"When such a window is found and its name matches any string from a hardcoded list of bank-related strings, then and only then the malware initiates communication with its C&C server, sending requests at least once a second until terminated."
H January(68) February(106) March(112) April(110) June(37) July(4)
Brazilian Feds Dismantle Grandoreiro Banking Trojan, Arresting Top Operatives
31.1.24
Virus
The Hacker News
A Brazilian law enforcement operation has led to the
arrest of several Brazilian operators in charge of the Grandoreiro malware.
The Federal Police of Brazil said it served five temporary arrest warrants and 13 search and seizure warrants in the states of São Paulo, Santa Catarina, Pará, Goiás, and Mato Grosso.
Slovak cybersecurity firm ESET, which provided additional assistance in the effort, said it uncovered a design flaw in Grandoreiro's network protocol that helped it to identify the victimology patterns.
Grandoreiro is one of the many Latin American banking trojans such as Javali, Melcoz, Casabeniero, Mekotio, and Vadokrist, primarily targeting countries like Spain, Mexico, Brazil, and Argentina. It's known to be active since 2017.
In late October 2023, Proofpoint revealed details of a phishing campaign that distributed an updated version of the malware to targets in Mexico and Spain.
The banking trojan has capabilities to both steal data through keyloggers and screenshots as well as siphon bank login information from overlays when an infected victim visits pre-determined banking sites targeted by the threat actors. It can also display fake pop-up windows and block the victim's screen.
Attack chains typically leverage phishing lures bearing decoy documents or malicious URLs that, when opened or clicked, lead to the deployment of malware, which then establishes contact with a command-and-control (C&C) server for remotely controlling the machine in a manual fashion.
"Grandoreiro periodically monitors the foreground window to find one that belongs to a web browser process," ESET said.

"When such a window is found and its name matches any string from a hardcoded
list of bank-related strings, then and only then the malware initiates
communication with its C&C server, sending requests at least once a second until
terminated."
The threat actors behind the malware are also known to employ a domain generation algorithm (DGA) since around October 2020 to dynamically identify a destination domain for C&C traffic, making it harder to block, track, or take over the infrastructure.
A majority of the IP addresses these domains resolve to are provided primarily by Amazon Web Services (AWS) and Microsoft Azure, with the life span of the C&C IP addresses ranging anywhere between 1 day to 425 days. On average, there are 13 active and three new C&C IP addresses per day, respectively.
ESET also said that Grandoreiro's flawed implementation of its RealThinClient (RTC) network protocol for C&C made it possible to get information about the number of victims that are connected to the C&C server, which is 551 unique victims in a day on average mainly spread across Brazil, Mexico, and Spain.
Further investigation has found that an average number of 114 new unique victims connect to the C&C servers each day.
"The disruption operation led by the Federal Police of Brazil aimed at individuals who are believed to be high up in the Grandoreiro operation hierarchy," ESET said.
URGENT: Upgrade GitLab - Critical Workspace Creation Flaw Allows File Overwrite
31.1.24
Vulnerebility
The Hacker News
GitLab once again released fixes to address a critical security flaw in its Community Edition (CE) and Enterprise Edition (EE) that could be exploited to write arbitrary files while creating a workspace.
Tracked as CVE-2024-0402, the vulnerability has a CVSS score of 9.9 out of a maximum of 10.
"An issue has been discovered in GitLab CE/EE affecting all versions from 16.0 prior to 16.5.8, 16.6 prior to 16.6.6, 16.7 prior to 16.7.4, and 16.8 prior to 16.8.1 which allows an authenticated user to write files to arbitrary locations on the GitLab server while creating a workspace," GitLab said in an advisory released on January 25, 2024.
The company also noted patches for the bug have been backported to 16.5.8, 16.6.6, 16.7.4, and 16.8.1.
Also resolved by GitLab are four medium-severity flaws that could lead to a regular expression denial-of-service (ReDoS), HTML injection, and the disclosure of a user's public email address via the tags RSS feed.
The latest update arrives two weeks after the DevSecOps platform shipped fixes to close out two critical shortcomings, including one that could be exploited to take over accounts without requiring any user interaction (CVE-2023-7028, CVSS score: 10.0).
Users are advised to upgrade the installations to a patched version as soon as possible to mitigate potential risks. GitLab.com and GitLab Dedicated environments are already running the latest version.
China-Linked Hackers Target Myanmar's Top Ministries with Backdoor Blitz
31.1.24
APT
The Hacker News
The China-based threat actor known as Mustang Panda is
suspected to have targeted Myanmar's Ministry of Defence and Foreign Affairs as
part of twin campaigns designed to deploy backdoors and remote access trojans.
The findings come from CSIRT-CTI, which said the activities took place in November 2023 and January 2024 after artifacts in connection with the attacks were uploaded to the VirusTotal platform.
"The most prominent of these TTPs are the use of legitimate software including a binary developed by engineering firm Bernecker & Rainer (B&R) and a component of the Windows 10 upgrade assistant to sideload malicious dynamic-link libraries (DLLs)," CSIRT-CTI said.
Mustang Panda, active since at least 2012, is also recognized by the cybersecurity community under the names BASIN, Bronze President, Camaro Dragon, Earth Preta, HoneyMyte, RedDelta, Red Lich, Stately Taurus, and TEMP.Hex.
In recent months, the adversary has been attributed to attacks targeting an unnamed Southeast Asian government as well as the Philippines to deliver backdoors capable of harvesting sensitive information.
The November 2023 infection sequence starts with a phishing email bearing a booby-trapped ZIP archive attachment containing a legitimate executable ("Analysis of the third meeting of NDSC.exe") that's originally signed by B&R Industrial Automation GmbH and a DLL file ("BrMod104.dll").
The attack takes advantage of the fact that the binary is susceptible to DLL search order hijacking to side-load the rogue DLL and subsequently establish persistence and contact with a command-and-control (C2) server and retrieve a known backdoor called PUBLOAD, which, in turn, acts as a custom loader to drop the PlugX implant.
"The threat actors attempt to disguise the [C2] traffic as Microsoft update traffic by adding the 'Host: www.asia.microsoft.com' and 'User-Agent: Windows-Update-Agent' headers," CSIRT-CTI noted, mirror a May 2023 campaign disclosed by Lab52.
On the other hand, the second campaign observed earlier this month employs an optical disc image ("ASEAN Notes.iso") containing LNK shortcuts to trigger a multi-stage process that uses another bespoke loader called TONESHELL to likely deploy PlugX from a now-inaccessible C2 server.
It's worth noting that a similar attack chain attributed to Mustang Panda was previously unearthed by EclecticIQ in February 2023 in intrusions aimed at government and public sector organizations across Asia and Europe.
"Following the rebel attacks in northern Myanmar [in October 2023], China has expressed concern regarding its effect on trade routes and security around the Myanmar-China border," CSIRT-CTI said.
"Stately Taurus operations are known to align with geopolitical interests of the Chinese government, including multiple cyberespionage operations against Myanmar in the past."
Italian Data Protection Watchdog Accuses ChatGPT of Privacy Violations
31.1.24
AI
The Hacker News
Italy's data protection authority (DPA) has notified
ChatGPT-maker OpenAI of supposedly violating privacy laws in the region.
"The available evidence pointed to the existence of breaches of the provisions contained in the E.U. GDPR [General Data Protection Regulation]," the Garante per la protezione dei dati personali (aka the Garante) said in a statement on Monday.
It also said it will "take account of the work in progress within the ad-hoc task force set up by the European Data Protection Framework (EDPB) in its final determination on the case."
The development comes nearly 10 months after the watchdog imposed a temporary ban on ChatGPT in the country, weeks after which OpenAI announced a number of privacy controls, including an opt-out form to remove one's personal data from being processed by the large language model (LLM). Access to the tool was subsequently reinstated in late April 2023.
The Italian DPA said the latest findings, which have not been publicly disclosed, are the result of a multi-month investigation that was initiated at the same time. OpenAI has been given 30 days to respond to the allegations.
BBC reported that the transgressions are related to collecting personal data and age protections. OpenAI, in its help page, says that "ChatGPT is not meant for children under 13, and we require that children ages 13 to 18 obtain parental consent before using ChatGPT."
But there are also concerns that sensitive information could be exposed as well as younger users may be exposed to inappropriate content generated by the chatbot.
Indeed, Ars Technica reported this week that ChatGPT is leaking private conversations that include login credentials and other personal details of unrelated users who are said to be employees of a pharmacy prescription drug portal.
Then in September 2023, Google's Bard chatbot was found to have a bug in the sharing feature that allowed private chats to be indexed by Google search, inadvertently exposing sensitive information that may have been shared in the conversations.
Generative artificial intelligence tools like ChatGPT, Bard, and Anthropic Claude rely on being fed large amounts of data from multiple sources on the internet.
In a statement shared with TechCrunch, OpenAI said its "practices align with GDPR and other privacy laws, and we take additional steps to protect people's data and privacy."
Apple Warns Against Proposed U.K. Law#
The development comes as Apple said
it's "deeply concerned" about proposed amendments to the U.K. Investigatory
Powers Act (IPA) could give the government unprecedented power to "secretly
veto" privacy and security updates to its products and services.
"It's an unprecedented overreach by the government and, if enacted, the U.K. could attempt to secretly veto new user protections globally preventing us from ever offering them to customers," the tech giant told BBC.
The U.K. Home Office said adopting secure communications technologies, including end-to-end encryption, cannot come at the cost of public safety as well as protecting the nation from child sexual abusers and terrorists.
The changes are aimed at improving the intelligence services' ability to "respond with greater agility and speed to existing and emerging threats to national security."
Specifically, they require technology companies that field government data requests to notify the U.K. government of any technical changes that could affect their "existing lawful access capabilities."
"A key driver for this amendment is to give operational partners time to understand the change and adapt their investigative techniques where necessary, which may in some circumstances be all that is required to maintain lawful access," the government notes in a fact sheet, adding "it does not provide powers for the Secretary of State to approve or refuse technical changes."
Apple, in July 2023, said it would rather stop offering iMessage and FaceTime services in the U.K. than compromise on users' privacy and security.
New ZLoader Malware Variant Surfaces with 64-bit Windows Compatibility
31.1.24
Virus
The Hacker News
Threat hunters have identified a new campaign that
delivers the ZLoader malware, resurfacing nearly two years after the botnet's
infrastructure was dismantled in April 2022.
A new variant of the malware is said to have been in development since September 2023, Zscaler ThreatLabz said in an analysis published this month.
"The new version of Zloader made significant changes to the loader module, which added RSA encryption, updated the domain generation algorithm, and is now compiled for 64-bit Windows operating systems for the first time," researchers Santiago Vicente and Ismael Garcia Perez said.
ZLoader, also known by the names Terdot, DELoader, or Silent Night, is an offshoot of the Zeus banking trojan that first surfaced in 2015, before pivoting to functioning as a loader for next-stage payloads, including ransomware.
Typically distributed via phishing emails and malicious search engine ads, ZLoader suffered a huge blow after a group of companies led by Microsoft's Digital Crimes Unit (DCU) seized control of 65 domains that were used to control and communicate with the infected hosts.
The latest versions of the malware, tracked as 2.1.6.0 and 2.1.7.0, incorporate junk code and string obfuscation to resist analysis efforts. Each ZLoader artifact is also expected to have a specific filename for it to be executed on the compromised host.
"This could evade malware sandboxes that rename sample files," the researchers noted.
In addition to encrypting the static configuration using RC4 with a hard-coded alphanumeric key to conceal information related to the campaign name and the command-and-control (C2) servers, the malware has been observed relying on an updated version of the domain generation algorithm as a fallback measure in the event the primary C2 servers are inaccessible.
The backup communications method was first discovered in ZLoader version 1.1.22.0, which was propagated as part of phishing campaigns detected in March 2020.
"Zloader was a significant threat for many years and its comeback will likely result in new ransomware attacks," the researchers said. "The operational takedown temporarily stopped the activity, but not the threat group behind it."
The development comes as Red Canary warned of an increase in the volume of campaigns leveraging MSIX files to deliver malware such as NetSupport RAT, ZLoader, and FakeBat (aka EugenLoader), since July 2023, prompting Microsoft to disable the protocol handler by default in late December 2023.
It also follows the emergence of new stealer malware families such as Rage Stealer and Monster Stealer that are being used as an initial access pathway for information theft and as a launching pad for more severe cyber attacks.
Juniper Networks Releases Urgent Junos OS Updates for High-Severity Flaws
30.1.24
Vulnerebility
The Hacker News
Juniper Networks has released out-of-band updates to
address high-severity flaws in SRX Series and EX Series that could be exploited
by a threat actor to take control of susceptible systems.
The vulnerabilities, tracked as CVE-2024-21619 and CVE-2024-21620, are rooted in the J-Web component and impact all versions of Junos OS. Two other shortcomings, CVE-2023-36846 and CVE-2023-36851, were previously disclosed by the company in August 2023.
CVE-2024-21619 (CVSS score: 5.3) - A missing authentication vulnerability that
could lead to exposure of sensitive configuration information
CVE-2024-21620
(CVSS score: 8.8) - A cross-site scripting (XSS) vulnerability that could lead
to the execution of arbitrary commands with the target's permissions by means of
a specially crafted request
Cybersecurity firm watchTowr Labs has been
credited with discovering and reporting the issues. The two vulnerabilities have
been addressed in the following versions -
CVE-2024-21619 - 20.4R3-S9, 21.2R3-S7, 21.3R3-S5, 21.4R3-S6, 22.1R3-S5,
22.2R3-S3, 22.3R3-S2, 22.4R3, 23.2R1-S2, 23.2R2, 23.4R1, and all subsequent
releases
CVE-2024-21620 - 20.4R3-S10, 21.2R3-S8, 21.4R3-S6, 22.1R3-S5,
22.2R3-S3, 22.3R3-S2, 22.4R3-S1, 23.2R2, 23.4R2, and all subsequent releases
As temporary mitigations until the fixes are deployed, the company is
recommending that users disable J-Web or restrict access to only trusted hosts.
It's worth noting that both CVE-2023-36846 and CVE-2023-36851 were added to the Known Exploited Vulnerabilities (KEV) catalog in November 2023 by the U.S. Cybersecurity and Infrastructure Security Agency (CISA), based on evidence of active exploitation.
Earlier this month, Juniper Networks also shipped fixes to contain a critical vulnerability in the same products (CVE-2024-21591, CVSS score: 9.8) that could enable an attacker to cause a denial-of-service (DoS) or remote code execution and obtain root privileges on the device.
Researchers Uncover How Outlook Vulnerability Could Leak Your NTLM Passwords
30.1.24
Vulnerebility
The Hacker News

A now-patched security flaw in Microsoft Outlook could be exploited by threat
actors to access NT LAN Manager (NTLM) v2 hashed passwords when opening a
specially crafted file.
The issue, tracked as CVE-2023-35636 (CVSS score: 6.5), was addressed by the tech giant as part of its Patch Tuesday updates for December 2023.
"In an email attack scenario, an attacker could exploit the vulnerability by sending the specially crafted file to the user and convincing the user to open the file," Microsoft said in an advisory released last month.
"In a web-based attack scenario, an attacker could host a website (or leverage a compromised website that accepts or hosts user-provided content) containing a specially crafted file designed to exploit the vulnerability."
Put differently, the adversary would have to convince users to click a link, either embedded in a phishing email or sent via an instant message, and then deceive them into opening the file in question.
CVE-2023-35636 is rooted in the calendar-sharing function in the Outlook email application, wherein a malicious email message is created by inserting two headers "Content-Class" and "x-sharing-config-url" with crafted values in order to expose a victim's NTLM hash during authentication.
Varonis security researcher Dolev Taler, who has been credited with discovering and reporting the bug, said NTLM hashes could be leaked by leveraging Windows Performance Analyzer (WPA) and Windows File Explorer. These two attack methods, however, remain unpatched.
"What makes this interesting is that WPA attempts to authenticate using NTLM v2 over the open web," Taler said.
"Usually, NTLM v2 should be used when attempting to authenticate against internal IP-address-based services. However, when the NTLM v2 hash is passing through the open internet, it is vulnerable to relay and offline brute-force attacks."
The disclosure comes as Check Point revealed a case of "forced authentication" that could be weaponized to leak a Windows user's NTLM tokens by tricking a victim into opening a rogue Microsoft Access file.
Microsoft, in October 2023, announced plans to discontinue NTLM in Windows 11 in favor of Kerberos for improved security owing to the fact that it does not support cryptographic methods and is susceptible to relay attacks.
Albabat, Kasseika, Kuiper: New Ransomware Gangs Rise with Rust and Golang
30.1.24
Ransom
The Hacker News
Cybersecurity researchers have detected in the wild yet
another variant of the Phobos ransomware family known as Faust.
Fortinet FortiGuard Labs, which detailed the latest iteration of the ransomware, said it's being propagated by means of an infection that delivers a Microsoft Excel document (.XLAM) containing a VBA script.
"The attackers utilized the Gitea service to store several files encoded in Base64, each carrying a malicious binary," security researcher Cara Lin said in a technical report published last week. "When these files are injected into a system's memory, they initiate a file encryption attack."
Faust is the latest addition to several ransomware variants from the Phobos family, including Eking, Eight, Elbie, Devos, and 8Base. It's worth noting that Faust was previously documented by Cisco Talos in November 2023.
The cybersecurity firm described the variant as active since 2022 and "does not target specific industries or regions."
The attack chain commences with an XLAM document that, when opened, downloads Base64-encoded data from Gitea in order to save a harmless XLSX file, while also stealthily retrieving an executable that masquerades as an updater for the AVG AntiVirus software ("AVG updater.exe").
The binary, for its part, functions as a downloader to fetch and launch another executable named "SmartScreen Defender Windows.exe" in order to kick-start its encryption process by employing a fileless attack to deploy the malicious shellcode.
"The Faust variant exhibits the ability to maintain persistence in an environment and creates multiple threads for efficient execution," Lin said.
The development comes as new ransomware families such as Albabat (aka White
Bat), Kasseika, Kuiper, Mimus, and NONAME have gained traction, with the former
a Rust-based malware that's distributed in the form of fraudulent software such
as a fake Windows 10 digital activation tool and a cheat program for the
Counter-Strike 2 game.
Trellix, which examined the Windows, Linux, and macOS versions of Kuiper earlier this month, attributed the Golang-based ransomware to a threat actor named RobinHood, who first advertised it on underground forums in September 2023.
"The concurrency focused nature of Golang benefits the threat actor here, avoiding race conditions and other common problems when dealing with multiple threads, which would have otherwise been a (near) certainty," security researcher Max Kersten said.

"Another factor that the Kuiper ransomware leverages, which is also a reason for
Golang's increased popularity, are the language's cross-platform capabilities to
create builds for a variety of platforms. This flexibility allows attackers to
adapt their code with little effort, especially since the majority of the code
base (i.e., encryption-related activity) is pure Golang and requires no
rewriting for a different platform."
NONAME is also noteworthy for the fact that its data leak site imitates that of the LockBit group, raising the possibility that it could either be another LockBit or that it collects leaked databases shared by LockBit on the official leak portal, researcher Rakesh Krishnan pointed out.
The findings follow a report from French cybersecurity company Intrinsec that connected the nascent 3AM (also spelled ThreeAM) ransomware to the Royal/BlackSuit ransomware, which, in turn, emerged following the shutdown of the Conti cybercrime syndicate in May 2022.
The links stem from a "significant overlap" in tactics and communication channels between 3 AM ransomware and the "shared infrastructure of ex-Conti-Ryuk-TrickBot nexus."
That's not all. Ransomware actors have been observed once again using TeamViewer as an initial access vector to breach target environments and attempt to deploy encryptors based on the LockBit ransomware builder, which leaked in September 2022.
"Threat actors look for any available means of access to individual endpoints to
wreak havoc and possibly extend their reach further into the infrastructure,"
cybersecurity firm Huntress said.
In recent weeks, LockBit 3.0 has also been distributed in the form of Microsoft Word files disguised as resumes targeting entities in South Korea, according to the AhnLab Security Intelligence Center (ASEC).
Despite the amorphous and ever-evolving nature of the ransomware ecosystem, there are signs that victims are increasingly refusing to pay up, causing the proportion of ransomware victims that opted to pay to decline to 29% in Q4 2023, down from 41% in Q3 and 34% in Q2. A previous low of 28% was recorded in Q3 2022.
The average ransom payment for the time period dropped 33%, dropping from $850,700 to $568,705, figures shared by ransomware negotiation firm Coveware show. The median ransom payment, on the other hand, remained unchanged at $200,000, up from $190,424 in Q2 2023.
"The industry continues to get smarter on what can and cannot be reasonably obtained with a ransom payment," the company said. "This has led to better guidance to victims and fewer payments for intangible assurances."
NSA Admits Secretly Buying Your Internet Browsing Data without Warrants
29.1.24
BigBrothers
The Hacker News
The U.S. National Security Agency (NSA) has admitted to
buying internet browsing records from data brokers to identify the websites and
apps Americans use that would otherwise require a court order, U.S. Senator Ron
Wyden said last week.
"The U.S. government should not be funding and legitimizing a shady industry whose flagrant violations of Americans' privacy are not just unethical, but illegal," Wyden said in a letter to the Director of National Intelligence (DNI), Avril Haines, in addition to taking steps to "ensure that U.S. intelligence agencies only purchase data on Americans that has been obtained in a lawful manner."
Metadata about users' browsing habits can pose a serious privacy risk, as the information could be used to glean personal details about an individual based on the websites they frequent.
This could include websites that offer resources related to mental health, assistance for survivors of sexual assault or domestic abuse, and telehealth providers who focus on birth control or abortion medication.
In response to Wyden's queries, the NSA said it has developed compliance regimes and that it "takes steps to minimize the collection of U.S. person information" and "continues to acquire only the most useful data relevant to mission requirements."
The agency, however, said it does not buy and use location data collected from phones used in the U.S. without a court order. It also said it does not use location information obtained from automobile telematics systems from vehicles located in the country.
Ronald S. Moultrie, under secretary of defense for intelligence and security (USDI&S), said Departments of Defense (DoD) components acquire and use commercially available information (CAI) in a manner that "adheres to high standards of privacy and civil liberties protections" in support of lawful intelligence or cybersecurity missions.
The revelation is yet another indication that intelligence and law enforcement agencies are purchasing potentially sensitive data from companies that would necessitate a court order to acquire directly from communication companies. In early 2021, it was revealed the Defense Intelligence Agency (DIA) was buying and using domestic location data collected from smartphones via commercial data brokers.
The disclosure about warrantless purchase of personal data arrives in the aftermath of the Federal Trade Commission (FTC) prohibiting Outlogic (formerly X-Mode Social) and InMarket Media from selling precise location information to its customers without users' informed consent.
Outlogic, as part of its settlement with the FTC, has also been barred from collecting location data that could be used to track people's visits to sensitive locations such as medical and reproductive health clinics, domestic abuse shelters, and places of religious worship.
The purchase of sensitive data from these "shady companies" has existed in a legal gray area, Wyden noted, adding the data brokers that buy and resell this data are not known to consumers, who are often kept in the dark about who their data is being shared with or where it is being used.
Another notable aspect of these shadowy data practices is that third-party apps incorporating software development kits (SDKs) from these data brokers and ad-tech vendors do not notify users of the sale and sharing of location data, whether it be for advertising or national security.
"According to the FTC, it is not enough for a consumer to consent to an app or website collecting such data, the consumer must be told and agree to their data being sold to 'government contractors for national security purposes,'" the Oregon Democrat said.
"I am unaware of any company that provides such warnings to consumers before their data is collected. As such, the lawbreaking is likely industry-wide, and not limited to this particular data broker."
