
Articles 2015 November - English Press English Articles Page 1 2 3 4 5 6 2020 2019 2018 2017 2016 2015 2014 2013 2012
H Analysis Android Apple APT Attack BigBrothers BotNet Congress Crime Crypto Cryptocurrency Cyber CyberCrime CyberSpy CyberWar Exploit Forensics Hacking ICS Incindent iOS IT IoT Mobil OS Phishing Privacy Ransomware Safety Security Social Spam Virus Vulnerebility
Jednotlivé články jsou rozděleny podle měsíců a zde je najdete./The articles are broken down by month and can be found here.
2015 - January February March April May June July August September October November December
Today NSA has Stopped its Bulk Phone Surveillance Program
30.11.2015
Rejoice!
From this morning, you can call freely to anyone, talk anything without any fear of being spied by the United States National Security Agency (NSA), as the agency is not allowed to collect bulk phone records.
Until now we all are aware of the NSA's bulk phone surveillance program – thanks to former NSA employee Edward Snowden, who leaked the very first top secret documents of the agency in 2013.
However, more than two years later of the first revelation, that bulk phone surveillance program has finally come to an end.
End of Bulk Phone Surveillance Program
The White House announced Friday evening on the intelligence community's official Tumblr that the NSA will officially be shutting down its bulk phone surveillance program by Sunday, November 29.
Under this program, the US intelligence agency collected only the "metadata" that reveals data related to the called phone numbers (i.e. which numbers are calling and what time they place those calls). However, no content of the mobile conversations were recorded by the agency.
"Beginning Sunday, November 29, the government is prohibited from collecting telephone metadata records in bulk under Section 215, including of both U.S. and non-U.S. persons," the official announcement read.
The end of the vast surveillance program comes as a result of the USA Freedom Act passed by Congress back in June.
NSA's Bulk Metadata Collection is illegal
The bulk collection of metadata was ruled illegal by a court in May 2015. The USA Freedom Act ordered the spy agency to terminate collecting bulk phone metadata of U.S. Citizen, but the agency get the program extended until November 29 as a grace period.
The law put an end to the bulk phone data collection in an effort to sniff out suspicious activity. Instead, allow the agencies to request the records from telecom companies to enable monitoring of call records of specific people for up to 6 months if needed in terrorism investigations.
NSA to Request Records directs from the Telecoms
Now, the US spy agency is out of time, and the Obama administration says that it has a less invasive program ready to replace the old program.
So, from now on, the NSA will not be collecting your phone records in bulk – at least under the agencies laid out in Section 215 of the Patriot Act – and will have to request for data individually to telecommunication companies.
Swedish Court — 'We Can't Ban The Pirate Bay'
30.11.2015
Swedish court — 'We can't ban The Pirate Bay'
The controversial file-sharing website The Pirate Bay will still be running in Sweden as the District Court of Stockholm on Friday ruled that they be unable to force the internet service providers (ISPs) to block the website from operating.
The Pirate Bay is an infamous Swedish search engine predominantly used worldwide for pirating material, such as software, movies, music files and TV shows, entirely free of charge.
Numerous ISPs around Europe block the Pirate Bay, but the notorious site will not be inaccessible in its home country Sweden, at least for now, according to the local media.
Last year, a lawsuit was filed by Warner Music, Sony Music, Universal Music, Nordisk Film and the Swedish Film Industry in order to force Swedish ISP broadband companies to block the Pirate Bay, claiming them liable for the infringements of its customers.
Also Read: The Pirate Bay Runs on 21 "Raid-Proof" Virtual Machines To Avoids Detection
However, the Broadband companies refused to comply, stating that their only role is to provide their clients with access to the Internet while facilitating the free flow of information.
Sweden – We can't Ban The Pirate Bay
Now, a Stockholm District Court has handed down its decision in favor of ISPs, ruling that Sweden can not make them block the access to the Pirate Bay website, as those broadband companies are not responsible for what their customers do.
"A unanimous district court considers, therefore, that it is not in a position to authorize such a ban as the rights holders want, and, therefore, rejects their requests," presiding Chief Magistrate Anders Dereborg said.
In other words, the ISP networks are not participating in any crimes, according to the court ruling, as they are just the delivery medium.
Also Read: The Pirate Bay relaunch is FBI's Honeypot? Pirate Bay Team Responds,'NO WAY'
While it is possible that the group representing the copyright holders could appeal a higher court, in the meantime, the group will still have to pay the ISPs legal costs thus far, which amounts to more than $150,000.
So, before the group appeals a higher authority, this is something it might want to reconsider.
A few month back, The Pirate Bay co-founders Gottfrid Svartholm, Fredrik Neij, Peter Sunde and Carl Lundström cleared all the charges alleging criminal copyright infringement and abuse of electronic communications in a Belgian court.
The Hello Barbie doll, lights and shadows
30.11.2015
Mattel’s Hello Barbie has finally arrived in stores, but security experts have raised questions about security and privacy issues related to the technological toy.
Are you thinking of buying a Barbie for your daughter this Christmas?
Mattel’s Hello Barbie has finally arrived in stores, but security experts have raised questions about security and privacy issues related to the technological toy. The Hello Barbie doll is developed by the startup ToyTalk.
In February, The Register was one of the fist news agency reporting security and privacy implications of the Mattel’s Hello Barbie, and now that the popular doll is available for sale a security researcher has discovered security issues with the toy.
“Its Wi-Fi-connected Barbie toy has a microphone, a speaker, a small embedded computer with a battery that lasts about an hour, and Wi-Fi hardware. When you press a button on her belt buckle, Barbie wakes up, asks a question, and turns on its microphone while the switch is held down.” wrote the register.
Last week, the security expert Matt Jakubowski explained that the new Wi-Fi-Enabled Hello Barbie can be hacked, in the specific case to extract Wi-Fi network names, account IDs, and MP3 files from the toy.
“You can take that information and find out a person’s house or business. It’s just a matter of time until we are able to replace their servers with ours and have her say anything we want,” Jakubowski warned.

Oren Jacob, the ToyTalk CEO provided the following statement in response to the Jakubowski affirmation trying to rebuke the alarm.
“An enthusiastic researcher has reported finding some device data and called that a hack.” Jacob said. “While the path that the researcher used to find that data is not obvious and not user-friendly, it is important to note that all that information was already directly available to Hello Barbie customers through the Hello Barbie Companion App. No user data, no Barbie content, and no major security or privacy protections have been compromised to our knowledge.”
Jakubowski explained that it is quite easy to steal the account ID, this means that the attackers need get the password to gain access to the Hello Barbie account. Steal a password could be very simple for example with a spear phishing attack or by using other social engineering techniques.
Unfortunately, the experts at ToyTalk have a different opinion and consider the scenario improbable.
The Campaign for a Commercial-Free Childhood already asked Mattel to drop the Hello Barbie doll, a petition has already been signed by over 6,000 worried people.
We are approaching the holiday season, and recent data breach suffered by the giant VTech raised the question of children’s privacy.
Even if the Hello Barbie doll is secure today, this doesn’t mean that it will be the same tomorrow. Security experts could make a reverse engineering of its software components in order to discover security flaws.
Somerset Recon already reported the news that researchers have dumped the 16 megabits of firmware that runs the doll to analyze it.
“We began dumping the contents of the 16Mbit flash chip, and some pretty neat stuff popped up. Stay tuned for Part Two, where we’ll dive into the architecture of the system and its security implications.” wrote the Somerset Recon.
Stay Tuned!
ITAR (International Traffic in Arms Regulations) as cyber arms control
30.11.2015
That means that the State Department and the Pentagon are looking for an alternative framework, they might find it in the ITAR.
The US has failed to take the offensive cyber products to the Wassenaar agreement. That means that the State Department and the Pentagon are looking for an alternative framework. They might find it in ITAR [International Traffic in Arms Regulations].
The Obama administration understands that something has to be done to regulate the violence in the cyber domain. Cyber arms control and regulation are hot topics right now.
The last try to impose cyber arms control was with Wassenaar agreement that regulate dual use technologies. But, the big tech companies opposed, and the initiative failed.
I would like to argue that the Obama administration can choose to implement instead cyber arms control within the ITAR regulation.
ITAR
The ITAR is a set of United States Government regulations on the export and import of military related articles and services. Therefore, it can contain the offensive cyber technologies and give the US control over them.
One has to acknowledge that most of the cyber technologies are coming from US companies or companies that were funded by US money. It allows the US to use ITAR to control the export of those technologies.
The use of ITAR opens more possibilities in this context. For example, the US can decide that every code written on a CPU of Intel or AMD [US companies] is subject to ITAR. Equally, it can apply to any electronic product that is funded by US money or developed in the US.
If the US goes this way, others will follow. China is another country bothered with cyber defence. It is also a significant producer of electronics. That means that the Chinese government can apply a regulation like ITAR. Besides US and China, this is true for any “ITAR-Free” country.
To summarize, cyber technologies regulation is a must. There is no better option for the international community to decrease the violence in the cyber domain. The question on the table will it be by the Wassenaar Agreement, ITAR or a new one.
Recommended Reading:
http://insct.syr.edu/wp-content/uploads/2015/11/Herr_Rosenzweig_Cyber-Weapons-and-Export-Control.pdf
Trident nuclear weapons system could be vulnerable to cyber attacks
30.11.2015
The former British defence secretary Des Browne is warning that the Trident nuclear weapons system could be vulnerable to cyber-attack.
According to the Guardian, the former British defence secretary Des Browne called on the British Prime Minister to assess the resilience to cyber attacks of the Trident nuclear weapons system.
“The UK Trident programme encompasses the development, procurement and operation of the current generation of British nuclear weapons, and the means to deliver them.” states Wikipedia.
The Britain’s Trident nuclear weapons system may be obsolete soon unless David Cameron can protect it from cyber attacks of nation-state actors.
“The government … have an obligation to assure parliament that all of the systems of the nuclear deterrent have been assessed end-to-end against cyber attacks to understand possible weak spots and that those weak spots are protected against a high-tier cyber threat. If they are unable to do that then there is no guarantee that we will have a reliable deterrent or the prime minister will be able to use this system when he needs to reach for it.” states Browne.
The UK’s former defense secretary is seeking assurance from the Prime Minister that the Trident nuclear weapons system is secured against attacks from hostile persistent threat actors, such as Russia and China.
UK Trident nuclear weapons systems 2
According to a report issued by the US department of Defense on Resilient Military Systems, there is the concrete risk that the US and its allies could suffer a major attack on their military systems.
“The United States cannot be confident that our critical Information Technology (IT) systems will work under attack from a sophisticated and well-resourced opponent utilizing cyber capabilities in combination with all of their military and intelligence capabilities (a “full spectrum” adversary).” states the report. “While this is also true for others (e.g. Allies, rivals, and public/private networks), this Task Force strongly believes the DoD needs to take the lead and build an effective response to measurably increase confidence in the IT systems we depend on (public and private) and at the same time decrease a would-be attacker’s confidence in the effectiveness of their capabilities to compromise DoD systems. “
For the protection of the Trident nuclear weapons system it is essential to assess the military components searching for possible weaknesses and fix them.
According to the New Statesman, a spokesperson from the MoD explained that the Trident system is an air-gapped system, but we know that this is not sufficient to consider a system as security.
Security experts at FireEye discovered a Chinese hacking crew, dubbed APT 30, that was focusing its cyber espionage operations on air-gapped networks. The APT30 has many other tools in its arsenal that includes backdoors, malware with the ability to compromise air-gapped networks, downloaders and many others. Some of these tools were used only by the APT30 operators.
The British chancellor George Osborne last week to announce that the UK Government would allocate more than £3.2bn to cybersecurity over the next five years. Despite the significant effort, Browne expressed his skepticism on the protection of the Trident.
“My instinct is to think that £3.2bn over five years, comes nowhere near the scale of the cyber-threat challenge, if it includes ensuring cybersecurity for the command and control of our nuclear weapons. Also, this is the environment to which Moore’s law applies. Consequently, we can expect cyber-capacity to have doubled and doubled again since the report was published and to continue to increase.” said Browne.
Assassins in the darkweb, “Service catalogue” and Price list” updated
30.11.2015
Contract killers on darkweb have come up with updated “service-catalogue” with updated prices. Which are major changes and trends for prices?
Contract killers on darkweb have come up with updated “service-catalogue” with updated prices.
While comparing the recent screenshot of their “service-catalogue” captured from a C’thulhu Darksite with the published earlier, the following updates have been observed
They have done away with the “rank” systems, they have done away with the “rank” categorization for the target, and instead they have adopted a fairly simple categorization approach. The target would simply be categorized either as a “Regular Person” or a “public person”; there will not be any “medium” ranked targets. So, they have done away with “medium rank” categorization. Moreover, they have added the prices for higher difficulty levels; i.e., they have added the prices for the targets with the guards. Moreover, the prices vary based on the number of guards, if the target has 1 or 2 guards then the price would be higher than the target without the guards and if the target has 3-5 guards then the price for that would be the highest as the “difficulty level” would be the highest.
The old Pricelist found in the darkweb
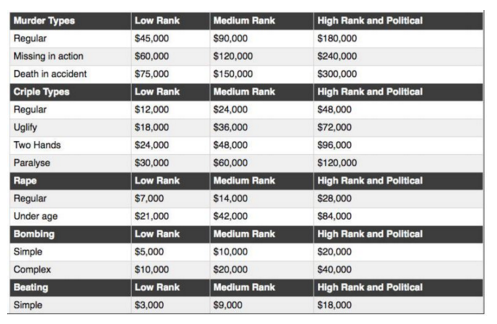
Below the new one
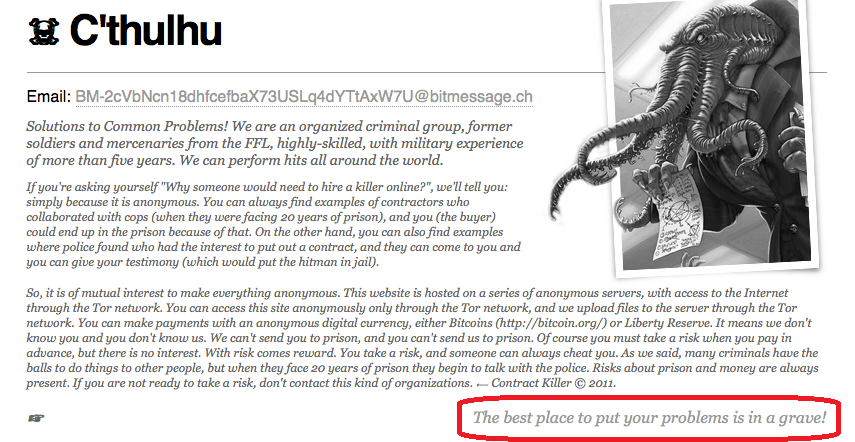
One more thing that drew the attention was that they have changed their tag-line as well; earlier, it used to be “The best place to put your all problems to grave!” the recent capture shows the tag-line as “ No fish is too big, no job too small – HITMAN does it all !”
Furthermore, if we observe the language used in Q&A, we can say that this was not written by a native English writer as there are conspicuous grammatical mistakes in writing.

Another known assassination market “Hitman Network” also updated its price list, they have significantly lowered the price than what was published/reported earlier. They have almost gone down by 50%.
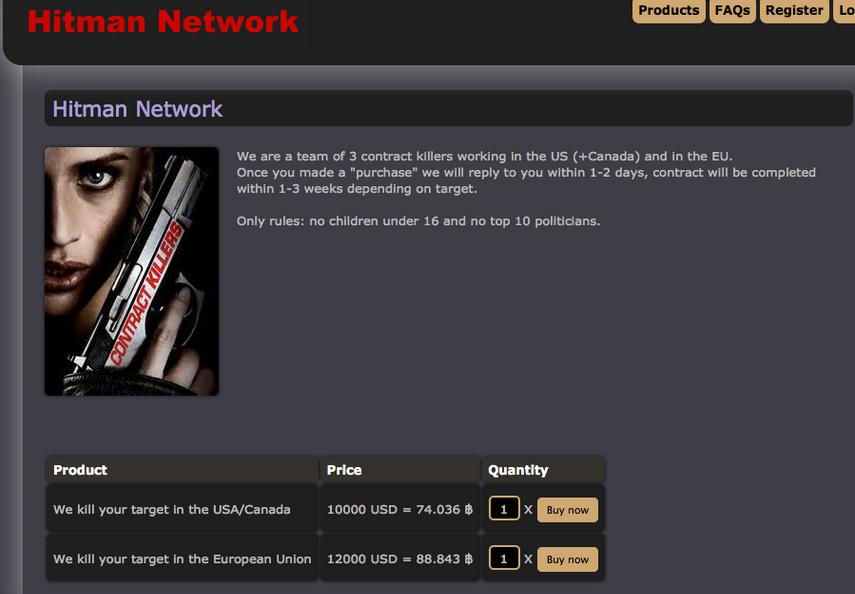

Moreover, the significant price difference was observed between these 2 killer markets, C’thulhu has got 45,000 USD for a regular target whereas Hitman has got only around 5000 USD for its target. We are not sure how many of these market offerings are legit.
Vtech hacked, data of thousands of kids exposed
30.11.2015
Toy maker Vtech has been hacked exposing data of thousands of kids, this hack is the fourth largest consumer data breach to date.
The greatest manufacturer of electronic toys Vtech, aka Video Technology Limited, was hacked. On 14 November, “an unauthorised party” managed to obtain access to the app store database of Vtech, the Learning Lodge.
The Learning Lodge includes apps, learning games, e-books, educational content and customer data (names, email IDs, passwords, questions and answers for password retrieval, IP addresses, and mailing addresses as well as download history), Vtech clarified that the database does not contain any financial data.

According to Motherboard the data breach may have exposed personal information of about five million parents who bought Vtech products and more 200,000 kids.
“The personal information of almost 5 million parents and more than 200,000 kids was exposed earlier this month after a hacker broke into the servers of a Chinese company that sells kids toys and gadgets, Motherboard has learned.” states Motherboard. “The hacked data includes names, email addresses, passwords, and home addresses of 4,833,678 parents who have bought products sold by VTech, which has almost $2 billion in revenue. The dump also includes the first names, genders and birthdays of more than 200,000 kids.”
The data stored in the app store database of Vtech belong to customers from several countries worldwide, including the US, China, the Netherlands, Denmark, Canada, the UK, Belgium, Ireland, France, Germany, Spain, Luxembourg, Latin America, Hong Kong, Australia and New Zealand.
The company issued an official statement admitting the data breach announcing an ongoing investigation.
“VTech Holdings Limited today announced that an unauthorized party accessed VTech customer data housed on our Learning Lodge app store database on November 14, 2015 HKT.” states the official statement. “Upon discovering the unauthorized access we immediately conducted a thorough investigation, which involved a comprehensive check of the affected site and implementation of measures to defend against any further attacks.”
The company received an email asking about the incident on 23 November, then started the investigation that revealed irregular activity on the Learning Lodge website.
The company announced that is working to improve security of the app store database and protect its customers.
“We are committed to protecting our customer information and their privacy, to ensure against any such incidents in the future.” added the company.
Motherboard analyzed the breached archive with the support of the security expert Troy Hunt, who maintains the website Have I Been Pwned.
Hunt discovered the archive contains “hashed” passwords or protected with an algorithm known as MD5, quite easy to break. The secret questions used for password or account recovery were stored in plaintext, crooks could potentially use them to take over other accounts belonging to the victims..
“That’s very negligent,” Hunt said. “They’ve obviously done a really bad job at storing passwords.”
As explained by Hunt, the most worrisome aspect of this data breach is the fact that it contains data about kids.
“When it includes their parents as well—along with their home address—and you can link the two and emphatically say ‘Here is 9 year old Mary, I know where she lives and I have other personally identifiable information about her parents (including their password and security question),’ I start to run out of superlatives to even describe how bad that is,” Hunt wrote in a blog post he published on Friday.
At the time of publishing VTech have taken services offline to fix the issue.
Russia deploys jamming systems in Syria as tensions rise
30.11.2015
Russia will deploy jamming systems in Syria to protect its air forces and prevent attacks against its aircraft.
The Russian army in Syria is planning to launch electronic warfare in the country with the institution of jamming systems. The jamming systems are an essential component of the Russian military strategy that aims to prevent attacks against its troops in the area.
On Tuesday, the Turkish Air Force brought down a Russian Su-24M Fencer bomber using an air-to-air missile in Syria near the Turkish border. Officially, the Turkish Air Force was carrying out strikes against terrorists in northern Syria.

According to the according to Lieutenant-General Evgeny Buzhinsky, Russia will have engage an electronic warfare to protect its pilots and prevent a similar attack.
The Russian forces will use both ground-based systems and specific equipment installed on a number of aircraft in the Russian aerial fleet.
It is a war scenario, the Russian military will install in Syria a highly sophisticated missile system to target any enemy aircraft flying over the area.
The incident is raising tensions between Russia and Turkey, Vladimir Putin used the following statement to describe the incident:
“a stab in the back by the accomplices of terrorism.”
The presence of a jamming system in the area will prevent a similar incident by interfering with electronic components of the attackers.
“Regarding the possible impact of this incident on the further developments of the operation in Syria, I think that from now on, our pilots will be more attentive and if the Turks continue behaving in such a manner, Russia will have to resort to electronic jamming and other warfare equipment, including special aircraft with special equipment on board, in order to protect our pilots from being stricken with missiles,” explained Buzhinsky.
In October the Russian news agency SputnikNews reported the presence of Russian cruiser mounted S-300 missile defense system in the shore of Latakia. Jamming systems were referred by the NATO’s supreme commander General Philip Breedlove described as the Russian A2/AD (anti-access/area denial) bubble in Syria.
The electronic equipment blinded NATO inside a bubble of 600 km in diameter centered on the Russian base in Latakia.
“The technology in question seems similar to the KRET Richag-AV system, although it apparently functions on a larger scale. A tactical version of this system was presented to journalists in April 2015.” reported the SputnikNews.
Turris Omnia Security Project protects home network users
30.11.2015
The non-profit security research Turris Omnia project originating from the Czech Republic focuses on safety of SoHo users.
The non-profit security research project originating from the Czech Republic, which focuses on safety of SoHo users, has recently entered a new phase. This project, whose users include such celebrities as Vint Cerf and Steve Crocker, is the work of CZ.NIC, the administrator of the Czech national domain .CZ and developer of globally used open-source projects, such as the authoritative DNS server KnotDNS or the routing daemon Bird.
In the original project, each user of the service received a Turris router, which extends standard functions of a home router to include the ability to analyze traffic between the Internet and the home network, while identifying suspicious data streams. If such data stream is detected, the router alerts the Turris central to a possible attack. The system central then compares data from many connected Turris routers and evaluates the detected threat.

If the threat is classified as attack, updates are created and distributed throughout the Turris network to help protect all other users. The router also includes other interesting safety-related features. One of them is the Majordomo tool which enables the user to check what public IP addresses the devices on their network communicated with. This tool was inspired by earlier problems of some IoT devices, such as TVs, which were caught sending data “home”.
Hardware and software developed within the project are completely open and accessible to the whole community. The aim of this project is to increase the safety of SoHo users while identifying new threats on the Internet. The Turris router supports IPv6, DNSSEC, automatic updates, and much more. The router, which is an important part of the project, was originally intended only for users from the Czech Republic. Due to the great success of the project, it was decided to create a similarly equipped device that would be available to users from other countries.
This is how the project of the Turris Omnia router came to be, which retained most important features of the original device.
The performance is provided by a 1.6GHz dual-core ARM CPU, 4GB of flash storage and 1GB of DDR3 RAM. Turris is ready for fast WAN and LAN: it has six 1Gb ports and dual-band Wi-Fi 802.11ac (3×3 MIMO)/ 802.11b/g/n (2×2 MIMO).
It also offers an SFP connector for optical Internet. Such a powerful router obviously suggests other possible uses, for example as a home NAS, that is why two USB 3.0 ports are also included. The router’s board has two Mini PCI Express ports, one mSATA, pins for GPIO, I²C, SPI and even a slot for a SIM card. Compared to the original Turris router, Turris Omnia brings one major change.

Participation in the research project is voluntary and the user can decide whether to enable the collection of anomalies on the device, for example.
Both versions of the router also allow their users to redirect certain ports to the common honeypot of the project, making the system central receive information about the behavior of attackers in the various networks, to which the routers are connected.
Thanks to this option, the project has already achieved success in detecting suspicious behavior of particular systems, protecting users from web pages spreading malware and identifying Turris clients’ computers that were members of the Zeus botnet. In the course of the last year’s investigation of attacks on users of the Synology Company, the company became interested in the anonymous data from the project.
The Turris project publishes information on curious findings on the CZ.NIC blog.
The Turris Omnia router can now be ordered in the crowdfunding campaign on Indiegogo either as the raw motherboard, or the complete device. The project remains non-profit, the price takes into account only the actual costs of CZ.NIC for the device production.
Terror alert spam detected by Symantec in the wild
30.11.2015
Cybercriminals impersonate law enforcement officials in Dubai, Bahrain, Turkey, and Canada to send terror alert spam and serve RATs.
No Doubts, cyber criminals are jackals always ready to exploit any event in the headlines, even the most dramatic incidents. We have assisted in the past many cases in which crooks exploited the media attention on news events, such as the mysterious skyjacking of the Malaysian Airlines flight MH370 or the incident occurred at the AirAsia flight QZ8501.
News of the day is that people from several countries, including Canada, Dubai, Bahrain and Turkey, have received fake “terror alert” emails. According to Symantec, the bogus notifications advise recipients reading the mail to keep them and their families and company secured from an imminent attack.

The specific campaign leveraged on malicious emails with two attachments which according to the content in the mail is a brief on measures to adopt to remain secure. One of the attachment is in reality a document containing indications on the measured to adopt, the second one is a malware used to infect the victim’s computer.
The malicious code is a multiplatform remote access Trojan (RAT) dubbed Jsocket (Backdoor.Sockrat), a RAT which was developed by the same authors of the AlienSpy RAT.
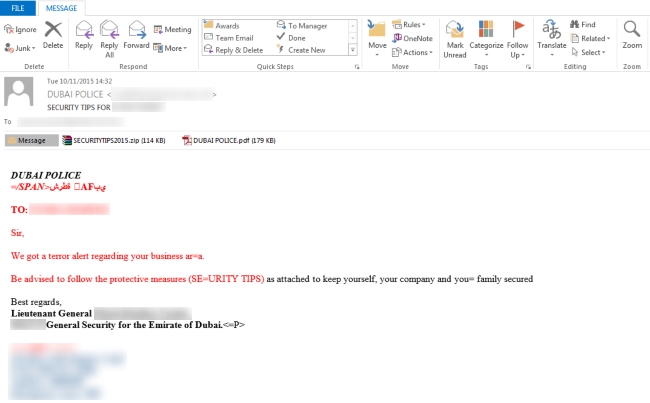
Operators behind the campaign used the signatures from local law enforcement agency’s officials in order to trick victims by giving more credibility to the messages.
“Earlier this month, Symantec observed malicious emails spoofing the email address of one United Arab Emirates (UAE) law enforcement agency, particularly the Dubai Police Force. These spear-phishing emails, which read like a warning from the Dubai Police, bank on users’ fear of terror attacks to trick them into executing the malicious attachments. The attachments are disguised as valuable security tips that could help recipients to protect themselves, as well as their companies and their families, from potential terror attacks that may occur in their business location.” states Symantec in a blog post.
“To add more credibility to the emails, the crooks impersonate the incumbent Dubai Police lieutenant general, who is also the head of general security for the emirate of Dubai, by signing the email with his name.”
The experts noticed that the spear phishing messages were well written and all officials used as alleged sender are currently in office.
Another element of interest highlighted by Symantec is represented by the effort spent by threat actors in targeting their victims, for example, the subject in most cases reflects the name of an employee who works for the targeted company. This circumstance leads the expert to believe that attackers have a specific knowledge of their victims.
Symantec experts confirm we may yet see more of these kinds of social engineering tactics preying on real-world fears, be careful!
Critical 'Port Fail' Vulnerability Reveals Real IP Addresses of VPN Users
27.11.2015
A newly discovered flaw affecting all VPN protocols and operating systems has the capability to reveal the real IP-addresses of users' computers, including BitTorrent users, with relative ease.
The vulnerability, dubbed Port Fail by VPN provider Perfect Privacy (PP) who discovered the issue, is a simple port forwarding trick and affects those services that:
Allow port forwarding
Have no protection against this specific attack
Port Forwarding trick means if an attacker uses the same VPN (Virtual Private Network) as the victim, then the real IP-address of the victim can be exposed by forwarding Internet traffic to a specific port.
"The crucial issue here is that a VPN user connecting to his own VPN server will use his default route with his real IP address, as this is required for the VPN connection to work," Perfect Privacy wrote in a blog post on Thursday.
Also Read: This Secure Operating System Can Protect You Even if You Get Hacked.
Port Fail affects all VPN protocols including…
OpenVPN
IPSec
…as well as applies to all operating systems, posing a huge privacy risk.
How Does 'Port Fail' Work?
A successful IP address leak attack requires an attacker to be on the same VPN network as the victim and to know the victim's VPN exit IP address, which could be discovered by tricking a victim into visiting a website control controlled by the attacker.
For example, an attacker with port forwarding enabled can see the request from the victim's actual IP addresses by tricking the victim into opening an image file.
The same attack is possible for BitTorrent users, but, in this case, there is no need for the attacker to redirect the victim to their page.
In this case, the attacker only with the activated port forwarding for the default BitTorrent port, can expose the real IP-address of a VPN user on the same network.
Also Read: Hackers Backdooring Cisco WebVPN To Steal Customers' Passwords
Affected VPN Providers
The flaw affected various large VPN providers. Perfect Privacy tested nine VPN providers out of which five were found to be vulnerable to this flaw and were alerted last week.
VPN providers including Private Internet Access (PIA), Ovpn.to and nVPN have fixed the issue before publication.
However, the company warned, "other VPN providers may be vulnerable to this attack as we could not possibly test all."
VPN aims to make you sure that your real identity remains anonymous on the Internet so that nobody could track the origin of your connection back to you, but this newly discovered flaw shows that it's quite easy to bypass this on some VPN providers.
Millions of IoT Devices Using Same Hard-Coded CRYPTO Keys
27.11.2015
Millions of embedded devices, including home routers, modems, IP cameras, VoIP phones, are shareing the same hard-coded SSH (Secure Shell) cryptographic keys or HTTPS (HTTP Secure) server certificates that expose them to various types of malicious attacks.
A new analysis by IT security consultancy SEC Consult shows that the lazy manufacturers of the Internet of Things (IoTs) and Home Routers are reusing the same set of hard-coded cryptographic keys, leaving devices open to Hijacking.
In simple words, this means that if you are able to access one device remotely, you can possibly log into hundreds of thousands of other devices – including the devices from different manufacturers.
Re-Using Same Encryption Keys
In its survey of IoT devices, the company studied 4,000 embedded devices from 70 different hardware vendors, ranging from simple home routers to Internet gateway servers, and discovered that…
…over 580 unique private cryptographic keys for SSH and HTTPS are re-shared between multiple devices from the same vendor and even from the different vendors.
The most common use of these static keys are:
SSH host keys
X.509 HTTPS certificates
SSH host keys verify the identity of a device that runs an SSH server using a public-private key pair. If an attacker steals the device's SSH host private key, he/she can impersonate the device and trick the victim's computer to talk to his computer instead.
Also Read: SSL Encryption — Securing Internet of Things (IoT)
The same happens in the case of websites if an attacker gains access to the device's HTTPS private certificate, which is actually used to encrypt traffic between users and its Web-based management interface.
The attacker can then decrypt the traffic to extract usernames, passwords and other sensitive data with the help of device's HTTPS private key.
MILLLLLIONS of Devices Open to Attacks
When scanned the Internet for those 580 keys, the researchers found that at least 230 crypto keys are actively being used by more than 4 Million IoT devices.
Moreover, the researchers recovered around 150 HTTPS server certificates that are used by 3.2 Million devices, along with 80 SSH host keys that are used by at least 900,000 devices.
Also Read: Most Vulnerable Smart Cities to Cyber Attack on Internet of Things (IoT).
The remaining crypto keys might be used by various other devices that are not connected to the Internet, but could still be vulnerable to man-in-the-middle (MITM) attacks within their respective local area networks.
As a result, potentially Millions of Internet-connected devices can be logged into by attackers, or their HTTPS web server connections can silently be decrypted by MitM attackers, using these crypto keys and certs once they're extracted from their firmware.
Where Does the actual Problem Reside?
The issue lies in the way vendors build and deploy their products. Typically, the vendors built their device's firmware based on software development kits (SDKs) received from chipmakers…
…without even bothering to change the source code or even the keys or certificates that are already present in those SDKs.
There are many reasons why this large number of devices are accessible from the Internet via HTTPS and SSH. These include:
Insecure default configurations by vendors
Automatic port forwarding via UPnP
Provisioning by ISPs that configure their subscribers' devices for remote management
"The source of the keys is an interesting aspect. Some keys are only found in one product or several products in the same product line. In other cases we found the same keys in products from various vendors," Sec Consult wrote in its blog post.
List of Vendors that are Re-Using Encryption Keys
Although SEC Consult identified more than 900 vulnerable products from roughly 50 manufacturers, the actual number could be even higher considering that its study only targeted firmware the company had access to.
Also Read: How Drones Can Find and Hack Internet-of-Things Devices From the Sky.
According to SEC Consult, these are the companies that were found reusing encryption keys:
ADB, AMX, Actiontec, Adtran, Alcatel-Lucent, Alpha Networks, Aruba Networks, Aztech, Bewan, Busch-Jaeger, CTC Union, Cisco, Clear, Comtrend, D-Link, Deutsche Telekom, DrayTek, Edimax, General Electric (GE), Green Packet, Huawei, Infomark, Innatech, Linksys, Motorola, Moxa, NETGEAR, NetComm Wireless, ONT, Observa Telecom, Opengear, Pace, Philips, Pirelli , Robustel, Sagemcom, Seagate, Seowon Intech, Sierra Wireless, Smart RG, TP-LINK, TRENDnet, Technicolor, Tenda, Totolink, unify, UPVEL, Ubee Interactive, Ubiquiti Networks, Vodafone, Western Digital, ZTE, Zhone and ZyXEL.
Most Affected Countries
Here's the list of Top 10 countries that are affected by SSH/HTTPS encryption key reuse:
United States
Mexico
Brazil
Spain
Colombia
Canada
China
Russian Federation
Taiwan
United Kingdom
SEC Consult has "worked together with CERT/CC to address this issue since early August 2015." and it recommends vendors to use securely random cryptographic keys for each IoT-capable device.
Moreover, ISPs are advised to make sure that there is no possibility to remotely access CPE (customer premises equipment) devices via WAN port. In case they need access for remote support purposes, "setting up a dedicated management VLAN with strict ACLs is recommended."
Nest camera, has a different definition for Turn off Mode
27.11.2015
Findings of a research show that the Nest camera is still operating even after it has been disabled through the mobile application.
People buy security cameras to have a higher level of control over their lives, but recently a research by a team at ABI Research found that users also must be worried about the security device itself.
nest camera
This news is about a security camera of Nest Company that was acquired by Google in 2014. The device is the latest product of Nest that enables users to see live video of their homes or to be notified about unusual motion or sound. Findings of research show that the camera is still operating even after it has been disabled through the mobile application. The LED indicator approves that the device is off, but the current drain illustrates something else. It is expected that current drain drops significantly when a device is disabled, but it’s not true in the case of Nest camera and current drain decline just 30 mA when the device in turn off mode.
“When a device goes to power down mode, you expect the current drain to drop quite a bit,” said Jim Mielke, a senior analyst at ABI Research.
The following table published by ABI research and depict current drain for different modes of operation.
Mode Resolution Current
Video Record – no motion 1080p 371mA
Video Record – no motion 720p 330mA
Video Record – no motion detected 720p 418mA
Video Record – no motion 360p 322mA
OFF Mode 343mA
“When Nest Cam is turned off from the user interface (UI), it does not fully power down, as we expect the camera to be turned on again at any point in time,” said Nest Labs in a statement. “With that said, when Nest Cam is turned off, it completely stops transmitting video to the cloud, meaning it no longer observes its surroundings.”
It can be argued that turn off mode has a unique definition universally and Nest approach to define turn off mode is bizarre. Even though Nest used 128-bit secure sockets layer (SSL) encryption, perfect forward secrecy and a 2,048-bit RSA key unique to each camera, but users might face new security risks. Lastly, this camera uses electricity constantly which is not an efficient practice in 21th century.
VPN users be aware , Port Fail flaw can reveal your identity
27.11.2015
Security experts at the VPN provider Perfect Privacy discovered a new vulnerability dubbed Port Fail that could be exploited to de-anonymize VPN users.
Security experts at the VPN provider Perfect Privacy discovered a new vulnerability dubbed Port Fail which affect all VPN (Virtual Private Network) protocols and operating systems. An attacker can exploit the Port Fail flaw to reveal the real IP-addresses of VPN users, including BitTorrent users.
Experts at Perfect Privacy tested nine VPN providers out of which five were found to be vulnerable to the Port fail flaw, the providers Private Internet Access (PIA), Ovpn.to and nVPN have fixed the issue before publication.
The experts at Perfect Privacy explained that the vulnerability is a simple port forwarding issue that affects all the services that implement the “port forwarding” feature and that doesn’t implement any defensive mechanism. The Port Fail affects all VPN protocols including the IPSec, OpenVPN, PPTP.
“We have discovered a vulnerability in a number of providers that allows an attacker to expose the real IP address of a victim. Port Fail affects VPN providers that offer port forwarding and have no protection against this specific attack.” Perfect Privacy wrote in a blog post on Thursday.
Basically, if the attacker uses the same VPN as the victim, then the real IP-address of the targeted user can be exposed by forwarding Internet traffic to a specific port. A successful Port Fail attack also required to know the victim’s VPN exit IP address, an information that is quite easy to discover by tricking a victim into visiting a website control controlled by the attacker.
VPN port fail 2
“The crucial issue here is that a VPN user connecting to his own VPN server will use his default route with his real IP address, as this is required for the VPN connection to work,” continues the post.
The attack works also against BitTorrent users and in this attack scenario there is no need for the attacker to redirect the victim to their page, the attacker only with the activated port forwarding for the default BitTorrent port can discover the real IP-address of a VPN user that share the same network.
The VPN affected by the vulnerability were already alerted by the company, but there is the risk that many other providers suffer the issue.
“other VPN providers may be vulnerable to this attack as we could not possibly test all.” states Perfect Privacy.
I suggest you giving a look to a blog post published by the penetration tester Darren Martyn describing the Port Fail attack scenario against Torrent users.
“I believe this kind of attack is probably going to be used heavily by copyright-litigation firms trying to prosecute Torrent users in the future, so it is probably best to double check that the VPN provider you are using does not suffer this vulnerability,” explained Martyn said.
How to Root Windows Phone and Unlock the Bootloader to Install Custom ROMs
27.11.2015
How to Root Windows Phone and Unlock the Bootloader to Install Custom ROM
Yes, Now it is possible to unlock a Windows Lumia Phone for Root Access and run custom ROMs.
Both Microsoft as well as Nokia have made Windows Lumia smartphones difficult to break into at a low-level by locking down their bootloaders, but a software hacker, who go by the name HeathCliff, has just proven that it is not impossible.
HeathCliff has released an excellent tool called "Windows Phone Internals" that allows Windows phone owners to unlock their smartphone's bootloaders, gain root access and even create and run custom ROMs.
What’s more interesting is the tool supports "most versions of Windows Phone 8.1 and Windows 10 Mobile".
HeathCliff is very well known XDA Developer and one of the Windows Phone legends. On Windows Phone part, HeathCliff is loved mostly for the WP7 Root Tools.
Windows Phone Internals or WP Internals is completely free to download though HeathCliff welcomes donations by those who have found the tool useful.
Also Read: Raspberry Pi Zero — The $5 Tiny Computer is Here
Here's the List of Things Windows Phone Internals can Do
You can unlock the bootloader of the specific Lumia Windows Phone models, and then enable Root Access
You can load your custom apps with higher privileges and without sandboxing in Windows Phone OS.
You can create Backup images of your phone and can also access the file-system in Mass Storage Mode.
You can even install your custom ROMs.
You can also watch the video provided by HeathCliff, showing what the tool is capable of doing.
Models Supported by Windows Phone Internals Tool
Here's the list of Lumia Phones Supported by the tool right now:
Lumia 520, 521 and 525
Lumia 620, 625
Lumia 720
Lumia 820
Lumia 920
Lumia 1020
Lumia 1320
Also Read: Meet Mr.Grey Hacker Who Stole 1.2 BILLION Login Credentials
How to Get Started?
Here's the introduction video for you to get started with Windows Phone Internals:
So, if you are ready to tinker with your Windows Phone then Download Windows Phone Internals for Free from here.
Also Read: Li-Fi is 100 times Faster than Wi-Fi: Real-World Tests Proved
Should You Root Your Phone?
However, I would caution against using this tool for those who do not understand the underlying architecture of their Windows Phones and Windows 10 Mobiles.
Rooting your phone gives you complete control over the OS, but that power can also be misused if you're not careful.
Heathcliff also states that after a tweak is completed, you should unroot your device to reduce the chance of malware or other bad stuff making their way on.
Using the tool without proper inspection could also result in damaged and unrecoverable data, for which neither The Hacker News nor I will be responsible. So please be careful before rooting your phone.
Windows Phone hacked with Windows Phone Internals
27.11.2015
Windows Phone Internals allows to unlock bootloader, enable Root access and create Custom ROM’s on selected Windows Lumia mobile devices.
We have spoken several times about jailbreaking and rooting activities explaining that these procedures allow to remove hardware restrictions implemented by the Apple and Google operating systems to give users root access allowing to download and install applications and themes from third-party stores.
But, what about Windows mobile devices?
Now, Windows users can now root their Windows Phones with the first Windows Phone root called Windows Phone Internals that was designed by Healthcliff74 (@Heathcliff74XDA).

Windows Phone Internals allows to unlock bootloaders of Windows Lumia and gain root access on the mobile, allowing to flash custom ROMs. This means that Windows Phone developer community will start developing good quality ROMs like the Android community does.
Healthcliff74 has launched a website dedicated to Windows Phone Internals with the intent to support users in rooting their devices.
“I am proud to announce the immediate availability of Windows Phone Internals 1.0. This tool allows you to unlock the bootloader of selected Lumia Windows Phone models. After unlocking the bootloader, you can enable Root Access on the phone or create and flash Custom ROM’s. I created a short introduction video to show the features of the tool.” said Healthcliff74.
“root Access allows you to load your own homebrew software onto the phone with high privileges. Apps can escape from their sandboxes. The tool can also create backup-images of the phone and access the file-system in Mass Storage mode. The tool supports most versions of Windows Phone 8.1 and Windows 10 Mobile. For a complete list of supported phones and Operating Systems have a look at the Getting Started section of the tool”.
In the following video is explained how to enable Root Access on Windows Phones and how to reate a Custom ROM.
The Windows Phone Internals tool works on most versions of Windows Phone 8.1 and Windows 10 Mobile.
Users can download and test the Windows Phone Internals on their device, but they have to consider that the operation has some risks to consider, such as the possibility to brick the Windows Phone.
Enjoy it!
Black Friday and Cyber Monday, Keep Yourself Safe
27.11.2015
Find out why there is increased risk of hacking during Black Friday and Cyber Monday and learn how to remain protected online.
Black Friday is here and so is Cyber Monday, with all the special seasonal offers that many consumers are craving! However, it seems that these are the days for which hackers have been preparing themselves all this time.
Unfortunately, there are more sophisticated threats that we should all beware of, as hackers have been gathering their strengths and are ready to unleash their wrath. Does this mean that we are better off abstaining from all purchases? Well, with the bargains that can be found online, good luck with your efforts to do that!
The Retail Cyber Intelligence Sharing Center has tried to inform people on the imminent risks that are piling up, when it comes to cyber threats on these days. In fact, they have published a report on what needs to be done on behalf of all consumers, in avoidance of negative consequences related to seasonal sales. It is worth reading through the report and find out why hackers understand the risks and how they overcome them, so as to get their hands on your money.
black friday scams
It is true that retailers have got their plates full and this means that they do not pay as much attention as they should be to preventive measures. As a result, hackers are left alone and they do what they know best – which is to intercept personal information and steal money online! ThreatMetrix has found an increase of 25% in the frauds prior to the holiday season.
What needs to be done, in order to avoid being compromised on Black Friday and Cyber Monday? Well, luckily things are not that devastating, assuming that you are vigilant. Here is what you should be focusing on, so that you can enjoy the holiday season and buy the things that you have been waiting for, without being tricked by anyone:
Only visit trusted websites, which are much safer to use. Do not trust any sites that you have never heard of, especially when you read through their offers and find them too good to be true. Search for the HTTPS on the address bar, since this is a great sign of security.
Allow encryption, as with this you will be able to prevent identity theft and the interception of your personal data (including the details of your credit card, apparently). VPN is a reliable method of using encryption throughout your web navigation and particularly throughout your financial transactions.
Do not click on any email links you find, even if they urge you to purchase an item of quality at half price or less. These links will most likely lead to your redirection somewhere unsafe and they can also be used for robbing you of your privacy.
Do not share your credit card credentials with anyone, even with your loved ones. More than that, you should not share them via an email or a private message on Facebook and other social media. This is a safe path to catastrophe!
Avoid Wi-Fi when purchasing something online, since publicly shared connections to the web include increased dangers and threats. Instead, use a private Internet connection that you know is secured and preferably encrypted.
Mobile devices are more prone to being hacked and they offer a more fertile ground for hackers to mislead you. Think about it, as you gaze through the merchandise of an e-shop from your limited sized screen and struggle to read the detailed description.
Enjoy Black Friday and Cyber Monday, taking full advantage of their special, limited offers for the holidays! Do so with absolute safety, though, since this is the best way to be jolly all-year-round!
Crooks use the Nuclear Exploit Kit to serve CryptoWall 4.0
27.11.2015
The popular Nuclear Exploit Kit has been used for the first time to serve the ransomware CryptoWall 4.0.
The Nuclear exploit kit is one of the privileged weapon in the arsenal of cyber criminal groups, now the popular crimeware kit has been used to serve the ransomware CryptoWall 4.0. In the past, criminal crews used the exploit kit to serve instances of the CryptoWall 3.0.
The discovery was made by the security researcher at Rackspace Brad Duncan, who explained that it is the first time that the new CryptoWall 4.0 ransomware is spread by using the an exploit kit.
Although Angler may dominate the exploit kit market at this time, the Nuclear exploit kit, arguably the second most prevalent exploit kit found in-the-wild today, has recently been observed utilizing payload delivery mechanisms that are much more efficient and more sophisticated in nature than ever seen before.
One of the primary advances made by the Nuclear Exploit Kit group is that the payloads delivered by the exploit kit are dynamic in nature. While payloads were often rotated during normal Nuclear EK operation, it has been discovered that the payloads delivered by recently-analyzed hosts serving the Nuclear EK have been exceptionally volatile in nature.
The Nuclear EK allows to serve malicious code by exploiting vulnerabilities in Java, Acrobat Reader, Flash, and Silverlight.
The most recent version(s) of the Nuclear EK utilizes effective techniques to evade detection, and even when it fails to exploit a target system, its anti-analysis techniques served to prevent malware analysts from re-creating and following/analyzing the infection chain employed by Nuclear.
Earlier this year, the security expert Maarten van Dantzig discovered a large number of Google ads sold through Bulgarian reseller EngageLab have been redirecting users to websites hosting the Nuclear exploit kit.
Duncan confirmed that samples of the CryptoWall 4.0 ransomware have been spotted in the wild since 2 November.
“Earlier this month, the BizCN gate actor switched IP addresses for its gate domains to 46.172.83.0/24. Also, as early as Friday 2015-11-20, this actor started sending CryptoWall 4.0 as one of its malware payloads from the Nuclear exploit kit (EK). Until now, I‘ve only associated CryptoWall 4.0 with malicious spam (malspam). This is the first time I’ve noticed CryptoWall 4.0 sent by an EK.” wrote Duncan. “Until now, I haven’t noticed CryptoWall 4.0 from any EKs. And now I’ve only seen it from the BizCN gate actor.”
Duncan dubbed the threat actors “BizCN gate actor” because it used domains registered through the Chinese registrar BizCN as a gate to hijack users to the domain hosting the Nuclear Exploit Kit.
“This actor uses dedicated servers for its gate domains. These gate domains tend to stick with one particular hosting provider. At times, the BizCN gate actor will switch hosting providers for its gates, and the IP address block for these gates will change.” states Duncan.

Duncan speculates that the disclosure of his analysis will force the BizCN gate actor to change tactics.
“Since this information is now public, the BizCN gate actor may change tactics. However, unless this actor initiates a drastic change, it can always be found again. I (and other security professionals) will continue to track the BizCN gate actor. Expect another diary on this subject if any significant changes occur.”
In order to protect your PC keep your software up to date.
Li-Fi is 100 times Faster than Wi-Fi Technology: Real-World Tests Prove
26.11.2015
Yes, it's time to shift from Wi-Fi to Li-Fi — an alternative technology that is 100 times faster than the average speeds of Wi-Fi.
Scientists have just field-tested the new wireless technology called Li-Fi for the first time and achieved marvelous wireless speeds that are 100 times faster than current WiFi speeds.
What is Li-Fi Technology?
Li-Fi is a new wireless technology that transmits high-speed data using light (i.e. Visible Light Communication or VLC) rather than radio bands.
In short, Li-Fi is a Super-Fast alternative to Wi-Fi.
Earlier this year, scientists achieved mind-blowing speeds of 224 gigabits per second (GBps) in the lab using Li-Fi. It's believed that this technology has the potential to change everything about the way we use the Internet today.
And Yes, it will.
Test Results: Li-Fi is 100 times Faster than Wi-Fi
An Estonian startup company called Velmenni took the technology out of the laboratories and into the real-world offices, and industrial environments in Tallinn for the first time and, believe me, it's really, really fast.
li-fi-wireless-internet-technology
The company was able to transmit data at 1GB per second, which is almost 100 times faster than the Wi-Fi speeds.
"We are doing a few pilot projects in different industries where we can utilize the VLC technology," Velmenni's CEO Deepak Solanki told IBTimes UK.
"Currently we have designed a smart lighting solution for an industrial environment where the data communication is done through the light. We're also doing a pilot project with a private client where we're setting up a Li-Fi network to access the Internet in [our] office space."
Unlike Wi-Fi network signals, Li-Fi is based on light and can't penetrate through walls, which makes it more secure from external sniffing. Meanwhile, it also means there is less interference from other devices.
Who Invented Li-Fi?
The Li-Fi technology was originated in 2011 by German physicist Harald Haas, who outlined the idea of using light bulbs as wireless routers during a TED Talk. He demonstrated that with a flickering light from an LED, one could transmit more data than a cellular tower.
You can watch the full video of Haas talk about the Li-Fi technology in 2011 given above.
IoT devices are re-using cryptographic keys, leaving in danger millions of devices
26.11.2015
Researchers from SEC consult analyzed more than 4000 firmware’s embedded devices, where is included devices belonging to 70 vendors. The findings are astonishing!
Researchers from SEC consult analyzed more than 4000 firmware’s embedded devices, where is included devices belonging to 70 vendors. The categories of devices analyzed include Internet gateways, routers, modems, IP cameras, VoIP phones, etc. SEC Consult was analyzing specifically the cryptographic keys (public keys, private keys, certificates) in firmware images of these devices, and concluded that most common keys are
SSH Host keys, that are required for operating a SSH server.
509 Certificates used for HTTPS which is the default server certificate for web based management.
These keys are generally used to access the IoT devices via SSH and HTTPS.
The experts analyzed 4000 firmware and found around 580 unique private keys, the use of Scans.io and Censys.io allowed them to discover that the same set of keys was widely re-used, on 580 keys, 230 are actively used.
“the private keys for more than 9% of all HTTPS hosts on the web (~150 server certificates, used by 3.2 million hosts)”
” the private keys for more than 6% of all SSH hosts on the web (~80 SSH host keys used by 0.9 million hosts)”
Embedded cryptographic key
The firmware running on the IoT device came with embedded keys used mainly for HTTPS, and SSH connections, this bad practice exposes end users to risk of attacks. Attackers can easily find the key and access a huge quantity of IoT devices that share it.
The experts at SEC consult also discovered:
“Some keys are only found in one product or several products in the same product line”
“In other cases, we found the same keys in products from various different vendors.”
The researchers mentioned real cases that demonstrate the alarming habit:
“A certificate issued to a “Daniel”, email (kiding@broadcom.com) is used in firmware from Actiontec, Aztech, Comtrend, Innatech, Linksys, Smart RG, Zhone and ZyXEL. More than 480.000 devices on the web are using this single certificate.”
“A certificate issued to Multitech in Bangalore, India is used in firmware from Aztech, Bewan, Observa Telecom, NetComm Wireless, Zhone, ZTE and ZyXEL. Over 300.000 devices on the web are using this certificate”.
“A certificate issued to “MatrixSSL Sample Server Cert” is used in WiMAX gateways from Green Packet, Huawei, Seowon Intech, ZTE and ZyXEL. All affected devices use the same code base, which is likely developed by ZyXEL. At least 80.000 devices on the web are using this certificate.”
Millions of devices exposed
SEC Consult’s researchers also uncovered another fact, many of these devices are directly accessible on the internet with insecure configurations and a used example is the case of Ubiquiti Networks, “who have remote management enabled by default in most products.”
Many Seagate GoFlex (80.000) are exposing HTTPS and SSH, and the blame should go the Seagate Share feature sets up port forwarding via UPnP.
In another case, the ISP exposes their clients’ IoT device by leaving their modems, routers and gateways with HTTPS and SSH remote administration features enabled by default.
The ISPs include, CenturyLink (500,000 exposed devices), TELMEX (1 million devices), Telefonica (170,000 devices), China Telecom (100,000 devices), VTR Globalcom (55,000 devices), Chunghwa Telecom (45,000) and Telstra (26,000 devices).
The counties with most affected hosts are:

SEC consult found more than 900 products from 50 vendors vulnerable, the list includes IoT devices proposed by:
ADB, AMX, Actiontec, Adtran, Alcatel-Lucent, Alpha Networks, Aruba Networks, Aztech, Bewan, Busch-Jaeger, CTC Union, Cisco, Clear, Comtrend, D-Link, Deutsche Telekom, DrayTek, Edimax, General Electric (GE), Green Packet, Huawei, Infomark, Innatech, Linksys, Motorola, Moxa, NETGEAR, NetComm Wireless, ONT, Observa Telecom, Opengear, Pace, Philips, Pirelli , Robustel, Sagemcom, Seagate, Seowon Intech, Sierra Wireless, Smart RG, TP-LINK, TRENDnet, Technicolor, Tenda, Totolink, unify, UPVEL, Ubee Interactive, Ubiquiti Networks, Vodafone, Western Digital, ZTE, Zhone and ZyXEL.
To avoid situations like these, the vendors have to ensure that each IoT device has its own unique cryptographic keys.
For the ISPs, if they need remote access for support purposes, they should set up a dedicated management VLAN with strict ACLs.
End users should change the SSH host keys and X.509 certificates of their IoT devices, an operation that is not allowed by some products, and in some cases users lack technical knowledge to change the settings.
All the problems emerged from the analysis have been reported by SEC consult to the CERT/CC which in August 2015 started informing device vendors, chipset manufacturers and affected ISPs. Some of them are already working on the fixes.
FBI is hunting MrGrey who has stolen 1.2 BILLION login credentials
26.11.2015
The FBI is convinced that there is a single hacker behind the theft of login credentials for over 1.2 Billion online accounts, his name is MrGrey.
According to a report published by the Reuters, the FBI is convinced that there is a single hacker behind the theft of login credentials for over 1.2 Billion online accounts, his name is MrGrey.
If confirmed, it could be the biggest heist of log-in credentials the FBI has investigated. My readers surely remember the case, last year the security firm Hold Security reported the amazing theft of the login credentials.
In August 2014, experts at Hold Security revealed to have discovered the biggest database of stolen user names and passwords and email addresses, the news is reported by The New York Times that hired an independent security expert who verified the authenticity of stolen data.
The security firm has discovered the amazing amount of data, nearly 1.2Billion credentials and half a billion email addresses, that is considered the single biggest amount of stolen Internet identity information ever collected. The experts believe that the data was collected by the Russian hacking group CyberVor from the numerous data breaches occurred all over the world in the last months and that hit around 420,000 websites vulnerable to SQL injection attacks.
fbi searching for MrGrey
The CyberVor hacking crew used botnets to search and hack vulnerable websites.
“To the best of our knowledge, [CyberVor] mostly focused on stealing credentials, eventually ending up with the largest cache of stolen personal [data], totalling over 1.2 Billion unique sets of emails and passwords,” Hold Security said in August last year.
By July 2014, criminals were able to collect 4.5 billion credentials, Hold Security discovered many duplications in the archive but anyway, it found that 1.2 billion of those records were unique and the archive included about 542 million unique email addresses. This is normal if we consider the bad habit to reuse same credentials for different web services.
Hold Security didn’t provide any information on the alleged breached websites, but according to Alex Holden, the company’s founder and chief information security officer, the list of compromised websites is long and include enterprises and small firms.
“Hold Security would not name the victims, citing nondisclosure agreements and a reluctance to name companies whose sites remained vulnerable. At the request of The New York Times, a security expert not affiliated with Hold Security analyzed the database of stolen credentials and confirmed it was authentic” reported The New York Times.
The Reuters has visioned court documents provided by the law enforcement to support its search warrant request in 2014.
“That hacker, known as “mr.grey,” was identified based on data from a cybersecurity firm that announced in August 2014 that it had determined an alleged Russian crime ring was responsible for stealing information from more than 420,000 websites, the documents said. The papers, made public last week by a federal court in Milwaukee, Wisconsin, provide a window into the Federal Bureau of Investigation’s probe of what would amount to the largest collection of stolen usernames and passwords.” states the Reuters.
The FBI associated MrGrey with the largest heist after discovering his Russian email address in spammer tools and posts on a Russian hacking forum offering to get user login credentials of Twitter, Facebook and Russian social network VK.
“The FBI also discovered an email address registered in 2010 contained in the spam utilities for a “mistergrey,” documents show. A search of Russian hacking forums by the FBI found posts by a “mr.grey,” who in November 2011 wrote that if anyone wanted account information for users of Facebook, Twitter and Russian-based social network VK, he could locate the records.” continues the Reuters
This circumstance leads Alex Holden from Hold Security to believe MrGrey likely operated or had access to the database containing the huge quantity of login credentials.
At the time I’m writing there is not news on how Mr.Grey obtained all the login credentials neither if this name is used by a single hacker or a hacking crew.
Mr. Grey Hacker (Wanted by FBI) Steals 1.2 BILLION Login Passwords
26.11.2015
That's a lot of Login credentials fetch by a single hacker.
The FBI believes a single hacker who goes by the moniker Mr.Grey has stolen login credentials for over 1.2 Billion online accounts – apparently the biggest heist of log-in credentials the FBI has investigated thus far.
Yeah, that's not Fifty, but 1.2 Billion Shades of Grey.
The information came from the court documents the federal agents submitted to support its search warrant request in 2014, Reuters reported.
The cyber security firm 'Hold Security' initially reported the theft of the credentials last year. It found out that Russian hacking group CyberVor has stolen 1.2 Billion login details and an additional 500 Million email accounts.
Botnet Breach
These data were said to have been harvested from over 420,000 websites via botnets looking for SQL injection flaws; the same technique recently used to hack TalkTalk.
Botnets are usually employed to attack an individual target, but in this case, they have been used as a huge scanner to scan websites on the Internet.
"To the best of our knowledge, [CyberVor] mostly focused on stealing credentials, eventually ending up with the largest cache of stolen personal [data], totalling over 1.2 Billion unique sets of emails and passwords," Hold Security said in August last year.
1.2 Billion Shades of Grey
The FBI is linking Mr.Grey to the largest heist after finding his Russian email address in spam-sending tools and posts on a Russian hacking forum offering to get user login credentials of Twitter, Facebook and Russian social network VK during its investigation.
Alex Holden, chief information security officer at Hold Security, believes those posts on online hacking forum prove that the hacker, "mr.grey" or "mistergrey", has access to a large database of stolen online credentials.
However, it's still unclear if Mr.Grey obtained all the login credentials by himself alone, or if Mr.Grey is just a single hacker or a group of hackers operating under one name.
Unfortunately, not much information is known about Mr.Grey's operations, but we will update soon if the FBI releases any new info.
Hackers are using Nuclear Exploit Kit to Spread Cryptowall 4.0 Ransomware
26.11.2015
Beware Internet Users!
Cryptowall 4.0 – the newest version of the world's worst Ransomware – has surfaced in the Nuclear exploit kit, one of the most potent exploit kits available in the underground market for hacking into computers.
Ransomware threat has emerged as one of the biggest threats to internet users in recent times. Typically, a Ransomware malware encrypts all files on victim’s computer with a strong cryptographic algorithm, then demand a ransom to be paid in Bitcoin (range between $200 and $10,000).
Cryptowall is currently among the most widespread and sophisticated family of Ransomware backed by a very robust back-end infrastructure.
Also Read: Anyone can Now Create their Own Ransomware using This Hacking ToolKit
The recent report dated back to last month suggested that the authors of Cryptowall 3.0 ransomware virus have managed to raise more than $325 Million in revenue in the past year alone.
With the debut of Cryptowall 4.0 at the beginning of this month, ransomware threat has become more sophisticated and advanced as Cryptowall 4.0 is employing "vastly improved" communications as well as better design code so that it can exploit more vulnerabilities.
Cryptowall 4.0 Delivered via Nuclear Exploit Kit
Now less than a month after its release, Cryptowall 4.0 ransomware has been spotted to be delivered as part of a Nuclear Exploit Kit, according to the security researchers at the SANS Internet Storm Center (ISC).
Until recently, Cryptowall 4.0 has been distributed only via malicious spam and phishing emails, but now it has been infecting machines via an Exploit Kit.
SANS security researcher Brad Duncan wrote in a blog post published Tuesday that a cyber criminal working off domains belonging to Chinese registrar BizCN has been spreading the Cryptowall 4.0 ransomware via the Nuclear Exploit Kit.
Duncan said the cyber gang, dubbed the "BizCN gate actor" by him, began distributing the ransomware in payloads from the exploit kit as early as November 20.
Also Read: Free Ransomware Decryption and Malware Removal ToolKit
Duncan published a whole technical analysis on the SANS ISC website that shows how Nuclear exploit kit infects a vulnerable Windows host.
"Since this information is now public, the BizCN gate actor may change [their] tactics," Duncan said in the post. "However, unless this actor initiates a drastic change, it can always be found again."
Cryptowall 4.0 made its debut earlier this month with upgrades that made it even more challenging for victims to recover files from compromised computers than its predecessor.
Cryptowall 4.0 now not only encrypts the data in your files but also encrypts the file names as well, with vastly improved communication capabilities.
What Should You do if You get Infected by Cryptowall 4.0?
Once your computer is infected by Cryptowall 4.0, unfortunately, there is not much you can do, as the encryption it uses is very strong and almost unbreakable.
The only options you are left with are:
Either, Format your computer and restore your data from the backup
Or, Pay the Ransom money for decryption key
However, we do not advise you to pay ransom as it does not guarantee that you'll get the decryption key and paying ransom would encourage criminal activities as well.
Prevention is the Best Practice
As I previously recommended, the best defense measure against Ransomware is creating awareness within the organizations, as well as maintaining backups that are regularly rotated.
Most viruses are introduced by opening infected attachments or clicking on links to malware usually contained in spam emails.
So, DO NOT CLICK on suspicious links provided in emails and attachments from unknown sources.
Also Read: Ransomware Attacks Threaten Wearable Devices and IoTs
Moreover, ensure that your systems are running the latest version of Antivirus software with up to date malware definitions.
Raspberry Pi Zero — The $5 Tiny Computer is Here
26.11.2015
Get ready for a ThanksGiving celebration from the Raspberry Pi Foundation.
Raspberry Pi, the charitable foundation behind the United Kingdom's best-selling computer, has just unveiled its latest wonder – the Raspberry Pi Zero.
Raspberry Pi Zero is a programmable computer that costs just $5 (or £4), may rank as the world's cheapest computer.
Raspberry Pi Zero: Just $5 Computer
Yes, Pi Zero is the smallest Raspberry Pi yet for just $5, but might be the biggest when looking at its specifications:
Broadcom BCM2835 application processor (same as Pi 1)
1GHz ARM11 core (40 percent faster than Raspberry Pi 1)
512MB of LPDDR2 SDRAM
Micro-SD card slot
MiniHDMI socket for 1080p60 video output
Micro-USB for data
Micro-USB for power
Unpopulated 40-pin GPIO connector
Identical pinout to Model A+/B+/2B
Unpopulated composite video connector
Smallest ever form factor (i.e. 65mm x 30mm x 5mm)
Get Your Raspberry Pi Zero Now!
The Raspberry Pi is responsible for the creation of credit card sized computers, but after years of working to lower the size and cost, founder Eben Upton says the foundation came up with Raspberry Pi Zero that is about the size of a stick of gum and costs just US$5.
Upton said the Pi Zero, made in Wales and runs full Raspbian and all your favorite applications including Scratch, Sonic Pi and Minecraft, was as revolutionary as the first Pi.
Also Read: CHIP — The World's First $9 Computer.
The Raspberry Pi Zero is on sale from today and is also given away with this month’s copy of the Raspberry Pi own magazine MagPi (available at Barnes & Noble and Microcenter).
You can order the Pi Zero, which is also available in the UK from element14, The Pi Hut and Pimoronia; in Europe from The Raspberry Pi Swag Store; and in the US from Adafruit and in Micro Center stores.
Note: Orders are limited to two per person at launch.
Facebook first discovered spear phishing attacks of Iranian hackers on State Department employees
26.11.2015
Facebook was the first company to notice the intrusion of Iranian Hackers in the e-mail accounts of US State Department officials focused on Iran. The attacks appear politically motivated and aimed to gather data about US-Iranian dual citizens in Iran.
Earlier this month, the computers at the US State Department and other government employees were targeted by hackers. The experts linked the attackers with the Iranian Revolutionary Guard, according to investigators the Facebook and e-mail accounts of US State Department officials focused on Iran were compromised to gather data about US-Iranian dual citizens in Iran and about the arrest of an Iranian-American businessman in Tehran in October.
The hackers have taken over social media accounts of junior State Department staff to launch a spear phishing campaign on the employees working in the State Department’s Office of Iranian Affairs and Bureau of Near Eastern Affairs and in the computers of some journalists.
US State Department e-mail system hacked Iranian hackers
Facebook was the first to notice the hacking campaign, the company alerted some of the affected users that their accounts had been compromised by a state-sponsored hackers.
The attack launched by the Iranian Revolutionary Guard hackers “was very carefully designed and showed the degree to which they understood which of our staff was working on Iran issues now that the nuclear deal is done,” an unnamed senior US official told the Times.
The recent wave of attacks came after a period of apparent calm, the cyber security experts noticed an evolution of the TTPs of the Iranian hackers. Iranian hackers were initially focused on targets belonging to the financial industry, their activities were limited to sabotage and disruption of the targeted infrastructures, such as in the attack on casino company Las Vegas Sands Corp. The fact that the Iranian hackers were more interested in destruction instead gathering intelligence lead the experts to believe that the threat actors were not state-sponsored but pro-Iranian “hacktivists.”
The recent attacks against The State Department attack is clearly a cyber espionage operation, they were initially attributed to Chinese hackers who may have infiltrated the department’s unclassified e-mail systems.
Russia, Hackers Stole $4 Million in cash with Reverse ATM Hack method
26.11.2015
Russian criminals Steal $4 Million In cash with a new technique dubbed reverse ATM Attack.
Russian hackers have adopted a new technique, dubbed Reverse ATM Attack to steal Millions of dollars from ATMs of financial institutions.
According to the experts at security firm GroupIB, the Reverse ATM Attack allowed criminal rings in Russia to steal 252 Million Rubles (roughly US$3.8 Million) from at least five different banks.

