
Ransomware Articles - H 2020 1 2 3 4 5 6 7 8 9 10 11 Ransomware List - H 2021 2020 2019 2018 1 Ransomware blog Ransomware blog
Ukrainian cyberpolice seized MeDoc servers while hackers withdrawn Bitcoin from NotPetya wallet
5.7.2017 securityaffairs Ransomware
The Ukraine’s cyber police seized the MeDoc servers after detecting a new suspicious activity and fearing new malware-based attacks.
The Ukrainian authorities have seized equipment from the online accounting firm MeDoc which is suspected to have had a significant role in the recent NotPetya attack.
The Ukraine’s cyber police have seized the servers after detecting a new suspicious activity, the seizure is containment measure that was adopted to “immediately stop the uncontrolled proliferation” of malware.

According to the Associated Press’s Raphael Satter that quotes the Cyberpolice spokesperson Yulia Kvitko, the company’s systems had either sent or were ready to send out a new update that might have been compromised by hackers.
“Tax software firm M.E. Doc was raided to “immediately stop the uncontrolled proliferation” of malware. In a series of messages, Cyberpolice spokeswoman Yulia Kvitko suggested that M.E. Doc had sent or was preparing to send a new update and added that swift action had prevented any further damage.” states the AP. ““Our experts stopped (it) on time,” she said.”
MeDoc technical staff provided its equipment to the Ukraine Cyberpolice to allow further detailed analysis. While the Ukraine Cyberpolice is investigating the case, the authorities urge people stop using the MeDoc application. The experts suggest turning off any computers running the MeDoc software, change their login credentials and get new digital signatures.
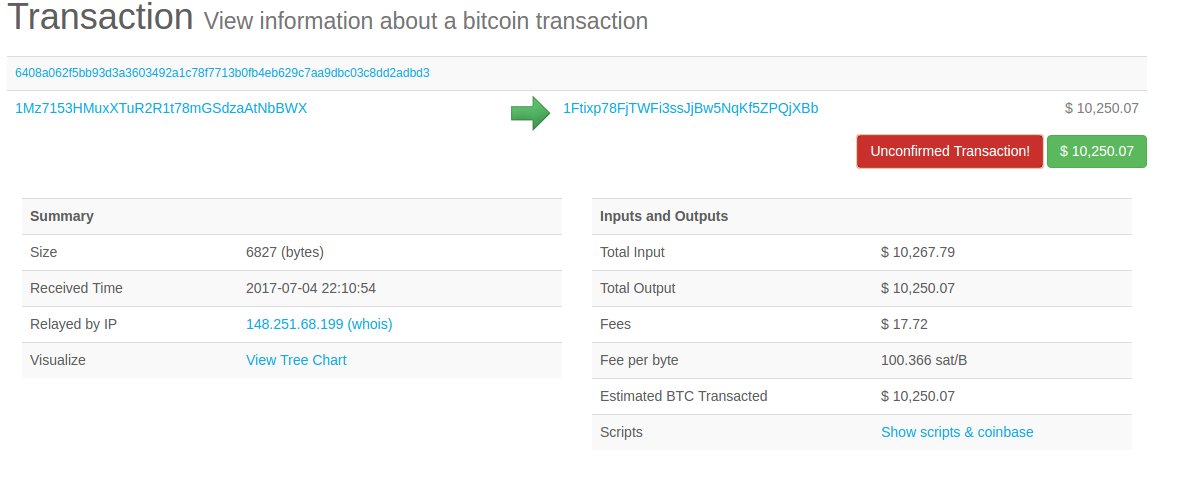
Back to the NotPetya massive attack, Kaspersky Lab analyst Aleks Gostev confirmed that alleged attackers cash out the sum paid by the victims, the Bitcoin collected in the original attack has been withdrawn.
codelancer @codelancer
And finally they withdraw everything ! Time to hunt, eh ? :) #notPetya money goes away
12:17 AM - 5 Jul 2017
9 9 Retweets 10 10 likes
Twitter Ads info and privacy
Roughly 3.96 Bitcoin ($10,382) was withdrawn from a wallet linked to NotPetya attack early on Wednesday morning.
Hackers used the money to pay for a Pastebin Pro account on the dark web, which was then used to post fresh ransomware drop instructions.
Follow
Kevin Beaumont ✔ @GossiTheDog
Haha the first Petya BitCoin transaction was to @pastebin for a Pastebin Pro account.
12:38 AM - 5 Jul 2017
11 11 Retweets 27 27 likes
Twitter Ads info and privacy
Follow
petya_payments @petya_payments
🚨 3.96983955 BTC ($10,381.86 USD) has just been withdrawn from a bitcoin wallet tied to #Petya ransomware https://blockchain.info/address/1Mz7153HMuxXTuR2R1t78mGSdzaAtNbBWX …
12:15 AM - 5 Jul 2017
170 170 Retweets 122 122 likes
Twitter Ads info and privacy
The AP closed its post reporting that Infrastructure Minister Volodymyr Omelyan told it his department had incurred “millions” in costs, with hundreds of workstations and two of its six servers knocked out.
Researchers Dissect Stealthy Backdoor Used by NotPetya Operators
5.7.2017 securityweek Ransomware
ESET security researchers have performed a detailed analysis of a stealthy backdoor used by the group behind the NotPetya destructive wiper and injected into the legitimate resources of tax accounting software M.E.Doc earlier this year.
Masquerading as ransomware, NotPetya was eventually found to be a wiper designed mainly to destroy data rather than hold it for ransom, and security researchers connected it to the persistent threat group TeleBots, which has launched several cyber-attacks against Ukraine before.
Previously referred to as BlackEnergy and Sandworm, the group allegedly compromised M.E.Doc earlier this year and injected their own code into one of the application’s modules. The malicious module was then pushed as an update to M.E.Doc clients and then used to distribute malware into the networks of these companies.
“It seems very unlikely that attackers could” inject a “very stealthy and cunning backdoor” into one of the software’s legitimate modules “without access to M.E.Doc’s source code,” ESET notes. Named ZvitPublishedObjects.dll, the backdoored module is written using the .NET Framework, is 5MB in size, and “contains a lot of legitimate code that can be called by other components, including the main M.E.Doc executable ezvit.exe.”
The malicious module was part of at least three updates released this year, on April 14, May 15, and June 22, yet M.E.Doc doesn’t appear to have been aware of the compromise, as several updates between April 24 and June 21 didn’t contain the backdoor. The malicious module was used for malware distribution at least twice: to drop the XData ransomware in May and NotPetya in June, ESET says.
“The main backdoor class is named MeCom and it is located in the ZvitPublishedObjects.Server namespace […]. The methods of the MeCom class are invoked by the IsNewUpdate method of UpdaterUtils in the ZvitPublishedObjects.Server namespace. The IsNewUpdate method is called periodically in order to check whether a new update is available,” ESET explains.
The attackers, ESET researchers say, knew exactly which organizations in Ukraine were using the backdoored M.E.Doc, courtesy of a unique legal entity identifier called the EDRPOU number that each company doing business in Ukraine has. Thus, the group could use tailored tactics against the computer network of the targeted organization, depending on their goals.
In addition to the EDRPOU numbers, the backdoor was used to collect proxy and email settings, including usernames and passwords, from the M.E.Doc application. The harvested information was written “into the Windows registry under the HKEY_CURRENT_USER\SOFTWARE\WC key using Cred and Prx value names.” These values can be used as evidence of compromise, ESET says.
The backdoor was using the M.E.Doc’s regular update check requests to the official M.E.Doc server upd.me-doc.com[.]ua to send the collected information in cookies. By not using external servers for command and control and not generating abnormal network traffic, the backdoor could remain completely hidden on the compromised networks.
Although forensic analysis on the M.E.Doc server wasn’t performed, ESET believes the server was compromised, especially since a PHP backdoor was found in a FTP directory on it. The researchers suggest that the attackers deployed on the server software allowing them to differentiate the requests coming from compromised machines.
The backdoor also includes code that allows the attackers to control the infected machines through a binary blob received via the official M.E.Doc server. After decryption and decompression, the binary reveals “an XML file that could contain several commands at once.”
“This remote control feature makes the backdoor a fully-featured cyberespionage and cybersabotage platform at the same time,” ESET notes.
Supported commands include RunCmd - shell command execution; DumpData - Base64 data decoding; MinInfo - information gathering (OS version, bitness (32 or 64), current privileges, UAC settings, proxy settings, email settings including login and password); GetFile - file collection; and Payload and AutoPayload - payload execution (as executable or as DLL - via rundll32.exe).
“As our analysis shows, this is a thoroughly well-planned and well-executed operation. We assume that the attackers had access to the M.E.Doc application source code. They had time to learn the code and incorporate a very stealthy and cunning backdoor. The size of the full M.E.Doc installation is about 1.5GB, and we have no way at this time to verify that there are no other injected backdoors,” ESET concludes.
The security researchers also note that further analysis is required to learn for how long the backdoor has been in use and whether the channel was used to push other commands and malware as well. They also note that there’s a possibility that the group might have compromised other software update supply chains but haven’t weaponized them yet.
In ExPetr/Petya’s shadow, FakeCry ransomware wave hits Ukraine
5.7.2017 Kaspersky Ransomware
FAKECRY RANSOMWARE
While the (cyber-)world was still shaking under the destructive ExPetr/Petya attack that hit on June 27, another ransomware attack targeting Ukraine at the same time went almost unnoticed.
So far, all theories regarding the spread of ExPetr/Petya point into two directions:
Distribution via trojanized updates to MeDoc users
Distribution via waterhole attacks in Ukrainian news websites (one case known)
While there is little doubt that MeDoc users were infected via malicious updates with ExPetr, it appears that ExPetr was not the only malware they received. Our telemetry confirms that MeDoc users received at least one other malicious program at the same time. This additional malware, which was run as “ed.exe” in the “MeDoc” program folder (eg. c:\programdata\medoc\medoc\ed.exe) was run on victim machines by the parent process ezvit.exe, a component of the MeDoc software. This suggests the delivery mechanism abused the same MeDoc updates vector as ExPetr.
The malware, which unsurprisingly, is also ransomware, is written in .NET and includes a “WNCRY” string, which obviously refers to the massive WannaCry epidemic that hit global businesses back in May 2017.
A “forgotten” PDB path inside also points to the project’s name being “WannaCry”:
Amusingly, in what we believe to be a false flag, it pretends to be “made in China”:
Based on the strings and the pretense that it’s WannaCry, we’ve decided to call this “FakeCry”.
FakeCry technical details
Sample:MD5: 0BDE638B274C7F9C6C356D3987ED1A2D
Size: 3,880,448 bytes
Compilation timestamp: Fri Jan 01 01:25:26 2016
First seen in the wild: 2017.06.27 12:34:00 (GMT)
Filename on disk: wc.exe
This program acts as a dropper for a ransomware module.
The dropper supports the following commands:
extract – drops the ransomware component
ed – begin encryption
dd – begin decryption
<Key>:
If ed is passed then it is a public key
If dd is passed then it is a private key
demo (encryption or decryption with hardcoded RSA keys)
The ransomware component has the following identification data:
MD5: 5C7C894A1CCFD8C8E0F174B0149A6601
Size: 442,880 bytes
Compilation timestamp: Fri Jan 01 01:20:53 2016
First seen in the wild: 2017.06.27 12:34:00 (GMT)
Filename on disk: ed.exe
The ransomware component supports the following command
genrsa – generate RSA-2048 key pair
Df – decrypt file
Dd – decrypt disk
ef- encrypt file
Ed – encrypt disk
delshadowcopies – delete shadow copies on machine
Example command line for the execution of the ransomware component:
exe -ed C:\ 3ds,uot,stw,sxw,ott,odt,pem,p12,csr,crt,key,pfx,der windows BgIAAACkAABSU0ExAAgA….
When run, the ransomware executes the following steps:
deletes shadow copies
initializes keys
creates file list for encryption
encrypts files
shows window with the ransom demand
Keys initialization process
The malware creates a RSA key pair for encryption. The private RSA key is encrypted with the attacker’s public RSA key, which is passed via arguments.
The generated, the public RSA key and encrypted private RSA key are stored in this registry key:
HKCU\Software\WC
File encryption process
List of extensions targeted for encryption:
doc,docx,xls,xlsx,ppt,pptx,pst,ost,msg,eml
vsd,vsdx,txt,csv,rtf,123,wks,wk1,pdf,dwg
onetoc2,snt,docb,docm,dot,dotm,dotx,xlsm,xlsb,xlw
xlt,xlm,xlc,xltx,xltm,pptm,pot,pps,ppsm,ppsx
ppam,potx,potm,edb,hwp,602,sxi,sti,sldx,sldm
sldm,vdi,vmdk,vmx,gpg,aes,ARC,PAQ,bz2,tbk
bak,tar,tgz,gz,7z,rar,zip,backup,iso,vcd
raw,cgm,tiff,nef,psd,ai,svg,djvu,m4u,m3u
mid,wma,flv,3g2,mkv,3gp,mp4,mov,avi,asf
mpeg,vob,mpg,wmv,fla,swf,wav,mp3,sh,class
jar,java,rb,asp,php,jsp,brd,sch,dch,dip
pl,vb,vbs,ps1,bat,cmd,js,asm,h,pas
cpp,c,cs,suo,sln,ldf,mdf,ibd,myi,myd
frm,odb,dbf,db,mdb,accdb,sql,sqlitedb,sqlite3,asc
lay6,lay,mml,sxm,otg,odg,uop,std,sxd,otp
odp,wb2,slk,dif,stc,sxc,ots,ods,3dm,max
3ds,uot,stw,sxw,ott,odt,pem,p12,csr,crt,key,pfx,der
If a file to be encrypted is locked by other processes, the ransomware can kill this process, using a Sysinternals tool (Handler Viewer) to accomplish the task.
The file encryption algorithm in a nutshell:
Attacker’s RSA public key is received by the ransomware via command line
“Session” RSA-2048 key-pair is generated
“Session” RSA private key is encrypted with public RSA key (which was received in point №1)
For each file, an AES-256 key and IV are generated
Key and IV are encrypted with generated “Session” RSA key and saved in the encrypted file
Interestingly, the ransomware contains a list of extensions called “DEMO_EXTENSIONS”. The attackers provide the claim that that the files from this DEMO_EXTENSION list (which contains only image file extensions – “jpg, jpeg, png, tif, gif, bmp”) will be decrypted for free, something that appears to be working as advertised.
Here’s a screenshot of the ransomware component running on a victim machine:
To decrypt the files, the attackers are asking for 0.1BTC, which is approximately 260$ at today’s exchange price. The wallet number is fixed, 13KBb1G7pkqcJcxpRHg387roBj2NX7Ufyf for all infections. Interestingly, the wallet has received seven payments so far, totalling 0.51 BTC. Most of the 0.1 payments took place on June 26, suggesting that was the day when the attack peaked. Interestingly, the attackers have withdrawn 0.41 BTC from the ransom account.
Transaction for wallet FakeCry
So far, there is no further activity on the receiving wallet 1FW1xW8kqNg4joJFyTnw6v5bXUNyzKXtTh.
To check the payment and receive the decryption key, the malware uses an Onion server as C2, which is “4gxdnocmhl2tzx3z[.]onion”.
Conclusions
Although the software company developing the MeDoc software has been so far denying all evidence that its users have been infected through malicious updates, our telemetry suggests that the vast majority of the ExPetr/Petya victims on June 27, 2017 were attacked this way.
Unfortunately ExPetr/Petya was not the only ransomware that was distributed via MeDoc updates on June 27. In parallel, another ransomware, FakeCry, was also distributed to MeDoc users at exactly the same time as ExPetr/Petya. Our telemetry shows about 90 attacked organizations received the FakeCry ransomware, almost all in Ukraine.
What makes FakeCry interesting is the fact that it appears to have been designed with false flags in mind. Its interface and messages closely emulate those of WannaCry, yet this is an entirely different malware. In what we believe to be a false flag, samples also include a “made in china” string.
Of course, one of the biggest questions here is if FakeCry and ExPetr are related. So far, the most important evidence that would suggest it, is the fact they were both distributed through MeDoc updates, at the same time.
As usual, our recommendations to protect against ransomware include:
Here’s our shortlist of recommendations on how to survive ransomware attacks:
Run a robust anti-malware suite with embedded anti-ransomware protection such as System Watcher from Kaspersky Internet Security.
Make sure you update Microsoft Windows and all third party software. It’s crucial to apply the MS17-010 bulletin immediately.
Do not run open attachments from untrusted sources.
Backup sensitive data to external storage and keep it offline.
Last but not least, never pay the ransom. Paying the ransom funds the next wave of attacks.
For sysadmins, our products detect the samples used in the attack by these verdicts:
UDS:DangerousObject.Multi.Generic
PDM:Trojan.Win32.Generic
Our behavior detection engine SystemWatcher detects the threat as:
PDM:Trojan.Win32.Generic
PDM:Exploit.Win32.Generic
NotPetya Connected to BlackEnergy/KillDisk: Researchers
3.7.2017 securityweek Ransomware
Last week’s devastating NotPetya attack might have been launched by the same threat group that previously used the Russia-linked BlackEnergy malware family in attacks against Ukraine, security researchers reveal.
Initially believed to be a ransomware incident employing the same distribution tools as WannaCry, the NotPetya malware eventually proved to be a disk wiper spreading with the sole purpose of damaging infected computers. Similar to WannaCry, NotPetya hit Windows 7 machines the most.
The malware eventually hit systems in more than 65 countries, but most of its victims are located in Ukraine. Of a total of less than 20,000 machines infected by NotPetya (also referred to as PetrWrap, exPetr, GoldenEye, and Diskcoder.C), more than 70% are in Ukraine, Microsoft says.
Late last week, security researchers also discovered the reason why Ukraine was hit the most: the attack was apparently launched by the same threat group that initiated numerous other attacks against the country’s power grid, mining and railway systems, and Ukrainian government organizations.
Dubbed TeleBots, the group was previously referred to as BlackEnergy or Sandworm Team. One of the tools associated with it is the KillDisk wiper that was packing ransomware capabilities in recent attacks, and which demanded a 222 Bitcoin ransom from its victims.
The NotPetya sample used in last week’s attack includes a series of similarities with the BlackEnergy and KillDisk malware families, Kaspersky Lab and ESET security researchers have discovered.
The list of targeted file extensions in NotPetya shows similarities to the list in a wiper the group was using in 2015, Kaspersky Lab reveals. The lists are similar in composition and formatting (stored in the same dot-separated formats), which suggests a possible link, the security researchers say.
According to Kaspersky, a Yara rule they created during analysis “fires on BlackEnergy and ExPetr samples only” when run on the company’s extensive malware collection. The strings used to create the rule can generate false positives when used alone, but “when combined together in this fashion, they become very precise,” the researchers say.
“Of course, this should not be considered a sign of a definitive link, but it does point to certain code design similarities between these malware families,” Kaspersky says.
ESET, on the other hand, appears more confident of the connection between TeleBots and NotPetya, and even suggests that this was the third major attack the group launched this year against Ukraine.
The first, they say, was launched in March and had as final payload a ransomware family detected as Filecoder.NKH. Tools used in the attack included the Python/TeleBot.A backdoor, a heavily obfuscated VBS backdoor, CredRaptor (password stealer), Plainpwd (modified Mimikatz to recover Windows credentials), and SysInternals’ PsExec (used for lateral movement). A Linux ransomware was used on non-Windows servers.
In late May, the group launched a second large ransomware attack against Ukraine, this time using a piece of malware known as XData (detected as Filecoder.AESNI.C). Five days into the attack, and 96% of the malware’s detections were in Ukraine, ESET was reporting on May 23.
The ransomware also packed code that allowed it to automatically move laterally within compromised networks: it featured an embedded Mimikatz DLL to extract Windows credentials, as well as SysInternals’ PsExec utility for spreading.
One month later, the group launched a third, more sophisticated ransomware attack against organizations in Ukraine. Borrowing code from last year’s Petya ransomware, the actors created a wiper and started using NSA-linked SMB exploits to maximize spreading capabilities.
“However, unlike the original Petya ransomware, Diskcoder.C’s authors modified the MBR code in such a way that recovery won’t be possible. Specifically, the attacker cannot provide a decryption key and the decryption key cannot be typed in the ransom screen, because the generated key contains non-acceptable characters,” ESET explains.
The initial infection vector in the NotPetya incident was the Ukrainian accounting software called MEDoc, the same as in the case of the XData attack. For the March attack, the group compromised another software company in Ukraine (not related to M.E. Doc), and gained access to the internal networks of several financial institutions using VPN tunnels.
“[The] Diskcoder.C outbreak suggests that the attackers had access to the update server of the legitimate software. Using access to this server, attackers pushed a malicious update that was applied automatically without user interaction. That’s why so many systems in Ukraine were affected by this attack,” ESET notes.
The security researchers also believe that M.E.Doc’s server, where they discovered a malicious PHP backdoor medoc_online.php in a FTP directory, might have been used as infection vector for other malware as well. Using malicious updates, the group supposedly deployed their own nefarious tools “in a stealthy way to computer networks that belong to high-value targets.”
The NotPetya ransomware is a Brick Through Your Windows
3.7.2017 securityaffairs Ransomware
The recent global outbreak of the “NotPetya” malware has some very curious features that have left security officials puzzled.
Despite the press coverage, NotPetya is not really a ransomware attack to hold your data hostage. It’s a killbot.
Several information security specialists have pointed a finger directly at Moscow; citing circumstantial evidence the source of NotPetya was the TELEBOTS group of hackers previously associated with attacks on Ukraine, in particular, the Ukraine power grid “BlackEnergy” attack. Others have noted the malware used features stolen from the US National Security Agency, specifically the EternalBlue exploit made famous by the previous WannaCry global ransomware attack.
First, the NotPetya attack does have components used by the Telebot attackers. According to Anton Cherepanov, a researcher at the Welivesecurity group, the NotPetya malware contains telltale clues in design that point toward the hacker group. Once executed, this ransomware-like design encrypts all files, except files located in the C:\Windows directory, using AES and RSA algorithms.
“As mentioned above, in the final stage of their attacks, the TeleBots attackers pushed ransomware using stolen Windows credentials and SysInternals’ PsExec. This new ransomware was detected by ESET products as Win32/Filecoder.NKH. Once executed, this ransomware encrypts all files (except files located in the C:\Windows directory) using AES-128 and RSA-1024 algorithms. The malware adds the .xcrypted file extension to already-encrypted files.” states the analysis published by ESET.
The malware deletes and overwrites the target files with a special software design called KillDisk. Telebot attackers have previously used the special KillDisk wiping system which appears inside NotPetya.
However, it is not just the KillDisk feature that points to the TELEBOT group. It is this feature combined with the poorly designed pay-off scheme inside NotPetya that indicates it is not ransomware at all but in fact a high-speed brick to destroy Windows data.
First, the NotPetya malware contains a single email address to contact the hacker which was quickly shut down in the first few hours of the attack. In addition, the Bitcoin area where the ransom was to be paid was easy to monitor, a very curious move by someone who wants to get money for crime. Finally, the data recovery section of the NotPetya malware was inoperable, leaving little chance of getting your data back even if the ransom was paid.
So, instead of being a kidnap your data scheme, NotPetya turned out to be a smash everything malware masquerading as a ransomware attack. Again, this charade of acting like a ransomware but actually being a destruction attack points toward the same MO (modus operandi) of the TELEBOT group.
While the NotPetya malware can use the stolen NSA EternalBlue exploit, which was later patched in a special Microsoft update, the prime method of spreading the attack was not the NSA software at all. Instead, NotPetya used common system features used inside some Microsoft networks to spread itself. One method is called PsExec, a light-weight telnet-replacement that lets you execute processes on other systems. PsExec is provided by Microsoft. The other method used by NotPetya is WMIC or Windows Management Instrumentation Command-line that is also provided by Microsoft.

