
The list of victims of the gang is long and includes the Steel sheet giant Hoa Sen Group, Southwire, Canon, LG Electronics, Xerox, and City of Pensacola.
Ransomware Articles - H 2020 1 2 3 4 5 6 7 8 9 10 11 Ransomware List - H 2021 2020 2019 2018 1 Ransomware blog Ransomware blog
Pioneers of "Double Extortion" Say Maze Ransomware Project is Over
3.11.20 Ransomware Securityaffairs
The Maze ransomware operators finally announced that they have officially shut down their operations and denies the creation of a cartel.
Today the Maze ransomware gang announced that they have officially shut down their operations, the news was anticipated last week.
The cybercrime gang announced that it will no longer leak data of new companies infected with their ransomware.
it was considered one of the most prominent and active ransomware crew since it began operating in May 2019. The gang was the first to introduce a double-extortion model in the cybercrime landscape at the end of 2019.
At the end of 2019, the Maze ransomware implemented data harvesting capabilities and started threatening the victims to release the stolen data for all those victims who refuse to pay the ransom.
The operators behind the Maze ransomware set up a leak site, dubbed Maze News, where they were publishing the list of the companies that allegedly refused to pay the ransom.
The leak site contains for each victim the data related to the infection, including the date of the attack, some stolen documents (Office, text and PDF files), the size of stolen data, and the list of IP addresses and machine names of the infected servers.
The Maze News site was also and used to publish press releases for the activities of the group.
Today, Maze operators released a press release on their site, the message titled “The Project is closed” warns that any other ransomware operation that will abuse its brand must be considered a scam.
“Maze Team Project is announcing it is officially closed.
All the links to out project, using of our brand, our work methods should be considered to be a scam.
We never had partners or official successors. Our specialists do not works with any other software. Nobody and never will be able to host new partners at our news website. The Maze cartel was never exists and is not existing now. It can be found only inside the heads of the journalists who wrote about it.”

The list of victims of the gang is long and includes the Steel sheet giant Hoa Sen Group, Southwire, Canon, LG Electronics, Xerox, and City of Pensacola.
Malware researchers that collaborate with Bleeping Computer first speculated that other malware, such as Egregor and Sekhmet ransomware borrows the code from Maze ransomware.
Since May, 2020, the Maze gang also started publishing information stolen from a different ransomware operation called LockBit, a circumstance that suggested the creation of a cartel with other gangs.
The press release published by Maze pointed out that ‘Maze Cartel only existed inside the heads of journalists who wrote about it.’
Pioneers of "Double Extortion" Say Maze Ransomware Project is Over
3.11.20 Ransomware Securityweek
The Maze ransomware group issued a press release on November, 1 2020 announcing, "it is officially closed." Maze was one of the pioneers of 'double extortion' -- stealing data before encrypting the victim's files. Ransoms could be demanded for both the decryption key, and for returning or deleting the stolen data.
The annoucement was published on Twitter by MalwareHunterTeam on November 2nd. Assuming its validity, the Maze group discusses four items.
Firstly, it denies that there was ever a 'Maze cartel'. The existence of a cartel was discussed in various media outlets during the summer of 2020. It seems to have originated from the discovery of data from competing ransomware groups on the Maze victim shaming website; but now Maze says there was never a cartel. "The Maze cartel was never exists and is not existing now. It can be found only inside the heads of the journalists who wrote about it." Anything that now claims to be Maze-related should be considered a scam, says the group -- adding that for those victims already included on their website, support will continue for another month.
The denial of a cartel may be somewhat simplistic. Jeremy Kennelly, Manager of Analysis at Mandiant Threat Intelligence, told SecurityWeek, "Mandiant has collected significant evidence suggesting that MAZE was operated via a profit-sharing arrangement where multiple discrete criminal groups collaborated to perpetrate their crimes -- one group operating the central MAZE infrastructure and various other individuals and teams working together to obtain access to victim networks and deploy MAZE ransomware. Furthermore," he added, "Mandiant has also seen clear cases where named threat actors such as FIN6 have worked with MAZE to monetize intrusions via ransomware distribution."
Secondly, the Maze group attempts to justify its actions. It was not about the money -- of course not -- it was about demonstrating poor security practices so that companies could improve matters. "This perspective from a highly successful ransomware group, who have profited millions from attacks," comments Jamie Hart, a cyber threat intelligence analyst at Digital Shadows, "shows their view of the crimes as somehow helpful. The group referred to their victims as clients," she added, "as if they believed the victim organizations indirectly hired the group as security professionals."
Maze goes on to warn that poor security threatens the national infrastructure, and that although Maze didn't attack the infrastructure, it will not be Maze, but some "radical psychos whose goals will not just to show you the weakness of security but to make a major damage."
Thirdly, under a section titled, 'What for?', the group seems to suggest that part of its purpose is to warn that society is surrendering its humanity to machines. This is not a unique viewpoint. It can almost be seen as a modern version of the Luddite viewpoint.
The Maze attitude focuses on the growth of digital currencies. As their value increases, Maze believes they will become concentrated in the hands of a few people. This is not so different from the current claims that just a few super-wealthy families already control the global economy -- but Maze believes that these people will then be able to crash fiat currency-based economies and drive everything online.
At that point, Maze suggests all will be lost. "You would not even notice when you will be tagged with chips or your DNA will be the only was {sic] to access the new digital world. As it will be the only place you can leave [sic] in, to get paid and consume." It's a fairly standard dystopian view of the future.
Finally, Maze says it will be back. "We will be back to you when the world will be transformed. We will return to show you again the errors and mistakes and to get you out of the Maze."
Overall, the announcement is fairly standard. The criminals deny they were motivated by money, but were more concerned to demonstrate the lack of security in their victims -- in other words, they were a public service. The view of the future is also standard sci-fi -- from Orwell's 1984 to the Wachowskis' Matrix.
Although this could possibly be the end of the Maze brand, the security industry does not believe the Maze operators will disappear quietly into retirement. "A service of this type may be wound down for a variety of reasons," said Kennelly, "including conflict between operators or the fallout from an exit scam, or alternatively it could be done in response to law enforcement scrutiny -- active or suspected. Services of this sort may also be deprecated in order to enable their operators to found a parallel operation using different malware or a different profit-sharing or operational model."
"The Maze threat is likely not finished," Hart told SecurityWeek. "Although the official reason for the announcement is unknown, the ransomware market's oversaturation may have motivated the group to cease operations. It's also possible that this is a similar exit strategy we witnessed with GandCrab in 2019. Another variant may emerge to take Maze's place; some operators have reportedly moved to the Egregor ransomware variant. Finally, they may be moving away from Maze to improve their operational security, decreasing the chance of being caught."
"We assess with high confidence," concluded Kennelly, "that many of the individuals and groups that collaborated to enable the MAZE ransomware service will likely to continue to engage in similar operations -- either working to support existing ransomware services or supporting novel operations in the future."
Maze ransomware is going out of the business
2.11.20 Ransomware Securityaffairs
The Maze ransomware operators are shutting down their operations for more than one year the appeared on the threat landscape in May 2019.
The Maze cybercrime gang is shutting down its operations, it was considered one of the most prominent and active ransomware crew since it began operating in May 2019. The gang was the first to introduce a double-extortion model in the cybercrime landscape at the end of 2019.
At the end of 2019, the Maze ransomware implemented data harvesting capabilities and started threatening the victims to release the stolen data for all those victims who refuse to pay the ransom.
The operators behind the Maze ransomware set up a leak site, dubbed Maze News, where they were publishing the list of the companies that allegedly refused to pay the ransom.
The leak site contains for each victim the data related to the infection, including the date of the attack, some stolen documents (Office, text and PDF files), the size of stolen data, and the list of IP addresses and machine names of the infected servers.
The Maze News site was also and used to publish press releases for the activities of the group.
The double-extortion technique was later adopted by other ransomware gangs, including REvil, DoppelPaymer, Nefilim, and Clop.
The list of victims of the gang is long and includes the Steel sheet giant Hoa Sen Group, Southwire, Canon, LG Electronics, Xerox, and City of Pensacola.
According to BleepingComputer, Maze had stopped encrypting new victims since September 2020 and is collecting the last ransom payments from victims.
This week, Maze has started to remove victims from their data leak site except for two organizations that already had all of their data published.
At the time it is not clear if Maze operators plan to release the keys to allow its victims to decrypt their files after they shut down the operations.
BleepingComputer speculates that Maze affiliates have switched to the Egregor operations, the gang that recently hit the game developer Crytek and leaked files allegedly stolen from the systems of the gaming firm Ubisoft.
“Egregor is believed to be the same underlying software as both Maze and Sekhmet as they utilize the same ransom notes, similar payment site naming, and share much of the same code.” states BleepingComputer.
“This was also confirmed by a ransomware threat actor who stated that Maze, Sekhmet, and Egregor were the same software.”
Ransomware Surge Imperils Hospitals as Pandemic Intensifies
1.11.20 Ransomware Securityweek
Hackers are stepping up attacks on health care systems with ransomware in the United States and other countries, creating new risks for medical care as the global coronavirus pandemic accelerates.
Alerts from US authorities and security researchers highlight a wave of cyberattacks on hospitals coping with rising virus infections.
An unusual warning this week from the FBI with the Departments of Homeland Security and Health and Human Services, underscored the threat.
The three agencies "have credible information of an increased and imminent cybercrime threat to US hospitals and health care providers," said the alert issued Wednesday, calling on health systems to "take timely and reasonable precautions to protect their networks from these threats."
Media reports have cited several US hospitals hit by ransomware.
One of them, the University of Vermont Medical Center, said in a statement Thursday it was working with law enforcement on "a now confirmed cyberattack that has affected some of our systems" which has had "variable impacts" on patient care.
Daniel dos Santos of the computer security firm Forescout said cash-strapped medical centers are particularly attractive targets for hackers and that at least 400 hospitals had been hit in the past few weeks in the US and Britain.
Hackers are aware that "health care is the most likely to pay the ransom because their services are critical," dos Santos said."Stopping services means that people will literally be dying."
For hospitals unable or willing to pay, "it would mean going back to pen and paper, which can cause huge slowdowns," he added.
Forescout said in a report that while many hospitals have upgraded computer systems, most use a variety of connected devices such as patient monitors or CT scanners which "act as the weak links in the network" because they transmit data over insecure channels.
In one sign of the troubles looming, dos Santos and fellow researchers said they discovered data on some three million US patients online, "unprotected and accessible to anyone who knows how to search for it.," the Forescout report said.
- Most targeted -
Ransomware is a longstanding security issue and health care has been a frequent target. A September attack disrupted Universal Health Services, which operates hospitals in the US and Britain.
But security experts say the attacks are accelerating as the pandemic worsens.
Researchers at the security firm Check Point said its survey showed health care has been the most targeted industry by ransomware, with a 71 percent jump in attacks on US providers in October from a month earlier.
Check Point said there have been significant rises in ransomware attacks on hospitals in Asia, Europe and the Middle East as well. Globally, the firm said ransomware attacks were up 50 percent in the third quarter compared with the first half of this year.
Many of the attacks use a strain of ransomware known as Ryuk, which security researchers say may be tied to North Korean or Russian cybercriminals.
The US government warning said health organizations are being targeted by phishing attacks to get access to the systems, with hackers using sophisticated tools including TrickBot software which can harvest credentials and exfiltrate data.
The Canadian government's Cyber Centre issued a similar warning in early October, warning of Ryuk ransomware "affecting multiple entities, including municipal governments and public health and safety organizations in Canada and abroad."
"The ransomware problem is steadily worsening and a solution desperately needs to be found," said Brett Callow of the security firm Emsisoft.
"We believe that solution is a prohibition on the payment of demands. Ransomware exists only because it's profitable. If the flow of cash stops, the attacks will stop and hospitals will no longer be at risk."
REvil ransomware gang hacked gaming firm Gaming Partners International
1.11.20 Ransomware Securityaffairs
The REvil ransomware operators made the headlines again, this time the gang claims to have hacked the Gaming Partners International (GPI).
Gaming Partners International (GPI) is a full-service supplier of gaming furniture and equipment for casinos worldwide. The REvil ransomware gang (aka Sodinokibi) claims to have stolen info from the systems at the company before encrypting them.
Recently, one of the members of the gang that goes online with the moniker UNKN, announced in an interview with Yelisey Boguslavskiy that they were planning an attack against a prominent organization in the gaming network.
The attack happened and today the REvil ransomware operators added Gaming Partners International to their dedicated leak site.
The cybercrime gang published some screenshots showing directories and files from the systems of the breached company.

Source Databreaches.net
The message published by the ransomware gang threatens to release the stolen data if the company will not pay the ransom within 72 hours.
The hackers claim to have stolen 540Gb of technical and financial documents stolen form the company.
“Absolutely all servers and working computers of the company are hacked and encrypted. There was a large data leak 540Gb of the most important information of the company, technical data, financial documents, contracts with ALL CASINO in LAS-VEGAS, MACAO, EUROPE, bank documents.” reads the message published by the ransomware operators.
The list of victims of the REvil ransomware gang is long and includes the London-based Travelex, the law firm of the stars, Grubman Shire Meiselas & Sacks (GSMLaw), the law firm Seyfarth Shaw, and US-based supplier of video delivery software solutions, SeaChange International.
Brooklyn & Vermont US hospitals hit by ransomware attacks
30.10.20 Ransomware Securityaffairs
Wyckoff Heights Medical Center in Brooklyn and the University of Vermont Health Network are the last victims of the Ryuk ransomware operators.
Ryuk ransomware operators continue the target the US healthcare industry, the last victims in order of time are the Wyckoff Heights Medical Center in Brooklyn and the University of Vermont Health Network.
The news of the attack comes a few hours after The FBI, the DHS’s Cybersecurity and Infrastructure Security Agency (CISA), and the Department of Health and Human Services (HHS) have issued a joint alert to warn hospitals and healthcare providers of imminent ransomware attacks from Russia.
This security advisory describes the tactics, techniques, and procedures (TTPs) associated with cyber criminals that could target organizations in the Healthcare and Public Health Sector (HPH) to infect systems with Ryuk ransomware.
The government agencies receive information about imminent attacks, threat actors are using the TrickBot botnet to deliver the infamous ransomware to the infected systems.
This week, the systems at Sky Lakes Medical Center in Oregon and St. Lawrence Health System in New York were infected with the Ryuk ransomware. In September, the Ryuk ransomware gang hit Universal Health Services, one of the largest hospital and healthcare services providers, forcing the company to shut down systems at healthcare facilities in the United States. The incident impacted over 200 medical facilities nationwide.
The news of the Ryuk ransomware attack at the Wycoff hospital was first published by Bleeping Computer that was informed by an employee of the organization.
Wyckoff Heights Medical Center is a 350-bed teaching hospital located in an ethnically diverse residential neighborhood directly on the border of northern Brooklyn and Western Queens, NY.
Wyckoff Hospital shut down portions of its network as part of the incident response procedure.
At the time of publishing this post, it is not known the extent of the incident and the impact on the operations of the hospitals.
University of Vermont Health Network also disclosed a similar cyber attack, the organization is working with the FBI and the Vermont Department of Public Safety on the investigation.
“People who are in urgent need of care are getting it and most appointments are happening,” Dr. Stephen Leffler, president of the University of Vermont Medical Center in Burlington, said at a news conference late Thursday outside the hospital. “Most surgeries will happen tomorrow. We did slow some down today as were switching systems.”
The ransomware attack has caused variable impacts at each of our affiliates, the family of ransomware involved in the attack is yet to be revealed.
“The attack has caused variable impacts at each of our affiliates. Staff are continuing to follow well-practiced standby procedures to ensure safe patient care. We understand the difficulty this causes for our patients and the community and apologize for the impact. There have been some changes to patient appointments and we are attempting to reach those patients who have been affected. We will continue to provide systems and patient service updates when they are available,” read a statement from the University of Vermont Health Network.
According to researchers at CheckPoint, Healthcare is the most targeted industry, by ransomware, in the US in October. Ransomware attacks against the US healthcare sector increased by 71%, experts also reported an increase of 33% in APAC and 36% in EMEA.
DoppelPaymer ransomware gang leaked Hall County, Georgia, voter info
30.10.20 Ransomware Securityaffairs
The DoppelPaymer ransomware operators have released data that was stolen from Hall County, Georgia earlier this month.
The DoppelPaymer ransomware operators have published online data that was stolen from Hall County, Georgia earlier this month.
The attack took place on October 7, it hit Hall County, in the northern part of the state and it disabled the county’s voter signature database.
The ransomware attack hit a Georgia county government and disabled a database used to verify voter signatures in the authentication of absentee ballots. It is a common process to validate absentee ballots sent by mail by analyzing signatures.
The media pointed out that this is the first reported case of a ransomware attack against a system used in the incoming 2020 Presidential election.
Ransomware attacks could have a dramatic impact on the elections, they could disrupt voting systems and raise doubts about the validity of the vote.
While the media reported that the ransomware operators leaked stolen data on their dark web leak site to force the organization to pay the ransom, Hall County stated that there was no indication that the hackers stole any unencrypted data before encrypting the systems.
“At this time, there is no evidence to show that citizen or employee data has been compromised. However, citizens and employees are encouraged to take precautionary measures to monitor and protect their personal information,” Hall County stated.
The DoppelPaymer ransomware gang finally published over 1 GB of files stolen from Hall County systems and revealed that 2,464 devices were encrypted during the attack.

Source Bleeping Computer
According to Bleeping Computer, The dump includes election documents, lobby comment cards, 911 spreadsheets, accounting and financial records.
“The election documents reviewed by BleepingComputer contain ballot proofs, poll worker lists, administrative documents, accounting and financial records, and city bulletins.” reported Bleeping Computer. “Also included are voter registration records containing resident’s voter registration ID, full name, address, and assigned ballot, which is, for the most part, public information.”
Most of the information leaked is public, but can be exploited by threat actors to carry out malicious activities against voters.
Recently the US government revealed that Iran-linked hackers were behind voter intimidation emails that were sent to Democrats in Florida and Alaska that pretended to be from the far-right Proud Boys group.
REvil Gang Promises a Big Video-Game Hit; Claims Massive Revenue
30.10.20 Ransomware Threatpost
In a wide-ranging interview, a REvil leader said the gang is earning $100 million per year, and provided insights into the life of a cybercriminal.
The REvil ransomware gang claims it will rake in $100 million by year’s end. That’s according to a REvil group leader in a rare Q&A with the YouTube Channel for tech blog “Russian OSINT.” During the live interview, the REvil hacker warned of a “big attack coming…linked to a very large video game developer.”
The boasting and threats come on the heels of REvil’s chief rivals, the Maze gang, announcing that it was closing up shop (see below).
The interview (Russian translation provided to Threatpost by Flashpoint) was wide-ranging and touches on the group’s operations, the money it makes, details on its high-profile attacks and the fact that the members are actively being hunted by governments around the world.
Operations
The Q&A first offered details into the group’s operations. For instance, the interviewee signaled an upcoming change in strategy.
While REvil already uses the double-extortion strategy (where companies’ files are not just encrypted but also stolen, with a threatened leak adding pressure to pay the ransom), the leader suggested that the future lie in taking that strategy further.
“Everything ultimately comes down to a shift toward leaking files and not locking them,” he said. “I personally really liked SunCrypt’s idea. DoS [denial of service] the site of the company and their infrastructure, combined with locking the files and threatening to publish them…[it] puts a lot of pressure on them…[We’re] thinking about employing a similar model.”
He also confirmed that REvil employs the ransomware-as-a-service model, where “affiliates” that carry out the attacks receive 70 to 80 percent of the “revenue” from the ransoms. The affiliates themselves are strictly vetted (much like the NetWalker gang), and are responsible for initial network infection, wiping out any backups and downloading files. REvil members meanwhile take care of ransom negotiations, software development and updates, receipt of the payment and the delivery of the decryptor.
When it comes to partners, “we have our own closed family, the selection is very rigorous and we don’t even bother talking to [amateurs],” he said. “Support only helps when it comes to negotiations. They have to master all the technical parts of the job by themselves.”
That said, the group also carries out its own attacks, he said, with a unit devoted to hacking companies – though the ransomware-as-a-service (RaaS) model is more lucrative.
He also said that Android or iOS ransomware is not in the cards for the group, because of the low value of the information stored on phones. “You have to be crazy to get involved in this,” he said. “I’m 100 percent against it.”
High-Profile Attacks
All of that business design has allowed REvil to claim some pretty big headlines. For instance, when asked what the biggest coups were for REvil, he cited, with pride, Travelex, Grubman Shire Meiselas & Sacks, and the 23 Texas municipalities that the gang attacked last summer.
The interviewee also took credit for two rumors associated with REvil. One, that it captured data on President Donald Trump and that REvil was behind Chile’s Banco Estado shutting all of its branches.
In the case of Trump, the files were reportedly lifted as part of the Grubman hack. “We just wished “good luck” to the NSA, FBI, and the U.S. Secret Service with the decryption of the files,” he said. “We didn’t demand money from Trump [directly]…The money for the [stolen] data was paid. I can’t tell you who bought it, though. The data had to do with tax-avoidance scheme affiliated with Trump.”
As for Banco Estado, the initial vector was email to bank employees, he said: “Yes, it really happened – we did it,” he alleged. “Often, companies do not disclose the source of the attack because they are afraid of reputational damage [affecting] their stock position.”
He added that around one-third of all companies quietly negotiate to pay the ransom, and that IT providers, insurance companies, law offices, manufacturing and the agro-industrial sector are the most-lucrative targets.
As for initial access, the interviewee said that harvesting and using administrative credentials with malware, brute-forcing Remote Desktop Protocol connections and exploiting bugs are the best avenues for attack.
“Grubman and Travelex…both were hacked through old versions of Pulsar and Citrix,” he said. “It is actually pretty stupid — we gained access to the [network] in minutes, and all due to one vulnerability that can be patched quickly.”
Attacks are likely to ramp up – and indeed the aforementioned video-game company attack is in the works but under wraps, the REvil operator claimed. But geopolitical realities will add to the momentum, according to Ilia Kolochenko, founder and CEO of web security company ImmuniWeb.
“The pandemic gradually exacerbates the situation, as budgets are being reduced, cybersecurity people are all exhausted, while employees working from home are considerably more vulnerable and susceptible to a wide spectrum of phishing attacks,” he said, via email. “Frequently, it is enough to breach one single user machine to get into a corporate network via VPN. Thus, cybercriminals are now enjoying a windfall of surging profits by effortlessly picking up low-hanging fruits in impunity. Worse, some cybersecurity professionals may sooner or later ponder all pros and cons, and given the unprecedented opportunities and low risks, will readily shift from their daily jobs to generous cyber-gangs.”
Money, Money, Money
All of this activity is in service of course to one thing: Personal enrichment.
The REvil leader noted that life as a cybercriminal started for him with video games.
“Once upon a time, when I was a kid, I installed CHLENIX [cheat config for Counter Strike] and really liked it,” he explained. That legacy lives on. The ransomware’s name is short for “Ransom Evil,” with the nomenclature inspired by the video game “Resident Evil,” according to the interview (only security researchers call it Sodinokibi, he said).
CHLENIX lead to more nefarious things, and now he’s leading a group that claims to be raking in $100 million per year. That’s less than what REvil’s precursor, GandCrab, was making. That group announced a shutdown in June 2019, after claiming to make $2 billion in a year and a half.
REvil was soon developed to take its place, and while the interviewee didn’t confirm the GandCrab connection specifically, he admitted that an earlier project was shut down to make way for a “better product.”
When asked when it would be time to step away form “the life,” he answered. “Personally, I should have stopped a long time ago. I have enough money for hundreds of years, but there is never too much money…[I hope to have] $1 billion, then $2 billion, and then if I’m in a good mood, $5 billion.”
“The [$100 million] number is merely a tip of the cybercrime revenue iceberg,” said Kolochenko. “Concomitant proliferation of cryptocurrencies makes such crimes technically uninvestigable, while law enforcement agencies and joint task forces are already overburdened with nation-state attacks, and transnational targeted attacks aimed to steal intellectual property from the largest Western companies.”
The Downside: Being Hunted
Conventional wisdom says that cyberattackers thrive in dark shadows and anonymity – but comments by the gang leader suggest that REvil members may not be as faceless as they would like.
When asked if group members could travel for instance, the answer was an uncategorical “nope.” The Russian-speaking interviewee added that, contrary to Kolochenko’s claim that being a ransomware operator is “low risk,” no one involved in ransomware would ever travel to Western countries or the United States for fear of being killed.
“We create serious problems and there is no justice for us, so killing us would be the only viable solution,” he said.
He said the group believes they are being hunted by the U.S. Secret Service, Europol and infosec companies on a daily basis, with CIA agents actively trying to infiltrate the group’s operations by posing as an affiliate applicant.
“But generally, their cover falls apart,” he noted. And as for hack-backs, “they have no idea what kind of OS we use on our servers or what kind of web servers we use… They are just hoping to get lucky. Our product…is configured to defend against them.”
Maze Closes Down
During the interview, the REvil leader also touched on its arch rival criminal group Maze, which is reportedly shuttering its operations.
According to someone identifying themselves as a Maze operator told Bleeping Computer this week that the group halted its encryption activities back in September, in order to focus on getting existing victims to pay up.
Soon after, Maze affiliates started porting over to the Egregor ransomware gang, the outlet reported.
Maze was a pioneer in the double-extortion tactic, first emerging last November. Since then, it has made waves with big strikes such as the one against Cognizant. And this summer it formed a cybercrime “cartel” – joining forces with various ransomware strains (including Egregor) sharing code, ideas and resources.
“Criminals don’t just have an epiphany and quit being criminals overnight,” said Lamar Bailey, senior director of security research at Tripwire, via email. “They shut down an operation when the return on their investment drops below the costs of running the ‘program’ or when they are about to get caught. This is no different.”
He added, “They are switching to something new, maybe Egregor, which miraculously came out at the same time Maze started shutting down. This is just like that one furniture store in town that is going out of business every few months only to reopen with a new name but with the same people and product.”
Kegtap, Singlemalt, Winekey Malware Serve Up Ransomware to Hospitals
30.10.20 Ransomware Threatpost
Amid an uptick in attacks on healthcare orgs, malware families, Kegtap, Singlemalt and Winekey are being used to deliver the Ryuk ransomware to already strained systems.
The boozy names might sound like the kind of thing conjured up in a frat-house common room, but malware families Kegtap, Singlemalt and Winekey are being used to gain initial network access in potentially lethal ransomware attacks on healthcare organizations in the midst of a global pandemic, researchers said in newly released findings.
The shot? The rampant spread of COVID-19 has put a tremendous strain on the U.S. healthcare system. The chaser? Cybercriminals are getting better than ever at exploiting that life-and-death crisis to turn a profit.
Who could use a drink?
Mandiant published a report this week laying out the signature tactics of the Kegtap/BEERBOT, Singlemalt/STILLBOT and Winekey/CORKBOT attacks, which researchers said have targeted hospitals, retirement communities and medical centers “… demonstrating a clear disregard for human life,” the report added.
Mandiant researchers observed the ransomware being used to hit a variety of sectors and organizations, in addition to healthcare, and found a few commonalities.
The Malware
Phishing emails, designed to mimic everyday business functions like contracts, personnel paperwork or complaints are sent with a link, not to a malware payload, but to a Google doc, PDF or some other document which would contain the in-line link to the malware.
“Hiding the final payload behind multiple links is a simple yet effective way to bypass some email filtering technologies,” the report said. “Various technologies have the ability to follow links in an email to try to identify malware or malicious domains; however, the number of links followed can vary. Additionally, embedding links within a PDF document further makes automated detection and link-following difficult.”
Kegtap, Singlemalt and Winekey (a.k.a. Bazar variants) act as first-stage loaders, which establish a foothold on a device before fetching malware for the next stage of the attack.
In this case, the criminals use them to download common penetration-testing frameworks like Cobalt Strike, Beacon and/or Powertrick to establish a presence. Following initial compromise, Cobalt Strike helps maintain the malware’s presence after reboot, the report said, and Beacon is the most often observed backdoor in these attacks.
Cobalt Strike, PowerShell Empire, Powersploit and Medasploit are a group of dual-use tools used for both legitimate tasks as well as nefarious ones, according to Cisco researcher Ben Nahorney. These pen-testing tools are intended to help security professionals identify weaknesses in their network defenses, but in the wrong hands they can supercharge attacks.
Beacon has also been used to deploy “PowerLurk’s Register-MaliciousWmiEvent cmdlet to register WMI events used to kill processes related to security tools and utilities, including Task Manager, WireShark, TCPView, ProcDump, Process Explorer, Process Monitor, NetStat, PSLoggedOn, LogonSessions, Process Hacker, Autoruns, AutorunsSC, RegEdit and RegShot,” the report said.
The malware then sets about escalating privileges, most often with valid credentials, according to the report, which are obtained through “exported copies of the ntds.dit Active Directory database and system, and security registry hives from a Domain Controller.”
Beacon, along with publicly available tools like Bloodhound, Sharphound or ADfind, is then deployed for reconnaissance, the researchers added, which enabled the actors to move laterally to expand their footprint across the compromised network.
The Ransomware Payload
The main goal of the mission, according to the report, is to deliver a Ryuk payload.
“There is evidence to suggest that Ryuk ransomware was likely deployed via PsExec, but other scripts or artifacts related to the distribution process were not available for forensic analysis,” the report continued.
This partnership between the developers behind Kegtap, Singlemalt and Winekey with the group behind Ryuk, makes this group particularly noteworthy. Ryuk is operated by an Eastern European actor called UNC1878 according to Mandiant, and continues to be a prolific threat against healthcare organizations — attacks which Charles Carmakal, senior vice president and CTO of Mandiant says pose unprecedented dangers to the U.S.
UNC1878’s Ryuk Threat
UNC1878’s Ryuk has been linked to ransomware spread throughout a Canadian government health organization and just this week was used in ransomware attacks against multiple healthcare systems, including Klamath Falls, Ore.-based Sky Lakes Medical Center and New York-based St. Lawrence Health System.
In September, Universal Health Services, a nationwide hospital operator, was hit by a ransomware attack suspected to have been Ryuk.
“UNC1878 is one of most brazen, heartless and disruptive threat actors I’ve observed over my career, Carmakal told Threatpost.
“Ransomware attacks on our healthcare system may be the most dangerous cybersecurity threat we’ve ever seen in the United States,” Carmakal continued. “Multiple hospitals have already been significantly impacted by Ryuk ransomware and their networks have been taken offline. As hospital capacity becomes more strained by COVID-19, the danger posed by this actor will only increase.”
Kegtap, Singlemalt and Winekey have also caught the attention of U.S. Cyber Command, which tweeted the Mandiant report with the comment, “The public and private sectors are united against ransomware, especially those actors targeting medical facilities during a pandemic.”
Stopping Ransomware Attacks on Healthcare
The key to stopping these attacks, according to the Mandiant report, is moving quickly to harden service accounts, prevent the use of privileged accounts for lateral movement, block internet service to servers where possible, block newly registered domains using DNS filers or web proxies, and update and install patches for Windows in addition to the network (including Zerologon, which has been observed in the attacks).
“The surge of malware campaigns on healthcare organizations is one of the most insidious attacks that can be unleashed by malicious actors — especially during a pandemic,” Jeff Horne, CSO at Order, told Threatpost by email. “These organizations are especially susceptible because many of their mission-critical, internet-connected devices run vulnerable operating systems that cannot be patched. There are nearly 650 million IoT/IoMT devices operating in the healthcare industry right now, and 82 percent of healthcare organizations have had their IoT/IoMT devices attacked.”
Horne adds these healthcare systems are up against a highly professional, well-equipped adversary and need to adapt an appropriate posture to defend their systems.
“These ‘ransomware-as-a-service’ groups are run by sophisticated and malicious developers operating like a criminal company with organized modern customer-focused services, online support, call centers and payment processors — making a considerable amount of money in the process,” Horne added. “This can’t just be addressed with antivirus software — these are focused, motivated and knowledgeable criminal operators that are targeting vulnerable healthcare organizations by exploiting vulnerabilities, gaining a foothold within their networks, and holding their important data hostage.”
FBI, CISA alert warns of imminent ransomware attacks on healthcare sector
30.10.20 Ransomware Securityaffairs
FBI and the DHS’s CISA agencies published a joint alert to warn hospitals and healthcare providers of imminent ransomware attacks from Russia.
The FBI, the DHS’s Cybersecurity and Infrastructure Security Agency (CISA), and the Department of Health and Human Services (HHS) has issued a joint alert to warn hospitals and healthcare providers of imminent ransomware attacks from Russia.
This security advisory describes the tactics, techniques, and procedures (TTPs) associated with cyber criminals that could target organizations in the Healthcare and Public Health Sector (HPH) to infect systems with Ryuk ransomware.
The government agencies receive information about imminent attacks, threat actors are using the TrickBot botnet to deliver the infamous ransomware to the infected systems.
“CISA, FBI, and HHS have credible information of an increased and imminent cybercrime threat to U.S. hospitals and healthcare providers. CISA, FBI, and HHS are sharing this information to provide warning to healthcare providers to ensure that they take timely and reasonable precautions to protect their networks from these threats.” reads the alert.
TrickBot is a popular banking Trojan that has been around since October 2016, its authors have continuously upgraded it by implementing new features.

