
Articles 2018 February - English Press English Articles Page 1 2 3 4 5 6 2020 2019 2018 2017 2016 2015 2014 2013 2012
H Analysis Android Apple APT Attack BigBrothers BotNet Congress Crime Crypto Cryptocurrency Cyber CyberCrime CyberSpy CyberWar Exploit Forensics Hacking ICS Incindent iOS IT IoT Mobil OS Phishing Privacy Ransomware Safety Security Social Spam Virus Vulnerebility
Jednotlivé články jsou rozděleny podle měsíců a zde je najdete./The articles are broken down by month and can be found here.
2018 - January February March April May June July August September October November December
Speciální antivirus pro chytré televize představil Eset
28.2.2018 SecurityWorld Zabezpečení
Smart TV Security, bezpečnostní aplikaci pro chytré televizory s Androidem, oznámil Eset. Novinka podle výrobce ochrání diváky před narůstajícími útoky pomocí malwaru včetně obrany před ransomwarem.
Prostřednictvím napadnutého chytrého televizoru mohou kyberzločinci proniknout i do jiných zařízení připojených do stejné domácí sítě, ale také provádět špionáž a shromažďovat citlivé osobní údaje. I kvůli tomu navrhnul Eset vlastní aplikaci na ochranu chytrých televizorů s operačním systémem Android TV.
„Vzhledem k rizikům, jež představují ohrožení bezpečnosti a soukromí, musí uživatelé řešit ochranu chytrých zařízení v domácnosti stejným způsobem, jako chrání své notebooky, tablety nebo mobilní telefony – nemohou k nim přistupovat jako k obyčejným televizím, varným konvicím nebo hodinkám,“ tvrdí Branislav Orlík, Mobile Security Product Manager společnosti Eset.
Chytré televizory s operačním systémem Android TV se podle něj stávají terčem nechvalně proslulého vyděračského ransomwaru určeného pro zařízení s Androidem, který se již řadu let zaměřuje na tablety a chytré mobilní telefony.
Hrozba se nyní rozšířila i na televizory s tímto operačním systémem, což vedlo k případům zašifrovaných obrazovek a požadavkům na výkupné za jejich odšifrování.
Aplikace Smart TV Security využívá při ochraně diváků různé bezpečnostní funkce, mezi něž patří:
Antivirová ochrana, jež brání v průniku rostoucímu počtu škodlivého softwaru určenému pro zařízení s Androidem.
Nástroj Anti-ransomware, který chrání před zašifrováním obrazovky. Pokud již do televizoru proniknul ransomware a zašifroval data, doporučuje se divákům vypnout a znovu zapnout chytrou televizi, provést aktualizaci virové databáze a spustit skenování malwaru. Pokud Smart TV Security detekuje ransomware, doporučí uživateli odinstalovat malware. Po potvrzení jeho odinstalování bude ransomware vymazán.
Skenování více zařízení na přítomnosti škodlivého softwaru, včetně těch, která se k chytré televizi připojují prostřednictvím USB.
Antiphishing na ochranu uživatelů před pokusy o krádež citlivých osobních dat. Tato funkce bude k dispozici pouze v prémiové verzi aplikace Smart TV Security.
Bezpečnostní aplikaci lze do televizoru stáhnout prostřednictvím obchodu Google Play.
Německá ministerstva obrany a zahraničí napadli ruští hackeři
28.2.2018 Novinky/Bezpečnost BigBrother
Německé bezpečnostní zdroje přiznaly, že se ruským hackerům podařilo v prosinci nepozorovaně nabourat počítačové sítě ministerstev obrany a zahraničí. Zdroje podle stanice Deutsche Welle uvedly, že škodlivý malware byl do sítí nainstalován o rok dříve.
Německá vláda přiznala, že se útok povedl ruské skupině APT28 známé taky jako Fancy Bear, která je spojována s ruským vojenským zpravodajstvím. Zdroj agentury DPA uvedl, že se hackerům zřejmě podařilo do klíčové vládní sítě nasadit malware, který tam mohl být rok. Infiltrovaná byla vládní síť Informationsverbund Berlin-Bonn (IVBB), což je speciálně navržená platforma pro komunikaci kancléřství, federálních ministerstev a několika bezpečnostních institucí v Berlíně a v Bonnu. Z bezpečnostních důvodů je oddělená od veřejné sítě.
Německé úřady čelily útokům hackerů i v minulosti, kdy se internetovým útočníkům podařilo proniknout například do sítě parlamentu.
Za útokem na Bundestag z roku 2015 je také skupina APT28. Byl tak rozsáhlý, že po něm musela německá vláda vyměnit celou IT infrastrukturu.
Německá vláda uvádí, že eviduje dvacet hackerských útoků denně.
Hackeři ukradli přes 150 miliónů korun. Policie nakonec dopadla jejich šéfa
28.2.2018 Novinky/Bezpečnost Kriminalita
Ukrajinská policie dopadla vůdce nebezpečné hackerské skupiny, která bankovním systémům po celém světě způsobila škody za stovky miliónů dolarů. Oznámila to agentura Unian. Úřady jméno zadrženého nezveřejnily, podle ukrajinských médií jde o šéfa skupiny Avalanche Gennadije Kapkanova.
družení hackerů Avalanche podle ukrajinských expertů organizuje kybernetické útoky sedm let, na dopadení jeho členů pracuje policie 30 zemí světa. Kapkanova už v listopadu 2016 zadrželi ukrajinští policisté v Poltavě jihovýchodně od Kyjeva, soud ale rozhodl o jeho stíhání na svobodě a hacker krátce nato zmizel.
Podle agentury Unian bude zatčený Kapkanov obviněn z kybernetických útoků, maření soudního rozhodnutí, praní špinavých peněz a finančních podvodů. Hrozí mu trest až patnácti let vězení. Členové skupiny Avalanche čelí trestnímu stíhání i v Německu, kde způsobili škody ve výši nejméně šesti miliónů eur (přes 150 miliónů korun).
Sdružení Avalanche se podle agentury AP specializovalo na metodu takzvaného phishingu, podvodné techniky používané na internetu k získávání citlivých údajů. V minulých letech byly phishingové útoky příčinou 95 procent všech neoprávněných čerpání peněz z účtů bankovních klientů přes kanály elektronického bankovnictví.
Hackeři široce zneužívají šifrované weby, i díky podvrženým certifikátům
28.2.2018 SecurityWorld Kryptografie
Důmyslnost hackerů stoupá nebývalým tempem -- ke svým útokům stále častěji využívají zašifrovanou webovou komunikaci i známé internetové služby jako jsou Dropbox či Google Docs. Více se zaměřují také na zařízení internetu věcí, které organizace často nechávají neaktualizovaná a zranitelná.
Tyto závěry přinesla studie Cisco 2018 Annual Cybersecurity Report. Ta dále říká, že nejčastější překážkou pro vybudování spolehlivé bezpečnostní architektury je nízký rozpočet, nekompatibilita jednotlivých bezpečnostních řešení a nedostatek IT specialistů na trhu.
Proto 74 % bezpečnostních profesionálů v obraně alespoň částečně spoléhá na umělou inteligenci a 83 % na automatizaci. Útoky jsou přitom stále ničivější. A tak zatímco dříve šlo útočníkům využívajícím vyděračský software (ransomware) především o zisk, dnes se stále častěji setkáváme s útoky, které se snaží napáchat maximální škody.
Letošní studie zjistila, že kybernetičtí útočníci stále častěji doručují škodlivý software prostřednictvím šifrované webové komunikace (typicky označované HTTPS). Jedním z klíčových faktorů, které nárůst ovlivňují, je snadné získání levných či dokonce bezplatných SSL certifikátů. Hackeři tak získávají mocný nástroj, jak doručit obětem škodlivý software.
„Šifrovaná komunikace na jedné straně představuje velmi dobrý způsob, jak ochránit soukromí uživatelů, avšak na té druhé otevírá útočníkům další možnosti, jak se vyhnout detekci. Proto podniky v dnešní době stále častěji vyhledávají bezpečnostní řešení, která využívají automatizaci a umělou inteligenci, neboť ta dokážou najít podobnosti mezi známým škodlivým softwarem a anonymním vzorkem dat,“ říká Milan Habrcetl, bezpečnostní expert společnosti Cisco.
Spam: útoky přichází ve vlnách
Nevyžádaná pošta (neboli spam) stále tvoří nejčastější způsob, jakým se útočníci snaží proniknout do zařízení. Z výzkumu škodlivých domén vyplynulo, že 60 % z nich je spojeno právě se spamovými kampaněmi.
Bez ohledu na to, jak se mění prostředí kybernetických hrozeb, zůstává email důležitým a mocným nástrojem útočníků. Počet doručovaných spamů není v průběhu času konstantní, ale přímo souvisí s aktivitou botnetů (internetoví roboti zasílající spamy), především pak botnetu Necurs, který je globálně hlavním šiřitelem infikovaných emailů.
Škodlivé přílohy emailů jsou nejčastěji ve formátu sady Office (.doc, .ppt, xls a další), a to v 37,7 % případů. Následují archivní formáty, tedy přílohy obsahující přípony .zip či .jar (36,8 %) a soubory s příponou .pdf (13,7 %).
Nové techniky hackerů
Kybernetičtí zločinci se, kromě šifrované komunikace, také stále častěji zaměřují na napadení uživatelů skrze známé a legitimní služby jako jsou například Google Docs, GitHub či Dropbox, jejichž prostřednictvím šíří command and control protokoly.
Zneužívání těchto legitimních aplikací souvisí s jejich velkou oblibou a mnoho zaměstnanců je využívá i přesto, že je podniková pravidla nepovolují. Navíc je velmi těžké, někdy až nemožné, takové útoky odhalit, neboť také využívají šifrovanou komunikaci.
Organizace podceňují aktualizace zařízení internetu věcí
Výzkumníci také zkoumali, jak se organizace zaměřují na zabezpečení svých zařízení internetu věcí a zjistili, že velmi podceňují aktualizování jejich softwaru. Test, ve kterém se zaměřili na citlivost na již známé typy malwaru, provedli na 7328 zařízeních internetu věcí, jako jsou požární alarmy, čtečky karet či senzory pro regulaci teploty.
Zkouška ukázala, že celých 83 % zařízení mělo kritickou zranitelnost a aktuální patch mělo nainstalováno pouze 17 % těchto zařízení. Infikovaná zařízení přitom mohou být využita nejen k napadení vlastní organizace, ale také k DDoS útokům.
V roce 2017 totiž kyberzločinci často využívali krátké (trvající v řádu sekund), ale intenzivní útoky a podle průzkumu se s nimi v loňském roce setkalo 42 % všech organizací.
Žák se naboural do systému školy a změnil známky
28.2.2018 Novinky/Bezpečnost Kriminalita
Až roční vězení hrozí mladistvému, který se na Karlovarsku naboural do počítačového systému základní školy a změnil známky. Policisté ho zadrželi a upozornili, že učitelé měli slabá hesla. O případu ve čtvrtek informovala mluvčí policie Kateřina Böhmová.
„Když se pedagogové přihlásili k systému elektronické žákovské knížky, zjistili, že žákům byla změněna klasifikace či přidány různé poznámky,“ uvedla Böhmová.
Případ oznámili a policisté začali pátrat po hackerovi. Našli lokalizační údaje, které ukazovaly na konkrétního člověka. Při domovní prohlídce následně kriminalisté zajistili techniku, která k útoku na školu sloužila. Mladistvému, jehož věk policie nesdělila, nyní hrozí až roční vězení.
„Takový kybernetický útok by se mladému muži nepodařilo uskutečnit, pokud by zaměstnanci základní školy jednali v souladu se zásadami bezpečného užívání počítačového systému,“ shrnula mluvčí policie.
Když šifrování snižuje bezpečnost a banka vyzrazuje číslo karty
28.2.2018 Root.cz Kryptografie
Šifrování je velmi užitečná věc, ale existují okrajové situace, kdy situaci zhoršuje. Příkladem je bankovní výpis, který je šifrovaný, což umožňuje zjistit téměř všechny informace o platební kartě.
Ne vždy je šifrování prospěšné, existuje malé množství případů, kdy je tomu přesně naopak. Takovým je třeba zabezpečení elektronických výpisů z účtu od české pobočky Raiffeisenbank. Začátek příběhu je už poměrně dávný:

🙋♂️
@denikembecka
Vrchol mé lenosti: Přišel mi výpis z banky, chráněný PINem. Než abych ho hledal, radši jsem bruteforcem uhádl heslo a nezvedl zadek z křesla
1:23 PM - Apr 22, 2017
168
55 people are talking about this
Twitter Ads info and privacy
Tento status proslavil Michal Špaček ve úvodu své přednášky o rizicích sdílení kódů, kterým nerozumíme. V tomto případě Tomáš Heřmanský, autor statusu, na snímku obrazovky sice rozmazal výsledné heslo, ale ponechal záhadné hexadecimální mezivýsledky, které, jak se později ukázalo, je možné použít k vypočítání hesla.
Na příběh jsem si vzpomněl v úterý, když mi poprvé přišel podobný výpis od téže banky. Vyzkoušel jsem tedy také nástroj pdfcrack, který čtyřmístné číselné heslo PDF souboru uhodl za desetinu sekundy. Co mě ale zarazilo, byl výběr číslic, které se banka rozhodla použít jako heslo.
E-mailová zpráva s popisem, jak se k heslu dobrat
Tím heslem totiž nejsou poslední čtyři číslice čísla karty, které se na mnoha místech zobrazují otevřeně za účelem určení konkrétní karty, ale naopak čtyři z šesti tajných číslic, které jsou v naprosté většině míst nahrazeny hvězdičkami či jinak. Jejich použití vypadá na první pohled logicky – zabezpečují, aby si výpis přečetl jen oprávněný držitel karty. Vezmeme-li ale v potaz fakt, že takto omezený prostor hesel je možné projít hrubou silou za desetinu sekundy, znamená to, že každý, kdo se takto šifrovanému PDF souboru dostane, okamžitě zjistí čtyři z šesti tajných číslic. Jak špatné to může být?
Co vytěžit z výpisu
Výpis ke kreditní kartě obsahuje všechny běžné náležitosti, mimo jiné:
datum výpisu
jméno držitele karty
jeho adresu
číslo karty bez šesti tajných číslic
přehled transakcí
stav konta bonusů za používání karty
předepsanou minimální splátku
číslo účtu a variabilní symbol, pod kterým lze úvěr splatit
úrokovou sazbu
Vžijeme-li se do role útočníka, který bude chtít nabyté údaje zneužít, musí znát minimálně číslo karty a datum konce platnosti. Většina obchodníků dnes také požaduje bezpečnostní kód z podpisového proužku karty či dodatečné ověření systémem 3-D Secure, ale stále je možné najít takové, kteří jej nepožadují.
Jedním z obchodů, které požadují minimum informací o kartě, je i gigant Amazon.
Začněme datem konce platnosti karty. To na výpisu sice není uvedeno, nicméně máme jako útočník několik možností, jak se k němu dobrat. Tou první může být už samotný způsob, jak jsme se k PDF souborům dostali. Pokud to bylo nabouráním se do něčí e-mailové schránky, pak zřejmě máme i informaci o tom, kdy byl doručen první výpis z účtu. Takový výpis také poznáme tak, že dluh z předchozího období bude nulový a nulový bude i stav bonusů, které se používáním kreditní karty sbírají. K vypočtení data konce platností tak stačí zjistit, na jak dlouho daná banka obvykle vydává platební karty, což je obvykle celistvý počet roků. Tato informace není nijak tajná a její zjištění nestojí velké úsilí.
Ze stovky na deset s Hansem Peterem Luhnem
Z šestnácti číslic čísla karty jich najdeme deset přímo na výpise, další čtyři jsou tvořeny uhodnutým heslem PDF souboru. K odhalení celého čísla karty tedy zbývá uhodnout dvě číslice, což dává prostor jedné stovky různých kombinací. Jako útočník ale máme velké štěstí – čísla karet jsou totiž zabezpečena Luhnovým algoritmem. Ten zajišťuje odolnost proti překlepům při opisování čísla karty přidáním kontrolní číslice tak, aby ciferný součet čísla karty (po určité transformaci sudých číslic zprava) byl beze zbytku dělitelný deseti.
Můžeme tedy jednoduše vytipovat, které dvojice hledaných čísel splňují podmínku Luhnova algoritmu, například tímto jednoduchým programem v Pythonu:
?
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
In [1]: import luhn
In [2]: for n in range(100):
...: ccnum = "531533{:02d}34567890".format(n)
...: if luhn.verify(ccnum):
...: print(ccnum)
...:
5315330134567890
5315331934567890
5315332734567890
5315333534567890
5315334334567890
5315335034567890
5315336834567890
5315337634567890
5315338434567890
5315339234567890
Máme tedy pouhých deset kandidátů na číslo karty, které můžeme postupně nebo lépe současně v různých obchodech vyzkoušet. Nepotřebovali jsme přitom nic jiného, než přístup k e-mailové schránce s výpisy z kreditní karty. Paradoxem je, že kdyby banka výpisy nešifrovala, nemá útočník jak zjistit čtyři tajné číslice a kandidátů by měl sto tisíc.
Zabezpečení čtyřmi číslicemi nedává smysl
Tohle je jeden z mála případů, kdy nějaké šifrování je prokazatelně horší než žádné šifrování. Použití čtyřmístného číselného hesla na místě, kde je možné provádět off-line neomezené množství pokusů o uhodnutí, je absolutní nesmysl, který odradí tak maximálně bankovního úředníka; ale jen takového, který se v práci nenudí natolik, aby všech deset tisíc kombinací vyzkoušel ručně. V kombinaci s použitím přísně tajného čísla v roli hesla pak jde o zbytečné hazardování s bezpečností.
Uvedený útok je naštěstí možné provést jen tam, kde obchodník nepožaduje zadání bezpečnostního kódu karty a/nebo potvrzení v systému 3-D Secure. Tím by mělo být pro případnou oběť snazší domoci se svých peněz zpět, neboť v případě nepoužití těchto doplňkových zabezpečení se zvyšuje obchodníkova odpovědnost za škody způsobené zneužitím platební karty. To ostatně ve své reakci (1, 2) tvrdí i přímo Raiffeisenbank:
Tato forma zabezpečení výpisu slouží především jako základní ochrana proti náhodnému přečtení. Velká většina obchodníků chrání transakce kartou na internetu pomocí CVC2 a 3DS kódu. Ano, existují i obchodníci, kde nakoupíte bez kódu, pokud by zde ke zneužití došlo, tak transakci vyreklamujeme zpět. Pokud hledáte jiný způsob zasílání výpisů, nabízíme možnost jeho stahování v rámci IB, které máte plně zabezpečené. K tomuto způsobu chceme do budoucna směřovat všechny klienty.
I tak je však na místě obezřetnost a rozumně nastavené limity. Stojí také za zvážení, zda nepožádat banku o nezasílání výpisů e-mailem; je možné je stáhnout nešifrované ze zabezpečeného webového bankovnictví.
Post scriptum: výpis obsahuje celé číslo karty
Andrei Badea
@0xabadea
Líný hacker si navíc všimne, že na první stránce výpisu je desetimístní variabilní symbol, který se nápadně shoduje s heslem výpisu (předposlední čtyřčíslí) a s posledním čtyřčíslím (obsaženým ve výpisu), takže ani nemusí nic hádat. https://twitter.com/Oskar456/status/966062292168269824 …
3:44 PM - Feb 21, 2018
20
See Andrei Badea's other Tweets
Twitter Ads info and privacy
Po napsání tohoto textu se ukázalo, že se zabezpečením čísla karty je to ještě horší a velká část předchozího textu přistupuje k problému až zbytečně složitě. V tomto konkrétním případě totiž všech šest tajných číslic z čísla karty je součástí variabilního symbolu, pod kterým je úvěr splácen. Hádat zbylé číslice tedy vlastně vůbec není nutné a vyzrazení čtyř číslic uhodnutím hesla je tedy vlastně jen podružný problém.
Ne, Elon Musk lidem neposílá ethereum. Je to podvod
28.2.2018 Živě.cz Spam
Ne, Elon Musk lidem neposílá ethereum. Je to podvod
Podvodníci si zase našli způsob, jak z důvěřivých lidí vytáhnout peníze. Tentokrát k tomu použili osobu vizionáře Elona Muska, pod jehož jménem založili falešný účet na Twitteru a slíbili, že lidem rozdají ethereum v hodnotě 4 milionů dolarů. Stačí jen, když mu lidé pošlou nějaký malý obnos, aby získal adresu jejich peněženky. Samozřejmě je to nesmysl.
Skutečný Elon Musk ve středu na Twitteru informoval o plánovaném startu satelitů Starlink. Příspěvek byl relativně nadšený. Nějakého podvodníka tak napadlo, že toho využije a založil téměř totožný účet @elonhmusk, ve kterém na příspěvek navázal jednoduchým sdělením - k příležitosti úspěchu rozdá lidem 5000 kusů etherea. Pokud kryptoměnu lidé chtějí získat, mají poslat nějaký malý obnos, aby Musk získal adresu jejich peněženky.
Účet je už z Twitteru odstraněný, zpráva vypadala takto:
To celebrate this, I'm also giving awaу 5,000 ЕTH!
To identify your address, just sеnd 0.5-1.0 ЕTH to the address bеlow and gеt 5-10 ЕTH back to the address you used for the transaсtion. ЕТH Аddress: ...
If you are latе, yоur EТH will bе sent back.
— Еlon Мusk (@elonhmusk)
Zní to jako jasný podvod a podvod to také je. Už samotný princip nedává smysl, adresu peněženky stačí sdělit, není potřeba z ní něco posílat. Nicméně mnoho lidí se nachytalo a podle sledování v blockchainu je možné zjistit, že podvodníkovi už lidé poslali ethereum v hodnotě více než 16 tisíc dolarů.
Účet lze přitom velice jednoduše odhalit. Není verifikovaný a má jinou adresu. Hlavně je třeba říct, že i když je Elon Musk znám jako šílenec, určitě by jen tak lidem neposlal skoro 4,3 miliony dolarů. A určitě by nechtěl, aby mu lidé něco posílali.
Není to letos poprvé, co se něco podobného stalo. Twitter už musel zrušit účty @elonmus_ a @elonnmuusk, které se pokoušely o něco podobného.
Smart Life od Avastu ochrání IoT před malwarem. Pomůže mu A.I.
28.2.2018 Živě.cz IoT
Smart Life od Avastu ochrání IoT před malwarem. Pomůže mu A.I.Smart Life od Avastu ochrání IoT před malwarem. Pomůže mu A.I.Smart Life od Avastu ochrání IoT před malwarem. Pomůže mu A.I.Smart Life od Avastu ochrání IoT před malwarem. Pomůže mu A.I.Smart Life od Avastu ochrání IoT před malwarem. Pomůže mu A.I.
Avast zprvu před malwarem chránil počítače, pak přibral chytré telefony a nyní se pokusí dohlédnout i na malou firemní a domácí síť s chytrými krabičkami IoT. Novou bezpečnostní platformu pojmenoval Smart Life.
Jak to bude fungovat v praxi? Vedle běžné detekce malwaru bude platforma pracovat i s prvky strojového učení a odhalování podezřelé aktivity. Když se tedy třeba chytrý termostat zapne v netradiční dobu, která neodpovídá dosavadnímu charakteru používání, a zároveň začne komunikovat s podezřelými IP adresami, Smart Life aktivitu vyhodnotí jako útok, zabrání pokračování a upozorní správce domácí sítě.
Podobným způsobem by měl bezpečnostní systém odhalit třeba podezřelou aktivitu chytrých televizorů, webkamer, všemožných přehrávačů a dalších prvků v domácím LANu, nebo v síti malé firmy. Ostatně jak upozorňuje sám Avast, hromadu podobných zařízení lze zneužít útočníkem třeba k těžbě kryptoměny Monero, kterou lze při větším množství napadených krabiček smysluplně těžit i na slabších armových čipsetech.
Smart Life je nicméně pouze software, takže aby mohl neustále skenovat vaši síť, musí běžet na nějakém železe. Tím bude buď přímo výkonnější Wi-Fi router některého ze smluvních partnerů, anebo dedikovaná krabička – sniffer – připojená do LANu. „Sniffer je v podstatě takové lepší Raspberry Pi postavené přímo pro nás,“ řekl nám bezpečnostní expert Avastu Filip Chytrý.
Internet věcí
Domácí IoT může vypadat všelijak počínaje komerčními krabičkami a konče DIY. Třeba takto, když si jej složíte a naprogramujete sami. Bezpečnostní a meteorologický systém autora článku obsahuje kameru s rybím okem, infračervený a mikrovlnný detektor pohybu, teploměr, vlhkoměr, tlakoměr, luxmetr, síť vnitřních i venkovních dálkových bezdrátových sond (868 MHz, LoRa), senzor CO2 a nakonec automatické spínání světel v bytě. Vše je postavené na Raspberry Pi Zero W, které může být také napadnutelné útočníky.
Bezpečnostní a meteorologická centrála postavená na Raspberry Pi Zero W
Samozřejmě jsme se Avastu zeptali i na to, jestli bude moci zkušenější uživatel nahodit celý systém i na některou z otevřených platforem – třeba na router s OpenWrt, kam patří i populární český router Turris. Ačkoliv se tomu Avast výhledově nebrání, zatím se bude soustředit pouze na železo od partnerů.
Pro Avast není Smart Life úplnou novinkou, podle Chytrého se totiž v podstatě jedná o evoluci platformy Chime, kterou vyvíjí AVG. No a AVG dnes patří pod křídla Avastu.
Siemens Releases BIOS Updates to Patch Intel Chip Flaws
28.2.2018 securityweek Vulnerebility
Siemens has released BIOS updates for several of its industrial devices to patch vulnerabilities discovered recently in Intel chips, including Meltdown, Spectre and flaws affecting the company’s Management Engine technology.
Following the disclosure of the Meltdown and Spectre attack methods, industrial control systems (ICS) manufacturers immediately started analyzing the impact of the flaws on their products. Advisories have been published by companies such as Siemens, Rockwell Automation, Schneider Electric, ABB, and Pepperl+Fuchs.
Siemens has determined that the security holes expose many of its product lines to attacks, including RUGGEDCOM, SIMATIC, SIMOTION, SINEMA, and SINUMERIK.
The company informed customers recently that it has started releasing BIOS updates for some of its impacted products, including SIMATIC industrial PCs, SIMATIC field PG rugged laptops, SIMATIC industrial tablet PCs (ITP), and SINUMERIK panel control units (PCU). In addition to firmware patches, users have been advised to install operating system updates, which should mitigate the Meltdown flaw and one variant of Spectre.
The BIOS updates released by the company for the aforementioned SIMATIC and SINUMERIK devices also patch several vulnerabilities discovered last year by researchers in Intel’s Management Engine (ME), Server Platform Services (SPS), and Trusted Execution Engine (TXE) technologies.
The flaws impacting these Intel products can be exploited – in most cases locally, but at least one bug is remotely exploitable – for arbitrary code execution, privilege escalation, and denial-of-service (DoS) attacks.
The firmware updates from Siemens also fix a vulnerability affecting the Trusted Platform Module (TPM) in chips made by German semiconductor manufacturer Infineon.
The flaw, CVE-2017-15361, is related to the RSA library in TPM and it could allow a remote attacker who knows the public key to obtain the private RSA key. The security hole affects the products of several major tech firms, including Microsoft, Google, HP, Lenovo and Fujitsu.
Siemens has published separate advisories to inform users about the availability of patches for Meltdown/Spectre, Intel ME, and Infineon TPM vulnerabilities. ICS-CERT has so far published an advisory only for the Infineon issue.
Fake ionCube Malware Hits Hundreds of Sites
28.2.2018 securityweek Virus
Hundreds of websites have been infected with malware that masquerades as legitimate ionCube-encoded files, SiteLock warns.
The malicious files were initially discovered in core directories of a WordPress site, featuring naming patterns usually associated with malware, namely “diff98.php” and “wrgcduzk.php.” Because the obfuscated files appear as if they had been encoded with ionCube, the researchers named the threat ionCube malware.
ionCube is an old and powerful PHP obfuscation technology that can be used to scramble text-based PHP files to hide the intellectual property. Due to licensing costs, ionCube isn’t usually used for malicious purposes.
Malicious attackers, however, found a way to pack their malware in a manner that resembles that of ionCube-encoded files, and started targeting various websites. Although the infection was initially spotted on a WordPress site, SiteLock's researchers discovered that Joomla and CodeIgniter sites have been infected as well.
According to SiteLock, the malware is likely to run on any web server running PHP, and could hide in plain sight by using filenames such as “inc.php” and “menu.php.” Overall, the researchers discovered over 7,000 infected files and say that over 700 sites were compromised.
Once decoded, the fake ionCube files turn into the malware itself, which still contains some obfuscation, along with some sort of access control, researchers discovered.
“While there’s still some degree of obfuscation, the presence of the $_POST and $_COOKIE superglobals and the eval request at the end of the file reveal its true purpose: to accept and execute remotely supplied code. It looks like the remote code supplied to this file is further obfuscated and there may be some sort of access control implemented, judging by the GUID-formatted string present,” SiteLock says.
Site administrators who haven’t specifically and intentionally installed ionCube-encoded files but do find such files on their servers were likely infected. If an infection is detected, the scanning of the entire site is recommended, to completely eliminate the threat.
According to SiteLock, differentiating between the fake and legitimate files can be very difficult as well, given the large number of malware variations out there. The researchers say it is common to see up to 100 slightly different variants of the malware on a single site.
Talos experts shared details of a remote code execution flaw in Adobe Acrobat Reader DC
28.2.2018 securityweek Vulnerebility
Security experts at Cisco Talos disclosed details of a remote code execution flaw that affects Adobe Acrobat Reader DC versions 2018.009.20050 and 2017.011.30070 and earlier.
Security experts at Cisco Talos shared details of a remote code execution vulnerability tracked as CVE-2018-4901, that affects Adobe Acrobat Reader DC.
A remote attacker can exploit the vulnerability tricking the victim into opening a malicious file or visiting a specially crafted webpage.
The flaw affects Adobe Acrobat Reader versions 2018.009.20050 and 2017.011.30070 and earlier. The vulnerability was disclosed on Dec. 7 and Adobe addressed it a few days ago, on February 13.
“Adobe Acrobat Reader is the most popular and most feature-rich PDF reader. It has a big user base, is usually a default PDF reader on systems and integrates into web browsers as a plugin for rendering PDFs. As such, tricking a user into visiting a malicious web page or sending a specially crafted email attachment can be enough to trigger this vulnerability.” reads the analysis published by the Talos team.
Adobe classified the flaw with a “priority 2” level that equals to “important”, this means that there is an “elevated risk” of exploitation. The good news is that there are currently no known exploits in the wild.
The researchers explained that the flaw could be used by attackers to embed a malicious JavaScript code in a PDF file to use document ID to perform unauthorized operations to trigger a stack-based buffer overflow when opening a specially crafted PDF document.
“A specific Javascript script embedded in a PDF file can cause the document ID field to be used in an unbounded copy operation leading to stack-based buffer overflow when opening a specially crafted PDF document in Adobe Acrobat Reader,” continues Talos.
Researchers at Talos also released Snort rules 45102-3 that could be used by administrators to detect exploitation attempts.
Experts warn Memcached DDoS attacks could be soon a dangerous threat
28.2.2018 securityweek Attack
Security experts started observing a dangerous trend in DDoS amplification technique, Memcached DDoS Attacks.
Security experts from some security firms have reported that threat actors have started abusing the memcached protocol to power distributed denial-of-service (DDoS) Attacks, so-called memcached DDoS attacks.
Memcached is a free and open source, high-performance, distributed memory caching system designed to speed up dynamic web applications by alleviating database load.
Clients communicate with memcached servers via TCP or UDP on port 11211.
Researchers from Cloudflare, Arbor Networks and security firm Qihoo 360 discovered that recently attackers are abusing the memcached for DDoS amplification attacks.
Chinese experts warned about abuses of memcached DDoS attacks in November.
Experts at Cloudflare dubbed this type of attack Memcrashed.
“Over last couple of days we’ve seen a big increase in an obscure amplification attack vector – using the memcached protocol, coming from UDP port 11211.” reads the analysis published by Cloudflare.
“An IP-spoofing capable attacker sends forged requests to a vulnerable UDP server. The UDP server, not knowing the request is forged, politely prepares the response. The problem happens when thousands of responses are delivered to an unsuspecting target host, overwhelming its resources – most typically the network itself.“
The involvement of memcached servers in DDoS Attacks is quite simple, the attacker sends a request to the targeted server on port 11211 spoofing the IP address of the victim. In a memcached DDoS attack, the request sent to the server is composed of a few bytes, while the response can be tens of thousands of times bigger, resulting in an amplification attack.

