
Ransomware Articles - H 2020 1 2 3 4 5 6 7 8 9 10 11 Ransomware List - H 2021 2020 2019 2018 1 Ransomware blog Ransomware blog
19 Million California Voter records held for ransom attack on a MongoDB instance
16.12.2017 securityaffairs Ransomware
Voter registration data for more than 19 million California residents stored in an unsecured MongoDB instance has been deleted and held for ransom.
Voter registration data for more than 19 million California residents that was stored in an unsecured MongoDB database has been deleted and held for ransom by attackers.
The incident was discovered by researchers at Kromtech, it is the last of a long string of ransom attacks targeting unsecured MongoDB database.
“In early December Kromtech security researchers discovered an unprotected instance of MongoDB database that appear to have contained voter data. The database named ‘cool_db’ contained two collections and was available for anybody with Internet connection to view and/or edit.
One was a manually crafted set of voter registration data for a local district and the other appeared to contain the entire state of California with 19,264,123 records, all open for public access.” reported Kromtech.
According to the LA Times California had 18.2 million registered voters in 2016 so this would logically be a complete list of their records.”
The attack sequence is similar to other hacks, the attacker scanned the internet for unsecured MongoDB databases, found this one containing the voter data, wiped the data in the archive and left a ransom request for 0.2 Bitcoin ($3,582 US at the current price).
Kromtech researchers were not able to identify the owner of the database because crooks deleted the content of the archive, they only analyzed stats data as well as a few records sample extracted from the database shortly before it has been wiped out.

It is impossible to determine if the attacker made a copy of the data before wiping the MongoDB database or if other hacker groups found and made a copy of the voter registration database before it was deleted.
“It is unclear who exactly compiled the database in question or the ownership, but researchers believe that this could have been a political action committee or a specific campaign based on the unofficial title of the repository (“cool_db”), but this is only a suspicion. Political firms assist campaigns in building voter profiles. This information of California voters is governed by state law that dictates what kind of information can be released, and for what purposes.” states Kromtech.
In June, security firm UpGuard found an Amazon S3 bucket containing the details of 198 million US voters.
Once in the hands of crooks, voter data could end up for sale on the Dark Web, in June 2016 a seller using the pseudonym of ‘DataDirect’ offered US voters’ registration records on the darknet marketplace “The Real Deal.”

Back to the case of the California Voter registration archive, Bob Diachenko, head of communications, Kromtech Security Center said:
“This is a massive amount of data and a wake up call for millions citizens of California who have done nothing more than fulfil the civic duty to vote. This discovery highlights how a simple human error of failing to enact the basic security measures can result in a serious risk to stored data. The MongoDB was left publically available and was later discovered by cyber criminals who seemed to steal the data, which origin is still unknown.”
If you are curious, like me, give a look at the transactions for the wallet in the ransom note and see if someone has paid 😉
https://blockchain.info/address/1EPA6qXtthvmp5kU82q8zTNkFfvUknsShS
New Spider Ransomware Emerges
13.12.2017 securityweek Ransomware
A new ransomware family discovered when analyzing a mid-scale campaign that started over the weekend uses decoy documents auto-synced to enterprise cloud storage and collaborations apps, security researchers have say.
Dubbed Spider, the new threat was observed being distributed via an Office document supposedly targeting users in Bosnia and Herzegovina, Serbia, and Croatia. The spam emails suggest the sender is looking to collect some debt from the recipient in attempt to trick the user into opening the attached file.
Obfuscated macro code embedded in the Office document, however, launches a Base64 encrypted PowerShell script to download the malicious payload, Netskope’s Amit Malik says.
If the malware is able to successfully infect a system, it starts encrypting user’s files and adds the ‘.spider’ extension the affected files.
A decrypter was designed to display the user interface and allow users decrypt the files using a decryption key. It is executed alongside the encrypter but runs in the background until the encryption process has been completed, BleepingComputer’s Lawrence Abrams explains.
According to Malik, the Spider decrypter monitors system processes and prevents the launch of tools such as taskmgr, procexp, msconfig, regedit, cmd, outlook, winword, excel, and msaccess.
During encryption, the malware skips files in the following folders: tmp, Videos, winnt, Application Data, Spider, PrefLogs, Program Files (x86), Program Files, ProgramData, Temp, Recycle, System Volume Information, Boot, and Windows.
After completing the encryption process, the decrypter displays a warning (available in English and Croatian) informing users on how they can decrypt their files. A help section is also included, with links and references to the resources needed to make the payment.
The ransom payment demanded is roughly $120.
“As ransomware continues to evolve, administrators should educate employees about the impact of ransomware and ensure the protection of the organization’s data by making a regular backup of critical data. In addition to disabling macros by default, users must also be cautious of documents that only contain a message to enable macros to view the contents and also not to execute unsigned macros and macros from untrusted sources,” Netskope says.
StorageCrypt Ransomware Targets NAS Devices via SambaCry Exploit
7.12.2017 securityweek Ransomware
A new ransomware family is using the SambaCry vulnerability that was patched in May to infect network-attached storage (NAS) devices, researchers have discovered.
Dubbed StorageCrypt, the ransomware demands between 0.4 and 2 Bitcoins ($5,000 to $25,000) from its victims for decrypting the affected files.
To infect NAS devices, StorageCrypt abuses the Linux Samba vulnerability known as SambaCry and tracked as CVE-2017-7494. Affecting devices from major vendors, the bug allows remote attackers to execute arbitrary code on targeted systems by uploading a shared library to a writable share, and then causing the server to load that library.
The first attempt to abuse the vulnerability resulted in targeted systems being infected with a cryptocurrency miner. During summer, a piece of malware dubbed SHELLBIND started abusing the flaw to infect NAS devices.
StorageCrypt leverages the SambaCry in the same manner as SHELLBIND did, BleepingComputer’s Lawrence Abrams reveals. The attack relies on the exploit executing a command to download a file called sambacry, store it in the /tmp folder as apaceha, and then running it.
What the security researcher couldn’t yet determine is whether the executable is only used to install the ransomware or is also serves as a backdoor for future attacks.
Once StorageCrypt is up and running on the infected device, it encrypts and renames the files and appends the .locked extension to them. It also drops a ransom note containing the ransom amount, the attackers’ Bitcoin address, and email address JeanRenoAParis@protonmail.com.
The malware was also observed dropping two files on the infected NAS devices, namely Autorun.inf and 美女与野兽.exe (which reportedly translates to Beauty and the beast). The former file is meant to spread the Windows executable to the machines the folders on the NAS device are accessed from.
To stay protected from this ransomware or other malware abusing SambaCry, users are advised to apply the latest patches to ensure their devices aren’t vulnerable, as well as to disconnect NAS devices from the Internet. Setting up a firewall and using a VPN for secure access to the NAS should also be taken into consideration.
The StorageCrypt ransomware is the last malware in order of time exploiting SambaCry to target NAS Devices
7.12.2017 securityaffairs Ransomware
StorageCrypt Ransomware is the last malware in order of time exploiting the SambaCry vulnerability, it was developed to target NAS Devices.
Experts discovered a new strain of malware exploiting the SambaCry vulnerability (CVE-2017-7494), it has been called StorageCrypt Ransomware because it targets NAS Devices via SambaCry Exploit.
The StorageCrypt ransomware demands between 0.4 and 2 Bitcoins ($5,000 to $25,000) for decrypting the encrypted files.
“Recently BleepingComputer has received a flurry of support requests for a new ransomware being named StorageCrypt that is targeting NAS devices such as the Western Digital My Cloud.” wrote the malware expert Lawrence Abrams from BleepingComputer.
“Victims have been reporting that their files have been encrypted and a note left with a ransom demand of between .4 and 2 bitcoins to get their files back.”
Experts discovered that the malware exploits the Linux Samba vulnerability, aka SambaCry, that was patched in May.
The vulnerability could be exploited by remote attackers to execute arbitrary code on targeted systems by uploading a shared library to a writable share, and then causing the server to load that library.
In July, experts discovered a malware dubbed SHELLBIND that exploited the CVE-2017-7494 Samba vulnerability in attacks against Internet of Things devices.
SHELLBIND infected most network-attached storage (NAS) appliances, it exploits the Samba vulnerability (also known as SambaCry and EternalRed) to upload a shared library to a writable share, and then cause the server to load that library.
CVE-2017-7494 is a seven-year-old remote code execution vulnerability that affects all versions of the Samba software since 3.5.0. The flaw has been patched by the development team of the project.
The CVE-2017-7494 flaw can be easily exploited, just a line of code could be used for the hack under specific conditions:
make file- and printer-sharing port 445 reachable on the Internet,
configure shared files to have write privileges.
use known or guessable server paths for those files
The Samba vulnerability affects the products of several major vendors, including NAS appliances.
The Samba bug appears to be a network wormable issue that could be exploited by a malicious code to self-replicate from vulnerable machine to vulnerable machine without requiring user interaction.
In June, researchers at Kaspersky Lab set up honeypots to detect SambaCry attacks in the wild. The experts spotted a malware campaign that was exploiting the SambaCry vulnerability to infect Linux systems and install a cryptocurrency miner.
According to Lawrence Abrams, the StorageCrypt Ransomware relies on the exploit executing a command to download a file called sambacry, store it in the /tmp folder as apaceha, and then executing it.
It is still unclear if the executable only installs the StorageCrypt ransomware or if it is also used as a backdoor.
Once the ransomware infected a device, it encrypts the files and renames them by appending the .locked extension to them.
“When a file is encrypted it will be renamed so that the .locked extension is appended to the filename. The ransomware will also drop a ransom note named _READ_ME_FOR_DECRYPT.txt that contains the ransom amount, the bitcoin address to send payment to, and the email address JeanRenoAParis@protonmail.com to contact after payment.” continues Abrams.

The ransomware drops two files on the infected NAS devices, namely Autorun.inf and 美女与野兽.exe, the latter file is meant to spread the Windows executable to the machines the folders on the NAS device are accessed from.
To avoid being infected by the StorageCrypt ransomware or other malware exploiting the SambaCry flaw, users need to apply the latest. Users also need to disconnect NAS devices from the Internet, set up a firewall to protect the storage device and use a VPN for secure access to it.
Experts discovered a new variant of Shadow BTCware Ransomware Variant
4.12.2017 securityaffairs Ransomware
The security expert Michael Gillespie discovered a new variant of the Shadow BTCware Ransomware which is manually installed on unsecured systems.
The security expert Michael Gillespie discovered a new variant of the BTCWare ransomware, the malicious code was spread by hacking into poorly protected remote desktop services and manually installed by crooks.
The new Shadow BTCware Ransomware variant appends the .[email]-id-id.shadow extension to the encrypted files, compared to previous versions it uses new email addresses a victim should contact to receive the instructions to pay the ransomware.
In the last version analyzed by the expert and reported by Bleeping Computer, the contact email address used by crooks is paydayz@cock.li.

The extension appended to encrypted files is also changed, the Shadow BTCware Ransomware variant appends the .[email]-id-[id].shadow extension to encrypted file’s name. (i.e. The file test.jpg is renamed to test.jpg.[paydayz@cock.li]-id-C0C.shadow).
“All your files have been encrypted!
All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail paydayz@cock.li
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the decryption tool that will decrypt all your files.
Free decryption as guarantee
Before paying you can send us up to 3 files for free decryption. The total size of files must be less than 1Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)
How to obtain Bitcoins.” reads an excerpt of the ransom note
As usual, to protect your system you need a proper cybersecurity posture. You should have a reliable and tested backup of data and of course, you have to use behavioral detections security solutions.
As usual, let me suggest to do not open attachments coming with unsolicited email messages, malware scan attachments with security tools (i.e. VirusTotal), make sure the OS and all the software are up to date.
Use strong passwords to protect your web services and never reuse the same password at multiple sites.
Further details, including the IoCs, have been published by Bleeping Computer.
Halloware Ransomware, a new malware offered for sale on the Dark Web for Only $40
3.12.2017 securityaffairs Ransomware
The Halloware ransomware is a new malware offered for sale in the dark web, the author that goes online with the moniker Luc1F3R is selling it for just $40.
According to the experts at Bleeping Computer, Luc1F3R started selling the Halloware this week through a dedicated portal on the Dark web. Luc1F3R claims to be a 17-year-old college student from Northeast India.
“Currently, the malware dev is selling and/or advertising his ransomware on a dedicated Dark Web portal, on Dark Web forums, two sites hosted on the public Internet, and via videos hosted on YouTube.” reported Bleeping Computer.
“The sites are offering a lifetime license for the Halloware ransomware for only $40.”
The low price has made the researchers suspicious, so they decided to investigate the case suspecting a scam.
Operational mistakes in the websites used by to Luc1F3R to sell the ransomware allowed the expert from Bleeping Computer to track down a web page where Luc1F3R was hosting the index of Halloware files, The page included weaponized documents used to deliver the malware.

One of the files in the list, hmavpncreck.exe, had the same SHA256 hash for which Luc1F3R included NoDistribute scan results in Halloware’s ad, confirming that it was the malware binary the experts were looking for.
Another file named ran.py seems to be Halloware’s source code.
“While the file was protected, Bleeping Computer managed to extract its source code, which will end up in the hands of other security researchers to create decrypters, in case someone buys this ransomware and uses it to infect real users.” continues the analysis from Bleeping Computer.
The researchers highlighted that Halloware is a working ransomware that encrypts files using a hardcoded AES-256 key and prepends the “(Lucifer)” string to encrypted file names. For example, once encrypted a file named image.png, it will appear as (Lucifer)image.png.
Once the Halloware ransomware has completed the encryption process it pops up a window showing a creepy clown with a ransom message containing the instruction to pay the ransom and decrypt the data. The victim’s desktop wallpaper, also displays a similar message, but experts noticed that Halloware ransomware does not drop text files with ransom notes on the infected PCs.

Wannabe criminals that buy the ransomware can generate their own install by changing two images and adding their customized payment site URL.
Anyway the experts noticed that the ransomware uses a hardcoded AES key and does not save any information on a remote server, this characteristic makes the malware not useful for the criminal underground.
According to Bleeping Computer Luc1F3R is a novice without particular skills. His tutorials published on YouTube describe basic hacking techniques or promote unsophisticated malware.
Some of the video tutorials include a Luc1F3R’s GitHub account that hosts four malware strains:
A Batch-based ransomware.
A Windows keylogger.
A Linux keylogger.
A bulk spoofed email sender.
Further details, including IoCs are available on the Bleeping Computer website.
New .NET-Based Ransomware Uses Open Source Code
2.12.2017 securityweek Ransomware
Two newly discovered .NET-based ransomware families are using open source repositories to encrypt users’ files, Zscaler security researchers say.
Dubbed Vortex and BUGWARE, the two ransomware families have been seen in live attacks carried out via spam emails containing malicious URLs. Both of the new malware families are compiled in Microsoft Intermediate Language (MSIL) and have been packed with the 'Confuser' packer.
The Vortex ransomware is written in Polish and makes use of the AES-256 cipher to encrypt image, video, audio, document, and other potentially important data files on the victim’s machine, Zscaler notes in an analysis report shared with SecurityWeek.
The same as other ransomware variants out there, the malware drops a ransom note once it has completed the encryption process, informing the victim on how they can restore their data and how to send the ransom money.
The malware allows users to decrypt two of their files for free and demands a $100 ransom, which supposedly increases to $200 in four days. Victims are encouraged to contact the attackers using the Hc9@2.pl or Hc9@goat.si email addresses.
After installation, the malware attempts to achieve persistence through creating a registry entry, as well as a registry key called “AESxWin.” The malware was also observed deleting shadow copies to prevent users from restoring their data without paying.
While analyzing the malware’s command and control (C&C) communication, the security researchers observed it sending system information and requesting a password API used for the encryption and decryption key.
Vortex is entirely based on AESxWin, a freeware encryption and decryption utility hosted on GitHub and created by Egyptian developer Eslam Hamouda. Thus, files can be decrypted using AESxWin, as long as the password used for encryption is known, Zscaler suggests.
BUGWARE, on the other hand, is based on the open source Hidden Tear code, which has been abused to create various ransomware families before.
The new threat also uses an invalid certificate pretending to be for GAS INFORMATICA LTDA and asks victims to pay the equivalent of a thousand Brazilian reals in Monero.
The malware creates a list of paths to encrypt and stores it in a file called Criptografia.pathstoencrypt. It also searches for all fixed, network, and removable drives and adds those paths to the list.
BUGWARE was observed generating the encryption key and using the AES 256-bit algorithm to encrypt users’ files, as well as renaming the encrypted files. The AES key is encrypted too, using a RSA public key, and the base64 encoded key is saved in the registry.
To achieve persistence, the malware creates a run key that ensures it is executed each time the user logs into the computer. If removable drives are detected, the threat drops a copy of itself on them, with the name “fatura-vencida.pdf.scr.”
The ransomware changes the victim’s desktop background using image files downloaded from “i[.]imgur.com/NpKQ3KZ.jpg."
A new version of the Scarab ransomware is now being distributed via the Necurs botnet
25.11.2017 securityaffairs Ransomware
The Scarab ransomware is now being distributed to millions of users via a massive spam campaign powered with the dreaded Necurs botnet.
Scarab is a strain of ransomware, first spotted in June by the security researcher Michael Gillespie, that is now being distributed to millions of users via a massive spam campaign powered with the dreaded Necurs botnet.
Security researchers believe that Necurs botnet was rented by a threat actor to spread the Scarab ransomware.
The Necurs botnet was used in the past months to push many other malware, including Locky, Jaff, GlobeImposter, Dridex and the Trickbot.
The ongoing spam campaign started on concurrently the Thanksgiving, most of the experts in the security community reporting the ongoing spam campaign, including security firms F-Secure and Forcepoint,
Forcepoint experts highlighted huge volume of spam emails sent in a few hours, 12.5 million emails.
“Forcepoint Security Labs have observed another piece of ransomware called “Scarab” being pushed by the infamous Necurs botnet. The massive email campaign started at approximately 07:30 UTC and is active as of 13:30 today, totalling over 12.5 million emails captured so far.” reads the analysis published by Forcepoint.

MalwareHunterTeam
@malwrhunterteam
Necurs now spreading Scarab (https://twitter.com/dvk01uk/status/933611940173066240 …).
Interesting...
🤔
Let's see if it will be more successful than Locky in past months...@BleepinComputer @demonslay335
cc @MalwareTechBlog
11:27 AM - Nov 23, 2017
1 1 Reply 13 13 Retweets 19 19 likes
Twitter Ads info and privacy
“Necurs’ spam botnet business is doing well as it is seemingly acquiring new customers. The Necurs botnet is the biggest deliverer of spam with 5 to 6 million infected hosts online monthly, and is responsible for the biggest single malware spam campaigns. Its service model provides the whole infection chain: from spam emails with malicious malware downloader attachments, to hosting the payloads on compromised websites.” reported F-Secure.
“The final payload (to our surprise) was Scarab ransomware, which we haven’t seen previously delivered in massive spam campaigns. Scarab ransomware is a relatively new ransomware variant first observed last June, and its code is based on the open source “ransomware proof-of-concept” called HiddenTear.”

The Necurs botnet pushed tens of millions of spam emails of the Scarab ransomware.
According to Forcepoint, by noon, Necurs had already sent out 12.5 million emails carrying what appeared to be a new version of the Scarab ransomware.

Necurs spam volume pushing Scarab ransomware
The massive Scarab ransomware campaign is evident also from data from the ID-Ransomware service that allows users to detect the type of ransomware that infected their system. The following graph shows the number of submissions for the Scarab ransomware per day.
Scarab emails disguised as archives carrying scanned images, email subjects are chose to trick victims into opening the archive, some of the most popular subject lines used in the campaign were:
Scanned from Lexmark
Scanned from HP
Scanned from Canon
Scanned from Epson
These emails carried a 7Zip archive that contained a Visual Basic script that act as a dropper of the Scarab ransomware.
Researchers observed that this Visual Basic script contained the same Game of Thrones references that were observed in other Necurs campaigns that delivered the Locky ransomware in September.
A first variant of the Scarab ransomware was discovered in June, in July the Malwarebytes researcher Marcelo Rivera spotted a second version that used the “.scorpio” extension.
18 Jun
Marcelo Rivero
@MarceloRivero
Replying to @demonslay335
#Scarab #Ransomware sample: ext ".[resque@plague.desi].scarab"https://www.virustotal.com/en/file/53f73dc2e8af9c059136029b3b535e885d4452d3375586eb9a0336d7a389aad5/analysis/1497737613/ … cc//@BleepinComputer @malwrhunterteam @Amigo_A_ pic.twitter.com/yuv3pF4Mfx
Marcelo Rivero
@MarceloRivero
#Scorpio #Ransomware (aka #Scarab) new sample, same rescue note, new ext: [Help-Mails@Ya.Ru].Scorpiohttps://www.virustotal.com/en/file/89258854adce5f5fd4d99ece5aad39b306f40585810ced9b0f79dad43fd8e036/analysis/ … pic.twitter.com/rZ9lyYDfdd
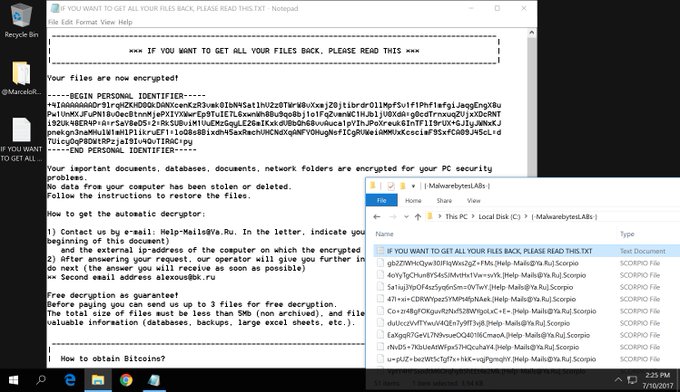
The variant currently used by crooks appends the “.[suupport@protonmail.com].scarab” extension to the original filenames of encrypted files.
The Scarab ransomware deletes shadow volume copies to make impossible to recovery the files, the malware drops a ransom note named “IF YOU WANT TO GET ALL YOUR FILES BACK, PLEASE READ THIS.TXT” on victims’ PCs.
The ransom does refer the ransom sum to pay, but urges victims to contact the Scarab authors via email or BitMessage as soon as possible to pay the smaller the ransom sum.
Necurs Returns With New Scarab Ransomware Campaign
25.11.2017 securityweek Ransomware
The world's largest spam botnet, Necurs, is delivering a new version of the Scarab ransomware. The campaign started at 07:30 UTC on Thanksgiving Day. By 13:30 UTC, security firm Forcepoint had already blocked more than 12.5 million Necurs emails.
The new campaign was also noted by F-Secure. "This morning at 9AM (Helsinki time, UTC +2) we observed the start of a campaign with malicious .vbs script downloaders compressed with 7zip," blogged researcher Paivi Tynninen on Thursday.
"Based on our telemetry," noted Forcepoint researchers, "the majority of the traffic is being sent to the .com top level domain (TLD). However, this was followed by region-specific TLDs for the United Kingdom, Australia, France and Germany."
Necurs, weaponizing between 5 and 6 million hosts per month, was originally best known for distributing the Dridex banking trojan, the Locky ransomware, and 'pump-and-dump' schemes. This year it has also spammed out Jaff and GlobeImposter ransomware. Scarab is new.
Scarab was first spotted in June 2017 by Michael Gillespie, creator of ID Ransomware (a service that allows users to submit a ransom note to discover which ransomware has infected them). According to F-Secure, Scarab's code "is based on the open source ìransomware proof-of-concept called HiddenTear."
Necurs is delivering a malicious VBS script downloader compressed with 7zip. As in previous campaigns, the script contains a number of Games of Thrones references, such as the strings 'Samwell' and 'JohnSnow'. The final payload is Scarab.
The email itself is typical Necurs: minimal text body with business-related subjects; in this case suggesting the attachment contains images of scanned documents. Popular subjects are 'Scanned from...' with either Lexmark, HP, Cannon or Epson added.
"The download domains used as part of this campaign were compromised sites which have previously been used by Necurs-based campaigns," notes Forcepoint. It is probable that many organizations will have these domains blacklisted, but the sheer size of the campaign will likely lead to many new Scarab infections.
If the downloader runs and Scarab is installed, it encrypts files and appends a new extension ending in '[suupport@protonmail.com].scarab'. The email address part of the extension is the same contact email provided in the ransom note.
The ransom note, with the filename ìIF YOU WANT TO GET ALL YOUR FILES BACK, PLEASE READ THIS.TXTî, is dropped into each affected folder. This note does not specify the amount of ransom required, saying instead that the amount will depend upon the speed of response from the victim. It does, however, offer to decrypt three files free of charge to prove the decryption will work: "Before paying you can send us up to 3 files for free decryption."
A second variant of the new Cryptomix Ransomware released in a few days
19.11.2017 securityaffairs Ransomware
Malware researchers at MalwareHunterTeam discovered a new variant of the CryptoMix ransomware, the second one in just a few days.
A new variant of the CryptoMix ransomware was recently discovered by the experts at the MalwareHunterTeam, it is the second release of new variants this week.
The latest variant appends the. 0000 extension to encrypted files and uses new contact emails, for example, a test file encrypted by this variant has an encrypted file name of 0D0A516824060636C21EC8BC280FEA12.0000.
The malware researcher Lawrence Abrams explained that this latest version of the ransomware uses the same encryption methods of previously discovered variants, but he noticed some slight differences.

