
Ransomware Articles - H 2020 1 2 3 4 5 6 7 8 9 10 11 Ransomware List - H 2021 2020 2019 2018 1 Ransomware blog Ransomware blog
Mamba ransomware is back and targets organizations in Brazil and Saudi Arabia
10.8.2017 securityaffairs Ransomware
Researchers at Kaspersky Lab discovered a new wave of attack leveraging the Mamba ransomware that hit organizations in Brazil and Saudi Arabia.
Mamba ransomware is one of the first malware that encrypted hard drives rather than files that was detected in public attacks.
Mamba leverages a disk-level encryption strategy instead of the conventional file-based one.
A similar Ransomware, called Petya, made the headlines for the recent massive attack and its disk encryption strategy. The first sample of Mamba Ransomware discovered in the wild were using a full disk encryption open source tool called DiskCryptor to strongly encrypt the data.
Mamba mostly targeted organizations in Brazil, it was also used by crooks in the attack against the San Francisco Municipal Transportation Agency occurred in November.
Researchers at Kaspersky Lab discovered a new wave of attack leveraging the Mamba ransomware that hit organizations in Brazil and Saudi Arabia.
Like the NotPetya massive attack, also Mamba appears to have been designed for sabotage, it is unclear if the malware was developed by crooks or by a nation-state actor.
Unlike the NotPetya attacks, it is not excluded that Mamba victims could decrypt their data.
“Authors of wiper malware are not able to decrypt victims’ machines. For example, if you remember the ExPetr [malware], it uses a randomly generated key to encrypt a victim machine, but the trojan doesn’t save the key for further decryption,” said Kaspersky Lab researcher Orkhan Memedov. “So, we have a reason to call it ‘a wiper.’ However, in case of Mamba the key should be passed to the trojan as a command line argument, it means that the criminal knows this key and, in theory, the criminal is able to decrypt the machine.”
Mamba was first spotted on September 2016 when experts at Morphus Labs discovered the infection of machines belonging to an energy company in Brazil with subsidiaries in the United States and India.
The researchers shared a detailed analysis on Security Affairs, they explained that once the malware has infected a Windows machine, it overwrites the existing Master Boot Record, with a custom MBR and encrypts the hard drive using the DiskCryptor tool.
“Unfortunately there is no way to decrypt data that has been encrypted with the DiskCryptor utility, because this legitimate utility uses strong encryption algorithms,” explained Kaspersky Lab.
The last samples of Mamba ransomware show an unusual ransom note that instead of demanding for money like the original Mamba, it provides two email addresses and an ID number to be used to recover the encryption key.

The threat actor behind the new wave of Mamba ransomware attacks leverages the PSEXEC utility to execute the malware on the corporate network once it has penetrated it. PSEXEC is the same tool used by NotPetya to spread within target networks.
The attack chain described by Kaspersky has two phases, in the first one attackers drop the DiskCryptor tool into a new folder created by the malware. The persistence is obtained by registering a system service called DefragmentService, then the system is rebooted.
The second phase sets up the new bootloader and encrypts disk partitions using DiskCryptor, then the machine is rebooted.
“It is important to mention that for each machine in a victim’s network, the threat actor generates a password for the DiskCryptor utility,” Kaspersky Lab said in its report. “This password is passed via command line arguments to the ransomware dropper.”
WannaCry Hero Marcus Hutchins pleads not guilty to malware claims
5.8.2017 securityaffairs Ransomware
Yesterday the judge approved to release the researcher Marcus Hutchins on bail for a bond of $30,000 under certain conditions.
Marcus Hutchins, also known as MalwareTech, is the 22-year-old security expert who made the headlines after discovering the “kill switch” that halted the outbreak of the WannaCry ransomware. Marcus Hutchins has been arrested in in Las Vegas after attending the Def Con hacking conference and was detained by the FBI in the state of Nevada.
The British security researcher was arrested on Thursday after being indicted on charges of creating the Kronos banking malware.
According to the investigators, Marcus Hutchins created the malware and shared it online, below the indictment issued by Eastern District of Wisconsin.
The prosecutors believe Hutchins created, shared, and masterminded the Kronos banking Trojan between July 2014 and July 2015.

On Friday, at 3pm Pacific Time, the young malware expert appeared before a judge, pleaded not guilty to the charges against him. The judge approved to release the researcher on bail for a bond of $30,000 under certain conditions.
MalwareTech is prohibited from accessing the Internet, he must wear a GPS tracker, and he cannot contact the unnamed co-defendant mentioned in the FBI’s indictment.
Unfortunately, even though that hearing finished at 3.30pm, Hutchins was not able to get to the bail office in time as it closes at 4pm, so he will spend the weekend in jail.
On Tuesday he will appear before a judge in Wisconsin for his next court appearance.
“He’s dedicated his life to researching malware and not trying to harm people,” said one of Hutchins attorneys, Adrian Lobo. “Using the internet for good is what he’s done.”
Lobo explained to the journalists that Hutchins was able to raise bail money from his supporters.
The US Department of Justice prosecutors mentioned a recent trip of the expert to a gun range as proof that he should be denied bail and kept in jail. Lobo defined the prosecution’s proposal as “garbage.”
Hutchins’ lawyers clarified the expert is not in any way behind the Kronos banking Trojan.
Wannacry authors make a $143,000 withdraw from Bitcoin wallets, whilst the internet is distracted!
5.8.2017 securityaffairs Ransomware
On Wednesday some very interesting and seemly unrelated events happened in regards to Wannacry. First Marcus Hutchins (AKA @Malwaretech), the security researcher who discovered the kill switch and stopped the spread of Wannacry was arrested whilst returning to the UK from Las Vegas- on suspicion of creating malware (covered here).
But the second event which will be covered in the article related to an event that seemed to of passed most of Twitter and the internet by. The WannaCry wallets from the orchestrators behind the ransomware outbreak (that famously affected companies globally including the NHS), were emptied to the tune of $143,000. Interestingly the Bitcoin generated through ransom payments from the global attack had not been touched until Wednesday.
A twitter bot created by Quartz, to monitor the wallets for payments during the original outbreak, first noticed the activity at 11:10pm ET, according to the twitter account a total of $70,000 was withdrawn from the following three transactions:
7.34128314 BTC ($20,055.52 USD) has just been withdrawn from a bitcoin wallet tied to #wcry ransomware. https://t.co/wX2k9pJLNQ
— actual ransom (@actual_ransom) August 3, 2017
8.73261636 BTC ($23,856.48 USD) has just been withdrawn from a bitcoin wallet tied to #wcry ransomware. https://t.co/KRxgNpBGgz
— actual ransom (@actual_ransom) August 3, 2017
9.67641378 BTC ($26,434.83 USD) has just been withdrawn from a bitcoin wallet tied to #wcry ransomware. https://t.co/CJLiu6cyvr
— actual ransom (@actual_ransom) August 3, 2017
Source QZ.com
The twitter bot the reported only 15 minutes later that the remainder of the monies were moved from the Bitcoin wallets, it is highly likely that these were laundered using a mixing service making it very hard to track the source and destination of the payments through making a high volume of small transactions to a large number of wallets.

Given the orchestrators of the Wannacry outbreak is widely suspected to be the Lazarus Group which have connections to North Korea, the timing and motivation of the BTC exfiltration could be a dig towards Marcus Hutchins, who stopped the spread of the attack, or just a coincidence, at this juncture there is no evidence to call it either way.
But it is also known that Lazarus, in particular, Bluenoroff are a financially motivated group, with the attacks on banks, financial, and trading companies in Bangladesh in 2014 and the now famous $81million Cyber-Heist of the Bangladesh central bank’s account at the Federal Reserve Bank of New York.
In summary, with the attackers behind Wannacry and NotPetya thought by many not to be financially motivated, it seems that even they still could not resist the opportunity to silently move their ill-gotten gains, whist the internet was distracted by other events!
Hackers Behind WannaCry Ransomware Withdraw $143,000 From Bitcoin Wallets
3.8.2017 thehackernews Ransomware
The cyber criminals behind the global WannaCry ransomware attack that caused chaos worldwide have finally cashed out their ransom payments.
Nearly three months ago, the WannaCry ransomware shut down hospitals, telecom providers, and many businesses worldwide, infecting hundreds of thousands of computers in more than 150 countries, encrypting files and then charging victims $300-$600 for the keys.
WannaCry was really bad, as the nasty ransomware forced the British NHS (National Health Service) to shut down hospitals and doctor's surgeries, and infected a Spanish telecommunications company and Russian mobile operator, among much more.
Even a month after the outbreak, the WannaCry ransomware was found infecting systems at Honda Motor Company, forcing the factory to shut down its production, and 55 speed and traffic light cameras in Victoria, Australia.
Overall, the hackers behind WannaCry made $140,000 in Bitcoins from the victims who paid for the decryption keys—but for almost three months, they did not touch three of their wallets where victims were instructed to send ransom payments.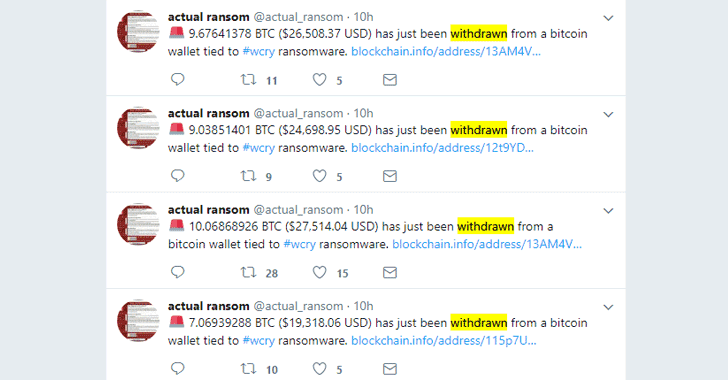
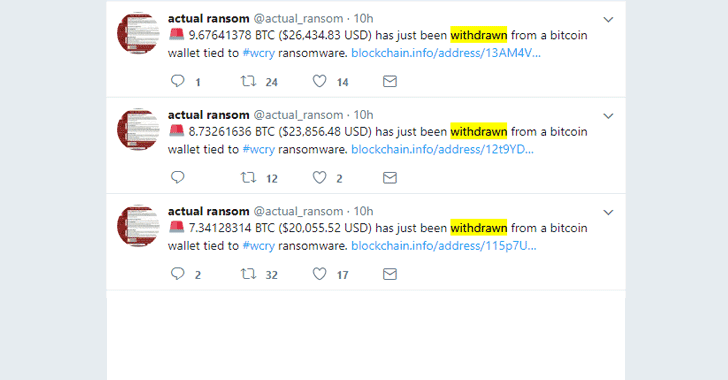
However, the WannaCry hackers started cashing out their cryptocurrencies on Wednesday night.
According to a Twitter bot tracking WannaCry ransom payments, only 338 victims paid the $300 in Bitcoin that totalled $140,000.
On Wednesday night, this money was withdrawn in 7 different payments within 15 minutes, although it is not clear where the money is being sent, or how the attacker will use it.
If you are unaware, we recently reported about Google's research on how cyber criminals and ransomware hackers cash out their stolen or looted cryptocurrencies via cryptocurrency exchanges that are involved in money laundering.
Last week, even German authorities arrested an alleged operator of the popular BTC-e Bitcoin exchange on charges of laundering over $4 billion in Bitcoin for culprits involved in hacking attacks, tax fraud and drug trafficking without identifying them.
The identity behind the WannaCry ransomware is still unknown, though some researchers traced back WannaCry to a state-sponsored hacking group called Lazarus in North Korea, while other believed the perpetrators might be Chinese.
The WannaCry epidemic was using self-spreading capabilities by leveraging leaked NSA's SMBv1 exploit, called EternalBlue, to infect vulnerable Windows computers, particularly those using older versions of the operating system.
While most of the affected organisations have now returned to normal, law enforcement agencies across the world are still on the hunt.
WannaCry Inspires Banking Trojan to Add Self-Spreading Ability
2.8.2017 thehackernews Ransomware
Although the wave of WannaCry and Petya ransomware has now been slowed down, money-motivated hackers and cyber criminals have taken lessons from the global outbreaks to make their malware more powerful.
Security researchers have now discovered at least one group of cyber criminals that are attempting to give its banking Trojan the self-spreading worm-like capabilities that made recent ransomware attacks go worldwide.
The new version of credential stealing TrickBot banking Trojan, known as "1000029" (v24), has been found using the Windows Server Message Block (SMB)—that allowed WannaCry and Petya to spread across the world quickly.
TrickBot is a banking Trojan malware that has been targeting financial institutions across the world since last year.
The Trojan generally spreads via email attachments impersonating invoices from a large unnamed "international financial institution," but actually leads victims to a fake login page used to steal credentials.
Last week, researchers at Flashpoint, who've been continually tracking TrickBot activities and its targets, have discovered that the TrickBot Trojan has just been evolved to spread locally across networks via Server Message Block (SMB).
Since the new version of TrickBot is still being tested, the new features are not fully implemented by the hacking gang behind the Trojan. It also doesn't have the ability to randomly scan external IPs for SMB connections, unlike WannaCry which exploited a vulnerability dubbed EternalBlue.
Flashpoint researchers said the trojan is modified to scan domains for lists of vulnerable servers via the NetServerEnum Windows API and enumerate other computers on the network via Lightweight Directory Access Protocol (LDAP).
The new TrickBot variant can also be disguised as 'setup.exe' and delivered through a PowerShell script to spread through interprocess communication and download additional version of TrickBot onto shared drives.
According to the researchers, the latest discovery of new TrickBot variant provides an insight into what the operators behind the malware might be using in the near-future.
"Flashpoint assesses with moderate confidence that the Trickbot gang will likely continue to be a formidable force in the near term," said Vitali Kremez, director of Research at Flashpoint.
"Even though the worm module appears to be rather crude in its present state, it's evident that the Trickbot gang learned from the global ransomware worm-like outbreaks of WannaCry and 'NotPetya' and is attempting to replicate their methodology."
In order to safeguard against such malware infection, you should always be suspicious of unwanted files and documents sent over an email and should never click on links inside them unless verifying the source.
To always have a tight grip on your valuable data, keep a good backup routine in place that makes their copies to an external storage device that is not always connected to your PC.
Moreover, make sure that you run an effective anti-virus security suite on your system, and keep it up-to-date.
Pharmaceutical giant Merck confirmed NotPetya attack disrupted operations worldwide
1.8.2017 securityaffairs Ransomware
The US pharmaceutical company Merck revealed that the massive NotPetya cyberattack has disrupted its worldwide operations.
The news was part of the Merck’s financial results announcement for the second quarter of 2017, according to the pharmaceutical giant the ransomware destructed operations in several critical sectors, including manufacturing, research, and sales.
The company didn’t disclose details on the cyber attacks, it believes that the NotPetya ransomware was the threat that hit the company on June 27th affecting tens of thousands of systems in more than 65 countries.
The analysis conducted on the ransomware reveals the threat was designed to look like ransomware but was wiper malware designed for sabotage purpose.
Researchers Matt Suiche, founder at Comae Technologies, explained that the analysis conducted by his team on Petya samples used in the attack revealed its wiper capabilities.
“we noticed that the current implementation that massively infected multiple entities in Ukraine was in fact a wiper which just trashed the 24 first sector blocks of the disk while replicating itself. Some noted that this was mainly slack space as only the first sector is relevant for most of machines — except few exceptions. ” states the analysis published by Comae Technologies.
“We believe the ransomware was in fact a lure to control the media narrative, especially after the WannaCryincidents to attract the attention on some mysterious hacker group rather than a national state attacker like we have seen in the past in cases that involved wipers such as Shamoon.”