The theft started in summer 2014 and finished in Q1 2015.
The experts provided a detailed description of the Reverse ATM Attack. The attacker would deposit sums of 5,000, 10,000 and 30,000 Rubles into legitimate bank accounts using ATMs, and immediately withdraw the same amounts of money accompanied by a printed receipt of the payment transaction. At this point the hackers send the details included in the receipt, including the payment reference number and the amount withdrawn, to a partner who had remote access to the infected POS terminals. Usually the partner is an individual located outside of Russia.
The partner hacker would then use the details on the receipt to perform a reversal operation on a POS terminal that would lead them into believing that the withdrawals were cancelled, thereby tricking thousands of point-of-sale (POS) terminals in the US and in the Czech Republic.
From the perspective of the bank, it would appear the attempt to withdraw cash was failing, a circumstance that for example occurs when the bank account has insufficient funds.
The cash out process is made through a global “money mule” network that will transfer the money to the attacker’s bank account.
“That information was sent to hackers who would use the data and their access to thousands of point of sale terminals, primarily based in the US and the Czech Republic, to create “a reversal operation” on a terminal that tricked the bank into believing the withdrawal of funds had been cancelled.” states Forbes. “At the point of sale terminal, this looked as though goods were returned or a payment declined, whilst to the banks it appeared the ATM withdrawal had been cancelled. Funds were returned to the account, though the crooks had already taken the cash. The process was repeated until there was no money remaining in the targeted ATM.”
As explained by the experts at Group-IB, the criminal gang leveraged weaknesses in the withdrawal, transfer and verification stages of credit card transactions used in Russia and managed to bypass checks recommended by VISA and MasterCard.
The problem is that when the reverse operation targets a single bank, transaction details provided by VISA are not verified by the targeted banks. When ATM Withdrawals were made in one country and cancelled/reversed in another, the verification process fails.
VISA brought together the affected banks so they could block reversal operations when funds were withdrawn from an ATM of the bank and reaccredited through a separate terminal.
“But that fix only addressed the issue of withdrawals from ATMs, not transfers from one card to another.” continues Forbes.
Group-IB is supporting law enforcement to investigate further fraudulent activities.
Hilton confirms some payment systems infected by malware
25.11.2015
The hotel chain Hilton Worldwide Holdings announced Tuesday that cyber criminals stole credit card information from some of its point-of-sale systems.
The hotel chain Hilton Worldwide Holdings admitted that crooks stole credit card information from some of its PoS systems, but hasn’t provided detailed info on the extent of the data breach. The company Hilton Worldwide is warning its customers who used credit cards at its hotels between November 18 and December 5 of last year or April 21 and July 27 of this year to monitor their banking account for any suspicious activity.
According to the Hilton global brands executive vice president Jim Holthouser, the malware infected the PoS systems, allowing the cyber criminals to steal customers’ data, including credit card holders’ names, card numbers, security codes and expiration dates.
Hilton
“Hilton Worldwide (NYSE: HLT) has identified and taken action to eradicate unauthorized malware that targeted payment card information in some point-of-sale systems. Hilton immediately launched an investigation and has further strengthened its systems.” reads a press release issued by the Hilton Worldwide Holdings.
“Hilton Worldwide worked closely with third-party forensics experts, law enforcement and payment card companies in this investigation, and determined that the specific payment card information was targeted by this malware. This information includes cardholder names, payment card numbers, security codes and expiration dates, but no addresses or personal identification numbers (PINs).”
It seems that customers’ addresses and personal identification numbers were not compromised in the data breach.
Hilton hired a forensic firm to investigate the cyber attack, along with law enforcement and payment card companies.
A few days ago another hotel chain was affected by a serious data breach, Starwood Hotels announced that hackers had infected payment systems, potentially exposing customers’ financial data, including credit card data.
If you are a customer of the popular hotel chain, visit hiltonworldwide.com/guestupdate for more details.
Russian ATM Hackers Steal $4 Million in Cash with 'Reverse ATM Hack' Technique
25.11.2015
Russian hackers have discovered a novel technique to rip off Millions of dollars from banks and ATMs.
Criminals in Russia used a technique, called “Reverse ATM Attack,” and stole 252 Million Rubles (US$3.8 Million) from at least five different banks, according to the information obtained by Russian digital intelligence firm Group-IB.
What is Reverse ATM Attack?
According to the intelligence firm, an attacker would deposit sums of 5,000, 10,000 and 30,000 Rubles into legitimate bank accounts using ATMs, and immediately withdraw the same amounts right away with a printed receipt of the payment transaction.
The details included in the receipt, containing a payment reference number and the amount withdrawn, would then be transferred to a partner hacker, who had remote access to the infected POS terminals, usually located outside of Russia.
Also Read: German Bank ATMs vulnerable to Hackers
The partner hacker would then use these details to perform a reversal operation on a POS terminal that would lead them into believing that the withdrawals were declined, thereby tricking thousands of American and Czech point-of-sale (POS) terminals, Forbes explained.
Meanwhile, it would appear to the bank as if the attempt to withdraw cash was cancelled, for example: when the customer has insufficient funds and then the same cash amount will be transferred to the attacker’s bank account using a global "money mule" network.
Now, Hackers would repeat these steps as long as the targeted ATM did not end cash.
Also Read: Beware of ATM Skimming Devices Installed on Vestibule Doors
Hackers Stole $3.8 Million in Cash from ATM Hack
Group-IB said the firm had seen at least five such incidents at five different Russian banks, the criminal activity starting in summer 2014 and finishing in the first quarter of 2015.
The hackers leveraged weaknesses in the withdrawal, transfer and verification stages of credit card transactions used in Russia and managed to bypass checks recommended by VISA and MasterCard.
Also Read: How Hackers Can Hack Your Chip-and-PIN Credit Cards
Here 'Checks' means:
When the reverse operation targets a single bank, transaction details provided by VISA is not verified by the affected banks.
When ATM Withdrawals were made in one country and cancelled/reversed in another, certain verification points were again missed.
Group-IB is working with the federal authorities to investigate further into the whole money laundering scheme.
How The Russian Abused Twitter as C&C in Hammertoss Malware? Python Answers
25.11.2015
Today, we will replicate a technique which has been used by recent, sophisticated and hard to trace a Russian malware called Hammertoss.
Today, we will replicate a technique which has been used by recent, sophisticated and hard to trace a Russian malware called Hammertoss, the creators of this malware has abused multiple well-known sites like Twitter and Github to defeat modern firewalls and torture whoever tracing their tracks.
In a nutshell, instead of getting a direct reverse connection back to the C&C server similar to what traditional malware does, this smart malware will jump between third party servers to perform its malicious activity, please take two minutes and watch this[https://www.fireeye.com/blog/threat-research/2015/07/hammertoss_stealthy.html/] short explanatory video from Fireeye so you will get a quick overview how the malware works.
Before the fun begins, I just want to mention that this code is a part of my new training course on Udemy called “Python for Offensive Pentest: A Complete Practical Course.”
All right, so the first stage of Hammertoss was to connect to a Twitter looking for a tweet created by the hackers which contains a URL for an image and hashtag as a part of the encryption key. Technically speaking, you don’t need to login into Twitter to parse someone’s tweet, so in this case, we just need to figure out the account URL to navigate and the HTML tags which contain the actual tweet, Keep in mind you can add other twitter accounts to hide the original one (which belongs to the hacker).
Obviously you should never your personal account while doing similar stuff, that’s why I created a new account holding my name and here’s is the link to my twitter home page:
https://twitter.com/HussamKhrais
Now from my Kali machine, I made a tweet saying “Hello from kali python” then I logged out, at this point once we click on the above URL, we should see something similar to this output

Now using your browser you can view the HTML source code of this page, in Chrome just do a right click anywhere in the page and select “View page source” or Ctrl+U for short, in the HTML if we search for our tweet, we will get the below HTML line:-
<meta name="description" content="The latest Tweets from Hussam Khrais (@HussamKhrais): "Hello from kali python"">

So technically if we code a simple script that will navigate to https://twitter.com/HussamKhrais
And retrieve the HTML page, then inside the HTML if we search for meta tag called name that has a value of description and asked for the value of content, then we should be able to grab our tweet.
Let’s translate this action to a code:-
fromBeautifulSoup import BeautifulSoup as soupy #1
importurllib #2
html = urllib.urlopen(‘https://twitter.com/HussamKhrais’).read() #3
soup = soupy(html) #4
x = soup.find(“meta”, {“name”:”description”})[‘content’] #5
print x #6
1# Import soupy function from BeautifulSoup library, we will use this function to search for the html tags
2# Import urllib which will be used to navigate to our twitter page and grab the html for us
3# Navigate to my twitter home page HussamKhrais, store the HTML page into html variable
4# Pass it to soupy function so we can parse it
5# Here we search for the HTML meta tags
6# Print the result out
The output for running the script would be

At this point, since we are only interested in having the string between the quotation marks, we can filter it out using regular expression, and that is exactly what the below script will do for us
importre
filter = re.findall(r'”(.*?)”‘,x)
tweet = filter[0]
print tweet
the “findall” function will grab the string between the ” ” and store it in a list data type called filter, finally we print the exact tweet.
After putting all the script pieces together, we got the below result

Please feel free to download the script and give it a try on your own tweet!
Now think about it for a second, can we use twitter to replace DDNS? Well, what will happen if we replace “Hello from kali python” with the attacker public IP, and each time the attacker IP changes, all what he needs to do is to send a tweet with the new IP to get the reverse connection for his victim!
A question for you…
After reading this article, do you think that can you code in Python a complete AV free remote shell and exfiltrate data without even having a single direct connection with your target? Please share your thoughts.
If you are interested on the topic you can go deeper following the course “Python For Offensive PenTest: A Complete Practical Course”

MagSpoof, how to predict American Express card numbers
25.11.2015
MagSpoof is a tiny device that can spoof/emulate any magnetic stripe or credit card. It can work wirelessly, even on standard magstripe/credit card readers.
When dealing with hacking we cannot avoid mention the popular hacker Samy Kamkar (@SamyKamkar), one of the most prolific experts that periodically presents to the security community his astonishing creations, including the Combo Breaker, OpenSesame and KeySweeper.
This time Kamkar has designed new cheap gadget (it goes for US$10) that can predict and store hundreds of American Express (AMEX) credit cards and use them for wireless transactions. The tiny gadget dubbed MagSpoof is a credit card/magstripe spoofer and can be used also at non-wireless payment terminals, it is composed of a micro-controller, motor-driver, wire, a resistor, switch, LED, and a battery.

“MagSpoof is a device that can spoof/emulate any magnetic stripe or credit card. It can work “wirelessly”, even on standard magstripe/credit card readers, by generating a strong electromagnetic field that emulates a traditional magnetic stripe card.” states Kamkar. “MagSpoof can be used as a traditional credit card and simply store all of your credit cards (and with modification, can technically disable chip requirements) in various impressive and exciting form factors, or can be used for security research in any area that would traditionally require a magstripe, such as readers for credit cards, drivers licenses, hotel room keys, automated parking lot tickets, etc.”
The hacker clarified that the device does not enable people to use credit cards that they don’t own because it is necessary to have the magstripes that they wish to emulate.
However, this means that crooks could use MagSpoof to rake cash after cards have been cancelled at businesses that do not require the CVV numbers on the back of cards.
After losing a card, Kamkar received a new one as a replacement, then he noticed many of the digits were similar. Analyzing other cards and replacements he discovered a pattern that allows him to predict AMIX card number by knowing a full card number, even if already reported lost or stolen.
“I pulled up the numbers to several other Amex cards I had, and then compared against more than 20 other Amex cards and replacements and found a global pattern that allows me to accurately predict American Express card numbers by knowing a full card number, even if already reported lost or stolen. This means if I were to obtain your Amex card and you called it in as lost or stolen, the moment you get a new card, I know your new credit card number.
I also know the new expiration date as the expiration date is fixed based on when the new card was requested, and you can determine if the new card has been requested by performing an auth on the existing card.”
Kamkar reported the issue to the American Express that is already working on a fix.
Magspoof is able to emit a strong “electromagnetic field” that emulates the effect obtained by physically swiping a card. Kamkar has released all the necessary to design a working device, including the source code and the instruction to build it.
“MagSpoof emulates a magnetic stripe by quickly changing the polarization of an electromagnet, producing a magnetic field similar to that of a normal magnetic stripe as if it’s being swiped. What’s incredible is that the magstripe reader requires no form of wireless receiver, NFC, or RFID — MagSpoof works wirelessly, even with standard magstripe readers. The stronger the electromagnet, the further away you can use it (a few inches in its current iteration).” continues the expert.
Of course, Kamkar precaution disabled the ability to deactivate EMV and has not released the prediction algorithm for the American Express card.
Kamkar has published a animated GIF image that shows how the tiny device works, below a video PoC published by Kamkar:
Kamkar explains that the device could be used to create by readers to create their own versions of Samsung MST or Coin.
Summarizing MagSpoof :
Allows you to store all of your credit cards and magstripes in one device
Works on traditional magstripe readers wirelessly (no NFC/RFID required)
Can disable Chip-and-PIN (code not included)
Correctly predicts Amex credit card numbers + expirations from previous card number (code not included)
Supports all three magnetic stripe tracks, and even supports Track 1+2 simultaneously
Easy to build using Arduino or other common parts
Person VUE Credential manager system has been compromised
25.11.2015
Person VUE, the world biggest learning, testing and certification company has announced that its Credential Manager system (PMC) has been breached.
On their website, Person VUE gives us some details of what might have happened, even though they don’t share who is the responsible for this breach.
“We recently were made aware that an unauthorized third party placed malware on Pearson VUE’s Credential Manager (PCM) system, which is a platform that supports adult professional certification and licenses. The unauthorized party improperly accessed certain information related to a limited set of Pearson VUE’s PCM system users. As of now, we do not believe that U.S. Social Security numbers or full payment card information were compromised as a result of this issue. “
Person VUE will keep PCM system offline for the necessary investigation.
“If your credentialing, certification or licensing organization has posted information about this or communicated with you about the issue directly, then it’s likely that you use this platform. It is important to note there is no indication at this time that the issue involved the Pearson VUE Testing System, the PearsonVUE.com website or any other Pearson/Pearson VUE systems. The issue is isolated to the PCM system. “the company added.
“Based on our investigation, there is no evidence at this time indicating that the VUE Testing System (VTS) or Exam Developer Software was affected by this issue.”
Since Person VUE is still trying to understand the scope of the data breach, they are not sure which data the attackers were able to get, but they think that no Social Security numbers or payment card information were in the leaked data.

The Pearson Credential Manager (PCM) system supports a number several companies’ certification tracking programs, including Cisco and F5 who posted some notes about the incident as well.
“According to Pearson VUE, an unauthorized party may have improperly gained access to information related to users that could include: names, postal addresses, phone numbers, email addresses, user IDs and, in some cases, last four digits of credit card numbers and dates of birth”, “As a precaution, Pearson VUE has taken its Credential Manager System offline and has informed us that it will remain offline until this matter has been resolved. As a result, all F5 certification processes are on hold until Pearson VUE gets its Credential Manager System back on line—our apologies for this inconvenience.” reported F5.
Since at least 14 November, the Cisco’s tracking system was down for “site maintenance,” but on Saturday, the company announced the Pearson VUE breach and stated its tracking system “will remain down until further notice”.
“PCM is an important part of Cisco’s certification ecosystem, as it enables individual users to manage and track their CCIE, CCNA, CCNP and other Cisco certifications directly through Pearson’s platform” said Cisco about the issue.
As I said before there is no certainty, about which data was leaked, but the news circulating on the Internet suggests that “just” name, mailing address, email address and phone number belonging to those who hold certifications were exposed.
Personally, that worries me, since I’m one the cases, as many of my colleagues in my field. The attackers may have many plans for this information, but one of them can be the mapping of all security/IT professionals.
We in Security Affairs will keep following this subject and will share with you if any news comes up.
Notorious Shm00p hacker Claims he helped the FBI find ISIS Hacker Junaid Hussain
25.11.2015
The hacker Shm00p claims he served as an FBI informant and helped the US law enforcement track down the hacker turned ISIS fighter Junaid Hussain.
When dealing with ISIS and cyber capabilities, the first name that experts cite is Junaid Hussain, the hacker that was killed in a targeted US drone strike in August this year.Now new details on Junaid Hussain and his death are circulating online.
The hacker Shm00p (@5hm00p), the same that hacked the Anonymous pseudo-official Twitter accounts @Anon_Central and @YourAnonNews, is claiming to have provided useful information to the FBI allowing to track Hussain.
In 2012, Hussain was sentenced to six months in prison in Britain for this crime. The jihadist was also cited by two gunmen responsible of the terrorist attack in Garland, Texas. The two men invited via Twitter to follow Hussain. In 2013, Hussain left the United Kingdom and joined ISIS.
On September 11 214, Fox News reported that leaders of the Islamic State of Iraq and Syria and Al Qaeda were stepping up efforts to seek a digital caliphate, speculating that one of the jihadist leaders, Hussain Al Britani, also known as Junaid Hussein, had allegedly hacked the Gmail account of former British Prime Minister Tony Blair.
“Jihadists in the Middle East are ramping up efforts to mount a massive cyber attack on the U.S., with leaders from both Islamic State and Al Qaeda – including a hacker who once broke into former British Prime Minister Tony Blair’s Gmail account – recruiting web savvy radicals, FoxNews.com has learned.”
According to Shm00p, he has served as an FBI informant to help the US intelligence under threat, and he is quite sure (“99.9% sure”) that the information he provided led to the extrajudicial killing of Hussain.
Shm00p, who lives in Las Vegas, is one of the members of the hacking group named Rustle League. On Sunday, he posted the following message:
“What the fuck have I done,” Shm00p tweeted.
A few hours later he sent a number of tweets at the FBI Twitter account.
“I lost a lot of good friendship and my fucking honor,” I am so embarrassed to show my face in public now because of this,”
Shm00p Tweets FBI Hussain
Shm00p and Hussain were affiliated with another notorious hacktivist group called Team Poison.
Jaime Cochran, a former member of Rustle League, told Motherboard that 5hm00p reached out to her after his Twitter confession to apologize, and confirmed his collaboration with the FBI.
5hm00p said told her that law enforcement forced him to provide information on two hackers who knew Hussain since their affiliation with the Team Poison.
“It seems believable to me. I dunno why someone would make this up,” Cochran told Motherboard in an encrypted chat.
It seems that in 2014, Hussain contacted Shm00p via the encrypted chat service Jabber, but Shm00p located the jihadist location and then passed it the FBI agents.
“I fucking helped you MURDER him [Junaid]. Do you know how I feel now when I sleep at night?”Shm00p tweeted. “Regardless that he was a terrorist and an animal I sure as fuck felt betrayed.”
Why did Shm00p pass information to the FBI?
The hacker explained that the FBI has forced him to disclose the Hussain’s location. Based on the tweets sent by Shm00p, the authorities forced him to provide support threatening his family.
The agents had him attempt to catch two of his friends while they were partying at the DefCon 2015 conference.
The FBI hasn’t commented the Shm00p’s declarations.
A source informed of the events told Motherboard that Shm00p did indeed help the US federal.
GlassRAT, the threat that remained stealth for years
25.11.2015
A new RAT dubbed GlassRAT was discovered by RSA, it targets mainly Chinese citizens working in multinational companies in and outside China.
According to the experts at RSA a remote access Trojan (RAT) dubbed GlassRAT managed to avoid detection by most antivirus software for several years.
The researchers explained that GlassRAT was used by threat actors in highly targeted attacks, the threat (also dubbed “zero detection” threat) has been around since at least September 2012.
GlassRAT was detected for the first time on December 2014 when a sample was only uploaded to VirusTotal.
The experts highlighted that the code of the GlassRAT dropper had been digitally signed with a legitimate certificate stolen from a popular Chinese software developer, a circumstance that allowed it to stay under the radar for several years. The dropper had been detected first in September 2015, it was uploaded to the public malware database from a Chinese IP address. The threat has been discovered on the computer of a Chinese national in February 2015.
GlassRAT has been used in highly targeted attacks on Chinese nationals and other Chinese speakers associated with large multinational corporations in China and other countries since at least early 2013.
The code of GlassRAT has many similarities with the one of the Taidoor threat and a malware family called Taleret. Taidoor has been around since 2008 and it has been mainly used in cyber espionage campaigns against organizations in Asia-Pacific region, including the Philippine military and the Mongolian government.
Experts linked the threat with cyber espionage campaigns leveraging Mirage, MagicFire and PlugX malware.
“The telemetry of GlassRAT and limited forensic samples suggest that targeting is narrowly focused,” reads the report published by RSA. “While several code similarities were found with other malware such as Taidoor and Taleret, the most interesting overlap with GlassRAT might be in the C2 infrastructure shared with geopolitical campaigns, which were reported earlier in this decade.”
The infection process is still not completely clear, experts believe the threat actors would use social engineering mixed with spear phishing attacks.
GlassRAT installs itself via a fake Flash installation package and then cleans any traces.
The threat is simple but effective, it included a classic reverse shell which allows attackers to gain complete control of the target system.
Who is behind the threat?
Experts at RSA pointed out that the nature of the targets and the technique adopted suggest that the operators belong to “subordinate departments of a much larger organization with shared infrastructure and developers run these campaigns.”
Hacker Claims He helped FBI Track Down ISIS Hacker (Who was killed in Drone-Strike)
24.11.2015
Junaid Hussain – a hacker turned ISIS cyber mastermind who was killed in a US drone strike in August this year.
But something has emerged what we don't know about the death of Hussain.
The infamous hacker who in the past hacked the Anonymous pseudo-official Twitter accounts, now claims he served as an FBI informant to help the US government track down Junaid Hussain.
The hacker, goes by the online alias Shm00p (@5hm00p), is a member of the hacking collective Rustle League and believes he is "99.9% sure" that the information given by him to the FBI agents led to the extrajudicial killing of Hussain.
"What the fuck have I done," Shm00p tweeted early Sunday morning.
Over 15 hours later after his first tweet, Shm00p made a series of tweets at the FBI Twitter account.
"I lost a lot of good friendship and my fucking honor," Shm00p tweeted at the FBI. You can see an archived copy of his now deleted tweets here. "I am so embarrassed to show my face in public now because of this," he continued.
Also Read: ISIS Hacker who Passed U.S. Military Data to Terrorists Arrested in Malaysia
Shm00p, who lives in Las Vegas, knew the British–born Hussain from their mutual affiliation with a notorious hacktivist group called Team Poison.
In 2014, Hussain reached out to Shm00p via the encrypted chat service Jabber. Shm00p was able to determine Hussain's location and then passed on the information to the FBI.
Shm00p said that he was very much sure this information led to the death of Junaid "TriCk" Hussain, who left the United Kingdom and joined ISIS in 2013.
"I fucking helped you MURDER him [Junaid]. Do you know how I feel now when I sleep at night?" Shm00p tweeted. "Regardless that he was a terrorist and an animal I sure as fuck felt betrayed."
Also Read: ISIS Supporter Hacks 54,000 Twitter Accounts & Posts Details of the CIA and FBI Heads
Based on his tweets, Shm00p was forced to help the FBI agents who threatened the livelihood of his family.
The FBI officials had him attempt to catch two of his friends while they were partying at the hacker conference DefCon in 2015, with the aim to get information on Hussain's whereabouts.
Although the FBI has declined to comment on the disclosure by Shm00p, a source with knowledge of the facts told Motherboard that Shm00p did indeed help the US federal agents locate Hussain.
ModPos, the most complex POS malware ever seen
24.11.2015
ModPOS is new POS malware discovered in systems of US retailers after the rush of Thanksgiving and experts speculate it is the most complex POS malware ever seen.
A new POS malware was discovered in US retailers, after the rush of Thanksgiving, and it looks like millions of US bank cards were affected.
The new POS malware is called ModPOS was found in some unnamed companies, but we know that we are talking about big retail companies, what makes the problem huge, because certainly means millions of dollars in damage.
The available information about the attackers are not a lot, but it’s known that they have been operating since 2013, and in a very professional way, never raised any suspicion, and that this malware was only discovered after weeks of painful research, and reverse-engineering by malware experts.
“This is POS [point-of-sale] malware on steroids,” “We have been examining POS malware forever, for at least the last eight years and we have never seen the level of sophistication in terms of development …[engineers say] it is the most sophisticated framework they have ever put their hands on.” Said iSight Partners senior director Steve Ward.
The malware experts took three weeks until reverse engineer one of the three kernel modules of the malware, and just to give you an idea, the same malware experts only needed 30 minutes to reverse engineer the Cheery Picker POS malware.
Steve Ward was impressed by the “incredibly talented” authors of the malware, and even refer that they did an “amazing job”, because their understanding of the security around POS was huge, “It is hard not to be impressed,” Ward said.
To give you another idea how good was this malware, the encryption used for network and C&C( command and control) data exfiltration and communication was protected with 128 and 256-bit encryption, and a new private key was needed peer customer.

Ward kept on saying that the authors of the malware must have spent a huge amount of money and time on each packed kernel driver module, which behaves like a rootkit, and it is difficult to detect and to reverse engineer.
It looks like the authors thought about this malware as an investment, designing the ModPOS to generate a large-scale, to be eventually able to get a return on their investment.
Now that the ModPOS was found and US retailers are aware of the problem, the attackers will need to change part of the base code to re-gain the obfuscation they had, but it looks like that some of these changes will be harder to implement, maybe more monetary investment will be needed again.
This is a new and very advanced malware, so we expect to keep hearing about more cases related with ModPOS and the attackers’ framework.
Dell's Laptops are Infected with 'Superfish-Like' pre-installed Malware
24.11.2015
Similar to the Superfish malware that surrounded Lenovo laptops in February, another big computer manufacturer Dell spotted selling PCs and laptops pre-installed with a rogue SSL certificate that could allow attackers:
To impersonate as any HTTPS-protected website and spy on when banking or shopping online.
The rogue certificate, dubbed eDellRoot, was first discovered over the weekend by a software programmer named Joe Nord. The certificate is so creepy that it automatically re-installs itself even when removed from the Windows operating system.
Also Read: Lenovo Caught Using Rootkit to Secretly Install Unremovable Software
Superfish 2.0: Unkillable Zombie
The self-signed transport layer security (TLS) credential came pre-installed as a root certificate on Dell PCs and laptops that are signed with the same private cryptographic key, which is stored locally.
That means an attacker with moderate technical skills can extract the key and abuse it to sign forged version of TLS certificates for any HTTPS-protected site on the Internet, exposing users to all manner of SSL attacks.
The certificate key can be used to conduct man-in-the-middle (MITM) attacks on Dell owners, silently stealing user names, passwords, session cookies, and other sensitive information when the affected Dell machines are connected to a malicious Wi-Fi hotspots in cafes, hospitals or airports.
The problem is similar to the scandal that hit Lenovo in February when the PC manufacturer was caught pre-installing an invasive adware program called Superfish with a similar self-signed cert to inject third-party advertisements into websites on browsers.
Must Read: Automatic Superfish Removal Tool
Although Dell's case is different as there is no indication that the certificate is being used to inject advertisements on the laptops, the resulting security issue is the same.
Affected PCs and Laptops
The self-signed certificate key was discovered to be pre-installed as a root certificate on at least three Dell laptop models:
Dell Inspiron 5000 series notebook
Dell XPS 15
Dell XPS 13
This indicates that the dangerous certificate may be present on a significant number of the Dell desktops and laptops currently on the market, specifically recent Dell Inspiron Desktop, XPS, and Precision M4800 and Latitude models.
To Check if Your Computer is Vulnerable
To discover the dangerous certificate:
Open up the Start menu
Select Run
Type in certmgr.msc – the Windows certificate manager – into the box and Hit Enter
Open up the Trusted Root Certification Authority folder on the left
Select Certificates
Search for eDellRoot
Once found, right-click over eDellRoot and hit "Remove." It appears to be gone, but actually it's not.
Reboot your computer and reopen certmgr.msc and search for the certificate "eDellRoot". Yeah, the removed root CA cert is back.
What Should You do? How to Remove?
It seems that even if the certificate is clearly fraudulent, Google Chrome and Microsoft Edge and Internet Explorer browsers always establish an encrypted Web session with no warnings.
But fortunately, Mozilla's Firefox web browser generates an alert warning that the certificate was not trusted.
So, Dell customers with new XPS, Precision, and Inspiron models are advised to use Firefox to browse the web.
To fix the issue completely, Dell users will need to manually revoke the certificate permissions, which is a complex and technically demanding task.
Moreover, security researcher Darren Kemp from Duo Security says that the problem may be even worse than what Nord suggested.
According to an analysis done by Kempa, a bundled plugin re-installs the root CA file when it is removed. So, to remove the eDellRoot certificate completely, you must:
First delete Dell.Foundation.Agent.Plugins.eDell.dll from your system
Then remove the eDellRoot root CA certificate
Dell's Response
In a statement, a Dell spokesperson said the company is investigating the report and looking into the certificate, but emphasized the company’s policy of minimizing pre-loaded software for security reasons.
- See more at: http://thehackernews.com/2015/11/superfish-malware-dell.html#sthash.Ojq5WPFZ.dpuf
Dell puts users at risk with dangerous eDellRoot root certificate
24.11.2015
Dell is in the headlines for shipping PCs with a pre-installed trusted root certificate dubbed eDellRoot that opens users to a number of cyber attacks.
Dell is in the headlines for shipping PCs with a pre-installed trusted root certificate that opens users to a number of cyber attacks. Hackers could exploit it to compromise the security of encrypted HTTPS connections. The case has several similarities to the Lenovo one, do you remember Superfish?
Early 2015, experts discovered that Lenovo was shipping laptops with Superfish malware , a malware that allows to steal web traffic using man-in-the-middle attacks. SuperFish is considered by many antivirus companies as a potentially unwanted program, adware, or a trojan.
The “Superfish” malware installed on laptops was able to steal web traffic using fake, self-signed, root certificates to inject advertisements into sessions. Lenovo has removed Superfish the malicious software after numerous users reported the embarrassing discovery on its forums by claiming to be victims of attacks.
A few months after the Lenovo case, Dell started deploying a trusted root certificate called eDellRoot.
The certificate is bundled with its private key, which open users to man-in-the-middle attacks, for example, if an affected Dell PC connects to a bogus Wi-Fi hotspot, attackers running the hotspot can exploit the eDellRoot certificate and the key to decrypt the victims’ web traffic and steal sensitive data.
The certificate as delivered on August 18 as part of an update to the Dell Foundation Services (DFS) application.
The eDellRoot certificate was discovered by researchers at Duo Labs who examined a Dell laptop, then the experts consulted the Censys project and discovered the certificate’s fingerprint in several locations.
What does this mean?
Simply that Dell has intentionally shipped the same keys in many other computers worldwide. In one case, the eDellRoot certificate was used to provide web services over HTTPS to a SCADA system.
“Given that this certificate can be used to sign SSL certificates for secure web communications, we talked to the good people at the Censys project. The Censys project uses zmap] to scan the whole IPv4 Internet and archive data, such as the SSL certificate that server sends when the scanner opens a connection. There do not appear to be any servers online that are using the initial eDellRoot certificate we discovered (98:A0:43:[…]).” states the report published by Duo Labs. “However, searching Censys for “eDellRoot” turned up another certificate, which was similar to the first one: same name and also self-signed. Normally, a given certificate would only be associated with one IP address, as it’s considered poor practice to share the private component of the certificate across multiple machines. Otherwise, it’s impossible to tell which computer actually sent a given message, a property that is often demanded in cryptosystems. “
The list of impacted systems includes XPS, OptiPlex, Inspiron, Vostoro, and Precision models.

“How this particular misconfiguration happened is unclear, but what is clear, is that this certificate is showing up in some extremely unusual and frankly concerning places,” continues the report.
Initially, Dell doesn’t explain the presence of eDellRoot, the company only declared that it “provides a core set of foundational services facilitating customer serviceability, messaging and support functions.”
Meantime, Dell updated the DFS application on Monday, after the news was circulating over the Internet. The company declared that it would be offering a tool to remove the certificate.
Unfortunately, the certificate cannot be simply removed due to a .DLL (–Dell.Foundation.Agent.Plugins.eDell.dll) included with the root certificate that reinstalls the file if it is deleted. Users have to delete both the .DLL and the certificate.
Dell plans to provide detailed information to remove the certificate and future machines will not include it.
“The recent situation raised is related to an on-the-box support certificate intended to provide a better, faster and easier customer support experience. Unfortunately, the certificate introduced an unintended security vulnerability.” is the official statement released by Dell.
Documents demonstrate NSA continued mass surveillance
24.11.2015
Newly disclosed documents show that the NSA had found a way to continue spying on American citizens’ email traffic from overseas.
The NSA continued to spy on the email messages of Americans, once again the US government has conducted a massive surveillance on the US soil. To curb internal law the US intelligence has is used overseas offices.
In response to the tragic attacks of the 9/11, the President Bush secretly authorized the US National Intelligence Agency to collect bulk metadata on emails sent by Americans. The mass collection didn’t include the email content, the US Foreign Intelligence Surveillance Court authorized it to help The War Against Terror (TWAT).
The collection of email of Americans on the US soil was stopped in 2011, but the NSA continued to monitor email traffic from Americans to people outside the nation’s borders.
A Freedom of Information Act lawsuit started by The New York Times against the NSA’s Inspector General allowed the disclosure of the document confirming the US Intelligence carried on collecting domestic data.
The report, published by the NYT, confirmed the existence of two distinct sources “assist in the identification of terrorists communicating with individuals in the United States, which addresses one of the original reasons for establishing” the bulk email records program.
“The report explained that there were two other legal ways to get such data. One was the collection of bulk data that had been gathered in other countries, where the N.S.A.’s activities are largely not subject to regulation by the Foreign Intelligence Surveillance Act and oversight by the intelligence court. Because of the way the Internet operates, domestic data is often found on fiber optic cables abroad.” states the NYT.
“The other replacement source for the data was collection under the FISA Amendments Act of 2008, which permits warrantless surveillance on domestic soil that targets specific noncitizens abroad, including their new or stored emails to or from Americans.”
Newly disclosed documents show that the NSA created a functional equivalent in continuing the surveillance activities.
“The shift has permitted the agency to continue analyzing social links revealed by Americans’ email patterns, but without collecting the data in bulk from American telecommunications companies — and with less oversight by the Foreign Intelligence Surveillance Court.” states the New York Times. “The disclosure comes as a sister program that collects Americans’ phone records in bulk is set to end this month. Under a law enacted in June, known as the U.S.A. Freedom Act, the program will be replaced with a system in which the N.S.A. can still gain access to the data to hunt for associates of terrorism suspects, but the bulk logs will stay in the hands of phone companies.”

The US Intelligence bypassed the restrictions on surveillance activities in the USA by using overseas offices to do the collection. The documents refer spy stations like RAF Menwith Hill in Yorkshire used for the collection of the metadata related to the American’s email traffic. Once the data were gathered by foreign offices, it was sent to the NSA headquarters in Maryland.
“We have known for some time that traffic analysis is more powerful than content analysis,” said Dan Geer, chief information security officer of the CIA’s venture capital firm In-Q-Tel.
“If I know everything about you, about who you communicate with, when, where, with what frequency, what length, and at what location, I know you. The soothing mendacity of proxies from the president that claim that it is only metadata, is to rely on the profound ignorance of the listener.”
The NSA still hasn’t commented the documents.
TrueCrypt is safer than previous examinations suggest
23.11.2015
A new security audit the TrueCrypt software confirmed that even if it is plagued by some vulnerabilities, the application is effective when it comes to protecting data.
TrueCrypt, secure or insecure … that is the question.
A group of Ten auditors from the Fraunhofer Institute for Secure Information Technology has conducted a six-month audit of TrueCrypt under contract from the German Government. The researchers have expressed a positive opinion of the popular freeware utility used for on-the-fly encryption (OTFE).
The experts have examined in detail the vulnerabilities affecting TrueCrypt and revealed that the popular application is safer than previous examinations suggest. The details of the analysis are included in a 77-page report, titled Security Analysis of TrueCrypt, that examined also extra vulnerabilities in the software.
The maintenance of TrueCrypt was mysteriously interrupted in May last year, a message on the official SourceForge-hosted page was encouraging users to adopt Microsoft Bitlocker because TrueCrypt was insecure.
“The development of TrueCrypt was ended in 5/2014 after Microsoft terminated support of Windows XP. Windows 8/7/Vista and later offer integrated support for encrypted disks and virtual disk images. Such integrated support is also available on other platforms (click here for more information). You should migrate any data encrypted by TrueCrypt to encrypted disks or virtual disk images supported on your platform,” states the message on Truecrypt website.

Rumors online states that developers were aware of a critical vulnerability or backdoor that would jeopardize the integrity of the software, and for this reason, they suspended the project.
Since then, a group of experts under the Open Crypto Audit Project who audited the software confirmed that it was “well-designed.” The report published by the OCAP highlights that popular appl is affected by several buffer overflow vulnerabilities, but tests conducted by Fraunhofer SIT researchers have demonstrated that these vulnerabilities cannot be exploited by hackers.
In September, the popular hackers James Foreshaw has discovered further privilege escalation vulnerabilities that were not reported in the previous security audits of the software.
Now the group of experts hired by the Germany’s Federal Office for Security in Information Technology has provided more details on the real level of security implemented by the encryption platform.
From a security standpoint, the group of researchers explained that despite there are security issued related to the software, it is good for protecting data stored on an unmounted hard drive or a USB flash drive.
“The AES implementation is not timing-resistant, key files are not used in a cryptographically secure way and the integrity of volume headers is not properly protected. There are many redundant implementations (sometimes for hardware-optimization) and disused algorithms are still present in a deactivated form in the source code,” state the report.
According to the experts, TrueCrypt is not resilient to attacks in which the attackers have privileged access to a running system, but this is not a novelty.
The experts evaluated the software not optimal but still effective under specific circumstances.
“Overall, the analysis did not identify any evidence that the guaranteed encryption characteristics are not fulfilled in the implementation of TrueCrypt. In particular, a comparison of the cryptographic functions with reference implementations or test vectors did not identify any deviations. The application of cryptography in TrueCrypt is not optimal. The AES implementation is not timing-resistant, key files are not used in a cryptographically secure way and the integrity of volume headers is not properly protected.”
Damballa revealed the secrets behind the Destover malware that infected the Sony Pictures
23.11.2015
Security researchers at Damballa Willis McDonald and Loucif Kharouni have conducted a deep analysis of the Destover malware used in the Sony Pictures attack.
Security researchers at Damballa Willis McDonald and Loucif Kharouni have conducted a deep analysis of the wiper used by threat actors in the Sony Pictures hack. The experts discovered that attackers used a highly sophisticated disk-cleaning code dubbed Destover malware that stayed hidden using newly-uncovered anti-forensics tools.
The experts noticed significant improvements in the variant of Destover malware that was used to erased data across systems at Sony Pictures in November. In December security experts at Kaspersky Lab have detected a strain of Destover Malware that has been digitally signed with the certificates stolen during Sony attack.
Destover has been linked to the Shamoon malware used in the attack on Saudi Aramco in 2012, experts have discovered several similarities among the wiping components implemented by the two malware.
Many hypotheses have been circulating about the Sony hack, the American authorities have blamed North Korea, but a part of the security community has pointed the finger at Russian hackers.
Experts at Damballa have discovered that the new variant of Destover use components to avoid detection and make hard forensic investigations, for example the strain of malware analyzed by McDonald and Kharouni has the ability to change file timestamps and erase the logs.
“The Destover trojan is a wiper that deletes files off of an infected system, rendering it useless … for ideological and political reasons not for financial gain,” the pair of researchers say. “
“Much was revealed In the weeks and months following these breaches, except for how attackers were able to stay undetected within the network long enough to expand their presence and exfiltrate Terabytes of sensitive information. While researching a newer sample of Destover, we came across two files that were identified by one antivirus product at the time under a generic signature. After analyzing further, we found two utilities closely related to Destover. Both utilities would be used during an attack to evade detection while moving laterally through a network to broaden the attack surface. Both utilities had usage statements and were named as setMFT and afset.”
The experts discovered two utilities used to manipulate the timestamps and wipe logs. The utility setMFT is used for timestomping, a term used to identify the copy the timestamp settings from a source file on disk to a destination file.
“setMFT is used to copy the timestamp settings from a source file on disk to a destination file, also called timestomping. Timestomping combined with similar file naming enables a file to blend in with legitimate files in the same directory. This can conceal a file’s existence from security personnel looking for malicious files or scans of files created after a certain date. Timestomping can get past a cursory check for malicious files. A thorough forensic examination will reveal that a file has been timestomped based on conflicting record dates and possibly log files.” states the post published by Damballa.
The afset utility is used to wipe Windows logs based on time and identity, and modify an executable’s properties, including build time and checksum.
“afset, like setMFT is also used to timestomp files plus clean Microsoft Windows logs based on criteria (id, time) from the user. It also changes the PE build time and checksum. afset provides more granular functionality to allow the user to set only certain timestamps on a file (sia, fna or both). “
The experts have no doubt, attackers behind the Destover-based attacks are very well organized, afset and setMFT utilities are part of their arsenal and allow them to remain under the radar for a long period.
“Gaining a foothold inside the victim’s network is a top priority. History tells us that in most of the high-profile hacks making news headlines, the attackers were able to spend months hidden inside the victim’s network exfiltrating Terabytes of data.”
The table below details the different steps attackers would go through to penetrate the targeted infrastructure, it is possible to note that they have used the two utilities for different purposes and at different steps.
STEPS TOOLS
Reconnaissance Scanners, Open source intelligence gathering
Breach Vulns, Exploits,
Foothold afset, setMFT, RATs, credential theft
Move laterally Stolen administrative credentials and RATs
Exfiltrate VPN accounts, RATs, out of band comms
Delete tracks afset, setMFT, Destover / Shamoon
Exit Publish stolen data, clean with Destover / Shamoon
Ransomware will target also Medical Devices
23.11.2015
“Want to keep using the pacemaker? “” pay us 2 bitcoins” Experts fear that ransomware will start targeting medical devices.
Technology has a huge role in our lives, we depend on it even more, including our smartwatch and also our medical device. Unfortunately, we usually forgot that even our medical devices, the ones they help to save lives, are also technological devices that could be affected by many security issues like a normal PC … and hackers can exploit these vulnerabilities!
A report issued by Forrester released some days ago, predict that for 2016 we will start seeing ransomware take advantage of medical devices.
Now imagine that a patient having a pacemaker suddenly receives a message on his phone saying “Want to keep using the pacemaker? “, ” pay us 2 bitcoins”, it may look bizarre, but its probably things that may happen in a near future.
It is a bold prediction by “Predictions 2016: Cybersecurity Swings To Prevention” report, but honestly it’s something that already crossed our minds.
“It’s definitely feasible from a technical standpoint,” “see it as something that could happen next year. All that would be required from an attacker standpoint is small modifications to the malware to make it work.” Explained Billy Rios, a popular hacker and medical device security researcher.
We could argue that it’s not correct to get a profit from situations like this, but many crooks, just don’t care.
The ICS-ALERT-13-164-01 from 2013 done by Rios and Terry McCorkle showed that 300 medical devices were using hard-coded passwords, that are set at the factory, that can’t be disabled or changed, these passwords are discriminated in the manual of the manufacturer.
The truth is, Cyber security exist probably since the last 15-25 years, but it’s something new in the Medical Industry and as Joshua Corman, founder of I Am the Cavalry says:
“While we’ve been doing this for 15-25 years in cyber, this is year zero or one for them [the healthcare industry],”“We can’t give them 15-25 years to catch up, although it’s not reasonable to get there overnight….We’re trying to approach this with teamwork and ambassador skill, not a pointing finger, but a helping hand.”
Ransomware is a huge business, and the major security vendors have been saying that 2015 had a huge increase in the Ransomware use and profit, and it tends to get even more with the IoT and all the devices connected to the internet.
Months ago on SecurityAffairs we talked about a list developed by I Am The Cavalry that was created to mitigate threat in cars, and now they are planning the same type of list but this time for medical devices.
There are many challenges ahead, when dealing with Medical devices, but we are starting to see many people worried about it, so I believe that many security researchers will focus their attention on them, but for this we also need the support of the medical devices manufacturers.
Police Body Cameras come with Conficker Worm
22.11.2015
Police body cameras sold by Martel Electronics have been found to be infected with the notorious Conficker worm.
Security experts at iPower Technologies while analyzing the body cam designed for police departments manufactured by Martel Electronics, discovered that the cameras were infected.
Martel Electronics is US company that design video systems used by law enforcement, including in-car and body cameras. iPower Technologies is working on developing a cloud-based system for law enforcement to store and manage video acquired by their cameras.
iPower discovered that the camera used for testing were infected with a variant of Conficker (aka Downup, Downadup and Kido). The malware is not complex and is actually detected by almost every antivirus software.
The cameras had been shipped with the worm, once the devices were connected to a computer, the malicious code attempted to contact the C&C server and infect other devices on the same network.
“During testing and evaluation of the Martel Electronics product, Jarrett Pavao and Charles Auchinleck, discovered that multiple body cameras had been shipped to iPower preloaded with the Win32/Conficker.B!inf worm virus. When the camera was connected to a computer, iPower’s antivirus software immediately caught the virus and quarantined it. However, if the computer did not have antivirus actively protecting the computer it would automatically run and start propagating itself through the network and internet.” states iPower in a blog post.
iPower attempted to report the issue to Martel before publicly disclose it, but it hasn’t received a response.
Conficker is a well-known threat, it was first detected in November 2008, when it has infected millions of computers across the world. Conficker is considered by security experts one of the largest botnets ever seen. Cyber security experts linked the threat also to Stuxnet, in fact, the worm was used to open back doors into computers in Iran, then infect them with Stuxnet … “Conficker was a door kicker,”
In 2009, Microsoft alongside security firms, academic researchers and domain registries teamed up to create the Conficker Working Group, a joint effort aiming to disrupt the botnet.
Unfortunately the threat is still active worldwide.
Shedun adware can install any malicious mobile app by exploiting Android Accessibility Service
22.11.2015
Shedun Trojanized adware family implements the ability to automatically install any app on the devices by exploiting the Android Accessibility Service.
Android is once again in the storm, threat actors can install any malicious third-party app on mobile devices remotely even if the users explicitly refuse it.
Security experts at mobile security firm Lookout have spotted Trojanized adware families that implement the ability to automatically install any mobile app on the devices by exploiting the Android accessibility features.
The researchers have found three Trojanized adware families, Shedun (GhostPush), Kemoge (ShiftyBug),
Shuanet.
These families root the infected device after being installed and gain persistence by embedding their code in the system partition. The root access allows attackers to gain unrestricted access to the mobile devices.
“Last week we told you about three trojanized adware families: Shuanet, ShiftyBug, and Shedun. These families root the victim’s device after being installed and then embed themselves in the system partition in order to persist, even after factory reset, becoming nearly impossible to remove. We call it “trojanized adware,” because the end goal of this malware is to install secondary applications and serve aggressive advertising.” reads the blog post published by
The malware researchers highlighted the capabilities of the Shedun adware family that seem to be out of the ordinary because it doesn’t exploit any vulnerability to hijack an Android device, instead it relies on the service’s legitimate functionality.

During the installation, mobile apps from the Shedun adware family tricks users into granting them access to the Android Accessibility Service, this means they will be able to read the text on the phone screen, determine an app installation prompt, scroll through the permission list and press the install button on the behalf of the user.
“Lookout observed Shedun abusing the Android Accessibility Service for its malicious means. Using the accessibility service toolset in the delivery of malware is pretty uncommon, so we took a deeper look.” states the post. “By gaining the permission to use the accessibility service, Shedun is able to read the text that appears on screen, determine if an application installation prompt is shown, scroll through the permission list, and finally, press the install button without any physical interaction from the user.”
The following video shows apps from the Shedun adware family gaining accessibility service privileges.
In this second video Shedun automatically install a trojanized app that masquerades itself as an official app available in Google Play Store and then is pushed to third-party markets.
It is important to note that the Android Accessibility Service is also used by legitimate applications, users are advised not to install applications from third-party app markets.
The new Nmap 7 version just released
22.11.2015
After 3.5 years, Fyodor has released the new version of the popular open-source network-exploration tool Nmap 7.
After 3.5 years, Fyodor has released the new version of the popular network-exploration tool Nmap 7. Nmap is one of the most popular open-source network mapper, the principal changes announced for this release are:
– 3,200 code commits since Nmap 6
– expanded capabilities for its scripting engine including 171 new NSE scripts
– Mature IPv6 support from host discovery, port scanning and OS detection
Serious vulnerabilities like Heartbleed, POODLE, and FREAK could be easily detected by using the automated scanners implemented by Nmap 7.
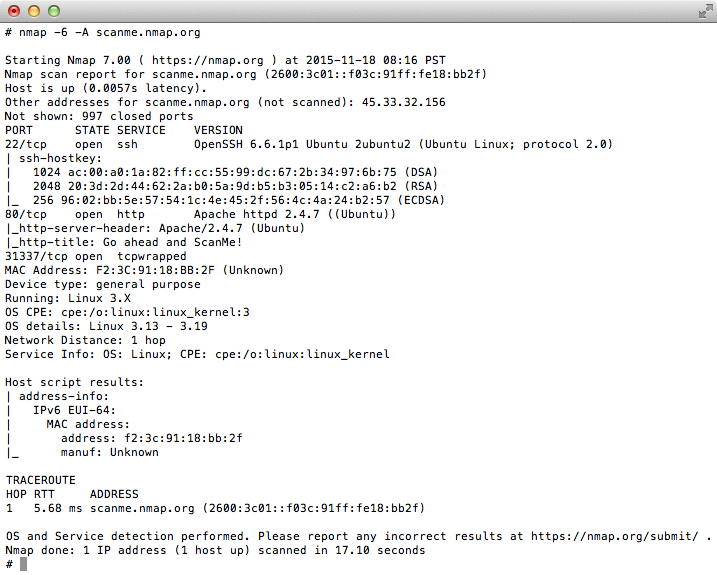
A new implementation for the ssl-enum-ciphers script allows to perform fast analysis of TLS connections by enumerating SSL/TLS protocol versions and cipher suites. It could allow to rapidly identify deployment problems.
The tool could be used to easily find vulnerable servers, Nmap 7 includes speedups and scanning improvements. The new version of the tool includes a newer and faster Nmap Scripting Engine (NSE), it also allows users to write Lua scripts.
“The venerable RPC grinder which used to run with -sV is now an NSE script: rpc-grind. This allowed us to cull a bunch of old C code in favor of more maintainable Lua, as well as make a noticeable improvement in scanning speed, all while using a fifth of the number of code lines.” states the post on the Nmap 7 version.
The library of scripts available in the Nmap 7 has expanded from 348 to 515. Some of the scripts included in the tool could be used to rapidly check for SSL vulnerabilities (i.e. Heartbleed, POODLE and Shellshock) and for HTTP flaws such as Slowloris and Misfortune Cookie.
The new engine can also output parsable XML and implements the support for shared libraries across scripts.
“NSE joins the rest of Nmap in being able to output parseable XML. Instead of just a text blob in Nmap’s XML output, scripts can now return structured information that can be quickly extracted with an XML parser. All new scripts produce structured output, most older scripts have been converted, and any script using the vulns library is automatically upgraded.”
If you want to download Nmap 7 click here.
DHS Information Security Program, Dozens secret databases vulnerable to hack
22.11.2015
Evaluation of DHS Information Security Program for Fiscal Year 2015 revealed the existence of dozens of top-secret unpatched databases.
The story I’m about to tell you is staggering, the US Department of Homeland Security is running dozens of unpatched and vulnerable databases, a number of them contained information rated as “secret” and even “top secret.”
The discovery emerged from the “Evaluation of DHS’ Information Security Program for Fiscal Year 2015” conducted on the department’s IT infrastructure by the US Government.
The audit of the DHS Information Security found serious security issues in the Government systems, including 136 systems that had expired “authorities to operate,” a circumstance that implies the stop of maintenance activities. The principal problem discovered by the inspectors is that a number of systems, despite are still operative and under maintenance have no up-to-date security patches, leaving them open to cyber attacks.
Of the 136 systems, 17 were containing information classified as “secret” or “top secret.”
Giving a deep look at the report on the DHS Information Security Program, it is possible to note that the Coast Guard runs 26 vulnerable databases, followed by FEMA with 25, Customs and Border Protection with 14, and the DHS’ headquarters with 11.

Although Secret Services have only two vulnerable databases, they have failed other targets.
It implemented proper security checks just for 75 percent of its secret or top secret databases, and just 58 per cent of its non-secret databases. The DHS targets are 100 per cent and 75 per cent respectively. The experts discovered several security issues affecting the majority of assessed systems, including PCs, databases and also browsers.
The assessments conducted to evaluate the DHS Information Security Program, revealed several deficiencies in the systems analyzed, for example, Windows 8.1 and Windows 7 workstations which were missing security patches for the principal software.
“We found additional vulnerabilities regarding Adobe Acrobat, Adobe Reader, and Oracle Java software on the Windows 7 workstations,” the department’s inspector general noted in a 66-page report. “If exploited, these vulnerabilities could allow unauthorized access to DHS data.”
The inspectors have found many other security issues in the DHS Information Security Program, including weak passwords, websites susceptible to cross-site and/or cross-frame vulnerabilities and poor security settings.
The Government environments suffer bureaucratic obstacles in bug fixing and patch management, it could take more than a year to fix a leak from the moment it is reported.
The results of the evaluation confirm that improvements have been made but there are a lot of serious issues that have to be urgently addressed.
“While improvements have been made, the Department must ensure compliance with information security requirements in other areas. For example, DHS does not include its classified system information as part of its monthly information security scorecard or its FISMA submission to OMB. In addition, USCG is not reporting its PIV data to the Department, which is a contradiction to the Under Secretary for Management’s guidance that requires Components to submit this information to the Department.5 In addition, we identified deficiencies with DHS’ enterprise management systems, including inaccurate or incomplete data.”
The report also provides a set of recommendations to solve the security issued emerged after the assessment.
The DHS has 90 days to fix the issues, two of which have been already solved.
Anonymous Hacking Group Takes Down 20,000 ISIS Twitter accounts
21.11.2015
Anonymous Hacking Group Takes Down 20,000 ISIS Twitter accounts
In the wake of horrific terror attacks in Paris, the online Hacktivist group Anonymous last week declared "total war" against the Islamic State militant group (ISIS) that claimed responsibility for the attacks.
While French, Russian, and US military are bombing ISIS from the sky, Anonymous members from all over the world are carrying out their very own cyber attack campaign, dubbed #OpParis, against the terrorist organization.
Anonymous has claimed to have taken down 20,000 ISIS-affiliated Twitter accounts in order to take revenge from ISIS for the deadly Paris attacks on November 13.
Anonymous Took Down 20,000 ISIS-affiliated Twitter Accounts
In a YouTube video posted on Wednesday, the group said:
"More than 20,000 Twitter accounts belonging to ISIS were taken down by Anonymous."
The group has provided a list of all the Twitter accounts that have been taken down.
On Tuesday, the hacktivist group claimed to have successfully taken down more than 5,500 pro-ISIS Twitter accounts from the Internet.
Also Read: Check Out How 'Idiot' Anonymous Hackers Can Disrupt your Online Propaganda
In the latest video provided by Anonymous, a spokesman in black behind the group’s signature Guy Fawkes mask said:
"Hello, citizens of the world. We are Anonymous. It is time to realize that social media is a solid platform for ISIS’s communication as well as neutering their ideas of terror amongst youth. However, at the same time, social media has proved it is an advanced weapon. We must all work together and use social media to eliminate the accounts used by terrorists."
Hey ISIS! We Will Hunt you Down from The Internet
ISIS' most interesting aspect is how it leverages the enormous power of social media platform to radicalize young people, spread its message around the globe, recruit foreign supporters to its fight and shock people into taking notice of its actions.
So, taking down the ISIS' social media presence is the real key to defeating the terror group, and it does make an impact at worst.
"ISIS, we will hunt you and take down your sites, accounts, emails and expose you. From now on, there is no safe place for you online. You will be treated like a virus, and we are the cure," the spokesman said in the video message.
Also Read: Anonymous declares War on ISIS: 'We will Hunt you Down!'
IDIOTS Answer to ISIS
Last week, when Anonymous declared war against ISIS and warned it of launching their "biggest operation ever" against the terrorist group, ISIS militants called Anonymous – "IDIOTS".
However, on the other side, the terror organization started spreading instructions through its affiliated official channels on Telegram on how to prevent getting hacked by Anonymous. This shows that ISIS knows the capability of Anonymous.
In the past, hackers and organizations associated with Anonymous brought down websites allegedly connected with ISIS and took down thousands of ISIS accounts, disrupting their social media recruitment efforts.
Zerodium price list for secret Hacking methods
21.11.2015
The Zerodium (Zero-day broker) company has published a price list for various classes of software targets and digital intrusion methods.
In an exceptional move on 18th of Nov (Wednesday), the Zerodium (Zero-day broker) published a price list for various classes of software targets and digital intrusion methods that is purchased from cyber criminals and resells to consumers like intelligence agencies and governments.
The chart, which describes the sums it pays for the techniques that effect a lot of operating systems and applications, symbolizes one of the most comprehensive views yet into the provocative and dark market for secret hacker activities.
“The first rule of [the] 0days biz is to never discuss prices publicly. So guess what: We’re going to publish our acquisition price list.” said Chaouki Bekrar, CEO of Zerodium.
According to the Zerodium, if an attack on a computer or remotely take control the user’s PC via her/his Internet Explorer or Safari, for example, fetches a cost of maximum $50,000. If the target is quite harder, like Google Chrome, the price will be $80,000. The price will increase further to $100,000 if the target is Windows phone device or Android. The price increment is not stopped here, iOS attack can earn an attacker $150,000, so far the top price on the chart.
Check out the Zerodium Chart below:
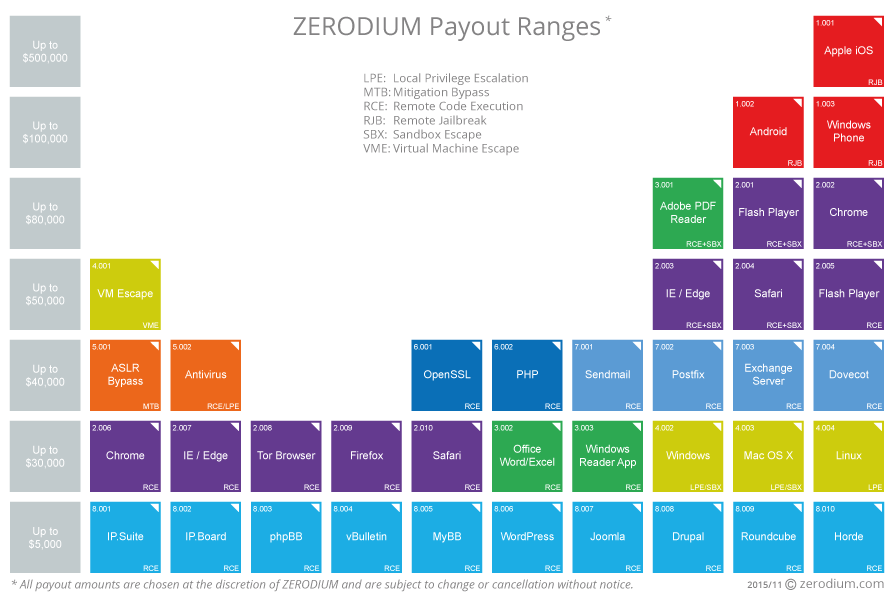
The firm explicitly advises brokers that any zero-day vulnerability we purchases must be for Zerodium’s eyes just; enterprising attackers cannot resell it to other customers or reveal it to the software’s seller, who might issue a patch that shields victims and renders the hack impractical. Zerodium specifies that it’ll pay the listed costs just for “exclusive, original, and previously unreported vulnerabilities.”
We can say, in other words, Zerodium is keeping its methods under wraps for its users. As per Zerodium FAQ page their customers include, “government organizations in need of specific and tailored cybersecurity capabilities.” On the other hand, Bekrar says, our customers pay subscription fee’s of minimum $500,000 annually for access to its vulnerabilities.
“Apple iOS, like all operating system, is often affected by critical security vulnerabilities, however due to the increasing number of security improvements and the effectiveness of exploit mitigations in place, Apple’s iOS is currently the most secure mobile OS. But don’t be fooled, secure does not mean unbreakable, it just means that iOS has currently the highest cost and complexity of vulnerability exploitation and here’s where the Million Dollar iOS 9 Bug Bounty comes into play.” said Zerodium in September.
In 2013, Muckrock requested to A Freedom of Information showed that NSA is one of the clients of Vupen. Openly trading in private intrusion methods has also made Zerodium’s CEO an easy object for criticism. Justin Schul from Google called Bekrar an “ethically challenged opportunist.” While on the other hand, Chris Soghoian a technologist called him Bekrar’s Vupen a “modern-day merchant of death,” selling “the bullets for cyber war.”
As per the Zerodium’s list, an iOS vulnerability is still top of the chart. Apple consumers may be discouraged to hear that the ability to attack their private device is as much a product as any other attacking method. However, nonetheless it is an exclusive one.
Anonymous Took Down 20,000 pro-ISIS Twitter accounts
21.11.2015
In the wake of Paris attacks Anonymous continues its campaign against the ISIS and announced to have taken down 20,000 pro-ISIS Twitter accounts.
In the wake of Paris attacks the hacking collective Anonymous launched its offensive against the ISIS with the intent to interfere with the online propaganda and reveal the identity of its members.
The #OpParis follows the precedent #OpISIS launched in the last months by Anonymous.
In the video message published by Anonymous, the groups announced that his members will catch ISIS members online. An avatar of Anonymous with a strong French accent declared “total war” to the terrorists.
In a new video published on YouTube on Wednesday, Anonymous announced to have identified and taken down More than 20,000 Pro-ISIS Twitter accounts:
“More than 20,000 Twitter accounts belonging to ISIS were taken down by Anonymous.”
Anonymous has also published the list of all the pro-ISIS Twitter accounts it has taken down.
A spokesman in the video announced:
“Hello, citizens of the world. We are Anonymous. It is time to realize that social media is a solid platform for ISIS’s communication as well as neutering their ideas of terror amongst youth. However, at the same time, social media has proved it is an advanced weapon. We must all work together and use social media to eliminate the accounts used by terrorists.” states the message.
“ISIS, we will hunt you and take down your sites, accounts, emails and expose you. From now on, there is no safe place for you online. You will be treated like a virus, and we are the cure,”
It is an escalation of the hacking activities started after the Paris Attacks, on Tuesday Anonymous claimed to have taken down more than 5,500 pro-ISIS Twitter accounts.
But, the ISIS is known to be a terrorist group with significant cyber abilities, especially the management of propaganda through social media.
The ISIS has considered strategic the use of technology, recently I described the content of the ISIS guide published by the organization to provide information to its members to avoid online surveillance.
Recently the US intelligence has also identified a training infrastructure that works with a sort of h24 help desk to provide information to the ISIS members and recruit new sympathizers.
Throw out the ISIS from the Internet is very challenging, the ISIS militants are ready to cyber jihad and called Anonymous “IDIOTS”.
Recently the group is making large use of the encrypting message service Telegram, security experts discovered broadcast messages used to provide instructions to the ISIS members on how to avoid getting hacked by Anonymous.
suggestions to pro-ISIS Twitter accounts
SilverPush technology tracks user habits with near-ultrasonic sounds
21.11.2015
The SilverPush technology allows advertising firm to track user habits with near-ultrasonic sounds.How does it work?
A few days ago, the Center for Democracy and Technology (CDT) warned that the Indian company SilverPush has developed a technology that allows adverts to ping inaudible commands to mobile devices.
SilverPush has issued also an SDK that could allow mobile developers to implement the technology in their mobile apps. This means that mobile apps running on the user’s device are able to receive near-ultrasonic sounds embedded in radio, TV or web browser advert. Humans are not able to capture the signals included in the ads because they are in the range of 18kHz to 19.95kHz, but the software can do it.
“Millions of mobile devices with SilverPush powered SDK are constantly listening to SilverPush patented audio beacons (ultrasonic) which are watermarked in Televison ad commercial. A pair is made once a SDK comes in proximity of audio beacon. The individual ID is mapped back to its audience genome and a brand-consumer journey has been started.” states the official description provided by SilverPush.
An application that implements the SilverPush technology car gather these near-ultrasonic messages by using the mobile microphone and then send data and mobile information (i.e. IMEI number, location, operating system version, and potentially the identity of the owner) to a server elsewhere.
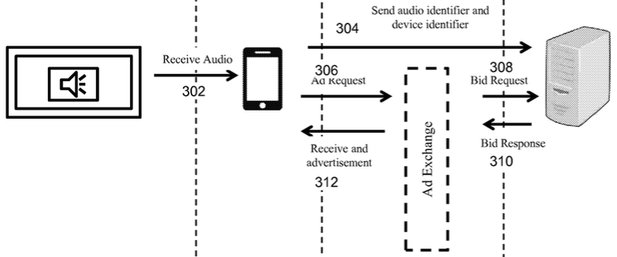
The application has a significant impact on the user’s privacy but represents a powerful instrument for the advertising industry. When the owner of a mobile device watches any advert embedding the SilverPush ultrasonic messages, his data are collected and sent back to a remote server.
A research has identified 30 applications using the SilverPush SDK, including shopping apps developed by companies in India and Far East.
Is it legal? Does the technology require the user’s consent?
“This kind of technology is fundamentally surreptitious in that it doesn’t require consent; if it did require it then the number of users would drop,” Joe Hall, chief technologist at CDT told The Register on Thursday. “It lacks the ability to have consumers say that they don’t want this and not be associated by the software.”
Another disconcerting aspect of the technology that the most applications that implement the SilverPush doesn’t notify it to the end-users.
In US and Europe end-user must explicitly give its consent, in Europe and in the US the exploitation of this kind of technology is not legal.
Imagine any abuse of the SilverPush technology by a repressive regime, the technology could allow a rogue government to track the mobile devices used by the dissidents.
How does it work?
The researcher Kevin Finisterre from Digital Munition firm analyzed the code of the SilverPush and has published his the results of the research on the GitHub.
The technology assigns letters of the alphabet to high-pitch tones (i.e. The letter ‘A’ is coded with a 18kHz tone, and 19.125kHz is a ‘P’). The combination of letters is used to identify TV ads, for example the ‘AP’ is associated to a Geico ad and display an image and link to the insurance biz.
Finisterre also demonstrated that is possible to spoof the sounds or interfere with the technology by generating randomly ultrasonic tones.
This Malware Can Secretly Auto-Install any Android App to Your Phone
20.11.2015
This Malware Can Secretly Auto-Install any Android App to Your Phone
Own an Android Smartphone?
Hackers can install any malicious third-party app on your smartphone remotely even if you have clearly tapped a reject button of the app.
Security researchers have uncovered a trojanized adware family that has the capability to automatically install any app on an Android device by abusing the operating system's accessibility features.
Michael Bentley, head of response at mobile security firm Lookout, warned in a blog post published Thursday that the team has found three adware families:
Shedun (GhostPush)
Kemoge (ShiftyBug)
Shuanet
Also Read: Android Malware Can Spy On You Even When Your Mobile Is Off
All the three adware families root-infect Android devices in order to prevent their removal and give attackers unrestricted access to the devices.
But, it seems that the Shedun adware family has capabilities that go beyond the reach of other adware families.
The Malware Doesn't Exploit Any Vulnerability
It is worth noting that the malware does not exploit any flaw in the service to hijack an Android device and instead relies on the service's legitimate functionality.
During the installation, apps from the Shedun adware family tricks users into granting them access to the Android Accessibility Service, which is meant to provide users alternative ways to interact with their smartphone devices.
Also Read: Kemoge: Latest Android Malware that Can Root Your Smartphone
By gaining access to the accessibility service, Shedun can:
Read the text that appears on the phone screen
Determine an app installation prompt
Scroll through the permission list
Finally, Press the install button without any physical interaction from the user
Video Demonstration:
You can watch the following video that shows the forced installation of an app in action.
The trojanized app actually masquerades itself as an official app available in Google Play Store and then is pushed to third-party markets.
The worrisome part is that Shedun apps can't be easily uninstalled, as the apps root the victim's device and then embed themselves in the system partition in an effort to persist even after factory reset.
Also Read: Android Bootkit Malware Infected Millions of Devices
Lookout categorized them as "Trojanized Adware" because the goal of this malware is to install third-party apps and serve aggressive advertising.
Legitimate applications also use the Android Accessibility Service for features like to grant expanded capability to phone tinkerers. So, users are, as always, advised to carefully make use of the third-party app markets.
The ISIS guide, how to stay secure online
20.11.2015
Which are the technological tools used by the ISIS? Do the terrorists know how to avoid the surveillance online? The ISIS guide has the replies to these questions.
In the wake of Paris attacks, intelligence agencies and law enforcement have raised again the debate about the encryption requesting IT giants to support them by introducing backdoors in their products.
But news reports of the Paris attacks have revealed that at least some of the time, the terrorists behind the attacks didn’t bother to use encryption while communicating, allowing authorities to intercept and read their messages.
Clearly the ability of law enforcement in intercepting communication is essential in fighting terrorism, the crusade against the online encryption is instrumented by part of the intelligence community. In some documented cases, the ISIS terrorists haven’t adopted the necessary measures to properly use encryption causing the exposure of their communications.
So what exactly are ISIS attackers doing for OPSEC?
Wired has published an interesting post to respond the question, it started from an ISIS guide to operational security that was available online.
The ISIS guide, which is written in Arabic, alongside with other documents were analyzed by Aaron Brantly and other researchers with the Combating Terrorism Center at West Point’s military academy.
The documents provide a long series of suggestion to the members of the organization to avoid online surveillance, for example it bans the use of Instagram meanwhile it suggests dozens of privacy and security applications, including the Tor browser and the Tails distro, Cryptocat, Wickr, and Telegram encrypted messaging systems, Hushmail and ProtonMail email services, and RedPhone and Signal for encrypted phone communications.
isis guide
The ISIS guide includes most of the recommendations provided by civil liberties, privacy defender, and journalist groups when dealing with surveillance operated by many regimes across the world.
“The documents indicate that the jihadis have not only studied these other guides closely, but also keep pace with the news to understand the latest privacy and security vulnerabilities uncovered in apps and software that could change their status on the jihadi greatest-hits list.” states Wired.
The ISIS guide invites members of the organizations to use Gmail only with false credentials and in conjunction with the Tor network or by protecting the access with a VPN (of course avoiding US VPN providers). The use of mobile OS is considered secure when data connections are routed through the Tor network.
In the list of the banned applications, there are also the Apple’s iMessage and WhatsApp, despite both implements end-to-end encryption the jihadists believe that companies spies on behalf of the US Government.
It also warns that mobile communications can be intercepted and recommends followers to use crypto phones like Cryptophone or BlackPhone instead.
“Instead of buying the [expensive] Blackphone, they’re trying to hack their own devices and route traffic through Tor,” explains Brantly who added that the ISIS demonstrating an increasing interest in hacking . “There’s a whole section on hacking [in the ISIS forums],” Brantley says. “They’re not super-talented hackers, but they’re reasonable.”
The manual also provides instructions to disable location services and geotagging when using mobile apps or taking photos and videos.
Dropbox is on the black list because Edward Snowden’s revelations, and because former Secretary of State Condoleezza Rice is on the company’s investors board.
“It uses a lot Services “Alclaud” or cloud services to store their files and photographs or make a backup copy of important and non-important files, and perhaps the most popular service in this area is a service Dropbox Drop Box, which joined Condoleezza Rice of the Council of your managed recently and is known to fight for privacy and support the absolute spy mail, so Adraor Snowden advised not to use the service and considered it .dangerous to personal security and privacy Here we put alternative and safe services and less than the paths of Xbox in .terms of space and features but much better ones”
Mega Services, SpiderOak service, SugarSync service and Copy.com service are cloud storages suggested in the manual.
“This is about as good at OPSEC as you can get without being formally trained by a government,” Brantly, a cyber fellow with the West Point center, told WIRED. “This is roughly [the same advice] I give to human rights activists and journalists to avoid state surveillance in other countries. If they do it right, then they can become pretty secure. [But] there’s a difference between telling somebody how to do it and then [them] doing it right.”
The manual provides instruction to assume a secure posture online avoiding to be infected by malware or get hacked. It suggests to carefully manage suspicious email and provides detailed instructions on how to set up a private Wi-Fi network.
Interesting the use of mobile apps like FireChat to share photos and text at short distances without needing to access the Internet.
Let’s close with two further elements emerged from the analysis of the ISIS guide, there is no reference to the use of gaming console as messaging platforms, neither the use of home-brewed encryption programs developed by ISIS members.
Jako Pat a Mat: Piráti omylem dali do viru i dešifrovací klíč
20.11.2015 Viry
Vyděračské viry z rodiny ransomware terorizují uživatele po celém světě již několik let. Jeho nová verze, která cílí na počítače s operačním systémem Linux, se tvůrcům ale opravdu nepovedla. Obsahuje totiž chybu, díky níž se lidé dostanou opět ke svým datům. Pirátům tak nemusí zaplatit ani korunu.
Nezvaný návštěvník požadující výkupné po uživatelích Linuxu pracuje úplně stejně jako jeho předchůdci. [celá zpráva]
Poté, co se se zabydlí v počítači, zašifruje na něm uživatelská data. Útočníci se pak snaží v majiteli napadeného stroje vzbudit dojem, že se k zašifrovaným datům dostane po zaplacení pokuty. Ta byla údajně vyměřena za používání nelegálního softwaru apod.
Když důvěřivci zaplatí, stejně se k datům nedostanou. Standardně je totiž nutné vyděračský virus z počítače odinstalovat a poté data odšifrovat.
Experti objevili v tomto ransomwaru chybu, díky které je možné získat klíče potřebné pro dešifrování souborů.
analytik Pavel Bašta z týmu CSIRT
A právě zde začíná ta vtipná část, která připomíná legendární pohádku Pat a Mat. Piráti si totiž nevedli při programování příliš dobře a nezvaný návštěvník zároveň prozrazuje klíč potřebný k dešifrování.
„Toto je dobrá zpráva pro všechny, jejichž soubory byly v posledních dnech zašifrovány ransomwarem známým jako Linux.Encoder1. Experti společnosti Bitdefender objevili v tomto ransomwaru chybu, díky které je možné získat klíče potřebné pro dešifrování souborů,“ uvedl analytik Pavel Bašta z Národního bezpečnostního týmu CSIRT, který je provozován sdružením CZ.NIC.
I když se nejčastěji vyděračské viry soustředí na klasické počítače, existují také výjimky. Loni v červnu bezpečnostní experti odhalili nezvaného návštěvníka, který požadoval výkupné i na mobilním telefonu.
Nested backdoor affects 600,000 Arris cable modems
20.11.2015
A Brazilian security researcher has discovered a nested backdoor affecting nearly 600,000 Arris cable modems. Arris is working to fix it.
The Security expert Bernardo Rodrigues (@bernardomr) has discovered the presence of a “backdoor-within-a-backdoor” in roughly 600,000 Arris cable modems.
Rodrigues is a vulnerability tester at Brazil’s Globo television network, he reported the undocumented library in three Arris cable modems, the company promptly replied that it is working to fix the issue.
Locate the Arris cable modems is quite easy with Shodan, in this way the expert exposed more that 600,000 affected devices.
In 2009 was reported for the first time a backdoor in the Arris cable modems, which were accessible using an admin password based on a known seed. Rodrigues has made a singular discovery, a backdoor affecting the hidden administrative shell that is implemented in the Arris cable modems.
“The default password for the SSH user ‘root’ is ‘arris’. When you access the telnet session or authenticate over SSH, the system spawns the ‘mini_cli’ shell asking for the backdoor password,” Rodrigues wrote in a blog post. “When you log using the password of the day, you are redirected to a restricted technician shell (‘/usr/sbin/cli’)”
The expert discovered that this nested backdoor uses a password based on the last five digits of the serial number of the device.
“They put a backdoor in the backdoor [which gives] a full busybox shell when you log on the Telnet/SSH session using these (serial number -based) passwords.”

A representative from the company ranked the risk as low and confirmed that the company is not aware of attacks in the wide.
“The risk related to this vulnerability is low, and we are unaware of any exploit related to it,” a spokeswoman says. “However, we take these issues very seriously and review them with the highest priority. Our team has been working around the clock on modem updates that address this reported vulnerability.”
Rodrigues also developed a keygen that can be used to calculate the password for the nested backdoor, a Metasploit module was already written to automate the exploitation of that flaw.

Rodrigues reported the flaws to CERT/CC which is already working with the vendor to solve the problem.
Below a video PoC of the nested backdoor in the Arris cable modems.
Hackers behind Dark Seoul are back
20.11.2015
The hacking group that behind the Dark Seoul Operation that hit entities in South Korea in 2013 may be back with new targets.
According to the experts at Palo Alto Networks, the hacking group behind the attacks that targeted banks, financial institutions, government websites and news agencies in South Korea is still active. The attacks occurred in 2013, the hacking campaign was labeled by security firms as Dark Seoul and Operation Troy. The experts noticed that the variant used in the recent attack doesn’t include the wiper component present in the version that targeted entities in the South Korea. The wiper deletes the Master Boot Record (MBR) making impossible the bootstrap of the machine.
The experts found many similarities between malware used in a recent attack in Europe and that malicious code spread in the attacks against entities in South Korea.

