
Articles 2015 December - English Press English Articles Page 1 2 3 4 5 6 2020 2019 2018 2017 2016 2015 2014 2013 2012
H Analysis Android Apple APT Attack BigBrothers BotNet Congress Crime Crypto Cryptocurrency Cyber CyberCrime CyberSpy CyberWar Exploit Forensics Hacking ICS Incindent iOS IT IoT Mobil OS Phishing Privacy Ransomware Safety Security Social Spam Virus Vulnerebility
Jednotlivé články jsou rozděleny podle měsíců a zde je najdete./The articles are broken down by month and can be found here.
2015 - January February March April May June July August September October November December
Microsoft will Inform You If Government is Spying on You
31.12.2015
Facebook will Inform You If Government is Spying on You
Following in the footsteps of Twitter, Facebook and Google, Microsoft promises to notify users of its e-mail (Outlook) and cloud storage (OneDrive) services if government hackers may have targeted their accounts.
The company already notifies users if an unauthorized person tries to access their Outlook or OneDrive accounts. But from now on, the company will also inform if it suspects government-sponsored hackers.
Ex-Employee: Microsoft Didn't Notify When China Spied Tibetans Leaders
The move could be taken in the wake of the claims made by Microsoft's former employees that several years ago Chinese government hacked into more than a thousand Hotmail email accounts of international leaders of Tibetan and Uighur minorities, but the company decided not to tell the victims, allowing the hackers to continue their campaign.
Instead of alerting those leaders of the hacking attempts, Microsoft simply recommended them to change their passwords without disclosing the reason, after an internal debate in 2011, Reuters reported.
However, Microsoft announced Wednesday that if the company strongly suspects that your account is being hijacked or targeted by hackers working in the interest of a nation-state, it will notify you via an email.
Here's what Microsoft Vice President Scott Charney writes:
"We're taking this additional step of specifically letting you know if we have evidence that the attacker may be 'state-sponsored' because it is likely that the attack could be more sophisticated or more sustained than attacks from cybercriminals and others. These notifications do not mean that Microsoft's own systems have in any way been compromised."
Just last week, Yahoo promised to alert its users whom it suspected were being spied on by state-sponsored hackers. Other big tech companies including Twitter, Facebook and Google, had previously assured their users that they would notify them of any potential government spying.
And now Microsoft is the latest company to join the list.
Government: We'll Sue You if You Do That!
This is a good news for Microsoft users, but it seems that the United Kingdom is not happy with this decision by all the major tech firms, because the country seeks access to personal communications in order to fight terrorism and protect national security.
The UK government is pushing a new Investigatory Powers Bill that will take the bosses of any company that warns its users that security organizations, such as GCHQ (the Government Communications Headquarters), MI5 and MI6, are spying on them.
Specifically, UK ministers want to make it a criminal offence for Twitter, Google and other tech firms under which they could face up to two years in prison.
Google will switch from Java APIs to OpenJDK
31.12.2015
Google confirms that the next Android versions will use Oracle’s open-source OpenJDK instead the Java APIs, a strategic choice.
Google is leaving Java application programming interfaces (APIs) in future versions of its mobile operating system Android. The company is planning to adopt as an alternative an open source solution.
What is this OpenJDK? It is an open-source implementation of the Java Platform, Standard Edition developed by Oracle, and related projects.
The news was first reported by Hacker News who quoted a “mysterious Android codebase commit.”
Google confirmed to the VentureBeat news portal that future Android versions, starting from Android N will use the Open JDK implementation, rather the official implementation of the Java APIs.
The experts have no doubts, this new change will allow the development community to easily interact and design better apps and produce quicker updates.
“Google is replacing its implementation of the Java application programming interfaces (APIs) in Android with OpenJDK, the open source version of Oracle’s Java Development Kit (JDK). The news first came by a “mysterious Android codebase commit” from last month submitted to Hacker News. Google confirmed to VentureBeat that Android N will rely on an OpenJDK implementation, rather Android’s own implementation of the Java APIs.” states VentureBeat.
OpenJDK
The reason of the choice is likely related to a legal dispute between Google and Oracle, this choice will protect Google with regards to future Android versions in the event the company loses.
The legal battle started when Oracle sued Google for copyright in 2010, claiming that Big G used a part of the Java APIs in the Android mobile OS.
Google replied sustaining the necessity to use Java APIs to allow different applications to interact, and, therefore, could not be copyrighted.
Google plans to introduce its resources into Open JDK having a significant impact on future development of the framework where the team can have a bigger impact on new features and improvements.
Google won a first legal dispute in 2012, but a Federal court lawsuit in 2014 expressed its favor to Oracle. Google reached out to the US Supreme Court to take the case, but the Supreme Court declined to hear Google’s appeal.
The experts believe that Google will be prohibited from using the copyrighted APIs, this is the principal motivation behind the choice to adopt the Open JDK.
Be aware, Open JDK is still under the Oracle’s control, but Google is legally authorized to implement it.
Tor Project to Start Bug Bounty Program — Get Paid for HACKING!
30.12.2015
The non-profit organization behind TOR – the largest online anonymity network that allows people to hide their real identity online – will soon be launching a "Bug Bounty Program" for researchers who find loopholes in Tor apps.
The bounty program was announced during the recurring 'State of the Onion' talk by Tor Project at Chaos Communication Congress held in Hamburg, Germany.
Bug bounty programs are cash rewards gave by companies or organizations to white hat hackers and researchers who hunt for serious security vulnerabilities in their website or products and then responsibly disclose them.
Bug bounties are designed to encourage security researchers and hackers to responsibly report the vulnerabilities they discovered, rather than exploiting it.
Here's what one of the founders of the Tor Project, Nick Mathewson, said about the bug bounty program as reported by Motherboard:
"We are grateful to the people who have looked at our code over the years, but the only way to continue to improve is to get more people involved...This program will encourage people to look at our code, find flaws in it, and help us to improve it."
The bug bounty program will start in the new year.
The Tor Project is following in the footsteps of a number of major technology companies, such as Facebook, Google, Paypal, and Mozilla, which offer bug bounties in thousands of Dollars.
Recently United Airlines made headlines by becoming the first airline to launch its own bug bounty program, eventually awarding millions of frequent-flyer miles to hackers and researchers.
The bug bounty could be in the wake of last month’s incident when Tor Project accused the FBI of paying the researchers of Carnegie Mellon University (CMU) at least $1 Million to help them Unmask Tor users and reveal their IP addresses. However, the FBI denies the claims.
Google 'Android N' Will Not Use Oracle's Java APIs
30.12.2015
Google appears to be no longer using Java application programming interfaces (APIs) from Oracle in future versions of its Android mobile operating system, and switching to an open source alternative instead.
Google will be making use of OpenJDK – an open source version of Oracle’s Java Development Kit (JDK) – for future Android builds.
This was first highlighted by a "mysterious Android codebase commit" submitted to Hacker News. However, Google confirmed to VentureBeat that the upcoming Android N will use OpenJDK, rather its own implementation of the Java APIs.
Google and Oracle have been fighting it out for years in a lawsuit, and it is hard to imagine that such a massive change is not related to the search engine giant's ongoing legal dispute with Oracle, however.
What Google and Oracle are Fighting About
The dispute started when Oracle sued Google for copyright in 2010, claiming that Google improperly used a part of its programming language called Java APIs and baked them into its Android mobile OS.
However, Google argued that the Java APIs in question were necessary for software innovation, allowing different applications to talk to each other, and, therefore, could not be copyrighted.
Google almost won the initial lawsuit in 2012, but a Federal court mostly reversed the decision in 2014 in Oracle's favor. Google reached out to the US Supreme Court to take the case, but Supreme Court declined to hear Google's appeal.
The final decision is yet to be made, but one possibility could be that the company will be prohibited from using the copyrighted APIs.
However, OpenJDK, the alternative to Java APIs, is still controlled by Oracle, but at least, Google is legally cleared to implement it.
As for how this new change in Android affects you and me, the new code should make it somewhat easier for Android N developers, perhaps resulting in better apps and quicker updates.
R.I.P Ian Murdock, Founder of Debian Linux, Dead at 42
30.12.2015
Ian Murdock, the founder the Debian Linux operating system and the creator of apt-get, has passed away.
Yes, it is very sad to announce that Ian Murdock is not between us. His death has touched the entire software community. He was just 42.
The announcement of Murdock death came out via a blog post on Docker website, where Murdock was working as a member of the technical staff.
The cause of death is unclear at present, but Murdock tweeted the same day that he would commit suicide that night. His Twitter account had since been deleted.
R.I.P Ian Murdock, The Founder of Debian Linux, Dead at 42
However, at that time, some people speculated that Murdock’s account had been hacked and that the tweets were not by him.
Murdock posted some Tweets on Monday suggesting he had been involved in a police case and has been beaten by the police and charged with battery.
However, neither Docker, nor the San Francisco Police Department immediately commented on Murdock’s actual cause of death.
Murdock developed Debian in August 1993 — and yes the “ian” in the project’s name is from Ian Murdock.
In the past, He also worked at Sun Microsystems and served as the CTO of the Linux Foundation.
It is with deep regret that we say goodbye to our great friend, the most significant contributor to Linux community, our beloved Ian Murdock.
Rip :(
DHS: Drug Traffickers are hacking surveillance drones on the border
30.12.2015
The U.S. Department of Homeland Security and local law enforcement confirmed that Drug Traffickers are hacking surveillance drones on the border.
Small drones are another powerful tool used by the US Department of Homeland Security to monitor its borders, but drug traffickers already adopting countermeasures. In order to avoid surveillance, drug traffickers are hacking US surveillance drones used to patrol the border.
According to Timothy Bennett, a Department of Homeland Security program manager, drug traffickers are using technology to spoof and jam the US surveillance drones.
“The bad guys on the border have lots of money. And what they are putting money into is spoofing and jamming of GPSs, so we are doing funding to look at small UAS that we can counter this,” Bennett said during a panel at the Center for Strategic & International Studies.
The principle behind the GPS spoofing attack is that sending to control system of the drone fake geographic coordinates it is possible to deceive the onboard system hijacking the vehicle in a different place for which it is commanded. Non-military GPS signals are not encrypted, this makes drones vulnerable to this kind of attacks.
Using jamming techniques against drones, it is possible to interrupt the GPS receiving transmitted to the UAVs. In this scenario the aircraft could potentially lose the capability to monitor its route and to calculate its location, altitude, and the direction in which it is traveling.
Both attack techniques are adopted by drug traffickers that belong to well-funded organizations that has access to modern advanced hacking technology.
DHS hasn’t provided further details on the attacks, but Bennett confirmed that the attacks are interfering with the operations conduced by members of the law enforcement.
“You’re out there looking, trying to find out this path [they’re] going through with drugs, and we can’t get good coordinate systems on it because we’re getting spoofed. That screws up the whole thing. We got to fix that problem,” Bennett told Defense One.
The Tor Project Is launching the Tor Bug Bounty Program
30.12.2015
The Tor officially announced to launch the Tor Bug Bounty Program in the next year, a great news for the Tor community.
The non-profit organization that is maintaining the TOR project plans to launch very soon a Tor Bug Bounty Program for researchers who find vulnerabilities in the popular anonymizing platform.
This is a great for all the researchers that fights for online anonymity and that wants to contribute to improve the security offered by the Tor system.
The imminent launch of the Tor bug bounty program was announced during the annual talk (“State of the Onion”) by representatives of the Tor Project at the Chaos Communication Congress held in Hamburg, Germany.
Tor Bug Bounty Program
The State of the Onion is arranged to cover technical, social, economic, political, and cultural issues pertaining to anonymity, the Tor Project, and the communities that use the system.
The Tor Bug Bounty Program will reward who report serious security vulnerabilities in the website or products managed by the Tor project.
The Tor Bug bounty project, like similar initiatives, aims to encourage hackers and security experts to responsibly report the loopholes affecting the Tor platform and that they discovered.
“We are grateful to the people who have looked at our code over the years, but the only way to continue to improve is to get more people involved…This program will encourage people to look at our code, find flaws in it, and help us to improve it.” Nick Mathewson, one of the founders of the Tor Project, told to Motherboard.
said about the bug bounty program as reported by Motherboard:
It is likely that the Tor bug bounty program will start in 2016. Clearly the bounty program can award researchers a lower fee respect that sum that could be offered by a government for a zero-day in a project considered strategic by intelligence agencies.
To give you an idea of the price of a zero-day, in November the zero-day trader Zerodium awarded $1 million for hacking the latest Apple iOS operating system, the same company offers Zwill pay $30,000 for an exploit that affects the Tor Browser.
Who pays the Tor bug bounty program?
“We have a sponsor, OTF [Open Technology Fund], who is paying HackerOne, a company that specializes in this, to help us do it,” explained Roger Dingledine, co-founder and research director of the Tor Project.
HackerOne used by experts that discover flaws in a software and desire to get in touch with the companies affected by them.
“The program will start out invite-only,” Mike Perry, lead developer of the Tor Browser, said during the talk, and added that vulnerabilities “specific to our applications” would fall into the program.
Recently a news monopolized the attention of the Tor community, security experts speculate that the FBI paid the researchers of Carnegie Mellon University (CMU) $1 Million to help them to de-anonymize Tor users, but FBI denies it.
North Korea's Red Star OS (Looks Like Mac OS X) Spies on its Own People
30.12.2015
North Korea's Red Star Computer OS (Just Looks Like Apple Mac OS X) Spies on Citizens
North Korea has its own homegrown computer operating system that looks remarkably just like Apple’s OS X, which not only prevents potential foreign hacking attempts but also provides extensive surveillance capabilities.
Two German researchers have just conducted an in-depth analysis of the secretive state's operating system and found that the OS does more than what is known about it.
Dubbed Red Star OS, the operating system based on a Linux 2009 version called Fedora 11 limits its users to a government-approved view of the world and has the tendency to 'watermark' files on USB sticks to track user’s shuttling contraband material.
Red Star OS Tracks User's Every Move
In short, whenever a user inserts a USB storage device containing photos, videos or other documents, into a computer running Red Star, the OS takes the current hard disk's serial number, encrypts that number, and writes that encrypted serial into the file, marking it.
north-koria-Red-Star-computer
The purpose of watermarking files is to track who actually has the particular file, who created that file, and who opened it.
Researchers previously reported this watermarking feature after analysing Red Star OS, but Florian Grunow and Niklaus Schiess of German IT company ERNW GmbH currently presented dive into Red Star OS goes further.
Makers have Full Control Over Red Star OS
Most of the Red Star's unique features, including its own version of encrypting files, were designed to grant its makers complete control over the operating system, making it independent from any code that could be compromised and exploited by foreign intelligence services, the duo said as they presented their findings at the Chaos Communication Congress in Hamburg on Sunday.
The researchers analysed the latest – third – version of Red Star OS coming out around 2013 and it is clear that software is as authoritarian as the country that developed it.
"This is a full-blown operating system where they control most of the code," Grunow said as quoted by Reuters. Moreover, the OS rigorously resists any changes made by its user and closely monitors every move of a user.
The Red Star OS provides its own firewall, antivirus system and web browser point to internal North Korean servers, and even the encryption is custom-developed.
No Tampering
However, the small program included in the OS constantly monitors the computer for any changes made to the system files.
As a result, any attempt by a user to tamper with the operating system's core functions, like disabling antivirus or firewall, would lead to the computer displaying an error message or rebooting itself.
Since, there is no sign in the OS of the kinds of cyber attack capability North Korea has been accused of, Red Star OS is also designed to crack down on the growing illegal exchange of foreign media content, including films, music or document files.
At the current, the duo has no information on how many computers in North Korea are using this operating system, as they found the OS from a website located outside the country, while visitors to North Korea say most computers there still use Windows XP.
A software bug caused the early release of 3,200 US prisoners
30.12.2015
The US Department of Corrections discovered a long-standing software bug that resulted in the early release of prisoners.
This news is disconcerting and demonstrates the importance to carefiìully consider the technology in our lives. The Washington State Department of Corrections (DoC) launched an investigation after it early released 3,200 prisoners over the course of 13 years.
It seems that a software bug present in the systems of the Department since 2002, caused errors in the calculation of time credits for the good behavior of individuals while imprisoned.
The bugs led errors in the calculation of sentence reductions for the US prisoners that had a good behavior, the experts estimated that in a 13-year period, the average number of days of those released early from prison was 49 days before the correct release date.
“This problem was allowed to continue for 13 years is deeply disappointing to me, totally unacceptable and, frankly, maddening,” is the comment of the Washington State Governor Jay Inslee. “I’ve [many] questions about how and why this happened, and I understand that members of the public will have those same queries.”
Gov. Jay Inslee today already ordered the Washington Department of Corrections to take the necessary actions to discover the bug that allowed criminals to leave the jail early.

The software bug was introduced in 2002, in that year the state’s supreme court introduced a change in the calculation of the “good time” credit system for all the prisoners in State Prisons and County jails,
Criteria for evaluating the good behavior of prisoners were introduced to allow guests of state prisons to reduce the period to be served.
The DoCs released a new version of software that implemented the new rules, but it introduced also a bug, but it is important to highlight that the Department of Corrections (DoC) has been informed of the software bug at least 3 years ago. In December, 2012 in fact, the familiars of an assault victim reported the issue to the Department of Corrections.
The US Department of Corrections accepted the claim and filed a request, ranking the error as “time sensitive.” This means that the US Department urged a solution as soon as possible, but something went wrong.
“Between December 2012 and this month, the software fix “was repeatedly delayed,” according to a DOC timeline of events. The delays occurred despite the fact a DOC worker who filed the service request labeled the fix as time sensitive and “ASAP.” Reported the SeattleTimes. “Typically, IT fixes are put into a queue according to priority, said Brown. But, “What we know, I think, at a bare minimum, is the proper prioritization did not occur,” he said.”
Three years to fix a time sensitive bug that could have effects on people security. Simply absurd!
Now something seems to be changing, Inslee assured that the software bug will be fixed within the January 7th.
Waiting for the fix, the US DOC has requested double checks before releasing any prisoner.
“The governor ordered DOC to halt all releases of impacted offenders from prison until a hand calculation is done to ensure the offender is being released on the correct date. A broader software fix is expected to be in place by Jan. 7, 2016.” continues the official statement.
“In addition, DOC is working swiftly to locate offenders who were released from prison prior to their actual earned release date and ensure they fulfill their sentences as required by law. In accordance with Supreme Court precedent, most of the offenders who were released early will be given with day for day credit for their time in the community. Depending on how much time they have left to serve, the offenders will go to work release or back to prison.”
Social Networks – A Bonanza for Cybercriminals
30.12.2015
On the unfortunate consequences of publishing your mobile phone number on your social media account
What do you think when you receive yet another spam or phishing message on your mobile phone? Most likely it is: “Who are these people, and how on earth did they get my phone number?” Initially, suspicion usually falls on an unscrupulous employee at some organization that you gave your number to. However, it’s not uncommon for spammers and cybercriminals to use a database harvested from a social network using special software, rather than a “leaked” database of cellphone subscribers.
Information security experts, including us, have for years reiterated: cybercriminals can make use of any information that you publish about yourself on a social network. However, a huge amount of users still continue to share news and a plethora of personal information with their virtual friends as well as incidental onlookers. This may lead to unpleasant and, at times, unforeseen consequences. To show that this isn’t just scaremongering, let me offer an example from the recent activities of our cybercrime investigation team.
A run-of-the-mill cybercrime
This autumn, we helped law enforcement agencies halt the activities of a small Russian cybercriminal gang that specialized in distributing Android malware and stealing money from online banking accounts. The group’s plan of action was fairly straightforward: they used a database of cellphone numbers they already had to send short messages containing a link to a banking Trojan. If infected successfully, the mobile device became part of a botnet, and the Trojan began to search for information about any banking services used by the victim, collecting any data required to access them. The cybercriminals then had the relatively simple task of transferring the victim’s money to their own accounts.
It is interesting to note that none of the cybercriminals were professional programmers. When people talk about hackers and stealing money, an image springs to mind of some corrupt programmer who writes malicious code and then uses it to infect the devices of unwitting users. This time, however, we are not talking about professionals with the relevant education and experience. Instead, we assume they spent just enough time on public hacking forums to garner the information and tools required to commit cybercrimes.
One of the tools they employed is of particular interest: it is a parser program that harvests mobile phone numbers from public profiles on the popular Russian social network VKontakte. With the help of this tool, the cybercriminals have created a database of cellphone numbers that was later used to send malicious messages. As far as we know, the social network was the sole source of information from which the cybercriminals harvested their data.
A post on a popular Russian hacker forum advertising an app to harvest the phone numbers of social network users
Russian cybercriminal forums (especially the open forums frequented by amateur fraudsters) have loads of adverts offering this type of software for sale or rent. It is capable of collecting and structuring all valuable information about users, including their first and last names, all published contact data and profile settings – not just mobile phone numbers. The availability of this information offers cybercriminals plenty of opportunities for fraud. The most obvious ways the gathered data can be used are: sending spam (including both advertising and malicious spam), stealing money through premium SMS services, and creating fake SIM cards.
In less than a year the cybercriminals have managed to steal an estimated 600,000 RUR (approximately $8,500). This is a relatively small amount compared to the millions stolen by larger, more advanced cybercriminal groups. However, in this case it is not the amount of money stolen that defines the scope of the problem, but rather the number of similar non-professional cybercriminal groups that are conducting the same sort of activity. Judging by the user complaints that get posted on the support forums of online banks, dozens of these criminal groups appear to be operating.
Beyond Russia
The fact that these types of fraudulent activities mostly take place in Russia and neighboring countries does not mean there is nothing to fear for people living in other countries.
For instance, the early banking Trojans for PCs and mobile devices mostly targeted users living in Russia. However, with time the Russian-language cybercriminals behind those Trojans either radically changed their target “audience” and switched to residents of other countries, or expanded it by creating versions that targeted the residents of other countries.
The criminal group we are looking at used an application that collected the personal information of users from just one social network – VKontakte. However, there are offers on hacking forums for similar tools designed to collect data from other social networks, including Facebook and Instagram. So, it is quite possible that similar schemes exploiting data collected from public sources are already emerging in countries beyond the former Soviet Union, or are likely to emerge in the near future.
An advert posted on a popular Russian public hacking forum offering a parser program designed to harvest users’ mobile phone numbers and other information from Instagram
The countries at most risk include those where pre-paid phone contracts are prevalent and various SMS services are popular, including those that allow bank card operations via SMS.
What to do?
In summary, we would like once again to urge users to publish as little information about themselves in social networks as possible. In particular, do not publish your mobile phone number, or remove it if you already have. This will not completely eliminate the problem of cybercriminals harvesting users’ personal information from social networks, but at least it prevents the easiest ways of stealing your money.
If you or your family and friends use mobile banking services, you should also apply these basic security measures:
Block installation of apps from third-party sources on the Android device you use for mobile banking;
Set withdrawal limits for your bank account;
Restrict or disable the sending of text messages to premium-rate numbers;
Use a reliable security solution capable of protecting your device from infections.
If you should still fall victim to an attack and your money is stolen, contact the appropriate law enforcement agencies. It is important you do this, because we are seeing an ominous trend: the broad availability of various tools, including malicious ones, and the perceived anonymity of cybercrime create a false sense of security in cybercriminals, which is only exacerbated by the passive attitude of the victims. This encourages an increasing number of people to start acting as cybercriminals in the hope of easy gains. The more cybercriminals that are arrested for these illegal activities, the more obvious it will be that cybercrime doesn’t pay and those contemplating it will be less likely to start committing crimes on the web. This will help make the Web a safer place.
Are Russian hackers infecting critical infrastructure in Ukraine?
30.12.2015
The Ukrainian Government is blaming Russians state-sponsored hackers for a number of electricity cut-offs occurred in Western Ukraine.
The Ukrainian Government is suffering a series of power outages in the Western region of the country likely caused by cyber attacks.
The Ukrainian Government believes that the power outages are caused by operations conducted by Russian nation-state actors.
“hacker attacks by Russia[n] special services”.
According to the Security Service of Ukraine (SBU), experts have discovered a malware infecting critical infrastructure of the country, the malicious code targeted networks of some utilities.
The malware infections were observed in concurrent with a “non-stop telephone flood at utility plants’ technical support departments.” According to the local media, the Ukraine is suffering information warfare attacks.
“Experts detected virus software was found in some networks, SBU says. The virus attack was timed with nonstop telephone flood at utility plants’ technical support departments.”
The Security Service of Ukrainian also confirmed that its experts reportedly foiled other attacks conducted by Russian hackers. Russian agents attempted to infiltrate computer networks of a number of electricity utility companies.
It is not the first time that the Ukrainian Government suffers attacks alleged launched by Russian hackers. The number of attacks during the dispute between the two countries on the control of the Crimea.
Last Christmas Eve, infrastructure in the Ukraine suffered numerous power outages that were attributed to cyber attacks operated by Russian hackers.
While the Government of Kiev is blaming Russian hackers, the Russian Government hasn’t replied to the accusation. There are also other possible explanations for the numerous power outages, including accidental failures caused by animals and weather conditions.
There are anyway, if confirmed the news of the presence of a malware targeting the national infrastructure it is more likely the involvement of a foreign government, but as usually happen in this case the problem of attribution has no simple resolution.
Employee Stole 'Yandex Search Engine' Source Code, Tried to Sell it for Just $29K
29.12.2015
A former employee of Russian search engine Yandex allegedly stole the source code and key algorithms for its search engine site and then attempted to sell them on the black market to fund his own startup.
Russian publication Kommersant reports that Dmitry Korobov downloaded a type of software nicknamed "Arcadia" from Yandex's servers, which contained highly critical information, including the source code and some of the "key algorithms," of its search engine.
Korobov then tried to sell the stolen codes to an electronics retailer called NIX, where a friend of his allegedly worked, and on the dark underground market in search of potential buyers.
But What's the Punchline?
The funniest part is that Korobov requested only $25,000 and 250,000 rubles (a total of almost $29,000) for Yandex's source code and algorithms, which actually cost "Billions of Rubles," or somewhere near $15 Million USD.
However, Korobov was arrested by Russia's Federal Security Service (FSB) before any transaction could take place.
If he had been succeeded, the code of Yandex's core service was floating freely over the Internet, resulting in serious consequences for the company.
The report noted that Korobov's court hearing took place earlier this month, and he received a suspended sentence of 2 years in jail after being accused of illegal possession as well as the distribution of commercial secrets.
The Arcadia software "is a key part of [the] company, it was related directly to Yandex's search engine, which is the [primary] source of the company's income," a Yandex representative said in court.
Yandex is the most popular search engine in Russia and is a big rival of Google. Its market share in November reached around 57 percent of all search queries within Russia, compared to Google's 35.2 percent.
Jail Authorities Mistakenly Early Released 3,200 Prisoners due to a Silly Software Bug
29.12.2015
Jailer Mistakenly Early Release 3,200 Prisoners due to a Silly Software Bug
Washington State Department of Corrections (DoC) is facing an investigation after it early released around 3,200 prisoners per year, since 2002, when a bug was introduced in the software used to calculate time credits for inmates' good behavior.
The software glitch led to a miscalculation of sentence reductions that US prisoners were receiving for their good behaviour.
Over the next 13 years, the median number of days of those released early from prison was 49 days before their correct release date.
"This problem was allowed to continue for 13 years is deeply disappointing to me, totally unacceptable and, frankly, maddening," Washington State Governor Jay Inslee said in a statement. "I've [many] questions about how and why this happened, and I understand that members of the public will have those same queries."
What's the Bug and How did it Remain Undetected for 13 Years?
The issue lies in DoC software that is used for calculating the release date for prisoners who showed good behavior while imprisoned.
The software bug was introduced in 2002, when the state's supreme court implemented a change to the "good time" credit system, allowing prisoners to claim credits for good behaviour while they are in:
State Prisons
County jails
These credits are then used to shorten the length of prisoner’s sentence. To apply these changes, DoCs around the United States released the new versions of software but unfortunately, the code that calculated prison sentences was faulty.
DoC First Informed of the Issue 3 Years Ago
What's even more disappointing is that the authorities first learned of the bug in December 2012, when the family of an assault victim alerted DoC that the attacker was going to be set free too soon.
At that time, DoC filed a request, labelling the error as "time sensitive" and to be implemented as quickly as possible.
However, the Washington DoC hired a new IT manager in November, who alerted the authorities of how serious the bug had become. Inslee assures that a full fix for the bug is expected to be rolled out by 7th January.
Until then the DoC has been ordered not to release any prisoner without manually checking their actual release date.
Microsoft maintains the recovery key of your new PC
29.12.2015
If you login to Windows 10 using your Microsoft account you have to know that your computer automatically uploaded a copy of your recovery key.
New Windows computers implement a built-in disk encryption feature that is turned on by default to protect user data in case the device is lost or stolen.
Be aware, this device encryption feature is different from the BitLocker which allows users to choose whether or not to backup their Recovery keys on Windows server.
The security feature is enabled by default in Microsoft systems since Windows 8.1, but what happen in case the user lost the encryption keys?
Microsoft maintains a copy of the Recovery Key, a circumstance that is raising a heated debate on the web because it represents a privacy violation according to many experts.
The Intercept revealed that when a user is logged into Windows 10 using his Microsoft account, the OS automatically uploads a copy of the recovery key to the Microsoft’s servers, and the bad news is that it is impossible to prevent it.
“But what is less well-known is that, if you are like most users and login to Windows 10 using your Microsoft account, your computer automatically uploaded a copy of your recovery key – which can be used to unlock your encrypted disk – to Microsoft’s servers, probably without your knowledge and without an option to opt-out.” states The Intercept.
Clearly this setting open users to a number of cyber attack, let’s think the case an attacker violates their Microsoft account, he would be able to access/copy the recovery key and delete it. A similar circumstance could occur if hackers compromise Microsoft servers and access the recovery keys of the users, or if an insider access to user recovery key.Even Law Enforcement or Spy agencies could also request Microsoft to hand over your recovery key.
Even law enforcement or intelligence agencies could force Microsoft to hand over the recovery key of a suspect.
“Your computer is now only as secure as that database of keys held by Microsoft, which means it may be vulnerable to hackers, foreign governments, and people who can extort Microsoft employees,” said Matthew Green, a cryptography professor at Johns Hopkins University.
The Intercept highlighted that storage of the recovery key on Microsoft’s servers makes the company an escrow agent, users can delete their recovery key, but they are not informed about this opportunity.
“The fact that new Windows devices require users to backup their recovery key on Microsoft’s servers is remarkably similar to a key escrow system, but with an important difference. Users can choose to delete recovery keys from their Microsoft accounts (you can skip to the bottom of this article to learn how) – something that people never had the option to do with the Clipper chip system. But they can only delete it after they’ve already uploaded it to the cloud.
How to Delete the Recovery Key from a Microsoft Account?
We said that it is not possible to prevent a new Windows computer from uploading the key at the very first time you log into your Microsoft account, you can delete the existing one from your Microsoft account and generate a new one.
Below the procedure to remove the encryption key from a Microsoft account:
Login in using the Microsoft Account to the Recovery Key Website:
The website maintains a list of recovery keys backed up to your Microsoft Account.
Backup Recovery Keys locally.
Delete the recovery key from the Microsoft Account.
recovery key windows encryption
The Intercept highlighted that even following the above procedure there is no guarantee that the key has been removed from the Microsoft servers, the unique possibility for the user is to generate a new recovery key without uploading it to Microsoft.
“After you finish setting up your Windows computer, you can login to your Microsoft account and delete the recovery key. Is this secure enough? “If Microsoft doesn’t keep backups, maybe,” says Green. “But it’s hard to guarantee that. And for people who aren’t aware of the risk, opt-out seems risky.”
Windows Pro or Enterprise users can create a new key by decrypting the hard disk and then re-encrypt the disk, below the procedure to do it.
Go to Start, type “bitlocker”, and click “Manage BitLocker.”
“Turn off BitLocker,” this command will trigger the decrypt of the entire disk.
Once completed, Click “Turn on BitLocker” again.
The OS will request you how to backup the Recovery Key. Make sure to DO NOT SELECT “Save to your Microsoft Account.”
That’s all!
Former Employee tried to sell Yandex Source Code for Just $29K
29.12.2015
A former employee at stole the source code of the Yandex Search Engine and its algorithms and tried to sell the for tens of thousands of euro.
A former employee, Dmitry Korobov, of Russian search engine Yandex is accused of stealing the source code and algorithms implemented by the company. The man alleged attempted to sell them on the black market to an electronics retailer called NIX.
The news was reported by the Russian publication Kommersant, Korobov downloaded has stolen a software called “Arcadia” from company’s servers which contained essential information, including the source code and some of the “key algorithms” implemented in its engine.
“According to the indictment read out by the prosecutor during the meeting, in March 2015, Dmitry Korobov, still working “Yandex”, “carried up from the server” Yandex “software” Arcadia “, containing the source code and algorithms of the search engine” Yandex “in for which is set to trade secrets on a removable storage medium for subsequent transfer to third parties. ” states Kommersant.
“Source: “b” familiar with the investigation affirms that the value of the stolen source code and search algorithms evaluated in the “billions of rubles, which, in fact, represents a significant part of the value of” Yandex “, as the search engine – the main service company.””
The most disconcerting aspect of this absurd story is that Korobov requested only $25,000 and 250,000 rubles (a total of almost $29,000) for both the Yandex’s source code and algorithms.
A few thousand dollars for software that worth “Billions of Rubles”! Consider that the leakage of the software would have been a disaster for the Russian company.
Korobov was identified and arrested by Russia’s Federal Security Service (FSB) before selling the precious software.
Korobov was already on a trial court, he received a suspended sentence of 2 years in jail after been accused of illegal possession as well as the distribution of commercial secrets. Yandex representative during the hearing in court explained the importance of the Arcadia software.
The Arcadia software “is a key part of [the] company, it was related directly to Yandex’s search engine, which is the [primary] source of the company’s income,” a Yandex representative said in court.
The incident raises once again the problem of the insiders and the importance to monitor the internal assets, including source code.
191 Million US Voters' Personal Info Exposed by Misconfigured Database
29.12.2015
BREAKING: A misconfigured database has resulted in the exposure of around 191 Million voter records including voters' full names, their home addresses, unique voter IDs, date of births and phone numbers.
The database was discovered on December 20th by Chris Vickery, a white hat hacker, who was able to access over 191 Million Americans’ personal identifying information (PII) that are just sitting in the public to be found by anyone looking for it.
Vickery is the same security researcher who uncovered personal details of 13 Million MacKeeper users two weeks ago, which included names, email addresses, usernames, password hashes, IP addresses, phone numbers, and system information.
However, the recent discovery made him shocked when he saw his own information in the database, according to DataBreaches.net, whom the researcher contacted and provided all the details about his finding.
300GB Trove of Voters' Information Leaked
Vickery has his hands on all 300GB of database contains a long list of voter records including:
Full name (first, middle, last)
Residential address
Mailing address
A unique voter ID
State voter ID
Gender
Date of birth
Date of registration
Phone number
Political affiliation
A detailed voting history since 2000
Fields for voter prediction scores
Not just his own, but Vickery also looked up a number of police officers in his city and confirmed the information was all correct. Reporters from CSO and DataBreaches.net also did the same and upheld the accuracy as well.
Fortunately, the database doesn't contain Social Security Numbers, driver license numbers, or any financial data, but it's still a massive amount of data when it comes to protecting users privacy and security.
What's even more Shocking?
The crazy part of the data breach is no one is taking responsibility for the exposed database.
Vickery, CSO and DataBreaches.net contacted various political tech groups and known voter information companies, but all denied the database belonged to them.
The FBI and Internet Crime Complaint Center were all approached by Vickery and DataBreaches.net; so let’s now see how long this information remains alive and accessible for anyone to see.
Patch now! Adobe releases Emergency Security Updates for Flash Player
29.12.2015
Adobe releases Emergency Security Updates for Flash Player
The Adobe Flash Player just said goodbye to the year with another bunch of vulnerability patches.
Adobe released an out-of-band security update on Monday to address Nineteen (19) vulnerabilities in its Flash Player, including one (CVE-2015-8651) that is being exploited in the wild.
All the programming loopholes could be abused to execute malicious code (here malicious Flash file on a web page) on victims' computers in order to hijack an unpatched PC or Mac entirely.
So, if you are running the Flash Player plugin on Windows, Mac OS X, Linux, or Chrome OS, it is time for you to upgrade your system as soon as possible before criminals start taking advantage of the bugs.
Here're the details of the Flash's 19 security vulnerabilities patched in the emergency APSB16-01 update posted Monday afternoon:
A Type Confusion Vulnerability that could lead to arbitrary code execution (CVE-2015-8644)
An Integer Overflow Vulnerability that also leads to code execution (CVE-2015-8651)
Use-After-Free() Vulnerabilities that could also lead to code execution
Memory Corruption Vulnerabilities that could also lead to code execution
The company did not provide many details about the attacks exploiting the Integer Overflow Vulnerability (CVE-2015-8651) discovered by Huawei, other than describing them as "limited, targeted attacks."
Upgrade your machines to the following patched versions of Flash Player:
Flash Player versions 20.0.0.267 and 18.0.0.324 for Windows and Mac users.
Flash Player version 20.0.0.267 for Google Chrome
Flash Player version 20.0.0.267 for Microsoft Edge and Internet Explorer 11 on Windows 10
Flash Player version 20.0.0.267 for IE 10 and 11 on Windows 8.x
Flash Player version 11.2.202.559 for Linux
You can also get the latest Flash Player versions from Adobe's website.
However, if you really want to get rid of these nasty bugs, you are advised to simply disable or completely uninstall Adobe Flash Player immediately.
Flash has plagued with several stability and security issues, which is why developers had hated the technology for years.
Moreover, this is the reason Adobe plans to kill Flash Player and re-brands it as Adobe Animate CC — Adobe's Premier Web animation tool for developing HTML5 content.
Microsoft Keeps Backup of Your Encryption Key on it's Server — Here's How to Delete it
29.12.2015
windows-disk-encryption-recovery-key-backup
Have you recently purchased a Windows computer?
Congratulations! As your new Windows computer has inbuilt disk encryption feature that is turned on by default in order to protect your data in case your device is lost or stolen.
Moreover, In case you lost your encryption keys then don't worry, Microsoft has a copy of your Recovery Key.
But Wait! If Microsoft already has your Disk Encryption Keys then what’s the use of using disk encryption feature? Doesn't Encryption mean Only you can unlock your disk?
Microsoft Probably Holds your Encryption Keys
Since the launch of Windows 8.1, Microsoft is offering disk encryption as a built-in feature for Windows laptops, Windows phones and other devices.
However, there is a little-known fact, highlighted by The Intercept, that if you have logged into Windows 10 using your Microsoft account, your system had automatically uploaded a copy of your recovery key to Microsoft’s servers secretly, and you can't prevent device encryption from sending your recovery key.
Note: Do not get confuse device encryption with BitLocker. Both works same but have different configuration options. BitLocker offers users a choice whether or not they want to backup their Recovery keys on Windows server.
Also Read: Mission '1 Billion' — Microsoft will Automatically Offer Windows 10 Upgrade
Why Should You Worry?
If a hacker hacks your Microsoft account, he can make a copy of your recovery key before you delete it (method described below).
Any Rogue employee at Microsoft with access to user data can access your recovery key.
If Microsoft itself get hacked, the hacker can have their hands on your recovery key.
Even Law Enforcement or Spy agencies could also request Microsoft to hand over your recovery key.
"Your computer is now only as secure as that database of keys held by Microsoft, which means it may be vulnerable to hackers, foreign governments, and people who can extort Microsoft employees," said Matthew Green, a cryptography professor at Johns Hopkins University.
How to Delete your Recovery Key from your Microsoft Account?
Although there's no way to prevent a new Windows computer from uploading the recovery key at the very first time you log into your Microsoft account, you can delete the existing recovery key from your Microsoft account and generate a new one.
Also Read: Intel launches Hardware-based Self-Encrypting Solid State Drives
Follow these simple steps in order to remove your recovery key from your Microsoft account:
Step 1: Open this website and log in with your Microsoft Account
Step 2: You will find list of recovery keys backed up to your Microsoft Account
Step 3: Take a back of your recovery Keys locally
Step 4: Go ahead and delete your recovery key from Microsoft Account.
Important Fact: Green also pointed out that even after deleting the recovery key from your Microsoft account, there is no guarantee that the key has been removed from the company's server.
Instant Solution: To solve this issue, Windows users are recommended to stop using their old encryption keys and generate a new one without sharing it with Microsoft.
How to Generate a New Encryption key (Without Sending a copy to Microsoft)?
Sorry for Windows Home Edition users, but Windows Pro or Enterprise users can create new key by decrypting whole hard disk and then re-encrypt the disk, and this time in such a way that you will actually get asked how you want to backup your Recovery Key.
Step 1: Go to Start, type "Bitlocker," and click "Manage BitLocker."
Step 2: Click "Turn off BitLocker" and it will decrypt your disk.
Step 3: Once done, Click "Turn on BitLocker" again.
how-to-install-bitlocker
Step 4: Then Windows will ask you: How you want to backup your Recovery Key. Make sure to DO NOT SELECT "Save to your Microsoft Account." That's it.
Congratulations!
Finally, the new Windows device you purchased specially for disk encryption feature has now enabled the feature, and Microsoft no longer can unlock it.
China passes its first Anti-Terrorism law
29.12.2015
China passed it first controversial Anti-Terrorism law that requires technology firms to help decrypt information and much more.
China Passes its first Anti-Terrorism law that will have a serious impact on all those companies that want to operate in the country.
The Anti-Terrorism law establishes that Operators of telecommunications and Internet services operating in China have to “offer technological assistance and cooperation with security departments to help prevent and investigate terrorist activities,” meanwhile financial organizations should immediately freeze relevant deposits and accounts belonging to suspects of terrorism.
Chinese controversial new anti-terrorism law requires tech companies to help the law enforcement and intelligence agencies to decrypt information or hand over encryption keys to officials when the Government needs to spy on suspects.
This implies that the Chinese government is requesting companies to provide encryption keys for the services they are offering, but the law wouldn’t require technology firms to install a “backdoor” in their products. A draft of the Anti-Terrorism law previously disclosed called for mandatory backdoor in the product and services of companies operating in China.
Anti-Terrorism law china
Chinese authorities defend the Anti-Terrorism law by saying that the Government og Beijing is simply doing what other Western nations already do to fight terror.
“This rule accords with the actual work need of fighting terrorism and is basically the same as what other major countries in the world do,” Li Shouwei, deputy head of the Chinese parliament’s criminal law division, told Reuters.
“Providers of telecommunications, Internet, finance, accommodation and passenger transport services should also check the identity of clients,” the law also states, effectively killing off online anonymity.
Someone compared the new Chinese Anti-Terrorism law to the US CALEA (Communications Assistance for Law Enforcement Act), which also requests ISPs to support the US authorities in investigating on suspects.
The Anti-Terrorism law also limits the liberties of media to “disseminate information on forged terrorist incidents, report on or disseminate details of terrorist activities that might lead to imitation, nor publish scenes of cruelty or inhumanity about terrorist activities.”
The Chinese Government is committing itself in respecting human rights.
Anyway, the most worrying aspect of the law is that it allows agents of the People’s Liberation Army to persecute terror suspects also overseas … what does it really imply?
A new emergency patch for Adobe Flash Zero-Day, update your system!
29.12.2015
Adobe has released security patches for Adobe Flash Player to fix critical vulnerabilities that could be exploited to take control of the affected system.
Adobe released an emergency patch for Flash Zero-Day (CVE-2015-8651) that is currently being exploited in targeted attacks. The out-of-band security update issued on Monday fix a number of security vulnerabilities that could be exploited by hackers to take control of an affected machine.
Adobe did not provide further details on the attacks exploiting the CVE-2015-8651 vulnerability, in the security bulletin it only confirms that the company is aware of a “limited, targeted attacks”.
“Adobe is aware of a report that an exploit for CVE-2015-8651 is being used in limited, targeted attacks.” states the security bulletin published by Adobe.
A company spokesperson confirmed that the vulnerability has been exploited in a spear phishing campaign.
The zero-day vulnerability affect all platforms, below the details Adobe provided in a security bulletin :
These updates resolve a type confusion vulnerability that could lead to code execution (CVE-2015-8644).
These updates resolve an integer overflow vulnerability that could lead to code execution (CVE-2015-8651).
These updates resolve use-after-free vulnerabilities that could lead to code execution (CVE-2015-8634, CVE-2015-8635, CVE-2015-8638, CVE-2015-8639, CVE-2015-8640, CVE-2015-8641, CVE-2015-8642, CVE-2015-8643, CVE-2015-8646, CVE-2015-8647, CVE-2015-8648, CVE-2015-8649, CVE-2015-8650).
These updates resolve memory corruption vulnerabilities that could lead to code execution (CVE-2015-8459, CVE-2015-8460, CVE-2015-8636, CVE-2015-8645).
Users must update their products as soon as possible. Unfortunately, Adobe Flash Player is a privileged target for hackers that exploit its flaws can compromise systems worldwide. The number of cyber attacks relying on Flash Player flaws this year is significant and urges Adobe to approach security issued in a different way.
adobe flash player update 2
In early December, Adobe presented Animated CC, the company is dismissing Adobe Flash Professional CC to introduce the new solution.
“For nearly two decades, Flash Professional has been the standard for producing rich animations on the web. ” Adobe has officially announced. “Today, over a third of all content created in Flash Professional uses HTML5, reaching over one billion devices worldwide. It has also been recognized as an HTML5 ad solution that complies with the latest Interactive Advertising Bureau (IAB) standards, and is widely used in the cartoon industry by powerhouse studios likeNickelodeon and Titmouse Inc.
Animate CC will continue supporting Flash (SWF) and AIR formats as first-class citizens. In addition, it can output animations to virtually any format (including SVG), through its extensible architecture.”
Many exponents of the security community fear that the Adobe Animate CC is the result of a marketing operation that would be still insecure.
Step by step the HTML5 language is replacing the flawed Flash, after YouTube also Facebook announced is leaving Flash to adopt it.
“We recently switched to HTML5 from a Flash-based video player for all Facebook web video surfaces, including videos in News Feed, on Pages, and in the Facebook embedded video player. We are continuing to work together with Adobe to deliver a reliable and secure Flash experience for games on our platform, but have shipped the change for video to all browsers by default.” States the announcement issued by Facebook.
191 Million US Voters' Personal Info Exposed by Misconfigured Database
28.12.2015
BREAKING: A misconfigured database has resulted in the exposure of around 191 Million voter records including voters' full names, their home addresses, unique voter IDs, date of births and phone numbers.
The database was discovered on December 20th by Chris Vickery, a white hat hacker, who was able to access over 191 Million Americans’ personal identifying information (PII) that are just sitting in the public to be found by anyone looking for it.
Vickery is the same security researcher who uncovered personal details of 13 Million MacKeeper users two weeks ago, which included names, email addresses, usernames, password hashes, IP addresses, phone numbers, and system information.
However, the recent discovery made him shocked when he saw his own information in the database, according to DataBreaches.net, whom the researcher contacted and provided all the details about his finding.
300GB Trove of Voters' Information Leaked
Vickery has his hands on all 300GB of database contains a long list of voter records including:
Full name (first, middle, last)
Residential address
Mailing address
A unique voter ID
State voter ID
Gender
Date of birth
Date of registration
Phone number
Political affiliation
A detailed voting history since 2000
Fields for voter prediction scores
Not just his own, but Vickery also looked up a number of police officers in his city and confirmed the information was all correct. Reporters from CSO and DataBreaches.net also did the same and upheld the accuracy as well.
Fortunately, the database doesn't contain Social Security Numbers, driver license numbers, or any financial data, but it's still a massive amount of data when it comes to protecting users privacy and security.
What's even more Shocking?
The crazy part of the data breach is no one is taking responsibility for the exposed database.
Vickery, CSO and DataBreaches.net contacted various political tech groups and known voter information companies, but all denied the database belonged to them.
The FBI and Internet Crime Complaint Center were all approached by Vickery and DataBreaches.net; so let’s now see how long this information remains alive and accessible for anyone to see.
CVE-2015-8562 – 16,000 Daily Attacks on vulnerable Joomla servers
28.12.2015
Experts at Symantec discovered that hackers quickly take advantage of CVE-2015-8562 remote code execution to compromise Joomla servers.
Joomla recently patched the CVE-2015-8562 vulnerability that could be exploited by attackers for remote code execution.
According to the security expert Daniel Cid from Sucuri, hundreds of attacks are now taking place.
“What is very concerning is that this vulnerability is already being exploited in the wild and has been for the last 2 days. Repeat: This has been in the wild as a 0-day for 2 days before there was a patch available.” States the blog post published by Sucuri.
“The wave of attacks is even bigger, with basically every site and honeypot we have being attacked [which] means that probably every other Joomla site out there is being targeted as well.”
The zero-day flaw could have a significant impact on the Internet users considering that Joomla is the most popular content management system having been downloaded more than 50 million times.
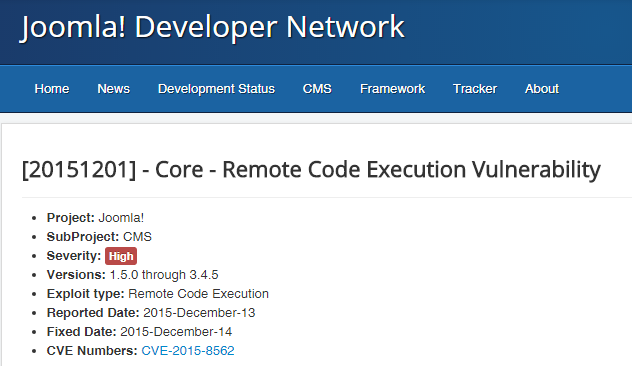
According to a security advisory published by Joomla, all versions above 1.5 are affected. It is important to update the CMS version to the patched version 3.4.6.
News of the day is that experts at Symantec have detected up to 20,000 daily attempts to exploit the Joomla CVE-2015-8562 vulnerability that has been fixed with the release of Joomla 3.4.6 and hotfixes for versions 1.5 and 2.5.

Symantec has been monitoring attack attempts against websites using vulnerable Joomla websites and detected, on average, 16,000 daily hits since the experts at Sucuri disclosed the flaw.
“Since the Joomla! RCE vulnerability was discovered, servers running vulnerable versions of the CMS are actively being scanned for and attacked. On average, we are detecting more than 16,600 attacks per day on vulnerable Joomla! servers.” states Symantec.
Cyber criminals exploit the CVE-2015-8562 vulnerability to fully compromise servers and abuse them to serve malware redirecting victims to exploit kits, or to launch other attacks such as distributed denial-of-service (DDoS) attacks.
“The exploit code is relatively easy to deploy and doesn’t require much skill, all that is needed is a single HTTP request. According to our telemetry, the methods attackers are using to scan for vulnerable versions of Joomla! is similar to methods we covered in a recent blog on an RCE vulnerability in the vBulletin platform.” states a blog post published by Symantec. “Attackers are scanning for servers running vulnerable versions of Joomla! by attempting to call a phpinfo() function or printing out an MD5 of a predetermined value.”

According to researchers, threat actors in the wild are scanning the Internet searching for vulnerable servers, they are sending out HTTP requests and analyzing responses when functions such asphpinfo() and eval(chr()) are executed.
Once the hackers identify a vulnerable server thay compromise it by installing a backdoor that allows them to control the machine and execute any kind of commands.
Administrators can check their web servers and examine access logs for suspicious activities, such as anomalous requests.
Database with 191 Million US voters’ personal data exposed online
28.12.2015
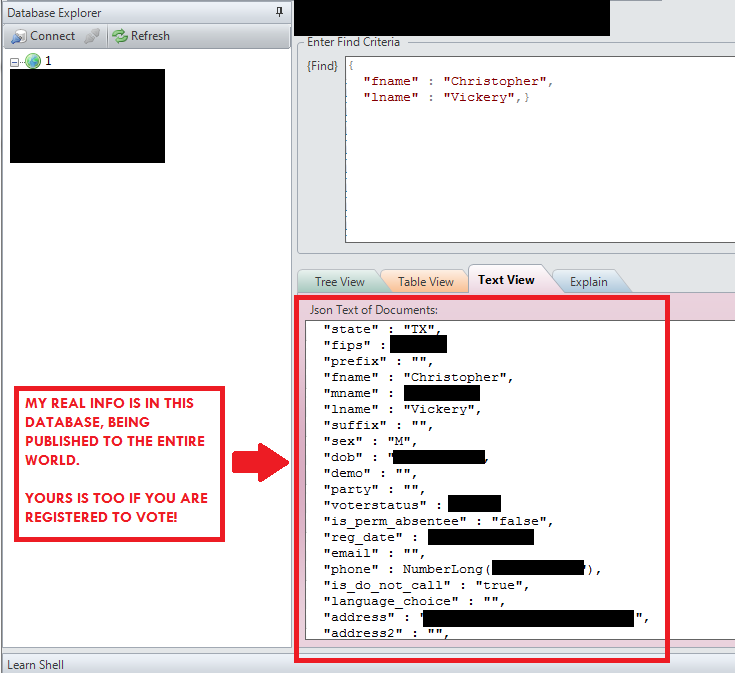
The security expert Chris Vickery has discovered a misconfigured archive exposes the personal details of 191 million U.S. voters.
A misconfigured database is the root cause of the exposure of around 191 Million voter records. The records include voters’ full names, unique voter IDs, unique voter IDs, date of births and phone numbers.
The database was discovered by the security expert Chris Vickery, the same expert that recently confirmed that information exposed in over 650 terabytes of MongoDB data was associated with 25 million user accounts from various apps and services, including 13 million users of the OS X optimization program MacKeeper.
The database containing voters’ information was discovered on December 20th, Vickery provided all the details about his disconcerting discovery to DataBreaches.net. The archive includes over 191 Million Americans’ personal identifying information (PII).
Vickery has found also his own information in the database containing 300GB of voters’ data.
“My immediate reaction was disbelief,” Vickery said. “I needed to know if this was real, so I quickly located the Texas records and ran a search for my own name. I was outraged at the result. Sitting right in front of my eyes, in a strange, random database I had found on the Internet, were details that could lead anyone straight to me. How could someone with 191 million such records be so careless?”
Below the detailed list of attributes stored in the leaked database.
Full name (first, middle, last)
Residential address
Mailing address
A unique voter ID
State voter ID
Gender
Date of birth
Date of registration
Phone number
Political affiliation
A detailed voting history since 2000
Fields for voter prediction scores
Vickery confirmed to have found in the voters’ database the records belonging to a number of police officers in his city, he has also verified the authenticity of the information.
The database doesn’t include Social Security Numbers, driver license numbers, or financial data, but the information it includes could be attractive for both cybercriminals and nation-state actors.
The principal media agencies are trying to identify possible responsible for the accidental exposure of so important data, but it is not clear who has misconfigured the archive.
Vickery and DataBreaches.net tried to contact voter information companies and various political groups, but all have denied any involvement in the incident.
“Salted Hash reached out to several political data firms in an effort to locate the owner of the exposed database. Dissent (admin of Databreaches.net) did the same thing. However, none of our efforts were successful.” reported Salted Hash. “The following firms were contacted by Salted Hash for this story: Catalist, Political Data, Aristotle, L2 Political, and NGP VAN. Databreaches.net reached out to Nation Builder. Speaking to Dissent, Nation Builder said that the IP address hosting the database wasn’t one of theirs, and it wasn’t an IP address for any of their hosted clients. As for the firms contacted by Salted Hash, each of them denied that the database was theirs, and in the case of NGP VAN, the technical aspects of the infrastructure (Linux vs. Windows) ruled them out because they’re a Windows shop and the data is housed as part of a Linux build. A later attempt to contact i360, another political data firm, was unsuccessful.”
Vickery also reported the issue to the FBI and Internet Crime Complaint Center, let’s hope the information will be removed as soon as possible.
China Passes Anti-Terrorism Law; Here's What You Need to Know
28.12.2015
If you rely on encrypted services to keep your data private and, unfortunately, you are in China, then you are about to be worried.
As of now Chinese government could snoop into the operations of technology companies as well as circumvent privacy protections in everyday gadgets.
China So-called Anti-Terrorism Law
Despite months of objections from major technology firms and concerns over human rights…
China passed its controversial new anti-terrorism law on Sunday that requires tech companies to help decrypt information or hand over encryption keys to officials when they want to spy on someone's communication in order to counter terror operations.
However, the officials swear that the law wouldn't require technology firms to install "backdoors" in their products, but it doesn't make any difference when the government mandate companies operating in China to provide encryption keys and passwords when requested.
Just like recent proposals from the intelligence agencies in the UK and US after the deadly assaults in Paris and California, China claims such law is necessary to fight against terrorism.
"Nowadays, the Internet is increasingly used by terror groups to spread their extremist ideas, recruit fighters, channel fund and plot attacks," said Xinhua, China's official news agency.
Concerns over New Anti-terrorism Law
However, critics are worried that the so-called anti-terrorism law could give the Chinese government right to snoop into the operations of major tech companies and ways to circumvent encryption protections in everyday gadgets, including smartphones, home routers and Smart devices.
Earlier this year, President Barack Obama raised his concerns over the then-draft law with China's President Xi Jinping, saying that the law would amount to a dangerous "back doors" to internet companies.
However, the government official assured that this law is meant to fight terrorism, so it will neither affect the normal operation of technology companies nor install any "backdoors" to infringe intellectual property rights or freedom of speech of every citizen on the Internet.
New Law in Effect from January 1
The country's first anti-terrorism law goes into effect on January 1st.
But, despite the requirements set out by the new law, major tech firms, such as iPhone maker Apple, do not hold the encryption keys, making itself incapable of providing access to users' data even if requested by the government.
That sets up a potential conflict.
So what will happen if Chinese authorities order these technology companies to fork over encryption keys that they can not possibly deliver?
Would they ban such companies from the country?
‘OR’
Would they fine those companies to pay an enormous amount? Just like US government imposed $5,000 per day fine on Lavabit founder for refusing to turn over the encryption keys.
But always keep in mind that no matter what, there would be many companies that will sacrifice your privacy in order to continue operating their business in the world's most populous nation.
Bitcoin Core Developers Quit Bitcoin Project to Launch a New Digital Currency
28.12.2015
Some of Bitcoin’s Core developers have left the Bitcoin project and started building their separate cryptocurrency called DECRED.
Decred aims to prevent the issues Bitcoin is currently facing regarding project governance and development funding.
CEO of 'Company 0', Mr. Jacob Yocom-Piatt, who has funded Bitcoin development since early 2013, said the actual development of the Bitcoin cryptocurrency is funded by external entities that forms a conflict of interests between the groups and the project's core developers.
According to Bitcoin's developers, these group puts limitations on input in Bitcoin's governance, selecting options that are favorable to their own interests only, and generally ignoring the developers' and project's best interests.
"The Bitcoin software is controlled by a small group of people who decide exclusively what can and cannot be changed," Jacob says in a press release.
"This is in part due to a lack of mechanisms and pathways for funding development work directly from the community, and, as a result, Bitcoin development is funded by external entities that create conflicts of interest between the developers and the representative power of the community that uses Bitcoin."
So, in order to address this issue, some of the Bitcoin developers have joined hands with the makers of the widely used BTCsuite and are now building their own new digital currency called DECRED.
What is DECRED?
Decred, managed and funded by Company 0 LLC, is an open and progressive cryptocurrency that will adopt a more decentralized community-based governance integrated into its blockchain.
The team has the advantage to make Decred a really great product as they already have experience with Bitcoin.
Some Highlights of DECRED
Decred intends to include a long list of features such as:
Implementation of consensus system based on proof-of-work and proof-of-stake system
Decred development is self-funded and open with block subsidy
Decred uses Blake-256 hashing algorithm
Decred may be compatible with Bitcoin
Decred community members will be involved in making bottom-up non-financial decision making easier
It will use secp256k1 signature scheme or Ed25519/secp256k1-Schnorr for better integration into existing software and make good use of the features offered by Schnorr signatures respectively
Decred uses Go as a codebase for development
Decred has an Airdrop scheduled for next month (20 days and a few hours from now) where they’ll be giving out 4 percent of the total Decred supply to all participants.
Interested developers can take part in the Airdrop by filling in their details on Decred website.
Somebody Offered Money to Raspberry Pi Foundation for Pre-Installing Malware
28.12.2015
The Raspberry Pi is now gaining attention from malware distributors who want the popular mini-computers to deliver with pre-install malware.
The Raspberry Pi Foundation has made a shocking revelation that the charitable foundation has been offered money to install malware onto the Raspberry Pi machines before they were shipped out to users.
The Raspberry Pi is an extremely simple computer that looks and feels very basic, but could be built into many geeky projects. Due to the low-cost appeal of the Raspberry Pi, the Foundation has sold over 4 million units.
Just Last month, Raspberry Pi unveiled its latest wonder: The Raspberry Pi Zero – a programmable computer that costs just $5 (or £4), may rank as the world's cheapest computer.
Last Wednesday, the Foundation tweeted a screenshot of an email in which "business officer" Linda effectively asked Foundation's director of communications Liz Uptonto to install a suspicious executable file onto Raspberry Pis for which the officer promised to offer a "price per install."
The email further explained that installing the executable file would create a shortcut icon on the user's desktop and opening the shortcut would take the user to the company's website. "Then this is our target," the email reads.
Here's the screenshot of the full email:
raspberry-pi-malware
However, the name of the company represented by Linda was not revealed by the Raspberry Pi Foundation.
Obviously, the paid-for-malware distributor pitched the wrong organisation, who declined the offer, describing the company as "evildoers," but the incident once again raises the question about this common, widespread issue.
Darkweb, a look back at 2015 events and 2016 predictions
28.12.2015
Which are the main events observed in the darkweb during the 2015 and what to expect in the next 12 months?
The DarkWeb is a set of publicly accessible content that are hosted on websites whose IP address is hidden, but to which anyone can access it as long as it knows the address. The same term is used to indicate a set of private content exchanged in a closed network of computers for file sharing.
A Darknet like the Tor network is so popular in the criminal ecosystem due to the anonymity it offers under specific conditions, law enforcement, and intelligence agencies face difficulties in de-anonymizing users and are not able to conduct a large-scale monitoring.
In 2015 the Darknet, and in particular the black markets assumed a crucial role in the criminal underground, it worked as an aggregator for the principal underground communities.
The most active actors in the darknet were cybercriminals and cyber terrorists, the first group exploited the anonymity of this part of the web to launch attacks against computer hardware and software, to conduct financial crimes and for child pornography.
Malware authors and botmasters have exploited darknets like the Tor Network and I2P to hide the Command and Control infrastructure.
Critroni, Cryptowall, Vawtrak and Dyre just a few samples of malware that exploit the Darknet to hide their control infrastructure.
Another phenomenon linked to the development of malware that exploit the darknet is the increase of the threat actors that started offering product and services to advantage the development and the deployment of malware.