Attackers might have used a diversionary strategy hide a state-sponsored attack on Ukraine critical infrastructure.
Experts from Kaspersky’s conducted a similar research that led to a similar conclusion.
Unlike other ransomware, Petya does not encrypt files on the infected systems but targets the hard drive’s master file table (MFT) and renders the master boot record (MBR) inoperable.
Petya locks the access to the users’ data by encrypting the master file table (MFT) and replaces the computer’s MBR with its own malicious code that displays the ransom note.
Petya overwrites the MBR of the hard drive causing Windows to crash. When the victim tries to reboot the PC, it will impossible to load the OS, even in Safe Mode.
The name of Merck was circulating on the internet shortly after the attack as one of the numerous victims of the NotPetya attack worldwide. Other major companies affected by the NotPetya attack were the Ukraine’s central bank, Russian oil giant Rosneft, advertising group WPP, the shipping giant A.P. Moller-Maersk, TNT Express and the law firm DLA Piper.
The company said it had still been working on restoring operations and minimizing the effects of the incident.
The company confirmed it had still been working on restoring operations:
“The company is in the process of restoring its manufacturing operations. To date, Merck has largely restored its packaging operations and has partially restored its formulation operations,” Merck said. “The company is in the process of restoring its Active Pharmaceutical Ingredient operations but is not yet producing bulk product. The company’s external manufacturing was not impacted. Throughout this time, Merck has continued to fulfill orders and ship product.”
Cyber attacks could have a significant impact on businesses, and two of the world’s largest consumer goods companies confirmed it. On July the companies Mondelez and Reckitt Benckiser warned of the impact of the NotPetya attack on their revenues.
The Mondelez International company estimated the NotPetya attack would cut three percentage points from second-quarter sales growth because of disruptions to shipping and invoices caused by the cyber attack.
the Reckitt Benckiser, the maker of Nurofen painkillers and Durex condoms, said it expected sales would be hit Q2 by an estimated £110m this year.
TOPransom: From eMail Attachment to Powning the Attacker’s Database
1.8.2017 securityaffairs Ransomware
TOPransom – Analyzing the entire process from getting an email attachment to powning the ransom server trying to stop the infection.
Hi folks, today I want to share a quick but intensive experience in fighting cybercrime. I wish you would appreciate the entire process of getting an email attachment to powning the ransom server trying to stop the infection and to alert everybody about the found threats. As a second step, I would try to identify the attacker in order to give additional information to law enforcements, those actions would not be published.
But, let’s start by having a little bit of context:
During the past few days a colleague of mine (MarcoT.) gave me an interesting eMail attachment called: 71878378709_708463.zip (sha256:fdd1da3bdd8f37dcc04353913b5b580dadda94ba).
By unzipping the attachment, it was interesting to see a single .vbs file. By double clicking a .vbs file the victim would run it through microsoft wscript.exe which fires up the infection process. The eMail belongs to a more complex spamming set spread over USA and coming few days ago to Europe as well.
The visual basic script was obfuscated, as you may appreciate from the following image, but the used obfuscation technique was quite weak to reverse. In fact only one round of packing was adopted and after few substitutions “clear text strings” were observable.

Obfuscated Dropper
Interesting techniques were introduced in this dropper. First of all a lot of junk code (apparently good code) was added in order to make reverse engineering process much harder. Very interesting the choice of such a code apparently taken from real droppers but not linked to the analized one. Another interesting adopted technique was on the “User-Agent” settings, which happened to be the key-factor to download the real payload. The dropper per-se is not interesting anymore. It basically uses a romantic WScript.Shell to execute a ‘MZ’ file once downloaded from compromised websites (IoC later on). The Dropped file is returned directly into the HTTP response body and saved with a static name in temporary user folder: saToHxy.exe. The dropper file renamed VB objects and VB functions to make everything a little harder.

Saving Dropper into user temporary file with static name
As today the dropping URLs are the following ones:
castillodepalazuelos.es/rf734rgf?
2010.sggt-wh.de/rf734rgf?
actt.gr/rf734rgf?
As mentioned a romantic Shell.Run would execute the dropped payload. The Payload (sha356:6a51d0cd9ea189babad031864217ddd3a7ddba84) looks like a one-stager payload. No heavy encryption nor multi staging delivery is involved, clear and intuitive user functions within enabled debugging headers.

No Packing found
Firing up IDA and reversing the sample showed up small encoded payload through XOR and some anti debugging tricks such as the timing control and performance monitoring as follows:
Anti-Debugging tricks: Timing and Performante control
Following on the analysis it becomes clear the spread use of Secure Handler Exception Chain exploiting technique. By triggering exceptions the attacker calls modified exception handler functions able to decode the payload and to allocate it directly on the new memory pages, ending up on “call eax” section. The following image shows the decoding loop.

Decoding Loop on 0x3001220
Following a piece of decoded memory area (configuration file), decoded by 0x03001220.
Decoded Memory Area
Dynamic Analysis took out the evidence of a Ransomware payload. In fact following on the decoded payload by getting far on memory site the analyst could observe the ransom HTML page (next image). I would prefer to show out a rendered “ransom request page” rather than a junk of hexadecimal bytes. (sha256: cdb3fef976270ab235db623d6a4a97ea93c41dd1) The ransom page looks looks like the following image.

I will call this Ransomware the “TOPransom” since the funny and evident mistake the attacker made in writing the ransom request file in where he suggested to download the TOP Browser rather then the TOR Browser 😀 (LOL). The TOPransom encrypts files and changes the file extensions with a alphanumeric extension, usually made of 3 characters (why “usually” ? Because looking at the attacker’s db it looks like that, but I didn’t find evidence on that). The modified extension is used as a hidden parameter in the ransom page. The following image shows some hidden features used by the attacker to bring informations to the control server.

POST request to buy the decrypter
Particularly interesting (at least in my persona point o view) the hidden input type called “FB” which looks like piggy backing two informations to the command and control (ransom server) such as: the extension and some hexadecimal content included in a crafted tag called “pre”. By clicking on “Yes I want to buy” the victim POST such a data and are prompted to the following page asking for 0.18 BTC in order to get files back.
Request for ransom
The FB hidden value “made me curious”. By changing the first value (the one before the statement “pre”) you would appreciate different BTC wallets with different asking prices. The following image shows the different results.
Request for ransom 2
This makes the system vulnerable to “balance enumeration” and to “denial of resources”. In fact by enumerating the attacker wallet space I will perform a duplice action: if the wallet exists I’ll take its balance, if the wallet does not exists the backend will create a new wallet, filling up the attacker reserved space for wallet creation. This action could block the new wallet creation ergo new infections. So lets’ write a simple dirty python script to force new wallet creation and money mapping.

Forcing New Wallets to limitate further infections (please do not consider this script as production ready script. Do not consider it as best implementation for such a goal)
Following on the analysis by playing a little bit further with that parameter (FB) I figured out it was vulnerable to SQL Injection. What a nice surprise !! The vulnerable parameter was the crafted tag called “pre” which vulnerable to code injection, which triggered SQLinjections.

SQLi on C&C server !
So let’s try to pown the Attacker ! As first sight you may observe a MySQL error with not a latin characters. Google Translator says it is a Russian language ! Now we know that the attacker belongs, with high probability, to the Russian community. By investigating a little bit harder on the DB, only TOR availability and super slow, I found the botids and the relatives tasks. Please have a look to incremental ids and try to immagine how big was that network.

Bot Ids and relative locations
Another interesting topic was to investigate which were the system users(a.k.a the attackers). In other words the users of such a ransomware-as-a-service-platform” which happened to be the real attackers. Since It looks like a “Ransomware as a service” platform figuring out how many dollars the attackers were able to gain over time its my next goal. The following obfuscated image shows some of the found usernames, passwords (chipertext) and wallets the attackers used to gain profit.

Attackers Username, Passwords and Wallets
My attention ended up on that guy: god.true@xmpp.jp
That guy is related to the following private wallet: 1P3t56jg5RQSkFDWkDK3xBj9JPtXhSwc3N
As you might guess there are two main wallet types:
– Public wallets which store the victim’s money. They are the public available wallets, everybody got infected must now them in order to pay the ransom.
– Private wallets which are the “real ones” belonging to attackers. Private wallets got money from public wallet once reached the end of the attack. Platform charges are applied during that transaction.
Having the private wallet means to have the possibility to track down transactions history. Transactions history is a great source to figure out if that guy made more illegal activity over the past months. Following the go.true@xmpp.jp ‘s private wallet. We may observe interesting transactions as showed in the following image

Transaction From 1P3t56jg5RQSkFDWkDK3xBj9JPtXhSwc3N
That wallet which is DB-related to god.true@xmpp.jp, made huge amount of transactions back on 2017-04-23 and 2017-04-20 by moving out from its wallet 81,87 BTC harvested by many small and similar transactions! If we include the harvested BTC from this attack which currently have balance 13 BTC, he or she is close to 100 BTC transactions. How about 2017-04 (do you remember any famous attack on that time ? :P) With high probability the attacker looks like abusing illegal activities (such as ransomware activities) more then once a time, this boy/girl — with a high probability — is a recurring attacker. By investigating a little bit more on that email address it’s easy to find heavy relations between got.true@xmpp.jp and https://vlmi.su/ which is a Russian based Market Place where attackers buy and sell attacking tools, information and experiences.
After few more crafted SQL queries I was able to extract the “inst” talbe. Fields names are the following ones:
ID, IP, FB, OS, TIMED, TIMEIN. COUNTRY, BRWSER
Yes come one ! This table records the infected clients, let’s see if we can do something to help them !
A simple DB count showed me more 2k infections so far. Not bad for being a plain new ransomware as a service. The Targets look like being very spread all over the world. So far it’s possible to extract the following country distribution.

TOPransom Victims Distribution
I will not disclosure IP addresses in order to guarantee victims privacy. Another interesting data comes from the victim browser distribution (another parameter collected by the attacker). Curiously the most used browser on windows devices is Chrome as the following image shows. [remember] The infection vector wasn’t through web browser but through wscript.exe which opens .vbs by double click on it. [/remember]

