
Ransomware Articles - H 2020 1 2 3 4 5 6 7 8 9 10 11 Ransomware List - H 2021 2020 2019 2018 1 Ransomware blog Ransomware blog
SeaChange video delivery provider discloses REVIL ransomware attack
10.9.20 Ransomware Securityaffairs
US-based supplier of video delivery software solutions, SeaChange International, revealed that a ransomware attack disrupted its operations in Q1 2020.
SeaChange International, a US-based supplier of video delivery software solutions, revealed that a ransomware attack has disrupted its operations during the first quarter of 2020.
SeaChange’s customers include major organizations such as BBC, Cox, Verizon, AT&T, Vodafone, Direct TV, Liberty Global, and Dish Network Corporation.
In April, SeaChange International was the victim of the Sodinokibi Ransomware gang.
At the time of the attack, the ransomware operators published images of the data they claim to have stolen before encrypting the systems at the company.
The news was also confirmed by the experts at the data breach notification service Under the Breach.
Sodinokibi/REVil ransomware operators posted images of SeaChange’s data on the leak site, they have created a page to the company containing images of allegedly stolen documents.
These images include a screenshot of folders on a SeaChange server compromised by the gang, insurance certificates, a driver’s license, and a cover letter for a proposal sent to the Pentagon.
After months of silence, SeaChange finally confirmed the ransomware attack, the company filed a 10-Q quarterly report with the US Securities and Exchange Commission (SEC).
“In the first quarter of fiscal 2021, we experienced a ransomware attack on our information technology system,” reads the report.
“While such attack did not have a material adverse effect on our business operation, it caused a temporary disruption. A forensic investigation is being conducted to determine if any data was compromised.”
The company did not disclose details of the attack, at the time the experts from BadPackets pointed out that attackers might have exploited the Pulse Secure VPN CVE-2019-11510 to compromise the company.
BadPackets reported that SeaChange had a Pulse Secure VPN server (https://vpn.schange.com ) vulnerable to CVE-2019-11510 from April 24, 2019 until March 24, 2020.
Recently, the Chilean bank BancoEstado, one of the country’s biggest banks, was forced to shut down all branches following a REVil ransomware attack..
The REvil ransomware gang is one of the most active groups, in the past, the operators have targeted Pulse Secure and Citrix VPN and enterprise gateway systems as entry points.
The list of victims is long and includes Telecom Argentina, Sri Lanka Telecom, Valley Health Systems, Australian firm Lion, Brown-Forman, the electrical energy company Light S.A., and Elexon electrical middleman.
Zeppelin Ransomware Returns with New Trojan on Board
10.9.20 Ransomware Threatpost
The malware has popped up in a targeted campaign and a new infection routine.
The Zeppelin ransomware has sailed back into relevance, after a hiatus of several months.
A wave of attacks were spotted in August by Juniper Threatlab researchers, making use of a new trojan downloader. These, like an initial Zeppelin wave observed in late 2019, start with phishing emails with Microsoft Word attachments (themed as “invoices”) that have malicious macros on board. Once a user enables macros, the infection process starts.
Threatpost Webinar Promo Bug Bounty
Click to Register
In the latest campaign, snippets of Visual Basic scripts are hidden among garbage text behind various images. The malicious macros parse and extract these scripts, and write them to a file at c:\wordpress\about1.vbs.
A second macro then looks for the string “winmgmts:Win32_Process” inside the document text, and uses it to execute about1.vbs from disk. About1.vbs is the aforementioned trojan downloader, which ultimately downloads the Zeppelin ransomware onto a victim’s machine.
The binary sleeps for 26 seconds “in an attempt to out-wait dynamic analysis in an automated sandbox and then runs the ransomware executable,” according to the recently released analysis. “As with previous versions, the Zeppelin executable checks the computer’s language settings and geolocation of the IP address of the potential victim to avoid infecting computers in Russia, Belarus, Kazakhstan and Ukraine.”
As for attribution, according to previous research from Vitali Kremez, Zeppelin is a simple piece of code that’s distributed via an affiliate business: The malware is generated via a GUI wizard and offered to distributors in return for a revenue share.
The latest campaign has affected around 64 known victims and targets, Juniper researchers noted, indicating a certain level of targeting. It may have started in June 4, when the command-and-control (C2) server that the malware uses was registered; and passive DNS data shows that it ran until at least Aug 28; August 28 is the most recent name resolution for the C2 domain, according to passive DNS data.
“[This] could indicate the malware has not infected new networks in the last few days,” according to the post.
Zeppelin is a variant of the Delphi-based ransomware-as-a-service (RaaS) family initially known as Vega or VegaLocker, which emerged at the beginning of 2019 in advertisements on the Russia-based Yandex.Direct – according to BlackBerry Cylance. Unlike its predecessor, Zeppelin is much more targeted, and first took aim at targeted tech and healthcare companies in Europe and the U.S.
Start of School in Hartford Delayed by Ransomware Attack
9.9.20 Ransomware Securityweek
One the worst cyberattacks yet against Connecticut’s capital city forced officials to postpone the first day of school Tuesday, disrupting the day for thousands of families as city computer experts rushed to restore systems vital for school operations.
Hartford Mayor Luke Bronin said the hacker or hackers indicated it was a ransomware attack, but only left an email address to contact and made no specific ransom demand. The problem was discovered Saturday and numerous systems were affected, including one used to communicate transportation routes and live information to school bus drivers.
Tuesday was supposed to be the first day of school for the district of about 18,000 students. Both in-person and remote learning have now been pushed back by the attack, officials said. A new start date has not been announced.
“We are often the subject of cyberattacks,” Bronin said at a news conference. “This was, however, the most extensive and significant attack that the city has been subject to ... certainly in the last five years.”
Much of the damage had been repaired by Monday night. The city’s $500,000 worth of cybersecurity improvements implemented last year prevented officials from being locked out of the city’s systems, Bronin said.
Superintendent of Schools Leslie Torres-Rodriguez announced the school opening postponement early Tuesday morning and said officials were checking to see if any school staff computers were affected by the attack.
“We are heavily relying on all of our technology and on our staff’s ability to access technology in order to deliver remote instruction, given that more than half of our student population has elected to learn remotely,” she said. “The team ... is trying to assess the impact throughout all of our 40 schools.”
Torres-Rodriguez said city schools were ready to open with a variety of coronavirus precautions. School officials said pre-kindergarten through ninth grade were to be fully in person, while a hybrid system of in-school and remote learning will be used for grades 10 through 12, under the currently low virus rate of fewer than 10 new cases per 100,000 population over a seven-day average.
Many parents took to social media Tuesday to express disappointment over the first day of school being postponed, with their children looking forward to returning to classes and seeing their friends. Some also were upset at what they called last-minute notice of the delay, noting officials knew about the problem since the weekend.
Kate Court said her 13-year-old son was already dressed and ready to go to the bus stop when she discovered the postponement. A New Britain resident and shipping warehouse worker, Court’s teenager attends a Hartford magnet school and her 8-year-old son goes to a Hartford elementary school.
“I didn’t get the message until 6 a.m.,” she said. “It’s pretty ridiculous. I’m a lucky one in that my mom was home to watch them. If not, I would have ... had to miss work.”
“This is crazy,” she said “We’re looking for normalcy again, whatever that may be.”
School officials said that while most of the computer systems were restored by Monday night, they did not learn until early Tuesday morning that the bus transportation system was still down.
Ransomware attacks targeting state and local governments have been on the rise, with cyber criminals seeking quick money by seizing data and holding it hostage until they get paid.
City officials say it wasn’t clear how the hacker or hackers gained access to city systems or if the attack was aimed at delaying the opening of school. Bronin said it appeared no sensitive personal or financial information was stolen in the attack.
More than 200 of the city’s 300 computer servers were disrupted. Besides the schools, the police department systems for report writing and video cameras also were affected, but there were no problems with the 911 system, Police Chief Jason Thody said.
City police were working with the FBI to try to identify who was behind the attack.
Newcastle University infected with DoppelPaymer Ransomware
8.9.20 Ransomware Securityaffairs
UK research university Newcastle University suffered a DoppelPaymer ransomware attack and took its systems offline in response to the attack.
UK research university Newcastle University was infected with the DoppelPaymer ransomware, in response to the incident it was forced to take systems offline on the morning of August 30th.
The Newcastle University did not provide info about the family of ransomware behind the attack, but the DoppelPaymer ransomware operators are claiming to be responsible. The gang already leaked 750Kb worth of stolen data on their data leak site ‘Dopple Leaks.’
IT staff at the university announced it will take several weeks to get the services back online after the attack.
The Newcastle University IT Service (NUIT) reported the incident to the UK Police and the National Crime Agency that is investigating the incident.
The Information Commissioner’s Office (ICO) and Office for Students were notified within 72 hours of the attack.
“On Sunday 30 August 2020, we became aware that the University had suffered a serious cyber incident which is causing operational disruption across our networks and IT systems,” reads the data breach notification.
“All University systems – with the exceptions of those listed in the communications (Office365 – including email and Teams, Canvas and Zoom) are either unavailable or available but with limitations. Access may cease at any point.”
At the time, the university hasn’t yet forced a password reset for its users, an action that could be adopted in the next hours as part of the incident response procedure conducted by the IT staff and external consultants.
Multiple services are still offline and other systems that are up and running could be taken offline if requested as part of the recovery and response procedure. The online payments portal is managed off-site by the university’s payment services provider and is not held on Newcastle University servers.
Students and employees can still access to a limited set of IT services including Office365 (email, Office apps, Teams), Canvas, and Zoom.
Students and staff are recommended to copy their files to their OneDrive accounts.
“Where appropriate, we advise you to copy and save business-critical data and files to your OneDrive,” reads an update provided by the university. “New files can also be created and saved on your OneDrive. Please only transfer essential files and do not copy or send files to your personal accounts.”
DoppelPaymer ransomware has been active since June 2019, in November Microsoft Security Response Center (MSRC) warned customers of the DoppelPaymer ransomware and provided useful information on the threat.
Chilean bank BancoEstado hit by REVil ransomware
8.9.20 Ransomware Securityaffairs
Chilean bank BancoEstado, one of the country’s biggest banks, was forced to shut down all branches following a ransomware attack.
Chilean bank BancoEstado, one of the country’s biggest banks, was hit with a ransomware attack that forced its branches to remain closed since September 7.
The ransomware encrypted most of the company servers and workstations.
The attack took place over the weekend, the closure of the BancoEstado breaches was announced by the bank through its Twitter account.
The bank disclosed the attack on Sunday via Twitter and decided to keep branches closed to investigate the incident and recover its systems.
“Our branches will not be operational and will remain closed today,” reads the statement published on Twitter.
The bank launched an investigation into the incident and reported it to Chilean police.
The Chilean CSIRT also issued a cyber-security alert warning about a ransomware campaign targeting the private sector.
According to ZDNet that cited a source close to the investigation, the Chilean bank was attacked by the REvil ransomware operators, but at the time of writing the BancoEstado’s data have yet to be published on the gang’s leak site.
“Investigators believe that on the night between Friday and Saturday, hackers used this backdoor to access the bank’s network and install ransomware.” reported ZDNet. “Bank employees working weekend shifts discovered the attack when they couldn’t access their work files on Saturday.”
Threat actors used the malicious Office file to deliver a backdoor on the bank’s infrastructure and use it as the entry point. It seems that the attack vector was a series of spam messages using weaponized Office documents.
According to the bank, its website, the banking portal, mobile apps, and the ATM network were not impacted thanks to a good design of the BancoEstado’s infrastructure.
The REvil ransomware gang is one of the most active groups, in the past, the operators have targeted Pulse Secure and Citrix VPN and enterprise gateway systems as entry points.
The list of victims is long and includes Telecom Argentina, Sri Lanka Telecom, Valley Health Systems, Australian firm Lion, Brown-Forman, the electrical energy company Light S.A., and Elexon electrical middleman.
In June 2018, North Korea-linked hackers hit another bank in Chile, the Banco de Chile infecting its system with a wiper.
Japan, France, New Zealand Warn of Sudden Uptick in Emotet Trojan Attacks
7.9.20 Ransomware Thehackernews
Cybersecurity agencies across Asia and Europe have issued multiple security alerts regarding the resurgence of email-based Emotet malware attacks targeting businesses in France, Japan, and New Zealand.
"The emails contain malicious attachments or links that the receiver is encouraged to download," New Zealand's Computer Emergency Response Team (CERT) said. "These links and attachments may look like genuine invoices, financial documents, shipping information, resumes, scanned documents, or information on COVID-19, but they are fake."
Echoing similar concerns, Japan's CERT (JPCERT/CC) cautioned it found a rapid increase in the number of domestic domain (.jp) email addresses that have been infected with the malware and can be misused to send spam emails in an attempt to spread the infection further.
First identified in 2014 and distributed by a threat group tracked as TA542 (or Mummy Spider), Emotet has since evolved from its original roots as a simple banking Trojan to a modular "Swiss Army knife" that can serve as a downloader, information stealer, and spambot depending on how it's deployed.
In recent months, the malware strain has been linked to several botnet-driven malspam campaigns and even capable of delivering more dangerous payloads such as Ryuk ransomware by renting its botnet of compromised machines to other malware groups.
The new uptick in Emotet activity coincides with their return on July 17 after a prolonged development period that lasted since February 7 earlier this year, with the malware sending as many as 500,000 emails on all weekdays targeting European organizations.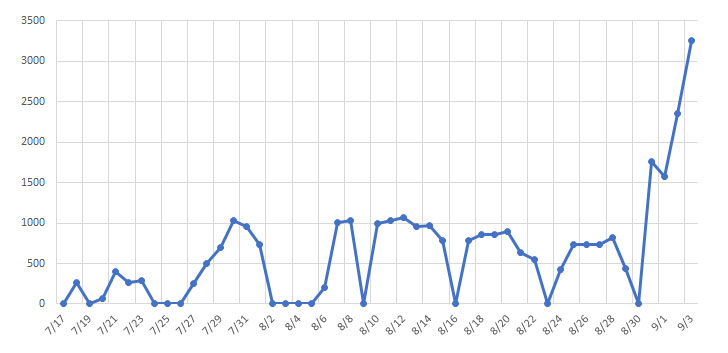
"Around February 7, Emotet entered a period of time where they stopped spamming and began working on developing their malware," Binary Defence outlined in a report last month detailing an exploit (called EmoCrash) to prevent the malware from affecting new systems.
Typically spread via large-scale phishing email campaigns involving malicious Microsoft Word or password-protected ZIP file attachments, the recent wave of attacks have taken advantage of a technique called email thread hijacking, using it to infect devices with the TrickBot and QakBot banking Trojans.
It works by exfiltrating email conversations and attachments from compromised mailboxes to craft convincing phishing lures that take the form of a malicious response to existing, ongoing email threads between the infected victim and other participants in order to make the emails seem more credible.
"TA542 also constructs phishing emails on the basis of information collected during the compromise of mailboxes, which it sends to exfiltrated contact lists, or more simply spoofs the image of entities, prior victims," the National Cybersecurity Agency of France (ANSSI) said.
In addition to using JPCERT/CC's EmoCheck tool to detect the Emotet trojan's presence on a Windows machine, it's recommended that network logs are routinely scanned for any connection to known Emotet command-and-control (C2) infrastructure.
"Since returning from an extended vacation, TA542 email campaigns are once again the most prevalent by message volume by a large margin, with only a few other actors coming close," Proofpoint said in an exhaustive analysis of Emotet last month.
"They have introduced code changes to their malware, such as updates to the email sending module, and picked up a new affiliate payload to distribute (Qbot), [and] expanded targeting of countries using native language lures.
Ransomware attack halts Argentinian border crossing for four hours
7.9.20 Ransomware Bleepingcomputer
Argentina's official immigration agency, Dirección Nacional de Migraciones, suffered a Netwalker ransomware attack that temporarily halted border crossing into and out of the country.
While ransomware attacks against cities and local agencies have become all too common, this may be a first known attack against a federal agency that has interrupted a country's operations.
According to a criminal complaint published by Argentina's cybercrime agency, Unidad Fiscal Especializada en Ciberdelincuencia, the government first learned of the ransomware attack after receiving numerous tech support calls from checkpoints at approximately 7 AM on August 27th.
"Being approximately 7 a.m. of the day indicated in the paragraph above, the Directorate of Technology and Communications under the Directorate General Information Systems and Technologies of this Organization received numerous calls from various checkpoints requesting technical support."
"This realized that it was not an ordinary situation, so it was evaluated the situation of the infrastructure of the Central Data Center and Servers Distributed, noting activity of a virus that had affected the systems MS Windows based files (ADAD SYSVOL and SYSTEM CENTER DPM mainly) and Microsoft Office files (Word, Excel, etc.) existing in users' jobs and shared folders," a translation of the complaint stated.
To prevent the ransomware from infecting further devices, the computer networks used by the immigration offices and control posts were shut down.
According to Argentinian news site Infobae, this led to a temporary suspension of border crossings for four hours while the servers were brought back online.
"The Comprehensive Migration Capture System (SICaM) that operates in international crossings was particularly affected, which caused delays in entry and exit to the national territory," the National Directorate of Migration (DNM) stated.
Government sources told Infobae that "they will not negotiate with hackers and neither they are too concerned with getting that data back."
Netwalker demands a $4 million ransom
When the Netwalker performs a ransomware attack, ransom notes will be left on devices that have been encrypted.
These ransom notes contain links to a dark web payment site that contains information on how to purchase a decryptor, the ransom amount, and information about any unencrypted files that were stolen during the attack.