In the criminal underground it is easy to find malware-construction kits that allow easy to build malicious code from existing templates. In May experts at McAfee discovered a sort of easy to use Ransomware builder, this family of malware is becoming even more popular in the criminal ecosystem and crooks are trying to capture this opportunity.
The ransomware-construction kits, dubbed Tox, was available online for free in the Dark Web since May 19.
Apart the sale of drugs, in 2015 we have assisted in the rapid growth of hacking communities in the darknet which were specialized in the sale of product and services for payment card frauds, in the sale of stolen data and hacking services and tools.
The most active underground communities were the Russian one, the US one, the Brazilian one, the Chinese one and also the emerging Japanese one.
Below a list of products/services offered in the principal black markets:
PII record for $1. (Trend Micro)
PayPal and eBay go up to $300 each. (Trend Micro)
Bank account offered for a price ranging from $200 and $500 per account (balance, history).
Document scans from $10 to $35 per document. (Trend Micro)
Credit card fraud CVVs ($3-$25), Dump ($20-$60), Fullz ($25-$125) [Data Preview -Annual Card Fraud Report IT Ministry of Treasury and Finance]
Counterfeit documents, including non-US passports, from $200 to $1000. Fake US driver’s licenses run for $100-$150, meanwhile counterfeit Social Security cards run between $250 and $400 on average.
Social media account hacking $50-$100 (FB, Twitter, etc.)
Remote Access Trojan $150-$400 (FB, Twitter, etc.)
Banking Malware Customization (i.e. Zeus source code) $900 – $1500
Rent a botnet for DDoS attack (24 hours) $900 – $1500
Giving a look to the principal 35 black marketplaces, security experts observed that they raked from $300,000 to $500,000 a day. About 70% of all sellers never managed to sell more than $1,000 worth of products, another 18% of sellers were observed to sell between $1,000 and $10,000 but only about 2% of vendors managed to sell more than $100,000.
But 2015 is considered the year of the terrorism, the ISIS terror is dramatically increased its power becoming the principal threat for the Western countries. The members of the IS exploited the darkweb to share videos and images for propaganda.
Hidden services were also used as repository of mobile apps used by the jihadists to communicate securely.
What to expect in the next 12 months?
Darkweb will continue to be a privileged environment for cyber criminal groups and terrorists.
Malware authors will exploit the Darknets basically as a backup mechanism for their botnet and to make them more resistant to various kinds of attacks operated by law enforcement.
The most interesting trend we will observe related to the growth of criminal-as-a-service model that will attack organized crime in the cyber criminal underground.
European credit card payment terminals are plagued with serious flaws
27.12.2015
Two German security experts have exposed a number of serious flaws in credit card payment systems that put users at risk.
The duo of German security experts, Karsten Nohl and Fabian Braunlein, found a new vulnerability in payment terminals that could be exploited by hackers to steal money. Differently from past attacks, this time, the hackers are targeting the protocol putting billions of customers at risk.
“Previous attacks exploit software bugs, like you would have on your computer. Ones that can be fixed with a software update,”
The experts discovered a set of vulnerabilities with payment terminals used in Europe that could allow hackers to steal the victim’s PIN code and magnetic strip from their card.
The experts tested payment terminals from five different payment processors that provide terminals to merchants, the systems tested used two different networks, both of which used the same back-end software.
“This is the only software used in Germany for this purpose, so everybody should be equally affected,” Nohl said.
The vulnerabilities could be exploited to force any terminal to send funds to any bank account in Germany, but the experts speculate that the flaw could affect systems in other European countries.
“Nohl and Bräunlein will lay out several different attacks, and they hinge on problems with two protocols that payment terminals use: ZVT and Poseidon. Protocols are essentially different languages that devices use to communicate.” reported MotherBoard.
The hack works wirelessly, the attacker only needs to be connected to the same wireless network.
“The companies responsible for these security vulnerabilities, including the banks – they certainly acknowledged the issue, but they are reluctant to react to it. They’re saying – ‘fraud is not happening yet’, but it’s just a matter of time. So, by not reacting now that it’s known – they’re adding insult to injury.” explained the popular German code-breaker Karsten Nohl of Security Research Labs in Berlin. “Now, what we’re attacking is the protocol itself. The devices work exactly as intended and are still vulnerable. So this is a risk that cannot easily be fixed with a patch.” “The entire system would have to be overhauled,”
Nohl explained that an attacker could trick victims into check their accounts charged for refunds that never took place in order to trigger the vulnerability. The vulnerability could be also used to clone credit card.
“Basically anything with a magnet strip and a PIN number is vulnerable to this,” Nohl said “This is the first time we’ve come across such a large deployment, with such serious issues, and don’t have an obvious fix.”
According to Karsten Nohl, a criminal organization could probably reproduce the attacks “within a couple of months.”
“The security of the PIN number is not quite as high as one wanted to believe, hence every system relying on the PIN is less secure than previously thought,” Nohl added.
The two experts have conducted several studies in the past warning about security issues affecting the SIM cards. Two years ago Karsten Nohl revealed to The New York Times that he identified a vulnerability in encryption technology used for SIM that could allow an attacker to obtain the 56-digit SIM card’s digital key necessary for the card modification. Roughly 750 million mobile phones were open to cyber attack.
Which is the response of the German banking organisation Deutsche Kreditwirtschaft?
According to Tagesschau, German banking organisation Deutsche Kreditwirtschaft who has analyzed the results of the study conducted by the experts, the system is secure. The organization claimed that the attack proposed by the experts only works under specific conditions. The Electronic commerce organisation BECN is also evaluating the results of the tests.
The Ramnit Botnet is back after the law enforcement takedown
27.12.2015
The Ramnit botnet that has been disrupted by European law enforcement in February is back and it’s targeting online banking worldwide.
Security researchers at IBM Security have discovered a new variant of the popular Ramnit Trojan. This year law enforcement agencies from several European countries coordinated by the Europol have taken over a the botnet composed by over 3.2 Million computers worldwide, but now a new malicious infrastructure is in the wild.
Ramnit was first spotted in 2010 as a worm, in 2011, its authors improved it starting from the leaked Zeus source code turning the malware into a banking Trojan. In 2014 it had the pinnacle of success, becoming the fourth largest botnet in the world.

The discovery represents the return of Ramnit after the law enforcement takedown.
“According to IBM X-Force researchers, that may have officially changed in December 2015. Not even a year after Ramnit was taken down, we are seeing what appears to be the first real re-emergence of the banking Trojan botnet. ” Limor Kessem, cyber intelligence expert at IBM Trusteer, wrote in a blog post.
The new Ramnit botnet uses a different command and control (C&C) infrastructure, the experts noticed that more than half of the infected machines are in Canada, followed by Australia, the US and Finland.
What’s new?
The source code of new Ramnit variant spotted by IBM is quite similar to the predecessor by it uses shorter configuration files and implements web injections mechanisms like other threats (i.e. Dridex, Shifu). The researchers speculate that operators behind the Ramnit botnet have acquired the web injection mechanism from other cyber criminal groups, the experts noticed that the code injected into banking websites by the malware is obtained in real time from a remote server.
“The only change in modus operandi is expressed in the web injections and the configuration file, which are both considered to be moving parts in the inner workings of any banking Trojan. Recent findings from IBM X-Force indicated that a number of other Trojans, like Shifu, Dridex and Neverquest, have been using the exact same web injections and remote servers, which can be indicative of gangs purchasing software-as-a-service (SaaS) from the same injection developers.” states the post.
The experts noticed several infection vectors, including malvertising campaigns that rely on the popular Angler exploit kit
“The new server commands newly infected machines that are receiving Ramnit through the Angler exploit kit. It regularly updates them with configurations and executable file builds. The new Ramnit also operates with a real-time webinjection server, selectively pulling attack schemes on the fly when infected users browse to a few major banks in Canada”
The old Ramnit botnet was operated by a single criminal crew that has never sold the source code for the malicious agent.
“From what we’ve learned so far, nothing seems to point to a notable change in terms of who is behind Ramnit. It is possible that a new gang has picked the project up, but attribution remains vague in this case,” added Kessem.
What about the future?
Experts believe the cyber criminals will expand their operation to other countries.
InterApp, the device that can hack any Smartphone
27.12.2015
The Tel Aviv-based Rayzone Group is offering for sale a gadget called InterApp that can intercept and exfiltrate information from nearby smartphones.
InterApp is a device designed by the Israeli Rayzone Group that can spy on any smartphone.
“InterApp system enables to get intimate information of any phone user, which is in the system’s ,proximity. The collected data includes: user email address and password, contact list, Dropbox, operating system of the phone, photos, internet history browsing, locations, and much more.” states the description published on the company website. “InterApp is fully transparent to the target and does not require any cooperation from the phone owner. The only required condition is that the WIFI transmitter of the mobile device will be open (No need to surf the web).”
The Interapp is an intrusion appliance that implements a number of zero-day exploits against common mobile OSs. According to the company, the gadget is able to infect a smartphone with a malware and compromise any nearby phone whose wifi is turned on.
The device can target launched hundreds of simultaneous attacks, without leaving forensic traces on the compromised smartwatches.InterApp can compromise a variety of mobile OSs and is very easy to use.
The InterApp is offered for sale to intelligence and law enforcement agencies, it is able to steal a user data, including contact list, photo gallery, and login credentials to several web services, including social networking apps and cloud storages.
The gadget is also able to get previous geographical locations of the smartphone and plot them on a map, it could be used to collect other details of the mobile device, including the IMEI, MSISDN data, MAC address, model, OS info, and personal information on the target (i.e. gender, age, address, education, and more).

Giving a look the products in the Rayzone portfolio we can find Piranha IMSI catcher, the TA9 big data analysis platform, the ArrowCell which is designed to neutralize IMSI catchers, and an advanced geo-location intelligence system called GeoMatrix.
A serious issue in Steam allowed access to other users’ accounts
26.12.2015
As a result of a configuration change a security issue allowed some Steam users to randomly see pages generated for other users for a period of less than an hour.
Bad news for the popular community of Steam gamers, some of the users are facing serious security issues. Several users online reported to be able to view other users’ account information. Numerous messages on Twitter, NeoGAF, and Reddit reported the problem highlighting that they were also able to access addresses and credit card data of other users.
“So, I went to go checkout on Steam after selecting a few games and I was taken to the checkout page which gave an error message, but still allowed me to select a payment method. When I went to choose a payment method, it opened the payment information forum like usual. Except, the information filled in wasn’t mine. I was for someone completely different than me that I’d never heard of before. Full name and address. The creditcard, thankfully, was not saved. As a IT security guy, this is some serious shit and could be a sign of a major vulnerability.” said a Reddit user.
The Valve company that owns the Steam platform confirmed the serious security, it was an internal error that the company has already fixed.
“Steam is back up and running without any known issues,” a company spokesperson said.
It seems that a wrong “configuration change” randomly let some Steam users view personal information of other users’ profile. The incident was limited to a one-hour period.
“We believe no unauthorized actions were allowed on accounts beyond the viewing of cached page information and no additional action is required by users,” he added.
The incident is serious and could have serious repercussion of the users’ security, at the time I was writing it is not clear the number of the affected users. Users also faced other problems, including difficulties in logging to the platform.
On December 25th, several users noticed that Visiting the Steam website or store the platform was returning an error, although there was no impact on the gaming service. There’s still no official explanation, but one popular theory holds that Steam is incorrectly caching account pages and rendering them for other users.
In a message on Steam’s forum one of the moderators explained that the platform has not been hacked and added that the personal information were not visible to other users.
“We’ve gotten reports that people sometimes see other people’s account information on the account page. Valve has been made aware of this and are working on a fix.
Some frequently asked questions:
– No, Steam is not hacked
– Creditcard info and phone numbers are, as required by law, censored and not visible to users“
Valve has released a statement to gamespot about the incident.
“Valve has issued a statement regarding today’s issues. “Steam is back up and running without any known issues,” a Valve spokesperson told GameSpot. “As a result of a configuration change earlier today, a caching issue allowed some users to randomly see pages generated for other users for a period of less than an hour. This issue has since been resolved. We believe no unauthorized actions were allowed on accounts beyond the viewing of cached page information and no additional action is required by users.”
Victims of the Gomasom Ransomware can now decrypt their files for free
26.12.2015
Fabian Wosar, security researcher at Emsisoft, created a tool for decrypting files locked by the Gomasom Ransomware.
Ransomware are the most threatening cyber threats for end-users, but today I have a good news for victims of the Gomasom ransomware, victims can rescue their locked files.
The news was spread by the security researcher Fabian Wosar that developed a tool that could be used by victims to decrypt their file locked by the Gomasom Ransomware.
Gomasom (“GOogle MAil ranSOM“) is a new threat in the criminal ecosystem, it encrypts users’ files, leaving a Gmail address in each file’s name, and adding the .crypt file extension at the end.
The tool analyzes the encrypted files allows users to get the decryption key and use it to decrypt their files. Wosar explained that the tool has a high success rate when the victim has the ability to analyze both the ransomware-encrypted and original version of a document.
Anyway it is always possible to retrieve the key with the tool because victims can take a PNG file encrypted with the ransomware, and compare it to a random PNG file from the Internet.
The tool to decrypt the file locked by Gomasom ransomware is available on the website of the Emsisoft security firm, meanwhile a user guide is available on the Bleeping Computer forum thread.

Zero knowledge proof as an enabler for Cyber weapon information sharing
26.12.2015
About the Zero knowledge proof and the ability to proof capability to attack or to defence implementing the cyber deterrence.
Successful deterrence based on three aspects – Capability, Threatening message and Transmitting the message to the opponent. Therefore, One of the critical issues in cyber deterrence is the ability to proof your capability to attack or to defence. If you can prove you can do it, the other side will be more convinced, and deterred.
Applying Deterrence by punishment force you to prove to the other side that you can compromise or damage his systems.
Applying Deterrence by denial force you to prove that you can defend your systems from a potential attack.
In both cases, the cost of the attack in the eyes of your opponent is rising. And with rising costs, he will think twice before carrying out one. However, why should one expose his secretive cyber weapon or defence structure before he has to use them?

Most of the Cyber weapons are disposable. Such are the defence solutions. If you expose your cyber weapon, your opponent will build a defence solution. If you do so with your defence structure, a hacker will find a way to bypass it. But what if there is a way to show your opponent your capabilities without reviling your secrets?
One method that potently could serve this propose is Zero knowledge proof [ZKP]. It’s a way in cryptography to prove to the other side that you hold the secret without exposing it to him.
Altho the Zero knowledge proof is used in cryptography, the abstract idea can play a role in Cyber deterrence to strengthen the capability projection of the player.
Let’s assume I have a cyber weapon that can destroy the opponent electric grid, and I want to use it to prevent him from destroying mine [I assume that he has an unknown, such weapon].
In that scenario, the first step is to convince him that I have such ability. But how can it be done? If I use it, deterrence will fail. If I don’t, it will leave a great deal of uncertainty, and deterrence will fail. It seems as “Catch 22” scenario.
However, if we add to this situation a Zero knowledge proof mechanism that will allow me to convince him that I have the ability without reviling it, deterrence can succeed.
There is no doubt it’s an initial idea. For now, the Zero knowledge proof is used in cryptography and reuse it as a cyber weapon or defence structure proof mechanism requires further research. But it gives hope to the possibility of applying a successful deterrence in the future cyber domain.
Additional reading
http://pages.cs.wisc.edu/~mkowalcz/628.pdf
http://blog.cryptographyengineering.com/2014/11/zero-knowledge-proofs-illustrated-primer.html
Turkish officers are in contact with members of the ISIS
26.12.2015
An investigation revealed that some Turkish officers on the Syrian border have communicated with terrorists of the ISIS in Syria.
According to a report published by the Turkey’s Cumhuriyet daily, Turkish authorities are in communication with members of the dreaded members of the Islamic State. The report cites an investigation by the Ankara Chief Prosecutor’s office which collected evidence of the alleged cooperation with the ISIS by eavesdropping on phone calls.
The discovery was accidental, the Ankara Chief Prosecutor’s office was investigating investigation into six missing Turkish citizens last year, the investigators believed they might have joined the ISIS militia in the area.
The authorities launched an investigation on 27 suspects, some of them in Syria.
“Prosecutors Derda Gökmen, sued about 27 suspects. Gökmen, “listening on the grounds that emerged during another crime” he has launched a separate investigation” the Cumhuriyet reported.
The Chief Prosecutor’s office was authorized to wiretap the phones of 19 suspects, the investigators speculate they had an important role in the case by putting the six missing persons in touch with the Islamic State.
isis islamic state selling oil
The investigation discovered a recruiting network, the wannabe militants received an “ideological training” to join into the organization.
“Those [who joined ISIS] from Ankara often used [the] Elbeyli district [of Kilis] as a throughway by traveling via Gaziantep and Kilis to the village of Able, which is subordinated to Syria’s Al-Bab district,” the report said, as cited by newspaper Today’s Zaman.
The information gathered during the investigation has been handed over to the Military Prosecutor’s office in March, because the Ankara Prosecutor’s office deemed the issue outside of its jurisdiction.
The Cumhuriyet also published some of the transcripts for the wiretapping, one of them allegedly states that the person indicated with the “X2” is a member of the military.
—Yes, brother.
X2: We are on the mined land where I delivered the vehicle. We have put our lights on. [We have the] material on us; come here with your men from that side…
The Turkish government has long been accused by opposition parties of inertia against the ISIS in Turkey. The Turkish authorities are not contrasting the ISIS militia through Turkey’s border with Syria.
A recent report revealed that the Turkey is acquiring oil from the ISIS that are offering the precious commodity at low prices.
The Russian Defense Ministry also released evidence of the illegal oil trade by IS with the support of the Turkey authorities, despite Ankara has denied the allegations.
Russian intelligence has recently spotted up to 12,000 tankers and trucks on the Turkish-Iraqi border.
“The [aerial] imagery was made in the vicinity of Zakho (a city in Iraqi Kurdistan), there were 11,775 tankers and trucks on both sides of the Turkish-Iraqi border,” Lieutenant-General Sergey Rudskoy told journalists on Friday.
“Heavy-duty trucks loaded with oil continue to cross the Turkish-Syrian border as well, Rudskoy said. At the same time, the number of tankers on the northern and western routes used for transporting oil from Syria is declining, the general added.” reported RT.com.
Turkish systems under attack. Is it information warfare?
26.12.2015
Turkish systems are suffering a major cyber attack which is causing serious problems to organizations in the country. Is is an act of Information warfare?
On Thursday, the non-governmental organization Nic.tr that manages IP addresses assigned to Turkish websites (the “tr” domain) confirmed that the Turkish Internet servers are suffering a powerful cyber attack that appeared to be from threat actors outside the country.
The attack appears to be managed by an “organized sources” outside Turkey and it is slowing banking services in the country.
Experts working in the Banking industry confirmed that the attack has created serious problems to the many banks causing the disruption of transactions.
The “tr” domain is used by websites belonging to Turkish ministries, financial institutions, and commercial enterprises.
turkish systems cyber attack
The Transport and Communications Minister Binali Yildirim confirmed that a “serious” cyber attack hit the systems of the country.and asked an Ankara-based university to beef up security measures, saying they were “insufficient”.
Who is behind the attack?
Intelligence experts believe that Russian hackers linked to the Kremlin are targeting the Turkish systems in response to the tension between the countries. In the past, Russian nation-state actors targeted systems of other countries in response to the military tension with the Russian Government. Last digital retaliation occurred in the peninsula of the Crimea, the scene of clashes between militias Ukrainian and Russian
Some newspapers also reported that the attack could have originated in Russia in retaliation in response to the shot down of the Russian fighter jet last month on the Syrian border.
Turkish systems are also under attack by members of the Anonymous collective that is accusing the Government of Ankara for supporting “supporting the Islamic State by buying their oil and tending to their injured fighters.”
Is Play Station Network under attack? Users reported issues
26.12.2015
The Phantom Squad started the attacks on the PlayStation Network and the EA (Electronic Arts) as announced a few days ago.
Last year hackers belonging to the hacking group of the Lizard Squad tool down at Christmas the online networks of both Microsoft Xbox Live and PlayStation network (PSN) highlighting security issues affecting the services of Sony and Microsoft.
This year another group known as Phantom Squad announced its intention to ruin Christmas for gamers. Phantom Squad also said that both platforms are vulnerable to attacks, and they add that they were able to take down Xbox live during the weekend.

The group launched small DDoS attacks on both Xbox Live and PSN causing short downtimes. In the last days, other groups announced their support. Hacking crews of VandaSec and PhantomSec also announced their support for the attack planned by Phantom Squad.
Phantom Squad previously targeted the Steam network and a number of servers for popular games, including Star Wars, Call of Duty: Black Ops 3, and Call of Duty: Black Ops 2 and Grand Theft Auto 5.
On December 24th, Phantom Squad started the announced attack, a severe DDoS attack hit the EA’s servers taking them down for the last three hours. The company confirmed the attack through the official Twitter account.
After the EA publicly disclosed the attacks, Phantom Squad stopped the attack and announced via their Twitter new attacks on the PlayStation Network.
After the PhantomSquad tweets, several users started reporting problems with PSN.
On December 24, 23:30, the PlayStation Network starts suffering the attack, the official EA’s website published the following warning message:
“Affected Platforms: PS4
Affected Services: You may have some difficulty launching games, applications, or online features. Our engineers are working to resolve the issue as soon as possible, and we thank you for your patience.”
I have installed my new Play Station 4 and I noticed several authentication errors while I was trying to access the Sony network.
According to the experts, something caused a temporary outage to the PlayStation Network, while its websites were not affected by downtimes. Is it the Phantom Squad attack? Is it a simple congestion caused by the huge traffic that reached the network in these days?
The Phantom Squad announced that a former LizardSquad member @RootedExploit will join to the attack, but confirmed that still haven’t targeted the SonyPlaystation network.
“We haven’t shut servers off yet because we are busy, we have family just like you guys do. Be patient!!!” they Tweeted.

Stay Tuned!
Want WhatsApp Free Video Calling? This Leaked Screenshot Reveals Upcoming Feature
24.12.2015
Raise your hands if you want Free Video Calling feature in WhatsApp.
I am in, and I think most of you people.
And the good news is that it looks like WhatsApp's much-awaited Free Video Calling feature is on its way, according to the recently leaked screenshots.
Free Video Calling Feature in WhatsApp
German technology blog Macerkopf.de has posted what it claims are screenshots from an unreleased version of the popular messaging client WhatsApp for iOS.
The screenshots are from an unreleased version of the software (version 2.12.16.2), which is currently being tested internally, but at present it is not clear whether or not those screenshots are legitimate.
But, if the leaked screenshots are real, and WhatsApp adds the Free Video Calling feature, then the company could take an enormous bite out of some of its top rival.
WhatsApp Video Calling feature will allow you to make video calls to your friends and family anywhere in the world for free as long as you have a Wi-Fi network or an effective data plan on your registered number.
Here are the allegedly leaked images of video calling feature in action:
how to activate whatsapp video calling
WhatsApp has added several new features to its messaging service in order to enhance the user experience. Just this year, WhatsApp finally added free voice call feature, and with the launch of video support, the messaging app will more firmly lock users into its ecosystem.
Someone wants infect millions of Raspberry Pi computers
24.12.2015
Liz Upton from the Raspberry Pi Foundation made a shocking revelation, someone has offered cash to install a malware into its tiny computers.
The Raspberry Pi Foundation made a shocking revelation, someone has offered cash to install a malware into its tiny computers.
Yes, the news is unbelievable, but Liz Upton, the Foundation’s director of communications, disclosed the content of an email from a “business officer” called Linda, who promised a “price per install” for a suspicious executable file.
“Amazing. This person seems to be very sincerely offering us money to install malware on your machines,” said Liz.
The name of the company represented by Linda was not disclosed, anyway the news is disconcerting.

The analysis of the email reveals the presence of numerous imperfections, a circumstance that suggests that the author is not an English-speaking individual.
The circumstance raises one again the question about the necessity of hardware validation, the possibility that a persistent attacker installs malicious implants and software onto consumer devices is a serious threat.
Someone is willing to pay to distribute malware, sometimes the developer directly inserts unauthorized code in their software, but in the majority of cases the malware is served by a third-party with the intent to compromise end-customer’s devices.
The offer to the Raspberry Pi Foundation is concrete and seems to be authentic, the choice of a tiny computer is strategic for attackers that could compromise an impressive number of users considering that the foundation has sold more than five million Raspberry Pi devices to date.
Obviously the The Raspberry Foundation declined the offer.
Hyatt Hotel Says Payment Systems Hacked with Credit-Card Stealing Malware
24.12.2015
Hyatt Hotels Corporation is notifying its customers that credit card numbers and other sensitive information may have been stolen after it found malware on the computers that process customer payments.
"We recently identified malware on computers that operate the payment processing systems for Hyatt-managed locations," the company announced on Wednesday. "As soon as we discovered the activity, we launched an investigation and engaged leading third-party cyber security experts."
What type of information?
The company didn't confirm whether the attackers succeeded in stealing payment card numbers, neither it say how long its network was infected or how many hotel chains were affected in the malware attack.
But as the payment processing system was infected with credit-card-stealing malware, there is a possibility that hackers may have stolen credit card numbers and other sensitive information.
What happened?
Hyatt spokeswoman Stephanie Sheppard said the company discovered malware on 30 November but did not justify why the company waited over three weeks to report the incident.
How many victims?
The company didn’t confirm how many clients could have been affected in the malware attack. However, the world’s leading hospitality corporation, headquartered in Chicago, owns a portfolio of 627 properties in 52 countries.
What was the response?
Hyatt said it had launched an investigation and hired leading third-party cyber security experts to help investigate the malware threat, as well as taken necessary steps to increase security on its computer systems.
What Hyatt customers should do?
Meanwhile, the company has also advised all its customers to review their payment card statements carefully and to report any unauthorized bank transactions.
Moreover, the company reassured its customers that "customers can feel confident using payment cards at Hyatt hotels worldwide."
Hyatt became the latest hotel chain to report a potential customer data breach this year, following the data breach in other hotel chains, including Hilton, Starwood, Mandarin Oriental, White Lodging and the Trump Collection that acknowledged finding malware in their payment systems.
India temporarily Bans Facebook's Free Internet Service
24.12.2015
Facebook's Free Internet access to India has hit a hurdle:
The Telecom Regulatory Authority of India (TRAI) has ordered the mobile carrier to temporary suspend the Facebook's Free Basics Internet program.
Facebook's Free Basics is an app that allows users to access certain Internet websites, including Facebook, for free.
However, India's independent regulatory body has asked Reliance Communications – the only mobile carrier that provides Free Basics in India – to disable the free internet service temporarily while the regulator investigates whether the service violates net neutrality.
Facebook's Free Basics – Free Internet for ALL
Facebook introduced Free Basics (then known as Internet.org) app to India in February this year, offering people access to more than three dozen Web services for free.
Users of Facebook’s Free Basics app must have a Reliance mobile network and are limited to a range of portals including Wikipedia, BBC News, AccuWeather, Bing, and sites dedicated to infant health, and of course, Facebook and Facebook Messenger.
But since its launch, Facebook's Free Basics has been controversial.
Free Basics Vs. Net Neutrality Advocates
While it offers limited internet resources to people who might not otherwise be able to afford it, on the other hand, the service also offers a huge advantage to the sites and services it includes.
For example, if the service includes Facebook Messenger to use for free, any other instant messaging app would not be able to upsurge in this competitive market, which is nothing but the violation of Net Neutrality.
However, Facebook argued to the contrary, saying Free Basics was "not in conflict" with Net Neutrality as it does not block or throttle other online services. But, Net Neutrality advocates argued that by providing some websites for free, users are discouraged from visiting other sites.
TRAI Bans Free Basics
Therefore, TRAI is concerned about whether mobile carriers should be allowed to charge different costs for different online content; in this case:
Free for selected websites
Charge for almost everything else on the Internet
"Unless that question is answered, it will not be appropriate for us to continue to make that happen," a senior government official told The Times of India (TOI), which first reported the news.
However, Facebook, on its part, said, "We are committed to Free Basics and to working with Reliance and the relevant authorities to help people in India get connected."
But he didn't comment on whether or not Free Basics has actually been banned.
Facebook Actively Lobbying to Keep Free Basics Alive in India
Facebook’s Save Free Basics In India Campaign: Last week, the social network called on Facebook users in India to send an automated email message to the TRAI showing their support to Free Basics.
However a few days ago, it came to light that the social media giant was overplaying its hand by sending notifications to Facebook users in the United States and the United Kingdom to do so the same.
And as usual, Facebook called the incident "accidental."
Moreover, this Facebook campaign has also proved controversial by net neutrality advocates and opponents, claiming its automated email undermines Net Neutrality in India.
Now, let’s just wait and watch that for how many days TRAI has suspended Free Basics in India, although the service is still available to subscribers even after the regulator ordered Reliance to block Free Basics two weeks ago.
Tis the season for shipping and phishing
24.12.2015
On the eve of major holidays such as Christmas and New Year, mail and delivery services face a dramatic increase in the amount of shipments they have to handle. People are buying far more goods online than usual, looking for bargains in the sales, and sending gifts by mail – both nationally and internationally – to friends and relatives. To ease their customers’ nerves, delivery services send email notifications and provide shipment tracking systems. However, this type of communication also creates the ideal conditions for cybercriminals to send phishing messages in the name of major delivery services, and we end up with an increase in the number of these messages.
The fraudsters have a clear aim: to trick unwitting users into downloading a malicious program or entering their confidential data on a phishing site. For example, one scam message detected by Kaspersky Lab asked the user to fill in and sign a delivery form in order to receive a shipment. The message had a DOC file attached to it containing the exploit Exploit.MSWord.Agent.gg, which allowed the cybercriminal to, among other things, gain remote access to the infected computer.
Tis the season for shipping and phishing
Phishing message containing Exploit.MSWord.Agent.gg
In another scam message the fraudsters write that the shipment is already at a DHL office, but the courier cannot deliver it because the delivery address is unclear. The recipient is asked to follow a link within 48 hours and enter the shipment number on the tracking page; otherwise, the shipment will be returned to the sender.
A closer inspection reveals that none of the links in the message lead to the DHL site; instead they all point to the same URL packed with the help of a URL shortening service. Another typical fraudster trick is also used in the email – the victim is warned there is a limited amount of time to react (in this case, 48 hours). If the user fails to follow the link in time, the shipment will be returned to the sender. The plan is simple – distract users with warnings about the urgency of doing something quickly rather than giving them time to think things through logically.
If unwitting users follow the link, they are taken to a specially crafted site in the corporate style of DHL, and are prompted to type in their login credentials to enter the shipment tracking system.
The data entered on sites like this is certain to end up in the hands of cybercriminals. The user will receive a message such as “Your account has been successfully updated”, and will be taken to the official DHL site, which will convince the victim that the operation was legitimate.
A similar situation exists around FedEx, another large delivery service provider. Kaspersky Lab has detected multiple phishing messages sent in the name of this company.
A fraudulent message sent in the name of FedEx
There’s nothing new about this scheme – the victim enters account credentials on a crafted site in order to view information about a shipment.
Phishing site masquerading as the FedEx site
The fact that this site is fraudulent and has nothing to do with FedEx is clear from the URL in the browser address bar.
The conclusion that can be made from the examples given above is that you shouldn’t be too trusting or inattentive while you are online. Never follow links in email messages; it’s safer if you manually type the URL of the required site in your browser address bar. Whenever a page prompts you to enter confidential data, always check the URL in the address bar first. If anything looks suspicious in the URL or in the website design, think twice before entering any personal data.
Last but not least, always keep your security software up to date; it should also include an anti-phishing tool that will help you keep your data confidential, and your money safe. That way, you will be in a good mood for the holidays.
Email accounts belonging to 130 Celebrities have been Hacked
24.12.2015
A man from the Bahamas has been charged after allegedly hacking into the email accounts belonging to 130 celebrities stealing personal information, movie scripts and sex tapes.
According to the U.S. Attorney’s Office for the Southern District of New York , Alonzo Knowles, aka “Jeff Moxey,” is a 23-year-old man suspected to have hacked into the email accounts of celebrities in an effort to steal private files, including scripts for upcoming movies and TV shows, unreleased music tracks and sexually explicit videos. According to the Attorney’s Office the attacker has also stolen social security numbers and passport copies of the victims.
celebrities hacked
The man is accused to have used malware-based attack and phishing messages to gain access to the email accounts of several professionals working in the entertainment, media and sports industries.
The investigation started after a man identified as Knowles proposed to a popular radio host the scripts for an upcoming season of a drama series. The radio host immediately informed the production of the show and reported the case to the law enforcement.
The criminal was presented to an undercover law enforcement agent, the man told to the agent he possessed a list of phone numbers and email addresses belonging at least 130 individuals.
Knowles was arrested in New York on December 21 while he was attempting to sell 15 scripts and the SSNs of three professional athletes and an actress. He offered for sale them at $80,000 to the undercover agent, for this reason, he has been charged with criminal copyright infringement and identity theft.
“This case has all of the elements of the kind of blockbuster script the defendant, Alonzo Knowles, is alleged to have stolen: hacks into celebrities’ private emails, identity theft, and attempts to sell victims’ information to the highest bidder. Unfortunately, these circumstances are all too real,” said Preet Bharara, the US Attorney for the Southern District of New York.
Celebrities are a privileged target for cyber criminals, the last incident in order of time occurred last year, when a number of celebrities have fallen victims of the Fappening case and hackers leaked online their nude pictures.
Roaming Tiger Hackers targets Russian organizations for espionage
24.12.2015
Security researchers from ESET uncovered the Roaming Tiger hacking campaign, bad actors in the wild are targeting Russian organizations.
Roaming Tiger is the name of a cyber espionage campaign targeting high profile organizations in Russia and former Soviet Union countries, including Belarus, Kazakhstan, Kyrgyzstan, Tajikistan, Ukraine and Uzbekistan.
The Roaming Tiger campaign was discovered by experts at ESET in 2014, the researcher Anton Cherepanov presented the findings of their investigation at the 2014 ZeroNights security conference.
According to the experts, the threat actors behind the Roaming Tiger relied on RTF exploits and the PlugX RAT, the analysis of the command and control (C&C) infrastructure suggests the involvement of Chinese hackers.
This summer, experts at Palo Alto Networks uncovered another hacking campaign having many similarities with the Roaming Tiger. The attacks targeted organizations in the same counties, but instead of PlugX, the hackers used a new tool dubbed BBSRAT.
” Based on data collected from Palo Alto Networks AutoFocus threat intelligence, we discovered continued operations of activity very similar to the Roaming Tiger attack campaign that began in the August 2015 timeframe, with a concentration of attacks in late October and continuing into December.” states a blog post published by PaloAlto Networks.
At least in one attack, the threat actors used spear phishing emails with a malicious Word document in attachment.

The Word document designed to exploit an old Microsoft Office vulnerability (CVE-2012-0158) to deliver the BBSRAT malware.
This flaw was also exploited in the attacks observed by ESET last year. Curiously the BBSRAT was using the same C&C architecture as in the Roaming Tiger campaign.
The experts at Palo Alto analyzed a malicious message trying to compromise the Vigstar company that specializes in the development of special-purpose wireless devices and satellite communications systems used by Russian defense and many security agencies.
Interestingly, experts pointed out that BBSRAT uses the same C&C domains as in the Roaming Tiger operation detailed by ESET. However, in the recent attacks, it appears the malicious actors deployed different malware variants and separate infrastructure for each of the targeted entities.
Summarizing the characteristics of the Roaming tiger campaign are
High profile victims in Russia
Use of RTF vulnerabilities (CVE-2012-0158 and CVE-2014-1761)
Win32/Korplug (aka PlugX RAT) • Win32/Farfli.BEK (aka Gh0st RAT)
Once again a threat actor is continuing to run espionage campaigns despite security researchers have discovered their tactics, techniques, and procedures (TTPs) .
“As in many of the previous articles regarding espionage-motivated adversaries and possible nation-state campaigns, what is being observed in this attack campaign is a continued operation and evolution by the adversary even after its tactics, techniques, and procedures (TTPs) have become public knowledge,” wrote Palo Alto Networks researchers in a blog post. “Despite the fact that the information about these attackers has been public for over a year, including a listing of many of the command and control servers, they continue to reuse much of their exposed playbook.”
Payment systems at Hyatt Hotels have been compromised
24.12.2015
Hyatt Hotels Corporation announced it recently discovered malware used to steal credit card data on its payment processing systems.
The Hyatt Hotels Corporation is the last victim of cyber criminals using PoS malware. The company announced Wednesday that a malware has infected its payment systems.
According to the official announcement issued by Hyatt the company is still investigating the incident, at the time I was writing it is still unclear if the malicious code has stolen credit card information from customers and how many customers have been impacted.
“We recently identified malware on computers that operate the payment processing systems for Hyatt-managed locations. As soon as we discovered the activity, we launched an investigation and engaged leading third-party cyber security experts.” states a message published on the company web site.
“The investigation is ongoing, and updates will be posted here at www.hyatt.com/protectingourcustomers. We have taken steps to strengthen the security of our systems, and customers can feel confident using payment cards at Hyatt hotels worldwide.”
Hyatt has taken steps to improve the security of its systems, the message wants to reassure the customers about security of payment systems at Hyatt hotels worldwide.

Hyatt is warning its customers to monitor their bank accounts looking for unauthorized charges, as always, it is essential to review payment card account statements closely and promptly any suspicious operation.
Customers who want to have more information can visit www.hyatt.com/protectingourcustomers or call 1-877-218-3036 (U.S. and Canada) or +1-814-201-3665 (International) from 7 a.m. to 9 p.m. EST.
Hyatt is the last hotel chains in order of time to have suffered a security breach, in the past year Hilton, Starwood, Mandarin Oriental, White Lodging and the Trump Collection were victims of similar attacks.
Microsoft bans Superfish-like adware methods starting in March 2016
24.12.2015
Microsoft declared war to Ad injection and “man-in-the-middle” techniques implemented by both malware and legitimate programs including adware.
Superfish adware was found already installed on new Lenovo portable PCs (laptops) earlier this year. The malware opens users to MITM (man in the middle) assaults in view of the way it infuses ads into web browsers.
It accompanies a self-marked root cert that produces certs for HTTPS associations, supplanting existing certs with its own particular all the while. Assailants (attackers) could exploit this situation—particularly after the secret word (password) for the certification that traveled with Superfish was found—to listen in on encoded correspondence.

Microsoft this week said it has upgraded its principles around adware, and now such projects that fabricate advertisements in the program are required to just utilize the program’s “upheld extensibility model for establishment, execution, crippling and evacuation.” Microsoft said in the beginning of March 2016 it will identify and start uprooting programs that could open the door to cyber attacks.
“The decision and control fit in with the general users online, and we are resolved to ensure that,” composed Barak Shein and Michael Johnson of Microsoft’s Malware Protection Center.
Lenovo immediately fixed the first Superfish issue and presently, browser creators, for example, Mozilla expelled the root cert from Firefox’s trusted root store.
Superfish’s capacity to perform SSL interference as a substitute was positively troubling conduct from an evidently trusted item, one that was all of a sudden opening the entryway to man-in-the-center assaults, as well as the control of DNS settings and other system layer assaults. More awful yet was that Superfish-like programming would not trigger notices about man-in-the-center assaults.
“These methods catch interchanges between the Internet and the PC to infuse notices and advancements into website pages from outside, without the control of the program,” Microsoft said. “Our expectation is to keep the client in control of their perusing knowledge and these systems lessen that control.”
130 Celebrities' Email Accounts Hacked; Hacker Stole Movie Scripts and Sex Tapes
23.12.2015
Breaking News: A 23-year-old Bahamian man has been arrested and charged with hacking into the email accounts of 130 celebrities and stealing the unreleased movie and TV scripts, sex tapes, explicit images and even the upcoming album of a famous A-List Celebrity.
The hacker named Alonzo Knowles contacted a famous radio host to sell the stolen scripts for the first six episodes of a hit television drama currently being filmed.
The unnamed host informed about it to the Homeland Security that cooked up a sting operation and had the radio host put the hacker in touch with an undercover investigator posing as an interested buyer.
The LOSE
Among the items he offered to sell were:
Scripts for three comedy films
A hip-hop biopic
Another television show
Social Security numbers for actors and professional athletes
Emails and phone numbers of at least 130 celebrities
Sex tapes of celebrities
The hacker was arrested on Monday in Manhattan, a day after arriving from the Bahamas to sell the agent 15 movie and TV shows scripts and the Social Security Numbers (SSNs) of a movie actress and two athletes for $80,000.
Besides this, Knowles also showed the agent a sex tape, saying the sex tape is just a "sample of things [he] can get," rather he had "more stuff along these [items] and can get more" if the undercover agent was interested.
How Did the Hacker Access Celebs Email Accounts?
The incident was neither linked to the stolen celebrity photos leaked late last year nor Sony Pictures hack, as the court document posted by NYT indicated that Knowles allegedly hacked into email accounts of celebrities by sending them a virus that allowed him to access their sensitive data.
Apart from gaining access to data via a virus, Knowles also sent fake automated text messages to the celebrities, making it look like their account had been hacked and asking for their passwords to secure their account.
Unfortunately, some of the celebrities replied with their passwords.
A federal criminal complaint noted his victims included movie and TV actors, a famous singer-songwriter, a casting director, and a hip-hop artist, but he did not identify the identity of celebrities, movies or TV shows involved.
Knowles was held without bail after an appearance Tuesday in Manhattan federal court on criminal copyright infringement and identity theft charges, which both have a maximum jail sentence of five years.
Aethra botnet made up of 12000 Italian devices threatens businesses
23.12.2015
Earlier this year experts at VoidSec discovered the Aethra botnet made up of 12000 Italian devices targeting businesses in various industries.
Earlier February, experts at VoidSec where performing ordinary maintenance on their personal website when noticed something of strange in the logs. It was a “strange” recurring pattern, revealing a brute force attack against the administrative interface of the WordPress website.
The experts noticed that all IPs involved in the attack (they were thousands) came from ranges of IP addresses associated to all the principal Italian Internet Service Providers. The involved IPS are
Fastweb
Albacom, now BT-Italia
Clouditalia
Qcom
WIND
BSI Assurance UK
The experts then tracked back the source of attack discovering that all the IPs involved were users by anAethra modem/router (BG1242W, BG8542W etc.).
As usual happen in this case, thousand of SOHO devices were compromised because they were using default credentials (blank: blank).
The interface of such devices is vulnerable to various reflected XSS, for example in the field username of the login form, in the “source host ping” field, mtrace etc. etc. – CSRF and to HTML5 cross-origin resource sharing (partly mitigated).
GET /cgi-bin/AmiWeb?path=/&operation=login&username=%3Cscript%3Ealert%28%27vsec%27%29%3B%3C/script%3E&password=&transaction=vnFS4Ztv_3@ HTTP/1.1
Host: 93.61.
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:42.0) Gecko/20100101 Firefox/42.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
DNT: 1
X-Requested-With: XMLHttpRequest
Connection: keep-alive
Summarizing the experts discovered a botnet of thousands of devices, by using Shodan they were able to extract some additional information about the infected devices.
“There are many Aethra devices around the world (~ 12,000), of which 10,866 are in Italy; filtering by type they are approximately 8000 Aethra Telecommunications PBX devices, the device involved in this specific attack.
The Aethra devices (including 104 models ranging from SIP / 2.0 to Aethra VegaX3_Series_4 Videoconference System) involve 254 unique providers around the world in fifty different countries.” States the report published by VoidSec.

The botnet is considered very dangerous because Aethra modems are mainly exclusively sold for business contracts, this means that vulnerable devices belong to business is various industries and could be used to facilitate targeted attacks towards those specific companies.
“From our statistics we noticed that 70% of those devices are vulnerable (default credentials), therefore 8400 devices with a business contract (ADSL 1Mbps upload / optic fiber 10Mbps) bring a maximum output power ranging from 8400 Mbps to 84000 Mbps, approximately 1-10 Gigabytes per second, that could be used for DDoS attacks.” continues the post.
The action of the Italian ISP Fastweb in a joint effort with Bug Hunters and Vendors allowed to identify and patch the vulnerability in just 7 business day. The operation allowed Voidsec to update their statistics revealing a more disturbing scenario.

“It appears that our initial estimates values, (made using only Shodan) were reductive and partly wrong; Fastweb has about 40,000 devices, but only 4% had default credentials, for a total output power ranging between 1.7 and 17 Gbps (based on average optic fiber coverage).”
Well done Fastweb!
Unfortunately, all BT Italia devices are still vulnerable.
Below the timeline published by VoidSec:
February 13: recognition of brute force and subsequent investigations; one of mine resource contacts someone in BT-Italy.
February 25: jrivett attempts to contact several times BT-Italia:
sent email to the abuse address on record for albacom.net, but every attempt bounced, saying that the user’s mailbox was full;
sent email to the technical contact on record for Albacom.net, but this was ignored;
tweeted about the problem on the main BT Twitter account, but my tweets were immediately deleted
During this period, numerous articles came out about the botnet used by LizardSquad during the famous attacks on Xbox Live and Play Station Network
Krebs on Security wrotes:
“The malicious code that converts vulnerable systems into stresser bots is a variation on a piece of rather crude malware first documented in November by Russian security firm Dr. Web, but the malware itself appears to date back to early 2014.
In addition to turning the infected host into attack zombies, the malicious code uses the infected system to scan the Internet for additional devices that also allow access via factory default credentials. In this way, each infected host is constantly trying to spread the infection to new home routers and other devices.
The botnet is not made entirely of home routers; some of the infected hosts appear to be commercial routers at universities and companies, and there are undoubtedly other devices involved.”
I think that Aethra routers may have contributed extensively to the LizardSquad botnet and its expansion.
March 2: the attacks are continuing, and BT has been warned about what happened.
April 15: attacks are decreasing and then resuming during the following weeks.
May 1: my resource has never received a response from BT-Italia.
December 11: (11 months later) According to our policy, I decided to proceed with a full disclosure, I have no reason to believe that the attacks have been stopped but rather that, they are reduced their intensity and they have changed targets.
December 11: Fastweb is made aware of the vulnerability, we agree some days of delay for the patch
December 22: responsible disclosure and happy ending, at least for Fastweb
Enjoy the report.
Kim Dotcom loses Fight Against Extradition to the US
23.12.2015
Kim Dotcom loses Fight Against Extradition to the US
Internet millionaire and Megaupload founder Kim Dotcom and his three associates are eligible for extradition to the US to face criminal charges over massive copyright infringement on Megaupload (now-shuttered), the court has ruled citing "overwhelming" evidence.
On Tuesday afternoon, New Zealand District Court Judge Nevin Dawson told the court that the United States had presented enough evidence against Dotcom and his co-defendants and that they should be surrendered to the US.
US prosecutors want Dotcom, and colleagues Mathias Ortmann, Bram van der Kolk and Finn Batato to stand trial on charges of copyright infringement, racketeering, and money laundering.
"No matter what happens in Court tomorrow, I'll be fine. Don't worry. Enjoy your Christmas & know that I'm grateful to have you, my friends," Dotcom tweeted before the court hearing.
The court ruling comes almost three years after the New Zealand police raided Dotcom's Auckland mansion at the request of the FBI and in the same year the US government launched extradition proceedings.
Video of High-Profile Armed Raid at Kim Dotcom's House
It was a high-profile armed raid (you can watch the raid video below), but it has taken almost four years for the courts to reach a decision on whether to send Dotcom to America.
Officials say Dotcom's file-sharing service Megaupload served copyright contents, including music, movies, electronic books, television programs, as well as business and entertainment software on 'a massive scale.'
The US government estimates the harm to film studios and record companies was more than $500 Million (£322 Million).
However, Dotcom and three defendants now have 15 days to appeal the court ruling.
"Justice was not served today," Dotcom's California-based lawyer Ira Rothken tweeted, confirming their plans to appeal the US extradition request in the High Court.
"The @KimDotcom team looks forward to having the US request for extradition reviewed in the High Court. We have no other comments at this time," Rothken said.
However, the defendants are allowed to remain out on bail in the meantime. Although the judge insisted that all the defendants should be ordered to report to probation every day.
Phantom Squad plans to hack PSN and Xbox, SkidNP hacks its website
21.12.2015
The hacking crew Phantom Squad announced a severe attack on PSN and Xbox Live networks, but SkidNP group defaced its website.
A few days ago a group of hackers dubbed Phantom Squad announced that it will take down the Xbox Live and PlayStation Network platforms during the upcoming Christmas holidays, emulating the clamorous attack conducted last year by Lizard Squad hackers.
However, it seems that there is an ongoing war between two group of hackers, the Phantom Squad and another group called SkidNP.
Yesterday Phantom Squad launched a first attack against both Xbox Live and PlayStation platforms, probably a test before the powerful attack announced for Christmas.
Curiously, the SkidNP today hacked the Phantom Squad’website (phantomsquad.ml). The Twitter account @SkidNP announced via twitter the hack, such as the SkidNP member @Obstructable that also spread the same news.

SkidNP defaced the Phantom Squad’s website and left the following message:
“Hello Phantom Squad. Your website has been taken over by Lizards.”
“You took credit for multiple attacks that you nor any of your members did. We are not so happy about this so we’ve taken over your site. Here is a suggestion. Quit while you have the chance because if you take credit for the Christmas attacks it will be the last thing you do.”
According to the techworm.net, @Obstructable told the reference to Lizard Squad was a joke and the group is not linked to the notorious hacking crew.
Regarding the Lizard Squad team, it appears to be inactive for a long, but there is the possibility that it is planning a new clamorous attack against PSN and Xbox Live servers. Yesterday AppleJ4ck, who seems to be a member of the hacking crew, announced an imminent attack.
skidnp group and lizard squad PSN and Xbox networks
The tweet which indicates that both the servers will be taken offline in 6 days i.e on 25th December.
The unique certainly at the moment is that several groups are planning to hack PSN and Xbox networks during the holidays.
Hillary Clinton calls tech companies to create a Manhattan Project for Encryption
21.12.2015
At tonight’s Democratic national debate Hillary Clinton Hillary Clinton calls tech companies to work on a new Manhattan Project for Encryption.
At tonight’s Democratic national debate Hillary Clinton calls tech companies cooperate to create “a Manhattan-like project.”
The US Government is expressing its concerns about the possible misuses of encryption that today represents a serious obstacle to the investigation of law enforcement and intelligence agencies.
The Manhattan Project was a research and development project conducted by the US in a joint effort with UK, and Canada that allowed the development of the first nuclear weapons during World War II.
Clinton hopes in a voluntary collaboration offered by the tech companies to provide back doors to their systems, but IT giants have already expressed their opposition.
“I would not want to go to that point,” Clinton said.
“Maybe the backdoor isn’t the right door,” she continued, emphasizing that she trusted Apple and other companies on the problem with the idea of encrypted tech.”
“I don’t know enough about the technology to say what it is,” Clinton said. “But I have a lot of confidence.”
The need of a Manhattan Project for cybersecurity was debated for a long, the recent wave of data breaches (i.e. OPM, Sony Pictures and Anthem hacks
The concept behind the proposal it to involve best experts in the fight against cyber threats, anyway such kind of declarations do not find a practical fundamental.
Fortunately Clinton has mentioned any law to force tech companies to insert a backdoor in their products, I remind you that the presence of security holes could also be exploited by hackers and persistent attackers such as a nation-state actor.
hilary clinton manhattan project encryption
Recently at a Senate hearing, the FBI Director James Comey called for tech companies currently providing users with end-to-end encryption to review “their business model” and stop implementing it.
The end-to-end encryption allows users to communicate securely on the internet making impossible for law enforcement to eavesdrop the traffic.
In the End-to-end Encryption model data is encrypted on the sender’s system before passing it to the servers of the service provider, which turn the encrypted data to the intended recipient, who is the only entity who can decrypt it.
Discovered a database containing data of 3.3 million Hello Kitty fans
21.12.2015
The researcher Chris Vickery has discovered a database leak that exposed 3.3 million accounts belonging to Hello Kitty fans.
The database of the official online community for Hello Kitty and other Sanrio characters, the sanriotown.com, has suffered a data breach. The researcher Chris Vickery has discovered online a database exposing 3.3 million accounts belonging to Hello Kitty fans.
According to Vickery not only the primary database sanriotown.com was affected, the fan portals of the following websites were also impacted by the leak:
hellokitty.com;
hellokitty.com.sg;
hellokitty.com.my;
hellokitty.in.th;
mymelody.com.
On Saturday evening, Vickery reported the discovery to Databreaches.net and Salted Hash.
The records exposed include first and last names, gender, encoded birthday (easily reversible), country, email addresses, SHA-1 hash passwords, password hint questions with corresponding answers, and other information.

The expert also discovered two additional backup servers containing mirrored data, then he notified the data leak to both Sanrio and the ISP being used to host the database.
This incident is raising great concern in the IT security industry because one again personal information of children are exposed online.
At the end of November, the VTech toy maker has been hacked exposing data of 11.6 million people, 6.4 million of them belonging to children.
The recent VTech data breach exposed 11.6 million people, and 6.4 million of them were children.
The identity theft of a child is even more insidious because crooks could abuse of the stolen data for years.
Every time I receive news of a data breach I suggest affected users to the change password for all the websites that share the same login credentials.
The same suggestion is valid for users that share the same hint question and answer across different websites.
Phone House – Personal data of 12+ million Dutch mobile customers open to hackers
20.12.2015
Basically all Dutch citizens who own a mobile phone are at risk of attack due to poor security practices at the Phone House.
The freelance IT security consultant Sijmen Ruwhof discovered that personal info of more than 12 million Dutch mobile phone are open to cyber attacks. Ruwhof detailed all the security issues he noticed in a blog post.
Basically, all Dutch citizens who own a mobile phone are at risk of attack, the Phone House is a Dutch phone retail company that is a dealer for all telecom operators in the country.
Phone House points of sale are located in the Media Markt stores across the country. Ruwhof went to a Phone House store in a Media Markt store in Utrecht to get information about his phone subscription, and made a disconcerting discovery; the employees at the Phone House had access to customer data of all Dutch telecoms via dealer portals, and this access seems to be very insecure.
“The sales guy starts renewing my Vodafone subscription and therefore needs to log in at a dealer portal from Vodafone. He doesn’t remember the login password, and, here it comes, on the screen he opens an Excel file which contains *all* their passwords,” Ruwhof observed. “Curiously and intensively I looked on the screen to get a picture of the treasure trove that was in front of me. Passwords to view and modify customer data of KPN, Vodafone, Telfort, T-Mobile, UPC, Tele2 and other companies were right in front of me.”
The expert also noticed that the Excel file containing the passwords was stored on Google Docs, and he was also able to see the login for the Google Account used by Phone House.
At a certain point, the sales guy has left unattended the PC, he didn’t close the file or lock the computer. The passwords were stored in the browser and the excel file remain always open and often visible on the screen.
Ruwhof visited several times the Phone House stores and always observed the same unsafe behavior, a circumstance that demonstrate the “fundamental lack of security and privacy awareness within Phone House and Media Markt.”
The expert also noticed that the passwords used by the operators were easy to guess and vulnerable to brute-force attacks.
The computers in the stores have easy to reach USB ports opening the door to a malware based attack via USB pen drive.

“I hope this story is a wake-up call for everyone who works with computers and handles personal data of others,” said Ruwhof.
Enjoy the Ruwhof’s post.
FBI investigates on Juniper hack, is it a nation-state attack?
20.12.2015
The FBI is investigating on the unauthorized code found in the operating system running on firewalls sold by Juniper Networks.
The FBI confirmed that is investigating on the alleged breach of Juniper Networks VPN software that resulted in the introduction of unauthorized code in the OS running on Juniper firewalls. Juniper Networks makes communications equipment for enterprises and government organizations, including the U.S. government.
An “unauthorized code” was discovered in the operating system for Juniper NetScreen firewalls. The company admitted the presence of the “unauthorized code” that could allow an attacker to decrypt VPN traffic.
[“unauthorized code”] “could allow a knowledgeable attacker to gain administrative access to NetScreen devices and to decrypt VPN connections.”
“During a recent internal code review, Juniper discovered unauthorized code in ScreenOS that could allow a knowledgeable attacker to gain administrative access to NetScreen devices and to decrypt VPN connections,” Juniper Chief Information officer Bob Worrall wrote. “Once we identified these vulnerabilities, we launched an investigation into the matter, and worked to develop and issue patched releases for the latest versions of ScreenOS.” states the advisory.
According to The Register, the presence of the unauthorized code could date back to 2008, the experts referred a 2008 notice issued by Juniper’s about a security issued that impacts ScreenOS 6.2.0r15 through 6.2.0r18 and 6.3.0r12 through 6.3.0r20. ScreenOS 6.2 was released. The Screen OS 6.3 was presented in 2009.
The U.S. officials are now investigating the security breach of Juniper Networks software over concerns the “backdoor entry” allowed nation-state hackers to spy on communications of the U.S. government.