The use of Microsoft-provided tools allowed NotPetya to spread undetected. The EternalBlue exploit has a known signature and can be detected by security and anti-virus software. Instead of drawing attention and perhaps even alerting the targets, the NotPetya designers utilized a special version of the Mimikatz tool to steal passwords and logins and then ran the PsExec and WMI software tools provided by Microsoft to move and replicate in a stealth fashion, undetected by anti-virus and security software.
“Specifically, the malware had an embedded Mimikatz DLL that it used to extract Windows account credentials from the memory of a compromised PC. With these credentials, the malware started to spread inside its host network using SysInternals’ PsExec utility.” continues the analysis.
The use of WMI and PsExec to move across a network is also a known signature of several malware designers including the TELEBOT group.
It is also clear the NotPetya software started with a very specific attack on the Ukraine. The initial attack was contained inside false updates tied to financial software used by the Ukraine called M.E.Doc. M.E.Doc software is one of only two software packages available for businesses have to pay their taxes in Ukraine. The attackers elected to concentrate against the M.E.Doc package because it appears they may have previously penetrated the small firm that distributed it and it was likely that a large number of users would have the software. Again, the intimate knowledge of Ukraine software updates and operations indicates that the TELEBOT group may have been the culprit.
However, what appears to not have been anticipated was that many of the Ukraine businesses included international partners with vulnerable connections on a global scale. The NotPetya virus spread through this international VPN and network connections to various companies around the globe including the US, UK, Australia, and Russia. It is this last nation-state attack by NotPetya that provided the awkward but convenient plausible deniability for Moscow that the malware wasn’t their doing.
This could be true since Moscow is known to work with a wide variety of hacker groups, some of which operate independently of Kremlin orders and often for their own profit. Russia employed such privateer hackers during the 2008 war against Georgia. The hackers were able to bring down a wide variety of Georgian targets including government communications and private companies which distributed power generators.
However, the privateers also were forced to live off the land so to speak. In order to finance many of the attacks, the groups utilized stolen US credit card information. The use of US money to finance an information warfare operation against Georgia did not sit well inside Washington and perhaps was one reason why the then Bush administration responded to deter Moscow from further combat.
It is not unfair to point out that other nations including the US, UK, China, and Israel have also been known to utilize privateer hackers for national security or nation-state style strikes. Many smaller nations which have limited resources in these areas have also employed private, often nefarious, hacker groups to penetrate political opponents, uncover leakers and distrust journalists. Sometimes when these attacks are revealed, the resulting scandal can damage the ruling party such as in the recent case of cyber attacks by the Mexican government.
However, the lack of pay-off for NotPetya to the designers shows at very worst it was a poorly designed nation-state attack that went out of control. Nation-state actors should take heed from the lessons of NotPetya and WannaCry. The fact is that software “weapons” can have collateral damage that extends far from the intended original target. Soft-warfare weapons are much like their bio-warfare cousins, they can spread and even attack the hand that created them.
US-CERT published an alert on the last variant of Petya ransomware, including countermeasures
2.7.2017 securityaffairs Ransomware
The Department of Homeland Security’s (DHS) US Computer Emergency Readiness Team (US-CERT) published the Alert (TA17-181A) on the Petya Ransomware.
The US-CERT urges organizations of updating their software and avoiding use unsupported applications and OSs.
The US-CERT confirmed it has received multiple reports of Petya ransomware infections related the recent massive attack. The ransomware leverages the ETERNALBLUE Exploit M2 MS17-010 to exploit vulnerabilities in Server Message Block (SMB) and makes devices unusable.
“The NCCIC Code Analysis Team produced a Malware Initial Findings Report (MIFR) to provide in-depth technical analysis of the malware. In coordination with public and private sector partners, NCCIC is also providing additional IOCs in comma-separated-value form for information sharing purposes.
Available Files:
MIFR-10130295.pdf
TA-17-181A_IOCs.csv
The scope of this Alert’s analysis is limited to the newest “Petya” variant that surfaced June 27, 2017, and this malware is referred to as “Petya” throughout this Alert.” states the alert.
“Based on initial reporting, this Petya campaign involves multiple methods of initial infection and propagation, including exploiting vulnerabilities in Server Message Block (SMB). “
The flaws exist in how the SMBv1 server handles certain requests, a remote attacker could execute code by sending specially crafted messages to [an SMBv1] server.
Experts at US-CERT that analyzed a sample of the last Petya ransomware discovered that this variant encrypts the victim’s files with a dynamically generated, 128-bit key and creates a unique ID of the victim. The experts haven’t found any link between the encryption key generation and the victim’s ID.
“However, there is no evidence of a relationship between the encryption key and the victim’s ID, which means it may not be possible for the attacker to decrypt the victim’s files even if the ransom is paid.” states the alerts.
“This Petya variant spreads using the SMB exploit as described in MS17-010 and by stealing the user’s Windows credentials. This variant of Petya is notable for installing a modified version of the Mimikatz tool, which can be used to obtain the user’s credentials. The stolen credentials can be used to access other systems on the network.”
The sample analyzed by the US-CERT will also attempt to identify other hosts on the network by checking the compromised system’s IP physical address mapping table.
The Petya variant writes a text file on the “C:\” drive containing the Bitcoin wallet address and the RSA keys for the ransom payment. The malicious code modifies the master boot record (MBR) to enable encryption of the master file table (MFT) and the original MBR, then it reboots the system to replace the MBR.
“Based on the encryption methods used, it appears unlikely that the files can be restored even if the attacker received the victim’s unique ID.”
The US-CERT suggests organizations following its best practices related to SMB, such as:
Disabling SMBv1
Blocking all versions of SMB at the network boundary by blocking TCP port 445 with related protocols on UDP ports 137-138 and TCP port 139, for all boundary devices.
“US-CERT cautions users and administrators that disabling or blocking SMB may create problems by obstructing access to shared files, data, or devices,” the agency states. “The benefits of mitigation should be weighed against potential disruptions to users.”

Below the complete list of recommended steps for prevention that was included in the alert:
Apply the Microsoft patch for the MS17-010 SMB vulnerability dated March 14, 2017.[5](link is external)
Enable strong spam filters to prevent phishing emails from reaching the end users and authenticate in-bound email using technologies like Sender Policy Framework (SPF), Domain Message Authentication Reporting and Conformance (DMARC), and DomainKeys Identified Mail (DKIM) to prevent email spoofing.
Scan all incoming and outgoing emails to detect threats and filter executable files from reaching the end users.
Ensure anti-virus and anti-malware solutions are set to automatically conduct regular scans.
Manage the use of privileged accounts. Implement the principle of least privilege. No users should be assigned administrative access unless absolutely needed. Those with a need for administrator accounts should only use them when necessary.
Configure access controls including file, directory, and network share permissions with least privilege in mind. If a user only needs to read specific files, they should not have write access to those files, directories, or shares.
Disable macro scripts from Microsoft Office files transmitted via email. Consider using Office Viewer software to open Microsoft Office files transmitted via email instead of full Office suite applications.
Develop, institute, and practice employee education programs for identifying scams, malicious links, and attempted social engineering.
Run regular penetration tests against the network, no less than once a year. Ideally, run these as often as possible and practical.
Test your backups to ensure they work correctly upon use.
Utilize host-based firewalls and block workstation-to-workstation communications.
From BlackEnergy to ExPetr
1.7.2017 Kaspersky Ransomware
A gut feeling of old acquaintances, new tools, and a common battleground
Much has been written about the recent ExPetr/NotPetya/Nyetya/Petya outbreak – you can read our findings here:Schroedinger’s Pet(ya) and ExPetr is a wiper, not ransomware.
As in the case of Wannacry, attribution is very difficult and finding links with previously known malware is challenging. In the case of Wannacry, Google’s Neel Mehta was able to identify a code fragment which became the most important clue in the story, and was later confirmed by further evidence, showing Wannacry as a pet project of the Lazarus group.
To date, nobody has been able to find any significant code sharing between ExPetr/Petya and older malware. Given our love for unsolved mysteries, we jumped right on it.
Analyzing the Similarities
At the beginning of the ExPetr outbreak, one of our team members pointed to the fact that the specific list of extensions used by ExPetr is very similar to the one used by BlackEnergy’s KillDisk ransomware from 2015 and 2016 (Anton Cherepanov from ESET made the same observation on Twitter).
The BlackEnergy APT is a sophisticated threat actor that is known to have used at least one zero day, coupled with destructive tools, and code geared towards attacking ICS systems. They are widely confirmed as the entity behind the Ukraine power grid attack from 2015 as well as a chain of other destructive attacks that plagued that country over the past years.
If you are interested in reading more about the BlackEnergy APT, be sure to check our previous blogs on the topic:
BE2 custom plugins, router abuse and target profiles
BE2 extraordinary plugins
BlackEnergy APT Attacks in Ukraine employ spearphishing with Word documents
Going back to the hunt for similarities, here’s how the targeted extensions lists looks in ExPetr and a version of a wiper used by the BE APT group in 2015:
ExPetr 2015 BlackEnergy wiper sample
3ds, .7z, .accdb, .ai, .asp, .aspx, .avhd, .back, .bak, .c, .cfg, .conf, .cpp, .cs, .ctl, .dbf, .disk, .djvu, .doc, .docx, .dwg, .eml, .fdb, .gz, .h, .hdd, .kdbx, .mail, .mdb, .msg, .nrg, .ora, .ost, .ova, .ovf, .pdf, .php, .pmf, .ppt, .pptx, .pst, .pvi, .py, .pyc, .rar, .rtf, .sln, .sql, .tar, .vbox, .vbs, .vcb, .vdi, .vfd, .vmc, .vmdk, .vmsd, .vmx, .vsdx, .vsv, .work, .xls
.3ds, .7z, .accdb, .accdc, .ai, .asp, .aspx, .avhd, .back, .bak, .bin, .bkf, .cer, .cfg, .conf, .crl, .crt, .csr, .csv, .dat, .db3, .db4, .dbc, .dbf, .dbx, .djvu, .doc, .docx, .dr, .dwg, .dxf, .edb, .eml, .fdb, .gdb, .git, .gz, .hdd, .ib, .ibz, .io, .jar, .jpeg, .jpg, .jrs, .js, .kdbx, .key, .mail, .max, .mdb, .mdbx, .mdf, .mkv, .mlk, .mp3, .msi, .my, .myd, .nsn, .oda, .ost, .ovf, .p7b, .p7c, .p7r, .pd, .pdf, .pem, .pfx, .php, .pio, .piz, .png, .ppt, .pptx, .ps, .ps1, .pst, .pvi, .pvk, .py, .pyc, .rar, .rb, .rtf, .sdb, .sdf, .sh, .sl3, .spc, .sql, .sqlite, .sqlite3, .tar, .tiff, .vbk, .vbm, .vbox, .vcb, .vdi, .vfd, .vhd, .vhdx, .vmc, .vmdk, .vmem, .vmfx, .vmsd, .vmx, .vmxf, .vsd, .vsdx, .vsv, .wav, .wdb, .xls, .xlsx, .xvd, .zip
Obviously, the lists are similar in composition and formatting, but not identical. Moreover, older versions of the BE destructive module have even longer lists. Here’s a snippet of an extensions list from a 2015 BE sample that is even longer:
Nevertheless, the lists were similar in the sense of being stored in the same dot-separated formats. Although this indicated a possible link, we wondered if we could find more similarities, especially in the code of older variants of BlackEnergy and ExPetr.
We continued to chase that hunch during the frenetic early analysis phase and shared this gut feeling of a similarity between ExPetr and BlackEnergy with our friends at Palo Alto Networks. Together, we tried to build a list of features that we could use to make a YARA rule to detect both ExPetr and BlackEnergy wipers.
During the analysis, we focused on the similar extensions list and the code responsible for parsing the file system for encryption or wiping. Here’s the code responsible for checking the extensions to target in the current version of ExPetr:
This works by going through the target file system in a recursive way, then checking if the extension for each file is included in the dot-separated list. Unfortunately for our theory, the way this is implemented in older BlackEnergy variants is quite different; the code is more generic and the list of extensions to target is initialized at the beginning, and passed down to the recursive disk listing function.
Instead, we took the results of automated code comparisons and paired them down to a signature that perfectly fit the mould of both in the hope of unearthing similarities. What we came up with is a combination of generic code and interesting strings that we put together into a cohesive rule to single out both BlackEnergy KillDisk components and ExPetr samples. The main example of this generic code is the inlined wcscmp function merged by the compiler’s optimization, meant to check if the filename is the current folder, which is named “.”. Of course, this code is pretty generic and can appear in other programs that recursively list files. It’s inclusion alongside a similar extension list makes it of particular interest to us –but remains a low confidence indicator.
Looking further, we identified some other candidate strings which, although not unique, when combined together allow us to fingerprint the binaries from our case in a more precise way. These include:
exe /r /f
ComSpec
InitiateSystemShutdown
When put together with the wcscmp inlined code that checks on the filename, we get the following YARA rule:
rule blackenergy_and_petya_similarities {
strings:
//shutdown.exe /r /f
$bytes00 = { 73 00 68 00 75 00 74 00 64 00 6f 00 77 00 6e 00 2e 00 65 00 78 00 65 00 }
//ComSpec
$bytes01 = { 43 00 6f 00 6d 00 53 00 70 00 65 00 63 00 }
//InitiateSystemShutdown
$bytes02 = { 49 6e 69 74 69 61 74 65 53 79 73 74 65 6d 53 68 75 74 64 6f 77 6e 45 78 57}
//68A4430110 push 0100143A4 ;’ntdll.dll’
//FF151CD10010 call GetModuleHandleA
//3BC7 cmp eax,edi
//7420 jz …
$bytes03 = { 68 ?? ?? ?1 ?0 ff 15 ?? ?? ?? ?0 3b c7 74 ?? }
// “/c”
$bytes04 = { 2f 00 63 00 }
//wcscmp(…
$hex_string = { b9 ?? ?? ?1 ?0 8d 44 24 ?c 66 8b 10 66 3b 11 75 1e 66
85 d2 74 15 66 8b 50 02 66 3b 51 02 75 0f 83 c0 04 83 c1 04 66 85 d2 75
de 33 c0 eb 05 1b c0 83 d8 ff 85 c0 0f 84 ?? 0? 00 00 b9 ?? ?? ?1 ?0 8d
44 24 ?c 66 8b 10 66 3b 11 75 1e 66 85 d2 74 15 66 8b 50 02 66 3b 51 02
75 0f 83 c0 04 83 c1 04 66 85 d2 75 de 33 c0 eb 05 1b c0 83 d8 ff 85 c0
0f 84 ?? 0? 00 00 }
condition:
((uint16(0) == 0x5A4D)) and (filesize < 5000000) and
(all of them)
}
rule blackenergy_and_petya_similarities {
strings:
//shutdown.exe /r /f
$bytes00 = { 73 00 68 00 75 00 74 00 64 00 6f 00 77 00 6e 00 2e 00 65 00 78 00 65 00 }
//ComSpec
$bytes01 = { 43 00 6f 00 6d 00 53 00 70 00 65 00 63 00 }
//InitiateSystemShutdown
$bytes02 = { 49 6e 69 74 69 61 74 65 53 79 73 74 65 6d 53 68 75 74 64 6f 77 6e 45 78 57}
//68A4430110 push 0100143A4 ;’ntdll.dll’
//FF151CD10010 call GetModuleHandleA
//3BC7 cmp eax,edi
//7420 jz …
$bytes03 = { 68 ?? ?? ?1 ?0 ff 15 ?? ?? ?? ?0 3b c7 74 ?? }
// “/c”
$bytes04 = { 2f 00 63 00 }
//wcscmp(…
$hex_string = { b9 ?? ?? ?1 ?0 8d 44 24 ?c 66 8b 10 66 3b 11 75 1e 66
85 d2 74 15 66 8b 50 02 66 3b 51 02 75 0f 83 c0 04 83 c1 04 66 85 d2 75
de 33 c0 eb 05 1b c0 83 d8 ff 85 c0 0f 84 ?? 0? 00 00 b9 ?? ?? ?1 ?0 8d
44 24 ?c 66 8b 10 66 3b 11 75 1e 66 85 d2 74 15 66 8b 50 02 66 3b 51 02
75 0f 83 c0 04 83 c1 04 66 85 d2 75 de 33 c0 eb 05 1b c0 83 d8 ff 85 c0
0f 84 ?? 0? 00 00 }
condition:
((uint16(0) == 0x5A4D)) and (filesize < 5000000) and
(all of them)
}
When run on our extensive (read: very big) malware collection, the YARA rule above fires on BlackEnergy and ExPetr samples only. Unsurprisingly, when used alone, each string can generate false positives or catch other unrelated malware. However, when combined together in this fashion, they become very precise. The technique of grouping generic or popular strings together into unique combinations is one of the most effective methods for writing powerful Yara rules.
Of course, this should not be considered a sign of a definitive link, but it does point to certain code design similarities between these malware families.
This low confidence but persistent hunch is what motivates us to ask other researchers around the world to join us in investigating these similarities and attempt to discover more facts about the origin of ExPetr/Petya. Looking back at other high profile cases, such as the Bangladesh Bank Heist or Wannacry, there were few facts linking them to the Lazarus group. In time, more evidence appeared and allowed us, and others, to link them together with high confidence. Further research can be crucial to connecting the dots, or, disproving these theories.
We’d like to think of this ongoing research as an opportunity for an open invitation to the larger security community to help nail down (or disprove) the link between BlackEnergy and ExPetr/Petya. Our colleagues at ESET have published their own excellent analysis suggesting a possible link between ExPetr/Petya and TeleBots (BlackEnergy). Be sure to check out their analysis. And as mentioned before, a special thanks to our friends at Palo Alto for their contributions on clustering BlackEnergy samples.
Hashes
ExPetr:
027cc450ef5f8c5f653329641ec1fed91f694e0d229928963b30f6b0d7d3a745
BE:
11b7b8a7965b52ebb213b023b6772dd2c76c66893fc96a18a9a33c8cf125af80
5d2b1abc7c35de73375dd54a4ec5f0b060ca80a1831dac46ad411b4fe4eac4c6
F52869474834be5a6b5df7f8f0c46cbc7e9b22fa5cb30bee0f363ec6eb056b95
368d5c536832b843c6de2513baf7b11bcafea1647c65df7b6f2648840fa50f75
A6a167e214acd34b4084237ba7f6476d2e999849281aa5b1b3f92138c7d91c7a
Edbc90c217eebabb7a9b618163716f430098202e904ddc16ce9db994c6509310
F9f3374d89baf1878854f1700c8d5a2e5cf40de36071d97c6b9ff6b55d837fca
Microsoft Tackles Ransomware with Controlled Folder Access
1.7.2017 securityweek Ransomware
In the wake of global malicious attacks such as WannaCry and NotPetya, Microsoft this week announced a new feature meant to keep users’ data safe from ransomware and other type of malware.
Dubbed Controlled folder access, the feature was included as a new option in the Windows Defender Security Center in Windows 10 Insider Preview Build 16232 for PC, and should become available for all users in the Windows 10 Fall Creators Update release, set to arrive sometime in October-November 2017.
This week, Microsoft also announced that the Fall Creators Update will make the Enhanced Mitigation Experience Toolkit (EMET) native to Windows 10, providing users with additional protection against exploits and other types of threats.
“In [Windows 10 Insider Preview Build 16232], we’re making it easier for you to protect valuable data from malicious apps and threats, such as ransomware. To enable the feature, search for and open the Windows Defender Security Center from Start, go to the Virus & threat protection settings section, and set the switch to On,” Dona Sarkar, Software Engineer, Windows and Devices Group, notes in a blog post.
The new feature, Sarkar explains, is meant to monitor the changes applications make to files in certain protected folders and blacklists any app that attempts to make such modifications, while also notifying the user on the action taken.
There will be a default list of folders included in the option (such as Documents, Pictures, Movies, and Desktop), but users will have the possibility to add more locations to the list. However, they won’t be able to modify the default list.
Users who don’t store their files in the default Windows libraries will certainly find the option to add more folders to the protected list a handy option.
“Click Protected folders in the Controlled folder access area and enter the full path of the folder you want to monitor. You can also enter network shares and mapped drives, but environment variables and wildcards are not supported (for right now),” Sarkar notes.
Controlled folder access should provide users with an extra layer of security in addition to the defenses already built into Windows 10. However, it users shouldn’t rely solely on it when it comes to data protection. Using a multi-layered approach to security is a better practice, as cybercriminals are constantly adapting in an attempt to bypass even the most sophisticated defenses.
Windows 10 to Get Built-in Protection Against Most Ransomware Attacks
30.6.2017 thehackernews Ransomware
Ransomware Ransomware Everywhere Not a Single Place to Hide!
But, Microsoft has a simple solution to this problem to protect millions of its users against most ransomware attacks.
Two massive ransomware attacks — WannaCry and Petya (also known as NotPetya) — in a month have caused chaos and disruption worldwide, forcing hospitals, ATMs, shipping companies, governments, airports and car companies to shut down their operations.
Most ransomware in the market, including WannaCry and NotPetya, are specifically designed to target computers running Windows operating system, which is why Microsoft has been blamed for not putting proper defensive measures in place to prevent such threats.
But not now!
In the wake of recent devastating global ransomware outbreaks, Microsoft has finally realized that its Windows operating system is deadly vulnerable to ransomware and other emerging threats that specifically targets its platform.
To tackle this serious issue, the tech giant has introduced a new anti-ransomware feature in its latest Windows 10 Insider Preview Build (16232) yesterday evening, along with several other security features.
Microsoft is planning to introduce these security features in Windows 10 Creator Update (also known as RedStone 3), which is expected to release sometime between September and October 2017.
The anti-ransomware feature, dubbed Controlled Folder Access, is part of Windows Defender that blocks unauthorized applications from making any modifications to your important files located in certain "protected" folders.
Applications on a whitelist can only access Protected folders. So you can add or remove the apps from the list. Certain applications will be whitelisted automatically, though the company doesn't specify which applications.
Once turned on, "Controlled folder access" will watch over files stored inside Protected folders and any attempt to access or modify a protected file by non-whitelisted apps will be blocked by Windows Defender, preventing most ransomware to encrypt your important files.
So, whenever an application tries to make changes to Protected files but is blacklisted by the feature, you will get a notification about the attempt.
How to Enable Controlled Folder Access, Whitelist Apps and Add or Remove Protected Folders
Here's how to enable the Controlled folder access feature:
Go to Start menu and Open the Windows Defender Security Center
Go to the Virus & Threat Protection settings section
Set the switch to On
Here's how to allow apps that you trust is being blocked by the Controlled folder access feature to access Protected folders:
Go to Start menu and Open the Windows Defender Security Center
Go to the Virus & Threat Protection settings section
Click 'Allow an app through Controlled folder access' in the Controlled folder access area
Click 'Add an allowed app' and select the app you want to allow
Windows library folders like Documents, Pictures, Movies, and Desktop are designated as being compulsorily "protected" by default, which can not be removed.
However, users can add or remove their personal folders to the list of protected folders. Here's how to add folders to Protected folders list:
Go to Start menu and Open the Windows Defender Security Center
Go to the Virus & Threat Protection settings section
Click 'Protected folders' in the Controlled folder access area
Enter the full path of the folder you want to monitor
Users can also enter network shares and mapped drives, but environment variables and wildcards are not supported at this moment.
Other Security Feature Introduced in Windows 10 Insider Program
With the release of Windows 10 Insider Preview Build 16232, Windows Defender Application Guard (WDAG) for Edge — a new system for running Microsoft Edge in a special virtual machine in order to protect the OS from browser-based flaws — also received improvements in usability.
Windows 10 Insider Preview Build also comes with support for Microsoft Edge data persistence when using WDAG.
"Once enabled, data such as your favorites, cookies, and saved passwords will be persisted across Application Guard sessions," Microsoft explains.
"The persisted data will be not be shared or surfaced on the host, but it will be available for future Microsoft Edge in Application Guard sessions."
Another new security feature called Exploit Protection has been introduced in Windows 10 16232, which blocks cyber attacks even when security patches are not available for them, which means the feature will be useful particularly in the case of zero-day vulnerabilities.
Exploit Protection works without Microsoft's Windows Defender Antivirus tool, but you can find the feature in Windows Defender Security Center → App & Browser Control → Exploit Protection.
In the Fall Creators Update for Windows 10, Microsoft has also planned to use a broad range of data from Redmond's cloud services, including Azure, Endpoint, and Office, to create an AI-driven Antivirus (Advanced Threat Protection) that can pick up on malware behavior and protect other PCs running the operating system.
Also, we reported about Microsoft's plan to build its EMET or Enhanced Mitigation Experience Toolkit into the kernel of the upcoming Windows 10 to boost the security of your PC against complex threats such as zero-day vulnerabilities.
Also, the company is planning to remove the SMBv1 (Server Message Block version 1) — a 30-year-old file sharing protocol which came to light last month after the devastating WannaCry outbreak — from the upcoming Windows 10 (1709) Redstone 3 Update.
Besides this, some other changes and improvements have also been introduced with the release, along with patches for several known issues.
NotPetya – Ukraine secret service announces a joint investigation with Europol, FBI, and NCA
30.6.2017 securityaffairs Ransomware
Ukraine secret service announces joint investigation with Europol, FBI, and NCA to attribute the recent Notpetya massive attack.
While security experts are investigating real motivation behind the massive NotPetya attack, Ukrainian authorities called for support in the investigation from European and US intelligence and law enforcement agencies.
The country’s security service SBU announced the international co-operation Europol, the FBI, and England’s National Crime Agency to investigate the incident and identify offenders.
Ukraine is the country with the largest number of NotPetya infections, a large number of critical infrastructure was affected in the attack.
According to the analysis conducted by Kaspersky, more than 50% of businesses targeted by NotPetya are industrial companies.