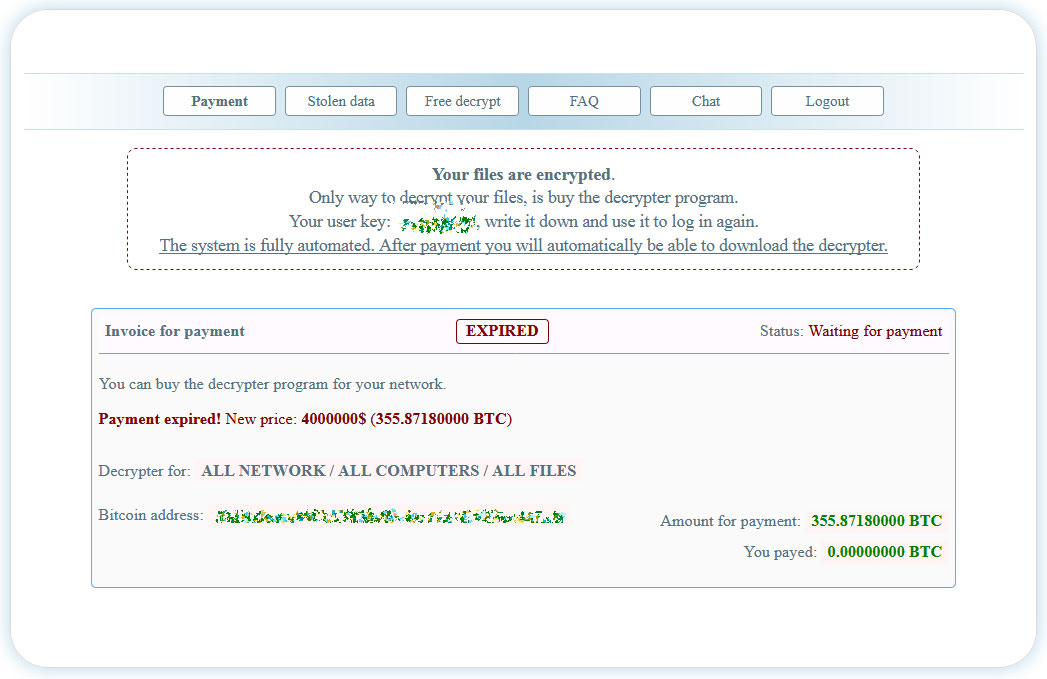
From a Netwalker Tor payment page shared with BleepingComputer, we have learned that the ransomware actors initially demanded a $2 million ransom.
After seven days passed, the ransom increased to $4 million, or approximately 355 bitcoins, as shown below in the image of Dirección Nacional de Migraciones's ransom page.
This Tor site also includes a 'Stolen Data' page that displays a screenshot of data stolen from "Migraciones Argentina" during this attack.
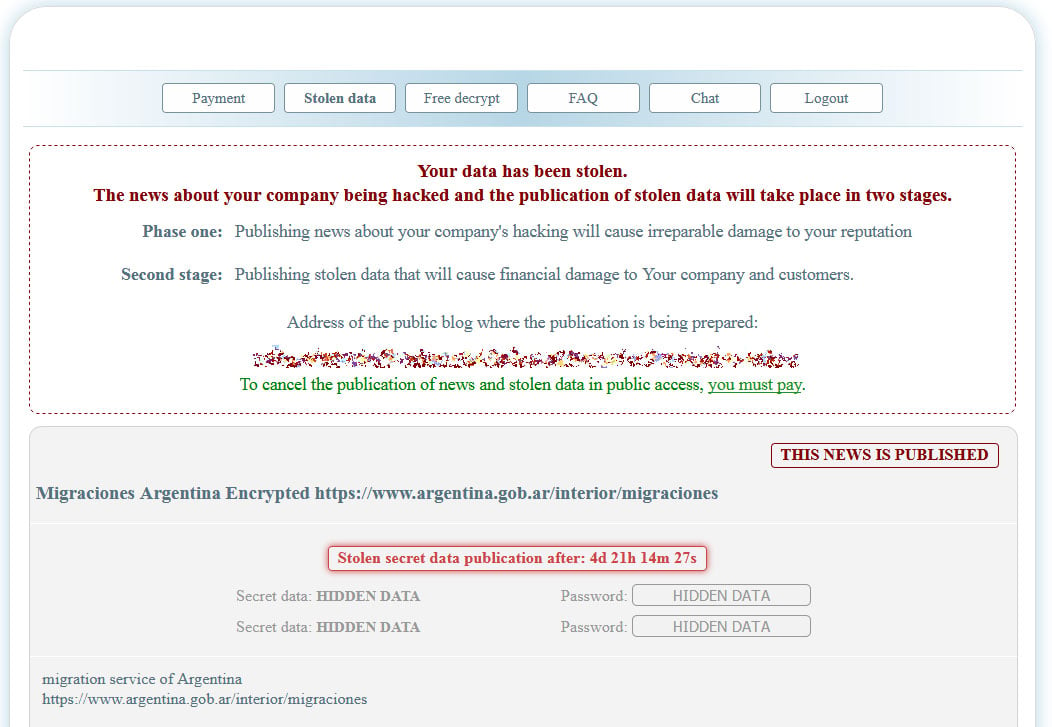
Due to this leaked data's potentially sensitive nature, BleepingComputer has decided not to post the data leak screenshots.
Thanos Ransomware adds Windows MBR locker that fails every time
7.9.20 Ransomware Bleepingcomputer
A new Thanos ransomware strain is trying and failing to deliver the ransom note onto compromised systems by overwriting the computers' Windows master boot record (MBR).
The new Windows MBR locker module has been discovered by security researchers at Palo Alto Networks' Unit 42 while analyzing two attacks were Thanos ransomware affiliates successfully encrypted devices of state-controlled organizations from the Middle East and North Africa during early July 2020.
"Overwriting the MBR is a more destructive approach to ransomware than usual," Unit 42 threat intelligence analyst Robert Falcone said. "Victims would have to expend more effort to recover their files – even if they paid the ransom."
"Fortunately, in this case, the code responsible for overwriting the MBR caused an exception because the ransom message contained invalid characters, which left the MBR intact and allowed the system to boot correctly."
Similar behavior was previously exhibited by Petya ransomware in 2016 when it was seen replacing infected devices' MBR to display a ransom note lock screen, as well as using a fake CHKDSK prompt to encrypt the Master File Table (MFT) in the background, rendering all files inaccessible.
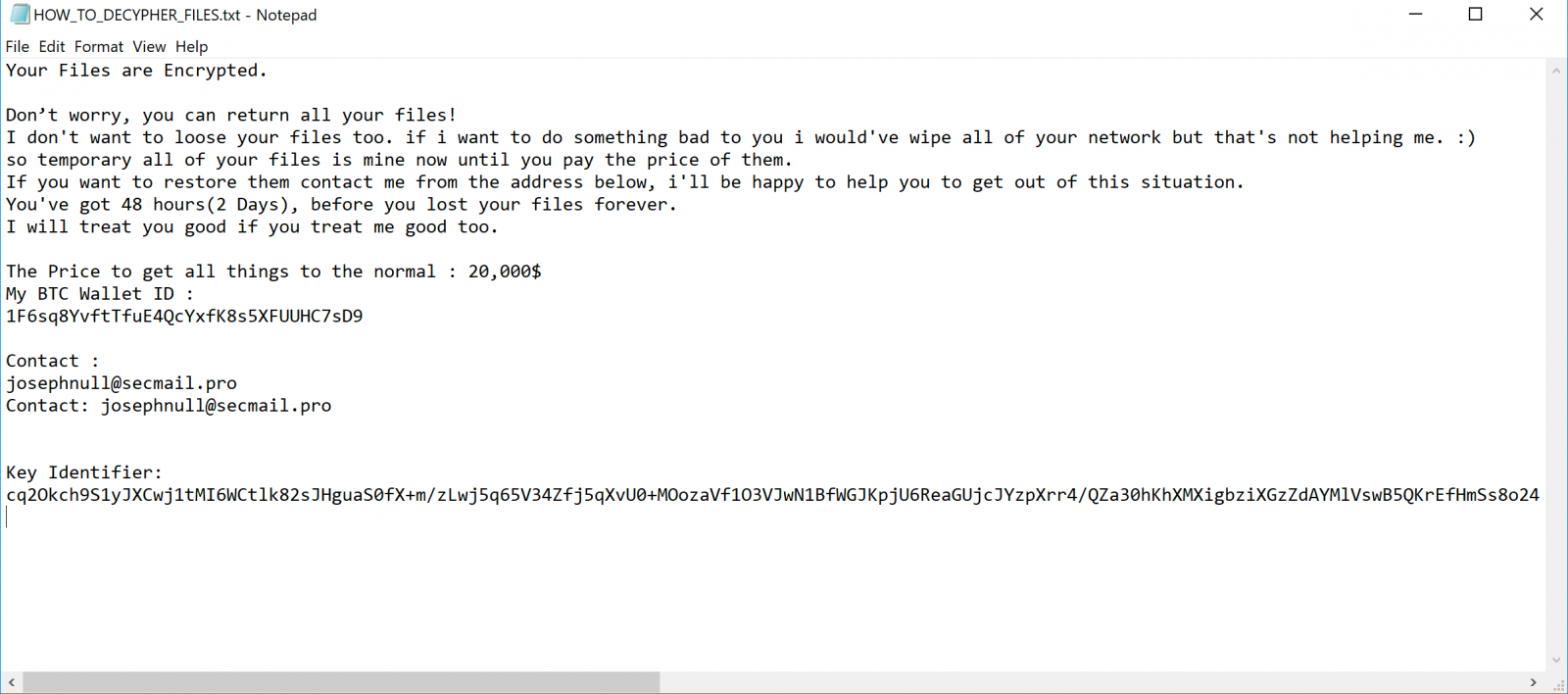
Thanos ransomware ransom note (Unit 42)
Even though they failed to overwrite the compromised computers' MBRs, the Thanos operators still dropped ransom note they regular way by creating HOW_TO_DECIPHER_FILES.txt text files and asking the victims to pay $20,000 to recover their data.
The researchers think that the attackers gained access to the targets' networks before the ransomware payloads were deployed since they were able to find valid credentials within the samples recovered after the attack.
The threat actors also used a layer-based approach to deliver the payloads, with custom PowerShell scripts, inline C# code, and shellcode being used to deliver the ransomware locally and to other systems on the victims' networks using the stolen credentials mentioned above.
While the two state-run entities from the Middle East and North Africa had their systems encrypted using Thanos ransomware payloads, Unit 42 has no info if the attackers were paid for their "efforts."
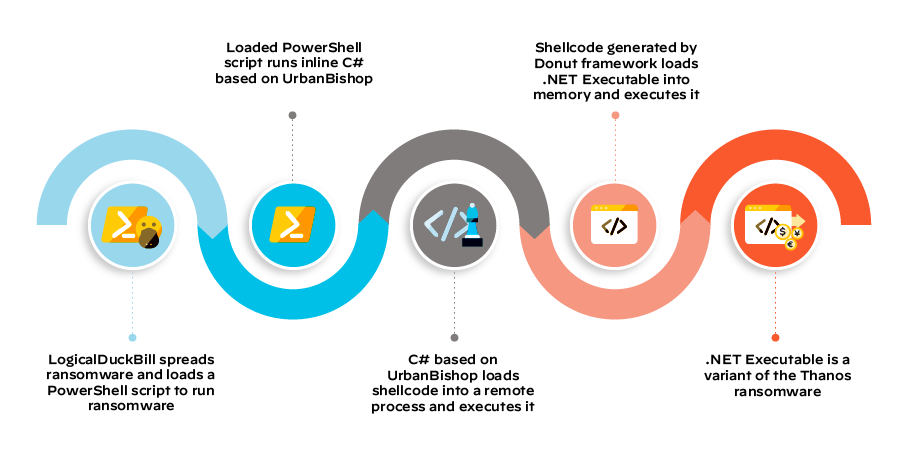
Thanos ransomware delivery (Unit 42)
Thanos ransomware is a Ransomware-as-a-Service (RaaS) operation advertised on several Russian-speaking hacker forums since February 2020 that enables affiliates to create custom ransomware payloads with the help of a builder provided by the developer.
Some Thanos samples have been previously tagged as Hakbit ransomware because of the different encryption extensions used by this RaaS' affiliates, but Recorded Future's Insikt Group says that they're the same malware based on core functionality, code similarity, and string reuse.v
Thanos is also the first to use the RIPlace anti-ransomware evasion technique together with numerous other quite advanced features designed to make it a serious threat as it can steal files and auto-spread between Windows devices using the PSExec program bundled with the SharpExec offensive security toolkit.
Three months ago, in June 2020, Thanos affiliates have failed to persuade multiple European companies from Austria, Switzerland, and Germany to pay €250 worth of bitcoins ransoms after encrypting their systems.
SunCrypt Ransomware shuts down North Carolina school district
7.9.20 Ransomware Bleepingcomputer
A school district in North Carolina has suffered a data breach after having unencrypted files stolen during an attack by the SunCrypt Ransomware operators, BleepingComputer has discovered.
The Haywood County School district in North Carolina announced that they had suffered a ransomware attack on August 24th, 2020, but had not stated what ransomware was used.
This attack caused the district to shut down its network and halt remote learning, which had started on August 17th.
"Our delay in restarting remote instruction is the uncertainty about the use of staff computers. We will know more when the forensic work is complete."
"We apologize for being unable to communicate as effectively as normal. Servers, Internet, and telephone services are still down in the school system. We will send another update at the end of the day," the Haywood County School District explained in their report to parents.
The school district has since resumed remote learning on August 31st, but with some school technology services still impacted.
Ransomware attack led to a data breach
After performing an investigation, the Haywood Country School District states that unencrypted data was stolen during the ransomware attack.
"In announcing the ransomware attack on Monday, we wanted everyone to understand a data breach was possible. We have now confirmed a data breach occurred. We are taking every possible step to eliminate any potential harm to staff, students, and affiliates. At this point, the forensic work has not determined the extent of specific data that was stolen. We ask staff, students, and parents to monitor for any suspicious activity," the school district announced in a new update this week.
BleepingComputer has learned that the SunCrypt Ransomware operators are behind the attack on the school district.
As part of their tactics, the SunCrypt operators will steal unencrypted data before encrypting an organization's devices and threaten to release the data if a ransom is not paid.
After not paying, the ransomware operators have published a 5GB archive containing data stolen from the school district.
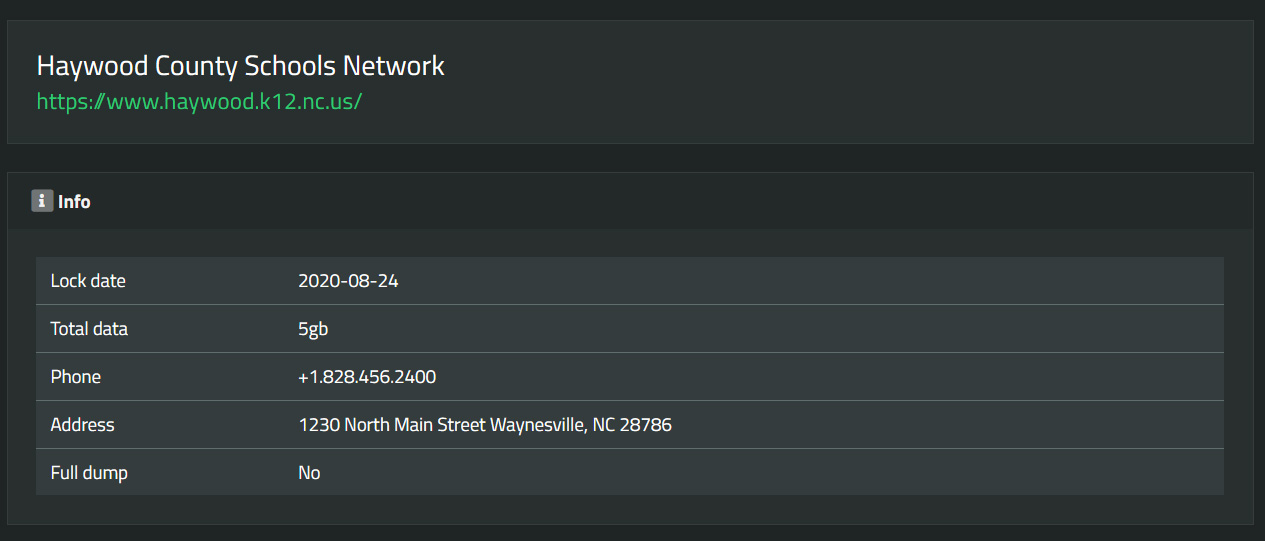
SunCrypt data leak site
This leaked data contains numerous sensitive documents and personal information related to the school district, students, and teachers.
A closer look at the Haywood County School District attack
When the SunCrypt ransomware operators perform an attack, they create a PowerShell script named after the victim and store it on the network's Windows domain controller.
BleepingComputer obtained the PowerShell script used in the Haywood County School District attack, as shown below. When executed on a device, it will launch the ransomware and encrypt the files on the computer.