TOPransomware victims browser distribution
On this post I’ve been describing the activity that took me from an email attachment to drop the entire attacker’s database on a Ransomware as a Service platform that I called TOPransom. I’ve being trying to enumerate attacker’s income and to mitigate the spreading vector by filling up wallets creation per user by writing a quick and durty python script.
Following IoC for your detection systems. Have fun !
IoC (summing up):
dropper .vba (sha256:fdd1da3bdd8f37dcc04353913b5b580dadda94ba)
saToHxy.exe (sha256:6a51d0cd9ea189babad031864217ddd3a7ddba84)
castillodepalazuelos.es/rf734rgf?
2010.sggt-wh.de/rf734rgf?
actt.gr/rf734rgf?
https://n224ezvhg4sgyamb.onion.link/efwdaq.php
RECOVER-FILES-html (sha256: cdb3fef976270ab235db623d6a4a97ea93c41dd1)
Bot location: http://oeirasdigital.pt
Bot Location: http://jflo.ca/
TOP Browser
How Hackers Cash Out Thousands of Bitcoins Received in Ransomware Attacks
29.7.2017 thehackernews Ransomware
Digital currencies have emerged as a favourite tool for hackers and cyber criminals, as digital currency transactions are nearly anonymous, allowing cyber criminals to use it in underground markets for illegal trading, and to receive thousands of dollars in ransomware attacks—WannaCry, Petya, LeakerLocker, Locky and Cerber to name a few.
Also, every other day we hear about some incidents of hacking of crypto currency exchange or digital wallets, in which hackers stole millions of dollars in Bitcoin or Ethereum.
The latest back-to-back series of thefts of Ethereum—one of the most popular and increasingly valuable cryptocurrencies—in which around half a billion dollars in total were stolen is the recent example of how much hackers are after crypto currencies.
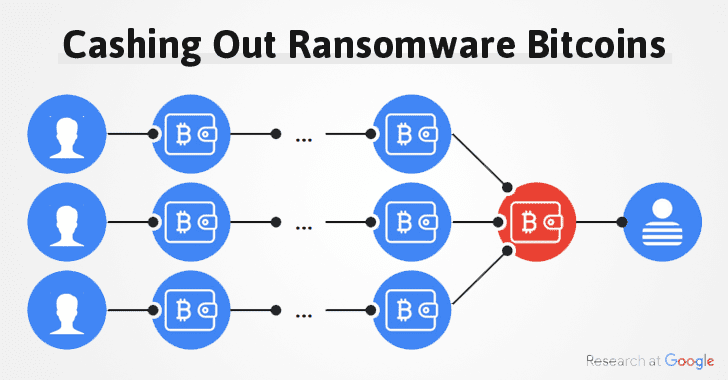
It's obvious that after ripping off hundreds of thousands of cryptocurrencies from exchanges, wallets and ransomware victims, cyber criminals would not hold them in just digital form—the next step is to cash them out into real-world money.
But how do they cash out without getting caught by law enforcement?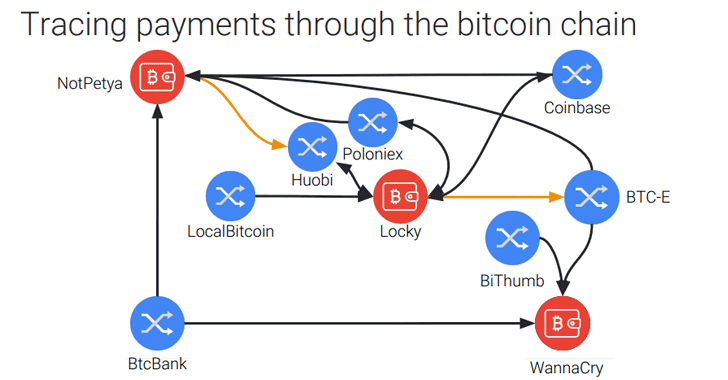
If you are unaware, there are some crypto currency exchanges involved in money laundering, who are illegally-operating to help hackers and cyber criminals easily cash out their digital currencies without identifying them, i.e. anonymously.
According to a recent research paper presented by three Google researchers, more than 95% of all Bitcoin payments collected from ransomware victims have been cashed out via a Russian cryptocurrency exchange, called BTC-e, since 2014.
Interestingly, just two days before Google presentation, one of the founders of BTC-e exchange, Alexander Vinnik, was arrested by Greek police on charges of laundering over $4 Billion in Bitcoin for culprits.
"We uncover the cash-out points, tracking how the money exits the Bitcoin network, enabling the authorities to pick up the money trail using conventional financial tracing means," the trio researchers, Luca Invernizzi, Kylie McRoberts and Elie Bursztein said.
Key Points — Tracking Ransomware Payments
The researchers followed the step-by-step money trail and got a look at the evolving ecosystem of ransomware families, which already helped make cyber-thieves at least $25 Million in the last two years.
Most Damaging Ransomware Families: According to the research, two families of ransomware strain helped hackers made most of the money — Locky and Cerber — while other variants are also starting to emerge.
Criminals looted In Millions: Locky has been the overall biggest earner for hackers at $7.8 Million and was the first ransomware infection to earn above $1 million a month to date, while Cerber has made $6.9 million to date with consistently making more than $200,000 a month.
Victim's Favorite Places to Buy Bitcoins: Obviously, victims also need BTC to pay out criminals, and most victims choose LocalBitcoins, Bithumb, and CoinBase to buy BTC, where 90% victims pay in a single transaction.
How Criminals Cash Out Cryptocurrency: According to the research, more than 95% of all Bitcoin payments for ransomware were cashed out via BTC-e, a service operational since 2011.
Criminals Renting Out Botnets: Cybercriminal gangs behind Dridex, Locky and Cerber have taken Necurs botnet—army of compromised machines—on rent to distribute their ransomware infections on a massive scale.
Google conducted the research in collaboration with the researchers from New York University, University of California San Diego and blockchain analyst firm Chainalysis.
When talking about BTC-e, the cryptocurrency exchange is believed to have been involved in cashing out Bitcoins stolen from the once-very popular Japanese bitcoin exchange Mt. Gox, which was shut down in 2014 following a massive series of mysterious robberies.
NoMoreRansom Says 28,000 Victim Devices Decrypted
27.7.2017 securityweek Ransomware
This week marks the one-year anniversary of the launch of the NoMoreRansom project. The project comprises an alliance of law enforcement agencies and private industry, currently totaling 109 partners. Its purpose is to gather all known ransomware decryptors in one location (the NoMoreRansom website) so that ransomware victims can at least attempt to decrypt encrypted files.
The project was launched on July 25, 2016 by the Dutch National Police, Europol, McAfee and Kaspersky Lab and now holds access to 54 decryption tools provided by 9 partners and covering 104 ransomware families. The site itself is available in 26 languages.
Since its inauguration it has helped decrypt 28,000 ransomware victim devices -- but, warns Europol, the threat is still escalating. "Ransomware has soared since 2012, with criminals lured by the promise of profit and ease of implementation. The threat continues to evolve, becoming stealthier and more destructive, increasingly targeting businesses more than individuals because the potential returns are much higher."
Europol notes that WannaCry alone claimed more than 300,000 business victims across 150 countries in its first few days; and that some organizations are still struggling to recover from the NotPetya attacks of June 27. It adds, "The total number of users who encountered ransomware between April 2016 and March 2017 rose by 11.4% compared to the previous 12 months, from 2,315,931 to 2,581,026 users around the world.
These figures demonstrate that NoMoreRansom is no solution to ransomware. It has benefited 28,000 users (and this should not be dismissed); but that figure is less than one-ninetieth of the total number of victims.
Europol recognizes this. "Prevention is no doubt better than cure. Internet users need to avoid becoming a victim in the first place. Many up to date prevention tips are available on www.nomoreransom.org." Its advice remains, "If you do become a victim, it is important not to pay the ransom and report your infection to the police."
It is equally clear, however, that many people do pay the ransom. At Black Hat this week, Google, Chainalysis, UC San Diego, and the NYU Tandon School of Engineering researchers presented details of their own investigation into ransomware payments. They have been able to track payments through the bitcoin blockchains from distribution sites to the cash-out points. It is hoped that law enforcement will be able to pick up the trail from here and use traditional money-tracking methods to locate the criminals.
The team tracked 34 separate ransomware families over the last two years, concluding that ransomware victims have paid out $25 million to the criminals; and that Locky alone generated $7 million. Cerber generated $6.9 million and CryptXXX generated $1.9 million.
With such figures, it is understandable that the usual 'official' advice from both law enforcement and security researchers is, "Don't pay the ransom: there is no guarantee that the criminals will decrypt your files, you paint a target on your back for further attacks, and you fund the whole criminal ecosystem."
One in Ten U.S. Organizations Hit by WannaCry: Study
25.7.207 securityweek Ransomware
A recent survey discovered that the vast majority of organizations in the United States weren’t prepared for the WannaCry ransomware attack, but just one in ten ended up being infected by the malware.
WannaCry stormed the world in mid-May by leveraging a previously patched exploit called EternalBlue, which hacker group Shadow Brokers allegedly stole from the NSA-linked Equation Group. The ransomware mostly infected Windows 7 computers that hadn’t been patched in due time, and also revealed the destructive impact of a global outbreak. NotPetya confirmed the risk in late June.
According to a survey (PDF) from software lifecycle automation solutions provider 1E, 86% of the organizations in the U.S. had to “divert significant resources” to safeguard themselves during the WannaCry attack. Only 14% of the respondents revealed their organization was prepared for such an attack.
The study also shows that 86% of organizations don’t apply patches immediately after they are released, thus leaving endpoints and entire networks exposed to such attacks. While 14% of respondents said they apply patches immediately, 36% apply them within one week after release, and 27% need up to a month for that, while 23% don’t apply patches within a month after release.
It’s no surprise that 70% of the 400+ U.S. IT professionals responding to the survey said they had to work over at least one weekend as a result of the WannaCry attack, while one in ten admitted to having worked three or more weekends.
The fact that most organizations aren’t prepared for attacks that exploit already patched vulnerabilities is also reflected in the percentage of respondents who said they already migrated to Windows 10: 11%. While 53% said they are currently migrating to Microsoft’s latest platform iteration, 28% said they are planning on doing so this year or the next, while 8% said they had no such plan.
Following the WannaCry incident, awareness appears to have increased regarding the benefits of applying the necessary patches in due time. 71% of respondents said their intent to stay updated has improved (the percentage rises to 87% when infected organizations are concerned), while 74% said “the experience of reacting to WannaCry has left them better prepared for future threats.”
However, 87% of organizations aren’t taking steps to accelerate their migration to Windows 10, despite the looming risks. Furthermore, 73% of respondents said management didn’t make more resources available to IT to help it apply patches faster and/or accelerate its OS migration.
“There is growing a concern that we have entered an era in which this kind of attack becomes the new normal. It's more important than ever that organizations stay current and ensure that software is kept up-to-date and fully patched at all times. WannaCry was a huge wakeup call that elevated security concerns to boardroom level -- IT teams can't afford to leave their organizations exposed,” Sumir Karayi, founder and CEO of 1E, said.
Researcher Analyzes Psychology of Ransomware Splash Screens
25.7.207 securityweek Ransomware
The 'splash screens' of seventy-six different types of ransomware have been analyzed by a cyber-psychologist from De Montfort University. Commissioned by SentinelOne, the subsequent report 'Exploring the Psychological Mechanisms used in Ransomware Splash Screens' (PDF) is designed to reveal how social engineering tactics are used by cyber criminals to manipulate and elicit payments from individuals.
All successful ransomware infections have one common factor -- an explanatory instruction screen to describe what has happened and explain how the victims can recover their files through the payment of a ransom. It is these explanatory screens that comprise the 'splash screens' that are analyzed.
The content and design of the splash screens varies widely but they all have the same intention: to ensure that the victim pays up. "The argument presented in the current report," writes the author, Dr Lee Hadlington, "suggests that these tactics are closely aligned to the concept of social engineering, working on aspects of fear, urgency, scarcity, authority and, in some cases, humor."
He admits that it isn't clear whether the use of archetypal social engineering methods is by design or imitation; but they do occur. The primary social engineering techniques are 'urgency' ('pay within a short deadline or the fee will double'); fear ('or you will lose all of your personal files'); authority ('you must do what I say'); and -- sometimes -- approachability ('email me if you need further instructions').
Hadlington says, "We know that psychology plays a significant part in cyber crime -- what's been most interesting from this study is uncovering the various ways that key social engineering techniques are used to intimidate or influence victims. With ransomware on the rise, it's important that we improve our understanding of this aspect of the attack and how language, imagery and other aspects of the initial ransom demand are used to coerce victims."
While the analysis of the splash screens is interesting and thorough, it does not explain why it is important to understand a technique (social engineering) that is already well-understood and thoroughly analyzed. Furthermore, there is no ability to study the effectiveness of the social engineering techniques (which would at least benefit social engineering research if not ransomware research).
One difficulty is that we do not fully understand the underlying purpose of this social engineering. David Harley, a senior research fellow with ESET, has his own thoughts. "As I see it, the importance of social engineering in notifications lies mostly in these areas," he told SecurityWeek in an emailed comment: "[firstly] pressuring the victim into taking the desirable action of paying up more or less immediately, rather than exploring other options. Especially if there's a risk that grey- or whitehat researchers will come up with a way of recovering data without paying.
"[Secondly] pressuring the victim into paying for recovery of data that aren't actually lost; and [thirdly] pressuring the victim into paying for recovery of data for which the criminals don't actually have a recovery mechanism, before some interfering security researcher points out that paying up doesn't achieve anything."
The big weakness in the report is the inability to measure the effectiveness of the splash screens. This is something that the author admits: "Not all splash screens are the same -- there is a distinct difference in terms of the level of sophistication of mechanisms used to gain payment, presentation of the splash screens and provision of information for further contact. However, there is no further data to explore how such differences map to their success in terms of eliciting payment."
Tony Rowan, a director at SentinelOne, accepts the difficulty in measuring the success of the different splash screens. "This is an interesting area," he told SecurityWeek, "and we have looked for data to use in a correlation exercise. At this stage, the payment data is too disparate and unverifiable to be useful for a correlation exercise, though this is an area we will continue to look at."
But as Harley adds, "As someone with a background in social sciences, I find these questions rather interesting; but from an academic point of view, without subjective data to draw on which aren't present in this study, they're just conjecture."
Without the ability to measure the effectiveness of the different splash screens, there can be no serious conclusions from the analysis. This is admitted: "By expanding the current work with more empirical research, a clearer understanding of why certain ransomware splash screens are more successful at eliciting a payment over others could be obtained," writes Hadlington. "Such information could in turn be used to provide effective mitigation techniques for such attacks, as well as giving both investigators and victims a clearer pathway for help and advice in the event of an attack."
But even then, it is not at all clear how understanding the efficiency of different social engineering techniques in splash screens could help provide 'effective mitigation techniques for such attacks'. It has to be said that this research will be of more interest to students of social engineering than to students of cyber security.
SLocker source code leaked online for free, a gift for crooks and hackers
24.7.2017 securityaffairs Ransomware
The SLocker source code leaked online, it is one of the oldest mobile lock screen and file-encrypting ransomware.
The source code of the SLocker Android malware, one of the most popular Android ransomware families, has been leaked online for free, allowing crooks to develop their own variant of the threat.
SLocker was first spotted in 2015, it is the first ransomware to encrypt Android files.
The SLocker source code has been leaked on GitHub by a user who uses the online moniker “fs0c1ety,” the hacker is inviting everyone to contribute to the code and submit bug reports.
“The SLocker family is one of the oldest mobile lock screen and file-encrypting ransomware and used to impersonate law enforcement agencies to convince victims to pay their ransom.” states fs0c1ety.
“All contributions are welcome, from code to documentation to design suggestions to bug reports. Please use GitHub to its fullest– contribute Pull Requests, contribute tutorials or other wiki content– whatever you have to offer, we can use it!”

The SLocker, aka Simple Locker, is a mobile ransomware that locks victims’ mobile devices and requests the payment of a ransom to unlock them.
The malware impersonates law enforcement agencies to convince victims to pay the ransom, it infected thousands of Android devices in 2016.
According to the experts, more than 400 new variants of the SLocker ransomware were observed in the wild in May, while in May researchers at Trend Micro found a variant mimicking the WannaCry GUI .
“This particular SLocker variant is notable for being an Android file-encrypting ransomware, and the first mobile ransomware to capitalize on the success of the previous WannaCry outbreak.” reads the analysis published by Trend Micro.
“While this SLocker variant is notable for being able to encrypt files on mobile, it was quite short-lived. Shortly after details about the ransomware surfaced, decrypt tools were published. And before long, more variants were found. Five days after its initial detection, a suspect supposedly responsible for the ransomware was arrested by the Chinese police. Luckily, due to the limited transmission channels (it was spread mostly through forums like QQ groups and Bulletin Board Systems), the number of victims was very low.”
Once infected the mobile device, SLocker runs silently in the background and encrypts any kind of file on the smartphone, including images, documents, and videos.
The ransomware is also able to hijack the mobile device, making impossible for the owners to access the device.
The availability of the SLocker source code will likely increase the number of samples that will be detected in the wild in the incoming weeks.
Lloyd’s of London: A massive cyber attack could cause an average of $53 billion of economic losses
23.7.2017 securityaffairs Ransomware
A major global cyber attack has the potential to trigger $53 billion of economic losses, the equivalent to a natural disaster like 2012’s Superstorm Sandy.
Events like the massive Wannacry attack or the Ukraine power outage raise the discussion about the possible economic losses caused by a cyber attack.
According to a new report published by the Lloyd’s of London (“Counting the cost: Cyber exposure decoded”), a massive cyber attack on a global scale could cause an average of $53 billion of economic losses. a figure on par with a catastrophic natural disaster such as U.S. Superstorm Sandy in 2012, Lloyd’s of London said in a report on Monday.
“A major global cyber-attack has the potential to trigger $53 billion of economic losses, roughly the equivalent to a catastrophic natural disaster like 2012’s Superstorm Sandy, according to a scenario described in new research by Lloyd’s, the world’s specialist insurance market, and Cyence, a leading cyber risk analytics modelling firm.” states a blog post published by Lloyd’s of London.
The figure is disconcerting, experts compared it with losses caused by a natural disaster such as the Superstorm Sandy that hit the US in 2012.
“The report, co-written with risk-modeling firm Cyence, examined potential economic losses from the hypothetical hacking of a cloud service provider and cyber attacks on computer operating systems run by businesses worldwide.” reported the Reuters.
Insurers are trying to estimate the economic impact of a cyber attack and the potential exposure to cyber risks, and believe me, it is very difficult to do it due to the lack of historical data on such kind of incidents.
“This report gives a real sense of the scale of damage a cyber-attack could cause the global economy. Just like some of the worst natural catastrophes, cyber events can cause a severe impact on businesses and economies, trigger multiple claims and dramatically increase insurers’ claims costs. Underwriters need to consider cyber cover in this way and ensure that premium calculations keep pace with the cyber threat reality.” said Lloyd’s of London Chief Executive Inga Beale.
“We have provided these scenarios to help insurers gain a better understanding of their cyber risk exposures so they can improve their portfolio exposure management and risk pricing, set appropriate limits and expand into this fast-growing, innovative insurance class with confidence.”
According to Cyence, economic costs in the hypothetical cloud provider attack could reach $8 billion global cost for cases like “WannaCry” ransomware that hit targets in more than 100 countries.

Economic costs could include business interruptions and computer repairs.
In June, the “NotPetya” ransomware infected systems worldwide causing $850 million in economic costs.
According to the report, in the hypothetical cloud service attack, hackers delivered a malware into a cloud provider’s software that was designed to trigger system crashes among users a year later.
The malware then propagates among the provider’s customers, infecting systems in almost any industry, from financial services to healthcare
The experts estimated average economic losses caused by the disruption of the victims’ operations could range from $4.6 billion to $53 billion for massive cyber attacks.
“But actual losses could be as high as $121 billion, the report said.” continues the Reuters.
“As much as $45 billion of that sum may not be covered by cyber policies due to companies underinsuring, the report said.”
The report estimates average losses for a scenario involving a hacking of operating systems ranged from $9.7 billion to $28.7 billion.
“Lloyd’s has a 20 percent to 25 percent share of the $2.5 billion cyber insurance market,” added Beale.
Download ‘Counting the cost: Cyber exposure decoded‘ report
A King’s Ransom It is Not
20.7.2017 Kaspersky Ransomware
Hidden motivations in separate but similar destructive events
EXPETR RANSOMWARE SHADOW BROKERS VULNERABILITIES AND EXPLOITS WANNACRY
The first half of 2017 began with two intriguing ransomware events, both partly enabled by wormable exploit technology dumped by a group calling themselves “The ShadowBrokers”. These WannaCry and ExPetr ransomware events are the biggest in the sense that they spread the quickest and most effectively of known ransomware to date. With this extraordinary effectiveness and speed, one might expect that at least one of the groups would walk away with a very large cash haul. But that is not the case.
King Richard the I, held for a King’s Ransom of 100,000 marks. The largest ransom in known history. At the time, twice England’s GDP
Both of these incidents were carried out by two very different groups that appear to have been capable of obtaining, but minimally interested in, a king’s ransom. This missing financial motivation is strange, considering the royal capabilities of the exploits that they used to deploy their ransomware.
Also unusual, and preceding and relevant to these 2017 ransomware events, is that groups carrying out aggressive, destructive acts were more straightforward about the matter. We first posted our destructive BlackEnergy (BE) findings in 2014, along with discussion of their “dstr” plugin and odd DDoS features. Allegedly BE later took down large parts of the electrical grid in Ukraine for almost a half day. Later we described the Destover components used in the worm-enabled, destructive, politically motivated Sony incident. And Shamoon and StonedDrill have been pushed in the Middle East around turbulent political situations as well. These components were all wiper technology, delivered in a very intentional and destructive manner. It’s interesting that these spectacles all coincided with large political events and interests. So this new need to cloak their destructive activity or sabotage is an interesting shared change in tactics.
WannaCry Deployment
WannaCry deployment efforts began much earlier than has been publicly discussed. Our private report subscribers received early information that the attackers were spearphishing targets globally by at least March 14th. These messages contained links to files hosted at file sharing services. When clicked, the link led to what recipients thought were resumes related to job applications with a filename “Resume.zip” containing “Job Inquiry – Resume 2017.exe”.
This executable maintained a modified Adobe pdf file icon, and dropped both more malware (droppers and downloader chains that later led to WannaCry installations) and immediately opened decoy job applications. Here is an image of one of the decoys. While we couldn’t find it online, it may be a rip of a legitimate document:
Most of these targets were soft (likely to run the exe and likely did not have advanced network defense programs in place), their locations dispersed globally, and their organizations’ profiles inconsistent.
The group attempted to deploy the first version of WannaCry ransomware to these and various other targets over the next two months, with no success or observable effort to collect bitcoin from this activity. And, even after the ETERNALBLUE spreader exploit with the DOUBLEPULSAR code and its oddly mistaken kill switch likely was hastily added to the ransomware, the attackers did not focus much more development or attention on collecting bitcoin. At one point, the actor sent a light set of messages encouraging users to pay BTC to their wallet.
This sort of inexpensive, two month long activity also may tell us a bit about the actor, their capabilities, and their interests — slow, practical, and somewhat hiding their interests in a very odd way.
While the Sony incident demonstrated the theft and use of stolen credentials and reliable lateral movement, even that credential theft itself required little effort on the part of the attackers. Entire spreadsheets of admin passwords were left open on network shares. Bizarre permission configurations were maintained within the network. The actor had little to do in order to spread a wiper with its audio-video payload to lob oddball jibes at Sony and its executives, and post pastebin threats at movie-goers and share the company’s dirty laundry over p2p. Understanding and co-opting a software update infrastructure was unnecessary in the Sony incident. But a low-tech worming component was also built into the toolset, highly effective most likely because of a low security environment, not because of a previously 0day component.
ExPetr Deployment
ExPetr deployment was sharp, advanced, and technically agile. The group precisely targeted a major accounting software supplier to Ukrainian organizations. They also compromised a news website in UA to further waterhole targets outside the reach of the M.E.Doc network.
Once inside the M.E.Doc network, they gained access to the software update infrastructure and used that access to further steal credentials within target customer organizations. It’s interesting that delivery of the original poisoned installer occurred in April, and the large scale wiping event occurred much later. Also, not all systems receiving attempted Telebot deployments later received an ExPetr deployment. And, not all systems receiving attempted ExPetr deployments had previously received an attempted Telebot deployment.
Oddly, the two month delay in delivering the worm-enabled ExPetr variant is unexpectedly similar to the delay we saw with WannaCry. Later, they delivered the WMI/PsExec/ETERNALBLUE/ETERNALROMANCE-weaponized ExPetr sabotage variant. But in a substantial advance from Wannacry, even if Windows systems were patched, the attackers had stolen credentials for effective lateral movement and could wipe/crypt target systems. This addition also tells us that this attacker wanted to focus on effectively operating the confines of Ukrainian-connected organizations. The worming components also didn’t generate random network connections outside of the target networks. The variant included both native win64 and win32 MSVC-compiled Mimikatz-inspired components dropped to disk and run, stealing passwords for maximum privilege and spread, like those for domain admin and various network service accounts.
The ExPetr attackers apparently did not return with widely spread taunts or messages for their targets, or drag out the incident by requesting BTC transactions for disk decryption.
Comparison Table
WannaCry ExPetr
Spearphishing Yes – dependent Minimal (if any) – reported initial entry
Waterholing No Yes
Supply side server compromise No Yes
Capable of developing wormable exploit No Seemingly not
Initial activity March 14 April 15
Ransomware/wiper spread date May 12 (two months later) June 27 (two months later)
Targeting Global and opportunistic Focused primarily within one country
ETERNALBLUE Yes Yes
ETERNALROMANCE No Yes
DOUBLEPULSAR Yes Yes (minor modification)
Advanced credential theft and spreading No Yes
Advanced anti-malware evasion No Yes
Wiper functionality No Yes
Properly implemented crypto No Yes
Rushed mistakes Unregistered kill switch domain Not really – possibly MBR overwrite algorithm (unlikely)
Financial draw No Minimal
Code sharing with other projects Yes Yes
The recent ETERNALBLUE/ETERNALROMANCE/DOUBLEPULSAR-enabled WannaCry and ExPetr incidents share similarities. Not in the sense that they were carried out by the same actor; it is most likely that they were not. One APT was rushed, opportunistic, not as technically capable as the other, while the other APT was practical, agile, and focused. But we are at the start of a trend emerging for this unusual tactic – APT camouflage destructive targeted activity behind ransomware.
FedEx May Have Permanently Lost Data Encrypted by NotPetya
20.7.2017 securityweek Ransomware
FedEx-owned international delivery services company TNT Express is still working on restoring systems hit last month by the destructive NotPetya malware attack, but some business data may never be recovered, FedEx said in a Securities and Exchange Commission (SEC) filing this week.
NotPetya (also known as Nyetya, PetrWrap, exPetr, GoldenEye, and Diskcoder.C) infected tens of thousands of systems, including ones belonging to major organizations, in more than 65 countries. Many of the victims were located in Ukraine, which is not surprising considering that the main attack vector was the update system of M.E. Doc, an accounting tool developed by Kiev-based tax software firm Intellect Service.
The infosec community initially believed NotPetya was a piece of ransomware, similar to WannaCry. However, closer analysis revealed that it was actually a wiper and it was unlikely that victims could recover their files, even if they paid the ransom.
TNT Express, whose Ukraine office uses the compromised tax software, was hit hard by the attack, which led to FedEx temporarily suspending trading of its shares on the New York Stock Exchange. It’s worth noting that FedEx was also impacted by the WannaCry attack.
In its annual report with the SEC on Form 10-K for fiscal year 2017, FedEx said the attack did not affect any other of its companies. While there is no evidence that any data was stolen by malicious actors from TNT systems, the attack had a significant impact on the company’s operations and communications.
A majority of TNT services are available by now, but FedEx informed customers of possible delays in service and invoicing due to the use of manual processes. The company is working on restoring critical systems, including operational, finance, back-office and secondary business systems, but it’s unclear how long the process will take.
Furthermore, FedEx believes it’s “reasonably possible” that TNT will not be able to fully restore all affected systems and recover all the critical business data encrypted by NotPetya.
“Given the recent timing and magnitude of the attack, in addition to our initial focus on restoring TNT operations and customer service functions, we are still evaluating the financial impact of the attack, but it is likely that it will be material,” FedEx said in a press statement. “We do not have cyber or other insurance in place that covers this attack. Although we cannot currently quantify the amounts, we have experienced loss of revenue due to decreased volumes at TNT and incremental costs associated with the implementation of contingency plans and the remediation of affected systems.”
FedEx is not the only shipping company hit by NotPetya. Danish shipping giant A.P. Moller-Maersk also had its systems infected, which prevented it from accepting new orders. Maersk-owned APM Terminals, a global port and cargo inland services provider, was also affected, causing problems at major ports in the United States and Europe.
According to Reuters, Maersk admitted that its antivirus software was not effective against the NotPetya malware, and the company now claims to have implemented additional security measures to prevent future incidents.
Two CryptoMix Ransomware variants emerged in a few days
19.7.2017 securityaffairs Ransomware
Two CryptoMix Ransomware variants emerged in a few days, a circumstance that suggests the operators behind the threat are very active.
Malwarebytes’ researcher Marcelo Rivero has spotted a new variant of the CryptoMix ransomware.

