
Ransomware Articles - H 2020 1 2 3 4 5 6 7 8 9 10 11 Ransomware List - H 2021 2020 2019 2018 1 Ransomware blog Ransomware blog
Ransomware infected systems at a luxury hotel locking guests in and out of the rooms
30.1.2017 securityaffairs Ransomware
The Romantik Seehotel Jäegerwirt 4-Star Superior Luxury Hotel was hit by a ransomware attack that locked guests in and out of the rooms.
Another singular incident involved a ransomware, the victims are hundreds of guests of a luxurious hotel in Austria, the Romantik Seehotel Jäegerwirt 4-Star Superior Hotel. The guests were locked in or out of their rooms. The malware infected the systems at the hotel and its administration opted to pay the ransom to restore a normal operation.

The administration of the Romantik Seehotel Jäegerwirt 4-Star Superior Hotel has admitted having paid €1,500 in Bitcoin to restore the electronic key card system that was compromised by the ransomware.The luxury hotel uses the electronic key card system to manage key cards of the hotel doors.
This isn’t the first cyber attack suffered by the luxury hotel, the hotel management confirmed its systems have been hit multiple times, but this time crooks compromised the internal key management system.
According to the news agency, cyber criminals gained control over the general computer system paralyzing almost any activity at the luxury hotel, including the reservation system and the cash desk system.
“One of Europe’s top hotels has admitted they had to pay thousands in Bitcoin ransom to cybercriminals who managed to hack their electronic key system, locking hundreds of guests in or out of their rooms until the money was paid.” reported The Local website.
I always suggest avoiding the payment of the ransom because there is no certainty that the files are decrypted. Fortunately, in the specific case, after the hotel management paid the ransom the systems were completely restored.
But never trust a cyber criminal!
Even after the payment of the ransom, hackers left a backdoor to the hotel system and conduct further attacks later.
The IT staff at the hotel detected the backdoor and neutralized it, it also adopted further security measures to repel further attacks.
Hotel managers decided to publicly disclose the story to warn hotel about the dangers of cyber attack.
“The house was totally booked with 180 guests; we had no other choice. Neither police nor insurance helps you in this case.” explained the Managing Director Christoph Brandstaetter.
“The restoration of our system after the first attack in summer has cost us several thousand Euros. We did not get any money from the insurance so far because none of those to blame could be found. Every euro that is paid to blackmailers hurts us. We know that other colleagues have been attacked, who have done similarly.”
Ransomware Hijacks Hotel Smart Keys to Lock Guests In and Out of the Rooms
29.1.2017 thehackernews Ransomware
Ransomware Hijacks Hotel Smart Keys to Lock Guests In and Out of the Rooms
What's the worst that could happen when a Ransomware hits a Hotel?
Recently, hundreds of guests of a luxurious hotel in Austria were locked in or out of their rooms when ransomware hit the hotel's IT system, and the hotel had no choice left except paying the attackers.
Today, we are living in a digital age that is creating a digital headache for people and organizations around the world with cyber attacks and data breaches on the rise.
Ransomware is one of them.
The threat has been around for a few years, but during 2016, it has turned into a noxious game of Hackers to get paid effortlessly by targeting hospitals, Universities, private businesses and even police departments and making hundreds of millions of dollars.
Now, the Romantik Seehotel Jäegerwirt 4-Star Superior Hotel has admitted it paid €1,500 (£1,275/$1,600) in Bitcoin ransom to cybercriminals who managed to break into their network and hack their electronic key card system that prevented its guests from entering or leaving their rooms.
The luxury hotel with a beautiful lakeside setting on the Alpine Turracher Hoehe Pass in Austria, like several other hotels in the industry, has a modern IT system that includes key cards for its hotel doors, which could not be programmed.
Also Read: This Tool Detects Never-Seen-Before Ransomware Before It Encrypts Your Data
According to the hotel management, the hotel has been hit multiple times by hackers, but this time they managed to take down the entire key system, preventing its guests to getting in or going out of their rooms, reported The Local.
Besides gaining control of the electronic key system, the hackers even gained control over the general computer system, shutting down all hotel computers, including the reservation system and the cash desk system.
Once the hotel made the payment, the system was completely restored that allowed the hotel staff to gain access to the network and hotel guests to enter and exit their rooms.
What's interesting? Even after the hotel fulfilled the hackers demand, the hackers left a backdoor to the hotel system in an attempt to conduct another cyber attack later.
Fortunately, the security standards of the hotel had been improved by its IT department, and critical networks had been separated to thwart the attack, giving attackers no chance to harm the hotel again.
Furious hotel managers decided to go public with the incident to warn others about the dangers of cyber attack, with Managing Director Christoph Brandstaetter said:
"The house was totally booked with 180 guests; we had no other choice. Neither police nor insurance helps you in this case.
The restoration of our system after the first attack in summer has cost us several thousand Euros. We did not get any money from the insurance so far because none of those to blame could be found.
Every euro that is paid to blackmailers hurts us. We know that other colleagues have been attacked, who have done similarly."
The Ransomware had stolen the nights of many businesses and organizations, as they would often be blamed to fight up to this nasty threat.
Ransomware criminals often demand the ransom in Bitcoin (BTC) for the surety of not getting caught, as Bitcoin transactions are non-trackable due to its decentralized nature.
The frequent payment to Ransomware encourages criminals to stash the cash and develop a more enticing framework for the next target. So, instead of paying or encouraging this scheme, keep your software and systems updated and avoid clicking suspicious links.
Nasty VirLocker Ransomware Returns
27.1.2017 SecurityWeek Ransomware
VirLocker, a nasty piece of ransomware that has been making the rounds for a few years, has recommenced its nefarious activity, Malwarebytes Labs researchers warn.
The one feature that sets this piece of polymorphic ransomware apart from other threats in the category is its ability to propagate through all the files it has touched. Specifically, VirLocker copies itself into the infected files, making it very easy for victims to accidentally leak it to their friends or to copy it to removable storage.
“Backups become infected, and even applications and EXE’s are not safe. Basically, when getting infected by VirLocker, you can no longer trust a single file that is on the affected machine,” Malwarebytes Labs’ Nathan Scott explains.
The main issue is to clean up the machine, because even the tools that the victim attempts to use for this process might be infected. What’s more, the malware attempts to infect newly downloaded files even before they are opened, so grabbing a disinfection tool from the web might not help either, the security researcher says.
VirLocker’s polymorphic abilities are the root cause of everyone’s headache, mainly because the malware can change a file differently every time it infects it: it can add fake code in certain sections to modify the file differently, can choose between multiple API’s in the main loader to avoid section fingerprinting, can use different XOR and ROL seeds to make the encrypted content of the exe entirely different, and more.
This makes the malware very difficult to detect, because infected files can’t be used in this regard, considering that any infected file is “practically different in many ways than any other version of itself:” the malware always seeds the encrypted code differently, and the stub can be different each creation.
“When the infection is executed, the FUD packer (which can be in some ways polymorphic itself) unpacks the first decryption function which is a mixture of Base64 and XOR and is always differently seeded. This new decryption function then decrypts another new decryption function that is a mixture of XOR/ROL and is always differently seeded. This decryption function then finally gets to the malicious code intended to run on the machine,” the security researcher notes.
The malware checks whether it has already infected the machine and if it was paid. If it has been paid, it switches to decrypting and extracting the original file that it had embedded inside of itself, then closes. If the user hasn’t paid, the ransomware opens the screen locker, if it’s not already open.
If the computer hasn’t been infected before, VirLocker opens the file embedded inside itself to trick the user into believing there’s no issue at all. In the background, however, the malware continues to infect the machine. Thus, the ransomware can spread without its author’s intervention: if a user sends an infected photo to a friend who opens it on their computer, the second machine is automatically infected.
“If anyone ever infected by VirLocker happened to send out any files after they were infected, thinking it was just a screen locker, those files will infect more people. This continuous loop of infection can cause VirLocker to spread like wildfire,” Scott notes.
Because extensions are turned off, users might not even see that the files on their machine have the .exe extension appended to it. What’s more, VirLocker adds itself to virtually every file on the computer, including media files and applications, and opening any of these files causes the malware to run again.
When trying to clean their machines, users are advised to first trick the malware into believing that the ransom has been paid, to avoid being infected once again. For that, when VirLock displays a screen lock, which usually impersonates some type of legal authority, users should enter a 64-length string in the “Transfer ID” text-box, and the ransomware will accept it as a real payment. This means that even typing in 64 zeros would do the trick.
After that, users should click on the “Pay Fine” button, to remove the ransom Lock Screen and to trick the malware into believing the ransom was paid. Next, users can start double-clicking on their infected files, as the malware will automatically extract the original files inside of them.
The security researchers recommend that users recover files that are important to them and save them on an external drive, while making sure that they avoid copying .exe files as well. Next, users should format the computer’s hard drive and re-install the operating system, for a fresh, clean start. “A complete reformat should be done, since nothing on the machine should be trusted after this infection,” Malwarebytes Labs says.
A few years back, ESET released a standalone cleaner for VirLock-infected files, available here.
Sage 2.0 Ransomware is spreading and demands a $2,000 Ransom
25.1.2017 securityaffairs Ransomware
A newly observed spam campaign is spreading a ransomware variant known as Sage 2.0 that is demanding a $2,000 ransom for the decryption key.
Sage 2.0 is a new ransomware recently spotted by security experts, it was first observed in December and not now it is distributed via malicious spam. Sage is considered a variant of CryLocker ransomware, it is being distributed by the Sundown and RIG exploit kits. The current campaign also leverages steganography to exfiltrate information about the victim’s PC inside a PNG image.

The malicious messages have a ZIP attachment that contains a Word document with malicious macros that once executed download and install the Sage ransomware. In some cases the experts also observed that the ZIP archive contains a .js file with the same functionality.
Duncan also explained that some of the malicious attachments are double-zipped and often the recipient’s name is part of the attachment’s file name.
“Emails from this particular campaign generally have no subject lines, and they always have no message text. The only content is a zip attachment containing a Word document with a malicious macro that downloads and installs ransomware. Sometimes, I’ll see a .js file instead of a Word document, but it does the same thing.” Duncan wrote in a report. “Often, the recipient’s name is part of the attachment’s file name. I replace those names with [recipient] before I share any info. A more interesting fact is the attachments are often double-zipped. They contain another zip archive before you get to the Word document or .js file.”
When the Sage 2.0 ransomware infects a Windows 7 machine it triggers the User Account Control (UAC) technology, this means that the user has to authorize its execution.
The ransom note includes instructions to pay an initial $2,000 ransom (or 2.22188 bitcoin). The ransomware uses a Tor-based domain with a decryptor screen.
In case of non-payment, the fee will increase over the time, but after a deadline reported on the Tor website the victim will be able possible to recover its files.
“The infected Windows host has an image of the decryption instructions as the desktop background. There’s also an HTML file with the same instructions dropped to the desktop. The same HTML file is also dropped to any directory with encrypted files. ‘.sage’ is the suffix for all encrypted files,” the security researcher explains.
The Sage ransomware maintains persistent on the infected machine by a scheduled task, and it’s stored as an executable in the user’s AppData\Roaming directory.
The Sage 2.0 ransomware generates post-infection traffic, like the CryLocker ransomware, in the form of HTTP POST requests. Sage traffic is different from CryLocker one because it is encrypted in some way.
“When the callback domains for Sage didn’t resolve in DNS, the infected host sent UDP packets sent to over 7,000 IP addresses. I think this could be UDP-based peer-to-peer (P2P) traffic, and it appears to be somehow encoded or encrypted,” added the security researcher.
“I’m not sure how widely-distributed Sage ransomware is. I’ve only seen it from this one malspam campaign, and I’ve only seen it one day so far. I’m also not sure how effective this particular campaign is. It seems these emails can easily be blocked, so few end users may have actually seen Sage 2.0. Still, Sage is another name in the wide variety of existing ransomware families. This illustrates how profitable ransomware remains for cyber criminals,” Duncan concludes.
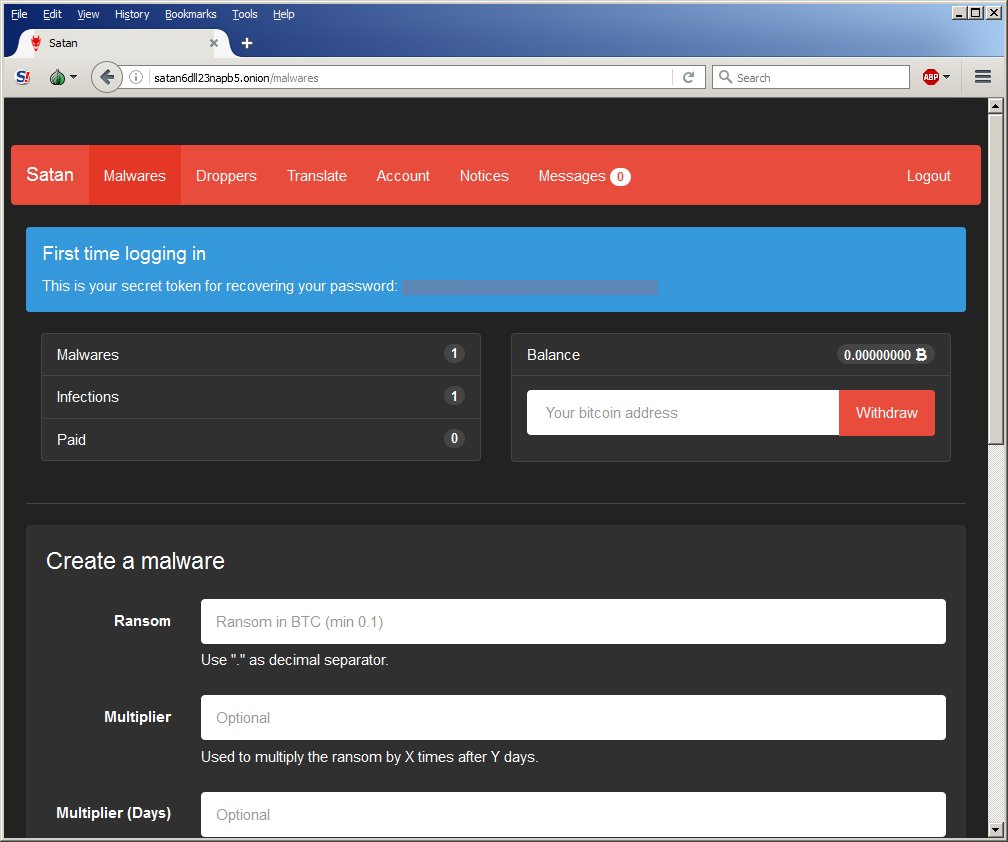
Satan, the ransomware-as-a-service surfaced in the dark web
20.1.2017 securityaffairs Ransomware
The independent malware research @Xylit0l discovered the Satan ransomware, a malware belonging to the Gen:Trojan.Heur2.FU family.
Yesterday the independent malware research @Xylit0l discovered the Satan ransomware, a malware belonging to the Gen:Trojan.Heur2.FU family. Satan is provided as a RaaS (Ransomware-as-a-Service).
Follow
Xylitol @Xylit0l
New #RaaS https://www.virustotal.com/en/file/c04836696d715c544382713eebf468aeff73c15616e1cd8248ca8c4c7e931505/analysis/1484756083/ …
5:34 PM - 18 Jan 2017
72 72 Retweets 72 72 likes
The Satan ransomware used RSA-2048 and AES-256 cryptography, it appends the names of encrypted files with the “.stn” extension.

“As mentioned above, Satan’s developers provide a service allowing prospective cyber criminals to make money by distributing this ransomware. In exchange, developers receive 30% of revenues generated by users.” Reads the analysis published on pcrisk.com.
“The Satan platform has a user-friendly interface, it is really simple to use to create your own ransomware. Users just need to have a Bitcoin wallet to use for ransom payment. Wannabe criminals must specify the ransom amount in Bitcoin and furthermore they can decide to increase the amount of money to pay after a specific deadline.”
“Now, the most important part: the bitcoin paid by the victim will be credited to your account. We will keep a 30% fee of the income, so, if you specified a 1 BTC ransom, you will get 0.7 BTC and we will get 0.3 BTC. The fee will become lower depending on the number of infections and payments you have.” Reads the adv for the Satan Platform.
The Satan platform implements multiple services, including a dropper builder that is able to obfuscate malware code to avoid detection by virus scanners.

The RaaS solutions also allows used to choose a language different from English or Portuguese. The platform also allows crooks to update their ransomware.

Satan, while crypt, changes files’ extension in .stn for example myfile.txt in myfile.txt.stn.
Satan, once encrypted the files, creates an HTML file (HELP_DECRYPT_FILES.html) on desktop containing the ransomware note and instructions for the payment.
Crooks encourage victims to pay ransom to receive the private key for decrypt files. But never pay any ransom or attempt to contact these cyber criminals, because there is no guarantee that your files will be decrypted!.
Satan uses several anti-evasion and anti-debugging techniques, for example, it doesn’t run on a virtual machine making it difficult to analyze.
In a couple of days, crooks already released two version of the Satan platform.
US cancer agency targeted by a singular ransomware attack
19.1.2017 securityaffairs Ransomware
A new ransomware campaign has targeted the not-for-profit cancer services organisation “Little Red Door” requesting a US$44,000 ransom.
A new ransomware campaign has targeted a not-for-profit cancer services organisation, the Little Red Door. The organization provides a number of cancer support services, including diagnostics and treatment.
The system at the agency was infected by a ransomware last Wednesday, January 11, 2017, at around 10:00 PM.
According to the Associated Press a ransomware infected its server and demanded a 50 bitcoin ransom (roughly US$44,000) in order to decrypt the files.
ransomware
“A ransomware group has infected the computers of an Indiana-based cancer agency and have asked for a large payment of 50 Bitcoin ($44,800).” reported Bleepingcomputer.com.
“The victim is Cancer Services of East Central Indiana-Little Red Door, an organization that helps “reduce the financial and emotional burdens of those dealing with a cancer diagnosis.“”
The Little Red Door Executive director, Aimee Fant, confirmed that data of the organization was stored in unspecified cloud storage.
The singularity of this specific ransomware attack it the fact crooks demanding the ransom directly to the cancer agency’s staff via phone and email.
“First, they sent text messages to the agency’s Executive Director, President, and Vice President phones, and then they sent a standardized “form letter” via email. The emails contained detailed payment instructions, but also several threats.” added bleepingcomputer.com.
According to the cancer agency’s Executive Director Aimee Fant, the group threatened to contact family members of living and deceased cancer clients, donors and community partners.
The organization, of course, will not pay the ransom because its money has to be used to provide the necessary services to cancer patients and their families.
“The agency will not raise money to pay the criminals’ ransom,” Fant said.
This is really a sad story, the organization has no choice, it has to replace the infected server and store the old one in the hope a security firm or law enforcement will find decryption keys during their operations.
The agency plans to replace the server with a “secure cloud-based” platform and hopes to be restored operations within the week.
The attack was reported by the organization to the FBI.
New campaign leverages RIG Exploit kit to deliver the Cerber Ransomware
16.1.2017 securityaffairs Ransomware
Experts from Heimdal Security warned of a spike in cyber attacks leveraging the popular RIG Exploit kit to deliver the Cerber Ransomware.
The RIG exploit kit is even more popular in the criminal ecosystem, a few days ago security experts at Heimdal Security warned of a spike in cyber attacks leveraging the popular Neutrino and RIG EKs.
Now security experts from Heimdal Security are warning of a new campaign leveraging the RIG exploit kit that targets outdated versions of popular applications to distribute the Cerber ransomware.
The attackers leverage an array of malicious domains to launch drive-by attacks against visitors trying to exploit flaws in outdated versions of popular applications such as Flash, Internet Explorer, or Microsoft Edge.
“At the moment, cybercriminals are using a swarm of malicious domains to launch drive-by attacks against unsuspecting users.” states the analysis published by Heimdal Security.
“The campaign works by injecting malicious scripts into insecure or compromised systems. Victims can get infected simply by browsing the compromised or infected websites, without clicking on anything. What exposes them to this attack are outdated versions of the following apps: Flash Player, Silverlight, Internet Explorer or Edge.”
The crooks compromise websites to inject malicious scripts that allow exploiting the flaws in the victim’s browser even without user interaction. reports.

This new campaign leverages on a RIG exploit kit that attempts to exploit the following 8 vulnerabilities:
CVE-2015-8651
CVE-2015-5122
CVE-2016-4117
CVE-2016-1019
CVE-2016-7200
CVE-2016-7201
CVE-2016-3298
CVE-2016-0034
According to the experts from Heimdal security, this variant of the RIG exploit is the Empire Pack version (RIG-E). Cyber criminals also abused domains that are part of the so-called Pseudo-Darkleech gateway that was also exploited by cyber gangs in June 2016 to deliver the CryptXXX ransomware in several campaigns leveraging on the Neutrino Exploit Kit.
It is important to highlight that the success of campaigns like this one is determined by the failure in applying security updates in popular software.
“As you can see, cybercriminals often use vulnerabilities already patched by the software developer in their attacks, because they know that most users fail to apply updates when they’re released. In spite of the wave of attacks, many Internet users still choose to ignore updates, but we hope that alerts such as this one will change their mind and make them more aware of the key security layer that updates represent.” states the report.
Spora Ransomware allows victims to pay for immunity from future attacks
12.1.2017 securityaffairs Ransomware
Security experts from Emsisoft spotted a new strain of malware, the Spora ransomware, that allows potential victims to pay for immunity from future attacks.
Security experts from Emsisoft spotted a new strain of ransomware dubbed Spora that implements a singular extortion mechanism, it allows potential victims to pay for immunity from future attacks.
According to the experts, the Spora ransomware appears well-written, it has a professional website for payment and offers several options to the victims that can pay to recover files, to remove the malware, and to gain immunity from future attacks.

The Spora ransomware implements a unique pricing model to determine how much a victim has to pay.
The attack vector is the email, victims receive messages with fake invoices as attachments. The attachments are ZIP archives with an HTA (HTML Application) file inside, masquerading as a PDF or DOC. When victims run the file, it extracts a JScript file in the %TEMP% folder, writes an encoded script into it, and then executes the file.
The malware encrypts file stored on both local files and network shares and doesn’t append an extension to them. The Spora ransomware doesn’t encrypt files located in specific directories to avoid compromise the machine operation.
According to Emsisoft, the ransomware leverages Windows CryptoAPI for encryption, it uses both RSA and AES to encrypt the files.
The encryption key management is quite complex as explained in the post published by the security firm.
“When Spora arrives on a system, it will first find and decrypt the malware author’s public RSA key embedded inside the malware executable using a hard-coded AES key. Once the malware author’s public RSA key has been successfully imported, the malware continues by creating a new 1024 bit RSA key pair, which we will call the victim’s RSA key pair, consisting of both a private and public key. It will also generate a new 256 bit AES key to encrypt the victim’s private RSA key with. Once the victim’s private RSA key is encrypted, the AES key used is then encrypted using the malware author’s public RSA key. The encrypted key material together with some additional information is then saved inside the .KEY file.” states the analysis published by Emsisoft.
“To encrypt a document or file on the system, Spora will first generate a new 256 bit per-file AES key. This per-file key serves to encrypt up to the first 5 MB of the file. Once done, the malware will encrypt the per-file key using the victim’s public RSA key and the RSA-encrypted per-file key is appended to the encrypted file.”
One of the most interesting abilities of the malware is that it is able to encrypt files without a command and control (C&C) server connection. Even if a security firm is able to analyze a decryption tool developed for one victim, they will not able to decrypt files of other users.
Experts believe the Spora ransomware is sold as a ransomware-as-a-service because instance of malware they analyzed have an hardcoded identify that is likely used to identify a specific campaign.
The aforementioned .KEY file contains multiple information such as the infection date, the username of the victim, and the locale of the infected system. These information are used by the author of the Spora ransomware to determine the ransom amount.
Los Angeles College Pays Hackers $28,000 Ransom To Get Its Files Back
10.1.2017 thehackernews Ransomware
Ransomware has turned on to a noxious game of Hackers to get paid effortlessly.
Once again the heat was felt by the Los Angeles Valley College (LAVC) when hackers managed to infect its computer network with ransomware and demanded US$28,000 payment in Bitcoins to get back online.
The cyber-attack occurred over winter break and caused widespread disruption to online, financial aid, email and voicemail systems, including locking out 1,800 students and staffs from their computers.
As the situation was gone out of its hand, the Los Angeles Community College District (LACCD) agreed to pay the ransom demand of $28,000 in Bitcoin to criminals to resume their operations after gaining the decryption keys, the school newspaper, The Valley Star, reports.
The cyber criminals gave the college a week to pay the ransom and threatened to delete all the data if they were not paid.
Also Read: RansomFree Tool Detects Never-Seen-Before Ransomware Before It Encrypts Your Data
Just like most ransomware victims the college obviously was not properly backing up the data. Therefore, the district agreed to pay up the ransom amount to quickly recover access to their systems and data.
However, according to the college officials, it was ultimately cheaper for them to pay the ransom than to remove the unknown ransomware virus from their systems to recover data and resume other services.
After paying the ransom, the college was given a ransomware decryption key to retaining access to its valuable data.
"LACCD and LAVC information technology staff, outside cybersecurity experts and law enforcement are working together to determine the specific nature and impact of this incident. Our top priority is the integrity of student, faculty and employee data, and we will continue to communicate with the LAVC community and the public as the investigation proceeds." the College wrote in a report [PDF].
The college was lucky this time, because, in the case of ransomware, there is no guarantee that one will get the right decryption key in return. For example, recently discovered KillDisk Ransomware that targets Linux machines, demands $218,000 to decrypt, but in return, wipes out data permanently.
One of the most notorious examples of ransomware attacks took place in March last year when crooks locked down the computers and sealed all sensitive files of a Los Angeles hospital, including patient data, which eventually made the hospital to pay $17,000.
Last year, we saw an enormous rise in Ransomware threats, both in numbers and sophistication, and the only way to secure your environment is to deploy automated and isolated backup mechanism.
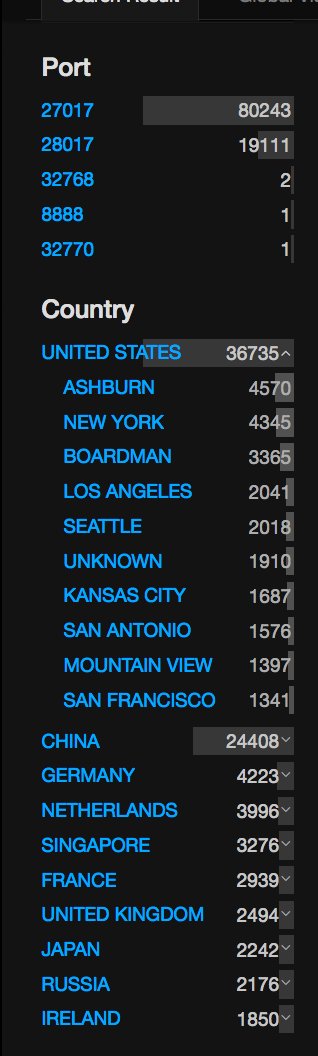
Number of MongoDB ransom attacks peaked 27,000 in a day
10.1.2017 securityaffairs Ransomware
According to the Australian Communications and Media Authority Antipodes the number of hacked MongoDB databases more than double to 27,000 in just a day.
MongoDB ransom attacks soar, according to the Australian Communications and Media Authority Antipodes the number of hacked systems more than double to 27,000 in just a day. According to the experts, the hackers are implementing an extortion mechanism copying and deleting data from vulnerable databases.
Crooks request the payment of a ransom in order to return data and help the company to fix the flaw they exploited. Last week I reported the story of a mysterious attacker that goes online with the harak1r1 moniker, he is breaking into unprotected MongoDB databases, stealing their content, and requesting for a 0.2 bitcoins (US$184) ransom to return the data.bitcoins (US$184) ransom to return the data.
The attacks were discovered by the Co-founder of the GDI Foundation, Victor Gevers, who warned of poor security for MongoDB installations in the wild. The security expert has discovered 196 instances of MongoDB that were wiped by Harak1r1 and being held for ransom.
The analysis of the Bitcoin wallet used by Harak1r1 revealed that at least 22 victims appeared to have paid.

5 Gen
Adrian Sanabria @sawaba
@SteveD3 @LawrenceHecht @achillean @akmalchaudhri @0xDUDE FWIW, in my experience, Shodan is a varying fraction of what's actually out there.
Segui
Victor Gevers @0xDUDE
@sawaba @SteveD3 @LawrenceHecht @achillean @akmalchaudhri That is why I am looking at different sources like Zoomeye (99,491 candidates) pic.twitter.com/VApFdRbF7g
18:17 - 5 Gen 2017
Visualizza l'immagine su Twitter
1 1 Retweet 3 3 Mi piace
According to the security researcher Niall Merrigan the number of attacks have soared from 12,000 earlier today to 27,633 in just 12 hours. According to the expert the attacks were powered by at least 15 different actors. One of the attackers goes online with the moniker ‘kraken0’ has compromised 15,482 MongoDB databases demanding victims the payment of 1 bitcoin ($US921).
Segui
Niall Merrigan @nmerrigan
Latest #Mongodb ransack looks like ~27K servers compromised from 12K this morning.. Numbers and info https://docs.google.com/spreadsheets/d/1QonE9oeMOQHVh8heFIyeqrjfKEViL0poLnY8mAakKhM/edit?usp=sharing … with @0xDUDE
23:03 - 8 Gen 2017
51 51 Retweet 30 30 Mi piace
The researcher is collecting information on the attacks including information provided by Victor Gevers.
The Australian Communications and Media Authority Antipodes is monitoring exposed MongoDB installations since July 2015 using intelligence provided by the ShadowServer nonprofit.
The organization reports about 400 exposed MongoDB databases a day to 90 percent of Australia’s network providers via the Australian Internet Security Initiative (AISI).

AISI statistics on Exposed MongoDB published by ElReg
Stay tuned …
Over 27,000 MongoDB Databases Held For Ransom Within A Week
9.1.2017 thehackernews Ransomware
The ransomware attacks on poorly secured MongoDB installations have doubled in just a day.
A hacker going by the handle Harak1r1 is accessing, copying and deleting unpatched or badly-configured MongoDB databases and then threatening administrators to ransom in exchange of the lost data.
It all started on Monday when security researcher Victor Gevers identified nearly 200 instances of a MongoDB installation that have been erased and held for ransom, asking victims to pay hefty ransoms for the data to be restored.
By Tuesday, this number reached approximately 2,000 databases as reported by Shodan Founder John Matherly, and by Friday, Gevers and fellow security researcher Niall Merrigan updated this count to 10,500.
However, according to recent statistics compiled by Merrigan, the number of compromised systems have reached more than double to 27,000, over the course of about 12 hours.
What's worse?
Initial attacks saw ransoms of 0.2 Bitcoins (nearly US$184) to the attacker, of which 22 victims appeared to have paid. But now the attacker is demanding up to 1BTC (around 906 USD).
The researchers have logged some 15 distinct attackers, of which an attacker using email handle kraken0 has compromised 15,482 MongoDB instances and is demanding 1 Bitcoin to return the lost data, though no one appears to have paid.
This means that after the initial story was made public, more hackers and the group of hackers are also doing same — accessing, copying and deleting badly-configured MongoDB databases — for ransom.
Who is responsible for the MongoDB Ransomware?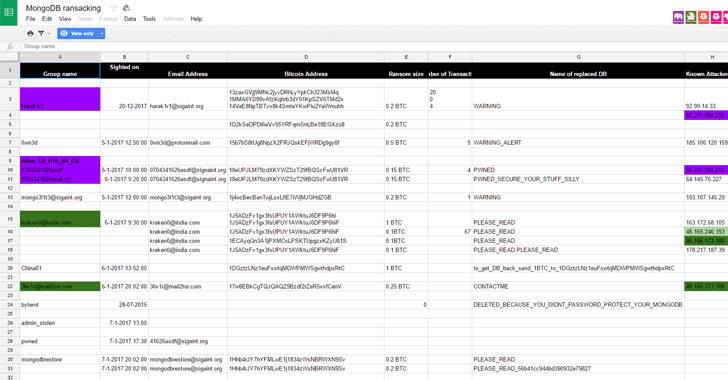
You! Yes, all those administrators who are using misconfigured MongoDB databases are the reason for this sudden spurt in these attacks.
In every case, the target MongoDB server had an administrator account that was configured without a password.
Many poorly secured MongoDB databases can be identified using Shodan search engine, which currently shows more than 99,000 vulnerable MongoDB instances.
This is the case when the company provides an easy way to set up authentication in MongoDB.
How to Protect Yourself?
Since there's no evidence the hackers had copied the data before deleting it, promises to restore the already-deleted databases in return for a hefty ransom are dubious.
Gevers advises affected MongoDB database owners not to pay and to get help from security professionals. He and Merrigan have helped some 112 victims secure their exposed MongoDB databases.
People who administer websites that use MongoDB are advised to follow these steps:
Enable authentication that provides you 'Defense in depth' if your network is compromised. Edit your MongoDB configuration file — auth = true.
Use firewalls — Disable remote access to the MongoDB, if possible. Avoid common pitfalls by blocking access to port 27017 or binding local IP addresses to limit access to servers.
Administrators are strongly recommended to update MongoDB software to the latest release.
Meanwhile, MongoDB developers have released an updated guide to MongoDB security, explaining these ransomware-inspired attacks and how you can detect and prevent them, along with the steps to check the integrity of your
Crooks target UK schools with ‘Department of Education’ ransomware
9.1.2017 securityaffairs Ransomware
Action Fraud is warning of ‘Department of Education’ ransomware, crooks are posing government officials to trick people into installing ransomware.
This is a story of another string of cyber attacks that leverage ransomware to compromise victims’ machines.
Cyber criminals are targeting schools in the UK, asking victims to pay up to £8,000 to unlock data to unlock encrypted documents.
The British Action Fraud is warning of fraudsters that are posing government officials from the Department of Education in order to trick people into installing ransomware on their computers.
The crooks are initially cold calling education establishments asking for the head teachers’ email addresses, then target them with malicious messages having zip attachments supposedly containing sensitive information. The attachments contain the ransomware.
“Fraudsters are initially cold calling education establishments claiming to be from the “Department of Education”. They then ask to be given the personal email and/or phone number of the head teacher/financial administrator.” reads the advisory published by ActionFraud.
“The fraudsters claim that they need to send guidance forms to the head teacher (these so far have varied from exam guidance to mental health assessments). The scammers on the phone will claim that they need to send these documents directly to the head teacher and not to a generic school inbox, using the argument that they contain sensitive information.”
Educational establishments must be vigilant of such kind of threats and have to check that their systems are up-to-date.
The Action Fraud organization added that similar scams have been carried on by fraudsters claiming to be from the Department for Work and Pensions and telecoms providers. In both cases the cyber criminals target the head teacher.
How to avoid such kind of scams?
First of all, being vigilant of any suspicious activity, even when attackers seem to know your personal details or have details about your staff. In the specific case, note that the “Department of Education” is not a real government department. Hackers used it instead of the real name Department for Education.
Having up-to-date defense solutions and software (i.e. OS and applications).
Never open attachments in unsolicited emails neither click on embedded links.
Make regular backups of your data. Be sure that the data are stored on an external storage system.
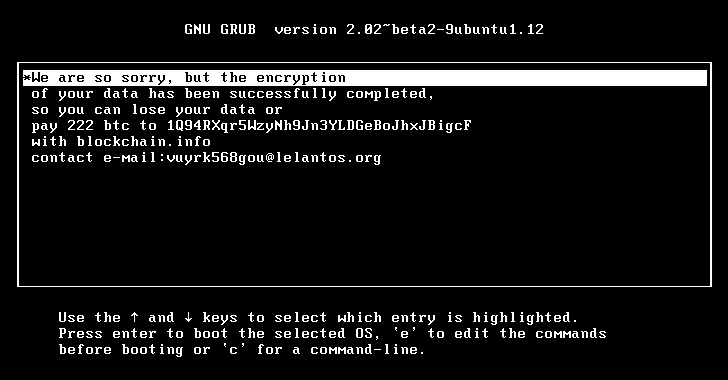
KillDisk Ransomware Targets Linux; Demands $250,000 Ransom, But Won't Decrypt Files
6.1.2017 thehackernews Ransomware
What you'll do if Ransomware infects you? Should you pay or not to recover your files?
Believe me, the FBI advises - Pay off the criminals to get your files back if you don't have a backup.
But paying off a ransom to cyber criminals is definitely not a wise option because there is no guarantee that you'll get the decryption key in return.
In the latest incident, the new variant of KillDisk ransomware has been found encrypting Linux machines, making them unbootable with data permanently lost.
What is KillDisk? KillDisk is a destructive data wiping malware that has previously been used to sabotage companies by randomly deleting files from the computers.
KillDisk is the same component associated with the Black Energy malware that was used to hit several Ukrainian power stations in 2015, cutting power for thousands of people.
But according to ESET security researchers, the nasty KillDisk disk wiper malware is back with new variants that target Windows and Linux desktops and servers, encrypt files and then ask for an unusually large ransom:
Around $218,000 in Bitcoins – possibly the world's most expensive ransom attacks.
What's even worst? Linux variant of the KillDisk ransomware does not store the encryption key anywhere on disk or command-and-control server.
So, even after you pay this extremely large ransom, you are not going to get any decryption key for recovery of your important files.
The good news is that ESET researchers have found a weakness in the encryption employed by the Linux variant which makes recovery of encrypted files possible, though difficult. But the same flaw doesn't exist in the Windows variant of the KillDisk ransomware.
KillDisk Deletes your Files Even After Paying $218,000
According to researchers, the files of victims targeted with the Linux variant of the malware are encrypted using "Triple-DES applied to 4096-byte file blocks," and each file on the computer is encrypted by a different set of 64-bit encryption keys.
The malware then displays the ransom note in an unusual manner: within the GRUB bootloader, which means the KillDisk Linux ransomware overwrites the bootloader entries to show ransom text that asks victims to pay 222 Bitcoin.
But paying off the criminals ransom will not bring your files back, as the Linux variant does not store decryption keys anywhere.
"KillDisk serves as another example of why paying ransom should not be considered an option. When dealing with criminals, there's no guarantee of getting your data back – in this case, the criminals clearly never intended to deliver on their promises," says Robert Lipovský, ESET Senior Researcher.
Prevention is the Best Practice
So, the only safe way of dealing with ransomware is prevention. As I previously recommended, the best defense against Ransomware is to create awareness within the organizations, as well as maintaining back-ups that are rotated regularly.
Most viruses are introduced by opening infected attachments or clicking on links to malware usually in spam emails. So, DO NOT CLICK on links provided in emails and attachments from unknown sources.
Moreover, ensure that your systems are running the latest version of Antivirus software with up to date malware definitions.
This Ransomware Unlocks Your Files For Free If You Read CyberSecurity Articles
5.1.2017 thehackernews Ransomware
Ransomware has been around for a few years, but in last two years, it has become one of the fastest growing threats to businesses and users across the world, so will be in 2017.
Ransomware is a piece of malware that encrypts files on your computer with strong encryption algorithms and then demands a ransom money in Bitcoin to decrypt the data so you can regain access to your encrypted files.
We have seen some nastier ransomware infections over the past couple of years. The most interesting one was Popcorn Time that decrypts victims files for free if they pass the infection on to other people.
Now, a new strain of ransomware takes the infection to a whole new level of craziness.
Dubbed Koolova, the ransomware will restore your encrypted files for free, just like Popcorn Time. The only difference between both the infections is that you don't have to infect others to get free decryption key.
Instead, all you have to do is educate yourself about ransomware by reading two cyber security awareness articles about avoiding the infection.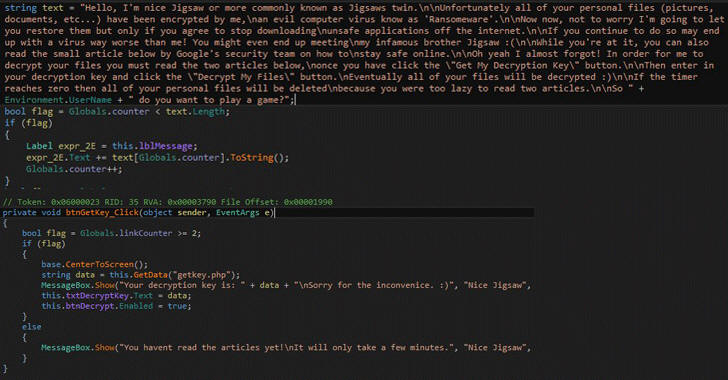
Discovered by security researcher Michael Gillespie and reported by BleepingComputer, the Koolova ransomware is not professionally coded and appears to be a work in progress.
The ransomware requires a lot of technical knowledge to get to the ransom demand screen that asks victims what they need do in order to avoid erasure of their data.
Once infected, Koolova encrypts the victim's files and then displays a warning screen where the text tells the victim to open and read two articles before they can get the ransomware decryption key.
If the victim is too lazy to read both articles, Koolova starts a countdown that if gets to zero, the ransomware will delete the encrypted files like Jigsaw malware.
But once the victim reads both articles, the Decrypt My Files (Decripta i Miei File) button becomes available. On clicking this button, Koolova will connect to the Command-and-Control (C&C) server and retrieve the decryption key.
The victim will then be able to take that decryption key and enter it into the key field to decrypt files.
Although the motive behind the ransomware attack is not to harm people, these kinds of actions are considered to be illegal in many countries. On January 1, a new law went into effect in California that outlaws the use of ransomware.
Do you consider educating people about any threat like this a good practice? Hit the comments below.
FireCrypt comes as a malware building kit and includes DDoS code
5.1.2017 securityaffairs Ransomware
Recently experts from MalwareHunterTeam discovered FireCrypt ransomware, a threat that comes as a malware building kit and includes DDoS code.
Ransomware has become one of the fastest growing threats, new malware implements sophisticated features to avoid detection and rapidly spread among the greatest number of machines.
Recently experts from MalwareHunterTeam discovered a new strain of ransomware dubbed FireCrypt, that includes also a component to launch DDoS attacks.
The experts noticed that FireCrypt continuously connects to s certain URL and downloads content from it and saves it to the local machine’s %Temp% folder. In this way, the malware fills the machine with junk files, the URL is hardcoded in the source code of the malware.
The DDoS component analyzed by the researchers targets the official portal of Pakistan’s Telecommunication Authority (http://www.pta.gov(.)pk/index.php) and downloads the content to a file in the %Temp% folder.
The FireCrypt ransomware is created with a malware builder dubbed BleedGreen and leverages a command-line application that automates the process of putting FireCrypt samples together. BleedGreen allows to rapidly customize the ransomware generating a unique executable with a custom name and a file icon chosen by the creator.
According to the malware researchers the ransomware builder is very trivial.
“Compared to other ransomware builders, this is a very low-end application. Similar builders usually allow crooks to customize a wider set of options, such as the Bitcoin address where to receive payments, the ransom demand value, contact email address, and more.” states a blog post published by Bleepingcomputer.com.