In early 2019, researchers spotted a new TrickBot backdoor framework dubbed Anchor that was using the anchor_dns tool for abusing the DNS protocol for C2 communications.
Several groups of experts linked both TrickBot and Ryuk threats to cybercrime gangs operating out of Russia. Ryuk first appeared in the threat landscape in August 2018 as a derivative of the Hermes 2.1 ransomware, that was first spotted in late 2017 and was available for sale on the open market as of August 2018
Unlike other ransomware gangs, Ryuk ransomware operators did not announce to avoid targeting healthcare organizations during the COVID-19
A few weeks ago, Universal Health Services (UHS), one of the largest hospital and healthcare services providers, has shut down systems at healthcare facilities in the United States after they were infected with the Ryuk ransomware.
A few days ago, Microsoft’s Defender team, FS-ISAC, ESET, Lumen’s Black Lotus Labs, NTT, and Broadcom’s cyber-security division Symantec joined the forces and announced a coordinated effort to take down the command and control infrastructure of the infamous TrickBot botnet.
Microsoft has taken down 120 of the 128 servers that were composing the Trickbot infrastructure.
Microsoft announced to have taken down 62 of the original 69 TrickBot C&C servers, seven servers that could not be brought down last week were Internet of Things (IoT) devices.
U.S. Hospitals Warned of Imminent Ransomware Attacks From Russia
29.10.20 Ransomware Securityweek
The U.S. government has warned hospitals and healthcare providers of an “increased and imminent” ransomware threat, which some experts have attributed to cybercriminals from Eastern Europe.
The alert was issued on Wednesday by the FBI, the DHS’s Cybersecurity and Infrastructure Security Agency (CISA), and the Department of Health and Human Services (HHS). The organizations say they’ve received credible information that threat actors are targeting the healthcare sector with the TrickBot malware in attacks that often lead to ransomware infections, data theft and disruption of healthcare services.
The alert focuses on TrickBot, particularly the Anchor evasion detection modules used in attacks aimed at high-profile organizations, and the Ryuk ransomware, which has often been delivered using the TrickBot botnet. Both TrickBot and Ryuk were previously linked to threat actors operating out of Russia.
Charles Carmakal, SVP and CTO of Mandiant, described it as “the most significant cyber security threat we’ve ever seen in the United States.”
“UNC1878, an Eastern European financially motivated threat actor, is deliberately targeting and disrupting U.S. hospitals, forcing them to divert patients to other healthcare providers. Patients may experience prolonged wait time to receive critical care,” Carmakal told SecurityWeek. “Multiple hospitals have already been significantly impacted by Ryuk ransomware and their networks have been taken offline. UNC1878 is one of most brazen, heartless, and disruptive threat actors I’ve observed over my career.”
While some ransomware operators have decided to avoid targeting healthcare organizations during the COVID-19 pandemic, that does not seem to be the case for Ryuk operators, who, according to what intelligence firm Hold Security told blogger Brian Krebs, have been planning on deploying ransomware at over 400 healthcare facilities in the United States.
According to various local media reports, several hospitals in the United States reported being hit by ransomware over the past days. A few weeks ago, hospital chain Universal Health Services reported that computers at all 250 of its US facilities were disrupted due to a cyberattacks that is believed to have involved Ryuk.
The TrickBot botnet was recently targeted for takedown by Microsoft and its partners, and in a separate operation by the U.S. government. While the operations appear to have been successful, at least to some extent, Ryuk attacks have continued.
More Hospitals Hit by Growing Wave of Ransomware Attacks
29.10.20 Ransomware Threatpost
Hospitals in New York and Oregon were targeted on Tuesday by threat actors who crippled systems and forced ambulances with sick patients to be rerouted, in some cases.
Two more hospitals were hit with ransomware attacks this week as a growing number of criminals target healthcare facilities during the COVID-19 pandemic.
On Tuesday, Klamath Falls, Ore.-based Sky Lakes Medical Center’s computer systems were compromised by a ransomware attack. On the same day, New York-based St. Lawrence Health System said computers at three of its hospitals (in Canton-Potsdam, Massena and Gouverneur) were attacked by the ransomware variant Ryuk.
Ransomware attacks have become an all-too-familiar reality for hospitals just as COVID-19 has forced many to spread themselves thin and accelerated the adoption of virtual care. This year, as hospitals have scrambled to save lives, cyberattacks targeting healthcare firms have grown 150 percent, according to a report by C5 Alliance.
Sky Lakes Medical Center said that its computer systems were “down” and and that scheduled procedures that require imaging services will need to be delayed. “Emergency and urgent care remain available,” it said in a statement.
The St. Lawrence Health System meanwhile said that within hours of the initial attack, its information systems department “disconnected all systems and shut down the affected network to prevent further propagation,” according to a statement.
Ryuk malware, used in the St. Lawrence attack, is a potent weapon which cybersecurity researchers describe as highly sophisticated. It’s used by threat groups such as North Korea’s Lazarus Group in targeted attacks. The active malware is responsible for a bevy of recent successful attacks, including one that recently shut down Universal Health Services, a Fortune-500 owner of a nationwide network of hospitals.
Cyberattacks in general have become a harrowing reality, threatening patient security tied to not just their data or a missed appointment. A ransomware attack against the Dusseldorf University Hospital in Germany is being blamed for a patient’s death. According to local reports, crippled computer systems forced an ambulance to be diverted to a more distant hospital – resulting in the patient’s death.
Similar to that situation, ambulances were also diverted from the Canton-Potsdam Hospital for a short period of time. And as of Wednesday, the Gouverneur Hospital said it continued to reroute ambulances away from its emergency room.
The attacks come three months after another N.Y.-based hospital, the Samaritan Medical Center, was hit with a ransomware attack on July 25. It took IT workers there 10 weeks to restore systems, the hospital confirmed in a statement. The attack “disrupted” its drug delivery, radiation therapy and medical-imaging services, and forced payroll and accounting to turn to paper records.
“Healthcare-delivery organizations, such as hospitals and clinics, are complex organizations where a broad range of information technology, internet of medical things, operational technology and internet-of-things devices are increasingly interconnected,” pointed out Forescout (PDF) in a recent report on the healthcare sector.
“The growing number and diversity of devices in [healthcare-delivery organizations] have introduced new cybersecurity risks,” according to the firm. “The ability to compromise devices and networks, and the possibility of monetizing patient data, have led to an increase in the number and sophistication of cyberattacks targeting healthcare-delivery organizations in recent years.”
The report said that attackers are attracted to hospitals because of the sheer complexity of their networks. Forescout said many struggle to manage a sprawling number of endpoints, ranging from computer systems, surgical equipment, telemedicine platforms, medical sensors and infusion pumps. All told, the report estimated that healthcare-delivery organizations contain an average of 20,000 devices.
The report urged hospitals to adopt network and device segmentation.
“Segmentation is a foundational control for risk mitigation in networks with a diversity of IT, IoT and OT devices,” according to the report’s authors. They warned, however, that over-segmentation with poorly defined zones only increases complexity with few benefits.
“However, segmentation requires well-defined trust zones based on device identity, risk profiles and compliance requirements for it to be effective in reducing the attack surface and minimizing blast radius,” according to the report.
FBI, DHS Warn Of Possible Major Ransomware Attacks On Healthcare Systems
29.10.20 Ransomware Thehackernews
The US Federal Bureau of Investigation (FBI), Departments of Homeland Security, and Health and Human Services (HHS) issued a joint alert Wednesday warning of an "imminent" increase in ransomware and other cyberattacks against hospitals and healthcare providers.
"Malicious cyber actors are targeting the [Healthcare and Public Health] Sector with TrickBot malware, often leading to ransomware attacks, data theft, and the disruption of healthcare services," the Cybersecurity and Infrastructure Security Agency said in its advisory.
The infamous botnet typically spreads via malicious spam email to unsuspecting recipients and can steal financial and personal data and drop other software, such as ransomware, onto infected systems.
It's worth noting that cybercriminals have already used TrickBot against a major healthcare provider, Universal Health Services, whose systems were crippled by Ryuk ransomware late last month.
TrickBot has also seen a severe disruption to its infrastructure in recent weeks, what with Microsoft orchestrating a coordinated takedown to make its command-and-control (C2) servers inaccessible.
"The challenge here is because of the attempted takedowns, the TrickBot infrastructure has changed and we don't have the same telemetry we had before," Hold Security's Alex Holden told The New York Times.
Although the federal report doesn't name any threat actor, the advisory makes a note of TrickBot's new Anchor backdoor framework, which has been recently ported to Linux to target more high-profile victims.
"These attacks often involved data exfiltration from networks and point-of-sale devices," CISA said. "As part of the new Anchor toolset, Trickbot developers created Anchor_DNS, a tool for sending and receiving data from victim machines using Domain Name System (DNS) tunneling."
As The Hacker News reported yesterday, Anchor_DNS is a backdoor that allows victim machines to communicate with C2 servers via DNS tunneling to evade network defense products and make their communications blend in with legitimate DNS traffic.
Also coinciding with the warning is a separate report by FireEye, which has called out a financially-motivated threat group it calls "UNC1878" for the deployment of Ryuk ransomware in a series of campaigns directed against hospitals, retirement communities, and medical centers.
Urging the HPH sector to patch operating systems and implement network segmentation, CISA also recommended not paying ransoms, adding it may encourage bad actors to target additional organizations.
"Regularly back up data, air gap, and password protect backup copies offline," the agency said. "Implement a recovery plan to maintain and retain multiple copies of sensitive or proprietary data and servers in a physically separate, secure location."
Enel Group suffered the second ransomware attack this year
28.10.20 Ransomware Securityaffairs
Multinational energy company Enel Group has been hit by Netwalker ransomware operators that are asking a $14 million ransom.
Systems at the multinational energy company Enel Group has been infected with Netwalker ransomware, it is the second ransomware attack suffered by the energy giant this year. Netwalker ransomware operators are asking a $14 million ransom for the decryption key, the hackers claim to have stolen several terabytes from the company and threaten to leak them if the ransom will be not paid.
Enel S.p.A., or the Enel Group, is an Italian multinational energy company that is active in the sectors of electricity generation and distribution, as well as in the distribution of natural gas.
The company has more than 61 million customers in 40 countries, it ranks 87 in Fortune Global 500, with $90 billion in revenues in 2019.
In June, Enel was hit by Snake ransomware, but the attack was quickly contained and the malware was not able to spread within its network.
The news of a possible ransomware attack against Enel Group was reported to BleepingComputer by a researcher on October 19.
The researcher shared with BleepingComputer a Netwalker ransom note that appeared to be used in the attack on Enel Group.

Source Bleeping Computer
BleepingComputer attempted to notify Enel Group last week without success. A few days later, Netwalker announced the leak of the company data through their support chat.
Enel never replied to the message of the ransomware operators, for this reason, the attackers started leaking a portion of the stolen data as proof of the data breach.
The operators are asking $14 million worth of Bitcoin (roughly 1234.02380000 BTC).

Source Bleeping Computer
Today, the Netwalker ransomware operators added Enel Group to their data leak site and some screenshots of unencrypted files stolen from the company.
The Italian cyber security firm TG soft publicly shared the news of the attack in a tweet:
The hackers stole about 5 terabytes of documents from the company and announced that they will “analyze every file for interesting things” and publish it on their leak site.
At the time of publishing this post, the company have yet to confirm the incident, let’s remember that the company conduct will have to be in compliance with the current EU privacy legislation GDPR.
Steelcase office furniture giant hit by Ryuk ransomware attack
28.10.20 Ransomware Securityaffairs
Office furniture company Steelcase was hit by Ryuk ransomware attack that forced it to shut down its network to avoid the malware from spreading.
Steelcase is a US-based furniture company that produces office furniture, architectural and technology products for office environments and the education, health care and retail industries. It is the largest office furniture manufacturer in the world. It has facilities, offices, and factories in the Americas, Europe, Asia, the Middle East, Australia and Africa.
Steelcase has 13,000 employees and $3.7 billion in 2020. The company is the last victim of the Ryuk ransomware operators, the attack forced the firm to shut down its network to avoid the malware from spreading.
In an 8-K form filed with the Securities and Exchange Commission (SEC), the company has disclosed the ransomware attack that took place on October 22nd, 2020.
“On October 22, 2020, Steelcase Inc. (the “Company”) detected a cyberattack on its information technology systems. The Company promptly implemented a series of containment measures to address this situation including temporarily shutting down the affected systems and related operations.” reads the 8-K form.
The company immediately started the incident response procedure in an attempt to restore the affected systems and return to normal operations as soon as possible. The company is not aware of data loss caused by the ransomware attack.
Bleeping Computer, citing a source in the cybersecurity industry, confirmed that Steelcase suffered a Ryuk ransomware attack.
“At this time, the Company is not aware of any data loss from its systems or any other loss of assets as a result of this attack. Although cyberattacks can be unpredictable, the Company does not currently expect this incident will have a material impact on its business operations or its financial results.” continues the form.
Ryuk ransomware operators were very active during the recent weeks, recently the gang infected systems at the Universal Health Services and French IT outsourcer Sopra Steria.
In March, the City of Durham shut down its network after Ryuk Ransomware attack.
A few days before, EVRAZ, one of the world’s largest multinational vertically integrated steel making and mining companies, has been hit by the Ryuk ransomware.
The list of the victims of the Ryuk ransomware is very long and includes the US government contractor Electronic Warfare Associates (EWA), US railroad company Railworks, Croatian petrol station chain INA Group, and parts manufacturer Visser Precision.
Threat actors behind Ryuk attacks often used the BazarLoader or TrickBot infections to gain a foothold in the target networks and then deploy Ryuk.
IT Services Giant Sopra Steria Hit by Ransomware
27.10.20 Ransomware Securityweek
European IT services provider Sopra Steria on Monday said its systems were recently infected with a new variant of the notorious Ryuk ransomware.
France-based Sopra Steria, which claims to have 46,000 employees across 25 countries, offers a wide range of IT services, including consulting, technology, software, system integration, business process, infrastructure management and cybersecurity.
The company reported on October 21 that it had detected an intrusion on its IT network the day before and that it had started working on containing the incident.
In an update shared on Monday, the IT giant said it was targeted in a cyberattack that involved a new variant of the Ryuk ransomware, a variant that allegedly was “previously unknown to antivirus software providers and security agencies.”
“Sopra Steria’s investigation teams immediately provided the competent authorities with all information required. The Group was able to quickly make this new version’s virus signature available to all antivirus software providers, in order for them to update their antivirus software,” the company said. “Moreover, it has also been established that the cyberattack was only launched a few days before it was detected.”
The fact that the attackers only gained access to Sopra Steria systems just days before the attack was uncovered is not surprising. The DFIR Report said recently that in one of the attacks it observed, only 29 hours passed between the first email being sent by the hackers and systems becoming fully compromised and encrypted.
Sopra Steria said the incident only impacted a “limited part” of its infrastructure and claimed that it had found no evidence of data leaks or damage to customer systems. However. the firm expects that it will take a few weeks until all operations return to normal.
Russia-linked cybercriminals who use the Ryuk ransomware have been known to also steal data from victims in an effort to increase their chances of getting paid.
The Ryuk ransomware has often been delivered via the TrickBot botnet, whose infrastructure was recently targeted for takedown by both the U.S. government and private sector companies. While the operation against TrickBot appears to have been successful — at least to some degree — it was reported just days before Sopra Steria was targeted that Ryuk attacks continued.
Ransomware attack disabled Georgia County Election database
26.10.20 Ransomware Securityaffairs
A ransomware attack recently hit Georgia county government and reportedly disabled a database used to verify voter signatures.
A ransomware attack hit a Georgia county government early this month and disabled a database used to verify voter signatures in the authentication of absentee ballots. It is a common process to validate absentee ballots sent by mail by analyzing signatures.
The media pointed out that this is the first reported case of a ransomware attack against a system used in the incoming 2020 Presidential election.
Ransomware attacks could have a dramatic impact on the elections, they could disrupt voting systems and raise doubts about the validity of the vote.
The attack took place on October 7, it hit Hall County, in the northern part of the state and it disabled the county’s voter signature database.
“One of the databases the county uses to verify voter signatures on absentee ballots is not working after some county network outages due to a ransomware attack on Oct. 7.” reported the Gainesville Times. “Registration Coordinator Kay Wimpye with the county elections office said employees can still verify voter signatures by manually pulling hard copies of voter registration cards, which is more time-consuming. Most voter signatures can be verified using a state database that has been unaffected by the outages, she said.”
The media reported that the Hall County attack was carried out by Doppelpaymer ransomware operators that also leaked stolen data on their dark web leak site to force the organization to pay the ransom.
The county website published an update to announce that the attack did not impact the voting process for citizens, a situation that is differed from the scenario reported by the Times.
Boyne Resorts ski and golf resort operator hit with WastedLocker ransomware
24.10.20 Ransomware Securityaffairs
The systems at the US-based ski and golf resort operator were infected with the WastedLocker ransomware, the incident impacted reservation systems.
Boyne Resorts is a collection of mountain and lakeside resorts, ski areas, and attractions spanning from British Columbia to Maine. The company owns and operates eleven properties and an outdoor lifestyle equipment/apparel retail division with stores in cities throughout Michigan. An industry leader in multiple U.S. regions, operations include snowsports and year-round mountain recreation, golf, an indoor waterpark, spas, food and beverage, lodging and real estate development.
Boyne Resorts was the victim of WastedLocker ransomware attack, the incident has impacted reservation systems.
According to BleepingComputer, the ransomware initially breached the corporate offices and then moved laterally targeting the IT systems of the resorts they operate. As result of the attack the company was forced to shut down portions of its network to prevent the ransomware from spreading.
Customers of the company were not able to make reservations at the resorts operated by the company. .
The ransomware encrypted files and renamed their filenames by adding the “.easy2lock” extension, this extension was previously associated with recent WastedLocker ransomware infections.
In July, Smartwatch and wearable device maker Garmin had to shut down some of its connected services and call centers following a WastedLocker Ransomware attack.
In June, security experts from Symantec reported that at least 31 organizations in the United States have been targeted with the recently discovered WastedLocker ransomware.
Researchers from the NCC Group’s report and later Symantec confirmed that malware was developed by the Russian cybercrime crew known as Evil Corp, which was behind the Dridex Trojan, and multiple ransomware like Locky , Bart, Jaff, and BitPaymer.
Most of the victims belong to the manufacturing industry, followed by IT and media and telecommunications sectors.
This group has been active since at least 2007, in December 2019, the U.S. Treasury Department imposed sanctioned on Evil Corp for causing more than $100 million in financial damages.
The U.S. Department of Justice (DoJ) has charged Russian citizens Maksim V. (32) and Igor Turashev (38) for distributing the infamous Dridex banking Trojan, and for their involvement in international bank fraud and computer hacking schemes.
Ransom payments to WastedLocker is not allowed by US authorities, this means that Boyne Resorts could face severe sanctions if it will pay the ransom.
Ransomware Takes Down Network of French IT Giant
24.10.20 Ransomware Threatpost
Sopra Steria hit with cyber attack that reportedly encrypted parts of their network on Oct. 20 but has remained mostly mum on details.
French IT giant Sopra Steria was hit with a cyber attack this week that disrupted the business of the firm and is widely believed to be the work of the threat actors behind Ryuk ransomware.
The company revealed the attack in a brief press statement released Oct. 22, two days after officials said the attack—which reportedly encrypted parts of the firm’s network—occurred.
“A cyberattack has been detected on Sopra Steria’s IT network on the evening of 20th October,” officials said. “Security measures have been implemented in order to contain risks.”
Sopra Steria employs 46,000 people in 25 countries and even has a cybersecurity arm that specializes in helping customers implement “reliable security and resiliency,” according to its website.
However the company, which did $4.4 billion in business last year, divulged nothing of exactly what type of attack it was and what services, systems and data were affected, sources in the French media claim it was Ryuk ransomware that took down the company.
If that’s true than the attackers behind Ryuk have been quite active lately. Earlier this week the group—also responsible for the TrickBot and BazarLoader infections used together with the ransomware—also struck in an unusually swift attack that went from sending a phishing email to complete encryption across the victim’s network in just five hours.
Ryuk also is behind a ransomware attack less than a month ago that shut down Universal Health Services, a Fortune-500 owner of a nationwide network of hospitals.
Sopra Steria is currently working to recover its systems “for a return to normal as quickly as possible” after the attack, as well as making “every effort … to ensure business continuity,” officials said in a statement. The company is working with authorities on the matter as well as staying in touch with customers and partners.
Still, it’s unfortunate that a company that specializes in IT services and cybersecurity would keep the public in the dark about key details of what went down during the attack and how it might affect their affiliates, observed Chloe Messdaghi, vice president of strategy for Point3 Security.
“One thing that is disappointing however is that Sopra Steria didn’t inform its customers in their public notification of exactly what types of data were exposed,” she said in an e-mail to Threatpost. “They also didn’t offer any advice on the kinds of attack attempts that end users whose data was exposed might expect and should be prepared to spot. Those potential attack strategies are dependent on the data exposed.”
This type of transparency with customers who could have been affected and exposed to risk is especially important for companies that specialize in IT services to uphold in these circumstances, Messdaghi said.
“As a digital transformation company, Sopra Steria is no doubt aware of these risks,” she said. “It’s crucially important that they share them, and quickly, with those whose data was exposed.”
Louisiana Calls Out National Guard to Fight Ransomware Surge
24.10.20 Ransomware Threatpost
An investigation showed a custom backdoor RAT and the Emotet trojan in the networks of municipal victims of the attacks.
The National Guard has been called in to help stop a series of government-focused ransomware attacks in Louisiana, according to a report.
Local government offices across the Pelican State have been besieged by ransomware strikes, according to a cybersecurity consultant speaking to Reuters, with “evidence suggesting a sophisticated hacking group was involved.”
The paper reported that a forensic investigation into the attacks unearthed a remote access trojan (RAT) buried in affected networks, which is often the calling card of an advanced persistent threat (APT) group known to be an arm of the North Korean government. That said, the “KimJongRat” backdoor has had its source code partially leaked, which could allow cyberattackers to copy it – thus casting doubt on that attribution.
The Emotet trojan was also found in victim networks, sources said, which can load other malware and self-propagate through networks. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued a warning earlier this month that state and local governments need to fortify their systems against the malware, amid a dramatic uptick in Emotet phishing attacks on municipalities since July.
“This increase has rendered Emotet one of the most prevalent ongoing threats,” the CISA alert read.
Sources said that the attacks were successful in locking up networks in several government offices in northern Louisiana, after staff were socially engineered via email into opening an attachment and triggering the infection chain. Further, the attackers took over victim email accounts to send malware to other employees under the guise of legitimate communications.
However, that cyberattack was stopped “in its early stages before significant harm was done,” according to the report.
It’s unclear which ransomware family was used in the attacks. The Louisiana National Guard has declined to comment on the incidents.
This is not the first time that Louisiana has called out the National Guard to combat cyberattacks. In July 2019, Louisiana’s governor declared a statewide state of emergency after ransomware hits on at least three school districts – Monroe City, Morehouse Parish and Sabine Parish. Declaring the state of emergency allowed coordination between cybersecurity experts from the National Guard, Louisiana State Police and the Office of Technology Services.
Ransomware attacks continue to surge in all sectors. Just this month, Software AG was struck by the Clop ransomware; French IT giant Sopra Steria was afflicted with Ryuk; and a county in Georgia found its voter-registration database caught up in an attack.
Georgia Election Data Hit in Ransomware Attack
24.10.20 Ransomware Threatpost
With Election Day approaching, local governments need to be prepared for malware attacks on election infrastructure.
Ransomware gangs have officially entered the 2020 election fray, with reports of one of the first breaches of the voting season, on Hall County, Ga. The county’s database of voter signatures was impacted in the attack along with other government systems.
Although the county said the voting process hasn’t been impacted by the ransomware attack, the incident is a warning to other municipalities to lock down their systems, particularly in these last days leading up to the election.
Hall County sits about an hour north of Atlanta and first reported the attack on Oct. 7.
Ransomware attacks involve a criminal introducing malware into the target’s systems, which then takes over an organization’s data and encrypts it until a ransom is paid.
Hall County’s Ransomware Attack
On Oct. 21, the Gainesville Times reported the county’s precinct map was down as a result of a ransomware attack, in addition to a voter-signature database.
It wasn’t until Oct. 22 that the county announced, “The voting process for citizens has not been impacted by the attack.”
“A ransomware attack has occurred involving critical systems within the Hall County government networks, including an interruption of phone services,” according to a news release. “As soon as it occurred, the county began working to investigate the cause, to restore operations and determine the effects of the incident.”
Hall County registration coordinator Kay Wimpye old the paper that some of the systems are already back up and running and if there is a question about a ballot signature, county employees are still able to pull voter-registration cards manually. But with record numbers of mail-in ballots being submitted, that could prove to be a time-consuming process.
Wimpye told the Times that her office sent out 27,573 absentee ballots as of Oct. 21, and 11,351 had been sent back. The Georgia Secretary of State reported that by Oct. 21, 2016, 103,239 mail-in ballots had been returned, compared to 805,442 on the same day in 2020, showing an explosion in the number of voters opting for mail-in voting this election cycle. Although the signatures are being verified now, the ballots won’t be tabulated until Election Day, according to the Times.
Ransomware & the Public Sector
Ransomware attacks timed this close to Election Day threaten to throw an already contentious competition into total disarray.
Brandon Hoffman, CIO at Netentrich, called the attack on voting infrastructure “inevitable.”
“The ransomware spree has gone essentially unchecked and it stands to reason that type of malware would be the one to hit,” he added. “On the other hand, with ransomware, election infrastructure probably wasn’t the main target.”
But, Hoffman warns, that could change.
“The fact that this was successful validates the attack path,” he said. “Attack-path validation is a key step in any attack sequence, and testing it on small-scale scenarios always makes sense. If security professionals working with voting technology were not already extra-vigilant, there’s no time to waste in getting over-prepared.”
Public-sector organizations are already a juicy target for malware attacks. More than half (52 percent) of public-sector organizations have been attacked and saw malware spread from a compromised user to colleagues, according to a recent report on public sector email security from Mimecast.
The report added that 9 percent of those attacked experienced more than a week of downtime as a result, the most of any other industry. And with the election just over a week away, that could spell disaster for getting votes tabulated in time.
Matthew Gardiner, cybersecurity strategist at Mimecast, told Threatpost by email that attackers see an easy payday in local governments.
“Ransomware-centric cybercriminals are focused on money,” he said. “Thus, they focus on hitting organizations that are relatively easy to get into and have an ability/willingness to pay the ransom. In general, cities, municipalities, towns, and school districts score high here.”
Once a ransom is paid, Gardiner compared it to “blood in the water for sharks,” drawing in more predators. The election deadline may up the price for the data or motivate targets to pay more quickly, but besides that, Gardiner doesn’t see the election outcome as a specific motivator for cybercriminals.
Patching & Training
To keep systems protected at such a sensitive time, two simple things can make a big difference: Patching and employee training, according to Daniel Norman, senior solutions analyst at Information Security Forum.
“Moving forward, end users should receive ample security awareness, education and training on the threat of ransomware, particularly its delivery mechanism,” Norman said in an emailed statement. “Typically, the success of ransomware is reliant on whether or not the target organization has patched its devices properly. Therefore, having all systems patched and up-to-date is a minimal for security.”
Ransomware is on the rise across the globe thanks to the pandemic, up more than 109 percent over last year, according to SonicWall’s 2020 Cyber Threat Report.
Hank Schless, senior manager with security solutions at Lookout, pointed out that workers scattered across the globe on mobile devices are more vulnerable than ever to socially engineered ploys as they toggle between personal and professional applications.
“As workers across the globe began working from home, organizations enabled their employees to stay productive by using mobile devices, and attackers know this,” Schless said.
“Organizations that are proactive about securing mobile devices with mobile security are at the forefront of innovation and demonstrate that they are adapting to today’s rapidly evolving threat landscape,” he added.
As for Hall County, their spokeswoman Katie Crumley declined to provide a comment to Threatpost, beyond the press release, “for security purposes.” The statement said the county “has enlisted the assistance of third-party cyber security professionals to expedite the recovery.”
Sopra Steria hit by the Ryuk ransomware gang
24.10.20 Ransomware Securityaffairs
French IT outsourcer Sopra Steria hit by ‘cyberattack’, Ryuk ransomware suspected
French IT outsourcer Sopra Steria has been hit by a ransomware attack, while the company did not reveal the family of malware that infected its systems, local media speculate the involvement of the Ryuk ransomware.
“A cyber attack was detected on the Sopra Steria computer network on the evening of October 20. Security measures have been taken to limit the risk of propagation.” reads the press release published by the company. “The Group’s teams are fully mobilized to ensure a return to normal as quickly as possible and everything is done to ensure business continuity. Sopra Steria is in close contact with its customers and partners as well as with the competent authorities.”
The European IT firm has 46,000 employees operating in 25 countries worldwide. It provides a wide range of IT services, including software development and consulting.
“According to our sources, the incident started to spread during the course of last night. The Active Directory infrastructure would be affected. And part of the information system would have been encrypted.” reported the website LeMagit. “Two sources tell us that the ransomware involved is none other than Ryuk. Surprise, researcher JamesWT_MHT found on VirusTotal a copy of an executable which two sources have confirmed to us is used internally at ESN for the generation of email signatures.”
French authorities are investigating the incident.
Sopra Steria is a member of France’s Cyber Campus, a French initiative to spread cybersecurity awareness, training, and product sales.
The Ryuk ransomware operators were very active early this year, in March they targeted hospitals even as these organizations are involved in the fight against the Coronavirus pandemic.
In September, the Universal Health Services (UHS) healthcare providers has reportedly shut down systems at healthcare facilities after a Ryuk ransomware attack.
In March, the City of Durham shut down its network after Ryuk Ransomware attack.
A few days before, EVRAZ, one of the world’s largest multinational vertically integrated steel making and mining companies, has been hit by the Ryuk ransomware.
The list of the victims of the Ryuk ransomware is very long and includes the US government contractor Electronic Warfare Associates (EWA), US railroad company Railworks, Croatian petrol station chain INA Group, and parts manufacturer Visser Precision.
Ransomware Group Makes Splashy $20K Donation to Charities
21.10.20 Ransomware Threatpost
Cybercriminal gang Darkside sent $20K in donations to charities in a ‘Robin Hood’ effort that’s likely intended to draw attention to future data dumps, according to experts.
The Darkside ransomware group has distinguished itself from its cybercriminal counterparts not by technical innovation, but by slapping a shiny corporate veneer on its attacks. The latest evolution in Darkside’s ransomware-as-a-corporation gimmick is a hefty $20,000 donation that the group made with stolen Bitcoin to two international charitable organizations, The Water Project and Children International, which they then mysteriously announced by a press release.
“Altruism isn’t a common trait in criminal extortion gangs, so it’s difficult to take their motivations at their word,” Chris Clements with Cerberus Sentinel said in a statement about the donations.
The Water Project did not immediately respond to Threatpost’s inquiries. Children’s International told Threatpost that the matter is being investigated.
“We are aware of the situation and are researching it internally,” Lauren Jurgens from Children’s International told Threatpost by email. “If the donation is linked to a hacker, we have no intention of keeping it.”
Darkside announced the deposits on October 13 through one of its corporatized “press releases” posted on a dark web portal, according to BBC, along with tax receipts for the donations for .88 Bitcoin for each group, or $10,000 apiece.
“The most troubling realization here is that the cybercriminals have made so much money through extortion that donating $20,000 is chump change to them,” Clements added.
Darkside’s Branding Effort
Darkside has devoted much of its time to trying to carve out a position as an altruistic, digital Robin Hood. The public relations ploy isn’t likely to have much sway with law-enforcement, and public sentiment has little to do with criminal activity.
“As we said in the first press release — we are targeting only large, profitable corporations,” the group wrote. “We think it’s fair that some of the money they’ve paid will go to charity. No matter how bad you think our work is, we are pleased to know that we helped change someone’s life.”
Javvad Malik, security awareness advocate with KnowBe4, told Threatpost that regardless of the messaging, the goal of ransomware crimes remains the same: To drive better outcomes for their breaches and steal more money.
“This [steal from the rich, give to the poor tactic] is not so much a shift in the narrative as a shift in the business model driving these criminal organizations,” he said, adding that bigger corporations give them more of what they want. “The more systems that can be disrupted, the more data that can be stolen, and the more public pressure that can be mounted on organizations — which means a greater likelihood for payout out and greater profit.”
Ransomware Goes Corporate
Digital Shadows has been tracking Darkside since it popped up last August, and a recent report pointed out that their tactics follow typical ransomware patterns. The exception is their chosen targets.
Stefano De Blasi with Digital Shadows said in that report that the group tries to differentiate itself by vowing not to attack organizations like schools, hospitals or governments, instead focusing on companies based on revenue.
Darkside uses customized ransomware for each attack and, according to Digital Shadows, combs through company’s financial data to pinpoint what they believe to be an appropriate ransom.
“The ransomware executes a PowerShell command that deletes shadow volume copies on the system. DarkSide then proceeds to terminate various databases, applications, and mail clients to prepare for encryption,” De Blasi wrote.
Personalized ransom notes from Darkside are then issued to the breached company with details on the type of data stolen, as well as how much and a link to their leak site, where the data will be published if ransom demands aren’t met.
Getting the criminal gang’s name in the headlines is one way to help make sure published, stolen data gets the most attention possible, causing the most damage possible to targets.
“Whether or not they’ll succeed in breaking the mold – only time will tell,” De Blasi added. “While the cyber-threat landscape can be unpredictable and volatile, a trend is a trend, and we will continue to monitor the cybercriminal bandwagon closely.”
Most researchers are not impressed by Darkside’s seeming altruism and careful victim selection.
“This latest ‘donation’ effort by ransomware operators is just an attempt to improve their image publicly,” Katie Nickels, director of intelligence at Red Canary, said via email. “When the pandemic first started, we saw ransomware operators claim that they wouldn’t target hospitals — yet we know many of them have. If ransomware operators truly cared about making the world a better place, they would stop ransoming victims, not make donations.”
Life of Maze ransomware
21.10.20 Ransomware Securelist
In the past year, Maze ransomware has become one of the most notorious malware families threatening businesses and large organizations. Dozens of organizations have fallen victim to this vile malware, including LG, Southwire, and the City of Pensacola.
The history of this ransomware began in the first half of 2019, and back then it didn’t have any distinct branding – the ransom note included the title “0010 System Failure 0010”, and it was referenced by researchers simply as ‘ChaCha ransomware’.
Ransom note of an early version of Maze/ChaCha ransomware
Shortly afterwards, new versions of this Trojan started calling themselves Maze and using a relevantly named website for the victims instead of the generic email address shown in the screenshot above.
Website used by a recent version of Maze ransomware
Infection scenarios
Mass campaigns
The distribution tactic of the Maze ransomware initially involved infections via exploit kits (namely, Fallout EK and Spelevo EK), as well as via spam with malicious attachments. Below is an example of one of these malicious spam messages containing an MS Word document with a macro that’s intended to download the Maze ransomware payload.
If the recipient opens the attached document, they will be prompted to enable editing mode and then enable the content. If they fall for it, the malicious macro contained inside the document will execute, which in turn will result in the victim’s PC being infected with Maze ransomware.
Tailored approach
In addition to these typical infection vectors, the threat actors behind Maze ransomware started targeting corporations and municipal organizations in order to maximize the amount of money extorted.
The initial compromise mechanism and subsequent tactics vary. Some incidents involved spear-phishing campaigns that installed Cobalt Strike RAT, while in other cases the network breach was the result of exploiting a vulnerable internet-facing service (e.g. Citrix ADC/Netscaler or Pulse Secure VPN). Weak RDP credentials on machines accessible from the internet also pose a threat as the operators of Maze may use this flaw as well.
Privilege escalation, reconnaissance and lateral movement tactics also tend to differ from case to case. During these stages, the use of the following tools has been observed: mimikatz, procdump, Cobalt Strike, Advanced IP Scanner, Bloodhound, PowerSploit, and others.
During these intermediate stages, the threat actors attempt to identify valuable data stored on the servers and workstations in the compromised network. They will then exfiltrate the victim’s confidential files in order to leverage them when negotiating the size of the ransom.
At the final stage of the intrusion, the malicious operators will install the Maze ransomware executable onto all the machines they can access. This results in the encryption of the victim’s valuable data and finalizes the attack.
Data leaks/doxing
Maze ransomware was one of the first ransomware families that threatened to leak the victims’ confidential data if they refused to cooperate.
In fact, this made Maze something of a trendsetter because this approach turned out to be so lucrative for the criminals that it’s now become standard for several notorious ransomware gangs, including REvil/Sodinokibi, DoppelPaymer, JSWorm/Nemty/Nefilim, RagnarLocker, and Snatch.
The authors of the Maze ransomware maintain a website where they list their recent victims and publish a partial or a full dump of the documents they have managed to exfiltrate following a network compromise.
Website with leaked data published by Maze operators
Ransomware cartel
In June 2020, the criminals behind Maze teamed up with two other threat actor groups, LockBit and RagnarLocker, essentially forming a ‘ransomware cartel’. The data stolen by these groups now gets published on the blog maintained by the Maze operators.
It wasn’t just the hosting of exfiltrated documents where the criminals pooled their efforts – apparently they are also sharing their expertise. Maze now uses execution techniques that were previously only used by RagnarLocker.
Brief technical overview
The Maze ransomware is typically distributed as a PE binary (EXE or DLL depending on the specific scenario) which is developed in C/C++ and obfuscated by a custom protector. It employs various tricks to hinder static analysis, including dynamic API function imports, control flow obfuscation using conditional jumps, replacing RET with JMP dword ptr [esp-4], replacing CALL with PUSH + JMP, and several other techniques.
To counter dynamic analysis, this Trojan will also terminate processes typically used by researchers, e.g. procmon, procexp, ida, x32dbg, etc.
The cryptographic scheme used by Maze consists of several levels:
To encrypt the content of the victim’s files, the Trojan securely generates unique keys and nonce values to use with the ChaCha stream cipher;
The ChaCha keys and nonce values are encrypted by a session public RSA-2048 key which is generated when the malware is launched;
The session private RSA-2048 key is encrypted by the master public RSA-2048 key hardcoded in the Trojan’s body.
This scheme is a variation of a more or less typical approach used by developers of modern ransomware. It allows the operators to keep their master private RSA key secret when selling decryptors for each individual victim, and it also ensures that a decryptor purchased by one victim won’t help others.
When executing on a machine, Maze ransomware will also attempt to determine what kind of PC it has infected. It tries to distinguish between different types of system (‘backup server’, ‘domain controller’, ‘standalone server’, etc.). Using this information in the ransom note, the Trojan aims to further scare the victims into thinking that the criminals know everything about the affected network.
Strings that Maze uses to generate the ransom note
Fragment of the procedure that generates the ransom note
How to avoid and prevent
Ransomware is evolving day by day, meaning a reactive approach to avoid and prevent infection is not profitable. The best defense against ransomware is proactive prevention because often it is too late to recover data once they have been encrypted.
There are a number of recommendations that may help prevent attacks like these:
Keep your OS and applications patched and up to date.
Train all employees on cybersecurity best practices.
Only use secure technology for remote connection in a company local network.
Use endpoint security with behavior detection and automatic file rollback, such asKaspersky Endpoint Security for Business.
Use the latest threat intelligence information to detect an attack quickly, understand what countermeasures are useful, and prevent it from spreading.
Detection
Kaspersky products protect against this ransomware, detecting it as Trojan-Ransom.Win32.Maze; it is blocked by Behavior-based Protection as PDM:Trojan.Win32.Generic.
We safeguard our customers with the best Ransomware Protection technologies.
TIP Cloud Sandbox report summary and execution map with mapping on MITRE ATT&CK Framework
Ryuk Ransomware Gang Uses Zerologon Bug for Lightning-Fast Attack
20.10.20 Ransomware Threatpost
Researchers said the group was able to move from initial phish to full domain-wide encryption in just five hours.
The Ryuk threat actors have struck again, moving from sending a phishing email to complete encryption across the victim’s network in just five hours.
That breakneck speed is partially the result of the gang using the Zerologon privilege-escalation bug (CVE-2020-1472), less than two hours after the initial phish, researchers said.
The Zerologon vulnerability allows an unauthenticated attacker with network access to a domain controller to completely compromise all Active Directory identity services, according to Microsoft. It was patched in August, but many organizations remain vulnerable.
In this particular attack, after the attackers elevated their privileges using Zerologon, they used a variety of commodity tools like Cobalt Strike, AdFind, WMI and PowerShell to accomplish their objective, according to the analysis from researchers at the DFIR Report, issued Sunday.
The Attack Begins
The attack started with a phishing email containing a version of the Bazar loader, researchers said. From there, the attackers performed basic mapping of the domain, using built-in Windows utilities such as Nltest. However, they needed to escalate their privileges to do any real damage, so they exploited the recently disclosed Zerologon vulnerability, researchers said.
Having gained elevated admin privileges, the cybercriminals were able to reset the machine password of the primary domain controller, according to the analysis.
Then, they moved laterally to the secondary domain controller, carrying out more domain discovery via Net and the PowerShell Active Directory module.
“From there, the threat actors appeared to use the default named pipe privilege escalation module on the server,” researchers said. “At this point, the threat actors used [Remote Desktop Protocol] RDP to connect from the secondary domain controller to the first domain controller, using the built-in administrator account.”
Cobalt Strike
Lateral movement was initiated via Server Message Block (SMB) and Windows Management Instrumentation (WMI) executions of Cobalt Strike beacons, researchers said. SMB is a networking file-share protocol included in Windows 10 that provides the ability to read and write files to network devices. WMI meanwhile enables management of data and operations on Windows-based operating systems.
Cobalt Strike belongs to a group of dual-use tools that are typically leveraged for both exploitation and post-exploitation tasks. Other examples in circulation include PowerShell Empire, Powersploit and Metasploit, according to recent findings from Cisco.
“From memory analysis, we were also able to conclude the actors were using a trial version of Cobalt Strike with the EICAR string present in the network configuration for the beacon. Both portable executable and DLL beacons were used,” researchers added.
Once on the main domain controller, another Cobalt Strike beacon was dropped and executed.
The analysis of the attack revealed that after about four hours and 10 minutes, the Ryuk gang pivoted from the primary domain controller, using RDP to connect to backup servers.
“Then more domain reconnaissance was performed using AdFind. Once this completed…the threat actors were ready for their final objective,” according to DFIR’s report.
Five Hours Later: Ryuk
For the final phase of the attack, the Ryuk operators first deployed their ransomware executable onto backup servers. After that, the malware was dropped on other servers in the environment, and then workstations.
Ryuk is a highly active malware, responsible for a string of recent hits, including a high-profile attack that shut down Universal Health Services (UHS), a Fortune-500 owner of a nationwide network of hospitals.
“The threat actors finished their objective by executing the ransomware on the primary domain controller, and at the five-hour mark, the attack completed,” researchers said.
The use of Zerologon made the cybrcriminals’ efforts much easier, since the attack didn’t need to be aimed at a high-privileged user who would likely have more security controls.
In fact, the toughest part of the campaign was the start of the attack – the successful installation of Bazar from the initial phishing email, which required user interaction. Researchers note that the user was a Domain User and did not have any other permissions – but that proved to be a non-issue, thanks to Zerologon.
The attack shows that organizations need to be ready to move more quickly than ever in response to any detected malicious activity.
“You need to be ready to act in less than an hour, to make sure you can effectively disrupt the threat actor,” according to researchers.
Zerologon Attacks Surge
The case study comes as exploitation attempts against Zerologon spike. Government officials last week warned that advanced persistent threat actors (APTs) are now leveraging the bug to target elections support systems.
That came just days after Microsoft sounded the alarm that an Iranian nation-state actor was actively exploiting the flaw (CVE-2020-1472). The APT is MERCURY (also known as MuddyWater, Static Kitten and Seedworm). And, Cisco Talos researchers also recently warned of a spike in exploitation attempts against Zerologon.
In September, the stakes got higher for risks tied to the bug when four public proof-of-concept exploits for the flaw were released on Github. This spurred the Secretary of Homeland Security to issue a rare emergency directive, ordering federal agencies to patch their Windows Servers against the flaw by Sept. 2.
Nefilim ransomware gang published Luxottica data on its leak site
20.10.20 Ransomware Securityaffairs
The Nefilim ransomware operators have posted a long list of files that appear to belong to Italian eyewear and eyecare giant Luxottica.
Luxottica Group S.p.A. is an Italian eyewear conglomerate and the world’s largest company in the eyewear industry. As a vertically integrated company, Luxottica designs, manufactures, distributes and retails its eyewear brands, including LensCrafters, Sunglass Hut, Apex by Sunglass Hut, Pearle Vision, Target Optical, Eyemed vision care plan, and Glasses.com. Its best known brands are Ray-Ban, Persol, and Oakley. Luxottica also makes sunglasses and prescription frames for designer brands such as Chanel, Prada, Giorgio Armani, Burberry, Versace, Dolce and Gabbana, Miu Miu, and Tory Burch.
Luxottica employs over 80,000 people and generated 9.4 billion in revenue for 2019.
On September 18, the company was hit by a cyberattack, some of the web sites operated by the company were not reachable, including Ray-Ban, Sunglass Hut, LensCrafters, EyeMed, and Pearle Vision.
Italian media outlets reported that the operations at the plants of Luxottica in Agordo and Sedico (Italy) were disrupted due to a computer system failure. Union sources confirmed that the personnel at the plants received an SMS in which they were notified that “the second workshift of today 21 September is suspended” due to “serious IT problems”.
BleepingComputer website, citing the security firm Bad Packets, speculates that the Italian was using a Citrix ADX controller device vulnerable to the critical CVE-2019-19781 vulnerability in Citrix devices.
At the time Luxottica has yet to release any official statement on the attack.
Security experts believe that threat actor exploited the above flaw to infect the systems at the company with ransomware.
Now we have more information about the incident, that seems to be the result of a ransomware attack.
The popular Italian cyber security expert Odysseus first revealed on the web site “Difesa e Sicurezza” that the Nefilim ransomware operators have posted a long list of files that appear to belong to Luxottica.
The huge trove of files appears to be related to the personnel office and finance departments.