Marcelo Rivero @MarceloRivero
#CryptoMix #Ransomware adds ext ".EXTE" to encrypted files, and the note "_HELP_INSTRUCTION.TXT" - md5: 1059676fbb9d811e88af96716cc1ffb5
12:07 AM - 14 Jul 2017
25 25 Retweets 18 18 likes
Twitter Ads info and privacy
The CryptoMix Malware family was spotted more than a year ago, numerous improvements were added across the time, except for the encryption method that remained the same.
Since the beginning of this year, researchers discovered at least three other CryptoMix variants in the wild, Wallet, CryptoShield, and Mole02.
The last variant observed by Rivero appends the ‘.EXTE’ extension to encrypted files.
Once the ransomware is launched on a computer, it drops a file in the ApplicationData folder and the ransom note in the targeted files’ folders. The ransomware creates a unique ID for each system and sends it to the C&C server.
Authors of the malware ask victims to pay the ransom in Bitcoins and use the email as a communication channel with the victims.
“While overall the encryption methods stay the same in this variant, there have been some differences. First and foremost, we have a new ransom note with a file name of _HELP_INSTRUCTION.TXT. ” wrote the researchers Lawrence Abrams from BleepingComputer.
“The next noticeable change is the extension appended to encrypted files. With this version, when a file is encrypted by the ransomware, it will modify the filename and then append the .EXTE extension to encrypted file’s name. For example, an test file encrypted by this variant has an encrypted file name of 32A1CD301F2322B032AA8C8625EC0768.EXTE.”
Lawrence also remarked that a different variant of the CryptoMix ransomware was observed appending the
. AZER extension to the encrypted files.

Researchers observed that this variant was using a different ransom not ( _INTERESTING_INFORMACION_FOR_DECRYPT.TXT) and different email addressed to receive communications from the victims.
The AZER CryptoMix ransomware is the first malware of the family that works completely offline, its code included ten different RSA-1024 public encryption keys and uses one of them to encrypt the AES key it uses to encrypt the files.
“Last, but not least, this version performs no network communication and is completely offline. It also embeds ten different RSA-1024 public encryption keys, which are listed below. One of these keys will be selected to encrypt the AES key used to encrypt a victim’s files. This is quite different compared to the Mole02 variant, which only included one public RSA-1024 key.” states BleepingComputer.
The same feature was also implemented in the latest EXTE version, the experts observed it also embeds the ten public RSA keys allowing the threat working in absence of connection.
The discovery of two variants of the CryptoMix ransomware in the wild in a few days suggests the operators behind the threat are very active.
CryptoMix Ransomware Variant EXTE Emerges
18.7.2017 securityweek Ransomware
A new variant of the CryptoMix ransomware was recently observed, appending the .EXTE extension to targeted files, security researchers warn.
Around for over a year, the CryptoMix ransomware family has seen numerous updates over time, but few major changes appear to have been added to it: although the ransom note and the used extension suffered modifications, the encryption method remained nearly the same from one variant to the other.
Once executed on the victim’s computer, the ransomware drops a file in the ApplicationData folder, while also dropping the ransom note in the targeted files’ folders. The malware also adds a series of registry keys, creates a unique ID and sends it to a remote location, after which it starts encrypting files using AES encryption.
In the ransom note, the malware demands users to contact the author via provided email addresses, while also asking them to pay the ransom amount in Bitcoins.
Discovered by Malwarebytes’ Marcelo Rivero, the latest malware variant uses the same encryption method as previous iterations, but does show some small updates, BleepingComputer’s Lawrence Abrams reveals.
The threat now adds the .EXTE extension to the encrypted files’ encrypted file name, while using a new ransom note named _HELP_INSTRUCTION.TXT (last year, CryptoMix used the HELP_YOUR_FILES.TXT ransom note). In this campaign, users are required to contact the ransomware authors at exte1@msgden.net, exte2@protonmail.com, and exte3@reddithub.com for payment information.
Earlier this month, a different variant of the malware was observed appending the .AZER extension to the encrypted files and using the _INTERESTING_INFORMACION_FOR_DECRYPT.TXT ransom note and webmafia@asia.com and donald@trampo.info email addresses.
Unlike previous variants, the AZER CryptoMix iteration performs no network communication and is completely offline. It embeds ten different RSA-1024 public encryption keys and uses one of them to encrypt the AES key it uses to encrypt the files.
The EXTE version, Abrams points out, also embeds the ten public RSA keys, meaning it too can work offline. The two variants emerged about one week of each other, which shows that the actor behind this ransomware variant is highly active. Since the beginning of this year, at least three other CryptoMix variants emerged: Wallet, CryptoShield, and Mole02.
NemucodAES ransomware and Kovter trojan bundled in the same campaigns
16.7.2017 securityaffairs Ransomware
Security experts at the SANS Institute discovered that that NemucodAES ransomware and Kovter trojan are being delivered together in spam campaigns.
Security experts at the SANS Institute Internet Storm Center, discovered that that two malware families, NemucodAES and Kovter are being delivered together in .zip attachments delivered via active spam campaigns.
Security Researcher Brad Duncan noticed in the last couple of weeks a significant increase in malicious spam delivering .zip archives with JavaScript files used to download and execute the NemucodAES ransomware and Kovter click-fraud malware.
NemucodAES is a variant of the Nemucod Trojan downloader, known for being used in different campaigns in 2016 distributing Locky and TeslaCrypt ransomware.
“By March 2016, we started seeing reports of ‘Nemucod ransomware’ that stopped downloading ransomware binaries in favor of using its own script-based ransomware component,” Duncan wrote in a SANS Institute Internet Storm Center posted Friday.
“And now in July 2017, we see the next phase of Nemucod ransomware: NemucodAES. Emisoft states this new variant is written in JavaScript and PHP. It uses AES and RSA to encrypt a victim’s files.”
The NemucodAES ransomware is easy to neutralize due to the availability of a decryptor, meanwhile, Kovter click-fraud is a fileless malware hard to detect. Kovter was also used by threat actors to steal personal information and download and execute additional malicious payloads.
Spam campaigns deliver the malicious .zip archives disguised as notices from the United Parcel Service.
“Malspam with Zip archives containing JavaScript files are easy for most organizations to detect… But some of these messages might slip past your filtering, and some people could possibly get infected. With the NemucodAES decryptor, people can recover their files, but I expect this ransomware will continue to evolve,” Duncan wrote.
Kovter was packaged with other ransomware in past campaigns, in February, experts at Microsoft’s Malware Protection Center spotted malicious email campaigns using .lnk attachments to spread Locky ransomware and Kovter.
Back to the recent campaign, NemucodAES and Kovter were bundled in malicious .zip archives. When victims unpack the archives a JavaScript file is extracted.
“Network traffic was typical for an infection by one of the .js files. We first see HTTP requests for the NemucodAES JavaScript, followed by requests for various executables. Then we see the post-infection Kovter traffic. NemucodAES doesn’t generate any traffic on its own,” according to the research report.
The NemucodAES ransomware encrypt files without appending any info to the original file names, then it delivers in the “AppData\Local\Temp” directory instructions (via an .hta file) to decrypt the files. It also uses a Windows desktop background (a .bmp file) as the ransomware note.