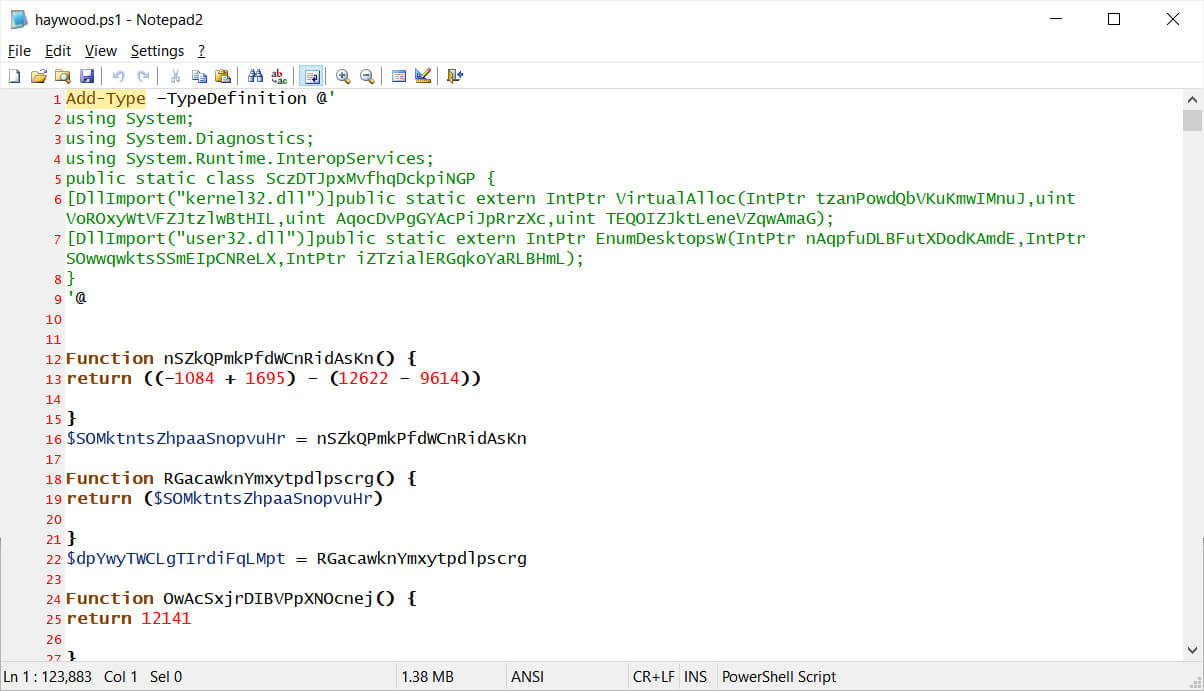
Haywood.ps1 PowerShell file
To launch the PowerShell script on every computer, the attackers will push a batch file to each Windows device on the network. When executed, this batch file will run the haywood.ps1 script stored on the domain controller and encrypt the computer.
By performing the attack in this way, attackers can compromise a network, quietly harvest files to steal, and then push out the ransomware to all of the devices simultaneously. This method allows the attackers to quickly encrypt all devices on the network without being detected.
Once done, the victims will be left with folders containing files that have been renamed and encrypted.
SunCrypt Encrypted Files
In each folder is a ransom note named YOUR_FILES_ARE_ENCRYPTED.HTML, which contains instructions on how to access the Tor payment site where a victim can negotiate with the ransomware operators.
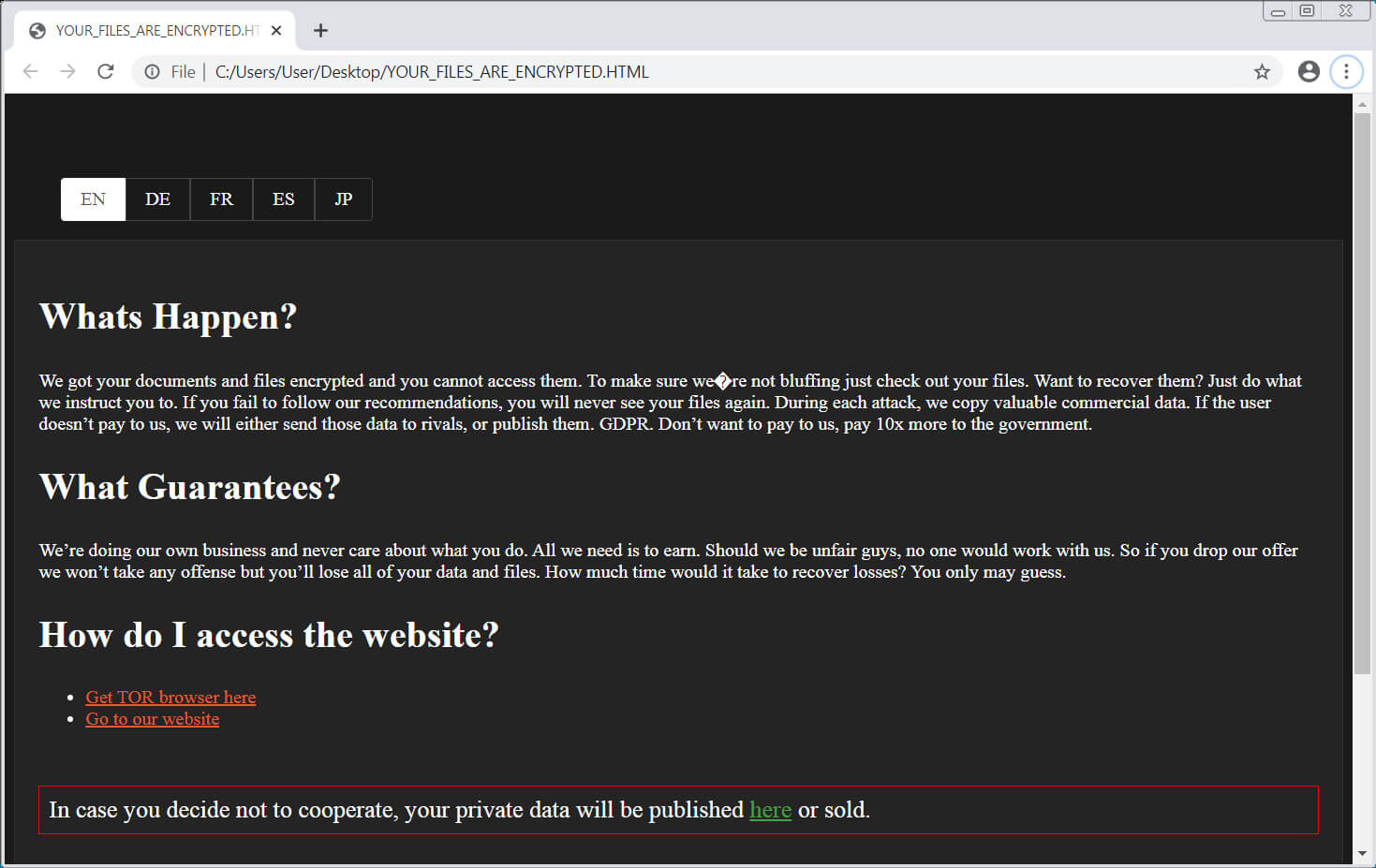
SunCrypt ransom note
Unfortunately, SunCrypt appears to be secure, which means there is no way to currently recover files for free.
FBI issues second alert about ProLock ransomware stealing data
7.9.20 BigBrothers Ransomware Bleepingcomputer
The FBI issued a second warning this week to alert US companies of ProLock ransomware operators stealing data from compromised networks before encrypting their victims' systems.
The 20200901-001 Private Industry Notification seen by BleepingComputer on September 1st comes after the MI-000125-MW Flash Alert on the same subject issued by the FBI four months ago, on May 4th, 2020.
FBI's previous alert also warned private industry partners that ProLock's decryptor is not working properly and that data will be lost since files over 64MB might be corrupted as part of the decryption process.
ProLock ransomware started as PwndLocker during late 2019, slowly making a reputation for itself while targeting both US businesses and local governments.
PwndLocker rebranded itself as ProLocker in March after fixing a bug that allowed free decryption of locked files, and its activity started to escalate as it started targeting corporate networks again.
The boost in activity was most likely caused by partnering with the QakBot banking trojan gang which made it a lot easier to gain access to new victims' networks.
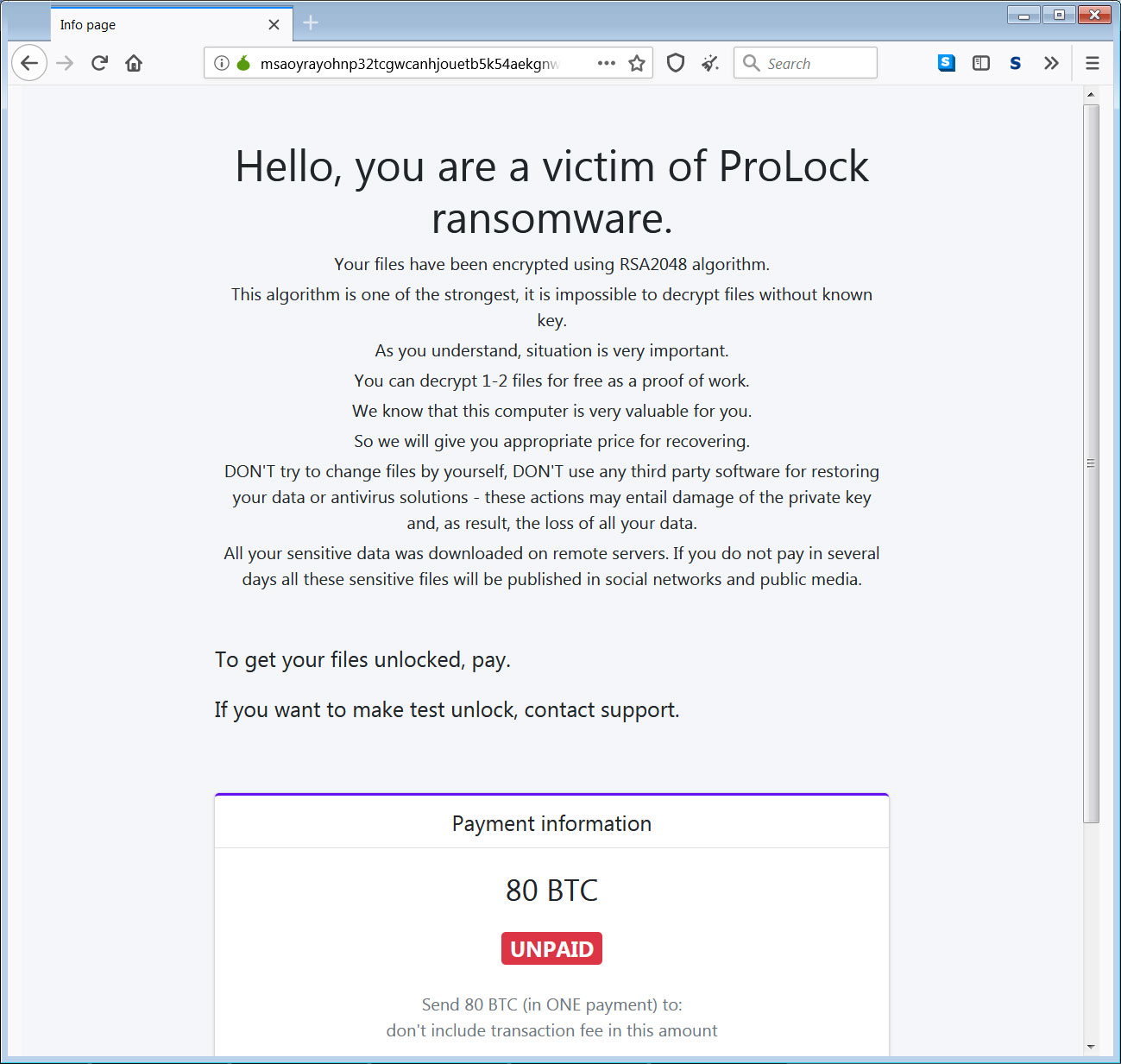
ProLock Tor payment site
ProLock ransoms can reach almost $700K
The operators behind the human-operated ProLock ransomware have been harvesting and exfiltrating information from their victims' devices before deploying their payloads since March 2020 according to the FBI.
The stolen data is later used by the threat actors as leverage in persuading the victim organizations into paying ransoms ranging between $175,000 to more than $660,000 depending on the size of the compromised network as BleepingComputer found.
So far, ProLock has successfully encrypted the networks of organizations around the world from multiple industry sectors including healthcare, construction, finance, and legal, including US government agencies and industrial entities.
ProLock's operators have used several attack vectors to breach their victims' systems including phishing emails with QakBot malicious attachments, using stolen credentials, and exploiting system configuration flaws.
The threat actors were observed archiving the stolen data and uploading to cloud storage platforms including OneDrive, Google Drive, and Mega with the help of the Rclone cloud storage sync command-line tool.
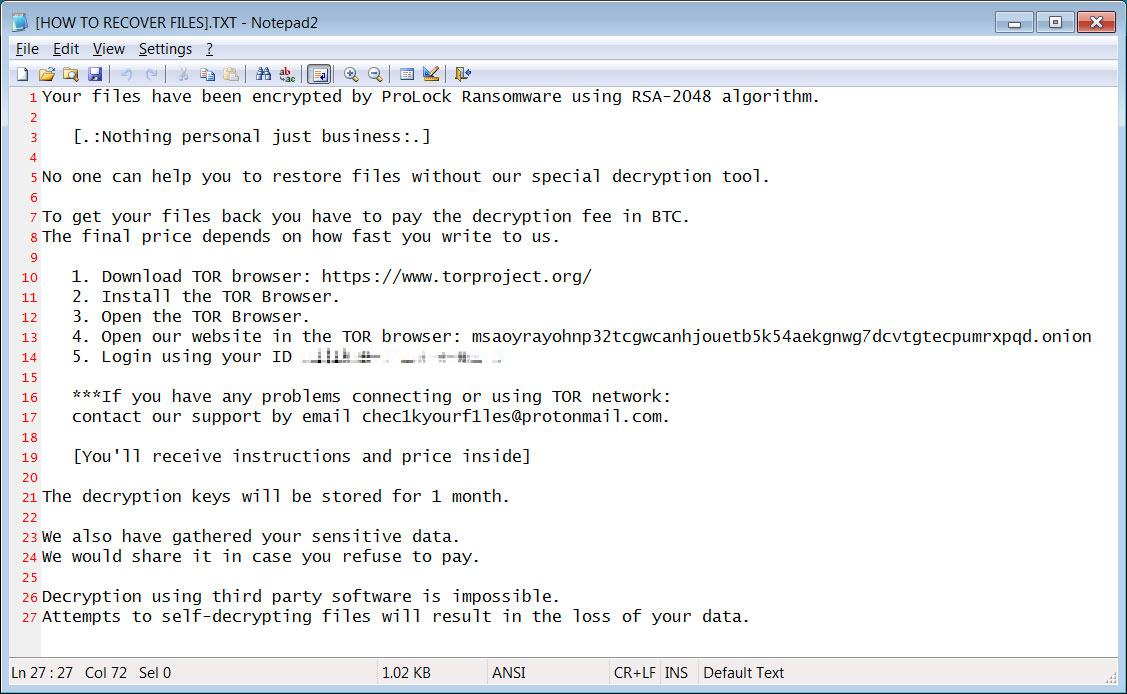
ProLock ransom note
Victims encouraged not to pay the ransoms
The FBI encourages private industry partners affected by ProLock ransomware attacks not to give in to the threat actors' demands and pay the ransoms.
Doing so would only embolden them to target other victims and will also directly fund their future illicit operations as the FBI explained.
However, the FBI recognizes the damages companies could face following such attacks and urges victims to report the attacks as soon as possible after having their systems infected with ProLock ransomware regardless of their decision to pay for a decryptor or not.
Reporting the attack to the local FBI field office to provide attack-related information such as phishing emails, recovered ransomware samples, ransom notes, and network traffic logs could help counter other attacks, as well as to identify and hold the attackers accountable for their activity.
The FBI recommends US orgs to periodically back up their data to an off-line/off-site backup location and to always keep their software up to date to patch any newly discovered security flaws the ProLock operators could exploit.
They are also recommended to make use of two-factor authentication (2FA) wherever possible, to disable unused Remote Desktop Protocol (RDP) instances, and to disable automatic attachment downloads in email clients.
Netwalker Ransomware hit Argentina’s official immigration agency
7.9.20 Ransomware Securityaffairs
Argentina’s official immigration agency, Dirección Nacional de Migraciones, is the last victim of the Netwalker ransomware operators.
Argentina’s official immigration agency, Dirección Nacional de Migraciones, was hit by a Netwalker ransomware attack that caused the interruption of the border crossing into and out of the country for four hours.
The ransomware operators also exfiltrated sensitive data from the agencies as reported by local media.
“A group of hackers entered the database of the National Directorate of Migration in the middle of the coronavirus pandemic, stole information and asks for a millionaire ransom to return the files , according to the body itself through its attorney, María Eugenia Lachalde” reported Infobae.
According to a criminal complaint published by Argentina’s Unidad Fiscal Especializada en Ciberdelincuencia, the agency started receiving numerous tech support calls from checkpoints at approximately 7 AM on August 27th.
In response to the infection, Argentina’s official immigration agency shut down its network to prevent the ransomware from spreading to other systems.
“Being approximately 7 a.m. of the day indicated in the paragraph above, the Directorate of Technology and Communications under the Directorate General Information Systems and Technologies of this Organization received numerous calls from various checkpoints requesting technical support.” reads the criminal complaint.
“This realized that it was not an ordinary situation, so it was evaluated the situation of the infrastructure of the Central Data Center and Servers Distributed, noting activity of a virus that had affected the systems MS Windows based files (ADAD SYSVOL and SYSTEM CENTER DPM mainly) and Microsoft Office files (Word, Excel, etc.) existing in users’ jobs and shared folders,”
The shut down of the network led to a temporary suspension of border crossings for four hours.
“The National Directorate of Migration (DNM), dependent on the Ministry of the Interior, reports that it managed to contain an attempted cyberattack on the body, which caused the fall of services, which are being gradually restored.” reads the advisory published by the National Directorate of Migration (DNM).
“The Integral System of Migratory Capture (SICaM) that operates in the international crossings was particularly affected, which caused delays in the entry and exit to the national territory.”
Government sources confirmed that they will not pay the ransom and will not negotiate with Netwalker ransomware operators which demand a $4 million ransom.
According to BleepingComputer, Netwalker ransomware operators initially demanded a $2 million ransom, the amount doubled after seven days passed.

Recently the FBI has issued a security alert about Netwalker ransomware attacks targeting U.S. and foreign government organizations.
The feds are recommending victims, not to pay the ransom and reporting incidents to their local FBI field offices.
The flash alert also includes indicators of compromise for the Netwalker ransomware along with mitigations.
The FBI warns of a new wave of Netwalker ransomware attacks that began in June, the list of victims includes the UCSF School of Medicine and the Australian logistics giant Toll Group.
The Netwalker ransomware operators have been very active since March and also took advantage of the ongoing COVID-19 outbreak to target organizations.