The builder is able to disguise the FireCrypt executable under a PDF or DOC icon, it is also able to make small changes to the binary to make harder the ransomware detection.
The infection process starts when a victim’s launches the executable (EXE file) generated by the builder. The ransomware first kills the Task Manager (taskmgr.exe) process and starts encrypting user’s files with AES-256 encryption.
Files encrypted by FireCrypt are easy to recognize because the malware appends the .firecrypt extension the file name. The ransomware drops a ransom note on the desktop that is identical to that used by the Deadly for a Good Purpose Ransomware and the two malware present many similarities.
“Compared to FireCrypt, the only difference is that the Deadly for a Good Purpose Ransomware also featured a logo at the top of the ransom note, now missing in FireCrypt. But, at a close inspection of Deadly’s source code, MalwareHunterTeam was able to discover that both ransomware versions used the same email and Bitcoin addresses, showing a clear connection between the two, with FireCrypt being a rebranded version of the original Deadly for a Good Purpose Ransomware.” continues the post on Bleepingcomputer.
Let’s close with a reflection on the DDoS component, the target URL cannot be modified by the ransomware builder and the DDoS attack is not effective because it requires to infect a huge number of PCs at the same time that would also be connected to the Internet simultaneously.
Koolova Ransomware decrypts files if victims read 2 posts about Ransomware
5.1.2017 securityaffairs Ransomware
The Koolova ransomware will decrypt the encrypted files for free it the victim read two blog posts about how to avoid ransomware infection.
Ransomware authors are very creative, in the last here we assisted a rapid evolution of the cyber extortion practice. Ransomware has become one of the fastest growing threats, new malware implements sophisticated features to avoid detection.
Recently security experts from MalwareHunterTeam spotted a singular strain of ransomware dubbed Popcorn Time that implemented an interesting mechanism to improve its efficiency.This ransomware comes with a singular feature, it allows victims to either pay up or they can opt to infect two others using a referral link. Then is the two other potential victims pay the ransom the original target receives a free key to unlock his encrypted files.
Now a new strain of ransomware dubbed Koolova appeared in the wild with a very singular feature. The Koolova ransomware will decrypt the encrypted files for free it the victim read two articles about how to avoid ransomware infection.
Once the Koolova ransomware infected a machine, it encrypts the files and then displays a warning screen where the text instructs the victim to open and read two awareness posts before they can get the ransomware decryption key.
Then Koolova starts a countdown that if gets to zero, the ransomware will definitively delete the files.
The two blog posts that the Koolova ransomware wants victims to read are:Google Security Blog called
“Stay safe while browsing” from Google Security Blog.
“Jigsaw Ransomware Decrypted: Will delete your files until you pay the Ransom” from BleepingComputer.
The threat was spotted by the security researcher Michael Gillespie, the malicious code appears to be a work in progress.
Visualizza l'immagine su TwitterVisualizza l'immagine su TwitterVisualizza l'immagine su TwitterVisualizza l'immagine su Twitter
Segui
Michael Gillespie @demonslay335
#Koolova #Ransomware based on #HiddenTear decrypts your files if you read @BleepinComputer & @Google articles on #Jigsaw and online security
00:29 - 19 Dic 2016
23 23 Retweet 19 19 Mi piace
“Koolova will encrypt a victim’s files and then display a screen similar to the Jigsaw Ransomware where the text is slowly shown on the screen. This text will tell the victim that they must read two articles before they can get a decryption key, It then tells you that if you are too lazy to read two articles before the countdown gets to zero, like Jigsaw, it will delete the encrypted files. This is not an idle threat as actually does delete the files.” reported BleepingComputer.com.
Once the victim reads both articles, he can rescue the encrypted files by clicking on the Decrypt My Files (the malware shows the string “Decripta i Miei File” which is Italian Language). The button “Decripta i Miei File” becomes available, when the user click on it the Koolova ransowmare will contact C&C server to get the decryption key.
Clearly, the author of this malware hasn’t developed it profit but just to spread awareness.
It has happened again, ransomware infected an LG Smart TV
3.1.2017 securityaffairs Ransomware
The software engineer Darren Cauthon reported his LG Smart TV was infected with ransomware on Christmas day, the malware asked for $500 to unlock the device
IoT Ransomware is a scaring reality, the threat will increase in the next months and security firms have been warning IT industry. Routers, smart TV, and CCTVs are all potential victims of such category of malware.
The latest incident in order of time involved an LG smart TV, the software engineer Darren Cauthon reported the device of one of his family members was infected with ransomware on Christmas day.
The TV got the ransomware when the programmer’s wife downloaded an app to the TV promising free movies, it was a ransomware demanding of US$500 to unlock the device.
The ransomware appears to be a version of the Cyber.Police ransomware, also known as FLocker and Frantic Locker.

FLocker isn’t a new threat, it has been around for a year and crooks delivered it to the victims via spam SMS campaigns or sharing malicious links.
The FLocker ransomware was first spotted on May 2015, security experts from Trend Micro detected more than 7,000 strains of the same malware. The threat actors behind the FLocker ransomware has updated over the time the threat improving it and making had its detection by security solutions. Over the past few months, the experts observed a number of spikes and drops in the number of iterations released in the wild, in the last wave of infection observed in the mid-April 2016 the researchers detected over 1,200 variants.

Visualizza l'immagine su Twitter
Segui
Darren Cauthon @darrencauthon
Family member's tv is bricked by Android malware. #lg wont disclose factory reset. Avoid these "smart tvs" like the plague.
19:59 - 25 Dic 2016
3.450 3.450 Retweet 2.836 2.836 Mi piace
Darren Cauthon’s LG smart TV runs Google TV, a project discontinued by Google in June 2014.
Currently, LG has moved to WebOS, an open-source Linux kernel-based multitask operating system.
Cauthon tried to reset the TV to factory settings, but the reset procedure available online didn’t work, so he decided to contact the customer service. The man was invited to go to a service center for assistance that implied a $340 bill for the support.
Resuming, the Ransomware asked for $500 to unlock the device, but the sad news is that also LG asks a $340 bit of the support.
The story has a happy ending, LG provided hidden reset instructions to remove the ransomware from the LG Smart TV.
The company offered factory reset steps which are not publicly available.
Below the video shared by The Register:
“With the TV powered off, place one finger on the settings symbol then another finger on the channel down symbol. Remove finger from settings, then from channel down, and navigate using volume keys to the wipe data/ factory reset option.” states the The Register.
25 Dic
Darren Cauthon @darrencauthon
Family member's tv is bricked by Android malware. #lg wont disclose factory reset. Avoid these "smart tvs" like the plague. pic.twitter.com/kNz9T1kA0p
Segui
Darren Cauthon @darrencauthon
The TV is saved! Thanks to LG for providing the factory reset instructions. I recorded a YouTube video of the fix: https://youtu.be/0WZ4uLFTHEE pic.twitter.com/hV62r68uit
06:15 - 29 Dic 2016
Dreaded KillDisk Malware now includes Ransomware abilities
29.12.2016 securityaffairs Ransomware
Researchers at security firm CyberX have recently discovered a variant of the KillDisk malware that also implements ransomware features.
KillDisk is a malware that has been used in attacks against industrial control systems (ICS), it was developed to wipe the hard drives of the infected machine in order to make it inoperable.
The new variant is able to encrypt the file with AES algorithm, the malware uses a unique key for each target and encrypt it with an RSA 1028 algorithm with a key stored in the body of the malware.
The variant of the KillDisk malware is able to encrypt a large number of files from both local partitions and network folders are targeted.
Victims are requested to pay 222 bitcoins ($206,000) to recover their files, a very exorbitant figure that suggests the intention of the author is to attack organizations with deep pockets.
The experts believe the variant has been developed by the TeleBots group, a Russian cybercriminal gang that developed its Telebots malware starting from the BlackEnergy one. The group was recently observed by experts from ESET targeting Ukrainian banks.
“This new variant of KillDisk was developed by the TeleBots gang, a group of Russian cybercriminals believed to have evolved from the Sandworm gang. The Sandworm gang is responsible for a string of attacks in the United States during 2014 that compromised industrial control system (ICS) and SCADA networks using a variant of the BlackEnergy malware” states the report published by the CyberX.
The researchers speculate the malware is being distributed via malicious Office attachments, a close look at the contact email used in the instructions reveals that hackers used the Tor anonymous email service lelantos.org.
The Bitcoin Wallet used by the hackers is still empty and there is no indication of past transactions.

CyberX noticed that the same RSA public key is used for all samples of malware it analyzed, this implies that it could be used to decrypt files for all victims.
According to CyberX, the KillDisk malware first elevate its privileges and then registers itself as a service. The malicious code kills various processes, not critical system ones and processes associated with anti-malware applications, to avoid triggering detection.
Victims of the CryptXXX v.3 can now use a free tool to decrypt their files
21.12.2016 securityaffairs Ransomware
Security researchers have released a decryption tool for unlocking files encrypted by the notorious CryptXXX v.3 ransomware.
CryptXXX v.3 ransomware was defeated, researchers have released a decryption tool for unlocking encrypted files. The decryption tool was included in the RannohDecryptor utility, a free application shared by the No Ransom Project.
The utility was already able to unlock a limited list of files encrypted by the CryptXXX v.3, but not it is able to recover almost any file targeted by the v.3.
The CryptXXX ransomware is one of the ransomware with the highest number of victims in the wild that targeted mostly US users. Russia, Germany and Japan are also in the top-targeted countries.
CryptXXX ransomware was first spotted in April, experts believe it allowed criminal organizations to earn a lot of money.
The experts noted an intense activity involving the malware that was spread in campaigns leveraging on Angler, Neutrino, and Magnitude exploit kits.
Since April, CryptXXX has rapidly evolved, according to the firm SentinelOne, in June a new campaign that fixed the security flaws that allowed decrypting locked files without paying the ransom.
In May, experts at Kaspersky Lab have updated their decryption tool to adapt to the second version of the CryptXXX ransomware in the RannohDecryptor 1.9.1.0.
Every time the author of the CryptXXX released a new version, experts from Kaspersky were able to exploit flaws in the code of the ransomware to unlock the encrypted files.
The researchers from Kaspersky Lab, discovered the malware leverage on a DLL written in Delphi and uses several encryption algorithms to lock the files.
Once CryptXXX v.3 locks files, it appends the extensions .crypt, .cryp1 and .crypz. The latest variant of the malware also includes a module called stiller.dll that is tasked with stealing account credentials from the victim’s machine
“After the files are encrypted and all the valuable data is transferred to the criminals, the Trojan displays a message to the victim demanding a ransom,” Kaspersky Lab researchers said.
If you are one of the victims of ransomware give a look at the list of available decryption utilities that was included in the No Ransom website.
RansomFree Tool Detects Never-Seen-Before Ransomware Before It Encrypts Your Data
20.12.2016 thehackernews Ransomware
Ransomware has risen dramatically since last few years, so rapidly that it might have already hit you or someone you know.
With hundred of thousands of ransomware variants emerging every day, it is quite difficult for traditional signature-based antivirus tools to keep their signature database up-to-date.
So, if signature-based techniques are not enough to detect ransomware infection, then what else can we do?
The solution is RansomFree.
Boston-based cyber security firm Cybereason has released RansomFree — a real-time ransomware detection and response software that can spot most strains of Ransomware before it starts encrypting files and alert the user to take action.
RansomFree is a free standalone product and is compatible with PCs running Windows 7, 8 and 10, as well as Windows Server 2010 R2 and 2008 R2.
Instead of regularly updated malware signatures to fight the bad programs, RansomFree uses "behavioral and proprietary deception" techniques to detect new ransomware variants in action before the threat has a chance to encrypt your data.
The company analyzed tens of thousands of ransomware variants belonging to more than 40 ransomware strains, including Locky, TeslaCrypt, Cryptowall, and Cerber and "identified the behavioral patterns that distinguish ransomware from legitimate applications."
"The ability to detect and stop never-before-seen ransomware is one of the features that makes RansomFree so unique," the company's spokesperson told The Hacker News. "The tool identifies ransomware behaviors including attempts targeting local disks, as well as detecting and stopping encryption over shared network drives."
If it finds any such behavior on your PC, RansomFree suspends that program and flags it for your review. It’s then up to you to either enable the program or allow RansomFree to stop it permanently.
By default, the anti-ransomware tool suspends any activity it finds suspicious — even if it is a legitimate encryption software that has some behavior in common with ransomware.
With this type of approach, even brand new ransomware infections will be stopped in their tracks without you having to worry about updates to the malicious software.
"Pervasive ransomware variants have outsmarted traditional endpoint defenses, such as antivirus software, leaving individuals exposed to the real dangers of cyber crime," said Uri Sternfield, Cybereason Senior Security Researcher.
"What's worse, a major part of the consumer population threatened by ransomware attacks have little recourse but to either pay the ransom, or risk losing their stolen content."
RansomFree can detect 99 percent of all ransomware strains and will also offer you protection against future ransomware strains, as the company said RansomFree would be updated daily in an attempt to stay ahead in this arms race.
RansomFree is free to download directly from Cybereason's official site.
Earlier this year, we also reported about another behavior-based anti-ransomware tool, dubbed RansomWhere, available for Mac OS X users that can identify ransomware-like behavior by continually monitoring the file-system for the creation of encrypted files by suspicious processes.
RansomWhere also works in a similar way like RansomFree, blocking the suspicious processes and waiting for the user to decide whether to allow or stop the process.
Besides using an anti-ransomware tool, you are also recommended to regularly backup your files, keep your OS and software programs up-to-date, disable Java and Flash when possible, do not download apps from unknown, untrusted websites, and be extra conscious when opening links and downloading attachments in an email.
Ransomware infections suffered by companies tripled in 12 months
13.12.2016 securityaffairs Ransomware
According to a new report published by Kaspersky Lab, the number of ransomware infections suffered by companies threefold from January to September.
The number of ransomware infections suffered by companies continues to increase and according to a new report published by the security firm Kaspersky Lab, it increased threefold from January to September.
One in every five businesses worldwide has been victims of a ransomware and the rate of ransomware attacks increased from one every two minutes to one every 40 seconds.
This alarming data confirm that the ransomware is one of the most dangerous threats in the current cyber security landscape.
Ransomware could have a dramatic impact on companies, 67 percent of the firm that was affected lost part or all of their corporate data and 25% victims spent several weeks trying to decrypt the data.
Experts from Kaspersky have detected 32,091 new ransomware variations in the third quarter, a significant increase compared to 2,900 variations discovered during the first quarter. According to the experts, 62 new ransomware families were observed in the wild this year.
The situation is even more worrisome when dealing with consumers, in their case the infection data reached one attack every 10 seconds in September.
In the criminal underground, such kind of threat is becoming even more popular, malware authors are developing new ransomware that presents sophisticated features and that are able to evade detection.
Ransomware allows criminal organizations to rapidly cash out their efforts, despite the numerous recommendation to avoid paying the ransom still a large number of victims prefer to pay it to decrypt their documents.
“Ransomware has completely dominated the current threat landscape,” explained Bharat Mistry, cyber-security consultant at Trend Micro.
“During the first part of 2016, we blocked and detected almost 80 million ransomware threats and identified 79 new ransomware families – comparing to 29 in the whole of 2015. That’s a 179 percent increase. Quite a few of those were built with routines that are designed to attack enterprise machine and endpoints. It’s time companies take heed.”
The analysis conducted by Kaspersky confirmed that SMBs are mostly targeted by ransomware, 42 percent of them suffered a ransomware-based attack over the past 12 months. Of those, one in three paid up the ransom, but one in five never got their files back, despite paying.
Giving a close look at the threats, CTB-Locker has represented one of the most dangerous threat. One of four ransomware victims was infected by the CTB-Locker. Other successful ransomware were Locky (7 percent) and TeslaCrypt (6.5 percent).
The researchers observed that ransomware infections are the result of more targeted attacks leveraging on spear-phishing messages and social engineering attacks against specific organizations.
Targeted attacks allow cyber criminals to maximize the likelihood victims will pay up the ransom.
How to defeat the ransomware?
Kaspersky urges companies to increase awareness about the threat by training its employees and to back up sensitive data regularly.
It is important to adopt security solutions and to maintain installed software up to date.
Below key figures of the report:
62 new ransomware families made their appearance.
There was an 11-fold increase in the number of ransomware modifications: from 2,900 new modifications in January/March, to 32,091 in July/September.
Attacks on business increased three-fold between January and the end of September: the difference between an attack every 2 minutes and one every 40 seconds.
For individuals the rate of increase went from every 20 seconds to every 10 seconds.
One in five small and medium-sized business who paid the ransom never got their data back.
I suggest you read the report.
Popcorn Time ransomware, pay up the ransom or spread it to decrypt the files
10.12.2016 securityaffairs Ransomware
Malware researchers from the MalwareHunterTeam have discovered a new strain of ransomware dubbed Popcorn Time on the Dark Web.
Malware researchers from MalwareHunterTeam have spotted a new ransomware, dubbed Popcorn Time, that appears to be still under development.
The researchers at MalwareHunterTeam found the Popcorn Time ransomware code on the Dark Web.
This ransomware comes with a singular feature, it allows victims to either pay up or they can opt to infect two others using a referral link. Then is the two other potential victims pay the ransom the original target receives a free key to unlock his encrypted files.
“Time that intends to give victim‘s a very unusual, and criminal, way of getting a free decryption key for their files. With Popcorn Time, not only can a victim pay a ransom to get their files back, but they can also try to infect two other people and have them pay the ransom in order to get a free key.” wrote Lawrence Abrams from BleepingComputer.com.
The researchers noticed that the ransom note offers two options, pay up the ransom or spread the infections.
“We are sorry to say that your computer and your files have been encrypted, but wait, don’t worry. There is a way you can restore your computer and all of your files… Send the link below to other people, if two or more people will install the file and pay, we will decrypt your files for free.” states the ransom note.

Lawrence explained that it is the first ransomware ever seen with this characteristic.
Abrams, who analyzed the code of the ransomware, said it is incomplete, some of the command and control servers are not working and there are many features that still have to be developed.
The ransom note demands 1 bitcoin, victims have a limited number of attempts to provide a decryption key.
“To make matters worse, there is unfinished code in the ransomware that may indicate that if a user enters the wrong decryption key 4 times, the ransomware will start deleting files.” added Abrams.
The Popcorn Time ransomware is able to encrypt more than 500 file types using AES-256 encryption. The malware appends the .filock extension to the encrypted files.
The ransom note reveals that the authors of the Popcorn Time ransomware developers claim to be “a group of computer science students from Syria.”
Another interesting aspect of this ransomware is the content of the note who promises that ransomware proceeds will go to food, medicine, and shelter for the victims of the civil war in Syria.
“We are extremely sorry that we are forcing you to pay,” states the note.
This Ransomware Unlocks Your Files For Free If You Infect Others
9.12.2016 thehackernews Ransomware
Is your PC infected with Ransomware? Either pay the ransom amount to the attacker or spread the infection further to get the decryption keys.
Yes, this new technique has been employed by cyber criminals with the latest round of ransomware threat, dubbed Popcorn Time.
Initially discovered by MalwareHunterTeam, the new Popcorn Time Ransomware has been designed to give the victim's a criminal way of getting a free decryption key for their encrypted files and folders.
Popcorn Time works similar to other popular ransomware threats, such as the Crysis Ransomware and TeslaCrypt, that encrypt various data stored on the infected computer and ask victims to pay a ransom amount to recover their data.
But to get their important files back, Popcorn Time gives victims option to pay a ransom to the cyber criminal or infect two other people and have them pay the ransom to get a free decryption key.
What's even worse? The victims are encouraged to pay the ransom of 1 Bitcoin (~$750) within seven days to receive decryption keys stored on a remote server owned by Popcorn Time's developers.
If the ransom is not paid within this duration, the decryption key will be permanently deleted and retrieve important files will become impossible.
Moreover, the code of the ransomware is incomplete that may indicate that if victims enter the wrong decryption key four times, the Popcorn Time ransomware will start deleting victims' files.
Here's How the Popcorn Time Ransomware Threat Works: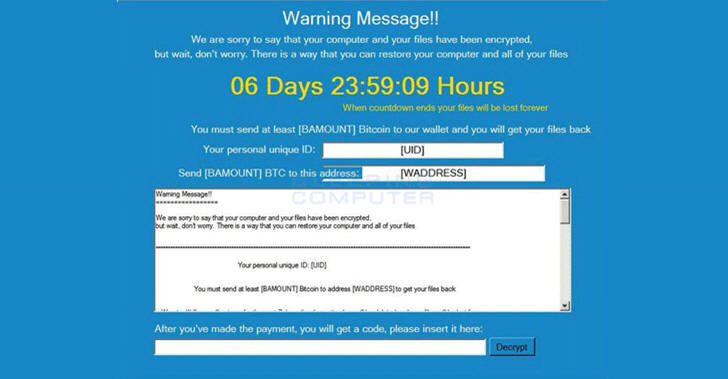
Once infected, the Popcorn Time Ransomware will check to see if the ransomware has been run already on the PC. If yes, the ransomware will terminate itself.
If not, the Popcorn Time Ransomware will either download various images to use as backgrounds or start encrypting the files using AES-256 encryption. The encrypted files will have the ".filock" or ".kok" extension appended to it.
While encrypting the data, the ransomware will display a fake screen that pretends to be the installation of the program.
As soon as the encryption is finished, it will convert two base64 strings, save them as ransom notes known as restore_your_files.html and restore_your_files.txt, and then automatically display the HTML ransom note asking for 1 Bitcoin.
Want a Free Decryption Key? Infect Two More People
The Popcorn Time author provides a "nasty way" for a victim to get the free decryption key: Spread the Ransomware to two other people via the victim's "referral" link."
If those two infected victims pay the ransom, then the first victim will supposedly get a free decryption key.
To make this possible, the ransom note contains a URL pointing to a file located on the Popcorn Time's TOR server.
Entering Wrong Decryption Key 4 Times and You are Screwed Up!
When executed, the Popcorn Time ransomware will display a lock screen filled in with various information relating to victim's particular installation.
The victim will also find a field where he/she can enter the decryption key given to them by the attacker after paying the ransom.
The source code for Popcorn Time contains a function that suggests the threat to delete files if the victim enters the wrong decryption code four times.
Since the Popcorn Time ransomware is still under development at the time of writing, many things are unclear and may change with time.
Customers of Liechtenstein banks blackmailed by ransomware
29.11.2016 securityaffairs Ransomware
Hackers are targeting Liechtenstein banks with ransomware-based attacks and are threatening to disclose customers sensitive information.
Hackers are targeting Liechtenstein banks with ransomware-based attacks. The situation is particularly concerning due to sensitive nature of the data that are stolen by crooks. Cyber criminals, in fact, are allegedly blackmailing customers by threatening to release their account data in case ransoms are not paid by the victims.
According to the Bild am Sonntag, the hackers gain access to account data from Valartis Bank Liechtenstein and stolen information on several clients, including politicians, actors, and other individuals.
hackers-are-targeting-liechtenstein-banks-with-ransomware
The director Andreas Insam told the newspaper Bild am Sonntag that its organization has already alerted the authorities.
“Attackers accused the bank board of not paying them for security services, likely bug poaching rather than legitimate testing, claiming their “intention is not to harm” and have to “resort to” extortion.” reported El Reg.
The cyber criminals are allegedly demanding up to 10 per cent of account balances in order to avoid disclosing customers’ information. The hackers, of course, accept payments in Bitcoin, they are threatening to disclose the information to authorities and media if the victms will not pay the ransom by December 7.
The Bild am Sonntag obtained three distinct messages (letter 1, letters, letter 3) from the hackers that claim to have siphoned several gigabytes of data from the targeted accounts. Information also includes the victims’ correspondence.
The letters published by media confirm the intention of the hacker to blackmail the victims by threatening with revealing alleged dirty affairs, including tax evasion.
At the time I’m writing the Bitcoin addresses used by the crooks for the payment were not disclosed in order to avoid tracking ransom payments of the victims.
San Francisco Metro System Hacked with Ransomware; Resulting in Free Rides
28.11.2016 thehackernews Ransomware
Nothing is immune to being hacked when hackers are motivated.
The same proved by hackers on Friday, when more than 2,000 computer systems at San Francisco's public transit agency were apparently got hacked.
San Francisco's Municipal Transportation Agency, also known as MUNI, offered free rides on November 26th after MUNI station payment systems and schedule monitors got hacked by ransomware and station screens across the city started displaying a message that reads:
"You Hacked, ALL Data Encrypted. Contact For Key(cryptom27@yandex.com)ID:681 ,Enter."
According to the San Francisco Examiner, MUNI confirmed a Ransomware attack against the station fare systems, which caused them to shut down ticket kiosks and make rides free this weekend.
As you can see, the above message delivered by the malware followed by an email address and ID number, which can then be used to arrange ransom payments.
MUNI Spokesman Paul Rose said his agency was investigating the matter and "working to resolve the situation," but did not provide details as of how MUNI got hacked.
"We are currently working to resolve the situation," said Rose. "There is an ongoing investigation, and it wouldn’t be appropriate to provide additional details."
Pay $73,000 to Free Systems from Ransomware
san-francisco-railway-hacked-ransomware-malware
Trains themselves were not affected by the malware attack, and the MUNI claimed that the payments were resumed on the morning of November 27th. The MUNI looks after trains, trams and buses around the city, including San Francisco's iconic cable cars.
It is yet not clear exactly who was responsible for the attack (besides a pseudonym "Andy Saolis"), but according to local media reports, the agency's computers were being held by ransomware until the MUNI paid the equivalent of more than $73,000 in Bitcoin.
Andy Saolis is a pseudonym commonly used in HDDCryptor ransom attacks, which uses commercial tools to encrypt hard drives and network shares on Windows machines using randomly generated keys and then overwrite the hard disks' MBRs to prevent systems from booting up properly.
The target machine is typically infected by accidentally opening a malicious executable in an email or download, and then the malware spreads out across the network.
The email address, cryptom27@yandex.com, used by anonymous criminal points the city to a Russian email address to arrange payment and has been linked to other cyber attacks as well.
The Hacker Linked to a Previous Ransomware Starin
When reaching at the provided email, the hacker provided a statement in broken English, which read:
"We don't attention to interview and propagate news! Our software working completely automatically and we don't have targeted attack to anywhere! SFMTA network was Very Open and 2000 Server/PC infected by software! So we are waiting for contact any responsible person in SFMTA but I think they don't want deal ! so we close this email tomorrow!"
The same email address, cryptom27@yandex.com, was linked to a ransomware strain called Mamba in September. The ransomware employs tactics similar to those demonstrated against the MUNI systems.
The hacker provided Hoodline a list of systems the hacker claimed to have infected in Muni's network, which came out to be 2,112 of the total 8,656 computer networks. The hacker also said that the MUNI had "one more day" to make a deal.
Not much about the hack is known; the extent of the hack and hacker's identity remain a mystery for now, but the incident once again reminds us that how vulnerable our critical infrastructure remains.
Two versions of the new Cerber 5.0 ransomware released in a few days
28.11.2016 securityaffairs Ransomware
Security experts from the CheckPoint firm discovered two different variants of the new Cerber 5.0 ransomware in a few weeks.
Security experts have spotted a new variant of the dreaded Cerber ransomware, the Cerber 5.0. This is the third version of the malware released this week that is able to encrypt files on all accessible network shares.
The Cerber ransomware was first spotted in March, since then it rapidly evolved. In June, Cloud security provider Avanan spotted a number of Cerber Ransomware variants that were targeting corporate Office 365 users with spam or phishing emails leveraging on malicious file attachments.
Cerber 2.0 was spotted in August when it was offered in the criminal underground via the ransomware-as-a-service model.
The Cerber 4.0 appeared in the wild in October, in the same month experts observed it killing common database-related processes like those of the MySQL, Oracle and Microsoft SQL servers to encrypt files.
The Cerber 4.0 appeared in the wild delivered by several exploit kits, including RIG, Neutrino, and Magnitude EKs.
The Cerber 4.0 is becoming very popular in the criminal ecosystem where it is still used to power several malvertising campaigns.
The latest, the Cerber 5.0 variant, included a .vbs file with a VBScript that implements a communication channel between victims and crooks.
Last week experts from CheckPoint security observed a rapid sequence of versions being released in the wild. Less than 24 hours after the release of the version 4.1.6, crooks distributed the Cerber 5.0 and the 5.0.1.
“Only yesterday (November 23rd, 2016) a new version of Cerber was released (4.1.6); however no prominent changes were noticeable in it. Less than 24 hours later, Cerber released the new version, 5.0, which is described in this article.” reads the analysis published by the firm CheckPoint.
“A notable change introduced in this Cerber version is the new IP ranges used for command and control communication. Cerber uses one IP range which was also used in its last version (4.1.6), while the rest of the IP ranges are new.”
The Ceber 5.0 leverages new IP ranges for the command and control (C&C) communication, only one of them was exploited in version 4.1.6. The malicious code multicasts messages to all IP addresses via UDP.
Cerber is currently distributed via spam e-mail campaigns and exploit kits, mostly Rig-V Exploit Kit. The malware uses randomly generated extensions for the encrypted file (4 random alphabetic letters).
Cerber informs victims which version of the ransomware they’ve been encrypted by, via a ransom note dropped on the desktop.

Experts from CheckPoint security speculate that Cerber creators constantly improve their code to avoid security vendors’ counter-measures.
There is no doubt, Cerber 5.0 will have many other successors.
Beware! Malicious JPG Images on Facebook Messenger Spreading Locky Ransomware
26.11.2016 thehackernews Ransomware
If you receive an image file sent by someone, even your friend, on your Facebook Messenger, LinkedIn or any other social media platform, just DO NOT CLICK ON IT.
Even JPG image file could eventually infect your computer with the infamous Locky Ransomware.
Earlier this week, we reported a new attack campaign that used Facebook Messenger to spread Locky Ransomware via .SVG image files, although Facebook denied this was the case.
Now, researchers have discovered that the ongoing spam campaign is also using boobytrapped .JPG image files in order to download and infect users with the Locky Ransomware via Facebook, LinkedIn, and other social networking platforms.
Security researchers from Israeli security firm Check Point have reportedly discovered how cyber criminals are hiding malware in image files, and how they are executing the malware code within these images to infect social media users with Locky variants.
According to researchers, malware authors have discovered security vulnerabilities in the Facebook and LinkedIn that forcibly download a maliciously coded image file on a user's computer, though in some cases, the user has to click on the image file to download.
When the user detect the automatic download and access that malformed image file, malicious code installs the Locky ransomware onto the user's computer, which encrypts all files on the infected computer until a ransom is paid.
Flaws in Facebook and LinkedIn Remain Unpatched
facebook-locky-ransomware
The security firm has declined to provide technical details as the vulnerability the malware relies on still impacts both Facebook and LinkedIn, among other unnamed web services.
"The attackers have built a new capability to embed malicious code into an image file and successfully upload it to the social media website," Check Point researchers say.
"The attackers exploit a misconfiguration on the social media infrastructure to deliberately force their victims to download the image file. This results in infection of the users' device as soon as the end-user clicks on the downloaded file."
CheckPoint says the firm reported the issue to both Facebook and LinkedIn back in September, but the vulnerabilities remain unpatched in both the platform, which is now actively being exploited by attackers.
Video Demonstration of the Attack
You can also watch the video demonstration of this attack, which CheckPoint dubbed ImageGate, which shows the attack in action.
Locky is Spreading Massively via Social Media Platform
Locky ransomware has been around since early this year and has become the biggest and most common ransomware family known today. It works by encrypting victims' files with RSA-2048 and AES-1024 algorithms and demands a ransom for the key.
Locky ransomware mainly spreads via phishing emails containing a malicious attachment disguised as a Word or Zip file. But since people spend time on social network sites, cyber crooks have turned their focus to finding a way into these platforms.
Check Point says that in the past week, they have noticed a "massive spread of the Locky ransomware via social media, particularly in its Facebook-based campaign."
To keep yourself safe, you are advised not to open any unsolicited file that has automatically downloaded onto your computer, especially image files with unusual extensions like SVG, JS, or HTA.
The bottom line: Don't be curious to look at image sent by someone, at least for the time being.
ESET Crysis decryptor to rescue files encrypted by the Crysis ransomware
23.11.2016 securityaffairs Ransomware
ESET security firm has included master decryption keys into a decryption tool that allows rescuing the encrypted files without paying the ransom.
Good news for the victims of the Crysis ransomware, ESET security firm has included master decryption keys into a tool that allows rescuing the encrypted files.
The decryption keys for the CrySis ransomware were posted online on the BleepingComputer.com forum by a user known as crss7777 who shared a link to a C header file containing the actual master decryption keys and information on how to utilize them.
“In a surprise move, the master decryption keys for the CrySiS Ransomware have been released early this morning in a post on the BleepingComputer.com forums. At approximately 1 AM EST, a member named crss7777 created a post in the CrySiS support topic at BleepingComputer with a Pastebin link to a C header file containing the actual master decryption keys and information on how to utilize them,” wrote Lawrence Abrams from BleepingComputer.
“These keys have already been used by Kaspersky Labs to update their RakhniDecryptor program so that it can be used to decrypt victim’s files.”

Lawrence Abrams speculates the user crss7777 could be a member of the development team.
“Though the identity of crss7777 is not currently known, the intimate knowledge they have regarding the structure of the master decryption keys and the fact that they released the keys as a C header file indicates that they may be one of the developers of the CrySiS ransomware,” said Abrams.
“Why the keys were released is also unknown, but it may be due to the increasing pressure by law enforcement on ransomware infections and the developers behind them.”
The CrySis ransomware was first spotted in February by ESET, it has infected systems mostly in Russia, Japan, South and North Korea, and Brazil.
The malware spreads via email attachments with double file extensions or via malicious links embedded in spam emails.
The ransomware is able to encrypt more than 200 file types searching for them on internal and external storage, and network shares, and deleting backup shadow files.
The CrySis ransomware appends the .xtbl extension to the encrypted files, the files are renamed following the following format [filename].id-[id].[email_address].xtbl.
In June the experts observed a peak in the number of infections, likely due to the dead of TeslaCrypt.
Security experts observed that in Australia and New Zealand the Crysis ransomware was targeted businesses exploiting remote desktop connections and compromising routers to re-infect cleaned up computers.
“Crysis (detected by Trend Micro as RANSOM_CRYSIS.A), a ransomware family first detected in February this year, has been spotted targeting businesses in Australia in New Zealand through remote desktop protocol (RDP) brute force attacks.” reported Trend Micro in a blog post.
It is not clear why crooks dropped the decryption keys, likely they tried to ease the pressure of law enforcement that were trying to identify the operators behind the malware.
ESET has included the decryption keys in a free tool, ESET Crysis decryptor, and published instructions to use it.
Watch out, Locky ransomware spread via SVG images on Facebook Messenger
21.11.2016 securityaffairs Ransomware
Researchers have discovered a new hacking campaign leveraging on Facebook Messenger to spread the Locky ransomware via SVG images.
The Locky Ransomware is spread via a downloader, experts noticed that it is able to bypass Facebook defense measures by pretending to be a harmless image file.
The campaign was first spotted during the weekend by the malware expert Bart Blaze and by the researchers Peter Kruse.
“Earlier today, a friend of mine notified me of something strange going on with his Facebook account; a message containing only an image (an .svg file in reality) had been sent automatically, effectively bypassing Facebook’s file extension filter:” wrote Bart Blaze in a blog post.