The Department of Homeland Security is working with Juniper in order to discover who inserted the bogus code in the Juniper devices and why.
“A senior U.S. official who declined to be named because of the sensitivity of the matter said the Department of Homeland Security is working with Juniper as it investigates the issue.” reported Reuters.
The unauthorized code could decrypt VPN devices without leaving a trace.
Juniper sustains that the unauthorized code it found had been inserted into its ScreenOS software.
“A skilled attacker would likely remove these entries from the local log file, thus effectively eliminating any reliable signature that the device had been compromised,”reads the Juniper’s security update.
Juniper also confirmed a second security issue that would allow an attacker monitoring VPN traffic.
A separate advisory issued by the company confirms the presence of two separate vulnerabilities in its products, the first one allows unauthorized remote administrative access to an affected device over SSH or telnet, “The second issue may allow a knowledgeable attacker who can monitor VPN traffic to decrypt that traffic,” the advisory said. “It is independent of the first issue. There is no way to detect that this vulnerability was exploited.”
At the time I was writing, Juniper confirmed it hadn’t discovered these security issues were exploited.
The disclosure of the security breach has prompted an investigation by the FBI into whether a foreign government wes trying to eavesdrop encrypted communication of U.S. government employees.
“The FBI is investigating the breach, which involved hackers installing a back door on computer equipment, U.S. officials told CNN.” continues the CNN. “The concern, U.S. officials said, is that sophisticated hackers who compromised the equipment could use their access to get into any company or government agency that used it. One U.S. official described it as akin to “stealing a master key to get into any government building.”
Instagram hacked! Hacker compromised the entire platform
19.12.2015
The researcher who hacked Instagram claims he was threatened by Facebook after he responsibly reported a series of security issues.
Every platform is potentially hackable, even the armored Facebook and Instagram and the independent security researcher Wesley Weinberg has demonstrated it.
Of course, if the hackers ethically report the flaw to the company usually nothing happen, but the story I’ll tell you seems to end up in taking legal actions against the expert.
The researcher Weinberg independent security researcher claims he was threatened by Facebook after he responsibly reported a series of security vulnerabilities and configuration flaws that allowed him to gain access to Instagram servers.
The expert confirmed to have had access to the following information:
Source Code of Instagram website
SSL Certificates and Private Keys for Instagram
Keys used to sign authentication cookies
Personal details of Instagram Users and Employees
Email server credentials
Keys for over a half-dozen critical other functions
Usually, experts that ethically report the vulnerabilities discovered are rewarded by the companies, but Facebook decided to sue the researcher of intentionally withholding flaws and information from its team.
Weinberg was analyzing Instagram systems after one of his friends suggested him to target potentially vulnerable server located at sensu.instagram.com.
The researcher discovered an RCE (Remote Code Execution) in the users’ session cookie management.
According to Weinberg, he exploited the Remote code execution vulnerability in Instagram system due to two weaknesses:
The Sensu-Admin web app running on the server contained a hard-coded Ruby secret token.
The host running a version of Ruby (3.x) that was susceptible to code execution via the Ruby session cookie.
Weinberg was able to access a database containing login details, including credentials, of both Instagram and Facebook employees.
The good news is that passwords were protected by bcrypt, but Weinberg was able to crack at least a dozen of weak passwords (i.e. instagram, password) in just a few minutes.
The expert then focused its efforts on the configuration of the server and discovered that one of the files contained some keys for Amazon Web Services accounts used by Istagram as data storage.
“These keys listed 82 Amazon S3 buckets (storage units), but these buckets were unique. He found nothing sensitive in the latest file in that bucket, but when he looked at the older version of the file, he found another key pair that let him read the contents of all 82 buckets.” state THN.
Weinberg has compromised the entire architecture of Instagram, he gained access to the platform source code, SSL certificates and private keys (including for instagram.com and *.instagram.com), API keys, users’ images, static content from the instagram.com website, email server credentials, iOS/Android app signing keys and much more.
“To say that I had gained access to basically all of Instagram’s secret key material would probably be a fair statement,” Weinberg wrote in his blog. “With the keys I obtained, I could now easily impersonate Instagram, or any valid user or staff member. While out of scope, I would have easily been able to gain full access to any user’s account, [personal] pictures and data.”
Weinberg reported his findings to Facebook, but the company reacted badly due to the exposure of employees’ data and excluded the expert from the bug bounty program.
In early December, Weinberg claims Synack CEO, Jay Kaplan, received a scary call from Facebook security chief Alex Stamos regarding the vulnerability discovered by Weinberg. Stamos sustains that the expert opened the users to cyber attack compromising the security of the entire platform.
“Alex informed my employer (as far as I am aware) that I had found a vulnerability, and had used it to access sensitive data. He then explained that the vulnerability I found was trivial and of little value, and at the same time said that my reporting and handling of the vulnerability submission had caused huge concern at Facebook. Alex then stated that he did not want to have to get Facebook’s legal team involved, but that he wasn’t sure if this was something he needed to go to law enforcement over.” Weinberg explained a blog post.
Stamos issued a statement, saying he “did not threaten legal action against Synack or [Weinberg] nor did [he] ask for [Weinberg] to be fired.”
Stamos published a post entitled “Bug Bounty Ethics” to reply Weinberg
“I told Jay that we couldn’t allow Wes to set a precedent that anybody can exfiltrate unnecessary amounts of data and call it a part of legitimate bug research, and that I wanted to keep this out of the hands of the lawyers on both sides. I did not threaten legal action against Synack or Wes nor did I ask for Wes to be fired. I did say that Wes’s behavior reflected poorly on him and on Synack, and that it was in our common best interests to focus on the legitimate RCE report and not the unnecessary pivot into S3 and downloading of data.” Stamos wrote.
“Condoning researchers going well above and beyond what is necessary to find and fix critical issues would create a precedent that could be used by those aiming to violate the privacy of our users, and such behavior by legitimate security researchers puts the future of paid bug bounties at risk,” he added.
Facebook assumed another position on the events, its security team says that Weinberg was never authorized to publish non-public information he accessed.
Facebook admitted the presence of the flaw and promised a $2,500 reward to Weinberg and his friend, but according to the company the expert has gone too far.
Beloo the full statement issued by Facebook:
“We are strong advocates of the security researcher community and have built positive relationships with thousands of people through our bug bounty program. These interactions must include trust, however, and that includes reporting the details of bugs that are found and not using them to access private information in an unauthorized manner. In this case, the researcher intentionally withheld bugs and information from our team and went far beyond the guidelines of our program to pull private, non-user data from internal systems.
We paid him for his initial bug report based on the quality, even though he was not the first to report it, but we didn’t pay for the subsequent information that he had withheld. At no point did we say he could not publish his findings — we asked that he refrain from disclosing the non-public information he accessed in violation of our program guidelines. We remain firmly committed to paying for high quality research and helping the community learn from researchers’ hard work.”
Let me close with a reflection …
What would happen if a nation-state actor exploits a similar flaw?
Over 650 terabytes of MongoDB data exposed on Internet
19.12.2015
The popular expert and Shodan creator John Matherly found over 650 terabytes of MongoDB data exposed on the Internet by vulnerable databases.
Last week my old hosting provider GoDaddy created me a lot of problems so I had no opportunity to write about this interesting story, now I passed to a better provider and I decided to do it.
There are at least 35,000 vulnerable MongoDB databases exposed on the Internet, the data they contain is exposed to cyber attacks. It has been estimated that nearly 684.8 terabytes of data are at risk, and most disconcerting aspect of the story is that this data is growing day by day.
The estimates are the result of a scan performed over the past few days by John Matherly, the popular cyber security expert, and creator of the Shodan search engine for Internet-connected devices.
MongoDB is a popular alternative to SQL, open source, many companies already use it, including “The New York Times”, “Ebay”, and “Foursquare.” John Matherly argues that around 30.000 databases are exposed because administrators are using old versions of MongoDB, and these old versions fail to bind to localhost
Matherly has already warned the IT industry about the presence of vulnerable MongoDB online, in July he revealed that many MongoDB administrators exposed something like 595.2 terabytes of data by adopting poor configurations, or un-patched versions of the MongoDB.
In July, he found nearly 30,000 unauthenticated MongoDB instances, then he decided to monitor the situation over the time.

Recently the security researcher Chris Vickery confirmed that information exposed in such databases was associated with 25 million user accounts from various apps and services, including 13 million users of the OS X optimization program MacKeeper. Vickery discovered that data records include names, email addresses, birth dates, postal addresses, private messages and insecure password hashes.
Matherly now discovered further 5,000 insecure instances since July, a somewhat surprising result giving that newer versions of the database no longer have a default insecure configuration.
“By default, newer versions of MongoDB only listen on localhost. The fact that MongoDB 3.0 is well-represented means that a lot of people are changing the default configuration of MongoDB to something less secure and aren’t enabling any firewall to protect their database.” Matherly wrote in a blog post Tuesday
“It could be that users are upgrading their instances but using their existing, insecure configuration files.”

Matherly observed the majority of vulnerable databases are hosted on cloud computing platforms run by Amazon.com, Alibaba Group and DigitalOcean.
Unfortunately, many other vulnerable databases are exposed on the Internet including Redis, CouchDB, Cassandra and Riak as confirmed by Matherly.
“Finally, I can’t stress enough that this problem is not unique to MongoDB:Redis, CouchDB, Cassandra and Riak are equally impacted by these sorts of misconfigurations.” explained Matherly.
Kaspersky Security Bulletin 2015. Evolution of cyber threats in the corporate sector
19.12.2015 Zdroj: Kaspersky
Top security stories
Overall statistics for 2015
Evolution of cyber threats in the corporate sector
Predictions 2016
In late 2014, we published predictions for how the world of cyber threats may evolve in 2015. Four of the nine predictions we made were directly connected with threats to businesses. Our predictions proved accurate – three of the four business-related threats have already been fulfilled:
Cybercriminals embrace APT tactics for targeted attacks – yes.
APT groups fragment, diversify attacks – yes.
Escalation of ATM and PoS attacks – yes.
Attacks against virtual payment systems – no.
Let’s have a look back at the major incidents of 2015 and at the new trends we have observed in information security within the business environment.
The year in figures
In 2015 one or more malware attacks were blocked on 58% of corporate computers. This is a 3 p.p. rise on the previous year.
29% of computers – i.e. almost every third business-owned computer – were subjected to one or more web-based attacks.
Malware exploiting vulnerabilities in office applications were used 3 times more often than in attacks against home users.
File antivirus detection was triggered on 41% of corporate computers (objects were detected on computers or on removable media connected to computers: flash drives, memory cards, telephones, external hard drives, or network disks).
Targeted attacks on businesses: APT and cybercriminals
2015 saw a number of APT attacks launched against businesses. The toolkits and methods used were very similar to those we observed when analyzing earlier APT attacks, but it was cybercriminals rather than state-sponsored groups who were behind the attacks. The methods used may not be characteristic of cybercriminals, but the main aim of their attacks remained the same: financial gain.
In 2015, one or more #malware attacks were blocked on 58% of corporate computers #KLReport
Tweet
The Carbanak campaign became a vivid example of how APT-class targeted attacks have shifted focus to financial organizations. The campaign was one of bona fide bank robberies in the digital age: the cybercriminals penetrated a bank’s network looking for a critical system, which they then used to siphon off money. After stealing a hefty sum (anywhere between $2.5 million and $10 million) from a bank, they moved on to the next victim.
Most of the organizations targeted were located in Eastern Europe. However, the Carbanak campaign has also targeted victims in the US, Germany and China. Up to 100 financial institutions have been affected across the globe, and the total losses could be as a high as $1 billion.
It shouldn’t be forgotten that information can also be of great value, especially if it can be used when making deals or trading on the stock exchange, be it in commodities, securities or currency markets, including cryptocurrency markets. One example of a targeted attack that may have been hunting for such information is Wild Neutron (aka Jripbot and Morpho). This cyber-espionage campaign first hit the headlines in 2013 when it affected several reputable companies, including Apple, Facebook, Twitter and Microsoft. After these incidents received widespread publicity the actors behind the cyberespionage campaign suspended their activities. However, about a year later Kaspersky Lab observed that Wild Neutron had resumed operations.
Our research has shown that the cyberespionage campaign caused infections on user computers in 11 countries and territories, namely Russia, France, Switzerland, Germany, Austria, Slovenia, Palestine, the United Arab Emirates, Kazakhstan, Algeria and the US. The victims included law firms, investment companies, bitcoin-related companies, enterprises and business groups involved in M&A deals, IT companies, healthcare companies, real estate companies, as well as individual users.
It should be noted that Wild Neutron used a code signing certificate stolen from Acer.
Stolen Acer certificate in the Wild Neutron installer
The trend towards the diversification of APT attacks is well illustrated by the change in targets attacked by the Chinese cybercriminal group Winnti. It was a long-held belief that Winnti only attacked computer gaming companies. However, in autumn 2015 evidence began to emerge that showed the group had performed a test run of their tools and methods and were trying to make money by attacking new targets. Their attention is no longer limited to the entertainment industry, with recent targets including pharmaceutical and telecom companies. Analysis of the new wave of Winnti attacks has revealed that (as with Wild Neutron) the Winnti rootkit was signed with a stolen certificate that belonged to a division at a major Japanese conglomerate.
Another development in 2015 was the expanding geographies of both the attacks and the attackers. For example, when Kaspersky Lab experts were investigating a Middle East incident, they came across activity by a previously unknown group conducting targeted attacks. The group, dubbed the Desert Falcons, is the first Arab actor to conduct full-blown cyberespionage attacks. At the time the group was detected, its victims numbered around 300, including financial organizations.
Another group named Blue Termite attacked organizations and companies in Japan:
Information about targeted attacks on businesses is available in the following Kaspersky Lab reports: Carbanak, Wild Neutron, Winnti, DarkHotel 2015, Desert Falcons, Blue Termit, Grabit. More detailed research results are provided to subscribers of the Kaspersky Intelligence Service.
Analysis of these attacks has identified several trends in the evolution of targeted attacks on businesses:
Financial organizations such as banks, funds and exchange-related companies, including cryptocurrency exchanges, have been subjected to attacks by cybercriminals.
The attacks are meticulously planned. The cybercriminals scrutinize the interests of potential victims (employees at the targeted company), and identify the websites they are most likely to visit; they examine the targeted company’s contacts, equipment and service providers.
The information collected at the preparation stage is then put to use. The attackers hack legitimate websites that have been identified and the business contact accounts of the targeted company’s employees. The sites and accounts are used for several hours to distribute malicious code, after which the infection is deactivated. This means the cybercriminals can re-use the compromised resources again later.
Signed files and legitimate software is used to collect information from the attacked network.
Attacks are diversifying to include small and medium-sized businesses.
The geography of attacks on businesses is expanding: a massive attack occurred in Japan, the emergence of new APT groups in Arab countries.
In 2015, 29% of business-owned computers were subjected to one or more web-based attacks #KLReport
Tweet
Although there are relatively few APT attacks launched by cybercriminals, the way they are developing will undoubtedly influence the methods and approaches employed by other cybercriminals in their operations against businesses.
Statistics
The statistics for corporate users (including the geography of attacks and ratings for detected objects) tend to coincide with those for home users. This is unsurprising because business users do not exist in an isolated environment and their computers are targeted by cybercriminals who spread malware irrespective of the nature of the target. These types of attacks and malware constitute the majority, while attacks specifically targeting business users have little impact on the overall statistics.
In 2015, one or more malware attack was blocked on 58% of corporate user computers, which is a 3 p.p. rise on last year.
Online threats (Web-based attacks)
In 2015, almost every third (29%) computer in a business environment was subjected to one or more web-based attacks.
TOP 10 web-based malicious programs
Please note that this ranking includes malicious programs only, and no adware. Although intrusive and annoying for users, adware does not cause any damage to a computer.
Name* % of unique users attacked**
1 Malicious URL 57.0
2 Trojan.Script.Generic 24.7
3 Trojan.Script.Iframer 16.0
4 Exploit.Script.Blocker 4.1
5 Trojan-Downloader.Win32.Generic 2.5
6 Trojan.Win32.Generic 2.3
7 Trojan-Downloader.JS.Iframe.diq 2.0
8 Exploit.Script.Generic 1.2
9 Packed.Multi.MultiPacked.gen 1.0
10 Trojan-Downloader.Script.Generic 0.9
*These statistics represent the detection verdicts of the web antivirus module. Information was provided by users of Kaspersky Lab products who consented to share their local statistical data.
**The percentage of all web attacks recorded on the computers of unique users.
This Top 10 consists almost exclusively of verdicts assigned to malicious objects that are used in drive-by attacks – Trojan downloaders and exploits.
Geography of web-based attacks
Geography of web-based attacks in 2015
(percentage of attacked corporate users in each country)
Local threats
The file antivirus detection was triggered on 41% of corporate user computers. The detected objects were located on computers or on removable media connected to the computers, such as flash drives, memory cards, telephones, external hard drives and network drives.
TOP 10 malicious programs detected on user computers
This ranking includes malicious programs only, and no adware. Although intrusive and annoying for users, adware does not cause any damage to a computer.
Name* % of unique users attacked**
1 DangerousObject.Multi.Generic 23.1
2 Trojan.Win32.Generic 18.8
3 Trojan.WinLNK.StartPage.gena 7.2
4 Trojan.Win32.AutoRun.gen 4.8
5 Worm.VBS.Dinihou.r 4.6
6 Net-Worm.Win32.Kido.ih 4.0
7 Virus.Win32.Sality.gen 4.0
8 Trojan.Script.Generic 2.9
9 DangerousPattern.Multi.Generic 2.7
10 Worm.Win32.Debris.a 2.6
* These statistics are compiled from malware detection verdicts generated by the on-access and on-demand scanner modules on the computers of those users running Kaspersky Lab products who have consented to submit their statistical data.
** The proportion of individual users on whose computers the antivirus module detected these objects as a percentage of all attacked individual users.
First place is occupied by various malicious programs that were detected with the help of cloud technologies, and assigned the umbrella verdict of ‘DangerousObject.Multi.Generic’. Cloud technologies work when antivirus databases do not yet contain signatures or heuristics to detect a malicious program but the company’s cloud antivirus database already includes information about the object. When a client company cannot send statistics to the cloud, Kaspersky Private Security Network is used instead, meaning that network computers receive protection from the cloud.
In 2015, file antivirus detection was triggered on 41% of corporate computers #KLReport
Tweet
Most of the remaining positions in the ranking are occupied by self-propagating malware programs and their components.
Geography of local threats
Geography of local threat detections in 2015
(percentage of attacked corporate users in each country)
Characteristics of attacks on businesses
The overall statistics for corporate users do not reflect the specific attributes of attacks launched against businesses; the stats are influenced more by the probability of a computer infection in a country, or by how popular a specific malware program is with cybercriminals.
However, a more detailed analysis reveals the peculiarities of attacks on corporate users:
exploits for vulnerabilities found in office applications are used three times more often than in attacks on home users;
use of malicious files signed with valid digital certificates;
use of legitimate programs in attacks, allowing the attackers to go undetected for longer.
We have also observed a rapid growth in the number of corporate user computers attacked by encryptor programs.
In this particular context, the majority of cases are not APT attacks: “standard” cybercriminals are simply focusing on corporate users, and sometimes on a particular company that is of interest to them.
Use of exploits in attacks on businesses
The ranking of vulnerable applications is compiled based on information about exploits blocked by Kaspersky Lab products and used by cybercriminals, both in web- and email-based attacks, as well as attempts to compromise local applications, including those on mobile devices.
Distribution of exploits used in cybercriminal attacks by type of attacked application
(corporate users, 2015)
Distribution of exploits used in cybercriminal attacks by type of attacked application
(home users, 2015)
If we compare the use of exploits by cybercriminals to attack home and corporate users, the first obvious difference is that exploits for office software vulnerabilities are used much more often in attacks launched against businesses. They are only used in 4% of attacks on home users, but when it comes to attacks on corporate users, they make up 12% of all exploits detected throughout the year.
Web browsers are the applications targeted most often by exploits in attacks on both home and corporate users. When viewing these statistics, it should be noted that Kaspersky Lab technologies detect exploits at various stages. Detection of landing pages from which exploits are distributed are also counted in the ‘Browsers’ category. We have observed that most often these are exploits for vulnerabilities in Adobe Flash Player.
Distribution of exploits used in cybercriminal attacks by type of attacked application in 2014 and 2015
The proportions of Java and PDF exploits have declined significantly compared to 2014, by 14 p.p. and 8 p.p., respectively. Java exploits have lost some of their popularity in spite of the fact that several zero-day vulnerabilities that been found during the year. The proportion of attacks launched using vulnerabilities in office software (+8 p.p.), browsers (+9 p.p.), Adobe Flash Player (+9 p.p), and Android software (+3 p.p.) have risen.
In 2015, @Kaspersky solutions detected ransomware on more than 50K computers in corporate networks #KLReport
Tweet
Investigations of security incidents have shown that even in targeted attacks on corporations, cybercriminals often use exploits for known vulnerabilities. This is because corporate environments are slow to install appropriate security patches. The proportion of exploits that target vulnerabilities in Android applications has risen to 7%, which suggests cybercriminals have a growing interest in corporate data stored on employees’ mobile devices.
Ransomware
Encryption Trojans were long considered to be a threat to home users only. Nowadays, however, we see ransomware actors paying more attention to organizations as targets.
In 2015, Kaspersky Lab solutions detected ransomware on more than 50,000 computers in corporate networks, which is double the figure for 2014. It is important to keep in mind that the real number of incidents is several times higher: the statistics reflect only the results of signature-based and heuristic detections, while in most cases Kaspersky Lab products detect encryption Trojans based on behavior recognition models.
The number of unique corporate users attacked by encryption Trojans in 2014 and 2015
There are two reasons for the surge in interest in businesses by ransomware actors. Firstly, they can receive much bigger ransoms from organizations than from individual users. Secondly, there is a better chance the ransom will be paid: some companies simply cannot continue their operations if information has been encrypted and is unavailable on critical computers and/or servers.
One of the most interesting developments of 2015 in this realm has been the emergence of the first Linux encryption malware (Kaspersky Lab products detect it as the verdict ‘Trojan-Ransom.Linux.Cryptor’), which targets websites, including online stores. The cybercriminals exploited vulnerabilities in web applications to gain access to websites, and then uploaded a malicious program to the sites that encrypted the server data. In the majority of cases, this brought the site down. The cybercriminals demanded a ransom of one bitcoin to restore the site. Around 2,000 websites are estimated to have been infected. Given the popularity of *nix servers in the business environment, it is reasonable to assume that next year there may be more ransomware attacks against non-Windows platforms.
TOP 10 encryptor Trojan families
Family % attacked users*
1 Scatter 21
2 Onion 16
3 Cryakl 15
4 Snocry 11
5 Cryptodef 8
6 Rakhni 7
7 Crypmod 6
8 Shade 5
9 Mor 3
10 Crypren 2
*The proportion of users attacked by malicious programs from this family, as a percentage of all attacked users.
Virtually all the ransomware families in the Top 10 demand ransoms in bitcoins.
The Scatter family of Trojans occupies first place. They encrypt files on the hard drive and leave encrypted files with the extension .vault. Scatter Trojans are multi-module, multi-purpose script-based malicious programs. This malware family has quickly evolved over a short period, developing new Email-Worm and Trojan-PSW capabilities on top of file encryption.
In second place is the Onion family of encryptors, known for the fact that their C&C servers are located within the Tor network. In third place is the Cryakl family of encryptors, which are written in Delphi and emerged back in April 2014.
In some cases, it may be possible to restore the data encrypted by these ransomware programs, usually when there are mistakes of some kind in their algorithms. However, it is currently impossible to decrypt data that has been encrypted by the latest versions of the malicious programs in the Top 10.
It is important for companies to understand that an infection by malware of this kind can interfere with business operations if critical business data is lost or a critical server operation is blocked due to encryption. Attacks like this can lead to huge losses, comparable to those caused by the Wiper malware attacks that destroyed data in corporate networks.
To address this threat, a number of measures should be taken:
deploy protection against exploits;
ensure behavioral detection methods are enabled in your security product (in Kaspersky Lab products, this is done in the System Watcher component);
configure a data backup procedure.
Attacks on PoS terminals
The security of point-of-sale (PoS) terminals has turned into another pressing issue for businesses, especially those involved in trading activities. Any computer with a special card reader device connected to it and the right software installed can be used as a PoS terminal. Cybercriminals hunt for these computers and infect them with malicious programs that allow them to steal the details of bank cards used to pay at the terminals.
Kaspersky Lab’s security products have blocked over 11,500 such attacks across the world. To date, there are 10 malware families in our collection that are designed to steal data from PoS terminals. Seven of these emerged this year. Despite the small number of attacks that are attempted, this risk should not be underestimated, because just one successful attack could compromise the details of tens of thousands of credit cards. Such a large number of potential victims is possible because business owners and system administrators do not see PoS terminals as devices that require protection. As a result, an infected terminal could go unnoticed for a long time, during which the malicious program sends the details of all the credit cards passing through the terminal to cybercriminals.
This problem is especially relevant in those countries where cards with EMV chips are not used. The adoption of EMV chip cards should make it far more difficult to obtain the data required to clone banking cards, although the adoption process could take a long time. In the meantime, there are some minimum measures that should be taken to protect PoS devices. Fortunately, for these devices it is fairly easy to configure the ‘default deny’ security policy, which blocks unknown programs from launching by default.
We expect that in the future cybercriminals will start targeting mobile PoS devices running under Android.
Conclusion
The data collected from Kaspersky Lab products shows that the tools used to attack businesses differ from those used against home users. In attacks on corporate users, exploits for office application vulnerabilities are used much more often, malicious files are often signed with valid digital certificates, and cybercriminals try to use legitimate software for their purposes, so they can go unnoticed for longer. We have also observed strong growth in the numbers of corporate user computers targeted by ransomware. This also applies to incidents not classified as APT attacks, where cybercriminals merely focus on corporate users, and sometimes on employees of specific companies.
The fact that cybercriminal groups use APT methods and programs to attack businesses takes them to a different level and makes them much more dangerous. Cybercriminals have begun to use these methods primarily to steal large sums of money from banks. They can use the same methods to steal a company’s money from bank accounts by gaining access to its corporate network.
@Kaspersky security products have blocked over 11.5K attacks on PoS terminals across the world #KLReport
Tweet
Cybercriminals rely on exploiting known vulnerabilities to conduct their attacks – this is due to the fact that many organizations are slow to implement software updates on their corporate computers. In addition, cybercriminals make use of signed malicious files and legitimate tools to create channels for extracting information: these tools include popular remote administration software, SSH clients, password restoration software, etc.
More and more frequently, corporate servers are being targeted by cybercriminals. Besides stealing data, there have been cases when the attacked servers were used to launch DDoS attacks, or the data on the servers was encrypted for ransom. Recent developments have shown that this is true for both Windows and Linux servers.
Many of the organizations that suffered attacks have received ransom demands asking for payments in return for halting an ongoing DDoS attack, unblocking encrypted data, or for not disclosing stolen information. When an organization faces such demands, the first thing they should do is contact law enforcement agencies and computer security specialists. Even if a ransom is paid, the cybercriminals may still not fulfil their promise, as was the case with the ProtonMail DDoS attack that continued after a ransom was paid.
Predictions
Growing numbers of attacks against financial organizations, financial fraud on exchange markets
In the coming year, we expect to see growing numbers of attacks launched against financial organizations, as well as a difference in the quality of these attacks. Besides transferring money to their own accounts and converting it to cash, we may also see cybercriminals employing some new techniques. These could include data manipulation on trading platforms where both traditional and new financial instruments, such as cryptocurrencies, are traded.
Attacks on infrastructure
Even if an organization is difficult to penetrate, it is now typical for organizations to store their valuable data on servers located in data centers rather than on the infrastructure located on their own premises. Attempts to gain unauthorized access to these outsourced components of a company’s infrastructure will become an important attack vector in 2016.
Exploiting IoT vulnerabilities to penetrate corporate networks
IoT (Internet of Things) devices can be found in almost every corporate network. Research conducted in 2015 has shown that there are a number of security problems with these devices and cybercriminals are likely to exploit them because they offer a convenient foothold at the initial stage of penetrating a corporate network.
More rigid security standards, cooperation with law enforcement agencies
In response to the growing number of computer incidents in business environments and the changes to the overall cyber-threat landscape, regulatory authorities will develop new security standards and update those already in effect. Organizations that are interested in the integrity and security of their digital values will cooperate more actively with law enforcement agencies, or find themselves obliged to do so by the standards mentioned above. This may lead to more concerted efforts to catch cybercriminals, so expect to hear about new arrests in 2016.
What to do?
In 2015, we have seen cybercriminals begin to actively use APT attack methods to penetrate company networks. We are talking here about reconnaissance that aims to identify weak spots in a corporate infrastructure and gathering information about employees. There is also the use of spear phishing and waterhole attacks, the active use of exploits to execute code and gain administrator rights, the use of legitimate software along with Trojans for remote administration, research of the targeted network and abuse of password restoration software. All this requires the development of methods and techniques to protect corporate networks.
As for specific recommendations, the TOP 35 cyber-intrusion mitigation strategies developed by the Australian Signals Directorate (ASD) should be consulted first of all. Through comprehensive, detailed analysis of local attacks and threats, ASD has found that at least 85% of targeted cyber intrusions could be mitigated by four basic strategies. Three of them are related to specialized security solutions. Kaspersky Lab products include technological solutions to cover the first three major strategies.
Below is a list of the four basic strategies that reduce the possibility of a successful targeted attack:
Use application whitelisting to help prevent malicious software and unapproved programs from running
Patch applications such as Java, PDF viewers, Flash, web browsers and Microsoft Office
Patch operating system vulnerabilities
Restrict administrative privileges to operating systems and applications, based on user duties.
For detailed information about the ASD mitigation strategies, consult the threat mitigation article in the Securelist encyclopedia.
Another important factor is the use of the latest threat data, i.e. threat intelligence services (Kaspersky Lab, for example, provides its own Kaspersky Intelligence Service ). A timely configuration and checkup of the corporate network using this data will help protect against attacks or detect an attack at an early stage.
The basic principles of ensuring security in corporate networks remain unchanged:
Train staff. Maintaining information security is not only the job of the corporate security service but also the responsibility of every employee.
Organize security procedures. The corporate security system must provide an adequate response to evolving threats.
Use new technologies and methods. Each added layer of protection helps reduce the risk of intrusion.
Kaspersky Security Bulletin 2015. Overall statistics for 2015
19.12.2015 Zdroj: Kaspersky
Top security stories
Evolution of cyber threats in the corporate sector
Overall statistics for 2015
Predictions 2016
The year in figures
In 2015, there were 1,966,324 registered notifications about attempted malware infections that aimed to steal money via online access to bank accounts.
Ransomware programs were detected on 753,684 computers of unique users; 179,209 computers were targeted by encryption ransomware.
Kaspersky Lab’s web antivirus detected 121,262,075 unique malicious objects: scripts, exploits, executable files, etc.
Kaspersky Lab solutions repelled 798,113,087 attacks launched from online resources located all over the world.
34.2% of user computers were subjected to at least one web attack over the year.
To carry out their attacks, cybercriminals used 6,563,145 unique hosts.
24% of web attacks neutralized by Kaspersky Lab products were carried out using malicious web resources located in the US.
Kaspersky Lab’s antivirus solutions detected a total of 4,000,000 unique malicious and potentially unwanted objects.
Vulnerable applications used in cyberattacks
In 2015, we saw the use of new techniques for masking exploits, shellcodes and payloads to make detecting infections and analyzing malicious code more difficult. Specifically, cybercriminals:
Used the Diffie-Hellman encryption protocol
Concealed exploit packs in Flash objects
The detection of two families of critical vulnerabilities for Android was one of the more remarkable events of the year. Exploiting Stagefright vulnerabilities enabled an attacker to remotely execute arbitrary code on a device by sending a specially crafted MMS to the victim’s number. Exploiting Stagefright 2 pursued the same purpose, but this time using a specially crafted media file.
In 2015, there were almost 2M attempts to steal money via online access to bank accounts #KLReport #banking
Tweet
Exploits for Adobe Flash Player were popular among malware writers in 2015. This can be explained by the fact that a large number of vulnerabilities were identified in the product throughout the year. In addition, cybercriminals used the information about unknown Flash Player vulnerabilities that became public as a result of the Hacking Team data breach.
When new Adobe Flash Player vulnerabilities were discovered, developers of various exploit packs were quick to respond by adding new exploits to their products. Here is the ‘devil’s dozen’ of Adobe Flash Player vulnerabilities that gained popularity among cybercriminals and were added to common exploit packs:
CVE-2015-0310
CVE-2015-0311
CVE-2015-0313
CVE-2015-0336
CVE-2015-0359
CVE-2015-3090
CVE-2015-3104
CVE-2015-3105
CVE-2015-3113
CVE-2015-5119
CVE-2015-5122
CVE-2015-5560
CVE-2015-7645
Some well-known exploit packs have traditionally included an exploit for an Internet Explorer vulnerability (CVE-2015-2419). We also saw a Microsoft Silverlight vulnerability (CVE-2015-1671) used in 2015 to infect users. It is worth noting, however, that this exploit is not popular with the main ‘players’ in the exploit market.
Distribution of exploits used in cyberattacks, by type of application attacked, 2015
Vulnerable applications were ranked based on data on exploits blocked by Kaspersky Lab products, used both for online attacks and to compromise local applications, including those on mobile devices.
Although the share of exploits for Adobe Flash Player in our ranking was only 4%, they are quite common in the wild. When looking at these statistics, it should be kept in mind that Kaspersky Lab technologies detect exploits at different stages. As a result, the Browsers category (62%) also includes the detection of landing pages that serve exploits. According to our observations, exploits for Adobe Flash Player are most commonly served by such pages.
We saw the number of cases which involved the use of Java exploits decrease over the year. In late 2014 their proportion of all the exploits blocked was 45%, but this proportion gradually diminished by 32 p.p. during the year, falling to 13%. Moreover, Java exploits have now been removed from all known exploit packs.
At the same time, the use of Microsoft Office exploits increased from 1% to 4%. Based on our observations, in 2015 these exploits were distributed via mass emailing.
Online threats in the banking sector
These statistics are based on the detection verdicts returned by the antivirus module, received from users of Kaspersky Lab products who have consented to provide their statistical data.
The annual statistics for 2015 are based on data received between November 2014 and October 2015.
In 2015, Kaspersky Lab solutions blocked attempts to launch malware capable of stealing money via online banking on 1,966,324 computers. This number is 2.8% higher than in 2014 (1,910,520).
The number of users attacked by financial malware, November 2014-October 2015
Number of users attacked by financial malware in 2014 and 2015
In 2015, the number of attacks grew steadily from February till April, with the peak in March-April. Another burst was recorded in June. In 2014, most users were targeted by financial malware in May and June. During the period between June and October in both 2014 and 2015 the number of users attacked fell gradually.
Geography of attacks
In order to evaluate the popularity of financial malware among cybercriminals and the risk of user computers around the world being infected by banking Trojans, we calculate the percentage of Kaspersky Lab users who encountered this type of threat during the reporting period in the country, relative to all users of our products in the county.
Geography of banking malware attacks in 2015 (users attacked by banking Trojans as a percentage of all users attacked by all types of malware)
TOP 10 countries by percentage of attacked users
Country* % attacked users**
1 Singapore 11.6
2 Austria 10.6
3 Switzerland 10.6
4 Australia 10.1
5 New Zealand 10.0
6 Brazil 9.8
7 Namibia 9.3
8 Hong Kong 9.0
9 Republic of South Africa 8.2
10 Lebanon 6.6
* We excluded those countries in which the number of Kaspersky Lab product users is relatively small (less than 10,000).
** Unique users whose computers have been targeted by web attacks as a percentage of all unique users of Kaspersky Lab products in the country.
Singapore leads this rating. Of all the Kaspersky Lab users attacked by malware in the country, 11.6% were targeted at least once by banking Trojans throughout the year. This reflects the popularity of financial threats in relation to all threats in the country.
5.4% of users attacked in Spain encountered a banking Trojan at least once in 2015. The figure for Italy was 5%; 5.1% in Britain; 3.8% in Germany; 2.9% in France; 3.2% in the US; and 2.5% in Japan.
2% of users attacked in Russia were targeted by banking Trojans.
The TOP 10 banking malware families
The table below shows the Top 10 malware families most commonly used in 2015 to attack online banking users (as a percentage of users attacked):
Name* % users attacked**
1 Trojan-Downloader.Win32.Upatre 42.36
2 Trojan-Spy.Win32.Zbot 26.38
3 Trojan-Banker.Win32.ChePro 9.22
4 Trojan-Banker.Win32.Shiotob 5.10
5 Trojan-Banker.Win32.Banbra 3.51
6 Trojan-Banker.Win32.Caphaw 3.14
7 Trojan-Banker.AndroidOS.Faketoken 2.76
8 Trojan-Banker.AndroidOS.Marcher 2.41
9 Trojan-Banker.Win32.Tinba 2.05
10 Trojan-Banker.JS.Agent 1.88
* These statistics are based on the detection verdicts returned by Kaspersky Lab’s products, received from users of Kaspersky Lab products who have consented to provide their statistical data.
** Unique users whose computers have been targeted by the malicious program, as a percentage of all unique users targeted by financial malware attacks.
The majority of the Top 10 malicious programs work by injecting random HTML code in the web page displayed by the browser and intercepting any payment data entered by the user in the original or inserted web forms.
The Trojan-Downloader.Win32.Upatre family of malicious programs remained at the top of the ranking throughout the year. The malware is no larger than 3.5 KB in size, and is limited to downloading the payload to the victim computer, most typically a banker Trojan from the Dyre/Dyzap/Dyreza family whose main aim is to steal the user’s payment details. Dyre does this by intercepting the data from a banking session between the victim’s browser and the online banking web app, in other words, by using a Man-in-the-Browser (MITB) technique. This malicious program is spread via specially created emails with an attachment containing a document with the downloader. In the summer of 2015, however, Trojan-Downloader.Win32.Upatre was spotted on compromised home routers, which is a testimony to how cybercriminals make use of this multi-purpose malware.
In 2015, #ransomware programs were detected on 753,684 computers of unique users #KLReport
Tweet
Yet another permanent resident of this ranking is Trojan-Spy.Win32.Zbot (in second place) which consistently occupies one of the leading positions. The Trojans of the Zbot family were among the first to use web injections to compromise the payment details of online banking users and to modify the contents of banking web pages. They encrypt their configuration files at several levels; the decrypted configuration file is never stored in the memory in its entirety, but is instead loaded in parts.
Representatives of the Trojan-Banker.Win32.ChePro family were first detected in October 2012. At that time, these banking Trojans were mostly aimed at users in Brazil, Portugal and Russia. Now they are being used to attack the users worldwide. Most programs of this type are downloaders which need other files to successfully infect the system. Generally, they are malicious banking programs, allowing the fraudsters to take screenshots, to intercept keystrokes, and to read the content of the copy buffer, i.e. they possess functionality that allows a malicious program to be used for attacks on almost any online banking system.
Of particular interest is the fact that two families of mobile banking Trojans are present in this ranking: Faketoken and Marcher. The malicious programs belonging to the latter family steal payment details from Android devices.
The representatives of the Trojan-Banker.AndroidOS.Faketoken family work in partnership with computer Trojans. To distribute this malware, cybercriminals use social engineering techniques. When a user visits his online banking account, the Trojan modifies the page, asking him to download an Android application which is allegedly required to securely confirm the transaction. In fact the link leads to the Faketoken application. Once Faketoken is on the user’s smartphone, the cybercriminals gain access to the user’s banking account via the computer infected with the banking Trojan and the compromised mobile device allows them to intercept the one-time confirmation code (mTAN).
The second family of mobile banking Trojans is Trojan-Banker.AndroidOS.Marcher. After infecting a device, the malware tracks the launch of just two apps – the mobile banking customer of a European bank and Google Play. If the user starts Google Play, Marcher displays a false window requesting credit card details which then go to the fraudsters. The same method is used by the Trojan if the user starts the banking application.
Tenth place in the 2015 ranking was occupied by the Trojan-Banker.JS.Agent family. This is the malicious JavaScript code that results from an injection into an online banking page. The aim of this code is to intercept payment details that the user enters into online banking forms.
2015 – an interesting year for ransomware
The Trojan-Ransom class represents malware intended for the unauthorized modification of user data that renders a computer inoperable (for example, encryptors), or for blocking the normal operation of a computer. In order to decrypt files and unblock a computer the malware owners usually demand a ransom from the victims.
Since its emergence with CryptoLocker in 2013, ransomware has come a long way. For example, in 2014 we spotted the first version of ransomware for Android. Just a year later, 17% of the infections we saw were on Android devices.
2015 also saw the first ransomware for Linux, which can be found in the Trojan-Ransom.Linux class. On the positive side, the malware authors made a small implementation error, which makes it possible to decrypt the files without paying a ransom.
Unfortunately, these implementation errors are occurring less and less. This prompted the FBI to state: “The ransomware is that good… To be honest, we often advise people just to pay the ransom”. That this is not always a good idea was also shown this year, when the Dutch police were able to apprehend two suspects behind the CoinVault malware. A little later we received all 14,000 encryption keys, which we added to a new decryption tool. All the CoinVault victims were then able to decrypt their files for free.
In 2015, 179,209 computers were targeted by encryption #ransomware #KLReport
Tweet
2015 was also the year that marked the birth of TeslaCrypt. TeslaCrypt has a history of using graphical interfaces from other ransomware families. Initially it was CryptoLocker, but this later changed to CryptoWall. This time they copied the HTML page in full from CryptoWall 3.0, only changing the URLs.
Number of users attacked
The following graph shows the rise in users with detected Trojan-Ransom within the last year:
Number of users attacked by Trojan-Ransom malware (Q4 2014 – Q3 2015)
Overall in 2015, Trojan-Ransom was detected on 753,684 computers. Ransomware is thus becoming more and more of a problem.
TOP 10 Trojan-Ransom families
The Top 10 most prevalent ransomware families are represented here. The list consists of browser-based extortion or blocker families and some notorious encryptors. So-called Windows blockers that restrict access to a system (for example, the Trojan-Ransom.Win32.Blocker family) and demand a ransom were very popular a few years ago – starting off in Russia then moving west – but are not as widespread anymore and are not represented in the Top 10.
Name* Users percentage**
1 Trojan-Ransom.HTML.Agent 38.0
2 Trojan-Ransom.JS.Blocker 20.7
3 Trojan-Ransom.JS.InstallExtension 8.0
4 Trojan-Ransom.NSIS.Onion 5.8
5 Trojan-Ransom.Win32.Cryakl 4.3
6 Trojan-Ransom.Win32.Cryptodef 3.1
7 Trojan-Ransom.Win32.Snocry 3.0
8 Trojan-Ransom.BAT.Scatter 3.0
9 Trojan-Ransom.Win32.Crypmod 1.8
10 Trojan-Ransom.Win32.Shade 1.8
*These statistics are based on the detection verdicts returned by Kaspersky Lab products, received from users of Kaspersky Lab products who have consented to provide their statistical data.
** Percentage of users attacked by a Trojan-Ransom family relative to all users attacked with Trojan-Ransom malware.
First place is occupied by Trojan-Ransom.HTML.Agent (38%) with the Trojan-Ransom.JS.Blocker family (20.7%) in second. They represent browser-blocking web pages with various unwanted content usually containing the extortion message (for example, a “warning” from a law enforcement agency) or containing JavaScript code that blocks the browser along with a message.
In third place is Trojan-Ransom.JS.InstallExtension (8%), a browser-blocking web page that imposes a Chrome extension installation on the user. When attempting to close the page a voice mp3 file is often played: “In order to close the page, press the ‘Add’ button”. The extensions involved are not harmful, but the offer is very obtrusive and difficult for the user to reject. This kind of extension propagation is used by a partnership program. These three families are particularly prevalent in Russia and almost as prevalent in some post-Soviet countries.
When we look at where ransomware is most prevalent (not just the three families mentioned above), we see that the top three consists of Kazakhstan, Russia and Ukraine.
Cryakl became relatively active in Q3 2015, when we saw peaks of up to 2300 attempted infections a day. An interesting aspect of Cryakl is its encryption scheme. Rather than encrypting the whole file, Cryakl encrypts the first 29 bytes plus three other blocks located randomly in the file. This is done to evade behavioral detection, while encrypting the first 29 bytes destroys the header.
In 2015, @kaspersky web antivirus detected 121,262,075 unique malicious objects #KLReport
Tweet
Cryptodef is the infamous Cryptowall ransomware. Cryptowall is found most often, in contrast to the other families discussed here, in the US. In fact, there are three times as many infections in the US than there are in Russia. Cryptowall is spread through spam emails, where the user receives a zipped JavaScript. Once executed, the JavaScript downloads Сryptowall and it starts encrypting files. A change in the ransom message is also observed: victims are now congratulated by the malware authors on “becoming part of the large Cryptowall community”.
Encryptors can be implemented not only as executables but also using simple scripting languages, as in the case of the Trojan-Ransom.BAT.Scatter family. The Scatter family appeared in 2014 and quickly evolved, providing itself with the functionality of Email-Worm and Trojan-PSW. Encryption makes use of two pairs of assymetric keys, making it possible to encrypt the user’s files without revealing their private key. It employs renamed legitimate utilities to encrypt files.
The Trojan-Ransom.Win32.Shade encryptor, which is also very prevalent in Russia, is able to request a list from the C&C server containing the URLs of additional malware. It then downloads that malware and installs it in the system. All its C&C servers are located in the Tor network. Shade is also suspected of propagating via a partnership program.
TOP 10 countries attacked by Trojan-Ransom malware
Country* % of users attacked by Trojan-Ransom**
1 Kazakhstan 5.47
2 Ukraine 3.75
3 Russian Federation 3.72
4 Netherlands 1.26
5 Belgium 1.08
6 Belarus 0.94
7 Kyrgyzstan 0.76
8 Uzbekistan 0.69
9 Tajikistan 0.69
10 Italy 0.57
* We excluded those countries in which the number of Kaspersky Lab product users is relatively small (less than 10,000).
**Unique users whose computers have been targeted by Trojan-Ransom as a percentage of all unique users of Kaspersky Lab products in the country.
Encryptors
Even if today’s encryptors are not as popular among cybercriminals as blockers were, they inflict more damage on users. So it’s worth investigating them separately.
The number of new Trojan-Ransom encryptors
The following graph represents the rise of newly created encryptor modifications per year.
Number of Trojan-Ransom encryptor modifications in Kaspersky Lab’s Virus Collection (2013 – 2015)
The overall number of encryptor modifications in our Virus Collection to date is at least 11,000. Ten new encryptor families were created in 2015.
The number of users attacked by encryptors
Number of users attacked by Trojan-Ransom encryptor malware (2012 – 2015)
In 2015, 179,209 unique users were attacked by encryptors. About 20% of those attacked were in the corporate sector.
It is important to keep in mind that the real number of incidents is several times higher: the statistics reflect only the results of signature-based and heuristic detections, while in most cases Kaspersky Lab products detect encryption Trojans based on behavior recognition models.
Top 10 countries attacked by encryptors
Country* % of users attacked by encryptors
1 Netherlands 1.06
2 Belgium 1.00
3 Russian Federation 0.65
4 Brazil 0.44
5 Kazakhstan 0.42
6 Italy 0.36
7 Latvia 0.34
8 Turkey 0.31
9 Ukraine 0.31
10 Austria 0.30
* We excluded those countries in which the number of Kaspersky Lab product users is relatively small (less than 10,000).
**Unique users whose computers have been targeted by Trojan-Ransom encryptor malware as a percentage of all unique users of Kaspersky Lab products in the country.
First place is occupied by the Netherlands. The most widespread encryptor family is CTB-Locker (Trojan-Ransom.Win32/NSIS.Onion). In 2015 an affiliate program utilizing CTB-Locker was launched and new languages were added including Dutch. Users are mainly infected by emails with malicious attachments. It appears there may be a native Dutch speaker involved in the infection campaign, as the emails are written in relatively good Dutch.
A similar situation exists in Belgium: CTB-Locker is the most widespread encryptor there, too.
In Russia, Trojan-Ransom.Win32.Cryakl tops the list of encryptors targeting users.
Online threats (Web-based attacks)
The statistics in this section were derived from web antivirus components that protect users from attempts to download malicious objects from a malicious/infected website. Malicious websites are deliberately created by malicious users; infected sites include those with user-contributed content (such as forums), as well as compromised legitimate resources.
The TOP 20 malicious objects detected online
Throughout 2015, Kaspersky Lab’s web antivirus detected 121,262,075 unique malicious objects: scripts, exploits, executable files, etc.
We identified the 20 malicious programs most actively involved in online attacks launched against computers in 2015. As in the previous year, advertising programs and their components occupy 12 positions in that Top 20. During the year, advertising programs and their components were registered on 26.1% of all user computers where our web antivirus is installed. The increase in the number of advertising programs, their aggressive distribution methods and their efforts to counteract anti-virus detection, continue the trend of 2014.
In 2015, @kaspersky solutions repelled ~800M attacks launched from online resources around the world #KLReport
Tweet
Although aggressive advertising does annoy users, it does not harm computers. That is why we have compiled another rating of exclusively malicious objects detected online that does not include the Adware or Riskware classes of program. These 20 programs accounted for 96.6% of all online attacks.
Name* % of all attacks**
1 Malicious URL 75.76
2 Trojan.Script.Generic 8.19
3 Trojan.Script.Iframer 8.08
4 Trojan.Win32.Generic 1.01
5 Expoit.Script.Blocker 0.79
6 Trojan-Downloader.Win32.Generic 0.69
7 Trojan-Downloader.Script.Generic 0.36
8 Trojan.JS.Redirector.ads 0.31
9 Trojan-Ransom.JS.Blocker.a 0.19
10 Trojan-Clicker.JS.Agent.pq 0.14
11 Trojan-Downloader.JS.Iframe.diq 0.13
12 Trojan.JS.Iframe.ajh 0.12
13 Exploit.Script.Generic 0.10
14 Packed.Multi.MultiPacked.gen 0.09
15 Exploit.Script.Blocker.u 0.09
16 Trojan.Script.Iframer.a 0.09
17 Trojan-Clicker.HTML.Iframe.ev 0.09
18 Hoax.HTML.ExtInstall.a 0.06
19 Trojan-Downloader.JS.Agent.hbs 0.06
20 Trojan-Downloader.Win32.Genome.qhcr 0.05
* These statistics represent detection verdicts from the web antivirus module. Information was provided by users of Kaspersky Lab products who consented to share their local data.
** The percentage of all malware web attacks recorded on the computers of unique users.
As is often the case, the TOP 20 is largely made up of objects used in drive-by attacks. They are heuristically detected as Trojan.Script.Generic, Expoit.Script.Blocker, Trojan-Downloader.Script.Generic, etc. These objects occupy seven positions in the ranking.
Malicious URL in first place is the verdict identifying links from our black list (links to web pages containing redirects to exploits, sites with exploits and other malicious programs, botnet control centers, extortion websites, etc.).
The Trojan.JS.Redirector.ads verdict (8th place) is assigned to script that cybercriminals place on infected web resources. It redirects users to other websites, such as those of online casinos. The fact that this verdict is included in the rating should serve as a reminder to web administrators of how easily their sites can be automatically infected by programs – even those that are not very complex.
In 2015, 34.2% of user computers were subjected to at least one web attack #KLReport
Tweet
The Trojan-Ransom.JS.Blocker.a verdict (9th place) is a script that tries to block the browser by means of a cyclic update of the page, and displays a message stating that a “fine” needs to be paid for viewing inappropriate materials. The user is told to transfer the money to a specified digital wallet. This script is mostly found on pornographic sites and is detected in Russia and CIS countries.
The script with the Trojan-Downloader.JS.Iframe.djq verdict (11th place) is found on infected sites running under WordPress, Joomla and Drupal. The campaign launched to infect sites with this script began on a massive scale in August 2015. First, it sends information about the header of the infected page, the current domain, and the address from which the user landed on the page with the script to the fraudsters’ server. Then, by using iframe, another script is downloaded in the user’s browser. It collects information about the system on the user’s computer, the time zone and the availability of Adobe Flash Player. After this and a series of redirects, the user ends up on sites that prompt him to install an update for Adobe Flash Player that is actually adware, or to install browser plugins.
The TOP 10 countries where online resources are seeded with malware
The following statistics are based on the physical location of the online resources that were used in attacks and blocked by our antivirus components (web pages containing redirects to exploits, sites containing exploits and other malware, botnet command centers, etc.). Any unique host could be the source of one or more web attacks. The statistics do not include sources used for distributing advertising programs or hosts linked to advertising program activity.
In order to determine the geographical source of web-based attacks, domain names are matched up against their actual domain IP addresses, and then the geographical location of a specific IP address (GEOIP) is established.
In 2015, Kaspersky Lab solutions blocked 798,113,087 attacks launched from web resources located in various countries around the world. To carry out their attacks, the fraudsters used 6,563,145 unique hosts.
80% of notifications about attacks blocked by antivirus components were received from online resources located in 10 countries.
The distribution of online resources seeded with malicious programs in 2015
The top four countries where online resources are seeded with malware remained unchanged from the previous year. France moved up from 7th to 5th place (5.07%) while Ukraine dropped from 5th to 7th position (4.16%). Canada and Vietnam left the Top 20. This year’s newcomers, China and Sweden, were in 9th and 10th places respectively.
This rating demonstrates that cybercriminals prefer to operate and use hosting services in different countries where the hosting market is well-developed.
Countries where users face the greatest risk of online infection
In order to assess the countries in which users most often face cyber threats, we calculated how often Kaspersky Lab users encountered detection verdicts on their machines in each country. The resulting data characterizes the risk of infection that computers are exposed to in different countries across the globe, providing an indicator of the aggressiveness of the environment facing computers in different parts of the world.
The TOP 20 countries where users face the greatest risk of online infection
Country* % of unique users**
1 Russia 48.90
2 Kazakhstan 46.27
3 Azerbaijan 43.23
4 Ukraine 40.40
5 Vietnam 39.55
6 Mongolia 38.27
7 Belarus 37.91
8 Armenia 36.63
9 Algeria 35.64
10 Qatar 35.55
11 Latvia 34.20
12 Nepal 33.94
13 Brazil 33.66
14 Kyrgyzstan 33.37
15 Moldova 33.28
16 China 33.12
17 Thailand 32.92
18 Lithuania 32.80
19 UAE 32.58
20 Portugal 32.31
These statistics are based on the detection verdicts returned by the web antivirus module, received from users of Kaspersky Lab products who have consented to provide their statistical data.
* We excluded those countries in which the number of Kaspersky Lab product users is relatively small (less than 10,000).
** Unique users whose computers have been targeted by web attacks as a percentage of all unique users of Kaspersky Lab products in the country.
In 2015, cybercriminals used 6,563,145 unique hosts to carry out their attacks #KLReport
Tweet
In 2015, the top three saw no change from the previous year. Russia remained in first place although the percentage of unique users in the country decreased by 4.9 p.p.
Germany, Tajikistan, Georgia, Saudi Arabia, Austria, Sri Lanka and Turkey left the Top 20. Among the newcomers are Latvia, Nepal, Brazil, China, Thailand, the United Arab Emirates and Portugal.
The countries can be divided into three groups that reflect the different levels of infection risk.
The high risk group (over 41%)
In 2015, this group includes the first three countries from the Top 20 – Russia, Kazakhstan and Azerbaijan.
The medium risk group (21-40.9%)
This group includes 109 countries; among them are France (32.1%), Germany (32.0%), India (31.6%), Spain (31.4%), Turkey (31.0%), Greece (30.3%), Canada (30.2%), Italy (29.4%), Switzerland (28.6%), Australia (28.0%), Bulgaria (27.0%), USA (26.4%), Georgia (26, 2%), Israel (25.8%), Mexico (24.3%), Egypt (23.9%), Romania (23.4%), UK (22.4%), Czech Republic (22.0% ), Ireland (21.6%), and Japan (21.1%).
The low risk group (0-20.9%)
The 52 countries with the safest online surfing environments include Kenya (20.8%), Hungary (20.7%), Malta (19.4%), the Netherlands (18.7%), Norway (18.3%), Argentina (18.3%), Singapore (18,2%), Sweden (18%), South Korea (17.2%), Finland (16.5%), and Denmark (15, 2%).
In 2015, 34.2% of computers were attacked at least once while their owners were online.
On average, the risk of being infected while surfing the Internet decreased by 4.1 p.p. over the year. This could be due to several factors:
Firstly, developers of browsers and search engines realized the necessity of securing their users and started to contribute to the fight against malicious sites
Secondly, users are using more and more mobile devices and tablets to surf the Internet.
Thirdly, many exploit packs have started to check if Kaspersky Lab’s product is installed on the user’s computer. If it is, the exploits do not even try to attack the computer.
Local threats
Local infection statistics for user computers are a very important indicator: they reflect threats that have penetrated computer systems by infecting files or removable media, or initially got on the computer in an encrypted format (for example, programs integrated in complex installers, encrypted files, etc.). In addition, these statistics include objects detected on user computers after the first scan of the system by Kaspersky Lab’s file antivirus.
This section contains an analysis of the statistical data obtained based on antivirus scans of files on the hard drive at the moment they are created or accessed, and the results of scanning various removable data storages.
In 2015, 24% of web attacks neutralized by @kaspersky were carried out using malicious sites located in US #KLReport
Tweet
In 2015, Kaspersky Lab’s antivirus solutions detected 4 million unique malicious and potentially unwanted objects, a twofold increase from the previous year.
The TOP 20 malicious objects detected on user computers
For this rating we identified the 20 most frequently detected threats on user computers in 2015. This rating does not include the Adware and Riskware classes of program.
Name* % of unique attacked users**
1 DangerousObject.Multi.Generic 39.70
2 Trojan.Win32.Generic 27.30
3 Trojan.WinLNK.StartPage.gena 17.19
4 Trojan.Win32.AutoRun.gen 6.29
5 Virus.Win32.Sality.gen 5.53
6 Worm.VBS.Dinihou.r 5.40
7 Trojan.Script.Generic 5.01
8 DangerousPattern.Multi.Generic 4.93
9 Trojan-Downloader.Win32.Generic 4.36
10 Trojan.WinLNK.Agent.ew 3.42
11 Worm.Win32.Debris.a 3.24
12 Trojan.VBS.Agent.ue 2.79
13 Trojan.Win32.Autoit.cfo 2.61
14 Virus.Win32.Nimnul.a 2.37
15 Worm.Script.Generic 2.23
16 Trojan.Win32.Starter.lgb 2.04
17 Worm.Win32.Autoit.aiy 1.97
18 Worm.Win32.Generic 1.94
19 HiddenObject.Multi.Generic 1.66
20 Trojan-Dropper.VBS.Agent.bp 1.55
These statistics are compiled from malware detection verdicts generated by the on-access and on-demand scanner modules on the computers of those users running Kaspersky Lab products who consented to submit their statistical data.
* Malware detection verdicts generated by the on-access and on-demand scanner modules on the computers of those users running Kaspersky Lab products who consented to submit their statistical data.
** The proportion of individual users on whose computers the antivirus module detected these objects as a percentage of all individual users of Kaspersky Lab products on whose computers a malicious program was detected.
The DangerousObject.Multi.Generic verdict, which is used for malware detected with the help of cloud technologies, is in 1st place (39.7%). Cloud technologies work when the antivirus databases do not yet contain either signatures or heuristics to detect a malicious program but the company’s cloud antivirus database already has information about the object. In fact, this is how the very latest malware is detected.
In 2015, @kaspersky solutions detected a total of 4M unique malicious & potentially unwanted objects #KLReport
Tweet
The proportion of viruses continues to decrease: for example, last year Virus.Win32.Sality.gen affected 6.69% of users while in 2015 – only 5.53%. For Virus.Win32.Nimnul these figures are 2.8% in 2014 and 2.37% in 2015. The Trojan-Dropper.VBS.Agent.bp verdict, which is 20th in the rating, is a VBS script that extracts Virus.Win32.Nimnul from itself and saves in to the disk.
In addition to heuristic verdicts and viruses the Top 20 includes verdicts for worms spread on removable media and their components. Their presence in this rating is due to the nature of their distribution and creation of multiple copies. A worm can continue to self-proliferate for a long time even if its management servers are no longer active.
Countries where users face the highest risk of local infection
For each country we calculated the number of file antivirus detections the users faced during the year. The data includes detected objects located on user computers or on removable media connected to the computers, such as flash drives, camera and phone memory cards, or external hard drives. This statistic reflects the level of infected personal computers in different countries around the world.
The TOP 20 countries by the level of infection
Country* % of unique users**
1 Vietnam 70.83
2 Bangladesh 69.55
3 Russia 68.81
4 Mongolia 66.30
5 Armenia 65.61
6 Somali 65.22
7 Georgia 65.20
8 Nepal 65.10
9 Yemen 64.65
10 Kazakhstan 63.71
11 Iraq 63.37
12 Iran 63.14
13 Laos 62.75
14 Algeria 62.68
15 Cambodia 61.66
16 Rwanda 61.37
17 Pakistan 61.36
18 Syria 61.00
19 Palestine 60.95
20 Ukraine 60.78
These statistics are based on the detection verdicts returned by the antivirus module, received from users of Kaspersky Lab products who have consented to provide their statistical data.
* When calculating, we excluded countries where there are fewer than 10,000 Kaspersky Lab users.
** The percentage of unique users in the country with computers that blocked local threats as a percentage of all unique users of Kaspersky Lab products.
For the third year in a row Vietnam topped the rating. Mongolia and Bangladesh swapped places – Bangladesh climbed from 4th to 2nd, while Mongolia moved from 2nd to 4th. Russia, which was not in last year’s Top 20, came third in 2015.
India, Afghanistan, Egypt, Saudi Arabia, Sudan, Sri Lanka, Myanmar, and Turkey all left the Top 20. The newcomers were Russia, Armenia, Somalia, Georgia, Iran, Rwanda, the Palestinian territories, and Ukraine.
In the Top 20 countries at least one malicious object was found on an average of 67.7% of computers, hard drives or removable media belonging to KSN users. The 2014 the figure was 58.7%.
The countries can be divided into several risk categories reflecting the level of local threats.
Maximum risk (over 60%): 22 countries, including Kyrgyzstan (60.77%), Afghanistan (60.54%)
High risk (41-60%): 98 countries including India (59.7%), Egypt (57.3%), Belarus (56.7%), Turkey (56.2%), Brazil (53.9%), China (53.4%), UAE (52.7%), Serbia (50.1%), Bulgaria (47.7%), Argentina (47.4%), Israel (47.3%), Latvia (45.9%), Spain (44.6%), Poland (44.3%), Germany (44%), Greece (42.8%), France (42.6%), Korea (41.7%), Austria (41.7%).
Moderate local infection rate (21-40.99%): 45 countries including Romania (40%), Italy (39.3%), Canada (39.2%), Australia (38.5%), Hungary (38.2%), Switzerland (37.2%), USA (36.7%), UK (34.7%), Ireland (32.7%), Netherlands (32.1%), Czech Republic (31.5%), Singapore (31.4%), Norway (30.5%), Finland (27.4%), Sweden (27.4%), Denmark (25.8%), Japan (25.6%).
The 10 safest countries were:
Country % of unique users*
1 Cuba 20.8
2 Seychelles 25.3
3 Japan 25.6
4 Denmark 25.8
5 Sweden 27.4
6 Finland 27.4
7 Andorra 28.7
8 Norway 30.5
9 Singapore 31.4
10 Czech Republic 31.5
* The percentage of unique users in the country with computers that blocked local threats as a percentage of all unique users of Kaspersky Lab products.
The appearance of Andorra, replacing Martinique, was the only change to this rating in 2015 compared to the previous year.
On average, 26.9% of user computers were attacked at least once during the year in the 10 safest countries. This is an increase of 3.9 p.p. compared to 2014.
Conclusion
Based on analysis of the statistics, we can highlight the main trends in cybercriminal activity:
Some of those involved in cybercrime are looking to minimize the risk of criminal prosecution and switching from malware attacks to the aggressive distribution of adware.
The proportion of relatively simple programs used in mass attacks is growing. This approach allows the attackers to quickly update malware which enhances the effectiveness of attacks.
Attackers have mastered non-Windows platforms – Android and Linux: almost all types of malicious programs are created and used for these platforms.
Cybercriminals are making active use of Tor anonymization technology to hide command servers, and Bitcoins for making transactions.
An increasing proportion of antivirus detections fall into a ‘gray zone’. This applies primarily to a variety of advertising programs and their modules. In our 2015 ranking of web-based threats, the representatives of this class of program occupy 12 places in the Top 20. During the year, advertising programs and their components were registered on 26.1% of all user computers where our web antivirus is installed. The growth in the volume of advertising programs, along with their aggressive distribution methods and attempts to counteract anti-virus detection, continues the trend of 2014. Spreading adware earns good money, and in the pursuit of profit the authors sometimes use the tricks and technologies typical of malicious programs.
In 2015, virus writers demonstrated a particular interest in exploits for Adobe Flash Player. According to our observations, landing pages with exploits are often downloaded by exploits for Adobe Flash Player. There are two factors at play here: firstly, a large number of vulnerabilities were detected in the product over the year; secondly, as a result of a data leak by Hacking Team, information about previously unknown vulnerabilities in Flash Player were made public, and attackers wasted no time in taking advantage.
The banking Trojan sphere witnessed an interesting development in 2015. The numerous modifications of ZeuS, which had continuously topped the ranking of the most commonly used malware families for several years, were dethroned by Trojan-Banker.Win32.Dyreza. Throughout the year, the rating for malicious programs designed to steal money via Internet banking systems was headed by Upatre, which downloads banking Trojans from the family known as Dyre/Dyzap/Dyreza to victims’ computers. In the banking Trojan sector as a whole, the share of users attacked by Dyreza exceeded 40%. The banker uses an effective of web injection method in order to steal data to access the online banking system.
Also of note is the fact that two families of mobile banking Trojans – Faketoken and Marcher – were included in the Top 10 banking Trojans most commonly used in 2015. Based on current trends, we can assume that next year mobile bankers will account for a much greater percentage in the rating.
In 2015, there were a number of changes in the ransomware camp:
While the popularity of blockers is gradually falling, the number of users attacked by encryption ransomware increased by 48.3% in 2015. Encrypting files instead of simply blocking the computer is a method that in most cases makes it very difficult for the victims to regain access to their information. The attackers are especially active in utilizing encryption ransomware for attacks on business users, who are more likely to pay a ransom than ordinary home users. This is confirmed by the appearance in 2015 of the first ransomware for Linux, targeting web servers.
At the same time, encryptors are becoming multi-module and, in addition to encryption, include functionality designed to steal data from user computers.
While Linux may only now have attracted the attention of fraudsters, the first ransomware Trojan for Android was detected back in 2014. In 2015, the number of attacks aimed at the Android OS grew rapidly, and by the end of the year 17% of attacks involving ransomware were blocked on Android devices.
The threat is actively spreading all over the planet: Kaspersky Lab products detected ransomware Trojans in 200 countries and territories, which is practically everywhere.
We expect that in 2016 cybercriminals will continue to develop encryption ransomware that targets non-Windows platforms: the proportion of encryptors targeting Android will increase, while others will emerge for Mac. Given that Android is widely used in consumer electronics, the first ransomware attack on ‘smart’ devices may occur.
You can’t be invulnerable, but you can be well protected
23.12.2015
Software vulnerabilities are one of those problems that potentially affect all users. A vulnerability is a fault in a program’s implementation that can be used by attackers to gain unauthorized access to data, inject malicious code or put a system out of operation. In most cases, vulnerabilities arise from a lack of attention to fine details at the design stage rather than programming errors. Sometimes a system can seem virtually invulnerable at the design stage, but then, at some point, a new technology arises and hackers prove that the system can be successfully attacked. A notable example is DES – a symmetric-key encryption algorithm developed in 1975, which was considered bulletproof at the time. However, in 1990 it was successfully broken in 39 days using an enormous computer network. A supercomputer built in 1998 succeeded in breaking DES in less than three days.
Continually testing popular software to identify vulnerabilities and releasing patches to close any vulnerabilities found is part of a program’s normal lifecycle. The more sophisticated and popular the program the higher the chances of vulnerabilities being found in it.
Searching for vulnerabilities
Most developers try to close any vulnerabilities found in their products in a timely manner. They analyze their software independently or with the help of external experts. However, third-party researchers also hunt for vulnerabilities. Some do this to improve the overall level of security online. Others are paid to search for vulnerabilities. Still others prefer to sell information on any vulnerabilities they discover on the black market.
They can do this because information on new vulnerabilities is valuable for cybercriminals. If a researcher finds a flaw in a system and proves that it can be exploited in practice (that is, if he writes an exploit), he can make tens of thousands of dollars on the black market. There is an entire sector of the cybercriminal underworld that specializes in finding and selling vulnerabilities.
Luckily, this business does not operate on a mass scale. One reason for this is that not all vulnerabilities can be exploited in the real world. A combination of different conditions is often needed to be able to do real harm and the chances of these combinations arising are not very high. A second reason is that it takes a highly skilled programmer to write an effective exploit, and there are not many of them around.
One more option for making money on vulnerabilities is to sell them to third-party companies that, at first glance, seem to have nothing to do with crime. This is what some researchers do. However, these companies may be involved in creating spyware for governments or special services, so the vulnerabilities will still be used to illegitimately manipulate information systems. Moreover, it turns out that the security of such companies is not always as good as it ought to be, so occasionally external parties are able to gain access to their knowledge, with dire consequences.
Idealists, who search for vulnerabilities for the sake of universal security, face a dilemma. On the one hand, the later they publicly announce their discovery, the more time the developers have to fix the problem. On the other, the earlier they publish the information the sooner users will learn about the danger posed by the vulnerability. In theory, cybercriminals might also discover the vulnerability and immediately take advantage of it. It should also be kept in mind that disclosing the information will inevitably result in attempts to abuse the newly discovered vulnerability. Sometimes, attacks can start within an hour of making information about a vulnerability public. This is what happened, for example, after the Shellshock disclosure.
What are the dangers of vulnerabilities?
An exploit is a program or code fragment that uses vulnerabilities to attack a computing system. In some cases, an exploit is used on a mass scale – that is, cybercriminals try to use it to attack a broad range of systems. In such cases, vulnerabilities in popular software (such as the Adobe Flash Player) are exploited to deliver payloads to user machines. This is commonly done via so-called drive-by attacks that attempt to download malicious code to the computers of all users visiting an infected website.
Sometimes cybercriminals develop targeted attacks. They analyze the software used by a particular company and write targeted exploits for those specific programs. One such highly tailored attack was carried out as part of the Duqu 2.0 APT.
The ‘useful’ life of exploits can vary. Some are used for years, even though developers release patches that close the relevant vulnerabilities. This is because some users are in no hurry to install those patches.
According to Kaspersky Lab data, today cybercriminals extensively use exploits for the vulnerabilities listed below:
Software product Vulnerability
Adobe Flash Player
CVE-2015-0310
CVE-2015-0311
CVE-2015-0313
CVE-2015-0336
CVE-2015-0359
CVE-2015-3090
CVE-2015-3104
CVE-2015-3105
CVE-2015-3113
CVE-2015-5119
CVE-2015-5122
CVE-2015-5560
CVE-2015-7645
Microsoft Internet Explorer
CVE-2014-6332
CVE-2015-2419
Microsoft Office CVE-2012-0158
Microsoft Windows CVE-2015-1701
It is easy to see from CVE identifiers that most of these vulnerabilities were discovered this year, but there are also some that date back to 2014 and even 2012. The fact that these vulnerabilities are still being exploited means that many users have not bothered to update the relevant software.
Defending against exploits
The main recommendations are really quite simple: remember to update your software regularly and do not use outdated software. The latter piece of advice can be hard to follow: it is sometimes difficult to find a new alternative to a familiar and convenient program that is outdated. While developers do not track vulnerabilities in obsolete software or release patches for them, cybercriminals continue to watch for an opportunity to exploit. The upshot is that you need additional protection to continue using such software.
There are dedicated tools designed to scan computers for known vulnerabilities and, if detected, automatically install updates. These tools include, for example, Kaspersky Systems Management components Vulnerability Assessment and Patch Management. Kaspersky Lab is also developing a similar solution for home users called Kaspersky Software Updater. The utility is currently in beta testing.
Kaspersky Lab uses a vulnerability naming system that is different from the codes used in the CVE (Common Vulnerabilities and Exposures) system. While an identifier in CVE always corresponds to one vulnerability, a code in our system can match a group of vulnerabilities (in most cases, vulnerabilities closed with one patch or vulnerabilities in one version of a program) – sometimes dozens of vulnerabilities are covered by one code (depending on the patches released by software vendors). As a result, the 20 KLA vulnerabilities listed below actually match 375 CVE vulnerabilities.
According to Kaspersky Security Network statistics, vulnerability scanning most often identifies the following sets of vulnerabilities on our users’ machines:
KLA Number of users Date of discovery Description
1 KLA10680 308219 2015-10-14 Code execution vulnerability in Adobe Flash Player
2 KLA10036 256383 2014-07-08 Multiple vulnerabilities in Adobe Flash and Adobe AIR
3 KLA10492 228454 2013-10-16 Multiple vulnerabilities in Oracle products
4 KLA10670 182972 2015-09-21 Multiple vulnerabilities in Adobe products
5 KLA10650 176435 2015-08-11 Multiple vulnerabilities in Adobe products
6 KLA10653 150987 2015-05-18 Code execution vulnerability in QuickTime
7 KLA10682 150960 2015-10-13 Multiple vulnerabilities in Adobe Acrobat and Reader
8 KLA10628 138039 2015-07-14 Multiple vulnerabilities in Adobe Acrobat
9 KLA10651 135291 2015-08-17 Code injection vulnerability in VLC Media Player
10 KLA10655 134824 2015-09-01 Multiple vulnerabilities in Google Chrome
11 KLA10672 108722 2015-09-22 Multiple vulnerabilities in Mozilla Firefox
12 KLA10654 107661 2015-08-27 Multiple vulnerabilities in Mozilla Firefox
13 KLA10691 103880 2015-11-10 Multiple vulnerabilities in Google Chrome
14 KLA10344 100311 2009-11-05 Multiple vulnerabilities in Sun Java SE
15 KLA10669 92345 2015-09-16 Multiple vulnerabilities in Apple iTunes
16 KLA10684 91013 2015-10-22 Code execution vulnerability in Flash plugin for Google Chrome
17 KLA10663 87898 2015-09-08 Code execution vulnerability in Adobe Shockwave Player
18 KLA10690 87478 2015-11-10 Multiple vulnerabilities in Adobe products
19 KLA10569 86657 2015-04-28 Vulnerability in OpenOffice
20 KLA10671 84380 2015-09-21 Flash Player update for Google Chrome
Vulnerability sets KLA10680 and KLA10650 are particularly notable. The former includes, among others, CVE-2015-7645, the latter — CVE-2015-5560. These vulnerabilities are also present in the first table above, which lists the most commonly exploited software flaws.
Naturally, security products also include technologies designed to block attempts to exploit vulnerabilities. They closely track application behavior (particularly that of applications known to be prone to vulnerabilities), identify and block suspicious activity.
How is the security industry doing?
Vulnerabilities can be found in security solutions, just like in any other software products. The only difference is that security vendors have a much greater responsibility, because security software is essentially the last line of defense. That is why Internet security companies are especially careful and thorough when it comes to checking products for vulnerabilities.
We cannot speak for the industry as a whole, so we are going to use the only example we are familiar with – that is, our own. We keep the security of our products in mind at all stages of development, from defining the attack surface at the design stage to special testing procedures aimed at identifying possible vulnerabilities in products that are nearly ready to be released. In the process of development, R&D staff not only create the necessary product functionality but also make certain that the new features cannot be used to compromise the program’s integrity.
We believe that this approach is more effective than a dedicated team responsible for tracking vulnerabilities in all of the company’s products. Which is not to say that we do not have such a team. A group of security architects regularly checks newly developed code for vulnerabilities using fuzz testing (so-called fuzzing) and penetration testing.
Fuzzing essentially means checking a program for unintended operations by inputting incorrect or random data. In other words, products are tested on abnormal or distorted data sets.
Penetration testing is carried out both internally and by external experts. It should be noted at this point, however, that in our experience, few external experts are sufficiently knowledgeable about the way security products work and can therefore effectively search for vulnerabilities. Additionally, Kaspersky Lab has a special team that specializes in searching third-party code for vulnerabilities (its services are used, among others, by banks seeking to verify the security of their applications). Even though third-party applications are the team’s top priority, these experts also analyze code developed in-house.
We also value the opinions of independent researchers. Any person who has found a vulnerability in our technologies can report it using a special communication channel that can be found here. Kaspersky Lab experts will thoroughly analyze all data coming via the channel. The procedure is as follows: first, our analysts confirm that there really is a vulnerability. After confirming this, we contact the independent researcher and agree on a time when this information will be made public. Meanwhile, the data is provided to the R&D team responsible for developing the technology; we also check whether the vulnerability is present in any other Kaspersky Lab products. It should be noted that sometimes independent researchers do draw our attention to serious issues. We really appreciate this!
A few practical recommendations
Since only software developers can significantly improve the situation, here are some recommendations:
As we have said many times before, update your software. If the developer provides an update for its product, the chances are that it does so for a good reason.
Do not disable automatic updates. True, this can be a bit of a nuisance if you have lots of programs, but security is what really counts.
Remove the programs you no longer use. There is no reason for this dead weight to remain on your hard drive. One day such programs could do you a grave disservice.
Do not use obsolete software. If it is really such a handy, useful program, there must be other similar programs available. True, it can be hard to abandon a familiar interface, but it is better to spend a few days getting used to a new one than using vulnerable software.
Regularly scan your computer for known vulnerabilities using dedicated utilities.
Hackers in the wild attempt to exploit the Juniper Backdoor
23.12.2015
A honeypot set up by researchers at the SANS institute has shown that hackers have already attempted to exploit the Juniper backdoor.
Shortly after Juniper posted the advisory related to the presence of unauthorized code in the OS of some of its Firewalls, HD Moore, the developer of the Rapid7′ Metasploit Framework, revealed that approximately 26,000 Netscreen devices are connected to the Internet with SSH open.
“Shortly after Juniper posted the advisory, an employee of Fox-IT stated that they were able to identify the backdoor password in six hours. A quick Shodan search identified approximately 26,000 internet-facing Netscreen devices with SSH open. Given the severity of this issue, we decided to investigate.” he wrote in a blog post.
Ronald Prins, founder and CTO of the Fox-IT security firm, explained that by reverse engineering the patch released by Juniper its experts were able to discover the master password backdoor (“<<< %s(un=’%s’) = %u,“).
“Once you know there is a backdoor there, … the patch [Juniper released] gives away where to look for [the backdoor] … which you can use to log into every [Juniper] device using the Screen OS software,” he told WIRED. “We are now capable of logging into all vulnerable firewalls in the same way as the actors [who installed the backdoor].” explained Prins.
The security firms Fox-IT has also released the Snort rules that can be used by the sys admins to detect unauthorized access to the Juniper devices through the backdoor.
News of the day is that a honeypot set up by researchers at the SANS Technology Institute’s Internet Storm Center (ISC) has identified attacks attempting to exploit the recently disclosed vulnerability in the Juniper firewalls. Let’s remind that the exploitation of the flaw could allow attackers to gain administrative access to the network devices.
“Since our initial announcement we’ve learned that the number of versions of ScreenO affected by each of the issues is more limited than originally believed. Administrative Access (CVE-2015-7755) only affects ScreenOS 6.3.0r17 through 6.3.0r20. VPN Decryption (CVE-2015-7756) only affects ScreenOS 6.2.0r15 through 6.2.0r18 and 6.3.0r12 through 6.3.0r20,” reported Juniper shared inviting administrators to apply the security updates as soon as possible.
The two vulnerabilities can be respectively exploited to remotely gain administrative access to a device via telnet or SSH (CVE-2015-7755) and to decrypt VPN traffic (CVE-2015-7756).
Researchers at the SANS Technology Institute have deployed a honeypot that emulates the Juniper devices running the ScreenOS, attracting threat actors in the wild. The researchers revealed that at the Technology Institute revealed that hackers have been using the backdoor password recently disclosed in an attempt to access the honeypot via SSH.
“Our honeypot doesn’t emulate ScreenOS beyond the login banner, so we do not know what the attackers are up to, but some of the attacks appear to be ‘manual’ in that we do see the attacker trying different commands,” said Johannes Ullrich from the SANS Technology Institute.