The threat actors initially leveraged phishing emails delivering a Visual Basic Scripting (VBS) loader, but since April 2020, Netwalker ransomware operators began exploiting vulnerable Virtual Private Network (VPN) appliances, user interface components in web apps, or weak passwords of Remote Desktop Protocol connections to gain access to their victims’ networks.
Recently the Netwalker ransomware operators were looking for new collaborators that can provide them with access to large enterprise networks.
Below the recommended mitigations provided by the FBI:
Back-up critical data offline.
Ensure copies of critical data are in the cloud or on an external hard drive or storage device.
Secure your back-ups and ensure data is not accessible for modification or deletion from the system where the data resides.
Install and regularly update anti-virus or anti-malware software on all hosts.
Only use secure networks and avoid using public Wi-Fi networks.
Consider installing and using a VPN.
Use two-factor authentication with strong passwords.
Keep computers, devices, and applications patched and up-to-date.
FBI issued a second flash alert about ProLock ransomware in a few months
6.9.20 Ransomware Securityaffairs
FBI issued a second flash alert about ProLock ransomware stealing data, four months after the first advisory published by the feds on the same threat.
The FBI has issued the 20200901-001 Private Industry Notification about ProLock ransomware stealing data on September 1st. The fresh alert is the second one related to this threat, the first one (MI-000125-MW Flash Alert) was published on May 4th, 2020.
At the time, Feds warned that the decryptor for the ProLock was not correctly working and using it could definitively destroy the data. The descriptor could corrupt files larger than 64MB during the decryption process.
The human-operated PwndLocker ransomware first appeared in the threat landscape in late 2019, operators’ demands have ranged from $175,000 to more than $660,000 worth of Bitcoin.
According to the FBI, operators behind the threat gain access to hacked networks via the Qakbot (Qbot) trojan, but experts from Group-IB added that they also target unprotected Remote Desktop Protocol (RDP)-servers with weak credentials. It is still unclear if the ProLock ransomware was managed by the Qakbot gang, or if the ProLock operators pay to gain access to hosts infected with Qakbot to deliver their malware.
“ProLock operators used two main vectors of initial access: QakBot (Qbot) and unprotected Remote Desktop Protocol (RDP)-servers with weak credentials.” reads a report published by Group-IB.
“The latter is a fairly common technique among ransomware operators. This kind of access is usually bought from a third party but may be obtained by group members as well.”
In March, threat actors behind PwndLocker changed the name of their malware to ProLock, immediately after security firm Emsisoft released a free decryptor tool.
The ProLock ransomware was employed in attacks against organizations worldwide from multiple sectors including construction, finance, healthcare, and legal. The malware was also used in attacks aimed at US government agencies and industrial entities.
The ransomware operators used to upload the stolen data to cloud storage platforms, including OneDrive, Google Drive, and Mega. Threat actors employed the Rclone cloud storage sync command-line tool.
The FBI is recommending victims of ransomware attacks to avoid paying the ransom to decrypt their files and immediately report attacks to the authorities.
The FBI also provides recommendations to mitigate the risks associated with ransomware attacks, such as periodically back up the data to an off-line backup system, keep any software up to date, disable unused RDP accesses, use of two-factor authentication (2FA) wherever possible.
SunCrypt Ransomware behind North Carolina school district data breach
5.9.20 Ransomware Securityaffairs
A school district in North Carolina disclosed a data breach after having unencrypted files stolen during a SunCrypt Ransomware attack.
The Haywood County School district in North Carolina has suffered a data breach after having unencrypted files stolen during a SunCrypt Ransomware attack.
The ransomware attack took place on August 24th, 2020, but at the time the family of malware that infected the school district was not revealed.
The infection forced the school district to shut down its systems and suspend remote instruction.
“Our delay in restarting remote instruction is the uncertainty about the use of staff computers. We will know more when the forensic work is complete.” reads a notice sent by the Haywood County School District to parents.
“We apologize for being unable to communicate as effectively as normal. Servers, Internet, and telephone services are still down in the school system. We will send another update at the end of the day.”
The school district partially resumed its operations on August 31st, including the remote learning, at the same time it has launched an investigation into the incident that revealed the theft of the data during the attack.
“In announcing the ransomware attack on Monday, we wanted everyone to understand a data breach was possible. We have now confirmed a data breach occurred. We are taking every possible step to eliminate any potential harm to staff, students, and affiliates.” reads an update on the incident published by the school district. “At this point, the forensic work has not determined the extent of specific data that was stolen. We ask staff, students, and parents to monitor for any suspicious activity.
According to BleepingComputer, the school district in North Carolina was hit by the SunCrypt Ransomware operators, that like other ransomware gangs (i.e. Maze, REVil) steal data before encrypting them and threaten victims to leak them if they will not pay the ransom.
“After not paying, the ransomware operators have published a 5GB archive containing data stolen from the school district.” reported BleepingComputer.
The archive leaked by the ransomware operators includes sensitive documents and personal information of the school district, students, and teachers.
BleepingComputer analyzed the attack against the Haywood County School District attack and published technical details on the attack chain employed in the incident.
Experts pointed out that currently there is no way to recovery file encrypted by the SunCrypt ransomware for free.
REvil ransomware operators breached healthcare org Valley Health Systems
28.8.20 Ransomware Securityaffairs
REvil ransomware operators claimed to have breached another healthcare organization, the victim is Valley Health Systems.
During ordinary monitoring activity of data leaks, the Cyble Research Team identified a leak disclosure post published by the REvil ransomware operators claiming to have breached a healthcare organization, the Valley Health Systems.
Healthcare organizations are a privileged target of hackers due to the sensitive data they manage. During this period, due to the ongoing COVID19 pandemic, these structures are under pressure and more exposed to cyber risks.
According to the Cisco/Cybersecurity Ventures Cybersecurity Almanac, the healthcare organizations suffered 2-3 more cyberattacks in 2019 than the average amount for the other industries.
“As the healthcare sector companies continues to improvise their treatment process and patient care with the availability of the new technologies, and on the same side cyber threat actors tends to exploit the vulnerabilities that are made with the technological advancements.” states the post published by Cyble.
“Recently, during the monitoring process of data leaks the Cyble Research Team identified a leak disclosure post in which the REvil ransomware operators claimed to have breached Valley Health Systems.”
The Valley Health Systems has been providing primary and preventative care to approximately 75,000 patients each year in southern West Virginia, southeastern Ohio, and eastern Kentucky. The organization operates over 40 healthcare facilities with over 400 employees working across all their centers.
Below is the post published by REvil operators: 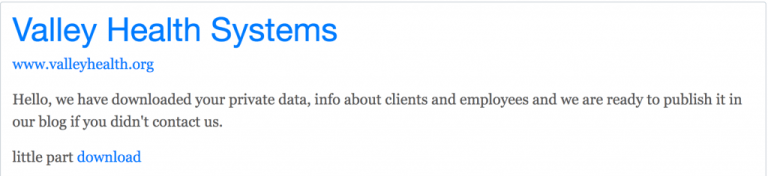
The REVil ransomware operators claim to have stolen company sensitive data, including info related to clients, employees, and patients.
Experts shared snapshots folders and also released a small part of a data leak containing the patient’s prescribed prescriptions, patient details (that include full name, date of birth, gender, patient ID), medical scan reports of patients, multiple Digital Imaging and Communications medical files, and much more.
Below a list of tips provided by Cyble to prevent ransomware attacks:
Never click on unverified/unidentified links
Do not open untrusted email attachments
Only download from sites you trust
Never use unfamiliar USBs
Use security software and keep it updated
Backup your data periodically
Isolate the infected system from the network
Use mail server content scanning and filtering
Never pay the ransom.
Iran-Linked ‘Newbie’ Hackers Spread Dharma Ransomware Via RDP Ports
24.8.20 Ransomware Threatpost
The recent Dharma campaign by Iran-linked script kiddies shows that the ransomware is being spread not just by sophisticated, state-sponsored actors anymore.
A group of ‘script kiddies’ tied to Iran are targeting companies worldwide with internet-facing Remote Desktop Protocol (RDP) ports and weak credentials in order to infect them with Dharma ransomware.
The Dharma malware (also known as Crysis) has been distributed as a ransomware-as-a-service (RaaS) model since at least 2016. While the ransomware was previously used by advance persistent threat (APT) actors, its source code surfaced in March 2020, making it available to a wider breadth of attackers. That is the case with this latest Iran-linked threat group, which researchers say is unsophisticated and has been targeting companies across Russia, Japan, China and India with the ransomware since June.
“The fact Dharma source code has been made widely available led to the increase in the number of operators deploying it,” Oleg Skulkin, senior digital forensics specialist with Group-IB, said in an analysis of the attacks posted Monday. “It’s surprising that Dharma landed in the hands of Iranian script kiddies who used it for financial gain, as Iran has traditionally been a land of state-sponsored attackers engaged in espionage and sabotage. Despite that these cybercriminals use quite common tactics, techniques and procedures they have been quite effective.”
The threat actors are unsophisticated because they use publicly available tools both to obtain initial access and move laterally – rather than using custom malware or post-exploitation frameworks, Group-IB senior DFIR analyst Oleg Skulkin told Threatpost.
“The threat actors use Persian language for Google searches on compromised servers and download tools from Iran-linked Telegram groups,” Skulkin told Threatpost. “In addition, Group-IB experts saw the threat actors’ attempt to brute-force accounts on an Iranian video streaming service.”
The attackers in this campaign first would scan ranges of IPs for hosts that contained these vulnerable RDP ports and weak credentials, researchers said. They did so using scanning software called Masscan (which has previously been utilized by bad actors like Fxmsp).
Once vulnerable hosts were identified, the attackers deployed a well-known RDP brute force application called NLBrute, which has been sold on forums for years. Using this tool, they were able to brute-force their way into the system, and then check the validity of obtained credentials on other accessible hosts in the network.
In some attacks, attackers also attempted to elevate privileges using an exploit for an elevation privilege flaw. This medium-severity flaw (CVE-2017-0213), which affects Windows systems, can be exploited when an attacker runs a specially crafted application.
Post compromise, “interestingly, the threat actors likely didn’t have a clear plan on what to do with the compromised networks,” said researchers, showing their lack of sophistication. In different attacks, attackers would download various publicly-available tools to perform reconnaissance or move laterally across the network.
dharma ransomware attackTo scan for accessible hosts in the compromised network, for instance, they used publicly-available tool Advanced Port Scanner. Other tools were downloaded by the attackers from Persian-language Telegram channels, researchers said.
“For instance, to disable built-in antivirus software, the attackers used Defender Control and Your Uninstaller,” said researchers. “The latter was downloaded from Iranian software sharing website — the Google search query in Persian language “دانلود نرم افزار youre unistaller” was discovered in the Chrome artifacts.”
Attackers would then move laterally across the network and deploy the Dharma variant executable, encrypt data, and leave a ransom note for the victim. Researchers said, hackers typically demanded a ransom between 1 to 5 BTC (worth between 12,000 to 59,000 USD at the time of writing).
Researchers said, though the exact number of victims in this campaign is unknown, the discovered forensic artifacts revealed a that the threat actors in this campaigb are “far behind the level of sophistication of big league Iranian APTs.”
“The newly discovered hacker group suggests that Iran, which has been known as a cradle of state-sponsored APT groups for years, now also accommodates financially motivated cybercriminals,” according to Group-IB researchers.
Researchers said part of this change may be attributed to the pandemic exposing a number of vulnerable hosts – with many employees working remotely – making an extremely popular attack vector for cybercriminals. Therefore, the default RDP port 3389 should be closed if not in use, they suggested.
“As the attackers usually need several attempts to brute force passwords and gain access to the RDP, it is important to enable account lockout policies by limiting the number of failed login attempts per user,” said researchers.
Canadian delivery company Canpar Express suffered a ransomware attack
24.8.20 Ransomware Securityaffairs
A ransomware attack hit TFI International’s four Canadian courier divisions last week, Canpar Express, ICS Courier, Loomis Express and TForce Integrated Solutions.
A couple of days after the transportation and logistics TFI International company raised millions of dollars in a share offering, the news of a ransomware attack against its four Canadian courier divisions (Canpar Express, ICS Courier, Loomis Express and TForce Integrated Solutions) made the headlines.
The news of the ransomware attack was published by the company on its website.
“On 19th Aug 2020 Canpar Express was the target of a ransomware attack that impacted some of our systems. We continue to meet most customer shipping needs and we are not aware of any misuse of client information.” states Canpar Express. “Canpar Express takes our obligation to protect customer information seriously. Upon learning of the incident, we immediately began an investigation and engaged cybersecurity experts to assist in the process. We have taken steps to contain and remediate the issue and are taking all necessary steps to help prevent a similar occurrences in the future.”
The experts are working to determine the extent of the attack, at the time the company did not disclose technical details on the attack, such as the family of ransomware that infected its systems.
“We continue to meet most customer shipping needs and we are not aware of any misuse of client information,” reads the notices from the company. “Out of an abundance of caution we want to make our clients aware of the incident, should you be experiencing any issues.”
TFI told its customers that it has launched an ongoing investigation.
TFI, Canada’s largest trucking and logistics company, raised $219 million (CA$290 million) in a share offering, which closed on Monday. It has a market cap of over $4.25 billion (CA$5.6 billion.)
The website of Canuck went offline for days due to the ransomware infection, according to the Reuters, the incident has a significant impact for America’s Hat residents, package tracking and scheduling pickups were blocked.
Financially-Motivated Iranian Hackers Adopt Dharma Ransomware
24.8.20 Ransomware Securityweek
Recent Dharma ransomware attacks show that more Iranian hackers have started to engage in financially-motivated operations, threat hunting firm Group-IB reports.
Also referred to as Crysis, the ransowmare family has been offered under a ransomware-as-a-service (RaaS) model since 2016, mainly associated with remote desktop protocol (RDP) attacks. In March this year, however, the malware’s source code became available for purchase.
In a report published on Monday, Group-IB revealed that Dharma ransomware attacks observed in June this year were the work of a newly discovered Iranian hacker group, and that organizations in China, India, Japan, and Russia were targeted. The attackers demanded ransom amounts ranging between 1 and 5 Bitcoin.
The attackers were observed mixing the ransomware with various publicly available tools and focusing their efforts on companies with Internet-facing RDP systems secured with weak credentials. The exact number of victims hasn’t been established yet.
Some of the tools employed in these attacks include the IP port scanner Masscan to identify vulnerable targets, and the RDP brute-forcing tool NLBrute to gain access to the identified machines. In some attacks, the hackers leveraged an exploit for CVE-2017-0213, in an attempt to elevate privileges.
“The newly discovered hacker group suggests that Iran, which has been known as a cradle of state-sponsored APT groups for years, now also accommodates financially motivated cybercriminals,” Group-IB notes.
The hackers behind these attacks, the security researchers note, are novices who likely did not have a clear plan of action once they gained access to the compromised networks.
Using the newly established RDP connection, the attackers attempted to disable built-in antivirus software using Defender Control and Your Uninstaller, while leveraging Advanced Port Scanner to discover accessible hosts in the network.
After network reconnaissance, the attackers attempted to move laterally using RDP. At the final stage of the attack, they would drop and manually execute a variant of Dharma ransomware onto the compromised hosts.
“The fact Dharma source code has been made widely available led to the increase in the number of operators deploying it,” said Oleg Skulkin, senior DFIR analyst at Group-IB. “It’s surprising that Dharma landed in the hands of Iranian script kiddies who used it for financial gain, as Iran has traditionally been a land of state-sponsored attackers engaged in espionage and sabotage.”
Steel sheet giant Hoa Sen Group hacked by Maze ransomware operators
21.8.20 Ransomware Securityaffairs
Experts at threat intelligence firm Cyble came across a post published by Maze ransomware operators claiming to have breached the steel sheet giant Hoa Sen Group.
During the ordinary monitoring of Deepweb and Darkweb, researchers at Cyble came across the leak disclosure post published by the Maze ransomware operators that claim the hack of the Hoa Sen Group.
Hoa Sen Group is the no.1 company in the field of manufacturing and trading steel sheet in Vietnam and the leading exporter of steel sheet in Southeast Asia.
The Hoa Sen Group (HSG) was founded in the year 2001, it has 7,100 employees across all its 343 companies and has been earning annual revenue of around $1.18 billion.
Maze ransomware operators claim to be in possession of the company’s sensitive data and are threatening to release it. Below a snapshot of the leak post published by the Maze Ransomware Operators:

Experts from Cyble analyzed the leaked data, an archive containing around 1.64 GB of files that correspond to the 5% of the overall stolen data. Maze ransomware operators have released documents containing data of Hoa Sen Group employees (i.e. offer letters released by the company). The archive also includes photos of people professionally dressed that appear to be employees of the company and resumes, academic documents, identity cards of current employees.
“Currently, the ransomware operators claims to have published 5% of company’s total data leak.” reads the post published by Cyble.
“Cyble has been reporting these data breaches to aware individuals of the risks associated with using online services.”
Below a list of tips provided by Cyble to prevent ransomware attacks:
Never click on unverified/unidentified links
Do not open untrusted email attachments
Only download from sites you trust
Never use unfamiliar USBs
Use security software and keep it updated
Backup your data periodically
Isolate the infected system from the network
Use mail server content scanning and filtering
Never pay the ransom.
University of Utah Pays $457,000 to Ransomware Operators
20.8.20 Ransomware Securityweek
The University of Utah on Thursday revealed that it paid approximately $457,000 to ransomware operators after servers in its College of Social and Behavioral Science (CSBS) were compromised.
The attack occurred on July 19, 2020, and resulted in the CSBS servers becoming temporarily inaccessible. Roughly .02% of the data stored on those servers was affected during the incident, the university claims.
Both employee and student information was impacted in the attack, and locally managed IT services and systems were restored from backup copies. The attack did not affect central university IT systems. The impacted servers were isolated immediately after the attack was identified.