The SVG image file could be used by attackers as a sort of container that can include a malicious code such as a Java Script.
In May 2015, researchers at the AppRiver security firm discovered a malicious campaign that was distributing a strain of ransomware by exploiting SVG files.
The SVG (Scalable Vector Graphics) is an XML-based vector image format for two-dimensional graphics with support for animation and interactivity. The SVG images include the definition of their behaviors in XML text files, this feature makes possible SVG image can be searched, indexed, scripted, and compressed. Despite SVG images can be created and edited with any text editor, more often they are created directly with a software that elaborates the images.
The experts at AppRiver noticed that threat actors in the wild were exploiting a small JavaScript entry contained in the SVG files that allow them to redirect victims to a website used to serve the Cryptowall malware.
“These SVG files however contained a small javascript entry that would open a webpage to download some malware.” AppRiver researchers said in a blog post. “The IP link in question ends up forwarding to another domain where a zip is downloaded of the actual exe payload. It didn’t auto execute, user interaction would still be needed for that. “
Back to the present, the new attack leverages a downloader called Nemucod that is spread via Facebook Messenger as a .svg file, as confirmed by Peter Kruse via Twitter.
Visualizza l'immagine su Twitter
Segui
peterkruse @peterkruse
Confirmed! #Locky spreading on #Facebook through #Nemucod camouflaged as .svg file. Bypasses FB file whitelist. https://www.virustotal.com/da/file/5e9e3f9f96ce2333473a4c7eae8e07a0d0a38b24cb9effc67f0063f2eaec4c92/analysis/ …
20:04 - 20 Nov 2016
159 159 Retweet 69 69 Mi piace
When the victim accesses the malicious SVG file it will be directed to a website that appears to be YouTube in design only, but once the page is loaded, the victim is asked to install a codec in order to play the video that is shown on the page.
“A website purporting to be Youtube, wih a video from Facebook – of course, you needed to install an additional extension to view it :)” continues Bart Blaze.
If the victim installs the Chrome extension as requested on the page, the attack is this spread further via Facebook Messenger. The experts observed that sometimes the malicious Chrome extension installs the Nemucod downloader, which launches the Locky ransomware attack.
The experts warn of several variants of the attack and likely several malicious extensions used to spread malware like the Locky Ransomware.
“Currently, I’m not exactly sure what this extension is supposed to do beside spreading itself automatically via Facebook, but likely it downloads other malware to your machine.” Blaze added in the post.
If you get infected remove asap the malicious extension from your browser.
CryptoLuck Ransomware spread through the RIG-E Exploit Kit
18.11.2016 securityaffairs Ransomware
CryptoLuck ransomware is a new strain of malware discovered by the researcher Kafeine, that is being distributed via the RIG-E exploit kit.
The notorious researcher Kafeine has spotted a new strain of ransomware dubbed CryptoLuck. The malware leverages DLL hijacking and exploits the legitimate GoogleUpdate.exe executable to infect computers.
The ransomware appends the .[victim_id]_luck extension to the encrypted files, it is able to lock hundreds of file extensions. It skips files that contain specific strings: Windows, Program Files, Program Files (x86), ProgramData, AppData, Application Data, Temporary Internet Files, Temp, Games, nvidia, intel, $Recycle.Bin, and Cookies.
The malware asks victims to pay a 2.1 Bitcoin (around $1,500) ransom within 72 hours in order to rescue the encrypted files.
The CryptoLuck ransomware is delivered through the RIG-Empire (RIG-E) exploit kit. Crooks leverages malvertising campaigns through adult websites, but likely they will adopt other infection vectors.
The ransomware is spread using a RAR SFX file which contains the crp.cfg, GoogleUpdate.exe, and goopdata.dll files, along with instructions to extract these into the %AppData%\76ff folder and to silently execute GoogleUpdate.exe.
The advantage for abusing the GoogleUpdate.exe is that is a legitimate Google program that is signed by Google.
The authors of the CryptoLuck ransomware have included a malicious goopdate.dll file in the package for the legitimate program to load into memory.
“When the GoogleUpdate.exe program is run, it will look for a DLL file called goopdate.dll file and load it. The problem is that it will first look for this file in the same folder that the GoogleUpdate.exe resides in. This allows a malware developer to create their own malicious goopdate.dll file and have it loaded by GoogleUpdate.” reads the analysis published by Lawrence Abrams from the BleepingComputer.com.
The CryptoLuck ransomware implements mechanisms to avoid analysis from security firms. It is able to determine if it is running in a virtual machine, and in this case, it halts itself. Once executed it scans all mounted drives and unmapped network shares for files to encrypt.
The ransomware uses an AES-256 encryption with a unique AES encryption key for each of file to encrypt. The key is encrypted with an embedded public RSA key and the resulting encrypted AES key is embedded in the encrypted file.
When the ransomware has completed the encryption of the files, it displays a ransom note that contains the instructions for the payment of the ransom.

Ransomware: How to recover your encrypted files, the last guide.
18.11.2016 securityaffairs Ransomware
In this guide, we will explain how to recover encrypted files focusing on the Data-Locker Ransomware that targets the Windows operating system.
Why my system asks me to pay?
A ransomware is a computer malware that limits the access of a system and ask for a ransom in order to remove that restriction.
The restriction applied to the system can change in the time and can be realized in various ways.
Based on the restriction applied on the system we can recognize two kinds of ransomware based on their behaviors:
Pc-Locker Ransomware:
They block the system showing a ransom page on the computer desktop where they intimidate the victim with a message and ask him to pay a ransom in order to unlock the machine.
Data-Locker Ransomware:
They encrypt a large amount of user data avoiding the encryption of the system files (in order to let the machine working) and then ask a ransom to unlock those files.
The main goal of the ransomware is to extort money from their victims using some technique (locking system, encrypting files) that can target different devices (desktop, laptop, tablet, smart watch, smart tv, smartphones) and different operating system (Windows, Linux, Os X).
When you get infected by a ransomware?
Anytime your system asks you to pay. As we said the main goal of the ransomware is to get money from their victims so the first action the ransomware does after an infection is to show a window containing the instructions (the ransom note) to make a payment trough a cryptocurrency, such as bitcoin.
It will never exist a ransomware that infects your system and will remain stealthy.
In this guide we will focus on the Data-Locker Ransomware that target the Windows operating system.
There are a lot of types of ransomware and every type, known as a family, act in a different way so there isn’t a general and always working methodology to recover your data.
Once you get infected by a ransomware you have to follow those steps if you want to restore your files and your system:
Unlock the screen and bypass the screen lock of the ransomware;
Restore/Decrypt the files;
Disinfection and removal of the ransomware persistence files.
Note that guide aims just to recover your encrypted files and not for the removal and disinfection of your machine.
We strongly recommend, once you recovered your files, to save them on an external drive and remove the ransomware from the system (or format the drive), because sometimes it could happen that ransomware trigger again its activity and encrypt all of your files recovered.
Some modern ransomware combines the technique of data-locker ransomware and pc-locker ransomware so you need to unlock the screen and bypass the screen lock of the ransomware before you start to recover your encrypted files.
In that case, we recommend runnig the operating system in safe boot with networking before you start to follow our methods to recover your files.
This avoids also to fight against some mechanism where the ransomware would delete the files after an amount of time.
The following methods we are explaining aren’t a way to fight this threat, the best way to fight ransomware are frequent backup and prevention.
That means if you get infected by a ransomware it’s already “late” and, also if a lot of researchers are fighting this threat developing ad-hoc decryption tool, there are some ransomware family really hard to deal with.
METHOD 1: Identification and Decryption Tool
If you get infected by a ransomware and you want to ask for helping other users (i.e. Forums, IRC, email…) or you want to check if some security firms have developed a decryption tool for that specific ransomware you have to recognize the family name of the ransomware.
Thanks to the malwarehunterteam, they set up a free web service that lets you host an infected file (or ransom note) and it will detect the ransomware family name and, in some cases, it will guide you to decrypt your files of that family.
ID Ransomware
Following a step-by-step real case of using this method to decrypt files from ransomware Teslacrypt 4.0

As we can see from the above image the id-ransomware home page allow you to upload a ransom note or a sample encrypted file for the family recognition.
In the case of Teslacrypt 4.0 we will use a ransom note because that family doesn’t add an extension to encrypted files so it would be more difficult to detect the family if we try to identify it by the encrypted file.
We strongly recommend to don’t upload huge files because the recognition doesn’t improve with the size of a file, that means it would be just a waste of resources.

Once the upload is completed, you have the result with the family name spotted by id-ransomware that matched the pattern matching of the ransom note uploaded.
In that case, Teslacrypt 4.0 is recoverable and they provide us a link that explains how to decrypt the files and which tools use.

We download the tool to decrypt our files developed by BloodDolly and we first need to set the key used by the ransomware to encrypt our files.

We need to do this because this is a multi purpose decryption tool for all the Teslacrypt versions (1 to 4).
Selecting the extension appended to the encrypted files by the ransomware will allow the tool to set the master key automatically.
In our case (Teslacrypt v 4) we will select the last one <as original> because that ransomware left unchanged the extension of our encrypted files.

Once we set up the key we can start to recover our files.
In our case, that tool decrypts the 100% of our files, as we can see in the following picture.

We also recommend to give Google a chance digiting “ <ransomware_family_name> decryption tool “ and look around if there is a decryption tool developed and not spotted by id-ransomware (rarely).
METHOD 2: Recover from shadow copies
The shadow copies service is a set of COM interfaces that implements a framework to allow volume backups to be performed while applications on a system continue to write to the volumes.
For example, when we took a restore point we are also saving a volume backup (containing the shadow copies) and we can restore files from that backup.
This is a built-in feature of all windows operating systems starting from win XP so, most probably, you have your shadow copies and you don’t know about it.
We will use a free tool that allows us to inspect in our shadow copies, this tool is called shadow explorer and you can download here.
Note that if you have Windows XP you have to download the old version of this tool.
If you renamed the vssadmin.exe utility for security reason, you must rename it and let it work normally if you want that tool will run correctly.
Following a step-by-step real case of using this method to restore files from ransomware Jigsaw.

The main window of shadow explorer allows us to choose the drive, we want to explore the shadow copies and the date of the shadow copies we want to consult, because it can be there are more than 1 snapshot of the volume back-up (i.e. 2 or more restore point).

Once you identify the data you want to recover you can right-click on the folder and you can export the files.

In our case, we recovered 100% of our files as we can see in the above picture because Jigsaw ransomware doesn’t delete the shadow copies.
This method is really effective not on the host infected directly by the ransomware because most ransomware delete shadow copies through vssadmin tool.
It’s really effective when ransomware spread over the network encrypting the files on all host linked to the local network and it can’t access to operating system functionalities like vssadmin utility.
So we have still the shadow copies alive on all the machine hit by ransomware indirectly.
We strongly recommend disabling vssadmin.exe service to prevent the ransomware deleting the shadow copies of windows that, in most cases, let the victim restore the files encrypted on the operating system hard drive.
METHOD 3: Data recovery tool
Data recovery is, simply, the salvaging and repair of data that has been lost.
Of course, data recovery won’t always be possible; sometimes a system can be too corrupted or damaged to get much of the data back.
In this guide we won’t cover the techniques used by data recovery tools to restore data, what we have to know is that the success of files recovering depends on a lot of variables (like operating system partitioning, priority on file overwriting, drive space handling …). If you want to have more information you can check this.
There are a lot of data recovery tools available on the web, you can check a list here.
In this guide, we will use a free data recovery tool called Recuva.
Following a step-by-step real case of using this method to restore files from ransomware Locky.Odin.

We strongly recommend to install Recuva on an external USB drive instead of installing it on your OS drive to increase the probability to recover your files.
Once installed, it will be prompted a wizard for a scan, we recommend to close it in order to set the following options for the scanning phase:

We recommend to set those options because by default they are not enabled.
Activating “Restore folder structure” will allow us to keep the directory tree structure and permit us to infer the name of all our encrypted files.
Then we can run our scan on the desired drive and wait for it:

When Recuva will finish scanning all the deleted files, it will prompt a window where you have all possible recoverable files.
Of course, not all the files can be recovered.
On the “State” tab we can realize if we can recover that file.
The “partly recoverable” files are that file that cannot be whole recovered, for example a txt file would contain half text recovered and other half corrupted.
On the “Comment” tab we can recognize the encrypted renamed files with the original name files.
In this way, also if we can’t recover the file, we can recover the filename.
We can check all the files we want to recover and decide where to export.
In the right corner we have the “switch to advanced mode” button that let us apply filters, based on the path of the files, on our recoverable files.
So we will apply the following filters:
C:\Personal_Data, C:\Users\Administrator\Personal_Data, C:\Users\Administrator\Desktop\Personal_Data
and we will check all the files we want to export.
We strongly recommend exporting all the data on an external drive in order to have more probability to recover more data.

On a total of 3002 files we have 915 files fully recovered that means the 30% and we considered just the fully recovered files.
This method is also useful for recovering the name and the path of the files encrypted because some ransomware rename our files in a random digits name and we can’t even recognize which file we lost.
OUR TEST
So how much effective are our methods?
We decided to group up a set of ransomware samples (the most recent families) and run them in our virtual machine in order to test the % recovered files of our methods.
To evaluate the recovering rate of each method for each ransomware we will use a folder (Personal_Data) containing 1000 elements (containing pdf, jpg, ppt, txt, doc, xls), placed in 3 different locations on the system:
C:\Personal_Data
C:\Users\Administrator\Personal_Data
C:\Users\Administrator\Desktop\Personal_Data
Then we will try to recover our files using our methods. We will calculate the % rate of successfully recovered files for each folder and we will execute this try running the ransomware 3 different times in different system states, in the end we will report an average of the % rate of recovered files.
For our test we will use the following samples of ransomware:
Cerber v.1 md5: 9a7f87c91bf7e602055a5503e80e2313
Jigsaw md5: 2773e3dc59472296cb0024ba7715a64e
TeslaCrypt v.4 md5: 0265f31968e56500218d87b3a97fa5d5
CryptXXX v.2 md5: 19127d5f095707b6f3b6b027d7704743
Bart md5: d9fe38122bb08d96ef0de61076aa4945
CryptXXX v.4 md5: 631c36f93b0fc53b8c7be269b02676d0
Bart v.2 md5: 4741852c23364619257c705aca9b1be3
Satana Ransomware md5: 46bfd4f1d581d7c0121d2b19a005d3df
Odin md5: 01f7db952b1b17d0a090b09018896105
Crypt888 md5: 86c85bd08dfac63df65eaeae82ed14f7
ransomware-recovery-guide-14

CrySis ransomware decryption keys published online
18.11.2016 securityaffairs Ransomware
The decryption keys for the CrySis ransomware were posted online on the BleepingComputer.com forum by a user known as crss7777.
Good news for the victims of the CrySis ransomware, on Sunday the master decryption keys were released to the public. Security experts from Kaspersky Lab have already included the decryption keys in the Rakhni decryptor allowing victims of CrySis versions 2 and 3 to recover their files.
The decryption keys for the CrySis ransomware were posted online on the BleepingComputer.com forum by a user known as crss7777 who shared a link to a C header file containing the actual master decryption keys and information on how to utilize them.
“In a surprise move, the master decryption keys for the CrySiS Ransomware have been released early this morning in a post on the BleepingComputer.com forums. At approximately 1 AM EST, a member named crss7777 created a post in the CrySiS support topic at BleepingComputer with a Pastebin link to a C header file containing the actual master decryption keys and information on how to utilize them,” wrote Lawrence Abrams from BleepingComputer.
“These keys have already been used by Kaspersky Labs to update their RakhniDecryptor program so that it can be used to decrypt victim’s files.”

Lawrence Abrams speculates the user crss7777 could be a member of the development team.
“Though the identity of crss7777 is not currently known, the intimate knowledge they have regarding the structure of the master decryption keys and the fact that they released the keys as a C header file indicates that they may be one of the developers of the CrySiS ransomware,” said Abrams.
“Why the keys were released is also unknown, but it may be due to the increasing pressure by law enforcement on ransomware infections and the developers behind them.”
The CrySis ransomware was first spotted in February by experts at Eset, the malware has infected systems mostly in Russia, Japan, South and North Korea, and Brazil.
The threat is spread via email attachments with double file extensions or via malicious links embedded in spam emails.
The CrySis ransomware appends the .xtbl extension to the encrypted files, the files are renamed following the following format [filename].id-[id].[email_address].xtbl.
Bleepingcomputer.com published detailed instructions to decrypt the files.
The “notification” ransomware lands in Brazil
26.10.2016 Kaspersky Ransomware
It’s unusual for a day to go by without finding some new variant of a known ransomware, or, what is even more interesting, a completely new one. Unlike the previously reported and now decrypted Xpan ransomware, this same-but-different threat from Brazil has recently been spotted in the wild. This time the infection vector is not a targeted remote desktop intrusion, but a more massively propagated malicious campaign relying on traditional spam email.
Since the infection is not done manually by the bad guys, their malware has a higher chance of being detected and we believe that is one of the reasons for them to have added one more level of protection to the code, resorting to a binary dropper to launch the malicious payload.
Given that this particular ransomware is fairly well known by now, instead of opting for the usual branding and marketing efforts in which most ransomware authors invest time, this group has decided to choose an unnamed campaign, showing only an email address for technical support and a bitcoin address for making the payment. It has become a kind of urban legend that if you can’t find something on Google, then it doesn’t exist.
Not very long ago, we saw the birth of truly autochthonous Brazilian ransomware, without much technical sophistication and mainly based on an open-source project. While there’s a long road ahead for local bad guys to achieve the level of the key players on the ransomware scene, this particular family is interesting to study since there have been versions in English, Italian, and now Brazilian Portuguese. Is this ransomware being sold as a commodity in underground forums with Brazilian crews just standing on the shoulders of giants? Or is this a regional operation just starting out?
As one of the very few ransomware variants that prepend a custom ‘Lock.’ extension to the encrypted files instead of appending it, the task of recognizing this malware is not particularly difficult. However, understanding its true origins could still be considered an ongoing debate.
The drop
If we trust that the first transaction corresponds to the very first victim, the campaign has probably been active since 2016-04-04 17:29:26 (April 4th, 2016). In reality, this is not exactly accurate. The timestamp of the original dropper shows that the sample was actually compiled at the beginning of October:
That would mean that the criminal behind the campaign might have had different ransomware campaigns running in the past, or is just using the same BTC wallet for more than his criminal deeds.
The dropper is protected by the popular .NET obfuscator SmartAssembly, as can be seen by the string “Powered by SmartAssembly 6.9.0.114”. Once executed, it tries to mask itself in the Alternate Data Stream of the NTFS file system in Windows:
“%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\Sims.exe:Zone.Identifier
It’s capable of disabling Windows LUA protection:
“HKLM\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM”; Key: “ENABLELUA”; Value: “00000000”
(cmd.exe /c %WINDIR%\System32\reg.exe ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f
Reg.exe ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f)
The mechanism used to write new information to the registry is quite unusual: it uses the official windows application ‘migwiz.exe’ in order to bypass the UAC screen, not requiring any action from the user to execute with elevated privileges.
The malware is able to do that by writing a library ‘cryptbase.dll’ to the same folder as the ‘migwiz.exe’ file. Then, as soon as it’s launched, the process will load this library, which has a WinExec call that will launch the command line provided by the parameter.
The reason why they are using MigWiz is because this process is one that is in Microsoft’s auto-elevate list, meaning it can be elevated without asking for explicit permission.
As a simple mean of information gathering, the dropper will read the name of the infected computer:
HKLM\SYSTEM\CONTROLSET001\CONTROL\COMPUTERNAME\ACTIVECOMPUTERNAME”; Key: “COMPUTERNAME
Moreover, it includes data stealer techniques, such as retrieving information from the clipboard, or while it’s being typed on the keyboard. Additionally it has the capability to reboot the user’s machine.
@4333be: push ebp
@4333bf: mov ebp, esp
@4333c1: sub esp, 14h
@4333c4: push ebx
@4333c5: mov ebx, dword ptr [ebp+08h]@4333c8: lea eax, dword ptr [ebp-04h]@4333cb: push eax
@4333cc: push 00000028h
@4333ce: call dword ptr [00482310h] ;GetCurrentProcess@KERNEL32.DLL
@4333d4: push eax
@4333d5: call dword ptr [0048202Ch] ;OpenProcessToken@ADVAPI32.DLL
@4333db: test eax, eax
@4333dd: je 0043341Eh
@4333df: lea ecx, dword ptr [ebp-10h]@4333e2: push ecx
@4333e3: push 00487D68h ;SeShutdownPrivilege
Finally, it drops and executes the file tmp.exe (corresponding hash B4FDC93E0C089F6B885FFC13024E4B9).
Hello sir, hello madam, your fines have been locked
After the infection has been completed, as is usual in all ransomware families, the ransom note is shown. This time, it is written in Brazilian Portuguese and demanding 2000 BRL, which equates to around 627 USD or 1 BTC at the time of writing.
The bitcoin address provided (1LaHiL3vTGdbXnzyQ9omsYt8nFkUafXzK4) for payment shows total deposits for 1.89 BTC although many transactions have been made since the creation of this wallet. This is leading us to believe that either the criminal has been using the wallet for other purposes or they have bargaining with the victims and offering them a lower price, as depicted by the amount in each transaction.
The ransom note is very succinct, without giving any special payment URL or any other type of information. The victim will have to learn about bitcoin payments the hard way, and should they need support they can reach the criminals through a single email point of contact.
AVISO
Ola Sr(a),
TODOS os seus arquivos foram BLOQUEADOS e esse bloqueio somente serão DESBLOQUEADOS
caso pague um valor em R$ 2000,00 (dois Mil reais) em Bitcoins
Após o pagamento desse valor, basta me enviar um print para o email
infomacaoh@gmail.com
que estarei lhe enviando o programa com a senha para descriptografar/desbloquear o seus arquivos.
Caso o pagamento não seja efetuado, todos os seus dados serão bloqueados
permanentemente e o seu computador sera totalmente formatado
(Perdendo assim, todas as informações contidas nele, incluindo senhas de email, bancárias…)
O pagamento deverá ser efetuado nesse endereço de Bitcoin:
1LaHiL3vTGdbXnzyQ9omsYt8nFkUafXzK4
Para converter seu saldo em bitcoins acesse o site:
https://www.mercadobitcoin.com.br/conta/register/
Growth of ransomware in Brazil
The growth of ransomware in Brazil has been nothing short of impressive, taking into consideration that during October 2016 alone the popular ransomware family Packed.NSIS.MyxaH.gen family grew by 287.96%, and another of the usual suspects Trojan-Ransom.Win32.CryptXXX.gen grew by 56.96%, (when compared to the previous month in each case.)
In 2016, the 3 most important families of ransomware have been Trojan-Ransom.Win32.Blocker, accounting for 49.63% of the total infections,
Trojan-Ransom.NSIS.Onion, 29.09%, and Trojan-Ransom.Win32.Locky, 3.99%.
Currently, Brazil is the eighth most affected country worldwide as far as ransomware infections go for this year, and ranked first in Latin America.
Indicators of compromise
File: 04.exe
Size: 1049600
MD5: 86C85BD08DFAC63DF65EAEAE82ED14F7
Compiled: Saturday, October 8 2016, 11:22:30 – 32 Bit .NET
File: tmp.exe
Size: 842220
MD5: BB4FDC93E0C089F6B885FFC13024E4B9
Compiled: Sunday, January 29 2012, 21:32:28 – 32 Bit
CryPy: ransomware behind Israeli lines
13.10.2016 Kaspersky Ransomware
A Tweet posted recently by AVG researcher, Jakub Kroustek, suggested that a new ransomware, written entirely in Python, had been found in the wild, joining the emerging trend for Pysomwares such as the latest HolyCrypt, Fs0ciety Locker and others.
This Python executable comprises two main files. One is called boot_common.py and the other encryptor.py. The first is responsible for error-logging on Windows platforms, while the second, the encryptor, is the actual locker. Within the encryptor are a number of functions including two calls to the C&C server. The C&C is hidden behind a compromised web server located in Israel. The Israeli server was compromised using a known vulnerability in a content management system called Magento, which allowed the threat actors to upload a PHP shell script as well as additional files that assist them in streaming data from the ransomware to the C&C and back.
A notable point to mention is that the server was also used for phishing attacks, and contained Paypal phishing pages. There are strong indications that a Hebrew-speaking threat actor was behind these phishing attacks. The stolen Paypal credentials were forwarded to another remote server located in Mexico and which contains the same arbitrary file upload technique, only with a different content management.
It is a known practice for attackers to look for low-hanging fruit into which they can inject their code in order to hide their C&C server. One such example was the CTB-Locker for web servers reported last March.
Ransomware Analysis
ICON:
SHA1: ad046bfa111a493619ca404909ef82cb0107f012
MD5: 8bd7cd1eee4594ad4886ac3f1a05273b
Size: 5.22 MB
Type: exe
To reverse the executable one should first conduct a number of checks using a convenient debugger. The universal steps for unpacking an unknown packer start with trying to set a memory breakpoint on popular functions that packers use, such as VirtualAlloc.
If the breakpoint hits, the next step involves switching to user mode and setting a hardware breakpoint (on access). That will assist in inspecting where exactly the program initializes the memory block. In most cases, an executable magic header (MZ) should appear in the memory block. However, in this case the following screenshot shows the readable data that was allocated to that memory block:
After the data was allocated to the memory block, it appeared to be using VM code (python vm) to execute the code. For those who are not familiar with the term, VM code is the process of creating new instruction sets based on the author’s request. The CPU uses those instruction sets to understand the instructions.
py2exe simply converts the code to x86 assembly, the architecture used on the CPU for communication, and, by loading a python DLLs, loads all the modules into the memory.
We found that the executable file was generated using py2exe. The first indicator was a stack PUSH instruction to add the string – PY2EXE_VERBOSE: a module that compiles Python scripts to Microsoft Windows executables.
PY2EXE module string disclosure
A module that reverse the operation of the py2exe can be found in Github and is called unpy2exe. This module will revert the executable back to its origin Python compiled code (i.e. .pyc file). From that format, another step will be required to fully revert to the original code. We randomly chose to use EasyPythonDecompiler.
Fully decompiled Python scripts
In it’s current state, the executable fails to encrypt the file system, simply because the threat actors must have migrated from the current server to another. By doing so, they deleted the remaining traces of the PHP files they used for data collection from a victim’s machine. The following is the log file that is generated upon exception:
Error log file being generated by the boot_common.py
The scripts in Python use two files:
Name: boot_common.py
md5: dfd6237e26babdbc2b32fa0d625c2d16
SHA1: 38fe7b64113e467375202e2708199b45a22b25a6
Size: 3Kb
This file throws an “error” to show that the program failed to execute if there is a problem.
Name: encryptor.py
md5: 1ed3f127a0e94394ef049965bbc952ef
SHA1: 73122712b4563fadcc9871eb3fe0efdcf70bb608
Size: 9Kb
This script encrypts the victim’s files.
The ransomware disables the following features from the compromised machine:
By overwriting the registry policies it disables Registry Tools, Task Manager, CMD and Run.
list of registry manipulations
It then continues with changing bcdedit to disable recovery and ignore boot status policy.
Upon successful encryption, the ransomware will encrypt the following file extensions:
*.mid, *.wma, *.flv, *.mkv, *.mov, *.avi, *.asf, *.mpeg, *.vob, *.mpg, *.wmv, *.fla, *.swf, *.wav, *.qcow2, *.vdi, *.vmdk, *.vmx, *.gpg, *.aes, *.ARC, *.PAQ, *.tar.bz2, *.tbk, *.bak, *.tar, *.tgz, *.rar, *.zip, *.djv, *.djvu, *.svg, *.bmp, *.png, *.gif, *.raw, *.cgm, *.jpeg, *.jpg, *.tif, *.tiff, *.NEF, *.psd, *.cmd, *.class, *.jar, *.java, *.asp, *.brd, *.sch, *.dch, *.dip, *.vbs, *.asm, *.pas, *.cpp, *.php, *.ldf, *.mdf, *.ibd, *.MYI, *.MYD, *.frm, *.odb, *.dbf, *.mdb, *.sql, *.SQLITEDB, *.SQLITE3, *.asc, *.lay6, *.lay, *.ms11 (Security copy), *.sldm, *.sldx, *.ppsm, *.ppsx, *.ppam, *.docb, *.mml, *.sxm, *.otg, *.odg, *.uop, *.potx, *.potm, *.pptx, *.pptm, *.std, *.sxd, *.pot, *.pps, *.sti, *.sxi, *.otp, *.odp, *.wks, *.xltx, *.xltm, *.xlsx, *.xlsm, *.xlsb, *.slk, *.xlw, *.xlt, *.xlm, *.xlc, *.dif, *.stc, *.sxc, *.ots, *.ods, *.hwp, *.dotm, *.dotx, *.docm, *.docx, *.DOT, *.max, *.xml, *.txt, *.CSV, *.uot, *.RTF, *.pdf, *.XLS, *.PPT, *.stw, *.sxw, *.ott, *.odt, *.DOC, *.pem, *.csr, *.crt, *.key and wallet.dat to encrypt crypto currency wallets
The files are encrypted using AES with CBC mode for the following paths:
D:\\
E:\\
[userhome]\\contacts
[userhome]\\Documents\\
[userhome]\\Downloads\\
[userhome]\\Favorites\\
[userhome]\\Links\\
[userhome]\\My Documents\\
[userhome]\\My Music\\
[userhome]\\My Pictures\\
[userhome]\\My Videos\\
F:\\
.
.
Z:\\
*userhome - The current user home directory
When the encryption step is done, the ransomware will remove the restore points and write the README_FOR_DECRYPT.txt file and execute it. The following screen shot is the ransom note:
CryPy Ransomware Note embedded in the Python code
The threat actor behind the attack asks the victim to contact it via email, and to send a request to the following two email addresses to receive the decryption program:
(1) m4n14k@sigaint[.]org
(2) blackone@sigaint[.]org
Note that the ransom note contains mistakes, implying that it has been written by a non-English speaker. First, the headline is missing a ‘T’ in “IMPORTAN INFORMATION”. Second, the sentence “Decrypting of your files…” is syntatically wrong. Native speakers will be able to find additional mistakes.
The threat actor claims that files will be deleted every 6 hours, which reflects the approach of more advanced ransomwares. However, it forgets to mention proof of decryption or a channel that can be used in cases where the payment process is not responsive. This points to the executable being at an early stage of development.
The ransomware survives a reboot by adding the following keys to the registry:
Software\\Microsoft\\Windows\\CurrentVersion\\Run
regkey Software\\Microsoft\\Windows\\CurrentVersion\\Run
subkey Adobe_ReaderX
data %TEMP%\\mw.exe
regkey Software\\Microsoft\\Windows\\CurrentVersion\\Run
subkey explore_
data [userhome]\\Appdata\\local\\DCBC2A71-70D8-4DAN-EHR8-E0D61DEA3FDF.exe
The code for adding the values to the registry are located on the functions autorun() and autorun2().
These keys cause the computer to execute the files after the computer is restarted.
Right before launching the ransom note, the script calls a delete_shadow() function that takes no arguments, and simply executes the following command line code to remove all shadow copies and prevent recovery from backup:
os.system("vssadmin Delete shadows /all /Quiet")
Lastly, the file calls autorun2() fuction that copies the ransomware from its current location to C:\\Users\\\\AppData\\Local with hardcoded name:
DCBC2A71-70D8-4DAN-EHR8-E0D61DEA3FDF.exe
C2 Communication
The ransomware hides behind an Israeli web server which was compromised using Shell script arbitrary upload written in PHP. The compromise and upload were possible because the server carried a vulnerable Magento CMS.
The executable transfers data over an unencrypted HTTP channel in clear-text. This allows for easy traffic inspection using a network listener. The following screenshot is the traffic being sent to the server:
Inspecting the Magento exploit and the compromised server, we found that the origin of the upload carries the title Pak Haxor – Auto Xploiter and the email ardiansyah09996@gmail[.]com and that the file was uploaded in August 2016, which aligns with the case in subject. The following screenshot reveals how attackers are using massive exploiters that scan for vulnerable web servers and exploit the vulnerability, which they later visit to expand their control over the server:
Part of such an exploitation technique is dropping additional PHP scripts to refine a more sophisticated attack, such as the CryPy ransomware.
One such script can be found hard-coded in the CryPy Python code, in the form of a GET request. The request is sent with two parameters to a script that was uploaded using the Auto Xploiter and carries the name victim.php. By reviewing the Python code it is easier to understand the type of data being presented in Base64 encoding format.
As seen in the screenshot above, the configurl parameter accepts a URL querystring where the victim_info input value of the info parameter is derived from the platform module.
uname() is used when one wants to return a tuple of system, node, release, version, machine and processor values. These are encoded with Base64.
The next parameter is ip which contains the socket.gethostname() which basically collects an IP address.
The querystring is then sent to urllib.urlopen(), which will send a GET request to the selected server and read the reponse content into glob_config.
The response contains a JSON format payload which is checked for the following keys:
x_ID – the victim’s unique ID to request their decryption keys after payment.
x_UDP – Not used; perhaps saved for future use.
x_PDP – Not used; perhaps saved for future use.
The second call is implemented in a function called generate_file() which is responsible for fetching a unique key for each file before encryption.
We have seen in recent lockers that, in order to demonstrate trust and integrity, the victim is able to decrypt one/two files before processing the payment. This proves decryptor validity. In order to randomly choose a file, the attacker must first generate a unique token for each one. The second PHP script found in the code is savekey.php which is described in the following screenshot and is suspected to have the C2 IP in it. It was however deleted long before we were able to reach it.
As for the first call, the second sends two parameters. The first is the file’s name and the other is the victim ID. In return, the server responds with two keys:
X – Unique key after encryption which will be appended to the file’s header.
Y – New filename which will be stored instead of the previous one.
These parameters are then sent to an encryption routine, along with the file’s original name.
IOCs
REG Keys
HKCU\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\System
HKCU\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\Explorer
HKCU\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\explore_
HKLM\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\Adobe_ReaderX
Domains
hxxp://www.baraherbs[.]co.il/js/owebia/victim.php
hxxp://www.baraherbs[.]co.il/js/owebia/savekey.php
Hashes
8bd7cd1eee4594ad4886ac3f1a05273b crypy.exe
1ed3f127a0e94394ef049965bbc952ef encryptor.py
Emails
m4n14k@sigaint[.]com
blackone@sigaint[.]com
DXXD Ransomware, displays legal notice and encrypts files on unmapped network shares
12.10.2016 securityaffairs Ransomware
The DXXD ransomware specifically targets servers and is able to encrypt files on network shares even if they haven’t been mapped.
Malware continues to evolve, the last threat in order of time that implemented a singular feature is the DXXD ransomware. The peculiarities of this threat is that it encrypts also file on network shares, even if they are, unmapped ( a feature already implemented by the Locky ransomware) and displays a legal notice.
The DXXD ransomware appends the. dxxd extension to the encrypted files, then it leaves a ransom note onto the infected machine. The DXXD ransom note contains instructions for the victims that need to contact rep_stosd@protonmail.com or rep_stosd@tuta.io.to the encrypted files, then it leaves a ransom note onto the infected machine. The DXXD ransom note contains instructions for the victims that need to contact rep_stosd@protonmail.com or rep_stosd@tuta.io.
Another interesting feature of the malware is its ability to configure a Windows Registry setting in order to display a sort of “legal notice” when people log into a computer. The VXers used this feature to allow a user who tries to login to the server to see the ransom note.
The DXXD ransomware changes the HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\LegalNoticeCaption registry key and the HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\LegalNoticeText to display the following note.
“When you start Windows, Windows Defender works to help protect your PC by scanning for malicious or unwanted software.”

It is still unclear the infection vector, Abrams speculate the threat is spread by abusing Remote Desktop Services.
“Based on information discovered, I believe that the ransomware developer is hacking into servers using Remote Desktop Services and brute forcing passwords. If you have been affected by the DXXD Ransomware, you should reset all the passwords for the affected machine.” wrote Lawrence Abrams.
According to Abrams, the author of the DXXD ransomware decided to taunt victims and experts who help victims by creating an account on BleepingComputer and claiming that a newer version of the threat it is more difficult to decrypt. The developer also claimed to have exploited a zero-day vulnerability to compromise servers and deliver the malware.

As usual, let me discourage from paying the ransomware because there is no guarantee that you will receive back your files. Don’t forget to back up your data frequently and use anti-malware solutions. In the specific case, it could be better to disable Remote Desktop Protocol (RDP) and files running from AppData/LocalAppData folders.
New Cerber ransomware variant kills common database-related processes
8.10.2016 securityaffairs Ransomware
A new variant of the Cerber ransomware kills common database-related processes like those of the MySQL, Oracle and Microsoft SQL servers to encrypt files.
According to experts the BleepingComputer.com forum, a new variant of the Cerber ransomware is the wild attempts to shut down database connections to increase the effects of the infection.
The principal goal of a ransomware it to encrypt some of the most important data stored on computers and servers in the shortest time.
In a business perspective, precious data are usually stored in databases, and the write access to them if usually blocked by the operating systems because other processes are already using them.
Clearly, the lock of the databases doesn’t allow the malware, including the Cerber ransomware, to have a write access to the archive preventing the ransomware from encrypting them.
In order to overwhelm this problem, the latest version of the Cerber attempts to kill the principal processes linked to many database-related activities.
“According to security researcher BloodDolly, this update also includes the addition of new database processes that are closed by the close_process directive in Cerber’s configuration. This directive tells Cerber to terminate certain processes before encryption begins.” states bleepingcomputer.com.
“The directive and the current list of processes being terminated are:
"close_process":
{
"close_process":1,
"process":["msftesql.exe","sqlagent.exe","sqlbrowser.exe","sqlservr.exe","sqlwriter.exe","oracle.exe","ocssd.exe","dbsnmp.exe","synctime.exe","mydesktopqos.exe","agntsvc.exeisqlplussvc.exe","xfssvccon.exe","mydesktopservice.exe","ocautoupds.exe","agntsvc.exeagntsvc.exe","agntsvc.exeencsvc.exe","firefoxconfig.exe","tbirdconfig.exe","ocomm.exe","mysqld.exe","mysqld-nt.exe","mysqld-opt.exe","dbeng50.exe","sqbcoreservice.exe"]
},
”
msftesql.exe, sqlagent.exe, sqlbrowser.exe, sqlservr.exe, sqlwriter.exe, oracle.exe, ocssd.exe, dbsnmp.exe, synctime.exe, mydesktopqos.exe, agntsvc.exeisqlplussvc.exe, xfssvccon.exe, mydesktopservice.exe, ocautoupds.exe, agntsvc.exeagntsvc.exe, agntsvc.exeencsvc.exe, firefoxconfig.exe, tbirdconfig.exe, ocomm.exe, mysqld.exe, mysqld-nt.exe, mysqld-opt.exe, dbeng50.exe and sqbcoreservice.exe.”
In order to kill the above processes, the ransomware needs to run from privileged accounts, a good reason to work with minimum privileges in a workspace.
The Cerber ransomware is a very common threat, it is offered on the criminal underground as a service and researchers estimate that the profits for the criminal organization behind is greater than a $1 million this year.
Cerber ransomware
Another worrisome trend is the increasing number of ransomware-bases attacks against businesses that need to adopt all the necessary countermeasure to defeat the threat.
The fall of the Encryptor RaaS also thanks to Shodan
10.10.2016 securityaffairs Ransomware
Law enforcement and security experts have dismantled the Encryptor RaaS architecture by localizing one of its servers with Shodan.
Shodan is a search engine for internet-connected devices, it is a precious instrument for IT experts and hackers that use it to find assess systems exposed on the Internet.
The information gathered via Shodan could allow attackers to identify and attack vulnerable and poorly protected systems online.
We cannon underestimate also its usefulness in the fight against botnets. This summer security experts and law enforcement used the popular search engine to shut down the Encryptor RaaS botnet used to spread ransomware.
The Encryptor RaaS botnet was offering ransomware as a service allowing wannabe criminals to create their own malware and distribute them without any specific knowledge.
This model of sale allows criminals to create the malware and rent the infrastructure to deploy it and collect the payments made by the victims. Operators behind the service maintain a fee for the service.
“Encryptor RaaS’s purveyor created a full web panel for his patrons, accessible only via the Tor network, that enabled them to manage victims’ systems. Bitcoin was the preferred transaction currency.” reads a blog post published by Trend Micro. “Compared to other ransomware such as Cerber, whose developers earn 40% in commissions, Encryptor RaaS has a more attractive proposition. Affiliates only had to dole out at least 5% of their revenue to continue distributing the ransomware.”
Encryptor was first spotted in 2015 and the experts noticed a spike in the number of victims in March 2016 when experts from Cylance spotted 1,818 victims.
“Encryptor RaaS has been around for nearly a year, since mid-2015. This piece of ransomware is available exclusively on an .onion domain on the TOR network. The ransomware author charges a 20% fee for every infected victim who pays the ransom, which is made in Bitcoin.
The Encryptor RasS numbers to date are as follows:
Total Number of Victims = 1818
Total Number of Victims Who Have Paid = 8 (0.44% of total users infected)” reads the analysis published by Cylance.
Bad actors behind the Encryptor RaaS advertise their malware as “fully undetectable” and it seems to be true according to data recently provided by NoDistribute online virus scanner (2 of 35 antivirus are able to detect the threat).
Security researchers and law enforcement have exploited the features implemented by Shodan to discover one of the servers of the Encryptor RaaS that was poorly configured and exposed to the Internet, instead of being hidden inside the Tor anonymizing network.
The authorities seized the server in June and localized other 3 machines in a few days.
“Encryptor RaaS seemed to be on a roll. Early into the investigation, however, one of its C&C servers—either abandoned by the developer or mistakenly left open to anyone on the Internet—was exposed and not anonymized by Tor. Accordingly indexed by Shodan, Encryptor RaaS was found hosting its systems on a legitimate cloud service. By late June, one of the systems was seized.” states TrendMicro.

