
Mandiant described the threat actor as having demonstrated a "nuanced understanding of the appliance and their ability to subvert detection throughout this campaign" and using living-off-the-land (LotL) techniques to fly under the radar.
H January(68) February(106) March(112) April(110) June(37) July(4)
Chinese Hackers Exploiting Ivanti VPN Flaws to Deploy New Malware
29.2.24
Virus
The Hacker News
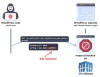
At least two different suspected China-linked cyber
espionage clusters, tracked as UNC5325 and UNC3886, have been attributed to the
exploitation of security flaws in Ivanti Connect Secure VPN appliances.
UNC5325 abused CVE-2024-21893 to deliver a wide range of new malware called LITTLELAMB.WOOLTEA, PITSTOP, PITDOG, PITJET, and PITHOOK, as well as attempted to maintain persistent access to compromised appliances, Mandiant said.
The Google-owned threat intelligence firm has assessed with moderate confidence that UNC5325 is associated with UNC3886 owing to source code overlaps in LITTLELAMB.WOOLTEA and PITHOOK with malware used by the latter.
It's worth pointing out that UNC3886 has a track record of leveraging zero-day flaws in Fortinet and VMware solutions to deploy a variety of implants like VIRTUALPITA, VIRTUALPIE, THINCRUST, and CASTLETAP.
"UNC3886 has primarily targeted the defense industrial base, technology, and telecommunication organizations located in the U.S. and [Asia-Pacific] regions," Mandiant researchers said.
The active exploitation of CVE-2024-21893 – a server-side request forgery (SSRF) vulnerability in the SAML component of Ivanti Connect Secure, Ivanti Policy Secure, and Ivanti Neurons for ZTA – by UNC5325 is said to have occurred as early as January 19, 2024, targeting a limited number of devices.
The attack chain entails combining CVE-2024-21893 with a previously disclosed command injection vulnerability tracked as CVE-2024-21887 to gain unauthorized access to susceptible appliances, ultimately leading to the deployment of a new version of BUSHWALK.
Some instances have also involved the misuse of legitimate Ivanti components, such as SparkGateway plugins, to drop additional payloads. This includes the PITFUEL plugin to load a malicious shared object codenamed LITTLELAMB.WOOLTEA, which comes with capabilities to persist across system upgrade events, patches, and factory resets.
“While the limited attempts observed to maintain persistence have not been successful to date due to a lack of logic in the malware’s code to account for an encryption key mismatch, it further demonstrates the lengths UNC5325 will go to maintain access to priority targets and highlights the importance of ensuring network appliances have the latest updates and patches,” the company pointed out.
It further acts as a backdoor that supports command execution, file management, shell creation, SOCKS proxy, and network traffic tunneling.
Also observed is another malicious SparkGateway plugin dubbed PITDOG that injects a shared object known as PITHOOK in order to persistently execute an implant referred to as PITSTOP that's designed for shell command execution, file write, and file read on the compromised appliance.

Mandiant described the threat actor as having demonstrated a "nuanced
understanding of the appliance and their ability to subvert detection throughout
this campaign" and using living-off-the-land (LotL) techniques to fly under the
radar.
The cybersecurity firm said it expects "UNC5325 as well as other China-nexus espionage actors to continue to leverage zero day vulnerabilities on network edge devices as well as appliance-specific malware to gain and maintain access to target environments."
Links Found Between Volt Typhoon and UTA0178#
The disclosure comes as
industrial cybersecurity company Dragos attributed China-sponsored Volt Typhoon
(aka Voltzite) to reconnaissance and enumeration activities aimed at multiple
U.S.-based electric companies, emergency services, telecommunication providers,
defense industrial bases, and satellite services.
"Voltzite's actions towards U.S. electric entities, telecommunications, and GIS systems signify clear objectives to identify vulnerabilities within the country's critical infrastructure that can be exploited in the future with destructive or disruptive cyber attacks," it said.
Volt Typhoon's victimology footprint has since expanded to include African electric transmission and distribution providers, with evidence connecting the adversary to UTA0178, a threat activity group linked to the zero-day exploitation of Ivanti Connect Secure flaws in early December 2023.
The cyber espionage actor, which heavily relies on LotL methods to sidestep detection, joins two other new groups, namely Gananite and Laurionite, that came to light in 2023, conducting long-term reconnaissance and intellectual property theft operations targeting critical infrastructure and government entities.
"Voltzite uses very minimal tooling and prefers to conduct their operations with as little a footprint as possible," Dragos explained. "Voltzite heavily focuses on detection evasion and long-term persistent access with the assessed intent of long-term espionage and data exfiltration."
(The story has been updated after publication to emphasize that the attempts to achieve persistence on the VPN appliances were unsuccessful.)
President Biden Blocks Mass Transfer of Personal Data to High-Risk Nations
29.2.24
BigBrothers
The Hacker News
U.S. President Joe Biden has issued an Executive Order
that prohibits the mass transfer of citizens' personal data to countries of
concern.
The Executive Order also "provides safeguards around other activities that can give those countries access to Americans' sensitive data," the White House said in a statement.
This includes sensitive information such as genomic data, biometric data, personal health data, geolocation data, financial data, and certain kinds of personally identifiable information (PII).
The U.S. government said threat actors could weaponize this information to track their citizens and pass that information to data brokers and foreign intelligence services, which can then be used for intrusive surveillance, scams, blackmail, and other violations of privacy.
"Commercial data brokers and other companies can sell this data to countries of concern, or entities controlled by those countries, and it can land in the hands of foreign intelligence services, militaries, or companies controlled by foreign governments," the government said.
In November 2023, researchers at Duke University revealed that it's trivial to "obtain sensitive data about active-duty members of the military, their families, and veterans, including non-public, individually identified, and sensitive data, such as health data, financial data, and information about religious practices" from data brokers for as low as $0.12 per record.
Stating that the sale of such data poses privacy, counterintelligence, blackmail, and national security risks, it added hostile nations could collect personal information on activists, journalists, dissidents, and marginalized communities with the goal of restricting freedom of expression and curbing dissent.
The government said the countries of concern have a "track record of collecting and misusing data on Americans." According to the U.S. Justice Department, the countries that fall under this category include China, Russia, Iran, North Korea, Cuba, and Venezuela.
The Executive Order directs the federal agencies to issue regulations that establish clear protections for sensitive personal and government-related data from access and exploitation, as well as set high-security standards to limit data access via commercial agreements.
Additionally, the order requires the Departments of Health and Human Services, Defense, and Veterans Affairs to ensure that Federal grants, contracts, and awards are not misused to facilitate access to sensitive data.
"The Administration's decision to limit personal data flows only to a handful of countries of concern, like China, is a mistake," Senator Ron Wyden said in a statement, and that the argument that the U.S. government cannot be banned from buying Americans' data is no longer valid.
"Authoritarian dictatorships like Saudi Arabia and U.A.E. cannot be trusted with Americans' personal data, both because they will likely use it to undermine U.S. national security and target U.S. based dissidents, but also because these countries lack effective privacy laws necessary to stop the data from being sold onwards to China."
The latest attempt to regulate the data broker industry comes as the U.S. added China's Chengdu Beizhan Electronics and Canadian network intelligence firm Sandvine to its Entity List after the latter's middleboxes were found to be used to deliver spyware targeting a former Egyptian member of parliament last year.
A report from Bloomberg in September 2023 also found that Sandvine's equipment had been used by governments in Egypt and Belarus to censor content on the internet.
Access Now said Sandvine's internet-blocking technologies facilitated human rights violations by repressive governments around the world, including in Azerbaijan, Jordan, Russia, Turkey, and the U.A.E., noting it played a "direct role" in shutting down the internet in Belarus in 2020.
"Sandvine supplies deep packet inspection tools, which have been used in mass web-monitoring and censorship to block news as well as in targeting political actors and human rights activists," the U.S. Department of State said, explaining its rationale behind adding the company to the trade restriction list. "This technology has been misused to inject commercial spyware into the devices of perceived critics and dissidents."
Iran-Linked UNC1549 Hackers Target Middle East Aerospace & Defense Sectors
29.2.24
APT
The Hacker News
An Iran-nexus threat actor known as UNC1549 has been
attributed with medium confidence to a new set of attacks targeting aerospace,
aviation, and defense industries in the Middle East, including Israel and the
U.A.E.
Other targets of the cyber espionage activity likely include Turkey, India, and Albania, Google-owned Mandiant said in a new analysis.
UNC1549 is said to overlap with Smoke Sandstorm (previously Bohrium) and Crimson Sandstorm (previously Curium), the latter of which is an Islamic Revolutionary Guard Corps (IRGC) affiliated group also known as Imperial Kitten, TA456, Tortoiseshell, and Yellow Liderc.
"This suspected UNC1549 activity has been active since at least June 2022 and is still ongoing as of February 2024," the company said. "While regional in nature and focused mostly in the Middle East, the targeting includes entities operating worldwide."
The attacks entail the use of Microsoft Azure cloud infrastructure for command-and-control (C2) and social engineering involving job-related lures to deliver two backdoors dubbed MINIBIKE and MINIBUS.
The spear-phishing emails are designed to disseminate links to fake websites containing Israel-Hamas related content or phony job offers, resulting in the deployment of a malicious payload. Also observed are bogus login pages mimicking major companies to harvest credentials.
The custom backdoors, upon establishing C2 access, act as a conduit for intelligence collection and for further access into the targeted network. Another tool deployed at this stage is a tunneling software called LIGHTRAIL that communicates using Azure cloud.
While MINIBIKE is based in C++ and capable of file exfiltration and upload, and command execution, MINIBUS serves as a more "robust successor" with enhanced reconnaissance features.
"The intelligence collected on these entities is of relevance to strategic Iranian interests and may be leveraged for espionage as well as kinetic operations," Mandiant said.
"The evasion methods deployed in this campaign, namely the tailored job-themed lures combined with the use of cloud infrastructure for C2, may make it challenging for network defenders to prevent, detect, and mitigate this activity."
CrowdStrike, in its Global Threat Report for 2024, described how "faketivists associated with Iranian state-nexus adversaries and hacktivists branding themselves as 'pro-Palestinian' focused on targeting critical infrastructure, Israeli aerial projectile warning systems, and activity intended for information operation purposes in 2023."
This includes Banished Kitten, which unleashed the BiBi wiper malware, and Vengeful Kitten, an alias for Moses Staff that has claimed data-wiping activity against more than 20 companies' industrial control systems (ICS) in Israel.
That said, Hamas-linked adversaries have been noticeably absent from conflict-related activity, something the cybersecurity firm has attributed to likely power and internet disruptions in the region.
FBI Warns U.S. Healthcare Sector of Targeted BlackCat Ransomware Attacks
28.2.24
Ransom
The Hacker News
The U.S. government is warning about the resurgence of BlackCat (aka ALPHV) ransomware attacks targeting the healthcare sector as recently as this month.
"Since mid-December 2023, of the nearly 70 leaked victims, the healthcare sector has been the most commonly victimized," the government said in an updated advisory.
"This is likely in response to the ALPHV/BlackCat administrator's post encouraging its affiliates to target hospitals after operational action against the group and its infrastructure in early December 2023."
The advisory comes from the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), and the Department of Health and Human Services (HHS).
The BlackCat ransomware operation suffered a major blow late last year after a coordinated law enforcement operation led to the seizure of its dark leak sites. But the takedown turned out to be a failure after the group managed to regain control of the sites and switched to a new TOR data leak portal that continues to remain active to date.
It has also ramped up against critical infrastructure organizations in recent weeks, having claimed responsibility for attacks on Prudential Financial, LoanDepot, Trans-Northern Pipelines, and UnitedHealth Group subsidiary Optum.
The development has prompted the U.S. government to announce financial rewards of up to $15 million for information leading to the identification of key members as well as affiliates of the e-crime group.
BlackCat's ransomware spree coincides with the return of LockBit after similar disruption efforts led by the U.K. National Crime Agency (NCA) last week.
According to a report from SC Magazine, threat actors breached Optum's network by leveraging the recently disclosed critical security flaws in ConnectWise's ScreenConnect remote desktop and access software.
The flaws, which allow for remote code execution on susceptible systems, have also been weaponized by the Black Basta and Bl00dy ransomware gangs as well as by other threat actors to deliver Cobalt Strike Beacons, XWorm, and even other remote management tools like Atera, Syncro, and another ScreenConnect client.
Attack surface management firm Censys said it observed more than 3,400 exposed potentially vulnerable ScreenConnect hosts online, with most of them located in the U.S., Canada, the U.K., Australia, Germany, France, India, the Netherlands, Turkey, and Ireland.

"It's clear that remote access software like ScreenConnect continues to be a
prime target for threat actors," Censys security researcher Himaja Motheram
said.
The findings come as ransomware groups like RansomHouse, Rhysida, and a Phobos variant called Backmydata have continued to compromise various organizations in the U.S., U.K., Europe, and the Middle East.
In a sign that these cybercrime groups are shifting to more nuanced and sophisticated tactics, RansomHouse has developed a custom tool dubbed MrAgent to deploy the file-encrypting malware at scale.
"MrAgent is a binary designed to run on [VMware ESXi] hypervisors, with the sole purpose of automating and tracking the deployment of ransomware across large environments with a high number of hypervisor systems," Trellix said. Details of MrAgent first came to light in September 2023.
Another significant tactic adopted by some ransomware groups is the sale of direct network access as a new monetization method via their own blogs, on Telegram channels, or data leak websites, KELA said.
It also follows the public release of a Linux-specific, C-based ransomware threat known as Kryptina, which surfaced in December 2023 on underground forums and has since been made available for free on BreachForums by its creator.

"The release of the RaaS source code, complete with extensive documentation,
could have significant implications for the spread and impact of ransomware
attacks against Linux systems," SentinelOne researcher Jim Walter said.
"It is likely to increase the ransomware builder's attractiveness and usability, drawing in yet more low-skilled participants to the cybercrime ecosystem. There is also significant risk that it will lead to the development of multiple spin-offs and an increase in attacks."
TimbreStealer Malware Spreading via Tax-themed Phishing Scam Targets IT Users
28.2.24
Phishing
The Hacker News
Mexican users have been targeted with tax-themed phishing
lures at least since November 2023 to distribute a previously undocumented
Windows malware called TimbreStealer.
Cisco Talos, which discovered the activity, described the authors as skilled and that the "threat actor has previously used similar tactics, techniques and procedures (TTPs) to distribute a banking trojan known as Mispadu in September 2023.
Besides employing sophisticated obfuscation techniques to sidestep detection and ensure persistence, the phishing campaign makes use of geofencing to single out users in Mexico, returning an innocuous blank PDF file instead of the malicious one if the payload sites are contacted from other locations.
Some of the notable evasive maneuvers include leveraging custom loaders and direct system calls to bypass conventional API monitoring, in addition to utilizing Heaven's Gate to execute 64-bit code within a 32-bit process, an approach that was also recently adopted by HijackLoader.
The malware comes with several embedded modules for orchestration, decryption, and protection of the main binary, while also running a series of checks to determine if it's running a sandbox environment, the system language is not Russian, and the timezone is within a Latin American region.
The orchestrator module also looks for files and registry keys to double-check that the machine hasn't been previously infected, before launching a payload installer component that displays a benign decoy file to the user, as it ultimately triggers the execution of TimbreStealer's primary payload.
The payload is designed to harvest a wide range of data, including credential information from different folders, system metadata, and the URLs accessed, look for files matching specific extensions, and verify the presence of remote desktop software.
TimbreStealer Malware
Cisco Talos said it identified overlaps with a Mispadu
spam campaign observed in September 2023, although the target industries of
TimbreStealer are varied and with a focus on manufacturing and transportation
sectors.
The disclosure comes amid the emergence of a new version of another information stealer called Atomic (aka AMOS), which is capable of gathering data from Apple macOS systems such as local user account passwords, credentials from Mozilla Firefox and Chromium-based browsers, crypto wallet information, and files of interest, using an unusual combination of Python and Apple Script code.
"The new variant drops and uses a Python script to stay covert," Bitdefender
researcher Andrei Lapusneanu said, noting the Apple Script block for collecting
sensitive files from the victim's computer exhibits a "significantly high level
of similarity" with the RustDoor backdoor.
It also follows the emergence of new stealer malware families such as XSSLite, which was released as part of a malware development competition hosted by the XSS forum, even as existing strains like Agent Tesla and Pony (aka Fareit or Siplog) continued to be used for information theft and subsequent sale on stealer logs marketplaces like Exodus.
Cybersecurity Agencies Warn Ubiquiti EdgeRouter Users of APT28's MooBot Threat
28.2.24
APT
The Hacker News
In a new joint advisory, cybersecurity and intelligence
agencies from the U.S. and other countries are urging users of Ubiquiti
EdgeRouter to take protective measures, weeks after a botnet comprising infected
routers was felled by law enforcement as part of an operation codenamed Dying
Ember.
The botnet, named MooBot, is said to have been used by a Russia-linked threat actor known as APT28 to facilitate covert cyber operations and drop custom malware for follow-on exploitation. APT28, affiliated with Russia's Main Directorate of the General Staff (GRU), is known to be active since at least 2007.
APT28 actors have "used compromised EdgeRouters globally to harvest credentials, collect NTLMv2 digests, proxy network traffic, and host spear-phishing landing pages and custom tools," the authorities said [PDF].
The adversary's use of EdgeRouters dates back to 2022, with the attacks targeting aerospace and defense, education, energy and utilities, governments, hospitality, manufacturing, oil and gas, retail, technology, and transportation sectors in the Czech Republic, Italy, Lithuania, Jordan, Montenegro, Poland, Slovakia, Turkey, Ukraine, the U.A.E., and the U.S.
MooBot attacks entail targeting routers with default or weak credentials to deploy OpenSSH trojans, with APT28 acquiring this access to deliver bash script and other ELF binaries to collect credentials, proxy network traffic, host phishing pages, and other tooling.
This includes Python scripts to upload account credentials belonging to specifically targeted webmail users, which are collected via cross-site scripting and browser-in-the-browser (BitB) spear-phishing campaigns.
APT28 has also been linked to the exploitation of CVE-2023-23397 (CVSS score: 9.8), a now-patched critical privilege escalation flaw in Microsoft Outlook that could enable the theft of NT LAN Manager (NTLM) hashes and mount a relay attack without requiring any user interaction.
Another tool in its malware arsenal is MASEPIE, a Python backdoor capable of executing arbitrary commands on victim machines utilizing compromised Ubiquiti EdgeRouters as command-and-control (C2) infrastructure.
"With root access to compromised Ubiquiti EdgeRouters, APT28 actors have unfettered access to Linux-based operating systems to install tooling and to obfuscate their identity while conducting malicious campaigns," the agencies noted.
Organizations are recommended to perform a hardware factory reset of the routers to flush file systems of malicious files, upgrade to the latest firmware version, change default credentials, and implement firewall rules to prevent exposure of remote management services.
The revelations are a sign that nation-state hackers are increasingly relying on routers as a launchpad for attacks, using them to create botnets such as VPNFilter, Cyclops Blink, and KV-botnet and conduct their malicious activities.
The bulletin arrives a day after the Five Eyes nations called out APT29 – the threat group affiliated with Russia's Foreign Intelligence Service (SVR) and the entity behind the attacks on SolarWinds, Microsoft, and HPE – for employing service accounts and dormant accounts to access cloud environments at target organizations.
WordPress LiteSpeed Plugin Vulnerability Puts 5 Million Sites at Risk
28.2.24
Vulnerebility
The Hacker News
A security vulnerability has been disclosed in the
LiteSpeed Cache plugin for WordPress that could enable unauthenticated users to
escalate their privileges.
Tracked as CVE-2023-40000, the vulnerability was addressed in October 2023 in version 5.7.0.1.
"This plugin suffers from unauthenticated site-wide stored [cross-site scripting] vulnerability and could allow any unauthenticated user from stealing sensitive information to, in this case, privilege escalation on the WordPress site by performing a single HTTP request," Patchstack researcher Rafie Muhammad said.
LiteSpeed Cache, which is used to improve site performance, has more than five million installations. The latest version of the plugin in 6.1, which was released on February 5, 2024.
The WordPress security company said CVE-2023-40000 is the result of a lack of user input sanitization and escaping output. The vulnerability is rooted in a function named update_cdn_status() and can be reproduced in a default installation.
"Since the XSS payload is placed as an admin notice and the admin notice could be displayed on any wp-admin endpoint, this vulnerability also could be easily triggered by any user that has access to the wp-admin area," Muhammad said.

The disclosure arrives four months after Wordfence revealed another XSS flaw in
the same plugin (CVE-2023-4372, CVSS score: 6.4) due to insufficient input
sanitization and output escaping on user supplied attributes. It was addressed
in version 5.7.
"This makes it possible for authenticated attackers with contributor-level and above permissions to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page," István Márton said.
Open-Source Xeno RAT Trojan Emerges as a Potent Threat on GitHub
28.2.24
Virus
The Hacker News
An "intricately designed" remote access trojan (RAT)
called Xeno RAT has been made available on GitHub, making it easily accessible
to other actors at no extra cost.
Written in C# and compatible with Windows 10 and Windows 11 operating systems, the open-source RAT comes with a "comprehensive set of features for remote system management," according to its developer, who goes by the name moom825.
It includes a SOCKS5 reverse proxy and the ability to record real-time audio, as well as incorporate a hidden virtual network computing (hVNC) module along the lines of DarkVNC, which allows attackers to gain remote access to an infected computer.
"Xeno RAT is developed entirely from scratch, ensuring a unique and tailored approach to remote access tools," the developer states in the project description. Another notable aspect is that it has a builder that enables the creation of bespoke variants of the malware.
It's worth noting that moom825 is also the developer of another C#-based RAT called DiscordRAT 2.0, which has been distributed by threat actors within a malicious npm package named node-hide-console-windows, as disclosed by ReversingLabs in October 2023.
Cybersecurity firm Cyfirma, in a report published last week, said it observed Xeno RAT being disseminated via the Discord content delivery network (CDN), once again underscoring how a rise in affordable and freely available malware is driving an increase in campaigns utilizing RATs.
"The primary vector in the form of a shortcut file, disguised as a WhatsApp
screenshot, acts as a downloader," the company said. "The downloader downloads
the ZIP archive from Discord CDN, extracts, and executes the next stage
payload."
The multi-stage sequence leverages a technique called DLL side-loading to launch a malicious DLL, while simultaneously taking steps to establish persistence and evade analysis and detection.
The development comes as the AhnLab Security Intelligence Center (ASEC) revealed the use of a Gh0st RAT variant called Nood RAT that's used in attacks targeting Linux systems, allowing adversaries to harvest sensitive information.
"Nood RAT is a backdoor malware that can receive commands from the C&C server to
perform malicious activities such as downloading malicious files, stealing
systems' internal files, and executing commands," ASEC said.
"Although simple in form, it is equipped with the encryption feature to avoid network packet detection and can receive commands from threat actors to carry out multiple malicious activities."
Five Eyes Agencies Expose APT29's Evolving Cloud Attack Tactics
28.2.24
APT
The Hacker News
Cybersecurity and intelligence agencies from the Five
Eyes nations have released a joint advisory detailing the evolving tactics of
the Russian state-sponsored threat actor known as APT29.
The hacking outfit, also known as BlueBravo, Cloaked Ursa, Cozy Bear, Midnight Blizzard (formerly Nobelium), and The Dukes, is assessed to be affiliated with the Foreign Intelligence Service (SVR) of the Russian Federation.
Previously attributed to the supply chain compromise of SolarWinds software, the cyber espionage group attracted attention in recent months for targeting Microsoft, Hewlett Packard Enterprise (HPE), and other organizations with an aim to further their strategic objectives.
"As organizations continue to modernize their systems and move to cloud-based infrastructure, the SVR has adapted to these changes in the operating environment," according to the security bulletin.
These include -
Obtaining access to cloud infrastructure via service and dormant accounts by
means of brute-force and password spraying attacks, pivoting away from
exploiting software vulnerabilities in on-premise networks
Using tokens to
access victims' accounts without the need for a password
Leveraging password
spraying and credential reuse techniques to seize control of personal accounts,
using prompt bombing to bypass multi-factor authentication (MFA) requirements,
and then registering their own device to gain access to the network
Making it
harder to distinguish malicious connections from typical users by utilizing
residential proxies to make the malicious traffic appear as if it's originating
from IP addresses within internet service provider (ISP) ranges used for
residential broadband customers and conceal their true origins
"For
organizations that have moved to cloud infrastructure, the first line of defense
against an actor such as SVR should be to protect against SVR' TTPs for initial
access," the agencies said. "Once the SVR gains initial access, the actor is
capable of deploying highly sophisticated post compromise capabilities such as
MagicWeb."
New Hugging Face Vulnerability Exposes AI Models to Supply Chain Attacks
28.2.24
AI
The Hacker News
Cybersecurity researchers have found that it's possible
to compromise the Hugging Face Safetensors conversion service to ultimately
hijack the models submitted by users and result in supply chain attacks.
"It's possible to send malicious pull requests with attacker-controlled data from the Hugging Face service to any repository on the platform, as well as hijack any models that are submitted through the conversion service," HiddenLayer said in a report published last week.
This, in turn, can be accomplished using a hijacked model that's meant to be converted by the service, thereby allowing malicious actors to request changes to any repository on the platform by masquerading as the conversion bot.
Hugging Face is a popular collaboration platform that helps users host pre-trained machine learning models and datasets, as well as build, deploy, and train them.
Safetensors is a format devised by the company to store tensors keeping security in mind, as opposed to pickles, which has been likely weaponized by threat actors to execute arbitrary code and deploy Cobalt Strike, Mythic, and Metasploit stagers.
It also comes with a conversion service that enables users to convert any PyTorch model (i.e., pickle) to its Safetensor equivalent via a pull request.
HiddenLayer's analysis of this module found that it's hypothetically possible for an attacker to hijack the hosted conversion service using a malicious PyTorch binary and compromise the system hosting it.
What's more, the token associated with SFConvertbot – an official bot designed to generate the pull request – could be exfiltrated to send a malicious pull request to any repository on the site, leading to a scenario where a threat actor could tamper with the model and implant neural backdoors.
"An attacker could run any arbitrary code any time someone attempted to convert their model," researchers Eoin Wickens and Kasimir Schulz noted. "Without any indication to the user themselves, their models could be hijacked upon conversion."
Should a user attempt to convert their own private repository, the attack could pave the way for the theft of their Hugging Face token, access otherwise internal models and datasets, and even poison them.
Complicating matters further, an adversary could take advantage of the fact that any user can submit a conversion request for a public repository to hijack or alter a widely used model, potentially resulting in a considerable supply chain risk.
"Despite the best intentions to secure machine learning models in the Hugging Face ecosystem, the conversion service has proven to be vulnerable and has had the potential to cause a widespread supply chain attack via the Hugging Face official service," the researchers said.
"An attacker could gain a foothold into the container running the service and compromise any model converted by the service."
The development comes a little over a month after Trail of Bits disclosed LeftoverLocals (CVE-2023-4969, CVSS score: 6.5), a vulnerability that allows recovery of data from Apple, Qualcomm, AMD, and Imagination general-purpose graphics processing units (GPGPUs).
The memory leak flaw, which stems from a failure to adequately isolate process memory, enables a local attacker to read memory from other processes, including another user's interactive session with a large language model (LLM).
"This data leaking can have severe security consequences, especially given the rise of ML systems, where local memory is used to store model inputs, outputs, and weights," security researchers Tyler Sorensen and Heidy Khlaaf said.
WordPress Plugin Alert - Critical SQLi Vulnerability Threatens 200K+ Websites
27.2.24
Vulnerebility
The Hacker News
A critical security flaw has been disclosed in a popular
WordPress plugin called Ultimate Member that has more than 200,000 active
installations.
The vulnerability, tracked as CVE-2024-1071, carries a CVSS score of 9.8 out of a maximum of 10. Security researcher Christiaan Swiers has been credited with discovering and reporting the flaw.
In an advisory published last week, WordPress security company Wordfence said the plugin is "vulnerable to SQL Injection via the 'sorting' parameter in versions 2.1.3 to 2.8.2 due to insufficient escaping on the user supplied parameter and lack of sufficient preparation on the existing SQL query."
As a result, unauthenticated attackers could take advantage of the flaw to append additional SQL queries into already existing queries and extract sensitive data from the database.
It's worth noting that the issue only affects users who have checked the "Enable custom table for usermeta" option in the plugin settings.
Following responsible disclosure on January 30, 2024, a fix for the flaw has been made available by the plugin developers with the release of version 2.8.3 on February 19.
Users are advised to update the plugin to the latest version as soon as possible to mitigate potential threats, especially in light of the fact that Wordfence has already blocked one attack attempting to exploit the flaw over the past 24 hours.
In July 2023, another shortcoming in the same plugin (CVE-2023-3460, CVSS score: 9.8) was actively exploited by threat actors to create rogue admin users and seize control of vulnerable sites.
The development comes amid a surge in a new campaign that leverages compromised
WordPress sites to inject crypto drainers such as Angel Drainer directly or
redirect site visitors to Web3 phishing sites that contain drainers.
"These attacks leverage phishing tactics and malicious injections to exploit the Web3 ecosystem's reliance on direct wallet interactions, presenting a significant risk to both website owners and the safety of user assets," Sucuri researcher Denis Sinegubko said.
It also follows the discovery of a new drainer-as-a-service (DaaS) scheme called CG (short for CryptoGrab) that runs a 10,000-member-strong affiliate program comprised of Russian, English, and Chinese speakers.
One of the threats actor-controlled Telegram channels "refers attackers to a telegram bot that enables them to run their fraud operations without any third-party dependencies," Cyfirma said in a report late last month.
"The bot allows a user to get a domain for free, clone an existing template for the new domain, set the wallet address where the scammed funds are supposed to be sent, and also provides Cloudflare protection for that new domain."
The threat group has also been observed using two custom telegram bots called SiteCloner and CloudflarePage to clone an existing, legitimate website and add Cloudflare protection to it, respectively. These pages are then distributed mostly using compromised X (formerly Twitter) accounts.
New IDAT Loader Attacks Using Steganography to Deploy Remcos RAT
27.2.24
Virus
The Hacker News
Ukrainian entities based in Finland have been targeted as part of a malicious campaign distributing a commercial remote access trojan known as Remcos RAT using a malware loader called IDAT Loader.
The attack has been attributed to a threat actor tracked by the Computer Emergency Response Team of Ukraine (CERT-UA) under the moniker UAC-0184.
"The attack, as part of the IDAT Loader, used steganography as a technique," Morphisec researcher Michael Dereviashkin said in a report shared with The Hacker News. "While steganographic, or 'Stego' techniques are well-known, it is important to understand their roles in defense evasion, to better understand how to defend against such tactics."
IDAT Loader, which overlaps with another loader family called Hijack Loader, has been used to serve additional payloads like DanaBot, SystemBC, and RedLine Stealer in recent months. It has also been used by a threat actor tracked as TA544 to distribute Remcos RAT and SystemBC via phishing attacks.
The phishing campaign – first disclosed by CERT-UA in early January 2024 – entail using war-themed lures as a starting point to kick-start an infection chain that leads to the deployment of IDAT Loader, which, in turn, uses an embedded steganographic PNG to locate and extract Remcos RAT.
The development comes as CERT-UA revealed that defense forces in the country have been targeted via the Signal instant messaging app to distribute a booby-trapped Microsoft Excel document that executes COOKBOX, a PowerShell-based malware that's capable of loading and executing cmdlets. CERT-UA has attributed the activity to a cluster dubbed UAC-0149.
It also follows the resurgence of malware campaigns propagating PikaBot malware since February 8, 2024, using an updated variant that appears to be currently under active development.
"This version of the PikaBot loader uses a new unpacking method and heavy obfuscation," Elastic Security Labs said. "The core module has added a new string decryption implementation, changes to obfuscation functionality, and various other modifications."
8,000+ Domains of Trusted Brands Hijacked for Massive Spam Operation
27.2.24
Spam
The Hacker News
More than 8,000 domains and 13,000 subdomains belonging to legitimate brands and institutions have been hijacked as part of a sophisticated distribution architecture for spam proliferation and click monetization.
Guardio Labs is tracking the coordinated malicious activity, which has been ongoing since at least September 2022, under the name SubdoMailing. The emails range from "counterfeit package delivery alerts to outright phishing for account credentials."
The Israeli security company attributed the campaign to a threat actor it calls ResurrecAds, which is known to resuscitate dead domains of or affiliated with big brands with the end goal of manipulating the digital advertising ecosystem for nefarious gains.
"'ResurrecAds' manages an extensive infrastructure encompassing a wide array of hosts, SMTP servers, IP addresses, and even private residential ISP connections, alongside many additional owned domain names," security researchers Nati Tal and Oleg Zaytsev said in a report shared with The Hacker News.
In particular, the campaign "leverages the trust associated with these domains to circulate spam and malicious phishing emails by the millions each day, cunningly using their credibility and stolen resources to slip past security measures."
These subdomains belong to or are affiliated with big brands and organizations such as ACLU, eBay, Lacoste, Marvel, McAfee, MSN, Pearson, PwC, Swatch, Symantec, The Economist, UNICEF, and VMware, among
The campaign is notable for its ability to bypass standard security blocks, with the entire body conceived as an image to evade text-based spam filters, clicking which initiates a series of redirections through different domains.
"These redirects check your device type and geographic location, leading to content tailored to maximize profit," the researchers explained.
"This could be anything from an annoying ad or affiliate link to more deceptive tactics like quiz scams, phishing sites, or even a malware download aimed at swindling you out of your money more directly."
Another crucial aspect of these emails is that they are also capable of circumventing Sender Policy Framework (SPF), an email authentication method that's designed to prevent spoofing by ensuring a mail server is authorized to send email for a given domain.
It's not just SPF, as the emails also pass DomainKeys Identified Mail (DKIM) and Domain-based Message Authentication, Reporting and Conformance (DMARC) checks that help prevent messages from being marked as spam.

In one example of a deceptive cloud storage warning email highlighted by
Guardio, the message originated from an SMTP server in Kyiv, yet was flagged as
being sent from Return_UlKvw@marthastewart.msn.com.
A closer examination of the DNS record for marthastewart.msn.com revealed that the subdomain is linked to another domain (msnmarthastewartsweeps[.]com) by means of a CNAME record, an aliasing technique that has been previously weaponized by advertising technology companies to get around third-party cookie blocking.
"This means that the subdomain inherits the entire behavior of msnmarthastewartsweeps[.]com , including its SPF policy," the researchers said. "In this case, the actor can send emails to anyone they wish as if msn[.]com and their approved mailers sent those emails!"

It's worth pointing out here that both the domains were legitimate and briefly
active at some point in 2001, before they were left in an abandoned state for 21
years. It wasn't until September 2022 when msnmarthastewartsweeps[.]com was
privately registered with Namecheap.
In other the hijacking scheme entails the threat actors systematically scanning for long-forgotten subdomains with dangling CNAME records of abandoned domains and then registering them to take control of them.
CNAME-takeover can also have serious consequences when such reputed subdomains are seized to host bogus phishing landing pages designed to harvest users' credentials. That said, there is no evidence that any of the hijacked subdomains have been used for this purpose.
Guardio said it also found instances where the DNS SPF record of a known domain holds abandoned domains associated with defunct email- or marketing-related services, thereby allowing attackers to grab ownership of such domains, inject their own IP addresses into the record, and ultimately send emails on behalf of the main domain name.
In an effort to counter the threat and dismantle the infrastructure, Guardio has made available a SubdoMailing Checker, a website that enables domain administrators and site owners to look for signs of compromise.
"This operation is meticulously designed to misuse these assets for distributing various malevolent 'Advertisements,' aiming to generate as many clicks as possible for these 'ad network' clients," the researchers said.
"Armed with a vast collection of compromised reputable domains, servers, and IP addresses, this ad network deftly navigates through the malicious email propagation process, seamlessly switching and hopping among its assets at will."
North Korean Hackers Targeting Developers with Malicious npm Packages
27.2.24
Virus
The Hacker News
A set of fake npm packages discovered on the Node.js
repository has been found to share ties with North Korean state-sponsored
actors, new findings from Phylum show.
The packages are named execution-time-async, data-time-utils, login-time-utils, mongodb-connection-utils, and mongodb-execution-utils.
One of the packages in question, execution-time-async, masquerades as its legitimate counterpart execution-time, a library with more than 27,000 weekly downloads. Execution-time is a Node.js utility used to measure execution time in code.
It "actually installs several malicious scripts including a cryptocurrency and credential stealer," Phylum said, describing the campaign as a software supply chain attack targeting developers. The package was downloaded 302 times since February 4, 2024, before being taken down.
In an interesting twist, the threat actors made efforts to conceal the obfuscated malicious code in a test file, which is designed to fetch next-stage payloads from a remote server, steal credentials from web browsers like Brave, Google Chrome, and Opera, and retrieve a Python script, which, in turn, downloads other scripts -
~/.n2/pay, which can run arbitrary commands, download and launch ~/.n2/bow and
~/.n2/adc, terminate Brave and Google Chrome, and even delete itself
~/.n2/bow, which is a Python-based browser password stealer
~/.n2/adc, which
installs AnyDesk on Windows
Phylum said it identified comments in the source
code ("/Users/ninoacuna/") that made it possible to track down a now-deleted
GitHub profile with the same name ("Nino Acuna" or binaryExDev) containing a
repository called File-Uploader.
Present within the repository were Python scripts referencing the same IP addresses (162.218.114[.]83 – subsequently changed to 45.61.169[.]99) used to fetch the aforementioned Python scripts.
It's suspected that the attack is a work in progress, as at least four more
packages with identical features have made their way to the npm package
repository, attracting a total of 325 downloads -
data-time-utils - 52 downloads starting from February 15
login-time-utils -
171 downloads starting from February 15
mongodb-connection-utils - 51
downloads starting from February 19
mongodb-execution-utils - 51 downloads
starting from February 19
Connections to North Korean Actors Emerge#
Phylum, which also analyzed the two GitHub accounts that binaryExDev follows,
uncovered another repository known as mave-finance-org/auth-playground, which
has been forked no less than a dozen times by other accounts.
While forking a repository in itself is not out of the ordinary, an unusual aspect of some of these forked repositories were that they were renamed as "auth-demo" or "auth-challenge," raising the possibility that the original repository may have been shared as part of a coding test for a job interview.
The repository was later moved to banus-finance-org/auth-sandbox, Dexbanus-org/live-coding-sandbox, and mave-finance/next-assessment, indicating attempts to actively get around GitHub's takedown attempts. All these accounts have been removed.
What's more, the next-assessment package was found to contain a dependency "json-mock-config-server" that's not listed on the npm registry, but rather served directly from the domain npm.mave[.]finance.
It's worth noting that Banus claims to be a decentralized perpetual spot exchange based in Hong Kong, with the company even posting a job opportunity for a senior frontend developer on February 21, 2024. It's currently not clear if this is a genuine job opening or if it's an elaborate social engineering scheme.
The connections to North Korean threat actors come from the fact that the obfuscated JavaScript embedded in the npm package overlaps with another JavaScript-based malware dubbed BeaverTail that's propagated via a similar mechanism. The campaign was codenamed Contagious Interview by Palo Alto Networks Unit 42 in November 2023.
Contagious Interview is a little different from Operation Dream Job – which is linked to the Lazarus Group – in that it's mainly focuses on targeting developers through fake identities in freelance job portals to trick them into installing rogue npm packages, Michael Sikorski, vice president and CTO of Palo Alto Networks Unit 42, told The Hacker News at the time.
One of the developers who fell victim to the campaign has since confirmed to Phylum that the repository is shared under the guise of a live coding interview, although they said they never installed it on their system.
"More than ever, it is important for both individual developers as well as software development organizations to remain vigilant against these attacks in open-source code," the company said.
Banking Trojans Target Latin America and Europe Through Google Cloud Run
27.2.24
Virus
The Hacker News
Cybersecurity researchers are warning about a spike in email phishing campaigns that are weaponizing the Google Cloud Run service to deliver various banking trojans such as Astaroth (aka Guildma), Mekotio, and Ousaban (aka Javali) to targets across Latin America (LATAM) and Europe.
"The infection chains associated with these malware families feature the use of malicious Microsoft Installers (MSIs) that function as droppers or downloaders for the final malware payload(s)," Cisco Talos researchers disclosed last week.
The high-volume malware distribution campaigns, observed since September 2023, have employed the same storage bucket within Google Cloud for propagation, suggesting potential links between the threat actors behind the distribution campaigns.
Google Cloud Run is a managed compute platform that enables users to run frontend and backend services, batch jobs, deploy websites and applications, and queue processing workloads without having to manage or scale the infrastructure.
"Adversaries may view Google Cloud Run as an inexpensive, yet effective way to deploy distribution infrastructure on platforms that most organizations likely do not prevent internal systems from accessing," the researchers said.
A majority of the systems used to send phishing messages originate from Brazil, followed by the U.S., Russia, Mexico, Argentina, Ecuador, South Africa, France, Spain, and Bangladesh. The emails bear themes related to invoices or financial and tax documents, in some cases purporting to be from local government tax agencies.
Embedded within these messages are links to a website hosted on run[.]app, resulting in the delivery of a ZIP archive containing a malicious MSI file either directly or via 302 redirects to a Google Cloud Storage location, where the installer is stored.
The threat actors have also been observed attempting to evade detection using geofencing tricks by redirecting visitors to these URLs to a legitimate site like Google when accessing them with a U.S. IP address.
Besides leveraging the same infrastructure to deliver both Mekotio and Astaroth, the infection chain associated with the latter acts as a conduit to distribute Ousaban.
Astaroth, Mekotio, and Ousaban are all designed to single out financial institutions, keeping tabs on users' web browsing activity as well as logging keystrokes and taking screenshots should one of the target bank websites be open.
Ousaban has a history of weaponizing cloud services to its advantage, having previously employed Amazon S3 and Microsoft Azure to download second-stage payloads, and Google Docs to retrieve command-and-control (C2) configuration.
The development comes amid phishing campaigns propagating malware families such as DCRat, Remcos RAT, and DarkVNC that are capable of harvesting sensitive data and taking control of compromised hosts.
It also follows an uptick in threat actors deploying QR codes in phishing and email-based attacks (aka quishing) to trick potential victims into installing malware on their mobile devices.