Victims are requested to pay a $1,500 ransom in Bitcoin.
Experts are investigating the presence of the Kovter malware in the campaigns. Kovter seems to be used only to check traffic and generating command-and-control traffic.
“I see a lot of post-infection events for Kovter command and control traffic. But I’m not certain click-fraud is involved any more,” Duncan said.
Give a look at the SANS’s analysis for further details about this campaign.
No Free Pass for ExPetr
14.7.2017 Kaspersky Ransomware
Recently, there have been discussions around the topic that if our product is installed, ExPetr malware won’t write the special malicious code which encrypts the MFT to MBR. Some have even speculated that some kind of conspiracy might be ongoing. Others have pointed out it’s plain and simple nonsense. As usual, Vesselin Bontchev, a legend in IT security, who’s become famous for usually getting things right, said it best:
So, what is going on here? As a wise man once said, “the code doesn’t lie,” so let’s analyze the ExPetr MBR disk infection/wiping code in details.
In a nutshell, the malware does these actions:
Checks administrator privileges
Enumerates running processes
Depending on the processes found, initialize a special runtime config
Depending on this runtime config, malware execution branches are chosen
The malware’s main function
The “check privileges” function
An interesting fact is that malware tries to find several running processes (it calculates a hash from running process names and compares it with several hard-coded values).
Enumerating running processes
The most interesting part that happens here is:
After this condition two malicious functions could be executed:
InfectMbr This routine will write the malicious GoldenEye encryptor code to the MBR. After reboot, this code will encrypt MFT and 1024 bytes of each file.
WipePhysicalDrive This routine will overwrite the first 10 sectors of the disk with random trash.
Let’s describe this condition in detail:
The WipePhysicalDrive function will be initiated if:
the special bit in runtime config is not set (that happens when malware finds the avp.exe running process).
the InfectMbr function fails.
This is what happens after an initial infection:
Graphic illustration of condition
Very important additions:
WipePhysicalDrive could be initiated regardless of whether the avp.exe process is running or not. This function will be called when the malware could not write the malicious code to MBR. For example, it could be caused by the activity of other security solutions blocking this write.
Regardless of whether MBR was infected with malicious code or was overwritten with random trash, malware will still try to encrypt the victim’s files using the AES and RSA ciphers and the attacker’s public key.
Overall, it appears that the group behind ExPetr have built what is usually called a stone soup. This is a mix of old code, new code, dirty hacks, test checks and parts of unusual code. For instance, there is a special condition block in which the AES file encryption doesn’t run at all, however, this condition is always false. It very much looks like something that was rushed out the door before it was polished and ready, from many points of view.
Why the rush, you may wonder? We do not know, but there could be several explanations. One of them could be they tried really hard to catch the EternalBlue/EternalRomance “train”. After WannaCry, a lot of organizations started patching their Windows installations to close these vulnerabilities, effectively shrinking the window of opportunity. It’s possible the authors of ExPetr wanted to infect as many targets as possible before these exploits were widely patched.
Despite the rush, the attackers were obviously aware of our technologies (and other companies’ technologies, obviously), notably System Watcher, which is extremely effective at fighting ransomware. System Watcher works by collecting information about the suspicious actions of running programs and builds a score. For instance, when a program reads a full file in memory, it then writes another file of similar size yet different format, then deletes the original, and the score increases. Other similar known bad behavior is used to increase the score and good behavior to decrease it. If multiple malicious actions happen several times, over and over, the score can reach a threshold where it’s pretty obvious that something is wrong. In that case, System Watcher warns the user and offers to terminate the offending process and restore the data.
To fight against this technology, the ExPetr authors have included multiple “counter measures.” One of them is to avoid writing the GoldenEye encryptor code to the MBR if our product is running. This is done in order to prevent raising the suspicion score and getting terminated too early. It actually seems that they put significant energy into trying to bypass our products and target our users, meaning they were pretty worried about being stopped. Nevertheless, these didn’t work too well, reinforcing the theory of a big pile of hacks, put together in a rush. The System Watcher component fires anyway and stops the file encryption, terminating the process and undoing the changes.
To conclude, our users have been protected despite the measures built into ExPetr to target them.
So why we are writing this longer explanation? With complex malware code and retro measures built to bypass antivirus products, it is complicated to understand all the functionality of today’s malware. It is easy to get tricked and believe certain code checks give a free pass to Kaspersky users. In reality, they were intended as a means of trying to pass under the System Watcher’s radar. In the end, it didn’t work. Our users do not need a free pass from ExPetr, since they have an universal “free pass” from our products and System Watcher.
New Ransomware Threatens to Send Your Internet History & Private Pics to All Your Friends
13.7.2017 thehackernews Ransomware
After WannaCry and Petya ransomware outbreaks, a scary (but rather creative) new strain of ransomware is spreading via bogus apps on the Google Play Store, this time targeting Android mobile users.
Dubbed LeakerLocker, the Android ransomware does not encrypt files on victim's device, unlike traditional ransomware, rather it secretly collects personal images, messages and browsing history and threatens to share it to their contacts if they don't pay $50 (£38).
Researchers at security firm McAfee spotted the LeakerLocker ransomware in at least two apps — Booster & Cleaner Pro and Wallpapers Blur HD — in the Google Play Store, both of which have thousands of downloads.
To evade detection of malicious functionality, the apps initially don’t contain any malicious payload and typical function like legitimate apps.
But once installed by users, the apps load malicious code from its command-and-control server, which instructs them to collect a vast number of sensitive data from the victim's phone — thanks to its victims granting unnecessary permissions blindly during installation.
The LeakerLocker ransomware then locks the home screen and displays a message that contains details of the data it claims to have stolen and holds instructions on how to pay the ransom to ensure the information is deleted.
The ransom message reads:
All personal data from your smartphone has been transferred to our secure cloud.
In less than 72 hours this data will be sent to every person on your telephone and email contacts list. To abort this action you have to pay a modest ransom of $50 (£38).
Please note that there is no way to delete your data from our secure but paying for them. Powering off or even damaging your smartphone won't affect your data in the cloud.
Although the ransomware claims that it has taken a backup of all of your sensitive information, including personal photos, contact numbers, SMS', calls and GPS locations and browsing and correspondence history, researchers believe only a limited amount of data on victims is collected.
According to researchers, LeakerLocker can read a victim's email address, random contacts, Chrome history, some text messages and calls, take a picture from the camera, and read some device information.
All the above information is randomly chosen to display on the device screen, which is enough to convince the victims that lots of data have been copied.
Both malicious apps have since been removed by Google from the Play Store, but it is likely that hackers will try to smuggle their software into other apps.
If you have installed any of the two apps, uninstall it right now.
But if you are hit by the ransomware and are worried about your sexy selfies and photographs being leaked to your friends and relatives, you might be thinking of paying a ransom.
Do not pay the Ransom! Doing so motivates cyber criminals to carry out similar attacks, and there is also no guarantee that the stolen information will be deleted by the hackers from their server and will not be used to blackmail victims again.
ICS Security Pros Increasingly Concerned About Ransomware: Survey
11.7.2017 securityweek ICS Ransomware
Many security practitioners in the field of industrial control systems (ICS) believe the level of risk is high, and they are increasingly concerned about ransomware and embedded controllers, according to the SANS Institute’s fourth annual ICS cyber security survey.
ICS security experts from organizations of all sizes told SANS that they believe the top threat vectors are devices that cannot protect themselves, such as embedded controllers (44%), internal threats, including accidents (43%), external threats, such as nation-state actors and hacktivists (40%), and ransomware and other extortion attempts (35%).
Ransomware has made a lot of headlines in the past year and industrial systems are at risk, as demonstrated by both theoretical attack scenarios and in-the-wild threats such as the WannaCry malware. As a result, the number of ICS security experts concerned about ransomware has nearly doubled compared to data from the previous SANS survey.
“Although ransomware primarily infects commercial OS-based systems (e.g., Windows, Linux), the integration of these into ICS environments and the dependence of ICS on devices running these operating systems has extended ransomware’s effectiveness and reach,” SANS said in its report. “Publicly known operational impacts remain few to date but, we expect more to follow, especially given public demonstrations of ransomware targeting ICS/SCADA.”
Recent ICS hacking demonstrations also appear to have contributed to an increasing awareness that embedded controllers and control system applications are at risk – nearly one-quarter of respondents believe controllers are most at risk. On the other hand, many still believe that computers running commercial operating systems are most at risk and have the greatest impact.
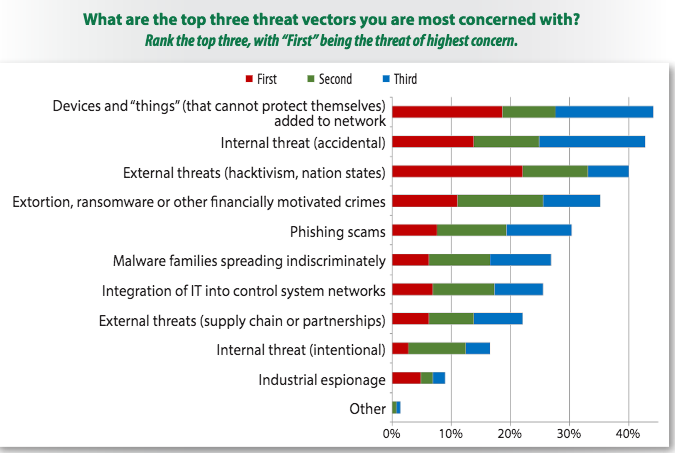
More than two-thirds of respondents believe the threat to ICS to be high or critical, and nearly half said their budgets for ICS security increased from the fiscal year 2016. Over the next 18 months, 20 percent or more of organizations have allocated budget for performing security assessments or audits of control systems, increase visibility into these systems, increase security awareness training, and implement anomaly and intrusion detection tools.
“Budgets for training and certification of staff responsible for implementing and maintaining security of control systems and control fell considerably, from 34% in 2016 to 26% in 2017. Rather than balancing this with increases in trained staff or outside consultants, budgets for these initiatives decreased, dropping, at 14%, below the top 10 budgetary initiatives,” SANS said. “At a time of increasing exposures and risk factors, this is counterintuitive. Rising threat levels and expanding attack surfaces require skilled professionals to address these risks.”
Of the organizations with more than 10,000 employees, 2.6 percent said they have a budget of more than $10 million for control system security in the fiscal year 2017, and 6 percent said they have a budget ranging between $1 million and $10 million. On the other hand, 2.6 percent of large companies admitted they don’t have a budget for ICS security.
The fact that some organizations have allocated budget for improving visibility is encouraging, considering that when asked if their control systems have been infected or infiltrated, 40 percent of respondents said “not that we know of,” which suggests they may have been breached, but lack visibility into their operational technology (OT) network.
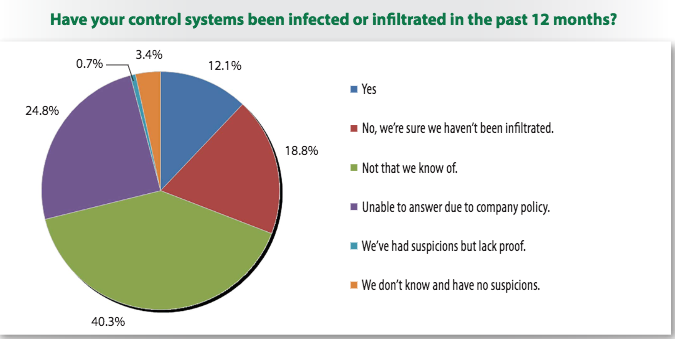
Roughly 12 percent of respondents said their control systems were infected or infiltrated in the past year. While most of them either did not know how many times their systems were breached or said they had only detected such events up to five times, some reported more than 50 incidents.
Calling Artificial Intelligence to Counter Ransomware Attacks
11.7.2017 securityaffairs Ransomware
The progression in Artificial Intelligence have incited intense debate worldwide, some experts are calling AI to counter malware attacks
In a short span of six weeks, the world was hit twice by major ransomware attacks — malicious software that seizes the data stored on your computer systems and would only release it to you upon receiving ransom money.
It goes without saying that the world is in dire need of better defense mechanism, and mercifully they have started to arise but in a rather slower and in patchwork fashion. The day we would feel completely secure, we may have artificial intelligence to thank.
Ransomware is not necessarily the trickiest or the most dangerous forms of malware that can hack into your computer, but it surely is infuriating and at many instances devastating. The majority types of infections that sneak into your systems don’t lock down your personal pictures or documents the way ransomware does and nor do they demand money.
Despite knowing the risks, there are many who aren’t very savvy enough to keep up with the security software updates. Both of the recent ransomware attacks thwacked users who were unsuccessful at installing the security update which Windows released a few months earlier.
Artificial Intelligence
The progression in Artificial Intelligence have incited intense debate worldwide. Science fiction is nearing reality and AI products are taking over households and workplace. Concerns about the potential takeover of AI over the job market is rising. Discussions are also live about the detrimental effects of an AI singularity, taking over the world and terminating the human race.
Though these debates are all valid, I strongly hold the opinion that AI should not only be concentrated to just home gadgets or on process optimization and automation. Instead, AI can be put to use in solving the greater problems the world is facing.