“The university notified appropriate law enforcement entities, and the university’s Information Security Office (ISO) investigated and resolved the incident in consultation with an external firm that specializes in responding to ransomware attacks,” University of Utah says.
The servers hosted data and services for CSBS and various colleges, departments and administrative units, and a password reset was prompted for students, staff, and faculty.
“After careful consideration, the university decided to work with its cyber insurance provider to pay a fee to the ransomware attacker. This was done as a proactive and preventive step to ensure information was not released on the internet,” the university reveals.
For the time being, the university hasn’t determined the exact nature of the data that might have been accessed during the incident, and only said that student and employee information was affected. All compromised servers have been cleaned.
It also noted that, despite significant investment in technology to keep its network protected from attacks, vulnerabilities still exist, because of the “decentralized nature and complex computing needs” the university has.
The vulnerability that led to this attack has been addressed and the University of Utah has also started moving college systems that contain private and restricted data to central services, to ensure they are better protected.
“The university is also unifying the campus to one central Active Directory and moving college networks into the centrally managed university network. These steps, in addition to individuals using strong passwords and two-factor authentication, are expected to reduce the likelihood of an incident like this occurring again,” the university says.
The organization also revealed that the $457,000 ransom was partly covered by the cyber insurance policy, and that it was not paid using tuition, grant, donation, state or taxpayer funds.
Cruise line operator Carnival Corporation suffers a ransomware attack
18.8.20 Ransomware Securityaffairs
The world’s largest cruise line operator Carnival Corporation has disclosed that one of their brands suffered a ransomware attack over the past weekend.
Cruise line operator Carnival Corporation has disclosed that one of their brands was hit with a ransomware attack over the past weekend.
Carnival Corporation & plc is a British-American cruise operator, currently the world’s largest travel leisure company, with a combined fleet of over 100 vessels across 10 cruise line brands. A dual-listed company,
Carnival Corporation has over 150,000 employees and 13 million guests annually. The cruise line operates under the brands Carnival Cruise Line, Costa, P&O Australia, P&O Cruises, Princess Cruises, Holland American Line, AIDA, Cunard, and their ultra-luxury cruise line Seabourn.
In an 8-K filing with the US Securities Exchange Commission (SEC), the cruise line operators revealed that the incident took place on August 15.
“On August 15, 2020, Carnival Corporation and Carnival plc (together, the “Company,” “we,” “us,” or “our”) detected a ransomware attack that accessed and encrypted a portion of one brand’s information technology systems. The unauthorized access also included the download of certain of our data files,” states the 8-K form filed with the SEC.
“Nonetheless, we expect that the security event included unauthorized access to personal data of guests and employees, which may result in potential claims from guests, employees, shareholders, or regulatory agencies,”
The Carnival IT staff confirms that the ransomware operators may have stolen personal data of guests and employees, according to the filing the unauthorized access also included the download of certain of our data files.
The filing does not provide details about the attack, it is not clear the family of ransomware that hit the company.
“Based on its preliminary assessment and on the information currently known (in particular, that the incident occurred in a portion of a brand’s information technology systems), the Company does not believe the incident will have a material impact on its business, operations or financial results. Nonetheless, we expect that the security event included unauthorized access to personal data of guests and employees, which may result in potential claims from guests, employees, shareholders, or regulatory agencies. Although we believe that no other information technology systems of the other Company’s brands have been impacted by this incident based upon our investigation to date, there can be no assurance that other information technology systems of the other Company’s brands will not be adversely affected.” continues the form 8-K.
Upon the discovery of the security incident, the Company launched an investigation and notified law enforcement, it also hired legal counsel and cyber security professionals. The company also announced to have already implemented a series of containment and remediation measures to respond to the incident and reinforce the security of its information technology systems.
In March, Carnival Corporation disclosed another data breach that took place in 2019. The company informed customers of the incident, a third-party gained unauthorized access to their personal information.
Exposed guests’ personal information included name, address, Social Security number, government identification number, such as passport number or driver’s license number, and health-related information. For some clients, credit card and financial account information might have been exposed.
It is interesting to note that according to cybersecurity intelligence firm Bad Packets, Carnival utilizes vulnerable Citrix devices that can be exploited by an attacker to access the corporate network.
The company was using Citrix servers vulnerable to the CVE-2019-19781 flaw that affects Citrix Application Delivery Controller (ADC), Citrix Gateway, and Citrix SD-WAN WANOP appliances.
BadPackets also speculate that another entry point in the Carnival network could be CVE-2020-2021 issue in the the PAN-OS operating system.
The flaw could allow unauthenticated network-based attackers to bypass authentication, it has been rated as critical severity and received a CVSS 3.x base score of 10.
Technology giant Konica Minolta hit by a ransomware attack
17.8.20 Ransomware Securityaffairs
IT giant Konica Minolta was hit with a ransomware attack at the end of July, its services have been impacted for almost a week.
A ransomware attack has impacted the services at the business technology giant Konica Minolta for almost a week, the attack took place at the end of July.
Konica Minolta is a Japanese multinational technology company headquartered in Marunouchi, Chiyoda, Tokyo, with offices in 49 countries worldwide. The company manufactures business and industrial imaging products, including copiers, laser printers, multi-functional peripherals (MFPs) and digital print systems for the production printing market.
The multinational business technology giant has almost 44,000 employees and over $9 billion in revenue for 2019.
Since July 30th, 2020, customers began reporting accessibility problems with the access to the company’s product supply and support site.
The site was displaying the following message:
“The Konica Minolta MyKMBS customer portal is temporarily unavailable. We are working hard to resolve the issue and apologize for any inconvenience this may have caused you. If you need immediate assistance for service, please call our Global Customer Services at 1-800-456-5664 (US) or 1-800-263-4410 (Canada).”
The outage lasted for an entire week, some Konica Minolta printers were also displaying a ‘Service Notification Failed’ error.
BleepingComputer that first reported the news attempted to contact the company without receiving any response.
“After some customers stated that their Konica contacts indicated a breach caused the outage, BleepingComputer attempted to contact the company numerous times via email and phone calls.” reads the post published by BleepingComputer.
“BleepingComputer never received a response to our inquiries.”
According to BleepingComputer, who received a copy of the ransom note (titled ‘!!KONICA_MINOLTA_README!!.txt,’) employed in the attack, the company was hit with a new strain of ransomware dubbed RansomEXX.
The ransomware encrypted the files and appended the ‘.K0N1M1N0’ extension appended to their filenames.
The RansomEXX is human-operated ransomware, this means that attackers manually infected the systems after gained access to the target network.
In June 2020, the same ransomware was employed in an attack on the Texas Department of Transportation.
The good news is that the RansomEXX ransom, unlike other families of ransomwawe, does not appear to exfiltrate data before encrypting target systems.
Sodinokibi ransomware gang stole 1TB of data from Brown-Forman
16.8.20 Ransomware Securityaffairs
Sodinokibi (REvil) ransomware operators announced on Friday to have hacked Brown-Forman, one of the largest U.S. firm in the spirits and wine business.
Sodinokibi (REvil) ransomware operators announced last week to have breached the network of the Brown-Forman, one of the largest U.S. firm in the spirits and wine business.
Threat actors claim to have exfiltrated 1TB of confidential data and plan to put it up for auction the most sensitive info and leak the rest.
Data accessed by the gang includes confidential employees’s info, company agreements, contracts, financial statements, and internal messages.
The Brown–Forman Corporation is one of the largest American-owned companies in the spirits and wine business. Based in Louisville, Kentucky, it manufactures several well-known brands throughout the world, including Jack Daniel’s, Early Times, Old Forester, Woodford Reserve, GlenDronach, BenRiach, Glenglassaugh, Finlandia, Herradura, Korbel, and Chambord.
Sodinokibi ransomware operators announced to have spent more than a month examining the infrastructure of the firm.
As a proof of the hack, Sodinokibi ransomware operators posted on their leak site multiple screenshots showing directories and files allegedly belonging to the company, and internal conversations between some employees.
The threat actors also published screenshots of database backup entries as recent as July 2020.

With this announcement, the REvil operators aim at forcing Brown-Forman into paying a ransom.
The company disclosed the incident in a statement, it added that was able to prevent its systems from being encrypted, suggesting the involvement of a ransomware. It only disclosed a few details about the incident, including when it happened or how the hackers accessed the data.
The company reported the incident to the authorities and retained a world class third-party data security experts to investigate the incident and resolve this situation as soon as possible. Brown-Forman also added that currently there are no active negotiations, but it suspects that some information has been exposed.
“Brown-Forman was the victim of a cybersecurity attack. Our quick actions upon discovering the attack prevented our systems from being encrypted” – said Brown-Forman spokesperson
“Unfortunately, we believe some information, including employee data, was impacted. We are working closely with law enforcement, as well as world-class third-party data security experts, to mitigate and resolve this situation as soon as possible,” the Brown-Forman spokesperson told Bloomberg.
If the company will pay the ransomware, the threat actor promises to delete all copies of the data.
“We still believe in the prudence of BROWN-FORMAN and are waiting for them to continue their discussion of a way out of this situation” Sodinokibi operators posted.
Maze ransomware gang leaked Canon USA’s stolen files
14.8.20 Ransomware Securityaffairs
Maze ransomware operators have leaked online the unencrypted files allegedly stolen from Canon during a recent ransomware attack.
According to an internal memo obtained by ZDNet last week, the recent outage suffered by Canon was caused by a ransomware attack, at the same time Maze ransomware operators were taking the credit for the incident.
The memo also reveals that the company has hired an external security firm to investigate the incident.
The problem was first reported by Bleepingcomputer, which tracked a suspicious outage on Canon’s image.canon cloud photo and video storage service. According to the media outlet, the incident resulted in the loss of data for users of their free 10GB storage feature.
The image.canon site suffered an outage on July 30th, 2020, that lasted for six days, until August 4th.
At the time the company only confirmed an internal investigation on a problem related to “10GB of data storage.”

Source BleepingComputer
According to Canon, some of the photo and image files saved prior to June 16 were “lost,” but it pointed out that they were not exposed in a data leak.
Now the Maze ransomware operators have published unencrypted files allegedly stolen the Canon during the ransomware attack.
BleepingComputer obtained from its source a portion of the ransom note and an internal notification that Canon sent to its employees.

Canon internal notice – Source BleepingComputer
BleepingComputer has obtained additional unpublished internal documents sent by the Canon IT department on August 10th to the employees about the restoration of services.
“We are only sharing a portion of the email below, as we do not want to reveal the company’s internal systems.” reads the post from BleepingComputer.
Maze ransomware operators have started to publish data stolen from the company on its data leak site.The gang has published a 2.2 GB archive called “STRATEGICPLANNINGpart62.zip” that attackers claim contain around 5% of the total amount of documents stolen during the attack,
The archive contains files related to Canon’s website and marketing materials, according to BleepingComputer’s source it do not appear to contain any financial information, employee information, or other sensitive data.
Maze ransomware operators recently published internal data from LG and Xerox after the company did not pay the ransom.
As usual, the Maze ransomware operators threaten the victims to pay the ransom to avoid their data being leaked online.
Maze ransomware operators have also breached the systems of the Xerox Corporation and stolen files before encrypting them.
In the past months Maze Ransomware gang breached the US chipmaker MaxLinear and Threadstone Advisors LLP, a US corporate advisory firm specialising in mergers ‘n’ acquisitions.
Maze operators were very active during the past months, they have also stolen data from US military contractor Westech and the ST Engineering group, and they have released credit card data stolen from the Bank of Costa Rica (BCR) threatening to leak other lots every week.
Previous victims of the ransomware gang include IT services firms Cognizant and Conduent.
City of Lafayette (Colorado) paid $45,000 ransom after ransowmare attack
12.8.20 Ransomware Securityaffairs
The City of Lafayette, Colorado, USA, has been forced to pay $45,000 because they were unable to restore necessary files from backup.
On July 27th, the systems at the City of Lafayette, Colorado, were infected with ransomware, the malicious code impacted phone services, email, and online payment reservation systems.
The City did not immediately disclose the cause of the outage of its systems and invited the citizens to use 911 or an alternate number for emergency services.
Now the City of Lafayette admitted they were a victim of a ransomware attack that encrypted its systems and confirmed that opted to pay a $45,000 ransom to receive a decryption tool to recover its files.
“After a thorough examination of the situation and cost scenarios, and considering the potential for lengthy inconvenient service outages for residents, we determined that obtaining the decryption tool far outweighed the cost and time to rebuild data and systems,” City of Lafayette Mayor Jamie Harkins explained in a video.
The City did not disclose technical details of the hack either the family of ransomware that infected its systems, it only stated that it does not believe any data was stolen. The City also added that credit card data was not stored on its systems, anyway it invited residents and employees to monitor their bank accounts for suspicious activity.
“Financial data appears to be recoverable from unaffected backups. Personal credit card information was not compromised, as the City uses external PCI-certified payment gateways.” reads the announcement published by the City. “There is no evidence to suggest personal data was compromised, but out of an abundance of caution, residents and employees are advised to be vigilant to monitor accounts for suspicious activity.”
The City is going to notify individuals who have personal information stored on the City’s network.
The small amount of money requested by the attackers suggests that the attackers are not one of the major ransomware gangs, like Maze, REvil, or Clop, that usually asks for a higher ransom.
Avaddon ransomware operators have launched their data leak site
11.8.20 Ransomware Securityaffairs
Avaddon ransomware operators, like other cybercrime groups, decided to launch a data leak site where publish data of victims who refuse to pay a ransom demand.
Avaddon ransomware operators announced the launch of their data leak site where they will publish the data stolen from the victims who do not pay a ransom demand.
The first group to adopt this strategy was the Maze ransomware gang in December 2019, since then other crews adopted the same stratefy, including REvil, Nefilim, and Netwalker.
The threat of exposing the victim’s sensitive data is used by the gang to force them into paying a ransom.
Cybersecurity intelligence firm Kela was the first to report that the Avaddon ransomware operators have announced on a Russian-speaking hacker forum their new data leak site.
Source BleepingComputer
The hackers have already published on the leak site 3.5MB of documents stolen from a construction company.
Let’s wait for new entries on the leak site!
Nefilim ransomware operators claim to have hacked the SPIE group
11.8.20 Ransomware Securityweek
Nefilim ransomware operators allegedly targeted the SPIE group, an independent European leader in multi-technical services.
Researchers from threat intelligence firm Cyble reported that Nefilim ransomware operators allegedly hacked The SPIE Group, an independent European leader in multi-technical services.
The number of ransomware attacks continues to increase, hackers also steal victims’ data and threaten them to release the stolen info if they don’t pay the ransom.
During darkweb and deepweb monitoring, the Cyble Research Team discovered a post from Nefilim ransomware operators in which they claimed to have breached The SPIE Group.

The ransomware gang also revealed to have stolen the company’s sensitive data.
The SPIE Group provides multi-technical services in the areas of energy and communications, it has more than 47,200 employees and in 2019 it reported consolidated revenues of €6.9 billion and consolidated EBITA of €416 million.
Nefilim ransomware operators also released the first batch of file threatens to release other documents. Cyble experts analyzed the material, the first lot of data contains around 11.5 GB.
“The data leak seems to consist of corporate operational documents which include the company’s telecom services contracts, dissolution legal documents, power of attorney documents, infrastructure group reconstructions contracts, and much more.” reported Cyble.
The Nefilim ransomware operators released a total of 65,042 files contained in 18,551 data folders.
Nefilim ransomware operators continue to be very active in this period, recently the group targeted the Dussmann group, the German largest private multi-service provider and Orange S.A., one of the largest mobile networks based in France.
Below a list of tips provided by Cyble to prevent ransomware attacks:
Never click on unverified/unidentified links
Do not open untrusted email attachments
Only download from sites you trust
Never use unfamiliar USBs
Use security software and keep it updated
Backup your data periodically
Isolate the infected system from the network
Use mail server content scanning and filtering
Never pay the ransom.
Did Maze ransomware operators steal 10 GB of data from Canon?
8.8.20 Ransomware Securityaffairs
An internal memo confirms that the prolonged outage suffered by Canon last week was caused by a ransomware infection, Maze operators took credit for it.
According to an internal memo obtained by ZDNet, the recent outage of Canon was caused by a ransomware attack, while Maze ransomware operators are taking the credit for the incident.
The memo also reveals that the company has hired an external security firm to investigate the incident.
The problem was first reported by Bleepingcomputer, which tracked a suspicious outage on Canon’s image.canon cloud photo and video storage service. According to the media outlet, the alleged incident resulted in the loss of data for users of their free 10GB storage feature.
The image.canon site suffered an outage on July 30th, 2020, that lasted for six days, until August 4th.
At the time the company only confirmed an internal investigation on a problem related to “10GB of data storage.”

Source BleepingComputer
According to Canon, some of the photo and image files saved prior to June 16 were “lost,” but it pointed out that they were not exposed in a data leak.
“Currently, the still image thumbnails of these lost image files can be viewed but not downloaded or transferred,” reads the notice issued by Canon. “If a user tries to download or transfer a still image thumbnail file, an error may be received.”
At the same time, the company issued an internal memo that warned employees of “company-wide” IT issues, which also impacted email systems.
Maze ransomware operators announced to have stolen 10TB of data as a result of a ransomware attack against the company but denied responsibility for the image.canon issues. If confirmed this means that the outage was not caused by the ransomware infection, but that anyway Maze operators have exfiltrated 10 GB of data from the company. Another memo sent to the employees specifically refers a “ransomware incident” and revealed that Canon has hired a cyber forensics firm to investigate the intrusion.
Maze ransomware operators recently published internal data from LG and Xerox after the company did not pay the ransom.
As usual, the Maze ransomware operators threaten the victims to pay the ransom to avoid their data being leaked online.
Maze ransomware operators have also breached the systems of the Xerox Corporation and stolen files before encrypting them.
In the past months Maze Ransomware gang breached the US chipmaker MaxLinear and Threadstone Advisors LLP, a US corporate advisory firm specialising in mergers ‘n’ acquisitions.