"In a separate attack, the adversaries sent targets spear-phishing emails with
malicious QR codes pointing to fake Microsoft Office 365 login pages that
eventually steal the user's login credentials when entered," Talos said.
"QR code attacks are particularly dangerous because they move the attack vector off a protected computer and onto the target's personal mobile device, which usually has fewer security protections in place and ultimately has the sensitive information that attackers are after."
Phishing campaigns have also set their eyes on the oil and gas sector to deploy an information stealer called Rhadamanthys, which has currently reached version 0.6.0, highlighting a steady stream of patches and updates by its developers.
"The campaign starts with a phishing email using a vehicle incident report to lure victims into interacting with an embedded link that abuses an open redirect on a legitimate domain, primarily Google Maps or Google Images," Cofense said.
Users who click on the link are then redirected to a website hosting a bogus PDF file, which, in reality, is a clickable image that contacts a GitHub repository and downloads a ZIP archive containing the stealer executable.
"Once a victim attempts to interact with the executable, the malware will unpack and start a connection with a command-and-control (C2) location that collects any stolen credentials, cryptocurrency wallets, or other sensitive information," the company added.
Other campaigns have abused email marketing tools like Twilio's SendGrid to obtain client mailing lists and take advantage of stolen credentials to send out convincing-looking phishing emails, per Kaspersky.
"What makes this campaign particularly insidious is that the phishing emails bypass traditional security measures," the Russian cybersecurity company noted. "Since they are sent through a legitimate service and contain no obvious signs of phishing, they may evade detection by automatic filters."
These phishing activities are further fueled by the easy availability of phishing kits such as Greatness and Tycoon, which have become a cost-effective and scalable means for aspiring cyber criminals to mount malicious campaigns.
"Tycoon Group [phishing-as-a-service] is sold and marketed on Telegram for as low as $120," Trustwave SpiderLabs researcher Rodel Mendrez said last week, noting the service first came into being around August 2023.
"Its key selling features include the ability to bypass Microsoft two-factor authentication, achieve 'link speed at the highest level,' and leveraging Cloudflare to evade antibot measures, ensuring the persistence of undetected phishing links."
LockBit Ransomware Group Resurfaces After Law Enforcement Takedown
27.2.24
Ransom
The Hacker News
The threat actors behind the LockBit ransomware operation have resurfaced on the dark web using new infrastructure, days after an international law enforcement exercise seized control of its servers.
To that end, the notorious group has moved its data leak portal to a new .onion address on the TOR network, listing 12 new victims as of writing.
The administrator behind LockBit, in a lengthy follow-up message, said some of their websites were confiscated by most likely exploiting a critical PHP flaw tracked as CVE-2023-3824, acknowledging that they didn't update PHP due to "personal negligence and irresponsibility."
"I realize that it may not have been this CVE, but something else like 0-day for PHP, but I can't be 100% sure, because the version installed on my servers was already known to have a known vulnerability, so this is most likely how the victims' admin and chat panel servers and the blog server were accessed," they noted.
Cybersecurity
They also claimed the U.S. Federal Bureau of Investigation
(FBI) "hacked" their infrastructure because of a ransomware attack on Fulton
County in January and the "stolen documents contain a lot of interesting things
and Donald Trump's court cases that could affect the upcoming U.S. election."
In addition to calling for attacking the ".gov sector" more often, they stated that the server from which the authorities obtained more than 1,000 decryption keys held almost 20,000 decryptors, most of which were protected and accounted for about half of the total number of decryptors generated since 2019.
The group further went on to add that the nicknames of the affiliates have "nothing to do with their real nicknames on forums and even nicknames in messengers."
That's not all. The post also attempted to discredit law enforcement agencies, claiming the real "Bassterlord" has not been identified, and that the FBI actions are "aimed at destroying the reputation of my affiliate program."
"Why did it take 4 days to recover? Because I had to edit the source code for the latest version of PHP, as there was incompatibility," they said.
"I will stop being lazy and make it so that absolutely every build loker will be with maximum protection, now there will be no automatic trial decrypt, all trial decrypts and the issuance of decryptors will be made only in manual mode. Thus in the possible next attack, the FBI will not be able to get a single decryptor for free."
Russia Arrests Three SugarLocker Members#
The development comes as Russian
law enforcement officials have arrested three individuals, including Aleksandr
Nenadkevichite Ermakov (aka blade_runner, GustaveDore, or JimJones), in
connection with the SugarLocker ransomware group.
"The attackers worked under the guise of a legitimate IT firm Shtazi-IT, which offers services for the development of landing pages, mobile applications, scripts, parsers, and online stores," Russian cybersecurity firm F.A.C.C.T. said. "The company openly posted ads for hiring new employees."
The operators have also been accused of developing custom malware, creating phishing sites for online stores, and driving user traffic to fraudulent schemes popular in Russia and the Commonwealth of Independent States (CIS) nations.
SugarLocker first appeared in early 2021 and later began to be offered under the ransomware-as-a-service (RaaS) model, leasing its malware to other partners under an affiliate program to breach targets and deploy the ransomware payload.
Cybersecurity
Nearly three-fourths of the ransom proceeds go to the
affiliates, a figure that jumps to 90% if the payment exceeds $5 million. The
cybercrime gang's links to Shtazi-IT were previously disclosed by Intel 471 last
month.
The arrest of Ermakov is notable, as it comes in the wake of Australia, the U.K., and the U.S. imposing financial sanctions against him for his alleged role in the 2022 ransomware attack against health insurance provider Medibank.
The ransomware attack, which took place in late October 2022 and attributed to the now-defunct REvil ransomware crew, led to the unauthorized access of approximately 9.7 million of its current and former customers.
The stolen information included names, dates of birth, Medicare numbers, and sensitive medical information, including records on mental health, sexual health, and drug use. Some of these records also found their way to the dark web.
It also follows a report from news agency TASS, which revealed that a 49-year-old Russian national is set to face trial on charges of carrying out a cyber attack on technological control systems that left 38 settlements of the Vologda region without power.
LockBit Saga — Timeline of Events#
FEBRUARY 20, 2024
LockBit Busted -
Authorities Seize Darknet Domains#
An international law enforcement
operation, including 11 countries and Europol, successfully seized darknet
domains linked to the ransomware group LockBit, which has extorted over $91
million since 2019. The operation, named Cronos, used a PHP security flaw to
disrupt LockBit's websites, marking a significant blow to the group's
activities.
FEBRUARY 21, 2024
LockBit Hackers Arrested - Decryption Tool Released#
UK's NCA shuts down LockBit ransomware, arrests 2 in Poland/Ukraine, freezes
200+ crypto accounts, indicts 2 Russians in US. Seized LockBit's code,
intelligence, dismantled 34 servers, retrieved 1k decryption keys. LockBit
affected 2.5k victims globally, netted $120M. Decryption tool available for
victims.
FEBRUARY 22, 2024
$15 Million Bounty on LockBit Ransomware Leaders#
US
State Dept offers $15M reward for info on LockBit ransomware leaders, involved
in 2k+ global attacks since 2020, causing $144M in damages. Law enforcement
disrupted LockBit, arresting affiliates and seizing assets. LockBit, known for
ransomware-as-a-service, extensive affiliate network, and innovative tactics
like a bug bounty program, remains a significant cyber threat despite setbacks.
FEBRUARY 25, 2024
LockBit Ransomware Kingpin 'Engages' with Police#
The
individual(s) behind the LockBit ransomware service, known as LockBitSupp, has
reportedly engaged with law enforcement following a significant international
crackdown on the ransomware-as-a-service operation named Operation Cronos.
FEBRUARY 26, 2024
LockBit is Back - Calls for Attacks on US Government#
The LockBit ransomware group has re-emerged on the dark web with a new
infrastructure shortly after law enforcement seized its servers. The group has
listed 12 new victims on its data leak portal and discussed the seizure of its
websites, attributing it to a potential exploitation of a PHP vulnerability.
Authorities Claim LockBit Admin "LockBitSupp" Has Engaged with Law Enforcement
25.2.24
Ransom
The Hacker News
LockBitSupp, the individual(s) behind the persona
representing the LockBit ransomware service on cybercrime forums such as Exploit
and XSS, "has engaged with law enforcement," authorities said.
The development comes following the takedown of the prolific ransomware-as-a-service (RaaS) operation as part of a coordinated international operation codenamed Cronos. Over 14,000 rogue accounts on third-party services like Mega, Protonmail, and Tutanota used by the criminals have been shuttered.
"We know who he is. We know where he lives. We know how much he is worth. LockbitSupp has engaged with law enforcement," according to a message posted on the now-seized (and offline) dark web data leak site.
The move has been interpreted by long-term watchers of LockBit as an attempt to create suspicion and sow the seeds of distrust among affiliates, ultimately undermining trust in the group within the cybercrime ecosystem.
According to research published by Analyst1 in August 2023, there is evidence to suggest that at least three different people have operated the "LockBit" and "LockBitSupp" accounts, one of them being the gang's leader itself.
However, speaking to malware research group VX-Underground, LockBit stated "they did not believe law enforcement know his/her/their identities." They also raised the bounty it offered to anyone who could message them their real names to $20 million. It's worth noting that the reward was increased from $1 million USD to $10 million late last month.
LockBit – also called Gold Mystic and Water Selkie – has had several iterations since its inception in September 2019, namely LockBit Red, LockBit Black, and LockBit Green, with the cybercrime syndicate also secretly developing a new version called LockBit-NG-Dev prior to its infrastructure being dismantled.
"LockBit-NG-Dev is now written in .NET and compiled using CoreRT," Trend Micro said. "When deployed alongside the .NET environment, this allows the code to be more platform-agnostic. It removed the self-propagating capabilities and the ability to print ransom notes via the user's printers."

One of the notable additions is the inclusion of a validity period, which
continues its operation only if the current date is within a specific date
range, suggesting attempts on the part of the developers to prevent the reuse of
the malware as well as resist automated analysis.
Work on the next generation variant is said to have been spurred by a number of logistical, technical, and reputational problems, prominently driven by the leak of the ransomware builder by a disgruntled developer in September 2022 and also misgivings that one of its administrators may have been replaced by government agents.
It also didn't help that the LockBit-managed accounts were banned from Exploit and XSS towards the end of January 2024 for failing to pay an initial access broker who provided them with access.
"The actor came across as someone who was 'too big to fail' and even showed disdain to the arbitrator who would make the decision on the outcome of the claim," Trend Micro said. "This discourse demonstrated that LockBitSupp is likely using their reputation to carry more weight when negotiating payment for access or the share of ransom payouts with affiliates."
PRODAFT, in its own analysis of the LockBit operation, said it identified over 28 affiliates, some of whom share ties with other Russian e-crime groups like Evil Corp, FIN7, and Wizard Spider (aka TrickBot).
These connections are also evidenced by the fact that the gang operated as a "nesting doll" with three distinct layers, giving an outward perception of an established RaaS scheme compromising dozens of affiliates while stealthily borrowing highly skilled pen testers from other ransomware groups by forging personal alliances.
The smokescreen materialized in the form of what's called a Ghost Group model, according to RedSense researchers Yelisey Bohuslavskiy and Marley Smith, with LockBitSupp serving "as a mere distraction for actual operations."
"A Ghost Group is a group that has very high capabilities but transfers them to another brand by allowing the other group to outsource operations to them," they said. "The clearest version of this is Zeon, who has been outsourcing their skills to LockBit and Akira."

The group is estimated to have made more than $120 million in illicit profits in
its multi-year run, emerging as the most active ransomware actor in history.
"Given that confirmed attacks by LockBit over their four years in operation total well over 2,000, this suggests that their impact globally is in the region of multi-billions of dollars," the U.K. National Crime Agency (NCA) said.
Needless to say, Operation Cronos has likely caused irreparable damage to the criminal outfit's ability to continue with ransomware activities, at least under its current brand.
"The rebuilding of the infrastructure is very unlikely; LockBit's leadership is very technically incapable," RedSense said. "People to whom they delegated their infrastructural development have long left LockBit, as seen by the primitivism of their infra."
"[Initial access brokers], which were the main source of LockBit's venture, will not trust their access to a group after a takedown, as they want their access to be turned into cash."
Microsoft Expands Free Logging Capabilities for all U.S. Federal Agencies
25.2.24
BigBrothers
The Hacker News
Microsoft has expanded free logging capabilities to all U.S. federal agencies using Microsoft Purview Audit irrespective of the license tier, more than six months after a China-linked cyber espionage campaign targeting two dozen organizations came to light.
"Microsoft will automatically enable the logs in customer accounts and increase the default log retention period from 90 days to 180 days," the U.S. Cybersecurity and Infrastructure Security Agency (CISA) said.
"Also, this data will provide new telemetry to help more federal agencies meet logging requirements mandated by [Office of Management and Budget] Memorandum M-21-31."
Microsoft, in July 2023, disclosed that a China-based nation-state activity group known as Storm-0558 gained unauthorized access to approximately 25 entities in the U.S. and Europe as well as a small number of related individual consumer accounts.
"Storm-0558 operates with a high degree of technical tradecraft and operational security," the company noted. "The actors are keenly aware of the target's environment, logging policies, authentication requirements, policies, and procedures."
The campaign is believed to have commenced in May 2023, but detected only a month later after a U.S. federal agency, later revealed to be the State Department, uncovered suspicious activity in unclassified Microsoft 365 audit logs and reported it to Microsoft.
The breach was detected by leveraging enhanced logging in Microsoft Purview Audit, specifically using the MailItemsAccessed mailbox-auditing action that's typically available for Premium subscribers.
The Windows maker subsequently acknowledged that a validation error in its source code allowed for Azure Active Directory (Azure AD) tokens to be forged by Storm-0558 using a Microsoft account (MSA) consumer signing key, and then use them to penetrate the mailboxes.
The attackers are estimated to have stolen at least 60,000 unclassified emails from Outlook accounts belonging to State Department officials stationed in East Asia, the Pacific, and Europe, Reuters reported in September 2023. Beijing has denied the allegations.
It also faced intense scrutiny for withholding basic-yet-crucial logging capabilities to entities that are on the more expensive E5 or G5 plan, prompting the company to make changes.
"We recognize the vital importance that advanced logging plays in enabling federal agencies to detect, respond to, and prevent even the most sophisticated cyberattacks from well-resourced, state-sponsored actors," Microsoft's Candice Ling said. "For this reason, we have been collaborating across the federal government to provide access to advanced audit logs."
Dormant PyPI Package Compromised to Spread Nova Sentinel Malware
24.2.24
Virus
The Hacker News
A dormant package available on the Python Package Index
(PyPI) repository was updated nearly after two years to propagate an information
stealer malware called Nova Sentinel.
The package, named django-log-tracker, was first published to PyPI in April 2022, according to software supply chain security firm Phylum, which detected an anomalous update to the library on February 21, 2024.
While the linked GitHub repository hasn't been updated since April 10, 2022, the introduction of a malicious update suggests a likely compromise of the PyPI account belonging to the developer.
Django-log-tracker has been downloaded 3,866 times to date, with the rogue version (1.0.4) downloaded 107 times on the date it was published. The package is no longer available for download from PyPI.
"In the malicious update, the attacker stripped the package of most of its original content, leaving only an __init__.py and example.py file behind," the company said.
The changes, simple and self-explanatory, involve fetching an executable named
"Updater_1.4.4_x64.exe" from a remote server ("45.88.180[.]54"), followed by
launching it using the Python os.startfile() function.
The binary, for its part, comes embedded with Nova Sentinel, a stealer malware that was first documented by Sekoia in November 2023 as being distributed in the form of fake Electron apps on bogus sites offering video game downloads.
"What's interesting about this particular case [...] is that the attack vector appeared to be an attempted supply-chain attack via a compromised PyPI account," Phylum said.
"If this had been a really popular package, any project with this package listed as a dependency without a version specified or a flexible version specified in their dependency file would have pulled the latest, malicious version of this package."
Microsoft Releases PyRIT - A Red Teaming Tool for Generative AI
23.2.24
Virus
The Hacker News
Microsoft has released an open access automation
framework called PyRIT (short for Python Risk Identification Tool) to
proactively identify risks in generative artificial intelligence (AI) systems.
The red teaming tool is designed to "enable every organization across the globe to innovate responsibly with the latest artificial intelligence advances," Ram Shankar Siva Kumar, AI red team lead at Microsoft, said.
The company said PyRIT could be used to assess the robustness of large language model (LLM) endpoints against different harm categories such as fabrication (e.g., hallucination), misuse (e.g., bias), and prohibited content (e.g., harassment).
It can also be used to identify security harms ranging from malware generation to jailbreaking, as well as privacy harms like identity theft.
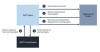
PyRIT comes with five interfaces: target, datasets, scoring engine, the ability to support multiple attack strategies, and incorporating a memory component that can either take the form of JSON or a database to store the intermediate input and output interactions.
The scoring engine also offers two different options for scoring the outputs from the target AI system, allowing red teamers to use a classical machine learning classifier or leverage an LLM endpoint for self-evaluation.
"The goal is to allow researchers to have a baseline of how well their model and entire inference pipeline is doing against different harm categories and to be able to compare that baseline to future iterations of their model," Microsoft said.
"This allows them to have empirical data on how well their model is doing today,
and detect any degradation of performance based on future improvements."
That said, the tech giant is careful to emphasize that PyRIT is not a replacement for manual red teaming of generative AI systems and that it complements a red team's existing domain expertise.
In other words, the tool is meant to highlight the risk "hot spots" by generating prompts that could be used to evaluate the AI system and flag areas that require further investigation.
Microsoft further acknowledged that red teaming generative AI systems requires probing for both security and responsible AI risks simultaneously and that the exercise is more probabilistic while also pointing out the wide differences in generative AI system architectures.
"Manual probing, though time-consuming, is often needed for identifying potential blind spots," Siva Kumar said. "Automation is needed for scaling but is not a replacement for manual probing."
The development comes as Protect AI disclosed multiple critical vulnerabilities in popular AI supply chain platforms such as ClearML, Hugging Face, MLflow, and Triton Inference Server that could result in arbitrary code execution and disclosure of sensitive information.
Researchers Detail Apple's Recent Zero-Click Shortcuts Vulnerability
23.2.24
OS
The Hacker News
Details have emerged about a now-patched high-severity
security flaw in Apple's Shortcuts app that could permit a shortcut to access
sensitive information on the device without users' consent.
The vulnerability, tracked as CVE-2024-23204 (CVSS score: 7.5), was addressed by Apple on January 22, 2024, with the release of iOS 17.3, iPadOS 17.3, macOS Sonoma 14.3, and watchOS 10.3.
"A shortcut may be able to use sensitive data with certain actions without prompting the user," the iPhone maker said in an advisory, stating it was fixed with "additional permissions checks."
Apple Shortcuts is a scripting application that allows users to create personalized workflows (aka macros) for executing specific tasks on their devices. It comes installed by default on iOS, iPadOS, macOS, and watchOS operating systems.
Bitdefender security researcher Jubaer Alnazi Jabin, who discovered and
reporting the Shortcuts bug, said it could be weaponized to create a malicious
shortcut such that it can bypass Transparency, Consent, and Control (TCC)
policies.
TCC is an Apple security framework that's designed to protect user data from
unauthorized access without requesting appropriate permissions in the first
place.
Specifically, the flaw is rooted in a shortcut action called "Expand URL," which
is capable of expanding and cleaning up URLs that have been shortened using a
URL shortening service like t.co or bit.ly, while also removing UTM tracking
parameters.
"By leveraging this functionality, it became possible to transmit the
Base64-encoded data of a photo to a malicious website," Alnazi Jabin explained.
"The method involves selecting any sensitive data (Photos, Contacts, Files, and
clipboard data) within Shortcuts, importing it, converting it using the base64
encode option, and ultimately forwarding it to the malicious server."
The exfiltrated data is then captured and saved as an image on the attacker's
end using a Flask application, paving the way for follow-on exploitation.
"Shortcuts can be exported and shared among users, a common practice in the
Shortcuts community," the researcher said. "This sharing mechanism extends the
potential reach of the vulnerability, as users unknowingly import shortcuts that
might exploit CVE-2024-23204."
FTC Slams Avast with $16.5 Million Fine for Selling Users' Browsing Data
23.2.24
BigBrothers
The Hacker News
The U.S. Federal Trade Commission (FTC) has hit antivirus vendor Avast with a $16.5 million fine over charges that the firm sold users' browsing data to advertisers after claiming its products would block online tracking.
In addition, the company has been banned from selling or licensing any web browsing data for advertising purposes. It will also have to notify users whose browsing data was sold to third parties without their consent.
The FTC, in its complaint, said Avast "unfairly collected consumers' browsing information through the company's browser extensions and antivirus software, stored it indefinitely, and sold it without adequate notice and without consumer consent."
It also accused the U.K.-based company of deceiving users by claiming that the software would block third-party tracking and protect users' privacy, but failing to inform them that it would sell their "detailed, re-identifiable browsing data" to more than 100 third-parties through its Jumpshot subsidiary.
What's more, data buyers could associate non-personally identifiable information with Avast users' browsing information, allowing other companies to track and associate users and their browsing histories with other information they already had.
The misleading data privacy practice came to light in January 2020 following a joint investigation by Motherboard and PCMag, calling out Google, Yelp, Microsoft, McKinsey, Pepsi, Home Depot, Condé Nast, and Intuit as some of Jumpshot's "past, present, and potential clients."
A month before, web browsers Google Chrome, Mozilla Firefox, and Opera removed Avast's browser add-ons from their respective stores, with prior research from security researcher Wladimir Palant in October 2019 deeming those extensions as spyware.
The data, which includes a user's Google searches, location lookups, and internet footprint, was collected via the Avast antivirus program installed on a person's computer without seeking their informed consent.
"Browsing data [sold by Jumpshot] included information about users' web searches and the web pages they visited – revealing consumers' religious beliefs, health concerns, political leanings, location, financial status, visits to child-directed content and other sensitive information," the FTC alleged.
Jumpshot described itself as the "only company that unlocks walled garden data," and claimed to have data from as many as 100 million devices as of August 2018. The browsing information is said to have been collected since at least 2014.
The privacy backlash prompted Avast to "terminate the Jumpshot data collection and wind down Jumpshot's operations, with immediate effect."
Avast has since merged with another cybersecurity company NortonLifeLock to form a new parent company called Gen Digital, which also includes other products like AVG, Avira, and CCleaner.
"Avast promised users that its products would protect the privacy of their browsing data but delivered the opposite," said Samuel Levine, director of the FTC's Bureau of Consumer Protection. "Avast's bait-and-switch surveillance tactics compromised consumers' privacy and broke the law."
Apple Unveils PQ3 Protocol - Post-Quantum Encryption for iMessage
23.2.24
Security
The Hacker News
Apple has announced a new post-quantum cryptographic
protocol called PQ3 that it said will be integrated into iMessage to secure the
messaging platform against future attacks arising from the threat of a practical
quantum computer.
"With compromise-resilient encryption and extensive defenses against even highly sophisticated quantum attacks, PQ3 is the first messaging protocol to reach what we call Level 3 security — providing protocol protections that surpass those in all other widely deployed messaging apps," Apple said.
The iPhone maker described the protocol as "groundbreaking," "state-of-the-art," and as having the "strongest security properties" of any cryptographic protocol deployed at scale.
PQ3 is the latest security guardrail erected by Apple in iMessage after it switched from RSA to Elliptic Curve cryptography (ECC), and by protecting encryption keys on devices with the Secure Enclave in 2019.
While the current algorithms that underpin public-key cryptography (or asymmetric cryptography) are based on mathematical problems that are easy to do in one direction but hard in reverse, a potential future breakthrough in quantum computing means classical mathematical problems deemed computationally intensive can be trivially solved, effectively threatening end-to-end encrypted (E2EE) communications.
The risk is compounded by the fact that threat actors could conduct what is known as a harvest now, decrypt later (HNDL) attack, wherein encrypted messages are stolen today in hopes of decoding them at a later point in time by means of a quantum computer once it becomes a reality.
In July 2022, the U.S. Department of Commerce's National Institute of Standards and Technology (NIST) chose Kyber as the post-quantum cryptographic algorithm for general encryption. Over the last year, Amazon Web Services (AWS), Cloudflare, Google, and Signal have announced support for quantum-resistant encryption in their products.

Apple is the latest to join the post-quantum cryptography (PQC) bandwagon with
PQ3, which combines Kyber and ECC and aims to achieve Level 3 security. In
contrast, Signal, which introduced its own PQXDH protocol, offers Level 2
security, which establishes a PQC key for encryption.
This refers to an approach where PQC is "used to secure both the initial key establishment and the ongoing message exchange, with the ability to rapidly and automatically restore the cryptographic security of a conversation even if a given key becomes compromised."
The protocol, per Apple, is also designed to mitigate the impact of key compromises by limiting how many past and future messages can be decrypted with a single compromised key. Specifically, its key rotation scheme guarantees that the keys are rotated every 50 messages at most and at least once every seven days.
Support for PQ3 is expected to start rolling out with the general availability of iOS 17.4, iPadOS 17.4, macOS 14.4, and watchOS 10.4 next month.
Cupertino's iMessage security upgrade follows the tech giant's surprise decision to bring Rich Communication Services (RCS) to its Messages app later this year, marking a much-needed shift from the non-secure SMS standard.
It also said it will work towards improving the security and encryption of RCS messages. It's worth noting that while RCS does not implement E2EE by default, Google's Messages app for Android uses the Signal Protocol to secure RCS conversations.
While the adoption of advanced protections is always a welcome step, it remains to be seen if this is expanded beyond iMessage to include RCS messages.
Cybercriminals Weaponizing Open-Source SSH-Snake Tool for Network Attacks
22.2.24
Hacking
The Hacker News
A recently open-sourced network mapping tool called SSH-Snake has been repurposed by threat actors to conduct malicious activities.
"SSH-Snake is a self-modifying worm that leverages SSH credentials discovered on a compromised system to start spreading itself throughout the network," Sysdig researcher Miguel Hernández said.
"The worm automatically searches through known credential locations and shell history files to determine its next move."
SSH-Snake was first released on GitHub in early January 2024, and is described by its developer as a "powerful tool" to carry out automatic network traversal using SSH private keys discovered on systems.
In doing so, it creates a comprehensive map of a network and its dependencies, helping determine the extent to which a network can be compromised using SSH and SSH private keys starting from a particular host. It also supports resolution of domains which have multiple IPv4 addresses.
"It's completely self-replicating and self-propagating – and completely fileless," according to the project's description. "In many ways, SSH-Snake is actually a worm: It replicates itself and spreads itself from one system to another as far as it can."
Sysdig said the shell script not only facilitates lateral movement, but also provides additional stealth and flexibility than other typical SSH worms.
The cloud security company said it observed threat actors deploying SSH-Snake in real-world attacks to harvest credentials, the IP addresses of the targets, and the bash command history following the discovery of a command-and-control (C2) server hosting the data.
"The usage of SSH keys is a recommended practice that SSH-Snake tries to take advantage of in order to spread," Hernández said. "It is smarter and more reliable which will allow threat actors to reach farther into a network once they gain a foothold."
When reached for comment, Joshua Rogers, the developer of SSH-Snake, told The Hacker News that the tool offers legitimate system owners a way to identify weaknesses in their infrastructure before attackers do, urging companies to use SSH-Snake to "discover the attack paths that exist – and fix them."
"It seems to be commonly believed that cyber terrorism 'just happens' all of a sudden to systems, which solely requires a reactive approach to security," Rogers said. "Instead, in my experience, systems should be designed and maintained with comprehensive security measures."
"If a cyber terrorist is able to run SSH-Snake on your infrastructure and access thousands of servers, focus should be put on the people that are in charge of the infrastructure, with a goal of revitalizing the infrastructure such that the compromise of a single host can't be replicated across thousands of others."
Rogers also called attention to the "negligent operations" by companies that design and implement insecure infrastructure, which can be easily taken over by a simple shell script.
"If systems were designed and maintained in a sane manner and system owners/companies actually cared about security, the fallout from such a script being executed would be minimized - as well as if the actions taken by SSH-Snake were manually performed by an attacker," Rogers added.
"Instead of reading privacy policies and performing data entry, security teams of companies worried about this type of script taking over their entire infrastructure should be performing total re-architecture of their systems by trained security specialists – not those that created the architecture in the first place."
The disclosure comes as Aqua uncovered a new botnet campaign named Lucifer that exploits misconfigurations and existing flaws in Apache Hadoop and Apache Druid to corral them into a network for mining cryptocurrency and staging distributed denial-of-service (DDoS) attacks.
The hybrid cryptojacking malware was first documented by Palo Alto Networks Unit 42 in June 2020, calling attention to its ability to exploit known security flaws to compromise Windows endpoints.

As many as 3,000 distinct attacks aimed at the Apache big data stack have been
detected over the past month, the cloud security firm said. This also comprises
those that single out susceptible Apache Flink instances to deploy miners and
rootkits.
"The attacker implements the attack by exploiting existing misconfigurations and vulnerabilities in those services," security researcher Nitzan Yaakov said.
"Apache open-source solutions are widely used by many users and contributors. Attackers may view this extensive use as an opportunity to have inexhaustible resources for implementing their attacks on them."
Russian Government Software Backdoored to Deploy Konni RAT Malware
22.2.24
Virus
The Hacker News
An installer for a tool likely used by the Russian Consular Department of the Ministry of Foreign Affairs (MID) has been backdoored to deliver a remote access trojan called Konni RAT (aka UpDog).
The findings come from German cybersecurity company DCSO, which linked the activity as originating from the Democratic People's Republic of Korea (DPRK)-nexus actors targeting Russia.
The Konni (aka Opal Sleet, Osmium, or TA406) activity cluster has an established pattern of deploying Konni RAT against Russian entities, with the threat actor also linked to attacks directed against MID at least since October 2021.
In November 2023, Fortinet FortiGuard Labs revealed the use of Russian-language Microsoft Word documents to deliver malware capable of harvesting sensitive information from compromised Windows hosts.
DCSO said the packaging of Konni RAT within software installers is a technique previously adopted by the group in October 2023, when it was found to leverage a backdoored Russian tax filing software named Spravki BK to distribute the trojan.
"In this instance, the backdoored installer appears to be for a tool named 'Statistika KZU' (Cтатистика КЗУ)," the Berlin-based company said.

"On the basis of install paths, file metadata, and user manuals bundled into the
installer, [...] the software is intended for internal use within the Russian
Ministry of Foreign Affairs (MID), specifically for the relaying of annual
report files from overseas consular posts (КЗУ — консульские загранучреждения)
to the Consular Department of the MID via a secure channel."
The trojanized installer is an MSI file that, when launched, initiates the infection sequence to establish contact with a command-and-control (C2) server to await further instructions.