The SBU considers the NotPetya attack an “act of cyberterrorism”, the joint investigation aims to attribute the attack to a specific threat actor.
“The SBU specialists in cooperation with the experts of FBI USA, NCA of Great Britain, Europol and also leading cyber security institutions, conduct coordinated joint events on localization of damaging software PetyaA distribution, final definition of methods of this act of cyberterrorism, establishing of the attack sources, its executors, organizers and paymasters.” states the announcement from the SBU. “Currently the mechanisms of virus program distribution, its activation and operation algorithms are already identified. At the same time the work on the search of possibilities for data decoding and groundwork of guidelines for prevention of virus distribution, neutralization of other negative consequences of this emergency is in process.”
The analysis conducted by many security firms suggest that Ukraine was a possible target of the attack.
According to experts from Cisco Talos Intelligence and Microsoft, the infection started in Ukraine, where local firm named MeDoc was targeted by attackers. Researchers believe that hackers infected software update to a Ukrainian tax accounting system called MeDoc, but MeDoc denies the allegations.
“At the time of updating the program, the system could not be infected with the virus directly from the update file,” translated version of MeDoc post reads. “We can argue that users of the MEDoc system can not infect their PC with viruses at the time of updating the program.”
However, several security researchers and even Microsoft agreed with Talo’s finding, saying MeDoc was breached and the virus was spread via updates.
“Initial infection appears to involve a software supply-chain threat involving the Ukrainian company M.E.Doc, which develops tax accounting software, MEDoc. Although this vector was speculated at length by news media and security researchers—including Ukraine’s own Cyber Police—there was only circumstantial evidence for this vector. Microsoft now has evidence that a few active infections of the ransomware initially started from the legitimate MEDoc updater process. ” states Microsoft.
Let me close with interesting hints from the investigation conducted by F-Secure:
“How does it compare to WannaCry (which also used these exploits)?
WannaCry clearly picked these exploits up after the Shadow Brokers dumped them into the public domain in April. Also, WannaCry didn’t do the best job at implementing these exploits correctly.
By comparison, this “Petya” looks well-implemented, and seems to have seen plenty of testing. It’s fully-baked.”
“But are you still skeptical about this malware being “nation state”?”
“Less and less so. We don’t think any current attribution is rock solid (attribution never really is). We feel this is definitely worth deeper investigation. And more pizza.
We’ve changed our minds on some of our earlier conclusions. Please note this if you’re reading any previous F-Secure analysis. And, of course, this is subject to further revision, as new facts come to light.
But the great mystery behind the attack is why the author of the malware failed to add proper decryption functionality to the MBR lock screen. It is not clear if it is an intentional choice or a clamorous mistake.
How to stop Petya?
When a computer is infected with Petya it will automatically attempt to reboot in order to encrypt the hard drive’s Master Boot Record. To block the malware it is necessary to halt the reboot and keep the PC running. Another way to immunize the machine consists of creating a read-only file “perfc” and placing it inside the Windows directory.
“If you’re lucky, Petya worm might see that file and will not encrypt your machine, BUT, it will continue to spread to other machines on the same network.” reads the analysis published PureVPN.
Original Author of Petya Ransomware is Back & He Wants to Help NotPetya Victims
29.6.2017 thehackernews Ransomware
The author of original Petya ransomware is back.
After a long 6 months of silence, the author of now infamous Petya ransomware appeared on Twitter today to help victims unlock their files encrypted by a new version of Petya, also known as NotPetya.
"We're back having a look in NotPetya," tweeted Janus, a name Petya creator previously chose for himself from a James Bond villain. "Maybe it's crackable with our privkey. Please upload the first 1MB of an infected device, that would help."
This statement made by Petya author suggests he may have held on a master decryption key, which if worked for the new variant of Petya infected files, victims would be able to decrypt their files locked in the recent cyber outcry.
Janus sold Petya as a Ransomware-as-a-Service (RaaS) to other hackers in March 2016, and like any regular ransomware, original Petya was designed to lock victim's computer, then return them when a ransom is paid.
This means anyone could launch the Petya ransomware attack with just the click of a button, encrypt anyone's system and demand a ransom to unlock it. If the victim pays, Janus gets a cut of the payment. But in December, he went silent.
However, On Tuesday, computer systems of the nation's critical infrastructure and corporates in Ukraine and 64 other countries were struck by a global cyber attack, which was similar to the WannaCry outbreak that crippled tens of thousands of systems worldwide.
Initially, a new variant of Petya ransomware, NotPetya, was blamed for infecting systems worldwide, but later, the NotPetya story took an interesting turn.
Yesterday, it researchers found that NotPetya is not a ransomware, rather it's a wiper malware that wipes systems outright, destroying all records from the targeted systems.
NotPetya also uses NSA's leaked Windows hacking exploit EternalBlue and EternalRomance to rapidly spread within the network, and WMIC and PSEXEC tools to remotely execute malware on the machines.
Experts even believe the real attack has been disguised to divert world's attention from a state-sponsored attack to a malware outbreak.
The source code to Petya has never been leaked, but some researchers are still trying hard to reverse engineer to find possible solutions.
Would this Really Help Victims?
Since Janus is examining the new code and even if his master key succeeds in decrypting victims’ hard drive's master file table (MFT), it won't be of much help until researchers find a way to repair MBR, which is wiped off by NotPetya without keeping any copy.
Tuesday's cyber outbreak is believed to be bigger than WannaCry, causing disaster to many critical infrastructures, including bricking computers at a Ukrainian power company, several banks in Ukraine, and the country's Kyiv Boryspil International Airport.
The NotPetya also canceled surgeries at two Pittsburgh-area hospitals, hit computers at the pharmaceutical company Merck and the law firm DLA Piper, as well as infected computers at the Dutch shipping company A.P. Moller-Maersk forced to shut down some container terminals in seaports from Los Angeles to Mumbai.
NotPetya - Destructive Wiper Disguised as Ransomware
29.6.2017 securityweek Ransomware
NotPetya/GoldenEye Malware Overwrites Master Boot Record
The Petya/NotPetya ransomware used in the global attack ongoing for the past two days was in fact hiding a wiper and was clearly aimed at data destruction, security researchers have discovered.
The attack started on June 27, with the largest number of victims being reported in Ukraine, where it apparently originated from. Within hours, the outbreak hit around 65 countries worldwide, including Belgium, Brazil, France, Germany, India, Russia, and the United States.
The attack would spread within local networks through various tools, including Mimikatz for credential gathering, and the EternalBlue exploit (also used by WannaCry), the EternalRomance exploit (Microsoft released patches for both in March), and WMIC (Windows Management Instrumentation Commandline) and PSExec for lateral movement.
The initial infection vector was the hijacked updater process of tax accounting software MEDoc, but researchers also discovered that the website of Ukrainian City of Bahmut might have been hacked and used to serve the malware as well.
Soon after the outbreak began, however, security researchers noticed that NotPetya wasn’t following the same rules as normal ransomware does when it comes to the payment process, and started sounding the alarm: an easy-to-block email address was used, a single Bitcoin address was hardcoded in the malware, and the payment process was rather counter-intuitive. The attackers weren’t seeking financial gains, multiple researchers said yesterday.
“A number of us in the security community are debating if the Petya attack on 27 June wasn’t a targeted attack on Ukraine, disguised as a ransomware attack on any organization caught up in the method used for infection,” Travis Farral, Director of Security Strategy at Anomali, told SecurityWeek in an emailed statement.
“There are details that support such a theory. The attackers behind the ransomware haven’t experienced much ROI despite the broad impact of the attack, they set up a weak payment process, launched the attack just prior to Ukraine’s Constitution Day and leveraged a malware family named for the pet name of Ukrainian President, Petro Poroshenko,” Farral continued.
During a phone call with SecurityWeek on Wednesday, Bitdefender senior e-threat analyst Bogdan Botezatu suggested that the attack might have had as final purpose data destruction rather than financial gains, and it didn’t take long for Matt Suiche, Microsoft MVP and founder of Comae Technologies, to reach the same conclusion.
“The ransomware was a lure for the media, this version of Petya actually wipes the first sectors of the disk like we have seen with malwares such as Shamoon,” Suiche says.
He reveals that, while the original Petya was meant to encrypt the Master Boot Record (MBR) and demand ransom to decrypt it, the malware used in this attack, which was referred to as Petya.A, Petrwrap, NotPetya, exPetr, and GoldenEye, is in fact overwriting MBR sectors without saving them elsewhere.
“We noticed that the current implemented that massively infected multiple entities Ukraine was in fact a wiper which just trashed the 25 first sector blocks of the disk,” Suiche says. The malware, he continues, “does permanent and irreversible damages to the disk.”
Comae also discovered that the attackers implemented a function to unconditionally wipe the first 10 sectors if two conditions were met: the hash command computed from a running process name (unknown so far) returned 0x2E214B44; the function that replaces the actual MBR returns an error (which should counter EDR trying to prevent bootloader modifications).
According to Kryptos Logic security researcher MalwareTech, however, the sectors that NotPetya overwrites in this attack don’t contain data at all. The malware supposedly saves the original first sector (MBR) elsewhere, but trashes the next 24 sectors.
“The 24 sectors following the MBR are completely empty on any standard Windows installation. […] Essentially on any standard Windows operating system there is nothing between sector 1 and sector 64,” the researcher points out.
Russian security firm Kaspersky Lab also reached the conclusion that the NotPetya campaign wasn’t designed as a ransomware attack, as everyone believed in the first place. Instead, it was “designed as a wiper pretending to be ransomware,” Kaspersky’s Anton Ivanov and Orkhan Mamedov explain in a recent blog post.
The first thing the researchers noticed was that the ransomware is actually generating random data when pretending to generate the installation ID showed to the victim. Without a valid ID, the attackers can’t decrypt the victims’ files.
“That means that the attacker cannot extract any decryption information from such a randomly generated string displayed on the victim, and as a result, the victims will not be able to decrypt any of the encrypted disks using the installation ID,” Kaspersky says.
On the one hand, this means that victims can’t restore their data even if they pay the ransom. On the other, it reinforces the idea that the main goal of the attack “was not financially motivated, but destructive.”
“The fact of pretending to be a ransomware while being in fact a nation state attack — especially since WannaCry proved that widely spread ransomware aren’t financially profitable — is in our opinion a very subtle way from the attacker to control the narrative of the attack,” Suiche notes.
“Perhaps this attack was never intended to make money, rather to simply disrupt a large number of Ukrainian organizations. Launching an attack that would wipe victim hard drives would achieve the same effect, however, that would be an overtly aggressive action. Effectively wiping hard drives through the pretense of ransomware confuses the issue,” Gavin O'Gorman, Symantec Security Response, points out.
Avira reveals that computers with Russian or Ukrainian language settings were impacted the most. The company also notes that the attack affected mostly older Windows systems running Windows 7 SP1, but that Windows 8 systems were affected as well.
Affected users are advised to refrain from paying the ransom as that would by no means help them decrypt their data. This advice is particularly true for the NotPetya incident, as the attackers have no means to restore victims’ data.
“Do not pay. You will not only be financing criminals, but it is unlikely that you will regain access to your files,” Europol notes. “Disconnect the infected device from the internet. If the infected device is part of a network, try to isolate it as soon as possible, in order to prevent the infection from spreading to other machines,” the agency continues.
ExPetr/Petya/NotPetya is a Wiper, Not Ransomware
29.6.2017 Kaspersky Ransomware
DATA ENCRYPTION PETYA RANSOMWARE WIPER
After an analysis of the encryption routine of the malware used in the Petya/ExPetr attacks, we have thought that the threat actor cannot decrypt victims’ disk, even if a payment was made.
This supports the theory that this malware campaign was not designed as a ransomware attack for financial gain. Instead, it appears it was designed as a wiper pretending to be ransomware.
Below the technical details are presented. First, in order to decrypt victim’s disk the attackers need the installation ID:
In previous versions of “similar” ransomware like Petya/Mischa/GoldenEye, this installation ID contains crucial information for the key recovery. After sending this information to the attacker they can extract the decryption key using their private key.
Here’s how this installation ID is generated in the ExPetr ransomware:
This installation ID in our test case is built using the CryptGenRandom function, which is basically generating random data.
The following buffer contains the randomly generated data in an encoded “BASE58” format:
If we compare this randomly generated data and the final installation ID shown in the first screen, they are the same. In a normal setup, this string should contain encrypted information that will be used to restore the decryption key. For ExPetr, the ID shown in the ransom screen is just plain random data.
That means that the attacker cannot extract any decryption information from such a randomly generated string displayed on the victim, and as a result, the victims will not be able to decrypt any of the encrypted disks using the installation ID.
What does it mean? Well, first of all, this is the worst-case news for the victims – even if they pay the ransom they will not get their data back. Secondly, this reinforces the theory that the main goal of the ExPetr attack was not financially motivated, but destructive.
Our friend Matt Suiche from Comae Technologies independently came to the same conclusion.
Turns Out New Petya is Not a Ransomware, It’s a Destructive Wiper Malware
29.6.2017 thehackernews Ransomware
What if I say the Tuesday's devastating global malware outbreak was not due to any ransomware infection?
Yes, the Petya ransomware attacks that began infecting computers in several countries, including Russia, Ukraine, France, India and the United States on Tuesday and demands $300 ransom was not designed with the intention of restoring the computers at all.
According to a new analysis, the virus was designed to look like ransomware but was wiper malware that wipes computers outright, destroying all records from the targeted systems.
Comae Technologies Founder Matt Suiche, who closely looked the operation of the malware, said after analyzing the virus, known as Petya, his team found that it was a "Wiper malware," not ransomware.
Security experts even believe the real attack has been disguised to divert world's attention from a state-sponsored attack on Ukraine to a malware outbreak.
"We believe the ransomware was, in fact, a lure to control the media narrative, especially after the WannaCry incident, to attract the attention on some mysterious hacker group rather than a national state attacker," Suiche writes.
Is Petya Ransomware Faulty or Over-Smart?
Petya is a nasty piece of malware that, unlike other traditional ransomware, does not encrypt files on a targeted system one by one.
Instead, Petya reboots victims computers and encrypts the hard drive's master file table (MFT) and renders the master boot record (MBR) inoperable, restricting access to the full system by seizing information about file names, sizes, and location on the physical disk.
Then Petya ransomware takes an encrypted copy of MBR and replaces it with its own malicious code that displays a ransom note, leaving computers unable to boot.
However, this new variant of Petya does not keep a copy of replaced MBR, mistakenly or purposely, leaving infected computers unbootable even if victims get the decryption keys.
Also, after infecting one machine, the Petya ransomware scans the local network and quickly infects all other machines (even fully-patched) on the same network, using EternalBlue SMB exploit, WMIC and PSEXEC tools.
Don't Pay Ransom; You Wouldn’t Get Your Files Back
So far, nearly 45 victims have already paid total $10,500 in Bitcoins in hope to get their locked files back, but unfortunately, they would not.
It's because the email address, which was being set-up by the attackers to communicate with victims and send decryption keys, was suspended by the German provider shortly after the outbreak.
Meaning, even if victims do pay the ransom, they will never recover their files. Kaspersky researchers also said same.
"Our analysis indicates there is little hope for victims to recover their data. We have analyzed the high-level code of the encryption routine, and we have figured out that after disk encryption, the threat actor could not decrypt victims’ disks," the security firm said.
"To decrypt a victim’s disk threat actors need the installation ID. In previous versions of 'similar' ransomware like Petya/Mischa/GoldenEye this installation ID contained the information necessary for key recovery."
If claims made by the researcher is correct that the new variant of Petya is a destructive malware designed to shut down and disrupt services around the world, the malware has successfully done its job.
However, it is still speculation, but the virus primarily and massively targeted multiple entities in Ukraine, including the country's local metro, Kiev's Boryspil airport, electricity supplier, the central bank, and the state telecom.
Other countries infected by the Petya virus included Russia, France, Spain, India, China, the United States, Brazil, Chile, Argentina, Turkey and South Korea.
How Did Petya get into the Computers in the First Place?
According to research conducted by Talos Intelligence, little-known Ukrainian firm MeDoc is likely the primary source of the yesterday's global ransomware outbreak.
Researchers said the virus has possibly been spread through a malicious software update to a Ukrainian tax accounting system called MeDoc, though MeDoc has denied the allegations in a lengthy Facebook post.
"At the time of updating the program, the system could not be infected with the virus directly from the update file," translated version of MeDoc post reads. "We can argue that users of the MEDoc system can not infect their PC with viruses at the time of updating the program."
However, several security researchers and even Microsoft agreed with Talo's finding, saying MeDoc was breached and the virus was spread via updates.
Petya/NotPetya: What We Know in the First 24 Hours
28.6.2017 securityweek Ransomware
Petya/NotPetya Ransomware May Not be a Financially Motivated Attack, Researchers Say
The Petya/NotPetya outbreak that originated in Ukraine on Tuesday but spread globally within hours might have been more than a financially motivated ransomware incident, security researchers suggest.
The attack caught security researchers’ attention because the same EternalBlue SMB exploit employed by WannaCry was used to spread to new machines, and because of the fast pace at which reports of infections started to emerge worldwide.
The malware used in this attack, however, wasn’t WannaCry, but a variant of the Petya ransomware that first emerged in March 2016. Also referred to as Petya.A, Petrwrap, NotPetya, exPetr, and GoldenEye, this Petya variant features a different encryption algorithm implementation than before and is targeting different file types than previously observed variations.
While the exact number of victims isn’t known at the moment, Kaspersky Lab has already confirmed over 2,000 attacks, most of which occurred in Ukraine. During a phone call, Bitdefender’s senior e-threat analyst Bogdan Botezatu confirmed to SecurityWeek that Ukraine was hit the most: “We’ve seen some hits in other countries, but Ukraine was ravaged.”
The Petya/NotPetya attack hit a total of 65 countries, including Belgium, Brazil, Germany, Russia, and the United States, Microsoft reveals. In Ukraine, more than 12,500 machines were affected by the ransomware attack, the tech giant says.
The attack hit Ukraine central bank, government computers, airports, the Kiev metro, the state power distributor Ukrenergo, Chernobyl’s radiation monitoring system, and other machines in the country. It also affected Russian oil giant Rosneft, DLA Piper law firm, U.S. biopharmaceutical giant Merck, British advertiser WPP, and Danish shipping and energy company Maersk, among others.
Jury still out on initial infection vector
What Botezatu couldn’t confirm as of now was the initial infection vector. “We know how the ransomware moves within a network once it has compromised a machine, but we can’t find evidence of the initial infection vector,” he said.
While Microsoft and Cisco suggest that the legitimate updater process of tax accounting software MEDoc was compromised and used as the initial infection vector, the Ukrainian company has already denied the allegations [Ukrainian], and Bitdefender says they confirmed breaches in organizations that don’t use the software.
Kryptos Logic suggests that a zero-day vulnerability might have been used, given that Petya/NotPetya is limited to spreading only to computers in internal networks, and because a spam campaign wouldn’t be as effective.
“We believe to reach such a velocity, this can accomplished by attacking update systems or software packages with 0-day vulnerabilities,” the company says.
Spam email was also considered a possibility, but “likely [wasn’t] responsible for the large number of public sector organizations hit in Ukraine,” a Kryptos Logic security researcher going by the name of MalwareTech says.
According to Costin Raiu, director of Global Research and Analysis Team at Kaspersky Lab, the website of Ukrainian City of Bahmut (Бахмут) might have been used as a secondary initial infection vector after being hacked and repurposed to serve the malware.
Encryption starts within an hour
The Petya/NotPetya variant used in this attack wouldn’t start encrypting infected computers immediately, but would wait for up to 60 minutes before doing so. However, given that the malware reboots the machine before starting the encryption, the delay window is supposedly used for credential gathering and network scanning operations.
“There appears to be a significant delay between running the malware and the beginning of the encryption process. Given that the malware reboots the machine, this is almost certainly to allow a reasonable amount of time to propagate across networks,” Forcepoint points out.
What fully set Petya/NotPetya apart from previous variants was the use of several tools for lateral movement. In addition to a modified EternalBlue exploit, the malware employs the EternalRomance exploit, Mimikatz for credential gathering, and WMIC (Windows Management Instrumentation Commandline) and PSExec for spreading within the compromised network.
The use of several tools allows the ransomware to compromise even up-to-date systems, and reports of companies that patched against EternalBlue but still got infected already emerged. As long as a single computer in the network is compromised, the malware can spread to the remaining ones, it seems.
“Once the ransomware has valid credentials, it scans the local network to establish valid connections on ports tcp/139 and tcp/445. A special behavior is reserved for Domain Controllers or servers: this ransomware attempts calls DhcpEnumSubnets() to enumerate DCP subnets all hosts on all DHCP subnets before scanning for tcp/139 and tcp/445 services. If it gets a response, the malware attempts to copy a binary on the remote machine using regular file-transfer functionalities with stolen credentials. It then tries to execute remotely the malware using either PSEXEC or WMIC tools,” Microsoft explains.
As soon as the encryption process starts, the machine is rebooted and the user is informed that the disk is being checked for errors. The same tactic was used by previous Petya variants: the malware would encrypt the Master Boot Record (MBR) while pretending to perform a check disk operation.
Petya/NotPetya uses an AES-128 key to encrypt all targeted files. It then encrypts the AES-128 with the attacker’s public RSA-2048 key and saves it to a README file. Because both keys are securely generated, this solid encryption scheme prevents researchers from creating decryption tools for the malware, “unless a subtle implementation mistake has been made,” Kaspersky says.
Paying not an option to recover files
While this has been said over and over again, it can’t be truer than in Petya/NotPetya’s case: paying is by no means a valid option. The main reason for this is that the attacker no longer has access to the “wowsmith123456@posteo.net” email address listed in the ransom note.
Midway through Tuesday, soon after learning that the email address was being used as part of a malware attack, Posteo decided to block the account straight away. The action is part of the company’s policy of not tolerating the misuse of its platform.
“Since midday it is no longer possible for the blackmailers to access the email account or send emails. Sending emails to the account is no longer possible either,” Posteo notes in a blog post.
While this seems like a logical step to take when encountering email accounts used for nefarious purposes, Posteo’s action certainly did more to hurt victims than help them, as they can no longer contact the attackers to ask for the decryption keys in exchange of payment proof.
The Bitcoin address the attackers ask victims to pay the ransom to already shows 43 transactions and 3.87408155 Bitcoin received, most probably in payments. Petya/NotPetya demands a $300 ransom from its victims.
Not a financially motivated attack
Despite using ransomware, the attack might not have been financially motivated, but rather aimed at data destruction or data theft, security researchers suggest.
“Many companies may be tempted to pay the ransom to get their systems back online. In this outbreak, it appears that the attackers never even attempted to be able to restore files to victims,” IBM’s Diana Kelley notes.
Bogdan Botezatu too notes that this campaign “might not have targeted financial gains but rather data destruction.” He further explains that the use of “a regular, non-bulletproof e-mail service provider,” is the first piece of evidence that the attackers weren’t really interested in getting paid.
Botezatu also told SecurityWeek that there are signs suggesting that the attack was initially targeted at specific companies, but became a global incident after getting out of hand.
He also cites “the lack of automation in the payment & key retrieval process” that “makes it really difficult for the attacking party to honor their end of the promise,” and the fact that the chosen payment confirmation option is rather difficult: “the user has to manually type an extremely long, mixed case “personal installation key” + “wallet” [which] is prone to typos.”
According to Recorded Future, there are reports that the Loki Bot information stealer might have been used in this attack as a secondary payload, suggesting that data theft could have been the purpose of the outbreak.
"Vaccine" available
Unlike the WannaCry outbreak, which was slowed down when a security researcher registered a kill-switch domain, no such option is available in Petya/NotPetya case. However, a vaccine is available, supposedly effective in preventing the ransomware from infecting compromised machines.
Discovered by Cybereason Principal Security Researcher Amit Serper, the vaccine involves the creation of a file named perfc (with no extension name) in the C:\Windows\ folder. Other security researchers also confirmed the finding.
Petwrap Ransomware massive attack – 24 hours later
28.6.2017 securityaffairs Ransomware
A new strain of the infamous Petya ransomware dubbed Petwrap, is infecting computers in different states, mostly in Ukraine and Russia.
This is the second massive ransomware-based attack in a few weeks, like WannaCry, the Petwrap ransomware exploits the MS17-010 SMB Remote Code Execution, so-called Eternal Blue, that Microsoft patched in March 2017.
Banks, financial institutions, businesses, energy firms, telecoms and systems in critical infrastructure were infected by the malware, among the victims the giant Maersk that confirmed the attack in an official statement on its Web site:
“We can confirm that Maersk IT systems are down across multiple sites and business units due to a cyber attack.”
Petwrap
Kaspersky telemetry on Petya ransomware
The “Eternal Blue” exploit was developed by the US National Security Agency, its code was leaked and in April by the hacker group Shadow Brokers.
Analyzis conducted by experts revealed that Petwrap also used other tricks to spread inside target networks.
According to the experts at Russian security firm Group-IB, the malware leverages a tool called “LSADump,” which can be used to collect login credentials from Windows computers and domain controllers on the network.
Follow
Group-IB @GroupIB_GIB
New #Petya uses #LSADump to get Admin password and infect all network. There is no need for #EternalBlue vulnerable PCs. #infosec
8:43 PM - 27 Jun 2017
40 40 Retweets 23 23 likes
Twitter Ads info and privacy
While I was writing, there is also news about illustrious victims in the US such as the global law firm DLA Piper that experienced severe issues at its systems.
Which is the attackers’ motivation?
According to security experts the attack presents various anomalies that led the experts into believing that hackers operated for sabotage.
According to Nicholas Weaver, a security researcher at the International Computer Science Institute Petya has been designed to be destructive while masquerading as a ransomware malware.
Weaver highlighted numerous anomalies in the ransomware-based attack, such as the use of a single Bitcoin address for every victim and the fact that the Petwrap operators urge victims to communicate with the them via an email address, while most of ransomware require victims to use Tor for communications.
“I’m willing to say with at least moderate confidence that this was a deliberate, malicious, destructive attack or perhaps a test disguised as ransomware,” states the Weaver’s comment published by Brian Krebs said. “The best way to put it is that Petya’s payment infrastructure is a fecal theater.”
Let me suggest to give a look at Yara rules and IOCs published by Kaspersky in the following analysis:
Schroedinger’s Pet(ya)
Shifr RaaS lets create a simple ransomware with just 3 steps
28.6.2017 securityaffairs Ransomware
Over the weekend, security experts discovered a new Ransomware-as-a-Service dubbed Shifr RaaS that allows creating a ransomware compiling 3 form fields.
Ransomware represents a profitable business for crooks, it is normal that the offer of Ransomware-as-a-Service (RaaS) will continue its success in the cyber criminal ecosystem.
Over the weekend, several security experts discovered a new Ransomware-as-a-Service website that allows wannabe cyber criminals to create their own ransomware just by filling in three form fields.
The website was hosted on the Dark Web and customers can pay their ransomware in Bitcoin.