The attack vector was the email with malicious attachments or containing harmful links, the European organization was recently targeted by a spear-phishing attack.
The malware had been wrapped into legitimate video player software that was hosted by an industrial control systems company,
Security experts Bryan Lee and Josh Grunzweig from Palo Alto explained that threat actors have trojanized a legitimate video player software that was hosted by an industrial control systems company.
“The initial attack was likely a spear-phishing email, which leveraged a trojanized version of a legitimate software installation executable hosted by a company in the industrial control systems sector. The modified executable still installs the legitimate video player software it claims to contain, but also infects the system.” reads the blog post published by Palo Alto Networks. “Based on deep analysis of the Trojan’s behavior, binary code, and previous reports of similar attacks, we have concluded that these samples were the same as the original tools used in the Dark Seoul/Operation Troy attacks” “It is likely the same adversary group is involved, although there is currently insufficient data to confirm this conclusion,”
In the analysis conducted by McAfee in 2013, the experts identified two parallel operations conducted by initially by two crews that appeared separated, the Whois Hacking Team and the NewRomanic Cyber Army Team. The evidence collected by McAfee lead the firm to concluded it was likely a single group behind both campaigns.
The malware used in the recent attack was controlled through compromised websites in South Korea and Europe. The attackers compromised these websites because they were running out-of-date software.
“The similarities in tactics however, do seem to outweigh the differences, and it is highly likely this is the same group or groups responsible for the original Dark Seoul/Operation Troy attacks, but with a new target and a new campaign,” Palo Alto wrote.
It is quite common to see three actors suspend their activities for a period, especially after the investigation of security firms. Usually, when these dormant threats reappear don’t adopt change completely their hacking arsenal and in many cases they reuse part of the uncovered control infrastructure.
The experts consider insufficient collected data at this time to clearly state why Dark Seoul/Operation Troy would resurface at this time, but they will continue to investigate on it.
EU plans to ban Bitcoin to curb terrorism funding
20.11.2015
According to a draft document seen by the Reuters the EU plans to ban bitcoin and any form of anonymous payment online to curb terrorism funding.
European Union countries are planning to ban virtual currencies and any form of anonymous payments online, even through pre-paid cards. According to a draft document seen by journalists at the Reuters Agency, the initiative aims to tackle terrorism financing after the recent tragic Paris attacks.
A crisis meeting will be held today in Brussels, EU interior and justice ministers will participate to discuss the measures to block any financing to the radical group ISIS.
The draft document will urge the European Commission to propose measures to “strengthen controls of non-banking payment methods such as electronic/anonymous payments and virtual currencies and transfers of gold, precious metals, by pre-paid cards,”. reads the draft document. [EU ministers also plan] “to curb more effectively the illicit trade in cultural goods,”
The Bitcoin is the most popular virtual currency, and authorities suspect that members of the ISIS could use it to rapidly transfer money to cells around the world.
At the Foreign Affairs Forum on Cryptocurrency Policy in May, government officials and Bitcoin entrepreneurs discussed the future of the cryptocurrency. Law enforcement fear possible abuses of the popular crypto currency, Jennifer Shasky Calvery, head of the US Treasury Department’s Financial Crimes Enforcement Network (FinCEN), which is charged with fighting money laundering and terrorist finance, explained that the virtual currency scheme could facilitate bad actors, including terrorists.
“What keeps me up at night when I am thinking about digital currency…the real threats out there, these days we’re thinking a lot about ISIL,” Calvery declared. “How they’re moving their money, and how potential US-based individuals are becoming foreign fighters: Are they moving their money, can we identify them from the movement of their money? What does it mean if they start moving their money through bitcoin? We’ve started to see some public articles suggesting that has occurred.”
Intelligence agencies and security experts are aware that alleged members of terrorist groups, including the ISIS, are exploring different opportunities to transfer money to militants operating in Western countries.
ISIS funds Bitcoin
A continuous flow of a small amount of money could be instantaneously transferred to numerous accounts used by ISIS members worldwide. Micro payments could exploit several channels, including systems like PayPal or virtual currencies like the Bitcoin.
Online it is possible to find a PDF document written by a user with the pseudonymous pseudonym of Amreeki Witness titled: Bitcoin wa Sadaqat alJihad which translates to: “Bitcoin and the Charity of Violent Physical Struggle”.Bitcoin and the Charity of Violent Physical Struggle”. The pseudonym Amreeki authored the PDF under is Taqi’ulDeen alMunthir. That name translates to Righteous in Faith the-Warner.
VirusTotal now Scans Mac OS X Apps for Malware
19.11.2015
Do Mac Computers Get Viruses?
Yes, Of Course, they do!
According to stats, malware for MAC OS X has appeared five times more in 2015 alone than the previous five years combined.
As malware for Macs is becoming more common, Google has decided to add support for Mac OS X malware detection to its VirusTotal web-based service.
VirusTotal — launched in 2004 and acquired by Google in 2012 — is a free and popular online service for security researchers and Hackers that lets you upload files to check them for viruses.
VirusTotal scans uploaded files with more than 55 different Antivirus products and Online scan engines to provide a combined report on the results.
VirusTotal also runs certain 'Windows PE files and Android apps' files in the Sandbox, a controlled research environment used for malware analysis.
According to the recent announcement, VirusTotal will also be able to execute suspicious Mac executable files inside its Sandbox environment to check them for viruses.
"We are happy to announce equal treatment for Mac OS X apps. Files scanned that are Mach-O executables, DMG files, or ZIP files containing a Mac app, will be sent to the sandbox to produce behavioral reports." Karl Hiramoto, Technical Account Manager at VirusTotal, said in a blog post.
You’ll be now able to see an extra tab, called "Behavioral Information," on the result page, where you can find:
Operations the executable file initiates
Processes the file starts
DNS queries the file makes
Mac users who wish to scan any file for detecting hidden threat can do so on www.virustotal.com website, or with an app or via the API.
Russian financial cybercrime: how it works
19.11.2015 Zdroj: Kaspersky
The Russian-language cybercrime market is known all over the world. By ‘Russian-language market’ we mean cybercriminals who are citizens of the Russian Federation and some former USSR countries, predominantly Ukraine and the Baltic states. Why is this market known worldwide? There are two main factors: the first of these is frequent global media coverage of the activity of Russian-language cybercriminals. The second is the open accessibility of online platforms used by the cybercriminal community for communications, promoting a variety of “services” and “products” and discussing their quality and methods of application, if not for making actual deals.
Over time, the range of “products” and “services” available through this underground market has evolved, becoming more focused on financial attacks, and with an ever-increasing level of sophistication. One of the most common types of cybercrime was (and still is) the turnover of stolen payment card data. With the emergence of online stores and other services involving e-payment transactions, DDoS-attacks and financial cybercrime have become especially popular with the fraudsters whose main targets are users’ payment data or the theft of money directly from user accounts or companies.
Attacks on users’ and companies’ e-wallets were initiated by the Trojan ibank in 2006; then came ZeuS (2007) and SpyEye (2009) followed by the groups Carberp (2010) and Carbanak (2013). And this list is incomplete; there are more Trojans out there, used by criminals to steal users’ money and data.
With online financial transactions becoming more common, the organizations supporting such operations are becoming more attractive to cybercriminals. Over the last few years, cybercriminals have been increasingly attacking not just the customers of banks and online stores, but the enabling banks and payments systems directly. The story of the Carbanak cybergroup which specializes in attacking banks and was exposed earlier this year by Kaspersky Lab is a clear confirmation of this trend.
Kaspersky Lab experts have been monitoring the Russian hacker underground since it first emerged. Kaspersky Lab regularly issues reports on financial cyber-threats which track changes in the number of financial malware attacks carried out over time. Information on the number of attacks may indicate the extent of the problem but does not reveal anything about who creates them and how. We hope that our review will help to shed light on this aspect of financial cybercrime.
Between 2012-15, law enforcement agencies arrested over 160 Russian-speaking cybercriminals
Tweet
The data presented in this article is compiled from dozens of investigations that Kaspersky Lab experts have participated in over the last few years, as well as their many years’ experience observing the Russian cybercrime market.
Situation overview
According to Kaspersky Lab, between 2012 and 2015, law enforcement agencies from a number of different countries, including the United States, Russia, Belarus, Ukraine and the EU arrested over 160 Russian-speaking cybercriminals who were members of small, medium-sized and large criminal groups. They were all suspected of being engaged in stealing money using malware. The total damage resulting from their worldwide activity exceeded $790 million dollars. (This estimate is based both on the analysis of public information about the arrests of people suspected of committing financial cybercrime in the period between 2012 and 2015 and on Kaspersky Lab’s own data.) Of this sum, about $509 million dollars was stolen outside the borders of the former USSR. Of course, this figure only includes confirmed losses, the details of which were obtained by law enforcement authorities during the investigation. In reality, cybercriminals could have stolen a much larger amount.
The number of arrests of Russian-speaking cybercriminals as officially announced during the period 2012 to 2015
Since 2013, Kaspersky Lab’s Computer Incidents Investigation team has participated in the investigation of more than 330 cybersecurity incidents. More than 95% of these were connected with the theft of money or financial information.
Although the number of arrests of Russian-language criminals suspected of financial cybercrime increased significantly in 2015 compared with the previous year, the cybercriminal market is still “crowded.” According to Kaspersky Lab experts, over the last three years Russian-language cybercrime has recruited up to a thousand people. These include people involved in the creation of infrastructure, and writing and distributing malware code to steal money, as well as those who either stole or cashed the stolen money. Most of those arrested are still not in prison.
We can calculate fairly precisely the number of people who make up the core structure of an active criminal group: the organizers, the money flow managers involved in withdrawing money from compromised accounts and the professional hackers. Across the cybercriminal underground, there are only around 20 of these core professionals. They are regular visitors of underground forums, and Kaspersky Lab experts have collected a considerable amount of information that suggests that these 20 people play leading roles in criminal activities that involve the online theft of money and information.
The exact number of groups operating across Russia and its neighboring countries is unknown: many of those involved in criminal activities participate in several thefts and then, for various reasons cease their activity. Some participants of known but apparently disbanded groups continue their criminal activities as part of new groups.
Kaspersky Lab’s Computer Incidents Investigation Department can now confirm the activity of at least five major cybercriminal groups specializing in financial crimes. These are the groups whose activities have been monitored by the company’s experts over the last few years.
All five groups came to the attention of the company’s experts in 2012-2013, and are still active. They each number between ten and 40 people. At least two of them are actively attacking targets not only in Russia but also in the USA, the UK, Australia, France, Italy and Germany.
There are ~20 of people, who make up the core structure of an active criminal group
Tweet
Since the investigation into these groups has not been completed, it is not possible to publish more detailed information on the activities of these groups. Kaspersky Lab continues to investigate their activity and is cooperating with the law enforcement agencies of Russia and other countries in order to curb their cybercriminal business.
Investigation into the activities of these groups has allowed Kaspersky Lab experts to form an idea about their methods of operation and the structure of the cybercriminal market.
The structure of the Russian-language cybercriminal market
“A Range of products and services”
The cybercriminal market usually comprises a set of “services” and “products”, used for various illegal actions in cyberspace. These “products” and “services” are offered to users of dedicated online communities, most of which are closed to outsiders.
The “products” include:
Software designed to gain unauthorized access to a computer or a mobile device, in order to steal data from an infected device or money from a victim’s account (the Trojans);
Software designed to take advantage of vulnerabilities in the software installed on a victim’s computer (exploits);
Databases of stolen credit card data and other valuable information;
Internet traffic (a certain number of visits to a customer-selected site by users with a specific profile.)
The “services” include:
Spam distribution;
Organization of DDoS attacks (overloading sites with requests in order to make them unavailable to legitimate users);
Testing malware for antivirus detection;
“Packing” of malware (changing malicious software with the help of special software (packers) so that it is not detected by antivirus software);
Renting out exploit packs;
Renting out dedicated servers;
VPN (providing anonymous access to web resources, protection of the data exchange);
Renting out abuse-resistant hosting (hosting that does not respond to complaints about malicious content, and therefore does not disable the server);
Renting out botnets;
Evaluation of the stolen credit card data;
Services to validate the data (fake calls, fake document scans);
Promotion of malicious and advertising sites in search results (Black SEO);
Mediation of transactions for the acquisition of “products” and “services”;
Withdrawal of money and cashing.
Payments for such “products” and “services” on the cybercriminal market are generally made via an e-payment system such as WebMoney, Perfect Money, Bitcoin and others.
All of these “products” and “services” are bought and sold in various combinations in order to enable four main types of crime. These types can also be combined in various ways depending on the criminal group:
DDoS attacks (ordered or carried out for the purpose of extortion);
Theft of personal information and data to access e-money (for the purpose of resale or money theft);
Theft of money from the accounts of banks or other organizations;
Domestic or corporate espionage;
Blocking access to data on the infected computer for the purpose of extortion;
According to Kaspersky Lab experts, the theft of money is currently the most widespread type of crime. The rest of this report therefore focuses on this segment of the Russian-language cybercrime market.
The “labor market” of financial cybercrime
The variety of skills required for the creation of “products” and the provision of “services” has given rise to a unique labor market of professionals involved in financial cybercrime.
The list of key roles is almost exactly the same as that seen in any IT-related company:
Programmers / encoders / virus writers (for the creation of new malicious software and modification of existing malware);
Web designers (for the creation of phishing pages, emails, etc.);
System administrators (for the construction and support of the IT infrastructure);
Testers (to test the malicious software);
“Cryptors” (responsible for the packing of malicious code to bypass antivirus detection).
The list does not include the heads of the criminal groups, the money flow managers engaged in withdrawing money from compromised accounts, and the heads of money mules supervising the process of cashing the stolen money. This is because the relationship between these elements of the criminal groups is not an employer-employee one, but more of a partnership.
Depending on the type and extent of the criminal enterprise, the heads of the groups either employ “staff” and pay them a fixed salary or work with them on a freelance basis paying for a particular project.
An offer of employment posted on a semi-closed forum inviting a programmer to join a cybercriminal group. The job requirements include experience in writing complex bots.
“Employees” are recruited either via sites where those involved in criminal activity traditionally gather or via resources for those interested in non-standard ways of making money online. In some cases, the ads are placed on mainstream job search sites or on the labor exchanges for remote employees.
We can confirm the activity of at least 5 major cybercriminal groups specializing in financial crimes
Tweet
In general, employees involved in cybercrime can be divided into two types: those who are aware of the illegality of the project or the work they are offered, and those who (at least in the beginning) know nothing about it. In the latter case, these are usually people performing relatively simple operations such as copying the interface of banking systems and sites.
By advertising “real” job vacancies, cybercriminals often expect to find employees from the remote regions of Russia and neighboring countries (mostly Ukraine) where problems with employment opportunities and salaries for IT specialists are quite severe.
A fraudster has advertised a job vacancy for java / flash specialists on a popular Ukrainian website. The job requirements include a good level of programming skills in Java, Flash, knowledge of JVM / AVM specifications, and others. The organizer offers remote work and full employment with a salary of $2,500.
The idea of searching for “employees” in these regions is simple – they carry a saving because staff can be paid less than employees based in large cities. Criminals also often give preference to candidates who have not previously been involved in cybercrime activity.
Often, such job offers are presented as legitimate work, with the true purpose of the work only becoming clear once the task is received.
In this example, the organizer of the criminal group offers a job to a javascript programmer, masking it under a vacancy at a “Web-innovation studio specializing in the development of highly sophisticated Internet applications.”
In the case of illegal job search sites, less-experienced candidates are expected.
This vacancy invites a C ++ developer to develop “custom” software. In this context “custom” software means malicious software.
The second reason in favor of remote “personnel” is the organizer’s aim of making the activity of the group as anonymous as possible, and to ensure that no single contractor possesses complete information about the group.
Options for organizing a criminal group
Criminal groups involved in stealing money or financial information that will enable them to get access to money, differ in the number of participants and scope of activities. There are three main types of involvement:
Affiliate programs
Single dealers, small and middle-sized groups (up to ten members)
Large organized groups (ten or more participants)
This division is nominal. The scale of the group’s activity depends on the skillfulness of its participants, their ambition and the overall level of organizational abilities. In some cases, Kaspersky Lab experts came across relatively small criminal groups performing tasks that usually require a greater number of participants.
Affiliate programs
Affiliate programs are the easiest and least expensive method of getting involved in cybercrime activities. The idea behind an affiliate program is that the organizers provide their “affiliates” with almost all the tools they need to commit a crime. The task of the “affiliates” is to generate as many successful malware infections as possible. In return, the owner or owners of the affiliate program share the income received as a result of these infections with the affiliates. Depending on the type of fraudulent scheme this could be a share of:
The sums stolen from the accounts of Internet banking users;
The money paid by the user as a ransom when cybercriminals use ransomware Trojans;
The money stolen from the “prepaid” accounts of mobile device users by sending out SMS messages to premium mobile numbers with the help of a malicious program.
Creating and supporting an affiliate program for the purpose of stealing money is a cybercrime committed, as a rule, by a group of users. However, such projects are often carried out by large organized groups whose activity is analyzed later in this document.
This advertisement announces the launch of the beta testing of an affiliate program used to distribute encrypting ransomware. Judging by its characteristics, the group’s activity is focused on companies located in the US and the UK. This is indicated by the comment saying that the malware distributed via the partner network is able to encrypt files with 80 different extensions, many of which are files of applications used in companies. The text on requirements for candidates to participate in testing includes a demonstration of the presence of traffic or downloads from the United States and the United Kingdom.
According to Kaspersky Lab experts, affiliate programs are becoming less popular with Russian-language cybercriminals. The main driver of their popularity had been fraudulent schemes used to infect users’ mobile devices with malicious programs which then sent out SMS messages to premium numbers. However, in the spring of 2014, the Russian regulator introduced new requirements for the organization of such services, which included a need to secure additional confirmation of subscription to a particular paid mobile service. This change was instrumental in reducing the number of malicious mobile partner programs to practically zero. Nevertheless, this type of joint cybercriminal activity is still used by groups specializing in the distribution of encrypting ransomware.
Small Groups
What distinguishes this form of cybercriminal activity from an affiliate program is that in this instance the criminal or criminals organize their own fraudulent scheme. Most of the components needed for the attack, such as malware and its modifications (“re-packed” malware), the traffic, the servers, etc., are bought on the black market. Often, members of such groups are not experts in the field of computer and network technologies; they learn about the components and organization of financial attacks from public sources, usually forums. The abilities of such groups can be restricted by a number of factors. Specifically, the use of widely-available malware results in rapid detection by security solutions. This, in turn, makes cybercriminals invest more money in the distribution of malware and in its “re-packing” to bypass detection. The end result is a significant drop in profits for the attacker.
Mistakes made by this type of cybercriminal often result in their identification and arrest. However, as a relatively low cost entry into the world of cybercriminal activity (from $ 200), this “amateur” format continues to attract new dealers.
An example of such an “amateur” criminal organization is the group that in 2012 was convicted by the Russian court for stealing more than 13 million rubles (then worth about $422,000) from a Russian bank’s online customers. During a comprehensive investigation Kaspersky Lab experts were able to collect the information that allowed law enforcement authorities to identify those behind the theft.
The court sentenced two members of the criminal group, giving each a suspended sentence of four and a half years. However, this verdict did not stop the criminals, and they continued to commit crimes, stealing almost as much again over the next two and a half years. They were re-arrested in May 2015.
Large organized criminal groups
Large criminal groups differ from the other players, both through a larger scale of activity and through a more thorough approach to the organization and operation of criminal schemes. Such groups can comprise up to several dozen people (not including money mules used for cashing and “laundering” money.) The targets of their attacks are not limited to individual online banking customers: they also attack small and medium-sized companies, while the largest and most sophisticated of them, such as Carbanak focus mostly on banks and e-payment systems.
The operational structure of large groups differs significantly from smaller groups. To a certain extent, the structure reflects that of an ordinary, average-sized company engaged in software development.
In particular, large groups have some form of regular staff – a group of associates who perform organizational tasks in return for a regular, fixed payment. However, even in these large, professional groups some of the tasks are passed to third-party contractors. For example, the “re-packing” of malware can be performed by the staff or hired virus writers or via third-party services where the process is automated with the help of special software. The same is true for many other elements of the IT infrastructure required for committing crime.
Examples of large, organized criminal groups are Carberp, whose members were arrested in Russia and Ukraine in 2012 and 2013 respectively, and Carbanak, unmasked by Kaspersky Lab in early 2015.
Although the damage from the activity of partner programs and small groups can run into hundreds of thousands of dollars, the large criminal groups are the most dangerous and destructive. The estimated damage caused by Carberp reaches several hundred million dollars (up to a billion). In this regard, studying how these groups function and the tactics they use is extremely important, as it strengthens our ability to effectively investigate their activity and – ultimately – to suppress it.
Distribution of roles in a large cybercriminal group
A major financial cybercrime undertaken by criminal “experts” in security and the finance sector can result in multi-million dollar losses for attacked organizations. As a rule, such crimes are preceded by many months of preparation. This preparation includes constructing complex infrastructure, and selecting and developing malicious software, as well as a thorough study of the target organization in order to clarify the details of its internal operations and security vulnerabilities. Each member of the criminal group has their own responsibilities.
The following role distribution is typical for a criminal group involved in stealing money. The distribution of roles in groups that specialize in other types of cybercrime may be different.
Virus writer/Programmer
A virus writer or programmer is responsible for creating malicious programs, i.e. the programs that allow the attackers to gain a foothold in the corporate network of the target organization, download additional malware that will help to obtain the necessary information, and ultimately steal money.
The significance of this group member and the nature of their relationship with the organizers may vary from group to group. For example, if the group uses ready-made malware taken from open sources or bought from other virus writers, their functions may be limited to setting and modifying malicious programs to work in the infrastructure created specifically for a certain cybercrime, or to adapt it for attacks on specific institutions. The most advanced groups, however, tend to rely on their own “developments” since it makes a malicious program less visible to most security solutions and provides more opportunities for malware modification. Where this is the case, the virus writer’s role becomes more important as they are responsible for the architecture and feature set of a malicious program.
A virus writer can also take on responsibility for malware “re-packing”. But this happens only when the organizer wants to keep the maximum number of tasks within the group, and where original software is used for malware “re-packing”. In most cases, however, this procedure is shifted to third-party contractors or packing-services.
Testers
The function of testers in a criminal group is not that different from testers working in legal IT companies. In both cases, testers receive from their managers the specifications for testing programs in different environments (different versions of operating systems, different sets of installed applications, etc.) and execute them. If a fraudulent scheme involves fake interfaces of remote banking or e-payment systems, the task of testers also includes monitoring the correct operation of these fakes.
Web designers and Web programmers
Typically, web designers and web programmers are remote employees, whose tasks include creating phishing pages and websites, fake application interfaces and web injects, all of which are used to steal data to get access to e-payment and e-banking system.
Distributors
Distributors aim to ensure the download of malicious software on as many devices as possible. The result is achieved by using several tools. Generally, the group organizer determines the profile of the users to be infected and buys the required type of traffic from the so-called traffic providers (services to attract users with certain characteristics to a particular website).
An advert offering to buy traffic. Cybercriminals are willing to pay only for the successful installation of malicious software at $ 140 per 1000 “call-backs” (a message that is sent by the malware to the command server after a successful infection).
The organizer can choose and order a spam mailing that will contain either an infected attached file or a link taking a victim to a malicious website. The organizers can also choose the site with the necessary target audience; involve hackers in breaking into it and placing the exploit pack on it. Of course, all these tools can be used in combination with each other.
Hackers
Often, in the course of an attack, the exploits and other malicious software the organizer has to hand is not enough to infect all the computers necessary for the attack and to anchor in them. It may become necessary to hack into a specific computer or site. In such cases, the organizers involve hackers, people who have considerable skills in information security and are able to perform non-standard tasks. In many of the cases examined by Kaspersky Lab experts, hackers were occasionally involved and were paid on a fee-for-service basis. However, if hacking is required regularly (e.g., for targeted attacks on financial institutions), a hacker becomes a “team member” and is often one of the cybercriminal group’s key participants, along with the organizers and money flow managers.
System administrators
System administrators in cybercriminal groups perform near-identical tasks to their counterparts in legitimate businesses: they implement the IT infrastructure and maintain it in working condition. Cybercriminal system administrators configure management servers, buy abuse-resistant hostings for servers, ensure the availability of tools for anonymous connection to the servers (VPN) and resolve other technical challenges, including the interaction with remote system administrators hired to perform small tasks.
Call services
Social engineering is important for the success of the cybercriminal business. Especially when it comes to attacks on organizations that result in the theft of huge sums of money. In most cases, even if the attackers are able to establish control over the computer from which the transaction could be performed, confirmation of its legitimacy is required to successfully complete the operation. This is what the “call service” is for. At the specified time, its “employees” play the role of an employee of the attacked organization or a bank with which the organization works, and confirm the legitimacy of the transaction.
“Call services” can participate in a particular cybercrime both as a subdivision of the criminal group, or as a third-party organization, performing a specific task on a fee-for-service basis. The forums that users involved in cybercrime use to communicate with each carry plenty of ads offering such services.
This advertisement offers “call services” in English, German, Dutch and French. The group specializes in calls to Internet stores and banks, as well to duped mules. Also, the group offers the quick creation of local toll-free numbers used to imitate support services in fraudulent schemes, receiving SMS messages, and receiving and sending faxes. The criminals ask from $10 to $12 for one call, $ 10 for receiving SMS and from $ 15 for creating toll-free numbers.
According to Kaspersky Lab, large cybercriminal groups prefer to have their own “call services” so they hardly ever turn to third-party providers.
Money flow managers
Money flow managers are members of the cybercriminal group who come into play when all the technical tasks for organizing the attack (choosing and infecting the target and anchoring in its infrastructure) are fulfilled, and everything is ready to commit the theft. Money flow managers are the people who withdraw money from compromised accounts. However, their participation is not limited to pressing the keys; they play a key role in the whole process.
The list of key roles in financial cyber gangs almost mirrors IT-companies
Tweet
Money flow managers usually thoroughly understand the internal rules of the attacked organization (they even know the lunch hours of the employee from whose computer the fraudulent transaction will be made). They know how the automated anti-fraud systems operate and how to bypass them. In other words, in addition to their criminal role of thieves, money flow managers perform “expert” tasks that are difficult or impossible to automate. Perhaps because of this special status, money flow managers are one of the few members of the criminal group who receive a percentage of the stolen money rather than a fixed “salary”.
Money flow managers often perform as botnet operators. i.e. members of the criminal group who analyze and classify the information obtained from infected computers (the access to the remote banking services, availability of money on the accounts which could be accessed, the organization where the infected computer is located, etc.).
Besides money loaders, these “working conditions” are only shared by the leaders of mule projects.
Head of Mules (Mule “project” leader)
Head of mules is a representative of the criminal group working closely with the people involved in the process of stealing money. The function of the mules is to get the stolen money, cash it and transfer to the criminal group its due share. To do this, the head of mules builds their own infrastructure, which consists of legal entities and individuals with their own bank accounts, to which the stolen money is transferred and from which it is later withdrawn and moved into the pockets of the fraudsters. The mule project leader cooperates with the organizer of the criminal group, and provides them with the numbers of the accounts to which the money loader sends the stolen money. Both mule project leaders and money flow managers work on commission which, according to the information obtained by Kaspersky Lab during the course of investigation, can amount to half the sum stolen.
Mule “projects”
Mule projects are a vital component of any financial cybercrime. Such groups comprise one or more organizers and up to several dozen individual mules.
A mule (or drop) is a holder of a means of payment who, on command from the money mules manager, cashes the money received into their/an account, or transfers it to another account as specified by the money mules manager.
Mules can be divided into two types: duped and non-duped. Duped mules are people who, at least at the beginning of their cooperation with the money mules manager, do not realize they are involved in a criminal scheme. As a rule, the task of getting and transferring money is presented to them under some plausible pretext. For example, the money mules manager can establish a legal entity and appoint to an executive position (the general or financial director, for example) a person who will perform the functions of the duped mule: such as signing corporate documents which will, in fact serve as a legal screen for withdrawing stolen money.
Non-duped mules are well aware of the real purpose of the money mules manager’s tasks.
The options used by the mule projects to withdraw money are manifold. Depending on the amount of money stolen, they may include individual credit card holders ready to cash money and give it to the representative of the money mules manager for a small fee, or specially created legal entities, whose representatives open “salary projects” (credit cards for transferring the salaries of company employees) at their corporate bank.
Yet another common method for constructing a mule scheme is for non-duped mules to open dozens of accounts at different banks.
This advert offers sets of payment cards (the card, the documents based on which the card was authorized, the SIM card with which the bank account of the card is associated) that can be used for cashing stolen money. For sale is the card issued by Russian banks and banks from neighboring countries, as well as banks from the countries of Europe, Asia and the United States. The Momentum-type set is costs 3000 rubles (less than $50), the set with the Platinum card – eight thousand rubles (about $120).
When the theft occurs outside of Russia, the role of the non-duped mules is performed by a citizen or group of citizens of an Eastern Europe country, who within a short period of time visit several countries on the continent and in each of them open accounts in their names. Then the non-dupe mules provide the money mules manager with the data to access all these accounts. These accounts are used later to withdraw the stolen money.
An example of an ad offering for sale a list of companies registered in the Russian Federation and in the offshore zone. The services of cybercriminals cost from $560 to $750.
Stuffers
The word “stuffer” comes from the word “stuff” (a colloquial word for “goods”). One way to withdraw stolen money is by buying goods in e-stores with the stolen money, reselling them and returning to the fraudsters their due percent. This is done by the stuffers, members of the cybercriminal groups engaged in spending money from compromised accounts on purchasing goods in online stores.
In fact, a stuffer is a variation of the money flow manager. Withdrawing money by purchasing goods is generally practiced if the stolen sums are relatively small. As a rule, the stuffers work in a team with the fences. Working “in tandem” often involves purchasing a certain type of goods, sometimes from a specific manufacturer or a clearly-defined model.
Organizer
If we consider cybercrime as a project, the organizer of the criminal group is its general manager. Their duties usually include financing the preparatory phase of the attack, allocating tasks to executors, monitoring their performance and interacting with third-party agents such as mule projects and call services (if the group does not have its own). The organizer determines the targets for attacks, selects the necessary “specialists” and negotiates with them.
Stages of the attacks
It should be noted that the above classifications are not set in stone. In some cases, a single member of the criminal group can combine several roles. Nevertheless, regardless of how many people execute them, each of the roles described can be found when investigating almost every money-related cybercriminal incident. Here’s how they work in “real time.”
Exploration. When it comes to targeted attacks on a specific company, the organizer first instructs the contractors to collect information about the company, which will help to develop a plausible social engineering scheme for the first stage of attack. If we are talking about an attack on individual users, the preliminary exploration stage is skipped or limited to choosing a “target audience” for the attack (for example, the users of the online banking service of a specific bank) and creating phishing emails and phishing sites with relevant content.
Infection. Penetration of the corporate network is performed by spear-phishing or a phishing mass-mailing that contains an attachment with the special document or a malicious web-link. Opening the attachment or following the link leads to malware infection. Often, infection occurs automatically without the user’s awareness or participation – after clicking on the link, a malicious program is automatically downloaded on the user’s computer (drive-by download) and runs on it.
In other cases, infection is carried out via compromised popular sites on which a tool is placed that invisibly redirects users to a third-party site containing a set of exploits. Once on this site, the user will be infected with malware.
Once inside the system cybercriminals use a number of malicious tools to consolidate their presence. For example, to ensure that internal sites of compromised organizations have the malware reinstalled when the organization’s security software deletes the previous version. In addition, attackers are often set up within the infrastructure software of the attacked organization, enabling easy access to the internal corporate network from outside.
Exploration and implementation. The programs for remote, hidden administration and management are downloaded onto compromised computers. They are used by cybercriminals to gain system administrators’ credentials. Legal programs for remote management and administration whose functionality is known to many users are often used for this.
Money theft. In the final stage, cybercriminals access the financial systems of the targeted organization and transfer money from its accounts to the accounts of the mule projects or withdraw money directly at ATMs.
Conclusion
Financial cybercrime backed by Russian-speaking criminals has become widespread in recent years and this growth is due to a number of causes. The main ones are:
Not enough qualified staff in law enforcement agencies;
Inadequate legislation allowing criminals in many cases to avoid responsibility or to receive a lighter sentence;
A lack of established procedures for international cooperation between law enforcement agencies and expert organizations in different countries.
Unlike the real world, a robbery in cyberspace usually goes unnoticed and there is a very small window for collecting digital evidence after the crime. Further, criminals have no need to stay in the country where the crime is committed.
Unfortunately, for Russian-speaking cybercriminals current conditions are more than favorable: the risk of prosecution is low while the potential rewards are high. As a result, the number of crimes and the damage caused by them is growing, and the market for cybercriminal services is increasing momentum.
A relatively low cost of entry ($ 200) to cybercrime attracts new dealers
Tweet
The lack of established mechanisms for international cooperation also plays into the hands of criminals: for example, Kaspersky Lab experts know that the members of some criminal groups permanently reside and work in Russia’s neighbors, while the citizens of the neighboring states involved in criminal activity often live and operate in the territory of the Russian Federation.
Kaspersky Lab is doing everything possible to terminate the activity of cybercriminal groups and encourages other companies and law enforcement agencies in all countries to cooperate.
The international investigation of Carbanak’s activity, initiated by Kaspersky Lab, is the first example of successful international cooperation. If the world is to see a serious and positive change there should be more such cases.
Reference. What is Kaspersky Lab Computer Incidents Investigation?
Kaspersky Lab is a well-known developer of anti-malware security solutions. But the company provides comprehensive protection, and this also includes services for computer incidents investigation.
Evidence of an incident, mainly presented in the form of digital data, needs to be collected and recorded so that there are no grounds for doubt in the investigation and trial when a victim makes a court application.
Kaspersky Lab Computer Incidents Investigation is responsible for:
Responding to IT security incidents and providing a quick analysis of the situation;
Collecting digital evidence and determining the circumstances of IT security incidents in accordance with established procedures;
Analyzing the evidence collected, searching the information related to the circumstances of the incident on the Internet and fixing them;
Preparing materials for the victim’s application to law enforcement agencies;
Providing expert support to investigative operations.
A huge amount of data is processed when responding to IT security incidents and supporting investigative operations. The analysis of this data, in combination with statistics on malicious objects detected identifies the trends of criminal behavior in cyberspace.
The Kaspersky Lab Computer Incidents Investigation Department was established in 2011 and involves six forensic experts.
New Dyre variant in the wild supports Windows 10 and Microsoft Edge
19.11.2015
The developers of the Dyre banking Trojan have released a new version of the malware that includes support for Windows 10 and Microsoft Edge.
The security firms Heimdal Security and F5 Networks have uncovered a new version of the Dyre (Dyreza) banking Trojan that includes support for Windows 10 and Microsoft Edge.
The new variant of Dyre now also targets Chrome, Firefox and Internet Explorer, and it is able to hook its code into the process of Microsoft Edge.
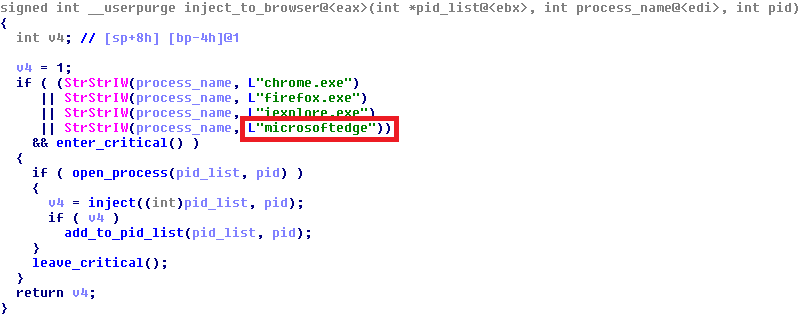
According to the Heimdal Security more than 80.000 machines are already infected with Dyre Trojan across the world.
The experts at F5 who analyzed the new Dyre Trojan have discovered that the authors have renamed some of the existing commands and have implemented new functionalities.
Below the list of new commands added to the new variant of the malware:
0xF1”lli” – Get the botid name
srvv – Get the C&C IP
dpsr – Get the data POST server IP
grop – Get the botnet name
seli – Get the self-IP
gcrc – Get the fake pages configuration
gcrp – Get the server-side webinjects configuration
pngd – Get the account information stolen by the pony module
sexe – Among other jobs, it copies the droppee path and its content both to Dyre’s special structure and the configuration file on disk. It also tries to get the anti-antivirus module from the C&C.
gsxe – Get the droppee path
The new commands are used to get the IP of the command and control (C&C) server, the botnet name, configuration for fake pages, configuration for server-side webinjects, account information stolen by the Pony module, and an anti-antivirus module.
The Dyte include a module specifically designed to locate security products installed on the infected machine and disable them, this module is named “aa32” on Windows 32-bit versions and “aa64” on 64-bit versions. The module is injected into the “spoolsv.exe” process and it is able to neutralize the principal antivirus software, including solutions designed by Avira, AVG, Malwarebytes, Fortinet, Trend Micro and also the Windows Defender service.
To make the malware more difficult to analyze, the authors of the last version have encrypted hardcoded debug strings and only decrypt them during runtime.
Previous versions of Dyre gain persistence by using a Run key in the registry, but the last one used a scheduled task that is run every minute.
“We conclude from the addition of these features that the authors of the malware strive to improve their resilience against anti-viruses, even at the cost of being more conspicuous,” is reported in the blog post published by F5. “They also wish to keep the malware up-to-date with current OS releases in order to be ‘compatible’ with as many victims as possible. There is little doubt that the frequent updating will continue, as the wicked require very little rest.”
Experts believe that the new variant of Dyre is spreading in the wild to monetize the coming holiday season.
“The timing of this new strain is just right: the season for Thanksgiving, Black Friday and Christmas shopping is ready to start, so financial malware will be set to collect a huge amount of financial data. Users will be busy, prone to multitasking and likely to choose convenience over safety online,” Heimdal Security noted.
Telegram — Secret Messaging app — Shuts Down 78 ISIS Channels
19.11.2015
The terrorist groups affiliated with the Islamic State have an extensive presence not only on social media accounts but also on the popular end-to-end encrypted messaging app Telegram through which they communicate with their followers and spread terror propaganda materials.
Telegram has always been terrorist's favorite, but ISIS had been using the app since October, when Telegram introduced an end-to-end encrypted Secret Chat feature that lets users broadcast messages to an unlimited number of subscribers.
Moreover, Telegram also provides self-destructing message feature that allows users to set their messages to self-destruct itself after a certain period of time.
But, the Good News is:
The nonprofit organization that runs Telegram has blocked around 78 ISIS-affiliated channels that the terrorists used to:
Communicate with their members
Spread propaganda
Recruit foreign supporters
Plan operations
Radicalize young people
"We were disturbed to learn that Telegram's public channels were being used by ISIS to spread their propaganda," Telegram writes. "As a result, this week alone we blocked 78 ISIS-related channels across 12 languages."
In the wake of the horrific Paris terrorist attacks, the Telegram creators said they are carefully reviewing all user-submitted reports sent to them and are taking appropriate action to block such channels that are used to spread terror-related contents.
Telegram — Secret Messaging app
Islamic State (ISIS) — Terror Has gone Social
Just after Anonymous declared war against ISIS, the militants started encouraging its members and followers to use Telegram secure instant messaging app, so that they can effectively make their conversations invisible from Government spies.
We also reported that ISIS issued some basic Internet safety tips to its followers via one of its Channel on Telegram, teaching terrorists how to avoid being caught or hacked by Anonymous.
No doubt, ISIS is leveraging the power of Social media to spread its message around the globe and deleting just 78 ISIS-affiliated Telegram Channels and 5,500 Twitter accounts won't stop them.
According to our analyses, there are still more than 100 other ISIS Telegram channels and thousands of Twitter and Facebook accounts affiliated with ISIS and each followed by thousands of Jihadists.
How to Report ISIS-related Abusive and Illegal Activities
Telegram — Secret Messaging app
So, if you come across any terror-related messages and want to contribute to preventing the terrorists from spreading their roots via social media platform, you can file your reports to the respective social media.
Is Telegram Really Secure? — 4 Major Privacy Issues Raised by Researcher
19.11.2015
The terrorist groups are encouraging its followers to use Telegram to make their propaganda invisible from law enforcement, but some security experts believe that Telegram may not be as secure as jihadi advocates may like to believe.
Telegram is an end-to-end encrypted messaging service that has been adopted by a lot more people than ISIS — as of last year, the company claimed more than 50 Million Telegram users sending 1 Billion messages per day.
Terrorists love Telegram because it not only provides an encrypted Secret Chat feature that lets its users broadcast messages to unlimited subscribers but also offers self-destructing message allowing users to set their messages to self-destruct itself after a certain period.
Is Telegram Really Secure?
In a blog post published Wednesday, the security researcher known as "the Grugq" pointed out several issues with Telegram that might obstruct terrorists from using it.
Here's the list of issues with Telegram:
1. Error prone
Telegram's end-to-end encrypted chat feature is not enabled by default. One has to select Secret Chat before start chatting, and it is not possible to encrypt an existing conversation.
Also Read: Anonymous Hackers Release Hacking Guide to Help Defeat ISIS Online Propaganda
2. Contact Theft
Telegram requires you to register a working phone number and uploads the entire Contacts database to its servers, helping it create a trail of breadcrumbs for law enforcement and investigators to follow.
"This allows Telegram to build a huge social network map of all its users and how they know each other," the Grugq wrote in his blog post.
3. Leak Voluminous Metadata
The use of a mobile phone can expose a wide range of metadata. Even if secure chat is enabled, law enforcement can collect other Metadata for sure by compromising the servers.
This could help them track down who talked to whom, at what time, from which location, which will be an enough information for agencies seeking for possible suspects.
For Example: If A and B are communicating with each other on encrypted channel, and A is on the suspect list of agencies, then they can at least figure out the connection between both using this Metadata.
Also Read: ISIS Called Anonymous "IDIOTS" and Issued Lame Tips to Avoid Getting Hacked
4. Wonky Homebrew Encryption
Some security experts are also worried about the encryption that Telegram uses, although its encryption hasn't been publicly broken.
Telegram has announced a contest to crack the app's encryption with a prize money of $300,000, but nobody claimed it.
However, when it comes to nation-state adversary, one wouldn't trust encryption protection in Telegram, as the app might work for the average user, but is not secure enough for terrorists.
Whatever be the privacy concerns regarding Telegram, the good news is:
Telegram has blocked 78 ISIS-affiliated Channels that the terrorist used to communicate with their members, spread propaganda and plan operations.
Blackhole Exploit Kit Resurfaces in the wild
19.11.2015
The experts at Malwarebytes have noticed that threat actors in the wild are reusing the Blackhole Exploit Kit despite its limited effectiveness.
The Blackhole exploit kit has reappeared in the wild surprising the security industry after that in October 2013 its author, know as Paunch, was arrested. Paunch was the author of two of the most popular exploit kits, Blackhole and the Cool Exploit Kit, that dominated the underground scene in recent years.
The Blackhole exploit kit was widely used to hack into several Web browsers and exploit flaws in popular software such as Adobe Reader. The winning factors for the success of Blackhole exploit kit were its efficiency, the availability of various models for sale (e.g. I was available for sale and rent in the underground market), availability of frequent updates and an affordable price (Blackhole was offered for rent as little as $200 to $300 per week).
The experts at Malwarebytes have noticed that threat actors in the wild are reusing the exploits despite their limited effectiveness. Malwarebytes observed the new variant of the BlackHole Exploit kit includes old PDF and Java exploits.
“The new drive-by download attacks we caught over the weekend rely on the same structure as the original Blackhole, even reusing the old PDF and Java exploits. The only difference is the malware payload being dropped, which is current and had very low detection on VirusTotal.” reports MalwareBytes.
The source code of the Blackhole was leaked online four years ago allowing cybercriminals to reuse it and add new features to the core modules. The numerous hacking communities could offer their variant of the Blackhole exploit kit that implements fresh exploits for vulnerabilities recently discovered.
Fortunately, the researchers at Malwarebytes have discovered that threat actors behind the new Blackhole campaign left the server that hosted the control infrastructure open on the Internet, a circumstance that allowed the expert to access it.
“The server used to host the exploit infrastructure happens to be fully browsable (thanks @MeJz024 for the tip). The folder structure shows with no doubt this is taken straight from the Blackhole source code that had been leaked.” reads the blog post.
The intent of the attacker is to try to compromise the numerous computer still vulnerable on the Internet, but the experts highlight the infection rate would be quite low due to the aging exploits
“Although the exploits are old, there are probably still vulnerable computers out there who could get compromised,” Segura wrote. “We are not quite sure why this old exploit kit is being used in live attacks considering the infection rate would be quite low due to the aging exploits.” said Jerome Segura, a senior security researcher for Malwarebytes.
MalwareBytes also published the Indicators of compromise on its website.
Telegram messaging service tries to ban ISIS, but..
19.11.2015
Telegram messaging service announced its actions against the abuses made by members of the ISIS, but it still allows communications in private groups.
In the wake of recent Paris attacks the experts increased their investigation on the communication channels used by members of the ISIS organization.
A few hours after the Paris attacks, investigators speculated terrorists were using the voice over IP implemented by the Play Station, but the unique certainly in this moment is that the terrorist organization is using the popular Telegram messaging service for its communications and to spread propaganda.
The terrorists are using the “Channels” feature implemented in the Telegram messaging service that allow users to subscribe to broadcast content published through a permanent URL. The feature allows publishers to reach a wide audience, the publishers can share messages, files, and images in an anonymous way both using a mobile device or PC.
Now the nonprofit organization running the Telegram messaging service announced that it is operating to ban the activities of terrorists. The organization has already identified several channels used by the ISIS and blocked them in response of abuse reports filed by Telegram users.
“We were disturbed to learn that Telegram’s public channels were being used by ISIS to spread their propaganda,” a Telegram spokesperson posted in the service’s Telegram News channel. “We are carefully reviewing all reports sent to us at abuse@telegram.org and are taking appropriate action to block such channels. As a result, this week alone we blocked 78 ISIS-related channels across 12 languages.”
Telegram messaging service
Telegram can block channels and also “sticker set” images, another feature abused to spread images through automated “bot” message applications.
strikers Telegram messaging service
Telegram clarifies that every time an abuse complaint is filed against public content, it checks the content alleged violated the publishing policy, then it evaluates to remove it:
“Please note that this does not apply to local restrictions on freedom of speech. For example, if criticizing the government is illegal in a country, Telegram won‘t be a part of such politically motivated censorship. This goes against our founders’ principles.”
“While we do block terrorist (e.g. ISIS-related) bots and channels, we will not block anybody who peacefully expresses alternative opinions.” states Telegram.
Unfortunately, terrorists could still establish private connections, Telegram admitted that it is not able to block communications that happen in private groups, which can include up to 200 users.
“All Telegram chats and group chats are private amongst their participants,” Telegram’s spokesperson wrote. “We do not process any requests related to them.”
This is a bad news because it means that group of ISIS members can still use the Telegram messaging service to share propaganda materials, operational instructions, and other information, within private groups.
French activist accuses Anonymous #OpParis of hindering Law Enforcement
19.11.2015
The collective Anonymous launched the #OpParis to track terrorists online, but a French activist accuses them of hindering Law Enforcement.
Just days following the horrific Paris attacks carried out by the ISIS, Anonymous hackers wedged a full-fledged war against the Islamic radicals, knocking out several thousand pro-ISIS Twitter accounts. However, a French blogger has spoken out against the hacker collective’s recent actions under the #OpParis campaign, saying they are hindering law enforcement’s ability to monitor and keep up with ISIS.
In a recent video published by Anonymous, the collective waged war against ISIS, saying “You should know that we will find you and we will not let you go under #OpISIS.”
#OpParis
Olivier Laurelli, a French citizen and computer security blogger said Anonymous shutting down pro-ISIS accounts is a bad idea as it leaves authorities blind to tracking activities of pro-ISIS members.
“To close those accounts is to leave police deaf and blind around some matters. It is important to know that one account is in France, another in Syria or in Iraq and if you see that someone who is connected to the attacks has a link to someone else, it’s important for police. Twitter has been quick to close down a large number of accounts, but I don’t know if it’s a good idea,” Laurelli told to AFP.
According to the blogger, the collectives relentless work to unmask ISIS members is an embarrassment for the police as it’s their duty to monitor the accounts and see who is spreading pro-ISIS propaganda. It’s also their job to keep the accounts under control from rapid growth on social media, exactly what Anonymous is currently doing.
Laurelli claims that the information Anonymous is destroying as part the #OpParis would have allowed law enforcement to properly counter the Paris attacks, in which 129 people lost their lives and 415 got injured.
Anonymous has taken #OPISIS strongly to social media, trying to get everyone to work together and unmask ISIS members. However, Facebook wasn’t too fond of the idea and decided to block a few Anonymous groups on Facebook for revealing the identity of an alleged ISIS member.
Laurelli’s comments come just after Anonymous published a list of more than 9,000 pro-ISIS twitter accounts that were promptly removed by Twitter.
Hey ISIS! Check Out How 'Idiot' Anonymous Hackers Can Disrupt your Online Propaganda
18.11.2015
The online Hacktivist group Anonymous declared War against the Islamic State militant group (ISIS) that claimed responsibility for the horrific terrorist attacks that rocked Paris last week.
In response to the Anonymous’ warning of launching their "biggest operation ever" against the terrorist group, ISIS militants called Anonymous – "IDIOTS".
It seems like Anonymous has taken ISIS response very seriously and the group has started carrying out their attacks against the terror organisation.
Anonymous First 'Cyber Attack' on ISIS
Soon after its war declaration, Anonymous claimed to have taken down more than 5,500 pro-ISIS Twitter accounts in #OpParis (Operation Paris).
In the past, hackers and organizations associated with Anonymous brought down websites allegedly connected with ISIS and claimed to have taken down thousands of ISIS accounts, disrupting their social media recruitment efforts.
Also Read: Would Encryption Backdoor Stop Paris-like Terror Attacks?
Anonymous' most famous targets include the white supremacist group Ku Klux Klan (KKK), the Vatican, the Westboro Baptist Church (known for its hate speech against the Jews, LGBT community, and liberal politicians), the governments, and even the CIA.
How Anonymous Can Disrupt ISIS's Online Propaganda
So, calling Anonymous idiots doesn’t make them idiots, because the hacktivist group has proved itself to be fully capable of launching successful attacks – and ISIS knows it.
That's why the terror organisation is spreading lame instructions through its affiliated official channels on Telegram on how to prevent getting hacked by Anonymous.
ISIS Online Propaganda: How They Manipulates Social Media
ISIS is a terrorist organisation whose most interesting aspect is how it leverages the huge power of Twitter and Facebook to radicalize young people, spread its message around the globe, recruit foreign supporters to its fight and shock people into taking notice of its actions.
Also Read: ISIS Issues 5 Lame Tips for its Members to Avoid Getting Hacked
Many ISIS militants maintain extremely active accounts on the popular social media platforms. They also have a strong presence on the most popular encrypted messaging app Telegram with more than 100,000 followers.
According to The Atlantic, there were more than 46,000 ISIS-affiliated Twitter accounts with an average of 1,000 followers each.
The group has also established a 24-hour Jihadi Help Desk to help its foot soldiers spread their message around the world, recruit followers and launch more terror attacks on foreign soil, NBC reports.
So How Anonymous can Defeat ISIS?
When taking into consideration ISIS's extensive presence on Twitter, taking down its social media presence is the actual key to defeating the terror group, and it does make an impact at worst.
So, taking down the group's 5,500 Twitter accounts could be the first step towards disrupting ISIS online propaganda.
No doubt, we doesn't have any silver bullet solution to this problem, neither cyber attacks can vanish ISIS from its roots, but at least hackers can disrupt their online propaganda that may disable them to plan or plot Paris-like terrorist attacks.
Also Read: We Can't Blame Edward Snowden and Encryption for Terror Attacks
Besides social media takeovers, the hacker collective is using "Distributed Denial of Service" (DDoS) attacks to shut down websites affiliated with ISIS, including its fundraising sites from where ISIS get fed.
Anonymous has previously used successful DDOS attacks to shut down services of companies or organizations the group deems fit for the attack, including the municipal computer system of Ferguson, Missouri in the wake of Michael Brown death.
Anonymous Releases Newbie "How-to" Hacking Guide
Now, this will really panic ISIS:
How Anonymous Can Disrupt ISIS's Online Propaganda
Anonymous group has also released a newbie How-to Hacking Guide for all wannabe hackers, in an effort to recruit more people in their Fight against Islamic State.
The Instruction set includes:
NoobGuide — Methods to hack websites associated with Islamic State
Reporter — How to set up a Twitter bot for uncovering IS accounts.
Searcher — How to identify and take down ISIS related websites and social media accounts
"Instead of sitting idle in the channel or lurking around and doing nothing, you can benefit greatly from the different tools and guides that have been provided to you. Your contribution means a lot and we encourage you to partake in all of the Op's activities if you can, the more the merrier," an anonymous member wrote.
It seems like, Anonymous is silently saying to ISIS… Just wait and watch what these idiots can do to you.
Kaspersky Security Bulletin. 2016 Predictions
18.11.2015 Zdroj: Kaspersky
It's the end of the world for APTs as we know it
As the year comes to an end, we have an opportunity to take stock of how the industry has evolved and to cast our predictions for the coming years. Taking advantage of a rare global meeting of our GReAT and Anti-Malware Research experts, we tossed ideas into the ring and I have the privilege of selecting some of the more noteworthy and plausible for both the coming year and the long-term future as we foresee it. The outlook for our rapidly evolving field of study is quite thought-provoking and will continue to present us with interesting challenges. By sticking to sober metrics, perhaps we can skip the usual science fiction fear mongering and come to some accurate predictions for both the short- and long-term.
No more APTs
Before you start celebrating, we should point out that we’re referring to the ‘Advanced’ and ‘Persistent’ elements – both of which the threat actors would gladly drop for overall stealth. We expect to see a decrease in the emphasis on persistence, placing a greater focus on memory-resident or fileless malware. The idea will be to reduce the traces left on an infected system and thus avoid detection altogether. Another approach will be to reduce the emphasis on advanced malware. Rather than investing in bootkits, rootkits, and custom malware that gets burned by research teams, we expect an increase in the repurposing of off-the-shelf malware. Not only does this mean that the malware platform isn’t burned upon discovery but it also has the added benefit of hiding the actor and his intentions in a larger crowd of mundane uses for a commercially available RAT. As the shine of cyber-capabilities wears off, return on investment will rule much of the decision-making of state-sponsored attackers – and nothing beats low initial investment for maximizing ROI.
APT: a decrease in the emphasis on persistence, a focus on memory-resident or fileless malware #KL2016Prediction
Tweet
The nightmare of ransomware continues
We expect to see the success of Ransomware spread to new frontiers. Ransomware has two advantages over traditional banking threats: direct monetization and relatively low cost per victim. This amounts to decreased interest from well-resourced third-parties such as banks, as well as low levels of reporting to law-enforcement agencies. Not only do we expect ransomware to gain ground on banking trojans but we also expect it to transition into other platforms. Weak attempts at bringing ransomware to mobile (Simplelocker) and Linux (Ransom.Linux.Cryptor, Trojan-Ransom.FreeBSD.Cryptor) have already been witnessed, but perhaps the more desirable target platform is OS X. We expect ransomware to cross the Rubicon to not only target Macs but also charge ‘Mac prices’. Then, in the longer term, there is the likelihood of IoT ransomware, begging the question, how much would you be willing to pay to regain access to your TV programming? Your fridge? Your car?
We expect ransomware to gain ground on banking trojans and to transition into other platforms #KL2016Prediction
Tweet
Betting against the house: financial crimes at the highest level
The merging of cybercrime and APT has emboldened financially motivated criminals who have gracefully transitioned from attacking end users to going after the financial institutions themselves. The past year has seen plenty of examples of attacks on point-of-sale systems and ATMs, not to mention the daring Carbanak heist that pilfered hundreds of millions of dollars. In the same vein, we expect cybercriminals to set their sights on novelties like alternate payment systems (ApplePay and AndroidPay) whose increasing rate of adoption should offer a new means of immediate monetization. Another inevitable point of interest is stock exchanges, the true mother lode. While frontal attacks may yield quick payoffs, we mustn’t overlook the possibility of more subtle means of interference, such as going after the black-box algorithms employed in high-frequency trading to ensure prolonged gains with a lower likelihood of getting caught.
Cybercriminals will set sights on novelties like alternate payment systems and stock exchanges #KL2016Prediction
Tweet
Attacks on security vendors
As attacks on security vendors rise, we foresee an interesting vector in compromising industry-standard reverse-engineering tools like IDA and Hiew, debugging tools like OllyDbg and WinDbg, or virtualization tools like the VMware suite and VirtualBox. CVE-2014-8485, a vulnerability in the Linux implementation of ‘strings’, presents an example of the vulnerable landscape of nontrivial security research tools that determined attackers may choose to exploit when targeting researchers themselves. In a similar vein, the sharing of freeware research tools through code repositories like Github is an area ripe for abuse, as users will more often than not pull code and execute it on their systems without so much as a glance. Perhaps we should also be casting a suspicious glance towards popular implementations of PGP so eagerly embraced by the infosec community.
We foresee a vector in compromising reverse-engineering, debugging & virtualization tools #KL2016Prediction
Tweet
Sabotage, extortion and shame
From dumps of celebrity nudes to the Sony and Ashley Madison hacks and the HackingTeam dump, there has been an undeniable increase in DOXing, public shaming, and extortion. Hacktivists, criminals, and state-sponsored attackers alike have embraced the strategic dumping of private pictures, information, customer lists, and code to shame their targets. While some of these attacks are strategically targeted, some are also the product of opportunism, taking advantage of poor cybersecurity to feign hacker prowess. Sadly, we can only expect this practice to continue to rise exponentially.
Whom do you trust?
Perhaps the scarcest commodity in the current internet age is trust. Abuse of trusted resources will further drive this scarcity. Attackers will continue to enlist open-source libraries and whitelisted resources for malicious purposes. We expect another form of trust to be abused, that of a company’s internal resources: as crafty attackers seek to expand their foothold on an infected network, they may target resources limited to the company intranet such as waterholing Sharepoint, file server, or ADP portals. Perhaps we’ll even witness the furthest extension of the already rampant abuse of trusted certificates as attackers establish an entirely fabricated certificate authority to issue certificates for their malware.
Attackers will enlist open-source libraries and whitelisted resources for malicious purposes #KL2016Prediction
Tweet
APT actors down the road
The profitability of cyberespionage has not escaped the attention of our foes and, as we expected, mercenaries have begun populating the scene. This trend will only increase to match the demand for cyber-capabilities by both companies as well as known APT actors looking to outsource less critical tasking without risking their tools and infrastructure. We could float the term ‘APT-as-a-Service’, but perhaps more interestingly we can expect the evolution of targeted attacks to yield ‘Access-as-a-Service’. The latter entails the sale of access to high-profile targets that have already fallen victim to mercenaries.
We'll see members of well-established APT teams potentially coming out of the shadows #KL2016Prediction
Tweet
Looking further into the future of cyberespionage, we see members of well-established APT teams (‘APT 1%ers’, if you will) potentially coming out of the shadows. This would happen in one of two forms: as part of the private sector with the proliferation of ‘hacking back’, or by sharing their insights with the larger infosec community, perhaps by joining us at conferences to share the other side of the story. In the meantime, we can expect the APT Tower of Babel to incorporate a few more languages.
The future of the Internet
The infrastructure of the internet itself has shown signs of tension and cracks in recent years. Concerns over massive router botnets, BGP hijacking and dampening, DNS attacks en masse, or server-powered DDoSes betray a lack of accountability and enforcement on a global scale. Looking further down the line to long-term predictions, we can consider what the internet might look like if that narrative of a globally connected village continues to wither. We may end up with a balkanized internet divided by national borders. At that point, concerns over availability may come down to attacks on the service junctures that provide access between different sections, or perhaps geopolitical tensions that target the cables that connect large swathes of the internet. Perhaps we’ll even see the rise of a black market for connectivity. Similarly, we can expect that as technologies that power the internet’s underbelly continue to gain mainstream attention and widespread adoption, developers with a stake in shadow markets, exchanges, and forums are likely to develop better technologies to keep the underground truly underground.
The internet's cracked: we may end up with a balkanized internet divided by national borders #KL2016Prediction
Tweet
The future of transportation
As investment and high-end research capabilities are dedicated to developing autonomous vehicles for both personal and commercial distribution, we will witness the rise of distributed systems to manage the routes and traffic of large volumes of these vehicles. The attacks may not focus on the distribution systems themselves, but perhaps on the interception and spoofing of the protocols they rely on (a proof of concept of the vulnerabilities of the widely adopted Global Star satcom system was presented by a Synack researcher at this year’s BlackHat conference). Foreseeable intentions behind these attacks include theft of high-value goods or kinetic damage resulting in loss of life.
Crypto: a breakdown in the reliability of standards and a need of 'post-quantum cryptography' #KL2016Prediction
Tweet
The cryptopocalypse is nigh
Finally, we cannot overemphasize the importance of cryptographic standards in maintaining the functional value of the internet as an information-sharing and transactional tool of unparalleled promise. These cryptographic standards rely on the expectation that the computational power required to break their encrypted output is simply above and beyond our combined means as a species. But what happens when we take a paradigmatic leap in computational capabilities as promised by future breakthroughs in quantum computing? Though quantum capabilities will not be initially available to the common cybercriminal, it signals a breakdown in the reliability of current crypto-standards and a need to design and implement ‘post-quantum cryptography’. Given the poor rate of adoption or proper implementation of high-quality cryptography as it is, we do not foresee a smooth transition to counterbalance cryptographic failures at scale.
Spam and phishing in Q3 2015
18.11.2015 Zdroj: Kaspersky
MALICIOUS SPAM MALWARE MALWARE DESCRIPTIONS PHISHING SPAM LETTERS SPAM REPORT SPAM STATISTICS SPAMMER TECHNIQUES TEMATIC SPAM
Download PDF version
Spam: features of the quarter
Online dating
The dating theme is typical for spam emails, but in the third quarter of 2015 we couldn’t help but notice the sheer variety appearing in these types of mailings. We came across some rather interesting attempts to deceive recipients and to bypass filters, as well as new types of spam mailings that were bordering on fraud.
The main aim of spammers exploiting the dating theme is usually to advertise recently created dating sites that are still relatively unknown. The owners of these sites resort to spamming to attract the largest possible audience to their resource. The messages often address different categories of recipients, for example, dating sites for older people, married people or the religious.
Yet another type of advert is for marriage agencies offering a selection of brides (mainly from Russia and Ukraine) to foreign suitors. This type of spam is usually distributed in the English-language segment of the Internet. The messages contain an invitation to register on a site, a short text promising to find the perfect life partner and a link leading to the advertised site.
Q3 2015, the percentage of spam in email traffic accounted for 54.2% #KLReport #infosec
Tweet
Similar emails can also be sent from a “bride”. This type of spam is closer to the fraudulent tactics used by ‘Nigerian letters’. The email is supposedly written by a girl who provides a few details about herself, about how hard her life is in the Russian hinterland, and her dreams of meeting Prince Charming. A photo is often attached, though not necessarily a photo of the “bride” – it could easily be taken from someone’s social networking page and attached to make the message look more convincing. That’s why emails from different girls may contain the same photos. However, the messages vary: a host of synonyms are used to bypass spam filters. The usual channel for receiving feedback is via email. The address is different for each email – they are obviously created in large quantities on free email services for each mass mailing. After replying, the user will, at best, receive a notification that the address is non-existent. The worst case scenarios will see his address targeted by further spam mailings and he may even get caught up in a scam where the girl asks for money to buy a ticket to come and see him. Once she gets the money, she disappears without a trace.
A similar method is used to advertise dating sites “for adults”. The emails contain either an invitation to register on the site and a promise of intimate dating, or a message from a girl who is looking for a partner for intimate relations plus a link to the resource with her alleged profile. This type of spam is often disguised as personal notifications on social networking sites, as well as image or audio files sent via instant messengers. As a result, the site is hidden, and the user cannot clearly identify what it is until he follows all the links. Of course, the contents of these messages aim to arouse the recipient’s interest and make him click the links, often due to the flirty content or heavy hints and intimate photos.
And finally, yet another type of spam we detected in Q3 was quite blatantly fraudulent. During the quarter we observed a mass mailing that prompted recipients to send a text message to a specific telephone number; in return a girl promised to send intimate photos of herself. The text of the emails varied, as did the mobile numbers specified in them. We sent messages to some of the numbers and found that they were not premium-rate numbers as might be expected, and users were not charged for sending a text message. We got a reply from a girl, but after a couple of answers it became clear we were dealing with a robot whose task was to make us download an application so we could continue chatting and receive the promised photos. As a result, we received several text messages containing short links that led to an article about useful mobile apps that appeared in a well-known American newspaper. During the redirect to the article an archive with mobile malware was downloaded to the user’s phone.
Seasonal malicious spam
The amount of seasonal spam traditionally increases in summer. This is true for both advertising and malicious spam. The holiday season saw spam with a travel theme: fake notifications from booking services, airlines and hotels were used to spread malicious programs.
Fake notifications from major international airlines and booking services were detected by Kaspersky Lab as Trojan-Downloader.JS.Agent.hhy and Trojan-Downloader.Win32.Upatre.
We came across similar emails supposedly sent by popular airlines that had messages in French. The text informed recipients that the attachment contained an e-ticket. In fact, the ZIP archive contained Trojan.Win32.Xtrat Trojan and the DDoS bot Nitol (the module used to organize DDoS attacks).
In July, fraudsters tried to trick users by sending fake notifications on behalf of hotels. The message thanked the recipients for staying in their hotel and asked them to view the attached bill. The attached archive actually contained Trojan-Downloader.Win32.Upatre.dhwi, which in turn downloaded and ran Trojan- Banker.Win32.Dyre (viewed as 98. ***. **. 39/cv17.rar) by clicking the links written in the body of the downloader.
In addition to fake emails sent on behalf of well-known companies we observed a message in English from an individual. The email contained a request to change a room booking because some friends had cancelled.
The text in the email could easily be seen as a legitimate request from a client; however, the ZIP attachment contained Trojan-Downloader.JS.Agent.hhi that downloaded Backdoor.Win32.Androm.
Spammer tricks
The text in a standard phishing email is usually in the body of the message, while personal information is entered on a web page that opens after clicking a fraudulent link in the text, or in the HTML fields of a page attached to the email, or is sent back in a reply email. The latter is most typical when asking recipients to confirm the address and the password for an email account.
Q3 2015, Top 3 biggest sources of spam globally were the #USA, #Vietnam & #China #KLReport
Tweet
In Q3 2015, cybercriminals came up with a new way of distributing phishing emails and bypassing spam filters. The text of the phishing email and the fake link were included in a PDF document attached to the email. After clicking the link, a standard phishing page opened and the user was asked to enter his personal information. The majority of emails utilizing the new technique imitated bank notifications. The body of these messages usually contained a short text describing the problem; sometimes there was no text at all.
It should be noted that the spammers used well-known phrases and tricks in the text of the emails: notifications about an account being blocked, the need to pass a verification procedure, security issues, an investigation into phishing incidents, etc. As usual, the fraudulent links were masked by legitimate links and text fragments.
However, there were emails with detailed text in the message body providing genuine links to official bank resources. The phishing notification was included in the PDF attachment.
Our colleagues also came across a different type of phishing message using Mediabox objects in attached PDF files.
A Mediabox object is a document opened by a mouse click and used to redirect the user to a phishing website.
Statistics
Proportion of spam in email traffic
Percentage of spam in email traffic, April-September 2015
After some relatively stable months in the second quarter the percentage of spam in global email traffic began to change again. A slight growth in July and August of 2015 was followed by a noticeable drop in September. As a result, the average percentage of spam in Q3 amounted to 54.19% – slightly higher than the average for the previous quarter.
Sources of spam by country, Q3 2015
The US (15.34%) remained the biggest source of spam in Q3. Vietnam was second with 8.42% of global spam, compared to 3.38% in the previous quarter. China rounded off the Top 3 (7.15%) – its share remained unchanged from the previous quarter.
Russia’s share (5.79%) dropped by 2.03 p.p., pushing it from second to fourth position. It was followed by Germany (4.39%) and France (3.32%) – their shares changed only slightly compared to Q2.
 Spam email size distribution, Q2 2015 and Q3 2015
Spam email size distribution, Q2 2015 and Q3 2015
The most commonly distributed emails were very small – up to 2 KB (79.05%). The proportion of these emails grew from the previous quarter (13.67 p.p.), while the share of emails sized 20-50 KB (3.32%) fell by approximately the same number of percentage points. The share of all other emails saw no significant change from Q2 of 2015.
Top 10 malicious programs sent by email, Q3 2015
Trojan-Spy.HTML.Fraud.gen remained the most popular malicious program sent by email. This program is a fake HTML page sent via email that imitates an important notification from a large commercial bank, online store, or software developer, etc.
Second and ninth places in the Top 10 are occupied by Trojan-Downloader.JS.Agent.hhi and Trojan-Downloader.JS.Agent.hfq, respectively. Both are an obfuscated Java-script. The downloaders use ADODB.Stream technology that allows them to download and run DLL, EXE and PDF files.
Trojan-Downloader.VBS.Small.lj and Trojan-Downloader.VBS.Agent.aqp came third and sixth, respectively. These VBS scripts, which also use the ADODB.Stream technology, download ZIP archives and run malware extracted from them.
Q3 2015, Upatre was the most common malware family sent by email #KLReport
Tweet
Trojan-Downloader.MSWord.Agent.oq came fourth. This malicious program is a DOC file with embedded VBS macros that run when the document is opened. The macros download another malicious VBS script from the cybercriminals’ site and run it on the victim’s computer.
Email-Worm.Win32.Mydoom.l rounds off the Top 5. This network worm is spread as an email attachment via file-sharing services and writable network resources. It harvests email addresses from infected computers so they can be used for further mass mailings. The worm also enables attackers to remotely control the infected computer.
Trojan-Downloader.HTML.Meta.ay, Trojan-Downloader.HTML.Agent.aax and Trojan-Downloader.HTML.Meta.aq were seventh, eighth and tenth in the rating, respectively. They all are HTML pages which, when opened, redirect users to a rigged site. Once there, a victim usually encounters a phishing page or is asked to download a program – Binbot, a binary option trading bot. The three malicious programs spread via email attachments and the only difference between them is the link which redirects users to the rigged sites.
Malware families
As in the previous two quarters, Upatre (9.46%) was the most common malware family. Malware from this family downloads the Trojan banker known as Dyre, Dyreza, Dyzap.
The MSWord.Agent family (5.55%) remained in second position. To recap, these malicious programs are DOC files with an embedded macro written in Visual Basic for Applications (VBA), which runs on opening the document. It downloads and runs other malware, such as malicious programs from the Andromeda family.
In third place was the VBS.Agent (5.44%) family. Unlike MSWord.Agent, the malicious programs of this family use the embedded VBS script. To download and run other malware on the user’s computer they use the ADODB.Stream technology.
Distribution of email antivirus verdicts by country, Q3 2015
There were some significant changes in the Top 3 countries targeted most often by mailshots in Q3 2015. Russia’s appearance in third place (7.56%) was the biggest surprise: its share grew by 2.82 p.p., pushing it up two places from fifth.
Germany (18.47%) remained on top, although its contribution dropped by 1.12 p.p. compared to Q2. Brazil ended the quarter in second place (11.7%) – the amount of malicious spam originating from there almost doubled compared to Q2.
The UK (4.56%), which was second in Q2, ended Q3 in sixth place.
Special features of malicious spam
In spam traffic at the beginning of September we came across a large-scale malicious mass mailing containing emails imitating a non-delivery auto-reply sent by an email server. The text and subject of the message looked very similar to an automatic notification; however, the sender address belonged to an individual, which raised doubts about the legitimacy of the email. The attached ZIP archive named Google_drive_1711 was also suspicious because notifications from email services do not normally contain attachments. Closer inspection revealed that the archive included Trojan Trojan-Downloader.JS.Agent.hhi, which in turn downloaded Backdoor.Win32.Androm.
At the beginning of the third quarter cybercriminals were actively sending out emails in French containing macro viruses. The macros that we detected belonged to a category of Trojan downloaders and were used to download and install the banking Trojan Dridex on victim computers. To deceive the recipient, the fraudsters imitated a notification about the receipt of an order or an invoice.
In July, spammers exploited the theme of loans to spread malicious files that are now traditional for advertising spam. Some scammer emails offered a loan attracting potential customers with very favorable terms, low interest rates, etc. Other messages notified the recipient that his loan application had been approved. Interestingly, this content can also be seen in ordinary advertising spam, but malicious spam usually contains an attachment masquerading as detailed information about the loan.
Interestingly, malicious emails with Trojan-Downloader.Win32.Upatre in the attachment were sent to employees at different companies.
Phishing
In Q3 2015, the Anti-Phishing system was triggered 36,300,537 times on computers of Kaspersky Lab users, which is 6 million times more than the previous quarter. Of them, 15,764,588 attempts were blocked by our heuristic detection components and 20,535,949 by signature detection components. 839,672 phishing wildcards were added to the Kaspersky Lab databases.
The country where the largest percentage of users is affected by phishing attacks was once again Brazil (21.7%). In Q3 2015, the share of those attacked increased by 11.33 p.p., meaning Brazil returned to the same sort of figures last seen in Q1.
Geography of phishing attacks*, Q3 2015
* Number of users on whose computers the Anti-Phishing system was triggered as a percentage of the total number of Kaspersky Lab users in the country
The percentage of attacked users in Japan and China also grew considerably (+10.9 p.p. and +7.85 p.p., respectively), which saw these countries ranked second and third in the rating.
Top 10 countries by percentage of users attacked:
Country % of users
1 Brazil 21.07
2 Japan 16.86
3 China 15.08
4 Vietnam 14.5
5 Bangladesh 13.32
6 Nigeria 13.05
7 Russia 12.91
8 Kazakhstan 12.85
9 India 12.44
10 Columbia 12.25
Organizations under attack
The statistics on phishing targets is based on detections of Kaspersky Lab’s anti-phishing component. It is activated every time a user enters a phishing page while information about it is not included in Kaspersky Lab databases. It does not matter how the user enters this page – by clicking the link contained in a phishing email or in the message in a social network or, for example, as a result of malware activity. After the activation of the security system, the user sees a banner in the browser warning about a potential threat.
In the third quarter of 2015, the ‘Global Internet portals’ category (30.93%) topped the rating of organizations attacked by phishers although its share decreased by 11.42 p.p. from the previous quarter. The share of ‘Social networking sites’ (21.44%) increased by 6.69 p.p. In third place came ‘Banks’ with 18.07% (+4.65 p.p.). The ‘Online games’ category also increased by half and accounted for 4.02%.
Distribution of organizations affected by phishing attacks, by category, Q3 2015
The proportion of phishing attacks on organizations in the ‘Cloud data storage’ category increased by 0.26 p.p. and amounted to 1.06%. Users are increasingly using cloud storage technology, thus attracting the attention of cybercriminals. The stolen information is used for blackmail, sold to third parties or used in targeted attacks.
This type of phishing is often distributed via email or social networks in the form of a message inviting users to download a document allegedly uploaded to a popular cloud service. Messages can arrive from a compromised account from a user’s friend list or, in the case of email, on behalf of a cloud service administrator.
Q3 2015, Anti-Phishing system was triggered more than 36M times on computers of @Kaspersky Lab users #KLReport
Tweet
Phishing pages imitating well-known cloud storage sites are used to distribute various malicious programs. In such cases, a user automatically downloads a malicious program to his computer by clicking the link on the page.
Below is an example of an attack where the user is asked to download an important PDF document. The link in the email leads to a phishing page imitating the site of the popular cloud service Dropbox.
Example of a phishing attack targeting users of Dropbox
In addition to stealing data stored in the cloud and spreading malware, cybercriminals often use the Dropbox name to steal the victim’s email account data.
Example of a phishing page using the Dropbox brand
Here is yet another example of phishing, with the scammers trying to steal the user’s AppleID and password for iCloud.
Example of a phishing attack on iCloud users
Among other things, if successful, the attackers gain access to any content purchased by the user as well as his email account.
Top 3 organizations attacked
Fraudsters continue to focus the greatest part of their non-spear phishing attacks on the most popular brands. In this way they are trying to increase the chances of success for their latest phishing attack. In more than half of cases the heuristic component of Anti-Phishing is triggered when a user follows a link to phishing pages hiding behind the names of more than 30 well-known companies.
The Top 3 organizations most often attacked by phishers account for 26.39% of all phishing links detected in Q3 2015.
Organization % of all detected phishing links
1 Yahoo! 15.38
2 VKontakte 9.44
3 Facebook 8.95
In Q3 2015, the leading three organizations targeted by phishers saw a few changes. Yahoo! remained top with 15.38%, although its share almost halved (-13.65 p.p.). The Russian social networking site VKontakte (9.44%) came second. Facebook (8.95%) fell by 1.49 p.p. and moved from second to third place.
Conclusion
In Q3 of 2015, the percentage of spam in email traffic accounted for 54.2%, a 0.8 p.p. drop from the previous quarter. The Top 3 biggest sources of spam distributed worldwide were: the US (15.3%), Vietnam (8.4%) and China (7.2%).
The holiday season saw an increase in tourism-related malicious spam. Cybercriminals sent out fake notifications from well-known booking services, airlines and hotels, as well as emails from individuals. They typically included attached archives with different Trojan downloaders.
Trojan-Spy.HTML.Fraud.gen remained the most popular malicious program sent by email. As in the previous two quarters, the rating of the most popular malware families was topped by Upatre. Germany topped the ranking of countries whose users were most often targeted by mailshots – 18.5% of antivirus detections were registered there.
A particular feature of Q3 was a new trick used in phishing emails – in order to bypass spam filters they placed the text of the email and fraudulent link in an attached PDF document rather than in the message body.
In Q3, Kaspersky Lab solutions blocked more than 36 million attempts to follow links to phishing pages, which is 6 million more than in the previous quarter. The country where the largest percentage of users is affected by phishing attacks was once again Brazil (21.7%).
Anonymous has taken down 5,500 ISIS accounts
18.11.2015
The collective of hackers Anonymous claimed Tuesday to have taken out 5,500 Twitter accounts used by the Islamic State organization.
The hacking collective Anonymous launched the operation #OpParis against the ISIS in response to the dramatic Paris attacks. The hackers belonging to Anonymous are targeting social media accounts used by members of the terrorist organization. Anonymous released a video on the Internet announcing that his members will catch ISIS members online. In the video, an avatar of Anonymous with a strong French accent declared war to the terrorists
In a couple of days, more than five thousand Twitter account were brought down by Anonymous, as announced by the collective in Tweet.
“We report that more than 5500 Twitter account of #ISIS are now #down! #OpParis #Anonymous #ExpectUs,” states the tweet published by Anonymous on Tuesday.
It is not clear how Anonymous has taken down the Twitter accounts used by the ISIS. Anonymous said it posted the accounts to an online forum using the hashtag #daeshbags (Daesh is the Arabic acronym for the Islamic State group).

