
Inside Egregor
Ransomware Articles - H 2020 1 2 3 4 5 6 7 8 9 10 11 Ransomware List - H 2021 2020 2019 2018 1 Ransomware blog Ransomware blog
Financial Impact of Ransomware Attack on Sopra Steria Could Reach €50 Million
27.11.20 Ransomware Securityweek
European IT services provider Sopra Steria estimates that a recent ransomware attack will have a financial impact ranging between €40 million ($48 million) and €50 million ($60 million).
Sopra Steria revealed one month ago that some of its systems were infected with a new variant of the Ryuk ransomware, which is believed to have been used by Russian cybercriminals.
The intrusion was detected on October 20, but the company’s investigation revealed that the attackers had only been in its systems for a few days before the breach was discovered, which is not surprising for attacks involving Ryuk.
In a statement released this week, the company said its IT and cybersecurity teams moved quickly to contain the attack and claimed that the malware only hit a “limited part” of its infrastructure.
“The secure remediation plan launched on 26 October is nearly complete. Access has progressively been restored to workstations, R&D and production servers, and in-house tools and applications. Customer connections have also been gradually restored,” Sopra Steria said.
Nevertheless, the company estimates that remediation efforts and the unavailability of various systems due to the incident will cost it up to €50 million ($60 million), of which €30 million ($36 million) should be covered by insurance. The firm says sales activity for the fourth quarter should not be significantly impacted by the ransomware attack.
“After including the items mentioned above, for financial year 2020 Sopra Steria expects to see negative organic revenue growth of between 4.5% and 5.0% (previously ‘between -2% and -4%’), an operating margin on business activity of around 6.5% (previously ‘between 6% and 7%’), and free cash flow of between €50 million and €100 million (previously ‘between €80m and €120m’),” Sopra Steria explained.
Sopra Steria offers a wide range of IT services, including consulting, technology, software, system integration, business process, infrastructure management and cybersecurity. The company says it has 46,000 employees across 25 countries.
Canon Says Data Stolen in August 2020 Ransomware Attack
27.11.20 Ransomware Securityweek
Canon, ransomware, Maze, data stolenImaging and optical giant Canon this week revealed that data was stolen in a ransomware attack it fell victim to in early August 2020.
The incident, discovered on August 4, resulted in threat actors having access to Canon’s network between July 20 and August 6.
Leveraging this access, the adversary obtained specific files “that contained information about current and former employees from 2005 to 2020 and their beneficiaries and dependents,” Canon U.S.A. reveals.
Compromised information, the company says, includes names, along with data such as date of birth, Social Security number, driver's license number, financial account number, government-issued identification number, and electronic signature.
“We wanted to notify our current and former employees and their beneficiaries and dependents of this incident and to assure them that we take it seriously,” Canon notes.
The ransomware family used in this attack was likely Maze, revealed a leaked ransom note that BleepingComputer got hold of in August.
The cybercriminals behind Maze are known for stealing victims’ data in an effort to convince them to pay the ransom, and they even put up a site where data of victims unwilling to pay is made public.
The attack targeting Canon was disclosed to employees within days, a screenshot of an internal message showed. In that message, the company noted that the ransomware attack was unrelated to an outage that affected a portion of long-term storage on image.canon, a cloud service for storing photos and videos.
At the time, Canon said that, while some files stored in the affected long-term storage were lost, no data leak occurred. In an update published on August 7, the company said that no unauthorized access to image.canon was identified.
The Maze ransomware’s operators announced in early November that they closed shop. The group, which claimed to have engaged in ransomware attacks to prove organizations’ poor security practices, is believed to have made millions from its illegal operations.
Danish news agency Ritzau hit by ransomware, but did not pay the ransom
27.11.20 Ransomware Securityaffairs
Ritzau, the biggest Danish news agency, was hit by a ransomware attack that brought it offline but refused to pay the ransom.
Ritzau, the biggest Danish news agency, was hit by a ransomware attack that brought it offline. The cyber attack hit a quarter of Ritzau ’s 100 servers that have been damaged. The agency confirmed that it has rejected the ransom demand but did not reveal its amount.
Ritzaus Bureau A/S, or Ritzau for short, is a Danish news agency founded by Erik Ritzau in 1866. It collaborates with three other Scandinavian news agencies to provide Nordic News, an English-language Scandinavian news service.
“Ritzau CEO Lars Vesterloekke couldn’t say how big the ransom demand was because those behind the “professional attack” had left “a file with a message” that the agency didn’t open following instructions from its advisers.” reported the Associated Press.
The news agency has transferred its emergency distribution to clients to six live blogs that provide a better overview.
“If it goes as expected, then we can gradually be back to normal on Thursday,” said Ritzau CEO Lars Vesterloekke Vesterloekke.
The agency launched an investigation into the incident with the help of an external security firm and its insurance company.
At the time of writing the family of ransomware that hit the agency has yet to be revealed, it is also not clear if the threat actors have stolen some data before encrypting the servers.
Ransomware hits US Fertility the largest US fertility network
27.11.20 Ransomware Securityaffairs
US Fertility, the largest network of fertility centers in the U.S., discloses a ransomware attack that took place in September 2020.
US Fertility, the largest network of fertility centers in the U.S., revealed that a ransomware attack hit its systems in September 2020.
The US Fertility (USF) network is comprised of 55 locations across 10 states that completed almost 25,000 IVF cycles in 2018 through its clinics with 130,000 babies have been born.
“On September 14, 2020, USF experienced an IT security event [..] that involved the inaccessibility of certain computer systems on our network as a result of a malware infection,” reads the Notice of Data Security Incident provided by the company.
“Through our immediate investigation and response, we determined that data on a number of servers and workstations connected to our domain had been encrypted by ransomware.”
The company immediately launched an investigation into the incident with the help of third-party forensic experts and notified the law enforcement agencies.
Once identified the impacted systems, the US Fertility took down them and completed the recovery operations on September 20.
Unfortunately, the investigation revealed that threat actors were able to steal a limited number of files containing various types of information for each impacted individual including names, addresses, dates of birth, MPI numbers, and for some individuals Social Security numbers.
The company confirmed that has been working with a specialized team of third-party data auditors to accurately identify the impacted individuals.
“The forensic investigation is now concluded and confirmed that the unauthorized actor acquired a limited number of files during the period of unauthorized access, which occurred between August 12, 2020, and September 14, 2020, when the ransomware was executed,” continues the breach notification.
USF has established a dedicated call center (855-914-4699) to provide information and support to its customers.
“We take this incident very seriously and are committed to protecting the security and confidentiality of health information we gather in providing services to individuals,” said Mark Segal, Chief Executive Officer of USF.
FBI issued an alert on Ragnar Locker ransomware activity
24.11.20 Ransomware Securityaffairs
The U.S. FBI is warning private industry partners of a surge in Ragnar Locker ransomware activity following a confirmed attack from April 2020.
The U.S. Federal Bureau of Investigation (FBI) issued a flash alert (MU-000140-MW) to warn private industry partners of an increase of the Ragnar Locker ransomware activity following a confirmed attack from April 2020.
The MU-000140-MW flash alert includes indicators of compromise to detect associated with this ransomware gang.
“The FBI first observed Ragnar Locker1ransomwarein April 2020, when unknown actors used it to encrypt a large corporation’s files for an approximately $11 million ransom and threatened to release 10 TB of sensitive company data,” reads the flash alert.
“Since then, Ragnar Locker has been deployed against an increasing list of victims, including cloud service providers, communication, construction, travel, and enterprise software companies. The FBI is providing details of Ragnar Locker ransomware to assist with understanding the code and identifying the activity.”
Threat actors behind the Ragnar Locker ransomware actors first obtain access to a target’s network, then perform reconnaissance to locate network resources and backups in the attempt to exfiltrate sensitive data. Once completed the reconnaissance phase, the operators manually deploy the
ransomware and start encrypting the victim’s data.
Operators behind the Ragnar Locker ransomware are frequently changing obfuscation techniques to avoid detection, they also used VMProtect, UPX, and custom packing algorithms for their malicious code.
Operators also use to deploy the Ragnar Locker within a custom Windows XP virtual machine on a target’s site to avoid detection.
Ragnar Locker doesn’t encrypt the system is it is found to be “Azerbaijani,” “Armenian,” “Belorussian,” “Kazakh,” “Kyrgyz,” “Moldavian,” “Tajik,” “Russian,” “Turkmen,” “Uzbek,” “Ukrainian,” or “Georgian.”
The report contains other technical details about the ransomware and provides the following recommendations to mitigate the threat:
Recommended Mitigations
Back-up critical data offline.
Ensure copies of critical data are in the cloud or on an external hard drive or storage device. This information should not be accessible from the compromised network.
Secure your back-ups and ensure data is not accessible for modification or deletion from the system where the data resides.
Install and regularly update anti-virus or anti-malware software on all hosts.
Only use secure networks and avoid using public Wi-Fi networks.
Consider installing and using a VPN.
Use multi-factor authentication with strong passwords.
Keep computers, devices, and applications patched and up-to-date.
QakBot Big Game Hunting continues: the operators drop ProLock ransomware for Egregor
20.11.20 Ransomware Securityweek
The QakBot banking trojan has dropped the ProLock ransomware, they are now opting for the Egregor ransomware in their operations.
Group-IB, a global threat hunting and intelligence company headquartered in Singapore, has discovered that QakBot (aka Qbot) operators have abandoned ProLock for Egregor ransomware. Egregor has been actively distributed since September 2020 and has so far hit at least 69 big companies in 16 countries. The biggest ransom demand detected by Group-IB team has been at $4 million worth of BTC.
During recent incident response engagements Group-IB DFIR (Digital Forensics and Incident Response) team has noticed a significant change in QakBot operators’ tactics, the gang started to deploy a new Egregor ransomware family. This ransomware strain emerged in September 2020, but the threat actors behind already managed to lock quite big companies, such as game developers Crytek, booksellers Barnes & Noble, and most recently a retail giant Cencosud from Chile.
ProLock = Egregor
The analysis of attacks where Egregor has been deployed revealed that the TTPs used by the threat actors are almost identical to the ones used by the ProLock operators, whose campaigns have been described in Group-IB blog post in May. First, the initial access is always gained via QakBot delivered through malicious Microsoft Excel documents impersonating DocuSign-encrypted spreadsheets. Moreover, Egregor operators have been using Rclone for data exfiltration – same as with ProLock. Same tools and naming convention have been used as well, for example md.exe, rdp.bat, svchost.exe. Hence, all of the above considered, Group-IB experts assess it’s very likely that QakBot operators have switched from ProLock to Egregor ransomware.
Geography and victims
The gang behind Egregor followed in Maze’s footsteps, who called it quits not long ago. Egregor operators leverage the intimidation tactics, they threaten to release sensitive info on the leak site they operate instead of just encrypting compromised networks. The biggest ransom demand registered by the Group-IB team so far was at $4 million worth of BTC.