Malicious PyPI Packages Slip WhiteSnake InfoStealer Malware onto Windows
Machines
29.1.24
Virus
The Hacker News
Cybersecurity researchers have identified malicious
packages on the open-source Python Package Index (PyPI) repository that deliver
an information stealing malware called WhiteSnake Stealer on Windows systems.
The malware-laced packages are named nigpal, figflix, telerer, seGMM, fbdebug, sGMM, myGens, NewGends, and TestLibs111. They have been uploaded by a threat actor named "WS."
"These packages incorporate Base64-encoded source code of PE or other Python scripts within their setup.py files," Fortinet FortiGuard Labs said in an analysis published last week.
"Depending on the victim devices' operating system, the final malicious payload is dropped and executed when these Python packages are installed."
While Windows systems are infected with WhiteSnake Stealer, compromised Linux hosts are served a Python script designed to harvest information. The activity, which predominantly targets Windows users, overlaps with a prior campaign that JFrog and Checkmarx disclosed last year.
"The Windows-specific payload was identified as a variant of the [...] WhiteSnake malware, which has an Anti-VM mechanism, communicates with a C&C server using the Tor protocol, and is capable of stealing information from the victim and executing commands," JFrog noted in April 2023.
It's also designed to capture data from web browsers, cryptocurrency wallets,
and apps like WinSCP, CoreFTP, Windscribe, Filezilla, AzireVPN, Snowflake,
Steam, Discord, Signal, and Telegram.
Checkmarx is tracking the threat actor behind the campaign under the moniker PYTA31, stating the end goal is to exfiltrate sensitive and particularly crypto wallet data from the target machines.
Some of the newly published rogue packages have also been observed incorporating clipper functionality to overwrite clipboard content with attacker-owned wallet addresses to carry out unauthorized transactions. A few others have been configured to steal data from browsers, applications, and crypto services.
Fortinet said the finding "demonstrates the ability of a single malware author to disseminate numerous info-stealing malware packages into the PyPI library over time, each featuring distinct payload intricacies."
The disclosure comes as ReversingLabs discovered two malicious packages on the npm package registry have been found to leverage GitHub to store Base64-encrypted SSH keys stolen from developer systems on which they were installed.
Experts Warn of macOS Backdoor Hidden in Pirated Versions of Popular Software
19.1.24
OS
The Hacker News
Pirated applications targeting Apple macOS users have
been observed containing a backdoor capable of granting attackers remote control
to infected machines.
"These applications are being hosted on Chinese pirating websites in order to gain victims," Jamf Threat Labs researchers Ferdous Saljooki and Jaron Bradley said.
"Once detonated, the malware will download and execute multiple payloads in the background in order to secretly compromise the victim's machine."
The backdoored disk image (DMG) files, which have been modified to establish communications with actor-controlled infrastructure, include legitimate software like Navicat Premium, UltraEdit, FinalShell, SecureCRT, and Microsoft Remote Desktop.
The unsigned applications, besides being hosted on a Chinese website named macyy[.]cn, incorporate a dropper component called "dylib" that's executed every time the application is opened.
The dropper then acts as a conduit to fetch a backdoor ("bd.log") as well as a downloader ("fl01.log") from a remote server, which is used to set up persistence and fetch additional payloads on the compromised machine.
The backdoor – written to the path "/tmp/.test" – is fully-featured and built atop an open-source post-exploitation toolkit called Khepri. The fact that it is located in the "/tmp" directory means it will be deleted when the system shuts down.
That said, it will be created again at the same location the next time the pirated application is loaded and the dropper is executed.
On the other hand, the downloader is written to the hidden path "/Users/Shared/.fseventsd," following which it creates a LaunchAgent to ensure persistence and sends an HTTP GET request to an actor-controlled server.
While the server is no longer accessible, the downloader is designed to write the HTTP response to a new file located at /tmp/.fseventsds and then launch it.
Jamf said the malware shares several similarities with ZuRu, which has been observed in the past spreading via pirated applications on Chinese sites.
"It's possible that this malware is a successor to the ZuRu malware given its targeted applications, modified load commands and attacker infrastructure," the researchers said.
Npm Trojan Bypasses UAC, Installs AnyDesk with "Oscompatible" Package
19.1.24
Virus
The Hacker News
A malicious package uploaded to the npm registry has been
found deploying a sophisticated remote access trojan on compromised Windows
machines.
The package, named "oscompatible," was published on January 9, 2024, attracting a total of 380 downloads before it was taken down.
oscompatible included a "few strange binaries," according to software supply chain security firm Phylum, including a single executable file, a dynamic-link library (DLL) and an encrypted DAT file, alongside a JavaScript file.
This JavaScript file ("index.js") executes an "autorun.bat" batch script but only after running a compatibility check to determine if the target machine runs on Microsoft Windows.
If the platform is not Windows, it displays an error message to the user, stating the script is running on Linux or an unrecognized operating system, urging them to run it on "Windows Server OS."
The batch script, for its part, verifies if it has admin privileges, and if not, runs a legitimate Microsoft Edge component called "cookie_exporter.exe" via a PowerShell command.
Attempting to run the binary will trigger a User Account Control (UAC) prompt asking the target to execute it with administrator credentials.
In doing so, the threat actor carries out the next stage of the attack by running the DLL ("msedge.dll") by taking advantage of a technique called DLL search order hijacking.
The trojanized version of the library is designed to decrypt the DAT file ("msedge.dat") and launch another DLL called "msedgedat.dll," which, in turn, establishes connections with an actor-controlled domain named "kdark1[.]com" to retrieve a ZIP archive.
The ZIP file comes fitted with the AnyDesk remote desktop software as well as a remote access trojan ("verify.dll") that's capable of fetching instructions from a command-and-control (C2) server via WebSockets and gathering sensitive information from the host.
It also "installs Chrome extensions to Secure Preferences, configures AnyDesk, hides the screen, and disables shutting down Windows, [and] captures keyboard and mouse events," Phylum said.
While "oscompatible" appears to be the only npm module employed as part of the campaign, the development is once again a sign that threat actors are increasingly targeting open-source software (OSS) ecosystems for supply chain attacks.
"From the binary side, the process of decrypting data, using a revoked certificate for signing, pulling other files from remote sources, and attempting to disguise itself as a standard Windows update process all along the way is relatively sophisticated compared to what we normally see in OSS ecosystems," the company said.
The disclosure comes as cloud security firm Aqua revealed that 21.2% of the top 50,000 most downloaded npm packages are deprecated, exposing users to security risks. In other words, the deprecated packages are downloaded an estimated 2.1 billion times weekly.
This includes archived and deleted GitHub repositories associated with the packages as well as those that are maintained without a visible repository, commit history, and issue tracking.
"This situation becomes critical when maintainers, instead of addressing security flaws with patches or CVE assignments, opt to deprecate affected packages," security researchers Ilay Goldman and Yakir Kadkoda said.
"What makes this particularly concerning is that, at times, these maintainers do not officially mark the package as deprecated on npm, leaving a security gap for users who may remain unaware of potential threats."
U.S. Cybersecurity Agency Warns of Actively Exploited Ivanti EPMM Vulnerability
19.1.24
BigBrothers
The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency
(CISA) on Thursday added a now-patched critical flaw impacting Ivanti Endpoint
Manager Mobile (EPMM) and MobileIron Core to its Known Exploited Vulnerabilities
(KEV) catalog, stating it's being actively exploited in the wild.
The vulnerability in question is CVE-2023-35082 (CVSS score: 9.8), an authentication bypass that's a patch bypass for another flaw in the same solution tracked as CVE-2023-35078 (CVSS score: 10.0).
"If exploited, this vulnerability enables an unauthorized, remote (internet-facing) actor to potentially access users' personally identifiable information and make limited changes to the server," Ivanti noted in August 2023.
All versions of Ivanti Endpoint Manager Mobile (EPMM) 11.10, 11.9 and 11.8, and MobileIron Core 11.7 and below are impacted by the vulnerability.
Cybersecurity firm Rapid7, which discovered and reported the flaw, said it can be chained with CVE-2023-35081 to permit an attacker to write malicious web shell files to the appliance.
There are currently no details on how the vulnerability is being weaponized in real-world attacks. Federal agencies are recommended to apply vendor-provided fixes by February 8, 2024.
The disclosure comes as two other zero-day flaws in Ivanti Connect Secure (ICS) virtual private network (VPN) devices (CVE-2023-46805 and CVE-2024-21887) have also come under mass exploitation to drop web shells and passive backdoors, with the company expected to release updates next week.
"We have observed the threat actor target the configuration and running cache of the system, which contains secrets important to the operation of the VPN," Ivanti said in an advisory.
"While we haven't observed this in every instance, out of an abundance of caution, Ivanti is recommending you rotate these secrets after rebuild."
Volexity, earlier this week, revealed that it has been able to find evidence of compromise of over 1,700 devices worldwide. While initial exploitation was linked to a suspected Chinese threat actor named UTA0178, additional threat actors have since joined the exploitation bandwagon.
Further reverse engineering of the twin flaws by Assetnote has uncovered an additional endpoint ("/api/v1/totp/user-backup-code") by which the authentication bypass flaw (CVE-2023-46805) could be abused on older versions of ICS and obtain a reverse shell.
Security researchers Shubham Shah and Dylan Pindur described it as "another example of a secure VPN device exposing itself to wide scale exploitation as the result of relatively simple security mistakes."
New Docker Malware Steals CPU for Crypto & Drives Fake Website Traffic
19.1.24
Virus
The Hacker News
Vulnerable Docker services are being targeted by a novel
campaign in which the threat actors are deploying XMRig cryptocurrency miner as
well as the 9Hits Viewer software as part of a multi-pronged monetization
strategy.
"This is the first documented case of malware deploying the 9Hits application as a payload," cloud security firm Cado said, adding the development is a sign that adversaries are always on the lookout for diversifying their strategies to make money off compromised hosts.
9Hits advertises itself as a "unique web traffic solution" and an "automatic traffic exchange" that allows members of the service to drive traffic to their sites in exchange for purchasing credits.
This is accomplished by means of a software called 9Hits Viewer, which runs a headless Chrome browser instance to visit websites requested by other members, for which they earn credits to pay for generating traffic to their sites.
The exact method used to spread the malware to vulnerable Docker hosts is currently unclear, but it's suspected to involve the use of search engines like Shodan to scan for prospective targets.
The servers are then breached to deploy two malicious containers via the Docker API and fetch off-the-shelf images from the Docker Hub library for the 9Hits and XMRig software.
"This is a common attack vector for campaigns targeting Docker, where instead of fetching a bespoke image for their purposes they pull a generic image off Dockerhub (which will almost always be accessible) and leverage it for their needs," security researcher Nate Bill said.
The 9Hits container is then used to execute code to generate credits for the attacker by authenticating with 9Hits using their session token and extracting the list of sites to visit.
The threat actors have also configured the scheme to allow visiting adult sites or sites that show popups, but prevent it from visiting cryptocurrency-related sites.
The other container is used to run an XMRig miner that connects to a private mining pool, making it impossible to determine the campaign's scale and profitability.
"The main impact of this campaign on compromised hosts is resource exhaustion, as the XMRig miner will use all available CPU resources it can while 9hits will use a large amount of bandwidth, memory, and what little CPU is left," Bill said.
"The result of this is that legitimate workloads on infected servers will be unable to perform as expected. In addition, the campaign could be updated to leave a remote shell on the system, potentially causing a more serious breach."
Russian COLDRIVER Hackers Expand Beyond Phishing with Custom Malware
19.1.24
BigBrothers
The Hacker News
The Russia-linked threat actor known as COLDRIVER has been observed evolving its tradecraft to go beyond credential harvesting to deliver its first-ever custom malware written in the Rust programming language.
Google's Threat Analysis Group (TAG), which shared details of the latest activity, said the attack chains leverage PDFs as decoy documents to trigger the infection sequence. The lures are sent from impersonation accounts.
COLDRIVER, also known by the names Blue Callisto, BlueCharlie (or TAG-53), Calisto (alternately spelled Callisto), Dancing Salome, Gossamer Bear, Star Blizzard (formerly SEABORGIUM), TA446, and UNC4057, is known to be active since 2019, targeting a wide range of sectors.
This includes academia, defense, governmental organizations, NGOs, think tanks, political outfits, and, recently, defense-industrial targets and energy facilities.
"Targets in the U.K. and U.S. appear to have been most affected by Star Blizzard activity, however activity has also been observed against targets in other NATO countries, and countries neighboring Russia," the U.S. government disclosed last month.
Spear-phishing campaigns mounted by the group are designed to engage and build trust with the prospective victims with the ultimate goal of sharing bogus sign-in pages in order to harvest their credentials and gain access to the accounts.
Microsoft, in an analysis of the COLDRIVER's tactics, called out its use of server-side scripts to prevent automated scanning of the actor-controlled infrastructure and determine targets of interest, before redirecting them to the phishing landing pages.
The latest findings from Google TAG show that the threat actor has been using benign PDF documents as a starting point as far back as November 2022 to entice the targets into opening the files.
"COLDRIVER presents these documents as a new op-ed or other type of article that the impersonation account is looking to publish, asking for feedback from the target," the tech giant said. "When the user opens the benign PDF, the text appears encrypted."
In the event the recipient responds to the message stating they cannot read the
document, the threat actor responds with a link to a purported decryption tool
("Proton-decrypter.exe") hosted on a cloud storage service.
The choice of the name "Proton-decrypter.exe" is notable because Microsoft had previously revealed that the adversary predominantly uses Proton Drive to send the PDF lures through the phishing messages.
Google TAG researchers told The Hacker News that the PDF document employed in the attack was hosted on Proton Drive and that the attackers say the tool is used to decrypt the file hosted on the cloud platform.
In reality, the decryptor is a backdoor named SPICA that grants COLDRIVER covert access to the machine, while simultaneously displaying a decoy document to keep up the ruse.
Prior findings from WithSecure (formerly F-Secure) have revealed the threat actor's use of a lightweight backdoor called Scout, a malware tool from the HackingTeam Remote Control System (RCS) Galileo hacking platform, as part of phishing campaigns observed in early 2016.
Scout is "intended to be used as an initial reconnaissance tool to gather basic system information and screenshots from a compromised computer, as well as enable the installation of additional malware," the Finnish cybersecurity company noted at the time.
SPICA, which is the first custom malware developed and used by COLDRIVER, uses JSON over WebSockets for command-and-control (C2), facilitating the execution of arbitrary shell commands, theft of cookies from web browsers, uploading and downloading files, and enumerating and exfiltrating files. Persistence is achieved by means of a scheduled task.
"Once executed, SPICA decodes an embedded PDF, writes it to disk, and opens it as a decoy for the user," Google TAG said. "In the background, it establishes persistence and starts the main C2 loop, waiting for commands to execute."
There is evidence to suggest that the nation-state actor's use of the implant goes back to November 2022, with the cybersecurity arm multiple variants of the "encrypted" PDF lure, indicating that there could be different versions of SPICA to to match the lure document sent to targets.
As part of its efforts to disrupt the campaign and prevent further exploitation, Google TAG said it added all known websites, domains, and files associated with the hacking crew to Safe Browsing blocklists.
Google said it does not have visibility into the number of victims who were successfully compromised with SPICA, but suspects it was only used in "very limited, targeted attacks," adding there has been a focus on "high profile individuals in NGOs, former intelligence and military officials, defense, and NATO governments."
The development comes over a month after the U.K. and the U.S. governments sanctioned two Russian members of COLDRIVER, Ruslan Aleksandrovich Peretyatko and Andrey Stanislavovich Korinets, for their involvement in conducting the spear-phishing operations.
French cybersecurity firm Sekoia has since publicized links between Korinets and known infrastructure used by the group, which comprises dozens of phishing domains and multiple servers.
"Calisto contributes to Russian intelligence efforts to support Moscow's strategic interests," the company said. "It seems that domain registration was one of [Korinets'] main skills, plausibly used by Russian intelligence, either directly or through a contractor relationship."
TensorFlow CI/CD Flaw Exposed Supply Chain to Poisoning Attacks
19.1.24
Vulnerebility
The Hacker News
Continuous integration and continuous delivery (CI/CD)
misconfigurations discovered in the open-source TensorFlow machine learning
framework could have been exploited to orchestrate supply chain attacks.
The misconfigurations could be abused by an attacker to "conduct a supply chain compromise of TensorFlow releases on GitHub and PyPi by compromising TensorFlow's build agents via a malicious pull request," Praetorian researchers Adnan Khan and John Stawinski said in a report published this week.
Successful exploitation of these issues could permit an external attacker to upload malicious releases to the GitHub repository, gain remote code execution on the self-hosted GitHub runner, and even retrieve a GitHub Personal Access Token (PAT) for the tensorflow-jenkins user.
TensorFlow uses GitHub Actions to automate the software build, test, and deployment pipeline. Runners, which refer to machines that execute jobs in a GitHub Actions workflow, can be either self-hosted or hosted by GitHub.
"We recommend that you only use self-hosted runners with private repositories," GitHub notes in its documentation. "This is because forks of your public repository can potentially run dangerous code on your self-hosted runner machine by creating a pull request that executes the code in a workflow."
Put differently, this allows any contributor to execute arbitrary code on the self-hosted runner by submitting a malicious pull request.
This, however, does not pose any security concern with GitHub-hosted runners, as each runner is ephemeral and is a clean, isolated virtual machine that's destroyed at the end of the job execution.
Praetorian said it was able to identify TensorFlow workflows that were executed on self-hosted runners, subsequently finding fork pull requests from previous contributors that automatically triggered the appropriate CI/CD workflows without requiring approval.
An adversary looking to trojanize a target repository could, therefore, fix a typo or make a small but legitimate code change, create a pull request for it, and then wait until the pull request is merged in order to become a contributor. This would then enable them to execute code on the runner sans raising any red flag by creating a rogue pull request.
Further examination of the workflow logs revealed that the self-hosted runner was not only non-ephemeral (thus opening the door for persistence), but also that the GITHUB_TOKEN permissions associated with the workflow came with extensive write permissions.
"Because the GITHUB_TOKEN had the contents:write permission, it could upload releases to https://github[.]com/tensorflow/tensorflow/releases/," the researchers pointed out. "An attacker that compromised one of these GITHUB_TOKEN's could add their own files to the Release Assets."
On top of that, the contents:write permissions could be weaponized to push code directly to the TensorFlow repository by covertly injecting the malicious code into a feature branch and getting it merged into the main branch.
That's not all. A threat actor could steal the AWS_PYPI_ACCOUNT_TOKEN used in the release workflow to authenticate to the Python Package Index (PyPI) registry and upload a malicious Python .whl file, effectively poisoning the package.
"An attacker could also use the GITHUB_TOKEN's permissions to compromise the JENKINS_TOKEN repository secret, even though this secret was not used within workflows that ran on the self-hosted runners," the researchers said.
Following responsible disclosure on August 1, 2023, the shortcomings were addressed by the project maintainers as of December 20, 2023, by requiring approval for workflows submitted from all fork pull requests, counting those from previous contributors, and by changing the GITHUB_TOKEN permissions to read-only for workflows that run on self-hosted runners.
"Similar CI/CD attacks are on the rise as more organizations automate their CI/CD processes," the researchers said.
"AI/ML companies are particularly vulnerable as many of their workflows require significant compute power that isn't available in GitHub-hosted runners, thus the prevalence of self-hosted runners."
The disclosure comes as both researchers revealed that several public GitHub repositories, including those associated with Chia Networks, Microsoft DeepSpeed, and PyTorch, are susceptible to malicious code injection via self-hosted GitHub Actions runners.
PixieFail UEFI Flaws Expose Millions of Computers to RCE, DoS, and Data Theft
19.1.24
Vulnerebility
The Hacker News
Multiple security vulnerabilities have been disclosed in
the TCP/IP network protocol stack of an open-source reference implementation of
the Unified Extensible Firmware Interface (UEFI) specification used widely in
modern computers.
Collectively dubbed PixieFail by Quarkslab, the nine issues reside in the TianoCore EFI Development Kit II (EDK II) and could be exploited to achieve remote code execution, denial-of-service (DoS), DNS cache poisoning, and leakage of sensitive information.
UEFI firmware – which is responsible for booting the operating system – from AMI, Intel, Insyde, and Phoenix Technologies are impacted by the shortcomings.
EDK II incorporates its own TCP/IP stack called NetworkPkg to enable network functionalities available during the initial Preboot eXecution Environment (PXE, pronounced "pixie") stage, which allows for management tasks in the absence of a running operating system.
In other words, it is a client-server interface to boot a device from its network interface card (NIC) and allows networked computers that are not yet loaded with an operating system to be configured and booted remotely by an administrator.
The code to PXE is included as part of the UEFI firmware on the motherboard or within the NIC firmware read-only memory (ROM).
The issues identified by Quarkslab within the EDKII's NetworkPkg encompass
overflow bugs, out-of-bounds read, infinite loops, and the use of weak
pseudorandom number generator (PRNG) that result in DNS and DHCP poisoning
attacks, information leakage, denial of service, and data insertion attacks at
the IPv4 and IPv6 layer.
The list of flaws is as follows -
CVE-2023-45229 (CVSS score: 6.5) - Integer underflow when processing IA_NA/IA_TA
options in a DHCPv6 Advertise message
CVE-2023-45230 (CVSS score: 8.3) -
Buffer overflow in the DHCPv6 client via a long Server ID option
CVE-2023-45231 (CVSS score: 6.5) - Out-of-bounds read when handling a ND
Redirect message with truncated options
CVE-2023-45232 (CVSS score: 7.5) -
Infinite loop when parsing unknown options in the Destination Options header
CVE-2023-45233 (CVSS score: 7.5) - Infinite loop when parsing a PadN option in
the Destination Options header
CVE-2023-45234 (CVSS score: 8.3) - Buffer
overflow when processing DNS Servers option in a DHCPv6 Advertise message
CVE-2023-45235 (CVSS score: 8.3) - Buffer overflow when handling Server ID
option from a DHCPv6 proxy Advertise message
CVE-2023-45236 (CVSS score: 5.8)
- Predictable TCP Initial Sequence Numbers
CVE-2023-45237 (CVSS score: 5.3) -
Use of a weak pseudorandom number generator
"The impact and exploitability of
these vulnerabilities depend on the specific firmware build and the default PXE
boot configuration," the CERT Coordination Center (CERT/CC) said in an advisory.
"An attacker within the local network (and, in certain scenarios remotely) could exploit these weaknesses to execute remote code, initiate DoS attacks, conduct DNS cache poisoning, or extract sensitive information."
Iranian Hackers Masquerade as Journalists to Spy on Israel-Hamas War Experts
18.1.24
BigBrothers
The Hacker News
High-profile individuals working on Middle Eastern affairs at universities and research organizations in Belgium, France, Gaza, Israel, the U.K., and the U.S. have been targeted by an Iranian cyber espionage group called Mind Sandstorm since November 2023.
The threat actor "used bespoke phishing lures in an attempt to socially engineer targets into downloading malicious files," the Microsoft Threat Intelligence team said in a Wednesday analysis, describing it as a "technically and operationally mature subgroup of Mind Sandstorm."
The attacks, in select cases, involve the use of a previously undocumented backdoor dubbed MediaPl, indicating ongoing endeavors by Iranian threat actors to refine their post-intrusion tradecraft.
Mint Sandstorm, also known as APT35, Charming Kitten, TA453, and Yellow Garuda, is known for its adept social engineering campaigns, even resorting to legitimate but compromised accounts to send bespoke phishing emails to prospective targets. It's assessed to be affiliated with Iran's Islamic Revolutionary Guard Corps (IRGC).