Unfortunately, the operators behind the Encryptor RaaS have wiped the master decryption key once spotted by the law enforcement, this means that victims of the ransomware will have no solution to rescue the encrypted files.
Polyglot – the fake CTB-locker
3.10.2016 Kaspersky Ransomware
Cryptor malware programs currently pose a very real cybersecurity threat to users and companies. Clearly, organizing effective security requires the use of security solutions that incorporate a broad range of technologies capable of preventing a cryptor program from landing on a potential victim’s computer or reacting quickly to stop an ongoing data encryption process and roll back any malicious changes. However, what can be done if an infection does occur and important data has been encrypted? (Infection can occur on nodes that, for whatever reason, were not protected by a security solution, or if the solution was disabled by an administrator.) In this case, the victim’s only hope is that the attackers made some mistakes when implementing the cryptographic algorithm, or used a weak encryption algorithm.
A brief description
The cryptor dubbed Polyglot emerged in late August. According to the information available to us, it is distributed in spam emails that contain a link to a malicious RAR archive. The archive contains the cryptor’s executable code.
Here are some examples of the links used:
hXXp://bank-info.gq/downloads/reshenie_suda.rar
hXXp://bank-info.gq/downloads/dogovor.rar
When the infected file is launched, nothing appears to happen. However, the cryptor copies itself under random names to a dozen or so places, writes itself to the autostart folder and to TaskScheduler. When the installation is complete, file encryption starts. The user’s files do not appear to change (their names remain the same), but the user is no longer able to open them.
When encryption is complete, the cryptor changes the desktop wallpaper, (interestingly, the wallpaper image is unique to each victim) and displays the ransom message.
The cryptor’s main window
New desktop wallpaper with the “open key” block unique to each victim computer
The user is offered the chance to decrypt several files for free.
The free trial decryption window
After this, the user is told to pay for file decryption in bitcoins. The cryptor contacts its C&C, which is located on the Tor network, for the ransom sum and the bitcoin address where it should be sent.
C&C communication window
From this moment on, the cryptor allows the user to check the ransom payment status on the C&C.
Ransom payment details
If the ransom is not paid on time, the cryptor notifies the user that it’s no longer possible to decrypt their files, and that it is about to ‘self-delete’.
Last window displayed by Polyglot
Imitating CTB-Locker
Initially, this cryptor caught our attention because it mimics all the features of another widespread cryptor – CTB-Locker (Trojan-Ransom.Win32.Onion). The graphical interface window, language switch, the sequence of actions for requesting the encryption key, the payment page, the desktop wallpapers – all of them are very similar to those used by CTB-Locker. The visual design has been copied very closely, while the messages in Polyglot’s windows have been copied word for word.
The main graphical interface windows:
List of encrypted files:
Polyglot - the fake CTB-locker Polyglot - the fake CTB-locker
Window for the trial decryption of 5 random files:
The private key request window:
The desktop wallpapers:
Polyglot - the fake CTB-locker
The ‘connection failed’ error message:
Offline decryption instructions:
Polyglot - the fake CTB-locker Polyglot - the fake CTB-locker
The similarities do not stop there. Even the encryption algorithms used by the cybercriminals have clearly been chosen to imitate those used in CTB-Locker.
Polyglot CTB-Locker
Algorithms used for file encryption File content is packed into a ZIP archive and then encrypted with AES-256. File content is compressed with Zlib and then encrypted with AES-256.
Algorithms used while working with the keys ECDH (elliptic curve Diffie-Hellman), curve25519, SHA256. ECDH (elliptic curve Diffie-Hellman), curve25519, SHA256.
Extensions of encrypted files File extensions are not changed. File extensions are changed, depending on version:
– .ctbl
– .ctb2
– 7 random lower-case Latin symbols
Demo decryption 5 files are decrypted for free as a demo. Their decryption keys and file names are saved in the registry. 5 files are decrypted for free as a demo. Their decryption keys are only stored in the RAM memory while the process is running.
C&C location C&C is in the Tor network, communication is via a public tor2web service. C&C is in the Tor network, communication is via a Tor client integrated into the Trojan, or (in some versions of CTB-Locker) via a public tor2web service.
Traffic protection / obfuscation Bitwise NOT operation. AES encryption.
That said, we should note the following: a detailed analysis has revealed that Polyglot was developed independently from CTB-Locker; in other words, no shared code has been detected in the two Trojans (except the publicly available DLL code). Perhaps the creators of Polyglot wanted to disorient the victims and researchers, and created a near carbon copy of CTB-Locker from scratch to make it look like a CTB-Locker attack and that there was no hope of getting files decrypted for free.
C&C communication
The Trojan contacts the C&C server located on Tor via a public tor2web service, using the HTTP protocol.
Prior to each of the below data requests, a POST request is sent with the just one parameter: “live=1”.
Request 1.
At the start of operation, the Trojan reports the successful infection to the C&C. The following data is sent to the C&C:
{
“ip”:”xxx.xxx.xxx.xxx”, //ip address of the infected computer
“method”:”register”, //action type. “register” = Trojan informs C&C of new infection
“uid”:”xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx”, //Infected computer’s ID
“version”:”10f”, //Trojan version contained in its body
“info”:”Microsoft (build xxxx), 64-bit”, //OS version on the infected computer
“description”:” “, //Always a whitespace (” “)
“start_time”:”14740xxxxx”, //Trojan’s start time
“end_time”:”0″, //Encryption finish time. 0 = no encryption has run yet
“user_id”:”5″ //Number hardwired in the sample
}
This data block is passed through a bitwise NOT operation, encoded into Base64 and sent to the C&C in a POST request.
Contents of the sent request
Parameters of the POST request:
signature – CRC32 from the sent data
ver – Trojan version
gcdata – data, with contents as described above.
Request 1 and the reply received from the C&C
Request 2.
When the Trojan has finished encrypting the user’s data, it sends another request to the C&C. The content of the request is identical to that of request 1 except the field “end_time”, which now shows the time encryption was completed.
Request 3.
This is sent to the C&C to request the bitcoin address for payment and the ransom sum to be paid.
{
“method”:”getbtcpay”
“uid”:”xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx”
}
The C&C replies to this request with the following data:
{
“code”:”0″,
“text”:”OK”,
“address”:”xxxxxxxx”, //bitcoin address (may vary)
“btc”:0.7, //amount to be paid in BTC (may vary)
“usd”:319.98 //amount to be paid in USD (may vary)
}
Request 4.
This is sent to request a file decryption key from the C&C.
{
“method”:”getkeys”,
“key”:””,
“uid”:”xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx”,
“info”:[“DYqbX3m9u0Pk9bE9Rg2Co3empC2M/yrnqgNS3r0AT2vwCw8Zas08bd4BNiO3XuAqi6/5WQ0VBiUkRUToo+YFL/QtPkiRIQ/D9RyKhzpBHlNpf2hPb9eloDzpkonQl7L6cQyJ2FipEG2ggZOdTDBcNAEAAAA=”]
}
Request 5.
The Trojan reports that data decryption has been completed and states the number of decrypted files to the C&C.
{
“method”:”setend”,
“uid”:”xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx”,
“decrypted”:”1″
}
Description of the encryption algorithm
During our analysis of the malicious code, it became evident that the Trojan encrypts files in three stages, creating intermediate files:
First, the original file is placed in a password-protected ZIP archive. The archive has the same name as the original file plus the extension “a19”;
Polyglot encrypts the password-protected archive with the AES-256-ECB algorithm. The resulting file again uses the name of the original file, but the extension is now changed to “ap19”;
The Trojan deletes the original file and the file with the extension “a19”. The extension of the resulting file is changed from “ap19” to that of the original file.
Flowchart of the search and file encryption actions performed by Polyglot
A separate AES key is generated for each file, and is nothing more than a ‘shared secret’ generated according to the Diffie-Hellman protocol on an elliptic curve. However, first things first.
Before encrypting any files, the Trojan generates two random sequences, each 32 bytes long. The SHA256 digests of each sequence become the private keys s_ec_priv_1 and s_ec_priv_2. Then, the Bernstein elliptic curve (Curve25519) is used to obtain public keys s_ec_pub_1 and s_ec_pub_2 (respectively) from each private key.
The Trojan creates the structure decryption_info and writes the following to it: a random sequence used as the basis for creating the key s_ec_priv_1, the string machine_guid taken from the registry, and a few zero bytes.
struct decryption_info
{
char s_rand_str_1[32];
char machine_guid[36];
char zeroes[12];
};
Using the private key s_ec_priv_2 and the cybercriminal’s public key mal_pub_key produces the shared secret mal_shared_secret = ECDH(s_ec_priv_2, mal_pub_key). The structure decryption_info is encrypted with algorithm AES-256-ECB using a key that is the SHA256 digest of this secret. For convenience, we shall call the obtained 80 bytes of the encrypted structure encrypted_info.
Only when Polyglot obtains the encrypted_info value does it proceed to generate the session key AES for the file. Using the above method, a new pair of keys is generated, f_priv_key and f_pub_key. Using f_priv_key and s_ec_pub_1 produces the shared secret f_shared_secret = ECDH(f_priv_key, s_ec_pub_1).
The SHA256 digest of this secret will be the AES key with which the file is encrypted.
To specify that the file has already been encrypted and that it’s possible to decrypt the file, the cybercriminals write the structure file_info to the start of each encrypted file:
struct file_info
{
char label[4] = {‘H’,’U’, ‘I ‘, 0x00};
uint32_t label2 = 1;
uint64_t archive_size;
char f_pub_key[32];
char s_ec_pub_1[32];
char s_ec_pub_2[32];
char encrypted_info[80];
};
The elliptic curve, the Diffie-Hellman protocol, AES-256, a password-protected archive – it was almost flawless. But not quite, because the creator of Polyglot made a few mistakes during implementation. This gave us the opportunity to help the victims and restore files that had been encrypted by Polyglot.
Mistakes made by the creators
As was mentioned earlier, all the created keys are based on a randomly generated array of characters. Therefore, the strength of the keys is determined by the generator’s strength. And we were surprised to see the implementation of this generator:
A graphical representation of the random sequence generation procedure
Let’s convert this function into pseudocode so it’s easier to follow:
Please note that when another random byte is selected, the entire result of the function rand() is not used, just the remainder of dividing the result by 32. Only the cybercriminal knows why they decided to make the random string this much weaker – an exhaustive search of the entire set of the possible keys produced by such a pseudo-random number generator will only take a few minutes on a standard PC.
Taking advantage of this mistake, we were able to calculate the AES key for an encrypted file. Although there was a password-protected archive below the layer of symmetric encryption, we already knew that the cybercriminal had made another mistake.
Let’s look at how the archive key is generated:
We can see that the key length is only 4 bytes; moreover, these are specific bytes from the string MachineGuid, the unique ID assigned to the computer by the operating system. Furthermore, a slightly modified MachineGuid string is displayed in the requirements text displayed to the victim; this means that if we know the positions in which the 4 characters of the ZIP archive password are located, we can easily unpack the archive.
The MachineGuid string displayed in the requirements screen
Conclusion
Files that are encrypted by this cryptor can be decrypted using Kaspersky Lab’s free anti-cryptor utility RannohDecryptor Version 1.9.3.0.
All Kaspersky Lab solutions detect this cryptor malware as:
Trojan-Ransom.Win32.Polyglot
PDM:Trojan.Win32.Generic
TeamXRat spreads ransomware via RDP brute-force attacks
2.10.2016 securityaffairs Ransomware
Malware researchers from Kaspersky have spotted the TeamXRat gang spreading a new ransomware in Brazil via RDP brute-force attacks.
Cyber criminals are using stolen or weak remote desktop credentials to access systems and deliver file-encrypting ransomware.
This is not a novelty in the criminal ecosystem, in March experts discovered a ransomware dubbed Surprise that was installed via TeamViewer and executes from memory.
In October 2015, experts at BleepingComputer blog reported a strain of ransomware dubbed LowLevel04 that was spreading via Remote Desktop and Terminal Service.
The hackers in both circumstances used stolen credentials for RDP software.
Now security researchers from the security firm Kaspersky Lab have spotted a new strain of ransomware, called Trojan-Ransom.Win32.Xpan, that was used in campaigns against hospitals and other organizations in Brazil.
According to Kaspersky, the new ransomware was developed by a gang called TeamXRat that was known for the development of remote access trojans (RATs).
teamxrat ransomware
The members of the TeamXRat perform brute-force attacks on the machine in order to access it via RDP and then manually install the Xpan ransomware on the hacked servers.
“Connecting remote desktop servers directly to the Internet is not recommended and brute forcing them is nothing new; but without the proper controls in place to prevent or at least detect and respond to compromised machines, brute force RDP attacks are still relevant and something that cybercriminals enjoy,” reads a blog post published by Kaspersky. “Once the server is compromised, the attacker manually disables the Antivirus product installed on the server and proceeds with the infection itself.”
The experts also highlighted that crooks exploit MS15-067 and MS15-030 vulnerabilities in the RDP protocol. Crooks could exploit them to remotely execute code by sending a specially crafted sequence of packets to a targeted system.
According to Kaspersky, Brazil is the country with the highest number of compromised RDP servers being sold on the underground market.
This summer experts from Kaspersky revealed the existence of the xDedic marketplace that was offering everyone from entry-level cybercriminals to APT groups fast, cheap and easy access to legitimate organizational servers.
The good news is that the TeamXRat has made an error while developing the encryption functionality of ransomware that has been exploited by the experts at Kaspersky Lab to recover the encrypted files without paying the ransom.
The victims of the Xpan have to contact Kaspersky to receive instructions and assistance to recover the files.
“But the good news is that the Kaspersky Anti-Ransom team was able to break the encryption used by the Xpan Trojan. This effort made possible the decryption of files belonging to a Hospital in Brazil, which was hit by this Ransomware family.” closes Kaspersky.
“If you’re a victim of this new Ransomware family and need help to decrypt your files, please DON’T PAY the ransom. Instead, contact us via support.”
TeamXRat: Brazilian cybercrime meets ransomware
29.9.2016 Kaspersky Ransomware
Brazilian cybercriminals are notorious for their ability to develop banking trojans but now they have started to focus their efforts in new areas, including ransomware. We discovered a new variant of a Brazilian-made ransomware, Trojan-Ransom.Win32.Xpan, that is being used to infect local companies and hospitals, directly affecting innocent people, encrypting their files using the extension “.___xratteamLucked” and asking to pay the ransom.
The Kaspersky Anti-Ransom team decrypted the Xpan Trojan, allowing them to rescue the files of a Hospital in Brazil that had fallen victim to this Ransomware family.
Actually, this is not the first ransomware to come out of Brazil. In the past, we investigated TorLocker and its flawed encryption, which was created and negotiated worldwide by a Brazilian cybercriminal. We also saw a lot of copycats use HiddenTear in local attacks. Trojan Ransom Xpan was created by an organized gang, which used targeted attacks via RDP that abused weak passwords and wrong implementations.
In this post, we’ll explain this new Ransomware family and how Brazilian coders are creating new ransomware from scratch.
The group behind the attack
The group identifies itself as “TeamXRat“and “CorporacaoXRat“.
(Translating from Portuguese to English as “CorporationXRat”)
Their first ransom trojan consisted of using a simple XOR based encryption, described by some victims here (most of the victims are from Brazil). The new version of Xpan Ransomware shows that the cybercriminals behind it have improved the code to make it more complex, also switching the encryption scheme.
The ransom texts used by the group are written in Portuguese from Brazil. The messages do not inform how much the victim has to pay to retrieve their files, nor the payment method required (which is usually Bitcoins). Instead, they instruct the victim to send an email to one of the anonymous email services Mail2Tor or Email.tg. For example, corporacaoxrat@mail2tor.com, xRatTeam@mail2tor.com and xratteam@email.tg providing the public key used by the ransomware to encrypt the files. Older versions of this ransomware also used e-mail accounts from another Email service – Protonmail, such as corporacaoxrat@protonmail.com, currently deactivated.
When the victim gets in touch with the group, they start to negotiate the ransom payment. All communication is in Portuguese and they request 1 btc (about 603 USD) to decrypt the files. The group also claims that the payment is a “donation” arguing that “they exploited flaws in your system and carried out the attack in order to make sure you increase your security”. Finally, the cybercriminals also offer to decrypt one file for free:
“For me only the ‘donation’ is important. Not your files. If your files are important to you, I advise you to make the donation; otherwise, you’ll lose all your files”
Xpan, how it works
The sample is UPX packed. Once executed it checks the default language of the infected system set in the following registry key: HKLM\SYSTEM\CONTROLSET001\CONTROL\NLS\LOCALE
In addition, it’s able to query local time and obtain the computer name from the registry using several commands like net.exe, sc.exe, and taskkill.exe. Interestingly, it also deletes any Proxy setting defined in the system, located in: HKCU\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP.
Since the targets are companies and corporations, the group might use proxies blocking access to certain Web resources. It is highly probable that this technique is used to “set victim’s free” while emailing the attackers or accessing BTC resources online.
After completing its execution, the ransomware displays the following image in the affected system:
“All your files were encrypted using a RSA 2048 bits encryption”
The sample is written in C++ and uses STL, being built as a console application. During the lenght of its execution, it logs all its actions to the console, only to clear it once the encryption process has finished.
The operation of this malware is ‘guided’ by the configuration data block stored inside the body of the Trojan:
Decrypted configuration block
The configuration contains the following details:
Drive letters which will be processed;
Blacklisted substrings: the files whose path contain any of these strings will not be encrypted;
Ransomware text message for the victim;
Extension of the encrypted files (in this case, .____xratteamLucked);
Name of the file with ransom notes;
Console commands to be executed prior to the process of file encryption;
Console commands to be executed after the encryption;
A public RSA-2048 key in the MSBLOB format.
Part of the pseudocode of the main procedure
From Xorist to Xpan
A previous ransomware sample that was believed to be part of the TeamXRat ransomware campaign used a simple encryption algorithm known as TEA (or Tiny Encryption Algorithm). After comparing this original version (dubbed Xorist) against this new Xpan variant, we could observe that now they are using an AES-256 encryption scheme.
Xorist ransomware TEA constant
Xpan ransomware now has evolved to use AES-256 encryption
Xorist Xpan
Will automatically start when user is logged in. It uses the following registry key for persistence: SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run No persistence used.
Tiny Encryption Algorithm AES-256
ASM, MS Linker C++, MinGW compiler
Includes a list of files that are to be encrypted. Will encrypt everything except .exe and .dll files and files with blacklisted substrings in the path.
The developers have clearly shifted their development procedures in the Xpan malware. It’s typical for cybercriminals to evolve their techniques once a decryption method has been found for their ransomware, or that specific variant is widely detected.
List of file extensions that Xorist ransomware will search and encrypt
File Encryption
The trojan uses the implementation of cryptographic algorithms provided by MS CryptoAPI. The files are encrypted by AES-256 in CBC mode.
There are 2 known versions of this trojan that can be distinguished by their extensions. The 1st one uses “___xratteamLucked” (3 ‘_’ symbols) and the second one – “____xratteamLucked” (4 ‘_’ symbols).
These 2 versions employ different techniques to encrypt the files, which we will describe in more detail.
Version 1 (3 ‘_’ symbols in the extension)
The trojan generates a single 255-symbol password for all files. This password is encrypted by RSA-2048 and put into the ransom note (concatenated with the public key). Then the trojan produces a 256-bit key from this password using the API CryptDeriveKey; this key will be used to encrypt all files.
When processing each file, the malware adds the string ‘NMoreira’ to the beginning of the original file and encrypts the file content by 245-byte blocks using the AES-256 algorithm in CBC mode. Each block is additionally XOR’ed with a random byte which is stored before the padding of the corresponding block.
Version 2 (4 ‘_’ symbols in the extension)
For each file, the trojan generates a new 255-symbol password, encrypts this password by RSA-2048 and puts this data into the beginning of each encrypted file. Then, the trojan produces a 256-bit key from this password using the API CryptDeriveKey, and uses this key to encrypt the original file content (AES-256 CBC).
File search and encryption is carried out by multiple threads, each thread processes its disk.
Ransomware in action: console output inform the files encrypted
After encryption is completed, the malware will change the wallpaper in the desktop and display this file, with the ransom note:
The ransom note, in Portuguese
Before encrypting the data in the affected system, the ransomware executes the following commands, aiming to stop popular database services, to be sure that database files will be encrypted as well, so they cause a greater damage to the victim:
echo Iniciando pre comandos
echo Parando Firbird
sc config FirebirdServerDefaultInstance start=disabled
taskkill /IM fb_inet_server.exe /F
net stop FirebirdServerDefaultInstance
echo parando SQL SERVE
taskkill /IM sqlservr.exe /F
sc config MSSQLSERVER start=disabled
sc config MSSQL$SQLEXPRESS start=disabled
net stop MSSQLSERVER
net stop MSSQL$SQLEXPRESS
echo parando poostgree
taskkill /IM pg_ctl.exe /F
sc config postgresql-9.0 start=disabled
net stop postgresql-9.0
After the execution, the ransomware deletes itself from the system, to remove the original infector:
@echo off
goto Delete
:WaitAndDelete
@timeout 5
:Delete
@del “path\sample_name.exe”
if exist “path\sample_name.exe”
goto WaitAndDelete
@del %0
After the encryption has finished, the trojan modifies the registry to add a custom handler for the action of double-clicking on any of the encrypted files. As a result, when the victim clicks on a file with the extension “.____xratteamLucked“, the command stored in the registry is executed, and this command shows the ransom notes in a new window using msg.exe (a standard utility which is a part of Windows distribution).
Windows Registry modified by the ransom
How they attack
Most of the attacks performed by TeamXRat are performed manually, installing the ransomware in the hacked server. To achieve that, they perform RDP (Remote Desktop Protocol) brute force attacks. Connecting remote desktop servers directly to the Internet is not recommended and brute forcing them is nothing new; but without the proper controls in place to prevent or at least detect and respond to compromised machines, brute force RDP attacks are still relevant and something that cybercriminals enjoy. Once the server is compromised, the attacker manually disables the Antivirus product installed on the server and proceeds with the infection itself.
We are also aware that vulnerabilities such as MS15-067 and MS15-030 in the RDP protocol, which allow remote code execution if an attacker sends a specially crafted sequence of packets to a targeted system, can be used by cybercriminals if a server is not patched and exposed to attacks.
As we saw in the recent xDedic research, vulnerable servers with exposed RDP connections are very valuable assets in the hands of cybercriminals. Not surprisingly, Brazil was the country with the most compromised servers being offered in the underground market to any cybercriminal.
xDedic: compromised Brazilian RDP servers were available in the underground market
Decryption: we can help!
If the victim pays the ransom, the cybercriminals will send this tool to decrypt the files:
Decryption tool sent by the bad guy after payment
But the good news is that the Kaspersky Anti-Ransom team was able to break the encryption used by the Xpan Trojan. This effort made possible the decryption of files belonging to a Hospital in Brazil, which was hit by this Ransomware family.
If you’re a victim of this new Ransomware family and need help to decrypt your files, please DON’T PAY the ransom. Instead, contact us via support.
Conclusion
As we can see, Brazilian bad guys are now diversifying their “business” with new ransomware families developed from scratch, abandoning older versions that used XOR encryption and adopting new, more robust encryption algorithms. This is a clear signal that they have started to explore new schemes with new targets and newer types of attacks.
As we forecasted in the beginning of this year, we expect ransomware attacks to gain ground on banking trojans and to transition into other platforms. Ransomware has two advantages over traditional banking threats: direct monetization using an anonymous payment system (usually Bitcoin), and relatively low cost per victim. Certainly, this is very attractive to Brazilian crooks, well-known for their banking trojans development. Brazilian law enforcement is very good at catching criminals (although they are not always convicted and imprisoned) by “following the money”, something that we know it’s not entirely possible for Bitcoin payments.
We detect this new threat as
Trojan-Ransom.Win32.Xpan.a and PDM:Trojan.Win32.Generic.
We’ll keep an eye out or new variants, which surely will appear from same or other threat actors.
MD5 reference: 34260178f9e3b2e769accdee56dac793
Mamba: The new Full Disk Encryption Ransomware Family Member
16.9.2016 securityaffairs Ransomware
A Brazilian Infosec research group, Morphus Labs, just discovered a new Full Disk Encryption (FDE) Ransomware this week, dubbed Mamba.
Mamba, as they named it, uses a disk-level encryption strategy instead of the conventional file-based one. This may be just the beginning of a new era for the Ransomwares.
In this article, Renato Marinho (@renato_marinho), the researcher responsible for the finding, explains more about this new threat [1].
About Mamba
“You are Hacked ! H.D.D Encrypted, Contact Us For Decryption Key (w889901665@yandex.com) YOURID: 123152”. This message is all that remains for the victims of this new Ransomware. To get the decryption key, it’s necessary to contact somebody through the informed e-mail address, give the ID and pay 1 BTC per infected host. Without that, the system even starts. For the matter of this article, we will call this Ransomware “Mamba”, a snake with a paralyzing poison.for the victims of this new Ransomware. To get the decryption key, it’s necessary to contact somebody through the informed e-mail address, give the ID and pay 1 BTC per infected host. Without that, the system even starts. For the matter of this article, we will call this Ransomware “Mamba”, a snake with a paralyzing poison..for the victims of this new Ransomware. To get the decryption key, it’s necessary to contact somebody through the informed e-mail address, give the ID and pay 1 BTC per infected host. Without that, the system even starts. For the matter of this article, we will call this Ransomware “Mamba”, a snake with a paralyzing poison.
It seems that the disk level Ransomware family is growing. A similar Ransomware, called Petya, got famous march this year because of the disk encryption strategy, although some analysis [2] says that the malware encrypts the master file table (MFT) and not the data itself. But Mamba Ransomware differs from Petya exactly at this point. It uses a full disk encryption open source tool called DiskCryptor [3] to strongly encrypt the data.disk encryption strategy, although some analysis [2] says that the malware encrypts the master file table (MFT) and not the data itself. But Mamba Ransomware differs from Petya exactly at this point. It uses a full disk encryption open source tool called DiskCryptor [3] to strongly encrypt the data..disk encryption strategy, although some analysis [2] says that the malware encrypts the master file table (MFT) and not the data itself. But Mamba Ransomware differs from Petya exactly at this point. It uses a full disk encryption open source tool called DiskCryptor [3] to strongly encrypt the data..disk encryption strategy, although some analysis [2] says that the malware encrypts the master file table (MFT) and not the data itself. But Mamba Ransomware differs from Petya exactly at this point. It uses a full disk encryption open source tool called DiskCryptor [3] to strongly encrypt the data..disk encryption strategy, although some analysis [2] says that the malware encrypts the master file table (MFT) and not the data itself. But Mamba Ransomware differs from Petya exactly at this point. It uses a full disk encryption open source tool called DiskCryptor [3] to strongly encrypt the data.
We found Mamba last September 7, during an incident response procedure for a multinational company that had some servers compromised by this malware in Brazil, EUA and India subsidiaries.
The goal of this article is to share some Mamba analysis results and to get some collaboration to better understand this threat and its intrusion vectors.
The ransom message
As stated in the introduction of this article, the ransomware hinders the operating system to boot up. It overwrites the boot disk master boot record (MBR) by a custom one that shows the ransom message and asks for the password like you can see in the Figure 1.ransomware hinders the operating system to boot up. It overwrites the boot disk master boot record (MBR) by a custom one that shows the ransom message and asks for the password like you can see in the Figure 1.1.ransomware hinders the operating system to boot up. It overwrites the boot disk master boot record (MBR) by a custom one that shows the ransom message and asks for the password like you can see in the Figure 1.1.ransomware hinders the operating system to boot up. It overwrites the boot disk master boot record (MBR) by a custom one that shows the ransom message and asks for the password like you can see in the Figure 1.1.1.ransomware hinders the operating system to boot up. It overwrites the boot disk master boot record (MBR) by a custom one that shows the ransom message and asks for the password like you can see in the Figure 1.

Figure 1: The ransom message at the beginning of the boot process
It’s not clear, but this new MBR also prompts the user for the decryption password.
Looking for the malware sample
As the whole data of the compromised servers HDD ware encrypted, including the Ransomware itself, we started to look for more information about it somewhere else.
The first strategy was looking for some parts of the ransom message in the Web. For our surprise, putting the text in the Web. For our surprise, putting the text in the Web. For our surprise, putting the text in the Web. For our surprise, putting the text “contact us for decryption key” YOURID, we received just one result from Google. It pointed to an analysis made using Malwr [4] sandbox on Aug/29. This result gave us some important information, like the file name (141.exe) and the hashes.Malwr [4] sandbox on Aug/29. This result gave us some important information, like the file name (141.exe) and the hashes..Malwr [4] sandbox on Aug/29. This result gave us some important information, like the file name (141.exe) and the hashes..Malwr [4] sandbox on Aug/29. This result gave us some important information, like the file name (141.exe) and the hashes..Malwr [4] sandbox on Aug/29. This result gave us some important information, like the file name (141.exe) and the hashes.

Figure 2: Google results for parts of the ransom message
Searching the “141.exe” file hash at VirusTotal, we found some AV engines linking the sample to a Ransomware malware, like TrendMicro calling it a “Ransom_HDDCRYPTOR.A”.engines linking the sample to a Ransomware malware, like TrendMicro calling it a “Ransom_HDDCRYPTOR.A”.engines linking the sample to a Ransomware malware, like TrendMicro calling it a “Ransom_HDDCRYPTOR.A”.engines linking the sample to a Ransomware malware, like TrendMicro calling it a “Ransom_HDDCRYPTOR.A”.engines linking the sample to a Ransomware malware, like TrendMicro calling it a “Ransom_HDDCRYPTOR.A”.engines linking the sample to a Ransomware malware, like TrendMicro calling it a “Ransom_HDDCRYPTOR.A”.

Figure 3: TrendMicro’s analysis for the “141.exe” sample
At the same time, we started to seek for the malware on other hosts of the company’s network. After some effort, using an anti-malware solution, we started to find out a malicious file in some different hosts. The file name was “152.exe”.of the company’s network. After some effort, using an anti-malware solution, we started to find out a malicious file in some different hosts. The file name was “152.exe”..of the company’s network. After some effort, using an anti-malware solution, we started to find out a malicious file in some different hosts. The file name was “152.exe”..of the company’s network. After some effort, using an anti-malware solution, we started to find out a malicious file in some different hosts. The file name was “152.exe”..of the company’s network. After some effort, using an anti-malware solution, we started to find out a malicious file in some different hosts. The file name was “152.exe”.
Conducting some dynamic analysis of “152.exe” with the TIV and Hybrid-Analysis [5] sandboxes, we started to find some similarities between the Mamba’s memory dump strings and the ransom message. To say the truth, we found exactly the message “You are Hacked ! H.D.D Encrypted, Contact Us For Decryption Key (w889901665@yandex.com) YOURID: 123152” – even the “YOURID” was the same! ! H.D.D Encrypted, Contact Us For Decryption Key (w889901665@yandex.com) YOURID: 123152” – even the “YOURID” was the same!
By the way, we found it very curious the fact that the “YOURID” information in the sandbox analysis be the same as the company’s compromised hosts. In other words, it seems like this is a static code.be the same as the company’s compromised hosts. In other words, it seems like this is a static code..be the same as the company’s compromised hosts. In other words, it seems like this is a static code..be the same as the company’s compromised hosts. In other words, it seems like this is a static code..be the same as the company’s compromised hosts. In other words, it seems like this is a static code.
Mamba’s initial analysis
To better understand how Mamba works, we started to perform some tests with it in our lab. In a first test, we basically ran the sample in a Windows 8.1 VM, but, unfortunately nothing happened unless a log file in the directory “C:\DC22” saying the password wasn’t informed.
On a second try, we gave a password as a parameter and the result was different. Some other files were created in the “C:\DC22”, as can be seen in the image below.

Figure 4: files created as the result of 152.exe execution with a password argument
After a few seconds, the Windows restarted and, when returned, the operating system was apparently normal and these were the messages found in the “log_file.txt”:
installing driver…
installing driver successfully..
getting share drive information…
Trying to create service…
creating service successfully. rebooting windows…
From this messages we got some more information:
– A new service was created – it doesn’t mention the name;
– They are apparently using the tool DiskCryptor;
– Maybe they intend to get some credentials from the machine using “netpass.exe”;
– The “netuse.txt” lists the shared folders mapped by the user;
So, we used Regshot to discover some more information about the changes caused by the malware in the SO, including the new service created by the malware. As the result, we discovered that one of the new services was called “DefragmentService”. We also discovered that the malware created a new user in the machine called “mythbusters” with the password “123456”.
These are the new service information:

Figure 5: Fake DefragmentService created by Mamba
So, according to this service, after the machine reboot, “152.exe” was expected to be called with the same parameters we give in the first run. We follow watching the machine process, but no 152.exe was running.
Then, we tried to reboot the machine again to check if the ransom message should appear, but the system booted up normally again.
Performing some analysis on “dcrypt.exe” and “dccon.exe”, the DiskCryptor GUI and command like, respectively, we found that the password parameter is preceded by a “-p”. So, we tried run “152.exe” with this parameter before diving into the reverse engineering job.
For our surprise, this time the encryption process worked and the ransom message was shown during the boot. The only thing to note here is that the password was the “-p” itself and not the password given by the following parameter as we expected. So, the thing is, Mamba was expecting a second argument to run properly.
The process that encrypted the disk was the “dccon.exe”, called by the “152.exe”. During the process, it was possible to follow the encryption with the command “dccon -info pt0” and the result was like follows:

Figure 6: Full disk encrypted by the Mamba Ransomware.
After the reboot, that didn’t occur automatically, the ransom message was shown exactly the same as the company’s compromised machines.

Figure 7: Lab machine compromised
At this stage, the log file looks like that:
installing driver…
installing driver successfully..
getting share drive information…
Trying to create service…
creating service successfully. rebooting windows…
Checking resources existence. They are OK…
driver installed before…
starting serviceMain…
ServiceMain: Entry
ServiceMain: Performing Service Start Operations
ServiceMain: Waiting for Worker Thread to complete
ServiceWorkerThread: Entry
ServiceCtrlHandler: Entry
ServiceCtrlHandler: Exit
Starting Mount app…
Checking resources existence. They are OK…
driver installed before…
mount:start…
pass:
123456
mount:mounting share drive…
mount:OS is win2003 or lower…
mount:share drive not found …
mount:exit Mount…
start hard drive encryption…
Checking resources existence. They are OK…
driver installed before…
Trying to create service…
As we can see, at some moment, the password used to encrypt the disk was printed to the log file.
Next steps
We’ve found some good information about this threat until now, but we didn’t find the infection vector yet. We know that the password used to encrypt the disk is given as a parameter, so, there may exists some script or other binary that calls the “152.exe” code giving it the clear text password that will be used. We also think that the password is the same for all the victims or may be something related to the victims’ environment, like the hostname, or something like that.
The actors in charge of this campaign seems to making some money. We contacted the e-mail address and they asked 1 BTC per infected machine.
This is the reply message we received:
andy saolis<w889901665@yandex.com>
Your HDD Encrypted By AES 2048Bit
send 1BTC Per HOST to My Bitcoin Wallet , then we give you Decryption key For Your Server HDD!!
My Bitcoin Wallet Address : 1NLnMNMPbxWeMJVtGuobnzWU3WozYz86Bf
We Only Accept Bitcoin , it’s So easy!
you can use Brokers to exchange your money to BTC ASAP
it’s Fast way!
Here:
https://localbitcoins.com/
if You Don’t Have a Account in Bitcoin , Read it First :
https://bitcoin.org/en/getting-started
bitcoin Market :
https://blockchain.info/
https://www.okcoin.com/
https://www.coinbase.com/
https://bitcoinwallet.com
One point that caught our attention was the mention to “server” in the message reply. Would their strategy be to compromise just servers? Corroborates to that hypothesis the fact that the other machines with the “152.exe” file weren’t compromised.
The bitcoin wallet given by the cybercriminal received 4 BTC by the time of this writing.

Figure 8: Cybercriminal bitcoin wallet balance
As Renato Marinho has stated, Morphus Labs is open to collaborate with the information security community finding more information about this threat. They have other samples of Mamba.
CSTO Ransomware, a malware that uses UDP and Google Maps
7.9.2016 securityaffairs Ransomware
CSTO ransomware it is able to query the Google Maps API to discover the victim’s location and connects to the C&C via UDP.
Ransomware is considered by the security experts one of the most dangerous threats to Internet users and organizations across the world.
Malware authors are developing new malicious codes that implement new features to improve evasion and spreading abilities.
Security researchers at BleepingComputer have reported a new ransomware dubbed Cry or CSTO because it pretends to come from the inexistent organization Central Security Treatment Organization.
The CSTO ransomware was first spotted by the malware researcher MalwareHunterTeam.
Once infected a machine the CSTO ransomware encrypts files and append the .cry extension to them. Like the Cerber ransomware, also the CSTO sends information to its command and control server via UDP.
After infecting a computer, the CSTO ransomware collects information on the host (Windows version, installed service pack, OS version, username, computer name, and CPU type) that sends via UDP to 4096 different IP addresses, but only one of them is the C&C server.
The Vxers have chosen the UDP protocol in an attempt to hide the location of the C&C server.
The threat requests the payment of a 1.1 Bitcoins (more than $600) ransom in order to decrypt the files.
The CSTO ransomware implements a singular feature, it leverages websites such as Imgur.com and Pastee.org to host information about victims, it is able to query the Google Maps API to discover the victim’s location using SSIDs of nearby wireless networks .
The ransomware uses the WlanGetNetworkBssList function to get the nearby SSIDs, in this way it is able to determine the victim’s location, but it is not clear how the malware uses this information.
“Furthermore, it will also use public sites such as Imgur.com and Pastee.org to host information about each of the victims. Last, but not least, it will query the Google Maps API to determine the victim’s location using nearby wireless SSIDs.” reported bleepingcomputer.com.