The researchers at Cloudflare observed a memcached DDoS attack that peaked at 260 Gbps while Arbor Networks reported observing attacks that peaked at 500 Gbps and even more.
“We have observed a considerable uptick in memcached reflection/amplification attacks ranging in size from a few hundred mb/sec up to 500gb/sec and larger. The amplified attack traffic is sourced from UDP/11211, with a packet size of 1428 bytes (1442 bytes with layer-2 Ethernet framing included), and no fragmentation (memcached segments large responses at layer-7, as does ntp).” reads the analysis published by Arbor Networks. “The attacker typically ‘primes’ a given set of memcached reflectors/amplifiers with arbitrary-length key/value pairs, and then issues memcached queries for those key/value pairs, spoofing the IP addresses of targeted hosts/networks.”
Researchers at Arbor Networks added that attackers can also send queries at TCP port 11211, but since TCP queries cannot be reliably spoofed, the hackers opted for UDP.
“I was surprised to learn that memcached does UDP, but there you go! The protocol specification shows that it’s one of the best protocols to use for amplification ever! There are absolutely zero checks, and the data WILL be delivered to the client, with blazing speed! Furthermore, the request can be tiny and the response huge (up to 1MB).” continues the analysis published by Cloudflare.
“Launching such an attack is easy. First the attacker implants a large payload on an exposed memcached server. Then, the attacker spoofs the “get” request message with target Source IP.”
According to Cloudflare, most of the memchached DDoS Attacks were launched from servers in North America and Europe, the majority of them is hosted by OVH, DigitalOcean, and Sakura.

The experts observed attacks from roughly 5,700 unique IPs associated with memcached servers.
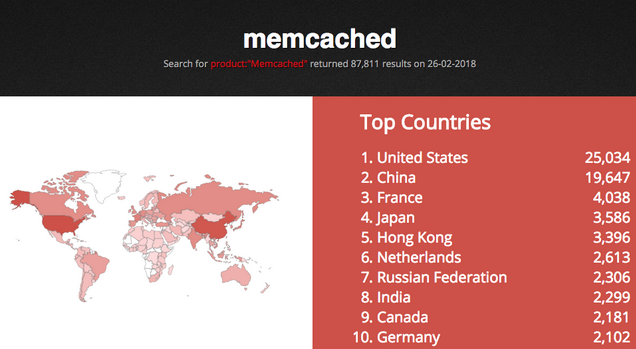
The situation can rapidly get worse because the result of a simple Shodan query shows nearly 88,000 unsecured memchached servers, most of them in the United States, China and France.
Cloudflare recommends disabling UDP support unless it’s needed and isolating memcached servers from the Internet. Internet service providers have to fix vulnerable protocols and prevent IP spoofing.
“Internet Service Providers – In order to defeat such attacks in future, we need to fix vulnerable protocols and also IP spoofing. As long as IP spoofing is permissible on the internet, we’ll be in trouble.” concluded Cloudflare.
“Developers – Please please please: Stop using UDP. If you must, please don’t enable it by default. If you do not know what an amplification attack is I hereby forbid you from ever typing
SOCK_DGRAM
into your editor.”
Memcached Servers Abused for Massive Amplification DDoS Attacks
28.2.2018 thehackernews Attack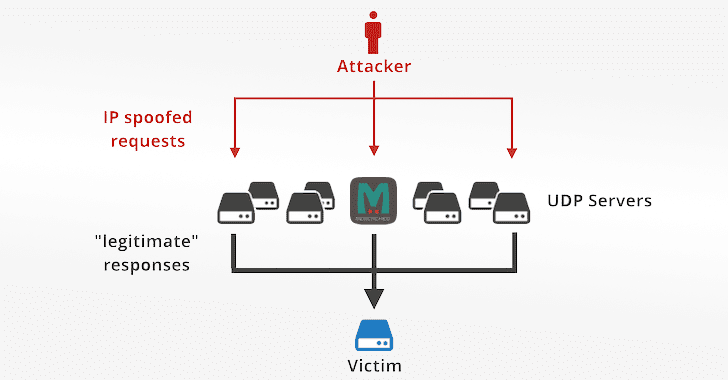
Cybercriminals have figured out a way to abuse widely-used Memcached servers to launch over 51,000 times powerful DDoS attacks than their original strength, which could result in knocking down of major websites and Internet infrastructure.
In recent days, security researchers at Cloudflare, Arbor Networks, and Chinese security firm Qihoo 360 noticed that hackers are now abusing "Memcached" to amplify their DDoS attacks by an unprecedented factor of 51,200.
Memcached is a popular open-source and easily deployable distributed caching system that allows objects to be stored in memory and has been designed to work with a large number of open connections. Memcached server runs over TCP or UDP port 11211.
The Memcached application has been designed to speed up dynamic web applications by reducing stress on the database that helps administrators to increase performance and scale web applications. It's widely used by thousands of websites, including Facebook, Flickr, Twitter, Reddit, YouTube, and Github.
Dubbed Memcrashed by Cloudflare, the attack apparently abuses unprotected Memcached servers that have UDP enabled in order to deliver DDoS attacks 51,200 times their original strength, making it the most prominent amplification method ever used in the wild so far.
How Memcrashed DDoS Amplification Attack Works?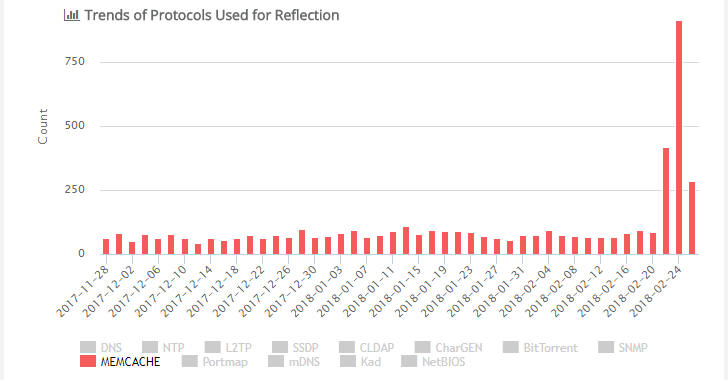
Like other amplification methods where hackers send a small request from a spoofed IP address to get a much larger response in return, Memcrashed amplification attack also works by sending a forged request to the targeted server (vulnerable UDP server) on port 11211 using a spoofed IP address that matches the victim's IP.
According to the researchers, just a few bytes of the request sent to the vulnerable server can trigger the response of tens of thousands of times bigger.
"15 bytes of request triggered 134KB of response. This is amplification factor of 10,000x! In practice we've seen a 15-byte request result in a 750kB response (that's a 51,200x amplification)," Cloudflare says.
According to the researchers, most of the Memcached servers being abused for amplification DDoS attacks are hosted at OVH, Digital Ocean, Sakura and other small hosting providers.
In total, researchers have seen only 5,729 unique source IP addresses associated with vulnerable Memcached servers, but they are "expecting to see much larger attacks in future, as Shodan reports 88,000 open Memcached servers." Cloudflare says.
"At peak we've seen 260Gbps of inbound UDP memcached traffic. This is massive for a new amplification vector. But the numbers don't lie. It's possible because all the reflected packets are very large," Cloudflare says.
Arbor Networks noted that the Memcached priming queries used in these attacks could also be directed towards TCP port 11211 on abusable Memcached servers.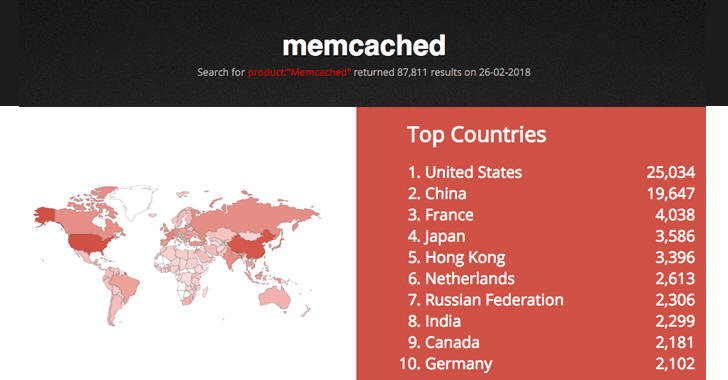
But TCP is not currently considered a high-risk Memcached reflection/amplification vector because TCP queries cannot be reliably spoofed.
The popularly known DDoS amplification attack vectors that we reported in the past include poorly secured domain name system (DNS) resolution servers, which amplify volumes by about 50 times, and network time protocol (NTP), which increases traffic volumes by nearly 58 times.
Mitigation: How to Fix Memcached Servers?
One of the easiest ways to prevent your Memcached servers from being abused as reflectors is firewalling, blocking or rate-limiting UDP on source port 11211.
Since Memcached listens on INADDR_ANY and runs with UDP support enabled by default, administrators are advised to disable UDP support if they are not using it.
The attack size potentially created by Memcached reflection cannot be easily defended against by Internet Service Providers (ISPs), as long as IP spoofing is permissible on the internet.
Hacker Who Never Hacked Anyone Gets 33-Month Prison Sentence
28.2.2018 thehackernews Crime
A hacker who was arrested and pleaded guilty last year—not because he hacked someone, but for creating and selling a remote access trojan that helped cyber criminals—has finally been sentenced to serve almost three years in prison.
Taylor Huddleston, 26, of Hot Springs, Arkansas, pleaded guilty in July 2017 to one charge of aiding and abetting computer intrusions by building and intentionally selling a remote access trojan (RAT), called NanoCore, to hackers for $25.
Huddleston was arrested in March, almost two months before the FBI raided his house in Hot Springs, Arkansas and left with his computers after 90 minutes, only to return eight weeks later with handcuffs.
This case is a rare example of the US Department of Justice (DOJ) charging someone not for actively using malware to hack victims' computers, but for developing and selling it to other cybercriminals.
Huddleston admitted to the court that he created his software knowing it would be used by other cybercriminals to break the law.
He initially started developing NanoCore in late 2012 with a motive to offer a low-budget remote management software for schools, IT-conscious businesses, and parents who desired to monitor their children's activities on the web.
However, Huddleston marketed and sold the NanoCore RAT for $25 in underground hacking forums that were extremely popular with cybercriminals around the world from January 2014 to February 2016. He then sold ownership of NanoCore to a third-party in 2016.
NanoCore RAT happens to be popular among cybercriminals on underground hacking forums and has been linked to intrusions in at least ten countries. Among the victims was a high-profile assault on Middle Eastern energy firms in 2015.
Huddleston also agreed with prosecutors that NanoCore RAT and available third-party plugins offered a full set of features including:
Stealing sensitive information from victim computers, such as passwords, emails, and instant messages.
Remotely activating and controlling connected webcams on the victims' computers in order to spy on them.
Ability to view, delete, and download files.
Locking infected PCs and holding them to ransom.
Using infected PCs to launch distributed denial of service (DDoS) attacks on websites and similar services.
In July plea, Huddleston also took responsibility for creating and operating a software licensing system called "Net Seal" that was used by another suspect, Zachary Shames, to sell thousands of copies of Limitless keylogger.
Shames used Net Seal to infect 3,000 people that were, in turn, used it to infect 16,000 computers, according to the DoJ.
In his guilty plea, Huddleston admitted that he intended his products to be used maliciously.
Besides the 33-month prison sentence handed down by judges on Friday, Huddleston also gets two years of supervised release.
Intel Releases Spectre Patches for Broadwell, Haswell CPUs
28.2.2018 securityweek Vulnerebility
Intel has released new firmware updates for its Broadwell and Haswell processors to address the Spectre vulnerability.
After the first round of Spectre patches released by the company caused more frequent reboots and other instability problems, Intel started working on new microcode updates.
The company first released new firmware updates for its Skylake processors, and last week it announced the availability of patches for several other CPUs, including Kaby Lake and Coffee Lake.
This week, the company updated the list of available firmware patches to state that the fixes for Haswell and Broadwell processors are also ready for use in production environments.
As of February 28, patches that can be deployed in production environments are available for the following products: Anniedale/Moorefield, Apollo Lake, Avoton/Rangeley, Broadwell (except Server EX), Broxton, Cherry View, Coffee Lake, Cougar Mountain, Denverton, Gemini Lake, Haswell (except Server EX), Kaby Lake, Knights Landing, Knights Mill, Skylake, SoFIA, Tangier, Valleyview/Bay Trail, and XGold.
Beta patches have been provided to OEMs for validation for Gladden, some Ivy Bridge, Sandy Bridge, and Skylake Xeon E3 processors. The microcode updates for Broadwell and Haswell Server EX processors, specifically the Xeon E7v4 and E7v3 product families, are also in beta phase.
As for the remaining CPUs, updates are either in pre-beta or planning phase, but pre-mitigation microcode updates are available for many of these products.
The patches will be delivered as OEM firmware updates. Device manufacturers started releasing BIOS updates to patch the Meltdown and Spectre vulnerabilities shortly after their disclosure, but a majority of firms decided to halt the updates due to instability issues. Some vendors have now resumed the distribution of firmware updates.
Meltdown attacks are possible due to a vulnerability tracked as CVE-2017-5754, while Spectre attacks are possible due to flaws tracked as CVE-2017-5753 (Variant 1) and CVE-2017-5715 (Variant 2). Meltdown and Spectre Variant 1 can be patched with software updates, but Spectre Variant 2 requires microcode updates for a complete fix.
Intel and AMD claim they are working on processors that will have built-in protections against these types of exploits.
Intel faces more than 30 lawsuits, including ones filed by customers and shareholders, over the Meltdown and Spectre vulnerabilities.
CSE Malware ZLab – Malware Analysis Report: A new variant of Mobef Ransomware
28.2.2018 securityaffairs Ransomware
Malware researchers at CSE Cybsec – ZLab have analyzed a new variant of Mobef ransomware, a malware that in the past mainly targeted Italian users.
Malware researchers at CSE Cybsec – ZLab have analyzed a new variant of Mobef ransomware, that was involved in past attacks against Italian users.
I personally obtained the sample by researchers at @MalwareHunterTeam and the Italian expert @Antelox and passed it to the experts at the ZLab.
24 Feb
MalwareHunterTeam
@malwrhunterteam
Thanks to @Antelox, we now have a sample for the ransomware that is targeting Italy (https://twitter.com/malwrhunterteam/status/967132494104530947 …): https://www.virustotal.com/en/file/aa2c9c02def2815aa24f5616051aa37e4ce002e62f507b3ce15aac191a36e162/analysis/1518986221/ …
Interesting packing/protection, maybe it's worth to dig into @hasherezade @VK_Intel.@BleepinComputer @demonslay335
cc @JAMESWT_MHT @forensico
MalwareHunterTeam
@malwrhunterteam
Seems it's a new version of Mobef (or maybe not even a new version, just a new note). Note that most of Mobef victims we seen in past year also were from Italy.
For this, we only seen victims from Italy till now. 1st on 16th this month.
The above sample also seen from Italy...
7:45 PM - Feb 24, 2018
7
See MalwareHunterTeam's other Tweets
Twitter Ads info and privacy
Like a classic ransomware, it encrypts all user files without changing the file extension and drops a file containing the instructions on how to pay the ransom.