The ransom note maintained the same file name _HELP_INSTRUCTION.TXT, but now uses the y0000@tuta.io, y0000@protonmail.com, y0000z@yandex.com, and y0000s@yandex.com emails for a victim to contact for payment information.
This variant of the CryptoMix ransomware contains 11 public RSA-1024 encryption keys that will be used to encrypt the AES key used to encrypt the files on the victim’s PC.
“This allows the ransomware to work completely offline with no network communication. This variant’s 11 public RSA keys are the same as the previous XZZX Cryptomix Ransomware variant.” wrote Abrams.
As usual, let me suggest to backup your data and test the backup files to avoid ugly surprises.
Install a security software and maintain it and any other application up to date. It could be useful to install specific anti-ransomware solution that implements behavioral.
Colleagues have published an interesting article on ransomware protection titled “How to Protect and Harden a Computer against Ransomware.”
City of Spring Hill in Tennessee still hasn’t recovered from ransomware attack
18.11.2017 securityaffairs Ransomware
In early November, the City of Spring Hill, Tenn, suffered a ransomware attack, but it still hasn’t recovered from attack attack.
In early November, the City of Spring Hill, Tenn, suffered a ransomware attack, but government officials refused to pay a $250,000 ransom demanded by the crooks and attempted to restore the database recovering the content from backups.
The malware caused serious damages to the city, many of the ordinary activities were affected, city workers were not able to access their email accounts, and residents were not able to make online payments or even use payment cards to pay utility bills or court fines, or conduct any other business transaction.
The situation is worse for emergency responders, the emergency dispatchers have had to log the calls, writing them by hand on a dry-erase board.
“This keeps track of our active police officers and medics out on a call,” said Director Brandi Smith about the white board.
“We write it down on paper, take the call number, put it behind them, so no matter who is working they know where the officer is, because despite all this, officer safety is still important to us,” she told News 2.

According to WKRN, the ransomware attack has shut down all mobile data terminals in the city’s police cars.
City officials announced that 911 system and city emails have been restored since Tuesday, the situation is more complicated for restoring direct deposits and online payments.
Investigators believe that the crooks haven’t stolen information from the city’s server.
Ransomware Targets SMBs via RDP Attacks
17.11.2017 securityweek Ransomware
A series of ransomware attacks against small-to-medium companies are leveraging Remote Desktop Protocol (RDP) access to infect systems, Sophos reports.
As part of these attacks, the mallicious actors abuse a commonly found issue in many business networks: weak passwords. After managing to crack and RDP password, attackers can easily install their malware onto the company’s systems with hopes to collect a ransom payment.
Discovering RDP ports exposed to the Internet isn’t difficult at all, Sophos explains. Cybercriminals can use specialized search engines such as Shodan for that and then abuse public or private tools to gain access to the discovered systems.
As part of the analyzed attacks, the actors used a tool called NLBrute to brute-force their way into the found systems by trying a variety of RDP passwords. Once they managed to find the right password, the attackers would immediately log into the network and create their own administrative accounts, Sophos says.
By doing so attackers can reconnect to the network even if the admin password they used for initial compromise has been changed. “They’ve already got backup accounts they can use to sneak back in later,” the researchers say.
Next, the attackers download and install low-level system tweaking software, such as Process Hacker, after which they turn off or reconfigure anti-malware applications. They also attempt to elevate privileges through abusing known vulnerabilities, including the CVE-2017-0213 and CVE-2016-0099 flaws that have been long patched by Microsoft.
The attackers also turn off database services to allow their malware to target databases, and also turn off the Windows live backup service called Volume Shadow Copy and delete existing backups, to prevent victims from restoring targeted files without paying. Next, they upload and run their ransomware.
According to Sophos, the attackers demanded a 1 Bitcoin ransom from their victims. Although numerous companies were hit, the attackers’ Bitcoin wallet shows a single transaction matching the demanded amount. Either victims have not paid, or they managed to negotiate lower payments, the security researchers say.
“The victims of this kind of attack are almost always small-to-medium companies: the largest business in our investigation had 120 staff, but most had 30 or fewer,” Sophos says.
To stay protected, organizations are advised to turn off RDP, or to protect it well if they need to use it regularly. They should also consider using a Virtual Private Network (VPN) for connections from outside their network, along with two-factor authentication (2FA), as well as to install available patches fast, to ensure their systems remain protected.
“You've probably heard the saying that 'if you want a job done properly, do it yourself’. Sadly, there's a niche of cybercrooks who have taken that advice to heart: if you've been sloppy setting up remote access to your network, they log in themselves and infect you with ransomware by simply running it directly, just like you or I might load Word or Notepad. This means the cyber criminals don’t need to mess around with emails, social engineering or malicious attachments,” said Paul Ducklin, Senior Technologist, Sophos.
The use of RDP to spread ransomware, however, isn’t a new practice. In fact, this attack method was so popular in the beginning of this year that it even topped email for ransomware distribution.
Last month, a BTCware ransomware variant called Payday was observed abusing the same method for infection. Security researchers investigating the attacks discovered that the malware operators were using brute-force attacks to crack RDP passwords and compromise the poorly secured systems.
Avira spotted a new strain of the dreaded Locky Ransomware in the wild
12.11.2017 securityaffairs Ransomware
Avira firm detected a new strain of the Locky ransomware that is spreading through malicious attachments disguised as legitimate Libre and Office documents.
Researchers at Avira Virus Lab detected a new strain of the Locky ransomware that is spreading through malicious attachments disguised as legitimate documents from productivity applications like Microsoft Word and Libre Office.
The new Lock Ransomware appends the same “.asasin” extension to the file names of encrypted documents as samples analyzed by security firm PhishMe in October.
The malware authors attempt to trick the victims into double-clicking the envelope.
“This new wave is being spread through Office Word documents, not only Microsoft but also other programs such as Libre Office, which look like the following image:”Locky Ransomware
“By doing so, this sets off a cascade of actions which will end in all valuable files being encrypted and the user getting the following message.” states the analysis published by Avira.
Once the users double-click the image, a series of actions is triggered, ending with the encryption of the files on the infected machine.
The analysis of the image included in the bait Word document revealed a LNK file (Windows shortcut), by pasting the command into a text editor, the researchers discovered it is meant to run a PowerShell script.
“The script is in clear text and can easily be read. Its intent is to download another PowerShell script from a link embedded in the script and then run this script by using the Invoke-Expression function.” continues the analysis.
The second script connects a server controlled by the operators and downloads a Windows executable file, which includes several stages of code obfuscation to confuse analysts and trick people into thinking it’s a clean file.
The new strain of Locky ransomware collects information about the operating system and sends it, encrypted, to the command-and-control server that in turn replies with the encryption key.
The rapid evolution of ransomware in the threat landscape is worrisome, and this case demonstrates it.
Security experts are observing a rapid evolution of the Locky ransomware, recently they have seen it spreading via spam campaigns that rely on the Necurs botnet. A couple of weeks ago, operators behind Locky ransomware campaigns have switched to new attack techniques to evade detection.
One of the new techniques adopted by the crooks is the use of the Dynamic Data Exchange (DDE) protocol designed to allow data transferring between applications.
Ordinypt is a wiper disguised as ransomware that targets German users
10.11.2017 securityaffairs Ransomware
Security experts spotted a new malware dubbed Ordinypt, it is a wiper disguised as ransomware that currently only targets German users
The malware researcher Michael Gillespie first reported a new strain of malware called Ordinypt that is currently targeting German users, but unfortunately instead of encrypting users’ files, the malware intentionally destroy them.
Early this week, the security researcher Karsten Hahn has spotted a sample that, based on VirusTotal detections, has been targeting only German users. The malware was spread via emails written in German, and delivering notes in an error-free language, it pretends to be a resume being sent in reply to job adverts.
The malware was first dubbed HSDFSDCrypt, but later G Data changed the name in Ordinypt ransomware.




These emails come with two files, a JPG file containing the resume and a curriculum vitae. The files in the observed samples use two attachments named Viktoria Henschel – Bewerbungsfoto.jpg and Viktoria Henschel – Bewerbungsunterlagen.zip.
“The ZIP archive contains two EXE files that use the old double-extension and custom icon tricks to fool users into thinking they’re different files. In this case, PDF files.” reported BleepingComputer.com.
“On Windows PCs that hide the file extensions by default, the EXE extension does not show up, and users just want to see the PDF part, which are legitimate PDFs, and not an executables.”

When the victim runs the executable will launch the Ordinypt ransomware, that in instead of encrypting files, wiper them by replacing files with random data.
9 Nov
Army Nael B. Leido @armynael
Replying to @demonslay335 and 4 others
It looks like its not encrypted before. It didn't even read the content of the file looking on its code. Also tested 300MB+ bait file and was replaced with a 21KB (very unlikely to be encrypted copy).
Philipp Mackensen @PMackensen
File names and content are generated by the same function (only needs a length as input) which randomly generates a string that consists of uppercase, lowercase and numeric characters . File size can differ between 8KB and 24KB (also random). Doesn't encrypt .png files tho.
11:42 AM - Nov 9, 2017
1 1 Reply 1 1 Retweet 6 6 likes
Twitter Ads info and privacy
The Ordinypt ransomware generates new “pseudo-encrypted-file’s” name, which is made up of 14 random alpha-numeric characters, the new files are sometimes more than half the size of the original ones.
The malware drops a ransom note in every folder where it wiped file content, the note is named where_sind_my_files.html. (translated which translates to where_are_my_files.html).

The fact that the Ordinypt is a wiper disguised as ransomware is also confirmed by its strange ransom note that doesn’t list an infection ID, nor does it ask for a file from where the ransomware’s authors can extract an ID.
The Ordinypt’s ransom note uses a bitcoin address from a hardcoded wallet address.
“The targeting of HR departments via job application emails also means that this is an intentional campaign to damage the operations of some Germany-based companies.” concluded Catalin Cimpanu from BleepingComputer.
“Furthermore, there’s no way of contacting the faux ransomware’s authors and verifying the payment. All evidence points to the fact that someone coded Ordinypt with the intention to damage computers.”
New GIBON Ransomware Emerges
7.11.2017 securityweek Ransomware
A newly discovered ransomware family called "GIBON" is targeting all files on machines that it has managed to infect, except those located in the Windows folder.
The ransomware is being sold on underground criminal forums for $500 and has been available there since at least May 2017. Despite that, however, security researchers got a glimpse of it only recently, and a decrypter for it was released last week.
The observed attack involving this threat was using malicious spam emails for distribution, but the exact delivery mechanism isn’t known at the moment.
Once it has infected a machine, GIBON connects to its command and control (C&C) server and registers the new victim by sending a base64 encoded string containing the timestamp, Windows version, and the "register" string (which tells the C&C that this is a new victim).
The server’s response contains a base64 encoded string that the ransomware uses as the ransom note. As BleepingComputer’s Lawrence Abrams notes, this setup allows the malware author to update the ransom note on the fly, without having to compile a new executable.
Once the victim has been registered, the ransomware generates an encryption key locally and then sends it to the C&C server as a base64 encoded string. The key is used to encrypt all of the files on the computer and appends the .encrypt extension to every encrypted file's name.
The threat continues to ping the server during the encryption process to inform it that the operation is still ongoing. When the process has been completed, it sends a final message to the server, containing the string "finish", a timestamp, Windows version, and the number of files encrypted.
GIBON drops a ransom note on each folder where a file has been encrypted, providing users with information on what happened and instructing them to contact the malware author via email at bomboms123@mail.ru or subsidiary:yourfood20@mail.ru for payment instructions.
While analyzing the advertisement for the malware, the researchers discovered that the author falsely claims that a RSA-2048 key is used for encryption. In fact, an addition cipher is used, and the ransomware then encrypts this cipher with a RSA-2048 key.
GIBON’s author also claims that files encrypted with the ransomware are impossible to decrypt, which is false as well, given that a decryptor has been already released.
The GIBON Ransomware appears in the threat landscape
6.11.2017 securityaffairs Ransomware
A new strain of ransomware dubbed GIBON ransomware was spotted by the ProofPoint researcher Matthew Mesa that observed it being distributed via malspam.
The spam messages use a malicious document as attachment containing macros that once enabled will download and install the ransomware on a victim’s machine.
The researcher dubbed the ransomware GIBON because of the presence of the string “GIBON” in two places. The experts first noticed this name in the user agent string of the malware using in the communications with the Command & Control server.

The second place where it is possible to find the string “GIBON” is the Admin panel for the ransomware, the logo is from the Russian television company VID.

When the GIBON ransomware is first executed, it will connect to the C&C and register a new victim by sending a base64 encoded string that contains the timestamp, the version of Windows, and the “register” string.
The C&C, in turn, will send back a response that contains a base64 encoded string that will be used by GIBON ransomware as the ransom note.
Once the infected machine is registered with the C&C, it will locally generate an encryption key and send it to the server as a base64 encoded string. The malware will use the key to encrypt all files on the target computer, it appends the .encrypt extension to the encrypted file’s name.
“Now that the victim has been registered and key transmitted to the C2, the ransomware will begin to encrypt the computer. While encrypting the computer, it will target all files regardless of the extension as long as they are not in the Windows folder.” reads the blog post published by Lawrence Abrams.
“During the encryption process, GIBON will routinely connect to the C2 server and send it a “PING” to indicate that it is still encrypting the computer.”
The malware drops a ransom note in each folder containing the encrypted files, it also generates a ransom note named READ_ME_NOW.txt.
“Attention! All the files are encrypted!
To restore the files, write to the mail:bomboms123@mail.ru
If you do not receive a response from this mail within 24 hours,
then write to the subsidiary:yourfood20@mail.ru”
Once the GIBON ransomware completed the file encryption a computer, it will send a message to the C&C server with the string “finish”, a timestamp, the Windows version, and the number of files that were encrypted.
The good news is that files encrypted by this ransomware can be decrypted using the GibonDecrypter.
Hacker threatens Canadian University to dump student info unless the university pay a ransom
5.11.2017 securityaffairs Ransomware
A hacker is attempting to extort the Canadian University of Fraser Valley (UFV), threatening to dump student information unless the university pays a ransom.
Extortion is a winning criminal model for crooks, a hacker is attempting to extort the Canadian University of Fraser Valley (UFV), threatening to dump student information unless the university pay 30,000 CAD (23,000 USD).
The University of Fraser Valley (UFV), is located in the Canadian town of Abbotsford, south-east of Vancouver.

The hackers breached the network at the university and gathered student information, including names, email addresses, phone numbers, physical addresses, grades information, some in some case financial data.
At the time it is not clear the time of the attack or the way hackers breached the university’s network, the Canadian University is still investigating the breach along with the local police.
Over last weekend, the hacker sent an email to UFV students with the personal information of 29 UVF students and a ransom demand of 30,000 CAD (23,000 USD). The hacker is threatening to release further details if the university will not pay the ransom in 48 hours.
The deadline has passed, but it’s unclear if the University paid the ransom.
The University admitted the security breach and issued four security alerts during the week.
“The students directly affected have been contacted and UFV is working with them to take steps to secure their privacy and personal information,” said a UFV spokesperson.
In response to the data breach, on Wednesday, the UFV shut down its email system announcing that it will be restored on November 6. The measure aims to prevent the spreading of emails containing data of other students.
CSE Malware ZLab – Full report of Bad Rabbit attack
1.11.2017 securityaffairs Ransomware
The researchers at CSE Cybsec ZLab have completed their analysis the Bad Rabbit ransomware, the report follows our preliminary analysis.
Introduction
Recently a new ransomware, called BadRabbit, infected systems in many countries, most of in East Europe, such as Ukraine and Russia. The malware was not totally new, it seems to be an evolution of the old NotPetya ransomware for some aspects, including:
The behavior after the reboot with a particular ransom note.
The spreading capability through lateral movements that relies on the SMB protocol and exploits a vulnerability based on vulnerability MS17-010.
There are also many differences with NotPetya, including, a more sophisticated behavior and the fixing of coding errors that transform NotPetya from a ransomware to a wiper, through the ad-hoc encrypting library “DiskCryptor”, for this purpose. These aspects suggest that the malware is a pure and correctly developed ransomware. Although there are some discrepancies:
The onion site indicated in the ransom note, “caforssztxqzf2nm[.]onion”, one the day after the initial infection, was no longer reachable. This implies that victims cannot pay the ransom to decrypt their files. But it’s strange that the onion site could be taken down so rapidly from authorities and it’s more probable that it could be taken down by the authors themselves.
Most of the compromised websites belong to restaurants, hotels and “house rental” services.
Most of the infected systems were in Ukraine, for example at the Odessa airport and Kiev metro. The targets are the same places previously targeted by NotPetya hackers.
These reasons make think that the malware isn’t a wiper for the design, but so de facto, because of the impossibility to pay the ransom and that the malware was written by the same authors of NotPetya and to be its evolution.
The full report includes technical details about the malware resulting from static and behavioral analysis. it also included Yara rules for the ransomware detection.
Malware Analysis Report: Bad Rabbit
Meet MBR-ONI, Bootkit Ransomware Used as a Targeted Wiper
1.11.2017 securityweek Ransomware
Earlier this year a new ransomware, dubbed ONI, was discovered in Japan. It is described as a sub-species of the GlobeImposter ransomware. Researchers blogged in July, "When it infects it, it encrypts the file, assigns the extension .oni to the filename, and asks for payment to decrypt it."
Cybereason now suggests that it is less ransomware, and more "a wiper to cover up an elaborate hacking operation." In a report published today, Cybereason researchers have tied the use of ONI to sophisticated attacks on Japanese industry. Unlike traditional ransomware attacks, these incursions lasted between three and nine months, and only culminated in the use of ransomware. The ransomware was, in effect, used to hide the purpose and effect of the hack.
In the same investigation, Cybereason discovered a new bootkit ransomware, MBR-ONI, which modifies the MBR and encrypts disk partitions. "We concluded that both ONI and MBR-ONI stem from the same threat actor since they were used in conjunction in the same targeted attacks and their ransom note contains the same email address," say the researchers.
The name ONI derives from the file extension of the encrypted files: '.oni'. It can mean 'devil' in Japanese. The term also appears in the contact email address used in the ransom notes: "Oninoy0ru", which can translate as Japanese for 'Night of the Devil'.
In the attack instances analyzed by Cybereason, a shared modus operandi was observed. This started with successful spear-phishing attacks leading to the introduction of the Ammyy Admin Rat. This was followed by a period of reconnaissance and credential theft, and lateral movement "ultimately compromising critical assets, including the domain controller (DC), to gain full control over the network."
The final stage of the attack is the use of log wipers and ONI distributed via a rogue group policy (GPO), in what Cybereason describes as a 'scorched earth policy'. The GPO would copy a batch script from the DC server, wiping clean the Windows' event logs to cover the attackers' tracks and avoid log-based detection. The batch file used the wevtutil command along with the "cl" flag, clearing events from more than 460 specified event logs. ONI would also be copied from the DC and executed, encrypting a large array of files.
The new MBR-ONI is used more sparingly against just a handful of the endpoints. These were the critical assets such as the AD server and file servers. Although both ONI and MBR-ONI could technically be decrypted (and can consequently be classified as ransomware rather than wipers), "We suspect," say the researchers, "that MBR-ONI was used as a wiper to conceal the operation's true motive."
The researchers also suspect that EternalBlue was used with other tools to spread through the networks. Although the log wiping and data corruption caused by the attacks makes this difficult to confirm with certainty, it was noted the EternalBlue patch had not been installed on the compromised machines, and the vulnerable SMBv1 was still enabled.
The ONI ransomware shares code with GlobeImposter, and shows Russian language traces. "While this type of evidence could have been left there on purpose by the attackers as decoy," say the researchers, "it can also suggest that the attacks were carried out by Russian speakers or, at the very least, that the ransomware was written by Russian speakers."
The MBR-ONI ransomware uses the same ransom message and ID for all infected machines (the ONI ransomware used a different ID for each encrypted system). A modified version of the open-source DiskCryptor tool was used for the encryption. Although this could be decrypted if the attackers supply the right key, "we suspect that the attackers never intended to provide recovery for the encrypted machines. Instead, the program was meant to be used as a wiper to cover the attackers' footprints and conceal the attack's motive."
The researchers believe it is highly unlikely that ransom extortion is the motive for these ONI attacks in Japan. Why would an attacker spend up to nine months -- at any point during which he could be detected and ejected -- before invoking the encryption?
"Until now the security community categorized ONI as ransomware. While ONI and the newly discovered MBR-ONI exhibit all the characteristics of ransomware, our analysis strongly suggests that they might have actually been used as wipers to cover an elaborate scheme," comments Assaf Dahan, director of advanced security services at Cybereason. "As someone who led red teams, I can tell you that taking over a network in order to mass-distribute ransomware can be achieved in a matter of a few hours or days. It doesn't make much sense to remain on the network for so long and risk exposure, unless they had other motives."
"We do not dismiss the possibility that financial gain was the motive behind these attacks," concludes Cybereason. "However, given the nature of the attacks and the profile of the targeted companies, other motives should not be dismissed lightly."
And while the researchers note that ONI is specific to Japan, they also point out that there are increasing reports of ransomware being used as a wiper by both cybercriminals and nation states in other parts of the world: PetWrap, Mamba, SamSam, NotPetya, Shamoon and Bad Rabbit are all possible examples. Such scorched earth tactics help to tie up incident responders in attempts to decrypt files, while making attribution to specific nation-state actors very difficult.
This is a tactic predicted by Carbon Black in a report in September 2017: Ransomware will increasingly be adopted by sophisticated groups who will use it in a targeted manner, often to augment or disguise other purposes – or simply as an obfuscated nation-state cyber weapon.
Cybereason raised $100 million in Series D funding from Tokyo-based SoftBank Corp in June 2017.
MBR-ONI ransomware involved in targeted attacks against Japanese organizations
1.11.2017 securityaffairs Ransomware
MBR-ONI is a new ransomware that is being used for targeted attacks in Japan, experts speculate it was used to cover larger hacking campaigns.
MBR-ONI is a new ransomware that is being used for targeted attacks in Japan, it is a bootkit ransomware that uses a modified version of the legitimate open-source disk encryption utility DiskCryptor to encrypt the file.
DiskCryptor is the same utility that was used by the recently discovered Bad Rabbit ransomware that targeted systems worldwide, mostly in Russia and Ukraine.
Experts from security intelligence firm Cybereason who analyzed the MBR-ONI malware speculate it has been used as wipers delete any track of targeted attacks against Japanese organizations.
“For several months Cybereason has been following the concerning rise of ONI, a family of ransomware involved in targeted attacks against Japanese companies.” states the analysis published by Cybereason.
“We suspect that the ONI ransomware was used as a wiper to cover up an elaborate hacking operation. These targeted attacks lasted between three to nine months and all ended with an attempt to encrypt hundreds of machines at once. “
The MBR-ONI was used by attackers in conjunction with ONI, that appears to be an earlier strain of ransomware developed by the same threat actors.
While ONI was used against most of the computers on targeted networks, MBR-ONI was used on only a limited number of endpoints. These endpoints were critical assets (Active Directory server, file servers, etc).
In the recent years, other wipers were used in targeted attacks including NotPetya, Mamba, SamSam, Shamoon and Bad Rabbit.
In the string of attacks against Japanese organizations, attackers leveraged on spear-phishing emails carrying weaponised Office documents that were used to deliver the Ammyy Admin RAT.
All the attacks that involved the ONI ransomware against Japanese companies across different industries shared the same pattern.
“The penetration vector used in the observed attacks consisted of spear-phishing emails that carried password-protected zip files containing weaponized Office documents.” continues the analysis.
“Once the victims extracted the zip file and opened the document, they were lured into enabling a macro. That launched a VBScript that downloaded and executed the Ammyy Admin RAT.”
Experts observed Ammyy Admin RAT installs on the compromised environment dated from December 2016 to September 2017, a circumstance that suggests that the attacks were carried over a period at least nine months.
Once the attackers penetrated the target’s environment, they will try to spread compromising critical assets such file servers, application servers and the domain controller (DC).
Researchers suspect that the threat actor used the NSA-leaked exploit EternalBlue, in conjunction with other tools to spread throughout the network.

ONI appears to share code with GlobeImposter ransomware, some routines are identical, while MBR-ONI shares a large portion of its code from DiskCryptor.
“While the ONI attacks presented in this blog are specific to Japan, we believe they also point to a concerning global trend. Using ransomware in targeted hacking operations is still quite uncommon compared to the popularity of ransomware in the overall cyber threat landscape.” concluded the experts.
Experts spotted a new strain of the Sage Ransomware that implements Anti-Analysis capabilities
1.11.2017 securityaffairs Ransomware
Security experts from Fortinet spotted a new strain of the Sage ransomware that included new functionalities, such as anti-analysis capabilities.
Sage 2.0 is a new ransomware first observed in December and not now it is distributed via malicious spam. Sage is considered a variant of CryLocker ransomware, it is being distributed by the Sundown and RIG exploit kits.
The malicious code discovered by Fortinet comes after a few months of apparent inactivity and were spread via spam emails with malicious JavaScript attachments.
“The Sage ransomware variant appears to have been out of circulation for a while in the malware scene. Since we published our article on Sage 2.0 last February, and the discovery of version 2.2 in March, the FortiGuard Labs team hasn’t seen significant activity with this malware for over six months.” states the analysis published by Fortinet.
“However, we just recently found new Sage samples that, while they appear to still be Sage 2.2, now have added tricks focused on anti-analysis and privilege escalation. In this article, we will share our findings of these recent updates.”
The Sage ransomware was also being distributed through weaponized documents, it leverages .info and .top top-level domain (TLD) names for malware delivery.
The ransomware implements the ChaCha20 encryption algorithm to encrypt the victim’s files and it doesn’t infect machines with Belarusian, Kazak, Uzbek, Russian, Ukrainian, Sakha, and Latvian keyboard layouts.
The threat actors behind this campaign have translated the ransom note into at least six languages, a circumstance that suggests they plan to target more countries in the future. in order to decrypt files, victims are instructed to access an onion site using the TOR browser and to pay a $2000 ransom to purchase the “SAGE Decrypter software.”