The threat encrypts the file, it uploads host information along with a list of encrypted files to Imgur.com by compiling all details in a fake PNG image file and sending it to a certain album.
Imgur, in turn, assigns a unique name for the image file and notifies it to the CSTO ransomware and then broadcasts the filename over UDP to inform the C&C server.
Similar to other ransomware, the Cry ransomware deletes the Shadow Volume Copies using the command vssadmin delete shadows /all /quiet. In this way it prevents victims from restoring the encrypted files.
The threat gains the persistency by creating a randomly named scheduled task that is triggered every time the user logs into Windows. The task also drops ransom notes on the desktop of the infected machine.
The ransom note includes instructions on how to access the Tor network to reach the payment site used by the authors.
“The ransom notes created by the Central Security Treatment Organization Ransomware contain links to a TOR payment site that has a Window title of User Cabinet. When a user visits this site, they will be prompted to login using the personal code from their ransom note.” continues bleepingcomputer.com.
The payment site includes a support page and offers victims the possibility to decryption just one file for free as proof that it is possible to decrypt all the locked files.
The researchers tested the free decryption feature, but it failed, another good reason to avoid paying the ransom.
New Locky Ransomware variant uses DLLs for distribution
27.8.2016 thehackernews Ransomware
A new Locky Ransomware variant has been spotted by researchers at Cyren, it uses DLLs for distribution.
The Locky Ransomware is one of the most popular threats since its first detection in the wild early 2016. The ransomware has evolved over the time, crooks have improved it adding new evasion detection features and changing the distribution methods.
Security experts observe the implementation of sophisticated sandbox evasion techniques, they documented a new strain of the malware that used a new extension (aka Zepto variant) for the encrypted files meanwhile another version was able to use of offline encryption.
When it first appeared in the threat landscape, Locky was leveraging on documents for its distribution, later it used malicious macros, JavaScript attachments and also Windows script (WSF) files.
Recently, experts from the security firm Cyren discovered a new variant that added a supplementary layer of obfuscation to its downloader script. The new strain of Locky is delivered via spam campaigns, each malicious email includes a ZIP-archived JavaScript.
“The email being sent in this latest wave, as often before, uses business finance-related topics to lure users into opening its attachment, which is ZIP-archived JavaScript. Comparing this variant to the earlier variants, it has added another layer of obfuscation which decrypts and executes the real Locky downloader script.” states the analysis published by Cyren.

The downloader script works in a way similar to other strain of the Locky ransomware, the downloaded files are decrypted and saved in the Windows Temp directory, but differently from the past, the malicious payload is DLL file instead a .EXE. The DLL library is loaded using rundll32.exe, it leverages a custom packer to prevent anti-malware scanners from detecting it.
Once it is executed, the new Locky ransomware searches for the affected system and network shares for files to encrypt, it uses the .zepto extension for locked file. When the encryption process has been completed, this variant of Locky ransomware drops and displays a ransom payment instruction page.
Researchers noticed that the .onion address provided in the ransom note directs victims to the same Locky decryptor page that has been used in previous campaigns.
“Clicking on the onion link directs the user to the same Locky Decryptor page we have seen in previous Locky waves.” closes the report.
A new LOCKY ransomware campaign targets the healthcare
20.8.2016 securityaffairs Ransomware
Malware researchers at FireEye security firm have spotted a new Locky ransomware campaign mainly targeting the healthcare sector.
Security experts from FireEye have spotted a Locky ransomware campaign mainly targeting the healthcare sector, Telecom and Transportation industries.

Attackers launched a massive phishing campaign to deliver the threat. The campaign bit organizations worldwide, mostly in the US, Japan, South Korea.
Threat actors behind this Locky campaign leveraged on DOCM FORMAT email attachments to deliver the ransomware, instead Javascript based downloaders.
“From our trend analysis, Locky ransomware started being delivered via DOCM format email attachments more extensively beginning in August. This marks a change from the large campaigns we observed in March, where a JavaScript based downloader was generally being used to infect systems.” reads the report published by FireEye.
“These detection spikes and change in tactics suggest that the cybercriminals are investing more to infect systems and maximize their profits. Additionally, we have observed that the delivery of Dridex via this distribution channel seems to have stopped, or nearly so, which could explain why we are seeing the Locky uptick.”
The researchers believe crooks are investing to compromise systems maximizing their efforts. Another interesting trend reported by FireEye is the pause in the distribution of the Dridex banking Trojan through the same channel.
Experts noticed many similarities in the macro code used by Attackers in three distinct Locky campaigns running on Aug. 9, Aug. 11 and Aug. 15.
The following are the key comparisons:
Each email campaign has a specific “one-off” campaign code that is used to download the Locky ransomware payload from the malicious malware server.
The malicious URL embedded within macro code is encoded using the same encoding function, but with a different key for each campaign. Each character is encoded by multiplying its ASCII code with a specified key (an integer). Hence, its decoder would perform a division using the specified integer.
The downloaded payload is encoded using 32 bytes rolling XOR key. A different key is used for each campaign. Rolling XOR is described as follows:
Plain [i] = Cipher [i] ^ Key [i % length of Key], where Plain is the computed plain text, Cipher is the cipher text, Key is the xor key, and i is the byte offset.
The evidence collected by the researchers suggest the involvement of a single or multiple attackers in a coordinated effort.
Hitler ransomware just deletes files instead encrypt them
14.8.2016 securityaffairs Ransomware
Security experts detected and analyzed a new threat, the Hitler ransomware, that doesn’t encrypt files but simply deletes them. Ransomware is one of the most dreaded threats for Internet users and a profitable business for crooks. In the last months, we have seen a number of malware belonging to this category, one of the most recent is a Hitler-themed ransomware that doesn’t encrypt files, but simply deletes them.

In reality, the threat appears to be a work in progress project developed by coders without specific skills.
The Windows ransomware displays a lock screen featuring Hitler, together with a message that warns users that files have been encrypted.
The ransomware requests the payment of only 25 euros, in the form of a Vodafone cash card. It is unusual for such kind of crimes.
The lock screen features a misspelling “Ransonware.”
The website Bleeping Computer published a detailed analysis of the Hitler ransomware that was first spotted by the malware analyst Jakub Kroustek from AVG.
“This ransomware appears to be a test variant based on the comments in the embedded batch file and because it does not encrypt any files at all. Instead this malware will remove the extension for all of the files under various directories, display a lock screen, and then show a one hour countdown as shown in the lock screen below.” reads the post published by Bleeping Computer “After that hour it will crash the victim’s computer, and on reboot, delete all of the files under the %UserProfile% of the victim. I hope this is not the actual code that this ransomware developer plans on using if it goes live.”
Visualizza l'immagine su Twitter
Segui
Jakub Kroustek @JakubKroustek
*sigh* #Hitler #Ransomware. #GrammarNazi. https://www.virustotal.com/en/file/06c8e0f6fa2616f4fa92c610a1faea23887ac31db8fa78cede49b6b8c80ec22f/analysis/1470566199 …
21:09 - 7 Ago 2016
27 27 Retweet 21 21 Mi piace
The experts have found the string “Das ist ein Test” (“This is a test”) in an embedded batch file, a circumstance that suggests the developer are German based.
Ransomware/RAT combo searches for solvent businesses
12.8.2016 helpnetsecurity Ransomware
The latest version of the Shade ransomware comes with a stealthy remote access Trojan, likely used to better gauge the amount of money the criminals can demand from the victims.
This variant of the Shade ransomware (also known as Troldesh) was made with specific targets in mind: companies in Russia and the CIS region.

The Trojan searches the list of installed applications and looks for strings associated with bank software
“For the initial check, the updated Trojan searches the list of installed applications and looks for strings associated with bank software. After that the ransomware looks for ‘BUH’, ‘BUGAL’, ‘БУХ’, ‘БУГАЛ’ (accounting) in the names of the computer and its user. If a match is found, the Trojan skips the standard file search and encryption procedure and instead downloads and executes a file from the URL stored in the Trojan’s configuration, and then exits,” Kaspersky Lab researchers have discovered.
The downloaded file is Teamspy, a modified version of the TeamViewer 6 legal remote control utility that doesn’t have a GUI or an icon. It also comes with two plugins: one that covertly installs the TeamViewer VPN driver, and one that installs the RDP Wrapper Library and opens a RDP connection on the computer.
Thus equipped, the infected computer is ready to be spied on.
Among the things Teamspy can do is record audio and video, allow the attackers to remotely access the machine, and to download and execute other malicious files.
That last capability will come in handy if the attackers decide that the target could be forced into paying a considerable ransom.
“The option of remote access to an infected accounting system allows the malefactor to secretly keep an eye on the victim’s activities and collect detailed information on the victim’s solvency in order to use the most efficient way of getting cash,” Kaspersky’s Fedor Sinitsyn noted.
They might ultimately opt for stealing banking credentials and try to syphon as much money as possible from the company account.
Victims of Shade ransomware versions 1 or 2 can try to decrypt encrypted files through the No More Ransom website, set up by the Dutch National Police, Europol, Intel Security and Kaspersky Lab.
Cerber2 ransomware released, no decryption tool available
8.8.2016 helpnetsecurity Ransomware
The author of the widely distributed Cerber ransomware has released a newer version, and files encrypted with Cerber2, unfortunately, can’t be decrypted without paying the ransom.
Cerber2
Several weeks ago, Trend Micro released a tool that can be used to decrypt files encrypted by a number of popular ransomware families and versions. Among these is the first version of Cerber (with certain limitations), but also CryptXXX, BadBlock, and TeslaCrypt.
But, as a Trend Micro researcher that goes by the online handle PanicAll recently discovered, the Cerber ransomware author must have looked at the Trend Micro tool’s code and found a way to foil it.
Files encrypted by Cerber2 get the .cerber2 extension, and the malware shows a new ransom message.
The encryption method has also changed: Cerber2 now uses the Microsoft API CryptGenRandom to generate the 32-bytes-long encryption key.
Finally, the new variant also uses a packer to make malware analysis more difficult.
The Trend Micro Ransomware File Decryptor tool has been updated on Friday, but unfortunately there is no solution yet for stumping Cerber2.
Users who have been hit can back up all their encrypted files and hope that one will be provided soon.
Teslacrypt decryption tool allows victims to restore their files
19.5.2016 Ransomware
A security researcher from ESET security firm issue a Teslacrypt decryption tool after the author closed the project and released a free master key.
The victims of the dreaded TeslaCrypt Ransomware now have the opportunity to restore their files by using a decryptor developed by experts from the ESET security Firm.
“Today, ESET® released a decryptor for recent variants of the TeslaCrypt ransomware. If you have been infected by one of the new variants (v3 or v4) of the notorious ransomware TeslaCrypt and the encrypted files have the extensions .xxx, .ttt, .micro, .mp3 or remained unchanged, then ESET has good news for you.” announced ESET.
A researcher from the company observed a decline in the number of victims of the TeslaCrypt ransomware, so he decided to the decryption key to the authors.
Incredibly, the author provided a free master key to the expert that developed a free universal Teslacrypt decryption tool.
Teslacrypt decryption tool

“In surprising end to TeslaCrypt, the developers shut down their ransomware and released the master decryption key. Over the past few weeks, an analyst for ESET had noticed that the developers of TeslaCrypt have been slowly closing their doors, while their previous distributors have been switching over to distributing the CryptXXX ransomware. ” reported Lawrence Abrams from bleepingcomputer.com that also published a step by step guide to use the Teslacrypt decryption Tool.
“When the ESET researcher realized what was happening, he took a shot in the dark and used the support chat on the Tesla payment site to ask if they would release the master TeslaCrypt decryption key. To his surprise and pleasure, they agreed to do so and posted it on their now defunct payment site.”

Ransomware is one of the most widespread threats. The last iteration of the TeslaCrypt ransomware spotted by experts at Endgame Inc. has been improved by the implementation of new sophisticated evasion techniques and the ability to target new file types.
The malware was used by crooks in numerous malvertising campaigns targeting high-traffic websites. The ransomware represents a serious threat for netizens and organizations. It is important to maintain aligned fresh backups of data in offline sources.
Recently experts at Kaspersky have issued a decryption tool for another ransomware, the Cryptxxx.
If you are one of the TeslaCrypt victims and want to have instruction on the Teslacrypt decryption tool, give a look to the step-by-step guide published by bleepingcomputer.com.
Experts also cracked the CryptXXX ransomware 2.0
16.5.2016 Ransomware
Security Experts at Kaspersky have updated their decryption tool to adapt to the second version of CryptXXX ransomware in the RannohDecryptor 1.9.1.0.
A couple of hours ago I published an interesting post the summarizes the ransomware activities in the last week, and unfortunately, this kind of malware is becoming even more popular in the criminal underground.
A few weeks ago a new threat appeared in the wild, it is the CryptXXX ransomware that was first spotted by the experts from Proofpoint in April. Researchers at ProofPoint discovered a number of compromised websites hosting the Angler exploit kit that were abused by crooks to serve the CryptXXX ransomware and infect Windows machines.
The CryptXXX ransomware has the ability to encrypt local files and any other document present on every connected data storage a short time after the PC has been infected. The threat also steals Bitcoins from the victim’s machines.
The malware authors use the delay in order to make harder for victims the identifications of the malicious website used to compromise their machines.
The files are encrypted with RSA4096 encryption and the CryptXXX ransomware demands the payment of a $500 ransom in bitcoins for decrypting the data back.
Like other ransomware, CryptXXX instructs victims about the payment process, it drops an image on the desktop containing the instructions to download the Tor browser and access an Onion service containing the instructions.

In April, experts at Kaspersky cracked the CryptXXX ransomware and released the RannohDecryptor utility, that was initially designed to recover files encrypted by the Rannoh ransomware.
A few days ago, the researchers from ProofPoint discovered that the CryptXXX ransomware had evolved making ineffective the RannohDecryptor.
In response, the experts from Kaspersky Lab have updated the decryption tool to defeat the second variant the CryptXXX ransomware, they released the RannohDecryptor tool version 1.9.1.0.
Victims of the new strain of the CryptXXX ransomware doesn’t need original copies to decrypt the file.
Below some notes published by the experts:
1. We support decryption of about 40 popular file formats, including documents, archives, images, etc. Unfortunately, there is no possibility to decrypt any arbitrary file format.
2. Decryption may take some time. Generally, the 1st file gets decrypted within several minutes, and all subsequent files in a matter of seconds (each). In the worst case every file will take several minutes. The utility notifies the user prior to start with the following message:
3. Original copy is not needed for Cryptxxx v2.
While this tool will help those infected decrypt their .crypt files, we know that criminals will always look to evolve to stop workarounds from good guys in cybersecurity. It is an unfortunate reality in the current world we live in. But fear not, we won’t rest and will stay vigilant to protect you.
Week in Ransomware – Week of May 13th, 2016
15.5.2016 Ransomware
Just in a week several new ransomware variants, services, and updates have been discovered in-the-wild, disclosed publicly, and thoroughly analyzed.
Statistical Summary
This week, in a span of just five (5) days (Monday, May 9th, 2016 – Friday, May 13th, 2016), through the collaborative efforts of several organizations and individual analysts around the globe, several new ransomware variants, services, and updates have been discovered in-the-wild, disclosed publicly, and thoroughly analyzed.
At the time of this writing (5/13/2016), the following metrics have been reported:
(6) New Ransomware Variants
(1) New Ransomware-as-a-Service (RaaS) Offering
(1) Update to an Existing Ransomware
Monday, May 9th, 2016
CryptXXX 2.0
The 2nd member of the CryptXXX family was released, dubbed CryptXXX 2.0.
Kaspersky released a decryption utility that decrypted files encrypted by CryptXXX’s first version.
However, Kaspersky’s decryption tool cannot decrypt files affected by this version of CryptXXX.
Appends the. crypt extension to all affected files.
Generates and assigns a unique identifier to the victim device.
Generates ransom notes whose filenames are created using this unique ID.
Its ransom notes are saved with the. html
Enigma
Targets Russian-speaking victims
Appends the. enigma extension to all affected files
Generates ransom notes named: txt
Tuesday, May 10th, 2016
Shujin
May possibly be the first ransomware discovered to be targeting only Chinese users
All associated files (including ransom notes) are written in Chinese
Generates ransom notes named: 文件解密帮助.txt
Wednesday, May 11th, 2016
German Netherlands Locker (GNL Locker)
Queries the target computer’s IP address and determine its geolocation
Only begins encryption process if device is located in either Germany or the Netherlands
Appends the. locked extension to all affected files.
Generates ransom notes using the following filenames and extensions:
txt
html
Thursday, May 12th, 2016
CryptoHitman
Actually a new version of the Jigsaw ransomware (created by the same developers)
Performs the same activities as the Jigsaw ransomware; the only differences between CryptoHitman and Jigsaw are, for the most part, aesthetic:
It now uses “Agent 47” of the “Hitman” videogame and movie series as their
logo, and includes an image of this character on the locker screen
The locker screen, however, also contains several pornographic images
Appends the. porno extension to all affected files.
Crypren
Heavily publicized this week, but has been around for a while.
Appends the. encrypted extension to all affected files.
Generates ransom notes named: html
New Version of Petya Ransomware with Additional Mischa Ransomware
New Version of Petya Ransomware
Utilizes a significantly modified installer
Some of the observed changes:
When executed, Petya will check to see if it can escalate to administrative privileges.
If so: the Petya ransomware will be installed
If not: the Mischa ransomware will be installed
Remember:
Petya encrypts the Master File Table (MFT) of the victim device.
It displays then an illegitimate screen created to resemble a legitimate “chkdsk” screen.
While the fake chkdsk screen is being displayed, encryption of the MFT is underway.
Once the encryption activities are finished, the victim device will present a lock screen with ransom payment instructions displayed.
Mischa
Generates ransom notes using the following filenames and extensions:
HTML
TXT
Unique in that it also encrypts executable files.
Friday, May 13th, 2016
Petya and Mischa Offered as Ransomware-as-a-Service (RaaS)
Allows distributors of malware to earn a portion of the revenue generated by Petya/Mischa by distributing their own unique installer of the malware.
Affiliate program is called “Janus”.
The name “Janus” is based on the criminal organization from the James Bond film, Goldeneye, which is named the “Janus Syndicate”.
RaaS has an official Twitter handle, @janussec
Alleged revenue share percentages are displayed below:
Volume/Week Shared %
< 5 BTC 25%
< 25 BTC 50%
< 125 BTC 75%
>= 125 BC 85%
petya ransomware
CryptXXX 2.0 Decryption Utility Released by Kaspersky
Kaspersky, who released a decryption utility for the earlier version of the CryptXXX ransomware, have thwarted the efforts of the CryptXXX authors once again.
Kaspersky modified their original CryptXXX decryption tool and released an updated version capable of decrypting files affected by the 2nd member of the CryptXXX family, CryptXXX 2.0.
Cerber Ransomware On The Rise, Fueled By Dridex Botnets
14.5.2016 Ransomware
Starting in April security experts at FireEye spotted a massive uptick in Cerber ransomware attacks delivered via a rolling wave of spam. Researchers there link the Cerber outbreaks to the fact that attackers are now leveraging the same spam infrastructure credited for making the potent Dridex financial Trojan extremely dangerous. Cerber, which is best known for its high-creep factor in using text-to-speech to “speak” its ransom note to victims, was first spotted in the wild in February. Its typical distribution method was via exploit kits, with Magnitude and Nuclear Pack exploiting a zero day in Adobe Flash Player (CVE-2016-1019). But as recently as May 4, FireEye reports, Cerber is now part of a spam campaign linked to Dridex botnets. “By partnering with the same spam distributor that has proven its capability by delivering Dridex on a large scale, Cerber is likely to become another serious email threat similar to Dridex and Locky,” wrote FireEye security analysts in a research blog posted Thursday. Dridex is a financial Trojan that has emerged as a significant threat to consumers and business, targeting the acquisition of financially related credentials. Its chief means of distribution is Dridex botnets that have been behind massive spam campaigns since February and are responsible for pushing out millions of targeted spam messages a day. Cerber ransomware, according to FireEye, follows the same spam framework as Dridex. Targets are sent emails with an attachment disguised as an invoice that contains malicious VBScript. Once the user opens the document, they’re encouraged to enable macros. In the case of Cerber, the malicious attachment obfuscates the offending VBScript that may be detected by an email gateway or spam filter. Instead, the macro downloads and installs the VBScript in the %appdata% path of the targeted PC. The VBScript is further manipulated to avoid detection and reverse engineering through the injection of junk code. Next, Cerber sniffs out whether a victim has an internet connection. If it does, the last piece of the Cerber ransomware is delivered. That’s when the VBScript sends an HTTP Range Request to fetch a JPEG file from a URL. “In the HTTP Request Headers, it sets the value of Range Header to: “bytes=11193-“. This indicates to the web server to return only the content starting at offset 11,193 of the JPG file,” FireEye wrote. This multi-stage technique of delivering the Cerber payload, FireEye said, is similar to HTTP Range Request checks leveraged by Dridex and Ursnif Trojans. Other similarities that Cerber has to Dridex include the fact that spam campaigns are typically English language only and are financially motivated booby-trapped with invoice, receipt, and order attachments. Once Cerber goes to work on a system, it targets email, Word documents, and Steam (gaming) related files appending encrypted files with the ‘.cerber’ file extension. Victims are directed to visit various versions of the “decrypttozxybarc” domain. In some instances, FireEye said, Cerber also installs a spambot module on the host PC. Attackers, FireEye suspect, are in the test stages of using infected PCs for distributing spam.
CryptXXX 2.0 foils decryption tool, locks PCs
14.5.2016 Ransomware
CryptXXX ransomware, first spotted in mid-April, has reached version 2.0, and a new level of nastiness. It’s also on its way to become one of the top ransomware families in the wild.
The malware’s first version would encrypt files but leave the rest of the infected computer alone, and victims would be able to use it to buy Bitcoin and pay the required ransom.
This also allowed them to deploy a decryption tool, developed by Kaspersky Lab researchers only a week after the first instance of the ransomware was spotted. The AV maker added the decryption capability to its decryptor tool meant initially for decrypting files taken hostage by the Rannoh ransomware.
But that option is not available any more, as CryptXXX 2.0 not only bypasses the decryption tool, but also locks the computer’s screen after popping-up the ransom request:

In addition to all this, the page where the crooks explain how the victims can effect the ransom payment mentions a Google Decrypter tool they will be able to use to decrypt their files. Proofpoint researchers believe that’s just a misdirection, to prevent victims to identify with which ransomware they have been hit.
“While new decryption tools may emerge, CryptXXX’s active development and rapid evolution suggest that this new ransomware will continue to compete strongly in malware ecosystems,” the researchers noted.
“As always, best practices for avoiding infection include patching systems and software, updating endpoint antimalware, deploying robust network protections, and regularly backing up all critical systems.”
STUPID LOCKY! Hackers disrupted a Locky ransomware Campaing
8.5.2016 Ransomware
Hackers have disrupted a Locky campaign after they compromised one of the cybercriminal servers used by the threat actors.
According to the security expert Sven Carlsen from Avira, hackers have dismantled a Locky campaign by hacking the command and control server. Carlsen explained that threat actors behind the Locky campaign spread the threat via spam email with a malicious attachment.
The attachment was a downloader that fetches the Locky ransomware from a server generated with a domain generation algorithm (DGA) and executes it.
While the researchers from Avira were analyzing the threat discovered that the downloader fetches a 12Kb executable containing the message “STUPID LOCKY,” instead the Locky Ransomware binary. Of course, this causes the failure of the attack resulting in an error message being displayed.

What happened?
Most likely hackers breached C&C server and replaced the code of the Locky ransomware with a harmless file.
“It seems that someone was able to access one of the command and control servers and replaced the original Locky ransomware with a dummy file. And I do mean dummy in the fullest expression of the word.” Carlsen wrote.
In the past, other cyber vigilantes have disrupted the hacking campaigns of crooks, Earlier 2016, white hats have attempted to shut down the distribution channels of the Dridex botnet and replaced the malware with a clean copy of an Avira antivirus application.
“I don’t believe that cybercriminals themselves would have initiated this operation because of the potential damage to their reputation and income stream. I also wouldn’t say that ‘Locky is dead’ after this operation,” Carlsen added. “As we know, they are still active and understand their ‘business’ very well. But after the examples of Dridex and now Locky, it shows that even cybercriminals, masters of camouflage, are also vulnerable.”
Like the CryptoWall ransomware, Locky uses to change the filenames of encrypted files to make harder data recovery.
When started, Locky creates and assigns a unique 16 hexadecimal number to the infected machine, then he will scan all drives and unmapped network shares for files to encrypt.
The malware uses the AES encryption algorithm and encrypts only file with extensions matching a certain criteria while it skips files containing certain strings in their full pathname and filename (i.e. tmp, winnt, Application Data, AppData, Program Files (x86), Program Files, temp, thumbs.db, $Recycle.Bin, System Volume Information, Boot, and Windows).
Locky is able to encrypt more than 160 different file types on compromised PCs and victims are asked to pay between $220 and $880 to recover their documents.
The Locky ransomware encrypts files renaming the to [unique_id][identifier].locky, the researchers also discovered that the unique ID and other information are embedded at the end of the encrypted file.
The malware will also delete all of the copies of documents in the Shadow Volume, making impossible to restore files.
Locky leaves a ransom note, the _Locky_recover_instructions.txtin, in each folder containing encrypted files.
Robin Hood CyptMix ransomware promises to donate fee to charity
6.5.2016 Ransomware
This is a novelty in the cyber criminal underground, crooks behind the new born CyptMix ransomware promise to donate the fee to charity.
No doubts, a very creative idea to extort money to the victims enticing them to pay for a good cause and telling them to think to have the opportunity to help the children.
Of course, the criminals don’t provide further details on the way they intend to donate the earnings.
“Your money will be spent for the children charity. So that is mean that You will get a participation in this process too. Many children will receive presents and medical help! And We trust that you are kind and honest person! Thank You very much! We wish You all the best! Your name will be in the main donors list and will stay in the charity history!” reads the ransom note sent to victims of the CyptMix ransomware shared by the experts at Heimdal Security who spotted the new threat.
It is the first time that experts see this kind of Psychological manipulation in ransomware-based attacks. This new strain of malware is spread through spam emails and drive-by attacks.
Even more curious is that the alleged benefactors called themselves the “Charity Team.”
Victims of the CyptMix ransomware need to pay 5 bitcoins (approximately $2200 at the current price per bitcoin), a ramson very expensive respect other similar threats.

The experts in Heimdal Security revealed that new threat re-uses large parts of open-source ransomware code. For example, this ransomware is a
“For example, this ransomware is a CryptoWall 4 variant and it also includes CryptXXX components.” states Heimdal Security.
The crooks behind the CyptMix ransomware have also fixed the developmental errors which made the decryption tool created by Kaspersky to work.
We can only hope that these criminals have truly noble intentions, as wrote Andra Zaharia, from Heimdal Security.
“We can hardly trust cyber criminals to have a kind and generous side to them,”
Petya: the two-in-one trojan
4.5.2016 Zdroj: Kaspersky Ransomware
Infecting the Master Boot Record (MBR) and encrypting files is nothing new in the world of malicious programs. Back in 1994, the virus OneHalf emerged that infected MBRs and encrypted the disk contents. However, that virus did not extort money. In 2011, MBR blocker Trojans began spreading (Trojan-Ransom.Win32.Mbro) that infected the MBR and prevented the operating system from loading further. The victim was prompted to pay a ransom to get rid of the problem. It was easy to treat a system infected by these blocker Trojans because, apart from the MBR, they usually didn’t encrypt any data on the disk.
Today, we have encountered a new threat that’s a blast from the past. The Petya Trojan (detected by Kaspersky Lab products as Trojan-Ransom.Win32.Petr) infects the MBR preventing normal system loading, and encrypts the Master File Table (MFT), an important part of the NT file system (NTFS), thus preventing normal access to files on the hard drive.
The infection scenario
The people spreading Petya attack their potential victims by sending spam messages containing links that download a ZIP archive. The archive contains the Trojan’s executable file and a JPEG image. The file names are in German (Bewerbungsunterlagen.PDF.exe, Bewerbungsmappe-gepackt.exe), are made to look like resumes for job candidates, and target HR staff in German-speaking countries.
Contents of the archives downloaded from links in spam
The cybercriminals didn’t bother with automatic escalation of privileges – the manifest of the Trojan’s executable file contains the following standard record:
If the user launches the malicious executable file Petya, Windows will show the standard UAC request for privilege escalation. If the system has been properly configured by the system administrators (i.e. UAC is enabled, and the user is not working from an administrator account), the Trojan won’t be able to run any further.
Unfortunately, a user who has the privileges to agree to a UAC request often underestimates the potential risks associated with launching unknown software with elevated rights.
How it works
The executable file and the packer
A Petya Trojan infection begins with the launch of the malicious executable file. The samples of the Trojan that Kaspersky Lab received for analysis are, just like most other malware samples, protected with a customized packer. When the executable file launches, the malicious packer’s code begins to work – it unpacks the malicious DLL Setup.dll into a newly designated RAM area, and then passes control to it.
Cybercriminals typically use packers to avoid detection – circumvent static signatures, trick the heuristic analyzer, etc. While investigating the Petya packer, we noticed an unusual trick used by the cybercriminals.
Cybercriminals often try to create the packer in such a way that a packed malicious executable file looks as similar as possible to a regular legitimate file. Sometimes, they take a legitimate file and substitute part of the code with malicious code. That’s what they did with Petya, with one interesting peculiarity: it was a part of the standard compiler-generated runtime DLL that was replaced with malicious code, while the function WinMain remained intact. The illustration below shows the transition, beginning from the entry point (“start”). As can be seen, the function of unpacking malicious code (which we dubbed “evil”) is called from the legal function __calloc_crt which is part of the runtime code.
Diagram of transitions between the malicious packer’s functions
Why do it that way? Obviously, the creators of the malicious packer were trying to trick an inattentive researcher or automatic analyzers: the file looks legitimate – WinMain doesn’t contain malicious code – so it’s possible that it will be overlooked. Besides, if the breakpoint is set at WinMain during debugging, then the malicious code works (and sends the system into BSOD, as we will discuss later in detail) and execution is over before the breakpoint is even reached.
Kaspersky Lab has detected Petya samples that masquerade as legitimate files written in C/C++ and in Delphi.
The malicious DLL
Setup.dll is a DLL with just one export: _ZuWQdweafdsg345312@0. It is written in C and compiled in Microsoft Visual Studio. The cybercriminals used an implementation of cryptographic algorithms available in the public library mbedtls (formerly polarssl). Setup.dll is not saved to the hard drive as a separate file, but always remains in the RAM.
When Setup.dll receives control, it decrypts the data contained in the section ‘.xxxx’ and then proceeds to infect the victim computer.
The encrypted ‘.xxxx’ section containing data
Fragment of the decrypted data from the ‘.xxxx’ section
At a higher degree of abstraction, the actions of Setup.dll come down to the following:
Re-write the boot record on the hard drive with its own malicious loader;
Generate a key, infection ID and other auxiliary information, and save them to the hard drive;
Cause a system abort and reboot, thereby passing control to the malicious loader.
Now let’s look in detail at how all of this is implemented in the Trojan. But before doing so, we need to define the terminology used.
Hard disk sector – the minimum addressable unit of a hard drive, typically 512 bytes.
Master boot record (MBR) – the code and the data written to Sector 0. After hardware is initialized, this code is used to boot the PC. Also, this sector contains the hard disks’ partition table. A disk partitioned with MBR may have up to four primary partitions, and the maximum partition size is ~2.2 TB.
GUID Partition Table (GPT) – a more modern standard of hard drive layout. It supports up to 128 partitions, each up to 9.4 ZB in size (1 ZB = 1021 bytes.)
Now let’s return to the Trojan under review. Setup.dll can infect disks partitioned according to either the older MBR standard or the more modern GPT standard. There are two alternative branches of execution sequences in the malicious program; the choice of execution branch depends on the data in the field PartitionStyle of the structure PARTITION_INFORMATION_EX.
Selection of the execution branch for disk infection, depending on whether the disk has MBR or GPT partitioning
Infecting an MBR disk
When infecting an MBR disk, Setup.dll performs the following actions:
Encrypts sector 0 (the original code and the MBR data) with the simple operation XOR 0x37 (ASCII ‘7’), writes the result to sector 56;
Encrypts sectors 1-33 with the same operation XOR 0x37;
Generates configuration data for the malicious loader, writes them to sector 54;
Creates the verification sector 55 populated with the repeating byte 0x37;
Copies the disk’s NT signature and the partition table saved from the original MBR into its own first-level loader; writes first-level malicious code to sector 0 of the disk, and writes second-level code to sectors 34-50 (referred to here as the malicious loader);
Calls the function NtRaiseHardError, which causes the operating system to crash (BSOD – the ‘blue screen of death’).
When an MBR disk has been infected, the beginning of the disk has the following structure:
Number of sector Content
0 First-level malicious loader
1 – 33 Encrypted sectors 1-33 (XOR 0x37)
34 – 50 Second-level malicious code
…
54 Configuration sector of the malicious program
55 Verification sector (populated with byte 0x37)
56 Encrypted original MBR code (XOR 0x37)
Infecting a GPT disk
When infecting a GPT disk, Setup.dll performs more actions:
Based on Primary GPT Header data, it receives the address of GPT header copy;
Encrypts the GPT header copy with XOR 0x37;
Performs all the actions that are performed when encrypting an MBR disk.
When a GPT disk has been infected, the beginning of the disk has the following structure:
Number of sector Content
0 First-level malicious loader
1 – 33 Encrypted sectors 1-33 (XOR 0x37)
34 – 50 Second-level malicious code
…
54 Configuration sector of the malicious program
55 Verification sector (populated with byte 0x37)
56 Encrypted original MBR code (XOR 0x37)
…
Backup LBA –
Backup LBA + 33 Encrypted copy of GPT Header (XOR 0x37)
Generation of configuration data
In the configuration sector (sector 54), the Trojan keeps the data it needs to encrypt MFT and decrypt it if the victim pays the ransom. Generation of the configuration data consists of the following steps:
Setup.dll generates a random string that is 16 characters long [1-9, a-x, A-X]; we will call this string password;
Generate a pair of keys: ec_session_priv (a private key, a random large integer number) + ec_session_pub (public key, a point on a standard elliptic curve secp192k1);
Calculate the session secret: session_secret = ECDH (ec_session_priv, ec_master_pub); the cybercriminals’ public key ec_master_pub is contained in the Trojan’s body;
Calculate the aes_key = SHA512(session_secret) – only the first 32 bytes of the hash sum are used;
Encrypt the ‘password’ string by XORing it with the first 16 bytes of ec_session_pub: password_xor = ec_session_pub[0, 15] xor password;
Encrypt the result using AES-256 with the key aes_key: password_aes_encr = AES_enc(password_xor);
Create the array ec_session_data = [ec_session_pub, password_aes_encr];
Calculate base58: ec_session_data_b58 = base58_enc(ec_session_data);
Use the result to calculate SHA256: digest = sha256(ec_session_data_b58);
Create array: ec_data = [check1, check2, ec_session_data_b58], where check1, check2 are bytes calculated by the formulas:
a = digest[0] & 0xF;
b = (digest[0] & 0xF) < 10;
check1 = (digest[0] >> 4) + 0x57 + ((digest[0] >> 4) < 10 ? 0xD9 : 0);
check2 = a + 0x57 + (b ? 0xD9 : 0);
Based on the ‘password’, create a key for MFT encryption;
Pseudocode creating a key for MFT encryption
Generate IV – 8 random bytes which will be used during MFT encryption;
Generate infection ID and use it to create “personalized” URLs for ransom payment webpages.
Ultimately, the configuration data structure looks like this:
In C language syntax, this structure can be presented as follows:
This is what the configuration data looks like after it is written to the hard drive:
Note that if the user turns off their computer after this stage and doesn’t switch it on again, only minimum damage will be done, as it is not difficult to decrypt data encrypted with 1-byte XOR. Therefore, a good piece of advice: if you launch an unknown file and your system suddenly crashes, showing a blue screen, you should switch off your computer and get help from a qualified specialist. The specialist should be able to identify a Petya infection and restore the disk sectors encrypted with XOR.
If, however, the computer was re-booted, then the Trojan’s third stage kicks in – the malicious code written to sectors 0 and 34–50.
The malicious loader
After rebooting, the code in sector 0 (the first-level loader) gains control. It loads the main second-level malicious code from sectors 34–50 into the memory and passes control to it. This code, in turn, receives information about the hard drives available in the system, searches for the disk where the configuration is written, reads the configuration data from sector 54 and, depending on the value in the field ‘config.state’, begins encryption (if the value is 0) or asks the user to enter the decryption key that they have purchased (if the value is 1).
Fragment of code implementing the Trojan’s logic
Encryption of MFT
The master file table (MFT) is a data structure with information about every file and directory on a volume formatted into NTFS, the file system that is used in all modern versions of Windows. The table contains the service data required to find each file on the disk. It can be compared to a table of contents in a book that tells you on which page to find a chapter. Similarly, MFT indicates which logical cluster a file is located in.
It is namely this critical area that is attacked by Petya. If the value of ‘config.state’ is equal to 0 during launch, it does the following:
Displays a fake disk check message:
Reads the key ‘config.salsa_key’ from the configuration sector into a local array; sets this field to zero on the disk, sets ‘config.state’ field at 1;
Encrypts the verification sector 55 with the stream cipher Salsa20; this sector is populated beforehand with the byte 0x37 (see the section ‘Infecting an MBR disk’ above);
Searches for each partition’s MFT on each connected hard drive;
Encrypts the MFT data with cipher Salsa20. Encryption is performed in parts of 8 sectors (i.e. the size of each part is 4 KB). A counter of the encrypted parts is kept in sector 57 of the first disk.
When encryption is over, it triggers a system reboot.
After the reboot, Petya displays an animated image of a flashing red and white skull drawn in ACCII-art style.
If the user presses any key, the Trojan displays a text which tells the victim in no uncertain terms what has happened.
Ransom demand and decryption
On this screen Petya displays links to the ransom payment webpages located in the Tor network (the addresses are specified in config.mal_urls), and the “personal decryption code” which the victim has to enter at either of the above sites. In reality, this “code” is the content of the field ‘config.ec_data’, hyphenated every six characters.
So, how do the cybercriminals plan to decrypt MFT, and are they even capable of doing so?
The ‘Key:’ field on this screen accepts a text string from the user. This string is checked for length (a 16-character long string is required), and then the Trojan uses it to calculate a 32-byte ‘salsa_key’ (following the algorithm discussed above in the section ‘Generation of configuration data’). The Trojan then attempts to decrypt the verification sector 55 with this key, and checks that the decrypted sector is completely populated with the byte 0x37. If it is, the key is considered correct, and Petya uses it to decrypt MFT. Then it decrypts all starting sectors encrypted with XOR 0x37, decrypts the original MBR and prompts the user to reboot the computer.
Thus, the correct string to be entered in the ‘Key:’ field is that very same ‘password‘ string that is generated in the first step when the configuration data is created.
Screen message displayed after successful decryption
The question remains: how do the cybercriminals know this string so they can communicate it to a victim who has paid the ransom? No automatic communication with C&C servers is established during the entire infection life cycle. The answer lies in the description of the algorithm for generating configuration data.
The victim is prompted to manually enter their “personal decryption code” ec_data on the ransom payment webpage. The cybercriminal can then perform the following actions:
Decode base58: base58_dec(ec_session_data_b58) = ec_session_data = [ec_session_pub, password_aes_encr]
Calculate session_secret = ECDH(ec_session_pub, ec_master_priv), in accordance with the Elliptic curve Diffie–Hellman properties, where ec_master_priv is a private key known to the Trojan’s creators only;
Calculate aes_key = SHA256(session_secret);
Decrypt AES-256: password_xor = AES_dec(password_encr);
Knowing ec_session_pub, calculate the original password based on password_xor.
The ransom payment webpage
When we visit the Tor site at the URL provided by the Trojan, we see a page that requires a CAPTCHA to be entered, after which the main ransom payment page is loaded. The design of the page immediately catches the eye, with its hammer and sickle and the word ‘ransomware’ in pseudo-Cyrillic. It looks like a USSR parody along the lines of the game Red Alert.
This page displays a countdown clock showing when the ransom price will be doubled, as well as regularly updated links to news and publications related to Petya.
When the ‘Start the decryption process’ button is pressed, you end up on a page that asks you to enter the value of ‘ec_data’, which is now called “your identifier” rather than “your personal decryption code”. It looks like the cybercriminals still haven’t decided what to call this part.
When the user enters this string, the site displays the amount of ransom in BTC, information on how to purchase bitcoins, and the address where the money should be sent.
As well as that, there are two other pages on the website: FAQ and Support.
The FAQ page
The FAQ page is interesting in that it contains false information: in reality, RSA is not used by the Trojan in any way, at any stage of infection.
The Support page
On the Support page, the user is given the option of sending a message to the cybercriminals. One phrase in particular stands out: “Please write your message in english, our russian speaking staff is not always available”. This implies that there is at least one person in the group who speaks Russian.
Geographic distribution
As we noted above, the spam messages target German-speaking victims. KSN statistics clearly show that Germany is the main target for the cybercriminals.
TOP 5 countries attacked by Petya Trojan by the number of attacked users:
Country Number of attacked users
1 Germany 579
2 China 19
3 India 8
4 Japan 5
5 Russian Federation 5
Conclusion
After analyzing the Petya Trojan, we discovered that it is an unusual hybrid of an MBR blocker and data encryptor: it prevents not only the operating system from booting but also blocks normal access to files located on the hard drives of the attacked system.
Although Petya is noticeably different from the majority of ransomware that has emerged in the recent years, it can hardly be described as a fundamentally new development. The ideas behind the Trojan have been seen before in earlier malware; the creators of Petya have simply combined them all in a single creation. That said, it should be acknowledged that it requires a certain degree of technical skill to implement a low-level code to encrypt and decrypt data prior to OS booting.
Another interesting peculiarity about Petya is the pseudo-Soviet graphic design on the ransom payment website; the name of the Trojan also fits into the image of a “Russian Trojan” designed by cybercriminals. There is no certainty as to whether the Trojan’s creators originally come from Russia or other former Soviet states; however, the text on the payment page suggests there is at least one Russian speaker in the gang.
Kaspersky Lab’s products protect users from this threat: Petya’s executable files are detected with the verdict Trojan-Ransom.Win32.Petr; in addition, the behavior analyzer proactively detects even unknown versions of this Trojan with the verdict PDM:Trojan.Win32.Generic.
P.S. How to decrypt your data without paying the ransom
On April 8, some independent researchers reported that they had found a method of restoring the password without paying the ransom to the cybercriminals. The method is based on a genetic algorithm; with the 8-byte long IV (stored in configuration sector 54) and the content of the encrypted verification sector 55, you can calculate the value of the password that generates the salsa key, which can then be used to decrypt the MFT.
Pirate Bay visitors infected with Cerber ransomware via bad ads
1.5.2016 Ransomware
Experts at MalwareBytes discovered that Pirate Bay users have been targeted by a malvertising campaign serving the Cerber crypto-ransomware.
Recently the visitors of the Pirate Bay website were infected with crypto-ransomware. Threat actors launched a malvertising attack on Pirate Bay and leveraged on bad ads to serve a ransomware.
According to the experts at Malwarebytes attackers used the Magnitude exploit kit and exploited the Cerber ransomware subscription service. The experts recognized the same modus operandi used in multiple Magnitude EK malvertising campaigns detected in the past.