Juniper attacks honeypot SANS
The experts observed tens of exploit attempts, most of which used the usernames “root” and “admin.” Below the complete list of username used by hackers:
+---------------+----------+
| username | count(*) |
+---------------+----------+
| root | 29 |
| admin | 18 |
| netscreen | 8 |
| login | 8 |
| administrator | 5 |
| test | 4 |
| system | 2 |
| bob | 1 |
| sdes | 1 |
| sqzeds | 1 |
| sqzds | 1 |
+---------------+----------+
The researchers also collected the source IP addresses used by attackers, in one case the IP 83.82.244.85 was involved in the 24 attacks.
Altogether 78 attacks were observed in about 5 hours, one of the IPs belongs to security firm Qualys, presumably the attacks from this source are the result of research activities.
+-----------------+----------+
| ip | count(*) |
+-----------------+----------+
| 83.82.244.85 | 24 |
| 84.104.21.148 | 8 |
| 176.10.99.201 | 7 |
| 88.169.13.26 | 7 |
| 76.18.66.48 | 5 |
| 64.39.109.5 | 4 |<- Qualys (probably "research")
| 198.50.145.72 | 4 |
| 2.239.22.90 | 4 |
| 86.195.19.248 | 4 |
| 80.123.56.190 | 3 |
| 64.39.108.99 | 2 |
| 79.120.10.98 | 2 |
| 62.42.12.8 | 1 |
| 192.99.168.52 | 1 |
| 94.210.22.151 | 1 |
| 174.114.144.109 | 1 |
+-----------------+----------+
After the disclosure of the presence of the unauthorized code in the Juniper network appliances, the networking giant Cisco decided to assess its products for the presence of malicious codes.
“Although our normal practices should detect unauthorized software, we recognize that no process can eliminate all risk,” Cisco’s Anthony Grieco said. “Our additional review includes penetration testing and code reviews by engineers with deep networking and cryptography experience.”
Oracle Ordered to Publicly Admit Misleading Java Security Updates
22.12.2015
Security issues have long tantalized over 850 Million users that have Oracle's Java software installed on their computers. The worst thing is that the software was not fully updated or secure for years, exposing millions of PCs to attack.
And for this reason, Oracle is now paying the price.
Oracle has been accused by the US government of misleading consumers about the security of its Java software.
Oracle is settling with the Federal Trade Commission (FTC) over charges that it "deceived" its customers by failing to warn them about the security upgrades.
Java is a software that comes pre-installed on many computers and helps them run web applications, including online calculators, chatrooms, games, and even 3D image viewing.
Oracle Left Over 850 Million PCs at Risk
The FTC has issued a press release that says it has won concessions in a settlement with Oracle over its failure to uninstall older and insecure Java SE software from customer PCs upon the upgrade process, which left up to 850 Million PCs susceptible to hacking attacks.
However, the company was only upgrading the most recent version of the software and ignoring the older versions that were often chock full of security loopholes that could be exploited by hackers in order to hack a targeted PC.
Oracle is Now Paying the Price
So, under the terms of the settlement with Oracle, announced by the FTC on Monday, Oracle is required to:
Notify Java customers about the issue via Twitter, Facebook, and its official website
Provide tools and instructions on how to remove older versions of Java software
Oracle has agreed to the settlement that is now subject to public comment for 30 days, although Oracle declined to comment on its part.
Meanwhile, the FTC wants Java users to know that if they have older versions of the software. Here is the website that will help you remove them: java.com/uninstall.
How to Crash Your Friends' WhatsApp Just By Sending Crazy Smileys
22.12.2015
What would require crashing the wildly popular WhatsApp messaging application?
Nearly 4000 Smileys.
Yes, you can crash your friends' WhatsApp, both WhatsApp Web and mobile application, by sending them not any specially crafted messages, but just Smileys.
Indrajeet Bhuyan, an independent researcher, has reported The Hacker News a new bug in WhatsApp that could allow anyone to remotely crash most popular messaging app just by sending nearly 4000 emojis to the target user, thereby affecting up to 1 Billion users.
Bhuyan is the same researcher who reported a very popular WhatsApp crash bug last year that required 2000 words (2kb in size) message in the special character set to remotely crash Whatsapp messenger app.
After this discovery, the company patched the bug by setting up the limits of characters in WhatsApp text messages, but unfortunately, it failed to set up limits for smileys send via WhatsApp.
"In WhatsApp Web, Whatsapp allows 65500-6600 characters, but after typing about 4200-4400 smiley browser starts to slow down," Bhuyan wrote in his blog post. "But since the limit is not yet reached so WhatsApp allows to go on inserting...when it receives it overflows the buffer and it crashes."
whatsapp
The recent bug tested on Android devices by multiple brands and successfully crashed:
WhatsApp for Android devices including Marshmallow, Lollipop and Kitkat
WhatsApp Web for Chrome, Opera and Firefox web browsers.
It is sure that the latest version of WhatsApp is affected by this bug.
Video Demonstration
You can also watch the Proof-of-Concept (PoC) video that shows the attack in work.
How to Protect Yourself
Bhuyan told The Hacker News that he had reported the WhatsApp crash bug to Facebook. However, before the company patches the issue, there is a simple way out.
If you become a victim of such message on WhatsApp, just open your messenger and delete the whole conversation with the sender.
However, remember, if you have kept some records of your chat with that particular friend, you’ll end up losing them all.
At the beginning of this year, Bhuyan also reported two separate bugs — WhatsApp Photo Privacy bug and WhatsApp Web Photo Sync Bug — in the WhatsApp web client that in some way exposes its users’ privacy.
Encrypted Email Servers Seized by German Authorities After School Bomb Threats
22.12.2015
In the wake of a hoax bomb threat, all public schools in Los Angeles were closed for a day last week, and now German authorities have seized an encrypted email server.
But, Does that make sense?
In a video statement posted on Monday, the administrator of Cock.li – an anonymous email provider service – said German authorities had seized a hard drive from one of its servers that used to host the service in a Bavarian data center.
The email provider was thought to have been used last week to send bomb threatening emails to several school districts across the United States, resulting in the closure of all schools in the Los Angeles Unified School District.
Despite The New York City Department of Education dismissed the e-mail as an obvious hoax, German authorities seized a hard drive that, according to the service admin, actually holds "all data" on the company.
According to the service administrator Vincent Canfield, "SSL keys and private keys and full mail content of all 64,500 of my users...hashed passwords, registration time, and the last seven days of logs were all confiscated and now are in the hands of German authorities."
Cock.li is Still Functional, but All Sensitive Data is in the Hands of Authorities
However, cock.li is still operational because it was hosted on a server utilizing a pair of drives in a RAID1 configuration – a method where data is stored to two hard drives simultaneously to minimize the chance of data being lost if one of the drives fails.
German authorities took one of the hard drives, but the other mirror drive is still in use.
But the significant risk still remains – the German authorities have had their hands on a lot of sensitive data of the users including:
SSL keys and Private keys
Full mail content of all users
Hashed passwords
Registration time
The last seven days of logs
Cock.li was launched in late 2013 and has since garnered more than 28,000 registered accounts under its domain.
Canfield has retained Jesselyn Radack, a well-known attorney who is representing former National Security Agency (NSA) contractor Edward Snowden as well as former NSA whistleblower Thomas Drake.
Who planted the Juniper ScreenOS Authentication Backdoor?
22.12.2015
Who planted the Authentication Backdoor in the Juniper ScreenOS? Security experts are making their speculation, but interesting revelations are coming out.
While the FBI is investigating the case searching for responsible for the introduction of a backdoor in a number of Juniper network devices, a number of speculation are circulating on the Internet. Juniper Networks is a technology provider for the US Government and many US federal agencies, including the FBI, this means that attackers may have had access to the traffic related to connections protected through VPNs.
Someone is blaming China, other the NSA, and the majority is pointing a more generic nation-state actor.
The experts that blame the Chinese Government sustain that the compromised appliance was originally developed by the NetScreen Technologies company that was acquired by Juniper Networks in 2004. The NetScreen Technologies was founded by Chinese nationals, for this reason some experts believe that Chinese experts have a deep knowledge of the compromised ScreenOS.
“It’s not hard to find evidence of ongoing work on ScreenOS in Beijing: a quick trawl of LinkedIn turns up several Juniper employees who work on the operating system. The Register in no way suggests that those who work in Juniper’s Beijing offices are in any way associated with the unauthorised code. We nonetheless asked Juniper if the code is known to have come from the Beijing facility.” states a blog post published by The Register.
Many experts speculate the involvement of the NSA, one of the documents leaked by Edward Snowden and disclosed by the German Der Spiegel revealed that the US intelligence had the ability to plant a backdoor in various network equipment, including Juniper firewalls.

There is also speculation that the two backdoors might not be the work of the same state-actor, as they are not connected.
According to the German online magazine, hackers belonging to the ANT division (Advanced or Access Network Technology), operating under the NSA’s department for Tailored Access Operations (TAO),
“In the case of Juniper, the name of this particular digital lock pick is “FEEDTROUGH.” This malware burrows into Juniper firewalls and makes it possible to smuggle other NSA programs into mainframe computers. Thanks to FEEDTROUGH, these implants can, by design, even survive “across reboots and software upgrades.” In this way, US government spies can secure themselves a permanent presence in computer networks. The catalog states that FEEDTROUGH “has been deployed on many target platforms.” states the Der Spiegel online.
HD Moore, the developer of the Rapid7′ Metasploit Framework, confirmed that there are roughly 26,000 Netscreen devices exposed on the Internet with SSH open.
“Shortly after Juniper posted the advisory, an employee of Fox-IT stated that they were able to identify the backdoor password in six hours. A quick Shodan search identified approximately 26,000 internet-facing Netscreen devices with SSH open. Given the severity of this issue, we decided to investigate.” he wrote in a blog post.
HD Moore added that the backdoor might date back to late 2013, and the encryption backdoor to 2012.
“This is interesting because although the first affected version was released in 2012, the authentication backdoor did not seem to get added until a release in late 2013 (either 6.3.0r15, 6.3.0r16, or 6.3.0r17).”
Ronald Prins, founder and CTO of Fox-IT, a Dutch security firm, explained that reverse engineering the patch released by Juniper he was able to discover the master password backdoor (“<<< %s(un=’%s’) = %u,“).
“Once you know there is a backdoor there, … the patch [Juniper released] gives away where to look for [the backdoor] … which you can use to log into every [Juniper] device using the Screen OS software,” he told WIRED. “We are now capable of logging into all vulnerable firewalls in the same way as the actors [who installed the backdoor].” explained Prins.
Fox-IT has also released the Snort rules that can be used by the sys admins to detect unauthorized access to the Juniper devices through the backdoor.
“Since our initial announcement we’ve learned that the number of versions of ScreenO affected by each of the issues is more limited than originally believed. Administrative Access (CVE-2015-7755) only affects ScreenOS 6.3.0r17 through 6.3.0r20. VPN Decryption (CVE-2015-7756) only affects ScreenOS 6.2.0r15 through 6.2.0r18 and 6.3.0r12 through 6.3.0r20,” reported Juniper shared inviting administrators to apply the security updates as soon as possible.
The unique certainly is that someone deliberately inserted a backdoor password into Juniper network devices.
Chinese hackers target Taiwanese Opposition Party and media
22.12.2015
Security experts at FireEye have uncovered a spear phishing campaign managed by Chinese hackers that is targeting Taiwan Opposition and Media ahead of the vote in January.
According to FireEye a group of Chinese hackers is targeting Taiwan’s opposition party and journalists, security experts and officials. The attacks are occurring weeks away from a Taiwanese presidential election.
The hackers are trying to compromise Taiwanese news organizations for intelligence purpose and obtain election-related information.
“Between November 26, 2015, and December 1, 2015, known and suspected China-based APT groups launched several spear phishing attacks targeting Japanese and Taiwanese organizations in the high-tech, government services, media and financial services industries. Each campaign delivered a malicious Microsoft Word document exploiting the aforementioned EPS dict copy use-after-free vulnerability, and the local Windows privilege escalation vulnerability CVE-2015-1701. The successful exploitation of both vulnerabilities led to the delivery of either a downloader that we refer to as IRONHALO, or a backdoor that we refer to as ELMER.” states the report published by FireEye.
The representatives of the main opposition Democratic Progressive Party (DPP) seem to have the favor of voters at the expense of the other party politics closer to the Chinese Government.

In the past, the Taiwanese government websites were constantly under attack from China, not experts at FireEye identified nation-state actor that is running a spear phishing campaign on Taiwanese journalists with the subject-line reading “DPP’s Contact Information Update” earlier this month.
“Each phishing message contained the same malicious Microsoft Word attachment. The malicious attachment resembled an article hosted on a legitimate Japanese defense-related website, as both discussed national defense topics and carried the same byline. The lure documents also used the Japanese calendar, as indicated by the 27th year in the Heisei period. This demonstrates that the threat actors understand conventional Japanese date notation.”
In March, the DPP’s website was brought down remaining down for at least four days, also in that case the experts blamed Chinese hackers.
“We often received fake emails pretending to come from our colleagues, asking us to click some links or download some documents,” said Ketty Chen, deputy director of the DPP’s international affairs department.
Analyzing the TTPs of the threat actors the experts at FireEye confirmed the Chinese origin of the threat and their intention to gather information relating to the upcoming election.
“Given the timing of these attacks, the reporters targeted, and the information used as a lure, it is possible that the attackers are seeking information relating to the upcoming election and about the DPP in particular,” Bryce Boland, chief technology officer for Asia Pacific at FireEye, told to Agence France-Presse
It is a state of emergency in Taiwan, and in particular for the Democratic Progressive Party, its politicians are a privileged target for alleged state-sponsored hackers.
A DPP official working for the cyber security of the Party, speaking on condition of anonymity, revealed that the organization is “constantly on guard” and conducts regular Internet security training for its staff.
Angler exploit kit includes the code of a recent Flash flaw
22.12.2015
A security researcher discovered a new variant of the Angler exploit kit that includes the exploit code for a recently patched Adobe Flash Player flaw.
The French security researcher “Kafeine” has discovered a new variant of the popular Angler exploit kit that includes the exploit code for a recently patched Adobe Flash Player vulnerability (CVE-2015-8446). Kafeine reported that new exploit code was added to the Angler exploit kit on December 14.
The new Angler exploit kit has been used by threat actors in the wild to spread the TeslaCrypt ransomware.
Once the ransomware infects a PC, it encrypts files and renames them with a .vvv extension requesting the payment of a $500 ransom within one week, after which the price to recover the files increases to $1,000.
The CVE-2015-8446 vulnerability is a Flash Player heap buffer overflow flaw that Adobe patched on December 8. had been added to Angler.
This vulnerability was discovered by an anonymous researcher who reported it via the Zero Day Initiative (ZDI). Recently Adobe released Flash Player 20.0.0.228 and 20.0.0.235 versions (Desktop Runtime with support for Firefox and Safari) that fixed 77 security issues.
Kafeine added that the exploit for the Flash vulnerability has been used by threat actors to deliver the Bedep Trojan Downloader.
Last week experts at Malwarebytes confirmed that the code for the CVE-2015-8446 exploit included in the Angler Exploit kit had been used by cyber criminals to serve the TeslaCrypt ransomware.
Once it infects a computer, the ransomware encrypts files and renames them with a .vvv extension. Victims are instructed to pay $500 within one week, after which the price for the private key needed to recover the files increases to $1,000.
The experts noticed that the new variant of the Angler Exploit Kit had a low detection rate at the time of its discovery.
Iranian hackers penetrated computers of a small dam in NY
22.12.2015
Iranian hackers penetrated the industrial control system of a dam near New York City in 2013, raising concerns about the security of US critical infrastructure.
It is official, Iranian hackers violated the online control system of a New York dam in 2013. According to reports, the hackers penetrated the control system of the dam and poked around inside the system.
The Wall Street Journal reported that hackers penetrated the system of the critical infrastructure through a cellular modem. The Journal cited an unclassified Homeland Security summary of the case. At the time I was writing the Department of Homeland Security has declined to comment on the cyber attack.
The Wall Street Journal cited to anonymous sources that revealed the hackers targeted the Bowman Avenue Dam, which is a small facility 20 miles outside of New York.
“It’s very, very small,” Rye City Manager Marcus Serrano told the newspaper, confirming that FBI agents investigated the case in 2013.
Fortunately, the intruders were not able to gain complete control of the control systems. The hackers used a machine that scanned the Internet for vulnerable US
The hackers used a machine that scanned the Internet for vulnerable US industrial control systems (ICS) , but the strange circumstance is that threat actors appeared to be focusing on a specific range of internet addresses.

The US cyber experts once discovered the attack have tracked back the intruders, the evidence collected suggests the involvement of Iranian hackers, probably the same groups that focused their operations on American companies and organizations.
Exactly one year ago, the experts at security firm Cylance revealed that Iranian hackers were targeting airlines, energy, defense companies worldwide as part of the Operation Cleaver campaign.
The fact that foreign hackers target US critical infrastructure is not a novelty, a report issued by The Department of Homeland Security (DHS) in November 2014 revealed that Russian hackers have infiltrated several critical infrastructure in the United States.
The US has the highest number of ICS and SCADA systems exposed on the internet and many of them are easily identifiable with search engines like Shodan or Censys. Researchers at Shodan recently revealed that the US have nearly 57,000 industrial control systems connected to the Internet.
A recent wave of attacks conducted by Iranian hackers came after a period of apparent calm. The cyber security experts noticed an evolution of the TTPs of the Iranian hackers that were initially focused on targets belonging to the financial industry, their activities were limited to sabotage and disruption of the targeted infrastructures, such as in the attack on casino company Las Vegas Sands Corp.
The recent attacks against The State Department attack is clearly a cyber espionage operation, they were initially attributed to Chinese hackers who may have infiltrated the department’s unclassified e-mail systems. Let’s remind that security experts at Facebook were first noticed the intrusion of Iranian Hackers in the e-mail accounts of US State Department officials focused on Iran.
Needless to emphasize the importance of activities of threat intelligence to prevent these accidents and mitigate cyber threats.
Top 8 Cyber Security Tips for Christmas Online Shopping
21.12.2015
As the most wonderful time of the year has come - Christmas, it has brought with itself the time of online shopping.
According to National Retail Federation, more than 151 million people shopped in store, but more than 100 Million shopped online during Cyber Monday sales and even why wouldn't it be so given the vast conveniences of online shopping.
It is quite visible in these days that more and more people are heading towards online shopping rather than the malls to purchase gifts for Christmas.
However, the main question arises: Is it safe to do so? Especially with so many users sharing credit card information online.
Here are some tips that you have to keep in mind before providing your credit card number and clicking, 'BUY'
1. DO NOT CLICK On Suspicious Links
Malicious links are sent by scammers who look more real than the original ones. As these links are specifically of the well-known sites like eBay and Flipkart, many online users fall victim.
The safest way of not getting tricked by these would be NOT to open them if provided via social media sites, messages or emails from unknown sources.
2. Keep your Eye on New Vendors
People tend to purchase goods and services from new vendors as they generally give attractive discounts.
However, one should always be safe from such vendors as sometimes the customer is trapped and exploited easily.
One of the main problems is FAKE CUSTOMERS REVIEW. Never rely totally on company or seller review information.
Always get a double confirmation of the things that are necessary including product purpose and suitability, materials and construction, quality, and other things like speedy shipping, prompt refunds, and returns.
Always try to start from minimum purchases and then shift to the major ones.
Always look before you leap.
Search online for other people's experiences online and also some sites like www.bbb.org and others.
3. Always Use Strong Passwords
This tip is one of the most obvious ones, but people do not intend to use it generally.
Always try to avoid easy to crack passwords by including a combination of upper and lowercase letters, numbers and special characters in your password.
Avoid using the most common passwords like your name, 123456 and password.
Most importantly don't use the same password for multiple sites.
4. Always Use Secured Websites
amazon-https
Before typing your sensitive information online, check to make sure if the website you just visited is a secure site.
Secure sites have a closed padlock in the status bar, and its URL starts with HTTPS, which means:
Communication is encrypted
SSL verifies authenticity
5. Avoid Using Debit Cards, Instead Use Credit Cards
For online shopping purposes, using a credit card is always considered to be a comparatively better option rather than using a debit card.
In a case, if someone manages to intercept your financial information online, they can do less damage.
Credit cards have spending limits but debit cards do not
Credit cards should also be used with low credit limits even as other option also given by the bank as "one-time use."
You can even make use of virtual credit cards that are specifically designed for online shopping only.
6. Important Things to Remember While Shopping
Always keep documentation of your online purchases, mostly an email is sent to the customer confirming the order.
It is the duty of every customer to print the document or save it somewhere safe till receiving the order.
Moreover, it is always suggested to log off from the retailer's website after making the purchase.
These are always considered to be the smarter options to adapt than to become a victim.
7. Do Not Provide Your Details to Every Website You Visit
Online stores provide an option for the customers to check out as a one time customer.
If you are not shopping regularly from any site, avoid filling unnecessary information, just in case, to be safe.
8. Check Your Bank Statements Regularly
Most of the banks now allow for setting up email notifications of any credit card transaction.
If you see any charges that are unusual, they have to get reported, and suitable actions should be taken that are needed to get a prompt refund.
Facebook wins Flash by knock out by switching to HTML5!
21.12.2015
Step by step the HTML5 language is replacing the flawed Flash that hackers have exploited in an impressive number of cyber attacks in the wild.
It may help the fact that Facebook is leaving Flash behind and it is adopting HTML5 (YouTube has done in the a recent past).
“We recently switched to HTML5 from a Flash-based video player for all Facebook web video surfaces, including videos in News Feed, on Pages, and in the Facebook embedded video player. We are continuing to work together with Adobe to deliver a reliable and secure Flash experience for games on our platform, but have shipped the change for video to all browsers by default.” States the announcement issued by Facebook.
“From development velocity to accessibility features, HTML5 offers a lot of benefits. Moving to HTML5 best enables us to continue to innovate quickly and at scale, given Facebook’s large size and complex needs.”
We are big supporters of the HTML5 since it eliminates the weakest link in the user environment and in terms of development, it makes the job easier for developers.
Facebook HTML5
Facebook explains the benefits of HTML5 that they will be using:
Development velocity
“Using web technologies allows us to tap into the excellent tooling that exists in browsers, among the open source community, and at Facebook in general. Not having to recompile code and being able to apply changes directly in the browser allow us to move fast.”
Testability
“We have an excellent testing infrastructure at Facebook. By moving to HTML5 video, we can avail ourselves of all the web tools in that infrastructure, like jest and WebDriver, at our disposal.”
Accessibility
“HTML5 made it possible for us to build a player that is fully accessible to screen readers and keyboard input. We can leverage the accessibility tools that HTML5 provides to make it easier for people with visual impairments to use our products. Making Facebook accessible to everyone is an important part of our mission to make the world more open and connected.”
When doing such a big move, there are challenges that needs to be overcome, and Facebook is no exception, and for that reason Facebook needed to:
Getting logging right
“To ensure logging correctness, we created a test suite that performs the same user-interaction scenarios against both video players and then validates that the logs are equivalent. This way we had high confidence in the data that our new HTML5 video player reports.”
Browser bugs
“One of the major issues we wanted to solve before shipping the HTML5 player was the number of bugs in various browsers around HTML5 videos. One specific bug in Chrome’s implementation of the SPDY protocol caused the browser to simply stop loading and playing videos in News Feed. We determined that the issue was triggered by loading too many videos concurrently, so we reduced the number of videos we load at the same time and make sure we cancel loading videos as soon as they are no longer required.”
Worse performance in older browsers
“In theory, most browsers in use support HTML5 video. However, in practice we noticed that a lot of the older browsers would simply perform worse using the HTML5 player than they had with the old Flash player. We saw more errors, longer loading times, and a generally worse experience. We decided to initially launch the HTML5 player to only a small set of browsers, and continuously roll out to more browsers, versions, and operating systems as we improved it and fixed small bugs. That’s why we waited until recently to ship the HTML5 player to all browsers by default, with the exception of a small set of them.”
Page load time regression
“The last major issue we faced while launching the HTML5 player was a regression in the time it takes to load Facebook. At Facebook, we care about the experience we provide to people. How long Facebook takes to load is a contributing factor we look at to gauge user experience. When we shipped the HTML5 player, we noticed that on average it took slightly longer for Facebook to load. By fixing several small performance regressions and making multiple micro-optimizations, we finally reached a level we felt happy with shipping.”
As said before, this can be a huge improvement for the user but also for the developers. On the user side, they will have an improved video experience, videos will start playing faster which is good.
It is good that big companies like Facebook and Google are adopting HTML5 forcing sooner or later other websites to switch to HTML5, making everyone a bit safer.
iOS Mobile Banking Apps, what is changed from 2013 tests?
21.12.2015
The security expert Ariel Sanchez presented the results of the test conducted on 40 iOS banking apps, comparing them to the ones obtained 2 years ago.
The banking industry is looking with an increasing interest in mobile platform, financial institutes are offering a growing number of services accessible through mobile devices, but what about security?
The security of mobile banking apps has been improved over the last years, but there is still a great scope for improvement.
Ariel Sanchez, a security consultant for IOActive, two years ago conducted a research on security implemented by iOS banking apps and now has decided to repeat the same tests. Sanchez evaluated the security level for 40 iOS banking apps and discovered a number of security weaknesses or vulnerabilities. The expert limited his analysis on client-side, avoiding to investigate the security offered on server-side.
For obvious reason, Sanchez hasn’t revealed the name of the apps or the banks who developed the mobile apps it tested.
What is changed?
Revisiting its research, Sanchez discovered that many of the problems emerged two years ago still remain despite the overall level of security is increased. Sanchez executed the following tests on each app:
Transport Security
Plaintext traffic
Improper session handling
Properly validate SSL certificates
Compiler Protection
Anti-jailbreak protection
Compiled with PIE
Compiled with stack cookies
Automatic reference counting
UIWebViews
Data validation (input, output)
UIWebView implementations
Insecure Data Storage
SQLlite database
File caching
Property list files
Log files
Logging
Custom logs
NSLog statements
Crash reports files
Binary Analysis
Disassemble the application
Detect obfuscation of the assembly code protections
Detect anti-tampering protections
Detect anti-debugging protections
Protocol handlers
Client-side injection
Third-party libraries
He discovered that five apps (12,5 per cent) failed to validate the authenticity of the SSL certificates presented, a circumstance that opens mobile users to Man-in-The-Middle (MiTM) attacks.
35 per cent of the mobile apps contained non-SSL links throughout the application, traffic to these links could be easily intercepted by attackers that could also inject arbitrary JavaScript/HTML code in an attempt to create a fake login prompt.
30 per cent of the iOS apps failed to validate incoming data, a circumstance that allows an attacker to potentially inject JavaScript. The expert noticed that this percentage is reduced respect the previous tests conducted in 2013.
40% of the apps leak information about user activity or client-server interactions.
“35% of the apps contained non-SSL links throughout the application. This allows an attacker to intercept traffic and inject arbitrary JavaScript/HTML code in an attempt to create a fake login prompts or similar scams. ” states the post published by Sanchez.
The expert also analyzed binary and file system revealing that 15 per cent of the iOS banking apps store unencrypted data and sensitive information. In some cases customers’ banking accounts and transaction history are archived in sqlite databases on the device or in plain text files.
In the following graphs are reported the results of the test conducted in 2013 and 2015.


Most of the apps have improved traffic protection and are properly validating SSL certificates, drastically reducing the exposure to MiTM attacks. It is interesting to note that there are still a high number of apps storing insecure data in their file system.
Sanchez concluded that despite the security implemented by the banking apps is increased it is still not enough because many apps remain vulnerable.
“While overall security has increased over the two-year period, it is not enough, and many apps remain vulnerable.” he added.
Enjoy the “(In)secure iOS Mobile Banking Apps – 2015 Edition” report.
AlienVault Unified Security Management: Real-Time Threat Detection Starting on Day 1
21.12.2015
As organizations expand their IT infrastructure to match their evolving business models and meet changing regulatory requirements, they often find that their networks have become extremely complex and challenging to manage.
A primary concern for many IT teams is detecting threats in the mountain of event data being generated every day.
Even a relatively small network can generate hundreds or thousands of events per second, with every system, application, and service generating events.
The sheer volume of data makes it virtually impossible to identify manually and link those few events that indicate a successful network breach and system compromise, before the exfiltration of data.
The AlienVault Unified Security Management (USM) platform is a solution to help IT teams with limited resources overcome the challenge of detecting threats in their network.
USM platform accelerates and simplifies your ability to detect, prioritize, and respond to the most critical threats targeting your network.
It enables any IT or security practitioner to see actionable results on day one and begin to improve their security posture immediately.
What can you do with USM?
All of USM’s built-in security controls are pre-integrated and optimized to work together out of the box. This unified approach eliminates the need for IT teams to configure and maintain numerous security point products.
Within minutes of installing USM, the platform begins generating detailed alerts. Additionally, it provides valuable insights into the assets and threats on your network with the following technologies:
Asset discovery
Vulnerability assessment
Intrusion detection
Behavioral monitoring
Security information and event management (SIEM)
Integrated threat intelligence from AlienVault Labs
This insight provides visibility into the software installed on your devices, their configuration, any vulnerabilities, as well as the specific threats targeting them.
Armed with this detailed threat information, you can focus on responding to the threats instead of trying to collect and analyze the information manually.
Integrated Threat Intelligence
The integrated threat intelligence, powered by AlienVault Labs and the , includes continuous updates to the built-in security controls as well as the latest information on emerging threats and bad actors.
The AlienVault Labs threat research team spends countless hours mapping out the different types of cyber attacks, the most recent threats, suspicious behavior, vulnerabilities and exploits they uncover across the entire threat landscape.
The team regularly delivers threat intelligence as a coordinated set of updates to the USM platform, which accelerates and simplifies threat detection and remediation.
OTX is the world’s first truly open threat intelligence community that enables collective defense with actionable, community-powered threat data.
It alerts you whenever an indicator of compromise (IOC) related to a new or emerging threat documented in the OTX database is detected in their network.
OTX enables everyone in the OTX community to collaborate actively and strengthen their defenses while helping others do the same.
Integrate Data from Existing Security Tools
The USM platform’s open architecture also enables you to utilize a much wider range of network and security data if you wish.
You can integrate security events from 3rd party tools, utilizing the extensive plugin library, or create custom plugins for unique applications running on your network.
Simplify Regulatory Compliance Requirements
AlienVault USM automatically identifies significant audit events that warrant immediate action. From file integrity monitoring to IDS to log management, USM makes compliance easier.
Not only does it provide the , but USM also gathers the information and generates the reports to give to auditors.
Additionally, USM includes a report library that provides flexible reporting and executive dashboards that make compliance measurement, reporting, and audits less painful.
USM allows you to demonstrate to auditors and management that your incident response program is robust and reliable for a range of regulations and guidelines, including PCI DSS, HIPAA, ISO 27002, SOX, GPG13 and more.
Deployment flexibility
The USM platform is also designed to meet a wide range of deployment requirements.
All of the AlienVault USM products are available in various models and form factors, based on size, scale, and configuration requirements.
You can quickly deploy AlienVault USM – as a dedicated hardware appliance, a virtual appliance, or as a cloud appliance within the Amazon AWS environment.
For one location, you can deploy a single USM All-in-One tool. The All-in-One appliance consolidates all USM functions into a single hardware or virtual appliance for reduced complexity and rapid deployment.
All event logs are forwarded to a single USM All-in-One appliance for collection, aggregation, analysis, correlation and reporting.
For larger networks, multiple locations, or locations with a high volume of events and/or performance requirements, you will want to deploy separate USM Standard or Enterprise components, either hardware or virtual appliances, to benefit from the improved performance.
Server – Aggregates and correlates information gathered by the Sensors, and provides single-pane-of-glass management, reporting, and administration.
Logger – Securely archives raw event log data for forensic investigations and compliance mandates.
Sensor – Deploys throughout the network to collect logs to provide the five essential security capabilities you need for complete visibility.
There is also a version of AlienVault USM or AWS that is built for the Amazon “shared responsibility” security model.
The AWS-native USM for AWS maximizes visibility into potential threats and misconfigurations and makes it easy to use built-in AWS security features like CloudTrail and Security Groups.
Try it for free
With USM you can achieve true security visibility in minutes, not months - If you'd like to take a closer look at AlienVault USM, you can , or you can on the AlienVault website.
How to Turn Any Non-Touch Screen PC Into a Touch Screen
21.12.2015
How to Turn Any Non-Touch Screen PC Into a Touch Screen
Want to buy a touch-screen laptop but couldn't afford it?
But what if I told you that you can turn your existing non-touch-screen laptop into a Touch Screen laptop?
Yes, it's possible. You can now convert your laptop or PC into a touch screen with the help of a new device called AirBar.
Touch screen has become a popular feature on laptops these days, and many laptops are moving toward having touch screens, but not every laptop or desktop model comes with the feature.
Swedish company Neonode has brought to you a new device, AirBar, that would bring the touch technology to virtually any computer from your non-touch laptops to notebooks.
What is AirBar and How does it Work?
AirBar is a small plug-and-touch bar that attaches magnetically to the bottom of your machine's display.
When connected to your laptop via an available USB port, AirBar starts emitting a beam of invisible light across your screen that is used to track touchscreen movements and gestures.
The movements and gestures are then translated into corresponding inputs, making you able to use all the gestures including poking, pinching, swiping, zooming and scrolling around with your hand, in the same way, like on a touchscreen PC.
Video Demonstration
AirBar turns any laptop, computer, or notebook into a touchscreen machine, without making any changes to its hardware.
You can watch the video below to know how really AirBar works.
And What's Great about AirBar is that…
…it even works if you have worn gloves, and with any other object.
AirBar works well with any device running Windows 8 or Windows 10 or even with a Chromebook, but it still needs to have proper OS X support.
The AirBar is going to retail for $49 next month with its public launch in January 2016 at the CES event in Las Vegas. 15.6-inch screens size at present. Currently, the only size that AirBar accommodates is 15.6-inch screens.
Kaspersky Security Bulletin 2015. Top security stories
19.12.2015 Zdroj: Kaspersky
Top security stories
Overall statistics for 2015
Evolution of cyber threats in the corporate sector
Predictions 2016
Targeted attacks and malware campaigns
Targeted attacks are now an established part of the threat landscape, so it’s no surprise to see such attacks feature in our yearly review. Last year, in our security forecast, we outlined what we saw as the likely future APT developments.
The merger of cybercrime and APT
Fragmentation of bigger APT groups
Evolving malware techniques
New methods of data exfiltration
APT arms race
Here are the major APT campaigns that we reported this year.
Carbanak combined cybercrime – in this case, stealing money from financial institutions – with the infiltration techniques typical of a targeted attack. The campaign was uncovered in spring 2015: Kaspersky Lab was invited to conduct a forensic investigation of a bank’s systems after some of its ATMs started to dispense cash ‘randomly’. It turned out that the bank was infected. Carbanak is a backdoor designed to carry out espionage, data exfiltration and remote control of infected computers. The attackers used APT-style methods to compromise their victims – sending spear-phishing e-mails to bank employees. Once installed on a bank’s computer, the attackers carried out reconnaissance to identify systems related to processing, accounting and ATMs and simply mimicked the activities of legitimate employees. Carbanak used three methods to steal money: (1) dispensing cash from ATMs, (2) transferring money to cybercriminals using the SWIFT network and (3) creating fake accounts and using mule services to collect the money. The attackers targeted around 100 financial institutions, with total losses amounting to almost $1 billion.