Mobef ransomware note
The analysis revealed that the ransomware was written in Delphi 4 and it doesn’t include useful strings. The Import Address Table is empty, this means that the malware isn’t as trivial as seems because it uses some technique to avoid the analysis.
After the execution, the ransomware creates three files:
4YOU: it contains the ransom note as shown in the popup window; it is stored in each folder in which there are encrypted files.
KEI: it contains the personal key used to identify the victim; it is stored in each folder in which there are encrypted files.
log: it contains the list of the encrypted files and it is stored in “C:\Windows”. This file represents also the kill-switch of the malware and the filename is the same for every infection.
Mobef ransomware – List of encrypted files
Once the encryption phase is complete, the new variant of the Mobef ransomware will try to contact an external server “mutaween.sa”, to exfiltrate a series of information.
It is interesting to note that the domain “mutaween.sa” doesn’t exist, it isn’t currently resolved by the DNS servers.
A deep analysis of the Mobef ransomware revealed that it implements a number of functionalities, such as the capability to encrypt files, not only on the local drive but also on removable drives and network shares.
Further details on the Mobef ransomware and Yara Rules are included in the report published by researchers at ZLAb.
IoT hack: how to break a smart home… again
28.2.2018 Kaspersky IoT
There can never be too many IoT gadgets – that’s what people usually think when buying yet another connected device with advanced functionality. From our perspective, we also think there can’t be too many IoT investigations. So, we have continued our experiments into checking and uncovering how vulnerable they are, and followed up our research focusing on smart home devices.
Researchers have already been analyzing connected devices for many years, but concerns around cybersecurity in the IoT world are still there, putting users under significant risk. In our previous analysis, possible attack vectors affecting both a device and a network to which it’s connected have been discovered. This time, we’ve chosen a smart hub designed to control sensors and devices installed at home. It can be used for different purposes, such as energy and water management, monitoring and even security systems.
This tiny box receives information from all the devices connected to it, and if something happens or goes wrong, it immediately notifies its user via phone, SMS or email in accordance with its preferences. An interesting thing is that it is also possible to connect the hub to local emergency services, thus alerts will be sent to them accordingly. So, what if someone was able to interrupt this smart home’s system and gain control over home controllers? It could turn life into a nightmare not only for its user, but also for the emergency services. We decided to check a hypothesis and as a result discovered logical vulnerabilities providing cybercriminals with several attack vectors opportunities.
Physical access
First, we decided to check what could be available for exploitation by an attacker being outside of the network. We discovered that the hub’s firmware is available publicly and can be downloaded without any subscription from the vendor’s servers. Therefore, once downloading it, anyone can easily revise the files inside it and analyze them.
We found that the password from the root account in the shadow file is encrypted with the Data Encryption Standard (DES) algorithm. As practice shows, this cryptographic algorithm is not considered to be secure or highly resistant to hacking, and therefore it is possible for an attacker to successfully obtain the hash through brute-force and find out the ‘root’ password.
To access the hub with ‘root’ rights and therefore modify files or execute different commands, physical access is needed. However, we don’t neglect the hardware hacking of devices and not all of them survive afterwards.
We explored the device physically, but of course not everyone would be able to do this. However, our further analysis showed there are other options to gain remote access over it.
Remote access
For hub control, users can either use a special mobile application or a web-portal through which they can set up a personal configuration and check all the connected systems.
To implement it, the owner sends a command for synchronization with the hub. At that moment, all settings are packed in the config.jar file, which the hub then downloads and implements.
But as we can see, the config.jar file is sent through HTTP and the device’s serial number is used as the device identifier. So, hackers can send the same request with an arbitrary serial number, and download an archive.
Some might think that serial numbers are very unique, but developers prove otherwise: serial numbers are not very well protected and can be brute-forced with a byte selection approach. To check the serial number, remote attackers can send a specially crafted request, and depending on the server’s reply, will receive information if the device is already registered in the system.
Moreover, our initial research has shown that users, without even realizing it, put themselves at risk by publishing their tech reviews online or posting photos of a hub in social networks and openly presenting devices’ serial numbers. And the security consequences will not be long in coming.
While analyzing the config.jar file archive, we found that it contains login and password details – all the necessary data to access a user’s account through the web-interface. Although the password is encrypted in the archive, it can be broken by hash decryption with the help of publicly available tools and open-sourced password databases. Importantly, during the initial registration of a user account in the system, there are no password complexity requirements (length, special characters, etc.). This makes password extraction easier.
As a result, we gained access to a user’s smart home with all the settings and sensor information being available for any changes and manipulations. The IP address is also listed there.
It is also possible that there might be other personal sensitive information in the archive, given the fact that users often upload their phone numbers into the system to receive alerts and notifications.
Thus, the few steps involved with generating and sending the right requests to the server can provide remote attackers with the possibility of downloading data to access the user’s web interface account, which doesn’t have any additional security layers, such as 2FA (Two Factor Authentication). As a result, attackers can take control over someone’s home and turn off the lights or water, or, even worse, open the doors. So, one day, someone’s smart life could be turned into a complete nightmare. We reported all the information about the discovered vulnerabilities to the vendor, which are now being fixed.
But there is always light at the end of the tunnel…
In addition to smart “boxes”, we had something smaller in our pocket – a smart light bulb, which doesn’t have any critical use, neither for safety or security. However, it also surprised us with a few – but still worrying – security issues.
The smart bulb is connected to a Wi-Fi network and controlled over a mobile application. To set it up a user needs to first download the mobile application (iOS or Android), switch on the bulb, connect to the Wi-Fi access point created by the bulb and provide the bulb with the SSID and password from a local Wi-Fi network.
From the application, users can switch it ON and OFF, set timers and change different aspect of the light, including its density and color. Our goal was to find out if the device might help an attacker in any way to gain access to a local network, from which it would eventually be possible to conduct an attack.
After several attempts, we were lucky to discover a way to get to the device’s firmware through the mobile application. An interesting fact is that the bulb does not interact with the mobile application directly. Instead, both the bulb and the mobile application are connected to a cloud service and communication goes through it. This explains why while sniffing the local network traffic, almost no interaction between the two were found.
We discovered that the bulb requests a firmware update from the server and downloads it through an HTTP protocol that doesn’t secure the communication with servers. If an attacker is in the same network, a man-in-the-middle kind of attack will be an easy task.
The hardware reconnaissance with flash dumping led us not only to the firmware, but to user data as well. With a quick look at the information shared with the cloud, no sensitive information seems to have been uploaded from the device or the internal network. But we found all the credentials of the Wi-Fi networks to which the bulb had connected before, which are stored in the device’s flash forever with no encryption – even after a “hard” reset of the device this data was still available. Thus, reselling it on online market places is certainly not a good idea.
Get ready
Our latest research has once again confirmed that ‘smart home’ doesn’t mean ‘secure home’. Several logical vulnerabilities (combined with an unconsciously published serial number) can literally open doors to your home and welcome in cybercriminals. Besides this, remote access and control over your smart hub can lead to a wide range of sabotage activities, which could cost you through high electricity bills, a flood or, even more importantly, your mental health.
But even if your smart hub is secure, never forget that the devil is in the details: a tiny thing such as a light bulb could serve as an entry-point for hackers as well, providing them with access to a local network.
That’s why it’s highly important for users to follow these simple cyber hygiene rules:
Always change the default password. Instead use a strict and complex one. Don’t forget to update it regularly.
Don’t share serial numbers, IP addresses and other sensitive information regarding your smart devices on social networks
Be aware and always check the latest information on discovered IoT vulnerabilities.
No less important is that vendors should improve and enhance their security approach to ensure their devices are adequately protected and, as a result, their users. In addition to a cybersecurity check, which is just as vital as testing other features before releasing a product, it is necessary to follow IoT cybersecurity standards. Kaspersky Lab has recently contributed to the ITU-T (International Telecommunication Union — Telecommunication sector) Recommendation, created to help maintain the proper protection of IoT systems, including smart cities, wearable and standalone medical devices and many others.
From IDF to Inc: The Israeli Cybersecurity Startup Conveyor Belt
28.7.2018 securityweek BigBrothers
Israeli Defense Force (IDF) Unit 820
Understanding Why Israel Produces Many Cybersecurity Firms Starts With Understanding the Talent That Israeli Defense Force (IDF) Unit 8200 Produces
One definition of 'entrepreneur' is "a person who organizes and manages any enterprise, especially a business, usually with considerable initiative and risk." If Israel were a business, then its founders were entrepreneurs; and there is little wonder that the nation is imbued with an entrepreneurial spirit.
This spirit shapes Israeli business. Peter Rousseau, now with The Hackett Group, wrote last year, "Seventy-six Israeli companies are currently traded on the NASDAQ, behind only the United States and China. Israel exports $1,246 worth of hi-tech goods and services per capita compared to $488 for the U.S. and $295 for the rest of the world."
Nowhere is the entrepreneurial spirit better demonstrated than in the quantity and quality of contemporary cybersecurity firms that have come from Israel -- starting, perhaps, with Check Point. Check Point was founded in 1993 by Gil Shwed, Shlomo Kramer, and Marius Nacht. Shwed and Kramer had served together in the Israeli Defense Force (IDF) Unit 8200. One of Check Point's earliest employees was Nir Zuk, who moved on to become the founder and CTO of Palo Alto Networks. Zuk also served in IDF Unit 8200 -- and Unit 8200 is a pervasive thread that dominates Israeli cybersecurity firms.
Unit 8200 is the signals intelligence (SIGINT) and web intelligence (WEBINT) unit of the Israeli military; and is generally considered among the elite of the world's intelligence agencies. It is not the only technology unit in the IDF; but it is the offensive or proactive unit. All young Israelis do between 32 and 36 months military service from the age of 18. Those with a particular aptitude for SIGINT are literally 'creamed off' into Unit 8200.
Development of Israel's SIGINT
Unit 8200 did not spring from nothing with the formation of Israel in 1948. Jewish intelligence groups had been working in Palestine both with the ruling British administration, and against the British and Arabs -- sometimes simultaneously -- for many years. After 1948, the Israeli military became the IDF and established a military intelligence group codenamed 'Rabbit'. Rabbit was charged with intercepting and decoding Arab communications; a charge born of necessity.
Unit 8200 evolved out of Rabbit. Initially with little budget and low manpower, it was forced to develop its own technology and techniques -- the entrepreneurial spirit of the nation co-existed within its intelligence agency from its very origins.
The modern Unit 8200, however, grew out of the Yom Kippur War in 1973. On that Atonement Day, Israel was simultaneously invaded by Egypt and Syria. Although Israel eventually defeated the invaders it was at heavy cost in both lives and finance. Subsequent analysis showed that a failure in intelligence had left the nation unprepared -- and subsequent Unit 8200 reorganization was designed to prevent this ever happening again. Part of this was the conscious encouragement of 'chutzpah', (or audacity) among its staff.
This is the basis of today's Unit 8200: the cream of youth, highly trained in signals intelligence, encouraged to be audacious in thought and action, and imbued with an entrepreneurial spirit. These young people are then released back into society following their required national service in their early twenties. This is a situation unique in the world.
Israeli Cybersecurity Startups
When talented youth join the NSA or FBI or GCHQ or any other national intelligence agency, they are expected to do so for life, not just for three years. No other nation has this constant stream of highly trained, audacious and entrepreneurial young people entering the job market every year. What else should the more entrepreneurial alumni do but start their own firms using the skills they have acquired; and what else should others do but work in the R&D departments of these firms?
IDF's cybersecurity training
SecurityWeek spoke to several founders of Israeli cybersecurity firms. All of them served in technology units, and most in Unit 8200. Other military units have their own technology sections; and these also lead to spin offs. Examples could include Yuval Diskin, former director of Shin Bet, who started the cyber-tech company Diskin Advanced Technologies LTD; and Haim Tomer, formerly head of the Mossad's Intelligence Division, who is now a cybersecurity consultant. Despite such examples, however, it is the alumni of 8200 that dominate the new start-ups.
Understanding why Israel produces so many cybersecurity firms starts with understanding the converyor belt of talent that 8200 produces. Lior Div (CEO), Yossi Nar (CVO), and Yonatan Striem-Amit (CTO) are the three ex-8200 co-founders of Cybereason. "It starts," explains Liv, "with how people are selected to get into 8200. The Unit interviews all new draftees, using a series of tests looking at background, math proficiency, programming capabilities and pure intelligence. 8200 gets 'first pick'."
Just two military units get the lion's share of the best of the best: pilots for the air force, and 8200 for cyber warriors. Draftees serve anything from three to five years. During this period, special talent is fast-tracked. "By the time I was 19, I already had 10 developers reporting to me," said Div.
But it is fast-tracking in a unique environment. In commercial terms, the 'projects' are now well-funded and manned. "You are taught one thing in particular," he continued: "there is no such thing as impossible -- there is no notion of what you can and cannot do. You are given a problem, you work like crazy and eventually you solve the problem. So by the time you are released, around age 22 or 23, you are trained to solve cybersecurity problems."
This training is unique. Having chosen its new intake, said Div, "the military undertakes intensive training. After six months, 'trainees' have learned what a traditional university would take four years to teach -- and they have learned the practice of their subject and not just the underlying theory. By the time they leave, they are trained and confident cybersecurity warriors with new ideas."
This is confirmed by Boris Vaynburg, co-founder and CEO of Solebit. He and his two co-founders, along with 95% of his R&D staff, are all IDF technology unit alumni. He points out that in order to stay one step ahead of Israel's adversaries, Unit 8200 must take advantage of all known and unknown vulnerabilities in order to get into target networks. In essence, 8200 members get constant on-the-job red team training; and by the time draftees leave the military, they have a thorough understanding -- through use -- of the techniques used by hackers.
Eddy Brobitsky, CEO and co-founder of Minerva Labs, did not serve in Unit 8200. "Neither I nor my 2 co-founders served with 8200," he said, "We served in the unit that builds defensive solutions for the IDF. IDF doesn't want to rely on off-the-shelf products only -- it's important to develop your own products, so nobody will know how they work. We were focused on developing scalable products for cybersecurity and IT." It's worth noting that the IDF is, in these terms, the largest company in Israel. Building security defenses suitable for the entire IDF and Israel government is equivalent to building a security product that will scale to the largest commercial organizations.
But it's not just the practical expertise of service that benefits budding entrepreneurs -- it is the whole culture. We've seen that 'nothing is impossible' and chutzpah is encouraged; but there is also a completely different 'product' development culture. "Inside the IDF," explained Brobitsky, "the motivation for developing new security is to save human life. It's not about financial profit. All I had to do was show that a vulnerability existed and that someone could be hurt if there was a compromise, and I would get the budget to execute the project and build a defense."
It's not the same in the commercial world. "Later, when I worked in a bank which was driven by money," he continued, "I needed to show that any investment in cybersecurity would not hurt income but actually increase income. Its a very different approach. For example, if you fail in the IDF, you don't get fired -- you're still in the army. The army is always encouraging you to try and not accept defeat in any project; so it encourages innovation." While serving in the IDF, Brobitsky was involved in the development of between 20 and 30 different cybersecurity solutions for the entire IDF and government.
"So the environment is to try and try again until you succeed. In the real world, if you fail you will sometimes lose your job; and if you've already lost one job through not succeeding, you're always a bit afraid to try a different approach to things wherever you go.
A second difference with the outside world is the extent of 'networking' within Israel's technology world. Although there are different technology units with different priorities, there is constant intercommunication between them. Everybody knows everybody, commented Amit Rahav, VP of business development at Secret Double Octopus, "with veterans of the Israeli intelligence units seeking to hire these young guys righty away, appreciating the pre-selection, training and experience of the units they themselves came out of. This is to some extent similar to what happens at Ivy league MBA programs in the US."
From new idea to new company
From here there is a well-trod path. Turning what has been learned into a new company requires funding. Early-stage venture capital is available in Israel for good ideas. Not all ideas are good; but Israeli investors have become savvy in technology. Nobody wanted to say that there is smart money and dumb money, but it was a common acknowledgment that Israeli money is smart. Good ideas get funded and dumb ideas never get off the ground.
"Israeli venture capital is available, but it is hard to get and getting harder," explained Solebit's Vaynburg. "Any new idea has to be disruptive and unique with a strong team behind it. It's easier to get VC outside of Israel," he continued, "because the Israeli VC firms have become very cybersecurity savvy, and there are so many approaches for what is already an overcrowded market."
At the same time, of course, the cost of getting a product presentation team together and flown to the U.S. to present to a U.S. venture capital firm is exorbitant for what is, at this stage, likely to be not much more than proof of concept on a new idea. Seed funding tends to come from Israel itself.
What this generally means is that when a new cybersecurity firm is ready to expand outside of Israel, it is already a fair bet. That expansion usually means a move to the U.S. rather than the UK or Europe. For this there are three motivations -- all of which SecurityWeek has already heard in different contexts . Firstly there is far more venture capital available in the US than elsewhere. It's just beginning in Europe: there's some in Berlin, but little in London.
Secondly, despite the European Union, there are at least six different cultures and different languages to understand within the member nations, as opposed to, basically, just one American culture and language. Thirdly, and perhaps most importantly, new technology early-adopters are more prevalent in America -- and especially on the West Coast -- than anywhere else.
The real decision is not America or Europe, but West Coast or East Coast. While the majority might be attracted to the entrepreneurial attitude of the West Coast, others are attracted by the big financial customers of the East Coast. Boston-based CyberArk is one. "We figured the biggest adoption for security would first come financial services firms, and that very much lent itself to the East Coast," commented CEO Udi Mokady, another 8200 alumni.
The path from concept to company is illustrated by Solebit itself. "Solebit was established 3 years ago," said Vaynburg. "R&D is based in Israel. Our headquarters, however, is currently relocating to the Bay Area. We raised our seed funding from an Israeli venture capital firm [$2 million from Glilot Capital Partners in 2015], and Round A funding from a U.S. venture capital firm." The Round A funding is so new that, although it has closed, it is yet to be announced.
Lessons from the Israeli cybersecurity model
The sad truth is that the IDF situation in Israel is unique, and could not be copied anywhere else in the world. It provides a constant source of technological competence trained to be audacious, persistent and positive. Other SIGINT organizations around the world do not release their staff on to the job market, preferring to keep them. Retired NSA, CIA and FBI staff tend to join the boards of existing large corporations; they do not tend to start new companies. In the UK, retired GCHQ and Ministry of Defence (MoD) officers might become private consultants, offering experience and expertise -- but rarely new ideas.
One idea alone could translate to other countries. The IDF, the largest company in Israel, funds the university fees for promising students, requiring only that they work for the IDF for a period after graduation. Large western organizations could do similar, finding and nurturing young talent. The idea of serious cybersecurity talent emerging with a sought-after degree and no student debt should be alluring to all sides.
Samsung Smartphones Get Encrypted Communications
28.7.2018 securityweek Krypto
KoolSpan this week announced a partnership with Samsung to implement secure communications on Samsung smartphones.
KoolSpan, a provider of encrypted secure voice and messaging solutions for mobiles, is already offering secure communications to enterprises. With support for mainstream phones, which are normally used within organizations, the solutions bring end-to-end encryption to all internal calls and texts within a company.
The end result of the partnership between KoolSpan and Samsung is TrustCall Native for Samsung, which provides native dialer integration on Samsung devices and which is being demonstrated at the Mobile World Congress in Barcelona.
The solution is aimed at tackling the rise in attacks on mobile communications, which normally consist of calls and messages being intercepted through the exploitation of vulnerabilities in mobile internetworking protocols.
Last year, the U.S. Department of Homeland Security (DHS) issued a report to underline some of the issues plaguing mobile communications, suggesting that both deliberate and accidental threats to mobile security continue to exist.
TrustCall Native for Samsung is focused on addressing such concerns by offering more secure communications on Samsung smartphones. To ensure ease-of-use, it integrates with Samsung native functionality for phone, messaging and contacts and applies encryption automatically.
KoolSpan’s solution is managed, deployed and configured across all smartphones within an organization by the IT department and is integrated with the phone’s native dialer and messenger. TrustCall Native Secure Communications for Samsung is available for customers with a Samsung Enterprise Alliance Program (SEAP) account and a subscription to KNOX Configure.
“We’re excited to partner with KoolSpan, which enables us to implement secure communications on Samsung smartphones. TrustCall Native, one of KoolSpan’s flagship products, is the best example of the universal understanding that security is only as good as it is easy to use,” Mike Kazmierczak, Samsung B2B Business Development Manager, Mobile B2B Team, EMEA, said.
Thanatos Ransomware Makes Data Recovery Impossible
28.7.2018 securityweek Ransomware
A newly discovered ransomware family is generating a different encryption key for each of the encrypted files but saves none of them, thus making data recovery impossible.
Dubbed Thanatos, the malware was discovered by MalwareHunterTeam and already analyzed by several other security researchers.
When encrypting files on a computer, the malware appends the .THANATOS extension to them. After completing the encryption, the malware connects to a specific URL to report back, thus allowing attackers to keep track of the number of infected victims.
The malware also generates an autorun key to open the ransom note every time the user logs in. In that note, the victim is instructed to send $200 to a listed crypto-coin address. Victims are also instructed to contact the attackers via email to receive a decryption program.
Thanatos’ operators allow victims to pay the ransom in Bitcoin, Ethereum, or Bitcoin Cash, thus becoming the first ransomware to accept Bitcoin Cash payments, Bleeping Computer’s Lawrence Abrams points out.
The issue with the new ransomware is that it, because it doesn’t save the encryption keys, files cannot be decrypted normally. However, victims don’t know that and might end up paying the ransom in the hope they can recover their files.
The good news regarding Thanatos, however, is that there might be a way to brute force the encryption keys, at least this is what security researcher Francesco Muroni suggests. However, this process would take a long time and would require for it to be a common file type with a known magic header.
Because of the botched encryption process, it is recommended to avoid paying the ransom if infected with Thanatos. Of course, this applies to every ransomware infection. It is also recommended to always keep applications up to date, and to use a security program capable of preventing this type of malware from compromising your systems.
Memcached Abused for DDoS Amplification Attacks
28.7.2018 securityweek Attack
Malicious actors have started abusing the memcached protocol to launch distributed denial-of-service (DDoS) attacks, Cloudflare and Arbor Networks warned on Tuesday.
Memcached is a free and open source distributed memory caching system designed to work with a large number of open connections. Clients can communicate with memcached servers via TCP or UDP on port 11211.
Cloudflare noticed in recent days that memcached has been abused for DDoS amplification attacks, and so have Arbor Networks and Chinese security firm Qihoo 360. Cloudflare has dubbed this type of attack Memcrashed.
Attackers are apparently abusing unprotected memcached servers that have UDP enabled. Similar to other amplification methods, the attacker sends a request to the targeted server on port 11211 using a spoofed IP address that matches the IP of the victim. The request sent to the server is just a few bytes, but the response can be tens of thousands of times bigger, resulting in a significant attack.
The largest memcached DDoS attack observed by Cloudflare peaked at 260 Gbps, but Arbor Networks reported seeing attacks that peaked at 500 Gbps and even more.
“I was surprised to learn that memcached does UDP, but there you go!” said CloudFlare’s Marek Majkowski. “The protocol specification shows that it's one of the best protocols to use for amplification ever! There are absolutely zero checks, and the data WILL be delivered to the client, with blazing speed! Furthermore, the request can be tiny and the response huge (up to 1MB).”
Arbor Networks noted that the type of queries used in these attacks can also be directed at TCP port 11211, but since TCP queries cannot be reliably spoofed, this protocol is less likely to be abused. The company pointed out that Chinese researchers warned about the possibility of attacks abusing memcached in November.
In the attacks seen by Cloudflare, attackers abused servers from all around the world, but mostly from North America and Europe. A majority of the servers are hosted by OVH, DigitalOcean and Sakura.
The attacks monitored by the content delivery network (CDN) came from roughly 5,700 unique IPs associated with memcached servers, but experts expect to see much larger attacks in the future considering that Shodan shows nearly 88,000 open servers. A majority of the exposed systems are in the United States, followed by China and France.
“Arbor’s current assessment is that, as with most other DDoS attack methodologies, memcached DDoS attacks were initially – and for a very brief interval – employed manually by skilled attackers; they have subsequently been weaponized and made available to attackers of all skill levels via so-called ‘booter/stresser’ DDoS-for-hire botnets,” Arbor Networks researchers said in a blog post. “The rapid increase in the prevalence of these attacks indicates that this relatively new attack vector was weaponized and broadly leveraged by attackers within a relatively short interval.”
Cloudflare recommends disabling UDP support unless it’s needed, and advised system administrators to ensure that their servers are not accessible from the Web. Internet service providers (ISPs) can also contribute to mitigating these and other types of amplification attacks by fixing vulnerable protocols and preventing IP spoofing.
Ad Network Performs In-Browser Cryptojacking
28.7.2018 securityweek CoinMine
An ad network provider is performing in-browser Coinhive cryptojacking on websites that use its service, 360 Netlab security researchers warn.
The practice has been ongoing since December 2017, several months after the ad network provider, a company called PopAds Publisher, started using domain generation algorithm (DGA) technology to bypass ad blockers, claiming it would allow customers to “monetize traffic that wasn’t monetized before.”
In mid-2017, the provider started to generate seemingly random domains that would ensure ads can reach end users. By the end of the year, however, these domains, which 360 Netlab refers to as DGA.popad, started participating in cryptojacking activities, all without end-users’ acknowledgement.
Given that many people use ad blockers to prevent sites from displaying ads to them, ad networks often attempt to bypass blockers, and this provider decided to use DGA domains to host its advertisements. With these domains changing daily, it becomes difficult to block the ads, the researchers point out.
What’s more, the ad network provider recently started using the DGA.popad domains to perform cryptojacking. These domains, the researchers discovered, have a strong connection with Coinhive family domains in DNS traffic and serve the coinhive.min.js web miner.
Some of the DGA.popad domains have a high ranking, with one of them found in the top 2000 sites on Alexa and several others in the top 3000 list.
Once a user accesses such a site, their computer’s CPU starts being used to the full. According to 360 Netlab, the favicon.ico on the DGA.popad sites was found to run as a web miner. Most of the sites that would redirect users to DGA.popad domains are providing adult content and downloading services.
Because the impacted sites contain advertisements from this ad network, the cryptojacking activities are performed regardless of whether the user has an ad blocker installed or not.
Normally, users would be sent to a standard domain (serve.popads.net) hosted by the provider. If an ad blocker is used, the standard domain is blocked, and the visitor is sent to one of the DGA.popad domains. Regardless of the delivery mechanism, both the ad and the cryptojacking script are served.
“We are not able to make a detailed assessment. This is because only part of all the traffic passing DGA.popad and serve.popads.net will be inserted a web miner, but we are not sure which part will be selected, for now,” the researchers note.
Trump Yet to Order Spies to Retaliate Against Russia: NSA Chief
28.7.2018 securityweek BigBrothers
President Donald Trump has not yet ordered his spy chiefs to retaliate against Russian interference in US elections, the head of the National Security Agency told lawmakers Tuesday.
"We have not opted to engage in some of the same behaviors we are seeing," said Admiral Michael Rogers, who heads both the NSA -- the leading US electronic eavesdropping agency -- and the new US Cyber Command, the military body charged with online combat.
Asked in a Senate Intelligence Committee hearing if he had received orders from Trump to fight back against Moscow's meddling, Rogers said: "No, I have not."
Rogers denied claims that the agency is doing nothing to push back against Russian hacking, theft of US cyber secrets and other activities.
However, he acknowledged: "They have not paid a price that is sufficient to change their behavior."
Rogers echoed the comments he and five other US intelligence chiefs made two weeks ago at the House Intelligence Committee, where all said they had not been ordered by Trump to counter the Russians.
The US has accused Russia of actively interfering in the 2016 presidential election, stealing Democratic party communications and pushing out disinformation through social media.
It also accuses Moscow of stealing hacking secrets of the US intelligence community.
Rogers said an order for Trump is needed before the US intelligence community and military can undertake offensive online operations against the Russians.
"What I see on the Cyber Command side leads me to believe that if we don't change the dynamic here, that this is going to continue, and 2016 won't be viewed as isolated," he said.
But he said that at a lower level, the NSA and Cyber Command could take some unspecified actions to rebuff attackers.
Asked about the exchange in Congress, White House spokeswoman Sarah Sanders suggested the president does not need to act.
"Nobody is denying him the authority," she said of Rogers.
A vulnerability in Facebook exposed email and details of page administrator
28.7.2018 securityaffairs Social
The security researcher Mohamed Baset discovered a vulnerability in Facebook that exposed email and other details of a page administrator.
Facebook has recently addressed an information disclosure vulnerability discovered by the security researcher Mohamed Baset that exposed page administrator.
According to Baset, the flaw is a “logical error” that he discovered after receiving an invitation to like a Facebook page on which he had liked a post.