The attack on Pirate Bay users relied on a ‘pop-under’ window to silently redirect visitors to the a website hosting the Magnitude exploit kit.
“The questionable advertiser was using a ‘pop-under’ to silently redirect users to the Magnitude exploit kit and infect them with the Cerber ransomware.” states the analysis published by Malwarebytes.
“This is part of the same Magnitude EK malvertising campaigns we have documented previously on this blog. The ad network changes (Traffic Holder in this case), but the modus operandi remains the same.”
The threat actors behind the Pirate Bay attack also targeted visitors of a number of porn and torrent websites.
The malvertising campaigns analyzed by experts at MalwareBytes exploited Adobe Flash Player vulnerabilities in order to infect users with vulnerable browsers.Magnitude EK recently showed some signs of additional refinements, first with the
“Magnitude EK recently showed some signs of additional refinements, first with the implementation of a fingerprinting gate before the exploit kit landing page as well as the integration of a new Adobe Flash Player zero-day, albeit not fully taken advantage of.” states a previous analysis published by the security firm.
The attack scheme is simple, attackers serve malicious ads compromising third-party ad networks, in this way they distribute the ads to high-traffic websites.
The researchers also noticed that the timing of the attacks is not casual, they targeted a number of torrent sites due to a huge spike in BitTorrent activity caused by users searching for the sixth season of Games of Thrones.
The Pirate Bay visitors infected with Cerber ransomware are asked to pay 1.25 bitcoin within the first seven days and after that 2.48 bitcoin.
Unfortunately, at the time I was writing there is no decryption tool for the files locked by the Cerber threat.
BWL Electric and Water Utility shut down by ransomware
30.4.2016 Ransomware
The Lansing Board of Water & Light (BWL) utility has had to shut down systems, phone lines in response to a ransomware-based attack.
Another ransomware attack against a critical infrastructure is in the headlines, this time the dreaded malware has infected and shut down an electric and water utility.
Other critical infrastructures across the world were targeted by ransomware in the past months, including hospitals and water facilities.
This specific category of malware allows crooks to easily monetize their efforts, demanding a ransom to restore the encrypted data.
Everything is connected to the internet is potentially exposed to ransomware-based attacks.
Everything that is connected to the Internet, including medical devices and Internet of Things systems.
The American public utility Lansing Board of Water & Light (BWL) has confirmed that the systems of the company have been infected by a ransomware that caused the paralysis of the internal computers.

The plant was infected earlier this week, according to the Lansing State Journal a member of the internal staff opened a malicious email attachment.
“As the infection spread, it encrypted files on other computers and required Peffley and staff to find a way to fight a virus that he said is “brand spanking new.”” reported the Lansing State Journal.
Once the employee has opened the malicious attachment, the malware was dropped and executed on the company system and began encrypting the files.
“A cyberattack this week on BWL’s internal network forced the utility to shut down its accounting system and email service indefinitely for about 250 employees. It also forced the utility to shut down phone lines, including a customer assistance line that’s often used for account inquiries. Power and water shutoffs by the utility are also suspended until further notice.” continues the Lansing State Journal.
Operators at BWL in response to the incident shut down the internal network and suspend internal operations, including Power and water, email service, and accounting for the internal staff.
At the time I was writing there isn’t information of the type of malware that infected the systems at the BWL. The FBI has launched an investigation about the incident alongside with local law enforcement authorities. There is no news if the BWL paid the ransom to the crooks.
The company confirmed that the incident hasn’t exposed personal information belonging to its 96,000 customers.
Ransomware Virus Shuts Down Electric and Water Utility
30.4.2016 Ransomware
Ransomware has become an albatross around the neck, targeting businesses, hospitals, and personal computers worldwide and extorting Millions of Dollars.
Typical Ransomware targets victim's computer encrypts files on it, and then demands a ransom -- typically about $500 in Bitcoin -- in exchange for a key that will decrypt the files.
Guess what could be the next target of ransomware malware?
Everything that is connected to the Internet.
There is a huge range of potential targets, from the pacemaker to cars to Internet of the Things, that may provide an opportunity for cybercriminals to launch ransomware attacks.
Recently, the American public utility Lansing Board of Water & Light (BWL) has announced that the company has become a victim of Ransomware attack that knocked the utility's internal computer systems offline.
Also Read: FBI Suggests Ransomware Victims — 'Just Pay the Ransom'.
The attack took place earlier this week when one of the company’s employees opened a malicious email attachment.
Once clicked, the malware installed on the computer and quickly began encrypting the organization's files, according to the Lansing State Journal.
BWL quickly decided to shut down its networks and suspend some services, including accounting and email service for its about 250 employees, in order to prevent further damages. Power and water shut-offs by BWL was also suspended.
Though the ransomware type is still unknown, the utility is currently working with the Federal Bureau of Investigation (FBI) and local law enforcement authorities to investigate the incident.
The company assured its 96,000 customers that no personal information related to its customers or employees has been compromised by the ransomware intrusion into the corporate computer network.
However, it is not yet clear whether the utility paid the Ransom in exchange of its data. The company said law enforcement has limited it from discussing the issue in public, at least for now.
Ran$umBin a dark web service dedicated to ransomware
28.4.2016 Ransomware
A group cyber criminals created Ran$umBin, A Dark web service which operates the one-stop shop for monetizing ransomware.
These days Ransomware are quite common and it is widespread and heavily used by cyber criminals as common tools to steal data as well as extort their owners. Few days back we had seen a new type of ransomware JIGSAW that caused psychological distress and then would probably encrypt all your data. This can be risky for the cyber criminals due to the fact that such operations require interaction with the victim and if the victim is ready to pay to get their stolen data back, it isn’t that easy to monetize such attacks. It’s just not an easy task for a cyber criminal to find a trustworthy Bitcoin launder, and to monetize their crime which can minimize the risk.
This can be risky for the cyber criminals due to the fact that such operations require interaction with the victim and if the victim is ready to pay to get their stolen data back, it isn’t that easy to monetize such attacks. It’s just not an easy task for a cyber criminal to find a trustworthy Bitcoin launder, and to monetize their crime which can minimize the risk.

A group of underground cyber criminals took advantage of this kind of situation and created Ran$umBin, A Dark web service which operates the one-stop shop for monetizing ransomware. Ran$umBin is specialized for both criminals as well as the victims. It lets the criminal upload stolen data which contains user credentials, credit data, stolen identities and any other kind of cyber-loot and on the other hand it lets the victims pay for the removal of those stolen data from the Dark Web, where any cyber criminal can buy the stolen data.
The below dump from Ran$sumBin contain’s username as well as password.

It has been found that Ran$umBin has been active for under two months. The business model is quite simple as well as its very user-friendly. Cyber criminals can upload stolen data and either sell it to other criminals or extort the data’s owner by the site takes some commission. The site’s combination is determined the identity of the data owner whether he is a criminal belonging to a pedophile would pay $100 and the site would take a 30% commission. On the other hand, if the criminal is looking for data related to the celebrity or a law enforcement representative, the site would double the commission to 40%. Alternatively, the criminal who uploads the data and either choose their own ransom demand and send their victim instruction on how to log into Ran$umBin and pay.
The site’s combination is determined the identity of the data owner whether he is a criminal belonging to a pedophile would pay $100 and the site would take a 30% commission. On the other hand, if the criminal is looking for data related to the celebrity or a law enforcement representative, the site would double the commission to 40%. Alternatively, the criminal who uploads the data and either choose their own ransom demand and send their victim instruction on how to log into Ran$umBin and pay.
The founder of Ran$umBin has defined the service as a new kind of one-stop ransom market. They will not send extortion messages to victims, and look themselves as responsible only for the safety as well as the privacy of their users.
But what in this case if a victim is being extorted again and again using Ran$sumbin?
The criminals assure that nobody gets extorted more than times in order to keep their offering fresh (No promises). But they assure that the stolen data is validated to make sure that the data isn’t old or irrelevant.
So far it is unknown who runs this operation, but based upon their language and their service structure, it is predicted that these are American Players. In fact, they also promote their service using a designated Twitter Account and have gained some traction among cyber criminals on the other hand this service has also been referred on different forums.
There is a huge team of cyber criminal teaming in the cyber underground with markets of all kinds, Certainly this type of market was to evolve. Ran$umBin’s operators are indeed American, their initiative might not hold for a long time. The North American underground market is less secretive than similar markets in Russia, Brazil, or the far east.
Often this kind of websites is taken down by authorities. In keeping a hope that in the future we and our loved ones shouldn’t be one of the victims.
Let’s keep a strong hope that this one will suffer and taken down immediately by the authorities.
Smile, you can recover files encrypted by the CryptXXX ransomware
27.4.2016 Ransomware
Security experts at Kaspersky have found a way to decrypt files locked by the CryptXXX ransomware by using the RannohDecryptor utility.
Good news for the victims of ransomware, the security experts at Kaspersky Lab have successfully cracked the CryptXXX ransomware.
The CryptXXX ransomware was first spotted by experts from Proofpoint in April when a number of compromised websites hosting the Angler exploit kit were abused to serve the threat and infect Windows machines.
CryptXXX encrypts local files and any other document present on every connected data storage a short time after the PC has been infected. The threat also steals Bitcoins from the victim’s machines.
The malware authors use the delay in order to make harder for victims the identifications of the malicious website used to compromise their machines.
The files are encrypted with RSA4096 encryption and the CryptXXX ransomware demands the payment of a $500 ransom in bitcoins for decrypting the data back.
Like other ransomware, CryptXXX instructs victims about the payment process, it drops an image on the desktop containing the instructions to download the Tor browser and access an Onion service containing the instructions.
CryptXXX ransomware instructions
Now experts at Kaspersky cracked the CryptXXX ransomware and released the RannohDecryptor utility, an initially that was initially designed to recover files encrypted by the Rannoh ransomware.
Victims of the CryptXXX ransomware have to use it by providing an original (not encrypted) version of at least one file present on the infected machine.
Below the instructions published by Kaspersky in a blog post:
Then you need to do the following:
Download the tool and launch it.
Open Settings and choose drive types (removable, network or hard drive) for scanning. Don’t check the “Delete crypted files after decryption” option until you are 100% that decrypted files open properly.
Click the “Start scan” link and choose where the encrypted .crypt file lies (that file, for which you have an unencrypted copy as well).
Then the tool will ask for the original file.
After that RannohDecryptor starts searching for all other files with “.crypt” extension and tries to decrypt all files, which weigh less than your original. The bigger file you’ve feed to the utility — the more files would be decrypted.
How to unlock a .crypt file
27.4.2016 Ransomware
April 26, 2016 John Snow Featured Post, News, Security, Threats 1 comment
The common user experience when it comes to ransomware looks like this: you open a website then accidentally download and install a piece of software. You might even not notice that you’ve done that. For some time nothing happens and suddenly you see a notification that all your files are encrypted by a Trojan that wants money to return them back. You check to see if it’s true and see: all your files refuse to open. You also see that they are updated with the ominous .crypt extension.
Decrypt CryptXXX
If you find yourself in this predicament, it looks like your system has been infected with CryptXXX ransomware. It’s a very mean Trojan that encrypts files and steals your personal data and bitcoins. But we have good news: there is a free tool, which can cure your system from this infection.
What is CryptXXX?
If you are looking for the files decryption manual you can skip this part — just scroll down the info you are looking for is later in the article. Here we are going to first cover several facts about the Trojan.
In April, 15 Proofpoint researchers discovered a brand new ransomware which used Angler exploit kit to infect Windows devices. As cybercriminals had not given any name to their creation the researchers called it CryptXXX. It is possible that they chose that name as the Trojan had a nasty habit of adding the .crypt extension to the names of all infected files and XXX is Anglers second name.
CryptXXX is an interesting ransomware sample. It encrypts files on all attached data storage a short time after the PC has been infected. The criminals put this delay in to confuse victims and make it harder to detect which websites spread the malware.
Having finished encryption the Trojan creates three manuals: a text file, an image and an HTML web page. The image is set as a desktop wallpaper (maybe, for greater clarity). The web-page is opened in a browser, while the text file is left on the hard drive just in case. All manuals contain similar text.
They inform the victims that their files are encrypted with the help of RSA4096 — a stronger encryption algorithm — and demand a $500 ransom in bitcoins for bringing the data back. The user has to install the Tor browser and follow the link in the manual to open an onion-website, which includes detailed instructions and the form of payment. There is even the Frequently Asked Question page — everything for the ease of use!
CryptXXX is also very curious and greedy: not only does it encrypt the files, but it also steals bitcoins kept on victims’ hard drives and copies other data, which can be useful for cybercriminals.
It’s awful but we have a cure!
Usually it’s very hard to find a universal decryption algorithm for modern ransomware. That’s why very often the only thing a victim can do is pay the ransom. We don’t recommend doing this unless it is the last resort.
Fortunately, CryptXXX turned out to be not that difficult to crack. Kaspersky Lab experts created a tool that can help users to restore encrypted files.
The RannohDecryptor utility was initially created to decrypt files, which suffered from Rannoh ransomware. In time it acquired additional and useful features. Now it can be used to cure your files from CryptXXX activity.
So if CryptXXX ransomware has found its way into your system, not everything is lost. To recover your files we will need the original (not encrypted) version of at least one file, which suffered from CryptXXX. If you have more files like this backed up, this will work.
Then you need to do the following:
Download the tool and launch it.
Open Settings and choose drive types (removable, network or hard drive) for scanning. Don’t check the “Delete crypted files after decryption” option until you are 100% that decrypted files open properly.
Click the “Start scan” link and choose where the encrypted .crypt file lies (that file, for which you have an unencrypted copy as well).
Then the tool will ask for the original file.
After that RannohDecryptor starts searching for all other files with “.crypt” extension and tries to decrypt all files, which weigh less than your original. The bigger file you’ve feed to the utility — the more files would be decrypted.
Get ready beforehand!
It’s better not to tempt fate and prevent CryptXXX from infecting your PC beforehand. Our decryption tool works today, but criminals can soon release a new version of the same ransomware that would be smarter. Very often culprits change malware code in such a way that it becomes impossible to decrypt infected files. For example, this already happened with TeslaCrypt ransomware: there was once a utility tool which successfully cured encrypted files but now it’s almost useless.
Let’s also remember that CryptXXX steals personal data and money — sharing them with criminals is surely a bad idea.
To protect yourself follow these cybersecurity rules.
Regularly make backups.
Install all critical updates for your OS and browsers. Angler exploit kit, which is used by CryptXXX, leverages software vulnerabilities to download and install the ransomware.
Install a proper security solution. Kaspersky Internet Security provides a multi-layered protection from ransomware. Kaspersky Total Security can complement the all-round protection with automatic backing up.
You can find more information on how to protect yourself from ransomware here.
New Decryptor Unlocks CryptXXX Ransomware
27.4.2016 Ransomware
When exploits kits, in particular Angler, spread ransomware infections, people get nervous. The latest strain to appear in the virulent Angler kit is CryptXXX, which researchers at Proofpoint and Fox IT tied to the same group dropping old-school Reveton ransomware and Bedep click-fraud malware. CryptXXX asks for a steep $500 in Bitcoin to unlock files it has encrypted, and given Angler’s penetration and frequent updates, CryptXXX quickly stepped to the forefront as ransomware to watch. CryptXXX is particularly nasty because it not only encrypts local files (encrypted files have a .crypt extension), but also those on all attached storage shortly after the initial infection. The malware also has other capabilities beyond encrypting local files. It copies files putting the victim at risk for identity theft and steals Bitcoins stored on the local hard drives. Researchers at Kaspersky Lab today published a solution for victims, a utility that helps recover files scrambled by CryptXXX. Fedor Sinitsyn, senior malware analyst at Kaspersky Lab, said the malware contained an undisclosed weakness in the malware’s crypto implementation that opened the door to the development of the decryptor. The decryptor was added to an existing ransomware utility that also recovers files lost to Rannoh, AutoIt, Fury, Crybola, and Cryaki. “It looks dangerous because of Angler (i.e. it has a potential for massive propagation),” Sinitsyn said. “Also, it has additional functionality to steal sensitive data, which is another big threat, even if the victim manages to decrypt the files.” Sinitsyn said, the decryptor requires at least one original copy of a file encrypted by CryptXXX. “If given a correct pair, the utility will decrypt all files with size less than or equal to the size of the file from the pair,” Sinitsyn said. “Most of the time the victim manages to find an original copy of one encrypted file. It can be on a disconnected flash drive, external hard drive, in their mailbox, in a cloud storage, on another PC, etc. In case of CryptXXX, if the victim finds a large original, it will allow to decrypt all affected files of this size or smaller.” CryptXXX was spotted by Proofpoint researchers on April 15 when an Angler infection that was moving Bedep was also moving a ransomware payload and Dridex banking malware, the company said in a blog post. The presence of Bedep tipped the researchers off that there may be more at play with CryptXXX. Bedep has been used in numerous other attacks to drop other malware such as the Pony password-stealing malware. In this case, Proofpoint said CryptXXX harvests data from instant messenger clients, local FTP client credentials, data from local mail clients, and browser information, including cookie data. Reventon ransomware has been relatively quiet since February 2015 when it was spotted in Angler infections. Proofpoint noted a half-dozen similarities between Reveton and CryptXXX such as both are written in Delphi, both use the same custom command and control protocol and both have a delayed start before targeting attached storage.
JIGSAW ransomware slowly deletes your files as you shilly-shally to pay the ransom
22.4.2016 Ransomware
A new threat is appeared in the wild it is the JIGSAW ransomware that slowly deletes your files as you shilly-shally to pay the ransom.
A new crypto-malware has appeared in the wild, its name is JIGSAW ransomware. The BitcoinBlackmailer.exe explains JIGSAW ransomware will encrypt your files adding ‘.FUN’ extension.
The author, in the Saw-movie style, displays the face of the character Billy the Puppet from the horror movie and then threatens to delete files if the ransom is not paid within a time limit.

Security Engineers at Forcepoint Security Labs were able to make a reverse engineering of the malware and obtain the encryption key used by JIGSAW to encrypt the file and 100 Bitcoin addresses used for payment of the ransom.
The use of horror movie images caused distress in the victim, it is a new tactic used by the malware author that also tried to obfuscate theirs .NET code to prevent analysis. Fortunately, it was easy for the experts to deobfuscate the source code allowing them a deep analysis of the JIGSAW ransomware. The malware was built with poor coding standards such that it can be easily reversed engineered by any entry-level malware analyst as the author failed to advise to strip out the text from the executable.
“Written in .NET, the malware can be reverse engineered without any great difficulty. This helps us greatly. So much so, that Forcepoint Security Labs are able to retrieve the encryption key (highlighted in yellow) used by the malware to encrypt the file” reads the analysis published by Forcepoint Security Labs.
The experts analyzed a number of the most recently seen variants of the JIGSAW ransomware, they took note of a number of attributes, including their sizes, time stamps (build date/time) and meta-data extracted from the images with the ExifTool.
The experts also discovered the author’s landing page as well as the JIGSAW malware kit offered for sale at $139 dollars on a Tor market place. The purchaser would get the source code for JIGSAW written in C# with step by step tutorial for deploying the malware. The malware had gone for sale 24 times since 04/03/2016.

The sample analyzed by the experts pointed to two distinct Bitcoin addresses used for the payment of the ransomware. One of the Bitcoin addresses has never received any ransom payment, meanwhile, the second one received a total of 89$ bitcoin.
The author provided also a well-documented tutorial on how to configure and build the software.
Let me suggest to give a look to the report published by Forcepoint.
RansomWhere, the free ransomware detection tool for Mac OS X
21.4.2016 Ransomware
The former NSA expert Patrick Wardle has designed RansomWhere, a free ransomware detection tool for the protection of Mac OS X systems.
The number of Ransomware-based attacks has risen in a dramatic way, every week the criminal underground community is presenting new threats with improved features that are causing significant economic losses to every industry.
Everyday security experts are detecting thousands of new ransomware samples, it is necessary a multi-layered approach to protect the systems from emerging threats. The traditional signature-based approach implemented by many antivirus solutions in many cases are not effective against a ransomware that rapidly changes.
Many antivirus vendors are improving their products by implementing behavior-based malware detection system, these solutions monitor for suspicious activities like the access to a large number of files, the use of encryption libraries, encrypting activities implemented by untrusted processes.
Now Mac users have a new defensive tool in their arsenal, it is a free generic ransomware detection tool dubbed RansomWhere.
RansomWhere
The tool implements a behavior-based malware detection system specifically designed for ransomware, this means that it continuously monitors the file system for the creation of encrypted files by suspicious processes. The tool was developed by Patrick Wardle, a former NSA expert who now leads a research team at the Synack security firm.
“RansomWhere? detects and blocks ransomware by detecting untrusted processes that are rapidly creating encrypted files. This is inherently reactive; and as such, the ransomware will likely encrypt a few files (ideally only two or three), before being detected and blocked. ” Wardle explained in a blog post.
The RansomWhere tool allows users to rapidly block the processes that are performing suspicious activities, then users have to decide the action to do to protect their system.
The tool works on the concept of “Trust,” it scans Mac apps and binaries that are signed with an Apple Developer ID and not by official Apple certificates.
The expert highlighted that the tool is not effective if ransomware abuses a signed Apple binary. Another limitation is that the tool inherently trusts applications that are already present on the system when it is installed, this means that is the system is already infected the malware could be not detected.
The expert demonstrated the efficiency of the RansomWhere against a number of threats, including the KeRanger and Gopher which is a proof-of-concept ransomware developed by Pedro Vilaca, last year.
The last limitation of the tool is that isn’t able to monitor activities on documents outside the user’s home directory, this means that sophisticated ransomware could move all the files outside the home directory and encrypt them.
Wardle highlighted the limitations of the tool explaining how it could be circumvented by attackers. The hacker Vilaca has already improved its PoC ransomware Gopher in order to deceive the monitoring operated by the RansomWhere tool.
A new strain of Teslacrypt implements sophisticated evasion
21.4.2016 Ransomware
The authors of the TeslaCrypt ransomware have improved it by implementing new sophisticated evasion techniques and targeting new file types.
The authors of the TeslaCrypt ransomware have introduced a couple of significant improvements, the new variant Version 4.1 has been in circulation for about a week. According to the experts at Endgame Inc., VXers have invested heavily in obfuscation and evasion techniques, and the malicious code can also encrypt new file extensions (.7z; .apk; .asset; .avi; .bak; .bik; .bsa; .csv; .d3dbsp; .das; .forge; .iwi; .lbf; .litemod; .litesql; .ltx; .m4a; .mp4; .rar; .re4; .sav; .slm; .sql; .tiff; .upk; .wma; .wmv; and .wallet).
“As our latest research on TeslaCrypt demonstrates, ransomware not only is becoming more widespread, but it is also becoming more sophisticated and adaptable. TeslaCrypt 4.1A is only a week old and contains an even greater variety of stealth and obfuscation techniques than its previous variants, the earliest of which is just over a year old.” states a report published by Endgame Inc.
The ransomware also targets backup files by deleting the Volume Shadow Copy, the new strain uses AES 256 for file encryption.
Like its predecessors, this new strain of Teslacrypt is spread as attachments of spam campaigns purporting to be shipping delivery notifications.
When the victims open the malicious .zip file sent as the attachment, a JavaScript downloader using Wscript is executed in order to download the TeslaCrypt ransomware from greetingsyoungqq[.]com/80.exe.
The Teslacrypt 4.1A ransomware also uses COM objects and deletes zone identifiers to evade the detection.

The ransomware also implements an anti-monitoring feature that terminates several Windows processes, including the Task Manager; Registry Editor; Command Shell, SysInternals Process Explorer and System Configuration.
This variant of TeslaCrypt maintains the persistence by making a copy of itself to the disk and creating a registry entry that points to the copy.
The ransomware attacks are the headlines in this first part of the year, and the situation is worsening.
“Only four months into 2016, as our timeline demonstrates, this may very well be the year of the ransomware attack. These kinds of opportunistic attacks can be very lucrative and sophisticated, and should increasingly be on the radar of both high-value organizations as well as individuals. ” close the post
Researcher releases Free Ransomware Detection Tool for Mac OS X Users
20.4.2015 Ransomware
Introducing RansomWhere, a free generic ransomware detection tool for Mac OS X users that can identify ransomware-like behavior by continually monitoring the file-system for the creation of encrypted files by suspicious processes.
This ransomware detection tool helps to block the suspicious processes and waits for the user to decide whether to allow or stop the process.
Ransomware has risen dramatically since last few years... so rapidly that it might have already hit someone you know.
With hundred of thousands of ransomware samples emerging every day, it is quite difficult for traditional signature-based antivirus products to keep their signature database up-to-date.
So, if signature-based techniques are not enough to detect ransomware infection, then what else can we do?
Some Antivirus companies have already upgraded their security solutions that detect suspicious behaviors like the sequential accessing of a large number of files, using encryption algorithms and key exchange mechanisms.
Here’s the latest ransomware detection tool for Mac OS X users:
RansomWhere? – a smart application that can identify ransomware-like behavior by detecting untrusted processes rapidly encrypting files, stop that suspicious process, and then alert the user.
How RansomWhere tool works
Patrick Wardle, a former NSA staffer who now leads research at bug hunting outfit Synack, has developed the RansomWhere tool, which aims at detecting and blocking generic ransomware on Mac OS X by regularly monitoring the user's local filesystem for the creation of encrypted files by any process.
"The ransomware will likely encrypt a few files (ideally only two or three), before being detected and blocked," Wardle wrote in a blog post.
This ransomware detection tool, by default, scans Mac apps and binaries that are signed with an Apple Developer ID and not by official Apple certificates.
If the tool detects any untrusted process, it suspends the suspicious process and alerts the user by showing a pop-up asking user to continue or terminate the process in question.
Wardle successfully tested RansomWhere against KeRanger as well as Gopher ransomware proof-of-concept, which was developed by a pro-Apple Mac hacker, Pedro Vilaca, last year.
Also Read: How Just Opening an MS Word Doc Can Hijack Every File On Your System.
Though Wardle admitted that his tool does not guarantee 100 percent result and that it could be circumvented by malicious hackers who can discover a way to bypass RansomWhere and avoid detection, it is always better to be somewhat safer than completely vulnerable.
Some known Limitations of RansomWhere tool?:
RansomWhere would not be able to help if any Ransomware malware abuses Apple-signed file or app.
RansomWhere detects ransomware infections after they have already encrypted some of your important files.
Files outside of your home directory are not protected by RansomWhere. So sophisticated ransomware could shift all your files outside home directory and lock them up.
Since hackers are always a step ahead of researchers, the RansomWhere tool has already been bypassed. Vilaca had tweaked his Gopher ransomware to bypass RansomWhere in a matter of minutes.
As mentioned in the limitations, Vilaca added just ten lines of code in its ransomware proof-of-concept to take the victim's files outside of the home directory and lock them up. You can watch the video above showing his hack.
Generic Ransomware Detection Comes to OS X
20.4.2016 Ransomware
With each new unrelenting ransomware sample, security researchers understand that no matter how quickly antivirus signatures are updated or how rapidly decryptors are built and shared, current defenses will continue to fall short. The problem is that most adequate defenses are sample-specific; Kaspersky Lab has built ransomware decryptors for CoinVault and Bitcryptor, and Cisco has a similar tool to unlock some TeslaCrypt infections, just to name two. Related Posts BlackBerry CEO Defends Lawful Access Principles, Supports Phone Hack April 19, 2016 , 4:55 pm Apple and FBI Faceoff at House Encryption Hearing April 19, 2016 , 4:12 pm 3.2 Million Servers Vulnerable to JBoss Attack April 18, 2016 , 2:11 pm Generic defense mechanisms are few and far between. Easy Sync Solutions’ CryptoMonitor, which was acquired in January by Malwarebytes, for example, detects and blocks numerous samples on the Windows side before they’re able to execute and begin encrypting files. On the OS X side there are admittedly few ransomware attacks, and even fewer generic detection mechanisms. Researcher Patrick Wardle, director of researcher at Synack and a known OS X hacker, today released his own generic OS X ransomware detector called RansomWhere? The utility monitors home directories on OS X machines for untrusted processes that are encrypting files. The user is presented with an alert while RansomWhere? blocks the process and waits for the user to decide whether to allow or terminate the process. “I saw that existing approaches aren’t working,” Wardle said “Antivirus has its shortcomings. KeRanger was signed with a legitimate Apple developer ID certificate that passed it off as a legitimate application. Gatekeeper is not going to block that. You’ve got to think outside the box and take an approach that is not specimen specific.” KeRanger surfaced last month and was quickly labeled the first functional OS X ransomware sample by researchers at Palo Alto Networks. KeRanger saddled itself aboard a Trojanized version of the Transmission BitTorrent client in an attempt to infect Mac users. The fact that it was signed with a real Apple cert gave it legitimacy and allowed it to slip native OS X protections. But the ransomware shot itself in the foot by including a three-day period during which it lay dormant. This gave researchers a window to inform Apple and Transmission to block the certificate and remove the malware from client downloads. “Ransomware is a great way for criminals to make a ton of money,” Wardle said. “If you hack a computer and get credit card numbers, most have no idea what to do with that [stolen] data. You have to approach someone to get money out of those credit cards. “Now, you can write ransomware, and maybe crack a version of an app, put it up on Pirate Bay, and get a ton of infections and send me ransoms in Bitcoin. That’s what’s driving this; it’s easy money and kinda crazy.” Wardle explains that his utility flags behavior as ransomware by first going through a number of checks, for example making a determination whether to trust a running process. Processes signed by Apple, or those approved by the user, are trusted, for example. It then monitors the behavior of untrusted processes to determine if new files that are created or modified are encrypted. If said processes create encrypted files quickly, the utility generates an alert that suspends the process and asks the user how to proceed. Wardle acknowledges that his 1.0 of version of the RansomWhere? utility has its limitations, and that the tool can be bypassed. Detection, he said, is reactive and the user is likely to lose a few files before an alert is generated and the offending process is suspended. The utility also will trust binaries signed by Apple and will not detect infections via injections into a signed binary. Wardle has published full technical details of how the utility detects ransomware and handles running processes. In the meantime, Wardle said he isn’t done. Future iterations of RansomWhere? would ideally monitor all files on an OS X machine, not just user directories. He’d also like to push detection into the kernel and afford more protection at that level. “This is the first tool where timing is paramount,” Wardle said.
How to decrypt Petya Ransomware for Free
13.4.2016 Ransomware
Ransomware has risen dramatically since last few years and is currently one of the most popular threats on the Internet.
The Ransomware infections have become so sophisticated with the time that victims end up paying ransom in order to get their critical and sensitive data back.
But if you are infected with Petya Ransomware, there is good news for you.
You can unlock your infected computer without paying the hefty ransom. Thanks to the Petya author who left a bug in the Ransomware code.
What is Petya Ransomware?
Petya is a nasty piece of ransomware that emerged two weeks ago and worked very differently from any other ransomware.
The ransomware targets the victims by rebooting their Windows computers, encrypting the hard drive's master boot file, and rendering the master boot record inoperable.
Also Read: How to Decrypt CoinVault and Bitcryptor Ransomware
A master boot record (MBR) is the information in the first sector of any hard disk that identifies how and where an OS is located while a master boot file is a file on NTFS volumes that includes the name, size, and location of all other files.
Once done, the infected PC restarts and the Petya ransomware code is booted rather than the operating system, displaying a ransom note that demands 0.9 Bitcoin (approx. US$381) in exchange for the decryption key to recover the system's files.
Now, without the decryption password, the infected PC would not boot up, making all files on the startup disk inaccessible.
However, a researcher who goes by the Twitter handle @leostone has developed a tool that generates the key Petya requires decrypting the master boot file.
Here's How to Unlock your Petya-infected Files for Free
The researcher discovered a weakness in the nasty malware's design after Petya infected his father-in-law's PC.
According to security researcher Lawrence Abrams from the Bleeping Computer, the key generator tool developed by Leostone could unlock a Petya-encrypted PC in just 7 seconds.
In order to use the Leostone's password generator tool, victims must remove the startup drive from the Petya affected computer and connect it to another Windows computer that's not infected.
The victim then needs to extract data from the hard disk, specifically:
the base-64-encoded 512 bytes that start at sector 55 (0x37h) with an offset of 0.
the 64-bit-encoded 8-byte nonce from sector 54 (0x36) offset 33 (0x21).
This data then needs to be used on this Web app (mirror site) created by Leostone to generate the key. The victim will then retrieve the key Petya used to decrypt the crucial file.
Here's a Simple Tool to Unlock your Files For Free
Since the Leostone's tool is not a straight-forward method, extracting the encrypted data is not easy for many victims.
The good news is that Fabian Wosar, a separate researcher, has created a free tool called the Petya Sector Extractor that can be used to easily extract the data in seconds.
In order to use Petya Sector Extractor, victims must run the tool on the uninfected Windows computer that is connected to the infected hard drive from the affected computer.
Abrams provided this step-by-step tutorial that will walk victims through the entire process.
This is a great solution to decrypt your infected files, but most likely, the Petya authors have already heard about this tool and are modifying their code to disable the solution. So, there is no guarantee the tool will continue to work indefinitely.
How to restore files encrypted by the Petya ransomware in less than 7 seconds
12.4.2016 Ransomware
Security Researchers have developed a decryption tool to restore the files encrypted by the Petya ransomware with a key generated in less than 10 seconds.
Security researchers have analyzed the code of Petya ransomware in order to devise a method to allow victims to restore encrypted files. The experts have been able to develop a decryption tool that should allow victims to generate keys in a few seconds.
The Twitter user @leostone announced to have elaborated a method to generate passwords in less than a minute. The user also developed a website to help victims generate keys for restoring encrypted files.
In order to generate a decryption key, the victim just needs to provide certain information on the infected drive. The researcher Fabian Wosar from Emisoft as developed an application that is able to automatize the process extracting data from infected Petya drives and generate the key for the data rescue.
The security experts Lawrence Abrams, who contribute at BleepingComputer.com blog, has prepared a guide on how to use the tool.
Abrams explained that the tool scans the infected drive searching for the Petya bootcode. Once detected the code, it selects it and allow users to simply copy both the sectors and nonce associated with it. These data (a Base64-encoded 512 bytes verification data and a Base64-encoded 8 bytes nonce) could be used to generate the password through the @leostone’s website.
“An individual going by the twitter handle leostone was able to create an algorithm that can generate the password used to decrypt a Petya encrypted computer. In my test this, this algorithm was able to generate my key in 7 seconds.” wrote Abrams in a blog post.
To discover the password, the user has to physically remove the drive from the infected machine and attach it to either a Windows machine or a USB drive docking station and to launch the Wosar’s tool.
“To use Leostone’s decryption tool you will need attach the Petya affected drive to another computer and extract specific data from it. The data that needs to be extracted is 512-bytes starting at sector 55 (0x37h) with an offset of 0 and the 8 byte nonce from sector 54 (0x36) offset: 33 (0x21). This data then needs to be converted to Base64 encoding and used on the https://petya-pay-no-ransom.herokuapp.com/ site to generate the key.” continues Abrams.
“Unfortunately, for many victims extracting this data is not an easy task. The good news is that Fabian Wosar created a special tool that can be used to easily extract this data. In order to use this tool, you need to take the encrypted drive from the affected computer and attach it to a Windows computer that is working properly. If your infected computer has multiple drives, you should only remove the drive that is the boot drive, or C:\ drive, for your computer.”
Once obtained the password, users should be able to reconnect their encrypted drive and enter it to restore the files encrypted by the Petya ransomware.
The identity of @leostone is still a mystery, he only explained to have decided to work on his decryption method after his father in law was infected by the Petya ransomware.
Unfortunately, it is likely that operators behind the Petya will soon improve their malware releasing a newer version with stronger encryption.
Petya ransomware encryption has been cracked
11.4.2016 Ransomware
Petya ransomware hit companies hard, but the good news is that there are now tools available to get the encrypted files and locked computers back.
The ransomware not only encrypts the victims’ files, but also their disk’s Master File Table (MFT), and it replaces the boot drive’s existing Master Boot Record (MBR) with a malicious loader.
Nearly two weeks ago a malware analyst that goes by the handle Hasherezade created a decoder that extracted the key Petya victims had to input in order to reverse the damage, but it only worked if the system was not rebooted after the infection (Stage 1).
But on Friday an unidentified programmer that goes by “Leo Stone” published another tool that manages to extract the key even if the computer was rebooted (Stage 2).
Apparently, his father in law fell victim to Petya, and didn’t want to pay the ransom, so Leo Stone went exploring to find a possible fix. The code for the tool (and technical details about his search) can be found on GitHub.
The tool can also be accessed here, and is ready for use. The only problem is that in order to use it, one has to extract two pieces of information from the infected disk, and that’s not that easy for tech-unsavvy users.
Luckily, Emsisoft researcher Fabian Wosar created another tool that will allow victims to the extract this info, but they will have to have another uninfected computer available and know how to remove a hard drive from one computer and attach it to another.
For more information about the whole process, check out these instructions by Bleeping Computer’s Lawrence Abrams.
When you finally input the info into Leo Stone’s tool and get the key, simply insert it into the ransomware lock screen, and wait for the damage to be reversed.
TA530 group, spear phishing meets ransomware
7.4.2016 Ransomware
A threat actor named TA530 group, has been targeting executives in an attempt to infect their machine with various malware, including ransomware.
Ransomware continues to represent one of the greatest threat for the Internet users, the FBI recently issued a confidential urgent “Flash” message to the businesses and organizations about the Samsam Ransomware.
Security firms are assisting to a rapid increase in the number of infections caused by the ransomware, US and Canada issued a joint warning about the recent surge in ransomware-based attacks. The most disconcerting aspect of the situation is the continuous improvement of such kind of malware and the techniques adopted by criminal organizations to spread it.
Today we will discuss a new threat that adopts a singular strategy to infect the victims, it relies on spear-phishing attacks to compromise users’machines.
Security firms use to observe spear-phishing attacks for espionage purposes, however, the adoption of these techniques in the criminal field contributes increasing their effectiveness.In a spear-phishing attack
In a spear-phishing attack, threat actors use a deep knowledge of the potential victims to target them, clearly this approach allows them to tailor the operation.
According to security experts at Proofpoint, a threat actor, named TA530 group, has been targeting executives and other high-level employees in an attempt to compromise their machine with various malware, including the CryptoWall ransomware.