Once the malicious code has encrypted a file it will append the .sage extension to it.
The malware researchers discovered encrypted strings in the source code of the malware, a clear attempt of the author of obfuscating the code. The strings are encrypted using the Chacha20 cipher, the experts noticed that every encrypted string has its own hard-coded decryption key.
The new Sage ransomware implements several anti-analysis checks, for example, it enumerates all active processes on the machine, calculates the hash for every each one, and then compares the hashes against a hardcoded list of blacklisted processes.
The malware also checks the full path of where it executes to determine if the filename or directory name contains strings that are commonly used in the paths for analyzing malware samples.
The new strain of the Sage ransomware also checks the computer and user names to determine if they match a list of names used in sandbox environments, a similar check is conducted on the x86 instruction CPUID to get the processor info.
On top of these, the ransomware checks whether an antivirus runs on the computer (by enumerating the services running under Service Control Manager) and checks it against a set of blacklisted MAC addresses.
The ransomware checks whether an antivirus software is running on the machine, it does it by enumerating the services running under Service Control Manager.
“it checks to see if the computer has an instance of a running Antivirus and checks it against a set of blacklisted MAC addresses. The malware checks if there is an Antivirus running by enumerating the services running under Service Control Manager, computing these services names to a Murmurhash3, and then checking them against its list of hard-coded hashes. Table 2 and Table 3, respectively, list some of the blacklisted Antivirus services names and MAC addresses.” continues the analysis.
The experts discovered that this variant of Sage is able to elevate its privilege either by exploiting a patched Windows kernel vulnerability (CVE-2015-0057) or by abusing eventvwr.exe and performing registry hijacking to bypass User Account Control (UAC).
Sage Ransomware Gets Anti-Analysis Capabilities
31.10.2017 securityweek Ransomware
The Sage ransomware, which emerged toward the beginning of this year, has added new functionality that allows it to escalate privileges and evade analysis, Fortinet warns.
The malware was highly active in early 2017, but hasn’t shown significant activity over the past six months. Recently found samples resembling a Sage variant observed in March this year, however, pack both anti-analysis and privilege escalation capabilities, Fortinet's security researchers warn.
Distributed via spam emails with malicious JavaScript attachments, Sage was also found to share the same distribution infrastructure with the Locky ransomware. The malware was also observed being distributed through document files with malicious macros. It leverages .info and .top top-level domain (TLD) names for malware delivery.
The ransomware uses the ChaCha20 encryption algorithm to encrypt the victim’s files and appends the .sage extension to them. Sage avoids infecting computers that have the following keyboard layouts: Belarusian, Kazak, Uzbek, Russian, Ukrainian, Sakha, and Latvian.
A look at Sage’s code shows that most strings have been encrypted in an attempt to conceal the malicious behavior. The authors used the ChaCha20 cipher for encryption and every encrypted string has its own hard-coded decryption key, Fortinet has discovered.
Furthermore, the malware now performs a variety of checks to determine if it is being loaded into a sandbox or a virtual machine for analysis.
The threat enumerates all active processes on the machine, computes a hash for every one of them, and then checks the hashes against a hardcoded list of blacklisted processes. It also checks the full path of where the malware executes and terminates if it includes strings such as sample, malw, sampel, virus, {sample’s MD5}, and {samples’s SHA1}.
The new Sage variant also checks the computer and user names to determine if they match a list of names normally used in sandbox environments. It also uses the x86 instruction CPUID to get the processor info and compare it to a list of blacklisted CPU IDs.
On top of these, the ransomware checks whether an antivirus runs on the computer (by enumerating the services running under Service Control Manager) and checks it against a set of blacklisted MAC addresses.
Sage was also found to be able to elevate its privilege either by exploiting a patched Windows kernel vulnerability (CVE-2015-0057) or by abusing eventvwr.exe and performing registry hijacking to bypass User Account Control (UAC).
The ransom note has been translated into six more languages, which suggests that the author may aim to target more countries in the future. Victims are instructed to access an onion site using the TOR browser and to pay a $2000 ransom to purchase the “SAGE Decrypter software.”
NotPetya Attack Had Significant Impact on Merck Revenue
30.10.2017 securityweek Ransomware
American pharmaceutical giant Merck reported last week that the recent NotPetya malware attack caused losses of hundreds of millions of dollars in revenue.
The company’s financial results for the third quarter show that worldwide sales decreased by 2 percent to $10.3 billion compared to the same quarter of 2016. This was partly blamed on sales reduced by roughly $240 million due to insufficient stock of Gardasil 9, a vaccine designed to prevent certain cancers and other diseases caused by human papillomavirus (HPV).
Merck said it had to borrow the product from the U.S. Centers for Disease Control and Prevention’s Pediatric Vaccine Stockpile due to a higher demand than originally planned and the temporary disruption to production caused by the NotPetya attack.
“Additionally, as expected, revenue was unfavorably impacted by approximately $135 million from lost sales in certain markets related to the cyber-attack,” the company said in its latest SEC filing.
Merck’s marketing and administrative expenses of $2.4 billion may have also been smaller if it wasn’t for remediation costs related to the cyberattack.
Shortly after the attack, the firm reported that the incident had disrupted its worldwide operations, including manufacturing, research and sales. By late July, the company had still not fully restored manufacturing operations.
Merck is one of several major companies hit by NotPetya, a piece of malware that infected tens of thousands of systems in more than 65 countries back in June. The malware initially appeared to be a piece of ransomware, but researchers later determined that it was actually a wiper as there was no way to recover encrypted files even if the ransom was paid.
FedEx reported losses of roughly $300 million, and Danish shipping giant AP Moller-Maersk estimated that the attack would cost it $200-$300 million. Significant losses were also reported by British consumer goods company Reckitt Benckiser ($130 million), Mondelez International ($150 million), and French construction giant Saint-Gobain ($387 million by the end of the year).
The threat group that launched the NotPetya attack may also be behind the recent Bad Rabbit ransomware campaign that hit many Russian organizations and some in Ukraine. While Bad Rabbit actually appears to be a piece of ransomware – users should be able to recover their files by paying the ransom and in some cases even if they don’t pay it – the number of affected organizations is much smaller.
Matrix Ransomware being distributed through malvertising
30.10.2017 securityaffairs Ransomware
Security expert Jérôme Segura from Malwarebytes has spotted that Matrix Ransomware has risen again, it is now being distributed through malvertising.
Malware researcher Jérôme Segura from Malwarebytes has discovered that Matrix Ransomware is now being distributed through malvertising campaign.


EKFiddle @EKFiddle
#RIGEK drops Matrix ransomware. Payload https://www.virustotal.com/#/file/522e7328b76109502231e9f80a2c83fb0c57c28db98b54e0e7f401e368401046/detection … SAZ https://drive.google.com/file/d/0B4QZ_nlBrTP5MngwY3lMeGQ4eTA/view?usp=sharing …
10:20 PM - Oct 26, 2017
1 1 Reply 28 28 Retweets 16 16 likes
Twitter Ads info and privacy
The Matrix Ransomware was first spotted in 2016, in April 2017 the threat intelligence expert Brad Duncan uncovered the EITest campaign using the RIG exploit kit to distribute this malware.
Since then the Matrix ransomware slightly disappeared from the threat landscape, but now it seems to be back and it is being delivered through malvertising campaign that triggers an Internet Explorer flaw (CVE-2016-0189) and Flash one(CVE-2015-8651).
When a computer is infected with the latest variant of the Matrix Ransomware, the malicious code will encrypt the files on the victim’s machine, scramble their file names, and append the .pyongyan001@yahoo.com extension to the file scrambled name.
The ransomware also drops a ransom note (#_#WhatWrongWithMyFiles#_#.rtf) in every folder that contains files it encrypted, then it will display a ransom screen.

To protect your system, it is essential to install all available security updates for any software installed on the machine, run a security software, and always backup your data.
Basetools underground hacking forum breached, hacker demands $50K ransom
29.10.2017securityaffairs Ransomware
Basetools underground hacking forum was breached, hackers demand a $50K ransom to avoid sharing stolen data, including admin identity, with law enforcement.
A hacker that goes online with the Twitter handle mat (@0xScripts) has breached a popular underground hacking forum and he is threatening to share the stolen archive to the law enforcement if the administrators will not pay $50,000.
The forum is Basetools.ws, its members trade any kind of illegal product and service, including stolen payment card data, hacking tools, and stolen account data.
The hacking forum accounts for over 150,000 users, and its listing includes more than 20,000 tools. The hackers published this week a sample of the stolen data online demanding a ransom to the operators of the forum.
The hacker ‘mat’ contacted also Security Affairs to notify the data breach.

Mat is threatening to share data on the forum’s administrator with US law enforcement agencies.
He provided me the evidence of the authenticity of the stolen data, he shared with me and BleepingComputer an image of the Basetools admin panel and an image containing the site admin’s login details and IP address.
“I dumped the tools they were selling, their login credentials for cpanel accounts” Mat @0xScripts told me, he also added the he hacked the forum alone.
“login credentials for shells backdoors spambot etc”
The listing includes:
credentials for RDP servers;
login credentials for shells and backdoors:
login credentials for spambots hosted on compromised websites;
login credentials for server SSH;
dump form several data breaches;
The data breach is very serious and could have significant consequences for cybercrime underground community. The stolen data includes Basetools seller data could be soon leaked online. The above credentials could be leaked online and used by many other threat actors in the wild.

Below another image published by BleepingComputer

At the time I was writing, the basetools underground hacking forum is offline
The hackers told me that he hacked the forum not only for money but also as a retaliation for the fact that its administrator has been manipulating stats.
“He’s not a reseller, basetools is manipulating the stats by putting him in top places everytime and earning stats are manipulated by basetools” the hacker told me.
“Basetools.pw is manipulating EARNING STATS & RESELLER STATS, Owner of this market has opened a reseller with name RedHat which always stays in First Place,” reads the ransom note.
Files Encrypted by Bad Rabbit Recoverable Without Paying Ransom
28.10.2017 securityweek Ransomware
Some users may be able to recover the files encrypted by the Bad Rabbit ransomware without paying the ransom, Kaspersky researchers discovered after analyzing the malware’s encryption functionality.
Once it infects a device, Bad Rabbit looks for certain file types and encrypts them. The disk is also encrypted and a ransom screen is displayed when the computer boots, preventing the victim from accessing the operating system. The disk encryption and bootloader functionality are provided by code derived from a legitimate utility named DiskCryptor.
Bad Rabbit has been linked to the NotPetya attack that caused significant disruptions to many companies back in late June. However, unlike NotPetya, which experts classified as a wiper due to the fact that victims could not recover their files even if they paid the ransom, files encrypted by Bad Rabbit can be recovered with the right decryption key.
While the encryption mechanisms used by the attackers, AES-128-CBC and RSA-2048, cannot be cracked, Kaspersky experts have identified some methods that may allow some victims to decrypt their disk and recover files.
When an infected computer boots up, users are informed that their files have been encrypted and they are instructed to make a payment in order to obtain the password needed for decryption. The same screen also allows victims who have already obtained a password to enter it and boot their system.
Kaspersky researchers discovered that the password needed to boot the system is not wiped from memory after it’s generated, giving users the opportunity to extract it before the process that creates the password, dispci.exe, is terminated. Entering this password boots the system and decrypts the disk, the security firm told SecurityWeek, but there is only a “slim chance” that victims will actually be able to extract the password.
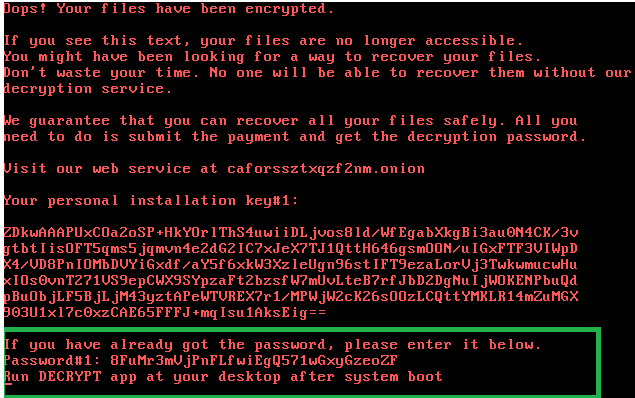
As for recovering files, experts noticed that Bad Rabbit does not delete shadow copies, which are backups made by Windows. If users enabled this backup functionality before the files were encrypted and the malware’s full disk encryption functionality failed for some reason or the disk is decrypted using the aforementioned method, the data can be restored via Windows or third-party utilities.
Kaspersky has also confirmed that Bad Rabbit does in fact use an NSA-linked exploit to spread; earlier reports claimed no exploits had been observed. The malware uses EternalRomance, which NotPetya also leveraged.
Based on the numerous similarities, the Bad Rabbit attack is believed to have been carried out by the same threat group that launched the NotPetya campaign, namely the Russia-linked threat actor known as BlackEnergy, TeleBots and Sandworm Team. Some are not convinced due to the fact that a majority of the victims were in Russia. Others pointed out, however, that the main target may have been Ukraine, where several major organizations were hit.
Documents encrypted by Bad Rabbit ransomware could be recovered without paying ransom
28.10.2017 securityaffairs Ransomware
Files Encrypted by Bad Rabbit Recoverable Without Paying Ransom.
Some victims of the recent Bad Rabbit attack may be able to recover their files encrypted by the ransomware without paying the ransom.
The discovery was made by researchers at Kaspersky Lab that analyzed the encryption functionality implemented by the ransomware.
Once the ransomware infects a computer, it encrypts certain file types, it also encrypts the disk and a ransom note is displayed when the computer boots.
The Bad Rabbit leverages the open source library DiskCryptor in order to encrypt the user files.
According to the preliminary analysis published by experts at the CSE Cybsec Zlab, the malware authors likely reused some pieces of NotPetya code increasing the complexity of the code itself and fixing coding errors that transform NotPetya from a ransomware to a wiper.
Now researchers from Kaspersky Lab discovered that files encrypted by Bad Rabbit can be recovered with following specific procedures.
When infected computer boots up, the victims are informed that their files have been encrypted by Bad Rabbit, and the malicious code provides instruction to complete the payment to obtain the decryption key.
Kaspersky noticed that Bad Rabbit uses the same screen to allows victims who have received the decryption key to enter it and boot their system.
Malware researchers discovered that after the ransomware the decryption key, this isn’t wiped from memory. Unfortunately, there is only a “slim chance” that victims will be able to extract the password.
The experts also discovered that Bad Rabbit does not delete shadow copies, allowing victims to restore the files through this windows backup functionality.
“We have discovered that Bad Rabbit does not delete shadow copies after encrypting the victim’s files. It means that if the shadow copies had been enabled prior to infection and if the full disk encryption did not occur for some reason, then the victim can restore the original versions of the encrypted files by the means of the standard Windows mechanism or 3rd-party utilities.” reads the analysis published by Kaspersky.

According to malware researchers, NotPetya has been linked to BlackEnergy APT, for this reason, some experts suggest the same threat actor could be behind the Bad Rabbit ransomware.
UK Government links the WannaCry attack that crippled NHS to North Korea
28.10.2017 securityaffairs Ransomware
UK Government blamed North Korea for the WannaCry attack that affected a third of English hospitals.
“This attack, we believe quite strongly that it came from a foreign state,” Ben Wallace, a junior minister for security, told BBC Radio 4’s Today programme.
“North Korea was the state that we believe was involved in this worldwide attack,” he said, adding that the government was “as sure as possible”.
The massive WannaCry attack infected more than 300,000 computers in 150 countries, including in Britain’s National Health Service (NHS), the US logistics company FedEx and a factory of the car vendor Honda.
WannaCry is a ransomware which encrypts all files stored in your system and demands a $300 ransomware in worth bitcoins if you want to decrypt and recover these files.
According to the Britain’s National Audit Office, computers at 81 hospital groups across England out of the total number of 236 were infected.
The WannaCry attack caused severe problems to the NHS England, it forced the cancellation of some 19,500 medical appointments and affected roughly 600 general practitioners.

The National Audit Office confirmed that most of the affected facilities were running Windows 7 OS that had not been updated.
“It was a relatively unsophisticated attack and could have been prevented by the NHS following basic IT security best practice,” NAO chief Amyas Morse said.
“There are more sophisticated cyber threats out there than WannaCry so the Department (of Health) and the NHS need to get their act together to ensure the NHS is better protected against future attacks,”.
Unfortunately, the numerous recommendations in the NHS about cybersecurity, in particular about the security updates, were ignored.
It was a terrible lesson for the NHS, according to Dan Taylor, NHS Digital’s head of security, the organization had “learned a lot” from WannaCry attack.
Taylor defined the WannaCry attack as “an international attack on an unprecedented scale”.
The good news is that according to the NAO report affected British organizations did not pay any ransom. The UK Government is still assessing the current impact of the WannaCry attack, it still “does not know how much the disruption to services cost.”
Shortly after the WannaCry attack many security experts and firms linked the ransomware to the North Korean APT Lazarus group.
Bad Rabbit Ransomware Uses Leaked 'EternalRomance' NSA Exploit to Spread
27.10.2017 thehackernews Ransomware
A new widespread ransomware worm, known as "Bad Rabbit," that hit over 200 major organisations, primarily in Russia and Ukraine this week leverages a stolen NSA exploit released by the Shadow Brokers this April to spread across victims' networks.
Earlier it was reported that this week's crypto-ransomware outbreak did not use any National Security Agency-developed exploits, neither EternalRomance nor EternalBlue, but a recent report from Cisco's Talos Security Intelligence revealed that the Bad Rabbit ransomware did use EternalRomance exploit.
NotPetya ransomware (also known as ExPetr and Nyetya) that infected tens of thousands of systems back in June also leveraged the EternalRomance exploit, along with another NSA's leaked Windows hacking exploit EternalBlue, which was used in the WannaCry ransomware outbreak.
Bad Rabbit Uses EternalRomance SMB RCE Exploit
Bad Rabbit does not use EternalBlue but does leverage EternalRomance RCE exploit to spread across victims' networks.
Microsoft and F-Secure have also confirmed the presence of the exploit in the Bad Rabbit ransomware.
EternalRomance is one of many hacking tools allegedly belonged to the NSA's elite hacking team called Equation Group that were leaked by the infamous hacking group calling itself Shadow Brokers in April this year.
EternalRomance is a remote code execution exploit that takes advantage of a flaw (CVE-2017-0145) in Microsoft's Windows Server Message Block (SMB), a protocol for transferring data between connected Windows computers, to bypass security over file-sharing connections, thereby enabling remote code execution on Windows clients and servers.
Along with EternalChampion, EternalBlue, EternalSynergy and other NSA exploits released by the Shadow Brokers, the EternalRomance vulnerability was also patched by Microsoft this March with the release of a security bulletin (MS17-010).
Bad Rabbit was reportedly distributed via drive-by download attacks via compromised Russian media sites, using fake Adobe Flash players installer to lure victims' into install malware unwittingly and demanding 0.05 bitcoin (~ $285) from victims to unlock their systems.
How Bad Rabbit Ransomware Spreads In a Network
According to the researchers, Bad Rabbit first scans the internal network for open SMB shares, tries a hardcoded list of commonly used credentials to drop malware, and also uses Mimikatz post-exploitation tool to extract credentials from the affected systems.
Bad Rabbit can also exploit the Windows Management Instrumentation Command-line (WMIC) scripting interface in an attempt to execute code on other Windows systems on the network remotely, noted EndGame.
However, according to Cisco's Talos, Bad Rabbit also carries a code that uses EternalRomance, which allows remote hackers to propagate from an infected computer to other targets more efficiently.
"We can be fairly confident that BadRabbit includes an EternalRomance implementation used to overwrite a kernel’s session security context to enable it to launch remote services, while in Nyetya it was used to install the DoublePulsar backdoor," Talos researchers wrote.
"Both actions are possible due to the fact that EternalRomance allows the attacker to read/write arbitrary data into the kernel memory space."
Is Same Hacking Group Behind Bad Rabbit and NotPetya?
Since both Bad Rabbit and NotPetya uses the commercial DiskCryptor code to encrypt the victim's hard drive and "wiper" code that could erase hard drives attached to the infected system, the researchers believe it is "highly likely" the attackers behind both the ransomware outbreaks are same.
"It is highly likely that the same group of hackers was behind BadRabbit ransomware attack on October the 25th, 2017 and the epidemic of the NotPetya virus, which attacked the energy, telecommunications and financial sectors in Ukraine in June 2017," Russian security firm Group IB noted.
"Research revealed that the BadRabbit code was compiled from NotPetya sources. BadRabbit has same functions for computing hashes, network distribution logic and logs removal process, etc."
NotPetya has previously been linked to the Russian hacking group known as BlackEnergy and Sandworm Team, but since Bad Rabbit is primarily targeting Russia as well, not everyone seems convinced with the above assumptions.
How to Protect Yourself from Ransomware Attacks?
In order to protect yourself from Bad Rabbit, users are advised to disable WMI service to prevent the malware from spreading over your network.
Also, make sure to update your systems regularly and keep a good and effective anti-virus security suite on your system.
Since most ransomware spread through phishing emails, malicious adverts on websites, and third-party apps and programs, you should always exercise caution before falling for any of these.
Most importantly, to always have a tight grip on your valuable data, keep a good backup routine in place that makes and saves copies of your files to an external storage device that isn't always connected to your PC.
Bad Rabbit Ransomware leverages the NSA Exploit for lateral movements
27.10.2017 securityaffairs Ransomware
Malware researchers at Cisco Talos team discovered the Bad Rabbit Ransomware leverages EternalRomance to propagate in the network.
New precious details emerge from the analysis of malware researchers at Cisco Talos and F-Secure who respectively discovered and confirmed the presence an NSA exploit in the Bad Rabbit ransomware.
On October 24, hundreds of organizations worldwide were hit by the Bad Rabbit ransomware, mostly in Russia and Ukraine.
The first reports on the ransomware revealed that the malicious code also relies on the Server Message Block (SMB) protocol to spread within the targeted network. Many experts excluded the use of the SMB exploits EternalBlue and EternalRomance for the lateral movements.
Previous reports confirmed that the Bad Rabbit ransomware does not use NSA-linked EternalBlue exploit, but researchers at Cisco Talos discovered the malicious code leverages EternalRomance to propagate in the network.
“Despite initial reports, we currently have no evidence that the EternalBlue exploit is being leveraged. However, we identified the usage of the EternalRomance exploit to propagate in the network. This exploit takes advantage of a vulnerability described in the Microsoft MS17-010 security bulletin. The vulnerability was also exploited during the Nyetya campaign.” reads the analysis published by the Talos team.