The analysis of the leaked files revealed that they contain confidential information regarding the recruitment process, professional resumes, and info about the internal structures of the Group’s human resource department.
The exposed financial data includes budgets, marketing forecast analysis, and other sensitive data.
Nefilim ransomware operators also published a message which accuses Luxottica of having failed the properly manage the attack.
In the past months, the number of ransomware attacks surged, numerous ransomware gangs made the headlines targeting organizations worldwide and threating the victims of releasing the stolen data if the ransom was not paid.
“Extortion it’s the “new deal” of the cybercrime: now, more than in the past, companies can’t “hide” the cyber attack anymore. Now it becomes mandatory “manage” the breach from the communication perspective: dissembling is useless and harmful.” explained Odysseus. “And again, defend the companies from the cyber attacks becomes even more strategic: data leaks damages can generate tremendus amount of costs for companies worldwide.”
One of the crews that adopted this double-extortion model is the Nefilim ransomware gang that targeted several organizations including the mobile network operator Orange, the independent European leader in multi-technical services The SPIE Group, the German largest private multi-service provider Dussman Group.
Ryuk Ransomware Attacks Continue Following TrickBot Takedown Attempt
20.10.20 Ransomware Securityweek
The threat actor behind the Ryuk ransomware continues to conduct attacks following the recent attempts to disrupt the TrickBot botnet, CrowdStrike reports.
Referred to as WIZARD SPIDER, the adversary has been widely using TrickBot for the distribution of ransomware, and the recent attempts by the U.S. Cyber Command and Microsoft to disrupt the botnet were expected to put an end to such operations.
However, the efforts had little effect on the botnet, and the threat actor is apparently able to continue operations at the same pace as before. With over one million infected machines, TrickBot represents a serious threat.
According to CrowdStrike, an initial swing at the botnet was observed on September 21, when a non-standard configuration file was being delivered to some of the infected machines, to instruct them to connect to a command and control (C&C) server address at 0.0.0.1 on TCP port 1.
As a result of this move, an unknown number of bots remained isolated from the network and became unreachable through the normal C&C channel. The non-standard config file was downloaded approximately 10,000 times, which translates into roughly one percent of systems infected with TrickBot being separated from the botnet.
“The operation against the TrickBot network was orchestrated to take down the botnet, thus reducing BGH infections by WIZARD SPIDER’s Ryuk and Conti ransomware families, with an ultimate goal of protecting the forthcoming U.S. elections from ransomware operations,” CrowdStrike notes.
TrickBot’s operators quickly switched to secondary channels to ensure their operations could continue. Emotet started deploying TrickBot last week, and WIZARD SPIDER added BazarLoader into the mix, an initial access tool the threat actor has used before.
Distributed through spam emails leading to Google Docs, BazarLoader features a backdoor component that provides the threat actor with the ability to run payloads and arbitrary scripts.
Starting September 2018, CrowdStrike notes, the Ryuk ransomware has been the most lucrative operation run by WIZARD SPIDER, as victims are believed to have paid over $61 million in ransom to recover files encrypted by Ryuk.
For an unknown reason, in March 2020, the group moved away from Ryuk and switched to the Conti ransomware, which emerged in an attack in June 2020. Conti, which has received weekly updates and improvements, is estimated to have been used to compromise more than 120 networks to date, most of them located in North America and Europe.
“Additional features, obfuscation techniques and code changes are integrated on an almost weekly basis. In August 2020, Conti’s technique shifted from fully encrypting files with AES-256 to a more strategic and efficient approach of selectively encrypting files with the ChaCha stream cipher. Conti’s host discovery and network share targeting functionality has also continued to evolve and is now comparable to that of Ryuk’s,” the security firm notes.
In September 2020, however, WIZARD SPIDER resumed Ryuk deployments and little code changes were observed between the ransomware’s April 2020 and September 2020 variants. The most notable of these modifications is the introduction of code obfuscation, although these are not as advanced as those used in Conti and BazarLoader.
“The ultimate goal of the disruption operation against the TrickBot network was to impact and prevent ransomware infections […]. While the valiant efforts of the cybersecurity teams involved in this complex operation undoubtedly had a short-term impact on WIZARD SPIDER’s TrickBot network, the response by the criminal actors has been swift, effective and efficient,” Crowdstrike concludes.
FIN11 gang started deploying ransomware to monetize its operations
19.10.20 Ransomware Securityaffairs
The financially-motivated hacker group FIN11 has started spreading ransomware to monetize its cyber criminal activities.
The financially-motivated hacker group FIN11 has switched tactics starting using ransomware as the main monetization method.
The group carried out multiple high-volume operations targeting companies across the world, most of them in North America and Europe.
In recent attacks, the group was observed deploying the Clop ransomware into the networks of its victims.
Since August, FIN11 started targeting organizations in many industries, including defense, energy, finance, healthcare, legal, pharmaceutical, telecommunications, technology, and transportation.
Researchers from FireEye’s Mandiant observed FIN11 hackers using spear-phishing messages distributing a malware downloader dubbed FRIENDSPEAK.
“Recently, FIN11 has deployed CLOP ransomware and threatened to publish exfiltrated data to pressure victims into paying ransom demands.” reads the analysis published by FireEye. “The group’s shifting monetization methods—from point-of-sale (POS) malware in 2018, to ransomware in 2019, and hybrid extortion in 2020—is part of a larger trend in which criminal actors have increasingly focused on post-compromise ransomware deployment and data theft extortion.”
The attack chain starts when the victims enable the macro embedded in an Excel spreadsheet that came with the phishing e-mails.
The macros download and execute the FRIENDSPEAK code, which in turn downloads the MIXLABEL malware.
Experts also reported that the threat actor modified the macros in Office documents used as bait and also added geofencing techniques.
Mandiant researchers highlighted an important with operations conducted by the TA505 cybercrime gang (aka Evil Corp), which has been active since 2014 focusing on retail and banking sectors.
TA505 also deployed the Clop ransomware in its malware campaigns and recently started exploiting the ZeroLogon critical flaw to compromise targeted organizations.
“Attribution of both historic TA505 activity and more recent FIN11 activity is complicated by the actors’ use of criminal service providers. Like most financially motivated actors, FIN11 doesn’t operate in a vacuum. We believe that the group has used services that provide anonymous domain registration, bulletproof hosting, code signing certificates, and private or semi-private malware.” reads the analysis. “Outsourcing work to these criminal service providers likely enables FIN11 to increase the scale and sophistication of their operations.”

The experts pointed out that the FIN11 actors after dropped the Clop ransomware did not abandon the target after losing access, at least in one case they re-compromised the target organization a few months later.
The researchers believe FIN11 operates from the Commonwealth of Independent States (CIS – former Soviet Union countries).
The experts observed Russian-language file metadata in the code of the malware and reported that the Clop ransomware was only deployed on machines with a keyboard layout used outside CIS countries.
Mandiant researchers speculate FIN11 will continue to target organizations with sensitive proprietary data and that will likely pay the ransom to recover their operations after the attacks.
Carnival Corp. Ransomware Attack Affects Three Cruise Lines
16.10.20 Ransomware Threatpost
Hackers accessed personal information of guests, employees and crew for Carnival Cruise, Holland America and Seabourn as well as casino operations.
Hackers accessed personal information of guests, employees and crew for three cruise line brands and the casino operations of Carnival Corp. in a ransomware attack the company suffered on Aug. 15, officials have confirmed.
Carnival Cruise Line, Holland America Line and Seabourn were the brands affected by the attack, which Carnival is still investigating, the company said in an update on the situation this week. Carnival has been working with cybersecurity consultants to recover its files and believes there is a a “low likelihood of the data being misused,” the company said.
Carnival had already revealed that it was the target of a ransomware attack two days after the incident, on Aug. 17. At the time acknowledged that hackers had accessed and encrypted a portion of one brand’s information technology systems, as well as downloaded data files from the company.
Carnival continues to work “as quickly as possible to identify the guests, employees, crew and other individuals whose personal information may have been impacted,” according to the update. Within 30 to 60 days, Carnival plans to complete the process and notify those known to be affected, provided the company has their current contact information.
In the meantime, anyone who believes they may have been affected can contact a dedicated call center the company set up to answer questions regarding the event, Carnival said. “When the investigation is complete, callers may confirm whether or not their information was affected,” the company said.
Cruise operators, like many other touristic services-oriented companies, have been hit hard during the COVID-19 pandemic, which has inspired hackers to take advantage of their troubled situation. Indeed, threat actors have been on nearly constant attack across industries since March when news of the pandemic first hit across the world, inspiring business closures and stay-at-home orders that left organizations vulnerable.
Calling the attack “yet another example of the importance of proper investment in cyber security programs to protect company and customer data,” Terence Jackson, CISO at cloud privileged access management solution provider Thycotic, stressed continued vigilance as the pandemic persists.
“Attackers are not taking it easy during the pandemic,” he said in an e-mail to Threatpost. “They are stepping the attacks up and we have to be ready.”
Business continuity and disaster recovery are two areas companies should consider bolstering during this unique time of vulnerability to attacks, noted Steve Durbin, managing director of the Information Security Forum.
“Established plans that depend on employees being able to work from home, for example, do not stand up to an attack that removes connectivity or personally targets individuals as a means of dropping ransomware into the corporate infrastructure,” he said in an e-mail to Threatpost. “Revised plans should cover threats to periods of operational downtime caused by attacks.”
For its part, Carnival said it is indeed taking proactive steps to bolster its security position, reviewing security and privacy policies and procedures and implementing changes when needed to enhance information security and privacy controls as it continues its review of the incident.
Egregor ransomware gang leaked data alleged stolen from Ubisoft, Crytek
16.10.20 Ransomware Securityaffairs
The Egregor ransomware gang has hit the game developer Crytek and leaked files allegedly stolen from the systems of the gaming firm Ubisoft.
A previously unknown ransomware gang dubbed Egregor has hit the game developer Crytek and leaked files allegedly stolen from the internal network of another leading gaming firm, Ubisoft.
A few days ago, the Egregor ransomware operators posted archives containing unencrypted files allegedly stolen in two distinct attacks from the two gaming firms.
Data allegedly stolen from the two companies were published on the Egregor’s gang dark web leak site. The ransomware operators leaked 300 MB from Crytek and 20 MB from Ubisoft.
The files stolen from Crytek contained data related to the development of games like Arena of Fate and Warface, along with the company’s old Gface social gaming network.