On the hacker side also the hackers belonging to the ISIS have released a statement in response to Anonymous’s #OpParis, the members of the ISIS called Anonymous – IDIOTS.
“The #Anonymous hackers threatened… that they will carry out a major hack operation on the Islamic state (idiots),” the message said.
The message was posted via the messaging service Telegram, the communication channel mostly used by the ISIS members in this period.

This is just the beginning, for sure in the next days the hackers will surprise us. Don’t forget that Anonymous is inviting its members to avoid to launch DDoS attacks against the ISIS websites, instead the collective is asking to hack them stealing sensitive data to disclose.
The ISIS is warning its members, on a separate Telegram Channel, Khilafah News, the ISIS spread a message to its followers that instructs them on how to prevent getting hacked by Anonymous.
Below the list of recommendations:
Don’t open any links unless sure of the source.
Change Internet Protocol addresses “constantly.”
Do not talk to people you do not know on Telegram.
Do not talk to people on Twitter direct messaging.
Do not make the same email as your username on Twitter.
Anonymous vs ISIS telegram darknet 3
The ISIS message was shared among various ISIS channels on Telegram.
JPMorgan hackers also hacked an anti-fraud corporation
18.11.2015
According to the Federal indictment about the JPMorgan case, the cyber gang also hacked an anti-fraud corporation labeled as “Victim #12” to remain hidden.
According to the Federal indictment about the JPMorgan case of 83 million stolen customer records, there is a firm labeled as “Victim #12,” that had been hacked to enable hackers to more easily push through payments for spam-advertised prescription drugs and fake antivirus schemes.
The US authorities have charged three individuals over the hack of the JPMorgan Chase and other financial institutions. The data breach suffered by the JPMorgan Chase is considered the largest ever hacking case in financial history.
According to Bloomberg, the cyber thieves have stolen details of “over 100 Million customers,” meanwhile the spokeswoman for JPMorgan Chase Patricia Wexler confirmed the number of affected customers was around 80 Million. The US Court of the Southern District of New York has charged three men, Gery Shalon, Ziv Orenstein, and Joshua Samuel Aaron, accusing them of hacking into a number of financial institutions, including JPMorgan Chase.
The Victim #12 is the G2 Web Services LLC based on many sources such as KrebsonSecurity and has the expertise in helping banks and financial institutions detect websites that are fraudulent or sell contraband.
“One of them, identified in the indictments only as “Victim #12,” is an entity that helps banks block transactions for dodgy goods advertised in spam. Turns out, the hackers targeted this company so that they could more easily push through payments for spam-advertised prescription drugs and fake antivirus schemes.” reported Brian Krebs.
Most probably, these hackers targeted the aforementioned victim to prevent blocking of the payments for the illegal transactions for fake anti-virus or pharmaceutical products. The gang that hacked also the JPMorgan has managed to monitor the detection processes of the victim and read staff emails that eventually enabled them arrange their steps to evade detection.
“Prosecutors say the ringleader of the cybercrime gang accused of breaking into JPMC,Scottrade, E-Trade and others is 31-year-old Gery Shalon, a resident of Tel Aviv and Moscow. Investigators allege Shalon and his co-conspirators monitored credit card transactions processed through their payment processing business to attempt to discern which, if any, were undercover transactions made on behalf of credit card companies attempting to identify unlawful merchants. The government also charges that beginning in or about 2012, Shalon and his co-conspirators hacked into the computer networks of Victim-12 (G2 Web Services).” continues Krebs.
In short, the hackers have blacklisted list of credit and debit cards belonging to employees of the Victim #12 used for detection of unlawful merchants and rejects all the transactions from the blacklist and as a consequence evade the detection.
“In particular, through their unlawful intrusion into Victim-12’s network, Shalon and his co-conspirators determined which credit and debit card numbers Victim-12 employees were using the make undercover purchases of illicit goods in the course of their effort to detect unlawful merchants,” reports the Shalon’s indictment. “Upon identifying those credit and debit card numbers, Shalon and his co-conspirators blacklisted the numbers from their payment processing business, automatically declining any transaction for which payment was offered through one of those credit or debit card numbers.”
jpmorgan
The moral of this story is the depth of organized cybercrimes and how cybercriminals are trying to keep their activities and business model in a covert manner.
“It’s a cat-and-mouse game. They go from one business into another.” said Alan Krumholz, principal data scientist at G2.
In conclusion, the above news helps us understand that all the companies co-operating are chained and lack of attention to security practices and standards of one of the parties may influence others even more traumatically.
Google’s $85 Chromebit Lets You Turn Any Monitor or TV into a Computer
18.11.2015
Asus and Google Chromebit Lets You Turn Any Monitor or TV into a Computer
Google and Asus are finally ready to release their new micro Chrome OS computer called the Chromebit — that retails at a great price, just $85.
That is quite cheap for what is essentially a portable computer that you can take anywhere in your pocket.
Also Read: CHIP — The World's First $9 Computer.
Announced back in March, the Chromebit is a fully featured Computer-on-a-Stick that plugs into TV or any screen and turns it into what Google calls a "full-fledged Chrome OS-based computer."
All you need to do is:
Plug the Chromebit into any HDMI port
Hook up the power cable, a Bluetooth keyboard and a mouse
Your instant computer is ready
It has a smarter clinch on the business end so that you can easily plug the Chromebit into practically any HDMI port without the need for any extension cable.
Also Read: Mouse Box — An Entire Computer inside a Mouse.
Despite its low price of just $85, the Chromebit offers you a complete Chrome OS experience, meaning you will be able to do everything you can do on your Chromebook or your Chromebox.
Asus and Google Chromebit Lets You Turn Any Monitor or TV into a Computer
Chromebit is currently available in United States, Australia, Canada, Denmark, Finland, Japan, New Zealand, Norway, Spain, Sweden, Taiwan and the UK. Users in the US can get the Chrombit from Amazon, Fry’s and Newegg.
ISIS Calls Anonymous "IDIOTS" and Issues 5 Lame Tips for its Members to Avoid Getting Hacked
18.11.2015
ISIS Calls Anonymous — IDIOTS — Issues Advice to Avoid Getting Hacked
The Anonymous Hacking group on Sunday declared Total War against the ISIS, the Islamic State terror organization that claimed responsibility for the Paris attacks on Friday that killed 129 people and hundreds more injured.
In a sinister video posted on YouTube, the Cyber Hacktivists said they will launch their "biggest operation ever" with the warning that "Anonymous from all over the world will hunt you down.”
Also Read: Would Encryption Backdoor Stop Paris-like Terror Attacks?
Now, The Islamic State militant group (ISIS) has released a statement, responding to Anonymous’s declaration of total war.
They (ISIS) called Anonymous – IDIOTS,
… and issued some anti-hacking tips to pro-ISIS supporters to protect against cyber attacks.
The message from ISIS to Anonymous came through one of the ISIS-affiliated official channels, dubbed ELITE SECTION of IS, on the messaging app Telegram.
The message read:
"The #Anonymous hackers threatened in a new video release that they will carry out a major hack operation on the Islamic state (idiots)."
ISIS issues 5 Lame Advice to Avoid Getting Hacked
isis-telegram-channels
On a separate Telegram Channel, Khilafah News, ISIS sent out a message to its supporters and followers that go on to provide instructions on how to prevent getting hacked by Anonymous.
These guidelines read:
Don't open any links unless sure of the source.
Change Internet Protocol addresses "constantly."
Do not talk to people you do not know on Telegram.
Do not talk to people on Twitter direct messaging.
Do not make the same email as your username on Twitter.
This ISIS message was then forwarded around to various other ISIS-affiliated Telegram channels to spread awareness among its members.
Also Read: ISIS Militants linked to Paris Attacks had a Bitcoin Wallet worth $3 Million
It seems like ISIS is taking Anonymous hackers seriously, as the hacktivist group has already taken down more than 5,500 Twitter accounts linked to ISIS supporters and members as a result of its #OpParis campaign.
Stop DDoS attacks in seconds
17.11.2015
An Israeli company named “L7 Defense” is trying to do the impossible – to stop application layer DDoS attacks in seconds instead of hours.
It wants to do so by using an automatic protection system based on an immune-biological model that combines with Real Time Big Data analysis.
“The body knows how to deal in real time with damage to critical systems. He is broadcasting warnings such as fever or other signs that activate the immune system. We found that combining biological model for analyzing the BIG DATA, identifies sophisticated DDoS attacks in real-time,” said Israel Gross, co-founder, and L7 Defense CMO.
Alongside Gross, the partners are Dr. Doron Chema (CEO) Bio-Information by Training, whom also developed the System model and Mr. Mark Ginsburg, a senior algorithmic developer who served in Elite Cyber Unit (IDF).
“DDoS attacks on the application layer are very challenging today. A major reason for this is the use of tools that successfully simulate human behavior and are tailor made for the specific target”, says Gross. “The trick in application layer DDoS is to attack a large number of vulnerabilities while exhausted the target servers’ resources in a short time period”.
DDOS Attack Concept.
Gross explains that today defense systems against DDoS attacks are mainly based on forwarding the traffic to human analysts for a test. “In reality, the average time to discovery and blockage of complex DDoS attacks is more than an hour,” says Gross. “We strive for detection and blocking in no more than a few seconds automatically, regardless of the number of attacking vectors. This protection model is patented”.
DDoS attacks began in the 90s when the original method is to “strangle” the network traffic. Over the years, this type of attack has become easier to identify and block. At the same time, a new trend was born in recent years – targeted attacks on system servers.
These attacks are called, “application layer DDoS” operate relatively modest volume of traffic, and very efficient due to their adaptation to the target. For example, in an e-commerce site, each search request could have a potential of serving as an attacking vector. One can carry out DDoS attack by using Bots, sending multiple search requests to products simultaneously. The result of the load focused on a search engine which usually supported by heavy mechanisms may bring down the entire site or at least a significant slowdown.
L7 Company’s system is software based, located within the boundaries of enterprise systems (DMZ) and can be installed in a public cloud (AMAZON, AZURE, etc.) and / or the customer’s server farm. The system is compact and can be installed as a single server, serving as a protective reverse proxy system.
The system operates at all times (ALWAYS ON), with no prior knowledge or accumulated memory (such as the use of a central signatures bank). From the moment of identifying an attack in real time, the system produces an unequivocal identification of each attack vector and stops them immediately.
“Demonstrations show that the system is dealing effectively with the detection and blocking of 4-5 vectors simultaneously without prior knowledge. It is not limited to blocking even more complex attacks,” says Gross.
“Recall that currently identifying and stopping more than one vector is a real challenge to the SOC personnel in various organizations and usually lasts a few hours by a team of dedicated experts.
“Our system is adapted to the current situation where organizations are attacked frequently and over days or even weeks. It does not require manual operation by teams of experts that the level their availability decrease and the level of cost increases accordingly”.
In July this year, the company raised 750 thousand dollars from Incubate (Elbit Systems Technology Venture) and Israeli office of the Chief Scientist (OCS). “Elbit is a strategic partner and it opens doors for us,” says Gross.
Defense L7 company began operating officially in last July and has been awarded first prize in start-up companies competition in Germany (Tech Ecosystems). “Winning the competition will expose us to the German market,” concludes Gros.
A flaw in D-Link Switches opens corporate networks to hack
17.11.2015
A flaw in certain D-Link switches can be exploited by remote attackers to access configuration data and hack corporate networks.
The independent security researcher Varang Amin and the chief architect at Elastica’s Cloud Threat Labs Aditya Sood have discovered a vulnerability in the D-Link Switches belonging to the DGS-1210 Series Gigabit Smart Switches.
The security experts revealed the existence of the flaw at the ToorCon security conference, but they avoided to disclose the details about the exploit to give the D-Link the necessary time to solve the issue.
D-Link Switches 2
This family of network devices allows the storage of backup files, including logs, firmware and configuration files, in the device’s flash memory or on a web server. Unfortunately, the system lacks of proper authorization and authentication mechanisms, allowing an attacker to access the stored backup files.
The experts discovered that file stored in the flash memory can be accessed remotely by simply knowing the IP address of the D-Link Switches. The exposition of information contained in the configuration files could give the attackers precious information on the targeted network, the attackers could also control internal traffic by compromising the D-Link Switches.
“Once the configuration file is accessed, all the details about the switch, including configuration, username, etc., can be obtained by the attacker. For example, the configuration can be uploaded on another switch (purchased from the market) to obtain the details. Log files reveal information about the clients that accessed the switch and other infrastructure-related information,” said Sood. “Compromising network switches can have disastrous consequences as the attacker can control the traffic flow.”
The duo of experts highlighted that also the root directory of the web server is easily accessible by hackers.
“Usually, when the backup option is selected, the log files and configuration file are stored on the flash drive. Logs are enabled by default in many versions, but a majority of administrators have backup configured so downloading these files is easy,” explained Sood.
Although the security vulnerability has been reported early October, D-Link hasn’t fixed it yet.
Paris Attacks — NO! We Can't Blame Edward Snowden and Encryption for Terror Attacks
17.11.2015
Terrorist groups are increasingly using high-grade, advanced end-to-end encryption technologies so that no law enforcement can catch them.
The deadliest terror attacks in Paris that killed 129 people were the latest example of it.
How did the Terrorists Communicate and Organize the Plot?
The Paris terrorists almost certainly used difficult-to-crack encryption technologies to organize the plot – locking law enforcement out, FBI Director James B. Comey told Congress Wednesday.
The ISIS mastermind behind the Friday's Paris massacre is identified to be Abdelhamid Abaaoud, who is based in Syria. So to transmit his plans to the suicide bombers and gunmen, he would have made use of secure communication to keep law enforcement out.
FBI's Comey believes ISIS is making use of popular social media platforms to reach out to potential recruits and smartphone messaging applications that are end-to-end encrypted, meaning even the company cannot read the messages.
Blame Game: Ex-CIA Director Blames Edward Snowden For Paris Attack
Ex-CIA Director James Woolsey, who once said Snowden "should be hanged by his neck until he is dead," has blamed NSA whistleblower Edward Snowden for revealing the agency's efforts to break encryption and for teaching terrorists how to avoid being caught.
Also Read: Anonymous declares War on ISIS: We will Hunt you Down!
Woolsey said, Snowden, who leaked a vast trove of classified files detailing the extent and workings of the United States intelligence system, is responsible for the Paris terror attacks and now has 'blood on his hands.'
According to Woolsey, it was Snowden's leak of top-secret documents about how American and British spy agencies monitor and track people worldwide that led terrorist groups like...
...ISIS and Al-Qaeda to adopt new communication methods, including end-to-end encryption channels, to avoid surveillance.
But, Why Blaming Snowden? It's Intelligence Failure
The tougher and more important question here is – If terrorists used encryption to plan the strikes in Paris, did they circumvent our spying agencies' Bulk Interception tools and offensive cyber operations?
"I was a bit surprised just by how quickly and blatantly – how shamelessly – some of them jumped to exploit the emotions prompted by the carnage in France to blame Snowden: doing so literally as the bodies still lay on the streets of Paris," the journalist Glenn Greenwald said, who has worked with Snowden to expose NSA secrets.
Bulk interception is the collection of the vast quantity of internet data, sometimes from thick undersea cables and then storing it in databases for a limited time.
However, the government's claims about the NSA bulk surveillance of email and phone records that the operations are to keep the country safe from terrorism are overblown and even misleading.
Also Read: ISIS Militants linked to Paris Attacks had a Bitcoin Wallet worth $3 Million
Surveillance of phone metadata has had no visible impact on preventing terrorist attacks, so it is a total failure of our intelligence agencies, and not Snowden.
The fact that, long before Snowden's leaks, our so-called intelligence agencies around the world failed to prevent many terrorist attacks, including:
The Bali bombing in 2002
The Madrid train bombing in 2004
The 7/7 London attacks in 2005
The series of attacks in Mumbai in 2008
The Boston Marathon bombing in 2013 that took place in the intense security at the leading annual event in a major American city
However, after all these terrorist attacks, the government response has been uniform – Give the intelligence agencies more powers and greater abilities to track, surveil and monitor anyone they believe is suspicious.
"The Snowden revelations were not significant because they told The Terrorists their communications were being monitored; everyone – especially The Terrorists – has known that forever," Greenwald said.
Moreover, one of the leaked GCHQ documents contains what the agency calls a "Jihadist Handbook" of security measures, which was written in 2003, that instructs terrorists to learn and use sophisticated, strong encryption techniques to avoid government surveillance.
So, how could we blame Snowden, who exposed law enforcement’s mass surveillance operations in 2013; almost 10 years after the Jihadist Handbook was written.
After Paris Attack, Government's arguments about Encryption and Backdoor
Now in the wake of the recent Paris terrorist attacks, the US government has renewed their assault on encryption and revived their efforts to force tech companies to install backdoors in their products, like encrypted messaging apps.
Also Read: US Court Rules NSA Phone surveillance Program is illegal.
The intelligence agencies have gotten it all wrong. Due to the bulk collection and interception, the overall volume of encrypted internet traffic has gone up and up, that the intercepted data has become inaccessible even to intelligence agencies.
So, it's not Snowden who is responsible for the Paris attacks, it's the Failure of our government and intelligence agencies.
Would Encryption Backdoor Stop Paris-like Terror Attacks?
17.11.2015
With 129 people killed in Paris terror attacks and dozens critically wounded, the law enforcement and intelligence officials are reviving their efforts to force companies to put some backdoors in encryption so that they can access your information.
How did the Intelligence agencies fail to Intercept terrorist plans of these attacks?
In the wake of the Paris terror attacks, Former CIA Director Michael Morell argued on TV that encrypted communication services may have aided the planning and plotting of the Paris attacks, blaming Edward Snowden and US companies for the attacks.
Also Read: NO, We Can't Blame Edward Snowden and Encryption for Terror Attacks
With more Surveillance and Encryption backdoor, Is it possible that Friday's attacks could have been stopped before they began?
Morell suggested that recalcitrant US companies should be forced to install government backdoors in their software and hand over encryption keys to the government, thinking that Encryption Backdoor could stop Paris-like Terror attacks.
NO, Encryption Backdoors Can't Stop Paris-like Terror Attacks
US intelligence and Law enforcement agencies have been warning for years that due to their inability to decrypt communication between computers and phones, they are unable to know what terrorist groups are planning.
But in my opinion, no backdoors can help law enforcement, and intelligence agencies tackle terrorism.
Here's Why:
Forcing US companies to put Backdoors in their encryption software and hand over encryption keys to the law enforcement would not help them catch terrorist suspects who are using their:
Jihadist's Home-Brewed Encryption products, or,
Services and Products made in Countries not controlled by US Laws.
You can not stop a terrorist from installing an app made in Russia or Brazil, neither you can stop them creating and using their own encryption apps. In both cases, such backdoors will be useless.
Also Read: Anonymous declares War on ISIS: 'We will Hunt you Down!'
Let's talk about some real examples where terrorist groups and online jihadists have proved that they are already aware of intelligence and law enforcement agencies' ability to track them.
Jihadist's Home-Brewed Encryption Softwares
Terrorist groups and jihadists were already making use of – and developing – secure communications software like:
1. Asrar al-Mujahideen (Message and File Encryption Software): Developed in 2007, Asrar al-Mujahideen is a Jihadi-themed encryption software package that encrypts messages and files between users and is promoted as a trusted and secure avenue for terrorist groups to communicate with one another.
2. Asrar Al-Dardashah (Encryption for Instant-messaging Services): Approximately four months before the Snowden's first revelation, GIMF introduced a new software package on February 7, 2013, that allows jihadi users to encrypt live conversations over instant messaging platform including Google Chat, Yahoo, MSN and Paltalk with the multi-platform instant messaging software Pidgin.
3. Tashfeer Al-Jawwal (Mobile Encryption Program): Developed on September 4, 2013, Tashfeer Al-Jawwal provides encryption for SMS messages and files sent on Android as well as Symbian-based mobile phones.
4. Amn al-Mujahid (Android-based Message Encryption software): Launched in late 2013 by Al-Qaida’s al-Fajr Media Center, Amn al-Mujahid is an encryption software for online communication with support for Android.
Don't Mess With Encryption
These examples are enough to provide you an overview that forcing companies to install backdoor will only leave us all vulnerable to the same type of surveillance from unauthorized entities, including hackers and spies from China, Russia, and other countries.
So, backdooring encryption software will never be a complete solution.
However, the FBI and NSA will continue their fight for gaining access to encrypted communications through backdoors, and possibly they will try their luck with the next presidential administration in 2017.
Meanwhile, in the wake of the Paris attacks, UK is willing to pass the Investigatory Powers Bill (IPB) that will grant intelligence agencies more powers to collect private communications in bulk.
Discovered an ISIL Bitcoin Address containing 3 Million dollars
17.11.2015
Hackers of the anti-Terrorism group Ghost Security Group have discovered ISIL militants had a bitcoin address containing 3 Million Dollars.
We have been dismayed by the recent Paris attacks, fear, disgust and anger are the emotions that many of us have felt seeing the images from the France.
While the Islamic State (ISIS) was claiming the responsibility for the attack, the collective of hackers Anonymous declared war on the terrorist organization by launching the operation #opParis.
The investigators are collecting every information regarding the Paris attacks trying to discover when and how the terrorist attacks were organized.
One of the principal problems for the authorities is to discover who is fundings the terrorists, which are the channels used by the ISIL to transfer money to the cells operating in various European countries.
The experts of the Anti-terrorism group of ethical hackers, Ghost Security Group (GSG), speculate that members of the ISIL regularly uses cryptocurrencies to fund the operations of its cells.
To proof their thesis, the hackers of the Ghost Security Group have searched for Bitcoin wallets used by the ISIL organization, and finally they have discovered them.
Members of the Ghost Security Group have uncovered several Bitcoin addresses that might be used by the ISIL to fund its operations. They also made a disconcerting discovery, one of the wallets they have analyzed contains $3 Million in US dollars worth of Bitcoins.
paris attacks
“Yes, we did detect several indicators of an attack impending and are currently in the process of collecting valuable evidence for United States government officials. I cannot go into more detail at the moment on current investigations.” a member of Ghost Security Group explained in an interview with NewsBTC.
“The Islamic State does use cryptocurrencies as a form of income to fund their ongoing operations, and we have managed to uncover several Bitcoin addresses used by them,” “We had discovered a BtC address linked to a known Islamic State deep website approximately three months ago and provided it to dw.com. They hired a team of blockchain analysts to trace the cryptocurrency to the estimated 3 million in BtC the discovered.”
The Ghost Security Group has identified several websites used by the ISIL on the darkweb and gathered information about the amount of money contained in the wallets the addresses of which are present on these sites.
“Most of the Bitcoin funding sites utilized by the Islamic State are on the deep web and we have managed to uncover several and successfully shut them down in order to limit the funding extremists receive through the use of cryptocurrencies.” continues the Ghost Security Group.
Although there are no proofs that these wallets were used to fund the cells involved in the Paris attacks, the Ghost Security Group linked it to the ISIL organization demonstrating the use of cryptocurrencies.
The hackers Ghost Security Group believe that Bitcoin is their prime form of cryptocurrency for the ISIL, but they have no information regarding the mining abilities of the group. It is likely that the ISIL receives donations on a regular basis by its sympathizers.
Anyone can assist the Ghost Security Group by reporting any tips they may receive to http://reportonlineterrorism.com. The group also accepts donations to purchase computer equipment for its activities.
GHOST SECURITY GROUP BITCOIN ADDRESS:
1MfUH1ThpU1dMjBAc5jcewLToE2efQxu7K
Windows Bitlocker disk encryption could be easily bypassed
17.11.2015
Microsoft recently fixed the a vulnerability in the Bitlocker disk encryption feature that could be exploited to easily bypassed it is a few seconds.
A disk encryption tool is a very important software for the protection of our data, million machines rely on them to protect user data, but we have to consider that also these applications could be affected by serious flaws.
In September, the security expert James Forshaw, a member of Google’s Project Zero team, has discovered two critical flaws in the driver that the popular disk encryption tool TrueCrypt installs on Windows systems. The vulnerabilities could be exploited by attackers to access protected data.
BitLocker is another popular disk encryption tool, it was designed by Microsoft and an amazing number of Windows users rely on its feature to protect their data.
The news in the headlines is that the BitLocker disk encryption tool could be easily bypassed prior to last week’s update.

According to a recent research conducted by the expert Ian Haken from the security firm Synopsys, the security feature implemented in BitLocker could be bypassed, and “does not require a sophisticated attacker.”
Prior to BitLocker, an attacker could simply boot up a live Linux distribution, mount the disk containing the user data and access his document. The full-disk encryption feature starts at the boot of the machine protecting data with unbreakable encryption.
One researcher, Ian Haken, a researcher at security firm Synopsys, said in a paper published late last week that the security feature could be bypassed, and “does not require a sophisticated attacker.”
Haken explained that PCs connected to domains were most exposed to the attack if the attacker is able to disconnect the machine from the network and the domain server couldn’t be reached. In this attack scenario the Windows machine uses a local username and password stored in the cache.
The researcher has discovered a method to access the cached password and modify it. In this way the attacker is able to bypass the full-disk encryption feature.
The researcher has demonstrated that by setting up a fake domain server with an identical name, the attacker only had to create a user account with a password created in the past by the user. This trick triggers a policy-based password change, at this point it is enough to change the password and log into the PC using the password that is set in its cache.
“Once logged in, the attacker now has access to all of the user’s data, such as emails, intellectual property, saved passwords, cached credentials, etc. If the user is a local administrator, the attacker could even dump the BitLocker key from kernel memory” wrote the researcher.
Microsoft has already fixed the bug, the last monthly security updates contain the fix for the flaw. Microsoft gave low priority to the flaw because its exploitation requests specific conditions, as reported in the MS15-122 security bulletin.
Clearly the classic attack scenario sees the attackers with access to a lost or stolen laptop, a circumstance not rare in an enterprise context.
The researcher excluded that the flaw has been exploited in the wild.
“As usual, the most important security procedure is to make sure you have applied all security updates to your effected systems,” the researcher wrote.
Hackers claim ISIS Militants linked to Paris Attacks had a Bitcoin Wallet worth $3 Million
16.11.2015
The world watched in horror as coordinate attacks in Paris Friday night killed more than 130 people and left over 352 injured.
Over 20 attackers have so far been part of the terrorist cell that planned the deadly Paris attacks, with seven suicide bombers dead, seven attackers under arrest and a total of six people on the run.
The attacks were carried out by Islamic State (ISIS), who later claimed responsibility for targeting innocent people at 'soft' locations that lack police or military protection, including Bataclan concert venue where at least 89 people lost their lives.
Following the bloody terror attacks, the hacktivist collective Anonymous declared war on the Islamic State (IS, formerly ISIS/ISIL) saying, "We will launch the biggest operation ever against you."
But the Question here is:
From Where did the terrorist cell that planned the brutal terrorist attacks in Paris get Fundings?
The Anti-terrorism group of ethical hackers, Ghost Security Group (GSG), said that ISIS regularly uses cryptocurrencies to fund its terrorist operations.
The anonymous member of GSG has uncovered several Bitcoin addresses that they said, might be used by ISIS. One of the accounts they analyzed was found to contain $3 Million in US dollars worth of Bitcoins.
Also Read: Anonymous Just Leaked list of 1000 ISIS Twitter Accounts.
"The Islamic State does use cryptocurrencies as a form of income to fund their ongoing operations, and we have managed to uncover several Bitcoin addresses used by them," a member of Ghost Security Group said in an interview with NewsBTC.
"We had discovered a BtC address linked to a known Islamic State deep website approximately three months ago and provided it to dw.com. They hired a team of blockchain analysts to trace the cryptocurrency to the estimated 3 million in BtC the discovered."
Although there are no actual proofs that cryptocurrencies were used to support the terrorist attacks in Paris, GSG claimed…
…it had uncovered several Bitcoin funding sites utilized by the ISIS on the dark web and successfully shut them down to limit the funding extremists receive through the use of cryptocurrencies.
Putin: ISIS Financed by 40 Countries, Including G20 Member States
At the recent G20 summit, Russian President Vladimir Putin said that ISIS is financed by individual businessmen from 40 countries, including some G20 members.
However, Putin hopes that the work with the G20 members in the fight against terrorism will continue. "I think that cooperation in fighting terrorism is very important," Putin told reporters.
Putin also calls out Obama for arming and training Fighters for ISIS, saying U.S.-trained rebels were leaving to join ISIS with weapons supplied by Washington.
“In my opinion, provision of military support to illegal structures runs counter to the principles of modern international law and the United Nations Charter,” Putin told reporters.
#ParisAttacks — Anonymous declares War on ISIS: 'We will Hunt you Down!'
16.11.2015
Following the bloody terror attacks in Paris where over 130 people were killed, the hacktivist collective Anonymous has declared total war against the Islamic State (IS, formerly ISIS/ISIL).
Anonymous released a video message, posted in French, on YouTube Sunday announcing the beginning of #OpParis, a coordinated campaign to hunt down ISIS's social media channels and every single supporter of the jihadist group online.
The combat mission #OpParis was announced as revenge for the recent ISIS terror attacks that took place in Paris on Friday, November 13, 2015.
Behind its signature Guy Fawkes mask, the group’s spokesperson speaking in French said, "Anonymous from all over the world will hunt you down. Expect massive cyber attacks. War is declared. Get prepared."
"You should know that we will find you, and we will not let you go. We will launch the biggest operation ever against you," the Anonymous spokesperson added. "The French people are stronger than you and will come out of this atrocity even stronger."
Under the #OpISIS online campaign, Anonymous members have been defending French cyber-borders following the Charlie Hebdo massacre in January. In #OpISIS, the group hacked, defaced, unmasked, and reported thousands of ISIS Twitter accounts.
Now, expect the same thing to happen again. In a separate tweet, the group posted a video message saying:
"We are upping our game, you will now be hit by major cyber attacks, I will be speaking to all the most prominent #OpIceISIS teams and supporters such as @TheBinarySec, @CtrlSec, @OpIceISIS and we will work together to take down all ISIS cyber communications and your accounts, haha good luck with keeping them."
More interestingly, the group has allegedly leaked a list of almost 1000 ISIS Twitter accounts in #OpParis.
The social network giant Facebook on Friday the 13th deleted an Anonymous group page, which has been exposing and reporting social media accounts linked to pro-ISIS, as well as banned all its administrators, without giving any prior warning.
The company said that the existence of the group was a "violation of Facebook Terms of Service and Community Standards."
How does the ISIS control the Internet?
16.11.2015
The ISIS, exactly as any other government, has adopted measures to control the access to the Internet in the territories occupied.
In these hours we are discussing the tragic Paris attacks, we are trying to collect the greatest amount of information as possible about the organization of the ISIS. How does the ISIS conduct its propaganda? Which are the communication channels they use? Which will be the next target?
Researching the topic on the web I have found an interesting post published by the Israel homeland Security website. We all know that the Western intelligence run Internet surveillance program and many governments apply a strict censorship on the online activities of their population. Probably the majority of you has read about the “The Great Firewall of China,” one of the most sophisticated surveillance system that is used by the Chinese Government to monitor the online activities of the population and block all the content not aligned with the policy of Beijing.
The Russian government has its surveillance system known as SORM exactly like the British government that manage a network of systems used to screen internet activities, experts refer it with the term “Hadrian’s Firewall.”
The question is … does the ISIS block online activities in the territories it has occupied? How does it do?
Paris attack ISIS darknet hub screenshot-from-2015-11-15-174423 2
The response is affirmative, the ISIS also controls and block Internet access from its region, it monitors the flow of information in and out of the provinces it occupies.
The mechanism is simple and effective, the self-proclaimed caliphate has banned every private access to the Internet.
“Since earlier in the year, ISIL has been monitoring access to the internet – quite literally, access to the internet itself. Previously, in cities likes Raqqa, Syria, “people would go to the cafes and pay money for internet and have a password or a username,” said Abu Ibrahim al-Raqqawi – an activist with the group Raqqa is Being Slaughtered Silently. “They were sitting in their homes and could access the internet” connecting to WiFi extenders operated by many neighbourhood internet cafes.” states the post published on the Israel homeland Security.
Basically every individual that wants to go online need to use a computer in an Internet cafè where he is tracked. The members of the ISIS in an unpredictable way inspect internet cafes and the machine used by the local people to check none has violated its rules.
Now, private internet access in banned. To go online, “you need to go to the internet cafe and you need to have your ID and they will register your name, the time you enter, and the time you’re out,” says Raqqawi, who uses a pseudonym.
Each offender is punished, and we all know the methods of ISIS.
Twittor tool uses Twitter direct messages to control botnets
16.11.2015
Twittor is a tool open source that was designed by the London-based researchers Paul Amar to control botnets via Direct Messages.
The expert has developed the Twittor tool to make life easier for botnet masters, allowing them to control their malicious architectute by sending out commands via Twitter accounts.
“I mostly wanted to create a PoC after Twitter decided to remove the 140 characters limit for Direct Messages,” wrote the security researcher.
The use of Twitter as a communication channel to control a botnet is not a novelty, any botmasters use social networks such as Facebook and Twitter as C&C. This is a winner’s choice because the technique makes it hard to detect botnet activities.
The interactions with social networking sites can be easily automated and “malicious” traffic directed to social media platforms is hard to identify due to large volumes. Attackers can set up a network of fake profiles on a social network and use them to post a specific set of encrypted commands to the malware. The infected machine queries the “bootmaster” profile for new commands, summarizing a botnet a using C&C in social media is extremely resilient and allows malware to run for long periods of time.
The attackers have improved their control techniques over time. Some malicious agents, in fact, don’t limit their activity to just interpreting messages from social networking but also receive commands hidden inside a picture posted by a profile related to the bootmaster.

The Twittor tool is open source and it is available on GitHub, and the researcher Amar is inviting developers to contribute to the project.
“A stealthy Python based backdoor that uses Twitter (Direct Messages) as a command and control server This project has been inspired by Gcat which does the same but using a Gmail account.” Amar wrote.
“fork the project, contribute, submit pull requests, and have fun.”
The Twittor tool is a Python-based backdoor, the attacker just needs a Twitter account, set up a Twitter app, and get Twitter API credentials.
Among the features already implemented by the twitter tool there is the listing of active boys, execution of commands on it, refreshing of the C&C control. All via features rely on the Direct Messages.
Amar explained that Twittor tool has been inspired by gcat, another open source backdoor that exploits Gmail as a command and control server.
A few hours the Paris attacks, a new ISIS propaganda hub appeared on the Darknet
16.11.2015
The popular security expert Scot Terban (aka @krypt3ia ) discovered a few hours after the Paris attacks, a new ISIS propaganda hub appeared on the Darknet.
The Paris attacks shocked the world, the war is overwhelmingly coming into our homes and the intelligence experts fear that this is just the beginning. The ISIS knows how to spread his message, none in the past was able to organize a so effective propaganda. Each media is masterfully handled by terrorists, social networks, instant messaging app, gaming platforms and forums course in the darknet.
In June, the Europol announced the creation of a team that aims to find key figures in propaganda campaigns run by ISIS members seeking to recruit foreign fighters. The Isis‘s machine propaganda is scaring as efficient, it generates something like 100.000 daily tweets, and it’s used to recruit foreign fighters to support the group.
The Isis is gaining a lot of power in the last years, for the first time a terrorist organization has resources and capabilities to proclaim itself a State.
For this reason, the Europol announced the creation of a new Europe-wide police unit to search for the core leaders of Isis’s social media propaganda campaign. The police unit will track the leaders responsible for an average of 100.000 tweets a day.
isis paris attacks post propaganda
The Paris attacks have raised the level of attention on the organizations that could have supported the terrorist operations from the inside. What are the channels used by terrorists to communicate and what technologies they used?
Many intelligence experts point to the revelations of Snowden as an element that has greatly benefited the terrorists to escape the control exercised by the police. Terrorists are aware that intelligence agencies are carefully monitoring telecom communications, emails, instant messaging apps and much more.
That’s why groups like the ISIS are looking for new channels to reach wider audiences, such as the gaming consoles and the Dark Web, two environments where it is necessary a significant effort to track and identify the source of the messages.
paris attacks
A few hours after the cruel Paris attack, Daesh (al-dowla al-islaamiyya fii-il-i’raaq wa-ash-shaam, a.k.a. ISIS/ISIL) launched his propaganda on the Dark Web.
The website contains translations in English, Turkish, and Russian from the recent statement issued by Daesh claiming credit for the Paris attacks.
The new propaganda center was discovered by the popular researcher Scot Terban (aka @krypt3ia ), who reported it to the colleagues at Salted HASH.
The expert noticed a post that explained the need to create a new hub for propaganda, this is the response to the numerous operations against other websites used by the ISIS that were seized by law enforcement of targeted by hacktivists online. The terrorists decided to move on the Darknet to make the Daesh more resilient to take over attempts.
“Terban came across the new Al-Hayat hub while performing jihadi research over the weekend.” states Salted HASH. “In a post on the Shamikh forum (a known jihadi bulletin board), someone posted the new address and instructions for reaching it.”
The new website includes a collection of propaganda video and images produced by Al-Hayat Media Center, the media division of Daesh. It is known to the intelligence because it is used to spread content glorifying the jihad against the infidel West, including poems for mujahids and songs (Nasheeds).
In the past, Daesh already had propaganda and recruitment hubs on the Darknet, but as explained by the expert it is the first time ever it published proof of those claims.
Terban has mirrored the website and its files, the intention of the expert is to analyze them and publish more details in the coming days. The site is a mine of information , it includes data from various sources, including standard bulletin boards used by the ISIS terrorists.
“The site mirrors many of the other standard bulletin boards that the jihadi’s have had over the years replete with videos and sections in all languages. Given that this site has popped up today in the Darknet just post the attacks in Paris, one has to assume that an all out media blitz is spinning up by Al-Hayat to capitalize on the situation,” Terban wrote.
The new Daesh hub demonstrates that even if the ISIS is aware of the Internet surveillance of western government, it considers the use of technology as strategical.
The Dark Web is a privileged environment for cyber criminals and state-sponsored hackers due to the anonymity offered by its services. The Dark Web is difficult to monitor for intelligence agencies and it is not so easy to locate members of terrorist organizations like the ISIS that share propaganda content. In the principal black markets hosted on the deep web it is possible to purchase any kind of illegal product and service, but in the dark part of the web it is possible to find propaganda videos and images. Hidden services in the Deep Web also offer the possibility to download the mobile apps used by the jihadists to communicate securely and to transfer Bitcoins to terrorist cells in every place of the world.
The new Daesh hub also suggests ISIS sympathizer the use of Telegram, a secret encrypted messaging platform that is largely adopted by terrorists.
Telegram is “A Secret Chat is a one-on-one chat wherein all messages are encrypted with a key held only by the chat’s participants.” It is an essential tool for all the individuals that need to protect their communication from prying eyes.
Telegram’s Channels used by the terrorists allow them to reach tens of thousand followers instantly.
Beaches, carnivals and cybercrime: a look inside the Brazilian underground
15.11.2015 Zdroj: Kaspersky
The Brazilian criminal underground includes some of the world’s most active and creative perpetrators of cybercrime. Like their counterparts in China and Russia, their cyberattacks have a strong local flavor. To fully understand them you need spend time in the country and understand its language and culture.
The Brazilian underground generates quite a lot of cyberthreats – mainly banking Trojans and phishing campaigns. These attacks can be quite creative and are designed to reflect the local landscape. In 2014, Brazil was ranked the most dangerous country for financial attacks, and the Brazilian banking Trojan, the ChePro family, was ranked the second most widespread Trojan after ZeuS.

Countries most affected by banking Trojans in 2014
The picture for phishing attacks is not that different, with Brazil also ranked in first place worldwide. Not surprisingly, quite a number of the brands and companies that feature in the most frequently attacked list are Brazilian.
Beaches, carnivals and cybercrime: a look inside the Brazilian underground

Countries most attacked by phishing attacks in 2014
Brazilian cybercriminals are adopting techniques that they have imported from Eastern Europe, inserting it into local malware to launch a series of geo-distributed attacks. These can include massive attacks against ISPs and modems and network devices or against popular, nationwide payment systems such as Boletos.
To understand what is going on in the Brazilian cybercriminal underground, we would like to take you on a journey into their world, to explore their attack strategy and their state of mind. We will look at the underworld market for stolen credit cards and personal data, the new techniques used in local malware and the ways in which they are cooperating with criminal in other countries.
For many people, Brazil is a country famous for its culture, beaches, samba and carnivals. For security professionals, it is equally renown as a prominent source of Banking Trojans.
Like Bonnie and Clyde: living the crazy life
The first impression you get is that Brazilian criminals like to flaunt how much money they have stolen and the high life they lead as a result of this. They compare themselves to Robin Hood: stealing from the ‘rich’ (in their eyes the banks, the financial systems and the government), in favor of the ‘poor’ (themselves). This is a widely-held conviction: they don’t regard themselves as stealing from individuals who bank online, but from the banks, since, according to local laws financial institutions are obliged to reimburse the victim for any money lost through theft.
There is a widespread sense of impunity, especially because, until recently cyber-crime was not legally defined as criminal activity under Brazilian law. The Carolina Dieckman law (named after a famous actress whose nude pictures were stolen from her computer) was approved in 2013, but the law is not very effective in punishing cybercriminals as the penalties are too lenient and the judicial system is very slow. It is very common for attackers to be arrested three or four times only to be released again without charge. The lack of effective legislation to combat cybercrime and high levels of police corruption provide the icing on the cake.
A strong indicator of just how immune to prosecution the cyber-criminals feel can be seen in the fact that it’s very easy to find videos and pictures of them online or to access their profiles on social networking sites. Invariably, they can be seen flaunting what appears to be stolen money, celebrating the high life, paying for prostitutes in Rio during the carnival, and more.

Brazil has achieved worldwide notoriety as a place where many ‘Bonnie and Clyde’ types are living decadent lives. How much do they steal? Quite a lot. According to the Brazilian Federation of Banks (FEBRABAN), in 2012 local banks lost 1.4 billion of reais (around US$500 million) paying for fraud perpetrated via Internet banking, by telephone, or through credit card cloning.
The target audience for cybercrime in Brazil is significant: the country has more than 100 million Internet users, 141 million citizens eligible to use Brazil’s e-voting system and more than 50 million people who use Internet banking services daily.
There are online videos celebrating the criminal life, like this song, the “Hacker’s Rap”. The lyrics celebrate the life of the criminals who use their knowledge to steal bank accounts and passwords:
The lyrics say: “I’m a virtual terrorist, a criminal; on the internet I spread terror, have nervous fingers; I’ll invade your PC, so heads up; you lose ‘playboy’, now your passwords are mine”.
Card-skimmers also celebrate and flaunt their profits in the “Cloned credit card rap”, also available on Youtube:
The lyrics include the words: “You work or you steal, we cloned the cards, I’m a 171, a professional fraudster and cloner, we steal from the rich, like Robin Hood, I’m a Raul…”
Recently the Brazilian Federal Police arrested the owner of a three million reais luxury mansion bought with funds stolen using Boleto malware. In Brazil, cybercrime pays, and pays very well.
C2C: Cybercrime to Cybercrime
As is the case with other underground fraternities, Brazilian cybercriminals are organized in small or medium-sized groups, each with their own expertise, selling their services to each other or working together. ‘Independent’ criminals are also common, but in general, most need to collaborate to do business.
The most common channels used by the Brazilian underworld to negotiate, buy and sell services or malware are Internet Relay Chat (IRC) channels. Some of them also use social networks such as Twitter and Facebook, but most of the juicy content is hidden inside IRC channels and closed forums that you can only join by invitation or with endorsement from an existing member. In these IRC chats criminals exchange data about attacks, hire out services among themselves, and sell personal data from hacked websites, while coders sell their malware and spammers sell their databases and services. These are true C2C (Cybercrime to Cybercrime) operations. The two most popular IRC networks used for such activity are FullNetwork and SilverLords.
However, a very common problem among the criminal fraternity is what it calls “calote” or deadbeats – those people who steal from the thieves, who buy criminal services or software underground without paying the seller. Revenge is taken quickly and in one of two ways. Firstly, the bad player may be “doxed”: their real identity published with the aim of alerting Law Enforcement. Secondly, they may find their name added to a big reputation database of bad and good debtors. This ‘black’ and ‘white’ list enables the ‘community’ to protect itself by checking out the reputation of a customer before doing business with them.

An underground reputation system from Fullnetwork.org: protection against deadbeats
“Doxing” and other attacks on competing gangs are common among the Brazilian underground – some groups even celebrate the arrest of other cyber-crooks. That’s what happened with Alexandre Pereira Barros, responsible for the SilverLords network. He and three other cybercriminals were arrested by the Brazilian Federal Police in April 2013 after a series of fraud attacks against financial systems, credit card cloning, hacktivism attacks, and more. The group owned a lottery retailer in the state of Goias, responsible for theft of $250.000. To ‘celebrate’ their arrest, other criminals posted a video on Youtube, in revenge for unpaid debts:

Brazilian cybercriminals arrested in 2013 – unfortunately, they did not end up in jail after all
A typical Brazilian cybercrime group include four or five members, but some groups can be bigger than that. Each member has their own role. The main character in this scenario is the “coder”, the person responsible for developing the malware, buying exploits, creating a quality assurance system for the malware and building a statistical system that will be used by the group to count victims; and then putting everything in a package that can be easily negotiated and used by other criminals. Some coders don’t limit themselves to a single group and may work with several, and most prefer to not get their hands dirty with any stolen money. Their earnings come from selling their creations to other criminals. A coder could be a leader of a group, but this is not common. They are rarely arrested.
Every group has one or two spammers, responsible for buying mailing lists, buying VPSs and designing the “engenharia” (the social engineering used in the mail messages sent to the victims). Their role also involves spreading the infection as widely as possible. It´s common to find spammers with experience in the defacement of web servers that then allow them to insert a malicious iframe into infected websites. Spammers don’t have a fixed salary: their earnings come from the number of people infected. That is why the coder needs to build a victim-counter into the malware, as this information is used to calculate how much the spammer will receive.
The group also has a recruiter, responsible for hiring the money mules (also known as “laranjas”). This is a very important task because this person will be in direct contact with people or hold responsibility for external activities, such as for coordinating the things necessary for transferring the money or withdrawing it from ATMs, paying the bills (generally at a lottery house) or receiving the products bought online with the stolen credit cards – do the “correria” (foray). It´s common for the people in this role to recruit their own family members to work as money mules, as they can earn up to 30% of the sums stolen and distributed among the money mule accounts. Generally, the money mules are the first to be arrested in police operations, followed by the recruiter.
The real leader of the group is responsible for coordinating the other members and all the activites, negotiating new “KLs” (keyloggers) with a coder, requesting a new “engenharia” from the spammers, or do the “correria” with recruiters. They are also responsible for recruiting new members to the group and negotiating their wares in with other criminal groups. Roles are not fixed; some members may perform a number of functions and work with more than one group, and their earnings may vary. Some criminals prefer to work independently, selling their services and goodies to several groups.
And some criminals have opened web stores to sell their goods and promote their services in a better and more user-friendly way. In these stores one can buy cryptors, hosting services, coding services for new Trojans, etc. That was the purpose of the “BlackStore” (now offline). Let’s check the prices of their ‘goodies’:
| A “crypter” 100% undetected, R$ 100 (U$ 30.00)
|
| Hosting: US$17
|
| Coding services: US$170 |
| Tester of stolen credit cards: US$130
Check out the pictures of the application on our database!” |
| DNS Network US$1500
|
| Malicious Java applet: US$25
|
| Viral Facebook: US$20 |
| VPS Spam sender: US$20
|
| SPAM PHP system: US$10
|
| KL (Keylogger): US$ 300 Targeted banks:
|
As a “professional” store, they also offer a receipt for your purchases:

Honest thieves: proof of your underground purchases
The professionalization of organized cybercrime, as observed in Eastern Europe, is now adopted by the Brazilian crime underground. Investment in technology and marketing is aimed at increasing their profits. In some closed forums criminals have even started advertising their services in a clear attempt to attract newcomers not used to developing their own tools:

The text says: “Buying any social engineering kit you also earn kits for banker, credit card and frequent flyer miles. 1 million free spam messages, from Bruno Dias smart solutions”. Other services that are increasingly offered include websites offering “malware as service”, cryptors, FUDs (fully undetected malware) and a complete system to manage information about stolen banking accounts:

“FUD as a service”, encryption service for already detected trojans
An “admin panel” manages the complete system that allow attackers to control infected machines, collect banking data, and bypass two-factor authentication (2FA) in any form (SMS, token, OTPs (one-time password cards) and more). Some systems also allow for the control of websites and domains used to spread the malware and to send spam and manage mail lists, all in a single solution.

Remote access tool sold on the underground intended to bypass the 2FA of Brazilian banks
The goods on offer also include DDoS attacks. Using the power of thousands of infected computers it’s not difficult to perform a distributed denial of service for other criminals, using SYN flood, amplified UDP, and more. The prices are listed below: 300 seconds: $8.3; 450 seconds: $13; 1000 seconds: $28; 3600 seconds: $40.

DDoS for hire: takedown your target paying by seconds of attacks
How much does your credit card cost?
Credit card dumps are among the most valuable data exchanged among criminals. These have often been cloned in different ways, including chupa cabras (skimmers) on ATMs and point-of-sale terminals, phishing pages, keyloggers installed on victims’ PCs, and more.
Brazil has one of the highest concentrations of ATM terminals, according to the World Bank. There are more than 160,000 opportunities for fraudsters to install a skimmer (also known as a “Chupa Cabra device”), and they do this all the time. Even during the day you can see them hanging about, wearing flip-flops and beachwear and in a very relaxed mood, installing skimmers in a crowded bank:
When it comes to credit card cloning, Brazil has some of the most creative and active criminals. Fortunately, most of the cards in use have CHIP and PIN technology built in. Despite recent news revealing some security flaws in this protocol, CHIP and PIN cards are still more secure and harder to clone than magnetic swipe cards. Because these EMV chips are used all over the country, most of the cloning activity happens online, using phishing attacks, fake bank pages, fake giveaways and compromised e-commerce portals, offering an expensive product for very attractive price. If you are engaged in any type of online business, sooner or later your card will be attacked: via phishing or through compromise of the e-commerce portal.
These highly sought-after dumps are sold online through specialized websites or even through IRC channels. And it’s not just carders and cybercriminals who are involved in this underground business, but many ‘traditional’ criminals connected to drug trafficking and other illegal activities.
The price of a cloned credit card depends in the bank, the country of origin, etc.
Infinity: flags such as American Express or international cards are sold at $42 apiece
Platinum: cards from multinational banks, $40 apiece
Black: cards by $30 apiece
Gold/ Premier: $25 apiece
Classic: from national banks, $22 apiece
Ad of a criminal selling dumps of stolen credit cards: you can even pay for it with your own credit card
Data breach incidents fueling cyberattacks
The Brazilian underground is hungry for personal data – and this allows cybercriminals to monetize identity theft, offering opportunities to buy products using “laranjas” or money mules, or even collect this data to empty your bank account, as several online services ask for personal data to confirm a customer’s identity.
Unfortunately, the country does not yet have specific laws in place to protect personal data – at this time politicians are still evaluating their options. As a result, data breaches in government organizations and private companies are widespread. Affected businesses currently are not obligated by law to contact customers affected by the breach or even to inform them that an incident has taken place.
Recently, we observed some very serious data breach incidents affecting major websites, and involving databases from the government, Receita Federal (IRS) and other institutions. It is common to find leaked databases being sold underground, such as the database of DETRAN (Traffic Department), with data on five million citizens costing only US$50:

Flaws on government websites are critical. In 2011 two very serious flaws in the Labor Ministry website exposed an entire database with six months’ worth of data on every citizen in the country. A flaw in the website’s security left sensitive data out in the open, with only a CPF number (Brazilian SSN) required to obtain further information about a person.

The CPF is one of the most important documents for anyone living in Brazil. The number is unique and is a prerequisite for a series of tasks like opening bank accounts, to get or renew a driver’s license, buy or sell real estate, obtain loans, apply for a jobs (especially in the public sector), and to get a passport or credit cards. Leaked data makes it possible for a cybercriminal to impersonate the victim and to steal their identity in order to, for example, get a loan from a bank.
This is a case of where a data leak meets the phishers. Information of such quality can only be obtained through data leak incidents. Not surprisingly, it is common for the Brazilian media to spot criminals selling CDs carrying data from the Brazilian IRS system which includes a lot of sensitive data, including the CPF numbers. You can find criminals selling CDs full of leaked database from several sources for a mere $100. As a result of such data breaches, Brazilian phishers have created attacks with messages displaying the complete name and the CPF number of the victim in an attempt to add legitimacy to a fake message. Attacks such this one have happened regularly since 2011:

A phishing message displaying the complete name of the victim and their CPF number
The abundance of personal data leaked from several sources has allowed Brazilian criminals to establish online services offering a searchable database with personal data from millions of citizens. Despite the efforts of the authorities to take down such websites, new services are created every month.

Having the CPF number is enough to find all your personal data
The problem of data brokers
Another problem related to the bad management of personal data is “Data brokers”, companies that collect information and then sell it on to companies that use it to target advertising and marketing at specific groups; or to verify a person’s identity for the purpose of fraud detection; or to sell to individuals and organizations so they can research particular individuals.
Local companies such as Serasa (now acquired by Experian) are a common target of phishers and malware authors. As they offer the biggest database in the country regarding fraud protection, and carry a complete profile of personal data for every citizen, the stolen credentials to access this database are valuable among fraudsters.
So, not surprisingly many fraudsters resell the results of their access to data broker services using stolen customer credentials, in packs that cost US$30 per 15 days or US$50 for 30 days of full access:

Other criminals go further, and build their own data broker services. Owners of these services market them to other fraudsters, offering a comprehensive package to search databases leaked from the government as well as those obtained from private sources. Such widespread activity gives the impression that in Brazil cybercrime will always be able to reach you, one way or another.

Govern and Data broker’s database together in the same underground service
To advertise their services, fraudsters use all channels, even social networks like Facebook. In a dossier published by Tecmundo they found evidence of public employees involved in the scheme, selling databases and credentials.

Access to stolen data service advertised on Facebook
How phishing attack compromised the Amazon forest
Could you imagine a phishing attack compromising the biggest rainforest in the world? That is what happened with IBAMA, the Brazilian Institute of Environment and Renewable Natural Resources. IBAMA is responsible for limiting the cutting of hardwood trees in the Amazon region, ensuring that only authorized companies are able to do that.
In a series of attacks against IBAMA’s employees (probably using phishing emails like the one below), Brazilian criminals were able to steal credentials and break into IBAMA’s online system. Then they unlocked 23 companies previously suspended for environmental crimes, allowing them to resume extracting wood from the forest. In just 10 days these companies extracted $11million in wood. The number of trees cut illegally was enough to fill 1,400 trucks.

Phishing page of IBAMA: to steal credentials and cut woods in the forest
Underground cooperation with Eastern Europe
We have sufficient evidence that Brazilian criminals are cooperating with the Eastern European gangs involved with ZeuS, SpyEye and other banking Trojans created in the region. This collaboration directly affects the quality and threat-level of local Brazilian malware, as its authors are adding new techniques to their creations.
It’s not unusual to find Brazilian criminals on Russian underground forums looking for samples, buying new crimeware and ATM/PoS malware, or negotiating and offering their services. The first result of this cooperation can be seen in the development of new attacks such the one affecting Boletos payments in Brazil.

Brazilian bad guy writing in (very bad) Russian, selling access to 400 infected PoS devices
They have also started to use the infrastructure of Eastern European criminals, sometimes buying bulletproof hosting or renting it. “João de Santo Cristo” (a fictional character that appears in a popular Brazilian tune) was one of them, buying and hosting 14 Boleto malware domains in Russia:

Not surprisingly we have started to see Russian websites hacked into and hosting fake Boleto websites:

These facts show how Brazilian cybercriminals are adopting new techniques as a result of collaboration with their European counterparts. We believe this is only the tip of the iceberg, as this kind of exchange tends to increase over the years as Brazilian crime develops and looks for new ways to attack businesses and regular people.
Advances in local malware
The contact with Eastern European cybercrime affects the quality of Brazilian malware. For example, we found in Boleto malware exactly the same encryption scheme that is used in payloads by ZeuS Gameover.

Encrypted payload of Boleto malware: the same encryption used by ZeuS
We also saw, for the first time, Brazilian malware using DGA (Domain Generation Algorithm). Trojan-Downloader.Win32.Crishi was one of them, distributed in messages like this one:

Further evidence of advances in Brazilian malware due to the cooperation with Eastern European criminals can be seen in the use of fast flux domains in Boleto attacks.
Conclusion
Brazil is one of the most dynamic and challenging markets in the world due to its particular characteristics and its important position in Latin America. The constant monitoring of Brazilian cybercriminals’ malicious activities provides IT security companies with a good opportunity to discover new attacks related to financial malware. In some cases these attacks are very unique as happened with the usage of malicious PAC files.

Message from bad guys in a malicious PAC file to yours truly: reaction due a good detection
To have a complete understanding of the Brazilian cybercrime scene, antimalware companies need to pay close attention to the reality of the country, collect files locally, build local honeypots, and retain local analysts to monitor the attacks, mostly because it’s common for criminals to restrict the reach of the infection and distribution of their creations to Brazilian users. As happens in Russia and China, Brazilian criminals have created their own, unique reality that’s very hard to understand from the outside.
Did terrorists use PlayStation 4 for communications in Paris attacks?
15.11.2015
Rumors circulating on the Internet sustain that terrorists behind the Paris attacks have used PlayStation 4 for their communications.
The Paris attacks have shocked the world, the ruthless terrorists of the ISIS killed defenseless people. The days after atrocity law enforcement are conducting an investigation on a large range to identify the logistic base of the group and the network of ISIS members that supported the men involved in the Paris attacks.
The roots of the Paris Attacks lie partly in Syria and Iraq, but we investigators have no doubt, they have deep ramifications in the principal European cities.
At the time I’m writing, 3 people suspected of having links with Paris Attacks have been arrested in Belgium, the countries that intelligence agencies consider the lair from which they started terrorists ISIS.
The ISIS has brought the terror in our cities, for the first time a group of terrorist has men, resources and money to proclaim itself a state.
The Paris attacks demonstrate the ISIS had high-level logistical organization, they coordinated such a mass terrorist attack avoiding being detected by the intelligence, despite the level of alert was high due to the alleged terrorist attack in Sinai and the tragedy of the Charlie Hebdo.
Such kind of attack needs a significant effort in communicating among members which remained hidden from the law enforcement and intelligence agencies despite the numerous surveillance programs of many governments.
Authorities are monitoring in every instant the communications, even messages exchanged over the Internet and probably among ISIS members crowding the Deep Web.
New of the last hours is that the IS terrorists involved in the Paris attacks may have used the most popular Sony PlayStation 4 gaming console as the platform to exchange messages.
A raid in nearby Brussels provided evidence that terrorists were using at least one PlayStation 4 console.
The Belgian federal home affairs minister Jan Jambon explained that the PS4 is used by ISIS members for their communications.
The choice is not casual, despite the effort of the intelligence agencies in monitoring communications over Gaming console, the ISIS members were aware of the difficulties to conduct a large-scale surveillance on the PlayStation 4 channels.
“The thing that keeps me awake at night is the guy behind his computer, looking for messages from [the Islamic State]and other hate preachers,” Jambon said last Friday, according to Brussels weekly, the Bulletin. “PlayStation 4 is even more difficult to keep track of than WhatsApp.”
ISIS Paris attacks PlayStation 4
The PlayStation’s IP-based voice systems are difficult to monitor and terrorists could send messages to each other within PlayStation games without speaking or typing a word.
At the time I’m writing there is no certainly, the investigators have no clear idea about a possible use of the Sony Play Station 4, anyway we cannot underestimate this option in the hand of terrorists that have significant technological abilities. A few days ago the popular Cyber security expert Mikko Hypponen, Chief Research Officer for F-Secure, said he worries about cyber extremists that could penetrate critical infrastructure and cause serious damages. The expert explained that the ISIS is probably the first group of terrorist that has hacking capabilities to manage a major attack against a government infrastructure, and the situation is getting worse because this group is gaining greater awareness of the effectiveness of an offensive launched by the cyberspace.
We have already discussed in the past the possibility that terrorist groups could exploit gaming console for internal communications. In 2013, I published a post describing the activities of the NSA and the British GCHQ to infiltrate the virtual world of online games considered as an attractive environment for cyber terrorists and hackers.
The Guardian published documents leaked by Snowden on the surveillance program in partnership with the New York Times and ProPublica, according the files the intelligence agencies have operated in virtual worlds and gaming communities to conduct intelligence operation and try to recruit informants.
Last documents published by the Guardian titled “Exploiting Terrorist Use of Games & Virtual Environments” are dated 2008 and remarked the necessity to monitor online gaming communities describing them as a “target-rich communications network” where intelligence targets could “hide in plain sight”.
The documents just provide a warning on the possible abuse of online gaming communities, but don’t contain an indication on real case discovered by the intelligence agencies.
The Secret Services have infiltrated the principal online game communities including Second Life to monitor users’ habits and snoop their communications, NSA and GCHQ have created human avatars to explore virtual reality and prevent terrorist initiatives.
Yes, but at that time there was no automatic system to monitor such kind of communication, what about today abilities?
Paris attacks must lead us to reflect seriously on the subject, the ISIS has skills and resources and it is not surprising that its members can exploit gaming console as communication channels.
Russia has a new anti wiretapping System
15.11.2015
A Russian manufacturer has built an advanced system for the protection of any channels of telephone communication against wiretapping.
The Russian Government has a new system for the protection of communication channels against the wiretapping, the news was disclosed by the director general of the Interstate Corporation of Development (ICD), Ivan Polyakov, and it was reported by the Russian News agency Tass.
The protection of telephone communication against wiretapping is strategic for any governments, the new system protecting any channels of telephone communication against espionage activities has been designed by a Russian manufacturer.
“The solution has been found that makes it possible to guarantee confidentiality of conversations irrespective of what systems and standards of communications you use,” Polyakov said.
“This is a very interesting solution, we believe it will be in demand on the market,” he said without providing further details on the solution.
surveillance wiretapping
The Russian authorities decided to develop a system for the protection of communication channels because the solution available on the don’t match the requirements of the Government.
“The options existing on the market could not satisfy us as a corporation. That is why we started with ourselves, and then decided to offer the product to the market,” he added.
Polyakov explained that components for the protection system were designed and produced directly at enterprises of the ICD.
As reported in the official website of the ICD, the purpose of Corporation establishment is the development of scientific, industrial and high-tech cooperation in Collective Security Treaty Organization (CSTO) countries.
The ICD was established on January 15, 2011, its is considered of the biggest Russian designers and producers of solution that could protect communication systems.
The Collective Security Treaty Organization is an military alliance, acting as counterpart to the NATO alliance, which was signed on 15 May 1992 and that includes Armenia, Belarus, Kazakhstan, Kyrgyzstan, Russia, Tajikistan and Uzbekistan.
Flaw in the Android Gmail app opens to email spoofing attacks
14.11.2015
A security loophole in the official Gmail Android app opens the email spoofing attacks allowing anyone to change the sender email name.
The independent security researcher Yan Zhu has discovered a serious security issue in the Gmail Android app allows ill-intentioned to send an email pretending to be someone else. Clearly a similar loophole could represent a gift for phishers and scammers, the issue dubbed Email Spoofing, enable the forgery of an e-mail header so that the email appears to have originated from someone else than the legitimate sender.
In a classic email spoofing attack, threat actors need an SMTP (Simple Mail Transfer Protocol) server to send the email and a mailing application.
The researchers Yan Zhu, discovered a flaw in the Gmail Android app that allowed her to change her display name in the account settings so that the final recipient will not be able to know the identity of the email sender.
Zhu provided a PoC of her attack by sending an email to someone by changing her display name to yan “”security@google.com,” as it visible in the following image.
“[This] extra quotes [in the display name] triggers a parsing bug in the Gmail app, which causes the real email to be invisible,” Zhu told Motherboard. “It’s always been possible to spoof email envelope addresses, but spoofed emails now usually get caught by spam filters or get displayed with a warning in Gmail, With this bug, a hacker can get around these protections.”
Wait! Now is arriving the interesting part of the story.
Zhu reported the issue to the Google Security team at the end of October, but unfortunately the experts rejected the bug report saying it is not a security vulnerability.
“Thanks for your note, we do not consider this [bug] to be a security vulnerability,” a Google Security Team member told Zhu.
“Filed a Gmail Android bug that lets me fake sender email address. [Google] said it’s not a security issue. ¯\_(ツ)_/¯.” Zhu tweeted.
You got it right! The security team of Google does not consider a security issue the e-mail spoofing.
Users that want to protect themselves from email spoofing attacks can read the following suggestions:
Enable antispam feature provided by your email service.
Analyze the Email message headers and search for the legitimate IP addresses of the sender. Every time you suspect an email spoofing give a look to the header and search for the real source.
Never Click on a Suspicious Link or open suspicious attachment. Be aware of any unsolicited email.
Keep your PC’s Antimalware Up-to-Date.
Bug in Gmail app for Android Allows anyone to Send Spoofed Emails
14.11.2015
A security researcher has discovered an interesting loophole in Gmail Android app that lets anyone send an email that looks like it was sent by someone else, potentially opening doors for Phishers.
This is something that we call E-mail Spoofing – the forgery of an e-mail header so that the email appears to have originated from someone other than the actual source.
Generally, to spoof email addresses, an attacker needs:
A working SMTP (Simple Mail Transfer Protocol) server to send email
A Mailing Software
However, an independent security researcher, Yan Zhu, discovered a similar bug in official Gmail Android app that allowed her to hide her real email address and change her display name in the account settings so that the receiver will not be able to know the actual sender.
How to Send Spoofed Emails via Gmail Android App?
To demonstrate her finding, Zhu sent an email to someone by changing her display name to yan ""security@google.com" (with an additional quote). You can see the below screenshot posted by Zhu on her Twitter timeline.
"[This] extra quotes [in the display name] triggers a parsing bug in the Gmail app, which causes the real email to be invisible," Zhu told Motherboard.
Gmail Android App Bug Allows anyone to Send Spoofed Emails
Once received, the email address could trick the receiver into believing that the mail has arrived from a legitimate Gmail security team, which is not.
Google – 'The Bug isn't a Security Vulnerability'
Zhu reported the loophole to Google's Security team at the end of October, but the team disapproved her bug report, saying the bug is not a security vulnerability.
"Thanks for your note, we do not consider this [bug] to be a security vulnerability," a Google Security Team member told Zhu.
"Filed a Gmail Android bug that lets me fake sender email address. [Google] said it's not a security issue. ¯\_(ツ)_/¯." Zhu tweeted.
Email spoofing can be used legitimately, but because spoofing an email address is surprisingly easy, spammers and phishers take advantage of it to harm people or organisation.
Here's How to Protect Yourself from Spoofed Emails
So, if you want to protect yourself from spoof messages, you can follow the given couple of things:
Turn on your Spam Filters – Almost every email service offers spam filters and junk boxes that dump spoof emails to your junk mail.
Learn to Read Email message headers, and Trace IP addresses – Tracking down the source of spam is a good practice. When you receive a suspicious email, open the header, and see if the IP address of the sender matches up with previous emails from the same person.
Never Click on a Suspicious Link or Download an Unfamiliar Attachment – Always pay attention to the emails you receive and avoid clicking links in email or downloading email attachments. Go to your bank's official website, or other websites directly from the browser and log into your account to find what they want you to see.
Keep your PC's Antimalware Up-to-Date.
FBI denies paying $1 MILLION to Unmask Tor Users
14.11.2015
Just day before yesterday, the Tor Project Director Roger Dingledine accused the FBI of paying the Carnegie Mellon University (CMU) at least $1 Million to disclose the technique they had discovered to unmask Tor users and reveal their IP addresses.
However, the Federal Bureau of Investigation has denied the claims.
In a statement, the FBI spokeswoman said, "The allegation that we paid [CMU] $1 Million to hack into Tor is inaccurate."
The Tor Project team discovered more than hundred new Tor relays that modified Tor protocol headers to track online people who were looking for Hidden Services, and the team believes that it belongs to the FBI in order to reveal the identity of Tor-masked IP addresses.
One such IP address belongs to Brian Richard Farrell, an alleged Silk Road 2 lieutenant who was arrested in January 2014.
The attack on Tor reportedly began in February 2014 and ran until July 2014, when the Tor Project discovered the flaw. Within few days, the team patched the vulnerability and updated its software, thereby rolling out new versions of code to block similar attacks in the future.
This week, Motherboard reviewed a new court filing in Farrell's case that proved the FBI had indeed recruited a "university-based research institute" to uncover the identity of Farrell by running systems on the Tor network.
The FBI spokeswoman didn't provide any further statement on the Tor Project claims, and it's still unclear which part of the FBI's statement is inaccurate – The Payment Amount or The FBI's Involvement Entirely.
What do you think? Hit the comments below.
You can buy a Cryptolocker/Cryptowall Ransomware Kit for $3,000
14.11.2015
Experts at BitDefender have discovered a Cryptolocker/Cryptowall Ransomware Kit offered for sale at $3,000, source code included.
Yesterday I wrote about a new Ransomware-as-a-service, the FAKBEN, surfaced from the criminal underground, requesting customers 10 percent profit cut. In the previous days I reported other cases involving ransomware, such as a malicious code that infected the UK Parliament, an off-line ransomware and a Linux.Encoder1 ransomware revealing the decryption key.
The cybercrime is looking with increasing interest to ransomware, today I want to write about the availability of the source code of Cryptolocker/Cryptowall in the underground.
According to Bitdefender, a Cryptolocker/Cryptowall Ransomware Kit is offered for sale for $3,000, including its source code.
The experts consider this offer for the Cryptolocker/Cryptowall Ransomware Kit not that expensive for the features it implements. We have seen that the return on investment for ransomware like Cryptowall could be very high.
Security researchers of the Cyber Threat Alliance have conducted an investigation into the cybercriminal operations leveraging CryptoWall 3.0 ransomware.
A Pastebin post also claims that the manual and free support is included along with Cryptolocker/Cryptowall Ransomware Kit source code, of course, buyers can pay it in Bitcoin.