The EternalRomance vulnerability was patched by Microsoft in March 2017 with the release of the MS17-010 security bulletin that also fixed the EternalChampion, EternalBlue and EternalSynergy exploits.
Both exploits were disclosed by the Shadow Brokers hacker group earlier this year when the crew leaked a portion of the arsenal of the NSA-Linked Equation Group, a database containing hacking tools and exploits.
Almost every analysis produced since the discovery of the Bad Rabbit ransomware revealed many similarities between Bad Rabbit and NotPetya, including the targeting of Ukraine and Russia, the usage of Mimikatz tool, and the same type of file encryption.
However, while NotPetya is a wiper disguised by a ransomware, Bad Rabbit appears to be a real ransomware.
Another interesting aspect emerged by further analysis is related to the alleged planning of the attack that seems to be dated back months ago. Some of the compromised domains used in the Bad Rabbit ransomware attack had been set up since at least July 2017 and some of the injection servers were first seen more than a year ago.
According to malware researchers, NotPetya has been linked to BlackEnergy APT, for this reason, some experts suggest the same threat actor could be behind the Bad Rabbit ransomware.
Profiling Tool Suggests 'Bad Rabbit' Not Financially Motivated
27.10.2017 securityweek Ransomware
Researchers at FireEye noticed that some of the websites redirecting users to the Bad Rabbit ransomware hosted a profiling framework, which could suggest that the attack was not financially motivated.
The Bad Rabbit attack, which led to the infection of hundreds of machines in Russia and Ukraine with ransomware, started with users being redirected to 1dnscontrol[.]com, a domain that served a malware dropper disguised as a Flash Player installer. Users had to manually execute the file in order to become infected.
FireEye noticed that several compromised websites redirecting to the 1dnscontrol domain had hosted a profiling tool. Tracked by the company as BACKSWING, the framework has been seen on more than 50 websites since September 2016, and four of them redirected users to Bad Rabbit ransomware this week.
BACKSWING is designed to collect information about a user’s browsing session - including User-Agent, HTTP Referrer, cookies, and the current domain - and sends it back to a command and control (C&C) server.
FireEye has seen two versions of the tool, the second version replacing the first one on several websites starting with October 5. BACKSWING v2 was mostly injected into legitimate JavaScript resources hosted by affected sites.
“Malicious profilers allow attackers to obtain more information about potential victims before deploying payloads (in this case, the BADRABBIT ‘flash update’ dropper),” FireEye researchers explained. “While FireEye has not directly observed BACKSWING delivering BADRABBIT, BACKSWING was observed on multiple websites that were seen referring FireEye customers to 1dnscontrol[.]com, which hosted the BADRABBIT dropper.”
If BACKSWING was in fact used by the threat group behind the Bad Rabbit ransomware, it would suggest that the attack was not financially motivated, as a profit-driven actor would not care about who they’re infecting as long as they make money.
This also reinforces the theory that the Bad Rabbit operation was conducted by the Russia-linked threat group known as BlackEnergy, TeleBots and Sandworm Team, which is also believed to be behind the NotPetya wiper attack that targeted Ukraine and other countries in June.
“We observed a spike of BACKSWING instances on Ukrainian sites, with a significant increase in May 2017. While some sites hosting BACKSWING do not have a clear strategic link, the pattern of deployment raises the possibility of a strategic sponsor with specific regional interests,” FireEye said.
While many similarities have been found between NotPetya and Bad Rabbit, one major difference is that the latter mainly hit enterprises and most of the victims are in Russia. However, the relatively small number of Ukrainian organizations affected by the malware include high profile targets, such as the airport in Odessa, the Kiev subway, the State Aviation Service of Ukraine, and the Transport Ministry of Ukraine.
Contrary to initial reports, the Bad Rabbit ransomware does in fact appear to leverage an NSA-linked exploit to spread within compromised networks. The exploit in question is called EternalRomance and its details were leaked by the hacker group Shadow Brokers back in April. The vulnerability leveraged by the exploit was patched by Microsoft in March. EternalRomance was also one of the exploits leveraged by the NotPetya wiper.
'Bad Rabbit' Ransomware Uses NSA Exploit to Spread
26.10.2017 securityweek Ransomware
Contrary to initial reports, the Bad Rabbit ransomware that hit Russia and Ukraine this week does in fact leverage an exploit linked to the U.S. National Security Agency (NSA).
Similar to the NotPetya wiper that infected tens of thousands of systems back in late June, Bad Rabbit also uses the Server Message Block (SMB) protocol to spread within the compromised network. However, researchers initially claimed that, unlike NotPetya, the ransomware did not use either of the SMB exploits tracked as EternalBlue and EternalRomance.
It turns out that while Bad Rabbit does not use EternalBlue, it does in fact leverage EternalRomance to propagate in the network. The presence of the exploit was first reported by Cisco Talos and later confirmed by F-Secure.
The EternalRomance vulnerability was addressed by Microsoft in March 2017 with the release of a security bulletin that also patched the EternalChampion, EternalBlue and EternalSynergy exploits.
Details of these flaws were made public by a hacker group calling itself Shadow Brokers earlier this year. The group claims to have obtained these and many other exploits from the NSA and that they were used by one of the agency’s teams known in the cybersecurity industry as the Equation Group.
When the exploits were made public by the Shadow Brokers in April, Microsoft pointed out that they had already been fixed, which has led some to believe that the tech giant learned about the vulnerabilities from the NSA itself.
The initial analysis showed many connections between Bad Rabbit and NotPetya, including targeting of Ukraine and Russia, binaries signed with expired certificates, use of Mimikatz for credential-grabbing, reboots and persistence via scheduled tasks, removal of event logs and USN change journals, and the same type of file encryption and ransomware functionality.
One of the most significant differences is the fact that Bad Rabbit appears to be an actual ransomware and, at least in theory, users can recover their encrypted files if they pay the ransom. NotPetya, on the other hand, has been classified as a wiper due to the fact that the ransom payment functionality is not implemented properly, making the recovery of files impossible.
Another major difference is the fact that Bad Rabbit mostly affected enterprises, particularly in Russia. However, it’s worth noting that many of the victims in Ukraine are high-profile organizations.
NotPetya has been linked to the Russian threat actor known as BlackEnergy, TeleBots and Sandworm Team, which suggests that the same group may be behind the Bad Rabbit attacks as well, although not everyone seems convinced.
An analysis of the Bad Rabbit infrastructure showed that some of the compromised domains used in the attack had been set up since at least July and some of the injection servers were first seen more than a year ago.
'Bad Rabbit' Attack Infrastructure Set Up Months Ago
26.10.2017 securityweek Ransomware
The infrastructure used by the Bad Rabbit ransomware was set up months ago and an increasing amount of evidence links the malware to the NotPetya attack launched in late June, which some experts believe was the work of a Russian threat actor.
A majority of the Bad Rabbit victims are in Russia – over 80% according to some reports – where the ransomware hit several media outlets, including Interfax. Significant infections have also been observed in Ukraine, where the malware reportedly hit major organizations such as the airport in Odessa, the Kiev subway, the State Aviation Service of Ukraine, and the Transport Ministry of Ukraine.
Infections have also been spotted in Bulgaria, Turkey, Germany, Japan, the United States, South Korea and Poland.
Unlike the NotPetya attack, which hit tens of thousands of systems in more than 65 countries, Bad Rabbit, delivered by attackers via fake Flash Player installers, only infected a few hundred machines mainly belonging to enterprises. The attack began on October 24 at around 10 AM UTC and the majority of infection attempts were detected in the first couple of hours.
Analysis conducted by researchers and security firms showed many connections between Bad Rabbit and NotPetya, including the use of legitimate features such as SMB to spread within the compromised network. However, Bad Rabbit does not use EternalBlue or any other exploit.
The security researcher known online as Bart Blaze has published a useful table summarizing the similarities and differences between NotPetya and Bad Rabbit. The similarities include targeting of Ukraine and Russia, binaries signed with expired certificates, use of Mimikatz for credential-grabbing, reboots and persistence via scheduled tasks, removal of event logs and USN change journals, and the same type of file encryption and ransomware functionality.
One of the most significant differences is the fact that Bad Rabbit appears to be an actual ransomware and, at least in theory, users can recover their encrypted files if they pay the ransom; unlike NotPetya, which has been classified as a wiper due to the fact that the ransom payment functionality is not implemented properly, making the recovery of files impossible.
Bad Rabbit infrastructure
Kaspersky Lab researcher Costin Raiu pointed out that several of the compromised domains used in the Bad Rabbit attack had been set up for malicious activity since at least July.
An analysis by RiskIQ shows that some of the injection servers involved in the attack were set up more than a year ago.
“While this list is most likely incomplete, it does show that it’s part of a long-running campaign. The operators of this campaign have been able to use this position to target unique visitors based on IP space they associate with their targets,” explained RiskIQ’s Yonathan Klijnsma.
“The thing we do not understand at this point is why they decided to burn this information position to mass distribute the BadRabbit ransomware rather than save it for another type of malware. The goal of the attack using ExPetya back in June was simple: cause as much disruption in the Ukraine and those associated with Ukraine as possible which also seems the case in the BadRabbit attack,” Klijnsma added.
Russian security firm Group-IB noted that the domain serving the fake Flash Player installer, 1dnscontrol[dot]com, was hosted by Inferno, which is run by the same people as 3NT Solutions and V3Servers. The activities of this hosting company were detailed back in 2014 by British researcher Conrad Longmore, who has now provided an updated list of IP addresses that he believes should be blocked by organizations.
“The domain name 1dnscontrol.com was registered on 22 March 2016 and is currently prolonged. There are a number of malicious domains associated with this site, which relate back to 2011. It is possible that these domains have also been compromised or are used for analogous attacks,” Group-IB said.
Links to BlackEnergy
NotPetya, which is also tracked as Diskcoder, Petya, Petrwrap, exPetr and GoldenEye, was linked back in early July to a threat group known as TeleBots, BlackEnergy and Sandworm Team, which experts have tied to Russia and which is believed to be behind cyberattacks on Ukraine’s power grid.
NotPetya was linked to BlackEnergy based on similarities to a wiper used by the threat actor, Yara rules detecting both BlackEnergy and NotPetya malware, and previous ransomware attacks that hit Ukraine.
Several security firms and researchers pointed out that if the NotPetya attack was conducted by BlackEnergy, and Bad Rabbit was created by the same developers that made NotPetya, the obvious conclusion would be that Bad Rabbit is also the work of the Russia-linked hackers.
Removal Attempt Turns Android Banking Trojan Into Ransomware
26.10.2017 securityweek Ransomware
Researchers at SfyLabs have detailed the capabilities of an Android banking Trojan named LokiBot that is designed to turn into a piece of ransomware when users attempt to remove it from their devices.
LokiBot has been around since at least June and its authors have been rolling out new features nearly every week.
Once it infects an Android device (running Android version 4.0 or later), the malware starts displaying overlay screens on top of banking and other popular apps in an effort to trick victims into handing over their information. The malware targets roughly 100 banking applications and popular apps such as WhatsApp, Skype and Outlook.
The malware can also open the user’s web browser and navigate to a specified page, reply to SMS messages, and launch banking apps.
“Combine this with the fact that LokiBot can show notifications which seem to come from other apps, containing for example a message that new funds have been deposited to the victim’s account and interesting phishing attack scenarios arise!” SfyLabs researchers said in a blog post. “The phishing notifications use the original icon of the application they try to impersonate. In addition, the phone is made to vibrate right before the notification is shown so the victim will take notice of it. When the notification is tapped it will trigger an overlay attack.”
The most interesting feature, which has led researchers to classify LokiBot as a hybrid Android malware, is its ability to turn into ransomware when users attempt to remove it.
Specifically, when users try to revoke its admin privileges, the malware initiates a procedure to encrypt all files on the device’s external storage and locks the screen with a typical ransom demand claiming that the phone is locked for “viewing child pornography.” Victims are given 48 hours to pay a $70 - $100 “fine” in bitcoin.
SfyLabs found that the bitcoin address provided by the cybercriminals already stores cryptocurrency worth roughly $1.5 million. However, it’s unlikely that the entire amount comes from LokiBot attacks as the campaigns spotted by experts generally have only around 1,000 bots and the cost of the Trojan itself is $2,000.
Researchers noticed that while the screen-locking functionality works, the malware doesn’t actually encrypt files. Due to an error, files are automatically restored after being encrypted, but with a different name.
The malware’s developers have implemented some mechanisms designed to prevent dynamic analysis, but they are not particularly sophisticated, especially compared to other malware.
It’s worth noting that there is another Loki Bot malware that targets Windows devices. This threat is designed to steal data from infected computers and it has reportedly been used as a secondary payload in the NotPetya attack launched in late June.
Bad Rabbit ransomware
25.10.2017 Kaspersky Ransomware
What happened?
On October 24th we observed notifications of mass attacks with ransomware called Bad Rabbit. It has been targeting organizations and consumers, mostly in Russia but there have also been reports of victims in Ukraine. Here’s what a ransom message looks like for the unlucky victims:
What is bad rabbit?
Bad Rabbit is a previously unknown ransomware family.
How is bad rabbit distributed?
The ransomware dropper was distributed with the help of drive-by attacks. While the target is visiting a legitimate website, a malware dropper is being downloaded from the threat actor’s infrastructure. No exploits were used, so the victim would have to manually execute the malware dropper, which pretends to be an Adobe Flash installer.
We’ve detected a number of compromised websites, all of which were news or media websites.
Whom does it target?
Most of the targets are located in Russia. Similar but fewer attacks have also been seen in other countries – Ukraine, Turkey and Germany. Overall, there are almost 200 targets, according to the KSN statistics.
Since when does Kaspersky Lab detect the threat?
We have been proactively detecting the original vector attack since it began on the morning of October 24. The attack lasted until midday, although we are still detecting ongoing attacks.
How is it different to ExPetr? Or it is the same malware?
Our observations suggest that this been a targeted attack against corporate networks, using methods similar to those used during the ExPetr attack.
Technical details
According to our telemetry, the ransomware is spread via a drive-by attack.
The ransomware dropper is distributed from hxxp://1dnscontrol[.]com/flash_install.php
Also according to our telemetry data, victims are redirected to this malware web resource from legitimate news websites.
The downloaded file named install_flash_player.exe needs to be manually launched by the victim. To operate correctly, it needs elevated administrative privileges which it attempts to obtain using the standard UAC prompt. If started, it will save the malicious DLL as C:\Windows\infpub.dat and launch it using rundll32.
Pseudocode of the procedure that installs the malicious DLL
infpub.dat appears to be capable of brute-forcing NTLM login credentials to Windows machines that have pseudo-random IP addresses.
The hard-coded list of credentials
infpub.dat will also install the malicious executable dispci.exe into C:\Windows and create a task to launch it.
Pseudocode of the procedure that creates the task which launches the malicious executable
What’s more, infpub.dat acts as a typical file encrypting ransomware: it finds the victim’s data files using an embedded extension list and encrypts them using the criminal’s public RSA-2048 key.
The public key of the criminals and the extension list
The criminal’s public key parameters:
Public-Key: (2048 bit)
Modulus:
00:e5:c9:43:b9:51:6b:e6:c4:31:67:e7:de:42:55:
6f:65:c1:0a:d2:4e:2e:09:21:79:4a:43:a4:17:d0:
37:b5:1e:8e:ff:10:2d:f3:df:cf:56:1a:30:be:ed:
93:7c:14:d1:b2:70:6c:f3:78:5c:14:7f:21:8c:6d:
95:e4:5e:43:c5:71:68:4b:1a:53:a9:5b:11:e2:53:
a6:e4:a0:76:4b:c6:a9:e1:38:a7:1b:f1:8d:fd:25:
4d:04:5c:25:96:94:61:57:fb:d1:58:d9:8a:80:a2:
1d:44:eb:e4:1f:1c:80:2e:e2:72:52:e0:99:94:8a:
1a:27:9b:41:d1:89:00:4c:41:c4:c9:1b:0b:72:7b:
59:62:c7:70:1f:53:fe:36:65:e2:36:0d:8c:1f:99:
59:f5:b1:0e:93:b6:13:31:fc:15:28:da:ad:1d:a5:
f4:2c:93:b2:02:4c:78:35:1d:03:3c:e1:4b:0d:03:
8d:5b:d3:8e:85:94:a4:47:1d:d5:ec:f0:b7:43:6f:
47:1e:1c:a2:29:50:8f:26:c3:96:d6:5d:66:36:dc:
0b:ec:a5:fe:ee:47:cd:7b:40:9e:7c:1c:84:59:f4:
81:b7:5b:5b:92:f8:dd:78:fd:b1:06:73:e3:6f:71:
84:d4:60:3f:a0:67:06:8e:b5:dc:eb:05:7c:58:ab:
1f:61
Exponent: 65537 (0x10001)
The executable dispci.exe appears to be derived from the code base of the legitimate utility DiskCryptor. It acts as the disk encryption module which also installs the modified bootloader and prevents the normal boot-up process of the infected machine.
An interesting detail that we noticed when analyzing the sample of this threat: it looks like the criminals behind this malware are fans of the famous books & TV show series Game Of Thrones. Some of the strings used throughout the code are the names of different characters from this series.
Dragon names from Game Of Thrones
Character name from Game Of Thrones
Kaspersky Lab experts are working on a detailed analysis of this ransomware to find possible flaws in its cryptographic routines.
Kaspersky Lab corporate customers are also advised to:
make sure that all protection mechanisms are activated as recommended; and that KSN and System Watcher components (which are enabled by default) are not disabled.
update the antivirus databases immediately.
The abovementioned measures should be sufficient. However, as additional precautions we advise the following:
restricting execution of files with the paths c:\windows\infpub.dat and C:\Windows\cscc.dat in Kaspersky Endpoint Security.
configuring and enabling Default Deny mode in the Application Startup Control component of Kaspersky Endpoint Security to ensure and enforce proactive defense against this and other attacks.
Kaspersky Lab products detect this threat with the following verdicts:
Trojan-Ransom.Win32.Gen.ftl
DangerousObject.Multi.Generic
PDM:Trojan.Win32.Generic
IOCs:
http://1dnscontrol[.]com/
fbbdc39af1139aebba4da004475e8839 – install_flash_player.exe
1d724f95c61f1055f0d02c2154bbccd3 – C:\Windows\infpub.dat
b14d8faf7f0cbcfad051cefe5f39645f – C:\Windows\dispci.exe
Bad Rabbit: New Ransomware Attack Rapidly Spreading Across Europe
25.10.2017 thehackernews Ransomware
A new widespread ransomware attack is spreading like wildfire around Europe and has already affected over 200 major organisations, primarily in Russia, Ukraine, Turkey and Germany, in the past few hours.
Dubbed "Bad Rabbit," is reportedly a new Petya-like targeted ransomware attack against corporate networks, demanding 0.05 bitcoin (~ $285) as ransom from victims to unlock their systems.
According to an initial analysis provided by the Kaspersky, the ransomware was distributed via drive-by download attacks, using fake Adobe Flash players installer to lure victims' in to install malware unwittingly.
"No exploits were used, so the victim would have to manually execute the malware dropper, which pretends to be an Adobe Flash installer. We’ve detected a number of compromised websites, all of which were news or media websites." Kaspersky Lab said.
However, security researchers at ESET have detected Bad Rabbit malware as 'Win32/Diskcoder.D' — a new variant of Petya ransomware, also known as Petrwrap, NotPetya, exPetr and GoldenEye.
Bad Rabbit ransomware uses DiskCryptor, an open source full drive encryption software, to encrypt files on infected computers with RSA 2048 keys.
bad-rabbit-ransomware
ESET believes the new wave of ransomware attack is not using EternalBlue exploit — the leaked SMB vulnerability which was used by WannaCry and Petya ransomware to spread through networks.
Instead it first scans internal network for open SMB shares, tries a hardcoded list of commonly used credentials to drop malware, and also uses Mimikatz post-exploitation tool to extract credentials from the affected systems.
The ransom note, shown above, asks victims to log into a Tor onion website to make the payment, which displays a countdown of 40 hours before the price of decryption goes up.
The affected organisations include Russian news agencies Interfax and Fontanka, payment systems on the Kiev Metro, Odessa International Airport and the Ministry of Infrastructure of Ukraine.
Researchers are still analyzing Bad Rabbit ransomware to check if there is a way to decrypt computers without paying ransomware and how to stop it from spreading further.
How to Protect Yourself from Ransomware Attacks?
Kaspersky suggest to disable WMI service to prevent the malware from spreading over your network.
Most ransomware spread through phishing emails, malicious adverts on websites, and third-party apps and programs.
So, you should always exercise caution when opening uninvited documents sent over an email and clicking on links inside those documents unless verifying the source to safeguard against such ransomware infection.
Also, never download any app from third-party sources, and read reviews even before installing apps from official stores.
To always have a tight grip on your valuable data, keep a good backup routine in place that makes their copies to an external storage device that isn't always connected to your PC.
Make sure that you run a good and effective anti-virus security suite on your system, and keep it up-to-date.
Bad Rabbit Linked to NotPetya, but Not as Widespread
25.10.2017 securityweek Ransomware
The Bad Rabbit ransomware attack that hit Russia and Ukraine on Tuesday has been linked to the recent NotPetya outbreak, but the number of infections appears to be far smaller.
Several cybersecurity firms have conducted an initial analysis of the threat, including Cisco Talos, Kaspersky, Malwarebytes, ESET, McAfee, Bitdefender and Trend Micro.
Bad Rabbit distribution
Researchers say the malware spreads via watering hole attacks that deliver a fake Flash Player installer. The malicious file has been delivered from compromised websites in Denmark, Ireland, Bulgaria, Turkey and Russia.
Researchers pointed out that victims need to manually launch the fake Flash installer to get infected, and the file needs to obtain administrative privileges, which causes Windows to display a User Account Control (UAC) prompt. The attackers have not made any effort to bypass UAC.
Once executed, the dropper copies the main module (infpub.dat) to the Windows folder and executes it through rundll32.exe, a Windows component used to run code in DLL files. Scheduled tasks, which have been given dragon names from the “Game of Thrones” TV show, are used to execute other malware components and reboot the system.
The ransom note is displayed in both text files dropped onto the system and via a bootlocker screen.
Bad Rabbit
Similar to NotPetya, Bad Rabbit does appear to rely on SMB to spread, but, contrary to initial reports, it does not use the NSA-linked EternalBlue exploit.
The malware scans the internal network for open SMB shares with a specific name. The threat relies on the Mimikatz post-exploitation tool to harvest credentials, but it also includes a hardcoded list of usernames and passwords.
Bad Rabbit file encryption
Once it infects a system, Bad Rabbit encrypts more than 100 file types, including archives, backups, databases, images, documents, source code, and virtual disk images. The encrypted files are given a .encrypted extension. Kaspersky’s Costin Raiu pointed out that the file types are similar to the ones targeted by NotPetya, but not identical.
Bad Rabbit clears security logs and deletes the update sequence number (USN) change journal, which logs all changes made to files on the volume, to prevent recovery.
The encryption relies on DiskCryptor, an open source full disk encryption software, and the attackers have used the AES-128-CBC cipher and an RSA-2048 public key.
It’s still unclear if files can be recovered without paying the ransom. However, unlike NotPetya, which made it impossible to decrypt files even if the ransom had been paid, researchers confirmed that data encrypted by Bad Rabbit is recoverable with the right key.
Victims are asked to pay 0.05 bitcoin, worth roughly $280, to get their files back, but the amount increases if the ransom is not paid within two days.
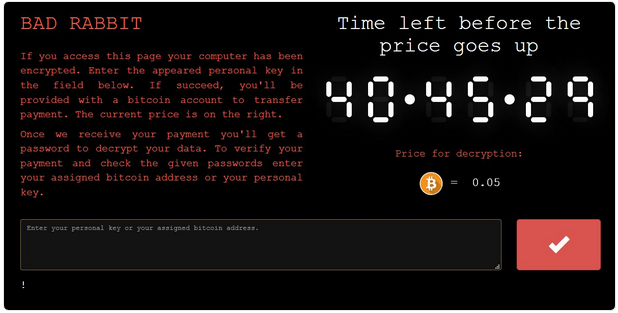
A majority of the victims are in Russia, where the ransomware hit several media outlets, including Interfax and Fontanka. A significant number of Infections has also been observed in Ukraine, where the malware reportedly hit the airport in Odessa, the Kiev subway, the State Aviation Service of Ukraine, and the Transport Ministry of Ukraine. Infections have also been spotted in Bulgaria, Turkey, Germany, Japan and other countries.
Some of the organizations whose systems have been compromised reported suffering significant disruptions.
Unlike the NotPetya attack, which hit tens of thousands of systems in more than 65 countries, Kaspersky reported that it had only seen roughly 200 victims. The security firm believes this may have been a targeted attack aimed at corporate networks.
Bad Rabbit links to NotPetya
Several security firms have classified Bad Rabbit as a variant of NotPetya, the malware that hit numerous organizations in late June and caused losses of millions of dollars for several major companies. NotPetya has also been tracked as Diskcoder, Petya, Petrwrap, exPetr and GoldenEye.
While NotPetya initially also appeared to be a piece of ransomware, researchers noticed that the encrypted files could not have been recovered even if the ransom had been paid. The malware was later reclassified as a wiper.
The list of similarities between NotPetya and Bad Rabbit includes the fact that both use SMB to spread, they create scheduled tasks to reboot the system, the ransom screen is very similar, both use .dat files as the main component, and some of the functionality and code is almost identical.
On the other hand, unlike NotPetya, Bad Rabbit does not use the EternalBlue exploit, its encryption functionality works properly and a more advanced crypter is used, it uses a different kernel and bootloader, and the attacks appear to have been more targeted. Another significant difference is the fact that NotPetya was delivered via a Ukraine-based company’s update server, while Bad Rabbit leverages drive-by attacks.
Bad Rabbit ransomware rapidly spreads, Ukraine and Russia most targeted countries
25.10.2017 securityaffairs Ransomware
A new strain of malware dubbed Bad Rabbit ransomware has been found rapidly spreading in Russia, Ukraine and elsewhere.
A new massive ransomware campaign is rapidly spreading around Europe, the malware dubbed Bad Rabbit has already affected over 200 major organizations mainly in Russia, Ukraine, Germany, Japan, and Turkey in a few hours.
The Bad Rabbit ransomware has infected several big Russian media outlets, the Interfax news agency and Fontanka.ru confirmed they were hit by the malware.
According to Kaspersky, the Odessa International Airport has reported on a cyberattack on its information system, but it is still unclear it is the same attack.
“In some of the companies, the work has been completely paralysed – servers and workstations are encrypted,” head of Russian cyber-security firm Group-IB, Ilya Sachkov, told the TASS news agency.
According to the malware experts, Bad Rabbit ransomware is Petya-like malware that is targeting corporate networks.
The malicious code demands 0.05 bitcoin ransom (~ $280) from victims to unlock their systems.
Experts from Kaspersky that analyzed the malware, believe the Dab Rabbit ransomware is spread via drive-by download attacks, attackers are using fake Adobe Flash players installer to trick victims into installing the malware.
“On October 24th we observed notifications of mass attacks with ransomware called Bad Rabbit. It has been targeting organizations and consumers, mostly in Russia but there have also been reports of victims in Ukraine. Here’s what a ransom message looks like for the unlucky victims:” reported Kaspersky Lab.

“No exploits were used, so the victim would have to manually execute the malware dropper, which pretends to be an Adobe Flash installer. We’ve detected a number of compromised websites, all of which were news or media websites.” continues the analysis published by Kaspersky Lab.
The experts from security firm ESET tracked the Bad Rabbit ransomware as ‘Win32/Diskcoder.D‘. According to ESET, the malware is a new variant of Petya ransomware. it relies on the open-source encryption software DiskCryptor, files are encrypted RSA 2048 keys.
The researchers excluded the new ransomware uses the EternalBlue exploit, instead, it first scans the target network for open SMB shares, tries to access them using hardcoded list of credentials to drop the malicious code, then uses the Mimikatz tool to extract credentials from the target.
“Win32/Diskcoder.D has the ability to spread via SMB. As opposed to some public claims, it does notuse the EthernalBlue vulnerability like the Win32/Diskcoder.C (Not-Petya) outbreak. First, it scans internal network for open SMB shares.” reads the analysis published by ESET.
“Mimikatz is launched on the compromised computer to harvest credentials. A hardcoded list username and password is also present.”