This is probably one of the easiest-to-use RaaS websites, the ransomware was dubbed Shifr due to the extension it appends to the encrypted files and is written in Go.
“We’ve called it Shifr based on the extension it adds to encrypted files, but G Data security researcher Karsten Hahn has told Bleeping Computer that an initial analysis of this new threat reveals clues that Shifr might be related to Trojan.Encoder.6491, the first ever ransomware written in Go, discovered last year by Dr.Web security researchers.” states a blog post published by BleepingComputer.
The process for the creation of the Shifr ransomware is simple, wannabe criminals have to provide the size of the ransom demanded by the malware, a Bitcoin address to handle victims’ payments and then they have to solve a CAPTCHA challenge and press a button.
“While other RaaS portals will ask for an entry fee or verify their clients to ensure only skilled crooks (and not security researchers) get their hands on ransomware samples, this service offers a fully weaponized sample in a few easy steps.” states Catalin Cimpanu from BleepingComputer.
After the deployment of the service, users started submitting Shifr samples to VirusTotal and many antivirus makers are currently detecting them as a threat.
Differently, from other RaaS services, operators behind Shifr maintain for them just 10% of the fee, it nothing is we consider that operators behind the Cerber RaaS keep for them 60% share.
We cannot exclude in this phase that the Shifr RaaS is a scam and that operators will not pay distributors their cuts.
The unique certainly is that the ransomware is not sophisticated and lack of many features, a circumstance that suggests it could be a work in progress project.
The researchers, for example, noticed that the crooks used the same servers to host the payment portal and the RaaS service, it isn’t a good practice.
It is quite easy to predict the rapid diffusion of RaaS services in the next month.
Schroedinger’s Pet(ya)
28.6.2017 Kaspersky Ransomware
DATA ENCRYPTION MALWARE DESCRIPTIONS MBR PETYA RANSOMWARE VULNERABILITIES AND EXPLOITS
Earlier today (June 27th), we received reports about a new wave of ransomware attacks spreading around the world, primarily targeting businesses in Ukraine, Russia and Western Europe. If you were one of the unfortunate victims, this screen might look familiar:
Kaspersky Lab solutions successfully stop the attack through the System Watcher component. This technology protects against ransomware attacks by monitoring system changes and rolling back any potentially destructive actions.
At this time, our telemetry indicates more than 2,000 attacks:
Our investigation is ongoing and our findings are far from final at this time. Despite rampant public speculation, the following is what we can confirm from our independent analysis:
How does the ransomware spread?
To capture credentials for spreading, the ransomware uses custom tools, a la Mimikatz. These extract credentials from the lsass.exe process. After extraction, credentials are passed to PsExec tools or WMIC for distribution inside a network.
Other observed infection vectors include:
A modified EternalBlue exploit, also used by WannaCry.
The EternalRomance exploit – a remote code execution exploit targeting Windows XP to Windows 2008 systems over TCP port 445 (Note: patched with MS17-010).
An attack against the update mechanism of a third-party Ukrainian software product called MeDoc.
IMPORTANT: A single infected system on the network possessing administrative credentials is capable of spreading this infection to all the other computers through WMI or PSEXEC.
What does the ransomware do?
The malware waits for 10-60 minutes after the infection to reboot the system. Reboot is scheduled using system facilities with “at” or “schtasks” and “shutdown.exe” tools.
Once it reboots, it starts to encrypt the MFT table in NTFS partitions, overwriting the MBR with a customized loader with a ransom note. More details on the ransom note below.
Network survey
The malware enumerates all network adapters, all known server names via NetBIOS and also retrieves the list of current DHCP leases, if available. Each and every IP on the local network and each server found is checked for open TCP ports 445 and 139. Those machines that have these ports open are then attacked with one of the methods described above.
Password extraction
Resources 1 and 2 of malware binary contain two versions of a standalone tool (32-bit and 64-bit) that tries to extract logins and passwords of logged on users. The tool is run by the main binary. All extracted data is transferred back to the main module via a named pipe with a random GUID-like name.
File Decryption
Are there any hopes of decrypting files for victims already infected? Unfortunately, the ransomware uses a standard, solid encryption scheme so this appears unlikely unless a subtle implementation mistake has been made. The following specifics apply to the encryption mechanism:
For all files, one AES-128 key is generated.
This AES key is encrypted with threat actors’ public RSA-2048 key.
Encrypted AES keys are saved to a README file.
Keys are securely generated.
The criminals behind this attack are asking for $300 in Bitcoins to deliver the key that decrypts the ransomed data, payable to a unified Bitcoin account. Unlike Wannacry, this technique would work because the attackers are asking the victims to send their wallet numbers by e-mail to “wowsmith123456@posteo.net”, thus confirming the transactions. We have seen reports this email account has already been shut down, effectively making the full chain decryption for existing victims impossible at this time.
At the time of writing, the Bitcoin wallet has accrued 24 transactions totalling 2.54 BTC or just under $6,000 USD.
Here’s our shortlist of recommendations on how to survive ransomware attacks:
Run a robust anti-malware suite with embedded anti-ransomware protection such as System Watcher from Kaspersky Internet Security.
Make sure you update Microsoft Windows and all third party software. It’s crucial to apply the MS17-010 bulletin immediately.
Do not run open attachments from untrusted sources.
Backup sensitive data to external storage and keep it offline.
For sysadmins, our products detect the samples used in the attack by these verdicts:
Trojan-Ransom.Win32.PetrWrap.d
HEUR:Trojan-Ransom.Win32.PetrWrap.d
PDM:Trojan.Win32.Generic
UDS: DangerousObject.Multi.Generic
Intrusion.Win.MS17-010.e
IOCs
71B6A493388E7D0B40C83CE903BC6B04
0df7179693755b810403a972f4466afb
42b2ff216d14c2c8387c8eabfb1ab7d0
E595c02185d8e12be347915865270cca
e285b6ce047015943e685e6638bd837e
Yara rules
rule ransomware_PetrWrap {
meta:
copyright = "Kaspersky Lab"
description = "Rule to detect PetrWrap ransomware samples"
last_modified = "2017-06-27"
author = "Kaspersky Lab"
hash = "71B6A493388E7D0B40C83CE903BC6B04"
version = "1.0"
strings:
$a1 = "MIIBCgKCAQEAxP/VqKc0yLe9JhVqFMQGwUITO6WpXWnKSNQAYT0O65Cr8PjIQInTeHkXEjfO2n2JmURWV/uHB0ZrlQ/wcYJBwLhQ9EqJ3iDqmN19Oo7NtyEUmbYmopcq+YLIBZzQ2ZTK0A2DtX4GRKxEEFLCy7vP12EYOPXknVy/+mf0JFWixz29QiTf5oLu15wVLONCuEibGaNNpgq+CXsPwfITDbDDmdrRIiUEUw6o3pt5pNOskfOJbMan2TZu" fullword wide
$a2 = ".3ds.7z.accdb.ai.asp.aspx.avhd.back.bak.c.cfg.conf.cpp.cs.ctl.dbf.disk.djvu.doc.docx.dwg.eml.fdb.gz.h.hdd.kdbx.mail.mdb.msg.nrg.ora.ost.ova.ovf.pdf.php.pmf.ppt.pptx.pst.pvi.py.pyc.rar.rtf.sln.sql.tar.vbox.vbs.vcb.vdi.vfd.vmc.vmdk.vmsd.vmx.vsdx.vsv.work.xls" fullword wide
$a3 = "DESTROY ALL OF YOUR DATA! PLEASE ENSURE THAT YOUR POWER CABLE IS PLUGGED" fullword ascii
$a4 = "1Mz7153HMuxXTuR2R1t78mGSdzaAtNbBWX" fullword ascii
$a5 = "wowsmith123456@posteo.net." fullword wide
condition:
uint16(0) == 0x5A4D and
filesize < 1000000 and any of them }
A new massive attack allegedly based on Petwrap #ransomware hits organizations in several states
27.6.2017 securityaffairs Ransomware
A new wave of cyber attacks is shocking the IT industry, a massive attack leveraging the Petwrap ransomware has infected systems across the world.
A new wave of cyber attacks is shocking the IT industry, a few weeks after the WannaCry massive attack, security experts are facing a new threat that is rapidly spreading.
Once again it is a ransomware that is infecting computers worldwide making chaos, systems at banks, power suppliers and businesses in Europe, Russia, Ukraine, and India have been targeted by Petwrap.
The Petwrap ransomware is a variant of the notorious Petya ransomware that encrypts files demanding $300 in bitcoins to the victims.
Like WannaCry, also Petwrap exploits the Windows SMBv1 vulnerability and the effects appear to be serious on a large scale highlighting the poor level of security of computers worldwide.
According to the security researchers Matt Suiche, founder of cyber security firm Comae Technologies, the malware use the same attack vector exploited by EternalBlue and the accompanying DoublePulsar rootkit.

Matthieu Suiche ✔ @msuiche
Byata builds SMBv1 headers in its code. This smells like ETERNALBLUE/DOUBLEPULSAR all over again. Will confirm shortly.
4:34 PM - 27 Jun 2017
32 32 Retweets 24 24 likes
Twitter Ads info and privacy
Unlike other ransomware, Petya does not encrypt files on the infected systems but targets the hard drive’s master file table (MFT) and renders the master boot record (MBR) inoperable.
Petya locks the access to the users’ data by encrypting the master file table (MFT) and replaces the computer’s MBR with its own malicious code that displays the ransom note.
Petya overwrites the MBR of the hard drive causing Windows to crash. When the victim tries to reboot the PC, it will impossible to load the OS, even in Safe Mode.
Below the ransom note that was displayed by the Petwrap ransomware:
“If you see this text, then your files are no longer accessible, because they are encrypted. Perhaps you are busy looking for a way to recover your files, but don’t waste your time. Nobody can recover your files without our decryption service.”

Another bad news is that currently, only a small portion of antivirus is able to detect the threat, according to VirusTotal, only 15 out of 61 anti-virus services are able to detect Petwrap.
News of attacks on financial institutions are circulating on the internet, the National Bank of Ukraine (NBU) is one of the victims of the ransomware.
The Perwrap ransomware has infected systems at Russian state-owned oil company Rosneft, while Ukrainian state electricity suppliers, “Kyivenergo” and “Ukrenergo,” were also targeted by the malware.
“We were attacked. Two hours ago, we had to turn off all our computers. We are waiting for permission from Ukraine’s Security Service (SBU) to switch them back on,” Kyivenergo’s press service said.
Many systems were infected in Ukraine, Ukrainian branch’s mining company Evraz also confirmed the infections along with the Ukraine’s local metro ,and Kiev’s Boryspil Airport.

Kyiv Metro Alerts @kyivmetroalerts
Друзі! Оплата банківськими картками наразі неможлива.
Хакерська атака. https://ain.ua/2017/06/27/kievenergo-i-ukrainskie-banki-podverglis-xakerskoj-atake …
2:00 PM - 27 Jun 2017
Photo published for «Киевэнерго» и украинские банки подверглись хакерской атаке
«Киевэнерго» и украинские банки подверглись хакерской атаке
Компьютерные сети энергокомпании 'Киевэнерго' пострадали от хакерской атаки. Компьютеры компании оказались заражены вирусом, подобным WannaCry. Об этом сообщает 'Интерфакс' со ссылкой на заявление...
ain.ua
79 79 Retweets 27 27 likes
Twitter Ads info and privacy
The giant logistic company Maersk was also targeted by the malware in a serious way.