The sellers also offer for sale ransomware binaries, a bundle of 8 goes for $400. However, the developer is opening to various models of sales, including the affiliate program in which he would share 50/50 the revenue with potential buyers.
“This is your chance to become a partner and join or buy build individual to you and use and to generate income and to convert and monetization,” reads the post. “If you are interested then contact i need a partnership and also iselling build to you.”
This is one of the few times when we can take a look at how the underground market works, the types of services offered, and maybe estimate the amount of money made from selling custom-made malware.

Cryptolocker/Cryptowall Ransomware Kit Sold for $3,000 - Source Code Included
Liviu Arsene, Security Researcher at Bitdefender, explained that buyers of Cryptolocker/Cryptowall Ransomware Kit will allegedly not only gain access to full support but paying an additional fee they fully customize their ransomware.
“Those who actually want to purchase the Cryptolocker/Cryptowall Ransomware Kit will allegedly not only gain access to full support, but can also ask for additional modules or customizations, such as preferred language interfaces for the access panel or custom deployments on VPS servers.” said Arsene.
Below the information provided by the seller, including the list of features implemented in the Cryptolocker/Cryptowall Ransomware Kit. It is interesting to note that the developer claims the ability of its ransomware of communicating with Command and Control servers over Tor without losing any connections, a unique technique that will only be disclosed once contacting support.
“Information for customers:
JID: whiterocks@richim.org
Price of binary: $400 (8/1 customers)
Price of source code and manual how edit code wallet btc i give you: $3000 (1 customer)
You keep 100% of payments
Free recompiles and support
Escrow accepted
Bitcoin (BTC) only!”
“Features:
Encryption algoritm BlowFish 448 bit (stronger then AES).
448 bit key is generated on computer and sent to C&C. Each computer generates unique key. Key is not stored on computer and is purged from RAM.
All C&C decryption keys are encrypted with the RSA-alg (1024 or 2048 Bit Keys). The Password used to decrypt the private key is not stored and only temporary used(conclusion: even if the server is raided or compromised the User-Passwords cannot be decrypted).
Locker can communicate with C&C over Tor, without losing any connections (contact support for more information – we are using a different technique).
Files in all locations (external media and network) are encrypted.
Encrypted extensions: odt, ods, odp, odm, odc, odb, doc, docx, docm, wps, xls, xlsx, xlsm, xlsb, xlk, ppt, pptx, pptm, mdb, accdb, pst, dwg, xf, dxg, wpd, rtf, wb2, mdf, dbf, psd, pdd, pdf, eps, ai, indd, cdr, jpg, jpe, dng, 3fr, arw, srf, sr2, bay, crw, cr2, dcr, kdc, erf, mef, mrwref, nrw, orf, raf, raw, rwl, rw2, r3d, ptx, pef, srw, x3f, der, cer, crt, pem, pfx, p12, p7b, p7c, c, cpp, txt, jpeg, png, gif, mp3, html, css, js, sql, mp4, flv, m3u, py, desc, con, htm, bin, wotreplay, unity3d , big, pak, rgss3a, epk , bik , slm , lbf, sav , lng ttarch2 , mpq, re4, apk, bsa , cab, ltx , forge ,asset , litemod, iwi, das , upk, bar, hkx, rofl, DayZProfile, db0, mpqge, vfs0 , mcmeta , m2, lrf , vpp_pc , ff , cfr, snx, lvl , arch00, ntl, fsh, w3x, rim ,psk , tor, vpk , iwd, kf, mlx, fpk , dazip, vtf, 001, esm , blob , dmp, layout, menu, ncf, sid, sis, ztmp, vdf, mcgame, fos, sb, itm , wmo , itm, map, wmo, sb, svg, cas, gho,iso ,rar, syncdb ,mdbackup , hkdb , hplg, hvpl, icxs, itdb, itl, mddata, sidd, sidn, bkf , qic, bkp , bc7 , bc6 ,pkpass, tax, gdb, qdf, t12,t13, ibank, sum, sie, sc2save ,d3dbsp, wmv, avi, wma, m4a, 7z, torrent, csv
AV software cannot decrypt files (Panda Ransomware Decrypt Tool, BitDefender Decrypt, Kaspersky).
Secure file erase (7 passes).
Message is displayed on GUI and inside of .txt files created in all folders. This message is configured on C&C, unique by country.
Compatible with crypters (no EOF).
Empty recycle bin (all drives).”
Unfortunately is even simpler for wannabe cyber criminals to arrange a ransomware campaign, they don’t need specific technical know-how to start developing and spreading their custom malware.
Chrome exploit leaves million Android devices open to attack
14.11.2015
At the MobilePwn2Own, a Chinese expert has demonstrated how to hijack an Android smartphone by exploiting a zero-day flaw in the Chrome browser.
The Chinese expert Guang Gong from Qihoo 360 has demonstrated how to hijack an Android smartphone by exploiting a flaw in the Chrome browser. The researcher demonstrated the hack at the MobilePwn2Own at the PacSec conference in Tokyo, the compromised device was running the latest version of the Android OS and the hacker exploited a JavaScript v8 flaw through the Chrome browser.
Gong hijacked a Google Project Fi Nexus 6 running the Android 6.0 Marshmallow and with all applications up-to-date gaining complete control of the smartphone.
The JavaScript v8 flaw allowed Gong to install an arbitrary application (he installed a BMX Bike game) on the targeted smartphone without requiring any user interaction. The attacker just needs to trick victims into visiting a bogus website he set up to compromise the device.
“PacSec speaker Guang Gong from Qihoo 360 just pwned my Google Project Fi Nexus 6 (which was fresh out of the box and only updated to the latest OS and apps) by having the Chrome browser visit the web server he set up on his laptop. As soon as the phone accessed the website the JavaScript v8 vulnerability in Chrome was used to install an arbitrary application (in this case a BMX Bike game) without any user interaction to demonstrate complete control of the phone. Interestingly, this was a one shot exploit that did everything in one go instead of chaining multiple vulnerabilities.” wrote the PacSec organizer Dragos Ruiu in a post on Google+.
The vulnerability did not reside in the Android OS but affects mobile devices running on the popular OS. Ruiu added that the exploit works also on some other mobile devices because it exploits the flaw in the JavaScript engine in Chrome this mean it could potentially affect all Android versions with the latest version of the Google browser installed.
“Off line we also tested his exploit on some other phones and it looks like it works on many targets – so I guess the three months he put into developing it delivered results. Since we don’t have any lavish prizes for him, I’m bringing him to Canada next year for some skiing/snowboarding at CanSecWest.” said Ruiu.
PWN2OWN Mobile: the information about the vulnerability in JavaScript v8 in latest Chrome is being given to Chrome security engineer here
Hackers Can Remotely Record and Listen Calls from Your Samsung Galaxy Phones
13.11.2015
Hackers Can Remotely Record and Listen Calls from Your Samsung Galaxy Phones
If you own a Samsung Galaxy Phone – S6, S6 Edge or Note 4, in particular – there are chances that a skilled hacker could remotely intercept your voice calls to listen in and even record all your voice conversations.
Two security researchers, Daniel Komaromy of San Francisco and Nico Golde of Berlin, have demonstrated exactly the same during a security conference in Tokyo.
The duo demonstrated a man-in-the-middle (MITM) attack on an out-of-the-box and most updated Samsung handset that allowed them to intercept voice calls by connecting the device to fake cellular base stations.
The issue actually resides in the Samsung's baseband chip, which comes in Samsung handsets, that handles voice calls but is not directly accessible to the end user.
How to Intercept Voice Calls?
The researchers set up a bogus OpenBTS base station that nearby Samsung devices, including the latest Samsung S6 and S6 Edge, think is a legitimate cellular tower.
Once connected to it, the bogus base station remotely tinkers with the phone's baseband processor even without any knowledge of the user.
This gives an attacker ability to intercept, listen, and even record your phone calls. In short, the hack attack is a cellular MITM attack, and users have no idea what's happening
Must Read: Chrome Zero-day Exploit leaves MILLIONS of Android devices vulnerable to Remote Hacking
However, given the requirements to make such an attack possible, an everyday hacker can not be able to execute the hack.
"Our example of modifying the baseband to hijack calls is just an example," Komaromy told the Reg. "The idea with hijacking would be that you can redirect calls to a proxy and that way you can man-in-the-middle the call. So that means the caller sees her original call connected – but it can be recorded in the proxy [which is how] it is like a wiretap implant."
The pair has reported their findings to Samsung and kept the details of the attack out of the reach of the public. Hopefully, the company will address the security hole promptly.
The Website of the Norwich airport hacked, a cue to reflect
13.11.2015
A hacker shut down the website of the Norwich airport in just a few minutes to demonstrate the importance of a proper approach to the cyber security.
A few days ago the website of the Norwich Airport was shut down by a hacker managed, the attack was conducted in a few minutes revealing serious problems of cyber security.
The hacker explained to the BBC that it was too easy to hack the website, he discovered a serious vulnerability by using sqlmap, the popular SQL injection and database takeover tool.
The hacker posted the following Video PoC on YouTtube to demonstrate that could be very easy to hack a vulnerable website just using the online material to identify a target, discover a security flaw and exploit it. In a few minutes the website of the Norwich Airport was shut down by the expert.
“In a world where computers rule nearly every aspect of our lives, privacy and security are now more important than ever before and failure to take basic steps is inexcusable even for the most basic websites,” he said. “With online guides and wiki pages detailing step by step, free and secure patch fixes to most hacks and an entire worldwide compendium of knowledge on every single aspect of the computer sciences this is not acceptable.”
Why did he hack the website?
The hacker explained that he decided to hack the website because a friend belonging the “Muslim Electronic Army” confided that he was “planning on having fun” with the security flaw in the website around Christmas time. During that period, an attack would have major repercussions causing many hardships, “alarm or disruption.”
The hacker raises the question about the security posture of a critical infrastructure such as an airport.
“Do you want to fly from an airport that may not have control of their own computers?” he added.
Sure, you can question me that no critical system has been impacted, but we cannot underestimate that a similar attack could have also serious consequences. Let think to a data breach, stolen data could be used by an attacker to extend the damage to other systems with lateral movement within a targeted network. Another possible attack scenario sees threat actors that use the compromised website to deliver malware to a huge number of visitors that could be a victim of more or less sophisticated fraud scheme.
“Imagine if the ‘official’ airport website is hacked and easily defaced with something designed specifically to cause public concern, or worse—panic. Or what if the site started delivering malware to visitors? Just because the site doesn’t store confidential information, it doesn’t mean its security can be ignored.” observed the WhiteHat Security founder, Jeremiah Grossman.
Chrome Zero-day Exploit leaves MILLIONS of Android devices vulnerable to Remote Hacking
13.11.2015
Hackers have found a new way to hack your Android smartphone and remotely gain total control of it, even if your device is running the most up-to-date version of the Android operating system.
Security researcher Guang Gong recently discovered a critical zero-day exploit in the latest version of Chrome for Android that allows an attacker to gain full administrative access to the victim's phone and works on every version of Android OS.
The exploit leverages a vulnerability in JavaScript v8 engine, which comes pre-installed on almost all (Millions) modern and updated Android phones.
All the attacker needs to do is tricking a victim to visit a website that contains malicious exploit code from Chrome browser.
Once the victim accessed the site, the vulnerability in Chrome is exploited to install any malware application without user interaction, allowing hackers to gain remotely full control of the victim’s phone.
Also Read: This Malware Can Delete and Replace Your Entire Chrome Browser with a lookalike
This Chrome for Android zero-day exploit was practically demonstrated by Gong in a hacking contest MobilePwn2Own during the 2015 PacSec conference in Tokyo.
Complete technical details on the exploit are not available yet, but the researcher has already alerted Google to the bug, and the company is expected to pay out a sizeable bug bounty for the exploit.
Just to be on the safer side, Android users are advised to use alternative browsers until Google patches the vulnerability.
Facebook is testing Self-Destructing Messages for Messenger App
13.11.2015
Facebook is testing a Self-Destructing Messages for its Messenger, at the moment the feature is available for some users in France.
This is the silent war of the social media, now Facebook is planning to offer its users a Snapchat-like feature in its Messenger app, the company is implementing the Self-Destructing Messages.
The new feature will allow Facebook users to send self-destructing messages.
Snapchat is a video messaging application that allows sending videos and messages, dubbed “Snaps,” that recipients can view for a limited time, it has been estimated that in May 2015 the app’s users were sending 2 billion photos and videos per day.
Facebook Self-Destructing messages
Now some Facebook users in France have discovered this new feature in the Messenger app that lets them send messages that Self-Destruct after an hour.
“Facebook is testing a disappearing message option within its Messenger app in France, giving users the option to have their messages self destruct one hour after sending them. The feature will bring ephemeral messaging to Facebook Messenger for the first time, taking a shot at Snapchat, the company’s biggest messaging competitor.” states Buzzfeed.
Users can enable the self-destructing message by tapping the hourglass icon on the top-right corner of the Messenger conversation. Enabling this mode Facebook sets the messages to self-destruct after an hour. To restore Facebook Messenger normal behavior user has to tap again the hourglass icon.
“We’re excited to announce the latest in an engaging line of optional product features geared towards making Messenger the best way to communicate with the people that matter most.” states Facebook.“Starting today, we’re conducting a small test in France of a feature that allows people to send messages that disappear an hour after they’re sent. Disappearing messages gives people another fun option to choose from when they communicate on Messenger. We look forward to hearing people’s feedback as they give it a try.”
Last year, Facebook has tested a similar self-destructing message feature, Slingshot, but without success.
At the time I’m writing, the feature is only available to a limited number of French users.
FAKBEN Ransomware-as-a-service emerges from the underground
13.11.2015
FAKBEN is offering a professional Ransomware-as-a-service that relies on a new CryptoLocker ransomware which can be downloaded through the executable file.
Ransomware is probably the most popular category of malicious code in this period, this week we have discussed a malicious code that infected the UK Parliament, an off-line ransomware and a Linux.Encoder1 ransomware revealing the decryption key.
News of the day is that a new Ransomware-as-a-service surfaces from the criminal underground, requesting customers 10 percent profit cut.
The FAKBEN Team is offering a professional Ransomware-as-a-service that relies on a new CryptoLocker ransomware which can be downloaded through the executable file. Users can customize their CryptoLocker variant and manage the campaign by using the CryptoLocker service developed by FAKBEN.
The service allows users to send the ransomware to a specific victim to ask for ransom money, the CryptoLocker service exploits the Tor Network to host a Hidden Service (https://24fkxhnr3cdtvwmy.onion/).
Customers can choose the total amount of victim to pay and the BTC wallet of destination.
“A new service launched this week is offering a new Ransomware product under the name CryptoLocker to anyone willing to pay ten percent of the collected ransom. In addition to the core Ransomware product, the ultimate goal of the business owner is to implement additional functions to the malware including linking it to recently produced exploits.” states a post published by Salted Hash. “Called CryptoLocker Service, the new venture launched this week on a standalone Darknet website. The new venture is being run by a person using the handle Fakben.”
Customers of the FAKBEN ransomware-as-a-service have to US$50 to download the CryptoLocker executable file, when one of the victims pay the ransom, the VXers keep 10 percent of the sum.
“You can download CryptoLocker executable file for $50 . When you have done the payment you will immediately be enabled to the building source of the ransomware so you can specify the amount of money you want to receive and the address destination for BTC. When crytpolocker file is executed to the victim’s machine it crypts all files. ” states FAKBEN.
“Then an automatic window is opened and is asked to the victim to pay in order to get the key for the decryption of the files. When the person pays for files decryption is important to be loyal and give him/her the key for the decryption. When money is payed we will take 10% for the service and then the other amount will be sent to the address you specified before.”
FAKBEN ransomware-as-a-service included a user-friendly interface that will show the number of infected machines and ransoms paid. This specific Ransomware-as-a-service surfaces is still not active, it will be launched in the coming days.
FAKBEN explained that the code used by the platform is completely different from the one of the original Cryptolocker, the malware actually only runs on Windows machines but there are plans to make it multiplatform.
Fakben explained that the ransomware cold be customized by adding a number of exploits targeting vulnerabilities in products such as Adobe and Java.
“Those additional services are not part of the core product. If they’re used, the customer would still pay the opening $50 USD fee, plus the exploit cost and development cost, as well as the ten percent commission on each ransom paid.” states Salted Hash.

Ransomware-as-a-service is not a novelty in the criminal ecosystem, recently crooks launched a similar service, the Tox ransomware-as-a-service, that anyway had no success and its creators decided to offer it for sale in the underground.
How to Build a Successful Incident Response Plan
13.11.2015
The fight to protect your company’s data isn’t for the faint of heart.
As an embattled IT warrior, with more systems, apps, and users to support than ever before, keeping everything up and running is a battle in itself.
When it comes to preventing the worst-case scenario from happening, you need all the help you can get, despite your super-hero status.
According to SANS, there are 6 key phases of an incident response plan.
Preparation - Preparing users and IT to handle potential incidents in case they happen
Identification - Figuring out what we mean by a “security incident” (which events can we ignore vs. which we must act on right now?)
Containment - Isolating affected systems to prevent further damage
Eradication - Finding and eliminating the root cause (removing affected systems from production)
Recovery - Permitting affected systems back into the production environment (and watching them closely)
Lessons Learned - Writing everything down and reviewing and analyzing with all team members so you can improve future incident response efforts
Here are three examples from the front lines of incident response that can help you at each phase as you build out your plan.
On Defining Success Incident Response Success
There are many levels of success in defensive work… the common wisdom is that the attacker only has to be right once, but the defender has to be right every time, but that’s not always true.
Attacks are not all-or-nothing affairs - they happen over time, with multiple stages before final success.
To remain undetected against an attentive defender, it is the attacker who must make every move correctly; if an astute defender detects them even once, they have the possibility to locate and stop the whole attack.
You aren't going to immediately detect everything that happens during an attack - but as long as you detect (and correctly identify) enough of an attack to stop it in its tracks, that’s success.
Don’t Panic. Stay Focused.
Execution is key - the range of ways to attack a target can seem limitless - expecting to be an expert on all of them is pointlessly unrealistic.
The most important part of incident response is to handle every situation in a way that limits damage, and reduces recovery time and costs.
At the end of the day, that’s how you’ll be measured on a job well done… not that you’ve covered every angle of every potential vulnerability.
Start with Simple Steps. Attackers are Lazy.
Attackers have technical and economic imperatives to use the minimum amount of effort and resources to breach their targets - the more you remove the low-hanging fruit on your network, the more you raise the actual level of work an attacker has to expend to successfully infiltrate it.
AlienVault has recently created a 5 chapter eBook titled the Insider’s Guide to Incident Response that goes further into fundamental strategies that can help you create an efficient and effective incident response plan.
The eBook covers:
Arming & Aiming Your Incident Response Team
Incident Response Process and Procedures
Types of Security Incidents
Incident Response Tools
Incident Response Training
You can download the entire eBook at AlienVault’s website here.
Learn more about AlienVault USM:
Download a free 30-day trial
Watch a demo on-demand
Play with USM in our product sandbox (no download required)
Facebook will Let You Send Self-Destructing Messages with Messenger App
13.11.2015
Facebook is planning to offer you the popular Snapchat feature in its Messenger app – 'Self-Destructing' Messages.
Yes, Facebook is testing a new feature within its Messenger app that will allow its users to send self-destructing messages.
Some Facebook users in France have spotted this new feature in the Messenger app that lets them send messages that only last for an hour.
How to Turn ON the Feature?
Users can turn on the self-destructing message feature within Messenger through an hourglass icon on the top-right corner of the conversation. The icon, when tapped, sets the messages to self-destruct after an hour of sending it.
Tapping the hourglass icon again will turn off the feature, with everything going back to normal.
Here's what Facebook says about the feature:
"We're excited to announce the latest in an engaging line of optional product features geared towards making Messenger the best way to communicate with the people that matter most."
"Starting today, we're conducting a small test in France of a feature that allows people to send messages that disappear an hour after they're sent. Disappearing messages gives people another fun option to choose from when they communicate on Messenger. We look forward to hearing people's feedback as they give it a try."
Snapchat has been offering similar feature since 2011 that allows its users to send images that self-destruct itself.
This is not the very first time Facebook has experimented with the self-destructing message feature. Last year, the social network giant tested a similar feature with Slingshot, a standalone app that allows users to send self-destructing messages, but it didn’t work.
Hopefully, by integrating self-destructing messages in its Messenger app with 700 Million users already, the company gets success this time.
So far the feature is only available to some users in France, but Facebook may roll out the feature outside of France if it's successful.
What do you think of this new feature? Hit the comments below.
Cherry Picker, a PoS Malware even more threatening
13.11.2015
Researchers at Trustwave have published the analysis of the Cherry Picker threat, a point-of-sale (PoS) malware that went undetected over the years.
A point-of-sale (PoS) malware that went largely undetected for the past several years has been analyzed by researchers at Trustwave.
Security experts at Trustwave have analyzed an insidious point-of-sale (PoS) malware dubbed Cherry Picker that threat has been around since at least 2011. The threat implements sophisticated evasion techniques that allowed it to remain under the radar across the years.
Cherry Picker Pos malware was detected for the first time in 2011 by experts at Trustwave, the researchers analyzed several samples and discovered that they were designed to inject processes managing cardholder data. One of the pieces of code analyzed by Trustwave consisted of two components, a command line interface (sr.exe), and the searcher.dll that is a code which is directly injected into targeted processes bysr.exe.
Cherry Picker Pos malware poseidon
Cherry Picker belongs to the family of the memory scrapers and uses a file infector for persistence.
“Cherry Picker’s use of configuration files, encryption, obfuscation, and command line arguments have allowed the malware to remain under the radar of many security companies and AV’s,” Trustwave researchers said. “The introduction of new way to parse memory and find CHD, a sophisticated file infector, and a targeted cleaner program have allowed this malware family to go largely unnoticed in the security community.”
The threat includes a cleaner module that allows it to remove all traces of the infection from the system.
The latest version of the Cherry Picker PoS malware uses the a set of API called QueryWorkingSet to scrape the memory and gather card data. The card data are then written into a file that is sent to the control servers.
“Once the data is exfiltrated, the cleaning process begins. The malware developers created a targeted cleaner tool designed to restore the infected system to a clean state. The threat relies on the popular remote control software TeamViewer to overwrite and remove files, logs and registry entries.” reported SecurityWeek.
The experts noticed that the presence of Cherry Picker was always accompanied to other threats, such as AutoIt PoS malware, and the Rdasrv that is one of the earliest PoS RAM scrapers.
Trustwave researchers reported spotting three different strains of the Cherry Picker PoS malware, the different versions account for the evolution of the other.
The researchers have noticed an evolution in the mechanism for persistence, earlier versions used a registry entry, in more recent instances, it uses an updated version of sr.exe, srf.exe, which has been used to install the malware and inject a DLL into processes.
The Cherry Picker PoS, different from similar threats focuses only on the process that manage card data, this process is reported in the configuration file. If the malware doesn’t find the process to inject on the machine it exits.
Central Shop, the evolution of credit card black markets
13.11.2015
Central Shop is a web portal dedicated to the sale of stolen credit card data that captures the attention of the experts due to its amazing interface.
The sale of stolen credit card data is one of the most prolific activities in the criminal ecosystem, in many black markets it is quite easy to acquire the precious commodities.
Today I desire to present you the Central Shop website, a portal dedicated to the sale of credit card data that captures the attention of the experts due to its amazing interface.
The first thing that immediately obvious when we access the site is an interactive map that allows visitors to chose the origins of stolen data they are searching for.
The possibility to choose the country for the stolen card data is very important for cyber criminals, by acquiring cards related to a specific region and operating the cash out activities in the same area could allow them to circumvent some of the controls implemented by identifying the ongoing fraudulent activities.
The same feature has been implemented by other actors in the underground, the popular expert Brian Krebs a couple of years ago reported the commercialization of the card information on the location of stores and point of sales where cards were used.
The financial security experts consider the information very precious for the arrangement of scams, the knowledge of the places where the cards were used allows the attackers to choose the points where to use the cards to reduce the risk of detection for the ongoing scam.
Location information included in the stolen card data allows buyers to use cloned versions of cards issued to people in their immediate vicinity.
“Later, I learned from a fraud expert that this feature is included because it allows customers of the shop to buy cards issued to cardholders that live nearby. This lets crooks who want to use the cards for in-store fraud avoid any knee-jerk fraud defenses in which a financial institution might block transactions that occur outside the legitimate cardholder’s immediate geographic region.” explained Brian Krebs.
The same feature was also implemented by operators of the AlphaBay black market, the recently announced a credit card “autoshop.”
By looking in the map it is possible to note that only a small number of countries are not covered, including Russia, Central Asia and Central and East Africa.

The site is available in several languages, such as Russian, English, Spanish and Chinese.
Researchers at Motherboard have tested the search function discovering that most of the cards come from the United States (nearly 50,000 cards).
Top 10 countries include also the United Kingdom (48,424 cards), Canada (34,048 cards), and Brazil (22,370 cards).

The domain was registered in June, but it’s not clear when operators behind Central Shop website started their activities.
At the time I’m writing it is no possible to register with the website …. stay tuned
FBI reportedly Paid $1 Million to University Researchers for UnMasking Tor Users
12.11.2015
The non-profit Tor Project has accused the FBI of paying the security researchers of Carnegie Mellon University (CMU) at least $1 Million to disclose the technique they had discovered that could help them…
…Unmask Tor users as well as Reveal their IP addresses as part of a criminal investigation.
As evidence, the Tor Project points to the cyber attack that it discovered last year in July.
The team discovered more than hundred new Tor relays that modified Tor protocol headers to track people who were looking for Hidden Services – web servers hosted on Tor that offers more privacy.
The Evidence
The unknown attackers used a combination of nodes and exit relays, along with some vulnerabilities in the Tor network protocol that let them uncovered users' real IP addresses.
The attack reportedly began in February 2014 and ran until July 2014, when the Tor Project discovered the vulnerability. Within few days, the team updated its software and rolled out new versions of code to block similar attacks in the future.
But who was behind this serious ethical breach was a mystery until the talk from Carnegie Mellon University's Michael McCord and Alexander Volynkin on de-anonymizing Tor users was cancelled at last year’s Black Hat hacking conference with no explanation.
UnMasking Tor Using Just $3,000 of Hardware
The Carnegie Mellon talk detailed a new way to "de-anonymize hundreds of thousands of Tor [users] and thousands of Hidden Services [underground sites] within a couple of months" using just $3,000 of hardware.
The researchers were going to prove their technique with examples of their own workaround identifying "suspected child pornographers and drug dealers."
However, after the ongoing attack on Tor network was discovered in July last year, the talk was abruptly canceled and suspicions were aroused that their techniques were used in the attacks discovered by the Tor Project.
The Tor Project also says the researchers stopped answering their emails, which made them more convinced of who was behind the attack – Carnegie Mellon's Computer Emergency Response Team (CERT).
"Such action is a violation of our trust and basic guidelines for ethical research. We strongly support independent research on our software and network, but this attack crosses the crucial line between research and endangering innocent users," The Tor Project Director Roger Dingledine wrote in a blog post published Wednesday.
However, the team is more confident that the Federal Bureau of Investigation (FBI) used the researchers of Carnegie Mellon University to circumvent federal hacking laws.
The FBI Paid $1 MILLLLLION to Unmask Tor Users
hack-tor-users
This week, Motherboard reviewed a court filing in the case of Brian Richard Farrell, an alleged Silk Road 2 lieutenant who was arrested in January 2014, that proved the FBI had indeed recruited a "university-based research institute" that was running systems on the Tor network to uncover the identity of Farrell.
"Apparently these researchers were paid by the FBI to attack hidden services users in a broad sweep, and then sift through their data to find people whom they could accuse of crimes," Dingledine wrote. "We have been told that the payment to CMU was at least $1 million."
Neither the FBI nor the Carnegie Mellon officials immediately responded to the Tor Project’s claims. If true, this incident would really make us think that…
Are these research by computer security researchers meant to help "identify vulnerabilities in the software" Or "endanger innocent people?"
What do you think? Let us know by hitting the comments below.
Did FBI pay the Carnegie Mellon to hack Tor?
12.11.2015
The Director of the Tor Project Roger Dingledine has accused the FBI of commissioning to the Carnegie Mellon boffins a study on methods to de-anonymize Tor users.
The experts at the Tor Project have collected more information about the attack launched last year by Carnegie Mellon researchers on the popular anonymizing system.
The Director of the Tor Project Roger Dingledine has accused the FBI of commissioning to the Carnegie Mellon boffins a study on methods to de-anonymize Tor users. The FBI has paid at least $1 million track Tor users and to reveal their IP addresses as part of a large criminal investigation.
“Apparently these researchers were paid by the FBI to attack hidden services users in a broad sweep, and then sift through their data to find people whom they could accuse of crimes. We publicized the attack last year, along with the steps we took to slow down or stop such an attack in the future:
https://blog.torproject.org/blog/tor-security-advisory-relay-early-traffic-confirmation-attack/
Here is the link to their (since withdrawn) submission to the Black Hat conference:
https://web.archive.org/web/20140705114447/http://blackhat.com/us-14/briefings.html#you-dont-have-to-be-the-nsa-to-break-tor-deanonymizing-users-on-a-budget
along with Ed Felten’s analysis at the time:
https://freedom-to-tinker.com/blog/felten/why-were-cert-researchers-attacking-tor/
We have been told that the payment to CMU was at least $1 million.” reads a blog post published by the Tor Project.
In 2014, researchers from Carnegie Mellon University’s computer emergency response team (Cert), Alexander Volynkin and Michael McCord, announced that they were able to de-anonymise Tor users and planned to reveal their discovery during the next Black Hat Conference in August.
A few weeks later the organization of the BlackHat had been contacted by the university’s lawyers which informed it that the researchers will not participate in the event.
“Unfortunately, Mr Volynkin will not be able to speak at the conference since the materials that he would be speaking about have not yet [been] approved by Carnegie Mellon University/Software Engineering Institute for public release,” states the message posted on the official website of the event.
The experts at the Tor Project are accusing the FBI of an attack on a large scale, the researchers confirmed that the offensive launched by the experts at the Carnegie Mellow University was not narrowly tailored to target specific individuals charged of criminal activity.
The attack represented a clear violation of trust and basic guidelines for ethical research.
“We strongly support independent research on our software and network, but this attack crosses the crucial line between research and endangering innocent users.” continues the post.
Neither the FBI not Carnegie Mellon representatives commented the accusation, Ed Desautels, a spokesman for Carnegie Mellon’s Software Engineering Institute only told Wired that he was not aware of any research activity commissioned to his institute.
“I’d like to see the substantiation for their claim,” said Ed Desautels. “I’m not aware of any payment.”
The evidence of the collaborations between the FBI and the Carnegie Mellon University has emerged also in a stand trial in federal court in Seattle later this month. The court was discussing the case of Brian Farrell, an alleged Silk Road 2 lieutenant, the law enforcement discovered the IP addresses belong to the suspect. A new filing in Farrell’s case states that a “university-based research institute” supported the investigation and helped the feds to de-anonymize Farrell.

According to a Homeland Security search warrant, between January 2014 and July 2014 a “source of information” provided law enforcement “with particular IP addresses” that had accessed the vendor side of Silk Road 2.
In July, the researchers at the Tor Project discovered a sustained attack against the Tor Network based on the technique described by the team of Carnegie Mellon University researchers.
“We think it’s unlikely they could have gotten a valid warrant for CMU’s attack as conducted, since it was not narrowly tailored to target criminals or criminal activity, but instead appears to have indiscriminately targeted many users at once. Such action is a violation of our trust and basic guidelines for ethical research. We strongly support independent research on our software and network, but this attack crosses the crucial line between research and endangering innocent users. This attack also sets a troubling precedent: Civil liberties are under attack if law enforcement believes it can circumvent the rules of evidence by outsourcing police work to universities. If academia uses “research” as a stalking horse for privacy invasion, the entire enterprise of security research will fall into disrepute. Legitimate privacy researchers study many online systems, including social networks — If this kind of FBI attack by university proxy is accepted, no one will have meaningful 4th Amendment protections online and everyone is at risk.”continues the post.
Snooping Samsung S6 calls with bogus base stations
12.11.2015
A duo of security researchers, Daniel Komaromy of San Francisco and Nico Golde of Berlin, demonstrated how to intercept calls using bogus base stations.
PacSec Modern Samsung devices, including the last generation Samsung S6, S6 Edge and Note 4, are vulnerable to phone eavesdropping. A duo of experts, Daniel Komaromy of San Francisco and Nico Golde of Berlin, demonstrated that is possible to intercept calls using malicious base stations.
The duo demonstrated the attacks on Samsung’s ‘Shannon’ line of baseband chips at the Mobile Pwn2Own competition at PacSec held in Toyko. Obviously the researchers haven’t publicly disclosed the details of their attack, they reported it to Samsung instead.
base stations MITM hack Samsung S6
Nico Golde and Daniel Komaromy at Pwn2Own today. (Drago Ruiu)
The experts targeted Samsung devices, including the Samsung S6, with a man-in-the-middle attack relying on an OpenBTS base station, tricking the handsets and forcing it to connect to the bogus station. Once connected to the bogus base station, the handset receives the baseband processor firmware, the module which is responsible handling voice calls.
“Our example of modifying the baseband to hijack calls is just an example,” Komaromy told Vulture South. “The idea with hijacking would be that you can redirect calls to a proxy (like a SIP proxy) and that way you can man-in-the-middle the call.” “So that means the caller sees her original call connected – but it can be recorded in the proxy [which is how] it’s like a wiretap implant.”
The attack works on Samsung S6 Edge running up updated software.
“I turned it on next to their radio and then dialled myself,” said PacSec organiser Dragos Ruiu. “And instead of ringing on my phone it rang on theirs.”
Android Tablets with Pre-loaded Cloudsota malware sold on Amazon
12.11.2015
Experts at Cheetah Mobile are warning about Android Tablet pre-loaded with Cloudsota Trojan sold on Amazon and other online stores.
Once again electronics equipment from China was offered for sale with pre-installed Trojan. This time, several models of Android tablets sold on Amazon and other online stores are sold with pre-loaded the Cloudsota malware.
Cheetah Mobile has identified more than 30 Android tablet brands pre-loaded with the Cloudsota malware, the majority of them are generic brand tablets equipped with Allwinner chips.
“Recently, researchers from the Cheetah Mobile Security Lab have found a dangerous Trojan, dubbed Cloudsota, pre-installed on certain Android tablets. Tablets infected with this Trojan are still on the shelves of Amazon, ready to be shipped to customers around the world.” states the post published by Cheetah Mobile.
The list of infected devices includes JYJ 7, JEJA 7 Zoll, FUSION5, Alldaymall Tablet, Yuntab SZ Wave, and Tagital. All the infected Android tablets are manufafured by Chinese companies.
The experts at Cheetah Mobile noticed several online reviews from customers who have purchased Android tablets infected with the malware.

It seems that the Cloudsota Trojan was deployed on several Android Tablet for many months, hackers used it to conduct several illegal activities, including install adware and hijack search results.
The researchers highlighted that the malware is able to restore itself after a reboot if the user attempts to remove it, this is possible because it runs with root permissions.
According to data collected by security products installed by the Cheetah Mobile, more than 17,000 infected tablets have been purchased in more than 150 countries.
The highest number of infections was observed in Mexico, the United States and Turkey. Unfortunately, it is impossible to have a reliable estimation of the number of infected devices because there are many Android Tablets that comes without Cheetah Mobile security products.
Tablets infected with Cloudsota have been traced to over 150 countries, with the highest number of infections in Mexico, the United States and Turkey.
The worst aspect of the story is that despite Cheetah Mobile has reported the issue to the affected manufacturers, none of them responded.
The experts at Cheetah Mobile who analyzed the malware code and the C&C servers suspect that the threat actors behind the Cloudsota Trojan are from China.
Mobile devices shipped with pre-loaded malware are not a novelty, in September experts from G Data revealed that malware had been found on over two dozen smartphone models from China.
Ransomware infected the UK Parliament’s computer networks
11.11.2015
A ransomware infected several PC at the UK Parliament, for the first time a threat hit the internal computer network, the Parliamentary Digital Service.
Ransomware is once again in the headlines, this time the attention of the media was caught due to the nature of the victim, the UK Parliament. Cyber criminals have infected the computers at the UK parliament’s network and demand ransom money from an MP.
In the first successful cyber-attack, the attackers infected a number of computers and raked sensitive data relating to Labour Party’s Shadow Digital Minister Chi Onwurah and her employees.
The IT staff detected the ransomware in May when the threat locked several files stored in a shared drive.
UK Government
The incident appeared serious due to a large number of users accessing the drive. Nearly 8,500 people in the UK Parliament were exposed to the threat, including MPs, lords and the internal employees.
The RT.com reported that ransomware rapidly spread within the UK Parliament’s computer network, but it was halted before encrypting highly confidential files.
“The hackers compromised several computer systems that held confidential documents relating to parliamentary work by Chi Onwurah, the shadow digital minister, and files containing information about her employees.The attack, which occurred in May, is the first report of a successful hack against the parliamentary network. It comes amid heightened fears that hackers are winning a cyber-arms race against companies and public bodies” reported The Times.
You can imagine the surprise when the MP for Newcastle-upon-Tyne Central was requested to pay a ransom to recover encrypted files.
Onwurah reported the incident to the IT staff which seized all of her computers, disconnected the machine from the internal network and wiped and replaced the hard disks.
“It’s important that everyone realizes how susceptible we all are to these attacks,” Onwurah told The Times newspaper. “There are reports that foreign intelligence agencies have targeted MPs’ computers, so the time has come to find out how well we are being protected, especially now we know what cyber-attackers can do,” “A lot of what I deal with is very confidential to the person concerned. They should expect a high level of confidentiality and a high level of security.”
Onwurah is determined to learn more about malware and risks of exposure to cyber-attacks on MPs.
Microsoft Security Updates November 2015
11.11.2015
Microsoft posted four critical bulletins today, along with another eight rated Important and lesser. Microsoft’s summary is at the Technet site. All in all, the software maker is patching a large number of vulnerabilities this month, with 37 CVE listed vulnerabilities being fixed with the four critical Bulletins alone. On the bright side, Microsoft claims that none of these exploits are being publicly exploited at the time of notification.
Software affected with Bulletins rated critical are listed here (MS15-112, MS15-113, MS15-114, MS15-115):
Web browsers Microsoft Edge and Internet Explorer
Windows Journal
Windows’ font handing code
Software affected with Bulletins rated important are listed here (MS15-116, MS15-117, MS15-118, MS15-119, MS15-120, MS15-121, MS15-122, MS15-123):
Microsoft Office
Windows NDIS, IPSEC, Schannel, and winsock (network software)
Microsoft .NET Framework
Kerberos
Services on Sharepoint and Office Web Apps
Skype for Business and Microsoft Lync
Of the Bulletins rated “Important”, 16 CVE listed vulnerabilities were being fixed.
For you travelers aware of your own operational security and shunners of pgp, it’s interesting that Bulletin MS15-122 provides fixes against BitLocker-encrypted drive attacks.
According to Microsoft, “Kerberos fails to check the password change of a user signing into a workstation. An attacker could bypass Kerberos authentication on a target machine and decrypt drives protected by BitLocker.
An attacker who has physical access to a target machine could bypass Kerberos authentication by connecting a workstation to a malicious Kerberos Key Distribution Center (KDC).
The following mitigating factors may be helpful in your situation:
This bypass can be exploited only if the target system has BitLocker enabled without a PIN or USB key.
A domain user must be logged on to the target machine for the attack to succeed.”
Its reporter, Ian Haken, will be presenting the attack in a couple of days at BlackHat EU in Amsterdam. Perhaps this is another indication that hardware assisted drive encryption is the way to go.
Significant updates today also include Google announcing their deprecation of support for the Chrome browser on Windows XP and Windows Vista, along with Mac OS X 10.6, 10.7, and 10.8. While some organizations in the ICS or health care space may want to continue running their investment into these systems on their plant floors or facilities, this deprecation is another reason to upgrade those systems.
What You Should Know about Triangulation Fraud and eBay
11.11.2015
The increasing phenomenon of triangulation fraud on eBay has led to a published analysis on behalf of the company, as to how buyers should get informed and what they should pay attention to.
Over the past few months, a new phenomenon has risen and its proportions have been growing exponentially. It seems that, even if you have ordered something on eBay from a legitimate seller, you can never be sure of having avoided fraud altogether. To be more specific, with the help of the triangulation fraud, somebody might be taking advantage of you and your desire to purchase something via this platform.
If you are not familiar with the exact process that takes place in the triangulation fraud, think of it like that:
You, as a carefree customer, order something and pay for it to be shipped to you
The seller uses stolen credit card data, in order to purchase what you have been searching for in the first place
He sends it to you, after having bought it from a legitimate e-Commerce site
You are happy, since you’ve got what you have ordered
The e-Commerce site is happy, because they have sold their goods
The seller is happy, as they have scammed everyone
The only one who’s left unhappy is the person, whose credit card data has been stolen
So, you get the picture! This is why most of the times there is no dispute filed as to any parties that are left discontent – in fact, they aren’t!
Elaborating more on that, eBay has published an analysis on triangulation fraud and the extent that it can take. Indeed, there may be more than a few scammers. In other words, the seller might employ someone to do all the hard work for them and ship the goods, so as not to raise any suspicions.
According to Ebay, the seller is normally an individual engaged in a “work at home” job, in some cases he doesn’t realize he is involved in a fraud scheme, and some do have a respectable selling history.
“Postings for seller positions are easily found on the web, and typically advertise the seller keeps a significant percentage of the sale − typically 30%.” states the analysis.

According to Ryan Moore, senior manager of global corporate affairs for eBay, working together is the key preventing such a mess.
“We believe collaboration and cooperation is the best way to combat fraud and organized retail crime of this nature, working in partnership with retailers and law enforcement”, he has stated. As he has added, this type of online crime “relies heavily on the tools that merchants use themselves, which includes understanding their customers and implementing the correct credit card authorization protocols”. explained Moore.
It is important to highlight just how crucial it can be for potential buyers to evaluate the offers on eBay and other platforms, prior to completing their order. If something sounds too good to be true moneywise, then it most probably is!
88 percent of company networks vulnerable to privileged account hacks
11.11.2015
A research published by CyberArk Labs focuses on targeted attacks against organizational networks, analyzing hackers’ methods, tools and techniques.
Bad news for network administrators, according to the security company CyberArk, 88 percent of networks are susceptible to privileged account hacks.
The report published by CyberArk entitled “Analyzing Real-World Exposure to Windows Credential Theft Attacks” reveals that corporate Windows networks are most of the times poorly configured and expose credentials for privileged user accounts. The analysis analyzes various credential abuse methods, including Kerberos attacks, Overpass-the-Hash and Pass-the-Hash attacks, providing suggestions for their mitigation.
The experts have searched for vulnerabilities and configuration issued that exposed credentials to hackers. They focused the investigation on the theft attacks, events that cause the exposure of the user’s credentials that could be used to log in impersonating the victim to exfiltrate data from the targeted machine.
The researchers at CyberArk assessed 51 corporate networks relying on Windows systems and discovered in over 88% of the cases “highly threatening machines” in the network’s architecture. The experts highlighted that 40 percent of Windows hosts could lead to a complete compromise if they were hacked.
“Every Windows network, no matter how large or small, could potentially be compromised by attackers through theft or privileged credentials,” states the report. 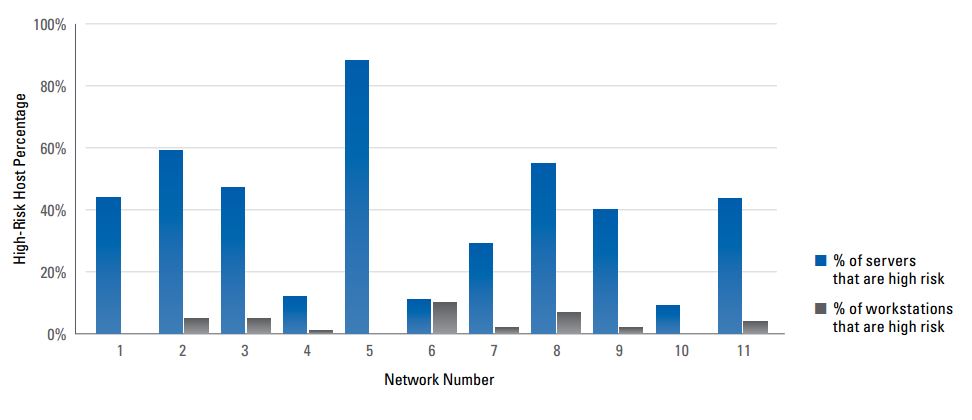
The worst scenario occurs when the attacker access credentials for privileged accounts, let us think to network administrators, and use them to lateral movement within the targeted organization.
Each machine is a mine of information for attackers that could gather them to penetrate more deeply targeted networks. Only 12 percent of the networks analyzed by the experts were classified at a“low exposure,” which are networks where less than 10 percent of the hosts had a high risk of being compromised.
Similar techniques were adopted by threat actors in the wild, such as the notorious cases of the giants of the retail industry, Target and Home Depot.
The report also mentions the abuse of privileged service accounts ordinary used to execute a number of functions implemented by the operating system.
“We’ve seen similar credential theft methods as the basis for major attacks across a number of organization,” said Andrey Dulkin, director of cyber innovation at CyberArk Labs. “Identifying these machines and securing the associated privileged credentials against theft and exploitation is a critical step in securing against advanced cyber attacks.”
Three men charged for the attack on the JPMorgan Chase
11.11.2015
U.S. Authorities have charged other three men in huge cyber fraud targeting JPMorgan, and at least another nine financial institutions.
The US authorities have charged three individuals over the hack of the JPMorgan Chase and other financial institutions. The data breach suffered by the JPMorgan Chase is considered the largest ever hacking case in financial history, data related nearly 76 million households and seven million small business accounts were exposed in the hack.
According to Bloomberg, the cyber thieves have stolen details of “over 100 Million customers,” meanwhile the spokeswoman for JPMorgan Chase Patricia Wexler confirmed the number of affected customers was around 80 Million.
“We appreciate the strong partnership with law enforcement in bringing the criminals to justice,” Wexler said in an email statement. “As we did here, we continue to cooperate with law enforcement in fighting cybercrime.” explained Wexler.
Now the US Court of the Southern District of New York has charged three men, Gery Shalon, Ziv Orenstein, and Joshua Samuel Aaron, accusing them of hacking into a number of financial institutions, including JPMorgan Chase.
The three hackers are added to another alleged criminal, Anthony Murgio, which was subjected to a separate indictment. Murgio was previously arrested for a cyber attack on JPMorgan as well as for operating an illegal Bitcoin exchange.
The Israeli Shalon, 31, and Orenstein, 40 were arrested in July, meanwhile American Murgio was arrested in the same period. Aaron, 31, is a U.S. citizen who has lived in Moscow and Tel Aviv.
“The new charges portray Shalon as the ringleader, having orchestrated hackings since 2012 against nine companies in which personal information for more than 100 million customers was stolen. He and Orenstein were accused of having since 2007 run at least 12 illegal Internet casinos, generating millions of dollars of profit each month.” states the Reuters.
“They allegedly also ran IDPay and Todur, through which they collected $18 million of fees to process hundreds of millions of dollars of transactions for criminals. According to the indictment, the illegal proceeds included tens of millions of dollars from manipulating the prices of stocks sold to customers whose information had been stolen.”
jpmorgan
The three alleged cyber criminals targeted at least nine financial organizations between 2012 and mid-2015, they were charged with 23 counts, including hacking, identity theft, securities fraud, and money laundering, among others.
Authorities said Shalon and Aaron exploited server located in Egypt to launch the attacks. The machines were rented under an alias that Shalon in all the hacking attacks.
E*Trade Financial Corp, TD Ameritrade Holding Corp and News Corp’s Dow Jones unit were among the victims of the hackers, a long list that includes also the Fidelity Investments and Scotttrade Inc.
The U.S. Attorney Preet Bharara explained at a press conference that “By any measure, the data breaches at these firms were breathtaking in scope and in size.”
GCHQ and NCA hunting criminals in the dark web
11.11.2015
The GCHQ and NCA join forces to fight online criminals in the Dark Web and formed a new unit called the Joint Operations Cell (JOC).
The dark web is a privileged environment for cyber criminals, the marketplaces hosted in this hidden part of the web are the right places where to buy and sell any kind of illegal service and product.
In the dark markets, it is possible to to find drugs, weapons, stolen data, and unfortunately also child pornography. British law enforcement and intelligence agencies, including the GCHQ and the National Crime Agency (NCA), have created a new unit, the JOC, that will specifically address the cyber crime.
The newborn unit will be initially focused on tackling online child sexual exploitation
“An NCA and GCHQ co-located Joint Operations Cell (JOC) opens officially today. The unit brings together officers from the two agencies to focus initially on tackling online child sexual exploitation.” states the press release published by the NSA.
In fact, the British Government is always in the forefront in the fight to online child sexual exploitation, in December 2014 the UK Prime Minister David Cameron announced the plan for the creation of a unit of cyber experts that will be involved in the investigation of crimes exploiting the dark web.
Prime Minister David Cameron revealed that national intelligence agencies will join the efforts to track and arrest online abusers and pedophiles. The British Prime Minister anticipated that the British Intelligence will have greater powers for online monitoring of suspects.
British authorities warned that up to 1,300 children are exposed to online abuse from pedophiles, it is a moral and social obligation to fight this social evil.
Cameron explained the strategy of the British Government at the #WeProtectChildren online global summit in London, announcing the creation of a new unit composed by members from the GCHQ and the National Crime Agency (NCA).
GCHQ against pedophilies Cameron
One of the most difficult goals of law enforcement that operate against online pedophiles, is to track this category of criminals that makes large use of anonymizing networks like Tor.
“The so-called ‘dark-net’ is increasingly used by paedophiles to view sickening images. I want them to hear loud and clear: we are shining a light on the web’s darkest corners; if you are thinking of offending, there will be nowhere for you to hide.” Cameron said.
The JOC will have the ambitious plan to fight any kind of online criminal activity.
“The Joint Operations Cell will increase our ability to identify and stop serious criminals, as well as those involved in child sexual exploitation and abuse online. This is a challenging task as we must detect them while they attempt to hide in the mass of data. We are committed to ensuring no part of the internet, including the dark web, can be used with impunity by criminals to conduct their illegal acts.” explained the GCHQ Director Robert Hannigan.
The GCHQ and the NCA have a long story of collaboration since the creation of the NCA in 2013. The NCA Director General Keith Bristow explained that the Joint Operations Cell wants to be the response to the significant increase in online illegal activities.
“The explosion in online communication channels has brought huge benefits for society. It has also significantly expanded the means by which criminals can share information, plan crimes including the sexual exploitation of children, and target victims. The JOC is a genuinely innovative development, using the best of our respective agencies’ skills to tackle the most complex cases and the most dangerous offenders online.” said the NCA Director General Keith Bristow.
I have no doubt, the Joint Operations Cell will give a hard time to criminals.
JPMorgan Hack — Three Men Charged in Biggest Bank Hack in History
10.11.2015
The US government has charged hackers over the largest ever hacking case in financial history.
The US Court of the Southern District of New York has charged three men accused of hacking into many financial institutions, including JPMorgan Chase that, according to the officials, was "the largest theft of user data from a U.S. financial institution in history."
JPMorgan Chase is one of the world's biggest banks that controls total assets worth more than $2.59 Trillion.
The Hackers targeted at least nine financial institutions between 2012 and mid-2015, including JPMorgan Chase, brokerages and a major business news publication, and stolen information of "over 100 Million customers," Bloomberg reported Tuesday.
The three men, including Gery Shalon, Ziv Orenstein, and Joshua Samuel Aaron were charged with 23 counts, including hacking, identity theft, securities fraud, and money laundering, among others.
A separate indictment was also filed against an alleged hacker, Anthony Murgio, who was previously arrested for a cyber attack on JPMorgan as well as for operating an illegal Bitcoin exchange.
The spokeswoman for JPMorgan Chase Patricia Wexler confirmed the bank's 2014 data breach hack that affected around 80 Million households.
"We appreciate the strong partnership with law enforcement in bringing the criminals to justice," Wexler said in an email statement. "As we did here, we continue to cooperate with law enforcement in fighting cybercrime."
U.S. Attorney Preet Bharara in Manhattan will announce the details of the indictments in a press conference that has been scheduled for later today at 1 St. Andrew's Plaza.
Disbanding the ‘Zoo’
10.11.2015
Two approaches to protecting virtualized data centers
Virtualized environments are exceptionally flexible, manageable, fault-tolerant and cost-effective. However, a number of difficulties have to be overcome to protect them from external threats. If this is not done successfully, problems will inevitably arise. This is true of individual virtual machines, as well as the data center as a whole.
Unfortunately, malware infections are a common occurrence in virtualized systems, particularly in VDI environments: customers’ employees do whatever they like on their virtual workstations without worrying about cyber-hygiene, believing that both their own IT department and the service provider will effectively block any malware.
It should be noted that, in most cases, the provider is not allowed access to customer machines and has to demand that customers use their own protection. Many customers, though not all, take a responsible approach and install endpoint protection solutions of their choice on their machines.
Sometimes, however, in spite of the provider’s recurring requests, customers resign themselves to the risk and do absolutely nothing about protection. There is no doubt that the provider will ultimately have to deal with all the problems arising from this approach. As a result, this turns into a major undertaking for the provider, who will have to change its protection strategy completely. (More information about security-related business problems faced by data centers can be found here.)
In virtualized data centers, information is stored and processed on virtual machines and in data storage systems. These are completely different technologies that require different approaches to protection, each having many subtle aspects.
The nuances of protecting virtualized environments
As mentioned above, if the service provider does not provide protection for customers’ virtual machines, customers will do it on their own, each in their own individual way. On the one hand, this is not a bad thing; each customer can choose a security solution that suits their needs. However, in practice, this approach is not only inefficient; the resulting chaotic ‘zoo’ of solutions on customer machines creates numerous problems of its own:
Excessive use of hardware resources. The security system on each machine includes a complete set of components: an antivirus engine, a signature database, a firewall, etc. Each takes up its share of CPU time, RAM and disk space.
‘Storms’. If scanning for malware is performed or antivirus databases are updated on several virtual machines at the same time, this leads to a surge in resource consumption, which can result in degradation of the entire platform’s performance or even in denial of service. Security software can of course be manually configured to avoid storms, but the time required to do this for hundreds of virtual machines will be very significant.
Panic attacks. A security system is often configured to step up protection when malware is detected on a machine. A ‘paranoid’ set of security rules is activated and out-of-schedule scans are launched. This can increase the load on the host machine’s hardware and negatively affect the performance of neighboring virtual machines.
‘Instant-on’ security gap. Virtual machines often remain inactive until they are started up when the need arises. While a machine is inactive, none of the security system components on it are updated and the machine remains vulnerable during the period from startup until an anti-malware solution update is completed.
Incompatibility. Virtual machines are similar to physical computers in many ways, but they are also different in some significant aspects of their operation. For example, they use dynamic hard disks and can migrate from one server to another without shutting down. Standard security systems for physical machines are not designed with virtualized systems in mind. This can lead to delays, faulty operation or even complete inability to operate.
All these issues will ultimately have to be addressed by the service provider – and on a regular basis. There is only one way to avoid this – prevent this ‘zoo’ from being created in the first place by putting customers in a situation where they have to choose between several proven dedicated security solutions for virtualized environments.
With or without an agent?
The key advantage of virtualization security systems like Kaspersky Security for Virtualization lies in the fact that the engine and the anti-malware databases are hosted on a separate virtual machine (Security Virtual Appliance, SVA) which provides protection for all machines running on the hypervisor.
This solution has obvious advantages: hundreds of machines can be protected by just one anti-malware engine running on the SVA, which operates all the time and receives timely updates. This means all machines receive a high level of protection, while the VM scanning schedule is designed to preclude any excess load on the environment.
Virtualization security software can be implemented in two substantially different ways: agent-based (light agent) or agentless. Customers have the freedom to choose the one that best suits their needs, or even combine the two.
The agentless security solution has all of its components running on the SVA, and has a number of serious limitations. It is only designed to operate in environments based on VMware products, and is not capable of working with processes running in virtual machine memories, so it only scans the file system and incoming network traffic. In other words, it can only scan files and block network attacks. In some cases, this is sufficient. An agentless solution also provides almost instant protection of virtual machines immediately after they are launched. No software needs to be installed on the customer’s machines.

Disbanding the 'Zoo': Two Approaches to Protecting Virtualized Data Centers
The agentless approach to securing virtual environments, based on the solution Kaspersky Security for Virtualization | Agentless
The light agent-based security system provides the entire range of security technologies (working with memory processes, application control, web browser protection, etc.) without using up lots of resources, as the scan engine and the databases are hosted on the SVA. Such an approach provides the functionality similar to Endpoint Protection-class solutions, while also being optimized and tested for virtual environments. However, a lightweight agent needs to be installed on each virtual machine so that the security solution has full access to the system. This can be seen as inconvenience, but many virtualization scenarios allow the use VM templates; in this case, the agent can be pre-installed into the template, so every VM spawned from it would have the agent as well, receiving instant protection right after being started.

The light agent-based approach to securing virtual environments, based on the solution Kaspersky Security for Virtualization | Light Agent
The choice between these two types of solutions depends on the accompanying circumstances.
Often the provider cannot guarantee the presence of a security solution at the customer’s facility, which potentially creates a gap in data center security. The customer may also have reasons for not allowing any third-party software to be installed on their machines. In this case, the agentless security solution is the optimal choice.
In other cases, the provider and the customer agree from the outset that a security solution will be installed on the virtual machines from a shortlist of tested and approved solutions. In this case, it is best to use specialized light agent-based security systems for virtual environments. This will provide the maximum level of security with minimum collateral problems.
A special case is that of a virtual desktop infrastructure (VDI) hosted in a data center. When virtual machines are used as workstations, each of them is exposed to a multitude of threats during everyday operations. An employee may pick up a malware program when visiting a dangerous website or receive an email with a malicious attachment, while it is not uncommon for malware to spread from a removable media device that has passed between other users.
When such a broad range of potential infection vectors is present, an agentless solution will be insufficient: with its limited functionality, the risk of infection is much higher. If an infection is detected, it will most probably happen too late to prevent any damage. On the other hand, a light agent-based security system is capable of protecting against a much broader range of threats by checking programs that are launched, preemptively blocking a user’s access to dangerous websites, and controlling the processes running in the system.
A third, more resource-intensive, protection option for virtual machines also exists – a ‘regular’, full-agent endpoint protection-class security product. This is a viable choice if there is no access to the hypervisor (e.g. in public clouds such as Amazon or Azure), or if a more obscure hypervisor is used at the data center that is incompatible with specialized security solutions. And finally, these ‘regular’ security systems are developed for a broader range of operating systems. For instance, they can be used to protect virtual machines running under Mac OS.
It should be noted that a security system that is not designed to work in a virtual environment may not be fully compatible with specific virtual machines and may not work properly or may not work at all. Solving these types of issues can take considerable time.
Taking care of data storages
An infected network data storage puts the entire data center at risk, and if anything requires anti-malware protection, it is data storage systems. If this need is not fulfilled, an epidemic may break out, especially if not all the machines located at the data center are connected to a security solution for virtual environments.
Storage Area Networks (SAN) are very easy to protect – all it takes is a security system on the server. This is no different from protecting any other server; in this case, a server solution is implemented, such as Kaspersky Security for File Servers. Things are different with Network Attached Storage (NAS), which all machines in the network are granted instant access to. In this case, a specialized NAS security solution is required.

Network data storage types
Data stored on NAS needs to be protected before it is available to customer machines, meaning support on the NAS side is required. Luckily, most NAS support a number of special protocols and are able to work with external security solutions.

Diagram showing how a NAS protection solution works
When a customer requests a file from NAS (1), the storage sends it to the security system’s server (2). The server scans the file and reports the result to the storage (3). Depending on the security solution’s verdict, NAS provides the file to the customer or denies access (4). For greater reliability, more than one security server can be present in a network. During normal operation, the data storage itself will balance the load between them.
Conclusion
When it comes to securing virtualized data centers, there is no silver bullet solution, nor can there be one, that would ideally solve all problems. What is possible is to choose the optimum security system based on all the relevant factors.
An agentless solution is best for protecting database servers, intranet web servers and machines that are not allowed to host any software besides a fixed set of applications.
If the customer has a choice of several specialized security solutions pre-approved by the provider, a light agent solution is the best option. This will meet the needs of protecting web servers, virtual workstations, and sensitive data processing servers.
Flexibility is particularly relevant when protecting virtual environments, so Kaspersky Lab provides both solutions – the agentless solution and the light agent solution – under one license. This gives the customer a choice between these two variants, and the capability to combine them when necessary, e.g. in environments with different hypervisors, or to address a variety of tasks more efficiently. More detailed information is available here.
The most important thing is to ensure that protection issues are addressed before any annoying and costly problems arise.
Flaw in Linux.Encoder1 ransomware reveals the decryption key
10.11.2015
Experts at Bitdefender have discovered a flaw in Linux Encryption Ransomware Linux.Encoder1 that exposes the decryption Key used to lock the files.
Last week security experts at Russian antivirus firm Doctor Web reported the discovery of a new Linux ransomware dubbed Linux.Encoder1 that is targeting Linux systems. It has been estimated that tens of users have already fallen victim to this Linux ransomware. The Linux.Encoder1 ransomware encrypts files present on the systems, once a machine is infected it downloads the files containing attackers’ demands and a file containing the path to a public RSA key. The Linux ransomware is launched as a daemon and deletes the original files, subsequently, the RSA key is used to store AES keys used to encrypt files.
“First, Linux.Encoder.1 encrypts all files in home directories and directories related to website administration. Then the Trojan recursively traverses the whole file system starting with the directory from which it is launched; next time, starting with a root directory (“/”). At that, the Trojan encrypts only files with specified extensions and only if a directory name starts with one of the strings indicated by cybercriminals.” states the post published by Dr Web last week.
The Encoder.1 , reportedly distributed via a vulnerability in eBay’s Magento ecommerce platform, demands the payment of one Bitcoin ($380) in exchange for the key needed to recover the files.
Linux.Encoder1 was spread by exploiting a vulnerability in the popular eBay’ Magento e-commerce platform, in order to recover the encrypted files, victims are asked to pay one Bitcoin (roughly $380 at today’s rate), once the ransom is paid the files are decrypted using a private RSA key that retrieves the AES key from encrypted files.
Despite the above algorithms are totally secure and impossible to crack, the researchers at Bitdefender discovered a flaw in the process for the generation of the AES key used by the ransomware.
“We mentioned that the AES key is generated locally on the victim’s computer. We looked into the way the key and initialization vector are generated by reverse-engineering the Linux.Encoder.1 sample in our lab. We realized that, rather than generating secure random keys and [initialization vectors], the sample would derive these two pieces of information from the libc rand() function seeded with the current system timestamp at the moment of encryption.” states the post published by BitDefender.
“This information can be easily retrieved by looking at the file’s timestamp,” Bitdefender said. “This is a huge design flaw that allows retrieval of the AES key without having to decrypt it with the RSA public key sold by the Trojan’s operator(s).”
The flaw allowed the experts at Bitdefender to develop a decryption tool that automatically recovers files encrypted by the Linux.Encoder1. The company also provided a script and the procedure to follow to restore the encrypted files. Given the complexity of the procedure, Bitdefender provides free support to any user in need of assistance.
Linux users are advised never to execute untrusted applications with root privileges, and it is important to perform regular backups that could allow them to recover encrypted file sin case of ransomware infections.
“Never run applications that you don’t completely trust as root user. This is a great security risk that will likely compromise your machine or the integrity of the data on it;
Backup early, backup often. If your computer falls victim to ransomware, it would be better to simply restore the affected files from an earlier backup than to pay the decryption fee. “
Yesterday I wrote about another useful tool released by Bitdefender to vaccine users against the CryptoWall 4.0 threat.
New insight on the Rocket Kitten Iranian hacking crew
10.11.2015
Experts from Check Point firm published a new report on the Rocket Kitten APT that include more insight into the activities of the group.
Do you remember the Rocket Kitten ATP?
The Rocket Kitten group has been suspected to be active since 2011 and have been increasing their activity since 2014. The main targets are based in the Middle East, and it seems that their targets are involved in policy research, diplomacy and international affairs like policy research, diplomacy and international affairs.
Several security firms have analyzed the operations conducted by the Rocket Kitten, experts have used different names to reference the hacking crew. FireEye linked the group to the cyber espionage campaign “Operation Saffron Rose“, the experts at iSIGHT Partners discovered the group was using a network of fake accounts on principal social media to spy on US officials and political staff worldwide, the NEWSCASTER network. Again, the experts from ClearSky uncovered the Thamar Reservoir operation that is targeting entities in the Middle East, meanwhile researchers at Trend Micro in March a new hacking campaign dubbed Operation Woolen GoldFish likely run by a threat actor group Rocket Kitten.
The Rocket Kitten group is very active and despite the numerous investigations of security firms it is continuing to conduct cyber espionage operations by using different tools in their arsenal for each hacking campaign.
The Rocket Kitten hackers are now in the headlines thanks to a new report published by the Check Point security firm. Check Point was investigating a phishing attack against one of its customers when discovered a server used by the Rocket Kitten group.
According to the report “Rocket Kitten: A Campaign with 9 Lives,” the hackers used a common XAMPP web server that was poorly configured, allowing the investigators to gain root access without authentication.
The experts at Check Point discovered that more than 1,800 victims were already successfully targeted by Rocket Kitten, their information was stored in the database present on the server.
The analysis of the logs from the phishing server revealed the most visitors came from Saudi Arabia (18%), the United States (17%), Iran (16%), the Netherlands (8%) and Israel (5%).
“This list was analyzed to confirm a strong alignment with nation-state political interests, with specific victims known as adversarial or of intelligence value to Iran.” states the report.

It is curious to note that nearly 26 percent of visitors provided their credentials.
Each victim was associated with a particular Rocket Kitten operator, in one case a single operator harvested details of nearly 700 victims. Another operator phished 522 users as part of a campaign targeting human rights activists, company executives and ministry officials in Saudi Arabia.
“Looking at user names, we can spot some potentially Persian names or aliases such as merah, kaveh, ahzab or amirhosein. These were potentially the campaign ‘operators’—tasked with social engineering and tailoring a phishing page per target.” states the report.
A third operator collected information belonging to 233 individuals in organizations operating in the defense sector, including in NATO countries, the United Arab Emirates, Afghanistan, Thailand, and Turkey.
The hackers also targeted Iranians living abroad, Israeli nuclear scientists, former military officials, national security and foreign policy researchers and Venezuelan entities.

The analysis of the phishing server allowed the investigators to reveal the identity of the main developer of the hacking crew, an individual using the nickname “Wool3n.H4T.”
“In this case, as in other previously reported cases, it can be assumed that an official body recruited local hackers and diverted them from defacing web sites to targeted espionage at the service of their country. As is often the case with such inexperienced personnel, their limited training reflects in lack of operational security awareness, leaving a myriad of traces to the origin of the attack and their true identities,” Check Point said in its report.
If you want to do deeper on the investigation give a look to the excellent “Rocket Kitten: A Campaign with 9 Lives” report published by Check Point.
200,000 Comcast login credentials available on the Dark Web
10.11.2015
During the weekend, nearly 590,000 Comcast email addresses and passwords were offered for sale on a BlackMarket in the dark web.
It is now the turn of Comcast, over the weekend nearly 590,000 Comcast email addresses and passwords were offered for sale on a BlackMarket in the dark web. As proof of the authenticity of the Comcast data, the seller published a list of 112 accounts requesting 300 USD for 100,000 accounts, the entire list of 590,000 accounts goes for $1,000 USD.
The discovery of the singular sale was made first by an individual owning the Twitter account @flanvel, which promptly contacted Salted Hash to report it the news.
Comcast was in possession of the list and it was checking the leaked data, it seems that of the 590,000 records offered for sale on the black marketplace about 200,000 of them were still active.