One of most talked-about news stories of Q1 2015 surrounded the Equation cyber-espionage group. The attackers behind Equation successfully infected the computers of thousands of victims in Iran, Russia, Syria, Afghanistan, the United States and elsewhere – victims included government and diplomatic institutions, telecommunications companies and energy firms. This is one of the most sophisticated APT campaigns we’ve seen: one of the many modules developed by the group modifies the firmware of hard drives – providing a level of stealth and persistence beyond other targeted attacks. It’s clear that development of the code stretches back to 2001 or earlier. It’s also related to other notorious attacks, Stuxnet and Flame – for example, its arsenal included two zero-day vulnerabilities that were later to be used in Stuxnet.
While investigating an incident in the Middle East, we uncovered the activity of a previously unknown group conducting targeted attacks. Desert Falcons is the first Arabic-speaking group that has been seen conducting full-scale cyber-espionage operations – apparently connected with the political situation in the region. The first signs of this campaign date back to 2011. The first infections took place in 2013, although the peak of activity was in late 2014 and early 2015. The group has stolen over 1 million files from more than 3,000 victims. The victims include political activists and leaders, government and military organizations, mass media and financial institutions – located primarily in Palestine, Egypt, Israel and Jordan. It’s clear that members of the Desert Falcons group aren’t beginners: they developed Windows and Android malware from scratch, and skillfully organized attacks that relied on phishing e-mails, fake web sites and fake social network accounts.
#Carbanak combined stealing from financial institutions with techniques typical of a targeted attack #KLReport
Tweet
In March 2015, we published our report on the Animal Farm APT, although information on the tools used in this campaign started appearing in the previous year. In March 2014, the French newspaper, Le Monde, published an article on a cyber-espionage toolset that had been identified by Communications Security Establishment Canada (CSEC): this toolset had been used in the ‘Snowglobe’ operation that targeted French-speaking media in Canada, as well as Greece, France, Norway and some African countries. CSEC believed that the operation might have been initiated by French intelligence agencies. A year later, security researchers published analyses (here, here and here) of malicious programs that had much in common with ‘Snowglobe’: in particular, the research included samples with the internal name ‘Babar’ – the name of the program mentioned by CSEC. Following analysis of the malicious programs, and the connections between them, Kaspersky Lab named the group behind the attacks as Animal Farm. The group’s arsenal included two of the three zero-day vulnerabilities that we had found in 2014 and that had been used by cybercriminals: for example, an attack from the compromised web site of the Syrian Ministry of Justice using CVE-2014-0515 exploits led to the download of an Animal Farm tool called ‘Casper’. One curious feature of this campaign is that one of its programs, ‘NBOT’, is designed to conduct DDoS (Distributed Denial of Service) attacks. This is rare for APT groups. One of the malicious ‘animals’ in the farm has the strange name ‘Tafacalou’ – possibly an Occitan word (a language spoken in France and some other places).
In April 2015, we reported the appearance of a new member of a growing ‘Duke’ family that already includes MiniDuke, CosmicDuke and OnionDuke. The CozyDuke APT (also known as ‘CozyBear’, ‘CozyCat’ and ‘Office Monkeys’) targets government organisations and businesses in the United States, Germany, South Korea and Uzbekistan. The attack implements a number of sophisticated techniques, including the use of encryption, anti-detection capabilities and a well-developed set of components that are structurally similar to earlier threats within the ‘Duke’ family. However, one of its most notable features is its use of social engineering. Some of the attackers’ spear-phishing e-mails contain a link to hacked web sites – including high-profile, legitimate sites – that host a ZIP archive. This archive contains a RAR SFX that installs the malware while showing an empty PDF as a decoy. Another approach is to send out fake flash videos as e-mail attachments. A notable example (one that gives the malware one of its names) is ‘OfficeMonkeys LOL Video.zip’. When run, this drops a CozyDuke executable on to the computer, while playing a ‘fun’ decoy video showing monkeys working in an office. This encourages victims to pass the video around the office, increasing the number of compromised computers. The successful use of social engineering to trick staff into doing something that jeopardises corporate security – by CozyDuke and so many other targeted attackers – underlines the need to make staff education a core component of any business security strategy.
The Naikon APT focused on sensitive targets in south-eastern Asia and around the South China Sea. The attackers, who seem to be Chinese-speaking and have been active for at least five years, target top-level government agencies and civil and military organisations in the Philippines, Malaysia, Cambodia, Indonesia, Vietnam, Myanmar, Singapore, Nepal, Thailand, Laos and China. Like so many targeted attack campaigns, Naikon makes extensive use of social engineering to trick employees of target organizations into installing the malware. The main module is a remote administration tool that supports 48 commands designed to exercise control over infected computers: these include commands to take a complete inventory, download and upload data, install add-on modules and the use of keyloggers to obtain employees’ credentials. The attackers assigned an operator to each target country, able to take advantage of local cultural features – for example, the tendency to use personal e-mail accounts for work. They also made use of a specific proxy server within a country’s borders, to manage connections to infected computers and transfer of data to the attackers’ Command-and-Control (C2) servers. You can find our main report and follow-up report on our web site
One of the many modules developed by the #Equation group modifies the firmware of hard drives #KLReport
Tweet
While researching Naikon, we also uncovered the activities of the Hellsing APT group. This group focused mainly on government and diplomatic organisations in Asia: most victims are located in Malaysia and the Philippines, although we have also seen victims in India, Indonesia and the US. In itself, Hellsing is a small and technically unremarkable cyber-espionage group (around 20 organisations have been targeted by Hellsing). What makes it interesting is that the group found itself on the receiving end of a spear-phishing attack by the Naikon APT group – and decided to strike back! The target of the e-mail questioned the authenticity of the e-mail with the sender. They subsequently received a response from the attacker, but didn’t open the attachment. Instead, shortly afterwards they sent an e-mail back to the attackers that contained their own malware. It’s clear that, having detected that they were being targeted, the Hellsing group was intent on identifying the attackers and gathering intelligence on their activities. In the past, we’ve seen APT groups accidentally treading on each other’s toes – for example, stealing address books from victims and then mass-mailing everyone on each of the lists. But an ATP-on-APT attack is unusual

Many targeted attack campaigns focus on large enterprises, government agencies and other high-profile organisations. So it’s easy to read the headlines and imagine that such organisations are the only ones on the radar of those behind targeted attacks. However, one of the campaigns we reported last quarter showed clearly that it’s not only ‘big fish’ that attackers are interested in. The Grabit cyber-espionage campaign is designed to steal data from small- and medium-sized organisations – mainly based in Thailand, Vietnam and India, although we have also seen victims in the US, UAE, Turkey, Russia, China, Germany and elsewhere. The targeted sectors include chemicals, nanotechnology, education, agriculture, media and construction. We estimate that the group behind the attacks has been able to steal around 10,000 files. There’s no question that every business is a potential target – for its own assets, or as a way of infiltrating another organisation
In spring 2015, during a security sweep, Kaspersky Lab detected a cyber-intrusion affecting several internal systems. The full-scale investigation that followed uncovered the development of a new malware platform from one of the most skilled, mysterious and powerful groups in the APT world – Duqu, sometimes referred to as the step-brother of Stuxnet. We named this new platform ‘Duqu 2.0’. In the case of Kaspersky Lab, the attack took advantage of a zero-day vulnerability in the Windows kernel (patched by Microsoft on 9 June 2015) and possibly up to two others (now patched) that were also zero-day vulnerabilities at the time. The main goal of the attackers was to spy on Kaspersky Lab technologies, ongoing research and internal processes. However, Kaspersky Lab was not the only target. Some Duqu 2.0 infections were linked to the P5+1 events related to negotiations with Iran about a nuclear deal: the attackers appear to have launched attacks at the venues for some of these high-level talks. In addition, the group launched a similar attack related to the 70th anniversary event of the liberation of Auschwitz-Birkenau. One of the most notable features of Duqu 2.0 was its lack of persistence, leaving almost no traces in the system. The malware made no changes to the disk or system settings: the malware platform was designed in such a way that it survives almost exclusively in the memory of infected systems. This suggests that the attackers were confident that they could maintain their presence in the system even if an individual victim’s computer was re-booted and the malware was cleared from memory. The Duqu 2.0 technical paper and analysis of the persistence module can be found on our web site
In August, we reported on the Blue Termite APT, a targeted attack campaign focused on stealing information from organisations in Japan. These include government agencies, local government bodies, public interest groups, universities, banks, financial services, energy, communication, heavy industry, chemical, automotive, electrical, news media, information services sector, health care, real estate, food, semiconductor, robotics, construction, insurance, transportation and more. One of the most high profile targets was the Japan Pension Service. The malware is customized according to the specific victim. The Blue Termite backdoor stores data about itself – including C2, API name, strings for anti-analysis, values of mutexes, as well as the MD5 checksum of backdoor commands and the internal proxy information. The data is stored in encrypted form, making analysis of the malware more difficult – a unique decryption key is required for each sample. The main method of infection, as with so many targeted attack campaigns, is via spear-phishing e-mails. However, we have other methods of infection. These include drive-by downloads using a Flash exploit (CVE-2015-5119) – one of the exploits leaked following the Hacking Team security breach – several Japanese web sites were compromised this way. We also found some watering-hole attacks, including one on a web site belonging to a prominent member of the Japanese government
#Hellsing group found itself on the receiving end of a spear-phishing attack by #Naikon & strike back #KLReport
Tweet
The group behind the Turla cyber-espionage campaign has been active for more than eight years now (our initial report, follow-up analysis and campaign overview can be found on securelist.com), infecting hundreds of computers in more than 45 countries. The attackers profile their victims using watering-hole attacks in the initial stages. However, as outlined in our latest report, for subsequent operations the group makes use of satellite communications to manage its C2 traffic. The method used by Turla to hijack downstream satellite links does not require a valid satellite Internet subscription. The key benefit is that it’s anonymous – it’s very hard to identify the attackers. The satellite receivers can be located anywhere within the area covered by the satellite (typically a wide area) and the true location and hardware of the C2 server can’t be identified easily or physically seized. It’s also cheaper than purchasing a satellite-based link and easier than hijacking traffic between the victim and the satellite operator and injecting packets along the way. The Turla group tends to focus on satellite Internet providers located in the Middle East and Africa, including Congo, Lebanon, Libya, Niger, Nigeria, Somalia and the UAE. Satellite broadcasts from these countries don’t normally cover European and North American countries, making it very hard for security researchers to investigate such attacks. The use of satellite-based Internet links is an interesting development. The hijacking of downstream bandwidth is cheap (around $1,000 for the initial investment and around $1,000 per year in maintenance), easy to do and offers a high degree of anonymity. On the other hand, it is not always as reliable as more traditional methods (bullet-proof hosting, multiple proxy levels and hacked web sites) – all of which Turla also uses. This makes it less likely that it will be used to maintain extensive botnets. Nevertheless, if this method becomes widespread among APT groups or cybercriminals, it will pose a serious problem for the IT security industry and law enforcement agencies

In August 2015, we published an update on the Darkhotel APT. These attacks were originally characterised by the misuse of stolen certificates, the deployment of HTA files using multiple methods and the infiltration of hotel Wi-Fi to place backdoors on targets’ computers
The #Turla group makes use of satellite communications to manage its C2 traffic #KLReport
Tweet
While the attackers behind this APT continue to use these methods, they have supplemented their armoury, shifting their attention more towards spear-phishing of their chosen victims. As well as using HTA files, they are also deploying infected RAR files, using the RTLO (right to left override) mechanism to mask the real extension of the file. The attackers also use Flash exploits, including a zero-day exploit leaked as a result of the Hacking Team security breach. The group has also extended its geographic reach to include victims in North Korea, Russia, South Korea, Japan, Bangladesh, Thailand, India, Mozambique and Germany
Data breaches
There has been a steady stream of security breaches this year. That such incidents have become routine is hardly surprising: personal information is a valuable commodity – not just for legitimate companies, but for cybercriminals too. Among the biggest incidents this year were attacks on Anthem, LastPass, Hacking Team, the United States Office of Personnel Management, Ashley Madison, Carphone Warehouse, Experian and TalkTalk. Some of these attacks resulted in the theft of huge amounts of data, highlighting the fact that many companies are failing to take adequate steps to defend themselves. It’s not simply a matter of defending the corporate perimeter. There’s no such thing as 100 per cent security, so it’s not possible to guarantee that systems can’t be breached, especially where someone on the inside is tricked into doing something that jeopardises corporate security. But any organisation that holds personal data has a duty of care to secure it effectively. This includes hashing and salting customer passwords and encrypting other sensitive data
On the other hand, consumers can limit the damage of a security breach at an online provider by ensuring that they choose passwords that are unique and complex: an ideal password is at least 15 characters long and consists of a mixture of letters, numbers and symbols from the entire keyboard. As an alternative, people can use a password manager application to handle all this for them automatically.
The issue of passwords is one that keeps surfacing. If we choose a password that is too easy to guess, we leave ourselves wide open to identify theft. The problem is compounded if we recycle the same password across multiple online accounts – if one accounts is compromised, they’re all at risk! This is why many providers, including Apple, Google and Microsoft, now offer two-factor authentication – i.e. requiring customers to enter a code generated by a hardware token, or one sent to a mobile device, in order to access a site, or at least in order to make changes to account settings. Two-factor authentication certainly enhances security – but only if it’s required, rather than just being an option
In 2015, there has been a steady stream of security breaches #KLReport
Tweet
The theft of personal data can have serious consequences for those affected. However, sometimes there can be serious knock-on effects. The Hacking Team breach resulted in the publication of 400GB of data: this included exploits used by the Italian company in its surveillance software. Some of the exploits were used in APT attacks – Darkhotel and Blue Termite. Unsurprisingly, the breach was followed by a scramble to patch the vulnerabilities exposed by the attackers
Smart (but not necessarily secure) devices
The Internet is woven into the fabric of our lives – literally in the case of the growing number of everyday objects used in the modern home – smart TVs, smart meters, baby monitors, kettles and more. You may remember that last year one of our security researchers investigated his own home, to determine whether it was really cyber-secure. You can find a follow-up to this research here. However, the ‘Internet of Things’ encompasses more than household devices.
Researchers have been investigating the potential security risks associated with connected cars for some years. In July 2014 Kaspersky Lab and IAB published a study looking at the potential problem areas of connected cars. Until this year, the focus was on accessing the car’s systems by means of a physical connection to the vehicle. This changed when researchers Charlie Miller and Chris Valasek found a way to gain wireless access to the critical systems of a Jeep Cherokee – successfully taking control and driving it off the road! (You can read the story here)
This story underlines some of the problems with connected devices that extend beyond the car industry – to any connected device. Unfortunately, security features are hard to sell; and in a competitive marketplace, things that make customers’ lives easier tend to take precedence. In addition, connectivity is often added to a pre-existing communication network that wasn’t created with security in mind. Finally, history shows that security tends to be retro-fitted only after something bad happens to demonstrate the impact of a security weakness. You can read more on these issues in a blog post written by Eugene Kaspersky published in the aftermath of the above research
Some of the problems with connected devices apply also to ‘smart cities’ #KLReport
Tweet
Such problems apply also to ‘smart cities‘. For example, the use of CCTV systems by governments and law enforcement agencies to monitor public places has grown enormously in recent years. Many CCTV cameras are connected wirelessly to the Internet, enabling police to monitor them remotely. However, they are not necessarily secure: there’s the potential for cybercriminals to passively monitor security camera feeds, to inject code into the network – thereby replacing a camera feed with fake footage – or to take systems offline. Two security researchers (Vasilios Hioureas from Kaspersky Lab and Thomas Kinsey from Exigent Systems) recently conducted research into the potential security weaknesses in CCTV systems in one city. You can read Vasilios’s report on our web site)
Unfortunately, there had been no attempt to mask the cameras, so it was easy to determine the makes and models of the cameras being used, examine at the relevant specifications and create their own scaled model in the lab. The equipment being used provided effective security controls, but these controls were not being implemented. Data packets passing across the mesh network were not being encrypted, so an attacker would be able to create their own version of the software and manipulate data travelling across it. One way this could potentially be used by attackers would be to spoof footage sent to a police station, making it appear as if there is an incident in one location, thereby distracting police from a real attack occurring somewhere else in the city
The researchers reported the issues to those in charge of the real world city surveillance system and they are in the process of fixing the security problems. In general, it’s important that WPA encryption, protected by a strong password, is implemented in such networks; that labelling is removed from hardware, to make it harder for would-be attackers to find out how the equipment operates; and to encrypt footage as it travels through the network
The wider issue here is that more and more aspects of everyday life are being made digital: if security isn’t considered at the design stage, the potential dangers could be far-reaching – and retro-fitting security might not be straightforward. The Securing Smart Cities initiative, supported by Kaspersky Lab, is designed to help those responsible for developing smart cities to do so with cyber-security in mind
International co-operation against cybercriminals
Cybercrime is now an established part of life, on the back of the ever-increasing online activities we engage in. This is now being reflected in official statistics. In the UK, for example, the Office for National Statistics now includes cybercrime among its estimates of the scale of crime, reflecting the fact that nature of crime in society is changing. While there’s no question that cybercrime can be lucrative, cybercriminals aren’t always able to act with impunity; and the actions of law enforcement agencies around the world can have a significant impact. International co-operation is particularly important, given the global nature of cybercrime. This year there have been some notable police operations
In April, Kaspersky Lab was involved in the take-down of the Simda botnet, co-ordinated by the Interpol Global Complex for Innovation. The investigation was started by Microsoft and expanded to other participants, including Trend Micro, the Cyber Defense Institute, officers from the Dutch National High Tech Crime Unit (NHTCU), the FBI, the Police Grand-Ducale Section Nouvelles Technologies in Luxembourg, and the Russian Ministry of the Interior’s Cybercrime Department ‘K’ supported by the INTERPOL National Central Bureau in Moscow. As a result of the operation, 14 servers in the Netherlands, the US, Luxembourg, Poland and Russia were taken down. Preliminary analysis of some of the sink-holed server logs revealed that 190 countries had been affected by the botnet
In 2015, there have been some notable international police operations #KLReport
Tweet
In September, the Dutch police arrested two men for suspected involvement in CoinVault ransomware attacks, following a joint effort by Kaspersky Lab, Panda Security and the Dutch National High Tech Crime Unit (NHTCU). This malware campaign started in May 2014 and continued into this year, targeting victims in more than 20 countries, with the majority of victims in the Netherlands, Germany, the United States, France and Great Britain. They successfully encrypted files on more than 1,500 Windows-based computers, demanding payment in bitcoin to decrypt data. The cybercriminals responsible for this ransomware campaign modified their creations several times to keep on targeting new victims. In November 2014, Kaspersky Lab and the Dutch NHTCU launched a web site to act as a repository of decryption keys; and we also made available online a decryption tool to help victims recover their data without having to pay the ransom. You can find our analysis of the twists and turns employed by the CoinVault authors here. Ransomware has become a notable fixture of the threat landscape. While this case shows that collaboration between researchers and law enforcement agencies can lead to positive results, it’s essential for consumers and businesses alike to take steps to mitigate the risks of this type of malware. Ransomware operations rely on their victims paying up. In September, an FBI agent caused controversy by suggesting that victims should pay the ransom in order to recover their data. While this might seem to be a pragmatic solution (not least because there are situations where recovery of data is not possible), it’s a dangerous strategy. First, there’s no guarantee that the cybercriminals will provide the necessary mechanism to decrypt the data. Second, it reinforces their business model and makes the further development of ransomware more likely. We would recommend that businesses and individuals alike make regular backups of data, to avoid being put in this invidious position
Attacks on industrial objects
Incidents caused by cybersecurity problems are a fairly regular occurrence at industrial objects. For example, according to US ICS CERT data, 245 such incidents were recorded in the US during the 2014 fiscal year, and 22 incidents in July and August 2015. However, we believe these numbers do not reflect the actual situation: there are many more cyber incidents than this. And while enterprise operators and owners prefer to keep quiet about some of these incidents, they are simply unaware of others
Let’s have a look at two cases that caught our attention in 2015
One is an incident that took place at a steel mill in Germany. Towards the end of 2014, the German Federal Office for Information Security (Bundesamt für Sicherheit in der Informationstechnik, BSI) published a report (see Appendix on English) which mentioned a cyber incident at a German steel mill. The incident resulted in physical damage to a blast furnace
This is the second cyberattack that we know of, after Stuxnet, to cause physical damage to industrial facilities. According to BSI, the attackers first used phishing emails to infect the enterprise’s office network, after which the hackers managed to infect a SCADA computer and attack the physical equipment. Unfortunately, BSI did not provide any additional information, so we do not know which malware was used and how it operated
This secrecy is bad for everybody: operators of other similar enterprises (with the possible exception of German facilities) will not be able to analyze the attack and implement countermeasures; cybersecurity experts are also in the dark and are unable to suggest security measures to their customers
Incident in Germany – the second cyberattack, after Stuxnet, to cause physical damage to facilities #KLReport
Tweet
Another curious incident was an attack against the Frederic Chopin Airport in Warsaw in June 2015., The computer system responsible for preparing flight plans for LOT, Poland’s national airline, was taken down for about five hours one Sunday. According to Reuters, this caused delays to a dozen flights
The airport management provided no details and experts had to form their opinions based on their experience. Ruben Santamarta, Principal Security Consultant at IOActive, has previously called attention to IT security issues in aviation. Based on what the LOT representatives said, he suggested that the company had fallen victim to a targeted attack: the system couldn’t generate flight plans because key nodes in the back office were compromised, or perhaps the attack targeted ground communication devices, resulting in the inability to perform or validate data loading on aircraft (including flight plans)
Our experts also responded to the incident, suggesting there could be two possible scenarios. The incident may have been the result of human error or equipment malfunction. Alternatively, the incident at the relatively small Warsaw airport could be a precursor of larger-scale attacks in other, much larger, airports
It was later announced that a DDoS attack had taken place and that no penetration had actually taken place. Once again, no detailed information about the incident was disclosed and we can either believe the official information or guess at the real reasons and goals of the attack
Whoever was behind the attacks described above and whatever goals they pursued, these incidents clearly demonstrate how significant a part of our lives computers have become and how vulnerable infrastructure objects have become in recent years
Unfortunately, today many governments and regulators resort to a policy of secrecy. We believe that transparency and the exchange of information about cyberattacks is an important part of providing adequate protection for industrial objects. Without this knowledge, it is very hard to protect these objects against future threats
In conclusion, we would like to mention one more trend that is already relevant and will continue to affect us all in the coming years: the hardware used by industrial enterprises is being actively connected to the Web. The Internet may have appeared quite a long time ago, but it is only now that it is being introduced to industrial processes. It is no exaggeration to say that this represents a new industrial revolution: we are witnessing the birth of the ‘Industrial Internet of Things’ or Enterprise 4.0. As a result, enterprises receive a whole host of additional benefits and can improve their manufacturing efficiency
We are witnessing the birth of a new industrial revolution – the ‘Industrial Internet of Things’ #KLReport
Tweet
In order to keep up with this trend, equipment manufacturers simply add sensors and controllers to proven, safe and reliable equipment originally developed for the ‘offline’ world, provide Internet connectivity for their devices and then offer this ‘new equipment’ to customers. They forget, however, that when online features are added to any device, this gives rise to new cybersecurity-related risks and threats. This is no longer a ‘physical’ device, but a ‘cyber-physical’ one
In the world of physical devices, all industrial devices, instruments, communication protocols, etc. were designed with safety in mind – in other words, they were built to be foolproof. This meant that if a device was designed to meet functional safety requirements, operating it without violating the safety rules would not result in any failures or damage to people or the environment
Enterprise 4.0 brings with it a new security dimension: IT security or protection against intentional external manipulation. You cannot simply connect an object or device from the pre-Internet era to the Internet: the consequences of this can be – and often are – disastrous
Engineers who embrace old ‘pre-revolutionary’ design principles often fail to realize that their devices can now be ‘operated’ not only by engineers, who know which actions are admissible and which are not, but also by hackers for whom there is no such thing as inadmissible remote object operations. This is one of the main reasons why today some well-established companies with many years of experience offer hardware that may be reliable from the point of view of functional safety, but which does not provide an adequate level of cybersecurity
In the world of cyber-physical devices, physical and cyber components are tightly integrated. A cyberattack can disrupt an industrial process, damage equipment or cause a technogenic disaster. Hackers are a real threat and anything that is connected to the Internet can be attacked. This is why equipment manufacturers, when designing new connected industrial equipment, should be as careful about implementing protection against cyberthreats as they are about designing functional safety features.
Conclusion
In 2015, perhaps for the first time in the entire history of the Internet, issues related to protecting networks and being protected online were discussed in connection with every sector of the economy and with people’s everyday life. Choose any sector of modern civilization – finances, industrial production, cars, planes, wearable devices, healthcare and many others – and you will be sure to find publications this year on incidents or cybersecurity problems related to that sector.
Regrettably, cybersecurity has now become inseparably linked with terrorism. Defensive, as well as offensive, methods used online are attracting lots of interest from various illegal organizations and groups.
Cybersecurity issues have risen to the level of top diplomats and government officials. In 2015, cybersecurity agreements were signed between Russia and China, China and the US, China and the UK. In these documents, governments not only agree to cooperate, but also accept the responsibility to refrain from any attacks on each other. At the same time, there was extensive discussion of recent changes to the Wassenaar Arrangement restricting spyware exports. A recurring theme of the year was the use of insecure email services by various political figures across the globe, including the then US Secretary of State Hillary Clinton.
All this has led to a huge surge in interest in cybersecurity issues, not only from the mass media but also from the entertainment industry. There were feature films and TV series produced, some of them starring cybersecurity experts, sometimes as themselves.
The word cybersecurity became fashionable in 2015, but this does not mean the problem has been solved. We are seeing what amounts to exponential growth in everything related to cybercrime, including increases in the number of attacks and attackers, the number of victims, defense and protection related costs, laws and agreements that regulate cybersecurity or establish new standards. For us, this is primarily about the sophistication of the attacks we detect. The confrontation is now in the active stage, with the final stage not even on the horizon.
Shocking! Instagram HACKED! Researcher hacked into Instagram Server and Admin Panel
18.12.2015
Ever wonder how to hack Instagram or how to hack a facebook account? Well, someone just did it!
But, remember, even responsibly reporting a security vulnerability could end up in taking legal actions against you.
An independent security researcher claims he was threatened by Facebook after he responsibly revealed a series of security vulnerabilities and configuration flaws that allowed him to successfully gained access to sensitive data stored on Instagram servers, including:
Source Code of Instagram website
SSL Certificates and Private Keys for Instagram
Keys used to sign authentication cookies
Personal details of Instagram Users and Employees
Email server credentials
Keys for over a half-dozen critical other functions
However, instead of paying him a reward, Facebook has threatened to sue the researcher of intentionally withholding flaws and information from its team.
Wesley Weinberg, a senior security researcher at Synack, participated in Facebook's bug bounty program and started analyzing Instagram systems after one of his friends hinted him to a potentially vulnerable server located at sensu.instagram.com
The researcher found an RCE (Remote Code Execution) bug in the way it processed users’ session cookies that are generally used to remember users' log-in details.
wesley-weinberg-security-researcher
Remote code execution bug was possible due to two weaknesses:
The Sensu-Admin web app running on the server contained a hard-coded Ruby secret token
The host running a version of Ruby (3.x) that was susceptible to code execution via the Ruby session cookie
Exploiting the vulnerability, Weinberg was able to force the server to vomit up a database containing login details, including credentials, of Instagram and Facebook employees.
Although the passwords were encrypted with ‘bcrypt’, Weinberg was able to crack a dozen of passwords that had been very weak (like changeme, instagram, password) in just a few minutes.
Exposed EVERYTHING including Your Selfies
Weinberg did not stop here. He took a close look at other configuration files he found on the server and discovered that one of the files contained some keys for Amazon Web Services accounts, the cloud computing service used to host Instagram's Sensu setup.
These keys listed 82 Amazon S3 buckets (storage units), but these buckets were unique. He found nothing sensitive in the latest file in that bucket, but when he looked at the older version of the file, he found another key pair that let him read the contents of all 82 buckets.
Instagram-admin-hacking
Weinberg had inadvertently stumbled upon almost EVERYTHING including:
Instagram's source code
SSL certificates and private keys (including for instagram.com and *.instagram.com)
API keys that are used for interacting with other services
Images uploaded by Instagram users
Static content from the instagram.com website
Email server credentials
iOS/Android app signing keys
Other sensitive data
"To say that I had gained access to basically all of Instagram's secret key material would probably be a fair statement," Weinberg wrote in his blog. "With the keys I obtained, I could now easily impersonate Instagram, or any valid user or staff member. While out of scope, I would have easily been able to gain full access to any user’s account, [personal] pictures and data."
Instagram-admin-hacking
Responsible Disclosure, but Facebook Threatens Lawsuit
Weinberg reported his findings to Facebook's security team, but the social media giant was concerned he had accessed private data of its users and employees while uncovering the issues.
Instead of receiving a reward from Facebook for his hard work, Weinberg was unqualified for the bug bounty program by Facebook.
In early December, Weinberg claims his boss Synack CEO, Jay Kaplan, received a scary call from Facebook security chief Alex Stamos regarding the weaknesses Weinberg discovered in Instagram that left Instagram and Facebook users wide open to a devastating attack.
Stamos "stated that he did not want to have to get Facebook's legal team involved, but that he was not sure if this was something he needed to go to law enforcement over," Weinberg wrote in his blog in a section entitled 'Threats and Intimidation.'
In response, Stamos issued a statement, saying he "did not threaten legal action against Synack or [Weinberg] nor did [he] ask for [Weinberg] to be fired."
Stamos said he only told Kaplan to "keep this out of the hands of the lawyers on both sides."
"Condoning researchers going well above and beyond what is necessary to find and fix critical issues would create a precedent that could be used by those aiming to violate the privacy of our users, and such behavior by legitimate security researchers puts the future of paid bug bounties at risk," Stamos added.
Facebook Responds
After the original publication by the researcher, Facebook issued its response, saying the claims are false and that Weinberg was never told not to publish his findings, rather only asked not to disclose the non-public information he accessed.
The social media giant confirmed the existence of the remote code execution bug in the sensu.instagram.com domain and promised a bug bounty of $2,500 as a reward to Weinberg and his friend who initially hinted that the server was openly accessible.
However, the other vulnerabilities that allowed Weinberg to gain access to sensitive data were not qualified, with Facebook saying he violated user privacy while accessing the data.
Here's the full statement by Facebook:
We are strong advocates of the security researcher community and have built positive relationships with thousands of people through our bug bounty program. These interactions must include trust, however, and that includes reporting the details of bugs that are found and not using them to access private information in an unauthorized manner. In this case, the researcher intentionally withheld bugs and information from our team and went far beyond the guidelines of our program to pull private, non-user data from internal systems.
We paid him for his initial bug report based on the quality, even though he was not the first to report it, but we didn't pay for the subsequent information that he had withheld. At no point did we say he could not publish his findings — we asked that he refrain from disclosing the non-public information he accessed in violation of our program guidelines. We remain firmly committed to paying for high quality research and helping the community learn from researchers' hard work.
Juniper Firewalls with ScreenOS Backdoored Since 2012
18.12.2015
Juniper Networks has announced that it has discovered "unauthorized code" in ScreenOS, the operating system for its NetScreen firewalls, that could allow an attacker to decrypt traffic sent through Virtual Private Networks (VPNs).
It's not clear what caused the code to get there or how long it has been there, but the release notes posted by Juniper suggest the earliest buggy versions of the software date back to at least 2012 and possibly earlier.
The backdoor impacts NetScreen firewalls using ScreenOS 6.2.0r15 through 6.2.0r18 and 6.3.0r12 through 6.3.0r20, states the advisory published by the company. However, there's no evidence right now that whether the backdoor was present in other Juniper OSes or devices.
The issue was uncovered during an internal code review of the software, according to Juniper chief information officer Bob Worrall, and requires immediate patching by upgrading to a new version of the software just released today.
"Juniper discovered unauthorized code in ScreenOS that could allow a knowledgeable attacker to gain administrative access to NetScreen devices and to decrypt VPN connections," Worrall said.
How Does the Backdoor Occur?
The backdoor occurred due to a pair of critical vulnerabilities:
First allows anyone to decrypt VPN traffic and leave no trace of their actions
Second allows anyone to complete compromise a device via an unauthorized remote access vulnerability over SSH or telnet.
In short, an attacker could remotely log-in to the firewall with administrator privileges, decrypt and spy on thought-to-be-secure traffic, and then even remove every trace of their activity.
Sounds awful, although Juniper claims the company has not heard of any exploitation in the wild so far and released patched versions of Screen OS that are available now on its download page.
Unauthorized code found in Juniper’s firewall OS
18.12.2015
An operating system running on firewalls sold by Juniper Networks contains unauthorized code that could be exploited to decrypt traffic sent through virtual private networks.
An “unauthorized code” was discovered in the operating system for Juniper NetScreen firewalls. The company admitted the presence of the “unauthorized code” that could allow an attacker to decrypt VPN traffic.
[“unauthorized code”] “could allow a knowledgeable attacker to gain administrative access to NetScreen devices and to decrypt VPN connections.”
According to The Register, the presence of the unauthorized code could date back to 2008, the experts referred a 2008 notice issued by Juniper’s about a security issued that impacts ScreenOS 6.2.0r15 through 6.2.0r18 and 6.3.0r12 through 6.3.0r20. ScreenOS 6.2 was released. The Screen OS 6.3 was presented in 2009.
“During a recent internal code review, Juniper discovered unauthorized code in ScreenOS that could allow a knowledgeable attacker to gain administrative access to NetScreen devices and to decrypt VPN connections,” Juniper Chief Information officer Bob Worrall wrote. “Once we identified these vulnerabilities, we launched an investigation into the matter, and worked to develop and issue patched releases for the latest versions of ScreenOS.” states the advisory.
The experts explained that there are several releases with numerous versions of the Juniper products and the unauthorized code was only found in some of them.
juniper firewall unauthorized code
A separate advisory issued by the company confirm the presence of two separate vulnerabilities in its products, the first one allows unauthorized remote administrative access to an affected device over SSH or telnet, “The second issue may allow a knowledgeable attacker who can monitor VPN traffic to decrypt that traffic,” the advisory said. “It is independent of the first issue. There is no way to detect that this vulnerability was exploited.”
The presence of unauthorized code is disconcerting, one of the most important vendors of security appliances inserted an unauthorized code in a number of its products.
Giving the nature of the code it is difficult to think that the code was accidentally “inserted” in the OS, it is likely that it was used to monitor customers’ confidential communications.
Users urge to update their products, Juniper has issued an out-of-band patch to fix the issue.
Microsoft Outlook flaw opens the door to “mailbomb” attacks
18.12.2015
Microsoft fixed a vulnerability in Microsoft Outlook that could allow remote code execution if the victim opens a specially crafted Office doc.
Microsoft recently fixed a number of critical bugs with the last “Patch Tuesday” issued on December 8, including an update to the Microsoft Office suite to fix a number of security issues. One of the flaws, the CVE-2015-6172 vulnerability, could be exploited by attackers for remote code execution through a “specially crafted Microsoft Office file”.
“This security update resolves vulnerabilities in Microsoft Office. The most severe of the vulnerabilities could allow remote code execution if a user opens a specially crafted Microsoft Office file. An attacker who successfully exploited the vulnerabilities could run arbitrary code in the context of the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.” states the Microsoft Security Bulletin.
The vulnerability affects Office 2010 and later, as well as Microsoft Word 2007 with Service Pack 3.
As explained by the security researcher Haifei Li in a paper entitled “BadWinmail: The ‘Enterprise Killer’ Attack Vector in Microsoft Outlook,” and attacker can exploit the vulnerability by sending a crafted attachment via e-mail to bypass Outlook’s layers of security by exploiting Office’s Object Linking and Embedding (OLE) capabilities and Outlook’s Transport Neutral Encapsulation Format (TNEF).
The winmail.dat file includes instructions on how to Microsoft Office handles attachments, before the patch release OLE objects were rendered within the e-mail and call code from the application they’re based on escaping the Outlook security “sandbox.”
“When the value of the ‘PidTagAttachMethod’ [within winmail.dat] is set to ATTACH_OLE (6),” Haifei wrote, “the ‘attachment file’ (which is another file contained in the winmail.dat file) will be rendered as an OLE object.”
As a result, an attacker could create a specific a TNEF e-mail and send it to the targeted user to launch the attack.
“Such a feature could allow us to “build” a TNEF email and send it to the user, when the user reads the email, the embedded OLE object will be loaded automatically. ” states the expert. ” According to the author’s tests, various OLE objects can be loaded via emails; this poses a big security problem.”

Phishing attacks that rely on this technique are very dangerous because to compromise the victim machine, it is sufficient that the malicious message is viewed by the user.
“By packing a Flash exploit in an OLE enabled TNEF e-mail, an attacker can [achieve] full code execution as long as the victim reads the e-mail,” he reported. “We use Flash OLE object as an example since Flash (zero-day) exploits are easy to obtain by attackers, but please note that there are other OLE objects [that] may be abused by [an] attacker.”
Haifei noted that the vulnerability could also be triggered by the content of the email instead the attachment because Outlook automatically considers .msg files as “safe” and opens them in an Outlook message view rather than sandboxing them. This means that OLE content embedded in the content of the email will be automatically opened.
Don’t waste time, apply the patch and turn off the message preview pane in Microsoft Outlook.
Haifei also suggested to change to registry keys with an “Office kill-bit” to block Flash content from automatically opening via OLE, by blocking the CLSID D27CDB6E-AE6D-11cf-96B8-444553540000.
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Office\Common\COM Compatibility\{D27CDB6E-AE6D-11cf-96B8-444553540000}]"Compatibility Flags"=dword:00000400
This setting will prevent protect you from OLE-embedded Flash exploits.
Hackers trace ISIS Twitter accounts back to the UK govt
18.12.2015
A group of hackers known as VandaSec claims three ISIS Twitter accounts trace back to computers belonging to the UK government.
According to the revelation of a group of hackers known as VandaSec, at least three Islamic State Twitter social media accounts are run from IP addresses linked to the British government’s Department for Work and Pensions (DWP).
VandaSec has discovered the internet protocol (IP) addresses used by three jihadists to access Twitter accounts involved in the activities of propaganda and online recruitment.
According to the Daily Mirror, the IP addresses belong to the DWP’s London offices.
“Hackers have claimed that a number of Islamic State supporters’ social media accounts are being run from internet addresses linked to the Department of Work and Pensions. A group of four young computer experts who call themselves VandaSec have unearthed evidence indicating that at least three ISIS-supporting accounts can be traced back to the DWP.”
“Don’t you think that’s strange?” said one of the hackers to the Daily Mirror. “We traced these accounts back to London, the home of the British intelligence services,” they added.
isis paris attacks post propaganda
There are two hypotheses on the strange discovery:
There are ISIS Sympathizers inside the British government.
The accounts are used by the British intelligence to identify wannabe terrorists and other members of the organization.
The addresses were thought to be based in Saudi Arabia, in reality, the Cabinet Office admitted to selling IP addresses to two Saudi companies earlier this year, this is the reason why the IP appears to be linked to the British Government.
“The government owns millions of unused IP addresses which we are selling to get a good return for hardworking taxpayers,” a Cabinet Office spokesperson said. “We have sold a number of these addresses to telecoms companies, both in the UK and internationally, to allow their customers to connect to the internet.” “We think carefully about which companies we sell addresses to, but how their customers use this internet connection is beyond our control.”
A secret cellphone spying devices catalog leaked online
18.12.2015
Someone in the Intelligence community leaked online a secret catalog of cellphone spying devices used by law enforcement.
The Intercept has leaked online a secret catalog of cellphone spying devices, the precious document has been given to the online publication by someone inside the intelligence community.
The person who passed the document to The Intercept declared to be concerned about the growing militarization of domestic law enforcement.
“The Intercept obtained the catalogue from a source within the intelligence community concerned about the militarization of domestic law enforcement. (The original is here.)” states the post published on the Intercept.
“A few of the devices can house a “target list” of as many as 10,000 unique phone identifiers. Most can be used to geolocate people, but the documents indicate that some have more advanced capabilities, like eavesdropping on calls and spying on SMS messages. Two systems, apparently designed for use on captured phones, are touted as having the ability to extract media files, address books, and notes, and one can retrieve deleted text messages.”

The catalog includes 53 cellphone spying devices, including Stingray I/II surveillance boxes and Boeing “dirt boxes.”
There are some devices small enough to fit in a backpack such as the REBUS Ground Based Geo-Location that “provides limited capability to isolate targets utilizing Firewall option.”
The document also includes many other cellphone spying devices that are less popular of the Stingray that could be used by law enforcement and intelligence agencies in various scenarios, including the deployment on drones and aircraft.
One of the spying devices is sold by the NSA, while another was designed for use by the CIA.
These systems are a long debated because they allow authorities to conduct dragnet surveillance, the cellphone spying devices have been used by local law enforcement agencies across the United States for a long time.
“The archetypical cell-site simulator, the Stingray, was trademarked by Harris Corp. in 2003 and initially used by the military, intelligence agencies, and federal law enforcement.” continues the post. “Another company, Digital Receiver Technology, now owned by Boeing, developed dirt boxes — more powerful cell-site simulators — which gained favor among the NSA, CIA, and U.S. military as good tools for hunting down suspected terrorists. The devices can reportedly track more than 200 phones over a wider range than the Stingray.”
The Intercept also reported the case of Marc Raimondi who was employed by the Harris company and that now is a Department of Justice spokesman who claim the agency’s use of Stingray cellphone spying devices is legal.
Jennifer Lynch, a senior staff attorney at the Electronic Frontier Foundation has repeatedly expressed its disappointment at the use of these devices in a domestic context.
“We’ve seen a trend in the years since 9/11 to bring sophisticated surveillance technologies that were originally designed for military use—like Stingrays or drones or biometrics—back home to the United States,” said Jennifer Lynch “But using these technologies for domestic law enforcement purposes raises a host of issues that are different from a military context.”
I suggest you to give a look to the document, it is full of interesting things.
You can Hack into a Linux Computer just by pressing 'Backspace' 28 times
17.12.2015
So what would anyone need to bypass password protection on your computer?
It just needs to hit the backspace key 28 times, for at least the computer running Linux operating system.
Wait, what?
A pair of security researchers from the University of Valencia have uncovered a bizarre bug in several distributions of Linux that could allow anyone to bypass any kind of authentication during boot-up just by pressing backspace key 28 times.
This time, the issue is neither in a kernel nor in an operating system itself, but rather the vulnerability actually resides in Grub2, the popular Grand Unified Bootloader, which is used by most Linux systems to boot the operating system when the PC starts.
Also Read: GPU-based Linux Rootkit and Keylogger.
The source of the vulnerability is nothing but an integer underflow fault that was introduced with single commit in Grub version 1.98 (December 2009) – b391bdb2f2c5ccf29da66cecdbfb7566656a704d – affecting the grub_password_get() function.
Here's How to Exploit the Linux Vulnerability
If your computer system is vulnerable to this bug:
Just hit the backspace key 28 times at the Grub username prompt during power-up. This will open a "Grub rescue shell" under Grub2 versions 1.98 to version 2.02.
This rescue shell allows unauthenticated access to a computer and the ability to load another environment.
From this shell, an attacker could gain access to all the data on your computer, and can misuse it to steal or delete all the data, or install persistent malware or rootkit, according to researchers Ismael Ripoll and Hector Marco, who published their research on Tuesday.
Here's How to Protect Linux System
The Grub vulnerability affects Linux systems from December 2009 to the present date, though older Linux systems may also be affected.
Also Read: Is This Security-Focused Linux Kernel Really UnHackable?
The good news is the researchers have made an emergency patch to fix the Grub2 vulnerability. So if you are a Linux user and worried your system might be vulnerable, you can apply this emergency patch, available here.
Meanwhile, many major distributions, including Ubuntu, Red Hat, and Debian have also released emergency patches to fix the issue.
Linux is often thought to be a super secure operating system compare to others, and this Grub vulnerability could be a good reminder that it's high time to take physical security just as seriously as network security.
Bad Santa! Microsoft Offers — 'Upgrade now' or 'Upgrade tonight' to Push Windows 10
17.12.2015
Many Windows 7 and Windows 8.1 users don't want to upgrade their machines to Microsoft’s newest Windows 10 operating system now or anytime soon. Isn't it?
But what if you wake up in the morning and found yourself a Windows 10 user?
That's exactly what Microsoft is doing to Windows 7 and 8.1 users.
Windows 10 Upgrade Becomes More Aggressive
Ever since Microsoft launched its new operating system over the summer, Windows 7 and 8.1 users have been forced several number of times to upgrade their machines to Windows 10.
It was relatively inoffensive at first, but as days have passed, Microsoft has become increasingly aggressive to push Windows users to upgrade to Windows 10.
Microsoft has left very little choice over whether to upgrade their systems to Windows 10 or not. At last, the users end up upgrading their machines to the latest Windows operating system.
Users now see a pop up on their computers, as InfoWorld reports, that displays only two choices for you:
Upgrade Now 'OR' Upgrade Tonight
But, What's the Catch?
Yes, there is a catch to get rid of Windows 10 upgrade, temporarily, anyways.
What users will see is the above two options but what they'll not see is the third option hiding in plain sight: The 'X' button in the top-right corner of the upgrade window.
Also Read: Reminder! If You Haven't yet, Turn Off Windows 10 Keylogger Now.
While you can click the 'X' button to make the upgrade go away, the less knowledgeable users would end up upgrading to Windows 10 either then and there or at that night.
Moreover, since the dialog box warns that "Upgrading to Windows 10 is Free for a Limited Time", some users could interpret that if they close the pop-up window, they may not be able to upgrade their machines Free at a later date.
Microsoft silently started pushing Windows 10 installation files on PCs running Windows 7 or Windows 8.1 over a month after its launch, even if users have not opted into the upgrade.
Almost two months ago, some Windows 7 and 8.1 users also claimed that Windows 10 had begun to install itself automatically on their PCs, which Microsoft later called it a mistake.
Although there is nothing we could predict what tweaks Microsoft has planned for future upgrades, the next time you may get a pop-up window with a single button that says "Upgrade Now."
19-Year-Old Teen Steals $150,000 by Hacking into Airline's Website
17.12.2015
What do you do to earn up to $150,000?
Somebody just hacks into airlines and sells fake tickets.
That's exactly what a 19-year-old teenager did and made approximately 1.1 Million Yuan (£110,000 or $150,000) by hacking into the official website of an airline and using the stolen booking information to defraud hundreds of passengers.
The teenager, identified as Zhang from Heilongjiang, north-east China, hacked into a Chinese airline website and illegally downloaded 1.6 Million passengers bookings details, including:
Flight details
Names
ID card numbers
Email addresses
Mobile phone numbers
Zhang then used this information to successfully defraud hundreds of customers by convincing them that there was some issue with their booking flights, and they had to pay extra fees, according to People's Daily Online.
Moreover, the hack caused the airline to lose almost 80,000 Yuan ($12,365 USD) as a result of customers requesting refunds.
The incident took place from 31 July to 20 August this year, and the suspect was arrested by the police on November in Dalian, north China.
A police officer said the hack was not highly sophisticated and was a result of a loophole in the airline's computer system. However, the name of the airline is not yet disclosed.
Phantom Squad wants to take down Playstation network and Xbox Live on Christmas
17.12.2015
Playstation network and Xbox Live risk to be taken down on Christmas by an anonymous group of hackers known as the Phantom Squad.
If you remember, last Christmas, both PlayStation network and Xbox Live were took down by hackers belonging to the group of hackers known as Lizard Squad. It looks like this year this new tradition may continue, all because a group called. posted on twitter a message announcing their intentions of taken down again both PlayStation network and Xbox live, menacing to keep down the services for a week.
“We are going to shut down Xbox live and PSN this year on christmas. And we are going to keep them down for one week straight #DramaAlert”
Phantom Squad (@PhantomSqaud) December 9, 2015
We have no information on the group, but probably the group wants to gain popularity, and these targets during the Christmas represent a great opportunity.
If they succeed, they will get the attention they want.
The intent of the Phantom Squad is to demonstrate that “cyber security does not exist” in both gaming platforms.
Phantom Squad also said that both platforms are vulnerable to attacks, and they add that they were able to take down Xbox live during the weekend:

Microsoft hasn’t confirmed the attack, but it confirmed that issues occurred in the Xbox live network on Saturday afternoon:
“We are currently investigating issues w/ signing in, managing friends, & matchmaking. Updates here while we work: http://xbx.lv/XBLstus,” said Microsoft’s XBox Support Twitter account.
As mention before, last Christmas, both platforms faced the same issue, the group Lizard Squad hit both networks with a powerful DDoS attack, the services provided by Sony and Microsoft were paralyzed for several days. After the attacks, an 18-year-old was arrested in the UK, on January 16th along with a 22-year-old Vincent Omari that was accused to be a member of the Lizard Squad group, but he always denied it and was released on bail.
Phantom Squad claims not be linked with Lizard Squad, and declared to be a group of Gray Hat hackers that like the popular Anonymous have declared war on the Islamic State group.
Elsio Pinto (@high54security) is at the moment the Lead McAfee Security Engineer at Swiss Re, but he also as knowledge in the areas of malware research, forensics, ethical hacking. He had previous experiences in major institutions being the European Parliament one of them. He is a security enthusiast and tries his best to pass his knowledge. He also owns his own blog McAfee Security Engineer at Swiss Re, but he also as knowledge in the areas of malware research, forensics, ethical hacking. He had previous experiences in major institutions being the European Parliament one of them. He is a security enthusiast and tries his best to pass his knowledge. He also owns his own blog McAfee Security Engineer at Swiss Re, but he also as knowledge in the areas of malware research, forensics, ethical hacking. He had previous experiences in major institutions being the European Parliament one of them. He is a security enthusiast and tries his best to pass his knowledge. He also owns his own blog http://high54security.blogspot.com/
Hackers Plan to Ruin Christmas Eve for Millions of PlayStation and Xbox Live Gamers
17.12.2015
Remember the notorious hacker group Lizard Squad that spoiled last Christmas holidays of many game lovers by knocking the PlayStation Network and Xbox Live offline with apparent Distributed Denial of Service (DDoS) attacks?
But, Will you be able to Play Xbox and PlayStation Game this Christmas?
Probably Not.
Because a new hacking group is threatening to carry out similar attacks by taking down the Xbox LIVE and PlayStation Network for a week during Christmas.
Be Ready this Christmas for Attacks on PSN and XBox LIVE
In a series of tweets, a bunch of DDoS hackers calling themselves "Phantom Group" (@PhantomSquad) announced that they will disrupt the XBox Live and PlayStation networks in a coordinated DoS attack.
The attacks could prevent millions of gamers worldwide from enjoying their newly opened Christmas gifts and accessing games online.
Also Read: PlayStation 4 Jailbreak Confirms.
Here are the tweets by Phantom Squad:
We are going to shut down Xbox live and PSN this year on Christmas. And we are going to keep them down for one-week straight #DramaAlert
Ok, think about this.... Xbox Live and PSN have millions upon millions of dollars... but do they use that money for better security?
No. PSN and Xbox do not use that money to improve their security... So until they open their eyes, Xbox Live and PSN will remain vulnerable.
Take Phantom Squad's Threats More Seriously
A few days ago, Phantom Squad claimed responsibility for knocking Reddit offline, and Reddit confirms that the issue, saying its databases coming "under extreme load" that could have been caused by a DDoS attack.
"Reddit #Offline Goodnight." — Phantom Squad tweeted on December 15, 2015.
Now, the group has turned its crosshairs toward the gaming networks.
However, neither Microsoft nor Sony responsible for managing PlayStation and XBox Live online networks respectively has confirmed the DDoS attacks, but Microsoft, at least, acknowledged issues with Xbox LIVE when Phantom Squad claimed responsibility.
"Xbox Live #Offline" — Phantom Squad tweeted on December 12, 2015.
As a proof, Phantom Squad also posted a video of its cyber attacks.
If the DDoS attack on PSN and XBox is carried out successfully for a week during Christmas, it will again ruin the Christmas holidays for millions of video game lovers worldwide, just like last year.
Since DDoS attacks are so easy to conduct nowadays when there are so many DDoS tools available online, the important point here is whether Microsoft and Sony have upgraded their DDoS defences enough to defend against the attacks.
So, What do you think about the declarations of war upon PSN and Xbox LIVE? Share your thoughts with us in the comments below.
Joomla under attack due to a zero-day. Patch your CMS now!
17.12.2015
The websites based on the popular Joomla CMS need to be updated as soon as possible due to a critical remote code execution vulnerability.
The websites based on the popular Joomla CMS need to be updated as soon as possible, Joomla has just released a security patch to fix a critical eight-year-old remote code execution vulnerability. The critical flaw was already exploited in the wild, during the weekend experts at the Sucuri firm observed an alarming increase in the number of attacks.
According to the security expert Daniel Cid from Sucuri, starting from Saturday hundreds of attacks are now taking place.
“What is very concerning is that this vulnerability is already being exploited in the wild and has been for the last 2 days. Repeat: This has been in the wild as a 0-day for 2 days before there was a patch available.” States the blog post published by Sucuri.
“The wave of attacks is even bigger, with basically every site and honeypot we have being attacked [which] means that probably every other Joomla site out there is being targeted as well.”
The zero-day flaw could have a significant impact on the Internet users considering that Joomla is the most popular content management system having been downloaded more than 50 million times.

According to a security advisory published by Joomla, all versions above 1.5 are affected. It is important to update the CMS version to the patched version 3.4.6.
“Browser information is not filtered properly while saving the session values into the database which leads to a remote code execution vulnerability,” it says.
Sucuri is inviting users to protect their websites and looking for possible indicators od compromise. The attackers are running object injection through the HTTP user agent with exploits from the IP address 74.3.170.33, 146.0.72.83, and 194.28.174.106.
“If you are a Joomla user, check your logs right away. Look for requests from 146.0.72.83 or 74.3.170.33 or 194.28.174.106 as they were the first IP addresses to start the exploitation. I also recommend searching your logs for “JDatabaseDriverMysqli” or “O:” in the User Agent as it has been used in the exploits. If you find them, consider your Joomla site compromised and move to the remediation / incident response phase.” States Sucuri.
Don’t waste time, check log and update your Joomla version asap.
GCHQ Gaffer database goes open source
17.12.2015
The British intelligence agency GCHQ has released the Gaffer database as an open source project.
Gaffer is sort of database written in Java that makes it “easy to store large-scale graphs in which the nodes and edges have statistics such as counts, histograms and sketches.”, its code is available for download on the code-sharing website Github.
“Gaffer is a framework that makes it easy to store large-scale graphs in which the nodes and edges have statistics such as counts, histograms and sketches. These statistics summarise the properties of the nodes and edges over time windows, and they can be dynamically updated over time.” states its description on the Github.
In reality the Gaffer is much more, it implements a framework for creating mass-scale databases, it is a powerful tool for the storage and analysis of the relationships between different pieces of data.
“Gaffer is a graph database, rather than a graph processing system. It is optimised for retrieving data on nodes of interest.” continues the description “Gaffer is distinguished from other graph storage systems by its ability to update properties within the store itself.”
The Gaffer implements features to carry out our several :
Allow the creation of graphs with summarised properties within Accumulo with a very less amount of coding.
Allow flexibility of stats that describe the entities and edges.
Allow easy addition of nodes and edges.
Allow quicker retrieval of data on nodes of interest.
Deal with data of different security levels – all data has a visibility, which is used to restrict who can access data based on their authorizations.
Support automatic age-off of data.
Gaffer is based on the Apache Accumulo that is a computer software project that developed a sorted, distributed key/value store based on the BigTable technology developed by Google.
Accumulo was created in 2008 by the US National Security Agency and it is released under the Apache 2.0 license.
Gaffer is distributed under the Apache 2.0 license that allows anyone to modify or distribute it.
GCHQ against pedophilies
Security experts speculate that Gaffer is used by the GCHQ for analyzing data related to a specific entity that could be a terrorist or any other element under investigation.
“Each node might be a surveilled terrorist or other source of data, and analysis of the graph might then show who or what is at the ‘center’ of that network,” said Andrii Degeler, a journalist at Ars Technica.
It is impossible to understand the motivation behind the release of the platform, but it is likely that the agency is trying to be attractive for young talents in the hacker community.
The GCHQ is currently working on Gaffer 2, as reported on Github:
“The version of Gaffer in this repo is no longer under active development because a project called Gaffer2 is in development. “
Press backspace 28 times to hack a Linux PC with Grub2
17.12.2015
The researchers Hector Marco and Ismael Ripoll have found that the Grub2 authentication could be easily defeated by hitting backspace 28 times.
A couple of researchers from the University of Valencia’s Cybersecurity research group, Hector Marco and Ismael Ripoll, have found that the Grub2 bootloader is plagued by a serious vulnerability that can be exploited by hackers to bypass password protection and compromise the targeted computer.
Nothing of complex, the researcher discovered that by pressing backspace 28 times, it’s possible to bypass authentication during boot-up on some Linux systems.
The duo explained that the flaw affects the Grub2 bootloader which is currently used by a large number of Linux machines, including some embedded systems, for the boot loading at system startup.
The researchers explained in the advisory that hitting the backspace key 28 times at the Grub username prompt during power-up will defeat the authentication mechanism, the action triggers a “rescue shell” under Grub2 versions 1.98 (December, 2009) to 2.02 (December, 2015).
“Exploiting the integer underflow can be used to cause an Off-by-two or an Out of bounds overwrite memory errors.” states the advisory. “An attacker which successfully exploits this vulnerability will obtain a Grub rescue shell. Grub rescue is a very powerful shell allowing to:
Elevation of privilege: The attacker is authenticated without knowing a valid username nor the password. The attacker has full access to the grub’s console (grub rescue).
Information disclosure: The attacker can load a customized kernel and initramfs (for example from a USB) and then from a more comfortable environment, copy the full disk or install a rootkit.
Denial of service: The attacker is able to destroy any data including the grub itself. Even in the case that the disk is ciphered the attacker can overwrite it, causing a DoS.“
An attacker can exploit the rescue shell to load another environment that allows him to fully compromise the machine, for example by installing a rootkit.
The integer underflow vulnerability affects Grub2 since 2009 and resides in the
grub_password_get()
function.
“The fault (bug) is in the code of Grub since version 1.98 (December, 2009). The commit which introduced the fault was
b391bdb2f2c5ccf29da66cecdbfb7566656a704d
, affecting the
grub_password_get()
function.” continues the advisory.

The duo also presented a proof-of-concept attack exploiting the flaw to inject a backdoor on the target system, fortunately, they have also released a fix that is available here.
N3XT — Advanced CHIP that Could Make Your Computer 1000 Times Faster
16.12.2015
Researchers have come up with an all new way to revolutionize the standard computer chip that comes inbuilt in all our electronics.
Researchers from Carnegie Mellon, Stanford, and the University of California, Berkeley among others, have invented a new material that could replace the 'silicon' in conventional chips – built in all electronic devices – making the device's processing speed 1,000 times faster.
This means that the new chip made with nano-material could solve complex problems in a fraction of the time our computers take.
The brand new chip, dubbed Nano-Engineered Computing Systems Technology (N3XT), takes the landscape from a resource-heavy single-storey layout to an efficient 'Skyscraper' approach, claims a Rebooting Computing special issue of the IEEE Computer journal.
Silicon Chip – A Resource-Heavy Single-Storey Layout
The standard silicon chips currently used in all electronic devices have one major issue:
The silicon chips are arranged like standalone houses in the suburbs.
This means these chips are single-storeys in which each "house" in the neighbourhood are connected with wires that carry digital data.
The drawback of silicon chips is that the data in these chips travels longer distances and wastes energy, often causing digital traffic jams while processing.
N3XT Chip – Skyscraper Approach is 1000 Times Faster
N3XT chips that are made from carbon nanotube transistors are tiny cylindrical molecules of carbon that efficiently conduct heat and electricity.
The N3XT model splits processors and memory into, say, different 'floors' in a skyscraper.
All those floors are then connected by millions of tiny electronic elevators, called 'vias,' that are used to transport data between chips.
The big advantage of Skyscraper approach – data moves much faster, and more efficiently over shorter distances (vertically) than across a larger area (horizontally) like in current silicon chips.
"When you combine higher speed with lower energy use, N3XT systems outperform conventional approaches by a factor of a thousand," said H. -S. Philip Wong, the Professor, who authored the paper.
Another Advantage of N3XT Over Silicon Chip
Another advantage of Skyscraper chips over Silicon chips is that:
Silicon chip cannot be piled on top of each other like in N3XT chip, because, during fabrication silicon chip gets extremely hot (almost 1,000 degrees centigrade) that ends up damaging the layers below.
Whereas the N3XT chip can be fabricated at much lower temperatures than silicon chip, so it can easily be layered without damaging the stacks below.
It sounds like an entirely different approach to computer memory and, of course, this kind of computing knowledge is new to me. But, it's interesting to know that the approach could bring a macro-level revolution in chip architecture that took place more than a century ago.
You can just check out the original report at Stanford News for more details and let me know what's your take on it.
Hacker claims Sony PlayStation 4 Jailbreak
16.12.2015
The dream comes true for many Sony PlayStation 4 users, a hacker has developed a Jailbreak for the popular armored console.
The Sony PlayStation 4 is considered one of the most protected platform, since now it was impossible to run pirated games, but a hacker who calls himself CTurt claimed to develop a fully jailbroken version of the PlayStation 4 with the help of a kernel exploit that he previously created.

CTurt exploited the hack in PlayStation 4 v1.76 to inject malicious code in the PS4 and gain control of the gaming platform.
“Just broke WebKit process out of a FreeBSD jail (cred->cr_prison = &prison0). Guess you could say the PS4 is now officially “jailbroken” :P” states a Tweet sent by CTurt.