“One day i liked one of the posts of a specific page but i didn’t liked or followed the page itself after a few days i got an email notification from facebook regarding an invitation to like the page that i did already liked one of its posts, I was amazed by the feature but i realized that this is a feature to target non-fans and i was wondering what could go wrong since this is a new feature ?” state the blog post published by the expert.
“From the investigations that i’m doing sometimes in the office of the fraud and phishing emails i’m always and blindly showing the “Original” of the message (that can be achieved by clicking on the little drop-down menu arrow beside the message reply button)”
The researchers analyzed the source code of the email sent by the social network and discovered it includes the name of the administrator of the page and other info.

The researcher reported the issue to Facebook that acknowledged it and decided to award the expert $2,500 as part of its bug bounty program.
Facebook announced to have paid out more than $880,000 for 400 vulnerability reports submitted by hackers.
Many of you may consider that the issue is not so serious, but this isn’t true because under certain circumstance the data exposure could represent a threat to the users’ privacy
In the case of business or community pages, revealing the identities of the administrators could get them targeted by messages and comments.
“For many individual Facebook pages, the administrator and the page will share an identity, so putting the admin’s name in the page’s email isn’t really giving away much. But for business or community pages, which might have a number of co-administrators, you wouldn’t expect Facebook to reveal anything more than the name of the page itself, at least not without asking.” reads the blog post published by Sophos. “If nothing else, this protects individual employees from getting bombarded with comments and questions – whether they’re praises or rants – in place of the account itself.”
Recently patched CVE-2018-4878 Adobe Flash Player flaw now exploited by cybercriminals
28.7.2018 securityaffairs Vulnerebility
Security researchers at Morphisec have uncovered a massive hacking campaign that is exploiting the recently patched CVE-2018-4878 Adobe Flash Player vulnerability.
Threat actors are exploiting the use-after-free flaw to deliver malware.
The CVE-2018-4878 vulnerability was fixed by Adobe on February 6, after security experts discovered it was used by North Korea-linked APT37 group in targeted attacks against South Korea.
Now the same vulnerability has been exploited by other threat actors in the wild as confirmed by Morphisec. The company spotted a campaign on February 22, the attackers were using a version of the exploit similar to the one used by the APT37 group.
The campaign is attributed to a financially motivated threat actor that exploited the CVE-2018-4878 in a malspam campaign, another thing highlighted by the researchers is that this exploit did not have a 64-bit version like the original one.
The attackers used spam emails containing a link to a document stored on safe-storage[.]biz. Once downloaded and opened, the document tries to trick victims with social engineering. It notifies users that an online preview is not available and instructs them to enable editing mode in order to view the content.
If the user enables the editing mode, the CVE-2018-4878 Adobe vulnerability is exploited and the Windows command prompt is executed. The associated cmd[.]exe file is then injected with malicious shellcode that connects to the attacker’s domain.
Security researchers at Morphisec have uncovered a massive hacking campaign that is exploiting the recently patched CVE-2018-4878 Adobe Flash Player vulnerability.
Threat actors are exploiting the use-after-free flaw to deliver malware.
The CVE-2018-4878 vulnerability was fixed by Adobe on February 6, after security experts discovered it was used by North Korea-linked APT37 group in targeted attacks against South Korea.
Now the same vulnerability has been exploited by other threat actors in the wild as confirmed by Morphisec. The company spotted a campaign on February 22, the attackers were using a version of the exploit similar to the one used by the APT37 group.
The campaign is attributed to a financially motivated threat actor that exploited the CVE-2018-4878 in a malspam campaign, another thing highlighted by the researchers is that this exploit did not have a 64-bit version like the original one.
The attackers used spam emails containing a link to a document stored on safe-storage[.]biz.
The URLs included in the emails is generated with Google’s URL shortening service, this circumstance allowed the researchers to determine the number of victims that clicked it. According to Morphisec each of the different links used in this campaign had been clicked tens and even hundreds of times within 3-4 days of being created.
Once downloaded and opened, the document tries to trick victims with social engineering. It notifies users that an online preview is not available and instructs them to enable editing mode in order to view the content.