The remote access trojan, which comes with capabilities for file transfers and
command execution, is believed to have been put to use as early as 2014, and has
also been utilized by other North Korean threat actors known as Kimsuky and
ScarCruft (aka APT37).
It's currently not clear how the threat actors managed to obtain the installer, given that it's not publicly obtainable. But it's suspected that the long history of espionage operations targeting Russia may have helped them identify prospective tools for subsequent attacks.
While North Korea's targeting of Russia is not new, the development comes amid growing geopolitical proximity between the two countries. State media from the Hermit Kingdom reported this week that Russian President Vladimir Putin has given leader Kim Jong Un a luxury Russian-made car.
"To some extent, this should not come as a surprise; increasing strategic proximity would not be expected to fully overwrite extant DPRK collection needs, with an ongoing need on the part of the DPRK to be able to assess and verify Russian foreign policy planning and objectives," DCSO said.
U.S. Offers $15 Million Bounty to Hunt Down LockBit Ransomware Leaders
22.2.24
Ransom
The Hacker News
The U.S. State Department has announced monetary rewards of up to $15 million for information that could lead to the identification of key leaders within the LockBit ransomware group and the arrest of any individual participating in the operation.
"Since January 2020, LockBit actors have executed over 2,000 attacks against victims in the United States, and around the world, causing costly disruptions to operations and the destruction or exfiltration of sensitive information," the State Department said.
"More than $144 million in ransom payments have been made to recover from LockBit ransomware events."
The development comes as a sweeping law enforcement operation led by the U.K. National Crime Agency (NCA) disrupted LockBit, a Russia-linked ransomware gang that has been active for more than four years, wreaking havoc on business and critical infrastructure entities around the world.
Ransomware-as-a-service (RaaS) operations like LockBit and others work by extorting companies by stealing their sensitive data and encrypting them, making it a lucrative business model for Russian e-crime groups that act with impunity by taking advantage of the fact that they are outside of the jurisdiction of Western law enforcement.
The core developers tend to tap into a network of affiliates who are recruited to carry out the attacks using LockBit's malicious software and infrastructure. The affiliates, in turn, are known to purchase access to targets of interest using initial access brokers (IABs).
"LockBit rose to be the most prolific ransomware group since Conti departed the scene in mid-2022," Chester Wisniewski, global field CTO at Sophos, said.
"The frequency of their attacks, combined with having no limits to what type of infrastructure they cripple has also made them the most destructive in recent years. Anything that disrupts their operations and sows distrust amongst their affiliates and suppliers is a huge win for law enforcement."
LockBit is also known to be the first ransomware group to announce a bug bounty program in 2022, offering rewards of up to $1 million for finding security issues in website and locker software.
"LockBit's operation grew in scale by consistently delivering new product
features, providing good customer support, and at times, marketing stunts that
included paying people to tattoo themselves with the group's logo," Intel 471
said.
Image Source: X
"LockBit flipped the script, letting its affiliates collect
the ransom and trusting them to pay it a portion. This made affiliates confident
that they were not going to lose out on a payment, thus attracting more
affiliates."
SecureWorks Counter Threat Unit (CTU), which is tracking the group under the name Gold Mystic, said it investigated 22 compromises featuring LockBit ransomware from July 2020 through January 2024, some of which relied solely on data theft to extort victims.
The cybersecurity company further pointed out that LockBit's practice of ceding control to its affiliates to handle ransom negotiation and payments allowed the syndicate to scale up and draw several affiliates over the years.
LockBit's takedown followed a months-long investigation that commenced in April 2022, leading to the arrest of three affiliates in Poland and Ukraine, the indictment in the U.S. of two other alleged members, as well as the seizure of 34 servers and 1,000 decryption keys that can help victims recover their data without making any payment.
These arrests include a 38-year-old man in Warsaw and a "father and son" duo from Ukraine. LockBit is estimated to have employed about 194 affiliates between January 31, 2022, and February 5, 2024, with the actors using a bespoke data exfiltration tool known as StealBit.
"StealBit is an example of LockBit's attempt to offer a full 'one-stop shop' service to its affiliates," the NCA said, adding the executable is used to export the data through the affiliate's own infrastructure before StealBit's in a likely effort to evade detection.
That said, the fluid structure of these RaaS brands means that shutting them down may not decisively impact the criminal enterprise, allowing them to regroup and resurface under a different name. If the recent history of similar takedowns is any indication, it won't be long before they rebrand and continue from where they left off.
"Comprehensive degradation of LockBit's infrastructure will likely result in a short cessation in activity from LockBit operatives before they resume operations – either under the LockBit name or an alternative banner," ZeroFox said.
"Even if we don't always get a complete victory, like has happened with QakBot, imposing disruption, fueling their fear of getting caught and increasing the friction of operating their criminal syndicate is still a win," Wisniewski added. "We must continue to band together to raise their costs ever higher until we can put all of them where they belong – in jail."
New Wi-Fi Vulnerabilities Expose Android and Linux Devices to Hackers
22.2.24
OS
The Hacker News
Cybersecurity researchers have identified two authentication bypass flaws in open-source Wi-Fi software found in Android, Linux, and ChromeOS devices that could trick users into joining a malicious clone of a legitimate network or allow an attacker to join a trusted network without a password.
The vulnerabilities, tracked as CVE-2023-52160 and CVE-2023-52161, have been discovered following a security evaluation of wpa_supplicant and Intel's iNet Wireless Daemon (IWD), respectively.
The flaws "allow attackers to trick victims into connecting to malicious clones of trusted networks and intercept their traffic, and join otherwise secure networks without needing the password," Top10VPN said in a new research conducted in collaboration with Mathy Vanhoef, who has previously uncovered Wi-Fi attacks like KRACK, DragonBlood, and TunnelCrack.
CVE-2023-52161, in particular, permits an adversary to gain unauthorized access to a protected Wi-Fi network, exposing existing users and devices to potential attacks such as malware infections, data theft, and business email compromise (BEC). It impacts IWD versions 2.12 and lower.
On the other hand, CVE-2023-52160 affects wpa_supplicant versions 2.10 and prior. It's also the more pressing of the two flaws owing to the fact that it's the default software used in Android devices to handle login requests to wireless networks.
That said, it only impacts Wi-Fi clients that aren't properly configured to
verify the certificate of the authentication server. CVE-2023-52161, however,
affects any network that uses a Linux device as a wireless access point (WAP).
Successful exploitation of CVE-2023-52160 banks on the prerequisite that the
attacker is in possession of the SSID of a Wi-Fi network to which the victim has
previously connected. It also requires the threat actor to be in physical
proximity to the victim.
"One possible such scenario might be where an attacker walks around a company's
building scanning for networks before targeting an employee leaving the office,"
the researchers said.
Major Linux distributions such as Debian (1, 2), Red Hat (1), SUSE (1, 2), and
Ubuntu (1, 2) have released advisories for the two flaws. The wpa_supplicant
issue has also been addressed in ChromeOS from versions 118 and later, but fixes
for Android are yet to be made available.
"In the meantime, it's critical, therefore, that Android users manually
configure the CA certificate of any saved enterprise networks to prevent the
attack," Top10VPN said.
Mustang Panda Targets Asia with Advanced PlugX Variant DOPLUGS
21.2.24
APT
The Hacker News
The China-linked threat actor known as Mustang Panda has targeted various Asian countries using a variant of the PlugX (aka Korplug) backdoor dubbed DOPLUGS.
"The piece of customized PlugX malware is dissimilar to the general type of the PlugX malware that contains a completed backdoor command module, and that the former is only used for downloading the latter," Trend Micro researchers Sunny Lu and Pierre Lee said in a new technical write-up.
Targets of DOPLUGS have been primarily located in Taiwan, and Vietnam, and to a lesser extent in Hong Kong, India, Japan, Malaysia, Mongolia, and even China.
PlugX is a staple tool of Mustang Panda, which is also tracked as BASIN, Bronze President, Camaro Dragon, Earth Preta, HoneyMyte, RedDelta, Red Lich, Stately Taurus, TA416, and TEMP.Hex. It's known to be active since at least 2012, although it first came to light in 2017.
The threat actor's tradecraft entails carrying out well-forged spear-phishing campaigns that are designed to deploy custom malware. It also has a track record of deploying its own customized PlugX variants such as RedDelta, Thor, Hodur, and DOPLUGS (distributed via a campaign named SmugX) since 2018.
Compromise chains leverage a set of distinct tactics, using phishing messages as a conduit to deliver a first-stage payload that, while displaying a decoy document to the recipient, covertly unpacks a legitimate, signed executable that's vulnerable to DLL side-loading in order to side-load a dynamic-link library (DLL), which, in turn, decrypts and executes PlugX.
The PlugX malware subsequently retrieves Poison Ivy remote access trojan (RAT) or Cobalt Strike Beacon to establish a connection with a Mustang Panda-controlled server.
In December 2023, Lab52 uncovered a Mustang Panda campaign targeting Taiwanese political, diplomatic, and governmental entities with DOPLUGS, but with a notable difference.
"The malicious DLL is written in the Nim programming language," Lab52 said. "This new variant uses its own implementation of the RC4 algorithm to decrypt PlugX, unlike previous versions that use the Windows Cryptsp.dll library."
DOPLUGS, first documented by Secureworks in September 2022, is a downloader with four backdoor commands, one of which is orchestrated to download the general type of the PlugX malware.
Trend Micro said it also identified DOPLUGS samples integrated with a module known as KillSomeOne, a plugin that's responsible for malware distribution, information collection, and document theft via USB drives.
This variant comes fitted with an extra launcher component that executes the legitimate executable to perform DLL-sideloading, in addition to supporting functionality to run commands and download the next-stage malware from an actor-controlled server.
It's worth noting that a customized PlugX variant, including the KillSomeOne module designed for spreading via USB, was uncovered as early as January 2020 by Avira as part of attacks directed against Hong Kong and Vietnam.
"This shows that Earth Preta has been refining its tools for some time now, constantly adding new functionalities and features," the researchers said. "The group remains highly active, particularly in Europe and Asia."
New 'VietCredCare' Stealer Targeting Facebook Advertisers in Vietnam
21.2.24
Social
The Hacker News
Facebook advertisers in Vietnam are the target of a previously unknown information stealer dubbed VietCredCare at least since August 2022.
The malware is "notable for its ability to automatically filter out Facebook session cookies and credentials stolen from compromised devices, and assess whether these accounts manage business profiles and if they maintain a positive Meta ad credit balance," Singapore-headquartered Group-IB said in a new report shared with The Hacker News.
The end goal of the large-scale malware distribution scheme is to facilitate the takeover of corporate Facebook accounts by targeting Vietnamese individuals who manage the Facebook profiles of prominent businesses and organizations.
Facebook accounts that have been successfully seized are then used by the threat actors behind the operation to post political content or to propagate phishing and affiliate scams for financial gain.
VietCredCare is offered to other aspiring cybercriminals under the stealer-as-a-service model and advertised on Facebook, YouTube, and Telegram. It's assessed to be managed by Vietnamese-speaking individuals.
Customers either have the option of purchasing access to a botnet managed by the malware's developers, or procure access to the source code for resale or personal use. They are also provided a bespoke Telegram bot to manage the exfiltration and delivery of credentials from an infected device.
The .NET-based malware is distributed via links to bogus sites on social media posts and instant messaging platforms, masquerading as legitimate software like Microsoft Office or Acrobat Reader to dupe visitors into installing them.
One of its major selling points is its ability to extract credentials, cookies, and session IDs from web browsers like Google Chrome, Microsoft Edge, and Cốc Cốc, indicating its Vietnamese focus.
It can also retrieve a victim's IP address, check if a Facebook is a business profile, and assess whether the account in question is currently managing any ads, while simultaneously taking steps to evade detection by disabling the Windows Antimalware Scan Interface (AMSI) and adding itself to the exclusion list of Windows Defender Antivirus.
"VietCredCare's core functionality to filter out Facebook credentials puts organizations in both the public and private sectors at risk of reputational and financial damages if their sensitive accounts are compromised," Vesta Matveeva, head of the High-Tech Crime Investigation Department for APAC, said.
Credentials belonging to several government agencies, universities, e-commerce platforms, banks, and Vietnamese companies have been siphoned via the stealer malware.
VietCredCare is also the latest addition to a long list of stealer malware, such as Ducktail and NodeStealer,that has originated from the Vietnamese cyber criminal ecosystem with the intent of targeting Facebook accounts.
That having said, Group-IB told The Hacker News there is no evidence at this stage that suggests connections between VietCredCare and the other strains.
"With Ducktail, the functions are different, and while there are some similarities with NodeStealer, we note that the latter uses a [command-and-control] server instead of Telegram, plus their choice of victims is different," the company said.
"The stealer-as-a-service business model enables threat actors with little to no technical skills to enter the cybercrime field, which results in more innocent victims being harmed."
Signal Introduces Usernames, Allowing Users to Keep Their Phone Numbers Private
21.2.24
Social
The Hacker News
End-to-end encrypted (E2EE) messaging app Signal said
it's piloting a new feature that allows users to create unique usernames (not to
be confused with profile names) and keep the phone numbers away from prying
eyes.
"If you use Signal, your phone number will no longer be visible to everyone you chat with by default," Signal's Randall Sarafa said. "People who have your number saved in their phone's contacts will still see your phone number since they already know it."
Setting a new username requires account holders to provide two or more numbers at the end of it (e.g., axolotl.99) in an effort to keep them "egalitarian and minimize spoofing." Usernames can be changed any number of times, but it's worth noting that they are not logins or handles.
Put differently, a username is an anonymous way to initiate conversations on the chat platform without having to share phone numbers. The feature is opt-in, although Signal said it's also taking steps to hide by default users' phone numbers from others who do not have them saved in their phone's contacts.
In addition, users can control who can find them by their numbers using another setting, restricting people from messaging them even if they are in possession of the phone numbers.
Both these options can be toggled via the following steps -
Settings > Privacy > Phone Number > Who Can See My Number > Everybody / Nobody
Settings > Privacy > Phone Number > Who Can Find Me By Number > Everybody /
Nobody
"Your phone number will no longer be visible to people you chat with
on Signal, unless they have it in their phone's contacts," Sarafa said. "You
will also be able to configure a new privacy setting to limit who can find you
by your phone number on Signal."
Russian Hackers Target Ukraine with Disinformation and Credential-Harvesting
Attacks
21.2.24
APT
The Hacker News
Cybersecurity researchers have unearthed a new influence operation targeting Ukraine that leverages spam emails to propagate war-related disinformation.
The activity has been linked to Russia-aligned threat actors by Slovak cybersecurity company ESET, which also identified a spear-phishing campaign aimed at a Ukrainian defense company in October 2023 and a European Union agency in November 2023 with an aim to harvest Microsoft login credentials using fake landing pages.
Operation Texonto, as the entire campaign has been codenamed, has not been attributed to a specific threat actor, although some elements of it, particularly the spear-phishing attacks, overlap with COLDRIVER, which has a history of harvesting credentials via bogus sign-in pages.
The disinformation operation took place over two waves in November and December 2023, with the email messages bearing PDF attachments and content related to heating interruptions, drug shortages, and food shortages.
The November wave targeted no less than a few hundred recipients in Ukraine, including the government, energy companies, and individuals. It's currently not known how the target list was created.
"What's interesting to note is that the email was sent from a domain masquerading as the Ministry of Agrarian Policy and Food of Ukraine, while the content is about drug shortages and the PDF is misusing the logo of the Ministry of Health of Ukraine," ESET said in a report shared with The Hacker News.
"It is possibly a mistake from the attackers or, at least, shows they did not care about all details."
The second disinformation email campaign that commenced on December 25, 2023, is notable for expanding its targeting beyond Ukraine to include Ukrainian speakers in other European nations. All the messages were written in Ukrainian and sent to a diverse set of targets ranging from the Ukrainian government to an Italian shoe
These messages, while wishing recipients a happy holiday season, also adopted a darker tone, going as far as to suggest that they ampute one of their arms or legs to avoid military deployment. "A couple of minutes of pain, but then a happy life!," the email goes.
ESET said one of the domains used to propagate the phishing emails in December 2023, infonotification[.]com, also engaged in sending hundreds of spam messages beginning January 7, 2024, redirecting potential victims to a fake Canadian pharmacy website.
It's exactly unclear why this email server was repurposed to propagate a pharmacy scam, but it's suspected that the threat actors decided to monetize their infrastructure for financial gain after realizing that their domains have been detected by defenders.
"Operation Texonto shows yet another use of technologies to try to influence the war," the company said.
The development comes as Meta, in its quarterly Adversarial Threat Report, said it took down three networks originating from China, Myanmar, and Ukraine across its platforms that engaged in coordinated inauthentic behavior (CIB).
While none of the networks were from Russia, social media analytics firm Graphika said posting volumes by Russian state-controlled media has declined 55% from pre-war levels and engagement has plummeted 94% compared to two years ago.
"Russian state media outlets have increased their focus on non-political infotainment content and self-promotional narratives about Russia since the start of the war," it said. "This could reflect a wider off-platform effort to cater to domestic Russian audiences after multiple Western countries blocked the outlets in 2022."
Midnight Blizzard and Cloudflare-Atlassian Cybersecurity Incidents: What to Know
21.2.24
Incindent
The Hacker News
The Midnight Blizzard and Cloudflare-Atlassian cybersecurity incidents raised alarms about the vulnerabilities inherent in major SaaS platforms. These incidents illustrate the stakes involved in SaaS breaches — safeguarding the integrity of SaaS apps and their sensitive data is critical but is not easy. Common threat vectors such as sophisticated spear-phishing, misconfigurations and vulnerabilities in third-party app integrations demonstrate the complex security challenges facing IT systems.
In the case of Midnight Blizzard, password spraying against a test environment was the initial attack vector. For Cloudflare-Atlassian, threat actors initiated the attack via compromised OAuth tokens from a prior breach at Okta, a SaaS identity security provider.
What Exactly Happened?#
Microsoft Midnight Blizzard Breach#
Microsoft was
targeted by the Russian "Midnight Blizzard" hackers (also known as Nobelium,
APT29, or Cozy Bear) who are linked to the SVR, the Kremlin's foreign
intelligence service unit.
In the Microsoft breach, the threat actors:
Used a password spray strategy on a legacy account and historic test accounts
that did not have multi-factor authentication (MFA) enabled. According to
Microsoft, the threat actors "[used] a low number of attempts to evade detection
and avoid account blocks based on the volume of failures."
Leveraged the
compromised legacy account as an initial entry point to then hijack a legacy
test OAuth app. This legacy OAuth app had high-level permissions to access
Microsoft's corporate environment.
Created malicious OAuth apps by exploiting
the legacy OAuth app's permissions. Because the threat actors controlled the
legacy OAuth app, they could maintain access to the applications even if they
lost access to the initially compromised account.
Granted admin Exchange
permissions and admin credentials to themselves.
Escalated privileges from
OAuth to a new user, which they controlled.
Consented to the malicious OAuth
applications using their newly created user account.
Escalated the legacy
application's access further by granting it full access to M365 Exchange Online
mailboxes. With this access, Midnight Blizzard could view M365 email accounts
belonging to senior staff members and exfiltrate corporate emails and
attachments.
Recreation of illustration by Amitai Cohen
Cloudflare-Atlassian Breach#
On
Thanksgiving Day, November 23, 2023, Cloudflare's Atlassian systems were also
compromised by a nation-state attack.
This breach, which started on November 15, 2023, was made possible through the
use of compromised credentials that had not been changed following a previous
breach at Okta in October 2023.
Attackers accessed Cloudflare's internal wiki
and bug database, enabling them to view 120 code repositories in Cloudflare's
Atlassian instance.
76 source code repositories related to key operational
technologies were potentially exfiltrated.
Cloudflare detected the threat
actor on November 23 because the threat actor connected a Smartsheet service
account to an admin group in Atlassian.
SaaS Security Guide
Can Your
Security Team Monitor 3rd Party Apps? 60% of Teams Can't
Think your SaaS
security is top-notch? Appomni surveyed over 600 global security practitioners,
and 79% of professionals felt the same – yet they faced cybersecurity incidents!
Dive into the insights of the AppOmni 2023 Report.
Learn How You Can
Threat Actors Increasingly Target SaaS #
These breaches
are part of a broader pattern of nation-state actors targeting SaaS service
providers, including but not limited to espionage and intelligence gathering.
Midnight Blizzard previously engaged in significant cyber operations, including
the 2021 SolarWinds attack.
These incidents underscore the importance of continuous monitoring of your SaaS environments and the ongoing risk posed by sophisticated cyber adversaries targeting critical infrastructure and operational tech stack. They also highlight significant vulnerabilities related to SaaS identity management and the necessity for stringent 3rd-party app risk management practices.
Attackers use common tactics, techniques and procedures (TTPs) to breach SaaS providers through the following kill chain:
Initial access: Password spray, hijacking OAuth
Persistence: Impersonates
admin, creates extra OAuth
Defense Evasion: Highly privileged OAuth, no MFA
Lateral Movement: Broader compromise of connected apps
Data Exfiltration:
Grab privileged and sensitive data out of apps
Breaking the SaaS Kill Chain#
One effective way to break the kill chain early is with continuous monitoring,
granular policy enforcement, and proactive lifecycle management over your SaaS
environments. A SaaS Security Posture Management (SSPM) platform like AppOmni
can help with detecting and alerting on:
Initial Access: Out-of-the-box rules to detect credential compromise, including
password spraying, brute force attacks, and unenforced MFA policies
Persistence: Scan and identify OAuth permissions and detect OAuth hijacking
Defense Evasion: Access policy checks, detect if a new identity provider (IdP)
is created, detect permission changes.
Lateral Movement: Monitor logins and
privileged access, detect toxic combinations, and understand the blast radius of
a potentially compromised account
Note: This expertly contributed article is written by Beverly Nevalga, AppOmni.
VMware Alert: Uninstall EAP Now - Critical Flaw Puts Active Directory at Risk
21.2.24
Vulnerebility
The Hacker News
VMware is urging users to uninstall the deprecated
Enhanced Authentication Plugin (EAP) following the discovery of a critical
security flaw.
Tracked as CVE-2024-22245 (CVSS score: 9.6), the vulnerability has been described as an arbitrary authentication relay bug.
"A malicious actor could trick a target domain user with EAP installed in their web browser into requesting and relaying service tickets for arbitrary Active Directory Service Principal Names (SPNs)," the company said in an advisory.
EAP, deprecated as of March 2021, is a software package that's designed to allow direct login to vSphere's management interfaces and tools through a web browser. It's not included by default and is not part of vCenter Server, ESXi, or Cloud Foundation.
Also discovered in the same tool is a session hijack flaw (CVE-2024-22250, CVSS score: 7.8) that could permit a malicious actor with unprivileged local access to a Windows operating system to seize a privileged EAP session.
Ceri Coburn from Pen Test Partners has been credited with discovering and reporting the twin vulnerabilities.
It's worth pointing out that the shortcomings only impact users who have added EAP to Microsoft Windows systems to connect to VMware vSphere via the vSphere Client.
The Broadcom-owned company said the vulnerabilities will not be addressed, instead recommending users to remove the plugin altogether to mitigate potential threats.
"The Enhanced Authentication Plugin can be removed from client systems using the client operating system's method of uninstalling software," it added.
The disclosure comes as SonarSource disclosed multiple cross-site scripting (XSS) flaws (CVE-2024-21726) impacting the Joomla! content management system. It has been addressed in versions 5.0.3 and 4.4.3.
"Inadequate content filtering leads to XSS vulnerabilities in various components," Joomla! said in its own advisory, assessing the bug as moderate in severity.
"Attackers can leverage the issue to gain remote code execution by tricking an administrator into clicking on a malicious link," security researcher Stefan Schiller said. Additional technical specifics about the flaw have been currently withheld.
In a related development, several high- and critical-severity vulnerabilities and misconfigurations have been identified in the Apex programming language developed by Salesforce to build business applications.
At the heart of the problem is the ability to run Apex code in "without sharing" mode, which ignores a user's permissions, thereby allowing malicious actors to read or exfiltrate data, and even provide specially crafted input to alter execution flow.
"If exploited, the vulnerabilities can lead to data leakage, data corruption, and damage to business functions in Salesforce," Varonix security researcher Nitay Bachrach said.
New Migo Malware Targeting Redis Servers for Cryptocurrency Mining
21.2.24
Cryptocurrency
The Hacker News
A novel malware campaign has been observed targeting
Redis servers for initial access with the ultimate goal of mining cryptocurrency
on compromised Linux hosts.
"This particular campaign involves the use of a number of novel system weakening techniques against the data store itself," Cado security researcher Matt Muir said in a technical report.
The cryptojacking attack is facilitated by a malware codenamed Migo, a Golang ELF binary that comes fitted with compile-time obfuscation and the ability to persist on Linux machines.
The cloud security company said it detected the campaign after it identified an "unusual series of commands" targeting its Redis honeypots that are engineered to lower security defenses by disabling the following configuration options -
protected-mode
replica-read-only
aof-rewrite-incremental-fsync, and
rdb-save-incremental-fsync
It's suspected that these options are turned off
in order to send additional commands to the Redis server from external networks
and facilitate future exploitation without attracting much attention.
This step is then followed by threat actors setting up two Redis keys, one pointing to an attacker-controlled SSH key and the other to a cron job that retrieves the malicious primary payload from a file transfer service named Transfer.sh, a technique previously spotted in early 2023.
The shell script to fetch Migo using Transfer.sh is embedded within a Pastebin file that's, in turn, obtained using a curl or wget command.
Redis Servers for Cryptocurrency Mining
The Go-based ELF binary, besides incorporating mechanisms to resist reverse engineering, acts as a downloader for an XMRig installer hosted on GitHub. It's also responsible for performing a series of steps to establish persistence, terminate competing miners, and launch the miner.
On top of that, Migo disables Security-Enhanced Linux (SELinux) and searches for uninstallation scripts for monitoring agents bundled in compute instances from cloud providers such as Qcloud and Alibaba Cloud. It further deploys a modified version ("libsystemd.so") of a popular user-mode rootkit named libprocesshider to hide processes and on-disk artifacts.
It's worth pointing out that these actions overlap with tactics adopted by known cryptojacking groups like TeamTNT, WatchDog, Rocke, and threat actors associated with the SkidMap malware.
"Interestingly, Migo appears to recursively iterate through files and directories under /etc," Muir noted. "The malware will simply read files in these locations and not do anything with the contents."
"One theory is this could be a (weak) attempt to confuse sandbox and dynamic analysis solutions by performing a large number of benign actions, resulting in a non-malicious classification."
Another hypothesis is that the malware is looking for an artifact that's specific to a target environment, although Cado said it found no evidence to support this line of reasoning.
"Migo demonstrates that cloud-focused attackers are continuing to refine their techniques and improve their ability to exploit web-facing services," Muir said.
"Although libprocesshider is frequently used by cryptojacking campaigns, this particular variant includes the ability to hide on-disk artifacts in addition to the malicious processes themselves."
LockBit Ransomware Operation Shut Down; Criminals Arrested; Decryption Keys
Released
21.2.24
Ransom
The Hacker News
The U.K. National Crime Agency (NCA) on Tuesday confirmed
that it obtained LockBit's source code as well as a wealth of intelligence
pertaining to its activities and their affiliates as part of a dedicated task
force called Operation Cronos.
"Some of the data on LockBit's systems belonged to victims who had paid a ransom to the threat actors, evidencing that even when a ransom is paid, it does not guarantee that data will be deleted, despite what the criminals have promised," the agency said.
It also announced the arrest of two LockBit actors in Poland and Ukraine. Over 200 cryptocurrency accounts linked to the group have been frozen. Indictments and sanctions have also been unsealed in the U.S. against two other Russian nationals who are alleged to have carried out LockBit attacks.
Artur Sungatov and Ivan Gennadievich Kondratiev (aka Bassterlord) have been accused of deploying LockBit against numerous victims throughout the U.S., including businesses nationwide in the manufacturing and other industries, as well as victims around the world in the semiconductor and other industries, per the U.S. Department of Justice (DoJ).
Kondratyev has also been charged with three criminal counts arising from his use of the Sodinokibi, also known as REvil, ransomware variant to encrypt data, exfiltrate victim information, and extort a ransom payment from a corporate victim based in Alameda County, California.
The development comes in the aftermath of an international disruption campaign targeting LockBit, which the NCA described as the "world's most harmful cyber crime group."
As part of the takedown efforts, the agency said it took control of LockBit's services and infiltrated its entire criminal enterprise. This includes the administration environment used by affiliates and the public-facing leak site hosted on the dark web.
In addition, 34 servers belonging to LockBit affiliates have also been dismantled and more than 1,000 decryption keys have been retrieved from the confiscated LockBit servers.
LockBit, since its debut in late 2019, runs a ransomware-as-a-service (RaaS)
scheme in which the encryptors are licensed to affiliates, who carry out the
attacks in exchange for a cut of the ransom proceeds. It is run by a threat
actor known as LockBitSupp.
The attacks follow a tactic called double extortion to steal sensitive data prior to encrypting them, with the threat actors applying pressure on victims to make a payment in order to decrypt their files and prevent their data from being published.
"The ransomware group is also infamous for experimenting with new methods for pressuring their victims into paying ransoms," Europol said.
"Triple extortion is one such method which includes the traditional methods of encrypting the victim's data and threatening to leak it, but also incorporates distributed denial-of-service (DDoS) attacks as an additional layer of pressure."
The data theft is facilitated by means of a custom data exfiltration tool codenamed StealBit. The infrastructure, which was used to organize and transfer victim data, has since been seized by authorities from three countries, counting the U.S.
According to Eurojust and DoJ, LockBit attacks are believed to have affected over 2,500 victims all over the world and netted more than $120 million in illicit profits. A decryption tool has also been made available via No More Ransom to recover files encrypted by the ransomware at no cost.
"Through our close collaboration, we have hacked the hackers; taken control of their infrastructure, seized their source code, and obtained keys that will help victims decrypt their systems," NCA Director General Graeme Biggar said.
"As of today, LockBit are locked out. We have damaged the capability and most notably, the credibility of a group that depended on secrecy and anonymity. LockBit may seek to rebuild their criminal enterprise. However, we know who they are, and how they operate."
New Malicious PyPI Packages Caught Using Covert Side-Loading Tactics
21.2.24
Virus
The Hacker News
Cybersecurity researchers have discovered two malicious packages on the Python Package Index (PyPI) repository that were found leveraging a technique called DLL side-loading to circumvent detection by security software and run malicious code.
The packages, named NP6HelperHttptest and NP6HelperHttper, were each downloaded 537 and 166 times, respectively, before they were taken down.
"The latest discovery is an example of DLL sideloading executed by an open-source package that suggests the scope of software supply chain threats is expanding," ReversingLabs researcher Petar Kirhmajer said in a report shared with The Hacker News.
The name NP6 is notable as it refers to a legitimate marketing automation solution made by ChapsVision. In particular, the fake packages are typosquats of NP6HelperHttp and NP6HelperConfig, which are helper tools published by one of ChapsVision's employees to PyPI.
In other words, the goal is to trick developers searching for NP6HelperHttp and NP6HelperConfig into downloading their rogue counterparts.
Contained within the two libraries is a setup.py script that's designed to download two files, an actual executable from Beijing-based Kingsoft Corporation ("ComServer.exe") that's vulnerable to DLL side-loading and the malicious DLL to be side-loaded ("dgdeskband64.dll").
In side-loading the DLL, the aim is to avoid detection of the malicious code, as observed previously in the case of an npm package called aabquerys that also leveraged the same technique to execute code capable of deploying a remote access trojan.
The DLL, for its part, reaches out to an attacker-controlled domain ("us.archive-ubuntu[.]top") to fetch a GIF file that, in reality, is a piece of shellcode for a Cobalt Strike Beacon, a post-exploitation toolkit used for red teaming.
There is evidence to suggest that the packages are part of a wider campaign that involves the distribution of similar executables that are susceptible to DLL side-loading.
"Development organizations need to be aware of the threats related to supply chain security and open-source package repositories," security researcher Karlo Zanki said.
"Even if they are not using open-source package repositories, that doesn't mean that threat actors won't abuse them to impersonate companies and their software products and tools."
New Report Reveals North Korean Hackers Targeting Defense Firms Worldwide
21.2.24
APT
The Hacker News
North Korean state-sponsored threat actors have been attributed to a cyber espionage campaign targeting the defense sector across the world.
In a joint advisory published by Germany's Federal Office for the Protection of the Constitution (BfV) and South Korea's National Intelligence Service (NIS), the agencies said the goal of the attacks is to plunder advanced defense technologies in a "cost-effective" manner.
"The regime is using the military technologies to modernize and improve the performance of conventional weapons and to develop new strategic weapon systems including ballistic missiles, reconnaissance satellites and submarines," they noted.
The infamous Lazarus Group has been blamed for one of the two hacking incidents, which involved the use of social engineering to infiltrate the defense sector as part of a long-standing operation called Dream Job. The campaign has been ongoing since August 2020 over several waves.
In these attacks, the threat actors either create a fake profile or leverage legitimate-but-compromised profiles on platforms like LinkedIn to approach prospective targets and build trust with them, before offering lucrative job opportunities and shifting the conversation to a different messaging service like WhatsApp to initiate the recruitment process.
Victims are then sent coding assignments and job offer documents laden with malware that, when launched, activate the infection procedure to compromise their computers.
"Universally, the circumstance that employees usually do not talk to their colleagues or employer about job offers plays into the hands of the attacker," the agencies said.
"The Lazarus Group changed its tools throughout the campaign and demonstrated more than once that it is capable of developing whatever is necessary to suit the situation."
The second case concerns an intrusion into a defense research center towards the end of 2022 by executing a software supply chain attack against an unnamed company responsible for maintaining one of the research center's web servers.
"The cyber actor further infiltrated the research facility by deploying remote-control malware through a patch management system (PMS) of the research center, and stole various account information of business portals and email contents," the BfV and NIS said.
The breach, which was carried by another North Korea-based threat actor, unfolded over five stages -
Hack into the web server maintenance company, steal SSH credentials, and gain
remote access to the research center's server
Download additional malicious
tooling using curl commands, including a tunneling software and a Python-based
downloader
Conduct lateral movement and plunder employee account credentials
Leverage the stolen security manager's account information to unsuccessfully
distribute a trojanized update that comes with capabilities to upload and
download files, execute code, and to collect system information
Persist
within target environment by weaponizing a file upload vulnerability in the
website to deploy a web shell for remote access and send spear-phishing emails
"The actor avoided carrying out a direct attack against its target, which
maintained a high level of security, but rather made an initial attack against
its vendor, the maintenance and repair company," the agencies explained. "This
indicates that the actor took advantage of the trustful relationship between the
two entities."
The security bulletin is the second to be published by BfV and NIS in as many years. In March 2023, the agencies warned of Kimsuky actors using rogue browser extensions to steal users' Gmail inboxes. Kimsuky was sanctioned by the U.S. government in November 2023.
The development comes as blockchain analytics firm Chainalysis revealed that the Lazarus Group has switched to using YoMix bitcoin mixer to launder stolen proceeds following the shutdown of Sinbad late last year, indicating their ability to adapt their modus operandi in response to law enforcement actions.
"Sinbad became a preferred mixer for North Korea-affiliated hackers in 2022, soon after the sanctioning of Tornado Cash, which had previously been the go-to for these sophisticated cybercriminals," the company said. "With Sinbad out of the picture, Bitcoin-based mixer YoMix has acted as a replacement."
The malicious activities are the work of a plethora of North Korean hacking units operating under the broad Lazarus umbrella, which are known to engage in an array of hacking operations ranging from cyber espionage to cryptocurrency thefts, ransomware, and supply chain attacks to achieve their strategic goals.
Critical Flaws Found in ConnectWise ScreenConnect Software - Patch Now
21.2.24
Vulnerebility
The Hacker News
ConnectWise has released software updates to address two security flaws in its ScreenConnect remote desktop and access software, including a critical bug that could enable remote code execution on affected systems.
The vulnerabilities, which currently lack CVE identifiers, are listed below -
Authentication bypass using an alternate path or channel (CVSS score: 10.0)
Improper limitation of a pathname to a restricted directory aka "path traversal"
(CVSS score: 8.4)
The company deemed the severity of the issues as critical,
citing they "could allow the ability to execute remote code or directly impact
confidential data or critical systems."
Both the vulnerabilities impact ScreenConnect versions 23.9.7 and prior, with fixes available in version 23.9.8. The flaws were reported to the company on February 13, 2024.
While there is no evidence that the shortcomings have been exploited in the wild, users who are running self-hosted or on-premise versions are recommended to update to the latest version as soon as possible.
"ConnectWise will also provide updated versions of releases 22.4 through 23.9.7
for the critical issue, but strongly recommend that partners update to
ScreenConnect version 23.9.8," the IT management software company said.
Source: John Hammond of HuntressLabs
Cybersecurity firm Huntress said it
found more than 8,800 servers running a vulnerable version of ScreenConnect. It
has also demonstrated a proof-of-concept (PoC) exploit that it said can be
"recreated with ease and required minimal technical knowledge" and used to
bypass authentication on unpatched ScreenConnect servers.
WordPress Bricks Theme Under Active Attack: Critical Flaw Impacts 25,000+ Sites
21.2.24
Vulnerebility
The Hacker News
A critical security flaw in the Bricks theme for WordPress is being actively exploited by threat actors to run arbitrary PHP code on susceptible installations.
The flaw, tracked as CVE-2024-25600 (CVSS score: 9.8), enables unauthenticated attackers to achieve remote code execution. It impacts all versions of the Bricks up to and including 1.9.6.
It has been addressed by the theme developers in version 1.9.6.1 released on February 13, 2024, merely days after WordPress security provider Snicco reported the flaw on February 10.
While a proof-of-concept (PoC) exploit has not been released, technical details have been released by both Snicco and Patchstack, noting that the underlying vulnerable code exists in the prepare_query_vars_from_settings() function.
Specifically, it concerns the use of security tokens called "nonces" for verifying permissions, which can then be used to pass arbitrary commands for execution, effectively allowing a threat actor to seize control of a targeted site.
The nonce value is publicly available on the frontend of a WordPress site, Patchstack said, adding there are no adequate role checks applied.
"Nonces should never be relied on for authentication, authorization, or access control," WordPress cautions in its documentation. "Protect your functions using current_user_can(), and always assume nonces can be compromised."
WordPress security company Wordfence said it detected over three dozen attack attempts exploiting the flaw as of February 19, 2024. Exploitation attempts are said to have commenced on February 14, a day after public disclosure.
A majority of the attacks are from the following IP addresses -
200.251.23[.]57
92.118.170[.]216
103.187.5[.]128
149.202.55[.]79
5.252.118[.]211
91.108.240[.]52
Bricks is estimated to have around 25,000
currently active installations. Users of the plugin are recommended to apply the
latest patches to mitigate potential threats.
Iran and Hezbollah Hackers Launch Attacks to Influence Israel-Hamas Narrative
21.2.24
BigBrothers
The Hacker News
Hackers backed by Iran and Hezbollah staged cyber attacks designed to undercut public support for the Israel-Hamas war after October 2023.
This includes destructive attacks against key Israeli organizations, hack-and-leak operations targeting entities in Israel and the U.S., phishing campaigns designed to steal intelligence, and information operations to turn public opinion against Israel.
Iran accounted for nearly 80% of all government-backed phishing activity targeting Israel in the six months leading up to the October 7 attacks, Google said in a new report.
"Hack-and-leak and information operations remain a key component in these and related threat actors' efforts to telegraph intent and capability throughout the war, both to their adversaries and to other audiences that they seek to influence," the tech giant said.
But what's also notable about the Israel-Hamas conflict is that the cyber operations appear to be executed independently of the kinetic and battlefield actions, unlike observed in the case of the Russo-Ukrainian war.
Such cyber capabilities can be quickly deployed at a lower cost to engage with regional rivals without direct military confrontation, the company added.
One of the Iran-affiliated groups, dubbed GREATRIFT (aka UNC4453 or Plaid Rain), is said to have propagated malware via fake "missing persons" site targeting visitors seeking updates on abducted Israelis. The threat actor also utilized blood donation-themed lure documents as a distribution vector.
At least two hacktivist personas named Karma and Handala Hack have leveraged wiper malware strains such as BiBi-Windows Wiper, BiBi-Linux Wiper, ChiLLWIPE, and COOLWIPE to stage destructive attacks against Israel and delete files from Windows and Linux systems, respectively.
Another Iranian nation-state hacking group called Charming Kitten (aka APT42 or CALANQUE) targeted media and non-governmental organizations (NGOs) with a PowerShell backdoor known as POWERPUG as part of a phishing campaign observed in late October and November 2023.
POWERPUG is also the latest addition to the adversary's long list of backdoors,
which comprises PowerLess, BellaCiao, POWERSTAR (aka GorjolEcho), NokNok, and
BASICSTAR.
Hamas-linked groups, on the other hand, targeted Israeli software engineers with coding assignment decoys in an attempt to dupe them into downloading SysJoker malware weeks before the October 7 attacks. The campaign has been attributed to a threat actor referred to as BLACKATOM.
"The attackers [...] posed as employees of legitimate companies and reached out via LinkedIn to invite targets to apply for software development freelance opportunities," Google said. "Targets included software engineers in the Israeli military, as well as Israel's aerospace and defense industry."
The California-headquartered company described the tactics adopted by Hamas cyber actors as simple but effective, noting their use of social engineering to deliver remote access trojans and backdoors like MAGNIFI to target users in both Palestine and Israel, which has been linked to BLACKSTEM (aka Molerats).
Adding another dimension to these campaigns is the use of spyware targeting Android phones that are capable of harvesting sensitive information and exfiltrating the data to attacker-controlled infrastructure.
The malware strains, called MOAAZDROID and LOVELYDROID, are the handiwork of the
Hamas-affiliated actor DESERTVARNISH, which is also tracked as Arid Viper,
Desert Falcons, Renegade Jackal, and UNC718. Details about the spyware were
previously documented by Cisco Talos in October 2023.
State-sponsored groups from Iran, such as MYSTICDOME (aka UNC1530), have also been observed targeting mobile devices in Israel with the MYTHDROID (aka AhMyth) Android remote access trojan as well as a bespoke spyware called SOLODROID for intelligence collection.
"MYSTICDOME distributed SOLODROID using Firebase projects that 302-redirected users to the Play store, where they were prompted to install the spyware," said Google, which has since taken down the apps from the digital marketplace.
Google further highlighted an Android malware called REDRUSE – a trojanized version of the legitimate Red Alert app used in Israel to warn of incoming rocket attacks – that exfiltrates contacts, messaging data, and location. It was propagated via SMS phishing messages that impersonated the police.
The ongoing war has also had an impact on Iran, with its critical infrastructure
disrupted by an actor named Gonjeshke Darande (meaning Predatory Sparrow in
Persian) in December 2023. The persona is believed to be linked to the Israeli
Military Intelligence Directorate.
The findings come as Microsoft revealed that Iranian government-aligned actors have "launched a series of cyberattacks and influence operations (IO) intended to help the Hamas cause and weaken Israel and its political allies and business partners."
Redmond described their early-stage cyber and influence operations as reactive and opportunistic, while also corroborating with Google's assessment that the attacks became "increasingly targeted and destructive and IO campaigns grew increasingly sophisticated and inauthentic" following the outbreak of the war.
Beside ramping up and expanding their attack focus beyond Israel to encompass
countries that Iran perceives as aiding Israel, including Albania, Bahrain, and
the U.S., Microsoft said it observed collaboration among Iran-affiliated groups
such as Pink Sandstorm (aka Agrius) and Hezbollah cyber units.
"Collaboration lowers the barrier to entry, allowing each group to contribute existing capabilities and removes the need for a single group to develop a full spectrum of tooling or tradecraft," Clint Watts, general manager at the Microsoft Threat Analysis Center (MTAC), said.
Last week, NBC News reported that the U.S. recently launched a cyber attack against an Iranian military ship named MV Behshad that had been collecting intelligence on cargo vessels in the Red Sea and the Gulf of Aden.
An analysis from Recorded Future last month also detailed how hacking personas and front groups in Iran are managed and operated through a variety of contracting firms in Iran, which carry out intelligence gathering and information operations to "foment instability in target countries."
"While Iranian groups rushed to conduct, or simply fabricate, operations in the early days of the war, Iranian groups have slowed their recent operations allowing them more time to gain desired access or develop more elaborate influence operations," Microsoft concluded.
LockBit Ransomware's Darknet Domains Seized in Global Law Enforcement Raid
21.2.24
Ransom
The Hacker News
Update: The U.K. National Crime Agency (NCA) has
confirmed the takedown of LockBit infrastructure. Read here for more details.
An international law enforcement operation has led to the seizure of multiple
darknet domains operated by LockBit, one of the most prolific ransomware groups,
marking the latest in a long list of digital takedowns.
While the full extent of the effort, codenamed Operation Cronos, is presently unknown, visiting the group's .onion website displays a seizure banner containing the message "The site is now under the control of law enforcement."
Authorities from 11 countries, Australia, Canada, Finland, France, Germany, Japan, the Netherlands, Sweden, Switzerland, the U.K., and the U.S., alongside Europol participated in the joint exercise.
Malware research group VX-Underground, in a message posted on X (formerly Twitter), said the websites were taken down by exploiting a critical security flaw impacting PHP (CVE-2023-3824, CVSS score: 9.8) that could result in remote code execution.
Law enforcement agencies also left on a note on the affiliate panel, stating they are in possession of the "source code, details of the victims you have attacked, the amount of money extorted, the data stolen, chats, and much, much more," adding it was made possible due to LockBit's "flawed infrastructure."
LockBit, which emerged on September 3, 2019, has been one of the most active and notorious ransomware gangs in history, claiming more than 2,000 victims to date. It's estimated to have extorted at least $91 million from U.S. organizations alone.
According to data shared by cybersecurity firm ReliaQuest, LockBit listed 275 victims on its data leak portal in the fourth quarter of 2023, dwarfing all its competitors.
There is no word as yet of any arrest or sanctions, but the development is a definite blow to LockBit's near-term operations and arrives two months after the BlackCat ransomware operation was dismantled by the U.S. government.
The coordinated takedown also coincides with the arrest of a 31-year-old Ukrainian national for gaining unauthorized access to Google and online bank accounts of American and Canadian users by deploying malware and selling access to other threat actors on the dark web for financial gain.
Meta Warns of 8 Spyware Firms Targeting iOS, Android, and Windows Devices
19.2.24
OS
The Hacker News
Meta Platforms said it took a series of steps to curtail
malicious activity from eight different firms based in Italy, Spain, and the
United Arab Emirates (U.A.E.) operating in the surveillance-for-hire industry.
The findings are part of its Adversarial Threat Report for the fourth quarter of 2023. The spyware targeted iOS, Android, and Windows devices.
"Their various malware included capabilities to collect and access device information, location, photos and media, contacts, calendar, email, SMS, social media, and messaging apps, and enable microphone,camera, and screenshot functionality," the company said.
The eight companies are Cy4Gate/ELT Group, RCS Labs, IPS Intelligence, Variston IT, TrueL IT, Protect Electronic Systems, Negg Group, and Mollitiam Industries.
These firms, per Meta, also engaged in scraping, social engineering, and phishing activity that targeted a wide range of platforms such as Facebook, Instagram, X (formerly Twitter), YouTube, Skype, GitHub, Reddit, Google, LinkedIn, Quora, Tumblr, VK, Flickr, TikTok, SnapChat, Gettr, Viber, Twitch and Telegram.
Specifically, a network of fictitious personas linked to RCS Labs, which is owned by Cy4Gate, is said to have tricked users into providing their phone numbers and email addresses, in addition to clicking on bogus links for conducting reconnaisance.
Another set of now-removed Facebook and Instagram accounts associated with Spanish spyware vendor Variston IT was employed for exploit development and testing, including sharing of malicious links. Last week, reports emerged that the company is shutting down its operations.
Cybersecurity
Meta also said it identified accounts used by Negg Group to
test the delivery of its spyware, as well as by Mollitiam Industries, a Spanish
firm that advertises a data collection service and spyware targeting Windows,
macOS, and Android, to scrape public information.
Elsewhere, the social media giant actioned on networks from China, Myanmar, and Ukraine exhibiting coordinated inauthentic behavior (CIB) by removing over 2,000 accounts, Pages, and Groups from Facebook and Instagram.
While the Chinese cluster targeted U.S. audiences with content related to criticism of U.S. foreign policy towards Taiwan and Israel and its support of Ukraine, the network originating from Myanmar targeted its own residents with original articles that praised the Burmese army and disparaged the ethnic armed organizations and minority groups.
The third cluster is notable for its use of fake Pages and Groups to post content that supported Ukrainian politician Viktor Razvadovskyi, while also sharing "supportive commentary about the current government and critical commentary about the opposition" in Kazakhstan.
The development comes as a coalition of government and tech companies, counting Meta, have signed an agreement to curb the abuse of commercial spyware to commit human rights abuses.
As countermeasures, the company has introduced new features like enabled Control Flow Integrity (CFI) on Messenger for Android and VoIP memory isolation for WhatsApp in an effort to make exploitation harder and reduce the overall attack surface.
That said, the surveillance industry continues to thrive in myriad, unexpected forms. Last month, 404 Media — building off prior research from the Irish Council for Civil Liberties (ICCL) in November 2023 — unmasked a surveillance tool called Patternz that leverages real-time bidding (RTB) advertising data gathered from popular apps like 9gag, Truecaller, and Kik to track mobile devices.
"Patternz allows national security agencies utilize real-time and historical user advertising generated data to detect, monitor and predict users actions, security threats and anomalies based on users' behavior, location patterns and mobile usage characteristics, ISA, the Israeli company behind the product claimed on its website.
Then last week, Enea took the wraps off a previously unknown mobile network attack known as MMS Fingerprint that's alleged to have been utilized by Pegasus-maker NSO Group. This information was included in a 2015 contract between the company and the telecom regulator of Ghana.
Cybersecurity
While the exact method used remains something of a mystery, the
Swedish telecom security firm suspects it likely involves the use of
MM1_notification.REQ, a special type of SMS message called a binary SMS that
notifies the recipient device of an MMS that's waiting for retrieval from the
Multimedia Messaging Service Center (MMSC).
The MMS is then fetched by means of MM1_retrieve.REQ and MM1_retrieve.RES, with the former being an HTTP GET request to the URL address contained in the MM1_notification.REQ message.
What's notable about this approach is that user device information such as User-Agent (different from a web browser User-Agent string) and x-wap-profile is embedded in the GET request, thereby acting as a fingerprint of sorts.
"The (MMS) User-Agent is a string that typically identifies the OS and device," Enea said. "x-wap-profile points to a UAProf (User Agent Profile) file that describes the capabilities of a mobile handset."
A threat actor looking to deploy spyware could use this information to exploit specific vulnerabilities, tailor their malicious payloads to the target device, or even craft more effective phishing campaigns. That said, there is no evidence that this security hole has been exploited in the wild in recent months.
Anatsa Android Trojan Bypasses Google Play Security, Expands Reach to New
Countries
19.2.24
OS
The Hacker News
The Android banking trojan known as Anatsa has expanded
its focus to include Slovakia, Slovenia, and Czechia as part of a new campaign
observed in November 2023.
"Some of the droppers in the campaign successfully exploited the accessibility service, despite Google Play's enhanced detection and protection mechanisms," ThreatFabric said in a report shared with The Hacker News.
"All droppers in this campaign have demonstrated the capability to bypass the restricted settings for accessibility service in Android 13." The campaign, in total, involves five droppers with more than 100,000 total installations.
Also known by the name TeaBot and Toddler, Anatsa is known to be distributed under the guise of seemingly innocuous apps on the Google Play Store. These apps, called droppers, facilitate the installation of the malware by circumventing security measures imposed by Google that seek to grant sensitive permissions.
In June 2023, the Dutch mobile security firm disclosed an Anatsa campaign that targeted banking customers in the U.S., the U.K., Germany, Austria, and Switzerland at least since March 2023 using dropper apps that were collectively downloaded over 30,000 times on the Play Store.
Anatsa comes fitted with capabilities to gain full control over infected devices and execute actions on a victim's behalf. It can also steal credentials to initiate fraudulent transactions.
The latest iteration observed in November 2023 is no different in that one of the droppers masqueraded as a phone cleaner app named "Phone Cleaner - File Explorer" (package name "com.volabs.androidcleaner") and leveraged a technique called versioning to introduce its malicious behavior.
While the app is no longer available for download from the official storefront for Android, it can still be downloaded via other sketchy third-party sources.
According to statistics available on app intelligence platform AppBrain, the app is estimated to have been downloaded about 12,000 times during the time it was available on the Google Play Store between November 13 and November 27, when it was unpublished.