Source ZDNet
At the time of writing the post, media outlets only confirmed the ransomware attack against Crytek, while it is not clear if Ubisoft suffered a security breach.
Files of the gaming firm were encrypted and the ransomware appended the’.CRYTEK’ extension to their filenames.
Egregor Ransomware operators also threatened to leak the source code of a popular upcoming Ubisoft game, the Watch Dogs: Legion.
Security researcher MalwareHunterTeam has attempted, without success, to warn Ubisoft for almost a year that their employees were the victims of phishing attacks.
FIN11 Hackers Spotted Using New Techniques In Ransomware Attacks
15.10.20 Ransomware Thehackernews
A financially-motivated threat actor known for its malware distribution campaigns has evolved its tactics to focus on ransomware and extortion.
According to FireEye's Mandiant threat intelligence team, the collective — known as FIN11 — has engaged in a pattern of cybercrime campaigns at least since 2016 that involves monetizing their access to organizations' networks, in addition to deploying point-of-sale (POS) malware targeting financial, retail, restaurant, and pharmaceutical sectors.
"Recent FIN11 intrusions have most commonly led to data theft, extortion and the disruption of victim networks via the distribution of CLOP ransomware," Mandiant said.
Although FIN11's activities in the past have been tied to malware such as FlawedAmmyy, FRIENDSPEAK, and MIXLABEL, Mandiant notes significant overlap in TTPs with another threat group that cybersecurity researchers call TA505, which is behind the infamous Dridex banking Trojan and Locky ransomware that's delivered through malspam campaigns via the Necurs botnet.
It's worth pointing that Microsoft orchestrated the takedown of the Necurs botnet earlier this March in an attempt to prevent the operators from registering new domains to execute further attacks in the future.
High-Volume Malspam Campaigns
FIN11, in addition to leveraging a high-volume malicious email distribution mechanism, has expanded its targeting to native language lures coupled with manipulated email sender information, such as spoofed email display names and email sender addresses, to make the messages appear more legitimate, with a strong bent towards attacking German organizations in their 2020 campaigns.
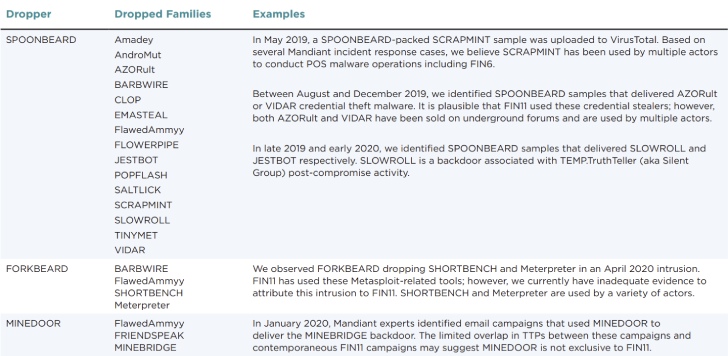
For instance, the adversary triggered an email campaign with email subjects such as "research report N-[five-digit number]" and "laboratory accident" in January 2020, followed by a second wave in March using phishing emails with the subject line "[pharmaceutical company name] 2020 YTD billing spreadsheet."
"FIN11's high-volume email distribution campaigns have continually evolved throughout the group's history," Andy Moore, senior technical analyst at Mandiant Threat Intelligence, told The Hacker News via email.
"Although we have not independently verified the connection, there is substantial public reporting to suggest that until sometime in 2018, FIN11 relied heavily on the Necurs botnet for malware distribution. Notably, observed downtime of the Necurs botnet has directly corresponded to lulls in the activity we attribute to FIN11."
Indeed, as per Mandiant's research, FIN11's operations appear to have ceased entirely from mid-March 2020 through late May 2020, before picking up again in June via phishing emails containing malicious HTML attachments to deliver malicious Microsoft Office files.
The Office files, in turn, made use of macros to fetch the MINEDOOR dropper and the FRIENDSPEAK downloader, which then dispatched the MIXLABEL backdoor on the infected device.
A Shift to Hybrid Extortion
In recent months, however, FIN11's monetization efforts have resulted in a number of organizations infected by CLOP ransomware, in addition to resorting to hybrid extortion attacks — combining ransomware with data theft — in a bid to force businesses into acquiescing to extortion payments that range from a few hundred thousand dollars up to 10 million dollars.
"FIN11's monetization of intrusions via ransomware and extortion follows a broader trend among financially motivated actors," Moore said.
"Monetization strategies that have been more common historically, such as the deployment of point-of-sale malware, limit criminals to targeting victims in certain industries, whereas ransomware distribution can allow actors to profit from an intrusion into the network of nearly any organization.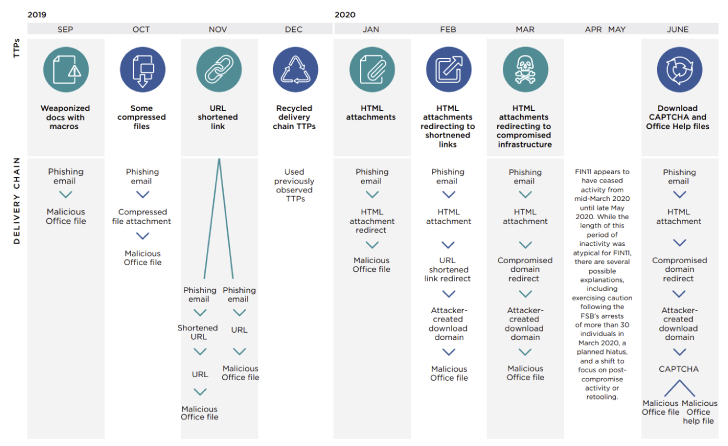
That flexibility, in combination with increasingly frequent reports of ballooning ransom payments, makes it an extremely attractive scheme for financially motivated actors," he added.
What's more, FIN11 is purported to have made use of a wide variety of tools (e.g., FORKBEARD, SPOONBEARD, and MINEDOOR) purchased from underground forums, thereby making attribution difficult or accidentally conflating activities of two disparate groups based on similar TTPs or indicators of compromise.
An Actor of Likely CIS Origin
As for the roots of FIN11, Mandiant stated with "moderate confidence" that the group operates out of the Commonwealth of Independent States (CIS) owing to the presence of Russian-language file metadata, avoidance of CLOP deployments in CIS countries, and the dramatic fall in activity coinciding the Russian New Year and Orthodox Christmas holiday period between January 1-8.
"Barring some sort of disruption to their operations, it is highly likely that FIN11 will continue to attack organizations with an aim to deploy ransomware and steal data to be used for extortion," Moore said.
"As the group has regularly updated their TTPs to evade detections and increase the effectiveness of their campaigns, it is also likely that these incremental changes will continue. Despite these changes, however, recent FIN11 campaigns have consistently relied on the use of macros embedded in malicious Office documents to deliver their payloads."
"Along with other security best practices, organizations can minimize the risk of being compromised by FIN11 by training users to identify phishing emails, disabling Office macros, and implementing detections for the FRIENDSPEAK downloader."
Software AG Data Released After Clop Ransomware Strike – Report
14.10.20 Ransomware Threatpost
The Clop group attacked Software AG, a German conglomerate with operations in more than 70 countries, threatening to dump stolen data if the whopping $23 million ransom isn’t paid.
Clop and the group’s signature malware has struck again — this time hitting a giant target in the form of German software conglomerate Software AG. The company isn’t paying a mammoth $23 million ransom (so far), and over the weekend it confirmed that the crooks were releasing company data, according to reports.
The Clop ransomware cybercriminals were able to infiltrate the company’s systems in early October. The company released a statement on October 5 publicly announcing the attack, adding, “While services to its customers, including its cloud-based services, remain unaffected, as a result, Software AG has shut down the internal systems in a controlled manner in accordance with the company’s internal security regulations,” the statement read.
But that assessment turned out to be prematurely rosy. Just days later, the company had to admit that Clop was, in fact, able to access and download customer data. And on Saturday, it admitted that the data was being released, according to Bloomberg.
Threatpost Webinar Promo Retail Security
Click to Register!
“Today, Software AG has obtained first evidence that data was downloaded from Software AG’s servers and employee notebooks,” the company said in its follow-up statement. “There are still no indications for services to the customers, including the cloud-based services, being disrupted.”
The company has shut down internal systems as a security precaution – as of the time of this writing, the effects of the cyberattack are dragging on.
“Ransomware gangs are becoming bolder and more sophisticated, going after larger and more lucrative targets with their criminal attacks,” said Saryu Nayyar, CEO at Gurucul, via email. “This recent attack against Germany’s Software AG is one of the largest ransomware attacks, but it will certainly not be the last. Even with a complete security stack and a mature security operations team, organizations can still be vulnerable. The best we can do is keep our defenses up to date, including behavioral analytics tools that can identify new attack vectors, and educate our users to reduce the attack surface.”
She added, “With little risk of punishment and potentially multi-million dollar payoffs, these attacks will continue until the equation changes.”
Clop’s Clout
“Scale and clout do not make an organization immune from ransomware attacks, and often make them a more vulnerable target,” Dan Piazza, technical product manager for Stealthbits Technologies said, via email. “An organization having deep pockets means attackers will devote vast resources towards compromising them, and more employees and networks means a larger attack surface. This also shows that threat actors are more motivated than ever and feel confident requesting exorbitant sums — likely due to past successes.”
Clop has emerged as a potent ransomware threat. First discovered in Feb. 2019 by the MalwareHunterTeam, the group continues to terrorize companies with a tactic called “double extortion,” meaning it steals the data and if their ransom demands aren’t met, the data is dumped on a criminal website for anyone to access.
Besides, Software AG, Clop recently hit ExecuPharm, a biopharmaceutical company, in April. And after the company refused to pay, the criminals leaked the compromised data. Other ransomware groups engage in similar tactics, including Maze, DoppelPaymer and Sodinokibi.
Just last month, the Maze gang dumped the personal information of students in Las Vegas on a shady underground forum, after the Clark County School District didn’t pay the ransom.
But Clop is distinguishing itself by going after top-flight companies, rather than the small- to midsize school districts and municipalities, which have emerged as the bread and butter of ransomware crooks everywhere.
MalwareHunterTeam shared excerpts from the ransom note sent by Clop to Software AG, which included the warm greeting, “HELLO DEAR SOFTWARE AG.” The ransom note continued more ominously, “If you refuse to cooperate, all data will be published for free download on our portal…”
Inside the Clop Malware
Researchers Alexandre Mundo and Marc Rivero Lopez at McAfee explained how Clop malware works in a recent blog post.
“The Clop ransomware is usually packed to hide its inner workings,” they wrote. “Signing a malicious binary, in this case ransomware, may trick security solutions to trust the binary and let it pass.” They also said the malware is equipped with the ability to terminate itself if it isn’t successfully installed as a service.
Once deployed, it compares the victim’s computer keyboard against hardcoded values.
“The malware checks that the layout is bigger than the value 0x0437 (Georgian), makes some calculations with the Russian language (0x0419) and with the Azerbaijan language (0x082C). This function will return 1 or 0, 1 if it belongs to Russia or another CIS country, or 0 in every other case,” Mundo and Lopez explained.
If it returns 0, the malware functions normally. If not, it fetches the entire screen context. It also determines whether the system uses a Russian character set, and if it does, the malware deletes itself. Otherwise, the malware marches on.
“This double-check circumvents users with a multisystem language, i.e. they have the Russian language installed but not active in the machine to avoid this type of malware,” they added.
Next, Clop’s ransomware creates a new thread and creates a folder entitled “Favorite” in a shared folder with the malware. It will then make a dummy call that the researchers think is intended to produce an error message, and loops for 666,000 times. If the malware discovers antivirus protections, it goes to sleep for five seconds, only to later continue its nefarious operation.
“The next action is to write this batch file in the same folder where the malware stays with the function ‘CreateFileA,'” they said. “The file created has the name ‘clearsystems-11-11.bat’. Later will launch it with ‘ShellExecuteA,’ wait for five seconds to finish, and delete the file with the function ‘DeleteFileA.'”
Clop’s use of .bat files indicates to Mundo and Lopez the authors aren’t very sophisticated programmers.
“All these actions could have been performed in the malware code itself, without the need of an external file that can be detected and removed,” they wrote.
A second version of Clop analyzed by the researchers shows an evolution of the malware, but with the same basic structure and intent.
Companies Wrangle with Clop
As Clop and other ransomware groups appear to be upping the ante on attacks, Piazza advises compromised organizations to be honest and up-front with customers about the security of their data. He points to Software AG’s clean up statement on Oct. 5 as a prime example of what not to do and that overly optimistic prognostications that must be recanted later are poisonous to the customer relationship.
“Customers want to be reassured their data is safe when an organization they do business with is the victim of ransomware, however when statements need to be later walked back it ends up doing more harm to an organization’s reputation than if they hadn’t issued the statement to begin with (at least until the extent of the attack is known),” Piazza advised, “Although statements such as these are typically done with good intentions, they can still have consequences if proven wrong and sensitive data is leaked.”
Software AG has not responded to inquiries.
Leading Law firm Seyfarth Shaw discloses ransomware attack
14.10.20 Ransomware Securityaffairs
Seyfarth Shaw, one of the leading global legal firms announced that it was a victim of an “aggressive malware” attack, likely a ransomware attack.
Seyfarth Shaw LLP is an international AmLaw 100 law firm headquartered in Chicago, Illinois, its clients include over 300 of the Fortune 500 companies, and its practice reflects virtually every industry and segment of the economy.
Seyfarth Shaw announced it was the victim of an “aggressive malware” attack, but the media immediately reported a ransomware infection later confirmed by the firm.
According to a statement published by the company, the attack took place on October 10, 2020.
“On October 10, 2020, Seyfarth was the victim of a sophisticated and aggressive malware attack. At this time, our email system remains down.” reads the statement published by the company.
“We understand that a number of other entities were simultaneously hit with this same attack. Our monitoring systems detected the unauthorized activity, and our IT team acted quickly to prevent its spread and protect our systems.”
The firm confirmed that many of its systems were encrypted and it is not aware of unauthorized access to its client or firm data,
“We have found no evidence that any of our client or firm data were accessed or removed.” continues the statement. “However, many of our systems were encrypted, and we have shut them down as a precautionary measure.”
The company notified law enforcement and it is supporting the investigation conducted by the FBI.
The firm added that an undisclosed number of companies was hit “simultaneously” by the same threat actors.
At the time of this post, the law firm did not disclose details about the attack, it is not clear the family of ransomware that hit the company and the extent of the security incident.
In the past other law firms suffered ransomware attacks, sometimes with dramatic consequences for their business like the Mossack Fonseca case.
In May, the Sodinokibi ransomware gang has stolen gigabytes of legal documents from the law firm of the stars, Grubman Shire Meiselas & Sacks (GSMLaw). In June 2017, the global law firm DLA Piper experienced severe issues at its systems after a ransomware attack.
Ransomware Attackers Buy Network Access in Cyberattack Shortcut
13.10.20 Ransomware Threatpost
Network access to various industries is being offered in underground forums at as little as $300 a pop – and researchers warn that ransomware groups like Maze and NetWalker could be buying in.
For prices between $300 and $10,000, ransomware groups have the opportunity to easily buy initial network access to already-compromised companies on underground forums. Researchers warn this opportunity gives groups like Maze or Sodinokibi the ability to more easily kickstart ransomware attacks across various industries.
The ability to purchase initial network access gives cybercriminals a quicker handle on infiltrating corporate and government networks, so that they can focus in on establishing persistence and moving laterally.
Threatpost Webinar Promo Retail Security
Click to Register!
“Network-access selling has progressed from a niche underground offering throughout 2017 to a central pillar of criminal underground activity in 2020,” said Thomas Willkan and Paul Mansfield, senior analysts with Accenture’s CTI Reconnaissance team, in a Monday post.
The salespeople behind this activity typically first develop an initial network vulnerability and infiltrate the victim network to gain complete corporate network access. Once that access is gained, the threat groups then sell it on dark web forums. The pricing depends on the size and revenue of the victim.
Network-access offerings are typically advertised on underground forums with victim industry info (such as banking or retail), the type of access for sale (VPN, Citrix or remote-desktop protocol, for instance), the number of the machines on the network, the country the victim operates in and more (such as the number of employees or revenue of the company).
In September, researchers tracked more than 25 persistent network-access sellers – with more entering the scene on a weekly basis. These sellers are operating on the same forums as actors associated with the ransomware gangs Maze, Lockbit, Avaddon, Exorcist, NetWalker, Sodinokibi and others, they said.
“Although it is difficult to prove that an advertised network access is linked to a specific ransomware attack, from analysis of threat-actor activity we assess with high confidence that some of the accesses are being purchased by ransomware groups and affiliates, thereby enabling potentially devastating ransomware attacks on corporate entities,” they said.
Upon closer inspection of these network access sellers, researchers noted that compromised RDP connections continue to be the most common attack vector – however, cybercriminals are increasingly offering up other vectors, including compromised Citrix and Pulse Secure VPN clients.
“We assess that network-access sellers are taking advantage of remote working tools as more of the workforce works from home as a result of the COVID-19 pandemic,” said researchers.
Another trend is that network-access sellers are starting to use zero-day exploits and sell the network access itself, as opposed to selling the zero-day exploit on its own. One threat actor named Frankknox, for instance, started by advertising for a zero-day targeting a popular mail server for $250,000 – however, he later killed that sale and started exploiting the zero-day himself, and went on to offer corporate network access to 36 companies instead. This network access has been marketed for between $2,000 up to $20,000 – and the threat group claimed to have sold access to at least 11 organizations.
Companies can protect themselves from network compromise and ransomware attacks by setting up monitoring capabilities, regularly backing up their data and employing best practices for using RDP, said researchers.
“We assess with high confidence that the relationship between initial access broker and ransomware group will continue to thrive in 2020 and beyond, earning the threat actors behind it huge profits,” they said. “This symbiotic relationship facilitates continuous targeting of government and corporate entities and streamlines the network compromise process, allowing cyber criminals to act quicker and more efficiently.”
Anatomy of Ryuk Attack: 29 Hours From Initial Email to Full Compromise
13.10.20 Ransomware Securityweek
An attack involving the Ryuk ransomware required 29 hours from an email being sent to the target to full environment compromise and the encryption of systems, according to the DFIR Report, a project that provides threat intelligence from real attacks observed by its honeypots.
Initially detailed in 2018, Ryuk was believed to be the work of North Korean hackers at first, due to similarities with the Hermes ransomware, but was then associated with Russian cybercriminals.
Over the past two years, Ryuk has been responsible for a significant number of high-profile attacks, including incidents involving Pennsylvania-based UHS and Alabama hospital chain DCH Health System.
In the case of the attack observed by the DFIR Report, it all started with a malicious email that carried a link to download the Bazar/Kegtap loader, which injects into multiple processes, and which performs reconnaissance on the infected system, using Windows utilities like nltest and net group, as well as third-party tool AdFind.
The malware remained quiet for roughly one day, after which a second reconnaissance phase was launched, using the same tools, plus Rubeus. Data was exfiltrated to a remote server and the attackers started lateral movement.
To compromise additional systems on the network, the attackers used various methods, including remote WMI, remote service execution with PowerShell, and a Cobalt Strike beacon dropped over SMB. Next, the Cobalt Strike beacon was used as the main pivotal point.
Additional beacons were then established across the environment and PowerShell was employed to disable Windows Defender. Ryuk was executed one minute after being transferred over SMB from the pivot and, once encryption started, the servers used to store backups were hit first.
The DFIR Report, which provides a comprehensive technical analysis of the attack, reveals that Ryuk was also transferred to the remaining hosts on the network via SMB, and that an RDP connection was leveraged to execute it from the pivot domain controller.
“In total, the campaign lasted 29 hours–from initial execution of the Bazar, to domain wide ransomware. If a defender missed the first day of recon, they would have had a little over 3 hours to respond before being ransomed,” The DFIR Report notes.
After the systems were encrypted, the attackers demanded approximately 600 Bitcoins (roughly $6 million) in ransom. However, the threat actors were willing to negotiate.
On Monday, Microsoft announced that it shut down the infrastructure of TrickBot, the botnet used as the main delivery channel for Ryuk ransomware.
Law Firm Seyfarth Shaw Hit by Damaging Ransomware Attack
13.10.20 Ransomware Securityweek
International law firm Seyfarth Shaw LLP has shut down many of its systems after being hit with a ransomware attack.
Founded in 1945 in Chicago, Illinois, Seyfarth has over 900 lawyers across 17 offices, providing clients all around the world with advisory, litigation, and transactional legal services. The Am Law 100 firm serves more than 300 of the Fortune 500 companies.
Over the weekend, the company fell victim to a ransomware attack that spread aggressively across its network and forced it to shut down its email service and other systems.
The firm says it was able to stop the attack soon after detection, but not before data on many systems was encrypted by the malware.
“On Saturday, October 10, 2020, Seyfarth was the victim of a sophisticated and aggressive malware attack that appears to be ransomware. […] many of our systems were encrypted, and we have shut them down as a precautionary measure,” Seyfarth announced.
The company claims that this appears to have been a coordinated attack targeting multiple entities at the same time.
“We understand that a number of other entities were simultaneously hit with this same attack. Our monitoring systems detected the unauthorized activity, and our IT team acted quickly to prevent its spread and protect our systems,” the law firm says.
Seyfarth also notes that it found no evidence that client or firm data was accessed or exfiltrated, but many recent ransomware attacks have resulted in sensitive information being stolen to convince the victim to pay the ransom.
As its email service remains inaccessible at the moment, the company advises clients to contact it via phone. An online contact form is also available.
“Our clients remain our top priority, and we will continue to do everything necessary to protect their confidential information and continue to serve them. We are coordinating with the FBI and are working around the clock to bring our systems back online as quickly and safely as possible,” Seyfarth continues.
Carnival Corp. Confirms Personal Information Compromised in Ransomware Incident
12.10.20 Ransomware Securityweek
Leisure travel company Carnival Corporation last week confirmed that personal information pertaining to guests, employees, and crew was compromised in an August 2020 ransomware attack.
Carnival, which owns 10 global cruise line brands and a tour company, employs more than 120,000 people and has a fleet of 102 ships. Prior to the COVID-19 pandemic, which forced the company to suspend operations, Carnival served more than 11 million guests per year.
In mid-August, the company announced that it detected a ransomware attack that resulted not only in some of its systems being encrypted, but also in the unauthorized download of some files.
In an 8-K form filed at the time with the U.S. Securities and Exchange Commission to announce the security incident, the company said the attack affected the technology systems for a cruise line brand, but did not mention which. An investigation was launched and law enforcement was alerted.
Last week, Carnival filed a 10-Q form with the SEC, confirming that certain personal data was compromised. However, it did not reveal the number of affected people or what type of information was accessed.
“On August 15, 2020, we detected a ransomware attack and unauthorized access to our information technology systems,” the filing reads. “While the investigation is ongoing, early indications are that the unauthorized third-party gained access to certain personal information relating to some guests, employees and crew for some of our operations.”
In the filing, Carnival also notes that it is not aware of the compromised data being misused.
“There is currently no indication of any misuse of this information. While at this time we do not believe that this information will be misused going forward or that this incident will have a material adverse effect on our business, operations or financial results, no assurances can be given and further we may be subject to future attacks or incidents that could have such a material adverse effect,” the company also said.
In March 2020, the cruise operator revealed a data breach that was initially identified in May 2019, and which resulted in large amounts of sensitive data pertaining to its guests being accessed by an unauthorized party.
Underestimating the FONIX – Ransomware as a Service could be an error
12.10.20 Ransomware Securityaffairs
FONIX is a new Ransomware as a Service available in the threat landscape that was analyzed by SentinelLabs researchers.
FONIX is a relatively new Ransomware as a Service (RaaS) analyzed by researchers from Sentinel Labs, its operators were previously specialized in the developers of binary crypters/packers.
The actors behind FONIX RaaS advertised several products on various cybercrime forums.
FONIX first appeared in the threat landscape in July 2020, fortunately, the number of infections associated with this threat is still small.
Experts pointed out that the ransomware authors don’t require the payment of a fee to become an affiliate of the service, the operators only keep a percentage of any ransoms from their affiliate network.
Experts believe that However the FONIX RaaS can quickly become rampant if security firms and authorities underestimate it.
“Notably, FONIX varies somewhat from many other current RaaS offerings in that it employs four methods of encryption for each file and has an overly-complex post-infection engagement cycle.” reads the analysis published by Sentinel Labs.

The communications with the RaaS operators are carried out via email. Any affiliate has to provide the operators files from a victim system to obtain the decryptor and key for the victim, in turn the operators keep for them 25% of the ransom.
“Based on current intelligence, we know that FONIX affiliates do not get provided with a decryptor utility or keys at first. Instead, victims first contact the affiliate (buyer) via email as described above. The affiliate then requests a few files from the victim. These include two small files for decryption: one is to provide proof to the victim, the other is the file “cpriv.key” from the infected host. The affiliate is then required to send those files to the FONIX authors, who decrypt the files, after which they can be sent to the victims.” continues the analysis.
“Presumably, once the victim is satisfied that decryption is possible, the affiliate provides a payment address (BTC wallet). The victim then pays the affiliate, with the affiliate in turn supplying the FONIX authors with their 25% cut.”
Obviously, the above process is a bit convoluted and far less user-friendly than most RaaS services.
The FONIX ransomware only targets Windows systems, by default it encrypts all file types, excluding critical Windows OS files.
The ransomware uses a combination of AES, Chacha, RSA, and Salsa20 to encrypt a victim’s files, it adds a .XINOF extension. Experts pointed out that the use of multiple encryption protocols makes the encryption process significantly slower than that of other ransomware.
Upon executing the payload with administrative privileges, the following system changes are made:
Task Manager is disabled
Persistence is achieved via scheduled task, Startup folder inclusion, and the registry (Run AND RunOnce)
System file permissions are modified
Persistent copies of the payload have their attributed set to hidden
A hidden service is created for persistence (Windows 10)
Drive / Volume labels are changed (to “XINOF”)
Volume Shadow Copies are deleted (vssadmin, wmic)
System recovery options are manipulated/disabled (bcdedit)
Safeboot options are manipulated
“a FONIX infection is notably aggressive – encrypting everything other than system files – and can be difficult to recover from once a device has been fully encrypted. Currently, FONIX does not appear to be threatening victims with additional consequences (such as public data exposure or DDoS attacks) for non-compliance.” concludes the report.
Tyler Technologies finally paid the ransom to receive the decryption key
11.10.20 Ransomware Securityaffairs
Tyler Technologies has finally decided to paid a ransom to obtain a decryption key and recover files encrypted in a recent ransomware attack.
Tyler Technologies, Inc. is the largest provider of software to the United States public sector. At the end of September, the company disclosed a ransomware attack and its customers reported finding suspicious logins and previously unseen remote access tools on their networks.
The ransomware attack took place on September 23, the threat actors breached the network of the company and deployed the malware.
Tyler notified law enforcement and hired a forensics firm to investigate the incident and determine the extent of the incident.
Immediately after the attack company representatives declared that the incident only impacted the internal network and phone systems.
Some reports circulating online speculate the company was infected with the RansomExx ransomware.
The RansomEXX is human-operated ransomware, this means that attackers manually infected the systems after gained access to the target network.
In June 2020, the same ransomware was employed in an attack on the Texas Department of Transportation, in September it infected the systems at the IPG Photonics high-performance laser developer.
According to BleepingComputer, which cited a source informed on the event, Tyler Technologies paid a ransom of an unspecified amount to receive the decryption key and recover encrypted files.
“When the ransomware encrypted Tyler Technologies’ files, they appended an extension similar to ‘.tylertech911-f1e1a2ac.'” reported BleepingComputer.
“To prove that the decryptor was valid, BleepingComputer was able to decrypt encrypted files [1, 2] uploaded to VirusTotal at the time of the ransomware attack.”
When decrypted, the Arin.txt file contained a list of IP ranges used by the company.
Experts pointed out that many school districts, court systems, and local and statement governments in the United States uses Tyler Technologies software, this means that the disclosure of data stolen during the ransomware attack could have serious consequences.
For this reason, the company decided to pay the ransom.
Enterprise Solutions Provider 'Software AG' Hit by Clop Ransomware
11.10.20 Ransomware Securityweek
German enterprise solutions giant Software AG revealed last week that it had been targeted by cybercriminals with the Clop ransomware.
Software AG operates across more than 70 countries around the world and it has over 5,000 employees. It claims that its solutions are used by more than 10,000 of the world’s biggest brands.
The company disclosed the incident on October 5, when it reported being hit by a malware attack on October 3. Software AG said at the time that it had shut down some internal systems in response to the breach.
The company said its helpdesk services and internal communications were impacted, but claimed that cloud-based services were not affected and that it found no evidence of customer information being compromised.
However, in an update shared on October 8, the company said the malware had not been fully contained and it had found evidence that the attackers did in fact download data from servers and employee notebooks.
Researchers at MalwareHunterTeam said on Saturday that the attack involved the Clop ransomware, and they noticed what appeared to be a new feature — the use of wevtutil.exe to clear event logs. They also noted that the sample that hit Software AG checked for the presence of McAfee software and attempted to uninstall it, but it’s unclear if the attackers somehow learned that the target was using McAfee products or if this functionality was added to the malware for a different target.
The Tor-hosted website where the group behind the Clop ransomware leaks data stolen from victims that refuse to pay the ransom claims that the first part of the stolen files will be made public soon.
Screenshots posted by the hackers show that they have obtained tens of gigabytes of data representing more than one million files. They appear to have obtained passport copies, invoices, and emails.
Bleeping Computer has learned from the Clop payment page associated with Software AG that the attackers have asked for more than 2,000 bitcoin, which is roughly $23 million.
SecurityWeek has reached out to Software AG for confirmation of the ransom demand and will update this article if the company responds.
The Clop ransomware is also known to have targeted the University of Maastricht in the Netherlands, which revealed earlier this year that it had paid a $240,000 ransom in response to the attack.
Watch Out — Microsoft Warns Android Users About A New Ransomware
11.10.20 Ransomware Thehackernews
Microsoft has warned about a new strain of mobile ransomware that takes advantage of incoming call notifications and Android's Home button to lock the device behind a ransom note.
The findings concern a variant of a known Android ransomware family dubbed "MalLocker.B" which has now resurfaced with new techniques, including a novel means to deliver the ransom demand on infected devices as well as an obfuscation mechanism to evade security solutions.
The development comes amid a huge surge in ransomware attacks against critical infrastructure across sectors, with a 50% increase in the daily average of ransomware attacks in the last three months compared to the first half of the year, and cybercriminals increasingly incorporating double extortion in their playbook.
MalLocker has been known for being hosted on malicious websites and circulated on online forums using various social engineering lures by masquerading as popular apps, cracked games, or video players.
Previous instances of Android ransomware have exploited Android accessibility features or permission called "SYSTEM_ALERT_WINDOW" to display a persistent window atop all other screens to display the ransom note, which typically masquerade as fake police notices or alerts about purportedly finding explicit images on the device.
But just as anti-malware software began detecting this behavior, the new Android ransomware variant has evolved its strategy to overcome this barrier. What's changed with MalLocker.B is the method by which it achieves the same goal via an entirely new tactic.
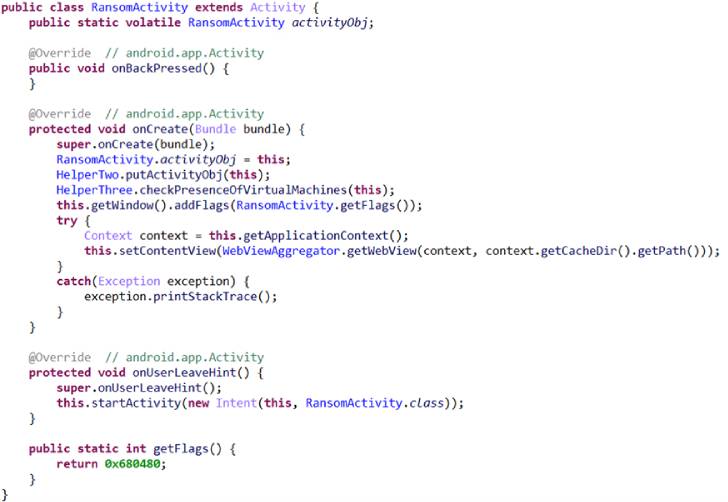
To do so, it leverages the "call" notification that's used to alert the user about incoming calls in order to display a window that covers the entire area of the screen, and subsequently combines it with a Home or Recents keypress to trigger the ransom note to the foreground and prevent the victim from switching to any other screen.
"This creates a chain of events that triggers the automatic pop-up of the ransomware screen without doing infinite redraw or posing as a system window," Microsoft said.
Aside from incrementally building on an array of aforementioned techniques to show the ransomware screen, the company also noted the presence of a yet-to-be-integrated machine learning model that could be used to fit the ransom note image within the screen without distortion, hinting at the next stage evolution of the malware.
Furthermore, in an attempt to mask its true purpose, the ransomware code is heavily obfuscated and made unreadable through name mangling and deliberate use of meaningless variable names and junk code to thwart analysis, the company said.
"This new mobile ransomware variant is an important discovery because the malware exhibits behaviors that have not been seen before and could open doors for other malware to follow," Microsoft 365 Defender Research Team said.
"It reinforces the need for comprehensive defense powered by broad visibility into attack surfaces as well as domain experts who track the threat landscape and uncover notable threats that might be hiding amidst massive threat data and signals."
Sophisticated Android Ransomware Executes with the Home Button
11.10.20 Ransomware Threatpost
The malware also has a unique machine-learning module.
A fresh variant of a sophisticated Android ransomware known as MalLocker locks up mobile devices – surfacing its ransom note when a user hits the Home button.
According to research from Microsoft, MalLocker is spreading via malicious website downloads (disguised as popular apps, cracked games or video players) and peddled in online forums, as it always has. However, “the new variant caught our attention because it’s an advanced malware with unmistakable malicious characteristic and behavior and yet manages to evade many available protections, registering a low detection rate against security solutions,” Microsoft researchers said, in a Thursday posting.
Threatpost Webinar Promo Retail Security
Click to register!
Android ransomware differs from its desktop counterparts by blocking access to the device with overlay screens containing ransom notes that prevent users from taking any action – it doesn’t actually encrypt anything. In MalLocker’s case, the overlay screen is surfaced using never-before-seen techniques that make use of certain Android features.
And, it has an open-source machine-learning module used to automatically fit the overlay screen to the device.
New Permissions
Researchers noted that typical Android ransomware uses a special permission called “SYSTEM_ALERT_WINDOW.” The note is hooked to that permission, so that whenever an app is opened that has this permission, the ransom note is presented and can’t be dismissed.
“No matter what button is pressed, the window stays on top of all other windows,” researchers said. “The notification was intended to be used for system alerts or errors, but Android threats misused it to force the attacker-controlled UI to fully occupy the screen, blocking access to the device. Attackers create this scenario to persuade users to pay the ransom so they can gain back access to the device.”
MalLocker is different though: It uses the “call” notification, among several categories of notifications that Android supports, which requires immediate user attention. It combines this with the “onUserLeaveHint()” callback method of the Android Activity, which is a bedrock Android function. It surfaces the typical GUI screen that Android users see after closing an app or when the user presses the Home key to send current activity to the background.
“The malware connects the dots and uses these two components to create a special type of notification that triggers the ransom screen via the callback,” according to Microsoft. “The malware overrides the onUserLeaveHint() callback function [and] triggers the automatic pop-up of the ransomware screen without…posing as system window.”
The analysis added, “The malware creates a notification builder [and builds] a very important notification that needs special privilege. The setFullScreenIntent()…API wires the notification to a GUI so that it pops up when the user taps on it.”
Machine Learning
MalLocker’s machine-learning module indicates continuous evolution of this Android ransomware family, researchers said.
“This ransomware is the latest variant of a malware family that has undergone several stages of evolution,” researchers said. “We expect it to churn out new variants with even more sophisticated techniques. In fact, recent variants contain code forked from an open-source machine-learning module used by developers to automatically resize and crop images based on screen size, a valuable function given the variety of Android devices.”
The latest MalLocker variant is also indicative that mobile threat actors continuously attempt to sidestep technological barriers and creatively find ways to accomplish their goal – and can open the door to new malware trends.
“This new mobile ransomware variant is an important discovery because the malware exhibits behaviors that have not been seen before and could open doors for other malware to follow,” Microsoft added.
Carnival confirms data breach as a result of the August ransomware attack
11.10.20 Ransomware Securityaffairs
Carnival Corporation, the world’s largest cruise line operator, has confirmed a data breach as a result of the august ransomware attack.
Carnival Corporation, the world’s largest cruise line operator, has confirmed a data breach as a result of the ransomware attack that took place in August. Ransomware operators have stolen the personal information of customers, employees, and ship crews during the attack.
Carnival Corporation & plc is a British-American cruise operator, currently the world’s largest travel leisure company, with a combined fleet of over 100 vessels across 10 cruise line brands. A dual-listed company,
Carnival Corporation has over 150,000 employees and 13 million guests annually. The cruise line operates under the brands Carnival Cruise Line, Costa, P&O Australia, P&O Cruises, Princess Cruises, Holland American Line, AIDA, Cunard, and their ultra-luxury cruise line Seabourn.

Source: Orlando Weekly
The company operates nine cruise line brands (Carnival Cruise Line, Costa, P&O Australia, P&O Cruises, Princess Cruises, Holland American Line, AIDA, Cunard, Seabourn) and a travel tour company (Holland America Princess Alaska Tours).
In an 8-K filing with the US Securities Exchange Commission (SEC), the cruise line operators revealed that the incident took place on August 15.
“On August 15, 2020, Carnival Corporation and Carnival plc (together, the “Company,” “we,” “us,” or “our”) detected a ransomware attack that accessed and encrypted a portion of one brand’s information technology systems. The unauthorized access also included the download of certain of our data files,” states the 8-K form filed with the SEC.
“Nonetheless, we expect that the security event included unauthorized access to personal data of guests and employees, which may result in potential claims from guests, employees, shareholders, or regulatory agencies,”
The company also notified law enforcement agencies and data regulators.
At the time, the company revealed that only one of its cruise line brands was affected by the security breach.
Upon the discovery of the security incident, the Company launched an investigation and notified law enforcement, it also hired legal counsel and cyber security professionals. The company also announced to have already implemented a series of containment and remediation measures to respond to the incident and reinforce the security of its information technology systems.
Now the company filed a new In a 10-Q form with the SEC, it confirmed that an unknown ransomware gang also stole the personal information of its customers and employees. The company added that it is not aware of any misuse of the exposed information.
“On August 15, 2020, we detected a ransomware attack and unauthorized access to our information technology systems. We engaged a major cybersecurity firm to investigate the matter and notified law enforcement and regulators of the incident.” reads the 10-Q form.
“While the investigation is ongoing, early indications are that the unauthorized third-party gained access to certain personal information relating to some guests, employees, and crew for some of our operations.” “There is currently no indication of any misuse of this information.”
The company warns its customers of future attacks or incidents that could be linked to this security breach.
“While at this time we do not believe that this information will be misused going forward or that this incident will have a material adverse effect on our business, operations, or financial results, no assurances can be given, and further, we may be subject to future attacks or incidents that could have such a material adverse effect.” states the company.
In August, researchers from cybersecurity intelligence firm Bad Packets noticed that Carnival was utilizing vulnerable Citrix devices at the time of the attack. The experts speculate that the vulnerable equipment was targeted by the attacker to access the corporate network.
BadPackets also speculate that another entry point in the Carnival network could be CVE-2020-2021 issue in the the PAN-OS operating system.
In March 2020, Carnival Corporation disclosed another data breach that took place in 2019. The company informed customers of the incident, a third-party gained unauthorized access to their personal information.
Exposed guests’ personal information included name, address, Social Security number, government identification number, such as passport number or driver’s license number, and health-related information. For some clients, credit card and financial account information might have been exposed
German tech firm Software AG hit by ransomware attack
10.10.20 Ransomware Securityaffairs
German tech firm Software AG has suffered a ransomware attack that took place during last weekend, media blamed the Clop ransomware gang.
The website ZDNet revealed in exclusive that German tech firm Software AG was hit by the Clop ransomware, the criminal gang is demanding more than $20 million ransom.
Software AG is an enterprise software company with over 10,000 enterprise customers in over 70 countries. The company is the second largest software vendor in Germany, and the seventh largest in Europe.
The incident took place on Saturday, October 3, and the company has not yet fully recovered from the ransomware infection.
“Earlier today, after negotiations failed, the Clop gang published screenshots of the company’s data on a website the hackers operate on the dark web (a so-called leak site).” reported ZDNet.
The screenshots shared by the Clop ransomware operators show employee passport and ID scans, employee emails, financial documents, and directories from the company’s internal network.