Jiri Kropac @jiriatvirlab
#ESET confirms Discoder/#Petya/#BadRabbit campaign live today, incorporating #Mimikatz distribuded via fake flash. More info soon.
4:42 PM - Oct 24, 2017
10 10 Replies 248 248 Retweets 147 147 likes
Twitter Ads info and privacy
Researchers from ESET reported that the payment website is hosted on the Tor network, the ransom note provided instructions to make the payment while displaying a countdown of 40 hours before the price of decryption increase.
Security experts are still analyzing the Bad Rabbit ransomware, meantime, malware researchers from Kaspersky are suggesting to disable WMI service to prevent the malware from spreading over the target network and to block the execution of files c:\windows\infpub.dat and c:\Windows\cscc.dat.
As usual stay vigilant when opening unsolicited mail containing documents or clicking on embedded links.
'Bad Rabbit' Ransomware Attack Hits Russia, Ukraine
24.10.2017 securityweek Ransomware
Several major organizations in Russia and Ukraine were hit in the past few hours by a ransomware named “Bad Rabbit.” The incident reminds of the massive attack involving NotPetya malware, which ended up costing companies millions of dollars.
Few details are known so far about the Bad Rabbit attack, which has the potential to cause significant damage.
Infected computers display a screen informing users that their files have been encrypted and instructing them to access a website over the Tor anonymity network. The Tor site tells victims to pay 0.05 bitcoin, worth roughly $283, to obtain the key needed to recover the encrypted files. However, the price goes up if the ransom is not paid within two days.

The list of organizations reportedly hit by the Bad Rabbit ransomware includes Russian media outlets Interfax and Fontanka, the airport in Odessa, the Kiev subway, the State Aviation Service of Ukraine, and the Transport Ministry of Ukraine. Interfax and others said the attack disrupted their operations.
Researchers are still analyzing the malware, but initial reports claim Bad Rabbit has been distributed via fake Flash Player updates. Some said the ransomware also leverages the Mimikatz post-exploitation tool for lateral movement within the compromised network. Kaspersky’s Anton Ivanov revealed that the threat uses code from a legitimate disk encryption utility named DiskCryptor.
Security firm ESET said the malware appears to be a new variant of NotPetya, also known as Diskcoder, Petya, Petrwrap, NotPetya, exPetr and GoldenEye. However, this has not been confirmed by other researchers. ESET reported that while most infections are in Russia and Ukraine, some compromised machines were also detected in Turkey, Bulgaria and other countries.
There are also some reports that Bad Rabbit uses SMB – specifically the NSA-linked EternalBlue exploit – to spread, just like NotPetya. However, this hasn’t been confirmed either.
The attack does remind of NotPetya, which started spreading via a software update from a Ukrainian company. However, NotPetya turned out to be a wiper instead of ransomware.
The fact that another major attack has hit Ukraine is not surprising considering that the country’s Security Service warned earlier this month about a possible large-scale cyberattack on state organizations and private companies. The agency said the purpose of the attack would be to disrupt IT systems and destabilize the situation in the country.
'Bad Rabbit' Ransomware Attack Hits Russia, Ukraine
24.10.2017 securityweek Ransomware
Several major organizations in Russia and Ukraine were hit in the past few hours by a ransomware named “Bad Rabbit.” The incident reminds of the massive attack involving NotPetya malware, which ended up costing companies millions of dollars.
Few details are known so far about the Bad Rabbit attack, which has the potential to cause significant damage.
Infected computers display a screen informing users that their files have been encrypted and instructing them to access a website over the Tor anonymity network. The Tor site tells victims to pay 0.05 bitcoin, worth roughly $283, to obtain the key needed to recover the encrypted files. However, the price goes up if the ransom is not paid within two days.

The list of organizations reportedly hit by the Bad Rabbit ransomware includes Russian media outlets Interfax and Fontanka, the airport in Odessa, the Kiev subway, the State Aviation Service of Ukraine, and the Transport Ministry of Ukraine. Interfax and others said the attack disrupted their operations.
Researchers are still analyzing the malware, but initial reports claim Bad Rabbit has been distributed via fake Flash Player updates. Some said the ransomware also leverages the Mimikatz post-exploitation tool for lateral movement within the compromised network. Kaspersky’s Anton Ivanov revealed that the threat uses code from a legitimate disk encryption utility named DiskCryptor.
Security firm ESET said the malware appears to be a new variant of NotPetya, also known as Diskcoder, Petya, Petrwrap, NotPetya, exPetr and GoldenEye. However, this has not been confirmed by other researchers. ESET reported that while most infections are in Russia and Ukraine, some compromised machines were also detected in Turkey, Bulgaria and other countries.
There are also some reports that Bad Rabbit uses SMB – specifically the NSA-linked EternalBlue exploit – to spread, just like NotPetya. However, this hasn’t been confirmed either.
The attack does remind of NotPetya, which started spreading via a software update from a Ukrainian company. However, NotPetya turned out to be a wiper instead of ransomware.
The fact that another major attack has hit Ukraine is not surprising considering that the country’s Security Service warned earlier this month about a possible large-scale cyberattack on state organizations and private companies. The agency said the purpose of the attack would be to disrupt IT systems and destabilize the situation in the country.
New Magniber Ransomware Emerges
19.10.2017 securityweek Ransomware
A brand new ransomware family currently being distributed through the Magnitude exploit kit appears to be targeting South Korean users exclusively, security researchers have discovered.
Dubbed Magniber, the threat checks the language of the compromised systems and only fully executes on machines featuring the locale identifier string 0x0412, which is the identifier for Korean, Trend Micro reports.
The new malware family was first observed this week, when Magnitude returned to activity after nearly a month of silence. The EK was usually distributing the Cerber ransomware, but it appears that its operators have moved to other payloads.
While most of the Magnitude attacks over the past two months and a half focused on Taiwan (81%), the security researchers noticed a shift toward South Korea on October 15. Magnitude campaigns use malvertising to infect users and deliver malicious payloads by exploiting the Internet Explorer vulnerability CVE-2016-0189, which Microsoft patched in May 2016.
Magnitude was the last exploit kit to have delivered Cerber, which appears to have disappeared from the threat landscape last month. Now, the toolkit is pushing a ransomware family that apparently uses the same payment system as Cerber.
This is why the security researchers who discovered the threat called it Magniber (Magnitude+Cerber), although there doesn’t seem to be code base resemblance between the two, Bleeping Computer’s Lawrence Abrams notes.
Specific to the new malware is the fact that it uses the victim’s unique ID as a subdomain to the payment portal on Tor. This subdomain is then displayed in the ransom note deployed on the infected system.
Once on the infected system, the malware starts searching for files to encrypt. At the moment, it is targeting over 700 file types, Malwarebytes says. The ransomware avoids encrypting files located in folders such as Windows, Program Files, Boot, Recycle Bin, Local Settings, and several Documents and Settings subfolders, among others.
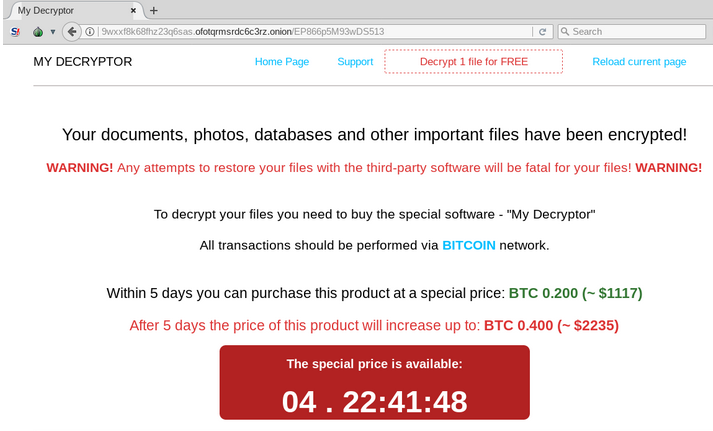
According to Trend Micro, Magniber’s code shows that the ransomware might still be under development. According to them, the threat could be still in experimental stages, supposedly built by Magnitude’s developers.
“Indeed, we’re bound to see more developments in both Magnitude and Magniber as their capabilities and tactics are fine-tuned. While Magnitude’s distribution of Magniber is still relatively muted, their ability to exploit security gaps in the system and encrypt its files makes their combination a credible threat,” the security researchers note.
According to Abrams, files encrypted by Magniber can be decrypted for free, so victims should refrain from paying the ransom. All users, however, are advised to keep their applications and operating systems updated at all times, and to install and maintain an anti-virus solution to avoid being infected in the first place. Users should also back up their data at all times, for easy recovery in the event of an infection.
Ransomware is a Booming Industry That Continues to Evolve
15.10.2017 securityweek Ransomware
The ransomware marketplace has grown by a phenomenal 2,502% from 2016 to 2017. This is the amount of money spent by criminals on ransomware software. It is a market fueled by the technical simplicity of the malware, the rise of Ransomware-as-a-Service, the guaranteed return on investment for criminals, the availability of Tor and crypto currencies to hide tracks; and a lack of fundamental security controls among victims.
Carbon Black's researchers monitored 21 of the largest dark web marketplaces trading ransomware (out of an estimated 6,300+ dark web marketplaces doing so) during August and September 2017. The results are astonishing, with more than 45,000 current listings. Prices range from Android lockscreen ransomware for $1.00 to custom code for more than $1000. The median cost of a ransomware offering is just $10.50.
The total amount of money involved is equally astonishing. According to FBI figures, ransom payments in 2016 were around $1 billion dollars; up from $24 million in 2015. According to Carbon Black's research, ransomware developers can expect to earn approximately $100,000 (tax free) per annum. This compares to an average salary of $69,000 (before tax) for legitimate software developers. The difference is even greater in many east European countries where much malware is thought to be developed. Ransomware sales on the dark web have grown from less then $400,000 in 2016 to around $6.25 million in 2017.
"The underground ransomware economy is now an industry that resembles commercial software — complete with development, support, distribution, quality assurance and even help desks," notes the report. Carbon Black's security strategist Rick McElroy expects this underground business to evolve and develop much like legitimate industries. "I expect that we will see consolidation between the developers and their products," he told SecurityWeek.
The simple reality is that the ransomware industry is growing because it is profitable. Dismantling the industry must therefore concentrate on removing that profitability. Carbon Black describes the industry as having a five-point supply chain: creation, distribution, encryption, payment and command and control. "If defenders can break or interrupt even one link of the chain," it suggests, "the entire attack falls apart."
Disrupting the creation will be impossible while young coders are unable to find legitimate jobs, and can earn attractive sums through developing ransomware. Distribution disruption is equally difficult when the marketplace can be hidden within the dark web. Encryption is similarly impossible to control -- powerful encryption systems are readily available in the public domain. Payment is the weakest link. In the supply chain it is the collection and tracking of ransoms paid -- but if no ransom is paid, then the entire industry will collapse.
"We need to STOP paying ransoms", says the report. "The system only works if victims choose to pay. Until people decide not to pay, this problem will only continue to grow." McElroy agreed in conversation that this is a difficult ask. Nevertheless, he believes that if enough victims in either a particular country, or target industry, refuse to pay, the criminals will simply target different areas or industries where the returns will be greater. It doesn't solve the problem, but it simply exports it elsewhere.
Preventing the need to pay a ransom would have a similar effect. This could relatively easily be achieved by improved security controls -- but ensuring that people and organizations have those controls in place is difficult if not impossible to achieve.
Against this background, the ransomware industry will continue to grow -- and it will continue to evolve. So far, ransomware has largely been in the hands of relatively unskilled coders; sophistication has not been necessary. Carbon Black sees this changing. To a certain extent the signs are already visible: WannaCry and NotPetya are examples. In the former, the ransomware was unsophisticated while in the latter decryption was never intended. However, the distribution of the ransomware via leaked NSA exploits was a new development.
Carbon Black describes this use of ransomware as a false flag. A closely related new development it expects will be the malware's use as a smokescreen. "Using already existing techniques of deleting Volume Shadow Copies, which deletes potential file backups, and the deletion of Windows event logs, adversaries can thwart many incident response efforts by forcing responders to focus on decrypting files instead of investigating data and credentials exfiltrated." The ransomware -- or more specifically the encryption element of ransomware -- will be used to hide and obfuscate traces of more traditional cyber thefts and cyberespionage.
All of this is likely as the ransomware industry evolves. McElroy told SecurityWeek he expects to see consolidation. The effect is likely to concentrate ransomware into the hands of more sophisticated coders. One effect of paying a ransom is that it tells the attackers that the victim can be coerced. Carbon Black expects to see more sophisticated developers employing more advanced morphing and persistence techniques to remain on the victim's network after decryption -- so that they can extort a second time in the future.
New Ransomware Not Just Encrypts Your Android But Also Changes PIN Lock
14.10.2017 thehackernews Ransomware
DoubleLocker—as the name suggests, it locks device twice.
Security researchers from Slovakia-based security software maker ESET have discovered a new Android ransomware that not just encrypts users’ data, but also locks them out of their devices by changing lock screen PIN.
On top of that:
DoubleLocker is the first-ever ransomware to misuse Android accessibility—a feature that provides users alternative ways to interact with their smartphone devices, and mainly misused by Android banking Trojans to steal banking credentials.
"Given its banking malware roots, DoubleLocker may well be turned into what could be called ransom-bankers," said Lukáš Štefanko, the malware researcher at ESET.
"Two-stage malware that first tries to wipe your bank or PayPal account and subsequently locks your device and data to request a ransom."
Researchers believe DoubleLocker ransomware could be upgraded in future to steal banking credentials as well, other than just extorting money as ransom.
First spotted in May this year, DoubleLocker Android ransomware is spreading as a fake Adobe Flash update via compromised websites.
Here's How the DoubleLocker Ransomware Works:
Once installed, the malware requests user for the activation of 'Google Play Services' accessibility feature, as shown in the demonstration video.
After obtaining this accessibility permission, the malware abuses it to gain device's administrator rights and sets itself as a default home application (the launcher)—all without the user's knowledge.
"Setting itself as a default home app – a launcher – is a trick that improves the malware's persistence," explains Štefanko.
"Whenever the user clicks on the home button, the ransomware gets activated, and the device gets locked again. Thanks to using the accessibility service, the user does not know that they launch malware by hitting Home."
Once executed, DoubleLocker first changes the device PIN to a random value that neither attacker knows nor stored anywhere and meanwhile the malware encrypts all the files using AES encryption algorithm.
DoubleLocker ransomware demands 0.0130 BTC (approximately USD 74.38 at time of writing) and threatens victims to pay the ransom within 24 hours.
If the ransom is paid, the attacker provides the decryption key to unlock the files and remotely resets the PIN to unlock the victim's device.
How to Protect Yourself From DoubleLocker Ransomware
According to the researchers, so far there is no way to unlock encrypted files, though, for non-rooted devices, users can factory-reset their phone to unlock the phone and get rid of the DoubleLocker ransomware.
However, for rooted Android devices with debugging mode enabled, victims can use Android Debug Bridge (ADB) tool to reset PIN without formatting their phones.
The best way to protect yourself from avoiding falling victims to such ransomware attacks is to always download apps from trusted sources, like Google play Store, and stick to verified developers.
Also, never click on links provided in SMS or emails. Even if the email looks legit, go directly to the website of origin and verify any possible updates.
Moreover, most importantly, keep a good antivirus app on your smartphone that can detect and block such malware before it can infect your device, and always keep it and other apps up-to-date.
Ransomware Attacks 'Global Epidemic', Says Europol
27.9.2017 securityweek Ransomware
An "epidemic" has erupted in global ransomware attacks, taking over computers as well as internet-linked devices like routers and CCTV cameras to turn them into tools for criminals, Europe's police agency said Wednesday.
"Ransomware attacks have eclipsed most other global cybercrime threats, with the first half of 2017 witnessing ransomware attacks on a scale previously unseen," Europol said, as it released its latest annual report on internet organised crime.
This included the WannaCry ransomware attack in May, believed to have rapidly infected as many as 300,000 targets in 150 countries including some high-profile ones such as Britain's National Health Service, Spanish telecoms company Telefonica, and logistics company Fed-Ex.
"The global impact of huge cyber security events such as the WannaCry ransomware epidemic has taken the threat from cybercrime to another level," Europol's chief Rob Wainwright said.
"Banks and other major businesses are now targeted on a scale not seen before," he said at the launch of the 80-page report.
At the same time, late 2016 saw the first "massive attacks" on insecure devices connected to the so-called internet of things.
In one case the notorious Mirai malware hacked into about 150,000 internet-linked devices like cellphones, routers, printers and security cameras to mount a "complex... sophisticated" attack.
The malware transformed them into botnets capable of launching a so-called distributed denial of service (DDoS) attack, Europol said.
They were responsible for a number of high profile attacks, including one which severely disrupted internet infrastructure on the West Coast of the United States.
Europol warned that the "collective response to cyber-criminals is still not good enough."
"In particular people and companies everywhere must do more to better protect themselves," it said.
The report also said that last year saw an unprecedented increase in data breaches with vast amounts of data being stolen, including over two billion records related to EU citizens reportedly leaked over a 12-month period.
European safety commissioner Julian King said Europol's latest report "shows online crime is the new frontier of law enforcement."
"We've all seen the impact of events like WannaCry. Whether attacks are carried out for financial or political reasons, we need to improve our resilience," King said.
RedBoot Ransomware Modifies Master Boot Record
25.9.2017 securityweek Ransomware
A newly discovered ransomware family has the ability to replace the Master Boot Record and modify the partition table, allowing the malware to function as a wiper.
Dubbed RedBoot, the malware was clearly designed for destructive purposes, as even the file-encryption operation is of a similar nature: it encrypts executables and DLLs along with normal data files, thus rendering the infected machine useless. Furthermore, by replacing the MBR, it prevents the computer from loading Windows.
The malware’s operations are similar to those of the Petya-Mischa pair – Petya would replace the MBR while Mischa would encrypt users’ files – which later evolved into the Goldeneye variant. This year, a global attack was using a destructive wiper masquerading as Petya.
Once executed on the target machine, the new RedBoot ransomware extracts 5 other files into a random folder in the same directory as the launcher: assembler.exe, boot.asm, main.exe, overwrite.exe, and protect.exe, BleepingComputer’s Lawrence Abrams notes.
assembler.exe, which is a renamed copy of nasm.exe, is used to compile the boot.asm assembly file into a new MBR boot.bin file. Next, overwrite.exe is used to overwrite the existing boot.bin with the newly compiled one.
The user mode encryption operation is performed by the main.exe file, while protect.exe was designed to terminate and prevent various programs from running on the infected machine, including Task Manager and Process Hacker.
After the files have been extracted, the launcher executes the necessary command to the new boot.bin file, and then deletes the boot.asm and assembly.exe files. Next, it overwrites boot.bin, and then starts main.exe to scan the computer for files to encrypt. protect.exe is also launched to prevent other programs from blocking or analyzing the infection.
The ransomware was designed to encrypt executables, DLLs, and normal data files on the infected machine, and appends the .locked extension to each of the encrypted files. As soon as the encryption process has been completed, the malware reboots the machine and the new master boot record displays a ransom note instead of loading Windows.
Although the ransom note claims that victims can recover their data if they contact the malware author at redboot@memeware.net to receive payment instructions, the researchers analyzing the threat suggest that this might not be the case.
Apparently, the malware “may also be modifying the partition table without providing a method to restore it,” Abrams says. Because of that, even if the victim contacts the malware author and pays the ransom, the hard drive might not be recoverable, the researcher explains.
It is currently unclear whether RedBoot is yet another wiper masquerading as ransomware, just as NotPetya, or if it is just poorly coded malware. The threat was compiled using AutoIT, which could suggest that an error resulted in it modifying the partition table without providing a way to input a key to recover it.
RedBoot ransomware also modifies partition table, is it a wiper?
25.9.2017 securityaffairs Ransomware
The RedBoot ransomware encrypts files on the infected computer, replaces the Master Boot Record and then modifies the partition table.
Malware Blocker researcher discovered a new bootlocker ransomware, dubbed RedBoot, that encrypts files on the infected computer, replaces the Master Boot Record (MBR) of the system drive and then modifies the partition table.
The experts noticed that there is no way to input a decryption key to restore the MBR and partition table, a circumstance that suggests this malware may be a wiper.
When the victim executes the RedBoot ransomware it will extract 5 other files into a random folder in the directory containing the launcher.
The five files are:
boot.asm. – it is an assembly file that will be compiled into the new master boot record. When the boot.asm has been compiled, it will generate the boot.bin file.
assembler.exe – it is a renamed copy of nasm.exe that is used to compile the boot.asm assembly file into the master boot record boot.bin file.
main.exe – It is the user mode encrypter that will encrypt the files on the computer
overwrite.exe. – It is used to overwrite the master boot record with the newly compiled boot.bin file.
protect.exe – It is the executable will terminate and prevent various programs from running such as the task manager and processhacker.
Once the files are extracted, the main launcher will compile the boot.asm file generating the boot.bin. The launcher executes the following command:
[Downloaded_Folder]\70281251\assembler.exe" -f bin "[Downloaded_Folder]\70281251\boot.asm" -o "[Downloaded_Folder]\70281251\boot.bin"
Once boot.bin has been compiled, the launcher will delete the boot.asm and assembly.exe files, then it will use the overwrite.exe program to overwrite the current master boot record with the compiled boot.bin using this command.
"[Downloaded_Folder]\70945836\overwrite.exe" "[Downloaded_Folder]\70945836\boot.bin"
At this point, the malware starts the encryption process, the launcher will start the main.exe that will scan the machine for files to encrypt appending the .locked extension onto each encrypted file. The main.exe program will also execute the protect.exe component to stop the execution of any software that can halt the infection.

Once all the files have been encrypted, the RedBoot ransomware will reboot the computer and will display a ransom note.
This ransom note provides the instruction to the victims to send their ID key to the email recipient redboot@memeware.net in order to get payment instructions.
Unfortunately, even if the victim contacted the developer and paid the ransom, the hard drive may not be recoverable because the RedBoot ransomware permanently modifies the partition table.
“While this ransomware is brand new and still being researched, based on preliminary analysis it does not look promising for any victims of this malware. This is because in addition to the files being encrypted and the MBR being overwritten, preliminary analysis shows that this ransomware may also be modifying the partition table without providing a method to restore it.” reads the analysis published by Lawrence Abrams.
Experts speculate the malware is a wiper disguised as a ransomware, but we cannot exclude that the author simply made some errors in the development phase.
“While this ransomware does perform standard user mode encryption, the modifying of the partition table and no way of inputting a key to recover it, may indicate that this is a wiper disguised as a ransomware. Then again, since the developer used a scripting language like AutoIT to develop this ransomware, it could very well be just a buggy and poorly coded ransomware.” concluded Lawrence Abrams.
Give a look at the analysis if you are interested in Indicators of Compromise (IoCs).
Authors of Locky Ransomware are big fans Game of Thrones series
25.9.2017 securityaffairs Ransomware
Researchers at PhishMe found the names of Game of Thrones show characters and other references into the script used to spread the Locky ransomware.
The fantasy drama television series Game of Thrones has an amazing number of fans, including the authors of the Locky ransomware.
The discovery was made by researchers at security firm PhishMe that found the names of show characters and other references into the source code of the Visual Basic script used by the crooks.
The Visual Basic script is included in the ZIP or RAR archive attached to email spam used in the ransomware campaign. When the victims open the archive and run the VB script contained within, it would download and install the Locky ransomware.
“Lightweight script applications designed to deliver malware often use rotating or pseudorandom variable names to ensure that the malware delivery tools look unique. In this case, many of the variables (some misspelled) referred to characters and events from the globally-popular television fantasy epic Game of Thrones.” states Phishme.
Experts discovered in the VB script reference to the TV show such as “Aria,” “SansaStark,” “RobertBaration,” “JohnSnow,” or “HoldTheDoor” .


According to BleepingComputer, the term “Throne” was used 70 times inside the script.
“The runtime for this script is indifferent to the variable names. The variable names could be anything, including completely random combinations of letters and numbers. However, the criminals responsible for this attack chose a distinctive theme for their variables, thereby revealing their interest in this pop culture phenomenon.” continues PhishMe.
Massive HerbaLife spam campaign spreads a variant of Locky ransomware
24.9.2017 securityaffairs Ransomware
Researchers spotted a new widespread ransomware campaign leveraging emails with malicious attachments using Herbalife branded messages.
Researchers at security firm Barracuda have spotted a new widespread ransomware campaign leveraging emails with malicious attachments, some of them pretend to be sent by the l multi-level marketing nutrition company Herbalife.
More than 20 million Herbalife branded emails were sent in a 24 hour period, since then, crooks sent out messages at a rate of about two million attacks per hour.
Most of the messages are sent from Vietnam other significant sources are India, Columbia, and Turkey and Greece.
“The Barracuda Advanced Technology Group is actively monitoring an aggressive ransomware threat that appears to come in the largest volume from Vietnam. Other significant sources of this attack include India, Columbia, and Turkey and Greece. Other countries appear to be distributing the same attack in very low volumes.” reads the analysis published by Barracuda. “So far we have seen roughly 20 million of these attacks in the last 24 hours, and that number is growing rapidly.”