Maersk @Maersk
2:35 PM - 27 Jun 2017
138 138 Retweets 56 56 likes
Twitter Ads info and privacy
At least three Ukrainian telecommunication operators, LifeCell, Kyivstar, Ukrtelecom, have also reported Petwrap ransomware infections.
While I was writing, different opinions about the threat are circulating on the Internet,
Kaspersky Lab malware analyst Vyacheslav Zakorzhevsky declared that infections were traced to a “new ransomware we haven’t seen before.Stay Tuned.
Petya Ransomware Spreading Rapidly Worldwide, Just Like WannaCry
27.6.2017 thehackernews Ransomware
Watch out, readers! It is ransomware, another WannaCry, another wide-spread attack.
The WannaCry ransomware is not dead yet and another large scale ransomware attack is making chaos worldwide, shutting down computers at corporates, power supplies, and banks across Russia, Ukraine, Spain, France, UK, India, and Europe and demanding demands $300 in bitcoins.
According to multiple sources, a new variant of Petya ransomware, also known as Petwrap, is spreading rapidly with the help of same Windows SMBv1 vulnerability that the WannaCry ransomware abused to infect 300,000 systems and servers worldwide in just 72 hours.
Petya is a nasty piece of ransomware and works very differently from any other ransomware malware. Unlike other traditional ransomware, Petya does not encrypt files on a targeted system one by one.
Instead, Petya reboots victims computers and encrypts the hard drive's master file table (MFT) and rendering the master boot record (MBR) inoperable, restricting access to the full system by seizing information about file names, sizes, and location on the physical disk.
Petya replaces the computer's MBR with its own malicious code that displays the ransom note and leaves computers unable to boot.
Petya! Petya! Another Worldwide Ransomware Attack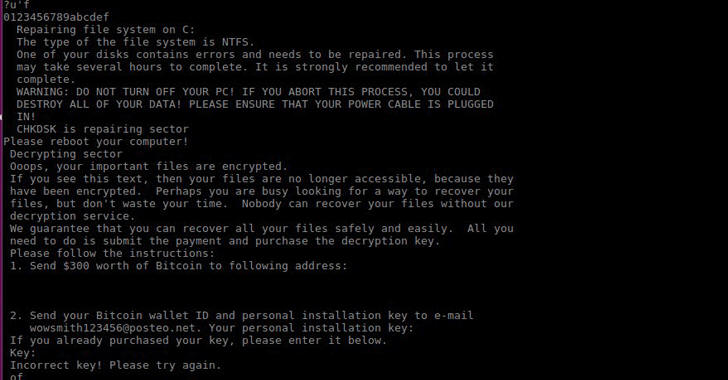
Screenshots of the latest Petya infection shared on Twitter shows that the ransomware displays a text, demanding $300 worth of Bitcoins. Here's what the text read:
"If you see this text, then your files are no longer accessible, because they are encrypted. Perhaps you are busy looking for a way to recover your files, but don't waste your time. Nobody can recover your files without our decryption service."
According to a recent VirusTotal scan, currently, only 13 out of 61 anti-virus services are successfully detecting the Petya virus.
Affected Power Companies:
Petya ransomware has already infected -- Russian state-owned oil giant Rosneft, Ukrainian state electricity suppliers, "Kyivenergo" and "Ukrenergo," in past few hours.
"We were attacked. Two hours ago, we had to turn off all our computers. We are waiting for permission from Ukraine's Security Service (SBU) to switch them back on," Kyivenergo's press service said.
Affected Banks and Financial Institutions:
There are reports from several banks, including National Bank of Ukraine (NBU), Oschadbank; and companies that they have been hit by the Petya ransomware attacks.
Affected Businesses:
Maersk, an international logistics company, has also confined on Twitter that the latest Petya attacks have shut down its IT systems at multiple locations and business units.
"We can confirm that Maersk IT systems are down across multiple sites and business units. We are currently asserting the situation. The safety of our employees, our operations and customers' business is our top priority. We will update when we have more information," the company said.
The ransomware also impacts multiple workstations at Ukrainian branch's mining company Evraz.
The most severe damages reported by Ukrainian businesses also include compromised systems at Ukraine's local metro, and Kiev's Boryspil Airport.
Affected Telecommunication Industry:
Three Ukrainian telecommunication operators, Kyivstar, LifeCell, Ukrtelecom, have also affected in the latest Petya attack.
Petya Victims Are Paying for Unlocking Files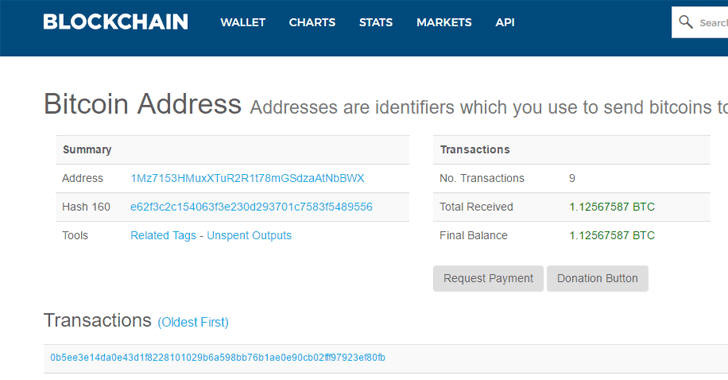
At the time of writing, 9 victims have paid in Bitcoin to '1Mz7153HMuxXTuR2R1t78mGSdzaAtNbBWX' address for decrypting their files infected by Petya, which total roughly $2700.
How Petya Ransomware Spreading So Fast?
So far, it is not yet confirmed that what's the reason behind the sudden rapid spreading of Petya, but security researchers on Twitter are arguing that like WannaCry, Petya is also exploiting SMBv1 EternalBlue exploit and taking advantage of unpatched Windows machines.
"Petya ransomware successful in spreading because it combines both a client-side attack (CVE-2017-0199) and a network based threat (MS17-010)" HackerFantastic tweeted, security researcher.
EternalBlue, a Windows SMB exploit leaked by the infamous hacking group Shadow Brokers in its April data dump, who claimed to have stolen it from the US intelligence agency NSA, along with other Windows exploits.
Microsoft has since patched the vulnerability for all versions of Windows operating systems, but many users remain vulnerable, and a string of malware variants are exploiting the flaw to deliver ransomware and mine cryptocurrency.
Just three days ago, we reported about the latest WannaCry attacks that hit Honda Motor Company and around 55 speed and traffic light cameras in Japan and Australia, respectively.
Well, it is quite surprising that even after knowing about the WannaCry issue for quite a decent amount of time, big corporates and companies have not yet implemented proper security measures to defend against the threat.
How to Protect Yourself from Ransomware attack
What to do immediately? Go and apply those goddamn patches against EternalBlue (MS17-010) and disable the unsecured, 30-year-old SMBv1 file-sharing protocol on your Windows systems and servers.
To safeguard against any ransomware infection, you should always be suspicious of unwanted files and documents sent over an email and should never click on links inside them unless verifying the source.
To always have a tight grip on your valuable data, keep a good back-up routine in place that makes their copies to an external storage device that isn't always connected to your PC.
Moreover, make sure that you run a good and effective anti-virus security suite on your system, and keep it up-to-date. Most importantly, always browse the Internet safely.
Petya Ransomware Outbreak Hits Organizations Globally
27.6.2017 securityweek Ransomware
Organizations worldwide are currently under a cyber-attack involving the year-old Petya ransomware, security experts report.
The attack already hit Ukraine central bank and Russian oil giant Rosneft. Government computers, airports, and large communication companies in Ukraine appear to have been affected as well. US biopharmaceutical giant Merck also confirmed that its network has been compromised as part of the global attack.
Allan Liska, Intelligence Architect, Recorded Future, told SecurityWeek in an emailed statement Spain and France were also hit, and that the first victims in the United States have started to emerge. Other security researchers observed attacks in the UK and India, and expect the outbreak to spread to other countries too.
Follow
Mikko Hypponen @mikko
There are now reports of Petya from Ukraine, Russia, UK, India. Business day starting in USA right now... https://twitter.com/ankit5934/status/879681380686340096 …
4:04 PM - 27 Jun 2017
168 168 Retweets 49 49 likes
Twitter Ads info and privacy
The massive spread comes only one month and a half after WannaCry affected hundreds of thousands of computers worldwide, spreading via a NSA-linked SMB exploit called EternalBlue. According to security company Avira, the currently unfolding attack is using the same exploit to spread like wildfire.
AlienVault also mentions the use of EternalBlue exploit, but notes that no confirmation on this has emerged as of now. The company reveals that the ransomware “leverages ARP scans and PsExec to spread. PsExec is dropped as dllhost.dat.”
Petya was initially spotted in March last year, when it stood out from the crowd because it wasn’t targeting individual files, as most ransomware families do, but was going after the Master Boot Record instead, thus completely cutting users’ access to the infected computers.
The malware was observed performing a two-step encryption process: it would first cause a PC crash with a BSOD and prompt for a reboot, and would manipulate the MBR during the boot-up sequence. Thus, users could avoid having their hard drives encrypted by preventing the computer from rebooting.
A few months later, Petya authors decided to bundle the malware with a ransomware family called Mischa, which would target individual files in the event the reboot failed. Thus, Mischa worked as an insurance policy, and the authors decided to adopt the Ransomware-as-a-Service business model.
By the end of 2016, another Petya variant called Goldeneye emerged, and researchers warned earlier this year of a malware variant called PetrWrap that was leveraging Petya and modifying it “on the fly” to control its execution.
According to Costin Raiu, director of Global Research and Analysis Team at Kaspersky Lab, the newly observed ransomware variant could be PetrWrap, and not the original Petya, while others say the ransomware variant is Petya.A. Raiu also notes that the sample he stumbled upon appears to have been compiled a week ago.
The Petya variant used in this attack demands a $300 ransom from its victims, and the first payments appear to have been made to the hardcoded Bitcoin wallet it uses.
According to Recorded Future’s Liska, other payloads might also be used in the attack: “There are also reports that the payload includes a variant of Loki Bot in addition to the ransomware. Loki Bot is a banking trojan, it steals usernames and passwords as well as other personal data from the victim machine and sends it to a command and control host. Which means this attack not only could make the victim's machine inoperable, it could steal valuable information that an attacker can take advantage of during the confusion.’”
SamSam ransomware attacks increase and crooks demand higher ransom
25.6.2017 securityaffairs Ransomware
Researchers at AlienVault observed a significant increase in the number of SamSam ransomware attacks, crooks are demanding $33,000 to the victims.
Security experts at AlienVault have observed a new string of attacks leveraging the SamSam ransomware, and this time crooks are demanding a $33,000 ransom to decrypt the files.
According to the researchers, crooks demand:
1.7 Bitcoin ($4,600) for a single machine
6 Bitcoins ($16,400) for half the machines (allowing the victim to confirm they can recover their files)
12 Bitcoins ($32,800) for all of the machines
The malware is installed on vulnerable systems through manual compromise, when the malware infects a machine it is able to spread to other computers on the network.
Experts believe the SamSam charges very high ransoms because of the effort of its operators in the operations. The FBI issued two alerts on the SamSam threat last year.
“MSIL or Samas (SAMSAM) was used to compromise the networks of multiple U.S. victims, including 2016 attacks on healthcare facilities that were running outdated versions of the JBoss content management application.” states the report published by the FBI. “SAMSAM exploits vulnerable Java-based Web servers. SAMSAM uses open-source tools to identify and compile a list of hosts reporting to the victim’s active directory. The actors then use psexec.exe to distribute the malware to each host on the network and encrypt most of the files on the system. The actors charge varying amounts in Bitcoin to provide the decryption keys to the victim.”
According to the researchers at AlienVault, SamSam attackers are using the following techniques to infect the machines:
Gain remote access through traditional attacks, such as JBoss exploits
Deploy web-shells
Connect to RDP over HTTP tunnels such as ReGeorg
Run batch scripts to deploy the ransomware over machines
SamSam was first spotted more than a year ago, it is written in C# language and once infected a machine the threat targets over 300 File types to encrypt.
Most recent variants show no changes compared to previous ones, it leverages the functions encc.myff1 and encc.EncryptFile for encryption.
Once encrypted the files. the SamSam ransomware will delete the original ones. Experts noticed the threat doesn’t clean the removed file sectors allowing users to recover their files or parts of them.
Researchers noticed a peak in the number of SamSam attack, its operators appear very active in this period. In April, systems at a New York hospital were infected with the ransomware, but the administration refused to pay the $44,000 ransom demanded by crooks.
“SamSam, which targets vulnerabilities in servers to infiltrate computer networks, is responsible for other attacks, including a major ransomware incident last year at 10-hospital Medstar Health in Maryland.” states buffalonews.com.
Experts who analyzed the transaction on the Bitcoin associated with SamSam operators noticed the attackers received $33,000 from its victims.
“The most recent attacks appear to have been successful, at least from the attacker’s point of view. The Bitcoin address associated with this week’s attacks has received $33,000,” states AlienVault.

SamSam Increases Ransom Demand to $33,000
24.6.2017 securityweek Ransomware
In newly observed attacks, the SamSam ransomware that has been active for more than a year is demanding a whopping $33,000 to decrypt all affected machines in a network.
SamSam isn’t distributed through automated tools such as exploit kits or spam botnets, as most ransomware families out there, but is installed on vulnerable systems through manual compromise instead.
Once a single machine in a network was breached, however, the threat can spread to other computers on the network. The ransomware’s operators are using remote desktop protocol (RDP), web shells and batch scripts to compromise networks and deploy the ransomware on every machine, AlienVault’s Chris Doman notes in a blog post.
Written in C#, the malware’s recent variants show no changes compared to previous samples, researchers say. On the compromised machines, the threat is targeting over 300 file types to encrypt, and uses the functions encc.myff1 and encc.EncryptFile for encryption, a researcher going by the name of Vallejo explains.
Recent SamSam attacks follow the same pattern as previous campaigns, albeit the demanded ransom is higher than before. The malware’s operators demand 1.7 Bitcoin (over $4,500) to decrypt a single machine, 6 Bitcoin (over $16,000) to decrypt data on half the machines, and 12 Bitcoins (around $33,000) to restore data on all of the infected machines.
“In addition, the group behind SamSam charges very high ransoms because of the amount of effort invested in their operations, which made them the subject of two FBI Alerts last year,” the researcher says.
According to AlienVault, the attacks appear to peak in waves, revealing when the ransomware’s authors are active. One notable recent SamSam incident involved a New York hospital that refused to pay the $44,000 ransom demanded after being infected with the ransomware in April.
“The most recent attacks appear to have been successful, at least from the attacker’s point of view. The Bitcoin address associated with this week’s attacks has received $33,000,” Doman reports.
After encrypting a file, SamSam deletes the original and leaves the encrypted variant instead. However, because the malware doesn’t appear to be cleaning the removed file sectors, affected users might be able to recover their files or parts of them.
No, WannaCry Is Not Dead! Hits Honda & Traffic Light Camera System
22.6.2017 thehackernews Ransomware
It's been over a month since the WannaCry ransomware caused chaos worldwide and people have started counting its name as 'the things of past,' but…
...WannaCry is not DEAD!
The self-spreading ransomware is still alive and is working absolutely fine.
The latest victims of WannaCry are Honda Motor Company and 55 speed and traffic light cameras in Australia.
The WannaCry ransomware shuts down hospitals, telecom providers, and many businesses worldwide, infecting over 300,000 Windows systems running SMBv1 in more than 150 countries within just 72 hours on 12th of May.
The worm was leveraging an NSA's Windows SMB exploit, dubbed EternalBlue, leaked by the infamous hacking group Shadow Brokers in its April data dump, along with other Windows exploits.
Honda Stops Production After WannaCry Hits its Computer
Honda Motor Company released a statement this week, saying the company was forced to halt its production for more than 24 hours at in one of its Japan-based factories after finding the WannaCry infections in its computer networks.
The automaker halted production of more than 1,000 at its Sayama plant, northwest of Tokyo, on Monday 19th June after it discovered that the ransomware had affected networks across Japan, North America, Europe, China, and other regions despite its efforts to secure systems in mid-May, according to a Wednesday report from Reuters.
While Honda did not say how WannaCry got into their networks 37 days after a researcher activated the kill switch, it's clear that the computers inside the Honda network were running unsupported versions of Windows OS or it did not install a highly critical patch released by Microsoft in March.
The Honda's Sayama plant, which produces the Accord sedan, Odyssey Minivan, Step Wagon compact multipurpose vehicle and more, produces around 1,000 vehicles per day.
Renault and Nissan were also infected by the WannaCry ransomware last month, which also forced them to temporarily stop their production at plants in Britain, India, Japan, France, and Romania.
WannaCry Hits 55 Traffic-Light and Speed Cameras in Australia
Another recent WannaCry victim was spotted in Australia when the Victoria Police confirmed that the ransomware infected a total of 55 red light cameras and speed cameras in Victoria via private camera operator Redflex.
The malware locked down critical files and demanded a ransom in return (WannaCry usually demands $300 to unlock files), according to the 3AW morning radio show.
"A system patch has been applied, which prevents the spread of the virus," the officials told the show. "The Department is in the process of removing the [WannaCry] virus from the affected cameras. The remaining websites will be rectified in the next couple of days."
The authorities believed the infection was the result of a targeted cyber attack, rather than 'human error,' likely on the part of a camera technician, and that WannaCry got onboard via a USB drive.
"Our advice at this stage is that a software virus has been detected however the camera system has not been compromised," the police said. "We will look into all incidents detected by the speed and red light cameras during the time in question as a matter of course. The integrity of the camera system has not been affected."
Well, it is quite surprising that even after knowing about the WannaCry issue for quite a decent amount of time, big companies have not yet implemented proper security measures to defend against the threat.
Ransomware has become an albatross around everyone's neck. Recently, a South Korean web hosting provider confirmed that the company had paid a record $1 Million ransom to hackers in return of its data following a ransomware attack over the weekend.
In cyberspace, Ignorance is not bliss. So, go and apply the goddamn patches and disable the unsecured, 30-year-old SMBv1 file-sharing protocol on your systems.
Necurs Botnet Distributing Locky Ransomware via Fake Invoices
22.6.2017 securityweek Ransomware
The Necurs spam botnet has switched back to distributing the Locky ransomware in a campaign featuring messages disguised as fake invoices, Cisco Talos security researchers reveal.
Last year, Necurs was the main driver behind Locky’s ascension to the top of the ransomware charts, and their activity was tightly connected. Following several months of vacation in early 2017, Necurs resumed activity in April, but distributed Locky only for a few weeks.
Starting around May 12, the same day WannaCy made its first appearance, Necurs switched to distributing a new ransomware family called Jaff. The malware was found to be tightly connected to Locky, as the same actor operated both ransomware families.
Earlier this month, however, Kaspersky Lab security researchers discovered vulnerabilities in Jaff and managed to create a decryptor for it, allowing victims to recover their data for free. Although three Jaff variants were observed to date, the decryption tool would work for all three of them.
The decryptor’s release apparently took Jaff out of the race, and Necurs returned to pushing Locky once again. The spam emails pushing the ransomware feature a double-zipped archive with an .exe file inside. Unlike previous Necurs-driven campaigns, which used themes such as order confirmations, payment receipts, and business documents, the new messages are fake invoices.
The newly observed campaign, Talos reports, features a notable volume of spam: during the first hour, it accounted for around 7% of the email volume registered by one of the company’s systems. The volume has decreased, but the campaign continues to be active, the security researchers say.
The campaign uses the same affiliate ID as before, but the ransomware itself appears to have suffered a series of changes, one of which prevents it from encrypting data on systems running under operating systems more recent than Windows XP.
The command and control (C&C) URL structure is another notable aspect of this campaign, the security researchers say: “Adversaries behind this latest Locky campaign have reused the /checkupdate path as part of the URL structure -- the same URL structure found in previous Locky campaigns. This is perhaps another indication that adversaries were hasty in their developing and distributing this campaign.”
Talos suggests that Locky’s operators are likely aware of the existing issues with the ransomware, and that an updated variant of the malware is likely to emerge soon, addressing the bug. At the moment, however, the Locky sample distributed via Necurs can encrypt only Windows XP systems.
“It's always risky clicking on links or opening attachments in strange email messages. Users that fail to heed this advice can easily become ransomware victims, and if the subsequent ransom is paid, the monies will no doubt fund another round of attacks. As always, organizations are encouraged to make regular backups of their data, practice restoring said data, and store backups offline far out of the reach of potential criminals,” Talos said.
Honda halted production in a factory after finding WannaCry traces in its networks
22.6.2017 securityaffairs Ransomware
The Honda company shuts down a factory in Japan after finding the WannaCry ransomware in its networks after 5 weeks its massive attack.
The WannaCry ransomware makes the headlines once again, The Honda Company to stopped the production in one of its plant in Japan after discovering the malware in its computer networks,
The Honda automaker halted the activities in the Sayama plant northwest of Tokyo on Monday after finding that the WannaCry ransomware had infected systems in its networks across Japan, North America, Europe, China, and other regions,
According to the Reuters agency, the experts discovered the infection on Sunday.
“The automaker shut production on Monday at its Sayama plant, northwest of Tokyo, which produces models including the Accord sedan, Odyssey Minivan and Step Wagon compact multipurpose vehicle and has a daily output of around 1,000 vehicles.” states the article.
“Honda discovered on Sunday that the virus had affected networks across Japan, North America, Europe, China and other regions, a spokeswoman said, despite efforts to secure its systems in mid-May when the virus caused widespread disruption at plants, hospitals and shops worldwide.”
According to the company, the production at other plants had not been affected, according to a Honda Spokesman, regular operations at the Sayama plant had resumed on Tuesday.
It is still unclear why the WannaCry ransomware was present in the Honda networks 5 weeks after its discovery,

the unique certainly is that the company had yet to patch its systems with the highly critical patch that Microsoft released in March.
One possibility is that IT staff at the company has inadvertently blocked the access to the kill switch domain that partially stopped the infections. That would have caused the WannaCry propagation inside the Honda networks.
We cannot exclude that the shutdown of Sayama plant was a precautionary measure to eradicate dormant instance of the ransomware.
Honda wasn’t the only company forced to shut down its networks due to WannaCry, other automakers like Renault and Nissan Motor were affected and were forced to halt productions in plants in Japan, Britain, France, Romania, and India.
It’s my opinion that the failure in responding the WannaCry attack was primarily caused by the failure of patch management processes. Don’t forget that systems across the world were infected by ransomware that was exploiting a flaw that was already fixed by a two-month-old patch.
South Korean hosting provider NAYANA infected by Erebus ransomware, it paid $1 Million to crooks
21.6.2017 securityaffairs Ransomware
South Korean web hosting company NAYANA was hit by the Erebus ransomware that infected 153 Linux servers and over 3,400 business websites the company hosts.
The South Korean web hosting provider NAYANA has paid $1 million in bitcoins to crooks after a Linux ransomware infected its systems. its 153 servers, encrypting 3,400 business websites and their data, hosted on them.
The ransomware encrypted files of 153 servers, roughly 3,400 business websites have been impacted.
“On June 10, South Korean web hosting company NAYANA was hit by Erebus ransomware (detected by Trend Micro as RANSOM_ELFEREBUS.A), infecting 153 Linux servers and over 3,400 business websites the company hosts.” reported Trend Micro that revealed the ransomware used in the attack is Erebus.
The attack happened on 10th June, the cyber criminals demanded a 550 bitcoins payment (over $1.6 million) to unlock the encrypted files. NAYANA after a negotiation with the cyber criminals has agreed to pay 397.6 bitcoins (around $1.01 million) in three installments.
The web hosting provider has already paid two installments and would complete the payment once recovered its data from two-third of the infected servers.
“On June 18, NAYANA started the process of recovering the servers in batches. Some of the servers in the second batch are currently experiencing database (DB) errors. A third payment installment is also expected to be paid after the first and second batches of servers have been successfully recovered.” continues Trend Micro.