Although they represent a minor part of the bulk data sold by crooks, we can not overlook the fact that the credentials offered could be used to take over the Comcast accounts.
According to the Comcast security team, the systems of the company have not been compromised, every user that will report suspicious activity on his account will be contacted singularly to solve the issue.
It is likely that the data still active and valid comes from a collection of data resulting from other data breaches, they are almost certainly recycled.
Online it is quite easy to find collections of data that come from malware-based attacks, data breaches, and phishing attacks. Unfortunately, users have the bad habit of sharing the same login credentials among different services online, when one of them is compromised attackers can access all the other web services.
In the specific case the list of Comcast login credentials was circulating online since last week, it is likely someone decided to offer it for sale.
Summarizing Comcast wasn’t the victim of a data breach, the company has reset nearly 200,000 passwords after customer list was discovered.
1-Click Way to Check If your Android Device is Vulnerable to Hacking
9.11.2015
Vulnerabilities are common these days and when we talk about mobile security, this year has been somewhat of a trouble for Android users. Almost every week we come across a new hack affecting Android devices.
One of the serious vulnerabilities is the Stagefright Security Bug, where all it needed to install malicious code on the Android devices was a simple text message.
Although Google patched these security holes in its latest Android update, manufacturers can take a long time to release their own updates, and it's even possible that older devices may not get the updates at all.
So, even after the release of patches for these critical vulnerabilities, it is difficult to say which Android devices are at risk of what bugs.
There is a one-click solution to this problem. One Android app can help educate you and help you know whether your devices is at risk.
One-Click Solution to Check Your Device for All Critical Bugs
Android Vulnerability Test Suite (VTS), developed by mobile security firm NowSecure, is a free vulnerability scanner that scans your Android device for 22 known device vulnerabilities including Stagefright, potentially alerting you to any of the known issues.
This free, open source Android vulnerability scanner tool is "meant to show the end user the attack surface that a given device is susceptible to."
As NowSecure says on the VTS' Google Play listing, "In implementing these checks we attempt to minimize or eliminate both false positives [as well as] false negatives without negatively affecting system stability."
Note: Your Antivirus product may detect this tool malicious in nature because it contains Stagefright detection code.
As VTS vulnerability scanner is an open-source project from a known and trusted developer, users and security researchers can file bugs or other issues on the GitHub repository.
How to Check your Android Device for All 22 Vulnerabilities?
This free Android vulnerability scanner app is available on Google Play Store, and its code is available on GitHub.
Install VTS for Android and hit the Search button when it appears to launch the Device Vulnerability Scanner.
After about 30 seconds, the Android vulnerability scanner will list all vulnerabilities your devices is vulnerable to.
I tested the app on my fully-patched OnePlus Two smartphone earlier this week and found my device is vulnerable to a few vulnerabilities, including the new variant of the Stagefright bug, Stagefright 2.0.
Cryptowall 4.0 comes from Russia, Bitdefender released a vaccine
9.11.2015
Security experts at Bitdefender speculate that the newborn Cryptowall 4.0 has a Russian origin. The company released a vaccine software.
Security experts at Bitdefender seem to have no doubt, the authors of the last variant of the popular Cryptowall ransomware, Cryptowall 4.0 are Russians. The experts came to this conclusion through evidence collected during their investigations, for example, the servers used for spamming the threat are located in Russia, and the Javascript used as a vector downloads the CriptoWall 4.0 payload from a Russian server.
The malware researchers also confirmed that encryption algorithm used to encrypt the victim’s files is the unbreakable AES 256 and the key is encrypted using RSA 2048.
The Cryptowall 4.0 infections were observed across the world, including in France, Italy, Germany, India, Romania, Spain, US, China, Kenya, South Africa, Kuwait and the Philippines.

As observed for other threats coming from Russia, Russian users seem to not interested by the ransomware because Cryptowall 4.0 doesn’t encrypt the files if it detects that the computer is using the Russian language.
“Cryptowall 4.0 spam servers are located in Russia, according to The Javascript-written malware downloads the CriptoWall component from a Russian server.” states the post published by Bitdefender.
CryptoWall is a profitable instrument in the hands of criminal organizations, the security researchers of the Cyber Threat Alliance have conducted an investigation into the cybercriminal operations leveraging CryptoWall 3.0 ransomware discovering that the criminals behind the dreaded ransomware already made $325 Million.
The victims have two possibilities, pay the ransom hoping to restore the encrypted documents or waiting that AV vendors will integrate the key used to encrypt their documents in their anti-ransomware solution. Unfortunately, this is possible only if security experts seize one of the C&C servers used by crooks and find on these machines the key used to encrypt the victim’s file.
To hamper the diffusion of the Cryptowall 4.0 Bitdefender has developed a software that allows users to immunize their computers and block file encryption process implemented by ransomware, including the Cryptowall 4.0.
Be aware, if the PC is already infected with CryptoWall 4.0, the “vaccine” will not sanitize it.
The tool is not a complete antivirus solution, but it is a supplementary layer of protection that could increase the resilience of the machine to malware based attacks.
The Infernal-Twin tool, easy hacking wireless networks
9.11.2015
The Infernal-Twin is an automated tool designed for penetration testing activities, it has been developed to automate the Evil Twin Attack.
The Infernal-Twin is an automated tool designed for penetration testing activities, it has been developed to assess wireless security by automating the Evil Twin Attack.
“The tool was created to help the auditors and penetration testers to perform wireless security assessment in a quick manner and easing complex attack vectors.” states Khalilov M, the author.
Be aware, as usually happen, penetration testing tool could be misused by hackers to conduct illicit activities, so I decided to present it to spread awareness about this potential weapon in the arsenal of attackers.
Let us start explaining the attack scenario, on the “Evil Twin” attack, the attacker set up a bogus Wi-Fi access point, purporting to provide wireless Internet services, but eavesdropping the user’s traffic.
The bogus Access Point is used to serve to the users in the network faked login pages to steal their Wi-Fi credentials and other sensitive data. The attack scenario could be exploited to run man-in-the-middle attacks or to serve malware to the computers in the targeted network.
First of all you need to install all the components necessary to use the tool, including the Apache module, the mysql database, the Scapy packet manipulation tool for computer networks and the wxtools debugging framework.
Then you have to install the Aircrack-ng utility and get the infernal-twin from the repository.
Aircrack-ng is a network software suite consisting of a detector, packet sniffer, WEP and WPA/WPA2-PSK cracker and analysis tool for 802.11 wireless LANs.
To install the components follow these steps
$ sudo apt-get install apache2
$ sudo apt-get install mysql-server libapache2-mod-auth-mysql php5-mysql
$ sudo apt-get install python-scapy
$ sudo apt-get install python-wxtools
$ sudo apt-get install python-mysqldb
$ sudo apt-get install aircrack-ng
$ git clone https://github.com/entropy1337/infernal-twin.git
$ cd infernal-twin
At this point launch the Infernal-Twin tool with super administrator privileges. Some users experienced problems connecting to the Database, the user @lightos provided the following solution to fix the issue.
Create a new user on the database and use it for launching the tool by following this procedure:
Delete dbconnect .conf file from the Infernal wireless folder
Run the following command from your mysql console.
mysql> use mysql;
mysql> CREATE USER ‘root2’@’localhost’ IDENTIFIED BY ‘enter the new password here’;
mysql> GRANT ALL PRIVILEGES ON \*.\* TO ‘root2’@’localhost’ WITH GRANT OPTION;
Try to run the tool again.
The Infernal -Twin tools implements several features, it provides all the necessary to hack a Wireless network (WPA2, WEP) and easily allows to run Wireless Social Engineering attacks. Below the principal features:
GUI Wireless security assessment SUIT
Impelemented
WPA2 hacking
WEP Hacking
WPA2 Enterprise hacking
Wireless Social Engineering
SSL Strip
Report generation
PDF Report
HTML Report
Note taking function
Data is saved into Database
Network mapping
MiTM
Probe Request
The author of the Infernal-Twin hacking tool, Khalilov M, aka 3ntr0py (entropy1337), announced that next releases will include parsing t-shark log files for gathering victim’s credentials and other data.
In the following video is it illustrated an attack on public network, the script should be able to go and modify the login page and alter the content of it with necessary variables.
Below another video turorial on the Infernal-Twin Tool.
If you are interested in Wireless hacking for penetration testing give a look also to WiFiPhisher, a WiFi social engineering tool that allows an attacker to steal credentials from users of secure WiFi networks.
WiFiPhisher was developed by the Greek security expert George Chatzisofroniou and is available for download on the software development website GitHub.
British NCA revealed to have hacking abilities, aka equipment interference
9.11.2015
Documents published by the UK Government reveal that the UK’s National Crime Agency has the hacking capabilities, so called equipment interference.
We have debated for a long time about hacking capabilities of principal law enforcement and intelligence agencies.
Many documents leaked by the whistleblower Edward Snowden revealed that the UK intelligence agency, the GCHQ has the ability to compromise practically every target, exactly like the cousin of the NSA.
Now for the first time the technological abilities of the UK’s National Crime Agency (NCA) have been revealed in a collection of documents, the British law enforcement agency has “equipment Interference” (EI) capabilities, which allow it to hack into mobile devices and computers.
Last week, the UK government published the draft Investigatory Powers Bill, a debated proposed of a legislation that would force internet service providers to store the internet browsing history of all citizens for up to one year.
Eric King, the deputy director of the Privacy International, who analyzed the document noticed that in a section there is the explicit reference to the capability of the UK law enforcement having the capability to conduct “equipment interference.”
“Equipment interference is currently used by law enforcement agencies and the security and intelligence agencies,” states the section. The documents also reveal that “more sensitive and intrusive techniques” are available to a “small number of law enforcement agencies, including the National Crime Agency.”
The document “Factsheet—Targeted Equipment Interference” published by the UK government a few days ago provides further information on the Equipment interference available at the National Crime Agency.
[The Equipment interference is] “the power to obtain a variety of data from equipment. This includes traditional computers of computer-like devices such as tablets, smart phones, cables, wires and static storage devices.”
Equipment interference, also known as “computer network exploitation,” has different levels of complexity. The agents at the National Crime Agency can use it to infect computers or to remotely deploy a spyware on mobile devices
[Sophisticated Equipment interference] allows NCS “remotely installing a piece of software on to a device.” the document reads. “the software could be delivered in a number of ways and then be used to obtain the necessary intelligence.” “Equipment interference capabilities have made a vital contribution to the UK from Islamist terrorism and have also enabled the disruption of paedophile-related crime.”
According to experts, there is little doubt that these practices could more simply be described as hacking.
The security research Claudio Guarnieri offered his comment to Motherboard about the Equipment interference capabilities of the British law enforcement Agency.
“However you put it, and regardless of ‘interference,’ it clearly speaks of equipment, so it most certainly isn’t referring to any sort of passive wiretapping. And the only thing you can do to equipment is, well, hack it,” explained Guarnieri “This appears to confirm for the very first time that British law enforcement are in the hacking business,” added King from Privacy International. “What statutory authority are the police claiming grants them these powers? How often have they been used? Has hacked material been used in criminal prosecutions? Have courts been notified evidence presented before them might have been tampered with by hacking?” King added.
ISIS Supporter Hacks 54,000 Twitter Accounts and Posts Details of Heads of the CIA and FBI
8.11.2015
ISIS Supporters Hack 54,000 Twitter Accounts and Posts Personal Data of Heads of the CIA and FBI
ISIS hackers have hacked tens of thousands of Twitter accounts, including the accounts of the members of CIA and the FBI, in revenge for the US drone strike that killed a British ISIS extremist in August.
The Cyber Caliphate, a hackers group set up by British ISIS member Junaid Hussain, urged its supporters and followers to hack Twitter accounts in order to take revenge of Husain's death.
Over 54,000 Twitter Accounts Hacked!
As a result, the hackers were able to hack more than 54,000 Twitter accounts. Most of the victims targeted by Jihadis appear to be based in Saudi Arabia though some of the them are British.
One of the victims based in Saudi Arabia, whose Twitter account was compromised by the ISIS extremists, said, "I am horrified at how they got hold of my details."
The extremists not only hacked thousands of Twitter accounts, but they also posted hacked personal information, including phone numbers and passwords, of the heads of:
The Central Intelligence Agency (CIA)
The Federal Bureau of Investigation (FBI)
The United States's National Security Agency
'We Are Back with a BANG'
Hussain was a British hacker who rose to prominence within Islamic State Terrorist group (better known as ISIS) in Syria as a top cyber expert to mastermind the ISIS online war before a US drone killed him in August.
After Hussain's death, Cyber Caliphate (@cyber_caliph), which took control of the official Twitter and YouTube accounts of the US military's Central Command (CENTCOM) in January, reappeared on Twitter last Sunday.
ISIS Supporters Hack 54,000 Twitter Accounts and Posts Personal Data of Heads of the CIA and FBI
"We are back," Cyber Caliphate declared in an opening tweet.
Before its accounts got suspended by Twitter, Cyber Caliphate tweeted a link to the database that contained stolen Twitter accounts, including passwords, although the data could not be verified yet.
The incident came just a day after another hacking group, Crackas With Attitude (CWA), claimed to have gained access to a Law Enforcement Portal that contains arrest records and tools for sharing information about terrorist events and active shooters.
Threat actors hacked the popular Touchnote company
8.11.2015
On 4th November 2015, Touchnote company received information confirming that is has been the victim of a data breach that exposed customer data.
Data breaches are becoming a daily event, the last one in the headlines it the hack suffered by the Touchnote postcard app.
Hackers have stolen customer data from Touchnote database, the popular app that is used to create postcards from pictures taken by the users. The app is very popular because is comes pre-installed on millions of handsets, nearly 4 million postcards have been sent via the Touchnote app since it was launched in 2008.
The company has already informed its customers via email, according the official statement issued by Touchnote hackers have accessed users’ personal information, including names, email and home addresses.
“On 4th November 2015 we received information confirming that Touchnote has been the victim of criminal activity, resulting in the theft of some of our customer data.
The data that was accessed included your name, email address, postal address and your Touchnote order history, registered with Touchnote does not store your full credit/debit card number, expiry date or security code. Therefore, this information was not accessed.
The data that was accessed included the last four digits of your card number (e.g. XXXX XXXX XXXX 1234) which on its own cannot be used for making financial transactions.” states the email.”
The company informed the customers that it is supporting investigation conducted by the UK’s National Cyber Crime Unit, at the time I’m writing there is no news regarding the real number of affected users.
The company highlighted that financial data was not exposed by the data breach, the hackers compromised only the last four digits from customer cards, but the firm clarified that it doesn’t store full card information (card numbers, expiration dates or security codes).
Touchnote stored passwords in an encrypted format, anyway it is recommending customers to change them.
“None of the data that may have been accessed is financially sensitive,” Touchnote said.
The company announced an improvement of its security measures.
Touchnote users are invited to carefully read the Q&A page published on the company website, other info will be provided via Twitter.
Cyber Caliphate Hacks 54k Twitter accounts, including ones of CIA and FBI officials
8.11.2015
The ISIS group known as the Cyber Caliphate hacked 54,000 Twitter accounts and leaked online data of heads of the CIA and FBI.
We have discussed several times about the cyber capabilities of the ISIS sympathizers, recently Mikko Hyppönen, Chief Research Officer for F-Secure, said he worries about cyber extremists that could penetrate critical infrastructure and cause serious damages.
The expert explained that the ISIS is probably the first group of terrorist that has hacking capabilities to manage a major attack against a government infrastructure, and the situation is getting worse because this group is gaining greater awareness of the effectiveness of an offensive launched by the cyberspace.
Now ISIS hackers are in the headline once again, they collective known as the Cyber Caliphate has hacked tens of thousands of Twitter accounts, including the accounts belonging to several members of the CIA and the FBI, in revenge for the US drone strike that killed the British Jihadist hacker Junaid Hussain in August.
“Jihadis have hacked tens of thousands of Twitter accounts in retaliation for the drone attack that killed a British Islamic State extremist. A group called Cyber Caliphate, set up by Junaid Hussain from Birmingham, urged its followers to take control of the accounts to spread IS propaganda. Most of the victims appear to be based in Saudi Arabia, though some are feared to be British. In what experts described as a worrying escalation of the global cyber war, details of more than 54,000 Twitter accounts, including passwords, were posted online last Sunday.” reported the DailyMail.
The intelligence analysts believe that the Cyber Caliphate is a group of hackers directly linked to the ISIS terrorist organization and Junaid Hussain was one of its founders.
The Cyber Caliphate is in hacking operation and propaganda on the Internet, it incites supporters and followers to hack Twitter accounts of Western Government and military organization in order to avenge the death of their brother.
The hackers hijacked more than 54,000 Twitter accounts, most of the accounts belong to users in Saudi Arabia. The hackers of the Cyber Caliphate leaked online personal information of the victims, including phone numbers and passwords, exposing them to serious risks.
“I am horrified at how they got hold of my details.” said one of the victims.
Among the victims of the Cyber Caliphate, there are senior officials of the Central Intelligence Agency (CIA), the Federal Bureau of Investigation (FBI), and The United States’s National Security Agency.
“We are back,” Cyber Caliphate declared via Twitter through an account that has been already suspended.
In May, the hackers of the Cyber Caliphate published a video threatening crippling cyber attacks against the Europe, United States, Europe and Australia. The terrorists claimed to have the necessary cyber capabilities to spy on Western communications.
“The electronic war has not yet begun,” the pro-ISIS hackers boasted in their latest video threatening the cyberattacks.
The group, which was involved in the hijacking of social media accounts belonging to the US CENTCOM, released a propaganda video threatening cyberattacks anticipating the operation of the terrorists on the Internet.
“Praise to Allah, today we extend on the land and in the internet. We send this message to America and Europe. We are the hackers of the Islamic State and the electronic war has not yet begun,” the video said with a distorted voice and picture of an Anonymous member. “What you have seen is just a preface of the future. We are able until this moment to hack the website of the American leadership and the website of the Australian airport and many other websites.”
What is Threat Intelligence and How It Helps to Identify Security Threats
8.11.2015
Simply put, threat intelligence is knowledge that helps you identify security threats and make informed decisions. Threat intelligence can help you solve the following problems:
How do I keep up to date on the overwhelming amount of information on security threats…including bad actors, methods, vulnerabilities, targets, etc.?
How do I get more proactive about future security threats?
How do I inform my leaders about the dangers and repercussions of specific security threats?
Threat Intelligence: What is it?
Threat intelligence has received a lot of attention lately. While there are many different definitions, here are a few that get quoted often:
Threat intelligence is evidence-based knowledge, including context, mechanisms, indicators, implications and actionable advice, about an existing or emerging menace or hazard to assets that can be used to inform decisions regarding the subject's response to that menace or hazard. – Gartner
The set of data collected, assessed and applied regarding security threats, threat actors, exploits, malware, vulnerabilities and compromise indicators – SANS Institute
Why is everyone talking about it?
Verizon’s 2015 DBIR estimated a financial loss of $400 million from 700 million compromised records, which resulted from 79,790 security incidents!
As long as security threats and breaches occur, every business will look for ways to protect their data. The threat landscape is always changing and the business risk is increasing because of our dependence on IT systems.
Threats come from internal as well as external sources. Bottom line is, organizations are under tremendous pressure to manage threats. Though information in the form of raw data is available abundantly, it is hard and time-consuming to get meaningful information based on which proactive measures can be set.
This naturally pulls more and more users towards threat intelligence as it helps to prioritize threats within the deluge of data, alerts, and attacks and provides actionable information.
The table below presents several common indicators of compromise that can be identified with threat intelligence feeds:
Category Indicators of Compromise Examples
Network
IP addresses
URLs
Domain names
Malware infections targeting internal hosts that are communicating with known bad actors
Email
Sender’s email address and email subject
Attachments
Links
Phishing attempts where internal hosts click on an unsuspecting email and “phone home” to a malicious command and control server
Host-Based
Filenames and file hashes (e.g. MD5)
Registry keys
Dynamic link libraries (DLLs)
Mutex names
External attacks from hosts that might be infected themselves or are already known for nefarious activity
Threat Intelligence capabilities
Attacks can be broadly categorized as user based, application based and infrastructure based threats. Some of the most common threats are SQL injections, DDoS, web application attacks and phishing.
It is important to have an IT security solution that provides threat intelligence capabilities to manage these attacks by being both proactive and responsive.
Attackers are constantly changing their methods to challenge security systems. Therefore, it becomes inevitable for organizations to get threat intelligence from a variety of sources.
One of the proven methods to stay on top of attacks is to detect and respond to threats with a SIEM (Security Information & Event Management system).
A SIEM can be used to track everything that happens in your environment and identify anomalous activities. Isolated incidents might look unrelated, but with event correlation and threat intelligence, you can see what is actually happening in your environment.
Nowadays, IT security professionals must operate under the assumed breach mentality. Comparing monitored traffic against known bad actors sourced from threat intelligence would help in identifying malicious activities.
However, this could be manual and time-consuming. Integrating indicator based threat intelligence to a SEIM security solution would help in identifying compromised system and possibly even prevent some attacks.
Best Practices
Integrating threat intelligence and responding to attacks is not enough to combat the ever-changing threat landscape. You need to analyze the situation and determine threats you are likely to face, based on which you can come up with precautionary measures.
Here is a list of several best practices:
Have an application whitelist and blacklist. This helps in preventing execution of malicious or unapproved programs including, .DLL files, scripts and installers.
Check your logs carefully to see if an attempted attack was an isolated event, or if the vulnerability had been exploited before.
Determine what was changed in the attempted attack.
Audit logs and identify why this incident happened – reasons could range from system vulnerability to an out-of-date driver.
What will threat intelligence enabled SIEM solve
A SIEM, like SolarWinds Log & Event Manager, collects and normalizes log data from monitored traffic and automatically tags suspicious events.
With integrated threat intelligence mechanism and built-in rules, the monitored events can be compared against the list of constantly updated known bad actors.
threat-intelligence
You can quickly search & monitor for hits from the bad actors against the log data in real time and identify common indicators of compromise.
You can automatically respond with actions like blocking known bad IP addresses, in case of malicious attack attempts.
Watch how threat intelligence works in a SIEM and download your free trial of a leading SIEM from SolarWinds.
Hackers have Hacked into US Arrest Records Database
8.11.2015
The Group of teenage hackers, which previously hacked into the personal email of the CIA director John Brennan and published a large trove of sensitive data, has now had its hands on even more important and presumably secure target.
Hackers Accessed Law Enforcement Private Portal
The hacking group, Crackas With Attitude (CWA), claims it has gained access to a Law Enforcement Portal through which one can access:
Arrest records
Tools for sharing information about terrorist events and active shooters
The system in question is reportedly known as the Joint Automated Booking System (JABS), which is only available to the Federal Bureau of Investigation (FBI) and law enforcement.
Hackers Gained Access to FBI's Real-Time Chat System
Moreover, the hacking group also says it has gained access to another tool that is something like a real-time chat system for the FBI to communicate with other law enforcement agents around the US.
Two days ago, CWA published a portion of the data it collected to Pastebin and Cryptobin, apparently releasing names, email addresses, and phone numbers of around 3,500 law enforcement and military personnel.
JABS System Hacked!
However, the group has been able to have its hands on many law enforcement tools that contain more sensitive information, and Wired verified that a screenshot of JABS shared by CWA was legitimate.
The CWA hackers told Wired they found a vulnerability that allowed them to gain access to the law enforcement private portal, giving the group access to dozen law enforcement tools, but the hackers didn't reveal anything about the vulnerability.
This system is noteworthy as it may allow anyone with access to view arrest records – whether the arrests are sealed or aren't available to the public.
It means, among other things, this system can expose secret informants and others who have been detained but are now working with the law enforcement agencies.
Although none of the information from these law enforcement tools has been shared publicly, the hacking group could bother government officials by releasing the sensitive information anytime soon.
Malvertising attack hit The Economist, anti-ad blocking service PageFair hacked
8.11.2015
PageFair, the anti-ad blocking analytics service used by The Economist’s was hacked on Halloween and the attackers used it to serve malware.
On Halloween, hackers have compromised the anti-ad blocking service PageFair used by The Economist exposing readers to malware infections.
PageFair allows publishers to measure how many visitors block their ads, users who visited The Economist’s website from October 31 to early hours of November 1 may have installed a keylogger disguised as an Adobe update onto their machines.
“On Oct. 31, 2015, one of economist.com’s vendors, PageFair, was hacked. If you visited economist.com at any time between Oct. 31, 23:52 GMT and Nov. 1, 01:15 GMT, using Windows OS and you do not have trusted anti-virus software installed, it is possible that malware, disguised as an Adobe update, was downloaded onto your PC. If you accepted what looked like an Adobe update when you visited economist.com,” states a security advisory published by The Economist.
The Economist hired a security firm to investigate the attack, the experts confirmed that the malware used by the threat actors is a Windows keylogger, it is likely attackers were interested in obtaining visitors’ personal data, including login credentials. 
The Economist confirmed that the company systems have not been compromised by the hacker that instead exploited the anti-ad blocking service PageFair.
Charles Barber, a spokesperson for the publication, told Quartz that only a limited number of visitors have been infected according to data provided by PageFair.
PageFair confirmed that its analytics network has been exploited to serve the malware for about 80, the malvertising attack was discovered after five minutes, but the company spent more than a hour to halt the attack.
“It is now six days since one of our CDNs was compromised for 83 minutes by a hacker. We have worked hard this week to analyse and disclose what happened to our clients and the world. Thanks to the cooperation of the NanoCore author and the dynamic DNS service Dyno, whatever access the hacker had to infected computers was shut down on Tuesday. In addition, for the last 4 days over 90% of antivirus tools (by market share) are detecting and cleaning the malware.” states PageFair in a official statement. “If you are a publisher using our free analytics service, you have good reason to be very angry and disappointed with us right now,” PageFair CEO Sean Blanchfield told MediaPost. “The attack was sophisticated and specifically targeted against PageFair, but it is unacceptable that the hackers could gain access to any of our systems.”
The Economist is just one of the 501 publishers that were affected by the security breach and 2.3% of their visitors were placed at risk,.
The Economist provided the following suggestions to its readers:
Change your passwords on all systems
Contact your financial providers and check bank and credit card statements for unusual activity
Run anti-virus software from a reputable provider. We recommend the following:
Windows Defender (if you have Windows 10 or 8.1)
Microsoft Security Essentials (if you have Windows 7 or Windows Vista)
Avast (free)
Malwarebytes (free)
Download and install the tool.
Run a full system scan.
The malware should be identified and removed.
Linux ransomware already infected at least tens of users
7.11.2015
Researchers at Russian antivirus company Doctor Web have discovered a Linux ransomware that has already infected tens of users.
Ransomware is a profitable instrument in the criminal ecosystem, security experts discover new variant on a weekly basis. This week the new variant of Cryptowall, the Cryptowall 4.0, appeared in the wild, meanwhile an offline ransomware is targeting Russian users.
News of the day is that researchers at Russian antivirus company Doctor Web have spotted a new file-encrypting ransomware, dubbed Linux.Encoder.1, that is targeting Linux systems. It has been estimated that tens of users have already fallen victim to this Linux ransomware.
“Doctor Web warns users about new encryption ransomware targeting Linux operating systems. Judging from the directories in which the Trojan encrypts files, one can draw a conclusion that the main target of cybercriminals is website administrators whose machines have web servers deployed on. Doctor Web security researchers presume that at least tens of users have already fallen victim to this Trojan.” states the blog post published by Doctor Web.
The Linux ransomware is written in C and leverages the PolarSSL library, it launches itself as a daemon that encrypt data and deletes the original files from the system

The Linux ransomware requires administrator privileges in order to work, once a machine is infected by the threat, the malware downloads the files containing attackers’ demands and a file containing the path to a public RSA key. The Linux ransomware is launched as a daemon and deletes the original files, subsequently, the RSA key is used to store AES keys used to encrypt files.
“First, Linux.Encoder.1 encrypts all files in home directories and directories related to website administration. Then the Trojan recursively traverses the whole file system starting with the directory from which it is launched; next time, starting with a root directory (“/”). At that, the Trojan encrypts only files with specified extensions and only if a directory name starts with one of the strings indicated by cybercriminals.” continues the post.
“To encrypt each file, the Trojan generates an AES key. After files are encrypted using AES-CBC-128, they are appended with the .encrypted extension. Into every directory that contains encrypted files, the Trojan plants a README_FOR_DECRYPT.txt file with a ransom demand,” Dr. Web explained.
In order to recover the encrypted files, victims are asked to pay one Bitcoin (roughly $380 at today’s rate), once the ransom is paid the files are decrypted using a private RSA key that retrieves the AES key from encrypted files.
Cracka hackers doxed more than 2,000 Government employees
7.11.2015
Cracka hackers who took over the personal email account of CIA Director John Brennan have now doxed more than 2000 Government employees.
The young hackers of the crew known as Crackas With Attitude (CWA) announced that they have doxed more than 2,000 Government employees.
The hackers are the same that accessed into the AOL email account of the CIA director and violated the email account of the FBI Deputy Director’s wife.
Now the hackers claim to have broken into government computers, on Thursday the official account of the Cracka group published a list of more than 2,000 names, phone numbers and email addresses of law enforcement and military personnel.

Cracka claimed to have broken into government systems and leaked the data belonging to government employees in support of Palestine
“Maybe the USgov should listen to us, I mean, we have enough information to make them look like the little bitches they are,” Cracka said in a tweet.
How did Cracka obtain the information?
Members of the group explained to Motherboard that they took over the account of an internal employee, then they got access to several “tools feds use” such as the JABS, a database containing information on the arrested people, the IC3, that is crime-reporting tool used by the FBI, and VCC, a sharing tool for law enforcement agencies.

Wired reported that hackers exploited a flaw to gain access to the private portal.
“The CWA hackers said they found a vulnerability that allowed them to gain access to the private portal, which is supposed to be available only to the FBI and other law enforcement agencies around the country. That portal in turn, they say, gave them access to more than a dozen law enforcement tools that are used for information sharing.” states Wired.
Cracka doesn’t provide information on the hacked account, it is clear that the employee is “high in the [government].” The hacker confirmed that they didn’t download all the data available.
“We let the [government] off by a lot, this could be so damaging it could affect the whole of USA by ALOT,” the hacker explained via online chat.
Cracka also published a tweet claiming to have stolen also “34,000 lines of emails, names, position and phone numbers of gov associates, including military.”
As correctly highlighted by Cracka, this kind of data breach could have serious consequence for the Homeland Security. The personal information belonging to government entities could be used by foreign state-sponsored hackers in cyber espionage operations.
“Just to clear this up, CWA did, indeed, have access to everybody in USA’s private information, now imagine if we was [sic] Russia or China,” he said in another tweet.
Journalists at Motherboard confirmed that at least five random numbers in the list they analyzed are legitimate.
The German Intelligence Systematically Spied on Allies
7.11.2015
The Der Spiegel magazine reported German Intelligence Agency BND “systematically spied” on its allies and several international organizations.
In the last months, the German Intelligence has accused the NSA of spying on Government members, including the Chancellor Angela Merkel.
In October, the German authorities have launched a probe into allegations of a new case of US espionage after they have found a laptop infected by the Regin Spyware.
The German Parliament also suffered numerous cyber attacks that spread a highly sophisticated malware inside the network of the Bundestag, the investigators speculate the involvement of nation-state actors, likely Russian state-sponsored hackers.
Victims or victimizers?
The German intelligence agency BND has already been accused of spying on officials at the French foreign ministry and the presidency, as well as the European Commission. The German spies alleged operated on behalf of the NSA.
Bundestag German Intelligence
In April 2015, the Der Spiegel revealed the German intelligence agency BND helped NSA in monitoring European politicians.
“At least since 2008 BND employees fell several times that some of these selectors contrary to the mission profile of the German foreign intelligence – and are not covered by the “Memorandum of Agreement”, which negotiated the Germans and the Americans to jointly combat global terrorism in 2002 had. Instead, the NSA was looking for specific information about over the defense group EADS, Eurocopter and French authorities. The BND did not take the obviously but as an opportunity to review the Selektorenliste systematically.
Only after the unveiling of the NSA scandal in the summer of 2013, a BND department dealt specifically with the NSA search terms.” states the Der Spiegel.
Now the RBB Radio and Spiegel Online are claiming that the BND is also responsible for cyber espionage on its own account on several embassies and administrations of “European states and allies”.
“the BND had systematically spied on ‘allies’ across the world, including on the interior ministries of the United States, Poland, Austria, Denmark and Croatia.” states the Spiegel.
According to the Der Spiegel, the German Secret Service spied on the US delegation at the European Union in Brussels and the UN in New York, the US Treasury, and several embassies in Germany, including those of the US, France, Britain, Sweden, Portugal, Greece, Spain, Italy, Switzerland, Austria and the Vatican.
The German intelligence appears very active, the German spies also spied on the Geneva-based International Committee of the Red Cross and Oxfam.
The unique certainly is that every government is currently conducting covert operations in the cyber space to gather intelligence and spy on allies and adversaries.
Kyberzločinci mají nový trik, jak šířit vyděračský virus
6.11.2015 Viry
Doslova jako mor se začaly internetem šířit podvodné e-maily, ve kterých straší kyberzločinci příjemce pozastavením funkčnosti domény. Ve skutečnosti se jim ale snaží do počítače propašovat nezvaného návštěvníka, jehož pomocí jej pak budou vydírat. Před novou hrozbou varoval český Národní bezpečnostní tým CSIRT.
„V posledních dnech probíhala v zahraničí phishingová kampaň zaměřená na držitele domén. V e-mailu, který držitelé domén obdrželi, byla informace o údajném pozastavení jejich domény kvůli porušování politiky jejich registrátora,“ uvedl analytik Pavel Bašta z týmu CSIRT, který je provozován sdružením CZ.NIC.
Riziko představují podvodné odkazy ve zprávách. „Odkazy v e-mailech vedou podle našich informací ke stažení ransomwaru,“ doplnil Bašta.
Ransomware se na internetu objevuje v různých obměnách. Jde o škodlivý kód, který dokáže zašifrovat data na pevném disku a za jejich obnovení požaduje výkupné. Vzhledem k tomu, že za odblokování počítače piráti požadují zpravidla 100 dolarů (2000 Kč), vyšplhá se ve výsledku „výkupné“ až na několik stovek tisíc korun denně.
Výkupné neplatit
Ani po zaplacení výkupného navíc nemají uživatelé jistotu, že se ke svým datům skutečně dostanou. Virus je nutné z počítače odinstalovat a data následně pomocí speciálního programu odšifrovat. [celá zpráva]
„Nelze vyloučit, že se podobný podvod v budoucnu objeví také v České republice. Držitelům domén proto doporučujeme v případě obdržení jakékoli podezřelé zprávy postupovat s rozvahou,“ uzavřel Bašta s tím, že zvýšená obezřetnost je vhodná také u tuzemských uživatelů.
Kybernetické útoky stály firmy za poslední rok 315 miliard dolarů
6.11.2015 Analýzy
Kybernetické útoky stály v posledních 12 měsících celosvětově firmy 315 miliard dolarů. Napadený byl přitom každý šestý podnik. Navzdory mediálně známým případům narušení bezpečnosti a stále častějším hackerským útokům se téměř polovina firem nadále vystavuje riziku tím, že nemají žádnou komplexní strategii pro prevenci digitální trestné činnosti. Vyplývá to ze studie společnosti Grant Thornton.
V Česku hrozí spíše útok na databáze osobních dat než kyberútok na strategickou infrastrukturu.
Podniky v EU zaznamenaly škody kolem 62 miliard dolarů, v Asii a Tichomoří 81 miliard a v Severní Americe 61 miliard USD. Průměrný kybernetický útok stojí podnik 1,2 procenta příjmů. Nejvíce ohrožený se cítí finanční sektor.
„Kybernetické útoky jsou stále významnějším nebezpečím pro podnikání. Nejedná se jen o náklady ve finančním smyslu, ale také o vážné poškození pověsti společnosti, jako se to stalo v případě webového portálu Ashley Madison, ze kterých se hackerům podařilo odcizit 36 miliónů e-mailů," uvedl partner Grant Thornton Advisory David Pirner.
V Česku hrozí spíše útok na databáze osobních dat než kyberútok na strategickou infrastrukturu. Bankovní sektor je podle Pirnera připraven relativně dobře. Ví totiž, na co se připravit, a navíc jsou banky pod palbou hackerů každý den. České banky byly zřejmě zčásti oběťmi loňského útoku mezinárodní skupiny Carbanak, která sérií napadení získala celosvětově přes 20 miliard korun.
Podle odborníků není v Česku pravděpodobný podobný masivní kybernetický útok, jenž nedávno postihl britského operátora TalkTalk, který mohl vést ke krádeži osobních údajů všech více než čtyř miliónů zákazníků, případně by spíše mířil na některého z virtuálních hráčů. „Velcí mobilní operátoři nevyužívají odlišné zabezpečovací systémy než jiné velké firmy a na bezpečnosti spíše nešetří. U nízkonákladových operátorů může být ale situace jiná," uvedl specialista na počítačovou bezpečnost společnosti DCIT Karel Miko.
Financial Reporting Council of Nigeria site used for phishing scam
6.11.2015
According to Netcraft, the website of Financial Reporting Council of Nigeria is used to serve a webmail phishing site from the legitim site of the agency.
The website of the Financial Reporting Council of Nigeria was used by cyber criminals in a phishing scam. According to the experts at Netcraft, the website of Financial Reporting Council of Nigeria is used to serve a webmail phishing site from the legitim site of the agency.
The attack is not complex, crooks used a common phishing kit that allows easily to create customised phishing pages.
“The phishing content is based on a ready-to-go phishing kit that is distributed as a zip file. It contains easily-customisable PHP scripts and images designed to trick victims into surrendering either their Yahoo, Gmail, Hotmail or AOL passwords.” states the report.
The hackers likely have compromised the government website and they have deployed the phishing web page into an images directory on the Financial Reporting Council of Nigeria website. The experts noticed also that the website of the Financial Reporting Council of Nigeria runs an older version 2.5.28 of the Joomla CMS which is no more supported.
The phishing page asks for user email credentials and the phone number used as backup login credentials for the Gmail service. When the victim has inserted the information they are transmitted via email directly to the cyber criminals. Then the phishing page redirects the victim’s browser to the Saatchi Art investment website at http://explore.saatchiart.com/invest-in-art/, but experts clarified that it is not involved in the scam.
“After a victim enters his or her email credentials into the phishing site, both the username and password are transmitted via email directly to the fraudster. These emails also contain the victim’s IP address, and a third-party web service is used to deduce which country the victim is in.” continues the post published by Netcraft.

The experts at Netcraft explained that this phishing scam is unusual because attackers seem to be more interested in collect users’ credentials shared among several web services, instead the victims’ banking account logins.
Netcraft reported that the majority of Nigeria’s government websites, including the one operated by the Financial Reporting Council, are hosted in the United States. They speculate the attacker exploited a flaw in the Joomla! CMS to deploy the phishing kit.
ProtonMail Paid Hackers $6000 Ransom in Bitcoin to Stop DDoS Attacks
6.11.2015
The Geneva-based encrypted email service ProtonMail was forced to pay a Ransom of almost $6,000 to stop sustained Denial-of-service (DDoS) attacks that have knocked its service offline since Tuesday.
ProtonMail – a full, end-to-end encrypted email service that launched last year – has been dealing with, what it called, the extremely powerful DDoS attack, and is still unavailable at the time of writing.
ProtonMail Paid $6,000 to Stop DDoS
In an official statement posted on a WordPress blog Thursday, officials of ProtonMail said the powerful DDoS attack by an unknown group of hackers forced them to pay 15 Bitcoins (about $5,850) in exchange for them halting the assault.
However, even after paying the ransom amount, the crippling DDoS attacks continued to the ProtonMail service.
DDoS Attack Continues Even After Paying Ransom
ProtonMail officials said, "We hoped that by paying [ransom], we could spare other companies impacted by the [DDoS] attack against us, but the attack continued nevertheless."
"Attacks against [key] infrastructure continued throughout the evening and to keep other customers online, our ISP [Internet Service Provider] was forced to stop announcing our IP range, effectively taking us offline."
Scary, Large-Scale DDoS attack
However, the criminals who extorted ProtonMail previously did not take responsibility for the second DDoS attack, which according to the company, was more "scary" and "a full-scale infrastructure attack."
"This coordinated assault on [our] key infrastructure eventually managed to bring down both the ISP and the datacenter, which impacted hundreds of other companies, not just ProtonMail," the company wrote.
Although the motive behind the attack is still unclear, ProtonMail promises that it is working hard to restore the service to its users.
Customers' Data Unaffected
The company is working with both the security officials in its Switzerland-based data center and others across the world to get the situation under control.
In its official Twitter account, ProtonMail reassured its customers that their data is "secure and untouched," but access to its site is unlikely, before confirming on Thursday that the service was under second DDoS attack.
ProtonMail offers an end-to-end encrypted webmail system designed by CERN scientists to fight snooping by law enforcement agencies like the NSA. Since its launch, the service has over 500,000 users worldwide.
FBI Deputy Director's Email Hacked by Teenager Who Hacked CIA Chief
6.11.2015
The same group of teenage hackers that hacked the AOL email account of the CIA director John Brennan two weeks ago has now hacked into AOL email accounts of the FBI Deputy Director, Mark Giuliano and his wife.
Yesterday, Cracka, a member of the teenage hacktivist group known as 'Crackas With Attitude' (CWA) posted a new trove of information belong to thousands of government employees online; however they claim to have accessed far more than that.
The hackers claimed to have obtained the personal information by hacking into AOL email accounts of the Giuliano and his wife.
More Than 3,500 Government Employees Doxxed
The published information includes more than 3,500 names, email addresses and contact numbers of law enforcement and military personnel.
Though the FBI officials couldn't immediately verify the claims, Infowars has confirmed the authenticity of several people listed, which includes everyone from local police officers to FBI and military intelligence analysts.
hacking-cia
Following the last CIA director's email hack, Mr. Giuliano made aggressive statements about catching the hackers and making an example out of CWA.
Also Read: WikiLeaks Publishes CIA Director's Hacked Emails
The CWA hacking group got angry over the statement made by Giuliano and moved forward to teach him a lesson by hacking his personal email account.
Cracka Twitter account was temporarily deleted, but before his account got deactivated by Twitter Thursday evening, Cracka claimed to have leaked the information in support of Palestine.
Hacker Made Phone Call to FBI Deputy Director
Motherboard spoke to the group of hackers that claimed they have access to a lot more than the information they shared Thursday.
Also Read: 4000 Malicious iOS Store Apps Linked to CIA
However, the FBI has declined to comment on whether or not Mark Giuliano was hacked, although Cracka said the group found deputy director's phone number in the email account’s contact lists.
The hacker also claimed to have called the number. "I called it and asked for Mark, and he is like 'I don't know you, but you better watch your back', and then he hung up, and I kept calling and he was getting mad then he didn't pick up," Cracka said.
ProtonMail paid a $6000 Ransom to stop DDoS Attacks
6.11.2015
ProtonMail has paid a $6000 Ransom to stop prolonged DDoS attacks that knocked its services offline since Tuesday. Unfortunately, the attacks are continuing.
The popular encrypted email service ProtonMail has suffered a prolonged major DDoS attack that knocked it offline since Tuesday. It was an extortion attempt, the attackers requested a ransom in order to stop the DDoS attack on the services of the company.
The company decided to pay a Ransom of almost $6,000 to stop the sustained Denial-of-service (DDoS) attacks, at the time of writing the ProtonMail encrypted email service is still down.
The news related the decision of ProtonMail of paying the ransom was published in an official statement posted on a the protonmaildotcom.wordpress.com blog on Thursday.
“As many of you know, ProtonMail came under sustained DDOS attack starting on November 3rd, 2015. At the current moment, we are not under attack and have been able to restore services, but we may come under attack again.” states the post.
The representatives of the ProtonMail explained that the company was victim of a powerful DDoS attack by an unknown group of hackers that requested 15 Bitcoins (about $5,850) in exchange for them stopping the DDoS attacks.
The hackers requested the payment of 15 Bitcoin on the address “1FxHcZzW3z9NRSUnQ9Pcp58ddYaSuN1T2y.” Below the history associated to this specific account used by crooks.
The real problem is that even if the company has paid the ransom the DDoS attacks continued, the attackers’ motivation is still unclear.
“We hoped that by paying [ransom], we could spare other companies impacted by the [DDoS] attack against us, but the attack continued nevertheless.” “Attacks against [key] infrastructure continued throughout the evening and to keep other customers online, our ISP [Internet Service Provider] was forced to stop announcing our IP range, effectively taking us offline.”
“This coordinated assault on [our] key infrastructure eventually managed to bring down both the ISP and the datacenter, which impacted hundreds of other companies, not just ProtonMail,” the company wrote.
ProtonMail is working to restore the service and is supporting the investigation conducted by the Swiss Governmental Computer Emergency Response Team (GovCERT), the Cybercrime Coordination Unit Switzerland (CYCO), and the Europol.
Below the description of the attack provided by ProtonMail:
“Slightly before midnight on November 3rd, 2015, we received a blackmail email from a group of criminals who have been responsible for a string of DDOS attacks which have happened across Switzerland in the past few weeks. This threat was followed by a DDOS attack which took us offline for approximately 15 minutes. We did not receive the next attack until approximately 11AM the next morning. At this point, our datacenter and their upstream provider began to take steps to mitigate the attack. However, within the span of a few hours, the attacks began to take on an unprecedented level of sophistication.” states the post. “At around 2PM, the attackers began directly attacking the infrastructure of our upstream providers and the datacenter itself. The coordinated assault on our ISP exceeded 100Gbps and attacked not only the datacenter, but also routers in Zurich, Frankfurt, and other locations where our ISP has nodes. This coordinated assault on key infrastructure eventually managed to bring down both the datacenter and the ISP, which impacted hundreds of other companies, not just ProtonMail.”
The company has confirmed that customer data are not affected by the ongoing attacks, they are “secure and untouched.”
ProtonMail’s also explained that its systems are still vulnerable to attacks of this magnitude, but it is thinking for a definitive solution to mitigate these events. The problem is that such kind of solutions is very expensive, the company requested users to Donate to the ProtonMail Defense Fund.
“At present, ProtonMail’s infrastructure is still vulnerable to attacks of this magnitude, but we have a comprehensive long term solution which is already being implemented. Protecting against a highly sophisticated attack like the second one which was launched against us requires sophisticated solutions as we also need to protect our datacenter and upstream providers. Cost estimates for these solutions are around $100,000 per year since there are few service providers able to fight off an attack of this size and sophistication”
The practice to hit companies with sustained DDoS attacks is quite common, according to a report published by Akamai in September, the DD4BC criminal group has been responsible for at least 114 DDoS attacks on its customers.
Avast uvedl na trh edice 2016 svých bezpečnostních řešení
6.11.2015 Ochrana
Nová bezpečnostní řešení pro PC a mobilní zařízení oznámil Avast. Verze 2016 pro PC přináší kromě jiného i multiplatformní řešení nazvané Hesla Avast (Avast Passwords), které uživatelům pomůže lépe se zorientovat v problematice spojené s ochranou osobních informací.
Avast 2016 přináší také rychlejší instalaci, zjednodušené uživatelské rozhraní a plnou kompatibilitu s Windows 10.
Hesla Avast představuje o multiplatformní řešení, které umožňuje synchronizovat všechna hesla napříč všemi zařízeními, včetně zařízení Android a iOS, dále umožňuje zkontrolovat úroveň bezpečnosti nastavených hesel a smazat všechna hesla uložená v internetovém prohlížeči.
Funkce Hesla Avast také umí uživatele upozornit na ztrátu ověřovacích údajů v případě úniku dat.
Novinky Avast 2016 pro PC podle dodavatele:
Hesla Avast — Tento správce hesel automaticky generuje silná hesla, která si uživatelé nemusí pamatovat — uživatelé si nastaví a zapamatují pouze jedno hlavní heslo, které jim umožní přístup ke všem ostatním heslům. Je dostupné ve všech verzích Avast 2016 pro PC, Android a iOS, podle výrobce bude brzy k dispozici i pro Mac.
Prohlížeč SafeZone — Izoluje všechny webové stránky týkající se on-line nakupování, bankovních převodů a finančních operací do „chráněného prostoru“, ve kterém otevírá i veškeré podezřelé webové stránky. SafeZone funguje zároveň i jako rozšíření prohlížeče, který nejen že blokuje nechtěné reklamy (díky vestavěnému Ad Blockeru), ale také umožňuje rychlejší načítání webových stránek. Pomocí další funkce rozšíření prohlížeče nazvané Do-Not-Track se mohou uživatelé dozvědět, které firmy sledují jejich chování na internetu a mohou se tak rozhodnout, kterým z nich toto povolí a kterým ne. SafeZone je součástí prémiových verzí produktů Avast 2016.
Vylepšená funkce Zabezpečení domácí sítě — Tato funkce nově odhalí dalších 12 typů zranitelností domácího routeru. Jedním kliknutím tak umožní zkontrolovat celou domácí síť včetně tiskáren, síťových disků a routeru.
Anonymous Group Leaks Identities of 1000 KKK Members
6.11.2015
The online hacktivist group Anonymous has followed through on its promise to disclose the identities of hundreds of Ku Klux Klan members.
On Monday, Anonymous vowed to release the full info dump of about 1,000 alleged Ku Klux Klan members with a chosen date of 5th of this November.
As promised, Anonymous posted a link to a Pastebin account with the names, aliases, Google Plus profiles, Facebook accounts and other identifying information of roughly 1,000 individuals the group believes are members of the Ku Klux Klan.
The hackers behind the leak tweeted a link to a Pastebin on a Twitter account, Operation KKK (@Operation_KKK) believed to be controlled by them.
Ku Klux Klan (KKK) is classified as a White Supremacist Racist group by the Anti-Defamation League and the Southern Poverty Law Center, allegedly having total 5,000 to 8,000 members.
"We hope Operation KKK will, in part, spark a bit of constructive dialogue about race, racism, racial terror and freedom of expression, across group lines. Public discourse about these topics can be honest, messy, snarky, offensive, humbling, infuriating, productive, and serious all at once," Anonymous wrote in the Pastebin post.
"The reality is that racism usually does NOT wear a hood, but it does permeate our culture on every level. Part of the reason we have taken the hoods off of these individuals is not because of their identities, but because of what their hoods symbolize to us in our broader society."
Anonymous also notes that the group collected the information of KKK members over 11 months through public documents, "digital espionage," interviews with experts and information from social media accounts of KKK affiliates.
However, the group has not published any personal information about the KKK members.
OmniRat RAT is currently being used by criminals in the wild
6.11.2015
Researchers at Avast have published an analysis of OmniRAT, a multi-platform remote administration tool (RAT) that has been used by criminals in the wild.
Researchers at Avast have conducted a brief analysis of OmniRAT, a multi-platform remote administration tool (RAT) that has been used for malicious purposes.
The malware researchers at Avast have published an interesting analysis of the multi-platform remote administration tool OmniRAT. The OmniRAT remote administration tool works on Android, Windows, Linux and Mac OS X OSs.
It is very popular and cheap, the OmniRAT lifetime license for servers and clients are offered for sale for $25 and $50, and operators also offer lifetime support.
Despite OmniRAT is not designed for illicit purposes, the experts at Avast have observed it being used my many crooks as a remote access Trojan.
The attackers use to spread the RAT via social engineering, a German user explained that his Android was infected via SMS containing a shortened URL link pointing to a website where the victim was instructed to enter a code and their phone number. The SMS was claiming that the victim had received an MMS that cannot be sent him because its mobile phone was affected by the Android StageFright vulnerability
When victims provide the information requested the website serve an APK reporting the icon labeled “MMS Retrieve” when installed. Then it is sufficient to click on the icon to start the installation of the OmniRAT.
OmniRAT 2
“A custom version of OmniRat is currently being spread via social engineering. A user on a German tech forum, Techboard-online, describes how a RAT was spread to his Android device via SMS. After researching the incident, I have come to the conclusion that a variant of OmniRat is being used.” is reported in the blog post published by Avast.
The malware analyst Nikolaos Chrysaidos from Avast explained that once criminals have infected the mobile device could access its contact list in order to spread OmniRat.
“The victim then has no idea their device is being controlled by someone else and that every move they make on the device is being recorded and sent back to a foreign server,” Chrysaidos said. “Furthermore, once cybercriminals have control over a device’s contact list, they can easily spread the malware to more people. Inside this variant of OmniRat, there is a function to send multiple SMS messages. What makes this especially dangerous is that the SMS spread via OmniRat from the infected device will appear to be from a known and trusted contact of the recipients, making them more likely to follow the link and infect their own device.”
OmniRat is quite to another RAT, DroidJack, that was used by several organizations in the criminal underground for illegal activities. OmniRat is cheaper that DroidJack which is offered for sale a nearly $210.
Mabouia: The first ransomware in the world targeting MAC OS X
5.11.2015
Rafael Salema Marques, a Brazilian researcher, published a PoC about the existence of Mabouia ransomware, the first ransomware that targets MAC OS X.
Imagine this scenario: You received a ransom warning on your computer stating that all your personal files had been locked. In order to unlock the files, you would have to pay $500.
This is the “modus operandi” imposed usually used by ransomware (ransom +software).
Ransomware encrypts files that are virtually impossible to decrypt with the computing means available to ordinary users. The only way to decrypt the files is paying to the malware creator to retrieve the password that unlocks the files… Which is exactly what you would do if I had not held up important files.
The definition of ransomware according to Wikipedia is as follows: “type of malware that restricts access to a computer system that it infects in some ways, and demands that the user pay a ransom to the operators of the malware to remove the restriction.” There are several actives ransomware in the world today, but no one had ever been designed to target Mac OS X until yesterday.
Mabouia ransomware
Rafael Salema Marques (@pegabizu), a Brazilian Cybersecurity Researcher, published yesterday a proof of concept about the existence of Mabouia ransomware, the first ransomware that targets MAC OS X.
The researcher’s goal is to alert the 66 million users of Mac OS X about the myth that there is no malware aimed at Apple’s personal computers.
The creator of the malicious code also mentions that Mac users are a good target for ransomware, because generally have a higher purchasing power and use the computer in a superficial way, usually by editing images and texts.
The malware name Mabouia refers to a kind of endemic lizard found on the island of Fernando de Noronha – Brazil. Is coded in C++ and uses the cryptographic algorithm XTEA with 32 rounds to encrypt the user files. Furthermore, it does not need superuser privileges for the execution of malicious code, considering that the ransomware will only modify the user’s personal files. Thus infection occurs with just one click.
In the link below you can see Mabouia ransomware in action:
Surviving in an IoT-enabled world
5.11.2015
Scare stories around the Internet of Things (IoT) conjure up images of bad guys in hoodies, who live for hacking and to make the lives of other people harder, inventing millions of ways to infiltrate your life through your gadgets. But is this perception a good enough reason to stop using smart devices? We don’t think so; we believe that customers should be aware of the potential risks and know how to mitigate them before embracing the IoT-enabled world.
More than a year ago, our colleague from the Global Research and Analysis Team, David Jacoby looked around his living-room, and decided to investigate how susceptible the devices he owned were to a cyber-attack. He discovered that almost all of them were vulnerable. So, we asked ourselves: was that a coincidence, or are the smart ‘IoT’ products currently on the market really that exposed? To find the answer, earlier this year we gathered up a random selection of connected home devices and took a look at how they work.
The devices we chose for our experiment were as follows:
a USB-dongle for video streaming (Google Chromecast);
a smartphone-controlled IP camera;
a smartphone-controlled coffee maker; and
a home security system, also smartphone-controlled.
The task we set ourselves was simple: to find out whether any of those products posed a security threat to their owner. The results of our investigation provide much food for thought.
Google Chromecast. IoT hacking for beginners
Risk: the content on the victim’s screen is streamed from a source owned by an attacker
Chromecast, which has been recently updated with a more advanced version, is an interesting device. It’s an inexpensive USB-dongle that allows you to stream media from your smartphone or tablet to a TV- or other display-screen. It works like this: the user connects it to a television’s HDMI in order to switch it on. After that the Chromecast launches its own Wi-Fi-network for initial setup. Once it has established a connection with a smartphone or a tablet, it switches its own Wi-Fi off and connects to the user’s home Wi-Fi network. It’s very convenient and user-friendly.
Surviving in an IoT-enabled world
But this could become less convenient and decidedly unfriendly if there is a hacker nearby. The famous “rickrolling” vulnerability, discovered by security consultant, Dan Petro, proves that. It allows the content on the victim’s screen to stream from a source owned by an attacker. This is how it works: the attacker floods the device with special ‘disconnect’ requests from a rogue Raspberry Pi-based device and then, as the Chromecast turns on its own Wi-Fi module in response, Google Chromecast is reconnected to the attacker’s device making it stream the content the attacker wants.
The only way to get rid of this is to switch off the TV, take the dongle out of range of your Wi-Fi hotspot and wait until the attacker gets bored and goes away.
The only limitation to this attack is that the attacker needs to be within range of the Wi-Fi network to which the target Chromecast is connected. However, we discovered in our own experiment that this not necessarily a restriction if you have a cheap directional Wi-Fi antenna and some Kali Linux software. When we used that, we found that Chromecast can be “rickrolled” across a far greater distance than the normal signal range for domestic Wi-Fi networks. What this means is that, while in the original hack by Dan Petro, the attacker would run the risk of being spotted by an angry Chromecast owner, with a directional antenna that risk no longer exists.
We don’t regard this “finding” as a new security discovery; it simply extends a previously-known and so far unpatched security issue. It’s an exercise for beginners in IoT hacking, although it could be used in a really harmful way – but we’ll get to that later. First we’ll go through the other findings of our brief research.
Mitigation: Use in remote parts of your house as this will lower the risk of attacks with a directional antenna
Status: Not patched
IP camera
Issue one
Risk: attackers get access to the email addresses of all the camera users who have experienced technical issues
The IP camera we investigated was positioned by its vendor as a baby monitor. You put the camera in a nursery, download an app on your smartphone, connect the camera to the app and the Wi-Fi, and off you go: you can watch your child whenever you want, from anywhere you like.
Surviving in an IoT-enabled world
Why would someone want to hack a baby monitor, you may well ask? Actually there are a number of recorded instances of baby monitor abuse dating back as early as 2013 (http://www.cbsnews.com/news/baby-monitor-hacked-spies-on-texas-child/) with a similar issue reported in 2015 (http://www.kwch.com/news/local-news/whitewater-woman-says-her-baby-monitor-was-hacked/32427912). So yes, there are people who, for some reason want to hack baby monitors.
When we investigated our camera (in the spring of 2015) there were two different apps available for customers that enabled them to communicate with the camera. Both contained security issues. We were later to learn from the vendor that one of these apps was a legacy app, however it was still being used by a number of camera owners. We discovered that this legacy app contained hardcoded credentials to a Gmail account.
public static final String EMAIL_FROM = “*****@gmail.com”;
public static final String EMAIL_PASSWORD = “*******”;
public static final String EMAIL_PORT = “465”;
public static final String EMAIL_SMTP_HOST = “smtp.gmail.com”;
public static final String EMAIL_TO;
public static final String EMAIL_TO_MAXIM = “maximidc@gmail.com”;
public static final String EMAIL_TO_PHILIPS = “*****@philips.com”;
public static final String EMAIL_USERNAME = “*****@gmail.com”;
The vendor later told us that the account was used to collect reports on technical issues from the camera users.
The problem here is that reports were being sent to this pre-installed account from users’ own email accounts. So an attacker would not even need to buy a camera; all they needed to do was download and reverse-engineer one of the apps to get access to the technical email account and to collect the email addresses of all the camera users who had experienced technical issues. Is it a big issue, that your email could have been exposed to a third party as a result of the exploitation of that vulnerability? It might be. However, realistically-speaking this vulnerability doesn’t appear to be a tempting target for mass-harvesting personal information, mainly because of its relatively small base of victims. Technical issues are rare and the app was old and not really popular at the time of our research. Baby monitors are also a niche product so not many email addresses are stored.
On the other hand, if you are the owner of a baby monitor, you’re most likely a parent and that fact makes you (and by extension your email address) a much more interesting target should an attacker plan a specific, tailored, fraud campaign.
In other words, this is not a critical security vulnerability but it could still be used by attackers. But that wasn’t the only vulnerability we found while investigating the camera and the app.
Status: fixed
Issue two
Risk: full control of the camera by an attacker
After looking at the legacy app we moved on to the more recent version and immediately discovered another interesting issue.
The application communicates with the camera through a cloud service and communication between the app and the cloud service is https-encrypted. The application uses Session ID for authentication which is changed automatically each time a user initiates a new session. It might sound secure, but it is in fact possible to intercept the Session ID and to control the camera through the cloud or to retrieve the password for local access to the camera.
Before the app starts streaming data from the camera, it sends an http request to the cloud service:
type=android&id=APA91bEjfHJc7p6vw3izKmMNFYt7wJQr995171iGq2kk_rD4XaMEHhTXqTmFaAALjWD15bnaVcyMuV2a7zvEFdtV13QXildHQn0PCvQbPikag2CPJwPwOWWsXtP7B0S-Jd3W-7n0JUo-nMFg3-Kv02yb1AldWBPfE3UghvwECCMANYU3tKZCb2A&sessionId=100-U3a9cd38a-45ab-4aca-98fe-29b27b2ce280
This request contains the Session ID which could be intercepted as the request is unencrypted. The Session ID is then used to retrieve the current password. We found that it could be done by creating a special link with the Session ID in the end.
https://*****/*****/*****sessionId=100-U3a9cd38a-45ab-4aca-98fe-29b27b2ce280
In return for this link the cloud service would send the password for the session.
https:// *****/*****/*****sessionId=100-U3a9cd38a-45ab-4aca-98fe-29b27b2ce280
… “local_view”:{“password”:”N2VmYmVlOGY4NGVj”,”port”:9090} …
Using the password it is possible to get full control of the camera, including the ability to watch the streamed video, listen to audio, and play audio on the camera.
It is important to note that this is not a remote attack – the attacker must be on the same network as the app user in order to intercept the initial request, making exploitation less likely. However, app users should still proceed with caution, especially if they are using large networks that can be accessed by many people. For example, if the app user is connecting to their camera from public Wi-Fi, they could be exposing themselves to risk from an attacker on the same network. In such conditions it would not be hard to imagine a real-life app-usage scenario that involved a third-party.
Status: fixed
Issue three
Risk: god mode – an attacker can do anything with camera firmware
The third issue we discovered while investigating our smartphone-controlled camera resided not in the app but in the camera itself. And the issue is rather simple: a factory root password for SSH in the firmware. It is simple because the camera is running on Linux and the root password enables god-mode for anyone who has access to the device and knows the password. You can do anything with camera firmware: modify it, wipe it – anything. All the attacker needs to do in order to extract the password is to download and extract the firmware from the vendor’s website (although the attacker would need to be in the same network with the attacked device to get the URL from which the firmware is being downloaded), extract it and follow this path: \\ubifs\\home/.config. There it is: in plain text.
CONFIG_*******_ROOT_PASSWORD=”sVGhNBRNyE57″
CONFIG_*******_ROOT_PASSWORD=”GFg7n0MfELfL”
What’s more worrying is that, unless they are a Linux expert, there is no way for an inexperienced user to remove or change this password by themself.
Why the SSH password was there is a mystery to us, but we have some suggestions. The root access would be of use to developers and technical support specialists in a situation where a customer encounters an unexpected technical problem that could not be fixed over the phone. In this case, a specialist could connect to the camera remotely, use the SSH password to get root access and fix an issue. Apparently this is a common practice for new models of such devices, which can contain bugs that were not discovered and fixed at the pre-release stage. We looked at the firmware of some other cameras from an alternative vendor and also discovered SSH passwords in there. So the story is: developers leave the SSH password in the firmware in order to have the ability to fix unexpected bugs there and then, and when a stable version of firmware is released they just forget to remove or encrypt the password.
Our second suggestion is that they just forgot it was there. As we discovered during our research, the part of the device where SSH passwords were found – the chipset – is usually shipped by a third-party vendor. And the third-party vendor leaves the SSH password in the camera by default for convenience, to make sure that the vendor of the end-product (the baby monitor) has the ability to tune up the chipset and to connect it with other hardware and software. So the vendor does this and then just forgets to remove the password. As simple as it sounds.
Status: fixed
Communications with the vendor
It wasn’t hard to discover these vulnerabilities and we have to admit that it wasn’t difficult to report them to the vendor and help them to patch them. The camera we investigated was branded by Philips, but was actually produced and maintained by Gibson Innovations. The representatives of the company were extremely quick to react to our report. As a result all the issues we reported have been patched, both in the camera and in the apps (Android and iOS).
This autumn, Rapid7 released a very interesting report about vulnerabilities in baby monitors, and a Philips product (a slightly different version of the camera we investigated) was on the list of vulnerable devices, with a number of vulnerabilities noted, some of them similar to those discovered in our research. But judging by the ‘from-discovery-to-patch’ timeline presented in the report, Gibson Innovations is one of only a few IoT vendors to treat security issues in their products seriously and to do so continuously. Kudos to them for such a responsible approach.
But back to our research.
One could say that the security issues we’ve discovered in the IP camera require access to the same network as the user of the camera or the camera itself, and they would be right. On the other hand, for an intruder that is not necessarily a major obstacle, especially if the user has another connected device in their network.
A smartphone-controlled coffee machine
What could possibly go wrong?
Risk: leakage of the password to the home wireless network
The coffee machine we’ve randomly chosen can remotely prepare a cup of coffee at the exact time you want. You just set the time and when the coffee is ready the app will send you a push-notification. You can also monitor the status of the machine through an app. For instance, it is possible to find out if it is brewing now or not, if it is ready for brewing or if it is time to refill the water container. In other words, a very nice device, which, unfortunately, gives an attacker a way to hijack the password of your local Wi-Fi network.
Surviving in an IoT-enabled world
Before you use it you have to set it up. It happens like this: when the device is plugged in, it creates a non-encrypted hotspot and listens to UPNP traffic. A smartphone running the application for communicating with the coffee machine connects to this hotspot and sends a broadcast UDP request asking if there are UPNP devices in the network. As our coffee machine is such a device, it responds to this request. After that a short communication containing the SSID and the password to the home wireless network, among other things, is sent from the smartphone to the device.
Surviving in an IoT-enabled world
This is where we detected a problem. Although the password is sent in encrypted form, the components of the encryption key are sent through an open, non-protected channel. These components are the coffee machine’s Ethernet address and some other unique credentials. Using these components, the encryption key is generated in the smartphone. The password to the home network is encrypted with this key using 128-bit AES, and sent in base64 form to the coffee machine. In the coffee machine, the key is also generated using these components, and the password can be decrypted. Then, the coffee machine connects to the home wireless network and ceases to be a hotspot until it is reset. From this moment on, the coffee machine is only accessible via the home wireless network. But it doesn’t matter, as by then the password is already compromised.
Status: the vulnerability is still in place
Communications with vendor
We’ve reported our findings to the vendor of the coffee machine, and the vendor has acknowledged the issue and provided us with the following statement:
“Both user experience and security are extremely important to us and we continually strive to strike the right balance between the two. The actual risks associated with the vulnerabilities you mentioned during set-up are extremely low. In order to gain access, a hacker would have to be physically within the radius of the home network at the exact time of set-up, which is a window of only a few minutes. In other words, a hacker would have to specifically target a smart coffee maker user and be around at the exact point of set-up, which is extremely unlikely. Because of this, we do not believe the potential vulnerabilities justify the significant negative impacts it will have on user experience if we make the suggested changes. Though no definite plans to change our set-up procedure are in the works, we are constantly reevaluating and wouldn’t hesitate to make changes if risks become more significant. Should something change in the near future we will let you know.”
We don’t entirely disagree with this statement and have to admit that the attack window is extremely short. The vulnerability could be patched in several ways, but based on the conclusions of our own analysis, almost all of these ways would involve either hardware changes (the Ethernet port on the coffee machine or a keyboard for the password would solve the problem) or the provision of a unique pin code for each coffee machine including those that have already been sold, which is not easy from a logistical point of view. Such changes would considerably impact the user experience and the set up process would become less straightforward.
The only software fix we can propose is to implement asymmetric encryption. In this case the coffee maker would have to send out the public encryption key to the user’s smartphone and only after that the sensitive data exchange would start. This, however, would still allow any user in a given Wi-Fi network, including the attacker, to take control of the coffee machine. The public key would be available to everyone, and the first user to receive it and establish the connection with the coffee maker will be able to control it. Nevertheless, the legitimate user of the coffee machine will at least have a clue that something is going wrong, as during/following? a successful attack they wouldn’t be able to communicate with the device. This is not the case with the current software running on the coffee machine.
So we can say that to some degree we understand the vendor logic: the level of risk this issue brings doesn’t match the level of complexity of measures that must be implemented in order to eliminate the issue. Besides that, it would be wrong to say that the vendor didn’t think about the security of their product at all: as we said earlier, the password is transmitted in protected form, and you have to hold the antenna in a special way.
However, the vulnerability still exists and for a smart criminal it wouldn’t be a problem to exploit it to obtain your Wi-Fi password. The situation is interesting: if you are a user of this coffee maker, every time you change the password for your home Wi-Fi network in order to make it more secure, you’re actually exposing this new password, because each time you implement a new password you have to set up the coffee machine again. And you would never know whether someone had sniffed your password or not. For some people this may not be an issue, but for others it is most certainly a security problem.
For this reason, we will not disclose the vendor or model so as not to draw unwanted attention to the vulnerable product. However, if you are a user of a smartphone-controlled coffee maker and you’re worried about this issue, do not hesitate to contact the vendor and ask them if our findings have something to do with the product that you own, or are planning to purchase.
Onto the final chapter of our journey into the insecure world of IoT.
Home security system vs physics
Risk: bypassing security sensors with no alarms
App-controlled home security systems are pretty popular nowadays. The market is full of different products intended to secure your home from physical intrusion. Usually such systems include a hub that is connected to your home network and to your smartphone, and a number of battery-powered sensors that communicate wirelessly with the hub. The sensors are usually door/window contact sensors that would inform the owner if the window or door they guard has been opened; motion sensors; cameras.
When we initially got our hands on a smart home security system we were excited. Previously we’d seen a lot of news about researchers finding severe vulnerabilities in such products, like the research from HP or another awesome piece of research on the insecurity of the ZigBee protocol used by such products, presented at this year’s Black Hat. We prepared ourselves for an easy job finding multiple security issues.
Surviving in an IoT-enabled world
But that wasn’t the case. The more we looked into the system the better we understood that, from a cyber-security perspective, it is a well-designed device. In order to set up the system, you have to connect the hub directly to your Wi-Fi router, and in order to make the app communicate with the hub, you have to create an account on the vendor’s website, provide your phone number and enter the secret pin code that is sent to you via SMS. All communications between the app and the system are routed through the vendor’s cloud service and everything is done over https.
When looking at how the hub downloads new versions of firmware, we found that the firmware is not signed, which is a bit of an issue as it potentially allows you to download any firmware onto the device. But at the same time, in order to do so you’d have to know the password and the login of the user account. Also, when on the same network as the security system it is possible to send commands to the hub, but to understand what kind of commands it is possible to send, you’d need to reverse-engineer the hub firmware which is not really security research, but aggressive hacking. We’re not aggressive hackers.
So from a software point of view – if you’re not intending to hack a device at all costs – the home security system we investigated was secure.
But then we looked at the sensors.
Defeating contact sensors with their own weapon
Intrusion or contact sensors, included in the package, consist of three main parts: the magnet (the part that you put on a door or on the moving part of a window), the radio transmitter, and the magnetic field sensor. It works as follows: the magnet emits a magnetic field and the magnetic field sensor registers it. If the door or window is opened, the sensor will stop registering the magnetic field and will send a notification to the hub, indicating that the door/window is open. But if the magnetic field is there, it will send no alarms, which means that all you need to bypass the sensor is a magnet powerful enough to replace the magnetic field. In our lab we put a magnet close to the sensor, and then we opened the window, got in, closed the window and removed the magnet. No alarms and no surprises.
One could say that it would only work with windows, where you can be lucky enough to locate easily the exact place where the sensor is placed. But magnetic fields are treacherous and they can walk through walls, and the simplest magnetic field detection app for the smartphone will locate a sensor precisely, even if you don’t have visual contact. So doors (if they’re not made of metal) are vulnerable too. Physics wins!
Motion sensor
Encouraged by an easy victory over contact sensors we moved on to the motion sensor and disassembled it to discover that it was a rather simple infrared sensor that detects the movement of a warm object. This means that if an object is not warm the sensor doesn’t care. As we discovered during our experiment, one would only need to put on a coat, glasses, a hat and/or a mask in order to become invisible to the sensor. Physics wins again!
Protection strategies
The bad news is that magnetic field sensor-based devices and low quality infrared motion sensors are used not only by the home security system we investigated. They’re pretty standard sensors which can be found in a number of other similar products. Just search the IoT e-shops and you’ll see for yourself. There is more bad news: it is impossible to fix the issue with a firmware update. The problem is in the technology itself.
The good news is that it is possible to protect yourself from the burglars who didn’t bunk off Physics in school. The basic rules here are as follows:
Do not rely only on contact sensors when protecting your home if you are using a system of the kind described above. Smart home security system vendors usually offer additional devices, like motion- and audio-sensing cameras, which are impossible to bypass with magnets. So it would be wise to supplement the contact sensors with some smart cameras even though it may cost more. Using contact sensors alone will turn your home security system into what is essentially a high-tech ‘toy’ security system.
If you’re using infrared motion sensors, try to put them in front of a radiator in rooms a burglar will have to walk through, should they make their way into your home. In this case the intruder, no matter what clothes they are wearing, will overshadow the radiator and the sensor will notice the change and report it to your smartphone.
Conclusions
Based on what we discovered during our brief experiment, vendors are doing their best not to forget about the cyber-security of the devices they’re producing, which is good. Nevertheless, any connected, app-controlled device that is usually called an IoT device is almost certain to have at least one security issue. However, the probability that they will be critical is not that high.
At the same time, the low severity of such security issues doesn’t guarantee that they won’t be used in an attack. At the beginning of this article we promised to describe how the safe and funny “rickrolling” vulnerability could be used in a dangerous attack. Here it is.
Just imagine that one day a TV with a Chromecast device connected to it, both belonging to an inexperienced user, starts showing error messages which report that, in order to fix this issue, the user has to reset their Wi-Fi router to factory settings. That means the user would have to reconnect all their devices, including their Wi-Fi-enabled coffee machine. The user resets the router and reconnects all the devices. After that the Chromecast works normally again as do all the other devices in the network. What the user doesn’t notice is that someone new has connected to the router, and then jumped to the baby monitor camera or other connected devices, ones that have no critical vulnerabilities but several non-critical ones.
Surviving in an IoT-enabled world
From an economic perspective it is still unclear why cybercriminals would attack connected home devices. But as the market of the Internet of Things takes off, and technologies are being popularized and standardized, it is only a matter of time before black hats find a way to monetize an IoT attack. Ransomware is obviously a possible way to go, but it’s certainly not the only one.
Besides that, cybercriminals are not the only ones who might become interested in IoT. For instance, this summer the Russian Ministry of Interior Affairs ordered (RU) to research possible ways of collecting forensic data from devices built with the use of smart technologies. And the Canadian military recently published a procurement request for a contractor that can “find vulnerabilities and security measures” for cars and will “develop and demonstrate exploits”.
This doesn’t mean that people should avoid using the IoT because of all the risks. The safe option is to choose wisely: consider what IoT device or system you want, what you plan to use it for and where.
Here is the list of suggestions from Kaspersky Lab:
Before buying an IoT device, search the Internet for news of any vulnerabilities. The Internet of Things is a very hot topic now, and a lot of researchers are doing a great job finding security issues in products of this kind: from baby monitors to app controlled rifles. It is likely that the device you are going to purchase has been already examined by security researchers and it is possible to find out whether the issues found in the device have been patched.
It is not always a great idea to buy the most recent products released on the market. Along with the standard bugs you get in new products, recently-launched devices might contain security issues that haven’t yet been discovered by security researchers. The best choice is to buy products that have already experienced several software updates.
When choosing what part of your life you’re going to make a little bit smarter, consider the security risks. If your home is the place where you store many items of material value, it would probably be a good idea to choose a professional alarm system that will replace or complement your existing app-controlled home alarm system; or set-up the existing system in such a way that any potential vulnerabilities would not affect its operation. Also, when choosing the device that will collect information about your personal life and the lives of your family, like a baby monitor, maybe it would be wise to choose the simplest RF-model, capable only of transmitting an audio signal, and without Internet connectivity. If that is not an option, than follow our first piece of advice – choose wisely!
As for the vendors of IoT-devices, we have only one, but important suggestion: to collaborate with the security community when creating new products and improving old ones. There are initiatives like Builditsecure.ly or OWASP Internet of Things project that could actually help to build an awesome connected device with no serious security issues. At Kaspersky Lab, we will also continue our research to get more information about connected devices and to find out how to protect people against the threats that such devices pose.
vBulletin security patches and zero-day exploit available online
5.11.2015
Rumors on the Internet says that the hackers who breached vBulletin forum website exploited a zero-day flaw, the company issued emergency security patches.
On Sunday, the vBulletin official website has been hacked, according to DataBreaches.net, vBulletin, Foxit Software forums have been hacked by Coldzer0 that has stolen hundreds of thousands of users’ records.
The hacker published screenshots that show he managed to upload a shell to the vBulletin forum website and accessed user personal information, including user IDs, names, email addresses, security questions and answers, and password salts).
In response to the attack, VBulletin Solutions has reset the passwords for over 300,000 accounts on the official website, and The vBulletin technical support has released an emergency security patch release for versions 5.1.4 through 5.1.9 of the vBulletin Internet forum software.
“Very recently, our security team discovered a sophisticated attack on our network. Our investigation indicates that the attacker may have accessed customer IDs and encrypted passwords on our systems,” explained a vBulletin support manager.
It’s not clear if the patches were released because the attacker exploited a zero-day flaw in the platform, the hacker in fact claimed to have compromised the vBulletin.com database exploiting an unknown vulnerability. On Monday, the hacker using the online moniker “Coldzer0” started offering for sale a zero-day vBulletin exploit (“vBulletin 5.x.x Remote Code Execution 0day Exploit”) on a website that specializes in the exploit trading.
Tuesday, after vBulletin released the security patches, a the Twitter account @_cutz published the details of a remote code execution flaw in vBulletin. The experts speculate the existence of the flaw for the past three years.
The offer also includes a video POC of the vBulleting zero-day Exploit:
vBulletin is a very popular platform, it is used by more than 100,000 community websites, including some operated by Electronic Arts, Sony Pictures and Valve Corporation.
VBulletin is urging all users to update their installations as soon as possible.
Offline Ransomware is spreading among Russian users
5.11.2015
Malware researchers at Check Point Technologies have discovered a new offline ransomware that is targeting mainly Russian users.
Malware researchers at Check Point Technologies have spotted a new “offline” ransomware that is targeting Russian users. The principal characteristic of this strain of malware is that it doesn’t need to communicate with a command and control (C&C) server in order to encrypt files.
This feature complicates the analysis of security firms because it is not possible to detect the communication with the control centers.
The offline ransomware has been around since at least June 2014, the experts highlighted that the threat actors behind the campaign have already released numerous variants of the malware.
The last version of the offline ransomware (CL 1.1.0.0) has been released in August 2015, the threat is well known to the principal security firms that detected it with various names (Ransomcrypt.U [Symantec], Win32.VBKryjetor.wfa [Kaspersky] and Troj/Ransom-AZT [Sophos].
Once the ransomware infects the victim’s PC, it encrypts his files and changes the desktop background displaying a message in the Russian language that includes the instructions to recover the files.