The attackers are using a Locky variant with a single identifier to track the infections.
“Barracuda researchers have confirmed that this attack is using a Locky variant with a single identifier. The identifier allows the attacker to identify the victim so that when the victim pays the ransom, the attacker can send that victim the decryptor,” continues the analysis. “In this attack, all victims get the same identifier, which means that victims who pay the ransom will not get a decryptor because it will be impossible for the criminal to identify them.”
The email attachment claims to be an invoice for an order placed through the company Herbalife. If the user opens the file, it will launch the ransomware dropper.
Attackers are also observing attachments that claim to impersonate invoicing from marketplace.amazon.uk. The researchers are also seeing other variants of the malicious emails that have appeared claiming to be a “copier” file delivery.
Barracuda researchers are now seeing also a wrapper in this campaign that impersonates a voicemail message, using the subject line “New voice message [phone number] in mailbox [phone number] from [“phone number”] [<alt phone number>].”>].”
Researchers detected at least 6,000 different versions of the malicious script used by the attackers, a circumstance that suggests crooks are randomizing a portion of the attack code to avoid detection.
“There have been approximately 6,000 fingerprints, which tells us that these attacks are being automatically generated using a template that randomizes parts of the files. The names of payload files and the domains used for downloading secondary payloads have been changing in order to stay ahead anti-virus engines.” continues the blog post.
The payloads delivered by the malicious emails and the domains used to host the second stage malware that infects the victim’s computer changed multiple times since the start of the ransomware campaign.
The researchers noted the attack code is checking the language files on a victim’s computer, suggesting the attackers are ready to target users worldwide.
All the messages come from a spoofed domain, making it appear as legitimate, give a look at the report for Indicators of Compromise (IoCs).
Due to the targets of the campaign experts believe the threat actors are primarily financially motivated,
CSE CybSec ZLAB Malware Analysis Report: Petya
24.9.2017 securityaffairs Ransomware
I’m proud to share with you the second report produced by Z-Lab, the Malware Lab launched by the company CSE CybSec. Enjoy the Analysis Report Petya.
CybSec Enterprise recently launched a malware Lab called it Z-Lab, that is composed of a group of skilled researchers and lead by Eng. Antonio Pirozzi.
It’s a pleasure for me to share with you the second analysis that we have recently conducted on the Petya Ransomware.
We have dissected the ransomware and discovered interesting details that are included in our report.
Below the abstract from the analysis, the detailed report is available for free on our website.
Abstract
In a modern environment, where data stored in computers play a fundamental role in the private and work routine, we must consider the problem of the risk of losing these data. In fact, the ever-increasing threat, that is spreading, is Ransomware. In the last 15 years, malware writers have realized that they may have anyone in their hand with his data.

Figure 1: Characteristic Petya Skull with the corresponding UI containing the payment ransom instructions.
In this context, we studied a well-known ransomware that has particularly hit the public, Petya. Petya first appeared in March 2016 affecting Windows systems propagating with e-mail attachments or Dropbox links. Unlike a classic ransomware that encrypts only files containing data (i.e. doc, pdf, xls, txt, jpg, and png… files) without tampering the OS. Petya works differently because it creeps in the Windows bootloader and enciphers the MFT (Master File Table) making the files inaccessible.
Thus, we created a strategy for analyse this ransomware divided into three macro-phases.
In the first phase, we have a look of the malware executable global view. We extracted from the binary some strings, among which “http://petya5koahtsf7sv[dot]onion/” and “http://petya37h5tbhyvki[dot]onion/”, referring the established Onion site (only reachable with TOR network) for the payment of the ransom. Other strings are related to the function names, and are used to retrieve, at runtime, the correspondent handle of the specific function that uses the API call to the “GetProcAddress()” routine. This is a technique widely used by malware writers, and it is named Runtime Linking.
In the behavior analysis phase, we discovered that the malware:
gains the access to the disk in order to overwrite the original MBR
enciphers the original MBR and moves it in another disk sector
writes after the Petya Bootloader its own kernel
reboots the system using an undocumented API call “NtRaiseHardError()”
shows a fake CHKDSK routine that actually crypts the MFT
displays the characteristic Petya interfaces
In the last phase, we focused on the reverse engineering of the Petya kernel. We analysed the code written on the disk deriving the control flow and the structures of the kernel, which contains:
routine for data encryption based on Salsa20 algorithm
routine for the validation of the key supplied by the Petya writers after the payment of the ransom
routine of MFT decryption and its restore
routine of MBR restore
Figure 2: Detail of Petya kernel
You can download the full ZLAB Malware Analysis Report at the following URL:
http://csecybsec.com/download/zlab/Report_petya_final
If you are intersted also into the first analysis conducted on NotPetya download the report at the following Link:
Ransomware: Where It's Been and Where It's Going
23.9.2017 securityweek Ransomware
About Ransomware Campaigns
Ransomware has become prevalent because it is an easy way for criminals to make a quick buck; and because in many ways defenders have forgotten the basics of cybersecurity. The efficiency of ransomware as an illicit means of making money is supported by the emergence of ransomware-as-a-service (RaaS), and Bitcoin as a secure method of ransom collection. These are conclusions drawn from an analysis of more than 1000 ransomware samples categorized into 150 families.
"Attackers are looking to make quick, easy money with unsophisticated malware combined with sophisticated delivery methods," say Carbon Black's researchers Brian Baskin and Param Singh in a blog post on Thursday. "The majority of today's ransomware aims to target the largest vulnerable population possible." As a result, ransomware campaigns are often delivered by large scale phishing/spam campaigns. "These 'spray and pray' attacks often rely on spamming and phishing campaigns to guarantee a small percentage of infections to extort money. Similar to many spam campaigns, ransomware has been sent en masse to thousands of email addresses at a single organization, requiring just one person to execute the payload for a successful attack."
Separately, Datto's State of the Channel Ransomware Report (PDF), also published Thursday, claims that an estimated $301 million was paid in ransoms from 2016-2017. Datto analyzed data from 1,700+ Managed Service Providers (MSPs) serving 100,000+ small-to-mid-sized businesses (SMBs) around the globe. Despite the success of ransomware, Datto notes, "With a reliable backup and recovery solution (BDR) in place, 96% of MSPs report clients fully recover from ransomware attacks."
Webroot's September Threat Trends Report suggests that "some 93% of all phishing emails now lead to ransomware". Merging these two statistics suggests that a combination of effective spam/phishing prevention and good BDR would go a long way to combating the ransomware epidemic. Clearly, this is not yet happening.
Carbon Black's research suggests that businesses have taken the decision to concentrate on recovery rather than prevention. "These businesses implemented policies to quickly re-image the machine with its most recent backup and move on." However, it adds, "WannaCry and NotPetya have changed that equation by including worm functionality to spread across networks... Businesses that had accepted the risk of handling few ransomware incidents now risked losing complete networks."
While improved phishing/spam detection could prevent a high proportion of current ransomware getting through to the target, this is unlikely ever to be 100% effective. The next line of defense would be anti-virus software. However, malware in general -- and including ransomware -- is moving towards fileless delivery, employing scripts embedded in attachments to effect the infection. In such circumstances, there is no file for traditional anti-virus to detect.
An example of a large scale fileless ransomware campaign was described by Trustwave's SpiderLabs at the end of August 2017. Dr. Fahim Abbasi and Nicholas Ramos describe a campaign that involved millions of spam messages with obfuscated JavaScript in the attachment. If the JavaScript ran, it caused either Cerber or FakeGlobe ransomware to be downloaded and executed.
"File-based solutions that focus on static indicators of files such as file names, unique strings, and hashes, are missing ransomware attacks as they don't have visibility into the 'DNA' of an attack," warns Carbon Black. "Without tracking malicious behavior and intent, such defensive methods could be unable to accurately predict future attacks involving volatile code leveraging such tools as JavaScript, PowerShell, Visual Basic, and Active Server Pages (ASP)."
Although ransomware uses the latest fileless techniques to beat defenses, the malware itself is often very simple. The Carbon Black researchers do not expect this to continue.
While most ransomware attacks Windows, they suggest that Linux will increasingly be targeted so that larger organizations can be extorted. "For example," they say, "attackers will increasingly look to conduct SQL injections to infect servers and charge a higher ransom price. We have already observed attacks hitting MongoDB earlier this year which provide an excellent foreshadowing." This will be in tandem with more focused targeting, both in sectors attacked and content encrypted. "A focused targeting of extensions can allow many ransomware samples to hide under the radar of many defenders."
Currently, most ransomware simply encrypts files. In the future, Baskin and Singh expect more of the malware to exfiltrate data prior to encrypting and ransoming files. They also believe that ransomware will increasingly be used as a smokescreen, just as DDoS attacks are already used to complicate response to financial fraud. In such circumstances, following large scale data exfiltration, "adversaries can thwart many incident response efforts by forcing responders to focus on decrypting files instead of investigating data and credentials exfiltrated."
More worryingly, the researchers also expect ransomware to become a false flag disguising a nation-state cyber weapon, "as seen with NotPetya. Solely from dynamic analysis it was perceived to be Petya, when more detailed analysis showed it wasn't. Such quick analysis also insinuated it to be obvious ransomware, but a greater depth of disassembly showed that data was not held at ransom; it was simply destroyed." Ransomware without decryption is nothing short of a wiper.
The simple message from Carbon Black is that despite the current success of ransomware, it is largely in the hands of relatively unskilled criminals. This won't continue. Ransomware will increasingly be adopted by sophisticated groups who will use it in a targeted manner, often to augment or disguise other purposes – or simply as an obfuscated nation-state cyber weapon. While the problem of ransomware is severe today, it will likely get much worse over the next few years.
Massive Spam Runs Distribute Locky Ransomware
23.9.2017 securityweek Ransomware
Locky ransomware, the infamous threat that dominated malware charts in 2016, is being aggressively distributed in a series of spam runs that have been ongoing for several weeks, security researchers warn.
First observed in early 2016 and mainly associated with spam campaigns fueled by the Necurs botnet, Locky was relatively silent in early 2017, but reemerged in new campaigns in April and June, and began ramping up activity in early August.
In late August, Locky started appearing in numerous campaigns, and is currently featured in attacks that ramp up to tens of millions of spam messages per day, targeting users all around the world. According to Trend Micro, the runs affect users in over 70 countries.
In most of the newly observed attacks, Locky has been distributed alongside another ransomware family calked FakeGlobe, also known as Globe Imposter, Trend Micro says. The spam messages, which feature either malicious links or macro-enabled documents, direct users to Locky for one hour, and then switch to FakeGlobe the next.
“This is not the first time we’ve seen download URLs serving different malware in rotation. However, typically the malware were different types, pairing information stealers and banking Trojans with ransomware. Now we see that cybercriminals are simply doubling up on ransomware, which is quite dangerous for users,” Trend Micro points out.
While Trend Micro says it was able to block nearly 600,000 emails carrying Locky, Barracuda researchers this week saw over 27 million of such emails during a 24-hour period alone.
Most of the emails were sent from Vietnam, but India, Columbia, Turkey and Greece also accounted for large numbers of messages (overall, spam originated from a total of 185 different countries). Most of the affected users were located in the US, Japan, Germany, and China.
Panda Security has also observed the massive distribution campaigns and confirms that the runs started to grow in volume on Tuesday. At the moment, the researchers say, the attackers send around 1 million phishing messages every hour.
Most of the messages are disguised as fake Amazon Marketplace and Herbalife invoices, but phony printer orders have been observed. The emails contain an archive as attachment. While in some cases .zip files are used, other emails feature .7z or 7-zip attachments.
While some of the ransomware samples observed recently used the .lukitus variant of Locky, more recent samples are appending the .ykcol extension to the encrypted files. The malware would also drop ransom notes named ykcol.htm and ykcol.bmp, demanding a .25 Bitcoin (around $1,000) ransom.
As Fortinet points out, the recently used .ykcol extension is actually the original .locky extension spelled backwards. The researchers also noticed that the second wave of spam carried email subject “Message from km_c224e,” which was previously used in campaigns delivering Dridex and Jaff ransomware.
“Despite a few minor alterations, Locky is still the same dangerous ransom malware from a year ago. It has the capabilities and distribution network necessary to cause significant damage to any system unfortunate enough to be hit by it. Over the past few months, we have seen it distributing massive spam campaigns and we don’t see it slowing down any time soon,” Fortinet notes.
FedEx announces $300m in lost business and response costs after NotPetya attack
21.9.2017 securityaffairs Ransomware
FedEx is the last firm in order of time that disclosed the cost caused by the massive NotPetya, roughly $300m in lost business and response costs.
The malware compromised systems worldwide, most of them in Ukraine, the list of victims is long and includes the US pharmaceutical company Merck, the shipping giant Maersk, the Ukraine’s central bank, Russian oil giant Rosneft, advertising group WPP, TNT Express and the law firm DLA Piper.
According to the second quarter earnings report published by Maersk, there were expecting losses between $200 million and $300 million due to “significant business interruption” because the company was forced to temporarily halt critical systems infected with the ransomware.
The situation announced by FedEx is also disconcerting, its systems will only be fully restored only at the end of September, three months after the incident.
“The worldwide operations of TNT Express were significantly affected during the first quarter by the June 27 NotPetya cyberattack. Most TNT Express services resumed during the quarter and substantially all TNT Express critical operational systems have been restored. However, TNT Express volume, revenue and profit still remain below previous levels,” the company said on Tuesday.
“Operating results declined due to an estimated $300 million impact from the cyberattack, which was partially offset by the benefits from revenue growth, lower incentive compensation accruals and ongoing cost management initiatives,”

During a conference call with financial analysts on Tuesday, FedEx chief information officer Rob Carter confirmed that the attack vector was an infected tax software update delivered to its system in Ukraine, clearly, it is referring the MeDoc accounting application.
Carter confirmed that the malware used in the attack was extremely disruptive, but also confirmed that customer data were not exposed.
“This attack was the result of [a] nation state targeting Ukraine and companies that do business there,” he explained.
TNT adopting further measured to protect its infrastructure, especially legacy systems in hubs and depots worldwide.
Other companies are counting the huge cost of attack, the consumer goods firm Reckitt Benckiser announced the attack cost it £100m ($136m), but the highest cost was announced by Saint Gobain, which expected $400 million losses.
ZLAB Malware Analysis Report: NotPetya
18.9.2017 securityweek Ransomware
I’m proud to share with you the first report produced by Z-Lab, the Malware Lab launched by the company CSE CybSec. Enjoy the Analysis Report NotPetya.
As most of you already know I have officially presented my new Co a couple of months ago, CybSec Enterprise is its name and we already started to work on strategic projects that we will reveal soon … meantime I apologize for the website that is still under construction.
We have already launched a malware Lab, let’s call it Z-Lab, composed by of group of skilled researchers and lead by Eng. Antonio Pirozzi.
It’s a pleasure for me to share with you one of the first analysis that we have recently conducted on the NotPetya Ransomware.
We have dissected the ransomware and discovered interesting details that are included in our report.
Below the abstract, the detailed report is available for free on our website.

Abstract
Due to the lack of updates performed by users on their machines, many threats spread out exploiting well-known vulnerabilities. This is what happened with the propagation of the NotPetya Ransomware, which infected a lot of users mostly in East Europe. This malware uses a famous exploit developed by NSA, Eternalblue, allowed by a vulnerability (MS17-010; CVE-2017-0143) in the Windows implementation of SMB protocol. The above-mentioned exploit was leaked in April 2017 and was used the first time with another malware, WannaCry, which caused more damage than NotPetya.
NotPetya’s could be confused with Petya ransomware (spread out in 2016) because of its behavior after the system reboot, but actually not because NotPetya is much more complex than the other one. In fact, Petya’s most known characteristic is the enciphering of the Windows MBR and MFT, instead, NotPetya propagates itself in the network as a worm.

In the above figure, we have a scheme of the malware’s behavior. We can see that the first phase is the searching of a file representing a kill-switch, to avoid infecting machines already compromised. Next steps are referred to the actual infection, synthesized below:
Take disk control
Replace the original MBR with its own
Schedule reboot after an hour
Crypt user files and concurrently spread itself using Eternalblue exploit
After the reboot, the next step is the fake CHKDSK routine, very similar to Petya, where the malware enciphers the MFT. After that, we no longer have the characteristic Petya skull, but directly the screen with the ransom note, including the e-mail address of the malware writer and the relative Bitcoin address for the ransom payment.
You can download the full ZLAB Malware Analysis Report at the following URL:
http://csecybsec.com/download/zlab/NotPetya-report.pdf
MongoDB improves security amid new wave of ransom-attacks
12.9.2017 securityaffairs Ransomware
MongoDB company implements new data security features in response to the recent wave of ransom attacks that hit installations worldwide.
You have to admit that the bad actors are very good at leveraging a vulnerability into a lucrative opportunity. The latest example comes from MongoDB, a popular, open source database commonly deployed for big data applications on the Internet.
The default installation for older versions of MongoDB did not force basic security controls such as a password for the administration account. Installed behind firewalls in a “traditional” data center configuration, the default installation is bad practice, but not necessarily a significant risk. Layers of protection mitigate the missing controls.
Unfortunately, many cloud hosting providers allow easy installation of MongoDB making it directly accessible from the Internet by default without a simple way to setup the security controls. Strip away layered security controls and do not force basic configuration security and you have a recipe for disaster.
“The most open and vulnerable MongoDBs can be found on the AWS platform because this is the most favorite place for organizations who want to work in a devops way,” Victor Gevers told Bleeping Computer. “About 78 percent of all these hosts were running known vulnerable versions.”
In December 2016, one bad actor started compromising vulnerable MongoDB databases. Contents were downloaded and replaced by a ransom note demanding payment in exchange for a return of the missing data. By January, many hacking groups were involved and over 20,000 vulnerable MongoDB installations were compromised. With that many groups in competition, databases were compromised multiple times and ransom notes from one group were replaced by ransom notes from another group. It was unclear for victims who had their missing data and who the ransom should be paid to. Victims paying the ransom were unlikely to get their data back.
After this flurry of activity in the first few months of 2016, the number of MongoDB attacks quieted over the Summer. Perhaps the victims had learned their lessons? Maybe they accepted their fate and couldn’t be ransomed again? Maybe the bad actors were taking the Summer off to spend their ill gotten gains? What we do know is that there are still thousands of vulnerable databases. Attacks against MongoDB databases picked up again in September — at a much faster pace. “[it] took attackers from the first wave of MongoDB attacks nearly a month to rack up 45,000 ransomed DBs. The Cru3lty group managed [22,000] only last week.”

Obviously, the bad actors have figured out how to script the attacks, but how do they find the targets? The same way most vulnerable systems are found on the Internet, SHODAN. The self-described “search engine for Internet-connected devices” is an easy place to find Internet of Things (IoT) devices. A great place to identify vulnerable web cams, refrigerators, industrial control systems (ICS), web apps and databases. If it is connected to the Internet you can find it in SHODAN. Once you know how to identify vulnerable MongoDB installations, add some scripting magic, exploit, ransom and repeat.
“New MongoDB instances which are not indexed by the famous search engine Shodan are not being hit. This means some groups don’t scan themselves but simply use OSINT,” said Victor Gevers, chairman of the GDI Foundation. One of the lead researchers tracking the ongoing exploits.
With all of the media coverage and the number of people affected at the beginning of the year, you might expect that everyone has checked and protected their MongoDB installations. But that is obviously not the case. According to a Google Docs spreadsheet maintained by the researchers, the count of compromised databases is almost 76,000. Obviously, the people installing MongoDB aren’t putting in the effort to secure their installations so the MongoDB team is changing their default installs to be more secure. If you are responsible for an existing MongoDB installation, you should check out the official MongoDB Security Checklist to ensure you are protected.
Other 26,000 MongoDB servers hit in a new wave of ransom attacks
5.9.2017 securityaffairs Ransomware
Security researchers Dylan Katz and Victor Gevers confirmed other 26,000 MongoDB servers were hit in a new wave of ransom attacks.
Ransom attacks on MongoDB databases revamped over the weekend after an apparent pause. According to the security researchers Dylan Katz and Victor Gevers, three new groups appeared on the threat landscape and hijacked over 26,000 servers, one of them, in particular, is responsible for hijacking 22,000 machines.
EMAIL ADDRESS VICTIMS RANSOM DEMAND BITCOIN ADDRESS
cru3lty@safe-mail.net 22,449 0.2 BTC Bitcoin address
wolsec@secmail.pro 3,516 0.05 BTC Bitcoin address
mongodb@tfwno.gf 839 0.15 BTC Bitcoin address
The security duo believes the attacks are the continuation of the wave of Ransom attack in MongoDB called MongoDB Apocalypse that peaked in January 2017.
The attacks were discovered by the Co-founder of the GDI Foundation, Victor Gevers, who warned of poor security for MongoDB installations in the wild. The security expert discovered in January 196 instances of MongoDB that were wiped by Harak1r1 and being held for ransom.
Multiple hacking groups scanned the internet for MongoDB installs left open for external connections and replaced their content with a ransom demand.
The analysis of the Bitcoin wallet used by Harak1r1 revealed that at least 22 victims appeared to have paid.
Many experts in the security community contributed in tracking the attacks, over 45,000 installs were compromised. Hackers targeted also other DBMS, such as MySQL, ElasticSearch, Hadoop, Cassandra, and CouchDB.
Back to the present, new groups launched a new wave of attacks against MongoDB databases. Compared with MongoDB Apocalypse, the number of compromised databases in decreased respect the first wave of attacks.
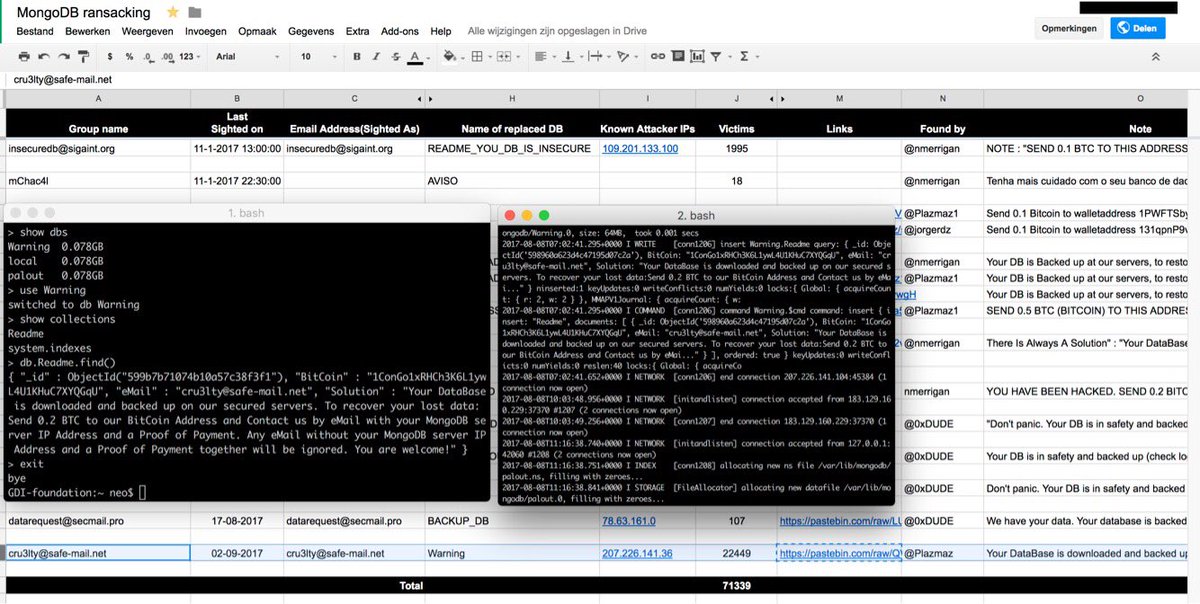
Victor Gevers @0xDUDE
MongoDBs are still being ransomed. A new attacker cru3lty@safe-mail.net made a record amount [22,449]
of victims: http://goo.gl/uCs16Q
9:46 PM - Sep 2, 2017 · The Netherlands
9 9 Replies 132 132 Retweets 112 112 likes
Twitter Ads info and privacy
Gevers told Bleeping Computer that even if there are fewer attackers, the impact is larger.
The experts are now investigating the cause of the success of the attacks.
US Government website was hosting a JavaScript downloader delivering Cerber ransomware
3.9.2017 Securityaffairs Ransomware
Security experts discovered last week that a US government website was hosting a JavaScript downloader used to deliver the Cerber ransomware.
The security researcher at NewSky Security Ankit Anubhav discovered last week that a US government website was hosting a malicious JavaScript downloader that was delivering the dreaded Cerber ransomware.