Maze operators were very active during the past months, they have also stolen data from US military contractor Westech and the ST Engineering group, and they have released credit card data stolen from the Bank of Costa Rica (BCR) threatening to leak other lots every week.
Previous victims of the ransomware gang include IT services firms Cognizant and Conduent.
Canon Admits Ransomware Attack in Employee Note, Report
7.8.20 Ransomware Threatpost
The consumer-electronics giant has suffered partial outages across its U.S. website and internal systems, reportedly thanks to the Maze gang.
A day after Canon was suspected of becoming the latest high-profile victim of a ransomware attack, an internal employee communique admitting just that has been leaked to media.
According to Bleeping Computer, the camera-maker has circulated a note to employees confirming that ransomware is to blame for outages across its main U.S. website, email, collaboration platforms and various internal systems.
“Canon U.S.A, Inc. and its subsidiaries understand the importance of maintaining the operational integrity and security of our systems,” reads the note, a screenshot of which has been posted by the outlet. “Access to some Canon systems is currently unavailable as a result of a ransomware incident we recently discovered. This is unrelated to the recent issue which affected image.canon.”
The Maze ransomware gang has taken credit for the outage, claiming to have lifted “10 terabytes of data, private databases etc.” in the process. This fits in with the known modus operandi of the group, which usually threatens to leak or sell sensitive data if the target doesn’t pay the ransom. In fact, researchers said in April that the Maze gang has created a dedicated web page, which lists the identities of their non-cooperative victims and regularly publishes samples of the stolen data. This so far includes details of dozens of companies, including law firms, medical service providers and insurance companies, that have not given in to their demands.
“Maze is a particularly malicious strain of ransomware, the criminal actors claim to steal their target’s data each time, and threaten to release it publicly if they refuse to pay the ransom,” Tiago Henriques, Coalition’s GM of customer security, told Threatpost. “Its ransom demands are also particularly costly – the average Maze demand we’ve seen is approximately five-and-a-half times larger than the overall average.”
The Canon USA website was still not up at the time of this writing, with a previous “the site is undergoing temporary maintenance” splash page now replaced with a picture of a hot-air balloon and the text, “Our heads aren’t in the clouds. We’re just busy updating our site. Please check back soon! In the Meantime [sic], please visit us at: Canon Online Store or Canon Forum.”
As the page indicates, other Canon assets, including its global website, appear to be unaffected, potentially meaning that the consumer-electronics giant’s security included working failsafe measures to limit the damage.
If so, Canon can count itself a rarity, according to researchers: “In our ethical hacking engagements we are typically able to gain complete control of networks in one to three days and the presence of security products rarely…prevent us from exploiting computer systems,” Chris Clements, vice president of solutions architecture at Cerberus Sentinel, said via email. “The Maze group has proven themselves as good as professional security testing organizations and the significant bounty the collect from extorting their victims means they are well funded to develop their own exploits and bypass methods. Given this, it’s not surprising that they have been able to compromise many large high-profile targets. The reality is that it is very difficult to protect yourself from a skilled adversary.”
The large-electronics-vendor-hit-by-ransomware situation is eerily similar to the recent attack on Garmin, which was the work of the WastedLocker ransomware and Evil Corp. In that case, the GPS specialist reportedly paid a multimillion-dollar ransom to retrieve its files.
“Ransomware has been taking businesses hostage (literally), and the tools, tactics and procedures criminal actors are using have become even more advanced in recent months,” Henriques said. “In the first half of 2020 alone, we observed a 279-percent increase in the frequency of ransomware attacks amongst our policyholders.”
Netwalker ransomware operators claim to have stolen data from Forsee Power
6.8.20 Ransomware Securityaffairs
Netwalker ransomware operators breached the networks of Forsee Power, a well-known player in the electromobility market.
A new company has been added to the list of the victims of the Netwalker ransomware operators, it is Forsee Power, which provides advanced lithium-ion battery systems for any mobility application.
The industrial group is based in France and in the US USA, it is one of the market leaders in Europe, Asia, and North America with annual revenue of around $65 million and over 200 employees.
Recently Cyble threat research group came across another disclosure from the Netwalker group that announced to have stolen sensitive data from Forsee Power.
Netwalker ransomware operators announced the attack with a message posted on their online blog and shared a few screenshots as proof of the security breach.
One of the images shared by the group shows a directory containing folders such as Accounts Receivable, Finance, collection letters, Expenses, and Employees.
Below some tips on how to prevent ransomware attacks provided by Cyble:
Never click on unverified/unidentified links
Do not open untrusted email attachments
Only download from sites you trust
Never use unfamiliar USBs
Use security software and keep it updated
Backup your data periodically
Isolate the infected system from the network
Use mail server content scanning and filtering
Never pay the ransom.
Recently the FBI has issued a security alert about Netwalker ransomware attacks targeting U.S. and foreign government organizations.
The feds are recommending victims, not to pay the ransom and reporting incidents to their local FBI field offices.
The flash alert also includes indicators of compromise for the Netwalker ransomware along with mitigations.
The FBI warns of a new wave of Netwalker ransomware attacks that began in June, the list of victims includes the UCSF School of Medicine and the Australian logistics giant Toll Group.
The Netwalker ransomware operators have been very active since March and also took advantage of the ongoing COVID-19 outbreak to target organizations.
The threat actors initially leveraged phishing emails delivering a Visual Basic Scripting (VBS) loader, but since April 2020, Netwalker ransomware operators began exploiting vulnerable Virtual Private Network (VPN) appliances, user interface components in web apps, or weak passwords of Remote Desktop Protocol connections to gain access to their victims’ networks.
Recently the Netwalker ransomware operators were looking for new collaborators that can provide them with access to large enterprise networks.
Below the recommended mitigations provided by the FBI:
Back-up critical data offline.
Ensure copies of critical data are in the cloud or on an external hard drive or storage device.
Secure your back-ups and ensure data is not accessible for modification or deletion from the system where the data resides.
Install and regularly update anti-virus or anti-malware software on all hosts.
Only use secure networks and avoid using public Wi-Fi networks.
Consider installing and using a VPN.
Use two-factor authentication with strong passwords.
Keep computers, devices, and applications patched and up-to-date.
Colorado City Pays $45,000 Ransom After Cyber-Attack
6.8.20 Ransomware Securityweek
Lafayette, Colorado, officials announced Tuesday the city’s computer systems were hacked and they were forced to pay a ransom to regain access.
Lafayette officials said hackers disabled the city’s network services and blocked its access until the city paid a $45,000 fee, the Daily Camera reported.
The attack caused city emails, phones, online payments and reservation systems to temporarily shut down.
The city’s system servers and computers are still in the process of being cleaned and rebuilt. Once finished, the relevant data will be restored into the system and operations will resume. In the meantime, the city is using temporary phone numbers and emails.
“In a cost/benefit scenario of rebuilding the city’s data versus paying the ransom, the ransom option far outweighed attempting to build,” the city said in a statement. “The inconvenience of a lengthy service outage for residents was also taken into consideration.”
A preliminary investigation shows the ransomware entered the city’s network through a phishing scam or by guessing passwords.
Mayor Jamie Harkins said using taxpayer dollars to pay a ransom was not ideal.
“We attempted to pursue any possible avenue to avoid paying the ransom,” Harkins said. “Staff worked to determine the severity of the attack while analyzing data and backups to find alternative solutions.”
The city said personal credit card information was not compromised. There was no evidence that showed personal data was stolen, but the city asked its residents to monitor their accounts for suspicious activity.
City officials said they would be sending security-breach notifications to those who have personal information on the city’s network.
In response to the attack, City Administrator Fritz Sprague enacted a declaration of local disaster emergency that allows for outside assistance from the state, neighboring jurisdictions and private contractors.
The declaration will be in effect for seven days unless it is extended by the City Council. The council is set to consider the extension on Tuesday.
To combat future attacks, the city said it is installing crypto-safe backups, deploying additional cybersecurity systems and implementing regular vulnerability assessments.
NetWalker Ransomware Rakes in $29M Since March
5.8.2020 Ransomware Threatpost
The ransomware has surged since moving to a RaaS model.
The NetWalker ransomware has been around for about a year, but it has really made a name for itself in 2020, racking up around $29 million in extortion gains just since March.
First detected in August 2019, NetWalker lingered around before surging in use in March through June, according to an analysis from McAfee Advanced Threat Research (ATR). The uptick coincided with the implementation of a robust ransomware-as-a-service (RaaS) model, which has been attracting technically advanced criminal affiliates.
“NetWalker RaaS prioritizes quality over quantity and is looking for people who are Russian-speaking and have experience with large networks,” the firm noted, in an analysis published Monday. “People who already have a foothold in a potential victim’s network and can exfiltrate data with ease are especially sought after. This is not surprising, considering that publishing a victims’ data is part of NetWalker’s model.”
This is reflected in some of the strikes attributed to the NetWalker malware, which are mainly targeted at large organizations in Europe and North America. These have included hits for transportation giant Toll Group, the University of California San Francisco and, most recently, French smart-battery company Forsee. Also, a recent FBI Alert warned that NetWalker ransomware attackers are now targeting U.S. and foreign government organizations.
Many organizations appear to be paying up: “McAfee discovered a large sum of Bitcoins linked to NetWalker, which suggests its extortion efforts are effective and that many victims have had no option other than to succumb to its criminal demands,” according to researchers.
Raking in Cash
The malware’s operators made some changes in their marketing approach that took effect in March, when its uptick began.
Someone going by the handle “Bugatti” began actively advertising the NetWalker RaaS at that time – and researchers speculated that, given the strength of NetWalker’s reputation on underground forums, “the individual behind Bugatti is most likely a well-respected and experienced cybercriminal.”
The individual is also highly proactive.
“Bugatti provides regular updates on the improvements in the ransomware, such as the popular Invoke-ReflectivePEInjection method, also commonly used by Sodinokibi,” researchers said in the posting. “In addition to the improvements in the ransomware, open slots for new affiliates are advertised. Bugatti strongly emphasized that they are primarily looking for experienced affiliates that focus on compromising the complete networks of organizations as opposed to end users. NetWalker is clearly following in the footsteps of its illustrious targeted ransomware peers like Sodinokibi, Maze and Ryuk.”
In the course of their investigation, researchers noticed one forum message that had screenshots of several partial Bitcoin addresses and dollar amounts. Using the CipherTrace software, they were able to track down the complete Bitcoin addresses from the screenshot and investigate the ledger further.
“Since the Bitcoin blockchain is a publicly accessible ledger, we can follow the money and see where the ransomware actors are transferring it to,” the report explained.
In one transaction, the amount was split between four different Bitcoin addresses – a common situation in RaaS transactions, analysts noted, because the payment is split between the RaaS operators and the affiliate(s). In this observed case, the splits were 80 percent, 10 percent and two 5 percent portions.
“While the [NetWalker operator] beneficiaries of the 5 percent cuts remain the same, the beneficiary of the 10 percent cut seems to change over time,” the researchers noted. “Based on the forum post, we assume these addresses also belong to the NetWalker actors.”
Meanwhile, around 30 unique Bitcoin addresses were the beneficiaries of the 80 percent splits – representing the affiliates.
The firm also found 23 transactions where the ransom payments were not split up, and the only beneficiaries were the two Bitcoin addresses receiving the 5-percent shares in the splits.
“The total amount of Bitcoin extorted this way between 1 March 2020 and 27 July 2020 is 677 BTC,” according to researchers. “Additionally, the amount received from remaining transactions following the ransomware-as-a-service scheme by these addresses between 1 March 2020 and 27 July 2020 is 188 BTC…[also we saw] a total of 1723 BTC being transferred to affiliates.”
In total, that adds up to 2,588 BTC, which at today’s exchange rate translates to $29,111,118.
Technical Changes
The malware itself has also undergone a few changes since March. For instance, the latest NetWalker ransom note drops a request for email communication from the proceedings, in favor of requiring victims to contact the attackers via a NetWalker Tor interface. There, after submitting a user key, victims are redirected to a chat with NetWalker technical support, where they can pay the ransom.
The actors also moved away from using legacy Bitcoin addresses to SegWit addresses.
“The benefits of using the newer SegWit addresses include faster transaction time and lower transaction cost,” according to researchers. “The NetWalker advertisement on the underground forum mentions instant and fully automatic payments around the time of this observed change. This makes us believe the ransomware actors were professionalizing their operation just before expanding to the ransomware-as-a-service model.”
The NetWalker malware uses a custom resource type (1337 or 31337) containing its entire configuration, researchers explained. NetWalker uses its configuration file in the resource to set its encryption mode, the name of the ransom note, contact information (post-March, that means specifying the NetWalker blog URL/payment page instead of an email address) and more.
“This file is extracted to memory and decrypted using the RC4 algorithm with a hard-coded key in the resource,” according to the analysis. “If the malware fails to get the configuration file, it will terminate itself.”
Overall, ransomware has evolved into a lucrative business for threat actors, especially with the rise of RaaS models – from underground forums selling ransomware, to offering services such as support portals to guide victims through acquiring crypto currency for payment, to the negotiation of the ransom.
“The recent shift to a business-centric model of ransomware-as-a-service is a clear sign that it is stepping up, so it seems that the NetWalker group is following in the footsteps of REvil and other successful RaaS groups,” the firm concluded. “The ransomware developers have proven the ability to refocus and capitalize on current world events and develop lures to help ensure the effectiveness of the ransomware, which has allowed them to become selective of their affiliates by limiting access to the ransomware to only those with vetted access to large organizations. As development of the ransomware continues, we have witnessed recent shifts in activity that closely follow in the footsteps of other ransomware developments, including threatening victims with the release of confidential information if the ransom is not met.”
NetWalker ransomware operators have made $25 million since March 2020
4.8.20 Ransomware Securityaffairs
NetWalker ransomware operators continue to be very active, according to McAfee the cybercrime gang has earned more than $25 million since March 2020.
McAfee researchers believe that the NetWalker ransomware operators continue to be very active, the gang is believed to have earned more than $25 million since March 2020.
The malware has been active at least since August 2019, over the months the NetWalker ransomware was made available through a ransomware-as-a-service (RaaS) model attracting criminal affiliates.
McAfee published a report about NetWalker’s operations, the researchers were able to track payments monitoring transactions to a pool of known Bitcoin addresses associated with the ransomware operators.
“Since 2019, NetWalker ransomware has reached a vast number of different targets, mostly based in western European countries and the US. Since the end of 2019, the NetWalker gang has indicated a preference for larger organisations rather than individuals.” reads the report. “During the COVID-19 pandemic, the adversaries behind NetWalker clearly stated that hospitals will not be targeted; whether they keep to their word remains to be seen.”
NetWalker ransomware operators have recently begun choosing affiliates specialized in targeted attacks against high-value entities in the attempt to maximize their effort with surgical operations.
High-value enterprises are expected to pay bigger ransom demands compared to small companies.
The affiliates used to deliver the threat via brute-forcing attacks on RDP servers or exploiting known vulnerabilities in VPN servers and firewalls.

The NetWalker author, who goes online with the moniker “Bugatti”, was only interested in doing business with Russian-speaking customers.
Threat actors spreading the NetWalker ransomware carried out cyber attacks that leveraged exploits in Oracle WebLogic and Apache Tomcat servers, brute-forcing RDP endpoints, and carrying out spear-phishing attacks on staff at major companies.
Last week, the FBI has issued a new security flash alert to warn of Netwalker ransomware attacks targeting U.S. and foreign government organizations. The feds are recommending victims, not to pay the ransom and reporting incidents to their local FBI field offices.
The flash alert also includes indicators of compromise for the Netwalker ransomware along with mitigations.
The FBI warns of a new wave of Netwalker ransomware attacks that began in June, the list of victims includes the UCSF School of Medicine and the Australian logistics giant Toll Group.
“As of June 2020, the FBI has received notifications of Netwalker ransomware attacks on U.S. and foreign government organizations, education entities, private companies, and health agencies by unidentified cyber actors.” reads the alert. “Netwalker became widely recognized in March 2020, after intrusions on an Australian transportation and logistics company and a U.S. public health organization. Cyber actors using Netwalker have since taken advantage of the COVID-19 pandemic to compromise an increasing number of unsuspecting victims.”
The Netwalker ransomware operators have been very active since March and also took advantage of the ongoing COVID-19 outbreak to target organizations.
The threat actors initially leveraged phishing emails delivering a Visual Basic Scripting (VBS) loader, but since April 2020, Netwalker ransomware operators began exploiting vulnerable Virtual Private Network (VPN) appliances, user interface components in web apps, or weak passwords of Remote Desktop Protocol connections to gain access to their victims’ networks.
Recently the Netwalker ransomware operators were looking for new collaborators that can provide them with access to large enterprise networks.
“Two of the most common vulnerabilities exploited by actors using Netwalker are Pulse Secure VPN (CVE-2019-11510) and Telerik UI (CVE-2019-18935).” continues the alert. “Once an actor has infiltrated a network with Netwalker, a combination of malicious programs may be executed to harvest administrator credentials, steal valuable data, and encrypt user files. In order to encrypt the user files on a victim network, the actors typically launch a malicious PowerShell script embedded with the Netwalker ransomware executable.”
The analysis of the transactions related bitcoin addresses involved in the Netwalker ransomware operations, McAfee observed 2,795 bitcoins being transferred between wallets operated by the gang between March 1st, 2020, and July 27th,2020.
“The total amount of extorted bitcoin that has been uncovered by tracing transactions to these NetWalker related addresses is 2795 BTC between 1 March 2020 and 27 July 2020. By using historic bitcoin to USD exchange rates, we estimate a total of 25 million USD was extorted with these NetWalker related transactions,” continues the McAfee’s report.
“Even though we do not have complete visibility into the BTC flow before NetWalker started ramping up, one thing is certain, this quarter alone it has been highly successful at extorting organisations for large amounts of money.”