AI in tackling Ransomware
2015 saw around 707 million cybersecurity breaches while in 2016 the figure reached 554 million in just the first half.
Detecting Malware
Earlier, the identification of malicious programs was done by matching the program’s code against a database of identified malware. Though this method was only as good as the database and would ultimately get outdated, allowing new malware variants to easily sneak in.
Hence, security companies started to gauge a malware by its behavior. For instance, in the case of ransomware, the software may go for repetitive tries to lock files by encrypting them. But this could also flag regular computer behavior for example file compression.
The modern techniques now include considering a combination of behaviors. Such as, a program which is encrypting files without displaying a progress bar on the monitor could be signaled as a surreptitious activity. But the drawback here is that it slows down the process of harmful software identification, also locking up some of the files.
Provision
The growing number of alerts being generated by the traditional tools is only increasing the struggle for the security teams. AI, with its ability to self-learn and automate, can raise the effectiveness and cut cost, guarding us from terrorism or attacks of rather smaller scale.
Moving further, the existing AI-centric solutions in the industry are more pro-active. They have the ability to anticipate attacks beforehand by detecting patterns and glitches pertaining to malicious content.
Secureworks utilizes the predictive competencies of AI for advanced threat recognition globally. SiftScience, Cylance, and Deep Instinct are using it to prevent frauds and for endpoint security, like smartphones and laptops. These technologies hold the potential to radically magnify the possibilities and scale of security specialists and enable them to sense incoming threats before they actually materialize.
Original Petya Master Decryption Key Released
10.7.2017 securityweek Ransomware
The master decryption key for last year’s Petya ransomware was made public last week and has since been confirmed to be genuine.
Petya ransomware first emerged in March 2016, distinguishing itself from similar malware by encrypting the Master Boot Record (MBR) instead of individual files. Soon after its initial appearance, Petya was paired with another ransomware, and the pair became available as a service a couple of months later.
The last known variant of the malware was spotted in December 2016 and was referred to as GoldenEye. Dubbed PetrWrap, a ransomware family observed in March this year was using Petya for its nefarious purposes, but wasn’t created by Janus Cybercrime Solutions, the name Petya’s author goes by.
NotPetya, the destructive wiper that hit numerous organizations in Ukraine and various other countries in late June, wasn’t the work of Janus either, but only borrowed code from Petya. In a tweet on June 28, Janus claimed no connection with NotPetya.
One week later, on July 5, the ransomware author posted a link to an encrypted and password protected file hosted on the mega.nz service. After opening the file, independent researcher and programmer Hasherezade found in it the master decryption key for all previous Petya variants.
Kaspersky security researcher Anton Ivanov has already confirmed that the key works for all Petya versions, including GoldenEye.
The release of the master decryption key is great news for those Petya victims who were unable to restore their files to date. Last year, security researchers managed to crack the first two versions of the ransomware, and the only variant not decrypted before was GoldenEye.
“Thanks to the currently published master key, all the people who have preserved the images of the disks encrypted by the relevant versions of Petya, may get a chance of getting their data back,” Hasherezade explains.
The newly released master key, however, won’t help users hit by NotPetya.
“This key cannot help in case of [NotPetya], since, in this particular case, the Salsa keys are not encrypted with Janus’ public key, but, instead of this, erased and lost forever. It can only help the people who were attacked by Petya/Goldeneye in the past,” Hasherezade notes.
Although the wiper’s alleged authors suggested last week they could provide decryption keys to help users with encrypted files, some researchers suggest decryption isn’t possible in NotPetya’s case. Others, however, explain decryption is possible if NotPetya was “unable to obtain administrator privileges when running.”
Windows 10 platform resilience against the Petya ransomware attack
10.7.2017 Ransomware
The Petya ransomware attack on June 27, 2017 (which we analyzed in-depth in this blog) may have been perceived as an outbreak worse than last month’s WannaCrypt (also known as WannaCry) attack. After all, it uses the same SMB exploit used by WannaCrypt and adds a second exploit and other lateral movement methods. However, our telemetry shows a less widespread attack:
The new Petya variant is highly sophisticated malware, but our telemetry shows it had far less reach than we expected given its worm-like spreading capabilities
The attack started in Ukraine; when the dust settled, more than 70% of the machines that encountered Petya were in Ukraine
It managed to spread to machines in other countries but in significantly lower volumes
The majority of infections were observed in Windows 7 machines
In this follow-up blog entry, we’ll discuss platform protection and mitigation in Windows 10 and Windows 10 S. The security configuration and reduced attack surface of Windows 10 S block this attack by default. As we previously discussed in a white paper, Windows 10 Creators Update has next-gen security technologies that help defend against ransomware attacks.
We will also present new findings from our continued investigation, specifically into the boot sector modification behavior of the ransomware.
Windows 10 protection and mitigation
The new Petya ransomware combines multiple well-known techniques for propagation and infection that are not new to security researchers. The noteworthy aspect is that Petya’s developer(s) took techniques normally used by penetration testers and hackers, and built a sophisticated multi-threaded automation of these techniques inside a single piece of code.
Such attacker techniques are part of the modern threat landscape and are continuously researched by security teams at Microsoft. Resulting new mitigations, hardening or defensive measures are then integrated into our products and operating systems.
Windows 10 follows this philosophy of continuous mitigation improvements. From our analysis of Petya, we were able to measure the defenses provided by Windows 10. Summarized in the diagram below are how mitigations and security features can help disrupt the different stages of this attack.
Petya’s kill-chain diagram with platform defenses able to mitigate or prevent certain techniques in Windows 10
Each mitigation in this diagram is placed on top of the specific malware techniques, which are either fully prevented or mitigated in Windows 10. For an overview and specific details of these mitigations included in Windows 10, see this page. Technical details of how each mitigation can help to block Petya’s techniques are listed below:
Device Guard can enforce strong code integrity policies to allow only trusted signed apps to run. It can thus block the entry vector of Petya (an updater running an untrusted binary) and also the further propagation attempts executing an untrusted DLL, either through PSEXEC or WMI.
Credential Guard uses virtualization-based security to isolate the LSASS process, so it fully protects from the credential dump executed by Petya using the external Mimikatz-like tool. It also protects the domain credentials stored in the Windows Credential Store. Access tokens exposed in memory can still be leveraged by Petya, but this is a less effective propagation mechanism, and it relies on third-party tools and other processes active in memory while Petya executes.
Several exploit mitigations such as better KASLR (randomization of kernel), NX HAL and PAGE POOL (non-executable kernel regions) are included by default in Windows 10 Anniversary and Creators Update, and they help mitigate SMB exploits like EternalBlue and EternalRomance. More mitigations like KCFG (control-flow guard for kernel) and HVCI (kernel code-integrity) are automatically enabled with Device Guard to provide additional resistance also to new exploits. Previous blogs discuss in detail how such mitigations were able to help mitigating unknown zero-day exploits, not effective against Windows 10.
UEFI Secure Boot is the security standard that uses hardware features to protect boot process and firmware against tampering. This protection will stop the dangerous disk encryption executed by Petya with a bootloader. After Petya’s forced reboot, a machine with Secure Boot will detect the anomalous bootloader and prevent further execution, containing the damage and preventing the very dangerous encryption of disk sectors leading to a complete loss of data. A machine in this state will be prevented from booting and can be recovered with the regular repair functionality from the Windows USB/DVD media. NOTE: Individual files encrypted by Petya in the limited time before reboot will remain encrypted and must be recovered from backup copies.
App Locker can also be used to block execution of certain programs (e.g. PSEXEC) or unsigned binaries (e.g. Petya’s DLL library) for machines that cannot benefit from Device Guard due to lack of the specific hardware requirements or due to older operating systems not supporting new mitigations (e.g. Windows 7).
Finally, administrators of networks with older operating systems like Windows 7 which do not benefit of modern hardware and software mitigations, may consider deploying some hardened configurations that could help to slow down or remove certain lateral movement techniques. Such hardened configurations may impact legitimate functionality such as file-sharing or remote management and so it needs to be evaluated carefully before deployment.
Block or restrict access to specific IPs for file-sharing services (SMB)
netsh firewall set service fileandprint
netsh firewall set service RemoteAdmin disable
Block remote execution through PSEXEC
FOR /F “usebackq tokens=2 delims=:” %a IN (`sc.exe sdshow scmanager`) DO sc.exe sdset scmanager D:(D;;0x00040002;;;NU)%a
ACL remote WMI access
Limited execution time
The impact of Petya’s worm behavior is limited by its design. As part of its execution command, it receives a time that it can run performing lateral movement and exploitation before rebooting the system.
If an argument is not passed, a default of 60mins is assumed. This value is later used to determine the time in the future for the system to reboot.
This means that the threat can only do lateral movement and exploitation of other machines during this limited time. This reduced the reach of the attack, as observed in our telemetry.
Also, the malware’s worm code does not persist across reboot; for example, if an infected machine is successfully rebooted, the worm does not run again.
Conditional behavior and boot sector modification
As discussed in our in-depth analysis of the Petya ransomware attack, beyond encrypting files, the ransomware also attempts to infect the Master Boot Record (MBR).
In addition to modifying the MBR, the malware modifies the second sector of the C: partition by overwriting it with uninitialized buffer, effectively destroying the Volume Boot Record (VBR) for that partition. The screenshot below shows the code that makes these changes:
It is not clear what the purpose of these modifications are, but the code appears to be buggy – it allocates 10 times the amount of memory it requires. In most modern machines, the VBR on the C: partition is not used for booting as there is a separate partition for the boot manager. Generally, for machines running Windows 7 or later that weren’t upgraded from XP, the malware’s VBR changes are unlikely to have any impact.
During malware initialization phase, this malware maintains a global variable that dictates its behavior. It alters its behavior based on the presence of processes related to certain antivirus applications running in the system.
Specifically, it looks for names of processes belonging to Kaspersky Antivirus and Symantec Antivirus and alters its behavior if it finds them. Below are the CRC values that threat checks and their corresponding process names.
CRC value Matching process name
0x651B3005 NS.exe
0x6403527E ccSvcHst.exe
0x2E214B44 avp.exe
Information controlling threats behavior is stored in a global variable (gConfig in the screenshots), which is then used to check during MBR modification.
If Kaspersky Antivirus process is found in the system or if the MBR infection is unsuccessful, the malware then proceeds to destroy the first 10 sectors of the hard drive. The code snippet below shows the threat logic:
Below snapshot shows threat code that destroys 10 sectors of \\\\.\\PhysicalDrive0, including the MBR sector.
On the other hand, if Symantec AV process names are found, the threat does not perform SMB exploitation.
We compared this new ransomware’s MBR infection functionality to the original Petya malware. Here are some of our findings:
Although the layout of the code and encrypted data in the sectors following the MBR varies between the two versions, the code itself is functionally very similar. The encryption process is the same: when the malicious MBR starts, it loads additional code from sectors after the MBR, which in turn proceeds to encrypt the Master File Table (MFT). After the encryption process is complete, the user is presented with the following ransom message, which is different from the typical ASCII skull and crossbones shown by the original Petya:
Ransom note from Petya after MBR infection
Interestingly, the first part of the text is the same message used by the WannaCrypt ransomware:
WannaCrypt ransom note
In terms of the malware code itself, there are some differences between the new Petya variant and the original malware. For example, the malware authors changed the constants for the key expansions of the encryption algorithm (Salsa20)— the standard string “expand 32-byte k” was replaced with the custom “-1nvalid s3ct-id”.
The code that is supposed to show the skull and crossbones ransom note is still physically present in the malicious MBR code, but it is only printing empty lines.
The strategy to cause a reboot to trigger the malicious MBR code has also been updated. The original version generated a serious system error by calling NtRaiseHardError with code 0xC0000350 (STATUS_HOST_DOWN), which forced the machine to reboot. The new Petya variant has also added a function to schedule a task that reboots the machine after a pre-configured number of minutes.
Fake victim ID
Below is the structure of the malware configuration stored by threat at Sector 32 (0x20):
typedef struct
{
BYTE Null;
BYTE SalsaKey[0x20];
BYTE SalsaIV[0x08];
BYTE BitcoinAddress[0x22];
BYTE Empty[0x5E];
BYTE VictimID[0x3C]; // 60 bytes
BYTE Empty2[0x11B];
}
The VictimID shown to the user is randomly generated using CryptGenRandom() and does not correspond to the MFT encryption, so the ID shown is of no value and is also independent from the per-drive file encryption ID written on README.TXT.
Below is a sample disk sector 32 written by the malware. Unlike the original Petya malware, elliptic curve data is empty.
Boot recovery options
Petya causes some damage to the operating system’s boot code. In certain cases, recovery to boot the infected machine to a clean state is possible.
Case 1: If machine is equipped with secure boot + UEFI
If an infected machine shows the message below, it means the threat couldn’t hijack the boot process and encrypt MFT. In this case, booting off a clean installation media and performing Startup Recovery can fix the issue, and the machine can be booted.
Case 2: If system is non-UEFI, installed with Kaspersky Antivirus, and in a state where boot completely fails
The ransomware attempts to destroy the first 10 sectors of the \\\\.\\PhysicalDrive0 if Kaspersky Antivirus is found or if the MBR infection is unsuccessful. Thus, boot process hijack through malicious MBR hasn’t been completed so the MFT (Master File table) contents are intact and not encrypted by the threat. In this case, the partition table information is destroyed by the threat. Given that it stores critical information needed in the booting process, a traditional boot repair process may not work. Rebuilding the partition table may require consultation with an expert.
Case 3: if a ransom message like below is seen, recovery is not possible
The image is shown if the machine reboots and the malicious MBR is executed successfully. In this case, it is likely that the malware successfully encrypted the MFT, a vital structure of the NTFS file system. Unfortunately, recovery is not possible, and the machine is not capable of booting anymore. One can take the hard disk to another clean system, use disk recovery tools to recover any recoverable personal files, and reimage the system.
Protection against ransomware attacks
The new Petya ransomware variant we saw this week is significantly more complex than the original. It also improved on WannaCrypt‘s spreading mechanisms by using a second exploit and adding more propagation methods. These lateral movement capabilities make this ransomware a higher risk for networks with an infected machine. Furthermore, the boot sector modification behavior discussed in this blog gives this ransomware more potential to cause damage to machines.
This Petya outbreak exemplifies the ever-increasing sophistication of ransomware attacks. A multi-layer defense stack is needed to protect computers and networks. At Microsoft, we strive to continuously enhance Windows 10 with next-generation features to protect customers. As described in this blog, Windows 10 has defenses that can mitigate ransomware attacks like Petya.
Windows Defender Antivirus and Windows Defender Advanced Threat Protection allows customers to detect, investigate, and respond to ransomware attacks. For enterprises, Device Guard locks down devices and provide kernel-level virtualization based security. Credential Guard protects domain credentials stored in the Windows Credential Store.
Keep your software up-to-date to block threats that attempt to exploit software vulnerabilities to infect machines or spread across networks. Additionally, secure privileged access to protect your network from credential theft.
To know more about security features in Windows 10, read out white paper “Next-gen ransomware protection with Windows 10 Creators Update”.
To find mitigation steps specific to this new Petya variant, refer to our blog “New ransomware, old techniques: Petya adds worm capabilities”.
Private Decryption Key For Original Petya Ransomware Released
7.7.2017 thehackernews Ransomware
Rejoice Petya-infected victims!
The master key for the original version of the Petya ransomware has been released by its creator, allowing Petya-infected victims to recover their encrypted files without paying any ransom money.
But wait, Petya is not NotPetya.
Do not confuse Petya ransomware with the latest destructive NotPetya ransomware (also known as ExPetr and Eternal Petya) attacks that wreaked havoc across the world last month, massively targeting multiple entities in Ukraine and parts of Europe.
The Petya ransomware has three variants that have infected many systems around the world, but now the author of the original malware, goes by the pseudonym Janus, made the master key available on Wednesday.
According to the security researchers, victims infected with previous variants of Petya ransomware, including Red Petya (first version) and Green Petya (second version) and early versions the GoldenEye ransomware can get their encrypted files back using the master key.
The authenticity of the master key has been verified by an independent Polish information security researcher known as Hasherezade.
"Similarly to the authors of TeslaCrypt, he released his private key, allowing all the victims of the previous Petya attacks, to get their files back," Hasherezade posted her finding on MalwareBytes on Thursday.
"Thanks to the currently published master key, all the people who have preserved the images of the disks encrypted by the relevant versions of Petya, may get a chance of getting their data back."
Although the first and second version of Petya was cracked last year, the private key released by Janus offers the fastest and most reliable way yet for Petya-infected victims to decrypt their files, especially locked with the uncrackable third version.
Meanwhile, Kaspersky Lab research analyst Anton Ivanov also analyzed the Janus' master key and confirmed that the key unlocks all versions of Petya ransomware, including GoldenEye.
Janus created the GoldenEye ransomware in 2016 and sold the variants as a Ransomware-as-a-Service (RaaS) to other hackers, allowing anyone to launch ransomware attacks with just one click and encrypt systems and demand a ransom to unlock it.
If the victim pays, Janus gets a cut of the payment. But in December, he went silent.
However, according to the Petya author, his malware has been modified by another threat actor to create NotPetya that targeted computers of critical infrastructure and corporations in Ukraine as well as 64 other countries.
The NotPetya ransomware also makes use of the NSA's leaked Windows hacking exploit EternalBlue and EternalRomance to rapidly spread within a network, and WMIC and PSEXEC tools to remotely execute malware on the machines.
Security experts even believe the real intention behind the recent ransomware outcry, which was believed to be bigger than the WannaCry ransomware, was to cause disruption, rather than just another ransomware attack.
According to researchers, NotPetya is in reality wiper malware that wipes systems outright, destroying all records from the targeted systems, and asking for ransom was just to divert world's attention from a state-sponsored attack to a malware outbreak.
Lucky are not those infected with NotPetya, but the master key can help people who were attacked by previous variants of Petya and Goldeneye ransomware in the past.
Security researchers are using the key to build free decryptors for victims who still have crypto-locked hard drives.
Private Decryption Key For Original Petya Ransomware Released Friday, July 07, 2017 Swati Khandelwal 133 189 0 327 Rejoice Petya-infected victims! The master key for the original version of the Petya ransomware has been released by its creator, allowing Petya-infected victims to recover their encrypted files without paying any ransom money. But wait, Petya is not NotPetya. Do not confuse Petya ransomware with the latest destructive NotPetya ransomware (also known as ExPetr and Eternal Petya) attacks that wreaked havoc across the world last month, massively targeting multiple entities in Ukraine and parts of Europe. The Petya ransomware has three variants that have infected many systems around the world, but now the author of the original malware, goes by the pseudonym Janus, made the master key available on Wednesday. According to the security researchers, victims infected with previous variants of Petya ransomware, including Red Petya (first version) and Green Petya (second version) and early versions the GoldenEye ransomware can get their encrypted files back using the master key. The authenticity of the master key has been verified by an independent Polish information security researcher known as Hasherezade. "Similarly to the authors of TeslaCrypt, he released his private key, allowing all the victims of the previous Petya attacks, to get their files back," Hasherezade posted her finding on MalwareBytes on Thursday. "Thanks to the currently published master key, all the people who have preserved the images of the disks encrypted by the relevant versions of Petya, may get a chance of getting their data back." Although the first and second version of Petya was cracked last year, the private key released by Janus offers the fastest and most reliable way yet for Petya-infected victims to decrypt their files, especially locked with the uncrackable third version. Meanwhile, Kaspersky Lab research analyst Anton Ivanov also analyzed the Janus' master key and confirmed that the key unlocks all versions of Petya ransomware, including GoldenEye. Janus created the GoldenEye ransomware in 2016 and sold the variants as a Ransomware-as-a-Service (RaaS) to other hackers, allowing anyone to launch ransomware attacks with just one click and encrypt systems and demand a ransom to unlock it. If the victim pays, Janus gets a cut of the payment. But in December, he went silent. However, according to the Petya author, his malware has been modified by another threat actor to create NotPetya that targeted computers of critical infrastructure and corporations in Ukraine as well as 64 other countries. The NotPetya ransomware also makes use of the NSA's leaked Windows hacking exploit EternalBlue and EternalRomance to rapidly spread within a network, and WMIC and PSEXEC tools to remotely execute malware on the machines. Security experts even believe the real intention behind the recent ransomware outcry, which was believed to be bigger than the WannaCry ransomware, was to cause disruption, rather than just another ransomware attack. According to researchers, NotPetya is in reality wiper malware that wipes systems outright, destroying all records from the targeted systems, and asking for ransom was just to divert world's attention from a state-sponsored attack to a malware outbreak. Lucky are not those infected with NotPetya, but the master key can help people who were attacked by previous variants of Petya and Goldeneye ransomware in the past. Security researchers are using the key to build free decryptors for victims who still have crypto-locked hard drives.
The author of the original Petya ransomware released the master key
7.7.2017 securityaffairs Ransomware
The author of the original variant of the Petya ransomware has made the master key available online, all the victims can decrypt their files for free.
Janus, the author of the original variant of Petya ransomware (that isn’t the NotPetya variant used in the recent massive attack) has made the master key available online.
All the victims of the original Petya ransomware can now use the master key for free to decrypt their files.
“As research concluded, the original author of Petya, Janus, was not involved in the latest attacks on Ukraine. His original malware was pirated and extended by an unknown actor (read more here).” reads a blog post published by MalwareByte “As a result of the recent events, Janus probably decided to shut down the Petya project. Similarly to the authors of TeslaCrypt, he released his private key, allowing all the victims of the previous Petya attacks, to get their files back.”
Follow
JANUS @JanusSecretary
"They're right in front of you and can open very large doors" https://mega.nz/#!lmow0Z7D!InyOTGaodVLX2M9pMGQvHJaGpvon11FyGep10ki4LHc … @hasherezade @MalwareTechBlog ;)
8:14 PM - 5 Jul 2017
28 28 Retweets 35 35 likes
Twitter Ads info and privacy
Researchers from KasperskyLab confirmed that the master key released by Janus works on files encrypted by the original Petya ransomware and early versions the GoldenEye ransomware.
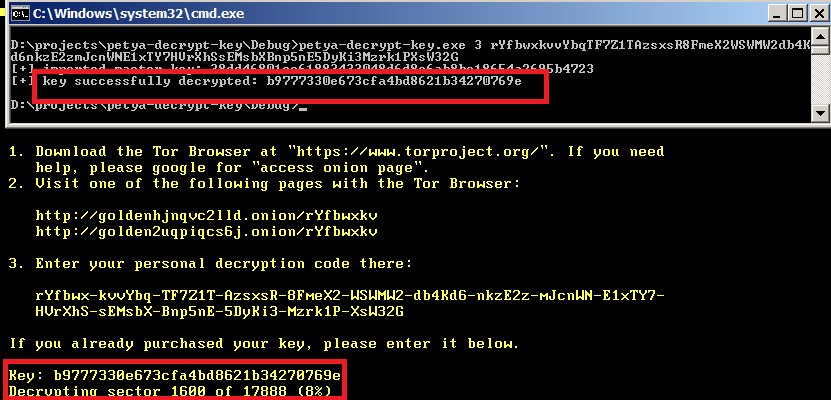
Anton Ivanov @antonivanovm
The published #Petya master key works for all versions including #GoldenEye
7:45 PM - 6 Jul 2017
495 495 Retweets 360 360 likes
Twitter Ads info and privacy
“The published #Petya master key works for all versions including #GoldenEye,” tweeted Ivanov from Kaspersky Lab.
GoldenEye is a ransomware created by Janus in 2016 that is based on the Petya code, unfortunately, someone has stolen the “compiled application” of the threat in 2017 and modified it.
“The source code of the original Petya has never been leaked publicly, so in case it was recompiled it proves that the original Petya’s author, Janus, is somehow linked to the current outbreak (either this is his work or he has sold the code to another actor).” wrote Hasherezade in one of its analysis.
Follow
hasherezade @hasherezade
My new post on #EternalPetya - proving that the code was indeed patched: https://blog.malwarebytes.com/threat-analysis/2017/06/eternalpetya-yet-another-stolen-piece-package/ …
6:56 PM - 30 Jun 2017
Photo published for EternalPetya - yet another stolen piece in the package? - Malwarebytes Labs
EternalPetya - yet another stolen piece in the package? - Malwarebytes Labs
In this post, we will try to fill this gap, by making step-by-step comparison of the current kernel and the one on which it is based (Goldeneye Petya).
blog.malwarebytes.com
251 251 Retweets 262 262 likes
Twitter Ads info and privacy
The expert confirmed that a stolen version of the ransomware that is based on the GoldenEye code was used in the massive NotPetya attack (aka ExPetr, Eternal Petya). Unlike previous versions, the NotPetya variant doesn’t implement the feature to decrypt files.
In April 2016, researchers developed a tool to decrypt files encrypted by early Petya ransomware versions. The Twitter user @leostone announced to have elaborated a method to generate passwords in less than a minute. The user also developed a website to help victims generate keys for restoring encrypted files.
In order to generate a decryption key, the victim just needs to provide certain information on the infected drive. The researcher Fabian Wosar from Emisoft as developed an application that is able to automatize the process extracting data from infected Petya drives and generate the key for the data rescue.
The security experts Lawrence Abrams, who contribute at BleepingComputer.com blog, has prepared a guide on how to use the tool.
Abrams explained that the tool scans the infected drive searching for the Petya bootcode. Once detected the code, it selects it and allow users to simply copy both the sectors and nonce associated with it. These data (a Base64-encoded 512 bytes verification data and a Base64-encoded 8 bytes nonce) could be used to generate the password through the @leostone’s website.
“An individual going by the twitter handle leostone was able to create an algorithm that can generate the password used to decrypt a Petya encrypted computer. In my test this, this algorithm was able to generate my key in 7 seconds.” wrote Abrams in a blog post.