On Monday, the software giant disclosed the ransomware attack and revealed that that the malware disrupted part of its internal network.
“The IT infrastructure of Software AG is affected by a malware attack since the evening of 3 October 2020. While services to its customers, including its cloud-based services, remain unaffected, as a result, Software AG has shut down the internal systems in a controlled manner in accordance with the company’s internal security regulations.” reads a statement released by the company. “The company is in the process of restoring its systems and data in order to resume orderly operation. However, helpdesk services and internal communication at Software AG are currently still being affected.”
New MalLocker.B ransomware displays ransom note in innovative way
9.10.20 Ransomware Securityaffairs
Microsoft warns of Android ransomware that activates when you press the Home button
Microsoft spotted a new strain of Amdroid ransomware tracked as MalLocker.B that activates when the users press the Home button.
Researchers from Microsoft spotted a new strain of Android ransomware that abuses the mechanisms behind the “incoming call” notification and the “Home” button to lock the screen on the victim’s device.
AndroidOS/MalLocker.B is distributed through tainted Android apps available for download on online forums and third-party websites.
The new variant also manages to evade many available protections, registering a low detection rate against security solutions.
Experts believe the malware is particularly sophisticated, but implements novel techniques and behavior.
Like other Android ransomware, MalLocker.B doesn’t actually encrypt the files on the devices but only inhibits the access to the phone.
Once installed, the ransomware displays a ransom note on the phone’s screen and prevents the victim from dismissing. The ransom note pretends to be a message from Russian law enforcement notifying users they have violated the law and must compensate by paying a fine.
Across time, security firms have spotted multiple mobile malware strains that have abused various features implemented by the Android operating systems to lock out the owners of the devices. For example, in 2017 ESET experts observed the DoubleLocker that was both encrypting user data and changing PIN Lock and that abused the Accessibility service to re-activate itself after users pressed the Home button.
What’s innovative about the MalLocker.B ransomware is how it displays its ransom note.
In the past, Android ransomware used the “SYSTEM_ALERT_WINDOW” a special permission to display their ransom note.
This permission allows apps to draw a window that belongs to the system group and can’t be dismissed, independently from any button pressed by the victims.
The actual mechanism implemented by the MalLocker.B ransomware to display the ransom note is composed of two parts.
The first part abuses the “call” notification that activates for incoming calls to show info about the caller. The ransomware abuses this feature to show a window that covers the entire screen of the device. The second part abuses the “onUserLeaveHint()” function which is called when users want to push an app into the background and switch to a new app. This feature is triggered everytime the users press buttons like Home or Recents. MalLocker.B abuses this function to prevent the victims from leaving the ransom note for the home screen or another app.
“The malware connects the dots and uses these two components to create a special type of notification that triggers the ransom screen via the callback.” reads the analysis published by Microsoft. “As the code snippet shows, the malware overrides the onUserLeaveHint() callback function of Activity class. The function onUserLeaveHint() is called whenever the malware screen is pushed to background, causing the in-call Activity to be automatically brought to the foreground. Recall that the malware hooked the RansomActivity intent with the notification that was created as a “call” type notification. This creates a chain of events that triggers the automatic pop-up of the ransomware screen without doing infinite redraw or posing as system window.”
This is the first time that experts observed the concurrent abuse of these two features in a ransomware that hijacks the Home button.
In order to avoid being infected with MalLocker.B and similar malware users are advised to avoid installing Android apps from third-party stores or forums.
Springfield Public Schools district hit with ransomware
9.10.20 Ransomware Securityaffairs
The Springfield Public Schools district in Massachusetts was forced to shut down its systems after a ransomware attack and closed the schools.
The Springfield Public Schools district, the third largest school district in Massachusetts, was forced to shut down its systems after a ransomware attack. The district, which has over 25,000 students, 4,500 employees, and more than sixty schools that were closed after the incident.
Due to the ongoing COVID-19 pandemic, the schools of the district were using remote learning model.
The district initially announced that the schools were closed due to “issues” with their network, but later it conformed that the problems were the result of a ransomware attack.
“Out of an abundance of caution the Springfield Public Schools have issued an early dismissal from school today and have temporarily suspended remote learning due to potential threats to the network that have been identified,” Mayor Domenic J. Sarno and Superintendent Daniel Warwick said in a statement.
Mayor Sarno and Superintendent Warwick, who initially announced the suspension of remote learning, has also confirmed the ransomware infection.
“Early this morning, the Springfield Public Schools identified a potential threat to their IT network. To ensure that the District can effectively mitigate the potential incident and restore access to all software and services as quickly as possible, school and remote learning activities are canceled for the remainder of today, Thursday, October 8th, 2020.” reads the official announcement. “It is anticipated that the risk will be cleared and resolved in the near future so that remote learning may continue,”
Bleeping computer, citing a source in the cyber security industry, was the first media to attribute the issues to a ransomware attack.
At the time the Springfield Public Schools has yet to reveal the family of ransomware that infected its systems and the number of devices impacted.
Unfortunately, it is likely that such kind of incident will become even more frequent in the incoming months.
In early September, the Hartford School District in Connecticut also suffered a ransomware attack that caused the delay of the school’s opening.
Microsoft Warns of Android Ransomware Abusing Notification Services
9.10.20 Ransomware Securityweek
Microsoft warned users on Thursday that it has spotted a sophisticated piece of Android ransomware that abuses notification services to display a ransom note.
Android ransomware typically allows cybercriminals to make a profit not by encrypting files — such as in the case of ransomware targeting desktop systems — but by displaying a full-screen ransom note that is difficult for the user to remove.
Microsoft says this particular Android ransomware family has been around for a while and its developers have continued to make improvements. Previous variants of the malware abused Android accessibility features or system alert windows to display the ransom note. However, Google has been taking steps to prevent abuse of these features, and some methods used by attackers can be easily spotted or bypassed by the victim.Android ransomware
In an effort to increase its chances of success, the latest version of the Android ransomware, which Microsoft tracks as AndroidOS/MalLocker.B, uses a new technique to display the ransom note and make it more difficult to remove.

The ransomware note is usually a fake police notice informing the victim that explicit images had been found on their device and instructing them to pay a fine within 24 hours.
The malware displays the ransom note using a “call” notification, which requires immediate attention from the user, combined with the “onUserLeaveHint()” callback method of the Activity class, which is called when an application is about to go into the background after the user has pressed the home key on their smartphone.
“The malware overrides the onUserLeaveHint() callback function of Activity class. The function onUserLeaveHint() is called whenever the malware screen is pushed to background, causing the in-call Activity to be automatically brought to the foreground,” explained Microsoft researcher Dinesh Venkatesan.
This ensures that the ransom note continues to be displayed on the screen regardless of what the victim does.
Microsoft also noted that it spotted a piece of code in the latest version that leverages an open source machine learning module which allows developers to automatically resize and crop an image based on the size of the device’s screen.
This code does not appear to be used in current versions of the ransomware, but if it’s fully implemented, it will ensure that the ransom note is displayed on the screen without being distorted, which Microsoft says makes the threats more believable and increases the chances of the ransom being paid.
Microsoft has published a blog post with technical details on how the malware works and how organizations can protect themselves against such threats.
University Hospital New Jersey paid a $670K ransom
4.10.20 Ransomware Securityaffairs
University Hospital New Jersey paid a $670,000 ransom this month to prevent the leak of 240 GB of stolen data, including patient information.
The University Hospital New Jersey (UHNJ) in Newark (New Jersey) has finally paid a $670,000 ransom to prevent the publishing of 240 GB of stolen data, including patient info.
In September, systems at the University Hospital New Jersey (UHNJ) were encrypted with the SunCrypt ransomware, threat actors also stolen documents from the institution and leaked a small portion of them online.
The UHNJ is a New Jersey state-owned teaching hospital with over 3,500 employees that was established in 1994. The hospital has a $626 million budget with over 172,000 annual outpatient visits.
SunCrypt ransomware operators first appeared in the threat landscape in October 2019, and over the past few months, they launched a dedicated leak site where they started publishing the data stolen from the victims.
BleepingComputer first reported the attack on the UHNJ, the SunCrypt Ransomware leaked a 1.7 GB archive containing over 48,000 documents, they claimed to have stolen 240 GB of data.
“This data leak includes patient information release authorization forms, copies of driving licenses, Social Security Numbers (SSNs), date of birth (DOB), and records about the Board of Directors.” reported Bleeping Computer.
A BleepingComputer’s source informed about the incident revealed that an employee of UHNJ was infected with the TrickBot trojan at the end of August before the ransomware attack took place.
The hospital contacted the ransomware operators via their Tor payment site, according to BleepingComputer the initial ransom demand was $1.7 million. Anyway, the threat actors were open to a negotiation of the ransom “due to COVID-19 situation.”
“We want to prevent any further leakage of our data and that is why we are here talking with you,” UHNJ told the ransomware operators.
The two parts finally agreed to pay a ransom of $672,744, approximately 61.90 bitcoins on September 19th.
SunCrypt ransomware operators provided to the University Hospital New Jersey a decryptor, the stolen data, a security report, and an agreement not to disclose any stolen data or attack UHNJ again.
The report states that the entry point was a phishing email that tricked an employee into providing the network credentials that allowed the attackers to log into UHNJ’s Citrix server and gain access to the network.
Researchers Mixed on Sanctions for Ransomware Negotiators
3.10.20 Ransomware Threatpost
Financial institutions, cyber-insurance firms, and security firms have all been put on notice by the U.S. Department of the Treasury.
Ransomware negotiators may have to pay up in new ways if they intercede with cybercriminals on companies’ behalf. Several researchers weighed in on the wisdom of the move, with mixed reactions.
The U.S. Department of the Treasury said Thursday that companies that facilitate ransomware payments to cyber-actors on behalf of victims may face sanctions for encouraging crime and future ransomware payment demands. These facilitators can fall into multiple camps, including financial institutions, cyber-insurance firms, and security firms involved in digital forensics and incident response.
The department has added multiple crimeware gangs to its sanctions program, prohibiting U.S. entities or citizens from doing business with them (i.e., pay a ransom). These include the developer of CryptoLocker, Evgeniy Mikhailovich Bogachev; the SamSam ransomware group; North Korea-linked Lazarus Group; and Evil Corp and its leader, Maksim Yakubets. This latest policy expands the sanctions’ applicability to anyone dealing with ransomware operators in general.
“Ransomware payments made to sanctioned persons or to comprehensively sanctioned jurisdictions could be used to fund activities adverse to the national security and foreign policy objectives of the United States. Ransomware payments may also embolden cyber-actors to engage in future attacks,” according to a website notice on the policy. “In addition, paying a ransom to cyber-actors does not guarantee that the victim will regain access to its stolen data.”
The Tresasury Department added that a lack of knowledge of the sanctions’ existence is not an excuse, and that people could still be held civilly liable in that case. However, if a company makes a “self-initiated, timely and complete report of a ransomware attack to law enforcement,” this will be taken into account and could lower any penalties for the organization.
The department did not specify the amount of any potential penalty.
To Pay or Not to Pay
While the feds have always recommended not paying ransoms, in reality, the decision to pay up or to not is an individual choice that has to be made given the context of any given situation, researchers said. Businesses that don’t have backups may be desperate to get their data back, for instance; or, many times, the ransomware payment is less than alternate investigation and remediation would cost (and often, firms can intercede for them and reduce the amount being extorted). Also, many gangs are stealing data as well, so sensitive data exposure is another consideration.
Because of that, the Treasury Department’s move could end up being counterproductive, some said.
“Penalizing businesses that pay off attackers sounds like it will make ransomware less lucrative,” said Melody Kaufmann, cybersecurity specialist for Saviynt, said via email. “The converse is true. This advisory will propagate ransomware rather than reduce it for three key reasons. First, it disincentivizes reporting ransomware attacks, robbing law enforcement, security professionals, and analysts of data vital to combat future attacks. Second, it fails to provide an effective data recovery alternative. Third, it favors big corporations while crushing small- to medium-sized businesses beneath its heel.”
Small and medium businesses are notorious for having weak security because maintaining an information security team is often cost-prohibitive. Lack of security increases their risk and the likelihood of infection, she added.
“This advisory discourages them from contacting law enforcement by increasing the chance of a fine,” she added. “Often paying the ransom is cheaper than the cost of losing their data or recovering from back-ups, which few small businesses even maintain. The treasury department will only learn of a ransomware attack on a small or medium business via a disgruntled employee or a media outlet reporting it.”
Tim Erlin, vice president of product management and strategy at Tripwire, added that ransomware affects every segment.
“It’s not just commercial organizations that have paid out for ransomware incidents,” he said via email. “There have been government agencies, cities and police departments that have fallen victim and ultimately paid the ransom as well. It’s easy to say that you should never pay the ransom because it just encourages more ransomware, but it’s much harder to follow one’s own advice when faced with the potential for sensitive data loss, publication, or the loss of your business.”
Not everyone saw the move as problematic.
“We need to change the economics of the bad guys if we want anything to change,” CynergisTek CEO Caleb Barlow said. “Ransomware payment got so much more difficult to do. The fact they’re using the Treasury Department to do this is brilliant. The reach of US Treasury is far broader – [and] applies to U.S. companies, allies, citizens – that they cannot aid and abet the enemy. A ransomware payment is no longer a get out of free jail card. Enterprises have to invest in defenses.”
He added that the fact that Garmin recently, knowingly paid an adversary on the sanction list “likely accelerated this decision.”
Nozomi Networks CEO Edgard Capdevielle also fell into the “don’t pay” camp.
“While it might be tempting to pay a ransom, doing so only fuels the fire,” he said via email. “We are seeing more instances where the public and private sector respond to the pressure and pay the ransom…choosing to pay a ransom is too often a short-sighted response that could come at a high cost. Research has shown that paying a ransom can double the cost of recovery. Building, maintaining and constantly improving an organization’s cybersecurity program is always the best approach and there are certainly tools available today that provide cost effective solutions.”
He added, “Organizations that give into hackers’ demands are only supporting the profitability and growth of ransomware activity. When it comes to ransomware attacks, prevention will always be better than a cure.”
One thing is certain – ransomware has reached epidemic proportions, according to Charles Carmakal, SVP and CTO of FireEye Mandiant.
“Ransomware is the most significant and prevalent cybersecurity threat facing corporations today,” he said. “Today’s ransomware and extortion problem is unbearable. Many ransomware operators steal a large volume of sensitive data from organizations prior to deploying encryptors and locking organizations out of their systems and data. Threat actors may ask for money for a decryption tool, a promise to not publish the stolen data, and a walkthrough of how they broke into the network.”
He said that these types of extortion demands are in the six-figure range for smaller companies and between seven and eight figures for larger companies.
“We are aware of several victim organizations that paid extortion demands between $10 million and $30 million,” he said. “Mandiant is aware of over 100 organizations in which ransomware operators had network access to in September alone, more than double what we were aware of in September of the previous year.”
Egregor Ransomware Threatens ‘Mass-Media’ Release of Corporate Data
3.10.20 Ransomware Threatpost
The newly discovered ransomware is hitting companies worldwide, including the GEFCO global logistics company.
A freshly discovered family of ransomware called Egregor has been spotted in the wild, using a tactic of siphoning off corporate information and threatening a “mass-media” release of it before encrypting all files.
Egregor is an occult term meant to signify the collective energy or force of a group of individuals, especially when the individuals are united toward a common purpose — apropos for a ransomware gang. According to an analysis from Appgate, the code seems to be a spinoff of the Sekhmet ransomware (itself named for the Egyptian goddess of healing) – a link that was also noted by other researchers..
“We found similarities in both Sekhmet and Egregor ransomware, such as obfuscation techniques, functions, API calls and strings, such as %Greetings2target% and %sekhmet_data% changing to %egregor_data%,” Gustavo Palazolo, security researcher at Appgate, told Threatpost. “Furthermore, the ransom note is also fairly similar.”
As far as other technical details, “The sample we analyzed has many anti-analysis techniques in place, such as code obfuscation and packed payloads,” according to the firm’s research, announced Friday. “Also, in one of the execution stages, the Egregor payload can only be decrypted if the correct key is provided in the process’ command line, which means that the file cannot be analyzed, either manually or using a sandbox, if the exact same command line that the attackers used to run the ransomware isn’t provided.”
Further, “we have found that Egregor can receive additional parameters via command line, such as ‘nomimikatz,’ ‘killrdp,’ ‘norename,’ among others,” Palazolo said. “At the moment, our team is still revers- engineering the malware to get the whole picture. Furthermore, we will continue to monitor any possible variant emerging from this family.”
Overall, he said, it has the same sophistication level as other ransomware families, however Egregor implements a high number of anti-analysis techniques, such as code obfuscation and payload encryption.
While Appgate researchers don’t know how long Egregor has been circulating, its first public appearance of Egregor was September 18 on Twitter, after it was spotted by @demonslay335 and @PolarToffee
Appgate researchers also found that the ransom note demands payment within three days – otherwise, the sensitive data will be leaked. In a twist from the usual double-extortion tactics used by ransomware families like NetWalker, the Egregor operators threaten to distribute stolen via “mass media,” so that a victim company’s partners and clients will know that the company was attacked.
This part of the ransom note, shared with Threatpost, reads: “What does it mean? It means that soon mass media, your partners and clients WILL KNOW about your PROBLEM.”
So far though, no mass-media events have occurred. “The only evidence we have is the deep web site in which they are publishing details about attacked companies, we have not identified any other news or information on data being released to any media organizations,” Palazolo said.
And indeed, the analysis uncovered a self-billed “Egregor news” website, hosted on the deep web, which the criminal group uses to leak stolen data.
“At the time of this advisory, there are at least 13 different companies listed in their ‘hall of shame,’ including the global logistics company GEFCO, which suffered a cyberattack last week,” according to the firm.
The Egregor ransom note also says that aside from decrypting all the files in the event the company pays the ransom, the operators will provide recommendations for securing the company’s network, “helping” them to avoid being breached again, “acting as some sort of black-hat pen-test team,” according to the Appgate research.
The note reads: “(In case the payment is done) … You WILL GET full DECRYPTION of your machines in the network, FULL FILE LISTING of downloaded data, confirmation of downloaded data DELETION from our servers, RECOMMENDATIONS for securing your network perimeter.”
“The ‘security recommendations’ caught our attention since it’s something unusual for a criminal group, they are trying to play good guys by suggesting they would try to help secure your network,” Palazolo said.
There’s no word yet on the initial infection vector for the malware, but ransomware seems to be equal-opportunity in terms of its targets, with samples affecting corporations in France, Germany, Italy, Japan, Mexico, Saudi Arabia and the US, according to the researcher.
As for the size of the ransom, the crimeware operators make victims jump through hoops.
“Unfortunately, there are no details on [the ransom payment amount] in the ransom note or on the Egregor website,” the researcher told Threatpost. “To get payment details, the victim needs to navigate to the deep web link Egregor provided and get instructions from the attacker through a live chat, which we have not performed.”
Blackbaud Says Bank Account Data, SSNs Impacted in Ransomware Incident
2.10.20 Ransomware Securityweek
Documents filed by cloud software provider Blackbaud with the United States Securities and Exchange Commission (SEC) this week reveal that bank account details and social security numbers might have been affected in a ransomware attack earlier this year.
In June 2020, Blackbaud, which is mainly known for the fundraising suites employed by charities and educational institutions, but which also offers payment services, announced publicly that it managed to stop a ransomware attack, but not before some data was stolen.
At the time, the company admitted to paying ransomware operators so that they would delete the data exfiltrated during the attack, but said that no personally identifiable information (PII) or bank account details were compromised.
In a Form 8-K filing this week, the cloud software company said a subsequent investigation revealed that the attackers were able to access data related to bank accounts, social security numbers, and login credentials.
“After July 16, further forensic investigation found that for some of the notified customers, the cybercriminal may have accessed some unencrypted fields intended for bank account information, social security numbers, usernames and/or passwords. In most cases, fields intended for sensitive information were encrypted and not accessible,” the company said.
Blackbaud said it took steps to inform the potentially impacted users in July, but that the new findings do not apply to all of those who were affected by the ransomware attack.
“Customers who we believe are using these fields for such information are being contacted the week of September 27, 2020 and are being provided with additional support,” Blackbaud noted in the filing.
The company also said that the investigation into the incident will continue, just as will security improvements to its systems. Customers, stockholders and other stakeholders will be informed of any new details that are uncovered during the investigation.
“Ransomware's double jeopardy factor is an effective attack vector for cybercriminals in this situation. It exfiltrates valuable original research data and IP for later sale on the dark web while locking the authors out of files that could potentially contain 100s of hours of irreplaceable work,” Matt Lock, UK Technical Director at Varonis, said in an emailed comment.
Netwalker ransomware operators leaked files stolen from K-Electric
2.10.20 Ransomware Securityaffairs
K-Electric, Pakistan’s largest private power company, did not pay the ransom and the Netwalker ransomware operators have leaked the stolen data.
In early September, K-Electric (KE), the electricity provider for the city of Karachi, Pakistan, was hit by a Netwalker ransomware attack that blocked billing and online services.
K-Electric is the largest power supplier in the country with 2.5 million customers and around 10,000 people.
Starting on September 7, the customers of the company were not able to access the services for their accounts. The good news is that the power supply has not been affected. In response to the incident, K-Electric is attempting to reroute users through a staging site, but the problems have yet to be solved.
The news of the incident was first reported by BleepingComputer which was informed by the ransomware researcher Ransom Leaks.
After being informed about this ransomware attack, security researchers confirmed that the Netwalker ransomware operators were behind the attack.
Netwalker ransomware operators are demanding the payment of $3,850,000 worth of Bitcoin. As usual, if the company will not pay the ransom within another seven days, the ransom will increase to $7.7 million.
Source BleepingComputer
The gang also claimed on the ‘Stolen data’ page of their Tor leak site that they have stolen unencrypted files from K-Electric before encrypting its systems. At the time it is not clear how many documents were stolen and which kind of information they contained.
News of the day is that Netwalker ransomware operators have released the victim’s data stolen during the attack, an 8.5 GB archive.
Researchers from cybersecurity firm Rewterz, who analyzed the content of the archive, told BleepingComputer that it contains some company’s sensitive information, including financial data, customer information, engineering reports, engineering diagrams for turbines, maintenance logs, and more.
Experts pointed out that threat actors had access to customer’s personal information that could be used to carry out multiple malicious activities.
Recently the Netwalker ransomware operators hit Argentina’s official immigration agency, Dirección Nacional de Migraciones, the attack caused the interruption of the border crossing into and out of the country for four hours.
Another victim of the group is the University of California San Francisco (UCSF), who decided to pay a $1.14 million ransom to recover its files.
Recently the FBI has issued a security alert about Netwalker ransomware attacks targeting U.S. and foreign government organizations.
The feds are recommending victims, not to pay the ransom and reporting incidents to their local FBI field offices.
The flash alert also includes indicators of compromise for the Netwalker ransomware along with mitigations.
The FBI warns of a new wave of Netwalker ransomware attacks that began in June, the list of victims includes the UCSF School of Medicine and the Australian logistics giant Toll Group.
The Netwalker ransomware operators have been very active since March and also took advantage of the ongoing COVID-19 outbreak to target organizations.
Below the recommended mitigations provided by the FBI:
Back-up critical data offline.
Ensure copies of critical data are in the cloud or on an external hard drive or storage device.
Secure your back-ups and ensure data is not accessible for modification or deletion from the system where the data resides.
Install and regularly update anti-virus or anti-malware software on all hosts.
Only use secure networks and avoid using public Wi-Fi networks.
Consider installing and using a VPN.
Use two-factor authentication with strong passwords.
Keep computers, devices, and applications patched and up-to-date.
Treasury Department Warns Ransomware Payment Facilitators of Legal Implications
2.10.20 Ransomware Securityweek
The U.S. Department of the Treasury this week issued an advisory to warn companies that facilitate ransomware payments of the potential legal implications resulting from sending money to sanctioned entities.
The Treasury Department’s Office of Foreign Assets Control (OFAC) says there has been a rise in ransomware attacks on U.S. organizations, which has resulted in an increase in the demand for ransomware payments.
Many organizations from around the world, including several cities and universities in the U.S., have paid significant amounts of money to recover their files following a ransomware attack.
However, the Treasury Department warns, companies that facilitate ransomware payments to cybercriminals on behalf of victims not only encourage future attacks, but also risk violating OFAC regulations. The advisory specifically lists cyber insurance companies, financial institutions, and providers of incident response and digital forensics services as organizations that can facilitate ransomware payments.
The OFAC noted that many cyber threat actors have been sanctioned over the past years, including for attacks involving malware such as Cryptolocker (linked to a Russian individual), SamSam (linked to Iranians), WannaCry (linked to North Korea) and Dridex (linked to a Russian organization).
Companies are informed that making a ransomware payment to sanctioned people or countries could be used to fund activities “adverse to the national security and foreign policy objectives of the United States.” The advisory also points out that paying the ransom not only encourages the threat actor to launch more attacks, but there is also no guarantee that the victim will regain access to the compromised data.
“OFAC may impose civil penalties for sanctions violations based on strict liability, meaning that a person subject to U.S. jurisdiction may be held civilly liable even if it did not know or have reason to know it was engaging in a transaction with a person that is prohibited under sanctions laws and regulations administered by OFAC,” the advisory notes.
In a fireside chat at SecurityWeek’s recent CISO Forum, Evan Wolff, a cyber-attorney and partner at international law firm Crowell & Moring, talked about the legal issues that CISOs could personally face due to their actions, and one of the examples he mentioned was paying to recover from a ransomware infection. The advisory from the Treasury Department reinforces Wolff’s warning about personal liability.
The advisory recommends that companies “implement a risk-based compliance program to mitigate exposure to sanctions-related violations,” and points out that reporting a ransomware attack to law enforcement in a timely manner and cooperating with law enforcement is considered a “significant mitigating factor in determining an appropriate enforcement outcome if the situation is later determined to have a sanctions nexus.”
“OFAC already provides a list of sanctioned entities. Victim organizations are required to check the list prior to paying extortion demands. However, the true identity of the cyber criminals extorting victims is usually not known, so it’s difficult for organizations to determine if they are unintentionally violating U.S. Treasury sanctions. Sometimes victims pay threat actors before they are sanctioned. For example, many victims have paid the ‘SamSam’ ransomware operators in the past, not knowing they were based in Iran at the time,” Charles Carmakal, SVP & CTO at FireEye Mandiant, told SecurityWeek.
“In recent months, the individuals (referred to as “EvilCorp”) involved with the Dridex banking malware have been connected with the WastedLocker ransomware family. Some extortion payment organizations have decided that they would not pay extortion demands associated with WastedLocker incidents out of fear of violating U.S. Treasury sanctions,” he added.
Las Vegas Students’ Personal Data Leaked, Post-Ransomware Attack
29.9.20 Ransomware Threatpost
A researcher said he discovered an open data cache with names, grades, birthdates and more, after the Clark County School District refused to pay the ransom.
Personal information for students in the Clark County School District, which includes Las Vegas, has reportedly turned up on an underground forum, following a ransomware attack that researchers say was carried out by the Maze gang.
In early September, the Associated Press reported that the district was crippled during its first week of school thanks to a ransomware attack, potentially exposing personal information of employees, including names and Social Security numbers. The Clark County School District (CCSD) quickly confirmed the reporting via a Facebook post, where it noted that three days after school began online, on August 27, it found many of the school’s files to be inaccessible – though online learning platforms weren’t affected. At the time it said that “some private information may have been accessed.”
This week, Brett Callow, a threat analyst with Emisoft, told the Wall Street Journal that student information has turned up in an underground forum.
Callow said that a warning shot was fired last week by the attackers, presumably in retribution for CCSD not paying the ransom of an undisclosed sum. Attackers, he said, released a non-sensitive file to show that they had data access. When that garnered no response they released a raft of sensitive information. That information included employee Social Security numbers, addresses and retirement paperwork; and student data such as names, grades, birth dates, addresses and the school attended. The hackers also announced that the data reveal represents all of the information that it stole from CCSD’s network.
When Threatpost reached out to Emisoft for more details on the data cache, Callow said that in total, the criminals — specifically, the Maze gang — published about 25GBs of data.
He also said that no password was needed for access to the information.
“The data was published on leak sites on both the clear and dark webs,” he told Threatpost. “It can be accessed by anybody with an internet connection who knows the URL.”
For its part, the district said in a statement Monday that the reporting has not been verified: “National media outlets are reporting information regarding the data security incident CCSD first announced on Aug. 27, 2020. CCSD is working diligently to determine the full nature and scope of the incident and is cooperating with law enforcement. The District is unable to verify many of the claims in the media reports. As the investigation continues, CCSD will be individually notifying affected individuals.”
Callow told Threatpost, “the data would certainly appear to be legitimate.”
Threatpost reached out to CCSD for more information on the ransom amount and other details. When it comes to the extortion piece, a similar attack in July on the Athens school district in Texas led to schools being delayed by a week and the district paying attackers a $50,000 ransom in exchange for a decryption key.
More ransomware operators are setting up pages where they threaten to publish compromised data from victims – an added pressure for victims to pay the ransom. The ransomware tactic, call “double extortion,” first emerged in late 2019 by Maze operators – but has been rapidly adopted over the past few months by various cybercriminals behind the Clop, DoppelPaymer and Sodinokibi ransomware families.
“The number of successful attacks on school districts has increased significantly in recent weeks, with at least 12 falling victim this month alone,” Callow told Threatpost. “The attacks have disrupted learning at up to 596 individual schools. The number of cases in which data is exfiltrated has also increased: at least five of the 12 districts had data stolen and published online.”
lia Kolochenko, founder and CEO of web security company ImmuniWeb, noted that the CCSD story could get messy if parents choose to sue the district over the attack and its handling of it.
“What may be tricky is an eventual lawsuit by the victims against the school,” he said via email. “The crunchy point will be whether a failure to pay a ransom, to preclude data from being published, may be construed as a failure to remediate the damage and thus make the school civilly liable for this specific leak and its consequences. The monetary damages will, however, likely be of a nominal value as evidenced by recent litigation in the US involving similar data breaches. The best avenue will likely be a settlement, providing the students with a necessary support to negate reasonably foreseeable consequences of the data breach and exposure of their PII [personally identifiable information.”
School Attacks Continue
A slew of ransomware attacks and other cyberthreats have plagued back-to-school plans — as if dealing with the pandemic weren’t stressful enough for administrators.
In addition to the Clark County and Athens incidents, an attack on Hartford, Conn. public schools earlier in September led to the postponement of the first day of school. According to a public announcement, ransomware caused an outage of critical systems, including the school district’s software system that delivers real-time information on bus routes.
Also, a recent ransomware attack against a North Carolina school district, Haywood County Schools, caused the school to close to students for days.
Security researchers have said that cyberattacks may likely become the new “snow day” – particularly with the advent of pandemic-driven online learning. As students prepare to return to school, schools are facing more complex cyber-threats. For instance, the need for data, monitoring and contact-tracing become key factors in students returning to in-person classes, and remote students will have longer periods of time where they are connected to the internet.
Meanwhile, researchers have warned of projected seven-fold increase in ransomware overall for 2020, compared to last year – with some strains being more worrisome than others.
“One ransomware variant that is particularly concerning is Ryuk, which has been attributed to North Korean and Russian threat actors,” said Jeff Horne, CSO at Ordr. “Ryuk can be difficult to detect and contain as the initial infection usually happens via spam/phishing and can propagate and infect IoT/IoMT devices, as we’ve seen with UHS hospital phones and radiology machines. Once on an infected host, it can pull passwords out of memory and then laterally moves through open shares, infecting documents and compromised accounts.”
He added that many of the ransomware attacks come with additional pain.
“Some threat actors are still piggybacking Ryuk behind some other trojans/bots like TrickBot, QakBot and Emotet, and some of those can use the EternalBlue vulnerability to propagate,” he said.
Arthur J. Gallagher (AJG) insurance giant discloses ransomware attack
29.9.20 Ransomware Securityaffairs
US-based Arthur J. Gallagher (AJG) insurance giant disclosed a ransomware attack, the security breach took place on Saturday.
US-based Arthur J. Gallagher (AJG) global insurance brokerage firm confirmed that it was his with a ransomware attack on Saturday, September 26. The company did not provide technical details about the attack, it is not clear how the ransomware operators breached the company and which is the family of malware that infected its systems.
According to the company profile, AJG has 33,300 employees and operates in 49 countries offering client-service capabilities in more than 150 countries around the world.
The company is currently ranked 429 on the Fortune 500 list.
The IT staff at the company detected the ransomware attack the same day, it added that only a “limited portion” of its internal systems was impacted and its operations were apparently not impacted.
“On September 26, 2020, Arthur J. Gallagher & Co. (the “Company”) detected a ransomware incident impacting a limited portion of our internal systems.” reads the 8-K form filed by the company with the U.S. Securities and Exchange Commission (SEC) on September 28th,
“We promptly took all of our global systems offline as a precautionary measure, initiated response protocols, launched an investigation, engaged the services of external cybersecurity and forensics professionals, and implemented our business continuity plans to minimize disruption to our customers”
The company is restarting its business systems and is investigating the incident. AJG added that it doesn’t expect the incident to have a material impact on its business, operations, or financial condition.
“Although we are in the early stages of assessing the incident, based on the information currently known, we do not expect the incident to have a material impact on our business, operations or financial condition.” continues the form.
AJG didn’t disclose a data breach, it is not clear if the ransomware operators have exfiltrated any customer or employee data during the attack.
The security researchers Troy Mursch, founder of the threat intelligence firm Bad Packets told Bleeping Computer via Twitter that AJG was using two F5 BIG-IP servers vulnerable to CVE-2020-5902, it is possible that ransomware operators exploited this flaw to target the company.
Maritime transport and logistics giant CMA CGM hit with ransomware
29.9.20 Ransomware Securityaffairs
The French maritime transport and logistics giant CMA CGM S.A. revealed it was the victim of a malware attack that affecting some servers on its network.
CMA CGM S.A., a French maritime transport and logistics giant, revealed that a malware attack affected some servers on its network.
The company is present in over 160 countries through 755 offices and 750 warehouses with 110,000 employees and 489 vessels. CMA CGM serves 420 of the world’s 521 commercial ports and operates on more than 200 shipping lines.
The company currently ranks fourth behind Maersk Line, MSC, and COSCO Shipping Lines, all companies that have been curiously hit by malware attacks in the past.
In response to the attack, the IT staff at the CMA CGM isolated some applications for the Internet to avoid the malware from spreading to other systems.
“The CMA CGM Group (excluding CEVA Logistics) is currently dealing with a cyber-attack impacting peripheral servers.” reads the security notice published by the company. “As soon as the security breach was detected, external access to applications was interrupted to prevent the malware from spreading.”
According to a report published by Lloyd’s List, the company’s Chinese offices were allegedly infected with the Ragnar Locker ransomware.