In less than 3 months Egregor operators have managed to successfully hit 69 companies around the world with 32 targets in the US, 7 victims in France and Italy each, 6 in Germany, and 4 in the UK. Other victims happened to be from the APAC, the Middle East, and Latin America. Egregor’s favorite sectors are Manufacturing (28.9% of victims) and Retail (14.5%). 
Inside Egregor
While TTP’s of Egregor operators are almost identical to that of ProLock, the analysis of Egregor ransomware sample obtained during a recent incident response engagement revealed that the executable code of Egregor is very similar to Sekhmet. The two strains share some core features, use similar obfuscation technique. Egregor source code bears similarities with Maze ransomware as well. The decryption of the final payload is based on the command-line provided password, so it is impossible to analyze Egregor if you don’t have command-line arguments provided by the attacker. Egregor operators use the combination of ChaCha8 stream cipher and RSA-2048 for file encryption.
The use of CobaltStike and QakBot is to watch when hunting for Egregor. More threat hunting and detection tips from Group-IB DFIR team as well as a detailed technical analysis of Egregor operations are available in Group-IB’s blog.
“Tactics, techniques and procedures observed are very similar to those seen in the past Qakbot’s Big Game Hunting operations,” comments Oleg Skulkin, senior DFIR analyst at Group-IB. At the same time, we see that these methods are still very effective and allow threat actors to compromise quite big companies with high success rate. It’s important to note, that the fact many Maze partners started to move to Egregor will most likely result in the shift in TTPs, so defenders should focus on known methods associated with Maze affiliates”.
Would you like to learn more about ransomware operations and TTPs in 2020, register now for Group-IB’s signature Threat Hunting and Intelligence conference, CyberCrimeCon. The eighth edition of the iconic event, held on November 25-26, will traditionally unite cybersecurity professionals from the financial and tech sectors, retail and industrial giants, as well as law enforcement agencies and will, in addition to two major streams — analytical and technological — contain a Threat Hunting Game. The conference’s speaker lineup includes representatives of Europol EC3, leading banks, FMCG companies, and independent researchers.
REvil ransomware demands 500K ransom to Managed.com hosting provider
19.11.20 Ransomware Securityaffairs
Managed web hosting provider Managed.com was hit with REvil ransomware that forced it to take down their servers and web hosting systems.
Managed web hosting provider Managed.com was hit by a REvil ransomware attack over the weekend that took their servers and web hosting systems offline.
At the time of writing this post, Managed.com hosting systems continue to be unavailable.
Early this week, the provider disclosed the incident and announced the launch of an investigation.
According to ZDNet, Managed.com initially said that the incident only impacted a limited number of customer sites, but a few hours later it was forced to take down its entire web hosting infrastructure.
Impacted systems included WordPress and DotNetNuke managed hosting platforms, online databases, email servers, DNS servers, RDP access points, and FTP servers.
The company reported the incident to law enforcement and started working to restore its infrastructure.
The company only disclosed the ransomware attack on Tuesday and explained that it was forced to shut down its infrastructure to protect the integrity of its customer’s data.
“November 17, 2020 – On Nov.16, the Managed.com environment was attacked by a coordinated ransomware campaign. To ensure the integrity of our customers’ data, the limited number of impacted sites were immediately taken offline. Upon further investigation and out of an abundance of caution, we took down our entire system to ensure further customer sites were not compromised. Our Technology and Information Security teams are working diligently to eliminate the threat and restore our customers to full capacity.” reads an update published by the company. “Our first priority is the safety and security of your data. We are working directly with law enforcement agencies to identify the entities involved in this attack. As more information is available, we will communicate directly with you,”
BleepingComputer, citing multiple sources, states that Managed.com was hit by the popular REvil ransomware gang that is demanding a $500,000 ransom in Monero to receive a decryptor.

Source Bleeping Computer
The REvil ransomware gang is known to use a double extortion model threatining to leak online files stolen from the victim, but it is not clear if they stole unencrypted files before encrypting devices of the provider.
REvil gang is one of the major ransomware operations, it has been active since April 2019, its operators claim to earn over $100 million a year through its RaaS service.
In a recent interview with the public-facing representative of REvil, the ransomware operation claims to earn over $100 million a year in extortion payments.
The list of the victims of the group is long and includes Travelex, Kenneth Cole, SeaChange, Brown-Forman, BancoEstado, Grubman Shire Meiselas & Sacks (GSMLaw), Valley Health Systems, Telecom Argentina, and Lion.
FireEye Predicts Ransomware Will Evolve and Expand in 2021
18.11.20 Ransomware Securityweek
FireEye Mandiant has delivered its cyber landscape predictions for the coming year, including growing and affiliate-supported espionage, increased targeting of OT by ransomware, and continued targeting of healthcare.
The COVID-19 pandemic and related cyber activity has dominated 2020. This will continue into 2021 (PDF), but the techniques learned and used through this year will expand beyond COVID into the future. Cyber espionage is a good example. There have been many recent stories about espionage attacks targeting COVID vaccine research-- but FireEye Mandiant sees cyber espionage evolving and increasing across the globe.
"A lot of espionage in 2021 will be similar to what we are already seeing," Jaimie Collier, cyber threat intelligence consultant at FireEye Mandiant, told SecurityWeek. "The Big Four (Russia, China, Iran and North Korea) are not going to fundamentally change what they are doing. But China's threat apparatus has grown with regard to espionage, and we expect to see more espionage activity from China."
Collier has also seen an uptick in activity from Vietnam and South Asia in general. "We're beginning to see more activity outside of the Big Four. Some of the countries that are just now getting into the business of cyber espionage will turn to third party intruder vendors for tools and capability enhancement. We've already seen that in the Dark Basin report earlier in the year."
The reverse of espionage -- which is the seeking of secrets -- is the information operation that seeks to sow falsehoods. "While it used to be just Russia targeting the U.S., the number of parties involved is growing rapidly. Iran is now involved, and there are pro-China and pro-Cuba regional networks in Argentina. All this space is getting more complex -- and a wider nexus of groups is trying to mimic legitimate media in their campaigns. We suspect that there are contractors, PR and marketing firms and other non-state actors now involved in these information operations."
Collier expects to see ransomware continue to evolve and expand. "Ransomware is transitioning from a bit of a nuisance to something that is a real strategic concern," he explained. "We're seeing the affiliate models expand, where different threat actors combine leading to a huge amount of specialization within the overall process. Some of the actors develop the ransomware, but work with others that specialize in gaining the initial access, and post-compromise exfiltration; all leading to a broader criminal ecosystem."
Part of this shows in the growing practice of double extortion -- using stolen data as an extra incentive for payment, or selling or exposing it if the victim still refuses to pay. But FireEye Mandiant also sees an increasing pivot towards ransomware targeting operational technology. "That's something we're watching keenly," Collier told SecurityWeek, "because of the potential for real world harm."
He believes the political profile around ransomware is also changing. In September 2020, the U.S. Department of the Treasury made it clear that paying a ransom could be considered contrary to the interests of national security. "The Australian Signals Directorate," he added, "has stated publicly that they will be proactive in going after financial/healthcare criminals. It's going to be interesting to see how other governments react, and see if other intelligence agencies start to go after financial criminals more than they have in the past."
But the pandemic and effects of the pandemic will continue to affect the cyber landscape through 2021. Surprisingly, FireEye Mandiant has not seen as much directly COVID-related phishing as has been reported elsewhere in 2020. "I think back in March," said Collier, "at the height of the first wave, COVID and Coronavirus was only featuring in around 2% of phishing emails." Although he believes it may have increased a little since then, the majority of phishing emails are still using traditional lures such as fake password resets and other lures that have been used for years. "For social engineering in general," he added, "it's important to look at Coronavirus as just another opportunity for the criminals."
The implication from this observation is that the continued increase in phishing cannot be explained by the pandemic, and that phishing is likely to continue its increase even after the pandemic eases. Spear-phishing will remain the most popular entry route for compromises, but FireEye Mandiant also believes that a wider number of nation-state actors will focus on intrusion techniques that don't require victim interaction -- such as exploiting web facing applications and password spraying.
A big problem through 2021 will, however, be the rapid and enforced move to increased remote working, and organizations' transition to a more expansive ecosystem. "As companies adopt remote work," he continued, "there is a push towards more niche areas for security -- from virtual conferencing to productivity platforms. We're introducing a lot of new systems and services into our organizations. A lot of these will be outsourced, working with third parties -- so there's a much more expansive ecosystem."
Much of this expansion overlaps with cloud security, with different providers for different services. These wider ecosystems were already evolving beyond the network perimeter. "One thing with cloud that we will be watching," said Collier, "is the issue around responsibility and the dynamic relationship between users and providers. Who is responsible for security?" Organizations will need to make the appropriate decisions in taking ownership of their data in the cloud, he warns, where inadvertent exposure is a growing problem.
Traditionally, security firms have been interested in adversary behavior -- but user behavior is the growing problem now that is likely to worsen with increased cloud usage. "One of the issues that will play out in 2021," he said, "is whether adversaries can take advantage of this new ecosystem faster than security teams can learn how to defend it." He worries that while security teams have been involved with company-wide cloud system usage, there is now a new reality. "A lot of different departments are going in different directions. You potentially have a marketing team experimenting with virtual conferencing platforms that may not automatically be perceived as part of the security team's purview. But if someone in marketing sets up a new virtual conference platform or new social media manager, is that going through the right channels -- because a lot of those areas have quite serious security issues. If you've got a corporate Twitter account with hundreds of thousands of followers, any compromise could lead to huge reputational damage. So, you have parts of the network that need to be secured, but are being run out of areas that are not usually seen as traditional security areas. Managing these areas in the remote world is the big question mark at the moment."
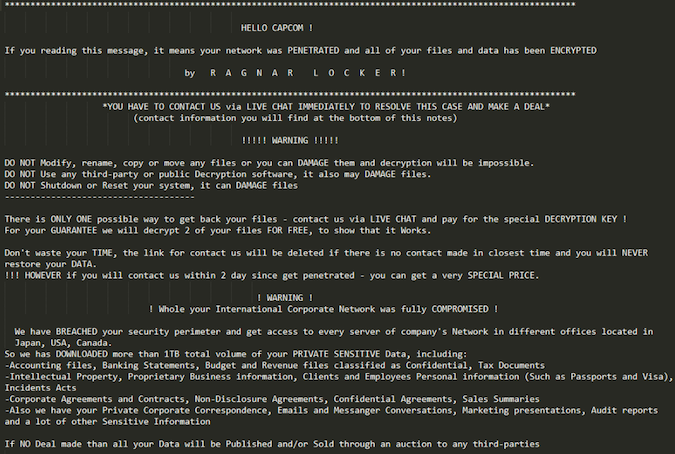
Capcom Confirms Hackers Stole Data in Recent Attack
17.11.20 Ransomware Securityweek
Japanese video game giant Capcom this week confirmed that a large amount of data was stolen from its systems during a ransomware attack several weeks ago.
Best known for multi-million-selling game franchises such as Ace Attorney, Devil May Cry, Resident Evil, and Street Fighter, Capcom has subsidiaries in Asia, Europe, and North America.