According to the above message, currently the exploit only works for PlayStation 4 firmware version 1.76, but the expert believes that it can be modified to work for more recent firmware.
How does it work?
According to the hacker, the jailbreak allows dumping of the Sony PlayStation 4 RAM from other processes and allows the installation of a custom firmware, which could be exploited by hackers to run homebrew applications that aren’t normally not allowed by the security restriction implemented by Sony.
“While it could take time before CTurt and other hackers are able to develop custom firmware along with the method to load it on the video game console, it should be noted that the exploit can also be taken advantage of to have the console run pirated software.” reported techtimes.com.
Clearly it the news will be confirmed we will observe a huge impact on the gaming market.
Which will be the reply of the Sony?
Obviously, the company will analyze the exploit in order to discover the vulnerabilities exploited by the hacker and fix them for the most recent version of Play Station 4 firmware.
Twitter warns victims of state-sponsored attacks
16.12.2015
Twitter has notified some of its users that they may have been targeted in an attack by state-sponsored hackers.
Twitter is warning users of state-sponsored cyber attacks, a small number of users, including a few connected to security and privacy advocacy, have been notified that their accounts were targeted by nation-state hackers.
The Twitter users received the notifications in the inboxes, the warning messages started a couple of days ago.
Twitter informed its users that hackers, likely associated with “a government,” were trying to compromise their account. The attackers were trying to steal users’ information, including email addresses, IP addresses and phone numbers linked to accounts.
“We believe that these actors (possibly associated with a government) may have been trying to obtain information such as email addresses, IP addresses and/or phone numbers,” Twitter said in its notification.
“At this time, we have no evidence they obtained your account information, but we’re actively investigating this matter,” “We wish we had more we could share, but we don’t have any additional information we can provide at this time.”
According to Motherboard, coldhack, a Canadian “nonprofit dedicated to furthering privacy, security and freedom of speech,” first twitted about the mysterious notification.

Colin Childs, one of the founding directors of coldhak, is a contractor for Tor Project , this could be a possible motivation for the alleged attack.
Another user of the popular platform that received the notification is Runa Sandvik, a privacy and security researcher and a former Tor Project member.
Twitter reported that targeted users belong organizations like the Electronic Frontier Foundation and Tor Project.
Ironically, the company is recommending the use of Tor to protect online privacy, because Twitter was accused in the past of blocking users who accessed its website via anonymizing networkand forcing them to verify their accounts by providing phone numbers.
It is the first time that Twitter warns its users of targeted attacks, in October Facebook launched a similar initiative warning its users of nation-state attacks. Back 2012, Google launched it notification service.
It is not clear how both Twitter and Facebook attribute the attacks to alleged state-sponsored attacks, in the case of the Twitter’s warnings it is not clear if the popular platform was hacked whether the accounts were targeted individually.
FireEye Appliances affected by a critical flaw simply exploitable
16.12.2015
Security experts at the Google Project Zero team have discovered a critical flaw in FireEye appliances that could be exploited via email.
A remote code execution vulnerability dubbed “666” affect FireEye Appliances, hackers can exploit the flaw simply by sending an email or tricking users into clicking on a link.
The 666 vulnerability resided in a module designed to analyze Java Archive (JAR) files, so the attacker can exploit it by sending a specially crafted JAR file across a network protected by FireEye appliances. The flaw has been coded “666” because of its ID in the Project Zero bug tracker.
This is possible by sending an email containing such a JAR file to the targeted organization, be aware because it is worth noting that the email would not have to be read for the malicious code to get executed because the appliances analyze the JAR archive anyway.
In the alternative, the attacker can share with someone in the organization a link pointing to a crafted JAR file. FireEye appliances automatically scan for files circulating in the network, but the same behavior could be exploited to trigger the RCE vulnerability without user interaction.

“The FireEye MPS (Malware Protection System) is vulnerable to a remote code execution vulnerability, simply from monitoring hostile traffic. FireEye is designed to operate as a passive network tap, so that it can see all the files and emails that enter a monitored network.” States the advisory published by the Project Zero. “This vulnerability allows an attacker to compromise the FireEye device, get a root shell and start monitoring all traffic on the victim network (emails, attachments, downloads, web browsing, etc). This is about the worst possible vulnerability that you can imagine for a FireEye user, it literally does not get worse than this.”
FireEye appliances are used by enterprise to monitor internal networks, they are able to monitor FTP, HTTP, SMTP and other protocols searching for potential threats.
The exploitation of the flaw could allow attackers to compromise networks protected by the security products.
This made it possible for the RCE vulnerability found by Google researchers to be exploited without user interaction.
Earlier this month, the researchers Tavis Ormandy and Natalie Silvanovich from the Google Project Zero announced the discovery of the critical flaw.
Frey immediately worked to fix the security issue reported by the hackers.
The experts announced last week that they had developed a reliable exploit for a remote code execution (RCE) vulnerability affecting FireEye’s Malware Protection System (MPS).
“Because FireEye devices typically have a secondary internet-connected interface for updates and management, the issue could even be wormable across the internet,” Ormandy explained.
Of course, they avoided providing further technical details, but Ormandy noted on Twitter that the bug likely affected “every version ever shipped.”
According to Tavis Ormandy and Natalie Silvanovich, the issue affected FireEye’s Network Security (NX), Email Security (EX), Malware Analysis (AX), and File Content Security (FX) products. The experts at FireEye promptly patched the remote code execution (RCE) vulnerability within two days even they issued a temporary workaround within hours.
FireEye released the security content version 427.334.
The flaw discovered by the Google Project Zero team is unique, the experts also discovered a privilege escalation vulnerability that could have been exploited to obtain root access to a FireEye device.
The details of this second flaw have not been disclosed because the vendor is still working on a permanent fix.
The joint exploitation of the two flaws could allow the a threat actor to compromise the internal network by deploying a stealth rootkit on the affected appliance and syphon sensitive data from the targeted host.
Top 10 — 2016 New Year's Resolutions for Cyber Security Professionals
16.12.2015
2016-New-Year-Resolutions-security-professionals
Billions of dollars are spent in securing business operations, and yet attackers still find ways to breach a network.
With the ever increasing growth in security attacks across all threat vectors, you should consider these New Year’s resolutions to help solve your security challenges in 2016:
Take stock of what you have
Segment your Network
Setup controls with ACLs
Secure protocols, network ports, & services
Monitor account activity
Monitor servers & databases
Make sure that your applications are secured
Ensure security policies are in place
Measure effectiveness and ensure your security products are doing their job
Add threat intelligence into your security operations
As you prepare for 2016 and reflect on all the security news stories from this year, these ten resolutions need to be on your “to-do” list:
1. Take stock of what you have
Knowing the genetic makeup of your environment is the key to securing your IT systems. It is critical to have an updated inventory of your systems, applications, and network devices as you cannot secure what you do not know about.
If you are starting up for the first time, you can use discovery inventory tools to create that initial inventory.
You should also consider using continuous discovery tools to identify what is connected to your private or internal network and what is connected to the public network or Internet.
As a best practice, you should use your inventory list and create device groups so that you can identify authorized users that perform critical tasks.
Eventually, feeding this information into a Security Information and Event Management (SIEM) product would help you to identify unauthorized access and mitigate threats before they become attacks.
2. Segment your Network
Managing network traffic and allocating bandwidth are typically seen as the main purposes of network segmentation, so some security aspects are often overlooked.
Adding new applications and making changes in the existing devices can drastically impact the security of your networks.
With proper segmentation in place, you will be able to apply appropriate security measures.
For example, the network that handles employees’ personal information and compensation details could be clearly marked off from your financial activities.
The key factors to consider when segmenting your networks should include:
knowledge of where your sensitive data resides
what applications and services your users need access to
capabilities of existing devices to implement segmentation
regulatory demand
how you will identify and respond when someone attempts to cross these boundaries
Based on this information you can allocate user and device permissions. Once you segment your networks based on required access, it will become easier for you to visualize how your devices interact across different segments and to identify suspicious activity.
3. Setup controls with Access Control Lists
Your firewalls and routers will permit or restrict data flow based on your ACLs. Ideally, you should be building your access control lists (ACLs) based on user need and in-line with your segmentation polices.
You need to identify what type of the controls are necessary for your applications and users.
With proper external ACLs, you could control IP spoofing in outbound and incoming traffic. For example, if incoming traffic shows an IP that falls within your organization’s IP range, then it is suspicious. Similarly, if outbound traffic shows an IP that does not fall in your IP range, then you have every reason to suspect a black cat.
You can make good use of your IP whitelists using your firewalls and routers and telling them how to handle incoming and outgoing traffic.
4. Secure protocols, network ports, & services
Whether it’s sensitive personal information or financial data, the demand for security of electronic communication is high for both private and business use.
To protect and keep your data secure, you need to secure your application, transport, network, and data link layers.
To ensure the availability of your critical business services, monitor your endpoints and detect traffic over restricted services, ports and protocols to mitigate malicious activities like:
malware infections that could enter via removable devices like USBs
unauthorized port scans, as attackers use this method often to gain entry into your network
Communicate best practices to your users and let them know what is acceptable and what is not - especially in terms of using BYOD, transferring files, and using VPNs.
5. Monitor account activity
Access rights to your devices need to be controlled and monitored. Apply the concept of least privilege enforcement to avoid abuse of privileges.
It is highly recommended that you monitor accounts that are given administrative privileges and set rules to log automatically off or disable that account if it is used for performing unauthorized activities.
For example, administrators can create local accounts with local administrative privileges. This is something an attacker or malicious insider would do to ensure they can retain access, even if they lose their privileged credentials.
Privileged accounts can, if unmanaged, lead to lack of accountability and increase your chances of credential theft. Stolen credentials lead to compromised networks which affect your customers, vendors, employees and eventually lead to loss of reputation.
6. Monitor servers & databases
Maintaining the integrity of sensitive information is vital. Keep track of changes made to files that contains business critical information or system data.
Since attackers like to modify local files or registry settings so they can embed themselves, monitor these changes. Correlate file audit events with user activity and system changes to thwart an attack.
7. Ensure security policies are in place
When regulatory agencies come up with compliance policies and procedures, they are trying to help you know how to defend attacks while also building customer confidence in doing business with your organization.
In reality, compliance standards will help you to identify ways to improve your IT infrastructure and act as a basis for your corporate security strategy.
For example, you should have clear internal policies when employees use their personal devices at work or when they use office devices/laptops at home.
These policies can help you prevent rogue users and devices from tampering with your data and network. In the case of mishaps, you should be able to take immediate action - remotely/automatically with your endpoint monitoring systems.
Implement change management for configurations of hardware and software on laptops, workstations, servers and network devices, to prevent policy violations and mistakes.
8. Make sure that your applications are secured
Patches are meant to plug security holes. You need to keep your systems patched with latest updates from vendors so that you do not have known vulnerabilities that could create unwanted issues.
Attackers find their targets based on known vulnerabilities - so if patches are not applied on time, you may be making yourself an easy target.
You should have a good patch management strategy in place to protect your environment from threats and unwanted malware that could result in a security breach.
9. Measure effectiveness and ensure your security products are doing their job
It has become an imperative to use multiple security systems like anti-virus & IDP/IDS.
Each of these systems is specialized and perform specific security functions. But, they operate in silos that could create gaps in data correlation and leave your organization vulnerable.
So, how do you measure overall effectiveness and ensure that your security products are working as expected?
Consider using a SIEM with continuous log monitoring capabilities so you can monitor and consolidate logs from all devices centrally and help ensure overall security of your environment.
Besides acting as a preventive measure, log monitoring also comes in handy for performing forensic analysis, in the case of a security incident.
10. Add Threat intelligence into your security operations
Threat intelligence data can help turn noise into actionable information to respond to attacks before a breach occurs.
Leverage this information with real-time event correlation to protect your environment from known bad actors.
As a best practice, send threat intelligence feeds into your SIEM since it’s the best solution for collecting, consolidating, and analyzing all of your log data and threat intelligence in one place.
A SIEM will help you detect attacks faster. Your SIEM should be able to alert you if it gets a match between threat intelligence (let’s say a bad actor IP address or URL) and what it is happening on your network.
Get Help Implementing These New Year’s Resolutions
If you need help with these 2016 New Year’s Resolutions, you really should check out these security products by SolarWinds.
For example, their Log & Event Manager is easy to use SIEM that comes with:
Log management,
automated security monitoring,
file integrity monitoring,
endpoint monitoring,
real-time event correlation,
And Threat intelligence with active response capabilities.
You can perform forensic analysis and look for specific data across monitored devices with powerful searches:
Solarwinds-Security-software
With Log & Event Manager you can:
Gain key insight into critical activities and improve security, stay compliant, and solve problems in a single virtual appliance.
Turn log data into real-time intelligence with in-memory event correlation and detect suspicious activities before it could harm your environment.
Automatically respond to security threats and known bad actors with built-in active responses, which requires no scripting.
Perform security audits and demonstrate compliance with predefined rules, templates and out-of-the-box reports.
Try Log & Event Manager - Download a free 30-day trial and have it up and running in less than an hour.
British Intelligence Open-Sources its Large-Scale Graph Database Software
16.12.2015
Open-Source-large-scale-database
UK's Secretive Spy Agency Government Communications Headquarters (GCHQ) has open-sourced one of its tools on code-sharing website GitHub for free...
A graph database called 'Gaffer.'
Gaffer, written in Java, is a kind of database that makes it "easy to store large-scale graphs in which the nodes and edges have statistics such as counts, histograms and sketches."
Github is a popular coding website that allows software developers to build their project on a single platform equipped with all the requirements that are gone in the making of a software.
Gaffer and its Functionalities
In short, Gaffer is a framework for creating mass-scale databases, to store and represent data, and is said to be useful for tasks including:
Allow the creation of graphs with summarised properties within Accumulo with a very less amount of coding.
Allow flexibility of stats that describe the entities and edges.
Allow easy addition of nodes and edges.
Allow quicker retrieval of data on nodes of interest.
Deal with data of different security levels – all data has a visibility, which is used to restrict who can access data based on their authorizations.
Support automatic age-off of data.
Gaffer actually uses the Apache Accumulo codebase that was originally open-sourced by the US National Security Agency (NSA) and is released under the Apache 2.0 licence.
Why GCHQ Open Sourced its Code?
It's pretty unusual for one of the most secretive intelligence agencies to release computer code online for anyone to use for free.
Because GCHQ is very well known for monitoring communications worldwide and is not at all expected to release its database types open source on GitHub.
However, maybe this GCHQ's move is part of its effort toward becoming friendlier in the hacker community and to attract new talents.
The spy agency also says that it is already started working on Gaffer2, a project the agency aims to take "the best parts of Gaffer... to create a more general purpose graph database system."
What do you think about this GCHQ's move? Feel free to tell us by hitting the comments below.
13 Million MacKeeper Users Hacked — 21 GB of Data Exposed
15.12.2015
13 Million MacKeeper Users Hacked — 21 GB of Data Exposed
MacKeeper anti-virus company is making headlines today for its lax security that exposed the database of 13 Million Mac users' records including names, email addresses, usernames, password hashes, IP addresses, phone numbers, and system information.
MacKeeper is a suite of software that claims to make Apple Macs more secure and stable, but today the anti-virus itself need some extra protection after a data breach exposed the personal and sensitive information for Millions of its customers.
The data breach was discovered by Chris Vickery, a white hat hacker who was able to download 13 Million customer records by simply entering a selection of IP addresses, with no username or password required to access the data.
21 GB Trove of MacKeeper Customer Data Leaked
31-year-old Vickery said he uncovered the 21 GB trove of MacKeeper customer data in a moment of boredom while searching for openly accessible databases on Shodan – a specialized search engine that looks for virtually anything connected to the Internet – that require no authentication.
"The search engine at Shodan.io had indexed their IPs as running publicly accessible MongoDB instances (as some have already guessed)," Vickery said in a Reddit post. "I had never even heard of MacKeeper or Kromtech until last night. I just happened upon it after being bored and doing a random "port:27017" search on Shodan."
As a result, four IP addresses took him straight to a MongoDB database, containing a range of personal information, including:
Customer Names
Email addresses
Usernames
Password hashes
Mobile phone numbers
IP addresses
System information
Software licenses and activation codes
Security Product Using Weak Algorithm to Hash Passwords
Although the passwords were encrypted, Vickery believes that MacKeeper was using weak MD5 hashes to protect its customer passwords, allowing anyone to crack the passwords in seconds using MD5 cracking tools.
The company responded to the issue after Vickery posted it on Reddit, saying that the company had no evidence the data was accessed by malicious parties.
"Analysis of our data storage system shows only one individual gained access performed by the security researcher himself," Kromtech, the maker of MacKeeper, said in a statement. "We have been in communication with Chris, and he has not shared or used the data inappropriately."
Though the company claims Vickery was the only person to access the MacKeeper users’'information; you should still change your MacKeeper passwords and passwords on websites that use the same password.
Hacker claims Sony PlayStation 4 Jailbreak
15.12.2015
The dream comes true for many Sony PlayStation 4 users, a hacker has developed a Jailbreak for the popular armored console.
The Sony PlayStation 4 is considered one of the most protected platform, since now it was impossible to run pirated games, but a hacker who calls himself CTurt claimed to develop a fully jailbroken version of the PlayStation 4 with the help of a kernel exploit that he previously created.

CTurt exploited the hack in PlayStation 4 v1.76 to inject malicious code in the PS4 and gain control of the gaming platform.
“Just broke WebKit process out of a FreeBSD jail (cred->cr_prison = &prison0). Guess you could say the PS4 is now officially “jailbroken” :P” states a Tweet sent by CTurt.

According to the above message, currently the exploit only works for PlayStation 4 firmware version 1.76, but the expert believes that it can be modified to work for more recent firmware.
How does it work?
According to the hacker, the jailbreak allows dumping of the Sony PlayStation 4 RAM from other processes and allows the installation of a custom firmware, which could be exploited by hackers to run homebrew applications that aren’t normally not allowed by the security restriction implemented by Sony.
“While it could take time before CTurt and other hackers are able to develop custom firmware along with the method to load it on the video game console, it should be noted that the exploit can also be taken advantage of to have the console run pirated software.” reported techtimes.com.
Clearly it the news will be confirmed we will observe a huge impact on the gaming market.
Which will be the reply of the Sony?
Obviously, the company will analyze the exploit in order to discover the vulnerabilities exploited by the hacker and fix them for the most recent version of Play Station 4 firmware.
Inside the German cybercriminal underground
14.12.2015
Trend Micro investigated on German crime forums and concluded that Germany possesses the most advanced cybercrime ecosystem in the European Union.
We have reported several times the news related to various criminal cybercriminal underground underground communities in the wild, such as American underground, the Russian underground, the Brazil underground, the Chinese underground and also the Japanese one.
What about the European cybercriminal underground?
This time, we will talk about the Germany cybercriminal underground, Trend Micro investigated on German crime forums and concluded that Germany possesses the most advanced cybercrime ecosystem in the European Union, beating known markets as the French and Spanish.
The Trend Micro survey examined 10 big crime forums, some of them holding a registered, active base between 20.000 and 70.000 users. The findings of the investigation are available in the paper titled U-Markt: Peering into the German Cybercriminal Underground.

“The German underground does not have as wide a selection of offerings as the Russian market. In most cases, it isn’t necessary to search for special goods and services in local communities because global (English-speaking) markets have more to offer. But when it comes to customized wares, it is harder to find appropriate equivalents. This is a niche that smaller communities (like the German underground) need to find in order to thrive and stay up.” Reads the paper-
In these places, it is quite easy to buy any kind of illegal product and service including:
Malware (Trojans, bank-stealers, and backdoors)
Drugs
Bulletproof hosts(BPHSs), to used to store malware components, exploit kits.
Fake IDs
Hacked accounts
Crypting services
In terms of banner ads, “are an easy way to promote partner sites (a marketplace run by those behind a certain forum in any community, most notably in the Russian underground). These can help marketplaces widen their client bases.”

Very interesting is the Packstation service described in the report as a delivery method exploited by criminals and that takes advantage of the German postal service.
“Most underground markets rely on droppers who cash in stolen credit cards and online accounts. There is no longer a need for droppers in the German underground. Users instead rely on the so-called “Packstation service” that takes advantage of the German postal service. This allows sellers to put goods sold in publicly accessible metal boxes for their buyers to pick up using their pTANs and access cards.”
The advantage of the “Packstation” redides in the fact that cybercriminals can easily perform “exchange of goods and payment. Users’ addresses cannot be tracked though they need to apply for the service using a physical (home) address and a mobile phone number (which are easy to fake) so they can receive short messaging service (SMS) notifications alongwith their pTANs to claim their parcels”

What does really make the Germany cybercriminal underground the most advanced cyber-crime in the all European Union? The answer is Russia, because both the German and the Russian underground forums are full of carding service banner ads. These adds are normally associated with Russian underground offerings but heavily advertised in German forums.
A good examples is “Rescator.cm”, one of Russia’s biggest stolen credit card marketplaces that is being advertised in the German underground, also “SecureVPN.to” but there are more.
Trend Micro also published the list of usernames per forums, probably to help future investigations.
I believe we will keep seeing more and more news about this cybercriminal underground due to the rapid growth of black markets.
This is How Tokyo Police Catching Rogue Drones in the Sky
14.12.2015
This Police Drone Fights Rogue Drones in the Sky
So how do you catch rogue drones that take your sky?
With another Giant Drone, of course!
This is exactly how the Tokyo Metropolitan Police Department is catching unwanted and potentially dangerous drones flying over the city, according to Japan Today.
The department is launching an anti-drone squad in order to prevent people from flying their drones overcrowded residential areas and important buildings in Tokyo, including the Prime Minister's Office.
How So?
Instead using a dragnet on the ground, the police authorities will use a drone armed with a net to scoop up the suspected drones and carry them away to safety.
Watch the Video:
The Tokyo Metropolitan Police have also released a video that shows its special Net-Wielding Drone in action. You can look at the video above.
It looks like the police are using a DJI Spreading Wings 900 with a 3 x 2 m² of Net tied to its feet.
As soon as a rogue drone is spotted in the sky, the squad will first attempt to contact its operator and order them to land the drone.
However, if the drone operator fails to comply, the anti-drone squad will release their Net-Wielding Drone to capture the drone and drag it away to safety.This move came in the wake of last April's incidence when they found a suspicious drone carrying radioactive material from the Fukushima Prefecture onto the roof of the Japan Prime Minister's Office.
Hacker Confirms PlayStation 4 Jailbreak! Exploit Could Open Doors for Pirated Games
14.12.2015
Sony's PlayStation 4 – the hottest-selling gaming console in the United States – has been in the market for a while now, and since its release, hackers have been tinkering with it to find a way to run unauthorized software.
Though breaking the protection on PlayStation 4 is a huge deal, a hacker who calls himself CTurt has claimed to develop a fully jailbroken version of the PlayStation 4 with the help of a kernel exploit that he previously created.
The current jailbreak allows dumping of the system RAM from other processes and installing custom firmware that can be used to run homebrew applications that aren't approved by Sony.
Of course, there is still a few other security issues to get by, but it is a foot in the door for game piracy, which can affect the gaming market as a whole.
The Twitter account of CTurt seems to indicate that currently the exploit only works for PlayStation 4 firmware version 1.76, but apparently it can be tweaked to work for more recent firmware.
ps4-PlayStation-jailbreak
CTurt successfully managed to take advantage of an exploit in PlayStation 4 v1.76 to inject an external code in the system, thereby taking control of the hardware.
Sony would certainly be unhappy with the launch of PlayStation 4 jailbreak and would be trying hard to eliminate any vulnerabilities for the most recent version of PS4 firmware.
Gift cards and return merchandise fraud scheme
14.12.2015
Be careful when using gift cards, cyber criminals have learned how to exploit this popular form of gift-giving, especially during the Holiday season.
Every day, users receive dozens of gift cards from top retailers for sale online, some of these are legitimate gift cards sold through third-party sites that resell used or unwanted cards, but a good portion result of illegal activities.
Some discounted gift cards are in fact the product of merchandise return fraud.
As explained by the security expert Brian Krebs, this kind of scam mainly impacts retailers that issue gift cards when clients return merchandise at a store without presenting a receipt.
Brian Krebs reported the case of one of his readers, who was aware that crooks steal merchandise from a physical store in the retail chain and return the merchandise to another store of the same chain without a receipt and then offer for sale the gift cards to websites like raise.com and cardpool.com at a discounted price.
Many stores for returns more than 60 days after the purchase, or if the receipt is unavailable, offer the value of the goods returned will be refunded to a merchandise card.
The Kreb’s reader confirmed she was not aware that the card was a merchandise return card, a fact that was printed on the front of the card she received.
gift cards
Krebs noticed searching for available gift cards for sale online discovered that the cards are routinely sold for at least 25 percent off their value.Clothier
“Clothier H&M’s cards average about 30 percent off.”
Krebs made other interesting discoveries analyzing discounts for industries that haven’t customers return (i.g. fuel stations, restaurants). The value of the cards from merchants that don’t take customer returns allows discounts that tends to be much lower, between 3 and 15 percent (i.e. gift cards from Starbucks and Chevron).
Twenty-five percent off is really high and experts invite customers to be wary of such offers.
“Normally, it is around 5 percent to 15 percent.” said Damon McCoy, an assistant professor at New York University and an expert on fraud involving stored value cards.
This means we are facing with a consolidated illegal activity, that according to the National Retail Foundation will cost U.S. retailers nearly $11 billion this year.
“Investigators say the crimes very often are tied to identity theft rings and drug addicts. Last month, authorities in Michigan convicted a 46-year-old father of four for running a large-scale fencing operation that used teams of prostitutes, heroin users, parolees and panhandlers to steal high-priced items from local Home Depot stores and then return the goods to a different Home Depot location in exchange for store debit cards.” wrote Krebs in a blog post.
Clearly gift cards are also a privileged cashout method for criminals specialized in the sale of stolen credit cards. Crooks used stolen card data to buy gift cards from a range of retailers and offer them for sale online at 20-30 percent discounts.
Is Vuvuzela the most secure SMS text messaging system?
14.12.2015
A group of computer scientists at the Massachusetts Institute of Technology has developed the most secure SMS text messaging system.
A group of computer scientists at the Massachusetts Institute of Technology (MIT) has developed a new SMS text messaging system, dubbed Vuvuzela, that is untraceable and could allow truly anonymous communications.
The researchers explained that their SMS text messaging system is resilient to traffic analysis, so more secure than the Tor anonymity network.
“Tor operates under the assumption that there’s not a global adversary that’s paying attention to every single link in the world,” said Nickolai Zeldovich, an associate professor of computer science and engineering, and co-leader of the Parallel and Distributed Operating Systems group at CSAIL.
“Maybe these days this is not as good of an assumption. Tor also assumes that no single bad guy controls a large number of nodes in their system. We’re also now thinking, maybe there are people who can compromise half of your servers.”
Scientists from MIT and the Qatar Computing Research Institute (QCRI), in July, claimed to be able to de-anonymize Tor hidden servers with up to 88% accuracy. The researcher demonstrated how to unmask Tor hidden services in the Tor Network by analyzing the traffic patterns of encrypted data passing through a single machine in the Tor network.
The researchers demonstrated that “simply by looking for patterns in the number of packets passing in each direction through a guard, machine-learning algorithms could, with 99 percent accuracy, determine whether the circuit was an ordinary Web-browsing circuit, an introduction-point circuit or a rendezvous-point circuit.”
“Furthermore, by using a Tor-enabled computer to connect to a range of different hidden services, they showed that a similar analysis of traffic patterns could identify those services with 88 per cent accuracy. That means that an adversary who lucked into the position of guard for a computer hosting a hidden service, could, with 88 per cent certainty, identify it as the service’s host.” States the MIT’s full press release .”
In October, the researchers presented their paper, titled “Vuvuzela: Scalable Private Messaging Resistant to Traffic Analysis” at the Association for Computing Machinery Symposium on Operating Systems Principles.
“Vuvuzela is a new scalable messaging system that offers strong privacy guarantees, hiding both message data and metadata. Vuvuzela is secure against adversaries that observe and tamper with all network traffic, and that control all nodes except for one server” states the paper.
A user that needs to send a message to another user leaves it at a specific location, such as a memory address on an internet-connected dead drop server, then its interlocutor retrieves the message from the same location.
In the simplest scenario were three people using the system but only two of them were sending text messages to each other, an attacker that analyze the traffic to the server is able to track the two users that exchanged messages.
To avoid traffic analysis in this scenario, the users, even not involved in any communication, send out regular messages to the dead-drop server making ineffective traffic analysis.
In this case, a persistent attacker running a traffic analysis will be only able to see traffic going through the server from multiple locations at all times.
The researchers explained that sending out regular spoof messages is not enough to avoid traffic analysis due to the possibility that an attacker can infiltrate the dead-drop server. In this case, the attacker would be able to see which users were actually sending out messages and who is its interlocutor.
To make the Vuvuzela resilient to this kind of attack, the SMS text messaging system uses three different dead drop servers.
All the messages, real and fake, are sent through the system wrapped in three layers of encryption.
” To make sure that exchange requests get mixed, each client encrypts their request with the public key of each server. If there are three servers, with public keys pk1, pk2, and pk3, then a user encrypts their request r to form Epk1 (Epk2 (Epk3 (r))). 5 This onion construction ensures that the request r can be decrypted only if each server removes its encryption layer in turn” states the paper.
The first server peels off the first layer of encryption on a message and then forward it to the second server. The first server also mixes up the order of the messages, and the second server does the same, so the third server is the unique one that can read the real messages.
The three layers of encryption allow the Vuvuzela SMS text messaging system to be effective even if one of the server is compromised.
Cyber Terrorists Can Get Their Hands on UK Infrastructure, Like the Net or Electricity
14.12.2015
Cyber terrorists can target UK infrastructure, with the odds being in favor of targeting the power grid, rather than the Internet broadband network.
Cyber terrorists are probably going to target the UK and more specifically focus on something that will create chaos in the country. After the devastating incidents of Paris in November, many people fear that ISIS and other extremist attackers will not rest. Instead, they will keep on escalating things and spreading terror all over the world. As far as the United Kingdom is concerned, some claim that the Internet broadband network will be an easy target. However, when it comes to escalating and causing severe damage, the electric grid would be far more catastrophic!
Of course, the net would die even in the case of turning off the lights all over the country. Furthermore, cyber terrorists can carry out a successful attack against the power grid jeopardizing human lives. This is what the extremists are after, right? So, it makes total sense that the electric power would be a more suitable target for them. Either way, the attacks would demand well-planned strategies and perfect coordination.

James Blessing is the Chair of the Internet Service Providers Association (ISPA) and has commented on the possibility of cyber criminals to target the UK network. He said that there are multiple locations to target and these locations have been created to be kept impenetrable:
“These places are not unsecure, they are in highly-guarded locations that as a network engineer are a pain to get into. They are in high security buildings and there’s usually a perimeter fence that is well away from the building. You would have to have a seriously big truckful, you’re talking a load of fertiliser bigger than the IRA used to use.”
On the targeting issue, Mr. Hypponen is a Chief Research Officer at cyber security specialists F-Secure and has analyzed his point of view:
“The Islamic State has demonstrated that they have the most credible offensive cyber capability of any of the jihadist extremist movements, and even they are far away from having this level of operational skills in their disposal … Why bother toying around taking down the net if you could take down the electric grid?”
An example of resilience in the governmental infrastructure that ought to be taken into consideration is that of Estonia. Ever since 2007, the whole governmental infrastructure can immediately bounce to international servers and thus jeopardize any of the data. So, without being physically located in one place, people have managed to eliminate the risks of being targeted at a specific place.
In the light of such a growing need for protection online, Britain has announced £1.9bn funding within a period of five years to safeguard the country against cyber-attacks, as well as the creation of a National Cyber Centre in the coming year, 2016.
European Space Agency domains hacked by Anonymous
14.12.2015
The collective Anonymous has compromised the subdomains of the European Space Agency website and leaked personal information of thousands of subscribers and officials.
The hacking collective Anonymous seems to be very active in this period, its last victim is the European Space Agency. Members of Anonymous have breached a number of subdomains of the European Space Agency website and leaked personal and login credentials of thousands of subscribers and officials.
”We did it for the Lulz” is the message left by Anonymous.

Anonymous conducted a cyber attack on the following subdomains of the European Space Agency (ESA) website:
due.esrin.esa.int
exploration.esa.int
sci.esa.int
The hackers exploited a blind SQL vulnerability in order to access the backend of the subdomains and exfiltrate data from the database.
The colleagues at the Hackread.com who disclosed the news, have analyzed the data leaked online by Anonymous confirming its authenticity. Anonymous leaked the stolen data into three separate files which include the website’s database, officials personal information and Subscribers’ data.
“The third file contains names, emails and clear-text passwords of 8000+ subscribers. The leaked data is available here → Database | Officials’ data |Subscribers’ data.”
Anonymous reported to HackRead the following message:
“BECAUSE XMAS IS COMING AND WE HAD TO DO SOMETHING FOR FUN SO WE DID IT FOR THE LULZ.”
It seems that the branch of the Anonymous collective that hacked the European Space Agency is the same that breached the databases at United Nations Climate Conference (Cop21) and the World Trade Organization.
Such kind of incidents opens the doors to further cyber attacks, the leaked data include information related to officials that could be targeted by criminal groups or nation-state actors for espionage.
Torrent websites infected 12 million Internet users per month
13.12.2015
According to a new study conducted by researchers at Digital Citizens Alliance and RiskIQ almost one-third of the 800 torrent websites served malware.
People believe that the best way to see a film or get a software is downloading from one of the numerous torrent websites online. Probably there is something that you should know.
According to a new study conducted by researchers at Digital Citizens Alliance and RiskIQ, almost one-third of the 800 torrent sites served malware on the users’ machine between June and August 2015.
About 12 million Internet users per month were infected by downloading material from the torrent files.
The experts cited the case of newly released video game Fallout 4 whose pirated copy was found embedded with a malicious code used by crooks to steal 4.88 bitcoins (nearly 2000 USD) from a gamer’s PC.
The researchers revealed that most torrent websites earn money by selling ads to malicious advertisers ho serve malware that criminal organizations use to harvest users’ data to resell on the black market.
According to the experts, the profit of this lucrative business allowed crooks to earn more than 70 million dollars.
“Baiting Internet users, stealing their personal information, and taking control of their computers is becoming big business—an estimated $70 million per year just from peddling malware.” states the report.
Most of the computers are infected via malicious ads spread through the torrent websites, the ads redirect victims to websites hosting malicious exploit kits.
“When you visit mainstreams sites, things are naturally happening without you clicking anything: pictures are being downloaded, ads are generating,” said Tom Galvin, executive director of Digital Citizens Alliance. “What’s happening now is that users can click on one of these content sites and decide not to watch a movie, but the malware is already on their computer scraping for their Social Security number. That’s used to mimic and adopt your online persona, access banking information, and in some cases, people are getting credit fraud notifications.”

Movie hubs deliver the majority of malware as explained by Galvin.
“Movies are digital bait,” added Galvin. “Consumers are defenseless, and this is really exploiting and abusing them.”
The researchers analyzed mainstream sites like Crackle and Hulu with torrent sites who provide movies like the Pirate Bay, Kickass Torrents, ExtraTorrent, multiple Torrentz forks, Putlocker and others.
Two percent of the mainstream sites were found serving malware each month and 33 percent of sites in the Content Theft Sample group had at least one malware incident in one month.
54% of all malicious code detected was classified as Trojan, 29 percent as Adware .

The researcher detected numerous variants of Remote access Trojans (RATs) which are used by crooks to steal financial information, login credentials and even access laptop’s camera.
The study includes the Top 10 RATs identified by the researchers, some of them are well-known threats used in numerous attacks in the wild. Xtreme Rat and Bifrost lead the list.

Unfortunately online piracy is one of the most profitable illegal activities and curbing it represent a major challenge for law enforcement.
You can give a contribute by stop download content from such websites that open you to cyber attacks and infections.
Give a look to this excellent report.
Iranian Government says Daesh doesn’t pose a threat to Iran
13.12.2015
The Iranian Cyber police (FATA) is actively monitoring the activities of the Daesh terrorist group (ISIS) in the country.
“Live by the sword, die by the sword,” Iranian hackers are intensifying their activities against the Western countries, recently security firms have uncovered several cyber espionage campaigns targeting US and European. organizations.
In November, experts from Check Point firm published a new report on the Rocket Kitten group, revealing the intensification of the Iranian activities in the cyberspace.
But Iranian experts are aware of possible threat originating from the cyberspace, not only Western governments, but also militant of the ISIS terrorist group.
The Daesh has a credible offensive cyber capability, this is the opinion of the cyber security expert Mikko Hyppönen which worries about cyber terrorists belonging to the Islamic State (Daesh, ISIL or ISIS) have a credible offensive cyber capability.
The Daesh is also threatening the Iranian Government, last week the Iran Chief Brigadier General Kamal Hadianfar announced at a Monday press conference that Iranian FATA (The Iranian Cyber Police) has identified and admonished an individual spreading the rumor that Daesh might pose a cyber threat to Iran. Hadianfar explained that the man admitted his error, but anyway he hasn’t done anything illegal.
“Hadianfar told a press conference that the person spreading the rumor that Daesh will pose threat to Iran on December 11 has been identified. He added he is living in northern Iran.” states a report published by the Islamic Republic News Agency (IRNA).
“FATA admonished the person for the issue, he said adding the person admitted to have made mistake, but, insisted that he has not committed any crime.”
According to the Islamic Republic News Agency (IRNA), the Chief Brigadier General Kamal Hadianfar explained that the FATA is monitoring the evolution of Daesh in the country, especially the activities exploiting the technological means.
132 websites linked to the terror group ISIS had been identified and shutdown, ha confirmed that all initiatives of propaganda has been nipped in the bud.
The commander of the Islamic Revolution Guards Corps (IRGC) anyway confirmed that no serious threat has been posed by Daesh for cyber attack.
I personally consider a serious error to underestimate every cyber threat, including the ISIS cyber capabilities.
The ISIS has the ability to make fake Syrian passports
13.12.2015
A new intelligence report shared with law enforcement warns of ISIS’ ability to create fake Syrian passports, it’s alarm.
According to a report issued by the US intelligence, the ISIS has the ability to create fake Syrian passports, the news was confirmed this week by a federal official.
The news was reported by the ABC news and the CNN, a spokeswoman for U.S. Immigration and Customs Enforcement confirmed the existence of the report but declined to provide a copy of it.
ABC News, which first reported the existence of the report on Thursday, confirmed the report was released to law enforcement by the Homeland Security Investigations agency. The US intelligence believes that the fake passports could be used by members of the ISIS organization to travel to the United States.
According to the US intelligence, members of the ISIS terrorist group have access to Syrian government passport printing machines and blank passports. This means that the organization is able to print travel documents for its members.
“The report warned that, based on U.S. Immigration and Customs Enforcement’s intelligence sources, ISIS has access to passport printing machines and blank passport books, raising the possibility the documents could be faked, according to the source.” states the CNN.
According to the CNN there was also concern that because the ISIS members had access to biographical and fingerprint data on Syrian citizens, there could expose Syrians to identity theft.
bitcoin isis 2
“The source noted that, beyond the report, there’s concern that this capability coupled with ISIS access to government buildings in Syria that contain valid biographical data and fingerprint info on Syrian citizens give rise to the threat of identity theft.” continues the CNN.
The experts don’t exclude that the fake passports have been already used by the ISIS to enter in the US.
“Since more than 17 months [have] passed since Raqqa and Deir ez–Zour fell to ISIS, it is possible that individuals from Syria with passports ‘issued’ in these ISIS-controlled cities or who had passport blanks, may have travelled to the U.S.,” states the ABC News.
The FBI Director James Comey discussed this week this issue in testimony on Capitol Hill.
“The intelligence community is concerned that they [Islamic State] have the ability, the capability to manufacture fraudulent passports, which is a concern in any setting.” said the FBI Director.
The Maine Independent Sen. Angus Kind told CNN that the US is moving toward developing a new generation of passports that cannot be faked due to the presence of a chip that has biometric data.
“I think this tells us that we’ve got to accelerate doing that. But in the world of threats, of course, this is the one of them, but there are lots of other things we have to attend to as well,” King said.
LATENTBOT, one the highly obfuscated backdoor in the wild
13.12.2015
Experts at FireEye have discovered a stealthy botnet relying on a backdoor called LATENTBOT has compromised companies around.
Experts at FireEye have discovered a stealthy botnet relying on a backdoor called LATENTBOT has compromised companies around. According to FireEye the LATENTBOT remained undetected since 2013 infecting computers in US, UK, South Korea, Brazil, United Arab Emirates, Singapore, Canada, Peru and Poland in 2015.
“FireEye Labs recently uncovered LATENTBOT, a new, highly obfuscated BOT that has been in the wild since mid-2013. It has managed to leave hardly any traces on the Internet, is capable of watching its victims without ever being noticed, and can even corrupt a hard disk, thus making a PC useless.” states the report published by FireEye.
The experts observed multiple campaigns targeting multiple industries, but the threat actors appear to be focused on the financial services and insurance sectors.
FireEye has uncovered similar samples in the wild across the time, using passive DNS information its experts dated the bot around mid-2013.
Giving a detailed look to the LATENTBOT botnet, the experts discovered that it implements a 6-stage obfuscation process, operates completely in memory (LATENTBOT will only keep its code in memory for the short time that is needed to infect the target), and implements a single exfiltration mechanism.
Below the list of features implemented by the LATENTBOT beckdoor.
a) Multiple layers of obfuscation
b) Decrypted strings in memory are removed after being used
c) Hiding applications in a different desktop
d) MBR wiping ability
e) Ransomlock similarities such as being able to lock the desktop
f) Hidden VNC Connection
g) Modular design, allowing easy updates on victim machines
h) Stealth: Callback Traffic, APIs, Registry keys and any other indicators are decrypted dynamically
i) Drops Pony malware as a module to act as infostealer
LATENTBOT is able to scan for cryptocurrency wallets via Pony stealer 2.0 malware plugin, it uses a custom encryption algorithm to protect command and control (C2) communications.
“LATENTBOT itself is not targeted in nature – it has been observed in multiple industries – but it is selective in the types of Windows systems to infect. For example, it won’t run in Windows Vista or Server 2008. LATENBOT also uses compromised websites as CnC infrastructure, making infection easier and detection harder.”
The researchers discovered that when the bot is running on a laptop, it will query the battery status via GetSystemPowerStatus and call SetThreadExecutionState in order to prevent the system from entering in sleep mode.
The threat actors exploit emails as attack vector, they have been using malicious messages containing an old word exploit created with Microsoft Word Intruder (MWI) exploit kit. When victims opened the document an embedded malicious executable runs, contacting the C&C server for campaign tracking and download the second stage binary, which turns out to be a LuminosityLink RAT.
“During our analysis, the Word documents downloaded LuminosityLink as the second stage binary. LuminosityLink is a full-featured RAT that has the ability to steal passwords, record keystrokes, transfer files and activate attached microphones or webcams.” continues the report.
“Since the running LuminosityLink is a RAT that offers multiple capabilities to fully control the infected box, it is surprising that another payload is being downloaded from a secondary C2 at emenike[.]no-ip.info (180.74.89.183),” FireEye detailed. That new module is LATENTBOT.
The report, published by FireEye includes full details on the back door, enjoy it!
The French Gov will not block Tor neither Free Wi-Fi
12.12.2015
According to the French Prime Minister Valls the Government will not ban Public Wi-Fi or the Tor Network.
Last week, documents leaked to Le Monde suggested that the French Government was planning to adopt drastic measures in response to the terrorist threat, including the ban of the Tor Network and curtail public Wi-Fi.
According to an internal document from the Ministry of Interior visioned by journalists at the French newspaper Le Monde, the French Prime Minister Manuel Valls ruled out introducing the above restrictions in response to the Paris terrorist attacks.
The document includes two proposals of legislation, one around the state of emergency, and the other related to counterterrorism measures.
The French Government was considering to “Forbid free and shared wi-fi connections,” the measures have to be adopted to avoid any abuse of public wi-fi networks. The law enforcement is difficult to track suspects and terrorists who use public wi-fi networks.
According to the legislation, the French Government was planning to give more powers to the authorities, including the enforce GPS tracking of rented cars, the block of Tor connections and the use of cellphone eavesdropping systems.
tor astoria
“Internet freedom is a great way to communicate with people, that’s a plus for the economy,” said Valls, adding it was “also a way for terrorists to communicate and spread their totalitarian ideology.” “The police look at all the aspects that better fight against terrorism, of course, but we must take effective measures,”
But Valls, clarified that the French Government will not ban the popular Tor network, neither to monitor its use. He said he had seen no proposals for such a scheme.
Anonymous Declares War On Donald Trump — #OpTrump
12.12.2015
Anonymous Declares War On Donald Trump
After targeting the Islamic State (ISIS) group in the wake of Deadly terror attacks in Paris, hacktivist group Anonymous has now turned its attention to controversial US presidential candidate Donald Trump.
The hacktivist group has declared war against Donald Trump following his recent radical speech stating he wanted to ban Muslims from entering the United States.
Anonymous vs. Donald Trump
On Wednesday, Anonymous slams Trump by posting a YouTube video in which a man in a Guy Fawkes mask says:
"Donald Trump, it has come to our attention that you want to ban all Muslims to enter the United States. This policy is going to have a huge impact. This is what ISIS wants. The more Muslims feel sad, the more ISIS feels that they can recruit them. Donald Trump, think twice before you speak anything. You have been warned, Donald Trump."
Watch the Video:
Anonymous Takes Down Donald Trump Website
Moreover, the group started #OpTrump hacking campaign against Donald Trump on Wednesday night and took down the website for New York City's Trump Towers (www.trumptowerny.com) by hitting it with Distributed Denial-of-Service (DDoS) attacks.
The website was reportedly down for hours. However, it appears to be operational now.
While the online hacktivist group has yet to officially claim responsibility for the DDOS attack on Trump's website, Twitter users showed their full support to Anonymous and its #OpTrump campaign.
Also Read: Telegram Shuts Down 78 ISIS Channels
This is not the first time the group has targeted Trump. Few months ago, Anonymous broke into Trump.com in an effort to deliver Jon Stewart a message as he was about to leave The Daily Show.
As we await Anonymous's next move, the group has already declared Friday to be a day to troll ISIS, urging Twitter users to troll ISIS using the #Daeshbags hashtag.
This Hack Lets You Find Which of Your Facebook Friends Like Trump
Meanwhile, a website known as FriendsWhoLikeTrump.com has been created to show you which of your Facebook friends have "Liked" Donald J. Trump.
Clicking on the site will land you to a Facebook search feature that shows what your friends have liked, or you can achieve the same yourself by simply typing "My friends who like Donald J. Trump" in the Facebook search bar.
You will get a list of anyone in your Facebook network who has clicked "Like" on Trump's Facebook page.
UK Gov could hack children’s smart toys to Spy on suspects
12.12.2015
The British Government as part of the Investigatory Powers Bill is planning to hack children’s smart toys to snoop on suspects.
We discussed several times the possibility to spy on people through smart device, including smart toys. A couple of weeks ago, the security expert Matt Jakubowski explained that the new Wi-Fi-Enabled Hello Barbie can be hacked to extract Wi-Fi network names, account IDs, and MP3 files from the toy.
News of the day is that as part of the Investigatory Powers Bill, children’s smart toys could be used by British law enforcement.
The "Hello Barbie" smart toys
According to Antony Walker, deputy chief executive officer of techUK, IoT devices, included smart toys, can be intercepted by the UK government and used for their investigation.
“In the context of the Internet of Things you have many types of connected devices … [such as] toys [that] children can interact [with].” Mr. Walker said at the second session on the Investigatory Powers Bill, :
“These devices may sit in a child’s bedroom, but they may be accessible. In theory, the manufacturer of the products could be subject to a warrant to enable equipment interference with those devices.”
The expert highlighted the implication of smart objects for the users’ privacy and security.
“We are moving beyond a world that is just about telephony, accessing messaging services and so on,” he stated.
“In an IOT type world the definitions that seem to apply to equipment seem to apply potentially to a huge range of devices that could be used for communications purposes and other purposes as well.”
The draft Investigatory Powers Bill would make it the legal duty of Internet service providers (ISPs) to support the law enforcement in exploiting smart devices, including smart toys, to snoop on suspects.
“A range of devices that have been in the news recently, in relation to a hack, are children’s toys that children can interact with,” Walker told the committee. “These are devices that may sit in a child’s bedroom but are accessible.”
According to the Investigatory Powers Bill, the UK Government would propose to make possible to break end-to-end encryption implemented by private companies for their services.
Hacker-Friendly Search Engine that Lists Every Internet-Connected Device
11.12.2015
Meet an all-new Hacker’s Search Engine similar to Shodan – Censys.
At the end of last month, security researchers from SEC Consult found that the lazy manufacturers of home routers and Internet of Things (IoT) devices have been re-using the same set of hard-coded cryptographic keys, leaving around 3 millions of IoT devices open to mass hijacking.
But how did the researchers get this number?
Researchers uncovered these devices with the help of Censys – a new search engine that daily scans the whole Internet for all the vulnerable devices.
Censys Maintains Complete Database of Everything on The Internet
Censys is similar to hacker's search engine Shodan, which is designed specifically to locate any devices that have been carelessly plugged into the Internet without much attempt at preventing unauthorized access.
However, Censys employs a more advanced method to find vulnerabilities in the devices and make the Internet a safer place.
Censys is a free search engine that was originally released in October by researchers from the University of Michigan and is powered by the world's biggest search engine Google.
Censys is part of an open source project that aims at maintaining a "complete database of everything on the Internet," helping researchers and companies unearth Online security mishaps and vulnerabilities in products and services.
How Does Censys Work?
Censys collects information on hosts and websites via daily scans of the IPv4 address space – the internet protocol version 4 that routes the majority of the Internet traffic today.
In order to do so, the new search engine uses two companion tools:
ZMap – an open-source network scanner
ZGrab – an application layer scanner
Censys then maintains a database of how hosts and websites are configured, allowing researchers to query the data through a search interface, report builder, and SQL engine.
ZMap scans over 4 Billion IP addresses on the Internet and collects new data every day. It also helps determine whether the machines on the internet have security vulnerabilities that should be fixed before being exploited by the hackers.
"We have found everything from ATMs and bank safes to industrial control systems for power plants. It's kind of scary," said Zakir Durumeric, the researcher leading the Censys project at the University of Michigan.
Obvious flaws in addition to issues caused by IT administrator failures can also be found.
Here's the MIT Technology Review on Censys, titled "A Search Engine for the Internet’s Dirty Secrets."
More details on the Censys architecture and functionalities are available in the team's research paper.
If you would like to give Censys a try, you can follow the step-by-step tutorial offered by the developers.
A well-funded cyber criminal group targets Asian organizations
11.12.2015
Trend Micro announced that the Asian market are being targeted more than ever by well-funded cyber criminal group that appears very organized.
The attacks rely on the Bifrose code to develop their backdoor, a malware that has been around since 2008. In 2014 it was reported that a new version of Bifrose appeared in the wild. Among the improvements observed in the new variant of Bifrose, the use of the Tor network to hide the C&C infrastructure.
“BIFROSE is mostly known for its keylogging routines, but it is capable of stealing far more information than just keystrokes,”. States Trend Micro,
It is a known fact that the Bifrose source code was sold in the past for around $10,000. The experts believe that the cyber criminal group behind the recent attacks against Asian entities is active since 2010 and that they bought the source code of Bifrose. The group has many human and financial resources and owns a wide variety of hacking tools in its arsenal.
“Our research indicates that the group has sufficient financial resources to purchase the source code of a widely available malware tool, and the human resources to design improved versions of its own backdoors based on this,”. Said Razor Huang, Trend Micro threats analyst.
The cyber criminal group most probably bought the Bifrose source code and improved its capabilities by adding new features
“improving its functions, the group then designed a new installation flow, developed a new builder to create unique loader-backdoor pairs, and made more simple and concise backdoor capabilities, resulting in a new backdoor—KIVARS. This could mean that the operation is either backed financially by its sponsors or the group has the funds and resources to improve on an existing backdoor.” Continues TrendMicro.
It is important to refer that the KIVARS backdoor could be used to target 64-bit systems. Trend Micro explains that KIVARS is most probably linked to Bifrose because they found that “some KIVARS backdoors’ PDB (program database) paths betray the code name of KIVARS to be “BR” + “{year}”. We think that BR mostly likely stands for Bifrose RAT.”
Another malware based on Bifrose developed by the same hacking group back in 2010 is XBOW. XBOW shows the “Recent,” “Desktop,” and “Program” folder paths, which are also present in the BIFROSE and KIVARS phone home messages.

Trend Micro monitored of a recent operation conducted by the cyber criminal group, dubbed Operation Shrouded Crossbow, that focused on the Asian market and in areas such as government contractors, privatized government agencies, and companies in the financial, healthcare, computer and consumer electronics sectors
The experts believe the cyber criminal group owns separated teams for each activity, one for development, another for the infiltration/targeting part, and another one to maintain their C&C infrastructure.
In my opinion, this shows the trend of the last 3 / 4 years, where more and more groups are becoming organized, like a legit company, where they are able to generate enough funds to keep going and improving their methods.
Government Could Hack Children's Toys to Spy on You
11.12.2015
Smartphones, Smart TVs, Smart Watches, Cell Phone Towers, Messaging services… but now, What's Next?
Smart Toys? Yes, probably.
Tech expert is warning that 'Smart Toys' could now be used by the government intelligence agencies to spy on suspects.
As part of the Investigatory Powers Bill, children's connected toys could be the next item to be used by the government in an effort to spy on people, claims Antony Walker, deputy CEO of technology trade association techUK.
The Snooper's Charter – Government's Spy Eyes
While speaking to the UK parliament's Commons Science and Technology Committee, Walker warned MPs of how the Draft Investigatory Powers Bill could be abused to turn any Internet-connected device into a snooping tool.
The draft Investigatory Powers Bill (or the Snooper's Charter) would make it the legal duty of Internet service providers (ISPs) to help and assist the British intelligence agencies in hacking into various connected devices if requested to do so.
Walker explained that anything connected to the Internet could theoretically be hacked into remotely and used by the authorities to snoop on criminals and suspects.
Smart Toys to Spy on People
"A range of devices that have been in the news recently, in relation to a hack, are children’s toys that children can interact with," Walker told the committee. "These are devices that may sit in a child’s bedroom but are accessible."
The innocent looking smart devices, including Smart Toys, such as Hello Barbie and My Friend Cayla – that come Wi-Fi enabled and have microphones and cameras built-in – could become spying tools for intelligence agencies to gain information such as:
What you just said.
What you watch on your home and what you don't.
The actual location of your washing machine, laundry baskets and dishwasher tables.
Where you put your keys, credit card, passport, and wallet.
"In theory, the manufacturer of those products could be the subject of a warrant to enable equipment interference with those devices," Walker said. "So the potential extent, I think, is something that needs to be carefully considered."
Walker also emphasised that the government should carefully consider how the "equipment interference" warrants should be used for electronic gadgets and make sure they're "only used when necessary and proportionate for a legitimate purpose."
Securing Smart Toys
Moreover, the security on connected devices should be tighter because it is not just government, but also criminals that can hack into these devices.
After concerns were raised early December by Bluebox Labs, Barbie's manufacturer Mattel reportedly tightened the security on Hello Barbie that allows kids to talk to dolls over a cloud server connection.
It's thought that other smart toy manufacturer companies will shortly follow the suite, especially after the news that Hong Kong toymaker VTech's systems were hacked, compromising 4.8 million records.
Hundreds of thousands of engine immobilizers remotely hackable
11.12.2015
A New Zealander expert has found hundred of thousands of vulnerable engine immobilizers are remotely hackable due to a flaw.
The New Zealander Lachlan Temple (@skooooch) has discovered hundred of thousands of vulnerable engine immobilizers are remotely hackable. The expert discovered a flaw in a popular cheap car tracking and immobilizer gadget that can allow remote attackers to locate, eavesdrop, and in some cases interrupting the fuel supply to the engine to hundreds of thousands of vehicles, and more alarming, even while they are in motion.
Once the users have installed the engine immobilizers on their car they are able to remotely track the vehicle, block the engine, enable microphone recording, enable geo-fencing, and track the car movements.
The gadgets are rebranded by various vendors, including the Chinese ThinkRace, meanwhile in Australia the engine immobilizers are branded as “Response” and offered for sale at electronics chain JayCar for about A$150.
One of the models available on the market is able to control the car fuel pumps, a feature implemented to remotely immobilize a stolen vehicle, but Temple discovered that a an attacker could exploit a flaw in the management of session cookies to enable this function.
This means that while you are driving, someone everywhere is able to stop your engine!
Temple presented his findings at the Kiwicon security confab in Wellington, he added that today the flaws allow attackers who log into any account, including a demo account, to log into any of the 360,000 units ThinkRace that are sold without need of a password.

Lachlan Temple. Photo by Darren Pauli / The Register
“You just brute force everyone account, you can increment each one,” Temple told Vulture South. “You could disable someone’s car if they have wired the relay, so if that happened on a freeway that is pretty dangerous.” “Most people would wire it this way, that’s the main point of it and the reason why mechanics sell it.”
Temple suggests users to wire the relay to the starter motor, in this way a remote hacker cannot stop the engine while in motion and instead would prevent it starting up once turned off.
The flaws could be also exploited by attackers to access user personal details, including phone numbers, or eavesdrop on cars through the a microphone installed in the set of the engine immobilizers.
Temple discovered that the same tracker is used by ThinkRace in the watches sold to track children, in this case, an attacker can eavesdrop on kids and track them.
Temple announced that he will focus next test on more expensive tracking solution available on the market, including engine immobilizers used by commercial fleets of vehicles.
Stay Tuned …
France will not Ban Public Wi-Fi Or Tor Network, Prime Minister Valls Confirms
11.12.2015
Despite the French Ministry of Interior's demands, France will not ban the TOR anonymity network or Free public Wi-Fi as a way to help the law enforcement fight terrorism.
French Prime Minister Manual Valls has gone on record saying that a ban on Free public Wi-Fi is "not a course of action envisaged," and he is not in favor of banning the TOR anonymity network, either.
Following the deadly terror attacks on Paris last month, an internal document obtained by Le Monde indicated that French government wanted to block communications of TOR as well as ban the use of Free Public Wi-Fi during states of emergency in an effort to fight terrorism more efficiently.
However, according to France PM, banning Encrypted Communications could affect the country's economy and security.
Must Read: FBI Director Asks Tech Companies to At least Don't Offer End-to-End Encryption
TOR and Free Wi-Fi Safe in France, PM Says
"A ban of [free public] Wi-Fi is not a course of action envisaged [and never has been]," Valls said (translated) on Wednesday.
Neither he is in favor of banning the TOR network, which encrypts and re-routes user traffic through a network of volunteer-operated servers, masking the real identities of users.
"Internet is a Freedom, is an extraordinary means of communication between people, it is a benefit to the economy," Valls added. "It's also a means for terrorists to communicate and spread their totalitarian ideology."
Therefore, he said the police must take some measures to improve their fight against terrorism in light of recent Paris attacks, but whatever measures they take to combat terrorism "must be effective."
The whole world response to recent Paris attacks involves lawmakers in the United States and Europe calling for new laws on technology, forcing the tech companies to put "backdoors" in their products and hand over encryption keys to the government on court orders.
New Spy Banker Trojan Telax exploits Google Cloud Servers
11.12.2015
Security firm Zscaler discovered a malicious campaign based on a new strain of the Spy Banker banking malware.
Security experts at Zscaler discovered a malware-based campaign relying on a new strain of Spy Banker banking malware.
Spy Banker is an old threat, it was first detected in 2009, the new variant spreads over social media, primary through Facebook, and relies on social engineering to trick users into clicking shortened Bit.ly URLs over the promise of coupons, vouchers or premium software downloads.
Zscaler experts also observed a number of victims were also compromised by drive-by downloads.
According to the researchers, the Spy Banker banking malware has been targeting Portuguese-speaking victims in Brazil.
“Zscaler ThreatLabZ has been closely monitoring a new Spy Banker Trojan campaign that has been targeting Portuguese-speaking users in Brazil. The malware authors are leveraging Google Cloud Servers to host the initial Spy Banker Downloader Trojan,which is responsible for downloading and installing Spy Banker Trojan Telax.” states the post published by Zscaler.
The campaign, spotted by researchers at Zscaler, spreads primarily over social media—Facebook for the most part—and uses convincing social engineering to trick users into clicking shortened Bit.ly URLs over the promise of coupons, vouchers or premium software downloads. A number of victims were also compromised by drive-by downloads.
The use of social media platforms to spread the malware is very effective, it exploits the user’s trust of messages coming from its network of contacts.
The malicious URLs point to a server hosted on Google Cloud Servers which host the Spy Banker downloader that is dropped on the victim’s machine. The downloader then downloads the Spy Banker Trojan Telax, whose aim is to steal online banking credentials.