Source Lloyds List
The Ragnar Locker appeared in the threat landscape at the end of the 2019 when it was employed in attacks against corporate networks.
One of the victims of the ransomware is the energy giant Energias de Portugal (EDP), where the attackers claimed to have stolen 10 TB of files.
“The French carrier was asked by hackers using the Ragnar Locker ransomware to contact them within two days ‘via live chat and pay for the special decryption key’. No ransom price has been named yet” reads the report.
At the time of writing, the external access to CMA CGM IT applications is currently unavailable. Customers have to contact their local agencies for all bookings.
The company is investigating the incident with the help of independent experts.
“An investigation is underway, conducted by our internal experts and by independent experts,” continues the notice. “A new communication will be issued at the end of the day.”
Ransomware attack on Tyler Technologies might be worse than initially thought
29.9.20 Ransomware Securityaffairs
Customers of Tyler Technologies are reporting finding suspicious logins and previously unseen remote access tools on their infrastructure
Tyler Technologies, Inc. is the largest provider of software to the United States public sector. The company last week disclosed a ransomware attack, and now its customers are reporting finding suspicious logins and previously unseen remote access tools on their networks.
The ransomware attack took place on September 23, the threat actors breached the network of the company and deployed the malware.
Tyler notified law enforcement and hired a forensics firm to investigate the incident and determine the extent of the incident.
Immediately after the attack company representatives declared that the incident only impacted the internal network and phone systems.
“Early in the morning on Wednesday, September 23, 2020, we became aware that an unauthorized intruder had disrupted access to some of our internal systems.” reads a statement issued by the company.
“We have confirmed that the malicious software the intruder used was ransomware.”
According to Tyler Technologies, the cloud infrastructure was not impacted and data of its customers were not affected.
“Based on the evidence available to-date, all indications are that the impact of this incident is limited to our internal corporate network and phone systems, and that there has been no impact on software we host for our clients.” continues the statement. “Our hosted environment is separate and segregated from our internal corporate environment.”
Further investigation revealed a different situation, as confirmed by some changes to the statement published by the company during the weekend. The statement explicitly refers to several suspicious logins to client systems that forced it to reset password as a precautionary measure.
“Because we have received reports of several suspicious logins to client systems, we believe precautionary password resets should be implemented,” the company said.
“If clients haven’t already done so, we strongly recommend that you reset passwords on your remote network access for Tyler staff and the credentials that Tyler personnel would use to access your applications, if applicable.”
Following the incident, some of Tyler’s customers also reported observing new remote access software, the Bomgar client, installed on their servers.
This circumstance suggests that attackers might have gained access to passwords for Tyler’s web-hosted infrastructure and moved to the company’s client networks.
“The hack prompted wide concern among local officials because some of Tyler’s programs are used to display election results, and U.S. intelligence agencies recently warned that foreign governments might try to sow mistrust by altering sites that report votes, which is seen as easier than changing the results themselves.” reported the Reuters.
“Tyler said the attack had no impact on the software it hosts for clients, and the software it sells that displays election results is hosted by Amazon and so was not at risk.”
According to Reuters, which first broke the story about the ransomware attack, some of Tyler’s software is also scheduled to be used in the upcoming US presidential election — for aggregating voting results from other sources into central dashboards.”
Some reports circulating online speculate the company was infected with the RansomExx ransomware.
The RansomEXX is human-operated ransomware, this means that attackers manually infected the systems after gained access to the target network.
In June 2020, the same ransomware was employed in an attack on the Texas Department of Transportation, in September it infected the systems at the IPG Photonics high-performance laser developer.
The good news is that the RansomEXX ransom, unlike other families of ransomware, does not appear to exfiltrate data before encrypting target systems.
UHS Shuts Down Systems in U.S. Hospitals Following Cyberattack
29.9.20 Ransomware Securityweek
Universal Health Services (UHS) over the weekend shut down the IT networks at multiple hospitals in the United States, after being hit with a cyberattack.
A Fortune 500 company operating more than 400 facilities in the United States, Puerto Rico, and the United Kingdom, the healthcare services provider has approximately 90,000 employees and claimed an annual revenue of $11.4 billion for 2019.
On Monday, some of the company’s employees took to Reddit to share information on a cyberattack that forced the shutdown of computers at UHS facilities nationwide. The hospital networks were shut down as well, but phone lines appear to have continued to operate throughout the incident.
“I work in a UHS facility and yes the system is down. Still have phones but that's it,” one person said.
Numerous Reddit users claiming to work at UHS facilities across the country revealed that systems started being shut down on Sunday, soon after midnight, and that employees were forbidden to turn on computers or the Internet.
Some claim that, prior to the shutdown, they observed some of the computers behaving strangely. Operation continued on paper, where possible, it seems.
“When the attack happened multiple antivirus programs were disabled by the attack and hard drives just lit up with activity. After 1min or so of this the computers logged out and shutdown. When you try to power back on the computers they automatically just shut down,” one of the users said.
While many said that patient care wasn’t critically affected, others detailed difficulties in receiving lab results or performing other types of investigations in a timely manner. There was also one unconfirmed report of patients dying due to such delays.
Also on Monday, UHS published a statement confirming that its IT network across facilities is suffering an outage due to a cyberattack.
“We implement extensive IT security protocols and are working diligently with our IT security partners to restore IT operations as quickly as possible. In the meantime, our facilities are using their established back-up processes including offline documentation methods. Patient care continues to be delivered safely and effectively,” the company revealed.
UHS also noted that patient and employee data does not appear to have been “accessed, copied or misused” during the incident.
While the company did not provide additional information on the incident, the manner in which the attack unfolded (based on employee reports) and the company’s reaction suggest ransomware was involved.
Some of the employees commenting on Reddit claimed that ransomware was indeed used and that the attackers demanded a ransom of tens of millions of dollars.
Furthermore, Bleeping Computer and TechCrunch report that information from people with knowledge of the incident leads to the conclusion that the Ryuk ransomware was used.
Hospitals in the Valley Health System, which appear affiliated to UHS, were also impacted, local news outlets report.
Universal Health Services Ransomware Attack Impacts Hospitals Nationwide
29.9.20 Ransomware Threatpost
The Ryuk ransomware is suspected to be the culprit.
A ransomware attack has shut down Universal Health Services, a Fortune-500 owner of a nationwide network of hospitals.
The attack occurred in the wee hours of the morning on Monday, according to reports coming in from employees on Reddit and other platforms.
On Reddit, a discussion with hundreds of comments indicated that many UHS locations were indeed down and requiring a return to manual processes.
“It was an epic cluster working ‘old school’ last night with everything on paper downtime forms,” one posted said. “It is true about sending patients away (called EMS diversion) but our lab is functional along with landlines. We have no access to anything computer based including old labs, EKGs or radiology studies. We have no access to our PACS radiology system.”
Another wrote, “UHS psych Georgia we’re definitely down. We are having to handwrite everything! We’re not allowed to turn computers on either.”
Meanwhile, one person told TechCrunch that “Everyone was told to turn off all the computers and not to turn them on again,” the person said. “We were told it will be days before the computers are up again.”
In an official statement given out on Monday, UHS noted: “The IT Network across Universal Health Services (UHS) facilities is currently offline, due to an IT security issue. We implement extensive IT security protocols and are working diligently with our IT security partners to restore IT operations as quickly as possible. In the meantime, our facilities are using their established back-up processes including offline documentation methods. Patient care continues to be delivered safely and effectively.”
It added, “No patient or employee data appears to have been accessed, copied or otherwise compromised.”
Reddit thread discussing the attack. Click to enlarge.
While UHS didn’t mention what kind of attack it suffered, other information coming from workers seems to point to the Ryuk ransomware as the culprit. An employee told BleepingComputer for instance that encrypted files are being appended with the .RYK extension; and, a ransom note that showed up on all affected computers referenced the phrase “Shadow of the Universe,” which is known to be included in Ryuk ransom notes.
Threatpost reached out to UHS for further comment.
Some on Reddit floated the specter of patients dying because of a lack of care, with an original poster stating (without evidence) that “four people died” as a result of the attack, because patient care was delayed.
“One of the busiest hospitals in the region is currently sending away all ambulances to different smaller hospitals because of this, and they themselves are losing patients while they are waiting for lab results to be delivered by courier….four people died tonight alone due to the waiting on results from the lab to see what was going on,” the post reads.
This is a similar situation to an incident this month at a Dusseldorf University hospital, where a ransomware attack resulted in emergency room diversions to other hospitals. According to a report by the NRW Minister of Justice, a patient died who had to be taken to a more distant hospital in Wuppertal because of the attack on the clinic’s servers. An investigation has been opened.
Some employees said they wouldn’t be surprised if patient care were impacted, despite the hospital system’s assurances.
“No patients died tonight in our ED but I can surely see how this could happen in large centers due to delay in patient care,” one poster said.
Another wrote, “I work at a UHS facility in Tucson and our sh*t is definitely down. They won’t even let us turn the computers on for going on over 24 hours. We’re a psych hospital so no one is dying from not getting their lab results back in time, but if the same thing happening to us is going on at any of UHS’s medical facilities then I can well imagine people dying.”
Again, there’s no confirmation that patient safety was compromised, let alone deaths, but the news does come as ransomware continues to explode. A report out from IBM X-Force found that this month, one in four observed attacks have been caused by ransomware.
“It is sad to see that despite hackers’ claims to stop healthcare cyber-attacks during COVID-19 crisis, such attacks still take place,” said Ilia Sotnikov, vice president of product management, Netwrix. “Ransomware attacks are especially disastrous for healthcare as they block access to IT systems and patient data in hospitals, leading to inability to treat people, and might eventually cost lives. Yet, the recent Netwrix 2020 Cyber Threats Report has found that every third healthcare organization experienced a ransomware attack during the past few months, which is the highest result among all the verticals. Reason for such high rates is easy: healthcare sector is an easy target for hackers, giving the shortage of resources, legacy systems and the pressure that the sector faces in the current situation.”
REvil ransomware operators are recruiting new affiliates
29.9.20 Ransomware Securityaffairs
REvil Ransomware (Sodinokibi) operators deposited $1 million in Bitcoins on a Russian-speaking hacker forum to demonstrate their willingness to involve new affiliates.
The REvil Ransomware (Sodinokibi) operators have deposited $1 million in bitcoins on a Russian-speaking hacker forum to prove to potential affiliates that they mean business.
Some hacker forum allows members to deposit funds that can be used to buy any kind of illicit services or product offered by other members.
Affiliates are essential to spread malicious code through hacking operations against businesses.
Usually, an affiliate gets 70-80% of the ransom payments they generate.
The REvil RaaS is a private operation, which means that potential affiliates are vetted and interviewed before they are allowed to join the program.
The selection of affiliates is a crucial process in the success of the cybercrime scheme, for this reason, REvil operators personally select each people they want to include in their program.
Now REvil ransomware operators have published a post on a cybercrime forum to recruiting new affiliates, preferably hackers with penetration testing capabilities.
As part of this recruitment process, REvil is looking for teams of skilled hackers at penetration testing or experienced individuals.
To attract the attention of the potential hackers to recruit as affiliates, the gang has deposited approximately $1 million (99 Bitcoins), on the hacker forum. Below an excerpt from the post published by REVil ransomware operators and shared by BleepingComputer:

Source BleepingComputer
The deposit demonstrates that the ransomware operators have a profitable business and trust the hacker forum and don’t fear an exit scam of its administrators
UHS hospitals hit by Ryuk ransomware attack
29.9.20 Ransomware Securityaffairs
Universal Health Services (UHS) healthcare providers has reportedly shut down systems at healthcare facilities after a Ryuk ransomware attack.
Universal Health Services (UHS), one of the largest hospital and healthcare services providers, has shut down systems at healthcare facilities in the United States after they were infected with the Ryuk ransomware.
The attack cyber-attack took place on Sunday morning, some patients have been redirected to other nearby hospitals because the UHS facilities were unable to operate.
Universal Health Services (UHS) is an American Fortune 500 company that provides hospital and healthcare services, in 2019, its annual revenues were $11.37 billion.
The company currently operates over 400 healthcare facilities in the US and the UK, has more than 90,000 employees. The Fortune 500 corporation had annual revenues of $11.4 billion in 2019.
According to reports from UHS’ employees, systems at some of the UHS hospitals in the US including those from California, Florida, Texas, Arizona, and Washington D.C. rebooted started displaying a ransom note. In response to the incident, the IT staff shut down its systems to avoid the propagation of the threat.
“I was sitting at my computer charting when all of this started. It was surreal and definitely seemed to propagate over the network. All machines in my department are Dell Win10 boxes.” reads one of the reports shared online.
“When the attack happened multiple antivirus programs were disabled by the attack and hard drives just lit up with activity. After 1min or so of this the computers logged out and shutdown. When you try to power back on the computers they automatically just shutdown. We have no access to anything computer based including old labs, ekg’s, or radiology studies. We have no access to our PACS radiology system.”
Some reports circulating online reveal that the ransomware added the “.ryk” extension to the filenames of encrypted documents, a circumstance that confirms a Ryuk ransomware infection.
The Ryuk ransomware operators were very active early this year, in March they targeted hospitals even as these organizations are involved in the fight against the Coronavirus pandemic.
The decision of the operators was not aligned with principal ransomware gangs that have announced they will no longer target health and medical organizations during the Coronavirus (COVID-19) pandemic.
Mount Locker ransomware operators demand multi-million dollar ransoms
28.9.20 Ransomware Securityaffairs
The operators behind new ransomware dubbed Mount Locker have adopted the same tactic of other gangs threatening the victims to leak stolen data.
A new ransomware gang named Mount Locker has started its operations stealing victims’ data before encrypting.
According to BleepingComputer, the ransomware operators are demanding multi-million dollar ransoms.
Like other ransomware operators, Mount Locker started targeting corporate networks, it has been active since the end of July 2020.
“From ransom notes shared with BleepingComputer by victims, the Mount Locker gang is demanding multi-million dollar ransom payments in some cases.” reported BleepingComputer.

Mount Locker ransom note (Source BleepingComputer)
In one of the attacks attributed to the group, the gang stole 400 GB of data from the victim and threatened it to share them with the its competitors, the media outlets, and TV channels, if the ransom is not paid.
The victim decided to not pay the ransom and the group published its data on its data leak site.
Currently, the data leak site includes the name of other alleged victims, and for one of them, it contained the leaked files.
Recently the ransomware operators claimed to have stolen the files from ThyssenKrupp System Engineering, from security company Gunnebo, and the provider of Nitonol components Memry, and Makalot.
According to the popular malware researchers Michael Gillespie, the Mount Locker uses ChaCha20 to encrypt the files and an embedded RSA-2048 public key to encrypt the encryption key.
The malware appends the extension .ReadManual.ID to the filenames of the encrypted files.
The ransom note, named RecoveryManual.html, includes instructions on how to access a Tor site, which is a chat service, that allows victims to communicate with the ransomware operators.
Experts confirmed that the encryption process implemented by the ransomware is not affected by any flaw, this means that it is not possible to recover the victims’ files for free.
Victims of ThunderX ransomware can recover their files for free
27.9.20 Ransomware Securityaffairs
Good news for the victims of the ThunderX ransomware, cybersecurity firm Tesorion has released a decryptor to recover their files for free.
Cybersecurity firm Tesorion has released a free decryptor for the ThunderX ransomware that allows victims to recover their files.
ThunderX is ransomware that appeared in the threat landscape recently, infections were discovered at the end of August 2020.
Researchers developed a decryptor for the ransomware after they have discovered a bug in the encryption process implemented by the threat.
This decryptor can recover for free files encrypted by the current version of the ThunderX ransomware that appends the .tx_locked extension to the filename of the decrypted files.
In order to recover the files, victims have to upload a copy of the readme.txt ransom note and an encrypted file to receive a decryption key.

The decryptor can be downloaded from the website of the NoMoreRansom project that already has helped victims of multiple ransomware to save more than one hundred million of ransom.
When the decryption process is completed, the decryptor will show a summary of the files successfully and those once for which the recovery failed.
Government Software Provider Tyler Technologies Confirms Ransomware Attack
25.9.20 Ransomware Securityweek
Tyler Technologies, a major provider of software and services for state and local governments in the United States, has confirmed that the recently disclosed cybersecurity incident involved ransomware.
Tyler this week shut down its website and started informing customers via email that its internal phone and IT systems were accessed without authorization by an unknown third party. The company said the attack disrupted access to some internal systems, and it decided to shut down points of access to external systems while investigating the incident.
Some industry professionals reported after the incident was disclosed that the attack appeared to involve a piece of ransomware named RansomExx.
In an update posted on its website on Thursday, Tyler confirmed that the attack involved ransomware, but it did not name the malware that was used and it did not provide other information on its response to the incident, citing an ongoing investigation.
RansomExx operators have not been observed stealing data from targeted companies and Tyler says it has found no evidence that customer data or servers are affected.
“Based on the evidence available to-date, all indications are that the impact of this incident is limited to our internal corporate network and phone systems, and that there has been no impact on software we host for our clients,” the company stated. “Our hosted environment is separate and segregated from our internal corporate environment. We have activated enhanced monitoring to supplement the monitoring services we already had in place, and we have detected no unauthorized or malicious activity or compromises in client systems that Tyler hosts.”
Tyler also provides election-related services to governments, which has raised some concerns, but the company has clarified that none of its products “is a system of record for voting or any other election- or voting-related activities.”
“Users of our open data solution may use our platform to post aggregated information about election returns, or to provide information about polling stations and campaign finance, but Tyler does not store individual voting records. Our open data solution is hosted offsite on AWS, not on Tyler's internal network that was impacted,” the company said.
When news of the breach broke, some reports claimed that the incident resulted in people being unable to pay utility bills or make court payments, but Tyler claims its online payment systems were not impacted and its employees have not found any evidence of disruption.
Russian Pleads Not Guilty in Foiled Tesla Ransomware Plot
25.9.20 Ransomware Securityweek
A Russian citizen accused of offering a Tesla employee $1 million to enable a ransomware attack at the electric car company’s plant in Nevada denied wrongdoing Thursday before a federal magistrate judge.
“I’m not guilty,” Egor Igorevich Kriuchkov said in response to a charge of conspiracy to intentionally cause damage to a protected computer.
He said earlier in the hearing that he wanted “to go through the whole process as fast as possible.”
Kriuchkov, 26, also told U.S. Magistrate Judge Carla Baldwin that he knew the Russian government was aware of his case. Authorities have not alleged that Kriuchkov has ties to the Kremlin. Authorities initially said he was 27.
The judge in Reno ordered Kriuchkov to remain in federal custody pending trial, scheduled Dec. 1 but likely to be postponed.
A conviction could bring a sentence of five years in prison and a $250,000 fine, said Nicholas Trutanich, U.S. attorney in Nevada. Deportation could follow a prison term.
Court documents say Kriuchkov was in the United States on a Russian passport and a tourist visa when he tried to recruit an employee of what was identified as “Company A” to install software enabling a computer hack.
Tesla CEO Elon Musk has acknowledged his company was the target of what he termed a serious effort to collect company secrets. Tesla has a massive factory near Reno that makes batteries for electric vehicles and energy storage units. Company officials did not immediately respond Thursday to messages.
Kriuchkov is accused of spending more than five weeks meeting, drinking, traveling and communicating by internet chat app with the unnamed employee, according to court documents. Some meetings were monitored and recorded by the FBI. It was not clear from the documents if money changed hands.
The plot was stopped before any damage occurred, the FBI said.
Kriuchkov spoke Thursday in English and had a Russian translator available.
His appointed attorneys, federal public defenders Sylvia Irvin and Brandon Jaroch, did not immediately respond to messages about his court appearance, which was held by videoconference due to restrictions on in-person gatherings amid the pandemic.
Kriuchkov was arrested Aug. 22 in Los Angeles, where prosecutors say he was heading to an airport to fly out of the country. He’s being held in the Washoe County Jail in Reno without bail.
The hack was designed to include a distributed denial-of-service attack, using junk data to flood the Tesla computer system, while a second intrusion would obtain files that could be dumped on the open internet if the company didn’t pay the ransom, according to court documents.
Other suspected co-conspirators are identified in a criminal complaint by nicknames. References are made to at least one other failed effort to target another unidentified company.
Government Software Provider Tyler Technologies Hit by Possible Ransomware Attack
24.9.20 Ransomware Securityweek
Tyler Technologies, a major Texas-based provider of software and services for the U.S. government, started informing customers on Wednesday of a security incident that is believed to have involved a piece of ransomware.
Tyler’s website is currently unavailable and in emails sent out to customers the company said its internal phone and IT systems were accessed without authorization by an “unknown third party.”
“Early this morning, we became aware that an unauthorized intruder had disrupted access to some of our internal systems. Upon discovery and out of an abundance of caution, we shut down points of access to external systems and immediately began investigating and remediating the problem,” reads the email, signed by the company’s CIO, Matt Bieri. “We have since engaged outside IT security and forensics experts to conduct a detailed review and help us securely restore affected equipment. We are implementing enhanced monitoring systems, and we have notified law enforcement.”
Bieri said only its internal network and phone systems appeared to have been impacted, and there was no evidence that client data, servers or hosted systems were affected.
SecurityWeek has reached out to Tyler for additional information on the incident and will update this article if the company responds.
In the meantime, Bleeping Computer reported that the company was targeted with a piece of ransomware named RansomExx. Cybercriminals are also said to have leveraged this piece of malware in attacks on the Texas Department of Transportation and Konica Minolta.
It’s unclear if the threat group that uses RansomExx also steals data from victim organizations. Ransomware operations increasingly involve the theft of sensitive data, which the attackers use for extortion and to increase their chances of getting paid by the victim.
Security blogger Brian Krebs learned from some Tyler customers in local government that the incident has resulted in people being unable to pay utility bills and make court payments.
Krebs also pointed out that Tyler provides customers a “survival guide” for ransomware attacks, including how to “respond to, and survive, a ransomware attack.” The measures proposed by the company may have helped lessen the impact of the attack, assuming that it has followed its own advice.
OldGremlin Ransomware Group Bedevils Russian Orgs
24.9.20 Ransomware Threatpost
The cybercriminal group has plagued firms with ransomware, sent via spear phishing emails with COVID-19 lures, since March.
A new cybercriminal group called OldGremlin has been targeting Russian companies – including banks, industrial enterprises and medical firms – with ransomware attacks.
OldGremlin relies on a bevy of tools, including custom backdoors called TinyPosh and TinyNode, to gain an initial foothold in the organization. It also uses tricky spear-phishing emails that utilize constantly evolving lures — from false coronavirus pandemic recommendations to fake requests for media interviews. And, the Russian-speaking cybercriminal group targets other Russian organizations, which researchers say is a big no-no within the Russian hacker community.
Researchers first discovered the group in August, when it targeted a large, unnamed medical company with a spear-phishing email purporting to be sent by the media holding company RBC. Instead, the email was an attack vector for OldGremlin to encrypt the company’s entire corporate network and demand a $50,000 ransom.
“According to Group-IB expert estimations, since the spring, OldGremlin has conducted at least seven phishing campaigns,” said researchers with Group-IB in a Wednesday post. “The hackers have impersonated the self-regulatory organization Mikrofinansirovaniye i Razvitiye (SRO MiR); a Russian metallurgical holding company; the Belarusian plant Minsk Tractor Works; a dental clinic; and the media holding company RBC.”
Attack Vector
The attack against the medical company is what put OldGremlin on researchers’ radar. In that case, the threat group sent targets a spear-phishing email with an attached ZIP archive, with the subject “Bill due” and purporting to be the finance department of RBC. Once the victim clicked on the .ZIP archive, a unique custom malware called TinyNode was used. TinyNode is a backdoor that downloads and launches additional malware.
“After the executable file was run for just 20 seconds, Windows Defender detected and deleted the malware,” said researchers. “Yet these 20 seconds were enough for the trojan to achieve persistence in the infected system. The victim failed to notice anything.”
After gaining remote access to the victim’s computer, the threat actors performed network reconnaissance, collected valuable data and propagated across the network, also utilizing the Cobalt Strike framework to make sure that any post-exploitation activity was as effective as possible.
“After the attackers conducted reconnaissance and made sure that they were in the domain that interested them, they continued to move laterally across the network, eventually obtaining domain administrator credentials,” said researchers. “They even created an additional account with the same privileges in case the main one was blocked.”
A few weeks after the initial attack, OldGremlin then wiped the organization’s backups, spreading TinyCryptor across hundreds of computers on the corporate network, with a ransom note demanding $50,000 in cryptocurrency in exchange for a decryption key.
OldGremlin History
Researchers said that OldGremlin’s first activities began between late March and early April. The group took advantage of the COVID-19 pandemic in early lures (a common theme for ransomware strains during this time period, as seen with the [F]Unicorn ransomware), sending financial institutions purported recommendations on how to organize a safe working environment during the pandemic, and impersonating the self-regulatory organization Mikrofinansirovaniye i Razvitiye (SRO MiR).
But OldGremlin has also constantly switched up its spear-phishing lures over time to mimic various organizations — from a Russian dental clinic to the Russian microfinance organization Edinstvo. The group has also commonly mimicked RBC in several campaigns. One spear-phishing email, for instance, purported to be sent by a Russian RBC journalist, who invited targets to take part in the “Nationwide survey of the banking and financial sectors during the coronavirus pandemic.” In later email exchanges, the attackers asked victims to click on a link, which then resulted in a custom trojan developed by the cybercriminals, TinyPosh, being downloaded to the victim’s computer.
oldgremlin cyberattack russia
Timeline of OldGremlin’s ransomware attacks. Credit: Group-IB
More recently, the group ramped up its activities in August after a short hiatus on August 13 and 14, sending around 250 malicious emails targeting Russian companies in the financial and industrial sectors. These campaigns also mimicked a journalist with the RBC group and a nickel-producing company.
Of note, OldGremlin appears to be made up of Russian speakers and yet is actively targeting Russian companies – which researchers said is a big transgression among the Russian underground.
“OldGremlin is the only Russian-speaking ransomware operator that violates the unspoken rule about not working within Russia and post-Soviet countries,” said Oleg Skulkin, senior digital forensics analyst at Group-IB. “They carry out multistage targeted attacks on Russian companies and banks using sophisticated tactics and techniques similar to those employed by APT groups.”
Group-IB detects a series of ransomware attacks by OldGremlin
23.9.20 Ransomware Securityaffairs
Researchers from threat hunting and intelligence firm Group-IB have detected a successful attack by a ransomware gang tracked as OldGremlin.
Group-IB, a global threat hunting and intelligence company headquartered in Singapore, has detected a successful attack by a ransomware gang, codenamed OldGremlin. The Russian-speaking threat actors are relatively new to the Big Game Hunting. Since March, the attackers have been trying to conduct multistage attacks on large corporate networks of medical labs, banks, manufacturers, and software developers in Russia. The operators use a suite of custom tools with the ultimate goal of encrypting files in the infected system and holding it for a ransom of about $50,000.
The first successful attack of OldGremlin, known to Group-IB team, has been detected in August. Group-IB Threat Intelligence team has also collected evidence of earlier campaigns dating back to the spring of this year. The group has targeted only Russian companies so far, which was typical for many Russian-speaking adversaries, such as Silence and Cobalt, at the beginning of their criminal path. Using Russia as a testing ground, these groups then switched to other geographies to distance themselves from vicious actions of the victim country’s police and decrease the chances of ending behind the bars.
Unsought invoice
As the initial vector of their attacks, OldGremlin use spear phishing emails, to which the group adopted creative approach. They, in particular, utilized the names of actually existing senders and, in one instance, sent out emails in several stages, making the victims think that they are arranging an interview with a journalist of a popular Russian business newspaper. In other instances, the gang exploited the COVID-19 theme and anti-government rallies in Belarus in their phishing emails.
The most recent successful attack, known to Group-IB Threat Intelligence team, took place in August, when OldGremlin targeted a clinical diagnostics laboratory operating throughout the country. The analysis of the incident revealed that the ransomware attack started with a phishing email sent on behalf of Russia’s major media holding company, with the “Invoice” subject. In their email, OldGremlin informed the recipient of their inability to contact the victim’s colleague highlighting the urgency to pay the bill, the link to which was included in the text body. By clicking the link, the victim downloaded a ZIP-archive that contained a unique custom backdoor, dubbed TinyNode. The backdoor downloads and installs additional malware on the infected machine.
The cybercriminals then used the remote access to the victim’s computer, obtained with the help of TinyNode, as a foothold for network reconnaissance, gathering data and lateral movement in the victim’s network. As part of post-exploitation activities, OldGremlin used Cobalt Strike to move laterally and obtain authentication data of domain administrator.
Several weeks after the attack’s launch, the cybercriminals deleted server backups before encrypting the victim’s network with the help of TinyCryptor ransomware (aka decr1pt), which is also OldGremlin’s brainchild. When the work of company’s regional branches had been paralyzed, they demanded about $50,000 in cryptocurrency. As a contact email, the threat actors gave an email registered with ProtonMail.
Up-to-date phishing
Group-IB Threat Intelligence experts have also detected other phishing campaigns carried out by the group, with the first of them having occurred in late March – early April. Back then, the group sent out emails to financial organizations from an email that mimicked that of a Russian microfinance organization, providing the recipients with the guidelines on how to organize safe remote work during the COVID-19. It was the first time when OldGremlin used their other custom backdoor – TinyPosh, which allowsthe attackers to download additional modules form their C2. To hide their C&C server, OldGremlin resorted to CloudFlare Workers server.
Two weeks after the above-mentioned malicious mailing, OldGremlin, keeping up with the urgent agenda, sent out emails with the subject “All-Russian study of the banking and financial sectors during the pandemic” purported to be from a real-life journalist with a major Russian media holding. The sender then asked for an online interview and schedule it with the Calendly and informed them that the questions for the interview had been uploaded to a cloud platform. As it was the case with their first campaigns, the link downloaded a custom TinyPosh Trojan.
Fig. 1 Phishing email sent on behalf of a Belarusian plant
Another round of phishing emails by OldGremlin was detected by CERT-GIB on August 19, when the group sent out messages exploiting the issue of protests in Belarus. The email that claimed to be from the CEO of the Minsk Tractor Works plant informed its partners of the fact that the enterprise was being probed by the country’s prosecutor’s office due to its participation in the anti-government protests and asked them to send missing documents. The list of the necessary documents was reportedly attached to the email, an attempt to download it, however, let TinyPosh in to the user’s computer. Between May and August, Group-IB detected nine campaigns conducted by the group.
“What distinguishes OldGremlin from other Russian-speaking threat actors is their fearlessness to work in Russia,” comments Group-IB senior Digital Forensics analyst Oleg Skulkin. “This indicates that the attackers are either fine-tuning their techniques benefiting from home advantage before going global, as it was the case with Silence and Cobalt, or they are representatives of some of Russia’s neighbors who have a strong command of Russian. Amid global tensions, cybercriminals have learned to navigate the political agenda, which gives us grounds to suggest that the attackers might come from some of the post-Soviet countries Russia has controversy or weak ties with.”
Despite the vim, showed by ransomware operators recently, there is still a number of measures that can be taken to fight off ransomware attacks. They include, among others, using multifactor authentication, complex passwords for the accounts used for access via RDP and changing them regularly, restricting the list of IP addresses that can be used to make external RDP connections, and etc. Relevant threat intelligence and proactive approach to threat hunting are paramount in building a resilient infrastructure. Implementing Group-IB Threat Detection System allows to hunt for advanced on both network and host levels. A technical analysis of OldGremlin’s operations along with IOCs is available at https://www.group-ib.com/blog/oldgremlin.