“Your files are encrypted, if you wish to retrieve them, send 1 encrypted file to the following mail address: Seven_Legion2@aol.com
ATTENTION!!! You have 1 week to mail me, after which the decryption will become impossible!!!!”
All the files on the machine infected by the CL 1.0.0.0 version, the one analyzed by the researchers at Check Point Technologies, were encrypted, and each one renamed to the following format:
email-[address to contact].ver-[Ransomware internal version].id-[Machine identifier]-[Date & Time][Random digits].randomname-[Random name given to the encrypted file].cbf
Example:
email-Seven_Legion2@aol.com.ver-CL 1.0.0.0.id-NPEULAODSHUJYMAPESHVKYNBQETHWKZOBQFT-10@6@2015 9@53@19 AM5109895.randomname-EFWMERGVKYNBPETHVKZNBQETHWKZNB.RGV.cbf
Victims are asked to pay a ransom between $300 and $380, depending on how fast they perform the payment, to receive a decryption tool and the key needed to recover their files.
The offline ransomware is written in Delphi and uses some Pascal modules, a choice not common for malware developers. The experts explained that the file-encrypting capabilities implemented by the offline ransomware are highly efficient, it is nearly impossible to recover the files once the threat has encrypted it.
Check Point has provided the following description of the file encryption process:
The beginning (first 30000 bytes) of each file is encrypted using two buffers of digits and letters that are randomly generated on the infected machine. The encryption process includes taking each original byte along with one byte from each of the randomly generated buffers and performing mathematical operations on them.
The remainder of each file (if it exists) is encrypted using an RSA public key (“local”) that is randomly generated on the infected machine, along with the matching local RSA private key required for decryption of the data.
The randomly generated buffers and the local RSA private key that are required for decryption are added as metadata to each encrypted file, and are then encrypted using three hardcoded RSA 768 public keys that the offender created in advance (“remote”). The matching remote RSA private keys required to unlock the metadata are located on the attacker’s side.
The threat actors used several email addresses in their campaign, most of them AOL and Gmail accounts. It is interesting to note that the unique account related to a Russian email provider, madeled@mail.ru, is also one of the emails associated with the original version of the offline ransomware. The address was no more used by crooks after the version 4.0.0.0.

Ransomware are very profitable for cyber criminals, according to security researchers of the Cyber Threat Alliance which have conducted an investigation into the cybercriminal operations leveraging CryptoWall ransomware, criminals behind CryptoWall 3.0 Made $325 Million.
On a weekly basis, new malware appears in the wild, recently the fourth version of the popular Cryptowall was detected online and new ones are expected to come.
Trojanized adware: already infected more than 20,000 Android Apps
5.11.2015
Researchers at Lookout firm have come across a new malicious adware family distributed via trojanized versions of popular Android applications.
Researchers at mobile security firm Lookout have come across a new malicious adware family distributed via trojanized versions of popular Android applications.
Security experts at Lookout have discovered a new strain of adware dubbed Shuanet, which is distributed via trojanized versions of popular Android apps, including the Okta’s two-factor authentication application, Candy Crush and Facebook.
Shuanet is able to gain root access to the infected device phone without the user’s knowledge, the threats install themselves as system applications and are very hard to remove from the devices.
The researchers at Lookout have discovered more than 20,000 popular Android applications that were trojanized with the adware Shuanet, Kemoge and Shuanet and distributed through third-party repositories. The trojanized versions of the mobile apps are fully functional, for this reason, they don’t raise suspicion. It is important to note that threat actors behind the campaign avoided compromising antivirus apps, a circumstance that suggests a high level of planning when creating these malware campaigns.
“Lookout has detected over 20,000 samples of this type of trojanized adware masquerading as legitimate top applications, including Candy Crush, Facebook, GoogleNow, NYTimes, Okta, Snapchat, Twitter, WhatsApp, and many others.” Lookout’s Michael Bentley wrote in a blog post. “Malicious actors behind these families repackage and inject malicious code into thousands of popular applications found in Google Play, and then later publish them to third-party app stores.”
The expert observed the majority of the Shuanet adware infections in the United States, Germany, Iran, Russia, India, Jamaica, Sudan, Brazil, Mexico, and Indonesia.
Lookout researchers believe that threat actors behind the adware campaigns Kemoge, Shedun and Shuanet are different groups, anyway the adware families appear to be linked. In some cases, the variants of malware analyzed share between 71 and 82 percent of their code, a circumstance that suggest the authors used the same pieces of code to build their versions of the auto-rooting adware.
Kemoge and Shuanet adware share at least three exploits to root devices.
“While historically adware hoped to convince the user to install new applications by showing banners and annoying pop ups, now it can install these third party apps without user consent. In this way it can heavily capitalize on the Cost Per Install paid out by web marketing companies,” Lookout’s Michael Bentley said in a blog post. “Unfortunately, should the revenue model change on clicks-per-install and ads, this may lead to malware authors using this privilege escalation for new monetization strategies.”
According to the experts, it is easy to predict that this type of trojanized adware will become even more sophisticated over the time.
“We expect this class of trojanized adware to continue gaining sophistication over time, leveraging its root privilege to further exploit user devices, allow additional malware to gain read or write privileges in the system directory, and better hide evidence of its presence and activities.”
Cracka hackers who doxed CIA Chief, not hit the FBI Deputy Director
5.11.2015
Cracka, the crew of young hackers who doxed the CIA Director John Brennan now hit the FBI Deputy Director Mark Giuliano ’s wife by hacking her email account.
I always say, give a keyboard and internet connection to a kid and he would destroy your company. It is not a joke, the effort needed to launch a cyber attack is smaller than in the past, and the economy of an attack advantages striker, who faces a very low cost compared to defense and would cause devastating damage.
Recently, four teens were arrested in connection with the TalkTalk data breach, meanwhile a group of alleged teenagers has hacked the personal email account of the CIA Director John Brennan.
The group of young hackers calls themselves “Crackass” (Cracka) and now it seems they are targeting other US Government Officials, they are arrogant and heedless of the fact that the Feds are on their tracks.
“Now the hackers are back at it, despite the fact that the FBI is investigating them, and that some law enforcement officials anonymously said the government is going to “make an example” out of them.” explained Lorenzo Bicchierai on Motherboard.
One of members of the cyber gang “Cracka” told Motherboard that they have now hacked the email account belonging another illustrious US official, the FBI Deputy Director Mark Giuliano.
This time the hackers violated a Comcast email account belonging to the Giuliano’s wife, they also published online a series of screenshots to prove they were in the account. The attackers haven’t provided further information on the method they used to take over the email account.
An email account, event your wife’s email is rich of precious information like your contact list, but it could include more data such as information related your next trip or the results of a clinical examination to which you have subjected. In this case, the hackers have found Giuliano’s mobile phone in the email account’s contact lists and called him.
“I called it and asked for Mark and he’s like ‘I don’t know you but you better watch your back’ and then he hung up and I kept calling and he was getting mad then he didn’t pick up,” Cracka told Motherboard via online chat.

The FBI still hasn’t commented the alleged hack of the Giuliano’s email.
The hacking crew targeted the FBI official because the Feds are investigating on them
Cracka said that they were not looking to get any information out of this hack, is an action conducted for revenge.
“We didn’t target him for anything interesting, we targeted him because FBI are [sic] investigating us,” he said.
Lorenzo Bicchierai who had the opportunity to view the screenshots shared by the Cracka confirmed that the account doesn’t appear to contain any sensitive information, except the contact list.
Anyway this contact list could be a good starting point for skilled hackers that could use is to target the family and friends of the couple in order to gather other information for a successive attack.
Stay tuned and thanks to Lorenzo Bicchierai for its excellent post.
CryptoWall 4.0 Released with a New Look and Several New Features
4.11.2015
The fourth member of the CryptoWall family of ransomware, CryptoWall 4.0, has just been released, complete with new features and a brand new look.
We recently reported that CryptoWall 3.0 has allegedly caused over $325 million in annual damages. CryptoWall first emerged in April 2014. Its first major upgrade was dubbed CryptoWall 2.0, and first emerged in October 2014. CryptoWall 3.0 then emerged in January 2015 and terrorized organizations on a global scale. Now, in November 2015, CryptoWall 4.0 has emerged.
New Features
New features such as the encryption of the names and extensions of affected files have emerged with the 4th member of the CryptoWall family. Additionally, CryptoWall 4.0 has changed the name of its ransom notes to HELP_YOUR_FILES.TXTand HELP_YOUR_FILES.HTML.
The ransom note itself contains payment instructions and also mocks the infected user.

Spread Method
The initially reported sample, provided by an infected user on the Bleeping Computer forums, was spread via e-mail through phishing e-mails with ZIP archive attachments claiming to be resumes. The file within the ZIP archive is a JavaScript file, that is obfuscated and beautified that downloads the CryptoWall 4.0 payload from a hard-coded URL.

However, it’s likely that exploit kits will begin to deliver CW4 as a payload very soon, if they are not already (especially the Angler EK).
Technical Information
The C&C communication and behavioural activity of CryptoWall 4.0’s payload is quite similar to its earlier versions. The specific sample that I have analyzed performed the following actions, as can be evidenced by the below images.
Contacted Domains

Added Files

Deleted Files

Modified Files

Added Registry Keys

Process Tree
INITIAL SAMPLE
exe
exe -k netsvcs
EXE “C:UsersAdministratorDesktopHELP_YOUR_FILES.TXT”
exe “C:UsersAdministratorDesktopHELP_YOUR_FILES.HTML”
exe Delete Shadows /All /Quiet
Voice as a threat: VoLTE, a new tool to compromise mobile networks
4.11.2015
While communication technology providers are seeking consensus over the future of 5G networks, carriers are wasting no time in rolling out new technologies available for the current 4G networks. Voice over LTE or simply VoLTE is one of these technologies. VoLTE allows transmitting voice calls over data layers.
Something's wrong with VoLTE
What exactly does that mean? Well, let us explain some technical details. Today’s cellular networks employ three ‘planes’: data, voice and control. We typically use the data plane for mobile Internet, and the voice plane for voice calls. The third plane, to put it simply, is used to manage everything what happens on the other two planes.
Traditional cellular networks handle voice calls through dedicated circuits. However, the 4G technology allows for the prioritization and transmission of voice traffic as packets with higher priority via the data plane. That is essentially VoLTE. The control plane packets have the highest priority. In essence, VoLTE is a sort of IP telephony (VoIP) adapted for use over cellular networks.
VoLTE brings a handful of benefits. First, ubiquitous VoLTE deployment will render existing 2G/3G infrastructures impractical and thus not necessary to support, since VoLTE won’t require a separate infrastructure to handle voice calls. Secondly, VoLTE offers higher bandwidth compared to 3G in boosting the voice quality.
The third benefit is that VoLTE can be used for video conferencing. Last but not least, mobile carriers claim VoLTE offers better call privacy and faster connection. All in all, it looks like VoLTE has a number of critical benefits with no particular drawbacks. At least upon first impression.
As it usually happens, every breakthrough technology has its growing pains. Researchers from the University of California, in joint effort with their colleagues of Shanghai Jiao Tong University and the Ohio State University, demonstrated practical attacks on VoLTE in two US Tier-1 carriers’ networks.
The researchers managed to demonstrate how a criminal can drop all of the victim’s calls, or to increase the amount of charges on the victim’s cellular bill, or vice versa to gain free mobile data access. The interesting thing is that criminals don’t need to hack networks to achieve their goals, or use expensive equipment to carry out the attacks. All they need is an unrooted or rooted smartphone.
The researchers’ key finding is that one can fool VoLTE and send ordinary data packets masqueraded as ‘the high priority’ signal or voice packets
This means that a potential attacker can have carte blanche. Signal packets are not charged for, so once you use this ‘wrapper’ for ordinary data packets, you can be freed from a responsibility of paying for your data plan. To offer a proof of concept, the researcher had a 10-minute Skype call and the carrier never registered their consumption of data traffic.
The signal (control) plane has the highest priority, which opens a pool of opportunities to culprits. If you jam up this layer with data packets masqueraded as signal packets, the signal packets won’t have enough bandwidth available. This method could be a means of cutting network access to someone or to launch a targeted attack and arrange network downtime by jamming it with faux signal packets.
Finally, attackers can use the same method to flood the victim with data packets which, provided the victim does not employ an unlimited data plan, might mean a lot of extra charges the target would need to pay to the carrier. Moreover, such attacks are not detected by firewalls, which are there to filter malicious traffic. In such an attack, a legitimate mobile traffic is used, which makes firewalls unable to detect an attack.
All of the above concerned the ability to transfer data packets via the signal (control) plane, but the same approach could work on the voice plane as well. For example, the researchers managed to subdue a voice call over VoLTE: a victim would accept the call but couldn’t hear anything, as voice packets were lost in the flood of faux signal packets.
The researchers offer a handful of solutions to at least partially solve the issues; both carriers whose networks were probed during the research have already deployed some of them.
How #hackers can exploit #VoLTE technology vulnerability to compromise #4G networks. #mobile #security
Tweet
Countries like Germany or Russia have just started to roll out VoLTE services – so it may well be the case that all the carriers won’t be that fast patching the vulnerabilities.
Unfortunately, some of the vulnerabilities cannot be patched without making changes in VoLTE as a standard. Of course, carriers would be more vigilant of what happens in their networks and make sure to cut off the transmission of the signal traffic between any devices, except for legitimate connections between a phone and a signal server, but it is never enough.
To fix all VoLTE issues, there is a need for a joint effort of OEMs, chipset vendors, carriers and standardization bodies.
That’s the reason why the researchers try to widely publicize this problem: the more widely acknowledged the problem would become, the faster the solutions would be found.
Users, on their end, should treat their mobile security more seriously: in order to carry out the described attacks, adversaries would have to install a malicious app on smartphones. Such mobile malware is very likely to be detected by a good security software.
And, finally, the absolute majority of popular devices and 4G active networks don’t support VoLTE at all so far. Let us hope that, by the time VoLTE becomes a ubiquitous service, all security issues will be solved.
GovRAT, the malware-signing-as-a-service platform in the underground
4.11.2015
Security Experts at InfoArmor discovered GovRAT, a malware-signing-as-a-service platform that is offered to APT groups in the underground.
In the past, I have explained why digital certificates are so attractive for crooks and intelligence agencies, one of the most interesting uses is the signature of malware code in order to fool antivirus. Naturally, digital certificates are becoming a precious commodity in the underground ecosystem, many operators in the black markets started this lucrative business.
A few weeks ago experts at IBM Security X-Force observed the offer of certificates in the Dark Web with a model of sale they called CaaS (Certificates as a service). Cybercriminals would use the Dark Web for selling high-grade code certificates -which they have obtained from trusted certificate authorities- to anyone that is interested in purchasing them.
The sale of code signing certificates has increased considerably over the past few months, a trend confirmed also by a recent research analysis conducted by the threat intelligence firm InfoArmor.
The research has given rise to a case in which a hacker tricked a legitimate certificate authority into issuing digital certificates for malware before offering a cyber-espionage tool called GovRAT.
GovRAT a hacking platform that allows the malware creation, it comes bundled with digital certificates for code signing. The same digital certificates were initially offered for sale on the black marketplace TheRealDeal Market hosted on the Tor network. GovRAT was offered for sale at 1.25 Bitcoin, but experts observed the creator is now selling it privately.

The GovRAT tool digitally signs malicious code with code-signing tools such as Microsoft SignTool, WinTrust, and Authenticode technology. The experts consider that final customer for GovRAT are APT groups targeting political, diplomatic and military employees of more than 15 governments worldwide.
The strains of malware analyzed by the researchers at InfoArmor were signed individually with different digital certificates.
InfoArmor reported also that seven banks, some in the US, and 30 defence contractors have also been targeted by the GovRAT. It has been estimated that more than 100 organizations have been hit by malware created by the GovRAT platform since early 2014.
Which is the price for code-signing digital certificates?
Experts at InfoArmor found the precious commodities on many underground black markets, they are offered for sale at a price between $600-$900 depending on the CA that issued them. It is quite easy to find code-signing digital certificates issued by Comodo, GoDaddy and Thawte. It is clear that digital certificates could be revoked by the CA, but as explained by numerous sellers the event is rare and often companies are very slow in invalidating them.
“[The buyers are] blackhats (mostly state-sponsored), malware developers,” Andrew Komarov, CIO at InfoArmor, told El Reg. “It is pretty professional audience, as typical script kiddies and cybercriminals don’t need such stuff. It is used in APTs, organised for targeted and stealth attacks. The appearance of such services on the blackmarket allow [hackers] to perform them much more easily, rather like Stuxnet.” “It is a pretty specific niche of modern underground market,” “It can’t be very big, as the number of certificates is pretty limited, and it is not easy to buy them, but according to our statistics, the number of such services is significantly growing.”
Stolen or fake certificates are a prerogative of state-sponsored attacks, they were used in numerous offensives including the Stuxnet and the Sony hack, the experts explained that cyber criminals are gaining digital certificates through resellers.
“Bad actors buy digital certificates through resellers, where the due diligence of customers is pretty poor,” Komarov explained. “They provide fake names, or fake information about the author and purpose on why they need this certificate, and receive it. After they have received such certificates, they trade it on the blackmarket for malware developers, allowing them to create signed malware for further APT in several minutes.”
InfoArmor reported the case of certs4you.org, a website offering malware-signing-as-a-service with prepared digital certificates. One such service ran from a website called certs4you.org before the domain was suspended.
Let me suggest reading the report on GovRAT published by InfoArmor.
Researcher releases Free Hacking Tool that Can Steal all Your Secrets from Password Manager
4.11.2015
Unless we are a human supercomputer, remembering a different password for every different site is not an easy task.
But to solve this problem, there is a growing market of password managers and lockers, which remembers your password for every single account and simultaneously provides an extra layer of protection by keeping them strong and encrypted.
However, it seems to be true only until a hacker released a hacking tool that can silently decrypt and extract all usernames, passwords, as well as notes stored by the popular password manager KeePass.
Dubbed KeeFarce, the hacking tool is developed by Kiwi hacker Denis Andzakovic and is available on GitHub for free download.
Hackers can execute KeeFarce on a computer when a user has logged into their KeePass vault, which makes them capable of decrypting the entire password archive and then dumping it to a file that attackers can steal remotely.
How Does KeeFarce Work?
KeeFarce obtains passwords by leveraging a technique called DLL (Dynamic Link Library) injection, which allows third-party apps to tamper with the processes of another app by injecting an external DLL code.
The injected code then calls an existing KeePass export method to export the contents of a currently open database, including user names, passwords, notes, and URLs to a clear-text CSV file.
The key takeaway here is:
KeyFarce is just a password extraction tool that could work perfectly like a password Stealer for remote hacking when combined with a computer malware.
If that happens, it is game over as you'll have much bigger things to worry about since most of your data is generally logged in already.
While KeeFarce is specifically designed to target KeePass password manager, it is possible that developers can create a similar tool that takes advantage of a compromised machine to target virtually every other password manager available today.
Fourth, a 16-year-old Hacker, Arrested over TalkTalk Hack
4.11.2015
Police have arrested a fourth person, a 16-year-old boy, from London in connection with the high-profile hack of British telecoms giant TalkTalk.
The investigating officers from the Metropolitan Police Cyber Crime Unit (MPCCU) arrested the teenager at his home in Norwich on suspicion of Computer Misuse Act offences.
TalkTalk was subjected to a 'significant and sustained' hacking attack on its official website two weeks back, which put the Bank Details and Personally Identifiable Information (PII) of its 4 Million customers at risk.
The telco confirmed last week that at most 1.2 Million names, email addresses and phone numbers and around 21,000 unique bank account numbers and sort codes were compromised in the attack.
However, TalkTalk said that the stolen credit card details were incomplete, so the payment cards could not be used for any false financial transactions. But, the company advised customers to remain vigilant against financial fraud.
Security experts believe that the recent hacking attack on TalkTalk may have taken place due to SQL injection (SQLi) attack, a method used to inject SQL commands to breach the database and get access to the users' personal data.
This is the fourth arrest since TalkTalk suffered a massive data breach and the 16-year-old boy remains in custody at a local police station.
The Police Service of Northern Ireland and MET detectives arrested a 20-year-old Staffordshire man on Sunday while 2 teenagers were also arrested in connection with the Data breach incident.
The first arrest came last week when police arrested and then bailed a 15-year-old boy from Northern Ireland while another 16-year-old boy from London was arrested and bailed on 30 October.
However, the connection between these four persons has not been known yet.
A Fourth Teenager was arrested over TalkTalk data breach
4.11.2015
British police announced Tuesday they had arrested a fourth teenager in connection with a data breach suffered by the Internet Service Provider TalkTalk.
The investigation of the TalkTalk data breach is still going, in a few days other two suspects have been arrested by law enforcement under the country’s Computer Misuse Act. The company suffered other two cyber attacks in eight months that caused the theft of customers’ data. A few days ago a third man was arrested in connection with the TalkTalk hack, he is a 20-year-old man from Staffordshire and he has been released on bail until March after he was arrested by law enforcement under the country’s Computer Misuse Act.
Investigators believe that he is a member of the group that hacked the telco firm TalkTalk stealing 1.2 million customer details (email addresses, names, and phone numbers, dates of birth) along with nearly 28,0000 partial credit and debit cards.
talktalk HQ
According to a statement from the Metropolitan Police, a fourth hacker was arrested, another teen that is from Norwich.
The TalkTalk ISP admitted some data are that were stolen by hackers are not encrypted, they classified the attack as “significant and sustained” but downgraded the risk of possible financial theft resulting from the hack.
TalkTalk confirmed that it is supporting the investigation conducted by the National Crime Agency and law enforcement. There are many aspects still no clear in the incident, let me remind you that the company was hit by a DDoS attack before the data breach and that an alleged LulzSec member claimed responsibility for the it denying any involvement in the data breach.
Someone also sent a ransom demand to TalkTalk, but no news has been provided on its origin and authenticity.
Chimera, a new strain of ransomware in the wild
4.11.2015
According to a German website, there is a new strain of ransomware dubbed Chimera that also threatens to publish personal data on the Internet.
A new strain of ransomware is targeting German companies, it is named Chimera and this time crooks don’t limit their extortion scheme to the file encrypting, they are also threatening victims to release sensitive data on the Internet.
The attack vector exploited by Chimera is the email, bogus emails are sent to the company employees to offer them a job or to apply for a job position. The malicious emails include a link to a Dropbox address, the messages try to trick employees into visiting the link claiming additional information.
When victims click on the link they download the Chimera ransomware that once installed encrypts user data present on the local system and on network connected drives. The ransomware displays victims the following message:
Victims need to pay 2.45 Bitcoin (around €630/$694) to decrypt the files. If the victims will not pay the ransom, the crooks will publish stolen data along with their name, on the Internet.
The researchers at Botfrei, who first spotted the malware, confirmed that here is no evidence that cyber criminals have leaked online the stolen data.
“There is so far no evidence or information whether the criminals have stolen from affected systems or are already published on the Internet personal information!” states a blog post published on Botfrei.
It is likely that the criminals have no ability to exfiltrate the encrypted data, that is expected to have a significant volume.
“Another problem with the edentulous threat posed by this ransomware is that the implication of a threatened personal information disclosure would assume that someone is combing through the files for that personal information,” explained the InfoSec analyst Bob Covello.
“This is a level of involvement that most ransomware criminals do not want to broach. Ransomware is designed for a quick payday for the criminals with little interaction with the victim.”
The primary defense against ransomware is to have the an updated backup of most important documents.
Project Zero Experts Found critical flaws in Samsung Galaxy S6 Edge
4.11.2015
Experts at Google’s Project Zero have discovered a number of high severity flaws in the Android OS version running on Samsung Galaxy S6 Edge smartphones.
Experts at Google Project Zero are conducting an analysis of the Android operating system running on the Android OS installed by other manufacturers on their mobile devices.
The principal manufactures have been using the Android Open Source Project (AOSP) source code to customize the Google OS for their systems, and experts at Project Zero wanted to test them.
“The majority of Android devices are not made by Google, but by external companies known as Original Equipment Manufacturers or OEMs which use the Android Open-Source Project (AOSP) as the basis for mobile devices which they manufacture.”states the blog post published by the Project Zero team.
“OEMs are an important area for Android security research, as they introduce additional (and possibly vulnerable) code into Android devices at all privilege levels, and they decide the frequency of the security updates that they provide for their devices to carriers.”
Recently a team of ten researchers from the Project Zero team and other Google security teams analyzed Samsung Galaxy S6 Edge smartphone searching for vulnerabilities in OS running on it.
They focused their efforts in evaluating the possibility to escalate kernel privileges from both local and remote starting point.
The researchers tried to gain remote access to data managed by the Android device, including contacts, messages and photos obtaining persistence in the mobile phone.
Samsung Galaxy S6 Edge 2
After a week of intense tests on the Samsung Galaxy S6 Edge, the team has found eleven high severity issues, the most important is a path traversal vulnerability (CVE-2015-7888) affecting the Samsung WifiHs20UtilityService service that can be exploited by attackers to write arbitrary files on the device.
“There is a process running a system on the device that scans for a zip file in /sdcard/Download/cred.zip and unzips the file. Unfortunately, the API used to unzip the file does not verify the file path, so it can be written in unexpected locations.” states the post.
Another serious flaw (CVE-2015-7889) discovered by the team in the Samsung Galaxy S6 Edge is affecting the email client (CVE-2015-7889) installed on the device. The flaw could be triggered by attackers to forward user’s emails to a different account via a series of intents from an unprivileged application. The experts also found another vulnerability (CVE-2015-7893) in the email client can be exploited to execute arbitrary JavaScript code embedded in an email.
The experts explained that the device drivers and media processing were affected by several issues that they have quickly identified.
“We found issues very quickly in these areas through fuzzing and code review.” states the post.
The discovered issues are related to the image parsing (CVE-2015-7894, CVE-2015-7895, CVE-2015-7896, CVE-2015-7897, CVE-2015-7898) and the drivers (CVE-2015-7890, CVE-2015-7891, CVE-2015-7892).
The Project Zero team reported the security vulnerabilities to Samsung in July, the company has fixed eight flaws in October, the remaining ones will be fixed this month.
#opKKK Anonymous denied involvement in recent leak
4.11.2015
#opKKK – The hacking collective Anonymous is denying involvement in the Monday leak of alleged Ku Klux Klan members that included several US senators.
A few days ago the popular Anonymous collective has posted a video message on YouTube and a message on Twitter to announce that it is holding a list of names of the Ku Klux Klan
members.
The popular collective announced its initiative under the operation dubbed #OpKKK, the target in this phase of the operation started last year is the Ghoul Squad, a group that is considered an organization belonging to the KKK.
“We will release, to the global public, the identities of up to 1,000 Klan members, Ghoul Squad affiliates and other close associates of various factions of the Ku Klux Klan across the United States.”
Unfortunately, other groups or individuals within the collective are abusing the Anonymous brand to conduct their personal initiatives and gain notoriety. As reported by the Register the group Anonymous” (PUTNAIOOACA) posted on Pastebin a message threatening to out members of the Ku Klux Klan too.
“we will be revealing about 1000 of your klan member identities.” the Anonymous PUTNAIOOACA said. “We are not attacking you because of what you believe in as we fight for freedom of speech, We are attacking you because of what you do to our brothers and sisters.” “You messed with our family and now we will mess with yours.”
But PUTNAIOOACA collective seems to be interested in revealing the identities of the KKK members working in the institutions ( Law enforcement, politicians, and any public servant or government representative)
As promised, early this week someone disclosed online a list of alleged Ku Klux Klan members that included several US senators. The official account for the @Operation_KKK took the distance from the announcement and posted the following message.
The information disclosed by other groups alleged to belong to Anonymous, but not members of #OpKKK, Pastebin, includes total phone numbers and email addresses allegedly belonging to KKK members. The list contains the names of at least 4 U.S. Senators and 5 City Mayors.


Obviously something went wrong, experts speculate that a faction of the collective has moved independently and it wants to influence the @Operation_KKK’s effort. Other experts speculate that someone want to use the Anonymous Brand and the #opKKK to launch a smear campaign against prominent personalities.
At the time I was writing Anonymous is inviting all to join it today for an ALL DAY town hall conversation on race, racism, terror & free speech.( #OpKKK #HoodsOff)
For any information about #OpKKK Anonymous invited to refer to the official .@Operation_KKK twitter account
Hey guys, tomorrow November 5 is Guy Fawkes’ Day … what will happen?
Komplexní zabezpečení firemní sítě zajistí nové UTM od Keria
4.11.2015

Nové UTM zařízení Control Box NG100, které uvedlo na trh Kerio, je určené pro sítě menších firmem, ideálně prý do deseti uživatelů.
Jde o relativně drobné, nicméně plně vybavené řešení pro unifikované zabezpečení sítí. Jeho součástí je firewall a směrovač, detekce a prevence útoků (IPS), antivirová ochrana, VPN a filtrování obsahu.
Nové zařízení je určeno pro menší firmy se zaměstnanci, kteří pracují buď na jednom místě, nebo jsou rozmístěni v menších týmech v různých lokalitách.
Podle výrobce chrání a zabezpečuje síť, uživatele i data a navíc prý přispívá i k vyšší produktivitě zaměstnanců.
NG100 lze monitorovat a přistupovat k němu kdykoli a z jakéhokoli zařízení prostřednictvím centralizované webové správy MyKerio.
Cena zařízení činí 14 688 Kč, cena ročního Software Maintenance je stanovená na 4 590 Kč.
Chimera, a new strain of ransomware in the wild
3.11.2015
According to a German website, there is a new strain of ransomware dubbed Chimera that also threatens to publish personal data on the Internet.
A new strain of ransomware is targeting German companies, it is named Chimera and this time crooks don’t limit their extortion scheme to the file encrypting, they are also threatening victims to release sensitive data on the Internet.
The attack vector exploited by Chimera is the email, bogus emails are sent to the company employees to offer them a job or to apply for a job position. The malicious emails include a link to a Dropbox address, the messages try to trick employees into visiting the link claiming additional information.
When victims click on the link they download the Chimera ransomware that once installed encrypts user data present on the local system and on network connected drives. The ransomware displays victims the following message:
chimera ransomware
Victims need to pay 2.45 Bitcoin (around €630/$694) to decrypt the files. If the victims will not pay the ransom, the crooks will publish stolen data along with their name, on the Internet.
The researchers at Botfrei, who first spotted the malware, confirmed that here is no evidence that cyber criminals have leaked online the stolen data.
“There is so far no evidence or information whether the criminals have stolen from affected systems or are already published on the Internet personal information!” states a blog post published on Botfrei.
It is likely that the criminals have no ability to exfiltrate the encrypted data, that is expected to have a significant volume.
“Another problem with the edentulous threat posed by this ransomware is that the implication of a threatened personal information disclosure would assume that someone is combing through the files for that personal information,” explained the InfoSec analyst Bob Covello.
“This is a level of involvement that most ransomware criminals do not want to broach. Ransomware is designed for a quick payday for the criminals with little interaction with the victim.”
The primary defense against ransomware is to have the an updated backup of most important documents.
More than 100 Million Android users at risk due to the Baidu Moplus SDK
3.11.2015
A vulnerability known as Wormhole affects the Baidu Moplus SDK and potentially exposes more than 100 Million users to cyber attacks.
The Moplus software development kit (SDK) distributed by the Chinese Search Engine Baidu includes a functionality that can be exploited to gain access to the user’s device. The backdoor-like feature potentially exposes more than 100 Million Android users to cyber attacks.
“A vulnerability known as Wormhole that reportedly affected the software development kit (SDK), Moplus by Baidu is making waves due to the severity of the impact once successfully exploited. The said vulnerability was discovered by WooYun.og, a vulnerability reporting platform in China.” states a blog post published by TrendMicro. “However, as our investigation on this security bug unfolded, we found out that the Moplus SDK has backdoor functionalities that are not necessarily due or related to a vulnerability. “
The Wormhole vulnerability in the Moplus SDK could be exploited by hackers to open an unsecured and unauthenticated HTTP server connection on the user’s device, and this connection is established in the background without the user’s knowledge.
The Moplus SDK automatically installs the Web server when a mobile app developed with the SDK is launched on the device. The server doesn’t implement authentication and can accept requests from any source. The server receives requests on both 6259 or 40310 ports, this means that an attacker can easily locate it by searching on a shared network the open ports.
“… the notion that it is vulnerability-related when in actual this SDK has backdoor routines such as pushing phishing pages, inserting arbitrary contacts, sending fake SMS, uploading local files to remote servers, and installing any applications to the Android devices without user’s authorization. ” continues the post.
The Moplus SDK is already used by more than 14,000 Android apps, nearly 4,000 of them are developed by Baidu. These apps have been already downloaded by more than 100 Million Android users.
Baidu moplus SDK
The Moplus SDK allows an attacker to perform many actions including:
Send SMS messages
ake phone calls
Get mobile phone details
Add new contacts
Get a list of local apps
Download files on the device
Upload files from the device
Silently install other apps (if the phone is rooted)
Push Web pages
Get phone’s geo-location, and many more
moplus SDK malicious featuresThe experts highlighted that the Wormhole flaw in the Moplus SDK is very dangerous because it is potentially easier to exploit than the Stagefright flaw. In this case in fact the hacker just need to locate a vulnerable device exposing the open ports.
The researchers at Trend Micro have confirmed the existence in the wild of a specific malware, dubbed ANDROIDOS_WORMHOLE.HRXA, which exploit the Wormhole in Moplus SDK.
Researchers reported the issue to Baidu and Google, the Chinese Giant has already pushed a partial fix for the issue in a new release of the Moplus SDK.
Be aware, the new version of SDK doesn’t completely solve all problems, for example the HTTP server remains exposed online.
A few days ago, another Chinese company has caught distributing malicious SDK which included spying features. According to according to Palo Alto Networks, nearly 18,000 Android Applications built using the Taomike SDK have been found to include SMS Stealing Library.
Anonymous Hackers to Leak 1000 of KKK Members Details on Million Mask March (Nov 5, 2015)
3.11.2015
The Online Hacktivist group Anonymous announced it plans to reveal the identities of about 1,000 Ku Klux Klan (KKK) members on 5th November, the day of the Global Protest movement known as the Million Mask March.
Million Mask March, where protesters don Guy Fawkes masks in hundreds of cities around the world, and march together against the corrupt Governments and corporations.
Ku Klux Klan (KKK) is classified as a White Supremacist Racist group by the Anti-Defamation League and the Southern Poverty Law Center, allegedly having total 5,000 to 8,000 members.
It was founded after the Civil War by former Confederate soldiers to fight against the reforms imposed by the North during Reconstruction.
“We've gained access to yet another KKK Twitter account. Using the info obtained, we will be revealing about 1000 Klan member identities.”, Anonymous Hackers tweeted last week.
The list of 1000 KKK Members, to be released on 5th November, apparently includes the names of US Politicians, according to the hackers affiliated with Anonymous — Operation KKK.
"You operate much more like terrorists, and you should be recognized as such. You are terrorists that hide your identities beneath sheets and infiltrate society on every level,” the hacker collective said.
"The privacy of the Ku Klux Klan no longer exists in cyberspace. You've had blood on your hands for nearly 200 years."
kkk-anonymous
Yesterday another group of Anonymous hackers, not members of Operation KKK, published the first batch of information (unverified) on Pastebin, which includes total 57 phone numbers and 23 email addresses allegedly belonging to KKK members, along with names of 4 U.S. Senators and 5 City Mayors.
However, Hackers affiliated with Operation KKK denies any connection with the above leak and promises to release its own 1000 KKK Members list on the 5th Nov.
Backdoor in Baidu Android SDK Puts 100 Million Devices at Risk
3.11.2015
The China's Google-like Search Engine Baidu is offering a software development kit (SDK) that contains functionality that can be abused to give backdoor-like access to a user's device, potentially exposing around 100 Million Android users to malicious hackers.
The SDK in question is Moplus, which may not be directly available to the public but has already made its way into more than 14,000 Android apps, of which around 4,000 are actually created by Baidu.
Overall, more than 100 Million Android users, who have downloaded these apps on their smartphones, are in danger.
Security researchers from Trend Micro have discovered a vulnerability in the Moplus SDK, called Wormhole, that allows attackers to launch an unsecured and unauthenticated HTTP server connection on affected devices, which works silently in the background, without the user's knowledge.
Also Read: More than 26 Android Phone Models Shipped with Pre-Installed Spyware
This unsecured server does not use authentication and can accept requests from anyone on the Internet. Though the server is controlled by the attacker, who can send requests to a particular port of this hidden HTTP server to execute malicious commands.
Malicious Functionalities of Wormhole
Currently, the researchers have identified that the SDK is using the port 6259 or 40310 to perform malicious activities on affected Android devices, which includes:
Send SMS messages
Make phone calls
Get mobile phone details
Add new contacts
Get a list of local apps
Download files on the device
Upload files from the device
Silently install other apps (if the phone is rooted)
Push Web pages
Get phone's geo-location, and many more
Since the SDK automatically installs the Web server when a Moplus SDK app is opened, hackers just need to scan a mobile network for port 6259 or 40310, thereby finding vulnerable devices they can abuse.
Also Read: Android Malware Can Spy On You Even When Your Mobile Is Off
Wormhole is More Dangerous than Stagefright
The vulnerability, according to researchers, is potentially easier to exploit than the Stagefright flaw, as Wormhole doesn't require social engineering to infect an unsuspecting user.
Trend Micro has also found at least one malware strain (detected as ANDROIDOS_WORMHOLE.HRXA) in the wild that takes advantage of Wormhole in Moplus SDK.
Researchers informed both Baidu as well as Google of the vulnerability.
As a result, Baidu has just pushed a partial fix for the problem by releasing a new version of the SDK that removed some of the SDK's functionality, but not all. The HTTP server remains online and active; however, Baidu assured its users that no backdoor exists now.
Must Read: Stagefright Bug 2.0 — One Billion Android SmartPhones Vulnerable to Hacking
This isn't the first time a Chinese company has caught distributing malicious SDK. Just a few days ago, the Taomike SDK – one of the biggest mobile ad solutions in China – was caught secretly spying on users' SMS messages and uploading them to a server in China.
The same malicious functionality was also discovered two weeks back in another SDK developed by Youmi; that affected 256 iOS apps, which were caught using private APIs to collect users private data. However, Apple eventually banned those apps from its App Store.
Kaspersky DDoS Intelligence Report Q3 2015
3.11.2015 Zdroj: Kaspersky
BOTNETS DDOS-ATTACKS
Download PDF version
Q3 events
Of all the Q3 2015 events in the world of DDoS attacks and the tools used to launch them, we picked out those that, in our opinion, best illustrate the main trends behind the evolution of these threats.
DDoS attacks targeting financial organizations for the purpose of extortion;
new techniques to increase the intensity of attacks by manipulating web pages;
active development of Linux-based botnets for DDoS attacks.
Attacks on financial organizations
In Q3 2015, there was increased activity by the cybercriminal group “DD4BC” responsible for a number of attacks on major banking organizations around the world. The group has been targeting banks, media groups and gaming companies since September, threatening to take down their customer websites unless they pay a ransom. The owner of the targeted resource is asked to pay between 25 and 200 bitcoins ($6,500 – $52,500), or have their servers disabled. Some of the first victims included organizations in Australia, New Zealand and Switzerland, while a warning was received by major financial institutions in Hong Kong. The Bank of China and the Bank of East Asia also reported that they were targeted by illegal activity. In the third quarter, a number of Russian financial institutions also received notifications from cybercriminals asking for a specific sum in cryptocurrency to terminate an attack.
Unusual attack scenario
The company CloudFlare reported a DDoS attack with an unusual scenario. A site belonging to one of CloudFlare’s customers was being subjected to an attack made up of 275,000 HTTP requests per second. Of particular interest was the fact that the attackers made use of malicious JavaScript embedded in adverts. An iframe with a malicious advert that contained the JavaScript was run on the browsers of lots of users, resulting in their workstations sending XHR requests to the victim. Experts believe that these malicious ads can also display some legitimate applications.
XOR DDoS bot activity
The specialists at Akamai Technologies witnessed growth in the capacity of a DDoS botnet consisting of Linux-based computers whose victims were mostly Asian sites belonging to educational institutions and gaming communities. A distinctive feature of the bot is the use of XOR-encryption both in the malicious program and for communication with the C&C servers. At the same time, in order to self-propagate the bot brute-forces passwords to the root account in Linux systems. Linux is often used as a server operating system, which means that the server also has the channel and computing resources that the attackers can use to launch DDoS attacks. Using SYN and DNS floods, this botnet has been successfully carrying out attacks with a capacity of 109-179 Gbps.
The proportion of DDoS attacks from Linux-based botnets in Q3 2015 was 45.6% #KLReport
Tweet
According to Kaspersky Lab data, the botnets from Linux-based servers infected by the XOR DDoS bot actively attacked resources located in China.
DDoS availability
On the one hand, the software that is used for DDoS attacks is becoming more complicated; on the other hand, the tools for DDoS attacks are becoming more freely available and easier to use. As a result, setting up and launching a DDoS attack no longer requires any special technical knowledge. A fairly competent criminal could easily unleash a powerful attack.
This fact is confirmed by attacks on the educational portal of the Republic of Tatarstan carried out by students attempting to block communication between teachers and parents. Throughout the year the attackers repeatedly tried to bring down the portal, which was protected by Kaspersky DDoS Protection. All their attempts were unsuccessful, but their persistence did succeed in attracting the attention of Kaspersky Lab’s experts.
The longest DDoS attack in Q3 2015 lasted for 320 hours #KLReport
Tweet
The availability and ease of use of the tools for DDoS attacks has resulted in the range of targets growing. It is generally accepted that DDoS attacks are mainly focused on financial institutions, government agencies, businesses and the media. Now, however, any resource that has attracted the ire of an unscrupulous web user could be subjected to a DDoS attack – even an educational portal.
Statistics of botnet-assisted DDoS attacks
Methodology
The DDoS Intelligence system (part of Kaspersky DDoS Protection) is designed to intercept and analyze commands sent to bots from command and control (C&C) servers, and does not have to wait until user devices are infected or cybercriminal commands are executed in order to gather data.
In this report, a single (separate) DDoS attack is defined as an incident during which any break in botnet activity lasts less than 24 hours. If the same web resource was attacked by the same botnet after a break of more than 24 hours, this is regarded as a separate DDoS attack. Attacks on the same web resource from two different botnets are also regarded as separate attacks.
In Q3 2015, 91.6% of resources, targeted by DDoS attacks, were located in 10 countries #KLReport
Tweet
The geographical distribution of DDoS victims and C&C servers is determined according to their IP addresses. In this report, the number of DDoS targets is calculated based on the number of unique IP addresses reported in the quarterly statistics.
It is important to note that DDoS Intelligence statistics are limited to those botnets that were detected and analyzed by Kaspersky Lab. It should also be highlighted that botnets are just one of the tools used to carry out DDoS attacks; therefore, the data presented in this report does not cover every DDoS attack that has occurred within the specified time period.
Q3 Summary
In Q3 2015, botnet-assisted DDoS attacks targeted victims in 79 countries around the world.
91.6% of targeted resources were located in 10 countries.
The largest numbers of DDoS attacks targeted victims in China, the US and South Korea.
The longest DDoS attack in Q3 2015 lasted for 320 hours (or 13.3 days).
SYN DDoS, TCP DDoS and HTTP DDoS were the most common DDoS attack scenarios.
Linux-based bots are actively used by cybercriminals; the proportion of DDoS attacks from Linux-based botnets in the third quarter was 45.6%.
Geography of attacks
In Q3, the targets of DDoS attacks were located in 79 countries around the world. 91.6% of attacked resources were located in 10 countries.
Distribution of unique DDoS attack targets by country, Q3 vs Q2 2015
China still leads the Top 10 ranking: in Q3 of 2015, 34.5% of DDoS attack targets were located there, an increase of 4.6 percentage points (p.p.) on the previous quarter. The US came second with 0.8%. South Korea remained in third place (17.7%) although its share increased considerably – by 7.9 p.p.
The Netherlands (1.1%) re-entered the Top 10. A newcomer to the rating was Japan whose share accounted for 1.3% of all attacked resources. Germany (1.0%) and Hong Kong (0.9%) left the Top 10.
If we look at the number of reported attacks, 92.3% of all attacks (an increase of 14.7 p.p. on Q2) had targets within the same Top 10 countries:
Distribution of DDoS attack by countries, Q3 vs Q2 2015
In the third quarter, China (37.9%), the US (22.7%) and South Korea (14.1%) remained in the leading three places. The Netherlands (1.1%) and Japan (1.3%) pushed France (0.9%) and Hong Kong (0.9%) out of the Top 10 in terms of the number of attacks. The biggest increase in the proportion of DDoS attacks in Q3 was observed in the US – the share of attacks grew by 5.4 p.p.
In Q3 2015, the largest numbers of DDoS attacks targeted victims in China, the US & South Korea #KLReport
Tweet
The figures for the leading three countries in both rankings – the number of attacks and the number of targets – increased by more than they did for the other Top 10 countries. The continued leadership of China and the US in the rankings is due to cheap web hosting in those countries, which explains why so many targeted web resources are located there.
The absolute leader in terms of the number of attacks was an IP address allegedly belonging to a data center in Hong Kong: throughout the quarter it was attacked 22 times.
Changes in DDoS attack numbers
In Q3 2015, DDoS activity was distributed unevenly, with two peaks: the first fell in mid-July, the second in late September. The quietest period was from early August to mid-September.
Number of DDoS attacks over time* in Q3 2015.
* DDoS attacks may last for several days. In this timeline, the same attack may be counted several times, i.e. one time for each day of its duration.
The peak number of attacks in one day was 1344, recorded on 24 September.
Tuesday was the most active day of the week in terms of DDoS attacks.
Distribution of DDoS attack numbers by days of the week
The fact that Tuesday leads is probably due to a dramatic rise in the number of DDoS attacks on that day of the week on 14 July and on 22 September. Particularly active on those two days were botnets from Linux-based servers infected by the XOR DDoS bot that attacked resources in China.
Types and duration of DDoS attacks
99.3% of DDoS targets in Q3 2015 (vs. 98.2% in Q2) were attacked by bots belonging to one family.
In only 0.7% of all cases cybercriminals launched attacks using bots from two different families (or the clients used the services of several attack agents). In 0.2% of cases, three or more bots were used.
In Q3 2015, SYN DDoS (51.7%) remained the most popular attack method. TCP DDoS (16.4%) and HTTP DDOS (14.9%) were second and third respectively. ICMP-DDoS, whose contribution doubled over the last two quarters and accounted for 5.1%, was fourth.
The distribution of DDoS attacks by types
Once again, most attacks lasted no longer than 24 hours in Q3 2015. However, the number of attacks that lasted a week or longer increased considerably.
The distribution of DDoS attacks by duration (hours)
The longest DDoS attack in the previous quarter lasted for 205 hours (8.5 days); in Q3, this record was beaten by an attack that lasted 320 hours (13.3 days).
C&C servers and botnet types
In Q3 2015, South Korea took the lead in terms of the number of C&C servers located on its territory; its share grew from 34% to 56.6%. Noticeably, in South Korea this quarter the number of C&C servers that control Nitol bots increased significantly. Nitol began to use Dynamic DNS services more actively, in particular, no-ip.org and codns.com. As mentioned above, the percentage of DDoS attacks targeting resources located in South Korea also increased.
The proportion of C&C servers located in the US and China dropped significantly – from 21% to 12.4% and from 14% to 6.9% respectively.
Distribution of botnet C&C servers by countries in Q3 2015
The activity of Windows and Linux botnets continued to fluctuate. After the previous quarter’s reduction in the share of Linux-based botnets, in Q3 they regained ground – the proportion of attacks by Linux bots grew from 37.6% to 45.6%.
Correlation between attacks launched from Windows and Linux botnets
The increase in the proportion of Linux bot activity was most probably down to insufficient protection for Linux-based machines and, quite importantly, their higher Internet speeds. This makes Linux more attractive to cybercriminals despite the relative complexity in developing, acquiring and exploiting Linux bots.
Attacks on banks
The third quarter of 2015 saw the return of DDoS extortionists to the cybercrime scene. A number of major banking institutions in a variety of countries were targeted by DDoS attacks that were then followed by demands for a large payment in cryptocurrency to stop the attack. This particular aspect of the attacks suggests they are the work of the cybercriminal group DD4BC (Distributed Denial of Service for Bitcoin), which demands bitcoin ransoms.
It appears the group has now reached Russia, where a number of financial institutions were also attacked. Some of the Russian banks that were targeted were either protected by Kaspersky DDoS Protection or quickly connected to the service as soon as the DDoS attacks began. This meant they avoided any damage and the banks’ websites and online banking systems continued to function smoothly.
Kaspersky Lab registered a wave of lengthy DDoS attacks on the online banking systems of eight well-known financial institutions, with some banks repeatedly targeted.
SYN DDoS, TCP DDoS and HTTP DDoS were the most common DDoS attack scenarios in Q3 2015 #KLReport
Tweet
For all attacks the cybercriminals used a complex combination of amplification attacks that disable online resource with minimal effort.
Three types of attack were used to overload the channel: NTP amplification, SSDP amplification and RIPv1 amplification which reached 40 Gbps. In some cases, the attacks were supplemented by a HTTPS flood attack that reached 150 Mbps from a botnet with about 2,000 attacking hosts.
The attacks lasted from one to four hours.
The attackers not only demanded a bitcoin ransom but also threatened the banks with unprecedented terabit attacks. However, these threats have not been implemented in practice.
We can assume that the peak attack parameters registered at the end of September were the attackers’ maximum – Kaspersky Lab experts recorded this particular aggregate capacity in simultaneous attacks on several banks.
Unfortunately, this does mean the power of attacks will not increase in the future.
Conclusion
The correlation between the number of attacks launched from Windows and Linux botnets marks an interesting trend, with criminals starting to actively use botnets from infected servers. There are several reasons for this.
Firstly, servers have a significantly bigger Internet channel than domestic machines, making it possible to organize powerful attacks with only a few C&C servers.
Secondly, the level of server protection is not always very high, leaving them vulnerable to hacking. If security patches are not regularly installed on the server, it quickly becomes an easy prey for cybercriminals: it does not take them long to discover such servers and exploit any known vulnerabilities. Then there is the expanded arsenal of available exploits that have appeared after a number of vulnerabilities were detected in open-source products such as exploits for the ghost vulnerability, which is still in use.
Thirdly, the power of a server botnet can be increased by renting additional servers.
In these circumstances, timely installation of security patches on servers becomes critical. For the owners of web resources, effective protection from DDoS attacks originating from server botnets is strongly recommended.
Kim Dotcom's Decentralized Internet — For You, Powered By You
3.11.2015
Imagine the internet that would offer you to communicate privately with anyone else without censorship, safe from the prying eyes of surveillance authorities….
… Decentralized, Encrypted, Peer-to-Peer Supported and especially a non-IP Address based Internet.
Yeah, a New Private Internet that would be harder to get Hacked.
This Internet is a dream of all Internet users today and, of course, Kim Dotcom – the Famous Internet entrepreneur who introduced legendary Megaupload and MEGA file sharing services to the World.
Kim Dotcom announced plans to start his very own private internet at the beginning of this year and has now revealed more details about MegaNet — a decentralized, non-IP based network that would share data via "Blockchains," the technology behind Bitcoins.
On Thursday, Dotcom remotely addressed a conference in Sydney, Australia, where he explained how MegaNet will utilize the power of mobile phones and laptops to operate.
How will MegaNet work?
MegaNet will work on non-IP-based Internet that will use blockchains and new protocols to communicate and exchange data while using the Internet's existing physical infrastructure.
MegaNet will actually rely on the unused processing power of people's smartphones and laptops.
Users with MegaNet on their smartphone would be able to donate their device's processing capability and storage bandwidth when they actually aren't using it.
Dotcom believes that once the service has enough subscribers, this would become an incredibly large amount of power, so much so that it can operate MegaNet.
MegaNet – The Internet For the People, From the People
"If you have a 100 Million smartphones that have the MegaNet app installed we'll have more online storage capacity, calculating power and bandwidth than the top 10 largest websites in the world combined [together], and that is the power of MegaNet," Dotcom said.
"Over the years with these new devices and capacity especially mobile bandwidth capacity, there will be no limitations."
So in short, MegaNet is a decentralized Internet, as Dotcom says, "from the people, for the people."
Encryption Used Won't be Cracked Even by Supercomputers
MegaNet will still use using the Internet's existing physical infrastructure people use today, but will add an extra layer of encryption running through all communications.
Dotcom did not reveal too much detail about the encryption he will be going to utilize, but said that he is going to harness very long keys, systems that won't be "reverse engineered or cracked by any supercomputer."
Difficult to Invade Privacy of Users
Most importantly, MegaNet will make it difficult for law enforcement agencies to invade its users privacy, as the entire network is fully encrypted.
"If you don't have IP addresses you can not hack the server, you can not execute denial of service [DDoS] attacks on gaming services or websites," Dotcom said from New Zealand, where he's currently awaiting the result of his extradition trial.
The millionaire is confident that MegaNet would be an excellent technology solution that will keep you secure over the Internet, without the requirement of any new infrastructure for users’ privacy.
With the launch of MegaNet, which is expected sometime in 2016, Dotcom hopes 100 Million users to sign-up within the first year of its launch.
Hackers win $1 million bounty for iOS 9 remote hack
3.11.2015
A team of hackers has received a million-dollar payout for disclosing a iOS zero-day vulnerability that could allow an attacker to remotely hack any Phone.
Bad news for the Apple users, a team of hackers have received a million-dollar payout for disclosing an iOS zero-day vulnerability that could allow an attacker to remotely hack any Phone running the latest version of iOS, i.e. iOS 9.
The unknown group of hackers has sold a zero-day vulnerability to Zerodium, the Exploit trade company controlled by the security firm Vupen which is specialized in Buys and Sells zero-day exploits.
In September Zerodium offered a million dollar prize to any person that finds unknown, unpatched bug in iOS 9 with the main purpose to jailbreak iThings.
The company announced the payment of a working exploit being able to do remote code execution on an iOS device via safari/chrome or by SMS/MMS, it also added that the zero-day exploit/jailbreak “must lead to and allow a remote, privileged, and persistent installation of an arbitrary app (e.g. Cydia) on a fully updated iOS 9 device.”
The working zero-day exploit can combine other vulnerabilities to perform a jailbreak without the need of a reboot or a connection to an external device.
“The whole exploitation/jailbreak process should be achievable remotely, reliably, silently, and without requiring any user interaction except visiting a web page or reading a SMS/MMS (attack vectors such as physical access, Bluetooth, NFC, or baseband are not eligible for the Million Dollar iOS 9 Bug Bounty. ZERODIUM may, at its sole discretion, make a distinct offer to acquire such attack vectors.).”
The exploit/jailbreak must support and work reliably on the following devices (32-bit and 64-bit when applicable):
– iPhone 6s / iPhone 6s Plus / iPhone 6 / iPhone 6 Plus
– iPhone 5 / iPhone 5c / iPhone 5s
– iPad Air 2 / iPad Air / iPad (4rd generation) / iPad (3th generation) / iPad mini 4 / iPad mini 2
Now it seems that someone has found the way to remotely hack the new IpPhone.
As I have explained several times the untethered jailbreaks allows users to gain root access to the operating system of the Apple devices allowing to bypass all the security features designed by Apple.
Jailbreaking a device is possible to install and execute software that could not otherwise be installed or run on that device, or to remove pre-installed software that could not otherwise be uninstalled.
In the attack scenario described by the group of hackers, they are able to exploit a zero-day in order to perform a remote browser-based jailbreak. Experts speculate that the new zero-day works on the new iPhone 6 and iPhone 5 models, iPad Air 2 and Air, iPad 4 and 3, and the iPad mini 4 and iPad mini 2.
The bug hunters have found three flaws in iOS 9.x and Google Chrome that lead them to remotely hack any iPhone running iOS 9.x.
“No software other than iOS really deserves such a high bug bounty,” founder Chaouki Bekrar told Vulture South. “Our bounty required much more work than a classic jailbreak as it had to be remote and browser-based, so this required two to three additional zero-days compared to a public jailbreak.” “The exploit chain includes a number of vulnerabilities affecting both Google Chrome browser and iOS, and bypassing almost all mitigations in place.”
According to Bekrar, the winners submitted the zero-day exploit a few hours before the contest closed, there was also another team of hacker that reported a partial jailbreak and could gain a partial reward.
Actually the experts at Zerodium are testing the zero-day exploit, obviously only the Zerodium clients will have the access to the remote browser-based untethered jailbreaking, the company confirmed that the zero-day will not be disclosed in public.
“We will first report the vulnerabilities to our customers, and we may later report them to Apple,” Bekrar added.
Who are the clients of companies like Zerodium and Vupen? Which is the final use of such kind of zero-day exploits?
The exploits could be acquired by totalitarian governments that could use them for surveillance and to track opponents. An attacker could use them to install any application that could allow to track individuals, including spyware and surveillance software.
Apple users have no choice, the must hope that security experts at Apple will find the zero-day bug and will fix it before someone could exploit it in the wild.
KeeFarce Hacking tool steals encrypted credentials from KeePass password manager
3.11.2015
KeeFarce is a recently released hacking tool that swipes encrypted credentials from the KeePass password manager through the DLL injection.
A password manager is considered one of the most secure tools to archive strong passwords in a computer. Unfortunately, the presence of a malware on the PC can expose passwords even if they are stored with a password manager.
A hacking tool recently released subbed KeeFarce is able to silently decrypts all usernames, passwords, and notes stored by the popular KeePass password manager and transcribes them information into a file.
“Indeed, if the operating system is owned, then it’s game over,” explained to Ars, Denis Andzakovic researcher at Security Assessment and the creator of KeeFarce.
Hackers can execute the KeeFarce tool on a computer where a logged in user has unlocked the KeePass database, under this condition, KeeFarce is able to decrypt the entire password archive.
“The point of KeeFarce is to actually obtain the contents of the password database. Say a penetration tester has achieved domain admin access to a network but also wants to obtain access to networking hardware, non-domain infrastructure, etcetera. The tester can compromise a sysadmin’s machine and use the tool to swipe the password details from the KeePass instance the sysadmin has open.” added Andzakovic.
KeeFarce is able to bypass the process memory protection implemented by the KeePass password manager, it extracts the passwords from the database by injecting a dynamic link library code. The injected DLL is able to invoke an existing function in KeePass that exports the contents of a currently open database to an external file in CSV format. The extracted data is in clear text and includes user names, passwords, notes, and URLs.
The DLL injection is a common process to allow programs to interoperate, but it could be abused to insert malicious code in the context of a running application.
KeeFarce works against KeePass 2.28, 2.29 and 2.30 running on Windows 8.1 (32 and 64 bit), it should also work on older Windows machines.
Tools like KeeFarce reminds us that password managers could represent a single point of failure that could be exploited with severe repercussion by hackers.
Similar tools could be used to hack also other commercial password managers.
Hackers WIN $1 Million Bounty for Remotely Hacking latest iOS 9 iPhone
3.11.2015
Well, here's some terrible news for all Apple iOS users…
Someone just found an iOS zero-day vulnerability that could allow an attacker to remotely hack your iPhone running the latest version of iOS, i.e. iOS 9.
Yes, an unknown group of hackers has sold a zero-day vulnerability to Zerodium, a startup by French-based company Vupen that Buys and Sells zero-day exploits.
And Guess what, in How much?
$1,000,000. Yes, $1 Million.
Last month, a Bug bounty challenge was announced by Zerodium for finding a hack that must allow an attacker to remotely compromise a non-jailbroken Apple device through:
A web page on Safari or Chrome browser,
In-app browsing action, or
Text message or MMS.
Zerodium's Founder Chaouki Bekrar confirmed on Twitter that an unnamed group of hackers has won this $1 Million Bounty for sufficiently submitting a remote browser-based iOS 9.1/9.2b Jailbreak (untethered) Exploit.
NO More Fun. It's Serious Threat to iOS Users
For those who are not aware, this remote Jailbreak is not really cool.
Why? Because…
The only difference between a malicious cyber attack and Jailbreak is – Payload, the code that executes on target system after exploitation.
A traditional jailbreak process is usually used to deploy an alternative App Store, but in hands of Hackers or law enforcement agencies, the same exploit can allow them to install any app they want with full privileges i.e. Spyware, Malware or Surveillance software.
Moreover, We know that Zerodium's parent company Vupen develops hacking techniques based on those bugs and typically sells them to multiple government customers.
Also Read: For Better Privacy & Security, Change these iOS 9 Settings Immediately.
So, the chances are high that the firm will resell the newly discovered and undisclosed remote iOS zero-day jailbreak exploit to its clients, which are said to include Spy agencies, Governments, and Law enforcement agencies.
Your Turn, Apple…
Let's see how much time Apple security team will now take to find out this open zero-day bug in its software and close the doors before it gets too late.
Meet The World's First Person Who Hacked His Body to Implant a Bitcoin Payment CHIP
3.11.2015
hacker Bitcoin mining chips
Hackers are now going crazy and trying new ways in Biohacking.
Until now, we have seen a hacker who implanted a small NFC chip in his hand in order to hack Android smartphones and bypass almost all security measures.
However, now the level of craziness has gone to a whole new level.
A Swedish hacker has devised a neat trick that makes him able to buy groceries or transfer money between bank accounts by just waving his hand.
Yes, you heard that right. Patric Lanhed, a software developer at DigitasLBi, implanted a small NFC (Near Field Communications) chip with the private key to his Bitcoin wallet under his skin.
So How Does the Trick Work?
So, while sending Bitcoin payment from one digital wallet to another, he just has to wave his hands against an NFC chip reader that will scan the data, and a custom software will confirm the authenticity of the key, triggering the money transfer.
A proof-of-concept video demonstration by Patric and his acquaintance Juanjo Tara Ortiz, an engineer at Arduino, shows a successful Bitcoin payment from one wallet to another. The transaction, what the duo claim, is…
The World's First "Bio-Payment" — a way to send and receive money using:
Data stored inside a human body
A custom software app built on top of a Bitcoin wallet’s developer API.
Bitcoin-related NFC technology has been around for a while, but this chip implant approach takes the potential of this technology to the next level.
$1 BILLION invested in Bitcoin Firms So Far
Major companies, including American Express (AXP), MasterCard, Bain Capital and the New York Stock Exchange, have invested overall, a record-breaking $1 Billion into Bitcoin-related tech startups.
The Bitcoin technology promises to transform the way we trade stocks, get paid, send money to each other, and much more. It has come up as an effective way to stop fraud.
So, one can see the future of Bitcoin payments using the bio-payment system.
The Future of Bio-Payments
Bitcoin is just the beginning of their research, as the duo believe that they can turn this payment transfer system into a bio-payment terminal system to be used in stores.
So in near future, the custom software developed by the duo will have the capability to allow people to store different types of data, including Bitcoin, on their chips.
They claim the applications besides a bio-payment will include:
Payments
Medical records
ID papers like an embedded Passport
Travel documents
ICE (In Case of Emergency) tags
Data authentication for consumer applications like vehicle entry, home security, computer authorization, and many more
VCard exchange over a phone and lot more applications
So be ready, as the age of Bio-Payments has arrived.
The official website of the popular vBulletin forum has been hacked
3.11.2015
The website of the vBulletin forum software is down for maintenance following a data breach that exposed personal information of hundreds of thousands users
On Sunday, the vBulletin official website has been hacked by an attacker using the moniker “Coldzer0.” The website has been defaced and the vBulletin forum was displaying the message “Hacked by Coldzer0.”
At the time I was writing the website is down for maintenance and there are no details on the attack, according to DataBreaches.net, vBulletin, Foxit Software forums have been hacked by Coldzer0 that has stolen hundreds of thousands of users’ records.
The hacker published screenshots that show he managed to upload a shell to the vBulletin forum website and accessed user personal information, including user IDs, names, email addresses, security questions and answers, and password salts).

I suggest users to change their passwords as soon as possible, especially if they share the same credentials across other websites.
DataBreaches.net has linked the online moniker “Coldzer0” to the malware analyst and security researcher Mohamed Osama. The Egyptian expert Osama has promptly removed all references to the vBulletin attack from his social media accounts. Osama has also deleted his personal website, coldroot.com, after his name was in the headlines due to the attack to vBulletin.