"Initially, the app appeared harmless, with no malicious code and its
accessibility service not engaging in any harmful activities," ThreatFabric
researchers said.
"However, a week after its release, an update introduced malicious code. This update altered the AccessibilityService functionality, enabling it to execute malicious actions such as automatically clicking buttons once it received a configuration from the [command-and-control] server."
What makes the dropper notable is that its abuse of the accessibility service is tailored to Samsung devices, suggesting that it was designed to exclusively target the company-made handsets at some point, although other droppers used in the campaign have been found to be manufacturer agnostic.
The droppers are also capable of circumventing Android 13's restricted settings by mimicking the process used by marketplaces to install new applications without having their access to the accessibility service functionalities disabled, as previously observed in the case of dropper services like SecuriDropper.
"These actors prefer concentrated attacks on specific regions rather than a global spread, periodically shifting their focus," ThreatFabric said. "This targeted approach enables them to concentrate on a limited number of financial organizations, leading to a high number of fraud cases in a short time."
The development comes as Fortinet FortiGuard Labs detailed another campaign that distributes the SpyNote remote access trojan by imitating a legitimate Singapore-based cryptocurrency wallet service known as imToken to replace destination wallet addresses and with actor-controlled ones and conduct illicit asset transfers.
"Like much Android malware today, this malware abuses the accessibility API," security researcher Axelle Apvrille said. "This SpyNote sample uses the Accessibility API to target famous crypto wallets."
Russian-Linked Hackers Target 80+ Organizations via Roundcube Flaws
19.2.24
APT
The Hacker News
Threat actors operating with interests aligned to Belarus and Russia have been linked to a new cyber espionage campaign that likely exploited cross-site scripting (XSS) vulnerabilities in Roundcube webmail servers to target over 80 organizations.
These entities are primarily located in Georgia, Poland, and Ukraine, according to Recorded Future, which attributed the intrusion set to a threat actor known as Winter Vivern, which is also known as TA473 and UAC0114. The cybersecurity firm is tracking the hacking outfit under the moniker Threat Activity Group 70 (TAG-70).
Winter Vivern's exploitation of security flaws in Roundcube and software was previously highlighted by ESET in October 2023, joining other Russia-linked threat actor groups such as APT28, APT29, and Sandworm that are known to target email software.
The adversary, which has been active since at least December 2020, has also been linked to the abuse of a now-patched vulnerability in Zimbra Collaboration email software last year to infiltrate organizations in Moldova and Tunisia in July 2023.
The campaign discovered by Recorded Future took place from the start of October 2023 and continued until the middle of the month with the goal of collecting intelligence on European political and military activities. The attacks overlap with additional TAG-70 activity against Uzbekistan government mail servers that were detected in March 2023.
"TAG70 has demonstrated a high level of sophistication in its attack methods," the company said. "The threat actors leveraged social engineering techniques and exploited cross-site scripting vulnerabilities in Roundcube webmail servers to gain unauthorized access to targeted mail servers, bypassing the defenses of government and military organizations."
The attack chains involve exploiting Roundcube flaws to deliver JavaScript payloads that are designed to exfiltrate user credentials to a command-and-control (C2) server.
Recorded Future said it also found evidence of TAG-70 targeting the Iranian embassies in Russia and the Netherlands, as well as the Georgian Embassy in Sweden.
"The targeting of Iranian embassies in Russia and the Netherlands suggests a broader geopolitical interest in assessing Iran's diplomatic activities, especially regarding its support for Russia in Ukraine," it said.
"Similarly, espionage against Georgian government entities reflects interests in monitoring Georgia's aspirations for European Union (EU) and NATO accession."
Iranian Hackers Target Middle East Policy Experts with New BASICSTAR Backdoor
19.2.24
APT
The Hacker News
The Iranian-origin threat actor known as Charming Kitten has been linked to a new set of attacks aimed at Middle East policy experts with a new backdoor called BASICSTAR by creating a fake webinar portal.
Charming Kitten, also called APT35, CharmingCypress, Mint Sandstorm, TA453, and Yellow Garuda, has a history of orchestrating a wide range of social engineering campaigns that cast a wide net in their targeting, often singling out think tanks, NGOs, and journalists.
"CharmingCypress often employs unusual social-engineering tactics, such as engaging targets in prolonged conversations over email before sending links to malicious content," Volexity researchers Ankur Saini, Callum Roxan, Charlie Gardner, and Damien Cash said.
Last month, Microsoft revealed that high-profile individuals working on Middle Eastern affairs have been targeted by the adversary to deploy malware such as MischiefTut and MediaPl (aka EYEGLASS) that are capable of harvesting sensitive information from a compromised host.
The group, assessed to be affiliated with Iran's Islamic Revolutionary Guard Corps (IRGC), has also distributed several other backdoors such as PowerLess, BellaCiao, POWERSTAR (aka GorjolEcho), and NokNok over the past year, emphasizing its determination to continue its cyber onslaught, adapting its tactics and methods despite public exposure.
The phishing attacks observed between September and October 2023 involved the Charming Kitten operators posing as the Rasanah International Institute for Iranian Studies (IIIS) to initiate and build trust with targets.
The phishing attempts are also characterized by the use of compromised email accounts belonging to legitimate contacts and multiple threat-actor-controlled email accounts, the latter of which is called Multi-Persona Impersonation (MPI).
The attack chains typically employ RAR archives containing LNK files as a starting point to distribute malware, with the messages urging prospective targets to join a fake webinar about topics that are of interest to them. One such multi-stage infection sequence has been observed to deploy BASICSTAR and KORKULOADER, a PowerShell downloader script.
BASICSTAR, a Visual Basic Script (VBS) malware, is capable of gathering basic system information, remotely executing commands relayed from a command-and-control (C2) server, and downloading and displaying a decoy PDF file.
What's more, some of these phishing attacks are engineered to serve different backdoors depending on the machine's operating system. While Windows victims are compromised with POWERLESS, Apple macOS victims are targeted with an infection chain culminating in NokNok via a functional VPN application that's laced with malware.
"This threat actor is highly committed to conducting surveillance on their targets in order to determine how best to manipulate them and deploy malware," the researchers said. "Additionally, few other threat actors have consistently churned out as many campaigns as CharmingCypress, dedicating human operators to support their ongoing efforts."
The disclosure comes as Recorded Future uncovered IRGC's targeting of Western countries using a network of contracting companies that also specialize in exporting technologies for surveillance and offensive purposes to countries like Iraq, Syria, and Lebanon.
The relationship between intelligence and military organizations and Iran-based contractors takes the form of various cyber centers that act as "firewalls" to conceal the sponsoring entity.
They include Ayandeh Sazan Sepher Aria (suspected to be associated with Emennet Pasargad), DSP Research Institute, Sabrin Kish, Soroush Saman, Mahak Rayan Afraz, and the Parnian Telecommunication and Electronic Company.
"Iranian contracting companies are established and run by a tight-knit network of personas, who, in some cases, represent the contractors as board members," the company said. "The individuals are closely associated with the IRGC, and in some cases, are even representatives of sanctioned entities (such as the IRGC Cooperative Foundation)."
FBI's Most-Wanted Zeus and IcedID Malware Mastermind Pleads Guilty
17.2.24
Crime
The Hacker News
A Ukrainian national has pleaded guilty in the U.S. to his role in two different malware schemes, Zeus and IcedID, between May 2009 and February 2021.
Vyacheslav Igorevich Penchukov (aka Vyacheslav Igoravich Andreev, father, and tank), 37, was arrested by Swiss authorities in October 2022 and extradited to the U.S. last year. He was added to the FBI's most-wanted list in 2012.
The U.S. Department of Justice (DoJ) described Penchukov as a "leader of two prolific malware groups" that infected thousands of computers with malware, leading to ransomware and the theft of millions of dollars.
This included the Zeus banking trojan that facilitated the theft of bank account information, passwords, personal identification numbers, and other details necessary to login to online banking accounts.
Penchukov and his co-conspirators, as part of the "wide-ranging racketeering enterprise" dubbed Jabber Zeus gang, then masqueraded as employees of the victims to initiate unauthorized fund transfers.
They also used individuals residing in the U.S. and other parts of the world as "money mules" to receive the wired funds, which were ultimately funneled to overseas accounts controlled by Penchukov et al. A successor to Zeus was dismantled in 2014.
The defendant has also been accused of facilitating malicious activity by helping lead attacks involving the IcedID (aka BokBot) malware from at least November 2018. The malware is capable of acting as an information stealer and a loader for other payloads, such as ransomware.
Ultimately, as investigative journalist Brian Krebs reported back in 2022, he managed to evade prosecution by Ukrainian cybercrime investigators for many years due to his political connections with former Ukrainian President Victor Yanukovych.
Following his arrest and extradition, Penchukov pleaded guilty to one count of conspiracy to commit a racketeer-influenced and corrupt organization (RICO) act offense for his leadership role in the Jabber Zeus group. He also pleaded guilty to one count of conspiracy to commit wire fraud for his leadership role in the IcedID malware group.
Penchukov is scheduled to be sentenced on May 9, 2024, and faces a maximum penalty of 20 years in prison for each count.
The development comes as the DoJ announced the extradition of a 28-year-old Ukrainian national from the Netherlands in connection with fraud, money laundering and aggravated identity theft by allegedly operating and advertising an information stealer known as Raccoon.
Mark Sokolovsky, who was arrested by Dutch authorities in March 2022, leased Raccoon to other cybercriminals on a malware-as-a-service (MaaS) model for $200 a month. It first became available in April 2019.
"These individuals used various ruses, such as email phishing, to install the malware onto the computers of unsuspecting victims," the DoJ said.
"Raccoon infostealer then stole personal data from victim computers, including login credentials, financial information, and other personal records. Stolen information was used to commit financial crimes or was sold to others on cybercrime forums."
At least 50 million unique credentials and forms of identification have been harvested by the malware, according to the U.S. Federal Bureau of Investigation (FBI) estimates.
Sokolovsky's arrest was accompanied by a coordinated takedown of Raccoon's digital infrastructure, but a new version of the stealer, called RecordBreaker, has since emerged in the wild.
He has been charged with one count of conspiracy to commit fraud and related activity in connection with computers, one count of conspiracy to commit wire fraud, one count of conspiracy to commit money laundering, and one count of aggravated identity theft.
Google Open Sources Magika: AI-Powered File Identification Tool
17.2.24
AI
The Hacker News
Google has announced that it's open-sourcing Magika, an
artificial intelligence (AI)-powered tool to identify file types, to help
defenders accurately detect binary and textual file types.
"Magika outperforms conventional file identification methods providing an overall 30% accuracy boost and up to 95% higher precision on traditionally hard to identify, but potentially problematic content such as VBA, JavaScript, and Powershell," the company said.
The software uses a "custom, highly optimized deep-learning model" that enables the precise identification of file types within milliseconds. Magika implements inference functions using the Open Neural Network Exchange (ONNX).
Google said it internally uses Magika at scale to help improve users' safety by routing Gmail, Drive, and Safe Browsing files to the proper security and content policy scanners.
In November 2023, the tech giant unveiled RETVec (short for Resilient and Efficient Text Vectorizer), a multilingual text processing model to detect potentially harmful content such as spam and malicious emails in Gmail.
Amid an ongoing debate on the risks of the rapidly developing technology and its abuse by nation-state actors associated with Russia, China, Iran, and North Korea to boost their hacking efforts, Google said deploying AI at scale can strengthen digital security and "tilt the cybersecurity balance from attackers to defenders."
It also emphasized the need for a balanced regulatory approach to AI usage and adoption in order to avoid a future where attackers can innovate, but defenders are restrained due to AI governance choices.
"AI allows security professionals and defenders to scale their work in threat detection, malware analysis, vulnerability detection, vulnerability fixing and incident response," the tech giant's Phil Venables and Royal Hansen noted. "AI affords the best opportunity to upend the Defender's Dilemma, and tilt the scales of cyberspace to give defenders a decisive advantage over attackers."
Concerns have also been raised about generative AI models' use of web-scraped data for training purposes, which may also include personal data.
"If you don't know what your model is going to be used for, how can you ensure its downstream use will respect data protection and people's rights and freedoms?," the U.K. Information Commissioner's Office (ICO) pointed out last month.
What's more, new research has shown that large language models can function as "sleeper agents" that may be seemingly innocuous but can be programmed to engage in deceptive or malicious behavior when specific criteria are met or special instructions are provided.
"Such backdoor behavior can be made persistent so that it is not removed by standard safety training techniques, including supervised fine-tuning, reinforcement learning, and adversarial training (eliciting unsafe behavior and then training to remove it), researchers from AI startup Anthropic said in the study.
CISA Warning: Akira Ransomware Exploiting Cisco ASA/FTD Vulnerability
17.2.24
Ransom
The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a now-patched security flaw impacting Cisco Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) software to its Known Exploited Vulnerabilities (KEV) catalog, following reports that it's being likely exploited in Akira ransomware attacks.
The vulnerability in question is CVE-2020-3259 (CVSS score: 7.5), a high-severity information disclosure issue that could allow an attacker to retrieve memory contents on an affected device. It was patched by Cisco as part of updates released in May 2020.
Late last month, cybersecurity firm Truesec said it found evidence suggesting that it has been weaponized by Akira ransomware actors to compromise multiple susceptible Cisco Anyconnect SSL VPN appliances over the past year.
"There is no publicly available exploit code for [...] CVE-2020-3259, meaning that a threat actor, such as Akira, exploiting that vulnerability would need to buy or produce exploit code themselves, which requires deep insights into the vulnerability," security researcher Heresh Zaremand said.
According to Palo Alto Networks Unit 42, Akira is one of the 25 groups with newly established data leak sites in 2023, with the ransomware group publicly claiming nearly 200 victims. First observed in March 2023, the group is believed to share connections with the notorious Conti syndicate based on the fact that the ransom proceeds have been routed to Conti-affiliated wallet addresses.
In the fourth quarter of 2023 alone, the e-crime group listed 49 victims on its data leak portal, putting it behind LockBit (275), Play (110), ALPHV/BlackCat (102), NoEscape (76), 8Base (75), and Black Basta (72).
Federal Civilian Executive Branch (FCEB) agencies are required to remediate identified vulnerabilities by March 7, 2024, to secure their networks against potential threats.
CVE-2020-3259 is far from the only flaw to be exploited for delivering ransomware. Earlier this month, Arctic Wolf Labs revealed the abuse of CVE-2023-22527 – a recently uncovered shortcoming in Atlassian Confluence Data Center and Confluence Server – to deploy C3RB3R ransomware, as well as cryptocurrency miners and remote access trojans.
The development comes as the U.S. State Department announced rewards of up to $10 million for information that could lead to the identification or location of BlackCat ransomware gang key members, in addition to offering up to $5 million for information leading to the arrest or conviction of its affiliates.
The ransomware-as-a-service (RaaS) scheme, much like Hive, compromised over 1,000 victims globally, netting at least $300 million in illicit profits since its emergence in late 2021. It was disrupted in December 2023 following an international coordinated operation.
The ransomware landscape has become a lucrative market, attracting the attention of cybercriminals looking for quick financial gain, leading to the rise of new players such as Alpha (not to be confused with ALPHV) and Wing.
There are indications that Alpha could be connected to NetWalker, which shuttered in January 2021 following an international law enforcement operation. The links pertain to overlaps in the source code and the tactics, techniques, and procedures (TTPs) used in attacks.
"Alpha may be an attempt at reviving the old ransomware operation by one or more of the original NetWalker developers," Broadcom-owned Symantec said. "Alternatively, the attackers behind Alpha may have acquired and modified the original NetWalker payload in order to launch their own ransomware operation."
The U.S. Government Accountability Office (GAO), in a report published towards the end of January 2024, called for enhanced oversight into recommended practices for addressing ransomware, specifically for organizations from critical manufacturing, energy, healthcare and public health, and transportation systems sectors.
RustDoor macOS Backdoor Targets Cryptocurrency Firms with Fake Job Offers
17.2.24
Cryptocurrency
The Hacker News
Multiple companies operating in the cryptocurrency sector
are the target of an ongoing malware campaign that involves a newly discovered
Apple macOS backdoor codenamed RustDoor.
RustDoor was first documented by Bitdefender last week, describing it as a Rust-based malware capable of harvesting and uploading files, as well as gathering information about the infected machines. It's distributed by masquerading itself as a Visual Studio update.
While prior evidence uncovered at least three different variants of the backdoor, the exact initial propagation mechanism remained unknown.
That said, the Romanian cybersecurity firm subsequently told The Hacker News that the malware was used as part of a targeted attack rather than a shotgun distribution campaign, noting that it found additional artifacts that are responsible for downloading and executing RustDoor.
"Some of these first stage downloaders claim to be PDF files with job offerings, but in reality, are scripts that download and execute the malware while also downloading and opening an innocuous PDF file that bills itself as a confidentiality agreement," Bogdan Botezatu, director of threat research and reporting at Bitdefender, said.
Since then, three more malicious samples that act as first-stage payloads have come to light, each of them purporting to be a job offering. These ZIP archives predate the earlier RustDoor binaries by nearly a month.
The new component of the attack chain – i.e., the archive files ("Jobinfo.app.zip" or "Jobinfo.zip") – contains a basic shell script that's responsible for fetching the implant from a website named turkishfurniture[.]blog. It's also engineered to preview a harmless decoy PDF file ("job.pdf") hosted on the same site as a distraction.

Bitdefender said it also detected four new Golang-based binaries that
communicate with an actor-controlled domain ("sarkerrentacars[.]com"), whose
purpose is to "collect information about the victim's machine and its network
connections using the system_profiler and networksetup utilities, which are part
of the macOS operating system.
In addition, the binaries are capable of extracting details about the disk via "diskutil list" as well as retrieving a wide list of kernel parameters and configuration values using the "sysctl -a" command.
A closer investigation of the command-and-control (C2) infrastructure has also revealed a leaky endpoint ("/client/bots") that makes it possible to glean details about the currently infected victims, including the timestamps when the infected host was registered and the last activity was observed.
"We know there are at least three victim companies until now," Botezatu said. "The attackers seem to target senior engineering staff – and this explains why the malware is disguised as a Visual Studio update. We don't know if there are any other companies compromised at this point, but we are still investigating this."
"It looks that the victims are indeed geographically linked – two of the victims are in Hong Kong, while the other one is in Lagos, Nigeria."
The development comes as South Korea's National Intelligence Service (NIS) revealed that an IT organization affiliated with the Workers' Party of North Korea's Office No. 39 is generating illicit revenue by selling thousands of malware-laced gambling websites to other cybercriminals for stealing sensitive data from unsuspecting gamblers.
The company behind the malware-as-a-service (MaaS) scheme is Gyeongheung (also spelled Gyonghung), a 15-member entity based in Dandong that has allegedly received $5,000 from an unidentified South Korean criminal organization in exchange for creating a single website and $3,000 per month for maintaining the website, Yonhap News Agency reported.
Malicious 'SNS Sender' Script Abuses AWS for Bulk Smishing Attacks
17.2.24
Virus
The Hacker News
A malicious Python script known as SNS Sender is being
advertised as a way for threat actors to send bulk smishing messages by abusing
Amazon Web Services (AWS) Simple Notification Service (SNS).
The SMS phishing messages are designed to propagate malicious links that are designed to capture victims' personally identifiable information (PII) and payment card details, SentinelOne said in a new report, attributing it to a threat actor named ARDUINO_DAS.
"The smishing scams often take the guise of a message from the United States Postal Service (USPS) regarding a missed package delivery," security researcher Alex Delamotte said.
SNS Sender is also the first tool observed in the wild that leverages AWS SNS to conduct SMS spamming attacks. SentinelOne said that it identified links between ARDUINO_DAS and more than 150 phishing kits offered for sale.
The malware requires a list of phishing links stored in a file named links.txt in its working directory, in addition to a list of AWS access keys, the phone numbers to target, the sender ID (aka display name), and the content of the message.
The mandatory inclusion of sender ID for sending the scam texts is noteworthy because support for sender IDs varies from country to country. This suggests that the author of SNS Sender is likely from a country where the sender ID is a conventional practice.
"For example, carriers in the United States don't support sender IDs at all, but carriers in India require senders to use sender IDs," Amazon says in its documentation.
There is evidence to suggest that this operation may have been active since at least July 2022, going by bank logs containing references to ARDUINO_DAS that have been shared on carding forums like Crax Pro.
A vast majority of the phishing kits are USPS-themed, with the campaigns directing users to bogus package tracking pages that prompt users to enter their personal and credit/debit card information, as evidenced by security researcher @JCyberSec_ on X (formerly Twitter) in early September 2022.
"Do you think the deploying actor knows all the kits have a hidden backdoor sending the logs to another place?," the researcher further noted.
If anything, the development represents commodity threat actors' ongoing attempts to exploit cloud environments for smishing campaigns. In April 2023, Permiso revealed an activity cluster that took advantage of previously exposed AWS access keys to infiltrate AWS servers and send SMS messages using SNS.
The findings also follow the discovery of a new dropper codenamed TicTacToe that's likely sold as a service to threat actors and has been observed being used to propagate a wide variety of information stealers and remote access trojans (RATs) targeting Windows users throughout 2023.
Fortinet FortiGuard Labs, which shed light on the malware, said it's deployed by means of a four-stage infection chain that starts with an ISO file embedded within email messages.
Another relevant example of threat actors continuously innovating their tactics concerns the use of advertising networks to stage effective spam campaigns and deploy malware such as DarkGate.
"The threat actor proxied links through an advertising network to evade detection and capture analytics about their victims," HP Wolf Security said. "The campaigns were initiated through malicious PDF attachments posing as OneDrive error messages, leading to the malware."
The infosec arm of the PC maker also highlighted the misuse of legitimate platforms like Discord to stage and distribute malware, a trend that has become increasingly common in recent years, prompting the company to switch to temporary file links by the end of last year.
"Discord is known for its robust and reliable infrastructure, and it is widely trusted," Intel 471 said. "Organizations often allowlist Discord, meaning that links and connections to it are not restricted. This makes its popularity among threat actors unsurprising given its reputation and widespread use."
U.S. State Government Network Breached via Former Employee's Account
17.2.24
BigBrothers
The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency
(CISA) has revealed that an unnamed state government organization's network
environment was compromised via an administrator account belonging to a former
employee.
"This allowed the threat actor to successfully authenticate to an internal virtual private network (VPN) access point," the agency said in a joint advisory published Thursday alongside the Multi-State Information Sharing and Analysis Center (MS-ISAC).
"The threat actor connected to the [virtual machine] through the victim's VPN with the intent to blend in with legitimate traffic to evade detection."
It's suspected that the threat actor obtained the credentials following a separate data breach owing to the fact that the credentials appeared in publicly available channels containing leaked account information.
The admin account, which had access to a virtualized SharePoint server, also enabled the attackers to access another set of credentials stored in the server, which had administrative privileges to both the on-premises network and the Azure Active Directory (now called Microsoft Entra ID).
This further made it possible to explore the victim's on-premises environment, and execute various lightweight directory access protocol (LDAP) queries against a domain controller. The attackers behind the malicious activity are presently unknown.
A deeper investigation into the incident has revealed no evidence that the adversary moved laterally from the on-premises environment to the Azure cloud infrastructure.
The attackers ultimately accessed host and user information and posted the information on the dark web for likely financial gain, the bulletin noted, prompting the organization to reset passwords for all users, disable the administrator account as well as remove the elevated privileges for the second account.
It's worth pointing out that neither of the two accounts had multi-factor authentication (MFA) enabled, underscoring the need for securing privileged accounts that grant access to critical systems. It's also recommended to implement the principle of least privilege and create separate administrator accounts to segment access to on-premises and cloud environments.
The development is a sign that threat actors leverage valid accounts, including those belonging to former employees that have not been properly removed from the Active Directory (AD), to gain unauthorized access to organizations.
"Unnecessary accounts, software, and services in the network create additional vectors for a threat actor to compromise," the agencies said.
"By default, in Azure AD all users can register and manage all aspects of applications they create. These default settings can enable a threat actor to access sensitive information and move laterally in the network. In addition, users who create an Azure AD automatically become the Global Administrator for that tenant. This could allow a threat actor to escalate privileges to execute malicious actions."
U.S. Government Disrupts Russia-Linked Botnet Engaged in Cyber Espionage
17.2.24
BigBrothers
The Hacker News
The U.S. government on Thursday said it disrupted a
botnet comprising hundreds of small office and home office (SOHO) routers in the
country that was put to use by the Russia-linked APT28 actor to conceal its
malicious activities.
"These crimes included vast spear-phishing and similar credential harvesting campaigns against targets of intelligence interest to the Russian government, such as U.S. and foreign governments and military, security, and corporate organizations," the U.S. Department of Justice (DoJ) said in a statement.
APT28, also tracked under the monikers BlueDelta, Fancy Bear, Fighting Ursa, Forest Blizzard (formerly Strontium), FROZENLAKE, Iron Twilight, Pawn Storm, Sednit, Sofacy, and TA422, is assessed to be linked to Unit 26165 of Russia's Main Directorate of the General Staff (GRU). It's known to be active since at least 2007.
Court documents allege that the attackers pulled off their cyber espionage campaigns by relying on MooBot, a Mirai-based botnet that has singled out routers made by Ubiquiti to co-opt them into a mesh of devices that can be modified to act as a proxy, relaying malicious traffic while shielding their actual IP addresses.
The botnet, the DoJ said, allowed the threat actors to mask their true location and harvest credentials and NT LAN Manager (NTLM) v2 hashes via bespoke scripts, as well as host spear-phishing landing pages and other custom tooling for brute-forcing passwords, stealing router user passwords, and propagating the MooBot malware to other appliances.
In a redacted affidavit filed by the U.S. Federal Bureau of Investigation (FBI), the agency said MooBot exploits vulnerable and publicly accessible Ubiquiti routers by using default credentials and implants an SSH malware that permits persistent remote access to the device.
"Non-GRU cybercriminals installed the MooBot malware on Ubiquiti Edge OS routers that still used publicly known default administrator passwords," the DoJ explained. "GRU hackers then used the MooBot malware to install their own bespoke scripts and files that repurposed the botnet, turning it into a global cyber espionage platform."
The APT28 actors are suspected to have found and illegally accessed compromised Ubiquiti routers by conducting public scans of the internet using a specific OpenSSH version number as a search parameter, and then using MooBot to access those routers.
Spear-phishing campaigns undertaken by the hacking group have also leveraged a then-zero-day in Outlook (CVE-2023-23397) to siphon login credentials and transmit them to the routers.
"In another identified campaign, APT28 actors designed a fake Yahoo! landing page to send credentials entered on the false page to a compromised Ubiquiti router to be collected by APT28 actors at their convenience," the FBI said.
As part of its efforts to disrupt the botnet in the U.S. and prevent further crime, a series of unspecified commands have been issued to copy the stolen data and malicious files prior to deleting them and modify firewall rules to block APT28's remote access to the routers.
The precise number of devices that were compromised in the U.S. has been censored, although the FBI noted that it could change. Infected Ubiquiti devices have been detected in "almost every state," it added.
The court-authorized operation – referred to as Dying Ember – comes merely weeks after the U.S. dismantled another state-sponsored hacking campaign originating from China that leveraged a different botnet codenamed KV-botnet to target critical infrastructure facilities.
Last May, the U.S. also announced the takedown of a global network compromised by an advanced malware strain dubbed Snake wielded by hackers associated with Russia's Federal Security Service (FSB), otherwise known as Turla.
Russian Turla Hackers Target Polish NGOs with New TinyTurla-NG Backdoor
17.2.24
Virus
The Hacker News
The Russia-linked threat actor known as Turla has been
observed using a new backdoor called TinyTurla-NG as part of a three-month-long
campaign targeting Polish non-governmental organizations in December 2023.
"TinyTurla-NG, just like TinyTurla, is a small 'last chance' backdoor that is left behind to be used when all other unauthorized access/backdoor mechanisms have failed or been detected on the infected systems," Cisco Talos said in a technical report published today.
TinyTurla-NG is so named for exhibiting similarities with TinyTurla, another implant used by the adversarial collective in intrusions aimed at the U.S., Germany, and Afghanistan since at least 2020. TinyTurla was first documented by the cybersecurity company in September 2021.
Turla, also known by the names Iron Hunter, Pensive Ursa, Secret Blizzard (formerly Krypton), Snake, Uroburos, and Venomous Bear, is a Russian state-affiliated threat actor linked to the Federal Security Service (FSB).
In recent months, the threat actor has singled out the defense sector in Ukraine and Eastern Europe with a novel .NET-based backdoor called DeliveryCheck, while also upgrading its staple second-stage implant referred to as Kazuar, which it has put to use as early as 2017.
The latest campaign involving TinyTurla-NG dates back to December 18, 2023, and is said to have been ongoing up until January 27, 2024. However, it's suspected that the activity may have actually commenced in November 2023 based on the malware compilation dates.
It's currently not known how the backdoor is distributed to victim environments, but it has been found to employ compromised WordPress-based websites as command-and-control (C2) endpoints to fetch and execute instructions, enabling it to run commands via PowerShell or Command Prompt (cmd.exe) as well as download/upload files.
TinyTurla-NG also acts as a conduit to deliver PowerShell scripts dubbed TurlaPower-NG that are designed to exfiltrate key material used to secure the password databases of popular password management software in the form of a ZIP archive.
"This campaign appears to be highly targeted and focused on a small number of organizations, of which until now we can only confirm Poland based ones," a Cisco Talos researcher told The Hacker News, noting that the assessment is based on the current visibility.
"This campaign is highly compartmentalized, a few compromised websites acting as C2s contact a few samples, meaning that it's not easy to pivot from one sample/C2 to others using the same infrastructure that would give us confidence they are related."
The disclosure comes as Microsoft and OpenAI revealed that nation-state actors from Russia are exploring generative artificial intelligence (AI) tools, including large language models (LLMs) like ChatGPT, to understand satellite communication protocols, radar imaging technologies, and seek support with scripting tasks.
Ivanti Pulse Secure Found Using 11-Year-Old Linux Version and Outdated Libraries
17.2.24
Vulnerebility
The Hacker News
A reverse engineering of the firmware running on Ivanti
Pulse Secure appliances has revealed numerous weaknesses, once again
underscoring the challenge of securing software supply chains.
Eclypsiusm, which acquired firmware version 9.1.18.2-24467.1 as part of the process, said the base operating system used by the Utah-based software company for the device is CentOS 6.4.
"Pulse Secure runs an 11-year-old version of Linux which hasn't been supported since November 2020," the firmware security company said in a report shared with The Hacker News.
The development comes as threat actors are capitalizing on a number of security flaws discovered in Ivanti Connect Secure, Policy Secure, and ZTA gateways to deliver a wide range of malware, including web shells, stealers, and backdoors.
The vulnerabilities that have come under active exploitation in recent months comprise CVE-2023-46805, CVE-2024-21887, and CVE-2024-21893. Last week, Ivanti also disclosed another bug in the software (CVE-2024-22024) that could permit threat actors to access otherwise restricted resources without any authentication.
In an alert published yesterday, web infrastructure company Akamai said it has observed "significant scanning activity" targeting CVE-2024-22024 starting February 9, 2024, following the publication of a proof-of-concept (PoC) by watchTowr.
Eclypsium said it leveraged a PoC exploit for CVE-2024-21893 that was released by Rapid7 earlier this month to obtain a reverse shell to the PSA3000 appliance, subsequently exporting the device image for follow-on analysis using the EMBA firmware security analyzer.
This not only uncovered a number of outdated packages – corroborating previous
findings from security researcher Will Dormann – but also a number of vulnerable
libraries that are cumulatively susceptible to 973 flaws, out of which 111 have
publicly known exploits.
Number of scanning requests per day targeting CVE-2024-22024
Perl, for
instance, hasn't been updated since version 5.6.1, which was released 23 years
ago on April 9, 2001. The Linux kernel version is 2.6.32, which reached
end-of-life (EoL) as of March 2016.
"These old software packages are components in the Ivanti Connect Secure product," Eclypsium said. "This is a perfect example as to why visibility into digital supply chains is important and why enterprise customers are increasingly demanding SBOMs from their vendors."
Furthermore, a deeper examination of the firmware unearthed 1,216 issues in 76
shell scripts, 5,218 vulnerabilities in 5,392 Python files, in addition to 133
outdated certificates.
The issues don't end there, for Eclypsium found a "security hole" in the logic of the Integrity Checker Tool (ICT) that Ivanti has recommended its customers to use in order to look for indicators of compromise (IoCs).
Specifically, the script has been found to exclude over a dozen directories such as /data, /etc, /tmp, and /var from being scanned, thereby hypothetically allowing an attacker to deploy their persistent implants in one of these paths and still pass the integrity check. The tool, however, scans the /home partition that stores all product-specific daemons and configuration files.
As a result, deploying the Sliver post-exploitation framework to the /data directory and executing ICT reports no issues, Eclypsium discovered, suggesting that the tool provides a "false sense of security."
It's worth noting that threat actors have also been observed tampering with the built-in ICT on compromised Ivanti Connect Secure devices in an attempt to sidestep detection.
In a theoretical attack demonstrated by Eclypsium, a threat actor could drop their next-stage tooling and store the harvested information in the /data partition and then abuse another zero-day flaw to gain access to the device and exfiltrate the data staged previously, all the while the integrity tool detects no signs of anomalous activity.
"There must be a system of checks and balances that allows customers and third-parties to validate product integrity and security," the company said. "The more open this process is, the better job we can do to validate the digital supply chain, namely the hardware, firmware, and software components used in their products."
"When vendors do not share information and/or operate a closed system, validation becomes difficult, as does visibility. Attackers will most certainly, as evidenced recently, take advantage of this situation and exploit the lack of controls and visibility into the system."
Chinese Hackers Using Deepfakes in Advanced Mobile Banking Malware Attacks
17.2.24
Virus
The Hacker News
A Chinese-speaking threat actor codenamed GoldFactory has been attributed to the
development of highly sophisticated banking trojans, including a previously
undocumented iOS malware called GoldPickaxe that's capable of harvesting
identity documents, facial recognition data, and intercepting SMS.
"The GoldPickaxe family is available for both iOS and Android platforms," Singapore-headquartered Group-IB said in an extensive report shared with The Hacker News. "GoldFactory is believed to be a well-organized Chinese-speaking cybercrime group with close connections to Gigabud."
Active since at least mid-2023, GoldFactory is also responsible for another Android-based banking malware called GoldDigger and its enhanced variant GoldDiggerPlus as well as GoldKefu, an embedded trojan inside GoldDiggerPlus.
Social engineering campaigns distributing the malware have been found to target the Asia-Pacific region, specifically Thailand and Vietnam, by masquerading as local banks and government organizations.
In these attacks, prospective victims are sent smishing and phishing messages and guided to switch the conversation to instant messaging apps like LINE, before sending bogus URLs that lead to the deployment of GoldPickaxe on the devices.
Some of these malicious apps targeting Android are hosted on counterfeit websites resembling Google Play Store pages or fake corporate websites to complete the installation process.
GoldPickaxe for iOS, however, employs a different distribution scheme, with successive iterations leveraging Apple's TestFlight platform and booby-trapped URLs that prompt users to download an Mobile Device Management (MDM) profile to grant complete control over the iOS devices and install the rogue app.
Both these propagation mechanisms were disclosed by the Thailand Banking Sector CERT (TB-CERT) and the Cyber Crime Investigation Bureau (CCIB), respectively, in November 2023.

The sophistication of GoldPickaxe is also evident in the fact that it's designed
to get around security measures imposed by Thailand that require users to
confirm larger transactions using facial recognition to prevent fraud.
"GoldPickaxe prompts the victim to record a video as a confirmation method in the fake application," security researchers Andrey Polovinkin and Sharmine Low said. "The recorded video is then used as raw material for the creation of deepfake videos facilitated by face-swapping artificial intelligence services."
Furthermore, the Android and iOS flavors of the malware are equipped to collect the victim's ID documents and photos, intercept incoming SMS messages, and proxy traffic through the compromised device. It's suspected that the GoldFactory actors use their own devices to sign-in to the bank application and perform unauthorized fund transfers.

That having said, the iOS variant exhibits fewer functionalities when compared
to its Android counterpart owing to the closed nature of the iOS operating
system and relatively stricter nature of iOS permissions.
The Android version – considered an evolutionary successor of GoldDiggerPlus – also poses as over 20 different applications from Thailand's government, the financial sector, and utility companies to steal login credentials from these services. However, it's currently not clear what the threat actors do with this information.
Another notable aspect of the malware is its abuse of Android's accessibility services to log keystrokes and extract on-screen content.

GoldDigger also shares code-level similarities to GoldPickaxe, although it is
chiefly designed to steal banking credentials, while the latter is geared more
towards gathering of personal information from victims. No GoldDigger artifacts
aimed at iOS devices have been identified to date.
"The primary feature of GoldDigger is that it targets over 50 applications from Vietnamese financial companies, including their packages' names in the trojan," the researchers said. "Whenever the targeted applications open, it will save the text displayed or written on the UI, including passwords, when they are entered."
The base version of GoldDigger, which was first discovered in June 2023 and continues to be still in circulation, has since paved the way for more upgraded variants, including GoldDiggerPlus, which comes embedded with another trojan APK component dubbed GoldKefu, to unleash the malicious actions.
GoldDiggerPlus is said to have emerged in September 2023, with GoldKefu impersonating a popular Vietnamese messaging app to siphon banking credentials associated with 10 financial institutions.
The Android trojan, which is used in conjunction with GoldKefu, uses fake overlays to collect the login information if the most recently opened application belongs to the target list, unlike GoldDigger which relies mainly on Android's accessibility services.
Goldkefu also integrates with the Agora Software Development Kit (SDK) to facilitate interactive voice and video calls and trick victims into contacting a bogus bank customer service by sending fake alerts that induce a false sense of urgency by claiming that a fund transfer to the tune of 3 million Thai Baht has taken place on their accounts.

If anything, the development is a sign that the mobile malware landscape remains
a lucrative market for cybercriminals looking for quick financial gain, even as
they find ways to circumvent defensive measures erected by banks to counter such
threats. It also demonstrates the ever-shifting and dynamic nature of social
engineering schemes that aim to deliver malware to victims' devices.
To mitigate the risks posed by GoldFactory and its suite of mobile banking malware, it's strongly advised not to click on suspicious links, install any app from untrusted sites, as they are a common vector for malware, and periodically review the permissions given to apps, particularly those requesting for Android's accessibility services.
"GoldFactory is a resourceful team adept at various tactics, including impersonation, accessibility keylogging, fake banking websites, fake bank alerts, fake call screens, identity, and facial recognition data collection," the researchers said. "The team comprises separate development and operator groups dedicated to specific regions."
"The gang has well-defined processes and operational maturity and constantly enhances its toolset to align with the targeted environment showcasing a high proficiency in malware development."
Critical Exchange Server Flaw (CVE-2024-21410) Under Active Exploitation
17.2.24
Vulnerebility
The Hacker News
Microsoft on Wednesday acknowledged that a newly
disclosed critical security flaw in Exchange Server has been actively exploited
in the wild, a day after it released fixes for the vulnerability as part of its
Patch Tuesday updates.
Tracked as CVE-2024-21410 (CVSS score: 9.8), the issue has been described as a case of privilege escalation impacting the Exchange Server.
"An attacker could target an NTLM client such as Outlook with an NTLM credentials-leaking type vulnerability," the company said in an advisory published this week.
"The leaked credentials can then be relayed against the Exchange server to gain privileges as the victim client and to perform operations on the Exchange server on the victim's behalf."
Successful exploitation of the flaw could permit an attacker to relay a user's leaked Net-NTLMv2 hash against a susceptible Exchange Server and authenticate as the user, Redmond added.
The tech giant, in an update to its bulletin, revised its Exploitability Assessment to "Exploitation Detected," noting that it has now enabled Extended Protection for Authentication (EPA) by default with the Exchange Server 2019 Cumulative Update 14 (CU14) update.
Details about the nature of the exploitation and the identity of the threat actors that may be abusing the flaw are currently unknown. However, Russian state-affiliated hacking crews such as APT28 (aka Forest Blizzard) have a history of exploiting flaws in Microsoft Outlook to stage NTLM relay attacks.
Earlier this month, Trend Micro implicated the adversary to NTLM relay attacks targeting high-value entities at least since April 2022. The intrusions targeted organizations dealing with foreign affairs, energy, defense, and transportation, as well as those involved with labor, social welfare, finance, parenthood, and local city councils.