In order to force the victims into paying the ransom, the gang set up a leak site where it publishes the data of the victim that refuse to pay. This tactic is becoming very common in the cybercrime ecosystem and many companies decided to pay to avoid having their name listed on the site and their data leaked online.
McAfee also shared YARA rules for the threat along with Indicators of Compromise and MITRE ATT&CK Techniques.
Maze Ransomware operators published data from LG and Xerox
4.8.20 Ransomware Securityweek
Maze ransomware operators published internal data from LG and Xerox after the company did not pay the ransom.
Ransomware crews are very active during these months, Maze ransomware operators have published tens of GB of internal data allegedly stolen from IT giants LG and Xerox following failed extortion attempts.
Maze ransomware operators published 50.2 GB from LG’s network and 25.8 GB from Xerox.
In June, researchers at threat intelligence firm Cyble discovered a data leak of LG Electronics published by Maze ransomware operators.
As usual, the Maze ransomware operators threaten the victims to pay the ransom to avoid their data being leaked online. A few days ago the group released a press release in which they warned the companies to not try to recover their files from their backup, it also announced the forthcoming LG Electronics data leak.
At the time, the Maze ransomware operators only released three screenshots as proof of the data breaches on the Maze ransomware leak site:
Researchers from ZDNet who analyzed the leaked data confirmed that it included source code for the firmware of various LG products, including phones and laptops.
“In an email in June, the Maze gang told ZDNet that they did not execute their ransomware on LG’s network, but they merely stole the company’s proprietary data and chose to skip to the second phase of their extortion attempts.” read a Maze’s statement reported by ZDNet.
“We decided not to execute [the] Maze [ransomware] because their clients are socially significant and we do not want to create disruption for their operations, so we only have exfiltrated the data,” the Maze gang told ZDNet via a contact form on their leak site.
Maze ransomware operators have also breached the systems of the Xerox Corporation and stolen files before encrypting them.
The company did not disclose the cyberattack, but early June the Maze ransomware operators published some screenshots that showed that a Xerox domain has been encrypted. One screenshot showed that hosts on “eu.xerox.net,” managed by Xerox Corporation, was hacked.
Another screenshot demonstrated that the ransomware operators were in the Xerox network till June 25th, 2020.
Xerox Corporation is an American corporation that sells print and digital document products and services in more than 160 countries. The company declared over $1.8 billion in revenue in Q1 2020 and has 27,000 employees across the globe. It’s currently tracking at 347 of the Fortune 500 list.
On June 24, Maze ransomware operators included Xerox in the list of the victims published on their leak site.
Anyway, it is still unclear the extent of the attack, what internal systems have been encrypted by Maze gang and which files have been exfiltrated.
Experts from threat intelligence company Bad Packets speculated that both company were hacked by exploiting the known CVE-2019-19781 vulnerability in Citrix ADC servers they were running. Bad Packets experts discovered that both organizations were running unpatched servers that could have been the entry point of the attackers.
In the past months Maze Ransomware gang breached the US chipmaker MaxLinear and Threadstone Advisors LLP, a US corporate advisory firm specialising in mergers ‘n’ acquisitions.
Maze operators were very active during the past months, they have also stolen data from US military contractor Westech and the ST Engineering group, and they have released credit card data stolen from the Bank of Costa Rica (BCR) threatening to leak other lots every week.
Previous victims of the ransomware gang include IT services firms Cognizant and Conduent.
Garmin Pays Up to Evil Corp After Ransomware Attack — Reports
4.8.20 Ransomware Threatpost
The ransom for the decryptor key in the WastedLocker attack could have topped $10 million, sources said.
Garmin, the GPS and aviation tech specialist, reportedly negotiated with Evil Corp for an decryption key to unlock its files in the wake of a WastedLocker ransomware attack.
The attack, which started on July 23, knocked out Garmin’s fitness-tracker services, customer-support outlets and commercial aviation offerings such as flight-plan filing, account-syncing and database-concierge capabilities. Garmin officially confirmed a cyberattack to Threatpost (and later in a web post), but declined to explain the specific cause.
However, sources reportedly shared photos with BleepingComputer of a Garmin computer with encrypted files with the .garminwasted extension on each file’s name. That indicated that WastedLocker was the malware involved. Soon, the company’s systems started coming back online, and as of Monday Garmin said its services are now fully restored.
BleepingComputer also said it obtained a copy of the working decryptor from the Garmin IT department with a time stamp of July 25, and that the original ransom amount requested was $10 million. Sky News meanwhile reported that the device-maker paid the ransom to Evil Corp, the gang behind the ransomware, via a ransomware-negotiation business called Arete IR.
If Garmin did indeed pay the ransom, the company could be in hot water from a legal perspective. The U.S. Treasury Department in December issued sanctions against Evil Corp, which state that “U.S. persons are generally prohibited from engaging in transactions” with Evil Corp or any of its individual members.
Evil Corp’s previous schemes involved capturing banking credentials with the Dridex banking trojan and then making unauthorized electronic funds transfers from unknowing victims’ bank accounts. Money mules would then receive these stolen funds into their bank accounts, and transport the funds overseas. Multiple companies have been targeted by Dridex, costing them millions of dollars; victims included two banks, a school district, a petroleum business, building materials supply company and others.
As a result, the U.S. authorities are offering up $5 million for information leading to the arrest of Evil Corp leader Maksim V. Yakubets, 32, of Russia, who goes under the moniker “aqua.”
Garmin has declined to comment on any of the investigative findings regarding the ransom or the decryptor.
“In organizations, one method to avoid paying is to assess whether their backups are available and not corrupted or deleted by cybercriminals,” James McQuiggan, security awareness advocate at KnowB4, said via email. “It’s crucial within an organization’s cybersecurity program to have a backup policy. This policy needs to include the planning and testing of backups regularly to determine their integrity. If the backup restoration process fails, it can mean additional risk to the organization’s revenue and reputation due to the downtime. Backups are just one part of a ransomware mitigation plan. Examining the root cause of most ransomware attacks is determined either to be a phishing attack or through vulnerable and unpatched systems.”
WastedLocker: A Look Inside
Kaspersky researcher Fedor Sinitsyn, in a recent post, said that there has been an increase in the use of WastedLocker in the first half of this year. In his technical analysis, the researcher highlighted several noteworthy features in the WastedLocker ransomware.
For one, it has a command line interface that attackers can use to control the way it operates; they can specify specific directories to target, and prioritize which sets of files are encrypted first. The CLI also allows attackers to encrypt files on specified network resources.
WastedLocker also features a bypass for User Account Control (UAC) on Windows machines, which is a security check meant to prevent malicious privilege escalation. If a program seeks to elevate privileges in order to function, a pop-up prompt will ask, “Do you want to allow the following program to make changes to this computer?” Device-owners or administrators can choose yes or no; but users that have been assigned a standard user access token will be prompted to enter admin credentials.
To get around this, WastedLocker can silently elevate its privileges using a known bypass technique, Sinitsyn said: “[This] sequence of actions results in WastedLocker being relaunched from the alternate [Windows NT file system (NTFS)] stream with elevated administrative privileges without displaying the UAC prompt.”
On the crypto front, WastedLocker uses a combination of AES and a publicly available reference implementation of an RSA algorithm named “rsaref,” according to the researcher, which is also seen elsewhere with other ransomwares. Also, it applies an MD5 hash of the original content of each encrypted file, which is used during decryption to ensure the correctness of the procedure.
“For each processed file, WastedLocker generates a unique 256 bit key and a 128 bit IV which will be used to encrypt the file content using the AES-256 algorithm in CBC mode,” he explained. “The AES key, IV and the MD5 hash of the original content, as well as some auxiliary information, are encrypted with a public RSA key embedded in the trojan’s body. The sample under consideration contains a 4096-bit public RSA key.”
The result of RSA encryption is Base64 encoded and saved in a new file with the extension .garminwasted_info, he added – and unusually, a new info file is created for each of the victim’s encrypted files.
“This is a rare approach that was previously used by the BitPaymer and DoppelPaymer trojans,” Sinitsyn said. “This WastedLocker sample we analyzed is targeted and crafted specifically to be used in this particular attack. It uses a ‘classic’ AES+RSA cryptographic scheme which is strong and properly implemented, and therefore the files encrypted by this sample cannot be decrypted without the threat actors’ private RSA key.”
To prevent ransomware attacks, users should maintain up-to-date OS and application versions; prevent Remote Desktop Protocol access via the internet and improve end-user awareness of these kinds of threats, he concluded, echoing McQuiggan.
“The Garmin incident is the next in a series of targeted attacks on large organizations involving crypto-ransomware,” Sinitsyn said. “Unfortunately, there is no reason to believe that this trend will decline in the near future.”
Belarussian authorities arrested GandCrab ransomware distributor
4.8.20 Ransomware Securityaffairs
Last week, the Minister of Internal Affairs of Belarus announced the arrest of a 31-year-old man that is accused of distributing the infamous GandCrab ransomware.
Last week, the Minister of Internal Affairs of Belarus announced the arrest of a man on charges of distributing the infamous GandCrab ransomware.
The arrest is the result of an investigation conducted with help from law enforcement from the UK and Romania.
The authorities did not reveal the name of the man, they arrested him in Gomel (Belarus). He had no previous criminal records at the time of the arrest, but it is known to be a member of a cybercrime forum to become an affiliate for the GandCrab ransomware operation.
He allegedly subscribed the GandCrab ransomware-as-a-service to create his own version of the malware and spread it running a spam campaign.
The GandCrab ransomware-as-a-service first emerged from Russian crime underground in early 2018.
The GandCrab was advertised in the Russian hacking community, researchers from LMNTRIX who discovered it noticed that authors was leveraging the RIG and GrandSoft exploit kits to distribute the malware.
As usually happen for Russian threat actors, members cannot use the ransomware to infect systems in countries in the former Soviet Republics that now comprise the Commonwealth of Independent States.
Below some interesting points from the first advertisement for this threat:
Prospective buyers are asked to join the ‘partner program’, in which profits from the ransomware are split 60:40
Large’ partners are able to increase their percentage of proceeds to 70 per cent
As a Ransomware-as-a-service offering, technical support and updates are offered to ‘partners’
Partners are prohibited from targeting countries in the Commonwealth of Independent States (Azerbaijan, Armenia, Belarus, Kazakhstan, Kyrgyzstan, Moldova, Russia, Tajikistan, Turkmenistan, Uzbekistan and Ukraine) – violating this rule results in account deletion
Partners must apply to use the ransomware, and there is a limited amount of ‘seats’ available.” reads the translation of the ad.
The operators behind the GandCrab RaaS offer they platform maintaining 40% of the ransom, the percentage is reduced for large partners.
Once infected, if the victim does not pay on time, he will have to pay a double ransom.
The authors of the GandCrab RaaS also offers technical support and updates to its members, they also published a video tutorial that shows how the ransomware is able to avoid antivirus detection.
The RaaS implements a user-friendly admin console, which is accessible via Tor Network, to allow malware customization (i.e. ransom amount, individual bots and encryption masks)
According to Belarussian authorities, the man infected more than 1,000 computers with his customized variant of GandCrab, but is not known how many victims paid the ransom. He was demanding the payment of around $1,200 worth of Bitcoin.
Officials believe that the man infected computers in more than 100 countries, most of them in India, the US, Ukraine, the UK, Germany, France, Italy, and Russia. GandCrab made more than 54,000 victims across the world, including 156 in Belarus, officials said.
Authorities also added that the man was involved in the distribution of cryptominers and wrote malware for other users on the same hacking forums.
The GandCrab Ransomware-as-a-Service shut down operations in June 2019 and told affiliates to stop distributing the ransomware. The authors of the ransomware are still unknown and are at large.
Security researchers Damian and David Montenegro, who follow the evolution of the GandCrab since its appearance, the GandCrab operators announced their decision of shutting down their operation in a post in popular hacking forums:
The operators revealed they have generated more than $2 billion in ransom payments, earning on average of $2.5 million dollars per week. The operators revealed to have earned a net of $150 million that now have invested in legal activities.
FBI issued a flash alert about Netwalker ransomware attacks
4.8.20 Ransomware Securityaffairs
The FBI has issued a security alert about Netwalker ransomware attacks targeting U.S. and foreign government organizations.
The FBI has issued a new security flash alert to warn of Netwalker ransomware attacks targeting U.S. and foreign government organizations. The feds are recommending victims, not to pay the ransom and reporting incidents to their local FBI field offices.
The flash alert also includes indicators of compromise for the Netwalker ransomware along with mitigations.
The FBI warns of a new wave of Netwalker ransomware attacks that began in June, the list of victims includes the UCSF School of Medicine and the Australian logistics giant Toll Group.
“As of June 2020, the FBI has received notifications of Netwalker ransomware attacks on U.S. and foreign government organizations, education entities, private companies, and health agencies by unidentified cyber actors.” reads the alert. “Netwalker became widely recognized in March 2020, after intrusions on an Australian transportation and logistics company and a U.S. public health organization. Cyber actors using Netwalker have since taken advantage of the COVID-19 pandemic to compromise an increasing number of unsuspecting victims.”
The Netwalker ransomware operators have been very active since March and also took advantage of the ongoing COVID-19 outbreak to target organizations.
The threat actors initially leveraged phishing emails delivering a Visual Basic Scripting (VBS) loader, but since April 2020, Netwalker ransomware operators began exploiting vulnerable Virtual Private Network (VPN) appliances, user interface components in web apps, or weak passwords of Remote Desktop Protocol connections to gain access to their victims’ networks.
Recently the Netwalker ransomware operators were looking for new collaborators that can provide them with access to large enterprise networks.
“Two of the most common vulnerabilities exploited by actors using Netwalker are Pulse Secure VPN (CVE-2019-11510) and Telerik UI (CVE-2019-18935).” continues the alert. “Once an actor has infiltrated a network with Netwalker, a combination of malicious programs may be executed to harvest administrator credentials, steal valuable data, and encrypt user files. In order to encrypt the user files on a victim network, the actors typically launch a malicious PowerShell script embedded with the Netwalker ransomware executable.”
Below the recommended mitigations provided by the FBI:
Back-up critical data offline.
Ensure copies of critical data are in the cloud or on an external hard drive or storage device.
Secure your back-ups and ensure data is not accessible for modification or deletion from the system where the data resides.
Install and regularly update anti-virus or anti-malware software on all hosts.
Only use secure networks and avoid using public Wi-Fi networks.
Consider installing and using a VPN.
Use two-factor authentication with strong passwords.
Keep computers, devices, and applications patched and up-to-date.
The FBI advises victims not to pay the ransom.
Garmin allegedly paid for a decryptor for WastedLocker ransomware
4.8.20 Ransomware Securityaffairs
BleepingComputer researchers confirmed that Garmin has received the decryption key to recover their files encrypted with the WastedLocker Ransomware.
BleepingComputer first revealed that Garmin has received the decryption key to recover the files encrypted with the WastedLocker Ransomware in the recent attack.
On July 23, smartwatch and wearables maker Garmin has shut down several of its services due to a ransomware attack that targeted its internal network and some production systems.
The outage also impacted the company call centers, making it impossible for the company to provide information to its users.
Most of the services used by customers of the company rely on the Garmin Connect service to sync data about runs and bike rides with its servers.
Even if the company did not provide technical details of the outage, several employees shared details about the alleged ransomware attack on social media.
Some employees later told BleepingComputer that the ransom demand was $10 million.
Some employees speculate the involvement of a new strain of ransomware called WastedLocker.
On July 27, the company announced that its computer networks were coming back after the ransomware attack.
Now BleepingComputer confirmed the malware family involved in the attack was the Wastedlocker ransomware after it has gained access to an executable created by the Garmin IT department to decrypt a workstation.
This means that the company allegedly paid the ransomware operators to obtain the decryptors for its files.
“To obtain a working decryption key, Garmin must have paid the ransom to the attackers. It is not known how much was paid, but as previously stated, an employee had told BleepingComputer that the original ransom demand was for $10 million.” reported BleepingComputer.
“When extracted, this restoration package includes various security software installers, a decryption key, a WastedLocker decryptor, and a script to run them all.”

Experts reported that upon executing the restoration package, it decrypts the files stored on the computer and then installs security software.
Bleepingcomputer reported that the script used by Garmin has a timestamp of 07/25/2020, a circumstance that suggests the company paid the ransom between July 24th and July 25th.
BleepingComputer researchers were able to encrypt a virtual machine using the sample of WastedLocker involved in the Garmin attack, then tested the decryptor.
The decryptor used by the company includes references to cybersecurity firm Emsisoft and ransomware negotiation service firm Coveware.
Both companies did not comment on this ransomware attacks
Emsisoft team is able to develop custom ransomware decryptors when the ransomware operators provide the victims the decryptor after the payment of the ransomware.
“If the ransom has been paid but the attacker-provided decryptor is slow or faulty, we can extract the decryption code and create a custom-built solution that decrypts up to 50 percent faster with less risk of data damage or loss,” Emsisoft’s ransomware recovery services page states.
Garmin did not comment the story.
Ransomware Feared as Possible Saboteur for November Election
4.8.20 Ransomware Securityweek
Federal authorities say one of the gravest threats to the November election is a well-timed ransomware attack that could paralyze voting operations. The threat isn’t just from foreign governments, but any fortune-seeking criminal.
Ransomware attacks targeting state and local governments have been on the rise, with cyber criminals seeking quick money by seizing data and holding it hostage until they get paid. The fear is that such attacks could affect voting systems directly or even indirectly, by infecting broader government networks that include electoral databases.
Even if a ransomware attack fails to disrupt elections, it could nonetheless rattle confidence in the vote.
On the spectrum of threats from the fantastical to the more probable, experts and officials say ransomware is a particularly realistic possibility because the attacks are already so pervasive and lucrative. The FBI and Department of Homeland Security have issued advisories to local governments, including recommendations for preventing attacks.
“From the standpoint of confidence in the system, I think it is much easier to disrupt a network and prevent it from operating than it is to change votes,” Adam Hickey, a Justice Department deputy assistant attorney general, said in an interview.