The sub-cluster, per Redmond, engages in resource-intensive social engineering to single out journalists, researchers, professors, and other individuals with insights on security and policy issues of interest to Tehran.
The latest intrusion set is characterized by the use of lures pertaining to the Israel-Hamas war, sending innocuous emails under the guise of journalists and other high-profile individuals to build rapport with targets and establish a level of trust before attempting to deliver malware to targets.
Microsoft said it's likely the campaign is an effort undertaken by the nation-state threat actor to collect perspectives on events related to the war.
The use of breached accounts belonging to the people they sought to impersonate in order to send the email messages is a new Mind Sandstorm tactic not seen before, as is its use of the curl command to connect to the command-and-control (C2) infrastructure.
Should the targets engage with the threat actor, they are sent a follow-up email containing a malicious link that points to a RAR archive file, which, when opened, leads to the retrieval of Visual Basic scripts from the C2 server to persist within the targets' environments.
The attack chains further pave the way for custom implants like MischiefTut or MediaPl, the former of which was first disclosed by Microsoft in October 2023.
Implemented in PowerShell, MischiefTut is a basic backdoor that can run reconnaissance commands, write outputs to a text file, and download additional tools on a compromised system. The first recorded use of the malware dates back to late 2022.
MediaPl, on the other hand, masquerades as Windows Media Player and is designed to transmit encrypted communications to its C2 server and launch command(s) it has received from the server.
"Mint Sandstorm continues to improve and modify the tooling used in targets' environments, activity that might help the group persist in a compromised environment and better evade detection," Microsoft said.
"The ability to obtain and maintain remote access to a target's system can enable Mint Sandstorm to conduct a range of activities that can adversely impact the confidentiality of a system."
The disclosure comes as Dutch newspaper De Volkskrant revealed earlier this month that Erik van Sabben, a Dutch engineer recruited by Israel and U.S. intelligence services, may have used a water pump to deploy an early variant of the now-infamous Stuxnet malware in an Iranian nuclear facility sometime in 2007.
PAX PoS Terminal Flaw Could Allow Attackers to Tamper with Transactions
18.1.24
Hacking
The Hacker News
The point-of-sale (PoS) terminals from PAX Technology are
impacted by a collection of high-severity vulnerabilities that can be weaponized
by threat actors to execute arbitrary code.
The STM Cyber R&D team, which reverse engineered the Android-based devices manufactured by the Chinese firm owing to their rapid deployment in Poland, said it unearthed half a dozen flaws that allow for privilege escalation and local code execution from the bootloader.
Details about one of the vulnerabilities (CVE-2023-42133) have been currently withheld. The other flaws are listed below -
CVE-2023-42134 & CVE-2023-42135 (CVSS score: 7.6) - Local code execution as root
via kernel parameter injection in fastboot (Impacts PAX A920Pro/PAX A50)
CVE-2023-42136 (CVSS score: 8.8) - Privilege escalation from any
user/application to system user via shell injection binder-exposed service
(Impacts All Android-based PAX PoS devices)
CVE-2023-42137 (CVSS score: 8.8)
- Privilege escalation from system/shell user to root via insecure operations in
systool_server daemon (Impacts All Android-based PAX PoS devices)
CVE-2023-4818 (CVSS score: 7.3) - Bootloader downgrade via improper tokenization
(Impacts PAX A920)
Successful exploitation of the aforementioned weaknesses
could permit an attacker to elevate their privileges to root and bypass
sandboxing protections, effectively gaining carte blanche access to perform any
operation.
This includes interfering with the payment operations to "modify data the merchant application sends to the [Secure Processor], which includes transaction amount," security researchers Adam Kliś and Hubert Jasudowicz said.
It's worth mentioning that exploiting CVE-2023-42136 and CVE-2023-42137 requires an attacker to have shell access to the device, while the remaining three necessitate that the threat actor has physical USB access to it.
The Warsaw-based penetration testing company said it responsibly disclosed the flaws to PAX Technology in early May 2023, following which patches were released by the latter in November 2023.
Feds Warn of AndroxGh0st Botnet Targeting AWS, Azure, and Office 365 Credentials
18.1.24
BigBrothers
The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency
(CISA) and the Federal Bureau of Investigation (FBI) warned that threat actors
deploying the AndroxGh0st malware are creating a botnet for "victim
identification and exploitation in target networks."
A Python-based malware, AndroxGh0st was first documented by Lacework in December 2022, with the malware inspiring several similar tools like AlienFox, GreenBot (aka Maintance), Legion, and Predator.
The cloud attack tool is capable of infiltrating servers vulnerable to known security flaws to access Laravel environment files and steal credentials for high-profile applications such as Amazon Web Services (AWS), Microsoft Office 365, SendGrid, and Twilio.
Some of the notable flaws weaponized by the attackers include CVE-2017-9841 (PHPUnit), CVE-2021-41773 (Apache HTTP Server), and CVE-2018-15133 (Laravel Framework).
"AndroxGh0st has multiple features to enable SMTP abuse including scanning, exploitation of exposed creds and APIs, and even deployment of web shells," Lacework said. "For AWS specifically, the malware scans for and parses AWS keys but also has the ability to generate keys for brute-force attacks."
The compromised AWS credentials are subsequently used to create new users and user policies, and in several instances, set up new AWS instances for additional, malicious scanning activity.
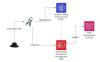
These features make AndroxGh0st a potent threat that can be used to download
additional payloads and retain persistent access to compromised systems.
"Androxgh0st is a consistent nuisance: we regularly see related user-agent strings in network connections scanning our honeypots," Alex Delamotte, senior threat researcher at SentinelLabs, told The Hacker News. "It's excellent to see CISA issuing an advisory against this type of threat, as cloud-focused malware advisories are uncommon."
The development arrives less than a week after SentinelOne revealed a related-but-distinct tool called FBot that is being employed by attackers to breach web servers, cloud services, content management systems (CMS), and SaaS platforms.
"The cloud threat landscape will continue to borrow code from other tools and integrate them into a holistic ecosystem, which is what we see with AlienFox and Legion doing with Androxgh0st and FBot respectively," Delamotte said.
"As actors find new ways to monetize cloud services, we can expect to see tailored tools emerge for those services, much like how these tools focus on exploiting mail services to conduct spamming attacks."
It also follows an alert from NETSCOUT about a significant spike in botnet scanning activity since mid-November 2023, touching a peak of nearly 1.3 million distinct devices on January 5, 2024. A majority of the source IP addresses are associated with the U.S., China, Vietnam, Taiwan, and Russia.
"Analysis of the activity has uncovered a rise in the use of cheap or free cloud and hosting servers that attackers are using to create botnet launch pads," the company said. "These servers are used via trials, free accounts, or low-cost accounts, which provide anonymity and minimal overhead to maintain."
New iShutdown Method Exposes Hidden Spyware Like Pegasus on Your iPhone
18.1.24
OS
The Hacker News
Cybersecurity researchers have identified a "lightweight
method" called iShutdown for reliably identifying signs of spyware on Apple iOS
devices, including notorious threats like NSO Group's Pegasus, QuaDream's Reign,
and Intellexa's Predator.
Kaspersky, which analyzed a set of iPhones that were compromised with Pegasus, said the infections left traces in a file named "Shutdown.log," a text-based system log file available on all iOS devices and which records every reboot event alongside its environment characteristics.
"Compared to more time-consuming acquisition methods like forensic device imaging or a full iOS backup, retrieving the Shutdown.log file is rather straightforward," security researcher Maher Yamout said. "The log file is stored in a sysdiagnose (sysdiag) archive."
The Russian cybersecurity firm said it identified entries in the log file that recorded instances where "sticky" processes, such as those associated with the spyware, caused a reboot delay, in some cases observing Pegasus-related processes in over four reboot delay notices.
What's more, the investigation revealed the presence of a similar filesystem path that's used by all the three spyware families – "/private/var/db/" for Pegasus and Reign, and "/private/var/tmp/" for Predator – thereby acting as an indicator of compromise.

That said, the success of this approach hinges on a caveat that the target user
reboots their device as often as possible, the frequency for which varies
according to their threat profile.
Kaspersky has also published a collection of Python scripts to extract, analyze, and parse the Shutdown.log in order to extract the reboot stats.
"The lightweight nature of this method makes it readily available and accessible," Yamout said. "Moreover, this log file can store entries for several years, making it a valuable forensic artifact for analyzing and identifying anomalous log entries."
The disclosure comes as SentinelOne revealed information stealers targeting macOS such as KeySteal, Atomic, and JaskaGo (aka CherryPie or Gary Stealer) are quickly adapting to circumvent Apple's built-in antivirus technology called XProtect.
"Despite solid efforts by Apple to update its XProtect signature database, these rapidly evolving malware strains continue to evade," security researcher Phil Stokes said. "Relying solely on signature-based detection is insufficient as threat actors have the means and motive to adapt at speed."
GitHub Rotates Keys After High-Severity Vulnerability Exposes Credentials
18.1.24
Vulnerebility
The Hacker News
GitHub has revealed that it has rotated some keys in
response to a security vulnerability that could be potentially exploited to gain
access to credentials within a production container.
The Microsoft-owned subsidiary said it was made aware of the problem on December 26, 2023, and that it addressed the issue the same day, in addition to rotating all potentially exposed credentials out of an abundance of caution.
The rotated keys include the GitHub commit signing key as well as GitHub Actions, GitHub Codespaces, and Dependabot customer encryption keys, necessitating users who rely on these keys to import the new ones.
There is no evidence that the high-severity vulnerability, tracked as CVE-2024-0200 (CVSS score: 7.2), has been previously found and exploited in the wild.
"This vulnerability is also present on GitHub Enterprise Server (GHES)," GitHub's Jacob DePriest said. "However, exploitation requires an authenticated user with an organization owner role to be logged into an account on the GHES instance, which is a significant set of mitigating circumstances to potential exploitation."
In a separate advisory, GitHub characterized the vulnerability as a case of "unsafe reflection" GHES that could lead to reflection injection and remote code execution. It has been patched in GHES versions 3.8.13, 3.9.8, 3.10.5, and 3.11.3.
Also addressed by GitHub is another high-severity bug tracked as CVE-2024-0507 (CVSS score: 6.5), which could permit an attacker with access to a Management Console user account with the editor role to escalate privileges via command injection.
The development comes nearly a year after the company took the step of replacing its RSA SSH host key used to secure Git operations "out of an abundance of caution" after it was briefly exposed in a public repository.
Citrix, VMware, and Atlassian Hit with Critical Flaws — Patch ASAP!
17.1.24
Vulnerebility
The Hacker News
Citrix is warning of two zero-day security
vulnerabilities in NetScaler ADC (formerly Citrix ADC) and NetScaler Gateway
(formerly Citrix Gateway) that are being actively exploited in the wild.
The flaws are listed below -
CVE-2023-6548 (CVSS score: 5.5) - Authenticated (low privileged) remote code
execution on Management Interface (requires access to NSIP, CLIP, or SNIP with
management interface access)
CVE-2023-6549 (CVSS score: 8.2) -
Denial-of-service (requires that the appliance be configured as a Gateway or
authorization and accounting, or AAA, virtual server)
The following
customer-managed versions of NetScaler ADC and NetScaler Gateway are impacted by
the shortcomings -
NetScaler ADC and NetScaler Gateway 14.1 before 14.1-12.35
NetScaler ADC and
NetScaler Gateway 13.1 before 13.1-51.15
NetScaler ADC and NetScaler
Gateway 13.0 before 13.0-92.21
NetScaler ADC and NetScaler Gateway version
12.1 (currently end-of-life)
NetScaler ADC 13.1-FIPS before 13.1-37.176
NetScaler ADC 12.1-FIPS before 12.1-55.302, and
NetScaler ADC 12.1-NDcPP
before 12.1-55.302
"Exploits of these CVEs on unmitigated appliances have
been observed," Citrix said, without sharing any additional specifics. Users of
NetScaler ADC and NetScaler Gateway version 12.1 are recommended to upgrade
their appliances to a supported version that patches the flaws.
It's also advised to not expose the management interface to the internet to reduce the risk of exploitation.
In recent months, multiple security vulnerabilities in Citrix appliances (CVE-2023-3519 and CVE-2023-4966) have been weaponized by threat actors to drop web shells and hijack existing authenticated sessions.
VMware Fixes Critical Aria Automation Flaw#
The disclosure comes as VMware
alerted customers of a critical security vulnerability in Aria Automation
(previously vRealize Automation) that could allow an authenticated attacker to
gain unauthorized access to remote organizations and workflows.
The issue has been assigned the CVE identifier CVE-2023-34063 (CVSS score: 9.9), with the Broadcom-owned virtualization services provider describing it as a "missing access control" flaw.
Commonwealth Scientific and Industrial Research Organization's (CSIRO) Scientific Computing Platforms team has been credited with discovering and reporting the security vulnerability.
The versions impacted by the vulnerability are provided below -
VMware Aria Automation (8.11.x, 8.12.x, 8.13.x, and 8.14.x)
VMware Cloud
Foundation (4.x and 5.x)
"The only supported upgrade path after applying the
patch is to version 8.16," VMware said. "If you upgrade to an intermediate
version, the vulnerability will be reintroduced, requiring an additional round
of patching."
Atlassian Discloses Critical Code Execution Bug#
The development also follows
Atlassian's release of patches for over two dozen vulnerabilities, including a
critical remote code execution (RCE) flaw impacting Confluence Data Center and
Confluence Server.
The vulnerability, CVE-2023-22527, has been assigned a CVSS score of 10.0, indicating maximum severity. It affects versions 8.0.x, 8.1.x, 8.2.x, 8.3.x, 8.4.x, and 8.5.0-8.5.3. It's worth noting that 7.19.x LTS versions are not affected by the vulnerability.
"A template injection vulnerability on out-of-date versions of Confluence Data Center and Server allows an unauthenticated attacker to achieve RCE on an affected version," the Australian company said.
The issue has been addressed in versions 8.5.4, 8.5.5 (Confluence Data Center and Server), 8.6.0, 8.7.1, and 8.7.2 (Data Center only). Users who are on out-of-date instances are recommended to update their installations to the latest version available.
Zero-Day Alert: Update Chrome Now to Fix New Actively Exploited Vulnerability
17.1.24
Exploit
The Hacker News
Google on Tuesday released updates to fix four security
issues in its Chrome browser, including an actively exploited zero-day flaw.
The issue, tracked as CVE-2024-0519, concerns an out-of-bounds memory access in the V8 JavaScript and WebAssembly engine, which can be weaponized by threat actors to trigger a crash.
"By reading out-of-bounds memory, an attacker might be able to get secret values, such as memory addresses, which can be bypass protection mechanisms such as ASLR in order to improve the reliability and likelihood of exploiting a separate weakness to achieve code execution instead of just denial of service," according to MITRE's Common Weakness Enumeration (CWE).
Additional details about the nature of the attacks and the threat actors that may be exploiting them have withheld in an attempt to prevent further exploitation. The issue was reported anonymously on January 11, 2024.
"Out-of-bounds memory access in V8 in Google Chrome prior to 120.0.6099.224 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page," reads a description of the flaw on the NIST's National Vulnerability Database (NVD).
The development marks the first actively exploited zero-day to be patched by Google in Chrome in 2024. Last year, the tech giant resolved a total of 8 such actively exploited zero-days in the browser.
Users are recommended to upgrade to Chrome version 120.0.6099.224/225 for Windows, 120.0.6099.234 for macOS, and 120.0.6099.224 for Linux to mitigate potential threats.
Users of Chromium-based browsers such as Microsoft Edge, Brave, Opera, and Vivaldi are also advised to apply the fixes as and when they become available.
Alert: Over 178,000 SonicWall Firewalls Potentially Vulnerable to Exploits - Act
Now
17.1.24
Exploit
The Hacker News
Over 178,000 SonicWall firewalls exposed over the internet are exploitable to at
least one of the two security flaws that could be potentially exploited to cause
a denial-of-service (DoS) condition and remote code execution (RCE).
"The two issues are fundamentally the same but exploitable at different HTTP URI paths due to reuse of a vulnerable code pattern," Jon Williams, a senior security engineer at Bishop Fox, said in a technical analysis shared with The Hacker News.
The vulnerabilities in question are listed below -
CVE-2022-22274 (CVSS score: 9.4) - A stack-based buffer overflow vulnerability
in the SonicOS via HTTP request allows a remote, unauthenticated attacker to
cause DoS or potentially result in code execution in the firewall.
CVE-2023-0656 (CVSS score: 7.5) - A stack-based buffer overflow vulnerability in
the SonicOS allows a remote, unauthenticated attacker to cause DoS, which could
result in a crash.
While there are no reports of exploitation of the flaws in
the wild, a proof-of-concept (PoC) for CVE-2023-0656 was published by the SSD
Secure Disclosure team in April 2023.
The cybersecurity firm revealed that the issues could be weaponized by bad actors to trigger repeated crashes and force the appliance to get into maintenance mode, requiring administrative action to restore normal functionality.
"Perhaps most astonishing was the discovery that over 146,000 publicly-accessible devices are vulnerable to a bug that was published almost two years ago," Williams said.
The development comes as watchTowr Labs uncovered multiple stack-based buffer overflow flaws in the SonicOS management web interface and SSL VPN portal that could lead to a firewall crash.
To safeguard against possible threats, it's recommended to update to the last version and ensure that the management interface isn't exposed to the internet.
Remcos RAT Spreading Through Adult Games in New Attack Wave
17.1.24
Virus
The Hacker News
The remote access trojan (RAT) known as Remcos RAT has been found being
propagated via webhards by disguising it as adult-themed games in South Korea.
WebHard, short for web hard drive, is a popular online file storage system used to upload, download, and share files in the country.
While webhards have been used in the past to deliver njRAT, UDP RAT, and DDoS botnet malware, the AhnLab Security Emergency Response Center's (ASEC) latest analysis shows that the technique has been adopted to distribute Remcos RAT.
In these attacks, users are tricked into opening booby-trapped files by passing them off as adult games, which, when launched, execute malicious Visual Basic scripts in order to run an intermediate binary named "ffmpeg.exe."
This results in the retrieval of Remcos RAT from an actor-controlled server.
A sophisticated RAT, Remcos (aka Remote Control and Surveillance) facilitates
unauthorized remote control and surveillance of compromised hosts, enabling
threat actors to exfiltrate sensitive data.
This malware, although originally marketed by Germany-based firm Breaking Security in 2016 as a bonafide remote administration tool, has metamorphosed into a potent weapon wielded by adversaries actors to infiltrate systems and establish unfettered control.
"Remcos RAT has evolved into a malicious tool employed by threat actors across various campaigns," Cyfirma noted in an analysis in August 2023.
"The malware's multifunctional capabilities, including keylogging, audio recording, screenshot capture, and more, highlight its potential to compromise user privacy, exfiltrate sensitive data, and manipulate systems. The RAT's ability to disable User Account Control (UAC) and establish persistence further amplifies its potential impact."
Inferno Malware Masqueraded as Coinbase, Drained $87 Million from 137,000
Victims
16.1.24
Cryptocurrency
The Hacker News
The operators behind the now-defunct Inferno Drainer created more than 16,000 unique malicious domains over a span of one year between 2022 and 2023.
The scheme “leveraged high-quality phishing pages to lure unsuspecting users into connecting their cryptocurrency wallets with the attackers’ infrastructure that spoofed Web3 protocols to trick victims into authorizing transactions,” Singapore-headquartered Group-IB said in a report shared with The Hacker News.
Inferno Drainer, which was active from November 2022 to November 2023, is estimated to have reaped over $87 million in illicit profits by scamming more than 137,000 victims.
The malware is part of a broader set of similar offerings that are available to affiliates under the scam-as-a-service (or drainer-as-a-service) model in exchange for a 20% cut of their earnings.
What’s more, customers of Inferno Drainer could either upload the malware to their own phishing sites, or make use of the developer’s service for creating and hosting phishing websites, either at no extra cost or charging 30% of the stolen assets in some cases.
According to Group-IB, the activity spoofed upwards of 100 cryptocurrency brands
via specially crafted pages that were hosted on over 16,000 unique domains.
Further analysis of 500 of these domains has revealed that the JavaScript-based drainer was hosted initially on a GitHub repository (kuzdaz.github[.]io/seaport/seaport.js) before incorporating them directly on the websites. The user “kuzdaz” currently does not exist.
In a similar fashion, another set of 350 sites included a JavaScript file, “coinbase-wallet-sdk.js,” on a different GitHub repository, “kasrlorcian.github[.]io.”
These sites were then propagated on sites like Discord and X (formerly Twitter), enticing potential victims into clicking them under the guise of offering free tokens (aka airdrops) and connecting their wallets, at which point their assets are drained once the transactions are approved.
In using the names seaport.js, coinbase.js and wallet-connect.js, the idea was to masquerade as popular Web3 protocols like Seaport, WalletConnect, and Coinbase to complete the unauthorized transactions. The earliest website containing one of these scripts dates back to May 15, 2023.
“Another typical feature of phishing websites belonging to Inferno Drainer was that users cannot open website source code by using hotkeys or right-clicking on the mouse,” Group-IB analyst Viacheslav Shevchenko said. “This means that the criminals attempted to hide their scripts and illegal activity from their victims.”
It’s worth noting that Google-owned Mandiant’s X account was compromised earlier this month to distribute links to a phishing page hosting a cryptocurrency drainer tracked as CLINKSINK.
“Inferno Drainer may have ceased its activity, but its prominence throughout 2023 highlights the severe risks to cryptocurrency holders as drainers continue to develop further,” Andrey Kolmakov, head of Group-IB’s High-Tech Crime Investigation Department, said.
Hackers Weaponize Windows Flaw to Deploy Crypto-Siphoning Phemedrone Stealer
16.1.24
Cryptocurrency
The Hacker News
Threat actors have been observed leveraging a now-patched
security flaw in Microsoft Windows to deploy an open-source information stealer
called Phemedrone Stealer.
"Phemedrone targets web browsers and data from cryptocurrency wallets and messaging apps such as Telegram, Steam, and Discord," Trend Micro researchers Peter Girnus, Aliakbar Zahravi, and Simon Zuckerbraun said.
"It also takes screenshots and gathers system information regarding hardware, location, and operating system details. The stolen data is then sent to the attackers via Telegram or their command-and-control (C&C) server."
The attacks leverage CVE-2023-36025 (CVSS score: 8.8), a security bypass vulnerability in Windows SmartScreen, that could be exploited by tricking a user into clicking on a specially crafted Internet Shortcut (.URL) or a hyperlink pointing to an Internet Shortcut file.
The actively-exploited shortcoming was addressed by Microsoft as part of its November 2023 Patch Tuesday updates.
The infection process involves the threat actor hosting malicious Internet Shortcut files on Discord or cloud services like FileTransfer.io, with the links also masked using URL shorteners such as Short URL.
The execution of the booby-trapped .URL file allows it to connect to an actor-controlled server and execute a control panel (.CPL) file in a manner that circumvents Windows Defender SmartScreen by taking advantage of CVE-2023-36025.
"When the malicious .CPL file is executed through the Windows Control Panel process binary, it in turn calls rundll32.exe to execute the DLL," the researchers said. "This malicious DLL acts as a loader that then calls on Windows PowerShell to download and execute the next stage of the attack, hosted on GitHub."
The follow-on payload is a PowerShell loader ("DATA3.txt") that acts as a launchpad for Donut, an open-source shellcode loader that decrypts and executes Phemedrone Stealer.