If the user enables the editing mode, the CVE-2018-4878 Adobe vulnerability is exploited and the Windows command prompt is executed. The associated cmd[.]exe file is then injected with malicious shellcode that connects to the attacker’s domain.
“On February 22, 2018, Morphisec Labs spotted several malicious word documents exploiting the latest Flash vulnerability CVE-2018-4878 in the wild in a massive malspam campaign.” states the analysis published by Morphisec.
“After downloading and opening the Word document, the attack exploits the Flash vulnerability 2018-4878 and opens a cmd[.]exe which is later remotely injected with a malicious shellcode that connects back to the malicious domain.”
Then the shellcode downloads a dll from the same domain, which is executed using Microsoft Register Server utility to bypass whitelisting solutions.
According to the experts, only a limited number of security solutions flag the bait documents as malicious.
“As expected and predicted, adversaries have quickly adopted the Flash exploit, which is easily reproducible. With small variations to the attack, they successfully launched a massive malspam campaign and bypassed most of the existing static scanning solutions once again.” concluded Morphisec.
Widespread Vulnerability Found in Single-Sign-On Products
27.7.2018 securityweek Vulnerebility
A behavioral quirk in SAML libraries has left many single-sign-on (SSO) implementations vulnerable to abuse. It allows an attacker that has gained any authenticated access to trick the system into granting further access as a different user without knowledge of that user's password.
This could be used by an attacker who has compromised a low level limited access account to acquire access to third-party cloud services -- or it could be used by a malicious insider seeking access to reserved network areas (such as the payroll databases, or HR records).
The vulnerability was discovered by the research team of Duo Security, itself an SSO provider; and is described in a blog posted today. It affects many of the leading SSO providers, and probably affects the majority of proprietary company SSO developments.
Duo has confirmed the flaw in OneLogin - python-saml (CVE-2017-11427); OneLogin - ruby-saml (CVE-2017-11428); Clever - saml2-js (CVE-2017-11429); OmniAuth-SAML (CVE-2017-11430); Shibboleth (CVE-2018-0489); and Duo Network Gateway (CVE-2018-7340).
Security Assertion Markup Language (SAML) is the underlying protocol used by most SSO implementations. It is what allows authentication to be passed between a company's identity store and, for example, a third-party service. Typically, a user will log onto the identity store. This contains the credentials that will allow the same user to access other services.
SAML is used to pass authentication, via the browser, from the identity provider to the third-party service, granting access. The flaw lies in how authentication is encoded by SAML in the provider's 'response'.
The SAML authentication response contains two primary elements: the assertion and the signature. The assertion element says this NameID is authenticated. The signature element is designed to prevent the authenticated user NameID being changed at any point between the identity provider and the service being accessed. "If the attacker can modify the 'NameID' without invalidating the signature, that would be bad," suggest the Duo researchers; and then proceed to explain how it can be done.
"One of the causes of this vulnerability is a subtle and arguably unexpected behavior of XML libraries like Python’s 'lxml' or Ruby’s 'REXML'," write the blog's authors. Comments can be included in the signature, but the canonicalization process of the SAML libraries tend to drop all text after the first text node to isolate the NameID.
"So," explain the researchers, "as an attacker with access to the account 'user@user.com.evil.com', I can modify *my own* SAML assertions to change the NameID to 'user@user.com' when processed by the SP." The seven characters are <!----> inserted before .evil.com. This causes the canonicalization process to drop '.evil.com', leaving the authenticated account as 'user@user.com'.
Not all SSO implementations are vulnerable to this glitch; but Duo has demonstrated that many are. All that is required from the attacker is a genuine account that he can 'modify' to his attack target, plus the relatively minor technical savvy to intercept and edit the SAML authentication as it passes through the browser.
"Remediation of this issue," notes the report, "somewhat depends on what relationship you have with SAML." It gets a bit complicated. "Duo has released updates for the Duo Network Gateway in version? ?1.2.10?. If you use the DNG as a SAML Service Provider and are not at version 1.2.10 or higher (at the time of writing this, 1.2.10 is the latest version), we recommend upgrading."
Different affected SSOs will have different specific recommendations, and it would be best to refer to them for guidance. Similarly, there are different recommendations for maintainers of identity or service providers, maintainers of SAML processing libraries, and maintainers of XML parsing libraries. One thing that would help, suggest the authors, is the ability to enforce multi-factor authentication, "because this vulnerability would only allow a bypass of a user’s first factor of authentication." But the authors also warn, "if your IdP is responsible for both first factor and second factor authentication, it’s likely that this vulnerability bypasses both!"
Because multiple vendors are affected by this vulnerability, Duo Security worked with CERT/CC to co-ordinate disclosure. It provided the vulnerability information to CERT/CC on 18 December 2017. By 20 February 2018, all notified affected vendors had confirmed they were ready for disclosure; and Duo Security has disclosed the vulnerability details today.
Ann Arbor, Michigan-based Duo Security, a cloud-based provider of identity and access management solutions, announced a $70 million Series D funding round led by Meritech Capital Partners and Lead Edge Capital in October 2017. This brought the total amount raised to $119 million, and valued the company at $1.17 billion.
Industrial Cybersecurity Firm CyberX Raises $18 Million
27.7.2018 securityweek IT
Industrial cybersecurity startup CyberX announced today that it has raised $18 million in a Series B funding round, bringing the total amount received to date by the company to $30 million.
The latest funding round was led by Norwest Venture Partners, which also invested in FireEye and Symantec-acquired Fireglass, with participation from previous investors Glilot Capital Partners, Flint Capital, ff Venture Capital, and OurCrow.
CyberX says it plans on using the additional funding to continue its expansion in Europe and the United States, drive international growth, and expand its product development, research, and threat intelligence teams.
Founded in 2013 by military cyber experts Nir Giller and Omer Schneider, CyberX offers a platform that continuously monitors networks and collects data to help detect potentially malicious activity. The company also recently unveiled simulation technology designed to help predict breach and attack vectors.
CyberX says its product has been used by Global 2000 organizations across the energy and utilities, chemical, oil and gas, manufacturing, and other critical infrastructure sectors.
“There is a growing need in many enterprises to connect their IIoT and ICS networks to corporate IT networks for performance, monitoring, and manageability reasons. This trend creates a new security risk which requires a modern, IIoT-optimized, security solution.” said Dror Nahumi, general partner at Norwest Venture Partners. “We are extremely impressed with CyberX’s solution and its successful adoption with top-tier enterprise customers across multiple verticals.”
“We’re proud that our team has delivered a series of industry-firsts, including the first anomaly detection platform to incorporate ICS-specific threat intelligence, risk and vulnerability assessments, and automated threat modeling, as well as native integration with SOC tools,” said Giller. “By providing SOC teams with deeper visibility into Operational Technology (OT) assets, behaviors, and threats, we’re helping organizations implement a unified approach across IT and OT security and remove silos between IT and OT -- thereby improving their combined IT/OT risk posture.”
CyberX previously raised $20,000 in 2013, $2 million in 2014, and another $9 million in 2016, which, along with some add-on investments to the Series A round brought the total raised so far to $30 million. The company noted that its latest funding is the largest B round to date in industrial cybersecurity.
Facebook Flaw Exposed Page Administrators
27.7.2018 securityweek Social
Facebook recently patched an information disclosure vulnerability that exposed page administrators, researcher Mohamed Baset reported this week.
Baset claimed he discovered the issue, which he described as a “logical error,” within a few minutes of receiving an invitation to like a Facebook page on which he had liked a post.
Looking at the email’s source code, the researcher noticed that it included the name of the page’s administrator and other details.
After being notified through its bug bounty program, Facebook acknowledged the vulnerability and decided to award the expert $2,500 for his findings.
Sophos’ Paul Ducklin has provided an explanation on why such an information disclosure flaw can pose a problem to Facebook page administrators.
“For many individual Facebook pages, the administrator and the page will share an identity, so putting the admin’s name in the page’s email isn’t really giving away much,” Ducklin said. “But for business or community pages, which might have a number of co-administrators, you wouldn’t expect Facebook to reveal anything more than the name of the page itself, at least not without asking.”
“If nothing else, this protects individual employees from getting bombarded with comments and questions – whether they’re praises or rants – in place of the account itself,” the expert added.
Baset, founder and lead penetration tester at Seekurity, said this was the second time he reported a vulnerability to Facebook without having to write any code to demonstrate his findings.
Facebook reported recently that last year it paid out more than $880,000 for 400 valid vulnerability reports submitted by white hat hackers.
Splunk to Acquire Security Orchestration Firm Phantom for $350 Million
27.7.2018 securityweek IT
Machine data solutions firm Splunk said on Tuesday that it has agreed to acquire Phantom Cyber, a provider of Security Orchestration, Automation and Response (SOAR) solutions.
Under the terms of the agreement, Splunk will pay approximately $350 million in cash and stock to acquire Palo Alto, Calif.-based Phantom.
Phantom, which has raised more than $23 million in funding, has developed a community-powered security automation and orchestration platform that currently has more than 200 “apps” which integrate with various security products. These apps are available for a wide range of security tools from partners including Cisco, McAfee, Palo Alto Networks, RSA Security, Symantec, Splunk, HPE, IBM and others.
By combining technologies from both companies, Splunk says that IT teams will be able to leverage automation capabilities to “help solve automation challenges in a widening range of use cases, including Artificial Intelligence for IT Operations (AIOps).”
Following the acquisition, Phantom founder and CEO Oliver Friedrichs will report to Haiyan Song, senior vice president and general manager of security markets at Splunk.
The acquisition is expected to close during the first half of 2018, subject to customary closing conditions and regulatory reviews.
“The majority of purchase price consideration will be paid from cash on our balance sheet. Total equity consideration plus Phantom employee retention incentives will result in less than one percent total dilution from this transaction,” said Dave Conte, chief financial officer, Splunk.
Investors in Phantom include, iconic Silicon Valley VC firm Kleiner Perkins, TechOperators Venture Capital, Blackstone, Foundation Capital, In-Q-Tel, Rein Capital, Zach Nelson, and John W. Thompson.
Changes in Apple’s iCloud Security Policies and Argument of China
27.7.2018 securityaffairs BigBrothers
Changes in Apple’s iCloud Security Policies – Apple announced to relocating the encryption key for users data in China; from the United States of America to some country in Asia!
The latest chaos in the digital world regarding Apple has stricken like a bullet, as the iPhone manufacturer announced to relocating the encryption key for users data in China; from the United States of America to some country in Asia!
Well, some security advocates argue that this is incorrect for the corporation itself as well as a privacy threat for users, but according to Apple Company; the codes are secure.
According to the reports, the users of iCloud in China are confused that in what way Apple will manage the confidentiality of their essential data.
Apple too fears that data protection employees have concerns about changing the privacy of iCloud users in China, as per two reports this week.
The classified data such as online emails, photographs, and messages stay protected from hackers by encryption. And now, Apple will store encryption keys in China instead of the United States of America (Reuters and the Wall Street Journal reports).
It means that the Chinese authorities do not need to go to USA law agencies to force Apple to provide the rights to the data. This step in reaction to newly introduced laws in China, according to which iCloud services offered to the citizens, should secure data within premises of the country and can be used by Chinese organizations.
By the end of the coming month, Apple is going to start transmitting coded information to China and will work closely with a Chinese government. Apple did not say when the encryption data keys would move abroad.
Data protection advocates said, “The change can cause problems for political and other dissidents”.
“Given that Apple is going to work in China, it is unlikely that government can get access to Apple’s data from the local community,” said the professor at the Toronto University, studying the actions of the Chinese government carefully.
Apple says, however, that the data keys stored in a secure place, still Apple will control them. Besides, Apple also claimed that it would provide data only on demand to China’s current legislative requirements and did not create loopholes for access.
Apple’s high-level officer said to news agencies that iCloud is a matter of concern for the recently introduced laws.
The spokeswoman also noted that Apple decision to break the service of iCloud in China would lead to reduced client’s interaction with Apple and would reduce the security and confidentiality of data for Chinese users.
Big multinationals like Microsoft and Amazon also work with Chinese companies to provide cloud storage service and use the vast Chinese market. Two technological giants of USA refused to inform the magazine, where the encryption keys of the company’s data store.
Apple informed the news agencies that they sent a warning about the transition to Chinese iCloud users, which will allow them to disable iCloud to avoid data storage in the country. Apple also told that no one will be touched before accepting new terms of use in China.
Users whose configurations allow another nation like Macao and Hong Kong have not registered their data on servers in China.
The Reuters also includes Taiwan in this list; the newspaper does not do this.
Apple Company and Amazon did not respond to our request for additional comments yet. Microsoft also denied giving any further comments.
Israeli mobile forensics firm Cellebrite can unlock every iPhone device on the market
27.7.2018 securityaffairs Apple
The Israeli mobile forensics firm Cellebrite has designed a technology that allows it to unlock almost any iPhone, including the latest iPhone X.
We have debated for a long time the legal dispute between Apple and the FBI for unlocking the San Bernardino shooter’s iPhone 5c.
The tech giant refused to help the US authorities to unlock the mobile device and the FBI paid over a million dollar to a third-party company to access data contained in the San Bernardino’s shooter’s iPhone.