The scenario is relatively simple: Plant malware on multiple networks that affect voter registration databases and activate it just before an election. Or target vote-reporting and tabulation systems.
“With the 2020 election, election infrastructure has a target on its back,” Colorado Secretary of State Jena Griswold said. “We know that election infrastructure was attempted to be undermined in 2016, and we know the techniques are shifting.”
The number of attacks has escalated in recent years, with targets including Texas’ transportation agency and city computers in New Orleans. A December report by cybersecurity firm Emsisoft tracked attacks against at least 966 entities that interrupted 911 services, rendered medical records inaccessible and hindered police background checks.
“We’re seeing state and local entities targeted with ransomware on a near daily basis,” said Geoff Hale, a top election security official with Homeland Security’s Cybersecurity and Infrastructure Security Agency.
Steps taken to improve security of voter registration systems after the 2016 election could help governments fend off election-related ransomware attacks. They’ve also acted to ensure they can recover quickly in the event of an attack.
Colorado, for example, stores redundant versions of its voter registration data at two separate secure locations so officials can easily shift operations. Backups are regular so the system can be quickly rebuilt if needed.
Even so, ransomware is an added concern for local election officials already confronting staffing and budget constraints while preparing for a shift from in-person voting to absentee balloting because of the pandemic.
In West Virginia, state officials are more concerned about the cyberthreat confronting its 55 county election offices than a direct attack on the statewide voter registration system. One click from a county employee falling victim to a spearphishing attack could grant a hacker access to the county network and eventually to election systems.
“I’m more worried that those people who are working extra hours and working more days, the temporary staff that may be brought in to help process the paperwork, that all this may create a certain malaise or fatigue when they are using tools like email,” said David Tackett, chief information officer for the secretary of state.
In states that rely heavily on in-person voting and use electronic systems to check in voters, a well-timed attack particularly during early voting could prevent officials from immediately verifying a voter’s eligibility, making paper backups critical.
For states conducting elections entirely by mail, including Colorado, an attack near Election Day may have little effect on voting because ballots are sent early to all voters, with few votes cast in-person. But it could disrupt vote-tallying, forcing officials to process ballots by hand.
In many states, local officials will face an influx of new ballot requests. That means they’ll need constant access to voter data as they handle these requests. An attack could cause major disruptions.
Hickey said he was unaware of ransomware attacks directly targeting election infrastructure. But local election offices are often connected to larger county networks and not properly insulated or protected.
A criminal targeting a county or state “may not even know what parts of the network they got into,” Hickey said. But as the malware creeps along and spreads, “what gets bricked is the entire network — and that includes but is not limited to election infrastructure.”
Even if election infrastructure isn’t directly targeted, there would likely be immediate assumptions it was, said Ron Bushar of the FireEye cybersecurity company.
A February advisory issued by the FBI and obtained by The Associated Press recommends local governments separate election-related systems from county and state systems to ensure they aren’t affected in an unrelated attack.
That’s how Louisiana’s election network survived multiple ransomware attacks: one occurred six days before the November election through an IT services company shared by the seven impacted counties. The second hit the state network a day after voting.
At a January meeting of state officials, Louisiana’s secretary of state highlighted the attacks as a blueprint for how an adversary like Russia could throw November into disarray.
Jason Ingalls, whose security firm responded to the Louisiana attacks, said in an interview: “You put me in charge of a platoon of Russian hackers and give me a couple of years to stage this and I could pull this off.”
CWT Travel Agency Faces $4.5M Ransom in Cyberattack, Report
1.8.2020 Ransomware Threatpost
The corporate-travel leader has confirmed an attack that knocked systems offline.
CWT, a giant in the corporate travel agency world with a global clientele, may have faced payment of $4.5 million to unknown hackers in the wake of a ransomware attack.
Independent malware hunter @JAMESWT tweeted on Thursday that a malware sample used against CWT (formerly known as Carlson Wagonlit Travel) had been uploaded to VirusTotal on July 27; he also included a ransom note indicating that the ransomware in question is Ragnar Locker.
In a media statement to Threatpost, CWT confirmed the cyberattack, which it said took place this past weekend: “We can confirm that after temporarily shutting down our systems as a precautionary measure, our systems are back online and the incident has now ceased.”
@JAMESWT also reported that the ransom demanded clocked in at 414 Bitcoin, or about $4.5 million at the current exchange rate. A CWT spokesperson declined to comment on whether the ransom was paid, or any technical details of the attack, or how it was able to recover so quickly.
Despite assurances of recovery, the impact of the incident could be wide: CWT says that it provides travel services to 33 percent of the Fortune 500 and countless smaller companies. And according to the ransom note uploaded by @JAMESWT, the hackers claim to have downloaded 2TB of the firm’s data, including “billing info, insurance cases, financial reports, business audit, banking accounts…corporate correspondence…[and] information about your clients such as AXA Equitable, Abbot Laboratories, AIG, Amazon, Boston Scientific, Facebook, J&J, SONOCO, Estee Lauder and many others.”
If true, the tactic fits in with the one-two punch trend that many ransomware operators have taken of late – locking up files, but also stealing and threatening to release sensitive data if victims don’t pay up. Such was the case of celebrity law firm Grubman Shire Meiselas & Sacks, which was hit with the REvil ransomware in May. Attackers threatened to leak 756 gigabytes of stolen data, including personal info on Lady Gaga, Drake and Madonna.
And in fact, the attackers behind the Ragnar Locker ransomware in particular are known for stealing data before encrypting networks, as was the case in April, in an attack on the North American network of Energias de Portugal (EDP). The cyberattackers claimed to have stolen 10 TB of sensitive company data, and demanded a payment of 1,580 Bitcoin (approximately $11 million).
“Ragnar Locker is a novel and insidious ransomware group, as Portuguese energy provider EDP found out earlier this year,” Matt Walmsley, EMEA director at Vectra, said via email. “Mirroring the ‘name and shame’ tactic used by Maze Group ransomware, victim’s data is exfiltrated prior to encryption and used to leverage ransomware payments. The bullying tactics used by these ransomware groups are making attacks even more expensive, and they are not going to stop any time soon, particularly within the current climate.”
However, if a data breach occurred in the CWT incident, the company has made no public disclosure on that aspect of the incident, and it has not yet reported the issue to the California Department of Justice (which requires data breach notifications for any incident affecting California residents within 30 days, under the California Consumer Protection Act).
CWT also said in its media statement that “While the investigation is at an early stage, we have no indication that PII/customer and traveler information has been affected. The security and integrity of our customers’ information is our top priority.”
According to the Register, certain CWT clients confirmed that they were notified of the incident by the travel agency.
Ragnar Locker typically uses exploits for managed service providers or Windows Remote Desktop Protocol (RDP) to gain a foothold on targeted networks, according to past analysis. The malware then looks to gain administrator-level access to the domain of a target and exfiltrate data, before using native Windows administrative tools such as Powershell and Windows Group Policy Objects (GPOs) to move laterally across the network to Windows clients and servers.
This M.O. could offer clues as to how the infection occurred, according to researchers.
“Ragnar Locker has used service providers as a means to distribute their payload,” Vectra’s Walmsley said. “These attackers will attempt to exploit, coerce and capitalize on organizations’ valuable digital assets, and now service companies with their extensive number of tantalizing downstream corporate customers, appear to have been targeted too.”
List of ransomware that leaks victims' stolen files if not paid
29.5.2020 Bleepingcomputer Ransomware
Starting last year, ransomware operators have escalated their extortion strategies by stealing files from victims before encrypting their data. These stolen files are then used as further leverage to force victims to pay.
Many ransomware operators have created data leak sites to publicly shame their victims and publish the files they stole.
As this is now a standard tactic for ransomware, all attacks must be treated as a data breaches.
Below is a list of ransomware operations that have a dedicated site for leaking data stolen from their victims.
The list of ransomware with data leak sites
AKO Ransomware
AKO ransomware began operating in January 2020 when they started to target corporate networks with exposed remote desktop services.
Unlike other ransomware, Ako requires larger companies with more valuable information to pay a ransom and an additional extortion demand to delete stolen data.
If payment is not made, the victim's data is published on their "Data Leak Blog."
AKO data leak site
CL0P Ransomware
CL0P started as a CryptoMix variant and soon became the ransomware of choice for an APT group known as TA505.
This group's ransomware activities gained media attention after encrypting 267 servers at Maastricht University.
In March 2020, CL0P released a data leak site called 'CL0P^-LEAKS', where they publish the victim's data.
CL0P data leak site
DoppelPaymer Ransomware
In July 2019, a new ransomware appeared that looked and acted just like another ransomware called BitPaymer.
Named DoppelPaymer by Crowdstrike researchers, it is thought that a member of the BitPaymer group split off and created this ransomware as a new operation.
Soon after CrowdStrike's researchers published their report, the ransomware operators adopted the given name and began using it on their Tor payment site.
DoppelPaymer targets its victims through remote desktop hacks and access given by the Dridex trojan.
High profile victims of DoppelPaymer include Bretagne Télécom and the City of Torrance in Los Angeles county.
In February 2020, DoppelPaymer launched a dedicated leak site that they call "Dopple Leaks" and have threatened to sell data on the dark web if a victim does not pay.
DoppelPaymer data leak site
Maze Ransomware
Maze ransomware is single-handedly to blame for the new tactic of stealing files and using them as leverage to get a victim to pay.
First spotted in May 2019, Maze quickly escalated their attacks through exploit kits, spam, and network breaches.
In November 2019, Maze published the stolen data of Allied Universal for not paying the ransom.
Since then, they started publishing the data for numerous victims through posts on hacker forums and eventually a dedicated leak site. Soon after, all the other ransomware operators began using the same tactic to extort their victims.
Maze is responsible for numerous high profile attacks, including ones against cyber insurer Chubb, the City of Pensacola, Bouygues Construction, and Banco BCR.
Maze data leak site
Nemty Ransomware
Originally launched in January 2019 as a Ransomware-as-a-Service (RaaS) called JSWorm, the ransomware rebranded as Nemty in August 2019.
As affiliates distribute this ransomware, it also uses a wide range of attacks, including exploit kits, spam, RDP hacks, and trojans.
In March, Nemty created a data leak site to publish the victim's data. This site is not accessible at this time.
Nemty leak site
Nephilim Ransomware
On March 30th, the Nemty ransomware operator began building a new team of affiliates for a private Ransomware-as-a-Service called Nephilim.
Unlike Nemty, a free-for-all RaaS that allowed anyone to join, Nephilim was built from the ground up by recruiting only experienced malware distributors and hackers.
Soon after, they created a site called 'Corporate Leaks' that they use to publish the stolen data of victims who refuse to pay a ransom.
Nephilim data leak site
Netwalker Ransomware
Starting as the Mailto ransomware in October 2019, the ransomware rebranded as Netwalker in February 2020.
Best known for its attack against the Australian transportation company Toll Group, Netwalker targets corporate networks through remote desktop hacks and spam.
In May 2020, Newalker started to recruit affiliates with the lure of huge payouts and an auto-publishing data leak site that uses a countdown to try and scare victims into paying.
Netwalker data leak site
Pysa Ransomware (Mespinoza)
Pysa first appeared in October 2019 when companies began reporting that a new ransomware had encrypted their servers.
When first starting, the ransomware used the .locked extension for encrypted files and switched to the .pysa extension in November 2019.
With ransom notes starting with "Hi Company" and victims reporting remote desktop hacks, this ransomware targets corporate networks.
For those interesting in reading more about this ransomware, CERT-FR has a great report on their TTPs.
The ransomware operators have created a data leak site called 'Pysa Homepage' where they publish the stolen files of their "partners" if a ransom is not paid.
Pysa / Mespinoza data leak site
Ragnar Locker Ransomware
First seen in February 2020, Ragnar Locker was the first to heavily target and terminate processes used by Managed Service Providers (MSP).
This tactic showed that they were targeting corporate networks and terminating these processes to evade detection by an MSP and make it harder for an ongoing attack to be stopped.
Ragnar Locker gained media attention after encrypting the Portuguese energy giant Energias de Portugal (EDP) and asked for a 1,580 BTC ransom.
RagnarLocker has created a web site called 'Ragnar Leaks News' where they publish the stolen data of victims who do not pay a ransom.
Ragnar Locker data leak site
REvil / Sodinokibi Ransomware
Sodinokibi burst into operation in April 2019 and is believed to be the successor of GandCrab, who shut down their ransomware operation in 2019.
Also known as REvil, Sodinokibi has been a scourge on corporate networks after recruiting an all-star team of affiliates who focus on high-level attacks utilizing exploits, hacked MSPs, and spam.
Known victims of the REvil ransomware include Grubman Shire Meiselas & Sacks (GSMLaw), SeaChange, Travelex, Kenneth Cole, and GEDIA Automotive Group.
After Maze began publishing stolen files, Sodinokibi followed suit by first publishing stolen data on a hacker forum and then launching a dedicated "Happy Blog" data leak site
REvil / Sodinokibi data leak site
Sekhmet Ransomware
Sekhmet appeared in March 2020 when it began targeting corporate networks.
"Your company network has been hacked and breached. We downloaded confidential and private data. In case of not contacting us in 3 business days this data will be published on a special website available for public view," states Sekhmet's ransom note.
The Sekhmet operators have created a web site titled 'Leaks leaks and leaks' where they publish data stolen from their victims.
Sekhmet data leak site
Snatch Ransomware
In operation since the end of 2018, Snatch was one of the first ransomware infections to steal data and threaten to publish it.
They previously had a leak site created at multiple TOR addresses, but they have since been shut down. It is not known if they are continuing to steal data.
Snatch ransom note
(Source: Zerofox)
Ransomware who leak data without dedicated sites
Instead of creating dedicated "leak" sites, the ransomware operations below leak stolen files on hacker forums or by sending emails to the media.
CryLock Ransomware
Operating since 2014/2015, the ransomware known as Cryakl rebranded this year as CryLock.
As part of the rebrand, they also began stealing data from companies before encrypting their files and leaking them if not paid.
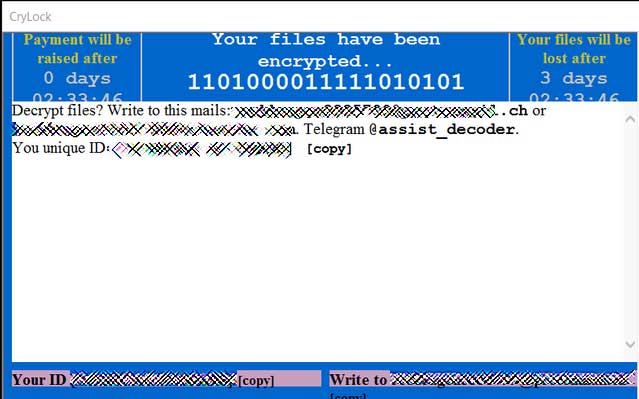
CryLock lock screen
ProLock Ransomware
The ProLock Ransomware started out as PwndLcker in 2019 when they started targeting corporate networks with ransom demands ranging between $175,000 to over $660,000.
After a weakness allowed a decryptor to be made, the ransomware operators fixed the bug and rebranded as the ProLock ransomware.
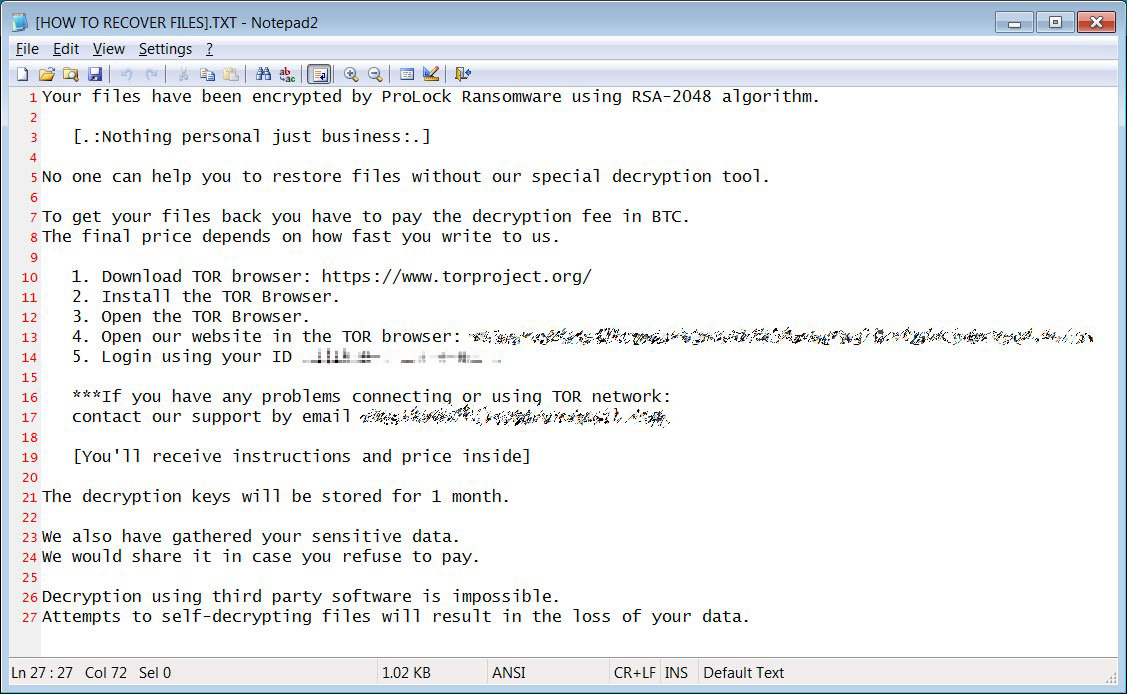
ProLock ransom note
Snake Ransomware
Snake ransomware began operating at the beginning of January 2020 when they started to target businesses in network-wide attacks.
Most recently, Snake released the patient data for the French hospital operator Fresenius Medical Care.
Snake ransom note
This list will be updated as other ransomware infections begin to leak data.