Written in C#, Phemedrone Stealer is actively maintained by its developers on GitHub and Telegram, facilitating the theft of sensitive information from compromised systems.
The development is once again a sign that threat actors are getting increasingly flexible and quickly adapting their attack chains to capitalize on newly disclosed exploits and inflict maximum damage.
"Despite having been patched, threat actors continue to find ways to exploit CVE-2023-36025 and evade Windows Defender SmartScreen protections to infect users with a plethora of malware types, including ransomware and stealers like Phemedrone Stealer," the researchers said.
Opera MyFlaw Bug Could Let Hackers Run ANY File on Your Mac or Windows
16.1.24
Vulnerebility
The Hacker News
Cybersecurity researchers have disclosed a now-patched security flaw in the
Opera web browser for Microsoft Windows and Apple macOS that could be exploited
to execute any file on the underlying operating system.
The remote code execution vulnerability has been codenamed MyFlaw by the Guardio Labs research team owing to the fact that it takes advantage of a feature called My Flow that makes it possible to sync messages and files between mobile and desktop devices.
"This is achieved through a controlled browser extension, effectively bypassing the browser's sandbox and the entire browser process," the company said in a statement shared with The Hacker News.
The issue impacts both the Opera browser and Opera GX. Following responsible disclosure on November 17, 2023, it was addressed as part of updates shipped on November 22, 2023.
My Flow features a chat-like interface to exchange notes and files, the latter of which can be opened via a web interface, meaning a file can be executed outside of the browser's security boundaries.
It is pre-installed in the browser and facilitated by means of a built-in (or internal) browser extension called "Opera Touch Background," which is responsible for communicating with its mobile counterpart.
This also means that the extension comes with its own manifest file specifying all the required permissions and its behavior, including a property known as externally_connectable that declares which other web pages and extensions can connect to it.

In the case of Opera, the domains that can talk to the extension should match
the patterns "*.flow.opera.com" and ".flow.op-test.net" – both controlled by the
browser vendor itself.
"This exposes the messaging API to any page that matches the URL patterns you specify," Google notes in its documentation. "The URL pattern must contain at least a second-level domain."
Guardio Labs said it was able to unearth a "long-forgotten" version of the My Flow landing page hosted on the domain "web.flow.opera.com" using the urlscan.io website scanner tool.
"The page itself looks quite the same as the current one in production, but
changes lie under the hood: Not only that it lacks the [content security policy]
meta tag, but it also holds a script tag calling for a JavaScript file without
any integrity check," the company said.
"This is exactly what an attacker needs – an unsafe, forgotten, vulnerable to code injection asset, and most importantly, has access to (very) high permission native browser API."
The attack chain then hinges, creating a specially crafted extension that masquerades as a mobile device to pair with the victim's computer and transmit an encrypted malicious payload via the modified JavaScript file to the host for subsequent execution by prompting the user to click anywhere on the screen.
The findings highlight the increasing complexity of browser-based attacks and the different vectors that can be exploited by threat actors to their advantage.
"Despite operating in sandboxed environments, extensions can be powerful tools for hackers, enabling them to steal information and breach browser security boundaries," the company told The Hacker News.
"This underscores the need for internal design changes at Opera and improvements in Chromium's infrastructure. For instance, disabling third-party extension permissions on dedicated production domains, similar to Chrome's web store, is recommended but has not yet been implemented by Opera."
When reached for comment, Opera said it moved quickly to close the security hole and implement a fix on the server side and that it's taking steps to prevent such issues from happening again.
"Our current structure uses an HTML standard, and is the safest option that does not break key functionality," the company said. "After Guardio alerted us to this vulnerability, we removed the cause of these issues and we are making sure that similar problems will not appear in the future."
"We would like to thank Guardio Labs for their work on uncovering and immediately alerting us to this vulnerability. This collaboration demonstrates how we work together with security experts and researchers around the world to complement our own efforts at maintaining and improving the security of our products and ensuring our users have a safe online experience."
High-Severity Flaws Uncovered in Bosch Thermostats and Smart Nutrunners
15.1.24
Vulnerebility
The Hacker News
Multiple security vulnerabilities have been disclosed in
Bosch BCC100 thermostats and Rexroth NXA015S-36V-B smart nutrunners that, if
successfully exploited, could allow attackers to execute arbitrary code on
affected systems.
Romanian cybersecurity firm Bitdefender, which discovered the flaw in Bosch BCC100 thermostats last August, said the issue could be weaponized by an attacker to alter the device firmware and implant a rogue version.
Tracked as CVE-2023-49722 (CVSS score: 8.3), the high-severity vulnerability was addressed by Bosch in November 2023.
"A network port 8899 is always open in BCC101/BCC102/BCC50 thermostat products, which allows an unauthenticated connection from a local WiFi network," the company said in an advisory.
The issue, at its core, impacts the WiFi microcontroller that acts as a network gateway for the thermostat's logic microcontroller.
By exploiting the flaw, an attacker could send commands to the thermostat, including writing a malicious update to the device that could either render the device inoperable or act as a backdoor to sniff traffic, pivot onto other devices, and other nefarious activities.
Bosch has corrected the shortcoming in firmware version 4.13.33 by closing the port 8899, which it said was used for debugging purposes.
The German engineering and tech company has also been made aware of over two dozen flaws in Rexroth Nexo cordless nutrunners that an unauthenticated attacker could abuse to disrupt operations, tamper with critical configurations, and even install ransomware.
"Given that the NXA015S-36V-B is certified for safety-critical tasks, an attacker could compromise the safety of the assembled product by inducing suboptimal tightening, or cause damage to it due to excessive tightening," Nozomi Networks said.
The flaws, the operational technology (OT) security firm added, could be used to obtain remote execution of arbitrary code (RCE) with root privileges, and make the pneumatic torque wrench unusable by hijacking the onboard display and disabling the trigger button to demand a ransom.
"Given the ease with which this attack can be automated across numerous devices, an attacker could swiftly render all tools on a production line inaccessible, potentially causing significant disruptions to the final asset owner," the company added.
Patches for the vulnerabilities, which impact several NXA, NXP, and NXV series devices, are expected to be shipped by Bosch by the end of January 2024. In the interim, users are recommended to limit the network reachability of the device as much as possible and review accounts that have login access to the device.
The development comes as Pentagrid identified several vulnerabilities in Lantronix EDS-MD IoT gateway for medical devices, one which could be leveraged by a user with access to the web interface to execute arbitrary commands as root on the underlying Linux host.
Balada Injector Infects Over 7,100 WordPress Sites Using Plugin Vulnerability
15.1.24
Virus
The Hacker News
Thousands of WordPress sites using a vulnerable version
of the Popup Builder plugin have been compromised with a malware called Balada
Injector.
First documented by Doctor Web in January 2023, the campaign takes place in a series of periodic attack waves, weaponizing security flaws WordPress plugins to inject backdoor designed to redirect visitors of infected sites to bogus tech support pages, fraudulent lottery wins, and push notification scams.
Subsequent findings unearthed by Sucuri have revealed the massive scale of the operation, which is said to have been active since 2017 and infiltrated no less than 1 million sites since then.
The GoDaddy-owned website security company, which detected the latest Balada Injector activity on December 13, 2023, said it identified the injections on over 7,100 sites.
These attacks take advantage of a high-severity flaw in Popup Builder (CVE-2023-6000, CVSS score: 8.8) – a plugin with more than 200,000 active installs – that was publicly disclosed by WPScan a day before. The issue was addressed in version 4.2.3.
"When successfully exploited, this vulnerability may let attackers perform any action the logged‑in administrator they targeted is allowed to do on the targeted site, including installing arbitrary plugins, and creating new rogue Administrator users," WPScan researcher Marc Montpas said.
The ultimate goal of the campaign is to insert a malicious JavaScript file hosted on specialcraftbox[.]com and use it to take control of the website and load additional JavaScript in order to facilitate malicious redirects.
Furthermore, the threat actors behind Balada Injector are known to establish persistent control over compromised sites by uploading backdoors, adding malicious plugins, and creating rogue blog administrators.
This is often accomplished by using the JavaScript injections to specifically target logged-in site administrators.
"The idea is when a blog administrator logs into a website, their browser contains cookies that allow them to do all their administrative tasks without having to authenticate themselves on every new page," Sucuri researcher Denis Sinegubko noted last year.
"So, if their browser loads a script that tries to emulate administrator activity, it will be able to do almost anything that can be done via the WordPress admin interface."
The new wave is no exception in that if logged-in admin cookies are detected, it weaponizes the elevated privileges to install and activate a rogue backdoor plugin ("wp-felody.php" or "Wp Felody") so as to fetch a second-stage payload from the aforementioned domain.
The payload, another backdoor, is saved under the name "sasas" to the directory where temporary files are stored, and is then executed and deleted from disk.
"It checks up to three levels above the current directory, looking for the root directory of the current site and any other sites that may share the same server account," Sinegubko said.
"Then, in the detected site root directories, it modifies the wp-blog-header.php file to inject the same Balada JavaScript malware as was originally injected via the Popup Builder vulnerability."
DDoS Attacks on the Environmental Services Industry Surge by 61,839% in 2023
15.1.24
Attack
The Hacker News
The environmental services industry witnessed an
"unprecedented surge" in HTTP-based distributed denial-of-service (DDoS)
attacks, accounting for half of all its HTTP traffic.
This marks a 61,839% increase in DDoS attack traffic year-over-year, web infrastructure and security company Cloudflare said in its DDoS threat report for 2023 Q4 published last week.
"This surge in cyber attacks coincided with COP 28, which ran from November 30th to December 12th, 2023," security researchers Omer Yoachimik and Jorge Pacheco said, describing it as a "disturbing trend in the cyber threat landscape."
The uptick in HTTP attacks targeting environmental services websites is part of a larger trend observed annually over the past few years, specifically during COP 26 and COP 27, as well as other United Nations environment-related resolutions or announcements.
"This recurring pattern underscores the growing intersection between environmental issues and cyber security, a nexus that is increasingly becoming a focal point for attackers in the digital age," the researchers said.
Despite the environmental services sector becoming a new target in Q4 2023, the cryptocurrency industry continues to be the primary casualty in terms of the volume of HTTP DDoS attack requests.
With more than 330 billion HTTP requests targeting it, the attack traffic represents more than 4% of all HTTP DDoS traffic for the quarter. Gaming and gambling and telecommunications emerged as the second and third most attacked industries.
On the other end of the spectrum are the U.S. and China, acting as the main sources of HTTP DDoS attack traffic. It's worth noting that the U.S. has been the largest source of HTTP DDoS attacks for five consecutive quarters since Q4 2022.

"Together, China and the U.S. account for a little over a quarter of all HTTP
DDoS attack traffic in the world," the researchers said. "Brazil, Germany,
Indonesia, and Argentina account for the next 25%."
The development comes amid a heavy onslaught of DDoS attacks targeting Palestinian banking, information technology (IT), and internet platforms following the onset of the Israel-Hamas War and Israel's counteroffensive codenamed Operation Iron Swords.
The percentage of DDoS attack traffic targeting Palestinian websites grew by 1,126% quarter-over-quarter, Cloudflare said, adding DDoS attack traffic targeting Taiwan registered a 3,370% growth amidst the Taiwanese presidential elections and rising tensions with China.
Akamai, which also published its own retrospective on DDoS Trends in 2023, said "DDoS attacks became more frequent, longer, highly sophisticated (with multiple vectors), and focused on horizontal targets (attacking multiple IP destinations in the same attack event)."
The findings also follow a report from Cloudflare about the increasing threat posed by unmanaged or unsecured API endpoints, which could enable threat actors to exfiltrate potentially sensitive information.
"HTTP anomalies — the most frequent threat toward APIs — are common signals of malicious API requests," the company said. "More than half (51.6%) of traffic errors from API origins comprised '429' error codes: 'Too Many Requests.'"
New Findings Challenge Attribution in Denmark's Energy Sector Cyberattacks
14.1.24
BigBrothers
The Hacker News
The cyber attacks targeting the energy sector in Denmark
last year may not have had the involvement of the Russia-linked Sandworm hacking
group, new findings from Forescout show.
The intrusions, which targeted around 22 Danish energy organizations in May 2023, occurred in two distinct waves, one which exploited a security flaw in Zyxel firewall (CVE-2023-28771) and a follow-on activity cluster that saw the attackers deploy Mirai botnet variants on infected hosts via an as-yet-unknown initial access vector.
The first wave took place on May 11, while the second wave lasted from May 22 to 31, 2023. In one such attack detected on May 24, it was observed that the compromised system was communicating with IP addresses (217.57.80[.]18 and 70.62.153[.]174) that were previously used as command-and-control (C2) for the now-dismantled Cyclops Blink botnet.
Forescout's closer examination of the attack campaign, however, has revealed
that not only were the two waves unrelated, but also unlikely the work of the
state-sponsored group owing to the fact the second wave was part of a broader
mass exploitation campaign against unpatched Zyxel firewalls. It's currently not
known who is behind the twin sets of attacks.
"The campaign described as the 'second wave' of attacks on Denmark, started before and continued after [the 10-day time period], targeting firewalls indiscriminately in a very similar manner, only changing staging servers periodically," the company said in a report aptly titled "Clearing the Fog of War."
There is evidence to suggest that the attacks may have started as early as February 16 using other known flaws Zyxel devices (CVE-2020-9054 and CVE-2022-30525) alongside CVE-2023-28771, and persisted as late as October 2023, with the activity singling out various entities across Europe and the U.S.
"This is further evidence that exploitation of CVE-2023-27881, rather than being limited to Danish critical infrastructure, is ongoing and targeting exposed devices, some of which just happen to be Zyxel firewalls safeguarding critical infrastructure organizations," Forescout added.
Critical RCE Vulnerability Uncovered in Juniper SRX Firewalls and EX Switches
13.1.24
Vulnerebility
The Hacker News
Juniper Networks has released updates to fix a critical
remote code execution (RCE) vulnerability in its SRX Series firewalls and EX
Series switches.
The issue, tracked as CVE-2024-21591, is rated 9.8 on the CVSS scoring system.
"An out-of-bounds write vulnerability in J-Web of Juniper Networks Junos OS SRX Series and EX Series allows an unauthenticated, network-based attacker to cause a Denial-of-Service (DoS) or Remote Code Execution (RCE) and obtain root privileges on the device," the company said in an advisory.
The networking equipment major, which is set to be acquired by Hewlett Packard Enterprise (HPE) for $14 billion, said the issue is caused by use of an insecure function allowing a bad actor to overwrite arbitrary memory.
The flaw impacts the following versions, and has been fixed in versions 20.4R3-S9, 21.2R3-S7, 21.3R3-S5, 21.4R3-S5, 22.1R3-S4, 22.2R3-S3, 22.3R3-S2, 22.4R2-S2, 22.4R3, 23.2R1-S1, 23.2R2, 23.4R1, and later -
Junos OS versions earlier than 20.4R3-S9
Junos OS 21.2 versions earlier than
21.2R3-S7
Junos OS 21.3 versions earlier than 21.3R3-S5
Junos OS 21.4
versions earlier than 21.4R3-S5
Junos OS 22.1 versions earlier than 22.1R3-S4
Junos OS 22.2 versions earlier than 22.2R3-S3
Junos OS 22.3 versions earlier
than 22.3R3-S2, and
Junos OS 22.4 versions earlier than 22.4R2-S2, 22.4R3
As temporary workarounds until the fixes are deployed, the company recommends
that users disable J-Web or restrict access to only trusted hosts.
Also resolved by Juniper Networks is a high-severity bug in Junos OS and Junos OS Evolved (CVE-2024-21611, CVSS score: 7.5) that could be weaponized by an unauthenticated, network-based attacker to cause a DoS condition.
While there is evidence that the vulnerabilities are being exploited in the wild, multiple security shortcomings affecting the company's SRX firewalls and EX switches were abused by threat actors last year.
29-Year-Old Ukrainian Cryptojacking Kingpin Arrested for Exploiting Cloud
Services
13.1.24
Cryptocurrency
The Hacker News
A 29-year-old Ukrainian national has been arrested in connection with running a
"sophisticated cryptojacking scheme," netting them over $2 million (€1.8
million) in illicit profits.
The person was apprehended in Mykolaiv, Ukraine, on January 9 by the National Police of Ukraine with support from Europol and an unnamed cloud service provider following "months of intensive collaboration."
"A cloud provider approached Europol back in January 2023 with information regarding compromised cloud user accounts of theirs," Europol said, adding it shared the intelligence with the Ukrainian authorities.
As part of the probe, three properties were searched to unearth evidence against the suspect.
Cryptojacking refers to a type of cyber crime that entails the unauthorized use of a person's or organization's computing resources to mine cryptocurrencies.
On the cloud, such attacks are typically carried out by infiltrating the infrastructure via compromised credentials obtained through other means and installing miners that use the infected host's processing power to mine crypto without their knowledge or consent.
"If the credentials do not have the threat actors' desired permissions, privilege escalation techniques are used to obtain additional permissions," Microsoft noted in July 2023. "In some cases, threat actors hijack existing subscriptions to further obfuscate their operations."
The core idea is to avoid paying for necessary infrastructure required to mine cryptocurrencies, either by taking advantage of free trials or compromising legitimate tenants to conduct cryptojacking attacks.
In October 2023, Palo Alto Networks Unit 42 detailed a cryptojacking campaign in which threat actors were found stealing Amazon Web Services (AWS) credentials from GitHub repositories within five minutes of their public disclosure to mine Monero.
Nation-State Actors Weaponize Ivanti VPN Zero-Days, Deploying 5 Malware Families
13.1.24
Exploit
The Hacker News
As many as five different malware families were deployed
by suspected nation-state actors as part of post-exploitation activities
leveraging two zero-day vulnerabilities in Ivanti Connect Secure (ICS) VPN
appliances since early December 2023.
"These families allow the threat actors to circumvent authentication and provide backdoor access to these devices," Mandiant said in an analysis published this week. The Google-owned threat intelligence firm is tracking the threat actor under the moniker UNC5221.
The attacks leverage an exploit chain comprising an authentication bypass flaw (CVE-2023-46805) and a code injection vulnerability (CVE-2024-21887) to take over susceptible instances.
Volexity, which attributed the activity to a suspected Chinese espionage actor named UTA0178, said the twin flaws were used to gain initial access, deploy webshells, backdoor legitimate files, capture credentials and configuration data, and pivot further into the victim environment.
According to Ivanti, the intrusions impacted less than 10 customers, indicating that this could be a highly-targeted campaign. Patches for the two vulnerabilities (informally called ConnectAround) are expected to become available in the week of January 22.
Mandiant's analysis of the attacks has revealed the presence of five different custom malware families, besides injecting malicious code into legitimate files within ICS and using other legitimate tools like BusyBox and PySoxy to facilitate subsequent activity.
"Due to certain sections of the device being read-only, UNC5221 leveraged a Perl script (sessionserver.pl) to remount the filesystem as read/write and enable the deployment of THINSPOOL, a shell script dropper that writes the web shell LIGHTWIRE to a legitimate Connect Secure file, and other follow-on tooling," the company said.
LIGHTWIRE is one of the two web shells, the other being WIREFIRE, which are "lightweight footholds" designed to ensure persistent remote access to compromised devices. While LIGHTWIRE is written in Perl CGI, WIREFIRE is implemented in Python.
Also used in the attacks are a JavaScript-based credential stealer dubbed WARPWIRE and a passive backdoor named ZIPLINE that's capable of downloading/uploading files, establishing a reverse shell, creating a proxy server, and setting up a tunneling server to dispatch traffic between multiple endpoints.
"This indicates that these are not opportunistic attacks, and UNC5221 intended to maintain its presence on a subset of high priority targets that it compromised after a patch was inevitably released," Mandiant further added.
UNC5221 has not been linked to any previously known group or a particular country, although the targeting of edge infrastructure by weaponizing zero-day flaws and the use of compromise command-and-control (C2) infrastructure to bypass detection bears all the hallmarks of an advanced persistent threat (APT).
"UNC5221's activity demonstrates that exploiting and living on the edge of networks remains a viable and attractive target for espionage actors," Mandiant said.
Medusa Ransomware on the Rise: From Data Leaks to Physical Threats
12.1.24
Ransom
The Hacker News
The threat actors associated with the Medusa ransomware
have ramped up their activities following the debut of a dedicated data leak
site on the dark web in February 2023 to publish sensitive data of victims who
are unwilling to agree to their demands.
"As part of their multi-extortion strategy, this group will provide victims with multiple options when their data is posted on their leak site, such as time extension, data deletion or download of all the data," Palo Alto Networks Unit 42 researchers Anthony Galiette and Doel Santos said in a report shared with The Hacker News.
"All of these options have a price tag depending on the organization impacted by this group."
Medusa (not to be confused with Medusa Locker) refers to a ransomware family that appeared in late 2022 before coming into prominence in 2023. It's known for opportunistically targeting a wide range of industries such as high technology, education, manufacturing, healthcare, and retail.
As many as 74 organizations, mostly in the U.S., the U.K., France, Italy, Spain, and India, are estimated to have been impacted by the ransomware in 2023.
Ransomware attacks orchestrated by the group commence with the exploitation of internet-facing assets or applications with known unpatched vulnerabilities and hijacking of legitimate accounts, often employing initial access brokers to obtain a foothold to target networks.
In one instance observed by the cybersecurity firm, a Microsoft Exchange Server was exploited to upload a web shell, which was then used as a conduit to install and execute the ConnectWise remote monitoring and management (RMM) software.
A notable aspect of the infections is the reliance on living-off-the-land (LotL) techniques to blend in with legitimate activity and sidestep detection. Also observed is the use of a pair of kernel drivers to terminate a hard-coded list of security products.
The initial access phase is followed by discovery and reconnaissance of the compromised network, with the actors ultimately launching the ransomware to enumerate and encrypt all files save for those with the extensions .dll, .exe, .lnk, and .medusa (the extension given to the encrypted files).
For each compromised victim, Medusa's leak site displays information about the organizations, ransom demanded, the amount of time left before the stolen data is released publicly, and the number of views in a bid to exert pressure on the company.
The actors also offer different choices to the victim, all of which involve some
form of extortion to delete or download the pilfered data and seek a time
extension to prevent the data from being released.
As ransomware continues to be a rampant threat, targeting tech companies, healthcare, critical infrastructure, and everything in between, the threat actors behind it are getting more brazen with their tactics, going beyond publicly naming and shaming organizations by resorting to threats of physical violence and even dedicated public relations channels.
"Ransomware has changed many facets of the threat landscape, but a key recent development is its increasing commoditization and professionalization," Sophos researchers said last month, calling ransomware gangs "increasingly media-savvy."
Medusa, per Unit 42, not only has a media team to likely handle their branding efforts, but also leverages a public Telegram channel named "information support," where files of compromised organizations are shared and can be accessed over the clearnet. The channel was set up in July 2021.
"The emergence of the Medusa ransomware in late 2022 and its notoriety in 2023 marks a significant development in the ransomware landscape," the researchers said. "This operation showcases complex propagation methods, leveraging both system vulnerabilities and initial access brokers, while adeptly avoiding detection through living-off-the-land techniques."
The development comes as Arctic Wolf Labs publicized two cases in which victims of Akira and Royal ransomware gangs were targeted by malicious third-parties posing as security researchers for secondary extortion attempts.
"Threat actors spun a narrative of trying to help victim organizations, offering to hack into the server infrastructure of the original ransomware groups involved to delete exfiltrated data," security researchers Stefan Hostetler and Steven Campbell said, noting the threat actor sought about 5 bitcoin in exchange for the service.