Ankit Anubhav @ankit_anubhav
#Javascript #malware using #powershell hosted on US Government site. Link is still live! cc @USCERT_gov
IOC :: https://pastebin.com/0eAPV7Lc
1:58 PM - Aug 30, 2017
5 5 Replies 67 67 Retweets 48 48 likes
Twitter Ads info and privacy
“Javascript malware hosted on US government site which launches powershell to connect to C2.” said the researcher Ankit Anubhav from NewSky Security.
The website was hosting a .zip archive that contained JavaScript that included obfuscated PowerShell. The PowerShell downloads a gif file which is in reality a Cerber executable.Below the malicious link:
hxxp://dms(dot)nwcg(dot)gov/pipermail/ross-suggestion/attachments/20170304/9ee8a89e/attachment.zip
The downloader was spotted on Wednesday, and within hours, the malicious code was removed.
It is not clear how the attackers installed the malicious code onto the .gov site and how many visitors have been infected.
Anubhav believes that the site was compromised, another possibility is that the site was used as a storage for email attachments from government officials’ emails and probably the malware was attached to one of the messages.
The expert highlighted many similarities with the Blank Slate spam campaign which earlier this year was spreading the Cerber ransomware. The email used by crooks in this campaign contained a double-zip archive with the second containing either a malicious JavaScript file or a malicious Microsoft Word document.
“An interesting aspect of this campaign is that the file attachments are double-zipped. There’s a zip archive within the zip archive. Within that second zip archive, you’ll find a malicious JavaScript (.js) file or a Microsoft Word document. These files are designed to infect a computer with ransomware.” reported the analysis from SANS.
“Blank Slate has pushed different types of ransomware. However, the vast majority of ransomware from this campaign has been Cerber.”
According to an analysis published by Anubhav along with the malware analyst at Spanish telco Telefonica, Mariano Palomo Villafranca, high reputation websites like the US one hosting the malware represent a privileged attack vector for crooks.
“Often security solutions blacklist an entire range of IP addresses and the potential target is saved from such attack (because the site is blocked before they visit it). To counter this measure, attackers focus on hosting malware in legitimate places, such as Google documents, or websites which are “known/proven clean”. As it turns out, one ideal scenario for an attacker would be to host malware on a government site.” states the analysis published by the security duo.
In an attack scenario, a victim could receive a link to the page hosting the .zip file. Once the victim clicks on the link the obfuscated JavaScript is extracted and launches PowerShell which downloads the malware from a known a domain compromised by the attacker.

According to the analysis, the gif executable was a NSIS installer which was used to extract the Cerber JSON file configuration.
“The link is down as of now. However, when we analysed archived data, we found that this particular payload was Cerber ransomware with a SHA256 1f15415da53df8a8e0197aa7e17e594d24ea6d7fbe80fe3bb4a5cd41bc8f09f6.”
Defray Ransomware Used in Selective Attacks Against Multiple Sectors
29.8.2017 securityweek Ransomware
A newly discovered ransomware variant has been used in small, selectively targeted attacks aimed at healthcare and education, and manufacturing and technology, respectively.
Dubbed Defray and discovered by Proofpoint earlier this month, the malware appears to have been involved only in two attacks, distributed via Word documents attached to phishing emails. The campaigns consisted of only several messages each, while the lures were specifically crafted for the intended targets.
The Microsoft Word documents carrying the ransomware contain an embedded OLE packager shell object. When the victim opens the document, the malware is dropped in the %TEMP% folder, and a file named taskmgr.exe or explorer.exe is then executed.
Defray contains a hardcoded list of around 120 file extensions to encrypt, though security researchers from Proofpoint noticed that the malware would also encrypt files with extensions that are not on the list (such as .lnk and .exe). The ransomware doesn’t change the extension of the encrypted files, Proofpoint says.
The threat communicates with the command and control server via both HTTP (clear-text) and HTTPS, to send infection information. After completing the encryption process, the malware disables startup recovery and deletes volume shadow copies. On Windows 7, Defray would also monitor and kill running programs such as the Task Manager and browsers.
To inform the victim of what happened with the files, the ransomware creates a ransom note called FILES.TXT in “many folders throughout the system,” along with a file called HELP.txt on the desktop (with identical content).
“The ransom note […] follows a recent trend of fairly high ransom demands; in this case, $5000. However, the actors do provide email addresses so that victims can potentially negotiate a smaller ransom or ask questions, and even go so far as to recommend BitMessage as an alternative for receiving more timely responses. At the same time, they also recommend that organizations maintain offline backups to prevent future infections,” Proofpoint reveals.
To date, the malware was observed only in two distinct attacks, one targeting Manufacturing and Technology verticals, on August 15, and another primarily aimed at Healthcare and Education, on August 22. As part of the first campaign, the emails featured the subject “Order/Quote” and referenced a UK-based aquarium with international locations. In the second campaign, the emails used a UK hospital logo, purporting to be from the Director of Information Management & Technology at the hospital.
“Defray Ransomware is somewhat unusual in its use in small, targeted attacks. Although we are beginning to see a trend of more frequent targeting in ransomware attacks, it still remains less common than large-scale “spray and pray” campaigns. It is also likely that Defray is not for sale, either as a service or as a licensed application like many ransomware strains. Instead, it appears that Defray may be for the personal use of specific threat actors, making its continued distribution in small, targeted attacks more likely,” Proofpoint concludes.
Defray Ransomware used in targeted attacks on Education and Healthcare verticals
27.8.2017 securityaffairs Ransomware
Researchers at Proofpoint spotted Defray Ransomware, a new ransomware used in a targeted campaign against education and healthcare organizations.
Earlier this month, researchers at Proofpoint spotted a targeted ransomware campaign against education and healthcare organizations. The ransomware used in the campaign was dubbed Defray, based on the command and control (C&C) server hostname used for the first observed attack:
defrayable-listings[.]000webhostapp[.]com
The ransomware is being spread via Microsoft Word document attachments in email.
The researchers observed two targeted attack on Aug. 15, and on Aug. 22, and both appeared to be designed for specific organizations.
The attack on August 22, aimed primarily at Healthcare and Education involving messages with a Microsoft Word document containing an embedded executable (specifically, an OLE packager shell object). The attachment features a UK hospital logo in the upper right and purports to be from the Director of Information Management & Technology at the hospital.
The attack on August 15 targeted Manufacturing and Technology verticals, attackers used messages with the subject “Order/Quote” and a Microsoft Word document containing an embedded executable (also an OLE packager shell object).
The attachment used a lure referencing a UK-based aquarium purported to be from a representative of the aquarium.

The attackers behind the Defray ransomware ask for $5,000, but researchers highlighted that the ransom note contains several email addresses, presumably of the cybercriminal Igor Glushkov,to allow victims to “negotiate a smaller ransom or ask questions.”
The Defray ransomware targets a hardcoded list of file types but doesn’t change the file extension names. After encryption is complete, the Defray ransomware may cause other general havoc on the system by disabling startup recovery and deleting volume shadow copies. On Windows 7, it monitors and kills running programs with a GUI, such as the task manager and browsers.
Experts speculate the threat could be being used privately and for this reason, it is less likely Defray ransomware will continue to be used in limited, targeted attacks.
“Defray Ransomware is somewhat unusual in its use in small, targeted attacks. Although we are beginning to see a trend of more frequent targeting in ransomware attacks, it still remains less common than large-scale “spray and pray” campaigns. It is also likely that Defray is not for sale, either as a service or as a licensed application like many ransomware strains. Instead, it appears that Defray may be for the personal use of specific threat actors, making its continued distribution in small, targeted attacks more likely” concluded Proofpoint.
Easy-to-Use Apps Allow Anyone to Create Android Ransomware Within Seconds
25.8.2017 thehackernews Ransomware
"Ransomware" threat is on the rise, and cyber criminals are making millions of dollars by victimizing as many people as they can—with WannaCry, NotPetya and LeakerLocker being the ransomware threats that made headlines recently.
What's BAD? Hacker even started selling ransomware-as-a-service (RaaS) kits in an attempt to spread this creepy threat more easily, so that even a non-tech user can create their own ransomware and distribute the threat to a wider audience.
The WORSE—You could see a massive increase in the number of ransomware campaigns during the next several months—thanks to new Android apps available for anyone to download that let them quickly and easily create Android ransomware with their own devices.
Security researchers at Antivirus firm Symantec have spotted some Android apps available on hacking forums and through advertisements on a social networking messaging service popular in China, which let any wannabe hacker download and use Trojan Development Kits (TDKs).
How to Create Your Own Android Ransomware
With an easy-to-use interface, these apps are no different from any other Android app apart from the fact that it allows users to create their custom mobile malware with little to no programming knowledge.
To create customized ransomware, users can download one such app (for an obvious reason we are not sharing the links), install and open it, where it offers to choose from the following options, which are displayed on the app's on-screen form:
The message that is to be shown on the locked screen of the infected device
The key to be used to unlock that infected device
The icon to be used by their malware
Custom mathematical operations to randomize the code
Type of animation to be displayed on the infected device
Once all of the information has been filled in, users just require hitting the "Create" button.
If the user hasn't before, the app will prompt him/her to subscribe to the service before proceeding. The app allows the user to start an online chat with its developer where he/she can arrange a one-time payment.
After the payment has been made, the "malware is created and stored in the external storage in ready-to-ship condition," and then the user can continue with the process, making as many as victims as the user can.
"Anyone unlucky enough to be tricked into installing the malware will end up with a locked device held to ransom," Symantec researchers say.
"The malware created using this automation process follows the typical Lockdroid behavior of locking the device’s screen with a SYSTEM_ALERT_WINDOW and displaying a text field for the victim to enter the unlock code."
The Lockdroid ransomware has the ability to lock the infected device, change the device PIN, and delete all of its user data through a factory reset, and even prevent the user from uninstalling the malware.
Such apps allow anyone interested in hacking and criminal activities to develop a ready-to-use piece of ransomware malware just by using their smartphones without any need to write a single line of code.
"However, these apps are not just useful for aspiring and inexperienced cyber criminals as even hardened malware authors could find these easy-to-use kits an efficient alternative to putting the work in themselves," the researchers say.
So, get ready to expect an increase in mobile ransomware variants in coming months.
How to Protect Your Android Devices from Ransomware Attacks
In order to protect against such threats on mobile devices, you are recommended to:
Always keep regular backups of your important data.
Make sure that you run an active anti-virus security suite of tools on your machine.
Avoid downloading apps from unknown sites and third-party app stores.
Always pay close attention to the permissions requested by an app, even if it is downloaded from an official app store.
Do not open any email attachments from unknown sources.
Finally, browse the Internet safely.
SyncCrypt Ransomware hides its components in image files
21.8.2017 securityaffairs Ransomware
A new strain of ransomware distributed through spam emails, dubbed SyncCrypt, hides its components inside harmless-looking images.
A new strain of ransomware recently discovered, dubbed SyncCrypt, hides its components inside harmless-looking images.
The SyncCrypt ransomware is distributed through spam emails that use attachments containing WSF files pretending to be court orders.
Once the victims execute the attachment, an embedded JScript fetches seemingly innocuous images from specific locations and extracts ransomware components they hide.
The ransomware components are stored into the images as ZIP files.
According to the BleepingComputer malware expert Lawrence Abrams, the JScript also extracts the hidden malicious components (sync.exe, readme.html, andreadme.png).
“If a user was to open one of these image URLs directly, they would just just see an image that contains the logo for Olafur Arnalds’ album titled “& They Have Escaped the Weight of Darkness”.” states the analysis published by Lawrence Abrams.
“Embedded in this image, though, is a zip file containing the sync.exe, readme.html, and readme.png files. These files are the core components of the SyncCrypt ransomware.”

The WSF file also creates a Windows scheduled task called Sync that once is executed, it starts scanning the infected system for certain file types and encrypts them using AES encryption.
The SyncCrypt ransomware uses an embedded RSA-4096 public encryption key to encrypt the used AES key.
The ransomware targets more than 350 file types and appends the .kk extension to them after encryption. The researcher observed that the ransomware skips files located in several folders, including\windows\, \program files (x86)\, \program files\, \programdata\, \winnt\, \system volume information\, \desktop\readme\, and\$recycle.bin\.
The ransomware demands around $429 to be paid to decrypt the files, after the payment was completed by the victims they have to send an email containing the key file to one of the emails getmyfiles@keemail.me, getmyfiles@scryptmail.com, or getmyfiles@mail2tor.com to get a decrypter.
According to Abrams, the distribution process is able to evade the detection, only one of the 58 vendors in VirusTotal could detect the malicious images at the time of analysis. The researchers noticed that the Sync.exe, on the other hand, had a detection rate of 28 out of 63.
Unfortunately, at this time there is no way to decrypt files encrypted by the SyncCrypt ransomware for free.
Abrams analysis includes IoCs and provides the following recommendations to avoid being infected by ransomware.
Backup, Backup, Backup!
Do not open attachments if you do not know who sent them.
Do not open attachments until you confirm that the person actually sent you them,
Scan attachments with tools like VirusTotal.
Make sure all Windows updates are installed as soon as they come out! Also make sure you update all programs, especially Java, Flash, and Adobe Reader. Older programs contain security vulnerabilities that are commonly exploited by malware distributors. Therefore it is important to keep them updated.
Make sure you use have some sort of security software installed.
Use hard passwords and never reuse the same password at multiple sites.
For a complete guide on ransomware protection, give a look at How to Protect and Harden a Computer against Ransomware article.
The Ukrainian central bank warned of new NotPetya-style massive attack risk
19.8.2017 securityaffairs Ransomware
The Ukrainian central bank warned state-owned and private lenders of the appearance of new the NotPetya-like attack that would target national businesses.
On Friday, the Ukrainian central bank warned of new malware-based attack risk. According to the Reuters, the Ukrainian central bank warned state-owned and private lenders of the spreading of new infections like the NotPetya attack that hit the critical infrastructure of the country in June.
“The Ukrainian central bank said on Friday it had warned state-owned and private lenders of the appearance of new malware as security services said Ukraine faced cyber attacks like those that knocked out global systems in June.” states post published by the Reuters.
“The June 27 attack, dubbed NotPetya, took down many Ukrainian government agencies and businesses, before spreading rapidly through corporate networks of multinationals with operations or suppliers in eastern Europe.”
The Ukrainian central bank is closely working with the national CERT and local authorities to improve the resilience to cyber attacks of its critical infrastructures, especially the ones of the Ukrainian banking sector.
“Therefore on Aug. 11…, the central bank promptly informed banks about the appearance of new malicious code, its features, compromise indicators and the need to implement precautionary measures to prevent infection,” the central bank told Reuters in emailed comments.
The Reuters has seen the letter sent by the Ukrainian central bank to the national banks, the message warns of a new strain of malware is spread via phishing email using weaponized word documents.

The experts warn of a possible massive cyber attack on Ukrainian companies, the malicious code is currently able to evade antivirus solutions.
“The nature of this malicious code, its mass distribution, and the fact that at the time of its distribution it was not detected by any anti-virus software, suggest that this attack is preparation for a mass cyber-attack on the corporate networks of Ukrainian businesses,” the letter said.
Of course, the first suspect according to the experts is Russia that has many interests in the country, in many cases, Ukraine blamed the Kremlin for cyber attacks on its infrastructure, including the power grid and financial systems.
The state cyber police and Security and Defence Council already warned of a potential imminent cyber attack against Ukraine. Authorities believe Ukraine could be targeted on Aug. 24 with a NotPetya-style massive attack aimed at destabilizing the country as it celebrates its 1991 independence from the Soviet Union.
SyncCrypt Ransomware Hides Components in Image Files
18.8.2017 securityweek Ransomware
A newly discovered piece of ransomware hides its components inside online harmless-looking images that don’t trigger anti-virus detection.
Dubbed SyncCrypt, the ransomware is distributed through spam emails that feature attachments containing WSF files pretending to be court orders. Once the attachments are executed, embedded JScript fetches seemingly innocuous images from specific locations and extracts malicious components hidden inside them.
The ransomware components are stored inside the images as ZIP files, and they aren’t triggered if the user simply accesses their URL via browser. The aforementioned JScript, however, not only downloads the images, but also extracts the hidden malicious components (sync.exe, readme.html, and readme.png), BleepingComputer’s Lawrence Abrams reveals.
The WSF file also creates a Windows scheduled task called Sync. Once the sync.exe file is executed, it starts scanning the victim’s computer for certain file types and encrypts them using AES encryption. The malware encrypts the used AES key with an embedded RSA-4096 public encryption key.
The ransomware targets over 350 file types and appends the .kk extension to them after encryption. The threat skips files located in several folders, namely \windows\, \program files (x86)\, \program files\, \programdata\, \winnt\, \system volume information\, \desktop\readme\, and \$recycle.bin\.
The ransomware demands around $430 to be paid to retrieve the decryption key. The attackers instruct victims to provide them with the key file after paying the ransom to receive a decrypter. The email addresses used as part of the analyzed attack include getmyfiles@keemail.me, getmyfiles@scryptmail.com, and getmyfiles@mail2tor.com.
The distribution of this ransomware is highly effective because of its ability to bypass detection. According to Abrams, only one of the 58 vendors in VirusTotal could detect the malicious images at the time of analysis. Sync.exe, on the other hand, had a detection rate of 28 out of 63.
To stay protected, users should pay extra care when opening attachments or clicking on URLs in emails received from unknown sources. They should also keep their files backed up at all times, to ensure they can recover their data without having to pay a ransom. Keeping all software on the machine updated at all times should decrease the chances of becoming infected.
Locky Ransomware Campaign Ramps Up
17.8.2017 securityweek Ransomware
The Locky ransomware family that dominated the charts last year has returned, and has been distributed through high volume campaigns over the past week.
Closely tied to the activity of the Necurs botnet, Locky has been nearly completely absent from the threat landscape this year. Following several months of total silence, the ransomware was present in spam runs in April and May, but went under the radar within weeks, as Necurs switched to distributing the Jaff ransomware.
On August 9, however, new spam campaigns dropping Locky caught the attention of security researchers. The first to observe the new ransomware variant was Racco42, who revealed that the spam messages contained subject lines similar to E [date] (random_numer).docx.
The Locky variant featured in that campaign was appending the .diablo6 extension to encrypted files and was downloaded by a VBS script packed inside a ZIP attachment. The malware demands a 0.49 Bitcoin ransom (currently about $2,250).
According to Fortinet, the malicious emails were mainly targeted at victims in the United States (37%) and Austria (36%). A large portion of them (10%) hit users in the UK. The security researchers also note that the new Locky variant packs the same capabilities as the last year version, and that free decryption isn’t possible.
Comodo, which performed a detailed analysis of the recent Locky attacks, calls the new ransomware variant IKARUSdilapidated, based on the appearance of the word in the code string. The security firm also says that tens of thousands of phishing emails featuring subject lines and attachments named similar to E [date] (random_numer) were observed over the course of several days dropping Locky.
A closer look at these emails revealed that 11,625 different IP addresses from 133 countries were used in this campaign, with Vietnam, India, Mexico, Turkey, and Indonesia being the top five. Most of the IP owners are telecom companies and ISPs, meaning that they belong “to infected, now compromised computers,” essentially forming a botnet, Comodo notes in a report shared with SecurityWeek.
Earlier this week, another Locky variant emerged, one that would append the .Lukitus extension to the encrypted files, Malwarebytes says. The spam emails feature either no subject or something similar to Emailing - CSI-034183_MB_S_7727518b6bab2 as subject line, and include a RAR or ZIP attachment that has JS files inside, which in turn download Locky.
To stay protected, users should keep their files backed up at all times and should also avoid opening attachments or clicking on links coming via email from unknown sources. Keeping the operating system and all applications on the computer updated at all times should also prevent infections from happening.
“It’s still too early to say if this campaign signals the start of Locky diving back into the ransomware race or if it is just testing the waters. We’ll probably see in the next few weeks or months,” Fortinet says.
NotPetya Attack Costs Big Companies Millions
17.8.2017 securityweek Ransomware
Some of the big companies hit by the NotPetya malware in late June have reported losing hundreds of millions of dollars due to the cyberattack.
The NotPetya malware outbreak affected tens of thousands of systems in more than 65 countries, including ones belonging to major organizations such as Rosneft, AP Moller-Maersk, Merck, FedEx, Mondelez International, Nuance Communications, Reckitt Benckiser and Saint-Gobain. Many of the victims were located in Ukraine, the home of a tax software firm whose product was used as the main attack vector.
Researchers initially believed NotPetya (aka PetrWrap, exPetr, GoldenEye and Diskcoder.C) was a piece of ransomware, similar to WannaCry. However, a closer analysis revealed that it was actually a wiper and it was unlikely that victims could recover their files, even if they paid the ransom.
Financial reports published by the affected companies in the past few weeks show that the cyberattack has caused serious damage in many cases. FedEx-owned international delivery services company TNT Express, for instance, said there was a possibility that some business data may never be recovered.
Danish shipping giant AP Moller-Maersk estimates that the attack has cost it $200-$300 million. The conglomerate believes the cyberattack will have a significant impact on its finances in the third quarter due to revenue lost in July.
American pharmaceutical giant Merck had still been working on restoring operations in late July. In its latest financial results announcement, the firm said the cyberattack had disrupted its worldwide operations, including manufacturing, research and sales, but did not specify the exact losses caused by the incident.
Reckitt Benckiser, the British consumer goods company that makes Nurofen, Dettol and Durex, said the attack disrupted its ability to manufacture and distribute products. It estimated that the incident could have an impact of $130 million on its revenue.
Voice and language solutions provider Nuance Communications reported GAAP revenue of $486.2 million and non‑GAAP revenue of $495.6 million in the third quarter. The company estimates that the third-quarter GAAP revenues would have been $501.6 million and non-GAAP revenues $511.0 million had the malware incident not taken place. Nuance said its healthcare business was the most impacted.
Mondelez International, owner of U.K. chocolate maker Cadbury, estimated the cost of the attack at just over $150 million in lost sales and incremental expenses. The company, whose sales, distribution and financial networks were impacted by the malware, expects the recovery process to continue into the second half of 2017.
French construction giant Saint-Gobain said the attack led to donwtime of IT systems and supply chain disruptions. The NotPetya attack has had a negative impact of €220 million ($258 million) on sales and €65 million ($76 million) on operating income in the first half of 2017. Until the end of the year, total losses are expected to rise to €330 million ($387 million).
German consumer goods provider Beiersdorf was also hit by the attack and while it expects sales worth roughly €35 million ($41 million) to be shifted from the second quarter to the third, the company does not expect a material impact on its profits for this year.
NotPetya ransomware caused $300m losses to the shipping giant Maersk
17.8.2017 securityaffairs Ransomware
The transportation giant Maersk announced that it would incur hundreds of millions in U.S. dollar losses due to the NotPetya ransomware massive attack.
A.P. Moller-Maersk, the transportation and logistics firm, announced Tuesday that it would incur hundreds of millions in U.S. dollar losses due to the NotPetya ransomware massive attack.
According to the second quarter earnings report, there were expecting losses between $200 million and $300 million due to “significant business interruption” because the company was forced to temporarily halt critical systems infected with the ransomware.
“As soon as A.P. Moller – Maersk became aware that systems had been affected, action to respond was initiated including closing down infected networks. The malware was contained to only impact the container related businesses of A.P. Moller” reads the report. “A.P. Moller – Maersk also remained in full control of all vessels throughout the situation, and all employees were safe.”
The company said its Maersk Line APM Terminals and Damco systems were completely shut down in response to the incident as a precaution measure.
“These system shutdowns resulted in significant business interruption during the shutdown period, with limited financial impact in Q2, while the impact in Q3 is larger, due to temporary lost revenue in July (see guidance for 2017),” continues the report.
NotPetya hit hundreds of companies causing serious million of dollars damages, early August, the US pharmaceutical company Merck revealed that the massive NotPetya cyberattack has disrupted its worldwide operations.

Other major companies affected by the NotPetya attack were the Ukraine’s central bank, Russian oil giant Rosneft, advertising group WPP, and the law firm DLA Piper.
Two of the world’s largest consumer goods companies suffered serious problems, on July the companies Mondelez and Reckitt Benckiser warned of the impact of the NotPetya attack on their revenues.
The Mondelez International company estimated the NotPetya attack would cut three percentage points from second-quarter sales growth because of disruptions to shipping and invoices caused by the cyber attack.
The Reckitt Benckiser, the maker of Nurofen painkillers and Durex condoms, said it expected sales would be hit Q2 by an estimated £110m this year.
The company said that its expected overall profit to still exceed 2016 margins despite the impact of the cyberattack.
“This cyber-attack was a previously unseen type of malware, and updates and patches applied to both the Windows systems and antivirus were not an effective protection in this case,” the company said. “In response to this new type of malware, A.P. Moller – Maersk has put in place different and further protective measures and is continuing to review its systems to defend against attacks.”
Cerber Ransomware now includes a feature to avoid canary files anti-malware
16.8.2017 securityaffairs Ransomware
Researchers at Cybereason have discovered a new strain of the Cerber ransomware that implements a new feature to avoid triggering canary files.
The canary files are a security measure for the early detection of threat like ransomware.
These files are located in specific positions of systems and an anti-ransomware application watches for any modification. If the watching anti-ransomware detects any attempt to encrypt these file the defense solution will trigger the necessary countermeasures.