CVE-2024-21410 adds to two other Windows flaws – CVE-2024-21351 (CVSS score:
7.6) and CVE-2024-21412 (CVSS score: 8.1) – that have been patched by Microsoft
this week and actively weaponized in real-world attacks.
The exploitation of CVE-2024-21412, a bug that enables a bypass of Windows SmartScreen protections, has been attributed to an advanced persistent threat dubbed Water Hydra (aka DarkCasino), which has previously leveraged zero-days in WinRAR to deploy the DarkMe trojan.
"The group used internet shortcuts disguised as a JPEG image that, when selected by the user, allows the threat actor to exploit CVE-2024-21412," Trend Micro said. "The group can then bypass Microsoft Defender SmartScreen and fully compromise the Windows host as part of its attack chain."
Microsoft's Patch Tuesday update also addresses CVE-2024-21413, another critical shortcoming affecting the Outlook email software that could result in remote code execution by trivially circumventing security measures such as Protected View.
Codenamed MonikerLink by Check Point, the issue "allows for a wide and serious impact, varying from leaking of local NTLM credential information to arbitrary code execution."
The vulnerability stems from the incorrect parsing of "file://" hyperlinks, which makes it possible to achieve code execution by adding an exclamation mark to URLs pointing to arbitrary payloads hosted on attacker-controlled servers (e.g., "file:///\\10.10.111.111\test\test.rtf!something").
"The bug not only allows the leaking of the local NTLM information, but it may also allow remote code execution and more as an attack vector," the cybersecurity firm said. "It could also bypass the Office Protected View when it's used as an attack vector to target other Office applications."
Microsoft, OpenAI Warn of Nation-State Hackers Weaponizing AI for Cyber Attacks
17.2.24
AI
The Hacker News
Nation-state actors associated with Russia, North Korea,
Iran, and China are experimenting with artificial intelligence (AI) and large
language models (LLMs) to complement their ongoing cyber attack operations.
The findings come from a report published by Microsoft in collaboration with OpenAI, both of which said they disrupted efforts made by five state-affiliated actors that used its AI services to perform malicious cyber activities by terminating their assets and accounts.
"Language support is a natural feature of LLMs and is attractive for threat actors with continuous focus on social engineering and other techniques relying on false, deceptive communications tailored to their targets' jobs, professional networks, and other relationships," Microsoft said in a report shared with The Hacker News.
While no significant or novel attacks employing the LLMs have been detected to date, adversarial exploration of AI technologies has transcended various phases of the attack chain, such as reconnaissance, coding assistance, and malware development.
"These actors generally sought to use OpenAI services for querying open-source information, translating, finding coding errors, and running basic coding tasks," the AI firm said.
For instance, the Russian nation-state group tracked as Forest Blizzard (aka APT28) is said to have used its offerings to conduct open-source research into satellite communication protocols and radar imaging technology, as well as for support with scripting tasks.
Some of the other notable hacking crews are listed below -
Emerald Sleet (aka Kimusky), a North Korean threat actor, has used LLMs to
identify experts, think tanks, and organizations focused on defense issues in
the Asia-Pacific region, understand publicly available flaws, help with basic
scripting tasks, and draft content that could be used in phishing campaigns.
Crimson Sandstorm (aka Imperial Kitten), an Iranian threat actor who has used
LLMs to create code snippets related to app and web development, generate
phishing emails, and research common ways malware could evade detection
Charcoal Typhoon (aka Aquatic Panda), a Chinese threat actor which has used LLMs
to research various companies and vulnerabilities, generate scripts, create
content likely for use in phishing campaigns, and identify techniques for
post-compromise behavior
Salmon Typhoon (aka Maverick Panda), a Chinese
threat actor which has used LLMs to translate technical papers, retrieve
publicly available information on multiple intelligence agencies and regional
threat actors, resolve coding errors, and find concealment tactics to evade
detection
Microsoft said it's also formulating a set of principles to
mitigate the risks posed by the malicious use of AI tools and APIs by
nation-state advanced persistent threats (APTs), advanced persistent
manipulators (APMs), and cybercriminal syndicates and conceive effective
guardrails and safety mechanisms around its models.
"These principles include identification and action against malicious threat actors' use notification to other AI service providers, collaboration with other stakeholders, and transparency," Redmond said.
Ubuntu 'command-not-found' Tool Could Trick Users into Installing Rogue Packages
17.2.24
Hacking
The Hacker News
Cybersecurity researchers have found that it's possible
for threat actors to exploit a well-known utility called command-not-found to
recommend their own rogue packages and compromise systems running Ubuntu
operating system.
"While 'command-not-found' serves as a convenient tool for suggesting installations for uninstalled commands, it can be inadvertently manipulated by attackers through the snap repository, leading to deceptive recommendations of malicious packages," cloud security firm Aqua said in a report shared with The Hacker News.
Installed by default on Ubuntu systems, command-not-found suggests packages to install in interactive bash sessions when attempting to run commands that are not available. The suggestions include both the Advanced Packaging Tool (APT) and snap packages.
When the tool uses an internal database ("/var/lib/command-not-found/commands.db") to suggest APT packages, it relies on the "advise-snap" command to suggest snaps that provide the given command.
Thus, should an attacker be able to game this system and have their malicious package recommended by the command-not-found package, it could pave the way for software supply chain attacks.
Aqua said it found a security loophole wherein the alias mechanism can be exploited by the threat actor to potentially register the corresponding snap name associated with an alias and trick users into installing the malicious package.
What's more, an attacker could claim the snap name related to an APT package and upload a malicious snap, which then ends up being suggested when a user types in the command on their terminal.

"The maintainers of the 'jupyter-notebook' APT package had not claimed the
corresponding snap name," Aqua security researcher Ilay Goldman said. "This
oversight left a window of opportunity for an attacker to claim it and upload a
malicious snap named 'jupyter-notebook.'"
To make matters worse, the command-not-found utility suggests the snap package above the legitimate APT package for jupyter-notebook, misleading users into installing the fake snap package.
As many as 26% of the APT package commands are vulnerable to impersonation by malicious actors, Aqua noted, presenting a substantial security risk, as they could be registered under an attacker's account.
A third category entails typosquatting attacks in which typographical errors made by users (e.g., ifconfigg instead of ifconfig) are leveraged to suggest bogus snap packages by registering a fraudulent package with the name "ifconfigg."
In such a case, command-not-found "would mistakenly match it to this incorrect command and recommend the malicious snap, bypassing the suggestion for 'net-tools' altogether," Aqua researchers explained.
Describing the abuse of the command-not-found utility to recommend counterfeit packages as a pressing concern, the company is urging users to verify the source of a package before installation and check the maintainers' credibility.
Developers of APT and snap packages have also been advised to register the associated snap name for their commands to prevent them from being misused.
"It remains uncertain how extensively these capabilities have been exploited, underscoring the urgency for heightened vigilance and proactive defense strategies," Aqua said.
Bumblebee Malware Returns with New Tricks, Targeting U.S. Businesses
17.2.24
Virus
The Hacker News
The infamous malware loader and initial access broker
known as Bumblebee has resurfaced after a four-month absence as part of a new
phishing campaign observed in February 2024.
Enterprise security firm Proofpoint said the activity targets organizations in the U.S. with voicemail-themed lures containing links to OneDrive URLs.
"The URLs led to a Word file with names such as "ReleaseEvans#96.docm" (the digits before the file extension varied)," the company said in a Tuesday report. "The Word document spoofed the consumer electronics company Humane."
Opening the document leverages VBA macros to launch a PowerShell command to download and execute another PowerShell script from a remote server that, in turn, retrieves and runs the Bumblebee loader.
Bumblebee, first spotted in March 2022, is mainly designed to download and execute follow-on payloads such as ransomware. It has been put to use by multiple crimeware threat actors that previously observed delivering BazaLoader (aka BazarLoader) and IcedID.
It's also suspected to be developed by threat actors the Conti and TrickBot cybercrime syndicate as a replacement for BazarLoader. In September 2023, Intel 471 disclosed a Bumblebee distribution campaign that employed Web Distributed Authoring and Versioning (WebDAV) servers to disseminate the loader.
The attack chain is notable for its reliance on macro-enabled documents in the attack chain, especially considering Microsoft began blocking macros in Office files downloaded from the internet by default starting July 2022, prompting threat actors to modify and diversify their approaches.
The macro-based attack is also markedly different from pre-hiatus campaigns in which the phishing emails came with zipped LNK files bearing Bumblebee executables or HTML attachments that leveraged HTML smuggling to drop a RAR file, which exploited the WinRAR flaw tracked as CVE-2023-38831 to install the loader.
The return of Bumblebee also coincides with the reappearance of new variants of QakBot, ZLoader, and PikaBot, with samples of QakBot distributed in the form of Microsoft Software Installer (MSI) files.
"The .MSI drops a Windows .cab (Cabinet) archive, which in turn contains a DLL," cybersecurity firm Sophos said on Mastodon. "The .MSI extracts the DLL from the .cab, and executes it using shellcode. The shellcode causes the DLL to spawn a second copy of itself and inject the bot code into the second instance's memory space."
The latest QakBot artifacts have been found to harden the encryption used to conceal strings and other information, including employing a crypter malware called DaveCrypter, making it more challenging to analyze. The new generation also reinstates the ability to detect whether the malware was running inside a virtual machine or sandbox.
Another crucial modification includes encrypting all communications between the malware and the command-and-control (C2) server using AES-256, a stronger method than was used in versions prior to the dismantling of QakBot's infrastructure in late August 2023.
"The takedown of the QakBot botnet infrastructure was a victory, but the bot's creators remain free, and someone who has access to QakBot's original source code has been experimenting with new builds and testing the waters with these latest variants," Andrew Brandt, principal researcher at Sophos X-Ops, said.
"One of the most notable changes involve a change to the encryption algorithm the bot uses to conceal default configurations hardcoded into the bot, making it more difficult for analysts to see how the malware operates; the attackers are also restoring previously deprecated features, such as virtual machine (VM) awareness, and testing them out in these new versions."
QakBot has also emerged as the second most prevalent malware for January 2024, trailing behind FakeUpdates (aka SocGholish) but ahead of other families like Formbook, Nanocore, AsyncRAT, Remcos RAT, and Agent Tesla.
The development comes as Malwarebytes revealed a new campaign in which phishing sites mimicking financial institutions like Barclays trick potential targets into downloading legitimate remote desktop software like AnyDesk to purportedly resolve non-existent issues and ultimately allow threat actors to gain control of the machine.
DarkMe Malware Targets Traders Using Microsoft SmartScreen Zero-Day
Vulnerability
17.2.24
Virus
The Hacker News
A newly disclosed security flaw in the Microsoft Defender SmartScreen has been
exploited as a zero-day by an advanced persistent threat actor called Water
Hydra (aka DarkCasino) targeting financial market traders.
Trend Micro, which began tracking the campaign in late December 2023, said it entails the exploitation of CVE-2024-21412, a security bypass vulnerability related to Internet Shortcut Files (.URL).
"In this attack chain, the threat actor leveraged CVE-2024-21412 to bypass Microsoft Defender SmartScreen and infect victims with the DarkMe malware," the cybersecurity firm said in a Tuesday report.
Microsoft, which addressed the flaw in its February Patch Tuesday update, said an unauthenticated attacker could exploit the flaw by sending the targeted user a specially crafted file in order to bypass displayed security checks.
However, successful exploitation banks on the prerequisite that the threat actor convinces the victim to click on the file link to view the attacker-controlled content.
The infection procedure documented by Trend Micro weaponizes CVE-2024-21412 to drop a malicious installer file ("7z.msi") by clicking on a booby-trapped URL ("fxbulls[.]ru") distributed via forex trading forums under the pretext of sharing a link to a stock chart image that, in reality, is an internet shortcut file ("photo_2023-12-29.jpg.url").
"The landing page on fxbulls[.]ru contains a link to a malicious WebDAV share with a filtered crafted view," security researchers Peter Girnus, Aliakbar Zahravi, and Simon Zuckerbraun said.
"When users click on this link, the browser will ask them to open the link in Windows Explorer. This is not a security prompt, so the user might not think that this link is malicious."
The clever trick that makes this possible is the threat actor's abuse of the search: application protocol, which is used for calling the desktop search application on Windows and has been abused in the past to deliver malware.
The rogue internet shortcut file, for its part, points to another internet shortcut file hosted on a remote server ("2.url"), which, in turn, points to a CMD shell script within a ZIP archive hosted on the same server ("a2.zip/a2.cmd").
This unusual referencing stems from the fact that "calling a shortcut within another shortcut was sufficient to evade SmartScreen, which failed to properly apply Mark of the Web (MotW), a critical Windows component that alerts users when opening or running files from an untrusted source."
The end goal of the campaign is to deliver a Visual Basic trojan known as DarkMe stealthily in the background while displaying the stock graph to the victim to keep up the ruse upon completion of the exploitation and infection chain.
DarkMe comes with capabilities to download and execute additional instructions, alongside registering itself with a command-and-control (C2) server and gathering information from the compromised system.
The development comes amid a new trend where zero-days found by cybercrime groups end up getting incorporated into attack chains deployed by nation-state hacking groups to launch sophisticated attacks.
"Water Hydra possess the technical knowledge and tools to discover and exploit zero-day vulnerabilities in advanced campaigns, deploying highly destructive malware such as DarkMe," the researchers said.
Microsoft Rolls Out Patches for 73 Flaws, Including 2 Windows Zero-Days
17.2.24
Vulnerebility
The Hacker News
Microsoft has released patches to address 73 security
flaws spanning its software lineup as part of its Patch Tuesday updates for
February 2024, including two zero-days that have come under active exploitation.
Of the 73 vulnerabilities, 5 are rated Critical, 65 are rated Important, and three and rated Moderate in severity. This is in addition to 24 flaws that have been fixed in the Chromium-based Edge browser since the release of the January 2024 Patch Tuesday updates.
The two flaws that are listed as under active attack at the time of release are below -
CVE-2024-21351 (CVSS score: 7.6) - Windows SmartScreen Security Feature Bypass
Vulnerability
CVE-2024-21412 (CVSS score: 8.1) - Internet Shortcut Files
Security Feature Bypass Vulnerability
"The vulnerability allows a malicious
actor to inject code into SmartScreen and potentially gain code execution, which
could potentially lead to some data exposure, lack of system availability, or
both," Microsoft said about CVE-2024-21351.
Successful exploitation of the flaw could allow an attacker to circumvent SmartScreen protections and run arbitrary code. However, for the attack to work, the threat actor must send the user a malicious file and convince the user to open it.
CVE-2024-21412, in a similar manner, permits an unauthenticated attacker to bypass displayed security checks by sending a specially crafted file to a targeted user.
"However, the attacker would have no way to force a user to view the attacker-controlled content." Redmond noted. "Instead, the attacker would have to convince them to take action by clicking on the file link."
CVE-2024-21351 is the second bypass bug to be discovered in SmartScreen after CVE-2023-36025 (CVSS score: 8.8), which was plugged by the tech giant in November 2023. The flaw has since been exploited by multiple hacking groups to proliferate DarkGate, Phemedrone Stealer, and Mispadu.
Trend Micro, which detailed an attack campaign undertaken by Water Hydra (aka DarkCasino) targeting financial market traders by means of a sophisticated zero-day attack chain leveraging CVE-2024-21412, described CVE-2024-21412 as a bypass for CVE-2023-36025, thereby enabling threat actors to evade SmartScreen checks.
Water Hydra, first detected in 2021, has a track record of launching attacks against banks, cryptocurrency platforms, trading services, gambling sites, and casinos to deliver a trojan called DarkMe using zero-day exploits, including the WinRAR flaw that came to light in August 2023 (CVE-2023-38831, CVSS score: 7.8).
Late last year, Chinese cybersecurity company NSFOCUS graduated the "economically motivated" hacking group to an entirely new advanced persistent threat (APT).
"In January 2024, Water Hydra updated its infection chain exploiting CVE-2024-21412 to execute a malicious Microsoft Installer File (.MSI), streamlining the DarkMe infection process," Trend Micro said.
Both vulnerabilities have since been added to the Known Exploited Vulnerabilities (KEV) catalog by the U.S. Cybersecurity and Infrastructure Security Agency (CISA), urging federal agencies to apply the latest updates by March 5, 2024.
Also patched by Microsoft are five critical flaws -
CVE-2024-20684 (CVSS score: 6.5) - Windows Hyper-V Denial of Service
Vulnerability
CVE-2024-21357 (CVSS score: 7.5) - Windows Pragmatic General
Multicast (PGM) Remote Code Execution Vulnerability
CVE-2024-21380 (CVSS
score: 8.0) - Microsoft Dynamics Business Central/NAV Information Disclosure
Vulnerability
CVE-2024-21410 (CVSS score: 9.8) - Microsoft Exchange Server
Elevation of Privilege Vulnerability
CVE-2024-21413 (CVSS score: 9.8) -
Microsoft Outlook Remote Code Execution Vulnerability
"CVE-2024-21410 is an
elevation of privilege vulnerability in Microsoft Exchange Server," Satnam
Narang, senior staff research engineer at Tenable, said in a statement. "This
flaw is more likely to be exploited by attackers according to Microsoft."
"Exploiting this vulnerability could result in the disclosure of a targeted user's Net-New Technology LAN Manager (NTLM) version 2 hash, which could be relayed back to a vulnerable Exchange Server in an NTLM relay or pass-the-hash attack, which would allow the attacker to authenticate as the targeted user."
The security update further resolves 15 remote code execution flaws in Microsoft WDAC OLE DB provider for SQL Server that an attacker could exploit by tricking an authenticated user into attempting to connect to a malicious SQL server via OLEDB.
Rounding off the patch is a fix for CVE-2023-50387 (CVSS score: 7.5), a 24-year-old design flaw in the DNSSEC specification that can be abused to exhaust CPU resources and stall DNS resolvers, resulting in a denial-of-service (DoS).
The vulnerability has been codenamed KeyTrap by the National Research Center for Applied Cybersecurity (ATHENE) in Darmstadt.
"[The researchers] demonstrated that just with a single DNS packet the attack can exhaust the CPU and stall all widely used DNS implementations and public DNS providers, such as Google Public DNS and Cloudflare," ATHENE said. "In fact, the popular BIND 9 DNS implementation can be stalled for as long as 16 hours."
Glupteba Botnet Evades Detection with Undocumented UEFI Bootkit
17.2.24
Virus
The Hacker News
The Glupteba botnet has been found to incorporate a
previously undocumented Unified Extensible Firmware Interface (UEFI) bootkit
feature, adding another layer of sophistication and stealth to the malware.
"This bootkit can intervene and control the [operating system] boot process, enabling Glupteba to hide itself and create a stealthy persistence that can be extremely difficult to detect and remove," Palo Alto Networks Unit 42 researchers Lior Rochberger and Dan Yashnik said in a Monday analysis.
Glupteba is a fully-featured information stealer and backdoor capable of facilitating illicit cryptocurrency mining and deploying proxy components on infected hosts. It's also known to leverage the Bitcoin blockchain as a backup command-and-control (C2) system, making it resilient to takedown efforts.
Some of the other functions allow it to deliver additional payloads, siphon credentials, and credit card data, perform ad fraud, and even exploit routers to gain credentials and remote administrative access.
Over the past decade, the modular malware has metamorphosed into a sophisticated threat employing elaborate multi-stage infection chains to sidestep detection by security solutions.
A November 2023 campaign observed by the cybersecurity firm entails the use of pay-per-install (PPI) services such as Ruzki to distribute Glupteba. In September 2022, Sekoia linked Ruzki to activity clusters leveraging PrivateLoader as a conduit to propagate next-stage malware.
This takes the form of large-scale phishing attacks in which PrivateLoader is delivered under the guise of installation files for cracked software, which then loads SmokeLoader that, in turn, launches RedLine Stealer and Amadey, with the latter ultimately dropping Glupteba.

"Threat actors often distribute Glupteba as part of a complex infection chain
spreading several malware families at the same time," the researchers explained.
"This infection chain often starts with a PrivateLoader or SmokeLoader infection
that loads other malware families, then loads Glupteba."
In a sign that the malware is being actively maintained, Glupteba comes fitted with a UEFI bootkit by incorporating a modified version of an open-source project called EfiGuard, which is capable of disabling PatchGuard and Driver Signature Enforcement (DSE) at boot time.
It's worth pointing out that previous versions of the malware were found to "install a kernel driver the bot uses as a rootkit, and make other changes that weaken the security posture of an infected host."
Glupteba's resurfaced campaign in 2023 has been described as widespread and affecting multiple regions and industries spread across countries as varied as Greece, Nepal, Bangladesh, Brazil, Korea, Algeria, Ukraine, Slovakia, Turkey, Italy, and Sweden.
"Glupteba malware continues to stand out as a notable example of the complexity and adaptability exhibited by modern cybercriminals," the researchers said.
"The identification of an undocumented UEFI bypass technique within Glupteba underscores this malware's capacity for innovation and evasion. Furthermore, with its role in distributing Glupteba, the PPI ecosystem highlights the collaboration and monetization strategies employed by cybercriminals in their attempts at mass infections."
PikaBot Resurfaces with Streamlined Code and Deceptive Tactics
17.2.24
Virus
The Hacker News
The threat actors behind the PikaBot malware have made
significant changes to the malware in what has been described as a case of
"devolution."
"Although it appears to be in a new development cycle and testing phase, the developers have reduced the complexity of the code by removing advanced obfuscation techniques and changing the network communications," Zscaler ThreatLabz researcher Nikolaos Pantazopoulos said.
PikaBot, first documented by the cybersecurity firm in May 2023, is a malware loader and a backdoor that can execute commands and inject payloads from a command-and-control (C2) server as well as allow the attacker to control the infected host.
It is also known to halt its execution should the system's language be Russian or Ukrainian, indicating that the operators are either based in Russia or Ukraine.
In recent months, both PikaBot and another loader called DarkGate have emerged as attractive replacements for threat actors such as Water Curupira (aka TA577) to obtain initial access to target networks via phishing campaigns and drop Cobalt Strike.
Zscaler's analysis of a new version of PikaBot (version 1.18.32) observed this month has revealed its continued focus on obfuscation, albeit with simpler encryption algorithms, and insertion of junk code between valid instructions as part of its efforts to resist analysis.
Another crucial modification observed in the latest iteration is that the entire bot configuration -- which is similar to that of QakBot -- is stored in plaintext in a single memory block as opposed to encrypting each element and decoding them at runtime.
A third change concerns the C2 server network communications, with the malware developers tweaking the command IDs and the encryption algorithm used to secure the traffic.
"Despite its recent inactivity, PikaBot continues to be a significant cyber threat and in constant development," the researchers concluded.
"However, the developers have decided to take a different approach and decrease the complexity level of PikaBot's code by removing advanced obfuscation features."
The development comes as Proofpoint alerted of an ongoing cloud account takeover (ATO) campaign that has targeted dozens of Microsoft Azure environments and compromised hundreds of user accounts, including those belonging to senior executives.
The activity, underway since November 2023, singles out users with individualized phishing lures bearing decoy files that contain links to malicious phishing web pages for credential harvesting, and use them for follow-on data exfiltration, internal and external phishing, and financial fraud.
Ivanti Vulnerability Exploited to Install 'DSLog' Backdoor on 670+ IT
Infrastructures
17.2.24
Vulnerebility
The Hacker News
Threat actors are leveraging a recently disclosed
security flaw impacting Ivanti Connect Secure, Policy Secure, and ZTA gateways
to deploy a backdoor codenamed DSLog on susceptible devices.
That's according to findings from Orange Cyberdefense, which said it observed the exploitation of CVE-2024-21893 within hours of the public release of the proof-the-concept (PoC) code.
CVE-2024-21893, which was disclosed by Ivanti late last month alongside CVE-2024-21888, refers to a server-side request forgery (SSRF) vulnerability in the SAML module that, if successfully exploited, could permit access to otherwise restricted resources sans any authentication.
The Utah-based company has since acknowledged that the flaw has limited targeted attacks, although the exact scale of the compromises is unclear.
Then, last week, the Shadowserver Foundation revealed a surge in exploitation attempts targeting the vulnerability originating from over 170 unique IP addresses, shortly after both Rapid7 and AssetNote shared additional technical specifics.
Orange Cyberdefense's latest analysis shows that compromises have been detected as early as February 3, with the attack targeting an unnamed customer to inject a backdoor that grants persistent remote access.
"The backdoor is inserted into an existing Perl file called 'DSLog.pm,'" the company said, highlighting an ongoing pattern in which existing legitimate components – in this case, a logging module – are modified to add the malicious code.
DSLog, the implant, comes fitted with its own tricks to hamper analysis and
detection, including embedding a unique hash per appliance, thereby making it
impossible to use the hash to contact the same backdoor on another device.
The same hash value is supplied by the attackers to the User-Agent header field in an HTTP request to the appliance to allow the malware to extract the command to be executed from a query parameter called "cdi." The decoded instruction is then run as the root user.
"The web shell does not return status/code when trying to contact it," Orange Cyberdefense said. "There is no known way to detect it directly."
It further observed evidence of threat actors erasing ".access" logs on "multiple" appliances in a bid to cover up the forensic trail and fly under the radar.
But by checking the artifacts that were created when triggering the SSRF vulnerability, the company said it was able to detect 670 compromised assets during an initial scan on February 3, a number that has dropped to 524 as of February 7.
In light of the continued exploitation of Ivanti devices, it's highly recommended that "all customers factory reset their appliance before applying the patch to prevent the threat actor from gaining upgrade persistence in your environment."
Alert: CISA Warns of Active 'Roundcube' Email Attacks - Patch Now
17.2.24
BigBrothers
The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency
(CISA) on Monday added a medium-severity security flaw impacting Roundcube email
software to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence
of active exploitation.
The issue, tracked as CVE-2023-43770 (CVSS score: 6.1), relates to a cross-site scripting (XSS) flaw that stems from the handling of linkrefs in plain text messages.
"Roundcube Webmail contains a persistent cross-site scripting (XSS) vulnerability that can lead to information disclosure via malicious link references in plain/text messages," CISA said.
According to a description of the bug on NIST's National Vulnerability Database (NVD), the vulnerability impacts Roundcube versions before 1.4.14, 1.5.x before 1.5.4, and 1.6.x before 1.6.3.
The flaw was addressed by Roundcube maintainers with version 1.6.3, which was released on September 15, 2023. Zscaler security researcher Niraj Shivtarkar has been credited with discovering and reporting the vulnerability.
It's currently not known how the vulnerability is being exploited in the wild, but flaws in the web-based email client have been weaponized by Russia-linked threat actors like APT28 and Winter Vivern over the past year.
U.S. Federal Civilian Executive Branch (FCEB) agencies have been mandated to apply vendor-provided fixes by March 4, 2024, to secure their networks against potential threats.
Rhysida Ransomware Cracked, Free Decryption Tool Released
12.2.24
Ransom
The Hacker News
Cybersecurity researchers have uncovered an
"implementation vulnerability" that has made it possible to reconstruct
encryption keys and decrypt data locked by Rhysida ransomware.
The findings were published last week by a group of researchers from Kookmin University and the Korea Internet and Security Agency (KISA).
"Through a comprehensive analysis of Rhysida Ransomware, we identified an implementation vulnerability, enabling us to regenerate the encryption key used by the malware," the researchers said.
The development marks the first successful decryption of the ransomware strain, which first made its appearance in May 2023. A recovery tool is being distributed through KISA.
The study is also the latest to achieve data decryption by exploiting implementation vulnerabilities in ransomware, after Magniber v2, Ragnar Locker, Avaddon, and Hive.
Rhysida, which is known to share overlaps with another ransomware crew called
Vice Society, leverages a tactic known as double extortion to apply pressure on
victims into paying up by threatening to release their stolen data.
An advisory published by the U.S. government in November 2023 called out the threat actors for staging opportunistic attacks targeting education, manufacturing, information technology, and government sectors.
A thorough examination of the ransomware's inner workings has revealed its use
of LibTomCrypt for encryption as well as parallel processing to speed up the
process. It has also been found to implement intermittent encryption (aka
partial encryption) to evade detection by security solutions.
"Rhysida ransomware uses a cryptographically secure pseudo-random number generator (CSPRNG) to generate the encryption key," the researchers said. "This generator uses a cryptographically secure algorithm to generate random numbers."
Specifically, the CSPRNG is based on the ChaCha20 algorithm provided by the LibTomCrypt library, with the random number generated also correlated to the time at which Rhysida ransomware is running.
That's not all. The main process of Rhysida ransomware compiles a list of files to be encrypted. This list is subsequently referenced by various threads created to simultaneously encrypt the files in a specific order.
"In the encryption process of the Rhysida ransomware, the encryption thread generates 80 bytes of random numbers when encrypting a single file," the researchers noted. "Of these, the first 48 bytes are used as the encryption key and the [initialization vector]."
Using these observations as reference points, the researchers said they were able to retrieve the initial seed for decrypting the ransomware, determine the "randomized" order in which the files were encrypted, and ultimately recover the data without having to pay a ransom.
"Although these studies have a limited scope, it is important to acknowledge that certain ransomwares [...] can be successfully decrypted," the researchers concluded.
CISA and OpenSSF Release Framework for Package Repository Security
12.2.24
BigBrothers
The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency
(CISA) announced that it's partnering with the Open Source Security Foundation
(OpenSSF) Securing Software Repositories Working Group to publish a new
framework to secure package repositories.
Called the Principles for Package Repository Security, the framework aims to establish a set of foundational rules for package managers and further harden open-source software ecosystems.
"Package repositories are at a critical point in the open-source ecosystem to help prevent or mitigate such attacks," OpenSSF said.
"Even simple actions like having a documented account recovery policy can lead to robust security improvements. At the same time, capabilities must be balanced with resource constraints of package repositories, many of which are operated by non-profit organizations."
Notably, the principles lay out four security maturity levels for package repositories across four categories of authentication, authorization, general capabilities, and command-line interface (CLI) tooling -
Level 0 - Having very little security maturity.
Level 1 - Having basic
security maturity, such as multi-factor authentication (MFA) and allowing
security researchers to report vulnerabilities
Level 2 - Having moderate
security, which includes actions like requiring MFA for critical packages
and warning users of known security vulnerabilities
Level 3 - Having
advanced security, which requires MFA for all maintainers and supports build
provenance for packages
All package management ecosystems should be
working towards at least Level 1, the framework authors Jack Cable and Zach
Steindler note.
The ultimate objective is to allow package repositories to self-assess their security maturity and formulate a plan to bolster their guardrails over time in the form of security improvements.
"Security threats change over time, as do the security capabilities that address those threats," OpenSSF said. "Our goal is to help package repositories more quickly deliver the security capabilities that best help strengthen the security of their ecosystems."
The development comes as the U.S. Department of Health and Human Services' Health Sector Cybersecurity Coordination Center (HC3) warned of security risks arising as a result of using open-source software for maintaining patient records, inventory management, prescriptions, and billing.
"While open-source software is the bedrock of modern software development, it is also often the weakest link in the software supply chain," it said in a threat brief published in December 2023.
Microsoft Introduces Linux-Like 'sudo' Command to Windows 11
12.2.24
OS
The Hacker News
Microsoft said it's introducing Sudo for Windows 11 as part of an early preview version to help users execute commands with administrator privileges.
"Sudo for Windows is a new way for users to run elevated commands directly from an unelevated console session," Microsoft Product Manager Jordi Adoumie said.
"It is an ergonomic and familiar solution for users who want to elevate a command without having to first open a new elevated console."
Sudo, short for superuser do, is a program for Unix-like computer operating systems that allows users to run programs with the security privileges of another user, usually a user with elevated permissions (e.g., administrator).
The feature is available for Windows 11 builds 26045 and later. It can be enabled by heading to Settings > System > For Developers, and setting "Enable sudo" to On.
Sudo for Windows comes with three options: run applications in a new elevated console window, run the elevated process in the current window but with the input stream (stdin) closed, and in inline mode.
Sudo for Windows 11
"An unelevated process can send input to the elevated process within the same
console windows or get information from the output in the current windows in
this configuration."
Microsoft said it's also in the process of open-sourcing the project on GitHub,
urging other users to contribute to the initiative as well as report issues and
file feature requests.
"The inline configuration option runs the elevated
process in the current window and the process is able to receive input from the
current console session," Redmond warns in its documentation.
U.S. Offers $10 Million Bounty for Info Leading to Arrest of Hive Ransomware
Leaders
12.2.24
BigBrothers
The Hacker News
The U.S. Department of State has announced monetary rewards of up to $10 million for information about individuals holding key positions within the Hive ransomware operation.
It is also giving away an additional $5 million for specifics that could lead to the arrest and/or conviction of any person "conspiring to participate in or attempting to participate in Hive ransomware activity."
The multi-million-dollar rewards come a little over a year after a coordinated law enforcement effort covertly infiltrated and dismantled the darknet infrastructure associated with the Hive ransomware-as-a-service (RaaS) gang. One person with suspected ties to the group was arrested in Paris in December 2023.
Hive, which emerged in mid-2021, targeted more than 1,500 victims in over 80 countries, netting about $100 million in illegal revenues. In November 2023, Bitdefender revealed that a new ransomware group called Hunters International had acquired the source code and infrastructure from Hive to kick-start its own efforts.
There is some evidence to suggest that the threat actors associated with Hunters International are likely based in Nigeria, specifically an individual named Olowo Kehinde, per information gathered by Netenrich security researcher Rakesh Krishnan, although it could also be a fake persona adopted by the actors to cover up their true origins.
Blockchain analytics firm Chainalysis, in its 2023 review published last week, estimated that ransomware crews raked in $1.1 billion in extorted cryptocurrency payments from victims last year, compared to $567 million in 2022, all but confirming that ransomware rebounded in 2023 following a relative drop off in 2022.
"2023 marks a major comeback for ransomware, with record-breaking payments and a substantial increase in the scope and complexity of attacks — a significant reversal from the decline observed in 2022," it said.
The decline in ransomware activity in 2022 has been deemed a statistical aberration, with the downturn attributed to the Russo-Ukrainian war and the disruption of Hive. What's more, the total number of victims posted on data leak sites in 2023 was 4,496, up from 3,048 in 2021 and 2,670 in 2022.
Palo Alto Networks Unit 42, in its own analysis of ransomware gangs' public listings of victims on dark web sites, called out manufacturing as the most impacted industry vertical in 2023, followed by profession and legal services, high technology, retail, construction, and healthcare sectors.
While the law enforcement action prevented approximately $130 million in ransom payments to Hive, it's said that the takedown also "likely affected the broader activities of Hive affiliates, potentially lessening the number of additional attacks they could carry out." In total, the effort may have averted at least $210.4 million in payments.
Adding to the escalation in the regularity, scope, and volume of attacks, last year also witnessed a surge in new entrants and offshoots, a sign that the ransomware ecosystem is attracting a steady stream of new players who are attracted by the prospect of high profits and lower barriers to entry.
Cyber insurance provider Corvus said the number of active ransomware gangs registered a "significant" 34% increase between Q1 and Q4 2023, growing from 35 to 47 either due to fracturing and rebranding or other actors getting hold of leaked encryptors. Twenty-five new ransomware groups emerged in 2023.
"The frequency of rebranding, especially among actors behind the biggest and most notorious strains, is an important reminder that the ransomware ecosystem is smaller than the large number of strains would make it appear," Chainalysis said.
Besides a notable shift to big game hunting – which refers to the tactic of targeting very large companies to extract hefty ransoms – ransom payments are being steadily routed through cross-chain bridges, instant exchangers, and gambling services, indicating that e-crime groups are slowly moving away from centralized exchanges and mixers in pursuit of new avenues for money laundering.
In November 2023, the U.S. Treasury Department imposed sanctions against Sinbad, a virtual currency mixer that has been put to use by the North Korea-linked Lazarus Group to launder ill-gotten proceeds. Some of the other sanctioned mixers include Blender, Tornado Cash, and ChipMixer.
The pivot to big game hunting is also a consequence of companies increasingly refusing to settle, as the number of victims who chose to pay dropped to a new low of 29% in the last quarter of 2023, according to data from Coveware.
"Another factor contributing to higher ransomware numbers in 2023 was a major shift in threat actors' use of vulnerabilities," Corvus said, highlighting Cl0p's exploitation of flaws in Fortra GoAnywhere and Progress MOVEit Transfer.
"If malware, like infostealers, provide a steady drip of new ransomware victims, then a major vulnerability is like turning on a faucet. With some vulnerabilities, relatively easy access to thousands of victims can materialize seemingly overnight."
Cybersecurity company Recorded Future revealed that ransomware groups' weaponization of security vulnerabilities falls into two clear categories: vulnerabilities that have only been exploited by one or two groups and those that have been widely exploited by multiple threat actors.
"Magniber has uniquely focused on Microsoft vulnerabilities, with half of its unique exploits focusing on Windows Smart Screen," it noted. "Cl0p has uniquely and infamously focused on file transfer software from Accellion, SolarWinds, and MOVEit. ALPHV has uniquely focused on data backup software from Veritas and Veeam. REvil has uniquely focused on server software from Oracle, Atlassian, and Kaseya."
The continuous adaptation observed among cybercrime crews is also evidenced in the uptick in DarkGate and PikaBot infections following the takedown of the QakBot malware network, which had been the preferred initial entry pathway into target networks for ransomware deployment.
Chainalysis further said it found a "correlation" between inflows to initial access broker (IAB) wallets and a spike in ransomware payments, suggesting that keeping tabs on IABs blockchain trails could provide early warning signs for potential intervention and mitigation of attacks.
"Ransomware groups such as Cl0p have used zero-day exploits against newly discovered critical vulnerabilities, which represent a complex challenge for potential victims," Unit 42 said.
"While ransomware leak site data can provide valuable insight on the threat landscape, this data might not accurately reflect the full impact of a vulnerability. Organizations must not only be vigilant about known vulnerabilities, but they must also develop strategies to quickly respond to and mitigate the impact of zero-day exploits."
U.S. DoJ Dismantles Warzone RAT Infrastructure, Arrests Key Operators
12.2.24
Virus
The Hacker News
The U.S. Justice Department (DoJ) on Friday announced the seizure of online infrastructure that was used to sell a remote access trojan (RAT) called Warzone RAT.
The domains – www.warzone[.]ws and three others – were "used to sell computer malware used by cybercriminals to secretly access and steal data from victims' computers," the DoJ said.
Alongside the takedown, the international law enforcement effort has arrested and indicted two individuals in Malta and Nigeria for their involvement in selling and supporting the malware and helping other cybercriminals use the RAT for malicious purposes.
The defendants, Daniel Meli (27) and Prince Onyeoziri Odinakachi (31) have been charged with unauthorized damage to protected computers, with the former also accused of "illegally selling and advertising an electronic interception device and participating in a conspiracy to commit several computer intrusion offenses."
Cybersecurity
Meli is alleged to have offered malware services at least since
2012 through online hacking forums, sharing e-books, and helping other criminals
use RATs to carry out cyber attacks. Prior to Warzone RAT, he had sold another
RAT known as Pegasus RAT.
Like Meli, Odinakachi also provided online customer support to purchasers of Warzone RAT malware between June 2019 and no earlier than March 2023. Both individuals were arrested on February 7, 2024.
Warzone RAT, also known as Ave Maria, was first documented by Yoroi in January 2019 as part of a cyber attack targeting an Italian organization in the oil and gas sector towards the end of 2018 using phishing emails bearing bogus Microsoft Excel files exploiting a known security flaw in the Equation Editor (CVE-2017-11882).
Sold under the malware-as-a-service (Maas) model for $38 a month (or $196 for a year), it functions as an information stealer and facilitates remote control, thereby allowing threat actors to commandeer the infected hosts for follow-on exploitation.
Some of the notable features of the malware include the ability to browse victim file systems, take screenshots, record keystrokes, steal victim usernames and passwords, and activate the computer's webcams without the victim's knowledge or consent.
"Ave Maria attacks are initiated via phishing emails, once the dropped payload infects the victim's machine with the malware, it establishes communication with the attacker's command-and-control (C2) server on non-HTTP protocol, after decrypting its C2 connection using RC4 algorithm," Zscaler ThreatLabz said in early 2023.
Cybersecurity
On one of the now-dismantled websites, which had the tagline
"Serving you loyally since 2018," the developers of the C/C++ malware described
it as reliable and easy to use. They also provided the ability for customers to
contact them via email (solmyr@warzone[.]ws), Telegram (@solwz and
@sammysamwarzone), Skype (vuln.hf), as well as via a dedicated "client area."
An additional contact avenue was Discord, where the users were asked to get in touch with an account with the ID Meli#4472. Another Telegram account linked to Meli was @daniel96420.
Outside of cybercrime groups, the malware has also been put to use by several advanced threat actors like YoroTrooper as well as those associated with Russia over the past year.
The DoJ said the U.S. Federal Bureau of Investigation (FBI) covertly purchased copies of Warzone RAT and confirmed its nefarious functions. The coordinated exercise involved assistance from authorities in Australia, Canada, Croatia, Finland, Germany, Japan, Malta, the Netherlands, Nigeria, Romania, and Europol.
Alert: New Stealthy "RustDoor" Backdoor Targeting Apple macOS Devices
10.2.24
OS
The Hacker News
Apple macOS users are the target of a new Rust-based backdoor that has been operating under the radar since November 2023.
The backdoor, codenamed RustDoor by Bitdefender, has been found to impersonate an update for Microsoft Visual Studio and target both Intel and Arm architectures.
The exact initial access pathway used to propagate the implant is currently not known, although it's said to be distributed as FAT binaries that contain Mach-O files.
Multiple variants of the malware with minor modifications have been detected to date, likely indicating active development. The earliest sample of RustDoor dates back to November 2, 2023.
It comes with a wide range of commands that allow it to gather and upload files, and harvest information about the compromised endpoint.
Some versions also include configurations with details about what data to collect, the list of targeted extensions and directories, and the directories to exclude.
The captured information is then exfiltrated to a command-and-control (C2) server.
The Romanian cybersecurity firm said the malware is likely linked to prominent ransomware families like Black Basta and BlackCat owing to overlaps in C2 infrastructure.
"ALPHV/BlackCat is a ransomware family (also written in Rust), that first made its appearance in November 2021, and that has pioneered the public leaks business model," security researcher Andrei Lapusneau said.
In December 2023, the U.S. government announced that it took down the BlackCat ransomware operation and released a decryption tool that more than 500 affected victims can use to regain access to files locked by the malware.
Raspberry Robin Malware Upgrades with Discord Spread and New Exploits
10.2.24
Exploit
The Hacker News
The operators of Raspberry Robin are now using two new
one-day exploits to achieve local privilege escalation, even as the malware
continues to be refined and improved to make it stealthier than before.
This means that "Raspberry Robin has access to an exploit seller or its authors develop the exploits themselves in a short period of time," Check Point said in a report this week.
Raspberry Robin (aka QNAP worm), first documented in 2021, is an evasive malware family that's known to act as one of the top initial access facilitators for other malicious payloads, including ransomware.
Attributed to a threat actor named Storm-0856 (previously DEV-0856), it's propagated via several entry vectors, including infected USB drives, with Microsoft describing it as part of a "complex and interconnected malware ecosystem" with ties to other e-crime groups like Evil Corp, Silence, and TA505.
Raspberry Robin's use of one-day exploits such as CVE-2020-1054 and CVE-2021-1732 for privilege escalation was previously highlighted by Check Point in April 2023.
The cybersecurity firm, which detected "large waves of attacks" since October 2023, said the threat actors have implemented additional anti-analysis and obfuscation techniques to make it harder to detect and analyze.
"Most importantly, Raspberry Robin continues to use different exploits for vulnerabilities either before or only a short time after they were publicly disclosed," it noted.
"Those one-day exploits were not publicly disclosed at the time of their use. An exploit for one of the vulnerabilities, CVE-2023-36802, was also used in the wild as a zero-day and was sold on the dark web."
A report from Cyfirma late last year revealed that an exploit for CVE-2023-36802 was being advertised on dark web forums in February 2023. This was seven months before Microsoft and CISA released an advisory on active exploitation. It was patched by the Windows maker in September 2023.