It also follows a new advisory from the Finnish National Cyber Security Centre (NCSC-FI) about a spike in Akira ransomware incidents in the country towards the end of 2023 by exploiting a security flaw in Cisco VPN appliances (CVE-2023-20269, CVSS score: 5.0) to breach domestic entities.
Cryptominers Targeting Misconfigured Apache Hadoop and Flink with Rootkit in New
Attacks
12.1.24
Cryptocurrency
The Hacker News
Cybersecurity researchers have identified a new attack
that exploits misconfigurations in Apache Hadoop and Flink to deploy
cryptocurrency miners within targeted environments.
"This attack is particularly intriguing due to the attacker's use of packers and rootkits to conceal the malware," Aqua security researchers Nitzan Yaakov and Assaf Morag said in an analysis published earlier this week. "The malware deletes contents of specific directories and modifies system configurations to evade detection."
The infection chain targeting Hadoop leverages a misconfiguration in the YARN's (Yet Another Resource Negotiator) ResourceManager, which is responsible for tracking resources in a cluster and scheduling applications.
Specifically, the misconfiguration can be exploited by an unauthenticated, remote threat actor to execute arbitrary code by means of a crafted HTTP request, subject to the privileges of the user on the node where the code is executed.
The attacks aimed at Apache Flink, likewise, take aim at a misconfiguration that permits a remote attacker to achieve code execution sans any authentication.
These misconfigurations are not novel and have been exploited in the past by financially motivated groups like TeamTNT, which is known for its history of targeting Docker and Kubernetes environments for the purpose of cryptojacking and other malicious activities.
But what makes the latest set of attacks noteworthy is the use of rootkits to hide crypto mining processes after obtaining an initial foothold into Hadoop and Flink applications.
"The attacker sends an unauthenticated request to deploy a new application," the researchers explained. "The attacker is able to run a remote code by sending a POST request to the YARN, requesting to launch the new application with the attacker's command."
The command is purpose-built to clear the /tmp directory of all existing content, fetch a file called "dca" from a remote server, and execute it, followed by deleting all files in the /tmp directory once again.
The executed payload is a packed ELF binary that acts as a downloader to retrieve two rootkits and a Monero cryptocurrency miner binary. It's worth pointing out that various adversaries, including Kinsing, have resorted to employing rootkits to conceal the presence of the mining process.
To achieve persistence, a cron job is created to download and execute a shell script that deploys the 'dca' binary. Further analysis of the threat actor's infrastructure reveals that the staging server used to fetch the downloader was registered on October 31, 2023.
As mitigations, it's recommended that organizations deploy agent-based security solutions to detect cryptominers, rootkits, obfuscated or packed binaries, as well as other suspicious runtime behaviors.
Act Now: CISA Flags Active Exploitation of Microsoft SharePoint Vulnerability
12.1.24
Exploit
The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical security vulnerability impacting Microsoft SharePoint Server to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation.
The issue, tracked as CVE-2023-29357 (CVSS score: 9.8), is a privilege escalation flaw that could be exploited by an attacker to gain administrator privileges. Microsoft released patches for the bug as part of its June 2023 Patch Tuesday updates.
"An attacker who has gained access to spoofed JWT authentication tokens can use them to execute a network attack which bypasses authentication and allows them to gain access to the privileges of an authenticated user," Redmond said. "The attacker needs no privileges nor does the user need to perform any action."
Security researcher Nguyễn Tiến Giang (Jang) of StarLabs SG demonstrated an exploit for the flaw at the Pwn2Own Vancouver hacking contest last year, earning a $100,000 prize.
The pre-authenticated remote code execution chain combines authentication bypass (CVE-2023–29357) with a code injection bug (CVE-2023-24955, CVSS score: 7.2), the latter of which was patched by Microsoft in May 2023.
"The process of discovering and crafting the exploit chain consumed nearly a year of meticulous effort and research to complete the full exploit chain," Tiến Giang noted in a technical report published in September 2023.
Additional specifics of the real-world exploitation of CVE-2023–29357 and the identity of the threat actors that may be abusing them are presently unknown. That said, federal agencies are recommended to apply the patches by January 31, 2024, to secure against the active threat.
Threat Actors Increasingly Abusing GitHub for Malicious Purposes
12.1.24
Virus
The Hacker News
The ubiquity of GitHub in information technology (IT)
environments has made it a lucrative choice for threat actors to host and
deliver malicious payloads and act as dead drop resolvers, command-and-control,
and data exfiltration points.
"Using GitHub services for malicious infrastructure allows adversaries to blend in with legitimate network traffic, often bypassing traditional security defenses and making upstream infrastructure tracking and actor attribution more difficult," Recorded Future said in a report shared with The Hacker News.
The cybersecurity firm described the approach as "living-off-trusted-sites" (LOTS), a spin on the living-off-the-land (LotL) techniques often adopted by threat actors to conceal rogue activity and fly under the radar.
Prominent among the methods by which GitHub is abused relates to payload delivery, with some actors leveraging its features for command-and-control (C2) obfuscation. Last month, ReversingLabs detailed a number of rogue Python packages that relied on a secret gist hosted on GitHub to receive malicious commands on the compromised hosts.
While full-fledged C2 implementations in GitHub are uncommon in comparison to other infrastructure schemes, its use by threat actors as a dead drop resolver – wherein the information from an actor-controlled GitHub repository is used to obtain the actual C2 URL – is a lot more prevalent, as evidenced in the case of malware like Drokbk and ShellBox.
Also rarely observed is the abuse of GitHub for data exfiltration, which, per Recorded Future, is likely due to file size and storage limitations and concerns around discoverability.
Outside of these four main schemes, the platform's offerings are put to use in various other ways in order to meet infrastructure-related purposes. For instance, GitHub Pages have been used as phishing hosts or traffic redirectors, with some campaigns utilizing GitHub repositories as a backup C2 channel.
The development speaks to the broader trend of legitimate internet services such as Google Drive, Microsoft OneDrive, Dropbox, Notion, Firebase, Trello, and Discord being exploited by threat actors. This also extends to other source code and version control platforms like GitLab, BitBucket, and Codeberg.
"There is no universal solution for GitHub abuse detection," the company said. "A mix of detection strategies is needed, influenced by specific environments and factors such as the availability of logs, organizational structure, service usage patterns, and risk tolerance, among others."
New PoC Exploit for Apache OfBiz Vulnerability Poses Risk to ERP Systems
12.1.24
Exploit
The Hacker News
Cybersecurity researchers have developed a
proof-of-concept (PoC) code that exploits a recently disclosed critical flaw in
the Apache OfBiz open-source Enterprise Resource Planning (ERP) system to
execute a memory-resident payload.
The vulnerability in question is CVE-2023-51467 (CVSS score: 9.8), a bypass for another severe shortcoming in the same software (CVE-2023-49070, CVSS score: 9.8) that could be weaponized to bypass authentication and remotely execute arbitrary code.
While it was fixed in Apache OFbiz version 18.12.11 released last month, threat actors have been observed attempting to exploit the flaw, targeting vulnerable instances.
The latest findings from VulnCheck show that CVE-2023-51467 can be exploited to execute a payload directly from memory, leaving little to no traces of malicious activity.
Security flaws disclosed in Apache OFBiz (e.g., CVE-2020-9496) have been exploited by threat actors in the past, including by threat actors associated with the Sysrv botnet. Another three-year-old bug in the software (CVE-2021-29200) has witnessed exploitation attempts from 29 unique IP addresses over the past 30 days, per data from GreyNoise.
What's more, Apache OFBiz was also one of the first products to have a public exploit for Log4Shell (CVE-2021-44228), illustrating that it continues to be of interest to both defenders and attackers alike.
CVE-2023-51467 is no exception, with details about a remote code execution
endpoint ("/webtools/control/ProgramExport") as well as PoC for command
execution emerging merely days after public disclosure.
While security guardrails (i.e., Groovy sandbox) have been erected such that they block any attempts to upload arbitrary web shells or run Java code via the endpoint, the incomplete nature of the sandbox means that an attacker could run curl commands and obtain a bash reverse shell on Linux systems.
"For an advanced attacker, though, these payloads aren't ideal," VulnCheck's Chief Technology Officer Jacob Baines said. "They touch the disk and rely on Linux-specific behavior."
The Go-based exploit devised by VulnCheck is a cross-platform solution that works on both Windows and Linux as well as gets around the denylist by taking advantage of groovy.util.Eval functions to launch an in-memory Nashorn reverse shell as the payload.
"OFBiz is not widely popular, but it has been exploited in the past. There is a fair deal of hype around CVE-2023-51467 but no public weaponized payload, which called into question if it was even possible," Baines said. "We've concluded that not only is it possible, but we can achieve arbitrary in memory code execution."
New Python-based FBot Hacking Toolkit Aims at Cloud and SaaS Platforms
12.1.24
Hacking
The Hacker News
A new Python-based hacking tool called FBot has been uncovered targeting web
servers, cloud services, content management systems (CMS), and SaaS platforms
such as Amazon Web Services (AWS), Microsoft 365, PayPal, Sendgrid, and Twilio.
"Key features include credential harvesting for spamming attacks, AWS account hijacking tools, and functions to enable attacks against PayPal and various SaaS accounts," SentinelOne security researcher Alex Delamotte said in a report shared with The Hacker News.
FBot is the latest addition to the list of cloud hacking tools like AlienFox, GreenBot (aka Maintance), Legion, and Predator, the latter four of which share code-level overlaps with AndroxGh0st.
SentinelOne described FBot as "related but distinct from these families," owing to the fact that it does not reference any source code from AndroxGh0st, although it exhibits similarities with Legion, which first came to light last year.
The end goal of the tool is to hijack cloud, SaaS, and web services as well as harvest credentials to obtain initial access and monetize it by selling the access to other actors.
FBot, in addition to generating API keys for AWS and Sendgrid, packs an assortment of features to generate random IP addresses, run reverse IP scanners, and even validate PayPal accounts and the email addresses associated with those accounts.
"The script initiates the Paypal API request via the website hxxps://www.robertkalinkin.com/index.php, which is a Lithuanian fashion designer's retail sales website," Delamotte noted. "Interestingly, all identified FBot samples use this website to authenticate the Paypal API requests, and several Legion Stealer samples do as well."
On top of that, FBot packs in AWS-specific features to check for AWS Simple Email Service (SES) email configuration details and determine the targeted account's EC2 service quotas. The Twilio-related functionality, likewise, is utilized to gather specifics about the account, namely the balance, currency, and phone numbers connected to the account.
The features don't end there, for the malware is also capable of extracting credentials from Laravel environment files.
The cybersecurity firm said it uncovered samples starting from July 2022 to as recently as this month, suggesting that it is being actively used in the wild. That said, it's currently not known if the tool is actively maintained and how it's distributed to other players.
"We found indications that FBot is the product of private development work, so contemporary builds may be distributed through a smaller scale operation," Delamotte said.
"This aligns with the theme of cloud attack tools being bespoke 'private bots' tailored for the individual buyer, which is a theme prevalent among AlienFox builds."
Atomic Stealer Gets an Upgrade - Targeting Mac Users with Encrypted Payload
11.1.24
OS
The Hacker News
Cybersecurity researchers have identified an updated
version of a macOS information stealer called Atomic (or AMOS), indicating that
the threat actors behind the malware are actively enhancing its capabilities.
"It looks like Atomic Stealer was updated around mid to late December 2023, where its developers introduced payload encryption in an effort to bypass detection rules," Malwarebytes' Jérôme Segura said in a Wednesday report.
Atomic Stealer first emerged in April 2023 for a monthly subscription of $1,000. It's capable of harvesting sensitive information from a compromised host, including Keychain passwords, session cookies, files, crypto wallets, system metadata, and the machine's password via a fake prompt.
Over the past several months, the malware has been observed propagated via malvertising and compromised sites under the guise of legitimate software and web browser updates.
Malwarebytes' latest analysis shows that Atomic Stealer is now being sold for a hefty $3,000/month rental fee, with the actors running a promotion coinciding with Christmas, offering the malware for a discounted price of $2,000.
Besides incorporating encryption to thwart detection by security software,
campaigns distributing Atomic Stealer have undergone a slight shift, wherein
Google search ads impersonating Slack are used as conduits to deploy Atomic
Stealer or a malware loader called EugenLoader (aka FakeBat) depending on the
operating system.
It's worth noting that a malvertising campaign spotted in September 2023 leveraged a fraudulent site for the TradingView charting platform to deliver NetSupport RAT, if visited from Windows, and Atomic Stealer, if the operating system is macOS.
The rogue Slack disk image (DMG) file, upon opening, prompts the victim to enter their system password, thereby allowing threat actors to gather sensitive information that are access-restricted. Another crucial aspect of the new version is the use of obfuscation to conceal the command-and-control server that receives the stolen information.
"As stealers continue to be a top threat for Mac users, it is important to download software from trusted locations," Segura said. "Malicious ads and decoy sites can be very misleading though and it only takes a single mistake (entering your password) for the malware to collect and exfiltrate your data."
Mandiant's X Account Was Hacked Using Brute-Force Attack
11.1.24
Attack
The Hacker News
The compromise of Mandiant's X (formerly Twitter) account
last week was likely the result of a "brute-force password attack," attributing
the hack to a drainer-as-a-service (DaaS) group.
"Normally, [two-factor authentication] would have mitigated this, but due to some team transitions and a change in X's 2FA policy, we were not adequately protected," the threat intelligence firm said in a post shared on X.
The attack, which took place on January 3, 2023, enabled the threat actor to take control of the company's X account and distribute links to a phishing page hosting a cryptocurrency drainer tracked as CLINKSINK.
Drainers refer to malicious scripts and smart contracts that facilitate the theft of digital assets from the victim's wallets after they are tricked into approving the transactions.
According to the Google-owned subsidiary, multiple threat actors are believed to have leveraged CLINKSINK since December 2023 to siphon funds and tokens from Solana (SOL) cryptocurrency users.
As observed in the case of other drainers like Angel Drainer and Inferno Drainer, affiliates are roped in by the DaaS operators to conduct the attacks in exchange for a cut (typically 20%) of the stolen assets.
The identified activity cluster involves at least 35 affiliate IDs and 42 unique Solana wallet addresses, collectively netting the actors no less than $900,000 in illegal profits.
The attack chains involve the use of social media and chat applications such as X and Discord to distribute cryptocurrency-themed phishing pages that encourage the targets to connect their wallets to claim a bogus token airdrop.
"After connecting their wallet, the victim is then prompted to sign a transaction to the drainer service, which allows it to siphon funds from the victim," security researchers Zach Riddle, Joe Dobson, Lukasz Lamparski, and Stephen Eckels said.
CLINKSINK, a JavaScript drainer, is designed to open a pathway to the targeted wallets, check the current balance on the wallet, and ultimately pull off the theft after asking the victim to sign a fraudulent transaction. This also means that the attempted theft will not succeed if the victim rejects the transaction.
The drainer has also spawned several variants, including Chick Drainer (or Rainbow Drainer), raising the possibility that the source code is available to multiple threat actors, allowing them to mount independent draining campaigns.
"The wide availability and low cost of many drainers, combined with a relatively high potential for profit, likely makes them attractive operations for many financially motivated actors," Mandiant said.
"Given the increase in cryptocurrency values and the low barrier to entry for draining operations, we anticipate that financially motivated threat actors of varying levels of sophistication will continue to conduct drainer operations for the foreseeable future."
The development comes amid an uptick in attacks targeting legitimate X accounts to spread cryptocurrency scams.
Earlier this week, the X account associated with the U.S. Securities and Exchange Commission (SEC) was breached to falsely claim that the regulatory body had approved the "listing and trading of spot bitcoin exchange-traded products," causing bitcoin prices to spike briefly.
X has since revealed the hack was the result of "an unidentified individual obtaining control over a phone number associated with the @SECGov account through a third-party," and that the account did not have two-factor authentication enabled.
Chinese Hackers Exploit Zero-Day Flaws in Ivanti Connect Secure and Policy
Secure
11.1.24
Vulnerebility
The Hacker News
A pair of zero-day flaws identified in Ivanti Connect
Secure (ICS) and Policy Secure have been chained by suspected China-linked
nation-state actors to breach less than 10 customers.
Cybersecurity firm Volexity, which identified the activity on the network of one of its customers in the second week of December 2023, attributed it to a hacking group it tracks under the name UTA0178. There is evidence to suggest that the VPN appliance may have been compromised as early as December 3, 2023.
The two vulnerabilities that have been exploited in the wild to achieve unauthenticated command execution on the ICS device are as follows -
CVE-2023-46805 (CVSS score: 8.2) - An authentication bypass vulnerability in the
web component of Ivanti Connect Secure (9.x, 22.x) and Ivanti Policy Secure
allows a remote attacker to access restricted resources by bypassing control
checks.
CVE-2024-21887 (CVSS score: 9.1) - A command injection vulnerability
in web components of Ivanti Connect Secure (9.x, 22.x) and Ivanti Policy Secure
allows an authenticated administrator to send specially crafted requests and
execute arbitrary commands on the appliance.
The vulnerabilities can be
fashioned into an exploit chain to take over susceptible instances over the
internet.
"If CVE-2024-21887 is used in conjunction with CVE-2023-46805, exploitation does not require authentication and enables a threat actor to craft malicious requests and execute arbitrary commands on the system," Ivanti said in an advisory.
The company said it has observed attempts on the part of the threat actors to manipulate Ivanti's internal integrity checker (ICT), which offers a snapshot of the current state of the appliance.
Patches are expected to be released in a staggered manner starting from the week of January 22, 2024. In the interim, users have been recommended to apply a workaround to safeguard against potential threats.
In the incident analyzed by Volexity, the twin flaws are said to have been employed to "steal configuration data, modify existing files, download remote files, and reverse tunnel from the ICS VPN appliance."
The attacker further modified a legitimate CGI file (compcheck.cgi) on the ICS VPN appliance to allow command execution. In addition, a JavaScript file loaded by the Web SSL VPN login page was altered to log keystrokes and exfiltrate credentials associated with users logging into the device.
"The information and credentials collected by the attacker allowed them to pivot to a handful of systems internally, and ultimately gain unfettered access to systems on the network," Volexity researchers Matthew Meltzer, Robert Jan Mora, Sean Koessel, Steven Adair, and Thomas Lancaster said.
The attacks are also characterized by reconnaissance efforts, lateral movement, and the deployment of a custom web shell dubbed GLASSTOKEN via the backdoored CGI file to maintain persistent remote access to the external-facing web servers.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA), in an alert of its own, said it has added the two shortcomings to its Known Exploited Vulnerabilities (KEV) catalog, urging federal agencies to apply the fixes by January 31, 2024.
"Internet-accessible systems, especially critical devices like VPN appliances and firewalls, have once again become a favorite target of attackers," Volexity said.
"These systems often sit on critical parts of the network, cannot run traditional security software, and typically sit at the perfect place for an attacker to operate. Organizations need to make sure they have a strategy in place to be able to monitor activity from these devices and quickly respond if something unexpected occurs."
Cisco Fixes High-Risk Vulnerability Impacting Unity Connection Software
11.1.24
Vulnerebility
The Hacker News
Cisco has released software updates to address a critical
security flaw impacting Unity Connection that could permit an adversary to
execute arbitrary commands on the underlying system.
Tracked as CVE-2024-20272 (CVSS score: 7.3), the vulnerability is an arbitrary file upload bug residing in the web-based management interface and is the result of a lack of authentication in a specific API and improper validation of user-supplied data.
"An attacker could exploit this vulnerability by uploading arbitrary files to an affected system," Cisco said in an advisory released Wednesday. "A successful exploit could allow the attacker to store malicious files on the system, execute arbitrary commands on the operating system, and elevate privileges to root."
The flaw impacts the following versions of Cisco Unity Connection. Version 15 is not vulnerable.
12.5 and earlier (Fixed in version 12.5.1.19017-4)
14 (Fixed in version
14.0.1.14006-5)
Security researcher Maxim Suslov has been credited with
discovering and reporting the flaw. Cisco makes no mention of the bug being
exploited in the wild, but it's advised that users update to a fixed version to
mitigate potential threats.
Alongside the patch for CVE-2024-20272, Cisco has also shipped updates to resolve 11 medium-severity vulnerabilities spanning its software, including Identity Services Engine, WAP371 Wireless Access Point, ThousandEyes Enterprise Agent, and TelePresence Management Suite (TMS).
Cisco, however, noted that it does not intend to release a fix for the command injection bug in WAP371 (CVE-2024-20287, CVSS score: 6.5), stating that the device has reached end-of-life (EoL) as of June 2019. It's instead recommending customers migrate to the Cisco Business 240AC Access Point.
NoaBot: Latest Mirai-Based Botnet Targeting SSH Servers for Crypto Mining
11.1.24
BotNet
The Hacker News
A new Mirai-based botnet called NoaBot is being used by
threat actors as part of a crypto mining campaign since the beginning of 2023.
"The capabilities of the new botnet, NoaBot, include a wormable self-spreader and an SSH key backdoor to download and execute additional binaries or spread itself to new victims," Akamai security researcher Stiv Kupchik said in a report shared with The Hacker News.
Mirai, which had its source code leaked in 2016, has been the progenitor of a number of botnets, the most recent being InfectedSlurs, which is capable of mounting distributed denial-of-service (DDoS) attacks.
There are indications that NoaBot could be linked to another botnet campaign involving a Rust-based malware family known as P2PInfect, which recently received an update to target routers and IoT devices.
This is based on the fact that threat actors have also experimented with dropping P2PInfect in place of NoaBot in recent attacks targeting SSH servers, indicating likely attempts to pivot to custom malware.
Despite NaoBot's Mirai foundations, its spreader module leverages an SSH scanner to search for servers susceptible to dictionary attack in order to brute-force them and add an SSH public key in the .ssh/authorized_keys file for remote access. Optionally, it can also download and execute additional binaries post successful exploitation or propagate itself to new victims.
"NoaBot is compiled with uClibc, which seems to change how antivirus engines
detect the malware," Kupchik noted. "While other Mirai variants are usually
detected with a Mirai signature, NoaBot's antivirus signatures are of an SSH
scanner or a generic trojan."
Besides incorporating obfuscation tactics to render analysis challenging, the attack chain ultimately results in the deployment of a modified version of the XMRig coin miner.
What makes the new variant a cut above other similar Mirai botnet-based campaigns is that it does not contain any information about the mining pool or the wallet address, thereby making it impossible to assess the profitability of the illicit cryptocurrency mining scheme.
"The miner obfuscates its configuration and also uses a custom mining pool to avoid exposing the wallet address used by the miner," Kupchik said, highlighting some level of preparedness of the threat actors.
Akamai said it identified 849 victim IP addresses to date that are spread geographically across the world, with high concentrations reported in China, so much so that it amounts to almost 10% of all attacks against its honeypots in 2023.
"The malware's method of lateral movement is via plain old SSH credentials dictionary attacks," Kupchik said. "Restricting arbitrary internet SSH access to your network greatly diminishes the risks of infection. In addition, using strong (not default or randomly generated) passwords also makes your network more secure, as the malware uses a basic list of guessable passwords."