In early November, Capcom announced that it was forced to suspend some operations due to unauthorized access to its internal network and that email and file servers were affected.
The Ragnar Locker ransomware gang, which was responsible for the attack, claimed at the time that it managed to steal vast troves of data from Capcom, including bank statements, financial documents, intellectual property, personal information of both customers and employees, emails and private chats, and other data.
On Monday, Capcom revealed that its investigation into the incident has indeed confirmed that data was stolen during the ransomware attack, including personal information of current and former employees, sales reports, and financial information.
The stolen data, the company says, includes names and signatures, addresses, passport information, and human resources information.
According to the game maker, a large amount of other information might have been stolen as well, including help desk information (Japan), store member and esports operations website member information (North America), a list of shareholders, and former employee and applicant data.
The potentially affected information includes names, addresses, emails, phone numbers, photos, birthdates, shareholder numbers, and amount of shareholdings. More than 350,000 people could be affected, Capcom revealed.
Additionally, the game maker says confidential corporate data — including partner information, sales data and documents, development documents, and more — might have been compromised as well.
“None of the at-risk data contains credit card information. All online transactions etc. are handled by a third-party service provider, and as such Capcom does not maintain any such information internally,” the company says.
Capcom also noted that it could not determine the exact number of impacted people or the amount of stolen data, so it decided to list the “maximum number of items it has determined to potentially have been affected at the present time.”
While the investigation continues, the video game giant is in the process of informing affected people of the incident.
The company also confirmed that the attack, which was identified on November 2, was indeed the work of the Ragnar Locker gang, and revealed that some of the actions it took following the discovery include shutting down the infected systems, contacting the authorities, strengthening its security posture, and engaging with a third-party security company to investigate the incident.
“Investigation and analysis, etc., of this incident took additional time due to issues such as the information saved on servers being encrypted and access logs being deleted in the attack,” the company also explains.
Capcom also noted that this was a targeted attack and that the employed ransomware appears to have been specifically tailored to encrypt data on its systems and delete access logs. Additional information will be revealed as the investigation advances.
“While it’s good that no payment information was taken in this breach, the amount of personal data stolen amounts to something worse. A stolen credit card can be stopped and payments refused, but we only get one identity – if the digital version is stolen in a breach, then that is much harder to replace. Capcom needs to contact affected members immediately and should be providing information on the steps they are taking to provide identity protection, as well as what members can do to protect themselves,” Laurence Pitt, Technical Security Lead, Juniper Networks, said in an emailed comment.
Chilean-based retail giant Cencosud hit by Egregor Ransomware
16.11.20 Ransomware Securityaffairs
Chilean-based retail giant Cencosud has suffered a ransomware attack that impacted operations at its stores, Egregor ransomware appears to be involved.
A ransomware attack, allegedly launched by the Egregor ransomware gang, hit the Chilean-based retail giant Cencosud, the incident impacted operations at its stores.
Cencosud the largest retail company in Chile and the third largest listed retail company in Latin America, competing with the Brazilian Companhia Brasileira de Distribuição and the Mexican Walmart de México y Centroamérica as one of the largest retail companies in the region. The company has more than 1045 stores in Latin America (Argentina, Brazil, Chile, Colombia, and Peru) with over 140,000 employees and $15 billion in revenue for 2019. The company’s stores include Easy home goods, Jumbo, Paris, Costanera Center, Santa Isabel, Vea, Disco, Metro, Johnson and Shopping Center.
“The Chilean multinational Cencosud (Centros Comerciales Sudamericanos SA) was hacked by cybercriminals who would have in their possession information from customers of supermarkets such as Disco, Jumbo and Vea and would ask for millions of dollars to return it.” reads the post published by the Argentinian media outlet Clarín.
The incident took place this week, according to local media and Bleeping Computer, customets could not use the ‘Cencosud Card’ credit card or pickup their web purchases at the impated stores due to the reansomware attack.
Clarins website pointed out that Cencosud has its own credit card, this means that threat actors could use the stolen information to make purchases and thus steal money from customers.
BleepingComputer was the first to confirm that the retail giant was hit by Egregor ransomware after it obtained the ransom note.
“After learning of the attack, BleepingComputer obtain the ransom note and can confirm it was conducted by Egregor and targeted the ‘Cencosud’ Windows domain.” reported Bleeping Computer.
Egregor ransomware has been active since September as a ransomware-as-a-service operation, many affiliates of the Maze ransomware operations have chosen it after Maze shut down its activities. Some of the victims of the group are Egregor Crytek, Barnes and Noble, and Ubisoft.
Malware researchers that collaborate with Bleeping Computer first speculated that other malware, such as Egregor and Sekhmet ransomware borrows the code from Maze ransomware.
Local media also reported that printers in multiple retail outlets in Chile and Argentina began printing out ransom notes while the ransomware was encrypting the systems.
“The ransom note does not provide links to proof of stolen data, but Egregor has a history of stealing unencrypted files before deploying their ransomware.” continues Bleeping Computer.
Biotech research firm Miltenyi Biotec hit by Mount Locker ransomware
15.11.20 Ransomware Securityaffairs
Biotech research firm Miltenyi Biotec disclosed a ransomware attack that took place in October and affected its IT infrastructure worldwide.
Biotech research firm Miltenyi Biotec was hit with a ransomware attack that took place in October and affected its IT infrastructure worldwide.
The company announced that it has fully restored systems after the attack, anyway in some countries local employees are still facing problems with mail and telephone systems.
Miltenyi Biotec is a global biotechnology company headquartered in Cologne, Germany, that provides products and services that support scientists, clinical researchers, and physicians across basic research, translational research, and clinical applications. The company offers solutions covering techniques of sample preparation, cell separation, cell sorting, flow cytometry, cell culture, molecular analysis, clinical applications and small animal imaging. Miltenyi Biotec has more than 3,000 employees in 28 countries and more than 17,000 products.
Miltenyi Biotec is providing the above products, including SARS-CoV-2 antigens, to clinicians and researchers who are working on COVID-19 vaccines and treatments.
“During the last two weeks, there have been isolated cases where order processing was impaired by malware in parts of our global IT infrastructure. Rest assured, all necessary measures have now been taken to contain the issue and recover all affected systems. Based on our current knowledge, we have no indication that the malware has been inadvertently distributed to customers or partners.” reads the announcement published by Miltenyi Biotec.
“As of this time, our operational processes have been fully restored. Should you have experienced any delays with your orders, we ask you to be patient for just a little longer, and to get in contact with us in urgent cases. Please accept our apologies for any inconvenience this may have caused you.”
The company is not aware of data leak resulting from the malware infection. Customers should expect order delays caused by the incident that impacted their systems across the last two weeks.
Customers experiencing difficulties can contact the company using a list of contact numbers available here.
Miltenyi Biotec did not disclose the family of malware that infected its systems, anyway, Bleeping Computer speculates the involvement of Mount Locker ransomware.
“Even though Miltenyi Biotec has not disclosed the nature of the malware that caused the operational downtime during the last two weeks, the Mount Locker ransomware gang has claimed the attack earlier this month.” reported Bleeping Computer.
On November 4, 2020, Mount Locker ransomware operators have leaked on their data leak site (‘Mount Locker News & Leaks’) 5% out of the 150 GB of data they have allegedly stolen from the company.
Mount Locker ransomware operators have been active since July 2020 and targeted multiple organizations demanding multi-million dollar ransoms.
To make pressure on the victims, Mount Locker operators also threaten them to contact the media, TV channels, and newspapers if the ransom is not paid.
Ragnar Locker Ransomware Gang Takes Out Facebook Ads in Key New Tactic
12.11.20 Ransomware Threatpost
Following a Nov. 3 ransomware attack against Campari, Ragnar Locker group took out public Facebook ads threatening to release stolen data.
The Ragnar Locker ransomware group has decided to ratchet up the pressure on its latest high-profile victim, Italian liquor conglomerate Campari, by taking out Facebook ads threatening to release the 2TB of sensitive data it stole in a Nov. 3 attack – unless a $15 million ransom is paid in Bitcoin.
Campari Group, which is behind a bevy of global brands including SKYY, Grand Marnier and Wild Turkey, has acknowledged the ransomware attack.
Double-Extortion-Plus
This is a new spin on the double-extortion ransomware tactic, where criminals not only lock organizations out of their systems, but also threaten to release sensitive stolen data to the public if their demands aren’t met. The Facebook ads pile on an entirely new layer of extortion pressure, letting the public know that Campari data is compromised and that the liquor giant is refusing to pay to keep it secure.
The ads, first spotted by researcher Brian Krebs on Nov. 9, were to-the-point and entitled, “Security Breach of Campari Group Network.” Ragnar Locker bought the ads using a hacked Facebook account, which Krebs said were subsequently shown to more than 7,000 users before Facebook caught on and pulled them down.
“Cybercrime groups have no shame in their extortion attempts,” Chris Clements, vice president of solutions architecture with Cerberus Sentinel said. “They will use any and all options available to them to extract whatever money they can from their victims. The use of compromised Facebook user accounts to buy ad campaigns to further harass their victims is novel, but not at all out-of-character.”
The ‘Wall of Shame’ Moves to Facebook
First observed in 2019, the Ragnar Locker group started using the threat of making stolen data public last April, when it launched a Wall of Shame site, security researcher who uses the handle Pancak3 recently explained in a DM exchange with Threatpost.
He added that the executables for both the Campari ransomware attack and a recent high-profile breach of gaming giant Capcom were signed by the same cert, linking both to the Ragnar Locker group. Pancak3 added that he thinks it shows that the Ragnar Locker ransomware operators are getting “more confident in their intrusion methods.”
Now, with the development of public advertising to increase pressure for victims to pay, it would appear the group is not even trying to hide their malicious activities any longer. In fact, they’re publicizing them.
In added criminal twist, everyday Facebook advertisers are now vulnerable to Ragnar Locker attacks.
“What this does show is that every online user is vulnerable to compromise and false financial charges should their social-media accounts be compromised and used to purchase ad campaigns on the corresponding platforms,” Clements said. “Users should ensure that two-factor authentication is enabled on all of their online accounts and that they do not reuse the same password across different websites or mobile applications. ”
Facebook has not responded to Threatpost’s request for comment.
Backing up bad actions with public advertising is likely to be emulated. Ragnar Locker appears to be somewhat of an influential group within the ransomware community. In Sept. researchers observed the Maze group picking up the Ragnar Locker trick of distributing ransomware with virtual machines, an approach experts at Sophos Managed Threat Response called “radical.”
Still, experts say, keeping individual accounts secure goes a long way to mitigating the threat that groups like these have on the public — and 2FA is a good place to start despite any inconvenience that managing multiple unique passwords can present.
“Password-manager applications can help alleviate the burden of remembering unique passwords across multiple sites or applications but carry their own risk should they become compromised.” Clements advised. “Still, the benefits of using a password manager usually greatly outweigh the potential downsides.”
Ragnar Locker Ransomware Gang Takes Out Facebook Ads in Key New Tactic
12.11.20 Ransomware Threatpost
Following a Nov. 3 ransomware attack against Campari, Ragnar Locker group took out public Facebook ads threatening to release stolen data.