Raspberry Robin is said to have started utilizing an exploit for the flaw
sometime in October 2023, the same month a public exploit code was made
available, as well as for CVE-2023-29360 in August. The latter was publicly
disclosed in June 2023, but an exploit for the bug did not appear until
September 2023.
It's assessed that the threat actors purchase these exploits rather than developing them in-house owing to the fact that they are used as an external 64-bit executable and are not as heavily obfuscated as the malware's core module.
"Raspberry Robin's ability to quickly incorporate newly disclosed exploits into its arsenal further demonstrates a significant threat level, exploiting vulnerabilities before many organizations have applied patches," the company said.
One of the other significant changes concerns the initial access pathway itself, leveraging rogue RAR archive files containing Raspberry Robin samples that are hosted on Discord.
Also modified in the newer variants is the lateral movement logic, which now uses PAExec.exe instead of PsExec.exe, and the command-and-control (C2) communication method by randomly choosing a V3 onion address from a list of 60 hardcoded onion addresses.
"It starts with trying to contact legitimate and well-known Tor domains and checking if it gets any response," Check Point explained. "If there is no response, Raspberry Robin doesn't try to communicate with the real C2 servers."
MoqHao Android Malware Evolves with Auto-Execution Capability
9.2.24
OS
The Hacker News
Threat hunters have identified a new variant of Android malware called MoqHao that automatically executes on infected devices without requiring any user interaction.
"Typical MoqHao requires users to install and launch the app to get their desired purpose, but this new variant requires no execution," McAfee Labs said in a report published this week. "While the app is installed, their malicious activity starts automatically."
The campaign's targets include Android users located in France, Germany, India, Japan, and South Korea.
MoqHao, also called Wroba and XLoader (not to be confused with the Windows and macOS malware of the same name), is an Android-based mobile threat that's associated with a Chinese financially motivated cluster dubbed Roaming Mantis (aka Shaoye).
Typical attack chains commence with package delivery-themed SMS messages bearing fraudulent links that, when clicked from Android devices, lead to the deployment of the malware but redirect victims to credential harvesting pages impersonating Apple's iCloud login page when visited from an iPhone.
In July 2022, Sekoia detailed a campaign that compromised at least 70,000 Android devices in France. As of early last year, updated versions of MoqHao have been found to infiltrate Wi-Fi routers and undertake Domain Name System (DNS) hijacking, revealing the adversary's commitment to innovating its arsenal.
The latest iteration of MoqHao continues to be distributed via smishing techniques, but what has changed is that the malicious payload is run automatically upon installation and prompts the victim to grant it risky permissions without launching the app, a behavior previously spotted with bogus apps containing the HiddenAds malware.
What's also received a facelift is that the links shared in the SMS messages themselves are hidden using URL shorteners to increase the likelihood of the attack's success. The content for these messages is extracted from the bio (or description) field from fraudulent Pinterest profiles set up for this purpose.
MoqHao is equipped with several features that allow it to stealthily harvest sensitive information like device metadata, contacts, SMS messages, and photos, call specific numbers with silent mode, and enable/disable Wi-Fi, among others.
McAfee said it has reported the findings to Google, which is said to be "already working on the implementation of mitigations to prevent this type of auto-execution in a future Android version."
The development comes as Chinese cybersecurity firm QiAnXin revealed that a previously unknown cybercrime syndicate named Bigpanzi has been linked to the compromise of Android-based smart TVs and set-top boxes (STBs) in order to corral them into a botnet for conducting distributed denial-of-service (DDoS) attacks.
The operation, active since at least 2015, is estimated to control a botnet comprising 170,000 daily active bots, most of which are located in Brazil. However, 1.3 million distinct Brazilian IP addresses have been associated with Bigpanzi since August 2023.
The infections are made possible by tricking users into installing booby-trapped apps for streaming pirated movies and TV shows through sketchy websites. The campaign was first disclosed by Russian antivirus vendor Doctor Web in September 2023.
"Once installed, these devices transform into operational nodes within their illicit streaming media platform, catering to services like traffic proxying, DDoS attacks, OTT content provision, and pirate traffic," QiAnXin researchers said.
"The potential for Bigpanzi-controlled TVs and STBs to broadcast violent, terroristic, or pornographic content, or to employ increasingly convincing AI-generated videos for political propaganda, poses a significant threat to social order and stability."
New Coyote Trojan Targets 61 Brazilian Banks with Nim-Powered Attack
9.2.24
Virus
The Hacker News
Sixty-one banking institutions, all of them originating
from Brazil, are the target of a new banking trojan called Coyote.
"This malware utilizes the Squirrel installer for distribution, leveraging Node.js and a relatively new multi-platform programming language called Nim as a loader to complete its infection," Russian cybersecurity firm Kaspersky said in a Thursday report.
What makes Coyote a different breed from other banking trojans of its kind is the use of the open-source Squirrel framework for installing and updating Windows apps. Another notable departure is the shift from Delphi – which is prevalent among banking malware families targeting Latin America – to an uncommon programming language like Nim.
In the attack chain documented by Kaspersky, a Squirrel installer executable is used as a launchpad for a Node.js application compiled with Electron, which, in turn, runs a Nim-based loader to trigger the execution of the malicious Coyote payload by means of DLL side-loading.
The malicious dynamic-link library, named "libcef.dll," is side-loaded by means of a legitimate executable named "obs-browser-page.exe," which is also included in the Node.js project. It's worth noting that the original libcef.dll is part of the Chromium Embedded Framework (CEF).
Coyote, once executed, "monitors all open applications on the victim's system and waits for the specific banking application or website to be accessed," subsequently contacting an actor-controlled server to fetch next-stage directives.
It has the capability to execute a wide range of commands to take screenshots,
log keystrokes, terminate processes, display fake overlays, move the mouse
cursor to a specific location, and even shut down the machine. It can also
outright block the machine with a bogus "Working on updates..." message while
executing malicious actions in the background.
"The addition of Nim as a loader adds complexity to the trojan's design," Kaspersky said. "This evolution highlights the increasing sophistication within the threat landscape and shows how threat actors are adapting and using the latest languages and tools in their malicious campaigns."
The development comes as Brazilian law enforcement authorities dismantled the Grandoreiro operation and issued five temporary arrest warrants and 13 search and seizure warrants for the masterminds behind the malware across five Brazilian states.
It also follows the discovery of a new Python-based information stealer that's related to the Vietnamese architects associated with MrTonyScam and distributed via booby-trapped Microsoft Excel and Word documents.
The stealer "collects browsers' cookies and login data [...] from a wide range of browsers, from familiar browsers such as Chrome and Edge to browsers focused on the local market, like the Cốc Cốc browser," Fortinet FortiGuard Labs said in a report published this week.
Fortinet Warns of Critical FortiOS SSL VPN Flaw Likely Under Active Exploitation
9.2.24
Exploit
The Hacker News
Fortinet has disclosed a new critical security flaw in
FortiOS SSL VPN that it said is likely being exploited in the wild.
The vulnerability, CVE-2024-21762 (CVSS score: 9.6), allows for the execution of arbitrary code and commands.
"A out-of-bounds write vulnerability [CWE-787] in FortiOS may allow a remote unauthenticated attacker to execute arbitrary code or command via specially crafted HTTP requests," the company said in a bulletin released Thursday.
It further acknowledged that the issue is "potentially being exploited in the wild," without giving additional specifics about how it's being weaponized and by whom.
The following versions are impacted by the vulnerability. It's worth noting that FortiOS 7.6 is not affected.
FortiOS 7.4 (versions 7.4.0 through 7.4.2) - Upgrade to 7.4.3 or above
FortiOS 7.2 (versions 7.2.0 through 7.2.6) - Upgrade to 7.2.7 or above
FortiOS 7.0 (versions 7.0.0 through 7.0.13) - Upgrade to 7.0.14 or above
FortiOS 6.4 (versions 6.4.0 through 6.4.14) - Upgrade to 6.4.15 or above
FortiOS 6.2 (versions 6.2.0 through 6.2.15) - Upgrade to 6.2.16 or above
FortiOS 6.0 (versions 6.0 all versions) - Migrate to a fixed release
The
development comes as Fortinet issued patches for CVE-2024-23108 and
CVE-2024-23109, impacting FortiSIEM supervisor, allowing a remote
unauthenticated attacker to execute unauthorized commands via crafted API
requests.
Earlier this week, the Netherlands government revealed a computer network used by the armed forces was infiltrated by Chinese state-sponsored actors by exploiting known flaws in Fortinet FortiGate devices to deliver a backdoor called COATHANGER.
The company, in a report published this week, divulged that N-day security vulnerabilities in its software, such as CVE-2022-42475 and CVE-2023-27997, are being exploited by multiple activity clusters to target governments, service providers, consultancies, manufacturing, and large critical infrastructure organizations.
Previously, Chinese threat actors have been linked to the zero-day exploitation of security flaws in Fortinet appliances to deliver a wide range of implants, such as BOLDMOVE, THINCRUST, and CASTLETAP.
It also follows an advisory from the U.S. government about a Chinese nation-state group dubbed Volt Typhoon, which has targeted critical infrastructure in the country for long-term undiscovered persistence by taking advantage of known and zero-day flaws in networking appliances such as those from Fortinet, Ivanti Connect Secure, NETGEAR, Citrix, and Cisco for initial access.
China, which has denied the allegations, accused the U.S. of conducting its own cyber attacks.
If anything, the campaigns waged by China and Russia underscore the growing threat faced by internet-facing edge devices in recent years owing to the fact that such technologies lack endpoint detection and response (EDR) support, making them ripe for abuse.
"These attacks demonstrate the use of already resolved N-day vulnerabilities and subsequent [living-off-the-land] techniques, which are highly indicative of the behavior employed by the cyber actor or group of actors known as Volt Typhoon, which has been using these methods to target critical infrastructure and potentially other adjacent actors," Fortinet said.
Warning: New Ivanti Auth Bypass Flaw Affects Connect Secure and ZTA Gateways
9.2.24
Vulnerebility
The Hacker News
Ivanti has alerted customers of yet another high-severity
security flaw in its Connect Secure, Policy Secure, and ZTA gateway devices that
could allow attackers to bypass authentication.
The issue, tracked as CVE-2024-22024, is rated 8.3 out of 10 on the CVSS scoring system.
"An XML external entity or XXE vulnerability in the SAML component of Ivanti Connect Secure (9.x, 22.x), Ivanti Policy Secure (9.x, 22.x) and ZTA gateways which allows an attacker to access certain restricted resources without authentication," the company said in an advisory.
The company said it discovered the flaw during an internal review as part of its ongoing investigation into multiple security weaknesses in the products that have come to light since the start of the year, including CVE-2023-46805, CVE-2024-21887, CVE-2024-21888, and CVE-2024-21893.
CVE-2024-22024 affects the following versions of the products -
Ivanti Connect Secure (versions 9.1R14.4, 9.1R17.2, 9.1R18.3, 22.4R2.2, and
22.5R1.1)
Ivanti Policy Secure (version 22.5R1.1)
ZTA (version 22.6R1.3)
Patches for the bug are available in Connect Secure versions 9.1R14.5, 9.1R17.3,
9.1R18.4, 22.4R2.3, 22.5R1.2, 22.5R2.3, and 22.6R2.2; Policy Secure versions
9.1R17.3, 9.1R18.4, and 22.5R1.2; and ZTA versions 22.5R1.6, 22.6R1.5, and
22.6R1.7.
Ivanti said there is no evidence of active exploitation of the flaw, but with CVE-2023-46805, CVE-2024-21887, and CVE-2024-21893 coming under broad abuse, it's imperative that users move quickly to apply the latest fixes.
Stealthy Zardoor Backdoor Targets Saudi Islamic Charity Organization
9.2.24
Virus
The Hacker News
An unnamed Islamic non-profit organization in Saudi
Arabia has been targeted as part of a stealthy cyber espionage campaign designed
to drop a previously undocumented backdoor called Zardoor.
Cisco Talos, which discovered the activity in May 2023, said the campaign has likely persisted since at least March 2021, adding it has identified only one compromised target to date, although it's suspected that there could be other victims.
"Throughout the campaign, the adversary used living-off-the-land binaries (LoLBins) to deploy backdoors, establish command-and-control (C2), and maintain persistence," security researchers Jungsoo An, Wayne Lee, and Vanja Svajcer said, calling out the threat actor's ability to maintain long-term access to victim environments without attracting attention.
The intrusion targeting the Islamic charitable organization involved the periodic exfiltration of data roughly twice a month. The exact initial access vector used to infiltrate the entity is currently unknown.

The foothold obtained, however, has been leveraged to drop Zardoor for
persistence, followed by establishing C2 connections using open-source reverse
proxy tools such as Fast Reverse Proxy (FRP), sSocks, and Venom.
"Once a connection was established, the threat actor used Windows Management Instrumentation (WMI) to move laterally and spread the attacker's tools — including Zardoor — by spawning processes on the target system and executing commands received from the C2," the researchers said.
The as-yet-undetermined infection pathway paves the way for a dropper component that, in turn, deploys a malicious dynamic-link library ("oci.dll") that's responsible for delivering two backdoor modules, "zar32.dll" and "zor32.dll."
While the former is the core backdoor element that facilitates C2 communications, the latter ensures that "zar32.dll" has been deployed with administrator privileges. Zardoor is capable of exfiltrating data, executing remotely fetched executables and shellcode, updating the C2 IP address, and deleting itself from the host.
The origins of the threat actor behind the campaign are unclear, and it does not share any tactical overlaps with a known, publicly reported threat actor at this time. That said, it's assessed to be the work of an "advanced threat actor."
Chinese Hackers Operate Undetected in U.S. Critical Infrastructure for Half a
Decade
8.2.24
BigBrothers
The Hacker News
The U.S. government on Wednesday said the Chinese state-sponsored hacking group known as Volt Typhoon had been embedded into some critical infrastructure networks in the country for at least five years.
Targets of the threat actor include communications, energy, transportation, and water and wastewater systems sectors in the U.S. and Guam.
"Volt Typhoon's choice of targets and pattern of behavior is not consistent with traditional cyber espionage or intelligence gathering operations, and the U.S. authoring agencies assess with high confidence that Volt Typhoon actors are pre-positioning themselves on IT networks to enable lateral movement to OT assets to disrupt functions," the U.S. government said.
The joint advisory, which was released by the Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency (NSA), and the Federal Bureau of Investigation (FBI), was also backed by other nations that are part of the Five Eyes (FVEY) intelligence alliance comprising Australia, Canada, New Zealand, the U.K.
Volt Typhoon – which is also called Bronze Silhouette, Insidious Taurus, UNC3236, Vanguard Panda, or Voltzite – a stealthy China-based cyber espionage group that's believed to be active since June 2021.
It first came to light in May 2023 when Microsoft revealed that the hacking crew managed to establish a persistent foothold into critical infrastructure organizations in the U.S. and Guam for extended periods of time sans getting detected by principally leveraging living-off-the-land (LotL) techniques.
"This kind of tradecraft, known as 'living off the land,' allows attackers to operate discreetly, with malicious activity blending in with legitimate system and network behavior making it difficult to differentiate – even by organizations with more mature security postures," the U.K. National Cyber Security Centre (NCSC) said.
Another hallmark tactic adopted by Volt Typhoon is the use of multi-hop proxies like KV-botnet to route malicious traffic through a network of compromised routers and firewalls in the U.S. to mask its true origins.
Cybersecurity firm CrowdStrike, in a report published in June 2023, called out its reliance on an extensive arsenal of open-source tooling against a narrow set of victims to achieve its strategic goals.
"Volt Typhoon actors conduct extensive pre-exploitation reconnaissance to learn about the target organization and its environment; tailor their tactics, techniques, and procedures (TTPs) to the victim's environment; and dedicate ongoing resources to maintaining persistence and understanding the target environment over time, even after initial compromise," the agencies noted.
U.S. Infrastructure
"The group also relies on valid accounts and leverages
strong operational security, which combined, allows for long-term undiscovered
persistence."
Furthermore, the nation-state has been observed attempting to obtain administrator credentials within the network by exploiting privilege escalation flaws, subsequently leveraging the elevated access to facilitate lateral movement, reconnaissance, and full domain compromise.
The ultimate goal of the campaign is to retain access to the compromised environments, "methodically" re-targeting them over years to validate and expand their unauthorized accesses. This meticulous approach, per the agencies, is evidenced in cases where they have repeatedly exfiltrated domain credentials to ensure access to current and valid accounts.
"In addition to leveraging stolen account credentials, the actors use LOTL techniques and avoid leaving malware artifacts on systems that would cause alerts," CISA, FBI, and NSA said.
"Their strong focus on stealth and operational security allows them to maintain long-term, undiscovered persistence. Further, Volt Typhoon's operational security is enhanced by targeted log deletion to conceal their actions within the compromised environment."
The development comes as the Citizen Lab revealed a network of at least 123 websites impersonating local news outlets spanning 30 countries in Europe, Asia, and Latin America that's pushing pro-China content in a widespread influence campaign linked to a Beijing public relations firm named Shenzhen Haimaiyunxiang Media Co., Ltd.
The Toronto-based digital watchdog, which dubbed the influence operation PAPERWALL, said it shares similarities with HaiEnergy, albeit with different operators and unique TTPs.
"A central feature of PAPERWALL, observed across the network of websites, is the ephemeral nature of its most aggressive components, whereby articles attacking Beijing's critics are routinely removed from these websites some time after they are published," the Citizen Lab said.
In a statement shared with Reuters, a spokesperson for China's embassy in Washington said "it is a typical bias and double standard to allege that the pro-China contents and reports are 'disinformation,' and to call the anti-China ones' true information.'"
HijackLoader Evolves: Researchers Decode the Latest Evasion Methods
8.2.24
Virus
The Hacker News

The threat actors behind a loader malware called HijackLoader have added new
techniques for defense evasion, as the malware continues to be increasingly used
by other threat actors to deliver additional payloads and tooling.
"The malware developer used a standard process hollowing technique coupled with an additional trigger that was activated by the parent process writing to a pipe," CrowdStrike researchers Donato Onofri and Emanuele Calvelli said in a Wednesday analysis. "This new approach has the potential to make defense evasion stealthier."
HijackLoader was first documented by Zscaler ThreatLabz in September 2023 as having been used as a conduit to deliver DanaBot, SystemBC, and RedLine Stealer. It's also known to share a high degree of similarity with another loader known as IDAT Loader.
Both the loaders are assessed to be operated by the same cybercrime group. In the intervening months, HijackLoader has been propagated via ClearFake and put to use by TA544 (aka Narwhal Spider, Gold Essex, and Ursnif Gang) to deliver Remcos RAT and SystemBC via phishing messages.
"Think of loaders like wolves in sheep's clothing. Their purpose is to sneak in, introduce and execute more sophisticated threats and tools," Liviu Arsene, director of threat research and reporting at CrowdStrike, said in a statement shared with The Hacker News.
"This recent variant of HijackLoader (aka IDAT Loader) steps up its sneaking game by adding and experimenting with new techniques. This is similar to enhancing its disguise, making it stealthier, more complex, and more difficult to analyze. In essence, they're refining their digital camouflage."
The starting point of the multi-stage attack chain is an executable ("streaming_client.exe") that checks for an active internet connection and proceeds to download a second-stage configuration from a remote server.
The executable then loads a legitimate dynamic-link library (DLL) specified in the configuration to activate shellcode responsible for launching the HijackLoader payload via a combination of process doppelgänging and process hollowing techniques that increases the complexity of analysis and the defense evasion capabilities.
"The HijackLoader second-stage, position-independent shellcode then performs some evasion activities to bypass user mode hooks using Heaven's Gate and injects subsequent shellcode into cmd.exe," the researchers said.
"The injection of the third-stage shellcode is accomplished via a variation of process hollowing that results in an injected hollowed mshtml.dll into the newly spawned cmd.exe child process."
Heaven's Gate refers to a stealthy trick that allows malicious software to evade endpoint security products by invoking 64-bit code in 32-bit processes in Windows, effectively bypassing user-mode hooks.
One of the key evasion techniques observed in HijackLoader attack sequences is the use of a process injection mechanism called transacted hollowing, which has been previously observed in malware such as the Osiris banking trojan.
"Loaders are meant to act as stealth launch platforms for adversaries to introduce and execute more sophisticated malware and tools without burning their assets in the initial stages," Arsene said.
"Investing in new defense evasion capabilities for HijackLoader (aka IDAT Loader) is potentially an attempt to make it stealthier and fly below the radar of traditional security solutions. The new techniques signal both a deliberate and experimental evolution of the existing defense evasion capabilities while also increasing the complexity of analysis for threat researchers."
Google Starts Blocking Sideloading of Potentially Dangerous Android Apps in
Singapore
8.2.24
OS
The Hacker News
Google has unveiled a new pilot program in Singapore that aims to prevent users from sideloading certain apps that abuse Android app permissions to read one-time passwords and gather sensitive data.
"This enhanced fraud protection will analyze and automatically block the installation of apps that may use sensitive runtime permissions frequently abused for financial fraud when the user attempts to install the app from an Internet-sideloading source (web browsers, messaging apps or file managers)," the company said.
The feature is designed to examine the permissions declared by a third-party app in real-time and look for those that seek to gain access to sensitive permissions associated with reading SMS messages, deciphering or dismissing notifications from legitimate apps, and accessibility services that have been routinely abused by Android-based malware for extracting valuable information.
As part of the test, users in Singapore who attempt to sideload such apps (or APK files) will be blocked from doing so via Google Play Protect and displayed a pop-up message that reads: "This app can request access to sensitive data. This can increase the risk of identity theft or financial fraud."
"These permissions are frequently abused by fraudsters to intercept one-time passwords via SMS or notifications, as well as spy on-screen content," Eugene Liderman, director of the mobile security strategy at Google, said.
The change is part of a collaborative effort to combat mobile fraud, the tech giant said, urging app developers to follow best practices and review their apps' device permissions to ensure it does not violate the Mobile Unwanted Software principles.
Google, which launched Google Play Protect real-time scanning at the code level
to detect novel Android malware in select markets like India, Thailand,
Singapore, and Brazil, said the effort allowed it to detect 515,000 new
malicious apps and that it issued no less than 3.1 million warnings or blocks of
those apps.
The development also comes as Apple announced sweeping changes to the App Store in the European Union to comply with the Digital Markets Act (DMA) ahead of the March 6, 2024, deadline. The changes, including Notarization for iOS apps, are expected to go live with iOS 17.4.
The iPhone maker, however, repeatedly emphasized that distributing iOS apps from alternative app marketplaces exposes E.U. users to "increased privacy and security threats," and that it does not intend to bring them to other regions.
"This includes new avenues for malware, fraud and scams, illicit and harmful content, and other privacy and security threats," Apple said. "These changes also compromise Apple's ability to detect, prevent, and take action against malicious apps on iOS and to support users impacted by issues with apps downloaded outside of the App Store."
Kimsuky's New Golang Stealer 'Troll' and 'GoBear' Backdoor Target South Korea
8.2.24
APT
The Hacker News
The North Korea-linked nation-state actor known as
Kimsuky is suspected of using a previously undocumented Golang-based information
stealer called Troll Stealer.
The malware steals "SSH, FileZilla, C drive files/directories, browsers, system information, [and] screen captures" from infected systems, South Korean cybersecurity company S2W said in a new technical report.
Troll Stealer's links to Kimsuky stem from its similarities to known malware families, such as AppleSeed and AlphaSeed malware that have been attributed to the group.
Kimsuky, also tracked under the names APT43, ARCHIPELAGO, Black Banshee, Emerald Sleet (previously Thallium), Nickel Kimball, and Velvet Chollima, is well known for its propensity to steal sensitive, confidential information in offensive cyber operations.
In late November 2023, the threat actors were sanctioned by the U.S. Treasury Department's Office of Foreign Assets Control (OFAC) for gathering intelligence to further North Korea's strategic objectives.
The adversarial collective, in recent months, has been attributed to spear-phishing attacks targeting South Korean entities to deliver a variety of backdoors, including AppleSeed and AlphaSeed.
S2W's latest analysis reveals the use of a dropper that masquerades as a security program installation file from a South Korean company named SGA Solutions to launch the stealer, which gets its name from the path "D:/~/repo/golang/src/root.go/s/troll/agent" that's embedded in it.
"The dropper runs as a legitimate installer alongside the malware, and both the dropper and malware are signed with a valid, legitimate D2Innovation Co.,LTD' certificate, suggesting that the company's certificate was actually stolen," the company said.
A stand-out feature of Troll Stealer is its ability to pilfer the GPKI folder on infected systems, raising the possibility that the malware has been put to use in attacks targeting administrative and public organizations in the country.
Given the absence of Kimsuky campaigns documenting the theft of GPKI folders, it has raised the possibility that the new behavior is either a shift in tactics or the work of another threat actor closely associated with the group that also has access to the source code of AppleSeed and AlphaSeed.
There are also signs that the threat actor may be involved with a Go-based backdoor codenamed GoBear that's also signed with a legitimate certificate associated with D2Innovation Co., LTD and executes instructions received from a command-and-control (C2) server.
"The strings contained in the names of the functions it calls have been found to overlap with the commands used by BetaSeed, a C++-based backdoor malware used by the Kimsuky group," S2W said. "It is noteworthy that GoBear adds SOCKS5 proxy functionality, which was not previously supported by the Kimsuky group's backdoor malware."
Critical Patches Released for New Flaws in Cisco, Fortinet, VMware Products
8.2.24
Exploit
The Hacker News
Cisco, Fortinet, and VMware have released security fixes for multiple security vulnerabilities, including critical weaknesses that could be exploited to perform arbitrary actions on affected devices.
The first set from Cisco consists of three flaws – CVE-2024-20252 and CVE-2024-20254 (CVSS score: 9.6) and CVE-2024-20255 (CVSS score: 8.2) – impacting Cisco Expressway Series that could allow an unauthenticated, remote attacker to conduct cross-site request forgery (CSRF) attacks.
All the issues, which were found during internal security testing, stem from insufficient CSRF protections for the web-based management interface that could permit an attacker to perform arbitrary actions with the privilege level of the affected user.
"If the affected user has administrative privileges, these actions could include modifying the system configuration and creating new privileged accounts," Cisco said about CVE-2024-20252 and CVE-2024-20254.
On the other hand, successful exploitation of CVE-2024-20255 targeting a user with administrative privileges could enable the threat actor to overwrite system configuration settings, resulting in a denial-of-service (DoS) condition.
Another crucial difference between the two sets of flaws is that while the former two affect Cisco Expressway Series devices in the default configuration, CVE-2024-20252 only impacts them if the cluster database (CDB) API feature has been enabled. It's disabled by default.
Patches for the vulnerabilities are available in Cisco Expressway Series Release versions 14.3.4 and 15.0.0.
Fortinet, for its part, has released a second round of updates to address what are bypasses for a previously disclosed critical flaw (CVE-2023-34992, CVSS score: 9.7) in FortiSIEM supervisor that could result in the execution of arbitrary code, according to Horizon3.ai researcher Zach Hanley.
Tracked as CVE-2024-23108 and CVE-2024-23109 (CVSS scores: 9.8), the flaws "may allow a remote unauthenticated attacker to execute unauthorized commands via crafted API requests."
It's worth noting that Fortinet resolved another variant of CVE-2023-34992 by closing out CVE-2023-36553 (CVSS score: 9.3) in November 2023. The two new vulnerabilities are/will be plugged in the following versions -
FortiSIEM version 7.1.2 or above
FortiSIEM version 7.2.0 or above (upcoming)
FortiSIEM version 7.0.3 or above (upcoming)
FortiSIEM version 6.7.9 or above
(upcoming)
FortiSIEM version 6.6.5 or above (upcoming)
FortiSIEM version
6.5.3 or above (upcoming), and
FortiSIEM version 6.4.4 or above (upcoming)
Completing the trifecta is VMware, which has warned of five
moderate-to-important severity flaws in Aria Operations for Networks (formerly
vRealize Network Insight) -
CVE-2024-22237 (CVSS score: 7.8) - Local privilege escalation vulnerability that
allows a console user to gain regular root access
CVE-2024-22238 (CVSS score:
6.4) - Cross-site scripting (XSS) vulnerability that allows a malicious actor
with admin privileges to inject malicious code into user profile configurations
CVE-2024-22239 (CVSS score: 5.3) - Local privilege escalation vulnerability that
allows a console user to gain regular shell access
CVE-2024-22240 (CVSS
score: 4.9) - Local file read vulnerability that allows a malicious actor with
admin privileges to access sensitive information
CVE-2024-22241 (CVSS score:
4.3) - Cross-site scripting (XSS) vulnerability that allows a malicious actor
with admin privileges to inject malicious code and take over the user account
To mitigate the risks, all users of VMware Aria Operations for Networks version
6.x are being recommended to upgrade to version 6.12.0.
Considering the history of exploitation when it comes to Cisco, Fortinet, and VMware flaws, patching is a necessary and crucial first step that organizations need to take to handle the shortcomings.
After FBI Takedown, KV-Botnet Operators Shift Tactics in Attempt to Bounce Back
8.2.24
BotNet
The Hacker News
The threat actors behind the KV-botnet made "behavioral
changes" to the malicious network as U.S. law enforcement began issuing commands
to neutralize the activity.
KV-botnet is the name given to a network of compromised small office and home office (SOHO) routers and firewall devices across the world, with one specific cluster acting as a covert data transfer system for other Chinese state-sponsored actors, including Volt Typhoon (aka Bronze Silhouette, Insidious Taurus, or Vanguard Panda).
Active since at least February 2022, it was first documented by the Black Lotus Labs team at Lumen Technologies in mid-December 2023. The botnet is known to comprise two main sub-groups, viz. KV and JDY, with the latter principally used for scanning potential targets for reconnaissance.
Late last month, the U.S. government announced a court-authorized disruption effort to take down the KV cluster, which is typically reserved for manual operations against high-profile targets chosen after broader scanning via the JDY sub-group.
Now, according to new findings from the cybersecurity firm, the JDY cluster fell silent for roughly fifteen days following public disclosure and as a byproduct of the U.S. Federal Bureau of Investigation (FBI) undertaking.
"In mid-December 2023, we observed this activity cluster hovering around 1,500 active bots," security researcher Ryan English said. "When we sampled the size of this cluster in mid-January 2024 its size dwindled to approximately 650 bots."
Given that the takedown actions began with a signed warrant issued on December 6, 2023, it's fair to assume that the FBI began transmitting commands to routers located in the U.S. sometime on or after that date to wipe the botnet payload and prevent them from being re-infected.
"We observed the KV-botnet operators begin to restructure, committing eight
straight hours of activity on December 8, 2023, nearly ten hours of operations
the following day on December 9, 2023, followed by one hour on December 11,
2023," Lumen said in a technical report shared with The Hacker News.
During this four-day period, the threat actor was spotted interacting with 3,045 unique IP addresses that were associated with NETGEAR ProSAFEs (2,158), Cisco RV320/325 (310), Axis IP cameras (29), DrayTek Vigor routers (17), and other unidentified devices (531).
Also observed in early December 2023 was a massive spike in exploitation attempts from the payload server, indicating the adversary's likely attempts to re-exploit the devices as they detected their infrastructure going offline. Lumen said it also took steps to null-route another set of backup servers that became operational around the same time.
It's worth noting that the operators of the KV-botnet are known to perform their own reconnaissance and targeting while also supporting multiple groups like Volt Typhoon. Interestingly, the timestamps associated with exploitation of the bots correlates to China working hours.
"Our telemetry indicates that there were administrative connections into the known payload servers from IP addresses associated with China Telecom," Danny Adamitis, principal information security engineer at Black Lotus Labs, told The Hacker News.