The Erebus Linux ransomware was first spotted in September 2016, in February a new version was improved implementing Windows’ User Account Control bypass capabilities.
The experts observed that the servers of the Korean hosting provider were running on Linux kernel 2.6.24.2, a circumstance that exposed them to known attacks such as DIRTY COW Linux exploit. It is also possible that the attackers exploited flaws in outdated Apache version 1.3.36 used by the company.
“NAYANA’s website runs on Linux kernel 2.6.24.2, which was compiled back in 2008. Security flaws like DIRTY COW that can provide attackers root access to vulnerable Linux systems are just some of the threats it may have been exposed to.” states Trend Micro..
“Additionally, NAYANA’s website uses Apache version 1.3.36 and PHP version 5.1.4, both of which were released back in 2006. Apache vulnerabilities and PHP exploits are well-known; in fact, there was even a tool sold in the Chinese underground expressly for exploiting Apache Struts.”
The Erebus ransomware is targeting users in South Korea, it leveraged RSA-2048 algorithm to encrypt office documents, databases, archives, and multimedia files. The private key is encrypted using AES encryption and another randomly generated key.
The malicious code appends a .ecrypt extension to the encrypted files.
“The file is first scrambled with RC4 encryption in 500kB blocks with randomly generated keys,” continues the analysis. “The RC4 key is then encoded with AES encryption algorithm, which is stored in the file. The AES key is again encrypted using RSA-2048 algorithm that is also stored in the file.”
Web Hosting Company Pays $1 Million to Ransomware Hackers to Get Files Back
20.6.2017 thehackernews Ransomware
South Korean web hosting provider has agreed to pay $1 million in bitcoins to hackers after a Linux ransomware infected its 153 servers, encrypting 3,400 business websites and their data, hosted on them.
According to a blog post published by NAYANA, the web hosting company, this unfortunate event happened on 10th June when ransomware malware hit its hosting servers and attacker demanded 550 bitcoins (over $1.6 million) to unlock the encrypted files.
However, the company later negotiated with the cyber criminals and agreed to pay 397.6 bitcoins (around $1.01 million) in three installments to get their files decrypted.
The hosting company has already paid two installments at the time of writing and would pay the last installment of ransom after recovering data from two-third of its infected servers.
According to the security firm Trend Micro, the ransomware used in the attack was Erebus that was first spotted in September last year and was seen in February this year with Windows’ User Account Control bypass capabilities.
Since the hosting servers were running on Linux kernel 2.6.24.2, researchers believe that Erebus Linux ransomware might have used known vulnerabilities, like DIRTY COW; or a local Linux exploits to take over the root access of the system.
“The version of Apache NAYANA used is run as a user of nobody(uid=99), which indicates that a local exploit may have also been used in the attack,” researchers note.
“Additionally, NAYANA’s website uses Apache version 1.3.36 and PHP version 5.1.4, both of which were released back in 2006.”
Erebus, the ransomware primarily targeting users in South Korea, encrypts office documents, databases, archives, and multimedia files using the RSA-2048 algorithm and then appends them with a .ecrypt extension before displaying the ransom note.
“The file is first scrambled with RC4 encryption in 500kB blocks with randomly generated keys,” researchers say. “The RC4 key is then encoded with AES encryption algorithm, which is stored in the file. The AES key is again encrypted using RSA-2018 algorithm that is also stored in the file.”
The public key which is generated locally is shared, while the private key is encrypted using AES encryption and another randomly generated key.
According to analysis conducted by the Trend Micro researchers, decryption of infected files is not possible without getting hold of the RSA keys.
So, the only safe way of dealing with ransomware attacks is prevention. As we have previously recommended, the best defense against Ransomware is to create awareness within the organizations, as well as to maintain back-ups that are rotated regularly.
Most viruses are introduced by opening infected attachments or clicking on links to malware usually in spam emails. So, DO NOT CLICK on links provided in emails and attachments from unknown sources.
Moreover, ensure that your systems are running the latest version of installed applications.
Fileless, Code-Injecting Ransomware SOREBRECT Emerges
19.6.2017 securityweek Ransomware
A newly discovered ransomware family incorporates a combination of fileless attack and code-injection, Trend Micro security researchers warn.
Dubbed SOREBRECT, the threat was initially spotted a couple of months ago, when it managed to infect the systems and networks of organizations in the Middle East. The ransomware packs unusual encryption techniques, is abusing the PsExec utility to leverage code injection, and also focuses on remaining stealthy, the security company says.
The ransomware was fitted with a self-destruct routine that turns it into a fileless threat: it injects code into a legitimate system process before terminating its main binary. Furthermore, it goes to lengths to delete the affected system’s event logs and other artifacts in an attempt to hinder forensic analysis and prevent researchers from tracking the threat’s activities.
When discovered, SOREBRECT had a low distribution and concentrated on Middle Eastern countries like Kuwait and Lebanon. By early May, however, it was already found on computers in Canada, China, Croatia, Italy, Japan, Mexico, Russia, Taiwan, and the U.S., infecting industries including manufacturing, technology, and telecommunications.
“Given ransomware’s potential impact and profitability, it wouldn’t be a surprise if SOREBRECT turns up in other parts of the world, or even in the cybercriminal underground where it can be peddled as a service,” Trend Micro says.
During attacks, the malware abuses PsExec, a legitimate Windows command-line utility used by system admins to execute commands or run executable files on remote systems. This, researchers say, means that attackers are already in the possession of administrator credentials or that the remote machines were exposed or brute-forced.
SOREBRECT, however, isn’t the first ransomware family to misuse PsExec, with SamSam, Petya, and its derivative, PetrWrap also abusing the utility to install the ransomware on compromised servers or endpoints. The new threat, however, maliciously deploys PsExec and performs code injection.
“It injects its code into Windows’ svchost.exe process, while the main binary self-destructs. The combination is potent: once the deployed ransomware binary finishes execution and self-termination, the injected svchost.exe—a legitimate Windows service-hosting system process—resumes the execution of the payload (file encryption),” Trend Micro explains.
The researchers also argue that the ransomware’s code injection capability makes the attack more effective compared to using the Remote Desktop Protocol (RDP). Through PsExec, attackers can remotely execute commands, instead of providing a log-in session or manually transferring the malware to the target machine.
The ransomware also uses wevtutil.exe to delete the system’s event logs, and vssadmin to delete shadow copies, thus covering its tracks and preventing users from recovering their files. The malware also uses the TOR network to communicate with its command and control (C&C) server.
The threat can also encrypt files on network shares, the researchers warn. For that, it scans the network for asset discovery and enumerates open shares, including folders, content or peripherals that are readily accessible through the network. Next, it initiates a connection to the discovered share and, if both read and write access are available, it encrypts it.
To stay protected, IT/system administrators and information security professionals are advised to restrict user write permissions and limit privileges for PsExec. As usually, keeping files backed up at all times and both systems and networks updated can prove helpful in case of an attack. Training employees on security and deploying multilayered security mechanisms are also highly important.
New Code-injecting SOREBRECT Fileless Ransomware detected in the wild
16.6.2017 securityaffairs Ransomware
The number of fileless malware continues to increase, recently security researchers spotted a new Fileless Ransomware dubbed Sorebrect.
Sorebrect is able to inject malicious code into a legitimate system process (svchost.exe) on a targeted system and it terminates its binary to evade detection. It also make hard forensics analysis by deleting the affected system’s event logs using wevtutil.exe and shadow copies with vssadmin,and other artifacts such as files executed on the system.
SOREBRECT leveraged on Tor network to anonymize communications to command-and-control (C&C) server.
Unlike other ransomware, Sorebrect has been designed to specifically target enterprise’s systems in various industries (manufacturing, technology, and telecommunications), the malicious code it injects is tasked of file encryption on the local machine and connected network shares. The Sorebrect ransomware scans the local network for other connected systems with open shares and encrypts files stored on them.
“Extracting and analyzing the SOREBRECT samples revealed the unusual techniques it employs to encrypt its victim’s data. Its abuse of the PsExec utility is also notable; SOREBRECT’s operators apparently use it to leverage the ransomware’s code injection capability.” states the analysis shared by Trend Micro.
“While file encryption is SOREBRECT’s endgame, stealth is its mainstay. The ransomware’s self-destruct routine makes SOREBRECT a fileless threat. The ransomware does this by injecting code to a legitimate system process (which executes the encryption routine) before terminating its main binary.”

The experts noticed that the SOREBRECT fileless ransomware first compromises administrator credentials (i.e. by brute forcing attacks), then leverage Microsoft Sysinternals PsExec command-line utility to encrypt files.
“Why PsExec? While attackers can both use Remote Desktop Protocol (RDP) and PsExec to install SOREBRECT in the affected machine, its code injection capability makes the attack more effective. Compared to using RDP, utilizing PsExec is simpler and can take advantage of SOREBRECT’s fileless and code injection capabilities.” continues the analysis.
“PsExec can enable attackers to run remotely executed commands, instead of providing and using an entire interactive login session, or manually transferring the malware into a remote machine, like in RDPs,” Trend Micro says.
The fileless ransomware was first spotted in Middle Eastern countries like Kuwait and Lebanon, recently experts observed attacks against systems in Canada, China, Croatia, Italy, Japan, Mexico, Russia, Taiwan, and the U.S.
Below the best practices for securing systems and networks suggested by TrendMicro.
Restrict user write permissions.
Limit privilege for PsExec.
Back up files.
Keep the system and network updated.
Deploy multilayered security mechanisms.
New Fileless Ransomware with Code Injection Ability Detected in the Wild
16.6.2017 thehackernews Ransomware
It is no secret that hackers and cybercriminals are becoming dramatically more adept, innovative, and stealthy with each passing day.
While new forms of cybercrime are on the rise, traditional activities seem to be shifting towards more clandestine techniques that come with limitless attack vectors with low detection rates.
Security researchers have recently discovered a new fileless ransomware, dubbed "Sorebrect," which injects malicious code into a legitimate system process (svchost.exe) on a targeted system and then self-destruct itself in order to evade detection.
Unlike traditional ransomware, Sorebrect has been designed to target enterprise's servers and endpoint. The injected code then initiates the file encryption process on the local machine and connected network shares.
This fileless ransomware first compromises administrator credentials by brute forcing or some other means and then uses Microsoft’s Sysinternals PsExec command-line utility to encrypt files.
"PsExec can enable attackers to run remotely executed commands, instead of providing and using an entire interactive login session, or manually transferring the malware into a remote machine, like in RDPs," Trend Micro says.
Sorebrect Also Encrypts Network Shares
Sorebrect also scans the local network for other connected computers with open shares and locks files available on them as well.
"If the share has been set up such that anyone connected to it has read-and-write access to it, the share will also be encrypted," researchers say.
The nasty ransomware then deletes all event logs (using wevtutil.exe) and shadow copies (using vssadmin) on the infected machine that could provide forensic evidence such as files executed on the system and their timestamps, which makes this threat hard-to-detect.
In addition, Sorebrect uses the Tor network protocol in an attempt to anonymize its communication with its command-and-control (C&C) server, just like almost every other malware.
Sorebrect Ransomware Spreads Worldwide
The Sorebrect fileless ransomware has been designed to target systems from various industries including manufacturing, technology, and telecommunications.
According to Trend Micro, Sorebrect was initially targeting Middle Eastern countries like Kuwait and Lebanon, but from last month, this threat has started infecting people in Canada, China, Croatia, Italy, Japan, Mexico, Russia, Taiwan, and the U.S.
"Given ransomware’s potential impact and profitability, it wouldn’t be a surprise if SOREBRECT turns up in other parts of the world, or even in the cybercriminal underground where it can be peddled as a service," the researchers note.
This is not the first time when researchers have come across Fileless malware. Two months ago, Talos researchers discovered a DNSMessenger attack that was completely Fileless and used DNS TXT messaging capabilities to compromise systems.
In February, Kaspersky researchers also discovered fileless malware that resided solely in the memory of the compromised computers, which was found targeting banks, telecommunication companies, and government organizations in 40 countries.
Ways to Protect Against Ransomware Attacks
Since the ransomware does not target individuals but organizations, sysadmins and information security professionals can protect themselves by:
Restricting user write permissions: a significant factor that exposes network shares to ransomware by giving users full permissions.
Limiting privilege for PsExec: Limit PsExec and provide permission to run them only to system administrators.
Keeping your system and network up-to-date: Always keep your operating system, software, and other applications updated.
Backing up your data regularly: To always have a tight grip on all your important files and documents, keep a good backup routine in place that makes their copies to an external storage device that is not always connected to your PC.
Adopting a cyber security-aware workforce: Educating your employees about malware, threat vectors and security measure always plays a major role in any organization.
U.K. Center of Security Excellence Hit by Ransomware
16.6.2017 securityweek Ransomware
One of the world's top ten universities, awarded the status of "centre of excellence in cyber-security research" by the UK's GCHQ, has been hit by a so-far unrecognized strain of ransomware. This comes just one month after many UK health trusts were struck by the global WannaCry ransomware.
In a statement originally issued yesterday and updated today, University College London (UCL) described the current and ongoing ransomware. "We are continuing to investigate the infection that is affecting UCL users. Our current hypothesis is that the malware infection occurred through users visiting a website that had been compromised rather than being spread via email attachments. However, this remains unconfirmed at the moment."
UCL believes it has now contained the outbreak by isolating the infected storage/devices, and does not expect any further infections. Twelve users had their local or shared drives infected and encrypted.
We believe, says UCL, "that the infection started as a result of UCL users visiting a website that had been compromised. Clicking on a popup or even just visiting a compromised site may have then introduced the malware to their device. The website could be one that they use regularly. We are still trying to confirm this and determine the site that may have caused the infection."
For now, UCL cannot confirm the type of ransomware that was used; but it seems to be Windows only. Its anti-virus defenses were, it says, up-to-date.
For now, UCL's comments ask as many questions as they answer. While there is no 100% secure defense against phishing (it will always catch someone), was this one person tricked and 12 users affected by the ransomware spreading through local shares; or twelve people tricked?
Or was there no phishing attack? Could this have been a watering hole attack -- hinted at by UCL's comment that the poisoned website could be one used regularly. Either way, was the user, or users, operating unpatched software? If the delivering exploit were a zero-day exploit, it wouldn't matter; but there is no immediate news of any widespread use of a zero-day elsewhere -- and it is unlikely that a criminal actor would waste a zero-day on a single UK university.
It is possible, then that this ransomware managed to get into UCL by just one user operating an unpatched browser. But whatever the infection vector, it seems that existing anti-malware failed to detect and stop it. "Clearly, we are seeing again that the old guard of AV isn't able to deal with evolving threats, even the obvious ransomware," comments Tony Rowan, security consultant at SentinelOne. "For each case of ransomware, we have to ask ourselves how many silent attacks are going unnoticed?"
Andrew Stuart, MD at Datto takes a similar view that AV alone is not enough against modern malware. "What this attack highlights," he claims, "is that anti-virus alone is simply not sufficient enough to prevent ransomware. Along with vulnerability patching, these AV tools might be capable of catching known strains of malware, but newer ones too often pass through defenses undetected." His own view is that regular back-up snapshots are the best solution. "If companies take regular snapshots of their systems, they are able to quickly spin-up systems to a 'healthy' point before the ransomware took hold."
Jason Allaway, VP at RES, sees the solution -- at least partly -- in education. "Everyone involved in a university needs to be prepared, as after all, lecturers and other staff members are just as weak a link in the security chain if they don't know what to look for. Organizations should provide informative materials and classes on the techniques of hackers, such as phishing emails, how to spot these and how to counter-act them."
Mike Viscuso, CTO at Carbon Black, agrees on all counts. "Organizations can better set themselves up to deal with ransomware attacks by consistently backing up critical files, educating employees on proper cybersecurity hygiene, and patching vulnerabilities in a timely manner. The fact this attack on UCL appears to have circumvented AV filters shows the inadequacy traditional AV protection provides."
Steven Malone, director of security product management at Mimecast, believes that UCL's problem is typical of organizations that do not sufficiently consider email as an attack vector. "UCL appears to be running 'naked' Office 365 for its email security gateway. This is case in point for why all organizations need to ask if they are happy to trade defense-in-depth strategies for single vendor reliance when moving to the cloud...
"The vast majority of ransomware attacks are spread by email yet many organizations have still not put any additional security controls in place. Real-time checks on links and converting all incoming attachments to safe formats seriously reduces the risk of infection."
The reality, however, is that we do not yet have enough information to know what went wrong, where or why. It is worth remembering that in a campus of almost 50,000 staff and students, UCL contained this outbreak to just 12 users.
Victims of Jaff Ransomware now can decrypt their locked files for free thanks to Kaspersky
15.6.2017 securityaffairs Ransomware
Victims of the Jaff ransomware can use an updated version of the Kaspersky Labs’s RakhniDecryptor tool to decrypt their encrypted files.
Security researchers at Kaspersky Lab have discovered a weakness in the Jaff ransomware that allowed the researchers creating of decryption keys to unlock files encrypted by the malware.
Once the victims were infected by the Jaff ransomware, crooks then demanded a ransom of between 0.5 to 2 Bitcoin (approximately $1,500 – $5,000, based on current exchange rates).
That weakness can be exploited by a free tool that has been included in the list of free ransomware decryptors shared by Kaspersky Lab. The tools allow recovering files encrypted by the ransomware like Rannoh and CoinVault.
“We have found a vulnerability in Jaff’s code for all the variants to date. Thanks to this, it is now possible to recover users’ files (encrypted with the .jaff, .wlu, or .sVn extensions) for free,” Kaspersky Lab said in a statement announcing the availability of the decryption keys.
The free decryption tool for unlocking files has been added to the RakhniDecryptor (version 1.21.2.1).
The Jaff ransomware was first spotted in May while it was being distributed by Necurs botnet previously used to spread the Locky and Dridex malware.
A few days ago, security researchers at Heimdal Security who were investigating a new strain of Jaff ransomware discovered that the malware is sharing the backend infrastructure with a black market offering for sale stolen card data and account information.
The Jaff ransomware has been recently discovered, it was involved in a number of large-scale email campaigns each using a PDF attachment with an embedded Microsoft Word document embedding macros that download and execute the malicious code.

According to Kaspersky Lab, top countries impacted by the ransomware are China, India, Russia, Egypt, and Germany.
Let me suggest giving a look at the numerous decryption utilities published by Kaspersky Lab under the No Ransom Project.
Kaspersky is very active in the fight against ransomware, one year ago it launched, along with the Europol and other security firms, the ‘NO More Ransom’ initiative.
Jaff Ransomware Decryption Tool Released – Don't Pay, Unlock Files for Free
15.6.2017 thehackernews Ransomware
Hit by Jaff Ransomware? Don't pay the Ransom. You can unlock your files for Free!
Kaspersky Labs has released an updated version 1.21.2.1 of its free ransomware decryption tool, RakhniDecryptor, which can now also decrypt files locked by the Jaff ransomware.
Security researchers at Kaspersky Labs have discovered a weakness in the Jaff ransomware code that makes it possible for victims to unlock their Jaff-infected files for free.
First identified last month, Jaff is relatively new ransomware that's being distributed with the help of 'Necurs botnet' that currently controls over 6 million infected computers worldwide.
Necurs botnet is the same botnet – army of compromised internet connected devices – that was used to distribute Dridex Banking Trojan and Locky ransomware, which also infects users’ machines, encrypt files and then demand a ransom before unlocking them.
Jaff ransomware (Trojan-Ransom.Win32.Jaff) attack is primarily carried out by sending spam emails to millions of users with an attached PDF, which if clicked, opens up an embedded Word document with a malicious macro script to downloads and execute the ransomware.
Once victims download and enable a Word macro associated with the .PDF, the Jaff ransomware gets downloaded onto their computer, encrypting victims files and then demanding a ransom of between 0.5 to 2 Bitcoin (~$1,500 to $5,000 today).
The Jaff attack started on May 12 – the same day when the devastating WannaCry ransomware debuted – by sending spam emails at the speed of 5 Million emails per hour.
How to Use RakhniDecryptor
Kaspersky RakhniDecryptor tool is a lightweight and portable piece of software designed to decrypt files encrypted by several variants of ransomware including Lobzik, Rakhni, Mircop, Crusis and 17 others.
RakhniDecryptor is very easy to use and doesn't require any technical knowledge. Here's the list of simple steps to use this tool:
Download RakhniDecryptor 1.21.2.1
Run the RakhniDecryptor.exe file on the infected computer
Click 'Change parameters' to select the objects to scan (hard drives/removable drives/network drives)
Click the 'Start Scan' button and then choose the specify path to one of the encrypted files
The RakhniDecryptor utility will then recover the decryption password to unlock files
How to Protect Yourself From Ransomware Attacks
Whether it's Jaff, Locky, CoinVault, TeslaCrypt, or any other ransomware, the protection measures are standard.
To safeguard against ransomware infections, you should always be suspicious of uninvited documents sent in an email and never click on links inside those documents unless verifying their source.
Check if macros are disabled in your MS Office apps. If not, block macros from running in MS Office files from the Internet. In enterprises, your system administrators can set the default setting for macros.
In order to always have a tight grip on all your important documents, keep a good backup routine in place that makes copies of your files to an external storage device which is not always connected to your PC.
Moreover, make sure that you run an active anti-virus security suite of tools on your system and keep them up-to-date, and most importantly, always browse the Internet safely.
MacRansom: The first Mac ransomware offered as a RaaS Service
12.6.2017 securityaffairs Ransomware
Malware researchers at security firm Fortinet have spotted MacRansom, it is the first Mac ransomware offered as a RaaS Service.
Malware researchers at security firm Fortinet have spotted a new strain of ransomware dubbed MacRansom that targets Mac machines.
The malware is available with Ransomware-as-a-service (RaaS) model through a hidden service in the TOR network. Experts believe this is the first time a Mac ransomware is offered as RaaS.
“Just recently, we here at FortiGuard Labs discovered a Ransomware-as-a-service (RaaS) that uses a web portal hosted in a TOR network which has become a trend nowadays. However, in this case it was rather interesting to see cybercriminals attack an operating system other than Windows. And this could be the first time to see RaaS that targets Mac OS.” states the analysis published by Fortinet.
Despite the threat is not sophisticated like other similar threats it could cause serious problems to the victims because it encrypts victim’s files. The availability of MacRansom as RaaS makes it easy to arranges ransomware campaign to crooks that have no specific skills.
MacRansom variant is not readily available through the Tor portal, would-be crooks can contact the author of the ransomware in order to receive their version of the threat.
“This MacRansom variant is not readily available through the portal. It is necessary to contact the author directly to build the ransomware. At first, we thought of it as a scam since there was no sample but to verify this we dropped the author an email and unexpectedly received a response.” continues the analysis.