The Ragnar Locker ransomware group has decided to ratchet up the pressure on its latest high-profile victim, Italian liquor conglomerate Campari, by taking out Facebook ads threatening to release the 2TB of sensitive data it stole in a Nov. 3 attack – unless a $15 million ransom is paid in Bitcoin.
Campari Group, which is behind a bevy of global brands including SKYY, Grand Marnier and Wild Turkey, has acknowledged the ransomware attack.
Double-Extortion-Plus
This is a new spin on the double-extortion ransomware tactic, where criminals not only lock organizations out of their systems, but also threaten to release sensitive stolen data to the public if their demands aren’t met. The Facebook ads pile on an entirely new layer of extortion pressure, letting the public know that Campari data is compromised and that the liquor giant is refusing to pay to keep it secure.
The ads, first spotted by researcher Brian Krebs on Nov. 9, were to-the-point and entitled, “Security Breach of Campari Group Network.” Ragnar Locker bought the ads using a hacked Facebook account, which Krebs said were subsequently shown to more than 7,000 users before Facebook caught on and pulled them down.
“Cybercrime groups have no shame in their extortion attempts,” Chris Clements, vice president of solutions architecture with Cerberus Sentinel said. “They will use any and all options available to them to extract whatever money they can from their victims. The use of compromised Facebook user accounts to buy ad campaigns to further harass their victims is novel, but not at all out-of-character.”
The ‘Wall of Shame’ Moves to Facebook
First observed in 2019, the Ragnar Locker group started using the threat of making stolen data public last April, when it launched a Wall of Shame site, security researcher who uses the handle Pancak3 recently explained in a DM exchange with Threatpost.
He added that the executables for both the Campari ransomware attack and a recent high-profile breach of gaming giant Capcom were signed by the same cert, linking both to the Ragnar Locker group. Pancak3 added that he thinks it shows that the Ragnar Locker ransomware operators are getting “more confident in their intrusion methods.”
Now, with the development of public advertising to increase pressure for victims to pay, it would appear the group is not even trying to hide their malicious activities any longer. In fact, they’re publicizing them.
In added criminal twist, everyday Facebook advertisers are now vulnerable to Ragnar Locker attacks.
“What this does show is that every online user is vulnerable to compromise and false financial charges should their social-media accounts be compromised and used to purchase ad campaigns on the corresponding platforms,” Clements said. “Users should ensure that two-factor authentication is enabled on all of their online accounts and that they do not reuse the same password across different websites or mobile applications. ”
Facebook has not responded to Threatpost’s request for comment.
Backing up bad actions with public advertising is likely to be emulated. Ragnar Locker appears to be somewhat of an influential group within the ransomware community. In Sept. researchers observed the Maze group picking up the Ragnar Locker trick of distributing ransomware with virtual machines, an approach experts at Sophos Managed Threat Response called “radical.”
Still, experts say, keeping individual accounts secure goes a long way to mitigating the threat that groups like these have on the public — and 2FA is a good place to start despite any inconvenience that managing multiple unique passwords can present.
“Password-manager applications can help alleviate the burden of remembering unique passwords across multiple sites or applications but carry their own risk should they become compromised.” Clements advised. “Still, the benefits of using a password manager usually greatly outweigh the potential downsides.”
Ragnar Locker ransomware gang advertises Campari hack on Facebook
12.11.20 Ransomware Securityaffairs
Ragnar Locker Ransomware operators have started to run Facebook advertisements to force their victims into paying the ransom.
In November 2019, ransomware operators have started adopting a new double-extortion strategy first used by the Maze gang that sees threat actors also stealing unencrypted files before encrypting infected systems. Then the attackers threaten to release the stolen files if a ransom is not paid.
Ransomware operators are adopting multiple tricks to make pressure on the victims, such as publishing post press releases about their attacks.
Ragnar Locker Ransomware operators are improving their extortion technique and started running Facebook advertisements to make pressure on their victims and force them to pay the ransom.
Ragnar Locker gangs started hacking into a Facebook advertiser’s account and creating advertisements their hack, this has already happened with the recent attack on the Italian liquor company Campari Group.
Ragnar Locker ransomware gang breached the Campari Group’s network last week and claims to have stolen 2 TB of unencrypted files before encrypting the infected systems. The threat actors demanded a $15 million ransom to provide a decryptor to recover the files.

“Now, one crime group has started using hacked Facebook accounts to run ads publicly pressuring their ransomware victims into paying up.” states the popular investigator Brian Krebs that first reported the news about the new extortion scheme. “The ad was designed to turn the screws to the Italian beverage vendor Campari Group, which acknowledged on Nov. 3 that its computer systems had been sidelined by a malware attack.”
The advertising campaign has begun on the evening of Monday, Nov. 9, on Facebook.

This Facebook advertisement campaign run by the Ragnar ransomware Team was titled “Security breach of Campari Group network,” it warned the victims of further sensitive data would be released.
The owner of the account hacked by the ransomware gang told Brian Krebs that the advertisement was shown to over 7,000 Facebook users before Facebook detected it as a fraudulent campaign.
Chris Hodson told Krebs that the hacked Facebook account belongs to his deejay activity named Hodson Event Entertainment, the attackers had budgeted $500 for this campaign. Hodson said that the fraudulent advertisement was shown to 7,150 Facebook users before Facebook blocked it and generated 770 clicks.
“
“I thought I had two-step verification turned on for all my accounts, but now it looks like the only one I didn’t have it set for was Facebook,” Hodson said.
Hodson said that Facebook billed him $35 for the first part of the campaign, the company, but the social network giant detected the ads as fraudulent just before his account could be billed another $159 for the campaign.
Facebook said the company is still investigating the incident.
The new extortion tactic demonstrates the continuous evolution of the ransomware extortion model, it is easy to prodict further sophisticated schema in the future.
Targeted ransomware: it’s not just about encrypting your data!
11.11.20 Ransomware Securelist
Part 1 - “Old and New Friends”
When we talk about ransomware, we need to draw a line between what it used to be and what it currently is. Why? Because nowadays ransomware is not just about encrypting data – it’s primarily about data exfiltration. After that, it’s about data encryption and leaving convincing proof that the attacker was in the network, and finally, it’s extortion. And again, it’s not about the data loss itself but about publishing stolen data on the internet. Let’s call it “Ransomware 2.0”.
Why is it so important to state this? Because many organizations still believe that it’s all about malware, and if your anti-malware protection is good enough, you’ll be OK. As long as people think this way, the ransomware threat actors will continue to succeed again and again.
In most cases, the initial vector of attack is exploiting some already known vulnerabilities in commercial VPN software. Other cases involve abusing RDP-enabled machines exposed to the internet. Then there’s the exploitation of the vulnerable router firmware. As you can see, it’s not necessarily about malware but also bad practices, a lack of patching cycles, and general security procedures.
Sometimes ransomware threat actors may rely on traditional malware like botnet implants previously dropped by other cybercriminal groups. And finally, if we recall the Tesla story, the attempt to infect that factory was through someone working at the company. That means physical human access is also a vector. It is complex.
In all cases, the original entry point is to start network reconnaissance, then lateral movement, then data exfiltration. Once it is done, it finally comes to the “coup de grace” – the ransomware. By the time ransomware is deployed, the anti-malware product might be already deleted or disabled by the threat actor because they already had full control over the domain network and could operate as legitimate administrators. So it is about a full red team operation that relies on different hacking techniques, including those to disable anti-malware solutions mostly through legitimate tools and misc scripts. That way, the threat actor doesn’t bother if the ransomware itself will be detected or not.
Different ransomware groups use different TTPs and different encryption techniques. Today we want to talk about two of them: Ragnar Locker and Egregor – a veteran and a newbie. Both singular and distant at the same time.
Ragnar Locker
Early variants of this malware were discovered in 2019; however, Ragnar Locker gained notoriety in the first half of 2020 when it started to attack large organizations.
Ragnar Locker is highly targeted, to the extent that each individual sample is specifically tailored for the organization the actors are attacking. The group behind it loves to abuse RDP, while their preferred payment method is bitcoins.
This group owns three .onion domains available on Tor and one Surface Web domain registered on June 16, 2020.
If the victims refuse to pay, their stolen data is published in a so-called Wall of Shame section.
Screenshot of the Wall of Shame where stolen data is exposed
Curiously, this group is positioning itself as a bug bounty hunting group. They claim the payment is their bounty for discovering vulnerabilities that were exploited and to provide decryption for the files and OpSec training for the victim; and, finally, for not publishing the stolen data. Of course, if the victim refuses to pay, the data goes public. Besides that, if the victim chats with the Ragnar Locker threat actor and fails to pay, then the chat is exposed along with the stolen data.
In July 2020, Ragnar Locker made a public announcement that they had joined so-called “Maze Cartel” distraction concept. It means to say that the groups cooperated, exchanging information stolen from victims and publishing it on their websites.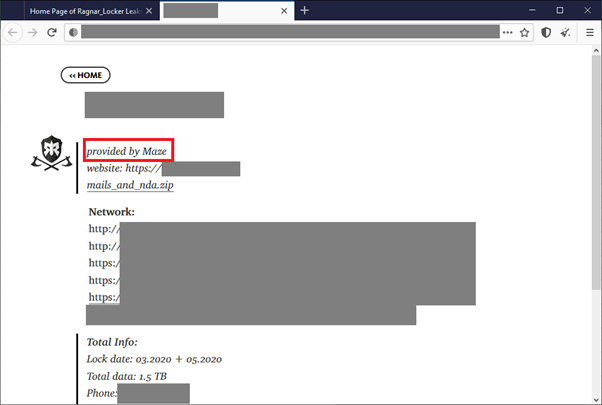
Example of a victim allegedly provided by Maze and published on the Ragnar Locker Wall of Shame page
You can read more about Maze Ransomware here.
Based on the list of victims who refused to pay, the main target of Ragnar Locker are US based companies, while the type of industry varies.
Geography of Ragnar Locker victims (download)
Ragnar Locker victims by industry (download)
Technical description
For our analysis we chose a recently encountered sample of the malware: 1195d0d18be9362fb8dd9e1738404c9d
When started, Ragnar Locker checks the system locale of the machine it is executing on. If determines that it is the locale of one of the countries listed in the screenshot below, it will cease operation and exit without doing anything else.
For countries not on the above list, it will proceed to stop services with names containing any of the substrings hardcoded in the malware sample and obfuscated by RC4:
Afterwards, Rangar Locker will terminate running processes according to another substring list contained inside the Trojan body:
Finally, when all the preparation is done, the Trojan will search for available drives and encrypt the victim’s files.
For file encryption RagnarLocker uses a custom stream cipher based on the Salsa20 cipher. Instead of the standard initialization ‘magic’ constants sigma = “expand 32-byte k” and tau = “expand 16-byte k” normally used in Salsa20, the Trojan generates new random values for each processed file. This is an unnecessary step which makes the cipher incompatible with the standard Salsa20, but doesn’t in fact enhance its security.