Microsoft January 2024 Patch Tuesday
10.1.24 Vulnerebility The Hacker News
| Description | |||||||
|---|---|---|---|---|---|---|---|
| CVE | Disclosed | Exploited | Exploitability (old versions) | current version | Severity | CVSS Base (AVG) | CVSS Temporal (AVG) |
| .NET Core and Visual Studio Denial of Service Vulnerability | |||||||
| CVE-2024-20672 | No | No | - | - | Important | 7.5 | 6.7 |
| .NET Framework Denial of Service Vulnerability | |||||||
| CVE-2024-21312 | No | No | - | - | Important | 7.5 | 6.7 |
| Azure Storage Mover Remote Code Execution Vulnerability | |||||||
| CVE-2024-20676 | No | No | - | - | Important | 8.0 | 7.0 |
| BitLocker Security Feature Bypass Vulnerability | |||||||
| CVE-2024-20666 | No | No | - | - | Important | 6.6 | 5.8 |
| Chromium: CVE-2024-0222 Use after free in ANGLE | |||||||
| CVE-2024-0222 | No | No | - | - | - | ||
| Chromium: CVE-2024-0223 Heap buffer overflow in ANGLE | |||||||
| CVE-2024-0223 | No | No | - | - | - | ||
| Chromium: CVE-2024-0224 Use after free in WebAudio | |||||||
| CVE-2024-0224 | No | No | - | - | - | ||
| Chromium: CVE-2024-0225 Use after free in WebGPU | |||||||
| CVE-2024-0225 | No | No | - | - | - | ||
| Hypervisor-Protected Code Integrity (HVCI) Security Feature Bypass Vulnerability | |||||||
| CVE-2024-21305 | No | No | - | - | Important | 4.4 | 3.9 |
| MITRE: CVE-2022-35737 SQLite allows an array-bounds overflow | |||||||
| CVE-2022-35737 | No | No | - | - | - | ||
| Microsoft AllJoyn API Denial of Service Vulnerability | |||||||
| CVE-2024-20687 | No | No | - | - | Important | 7.5 | 6.5 |
| Microsoft Bluetooth Driver Spoofing Vulnerability | |||||||
| CVE-2024-21306 | No | No | - | - | Important | 5.7 | 5.0 |
| Microsoft Common Log File System Elevation of Privilege Vulnerability | |||||||
| CVE-2024-20653 | No | No | - | - | Important | 7.8 | 6.8 |
| Microsoft Identity Denial of service vulnerability | |||||||
| CVE-2024-21319 | No | No | - | - | Important | 6.8 | 5.9 |
| Microsoft Local Security Authority Subsystem Service Information Disclosure Vulnerability | |||||||
| CVE-2024-20692 | No | No | - | - | Important | 5.7 | 5.0 |
| Microsoft Message Queuing Denial of Service Vulnerability | |||||||
| CVE-2024-20661 | No | No | - | - | Important | 7.5 | 6.5 |
| Microsoft Message Queuing Information Disclosure Vulnerability | |||||||
| CVE-2024-20660 | No | No | - | - | Important | 6.5 | 5.7 |
| CVE-2024-20664 | No | No | - | - | Important | 6.5 | 5.7 |
| CVE-2024-21314 | No | No | - | - | Important | 6.5 | 5.7 |
| Microsoft ODBC Driver Remote Code Execution Vulnerability | |||||||
| CVE-2024-20654 | No | No | - | - | Important | 8.0 | 7.0 |
| Microsoft Office Remote Code Execution Vulnerability | |||||||
| CVE-2024-20677 | No | No | - | - | Important | 7.8 | 6.8 |
| Microsoft Online Certificate Status Protocol (OCSP) Remote Code Execution Vulnerability | |||||||
| CVE-2024-20655 | No | No | - | - | Important | 6.6 | 5.8 |
| Microsoft Printer Metadata Troubleshooter Tool Remote Code Execution Vulnerability | |||||||
| CVE-2024-21325 | No | No | - | - | Important | ||
| Microsoft SharePoint Server Remote Code Execution Vulnerability | |||||||
| CVE-2024-21318 | No | No | - | - | Important | 8.8 | 7.7 |
| Microsoft Virtual Hard Disk Elevation of Privilege Vulnerability | |||||||
| CVE-2024-20658 | No | No | - | - | Important | 7.8 | 6.8 |
| Microsoft.Data.SqlClient and System.Data.SqlClient SQL Data Provider Security Feature Bypass Vulnerability | |||||||
| CVE-2024-0056 | No | No | - | - | Important | 8.7 | 7.6 |
| NET, .NET Framework, and Visual Studio Security Feature Bypass Vulnerability | |||||||
| CVE-2024-0057 | No | No | - | - | Important | 9.1 | 8.2 |
| Remote Desktop Client Remote Code Execution Vulnerability | |||||||
| CVE-2024-21307 | No | No | - | - | Important | 7.5 | 6.5 |
| Visual Studio Elevation of Privilege Vulnerability | |||||||
| CVE-2024-20656 | No | No | - | - | Important | 7.8 | 6.8 |
| Win32k Elevation of Privilege Vulnerability | |||||||
| CVE-2024-20683 | No | No | - | - | Important | 7.8 | 6.8 |
| CVE-2024-20686 | No | No | - | - | Important | 7.8 | 6.8 |
| Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability | |||||||
| CVE-2024-21310 | No | No | - | - | Important | 7.8 | 6.8 |
| Windows CoreMessaging Information Disclosure Vulnerability | |||||||
| CVE-2024-20694 | No | No | - | - | Important | 5.5 | 4.8 |
| Windows Cryptographic Services Information Disclosure Vulnerability | |||||||
| CVE-2024-21311 | No | No | - | - | Important | 5.5 | 4.8 |
| Windows Cryptographic Services Remote Code Execution Vulnerability | |||||||
| CVE-2024-20682 | No | No | - | - | Important | 7.8 | 6.8 |
| Windows Group Policy Elevation of Privilege Vulnerability | |||||||
| CVE-2024-20657 | No | No | - | - | Important | 7.0 | 6.1 |
| Windows HTML Platforms Security Feature Bypass Vulnerability | |||||||
| CVE-2024-20652 | No | No | - | - | Important | 7.5 | 6.5 |
| Windows Hyper-V Denial of Service Vulnerability | |||||||
| CVE-2024-20699 | No | No | - | - | Important | 5.5 | 4.8 |
| Windows Hyper-V Remote Code Execution Vulnerability | |||||||
| CVE-2024-20700 | No | No | - | - | Critical | 7.5 | 6.5 |
| Windows Kerberos Security Feature Bypass Vulnerability | |||||||
| CVE-2024-20674 | No | No | - | - | Critical | 9.0 | 7.8 |
| Windows Kernel Elevation of Privilege Vulnerability | |||||||
| CVE-2024-20698 | No | No | - | - | Important | 7.8 | 6.8 |
| Windows Kernel-Mode Driver Elevation of Privilege Vulnerability | |||||||
| CVE-2024-21309 | No | No | - | - | Important | 7.8 | 6.8 |
| Windows Libarchive Remote Code Execution Vulnerability | |||||||
| CVE-2024-20696 | No | No | - | - | Important | 7.3 | 6.4 |
| CVE-2024-20697 | No | No | - | - | Important | 7.3 | 6.4 |
| Windows Message Queuing Client (MSMQC) Information Disclosure | |||||||
| CVE-2024-20680 | No | No | - | - | Important | 6.5 | 5.7 |
| CVE-2024-20663 | No | No | - | - | Important | 6.5 | 5.7 |
| Windows Nearby Sharing Spoofing Vulnerability | |||||||
| CVE-2024-20690 | No | No | - | - | Important | 6.5 | 5.9 |
| Windows Online Certificate Status Protocol (OCSP) Information Disclosure Vulnerability | |||||||
| CVE-2024-20662 | No | No | - | - | Important | 4.9 | 4.3 |
| Windows Server Key Distribution Service Security Feature Bypass | |||||||
| CVE-2024-21316 | No | No | - | - | Important | 6.1 | 5.3 |
| Windows Subsystem for Linux Elevation of Privilege Vulnerability | |||||||
| CVE-2024-20681 | No | No | - | - | Important | 7.8 | 6.8 |
| Windows TCP/IP Information Disclosure Vulnerability | |||||||
| CVE-2024-21313 | No | No | - | - | Important | 5.3 | 4.6 |
| Windows Themes Information Disclosure Vulnerability | |||||||
| CVE-2024-20691 | No | No | - | - | Important | 4.7 | 4.1 |
| Windows Themes Spoofing Vulnerability | |||||||
| CVE-2024-21320 | No | No | - | - | Important | 6.5 | 5.7 |
Free Decryptor Released for Black Basta and Babuk's Tortilla Ransomware Victims
10.1.24
Ransom
The Hacker News
Free Ransomware Decryptor
A decryptor for the Tortilla
variant of the Babuk ransomware has been released by Cisco Talos, allowing
victims targeted by the malware to regain access to their files.
The cybersecurity firm said the threat intelligence it shared with Dutch law enforcement authorities made it possible to arrest the threat actor behind the operations.
The encryption key has also been shared with Avast, which had previously released a decryptor for Babuk ransomware after its source code was leaked in September 2021. The updated decryptor can be accessed here [EXE file].
"A single private key is used for all victims of the Tortilla threat actor," Avast noted. "This makes the update to the decryptor especially useful, as all victims of the campaign can use it to decrypt their files."
The Tortilla campaign was first disclosed by Talos in November 2021, with the attacks leveraging ProxyShell flaws in Microsoft Exchange servers to drop the ransomware within victim environments.

Tortilla is one among the many ransomware variants that have based their
file-encrypting malware on the leaked Babuk source code. This includes Rook,
Night Sky, Pandora, Nokoyawa, Cheerscrypt, AstraLocker 2.0, ESXiArgs, Rorschach,
RTM Locker, and RA Group.
The development comes as German cybersecurity firm Security Research Labs (SRLabs) released a decryptor for Black Basta ransomware called Black Basta Buster by taking advantage of a cryptographic weakness to recover a file either partially or fully.
"Files can be recovered if the plaintext of 64 encrypted bytes is known," SRLabs said. "Whether a file is fully or partially recoverable depends on the size of the file."
"Files below the size of 5000 bytes cannot be recovered. For files between 5000 bytes and 1GB in size, full recovery is possible. For files larger than 1GB, the first 5000 bytes will be lost but the remainder can be recovered."
Bleeping Computer reported late last month that the Black Basta developers have since fixed the issue, preventing the tool from working with newer infections.
FTC Bans Outlogic (X-Mode) From Selling Sensitive Location Data
10.1.24
BigBrothers
The Hacker News
The U.S. Federal Trade Commission (FTC) on Tuesday
prohibited data broker Outlogic, which was previously known as X-Mode Social,
from sharing or selling any sensitive location data with third-parties.
The ban is part of a settlement over allegations that the company "sold precise location data that could be used to track people's visits to sensitive locations such as medical and reproductive health clinics, places of religious worship and domestic abuse shelters."
The proposed order also requires it to destroy all the location data it previously gathered unless it obtains consumer consent or ensures the data has been de-identified or rendered non-sensitive as well as maintain a comprehensive list of sensitive locations and develop a comprehensive privacy program with a data retention schedule to prevent abuse.
The FTC accused X-Mode Social and Outlogic of failing to establish adequate safeguards to prevent the misuse of such data by downstream customers. The development marks the first-ever ban on the use and sale of sensitive location data.
X-Mode, which first attracted attention in 2020 for selling location data to the U.S. military, works by offering precise location data that it collects from proprietary apps and third-party apps that incorporate its software development kit (SDK) into its apps. It's also said to have procured location data from other data brokers and aggregators.
Following the revelations in 2020, both Apple and Google urged app developers to remove the SDK from their apps or face a ban from their respective app stores.
"The raw location data that X-Mode/Outlogic has sold is associated with mobile advertising IDs, which are unique identifiers associated with each mobile device," the FTC said. "This raw location data is not anonymized, and is capable of matching an individual consumer's mobile device with the locations they visited."
The agency further said that the company, until May 2023, did not have any policies in place to remove sensitive locations from the location data it sold, not only putting users' privacy at risk, but also exposing them to potential discrimination, physical violence, emotional distress, and other harms.
The FTC also called out X-Mode for not being transparent about which entities would receive the data when a customer used a third-party app with its SDK and that it failed to ensure that these apps sought informed consumer consent to grant it permission to access their location information in the first place.
Lastly, X-Mode was alleged to have been negligent in honoring requests made by some Android users to opt out of tracking and personalized ads.
In a statement provided to news agency Reuters, Outlogic said it disagreed with the "implications" of the FTC announcement, and there was no finding it misused location data.
"I commend the FTC for taking tough action to hold this shady location data broker responsible for its sale of Americans' location data," U.S. Senator Ron Wyden said in a statement shared with The Hacker News.
"In 2020, I discovered that the company had sold Americans' location data to U.S. military customers through defense contractors. While the FTC's action is encouraging, the agency should not have to play data broker whack-a-mole. Congress needs to pass tough privacy legislation to protect Americans' personal information and prevent government agencies from going around the courts by buying our data from data brokers."
Microsoft's January 2024 Windows Update Patches 48 New Vulnerabilities
10.1.24
OS
The Hacker News
Microsoft has addressed a total of 48 security flaws
spanning its software as part of its Patch Tuesday updates for January 2024.
Of the 48 bugs, two are rated Critical and 46 are rated Important in severity. There is no evidence that any of the issues are publicly known or under active attack at the time of release, making it the second consecutive Patch Tuesday with no zero-days.
The fixes are in addition to nine security vulnerabilities that have been resolved in the Chromium-based Edge browser since the release of December 2023 Patch Tuesday updates. This also includes a fix for a zero-day (CVE-2023-7024, CVSS score: 8.8) that Google said has been actively exploited in the wild.
The most critical among the flaws patched this month are as follows -
CVE-2024-20674 (CVSS score: 9.0) - Windows Kerberos Security Feature Bypass
Vulnerability
CVE-2024-20700 (CVSS score: 7.5) - Windows Hyper-V Remote Code
Execution Vulnerability
"The authentication feature could be bypassed as this
vulnerability allows impersonation," Microsoft said in an advisory for
CVE-2024-20674.
"An authenticated attacker could exploit this vulnerability by establishing a machine-in-the-middle (MitM) attack or other local network spoofing technique, then sending a malicious Kerberos message to the client victim machine to spoof itself as the Kerberos authentication server."
However, the company noted that successful exploitation requires an attacker to gain access to the restricted network first. Security researcher ldwilmore34 has been credited with discovering and reporting the flaw.
CVE-2024-20700, on the other hand, neither requires authentication nor user interaction to achieve remote code execution, although winning a race condition is a prerequisite to staging an attack.
"It isn't clear exactly where the attacker must be located — the LAN on which the hypervisor resides, or a virtual network created and managed by the hypervisor — or in what context the remote code execution would occur," Adam Barnett, lead software engineer at Rapid7, told The Hacker News.
Other notable flaws include CVE-2024-20653 (CVSS score: 7.8), a privilege escalation flaw impacting the Common Log File System (CLFS) driver, and CVE-2024-0056 (CVSS score: 8.7), a security bypass affecting System.Data.SqlClient and Microsoft.Data.SqlClient.
"An attacker who successfully exploited this vulnerability could carry out a machine-in-the-middle (MitM) attack and could decrypt and read or modify TLS traffic between the client and server," Redmond said about CVE-2024-0056.
Microsoft further noted that it's disabling the ability to insert FBX files in Word, Excel, PowerPoint, and Outlook in Windows by default due to a security flaw (CVE-2024-20677, CVSS score: 7.8) that could lead to remote code execution.
"3D models in Office documents that were previously inserted from an FBX file will continue to work as expected unless the 'Link to File' option was chosen at the insert time," Microsoft said in a separate alert. "GLB (Binary GL Transmission Format) is the recommended substitute 3D file format for use in Office."
It's worth noting that Microsoft took a similar step of disabling the SketchUp (SKP) file format in Office last year following Zscaler's discovery of 117 security flaws in Microsoft 365 applications.
CISA Flags 6 Vulnerabilities - Apple, Apache, Adobe , D-Link, Joomla Under
Attack
10.1.24
BigBrothers
The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency
(CISA) has added six security flaws to its Known Exploited Vulnerabilities (KEV)
catalog, citing evidence of active exploitation.
This includes CVE-2023-27524 (CVSS score: 8.9), a high-severity vulnerability impacting the Apache Superset open-source data visualization software that could enable remote code execution. It was fixed in version 2.1.
Details of the issue first came to light in April 2023, with Horizon3.ai's Naveen Sunkavally describing it as a "dangerous default configuration in Apache Superset that allows an unauthenticated attacker to gain remote code execution, harvest credentials, and compromise data."
It's currently not known how the vulnerability is being exploited in the wild. Also added by CISA are five other flaws -
CVE-2023-38203 (CVSS score: 9.8) - Adobe ColdFusion Deserialization of Untrusted
Data Vulnerability
CVE-2023-29300 (CVSS score: 9.8) - Adobe ColdFusion
Deserialization of Untrusted Data Vulnerability
CVE-2023-41990 (CVSS score:
7.8) - Apple Multiple Products Code Execution Vulnerability
CVE-2016-20017
(CVSS score: 9.8) - D-Link DSL-2750B Devices Command Injection Vulnerability
CVE-2023-23752 (CVSS score: 5.3) - Joomla! Improper Access Control Vulnerability
It's worth noting that CVE-2023-41990, patched by Apple in iOS 15.7.8 and iOS
16.3, was used by unknown actors as part of Operation Triangulation spyware
attacks to achieve remote code execution when processing a specially crafted
iMessage PDF attachment.
Federal Civilian Executive Branch (FCEB) agencies have been recommended to apply fixes for the aforementioned bugs by January 29, 2024, to secure their networks against active threats.
Alert: Water Curupira Hackers Actively Distributing PikaBot Loader Malware
10.1.24
Virus
The Hacker News
A threat actor called Water Curupira has been observed actively distributing the
PikaBot loader malware as part of spam campaigns in 2023.
"PikaBot's operators ran phishing campaigns, targeting victims via its two components — a loader and a core module — which enabled unauthorized remote access and allowed the execution of arbitrary commands through an established connection with their command-and-control (C&C) server," Trend Micro said in a report published today.
The activity began in the first quarter of 2023 that lasted till the end of June, before ramping up again in September. It also overlaps with prior campaigns that have used similar tactics to deliver QakBot, specifically those orchestrated by cybercrime groups known as TA571 and TA577.
It's believed that the increase in the number of phishing campaigns related to PikaBot is the result of QakBot's takedown in August, with DarkGate emerging as another replacement.
PikaBot is primarily a loader, which means it's designed to launch another payload, including Cobalt Strike, a legitimate post-exploitation toolkit that typically acts as a precursor for ransomware deployment.
The attack chains leverage a technique called email thread hijacking, employing existing email threads to trick recipients into opening malicious links or attachments, effectively activating the malware execution sequence.
The ZIP archive attachments, which either contain JavaScript or IMG files, are used as a launchpad for PikaBot. The malware, for its part, checks the system's language and halts execution should it be either Russian or Ukrainian.
In the next step, it collects details about the victim's system and forwards them to a C&C server in JSON format. Water Curupira's campaigns are for the purpose of dropping Cobalt Strike, which subsequently lead to the deployment of Black Basta ransomware.
"The threat actor also conducted several DarkGate spam campaigns and a small number of IcedID campaigns during the early weeks of the third quarter of 2023, but has since pivoted exclusively to PikaBot," Trend Micro said.
Turkish Hackers Exploiting Poorly Secured MS SQL Servers Across the Globe
10.1.24
Exploit
The Hacker News
Poorly secured Microsoft SQL (MS SQL) servers are being
targeted in the U.S., European Union, and Latin American (LATAM) regions as part
of an ongoing financially motivated campaign to gain initial access.
"The analyzed threat campaign appears to end in one of two ways, either the selling of 'access' to the compromised host, or the ultimate delivery of ransomware payloads," Securonix researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov said in a technical report shared with The Hacker News.
The campaign, linked to actors of Turkish origin, has been codenamed RE#TURGENCE by the cybersecurity firm.
Initial access to the servers entails conducting brute-force attacks, followed by the use of xp_cmdshell configuration option to run shell commands on the compromised host. This activity mirrors that of a prior campaign dubbed DB#JAMMER that came to light in September 2023.
This stage paves the way for the retrieval of a PowerShell script from a remote server that's responsible for fetching an obfuscated Cobalt Strike beacon payload.
The post-exploitation toolkit is then used to download the AnyDesk remote desktop application from a mounted network share for accessing the machine and downloading additional tools such as Mimikatz to harvest credentials and Advanced Port Scanner to carry out reconnaissance.

Lateral movement is accomplished by means of a legitimate system administration
utility called PsExec, which can execute programs on remote Windows hosts.
That attack chain, ultimately, culminates with the deployment of Mimic ransomware, a variant of which was also used in the DB#JAMMER campaign.
“The indicators as well as malicious TTPs used in the two campaigns are completely different, so there is a very high chance these are two disparate campaigns,” Kolesnikov told The Hacker News.
“More specifically, while the initial infiltration methods are similar, DB#JAMMER was slightly more sophisticated and used tunneling. RE#TURGENCE is more targeted and tends to use legitimate tools and remote monitoring and management, such as AnyDesk, in an attempt to blend in with normal activity.”
Securonix said it uncovered an operational security (OPSEC) blunder made by the threat actors that allowed it to monitor clipboard activity owing to the fact that the clipboard sharing feature of AnyDesk was enabled.
This made it possible to glean their Turkish origins and their online alias atseverse, which also corresponds to a profile on Steam and a Turkish hacking forum called SpyHack.
"Always refrain from exposing critical servers directly to the internet," the researchers cautioned. "With the case of RE#TURGENCE attackers were directly able to brute force their way into the server from outside the main network."
Alert: New Vulnerabilities Discovered in QNAP and Kyocera Device Manager
9.1.24
Vulnerebility
The Hacker News
A security flaw has been disclosed in Kyocera's Device
Manager product that could be exploited by bad actors to carry out malicious
activities on affected systems.
"This vulnerability allows attackers to coerce authentication attempts to their own resources, such as a malicious SMB share, to capture or relay Active Directory hashed credentials if the 'Restrict NTLM: Outgoing NTLM traffic to remote servers' security policy is not enabled," Trustwave said.
Tracked as CVE-2023-50916, Kyocera, in an advisory released late last month, described it as a path traversal issue that enables an attacker to intercept and alter a local path pointing to the backup location of the database to a universal naming convention (UNC) path.
Cybersecurity
This, in turn, causes the web application to attempt to
authenticate the rogue UNC path, resulting in unauthorized access to clients'
accounts and data theft. Furthermore, depending on the configuration of the
environment, it could be exploited to pull off NTLM relay attacks.
The shortcoming has been addressed in Kyocera Device Manager version 3.1.1213.0.
QNAP Releases Fixes for Several Flaws#
The development comes as QNAP released
fixes for several flaws, including high-severity vulnerabilities impacting QTS
and QuTS hero, QuMagie, Netatalk and Video Station.
This comprises CVE-2023-39296, a prototype pollution vulnerability that could allow remote attackers to "override existing attributes with ones that have an incompatible type, which may cause the system to crash."
The shortcoming has been addressed in versions QTS 5.1.3.2578 build 20231110 and QuTS hero h5.1.3.2578 build 20231110.
Cybersecurity
A brief description of the other notable flaws is as follows -
CVE-2023-47559 - A cross-site scripting (XSS) vulnerability in QuMagie that
could allow authenticated users to inject malicious code via a network
(Addressed in QuMagie 2.2.1 and later)
CVE-2023-47560 - An operating system
command injection vulnerability in QuMagie that could allow authenticated users
to execute commands via a network (Addressed in QuMagie 2.2.1 and later)
CVE-2023-41287 - An SQL injection vulnerability in Video Station that could
allow users to inject malicious code via a network (Addressed in Video Station
5.7.2 and later)
CVE-2023-41288 - An operating system command injection
vulnerability in Video Station that could allow users to execute commands via a
network (Addressed in Video Station 5.7.2 and later)
CVE-2022-43634 - An
unauthenticated remote code execution vulnerability in Netatalk that could allow
attackers to execute arbitrary code (Addressed in QTS 5.1.3.2578 build 20231110
and QuTS hero h5.1.3.2578 build 20231110)
While there is no evidence that the
flaws have been exploited in the wild, it's recommended that users take steps to
update their installations to the latest version to mitigate potential risks.