In sample analyzed by Zscaler, the short URL points to a PHP files that’s hosted on a Google Cloud server. The PHP file then does a 302 redirect to download the initial Spy Banker Downloader Trojan payload.
In the attack illustrated by the experts, the executable file receitanet.com is posing to be Brazil’s federal revenue online tax returns service. In other cases observed by the researchers, the crooks used different themes offering discount vouchers and fake premium software applications.
The researchers revealed that this specific short URL had been clicked more than 103,000 times, 102,000 of which come Facebook.

Google has already cleaned up the cloud servers involved in the malicious campaign.
“It is important to note that Google has already cleaned up the cloud servers being currently redirected by these two active sites and hence the infection cycle will fail with a 404 Not Found message,” Zscaler said.
Zscaler published a detailed analysis of the new variant of the Spy Banker Trojan Telax … enjoy it!
ZeroDB, the end-to-end encrypted database, goes open source
10.12.2015
The End-to-end encrypted database ZeroDB becomes open source and its code is available on GitHub, try it and contribute to the community with your experience.
While politicians and experts are debating around encryption, the End-to-end encrypted database ZeroDB becomes open source and its code is available on GitHub.
ZeroDB is an end-to-end encrypted database in which the storage server knows nothing about the data it is storing, as reported on the official website query logic is performed client-side against encrypted data on a remote server, in this way even if the storage server is hacked, an attacker will not be able to view the unencrypted data.
ZeroDB allows users to develop applications with strong security with specific care to the end-user privacy. ZeroDB is particularly suitable for applications that need to store encrypted information on untrusted servers such as a public cloud storage.

The database is based on Zope Object Database (ZODB), which is an object-oriented database for transparently and persistently storing Python objects, and written inPython.
“In ZeroDB, the client is responsible for the database logic. Data encryption, decryption and compression also happen client side. Therefore, the server never has any knowledge about the data, its structure or order,” it is explained in the documentation. “Since the server has no insight into the nature of the data, the risk of a server-side data breach is eliminated. Even if attackers successfully infiltrate the server, they won’t have access to the cleartext data,” the developers pointed out.
The user data on the server is always encrypted, at rest, in transit, and even when used. The developers behind the ZeroDB project, MacLane Wilkison and Michael Egorov, changed the license from proprietary to AGPLv3 early this week.
“Now that it’s open source, we want your help to make it better. Try it, build awesome things with it, break it. Then tell us about it.” states the post the officially announces ZeroDB goes open source. “Today, we’re releasing a Python implementation. A JavaScript client will be following soon.”
The ZeroDB is recommended for companies in the financial services industry, healthcare industry, government agencies, media companies and telecoms.
The announcement related to ZeroDB comes a few days after the one of Hashcat, the popular password recovery tool that has been released as open source under the MIT license.
FBI Director Asks Tech Companies to At least Don't Offer End-to-End Encryption
10.12.2015
FBI Director Asks Tech Companies to At least Don't Offer End-to-End Encryption
FBI declared War against Encryption.
Encryption is defeating government intelligence agencies to detect terrorist activities and after the recent ISIS-linked terror attacks in Paris and California, the issue has once again become a political target in Washington.
...and meanwhile, Kazakhstan plans to make it Mandatory for its Citizens to Install Internet Backdoor, allowing the government to intercept users' traffic to any secure website and access everything from web browsing history to usernames and passwords.
FBI: For God's Sake, Don't Use End-to-End Encryption
At a Senate hearing on Wednesday, FBI's Director James Comey called for tech companies currently providing users with end-to-end encryption to reconsider "their business model" and simply stop doing that, reported The Intercept.
Yes, instead of asking companies for a "backdoor" this time, Comey suggested them to adopt encryption techniques that help federal agencies intercept and turn over end-to-end encrypted communications when necessary.
"The government doesn't want a backdoor, but [it] hopes to get to a place where if a judge issues an order, the company figures out how to supply that information to the judge and figures out on its own the best way to do that," said Comey.
Comey: Keep Readable Version of Customers' Messages
End-to-end Encryption is a secure communication that encrypts the data on the sender's system before passing it to a company server. The company then passes the encrypted data to the intended recipient, who is the only person who can decrypt it.
Recommended Read: How to Install Let's Encrypt Free SSL Certificate On Your Website.
Nobody in between, be an application service provider, an Internet service provider (ISP), hacker, or even law enforcement officials, can read the data or tamper with it.
However, Comey is asking for the technology companies to retain a readable version of that initial data, just in case the authorities need it.
"There are plenty of companies today that provide secure services to their customers and still comply with court orders," he said. "There are plenty of folks who make good phones [and] are able to unlock them in response to a court order."
Terrorists and Encryption
Moreover, Comey also gave an example of a situation in which law enforcement officials faced obstacle because of encryption.
Also Read: Peerio — End-to-End Encrypted Secure Messenger and File Sharing App.
Here's the example Comey provided:
"In May, when two terrorists attempted to kill a whole lot of people in Garland, Texas, and were stopped by the action of great local law enforcement. That morning, before one of those terrorists, left to try to commit mass murder, he exchanged 109 messages with an overseas terrorist. We have no idea what he said because those messages were encrypted. That is a big problem."
You can watch his full speech at the Senate hearing in the video given below:
So at last, the FBI director did not actually make crystal clear exactly what measures he wants tech companies to adopt, or whether he had favor laws to force the companies to do it. But, he made partially clear that he is not at all satisfied with the current need to encrypt devices.
AVG, McAfee, and Kaspersky antivirus were vulnerable to critical flaw
10.12.2015
Experts at enSilo have found a critical security vulnerability in various antivirus (AV) software that could be exploited by attackers to turn the AntiVirus to an attack-enabler tool.
Some of the most important security firms have had an ugly surprise, the security software they offer to their clints have been compromised by a serious vulnerability flaw that could be exploited to hack computers.
In March, the security researchers at enSilo firm discovered a serious vulnerability in the popular free antivirus engine AVG Internet Security 2015. The researchers discovered that the software was allocating memory for read, write, and execute (RWX) permissions in a predictable address. The knowledge of the memory address could be exploited by an attacker could to inject malicious code into the target system and execute it.
enSilo reported the vulnerability to AVG that promptly fixed it within a couple of days. The experts at enSilo decided to analyze other software commercialized by the principal security firms, including McAfee and Kaspersky.
They discovered that VirusScan Enterprise version 8.8 and Kaspersky Total Security 2015 were also affected by the vulnerability. Below the list of vulnerable products discovered by the experts:
For now we have found this vulnerability in the following Anti-Virus products. We’ll continue updating this list as we receive more information.
McAfee Virus scan Enterprise version 8.8. This vulnerability appears in their Anti Malware + Add-on Modules , scan engine version (32 bit) 5700.7163 , DAT version 7827.0000 , Buffer Overflow and Access Protection DAT version 659 , Installed patches: 4. We have notified McAfee and they have silently fixed it in their patch dated Aug. 20, 2015.
Kaspersky Total Security 2015 – 15.0.2.361 – kts15.0.2.361en_7342. We have notified Kaspersky and they have silently fixed it in their patch dated Sept. 24, 2015.
AVG Internet Security 2015 build 5736 + Virus database 8919. As mentioned above, AVG has released their patch on March 12th.
The researchers plan to analyze other solutions and update the readers about the status of their security software.
“We’ll continue updating this list as we receive more information,” said Tomer Bitton, VP of research at enSilo, in a blog post.
“Given that this is a repetitive coding issue amongst Anti-Virus – an intrusive product, we believe that this vulnerability is also likely to appear in other intrusive products, non-security related, such as application-performing products.”
Other experts wrote about the security issue, Tavis Ormandy, security expert at Google, has written about a similar issue with Kaspersky software. In the blog post the hacker detailed how it is possible to exploit the security issue.

Considering the gravity of the problem and its widespread nature, enSilo has created a free checking tool called AVulnerabilityChecker to allow users checking if their machine is vulnerable.
“Considering the gravity of this issue, we created a tool – AVulnerabilityChecker – that checks whether an application running on your machine is vulnerable to this flaw. If vulnerable, AVulnerabilityChecker will not be able to tell you which application contains the flaw, but it will point out where to start the analysis.” states enSilo.
McAfee and Kaspersky have already fixed the security issue.
Internet root servers flooded with 5 million queries a second
10.12.2015
Two anomalous DDoS attacks have flooded the Internet root servers that received more than 5 million queries a second.
Early last week, anomalous DDoS attacks have threatened the Internet root servers that received more than 5 million queries a second.
“The authoritative name servers that serve the DNS root zone, commonly known as the “root servers”, are a network of hundreds of servers in many countries around the world. They are configured in the DNS root zone as 13 named authorities, as follows.” reads the IANA website.

The Internet root servers are critical components of the global Internet infrastructure, they were targeted two times for an hour or more each. Multiple domain name system root servers were hit in the attacks, these systems are essential to associate a logical address to the IP address.
“On November 30, 2015 and December 1, 2015, over two separate intervals, several of the Internet Domain Name System’s root name servers received a high rate of queries. This report explains the nature and impact of the incident.” states an advisory published Friday “While it’s common for the root name servers to see anomalous traffic, including high query loads for varying periods of time, this event was large, noticeable via external monitoring systems, and fairly unique in nature, so this report is offered in the interests of transparency.”
The first DDoS attack occurred on Monday, November 30, and the Internet root servers were flooded for about two hours and 40 minutes. The second attack took place on December 1 and lasted an hour. The majority of the Internet root servers was hit in the cyber attacks which flooded the machines with billions of valid queries for two undisclosed domain names, one for each attack.
Despite a significant volume of traffic flooded the Internet Root servers, the Internet users did not suffer any disservice because root servers are involved in the address resolution only when a much larger network of intermediate DNS servers fail to do so.
Who it behind a so powerful attack?
At the rime I’m writing, there is no indication of a possible responsible, the unique certainly is a so powerful DDoS attack request a significant computing power and bandwidth.
The name servers targeted in the attack use IP Anycast, it is a network routing methodology in which datagrams from a single sender are routed to the topologically nearest node in a group of potential receivers, though it may be sent to several nodes, all identified by the same destination address.
The fact that attackers hit IP Anycast servers indicates that attackers coordinated resources geographically dispersed.
“This event was notable for the fact that source addresses were widely and evenly distributed, while the query name was not,” continues the advisory. “This incident, therefore, is different from typical DNS amplification attacks whereby DNS name servers (including the DNS root name servers) have been used as reflection points to overwhelm some third party.”
The experts speculate the involvement of a large botnet, likely composed of a huge number of IoT devices. Such kind of attacks could be prevented by implementing the BCP 38, the Internet Engineering Task Force standard for defeating IP address spoofing.
NCA launched #CyberChoice campaign, to prevent youngsters become cyber criminals
10.12.2015
The Britain’s National Crime Agency (NCA) has launched this week #CyberChoices campaign that targets parents of youngsters aged 12-15 to explain them how it is easy to be involved in cyber criminal activities.
Are script kiddies a real threat? The Britain’s National Crime Agency (NCA) thinks so and launched a campaign to discourage teens from hacking activities after it has found the average age of suspects had plummeted to 17.
The decision is not unreasonable, the law enforcement noticed that the average age of the suspects has plummeted to 17. Hacking is becoming an attractive lifestyle, it’s cool, and a growing number are approaching it without having the perception of the consequences.
“Over the past few years the NCA has seen the people engaging in cyber crime becoming younger and younger,” said Richard Jones, head of the National Cyber Crime Unit’s Prevent team.
According to the officers from the NCA, the average age of suspected cyber criminals featured in investigations involving the NCA in 2015 year was 17, compared to 24 observed in 2014.
“We know that simply criminalizing young people cannot be the solution to this and so the campaign seeks to help motivate children to use their skills more positively,” Jones added.
“These individuals are really bright and have real potential to go on to exciting and fulfilling jobs. But by choosing the criminal path they can move from low level ‘pranking’ to higher level cyber crime quite quickly,”
NCA computer
The NCA has launched the #CyberChoices campaign that targets parents of youngsters aged 12-15 to explain them how it is easy to be involved in cyber criminal activities, even without their knowledge.
The official advertisement presented by the NCA features a young boy with his family on a sofa, with the parents vaunting about IT expertise of their son.
But when the parents reveal that he joked about robbing a bank that the they realize their son is cyber criminal. The spot ends with the entire family being quizzed by officers from the NCA.
The campaign #CyberChoices was launched by the UK Government to educate parents on common forms of cyber crime, the lack of knowledge has a significant impact of the perception on cybercrime for their son. Malware, Distributed Denial of Service (DDoS), ransomware, Dark Web are unknown terms for parents, but not for their children and the risk of being involved in criminal activities is high.
“The campaign aims to educate parents on the common forms of cyber crime potentially undertaken by teenagers. In an operation targeting users of Lizard Stresser, a Distributed Denial of Service (DDoS) tool which can knock websites offline by flooding them with data, all of the seven people arrested were under the age of 18.” reads the post published by the Agency
Younger hackers have also increasingly used Remote Access Trojans (RATs) that allow them to remotely control the PC of their victims, the agency revealed that youngest purchaser of a RAT was just 12 years old.
“Other types of malicious software called Remote Access Trojans (RATs) can also be popular amongst younger users. They allow people to remotely monitor and take full control of another computer. During an operation targeting users of the Blackshades RAT the average age of the 22 people arrested was 18, with the youngest purchaser of Blackshades just 12 years old.”
Giving a look to some of the most glamorous security breached, like the attack against the British IPS TalkTalk and the Christmas attack against PSN network and XBox live network conducted by Lizard Squad hacking crew it is possible to note that the groups were composed of young hackers, often minors …
It’s time to act!
Someone Just Tried to Take Down Internet's Backbone with 5 Million Queries/Sec
10.12.2015
Someone just DDoSed one of the most critical organs of the Internet anatomy – The Internet's DNS Root Servers.
Early last week, a flood of as many as 5 Million queries per second hit many of the Internet's DNS (Domain Name System) Root Servers that act as the authoritative reference for mapping domain names to IP addresses and are a total of 13 in numbers.
The attack, commonly known as Distributed Denial of Service (DDoS) attack, took place on two separate occasions.
The first DDoS attack to the Internet's backbone root servers launched on November 30 that lasted 160 minutes (almost 3 hours), and the second one started on December 1 that lasted almost an hour.
Massive Attacks Knocked Many of the 13 Root Servers Offline
The DDoS attack was able to knock 3 out of the 13 DNS root servers of the Internet offline for a couple of hours.
Also Read: Secure Email Service Paid Hackers $6000 Ransom to Stop DDoS Attacks.
The request queries fired at the servers were valid DNS messages addressed towards a single domain name in the first DDoS attack, and the second day's DDoS attack addressed towards a different domain name.
According to the analysis published by the root server operators on Tuesday, each attack fired up to 5 million queries/second per DNS root name server that was enough to flood the network and cause timeouts on the B, C, G, and H root servers.
There is no indication of who or what was behind the large-scale DDoS attacks because the source IP addresses used in the attacks were very well distributed and randomized across the entire IPv4 address space.
Interesting Read: Record-breaking 1Tbps Speed achieved Over 5G Mobile Connection.
However, the DDoS attacks did not cause any serious damage to the Internet, but a mere delay for some of the Internet users who made DNS queries through their web browser, FTP, SSH, or other clients.
This Smart Design Defends DNS Protocol Infrastructure
The motive for such attacks is still unclear because disabling or knocking down a root server won't have a severe impact on the Internet as there are several thousand of other DNS servers managing DNS queries.
"The DNS Root Name Server system functioned as [it's] designed, demonstrating overall robustness in the face of [massive] traffic floods observed at numerous DNS Root Name Servers," Root Server Operators says (PDF), referring to the backup system employed by DNS servers.
Like the Internet, DNS is constructed on a mesh-like structure, so if one server doesn't respond to a request, other servers step in and provide a DNS query result.
According to the DNS root server operators, the attack was not the result of a reflective DDoS attack in which open and misconfigured DNS is used to launch high-bandwidth DDoS attacks on the target.
Recommended Read: Over 20Gbps DDoS attacks Now Become Common for Hackers.
Despite all the facts, any attack on the critical infrastructure of the Internet is taken extremely seriously.
The DNS root server operators recommended the Internet Service Providers (ISPs) to implement Source Address Validation and BCP 38, an Internet Engineering Task Force standard that helps defeat IP address spoofing.
xboxlive digital certificate exposed opens users to MITM attacks
9.12.2015
Microsoft has issued an advisory to notify customers that the private keys for an SSL/TLS digital certificate for *xboxlive.com have been disclosed.
According to a security advisory published by Microsoft, the company is propagating a new certificate for the *.xboxlive.com domain because it has “inadvertently disclosed” the certificate’s contents.
Microsoft confirmed the accidental disclosure of the digital certificate private keys for the above domain, a circumstance that opens customers to man-in-the-middle attacks, although the certificate “cannot be used to issue other certificates, impersonate other domains, or sign code”.
The Xboxlive certificate is included in all supported releases of Microsoft Windows.
“Microsoft is aware of an SSL/TLS digital certificate for *.xboxlive.com for which the private keys were inadvertently disclosed. The certificate could be used in attempts to perform man-in-the-middle attacks. It cannot be used to issue other certificates, impersonate other domains, or sign code. This issue affects all supported releases of Microsoft Windows. Microsoft is not currently aware of attacks related to this issue. ” reads the Microsoft advisory.
Microsoft confirmed that revocation of the Xboxlive SSL server certificates should propagate to everybody automatically, however. The company hasn’t provided additional information on how many people may have seen the certificate, but it is unlike that the accidental disclosure has been exploited in attacks in the wild.
xboxlive
Users of Windows have nothing to do, meanwhile users of Vista, Windows 7, Windows Server 2008 or Windows Server 2008 R2 will need to enable the automatic certificate updater.
Users not covered by the automatic update should add the compromised certificate to the list of untrusted certificates by using the Certificates MMC snap-in.
After applying the update, how can users verify the certificates in the Microsoft Untrusted Certificates Store?
For Windows Vista, Windows 7, Windows Server 2008, and Windows Server 2008 R2 systems that are using the automatic updater of certificate trust lists (see Microsoft Knowledge Base Article 2677070 for details), and for Windows 8, Windows 8.1, Windows RT, Windows RT 8.1, Windows Server 2012, Windows Server 2012 R2, Windows 10, and Windows 10 Version 1511 systems, users can check the Application log in the Event Viewer for an entry with the following values:
Source: CAPI2
Level: Information
Event ID: 4112
Description: Successful auto update of disallowed certificate list with effective date: Tuesday, December 1, 2015 (or later).
For systems not using the automatic updater of certificate trust lists, in the Certificates MMC snap-in, verify that the following certificate has been added to the Untrusted Certificates folder:
Certificate Issued by Thumbprint
xboxlive.com Microsoft IT SSL SHA2 8b 2e 65 a5 da 17 fc cc bc de 7e f8 7b 0c 0e d5 d0 70 1f 9f
It Works! Google's Quantum Computer is '100 Million Times Faster' than a PC
9.12.2015
It Works! Google's D-Wave 2X Quantum Computer is '100 Million Times Faster'
Announcing the results of its experiment, Google says Quantum Computer is More than 100 Million times faster than a regular PC.
Two years ago, Google and NASA (National Aeronautics and Space Administration) bought a D-Wave 2X quantum computer, which they have been experimenting at the U.S. space agency's Ames Research Center in Mountain View, California for the past two years.
The goal is to create a better way to solve highly complex problems in seconds rather than years.
Also Read: Fastest Operating System for Quantum Computing Developed By Researchers
Now, a Google's Quantum AI team appears to have announced the results of its latest test on D-Wave 2X quantum computer, demonstrating that quantum annealing can outperform simulated annealing by over 108 times – that is 100,000,000 times faster.
What is Quantum Computers?
Google's D-Wave 2X Quantum Computer
Quantum computers can theoretically be so much faster because they take advantage of quantum mechanics. While traditional computers use the "bits" to represent information as a 0 or a 1, quantum computers use "qubits" to represent information as a 0, 1, or both at the same time.
In turn, this allows Quantum computers to achieve a correct answer much faster and efficiently through parallel processing.
Now, the Google Quantum Artificial Intelligence Lab has announced that its D-Wave machine is considerably much faster than simulated annealing – quantum computation simulation on a classical computer chip.
"We found that for problem instances involving nearly 1000 binary variables, quantum annealing significantly outperforms its classical counterpart, simulated annealing. It is more than 108 times faster than simulated annealing running on a single core," said Hartmut Neven, Google's director of engineering.
Also Read: Web Encryption Protocol That Even Quantum Computers Can't Crack
Google: Our Quantum Machine is 100 Million Times Faster
Google has also published a paper [PDF] on the findings, claiming that the team was able to perform a calculation with the quantum computing technology that was significantly faster than a conventional computer with a single core processor.
Google's D-Wave 2X Quantum Computer
The researchers emphasized that their research on quantum computing is still in the early stages and has yet to be commercialized which could take decades.
"While these results are intriguing and very encouraging, there is more work ahead to turn quantum enhanced optimization into a practical technology," Neven wrote.
However, the team of Google and NASA researchers announced on Tuesday that the tests on D-Wave machines using Quantum Monte Carlo algorithm simulates running an optimization problem on ordinary silicon, and again the results were more than 100 Million times faster than a conventional computer.
The North American cyber-criminal underground it’s easy to access!
9.12.2015
According to a new report published by Trend Micro, the North American cyber criminal underground is very easy to access.
The new report released by Trend Micro reveals that the cyber criminal underground market in North America isn’t so hidden like in other countries.
“It doesn’t exist in the dark web as much as other undergrounds do, or practice as much security,” ,”Essentially, it’s become a gun show for everyone as long as they can participate and are willing to pay.” says Tom Kellermann, chief cybersecurity officer at Trend Micro.
“The North American Underground primarily caters to customers within the region–users based in the United States (US) and Canada. Unsurprisingly, most of the offerings (stolen accounts, products and services, and fake documents) are US based. This is consistent with what we see in the Japanese1 and Brazilian2 undergrounds and suggests that US-based information is most sought after in it.” states the report.
Gigging in the underground markets users can buy, guns, drugs, hacking services, bulletproof vests, and even money laundering services or maybe hire a murder.
It could be useful to help different criminal activities, tradition organized criminals are becoming “cyber aware” and now do their business through the internet.
“We’ve done studies and exposes of the most significant undergrounds in the world,” “The U.S. underground doesn’t practice operational security. They’ve essentially become a shopping mall.”
Of course, law enforcement is aware of this trend and probably in the future more of these underground markets in response to the increasing pressure of the authorities will migrate to the darkweb, where they would be more protected.
In the decade of 2000, law enforcement agencies were doing very well, and almost every U.S cyber-criminal underground was dismantled, but in the last 3 years, the criminal underground market did a came back and its getting stronger.
“It’s larger because it’s providing a wider multiplicity of goods and services,”. “They’re there for the drugs, weapons, passports, stolen cards, and murder for hire.
Looking at the numbers, it can be seen that drugs it’s the popular item in the criminal underground ecosystem, getting 62% of the market, but also its interesting to see that stolen data dumps account gets 16%, fake documents 4%, weapons 2%, and murder for hire 1%.


North America criminal Underground Trend Micro drugs
In terms of “murder for hire“, you have some options available like a simple beating for $3,000, or an “accidental death” for $900,000.
The last bit that we hadn’t covered yet was the crimeware that takes 15% of the market and include things like, buying malware, hacking services.
Other best seller besides drugs are malware, and the service provider for the malware does his homework, encrypting the malware multiple times as needed until the malware can pass undetectable through the endpoint products.
“it’s why targeted attacks have become so prevalent,”,”They will make sure their attacks cannot be stopped by perimeter defenses.”


Talking about differences in countries, Kellerman explains:
“In the Russian or Chinese underground, they won’t sell you the back door into the system,”,”That’s a North American phenomenon. It’s like, I broke into a house last night, I made a duplicate of the key. You want it, you got it.”
One of the main reasons why nowadays we read about the cyber criminal underground in the news is because doing illegal activities in the cyberspace is becoming even more easy and cheap.
The model of sale known as crime-as-a-service is attracting the organized crime and is allowing a rapid growth of illegal activities online.
Is he Satoshi Nakamoto? Australian Police raid home of the alleged Bitcoin father
9.12.2015
While media announced to have found the real identity of the Bitcoin creator Satoshi Nakamoto, Australian police raided his home in Sidney.
A few hours after the media indicated the Australian expert Craig Steven Wright as the possible man behind the popular name Satoshi Nakamoto, the anonymous creator of Bitcoin, the Australian Police raided his home in Sydney.
Wright was identified as the mysterious creator of Bitcoin, Satoshi Nakamoto, based on leaked transcripts of legal interviews and a number of emails and blog posts.
At the time I was writing, there is no confirmation about the identity of the Bitcoin creator. A dozen of police agents raided Wright’s home on Wednesday afternoon searching, they broke down the door and ransacked the house.
It is important to clarify that the raid seems to be not associated with the recent revelation on the Satoshi Nakamoto’s real identity, the Guardian who reported the news states that the operation is linked to the Australian Taxation Office investigation
“On Wednesday afternoon, police gained entry to a home belonging to Craig Wright, who had hours earlier been identified in investigations by Gizmodo and Wired, based on leaked transcripts of legal interviews and files. Both publications have indicated that they believe Wright to have been involved in the creation of the cryptocurrency.” reported the Guardian.
Bitcoin
The Australian Federal police issued an official statement explaining that the raids were not related to the bitcoin claims.
“The AFP can confirm it has conducted search warrants to assist the Australian Taxation Office at a residence in Gordon and a business premises in Ryde, Sydney. This matter is unrelated to recent media reporting regarding the digital currency bitcoin.”
One officer told Reuters they were “clearing the house”, Reuters also reported that also the Wright’s offices have been raided.
The emails cited by Gizmodo don’t state that Wright is a founder of the Bitcoin, instead, suggest his involvement in the development of the cryptocurrency. Wright was trying to persuade the Australian Taxation Office to tax his Bitcoin holdings as a currency and not as an asset.
Another thing that suspicious experts is that Nakamoto reportedly has some 1.1 Million Bitcoins to his name in a trust fund that amounts to roughly 455 Million in US Dollars, it is exactly the same amount that Wright is believed to own.
“An email to a Clayton Utz lawyer identified as Wright’s lawyer in the ATO transcripts was sent from an address linked to Nakamoto and is signed “Craig (possibly).” “The email discussed whether contact should be made with Australia’s then assistant treasurer Arthur Sinodinos in January 2014 over the regulatory issues in Australia surrounding bitcoin.” continues the Guardian.
“The treatment of bitcoin for tax purposes in Australia has been the subject of considerable debate. The ATO ruled in December 2014 that cryptocurrency should be considered an asset for capital gains tax purposes.”
The Australian Taxation Office authorities will continue its investigation, for sure they will clarify if Wright is the mysterious Satoshi Nakamoto, or he is the wrong person.
Bitcoin Creator 'Satoshi Nakamoto' Unmasked! An Australian Man 'Craig Wright' identified...
9.12.2015
Breaking Update: Police Raid alleged Bitcoin Creator Craig Wright's Home in Sydney.
Yes, Satoshi Nakamoto, the mysterious creator of the Bitcoin digital cryptocurrency has possibly been identified as an Australian entrepreneur, according to investigations independently done by Wired and Gizmodo.
His name is Craig Steven Wright…
...at least based on some convincing evidence shown by both the publications.
Bitcoin is a revolutionary virtual currency developed around Blockchain, a complicated cryptographic protocol and a global computers network that oversees and verifies which Bitcoins have been spent by whom.
The identity of the ones spending Bitcoins are extremely difficult to trace because of its anonymous nature, therefore, are very popular among criminals.
Also Read: Meet The World's First Person Who Hacked His Body to Implant a Bitcoin Payment CHIP
Satoshi Nakamoto is not only the father of an entire economy worth Billions of dollars, but also a multi-multi-millionaire himself.
Some Evidence that... Satoshi Nakamoto = Craig Steven Wright
The 44-year-old Australian academic – described as a "climate-change denier, a serial entrepreneur and an eccentric" – fits the profile of Bitcoin's creator in nearly every detail.
who-is-satoshi-nakamoto-bitcoin
Wired claimed that Wright knew about Bitcoin before it was ever made public in 2009. We can say this based on the following evidence:
Wright apparently published some blog posts sharing and seeking expertise on developing crypto currencies just before the launch of Bitcoin.
His PGP keys for email were previously linked to someone identifying themselves as being Satoshi Nakamoto.
A blog post announcing the launch of Bitcoin, which was then deleted and replaced with a short note saying "the best way to hide is right in the open."
The Documents that were either "Leaked" or "Hacked" by an anonymous source close to Wright include e-mails dating back to 2008 — before the creation of Bitcoin — in which Wright discusses his work on Bitcoin.
Wright has 1.1 Million Bitcoins Worth $400
As evidence, the report cites a Legal Contract that Mr. Wright and his American business partner, Dave Kleiman (computer forensics expert) who died in 2013, were involved in the development of the Bitcoin digital currency.
According to the contract, Wright and Kleiman allegedly have access to 1.1 Million Bitcoins. This sum, worth about $400 Million today, is the same amount that Nakamoto is believed to own.
Also Read: World's 9 Biggest Banks to adopt Bitcoin's Blockchain Technology.
Leaked Conversation b/w Wright and his Lawyer
Another leaked document shows conversations between Wright and his lawyers in which Wright said:
"I did my best to try and hide the fact that I have been running Bitcoin since 2009;" however "by the end of this I think half the world is going to bloody know."
Shortly after Wired published its report, Wright blog was taken offline as well as his Twitter account went deleted altogether.
Wright's Ex-Wife Knew his Research on Digital Money
The Gizmodo story includes interviews with Wright's ex-wife Lynn, who confirmed that her husband worked on digital currency ideas many years ago, but noted that he 'didn’t call it Bitcoin' at first.
Another reporter approached his current wife, who is a director at his company DeMorgan, and asked if Wright was the inventor of Bitcoin, Guess What?
She smiled and closed the door, declining to comment on it.
Wright Announced World's First Bitcoin Bank
Wright publicly announced last year his plans to establish the "World's First Bitcoin Bank" and described himself as CEO DeMorgan company.
DeMorgan – a company "focused on alternative currency, next generation banking and educational products with a focus on security and creating a simple user experience."
However, evidence can go wrong. Various attempts to prove Satoshi Nakamoto's identity in the past have proved unsuccessful.
Also Read: 'Bitcoin is Now Officially a Commodity' — US Regulator Declared
Last year, Newsweek created headlines worldwide, claiming to "outed" the creator of Bitcoin 'Satoshi' as being a 64-year-old Japanese-American, who lives near Los Angeles.
However, Wright's name has never appeared on the list of the possible creators of Bitcoin. So this time as well, the whole story could be nothing but just a big Hoax and the unverified leaked documents could also be faked in whole or in part.
Police Raid alleged Bitcoin Creator Craig Wright's Home in Sydney
9.12.2015
Just hours after the Australian man 'Craig Steven Wright' outed as the possible real identity of Satoshi Nakamoto, the anonymous creator of Bitcoin, Australian Police raided his home in Sydney.
Over 10 police officers raided Wright's home in the Sydney suburbs on Wednesday afternoon. They forcefully opened the door, and 'started searching the cupboards and surfaces of the garage.'
However, the Sydney police raid at Wright's home is not associated with the claims of his being involved in creating Bitcoins, rather related to the Australian Taxation Office investigation, the Guardian reported.
Wright was recently identified as the mysterious creator of Bitcoin, based on leaked transcripts of legal interviews and a number of emails and blog posts.
However, neither Dr. Wright nor anyone else has publicly confirmed the real identity of the founder of Bitcoin Satoshi Nakamoto.
In a statement, the Australian Federal Police (AFP) officers said the raids weren't at all associated with the recent Bitcoin claims on Wright.
"The AFP can confirm it has conducted search warrants to assist the Australian Taxation Office at a residence in Gordon and a business premises in Ryde, Sydney," the police said. "This matter is unrelated to recent media reporting regarding the digital currency bitcoin."
Wright appears to be persuading the Australian Taxation Office to tax his Bitcoin holdings as a currency and not as an asset.
Nakamoto reportedly has some 1.1 Million Bitcoins to his name in a trust fund that amounts to roughly 455 Million in US Dollars — the same amount that Wright is believed to own.
The recent investigations hinted at a direct link between Wright and Nakamoto, but the evidence could be fake in whole or part and there is a possibility that Wright could also be the wrong man.
Maybe the Australian Taxation Office authorities will have the better luck in figuring out the mystery — The Face behind Bitcoin.
Cadelle and Chafer, Iranian hackers are tracking dissidents and activists
9.12.2015
Symantec has uncovered Cadelle and Chafer groups, two Iran-based hacking teams that are tracking dissidents and activists.
According to a new report published by Symantec. Iranian hackers have been using malware to track individuals, including Iranian activists and dissidents.
The researchers have identified two groups of Iran-based hackers, dubbed Cadelle and Chafer, which were distributing data stealer malware since at least mid-2014. The experts uncovered the command-and-control servers explaining that registration details indicate the Iranian hackers may have been operating since 2011.
There are a number of indicators that suggest both groups are based in Iran, the Cadelle and Chafer teams are most active during the day time within Iran’s time zone and primarily operate during Iran’s business week (Saturday through Thursday).
“Two Iran-based attack groups that appear to be connected, Cadelle and Chafer, have been using Backdoor.Cadelspy and Backdoor.Remexi to spy on Iranian individuals and Middle Eastern organizations.” states a report published by Symantec.
The hackers used custom-made malware that isn’t particularly sophisticated, the attackers remained under the radar for a long time and gained access to “an enormous amount of sensitive information.”
Let’s give a close look to the malware used by the Iran-based hackers, Cadelle uses a piece of malware called backdoor.cadellespy, meanwhile Chafer relies uses on the backdoor.remexi.
The researchers collected evidence to suggest that the two teams may be connected, Chafer was used to compromise web servers, likely through SQL injection attacks, to drop Backdoor.Remexi onto targeted systems. The Remexi botnet was used to gain control over the victim’s PC stealing user login credentials to use in lateral movements.
The analysis of Cadelspy’s file strings revealed that some dates use the Solar Hijri calendar format, a format very common in Afghanistan and Iran.
Most of affected organizations are based in the Middle East region in countries such as Saudi Arabia and Afghanistan, while one of the victim organization is located in the US.

Both groups are small, the experts at Symantec speculate they are composed of five to 10 people, but they don’t share the same attack infrastructure.
“The Cadelle and Chafer groups also keep the same working hours and focus on similar targets. However, no sharing of C&C infrastructure between the teams has been observed.” reads the report.
“If Cadelle and Chafer are not directly linked, then they may be separately working for a single entity. Their victim profile may be of interest to a nation state.”
Another interesting aspect related to the two Iran-based groups, is that several machines resulted infected with both Cadelyspy and Remexi malware, and the infections occurred within minutes of one another.
“One computer that was infected with both Cadelspy and Remexi was a system that ran a SIM card editing application,” Symantec wrote. “Other compromised computers included those belonging to web developers or are file and database servers.”
The malware also targeted people using anonymous proxies, used by activists and dissidents to hide their identity online and avoid censorship.
“Reports have shown that many Iranians avail of these services to access sites that are blocked by the government’s Internet censorship,” Symantec wrote. “Dissidents, activists, and researchers in the region may use these proxies in an attempt to keep their online activities private.”
Symantec confirmed that Cadelle and Chafer are still active today and will continue their operations.
EU regulation to Impose rules on firms to improve cybersecurity
9.12.2015
EU member states and lawmakers have prepared a first draft of the EU regulation in cyber security that will force companies to improve security and report security breaches and cyber incidents.
EU member states plan to impose rules in the company to prevent cyber attacks, on Monday they agreed the first draft of the regulation that will force companies in various industries to increase cyber security and disclose any incident reporting it to the authorities.
The regulation will impact any sector, including financial, health care and transportation.
“This agreement is a major step in raising the level of cybersecurity in Europe, one of the objectives of the EU cybersecurity strategy and a cornerstone in our efforts towards a Digital Single Market” the European’s Union’s digital commissioner Guenther Oettinger wrote on his blog.
The EU regulation will oblige IT giants, Internet and cloud service providers, and online marketplaces like Amazon, eBay, and Google to ensure the safety of their infrastructure and to disclose and share information about major incidents.
In this phase small digital companies will be exempted from the rules, however I believe that the regulation will be adapted to consider in the future also the specific situation of this category of businesses.
EU regulation
As explained by Oettinger, the EU regulation is a necessary action to respond to the cybercrime and mitigate its impact on the economy of the EU.
“Every day, cybercrime and cyberattacks cause major economic damage to European businesses and our economy. This amounts to hundreds of billions of euro each year. Even ordinary families and children cannot escape this risk.” Oettinger says. “I will not sit back and let these criminals and cyber terrorists attack our businesses, intrude into our private lives and destroy trust in our digital economy and society,”
The new EU rules in cyber security will act on three levels:
improving cybersecurity in EU countries by forcing Member States to have a national strategy.
improving cooperation between Computer Security Incident response teams of the State Members and to share information about cyber attacks and risks.
forcing companies that provide essential services (i.e. power companies, financial institutions, transport providers, healthcare and digital infrastructure) to take appropriate security measures and inform the authorities when they suffer a major cyber incident.
“The rules will make digital networks and services more secure and reliable. Consumers will have more confidence in the technologies, services and systems they rely on day-to-day. The EU economy will benefit as sectors that depend on Network and Information Security will be backed up by cybersecurity teams at home and across Europe. Governments and businesses can be confident that digital networks and critical infrastructure such as the electricity, gas and transport sectors can securely provide their essential services at home and across borders. ” continues the post.
The new rules will impact also companies that operate in the IT sectors but that rely on technologies to provide their services, gas and transport sectors “can securely provide their essential services at home and across borders,”.
The EU regulation in cyber security has to be approved by the European Parliament, but cyber security experts believe that the 28 EU member states will accelerate the process for the criticality in the field.
Nemesis Bootkit — A New Stealthy Payment Card Malware
8.12.2015
Another day, another stunning Malware – this time targeting banks, payment card processors, and other financial services.
Security researchers have uncovered a sophisticated payment card malware that executes before the operating system boots, making the malware very difficult to detect and much less remove.
The malware in question is part of "Nemesis" – a malware suite that includes all software programs for capturing screens, transferring files, injecting processes, logging keystrokes, and carrying out other malicious activities on the infected computers.
Nemesis malware family has been seen in the past, targeting banks, ATMs, financial transaction processing, credit unions, and financial business service companies.
Nemesis Bootkit Malware – Reappears even after Re-installation of the OS
The malware with bootkit functionality has been in operation since early this year and has the ability to modify the legitimate VBR (Volume Boot Record) that makes the malware possible to load before Windows starts.
This makes the malicious threat hard to detect and remove using traditional security approaches.
Moreover, the malware resides in a low-level portion of a hard drive.
This makes the malware infection reappears even after the complete reinstallation of the Windows operating system.
"The malware that persists outside of the operating system (OS) requires a different approach to detection and eradication," security analysts from FireEye wrote in a blog post published Monday.
"Malware with bootkit functionality can be installed and executed almost entirely independent of the Windows [OS]. As a result, incident responders will need tools that can access and search raw disks at scale for evidence of bootkits."
How Does the Malware Work?
Early this year, the cyber criminals tweaked Nemesis to include a utility called BOOTRASH that has the ability to modify an infected computer’s boot process.
In a normal boot, any Windows PC reads data from a hard drive's MBR (Master Boot Record) that loads the VBR – a piece of code specific to an operating system containing instructions for the OS to begin the boot process.
The process typically looks like this:
banking-malware
The VBR then normally loads the operating system code, but BOOTRASH loads:
First, the malicious code that injects the Nemesis components stored in the virtual file system into the Windows kernel
Then the Operating System code
Since BOOTRASH is loaded outside of the machine's OS, it is not subject to any kind of integrity checks, nor are any of its components scanned by system's Anti-Virus program, which helps the malware evade detection.
According to the researchers, versions of BOOTRASH are targeting both 32-bit and 64-bit Windows architectures. Moreover, due to this newly added Bootkit component, reinstalling the OS will not remove the Nemesis malware.
Hackers behind Nemesis Malware
FireEye researchers believe the Nemesis bootkit malware belongs to a financial crime group of hackers, likely based in Russia, called FIN1.
"We identified the presence of a financially motivated threat group that we track as FIN1, whose activity at the organization dated back several years," FireEye researcher wrote. "The threat group deployed numerous malicious files and utilities, all of which were part of a malware ecosystem referred to as ‘Nemesis’ by the malware developer(s)."
The researchers believe that the FIN1 hacking group used this malware, most of the times, to access victims environment and steal cardholders data. In the past, the researchers came across different versions of the Nemesis family when they analyzed FIN1's malware.
How to Protect Your Systems From Nemesis Bootkit Malware?
Re-installing the operating system of your Windows machine is not a sufficient method to get rid of this malware.
The solution against this malware threat is to use software tools that can access and scan raw disks at scale for evidence of Bootkits, or physically wipe the disks before reinstalling the operating system.
"System administrators should perform a complete physical wipe of any systems compromised with a bootkit and then reload the operating system," FireEye researchers recommend.
Nemesis is by no means the first malware family to hijack normal boot process of a PC in an effort to gain persistence and stealth, but it is not the first malware family that contains bootkit functionality.
In the past, researchers detected malicious threats such as TDL4 (Olmarik), Rovnix, Necurs, and Carberp. Among these, Carberp banking trojan targeted financial institutions.
Like it or not, Microsoft Plans to Push Windows 10 Upgrade more Aggressively
8.12.2015
Like it or not, Microsoft plans to Push Windows 10 Upgrade with new Strategy
This is no surprise that Microsoft wants you to install Windows 10.
But, Hey Microsoft, Not everyone wants to upgrade to Windows 10. Many people are happy with Windows 7 or Windows 8.1 OS and don’t want to switch to the newest Windows 10 operating system.
Days after the launch of Windows 10, Microsoft started offering Free Windows 10 installation to every Windows user. The marketing strategy successfully worked for Microsoft and just within a week after the launch, Windows 10 started running on millions of PCs.
Then the company went into planning other tricks in order to get on to the maximum number of PCs as possible. It silently started pushing Windows 10 installation files on PCs running Windows 7 or Windows 8.1, even if users have not opted into the upgrade.
Also Read: Reminder! If You Haven't yet, Turn Off Windows 10 Keylogger Now.
Less than two months ago, some Windows 7 and 8.1 users also claimed that Windows 10 had begun to install itself automatically on their PCs, which Microsoft later called it a mistake.
More Aggressive Windows 10 Upgrade Strategy
Now, Microsoft is going to kick off a more aggressive Windows 10 Upgrade strategy.
The new operating system that showed up first as optional, and then as recommended download in Windows Update, will soon show up – "Yes, I want to upgrade."
Yes, those Windows 7 or 8.1 users who are trying to block the Windows 10 upgrade will find that the upgrade has just not gone away.
Must Read: Just Like Windows 10, Windows 7 and 8 Also Spy on You – Here's How to Stop Them.
This is because Microsoft has recently made some changes to settings on Windows 7 and 8.1 machines that were previously configured not to receive the Windows 10 upgrade.
The settings have been reset in such a way that one of the updates that the company deployed on Windows 7 and Windows 8.1 machines keeps on checking every day to make sure that no other changes are made to this behavior.
Windows 10 Update Being Re-offered Several Times
The issue was reported by Josh Mayfield, the creator of GWX Control Panel, an app used to block the upgrade to Windows 10.
The developer received several reports from its users who specified that their preferences of not upgrading to Windows 10 reset up to several times a day and the Windows 10 update presented to them again.
"Over Thanksgiving weekend I started getting reports that the Windows Update 'AllowOSUpgrade' setting was getting flipped back on on a number of peoples' PCs, and it keeps resetting itself at least once a day if they switch it back off," Josh Mayfield said as reported by Computerworld.
Microsoft stated about a month ago that it intends to push the new operating system much more aggressively in the new year, re-categorizing Windows 10 as a "Recommended Update" in its Windows Update service.
So don’t be surprised if, in coming days, the Windows 10 installation process starts again, and again, until you finally lay down your arms and allow the Windows 10 upgrade, or simply move on to another operating system.
BackStab Malware steals iOS and BlackBerry Backups
8.12.2015
Security experts at Palo Alto Networks have uncovered a new strain of malware dubbed BackStab that steals local mobile data backups.
Security experts at Palo Alto Networks have uncovered a new strain of malware dubbed BackStab that steals local mobile data backups and transfer it to the C&C server.
The malware is not able to steal data from the mobile device, instead it searches for data backup from the infected PCs. The malware scans for backups created by the mobile devices or by any other software that creates automatic backups.
BackStab Malware is able to Steal both iOS and BlackBerry Backups via compromised computers.
The malware exploits the fact that many backup tools don’t implements encryption, so the malicious code easily finds the backups and access data it contains.
As explained by the experts, the BackStab malware doesn’t need to have higher-level privileges or root access to the device or the infected computer.
BackStab has been in the wild for over five years, the experts at Palo Alto Networks have discovered six trojan families that used the technique to steal backup data in attacks across 30 countries.
“We have identified 704 samples of six Trojan, adware and HackTool families for Windows or Mac OS X systems that used this technique to steal data from iOS and BlackBerry devices. These attacks have been in the wild for over five years, and we have observed them deployed in over 30 countries around the world.” state a blog post published by PaloAlto Networks

According to Palo Alto researchers BackStab still not supports Android backups.
The experts provided a detailed description about how the BackStab works and mitigation strategies.
“Under certain conditions, mobile devices automatically create un-encrypted backup files on a local computer when they are attached through a USB port. Apple iOS devices began doing this when iTunes backup was introduced with the first generation iPhone in 2007. When users choose the default backup options, the contents of their phone is stored, unencrypted on their computers local hard drive in a well-known location. Forensics experts have known about this behavior for years and have exploited it to gain access to iOS device content even when they cannot directly access an iPhone due to it’s strong protections.”
Security experts suggest users to use a backup solution that implement data encryption, keep the OS and the application up to date, and “do not click “Trust” on the popup that appears every time they connect their phone to a new computer.”
Nemesis, a bootkit used to steal payment card data
8.12.2015
Nemesis is a new strain of malware, very hard to detect and remove, designed to steal payment card data and implementing bootkit functionalities.
Experts at FireEye have discovered a new strain of malware designed to steal payment card data. Nothing new, you are probably saying, but this malware dubbed Nemesis is very difficult to detect and remove.
FireEye has identified the threat actor behind the new Nemesis malware, it is the hacking crews FIN1, which is suspected of being a group of criminals from Russia.
The FIN1 criminal gang has been known to target financial institutions worldwide, it used the Nemesis malicious code to compromise an unknown organization that processes financial transactions.
Nemesis malware
Organizations in the retail industry who manage payment card data are privileged targets of cyber criminal gangs, Target, Home Depot, Neiman Marcus are just a names of illustrious victims of the cyber crime.
Nemesis belong to the family of malware identified as bootkit, BIOS bootkits was mentioned when Snowden disclosed the catalog of surveillance tools used by the NSA ANT division, these malware are able to compromise the BIOS of the victim’s machine ensuring persistence and implementing sophisticated evasion techniques.
“In September, Mandiant Consulting identified a financially motivated threat group targeting payment card data using sophisticated malware that executes before the operating system boots. This rarely seen technique, referred to as a ‘bootkit’, infects lower-level system components making it very difficult to identify and detect.” states FireEye in a blog post“The malware’s installation location also means it will persist even after re-installing the operating system, widely considered the most effective way to eradicate malware.”
Even when the operating system is reinstalled, the bootkit can remain in place.
“Malware with bootkit functionality can be installed and executed almost completely independent of the Windows operating system,” the post continues.
In early 2015, the FIN1 threat actors added to its arsenal a utility that modifies the legitimate system Volume Boot Record (VBR) and hijacks the system boot process, in this way the criminals ensure the loading of the Nemesis malware before the Windows operating system. The utility was called by the experts at FireEye BOOTRASH, the only way to detect it is to use a raw disk scanner.
“Similarly, re-installing the operating system after a compromise is no longer sufficient. System administrators should perform a complete physical wipe of any systems compromised with a bootkit and then reload the operating system.”
The experts at FireEye Mandiant have found the bootkit by using a tool called Mandiant Intelligent Response (MIR) that allows for raw disk access and scan.
Linksys wireless routers are open to cyber attacks
8.12.2015
According to an advisory published by the KoreLogic firm the Linksys EA6100-6300 wireless routers are vulnerable to attacks due to flawed CGI scripts.
Once again IoT devices are in the headlines, once again SOHO routers are affected by a security vulnerability that opens users to cyber attacks. According to the KoreLogic firm, the flawed devices are the Linksys EA6100-6300 wireless routers, the company has published an advisory reporting that security issues affect the CGI scripts in the admin interface opening the device to remote attacks.
“Multiple CGI scripts in the web-based administrative interface of the Linksys EA6100 – EA6300 Wireless Router allow unauthenticated access to the high-level administrative functions of the device.” the advisory says
“This vulnerability can be leveraged by an unauthenticated attacker to obtain the router’s administrative password and subsequently arbitrarily configure the device.”
Linksys EA6100 - EA6300 Wireless Router
Many of the CGI scripts in the admin interface provide an attacker with unauthenticated access to the device allowing him to get the router’s admin password.
“Other CGI files that are accessible from an unauthenticated perspective can be used to configure settings for the affected device. This led to the development of an exploit to abuse these vulnerabilities.” the advisory continues.
The flawed scripts include the bootloader, sysinfo.cgi, ezwifi_cfg.cgi, qos_info.cgi and others.
The company the security issued to Linksys, but it still waiting for a reply, the Linksys EA6100-6300 wireless routers are consumer products, this means that once the security update will be available end-users will have to apply it. Unfortunately in many cases end-users fail to apply the patches and end users remain open to cyber attacks.
Matt Bergin of KoreLogic also published a proof-of-concept code provided with the advisory. The PoC includes the code for testing the Linksys EA6100-6300 wireless routers to see if they still use the factory admin password.
Waiting for a fix let me suggest to disable the remote admin access to your Linksys EA6100-6300 wireless router.
Hashcat, the fastest Password Cracking utility is now Open Source
8.12.2015
Hashcat, the popular password recovery tool has been released as open source under the MIT license. You can contribute to it.
The popular password cracking tool Hashcat is not an open source software, the announcement was first made on December 4 on Twitter via an MD5 hash that posted the following message:
“hashcat open source”
The source code for both utilities Hashcat and oclHashcat is now available on the GitHub repository.
The main Hashcat developer, Jens ‘atom’ Steube, has later published a post on the Hashcat official forum to announce the availability of the source code for both Hashcat and oclHashcat software.
Hashcat is the a fast and advanced GPGPU-based password recovery utility, meanwhile oclHashcat is the respective GPU-based version.

Why Does Hashcat go Open Source?
Steube, who is a strong supporter of open source software, decided to release the software to allow software and security experts to review the code and improve it, for example integrating external libraries.
The software is under the MIT license to allow an easy integration or packaging for the most common Linux distributions.
“Actually, I am a big fan of open source software, and I’ve always held the idea of eventually going open source at some point in the future. The difficult questions were when would we be ready to do so, and when would be the best time to do it.” states the post.
Up until now, Hashcat is not supported on OS X because Apple does not allow “offline” compiling of kernel code. Now that the Hashcat project goes open source, users will be able to compile the GPU kernels and use oclHashcat also on OS X.
“Currently there is no native support for OSX. The main reason for this is that Apple does not support “offline” compiling of the kernel code. Technically, the missing piece is what AMD allows through CL_CONTEXT_OFFLINE_DEVICES_AMD in its OpenCL runtime. This would allow the compilation of GPU kernels for devices which are not currently attached to the development system. With an open source project, you can easily compile the kernels using the Apple OpenCL Runtime “just in time”, also known as JIT, and hence lift that restriction. This means that support for oclHashcat on OSX would be possible for the first time.” Steube explains.
Steube in the past worked with the experts at Kaspersky Lab, assisting them in cracking hashes related to the Gauss malware and the Equation group.
Experts at Kaspersky Lab published a blog post early this week to explain the benefits of password cracking tools going open source.
“One of the main [password cracking tool] user-groups are penetration-testers. Their job is to evaluate the security in given areas including evaluation of password security. Also forensic-examiners use these tools in order to gain access to required evidence. These cases and tasks are often highly sensitive and apply to strict rules,” explained Marco Preuss. “OpenSource offers the possibility of developing customized extensions without leaking any potential sensitive information to external developers of such tools. This applies if different hash-algorithms are required to be audited while pentesting or specific requirements are set in forensic cases e.g. criminal evidence collection for an upcoming lawsuit.”
Steube will continue to support the Hashcat project
“No way I’d do that! I’ll stay here, providing the same effort as before,” the developer said.
Every but could be submitted to the development team, along with new features.
Notebooky od Lenova, Toshiby a Dellu obsahují nebezpečný software
8.12.2015
Bezpečnostních chyb nalezených v podpůrném softwaru předinstalovaném výrobci přenosných počítačů přibývá.
Nové chyby byly objeveny v aplikacích Lenovo Solution Center, Toshiba Service Station a Dell System Detect, přičemž jako nejzranitelnější se jeví první jmenovaná, která na počítačích s operačním systémem Windows může šikovným útočníkům dovolit prostřednictvím webových stránek spustit škodlivý kód.
Chyby objevil a upozornil na ně hacker z řad veřejnosti a přiměl tak k reakci koordinační centrum CERT z Carnegie Mellon University, které vydalo bezpečnostní výstrahu.
Jeden z problémů způsobuje LSCTaskService, služba vytvářená aplikací Lenovo Solution Center, na kterou jsou navázána systémová oprávnění. Služba otevírá http démon na portu (55555), který je schopen přijímat příkazy. Jeden z nich, s názvem RunInstaller, přitom kontroluje soubory umístěné v %APPDATA%\LSC\Local Store folder.
Do tohoto adresáře může zapisovat kterýkoliv uživatel, bez ohledu na oprávnění, nicméně soubory jsou spouštěny jako systémové, což znamená, že i cizí uživatel může využít této chyby a získat plnou kontrolu nad systémem.
Díky návazné chybě navíc útočník ani nemusí vkládat vlastní soubory do zmíněného adresáře. A aby toho nebylo málo, LSCTaskService je zranitelná i skrz takzvanou cross-site request forgery (CSRF), útok do internetových aplikací pracující na bázi nezamýšleného požadavku pro vykonání určité akce v této aplikaci, který ovšem pochází z nelegitimního zdroje.
Což ale znamená, že aby útočník zneužil první dvě chyby, nemusí mít ani lokální přístup do systému, ve kterém je nainstalováno Lenovo Solution Center a stačí mu uživatele dostat na škodnou webovou stránku.
Chyby dalších jmenovaných výrobců už tolik závažné nejsou. Aplikace Toshiba Service Station vytváří službu TMachInfo, která běží jako systémová a přijímá příkazy skrz UDP port 1233. Jeden z nich, nazvaný Reg.Read, lze využít ke čtení většiny registrů Windows jako systémový uživatel. „Nevím, k čemu to využít, ale někdo jiný by mohl vědět,“ píše ve své zprávě hacker s nickem slipstream.
A chyba, kterou objevil v Dell System Detect paradoxně vyplynula z řešení, kterým se Dell pokusil záplatovat předchozí jinou chybu. Týká se ověřovacích podpisů RSA-1024, u nichž je údajně potíž v tom, že je firma umístila na své webové stránky, kde s k nim mohou dostat útočníci a následně je zneužít.
Lenovo uvedlo, že chyby prověří a poskytne potřebné záplaty, než tak ale učiní, uživatelé si prý mohou Lenovo Solution Center odinstalovat. Toshiba a Dell se k problémům zatím nevyjádřily.
Stepping out of the dark: Hashcat went OpenSource
8.12.2015
While passwords are still an essential topic in IT-Security, the recovery and cracking of those is as well. There are several tools focusing on password recovery while two of them stand out of the crowd: Hashcat/oclHashcat and John-the-Ripper (JtR).
We already mentioned Hashcat in our blog on account password security here.
Jens Steube – the mind behind Hashcat -also supported our research on the Gauss malware by creating the oclGaussCrack.
Beginning of this year we also asked for help on the Equationgroup MD5 “e6d290a03b70cfa5d4451da444bdea39”. Jens Steube and Philipp Schmidt solved it as arabic word for “unregistered”.
Last Friday, a “cryptic” message was posted on Twitter by @hashcat

The MD5 revealed a major step for Hashcat: “hashcat open source” – Jens ‘atom’ Steube decided to go OpenSource with his well-known Password recovering/cracking tool Hashcat/oclHashcat. Over this weekend, the github repository of Hashcat was among the top trending and collected already more than 1,000 “stars“.