The key and nonce values are also uniquely generated for each file, and will be encrypted along with the constants described above by RSA using the public 2048-bit key hardcoded in the Trojan’s body.
The RNG is based on the MS CryptoAPI function CryptGenRandom, which is considered secure, and the SHA-256 hash algorithm. The RNG implementation looks a bit awkward, but we haven’t found any critical flaws in it.
The RNG procedure pseudocode used by a recent Ragnar Locker variant
After encrypting the content of each of the victim’s files, Ragnar Locker will append the encrypted key, nonce and initialization constants to the encrypted file, and finalize by adding the marker “!@#_®agna®_#@!”
Trailing bytes of a file encrypted by Ragnar Locker
The ransom notes dropped by the Trojan contain the name of the victim organization which clearly indicates that the criminals utilize a targeted approach, identify their victim and carefully prepare the attack.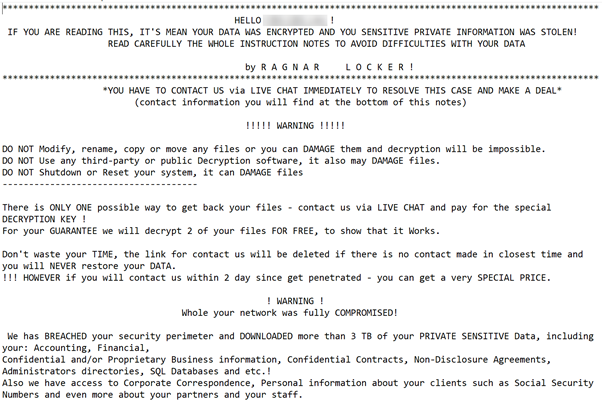
The ransom note also attempts to further scare the victim into paying by emphasizing that the threat actors have stolen confidential data in addition to the file encryption performed by the Trojan.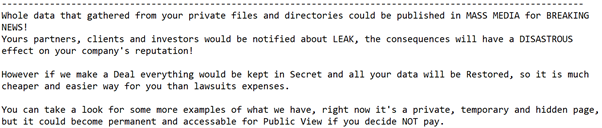
Egregor
Egregor ransomware is a new strain that was discovered in September 2020, and after the initial analysis we noticed code similarities between this new threat and Sekhmet ransomware, as well as the notorious Maze ransomware, which announced on November 1st, 2020 that they shut down.
Egregor keeps at least one .onion domain and two Surface Web domains. The first Surface Web domain was registered on September 6, 2020 and the second one on October 19, 2020. At the time of writing, both Surface Web domains were intermittent. That is probably why on the main page of the Onion domain, there is a big disclaimer with this notice:
The Egregor ransomware is typically distributed by the criminals following a network breach. The malware sample is a DLL file that needs to be launched with the correct password given as a command line argument. The DLL is usually dropped from the Internet. On occasions, the domains used to spread it exploit names or words used in the victim’s industry.
Egregor is probably the most aggressive Ransomware family in terms of negotiation with the victims. It gives only 72 hours to contact the threat actor. Otherwise, the victim’s data is processed for publishing.
The ransomware payment is negotiated and agreed upon via a special chat assigned to each victim. The payment is received in BTC.
Example of a chat negotiating to pay the ransom
Technical description
b21930306869a3cdb85ca0d073a738c5
As mentioned above, the malware sample only works if a correct password is provided during launch. The packer of the malware will use this password to decrypt the payload binary. A missing or incorrect argument will result in an incorrect decryption of the payload, which will be unable to execute and will crash instead.
This technique is intended to hinder both automatic analysis in sandbox-type systems, and manual analysis by researchers: without the correct password it is impossible to unpack and analyze the payload binary.
After unpacking two layers of the malicious packer, we end up with an obfuscated binary which is still not suitable for static analysis. The obfuscation techniques used in Egregor strongly resemble those in Maze and Sekhmet: the code is ‘torn apart’ by control flow obfuscation using conditional and unconditional jumps, PUSH+JMP instead of RETN, and so on.
Control flow obfuscation example
When the payload starts executing, first of all, it will check the system and user language of the OS to avoid encrypting machines having one of the following languages installed:
Armenian (Armenia)
Azerbaijani (Cyrillic, Azerbaijan)
Azerbaijani (Latin, Azerbaijan)
Belarusian (Belarus)
Georgian (Georgia)
Kazakh (Kazakhstan)
Kyrgyz (Kyrgyzstan)
Romanian (Moldova)
Russian (Moldova)
Russian (Russia)
Tajik (Cyrillic, Tajikistan)
Tatar (Russia)
Turkmen (Turkmenistan)
Ukrainian (Ukraine)
Uzbek (Latin, Uzbekistan)
Then it will attempt to terminate the following processes: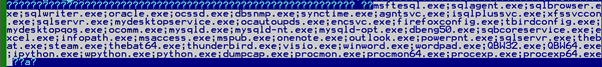
This is intended to make writable potentially valuable files such as documents or databases that may have been in use at the moment of infection. In addition, some programs typically used by researchers, e.g., procmon or dumpcap, are also listed for termination to further hinder dynamic analysis.
Egregor uses a hybrid file encryption scheme based on the stream cipher ChaCha and the asymmetric cipher RSA.
The RSA-2048 master public key of the criminals is embedded in the trojan’s body.
When executing on a victim’s machine, Egregor generates a new unique pair of session RSA keys. The session private RSA key is exported and encrypted by ChaCha with a uniquely generated key + nonce, then the key and nonce are encrypted by the master public RSA key. The results are saved in a binary file (in our case it’s named C:\ProgramData\dtb.dat), as well as a base64-encoded string in the ransom notes.
For each data file Egregor processes, it generates a new 256-bit ChaCha key and 64-bit nonce, encrypts the file content by ChaCha, then encrypts them using the session public RSA key, and saves them along with some auxiliary information in the end of the encrypted file.
The last 16 bytes of each encrypted file are comprised of a dynamic marker: a random DWORD and this same DWORD xor’ed with the value 0xB16B00B5 which equals ‘BIGBOOBS’ in so-called leet speak, originally used by “hackers, crackers and script kiddies”, according to Wikipedia.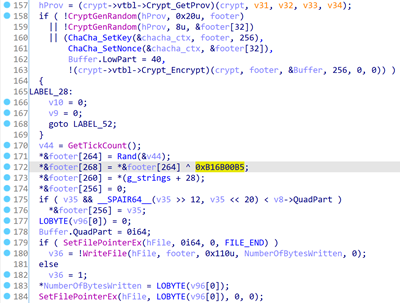
Part of the file encryption procedure pseudocode
The main page of the data leak website contains news about recently attacked companies along with some sarcastic remarks written by the ransomware group.
The archive section of the site lists the victims of the extortionists and the links to download the stolen data.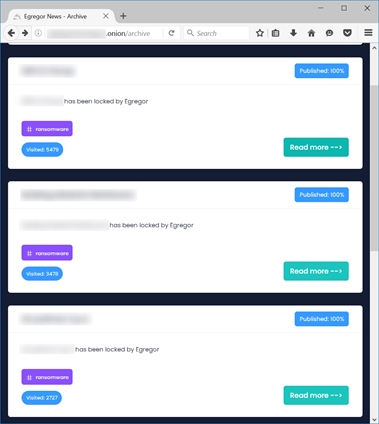
Based on the information of those victims who refused to pay, the geographic reach of Egregor is way more extensive than that of Ragnar Locker:
Geography of Egregor victims (download)
The same is true for the number of attacked industries:
Egregor victims by industry (download)
Conclusions
Unfortunately, Ransomware 2.0 is here to stay. When we talk about 2.0, we mean targeted ransomware with data exfiltration. The whole extortion process is primarily about the victims’ data not being published on the internet and only then about decryption. Why is it so important for the victims that their data is not published? Because possible lawsuits and fines due to violations of regulations like HIPAA, PIC or GDPR can result in immense financial losses, reputational damage and potential bankruptcy.
As long as companies see ransomware threat actors as typical malware threats, they will also fail. It is not about just endpoint protection; it is about red teaming, business analysts working with exfiltrated documents evaluating the ransom to pay. It is also about data theft, of course, and public shaming, leading to all sorts of problems in the end.
Our next chapter will cover something else – a perfect umbrella for different threat actors with different motivations operating under the aegis of Ransomware 2.0.
Ransomware operators use fake Microsoft Teams updates to deploy Cobalt Strike
11.11.20 Ransomware Securityaffairs
Ransomware operators use fake Microsoft Teams updates to deploy Cobalt Strike and compromise the target networks.
Ransomware operators are using malicious fake Microsoft Teams updates to deliver backdoors that lead the installation of the Cobalt Strike post-exploitation tool and compromise the target network.
The ongoing COVID-19 pandemic is forcing a growing number of organizations and businesses in using videoconferencing solutions, and threat actors are attempting to exploit this scenario.
BleepingComputer has seen a non-public security advisory issued by Microsoft that is warning its customers of malware campaigns using fake Microsoft Teams updates.
The technique is not new and threat actors already exploited it in attacks in the wild. In 2019, DoppelPaymer ransomware operators used this trick to target Microsoft users in 2019, this year WastedLocker operators evolved the technique by using a multi-state attack chain and employing signed binaries to evade the detection.
Recently threat actors carried out black SEO campaigns to trick Internet users into visiting compromised websites hosting fake ads that lure users into clicking it to install an update.
“In at least one attack Microsoft detected, the crooks purchased a search engine ad that caused top results for Teams software to point to a domain under their control.” reported Bleeping Computer.
“Clicking on the link downloaded a payload that executed a PowerShell script to retrieve more malicious content. It also installed a legitimate copy of Microsoft Teams on the system to keep victims unaware of the attack.”
In one of the attacks spotted by Microsoft, threat actors were spreading a tainted copy of Microsoft Teams. In the early stage of the attack chain, hackers used the Predator the Thief infostealer to gather sensitive information on the target, including credentials and payment data. Threat actors also distributed other malware, like the Bladabindi (NJRat) backdoor and ZLoader info-stealer, and of course Cobalt Strike.
Cobalt Strike was employed by ransomware operators to move laterally across the target network, below an attack chain shared by Microsoft with Bleeping Computer.

Source Microsoft for BleepingComputer
Experts from Microsoft observed multiple campaigns using fake Microsoft Teams updates as a lure, the attacks were likely conducted by the same threat actor.
The security advisory includes a series of recommendations such as:
using web browsers that can filter and block malicious websites;
using strong, random passwords for local administrators;
limiting admin privileges to essential users;
blocking executable files that do not meet specific criteria;
blocking JavaScript and VBScript code from downloading executable content.
Compal, the Taiwanese giant laptop manufacturer hit by ransomware
10.11.20 Ransomware Securityaffairs
The Taiwanese electronics manufacture Compal suffered a ransomware attack over the weekend, media blames the DoppelPaymer ransomware gang.