Beware! YouTube Videos Promoting Cracked Software Distribute Lumma Stealer
9.1.24
Virus
The Hacker News
Threat actors are resorting to YouTube videos featuring content related to
cracked software in order to entice users into downloading an information
stealer malware called Lumma.
"These YouTube videos typically feature content related to cracked applications, presenting users with similar installation guides and incorporating malicious URLs often shortened using services like TinyURL and Cuttly," Fortinet FortiGuard Labs researcher Cara Lin said in a Monday analysis.
This is not the first time pirated software videos on YouTube have emerged as an effective bait for stealer malware. Previously similar attack chains were observed delivering stealers, clippers, and crypto miner malware.
In doing so, threat actors can leverage the compromised machines for not only information and cryptocurrency theft, but also abuse the resources for illicit mining.
In the latest attack sequence documented by Fortinet, users searching for cracked versions of legitimate video editing tools like Vegas Pro on YouTube are prompted to click on a link located in the video's description, leading to the download of a bogus installer hosted on MediaFire.
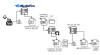
The ZIP installer, once unpacked, features a Windows shortcut (LNK) masquerading
as a setup file that downloads a .NET loader from a GitHub repository, which, in
turn, loads the stealer payload, but not before performing a series of
anti-virtual machine and anti-debugging checks.
Lumma Stealer, written in C and offered for sale on underground forums since late 2022, is capable of harvesting and exfiltrating sensitive data to an actor-controlled server.
The development comes as Bitdefender warned of stream-jacking attacks on YouTube in which cybercriminals take over high-profile accounts via phishing attacks that deploy the RedLine Stealer malware to siphon their credentials and session cookies, and ultimately promote various crypto scams.
It also follows the discovery of an 11-month-old AsyncRAT campaign that employs phishing lures to download an obfuscated JavaScript file that's then utilized to drop the remote access trojan.
"The victims and their companies are carefully selected to broaden the impact of the campaign," AT&T Alien Labs researcher Fernando Martinez said. "Some of the identified targets manage key infrastructure in the U.S."
Syrian Hackers Distributing Stealthy C#-Based Silver RAT to Cybercriminals
9.1.24
Virus
The Hacker News
Threat actors operating under the name Anonymous Arabic
have released a remote access trojan (RAT) called Silver RAT that's equipped to
bypass security software and stealthily launch hidden applications.
"The developers operate on multiple hacker forums and social media platforms, showcasing an active and sophisticated presence," cybersecurity firm Cyfirma said in a report published last week.
The actors, assessed to be of Syrian origin and linked to the development of another RAT known as S500 RAT, also run a Telegram channel offering various services such as the distribution of cracked RATs, leaked databases, carding activities, and the sale of Facebook and X (formerly Twitter) bots.
The social media bots are then utilized by other cyber criminals to promote various illicit services by automatically engaging with and commenting on user content.
In-the-wild detections of Silver RAT v1.0 were first observed in November 2023, although the threat actor's plans to release the trojan were first made official a year before. It was cracked and leaked on Telegram around October 2023.
The C#-based malware boasts of a wide range of features to connect to a command-and-control (C2) server, log keystrokes, destroy system restore points, and even encrypt data using ransomware. There are also indications that an Android version is in the works.
"While generating a payload using Silver RAT's builder, threat actors can select
various options with a payload size up to a maximum of 50kb," the company noted.
"Once connected, the victim appears on the attacker-controlled Silver RAT panel,
which displays the logs from the victim based on the functionalities chosen."
An interesting evasion feature built into Silver RAT is its ability to delay the execution of the payload by a specific time as well as covertly launch apps and take control of the compromised host.
Further analysis of the malware author's online footprint shows that one of the members of the group is likely in their mid-20s and based in Damascus.
"The developer [...] appears supportive of Palestine based on their Telegram posts, and members associated with this group are active across various arenas, including social media, development platforms, underground forums, and Clearnet websites, suggesting their involvement in distributing various malware," Cyfirma said.
NIST Warns of Security and Privacy Risks from Rapid AI System Deployment
8.1.24
AI
The Hacker News
The U.S. National Institute of Standards and Technology (NIST) is calling attention to the privacy and security challenges that arise as a result of increased deployment of artificial intelligence (AI) systems in recent years.
"These security and privacy challenges include the potential for adversarial manipulation of training data, adversarial exploitation of model vulnerabilities to adversely affect the performance of the AI system, and even malicious manipulations, modifications or mere interaction with models to exfiltrate sensitive information about people represented in the data, about the model itself, or proprietary enterprise data," NIST said.
As AI systems become integrated into online services at a rapid pace, in part driven by the emergence of generative AI systems like OpenAI ChatGPT and Google Bard, models powering these technologies face a number of threats at various stages of the machine learning operations.
These include corrupted training data, security flaws in the software components, data model poisoning, supply chain weaknesses, and privacy breaches arising as a result of prompt injection attacks.
"For the most part, software developers need more people to use their product so it can get better with exposure," NIST computer scientist Apostol Vassilev said. "But there is no guarantee the exposure will be good. A chatbot can spew out bad or toxic information when prompted with carefully designed language."
The attacks, which can have significant impacts on availability, integrity, and privacy, are broadly classified as follows -
Evasion attacks, which aim to generate adversarial output after a model is
deployed
Poisoning attacks, which target the training phase of the algorithm
by introducing corrupted data
Privacy attacks, which aim to glean sensitive
information about the system or the data it was trained on by posing questions
that circumvent existing guardrails
Abuse attacks, which aim to compromise
legitimate sources of information, such as a web page with incorrect pieces of
information, to repurpose the system's intended use
Such attacks, NIST said,
can be carried out by threat actors with full knowledge (white-box), minimal
knowledge (black-box), or have a partial understanding of some of the aspects of
the AI system (gray-box).
The agency further noted the lack of robust mitigation measures to counter these risks, urging the broader tech community to "come up with better defenses."
The development arrives more than a month after the U.K., the U.S., and international partners from 16 other countries released guidelines for the development of secure artificial intelligence (AI) systems.
"Despite the significant progress AI and machine learning have made, these technologies are vulnerable to attacks that can cause spectacular failures with dire consequences," Vassilev said. "There are theoretical problems with securing AI algorithms that simply haven't been solved yet. If anyone says differently, they are selling snake oil."
DoJ Charges 19 Worldwide in $68 Million xDedic Dark Web Marketplace Fraud
8.1.24
Crime
The Hacker News
The U.S. Department of Justice (DoJ) said it charged 19
individuals worldwide in connection with the now-defunct xDedic Marketplace,
which is estimated to have facilitated more than $68 million in fraud.
In wrapping up its investigation into the dark web portal, the agency said the transnational operation was the result of close cooperation with law enforcement authorities from Belgium, Germany, the Netherlands, Ukraine, and Europol.
Of the 19 defendants, three have been sentenced to 6.5 years in prison, eight have been awarded jail terms ranging from one year to five years, and one individual has been ordered to serve five years' probation.
One among them includes Glib Oleksandr Ivanov-Tolpintsev, a Ukrainian national who was sentenced to four years in prison in May 2022 for selling compromised credentials on xDedic and making $82,648 in illegal profits.
Cybersecurity
Dariy Pankov, described by the DoJ as one of the highest
sellers by volume, offered credentials of no less than 35,000 hacked servers
located all over the world and obtaining more than $350,000 in illicit proceeds.
The servers were infiltrated using a custom tool named NLBrute that was capable of breaking into protected computers by decrypting login credentials.
Also of note is a Nigerian national named Allen Levinson, who was a "prolific buyer" with a particular interest in purchasing access to U.S.-based Certified Public Accounting firms in order to file bogus tax returns with the U.S. government.
Five others, who have been accused of a conspiracy to commit wire fraud, are pending sentencing.
Alongside these administrators and sellers, two buyers named Olufemi Odedeyi and Oluwaseyi Shodipe have been charged with conspiracy to commit wire fraud and aggravated identity theft. Shodipe has also been charged with making false claims and theft of government funds.
Both individuals are yet to be extradited from the U.K. If convicted, they each face a maximum penalty of 20 years in federal prison.
Cybersecurity
The marketplace, until its takedown in January 2019, allowed
cybercriminals to buy or sell stolen credentials to more than 700,000 hacked
computers and servers across the world and personally identifiable information
of U.S. residents, such as dates of birth and Social Security numbers.
Alexandru Habasescu and Pavlo Kharmanskyi functioned as the marketplace's administrators. Habasescu, from Moldova, was the lead developer, while Kharmanskyi, who lived in Ukraine, managed advertising, payments, and customer support to buyers.
"Once purchased, criminals used these servers to facilitate a wide range of illegal activity that included tax fraud and ransomware attacks," the DoJ said.
Targets of these attacks comprised government infrastructure, hospitals, 911 and emergency services, call centers, major metropolitan transit authorities, accounting and law firms, pension funds, and universities.
North Korea's Cyber Heist: DPRK Hackers Stole $600 Million in Cryptocurrency in
2023
8.1.24
Cryptocurrency
The Hacker News
Threat actors affiliated with the Democratic People's
Republic of Korea (also known as North Korea) have plundered at least $600
million in cryptocurrency in 2023.
The DPRK "was responsible for almost a third of all funds stolen in crypto attacks last year, despite a 30% reduction from the USD 850 million haul in 2022," blockchain analytics firm TRM Labs said last week.
"Hacks perpetrated by the DPRK were on average ten times as damaging as those not linked to North Korea."
There are indications that additional breaches targeting the crypto sector towards the end of 2023 could push this figure higher to around $700 million.
The targeting of cryptocurrency companies is not new for North Korean state-sponsored actors, who have stolen about $3 billion since 2017.
These financially motivated attacks are seen as a crucial revenue-generation mechanism for the sanctions-hit nation, funding its weapons of mass destruction (WMD) and ballistic missile programs.

The intrusions leverage social engineering to lure targets and typically aim to
compromise private keys and seed phrases – which are used to safeguard digital
wallets – and then use them to gain unauthorized access to the victims' assets
and transfer them to wallets under the threat actor's control.
"They are then swapped mostly for USDT or Tron and converted to hard currency using high-volume OTC brokers," TRM Labs said.
The company further noted that DPRK hackers continued to explore other money laundering tools after the U.S. Treasury Department sanctioned a crypto mixer service known as Sinbad for processing a chunk of their proceeds, indicating constant evolution despite law enforcement pressure.
"With nearly USD 1.5 billion stolen in the past two years alone, North Korea's hacking prowess demands continuous vigilance and innovation from business and governments," TRM Labs said.
Sea Turtle Cyber Espionage Campaign Targets Dutch IT and Telecom Companies
7.1.24
BigBrothers
The Hacker News
Telecommunication, media, internet service providers
(ISPs), information technology (IT)-service providers, and Kurdish websites in
the Netherlands have been targeted as part of a new cyber espionage campaign
undertaken by a Türkiye-nexus threat actor known as Sea Turtle.
"The infrastructure of the targets was susceptible to supply chain and island-hopping attacks, which the attack group used to collect politically motivated information such as personal information on minority groups and potential political dissents," Dutch security firm Hunt & Hackett said in a Friday analysis.
"The stolen information is likely to be exploited for surveillance or intelligence gathering on specific groups and or individuals."
Sea Turtle, also known by the names Cosmic Wolf, Marbled Dust (formerly Silicon), Teal Kurma, and UNC1326, was first documented by Cisco Talos in April 2019, detailing state-sponsored attacks targeting public and private entities in the Middle East and North Africa.
Activities associated with the group are believed to have been ongoing since January 2017, primarily leveraging DNS hijacking to redirect prospective targets attempting to query a specific domain to an actor-controlled server capable of harvesting their credentials.
"The Sea Turtle campaign almost certainly poses a more severe threat than DNSpionage given the actor's methodology in targeting various DNS registrars and registries," Talos said at the time.
In late 2021, Microsoft noted that the adversary carries out intelligence collection to meet strategic Turkish interests from countries like Armenia, Cyprus, Greece, Iraq, and Syria, striking telecom and IT companies with an aim to "establish a foothold upstream of their desired target" via exploitation of known vulnerabilities.
Then last month, the adversary was revealed to be using a simple reverse TCP shell for Linux (and Unix) systems called SnappyTCP in attacks carried out between 2021 and 2023, according to the PricewaterhouseCoopers (PwC) Threat Intelligence team.
"The web shell is a simple reverse TCP shell for Linux/Unix that has basic [command-and-control] capabilities, and is also likely used for establishing persistence," the company said. "There are at least two main variants; one which uses OpenSSL to create a secure connection over TLS, while the other omits this capability and sends requests in cleartext."
The latest findings from Hunt & Hackett show that Sea Turtle continues to be a stealthy espionage-focused group, performing defense evasion techniques to fly under the radar and harvest email archives.
In one of the attacks observed in 2023, a compromised-but-legitimate cPanel account was used as an initial access vector to deploy SnappyTCP on the system. It's currently not known how the attackers obtained the credentials.
"Using SnappyTCP, the threat actor sent commands to the system to create a copy of an email archive created with the tool tar, in the public web directory of the website that was accessible from the internet," the firm noted.
"It is highly likely that the threat actor exfiltrated the email archive by downloading the file directly from the web directory."
To mitigate the risks posed by such attacks, it's advised that organizations enforce strong password policies, implement two-factor authentication (2FA), rate limit login attempts to reduce the chances of brute-force attempts, monitor SSH traffic, and keep all systems and software up-to-date.
Pro-Iranian Hacker Group Targeting Albania with No-Justice Wiper Malware
6.1.24
BigBrothers
The Hacker News
The recent wave of cyber attacks targeting Albanian
organizations involved the use of a wiper called No-Justice.
The findings come from cybersecurity company ClearSky, which said the Windows-based malware "crashes the operating system in a way that it cannot be rebooted."
The intrusions have been attributed to an Iranian "psychological operation group" called Homeland Justice, which has been operating since July 2022, specifically orchestrating destructive attacks against Albania.
On December 24, 2023, the adversary resurfaced after a hiatus, stating it's "back to destroy supporters of terrorists," describing its latest campaign as #DestroyDurresMilitaryCamp. The Albanian city of Durrës currently hosts the dissident group People's Mojahedin Organization of Iran (MEK).
Targets of the attack included ONE Albania, Eagle Mobile Albania, Air Albania, and the Albanian parliament.
Two of the primary tools deployed during the campaign include an executable wiper and a PowerShell script that's designed to propagate the former to other machines in the target network after enabling Windows Remote Management (WinRM).
The No-Justice wiper (NACL.exe) is a 220.34 KB binary that requires administrator privileges to erase the data on the computer.
This is accomplished by removing the boot signature from the Master Boot Record (MBR), which refers to the first sector of any hard disk that identifies where the operating system is located in the disk so that it can be loaded into a computer's RAM.
Also delivered over the course of the attack are legitimate tools like Plink (aka PuTTY Link), RevSocks, and the Windows 2000 resource kit to facilitate reconnaissance, lateral movement, and persistent remote access.

The development comes as pro-Iranian threat actors such as Cyber Av3ngers, Cyber
Toufan, Haghjoyan, and YareGomnam Team have increasingly set their sights on
Israel and the U.S. amid continuing geopolitical tensions in the Middle East.
"Groups such as Cyber Av3ngers and Cyber Toufan appear to be adopting a narrative of retaliation in their cyber attacks," Check Point disclosed last month.
"By opportunistically targeting U.S. entities using Israeli technology, these hacktivist proxies try to achieve a dual retaliation strategy – claiming to target both Israel and the U.S. in a single, orchestrated cyber assault."
Cyber Toufan, in particular, has been linked to a deluge of hack-and-leak operations targeting over 100 organizations, wiping infected hosts and releasing stolen data on their Telegram channel.
"They've caused so much damage that many of the orgs – almost a third, in fact, haven't been able to recover," security researcher Kevin Beaumont said. "Some of these are still fully offline over a month later, and the wiped victims are a mix of private companies and Israeli state government entities."
Last month, the Israel National Cyber Directorate (INCD) said it's currently tracking roughly 15 hacker groups associated with Iran, Hamas, and Hezbollah that are maliciously operating in Israeli cyberspace since the onset of the Israel-Hamas war in October 2023.
The agency further noted that the techniques and tactics employed share similarities with those used in the Ukraine-Russia war, leveraging psychological warfare and wiper malware to destroy information.
SpectralBlur: New macOS Backdoor Threat from North Korean Hackers
5.1.24
OS
The Hacker News
Cybersecurity researchers have discovered a new Apple
macOS backdoor called SpectralBlur that overlaps with a known malware family
that has been attributed to North Korean threat actors.
"SpectralBlur is a moderately capable backdoor that can upload/download files, run a shell, update its configuration, delete files, hibernate, or sleep, based on commands issued from the [command-and-control] server," security researcher Greg Lesnewich said.
The malware shares similarities with KANDYKORN (aka SockRacket), an advanced implant that functions as a remote access trojan capable of taking control of a compromised host.
It's worth noting that the KANDYKORN activity also intersects with another campaign orchestrated by the Lazarus sub-group known as BlueNoroff (aka TA444) which culminates in the deployment of a backdoor referred to as RustBucket and a late-stage payload dubbed ObjCShellz.
In recent months, the threat actor has been observed combining disparate pieces of these two infection chains, leveraging RustBucket droppers to deliver KANDYKORN.
The latest findings are another sign that North Korean threat actors are increasingly setting their sights on macOS to infiltrate high-value targets, particularly those within the cryptocurrency and the blockchain industries.
"TA444 keeps running fast and furious with these new macOS malware families," Lesnewich said.
Security researcher Patrick Wardle, who shared additional insights into the inner workings of SpectralBlur, said the Mach-O binary was uploaded to the VirusTotal malware scanning service in August 2023 from Colombia.
The functional similarities between KANDYKORN and SpectralBlur have raised the possibility that they may have been built by different developers keeping the same requirements in mind.
What makes the malware stand out are its attempts to hinder analysis and evade detection while using grantpt to set up a pseudo-terminal and execute shell commands received from the C2 server.
The disclosure comes as a total of 21 new malware families designed to target macOS systems, including ransomware, information stealers, remote access trojans, and nation-state-backed malware, were discovered in 2023, up from 13 identified in 2022.
"With the continued growth and popularity of macOS (especially in the enterprise!), 2024 will surely bring a bevy of new macOS malware," Wardle noted.
Orange Spain Faces BGP Traffic Hijack After RIPE Account Hacked by Malware
5.1.24
Hacking
The Hacker News
Mobile network operator Orange Spain suffered an internet
outage for several hours on January 3 after a threat actor used administrator
credentials captured by means of stealer malware to hijack the border gateway
protocol (BGP) traffic.
"The Orange account in the IP network coordination center (RIPE) has suffered improper access that has affected the browsing of some of our customers," the company said in a message posted on X (formerly Twitter).
However, the company emphasized no personal data was compromised and that the incident only affected some browsing services.
The threat actor, who goes by the name Ms_Snow_OwO on X, claimed to have gained access to Orange Spain's RIPE account. RIPE is a regional Internet registry (RIR) that oversees the allocation and registration of IP addresses and autonomous system (AS) numbers in Europe, Central Asia, Russia, and West Asia.
"Using the stolen account, the threat actor modified the AS number belonging to Orange's IP address, resulting in major disruptions to Orange and a 50% loss in traffic," cybersecurity firm Hudson Rock said.
Further analysis has revealed that the email address of the admin account is
associated with the computer of an Orange Spain employee who was infiltrated by
Raccoon Stealer malware on September 4, 2023.
It's currently not known how the stealer found its way to the employee's system, but such malware families are typically propagated via malvertising or phishing scams.
"Among the corporate credentials identified on the machine, the employee had specific credentials to 'https://access.ripe.net' using the email address which was revealed by the threat actor (adminripe-ipnt@orange.es)," the company added.
Even worse, the password used to secure Orange's RIPE administrator account was "ripeadmin," which is both weak and easily predictable.
Security researcher Kevin Beaumont further noted that RIPE neither mandates two-factor authentication (2FA) nor enforces a strong password policy for its accounts, making it ripe for abuse.
"Currently, infostealer marketplaces are selling thousands of credentials to access.ripe.net — effectively allowing you to repeat this at organizations and ISPs across Europe," Beaumont said.
RIPE, which is currently investigating to see if any other accounts have been affected in a similar manner, said it will directly reach out to affected account holders. It has also urged RIPE NCC Access account users to update their passwords and enable multi-factor authentication for their accounts.
"In the long term, we're expediting the 2FA implementation to make it mandatory for all RIPE NCC Access accounts as soon as possible and to introduce a variety of verification mechanisms," it added.
The incident serves to highlight the consequences of infostealer infections, necessitating that organizations take steps to secure their networks from known initial attack vectors.
Alert: Ivanti Releases Patch for Critical Vulnerability in Endpoint Manager
Solution
5.1.24
Vulnerebility
The Hacker News
Ivanti has released security updates to address a
critical flaw impacting its Endpoint Manager (EPM) solution that, if
successfully exploited, could result in remote code execution (RCE) on
susceptible servers.
Tracked as CVE-2023-39336, the vulnerability has been rated 9.6 out of 10 on the CVSS scoring system. The shortcoming impacts EPM 2021 and EPM 2022 prior to SU5.
"If exploited, an attacker with access to the internal network can leverage an unspecified SQL injection to execute arbitrary SQL queries and retrieve output without the need for authentication," Ivanti said in an advisory.
"This can then allow the attacker control over machines running the EPM agent. When the core server is configured to use SQL express, this might lead to RCE on the core server."
The disclosure arrived weeks after the company resolved nearly two dozen security flaws in its Avalanche enterprise mobile device management (MDM) solution.
Of the 21 issues, 13 are rated critical (CVSS scores: 9.8) and have been characterized as unauthenticated buffer overflows. They have been patched in Avalanche 6.4.2.
"An attacker sending specially crafted data packets to the Mobile Device Server can cause memory corruption which could result in a denial-of-service (DoS) or code execution," Ivanti said.
While there is no evidence that these aforementioned weaknesses have been exploited in the wild, state-backed actors have, in the past, exploited zero-day flaws (CVE-2023-35078 and CVE-2023-35081) in Ivanti Endpoint Manager Mobile (EPMM) to infiltrate the networks of multiple Norwegian government organizations.
A month later, another critical vulnerability in the Ivanti Sentry product (CVE-2023-38035, CVSS score: 9.8) came under active exploitation as a zero-day.
Russian Hackers Had Covert Access to Ukraine's Telecom Giant for Months
5.1.24
BigBrothers
The Hacker News
Ukrainian cybersecurity authorities have disclosed that
the Russian state-sponsored threat actor known as Sandworm was inside telecom
operator Kyivstar's systems at least since May 2023.
The development was first reported by Reuters.
The incident, described as a "powerful hacker attack," first came to light last month, knocking out access to mobile and internet services for millions of customers. Soon after the incident, a Russia-linked hacking group called Solntsepyok took responsibility for the breach.
Solntsepyok has been assessed to be a Russian threat group with affiliations to the Main Directorate of the General Staff of the Armed Forces of the Russian Federation (GRU), which also operates Sandworm.
The advanced persistent threat (APT) actor has a track record of orchestrating disruptive cyber attacks, with Denmark accusing the hacking outfit of targeting 22 energy sector companies last year.