Such kind of dispute would not happen in the future, the Israeli mobile forensics firm Cellebrite has designed a technology that allows it to unlock almost any iPhone, including the latest iPhone X.
The Israeli mobile forensics firm Cellebrite that is one of the leading companies in the world in the field of digital forensics. The company already works with the principal law enforcement and intelligence agencies worldwide.
Cellebrite provides the FBI with decryption technology as part of a contract signed in 2013, its technology allows investigators to extract information from mobile devices.
The company’s Advanced Unlocking and Extraction Services could be used to unlock every iPhone running iOS 11 and older versions.
“Cellebrite, a Petah Tikva, Israel-based vendor that’s become the U.S. government’s company of choice when it comes to unlocking mobile devices, is this month telling customers its engineers currently have the ability to get around the security of devices running iOS 11.” reads a post published by Forbes.
“That includes the iPhone X, a model that Forbes has learned was successfully raided for data by the Department for Homeland Security back in November 2017, most likely with Cellebrite technology.”
Cellebrite says it advanced services can hack into “Apple iOS devices and operating systems, including iPhone, iPad, iPad mini, iPad Pro and iPod touch, running iOS 5 to iOS 11.”
According to Forbes, anonymous sources confirmed that Cellebrite could also unlock the iPhone 8, and likely the iPhone X.
“a source in the police forensics community told Forbes he’d been told by Cellebrite it could unlock the iPhone 8. He believed the same was most probably true for the iPhone X, as security across both of Apple’s newest devices worked in much the same way.” continues Forbes.
Law enforcement agencies that need to unlock a device (iOS or Android) simply need to send it to the company Labs where a pool of experts will do the job, the service costs as little as $1,500 per unlock.
“In its labs, the company then uses whatever secret exploits it has to crack the lock and either hands it back to investigators so they can take data from the device, or Cellebrite can do that for them. As Forbes previously detailed, this can be relatively inexpensive, costing as little as $1,500 per unlock.” states Forbes.
It also appears the FBI has already tried out Cellebrite service on the latest Apple devices, the iPhone X. According to a warrant viewed by Forbes related to a suspect in an arms trafficking (Abdulmajid Saidi), his iPhone X was sent to a Cellebrite specialist at the DHS Homeland Security Investigations Grand Rapids labs and the data extracted on December 5.
Cellebrite hasn’t commented on the latest report.
Flaw in Popular μTorrent Software Lets Hackers Control Your PC Remotely
27.2.2018 thehackernews Vulnerebility

If you have installed world's most popular torrent download software, μTorrent, then you should download its latest version for Windows as soon as possible.
Google's security researcher at Project Zero discovered a serious remote code execution vulnerability in both the 'μTorrent desktop app for Windows' and newly launched 'μTorrent Web' that allows users to download and stream torrents directly into their web browser.
μTorrent Classic and μTorrent Web apps run in the background on the Windows machine and start a locally hosted HTTP RPC server on ports 10000 and 19575, respectively, using which users can access its interfaces over any web browser.
However, Project Zero researcher Tavis Ormandy found that several issues with these RPC servers could allow remote attackers to take control of the torrent download software with little user interaction.
According to Ormandy, uTorrent apps are vulnerable to a hacking technique called the "domain name system rebinding" that could allow any malicious website a user visits to execute malicious code on user's computer remotely.
To execute DNS rebinding attack, one can simply create a malicious website with a DNS name that resolves to the local IP address of the computer running a vulnerable uTorrent app.
"This requires some simple DNS rebinding to attack remotely, but once you have the secret you can just change the directory torrents are saved to, and then download any file anywhere writable," Ormandy explained.
Proof-of-Concept Exploits for uTorrent Software Released Publicly
Ormandy also provided proof-of-concept exploits for μTorrent Web and μTorrent desktop (1 and 2), which are capable of passing malicious commands through the domain in order to get them to execute on the targeted computer.
Last month, Ormandy demonstrated same attack technique against the Transmission BitTorrent app.
Ormandy reported BitTorrent of the issues with the uTorrent client in November 2017 with a 90-days disclosure deadline, but a patch was made public on Tuesday—that's almost 80 days after the initial disclosure.
What's more? The re-issued new security patches the same day after Ormandy found that his exploits continued to work successfully in the default configuration with a small tweak.
"This issue is still exploitable," Ormandy said. "The vulnerability is now public because a patch is available, and BitTorrent have already exhausted their 90 days anyway."
"I see no other option for affected users but to stop using uTorrent Web and contact BitTorrent and request a comprehensive patch."
Patch your uTorrent Software NOW!
The company assured its users that all vulnerabilities reported by Ormandy it two of its products had been addressed with the release of:
μTorrent Stable 3.5.3.44358
BitTorrent Stable 7.10.3.44359
μTorrent Beta 3.5.3.44352
μTorrent Web 0.12.0.502
All users are urged to update their software immediately.
Phone-Cracking Firm Found a Way to Unlock Any iPhone Model
27.2.2018 thehackernews Apple
Remember the infamous encryption fight between Apple and the FBI for unlocking an iPhone belonging to a terrorist behind the San Bernardino mass shooting that took place two years ago?
After Apple refused to help the feds access data on the locked iPhone, the FBI eventually paid over a million dollar to a third-party company for unlocking the shooter's iPhone 5c.
Now, it appears that the federal agency will not have to fight Apple over unlocking iPhones since the Israeli mobile forensics firm Cellebrite has reportedly figured out a way to unlock almost any iPhone in the market, including the latest iPhone X.
Cellebrite, a major security contractor to the United States law enforcement agencies, claims to have a new hacking tool for unlocking pretty much every iPhone running iOS 11 and older versions, Forbes reports.
In its own literature [PDF] "Advanced Unlocking and Extraction Services," Cellebrite says its services can break the security of "Apple iOS devices and operating systems, including iPhone, iPad, iPad mini, iPad Pro and iPod touch, running iOS 5 to iOS 11."
Citing anonymous sources, the publication reported that Cellebrite could also unlock the iPhone 8, and since the security across Apple's newest iPhone devices worked in much the same way, the company can break the security of the iPhone X as well.
Besides Apple's devices, Cellebrite can also break into Google Android-powered smartphones from Samsung (Galaxy and Note series), Alcatel, Google Nexus, HTC, Huawei, LG, Motorola, ZTE and many more.
"Cellebrite Advanced Unlocking Services is the industry's only solution for overcoming many types of complex locks on market-leading devices," Cellebrite literature explains.
"This can determine or disable the PIN, pattern, password screen locks or passcodes on the latest Apple iOS and Google Android devices."
Last November, the Department of Homeland Security reportedly managed to get into an iPhone X owned by a suspect in an arms trafficking case, probably with the help of a Cellebrite-trained specialist.
However, a warrant discovered by Forbes does not mention the method or technology used by law enforcement to hack into the iPhone X.
Founded in 1999, Cellebrite provides digital forensics tools and software for mobile phones to its customers, which also includes the US government.
One of its main products is the Universal Forensic Extraction Device (UFED) that claims to help investigators extract all data and passwords from mobile phones.
While the Cellebrite's iPhone hacking tool has the potential to affect hundreds of millions of Apple users, Apple also rolls out software updates and patches on a regular basis.
So users are advised to keep their devices up-to-date, as its hard to say if the company's hacks work on the latest updates of iOS 11.
Neither Cellebrite nor Apple immediately commented on the latest report.
Android P Will Block Background Apps from Accessing Your Camera, Microphone
27.2.2018 thehackernews Android
Yes, your smartphone is spying on you. But, the real question is, should you care?
We have published thousands of articles on The Hacker News, warning how any mobile app can turn your smartphone into a bugging device—'Facebook is listening to your conversations', 'Stealing Passwords Using SmartPhone Sensors', 'Your Headphones Can Spy On You' and 'Android Malware Found Spying Military Personnel' to name a few.
All these stories have different objectives and targets but have one thing in common, i.e., apps running in the background covertly abuse ‘permissions’ without notifying users.
Installing a single malicious app unknowingly could allow remote attackers to covertly record audio, video, and taking photos in the background.
But, not anymore!
In a boost to user privacy, the next version of Google's mobile operating system, Android P, will apparently block apps idling in the background from accessing your smartphone's camera and microphone.
According to the Android Open Source Project (AOSP) commit, Google is working on two built-in features in Android P to protect its users from malicious apps spying on them using smartphones’ camera or microphone.
First spotted by XDA developers, the source code commit for both the camera and microphone changes notes that apps that are "idle" (aka running in the background) "for more than a certain amount of time" without specifying themselves will not be able to use the microphone or camera.
To do so, the Android P mobile operating system would target something known as an app's User ID (UID)—a unique ID assigned to an app when a user downloads it on his/her Android device that cannot be altered and are permanent until the app is uninstalled.
Android P would keep an eye on the app’s UID and block it from accessing the camera and microphone in any way whenever that UID is idle. Repeated attempts of requesting access to the camera would generate errors.
However, microphone-using apps will not be cut off from the microphone, but will "report empty data (all zeros in the byte array), and once the process goes in an active state, we report the real mic data."
It should also be noted that users talking on the smartphone while using other apps will not have to worry about these new features because the dialer application went into the background while active.
Imposing such limitations on apps would surely alleviate spying fears for Android users as of today when advertisers misuse such features to listen in on app users and Android malware capable of capturing audio, video, and images in the background are out there, for example, Skygofree and Lipizzan.
Android P is still in development and is not yet named. The company seems to release the next major version of Android in this year's Google I/O developer conference that will take place from May 8 to May 10 at the Shoreline Amphitheatre in Mountain View, California.
North Korea's Flash Player Flaw Now Exploited by Cybercriminals
27.2.2018 securityweek BigBrothers
Endpoint security firm Morphisec has spotted a massive campaign that exploits a recently patched Adobe Flash Player vulnerability to deliver malware.
The flaw in question, CVE-2018-4878, is a use-after-free bug that Adobe patched on February 6, following reports that North Korean hackers had been exploiting the vulnerability in attacks aimed at South Korea. The threat group, tracked as APT37, Reaper, Group123 and ScarCruft, has been expanding the scope and sophistication of its campaigns.
After Adobe patched the security hole, which allows remote code execution, other malicious actors started looking into ways to exploit CVE-2018-4878.
Morphisec said it spotted a campaign on February 22, which had been using a version of the exploit similar to the one developed by APT37. However, researchers pointed out that the exploit in the malspam campaign, unlike the one used in the original attacks, did not have a 64-bit version.
The attack starts with a spam email containing a link to a document stored on safe-storage[.]biz. Once downloaded and opened, the document informs users that an online preview is not available and instructs them to enable editing mode in order to view the content.
If users comply, the Flash vulnerability is exploited and the Windows command prompt is executed. The associated cmd.exe file is then injected with malicious shellcode that connects to the attacker’s domain.
A DLL file is then downloaded by the shellcode and executed using the Microsoft Register Server (regsvr32) utility. The legitimate tool is abused in an effort to bypass whitelisting products.
The malicious documents and the Flash exploit were only detected by a few security solutions based on their signature at the time of Morphisec’s analysis.
Since the URLs included in the spam emails were created using Google’s URL shortening service, researchers determined that each of the different links delivered in this campaign had been clicked tens and even hundreds of times within 3-4 days of being created. Users clicked on the links from various browsers and email services, including Outlook, Gmail and Aruba.it.
“As expected and predicted, adversaries have quickly adopted the Flash exploit, which is easily reproducible,” Morphisec’s Michael Gorelik explained in a blog post. “With small variations to the attack, they successfully launched a massive malspam campaign and bypassed most of the existing static scanning solutions once again.”
Evrial: The Latest Malware That Steals Bitcoins Using the Clipboard
27.2.2018 securityaffairs Virus
Evrial is a cryptocoin malware stealer discovered by the researchers at ElevenPaths which takes control of the clipboard to get “easy money”.
Evrial is a cryptocoin malware stealer which takes control of the clipboard to get “easy money”.
ElevenPaths has taken a deep technical dive into the malware itself, to show how it technically works, with a quite self-explanatory video. Aside, we have followed the steps of its Russian creator and found that his scam has been targeting other scammers themselves.