Compal Electronics is a Taiwanese original design manufacturer (ODM), handling the production of notebook computers, monitors, tablets and televisions for a variety of clients around the world, including Apple Inc., Acer, Lenovo, Dell, Toshiba, Hewlett-Packard and Fujitsu. It also licenses brands of its clients. It is the second-largest contract laptop manufacturer in the world behind Quanta Computer.
Compal suffered a ransomware attack over the weekend, a screenshot of the ransom note shared by the employees of the company is circulating online.
Responsible for the breach is believed to be the DoppelPaymer ransomware gang, according to a screenshot of the ransom note shared by Compal employees with Yahoo Taiwan reporters and reported by ZDNet.
ZDNet reviewed the ransom note and confirmed that the ransomware gang behind the attack could be the DoppelPaymer crew.

Source ZDNet
The cyber attack took place over the weekend and was discovered on Sunday morning, according to local media it might have impacted around 30% of Compal’s computer fleet. In response to the incident, the company network was shut down to avoid the ransomware from spreading
“It is understood that the information security personnel had an emergency meeting in Xu Shengxiong’s chairman’s room early in the morning to discuss solutions, because the IT staff discovered from Sunday that the internal network was abnormal, but it continued to affect it on Monday, and the company’s internal company also posted A letter teaches employees how to deal with abnormal computers.” reported Yahoo Taiwan finance. “According to the Internet PTT, 30% of the computers have been hit. A bunch of employees fell early, the internal network was completely disconnected, and the network was disconnected late.”
On Monday, employees that returned to work received a notice from Compal’s IT staff asking them to check the status of their workstations and back up important files on systems that were not infected with the ransomware.
The company is working to recover the impacted systems using the backups.
Today, Compal Deputy Manager Director Qingxiong Lu disclosed the security breach but explained that the network issues were not caused by a ransomware attack. The executive pointed out that the Compal production lines were not impacted by the cyber attack.
“[the company] is not being blackmailed by hackers as it is rumored by the outside world,” Qingxiong Lu told local media.
The company s expected to fully recover its impacted systems today.
E-commerce platform X-Cart hit by a ransomware attack
10.11.20 Ransomware Securityaffairs
The e-commerce software platform X-Cart suffered a ransomware attack at the end of October, e-stores hosted by the company went down.
At the end of October, the e-commerce software platform X-Cart suffered a ransomware attack, the infection brought down customers’ e-stores hosted by the company on its platform.
The software and services company X-Cart was recently acquired by Seller Labs, the premier software and services provider for Amazon sellers and brands.
The company immediately launched an internal investigation and discovered that threat actors exploited a vulnerability in third-party software management tool to access the hosting platform and install the ransomware.
“On October 21, 2020, at approximately 11 am EST, X-Cart in cooperation with our infrastructure provider identified that some of our servers were down due to a ransomware attack. All customer websites have since been restored.
The vulnerability was in a 3rd party software tool we used to manage our service infrastructure. We have removed this tool from our systems and are working with a security firm to confirm the source of entry and identify the ransomware strain. Once that report is ready, we will share it with our customers.” Jeff Cohen, vice president of marketing at X-cart, told The Daily Swig.
“An outage of any kind is disruptive to our customers and impacts each of them differently. The X-Cart team remains focused on helping customers get back to business.”
According to Cohen, threat actors gained access to a small portion of the platform and encrypted some of its servers bringing down the X-Cart stores they were hosting.
Users reported that the systems were down for several days, is some cases customers restored their operations but claimed to have missed order information and settings changes.
“Email servers were also impacted as DKIM records and such weren’’t set up,” states The Daily Swig.
The company claims that its core systems were not impacted and states that all customer websites have since been restored.
X-Cart pointed out that the outage was “limited to customers that were on our shared hosting plans” and none of its dedicated hosting clients were impacted.
In response to this initiative, Cohen said the company’s “first priority” during the ransomware attack “has been to get every customer back online and ensure we have a stable and secure system.”
According to Cohen, the company did not pay the ransom and recoverd its files from backups. He also added that the threat actors didn’t provide any way to communicate with them, and this is very strange for ransomware attacks.
“At this time, we believe we know the third-party tool but do not want to disclose it until our security agency confirms and completes the audit,” Cohen explained. “They have narrowed down the ransomware strain but have not reported the final findings.” concludes Cohen.
“The ransomware hackers do not provide a way to communicate so to comply with US laws we had to work on a recovery process.”
At the time, it is not clear the family of ransomware that infected the systems at the hosting platform.
E-commerce platform X-Cart hit by a ransomware attack
9.11.20 Ransomware Securityaffairs
The e-commerce software platform X-Cart suffered a ransomware attack at the end of October, e-stores hosted by the company went down.
At the end of October, the e-commerce software platform X-Cart suffered a ransomware attack, the infection brought down customers’ e-stores hosted by the company on its platform.
The software and services company X-Cart was recently acquired by Seller Labs, the premier software and services provider for Amazon sellers and brands.
The company immediately launched an internal investigation and discovered that threat actors exploited a vulnerability in third-party software management tool to access the hosting platform and install the ransomware.
“On October 21, 2020, at approximately 11 am EST, X-Cart in cooperation with our infrastructure provider identified that some of our servers were down due to a ransomware attack. All customer websites have since been restored.
The vulnerability was in a 3rd party software tool we used to manage our service infrastructure. We have removed this tool from our systems and are working with a security firm to confirm the source of entry and identify the ransomware strain. Once that report is ready, we will share it with our customers.” Jeff Cohen, vice president of marketing at X-cart, told The Daily Swig.
“An outage of any kind is disruptive to our customers and impacts each of them differently. The X-Cart team remains focused on helping customers get back to business.”
According to Cohen, threat actors gained access to a small portion of the platform and encrypted some of its servers bringing down the X-Cart stores they were hosting.
Users reported that the systems were down for several days, is some cases customers restored their operations but claimed to have missed order information and settings changes.
“Email servers were also impacted as DKIM records and such weren’’t set up,” states The Daily Swig.
The company claims that its core systems were not impacted and states that all customer websites have since been restored.
X-Cart pointed out that the outage was “limited to customers that were on our shared hosting plans” and none of its dedicated hosting clients were impacted.
In response to this initiative, Cohen said the company’s “first priority” during the ransomware attack “has been to get every customer back online and ensure we have a stable and secure system.”
According to Cohen, the company did not pay the ransom and recoverd its files from backups. He also added that the threat actors didn’t provide any way to communicate with them, and this is very strange for ransomware attacks.
“At this time, we believe we know the third-party tool but do not want to disclose it until our security agency confirms and completes the audit,” Cohen explained. “They have narrowed down the ransomware strain but have not reported the final findings.” concludes Cohen.
“The ransomware hackers do not provide a way to communicate so to comply with US laws we had to work on a recovery process.”
At the time, it is not clear the family of ransomware that infected the systems at the hosting platform.
Ransomware operators target CVE-2020-14882 WebLogic flaw
8.11.20 Ransomware Securityaffairs
At least one ransomware operator appears to have exploited the recently patched CVE-2020-14882 vulnerability affecting Oracle WebLogic.
At least one ransomware operator appears is exploiting the recently patched CVE-2020-14882 vulnerability in Oracle WebLogic.
At the end of October, threat actors have started scanning the Internet for servers running vulnerable installs of Oracle WebLogic in the attempt of exploiting the CVE-2020-14882 flaw.
The CVE-2020-14882 can be exploited by unauthenticated attackers to take over the system by sending a simple HTTP GET request.
The vulnerability received a severity rating 9.8 out of 10, it was addressed by Oracle in this month’s release of Critical Patch Update (CPU).
The issue affects versions of Oracle WebLogic Server are 10.3.6.0.0, 12.1.3.0.0, 12.2.1.3.0, 12.2.1.4.0 and 14.1.1.0.
The flaw was discovered by the security researcher Voidfyoo from Chaitin Security Research Lab, it was addressed in Oracle’s October 2020 Critical Patch Update.
In early November, Oracle issued an out-of-band security update to address another critical remote code execution (RCE) vulnerability, tracked as CVE-2020-14882.
Renato Marinho, a security researcher at Morphus Labs and SANS ISC handler reported that the WebLogic honeypots he set up were targeted by a large number of scans for CVE-2020–14882.
“Starting late last week, we observed a large number of scans against our WebLogic honeypots to detect if they are vulnerable to CVE-2020–14882.” reads the analysis published by the expert. “CVE-2020–14882 was patched about two weeks ago as part of Oracle’s quarterly critical patch update. In addition to scans simply enumerating vulnerable servers, we saw a small number of scans starting on Friday (Oct. 30th) attempting to install crypto-mining tools.”
The expert spotted a small number of scans starting on October 30 attempting to install crypto-mining tools.
Over the weekend, the experts uncovered a campaign targeting the same vulnerability and leveraging a chain of obfuscated PowerShell scripts to fetch a Cobalt Strike payload.
Cisco Talos Q4 2020 CTIR report revealed that 66% of all ransomware attacks in Q4 involved the use of Cobalt Strike, for this reason, experts speculate that threat actors were exploiting the CVE-2020–14882 to deploy this specific kind of malware.
The only way to prevent these attacks is to apply the security updates to the WebLogic installs as soon as possible. The analysis published by Morphus Labs also includes Indicators of Compromise (IoCs) for these attacks.
Campari Site Suffers Ransomware Hangover
7.11.20 Ransomware Threatpost
The Ragnar Locker operators released a stolen contract between Wild Turkey and actor Matthew McConaughey, as proof of compromise.
Italian spirits brand Campari has restored its company website following a recent ransomware attack. According to the ransom note, the group behind the breach used Ragnar Locker to encrypt most of Campari’s servers and was holding the data hostage for $15 million in Bitcoin.
Campari Group is behind liquor brands Aperol, SKYY, Grand Marnier and Wild Turkey. The company announced on Nov. 3 it was the victim of a Nov. 1 malware attack.
“The group’s IT department, with the support of IT security experts, immediately took action to limit the spread of malware in data and systems,” the Campari Group statement said. “Therefore, the company has implemented a temporary suspension of IT services, as some systems have been isolated in order to allow their sanitation and progressive restart in safe conditions for a timely restoration of ordinary operations. At the same time, an investigation into the attack was launched, which is still ongoing. It is believed that the temporary suspension of the IT systems cannot have any significant impact on the Group’s results.”
The Ransom Note
Malware researcher Pancak3 shared a copy of the ransom note with Threatpost.
The ransom note. Source: Pancak3.
“We have BREACHED your security perimeter and get [sic] access to every server of the company’s network in different countries across all your international offices,” the note reads, in part. It goes on to detail the types of data compromised, including accounting files, bank statements, employee personal information and more. The note said the scammers were able to steal a total of 2TB of data.
“If no deal is made than [sic] all your data with be published and/or sold through an auction to any third parties,” the note threatens.
Compromised documents posted on a leak site for the group included a contract between Wild Turkey and actor Matthew McConaughey, according to ZDNet, as proof they had the goods.
Campari Group has not responded to Threatpost’s request for comment.