To discover the password, the user has to physically remove the drive from the infected machine and attach it to either a Windows machine or a USB drive docking station and to launch the Wosar’s tool.
“To use Leostone’s decryption tool you will need attach the Petya affected drive to another computer and extract specific data from it. The data that needs to be extracted is 512-bytes starting at sector 55 (0x37h) with an offset of 0 and the 8 byte nonce from sector 54 (0x36) offset: 33 (0x21). This data then needs to be converted to Base64 encoding and used on the https://petya-pay-no-ransom.herokuapp.com/ site to generate the key.” continues Abrams.
“Unfortunately, for many victims extracting this data is not an easy task. The good news is that Fabian Wosar created a special tool that can be used to easily extract this data. In order to use this tool, you need to take the encrypted drive from the affected computer and attach it to a Windows computer that is working properly. If your infected computer has multiple drives, you should only remove the drive that is the boot drive, or C:\ drive, for your computer.”
Once obtained the password, users should be able to reconnect their encrypted drive and enter it to restore the files encrypted by the Petya ransomware.
In response to the tool, the Petya’s author updated the ransomware neutralizing it.
“Thanks to the currently published master key, all the people who have preserved the images of the disks encrypted by the relevant versions of Petya, may get a chance of getting their data back,” Hasherezade wrote.
NotPetya Operators Accessed M.E.Doc Server Using Stolen Credentials: Cisco
6.7.2017 securityweek Ransomware
The group behind last week’s destructive NotPetya attack was able to access M.E.Doc’s update server and use it for their nefarious purposes courtesy of stolen credentials, Cisco has discovered.
Last week, multiple security companies determined that the tax software company’s update server was used as the initial attack vector. Although M.E.Doc denied possible compromise several times during the first days of the outbreak, it eventually agreed to allow a security firm to perform forensic analysis of the server.
Earlier this week, Ukraine police seized the M.E.Doc servers believed to have been used in the incident, to prevent any subsequent attacks from happening. The local authorities suggested the threat group might use the server for further attacks, and not without reason, it seems: a fake WannaCry ransomware family was distributed in the shadow of NotPetya using the same vector.
Cisco was the security company M.E.Doc provided with access to its server, and the company now confirms not only that the server was compromised, but also that the attack was destructive in nature, and that a backdoored module was pushed to M.E.Doc clients several times over the past months.
RSA Webinar - July 13 at 1PM ET: Evolution from Two-Factor Authentication to Identity Assurance
Disguised as ransomware, the NotPetya wiper (which Cisco refers to as Nyetya), was designed to overwrite the infected system’s Master Boot Record (MBR) to prevent access to the operating system. The malware also encrypts specific file types, but the process wasn’t meant to allow file decryption, the security researchers suggested.
In a new report presenting the findings of their analysis of the M.E.Doc server, Cisco confirms that the attack was destructive in nature and that all malware installations came through the M.E.Doc update system.
The investigators discovered a web shell at http://www.me-doc[.]com[.]ua/TESTUpdate/medoc_online.php and found it to be a slightly modified version of the open source PHP web shell PAS. Stored in an encrypted form, the web shell requires a passphrase to decrypt.
Using stolen admin credentials, the malicious actor logged into the M.E.Doc server, acquired root privileges, and started modifying the configuration file for the NGINX web server so that “any traffic to upd.me-doc.com.ua would be proxied through the update server and to a host in the OVH IP space with an IP of 176.31.182.167.”
The actor restored the original server configuration several hours later. They also wiped the OVH server to erase evidence.
Further analysis confirms the ESET report claiming that a backdoor had been inserted into the M.E.Doc software on multiple occasions: on April 14, May 15, and June 22. The malicious actor behind this activity was TeleBots, also known as BlackEnergy and Sandworm, ESET revealed.
“The .net code in ZvitPublishedObjects.dll had been modified on multiple occasions to allow for a malicious actor to gather data and download and execute arbitrary code,” Cisco notes.
The backdoor, the security company confirms, was used to retrieve the EDRPOU and name of M.E.Doc clients, as well as to steal sensitive information (SMTP hosts, usernames, passwords, and email addresses) and download and execute payloads. All traffic was masqueraded as requests to the legitimate M.E.Doc server.
According to Cisco, the concerning matter is that the actor behind NotPetya “burned a significant capability in this attack” by compromising both “the backdoor in the M.E.Doc software and their ability to manipulate the server configuration in the update server.” The actor was able to “deliver arbitrary code to the 80% of UA businesses that use M.E.Doc,” as well as to any other multinational corporation using the software.
“This is a significant loss in operational capability, and the Threat Intelligence and Interdiction team assesses with moderate confidence that it is unlikely that they would have expended this capability without confidence that they now have or can easily obtain similar capability in target networks of highest priority to the threat actor,” Cisco continues.
The company also advises organizations with ties to Ukraine software like M.E.Doc and with systems in Ukraine to take extra caution, given that these resources have been shown to be targeted by advanced threat actors. The security firm advises companies to use separate network architectures and increased monitoring, as well as to patch their systems for any known vulnerabilities, and even upgrade to more secure platform versions.
“Talos places this attack in the supply-chain category. Rather than targeting organizations directly, an actor compromises trusted hardware and software vendors to deliver compromised assets to a high-priority environment. We believe that these types of malicious capabilities are highly desired by sophisticated actors. All vendors, regardless of size or geographic region, must be increasingly vigilant,” the company concludes.
NotPetya Decryption Key Sale - Genuine or Curveball Charade?
6.7.2017 securityweek Ransomware
Confusion over the source and motive behind the NotPetya ransomware outbreak was given an extra stir with the offer for sale of a private decryption key. Posts appeared Tuesday on both Pastebin and DeepPaste: "Send me 100 Bitcoins and you will get my private key to decrypt any harddisk (except boot disks)."
The posts appear to be genuine, and the key proofs have been tested. "It means that whoever posted this message has [the] private key to decrypt the data encrypted by the NotPetya malware," Anton Cherepanov, ESET senior malware researcher, told Forbes.
Catalin Cimpanu at BleepingComputer suggests a different verification. Just before the posts appeared, he points out that two small payments (of around $285 and $300) were made from the ransomware's Bitcoin wallets to wallets associated with the Pastebin and DeepPaste text sharing services. On the reasonable assumption that the payments and the posts are associated, it is further proof that the offer comes from the NotPetya group. "
The announcement made yesterday night is verified by the two Bitcoin payments the group made to the two services where they hosted their statements," Cimpanu wrote.
Shortly after the posts, the entire remaining funds (about $10,000) were moved out of the ransomware wallet in what seems to be the start of the group striving to hide their tracks.
On the surface, this appears to be a logical process. A faulty encryption routine used by the malware made the recovery of files by victims impossible. F-Secure has pointed out that decryption can be achieved with difficulty: "In order to decrypt the files successfully, the files should be enumerated in the exact same order as during encryption, and with the same "bug" in place."
This still requires a decryptor obtained separately by the victims; but the group's webmail provider has shut down their inbox so they can no longer read emails or reply with decryption keys.
With no possibility of collecting more ransoms, the private key is the only asset of value left to the group -- so selling that in a single transaction for a large amount would make sense. This is what you might expect criminals to do.
The confusion comes from a strong body of opinion that suggests the perpetrators are not simple criminals but a state-sponsored group. NotPetya, says this theory, is actually a cyber weapon disguised as ransomware delivered by Russia primarily against the Ukraine as part of the ongoing cyber conflict between the two nations.
"Since the outbreak," explains David Kennerley, director of threat research at Webroot, "many analysts have pointed towards possible state involvement in the ransomware attack, and the ‘mistakes' made by the authors of NotPetya, lent to theories their main intention wasn't primarily monetary gain. And the most likely the aim was to cause as much damage and havoc as possible under the guise of ransomware – with the primary target being Ukrainian entities."
Further indications that the group might not be serious about collecting money comes from Cimpanu. The Pastebin/DeepPaste messages include a link to "a Dark Web portal running Mattermost, an open source, self-hosted Slack-like online chat application." He engaged with the group, but got little response to his queries, and the chat room is now deactivated. Yesterday he tweeted, "NotPetya public chat is down. Charade over."
The bottom-line is that this sale initially looks like the act of a criminal gang, but proves nothing. "We've been told that the hackers, portraying to be the ransomware creators, have successfully decrypted a number of files encrypted by NotPetya – this definitely points towards inside knowledge of the ransomware itself," comments Kennerley.
"Are they the creators? Are they close to the creators, or has another group independently found a possible weakness in NotPetya's encryption routine and is now attempting to make a quick buck? A number of files have been decrypted, this doesn't mean they have the ability to decrypt all files, but again it adds a twist to the story. At least from a distance, it adds an argument against the theories that this wasn't about the money – or is this a smoking gun to throw investigators of the scent, or even an attempt at good old internet trolling? Whatever it turns out to be - At 100 bitcoins, it's very unlikely anyone will take them up on their offer."
"Unfortunately, this doesn't really clear anything up about the case," comments F-Secure security adviser Andy Patel. "100BTC for the master key that will decrypt all files encrypted by NotPetya isn't really worth it, considering a majority of victims probably have corrupted master file tables, and hence can't even access that data anymore."
So, despite the apparent criminal offer for sale, it is still unclear whther NotPetya is a cyberweapon aimed at the Ukraine or a flawed criminal act. It isn't clear whether the private key sale is genuinely from the perpetrator, or a curveball from a state group.
Android Ransomware Mimics WannaCry
6.7.2017 securityweek Ransomware
Android file-encrypting ransomware SLocker was recently observed using an interface similar to that of the WannaCry malware that hit Windows systems worldwide last month, TrendMicro security researchers reveal.
One of the first Android ransomware families to encrypt files on compromised devices, SLocker had a short lived success before, as the suspect supposedly responsible for it was arrested within five days after the initial detection.
The malware initally infected a small number of users because of limited transmission channels (forums like QQ groups and Bulletin Board Systems), but is back in an attempt to capitalize on the success of the WannaCry outbreak.
According to Trend Micro, the original ransomware sample found earlier this month was named King of Glory Auxiliary and was posing as a cheating tool for the game King of Glory. Once installed, however, the ransomware featured a similar appearance to WannaCry.
To lure users into installing it, the SLocker ransomware also disguises as video players, and other types of programs. After the application is first run, however, it changes the icon and name, along with the wallpaper of the infected device.
It also checks whether it has been run before, and generates a random number and stores it in SharedPreferences if not. Next, the threat locates the device’s external storage directory and starts a new thread that will first go through the directory to find files that meet specific requirements.
“We see that the ransomware avoids encrypting system files, focuses on downloaded files and pictures, and will only encrypt files that have suffixes (text files, pictures, videos). When a file that meets all the requirements is found, the thread will use ExecutorService (a way for Java to run asynchronous tasks) to run a new task,” the security researchers explain.
The malware generates a cipher based on the previously generated random number and feeds the string to construct the final key for AES before using AES to encrypt files.
SLocker victims are provided three options to pay the ransom, but all three lead to the same QR code requesting victims to pay via popular Chinese mobile payment service QQ. The malware also threatens victims that the ransom amount will increase after three days and that files will be deleted after a week.
The malware analysis also revealed that the decryption key is compared with the value in MainActivity.m, which is the previously generated random number plus 520. Thus, users can decrypt their files for free if they can figure out the method for generating the decrypt key, TrendMicro notes.
“Compared to the ransomware we’ve seen before, this ransomware is relatively simple. It is actually quite easy for a security engineer to reverse the ransomware and find a way to decrypt files. However, the proliferation of new variants so quickly after the first one shows that these malicious actors are not slowing down. Even though a suspect was caught, more advanced ransomware may be just around the corner,” TrendMicro notes.
To stay protected, users should install only apps downloaded from legitimate app stores, and should also check the permissions requested by each app, especially when they allow the software to read/write on external storage. Users should also back up their data regularly and install and maintain a comprehensive antivirus solution.
[Video] Ukrainian Police Seize Servers of Software Firm Linked to NotPetya Cyberattack
6.7.2017 thehackernews Ransomware
Ukrainian National Police has released a video showing officers raiding company of M.E.Doc accounting software makers, whose systems have been linked to outbreak of Petya (NotPetya) ransomware that recently infected computers of several major companies worldwide.
On 4th July, masked police officers from Ukrainian anti-cybercrime unit — carrying shotguns and assault rifles — raided the software development firm “Intellect Service,” in the capital city Kyiv and seized their servers, which were reportedly compromised by hackers to spread (ExPetr, PetrWrap, Petya, NotPetya) ransomware.
Researchers from ESET security firm have found a very stealthy malicious code in the M.E.Doc software update which was injected by an unknown hacker or group of hackers in mid-April by exploiting a vulnerability.
The malicious software upgrade, designed to install a backdoor and give unauthorized remote access to attackers, was then delivered as an update to nearly 1 million computers belonging to its client companies.
Researchers explain that the backdoor installed in endpoint computers was designed to allow hackers to execute various commands remotely and further install other malicious programs, eventually used to conduct WannaCry like global ransomware attack.
The software company previously denied its servers had been compromised, but several researchers and even Microsoft blamed the company for being "patient zero" for the NotPetya attack.
Ukrainian authority has also said that the company could face charges.
Moreover, the Petya investigation took interesting twist last week when researchers found that NotPetya is not a ransomware; instead, it’s a destructive piece of “wiper” malware designed to destroy all records from the targeted systems, making organizations to shut down their operations.
Ukrainian authority has recommended M.E.Doc customers to stop using its accounting software until further notice. So, you are supposed to turn off your computers if it has the M.E.Doc software installed on and change your passwords.
Ukraine believes Russia is behind the NotPetya cyber attack that shut down the nation's critical operations, including the airport, local metro, hospitals, and government, but authorities are still investigating the case.
NotPetya Hacker Demands 100 Bitcoins for the Decryption Key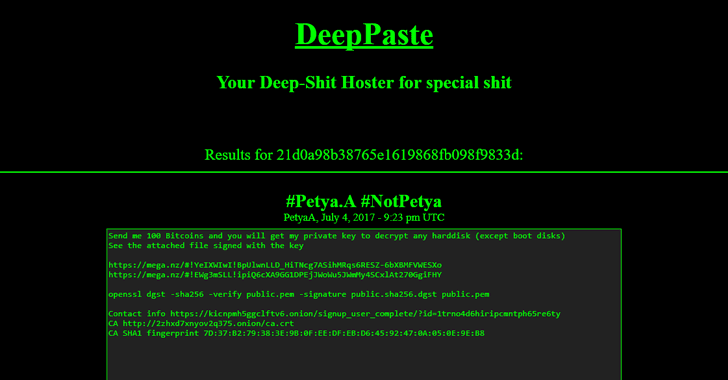
It was also reported today that the hackers connected to the NotPetya ransomware moved $10,000 worth of Bitcoins from the online wallet they were using to receive payments from victims to a different wallet.
After that someone claimed to be connected to NotPetya Posted an announcement on DeepPaste and Pastebin, asking for 100 Bitcoins (roughly $256,000) for the private key that supposedly decrypts any file encrypted with NotPetya.
Risks of hacking attacks: Ransomware – Cryptolocker and tutorials for Italian SMEs in the light of the Network and Information Security (NIS) Directive.
6.7.2017 securityaffairs Ransomware
As was anticipated by Minister Pier Carlo Padoan, the Taormina G7, he would have to face, inter alia, the overwhelming problem of Web security and the protection of sensitive data.
The issue is much more urgent in the light of cyber attacks on computer systems of some key service providers in several EU Member States and in the UK, including the National Public Health Service (public body) or Against that of Renault in France (private body) that had the effect of completely blocking both the structures mentioned and not only.
These attacks, in fact, have been carried out on a large scale and involved hundreds of computer systems at the European level. Ransomware technology, a type of malware used in this case by hackers, has already been used on several occasions and is spreading very rapidly so that it may become, as early as 2017, a serious problem as DDoS attacks ( Distributed Denial of Service) (source: David Gubiani, Check Point Security Engineering Manager).
Even at a non-Community level, the UN Security Council has dealt with this issue with Resolution 2341/2017, in which United Nations Member States have been encouraged to co-ordinate each other by exchanging their knowledge about each other to attacks perpetrated via the Web.
On this point, it is interesting to note that Jurgen Stock (Head of Interpol) has complained of a structural disconnection that exists at present between the United Nations Members States.
And as Professor Pierluigi Paganini, Chief Technologist of CyberSec Enterprise, said in his speech: “From the Wannacry case to the NIS Directive, critical infrastructures are still too vulnerable:” While in Europe there is a debate about the need to calibrate infrastructures, criticisms and adopting security measures that will make them resilient to cyberattacks, and such events demonstrate how vulnerable network infrastructure is exposed to small-scale threats.
Think of the potential large-scale impact of a ransomware such as WannaCry that exploits a zero-day flaw, which is not known at the time of the attack and is therefore extremely dangerous. ”
In the debate on Resolution 2341/2017, particular interest can be attributed to the point where it has been shown that the key role in cyber attack prevention lies in cooperation between public and private sectors; It was therefore hoped that a Memorandum of Understanding would be established between the Member States regarding the information on the acquired data.
It appears that ictu oculi – as in the NIS Directive at Community level and in UN Security Council Resolution 2341/2017 – the phrase “wishes cooperation between the Member States” stresses how information exchange can prove to be crucial and limited cyber attacks, which can provide effective prevention and, consequently, limitations of related harm to IT systems.
However, the appearance that is particularly alarming is that for such attacks, hackers used a Ransomware called “WannaCry” a virus that, like Cryptocker, was created by scammers with high-level knowledge in the field of computer programming.
Scammers can infiltrate a PC in a variety of ways, for example through an attachment of an infected mail or through the browser, when a website is infected with this kind of malware. The word ransom means requiring a ransom, to be paid to remove the limitation and to get the possibility of access to the PC (source Avast), actually doing a real extortion by the use of the computer system. It is therefore evident that there is a consequent risk for those who give up on what is required by extortionists to feed a funding channel for occult criminal organizations and terrorist organizations (Europol sources).
However, 2016, as Gabriele Faggioli, Legal, Ceo Partners4innovation said, with the NIS Directive of the Parliament and the European Council of July 6, will be remembered as the year that will mark the course of the decades on the issue of computer security.
The future of this issue in Europe is essentially due to the rules of a broad package of will be remembered as the year that will mark the course of the next decades on the issue of computer security.
The future of this issue in Europe is essentially attributable to the rules of a large EU reform package, which has been in force and in part already applicable since this year as Regulation no. 679/2016, General Data Protection Regulation (RGPD). This legislation, which entered into force on 24 May and applicable from 24 May 2018, replaces Directive 95/46 / EC. There is, moreover, Directive n. 1148/2016, the Network and Information Security Directive (NIS Directive), which entered into force on 8 August, laying down measures for a common high level of network security and information systems in the Union.
The text of the Directive states that Member States shall ensure that public administrations and market operators take appropriate technical and organizational measures to manage network security risks and the information systems that control and use in their operations.
Given the state of the art attacks, these measures must ensure a level of safety appropriate to the actual level of risk involved.
In particular, measures should be taken to prevent and minimize the impact of accidents attacks affecting their network and the information systems on the basic services they provide and, therefore, to ensure the continuity of the services incurred by these networks and information systems.
The Legislator has undertaken to ensure that the contents of these provisions are effective, work in practice, and last for at least a generation. The provisions are dense with technical-informational references and address the challenges imposed by new technologies in data protection and system and network security.
As Antonello Salerno said, “The future of cybersecurity in Italy could be decided on two key aspects: the role of the PA as an example and a spur for the private and the training of excellence skills remaining in the country.here” Of course, there are adequate investments to protect critical infrastructures. To reach this goal, the implementation of the European Network and Information Security Directive will be important.
If, from a formal point of view, the NIS Directive, which was adopted in July, is yet to be adopted (the deadline for transposition is by May 2018), Italy has already substantially aligned with many of the requirements of the new Community legislation, and can now focus on details to make the strategy more effective.
The hubs are those of the Decree of the President of the Council of Ministers of 24 January 2013, which contains a first model of cybersecurity governance and indicates in the DSI or DIS (Department of Security Information) and in the CISR (Interministerial Security Committee of the Republic) the main coordinating references. a
Under the NIS Directive, you will need to identify the essential service providers. The legislator could only point to the obligation to notify the attacks only for large national players, leaving the majority of Italian business fabric (mainly composed of SMEs) or, as it may be desirable, extend this obligation also to actors of relatively small size, such as many municipal or local companies, but which rely on large user bases and whose contribution on a national scale could be extremely significant.
The specific methods of allocating these resources will depend on the effectiveness of the Italian action on computer security. “The opportunity – emphasizes Andrea Rigoni (cybersecurity expert and partner of Intellium, strategic consultancy for NATO), governments and large infrastructures – is that with the adoption of the NIS directive we are back with the plan and it is decided to allocate more clearly and timely the funding for network security.”
Particularly interesting will be the role of the Public Administration, as has happened in the past on other occasions, starting with electronic billing, for example, can make a changeover for the private, thanks to compliance mechanisms. While on the one hand, the public has to make their own infrastructures and management systems compliant with international standards that the Government is required to identify and detail, and on the other hand, it may ask the same security standards for companies interested in working with the Public Administration, thus triggering a virtuous circle that will involve the private sector through the certification of the PA chain.
The risk for companies operating in any economic sector is high as evidenced by the outcome of a study that says Prof. Pierluigi Paganini is “surprising”, only 3 threats have been designed with the intent of striking critical industrial systems and infrastructures – Stuxnet, Havex, and BlackEnergy2. That data continues Paganini, “confirms that industrial systems today continue to be most exposed to generic threats, given alarming if we think an attack designed to hit these systems could have disastrous effects.
Stuxnet first, and the latest attacks in Ukraine with BlackEnergy malware have demonstrated the effectiveness of a malware in an offensive against an industrial system in a critical infrastructure. ”
From what has just been reported, additional business risks seem to derive from the use of computer media such as smartphones and tablets. Many companies, both public and private, provide computer support to their employees. With a 394% increase in smartphone and 1700% of the tablet in the past four years, it’s no wonder that mobile attacks are steadily increasing. According to the Check Point Security Report 2016, a five-person employee will be the author of a violation of his business data via mobile malware or malicious Wi-Fi, both highly effective attack devices on mobile devices.
As this trend is steadily growing, Check Point points out that mobile business-related violations is becoming an increasingly significant problem for a company’s security since these computer-based media are particularly vulnerable and vulnerable to an absence of a frequent update of the antivirus used.
Recent attacks involving some of the journalists’ phones show how attack techniques are “in the wild” and that we should expect more and more to see criminal bands using them. However, mobile security remains a challenge for businesses, a push-pull between productivity, privacy and protection.
In 2017, organizations should take into account the spread of cyber attacks through the “Industrial Internet of Things”, not only through smartphones and corporate tablets, but also, for example, by printers or other types of devices.
Convergence between IT and Operational Technology (OT) is making both the most vulnerable environments and therefore it will be necessary to extend physical control systems and physical security to logical space and implement threat prevention solutions in IT and OT environments. Critical infrastructures, including nuclear power plants, electricity and telecommunications networks, remain highly vulnerable to possible cyber attacks. Almost all infrastructures have been designed and built before the threat of cyber attacks and for this reason, even the simplest computer security principles in most cases have not been taken into account within the projects.
In this regard, it is interesting and also worrying as it has emerged in the quoted work of Prof. Pierluigi Paganini, which, as revealed by the research of the US – ICS CERT, states that: “… the energy sector is one of the most sought after and confirmed in the many attacks that have been observed over recent months by groups of criminals and nation-state actors. According to a recent analysis released by IBM Managed Security Services, the number of attacks against industrial systems has increased by 110% compared to last year. IBM experts observed a significant increase in brute-force attacks against SCADA systems. … The US leads the rankings of the five major nations affected by the attacks, not surprising if we consider the largest number of ICS systems in the United States. ”
Only at the beginning of 2016 was the first intentional blackout caused by a computer attack.
Critical Infrastructure Security Officers must, therefore, be prepared for their networks and systems to be systematically attacked by different actors: other States, terrorists and organized crime.
Check Point’s Security Report 2016 revealed that the number of unknown malware volumes that attack organizations is nearly 10,000, with about 12 million new malware variants identified each month.
In the Security report, it is evident that: “These technologies are in fact part of our business and cybercriminals have consequently innovated their hacking techniques.”
“Hackers have become smarter when it comes to malware and ransomware, releasing every minute new variations.”
“The era of signature-based antivirus to detect malware is far away.”
“With these predictions, companies can develop their IT security plans to keep them one step ahead of emerging threats by preventing attacks before they can cause damage.”
To ensure convergence in the implementation of Article 14, Member States of the U.E. encourage the use of network standards and/or technical specifications and information security.
Just to counter the risks of attacks on computer systems, as has been previously stressed, 2016 is remembered not only for the NIS Directive but also for privacy legislation.
Member States’ legislation identifies competent authorities both in the protection of sensitive data and in identifying the Computer Security Incident Response Team (CSIRT), but the NIS Directive, since many incidents compromise personal data, also provides that the competent authority should operate in close cooperation with the authorities that supervise the protection of data in cases of incidents involving personal data breaches.
However, the two disciplines cannot be confused, as they are directed to regulate the activities of distinct subjects. It is foreseen that NIS will only be applied to providers of essential services and Internet service providers, while the privacy and data protection regulations also apply to individuals.
However, the rules in question may overlap in cases where a computer incedent also involves a violation of personal data. In this case, the affected parties will have to act to report the incidents under the two directives, either they will have to report both the incidents referred to in the NIS Directive and the notification of the violation of personal data provided by the RGPD.
The hope is that, in a juncture and in the process of transposition into our legal order of both Directives, the Authorities responsible for the surveillance and management of cyberattacks and on the protection of the preservation of personal data examine the guidelines which can help businesses cope with security incidents, so as to ensure and insure compliance with both regulations.
Notwithstanding the NIS Directive applies only to “macro categories” i.e. to essential service operators (energy, transport, banking, health, etc.), while Regulation NIS no. 679/2016 applies to all companies, it is to be noted that the business fabric present on Italian territory is predominantly made up of SMEs which as such cannot benefit from the protection provided by the NIS; therefore, it would be desirable, in addition to an either convergence of the norms now cited, and the creation within the various trade associations (such as Confindustria, Confagricoltori, Confartigianato), of structures capable of receiving news of any incidents that have occurred to their associates and then, in turn, communicating them and CSIRT.
The constituent entity, within the category of associations, should essentially reflect the structure of the CSIRTs as set out in the NIS Directive, assuming a dual function: first, the protection of small and medium-sized enterprises from potential cyber attacks that could hurt or even blocking production by violating the informative and sensitive data present in the servers of the companies themselves; and second the assessment of the reliability of affiliated companies, in that way, for the development of a sort of “computer reliability rating” both on the prevention of computer accidents and on the contrary, and by ensuring a high level of protection of sensitive data.
It is believed that any user of the services produced by the subjects concerned should be able to know whether the company to which it is addressed is substantially reliable from a computer point of view and to know how to hold sensitive data on the servers of the company itself. Think, for example, of the case of a clinic and a patient who may be affected by a disease, a condition that, if spread, could severely damage the patient’s reputation. Or the case of a large company that would like to take advantage of the collaboration of a company for the development of the inductor: it is evident that it is useful to be aware of the reliability of the computer systems used.
To ensure the full operation of the description, it would be necessary to have the “mini CSIRT or CSIRT category” within each category association linked to a national CSIRT, which is then connected to the CSIRT network at a community level.
In addition, in a top-down view, the “CSIRT category”, present within each category association, are linked to a national CSIRT, which is then linked to the CSIRT network at Community again at a community level.
Furthermore, in a top-down view, the “CSIRT category”, if aware of an incident that happened to one of its associates, must report the incident not only to the national CSIRT but also to the other members of the association, avoiding possibly spreading the name of the affected affiliate for reasons of company reputation.
Companies will also have to set up a biennial plan to prevent computer attacks and protect sensitive data contained in their servers.
Consequently, every two years, the CSIRT category will list a list of associated companies by providing a rating of their reliability based on the level of prevention from computer incidents reached. This will greatly contribute to protecting the members of the association and improving prevention against cyber attacks and supporting actions in the event of a wasted attack.
Such a system, which, moreover, refers to a duty of cooperation enshrined in the world as well as in the community, can guarantee to public companies, private individuals and users of the services produced, more and more secure computer systems and the capability of dealing with hacker attacks while not abandoning victims and their users to their destiny, without specific reference points.
I conclude by making the conclusions of Prof. Pierluigi Paganini in his intervention “From the Wannacry case to the NIS Directive, critical infrastructures are still too vulnerable” in which it was expressly stated that: “… recalling that the security of our infrastructures also depends on the posture of the citizens. We need to learn about computer threats and how to defend ourselves from them. We are the knot of a global network with which we exchange a huge amount of information filtering or configuration errors in the systems we use every day could lead to risk situations for the entire community. ”