A New Hacking Group Hitting Russian Companies With Ransomware
23.9.20 Ransomware Thehackernews
As ransomware attacks against critical infrastructure continue to spike in recent months, cybersecurity researchers have uncovered a new entrant that has been actively trying to conduct multistage attacks on large corporate networks of medical labs, banks, manufacturers, and software developers in Russia.
The ransomware gang, codenamed "OldGremlin" and believed to be a Russian-speaking threat actor, has been linked to a series of campaigns at least since March, including a successful attack against a clinical diagnostics laboratory that occurred last month on August 11.
"The group has targeted only Russian companies so far, which was typical for many Russian-speaking adversaries, such as Silence and Cobalt, at the beginning of their criminal path," Singaporean cybersecurity firm Group-IB said in a report published today and shared with The Hacker News.
"Using Russia as a testing ground, these groups then switched to other geographies to distance themselves from vicious actions of the victim country's police and decrease the chances of ending behind the bars."
OldGremlin's modus operandi involves using custom backdoors — such as TinyNode and TinyPosh to download additional payloads — with the ultimate goal of encrypting files in the infected system using TinyCryptor ransomware (aka decr1pt) and holding it hostage for about $50,000.
In addition, the operators gained an initial foothold on the network using a phishing email sent on behalf of Russia's RBC Group, a Moscow-based major media group, with "Invoice" in the subject line.
The message informed the recipient of their inability to contact the victim's colleague with regards to an urgent bill payment along with a malicious link to pay the bill that, when clicked, downloaded the TinyNode malware.
Upon finding their way in, the bad actor used remote access to the infected computer, leveraging it to laterally move across the network via Cobalt Strike and gather authentication data of the domain administrator.
In a different variant of the attack observed in March and April, the cybercriminals were found using COVID-themed phishing lures to financial enterprises that masqueraded as a Russian microfinance organization to deliver the TinyPosh Trojan.
Subsequently, a separate wave of the campaign was detected on August 19, when the cybercriminals sent out spear-phishing messages exploiting the ongoing protests in Belarus decrying the government, proving once again that threat actors are adept at capitalizing world events to their advantage.
In all, OldGremlin has been behind nine campaigns between May and August, according to Group-IB.
"What distinguishes OldGremlin from other Russian-speaking threat actors is their fearlessness to work in Russia," Oleg Skulkin, a senior digital forensics analyst at Group-IB, said.
"This indicates that the attackers are either fine-tuning their techniques benefiting from home advantage before going global, as it was the case with Silence and Cobalt, or they are representatives of some of Russia's neighbors who have a strong command of Russian."
A Patient Dies After Ransomware Attack Paralyzes German Hospital Systems
21.9.20 Ransomware Thehackernews
German authorities last week disclosed that a ransomware attack on the University Hospital of Düsseldorf (UKD) caused a failure of IT systems, resulting in the death of a woman who had to be sent to another hospital that was 20 miles away.
The incident marks the first recorded casualty as a consequence of cyberattacks on critical healthcare facilities, which has ramped up in recent months.
The attack, which exploited a Citrix ADC CVE-2019-19781 vulnerability to cripple the hospital systems on September 10, is said to have been "misdirected" in that it was originally intended for Heinrich Heine University, according to an extortion note left by the perpetrators.
After law enforcement contacted the threat actors and informed them that they had encrypted a hospital, the operators behind the attack withdrew the ransom demand and provided the decryption key.
The case is currently being treated as a homicide, BBC News reported over the weekend.
Unpatched Vulnerabilities Become Gateway to Ransomware Attacks
Although several ransomware gangs said early on in the pandemic that they would not deliberately target hospitals or medical facilities, the recurring attacks prompted the Interpol to issue a warning cautioning hospitals against ransomware attacks designed to lock them out of their critical systems in an attempt to extort payments.
Weak credentials and VPN vulnerabilities have proven to be a blessing in disguise for threat actors to break into the internal networks of businesses and organizations, leading cybersecurity agencies in the U.S. and U.K. to publish multiple advisories about active exploitation of the flaws.
"The [Federal Office for Information Security] is becoming increasingly aware of incidents in which Citrix systems were compromised before the security updates that were made available in January 2020 were installed," the German cybersecurity agency said in an alert last week.
"This means that attackers still have access to the system and the networks behind it even after the security gap has been closed. This possibility is currently increasingly being used to carry out attacks on affected organizations."
The development also coincides with a fresh advisory from the U.K. National Cyber Security Centre (NCSC), which said it's observed an uptick in ransomware incidents targeting educational institutions at least since August 2020, while urging schools and universities to implement a "defence in depth" strategy to defend against such malware attacks.
Some of the affected institutions included Newcastle and Northumbria Universities, among others.
Citing Remote Desktop Protocol (RDP), vulnerable software or hardware, and email phishing as the three most common infection vectors, the agency recommended organizations to maintain up-to-date offline backups, adopt endpoint malware protection, secure RDP services using multi-factor authentication, and have an effective patch management strategy in place.
A Spike in Ransomware Infections
If anything, the ransomware crisis seems to be only getting worse. Historical data gathered by Temple University's CARE cybersecurity lab has shown that there have been a total of 687 publicly disclosed cases in the U.S. since 2013, with 2019 and 2020 alone accounting for more than half of all reported incidents (440).
Government facilities, educational institutions, and healthcare organizations are the most frequently hit sectors, as per the analysis.
And if 2020 is any indication, attacks against colleges and universities are showing no signs of slowing down.
Allan Liska, a threat intelligence analyst at Recorded Future, revealed there had been at least 80 publicly reported ransomware infections targeting the education sector to date this year, a massive jump from 43 ransomware attacks for the whole of 2019.
"Part of this change can be attributed to extortion sites, which force more victims to announce attacks," Liska said in a tweet. "But, in general, ransomware actors have more interest in going after colleges and universities, and they are often easy targets."
You can read more about NCSC's mitigation measures here. For more guidance on proofing businesses against ransomware attacks, head to US Cybersecurity Security and Infrastructure Security Agency's response guide here.
NCSC warns of a surge in ransomware attacks on education institutions
21.9.20 Ransomware Securityaffairs
The U.K. National Cyber Security Centre (NCSC) has issued an alert about a surge in ransomware attacks targeting education institutions.
The U.K. National Cyber Security Centre (NCSC), has issued an alert about a surge in ransomware attacks against education institutions. The British security agency is urging the institutions in the industry to follow the recommendations to mitigate the risk of exposure to ransomware attacks.
“This criminal targeting of the education sector, particularly at such a challenging time, is utterly reprehensible.” “While these have been isolated incidents, I would strongly urge all academic institutions to take heed of our alert and put in place the steps we suggest, to help ensure young people are able to return to education undisrupted.” Paul Chichester, Director of Operations at the NCSC, said.
“We are absolutely committed to ensuring UK academia is as safe as possible from cyber threats, and will not hesitate to act when that threat evolves.”
This summer the NCSC investigated an increased number of cyber attacks on universities, schools, and colleges, most of them were hit with ransomware.
The attacks continued over time, recently the Newcastle University was hit with DoppelPaymer ransomware.
“With institutions either welcoming pupils and students back for a new term, or preparing to do so, the NCSC’s alert urges them to take immediate steps such as ensuring data is backed up and also stored on copies offline.” reads the advisory. “They are also urged to read the NCSC’s newly-updated guidance on mitigating malware and ransomware attacks, and to develop an incident response plan which they regularly test.”
The NCSC also provided info about the initial infection vectors observed in the ransomware attacks:
Insecure Remote Desktop Protocol (RDP) configurations
Vulnerable Software or Hardware
Phishing emails
The agency recommends to implement an effective vulnerability management and patch management process, and of course to secure RDP services.
Once gained the foothold in the target network, the attackers will attempt lateral movements to elevate the privileges and search for high-value machines to encrypt (i.e. backup servers, network shares, servers, auditing devices).
In some attacks, government experts also observed the sabotage of backup or auditing devices to make recovery more difficult, the encryption of entire virtual servers, the use of scripting environments (i.e. PowerShell) to easily deploy tooling or ransomware.
NCSC education institutions
Below the list of recommendations provided by the agency that includes the use of updated antivirus software and anti-phishing defense measures:
centrally manage devices in order to only permit applications trusted by the enterprise to run on devices, using technologies including AppLocker, or from trusted app stores (or other trusted locations)
consider whether enterprise antivirus or anti-malware products are necessary, and keep the software (and its definition files) up to date
provide security education and awareness training to your people, for example NCSC’s Top Tips for Staff
disable or constrain scripting environments and macros, by:
enforcing PowerShell Constrained Language mode via a User Mode Code Integrity (UMCI) policy – you can use AppLocker as an interface to UMCI to automatically apply Constrained Language mode
protecting your systems from malicious Microsoft Office macros
disable autorun for mounted media (prevent the use of removable media if it is not needed)
To prevent attackers exploiting flaws to force the execution of their code the organization recommends:
install security updates as soon as they become available in order to fix exploitable bugs in your products
enable automatic updates for OSs, applications, and firmware if you can
use the latest versions of OSs and applications to take advantage of the latest security features
configure host-based and network firewalls, disallowing inbound connections by default
Recently Check Point researchers warned of a surge in the DDoS attacks against education institutions and the academic industry across the world.
IPG Photonics high-performance laser developer hit with ransomware
21.9.20 Ransomware Securityaffairs
IPG Photonics, a leading U.S. manufacturer of high-performance fiber lasers for diverse applications and industries was hit by a ransomware attack that disrupted its operations.
IPG Photonics manufactures high-performance fiber lasers, amplifiers, and laser systems for diverse applications and industries.
The company was founded in 1990 in Russia by physicist Valentin Gapontsev, it employs over 4,000 people and has a $1.3 billion revenue in 2019.
The laser systems designed by the company were part of the U.S. Navy’s arsenal.
The news of the attack was first reported by BleepingComputer which was contacted on Monday by a source with knowledge of the attack.
The source told BleepingComputer that the ransomware attack had disrupted the operations worldwide of the company.
The attack affected email, phones, and network connectivity in the offices.
“Due to the attack, IPG Photonics IT systems are shutdown worldwide, affecting email, phones, and network connectivity in the offices.” reported BleepingComputer. “With these systems down, BleepingComputer is also being told that manufacturing parts and shipping have become unavailable.”
BleepingComputer speculates that the attack was carried out by RansomExx ransomware operators, the same gang that recently hit the IT giant Konica Minolta.
The RansomEXX is human-operated ransomware, this means that attackers manually infected the systems after gained access to the target network.
In June 2020, the same ransomware was employed in an attack on the Texas Department of Transportation.
The good news is that the RansomEXX ransom, unlike other families of ransomware, does not appear to exfiltrate data before encrypting target systems.
Maze Ransomware Adopts Ragnar Locker Virtual-Machine Approach
19.9.20 Ransomware Threatpost
Maze continues to adopt tactics from rival cybercrime gangs.
The operators of the Maze ransomware have added a fresh trick to their bag of badness: Distributing ransomware payloads via virtual machines (VM). It’s a “radical” approach, according to researchers, meant to help the ransomware get around endpoint defense.
That’s according to researchers with Sophos Managed Threat Response (MTR), who said that the threat actors were recently seen distributing the malware in the form of a VirtualBox virtual disk image (a VDI file). The VDI file itself was delivered inside of a Windows MSI file, which is a format used for installation, storage and removal of programs.
In order to set up the VM on the target, “the attackers also bundled a stripped down, 11-year-old copy of the VirtualBox hypervisor inside the .MSI file, which runs the VM as a ‘headless’ device, with no user-facing interface,” researchers said, in a Thursday posting.
The VM would run as a trusted application, which helps the ransomware conceal itself. Also, most endpoint solutions only have visibility into physical drives, not VMs – virtual environments usually require their own separate security monitoring solution.
“Since the…ransomware application runs inside the virtual guest machine, its process and behaviors can run unhindered, because they’re out-of-reach for security software on the physical host machine,” Sophos explained in an earlier blog post. “The data on disks and drives accessible on the physical machine are attacked by the ‘legitimate’ VboxHeadless.exe process, the VirtualBox virtualization software.”
In employing the strategy, the Maze authors are taking a page from the Ragnar Locker ransomware, according to Sophos’ analysts, who uncovered the latter using the same technique earlier this year.
“In an earlier attack, Ragnar Locker also deployed a virtual machine in an attempt to bypass protection measures,” Sophos researchers explained. In that attack, they added, “Ragnar Locker was deployed inside an Oracle VirtualBox Windows XP virtual machine. The attack payload was a 122 MB installer with a 282 MB virtual image inside—all to conceal a 49 KB ransomware executable.”
Technical Details
In the Maze ransomware incident, the attack payload was a 733 MB installer with a 1.9 GB Windows 7 virtual image inside (uncompressed) — concealing a 494 KB ransomware executable.
The file sizes are much larger than the Ragnar Locker approach. The Maze infection routine included an installer for both the 32-bit and 64-bit versions of VirtualBox 3.0.4 inside of the MSI file, for one (the VirtualBox version dates back to 2009 and is still branded with its then-publisher’s name, Sun Microsystems). And, the threat actors chose to use Windows 7.
“Using a virtual Windows 7 machine instead of XP significantly increases the size of the virtual disk, but also adds some new functionality that wasn’t available in the Ragnar Locker version,” according to the Sophos writeup. “Specifically, the VM is configured in such a way that it “allows easy insertion of another ransomware on the attacker’s ‘builder’ machine.”
The root of the virtual disk contains three files associated with the Maze ransomware: preload.bat, vrun.exe (the VM itself) and a file just named payload (with no file extension), which is the actual Maze DLL payload.
“The preload.bat file (shown below) modifies the computer name of the virtual machine, generating a series of random numbers to use as the name, and joins the virtual machine to the network domain of the victim organization’s network using a WMI command-line function,” explained Sophos analysts.
For persistence, the malware also adds a file named startup_vrun.bat to the Windows Start menu.
“The script copies the same three files found on the root of the VM disk (the vrun.exe and payload DLL binaries, and the preload.bat batch script) to other disks, then issues a command to shut down the computer immediately,” according to the analysis. “When someone powers the computer on again, the script executes vrun.exe.”
When the MSI file first runs, the VM creates the C:\SDRSMLINK\ folder location, which acts as a clearinghouse for specific folders the malware wants to track – Maze does so using symbolic links (symlinks), which act as shortcuts to folders on the local hard drive. This folder is shared with the rest of the network.
Ultimately, a batch script called starter.bat is used launch the ransomware payload from within the VM.
Recon Before Deployment
Sophos researchers said that telemetry analysis revealed that the attackers had penetrated the network at least six days prior to delivering the ransomware payload.
“The attackers had spent days preparing to launch the ransomware by building lists of IP addresses inside the target’s network, using one of the target’s domain controller servers and exfiltrating data to cloud storage provider Mega.nz,” researchers explained.
Also, the VM was apparently configured in advance by someone who was intimately familiar with the victim’s network, they said.
The threat actors initially demanded a $15 million ransom from the target of the attack. The target did not pay the ransom, according to Sophos.
The [virtual machine’s] configuration file (micro.xml) maps two drive letters that are used as shared network drives in this particular organization, presumably so it can encrypt the files on those shares as well as on the local machine,” according to the analysis.
Meanwhile, the operators behind the Maze ransomware have been busy in 2020, usually going after very high-profile fish. In June Maze attacked a U.S. military contractor involved in the maintenance of the country’s Minuteman III nuclear arsenal. In April they hit IT services giant Cognizant, causing service disruptions; Cognizant, a Fortune 500 company, employs close to 300,000 people. The malware was also behind the December cyberattack on the City of Pensacola, Fla., which shut down the city’s computer networks and affected its systems. Other targets have included Allied Systems and Pitney Bowes.
The Maze operators continue to evolve their tactics as well. For instance, they often now carry out “double extortion” attacks, in which they leak information on an underground forum unless victims pay up. In fact, researchers said in April that the Maze gang has created a dedicated web page, which lists the identities of their non-cooperative victims and regularly publishes samples of the stolen data. This so far includes details of dozens of companies, including law firms, medical service providers and insurance companies, that have not given in to their demands.
“The Maze threat actors have proven to be adept at adopting the techniques demonstrated to be successful by other ransomware gangs, including the use of extortion as a means to extract payment from victims,” Sophos researchers concluded. “As endpoint protection products improve their abilities to defend against ransomware, attackers are forced to expend greater effort to make an end-run around those protections.”
Ransomware en masse on the wane: top threats inside web-phishing in H1 2020
18.9.20 Ransomware Securityaffairs
Web-phishing targeting various online services almost doubled during the COVID-19 pandemic, it accounted for 46 percent of the total number of fake web pages.
Singapore, 09/18/2020 — Group-IB, a global threat hunting and intelligence company headquartered in Singapore, evidenced the transformation of the threat portfolio over the first half of 2020. It came as no surprise that web-phishing targeting various online services almost doubled during the COVID-19 pandemic: it accounted for 46 percent of the total number of fake web pages. Ransomware, the headliner of the previous half-year, walked off stage: only 1 percent of emails analyzed by Group-IB’s Computer Emergency Response Team (CERT-GIB) contained this kind of malware. Every third email, meanwhile, contained spyware, which is used by threat actors to steal payment data or other sensitive info to then put it on sale in the darknet or blackmail its owner.
Downloaders, intended for the installation of additional malware,and backdoors, granting cybercriminals remote access to victims’ computers, also made it to top-3. They are followed by banking Trojans, whose share in the total amount of malicious attachments showed growth for the first time in a while.
Opened email lets spy in
CERT-GIB’s report is based on data collected and analyzed by the Threat Detection System (TDS) Polygon as part of operations to prevent and detect threats distributed online in H1 2020. According to the data of CERT-GIB, in H1 2020, 43 percent of the malicious mails on the radars of Group-IB Threat Detection System had attachments with spyware or links leading to their downloading. Another 17 percent contained downloaders, while backdoors and banking Trojans came third with a 16- and 15-percent shares, respectively. Ransomware, which in the second half of 2019 hid in every second malicious email, almost disappeared from the mailboxes in the first six months of this year with a share of less than 1 percent.
These findings confirm adversaries’ growing interest in Big Game Hunting. According to Group-IB’s recent white paper “Ransomware Uncovered: Attackers’ Latest Methods”: ransomware operators have switched from attacks en masse on individuals to corporate networks. Thus, when attacking large companies, instead of infecting the computer of a separate individual immediately after the compromise, attackers use the infected machine to move laterally in the network, escalate the privileges in the system and distribute ransomware on as many hosts as possible.
Top-10 tools used in attacks tracked by CERT-GIB in the reporting period were banking Trojan RTM (30%); spyware LOKI PWS (24%), AgentTesla (10%), Hawkeye (5%), and Azorult (1%); and backdoors Formbook (12%), Nanocore (7%), Adwind (3%), Emotet (1%), and Netwire (1%). The new instruments detected in the first half of the year included Quasar, a remote access tool based on the open source; spyware Gomorrah that extracts login credentials of users from various applications; and 404 Keylogger, a software for harvesting user data that is distributed under malware-as-a-service model.
Almost 70 percent of malicious files were delivered to the victim’s computer with the help of archives, another 18% percent of malicious files were masked as office documents (with .doc, .xls and .pdf file extensions), while 14% more were disguised as executable files and scripts.

Secure web-phishing
In the first six months of 2020, CERT-GIB blocked a total of 9 304 phishing web resources, which is an increase of 9 percent compared to the previous year. The main trend of the observed period was the two-fold surge in the number of resources using safe SSL/TLS connection – their amount grew from 33 percent to 69 percent in just half a year.
This is explained by the cybercriminals’ desire to retain their victim pool – the majority of web browsers label websites without SSL/TLS connection as a priori dangerous, which has a negative impact on the effectiveness of phishing campaigns. Group-IB experts predict that the share of web-phishing with insecure connection will continue to decrease, while websites that do not support SSL/TLS will become an exception.
Pandemic chronicle
Just as it was the case in the second half of 2019, in the first half of this year, online services like ecommerce websites turned out to be the main target of web-phishers. In the light of global pandemic and the businesses’ dive into online world, the share of this phishing category increased to remarkable 46 percent. The attractiveness of online services is explained by the fact that by stealing user login credentials, threat actors also gain access to the data of bank cards linked to user accounts.
Online services are followed by email service providers (24%), whose share, after a decline in 2019, resumed growth in 2020, and financial organizations (11%). Main web-phishing target categories also included payment services, cloud storages, social networks, and dating websites.
The leadership in terms of the number of phishing resources registered has persistently been held by .com domain zone – it accounts for nearly a half (44%) of detected phishing resources in the review period. Other domain zones popular among the phishers included .ru (9%), .br (6%), .net (3%) and .org (2%).

“The beginning of this year was marked by changes in the top of urgent threats that are hiding in malicious emails, — comments CERT-GIB deputy head Yaroslav Kargalev.—Ransomware operators have focused on targeted attacks,choosing large victims with a higher payment capacity. The precise elaboration of these separate attacks affected the ransomware share in the top threats distributed via email en masse. Their place was taken by backdoors and spyware, with the help of which threat actors first steal sensitive information and then blackmail the victim, demanding a ransom, and, in case the demand is refused, releasing the info publicly. The ransomware operators’ desire to make a good score is likely to result in the increase of the number of targeted attacks. As email phishing remains the main channel of their distribution, the urgency of securing mail communication is more relevant than ever.”
California Elementary Kids Kicked Off Online Learning by Ransomware
18.9.20 Ransomware Threatpost
The attack on the Newhall District in Valencia is part of a wave of ransomware attacks on the education sector, which shows no sign of dissipating.
As students head back to the classroom, the spate of ransomware attacks against schools is continuing. The latest is a strike against a California school district that closed down remote learning for 6,000 elementary school students, according to city officials.
The cyberattack, against the Newhall School District in Valencia, affected all distance learning across 10 different grade schools, Newhall Superintendent Jeff Pelzel told the Los Angeles Times. He said the cybercriminals struck overnight Sunday into Monday morning, and that he noticed something awry after getting consistent error messages when trying to access Outlook and email. Shortly after, it became apparent that the district had been victimized by malware.
Interestingly, there has been no extortion demand yet, Pelzel told the outlet. But meanwhile, Newhall’s servers have been shut down while a forensic investigation plays out, and the kids are back to using pencil and paper to work on take-home assignments.
The news comes as officials issue warnings on increased ransomware attacks in the education sector, largely tied to remote learning and the increased use of technology for instruction – which widens the attack surface. The U.K.’s National Cyber Security Centre (NCSC) for instance flagged an uptick of attacks against grammar schools, colleges and universities in that country, warning that vulnerable remote desktop protocol (RDP), unpatched software and hardware being used by remote learners, and successful phishing emails are all common attack vectors.
Here in the U.S., ransomware has unfortunately become part of the curriculum for some institutions. Over the summer, as they were preparing to welcome students back, four different universities fell victim to the NetWalker ransomware gang, according to tallies from Avira: The University of Utah (which paid almost half a million dollars); Columbia College in Chicago (ransom status unknown); Michigan State University (no ransom paid); and the University of California San Francisco (which paid $1.14 million).
Ransomware operators are targeting colleges and universities because of the sheer value of the information they hold, according to Avira.
“Universities have vast databases on thousands of students and faculty, which can include items of great interest to cybercriminals,” according to a Thursday blog. “This includes personal information like names, birth dates, telephone numbers and email addresses, as well as financial records. But some of the data stored in university databases can be of even more value. Cutting-edge research takes place at universities, and the theft, manipulation or destruction of this data can be enough motivation for hackers.”
Meanwhile, on the K-12 front, the attack on Newhall is hardly unique: Last week, attacks in Hartford, Conn., Fairfax County Va. and Clark County, Nev. (home of Las Vegas) forced public schools to postpone the first day of school. In August, a cyberattack on the Rialto Unified School District in San Bernardino County forced online class suspension. And earlier in July on the Athens school district in Texas led to schools being delayed by a week (and the district paying attackers a $50,000 ransom in exchange for a decryption key).
Security firm Check Point said in a report this week that the U.S. is responsible for the highest increase in education-related attacks globally, including ransomware, DDoS and other campaigns. Between July and August 2020, the average number of weekly attacks per education organization in the U.S. increased by 30 percent, from 468 cyberattacks to 608, when compared to the previous two months. For comparison, cyberattacks against all other sectors increased by only 6.5 percent.
The trend will likely continue as long as distance learning remains the new normal, the firm warned.
“The coronavirus pandemic has been a forcing function for not only remote work, but remote learning,” said Omer Dembinsky, manager of data intelligence at Check Point, via email. “These numbers are staggering, and an ominous trend is clear: Hackers are eyeing students returning to virtual classes as easy targets. These attacks can include malicious phishing emails, “Zoombombs” and even ransomware…I strongly urge students, parents and institutions to be extra careful these next few months, as I believe the attack numbers and methods will only get worse. As remote learning stays, hackers also stay.”
Major Duesseldorf hospital infected with ransomware, patient died for consequences
18.9.20 Ransomware Securityaffairs
A major hospital in Duesseldorf was hit by a cyber attack, a woman who needed urgent admission died after she had to be hijacked to another city.
The news is shocking, German authorities revealed that a cyber attack hit a major hospital in Duesseldorf, the Duesseldorf University Clinic, and a woman who needed urgent admission died after she had to be taken to another city for treatment.
“The Duesseldorf University Clinic’s systems have been disrupted since last Thursday.” states the Associated Press.
The treatment for the women was delayed for an hour that caused the death of the patient.
The cyber attack took place last Thursday, since then the systems at the Duesseldorf University Clinic were not available. The authorities investigated the incident and discovered that the IT systems were disrupted by a cyber attack that targeted a widely used commercial add-on software.
The attack caused systems gradually crashing, it paralyzed the operations at the hospital and emergency patients were hijacked in other structures while surgical operations postponed.
The hospital confirmed that there was no concrete ransom demand and reported that there are no indications that data is irretrievably lost.
Currently the hospital is restoring its IT systems and resuming the operations. The news agency dpa reported that a report from North Rhine-Westphalia state’s justice minister revealed that the hospital was hit by a ransomware attack, which infected 30 servers at its network and an extortion note was found on one of the systems. The ransom note includes details to contact the attackers but doesn’t contain any sum.
Duesseldorf law enforcement contacted the ransomware gang and told them the hospital had been affected, endangering the life of patients. The ransomware operators then decided to withdraw the extortion attempt and provided a digital key to decrypt the data.
The justice minister’s report confirmed that the perpetrators are no longer reachable.
“Prosecutors launched an investigation against the unknown perpetrators on suspicion of negligent manslaughter because a patient in a life-threatening condition who was supposed to be taken to the hospital last Friday night was sent instead to a hospital in Wuppertal, a roughly 32-kilometer (20-mile) drive.” concludes the AP agency.
Maze ransomware uses Ragnar Locker virtual machine technique
18.9.20 Ransomware Securityaffairs
The Maze ransomware operators now use a virtual machine to encrypt a computer, a tactic previously adopted by the Ragnar Locker malware.
The Maze ransomware operators have adopted a new tactic to evade detection, their malware now encrypts a computer from within a virtual machine. This technique was first adopted by Ragnar Locker gang in May, at the time the Ragnar Locker was deploying Windows XP virtual machines to encrypt victim’s files while bypassing security measures.
The malware leverages a VirtualBox feature that allows the host operating system to share folders and drives as a network share inside a virtual machine. The virtual machine mounts the shared path as a network drive from the \\VBOXSVR virtual computer to access their content.
The virtual machine then runs the ransomware in the virtual machine to encrypt the share’s files.
As the security software running on the victim’s host will not detect the ransomware executable or activity on the virtual machine, it will happily keep running without detecting that the victim’s files are now being encrypted.
Now Maze ransomware operators are using the same technique, according to researchers from Sophos that blocked some of their attacks.
“While conducting an investigation into an attack in July in which the attackers repeatedly attempted to infect computers with Maze ransomware, analysts with Sophos’ Managed Threat Response (MTR) discovered that the attackers had adopted a technique pioneered by the threat actors behind Ragnar Locker earlier this year, in which the ransomware payload was distributed inside of a virtual machine (VM).” reads the analysis published by Sophos.
In the two attempts blocked by the Sophos end-point, the Maze operators attempted to launch various ransomware executables using scheduled tasks named ‘Windows Update Security,’ or ‘Windows Update Security Patches,’ or ‘Google Chrome Security Update.’
In the third attack blocked by Sophos, Maze ransomware operators deployed an MSI file that installed the VirtualBox VM software on the server along with a customized Windows 7 virtual machine.
Upon executing the virtual machine, a batch file named startup_vrun.bat batch file would be executed that drops the Maze executables in the machine.
The startup_vrun.bat file is located at c:\users\Administrator\AppData\Roaming\Microsoft\Windows\Start Menu\Startup to achieve persistence.
“The root of that virtual disk contained three files associated with the Maze ransomware: preload.bat, vrun.exe, and a file just named payload (with no file extension), which is the actual Maze DLL payload.” continues the analysis.
“The script copies the same three files found on the root of the VM disk (the vrun.exe and payload DLL binaries, and the preload.bat batch script) to other disks, then issues a command to shut down the computer immediately. When someone powers the computer on again, the script executes vrun.exe.”

The machine is then shut down, after restarting it the vrun.exe will be launched to encrypt the host’s files.
Experts pointed out that the size of the disk used in this attack is greater than the one observed in the previous Ragnar Locker’s attacks.
The Ragnar Locker attack used a VM containing a Windows XP image that was only 404 MB in size. As Maze used Windows 7 image, the size of the file employed was of 2.6 GB.
“The Maze threat actors have proven to be adept at adopting the techniques demonstrated to be successful by other ransomware gangs, including the use of extortion as a means to extract payment from victims.” concludes the report. “As endpoint protection products improve their abilities to defend against ransomware, attackers are forced to expend greater effort to make an end-run around those protections.”
SunCrypt ransomware operators leak data of University Hospital New Jersey
17.9.20 Ransomware Securityaffairs
University Hospital New Jersey (UHNJ) has suffered a ransomware attack, SunCrypt ransomware operators also leaked the data they have stolen.
Systems at the University Hospital New Jersey (UHNJ) were encrypted with the SunCrypt ransomware, threat actors also stolen documents from the institution and leaked it online. The incident took place in September.
The UHNJ is a New Jersey state-owned teaching hospital with over 3,500 employees that was established in 1994.
The hospital has a $626 million budget with over 172,000 annual outpatient visits.
The SunCrypt ransomware operation has leaked data allegedly stolen from UHNJ in a September ransomware attack.
SunCrypt ransomware operators first appeared in the threat landscape in October 2019, and over the past few months, they launched a dedicated leak site where they started publishing the data stolen from the victims.
In early Septembers, the Haywood County School district in North Carolina has suffered a data breach after having unencrypted files stolen during a SunCrypt Ransomware attack.
The ransomware attack took place on August 24th, 2020, but at the time the family of malware that infected the school district was not revealed.
The infection forced the school district to shut down its systems and suspend remote instruction
Now BleepingComputer first reported the attack on the UHNJ, the SunCrypt Ransomware leaked a 1.7 GB archive containing over 48,000 documents, they claimed to have stolen 240 GB of data.
“This data leak includes patient information release authorization forms, copies of driving licenses, Social Security Numbers (SSNs), date of birth (DOB), and records about the Board of Directors.” reported Bleeping Computer.
A BleepingComputer’s source informed about the incident revealed that an employee of UHNJ was infected with the TrickBot trojan at the end of August before the ransomware attack took place.
If confirmed, it is possible that threat actors used TrickBot to gain a foothold in the target network and then infect the largest number of systems as possible.
BleepingComputer made an interesting observation, while Maze denies any link with the SunCrypt gang, the SunCrypt ransomware operators told BleepingComputer that they are part of the Maze gang.
Experts also noticed that systems infected with SunCrypt connect to an IP address previously associated with Maze ransomware operations.
Development Bank of Seychelles Hit by Ransomware
14.9.20 Ransomware Securityweek
The Central Bank of Seychelles (CBS) on Friday announced that the network of the Development Bank of Seychelles (DBS) was recently targeted in a ransomware attack.
Established in 1977, DBS is majority owned by the government of Seychelles, but it is non-budgetary dependent and operates on a commercial basis.
The newly disclosed security incident, CBS reveals, was communicated by DBS on September 9, and an investigation was launched into the matter.
“Since then, CBS has been engaging with DBS to establish the exact nature and circumstances of the incident and closely monitor the developments, including the possible impact on DBS' operations,” the bank said in a Friday announcement.
CBS did not provide additional information on the attack, but revealed that it has encouraged DBS to keep customers and stakeholders informed on the investigation, and that more will be shared publicly once the details surrounding the incident are uncovered.
“The CBS has stressed on the need for DBS to maintain communication with its clients and other stakeholders, particularly within the banking sector, throughout this process. […]The CBS will be providing further details to the general public once the full extent of this reality has been clearly understood,” the bank announced.
Furthermore, CBS says that the incident is also expected to help identify “areas of vulnerability that could have led to the ransomware attack.”
The bank has yet to reveal whether customer data was compromised in the incident. Many of the ransomware attacks over the past couple of years, however, did result in sensitive data being stolen, to entice victim companies into paying the ransom.
CIRWA Project tracks ransomware attacks on critical infrastructure
14.9.20 Ransomware Securityaffairs
Researchers from Temple University have been tracking ransomware attacks on critical infrastructure all over the world.
A team of researchers at Temple University in Philadelphia has presented a project named CIRWA (repository of critical infrastructure ransomware attacks) that aims at tracking ransomware attacks on critical infrastructure worldwide.
The project was launched in September 2019 and as of August 2020, the experts collected 680 records of ransomware attacks that took place since November 2013. The maintainers of the project also mapped the attacks to the MITRE ATT&CK framework.
“In September 2019, we started a repository of Critical Infrastructures Ransomware Attacks (CIRWAs). These are based on publicly disclosed incidents in the media or security reports.” reads the project description. “This repository (version 10.2) now has 687 records assembled from publicly disclosed incidents between November 2013 and August 2020.”
Anyone can request access to the data by compiling this form.
For each ransomware attack, the researchers collected a broad range of information, including the targeted organization, data of the attack, the date when the attack started, location of the targeted organization, duration of the attack, the ransomware family, the ransom amount, the payment method, industry, whether the amount was paid, and the source of the information.
According to the summary findings related to the period 2013-2020, the most targeted critical infrastructures are government facilities, followed by education and healthcare. The threat actor most active against critical infrastructure are the Maze ransomware operators, while the typical duration of a ransomware attack is of 1 week or less, and the most commonly demanded ransom amount is $50,000 or less.
Exerts pointed out that there are 13 known incidents where the ransomware operators demanded more than $5 million.