Rise of Ragnar Locker Ransomware
“The operators are professionals,” Pancak3 told Threatpost. “They have good knowledge of penetration tactics that enable them to gain initial entry, perform recon, and steal data prior to deploying their ransomware. Back in April they first started their public shaming site, “WALL OF SHAME,” to post details of non-paying victims. It’s believed that Ragnar Locker partnered with Maze operators earlier this year.”
Ragnar Locker ransomware, Pancak3 added, is a relatively new malware written in C and C++.
“(It was) first was observed in late 2019,” Pancak3 explained. “Ragnar Locker allows operators to customize the way it behaves on the infected host.”
The Capari compromise looks almost identical to the Capcom Ragnar Locker attack, according to Pancak3.
In that attack, Ragnar Locker was also reportedly used this week to attack Japanese gaming juggernaut Capcom, to steal data from networks in the U.S., Japan and Canada. And Pancak3 noticed some similarities between the two attacks.
“The executables for both Capcom and Campari are signed with the same cert.,” he told Threatpost. Adding, it shows that the group is getting a bit complacent.
“I think it shows that they are confident in their intrusion methods,” Pancak3 said.
Ransomware attacks have been on the rise since the beginning of the pandemic last spring. Last July, SonicWall’s 2020 Cyber Threat Report said ransomware attacks have more than doubled over last year.
“As we’ve seen with Campari and many others, ransomware continues to be a significant threat to organizations large and small,” Wade Lance, CTO at Illusive Networks said via email. “Cybercriminals only need to get lucky once when they attack with ransomware to be successful. On the other hand, large organizations must stop every attempted cyberattack aimed at them, and if they are wrong even once the consequences are catastrophic.”
RansomEXX Trojan attacks Linux systems
7.11.20 Ransomware Securelist
We recently discovered a new file-encrypting Trojan built as an ELF executable and intended to encrypt data on machines controlled by Linux-based operating systems.
After the initial analysis we noticed similarities in the code of the Trojan, the text of the ransom notes and the general approach to extortion, which suggested that we had in fact encountered a Linux build of the previously known ransomware family RansomEXX. This malware is notorious for attacking large organizations and was most active earlier this year.
RansomEXX is a highly targeted Trojan. Each sample of the malware contains a hardcoded name of the victim organization. Moreover, both the encrypted file extension and the email address for contacting the extortionists make use of the victim’s name.
Several companies have fallen victim to this malware in recent months, including the Texas Department of Transportation (TxDOT) and Konica Minolta.
Technical description
The sample we came across – aa1ddf0c8312349be614ff43e80a262f – is a 64-bit ELF executable. The Trojan implements its cryptographic scheme using functions from the open-source library mbedtls.
When launched, the Trojan generates a 256-bit key and uses it to encrypt all the files belonging to the victim that it can reach using the AES block cipher in ECB mode. The AES key is encrypted by a public RSA-4096 key embedded in the Trojan’s body and appended to each encrypted file.
Additionally, the malware launches a thread that regenerates and re-encrypts the AES key every 0.18 seconds. However, based on an analysis of the implementation, the keys actually only differ every second.
Apart from encrypting the files and leaving ransom notes, the sample has none of the additional functionality that other threat actors tend to use in their Trojans: no C&C communication, no termination of running processes, no anti-analysis tricks, etc.
Fragment of the file encryption procedure pseudocode; variable and function names are saved in the debug information and must match the original source code
Curiously, the ELF binary contains some debug information, including names of functions, global variables and source code files used by the malware developers.
Original names of source files embedded in the trojan’s body
Execution log of the trojan in Kaspersky Linux Sandbox
Similarities with Windows builds of RansomEXX
Despite the fact that previously discovered PE builds of RansomEXX use WinAPI (functions specific to Windows OS), the organization of the Trojan’s code and the method of using specific functions from the mbedtls library hint that both ELF and PE may be derived from the same source code.
In the screenshot below, we see a comparison of the procedures that encrypt the AES key. On the left is the ELF sample aa1ddf0c8312349be614ff43e80a262f; on the right is the PE sample fcd21c6fca3b9378961aa1865bee7ecb used in the TxDOT attack.
Despite being built by different compilers with different optimization options and for different platforms, the similarity is quite obvious.
We also observe resemblances in the procedure that encrypts the file content, and in the overall layout of the code.
What’s more, the text of the ransom note is also practically the same, with the name of the victim in the title and equivalent phrasing.
Parallels with a recent attack in Brazil
As reported by the media, one of the country’s government institutions has just been attacked by a targeted ransomware Trojan.
Based on the ransom note, which is almost identical to the one in the sample we described, and the news article mentioned above, there is a high probability that the target is the victim of another variant of RansomEXX.
Ransom note from the sample aa1ddf0c8312349be614ff43e80a262f
Ransom note from the Bleeping Computer post about the most recent attack in Brazil
Our products protect against this threat and detect it as Trojan-Ransom.Linux.Ransomexx
Kaspersky Threat Attribution Engine identifies Ransomexx malware family
Indicators of compromise
Recent Linux version: aa1ddf0c8312349be614ff43e80a262f
Earlier Windows version: fcd21c6fca3b9378961aa1865bee7ecb
RansomExx ransomware now targets also Linux systems
7.11.20 Ransomware Securityaffairs
The RansomExx Ransomware gang is expanding its operations by creating a new version that is able to infect Linux machines.
RansomExx ransomware operators are expanding their operations by developing a Linux version of their malware.
Kaspersky researchers have analyzed the Linux version of the RansomExx ransomware, also tracked as Defray777.
This week the RansomExx ransomware has been involved in the attacks against Brazil’s Superior Court of Justice.
The RansomEXX is human-operated ransomware, this means that attackers manually infected the systems after gained access to the target network.
In June 2020, the same ransomware was employed in an attack on the Texas Department of Transportation, in August is infected systems at the multinational technology Konica Minolta, in September it infected the systems at the IPG Photonics high-performance laser developer and at the software provider Tyler Technologies.
The recently discovered Linux version of the RansomExx ransomware is built as an ELF executable named ‘svc-new’ that encrypts the target’s server.
“After the initial analysis we noticed similarities in the code of the Trojan, the text of the ransom notes and the general approach to extortion, which suggested that we had in fact encountered a Linux build of the previously known ransomware family RansomEXX,” reads the report published by Kaspersky.
Upon launching the Trojan, it generates a 256-bit key that is used to encrypt all the victim’s files that it can reach using the AES block cipher in ECB mode. The AES key is encrypted by a public RSA-4096 key embedded in the code of the malware and appended to all the encrypted file.
Experts pointed out that the ransomware lacks additional functionalities implemented by other Trojans, such as C2 communication, anti-analysis features, and the ability to kill processes.
Unlike the Windows version, the Linux variant doesn’t wipe free space.
Experts noticed that when a victim pays the ransom, they will receive both a Linux and Windows decryptor with the corresponding RSA-4096 private key and encrypted file extension embedded in the executable.
Despite the Windows and Linux variants have been built by different compilers with different optimization options and for different platforms, their similarity is clear: 
Kaspersky’s report also includes Indicators of Compromise (IoCs) for the new variant.
Recent WebLogic Vulnerability Likely Exploited by Ransomware Operators
7.11.20 Ransomware Securityweek
At least one ransomware operator appears to have added to their arsenal an exploit for a recently patched vulnerability in Oracle WebLogic.
Tracked as CVE-2020-14882 and considered critical severity, the vulnerability was addressed in Oracle’s October 2020 Critical Patch Update. It can be exploited remotely and does not require authentication for that.
The first attacks targeting the vulnerability appeared within the first week after patches were released.
One week later, Oracle announced the release of an out-of-band update for another critical WebLogic vulnerability, CVE-2020-14750 (CVSS score of 9.8), related to CVE-2020-14882 and also remotely exploitable without authentication.
CVE-2020-14750 was patched soon after a security researcher revealed how easy it is to bypass the initial patch for CVE-2020-14882.
Now, Morphus Labs security researcher and SANS ISC handler Renato Marinho reveals that WebLogic honeypots have detected a large number of scans for CVE-2020–14882, with some of them performed by crypto-mining operators.
“In addition to scans simply enumerating vulnerable servers, we saw a small number of scans starting on Friday (Oct. 30th) attempting to install crypto-mining tools,” Marinho explains.
Over the weekend, he also explains, one campaign targeting the vulnerability started leveraging a series of obfuscated PowerShell scripts to fetch a Cobalt Strike payload.
Given that roughly two-thirds of all of the ransomware attacks observed over the past quarter have leveraged Cobalt Strike, the new set of scans was likely the doing of a ransomware operator.
“Thus, as expected, there is a high probability ransomware gang included CVE-2020–14882 exploit in their arsenal,” Marinho says.
Users are advised to apply the available WebLogic patches as soon as possible, to ensure their environments remain secure. The two critical vulnerabilities can be abused to completely take over the affected systems.
Brazil’s court system shut down after a massive ransomware attack
6.11.20 Ransomware Securityaffairs
This week, Brazil’s Superior Court of Justice has temporarily shut down its operation following a ransomware attack during judgment sessions.
Brazil’s Superior Court of Justice was hit by a ransomware attack on Tuesday during judgment sessions, the attack forced a temporary shut down of the court’s information technology network.
“The Superior Court of Justice (STJ) announces that the court’s information technology network suffered a hacker attack, this Tuesday (3), during the afternoon, when the six group classes’ judgment sessions were taking place. The presidency of the court has already called the Federal Police to investigate the cyber attack.” announced STJ President Humberto Martins in an official statement on the Supreme Federal Court’s website.
The attack was discovered on November 3 and the IT staff shut down the court’s network to prevent the malware from spreading.
According to the announcement, the institution is going to restore its systems and court activities are expected to resume on November 9.
All judgment sessions, virtual and by video conference will be either suspended or canceled until the court network’s security will be restored, likely on November 9.
As a result of the attack, the websites of several Brazilian federal government agencies are also currently offline.
According to local media, Brazilian president Jair Bolsonaro announced that the authorities have identified the threat actors behind the attack.
Two days after the ransomware attack took place, the Superior Court of Justice systems are still offline.
Brazilian media outlet CISO Advisor claims it has viewed an internal report on the security breach incident that suggests the threat actor was a cybercrime organization financially motivated.
“An audio report by an IT official at the agency, to which the CISO Advisor had access, indicates that more than 1,200 servers, mostly virtual machines, have been encrypted. At this time, the STJ website remains down. Our report tried to contact the agency’s press office, but the contact information has even disappeared from Google’s cache.” reads the CISO Advisor.
“The report obtained by CISO Advisor says that the attack “was a planned coup; it is believed that it was something orchestrated and ordered perhaps even by some criminal organization such as PCC, Comando Vermelho or Família do Norte, together with international gangs that make cyber attacks, and receive for that and that may have used outsourced servers.”
The hackers infected thousands of systems, most of them are virtual machines that were encrypted and deleted.
One of the technicians at the court confirmed that attackers take over a Domain Admin account.
“It was basically a ransomware attack . A Domain Admin account was exploited which allowed the hacker to have access to our servers, to join the administration groups of the virtual environment and, finally, encrypt a good part of our virtual machines “.