Other threats in the malware arsenal of the TA530 are:
Ursnif ISFB – banking Trojan configured to target Australian banks
Fileless Ursnif/RecoLoad – Point of Sale (PoS) reconnaissance Trojan targeted at Retail and Hospitality. It was first featured in Kafeine’s blog [1] in July of 2015, which suggests that it has been in distribution since 2014; shortly after, it was described with more detail by Trend Micro [2].
Tiny Loader – a downloader used in campaigns targeting Retail and Hospitality verticals. We have not observed it download secondary payloads, but previously it has been used to download malware such as AbaddonPOS [3].
TeamSpy/TVSpy – RAT utilizing Teamviewer [4], primarily targeted at Retail and Hospitality
CryptoWall – File encrypting ransomware targeted at a variety of companies
Nymaim – Installs a banking Trojan [5] primarily targeted at Financial companies
Dridex Botnet 222 – banking Trojan botnet with UK targeting. Proofpoint first observed this botnet when it was dropped by Bedep in January 2016 [6]
The attackers were able to profile victims, targeting specific industries and geographic areas.
The approach is simple, targeting executives there is a high likelihood that victims will pay to restore high-value information and usually people in these positions are more likely to have access to corporate online bank accounts and other online services.
“Additionally, TA530 customizes TA530 customizes the e-mail to each target by specifying the target’s name, job title, phone number, and company name in the email body, subject, and attachment names. On several occasions, we verified that these details are correct for the intended victim. While we do not know for sure the source of these details, they frequently appear on public websites, such as LinkedIn or the company’s own website. The customization doesn’t end with the lure; the malware used in the campaigns is also targeted by region and vertical.” states the blog post published Tuesday
The TA530 group targets tens of thousands of recipients in US, UK, and Australian organizations, the figures are very interesting if we consider that are related to spear-phishing attacks.
“We observed TA530 at times targeting only a specific and narrow vertical, such as Retail and Hospitality. At other times, the campaigns appear more widespread. Overall, the volume of messages targeting each vertical is shown below:

The experts believe that the TA530 will intensify his spear-phishing campaign including new malicious payloads into its arsenal and adopting news delivery methods.
“Based on what we have seen in these examples from TA530, we expect this actor to continue to use personalization and to diversify payloads and delivery methods,” states ProofPoint. “The personalization of email messages is not new, but this actor seems to have incorporated and automated a high level of personalization, previously not seen at this scale, in their spam campaigns.”
Locky: the encryptor taking the world by storm
7.4.2016 Zdroj: Kaspersky Ransomware
In February 2016, the Internet was shaken by an epidemic caused by the new ransomware Trojan Locky (detected by Kaspersky Lab products as Trojan-Ransom.Win32.Locky). The Trojan has been actively propagating up to the present day. Kaspersky Lab products have reported attempts to infect users with the Trojan in 114 countries around the world.
Analysis of the samples has shown that this Trojan is a brand new ransomware threat, written from scratch. So, what is Locky, and how can we protect against it?
Propagation
In order to spread the Trojan, cybercriminals sent out mass mailings with malicious loaders attached to spam messages.
Initially, the malicious spam messages contained an attached DOC file with a macro that downloaded the Locky Trojan from a remote server and executed it.
An early-stage spam message with a malicious document attached
A fragment of the malicious macro
Kaspersky Lab products detect files with malicious macros as Trojan-Downloader.MSWord.Agent and HEUR:Trojan-Downloader.Script.Generic.
We should note that in modern versions of Microsoft Office, automatic execution of macros is disabled for security reasons. However, practice shows that users often enable macros manually, even in documents from unknown sources, which may lead to some damaging consequences.
At the time of writing, the malicious spam is still being sent, but instead of the DOC files being attached there are now ZIP archives containing one or more obfuscated scripts in JavaScript. The messages are mostly in English, though some bilingual variants have appeared.
Spam message in English with the archive attached
Message in German and English with the archive attached
The user is prompted to manually launch the scripts.
Contents of the archive attached to the message
Fragment of the archived script
When launched, the script downloads the Locky Trojan from a remote server and launches it.
Kaspersky Lab products detect these script loaders as Trojan-Downloader.JS.Agent and HEUR:Trojan-Downloader.Script.Generic.
Geography of attacks
Kaspersky Security Network has reported Locky attacks in 114 countries. Below is a list of countries where the Trojan was detected most often:
Country Number of attacks
Germany 3989
France 2372
Kuwait 976
India 512
China 427
South Africa 220
United States 188
Italy 128
Spain 105
Mexico 92
We should note that these statistics only include cases where the actual Trojan was detected, and does not include early-stage detections reported as malicious spam or malicious downloaders.
The geography of Trojan-Ransom.Win32.Locky attacks
As we can see, the Trojan carries out attacks in practically all regions of the world. We can assume which countries the cybercriminals see as their main targets based on the list of languages used on the ransom payment webpage (see details below).
How it works
The Locky Trojan is an executable file, about 100 kb in size. It is written in C++ using STL, and is compiled in Microsoft Visual Studio. When launching, it copies itself to %TEMP%\svchost.exe and deletes the NTFS data stream Zone.Identifier from its copy – this is done to ensure that when the file is launched, Windows does not display a notification saying that the file has been downloaded from the Internet and may be potentially dangerous. The Trojan then launches from %TEMP%.
Once launched, the Trojan checks for the presence and the contents of the below registry keys.
Path Type Value
HKEY_CURRENT_USER\Software\Locky\id REG_SZ Infection ID
HKEY_CURRENT_USER\Software\Locky\pubkey REG_BINARY Public RSA key in MSBLOB format
HKEY_CURRENT_USER\Software\Locky\paytext REG_BINARY Text shown to the victim
HKEY_CURRENT_USER\Software\Locky\completed REG_DWORD Status (whether encryption is completed)
If data already exists in the registry keys (this is the case if the Trojan has launched before, but its previous session aborted for some reason), Locky reads that data and continues with the infection process.
If launched for the first time, the Trojan performs the following actions:
Contacts C&C and reports infection;
Receives a public RSA-2048 key and infection ID from C&C, saves them in the registry;
Sends information about the language of the infected operating system, receives the cybercriminals’ ransom demand text that will be shown to the victim, saves the text in the registry;
Searches for files with specific extensions on local disk drives, encrypts them;
Deletes shadow copies of files;
Registers itself for autostart (HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run);
Searches for and encrypts files with specific extensions on network drives and on network file resources with no assigned drive letter;
Displays the cybercriminals’ ransom demands to the victim;
Terminates its process and removes itself.
Fragment of code that determines the language of the operating system
File encryption
The Trojan searches for files matching a given list of extensions. Then, these files are encrypted as described below.
List of file extensions that are subject to encryption
For each file that matches an extension on the list, the Trojan generates a new 128-bit key and encrypts the file’s contents with the algorithm AES-128 in CTR mode. The encrypted file is given the name <16 HEX characters as ID><16 random HEX characters>.locky. Then the following structure is added to the end of the file:
Structure appended by the Trojan to the end of an encrypted file
In C language syntax, this structure may be described as follows:
struct file_data
{
uint32_t start_marker; //Structure start marker = 0x8956FE93
char id[16]; //Infection ID
uint8_t aes_key[256]; //AES key encrypted with RSA-2048
uint32_t name_marker; //Name start marker encrypted with AES (= 0xD41BA12A after decryption)
uint8_t orig_name[520]; //Original file name encrypted with AES
WIN32_FILE_ATTRIBUTE_DATA attr; //Original file attributes encrypted with AES
};
1
2
3
4
5
6
7
8
9
struct file_data
{
uint32_t start_marker; //Structure start marker = 0x8956FE93
char id[16]; //Infection ID
uint8_t aes_key[256]; //AES key encrypted with RSA-2048
uint32_t name_marker; //Name start marker encrypted with AES (= 0xD41BA12A after decryption)
uint8_t orig_name[520]; //Original file name encrypted with AES
WIN32_FILE_ATTRIBUTE_DATA attr; //Original file attributes encrypted with AES
};
Appended structure described in C language syntax
Ransom demands
After encrypting the user’s files, the Trojan displays the following message with the cybercriminals’ ransom demands.
Ransom demand in English
Ransom demand in German
The ransom message contains the address of the cybercriminals’ ‘secret server’ where they placed information about the ransom they demand for the decryption program. All four links in the message lead to the same website in the Tor network.
During the early spamming campaigns, the ransom payment page looked like this:
Early version of Locky’s ransom demand page
On this page, the cybercriminals suggested that the victims pay in bitcoins to decrypt the affected files on their computer. They also gave recommendations about where and how to get the cryptocurrency.
The contents and the design of the page changed with time. Today, the page is available in more than 20 languages (that can be selected from a dropdown list), and looks like this:
Latest version of Locky’s ransom payment page
If we look at the page’s source code, we will see a complete list of supported languages. The cybercriminals obviously see the corresponding countries as the main targets for this ransomware Trojan. Interestingly, Russian and other CIS languages are not on the list. For some reason the cybercriminals are not that keen on targeting users in countries where those languages are spoken – something that KSN statistics confirm.
List of languages supported on Locky ransom payment page
Communication with C&C
The Trojan’s code contains between one and three C&C IP addresses. On top of that, the code contains an algorithm generating new C&C addresses (DGA, domain generation algorithm) depending on the current day, month and year. With this algorithm, six C&C addresses are generated each day. The pseudo-code to illustrate the DGA Locky algorithm is highlighted in the screenshot below.
Pseudo-code of Locky C&C domain generation algorithm
Communication with a C&C is performed using the HTTP protocol. The Trojan sends a POST request to an address with the format http://<cnc_url>/main.php; the transmitted data is encrypted with a simple symmetric algorithm.
Let’s have a look at the possible types of transmitted parameters.
Notification about infection and request for key.
id=<infection id>
&act=getkey&affid=<partner id contained in the Trojan’s body>
&lang=<language of the operating system>
&corp=<whether the OS is a corporate OS>
&serv=<whether the OS is a server OS>
&os=<OS version>
&sp=<version of OS service pack>
&x64=<whether the OS is 32- or 64-bit>
Judging by the affid parameter, Locky is distributed via an affiliate, or partnership, program.
Sending list of encrypted paths.
id=<infection id>
&act=report&data=<list of paths>
For each disk drive it has handled, the Trojan sends the C&C a list of all paths to all encrypted files.
Sending statistics for each handled disk drive.
id=<infection id>
&act=stats&path=<path>
&encrypted=<number of files encrypted>
&failed=<number of errors>
&length=<total size of encrypted files>
It should be noted that the cybercriminal collects very detailed statistics for each infection. Other ransomware families that we analyzed earlier were not this thorough at collecting statistics.
Countermeasures
Kaspersky Lab products protect against the Locky ransomware Trojan at all stages of the attack:
The anti-spam module detects emails sent by the Trojan’s distributors;
Script loaders are detected by static and heuristic signatures of email and file antivirus with the verdicts Trojan-Downloader.MSWord.Agent, Trojan-Downloader.JS.Agent, HEUR:Trojan-Downloader.Script.Generic;
The Trojan’s executable file is detected by file antivirus signatures as Trojan-Ransom.Win32.Locky;
Unknown samples of Locky are proactively detected by the System Watcher module with the verdict PDM:Trojan.Win32.Generic.
Preventing infections
Locky is a typical ransomware Trojan, and it exhibits no major differences from other ransomware families in its internal arrangement or its principles of operation. However, it caught the attention of researchers because it was so active and so widespread. According to KSN data, Kaspersky Lab products have blocked Locky attacks in over 100 countries around the world – no other ransomware Trojan to date has attacked so many countries at once.
To protect yourself from this ransomware Trojan, follow these preventive measures:
Do not open attachments in emails from senders you don’t know;
Back up your files on a regular basis and store the backup copies on removable storage media or in cloud storages – not on your computer;
Regularly run updates for your antivirus databases, operating system and other software installed on your computer;
Create a separate network folder for each user when managing access to shared network folders.
Why malware like the Samsam ransomware are so dangerous for hospitals?
4.4.2016 Ransomware
The FBI issued a confidential urgent “Flash” message to the businesses and organizations about the Samsam Ransomware, why it is so dangerous?
It is emergency, every week security experts launch an alert on a new ransomware, the extortion practice is becoming a profitable business for criminal gangs worldwide. Recently the US and Canada issued a joint warning about the recent surge in ransomware infections. According to the Reuters, the FBI issued a confidential urgent “Flash” message to the businesses and organizations about the Samsam Ransomware, that targeted several hospitals. The law enforcement Agency also shared IoC for the Samsam threat to help organizations monitoring for infections.
The law enforcement Agency also shared IoC for the Samsam threat to help organizations monitoring for infections.
“The FBI is distributing these indicators to enable network defense activities and reduce the risk of similar attacks in the future,” the advisory said.” states the advisory.Among the victims of the Samsam Ransomware there is the MedStar non-profit group that manages 10 hospitals in the Baltimore and Washington area.The bad actors behind the attack on MedStar requested 45 Bitcoins (about US$18,500) for restoring the encrypted files.
MedStar did not pay the Ransom because it has a backup of the encrypted information, a situation rare that advantage the attackers behind ransomware-based campaigns.
The IT department of the MedStar Hospital detected the infection at an early stage and was able to stop the Samsam Ransomware from infecting internal systems.
The MedStar incident demonstrates that a proper security posture, an early response and the implementation of effective best practices like data backup are necessary steps for a right approach to prevent damage from ransomware-based attacks.
In the specific case, the Samsam ransomware is not a new threat, it has been around since last few years targeting businesses and organizations worldwide.
Samsam is considered a very interesting threat by experts because it doesn’t require the victim’s interaction.
Typical victims get a ransomware infection by clicking on a malicious link, by opening an attachment or through a malvertising, but the Samsam ransomware targets servers instead end-users.
The threat first exploits unpatched vulnerabilities in JBoss application servers by using JexBoss, an open-source penetration testing tool. Once exploited the flaws, the attackers get remote shell access to the infected servers and install the Samsam ransomware onto the targeted Web application server.
Once the server has been compromised, attackers use it to spread the ransomware client to Windows machines and encrypt their files.
“The Samas infection chain diagram illustrates how Ransom:MSIL/Samas gets into the system. It starts with a pen-testing/attack server searching for potential vulnerable networks to exploit with the help of a publicly-available tool named reGeorg, which is used for tunnelling. Java-based vulnerabilities were also observed to have been utilized, such as Java-based vulnerabilities were also observed to have been utilized, such as CVE-2010-0738 related to outdated JBOSS server applications.
It can use other information-stealing malware (Derusbi/Bladabindi) to gather login credentials as well. When it has done so, it will list the stolen credentials into a text file, for example, list.txt, and use this to deploy the malware and its components through a third party tool named psexec.exe through batch files that we detect as Trojan:BAT/Samas.B and Trojan:BAT/Samas.C.” states a blog post published by Microsoft on the threat.”

Such kind of threat is particularly insidious for any organizations, especially the ones that works directly with the public, like transportation services and hospitals.
The number of ransomware infections in the healthcare industry is rapidly increasing, the threats in many cases are able to cause the paralysis of the infrastructure with serious damages in the middle and long term.
In February, two German hospitals were infected by a ransomware, in a similar way occurred recently at the US Hollywood Presbyterian Medical Center. The Los Angeles hospital paid about $17,000 to the crooks for restoring patients’ files.
Recently the systems at the Methodist Hospital in Kentucky that’s been infected. According to NewsChannel10, the Methodist Hospital in Henderson was hit my a ransomware that locked patients’ files and is demanding money for to regain access to them. Officials say that the hospital paid about $17,000 to those hackers for the access back to the patients’ files.
Ransomware attacks on Hospitals put Patients at Risk
4.4.2016 Ransomware
Just last week, the Federal Bureau of Investigation (FBI) issued an urgent "Flash" message to the businesses and organisations about the threat of Samsam Ransomware, but the ransomware has already wreaked havoc on some critical infrastructure.
MedStar, a non-profit group that runs 10 hospitals in the Baltimore and Washington area, was attacked with Samsam, also known as Samas and MSIL, last week, which encrypted sensitive data at the hospitals.
After compromising the MedStar Medical System, the operators of the ransomware offered a bulk deal: 45 Bitcoins (about US$18,500) for the decryption keys to unlock all the infected systems.
But unlike other businesses or hospitals, MedStar did not pay the Ransom to entertain the hackers.
So, you might be thinking that the hospitals lost all its important and critical data. Right?
But that was not the case in MedStar.
Here's How MetStar Successfully dealt with SAMSAM Ransomware
MetStar sets an example for all those businesses and organisations that pay ransom amount to attackers, motivating their criminal minds to spread the infection further.
The IT department of the MedStar Hospital was initially able to detect the intrusion in their servers and stop the Ransomware from spreading further in its internal network by shutting down most of its network operations.
Besides this, the IT engineers successfully restored three main clinical information systems from the backups (rest of the restoration process is in progress) – a practice that all organisation should follow.
This quick and active approach of hospital’s IT department ultimately saved not only the hospital reputation but also the lives of admitted patients, said Ann Nickels, a spokeswoman for the nonprofit MedStar medical system.
Even though the prevention of Ransomware attack is complex, it is noticeable from the MedStar incident that the automatic backup is not an optional step but a must-follow step, to prevent these kinds of attacks.
What is Samsam and How Does it Work?
Ransomware has been around since last few years targeting businesses and organisations, but Samsam is yet the most interesting innovation of ransomware that requires no human interaction from the target.
Typical ransomware infects victim's machine by a malicious email link or attachment or a malicious advertisement. But Samsam ransomware doesn't target humans. It targets servers.
Samsam first exploits the unpatched vulnerabilities in both JBoss application servers by using JexBoss, an open-source penetration testing tool.
The hacker then uses these exploits to get remote shell access to the affected server and install Samsam onto the targeted Web application server.
Now, the hacker uses the infected server to spread the ransomware client to Windows machines and encrypt their files. Once the server is compromised, there is no communication with the command and control network.
You can find more detailed information about Samsam here.
Why Hospitals are Soft Target?
With the advent of Ransomware, we have seen an enormous growth in the malware business.
The countless transactions of Bitcoins into the dark web wallets had energized the Ransomware authors to spread and adopt new methods of infection for the higher successful rate.
Nowadays ransomware had been a soft target for both Corporates and Hospitals.
Since earlier this year, at least, a dozen hospitals have been affected by ransomware, enforcing them to pay the ransom as per the demand by freezing the central medical systems.
Technological advancement in the medical arena had digitalized patients data in the form of Electronic Medical Record (EMR) to save them into the hospital’s central database.
Since the delay in patients treatment by temporary locking down their data could even result in the patient’s death, the ransomware attackers seek 100% guarantee ransom by infecting hospitals.
Due to this reason, in most of the cases, hospitals generally agrees to pay the ransom amount to the attacker in order to obtain the decryption keys from the attackers.
Recently, Hollywood Presbyterian Medical Centre in Los Angeles paid US$17,000 to the ransomware attackers to (or "intending to") regaining access to their patient's data.
Followingly, many more hospitals like Methodist Hospital in Henderson and Kentucky, Chino Valley Medical Center and Desert Valley Hospital in California have been infected with Ransomware and became fresh victims of the ransomware attacks.
F-Secure provides more details on the Petya ransomware
2.4.2016 Ransomware
The best way to address a threat is to know it so security experts at F-Secure shared a detailed analysis on the new Petya ransomware.
Several days ago, I wrote about a new singular Ransomware dubbed Petya that captured the attention of security experts because it causes a blue screen of death (BSoD) by overwriting the MBR.
Now security firm F-Secure has issued an alert on the Petya ransomware, sharing the results of its analysis about the threat.
The malware encrypts the entire disk instead of encrypting files on the infected system like any other ransomware,
The Petya ransomware encrypts the filesystem’s master file table (MFT) making impossible for the operating system the access to any file and making the machine unusable.
The MFT contains at least one entry for every file, including the MFT itself.
” Specifically, it will encrypt the filesystem’s master file table (MFT), which means the operating system is not able to locate files.” wrote Jarkko Turkulainen, F-Secure senior security researcher.
“It installs itself to the disk’s master boot record (MBR) like a bootkit. But instead of covert actions, it displays a red screen with instructions on how to restore the system.”
Why encrypt the MFT?
Because the encryption of an MFT is less consuming than the encryption of all the files contained on the disk, and the result is the same.
Even restoring the MBR with recovery system won’t help, because the MFT remains encrypted.
The attack of a generic ransomware is very slow respect an attack based on the Petya ransomware, this means that victims aware of the threat could act to limit the effects of the malware.
Petya is able to compromise the MFT in a few seconds, causing the system crash and forcing a restart, and according to F-Secure experts, in an enterprise environment there would be no time to take mitigation measures.
Another effect of the Petya infection is that the victim would need to use a machine different from the infected computer to pay the ransom.
Petya operates in two stages, in the first one is the main dropper that performs the following operations:
Infects the MBR using direct \\.\PhysicalDrive manipulation.
Generates a set of crypto keys, including a disk encryption 16-byte key consisting of ASCII characters. It also wraps up a special decryption code, which only the server can open. This code contains the actual disk encryption key.
Saves the crypto keys to disk for later use in the MBR infection code.
Shuts down the machine without any warning to boot to MBR code.
In the second phase, once infected the PC, the machine boots to MBR code, which:
First checks to see if the disk is infected.
If not, it will present a fake CHKDSK screen and will encrypt the MFT using the shared secret as the encryption key.
Uses salsa20 for disk encryption, and destroys the key after encryption.
Presents the red “skull screen” and then the screen with Tor hidden service URLs, and the “decryption code”, which is an encrypted message only the server can open.
The Petya ransomware implements a custom Elliptic Curve encryption scheme for file encryption, the dropper ships with a 192-bit public key and secp192k1 curve parameters hardcoded in the code.
Wanting to make a critical to the authors, the Petya ransomware doesn’t implement a mechanism for paying the ransom, instead, it just share a URL with victims.

“Somewhat ironically, in making it harder for victims to pay a ransom, Petya’s authors may have also lowered their own chances of profiting from it” F-Secure security advisor Sean Sullivan explained to Dark Reading. “As a result, the likelihood of the same technique being used more widely will depend on the success malware authors have in monetizing Petya.”
It is important to notice that only the server can restore the encryption key used to encrypt the files with the EC algorithm.
“The only way to restore the machine without the help of the server is to catch the salsa20 key inline of the infection process, using debuggers. Not a very attractive counter measure for the average computer user:).” states F-Secure.
Ransomware is a serious threat, this form of digital extortion is becoming a common and profitable practice in the criminal underground.In recent months, ransomware samples like
In recent months, many ransomware strains like TeslaCrypt, Locky and CryptoWall have infected a large number of victims worldwide.
The U.S DHS issued an alert warning users of the threat. The alert, issued late Thursday, warned consumers and businesses about the “devastating” consequences of a ransomware attack.
“In early 2016, destructive ransomware variants such as Locky and Samas were observed infecting computers belonging to individuals and businesses, which included healthcare facilities and hospitals worldwide. Ransomware is a type of malicious software that infects a computer and restricts users’ access to it until a ransom is paid to unlock it.” states the alert.
“The United States Department of Homeland Security (DHS), in collaboration with Canadian Cyber Incident Response Centre (CCIRC), is releasing this Alert to provide further information on ransomware, specifically its main characteristics, its prevalence, variants that may be proliferating, and how users can prevent and mitigate against ransomware.”
The KimcilWare Ransomware targets Magento Platforms
31.3.2016 Ransomware
Security experts from the MalwareHunterTeam have discovered KimcilWare ransomware, a malware specifically designed to target Magento e-commerce platforms.
Security experts from the MalwareHunterTeam have spotted a news train of ransomware, called KimcilWare, specifically designed to target Web servers, and more specifically Magento e-commerce platforms.
“A new ransomware called KimcilWare has been discovered that appears to be targeting web sites using the Magento eCommerce solution. It is currently unknown how these sites are being compromised, but victims will have their web site files encrypted using a Rijndael block cipher and then ransomed for anywhere between $140 USD and $415 USD depending on the variant that infected them. Unfortunately, at this time there is no way to decrypt the data for free.” states a blog post published on BleepingComputer.
The KimcilWare ransomware encrypts the files of the Magento platform, it is easy to recognize because it appends the “.kimcilware” extension at the end of each file. rendering the store useless.
“One script will encrypt all data on the web site and append the .kimcilware extension to all encrypted files. It will also insert a index.html file that displays the ransom note shown above. The KimcilWare variant has a ransom amount of $140 USD. You can see an example of a folder encrypted with the KimcilWare script below. ” continues BleepingComputer.

Source BleepingComputer
The malware also uses its index file in order to publish a black page that informs the victims that the server had been encrypted.

“Webserver Encrypted” states the message on the home page “Your webserver files has been encrypted with a unix algorithm encryptor. You must paw 140$ to decrypt your webserver files. Payment via Bitcoin only. For more information contact me at tuyuljahat@hotmail.com.”
Of course, the e-commerce becomes useless once the malware has encrypted all the files.
The bad news is that it is still unknown the infection process, but fortunately, the number of infections is still limited.
The KimcilWare ransomware was first reported on March 3 by the owner of a Magento store (version 1.9.1.0) on StackExchange. The administrator noticed that only one site on a server with multiple Magento instances was infected.
A second case was reported a few days later on Magento’s official forum, from a store owner running version 1.9.2.4. The Magento admin speculates a security issue affecting the Helios Vimeo Video Gallery extension.
Another ransomware having similar capabilities was discovered by the security researcher Jack (@Malwareforme). This second malware is called MireWare and uses the same tuyuljahat@hotmail.com email address in its ransom note included in the index page. From his analysis, MireWare is a variant of the
Jack noticed that MireWare is a variant of the Hidden Tear open source ransomware published by the Turkish security researchers Utku Sen for educational purposes.
The Hidden Tear was intentionally designed with security flaws and Bleeping Computer’s researchers Lawrence Abrams who analyzed MireWare confirmed that also this threat is currently broken due to the lack of a valid SSL certificate for its C&C server.
Experts believe that the KimcilWare ransomware is in its early stages, but that it might rapidly evolve.
If you administrate a Magento store update to the latest Magento store versions and use strong passwords for the admin accounts.
Bitdefender Vaccine now supports also CTB-Locker, Locky, TeslaCrypt
30.3.2016 Ransomware
The prevention is better that the cure, users can immunize their PC against CTB-Locker, Locky and TeslaCrypt using Bitdefender Anti-ransomware vaccine.
Security experts from the Romanian security vendor Bitdefender have updated their anti-ransomware vaccine in order to protect machines from the latest versions of the CTB-Locker, Locky and TeslaCrypt ransomware.
According data recently published by Fortinet, top ransomware families are CryptoWall, Locky, and TeslaCrypt, while Cryptowall is predominant, Lock is rapidly spreading.
ransomware infections statistics
The Bitdefender Anti-Ransomware toolkit was developed by the company years ago to help victims of crypto-ransomware to prevent infections.
Some ransomware-decryptors tries to exploit encryption flaws in the ransomware implementation to decrypt files or use encryption keys discovered by law enforcement during their activity.
These conditions are not easy to match, so Bitdefender is promoting the prevention instead the cure by spreading its anti-ransomware vaccine.

The most recent version, 1.0.11.26, includes detection for the latest variant of ransomware in the wild, including CTB-Locker, Locky and TeslaCrypt.
These three ransomware had a different evolution in the last weeks, Locky for example is rapidly spreading meanwhile a new strain of TeslaCrypt appeared in the wild, the version 4.0 with implements significant improvements.
We have no news regarding the CTB-Locker, in fact, there are no new infections in the wild.
“Bitdefender anti-malware researchers have released a new vaccine tool which can protect against known and possible future versions of the CTB-Locker, Locky and TeslaCrypt crypto ransomware families.” state the announcement published by BitDefender.
“The new tool is an outgrowth of the Cryptowall vaccine program, in a way.” Chief Security Strategist Catalin Cosoi explained. “We had been looking at ways to prevent this ransomware from encrypting files even on computers that were not protected by Bitdefender antivirus and we realized we could extend the idea.”
Download the Bitdefender Anti-ransomware vaccine from the company website.
PowerWare ransomware, a new fileless threat in the wild
28.3.2016 Ransomware
Experts at Carbon Black spotted in the wild a new threat dubbed PowerWare ransomware that exploits PowerShell, the native Windows framework.
Authors of ransomware are implementing new features to make their malware even more dangerous and effective. Yesterday I wrote about the new Petya ransomware, which overwrites MBR causing a blue screen of death, now I will introduce you a threat targeting the healthcare industry.
The new ransomware is called PowerWare and was discovered a week ago by security researchers at the Carbon Black firm.

The most interesting feature implemented in the PowerWare ransomware is that it is fileless. Many malware in the wild are fileless, including one of the variants of the popular Angler Exploit Kit, but this feature is rare for ransomware.
Criminal gangs behind PowerWare are spreading it using spam messages including a Word document attachment purporting to be an invoice. The attackers use an old trick in order to convince victims in enabling the macros, they request to enable macros to correctly view the document.
The macros runs the cmd.exe which launches the PowerShell, the native Windows framework that uses a command-line shell to perform several tasks.
The use of PowerShell allows the ransomware to avoid writing files to the disk and make hard the threat detection. It also allows the ransomware to encrypt files on the victim’s PC.
“The macros are there to launch PowerShell and pull down the ransomware script. Lots of malware can be distributed via macros in Word docs. Most of the time they download additional binaries to do more bad stuff (backdoors, etc.),” Valdez said.
“This does not pull down any additional binaries (executables), and leverages PowerShell (already on the system and approved to be there) to do the dirty work.”
“This means no ‘traditional’ malware – no additional executable needed – just a text document (script).”
The PowerShell ransomware requests victims to pay a $500 ransom to restored the encrypted files. Also in this case, the ransom double if the victim’s doesn’t respect the deadline.
Fileless ransomware could become rapidly popular in the criminal ecosystem, on March 11, the researchers at Palo Alto Networks, spotted a new malware family called PowerSniff that has many similarities with PowerWare, including the fileless capability.
PETYA ransomware overwrites MBR causing a blue screen of death
27.3.2016 Ransomware
The Petya ransomware causes a blue screen of death (BSoD) by overwriting the MBR and leaves a ransom note at system startup.
Ransomware is one of the most dangerous threats of this first part of the year, recently experts at TrendMicro has spotted a new malicious code dubbed Petya (RANSOM_PETYA.A) that overwrites MBR to lock users out of the infected machines.
The Petya ransomware causes a blue screen of death (BSoD) by overwriting the MBR and leaves a ransom note at system startup.
Petya overwrites the MBR of the hard drive causing Windows to crash. When the victim tries to reboot the PC, it will impossible to load the OS, even in Safe Mode.
Users turning on the computer are displayed a flashing red and white screen with a skull-and-crossbones instead.

“As if encrypting files and holding them hostage is not enough, cybercriminals who create and spread crypto-ransomware are now resorting to causing blue screen of death (BSoD) and putting their ransom notes at system startup—as in, even before the operating system loads.” states the post published by Trend Micro.
“Imagine turning on your computer and instead of the usual Windows icon loading, you get a flashing red and white screen with a skull-and-crossbones instead.”
Another interesting aspect of the Petya is the delivery mechanism used by crooks that relies on legitimate cloud storage services like Dropbox.
“this is the first time (in a long time) that leads to crypto-ransomware infection. It is also a departure from the typical infection chain, wherein the malicious files are attached to emails or hosted in malicious sites and delivered by exploit kits.” continues the post.
Victims would receive an email that appears to be from an applicant seeking a position in a company, it includes a link to a Dropbox folder that contains its alleged CV.
The experts explained that one of the samples they analyzed, the Dropbox folder was containing contains two files, a self-extracting executable file that purports to be the CV, and a photo of the applicant.
The researcher discovered that the photo is a stock image.
The self-extracting executable is used to serve a Trojan onto the victim’s machine, the malware first disable any antivirus programs installed, then downloads and executes the Petya Ransomware.
In the following image are reported the instructions provided by the Petya ransomware to the victims in order to pay the ransom and restore the encrypted files.
The instruction includes a link to the Tor Project and how to download the Tor Browser to visit a page where purchase the decryption key to restore the data.

The crooks behind the Petya ransomware request the payment of 0.99 Bitcoins (nearly US$430), but the price would be doubled if the payment is not completed within a deadline.
The FBI is investigating ransomware-based attack at Methodist Hospital
23.3.2016 Ransomware
The FBI is investigating cyber-attack at Methodist Hospital in Henderson, once again a ransomware hit a critical infrastructure.
Ransomware is one of the most dangerous cyber threats for businesses and government organizations, the number of infections worldwide is in constant increase. Recently I reported the discovery in the wild of the a new variant of the TeslaCrypt, meanwhile security firms are warning on a spike in the number of attacks bases on the Locky malware.
What happen when ransomware hits a critical infrastructure?
The impact could be serious, in the last months, a ransomware hit Israeli Public Utility Authority with a severe impact on its operations, meanwhile several attacks hit computer systems of hospitals in the US and Germany.
In February, two German hospitals were infected by a ransomware, in a similar way occurred recently at the US Hollywood Presbyterian Medical Center. The Los Angeles hospital paid about $17,000 to the crooks for restoring patients’ files.
News of the day, the systems at another US hospital have been infected by ransomware, it is the Methodist Hospital in Kentucky that’s been infected.
According to NewsChannel10, the Methodist Hospital in Henderson was hit my a ransomware that locked patients’ files and is demanding money for to regain access to them. Officials say that the hospital paid about $17,000 to those hackers for the access back to the patients’ files.
“In the past, we haven’t seen crimes in such a large scale like Methodist,” said KSP trooper Shane Settle. “In general, the more a criminal commits a crime, the more confident they get, especially if they get away with it. I think that’s what you’re seeing here is they are shooting for a much larger target and more money.”
“We’ve notified the FBI, we’re dealing with federal authorities on how to deal with it,” said David Park, Methodist Hospital COO. “Depending upon the number of records that were locked, depends upon whether we’re going to consider looking into whether we pay anything or not.”
The ransomware copies the patients’ files, encrypted them and then the deleted the originals. The good news is that the IT staff at the Methodist Hospital in Henderson has updated backups, this drastically limits the effects of the ransomware on the infrastructure.
In a press release, Methodist Hospital officials reassured patients their information is secure, the hospital is currently working with a backup infrastructure while the internal staff is sanitizing the systems
ransomware hit Methodist Hospital Henderson
We must expect similar attacks in the next future, medical data are a precious commodity in the underground.
According to The Ponemon Institute’s 2015 Global Cost of Data Breach Study, the health care industry suffered the highest costs that were estimated at an average of $363 per record, a data that doesn’t surprise the experts due to the higher value of medical records respect credit card data.

A set of complete health insurance credentials sold for $20 on the underground markets in 2013 — 10 to 20 times the price of a U.S. credit card number with a security code, according to Dell.
Caleb Barlow, vice president at IBM Security, explained that data in a medical record have a much longer shelf life than that of a credit card number.
“With credit cards, the time frame from the breach to mitigation is very short,” Barlow explained. “But the health care record can be used to establish access in perpetuity,” “it can be used to establish credit or steal your identity ten or fifteen years from now,” he added. “Once this information is out there, you can’t get the genie back in the bottle.”
Be aware the unbreakable TeslaCrypt 4 was detected in the wild
19.3.2016 Ransomware
According to the experts at Heimdal Security firm, the ransomware Teslacrypt 4 arrived and it is infecting systems in the wild.
According to the experts at Heimdal Security, the fourth version of the infamous Teslacrypt ransomware has just been launched. Teslacrypt 4 implements new functionalities and is more stable of previous versions, stability, it also fixed various bugs, including one related to encryption of large data files. In the previous variants, files larger than 4 GB would get permanently damaged when the ransomware tried to encrypt them.
Teslacrypt 4 used RSA 4096 for data encryption, this makes impossible to recover data encrypted by the ransomware.
“Consequently, the encrypted data will be impossible to recover, which can determine information loss if the victim doesn’t have a backup for the affected data.” states a report published by Heimdal Security.
The bad news for the victims is that the TeslaDecoder tool used to rescue the files encrypted by the previous variants of the ransomware no longer works with Teslacrypt 4.0.
Victims of the Teslacryt 4 ransomware have to possibility to recover information, they can only restore files from a previous backup or pay the ransom with no guarantee of success.
Researchers spotted TeslaCrypt 4 in the wild, crooks used drive-by attacks to spread the ransomware leveraging on the Angler exloit kit.
The researchers already blocked more than 600 domains hosting the Angler EK in just one day. It has been estimated that daily average of domain spreading Angler EK blocked by the security firsm will reach soon 1200 domains per day, on average.