Data collected by the researchers are very interesting and very useful for future research projects on the security of the critical infrastructure.
The researchers highlighted the importance of the contribution from the security community, anyone could submit info related to attacks to CIRWA using this form.
Fairfax County Public Schools hit by Maze ransomware
14.9.20 Ransomware Securityaffairs
Fairfax County Public Schools (FCPS), one of the largest school divisions in the US, was hit by Maze ransomware operators.
Fairfax County Public Schools (FCPS) was victim of an attack carried out by the Maze ransomware operators.
FCPS is one of the largest school districts in the US with an approved budget of $3.2 billion for 2021.
The Fairfax County Public Schools has more than 188,000 students in grades prekindergarten through 12 and approximately 25,000 full-time employees working in 198 schools and centers within the U.S. commonwealth of Virginia.
“FCPS recently learned that ransomware was placed on some of our technology systems. We are taking this matter very seriously and are working diligently to address the issue.” reads a statement published by FCPS. “We currently believe we may have been victimized by cyber criminals who have been connected to dozens of ransomware attacks in other school systems and corporations worldwide. We are coordinating with the FBI on the matter.”
The institution has notified the authorities and is investigating the incident with leading security experts to determine the extent of the attack.
At the moment the exact date when the ransomware impacted FCPS’s network is not yet known but the school district says that it collaborating with the FBI to determine what ransomware gang is behind the attack.
“FCPS is committed to protecting the information of our students, our staff, and their families,” concludes the statement. “We will work with law enforcement to the fullest extent to prosecute any individuals or groups that attack our systems.”
The statement did not disclose the threat actors behind the attack, it only pointed out that the same ransomware gangs has been connected to dozens of similar attacks against school districts and businesses worldwide.
The Maze ransomware operators claimed responsibility for the attack and leaked an archive of roughly 100MB (2% of the total amount of stolen data).
The leaked archive contains students’ info, administrative documents, and an LSASS dump that could allow retrieving Windows credentials.
An update sent Saturday afternoon to the school community said the school system is “working diligently to protect the information of our staff, students and their families.”
The institution added that the ransomware intrusion did not disrupt the school system’s distance learning program.
Lucy Caldwell, a spokesperson for Fairfax County Public Schools, told WTOP that she expected remote learning will be not impacted by the infection.
In August, experts at threat intelligence firm Cyble came across a post published by Maze ransomware operators claiming to have breached the steel sheet giant Hoa Sen Group.
A few days before, Maze ransomware operators also published internal data from LG, Xerox, and Canon after the companies did not pay the ransom.
The list of victims of the Maze ransomware gang includes Conduent, IT services giant Cognizant, system-on-chip (SOC) maker MaxLinear, and Banco BCR,
Bank of Seychelles hit by a ransomware attack
13.9.20 Ransomware Securityaffairs
The Development Bank of Seychelles (DBS) was hit by a ransomware attack disclose the Central Bank of Seychelles (CBS).
The Central Bank of Seychelles (CBS) disclosed via a press statement that the Development Bank of Seychelles (DBS) was hit by a ransomware attack.
DBS is a joint venture by the Seychelles government and some shareholders including Bank, Caisse Francaise de Cooperation, European Investment Bank, DEG, Standard Chartered Bank, and Barclays Bank.
Since its creation, the shares of Standard Chartered Bank were taken over by Nouvobanq. DBS bought back Barclays’ share and Government purchased the shares of DEG, hence, increasing its shareholding to 60.50%.
Since then, the government and DBS bought the shares of Barclays Bank and DEG, allowing the Seychelles government to reach the control of 60,50% of the bank’s shares.
“The Central Bank of Seychelles (CBS) has been informed of a ransomware attack on the network of the Development Bank of Seychelles (DBS).” reads the statement.”The incident was communicated to CBS on Wednesday 9 September 2020. Since then, CBS has been engaging with DBS to establish the exact nature and circumstances of the incident and closely monitor the developments, including the possible impact on DBS’ operations.”
According to the press release, the ransomware attack took place on September 9, 2020. CBS and DBS immediately launched an investigation into the incident and are assessing the extent of the attack.
The bank did not provide technical details of attack such as the family of ransomware that infected its systems.
At the time it is not clear if the attackers have also exfiltrated some data before encrypting the bank’s systems.
“The CBS has stressed on the need for DBS to maintain communication with its clients and other stakeholders, particularly within the banking sector, throughout this process.” continues the statement. “The CBS will be providing further details to the general public once the full extent of this reality has been clearly understood.”
CBS concluded announcing the adoption of appropriate measures to protect the integrity of the financial system and maintain confidence in the banking sector.
CBS is committed to updating customers and stakeholders on the evolution of the event and on the investigation.
Recently another bank disclosed a ransomware attack, Chilean bank BancoEstado was also forced to shut down its branches following an infection.
Data Center Provider Equinix Hit by Ransomware
11.9.20 Ransomware Securityweek
Data center and colocation services provider Equinix this week revealed that it was the victim of a ransomware attack.
Headquartered in Redwood City, California, Equinix operates over 200 data centers across 25 countries around the world.
The incident, which the data center giant disclosed earlier this week, has only impacted some of the company’s internal systems.
According to Equinix, it was able to quickly address the security incident and its teams are currently investigating the attack. Law enforcement was alerted as well.
“Our data centers and our service offerings, including managed services, remain fully operational, and the incident has not affected our ability to support our customers,” the company said.
Furthermore, Equinix points out that most of its customers “operate their own equipment within Equinix data centers,” meaning that the attack did not affect their operations. Furthermore, data on customer equipment at Equinix was not impacted either, the data center giant claims.
“The security of the data in our systems is always a top priority and we intend to take all necessary actions, as appropriate, based on the results of our investigation,” the company continues.
Equinix did not provide information on how the attackers were able to breach its systems, nor on the type of ransomware used, but BleepingComputer claims that the NetWalker ransomware was used.
The attackers apparently demanded a $4.5 million (455 bitcoin) ransom from Equinix, claiming they were able to download sensitive data from the company’s servers and threatening they would make the data public unless the ransom is paid.
In July 2020, the FBI issued an alert on NetWalker attacks targeting businesses in the United States and abroad, explaining that the malware’s operators exploit known vulnerabilities in VPN appliances and web apps, and Remote Desktop Protocol connections.
With Equinix having the credentials for tens of RDP servers sold on the dark web, it’s likely that this was the attack vector used in this incident.
“This attack once again demonstrates the importance of having security visibility into all of your company’s digital assets - both inside and outside of your perimeter. Anything that connects to your corporate infrastructure can act as an entry point for threat actors,” Hank Schless, Senior Manager, Security Solutions at Lookout, said in an emailed comment.
“Equinix is doing the right thing by putting out a statement within 72 hours, which aligns them with Article 33 of the GDPR that requires notification of a breach within that time frame. This will help minimize the long term impacts,” Schless continued.
Jamie Hart, Cyber Threat Intelligence Analyst at Digital Shadows, commented, “Organizations need to ensure that RDP servers are secure, such as prohibiting RDP connections over the open internet, using complex passwords and multifactor authentication, limiting privileged access and minimizing the number of local administrator accounts, and using Firewalls to restrict access. Also, keep software and operating systems updated and maintain a relevant and well-practiced response plan per your organization’s threat model is imperative. Finally, conduct regular security awareness training that includes instruction on how to spot phishing email, how to report suspicious emails, and when to be critical of links or attachments.”
Ransomware And Zoom-Bombing: Cyberattacks Disrupt Back-to-School Plans
11.9.20 Ransomware Threatpost
Cyberattacks have caused several school systems to delay students’ first day back – and experts warn that new COVID-related delays could be the new “snow days.”
A slew of ransomware attacks and other cyberthreats have plagued back-to-school plans — as if dealing with the pandemic weren’t stressful enough for administrators. Just this week, attacks in Hartford, Conn. and Clark County, Nev. forced public schools to postpone the first day of school, in what security experts say is a sign of more cyberattacks to come as more students head back to the classroom.
According to a Tuesday public announcement, Hartford’s ransomware attack caused an outage of critical systems, including the school district’s software system that delivers real-time information on bus routes. That led school leaders to delay Tuesday’s first day of classes – a mix of both virtual classes and in-person learning – until Wednesday.
Security researchers point to the incident as a sign that this year, cyberattacks may likely become the new “snow day” – particularly with the advent of pandemic-driven online learning. As students prepare to return to school, whether in-person or virtually, school districts are battling a slew of ransomware, phishing and virtual classroom hijacking attacks.
Threatpost Webinar Promo Bug Bounty
Click to Register
“In 2020, schools are facing more complex cyber-threats as the need for data, monitoring and contact tracing become key factors in students returning to in-person classes,” Heather Paunet, senior vice president of product management at Untangle, told Threatpost. “The other side of the coin is that many schools are beginning the year remotely, meaning that students will have longer periods of time where they are connected to the internet, and being a possible point of access. Managing student data and network access will be essential in both cases.”
Other recent ransomware attacks include one that hit the Clark County school district, which includes Las Vegas, during its first week of school, potentially exposing personal information of employees. And two weeks ago a ransomware attack against a North Carolina school district, Haywood County Schools, caused the school to close to students for days.
Another cyberattack earlier in July on the Athens school district in Texas led to schools being delayed by a week (and the district paying attackers a $50,000 ransom in exchange for a decryption key).
According to Recorded Future’s research, there have been nine recorded attacks against school districts in July, August and September (so far) this year. Additionally, there have been four attacks against colleges/universities during the same time frame.
Even in a pre-COVID world, schools are an attractive target for ransomware attackers because they can time the attack to disrupt the start of the school year, which may force schools’ hands in paying the ransom, Allan Liska, solutions architect at Recorded Future, told Threatpost.
“Ransomware actors target schools systems because, frankly, they are easy targets,” Liska told Threatpost. “Security teams are usually not part of school systems, which means you often have IT staff performing double-duty managing infrastructure as well as attempting to secure it.”
That was the case with Hartford’s ransomware attack, which hit the Metro Hartford Information Services (MHIS), the city of Hartford’s shared-services team that manages Hartford Public Schools’ network infrastructure. Threatpost has reached out to the City of Hartford for more information on the cyberattack.
Zoom-Bombing Continues
Beyond ransomware, schools face a slew of more novice threats as students return to learning during the global pandemic – including Zoom-bombing, a trend that began earlier in 2020 as the coronavirus lockdowns led to massive spikes in the videoconferencing service’s usage. These attacks occur when a bad actor gains access to the dial-in information and “crashes” a Zoom session – often sharing adult or otherwise disturbing content.
One 14-year-old boy from Park Ridge, Ill. was recently accused of sharing login information for remote-learning sessions at a high school, for instance, which resulted in Zoom-bombers hijacking virtual classes during the first week of school (Aug. 25 through 27). Meanwhile, a man was arrested after Zoom-bombing an online lecture by the University of Houston and making physical-bomb threats.
Kashif Hafeez, senior director at WhiteHat Security, told Threatpost that the sudden shift to remote learning has opened up many unprecedented attack surfaces that school systems were not prepared to support, and has left them vulnerable to a major security incident.
“As technology in our school systems continue to evolve, so do the challenges that comes with it, especially the cyber-risks which only continue to intensify in the education sector,” Hafeez told Threatpost.
For instance, phishing is another common back-to-school scam that cybercriminals will be looking to tap into with the surge of virtual learning. In 2019, researchers warned that students at hundreds of universities worldwide were being targeted with fake emails, which contained attachments or links to cloned university login portals or impersonations of university library administration login pages.
“In today’s environment, where schools are now operating remotely, they have significantly increased use of technology for teaching, learning and managing day-to-day operations,” said Hafeez. “This provides cybercriminals with new opportunities, significantly increasing the attack surface, and schools have now become more vulnerable to cyberattacks.”
Overcoming the Security Learning Curve
Taking even basic security measures — including educating teachers and students against clicking potential phishing links — are important for securing school systems. Securing students’ data, including student transportation, attendance and even, in pandemic times, health data like their temperature, is another risk that schools need to manage, Paunet told Threatpost.
“Administrators who are working with students remotely will need to ensure that both students and teachers are accessing their eLearning platforms through VPN connections or other secure login portals,” Paunet said. “These logins should have two-factor authentication when available, and ongoing training for teachers and administrators should be considered, so phishing emails, suspicious activity or unauthorized updates to their credentials can be avoided or identified.”
When it comes to ransomware attacks, such as the one this week against the Hartford Public School system, it’s also essential to ensure that systems are segmented throughout the network and that data is backed up, experts said.
“We often encourage network administrators to create access layers within their systems, like in this case,” said Paunet. “So, as they are diligently working to back up and regain access to student records, attendance and other information, they can ensure that once this data is regained, it won’t be compromised a second time through the other system.”
Colocation data centers giant Equinix data hit by Netwalker Ransomware
11.9.20 Ransomware Securityaffairs
Equinix, one of the world’s largest providers of colocation data centers and Internet connection announced it was hit by Netwalker Ransomware.
Equinix, one of the leaders in the global colocation data center market share, with 205 data centers in 25 countries on five continents, was hit by Netwalker ransomware operators.
The popular cybercrime gang is demanding a $4.5 million ransom for a decryptor and to prevent the release of the stolen data.
The company disclosed the incident in a statement published on its website, it confirmed the ransomware attack that hit many internal systems, fortunately, the main core of its services to the customers was not impacted unaffected.
“Equinix is currently investigating a security incident we detected that involves ransomware on some of our internal systems.” reads the statement.
“Our data centers and our service offerings, including managed services, remain fully operational, and the incident has not affected our ability to support our customers.”
The ransom note employed in this attack was specifically crafted for Equinix and includes a link to a screenshot of the stolen data.
The screenshot shared by the Netwalker ransomware operators shows folders from infected systems allegedly containing company data, including financial information and data center reports.
The Netwalker ransomware gang is asking the victims to contact them within 3 days to avoid the leak of the stolen data.
Below the text of the ransom note shared by BleepingComputer.
“LOOK AT THIS SCREENSHOT https://prnt.sc/[redacted]
IF YOU NOT CONTACT US WE WILL PUBLISH YOUR DATA TO PUBLIC ACCESS. YOU CAN TAKE A LOOK AT OUR BLOG [redacted]
YOU HAVE 3 DAYS TO CONTACT US OR WE WILL MAKE POST IN OUR BLOG, CONTACT ALL POSSIBLE NEWS SITES AND TELL THEM ABOUT DATA BREACH “
The ransom note also includes a link to the Netwalker Tor payment site, threat actors are demanding a $4.5 million ransom (455 bitcoin). If the company will not pay in time, the ransom would double.
Source BleepingComputer
The latest timestamp on the folders is 9/7/20, a circumstance that suggests the security breach took place recently.
“Note that as most customers operate their own equipment within Equinix data centers, this incident has had no impact on their operations or the data on their equipment at Equinix.” concludes the statement. “The security of the data in our systems is always a top priority and we intend to take all necessary actions, as appropriate, based on the results of our investigation.”
Netwalker ransomware gang is very active in this period, in a few days it announced the hack of K-Electric, the major Pakistani electricity provider, and Argentina’s official immigration agency, Dirección Nacional de Migraciones.
Another victim of the group is the University of California San Francisco (UCSF), who decided to pay a $1.14 million ransom to recover its files.
Recently the FBI has issued a security alert about Netwalker ransomware attacks targeting U.S. and foreign government organizations.
The feds are recommending victims, not to pay the ransom and reporting incidents to their local FBI field offices.
The flash alert also includes indicators of compromise for the Netwalker ransomware along with mitigations.
The FBI warns of a new wave of Netwalker ransomware attacks that began in June, the list of victims includes the UCSF School of Medicine and the Australian logistics giant Toll Group.
The Netwalker ransomware operators have been very active since March and also took advantage of the ongoing COVID-19 outbreak to target organizations.
The threat actors initially leveraged phishing emails delivering a Visual Basic Scripting (VBS) loader, but since April 2020, Netwalker ransomware operators began exploiting vulnerable Virtual Private Network (VPN) appliances, user interface components in web apps, or weak passwords of Remote Desktop Protocol connections to gain access to their victims’ networks.
Recently the Netwalker ransomware operators were looking for new collaborators that can provide them with access to large enterprise networks.
Below the recommended mitigations provided by the FBI:
Back-up critical data offline.
Ensure copies of critical data are in the cloud or on an external hard drive or storage device.
Secure your back-ups and ensure data is not accessible for modification or deletion from the system where the data resides.
Install and regularly update anti-virus or anti-malware software on all hosts.
Only use secure networks and avoid using public Wi-Fi networks.
Consider installing and using a VPN.
Use two-factor authentication with strong passwords.
Keep computers, devices, and applications patched and up-to-date.
An overview of targeted attacks and APTs on Linux
10.9.20 Ransomware Securelist
Perhaps unsurprisingly, a lot has been written about targeted attacks on Windows systems. Windows is, due to its popularity, the platform for which we discover most APT attack tools. At the same time, there’s a widely held opinion that Linux is a secure-by-default operating system that isn’t susceptible to malicious code. It’s certainly true that Linux hasn’t faced the deluge of viruses, worms and Trojans faced by those running Windows systems over the years. However, there is certainly malware for Linux – including PHP backdoors, rootkits and exploit code. Moreover, numbers can be misleading. The strategic importance of servers running Linux makes them an attractive target for attackers of all kinds. If an attacker is able to compromise a server running Linux, they not only gain access to data stored on the server but can also target endpoints connected to it running Windows or macOS – for example, through a drive-by download. Furthermore, Linux computers are more likely to be left unprotected, so that such a compromise might well go unnoticed. When the Heartbleed and Shellshock vulnerabilities were first reported in 2014, two major concerns were that compromised Linux servers could become an attacker’s gateway into a corporate network and could give an attacker access to sensitive corporate data.
The Global Research and Analysis Team (GReAT) at Kaspersky publishes regular summaries of advanced persistent threat (APT) activity, based on the threat intelligence research discussed in greater detail in our private APT reports. In this report, we focus on the targeting of Linux resources by APT threat actors.
Readers who would like to learn more about our intelligence reports or request more information on a specific report are encouraged to contact intelreports@kaspersky.com.
Barium
We first wrote about the Winnti APT group (aka APT41 or Barium) in 2013, when they were targeting mostly gaming companies for direct financial profit. Meanwhile, they grew their operations, developed tons of new tools and went for much more complex targets. MESSAGETAP is Linux malware used by this group to selectively intercept SMS messages from the infrastructure of telecoms operators. According to FireEye, the group deployed this malware on SMS gateway systems as part of its operations to infiltrate ISPs and telecoms companies in order to build a surveillance grid.
Recently, we discovered another suspected Barium/APT41 tool, written in the programming language Go (also known as Golang) that implements a dynamic, C2-controlled packet corruption/network attack tool for Linux machines. Although it’s not 100% clear if this is a tool developed for system administration tasks or if it is also part of the APT41 toolset, the fact that the functionality it offers can also be achieved through other system management tools suggests that its purpose may not be legitimate. Also, its name on disk is rather generic and is unrelated to its functionality, again suggesting that it is potentially a covert tool used for carrying out certain types of destructive attacks. More details about this tool can be found in our private report “Suspected Barium network control tool in GO for Linux”.
Cloud Snooper
In February 2020, Sophos published a report describing a set of malicious tools it attributes to a previously unknown threat actor called Cloud Snooper. The centerpiece is a server-oriented Linux kernel rootkit that hooks netfilter traffic control functions in order to enable firewall-traversing covert C2 (command-and-control) communications. We analyzed and described the rootkit’s userland companion backdoor, dubbed ‘Snoopy’, and were able to design detection and scanning methods to identify the rootkit at scale. We also discovered more samples, as well as targeted servers in Asia. We believe that this evolved toolset might have been in development since at least 2016.
DarkHotel
DarkHotel is one threat actor that has targeted Linux systems to use as part of its supporting infrastructure. For example, in November 2018, when we reported a DarkHotel campaign targeting diplomatic entities in the APAC region and Europe using the GreezeShell backdoor, we observed that some of the C2 servers were running Ubuntu Linux. The servers all had standard SSH and SMTP ports open; and, in addition, they all used Apache web server version 2.4.18.
Equation
We uncovered the Equation group in 2015. This is a highly sophisticated threat actor that has been engaged in multiple CNE (computer network exploitation) operations dating back to 2001, and perhaps as early as 1996. For many years this threat actor interacted or worked together with other powerful APT groups, for projects such as Stuxnet and Flame. The group has a powerful arsenal of implants. Among those we found were: ‘EQUATIONLASER’, ‘EQUATIONDRUG’, ‘DOUBLEFANTASY’, ‘TRIPLEFANTASY’, ‘FANNY’ and ‘GRAYFISH’. The innovations of the Equation group aren’t limited to the Windows platform. The group’s POSIX-compliant codebase allows for parallel developments on other platforms. In 2015, we came by the early-stage DOUBLEFANTASY malware for Linux. This implant collects system information and credentials and provides generic access to an infected computer. Given the role this module plays in the infection lifecycle, it would suggest the presence of analogous later-stage, more sophisticated implants, although we weren’t able to find any.
HackingTeam
HackingTeam was an Italian information technology company that developed and sold intrusion and so called “legal surveillance software” to governments, law enforcement agencies and businesses around the world. Unfortunately for them, they were hacked and suffered a data breach in 2015, at the hands of the activist known as Phineas Phisher. The subsequent leak of 400GB of stolen company data, including source code and customer information, allowed these tools to be acquired, adapted and used by threat actors around the world, such as DancingSalome (aka Callisto). The leaked tools included a zero-day exploit for Adobe Flash (CVE-2015-5119) as well as sophisticated platforms capable of providing remote access, keylogging, general information recording and exfiltration, and perhaps most notably, the ability to retrieve Skype audio and video frames directly from memory, bypassing stream encryption. The RCS (Remote Control System) malware (aka Galileo, Da Vinci, Korablin, Morcut and Crisis) includes multiple components, including desktop agents for Windows, macOS and perhaps unsurprisingly… Linux.
Lazarus
In late 2018, we discovered a previously unknown malicious framework that we named MATA internally. This framework was used to target commercial companies in Korea, India, Germany and Poland. While we weren’t able to find code overlaps with any other known actor, the Kaspersky Threat Attribution engine showed code similarities with Manuscrypt, complex malware used by Lazarus (aka Hidden Cobra). This framework, as with earlier malware developed by Lazarus, included a Windows backdoor. However, we also found a Linux variant that we believe was designed for networking devices.
In June 2020, we analyzed new macOS samples linked to Lazarus Operation AppleJeus and TangoDaiwbo campaigns, used in financial and espionage attacks. The samples had been uploaded to VirusTotal. The uploaded files also included a Linux malware variant that included similar functionality to the macOS TangoDaiwbo malware. These samples confirm a development that we had highlighted two years earlier – that the group was actively developing non-Windows malware.
Sofacy
Sofacy (aka APT28, Fancy Bear, STRONTIUM, Sednit and Tsar Team) is a highly active and prolific APT threat actor. From its high-volume zero-day deployment to its innovative, broad malware set, Sofacy is one of the top groups that we monitor. Among the tools in the group’s arsenal is SPLM (also known as CHOPSTICK and XAgent), a second-stage tool used selectively against targets around the world. Over the years, Sofacy has developed modules for several platforms, including, in 2016, modules for Linux, detected as ‘Fysbis’. The consistent artefacts seen over the years and across Windows, macOS, iOS and Linux suggests that the same developers, or a small core team, is modifying and maintaining the code.
The Dukes
The Dukes is a sophisticated threat actor that was first documented by us in 2013, but whose tools have been used in attacks dating back to 2008. The group is responsible for attacks against targets in Chechnya, Ukraine, Georgia, as well as western governments and NGOs, NATO and individuals – the group is thought to be behind the hack of the Democratic National Congress in 2016. The Dukes’ toolset includes a comprehensive set of malware implementing similar functionality but coded in several different programming languages. The group’s malware and campaigns include PinchDuke, GeminiDuke, CosmicDuke, MiniDuke, CozyDuke, OnionDuke, SeaDuke, HammerDuke and CloudDuke. At least one of these, SeaDuke, includes a Linux variant.
The Lamberts
The Lamberts is a highly sophisticated threat actor group which is known to possess a huge malware arsenal, including passive, network-driven backdoors, several generations of modular backdoors, harvesting tools and wipers for carrying out destructive attacks. We created a color scheme to distinguish the various tools and implants used against different victims around the world.
Lamberts discovery timeline
In 2017, we published an overview of the Lamberts family; and further updates (GoldLambert, SilverLambert, RedLambert, BrownLambert) are available to customers of our threat intelligence reports. The focus of the various Lamberts variants is definitely Windows. Nevertheless, signatures that we created for Green Lambert for Windows also triggered on a macOS variant of Green Lambert that was functionally similar to the Windows version. In addition, we also identified samples of the SilverLambert backdoor compiled for both Windows and Linux.
Tsunami backdoor
Tsunami (aka Kaiten) is a UNIX backdoor used by multiple threat actors since it was first seen in the wild in 2002. The source code was made public some years ago; and there are now more than 70 variants. The source code compiles smoothly on a wide range of embedded devices; and there are versions for ARM, MIPS, Sparc and Cisco 4500/PowerPC. Tsunami remains a threat for Linux-based routers, DVRs and the increasing number of IoT (internet of things) devices. In 2016, a variant of Tsunami was used in the Linux Mint hack, where an unknown threat actor compromised the Linux Mint distribution ISOs to include a backdoor. We also observed the use of the Tsunami backdoor to surgically target a number of cryptocurrency users on Linux.
Turla
Turla (aka Uroboros, Venomous Bear and Waterbug) is a prolific Russian-speaking group known for its covert exfiltration tactics such as the use of hijacked satellite connections, water-holing of government websites, covert channel backdoors, rootkits and deception tactics. This threat actor, like other APT groups, has made significant changes to its toolset over the years. Until 2014, every malware sample used by Turla that we had seen was designed for 32- or 64-bit versions of Windows.
Then in December 2014, we published our report on Penguin Turla, a Linux component in the Turla arsenal. This is a stealth backdoor that didn’t require elevated privileges, i.e. administrator or root rights. Even if someone with limited access to the system launches it, the backdoor can intercept incoming packets and run commands from the attackers on the system while maintaining stealth. It is also rather hard to uncover, so if it’s installed on a compromised server, it could sit there unnoticed for a long time. Further research on Penguin Turla revealed that its roots stretch back to the Moonlight Maze operation in the mid-1990s. In May this year, researchers from Leonardo published a report about Penguin_x64, a previously undocumented variant of the Penguin Turla Linux backdoor. Based on this report, we generated network probes that detect Penquin_x64 infected hosts at scale, allowing us to discover a couple dozen infected servers in Europe and the US, as recent as July 2020. We believe that, following public documentation of GNU/Linux tools, Turla may have been repurposing Penguin to conduct operations other than traditional intelligence gathering.
Two-Sail Junk
In January 2020, a watering hole was discovered that utilized a full remote iOS exploit chain to deploy a feature-rich implant named LightSpy. The site appears to have been designed to target users in Hong Kong, based on the content of the landing page. For the time being, until we can link the campaign to a known group, we have given the name Two-Sail Junk to the threat actor behind this implant. However, while our public report focused on the iOS implant, the project is broader than previously thought, supporting an Android implant, and probably supporting implants for Windows, Linux and MacOS.
WellMess
In March 2020, we began to actively track new C2 servers associated with malware commonly referred to as WellMess, indicating a potentially massive new wave of activity. This malware was initially documented by JPCERT in July 2018 and has been sporadically active since then. There were rumors that hint at a possible connection with CozyDuke (aka APT29), along with speculation that the current activity was focused on the healthcare industry, although we were unable to verify either claim. WellMess is a Remote Access Trojan, written in .NET and Go (Golang), cross-compiled to be compatible with both Windows and Linux.
WildNeutron
We first published about WildNeutron in 2015, together with our colleagues from Symantec, who call it Morpho or Butterfly. This group, which rose to prominence with their 2012-2013 attacks on Twitter, Microsoft, Apple and Facebook, are one of the most elusive, mysterious and dynamic we have seen. Their arsenal included many interesting and innovative tools, such as LSA backdoors or IIS plugins, coupled with both zero-day-based and physical deployment. Unsurprisingly, in several known attacks WildNeutron used a custom Linux backdoor as well.
Zebrocy
Zebrocy is custom malware that we have been tracking since 2015. The group using this malware started as a subset of Sofacy, but also has similarities and overlaps with other APT groups. The group has developed malware in several languages, including Delphi, AutoIT, .NET, C#, PowerShell and Go. Zebrocy has mainly targeted Central Asian government-related organizations, both in-country and in remote locations. The group makes extensive use of spear phishing to compromise Windows endpoints. However, its backdoors are configured to communicate directly with IP-assigned web server hosts over port 80; and the group seems to favor Linux for this part of its infrastructure – specifically, Apache 2.4.10 running on Debian Linux.
Recommendations for protecting Linux systems
One of the main reasons that Linux systems go unprotected is a false sense of security from using Linux instead of the far more popular (and more targeted) Windows. Nevertheless, we hope all the aforementioned points are convincing enough for you to start securing your Linux-based machines in a serious way.
The very first recommendation is to maintain a list of trusted sources of your software. Think about this in the same way as the recommended approach to Android or iOS apps – only installing applications from official repositories. In the Linux world we enjoy more freedom: for example, even if you are using Ubuntu, you’re not restricted only to Canonical’s own repository. Any .DEB file, or even application source code from GitHub, is at your service. But please choose these sources wisely. Don’t just blindly follow instructions like “Run this script from our server to install”; or “curl https://install-url | sudo bash” – which is a security nightmare.
Please also be mindful of the secure way to get applications from these trusted repositories. Your channels to update the apps have to be encrypted using HTTPS or SSH protocols. Besides your trust in software sources and its delivery channel, it’s critical for updates to arrive in a timely fashion. Most modern Linux flavors are able to do this for you, but a simple cron script would help you to stay more protected and to get all the patches as soon as they are released by developers.
The next thing we would recommend is checking network-related settings. With commands like “netstat -a” you could filter out all unnecessary opened ports on your host. Please avoid network applications you really don’t need or don’t use to minimize your network footprint. Also, it would be strongly recommended to properly set up the firewall from your Linux distributive, to filter traffic and store the host’s network activity. It’s also a very good idea not to go online directly, but through NAT.
To continue with the network-related security rules, we recommend protecting your locally stored SSH keys (used for your network services) using passwords at least. In more “paranoid” mode you could even store the keys on external protected storage, like tokens from any trusted vendor. On the server side of connections, nowadays it’s not that hard to set up multi-factor authentication for SSH sessions, like the messages to your phone or other mechanisms such as authenticator apps.
So far, our recommendations have covered software sources, application delivery channel, avoiding unnecessary network footprint and protection of encryption keys. One more idea we recommend for monitoring threats you couldn’t find at the filesystem level is to keep and analyze the network activity logs. You could install and use an out-of-band network tap to independently monitor and analyze the network communications of your Linux systems.
As part of your threat model, you need to consider the possibility that, despite all the aforementioned measures, attackers can compromise your protection. Think about the next protection step in terms of an attacker’s persistence in the system. They will probably make changes to be able to start their Trojan automatically after the system reboots. So, you need to regularly monitor the main configuration files as well as the integrity of system binaries, just in case of file viruses. The logs mentioned above for monitoring network communication, is fully applicable here: the Linux auditing system collects system calls and file access records. Additional daemons such as “osquery” can be used for the same task. . Any suspicious files, URLs, and IP addresses can be checked at Kaspersky Threat Intelligence Portal.
Physical security of devices is also important. It doesn’t matter how much attention you pay to network and system level hardening if your laptop ends up in an attacker’s hands and you haven’t taken steps to protect it from this attack vector. You should consider full disk encryption and safe boot mechanisms for physical security. A more spy-like approach would be to place tamper-evident security tape on your most critical hardware.
Dedicated solution with Linux security can simplify the protection task: web threat protection detects malicious and phishing websites; network threat protection detects network attacks in incoming traffic; behavior analysis detects malicious activity, while device control allows management of connected devices and access to them.
Our final recommendation relates to Docker. This is not a theoretical threat: infection of containers is a very real issue. Containerization doesn’t provide security by itself. Some containers are quite isolated from the host, but not all – network and file system interfaces exist in them and in most cases there are bridges between physical and containerized worlds.
Therefore, you can use security solution that allows to add security into development process. Kaspersky Hybrid Cloud Security includes integration with CI/CD platforms, such as Jenkins, through a script to scan Docker images for malicious elements at different stages.
To prevent supply-chain attacks, On-Access Scanning (OAS) and On-Demand Scanning (ODS) of containers, images, and local and remote repositories can be used. Namespace monitoring, flexible mask-based scan scope control and the ability to scan different layers of containers help to enforce secure development best practices.
We have broken down this list of recommendations into logical sections. Please bear in mind that, besides applying all the measures we have mentioned, you should also audit and check all the generated logs and any other messages regularly. Otherwise you could miss signs of intrusion. A final idea, for security enthusiasts, is to adopt active measures – to provide system penetration testing from time to time.
Summary of recommendations:
Maintain a list of trusted software sources, avoid using unencrypted update channels.
Do not run binaries and scripts from untrusted sources. A widely advertised way to install programs with commands like “curl https://install-url | sudo bash” is a security nightmare.
Make sure your update procedure is effective. Set up automatic security updates.
Spend time to set up your firewall properly: make sure it logs network activity, block all ports you don’t use, minimize your network footprint.
Use key-based SSH authentication, protect keys with passwords.
Use 2FA and store sensitive keys on external token devices (e.g. Yubikey).
Use an out-of-band network tap to independently monitor and analyze network communications of your Linux systems.
Maintain system executable file integrity. Review configuration file changes regularly.
Be prepared for insider/physical attacks: use full disk encryption, trusted/safe boot and put tamper-evident security tape on your critical hardware.
Audit the system, check logs for indicators of attacks.
Run penetration tests on your Linux setup.
Use a dedicated security solution for Linux with web and network protection, as well as features for DevOps protection.