The court’s IT department informed judges, interns, and outsourced workers that cannot use their computers if they were connected to the court’s network at the time of the attack
“According to the resolution, administrative, civil and criminal procedural deadlines are suspended from the 3rd to the 9th of November (inclusive), returning to flow on the 10th,” reads a statement on the court’s website.
“For the purpose of counting the term in criminal proceedings, the suspension period will be considered a reason of force majeure, according to the provision of paragraph 4 of article 798 of the Code of Criminal Procedure (CPP). Also according to the resolution, the measures can be reviewed at any time, depending on the result of efforts to normalize the systems.”
Bleeping Computer, after receiving a copy of the ransom that was found on the systems of the STJ, confirmed that the court was a victim of an attack launched by the RansomExx ransomware gang.
The RansomEXX is human-operated ransomware, this means that attackers manually infected the systems after gained access to the target network.
In June 2020, the same ransomware was employed in an attack on the Texas Department of Transportation, in August is infected systems at the multinational technology Konica Minolta, in September it infected the systems at the IPG Photonics high-performance laser developer and at the software provider Tyler Technologies.
Prominent Italian firms under attack, Campari is the last one
6.11.20 Ransomware Securityaffairs
Campari Group, the Italian beverage giant has been hit by a ransomware attack that forced the company to shut down a large part of its IT network.
The Italian company is active since 1860, it produces spirits, wines, and soft drinks. The company owns multiple brands including Aperol, Appleton, Campari, Dreher, Cinzano, SKYY Vodka, Espolón, Wild Turkey and Forty Creek Whisky.
The attack took place over the weekend, the systems at Campary were infected with the RagnarLocker ransomware as confirmed by a copy of the ransomware that is circulating online.
“Campari Group informs that, presumably on 1 November 2020, it was the subject of a malware attack (computer virus), which was promptly identified. The Group’s IT department, with the support of IT security experts, immediately took action to limit the spread of malware in data and systems. Therefore, the company has implemented a temporary suspension of IT services, as some systems have been isolated in order to allow their sanitation and progressive restart in safe conditions for a timely restoration of ordinary operations.” reads the statement published by the company (Italian).
The Ragnar Locker ransomware operators claim to have stolen 2 TB of unencrypted files and to recover their files, the gang is demanding $15 million.
“Pancak3 told BleepingComputer that Ragnar Locker claims to have encrypted most of Campari Group’s servers from twenty-four countries and are demanding $15,000,000 in bitcoins for a decryptor.” reported Bleeping Computer.
Source ZDNet
The ransom note includes URLs to screenshots of some of the stolen data, including sensitive documents such as bank statements, a spreadsheet containing SSNs, and a confidentiality agreement.
Like other ransomware gangs, also RagnarLocker operators are threatening to release files stolen from Campari before they have encrypted its systems.
To force the Campari into paying the ransom the RagnarLocker operators have published screenshots of the company’s network and other documents on their dark web leak site.
Campari has refused to pay the ransom and decided to restore its backup. The company notified the authorities and immediately launched an investigation into the security breach. Campari announced that it’s working on a “progressive restart in safety conditions,” it also added that the temporary suspension of the IT systems cannot have any significant impact on the Group’s financial results.
Six days after the attack, the company websites and email servers are still down.
Other prominent Italian firms have been victims of ransomware attacks in the last months, including ENEL, Luxottica, Geox, and Carraro. In some cases, the attacks blocked operations of the victims and their employees remained at home.
Hackers Demand $11 Million From Capcom After Ransomware Attack
6.11.20 Ransomware Securityweek
A group of cybercriminals that breached the systems of Japanese video game giant Capcom is demanding $11 million after deploying ransomware and stealing vast amounts of data.
Capcom, which has operations in the US, Europe and East Asia, is best known for games such as Resident Evil, Street Fighter, Devil May Cry, Monster Hunter, Ace Attorney and Mega Man.
The company revealed on November 4 in a press release that it detected unauthorized access to its internal networks a couple of days earlier. Capcom said it was forced to halt some operations and that the incident impacted its email and file servers, among other systems. It claimed that it had found no evidence of customer information being compromised.
However, the cybercriminals who breached Capcom, a group that uses the ransomware known as Ragnar Locker, claim to have stolen more than 1 TB of files, including accounting files, banking statements, financial reports, tax documents, intellectual property, proprietary business information, personal information of employees and customers, corporate contracts, emails, private chats, and various other types of information.

A researcher who uses the online moniker pancak3 told SecurityWeek that he learned from the attackers that they are initially asking Capcom to pay $11 million in bitcoin.
The researcher says the hackers claim their ransomware encrypted roughly 2,000 Capcom servers, including file servers. The attackers have posted some screenshots to prove that they’ve gained access to sensitive information.
Ragnar Locker operators demanded a similar ransom from renewable energy company EDP, whose systems they breached in May. The same ransomware is also believed to have been involved in recent attacks targeting the United Nations’ International Maritime Organization and French shipping giant CMA CGM.
Toymaker giant Mattel disclosed a ransomware attack
5.11.20 Ransomware Securityaffairs
Toymaker giant Mattel disclosed a ransomware attack, the incident took place in July and impacted some of its business operations.
Toy industry giant Mattel announced that it has suffered a ransomware attack that took place on July 28th, 2020, and impacted some of its business operations.
The good news that the company excluded the theft of internal information.
The toymaker is one of the largest toymakers in the world with 24,000 employees and $5.7 billion in revenue for 2019.
Mattel is known for its popular brands, including Barbie, Hot Wheels, Fisher-Price, Fuhu, American Girl, Thomas & Friends, and Tyco Toys.
The company filed a 10-Q form with the Securities and Exchange Commission (SEC), Mattel disclosed that it suffered a ransomware attack on July 28th, 2020.
“On July 28, 2020, Mattel discovered that it was the victim of a ransomware attack on its information technology systems that caused data on a number of systems to be encrypted. Promptly upon detection of the attack, Mattel began enacting its response protocols and taking a series of measures to stop the attack and restore impacted systems. Mattel contained the attack and, although some business functions were temporarily impacted, Mattel restored its operations.” reads the 10-Q form. “A forensic investigation of the incident has concluded, and no exfiltration of any sensitive business data or retail customer, supplier, consumer, or employee data was identified. There has been no material impact to Mattel’s operations or financial condition as a result of the incident.”
The company immediately launched an investigation that leads it to conclude that attackers did not exfiltrate any sensitive business data or internal data.
According to BleepingComputer, in July, systems at the toymaker were infected with the TrickBot malware which was used by several cybercrime gangs to deliver malware like Ryuk or Conti.
REvil Ransomware Operator Bids for KPot Stealer Source Code
5.11.20 Ransomware Securityweek
The source code for the KPot information stealer was put up for auction, with the REvil ransomware operators apparently being the sole bidders, threat intelligence provider Cyjax reports.
Initially spotted in 2018 and offered as a Malware-as-a-Service (MaaS), KPot was designed to steal account information, as well as other types of data from browsers (e.g. cookies and autofill forms), messaging and email applications, and other software, including VPNs, RDP and FTP tools, cryptocurrency apps, and gaming software.
Written in C/C++, the malware relies on HTTP for command and control (C&C) communication and includes support for a variety of commands, to steal desired information and files from the victim machine, to remove itself, or take screenshots.
The KPot developers announced a couple of weeks ago that they were auctioning the malware’s source code, with a starting price of $6,500. They were also offering the source code for $10,000 upfront.
This week, Cyjax revealed that a representative of the REvil (Sodinokibi) ransomware gang was the only bidder in the auction. They also note that the auction was closed soon after the group made the bid.
“While the closed nature of these sales makes it impossible to definitively state REvil are now the owner of the KPot stealer, this seems highly likely. They were the only public bidder for this product and could almost certainly outbid other interested parties,” Cyjax notes.
First observed in early 2019 and offered as a ransomware-as-a-service (RaaS), REvil is believed to be operated by the gang behind the GandCrab ransomware, which retired in June 2019.
In a recent interview, the REvil gang said they top $100 million in annual earnings from the ransomware business. The GandCrab group claimed it managed to earn over $2 billion.
“If REvil has purchased the source code for KPot stealer, then this will likely be incorporated into future ransomware attacks,” Cyjax also says.
The move would not be surprising, considering that many ransomware gangs have been observed stealing victim data in an effort to convince them to pay the ransom by threatening to make the information public.
Media Comms Giant Says Ransomware Hit Will Cost Millions
4.11.20 Ransomware Threatpost
Aussie firm Isentia said “remediation and foregone revenue” could total $8.5 million AUS or more.
Media communications giant Isentia is reporting that its coffers will be emptied of as much as $6 million ($8.5 million AUS) in the wake of a ransomware attack last week.
The company is a media-intelligence and data-analytics firm headquartered in Australia, with a presence throughout Southeast Asia. It’s known for its Mediaportal platform, which aggregates news about customers’ brands and is used by public relations and marketing teams globally. According to its website, customers include a variety of major clients, including the Australian government, Singtel, Samsung and the Walt Disney Corp.
Isentia said that remediation costs and lost business stemming from its systems being locked up by the attack will create a big hit to its bottom line for fiscal year 2021, with an estimate that this will total $7 million to $8.5 million AUS.
CEO Ed Harrison however said that “it is difficult to fully assess the impact on our FY21 pre-tax earnings” given that the estimate is based on an ongoing assessment of the incident – so the amount could be revised upward.
In a statement issued on Tuesday (obtained by Bitdefender), the firm also said that the attack happened as the company was transitioning to a new debt facility with the Commonwealth Bank of Australia (CBA), meaning that the timeline for the drawdown of the CBA facility has been elongated – potentially also affecting its earnings results.
The ransomware attack happened on Oct. 27, after which the Mediaportal was downed, both for customers and staff. Workers resorted to preparing media reports manually, according to reports. The company and the Australian Cybersecurity Centre both quickly confirmed the attack.
“The impact of Isentia, a media-monitoring firm, being hit by a cyberattack demonstrates the interconnected world of national cyber-defense,” said Steve Forbes, government cybersecurity expert at Nominet, via email. “While a media-monitoring firm wouldn’t typically be considered part of critical infrastructure, its work with many government departments and large organizations – such as the Australian Stock Exchange – [was] put on hold due to the cyberattack.”
In Tuesday’s notice, it said that Mediaportal has been restored, while other IT systems are still inaccessible. “Key elements of our services” are being restored each day, according to Harrison, and the company is “making good progress.
There’s no word on which ransomware was behind the attack, or what the initial infection vector was.
“This incident also reminds us of the importance of vetting third parties in terms of their cyber resilience,” Forbes said. “While the full details of this particular security breach are yet to emerge, best practice advice is to ensure third parties have at least similar practices and procedures as your own to keep sensitive data safe.”
The news comes as ransomware attacks continue to crest, particularly in attacks against hospitals, and helped along by tools like an exploit for the Zerologon bug.
In a warning last week, the Cybersecurity and Infrastructure Security Agency (CISA) said it was tracking mass ransomware activity, as well as the use of the malware Trickbot against healthcare facilities.