The hacker claims to have exploited a zero-day vulnerability affecting the vBulletin forum to hack the popular application.
It is not the first time that hackers target vBulletin, in 2013 experts at Security firm Imperva discovered that more than 35000 websites based on vBulletin CMS were hacked exploiting a known vulnerability.
IT threat evolution in Q3 2015
2.11.2015 Zdroj: Kaspersky
APT CYBER ESPIONAGE FINANCIAL MALWARE INTERNET BANKING MALWARE STATISTICS MOBILE MALWARE TROJAN-BANKERS VULNERABILITIES AND EXPLOITS
Download PDF version
Q3 in figures
According to KSN data, Kaspersky Lab solutions detected and repelled a total of 235,415,870 malicious attacks from online resources located all over the world.
75,408,543 unique URLs were recognized as malicious by web antivirus components.
Kaspersky Lab’s web antivirus detected 38,233,047 unique malicious objects: scripts, exploits, executable files, etc.
There were 5,686,755 registered notifications about attempted malware infections that aim to steal money via online access to bank accounts.
Kaspersky Lab’s file antivirus detected a total of 145,137,553 unique malicious and potentially unwanted objects.
Kaspersky Lab mobile security products detected:
1,583,094 malicious installation packages;
323,374 new malicious mobile programs;
2516 mobile banker Trojans.
Overview
Targeted attacks
Turla’s ‘eye in the sky’
We’ve written about Turla several times over the last year or so (our initial report, follow-up analysis and campaign overview can be found on securelist.com). The group behind this cyber-espionage campaign has been active for more than eight years, infecting hundreds of computers in more than 45 countries. The organizations targeted include government agencies, embassies, military, education, research and pharmaceutical companies.
The Turla group profiles its victims, using watering-hole attacks in the initial stages. However, as outlined in our latest report, for subsequent operations the group makes use of satellite communications to manage its C2 (Command-and-Control) traffic.
Most people think of satellite communications as a means of broadcasting TV, but they are also used to provide Internet access. Typically, this is done in remote locations where other types of Internet access are slow, unstable or unavailable. One of the most widespread and least expensive means of obtaining satellite-based access is through a downstream-only connection.
Turla gang turns to satellites for #cybercrime #KLRreport
Tweet
The method used by Turla to hijack downstream satellite links does not require a valid satellite Internet subscription. The key benefit is that it’s anonymous – it’s very hard to identify the attackers. The satellite receivers can be located anywhere within the area covered by the satellite (typically a wide area) and the true location and hardware of the C2 server can’t be easily identified or physically seized. It’s also cheaper than purchasing a satellite-based link and easier than hijacking traffic between the victim and the satellite operator and injecting packets along the way.
In order to attack satellite-based Internet connections, both the legitimate users of these links, as well as the attackers’ own satellite dishes, point to the specific satellite that is broadcasting the traffic. The attackers exploit the fact that packets are unencrypted. Once an IP address that is routed through the satellite’s downstream link has been identified, the attackers start listening for packets coming from the Internet to this specific IP. Once a packet has been identified, they identify the source and spoof a reply packet back to the source using a conventional Internet line. At the same time, the legitimate user of the link just ignores the packet as it goes to an otherwise unused port (for instance, port 80 or 10080). You can find a graphical explanation of how Turla uses satellite links here.
The Turla group tends to focus on satellite Internet providers located in the Middle East and Africa, including Congo, Lebanon, Libya, Niger, Nigeria, Somalia and the UAE. Satellite broadcasts from these countries don’t normally cover European and North American countries, making it very hard for security researchers to investigate such attacks.
The use of satellite-based Internet links is an interesting development. The hijacking of downstream bandwidth is cheap (around $1,000 for the initial investment and around $1,000 per year in maintenance), easy to do and offers a high degree of anonymity. On the downside, it’s not always as reliable as more traditional methods such as bullet-proof hosting, multiple proxy levels and hacked web sites – all of which Turla also uses. This makes it less likely that it will be used to maintain extensive botnets. Nevertheless, if this method becomes widespread among APT groups or cybercriminals, it will pose a serious problem for the IT security industry and law enforcement agencies.
Darkhotel extends its ‘guest’ list
In November 2014, we reported on the Darkhotel APT. These attacks were characterized by the misuse of stolen certificates, the deployment of HTA files using multiple methods and the infiltration of hotel Wi-Fi networks to place backdoors on targets’ computers.
Recently we published an update on Darkhotel. While the attackers behind this APT continue to use the above methods, they have also supplemented their armoury. They have shifted their attention more towards spear-phishing of their chosen victims. As well as using HTA files, they are also deploying infected RAR files, using the RTLO (right to left override) mechanism to mask the real extension of the file. The attackers also use Flash exploits, including a zero-day exploit leaked as a result of the Hacking Team security breach.
In 2015, Darkhotel extended its geographic reach, to include victims in North Korea, Russia, South Korea, Japan, Bangladesh, Thailand, India, Mozambique and Germany.
Blue Termite
In August, we reported on the Blue Termite APT, a targeted attack campaign focused on stealing information from organizations in Japan. These include government agencies, local government bodies, public interest groups, universities, banks, financial services, as well as companies working in sectors such as energy, communication, heavy industry, chemical, automotive, electrical, news media, information services, health care, real estate, food, semiconductor, robotics, construction, insurance, transportation, and more. One of the most high profile targets was the Japan Pension Service.
The malware is customized according to the specific victim. The Blue Termite backdoor stores data about itself – including C2, API name, strings for anti-analysis, values of mutexes, as well as the MD5 checksum of backdoor commands and the internal proxy information. The data are stored in encrypted form, making analysis of the malware more difficult – a unique decryption key is required for each sample.
The main method of infection, as with so many targeted attack campaigns, is via spear-phishing e-mails. However, we have detected other methods of infection. These include drive-by downloads using a Flash exploit (CVE-2015-5119) – one of the exploits leaked following the Hacking Team security breach. Several Japanese web sites were compromised this way. We also found some watering-hole attacks, including one on a web site belonging to a prominent member of the Japanese government.
Malware stories
End of the line for CoinVault?
On 14 September 2015, Dutch police arrested two men for suspected involvement in CoinVault ransomware attacks, following a joint effort by Kaspersky Lab, Panda Security and the Dutch National High Tech Crime Unit (NHTCU) – highlighting the benefit of collaboration between police and security researchers. This malware campaign started in May 2014 and continued into this year, targeting victims in more than 20 countries, with the majority of victims in the Netherlands, Germany, the United States, France and Great Britain. They successfully encrypted files on more than 1,500 Windows-based computers, demanding payment in bitcoin to decrypt data on victims’ machines.
The cybercriminals responsible for this ransomware campaign modified their creations several times to keep on targeting new victims. We published our first analysis of CoinVault in November 2014, soon after the first sample of the malicious program appeared. The campaign then stopped until April 2015, when we found a new sample. In the same month, Kaspersky Lab and the Dutch NHTCU launched a web site to act as a repository of decryption keys. In addition, we also made available online a decryption tool to help victims recover their data without having to pay the ransom.
Arrests made in #CoinVault #ransomware attacks by Dutch Authorities with assist from @Kaspersky #KLReport
Tweet
After publishing the site, Kaspersky Lab was contacted by Panda Security, which had found information about additional malware samples. We were able to confirm that the samples were related to CoinVault. We passed this information to the Dutch NHTCU.
You can find our analysis of the twists and turns employed by the CoinVault authors here.
Ransomware has become a notable fixture of the threat landscape. While this case shows that collaboration between researchers and law enforcement agencies can lead to positive results, it’s essential for consumers and businesses alike to take steps to mitigate the risks of this type of malware. Ransomware operations rely on their victims paying up. On top of anti-malware protection, it’s important to make regular backups of data, to avoid data loss and the need to make such ransom payments.
A serpent in Apple’s walled garden
The recent appearance of malicious apps in the App Store has made it clear that, contrary to what many people believe, iOS is not immune to malware.
The malware, called ‘Xcodeghost’, infected dozens of apps, including WeChat, NetEase’s music download app, business card scanner CamCard and Didi Kuadi’s car-hailing app. The Chinese versions of Angry Birds 2 were also infected.
The attackers didn’t hack the App Store, but hosted a malicious version of Apple’s Xcode. Xcode is a free suite of tools used by software developers to create iOS apps. It is officially distributed by Apple, but also unofficially by third parties: someone in China hosted a version of Xcode that contained XcodeGhost. Some Chinese developers choose to download development tools such as this from local servers because it is much quicker.
Any apps created using the modified version of Xcode would be infected. The infected apps steal data from their victims and send it to the attackers. It was initially believed that 39 infected apps had bypassed Apple’s scanning process and had been successfully uploaded to the App Store. Infected apps have been removed by Apple. However, the compromised version of Xcode has been available for around six months, so the total number of infected apps could be much higher, not least because the source code for XcodeGhost has been published on Github.
You can find an analysis of XcodeGhost by researchers at Palo Alto Networks here.
The incident highlights the danger of programs being infected at source if tools used by developers are compromised.
The Gaza cyber-gang
At the end of September we reported on the activities of another regional APT, the Gaza cyber-gang. This is a politically motivated Arabic group operating in the MENA region (Middle East and North Africa) – mainly focused on Egypt, the UAE and Yemen. The group is interested in government agencies – especially embassies, where security and IT operations might not be well-established or reliable. The Gaza cyber-gang has been active since 2012, but became particularly active in the second quarter of 2015.
The gang actively sends malware to IT and Incident Response (IR) staff in target organizations: the file names they use reflect IT functions and IR tools used to investigate cyber-attacks. It’s not hard to work out why. IT staff typically have greater access rights than other employees, because it’s their job to manage the corporate infrastructure. IR employees are likely to have access to sensitive data related to ongoing cyber-investigations, as well as extended access rights to help them look for suspicious activities across the network. This means the attackers not only gain access to the target organization but also extend their reach across the network.
The main infection modules used by the group are widely used remote access Trojans (RATs): XtremeRAT and PoisonIvy. Their activities are heavily reliant on social engineering. They use filenames related to IT and IR functions and content and domain names that are likely to be of interest to their victims (e.g. ‘.gov.uae.kim’).
Statistics
All the statistics used in this report were obtained using Kaspersky Security Network (KSN), a distributed antivirus network that works with various anti-malware protection components. The data was collected from KSN users who agreed to provide it. Millions of Kaspersky Lab product users from 213 countries and territories worldwide participate in this global exchange of information about malicious activity.
Mobile threats
Displaying adverts to users is still the main method of making money from mobile threats. The number of programs displaying intrusive advertising on mobile devices (adware) continued to grow in the third quarter and accounted for more than half of all detected mobile objects.
We have also observed a growing number of programs that use advertising as the main monetization method while also using other methods from the virus writers’ arsenal. They often root the device of a victim and use superuser privileges, making it very difficult, if not impossible, to combat them. In Q3 2015, these Trojans accounted for more than half of the Top 20 most popular mobile malware.
In Q3, @Kaspersky mobile security products detected 323,374 new malicious mobile programs #klreport
Tweet
SMS Trojans are still relevant as a monetization method, especially in Russia. These programs send paid messages from an infected device without the user’s knowledge. Although their overall traffic share among mobile threats continues to fall, the malicious mobile Trojan-SMS still leads in terms of the number of new samples detected in the third quarter.
The pursuit of profit is not limited to displaying adverts or sending paid text messages – cybercriminals are also very interested in users’ bank accounts. In Q3 2015, the total share of mobile bankers and spyware designed to steal personal information exceeded that of SMS Trojans in new mobile malware traffic by 0.7 p.p.
The number of new mobile threats
In Q3 2015, Kaspersky Lab mobile security products detected 323,374 new malicious mobile programs – a 1.1-fold increase on Q2 2015 and a 3.1-fold increase on Q1.
The number of malicious installation packages detected was 1,583,094 – this is 1.5 times more than in the previous quarter.
Number of malicious installation packages and new malicious mobile programs detected
(Q1 2015 – Q3 2015)
Distribution of mobile malware by type
Distribution of new mobile malware by type, Q2 and Q3 2015
Potentially unwanted advertising programs (adware) headed the ranking of detected objects for mobile devices in Q3 2015. In the previous quarter this category of programs occupied second place with 19%; in Q3 their share grew considerably and reached 52.2%.
Second came RiskTool. The programs in this category are legitimate applications that are potentially dangerous for users – if used carelessly or manipulated by a cybercriminal, they could lead to financial losses. RiskTool was knocked off top spot after its share decreased by 16.6 p.p. from the previous quarter.
The percentage of SMS Trojans in the overall flow of mobile threats decreased by another 1.9 p.p. and amounted to 6.2%. Despite this, they are still among the leading mobile malicious programs.
SMS Trojans were followed by Spy Trojans (5.4%). These programs steal personal data from users, including incoming text messages (mTANs) from banks.
Q3 2015, @kaspersky detected 2,516 #mobile banker Trojans, which is a 4X increase on the previous quarter #KLReport
Tweet
In the third quarter of 2015, the biggest growth rates were demonstrated by Trojan-Banker whose share more than doubled and accounted for 1.5% compared to 0.6% in the previous quarter. In Q2, 630 of these programs were detected, while Q3 saw their number increase four-fold and exceed 2500.
Top 20 malicious mobile programs
Please note that the ranking of malicious programs does not include potentially dangerous or unwanted programs such as RiskTool or adware.
Name % of attacked users*
1 DangerousObject.Multi.Generic 46.6
2 Trojan.AndroidOS.Rootnik.d 9.9
3 Trojan-SMS.AndroidOS.Podec.a 7.4
4 Trojan-Downloader.AndroidOS.Leech.a 6.0
5 Trojan.AndroidOS.Ztorg.a 5.5
6 Exploit.AndroidOS.Lotoor.be 4.9
7 Trojan-Dropper.AndroidOS.Gorpo.a 3.3
8 Trojan-SMS.AndroidOS.Opfake.a 3.0
9 Trojan.AndroidOS.Guerrilla.a 2.9
10 Trojan-SMS.AndroidOS.FakeInst.fz 2.6
11 Trojan-Ransom.AndroidOS.Small.o 2.3
12 Trojan-Spy.AndroidOS.Agent.el 2.1
13 Trojan.AndroidOS.Ventica.a 1.9
14 Trojan.AndroidOS.Ztorg.b 1.9
15 Trojan.AndroidOS.Ztorg.pac 1.8
16 Trojan.AndroidOS.Fadeb.a 1.6
17 Trojan-SMS.AndroidOS.Smaps.a 1.5
18 Trojan.AndroidOS.Iop.a 1.5
19 Trojan.AndroidOS.Guerrilla.b 1.5
20 Trojan-SMS.AndroidOS.FakeInst.fi 1.4
* Percentage of users attacked by the malware in question, relative to all users attacked.
The top position in the rankings was occupied by DangerousObject.Multi.Generic (46.6%). This is how new malicious applications are detected by the KSN cloud technologies, which help our products to significantly shorten the response time to new and unknown threats. The proportion of DangerousObject.Multi.Generic increased almost three-fold: from 17.5% in Q2 to 46.6% in Q3.
The number of Trojans that use advertising as the main means of monetization significantly increased from the previous quarter. In the second quarter of 2015 this Top 20 included six of these programs, while in Q3 their number increased to 11: three programs belong to the Trojan.AndroidOS.Ztorg family, and two each belong to the Trojan.AndroidOS.Guerrilla, Trojan.AndroidOS.Rootnik.d, Trojan-Downloader.AndroidOS .Leech.a, Trojan-Dropper.AndroidOS.Gorpo.a, Trojan-Spy.AndroidOS.Agent.el, Trojan.AndroidOS.Ventica.a and Trojan.AndroidOS.Fadeb.a families.
Unlike the usual advertising modules, these programs do not contain any useful functionality. Their goal is to deliver as many adverts as possible to the recipient using a variety of methods, including the installation of new advertising programs. These Trojans can use superuser privileges to conceal their presence in the system folder, from where it will be very difficult to remove them.
Of special note is Trojan-Spy.AndroidOS.Agent.el, which is even encountered in the official firmware of some developers.
Trojan-SMS.AndroidOS.Podec.a (7.4%) has been among the Top 3 malicious mobile programs for four quarters in a row due to how actively it is spread. It is worth mentioning that the functionality of the latest versions of this Trojan has changed and no longer includes the sending of text messages. The Trojan is now fully focused on paid subscriptions, making use of CAPTCHA recognition.
Seventeenth place is occupied by Trojan-SMS.AndroidOS.Smaps.a. Some of its versions are able to send spam upon receiving a command from the server via the Viber app if it is installed on the victim’s device. No special permission or actions on the part of the user are required by the Trojan to do this.
The geography of mobile threats
The geography of mobile malware infection attempts in Q3 2015 (percentage of all users attacked)
Top 10 counties attacked by mobile malware (ranked by percentage of users attacked)
Country* % of users attacked **
1 Bangladesh 22.57
2 China 21.45
3 Nigeria 16.01
4 Tanzania 15.77
5 Iran 13.88
6 Malaysia 13.65
7 Algeria 12.73
8 Nepal 12.09
9 Kenya 11.17
10 Indonesia 10.82
* We eliminated countries from this ranking where the number of users of Kaspersky Lab’s mobile security product is lower than 10,000.
** Percentage of unique users attacked in each country relative to all users of Kaspersky Lab’s mobile security product in the country.
Most secure country v. #Mobile #Malware Japan (1.13%) Where does your country rank? #KLReport
Tweet
The most secure countries in this respect are:
Country % of users attacked **
1 Japan 1.13
2 Canada 2.87
3 Denmark 3.20
4 Sweden 3.45
5 Australia 3.48
Although Australia is included in the Top 5 most secure countries, when it comes to mobile malware infections the situation is not as safe as would be expected: in the third quarter of 2015, users in Australia were attacked by mobile banker Trojans more often than users in other countries (see below.).
Mobile banker Trojans
In Q3 2015, we detected 2,516 mobile banker Trojans, which is a four-fold increase on the previous quarter.
Number of mobile banker Trojans detected by Kaspersky Lab’s solutions (Q4 2014 – Q3 2015)
Geography of mobile banking threats in Q3 2015 (number of users attacked)
The number of attacked users depends on the overall number of users within each individual country. To assess the risk of a mobile banker Trojan infection in each country, and to compare it across countries, we made a country ranking according to the percentage of users attacked by mobile banker Trojans.
Top 10 counties attacked by mobile banker Trojans (ranked by percentage of users attacked)
Country* % of users attacked by mobile bankers**
1 Australia 0.85
2 Republic of Korea 0.40
3 Russia 0.32
4 Cyprus 0.32
5 Czech Republic 0.31
6 Austria 0.27
7 Kyrgyzstan 0.26
8 Bulgaria 0.24
9 Romania 0.23
10 Uzbekistan 0.23
* We eliminated countries from this ranking where the number of users of Kaspersky Lab’s mobile security product is lower than 10,000.
** Percentage of unique users in each country attacked by mobile banker Trojans, relative to all users of Kaspersky Lab’s mobile security product in the country.
Australia, which was ranked eighth in the previous quarter, took the lead in Q3 2015. The percentage of users attacked by mobile bankers in Australia increased six-fold (from 0.14% to 0.85%). Such significant growth was caused by fraudsters making active use of Trojan-Banker.AndroidOS.Agent.ad. This Trojan steals credentials used to enter the online banking system of one of Australia’s largest banks. It also tries to steal users’ credit card details (cardholder’s name, card number, CVV, card expiry date).
At the same time, Korea, which topped the Q2 rating, saw its share decrease six-fold (from 2.37% to 0.4%) and dropped to second place in the ranking.
Top 10 countries by the percentage of users attacked by mobile bankers relative to all attacked users
An indication of how popular mobile banker Trojans are with cybercriminals in each country can be provided by the percentage of users who were attacked at least once by mobile banker Trojans during the quarter, relative to all users in the same country whose mobile security product was activated at least once in the reporting period. This ranking differs from the one above:
Country* % of users attacked by mobile bankers, relative to all attacked users **
1 Australia 24.31
2 Austria 7.02
3 Montenegro 5.92
4 Republic of Korea 5.69
5 France 5.66
6 Cyprus 5.56
7 Russia 5.09
8 Czech Republic 4.98
9 Sweden 4.81
10 Finland 4.56
* We eliminated countries from this ranking where the number of users of Kaspersky Lab’s mobile security product is lower than 10,000.
** Percentage of unique users in each country attacked by mobile banker Trojans, relative to all unique users attacked by mobile malware in the country.
In Australia, which topped the ranking, slightly less than a quarter of all users attacked by mobile malware were targeted by mobile bankers.
The share of bankers among all mobile malware attacks in Russia halved – from 10.35% to 5.09%. This was due to a significant drop in the activity of the Trojan-Banker.AndroidOS.Marcher family which was one of the most popular in the country. In the third quarter the number of attacks using this malware fell almost ten-fold compared to the previous quarter.
Vulnerable applications used by cybercriminals
The ranking of vulnerable applications below is based on information about the exploits blocked by our products. These exploits were used by cybercriminals in Internet attacks and in attempts to compromise local applications, including those installed on mobile devices.
Distribution of exploits used in attacks by type of application attacked, Q3 2015
Compared to Q2 2015, the following changes have taken place:
The proportion of Adobe Flash Player exploits has risen by 2 percentage points (p.p.).
The proportion of Adobe Reader exploits has decreased by 5 p.p.
In Q3, just like the rest of the year, exploits for Adobe Flash Player were in demand. Their share was only 5%, but there are more of them ‘in the wild’ and at the current time nearly all exploit packs are using vulnerabilities in this software. As was the case in the previous quarter, the share of Java exploits (11%) has continued to decrease in Q3. We have not observed any exploits for this software included in recent exploit packs.
In Q3, the most common exploit packs included exploits for the following vulnerabilities:
CVE-2015-5560 (Adobe Flash; this exploit was described in a Kaspersky Lab article)
CVE-2015-2419 (Internet Explorer)
CVE-2015-1671 (Silverlight)
The previous quarter saw a dramatic increase in the number of spam messages containing malicious PDF documents. This quarter, the number of these messages decreased significantly, so the proportion of Adobe Reader exploits also decreased.
The overall trend so far for 2015 has continued in Q3: exploits for Adobe Flash Player and Internet Explorer are most popular with cybercriminals. In the pie chart above, the latter falls into the ‘Browsers’ category; the landing pages from which the exploits spread are also classified here.
Online threats (Web-based attacks)
The statistics in this section were derived from web antivirus components that protect users from attempts to download malicious objects from a malicious/infected website. Malicious websites are created deliberately by malicious users; infected sites include those with user-contributed content (such as forums), as well as compromised legitimate resources.
Online threats in the banking sector
These statistics are based on the detection verdicts returned by the antivirus module, received from users of Kaspersky Lab products who have consented to provide their statistical data.
In Q3 2015, Kaspersky Lab solutions blocked attempts to launch malware capable of stealing money via online banking on the 625,669 computers. This number is 17.2 p.p. lower than in Q2 2015 (755,642). A year ago, in Q3 2014 this number was 591,688.
Kaspersky Lab’s solutions produced a total of 5,686,755 notifications about attempted malware infections aimed at stealing money via online access to bank accounts in Q3 2015.
Number of attacks by financial users, Q3 2015
Geography of attacks
To evaluate and compare the degree of risk of being infected by banking Trojans which user computers are exposed to worldwide, we calculate the percentage of Kaspersky Lab product users who encountered this type of threat during the reporting period in the country, relative to all users of our products in the county.
Geography of banking malware attacks in Q3 2015 (percent of attacked users)
Top 10 countries by the percentage of attacked users
Country* % attacked users**
1 Austria 4.98
2 Singapore 4.23
3 Turkey 3.04
4 Namibia 2.91
5 New Zealand 2.86
6 Hong Kong 2.81
7 Australia 2.78
8 Lebanon 2.60
9 United Arab emirates 2.54
10 Switzerland 2.46
* We excluded those countries in which the number of Kaspersky Lab product users is relatively small (less than 10,000).
** Unique users whose computers have been targeted by web attacks as a percentage of all unique users of Kaspersky Lab products in the country.
In Q3 2015, Austria became the leader in terms of the percentage of Kaspersky Lab users who were attacked by banking Trojans. Singapore, last quarter’s leader, is now in second place. It should be noted that most countries in the Top 10 have significant numbers of online banking users, and this attracts the cybercriminals.
In Russia, 0.71% of users encountered a banking Trojan at least once in Q3; this number is little different from the Q2 figure of 0.75%. In the US, the figure was 0.59%, which is 0.3 p.p. lower than in Q2. The countries of Western Europe also saw a small decrease in the percentages of users attacked by banking malware compared to Q2: Spain stood at 1.95%, or 0.07 p.p. less than in Q2; the UK (1.24%) was down 0.34 p.p.; Italy (1.16%) saw a decrease of 0.41 p.p.; while Germany (1.03%) was 0.13 p.p. lower.
The Top 10 banking malware families
The table below shows the Top 10 malware families most commonly used in Q3 2015 to attack online banking users:
Name* Percentage of attacks**
1 Trojan-Downloader.Win32.Upatre 63.13
2 Trojan-Spy.Win32.Zbot 17.86
3 Trojan-Banker.JS.Agent 1.70
4 Trojan-Banker.Win32.ChePro 1.97
5 Backdoor.Win32.Caphaw 1.14
6 Trojan-Banker.Win32.Banbra 1.93
7 Trojan-Banker.AndroidOS.Faketoken 0.90
8 Trojan-Banker.AndroidOS.Agent 0.57
9 Trojan-Banker.Win32.Tinba 1.93
10 Trojan-Banker.AndroidOS.Marcher 0.55
*These statistics are based on the detection verdicts returned by Kaspersky Lab’s products, received from users of Kaspersky Lab products who have consented to provide their statistical data.
**Unique users whose computers have been targeted by the malicious program, as a percentage of all unique users targeted by financial malware attacks.
The majority of the Top 10 malicious programs work by injecting random HTML code in the web page displayed by the browser and intercepting any payment data entered by the user in the original or inserted web forms.
The Trojan-Downloader.Win32.Upatre family of malicious programs remains at the top of the ranking. The malware is no larger than 3.5 KB in size, and is limited to downloading the payload to the victim computer, most typically a banker Trojan from the Dyre/Dyzap/Dyreza family. The first malicious program from this family was detected in June 2014, and its main aim is to steal the user’s payment details. Dyre does this by intercepting the data from a banking session between the victim’s browser and the online banking web app. In the summer of 2015, however, Trojan-Downloader.Win32.Upatre was spotted on compromised home routers, which is a testimony to how cybercriminals make use of this multiple-purpose malware.
Trojan-Spy.Win32.Zbot, in second place, has become a permanent resident of this ranking, and it is no coincidence that it consistently occupies a leading position. The Trojans of the Zbot family were among the first to use web injections to compromise the payment details of online banking users and to modify the contents of banking web pages. They encrypt their configuration files at several levels; the decrypted configuration file is never stored in the memory in its entirety, but is instead loaded in parts. This gives the Trojans of the Trojan-Spy.Win32.Zbot family a technological edge over other malware programs.
Third place in the Q3 ranking was occupied by the Trojan-Banker.JS.Agent family. This is the malicious JavaScript code that results from an injection into an online banking page. The aim of this code is to intercept payment details that the user enters into online banking forms.
Of particular interest is the fact that three families of mobile banking Trojans are present in this ranking: Trojan-Banker.AndroidOS.Faketoken, Trojan-Banker.AndroidOS.Marcher (we wrote about these two in in the Q2 report), and a newcomer to this ranking – Trojan-Banker.AndroidOS.Agent. The malicious programs belonging to the latter family steal payment details from Android devices.
The Top 10 operating systems attacked by banker Trojans
In Q3, users of Windows operating systems encountered the largest number of financial malware attacks (which comes as no surprise given how widespread Windows devices are). That said, users of Windows 7 x64 Edition encountered banking Trojans more often, accounting for 42.2% of all banking Trojan attacks. Android also made it into the list of attacked operating systems.
Operating system Percentage of attacks*
Windows 7 x64 Edition 42.2
Windows 7 11.6
Windows 7 Home x64 Edition 5.5
Windows XP Professional 7.0
Windows 8.1 Home x64 Edition 3.7
Windows 8.1 x64 Edition 2.3
Windows 7 Home 1.3
Windows 10 x64 Edition 1.2
Android 4.4.2 0.6
Windows NT 6.3 x64 Edition 0.7
*These percentage numbers are relative to all financial malware attacks detected on the computers of unique users who have consented to provide their statistical data.
It should be noted that although the family of Mac OS X operating systems did not make it to the Top 10, users of this operating system should not see themselves as being immune: in Q3 2015, computers running under Mac OS X were attacked 12,492 times.
TOP 20 malicious objects detected online
In the third quarter of 2015, Kaspersky Lab’s web antivirus detected 38,233,047 unique malicious objects (scripts, exploits, executable files, etc.) and reported 75,408,543 unique URLs as malicious.
In Q3 2015, @Kaspersky Lab's web antivirus detected 38,233,047 unique malicious objects #KLReport
Tweet
Of all malicious or potentially unwanted objects, we identified the 20 most active. These 20 accounted for 95% of all attacks on the Internet.
Top 20 malicious objects detected online
Name* % of all attacks**
1 Malicious URL 53.63
2 AdWare.JS.Agent.bg 16.71
3 AdWare.Script.Generic 7.14
4 Trojan.Script.Generic 6.30
5 Trojan.Script.Iframer 3.15
6 Trojan.Win32.Generic 1.52
7 AdWare.Win32.SoftPulse.heur 1.31
8 AdWare.JS.Agent.bt 1.09
9 AdWare.Win32.OutBrowse.heur 0.84
10 Trojan-Downloader.Win32.Generic 0.63
11 AdWare.NSIS.Vopak.heur 0.46
12 Exploit.Script.Blocker 0.46
13 Trojan-Downloader.JS.Iframe.diq 0.30
14 AdWare.Win32.Amonetize.aqxd 0.30
15 Trojan-Downloader.Win32.Genome.tqbx 0.24
16 AdWare.Win32.Eorezo.abyb 0.23
17 Hoax.HTML.ExtInstall.a 0.19
18 Trojan-Clicker.HTML.Iframe.ev 0.17
19 AdWare.Win32.Amonetize.bgnd 0.15
20 Trojan.Win32.Invader 0.14
* These statistics represent the detection verdicts of the web antivirus module. Information was provided by users of Kaspersky Lab products who consented to share their local statistical data.
** The percentage of all web attacks recorded on the computers of unique users.
The Top 20 is largely made up of verdicts assigned to objects used in drive-by attacks, as well as adware programs. This quarter, adware verdicts occupied nine positions in this ranking.
Of interest is the verdict Hoax.HTML.ExtInstall.a, assigned to a web page which blocks the browser and urges the user to install a Chrome extension. When the user tries to close the page, the voice file ‘voice.mp3’ is often played – “Click on the ‘Add’ button to close this page”.

Web page urging users to install a Chrome extension
(translation: “Press ‘Add’ to continue”)
The extensions that are offered do not cause any harm to users. However, the prompt is very intrusive and it is practically impossible for the user to reject it. This is why Kaspersky Lab products detect the corresponding web page with its popup window as malicious. There is a partnership program that uses this method to distribute the extension.
Top 10 countries where online resources are seeded with malware
The following statistics are based on the physical location of the online resources that were used in attacks and blocked by our antivirus components (web pages containing redirects to exploits, sites containing exploits and other malware, botnet command centers, etc.). Any unique host could be the source of one or more web attacks.
In order to determine the geographical source of web-based attacks, domain names are matched up against their actual domain IP addresses, and then the geographical location of a specific IP address (GEOIP) is established.
The #USA is top country with malicious web-based attack resources in Q3 #KLReport
Tweet
In Q3 2015, Kaspersky Lab solutions blocked 235,415,870 attacks launched from web resources located in various countries around the world. 80% of notifications on blocked web attacks were triggered by attacks coming from web resources located in 10 countries.
Distribution of web attack sources by country, Q3 2015
Q3 saw the US take over first place (with 26.9%) from Russia (18.8%). The Virgin Islands and Singapore have fallen out of the Top 10, while there are two newcomers – Sweden (1.43%) and Canada (1.42%).
Countries where users faced the greatest risk of online infection
In order to assess the risk of online infection faced by users in different countries, we calculated the percentage of Kaspersky Lab users in each country who encountered detection verdicts on their machines during the quarter. The resulting data provide an indication of the aggressiveness of the environment in which computers work in different countries.
Country* % of unique users attacked**
1 Russia 38.20
2 Nepal 36.16
3 Kazakhstan 33.79
4 Ukraine 33.55
5 Syria 32.10
6 Azerbaijan 32.01
7 Belarus 30.68
8 Vietnam 30.26
9 China 27.82
10 Thailand 27.68
11 Armenia 27.65
12 Brazil 26.47
13 Algeria 26.16
14 Turkey 25.13
15 Mongolia 25.10
16 Kyrgyzstan 23.96
17 Macedonia 23.84
18 Lithuania 23.59
19 Bangladesh 23.56
20 Moldavia 23.36
These statistics are based on the detection verdicts returned by the web antivirus module, received from users of Kaspersky Lab products who have consented to provide their statistical data.
*These calculations excluded countries where the number of Kaspersky Lab users is relatively small (fewer than 10,000 users).
**Unique users whose computers have been targeted by web attacks as a percentage of all unique users of Kaspersky Lab products in the country.
The leader of this ranking remained unchanged – it is still Russia with 38.2%. Since the previous quarter, Georgia, Croatia, Qatar, Bosnia and Herzegovina and Greece have left the Top 20. Newcomers to the ranking are Nepal, which went straight in at number two (36.16%), Brazil in 12th place (26.47%), Turkey in 14th (25.13%), Lithuania in 18th (23.59%), and Bangladesh (23.56%) in 19th.
23.4% of computers connected to the Internet globally were subjected to at least one web attack during Q3 #KLReport
Tweet
The countries with the safest online surfing environments included Switzerland (17%), the Czech Republic (16%), the US (16.3%), Singapore (15%), Hungary (13.8%), Norway (13%), Ireland (12.2%), and Sweden (10.8%).

On average, 23.4% of computers connected to the Internet globally were subjected to at least one web attack during the three months. This is a 0.5 p.p. decrease on Q2.
Local threats
Local infection statistics for users computers are a very important indicator: they reflect threats that have penetrated computer systems using means other than the Internet, email, or network ports.
Data in this section is based on analyzing statistics produced by antivirus scans of files on the hard drive at the moment they were created or accessed, and the results of scanning removable storage media.
In Q3 2015, Kaspersky Lab’s file antivirus modules detected 145,137,553 unique malicious and potentially unwanted objects.
Top 20 malicious objects detected on user computers
Name* % of unique users attacked**
1 DangerousObject.Multi.Generic 19.76
2 Trojan.Win32.Generic 14.51
3 Trojan.WinLNK.StartPage.gena 5.56
4 WebToolbar.JS.Condonit.a 4.98
5 AdWare.Script.Generic 4.97
6 WebToolbar.Win32.Agent.azm 4.48
7 RiskTool.Win32.GlobalUpdate.dx 3.63
8 WebToolbar.JS.AgentBar.e 3.63
9 WebToolbar.JS.CroRi.b 3.32
10 Downloader.Win32.Agent.bxib 3.20
11 AdWare.Win32.OutBrowse.heur 3.13
12 Adware.NSIS.ConvertAd.heur 3.08
13 AdWare.Win32.Generic 3.06
14 Downloader.Win32.MediaGet.elo 2.98
15 Trojan.Win32.AutoRun.gen 2.92
16 AdWare.Win32.BrowseFox.e 2.91
17 WebToolbar.Win32.MyWebSearch.si 2.82
18 AdWare.Win32.MultiPlug.heur 2.66
19 Virus.Win32.Sality.gen 2.61
20 RiskTool.Win32.BackupMyPC.a 2.57
*These statistics are compiled from malware detection verdicts generated by the on-access and on-demand scanner modules on the computers of those users running Kaspersky Lab products who have consented to submit their statistical data.
**The proportion of individual users on whose computers the antivirus module detected these objects as a percentage of all individual users of Kaspersky Lab products on whose computers a file antivirus detection was triggered.
In line with the established practice, this ranking represents the verdicts assigned to adware programs or their components, and to worms distributed on removable drives.
The only virus in the rankings – Virus.Win32.Sality.gen – continues to lose ground. The proportion of user machines infected by this virus has been diminishing for a long time. In Q3 2015, Sality was in 19th place with 2.61%, which is a 0.25 p.p. decrease on Q2.
Countries where users faced the highest risk of local infection
For each of the countries, we calculated the percentage of Kaspersky Lab product users on whose computers the file antivirus had been triggered during the quarter. These statistics reflect the level of personal computer infection in different countries.
Top 20 countries with the highest levels of computer infection
Country* % of unique users**
1 Bangladesh 64.44
2 Vietnam 60.20
3 Nepal 60.19
4 Georgia 59.48
5 Somalia 59.33
6 Laos 58.33
7 Russia 57.79
8 Armenia 57.56
9 Afghanistan 56.42
10 Ethiopia 56.34
11 Rwanda 56.21
12 Syria 55.82
13 Mozambique 55.79
14 Yemen 55.17
15 Cambodia 55.12
16 Algeria 55.03
17 Iraq 55.01
18 Kazakhstan 54.83
19 Mongolia 54.65
20 Ukraine 54.19
These statistics are based on the detection verdicts returned by on-access and on-demand antivirus modules, received from users of Kaspersky Lab products who have consented to provide their statistical data. The data include detections of malicious programs located on users’ computers or on removable media connected to the computers, such as flash drives, camera and phone memory cards, or external hard drives.
* These calculations exclude countries where the number of Kaspersky Lab users is relatively small (fewer than 10,000 users).
** The percentage of unique users in the country with computers that blocked local threats as a percentage of all unique users of Kaspersky Lab products.
The newcomers to this ranking are Mozambique in 13th position (55.8%), and Yemen in 14th (55.2%).
42.2% of computers globally faced at least one local threat during Q3 2015 #KLReport
Tweet
The safest countries in terms of local infection risks were Sweden (21.4%), Denmark (19.8%) and Japan (18.0%).

An average of 42.2% of computers globally faced at least one local threat during Q3 2015, which is 2.2% p.p. more than in Q2 2015.
Are we putting our finances at risk with our online shopping and banking?
2.11.2015
Nearly everyone has faced a cyber criminal’s activity at one point or another. You have probably received a magical SMS that read something like: “You are the winner!!! Your Ferrari and $1M await you! Call XXXXXX right now!!!” Up until now, these well-known tricks have worked surprisingly well. Even if you’ve never taken the bait yourself, you probably know somebody who did.
Don't endanger your online transactions That person (or you) is not alone. Employees of huge corporations have also been taken by schemes from cyber criminals. For example, over the course of two years the Carbanak cybergang stole funds from dozens of financial institutions worldwide to the tune of roughly $1 Billion. Right now, there is a type of mobile malware targeting mobile banking.
To earn easy money, hackers, for example, make specific malware, which replaces legitimate banking interfaces with custom imagery and code. But before stealing your money, a malware needs to be installed on your device. So how does it find a loophole?
A test, recently conducted by Kaspersky Lab, shows that many users do not follow basic security rules when make online payments or log into an online banking system. 50% of the people surveyed do not check if they use the authentic website of their bank or payment system. They don’t pay attention at the https prefix, which indicates an encrypted connection; some of the surveyed have even selected a website with a misspelled address — an obvious sign of a fake phishing page.
It seems that a key logger will also find its victim: only each fifth of those surveyed prefer to use a virtual keyboard to protect their passwords from interception by malware. In the survey other users stated that they choose the “incognito” mode to protect a payment, or resort to an anonymizer, or even try to enter and wipe the data repeatedly in order “to confuse viruses.” Unfortunately, these actions do nothing to protect a user’s financial information.
Are we putting our #finances at risk with our #online shopping and #banking?
Tweet
What’s more surprising it’s that 20% of the users do not think of protecting their banking accounts even offline. For example, in a restaurant they are ready to give their banking card to a nice waitress or a polite waiter and let them take it out of their site.
This is a bad idea. Please, remember: if fraudsters receive access to your card at least for a minute, they can make a full-fledged copy very quickly.
Banks cannot guarantee 100% protection simply because to large extend security depends on users behavior. Besides, not all payment systems care about cyber security that much. That’s why users, especially the less cyber savvy, should install specific solution to secure their online payments.
For example, one can have a look at the award-winning Safe Money technology for Windows and Mac OS X integrated in Kaspersky Internet Security – Multi-Device and Kaspersky Total Security – Multi-Device. Safe Money enables a multi-layered defense. It checks if the site is secure, ensures you’re not being tricked by a fake page and then opens the website in a special, protected mode.
Flaws in ATMs of a German Bank open the doors to cyber attacks
2.11.2015
A security researcher at the Vulnerability Lab discovered that ATMs at the German savings bank Sparkasse can leak sensitive info during software updates.
The security researcher Benjamin Kunz-Mejri, CEO of the Vulnerability Lab, discovered that ATMs at the German savings bank Sparkasse can leak sensitive data during software updates.
The discovery of the anomaly was casual, Benjamin Kunz-Mejri was was using the ATM when it ejected his card and resulted “temporarily not available.” The expert tried to interact with the ATM and observed a Windows command prompt showing on ongoing update process, he took a video of the information displayed on the terminal.
The change of the status was caused by a software update, and the researcher used the term “timing attack” to describe his interaction with the ATM.
He was surprised that the ATM keyboard was not disabled, allowing an attacker to execute system commands via the command prompt. He also noticed that the card reader remained usable during the update process.

Video recording has allowed the expert to analyze the information displayed on the screen, he noticed that many sensitive data was revealed, including the bank’s main system branch usernames, serial numbers, network and firewall configurations, device IDs, ATM settings, and two system passwords.
The ATM machines analyzed by the researcher are manufactured by Wincor Nixdorf, one of the most important company of the retail and banking industry. The flawed terminals are running Windows 7 and Windows XP operating systems. It is likely that other banks which are using the Wincor Nixdorf ATMs might be affected as well.
The experts warn about a large scale attack coordinated by a criminal ring in conjunction with a planned update, they described the following possible attack scenarios:
The attacker could use the information disclosed during the update process to run a man-in-the-middle (MitM) attack on the targeted bank’s local network. This attacker needs a physical access to bank network.
The attacker could push a bogus update to reconfigure the ATMs, also in this case he needs a physical access to bank network.
The Attacker could conduct fraudulent transactions by forcing the ATM crash and corrupt the logging or debugging mechanism.
The Vulnerability Lab reported the security issue to Sparkasse’s Security and Data Protection team in May, the flaw was confirmed after the vulnerability report was received by the internal Finance Security Center.
The Sparkasse bank has already pushed out updates that fix the issue to a limited number of ATMs in the city of Kassel. The purpose is to run further tests before issuing the update to all the ATMs used by the organization.
It is the first time that a German bank admits the security vulnerability in an ATM and reward the researchers.
Third suspect arrested in connection with the TalkTalk breach
2.11.2015
A third suspect has been arrested by the British authorities in connection with the TalkTalk breach, he is a 20-year-old from Staffordshire.
While the investigation of the TalkTalk data breach is going on, a third man has been arrested in connection with the hack. The third unnamed suspect is a 20-year-old man from Staffordshire, he has been released on bail until March after he was arrested by law enforcement under the country’s Computer Misuse Act.
Investigators believe that he is a member of the group that hacked the telco firm TalkTalk stealing 1.2 million customer details (email addresses, names, and phone numbers, dates of birth) along with nearly 28,0000 partial credit and debit cards.
On October 26, the UK Metropolitan Police has announced the arrest of a 15-Year-Old in connection to the data breach. Law enforcement from the Police Service of Northern Ireland (PSNI) have identified the youngster and arrested him on suspicion of Computer Misuse Act offenses.
TalkTalk
In a statement, the UK Metropolitan Police announced that officers from the Police Service of Northern Ireland, working with detectives from the MPCCU (MET Cyber Crime Unit) executed a search warrant at an address in County Antrim, Northern Ireland.
“At the address, a 15-year-old boy was arrested on suspicion of Computer Misuse Act offences. He has been taken into custody at a County Antrim police station where he will later be interviewed. A search of the address is ongoing and enquiries continue. This is a joint investigation by MPCCU detectives, the PSNI’s Cyber Crime Centre (CCC) and the National Crime Agency,” the statement added.
Some days later, on October 20, the UK Police have arrested a second individual as part of the investigation into the TalkTalk security breach, also in this case the suspect is a teenager. According to the Metropolitan Police, the second suspect is a 16-year-old boy from Feltham. The teen was arrested by the agents of the Cyber Crime Unit on suspicion of Computer Misuse Act offences and was later bailed.
The Register reported that victims of the cyber attack have the faculty to leave TalkTalk and terminate the contract without problem.
“Customers wanting to leave the popped telco will need to have had money stolen on or after 21 October as a result of the hack, and have contacted the fraud department.” states the The Register “TalkTalk says it is not accepting liability for other possible expenses customers may have to bear as a result of the breach.”
CISA Passes Senate, criticism about privacy and security
2.11.2015
The CISA cyber security bill passes US Senate despite tech giants, privacy advocates, and civil liberties groups express their disappointment.
The US Senate voted overwhelmingly to pass a version of the Cybersecurity Information Sharing Act (CISA), a bill that has been debated for a long because it will authorize government pervasive monitoring of citizens.
Many politicians, tech giants, privacy advocates, and civil liberties groups are expressing their disappointment and consternation to the decision of the US Senate. The CISA bill passed with a final vote of 74 to 21, it requires companies to share information about potential threats with the government.
White House
The exponents of the senate that voted the bill consider it a necessary a measure against the numerous data breaches suffered by the US companies, including Sony Pictures, JP Morgan Chase, Anthem and the Office of Personnel Management.
The CISA is severely criticized because it will only advantage the Government Agencies to collect information about users, data that will be collected by the Department of Homeland Security and shared with the FBI and NSA.
The privacy advocates and part of the security industry believe that the CISA bill doesn’t address the problems that caused the long series of data breaches.
“The bill is fundamentally flawed due to its broad immunity clauses, vague definitions, and aggressive spying authorities. The bill now moves to a conference committee despite its inability to address problems that caused recent highly publicized computer data breaches, like unencrypted files, poor computer architecture, un-updated servers, and employees (or contractors) clicking malware links.” states the EFF disappointing as CISA Passes Senate.
The conference committee between the House of Representatives and the Senate will determine the bill’s final language, but experts are skeptical about the possibility to modify it to address the real cybersecurity problems in a correct way.
The Cybersecurity Information Sharing Act is considered the reincarnation in a new guise of the CISPA that passed in the United States House of Representatives on April 18, 2013,but has been blocked by the Senate.
While the CISPA was hampered by the Obama administration due to privacy concerns, the CISA has received the consensus of the President.
“The passage of CISA reflects the misunderstanding many lawmakers have about technology and security,” continues the EFF. “With security breaches like T-mobile, Target, and OPM becoming the norm, Congress knows it needs to do something about cybersecurity. It chose to do the wrong thing. EFF will continue to fight against the bill by urging the conference committee to incorporate pro-privacy language.”
CISA requests sharing of “cyber threat indicators,” but doesn’t address privacy issues.
The Sen. Ron Wyden (D-Ore) is one of the opponents of the CISA bill that he considers “flawed” and just “feel-good legislation.”He warned about the abuses that could result from the application of the CISA.
“The fight to secure Americans’ private, personal data has just begun,” said Wyden. “Today’s vote is simply an early, flawed step in what is sure to be a long debate over how the U.S. can best defend itself against cyber threats.”
Prior to the final vote, the principal IT companies, including Apple, Google and Microsoft, also expressed their privacy concerns over the CISA and its request to share sensitive customer data to the US Agencies.
“We don’t support the current CISA proposal. The trust of our customers means everything to us and we don’t believe security should come at the expense of their privacy.” said an Apple spokesperson before the final vote.
Report: German Bank ATMs vulnerable to Hackers
2.11.2015
Avoiding Credit Card Fraud is simply easy as long as you use cash. But, what if you even get hacked while withdrawing cash from an ATM?
If you are living in Germany or traveling there, then think twice before using your payment cards in the ATMs.
Here’s why:
A Security researcher in Germany has managed to hack ATM and self-service terminal from Sparkasse Bank that allowed him to reveal the sensitive details from the payment card inserted into the machine.
Benjamin Kunz-Mejri, CEO of Germany-based security firm Vulnerability Lab, discovered a vulnerability while using a Sparkasse terminal that suddenly ejected his card, and changed status to "temporarily not available."
Meanwhile, the machine automatically started performing software update process in the background. However, Benjamin used a special keyboard combination to trick the ATM into another mode.
Benjamin’s trick forced ATM system to put update process console (cmd) in the foreground of the warning message.
"At that moment the researcher realized that there is a gap and used his iPhone to capture the bootChkN console output (Wincor Nixdorf) of the branch administrator," a blog post on Vulnerability-Lab stated.
how-to-hack-atm
After saving the data and reviewing the recording, Benjamin was able to reveal a lot of sensitive information, including the bank’s main branch office:
Usernames
Serial numbers
Firewall settings
Network information
Computer name
Device IDs
ATM settings
Two system passwords
Other hardware related information
"Benjamin reported the critical issue to the Sparkasse Bank, which acknowledged the issue and has now started patching its ATMs and self-service terminals in a pilot program to prevent attacks." Sparkasse Bank said in a statement.
The ATM (Automated Teller Machine) analyzed by Benjamin is manufactured by Wincor Nixdorf, one of the most famous company in the retail and banking industry.
Therefore, the chances are high that other banks that are using the Wincor Nixdorf ATMs and self-service terminals are also affected, along with Sparkasse Bank.
Benjamin reported the critical issue to the Sparkasse Bank, which acknowledged the issue and has now started patching its ATMs and self-service terminals to prevent attacks.
Některé oběti ransomwaru už mohou svá data odemknout zdarma
2.11.2015 Viry
Napadl vás ransomware CoinVault a Bitcryptor? S největší pravděpodobností můžete svá data odemknout zdarma, protože k dispozici je 14 tisíc klíčů, které to umožňují -- získal je Kaspersky Lab a úřady v Holadsku.
Oba typy tohoto zákeřného malwru jsou podle všeho mrtvé. Jejich autoři byli zadrženi, což vedlo i k získání zhruba čtrnácti tisíc dešifrovacích klíčů, pomocí kterých teď můžou oběti svá data odemknout.
Hrozba CoinVaultu a Bitcryptoru se objevila loni v květnu, kdy ransomware infikoval velké množství počítačů, ve kterých zablokoval cenná data. Za jejich odblokování pak tvůrci škodlivého programu požadovali výkupné (ransom) v hodnotě stovek dolarů ve formě Bitcoinů.
Policie pachatele zadržela před několika týdny v nizozemském Amersfoortu, jednalo se o dva mladíky ve věku osmnáct a dvaadvacet let. Na jejich odhalení měla podíl i společnost Kaspersky Lab, jejíž pracovníci se dostali ke zhruba čtrnácti tisícům dešifrovacím klíčům, které teď pro použití napadenými uživateli přidali do své databáze noransom.kaspersky.com. Podle Kaspersky Lab je tak kauza CoinVaultu, respektive Bitcryptoru uzavřená.
Oběti útoků jiného ransomwaru však takové štěstí nemají. Americká FBI, která se touto problematikou zabývá, připustila, že je na většinu podobných útoků krátká. „Abych byl upřímný, často lidem doporučujeme, ať výkupné prostě zaplatí,“ uvedl jeden z agentů Joseph Bonavolonta.
Případů napadení ransomwarem přitom v posledních letech dramaticky přibývá. Počet uživatelů napadených nejrozšířenějším ransomwarem CryptoWall version 3 už se pohybuje v řádech stovek tisíců, přičemž skupina, která je za něj zodpovědná, si tak na výkupném přišla už na více než 325 milionů dolarů.
Pokročilé hrozby dokáže odhalit novinka firmy Symantec
2.11.2015 Zabezpečení
Řešení Advanced Threat Protection (ATP) podle výrobce umožňuje odhalit bezpečnostní hrozby, zjistit jejich závažnost a odstranit je napříč celou infrastrukturou.
Bezpečnostní řešení navržené speciálně proti pokročilým hrozbám oznámil Symantec. Ke sledování hrozeb prý postačuje jediná konzole, vykonání všech důležitých akcí vyžaduje pouze jediné kliknutí myši a na koncové body není nutné instalovat žádné nové agenty.
Řešení ATP koreluje podezřelé aktivity ze všech kontrolních bodů a řadí události podle jejich priority tak, aby bylo možné ihned zjistit, jaké z nich představují pro organizaci největší riziko.
Jakmile je kritická hrozba identifikovaná, lze snadno a rychle zablokovat její veškeré instance (kopie na dalších bodech, různé projevy v podnikové síti apod.).
K hlavním pokročilým hrozbám dnes patří ransomware (malware vydírající oběti), trojské koně umožňující útočníkovi vzdálený přístup, pokročilé přetrvávající hrozby (advanced persistent threats, APT) nebo útoky zero day (zneužití chyb softwaru v době, než jeho výrobce vydá opravu).
ATP obsahuje mj. technologii Cynic, což je nová technologie sandboxu, na cloudu založené simulační prostředí, které umožňuje stanovit závažnost jednotlivých hrozeb.
Součástí ATP je rovněž funkcionalita Synapse, tedy technologie fungující napříč jednotlivými kontrolními body, která analyzuje podezřelé aktivity na úrovni koncových bodů, sítí a e-mailu, přičemž opět pomáhá určit, co aktuálně představuje pro organizaci největší riziko.
Řešení bude k dispozici na konci roku 2015.
Hackers have accessed details of 1,827 Vodafone customers
2.11.2015
According to Vodafone UK, criminals used the stolen data obtained from “an unknown source” to try to access customers’ accounts.
Personal details belonging to roughly 2,000 Vodafone customers have been compromised.
According to Vodafone, cyber criminals used the stolen data (emails and passwords) obtained from “an unknown source” to try to access customers’ accounts between Wednesday and Thursday.
“We can confirm that Vodafone UK was subject to an attempt to access some customers’ account details between midnight on Wednesday 28 October and midday on Thursday 29 October. At that point we initiated a comprehensive investigation to fully understand the facts so that we could give any affected customers the best possible advice. We informed the National Crime Agency (NCA), the ICO and Ofcom of the issue on the evening of Friday 30 October.” states the message issued by Vodafone UK.
According to telecommunications company the criminals accessed 1,827 customers accounts, gaining their names, mobile phone number, bank short code and the last 4 digits of their bank account.
No credit or debit card numbers or details were obtained, but it is important to keep in mind that data accessed by criminals could be used for fraudulent activities.
Also in this case, the company is saying that its systems had not been breached, a circumstance similar to the security breach occurred recently to the British Gas company that caused the exposure of 2,200 records.
In response to the security breach, Vodafone has blocked the customers’ accounts involved in the incident and it is contacting affected customers to assist them with changing their account details.
Vodafone has already contacted the banks of affected customers to alert them to potential risks for the individual involved. Vodafone is now working with the National Crime Agency (NCA) and has already informed the ICO and Ofcom of the issue on the evening of Friday 30 October.
“The NCA can confirm that we have been contacted by Vodafone in relation to a compromise of customer data, and we are in dialogue with the company.” said an NCA spokeswoman said. “Anyone who thinks they have been subject to attempted or successful fraud, or other online crime, should report it to action fraud at www.actionfraud.police.uk.”
We will also be loading customers’ details into the Credit Industry Fraud Avoidance Service (CIFAS) database, which will ensure that bank or mobile operators will make additional checks to avoid fraud.
Victims of the security breach should:
Carefully monitor their banks and report any unusual activity. Users in England, Wales or Northern Ireland can contact the national fraud and internet crime reporting centre Action Fraud on 0300 123 2040 or www.actionfraud.police.uk. Scottish users can call Police Scotland.
Be aware of phishing emails.
Avoid giving out personal and financial data.
Criminals behind CryptoWall 3.0 Made $325 Million
2.11.2015
Security researchers of the Cyber Threat Alliance have conducted an investigation into the cybercriminal operations leveraging CryptoWall 3.0 ransomware.
Brief Background
Ransomware, specifically crypto-ransomware, is a malware classification that encompasses Trojans that enumerate the file system of an infected host, in order to discover and compromise any and every document possible. Crypto-ransomware encrypts the contents of supported data files, rendering these files useless to their rightful owner.
This malware classification is quite self-explanatory; ransomware will often drop ransom notes in many areas within the affected file system, in varying formats and/or languages, that demand that the victim pays a ransom in order to recover their files. This ransom is usually paid in Bitcoin, with a (sometimes empty) promise of providing a decryption utility in order to recover all affected files, as a result of a successful, cleared ransom payment.
The CryptoWall family of ransomware first emerged in April 2014. Its first major revision came with the upgrade to CryptoWall 2.0, in October 2014. The most recent variant of the CryptoWall ransomware, CryptoWall 3.0, emerged in-the-wild beginning in January 2015.

The sophistication of CryptoWall 3.0 has skyrocketed exponentially since its initial inception; CryptoWall 3.0 is the most advanced, and the most prevalent ransomware actively distributed in-the-wild today.
Statistical Information
Through a collaborative effort between several large, well-respected information security firms, several CryptoWall 3.0 campaigns were able to analyze with great granularity, revealing a wealth of information behind the threat actor(s) and their effectiveness. The information security firms that participated in this analysis includes: Intel Security, Fortinet, Symantec, Palo Alto Networks, and several other members of the Cyber Threat Alliance.
Monetary Damages: Approximately $325 Million
Analyzed Malware Samples: Over 4,000
Discovered C&C URLs: Approximately 839
Discovered 2nd-Tier C&C IP Addresses: Approximately 5
Total Infection Attempts: Over 400,000 Across 49 CryptoWall 3.0 Campaigns
Region Most Affected: North America
Across 49 analyzed CryptoWall 3.0 campaigns, over 400,000 infection attempts were logged. CryptoWall 3.0 is commonly delivered via phishing e-mail, but it is also quite commonly delivered as a payload of an exploit kit. Specifically, CryptoWall 3.0 seems to be the most commonly delivered payload by the Angler EK; the most active, sophisticated exploit kit found in-the-wild today. CryptoWall 3.0 ransom payments accounted for an estimated total of more than $60 million in revenue for an Angler EK group exposed by Cisco’s Talos Group earlier this year.
Closing
It just goes to show that the prevalence of ransomware in-the-wild is on the uprise, and the exponential growth of ransomware in sophistication and quantity of variants is not slowing down. Malware authors have been leveraging exploit kits to deliver their ransomware; a very effective infection method that is only becoming increasingly hard to defend against.
Free Ransomware Decryption Tool — CoinVault and Bitcryptor
1.11.2015
Have you been infected with the insidious CoinVault or Bitcryptor ransomware?
If so, there is some potentially good news for you.
You may now recover your encrypted files for FREE! – Thanks to the efforts of Dutch police and antivirus maker Kaspersky Lab.
Security researchers from Kaspersky Lab and the Dutch Public Prosecution Service have obtained and published the last set of encryption keys from command-and-control (C&C) servers used by two related ransomware threats – CoinVault and Bitcryptor.
Security researchers first observed CoinVault ransomware attacks in May 2014. Since then, CoinVault has made more than 1,500 victims in more than 108 countries.
In April 2015, the Dutch police obtained 'Decryption keys' database from a seized command and control server of CoinVault.
Ransomware Decryption Tool
Those decryption keys were then used by Kaspersky Lab to set up a Ransomware Decryptor Service, which included a set of around 750 decryption keys recovered from CoinVault servers hosted in the Netherlands.
After that raid, the CoinVault's authors slowly updated their code, eventually releasing a second-generation CoinVault version that they named Bitcryptor.
However, last month, the Dutch authorities arrested two men in connection with CoinVault and Bitcryptor ransomware attacks, leading to the recovery of additional 14,031 decryption keys.
The keys have now been updated to the Kaspersky's Ransomware Decryptor Service and published on the noransom.kaspersky.com website.
Those victims that had their PCs infected by these ransomware programs and still have the encrypted data lying around can now download these keys to unlock their personal files.
How to Decrypt CoinVault and Bitcryptor Ransomware:
Step 1: Note down the Bitcoin wallet address mentioned by the malware.
Step 2: Get the encrypted file list from the ransomware interface.
Step 3: Then download an effective antivirus and remove CoinVault Ransomware.
Step 4: Open https://noransom.kaspersky.com and download the decryption tool released by Kaspersky Labs.
Step 5: Install additional libraries and Decrypt your files.
However, there's only one catch:
"If you get infected by this ransomware in the near future, you are out of luck."
Ransomware on Rise
Ransomware has emerged as one of the biggest Internet threats to the web users in recent years.
The authors of the notorious CryptoWall ransomware have raised more than $325 MILLION (£212 million) in this past year alone.
Typically, hackers primarily gain access to a user's computer using ransomware malware that heavily encrypts data files with a strong cryptographic algorithm, and then demand a ransom money (to be paid in Bitcoin), which ranges from $200 to $10,000.
How to Prevent Yourself Against Ransomware Attacks?
Just few days back, the Federal Bureau of Investigation (FBI) advised ransomware victims to just pay off the criminals in order to see their valuable data again.
However, in my opinion, the best defense against these threats is to ensure that all your important files are regularly backed up to a separate drive or storage that are only temporarily connected and can not be reached by the attackers.
A few more things you should keep in mind to prevent your Computer from getting infected with ransomware and other malware threats are:
Ensure your system software and antivirus definitions are up-to-date.
Avoid visiting suspicious websites.
Avoid Opening Emails and attachments from unknown sources.
Hacking Team Offering Encryption Cracking Tools to Law Enforcement Agencies
1.11.2015
Hacking Team, the infamous Italy-based spyware company that had more than 400 GB of its confidential information stolen earlier this year, has resumed its operations and started pitching new hacking tools to help US law enforcement gets around their encryption issues.
Yes, Hacking Team is back with a new set of Encryption Cracking Tools for government agencies as well as other customers to break encrypted communications.
The announcement came in an email pitch sent to existing and potential new customers on October 19 when Hacking Team CEO David Vincenzetti confirmed that Hacking Team is now "finalizing [its] brand new and totally unprecedented cyber investigation solutions."
The e-mail is not made public, but Motherboard has been able to obtain a copy of it that states:
"Most [government agencies] in the United States and abroad will become 'blind,' they will 'go dark,' they will simply be unable to fight vicious phenomena such as terrorism," wrote Vincenzetti. "Only the private companies can help here; we are one of them."
"It is crystal clear that the present American administration does not have the stomach to oppose the American IT conglomerates and to approve unpopularly, yet totally necessary, regulations," He added.
Game Changers
The brand new cyber investigation solutions here, of which Vincenzetti is talking about, will be "Game Changers."
The announcement came roughly 4 months after a mysterious hacker or group of hackers hacked into Hacking Team's servers, leaking more than 400 gigabytes of internal data, including:
Internal emails
Hacking tools
Zero-day exploits
Surveillance tools
Source code for Spyware suite, called Remote Control System (RCS)
A spreadsheet listing every government client with date of purchase and amount paid
Remote Control System Version 10 (RCS 10)
Since then, Hacking Team has reportedly been working on launching a new revamped 10th edition of its proprietary Remote Control System, RCS 10.
Hacking Team is known for its Remote Control System (RCS) spyware, also known as Galileo, which is loaded with a number of zero-day exploits that have the ability to monitor the computers of its targets remotely.
However, it's still unclear when the company will actually release RCS 10. Also, it is all set to be seen as to which law enforcement agencies will take the Hacking Team offer, given its recent security breach.
Anonymous will reveal names of about 1,000 KKK members
1.11.2015
“Ku Klux Klan, We never stopped watching you,” “We know who you are.” Anonymous plans to reveal the identities of up to 1,000 Ku Klux Klan members.
The popular Anonymous collective has declared war to the white supremacy group Ku Klux Klan (KKK), the hacktivist has posted a video message on YouTube and a message on Twitter to announce that it is holding a list of names of the Klan members.

Anonymous confirmed that they hacked a Twitter account and that obtained through it about 1000 klan member identities.
We’ve gained access to yet another KKK Twitter account. Using the info obtained, we will be revealing about 1000 klan member identities.
— Operation KKK (@Operation_KKK) 22 Ottobre 2015
“All will be revealed next month around the one year anniversary of #OpKKK,” it tweeted, under the handle @Operation_KKK. The Anonymous campaign dubbed #OpKKK has begun in November 2014 in response to the menaces that KKK members made against peaceful protesters in Ferguson. Ferguson (Missuri) has become the center of racial tensions after the officer Darren Wilson killed the 18-year-old black boy, Michael Brown, in August 2014.
“You are more than extremists. You are more than a hate group,” states the Anonymous’s message.” “You operate much more like terrorists and you should be recognized as such. You are terrorists that hide your identities beneath sheets and infiltrate society on every level.” “The privacy of the Ku Klux Klan no longer exists in cyberspace. You’ve had blood on your hands for nearly 200 years.” Anonymous also announced the imminent disclosure of the identities of 1000 members of the KKK.
“We will release, to the global public, the identities of up to 1,000 Klan members, Ghoul Squad affiliates and other close associates of various factions of the Ku Klux Klan across the United States.”
The Ghoul Squad is considered an organization belonging to the KKK.
We’ve gained access to yet another KKK Twitter account. Using the info obtained, we will be revealing about 1000 klan member identities. — Operation KKK (@Operation_KKK) 22 Ottobre 2015
Stay Tuned …. this is just the beginning.
How CoinVault or Bitcryptor victims could try to recover their files
1.11.2015
Victims of CoinVault ransomware can now rely on a new set of encryption keys added to the free CoinVault Ransomware Decryptor tool to recover their files.
Every day, dozens of users ask me how to decrypt their data locked by various ransomware such as CoinVault or Bitcryptor?
Now I have a good news for them, it is possible to use a free tool to recover the encrypted files.
The tool was designed by the experts of the Kaspersky Lab in collaboration with the Dutch police, the experts have used a set of encryption keys extracted from command-and-control (C&C) servers used by two groups that were using CoinVault and Bitcryptor.
In May 2014, the investigators detected numerous attacks based on the CoinVault ransomware that infected more than 1,500 victims in more than 108 countries.
In April 2015, the Dutch Public Prosecution Service extracted a set of CoinVault Decryption keys from a database present on a seized command and control server.
In April 2015, the expert from Kaspersky Lab announced the development of the tool called “CoinVault Ransomware Decryptor”, the researcher teamed up with The National High Tech Crime Unit (NHTCU) of the Dutch Police.
CoinVault malware
The tool included a set of around 750 decryption keys recovered from CoinVault servers hosted in the Netherlands.
In response to the action of the law enforcement, the authors of CoinVault updated their code and released a new version dubbed Bitcryptor.
Now the law enforcement could rely on additional 14,031 decryption keys obtained last month by the Dutch authorities following the arrest of two men in connection with CoinVault and Bitcryptor ransomware attacks.
The keys have been included in the Kaspersky’s Ransomware Decryptor Service which is available on the noransom.kaspersky.com website.
If you are a victim of CoinVault and Bitcryptor ransomware attacks you can try to download these keys to unlock the encrypted files.
To decrypt the file use the following procedure:
Step 1: If you are infected with CoinVault, just note down the Bitcoin wallet address mentioned by the malware on the screen.
Step 2: Get the encrypted file list from ransomware interface.
Step 3: Download an effective antivirus and remove CoinVault Ransomware first.
Step 4: Open https://noransom.kaspersky.com and download the decryption tool released by Kaspersky Labs.
Step 5: Install additional libraries and Decrypt your files.
In order to protect your computer from malware:
Ensure your system software and antivirus definitions are up-to-date.
Avoid visits suspicious websites.
Regularly backup your important files to a separate drive or storage that are only temporarily connected.
Be on high alert for pop-ups, spam, and unexpected email attachments.
Hacking discipline, EOL of computer science in the cyber domain
1.11.2015
The hacking world will change. Instead of hacking based on computer programming as today, the hacking will be based on chemistry, biology, and physics.
In the medium term future, the hacking world will change. Instead of hacking based on computer programming as today, the hacking will be based on chemistry, biology and physics. This article will explain this claim. For the discussion, I will split the hacking scene to two main scenarios – Hacking to autonomic machines and hacking to the human body.
In “autonomous machines”, I refer to self-healing machines that can find and fix vulnerabilities in the code by them self. When this kind of machines will be developed, they will turn the hackers useless. In this future reality, only machines will hack each other. I will come back to this future later.
hacking
In the other scenario, humans control the machines, and hackers are manipulating them to hack the machines. In a deeper vision, humans are building the machines, programming them, using and fixing them. All the life-cycle of the machines is controlled by humans. Therefore, by hacking the human behavior, one can control the machine.
To make it clearer, when one hacks a machine, he exploits the code that another human has written for the machine or the behavior of human that uses the machine. Zero-day vulnerabilities, backdoor’s or logic bombs, are all failures of humans. When the autonomous machines are developed, all those failures will be reduced to a minimum or even disappear with time.
In “minimize failures” reality, it will become much harder for hackers to hack the machines, forcing them to go mostly after humans. One can imagine the machinery infrastructure as the transport and storage layer of human knowledge. And if that layer becomes unhackable, we are talking about hacking the human brain or body to get the knowledge or behavior we want to get.
Going back to the second scenario, hacking will turn to biological computing systems [as the human body] rather than machinery based systems as today. It will change the hacking profession. Computer science will be replaced with chemistry, biology and physics.
While it seems like science fiction to some, I believe it’s the future. Any country that will want to maintain a competitive advantage with others in the futuristic cyber domain, should educate the young generation in those professions. It should be noticed that educating someone in chemistry, biology or physics [MA\Phd] takes a longer period than to do it for computer science \ programming.
This conclusion is applicable also to the business world. The change won’t be linear. When autonomic machines will enter the market, all the existing cyber solutions will be obsolete. No human will be able to write a code that protects against a cyber attack by autonomous machine. It will be companies that developed offense \ defense solutions for the human body that will survive.
To summarize, the cyber domain is a dynamic technology field based today on machines. And because of that, the machines are becoming more efficient in their way to an autonomous degree.
It’s not “if,” but a “When” question. It will be who understand it and embrace it that will lead the future cyber domain. Those who will keep “Hold a bull’s horn” will become irrelevant.
About the Author Ami Rojkes Dombe
Ami is An Israeli-based writer, tech corresponded of the Israel Defense magazine. Covers the Israeli cyber industry, defense industries and the ICT scene. Passions include futuristic technologies, science and geopolitical aspect of technology. MA in political science with thesis in Cyber deterrence.
The surveillance firm Hacking Team is back stronger than before
1.11.2015
Motherboard has obtained a non-public email sent by the Hacking Team CEO to its customers that announce a new generation of hacking tools.
Hacking Team is the popular surveillance company that suffered a serious data breach this year. More than 400 GB of its sensitive data were exfiltrated from the Italian company, including internal emails, zero-day exploits, surveillance tools, source code for the Remote Control System (RCS) spyware and a spreadsheet listing government clients.
The company has resumed its operations and as expected by the experts started is working with a new set of tools for its arsenal.
Among the numerous clients of the Hacking Team, there are several US law enforcement and intelligence agencies.

Hacking Team RCS alleged clients
News of the day is that the company is offering to its clients Encryption Cracking Tools to circumvent the Internet encryption.
The Encryption Cracking Tools allow the company’s customers to break encrypted communications.
The news was reported by Motherboard that obtained a copy of a non-public email sent by the CEO David Vincenzetti to a mailing list made of potential and current customers on October 19.
“Most [law enforcement agencies] in the US and abroad will become ‘blind,’ they will ‘go dark:’ they will be simply be [sic] unable to fight vicious phenomena such as terrorism,” states the email sent by the Hacking Team’s CEO David Vincenzetti. “Only the private companies can help here, we are one of them.” “It is crystal clear that the present American administration does not have the stomach to oppose the American IT conglomerates and to approve unpopularly, yet totally necessary, regulations,”
Following the data breach, the Hacking Team went into “full on emergency mode,” asking its customers to shut off their surveillance systems.
In response to the hack, the firm has been working on new version of its surveillance software and hacking tools, including a new version of the RCS 10.
Vincenzetti announced in the email message a totally new cyber arsenal, he defined its new tools as game changers,
[Hacking Team is] “finalizing brand new and totally unprecedented cyber investigation solutions, game changers, to say the least.”
Motherboard mentions a totally a new RCS version, RCS 10, a powerful tool that is able to load a number zero-day exploits designed by the experts of the company.
How to steal Jaguar XFR cars in 60 seconds by hacking them
1.11.2015
Hackers are able to steal Jaguar XFR cars by exploiting a hacking device that sends out a fake signal emulating a wireless key.
According to the CCTV footage, a Jaguar XFR parked in a parking lot in Auckland (New Zealand) was stolen with this technique. The video shows the thief that walks towards the car, opens the door and jump in.
According to the law enforcement, hacking devices like the one used in the theft are offered for sale on the Internet and could be easily configured to target specific car models using wireless systems.
In 2014, nearly 6000 cars have been stolen in London with this technique.
“This guy is a professional, it’s sophisticated. It’s something that has been organised. It’s not your everyday car theft.” said Mr Beacham, the manager of the dealership. “We never heard anything and only realised an hour later … that the car was missing.” “The CCTV shows him speeding off down Great South Rd in broad daylight.
Unfortunately, such kind of hack seems to very common, hackers are using devices that are designed to deceive the authentication process implemented by wireless car.
These devices act as a jamming device and are also able to capture legitimate signals sent by the owner of the vehicle when he tries to unlock the car.
To better understand how these devices work, let me introduce you the RollJam, a cheap device designed by the popular hacker Samy Kamkar, composed of a microcontroller and a battery. RollJam is capable unlocking any car or garage door, it is easy to use and costs under $30.
RollJam exploits security vulnerabilities in the wireless unlocking technology that is currently implemented by the majority of car manufacturers.
Keyless cars thefts is rising 1
Keyless entry systems allow car owners to unlock the vehicle remotely within a range of 20 meters.
RollJam was designed to steal the secret codes, also known as Rolling Code, that is generated by Keyless entry systems when the car owner presses the unlock or lock button on his wireless key. The Rolling code is a one-time code randomly generated and sent over a radio frequency to the car when the car owner presses the button of its key fob.
When the Rolling code is used the car generates a new one to use for the next time.
How does RollJam work?
The principle is simple, when the car owner presses the key fob to unlock the car, RollJam used its radio frequency to block the signal and then records it.
The car will never receive the code and the car owner likely will press the button again. When the button is pressed the second time, the RollJam again jams the signal and record also this second code, meantime it reply to the challenge mechanism by providing the first code it intercepted, unlocking the car.
When the victim parks the vehicle in his/her car, you can use that stolen signal to unlock the car. “Because I jammed two signals,” Kamkar said, “I still have one that I can use in the future.”
The RollJam works on several cars, Kamkar discovered that the attack works against widely adopted chips, including the High-Security Rolling Code Generator made by National Semiconductor and the KeeLoq access control system from Microchip Technology.
Among the car makers vulnerable to the RollJam device there are Chrysler, Fiat, Honda, Toyota, Daewoo, GM, Volvo, Volkswagen Group, and Jaguar.