What's more, the press statement from the U.S. Justice Department described the
botnet as controlled by "People's Republic of China (PRC) state-sponsored
hackers."
This raises the possibility that the botnet "was created by an organization supporting the Volt Typhoon hackers; whereas if the botnet was created by Volt Typhoon, we suspect they would have said 'nation-state' actors," Adamitis added.
There are also signs that the threat actors established a third related-but-distinct botnet cluster dubbed x.sh as early as January 2023 that's composed of infected Cisco routers by deploying a web shell named "fys.sh," as highlighted by SecurityScorecard last month.
But with KV-botnet being just "one form of infrastructure used by Volt Typhoon to obfuscate their activity," it's expected that the recent wave of actions will prompt the advanced persistent threat (APT) actors to presumably transition to another covert network in order to meet their strategic goals.
"A significant percent of all networking equipment in use around the world is functioning perfectly well, but is no longer supported," English said. "End users have a difficult financial choice when a device reaches that point, and many aren't even aware that a router or firewall is at the end of its supported life.
"Advanced threat actors are well aware that this represents fertile ground for exploitation. Replacing unsupported devices is always the best choice, but not always feasible."
"Mitigation involves defenders adding their edge devices to the long list of those they already have to patch and update as often as available, rebooting devices and configuring EDR or SASE solutions where applicable, and keeping an eye on large data transfers out of the network. Geofencing is not a defense to rely on, when the threat actor can hop from a nearby point."
Critical Bootloader Vulnerability in Shim Impacts Nearly All Linux Distros
7.2.24
Vulnerebility
The Hacker News
The maintainers of shim have released version 15.8 to
address six security flaws, including a critical bug that could pave the way for
remote code execution under specific circumstances.
Tracked as CVE-2023-40547 (CVSS score: 9.8), the vulnerability could be exploited to achieve a Secure Boot bypass. Bill Demirkapi of the Microsoft Security Response Center (MSRC) has been credited with discovering and reporting the bug.
"The shim's http boot support (httpboot.c) trusts attacker-controlled values when parsing an HTTP response, leading to a completely controlled out-of-bounds write primitive," Oracle's Alan Coopersmith noted in a message shared on the Open Source Security mailing list oss-security.
Demirkapi, in a post shared on X (formerly Twitter) late last month, said the vulnerability "exists in every Linux boot loader signed in the past decade."
shim refers to a "trivial" software package that's designed to work as a first-stage boot loader on Unified Extensible Firmware Interface (UEFI) systems.
Firmware security firm Eclypsium said CVE-2023-40547 "stems from HTTP protocol handling, leading to an out-of-bounds write that can lead to complete system compromise."
In a hypothetical attack scenario, a threat actor on the same network could leverage the flaw to load a vulnerable shim boot loader, or by a local adversary with adequate privileges to manipulate data on the EFI partition.
"An attacker could perform a MiTM (Man-in-the-Middle) attack and intercept HTTP traffic between the victim and the HTTP server used to serve files to support HTTP boot," the company added. "The attacker could be located on any network segment between the victim and the legitimate server."
That said, obtaining the ability to execute code during the boot process – which occurs before the main operating system starts – grants the attacker carte blanche access to deploy stealthy bootkits that can give near-total control over the compromised host.
The five other vulnerabilities fixed in shim version 15.8 are below -
CVE-2023-40546 (CVSS score: 5.3) - Out-of-bounds read when printing error
messages, resulting in a denial-of-service (DoS) condition
CVE-2023-40548
(CVSS score: 7.4) - Buffer overflow in shim when compiled for 32-bit processors
that can lead to a crash or data integrity issues during the boot phase
CVE-2023-40549 (CVSS score: 5.5) - Out-of-bounds read in the authenticode
function that could permit an attacker to trigger a DoS by providing a malformed
binary
CVE-2023-40550 (CVSS score: 5.5) - Out-of-bounds read when validating
Secure Boot Advanced Targeting (SBAT) information that could result in
information disclosure
CVE-2023-40551 (CVSS score: 7.1) - Out-of-bounds read
when parsing MZ binaries, leading to a crash or possible exposure of sensitive
data
"An attacker exploiting this vulnerability gains control of the system
before the kernel is loaded, which means they have privileged access and the
ability to circumvent any controls implemented by the kernel and operating
system," Eclypsium noted.
Global Coalition and Tech Giants Unite Against Commercial Spyware Abuse
7.2.24
BigBrothers
The Hacker News
A coalition of dozens of countries, including France, the
U.K., and the U.S., along with tech companies such as Google, MDSec, Meta, and
Microsoft, have signed a joint agreement to curb the abuse of commercial spyware
to commit human rights abuses.
The initiative, dubbed the Pall Mall Process, aims to tackle the proliferation and irresponsible use of commercial cyber intrusion tools by establishing guiding principles and policy options for States, industry, and civil society in relation to the development, facilitation, purchase, and use of such tools.
The declaration stated that "uncontrolled dissemination" of spyware offerings contributes to "unintentional escalation in cyberspace," noting it poses risks to cyber stability, human rights, national security, and digital security.
"Where these tools are used maliciously, attacks can access victims' devices, listen to calls, obtain photos and remotely operate a camera and microphone via 'zero-click' spyware, meaning no user interaction is needed," the U.K. government said in a press release.
According to the National Cyber Security Centre (NCSC), thousands of individuals are estimated to have been globally targeted by spyware campaigns every year.
"And as the commercial market for these tools grows, so too will the number and severity of cyber attacks compromising our devices and our digital systems, causing increasingly expensive damage and making it more challenging than ever for our cyber defenses to protect public institutions and services," Deputy Prime Minister Oliver Dowden said at the U.K.-France Cyber Proliferation conference.
Notably missing from the list of countries that participated in the event is Israel, which is home to a number of private sector offensive actors (PSOAs) or commercial surveillance vendors (CSVs) such as Candiru, Intellexa (Cytrox), NSO Group, and QuaDream.
Recorded Future News reported that Hungary, Mexico, Spain, and Thailand – which have been linked to spyware abuses in the past – did not sign the pledge.
The multi-stakeholder action coincides with an announcement by the U.S. Department of State to deny visas for individuals that it deems to be involved with the misuse of dangerous spyware technology.
"Until recently, a lack of accountability has enabled the spyware industry to proliferate dangerous surveillance tools around the world," Google said in a statement shared with The Hacker News. "Limiting spyware vendors' ability to operate in the U.S. helps to change the incentive structure which has allowed their continued growth."
One hand, spyware such as Chrysaor and Pegasus are licensed to government customers for use in law enforcement and counterterrorism. On the other hand, they have also been routinely abused by oppressive regimes to target journalists, activists, lawyers, human rights defenders, dissidents, political opponents, and other civil society members.
Such intrusions typically leverage zero-click (or one-click) exploits to surreptitiously deliver the surveillanceware onto the targets' Google Android and Apple iOS devices with the goal of harvesting sensitive information.
That having said, ongoing efforts to combat and contain the spyware ecosystem have been something of a whack-a-mole, underscoring the challenge of fending off recurring and lesser-known players who provide or come up with similar cyber weapons.
This also extends to the fact that CSVs continue to expend effort developing new exploit chains as companies like Apple, Google, and others discover and plug the zero-day vulnerabilities.
Source: Google's Threat Analysis Group (TAG)
"As long as there is a demand
for surveillance capabilities, there will be incentives for CSVs to continue
developing and selling tools, perpetrating an industry that harms high risk
users and society at large," Google's Threat Analysis Group (TAG) said.
An extensive report published by TAG this week revealed that the company is tracking roughly 40 commercial spyware companies that sell their products to government agencies, with 11 of them linked to the exploitation of 74 zero-days in Google Chrome (24), Android (20), iOS (16), Windows (6), Adobe (2), Mozilla Firefox (1) over the past decade.
Unknown state-sponsored actors, for example, exploited three flaws in iOS (CVE-2023-28205, CVE-2023-28206, and CVE-2023-32409) as a zero-day last year to infect victims with spyware developed by Barcelona-based Variston. The flaws were patched by Apple in April and May 2023.
The campaign, discovered in March 2023, delivered a link via SMS and targeted iPhones located in Indonesia running iOS versions 16.3.0 and 16.3.1 with an aim to deploy the BridgeHead spyware implant via the Heliconia exploitation framework. Also weaponized by Variston is a high-severity security shortcoming in Qualcomm chips (CVE-2023-33063) that first came to light in October 2023.
The complete list of zero-day vulnerabilities in Apple iOS and Google Chrome that were discovered in 2023 and have been tied to specific spyware vendors is as follows:
Zero-day Exploit Associated Spyware Vendor
CVE-2023-28205 and CVE-2023-28206
(Apple iOS) Variston (BridgeHead)
CVE-2023-2033 (Google Chrome)
Intellexa/Cytrox (Predator)
CVE-2023-2136 (Google Chrome) Intellexa/Cytrox
(Predator)
CVE-2023-32409 (Apple iOS) Variston (BridgeHead)
CVE-2023-3079
(Google Chrome) Intellexa/Cytrox (Predator)
CVE-2023-41061 and CVE-2023-41064
(Apple iOS) NSO Group (Pegasus)
CVE-2023-41991, CVE-2023-41992, and
CVE-2023-41993 (Apple iOS) Intellexa/Cytrox (Predator)
CVE-2023-5217 (Google
Chrome) Candiru (DevilsTongue)
CVE-2023-4211 (Arm Mali GPU) Cy4Gate (Epeius)
CVE-2023-33063 (Qualcomm Adreno GPU) Variston (BridgeHead)
CVE-2023-33106 and
CVE-2023-33107 (Qualcomm Adreno GPU) Cy4Gate (Epeius)
CVE-2023-42916 and
CVE-2023-42917 (Apple iOS) PARS Defense
CVE-2023-7024 (Google Chrome) NSO
Group (Pegasus)
"Private sector firms have been involved in discovering and
selling exploits for many years, but the rise of turnkey espionage solutions is
a newer phenomena," the tech giant said.
"CSVs operate with deep technical expertise to offer 'pay-to-play' tools that bundle an exploit chain designed to get past the defenses of a selected device, the spyware, and the necessary infrastructure, all to collect the desired data from an individual's device."
Chinese Hackers Exploited FortiGate Flaw to Breach Dutch Military Network
7.2.24
Exploit
The Hacker News
Chinese state-backed hackers broke into a computer network that's used by the Dutch armed forces by targeting Fortinet FortiGate devices.
"This [computer network] was used for unclassified research and development (R&D)," the Dutch Military Intelligence and Security Service (MIVD) said in a statement. "Because this system was self-contained, it did not lead to any damage to the defense network." The network had less than 50 users.
The intrusion, which took place in 2023, leveraged a known critical security flaw in FortiOS SSL-VPN (CVE-2022-42475, CVSS score: 9.3) that allows an unauthenticated attacker to execute arbitrary code via specially crafted requests.
Successful exploitation of the flaw paved the way for the deployment of a backdoor dubbed COATHANGER from an actor-controlled server that's designed to grant persistent remote access to the compromised appliances.
"The COATHANGER malware is stealthy and persistent," the Dutch National Cyber Security Centre (NCSC) said. "It hides itself by hooking system calls that could reveal its presence. It survives reboots and firmware upgrades."
COATHANGER is distinct from BOLDMOVE, another backdoor linked to a suspected China-based threat actor that's known to have exploited CVE-2022-42475 as a zero-day in attacks targeting a European government entity and a managed service provider (MSP) located in Africa as early as October 2022.
The development marks the first time the Netherlands has publicly attributed a cyber espionage campaign to China. Reuters, which broke the story, said the malware is named after a code snippet that contained a line from Lamb to the Slaughter, a short story by British author Roald Dahl.
It also arrives days after U.S. authorities took steps to dismantle a botnet comprising out-of-date Cisco and NetGear routers that were used by Chinese threat actors like Volt Typhoon to conceal the origins of malicious traffic.
Last year, Google-owned Mandiant revealed that a China-nexus cyber espionage group tracked as UNC3886 exploited zero-days in Fortinet appliances to deploy THINCRUST and CASTLETAP implants for executing arbitrary commands received from a remote server and exfiltrating sensitive data.
Critical JetBrains TeamCity On-Premises Flaw Exposes Servers to Takeover - Patch
Now
7.2.24
Vulnerebility
The Hacker News
JetBrains is alerting customers of a critical security
flaw in its TeamCity On-Premises continuous integration and continuous
deployment (CI/CD) software that could be exploited by threat actors to take
over susceptible instances.
The vulnerability, tracked as CVE-2024-23917, carries a CVSS rating of 9.8 out of 10, indicative of its severity.
"The vulnerability may enable an unauthenticated attacker with HTTP(S) access to a TeamCity server to bypass authentication checks and gain administrative control of that TeamCity server," the company said.
The issue impacts all TeamCity On-Premises versions from 2017.1 through 2023.11.2. It has been addressed in version 2023.11.3. An unnamed external security researcher has been credited with discovering and reporting the flaw on January 19, 2024.
Users who are unable to update their servers to version 2023.11.3 can alternately download a security patch plugin to apply fixes for the flaw.
"If your server is publicly accessible over the internet and you are unable to take one of the above mitigation steps immediately, we recommend temporarily making it inaccessible until mitigation actions have been completed," JetBrains advised.
While there is no evidence that the shortcoming has been abused in the wild, a similar flaw in the same product (CVE-2023-42793, CVSS score: 9.8) came under active exploitation last year within days of public disclosure by multiple threat actors, including ransomware gangs and state-sponsored groups affiliated with North Korea and Russia.
Beware: Fake Facebook Job Ads Spreading 'Ov3r_Stealer' to Steal Crypto and
Credentials
6.2.24
Virus
The Hacker News
Threat actors are leveraging bogus Facebook job
advertisements as a lure to trick prospective targets into installing a new
Windows-based stealer malware codenamed Ov3r_Stealer.
"This malware is designed to steal credentials and crypto wallets and send those to a Telegram channel that the threat actor monitors," Trustwave SpiderLabs said in a report shared with The Hacker News.
Ov3r_Stealer is capable of siphoning IP address-based location, hardware info, passwords, cookies, credit card information, auto-fills, browser extensions, crypto wallets, Microsoft Office documents, and a list of antivirus products installed on the compromised host.
While the exact end goal of the campaign is unknown, it's likely that the stolen information is offered for sale to other threat actors. Another possibility is that Ov3r_Stealer could be updated over time to act as a QakBot-like loader for additional payloads, including ransomware.
The starting point of the attack is a weaponized PDF file that purports to be a file hosted on OneDrive, urging users to click on an "Access Document" button embedded into it.
Trustwave said it identified the PDF file being shared on a fake Facebook account impersonating Amazon CEO Andy Jassy as well as via Facebook ads for digital advertising jobs.
Users who end up clicking on the button are served an internet shortcut (.URL) file that masquerades as a DocuSign document hosted on Discord's content delivery network (CDN). The shortcut file then acts as a conduit to deliver a control panel item (.CPL) file, which is then executed using the Windows Control Panel process binary ("control.exe").
The execution of the CPL file leads to the retrieval of a PowerShell loader ("DATA1.txt") from a GitHub repository to ultimately launch Ov3r_Stealer.
It's worth noting at this stage that a near-identical infection chain was recently disclosed by Trend Micro as having put to use by threat actors to drop another stealer called Phemedrone Stealer by exploiting the Microsoft Windows Defender SmartScreen bypass flaw (CVE-2023-36025, CVSS score: 8.8).
The similarities extend to the GitHub repository used (nateeintanan2527) and the fact that Ov3r_Stealer shares code-level overlaps with Phemedrone.
"This malware has recently been reported, and it may be that Phemedrone was re-purposed and renamed to Ov3r_Stealer," Trustwave said. "The main difference between the two is that Phemedrone is written in C#."
The findings come as Hudson Rock revealed that threat actors are advertising their access to law enforcement request portals of major organizations like Binance, Google, Meta, and TikTok by exploiting credentials obtained from infostealer infections.
They also follow the emergence of a category of infections called CrackedCantil that take leverage cracked software as an initial access vector to drop loaders like PrivateLoader and SmokeLoader, when subsequently act as a delivery mechanism for information stealers, crypto miners, proxy botnets, and ransomware.
Experts Detail New Flaws in Azure HDInsight Spark, Kafka, and Hadoop Services
6.2.24
Vulnerebility
The Hacker News
Three new security vulnerabilities have been discovered
in Azure HDInsight's Apache Hadoop, Kafka, and Spark services that could be
exploited to achieve privilege escalation and a regular expression
denial-of-service (ReDoS) condition.
"The new vulnerabilities affect any authenticated user of Azure HDInsight services such as Apache Ambari and Apache Oozie," Orca security researcher Lidor Ben Shitrit said in a technical report shared with The Hacker News.
The list of flaws is as follows -
CVE-2023-36419 (CVSS score: 8.8) - Azure HDInsight Apache Oozie Workflow
Scheduler XML External Entity (XXE) Injection Elevation of Privilege
Vulnerability
CVE-2023-38156 (CVSS score: 7.2) - Azure HDInsight Apache
Ambari Java Database Connectivity (JDBC) Injection Elevation of Privilege
Vulnerability
Azure HDInsight Apache Oozie Regular Expression
Denial-of-Service (ReDoS) Vulnerability (no CVE)
The two privilege escalation
flaws could be exploited by an authenticated attacker with access to the target
HDI cluster to send a specially crafted network request and gain cluster
administrator privileges.

The XXE flaw is the result of a lack of user input validation that allows for
root-level file reading and privilege escalation, while the JDBC injection flaw
could be weaponized to obtain a reverse shell as root.
"The ReDoS vulnerability on Apache Oozie was caused by a lack of proper input validation and constraint enforcement, and allowed an attacker to request a large range of action IDs and cause an intensive loop operation, leading to a denial-of-service (DoS)," Ben Shitrit explained.
Successful exploitation of the ReDoS vulnerability could result in a disruption of the system's operations, cause performance degradation, and negatively impact both the availability and reliability of the service.
Following responsible disclosure, Microsoft has rolled out fixes as part of updates released on October 26, 2023.
The development arrives nearly five months after Orca detailed a collection of eight flaws in the open-source analytics service that could be exploited for data access, session hijacking, and delivering malicious payloads.
In December 2023, Orca also highlighted a "potential abuse risk" impacting Google Cloud Dataproc clusters that take advantage of a lack of security controls in Apache Hadoop's web interfaces and default settings when creating resources to access any data on the Apache Hadoop Distributed File System (HDFS) without any authentication.
Hackers Exploit Job Boards, Stealing Millions of Resumes and Personal Data
6.2.24
Incindent
The Hacker News
Employment agencies and retail companies chiefly located in the Asia-Pacific
(APAC) region have been targeted by a previously undocumented threat actor known
as ResumeLooters since early 2023 with the goal of stealing sensitive data.
Singapore-headquartered Group-IB said the hacking crew's activities are geared towards job search platforms and the theft of resumes, with as many as 65 websites compromised between November 2023 and December 2023.
The stolen files are estimated to contain 2,188,444 user data records, of which 510,259 have been taken from job search websites. Over two million unique email addresses are present within the dataset.
"By using SQL injection attacks against websites, the threat actor attempts to steal user databases that may include names, phone numbers, emails, and DoBs, as well as information about job seekers' experience, employment history, and other sensitive personal data," security researcher Nikita Rostovcev said in a report shared with The Hacker News.
"The stolen data is then put up for sale by the threat actor in Telegram channels."
Group-IB said it also uncovered evidence of cross-site scripting (XSS) infections on at least four legitimate job search websites that are designed to load malicious scripts responsible for displaying phishing pages capable of harvesting administrator credentials.
ResumeLooters is the second group after GambleForce that has been found staging SQL injection attacks in the APAC region since late December 2023.
A majority of the compromised websites are based in India, Taiwan, Thailand, Vietnam, China, Australia, and Turkey, although compromises have also been reported from Brazil, the U.S., Turkey, Russia, Mexico, and Italy.
The modus operandi of ResumeLooters involves the use of the open-source sqlmap tool to carry out SQL injection attacks and drop and execute additional payloads such as the BeEF (short for Browser Exploitation Framework) penetration testing tool and rogue JavaScript code designed to gather sensitive data and redirect users to credential harvesting pages.
The cybersecurity company's analysis of the threat actor's infrastructure reveals the presence of other tools like Metasploit, dirsearch, and xray, alongside a folder hosting the pilfered data.
The campaign appears to be financially motivated, given the fact that ResumeLooters have set up two Telegram channels named 渗透数据中心 and 万国数据阿力 last year to sell the information.
"ResumeLooters is yet another example of how much damage can be made with just a handful of publicly available tools," Rostovcev said. "These attacks are fueled by poor security as well as inadequate database and website management practices."
"It is striking to see how some of the oldest yet remarkably effective SQL attacks remain prevalent in the region. However, the tenacity of the ResumeLooters group stands out as they experiment with diverse methods of exploiting vulnerabilities, including XSS attacks."
Recent SSRF Flaw in Ivanti VPN Products Undergoes Mass Exploitation
6.2.24
Exploit
The Hacker News
A recently disclosed server-side request forgery (SSRF)
vulnerability impacting Ivanti Connect Secure and Policy Secure products has
come under mass exploitation.
The Shadowserver Foundation said it observed exploitation attempts originating from more than 170 unique IP addresses that aim to establish a reverse shell, among others.
The attacks exploit CVE-2024-21893 (CVSS score: 8.2), an SSRF flaw in the SAML component of Ivanti Connect Secure, Policy Secure, and Neurons for ZTA that allows an attacker to access otherwise restricted resources without authentication.
Ivanti had previously divulged that the vulnerability had been exploited in targeted attacks aimed at a "limited number of customers," but cautioned the status quo could change post public disclosure.
That's exactly what appears to have happened, especially following the release of a proof-of-concept (PoC) exploit by cybersecurity firm Rapid7 last week.
The PoC involves fashioning an exploit chain that combines CVE-2024-21893 with CVE-2024-21887, a previously patched command injection flaw, to achieve unauthenticated remote code execution.
It's worth noting here that CVE-2024-21893 is an alias for CVE-2023-36661 (CVSS score: 7.5), an SSRF vulnerability present in the open-source Shibboleth XMLTooling library. It was fixed by the maintainers in June 2023 with the release of version 3.2.4.
Security researcher Will Dormann further pointed out other out-of-date open-source components used by Ivanti VPN appliances, such as curl 7.19.7, openssl 1.0.2n-fips, perl 5.6.1, psql 9.6.14, cabextract 0.5, ssh 5.3p1, and unzip 6.00, thus opening the door for more attacks.
The development comes as threat actors have found a way to bypass Ivanti's initial mitigation, prompting the Utah-based company to release a second mitigation file. As of February 1, 2024, it has begun releasing official patches to address all the vulnerabilities.
Last week, Google-owned Mandiant revealed that several threat actors are leveraging CVE-2023-46805 and CVE-2024-21887 to deploy an array of custom web shells tracked as BUSHWALK, CHAINLINE, FRAMESTING, and LIGHTWIRE.
Palo Alto Networks Unit 42 said it observed 28,474 exposed instances of Ivanti Connect Secure and Policy Secure in 145 countries between January 26 and 30, 2024, with 610 compromised instances detected in 44 countries as of January 23, 2024.
U.S. Imposes Visa Restrictions on those Involved in Illegal Spyware Surveillance
6.2.24
BigBrothers
The Hacker News
The U.S. State Department said it's implementing a new
policy that imposes visa restrictions on individuals who are linked to the
illegal use of commercial spyware to surveil civil society members.
"The misuse of commercial spyware threatens privacy and freedoms of expression, peaceful assembly, and association," Secretary of State Antony Blinken said. "Such targeting has been linked to arbitrary detentions, forced disappearances, and extrajudicial killings in the most egregious of cases."
The latest measures, underscoring continued efforts on part of the U.S. government to curtail the proliferation of surveillance tools, are designed to "promote accountability" for individuals involved in commercial spyware misuse.
The new policy covers people who have used such tools to "unlawfully surveil, harass, suppress, or intimidate individuals," as well as those who stand to financially benefit from the misuse.
It also includes the companies (aka private sector offensive actors or PSOAs) that develop and sell the spyware to governments and other entities. It's currently not clear how the new restrictions will be enforced for individuals who possess passports that don't require a visa to enter the U.S.
However, CyberScoop notes that executives potentially affected by the ban would no longer be eligible to participate in the visa waiver program, and that they would need to apply for a visa to travel to the U.S.
The development comes days after Access Now and the Citizen Lab revealed that 35 journalists, lawyers, and human-rights activists in the Middle Eastern nation of Jordan were targeted with NSO Group's Pegasus spyware.
In November 2021, the U.S. government sanctioned NSO Group and Candiru, another spyware vendor, for developing and supplying cyber weapons to foreign governments that "used these tools to maliciously target government officials, journalists, businesspeople, activists, academics, and embassy workers."
Then early last year, U.S. President Joe Biden signed an executive order barring federal government agencies from using commercial spyware that could pose national security risks. In July 2023, the U.S. also placed Intellexa and Cytrox on a trade blocklist.
According to an intelligence assessment released by the U.K. Government Communications Headquarters (GCHQ) in April 2023, at least 80 countries have purchased commercial cyber intrusion software over the past decade.
Google's Threat Analysis Group (TAG), in a comprehensive report about the commercial spyware landscape shared with The Hacker News, said there are dozens of smaller vendors such as Cy4Gate, Negg Group, and Variston who "enable the proliferation of dangerous tools and capabilities used by governments against individuals."
For example, Italian company Cy4Gate, which acquired RCS Lab in March 2022, is the maker of Android and iOS spyware known as Epeius. Negg Group, which is also from Italy, develops a strain of mobile spyware codenamed VBiss that's delivered via one-click exploit chains. It has also been linked to another Android malware known as Skygofree.
"If governments ever had a monopoly on the most sophisticated capabilities, that era is certainly over," TAG said, adding it's tracking nearly 40 companies with varying levels of sophistication. "The private sector is now responsible for a significant portion of the most sophisticated tools we detect."
This is exemplified by the fact that of the 25 zero-days that were exploited in the wild in 2023, 20 were weaponized by PSOAs. Furthermore, 35 out of 72 zero-days found in Google products since 2014 have been actively exploited by commercial vendors.
"The development of surveillance technology often begins with the discovery of a vulnerability and ends with a government customer collecting data from spyware installed on a high risk user's device," TAG further noted, calling out the roles played by exploit developers, exploit brokers, and the vendors themselves, who sell the spyware as a product along with the initial delivery mechanisms and the exploits.
(The story was updated after publication to include additional insights shared by Google's Threat Analysis Group.)
Belarusian National Linked to BTC-e Faces 25 Years for $4 Billion Crypto Money
Laundering
6.2.24
Cryptocurrency
The Hacker News
A 42-year-old Belarusian and Cypriot national with
alleged connections to the now-defunct cryptocurrency exchange BTC-e is facing
charges related to money laundering and operating an unlicensed money services
business.
Aliaksandr Klimenka, who was arrested in Latvia on December 21, 2023, was extradited to the U.S. and is currently being held in custody. If convicted, he faces a maximum penalty of 25 years in prison.
BTC-e, which had been operating since 2011, was seized by law enforcement authorities in late July 2017 following the arrest of another key member Alexander Vinnik, in Greece.
The exchange is alleged to have received deposits valued at over $4 billion, with Vinnik laundering funds received from the hack of another digital exchange, Mt. Gox, through various online exchanges, including BTC-e.
Court documents allege that the exchange was a "significant cybercrime and online money laundering entity," allowing its users to trade in bitcoin with high levels of anonymity, thereby building a customer base that engaged in criminal activity.
This included hacking incidents, ransomware scams, identity theft schemes, and narcotics distribution rings.
"BTC-e's servers, maintained in the United States, were allegedly one of the primary ways in which BTC-e and its operators effectuated their scheme," the U.S. Department of Justice (DoJ) said.
These servers were leased to and maintained by Klimenka and Soft-FX, a technology services company controlled by the defendant.
BTC-e has also been accused of failing to establish an anti-money laundering process or know-your-customer (KYC) verification in accordance with U.S. federal laws.
In June 2023, two Russian nationals – Alexey Bilyuchenko and Aleksandr Verner – were charged for their roles in masterminding the 2014 digital heist of Mt. Gox.
News of Klimenka's indictment comes as the DoJ charged Noah Michael Urban, 19, of Palm Coast, Florida, with wire fraud and aggravated identity theft for offenses that led to the theft of $800,000 from at least five different victims between August 2022 and March 2023.
Urban, who went by the aliases Sosa, Elijah, King Bob, Anthony Ramirez, and Gustavo Fring, is said to be a key member of the cybercrime group known as Scattered Spider, according to KrebsOnSecurity, as well as a "top member" of a broader cybercrime ecosystem that calls itself The Com.
It also follows the Justice Department's announcement of charges against three individuals, Robert Powell, Carter Rohn, and Emily Hernandez, in relation to a SIM swapping attack aimed at crypto exchange FTX to steal more than $400 million at the time of its collapse in 2022.
Powell (aka R, R$, and ElSwapo1), Rohn (aka Carti and Punslayer), and Hernandez (aka Em) are accused of running a massive cybercriminal theft ring dubbed the Powell SIM Swapping Crew that orchestrated SIM swapping attacks between March 2021 and April 2023 and stole hundreds of millions of dollars from victims' accounts.
Blockchain analytics firm Elliptic, in October 2023, said the plunder assets had been laundered through cross-chain crime in collaboration with Russia-nexus intermediaries in an attempt to obscure the trail.
Patchwork Using Romance Scam Lures to Infect Android Devices with VajraSpy
Malware
5.2.24
OS
The Hacker News
The threat actor known as Patchwork likely used romance scam lures to trap
victims in Pakistan and India, and infect their Android devices with a remote
access trojan called VajraSpy.
Slovak cybersecurity firm ESET said it uncovered 12 espionage apps, six of which were available for download from the official Google Play Store and were collectively downloaded more than 1,400 times between April 2021 and March 2023.
"VajraSpy has a range of espionage functionalities that can be expanded based on the permissions granted to the app bundled with its code," security researcher Lukáš Štefanko said. "It steals contacts, files, call logs, and SMS messages, but some of its implementations can even extract WhatsApp and Signal messages, record phone calls, and take pictures with the camera."
As many as 148 devices in Pakistan and India are estimated to have been compromised in the wild. The malicious apps distributed via Google Play and elsewhere primarily masqueraded as messaging applications, with the most recent ones propagated as recently as September 2023.
Privee Talk (com.priv.talk)
MeetMe (com.meeete.org)
Let's Chat
(com.letsm.chat)
Quick Chat (com.qqc.chat)
Rafaqat رفاق (com.rafaqat.news)
Chit Chat (com.chit.chat)
YohooTalk (com.yoho.talk)
TikTalk (com.tik.talk)
Hello Chat (com.hello.chat)
Nidus (com.nidus.no or com.nionio.org)
GlowChat (com.glow.glow)
Wave Chat (com.wave.chat)
Rafaqat رفاق is notable
for the fact that it's the only non-messaging app and was advertised as a way to
access the latest news. It was uploaded to Google Play on October 26, 2022, by a
developer named Mohammad Rizwan and amassed a total of 1,000 downloads before it
was taken down by Google.
The exact distribution vector for the malware is currently not clear, although the nature of the apps suggests that the targets were tricked into downloading them as part of a honey-trap romance scam, where the perpetrators convince them to install these bogus apps under the pretext of having a more secure conversation.
This is not the first time Patchwork – a threat actor with suspected ties to India – has leveraged this technique. In March 2023, Meta revealed that the hacking crew created fictitious personas on Facebook and Instagram to share links to rogue apps to target victims in Pakistan, India, Bangladesh, Sri Lanka, Tibet, and China.
It's also not the first time that the attackers have been observed deploying VajraRAT, which was previously documented by Chinese cybersecurity company QiAnXin in early 2022 as having been used in a campaign aimed at Pakistani government and military entities. Vajra gets its name from the Sanskrit word for thunderbolt.

Qihoo 360, in its own analysis of the malware in November 2023, tied it to a
threat actor it tracks under the moniker Fire Demon Snake (aka APT-C-52).
Outside of Pakistan and India, Nepalese government entities have also been likely targeted via a phishing campaign that delivers a Nim-based backdoor. It has been attributed to the SideWinder group, another group that has been flagged as operating with Indian interests in mind.
The development comes as financially motivated threat actors from Pakistan and India have been found targeting Indian Android users with a fake loan app (Moneyfine or "com.moneyfine.fine") as part of an extortion scam that manipulates the selfie uploaded as part of a know your customer (KYC) process to create a nude image and threatens victims to make a payment or risk getting the doctored photos distributed to their contacts.
"These unknown, financially motivated threat actors make enticing promises of quick loans with minimal formalities, deliver malware to compromise their devices, and employ threats to extort money," Cyfirma said in an analysis late last month.
It also comes amid a broader trend of people falling prey to predatory loan apps, which are known to harvest sensitive information from infected devices, and employ blackmail and harassment tactics to pressure victims into making the payments.
According to a recent report published by the Network Contagion Research Institute (NCRI), teenagers from Australia, Canada, and the U.S. are increasingly targeted by financial sextortion attacks conducted by Nigeria-based cybercriminal group known as Yahoo Boys.
"Nearly all of this activity is linked to West African cybercriminals known as the Yahoo Boys, who are primarily targeting English-speaking minors and young adults on Instagram, Snapchat, and Wizz," NCRI said.
Wizz, which has since had its Android and iOS apps taken down from the Apple App Store and the Google Play Store, countered the NCRI report, stating it's "not aware of any successful extortion attempts that occurred while communicating on the Wizz app."
Pegasus Spyware Targeted iPhones of Journalists and Activists in Jordan
5.2.24
OS
The Hacker News
The iPhones belonging to nearly three dozen journalists,
activists, human rights lawyers, and civil society members in Jordan have been
targeted with NSO Group's Pegasus spyware, according to joint findings from
Access Now and the Citizen Lab.
Nine of the 35 individuals have been publicly confirmed as targeted, out of whom six had their devices compromised with the mercenary surveillanceware tool. The infections are estimated to have taken place from at least 2019 until September 2023.
"In some cases, perpetrators posed as journalists, seeking an interview or a quote from victims, while embedding malicious links to Pegasus spyware amid and in between their messages," Access Now said.
"A number of victims were reinfected with Pegasus spyware multiple times — demonstrating the relentless nature of this targeted surveillance campaign."
The Israeli company has been under the radar for failing to implement rigorous human rights safeguards prior to selling its cyber intelligence technology to government clients and law enforcement agencies for "preventing and investigating terrorism and serious crimes."
NSO Group, in its 2023 Transparency and Responsibility Report, touted a "significant decrease" in reports of product misuse during 2022 and 2023, attributing the downturn to its due diligence and review process.
"Cyber intelligence technology enables government intelligence and law enforcement agencies to carry out their basic duties to prevent violence and safeguard the public," the company noted.
"Importantly, it allows them to counter the widespread deployment of end-to-end encryption applications by terrorists and criminals without engaging in mass surveillance or obtaining backdoor access to the devices of all users."
It further sought to "dispel falsehoods" about Pegasus, stating it is not a mass surveillance tool, that it's licensed to legitimate, vetted intelligence and law enforcement agencies, and that it cannot take control of a device or penetrate computer networks, desktop or laptop operating systems.
"It is technologically impossible for Pegasus to add, alter, delete, or otherwise manipulate data on targeted mobile devices, or perform any other activities beyond viewing and/or extracting certain data," NSO Group said.
Despite these assurances, the invasive spyware attacks targeting Jordan civil society members underscores the continued pattern of abuse that run counter to the company's claims.
Access Now said the victims' devices were infiltrated with both zero-click and one-click attacks using Apple iOS exploits like FORCEDENTRY, FINDMYPWN, PWNYOURHOME, and BLASTPASS to breach security guardrails and deliver Pegasus via social engineering attacks.
The attacks were characterized by the propagation of malicious links to victims via WhatsApp and SMS, with the attackers posing as journalists to increase the likelihood of success of the campaign.
The non-profit further said that enabling Lockdown Mode on the iPhones likely prevented some of the devices from being re-infected again with the spyware. It also called on world governments, including Jordan's, to halt the use of such tools and enforce a moratorium on their sale until adequate countermeasures are adopted.
"Surveillance technologies and cyberweapons such as NSO Group's Pegasus spyware are used to target human rights defenders and journalists, to intimidate and dissuade them from their work, to infiltrate their networks, and to gather information for use against other targets," Access Now said.
"The targeted surveillance of individuals violates their right to privacy, freedom of expression, association, and peaceful assembly. It also creates a chilling effect, forcing individuals to self-censor and cease their activism or journalistic work, for fear of reprisal."
New Mispadu Banking Trojan Exploiting Windows SmartScreen Flaw
5.2.24
Exploit
The Hacker News
The threat actors behind the Mispadu banking Trojan have
become the latest to exploit a now-patched Windows SmartScreen security bypass
flaw to compromise users in Mexico.
The attacks entail a new variant of the malware that was first observed in 2019, Palo Alto Networks Unit 42 said in a report published last week.
Propagated via phishing mails, Mispadu is a Delphi-based information stealer known to specifically infect victims in the Latin American (LATAM) region. In March 2023, Metabase Q revealed that Mispadu spam campaigns harvested no less than 90,000 bank account credentials since August 2022.
It's also part of the larger family of LATAM banking malware, including Grandoreiro, which was dismantled by Brazilian law enforcement authorities last week.
The latest infection chain identified by Unit 42 employs rogue internet shortcut files contained within bogus ZIP archive files that leverage CVE-2023-36025 (CVSS score: 8.8), a high-severity bypass flaw in Windows SmartScreen. It was addressed by Microsoft in November 2023.
"This exploit revolves around the creation of a specifically crafted internet shortcut file (.URL) or a hyperlink pointing to malicious files that can bypass SmartScreen's warnings," security researchers Daniela Shalev and Josh Grunzweig said.
"The bypass is simple and relies on a parameter that references a network share, rather than a URL. The crafted .URL file contains a link to a threat actor's network share with a malicious binary."
Mispadu, once launched, reveals its true colors by selectively targeting victims based on their geographic location (i.e., Americas or Western Europe) and system configurations, and then proceeds to establish contact with a command-and-control (C2) server for follow-on data exfiltration.
In recent months, the Windows flaw has been exploited in the wild by multiple cybercrime groups to deliver DarkGate and Phemedrone Stealer malware in recent months.
Mexico has also emerged as a top target for several campaigns over the past year that have been found to propagate information stealers and remote access trojans like AllaKore RAT, AsyncRAT, Babylon RAT. This constitutes a financially-motivated group dubbed TA558 that has attacked the hospitality and travel sectors in the LATAM region since 2018.
The development comes as Sekoia detailed the inner workings of DICELOADER (aka Lizar or Tirion), a time-tested custom downloader used by the Russian e-crime group tracked as FIN7. The malware has been observed delivered via malicious USB drives (aka BadUSB) in the past.
"DICELOADER is dropped by a PowerShell script along with other malware of the intrusion set's arsenal such as Carbanak RAT," the French cybersecurity firm said, calling out its sophisticated obfuscation methods to conceal the C2 IP addresses and the network communications.
It also follows AhnLab's discovery of two new malicious cryptocurrency mining campaigns that employ booby-trapped archives and game hacks to deploy miner malware that mine Monero and Zephyr.
U.S. Sanctions 6 Iranian Officials for Critical Infrastructure Cyber Attacks
3.2.24
BigBrothers
The Hacker News
The U.S. Treasury Department's Office of Foreign Assets
Control (OFAC) announced sanctions against six officials associated with the
Iranian intelligence agency for attacking critical infrastructure entities in
the U.S. and other countries.
The officials include Hamid Reza Lashgarian, Mahdi Lashgarian, Hamid Homayunfal, Milad Mansuri, Mohammad Bagher Shirinkar, and Reza Mohammad Amin Saberian, who are part of the Iranian Islamic Revolutionary Guard Corps Cyber-Electronic Command (IRGC-CEC).
Reza Lashgarian is also the head of the IRGC-CEC and a commander in the IRGC-Qods Force. He is alleged to have been involved in various IRGC cyber and intelligence operations.
The Treasury Department said it's holding these individuals responsible for carrying out "cyber operations in which they hacked and posted images on the screens of programmable logic controllers manufactured by Unitronics, an Israeli company."
In late November 2023, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) revealed that the Municipal Water Authority of Aliquippa in western Pennsylvania was targeted by Iranian threat actors by exploiting Unitronics PLCs.
The attack was attributed to an Iranian hacktivist persona dubbed Cyber Av3ngers, which came to the forefront in the aftermath of the Israel-Hamas conflict, staging destructive attacks against entities in Israel and the U.S.
The group, which has been active since 2020, is also said to be behind several other cyber attacks, including one targeting Boston Children's Hospital in 2021 and others in Europe and Israel.
"Industrial control devices, such as programmable logic controllers, used in water and other critical infrastructure systems, are sensitive targets," the Treasury Department noted.
"Although this particular operation did not disrupt any critical services, unauthorized access to critical infrastructure systems can enable actions that harm the public and cause devastating humanitarian consequences."
The development comes as another pro-Iranian "psychological operation group" known as Homeland Justice said it attacked Albania's Institute of Statistics (INSTAT) and claimed to have stolen terabytes of data.
Homeland Justice has a track record of targeting Albania since mid-July 2022, with the threat actor most recently observed delivering a wiper malware codenamed No-Justice.
Mastodon Vulnerability Allows Hackers to Hijack Any Decentralized Account
3.2.24
Vulnerebility
The Hacker News
The decentralized social network Mastodon has disclosed a
critical security flaw that enables malicious actors to impersonate and take
over any account.
"Due to insufficient origin validation in all Mastodon, attackers can impersonate and take over any remote account," the maintainers said in a terse advisory.
The vulnerability, tracked as CVE-2024-23832, has a severity rating of 9.4 out of a maximum of 10. Security researcher arcanicanis has been credited with discovering and reporting it.
It has been described as an "origin validation error" (CWE-346), which can typically allow an attacker to "access any functionality that is inadvertently accessible to the source."
Every Mastodon version prior to 3.5.17 is vulnerable, as are 4.0.x versions before 4.0.13, 4.1.x versions before 4.1.13, and 4.2.x versions before 4.2.5.
Mastodon said it's withholding additional technical specifics about the flaw until February 15, 2024, to give admins ample time to update the server instances and prevent the likelihood of exploitation.
"Any amount of detail would make it very easy to come up with an exploit," it said.
The federated nature of the platform means that it runs on separate servers (aka instances), independently hosted and operated by respective administrators who create their own rules and regulations that are enforced locally.
This also means that not only each instance has a unique code of conduct, terms of service, privacy policy, and content moderation guidelines, but it also requires each administrator to apply security updates in a timely fashion to secure the instances against potential risks.
The disclosure arrives nearly seven months after Mastodon addressed two other critical flaws (CVE-2023-36460 and 2023-36459) that could have been weaponized by adversaries to cause denial-of-service (DoS) or achieve remote code execution.
AnyDesk Hacked: Popular Remote Desktop Software Mandates Password Reset
3.2.24
Incindent
The Hacker News
Remote desktop software maker AnyDesk disclosed on Friday
that it suffered a cyber attack that led to a compromise of its production
systems.
The German company said the incident, which it discovered following a security audit, is not a ransomware attack and that it has notified relevant authorities.
"We have revoked all security-related certificates and systems have been remediated or replaced where necessary," the company said in a statement. "We will be revoking the previous code signing certificate for our binaries shortly and have already started replacing it with a new one."
Out of an abundance of caution, AnyDesk has also revoked all passwords to its web portal, my.anydesk[.]com, and it's urging users to change their passwords if the same passwords have been reused on other online services.
It's also recommending that users download the latest version of the software, which comes with a new code signing certificate.
AnyDesk did not disclose when and how its production systems were breached. It's currently not known if any information was stolen following the hack. However, it emphasized there is no evidence that any end-user systems have been affected.
Earlier this week, Günter Born of BornCity disclosed that AnyDesk had been under maintenance since January 29. The issue was addressed on February 1. Previously, on January 24, the company also alerted users of "intermittent timeouts" and "service degradation" with its Customer Portal.
AnyDesk boasts over 170,000 customers, including Amedes, AutoForm Engineering, LG Electronics, Samsung Electronics, Spidercam, and Thales.
The disclosure comes a day after Cloudflare said it was breached by a suspected nation-state attacker using stolen credentials to gain unauthorized access to its Atlassian server and ultimately access some documentation and a limited amount of source code.
Russian APT28 Hackers Targeting High-Value Orgs with NTLM Relay Attacks
3.2.24
APT
The Hacker News
Russian state-sponsored actors have staged NT LAN Manager
(NTLM) v2 hash relay attacks through various methods from April 2022 to November
2023, targeting high-value targets worldwide.
The attacks, attributed to an "aggressive" hacking crew called APT28, have set their eyes on organizations dealing with foreign affairs, energy, defense, and transportation, as well as those involved with labor, social welfare, finance, parenthood, and local city councils.
Cybersecurity firm Trend Micro assessed these intrusions as a "cost-efficient method of automating attempts to brute-force its way into the networks" of its targets, noting the adversary may have compromised thousands of email accounts over time.
APT28 is also tracked by the broader cybersecurity community under the names Blue Athena, BlueDelta, Fancy Bear, Fighting Ursa, Forest Blizzard (formerly Strontium), FROZENLAKE, Iron Twilight, ITG05, Pawn Storm, Sednit, Sofacy, and TA422.
The group, believed to be active since at least 2009, is operated by Russia's GRU military intelligence service and has a track record of orchestrating spear-phishing containing malicious attachments or strategic web compromises to activate the infection chains.
In April 2023, APT28 was implicated in attacks leveraging now-patched flaws in networking equipment from Cisco to conduct reconnaissance and deploy malware against select targets.
The nation-state actor, in December, came under the spotlight for exploiting a privilege escalation flaw in Microsoft Outlook (CVE-2023-23397, CVSS score: 9.8) and WinRAR (CVE-2023-38831, CVSS score: 7.8) to access a user's Net-NTLMv2 hash and use it to stage an NTLM Relay attack against another service to authenticate as the user.
An exploit for CVE-2023-23397 is said to have been used to target Ukrainian entities as early as April 2022, according to a March 2023 advisory from CERT-EU.
It has also been observed leveraging lures related to the ongoing Israel-Hamas war to facilitate the delivery of a custom backdoor called HeadLace, alongside striking Ukrainian government entities and Polish organizations with phishing messages designed to deploy backdoors and information stealers like OCEANMAP, MASEPIE, and STEELHOOK.
One of the significant aspects of the threat actor's attacks is the continuous attempt to improve its operational playbook, fine-tuning and tinkering with its approaches to evade detection.
This includes the addition of anonymization layers such as VPN services, Tor, data center IP addresses, and compromised EdgeOS routers to carry out scanning and probing activities. Another tactic entails sending spear-phishing messages from compromised email accounts over Tor or VPN.
"Pawn Storm has also been using EdgeOS routers to send spear-phishing emails, perform callbacks of CVE-2023-23397 exploits in Outlook, and proxy credential theft on credential phishing websites," security researchers Feike Hacquebord and Fernando Merces said.
"Part of the group's post-exploitation activities involve the modification of folder permissions within the victim's mailbox, leading to enhanced persistence," the researchers said. "Using the victim's email accounts, lateral movement is possible by sending additional malicious email messages from within the victim organization."
It's currently not known if the threat actor themselves breached these routers, or if it is using routers that were already compromised by a third-party actor. That said, no less than 100 EdgeOS routers are estimated to have been infected.
Furthermore, recent credential harvesting campaigns against European governments have used bogus login pages mimicking Microsoft Outlook that are hosted on webhook[.]site URLs, a pattern previously attributed to the group.
An October 2022 phishing campaign, however, singled out embassies and other high-profile entities to deliver a "simple" information stealer via emails that captured files matching specific extensions and exfiltrated them to a free file-sharing service named Keep.sh.
"The loudness of the repetitive, oftentimes crude and aggressive campaigns, drown out the silence, subtlety, and complexity of the initial intrusion, as well as the post-exploitation actions that might occur once Pawn Storm gets an initial foothold in victim organizations," the researchers said.
The development comes as Recorded Future News revealed an ongoing hacking campaign undertaken by the Russian threat actor COLDRIVER (aka Calisto, Iron Frontier, or Star Blizzard) that impersonates researchers and academics to redirect prospective victims to credential harvesting pages.
DirtyMoe Malware Infects 2,000+ Ukrainian Computers for DDoS and Cryptojacking
3.2.24
Virus
The Hacker News
The Computer Emergency Response Team of Ukraine (CERT-UA) has warned that more than 2,000 computers in the country have been infected by a strain of malware called DirtyMoe.
The agency attributed the campaign to a threat actor it calls UAC-0027.
DirtyMoe, active since at least 2016, is capable of carrying out cryptojacking and distributed denial-of-service (DDoS) attacks. In March 2022, cybersecurity firm Avast revealed the malware's ability to propagate in a worm-like fashion by taking advantage of known security flaws.
The DDoS botnet is known to be delivered by means of another malware referred to as Purple Fox or via bogus MSI installer packages for popular software such as Telegram. Purple Fox is also equipped with a rootkit that allows the threat actors to hide the malware on the machine and make it difficult to detect and remove.
The exact initial access vector used in the campaign targeting Ukraine is currently unknown. CERT-UA is recommending that organizations keep their systems up-to-date, enforce network segmentation, and monitor network traffic for any anomalous activity.
The disclosure comes as Securonix detailed an ongoing phishing campaign known as STEADY#URSA targeting Ukrainian military personnel with the goal of delivering a bespoke PowerShell backdoor dubbed SUBTLE-PAWS.
"The exploitation chain is relatively simple: it involves the target executing a malicious shortcut (.lnk) file which loads and executes a new PowerShell backdoor payload code (found inside another file contained within the same archive)," security researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov said.
The attack is said to be related to a threat actor known as Shuckworm, which is also known as Aqua Blizzard (formerly Actinium), Armageddon, Gamaredon, Iron Tilden, Primitive Bear, Trident Ursa, UNC530, and Winterflounder. Active since at least 2013, it's assessed to be part of Russia's Federal Security Service (FSB).
SUBTLE-PAWS, in addition to setting up persistence on the host, uses Telegram's blogging platform called Telegraph to retrieve the command-and-control (C2) information, a technique previously identified as associated with the adversary since early 2023, and can propagate through removable attached drives.
Gamaredon's ability to spread via USB drives was also documented by Check Point in November 2023, which named the PowerShell-based USB worm LitterDrifter.
"The SUBTLE-PAWS backdoor uses advanced techniques to execute malicious payloads dynamically," the researchers said.
"They store and retrieve executable PowerShell code from the Windows Registry which can assist in evading traditional file-based detection methods. This approach also aids in maintaining persistence on the infected system, as the malware can initiate itself again after reboots or other interruptions."
Former CIA Engineer Sentenced to 40 Years for Leaking Classified Documents
3.2.24
BigBrothers
The Hacker News
A former software engineer with the U.S. Central
Intelligence Agency (CIA) has been sentenced to 40 years in prison by the
Southern District of New York (SDNY) for transmitting classified documents to
WikiLeaks and for possessing child pornographic material.
Joshua Adam Schulte, 35, was originally charged in June 2018. He was found guilty in July 2022. On September 13, 2023, he was convicted on charges of receiving, possessing, and transporting child pornography. In addition to the prison term, Schulte has been sentenced to a lifetime of supervised release.
"Schulte's theft is the largest data breach in the history of the CIA, and his transmission of that stolen information to WikiLeaks is one of the largest unauthorized disclosures of classified information in the history of the U.S.," the U.S. Department of Justice (DoJ) said.
The sensitive information shared by Schulte included a tranche of hacking tools and exploits that were denominated as Vault 7 and Vault 8. It was published by WikiLeaks starting March 7, 2017, over a period of eight months.
Schulte was employed as a software developer in the Center for Cyber Intelligence (CCI) from 2012 to 2016, where he worked on tools pertaining to offensive cyber operations conducted by the CIA, subsequently abusing his administrator privileges to plunder "copies of the entire CCI tool development archives" in 2016.
This information included methods to "collect foreign intelligence against America's adversaries," including an arsenal of cyber weapons and zero-day exploits that made it possible to compromise cars, smart TVs, web browsers, and widely-used desktop and mobile operating systems.
The leak, described as a "digital Pearl Harbor," cost the agency "hundreds of millions of dollars" and "severely harmed U.S. national security and directly risked the lives of CIA personnel," prosecutors said.
Schulte was also accused of repeatedly lying to the U.S. Federal Bureau of Investigation (FBI) about his involvement as well as "spinning fake narratives" about how the information could have been obtained from CIA computers in an attempt to deflect suspicion.
A subsequent search of his New York apartment in March 2017 unearthed a stockpile of child sexual abuse material (CSAM) encompassing approximately 3,400 images and videos, some of which were collected during his employment with the CIA from the dark web and Russian websites.
During detention pending trial, he was found to have used contraband cell phones in jail to create anonymous, encrypted email, and social media accounts, and attempted to transmit protected discovery materials to WikiLeaks and publish classified information about CIA cyber techniques and tools.
Schulte's goal, the DoJ said, quoting a journal maintained by him, was to "break up diplomatic relationships, close embassies, [and] end U.S. occupation across the world."
"Joshua Schulte was rightly punished not only for his betrayal of our country, but for his substantial possession of horrific child pornographic material," FBI Assistant Director in Charge James Smith said. "The severity of his actions is evident, and the sentence imposed reflects the magnitude of the disturbing and harmful threat posed by his criminal conduct."
INTERPOL Arrests 31 in Global Operation, Identifies 1,900+ Ransomware-Linked IPs
3.2.24
Crime
The Hacker News
An INTERPOL-led collaborative operation targeting phishing, banking malware, and ransomware attacks has led to the identification of 1,300 suspicious IP addresses and URLs.
The law enforcement effort, codenamed Synergia, took place between September and November 2023 in an attempt to blunt the "growth, escalation and professionalization of transnational cybercrime."
Involving 60 law enforcement agencies spanning 55 member countries, the exercise paved the way for the detection of more than 1,300 malicious servers, 70% of which have already been taken down in Europe. Hong Kong and Singapore authorities took down 153 and 86 servers, respectively.
Servers, as well as electronic devices, were confiscated following over 30 house searches. Seventy suspects have been identified to date, and 31 from Europe, South Sudan, and Zimbabwe have been arrested.
Singapore-headquartered Group-IB, which also contributed to the operation, said it identified "more than 500 IP addresses hosting phishing resources and over 1,900 IP addresses associated with ransomware, Trojans, and banking malware operations."
The rogue infrastructure was hosted in Australia, Canada, Hong Kong, and Singapore, among others, with the resources distributed across more than 200 web hosting providers around the world.
"The results of this operation, achieved through the collective efforts of multiple countries and partners, show our unwavering commitment to safeguarding the digital space," Bernardo Pillot, assistant director to INTERPOL Cybercrime Directorate, said.
"By dismantling the infrastructure behind phishing, banking malware, and ransomware attacks, we are one step closer to protecting our digital ecosystems and a safer, more secure online experience for all."
The development arrives more than a month after another six-month-long international police operation dubbed HAECHI-IV has resulted in the arrests of nearly 3,500 individuals and seizures worth $300 million across 34 countries.
Cloudflare Breach: Nation-State Hackers Access Source Code and Internal Docs
3.2.24
Incindent
The Hacker News
Cloudflare has revealed that it was the target of a
likely nation-state attack in which the threat actor leveraged stolen
credentials to gain unauthorized access to its Atlassian server and ultimately
access some documentation and a limited amount of source code.
The intrusion, which took place between November 14 and 24, 2023, and detected on November 23, was carried out "with the goal of obtaining persistent and widespread access to Cloudflare's global network," the web infrastructure company said, describing the actor as "sophisticated" and one who "operated in a thoughtful and methodical manner."
As a precautionary measure, the company further said it rotated more than 5,000 production credentials, physically segmented test and staging systems, carried out forensic triages on 4,893 systems, reimaged and rebooted every machine across its global network.
The incident involved a four-day reconnaissance period to access Atlassian Confluence and Jira portals, following which the adversary created a rogue Atlassian user account and established persistent access to its Atlassian server to ultimately obtain access to the Bitbucket source code management system by means of the Sliver adversary simulation framework.
As many as 120 code repositories were viewed, out of which 76 are estimated to have been exfiltrated by the attacker.
"The 76 source code repositories were almost all related to how backups work, how the global network is configured and managed, how identity works at Cloudflare, remote access, and our use of Terraform and Kubernetes," Cloudflare said.
"A small number of the repositories contained encrypted secrets which were rotated immediately even though they were strongly encrypted themselves."
The threat actor is then said to have unsuccessfully attempted to "access a console server that had access to the data center that Cloudflare had not yet put into production in São Paulo, Brazil."
The attack was made possible by using one access token and three service account credentials associated with Amazon Web Services (AWS), Atlassian Bitbucket, Moveworks, and Smartsheet that were stolen following the October 2023 hack of Okta's support case management system.
Cloudflare acknowledged that it had failed to rotate these credentials, mistakenly assuming they were unused.
The company also said it took steps to terminate all malicious connections originating from the threat actor on November 24, 2023. It also involved cybersecurity firm CrowdStrike to perform an independent assessment of the incident.
"The only production systems the threat actor could access using the stolen credentials was our Atlassian environment. Analyzing the wiki pages they accessed, bug database issues, and source code repositories, it appears they were looking for information about the architecture, security, and management of our global network," Cloudflare said.
FritzFrog Returns with Log4Shell and PwnKit, Spreading Malware Inside Your
Network
2.2.24
BotNet
The Hacker News
The threat actor behind a peer-to-peer (P2P) botnet known
as FritzFrog has made a return with a new variant that leverages the Log4Shell
vulnerability to propagate internally within an already compromised network.
"The vulnerability is exploited in a brute-force manner that attempts to target as many vulnerable Java applications as possible," web infrastructure and security company Akamai said in a report shared with The Hacker News.
FritzFrog, first documented by Guardicore (now part of Akamai) in August 2020, is a Golang-based malware that primarily targets internet-facing servers with weak SSH credentials. It's known to be active since January 2020.
It has since evolved to strike healthcare, education, and government sectors as well as improved its capabilities to ultimately deploy cryptocurrency miners on infected hosts.
What's novel about the latest version is the use of the Log4Shell vulnerability as a secondary infection vector to specifically single out internal hosts rather than targeting vulnerable publicly-accessible assets.
"When the vulnerability was first discovered, internet-facing applications were prioritized for patching because of their significant risk of compromise," security researcher Ori David said.
"Contrastly, internal machines, which were less likely to be exploited, were often neglected and remained unpatched — a circumstance that FritzFrog takes advantage of."
This means that even if the internet-facing applications have been patched, a
breach of any other endpoint can expose unpatched internal systems to
exploitation and propagate the malware.
The SSH brute-force component of FritzFrog has also received a facelift of its own to identify specific SSH targets by enumerating several system logs on each of its victims.
Another notable change in the malware is use of the PwnKit flaw tracked as CVE-2021-4034 to achieve local privilege escalation.
"FritzFrog continues to employ tactics to remain hidden and avoid detection," David said. "In particular, it takes special care to avoid dropping files to disk when possible."
This is accomplished by means of the shared memory location /dev/shm, which has also been put to use by other Linux-based malware such as BPFDoor and Commando Cat, and memfd_create to execute memory-resident payloads.
The disclosure comes as Akamai revealed that the InfectedSlurs botnet is actively exploiting now-patched security flaws (from CVE-2024-22768 through CVE-2024-22772, and CVE-2024-23842) impacting multiple DVR device models from Hitron Systems to launch distributed denial-of-service (DDoS) attacks.
Exposed Docker APIs Under Attack in 'Commando Cat' Cryptojacking Campaign
2.2.24
Cryptocurrency
The Hacker News
Exposed Docker API endpoints over the internet are under
assault from a sophisticated cryptojacking campaign called Commando Cat.
"The campaign deploys a benign container generated using the Commando project," Cado security researchers Nate Bill and Matt Muir said in a new report published today. "The attacker escapes this container and runs multiple payloads on the Docker host."
The campaign is believed to have been active since the start of 2024, making it the second such campaign to be discovered in as many months. In mid-January, the cloud security firm also shed light on another activity cluster that targets vulnerable Docker hosts to deploy XMRig cryptocurrency miner as well as the 9Hits Viewer software.
Commando Cat employs Docker as an initial access vector to deliver a collection of interdependent payloads from an actor-controlled server that is responsible for registering persistence, backdooring the host, exfiltrating cloud service provider (CSP) credentials, and launching the miner.
The foothold obtained by breaching susceptible Docker instances is subsequently abused to deploy a harmless container using the Commando open-source tool and execute a malicious command that allows it to escape the confines of the container via the chroot command.
It also runs a series of checks to determine if services named "sys-kernel-debugger," "gsc," "c3pool_miner," and "dockercache" are active on the compromised system, and proceeds to the next stage only if this step passes.
"The purpose of the check for sys-kernel-debugger is unclear – this service is not used anywhere in the malware, nor is it part of Linux," the researchers said. "It is possible that the service is part of another campaign that the attacker does not want to compete with."
The succeeding phase entails dropping additional payloads from the command-and-control (C2) server, including a shell script backdoor (user.sh) that's capable of adding an SSH key to the ~/.ssh/authorized_keys file and creating a rogue user named "games" with an attacker-known password and including it in the /etc/sudoers file.