Teslacrypt 4 could be also used by attackers to harvest user’s data, including the “MachineGuid”, “DigitalProductID” and “SystemBiosDate” .
Experts at Heimdal Security have published the following Indicators of Compromise for the Teslacrypt 4.0:
%UserProfile%\Desktop\RECOVER[%5 random signs%].html
%UserProfile%\Desktop\RECOVER[%5 random signs %].png
%UserProfile%\Desktop\RECOVER[%5 random signs %].txt %UserProfile%\Documents\[random file name].exe %UserProfile%\Documents\recover_file.txt
TeslaCrypt 4 also creates the following value in the registry:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\_[random name] C:\Windows\SYSTEM32\CMD.EXE /C START %user account%\Documents\[random name].exe
The current list of Teslacrypt 4 Control & Command servers is the folowing:
http://commonsenseprotection[.]com/phsys.php
http://ebookstoreforyou[.]com/phsys.php
http://esbook[.]com/phsys.php
http://exaltation[.]info/plugins/phsys.php
http://hmgame[.]net/phsys.php
http://shampooherbal[.]com/phsys.php
This new variant of TeslaCrypt demosntrates the rapid evolution of the threat that first appeared in March 2015, meanwhile the version 2.o appeared in the wild in July 2015 and the TeslaCrypt 3.0 in January 2016.
Malvertising Campaign Hits Top Websites to Spread Ransomware
18.3.2016 Ransomware
Malvertising Campaign Hits Top Websites to Spread Ransomware
Hackers are always in search for an elite method to create loopholes in the cyberspace to implement the dark rules in the form of vulnerability exploitation.
Top Trustworthy sites such as The New York Times, BBC, MSN, AOL and many more are on the verge of losing their face value as a malwertized advertisement campaign are looming around the websites, according to SpiderLabs.
Here's what Happens to Users when Clicking Ads on these Big Brand Sites:
The advertisements on the legit sites trick users into clicking on it, making them believe that these circulated ads come from a trusted networks.
Once clicked, the malicious Ad redirects the user to a malicious website that hosts Angler Exploit Kit (AEK) to infect visitors by installing malware and ransomware on their computer.
Angler Exploit Kit includes many malicious hacking tools and zero-day exploits that let hackers execute drive-by attacks on visitors' computers.
In this case, the Angler kit scans for the vulnerable PCs and loads Bedep Trojan and TeslaCrypt Ransomware, opening doors for hackers to further install a variety of malicious programs.
Buying Media-Related Domains to Spread Malicious Campaigns
While conducting the background check, the security firm discovered that cyber criminals behind this advertising campaign made use of an expired website domain of Brentsmedia, an online marketing solution who discontinued their service earlier 2016.
According to the web registrar records, Brentsmedia's domain was purchased by Pavel G Ashtahov on March 6th, the day just before the malvertising campaign kickstarted.
Malvertising Campaign Hits Top Websites Worldwide to Spread Ransomware
Detailed analysis of this mischievous Ad campaign revealed that when a user tends to click on the malwertized Ad, it triggers a JSON file (Javascript Object Notation), which contains a list of security products for cross checking their presence in the victim's system.
If any of the pre-defined products found installed, the malvertising Ads avoid loading the malicious payload to evade the detection by antivirus firms that could block the campaign if detected.
But if not present, it will carry out the exploitation in a stealth mode, ultimately redirecting the user to the malicious page.
The Intensity of the Malvertising!
According to the researchers telemetry, these malicious Ads were delivered through two affiliate networks namely Adnxs, which has already resolved the issue, and Taggify, which has not paid any attention to the seriousness of the problem.
Two more expired media-related domains exhibiting the same characteristics as brentsmedia[.]com: "envangmedia[.]com" and "markets.shangjiamedia[.]com", shows that another similarly named domain has already been registered.
So there might be a possibility of hijacking "media" related branded domains for running malvertising campaigns, as a new generation threat to the global leaders.
EDA2, derived from the educational ransomware, is easy to break
16.3.2016 Ransomware
The new strain of educational ransomware EDA2 is infecting systems in the wild, but experts discovered that it is quite easy to neutralize.
Do you remember the EDA2 ransomware?
It is one of the educational ransomware developed by the security expert Utku Sen, now a new variant of the EDA2 educational ransomware appeared in the wild and the good news is that this variant is quite easy to neutralize.
The EDA2 ransomware encrypts victims’ files using AES encryption, then it appends the .locked extension to them. In a way similar to other ransomware, EDA2 also drops notes on the infected machines and informs users that they need to pay .5 bitcoins to restore their files.
According to the experts at Bleeping Computer, the educational ransomware has already infected more than 650 machines and the analysis of the Bitcoin address associated with the ransom request revealed that only 3 victims have paid.
The crooks are targeting online gamers, the EDA2 educational ransomware spread via a link associated with a YouTube video that explains how to crack the Far Cry Primal videogame. When victims try to execute the file crack are infected by the ransomware that encrypts users’ files.

The new strain of educational ransomware EDA2 is infecting systems in the wild, but experts discovered that it is quite easy to neutralize.
Do you remember the EDA2 ransomware?
It is one of the educational ransomware developed by the security expert Utku Sen, now a new variant of the EDA2 educational ransomware appeared in the wild and the good news is that this variant is quite easy to neutralize.
The EDA2 ransomware encrypts victims’ files using AES encryption, then it appends the .locked extension to them. In a way similar to other ransomware, EDA2 also drops notes on the infected machines and informs users that they need to pay .5 bitcoins to restore their files.
According to the experts at Bleeping Computer, the educational ransomware has already infected more than 650 machines and the analysis of the Bitcoin address associated with the ransom request revealed that only 3 victims have paid.
The crooks are targeting online gamers, the EDA2 educational ransomware spread via a link associated with a YouTube video that explains how to crack the Far Cry Primal videogame. When victims try to execute the file crack are infected by the ransomware that encrypts users’ files.

The author of the malware in a bold manner writes in the note that he would never get caught by the authorities.
Utku Sen, the developer that created the educational ransomware, seems to have deliberately inserted security flaws in both the Hidden Tear and EDA2 to sabotage cyber criminals using the proof-of-concept ransomware.
The Sen’s plan worked with the Hidden Tear allowing the recovery of the file encrypted by the Linux.Encoder and Cryptear.B ransomware, meanwhile failed with EDA2.
The developer also inserted vulnerabilities in the EDA2’s control script in order to retrieve decryption keys allowing victims to restore their files.
The keys are then published online giving the opportunity to the victims to restore their files by using the Hidden Tear Decryptor.
Other educational ransomware developed by the Hidden Tear are Magic, Linux.Encoder, and Cryptear.B, all these threats were deliberately affected by a flaw that allows researchers easily to decrypt documents.
A new massive spam campaign is spreading Locky ransomware downloaders
13.3.2016 Ransomware
Experts at Trustwave observed a new massive spam campaign that was sending a JavaScript attachment that downloads Locky ransomware.
Ransomware continues to be among most insidious threats in this first part of the year, security researcher have recently observed a spike in the number of Locky ransomware infections.
The experts from Trustwave security firm highlighted the worrying intensification around this threat.
The security researchers observed a new massive spam campaign serving Locky ransomware downloaders in the form of JavaScript attachments.
According to Trustwave, spam campaign aiming to spread malware has represented 18 percent of total spam in the last weeks, while typically this specific kind of spam represents less than 2 percent of total spam.
The experts linked the increment to the diffusion of ransomware JavaScript downloaders, Trustwave also noticed that the malicious spam was concentrated in bursts.
“Our Spam Research Database saw around 4 million malware spams in the last seven days, and the malware category as a whole accounted for 18% of total spam arriving at our spam traps.” states a blog post published by Trustwave. “The graph below shows hourly spam traffic for the malware category for the past 30 days – note the relatively low levels of activity to the left, and huge peaks on the right, representing the ransomware downloader campaigns. As you can see the campaigns are not continuous, but concentrated bursts, with peaks of 200K emails hitting our servers in a single hour.”

The researchers discovered that the Locky ransomware was spread through the same botnet used to spread the Dridex trojan.
“These campaigns are coming from the same botnet responsible for previously spammed documents with malicious macros which downloaded the Dridex trojan. The actors behind the campaigns have merely changed the delivery mechanism (.js attachment) and the end malware (ransomware).” states the report published by Trustwave.
The threat actors simply changed tactic and malware, in the case os Dridex they used email attachment disguised as an invoice, typically documents embedding malicious macro, the recent Locky ransomware campaign relies on JavaScript attachment that downloads the Locky code.
The Locky ransomware uses AES encryption algorithm to encrypt both local files and files on network shares, even if they are unmapped.
When started, Locky creates and assigns a unique 16 hexadecimal number to the infected machine, then he will scan all drives and unmapped network shares for files to encrypt.
The malware uses the AES encryption algorithm and encrypts only file with extensions matching a certain criteria while it skips files containing certain strings in their full pathname and filename (i.e. tmp, winnt, Application Data, AppData, Program Files (x86), Program Files, temp, thumbs.db, $Recycle.Bin, System Volume Information, Boot, and Windows).
The Locky ransomware encrypts files renaming the to [unique_id][identifier].locky, the researchers also discovered that the unique ID and other information are embedded at the end of the encrypted file.
The malware will also delete all of the copies of documents in the Shadow Volume, making impossible to restore files.
“Inside the Locky ransom notes are links to a Tor site called the Locky Decrypter Page. This page is located at 6dtxgqam4crv6rr6.onion and contains the amount of bitcoins to send as a payment, how to purchase thebitcoins, and the bitcoin address you should send payment to. Once a victim sends payment to the assigned bitcoin address, this page will provide a decrypter that can be used to decrypt their files.” BleepingComputer reports in a blog post.
KeRanger, the new MAC OS X ransomware that hit Apple users on the weekend
7.3.2016 Apple Ransomware
Over the weekend Apple customers who were looking for the latest version of Transmission were infected by KeRanger MAC OS X ransomware.
Bad news for Apple customers, their systems were targeted for the first time over the weekend by a ransomware campaign. The experts at Palo Alto Networks Unit 42 who discovered the malicious campaign reported that Apple customers who were looking for the latest version of Transmission, a popular BitTorrent client, were infected with a new family of Ransomware that was specifically designed to target OS X installations.
“On March 4, we detected that the Transmission BitTorrent ailient installer for OS X was infected with ransomware, just a few hours after installers were initially posted. We have named this Ransomware “KeRanger.” states the report published by Palo Alto Networks.
The researchers named this new Ransomware family KeRanger, they also released a technical analysis of the malware.
Ransomware attacks on MAC OS X systems is a novelty, in the past the unique malware with similar characteristics was FileCoder, a malicious code detected by Kaspersky Lab in 2014.
“The only previous ransomware for OS X we are aware of is FileCoder, discovered by Kaspersky Lab in 2014. As FileCoder was incomplete at the time of its discovery, we believe KeRanger is the first fully functional ransomware seen on the OS X platform.” continues the post.

According to the report, users who have directly downloaded Transmission installer from the official website in a specific time interval may be been infected by KeRanger MAC OS X ransomware.
“Users who have directly downloaded Transmission installer from official website after 11:00am PST, March 4, 2016 and before 7:00pm PST, March 5, 2016, may be been infected by KeRanger.”
The Transmission project promptly removed the malicious installers on Saturday (March 5) and it is urging its users to update to the latest version (2.92).
The experts discovered that the malware was embedded within the Transmission DMG file itself, but this was not enough to install the malware. The author of KeRanger also signed the installer with a valid code-signing certificate, issued to Polisan Boya Sanayi ve Ticaret A.ª., a holding company in Istanbul, to bypass security measured implemented by the Apple’s Gatekeeper.
The experts noticed that authors have used hidden services to masquerade the command and control infrastructure, once infected a machine the KeRanger MAC OS ransomware will wait three days before contacting a Command & Control server. Below the list of services in the Tor network used in the by the ransomware.
lclebb6kvohlkcml.onion[.]link
lclebb6kvohlkcml.onion[.]nu
bmacyzmea723xyaz.onion[.]link
bmacyzmea723xyaz.onion[.]nu
nejdtkok7oz5kjoc.onion[.]link
nejdtkok7oz5kjoc.onion[.]nu
Once the ransomware has contacted the server it starts encrypting documents having more than 300 different extensions:
Documents: .doc, .docx, .docm, .dot, .dotm, .ppt, .pptx, .pptm, .pot, .potx, .potm, .pps, .ppsm, .ppsx, .xls, .xlsx, .xlsm, .xlt, .xltm, .xltx, .txt, .csv, .rtf, .tex
Images: .jpg, .jpeg,
Audio and video: .mp3, .mp4, .avi, .mpg, .wav, .flac
Archives: .zip, .rar., .tar, .gzip
Source code: .cpp, .asp, .csh, .class, .java, .lua
Database: .db, .sql
Email: .eml
Certificate: .pem
It is interesting to note that the ransomware is not able to start the encrypting process without making the initial contact to C&C servers.
When the files are encrypted, the KeRanger MAC OS ransomware demands $400.00 USD to the victims
The researchers suspect that the KeRanger MAC OS ransomware is still under development, in fact, they noticed the malware doesn’t encrypt Time Machine backup files, but the analysis of the code revealed that the is code to perform this action is already present in the malware, but it is still not active.
“Additionally, KeRanger appears to still be under active development and it seems the malware is also attempting to encrypt Time Machine backup files to prevent victims from recovering their back-up data.”
To mitigate the infections, the digital certificate used to sign the code has been already revoked. Apple added the installers to the Gatekeeper blacklist and also updated XProtect signatures to include the new KeRanger Ransomware family.
CTB-Locker is back: the web server edition
1.3.2016 Zdroj: Kaspersky Ransomware
Cryptolockers have become more and more sophisticated, bypassing system protections and terrifying anyone in their path. TeslaCrypt, CryptoWall, TorrentLocker, Locky and CTB-Locker are only some of the malware we have protected from for the past two years. We have seen many shapes and colors of cryptolockers, but the new CTB-Locker variant says it all. The world of cybercriminals is investing in how to reinvent cryptolockers.
Before, CTB-Locker, or Onion Ransomware, differed from other ransomware in the usage of the Tor Project’s anonymity network to shield itself from takedown efforts that rely largely on static malware command and control servers. Its use of Tor also helped evading detection and blocking. Another thing that protected CTB-Locker controllers was accepting as payment only Bitcoins, the decentralized and largely anonymous crypto-currency known.
A new variant of the CTB-Locker targets web servers only, and to our knowledge it has already successfully encrypted web-root files in more than 70 servers located in 10 countries.
In this blogpost I will take you into the “lion’s den”, after victims were kind enough to share the cryptors that had been deployed into their web servers.
Step 1: defacement
This new variant aims to encrypt web servers and demand less than half a bitcoin as a ransom (~150 USD). If payment isn’t sent on time the ransom is doubled to approximately 300 USD. When paid, the decryption key is generated and is used to decrypt the web server’s files.
It has become clear that the web servers infected with this variant were targeted due to a security hole in their web server. Once exploited, the website is defaced. Defacement is a well-known method for hacking groups to show their victims they mean business. The most recent cases we’ve witnessed are not random, but mostly about political affiliations and cultural perspectives.
In this case, the defacement, which contains a replacement of the main php/html page, is used as the message carrier and contains all the means necessary for the attack to leave the right impression on the victim. We will deep-dive into it in the next steps.
It is important to mention that the original code is not deleted. It is stored safely in the web root with a different name in an encrypted state.
The message
As variants of malware of this kind are based on the simple fact that a victim cares more about his content than about paying a ransom, the authors usually leave a very detailed message for everyone to see.
The following quote is a part of the information that is left on the main page:
The decryption key is stored on a remote server, but the attackers were “kind enough” to allow the victim to decrypt two files free, as a sign of authenticity.
The other function that exists on the attacked website allows the victim to communicate with the attacker via chat: it requires a personal signature/code which is available for victims only.
At the moment, no decryption tool exists in the wild, thus there is no way to decrypt the files encrypted by the new CTB-Locker. The only way to remove this threat in a matter of seconds is to keep file backups in a separate location.
Although this seems like a big concern, we tend to believe that it is not. Large websites tend to have multiple versions of their content, spreading over a number of webservers. In many other cases, they are supervised and tested by professional security penetration testing firms and so are constantly under the magnifier.
Step 2: encryption process
We still don’t know how the CTB-Locker is being deployed on web servers, but there is one common thing among many of the attacked servers – they use the WordPress platform as a content management tool. WordPress contains many vulnerabilities in its non-updated versions and we already seen critical vulnerabilities presented last year. In addition, WordPress also has another weak spot – plugins. Those tiny enhancement features helps WordPress become what it is – a leader in the world of CMS. However, having third party plugins also makes the server more vulnerable to attacks, as plugin authors are not committed to any type of security measurements.
Once the malware author is inside WordPress system, he is able to replace the main website file and execute the encryption routine. The main file is renamed and saved in an encrypted state.
Two different AES-256 keys are deployed to the victim server:
create_aes_cipher($keytest) – encrypts the two files which can be decrypted free.
create_aes_cipher($keypass) – encrypts the rest of the files hosted on the server web root.
The two files are chosen by the authors and their names are saved in a text file.
The create_aes_cipher() accepts one parameter as the key and sends it to the standard Crypt_AES() function:
function create_aes_cipher($key) {
$aes = new Crypt_AES();
$aes->setKeyLength(256);
$aes->setKey($key);
return $aes;
}
1
2
3
4
5
6
function create_aes_cipher($key) {
$aes = new Crypt_AES();
$aes–>setKeyLength(256);
$aes–>setKey($key);
return $aes;
}
When encrypting the site, the script first uses the test key to encrypt the two files that will be used for free decryption. It will then generate a list of files that match specific file extensions and encrypt them using AES-256 encryption. The extensions that will be encrypted are read from the ./extensions.txt file and are currently:
Files that contain the following strings will be excluded from the encryption process:
“/crypt/”
“secret_”
In addition, files which are populated with data that will later assist the user with the decryption process would obviously be excluded as well.
./index.php – as described above, this file is the main door for the victim to analyze the attack and contains PHP code of the encryption/decryption routine.
./allenc.txt – contains a list of all encrypted files.
./test.txt – contains the files which are freely available for decryption.
./victims.txt – contains a list of all the files that are being encrypted or have already been encrypted.
./extensions.txt – contains the list of file extensions (see above).
./secret_ – as said, the victim is required to identify himself before the free decryption or chat is even possible.
On the main page of the CTB-Locker, attackers are using JQUERY to query proxy servers and verify payments. The following code was found in the page source code and the servers listed on the top are proxies which are used as another layer of protection, instead of the main server of the attackers:
Proxy servers which are part of the decryption process:
http://erdeni.ru/access.php
http://studiogreystar.com/access.php
http://a1hose.com/access.php
The ransomware servers are not permanent and are being replaced by new ones every certain period of time. We have identified the threat actor inspecting the server logs and analytics, as sometimes different checks resulted in the server shutting down and turned back on.
Step 3: proxy to C&C
The attackers are utilizing servers which were already attacked to traffic through another layer of protection. On a victim server’s source code, a JavaScript code reveals how the decryption process is sent through three different servers randomly, however those are not the C&C.
The above screenshot was taken from the access.php page, supposedly located in each one of the bot servers used as a proxy for the decryption process.
In white block is the actual C&C which has been hardcoded on each of the PHP pages (access.php).
When POST request is being sent with the right parameters, a socket instance is being created and sends a connect beam to the attacker’s C&C server. Later it is being determined if the decryption process succeeded.
Free decrypt
The ransomware allows the victim to freely decrypt not more than two files. It is not for the victim to choose, since the files are pre-chosen and can be found in the malware’s designated file as listed above. The two files are randomly picked during the course of the encryption process.
The following image is an illustration of the free decrypt module:
In order to decrypt the two free files, the victim is required to enter the secret_ file name. Once you click the DECRYPT IT FREE button, the client-side script builds a POST request and sends it to one of the C&C servers. We were able to imitate the PHP calculation and run the exit() function of the free decryption routine:
The following is the PHP code at the back-end. The function secret_ok() verifies the identity of the victim, based on his domain name and other indicators:
if (isset($_GET[‘dectest’]) && secret_ok()) {
decrypt_files(‘test.txt’, $_GET[‘dectest’]);
exit(‘Congratulations! TEST FILES WAS DECRYPTED!!’);
}
1
2
3
4
if (isset($_GET[‘dectest’]) && secret_ok()) {
decrypt_files(‘test.txt’, $_GET[‘dectest’]);
exit(‘Congratulations! TEST FILES WAS DECRYPTED!!’);
}
Threat actor’s chat room
The ransomware also includes functionality to communicate with the malware authors. As already said, the victim is required to use the secret_ key in order to open the chat. Without it, the chat will remain unresponsive.
We have come to the conclusion that ransomware is the new-generation malware for an attacker interested in financial gain. They are very effective, there is no solid solution against this threat thus far, and they are flexible to attack not only desktop operating systems, but now web servers as well.
We urge anyone to backup all important data; and to be cautious about emails which are not specifically meant for the user, or attractive ads that appear online. In addition, third party software must not be trusted automatically by its hash. This identifier can be changed by an attacker once a server has been compromised. Be sure to use other routine checks to ensure that the software is legitimate.
CTB-Locker Ransomware Spreading Rapidly, Infects Thousands of Web Servers
27.2.2016 Ransomware
In last few years, we saw an innumerable rise in ransomware threats ranging from Cryptowall to Locky ransomware discovered last week.
Now, another genre of ransomware had been branched out from the family of CTB-Locker Ransomware with an update to infect "Websites".
The newly transformed ransomware dubbed "CTB-Locker for Websites" exclusively hijacks the websites by locking out its data, which would only be decrypted after making a payment of 0.4 BTC.
This seems to be the very first time when any ransomware has actually defaced a website in an attempt to convince its administrator to comply with the ransom demand.
However, the infected website admins can unlock any 2 files by the random generator for free as a proof of decryption key works.
Here's How CTB-Locker for Websites Ransomware Works
The CTB-Locker ransomware replaces the index page (the original index.php or index.html) of the servers hosting websites with the attacker's defacement page (a new affected index.php).
The defacement page serves a message informing the site owners that their files have been encrypted, and they need to pay a ransom before a certain deadline.
Once encrypted, the compromised websites display the following message:
"Your scripts, documents, photos, databases and other important files have been encrypted with strongest encryption algorithm AES-256 and unique key, generated for this site."
The message also contains a step-by-step guide that helps the CTB-Locker victims to make the payment to a specific Bitcoin address.
FREE Key to Decrypt Any 2 Random Files
Soon after gaining the website control, the ransomware attacker submits two different AES-256 decryption keys to the affected index.php.
The first key would be used to decrypt any 2 random files from the locked files for free under the name of "test" which are chosen to demonstrate the decryption procedure.
Once the site administrator enters the filename and hit "Decrypt for Free," jquery would be fired up upon the request to test the decryption key in a C&C Server. When the key is received, it'll decrypt any 2 random files and display 'Congratulations! TEST FILES WAS DECRYPTED!!'
The other decryption key would be the one to decrypt rest of the seized files, after making the payment in Bitcoin to the attacker.
All the website's content would be encrypted using an AES-256 algorithm, and a unique ID would be generated for each infected website.
Nearly all possible types of files extensions are being affected by CTB-Locker Ransomware.
Live Session with Ransomware Attackers
Another unique characteristic of the ransomware is giving victims the ability to exchange messages with the ransomware attackers.
The ransomware developers have organized a chat room in such a way that the victims could talk with the ransomware creators after the specifying name of the secret file which is present in the same directory with index.php.
CTB Locker for Website → Modifies Packages in the Server
The CTB-Locker for Website package utilizes a variety of files described below:
index.php : The Main component of CTB-Locker for Websites and contains the encryption and decryption routines as well as the payment page.
allenc.txt : Contains a list of all encrypted files.
test.txt : Contains the path and filenames to two prechosen files that can be decrypted for free.
victims.txt : It contains a list of all files that are to be encrypted. However, the files that are already encrypted will remain in this list.
extensions.txt - The list of file extensions that should be encrypted.
secret_[site_specific_string] : The secret file used by the Free Decrypt and Chat functions and is located in the same folder as the index.php file.
Command and Control Server Location:
According to Benkow Wokned (@benkow_), a security researcher who discovered CTB-Locker for Website, found that the index.php page utilizes the jQuery.post() function to communicate and POST data to the Ransomware's Command and Control (C&C) servers.
Currently, there are three Command and Control servers for CTB-Locker for Websites uncovered by the researchers:
http://erdeni.ru/access.php
http://studiogreystar.com/access.php
http://a1hose.com/access.php
The ransomware also gives a timeslot for the website administrators to recover the files. However, failure to pay the BTC in time would double the ransom amount by 0.8 BTC.
CTB-Locker for Windows
CTB-Locker for Websites isn't the only latest development with this family of ransomware. The ransomware has come to the Windows environment by using executables code signed with a stolen certificate.
Usually, the purpose of digital signature is to authenticate the public about the genuinity of the products. The certificates are provided only after a background check conducted by the Certificate Authorities (CA) like Verizon, DigiCert.
But the cybercriminal group behind the CTB-Locker ransomware has tampered the genuinity of digital certificates. The executable version in the Windows of the CTB Ransomware comes with a pre-signed digital signature.
Uses Encryptor Raas For Code-Signing Certificate
The group behind CBT believed to had taken the advantage of Jeiphoos, another ransomware developer who lets people go to his "Encryptor RaaS" Tor site that provides free digital signature certificates and sign any executable using stolen code-signing certificate.
The act of stealing digital signatures is not new as they are included in the frames from the past years.
Hijacking a company website would economically affect the services that are being offered to users via websites, elevating the issue to another level. However, the major part lies in the POS (Point of Sale) attack, if the threat infects an e-commercial website.
Currently, many websites had been compromised by "CBT-Locker for Website." As per the analysis, many wordpress sites (most of the static web pages) has been found to be targeted by CBT Website Locker.
Since this is not a serious issue like the Locky ransomware that utilizes Macros, the website administrator can make use of the untouched mirrors (backups) to bring back the site into action.
Ransomware attacks paralyzed at least two German hospitals
27.6.2016 Ransomware
New ransomware infections hit hospitals in Germany, at least two of them were infected by the dreaded malware.
According to local reports, the systems at two German hospitals were infected by a ransomware, in a similar way occurred recently at the US Hollywood Presbyterian Medical Center.
According to the German broadcaster Deutsche Welle, the German hospitals infected by the ransomware are the Lukas Hospital in the city of Neuss and the Klinikum Arnsberg hospital in North Rhine-Westphalia.
German hospitals infected by malware Lukas Hospital in the city of Neuss
“Several hospitals in Germany have come under attack by ransomware, a type of virus that locks files and demands cash to free data it maliciously encrypted. It will take weeks until all systems are up and running again.” reported the broadcaster.
A few weeks ago, the staff at the Lukas Hospital noticed a progressive deterioration of system performance, while error messages were popping up.
“We then pulled the plug on everything,” spokesperson Dr. Andreas Kremer told DW. “Computers, servers, even the email server, and we went offline.”
The ransomware paralyzed the hospital’s architecture, the incident occurred on February 10, 2016. The internal IT staff will take weeks until everything’s back to normal.
“Our IT department quickly realized that we caught malware that encrypts data. So if the X-ray system wants to access system data, it failed to find it because it’s been encrypted, so it displays an error message,” Kremer said.
The staff at the hospital used phone and fax to communicate with patients, the staff explained that a number of high-risk surgeries have been postponed because of the cyber attack.
The hospital reported the incident to the authorities and to the State Criminal Investigation Office (LKA) which are currently investigating on the case.
“We haven’t received a concrete demand for money, but we’ve seen these pop up windows that appear if you don’t stop the ransomware on a computer,” he told DW. The message in broken English points to an anonymous email address to get in touch with. “Following the Criminal Police Office’s advice, we didn’t do that,” Kremer said.
Fortunately, the IT staff at the hospital makes regular backups of the data.
“We have regular backups, so that isn’t a problem. If the virus encrypted data we have backed up, we just restore the backup files,” Kremer said.
The incident at Klinikum Arnsberg occurred a couple of days later, also in this case the systems were infected by a ransomware that was spread through phishing emails.
In this case, only one of 200 servers was infected by the malware, the IT staff recovered the situation by restoring a working backup.
“According to present knowledge, it was an attachment in an email that allowed the virus to enter the system,” Klinikum Arnsberg spokesperson Richard Bornkeßel told DW. “Fortunately, it was only one server that was affected. The virus had started to encrypt files, but we could simply restore them from a backup,”
Both German hospitals haven’t paid the ransom.
Admedia attacks now rely also on Joomla to serve ransomware
22.2.2016 Ransomware
Operators running websites based on the WordPress and Joomla must be aware of a spike in the number of compromised platforms used in Admedia attacks.
Not only WordPress CMS, threat actors behind the “Admedia attacks” are now looking with increasing interest to Joomla. This is the discovery made by the experts at the Internet Storm Center (ISC) that discovered the presence of the bad actors responsible of the Admedia attacks, behind a hacking campaign that targeted Joomla-hosted sites.
Early February, experts at Sucuri reported a spike in compromised WordPress sites generating hidden iframes with malicious URLs referencing domain hosting exploit kit. The researchers at Sucuri observed the use of the string “admedia” in most URLs generated by the iframes.
“These “admedia” URLs act as a gate between the compromised website and the EK server. EK traffic associated with this campaign has generally sent TeslaCrypt ransomware. However, characteristics of this campaign have evolved since Sucuri’s original blog post.” states an analysis published by the Internet Storm Center (ISC).
The campaign is evolving, on Wednesday 2016-02-17 Brad Duncan, security researcher at Rackspace, discovered the new attack chain. The attacks started with a compromised website that generated an admedia gate, which led to Angler EK that is used to serve TeslaCrypt to vulnerable machines. The experts also highlighted that crooks behind the admedia attacks that initially relied on Nuclear exploit kit on compromised sites, now added the Angler exploit kit.
The analysis of the traffic generated by the malware allowed the ISC to identify the following components:
178.62.122.211 – img.belayamorda.info – admedia gate
185.46.11.113 – ssd.summerspellman.com – Angler EK
192.185.39.64 – clothdiapersexpert.com – TeslaCrypt callback traffic
The attackers compromised website generate the admedia gate by injecting malicious scripts.
“As the Sucuri blog already reported, each .js file returned by the compromised site had malicious script appended to it. In a case on 2016-02-15, I also saw the same type of script included in an HTML page from the compromised website; however, today’s traffic only shows injected script in the .js files.” Duncan wrote.

The above image demonstrates that attackers have started using “megaadvertize” in their gateway URLs, instead of “admedia.”
Locky Ransomware uses AES to encrypt Local Files and Unmapped Network Shares
20.2.2016 Ransomware
Security researchers discovered a strain of ransomware called Locky that uses AES encryption to encrypt local files and files on network shares.
Security researchers have discovered a new piece of ransomware called Locky, which uses AES encryption algorithm to encrypt both local files and files on network shares, even if they are unmapped.
Security experts at BleepingComputer spotted a new strain of ransomware dubbed Locky that encrypts local files and files on network shares by using the AES encryption.
“A new ransomware has been discovered called Locky that encrypts your data using AES encryption and then demands .5 bitcoins to decrypt your files. ” BleepingComputer reports in a blog post.
The experts noticed that Locky is the second ransomware spotted in the last months that is able to encrypt files on unmapped network shares, a trend that results from the availability online of the source code of ransomware like Hidden Tear.
The Locky ransomware is being spread via malicious emails with Word document attachments that pretend to be an invoice, but that includes malicious macros. When the victim enables macros to view the document, it triggers a downloader for the Locky ransomware. The malware is then downloaded from a remote server and executed.
Like the CryptoWall ransomware, Locky uses to change the filenames of encrypted files to make harder data recovery.
When started, Locky creates and assigns a unique 16 hexadecimal number to the infected machine, then he will scan all drives and unmapped network shares for files to encrypt.
The malware uses the AES encryption algorithm and encrypts only file with extensions matching a certain criteria while it skips files containing certain strings in their full pathname and filename (i.e. tmp, winnt, Application Data, AppData, Program Files (x86), Program Files, temp, thumbs.db, $Recycle.Bin, System Volume Information, Boot, and Windows).
The Locky ransomware encrypts files renaming the to [unique_id][identifier].locky, the researchers also discovered that the unique ID and other information are embedded at the end of the encrypted file.
The malware will also delete all of the copies of documents in the Shadow Volume, making impossible to restore files.
Locky leaves a ransom note, the _Locky_recover_instructions.txtin, in each folder containing encrypted files.

“Inside the Locky ransom notes are links to a Tor site called the Locky Decrypter Page. This page is located at 6dtxgqam4crv6rr6.onion and contains the amount of bitcoins to send as a payment, how to purchase the bitcoins, and the bitcoin address you should send payment to. Once a victim sends payment to the assigned bitcoin address, this page will provide a decrypter that can be used to decrypt their files.” continues the post.
“Locky will change the Windows wallpaper to %UserpProfile%\Desktop\_Locky_recover_instructions.bmp, which contains the same instructions as the text ransom notes.”
Ransomware demanded $3.6M after takes offline the Hollywood Presbyterian Medical Center
16.2.2016 Ransomware
Cyber criminals demanded $3.6M after a ransomware-based attack takes offline the systems at the Hollywood Presbyterian Medical Center.
In the “2016 Cyber Security Predictions: From Extortion to Nation-state Attacks” I published at the end of 2015 I have predicted the criminal practices of the extortion will reach levels never seen before.
“Cyber criminals will use threaten victims with ransomware and DDoS attack in an attempt to extort money to stop the attacks or to allow victims to rescue the locked files. Ransomware will be used to target IoT devices like SmartTV, wearables and medical devices.” I wrote in a blog post, and the facts are confirming my expectations.
In the last weeks, a new wave of ransomware targeted million users in Europe, but probably the news is more sensational when the victims are public services like hospitals or power facilities. In January, the Israeli Public Utility Authority suffered a serious incident that caused problems with the systems of the institution, now we discuss other disconcerting news, the computers at Hollywood Presbyterian Medical Center have been down for more than a week due to a ransomware infection.
A local computer consultant revealed to the media that the ransom being demanded was about 9,000 BTC, or just over $3.6 million dollars.
Now the situation has been restored and all the machines have been sanitized, while law enforcement is still investigating the case. Computers storing patients’ data, CT scans, Hospital’s documentation, and lab data went offline.
Hollywood Presbyterian Medical Center ransomware
Unfortunately, the staff at Hollywood Presbyterian Medical Center faced the paralysis of internal services due to the cyber attack.
[The Hollywood Presbyterian Medical Center] reported “significant IT issues and declared an internal emergency” Feb. 5, said hospital president and CEO Allen Stefanek.
The NBC Los Angeles reported the case of a patient that had to drive more than an hour to Palmdale to pick up medical tests in person.
Stefanek also added that hospital’s emergency room systems have been sporadically impacted by the ransomware forcing the displacement of some patients to other hospitals.
The Hospital continued to work but any activity relying on IT system was impacted, registrations and medical records were logged on paper.
The experts at the Hollywood Presbyterian Medical Center haven’t provided technical details about the incident, it is not clear which family of malware infected the systems.
Here's How to Decrypt Hydracrypt & Umbrecrypt Ransomware Files
13.2.2016 Ransomware
Over the last few years, we have seen several types of Ransomware malware that demand a whopping amount of money from users for the retrieval of their locked, compromised sensitive files.
We have also witnessed the birth of decryption solution for some of the Ransomware like Cryptolocker (partial), Coinvault, Rescue Kit.
One more solution has recently been released for decryption of newly emerging ransomware, dubbed as Hydracrypt and Umbrecrypt that are propagated through Angler Exploit Kit.
Both of the malware belong to CrypBoss ransomware family.
The source code of CrypBoss Ransomware was leaked last year on Pastebin, which was later analyzed by Fabian Wosar, a security researcher at Emsisoft.
With the help of CrypBoss Source code, Wosar was successfully able to crack the encryption algorithm of the ransomware and quickly made the decryption tool for CrypBoss and its variants (Hydracrypt and Umbrecrypt).
It is found that both Hydracrypt and Umbrecrypt share the same genealogy which got traced back to CrypBoss Ransomware with small modifications in the implementation by its authors.
"Unfortunately the changes made by the HydraCrypt and UmbreCrypt authors cause up to 15 bytes at the end of the file to be damaged irrecoverably" Wosar stated.
The damaged bytes in the encrypted files are trivial (in most of the cases) since it would be used as a buffer data or some trailing bytes, which could easily be re-build by using any file repairing tool (for those 15 bytes).
This doesn't affect much of the decryption process as 99 percent of the files are retrieved without any harm using the released decryptor tool that is available Free to download.
How to Decrypt Ransomware Files?
Double clicking the decryptor executable would initialize the decryption process, and you would get the key once the task gets completed. The time taken to crack the encryption would also depend upon your system's Flip-Flop power.
Once the decryption key is generated, it is better to save it as a hard copy (by writing down in the paper). Now you can run the decryptor tool and select the intended folders to get unlocked. Enter the key once the decryptor tool prompts for it.
To avoid a hotch-potch, users are advised to:
Run the decryptor for a small number of files initially to check whether the decryption procedure is being executed properly.
This would deliver the file ensurity and saves your time.
Make sure whether enough space is present in the hard-drive, so as to take place the decryption.
How to Ensure your Decrypted Data is Legit?
Here's How to Decrypt Hydracrypt & Umbrecrypt Ransomware Files
However, the security team also stated that the result of the Decryption might not be correct as the ransomware, unfortunately, does not leave any information about the original file behind.
To ensure the proper file recovery, initially you have to select the encrypted file along with its original version (somewhere in your cloud or anywhere) and pass it to the decryptor executable by a simple drag-and-drop.
[Note: If you haven't found such, then users can also get a random encrypted file and a random PNG image off the Internet.]
If the resultant output is legit, then you can carry out the same task with the remaining files. As the same algorithm is being followed in the remaining encrypted files, then you would get your files back as normal.
Emergency. Hundreds of compromised WordPress sites serve TeslaCrypt ransomware
5.2.2016 Ransomware
Operators running websites based on the WordPress must be aware of a spike in the number of compromised platforms used to deliver the TeslaCrypt ransomware.
Administrators running websites based on the popular WordPress CMS must be aware of a spike in hacks that are resulting in the silent delivery of ransomware to the visitors.
According to the experts at the Heimdal Security, threat actors hacked WordPress-based sites to redirect victims to other domains hosting the Nuclear Exploit Kit.
People who visit the compromised WordPress sites using out-of-date versions of popular software, including Flash Player, Adobe Reader and Internet Explorer, can be infected with the Teslacrypt ransomware. The experts at Heimdal discovered that the attackers behind the current WordPress compromises were exploiting an unidentified vulnerability with obfuscated JavaScript. The code redirects victim to the domain chrenovuihren that serves an online ad that forces traffic to the site hosting Nuclear.
“Our team warns that a disproportionate amount of websites that employ the WordPress platform have been compromised by cyber criminals. Hundreds of WordPress websites spreading malware. The attackers fed obfuscated Javascript code to these websites. The users who end up on the hacked websites are redirected on a domain called “chrenovuihren” via multiple servers.” states a blog post published by Heimdal Security.

It isn’t the first time that the Nuclear Exploit Kit is used to drop ransomware, in November it Kit has been used for the first time to serve the ransomware CryptoWall 4.0, meanwhile in the past criminal groups used it to serve instances of the CryptoWall 3.0.
The Heimdal Security researchers identified three IP addresses of Nuclear EK gateways:
159,203.24 [.] 40
164,132.80 [.] 71
162,243.77 [.] 214
The campaign relies on a number of domains to spread the malware, the domains are all subdomains of the chrenovuihren.
“The campaign makes use of several domains to deliver the malicious code, which is why active servers can quickly change depending on which IP as DNS lookup they use,” continues the post.
“We have already blocked more than 85 domains that are being actively used in this campaign, and the list will most likely increase.”
The bad news it the low detection rate for this threat, just 2 of 66 antivirus solutions on VirusTotal are able to detect the malicious agent.
This last campaign based on compromised WordPress-based websites comes a few days later another massive hacking campaign has been identified by experts at Sucuri, the researchers at Heimdal speculate the involvement of the same threat actors for both campaigns.
Website owners based on WordPress must protect their servers and let me share with you, once again, the following key recommendations to get protected against ransomware:
Keep software and your operating system updated at all times
Backup your data, do it often and in multiple locations
Use a security tool that can filter your web traffic and protect you against ransomware, which traditional antivirus cannot detect or block.