MacRansom implements symmetric encryption with a hard-coded key and the ransomware only encrypts a maximum of 128 files, it demands 0.25 bitcoin (around $700) for decryption keys.
Researchers found two sets of symmetric keys used by the ransomware:
ReadmeKey: 0x3127DE5F0F9BA796
TargetFileKey: 0x39A622DDB50B49E9
The ReadmeKey is used to decrypt ._README_ file that contains the ransom notes and instructions, while the TargetFileKey is used to encrypt and decrypt the victim’s files.
The malicious code implements anti-analysis activity, the first thing the ransomware does is to check if the sample is being run in a non-Mac environment or if it is running in debugged environment.
The author gives 30 per cent to the Bitcoin address of the customer once the victim has paid the ransom.
Customers just have to spread the threat, for example delivering it via spam emails on through drive-by download attacks.
The author discourages drive-by download attacks or other approaches that involve uploading customized versions of MacRansom.
“It is not every day that we see new ransomware specifically targeting Mac OS platform. Even if it is far inferior from most current ransomware targeting Windows, it doesn’t fail to encrypt victim’s files or prevent access to important files, thereby causing real damage.” concluded Fortinet.
“Last but not the least, this MacRansom variant is potentially being brewed by copycats as we saw quite a lot of similar code and ideas taken from previous OSX ransomware. Even though it utilizes anti-analysis tricks, which differs from previous OSX ransomware, these are well-known techniques widely deployed by many malware authors. MacRansom is yet another example of the prevalence of the ransomware threat, regardless of the OS platform being run.”
French Police Seize 6 Tor Relay Servers in WannaCry Investigation
12.6.2017 thehackernews Ransomware
WannaCry, the biggest ransomware attack in the history, gained prominence very rapidly in the media globally after the ransomware infected more than 300,000 computers in over 150 countries within just 72 hours.
Governments, Intelligence agencies and law enforcement around the world have already started their investigations and are working closely with affected companies to track down hackers responsible for the global cyber attack launched on Friday, 12th May.
Some researchers traced back WannaCry to a state-sponsored hacking group in North Korea, while other believed the perpetrators might be Chinese.
If you have been following WannaCry coverage on The Hacker News, you should be aware of that the WannaCry ransomware uses Tor hidden service to communicate with its command-and-control server.
Just yesterday, we came to know that French authorities had seized at least 6 Tor's entry guard node servers, hosted on France-based hosting providers, just two days after the outbreak of ransomware attack while investigating the WannaCry incident.
On 15th May, a French hacktivist, who uses online moniker ‘Aeris,’ informed Tor community that the official from Central Office for Combating Crime Related to Information and Communication Technologies (OCLCTIC) raided the Online.net hosting provider and have seized his "kitten1" and "kitten2" (torguard and fallback directory) servers on 14th May.
"Cops raided OVH, Online.net and FirstHeberg hosting providers on the basis of a complaint filed by French Renault company that was one of the victims of the WannaCry infection," Aeris told The Hacker News.
"I went to court to have access to information about the seizer of my servers, but it refused to provide me with any information, and even the providers are under gag order."
Aeris told THN that he is aware of the seizer of total 6 Tor relays, operated by 5 operators.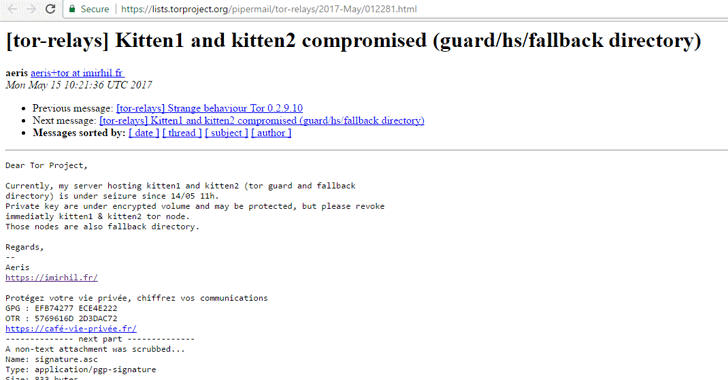
Perhaps nobody was aware of the takedown of these servers in question until the author of Deepdotweb first reported about this incident on Saturday.
Aeris also claimed that the French authorities had taken this action after a victim company (possibly Renault, a France-based multinational automobile manufacturer) contacted the agency for help and provided network traffic logs to assist the investigation.
Since the Tor nodes have been securely implemented to protect the privacy of Tor users and no actual data had been retained on them, the law enforcement authorities would hardly find any evidence related to the WannaCry gang.
"Private key are under encrypted volume and may be protected, but please revoke immediately kitten1 & kitten2 tor node. Those nodes are also fallback directory." Aeris warned.
WannaCry epidemic that hit victims worldwide was using self-spreading capabilities to infect vulnerable Windows computers, particularly those using older versions of the operating system.
While most of the affected organisations have now returned to normal, law enforcement agencies across the world are still on the hunt.
Police seized two Tor relays investigating WannaCry attack, others disappeared in the same period
11.6.2017 securityaffairs Ransomware
France’s cyber-crime investigation unit OCLCTIC seized one server running two Tor Relays Investigating the WannaCry attack.
A few days after the massive WannaCry attack the French authorities seized a server running two Tor relays in connection to the ransomware campaign, both relays were also working as Tor entry guard nodes, key components of Tor routing when users connect the anonymizing network.
The server was operated by the French activist Aeris that reported the police’s action through the Tor Project mailing on May 15 asking other Tor operators to revoke trust in the two seized relays.
The server was seized by France’s cyber-crime investigation unit OCLCTIC (L’Office Central de Lutte contre la Criminalité liée aux Technologies de l’Information et de la Communication).

According to Aeris, the police seized the server hosted at hosting company Online SAS, because the traffic associated with WannaCry ransomware that infected a big French company on May 12 was pointing the two Tor relays.
The WannaCry samples that infected the company were communicating with a command and control server hosted on the Tor Network, and it is likely that the server were used as a first hop of the Tor traffic.
“Most Tor servers are configured to log very few details, such as uptime and status metrics, so to safeguard the privacy of its users. Unless Aeris made customizations to default configs, French police have no chance of finding any useful information on the seized servers.” reported Catalin Cimpanu from Bleepingcomputer.com.
Aeris confirmed that tens of other Tor nodes in France disappeared just after the WannaCry attack, he provided Bleeping Computer a list of 30 servers he is currently investigating.
“We have confirmation of 6 Tor nodes seizures [from 5 operators],” the activist told Bleeping Computers. ” A seized relay is not of this list because of hosted on another provider.”
Warning! Hackers Started Using "SambaCry Flaw" to Hack Linux Systems
10.6.2017 thehackernews Ransomware
Remember SambaCry?
Two weeks ago we reported about a 7-year-old critical remote code execution vulnerability in Samba networking software (re-implementation of SMB networking protocol) that allows a remote hacker to take full control of a vulnerable Linux and Unix machines.
To know more about the SambaCry vulnerability (CVE-2017-7494) and how it works, you can read our previous article.
At that time, nearly 485,000 Samba-enabled computers were found to be exposed on the Internet, and researchers predicted that the SambaCry-based attacks also have potential to spread just like WannaCry ransomware widely.
The prediction came out to be quite accurate, as honeypots set up by the team of researchers from Kaspersky Lab have captured a malware campaign that is exploiting SambaCry vulnerability to infect Linux computers with cryptocurrency mining software.
Another security researcher, Omri Ben Bassat, independently discovered the same campaign and named it "EternalMiner."
According to the researchers, an unknown group of hackers has started hijacking Linux PCs just a week after the Samba flaw was disclosed publicly and installing an upgraded version of "CPUminer," a cryptocurrency mining software that mines "Monero" digital currency.
After compromising the vulnerable machines using SambaCry vulnerability, attackers execute two payloads on the targeted systems:
INAebsGB.so — A reverse-shell that provides remote access to the attackers.
cblRWuoCc.so — A backdoor that includes cryptocurrency mining utilities – CPUminer.
"Through the reverse-shell left in the system, the attackers can change the configuration of a miner already running or infect the victim’s computer with other types of malware," Kaspersky researchers say.
Mining cryptocurrencies can be a costly investment as it requires an enormous amount of computing power, but such cryptocurrency-mining malware makes it easier for cybercriminals by allowing them to utilise computing resources of compromised systems to make the profit.
If you have been following The Hacker News regularly, you must be aware of Adylkuzz, a cryptocurrency-mining malware that was using Windows SMB vulnerability at least two weeks before the outbreak of WannaCry ransomware attacks.
The Adylkuzz malware was also mining Monero by utilizing the enormous amount of computing resources of the compromised Windows systems.
The attackers behind SambaCry-based CPUminer attack have already earned 98 XMR, which worth 5,380 today and this figure is continuously rising with the increase in the number of compromised Linux systems.
"During the first day they gained about 1 XMR (about $55 according to the currency exchange rate for 08.06.2017), but during the last week they gained about 5 XMR per day," the researchers say.
The maintainers of Samba has already patched the issue in their new Samba versions 4.6.4/4.5.10/4.4.14, and are urging those using a vulnerable version of Samba to install the patch as soon as possible.
SambaCry is coming
10.6.2017 Kaspersky Ransomware
Not long ago, news appeared online of a younger sibling for the sensational vulnerability EternalBlue. The story was about a new vulnerability for *nix-based systems – EternalRed (aka SambaCry). This vulnerability (CVE-2017-7494) relates to all versions of Samba, starting from 3.5.0, which was released in 2010, and was patched only in the latest versions of the package (4.6.4/4.5.10/4.4.14).
On May 30th our honeypots captured the first attack to make use of this particular vulnerability, but the payload in this exploit had nothing in common with the Trojan-Crypt that was EternalBlue and WannaCry. Surprisingly, it was a cryptocurrency mining utility!
Vulnerability exploitation
In order to check that an unauthorized user has permissions to write to the network drive, the attackers first try to write a text file, consisting of 8 random symbols. If the attempt is successful they delete the file.
Writing and deleting the text file
After this check, it is time for the exploit’s payload (it is assembled as a Samba plugin). After successful exploitation of the vulnerability, this runs with super-user privileges, although first the attackers have to guess the full path to the dropped file with their payload, starting from the root directory of the drive. We can see such attempts in the traffic captured on our honeypot. They are just brute-forcing the most obvious paths (specified in different manuals, etc.), where files can be stored on the drive.
Bruteforcing the path to the payload
After the path to the file is found, it can be loaded and executed in the context of the Samba-server process, using the SambaCry vulnerability. Afterwards the file is deleted in order to hide the traces. From this moment it exists and runs only in the virtual memory.
In our case two files were uploaded and executed in such a way: INAebsGB.so (349d84b3b176bbc9834230351ef3bc2a – Backdoor.Linux.Agent.an) and cblRWuoCc.so (2009af3fed2a4704c224694dfc4b31dc – Trojan-Downloader.Linux.EternalMiner.a).
INAebsGB.so
This file stores the simplest reverse-shell. It connects to the particular port of the IP-address specified by its owner, giving him remote access to the shell (/bin/sh). As a result, the attackers have an ability to execute remotely any shell-commands. They can literally do anything they want, from downloading and running any programs from the Internet, to deleting all the data from the victim’s computer.
Listing of INAebsGB.so
It’s worth noting that a similar payload can be found in the implementation of the SambaCry exploit in Metasploit.
cblRWuoCc.so
The main functionality of this file is to download and execute one of the most popular open-source cryptocurrency mining utilities – cpuminer (miderd). It is done by the hardcoded shell-command, shown on the screenshot below.
The main functionality of cblRWuoCc.so
The file minerd64_s (8d8bdb58c5e57c565542040ed1988af9 — RiskTool.Linux.BitCoinMiner.a) downloaded in such a way is stored in /tmp/m on the victim’s system.
Cpuminer and what it actually mines
The interesting part is that the version of cpuminer used is “upgraded”, so it can be launched without any parameters to mine currency directly to the hardcoded attackers’ wallet. We obviously became interested in this wallet, so we decided to investigate a bit and uncover the balance of the attackers account.
Along with the attackers’ wallet number, the pool address (xmr.crypto-pool.fr:3333) can be found in the body of the miner. This pool is created for mining the open-source cryptocurrency – monero. Using all this data we managed to check out the balance on the attackers’ wallet and the full log of transactions. Let’s have a look:
Balance of the attackers’ account on 08.06.2017
Log of transactions with all the attackers’ cryptocurrency income
The mining utility is downloaded from the domain registered on April 29th 2017. According to the log of the transactions, the attackers received their first crypto-coins on the very next day, on April 30th. During the first day they gained about 1 XMR (about $55 according to the currency exchange rate for 08.06.2017), but during the last week they gained about 5 XMR per day. This means that the botnet of devices working for the profit of the attackers is growing.
Considering that the world discovered the EternalRed vulnerability only at the end of May, and the attackers had already adopted it, the rate of growth in the number of infected machines has significantly increased. After about a month of mining, the attackers gained 98 XMR, which means they earned about $5,500 according to the currency exchange rate at the time of writing.
Conclusion
As a result, the attacked machine turns into a workhorse on a large farm, mining crypto-currency for the attackers. In addition, through the reverse-shell left in the system, the attackers can change the configuration of a miner already running or infect the victim’s computer with other types of malware.
At the moment we don’t have any information about the actual scale of the attack. However, this is a great reason for system administrators and ordinary Linux users to update their Samba software to the latest version immediately to prevent future problems.
14-Year-Old Japanese Boy Arrested for Creating Ransomware
6.6.2017 thehackernews Ransomware
Japanese authorities have arrested a 14-year-old boy in Osaka, a prefecture and large port city, for allegedly creating and distributing a ransomware malware.
This is the first such arrest in Japan which involves a Ransomware-related crime.
Ransomware is a piece of malware that encrypts files on a victim's computer and makes them inaccessible until the victim pays a ransom, usually in Bitcoins, in order to get the decryption keys for the encrypted files.
Ransomware has been around for a few years, but currently, it has become a major cyber threat for businesses and users across the world.
Just last month, the WannaCry ransomware hit over 300,000 PCs within just 72 hours, wreaking havoc worldwide.
The recent arrest came after the teenager, who is a third-year junior high school student, created a ransomware virus and uploaded its source code on the Internet, according to multiple Japanese media.
The student, who admitted to the allegations, combined free encryption software to develop his own ransomware infection and then uploaded it to a foreign website and even taught people to download and use it to spread further for financial gain.
The teen also advertised the website through social media, including Twitter, telling users "I made ransomware. Please feel free to use it," the sources said.
According to Japanese police, the teen's ransomware allowed a downloader to infect victims' computers, demanding payment in digital currency. His ransomware framework has been downloaded over 100 times.
The authorities have not revealed the identity of the teenager, but have informed that the student just took about 3 days to create the ransomware program using his personal computer.
The student also told the authorities that he learned to code on his own and created the ransomware out of curiosity in order to become famous.
The Japanese police spotted the ransomware during "cyber patrolling" in January and confiscated the teen's computer after searching his house in April.
Learn How to Code — Though it is never recommended to develop a malware and spread it for fun, financial gain or other purposes, learning to code is not a crime.
If you're looking to 'learn how to code' and seeking a career as an expert-level programmer, you should know how to play with codes and make your own.
We have introduced an ultimate programming bundle that includes ten online training courses that could elevate your programming skills straight from beginner to advanced level.
The Ultimate Learn to Code 2017 Bundle, comes with lifetime access, offers you professional training courses on Python, Ruby, Java, iOS, HTML, CSS, AngularJS and other programming languages that are in high demands.
Jaff Ransomware Operation Tied to Cybercrime Store
5.6.2017 securityweek Ransomware
Jaff, a ransomware family that emerged on May 12, the same day WannaCry did, appears connected to wider operations, as a recent sample was found to share server space with a refined cybercrime marketplace, Heimdal Security warns.
Distributed via PDF documents attached to spam emails sent by the Necurs botnet, Jaff was already said to have been operated by the group behind Locky and Dridex, which also released the Bart ransomware last year.
Heimdal Security has revealed that Jaff shares server space with a cybercrime web shop that offers access to tens of thousands of compromised bank accounts, along with information on their balance, location, and attached email address.
The marketplace also allows cybercriminals to purchase stolen credit cards (some already verified), along with compromised accounts on PayPal, Amazon, eBay, and other online services. Some of the items sell for less than a dollar, while others are priced at several Bitcoins, the researchers say.
The marketplace doesn’t vet users, meaning that all types of malicious actors have access to the stolen goods.
The marketplace lists financial institutions from all around the world, with most of the compromised accounts seemingly originating from the U.S., Germany, France, Spain, Canada, Australia, Italy and New Zealand.
The marketplace also sells other types of user accounts that include financial data, such as those pertaining to portals like Apple, Bed Bath & Beyond, Barnes & Noble, Best Buy, Booking.com, Asos.com, and other ecommerce services.
“This doesn’t mean that those specific web shops have been compromised. Cyber criminals use a wide range of tactics to get into victims’ accounts, often focusing on breaking weak and/or reused passwords,” Heimdal Security evangelist Andra Zaharia notes.
The hackers can use these accounts to make fraudulent purchases or to harvest financial information pertaining to their owners. With access to stolen credit card data, cybercriminals can enjoy easy access to cash that can then be turned into untraceable Bitcoins.
According to Heimdal Security, the server this marketplace is hosted on is located in St. Petersburg, Russia, at IP 5.101.66 [.] 85. “The same server is also part of the infrastructure that fuels the Jaff ransomware attacks that have been sweeping across Europe and the rest of the world,” Zaharia says.
The domains used by this cybercrime marketplace include http://paysell[.]info, http://paysell[.]net, http://paysell[.]me, http://paysell[.]bz, http://paysell[.]org, and http://paysell[.]ws. Another domain is hosted on TOR (The Onion Router): paysellzh4l5lso7[.]onion.
Ransomware attacks often also aim at stealing as much user information as possible, but there doesn’t appear to be evidence that the stolen credentials available on this cybercrime marketplace were exfiltrated using Jaff.
In fact, Heimdal couldn’t share with SecurityWeek information on how the stolen data might have been acquired. Some possible explanations, however, include the use of other types of malware, or the exploit of the large number of credentials that emerged online last year as part of major data breaches affecting popular online platforms.
Jaff Ransomware campaigns linked to a black marketplace
4.6.2017 securityaffairs Ransomware
Security researchers linked Jaff ransomware campaigns to the backend infrastructure used by operators behind a black market.
Security researchers at Heimdal Security who are investigating a new strain of Jaff ransomware discovered that the malware is sharing the backend infrastructure with a black market offering for sale stolen card data and account information.
The black market is offering access to “tens of thousands of compromised bank accounts, complete with details about their balance, location, and attached email address.”
The black market offers compromised records for bank accounts most located in the United States, Germany, France, and Spain. Prices for the compromised accounts range from under $1 to several bitcoins, depending on the specific item.
“While analyzing a recent variant of Jaff, researchers have uncovered that this ransomware type shares server space with a refined cyber crime web store.” reads the analysis published by Heimdal Security.