And I would add that as for the contrast to the offenses committed by minors in the Network, the aspect of education and prevention is the most important thing for the prevention. One has to enter once and for all in the perspective for which no small or large world player (physical and/or juridical persons) can feel immune to attacks and therefore have to be cyber protectors while never underestimating the risk and it’s results. We must also educate ourselves that what is happening in the virtual world has more and more serious repercussions on the real world and on the fate of the cyber attack victim.
Fake WannaCry Ransomware Uses NotPetya's Distribution System
5.7.2017 securityweek Ransomware
The NotPetya wiper wasn’t the only piece of malware distributed last week using the compromised M.E.Doc update mechanism: a fake WannaCry ransomware variant was delivered using the same channel, Kaspersky Lab reports.
Called FakeCry, the ransomware was delivered to M.E.Doc users on June 27, the same day as the NotPetya outbreak started. According to Kaspersky, it was run as ed.exe in the M.E.Doc directory by the parent process ezvit.exe, suggesting it used the same delivery mechanism abused by NotPetya.
Written in .NET and including a “WNCRY” string, the ransomware was clearly making reference to the massive WannaCry epidemic in May 2017, and the same did a “forgotten” PDB path inside it. However, the malware also pretends to be “made in China,” which researchers suggest is a false flag.
Last month, some security researchers suggested WannaCry was the work of North Korean hackers, while others suggested it didn’t fit North Korea’s style. Linguistic analysis threat intelligence firm Flashpoint performed on 28 WannaCry ransom notes revealed that the attackers were fluent Chinese speakers who also appeared to know English.
Unlike WannaCry, which spread through the EternalBlue Windows exploit, FakeCry uses a dropper saved on disk as wc.exe. The dropper can execute several commands: drop the ransomware component; begin encryption; begin decryption; <Key> (public key for encryption and private key for decryption); and demo (encryption or decryption with hardcoded RSA keys).
The ransomware component, on the other hand, can generate the RSA-2048 key pair, encrypt/decrypt files, encrypt/decrypt disk, and delete shadow copies on the infected machine. When executed, the malware first deletes shadow copies, then initializes keys, creates the file list for encryption, proceeds to encrypt files, and then shows the ransom window.
FakeCry targets around 170 file types to encrypt and can kill processes if they use targeted files, to unlock them. It uses the Handler Viewer Sysinternals tool to accomplish the task. The ransomware also contains a list of extensions that contains only image file types (jpg, jpeg, png, tif, gif, and bmp), and which the attackers can decrypt for free, researchers say.
The ransom note displayed by this ransomware is similar to that of WannaCry. The attackers demand 0.1 Bitcoin (around $260) and use the same wallet number for all infections (seven payments have been made so far to the wallet). The ransomware uses a Tor server for command and control.
“Unfortunately ExPetr/Petya was not the only ransomware that was distributed via MeDoc updates on June 27. In parallel, another ransomware, FakeCry, was also distributed to MeDoc users at exactly the same time as ExPetr/Petya. Our telemetry shows about 90 attacked organizations received the FakeCry ransomware, almost all in Ukraine,” Kaspersky notes.
Ukraine’s authorities this week announced they raided and seized M.E.Doc servers fearing that the cybercriminals behind the NotPetya attack might still have access to these resources. In an official announcement, they advised users to turn off all computers on which the M.E.Doc software is running and to change passwords and electronic digital signatures.
Given that both malware families were distributed through the same vector at the same time suggests they might be related. However, the security researchers have yet to establish a definitive connection between the two.