Screenshot by https://twitter.com/jmgosney
Repository Official Announcement

Hashcat and oclHashcat
This project implements a rich set of features of attacks against a long list of algorithms. Hashcat is for CPU-based hash cracking while oclHashcat uses GPUs.
Why Password cracking tools and OpenSource?
There are many reasons why such tools are needed. One of the main user-groups are penetration-testers. Their job is to evaluate the security in given areas including evaluation of password security. Also forensic-examiners use these tools in order to gain access to required evidence. These cases and tasks are often highly sensitive and apply to strict rules. OpenSource offers the possibility of developing customized extensions without leaking any potential sensitive information to external developers of such tools. This applies if different hash-algorithms are required to be audited while pentesting or specific requirements are set in forensic cases e.g. criminal evidence collection for an upcoming lawsuit.
The implemented functionalities also try to push for stronger security by revealing unsecure hash-algorithms or vulnerabilities and weak passwords. This is must not be underestimated, as driving the evolution and development of new secure algorithms is an important and necessary step. [see Collision Vulnerabilities in MD5, SHA1 and SHA2.
Hashcat as OpenSource under the MIT License will now open possibilities of integrating other libraries and porting the software to other platforms. Hashcat may now also be integrated into Linux distributions and thereby opening up for a broader audience, since it’s even easier to use.
It’s difficult to foresee the future, but for sure we’ll see more development in this area – for a good reason.
Save the Date — 11th December: Anonymous to Celebrate 'ISIS Trolling Day'
7.12.2015
After hacking and taking down social media accounts of ISIS members, the online Hacktivist group Anonymous is back again with its new plan to harass the Islamic State (IS) militant group that was behind the horrific terror attack in Paris.
Anonymous declared total war against ISIS after the last month's Paris attacks and supposedly:
Took down thousands of Twitter and social media accounts used by the ISIS terrorists
Disrupted the terror group's primary communications platform
Replaced one of ISIS' websites with a Viagra ad
Now, the hacktivist group has declared December 11th to be "ISIS Trolling Day," planning an organized trolling campaign against ISIS by assaulting their image through Photoshopped images, memes, videos and jokes related to the terrorist organisation.
Also Read: ISIS Issues 5 Lame Tips for its Members to Avoid Getting Hacked
Vanish ISIS Online Presence
This campaign is also part of the group's ongoing effort to disrupt and dishonor the ISIS terror organization's online presence.
Western-living Muslims usually fall for ISIS' intimidating social media propaganda, so rebranding the militant group as a joke may be one of the best ideas Anonymous hackers ever had – attacking the ideas that ISIS is trying to spread online.
Anonymous has also asked netizens to be part of this trolling campaign as an effort to mock ISIS members and supporters for "the IDIOTS they are."
Also Read: Check Out How Anonymous Hackers Can Disrupt ISIS Online Propaganda
ISIS Trolling Day's Goals
According to a Ghostbin post, the trolling campaign will take place on Twitter, Facebook, Instagram, YouTube, and in the real world.
"We'll show them what they really are they don't stand for a religion, they don't stand for a God, they're brainwashers teaching from the young to the old their propaganda against the 'West' when in reality they're just increasing the distance between countries by giving many a bad name," the post reads.
Here are some of the campaign goals:
Use #Daesh or #Daeshbags (ISIS hates being called Daesh)
Post mocking photographs of ISIS on Instagram, Twitter, Facebook
Try to get #Daeshbags trending on Twitter
Post photographs of captured ISIS members and mock them
Use #'s that ISIS members use, but post mocking pictures instead
Make insulting videos of ISIS as well
Print out photos or stickers that mock ISIS and spread them around your city
JOIN US! DECEMBER 11, 2015! #OPISIS — Official #DayOfRage (@OpDayOfRage) December 5, 2015
Now, let's see what kind of real impact this campaign will make at the end of the day, but free speech and taunt can be a way more powerful tool when fighting a war of ideas.
Critical vulnerabilities found in Honeywell Midas Gas Detectors
7.12.2015
Another vulnerable IoT device is in the headlines, this time two serious vulnerabilities affect the Honeywell Midas gas detectors.
Honeywell has just released firmware updates for its Midas gas detectors to fix two high severity vulnerabilities.
The Midas gas detectors are a category of product manufactured by Honeywell to detect toxic, ambient and flammable gasses in the environment.
Midas gas detectors are usually used in light industrial manufacturing, university laboratories, semiconductor processing, and aerospace. Any unauthorized changes to the configuration of the Midas gas detectors could lead to wrong gas level measures, that could cause serious damage of industrial equipment and even the loss of human life.
According to the security expert Maxim Rupp, the Midas gas detectors running firmware versions 1.13b1 and prior, and Midas Black products running firmware versions 2.13b1 and prior are affected by two serious flaws (CVE-2015-7907, CVE-2015-7908) that can be easily exploited without having specific skills.
The first flaw (CVE-2015-7907) is a path traversal vulnerability that received the CVSS score of 8.6, it can be exploited by a remote attacker to bypass the authentication mechanism implemented to protect the web interface.
The access to the web interface gives the attackers full control on the configuration of the Midas gas detectors, ill-intentioned can exploit it to launch calibration and test processes.
The second flaw (CVE-2015-7908), that received the CVSS score of 9.4, is related to the transmission of the user passwords, the secret code are in fact transmitted in clear text.
“Successful exploitation of these vulnerabilities could allow a remote attacker to gain unauthenticated access to the device, potentially allowing configuration changes, as well as the initiation of calibration or test processes.” states the Advisory published by the ICS-CERT.
“Impact to individual organizations depends on many factors that are unique to each organization. NCCIC/ICS-CERT recommends that organizations evaluate the impact of these vulnerabilities based on their operational environment, architecture, and product implementation.”

Basically, the attacker can bypass authentication on the vulnerable Midas gas detectors simply by typing the URL of the page they want to access, for example, http://<host>/Network.htm. Rupp also discovered that the administrator password in embedded in clear text in the source code of the Security.htm page.
Rupp reported the flaws to the ICS-CERT which forwarded them to the Honeywell in July, the company fixed the vulnerabilities in October.
Honeywell urges its customers to apply the security patches, meantime protect the access to the Midas gas detectors, for example placing them in DMZs and using a firewall.
France wants to BAN Tor and Free Wi-Fi Services after Paris Terror Attacks
7.12.2015
Now this was to be done, Sooner or Later – The Government.
In the wake of the recent deadly Paris terror attacks, the French government is considering new laws that would Ban access to Free Wi-Fi and the Tor anonymity network, according to a recent report by French newspaper Le Monde.
The report cites an internal document from the Ministry of Interior by French Department of Civil Liberties and Legal Affairs (DLPAJ) that lists two proposed bills – one around the State of Emergency and the other on combating counter-terrorism.
Last month's Paris attacks started blame games, calling Edward Snowden and end-to-end encrypted services responsible for the ISIS-sponsored massacre.
Also Read: Anonymous declares War on ISIS: 'We will Hunt you Down!'
Now, the government has started renewing their assault on encryption and reviving their efforts to force tech companies to hand over encryption keys, and the document obtained by Le Monde hints the same.
Proposed Pieces of Legislation
State of Emergency Proposal: In this law, the French government is considering to Forbid the use of Free and Shared Wi-Fi connections during a state of emergency. Also, if the owners of public Wi-Fi networks did not disconnect, they could face criminal penalties.
According to the police, the reason behind restricting access to free or shared Wi-Fi is that it is apparently difficult to track suspects who use public Wi-Fi networks to communicate, so the law would shut down public Wi-Fi hotspots during a state of emergency.
The state of emergency increases the powers of the police in the country. During the state of emergency, French police may search residences without a warrant, tighten border controls, and even ban public protests.
Proposal for Combating Counter-Terrorism: This legislation proposal says the government is banning or blocking communications of the Tor network as well as requiring service providers to hand over encryption keys to police – not just during a state of emergency.
Indeed, in this section of the document, the Department of Civil Liberties and Legal Affairs questioned whether such proposed pieces of legislation might violate the French Constitution.
Also Read: Would Encryption Backdoor Stop Paris-like Terror Attacks?
The Onion Router, or TOR, is an anonymising network maintained by volunteers, which routes users’ data requests globally, making it very hard (but not impossible) to discover the actual user behind the computer screen.
Tor is an easy tool to hide your real identity on the Internet and is used not only by journalists, whistleblowers, and privacy concerned people, but also by terrorists, pedophiles, and cyber criminals.
Both pieces of legislation, according to Le Monde, could appear as soon as January 2016.
If block, France would be the first European country to block TOR. Though there is no easy way to block the anonymising network, China and Iran have both made successful attempts to block TOR.
Chakra JavaScript Engine: Microsoft Open-Sources the Heart of Edge browser
7.12.2015
Chakra: The Open-Source JavaScript Engine of Microsoft Edge browser
Microsoft has announced the plans to open source the core components of its "Chakra" – the JavaScript engine behind the new Edge browser – to GitHub code-sharing and collaboration repository next month.
The company made this announcement at the JSConf US Last Call conference in Florida this weekend.
What is Chakra?
"Chakra," developed in 2008, is a self-contained JavaScript virtual machine that Microsoft now lets developers implement in their own products and applications.
Though Chakra is at the core of only Microsoft's Edge, it is used across the Microsoft's newest operating system Windows 10 to power Universal Apps on Xbox, Windows Phone and tablets.
Chakra Going Open Source as ChakraCore
ChakraCore – is what Microsoft is calling the open source version of its Chakra – will be made available on GitHub under an MIT open source license in January 2016, with support from Intel, AMD, and NodeSource.
According to the Microsoft's official blog, "We're investing more than ever in improving Chakra and are excited to team up with our community to drive further improvements. In addition to the public [Microsoft means the 'open source community'], several organizations have already expressed interest in contributing to ChakraCore — among many others, we look forward to working with Intel, AMD and NodeSource as we develop this community."
ChakraCore Doesn't Include:
There are some differences between ChakraCore and Chakra as ships in Windows 10. The complete Chakra contains the adhesive between both:
The JavaScript engine and the browser's HTML engine
The JavaScript engine and the Universal Windows Platform
Chakra also has diagnostic APIs (Application Program Interfaces) that use COM and hence are Windows-specific.
However, neither of the above are part of the open source ChakraCore project. It only contains the 'core packages' for the engine, so doesn't expose Chakra's private bindings to the Edge browser or Universal Applications or make available COM diagnostic APIs.
What Does Chakra Offer?
The fully supported and open source ChakraCore project includes everything:
The parser
The interpreter
The JIT (just-in-time) compiler
The Garbage collector
The application programming interface (API) used to embed the engine into apps (like used in Edge)
It's an interesting and impressive move from the company like Microsoft that has rarely open sourced its projects. With this move, the company believes ChakraCore will be used in a large number of apps in the future, from cloud services to the Internet of Things (IoT).
Isn't that an exciting New Year gift for developers?
Arabian tales by ‘Nigerians’
7.12.2015 Zdroj: Kaspersky
The war in Syria, which began several years ago, has recently become one of the most widely reported events in the media. Along with the growing interest of the international community in Middle East events, “Nigerian” scammers have also jumped on the bandwagon. Over the last few months, we have recorded an increase in the number of fraudulent emails utilizing the Syrian theme.
The authors of most of the emails introduced themselves as Syrian citizens seeking asylum in Europe, and requested assistance in investing large sums of money. The messages were either short, with just enough info to arouse the recipient’s interest, or provide a detailed description of the offer.

Fraudsters often send out emails on behalf of women whose husbands have supposedly been killed or died. This theme was exploited with little or no changes in the Syria-related emails. A “widow” writes that her husbands had been killed and now she has a large sum of money that she wants to transfer to another country – she usually wants to get out of Syria too.

Fraudsters can also distribute emails on behalf of employees or owners of companies. To make the email more convincing, the text may include the names of real organizations. The authors of the emails provide a variety of stories to hook the recipient. For example, one of them says he has successfully transferred his assets to France but could not get a visa, so he is asking for help in case he cannot get to Europe.

The scammers are trying not only to get recipients interested by promising financial rewards but to evoke pity and compassion. In particular, the pseudo-Syrian citizens complain of harassment by the president and ask for help transferring and preserving their money.

English is the most popular language with the “Nigerian” scammers; however, we have come across emails in other languages: German, French and Arabic. The author of a German-language email introduced himself as an officer of the Syrian army fighting against ISIS; he writes that he wants to move $16 million earned by selling oil out of the country, and asks the recipient to contact him for more information. In particular, the fact that the citizens of Syria and other Arab countries have large amounts of money is often explained by various stories related to oil deals.

An email in French is written on behalf of a young Syrian refugee whose relatives were killed in the war in Syria and who is now staying in Germany. She complains about the unbearable cold in the tent she lives in, and about the promises of the authorities to improve the living conditions which are never fulfilled. She asks the recipient to take her in in exchange for a large sum of money.

Finally, the emails in Arabic, the official language of Syria, tell a sad story about a widow from Damascus, whose husband and children were killed during a bombardment using chemical weapons. The tale of the unhappy woman is intended to evoke the recipient’s sympathy while also mentioning a large sum of money that should tempt the recipient to help.

“Nigerian” scammers are trying to make their stories believable so they are using a standard set of tricks: links to legitimate news sources, detailed emotive stories where real events are mentioned, including well-known personalities, etc. However, it is worth remembering that emails from unknown senders offering you millions of dollars cannot be genuine. Therefore, the best solution is to simply delete the email and not enter into correspondence with the scammers.
Cyber spies of the Sofacy APT increased its operations tenfold
7.12.2015
According to a new report published by the Kaspersky Lab, the Sofacy APT has recently increased its activities.
According to a new report published by the Kaspersky Lab, the Advanced persistent threat group Sofacy (also known as APT28 , Fancy Bear, Sednit, and STRONTIUM) has increased its activity.
The Sofacy group has been active since 2008, targeting mostly military and government entities in NATO countries, the experts speculate that its is a nation-state actor.
The experts speculate that the Sofacy has increased its operations tenfold by targeting high-profile entities by using a new set of hacking tools.
In the last months, the researchers have uncovered a series of attacks, relying on a new set of tools and zero-day exploits, and targeting defense-related targets with specific focus with the Ukraine.
“In the months leading up to August, the Sofacy group launched several waves of attacks relying on zero-day exploits in Microsoft Office, Oracle Sun Java, Adobe Flash Player and Windows itself. For instance, its JHUHUGIT implant was delivered through a Flash zero-day and used a Windows EoP exploit to break out of the sandbox. ” state a blog post published by Kaspersky Lab.

The experts spotted a rare modification of the AZZY backdoor used by the threat actors for reconnaissance purposes. The first versions of the AZZY backdoor were discovered in August, once the attackers compromise the target they use more backdoor for lateral movements.
“The attackers deploy a rare modification of the AZZY backdoor, which is used for the initial reconnaissance. Once a foothold is established, they try to upload more backdoors, USB stealers as well as other hacking tools such as “Mimikatz” for lateral movement,” continues the post.
Kurt Baumgartner, principal security researcher at Kaspersky Lab, explained that the Sofacy APT group is very technically capable, it is able to design new hacking tools depending on the specific target.
“This quick work is a new characteristic of their work, and this stepped up urgency is something that is unusual. In general, APT intrusions can last months or longer, and in these cases, we see Sofacy acting with unusually ramped urgency,” Baumgartner said.
We will continue to follow the operations of the Sofacy APT group, stay tuned …
ISIS members have developed a mobile app for its communications
7.12.2015
Ghost Security Group has reportedly discovered an Android mobile application used by members of the ISIS organization for secure communications.
According to the Christian Science Monitor, the Ghost Security Group has reportedly discovered an Android mobile app used by members of the ISIS organization.
The Ghost Security Group is the notorious group of cyber experts in counter-terrorism networks that is involved in a series of initiatives against the ISIS radical group online.
In July, the group has supported US law enforcement and Intelligence agencies in thwarting ISIS terror plots in New York and Tunisia.
The Android app discovered by the experts is spread through hidden channels in popular messaging apps like Telegram. The ISIS members have developed the app as an alternative communication channel, the mobile application is reportedly used to spread propaganda and share information on the operations of the group.
“They want to create a broadcast capability that is more secure than just leveraging Twitter and Facebook,” Ghost Security Group chief operating officer Michael Smith II told the Christian Science Monitor. “Increasingly what you will see is the focus on developing means to control the distribution of their materials on a global scale.”
The discovery made by the Ghost Security Group demonstrates the cyber capabilities of the group, abilities that were discussed in the past by prominent experts, including the F-Secure Chief Research Officer Mikko Hypponen.
The popular expert said he worries about cyber extremists that could penetrate critical infrastructure and cause serious damages. The expert explained that the ISIS is probably the first group of terrorist that has hacking capabilities to manage a major attack against a government infrastructure, and the situation is getting worse because this group is gaining greater awareness of the effectiveness of an offensive launched by the cyberspace.
“The Islamic State is the first extremist group that has a credible offensive cyber capability,” said F-Secure Chief Research Officer Hyppönen, speaking last week at the Wall Street Journal’s WSJDLive conference in Laguna Beach, Calif. “Clearly, this situation isn’t getting better. It’s getting worse.”
In this period the US Congress is discussing the role of encryption in commercial products and services, and their potential abuse made by radical groups.

Intelligence agencies and law enforcement bodies worldwide claim that terrorists have exploited encryption implemented in commercial communications platform to arrange terrorist attacks, including the one that hit Paris on November, 13.
In August, a US security consultancy discovered another app dubbed Nasher developed by the member of the ISIS. Also in that case, the Android app was spread through unofficial channels. Users were required to download a special code shared among jihadist online communities and install the app on their device manually.
Islamic State uses the app – which it calls Nasher – to catalogue written reports, radio news and video files.
At the time of writing, the landing page for the app’s APK (Android application package) file had been viewed over 7,500 times although there’s no telling how many downloads have been made.

The French Gov wants to Block Tor and Forbid Free Wi-Fi
7.12.2015
In response to the recent Paris terror attacks, the French government is proposing to forbid and block the use of the Tor anonymity network.
According to an internal document from the Ministry of Interior visioned by journalists at the French newspaper Le Monde. The document includes two proposals of legislation, one around the state of emergency, and the other related to counterterrorism measures.
The French Government is considering to “Forbid free and shared wi-fi connections,” the measures have to be adopted to avoid any abuse of public wi-fi networks. The law enforcement is difficult to track suspects and terrorists who use public wi-fi networks.
The most controversial part of the piece of legislation is related to the ban of the Tor network, the legislation could be presented as early as January 2016.
It Tor the evil’s instrument?
The Tor is the most popular anonymizing network, it is currently maintained by volunteers. The anonymity of its users is ensured by routing the user’s traffic through unpredictable routes within the network of servers it includes, obfuscating the sources of data and masquerading the IP address.
Tor network is accused to be the kingdom of the evil, it hosts darkmarket places where it is possible to acquire any king of illegal product and service, including drugs, child pornography, weapons, and malware.
But we cannot ignore the importance of Tor, it allows journalists, whistleblowers and people who just want to protect their privacy online to avoid the censorship.
The Tor Project, the team that actually maintains the Tor network, did not immediately commented the news.
The Chinese authorities actively blocks connections to the Tor network preventing users from accessing the anonymizing network. The block is possible preventing the access to the public Tor entry nodes, anyway in countries where there is a strict control of the network it is possible to use non-public entry nodes, so-called “bridges,” to avoid the censorship.
Is the French ready to implement the Chinese censorship model? Is it constitutional? It this a good solution to prevent terrorist actions?
Let give a look to the Tor usage in the France in 2015 analyzing the number of direct connected users.

Focusing the analysis in the period before the Paris attacks, it is possible to note an increment of the connection in October.

There could be a number of causes responsible for the increment, including a botnet that used the Tor network to hide its C&C infrastructure. Anyway, in the days just before and after the attacks, there was nothing of strange.
It’s my personal opinion that ban the Tor network is a bad choice, there several options to stay online anonymously, recently we have discussed also the use of applications that could allow terrorists to exchange message hiding their identities.
Regarding the public WiFi, it could be a reasonable measure, but it is quite easy to find a poorly protected WiFi network to abuse. I made an experiment walking in my city, Napoli. I noticed an impressive amount of WiFi network apparently protected, but that use the default setting for their routers. Knowing the model of the router it quite easy to find online the login credentials. This circumstance would not be prevented by the measure proposed by the French Government.
3 OEMs Vulnerable To 3 Vulnerabilities. Your PCs At Risk
7.12.2015
Bad news for PC users, Lenovo machines can be hijacked by visiting a malicious website, meanwhile Dell and Toshiba PC are affected by serious flaws.
Security Researcher slipstream/RoL posted Proof-of-concept exploits online (3 OEMs Vulnerable To Three Vulnerability Your PCs At Risk) demonstrating how to compromise machines available on the market.
The US CERT has issued an alert about the vulnerabilities affecting the Lenovo machines, the Chinese firm is urging to uninstall its Solution Center as soon as possible.
“By convincing a user who has launched the Lenovo Solution Center to view a specially crafted HTML document (e.g., a web page or an HTML email message or attachment), an attacker may be able to execute arbitrary code with SYSTEM privileges. Additionally, a local user can execute arbitrary code with SYSTEM privileges,” said CERT, which is backed by the US Department of Homeland Security.
“The CERT/CC is currently unaware of a practical solution to this problem. However, please consider the following workaround: uninstall Lenovo Solution Center to prevent exploitation of these vulnerabilities. Closing any running instance of Lenovo Solution Center also prevents exploitation.”
Pc lenovo CERT
Lenovo Solution Center security advisory posted on company website confirms that the company is urgently working on a fix.
“We are urgently assessing the vulnerability report and will provide an update and applicable fixes as rapidly as possible. Additional information and updates will be posted to this security advisory page as they become available.” States the advisory.
Mitigation Strategy for Customers (what you should do to protect yourself) By Lenovo Solution Center : To remove the potential risk posed by this vulnerability, users can uninstall the Lenovo Solution Center application using the add / remove programs function.
By the way, the Lenovo Solution Center flaw is also exploitable remotely via CSRF, if the Lenovo Solution Center is open! Open Lenovo Solution Center and click here for a SYSTEM shell! Security Researcher Said
You can fetch exploit binaries and source code from oemdrop.
Summarizing the security vulnerabilities, according to CERT and Slipstream:
Lenovo
Lenovo Solution Center creates a process called LSCTaskService that runs with full administrator rights, and fires up a web server on port 55555. It can be instructed via GET and POST HTTP requests to execute code in a directory a local user can access.
Lenovo Solution Center will execute, again with full privileges, programs found in an arbitrary location on disk where the user can write to. Put some bad software in there, and it will be executed with admin rights.
A classic cross-site request forgery (CSRF) vulnerability exists in the LSCTaskService process, allowing any visited webpage to pass commands to the local web server to execute with full privileges.
Dell
Dell‘s bundled utility Dell System Detect can be made to gain admin privileges and execute arbitrary commands – by feeding it a security token downloaded from, er, dell.com: a token granting Dell System Detect permission to install manuals can be abused to execute programs (such as malware) with admin privileges. This can be exploited by software on your computer to fully compromise the machine.
Toshiba
Toshiba‘s bundled Service Station tool can be abused by normal users and unprivileged software to read the majority of the operating system’s registry as a SYSTEM-level user.
Remove Bloatware From Windows With Decrap My Computer
Decrap My Computer allows you to easily and safely remove all of the bloatware that comes pre-installed by the manufacturer on a new Windows PC. It can take hours or even days to get all the pre-installed software removed from your new computer, but with this little freeware utility you can completely uninstall all the unneeded software.
Best of all, Decrap My Computer can do all the operations needed to remove bloatware on its own, without any user input! It even clicks the usual “Next” and various other confirmation buttons of most common software uninstallers.
See how it works!
This video shows Decrap My Computer removes all the pre-installed software of a brand new Acer Aspire V3 laptop. Notice that after the final confirmation box has been closed, there is zero user input, all the uninstallers are automatically run by the Decrap My Computer program!
ISIS recruited experts set to wage chemical and biological attacks
7.12.2015
A European Parliament report has warned that the ISIS organization has already smuggled CBRN material into the EU, the risk of WMD attacks is real.
Intelligence experts suspect that the ISIS has recruited experts with chemistry, physics and computer science degrees to wage attacks with weapons of mass destruction.
“ISIS actually has already acquired the knowledge, and in some cases the human expertise, that would allow it to use CBRN materials as weapons of terror.” said Wolfgang Rudischhauser, Director of the Weapons of Mass Destruction Non-Proliferation Centre at NATO.
The shocking revelation is included in a report of the European Parliament that confirm the ISIS “may be planning to try to use internationally banned weapons of mass destruction in future attacks.”
The report comes after the recent Paris attacks and claims that the ISIS has already smuggled Weapon of Mass Destruction (WMD) material into Europe.
The report confirms the ISIS in recruiting foreign fighters with specific competencies in physics, chemistry and computer science.
“ISIL/Da’esh has recruited and continues to recruit hundreds of foreign fighters, including some with degrees in physics, chemistry and computer science, who experts believe have the ability to manufacture lethal weapons from raw substances.”

The British police forces have been conducting specific exercises to train its personnel to face various types of terrorist attacks, including chemical and biological ones.
“The European Union and its Member States must prepare for the possibility of a chemical or biological attack on their territory by the self-styled ‘Islamic State’ in Iraq and the Levant (known variously as IS, ISIS or ISIL, and by the Arabic acronym ‘Da’esh’).” states the report. “At present, European citizens are not seriously contemplating the possibility that extremist groups might use chemical, biological, radiological or nuclear (CBRN) materials during attacks in Europe. Under these circumstances, the impact of such an attack, should it occur, would be even more destabilising.”
European law enforcement agencies are facing the most serious terrorist and well-resourced organization of ever.
“We are dealing with a very serious, well-resourced, determined international terrorist organisation that is now active on the streets of Europe.” explained Rob Wainwright, head of Europol. “This represents the most serious terrorist threat faced in Europe for 10 years.”
Nomi Bar-Yaacov, Associate Fellow in Chatham House’s International Security Department, explained to the DailyMail that the risk is real.
“There is a very real risk of ISIS using unconventional weapons in Europe and beyond.” Nomi Bar-Yaacov.
The Western intelligence is trying to monitor Jihadi fighters, especially the for ‘specialist CBRN knowledge’.
EU governments have been warned to watch out for ‘other radicalised individuals, who have access to, or work in, sensitive areas’.
How is possible to steal CBRN material in Europe?
According to the 2014 Communication of the European Commission on a new EU approach to the detection and mitigation of CBRN-E risks, terrorist organizations have several opportunities to steal CBRN material.
The Commission confirmed thefts and misplacements of CBRN material occur on hundreds of occasions each year. Among the dangerous substances there is the sarin, ricin and anthrax.
“More than 150 cases of trafficking of radiological and nuclear materials are reported annually to the Incident and Trafficking Database of the International Atomic Energy Agency (IAEA);” states the report.
The intelligence is aware that CBRN substances have been illegally smuggled into the European Union, Interpol’s monthly CBRN intelligence reports report numerous examples of attempts to acquire, smuggle or use CBRN materials.
Sofacy APT hits high profile targets with updated toolset
6.12.2015 Zdroj: Kaspersky
Sofacy (also known as “Fancy Bear”, “Sednit”, “STRONTIUM” and “APT28”) is an advanced threat group that has been active since around 2008, targeting mostly military and government entities worldwide, with a focus on NATO countries. More recently, we have also seen an increase in activity targeting Ukraine.
Back in 2011-2012, the group used a relatively tiny implant (known as “Sofacy” or SOURFACE) as its first stage malware. The implant shared certain similarities with the old Miniduke implants. This led us to believe the two groups were connected, at least to begin with, although it appears they parted ways in 2014, with the original Miniduke group switching to the CosmicDuke implant.
At some point during 2013, the Sofacy group expanded its arsenal and added more backdoors and tools, including CORESHELL, SPLM (aka Xagent, aka CHOPSTICK), JHUHUGIT (which is built with code from the Carberp sources), AZZY (aka ADVSTORESHELL, NETUI, EVILTOSS, and spans across four to five generations) and a few others. We’ve seen quite a few versions of these implants and they were relatively widespread for a time.
#Sofacy group has been active since 2008, targeting mostly military and government entities in NATO countries
Tweet
Earlier this year, we noticed a new release of the AZZY implant which, at the time, was largely undetected by anti-malware products. We observed several waves of attacks using this version, most recently in October. The new waves of attacks also included a new generation of USB stealers deployed by the Sofacy actor, with the first versions dating back to February 2015, and which appear to be geared exclusively towards high profile targets.
Sofacy’s August 2015 attack wave
In the months leading up to August, the Sofacy group launched several waves of attacks relying on zero-day exploits in Microsoft Office, Oracle Sun Java, Adobe Flash Player and Windows itself. For instance, its JHUHUGIT implant was delivered through a Flash zero-day and used a Windows EoP exploit to break out of the sandbox. The JHUHUGIT implant became a relatively popular first stage for the Sofacy attacks and was used again with a Java zero-day (CVE-2015-2590) in July 2015.
While the JHUHUGIT (and more recently, “JKEYSKW”) implant used in most of the Sofacy attacks, high profile victims are being targeted with another first level implant, representing the latest evolution of their AZZYTrojan.
Two recurring characteristics of the #Sofacy group are speed and the use of multi-backdoor packages
Tweet
The first versions of the new AZZY implant appeared in August of this year. During a high profile incident we investigated, our products successfully detected and blocked a “standard” Sofacy “AZZY” sample that was used to target a range of defense contractors. The sample used in this attack (md5 A96F4B8AC7AA9DBF4624424B7602D4F7, compiled July 29th, 2015) was a pretty standard Sofacy x64 AZZY implant, which has the internal name “advshellstore.dll”.
Interestingly, the fact that the attack was blocked didn’t appear to stop the Sofacy team. Just an hour and a half later they had compiled and delivered another AZZY x64 backdoor (md5: 9D2F9E19DB8C20DC0D20D50869C7A373, compiled August 4th, 2015). This was no longer detectable with static signatures by our product. However, it was detected dynamically by the host intrusion prevention subsystem when it appeared in the system and was executed.

This recurring, blindingly-fast Sofacy attack attracted our attention as neither sample was delivered through a zero-day vulnerability — instead, they appeared to be downloaded and installed by another malware. This separate malware was installed by an unknown attack as “AppData\Local\Microsoft\Windows\msdeltemp.dll” (md5: CE8B99DF8642C065B6AF43FDE1F786A3).
The top level malware, CE8B99DF8642C065B6AF43FDE1F786A3 (named by its authors “msdeltemp.dll” according to internal strings, and compiled July 28th, 2015) is a rare type of the Sofacy AZZY implant. It has been modified to drop a separate C&C helper, (md5: 8C4D896957C36EC4ABEB07B2802268B9) as “tf394kv.dll“.
The dropped “tf394kv.dll” file is an external C&C communications library, compiled on July 24th, 2015 and used by the main backdoor for all Internet-based communications.

Decrypted configuration block of the C&C helper library “tf394kv.dll“
This code modification marks an unusual departure from the typical AZZY backdoors, with its C&C communication functions moved to an external DLL file. In the past, the Sofacy developers modified earlier AZZY backdoors to use a C&C server encoded in the registry, instead of storing it in the malware itself, so this code modularisation follows the same line of thinking.
In addition to the new AZZY backdoors with side-DLL for C&C, we observed a new set of data-theft modules deployed against victims by the Sofacy group. Among the most popular modern defense mechanisms against APTs are air-gaps — isolated network segments without Internet access, where sensitive data is stored. In the past, we’ve seen groups such as Equation and Flame use malware to steal data from air-gapped networks. The Sofacy group uses such tools as well.
The first versions of these new USB stealer modules appeared around February 2015 and the latest appear to have been compiled in May 2015. Older versions of these USBSTEALER modules were previously described by our colleagues from ESET.
One example of the new Sofacy USBSTEALER modules is 8b238931a7f64fddcad3057a96855f6c, which is named internally as msdetltemp.dll.

This data theft module appears to have been compiled in May 2015 and is designed to watch removable drives and collect files from them, depending on a set of rules defined by the attackers. The stolen data is copied into a hidden directory as “%MYPICTURES%\%volume serial number%“, from where it can be exfiltrated by the attackers using one of the AZZY implants. More details on the new USB stealers are available in the section on technical analysis.
Conclusions
Over the last year, the Sofacy group has increased its activity almost tenfold when compared to previous years, becoming one of the most prolific, agile and dynamic threat actors in the arena. This activity spiked in July 2015, when the group dropped two completely new exploits, an Office and Java zero-day.
At the beginning of August, Sofacy began a new wave of attacks, focusing on defense-related targets. As of November 2015, this wave of attacks is ongoing. The attackers deploy a rare modification of the AZZY backdoor, which is used for the initial reconnaissance. Once a foothold is established, they try to upload more backdoors, USB stealers as well as other hacking tools such as “Mimikatz” for lateral movement.
Over the last year, the #Sofacy group has increased its activity almost tenfold, that spiked in July 2015
Tweet
Two recurring characteristics of the Sofacy group that we keep seeing in its attacks are speed and the use of multi-backdoor packages for extreme resilience. In the past, the group used droppers that installed both the SPLM and AZZY backdoors on the same machine. If one of them was detected, the other one provided the attacker with continued access.
As usual, the best defense against targeted attacks is a multi-layered approach. Combine traditional anti-malware technologies with patch management, host intrusion detection and, ideally, whitelisting and default-deny strategies. According to a study by the Australian DSD, 85% of the targeted attacks analysed could have been stopped by four simple defense strategies. While it’s impossible to achieve 100% protection, in practice and most cases all you have to do is increase your defenses to the point where it becomes too expensive for the attacker – who will just give up and move on to other targets.
More information about the Sofacy group is available to customers of Kaspersky Intelligent Services.
Is there a ‘silver bullet’ to protect yourself against Sofacy? Learn more on Kaspersky Business blog.
Technical analysis
Internal name: DWN_DLL_MAIN.dll
File format: PE32 DLL
MD5: ce8b99df8642c065b6af43fde1f786a3
Linker version: 11.0, Microsoft Visual Studio
Linker timestamp: 2015.07.28 13:05:20 (GMT)
Exported functions:
10003F30: ?Applicate@@YGHXZ
10004270: ?SendDataToServer_2@@YGHPAEKEPAPAEPAK@Z
10003F60: ?k@@YGPAUHINSTANCE__@@PBD@Z
The library starts its main worker thread from the DllMain function.
Most of the strings inside the module are encrypted with a homebrew XOR-based algorithm. In addition to that, API function names are reversed, presumably to avoid detection in memory.
Once started, the code in the main thread resolves the basic API functions it needs and loads an additional library from the following location: “%TEMP%\tf394kv.dll”. If this file is not present, it is recreated from a hardcoded encrypted array inside the body of the DLL.
Next, the module enters an infinite loop. Every five minutes it collects basic system information and sends it to the C2 server:
Windows version number
Hardcoded string “4.3” (the backdoor’s internal version number)
List of running processes
The main thread also spawns a separate thread for receiving new commands from the C2 servers. Every 10 minutes, it sends a new request to the server. The server is expected to send back executable code and one of the following commands:
Write a new file “%LOCAL_APPDATA%\dllhost.exe” or “%TEMP%\dllhost.exe” and execute it, then delete the file
Write a new file “%LOCAL_APPDATA%\sechost.dll” or “%TEMP%\sechost.dll” and call its first exported function using “rundll32.exe” or Windows API, then delete the file
Run shellcode provided by the server in a new thread
While processing the commands, the backdoor logs all errors and execution results. The module also reads the contents of the file “%APPDATA%\chkdbg.log” and appends it to the results. It then sends the aggregated log back to the C2 server.
The module aborts the thread receiving C2 command after it fails to correctly execute commands more than six times in a row, i.e. if file or process creation fails.
The export called “k” is a wrapper for the “LoadLibraryA” API function.
The export called “SendDataToServer_2” does exactly what the name means: it encrypts all collected data, encodes it using Base64 encoding and calls its additional library to send the data to the C2 server. The names of the C2 servers are hardcoded.

Hardcoded C&C servers in the main module
The two C&C’s hardcoded in the configuration block of the main binary are:
intelnetservice[.]com
intelsupport[.]net
The export called “Applicate” runs a standard Windows application message loop until a “WM_ENDSESSION” message is received. It then terminates the main thread.
Internal name: snd.dll
File format: PE32 DLL
MD5: 8c4d896957c36ec4abeb07b2802268b9
Linker version: 11.0, Microsoft Visual Studio
Linker timestamp: 2015.07.24 12:07:27 (GMT)
Exported functions:
10001580: Init
10001620: InternetExchange
10001650: SendData
This external library implements a simple Wininet-based transport for the main module.
The strings inside the binary are encrypted using 3DES and XOR and reversed.
The DllMain function initializes the library and resolves all required Windows API functions.
The “Init” export establishes connection to port 80 of a C2 server using Wininet API. The user agent string employed is “MSIE 8.0”.
The “SendData” export sends a HTTP POST request using a hardcoded URI “/store/“. The reply, if its length is not equal to six and its contents do not contain “OK” is returned back to the caller.
The “InternetExchange” export closes the established connection and frees associated handles.
Sofacy AZZY 4.3 dropper analysis
File format: PE32 EXE
File size: 142,336 bytes
MD5: c3ae4a37094ecfe95c2badecf40bf5bb
Linker version: 11.0, Microsoft Visual Studio
Linker timestamp: 2015.02.10 10:01:59 (GMT)
Most of the strings and data in the file are encrypted using 3DES and XOR.
The code makes use of the Windows Crypto API for 3DES and the decryption key is stored as a standard Windows PUBLICKEYSTRUC structure:

Part of the decryption algorithm

Header of one encrypted data buffer containing the hardcoded 3DES key
First, it creates a new directory: “%LOCAL_APPDATA%\Microsoft\Windows”. If the directory creation fails it tries to install into “%TEMP%” directory instead.
Next it writes a hardcoded binary from its body to “msdeltemp.dll” into the target directory. If the file exists it then moves it to “__tmpdt.tmp” in the same directory and continues the installation. Sets file creation timestamp to that of “%SYSTEM%\sfc.dll”
To ensure the dropped payload starts automatically on user log-in it creates the following registry key:
[HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
StartUpChekTemp=RUNDLL32.EXE “%path to msdeltemp.dll%”,#1
Next, it starts the dropped dll using the same command line:
RUNDLL32.EXE “%path to msdeltemp.dll%“,#1
Finally, the program removes itself by starting the following command: “cmd /c DEL %path to self%“
The MD5 of the dropped file is f6f88caf49a3e32174387cacfa144a89
Dropper payload – downloader DLL
Internal name: msdetltemp.dll
File format: PE32 DLL
File size: 73 728 bytes
MD5: f6f88caf49a3e32174387cacfa144a89
Linker version: 11.0, Microsoft Visual Studio
Linker timestamp: 2015.02.10 07:20:02 (GMT)
Exported functions:
10002B55: Applicate
Most of the strings inside the binary are encrypted using a homebrew XOR-based algorithm and reversed.
The library is an older version of the “DWN_DLL_MAIN.dll” (md5: ce8b99df8642c065b6af43fde1f786a3).
The DllMain function is identical and starts the main thread; the “Applicate” function is identical to the one in the newer library. This version of the module does not rely on an external transport DLL for communicating with its C2 servers; instead it directly uses Wininet API functions.
The module contains the following hardcoded C2 server names:
drivres-update[.]info
softupdates[.]info
The module uses a hardcoded URL (“/check/“) for sending HTTP POST requests to its C2 servers.
The server is expected to send back executable code and one of the following commands:
Write a new file “%LOCAL_APPDATA%\svchost.exe” or “%TEMP%\svchost.exe” and execute it, then delete the file
Write a new file “%LOCAL_APPDATA%\conhost.dll” or “%TEMP%\conhost.dll” and call its first exported function using “rundll32.exe” or Windows API, then delete the file
Run shellcode provided by the server in a new thread
File collection module (“USB Stealer”)
Internal name: msdetltemp.dll (from resources)
File size: 50,176 bytes
File format: PE32 EXE
MD5: 0369620eb139c3875a62e36bb7abdae8
Linker version: 10.0, Microsoft Visual Studio
Linker timestamp: 2015.02.09 11:48:01 (GMT)
Most of the strings inside the binary are encrypted using 3DES and XOR and reversed.
The program creates the mutex “mtx” and an event named “WerTyQ34C”.
Upon start, it creates a window with the class name “Hello” and title “Program”, subscribes for device arrival notifications for that window and enters a standard Windows message processing loop. The message processing function waits for the WM_DEVICECHANGE event and starts a new thread on its arrival.
The module inspects every new disk volume attached to the system. For every disk it creates a “stash” directory in “%root stash directory location%\%volume serial number in hex%” with attributes FILE_ATTRIBUTE_HIDDEN and FILE_ATTRIBUTE_SYSTEM. The root stash directory location may be read from the configuration file or set to the default location which is “%MYPICTURES%”.
Then, it traverses the filesystem of the volume looking for files. Depending on the settings read from the configuration file, the scope may be narrowed to files with particular extensions and/or files created after a specified date.
It is worth noting that if the source file location contains the string “System Volume Information\S-1-5-21-1315235578-283289242\”, then the file is deleted after copying to the “stash” directory. There are known related samples that are able to create such directories on removable drives, i.e. the sample with md5: 8cb08140ddb00ac373d29d37657a03cc.
The configuration file is loaded from the same directory as the module and is expected to have a name “NvCpld.dat“. It is a text file that may contain the following configuration parameters:
Path – location of the root “stash” directory
Ext – search for files with one of these extensions only
Date – search for files not earlier than this date
Internal name: NvCpld.dll (from export table), msdetltemp.dll (from resources), IGFSRVC.dll (from resources)
File format: PE32 DLL
File size: 76,288 bytes
MD5s: 8b238931a7f64fddcad3057a96855f6c, ce151285e8f0e7b2b90162ba171a4b90
Linker version: 11.0, Microsoft Visual Studio
Linker timestamps: 2015.05.29 11:20:32 (GMT), 2006.11.25 04:39:15 (GMT)
Exported functions:
10002500: NvMswt
10002860: NvReg
10002880: NvStart
10002A80: NvStop
This library is a newer version of the file collection module (md5: 0369620eb139c3875a62e36bb7abdae8) wrapped in a DLL file.
There are two known variants of this module; they only differ in timestamp values and version information in the resource section.
The DllMain function only decrypts the data structures and initializes Windows API pointers.
The function “NvMswt” is a wrapper for the API function MsgWaitForMultipleObjects.
The function “NvReg” is a wrapper for the API function RegisterClassW.
The function “NvStart” is similar to the main function of the older module; it creates a window and enters the message loop waiting for device arrival notifications. The only difference introduced is that an event named “WerTyQ34C” can be signalled by the function “NvStop” to terminate the message loop and stop processing.
Indicators of compromise:
AZZY 4.3 installer:
c3ae4a37094ecfe95c2badecf40bf5bb
New generation (4.3) AZZY implants:
ce8b99df8642c065b6af43fde1f786a3
f6f88caf49a3e32174387cacfa144a89
Dropped C&C helper DLL for AZZY 4.3:
8c4d896957c36ec4abeb07b2802268b9
File collectors / USB stealers:
0369620eb139c3875a62e36bb7abdae8
8b238931a7f64fddcad3057a96855f6c
ce151285e8f0e7b2b90162ba171a4b90
f6f88caf49a3e32174387cacfa144a89
Stand-alone AZZY backdoors:
a96f4b8ac7aa9dbf4624424b7602d4f7
9d2f9e19db8c20dc0d20d50869c7a373
C&C hostnames:
drivres-update[.]info
intelnetservice[.]com
intelsupport[.]net
softupdates[.]info
Kaspersky Lab products detect the malware mentioned here with the following names:
Trojan.Win32.Sofacy.al
Trojan.Win32.Sofacy.be
Trojan.Win32.Sofacy.bf
Trojan.Win32.Sofacy.bg
Trojan.Win32.Sofacy.bi
Trojan.Win32.Sofacy.bj
Trojan.Win64.Sofacy.q
Trojan.Win64.Sofacy.s
HEUR:Trojan.Win32.Generic
Variety Jones, A Senior Adviser to Silk Road arrested in Thailand
6.12.2015
The man accused of being "a senior advisor" and mentor of Ross Ulbricht, the convicted operator of the illegal drug marketplace Silk Road, has been arrested in Thailand and charged with conspiring to traffic drugs and money laundering.
The US Department of Justice (DoJ) announced on Friday that Roger Thomas Clark, 54, is accused of being "Variety Jones," who was a close confidante of Ulbricht's who:
Advised Ulbricht on all aspects of Silk Road's operations
Helped Ulbricht grow the notorious website into an extensive criminal enterprise
Clark was arrested Thursday in Thailand and is now awaiting extradition to face United States charges of:
Narcotics Trafficking Conspiracy – carries a maximum sentence of life in prison.
Money Laundering Conspiracy – carries a maximum sentence of 20 years in prison.
Life in Prison
If convicted, Clark faces at least 10 years and as long as life in prison, according to a statement from Manhattan U.S. Attorney Preet Bharara.
According to the press release, Clark used the online aliases of Variety Jones, Cimon, and Plural of Mongoose, and was paid "hundreds of thousands of dollars" for his work on Silk Road.
"[Clark] was the biggest and strongest willed character I had met through the site thus far," Ross Ulbricht wrote in a 2011 journal entry. "He quickly proved to me that he had value by pointing out a major security hole in the site I was unaware of."
Also Read: Silk Road Mastermind Ross Ulbricht Sentenced To Life In Prison
Prosecutors also cited an online conversation in which Clark and Ulbricht discussed a plan to "track down" a certain Silk Road employee to ensure that he hadn't gone "off the rails." Clark reportedly commented: "Dude, we're criminal drug dealers – what line shouldn't we cross?"
When Silk Road was shut down and Ross Ulbricht was arrested by the law enforcement in October 2013, Variety Jones disappeared.
"The arrest of Roger Thomas Clark shows again that conducting criminal activities on the Dark Web does not keep a criminal out of law enforcement’s reach," said Diego Rodriguez, FBI assistant director.
"Clark may have thought residing in Thailand would keep him out of reach of U.S authorities, but our international partnerships have proven him wrong. We thank our law enforcement partners who have worked with the FBI on this case."
You can see the full press release of Clark case – U.S. v. Clark, 15-mj-01335, U.S. District Court, Southern District of New York (Manhattan) – here.
Serious, Yet Patched Flaw Exposes 6.1 Million IoT, Mobile Devices to Remote Code Execution
6.12.2015
Serious Security Flaw Exposes 6.1 Million IoT, Mobile Devices to Remote Code Execution
As much as you protect your electronics from being hacked, hackers are clever enough at finding new ways to get into your devices. But, you would hope that once a flaw discovered it would at least be fixed in few days or weeks, but that's not always the case.
A three-year-old security vulnerability within a software component used by more than 6.1 Million smart devices still remains unpatched by many vendors, thereby placing Smart TVs, Routers, Smartphones, and other Internet of Things (IoT) products at risk of exploit.
Security researchers at Trend Micro have brought the flaw to light that has been known since 2012 but has not been patched yet.
Remote Code Execution Vulnerabilities
Researchers discovered a collection of Remote Code Execution (RCE) vulnerabilities in the Portable SDK for UPnP, or libupnp component – a software library used by mobile devices, routers, smart TVs, and other IoT devices to stream media files over a network.
The flaws occur due to a buffer overflow in Simple Service Discovery Protocol (SSDP), potentially allowing hackers to take full control over the targeted device running the vulnerable version of the software development kit (SDK).
According to the researchers, the vulnerabilities were actually patched in 2012, but many applications still use the outdated versions of the library, allowing remote code execution attacks against devices with flawed apps installed.
"We found 547 apps that used older versions of libupnp, 326 of which are available on the Google Play store," Trend Micro mobile analyst Veo Zhang wrote in a blog post published Thursday.
Vulnerable Apps Downloaded by Millions of People
The biggest app affected by the flaw is QQMusic, which is used by over 100 Million people in China alone and has been downloaded by millions of Android users from the Google Play store. However, the security issue has since been fixed by the developers.
The Netflix application, also downloaded by Millions of people, was also thought to be affected by the flaw though the researchers say:
"Upon further clarification with Netflix, we learned that Netflix uses their own fork of libupnp due to an API that is no longer a part of newer libupnp versions. However, their fork contains the fixes from newer versions of libupnp as well, so we believe they are not affected by potential remote code execution attacks targeting this vulnerability."
Other popular applications using the outdated version of the library include nScreen Mirroring for Samsung, CameraAccess Plus and Smart TV Remote.
List of Vulnerable Apps
Here's the list of some apps, Trend Micro knows, are vulnerable and has actually tested:
Common Name
Package Name
AirSmartPlayer
com.gk.airsmart.main
Big2Small
com.alitech.dvbtoip
CameraAccess plus
jp.co.pixela.cameraaccessplus
G-MScreen
mktvsmart.screen
HexLink Remote (TV client)
hihex.sbrc.services
HexLink-SmartTV remote control
com.hihex.hexlink
Hisense Android TV Remote
com.hisense.commonremote
nScreen Mirroring for Samsung
com.ht.nscreen.mirroring
Ooredoo TV Oman
com.ooredootv.ooredoo
PictPrint – WiFi Print App –
jp.co.tandem.pictprint
qa.MozaicGO.Android
Mozaic GO
QQMusic
com.tencent.qqmusic
QQ音乐HD
com.tencent.qqmusicpad
Smart TV Remote
com.hisense.common
Wifi Entertainment
com.infogo.entertainment.wifi
モバイルTV(StationTV)
jp.pixela.px01.stationtv.localtuner.full.app
에브리온TV (무료 실시간 TV)
com.everyontv
多屏看看
com.letv.smartControl
海信分享
com.hisense.hishare.hall
Though the makers of QQMusic and LinPhone have addressed the issue and released fixes for their apps, users are advised to check their devices for one of these apps and if discovered, simply removed it or check for an update.
The security researchers are continuing to find out more vulnerable app.
Rekoobe a new malware targeting Linux users
6.12.2015
Experts at Russian anti-virus firm Dr.Web discovered Rekoobe, a new malware that is targeting Linux systems.
Rekoobe is a new malware that is targeting Linux systems, the discovery was made by experts at Russian anti-virus firm Dr.Web.
Dr.Web discovered the Rekoobe Trojan in October, then its experts analyzed the threat in the following two months.
The Rekoobe Trojan was initially developed to infect only Linux SPARC architectures, later it has been upgraded to target Linux PCs running on intel chips, on both 32 bit and 54-bit architectures.
Rekoobe linux malware
The experts explained that the Rekoobe Trojan is very simple by it is difficult to detect. The malware encryption to protect the configuration file and the data exchanged with the C&C server.
“Linux.Rekoobe.1 uses an encrypted configuration file. Once the file is read, the Trojan periodically refers to the C&C server to receive commands. Under specific circumstances, the connection to the server is established via a proxy server.” states a blog post published by Dr.Web. “The malware extracts the authorization data from its configuration file. All the sent and received information is split into separate blocks. Every block is encrypted and contains its own signature.”
The analysis of the Rebooke revealed that it could be used to deliver malicious payloads on the infected systems in order to obtain the full compromise of the target.
“Nevertheless,Linux.Rekoobe.1 can execute only three commands such as: to download or upload files, to send the received commands to the Linux interpreter, and to transmit the output to the remote server—thus, cybercriminals are able to interact with the compromised devise remotely.”
Unfortunately, the authors of Rekoobe have already ported the Trojan on other OS, including Android, Mac OS X and Windows.
Despite many users consider Linux systems immune from malware, other threats have been recently discovered, such as the Linux.Encoder.1 ransomware.
The senior advisor behind Silk Road has been arrested
6.12.2015
Roger Thomas Clark the alleged mentor of Ross Ulbricht, the owner of the most popular black market Silk Road, has been arrested in Thailand.
The alleged mentor of Ross Ulbricht, the owner of the most popular black market Silk Road, has been arrested in Thailand and charged with conspiring to traffic drugs and money laundering.
Roger Thomas Clark (54) accused of being the mind behind Silk Road, he served as a senior advisor and mentor of Ross Ulbricht.
Silk Road
The US Department of Justice (DoJ) announced yesterday Clark is charged being “Variety Jones” a key figure of the dark marketplace.
Clark was arrested Thursday and is now awaiting extradition to face United States charges of Narcotics Trafficking Conspiracy and Money Laundering Conspiracy, he risks a sentence that could bring him the life imprisonment
Roger Thomas Clark was a close collaborator of Ross Ulbricht’s who reported him on all activities of the Silk Road and helped Ulbricht to advertise the black market in the criminal underground.
The founder Ulbricht, also known as ‘Dread Pirate Roberts’, was arrested in San Francisco, he was reportedly in possession of 26,000 bitcoins with an estimated market value of $3.6 million USD.
After the arrest Roger Thomas Clark, aka Variety Jones, disappeared.
The Manhattan U.S. Attorney announced the arrest with the press release who refers Clark as the “Senior Adviser to the Operator Of The “Silk Road” Website.”
Clark used a number of aliases when operating online, including Variety Jones, Cimon, and Plural of Mongoose.
According to the press release, Clark used the online aliases of Variety Jones, Cimon, and Plural of Mongoose, and was paid “hundreds of thousands of dollars” for his work on the Silk Road.
“CLARK, who went by the online nicknames “Variety Jones,” “VJ,” “Cimon,” and “Plural of Mongoose,” was described by Ulbricht as a trusted “mentor,” who regularly advised him on the management of the Silk Road enterprise. Among other things, CLARK counseled Ulbricht on the improvement and expansion of Silk Road’s technical infrastructure, including helping Ulbricht hire and manage a computer programmer to assist with these projects.” reads the press release. “CLARK also helped Ulbricht develop and enforce the rules governing how Silk Road vendors and users could do business on the site, which were designed to maximize the commissions that Ulbricht received from Silk Road sales. CLARK further advised Ulbricht on how to conceal his involvement in, and hide his profits from, the operation of Silk Road, including helping Ulbricht devise cover stories to tell others and make plans to obtain foreign citizenship and offshore bank accounts. Finally, CLARK also advised Ulbricht on tactics to thwart efforts by law enforcement to investigate Silk Road. “
The full press release of U.S. v. Clark, 15-mj-01335, U.S. District Court, Southern District of New York (Manhattan) is available online.
Clark and Ulbricht used intimidation and violence to maintain control of the Silk Road support staff, discouraging them from cooperating with law enforcement.
Prosecutors also reported an online conversation between Clark and Ulbricht who were discussing to “track down” a certain Silk Road employee to ensure that he hadn’t gone “off the rails.” Clark reportedly commented: “Dude, we’re criminal drug dealers – what line shouldn’t we cross?
“In one such conversation, in which CLARK and Ulbricht discussed “track[ing] down” a certain Silk Road employee to ensure that he had not gone “[o]ff the rails,” CLARK commented, “[D]ude, we’re criminal drug dealers – what line shouldn’t we cross?””
The operation that allowed the arrest of Roger Thomas Clark is another success of the law enforcement, that identifies him despite the man adopted all the countermeasures to remain under the radar.
“The arrest of Roger Thomas Clark shows again that conducting criminal activities on the Dark Web does not keep a criminal out of law enforcement’s reach,” said Diego Rodriguez, FBI assistant director.
“Clark may have thought residing in Thailand would keep him out of reach of U.S authorities, but our international partnerships have proven him wrong. We thank our law enforcement partners who have worked with the FBI on this case.”
RCMP Cybercrime Strategy to fight online crimes
6.12.2015
The RCMP Cybercrime Strategy aims to improve Canada’s national police force in its fight against the rising and evolving threat of cybercrime.
Canadian Authorities consider online crimes serious threats to the Homeland security. Several times law enforcement tried to identify members of hacking crews like Anonymous, but in many cases the investigations haven’t obtained satisfactory results.
The Canadian law enforcement agency, the Royal Canadian Mounted Police plans to set up a special cyber crime unit to tackle “online threats to Canada’s “political, economic, and social integrity.”
The Royal Canadian Mounted Police revealed its four-years Action Plan this week. The law enforcement plans to recruit cyber specialists, acquire new tools for data analysis and set up better relationships with other law enforcement agencies worldwide.
“the RCMP Cybercrime Strategy is based on extensive internal and external consultation and focuses on ways to improve Canada’s national police force in its fight against the rising and evolving threat of cybercrime. “
The new unit will be based in Ottawa and it will be tasked to “investigate the most significant threats to Canada’s political, economic, and social integrity that would negatively affect Canada’s reputation and economy.”
[The team ]”will have the capacity to target cyber-related criminal activity targeting the federal government, national critical infrastructure, and key business assets.”
The Canadian Government revealed that its systems are under unceasing attacks, earlier this year, hacktivists accessed documents pertaining to the technology infrastructure at the Canadian Security Intelligence Service’s foreign bureaus.
In many cases, hackers targeted Government websites with DDoS attack in retaliation for government legislation.
cybercrime
The Royal Canadian Mounted Police consider the establishment of its cyber unit strategic.
“The team will enhance the RCMP’s ability to combat cybercrime-related offences where technology plays an integral role, such as investigating the unauthorized use of computers, mischief in relation to data, or the possession of a device to commit unauthorized computer use or data mischief,” the plan reads.
The ViceNews reported the statement of Jeff Adam, Chief Superintendent with Royal Canadian Mounted Police, which explained the difficulties law enforcement are facing when dealing online crime.
“Insofar as the apparent, as you say, lack of outcomes,” Adam said on a conference call presenting the action plan. “Cybercrime investigations, starting off, can involve encryption, the darknet, multinational jurisdictions — and, many times, many different national jurisdictions — and it is a complex and time-consuming task to both identify, gather the evidence on, and to bring those people into the realm of justice.
“And while there might not be, apparently, anything happening, this is not as simple as catching the car speeding down the street,””This is infinitely more complex and requires a whole new way of doing business.”
Darknet and encrypted communications complicate the investigation, the RCMP Commissioner Bob Paulson expressed his frustration with encryption at a security conference in November.
“It’s a very difficult proposition to bring traditional criminal justice strategies to bear in a place where anonymity is protected,” “We’re chasing the wrong Holy Grail. I am all for new legislation, I am all for warrantless access to subscriber info,”
But privacy advocates and activists consider the cryptographic practice as a pillar of the freedom of expression on the Internet,
“The intelligence services of the world claim that encryption is a problem,” said Jacob Appelbaum at the recent World Forum for Democracy conference. “But the evidence has come out that, in fact, the attacks in Paris were perpetrated by people who used credit cards in their real name, who used unencrypted text messages to say things like ‘let’s go.'”
Unfortunately, someone is riding the recent dramatic events like the Paris attacks to argument online surveillance activities, but the Canadian Liberal government seems to have a different policy on the online monitoring activities.
UK ANPR systems are one of the ‘world’s biggest surveillance systems’
6.12.2015
The automatic number plate recognition systems (ANPR) used by the UK police are one of the largest surveillance systems in the world.
When dealing surveillance systems the majority of people imagines skilled hackers that break their computers or communication lines in order to spy on specific targets.
The situation is quite different, we are surrounded by a number of systems that collect an impressive amount of data that could be used to spy on us.
If you are a Briton for example, you have to know that in your country there is a widespread use of automatic number plate recognition systems (ANPR). These systems are used by the UK law enforcement and are considered one of the largest surveillance systems in the world. The principal problem related to the use of the automatic number plate recognition systems is the absence of a legal framework that regulate its usage.
automatic number plate recognition systems ANPR
During a speech at Stirling University, the UK’s surveillance camera commissioner Tony Porter raised the issue related to usage of the automatic number plate recognition systems in the UK.
In the UK there are currently 8,300 ANPR cameras that every day collect the data related to 25-35 million ‘read.’ These records are sent to the National ANPR Data Centre, but there isn’t any legal framework governing this process, that clearly represent a mass data collection.
“ANPR in the UK must surely be one of the largest data gatherers of its citizens in the world,” Porter said. “I would like to put forward that the use of ANPR cameras has an extremely unsteady legal framework,”
The UK Government considers the automatic number plate recognition systems just one of the data source available to the law enforcement and, for this reason, they don’t need to be regulated.
I sincerely don’t this so, the ANPR systems of the country belong to one of the powerful “non-military” surveillance network and need to be clearly regulated. Aspect related to data management, data access and their protection have to be shared with the UK citizens.
“I am not 100 percent clear on this and when I’ve spoken to the Home Office they’ve informed me that ANPR is just another tool in the policing toolkit and does not require a statutory authority,” added Porter.
“So, as long as National ANPR Standards and Procedures offers sufficient safeguards to protect against the article 8 right against intrusion into privacy any legal challenge is set to fail. Or is it?”
“But who gave their consent to this? Where is the legislation, and where was the debate in parliament? So I argue that some forms of surveillance have no legislative framework whatsoever,” he added.
To support Porter it arrives the statements of Daniel Nesbitt, research director of Big Brother Watch, who argues the need to open a debate on the usage of number plate recognition systems.
“Although ANPR was first installed to tackle specific issues with 350 images now being captured every second it is impossible for motorists to travel without having their details captured and stored, regardless of whether or not they are doing anything wrong,” explained Daniel Nesbitt.
“An open and honest debate about how this technology is being used as well as how far it invades the privacy of ordinary motorists is now long overdue. For starters we need to see regular reports being published on how the system is being run and exactly what safeguards can be put in place to protect the public.”
When dealing with surveillance systems, especially civil ones, I’m always worried about the effective level of security they implement. A persistent attacker could breach them accessing an impressive amount of data that could be used to harm the Homeland security. I believe that also the security of these systems must be regulated in a legal framework to protect citizens.