The Jaff ransomware has been recently discovered, it was involved in a number of large-scale email campaigns each using a PDF attachment with an embedded Microsoft Word document embedding macros that download and execute the malicious code.
The discovery made by the experts at Heimdal Security confirms that hackers diversify their operations in order to maximize profits.
“As we know, a ransomware attack never stops at just encrypting data. It also harvests as much information as possible about the victim. By combining these informational assets, cyber criminals are engaging in both the long game, required to monetize stolen card data, and in quick wins, such as targeted ransomware attacks, whose simpler business model yields a fast return on investment,” continues the analysis.
The crooks used a server (IP address 5[.]101[.]66 [.] 85 ) located in St. Petersburg (Russia), the server is also involved in the campaign delivering the Jaff ransomware targeting users worldwide.
The cyber crime marketplace uses the following domains:
http://paysell[.]info
http://paysell[.]net
http://paysell[.]me
http://paysell[.]bz
http://paysell[.]org
http://paysell[.]ws
And TOR hidden service:
paysellzh4l5lso7[.]onion
Unfortunately, the case is not isolated, many criminal organizations used to diversify their activities to improve their operations.
“It can happen that we will see these two models combined, with data breaches becoming accompanied by subsequent ransomware attacks, which would make it a nightmare for companies to deal with,” concludes the analysis.
WannaCry Coding Mistakes Can Help Files Recovery Even After Infection
2.6.2017 thehackernews Ransomware
Last month WannaCry ransomware hit more than 300,000 PCs across the world within just 72 hours by using its self-spreading capabilities to infect vulnerable Windows PCs, particularly those using vulnerable versions of the OS, within the same network.
But that doesn't mean WannaCry was a high-quality piece of ransomware.
Security researchers have recently discovered some programming errors in the code of the WannaCrypt ransomware worm that might allow victims to restore their locked files without paying for any decryption key.
After deeply analysing the WannaCry code, security company at Kaspersky Lab found that the ransomware was full of mistakes that could allow some of its victims to restore their files with publicly available free recovery tools or even with simple commands.
Anton Ivanov, senior malware analyst at Kaspersky Lab, along with colleagues Fedor Sinitsyn and Orkhan Mamedov, detailed three critical errors made by WannaCry developers that could allow sysadmins to restore potentially lost files.
According to researchers, the issues reside in the way WannaCry ransomware deletes original files after encryption. In general, the malware first renames files to change their extension to ".WNCRYT," encrypt them and then delete the original files.
Recovering Read-only Files
Since it is not at all possible for malicious software to directly encrypt or modify read-only files, WannaCry copies the files and creates their encrypted copies.
While the original files remain untouched but are given a 'hidden' attribute, getting the original data back simply requires victims to restore their normal attributes.
That wasn't the only mistake within the WannaCry's code, as in some cases, the malware fails to delete the files after encrypting them properly.
Recovering Files from the System Drive (i.e. C drive)
Researchers have said that files stored on the important folders, like Desktop or Documents folder, can not be recovered without the decryption key because WannaCry has been designed to overwrite original files with random data before removal.
However, researchers noticed that other files stored outside of important folders on the system drive could be restored from the temporary folder using a data recovery software.
“...the original file will be moved to %TEMP%\%d.WNCRYT (where %d denotes a numeric value). These files contain the original data and are not overwritten,” researchers said.
Recovering Files from the Non-System Drives
Researchers also found that for non-system drives, the WannaCry Ransomware creates a hidden '$RECYCLE' folder and moves original files into this directory after encryption. You can recover those files just by unhiding the '$RECYCLE' folder.
Also, due to "synchronization errors" in WannaCry's code, in many cases the original files remain in the same directory, making it possible for victims to restore insecurely deleted files using available data recovery software.
Programming Blunders: The New Hope for WannaCry Victims
These programming errors in the code of WannaCry offer hope to many victims.
"If you were infected with WannaCry ransomware there is a good possibility that you will be able to restore a lot of the files on the affected computer," Kaspersky Lab wrote in a blog post published Thursday. "The code quality is very low."
"To restore files, you can use the free utilities available for data recovery."
The recovery of files infected by WannaCry was first made possible by French researchers Adrien Guinet and Benjamin Delpy, who made a free WannaCry decryption tool that works on Windows XP, Windows 7, Windows Vista, Windows Server 2003 and Server 2008.
It's been almost a month since WannaCry epidemic hit computers worldwide, but the hackers behind the self-spread ransomware, which leverages leaked NSA's Windows SMB exploits EternalBlue and DoublePulsar, have not been identified yet.
While police and cyber security firms continue to search for answers surrounding the origins of the WannaCry campaign, Dark web intelligence firm Flashpoint recently indicated the perpetrators might be Chinese, based on its linguistic analysis.
Decoy Files Found in PDFs Dropping Jaff Ransomware
1.6.2017 securityweek Ransomware
Spam campaigns distributing the Jaff ransomware have evolved and are using multiple decoy files hidden inside malicious PDF attachments, Trustwave security researchers say.
Jaff is a new ransomware family that emerged in early May, and has been distributed through the infamous Necurs spam botnet. After fueling a surge in malicious spam last year, Necurs went dark in December 2016, only to return in April 2017.
The Locky ransomware, historically associated with spam emails distributed by the Necurs botnet, went silent in December as well, and made only a brief return in April. As of early May, Necurs switched to distributing the Jaff ransomware and continues to do so.
The reason for this appears to be simple: Jaff was supposedly developed by the same group behind Locky and Dridex, considering the use of resources previously associated with these threats. The first Jaff variant even used a ransom note similar to Locky’s, but the second variant adopted a redesigned one, along with few other changes.
The distribution campaign uses PDF files attached to the spam emails, but with Word documents hidden inside. The email subject ranges from fake invoice notifications to fake payment receipts, and from alleged image scans to random file copies.
The ultimate goal remains the same: the Word document inside the PDF file is meant to download and drop a malware executable. According to Trustwave, however, the PDF campaigns have been evolving almost daily, with a larger number of embedded files discovered inside recent attachments and with additional layers of obfuscation.
“These additional files do nothing, and are probably just decoys. But the main .docm file, with its malicious macro, still acts as the malware downloader,” Trustwave’s Homer Pacag explains.
The PDF file contains an exportDataObject Launch instruction to drop and launch the embedded .docm file. When enabled, the Word document’s vbaProject macro component starts downloading the Jaff ransomware from a specific URL.
Over the past week or so, the Jaff variant being delivered via Necurs appends the .wlu extension to the encrypted files (the initial variant was using the .jaff extension). However, it continues to use the same URL to guide victims to where they can recover their encrypted files.
WannaCry mistakes that can help you restore files after infection
1.6.2017 Kaspersky Ransomware
Sometimes ransomware developers make mistakes in their code. These mistakes could help victims regain access to their original files after a ransomware infection. This article is a short description of several errors, which were made by the WannaCry ransomware developers.
Errors in file removal logic
When Wannacry encrypts its victim’s files, it reads from the original file, encrypts the content and saves it into the file with extension “.WNCRYT”. After encryption it moves “.WNCRYT” into “.WNCRY” and deletes the original file. This deletion logic may vary depending on the location and properties of the victim’s files.
The files are located on the system drive:
If the file is in an ‘important’ folder (from the malware developers’ point of view – e.g. Desktop and Documents), then the original file will be overwritten with random data before removal. In this case, unfortunately, there is no way to restore the original file content.
If the file is stored outside of ‘important’ folders, then the original file will be moved to %TEMP%\%d.WNCRYT (where %d denotes a numeric value). These files contain the original data and are not overwritten, they are simply deleted from the disk, which means there is a high chance it will be possible to restore them using data recovery software.
Renamed original files that can be restored from %TEMP%
The files are located on other (non-system) drives:
Ransomware creates the “$RECYCLE” folder and sets hidden+system attributes to this folder. This makes this folder invisible in Windows File Explorer if it has a default configuration. The malware intends to move the original files into this directory after encryption.
The procedure that determines the temporary directory to store original files before removal
However, because of synchronization errors in the ransomware code in many cases the original files stay in the same directory and are not moved into $RECYCLE.
The original files are deleted in an unsecure way. This fact makes it possible to restore the deleted files using data recovery software.
Original files that can be restored the from a non-system drive
The procedure that constructs the temporary path for an original file
The piece of code calling the above procedures
Read-only files processing error
While analysing WannaCry, we also discovered that this ransomware has a bug in its read-only file processing. If there are such files on the infected machine, then the ransomware won’t encrypt them at all. It will only create an encrypted copy of each original file, while the original files themselves only get the “hidden” attribute. When this happens, it is simple to find them and restore their normal attributes.
Original read-only files are not encrypted and stay in the same place
Conclusions
From our in depth research into this ransomware, it is clear that the ransomware developers have made a lot of mistakes and, as we pointed out, the code quality is very low.
If you were infected with WannaCry ransomware there is a good possibility that you will be able to restore a lot of the files on the affected computer. To restore files, you can use the free utilities available for file recovery. We advise organizations share this article with their system administrators – as they can use the file recovery utilities on affected machines in their network.
Linguistic Analysis Suggests WannaCry Hackers Could be From Southern China
30.5.2017 thehackernews Ransomware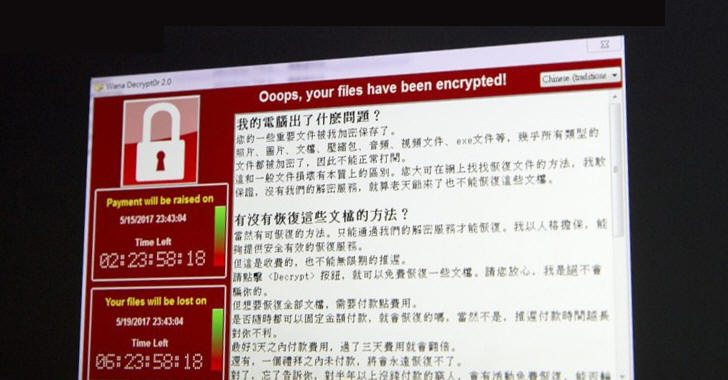
It’s been almost four weeks since the outcry of WannaCry ransomware, but the hackers behind the self-spread ransomware threat have not been identified yet.
However, two weeks ago researchers at Google, Kaspersky Lab, Intezer and Symantec linked WannaCry to ‘Lazarus Group,’ a state-sponsored hacking group believed to work for the North Korean government.
Now, new research from dark web intelligence firm Flashpoint indicates the perpetrators may be Chinese, based on its own linguistic analysis.
Flashpoint researchers Jon Condra and John Costello analyzed each of WannaCry's localized ransom notes, which is available in 28 languages, for content, accuracy, and style, and discovered that all the notes, except English and Chinese versions (Simplified and Traditional), had been translated via Google Translate.
According to the research, Chinese and English versions of the ransomware notes were most likely written by a human.
On further analysis, researchers discovered that the English ransom note contains a "glaring" grammatical error, which suggests the ransomware author may be a non-native English speaker.
“Though the English note appears to be written by someone with a strong command of English, a glaring grammatical error in the note suggest the speaker is non-native or perhaps poorly educated.”
And since Google Translate does not work good at translating Chinese to English and English to Chinese, and often produces inaccurate results, the English version could be written for translating the ransom note into other languages.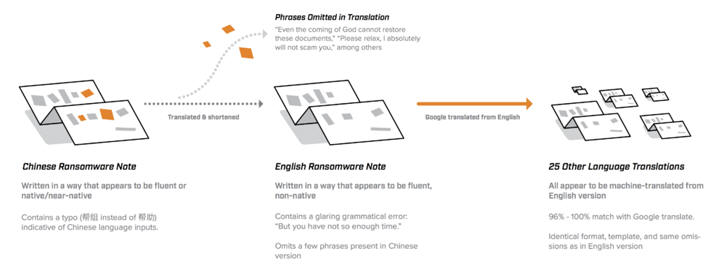
“Comparisons between the Google translated versions of the English ransomware note to the corresponding WannaCry ransom note yielded nearly identical results, producing a 96% or above match.”
According to the Flashpoint report, the Chinese ransom notes contain "substantial content not present in any other version of the note," and they are longer than and formatted differently from the English one.
The Chinese ransom notes also use proper grammar, punctuation, syntax, and character choice – indicating that the ransomware writer is fluent in the Chinese language.
"A typo in the note, bang zu (幫組) instead of bang zhu (幫助), which means ‘help,' strongly indicates the note was written using a Chinese-language input system rather than being translated from a different version," the researchers explain.
"The text uses certain terms that further narrow down a geographic location. One term, libai ( 禮拜 ) for ‘week,’ is more common in southern China, Hong Kong, Taiwan, and Singapore...The other “杀毒软件” for “anti-virus” is more common in the Chinese mainland."
All these clues made Flashpoint researchers into believing with high confidence that the unknown author or authors of WannaCry ransomware are fluent Chinese speaker and that the Chinese are the source of the English version of the ransom note.
However, Flashpoint researchers say it's hard to speculate the nationality of the WannaCry hackers as they may be affiliated to any Asian (China, Hong Kong, Taiwan, or Singapore).
WannaCry epidemic hit more than 300,000 PCs in more than 150 countries within just 72 hours, using self-spreading capabilities to infect vulnerable Windows PCs, particularly those using older versions of the operating system.
While most of the affected organisations have now returned to normal, law enforcement agencies across the world are on the hunt.
Linguistic Analysis Suggests WannaCry Authors Speak Chinese
26.5.2017 securityweek Ransomware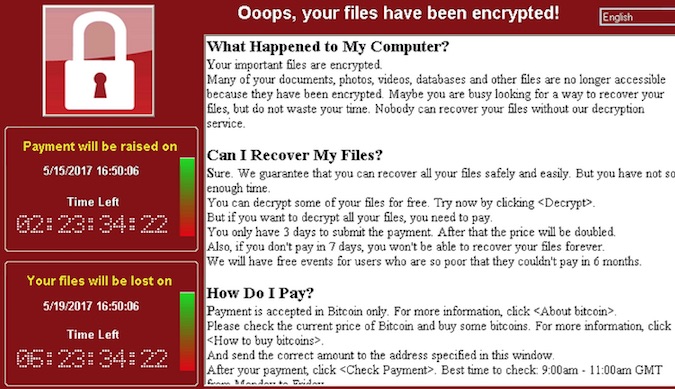
A linguistic analysis of more than two dozen ransom notes displayed by the WannaCry ransomware suggests that its authors are fluent Chinese speakers and they also appear to know English.
While malware code similarities suggest that WannaCry has been developed by the North Korea-linked threat actor known as Lazarus, some believe the attack does not fit Pyongyang’s style and interests.
Researchers at threat intelligence firm Flashpoint have analyzed 28 WannaCry ransom notes, including ones written in Chinese (both simplified and traditional), Danish, Dutch, English, French, German, Indonesian, Italian, Japanese, Korean, Norwegian, Portuguese, Romanian, Russian, Spanish, Swedish and Turkish.
The linguistic analysis showed that there are significant differences between the notes written in Chinese and the ones written in other languages. Evidence suggests that the Chinese note, which mostly uses proper grammar, punctuation and syntax, was actually written with a Chinese-language keyboard.
One of the words used in the Chinese note is more common in South China, Hong Kong, Singapore and Taiwan, while another term is more widely used in mainland China.
Experts pointed out that the note written in Chinese includes a significant amount of content that is not present in other versions, and they believe it may have served as the source for the English version.
The English note is also well written, but it contains a major grammar mistake that suggests its author is either not a native speaker or possibly someone who is not well educated.
Flashpoint has determined that the English note has been used to translate the text into other languages using a service such as Google Translate. Tests conducted by researchers show that there is a match of at least 96 percent between the WannaCry notes and Google-translated versions of the English message.
While WannaCry may have been developed by more than one individual, Flashpoint said with high confidence that the Chinese-language ransom note was written by someone who is fluent in Chinese. The English note was written by someone who knows English, but does not appear to be a native speaker, the company said.
“Given these facts, it is possible that Chinese is the author(s)’ native tongue, though other languages cannot be ruled out,” Flashpoint said. “It is also possible that the malware author(s)’ intentionally used a machine translation of their native tongue to mask their identity. It is worth noting that characteristics marking the Chinese note as authentic are subtle. It is thus possible, though unlikely, that they were intentionally included to mislead.”
While security firms such as Symantec and Kaspersky presented evidence linking WannaCry to North Korea, Cybereason questioned the apparent connection, pointing to differences in tactics and the fact that two of the most impacted countries, Russia and China, are North Korea’s biggest allies.
Researchers at Flashpoint are not the only ones who mentioned China. James Scott, a senior fellow at the Institute for Critical Infrastructure Technology, also believes the attack may have been conducted by hackers from China's People's Liberation Army "moonlighting" in their spare time, or freelance Chinese hackers hired by Pyongyang.
Jury Out on North Korea Link to Ransomware Attack
25.5.2017 securityweek Ransomware
Was North Korea behind the ransomware epidemic that hit global computer networks earlier this month?
That's the subject of heated debate in cybersecurity circles after analysts found similarities in the "WannaCry" worm to other malware attributed to North Korea, including the 2014 hack of Sony Pictures and a cyberheist of millions of dollars from the Bangladesh central bank.
The security firm Symantec this week said the shared code makes it "highly likely" that the attacks were connected to the hacker group given the code name Lazarus, which many believe is North Korean.
Israel-based cybersecurity firm Intezer last week reached a similar conclusion, finding that WannaCry had "strong links to other malware families, believed to be developed by North Korean hackers, or known to be used in attacks against South Korean organizations."
Russian-based security firm Kaspersky Lab and others also pointed to a likely North Korean link.
While the evidence is not conclusive -- hackers can often hide or "spoof" their real identities -- North Korea is emerging as one of the likely suspects despite a strong denial by the Pyongyang envoy to the United Nations, some analysts say.
Symantec researchers said that despite the likely North Korea link, the WannaCry attacks "do not bear the hallmarks of a nation-state campaign but are more typical of a cybercrime campaign."
- Desperate for cash -
"I could easily see North Korea doing this as a way to get money," said Paul Benda, a Pentagon and Department of Homeland Security official who is now chief technology officer at Global Security and Innovative Strategies, a Washington consultancy.
"With the sanctions they are under they need cold hard cash."
Other analysts have noted that sanctions squeezing Pyongyang may be prompting desperate actions to raise cash through various channels, including cybercrime.
"While years of sanctions have isolated the Hermit Kingdom from much of the global financial system, North Korea may be seeking to fund the state's coffers through a widespread cybercrime campaign," said FireEye analyst Luke McNamara in a recent post on the Lawfare blog.
Paradoxically, he said, the effort to persuade and other nations to pressure North Korea may be encouraging further cyberattacks: "Pyongyang would be left with few options to compensate for lost income that it could ramp up as quickly as cybercrime."
The attacks discovered last week caused havoc in global computer networks, affecting as many as 300,000 machines in 150 countries and disrupting governments and several industries. The hackers developed the virus to exploit a flaw exposed in leaked documents from the National Security Agency.
- Inconsistencies -
But despite the growing concerns over North Korea, some analysts say it's too soon to point the finger and cite inconsistencies with the Pyongyang connection.
The WannaCry attack appeared unsophisticated: researchers were able to halt the spread with a $10 purchase of a web domain that activated a "kill switch."
And various estimates showed the "ransom" raised amounted to a paltry $116,000 from 302 entities more than a week after computers were locked down.
James Scott, a senior fellow at the Institute for Critical Infrastructure Technology, said WannaCry was "barely functional" and spread widely only because of the large number of networks and computers which failed to upgrade security and were vulnerable to the self-replicating "worm."
The hackers known as Lazarus are a sophisticated cybermercenary group, Scott told AFP. "They use elaborate traps, obfuscation techniques and wipers to eliminate digital footprints. This (WannaCry) has none of that."
More likely, Scott said, is that the attacks were carried out by hackers from China's People's Liberation Army "moonlighting" in their spare time.
Scott, who disputes the widely held belief that the Lazarus group is North Korean, said it is possible that Pyongyang has outsourced some of its cybercrime to these freelance Chinese hackers.
Analysts at Boston-based security firm Cybereason also questions the role of North Korea.
"Nothing in North Korea's past cyber campaigns or in their conventional military and foreign policy fit this mold," the researchers said in a blog.
John Arquilla, chair of defense analysis at the Naval Postgraduate School, said that despite the common patterns in the recent attacks, cyber forensics still have a long way to go to positively identify the source of an attack.
"We are not at the level of CSI," he said, referring to the popular television criminal forensics show. "We have to be very careful about the potential for deception. I would not rush to take military or economically coercive actions on the basis of what might or might not be the truth" on the source of the attacks, Arquilla said.
Wanna Cry Again? NSA’s Windows 'EsteemAudit' RDP Exploit Remains Unpatched
25.5.2017 thehackernews Ransomware
Brace yourselves for a possible 'second wave' of massive global cyber attack, as SMB (Server Message Block) was not the only network protocol whose zero-day exploits created by NSA were exposed in the Shadow Brokers dump last month.
Although Microsoft released patches for SMB flaws for supported versions in March and unsupported versions immediately after the outbreak of the WannaCry ransomware, the company ignored to patch other three NSA hacking tools, dubbed "EnglishmanDentist," "EsteemAudit," and "ExplodingCan."
It has been almost two weeks since WannaCry ransomware began to spread, which infected nearly 300,000 computers in more than 150 countries within just 72 hours, though now it has been slowed down.
For those unaware, WannaCry exploited a Windows zero-day SMB bug that allowed remote hackers to hijack PCs running on unpatched Windows OS and then spread itself to other unpatched systems using its wormable capability.
EsteemAudit: Over 24,000 PCs Still Vulnerable
EsteemAudit is another dangerous NSA-developed Windows hacking tool leaked by the Shadow Brokers that targets RDP service (port 3389) on Microsoft Windows Server 2003 / Windows XP machines.
Since Microsoft no longer support Windows Server 2003 and Windows XP and unlike EternalBlue the company has not released any emergency patch for EsteemAudit exploit so far, over 24,000 vulnerable systems remains still exposed on the Internet for anyone to hack.
"Even one infected machine opens your enterprise to greater exploitation," says enSilo, a cyber security firm who came up with the AtomBombing attack last year and now has released an unofficial patch for EsteemAudit, which we have introduced later in this article.
EsteemAudit can also be used as a wormable malware, similar to the WannaCry ransomware, which allows hackers to propagate in the enterprise networks, leaving thousands of systems vulnerable to ransomware, espionage and other malicious attacks.
Ransomware authors, such as criminals behind CrySiS, Dharma, and SamSam, who are already infecting computers via RDP protocol using brute force attacks, can leverage EsteemAudit anytime for widespread and damaging attacks like WannaCry.
How to Secure Your Computers?
Due to the havoc caused by WannaCry, SMB service gained all the attention, neglecting RDP.
"Windows XP-based systems currently account for more than 7 percent of desktop operating systems still in use today, and the cyber security industry estimates that more than 600,000 web-facing computers, which host upwards of 175 million websites, still run Windows Server 2003 accounting for roughly 18 percent of the global market share," enSilo says.
Since Microsoft has not released any patch for this vulnerability, users and enterprises are advised to upgrade their systems to the higher versions to secure themselves from EsteenAudit attacks.
"Of the three remaining exploits, “EnglishmanDentist,” “EsteemAudit,” and “ExplodingCan,” none reproduces on supported platforms, which means that customers running Windows 7 and more recent versions of Windows or Exchange 2010 and newer versions of Exchange are not at risk," Microsoft says.
If it's hard for your enterprise to upgrade their systems immediately, it's good for them to secure their RDP port by either disabling it or putting it behind the firewall.
Meanwhile, enSilo has released a patch to help Windows XP and Server 2003 users secure their machines against EsteemAudit. You can apply the patch to secure your systems, but keep in mind, that it is not an official patch from Microsoft.
If you have any doubt on the patch, enSilo is a reputed cyber security company, though I expect Microsoft to release an official patch before any outcry like that of WannaCry.
Master Keys for Crysis ransomware released on a forum
25.5.2017 securityaffairs Ransomware
Researchers at ESET security firm have discovered that someone has released 200 master keys for the latest variants of the prominent Crysis ransomware.
While security experts continue to investigate the WannaCry attack, someone has released 200 master keys for the latest variants of the prominent Crysis ransomware. The file encrypted by this version have the .wallet and .onion extension added to their original name.
Antivirus firm ESET has used the leaked information to develop the ESET Crysis decrypting tool that is available for download on the company “utilities page.”
The master keys were posted by a new member of a forum at BleepingComputer.com that aim to help victims of this threat.

This is the third time that someone published the master key for the Crysis ransomware.
“This has become a habit of the Crysis operators lately – with this being the third time keys were released in this manner. Since the last set of decryption keys was published, Crysis ransomware attacks have been detected by our systems over ten thousand times.” reads the blog post published by ESET.
Decryption tools allow victims of the ransomware-based campaigns to restore their files without paying the ransom to the criminal organizations.
Recently the Quarkslab researcher, Adrien Guinet, has published a software, called Wanadecrypt, he used to recover the decryption key required to restore the files on an infected XP computer. The expert successfully tested the Wanadecrypt software on a small number of infected XP computers, but it is not clear if the technique works on every PC.
The technique devised by Adrien Guinet allows retrieving the secret encryption keys used by the WannaCry ransomware for free, it works on Windows XP, Windows 7, Windows Vista, Windows Server 2003 and 2008 operating systems.
Security researcher Benjamin Delpy developed another tool called WanaKiwi that not only retrieve the prime numbers from the memory but automate the whole decryption process of the WannaCry-infected files.
WanaKiwi works on Windows XP, Windows 7, Windows Vista, Windows Server 2003 and 2008 as explained by Matt Suiche from security firm Comae Technologies.
Despite the efforts of law enforcement and security firms in the fights against ransomware, this category of malware remains one of the most dangerous computer threats. Prevention is essential in keeping users safe.
“Prevention is essential in keeping users safe. Therefore, we recommend that all users keep their operating systems and software updated, use reliable security solutions with multiple layers of protection, and regularly back up all important and valuable data at an offline location (such as external storage).” concluded ESET.
New Jaff Ransomware Variant Emerges
25.5.2017 securityweek Ransomware
Although it dominated headlines over the past couple of weeks, WannaCry wasn’t the only ransomware family running rampant. Another active threats was Jaff, a ransomware family that emerged just days before the WannaCry outbreak.
Right from the start, Jaff stood out because it was being distributed by the Necurs botnet and was using a similar ransom page design as Locky. Thus, it didn’t take long for security researchers to associate the new threat with the actors behind Locky and Dridex, who also launched the Bart ransomware last year.
The ransomware was appending the .jaff extension to the encrypted files and demanding a huge ransom, at around 2 Bitcoin. The infection vector was .PDF files sent as attachments in spam emails.
A newly observed Jaff variant continues to use Necurs and PDF files for infection, but moved away from the .jaff extension and the Locky-like ransom note, Brad Duncan, Palo Alto Networks threat intelligence analyst and handler at the SANS Internet Storm Center, says.
The ransomware now appends the .wlu extension to the encrypted files and uses a ransom note featuring green fonts on a dark background. The security researcher also noticed that the ransomware authors ask for a 0.35630347 Bitcoin ransom now.
First observed on Tuesday, May 23, the spam emails distributing the new Jaff variant use a fake invoice theme. These messages feature a PDF attachment that contains an embedded Word document with malicious macros designed to infect the machine with rasomware.
“The Word macros generate an initial URL to download an encoded Jaff binary, then we see one other URL for post-infection callback from an infected host. The initial HTTP request for Jaff returns an encoded binary that's been XORed with the ASCII string I6cqcYo7wQ,” Duncan reveals.
The same as the initial Jaff variant, the new version targets over 400 file types. After completing the encryption process, it drops a ransom note to inform the victim on what happened and to provide information on how they can pay the ransom.
Because of its alleged connection with a large crime group, Jaff has the potential of becoming a major threat fast. WannaCry might have stolen the headlines for the past days, but Jaff is slowly growing to become a prevalent threat.