Illia Vitiuk, head of the Security Service of Ukraine's (SBU) cybersecurity department, said the attack against Kyivstar wiped out nearly everything from thousands of virtual servers and computers.
The incident, he said, "completely destroyed the core of a telecoms operator," noting the attackers had full access likely at least since November, months after obtaining an initial foothold into the company's infrastructure.
"The attack had been carefully prepared during many months," Vitiuk said in a statement shared on the SBU's website.
Kyivstar, which has since restored its operations, said there is no evidence that the personal data of subscribers has been compromised. It's currently not known how the threat actor penetrated its network.
It's worth noting that the company had previously dismissed speculations about the attackers destroying its computers and servers as "fake."
The development comes as the SBU revealed earlier this week that it took down two online surveillance cameras that were allegedly hacked by Russian intelligence agencies to spy on the defense forces and critical infrastructure in the capital city of Kyiv.
The agency said the compromise allowed the adversary to gain remote control of the cameras, adjust their viewing angles, and connect them to YouTube to capture "all visual information in the range of the camera."
New Bandook RAT Variant Resurfaces, Targeting Windows Machines
5.1.24
Virus
The Hacker News
A new variant of remote access trojan called Bandook has
been observed being propagated via phishing attacks with an aim to infiltrate
Windows machines, underscoring the continuous evolution of the malware.
Fortinet FortiGuard Labs, which identified the activity in October 2023, said the malware is distributed via a PDF file that embeds a link to a password-protected .7z archive.
"After the victim extracts the malware with the password in the PDF file, the malware injects its payload into msinfo32.exe," security researcher Pei Han Liao said.
Bandook, first detected in 2007, is an off-the-shelf malware that comes with a wide range of features to remotely gain control of the infected systems.
In July 2021, Slovak cybersecurity firm ESET detailed a cyber espionage campaign that leveraged an upgraded variant of Bandook to breach corporate networks in Spanish-speaking countries such as Venezuela.

The starting point of the latest attack sequence is an injector component that's
designed to decrypt and load the payload into msinfo32.exe, a legitimate Windows
binary that gathers system information to diagnose computer issues.
The malware, besides making Windows Registry changes to establish persistence on the compromised host, establishes contact with a command-and-control (C2) server to retrieve additional payloads and instructions.
"These actions can be roughly categorized as file manipulation, registry manipulation, download, information stealing, file execution, invocation of functions in DLLs from the C2, controlling the victim's computer, process killing, and uninstalling the malware," Han Liao said.
Beware: 3 Malicious PyPI Packages Found Targeting Linux with Crypto Miners
5.1.24
Virus
The Hacker News
Three new malicious packages have been discovered in the
Python Package Index (PyPI) open-source repository with capabilities to deploy a
cryptocurrency miner on affected Linux devices.
The three harmful packages, named modularseven, driftme, and catme, attracted a total of 431 downloads over the past month before they were taken down.
"These packages, upon initial use, deploy a CoinMiner executable on Linux devices," Fortinet FortiGuard Labs researcher Gabby Xiong said, adding the campaign shares overlaps with a prior campaign that involved the use of a package called culturestreak to deploy a crypto miner.
The malicious code resides in the __init__.py file, which decodes and retrieves the first stage from a remote server, a shell script ("unmi.sh") that fetches a configuration file for the mining activity as well as the CoinMiner file hosted on GitLab.
The ELF binary file is then executed in the background using the nohup command, thus ensuring that the process continues to run after exiting the session.
"Echoing the approach of the earlier 'culturestreak' package, these packages conceal their payload, effectively reducing the detectability of their malicious code by hosting it on a remote URL," Xiong said. "The payload is then incrementally released in various stages to execute its malicious activities."
The connections to the culturestreak package also stems from the fact that the configuration file is hosted on the domain papiculo[.]net and the coin mining executables are hosted on a public GitLab repository.
One notable improvement in the three new packages is the introduction of an extra stage by concealing their nefarious intent in the shell script, thereby helping it evade detection by security software and lengthening the exploitation process.
"Moreover, this malware inserts the malicious commands into the ~/.bashrc file," Xiong said. "This addition ensures the malware's persistence and reactivation on the user's device, effectively extending the duration of its covert operation. This strategy aids in the prolonged, stealthy exploitation of the user's device for the attacker's benefit."
UAC-0050 Group Using New Phishing Tactics to Distribute Remcos RAT
5.1.24
Virus
The Hacker News
The threat actor known as UAC-0050 is leveraging phishing attacks to distribute
Remcos RAT using new strategies to evade detection from security software.
"The group's weapon of choice is Remcos RAT, a notorious malware for remote surveillance and control, which has been at the forefront of its espionage arsenal," Uptycs security researchers Karthickkumar Kathiresan and Shilpesh Trivedi said in a Wednesday report.
"However, in their latest operational twist, the UAC-0050 group has integrated a pipe method for interprocess communication, showcasing their advanced adaptability."
UAC-0050, active since 2020, has a history of targeting Ukrainian and Polish entities via social engineering campaigns that impersonate legitimate organizations to trick recipients into opening malicious attachments.
In February 2023, the Computer Emergency Response Team of Ukraine (CERT-UA) attributed the adversary to a phishing campaign designed to deliver Remcos RAT.
Over the past few months, the same trojan has been distributed as part of at least three different phishing waves, with one such attack also leading to the deployment of an information stealer called Meduza Stealer.
The analysis from Uptycs is based on a LNK file it discovered on December 21, 2023. While the exact initial access vector is currently unknown, it's suspected to have involved phishing emails targeting Ukrainian military personnel that claim to advertise consultancy roles with the Israel Defense Forces (IDF).

The LNK file in question collects information regarding antivirus products
installed on the target computer, and then proceeds to retrieve and execute an
HTML application named "6.hta" from a remote server using mshta.exe, a
Windows-native binary for running HTA files.
This step paves the way for a PowerShell script that unpacks another PowerShell script to download two files called "word_update.exe" and "ofer.docx" from the domain new-tech-savvy[.]com.
Running word_update.exe causes it to create a copy of itself with the name fmTask_dbg.exe and establish persistence by creating a shortcut to the new executable in the Windows Startup folder.
The binary also employs unnamed pipes to facilitate the exchange of data between itself and a newly spawned child process for cmd.exe in order to ultimately decrypt and launch the Remcos RAT (version 4.9.2 Pro), which is capable of harvesting system data and cookies and login information from web browsers like Internet Explorer, Mozilla Firefox, and Google Chrome.
"Leveraging pipes within the Windows operating system provides a covert channel for data transfer, skillfully evading detection by Endpoint Detection and Response (EDR) and antivirus systems," the researchers said.
"Although not entirely new, this technique marks a significant leap in the sophistication of the group's strategies."
Mandiant's Twitter Account Restored After Six-Hour Crypto Scam Hack
4.1.24
Cryptocurrency
The Hacker News
American cybersecurity firm and Google Cloud subsidiary
Mandiant had its X (formerly Twitter) account compromised for more than six
hours by an unknown attacker to propagate a cryptocurrency scam.
As of writing, the account has been restored on the social media platform.
It's currently not clear how the account was breached. But the hacked Mandiant account was initially renamed to "@phantomsolw" to impersonate the Phantom crypto wallet service, according to MalwareHunterTeam and vx-underground.
Specifically, the scam posts from the account advertised an airdrop scam that urged users to click on a bogus link and earn free tokens, with follow-up messages asking Mandiant to "change password please" and "check bookmarks when you get account back."
Mandiant, a leading threat intelligence firm, was acquired by Google in March 2022 for $5.4 billion. It is now part of Google Cloud.
"The Mandiant Twitter account takeover could have happened [in] a number of ways," Rachel Tobac, CEO of SocialProof Security, said on X.
"Some folks are giving the advice to turn on MFA to prevent ATO and of course that is a good idea always *but it's also possible that someone in Support at Twitter was bribed or compromised which allowed the attacker access to Mandiant's account*."
The Hacker News has reached out to Mandiant for further comments, and we will update the story once we hear back.
Malware Using Google MultiLogin Exploit to Maintain Access Despite Password
Reset
3.1.24
Virus
The Hacker News
Information stealing malware are actively taking
advantage of an undocumented Google OAuth endpoint named MultiLogin to hijack
user sessions and allow continuous access to Google services even after a
password reset.
According to CloudSEK, the critical exploit facilitates session persistence and cookie generation, enabling threat actors to maintain access to a valid session in an unauthorized manner.
The technique was first revealed by a threat actor named PRISMA on October 20, 2023, on their Telegram channel. It has since been incorporated into various malware-as-a-service (MaaS) stealer families, such as Lumma, Rhadamanthys, Stealc, Meduza, RisePro, and WhiteSnake.
The MultiLogin authentication endpoint is primarily designed for synchronizing Google accounts across services when users sign in to their accounts in the Chrome web browser (i.e., profiles).
A reverse engineering of the Lumma Stealer code has revealed that the technique targets the "Chrome's token_service table of WebData to extract tokens and account IDs of chrome profiles logged in," security researcher Pavan Karthick M said. "This table contains two crucial columns: service (GAIA ID) and encrypted_token."
This token:GAIA ID pair is then combined with the MultiLogin endpoint to
regenerate Google authentication cookies.
When reached for comment, Google acknowledged the existence of the attack method but noted that users can revoke the stolen sessions by logging out of the impacted browser.
"Google is aware of recent reports of a malware family stealing session tokens," the company told The Hacker News. "Attacks involving malware that steal cookies and tokens are not new; we routinely upgrade our defenses against such techniques and to secure users who fall victim to malware. In this instance, Google has taken action to secure any compromised accounts detected."
"However, it's important to note a misconception in reports that suggests stolen tokens and cookies cannot be revoked by the user," it further added. "This is incorrect, as stolen sessions can be invalidated by simply signing out of the affected browser, or remotely revoked via the user's devices page. We will continue to monitor the situation and provide updates as needed."
The company further recommended users turn on Enhanced Safe Browsing in Chrome to protect against phishing and malware downloads.
SMTP Smuggling: New Flaw Lets Attackers Bypass Security and Spoof Emails
3.1.24
Exploit
The Hacker News
A new exploitation technique called Simple Mail Transfer Protocol (SMTP)
smuggling can be weaponized by threat actors to send spoofed emails with fake
sender addresses while bypassing security measures.
"Threat actors could abuse vulnerable SMTP servers worldwide to send malicious emails from arbitrary email addresses, allowing targeted phishing attacks," Timo Longin, a senior security consultant at SEC Consult, said in an analysis published last month.
SMTP is a TCP/IP protocol used to send and receive email messages over a network. To relay a message from an email client (aka mail user agent), an SMTP connection is established between the client and server in order to transmit the actual content of the email.
The server then relies on what's called a mail transfer agent (MTA) to check the domain of the recipient's email address, and if it's different from that of the sender, it queries the domain name system (DNS) to look up the MX (mail exchanger) record for the recipient's domain and complete the mail exchange.
The crux of SMTP smuggling is rooted in the inconsistencies that arise when outbound and inbound SMTP servers handle end-of-data sequences differently, potentially enabling threat actors to break out of the message data, "smuggle" arbitrary SMTP commands, and even send separate emails.

It borrows the concept from a known attack method referred to as HTTP request
smuggling, which takes advantage of discrepancies in the interpretation and
processing of the "Content-Length" and "Transfer-Encoding" HTTP headers to
prepend an ambiguous request to the inbound request chain.
Specifically, it exploits security flaws in messaging servers from Microsoft, GMX, and Cisco to send emails spoofing millions of domains. Also impacted are SMTP implementations from Postfix and Sendmail.
This allows for sending forged emails that seemingly look like they are originating from legitimate senders and defeat checks in place erected to ensure the authenticity of incoming messages – i.e., DomainKeys Identified Mail (DKIM), Domain-based Message Authentication, Reporting and Conformance (DMARC), and Sender Policy Framework (SPF).
While Microsoft and GMX have rectified the issues, Cisco said the findings do not constitute a "vulnerability, but a feature and that they will not change the default configuration." As a result, inbound SMTP smuggling to Cisco Secure Email instances is still possible with default configurations.
As a fix, SEC Consult recommends Cisco users change their settings from "Clean" to "Allow" in order to avoid receiving spoofed emails with valid DMARC checks.
DOJ Slams XCast with $10 Million Fine Over Massive Illegal Robocall Operation
3.1.24
Spam
The Hacker News
The U.S. Department of Justice (DoJ) on Tuesday said it
reached a settlement with VoIP service provider XCast over allegations that it
facilitated illegal telemarketing campaigns since at least January 2018, in
contravention of the Telemarketing Sales Rule (TSR).
In addition to prohibiting the company from violating the law, the stipulated order requires it to meet other compliance measures, including establishing a process for screening its customers and calling for potential illegal telemarketing. The order, which also imposes a $10 million civil penalty judgment, has been suspended due to XCast's inability to pay.
"XCast provided VoIP services that transmitted billions of illegal robocalls to American consumers, including scam calls fraudulently claiming to be from government agencies," the DoJ said in a press release.
These calls delivered prerecorded marketing messages, most of which were sent to numbers listed on the National Do Not Call Registry. To make matters worse, a majority of the calls falsely claimed to be affiliated with government entities or contained outright false or misleading information in an attempt to deceive victims into making purchases.
For instance, some of the calls claimed to be from the Social Security Administration and threatened to cut off a recipient's utility service unless immediate payments were made. In other cases, consumers were urged to act promptly to reverse bogus credit card charges.
As part of the proposed settlement, XCast has been ordered to cut ties with firms that do not adhere to the U.S. telemarketing laws.
The U.S. Federal Trade Commission (FTC), in a statement, said the Los Angeles-based company did nothing despite being warned several times that illegal robocallers were using its services.
"The order permanently bars XCast Labs from providing VoIP services to any company with which it does not have an automated procedure to block calls that display invalid Caller ID phone numbers or that are not authenticated through the FCC's STIR/SHAKEN Authentication Framework," the FTC said.
The development comes as the FTC announced a ban on Response Tree from making or assisting anyone else in making robocalls or calls to phone numbers on the Do Not Call Registry.
The complaint accused the Californian company of operating more than 50 websites, such as PatriotRefi[.]com, AbodeDefense[.]com, and TheRetailRewards[.]com, which used manipulative dark patterns to "trick consumers into providing their personal information for supposed mortgage refinancing loans and other services."
The defendants then allegedly sold the collected information of hundreds of thousands of consumers to telemarketers who used them to make millions of illegal telemarketing calls, including robocalls, to consumers across the country.
Google Settles $5 Billion Privacy Lawsuit Over Tracking Users in 'Incognito
Mode'
3.1.24
Security
The Hacker News
Google has agreed to settle a lawsuit filed in June 2020
that alleged that the company misled users by tracking their surfing activity
who thought that their internet use remained private when using the "incognito"
or "private" mode on web browsers.
The class-action lawsuit sought at least $5 billion in damages. The settlement terms were not disclosed.
The plaintiffs had alleged that Google violated federal wiretap laws and tracked users' activity using Google Analytics to collect information when in private mode.
They said this allowed the company to collect an "unaccountable trove of information" about users who assumed they had taken adequate steps to protect their privacy online.
Google subsequently attempted to get the lawsuit dismissed, pointing out the message it displayed when users turned on Chrome's incognito mode, which informs users that their activity might still be visible to websites you visit, employer or school, or their internet service provider.
It's worth noting here at this point that enabling incognito or private mode in a web browser only gives users the choice to search the internet without their activity being locally saved to the browser.
That said, websites using advertising technologies and analytics APIs can still continue to track users within that incognito session and can further correlate that activity by, for example, matching their IP addresses.
"Google's motion hinges on the idea that plaintiffs consented to Google collecting their data while they were browsing in private mode," U.S. District Judge Yvonne Gonzalez Rogers ruled.
"Because Google never explicitly told users that it does so, the Court cannot find as a matter of law that users explicitly consented to the at-issue data collection."
New Variant of DLL Search Order Hijacking Bypasses Windows 10 and 11 Protections
1.1.24
Hacking
The Hacker News
Security researchers have detailed a new variant of a
dynamic link library (DLL) search order hijacking technique that could be used
by threat actors to bypass security mechanisms and achieve execution of
malicious code on systems running Microsoft Windows 10 and Windows 11.
The approach "leverages executables commonly found in the trusted WinSxS folder and exploits them via the classic DLL search order hijacking technique," cybersecurity firm Security Joes said in a new report exclusively shared with The Hacker News.
In doing so, it allows adversaries to eliminate the need for elevated privileges when attempting to run nefarious code on a compromised machine as well as introduce potentially vulnerable binaries into the attack chain, as observed in the past.
DLL search order hijacking, as the name implies, involves gaming the search order used to load DLLs in order to execute malicious payloads for purposes of defense evasion, persistence, and privilege escalation.
Specifically, attacks exploiting the technique single out applications that do not specify the full path to the libraries they require, and instead, rely on a predefined search order to locate the necessary DLLs on disk.
Threat actors take advantage of this behavior by moving legitimate system binaries into non-standard directories that include malicious DLLs that are named after legitimate ones so that the library containing the attack code is picked up in place of the latter.
This, in turn, works because the process calling the DLL will search in the
directory it's executing from first before recursively iterating through other
locations in a particular order to locate and load the resource in question. To
put it in other words, the search order is as follows -
The directory from which the application is launched
The folder
"C:\Windows\System32"
The folder "C:\Windows\System"
The folder
"C:\Windows"
The current working directory
Directories listed in the
system's PATH environment variable
Directories listed in the user's PATH
environment variable
The novel twist devised by Security Joes targets files
located in the trusted "C:\Windows\WinSxS" folder. Short for Windows
side-by-side, WinSxS is a critical Windows component that's used for the
customization and updating of the operating system to ensure compatibility and
integrity.
Cybersecurity
"Our discovery diverges from this path, unveiling a more subtle and stealthy
method of exploitation."
The idea, in a nutshell, is to find vulnerable binaries in the WinSxS folder
(e.g., ngentask.exe and aspnet_wp.exe) and combine it with the regular DLL
search order hijacking methods by strategically placing a custom DLL with the
same name as the legitimate DLL into an actor-controlled directory to achieve
code execution.
As a result, simply executing a vulnerable file in the WinSxS folder by setting
the custom folder containing the rogue DLL as the current directory is enough to
trigger the execution of the DLL's contents without having to copy the
executable from the WinSxS folder to it.
Security Joes warned that there could be additional binaries in the WinSxS
folder that are susceptible to this kind of DLL search order hijacking,
necessitating that organizations take adequate precautions to mitigate the
exploitation method within their environments.
"Examine parent-child relationships between processes, with a specific focus on
trusted binaries," the company said. "Monitor closely all the activities
performed by the binaries residing in the WinSxS folder, focusing on both
network communications and file operations."
"This approach represents a novel application in cybersecurity:
traditionally, attackers have largely relied on well-known techniques like DLL
search order hijacking, a method that manipulates how Windows applications load
external libraries and executables," Ido Naor, co-founder and CEO of Security
Joes, said in a statement shared with The Hacker News.
New JinxLoader Targeting Users with Formbook and XLoader Malware
1.1.24
Virus
The Hacker News
A new Go-based malware loader called JinxLoader is being used by threat actors to deliver next-stage payloads such as Formbook and its successor XLoader.
The disclosure comes from cybersecurity firms Palo Alto Networks Unit 42 and Symantec, both of which highlighted multi-step attack sequences that led to the deployment of JinxLoader through phishing attacks.
"The malware pays homage to League of Legends character Jinx, featuring the character on its ad poster and [command-and-control] login panel," Symantec said. "JinxLoader's primary function is straightforward – loading malware."
Unit 42 revealed in late November 2023 that the malware service was first advertised on hackforums[.]net on April 30, 2023, for $60 a month, $120 a year, or for a lifetime fee of $200.
The attacks begin with phishing emails impersonating Abu Dhabi National Oil Company (ADNOC), urging recipients to open password-protected RAR archive attachments that, upon opening, drop the JinxLoader executable, which subsequently acts as a gateway for Formbook or XLoader.
The development comes as ESET revealed a spike in infections, delivering another novice loader malware family dubbed Rugmi to propagate a wide range of information stealers.
It also comes amid a surge in campaigns distributing DarkGate and PikaBot, with a threat actor known as TA544 (aka Narwal Spider) leveraging new variants of loader malware called IDAT Loader to deploy Remcos RAT or SystemBC malware.
What's more, the threat actors behind the Meduza Stealer have released an updated version of the malware (version 2.2) on the dark web with expanded support for browser-based cryptocurrency wallets and an improved credit card (CC) grabber.
In a sign that stealer malware continues to be a lucrative market for cybercriminals, researchers have discovered a new stealer family known as Vortex Stealer that's capable of exfiltrating browser data, Discord tokens, Telegram sessions, system information, and files that are less than 2 MB in size.
"Stolen information will be archived and uploaded to Gofile or Anonfiles; the malware will also post it onto the author's Discord using webhooks," Symantec said. "It's also capable of posting to Telegram via a Telegram bot."
New Terrapin Flaw Could Let Attackers Downgrade SSH Protocol Security
1.1.24
Attack
The Hacker News
Security researchers from Ruhr University Bochum have
discovered a vulnerability in the Secure Shell (SSH) cryptographic network
protocol that could allow an attacker to downgrade the connection's security by
breaking the integrity of the secure channel.
Called Terrapin (CVE-2023-48795, CVSS score: 5.9), the exploit has been described as the "first ever practically exploitable prefix truncation attack."
"By carefully adjusting the sequence numbers during the handshake, an attacker can remove an arbitrary amount of messages sent by the client or server at the beginning of the secure channel without the client or server noticing it," researchers Fabian Bäumer, Marcus Brinkmann, and Jörg Schwenk said.
SSH is a method for securely sending commands to a computer over an unsecured network. It relies on cryptography to authenticate and encrypt connections between devices.
This is accomplished by means of a handshake in which a client and server agree upon cryptographic primitives and exchange keys required for setting up a secure channel that can provide confidentiality and integrity guarantees.
However, a bad actor in an active adversary-in-the-middle (AitM) position with the ability to intercept and modify the connection's traffic at the TCP/IP layer can downgrade the security of an SSH connection when using SSH extension negotiation.
"The attack can be performed in practice, allowing an attacker to downgrade the connection's security by truncating the extension negotiation message (RFC8308) from the transcript," the researchers explained.
"The truncation can lead to using less secure client authentication algorithms and deactivating specific countermeasures against keystroke timing attacks in OpenSSH 9.5."
Another crucial prerequisite necessary to pulling off the attack is the use of a vulnerable encryption mode such as ChaCha20-Poly1305 or CBC with Encrypt-then-MAC to secure the connection.
"In a real-world scenario, an attacker could exploit this vulnerability to intercept sensitive data or gain control over critical systems using administrator privileged access," Qualys said. "This risk is particularly acute for organizations with large, interconnected networks that provide access to privileged data."
The flaw impacts many SSH client and server implementations, such as OpenSSH, Paramiko, PuTTY, KiTTY, WinSCP, libssh, libssh2, AsyncSSH, FileZilla, and Dropbear, prompting the maintainers to release patches to mitigate potential risks.
"Because SSH servers and OpenSSH in particular are so commonly used throughout cloud-based enterprise application environments, it's imperative for companies to ensure they have taken appropriate measures to patch their servers," Yair Mizrahi, senior security researcher of security research at JFrog, told The Hacker News.
"However, a vulnerable client connecting to a patched server will still result in an vulnerable connection. Thus, companies must also take steps to identify every vulnerable occurrence across their entire infrastructure and apply a mitigation immediately."