Researchers at Cybereason have discovered a new strain of the Cerber ransomware that implements a new feature to avoid triggering canary files.
“To avoid encrypting canary files and triggering anti-ransomware programs,” reports Uri Sternfield, Cybereason’s lead researcher, “a new feature in Cerber now searches computers for any image file (.png, .bmp, .tiff, .jpg, etc.) and checks whether they are valid. Image files are commonly used as canary files. If a malformed image is found, Cerber skips the entire directory in which it is located and does not encrypt it.”
Using this technique the Cerber ransomware is able to evade detection based on canary files. Experts pointed out that this mechanism could ble used against the Cerber ransomware by placing false modified canary files ( i.e. malformed image file ) in any important directory of the system. In this way users can vaccinate any folder containing valuable content.
“While this trick might allow Cerber to evade some canary-file anti-ransomware solutions, it also makes it vulnerable,” explains Sternfield; “a user can ‘vaccinate’ any important directory against Cerber by creating an invalid image file inside it, for example by copying any non-image file to this directory and renaming it to .jpg. Cerber will assume that the file is a canary file installed by an anti-ransomware program on the user’s machine and refuse to encrypt it!”
Cybereason’s developed a free application dubbed RansomFree that protects users from ransomware and automatically generates canary files in valuable folders.
Nevertheless, it is easy to create malformed canary files, for example, by renaming non-image file to jpeg.
“Simply take any non-image file and rename it to .jpg, then copy this file into any folder which holds important documents. This has to be performed for each folder
Cerber Ransomware Creates Self-Inflicted Canary Vaccine
16.8.2017 securityweek Ransomware
Researchers Say Cerber Ransomware Now Has a Feature to Avoid Triggering "Canary Files"
The old canary-in-the-coal-mine and the new canary file serve the same purpose. Both are threat detectors: the former to detect the presence of poisonous gas in a mine, and the latter to detect an unauthorized presence in a file system. The canary file is particularly useful as an early-warning system for the presence of ransomware.
The concept is very simple. A bogus file designed to look like a prime ransomware target is strategically placed and watched by an anti-ransomware application. There is no valid reason for this file to be encrypted. If the watching anti-ransomware detects any attempt to do so, it knows that ransomware is present and can take the necessary action.
Cybereason researchers have discovered that the Cerber ransomware now includes a new feature to avoid triggering canary files. "To avoid encrypting canary files and triggering antiransomware programs," reports Uri Sternfield, Cybereason's lead researcher, "a new feature in Cerber now searches computers for any image file (.png, .bmp, .tiff, .jpg, etc.) and checks whether they are valid. Image files are commonly used as canary files. If a malformed image is found, Cerber skips the entire directory in which it is located and does not encrypt it."
This is typical of the continuous battle between any attacker and defender: measures and countermeasures. The canary file is a countermeasure -- evading canary files is a counter-countermeasure. But Sternfield points out that there is a potential weakness in the counter-countermeasure -- it effectively introduces a vaccine against this version of Cerber that can be used by anyone.
"While this trick might allow Cerber to evade some canary-file anti-ransomware solutions, it also makes it vulnerable," explains Sternfield; "a user can 'vaccinate' any important directory against Cerber by creating an invalid image file inside it, for example by copying any non-image file to this directory and renaming it to .jpg. Cerber will assume that the file is a canary file installed by an anti-ransomware program on the user's machine and refuse to encrypt it!"
Put simply, any valuable folder can be vaccinated by the inclusion of a malformed image file, such as a bogus .jpg. Cybereason's own free RansomFree product automatically does this, but it "only generates canary files in key locations and important folders," Sternfield told SecurityWeek.
Nevertheless, it is an easy process for any user. "Simply take any non-image file and rename it to .jpg, then copy this file into any folder which holds important documents. This has to be performed for each folder separately," he explained.
While this process can be used to protect valuable files from this version of Cerber, it would be wrong to treat it as a solution against ransomware in general. What the story really illustrates is the manner in which attackers and defenders closely watch each others' moves, always trying to outsmart the other.
Cybereason has already updated its own products to make use of the 'vaccine' in strategic folders. If the authors of this version of Cerber detect that the vaccine becomes an effective defense against their attack, they might simply drop their canary file detection process. At this point, the infected user will have to rely on the more traditional monitoring of canary files by an anti-ransomware product.
Cybereason raised $100 million in Series D funding in June 2017, which brought the total amount raised by the cyber attack detection firm to $189 million since its inception in 2012.
Warning: Two Dangerous Ransomware Are Back – Protect Your Computers
15.8.2017 thehackernews Ransomware
Ransomware has been around for a few years but has become an albatross around everyone's neck—from big businesses and financial institutions to hospitals and individuals worldwide—with cyber criminals making millions of dollars.
In just past few months, we saw a scary strain of ransomware attacks including WannaCry, Petya and LeakerLocker, which made chaos worldwide by shutting down hospitals, vehicle manufacturing, telecommunications, banks and many businesses.
Before WannaCry and Petya, the infamous Mamba full-disk-encrypting ransomware and the Locky ransomware had made chaos across the world last year, and the bad news is—they are back with their new and more damaging variants than ever before.
Diablo6: New Variant of Locky Ransomware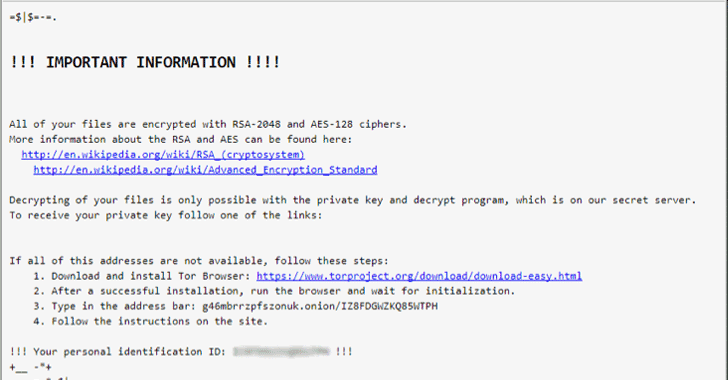
First surfaced in early 2016, Locky has been one of the largest distributed ransomware infections, infecting organisations across the globe.
By tricking victims into clicking on a malicious attachment, Locky ransomware encrypts nearly all file formats on a victim's computer and network and unlocks them until the ransom in Bitcoins is paid to attackers.
The ransomware has made many comebacks with its variants being distributed through Necurs botnet and Dridex botnet.
This time security researchers have discovered a fresh spam malware campaign distributing a new variant of Locky known as Diablo6 and targeting computers around the world, with the United States being the most targeted country, followed by Austria.
An independent security researcher using online alias Racco42 first spotted the new Locky variant that encrypts files on infected computers and appends the .diablo6 file extension.
Like usually, the ransomware variant comes in an email containing a Microsoft Word file as an attachment, which when opened, a VBS Downloader script is executed that then attempts to download the Locky Diablo6 payload from a remote file server.
The ransomware then encrypts the files using RSA-2048 key (AES CBC 256-bit encryption algorithm) on the infected computer before displaying a message that instructs victims to download and install Tor browser; and visit the attacker's site for further instructions and payments.
This Locky Diablo6 variant demands a sum of 0.49 Bitcoin (over $2,079) from victims to get their files back.
Unfortunately, at this time it is impossible to recover the files encrypted by the .Diablo6 extension, so users need to exercise caution while opening email attachments.
Return of Disk-Encrypting Mamba Ransomware
Mamba is another powerful and dangerous kind of ransomware infection that encrypts the entire hard disk on an affected computer instead of just files, leaving the system totally unusable unless a ransom is paid.
Similar tactics have also been employed by other ransomware attacks, including Petya and WannaCry, but the Mamba ransomware has been designed for destruction in corporates and other large organisations, rather than extorting Bitcoins.
Late last year, Mamba infected the San Francisco's Municipal Transportation Agency (MUNI) system's network over the Thanksgiving weekend, causing major train delays and forcing officials to shut down ticket machines and fare gates at some stations.
Now, security researchers at Kaspersky Lab have spotted a new campaign distributing Mamba infections, targeting corporate networks in countries, majorly in Brazil and Saudi Arabia.
Mamba is utilising a legitimate open source Windows disk encryption utility, called DiskCryptor, to fully lock up hard drives of computers in targeted organisations. So, there is no way to decrypt data as the encryption algorithms used by DiskCryptor are very strong.
Although it's not clear how the ransomware initially finds its way into a corporate network, researchers believe like most ransomware variants, Mamba might be using either an exploit kit on compromised or malicious sites or malicious attachments sent via an email.
The ransom note does not immediately demand money, rather the message displayed on the infected screen only claims that the victim's hard drive has been encrypted and offers two email addresses and a unique ID number to recover the key.
Here's How to Protect Yourself From Ransomware Attacks
Ransomware has become one of the largest threats to both individuals and enterprises with the last few months happening several widespread ransomware outbreaks.
Currently, there is no decryptor available to decrypt data locked by Mamba and Locky as well, so users are strongly advised to follow prevention measures in order to protect themselves.
Beware of Phishing emails: Always be suspicious of uninvited documents sent over an email and never click on links inside those documents unless verifying the source.
Backup Regularly: To always have a tight grip on all your important files and documents, keep a good backup routine in place that makes their copies to an external storage device that is not always connected to your PC.
Keep your Antivirus software and system Up-to-date: Always keep your antivirus software and systems updated to protect against latest threats.
WannaCry hero Marcus Hutchins pleads not guilty
15.8.2017 securityaffairs Ransomware
The 23-year-old expert Marcus Hutchins pleaded “not guilty” during a court hearing in Milwaukee, Wisconsin. His trial has been scheduled for October.
Yesterday, Marcus Hutchins, the WannaCry hero, has pleaded not guilty to charges of creating and selling malware at a hearing in Milwaukee, Wisconsin.
The court decided to relax the expert bail terms, allowing him to access the Internet and continues his ordinary working activities. The only restrictions on Hutchins is that the expert cannot visit the Wannacry server domain.
12h
MalwareTech ✔ @MalwareTechBlog
There's a lot of people I'd like to thank for amazing support over the past 11 days, which I will do when i get a chance to publish my blog.
Follow
MalwareTech ✔@MalwareTechBlog
i'm still on trial, still not allowed to go home, still on house arrest; but now i am allowed online. Will get my computers back soon.
9:58 PM - Aug 14, 2017
131 131 Replies 440 440 Retweets 1,715 1,715 likes
Twitter Ads info and privacy
The decision is unusual because computer crime suspects are not allowed to stay online.
The court allowed him to live in Los Angeles, where the company that hired him is located, but he is obliged to surrender his passport and he must wear a tracking device until his trial in October.
“Marcus Hutchins is a brilliant young man and a hero,” said Marcia Hofmann, founder of Zeigeist Law. “He is going to vigorously defend himself against these charges and when the evidence comes to light we are confident that he will be fully vindicated.”
Marcus Hutchins, also known as MalwareTech, is a 22-year-old security expert who made the headlines after discovering the “kill switch” that halted the outbreak of the WannaCry ransomware. Marcus Hutchins has been arrested in in Las Vegas after attending the Def Con hacking conference and was detained by the FBI in the state of Nevada.
The British security researcher was arrested on Thursday after being indicted on charges of creating the Kronos banking malware.
A second defendant whom identity was not revealed appears to be involved.
According to the investigators, Marcus Hutchins created the malware and shared it online, below the indictment issued by Eastern District of Wisconsin.
The prosecutors believe Hutchins created, shared, and masterminded the Kronos banking Trojan between July 2014 and July 2015.
“We are very pleased today that the court modified his terms to allow him to return to his important work,” said Hutchins lawyer Brian Klein, partner at Baker Marquart LLP.
HBO Offered Hackers $250,000 As Ransom to Prevent More Leaks
14.8.2017 thehackernews Ransomware
Hackers who recently hacked into HBO network and stole scripts, shows, and employee information documents, have now provided an email in which the United States cable channel offered them $250,000.
The company offered the payment as a "bounty payment" reward in which companies reward white-hat hackers for discovering cyber security vulnerabilities in their computer networks.
Late last month, the HBO hackers claimed to have obtained around 1.5 terabytes of information from HBO and dropped upcoming episodes of "Ballers" and "Room 104," and a script of the fourth episode of "Game of Thrones."
A week after that, the hackers released another half-gigabyte sample of its stolen HBO data, including company's emails, employment agreements, and financial balance sheets, along with the script of the upcoming episode of Game of Thrones, demanding a ransom—nearly $6 Million in Bitcoins.
Now, according to a screenshot of an email obtained by Variety, an HBO executive wrote that the company had not been able to acquire the amount of Bitcoin the hackers had demanded and requested them to extend the ransom payment deadline by one week.
"You have the advantage of having surprised us. In the spirit of professional cooperation, we are asking you to extend your deadline for one week," the HBO executive reportedly writes in the email.
"As a show of good faith on our side, we are willing to commit to making a bug bounty payment of $250,000 to you as soon as we can establish the necessary account and acquire Bitcoin, or we can wire the funds as soon as you give us the account information."
Since the offered amount is just 3 to 4 percent of what the hackers demanded, the proposal apparently failed to satisfy the greed of hackers, and they have threatened to release more files from its 1.5 terabytes of stolen data every Sunday until the ransom is paid.
Although HBO did not yet respond to the recently leaked email, a person familiar with HBO's response to the hack told Reuters that the company sent that email "as a stall tactic" and had never intended to make the $250,000 or the full $6 Million payment to the hackers.
The company previously said it was working with forensic experts and law enforcement.
"The review to date has not given us a reason to believe that our email system as a whole has been compromised. We continue to work around the clock with outside cyber security firms and law enforcement to resolve the incident," HBO spokesperson Jeff Cusson said.
If hackers have held on 1.5 terabytes of HBO data and the company refuses to pay the ransom, you should expect more leaks of upcoming episodes from your favourite shows.
Two days ago, the HBO hackers also released some of the stolen data from the company, including the home addresses and phone numbers belonging to some of the Game of Thrones show's stars.
At this moment, it is still unclear who is behind the hack. We will keep you updated with the latest information.
IPS as a Service Blocks WannaCry Spread Across the WAN
14.8.2017 thehackernews Ransomware
One of the most devastating aspects of the recent WannaCry ransomware attack was its self-propagating capability exploiting a vulnerability in the file access protocol, SMB v1.
Most enterprises defences are externally-facing, focused on stopping incoming email and web attacks. But, once attackers gain a foothold inside the network through malware, there are very few security controls that would prevent the spread of the attack between enterprise locations in the Wide Area Network (WAN).
This is partly due to the way enterprises deploy security tools, such as IPS appliances, and the effort needed to maintain those tools across multiple locations.
It’s for those reasons Cato Networks recently introduced a context-aware Intrusion Prevention System (IPS) as part of its secure SD-WAN service. There are several highlights in this announcement that challenge the basic concept of how IT security maintains an IPS device and sustains the effectiveness of its protection.
Cato Networks is a cloud-based, SD-WAN service provider that uniquely integrates network security into its SD-WAN offering.
The Cato IPS is fully converged with Cato’s other security services, which include next generation firewall (NGFW), secure web gateway (SWG), URL filtering, and malware protection.
With the IPS roll out, Cato continues its march towards providing secure networking everywhere while simplifying the overall IT stack for the enterprise.
Cato Networks IPS as a Service
With IPS as a service, Cato takes care of the work previously spent managing and maintaining the IPS appliances including sizing, capacity planning, patching, and signature management.
These are a complex task because IPS appliance performance is impacted by the mix of encrypted and unencrypted traffic and the number of active attack signatures.
Normally, IT professionals must spend time carefully calculating the effectiveness of a signature and its performance impact to avoid slowing-down traffic due to IPS appliance overload.
Cato addresses both issues. The Cato IPS leverages its elastic cloud platform to inspect any mix of encrypted and unencrypted traffic in real-time.
The decision of which signatures to deploy is made by the experts of Cato Research Labs. They consider the relevancy of the threat and the best way to describe it to the system. Often, an existing signature may already cover a specific attack vector.
New Kind of Signatures With Context-Aware Protection
The Cato IPS has another unique capability. Because it operates in the same software stack as all other network and security services and within a cloud network, it can access a rich set of context attributes.
This forms a foundation for very sophisticated signatures that are hard to compose with stand-alone IPS devices. The use of rich context makes Cato IPS signatures more accurate and more effective.
Context attributes include the application being accessed and the client being used to access it, user identity, geolocation, IP and domain reputation, the file type exchanged, and DNS activity associated with the session.
Cato shared on its blog how Cato IPS stopped the spread of the Wannacry ransomware across sites, and how Cato IPS detected command-and-control communication at one of its customer locations.
Interestingly, the IPS can extend its protection across sites and users without the need to deploy distributed appliances, another benefit of the system.
If you are a distributed enterprise and constraint by your ability to support a complex networking and security environment, Cato’s approach can improve your security posture while keeping overhead to a minimum.
Disclosure: This is a sponsored post from Cato Networks, and it is really coming at a great time because we were just thinking to share with you about how to prevent Wannacry like attacks from spreading across the enterprise networks.
Anti-Israel and pro-Palestinian IsraBye wiper spreads as a ransomware
14.8.2017 securityaffairs Ransomware
Malware researchers discovered an anti-Israel & pro-Palestinian data wiper dubbed IsraBye that is spreading as a ransomware.
Malware researcher Jakub Kroustek from Avast has recently discovered an anti-Israel & pro-Palestinian data wiper dubbed IsraBye. Even if the lock screen claims that the files can be recovered, their content is replaced with an anti-Israel message. 
Jakub Kroustek @JakubKroustek
This is Ahmed. Ahmed likes .NET. Ahmed hates #Israel. Ahmed created a #wiper. Ahmed, now GTFO. #MalwareWithSounds https://www.virustotal.com/en/file/5a209e40e0659b40d3d20899c00757fa33dc00ddcac38a3c8df004ab9051de0d/analysis/ …
10:45 PM - Jul 29, 2017
9 9 Replies 59 59 Retweets 88 88 likes
Twitter Ads info and privacy
The anti-Israel wiper was discovered concurrently the Al Aqsa crisis triggered by the decision of Israeli authorities to install metal detectors and other measures at the Al Aqsa mosque in Jerusalem. The measures were refused by Palestinians.
Researchers at Bleepingcomputer have published an interesting video on the IsraBye:
The wiper has a modular architecture composed of 5 different executables. The first executable is the launcher and wiper called IsraBye.exe. When executed IsraBye.exe silently begin to wipe all attached drives by replacing their contents with the following message:
Fuck-israel, [username] You Will never Recover your Files Until Israel disepeare
The wiper doesn’t encrypt the file, but destroy them and once completed the process, it extracts the files Cry.exe, Cur.exe, Lock.exe, and Index.exe from the IsraBye.exe executable and launches them.
The Cry.exe executable replaces the desktop’s wallpaper with an anti-Israel or pro-Palestinian image.

IsraBye wallpaper (Source Bleepingcomputer)
The Cur.exe attaches an image that included the message “End of Israel” to the mouse cursor.
The Lock.exe performs the following three functions:
it will look for the procexp64, ProcessHacker, taskmgr, procexp, xns5 processes in order to terminate them.
it will launch Index.exe if it is not already running.
it will copy the main Israbye.exe file to the root of other drives as a file called ClickMe.exe in order to spread the malware.
The researcher Ido Naor noticed that creating a file called ClickMe.exe in the %Temp% folder it is possible to make IsraBye crashes when first starting.

Ido Naor @IdoNaor1
#israhell #israbye Thought I'd put an empty "ClickMe.exe" and make it crash. Well it did, obviously. Kill switch is a new trend now?
1:35 PM - Aug 3, 2017
3 3 Replies 5 5 Retweets 5 5 likes
Twitter Ads info and privacy
The Index.exe executable displays the lock screen and extracts a wav file and play it.
The return of Mamba ransomware
13.8.2017 Kaspersky Ransomware
At the end of 2016, there was a major attack against San Francisco’s Municipal Transportation Agency. The attack was done using Mamba ransomware. This ransomware uses a legitimate utility called DiskCryptor for full disk encryption. This month, we noted that the group behind this ransomware has resumed their attacks against corporations.
Attack Geography
We are currently observing attacks against corporations that are located in:
Brazil
Saudi Arabia
Attack Vector
As usual, this group gains access to an organization’s network and uses the psexec utility to execute the ransomware. Also, it is important to mention that for each machine in the victim’s network, the threat executor generates a password for the DiskCryptor utility. This password is passed via command line arguments to the ransomware dropper.
Example of malware execution
Technical Analysis
In a nutshell, the malicious activity can be separated into two stages:
Stage 1 (Preparation):
Create folder “C:\xampp\http“
Drop DiskCryptor components into the folder
Install DiskCryptor driver
Register system service called DefragmentService
Reboot victim machine
Stage 2 (Encryption):
Setup bootloader to MBR and encrypt disk partitions using DiskCryptor software
Clean up
Reboot victim machine
Stage 1 (Preparation)
As the trojan uses the DiskCryptor utility, the first stage deals with installing this tool on a victim machine. The malicious dropper stores DiskCryptor’s modules in their own resources.
DiskCryptor modules
Depending on OS information, the malware is able to choose between 32- or 64-bit DiskCryptor modules. The necessary modules will be dropped into the “C:\xampp\http” folder.
The malware drops the necessary modules
After that, it launches the dropped DiskCryptor installer.
The call of the DiskCryptor installer
When DiskCryptor is installed, the malware creates a service that has SERVICE_ALL_ACCESS and SERVICE_AUTO_START parameters.
The creation of the malicious service’s function
The last step of Stage 1 is to reboot the system.
Force reboot function
Stage 2 (Encryption)
Using the DiskCryptor software, the malware sets up a new bootloader to MBR.
The call for setting up a bootloader to MBR
The bootloader contains the ransom message for the victim.
Ransomware note
After the bootloader is set, disk partitions would be encrypted using a password, previously specified as a command line argument for the dropper.
The call tree of encryption processes
When the encryption ends, the system will be rebooted, and a victim will see a ransom note on the screen.
Ransom notes
Kaspersky Lab products detect this threat with the help of the System Watcher component with the following verdict: PDM:Trojan.Win32.Generic.
Decryption
Unfortunately, there is no way to decrypt data that has been encrypted using the DiskCryptor utility because this legitimate utility uses strong encryption algorithms.
Ukrainian Man Arrested For Distributing NotPetya Ransomware And Helping Tax Evaders
12.8.2017 thehackernews Ransomware

Ukrainian authorities have arrested a 51-year-old man accused of distributing the infamous Petya ransomware (Petya.A, also known as NotPetya) — the same computer virus that massively hit numerous businesses, organisations and banks in Ukraine as well as different parts of Europe around 45 days ago.
However, the story is not as simple as it seems, which portrayed this man as a criminal. I recommend you to read complete article to understand the case better and then have an opinion accordingly.
Sergey Neverov (Сергей Неверов), father of two sons and the resident of the southern city of Nikopol, is a video blogger and computer enthusiast who was arrested by the Ukrainian police on Monday, August 7 from his home.
What Neverov Did?
According to a press release published on Thursday by the Ukrainian cyber police department, Neverov uploaded a video, showing how to infect a computer with Petya.A ransomware—and also shared a download link for NotPetya malware to his social media account.
After searching Neverov's home, the authorities seized his computers and other equipment, which were later analysed by the officers from the Ukrainian cyber-crime department, who discovered some files containing the malicious software.
However, the police confirmed that Neverov was neither the actual author of the NotPetya virus, nor he was behind the massive ransomware attack that crippled many businesses and banks in this summer.
The authorities charged Neverov of spreading a copy of NotPetya virus via his social media account that eventually infected at least 400 computers in Ukraine, and also believe that he had helped tax evaders — directly or indirectly.
Companies Intentionally Infected Their Computers to Avoid Paying Taxes & Fines
If you are not aware, 30th June was the last date in Ukraine for filing tax returns and unfortunately, during the same time NotPetya outcry began that encrypted sensitive files and documents for several businesses and organisations across the country.
Since firms that were infected by the virus were unable to submit tax reports on time and liable for paying huge fines for late submissions, the head of the parliamentary committee on tax and customs, Nina Yuzhanina, gave affected taxpayers some relief (through a statement on his Facebook profile) by extending the last date to 31st December, 2017.
Police believe the malware sample distributed by Neverov is being used by some businesses to deliberately infect their systems to avoid paying taxes on time as well as late tax return penalty.
Is Neverov a Hacker or Computer Enthusiast?
However, the story has another angle that indicates charges on Neverov are baseless.
As I mentioned, Neverov is a video-blogger with 11,000 followers on YouTube, who loves to play with computers and publish review videos on computer hardware and gadgets for informational purposes.
Neverov never tried to hide his identity, and even in some of his videos, he revealed his face and the exact GPS location to his house in Nikopol, which suggests that he had nothing to hide, neither his intentions were wrong.
When NotPetya outcry hit his country, Neverov got curious about the ransomware and started studying about the malware to understand how it works and to find a way to recover infected files without paying ransom to the attackers.
To get started, he downloaded a sample of NotPetya ransomware from the Internet and tested it on his computer, just like other malware analysts do.
In fact, while recording a video of the NotPetya infection to demonstrate its impact on a targeted computer, he failed two times in infecting his own computer.
When succeeded in the third attempt, Neverov uploaded the copy of NotPetya malware on file hosting website and shared the link on his social media account just for the informational purpose, saying "use at your own risk."
Moreover, it is important to note that Neverov would not be gaining any profit by distributing the ransomware because of NotPetya has been designed to blackmail victims into paying ransom amount to a specific Bitcoin address that belongs to the original attackers only.
If Convicted, Neverov Could Face 3 Years In Prison
Neverov, the computer enthusiast, has now been charged under article 361 (part 1) of the Criminal Code of Ukraine, which says:
"Unauthorized interference with the work of electronic computing machines (computers), automated systems, computer networks or telecommunication networks, ...which led to the leak, loss, fake, blocking information, distortion of the information processing or violation the established order it's routing."
Although this sanction provides maximum punishment of up to two years in prison, Neverov has been threatened to face up to three years in jail, according to the official comments from the law enforcement authorities.
The case seems somewhat similar to the one currently being faced by Marcus Hutchins, also known as MalwareTech, who gained famed for stopping the WannaCry ransomware.
Hutchins was arrested by the FBI while he was travelling to his home after attending Def Con event in the United States and has been charged with creating and distributing a banking malware.
Since Hutchins is a malware researcher, many infosec community members believe possibly a proof-of-concept code written and published by him publicly was re-used by the criminals to create the banking malware, which mistakenly framed him as the criminal mastermind.
Hutchins is set to face a hearing in the US district court on 14 August, so we still have to wait for more information about his case.