Also delivered in a similar manner are three more shell scripts – tshd.sh,
gsc.sh, aws.sh – which are designed to drop Tiny SHell and an improvised version
of netcat called gs-netcat, and exfiltrate credentials
The threat actors "run a command on the cmd.cat/chattr container that retrieves the payload from their own C2 infrastructure," Muir told The Hacker News, noting this is achieved by using curl or wget and piping the resulting payload directly into the bash command shell.
"Instead of using /tmp, [gsc.sh] also uses /dev/shm instead, which acts as a temporary file store but memory backed instead," the researchers said. "It is possible that this is an evasion mechanism, as it is much more common for malware to use /tmp."
"This also results in the artifacts not touching the disk, making forensics somewhat harder. This technique has been used before in BPFdoor – a high profile Linux campaign."
The attack culminates in the deployment of another payload that's delivered directly as a Base64-encoded script as opposed to being retrieved from the C2 server, which, in turn, drops the XMRig cryptocurrency miner but not before eliminating competing miner processes from the infected machine.
The exact origins of the threat actor behind Commando Cat are currently unclear, although the shell scripts and the C2 IP address have been observed to overlap with those linked to cryptojacking groups like TeamTNT in the past, raising the possibility that it may be a copycat group.
"The malware functions as a credential stealer, highly stealthy backdoor, and cryptocurrency miner all in one," the researchers said. "This makes it versatile and able to extract as much value from infected machines as possible."
U.S. Feds Shut Down China-Linked "KV-Botnet" Targeting SOHO Routers
2.2.24
BotNet
The Hacker News
The U.S. government on Wednesday said it took steps to
neutralize a botnet comprising hundreds of U.S.-based small office and home
office (SOHO) routers hijacked by a China-linked state-sponsored threat actor
called Volt Typhoon and blunt the impact posed by the hacking campaign.
The existence of the botnet, dubbed KV-botnet, was first disclosed by the Black Lotus Labs team at Lumen Technologies in mid-December 2023. The law enforcement effort was reported by Reuters earlier this week.
"The vast majority of routers that comprised the KV-botnet were Cisco and NetGear routers that were vulnerable because they had reached 'end of life' status; that is, they were no longer supported through their manufacturer's security patches or other software updates," the Department of Justice (DoJ) said in a press statement.
Volt Typhoon (aka DEV-0391, Bronze Silhouette, Insidious Taurus, or Vanguard Panda) is the moniker assigned to a China-based adversarial collective that has been attributed to cyber attacks targeting critical infrastructure sectors in the U.S. and Guam.
"Chinese cyber actors, including a group known as 'Volt Typhoon,' are burrowing deep into our critical infrastructure to be ready to launch destructive cyber attacks in the event of a major crisis or conflict with the United States," CISA Director Jen Easterly noted.
The cyber espionage group, believed to be active since 2021, is known for its reliance on legitimate tools and living-off-the-land (LotL) techniques to fly under the radar and persist within victim environments for extended periods of time to gather sensitive information.
Another important aspect of its modus operandi is that it tries to blend into normal network activity by routing traffic through compromised SOHO network equipment, including routers, firewalls, and VPN hardware, in an attempt to obfuscate their origins.
This is accomplished by means of the KV-botnet, which commandeers devices from Cisco, DrayTek, Fortinet, and NETGEAR for use as a covert data transfer network for advanced persistent threat actors. It's suspected that the botnet operators offer their services to other hacking outfits, including Volt Typhoon.
In January 2024, a report from cybersecurity firm SecurityScorecard revealed how the botnet has been responsible for compromising as much as 30% — or 325 of 1,116 — of end-of-life Cisco RV320/325 routers over a 37-day period from December 1, 2023, to January 7, 2024.
"Volt Typhoon is at least one user of the KV-botnet and [...] this botnet encompasses a subset of their operational infrastructure," Lumen Black Lotus Labs said, adding the botnet "has been active since at least February 2022."
The botnet is also designed to download a virtual private network (VPN) module to the vulnerable routers and set up a direct encrypted communication channel to control the botnet and use it as an intermediary relay node to achieve their operational goals.
"One function of the KV-botnet is to transmit encrypted traffic between the infected SOHO routers, allowing the hackers to anonymize their activities (i.e., the hackers appear to be operating from the SOHO routers, versus their actual computers in China)," according to affidavits filed by the U.S. Federal Bureau of Investigation (FBI).
As part of its efforts to disrupt the botnet, the agency said it remotely issued commands to target routers in the U.S. using the malware's communication protocols to delete the KV-botnet payload and prevent them from being re-infected. The FBI said it also notified every victim about the operation, either directly or via their internet service provider if contact information was not available.
"The court-authorized operation deleted the KV-botnet malware from the routers and took additional steps to sever their connection to the botnet, such as blocking communications with other devices used to control the botnet," the DoJ added.
It's important to point out here that the unspecified prevention measures employed to remove the routers from the botnet are temporary and cannot survive a reboot. In other words, simply restarting the devices would render them susceptible to re-infection.
"The Volt Typhoon malware enabled China to hide, among other things, pre-operational reconnaissance and network exploitation against critical infrastructure like our communications, energy, transportation, and water sectors – steps China was taking, in other words, to find and prepare to destroy or degrade the civilian critical infrastructure that keeps us safe and prosperous," FBI Director Christopher Wray said.
However, the Chinese government, in a statement shared with Reuters, denied any involvement in the attacks, dismissing it as a "disinformation campaign" and that it "has been categorical in opposing hacking attacks and the abuse of information technology."
Coinciding with the takedown, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) published new guidance urging SOHO device manufacturers to embrace a secure by design approach during development and shift the burden away from customers.
Specifically, it's recommending that manufacturers eliminate exploitable defects in SOHO router web management interfaces and modify default device configurations to support automatic update capabilities and require a manual override to remove security settings.
The compromise of edge devices such as routers for use in advanced persistent attacks mounted by Russia and China highlights a growing problem that's compounded by the fact that legacy devices no longer receive security patches and do not support endpoint detection and response (EDR) solutions.
"The creation of products that lack appropriate security controls is unacceptable given the current threat environment," CISA said. "This case exemplifies how a lack of secure by design practices can lead to real-world harm both to customers and, in this case, our nation's critical infrastructure."
HeadCrab 2.0 Goes Fileless, Targeting Redis Servers for Crypto Mining
2.2.24
Virus
The Hacker News
Cybersecurity researchers have detailed an updated
version of the malware HeadCrab that's known to target Redis database servers
across the world since early September 2021.
The development, which comes exactly a year after the malware was first publicly disclosed by Aqua, is a sign that the financially-motivated threat actor behind the campaign is actively adapting and refining their tactics and techniques to stay ahead of the detection curve.
The cloud security firm said that "the campaign has almost doubled the number of infected Redis servers," with an additional 1,100 compromised servers, up from 1,200 reported at the start of 2023.
HeadCrab is designed to infiltrate internet-exposed Redis servers and wrangle them into a botnet for illicitly mining cryptocurrency, while also leveraging the access in a manner that allows the threat actor to execute shell commands, load fileless kernel modules, and exfiltrate data to a remote server.
While the origins of the threat actor are presently not known, they make it a point to note in a "mini blog" embedded into the malware that the mining activity is "legal in my country" and that they do it because "it almost doesn't harm human life and feelings (if done right)."
The operator, however, acknowledges that it's a "parasitic and inefficient way" of making money, adding their aim is to make $15,000 per year.
"An integral aspect of the sophistication of HeadCrab 2.0 lies in its advanced evasion techniques," Aqua researchers Asaf Eitani and Nitzan Yaakov said. "In contrast to its predecessor (named HeadCrab 1.0), this new version employs a fileless loader mechanism, demonstrating the attacker's commitment to stealth and persistence."
It's worth noting that the previous iteration utilized the SLAVEOF command to
download and save the HeadCrab malware file to disk, thereby leaving artifact
traces on the file system.
HeadCrab 2.0, on the other hand, receives the malware's content over the Redis communication channel and stores it in a fileless location in a bid to minimize the forensic trail and make it much more challenging to detect.
Also changed in the new variant is the use of the Redis MGET command for command-and-control (C2) communications for added covertness.
"By hooking into this standard command, the malware gains the ability to control it during specific attacker-initiated requests," the researchers said.
"Those requests are achieved by sending a special string as an argument to the MGET command. When this specific string is detected, the malware recognizes the command as originating from the attacker, triggering the malicious C2 communication."
Describing HeadCrab 2.0 as an escalation in the sophistication of Redis malware, Aqua said its ability to masquerade its malicious activities under the guise of legitimate commands poses new problems for detection.
"This evolution underscores the necessity for continuous research and development in security tools and practices," the researchers concluded. "The engagement by the attacker and the subsequent evolution of the malware highlights the critical need for vigilant monitoring and intelligence gathering."
Warning: New Malware Emerges in Attacks Exploiting Ivanti VPN Vulnerabilities
2.2.24
Exploit
The Hacker News
Google-owned Mandiant said it identified new malware
employed by a China-nexus espionage threat actor known as UNC5221 and other
threat groups during post-exploitation activity targeting Ivanti Connect Secure
VPN and Policy Secure devices.
This includes custom web shells such as BUSHWALK, CHAINLINE, FRAMESTING, and a variant of LIGHTWIRE.
"CHAINLINE is a Python web shell backdoor that is embedded in a Ivanti Connect Secure Python package that enables arbitrary command execution," the company said, attributing it to UNC5221, adding it also detected multiple new versions of WARPWIRE, a JavaScript-based credential stealer.
The infection chains entail a successful exploitation of CVE-2023-46805 and CVE-2024-21887, which allow an unauthenticated threat actor to execute arbitrary commands on the Ivanti appliance with elevated privileges.
The flaws have been abused as zero-days since early December 2023. Germany's Federal Office for Information Security (BSI) said it's aware of "multiple compromised systems" in the country.
BUSHWALK, written in Perl and deployed by circumventing the Ivanti-issued mitigations in highly-targeted attacks, is embedded into a legitimate Connect Secure file named "querymanifest.cgi" and offers the ability to read or write to files to a server.
On the other hand, FRAMESTING is a Python web shell embedded in an Ivanti Connect Secure Python package (located in the following path "/home/venv3/lib/python3.6/site-packages/cav-0.1-py3.6.egg/cav/api/resources/category.py") that enables arbitrary command execution.
Mandiant's analysis of the ZIPLINE passive backdoor has also uncovered its use of "extensive functionality to ensure the authentication of its custom protocol used to establish command-and-control (C2)."
Furthermore, the attacks are characterized by the use of open-source utilities like Impacket, CrackMapExec, iodine, and Enum4linux to support post-exploitation activity on Ivanti CS appliances, including network reconnaissance, lateral movement, and data exfiltration within victim environments.
Ivanti has since disclosed two more security flaws, CVE-2024-21888 and CVE-2024-21893, the latter of which has come under active exploitation targeting a "limited number of customers." The company has also released the first round of fixes to address the four vulnerabilities.
UNC5221 is said to target a wide range of industries that are of strategic interest to China, with its infrastructure and tooling overlapping with past intrusions linked to China-based espionage actors.
"Linux-based tools identified in incident response investigations use code from multiple Chinese-language Github repositories," Mandiant said. "UNC5221 has largely leveraged TTPs associated with zero-day exploitation of edge infrastructure by suspected PRC nexus actors."
CISA Warns of Active Exploitation of Flaw in Apple iOS and macOS
2.2.24
BigBrothers
The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency
(CISA) on Wednesday added a high-severity flaw impacting iOS, iPadOS, macOS,
tvOS, and watchOS to its Known Exploited Vulnerabilities (KEV) catalog, based on
evidence of active exploitation.
The vulnerability, tracked as CVE-2022-48618 (CVSS score: 7.8), concerns a bug in the kernel component.
"An attacker with arbitrary read and write capability may be able to bypass Pointer Authentication," Apple said in an advisory, adding the issue "may have been exploited against versions of iOS released before iOS 15.7.1."
The iPhone maker said the problem was addressed with improved checks. It's currently not known how the vulnerability is being weaponized in real-world attacks.
Interestingly, patches for the flaw were released on December 13, 2022, with the release of iOS 16.2, iPadOS 16.2, macOS Ventura 13.1, tvOS 16.2, and watchOS 9.2, although it was only publicly disclosed more than a year later on January 9, 2024.
It's worth noting that Apple did resolve a similar flaw in the kernel (CVE-2022-32844, CVSS score: 6.3) in iOS 15.6 and iPadOS 15.6, which was shipped on July 20, 2022.
"An app with arbitrary kernel read and write capability may be able to bypass Pointer Authentication," the company said at the time. "A logic issue was addressed with improved state management."
In light of the active exploitation of CVE-2022-48618, CISA is recommending that Federal Civilian Executive Branch (FCEB) agencies apply the fixes by February 21, 2024.
The development also comes as Apple expanded patches for an actively exploited security flaw in the WebKit browser engine (CVE-2024-23222, CVSS score: 8.8) to include its Apple Vision Pro headset. The fix is available in visionOS 1.0.2.
RunC Flaws Enable Container Escapes, Granting Attackers Host Access
1.2.24
Exploit
The Hacker News
Multiple security vulnerabilities have been disclosed in the runC command line tool that could be exploited by threat actors to escape the bounds of the container and stage follow-on attacks.
The vulnerabilities, tracked as CVE-2024-21626, CVE-2024-23651, CVE-2024-23652, and CVE-2024-23653, have been collectively dubbed Leaky Vessels by cybersecurity vendor Snyk.
"These container escapes could allow an attacker to gain unauthorized access to the underlying host operating system from within the container and potentially permit access to sensitive data (credentials, customer info, etc.), and launch further attacks, especially when the access gained includes superuser privileges," the company said in a report shared with The Hacker News.
runC is a tool for spawning and running containers on Linux. It was originally developed as part of Docker and later spun out into a separate open-source library in 2015.
A brief description of each of the flaws is below -
CVE-2024-21626 - WORKDIR: Order of operations container breakout
CVE-2024-23651 - Mount Cache Race
CVE-2024-23652 - Buildkit Build-time
Container Teardown Arbitrary Delete
CVE-2024-23653 - Buildkit GRPC
SecurityMode Privilege Check
The most severe of the flaws is CVE-2024-21626,
which could result in a container escape centered around the `WORKDIR` command.
"This could occur by running a malicious image or by building a container image using a malicious Dockerfile or upstream image (i.e. when using `FROM`)," Snyk said.
There is no evidence that any of the newly discovered shortcomings have been exploited in the wild to date. That said, the issues have been addressed in runC version 1.1.12 released today.
"Because these vulnerabilities affect widely used low-level container engine components and container build tools, Snyk strongly recommends that users check for updates from any vendors providing their container runtime environments, including Docker, Kubernetes vendors, cloud container services, and open source communities," the company said.
In February 2019, runC maintainers addressed another high-severity flaw (CVE-2019-5736, CVSS score: 8.6) that could be abused by an attacker to break out of the container and obtain root access on the host.
Alert: Ivanti Discloses 2 New Zero-Day Flaws, One Under Active Exploitation
1.2.24
Exploit
The Hacker News
Ivanti is alerting of two new high-severity flaws in its
Connect Secure and Policy Secure products, one of which is said to have come
under targeted exploitation in the wild.
The list of vulnerabilities is as follows -
CVE-2024-21888 (CVSS score: 8.8) - A privilege escalation vulnerability in the
web component of Ivanti Connect Secure (9.x, 22.x) and Ivanti Policy Secure
(9.x, 22.x) allows a user to elevate privileges to that of an administrator
CVE-2024-21893 (CVSS score: 8.2) - A server-side request forgery vulnerability
in the SAML component of Ivanti Connect Secure (9.x, 22.x), Ivanti Policy Secure
(9.x, 22.x) and Ivanti Neurons for ZTA allows an attacker to access certain
restricted resources without authentication
The Utah-based software company
said it found no evidence of customers being impacted by CVE-2024-21888 so far,
but acknowledged "the exploitation of CVE-2024-21893 appears to be targeted."
It further noted that it "expects the threat actor to change their behavior and we expect a sharp increase in exploitation once this information is public."
In tandem to the public disclosure of the two new vulnerabilities, Ivanti has released fixes for Connect Secure versions 9.1R14.4, 9.1R17.2, 9.1R18.3, 22.4R2.2 and 22.5R1.1, and ZTA version 22.6R1.3.
"Out of an abundance of caution, we are recommending as a best practice that customers factory reset their appliance before applying the patch to prevent the threat actor from gaining upgrade persistence in your environment," it said. "Customers should expect this process to take 3-4 hours."
As temporary workarounds to address CVE-2024-21888 and CVE-2024-21893, users are recommended to import the "mitigation.release.20240126.5.xml" file.
The latest development comes as two other flaws in the same product – CVE-2023-46805 and CVE-2024-21887 – have come under broad exploitation by multiple threat actors to deploy backdoors, cryptocurrency miners, and a Rust-based loader called KrustyLoader.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA), in a fresh advisory published today, said adversaries are leveraging the two shortcomings to capture credentials and drop web shells that enable further compromise of enterprise networks.
"Some threat actors have recently developed workarounds to current mitigations and detection methods and have been able to exploit weaknesses, move laterally, and escalate privileges without detection," the agency said.
"Sophisticated threat actors have subverted the external integrity checker tool (ICT), further minimizing traces of their intrusion."
Telegram Marketplaces Fuel Phishing Attacks with Easy-to-Use Kits and Malware
1.2.24
Phishing
The Hacker News
Cybersecurity researchers are calling attention to the "democratization" of the
phishing ecosystem owing to the emergence of Telegram as an epicenter for
cybercrime, enabling threat actors to mount a mass attack for as little as $230.
"This messaging app has transformed into a bustling hub where seasoned cybercriminals and newcomers alike exchange illicit tools and insights creating a dark and well-oiled supply chain of tools and victims' data," Guardio Labs researchers Oleg Zaytsev and Nati Tal said in a new report.
"Free samples, tutorials, kits, even hackers-for-hire -- everything needed to construct a complete end-to-end malicious campaign."
This is not the first time the popular messaging platform has come under the radar for facilitating malicious activities, which are in part driven by its lenient moderation efforts.
As a result, what used to be available only on invite-only forums in the dark web is now readily accessible via public channels and groups, thereby opening the doors of cybercrime to aspiring and inexperienced cyber criminals.
In April 2023, Kaspersky revealed how phishers create Telegram channels to educate newbies about phishing as well as advertise bots that can automate the process of creating phishing pages for harvesting sensitive information such as login credentials.
One such malicious Telegram bot is Telekopye (aka Classiscam), which can craft fraudulent web pages, emails, SMS messages to help threat actors pull off large-scale phishing scams.
Guardio said the building blocks to construct a phishing campaign can be readily purchased off Telegram – "some offered at very low prices, and some even for free" – thereby making it possible to set up scam pages via a phishing kit, host the page on a compromised WordPress website via a web shell, and leverage a backdoor mailer to send the email messages.
Backdoor mailers, marketed on various Telegram groups, are PHP scripts injected into already infected-but-legitimate websites to send convincing emails using the legitimate domain of the exploited website to bypass spam filters.
"This situation highlights a dual responsibility for site owners," the researchers said. "They must safeguard not only their business interests but also protect against their platforms being used by scammers for hosting phishing operations, sending deceptive emails, and conducting other illicit activities, all unbeknownst to them."
To further increase the likelihood of success of such campaigns, digital
marketplaces on Telegram also provide what's known as "letters," which are
"expertly designed, branded templates" that make the email messages appear as
authentic as possible to trick the victims into clicking on the bogus link
pointing to the scam page.
Telegram is also host to bulk datasets containing valid and relevant email addresses and phone numbers to target. Referred to as "leads," they are sometimes "enriched" with personal information such as names and physical addresses to maximize the impact.
"These leads can be incredibly specific, tailored for any region, niche, demographic, specific company customers, and more," the researchers said. "Every piece of personal information adds to the effectiveness and credibility of these attacks."
The way these lead lists are prepared can vary from seller to seller. They can be procured either from cybercrime forums that sell data stolen from breached companies or through sketchy websites that urge visitors to complete a fake survey in order to win prizes.
Another crucial component of these phishing campaigns is a means to monetize the collected stolen credentials by selling them to other criminal groups in the form of "logs," netting the threat actors a 10-fold return on their investment based on the number of victims who end up providing valid details on the scam page.
"Social media account credentials are sold for as little as a dollar, while banking accounts and credit cards could be sold for hundreds of dollars — depending on their validity and funds," the researchers said.
"Unfortunately, with just a small investment, anyone can start a significant phishing operation, regardless of prior knowledge or connections in the criminal underworld."
Italian Businesses Hit by Weaponized USBs Spreading Cryptojacking Malware
1.2.24
Cryptocurrency
The Hacker News
A financially motivated threat actor known as UNC4990 is
leveraging weaponized USB devices as an initial infection vector to target
organizations in Italy.
Google-owned Mandiant said the attacks single out multiple industries, including health, transportation, construction, and logistics.
"UNC4990 operations generally involve widespread USB infection followed by the deployment of the EMPTYSPACE downloader," the company said in a Tuesday report.
"During these operations, the cluster relies on third-party websites such as GitHub, Vimeo, and Ars Technica to host encoded additional stages, which it downloads and decodes via PowerShell early in the execution chain."
UNC4990, active since late 2020, is assessed to be operating out of Italy based on the extensive use of Italian infrastructure for command-and-control (C2) purposes.
It's currently not known if UNC4990 functions only as an initial access facilitator for other actors. The end goal of the threat actor is also not clear, although in one instance an open-source cryptocurrency miner is said to have been deployed after months of beaconing activity.
Details of the campaign were previously documented by Fortgale and Yoroi in early December 2023, with the former tracking the adversary under the name Nebula Broker.
The infection begins when a victim double-clicks on a malicious LNK shortcut file on a removable USB device, leading to the execution of a PowerShell script that's responsible for downloading EMPTYSPACE (aka BrokerLoader or Vetta Loader) from a remote server via another intermedia PowerShell script hosted on Vimeo.

Yoroi said it identified four different variants of EMPTYSPACE written in
Golang, .NET, Node.js, and Python, which subsequently acts as a conduit for
fetching next-stage payloads over HTTP from the C2 server, including a backdoor
dubbed QUIETBOARD.
A notable aspect of this phase is the use of popular sites like Ars Technica, GitHub, GitLab, and Vimeo for hosting the malicious payload.
"The content hosted on these services posed no direct risk for the everyday users of these services, as the content hosted in isolation was completely benign," Mandiant researchers said. "Anyone who may have inadvertently clicked or viewed this content in the past was not at risk of being compromised."
QUIETBOARD, on the other hand, is a Python-based backdoor with a wide range of features that allow it to execute arbitrary commands, alter crypto wallet addresses copied to clipboard to redirect fund transfers to wallets under their control, propagate the malware to removable drives, take screenshots, and gather system information.
Additionally, the backdoor is capable of modular expansion and running independent Python modules like coin miners as well as dynamically fetching and executing Python code from the C2 server.
"The analysis of both EMPTYSPACE and QUIETBOARD suggests how the threat actors took a modular approach in developing their toolset," Mandiant said.
"The use of multiple programming languages to create different versions of the EMPTYSPACE downloader and the URL change when the Vimeo video was taken down show a predisposition for experimentation and adaptability on the threat actors' side."
Hackers Exploiting Ivanti VPN Flaws to Deploy KrustyLoader Malware
1.2.24
Virus
The Hacker News
A pair of recently disclosed zero-day flaws in Ivanti
Connect Secure (ICS) virtual private network (VPN) devices have been exploited
to deliver a Rust-based payload called KrustyLoader that's used to drop the
open-source Sliver adversary simulation tool.
The security vulnerabilities, tracked as CVE-2023-46805 (CVSS score: 8.2) and CVE-2024-21887 (CVSS score: 9.1), could be abused in tandem to achieve unauthenticated remote code execution on susceptible appliances.
As of January 26, patches for the two flaws have been delayed, although the software company has released a temporary mitigation through an XML file.
Volexity, which first shed light on the shortcomings, said they have been weaponized as zero-days since December 3, 2023, by a Chinese nation-state threat actor it tracks under the name UTA0178. Google-owned Mandiant has assigned the moniker UNC5221 to the group.
Following public disclosure earlier this month, the vulnerabilities have come under broad exploitation by other adversaries to drop XMRig cryptocurrency miners as well as Rust-based malware.
Synacktiv's analysis of the Rust malware, codenamed KrustyLoader, has revealed that it functions as a loader to download Sliver from a remote server and execute it on the compromised host.

Image Credit: Recorded Future
Sliver, developed by cybersecurity company
BishopFox, is a Golang-based cross-platform post-exploitation framework that has
emerged as a lucrative option for threat actors in comparison to other
well-known alternatives like Cobalt Strike.
That said, Cobalt Strike continues to be the top offensive security tool observed among attacker-controlled infrastructure in 2023, followed by Viper, and Meterpreter, according to a report published by Recorded Future earlier this month.
"Both Havoc and Mythic have also become relatively popular but are still observed in far lower numbers than Cobalt Strike, Meterpreter, or Viper," the company said. "Four other well-known frameworks are Sliver, Havoc, Brute Ratel (BRc4), and Mythic."
New Glibc Flaw Grants Attackers Root Access on Major Linux Distros
1.2.24
Vulnerebility
The Hacker News
Malicious local attackers can obtain full root access on
Linux machines by taking advantage of a newly disclosed security flaw in the GNU
C library (aka glibc).
Tracked as CVE-2023-6246, the heap-based buffer overflow vulnerability is rooted in glibc's __vsyslog_internal() function, which is used by syslog() and vsyslog() for system logging purposes. It's said to have been accidentally introduced in August 2022 with the release of glibc 2.37.
"This flaw allows local privilege escalation, enabling an unprivileged user to gain full root access," Saeed Abbasi, product manager of the Threat Research Unit at Qualys, said, adding it impacts major Linux distributions like Debian, Ubuntu, and Fedora.
A threat actor could exploit the flaw to obtain elevated permissions via specially crafted inputs to applications that employ these logging functions.
"Although the vulnerability requires specific conditions to be exploited (such as an unusually long argv[0] or openlog() ident argument), its impact is significant due to the widespread use of the affected library," Abbasi noted.
The cybersecurity firm said further analysis of glibc unearthed two more flaws in the __vsyslog_internal() function (CVE-2023-6779 and CVE-2023-6780) and a third bug in the library's qsort() function that can lead to memory corruption.
The vulnerability found in qsort() has affected all glibc versions released since 1992.
The development comes nearly four months after Qualys detailed another high-severity flaw in the same library called Looney Tunables (CVE-2023-4911, CVSS score: 7.8) that could result in privilege escalation.
"These flaws highlight the critical need for strict security measures in software development, especially for core libraries widely used across many systems and applications," Abbasi said.