By the end of 2017, CryptoShuffle was a malware sample capable of reading the clipboard and modifying cryptocurrency addresses found there. Later, someone realized that there could be some business on providing these features as a service and started to sell the platform itself calling it “Evrial”. The product was formed by a .NET malware sample capable of stealing passwords from browsers, FTP clients, Pidgin and it could also modify the clipboard on the fly so as to change any copied cryptocurrency address to whatever address he wanted to.
Evrial allows the attacker to control it all from a comfortable panel where the stolen data can be easily explored. When the attacker buys the application, he can set his “name” for logging into the panel which will be hardcoded in the code, so that the shipped Evrial version is unique for him.
When you want to make a Bitcoin transfer, you usually copy and paste the destination address. In this sense, the attacker waits until the user, trusting in the clipboard action, sends a new transaction to the copied cryptocurrency address, without knowing that the recipient’s address has been silently modified to one that belongs to the attacker. The malware performs this task in the background for different types of address including Bitcoin, Litecoin, Ethereum and Monero addresses as well as for Steam identifiers and Webmoney WMR and WMZ units.
The author exposes his username in Telegram: @Qutrachka. The account is in the source code in order to be able to contact him. Using this information and some other analysed samples, it has been possible to identify users in different deep web forums under the name Qutra whose main objective: sell this malicious software. There are also evidences that CryptoSuffer malware was linked to the same threat actor after identifying a publication in Pastebin explaining the functionalities of this family and published under the same user.
We are able to guess how much it is in every wallet. He has received a total of 21 transactions into the Bitcoin wallet, supposedly from his victims, collecting approximately 0.122 BTC. If ransomware wallets usually receive the same amount from its victims, here the range is wider because the legitimate payments that the victim wants to do are, of course, of different amounts.
The attacker has moved all the money to several addresses to try to blur the trail of his payments. The attacker has received 0.0131 Litecoins as well, but this amount is still available in his wallet. On the other hand, it has not been possible to track any payments related to his Monero account because of how this technology works so as to hide the information of which parties have been involved in each operation. At the same time, we could not find out any additional information linked to his various Webmoney accounts (WMR and WMZ). Anyway, what is clear is that this type of malicious behavior is technically viable while it is being used in the wild.
Line Between Nation-State, Criminal Hackers Increasingly Blurred: Report
26.2.2018 securityweek Crime
The line between the level of sophistication typically exhibited by state-sponsored threat groups and cybercriminals became increasingly blurred in the past year, according to CrowdStrike’s 2018 Global Threat Report.
CrowdStrike has analyzed various aspects of the cybersecurity landscape in the past year, including targeted attacks launched by nation state actors, the tools and operations of cybercriminals, hacktivism, law enforcement campaigns, and the effectiveness of attacks and defense mechanisms.
According to the security firm, there are several factors that led to the leveling of the playing field, but one of the most significant is the so-called “trickle-down effect.” This product adoption model states that a product initially too expensive for the masses eventually gets cheap enough for the general public to acquire.
Applying this model to the cybersecurity scene, we have the EternalBlue exploit, which is believed to have been developed by the U.S. National Security Agency (NSA), getting leaked by a group named Shadow Brokers. This has allowed other state-sponsored attackers – including in the WannaCry and NotPetya attacks believed to have been launched by North Korea and Russia – and profit-driven cybercriminals to use the exploit to accomplish their own goals.
On one hand, attacks such as the ones involving NotPetya and WannaCry malware have inspired cybercriminals, giving them ideas on how to maximize profits. On the other hand, state-sponsored actors have also taken inspiration from cybercriminals – both the NotPetya and WannaCry attacks were made to appear as if they were ransomware campaigns launched by profit-driven criminals.
Sophisticated supply chain attacks have been typically used by nation state groups, but last year saw several incidents that did not appear to be the work of state-sponsored cyberspies.
One incident involved rogue Python libraries being uploaded to the Python Package Index (PyPI). While the libraries included malicious code, it actually turned out to be benign, which has led some experts to believe that it may have been the work of a grey hat hacker.
Other incidents involved a piece of macOS malware called ProtonRAT, which attackers managed to deliver last year on at least two occasions after compromising websites hosting popular video conversion and media player apps. Operation WilySupply analyzed by Microsoft also falls into this category.
The list of supply chain attacks attributed to state-sponsored groups last year included the CCleaner and NetSarang incidents, which some linked to China, and the NotPetya campaign, whose initial infection vector was an updater for a Ukrainian tax accounting application.
“CrowdStrike's report is just one more in a long line of publications that demonstrates the increasing futility of technical attribution. The largest detriment of this trend of nation states hiding in the hacking noise is that the security industry no longer can have confidence in its traditional technical attribution models. Relying on code usage and IPs in a world where we know tool kits and techniques are shared, stolen, and sold amongst hackers is a recipe for misattribution,” Ross Rustici, senior director of intelligence services at Cybereason, commented on the CrowdStrike report.
“Hackers, especially the higher tier have proven time and again that they are capable and willing to play on cybersecurity's habit of confirmation bias by using false flags to point the community in the direction of a particular nation state or criminal group that is either: 1) currently the most talked about group making which plays into the self interest of the company of finding something that already garners a lot of media and PR attention; or 2) plays to the nationalism of the victim,” Rustici added.
NanoCore RAT Creator Sentenced to Prison
26.2.2018 securityweek Virus
A Hot Springs, Arkansas man who last year admitted in court to creating the NanoCore RAT (Remote Access Trojan) was sentenced to 33 months in prison.
Taylor Huddleston, 27, was sentenced on Friday for helping and assisting with computer intrusions through the development and marketing of malicious software, the Department of Justice announced. The programs he created were used to steal sensitive data from victims, spy on them, and conduct other illegal intrusions.
In addition to the 33 months in prison, Huddleston was ordered to serve two years of supervised release following his prison sentence.
Accused of developing, marketing, and distributing two malware families, Huddleston pleaded guilty in court in July 2017.
The first malicious program Huddleston developed is the NanoCore RAT, a backdoor that allows attackers to steal information from victim computers, including passwords, emails, instant messages, and other sensitive data. Used to infect and attempt to infect tens of thousands of systems, the RAT allows attackers to activate infected machines’ webcams to spy on victims.
NanoCore RAT was used in attacks targeting the finance departments of small and medium-sized businesses in the U.K., the U.S. and India, as well as in other global infection campaigns. Distribution methods included, among others, fileless tricks to the abuse of free Voice-over-IP (VoIP) service Discord.
Huddleston also admitted to creating Net Seal, licensing software that allowed him to distribute malware for co-conspirators for a fee. Huddleston is said to have used Net Seal to assist Zachary Shames in his attempt to infect 3,000 systems with malware that was in turn used to infect 16,000 computers.
Huddleston built Net Seal in 2012 and created NanoCore in 2014 (he marketed the RAT as a remote desktop management utility.
In his guilty plea last year, Huddleston admitted that he intended the programs to be used maliciously.
PhishMe Acquired at $400 Million Valuation, Rebranded as Cofense
26.2.2018 securityweek Phishing
Private Equity Deal Values Cofense at $400 Million
PhishMe, a security awareness firm that focuses on training employees on how to recognize and report phishing attacks, has been acquired by a private equity consortium in a deal that valued the company at $400 Million.
The company has also re-branded and changed its name to Cofense.
“PhishMe was founded to challenge the cliché - human is the weakest link,” said Rohyt Belani, CEO and Co-Founder of Cofense. “The Cofense solution set leverages internal employee-generated attack intelligence in concert with purpose-built response technologies to break the attack kill chain at delivery. Cofense reflects the full breadth of our portfolio of enterprise-wide attack detection, response, and orchestration solutions.”
Cofense LogoThe company says it currently has more than 1700 customers globally and that its PhishMe Reporter is installed on more 10 million endpoints.
In a recent survey by the Financial Services Information Sharing and Analysis Center (FS-ISAC) that polled more than 100 of its 7,000 global members, thirty-five percent of CISOs in the financial sector consider staff training to be the top priority for cyber defense.
“With cybersecurity a top priority for organizations everywhere, our goal is to continue bringing innovative products to markets around the globe to help stop active attacks faster than ever,” Belani added.
Cofense says it has experienced roughly 80% CAGR over the last four years, and has new offices opening in Australia, Singapore, Dubai, and Saudi Arabia.
The company has previously raised a total of roughly $58 million, including a large $42.5 million funding round in July 2016. The company had raised $2.5 million in July 2012 in a Series A round, followed by $13 Million in a Series B funding round in March 2015.
Security awareness firms have been the subject of significant funding and M&A transactions in recent months.
Earlier this month, security awareness training firm Wombat Security agreed to be acquired by Proofpoint for $225 million in cash. In August 2017, Webroot acquired Securecast, an Oregon-based company that specializes in security awareness training. In October 2017, security awareness training and simulated phishing firm KnowBe4 secured $30 million in Series B financing, which brought the total amounbt raised by KnowBe4 to $44 million. Security awareness training firm PhishMe has raised nearly $58 million in funding, including a $42.5 million series C funding round in July 2016.
Researchers Propose Improved Private Web Browsing System
26.2.2018 securityweek Privacy
A group of researchers from MIT and Harvard have presented a new system designed to make private browsing even more private.
Dubbed Veil, the system proposes additional protections for people who share computers with other people at the office, in hotel business centers, or university computing centers. The new system, the researchers claim, can be used in conjunction with existing private-browsing systems and anonymity networks. The system works even if users don’t visit a page using a browser’s native privacy mode.
In a paper (PDF) describing Veil, Frank Wang – MIT Computer Science and Artificial Intelligence Laboratory (CSAIL), Nickolai Zeldovich – MIT CSAIL, and James Mickens – Harvard, explain that the system is meant to prevent information leaks “through the file system, the browser cache, the DNS cache, and on-disk reflections of RAM such as the swap file.”
The researchers explain that existing private-browsing sessions rely on retrieving data, loading it into memory, and attempting to erase it when the session is over. However, because of a complex memory management process, some data could end up on a hard drive, where it could remain for days, with the browser not knowing what happened to that data.
The newly proposed system keeps all the data that the browse loads into memory encrypted until it is displayed on the screen, the researchers say. Users no longer type a URL into the browser, but access the Veil website and enter the URL there. With the help of a blinding server, the Veil format of the requested page is transmitted.
While the Veil page can be displayed in any browser, there is a bit of code in the page that executes a decryption algorithm and all of the data associated with the page is unreadable until it goes through that algorithm, the researchers say.
The system would also add decoy, meaningless code to every served page, so that the underlying source file is modified without affecting the way the page looks to the user. With no two transmissions of a page by the blinding sever similar, an attacker capable of recovering snippets of decrypted code after a Veil session should not be able to determine what page the user had visited.
“The blinding servers mutate content, making object fingerprinting more difficult; rewritten pages also automatically encrypt client-side persistent storage, and actively walk the heap to reduce the likelihood that in-memory RAM artifacts will swap to disk in cleartext form. In the extreme, Veil transforms a page into a thin client which does not include any page-specific, greppable RAM artifacts,” the paper reads.
One other option would be to have the blinding server opening the requested page itself, taking a picture of it, and sending the picture to the user’s computer. Should the user click anywhere on the image, the browser records the position of the click and sends the data to the server, which processes it and returns an image of the updated page.
Veil uses an opt-in model, meaning that the use of the new private browsing system requires developers to create Veil versions of their sites. To help in this regard, the researchers built a compiler to help admins convert sites automatically and is also capable of uploading the converted version of a site to a blinding server.
“To publish a new page, developers pass their HTML, CSS, and JavaScript files to Veil’s compiler; the compiler transforms the URLs in the content so that, when the page loads on a user’s browser, URLs are derived from a secret user key. The blinding service and the Veil page exchange encrypted data that is also protected by the user’s key. The result is that Veil pages can safely store encrypted content in the browser cache; furthermore, the URLs exposed to system interfaces like the DNS cache are unintelligible to attackers who do not possess the user’s key,” the paper reads.
The blinding servers, however, require maintenance, either by a network of private volunteers or a for-profit company. However, site admins would also have the option to host Veil-enabled versions of their sites themselves.
Ukraine Arrests 'Avalanche' Cybercrime Organizer: Police
26.2.2018 securityweek CyberCrime
Ukraine has detained one of the organizers of the massive Avalanche cybercrime network, police said on Monday, over a year after the global ring was busted in an international raid.
"An organizer of the international crime platform known as 'Avalanche' which infected up to half a million computers in the world daily was detained in Kiev Sunday," Ukraine's cyber police said in a statement.
Avalanche was a criminal network providing infrastructure for malware and DDoS (distributed denial of service) spam attacks across the world before it was busted in an unprecedented global sting operation.
Speaking to AFP, a cyber police spokeswoman confirmed the arrested man was Gennadiy Kapkanov, a Ukrainian citizen who was using a passport with a different identity.
Police also searched his rented flat, seizing a laptop and memory storage devices, it said.
In November 2016, police from more than 25 countries smashed the network and arrested its top bosses following a four-year operation.
Hundreds of servers were shut down or seized and 800,000 internet domains were blocked, Europol said at the time, in one of the biggest takedowns to date.
During the operation, Kapkanov was also detained in the sting at his home in Poltava, a city in central Ukraine, but the local court did not formally arrest him and he disappeared, Ukrainian media said.
Later on Monday, the same court will have to rule again on whether to formally place Kapkanov under arrest.
VISA – The adoption of chip-and-PIN card technology lead to 70% Drop in Counterfeit Fraud
26.2.2018 securityaffairs Crime
VISA – The cases of counterfeit fraud had dropped by 70% in September 2017 compared to December 2015 thanks to the diffusion of the diffusion in the storefronts of payment systems for EMV cards.
The introduction of chip-and-PIN card technology in the United States improved in a significant way the security of merchants and has reduced payment card fraud.
The cases of counterfeit fraud had dropped by 70% in September 2017 compared to December 2015 thanks to the diffusion of the diffusion in the storefronts of payment systems for EMV cards.
“For merchants who have completed the chip upgrade, counterfeit fraud dollars
EMV chip cards and chip-activated merchants combat counterfeit fraud in the U.S.
December 2017 Visa Chip Card Update in September 2017 compared to December 2015″ states VISA.
The process started in 2011 with the introduction of EMV (Europay, MasterCard, Visa) card technology in the United States.
The process was very slow, according to Visa, by September 2015, only roughly 392,000 merchants were accepting payment card using the new technology. at the same period, the number of Visa debit and credit cards using the EMV technology was only at 159 million.
Now Visa has shared data related to the adoption of the EMV technology by December 2017. The number of storefronts that currently accept payments with chip cars has reached 2.7 million in the U.S. (+570%), representing 59% of the total.

The number of Visa payment cards using EMV technology increased passed from 159 million to 481 million (202%), with 67% of Visa payment cards having chips.

It is an excellent result, according to VISA Chip transactions continue to increase in the US. EMV cards accounted for 96% of the overall payment volume in the United States in December 2017, with chip payment volume reaching $78 billion.

Cybercriminals have responded to the adoption of EMV chip cards focusing their efforts on card-not-present (CNP) fraud had that is today a serious concern for merchants.
Paypal issue allows disclosure of account balance and recent transactions
24.2.2018 securityaffairs Safety
Paypal issue allows for enumeration of the last four digits of payment method and for the disclosure of account balance and recent transactions of any given PayPal account.
Introduction
This post details an issue which allows for enumeration of the last four digits of payment method (such as a credit or debit card) and for the disclosure of account balance and recent transactions of any given PayPal account.
This attack was submitted to PayPal’s bug bounty program where it was classified as being out of scope, which is something that would admittedly be unavailing to refute since their program scope does not mention anything about attacks on their interactive voice response system.

Prerequisites and Reconnaissance
In order to get started, the attacker would require knowledge of two pieces of information pertaining to an account, which would be the e-mail address and phone number linked to it.
Armed with knowledge of the e-mail address and phone number linked to an account, the attacker would visit the Forgot Password page on PayPal’s website, and enter the e-mail address associated with the targeted account.
The attacker would then be presented with the type of card linked to the account, as well as the last two digits of the same.

Attacking the Interactive Voice Response System
On first glance, the interactive voice response system on PayPal’s phone-based customer support seemingly allows for a maximum of three attempts at submitting the correct last four digits per phone call.
However, if the first attempt at submission is incorrect, the caller will not be notified of a successful submission in subsequent attempts made during the same phone call. This makes any additional attempts given to a caller during the same phone call completely cosmetic.
To get around this presumed limitation, the attacker would have to make only one attempt at submitting a possible combination of the last four digits per phone call.

Additionally, limiting the number of attempts to one submission per phone call makes the task of enumerating the correct combination much more time-efficient, and not to mention, it allows for easily distinguishing between a correct attempt and an incorrect one.
Furthermore, upon have tested this theory with my own account, I have been able to conclude that there is no limit on the number of submission attempts which can be made in this manner, meaning that hypothetically, an attacker could call 100,000 times to enumerate the last four digits entirely on their own.
That would, however, be disregarding the last two digits retrieved from the Forgot Password page, the knowledge of which effectively makes the attack much more feasible–by reducing the number of possible combinations from 100,000 to just 100.
Once the correct combination of the last four digits has been found, the attacker would simply have to use the interactive voice response system to retrieve information about the account.
After having entered the correct last four digits, the account’s current balance will automatically read off by the machine.
Additionally, to retrieve information about recent transactions, an attacker would simply have to say “recent transactions”, and the same would then be read off.
Attack Efficacy and Efficiency
If the aforementioned prerequisites have been met, an attacker would without fail have the ability to enumerate the correct last four digits of the payment method linked to an account. This information could then further be used to retrieve the account’s current balance and recent transactions as well.
Moreover, after having timed various attempts at submission of the last four digits, it was found that an attempt at submission would on average take around 30 seconds. The fastest possible time would be 27 seconds per phone call.
If we take the fastest possible time as our average, enumerating all possible combinations from 00XX to 99XX would take at most around 45 minutes. This time could then be halved by adding another phone in the mix to consecutively make calls with.
Possible Fixes
Users should be allowed to opt for privacy settings which keep the amount of data revealed on the Forgot Password page to a minimum. This would be similar to how Twitter allows its users to hide information about the email address and/or phone number linked to their account when attempting to reset its password.
It would also be similar to how Facebook allows users to choose whether their full names show up or not when their e-mail address is entered on the password reset page.
Perhaps some measures could be deployed where the last two digits of credit or debit card, if they need to be shown at all, are only shown when the request matches a certain criteria, such as if/when the request has been made from a recognizable device or location.
Conclusion
This issue allows for enumeration of the last four digits of the payment method on an account, which then allows for the disclosure of the account’s current balance and recent transactions.
An attacker with knowledge of the targeted account’s email address and phone number would first use PayPal’s Forgot Password page to retrieve the last two digits of the payment method linked to the account.
The attacker would then be able to accurately enumerate the last four–or rather the first two of the last four digits–of the payment method on the account by making phone calls to PayPal’s phone-based customer support and interacting with the interactive voice response system.
Once the attacker has successfully enumerated the last four digits of credit/debit card or bank account linked to the account, they would then be able to query the current account balance and recent transaction information at will.
Lastly, I would like to note that since there is no human interaction required or involved in the attack, it would essentially be a backdoor into PayPal accounts–allowing attackers to query current account balance and recent transaction information of any given account, at any time.
Czech President Wants Hacker 'Extradited to Russia' Not US
24.2.2018 securityweek BigBrothers
The Czech Republic's pro-Moscow president has repeatedly lobbied for a Russian hacker held in Prague and wanted by the US to be extradited to Russia, the justice minister was quoted as saying Saturday.
Yevgeni Nikulin, sought by the US for alleged cyberattacks on social networks and also by his native Russia on fraud charges, has been in a Prague prison since he was arrested in the Czech capital in October 2016 in a joint operation with the FBI.
The case comes amid accusations by Washington that Russia tried to "interfere" through hacking in the 2016 US election won by Donald Trump, charges the Kremlin has dismissed.
Last May, a Prague court ruled that the 30-year-old Nikulin can be extradited to either Russia or the United States, with the final say left to Justice Minister Robert Pelikan.
"It's true that there have been two meetings this year at which the president (Milos Zeman) asked me to extradite a Russian citizen not to the United States, but to Russia," Pelikan told the aktualne.cz news site.
The site said the meetings had taken place in January, while earlier this week Pelikan received Vratislav Mynar, the head of Zeman's office, who also lobbied for Nikulin's extradition to Russia.
"It's none of your business, but I have handed the minister a letter from the detained Nikulin's mother," Mynar told aktualne.cz.
Zeman's spokesman Jiri Ovcacek declined to comment on the matter when asked by AFP.
Following Nikulin's arrest, Moscow accused Washington of harassing its citizens and vowed to fight Nikulin's extradition.
It then issued a separate arrest warrant for him over alleged theft from the WebMoney settlement system.
The US has charged Nikulin with hacking into social networks LinkedIn and Formspring and into the file hosting service Dropbox, Nikulin's lawyer Martin Sadilek told AFP earlier.
He also said Nikulin alleges that FBI investigators had tried twice to persuade him to confess to cyberattacks on the US Democratic Party.
Zeman, a 73-year-old ex-communist with strong pro-Russian, pro-Chinese and anti-Muslim views, won a second five-year term in a presidential vote in January.
2,000 Computers at Colorado DOT were infected with the SamSam Ransomware
24.2.2018 securityaffairs Ransomware
SamSam Ransomware hit the Colorado DOT, The Department of Transportation Agency Shuts Down 2,000 Computers after the infection.
SamSam ransomware made the headlines again, this time it infected over 2,000 computers at the Colorado Department of Transportation (DOT).
The DOT has shut down the infected workstations and is currently working with security firm McAfee to restore the ordinary operations. Officials confirmed the ransomware requested a bitcoin payment.
“The Colorado Department of Transportation has ordered an estimated 2,000 employees to shut down their computers following a ransomware attack Wednesday morning.” wrote the CBS Denver.
The CDOT spokesperson Amy Ford said employees were instructed to turn off their computers at the start of business Wednesday after ransomware infiltrated the CDOT network.
“We’re working on it right now,” added Ford.
The good news is that crucial systems at the Colorado DOT such as surveillance cameras, traffic alerts were not affected by the ransomware.
David McCurdy, OIT’s Chief Technology Officer, issued the following statement:
“Early this morning state security tools detected that a ransomware virus had infected systems at the Colorado Department of Transportation. The state moved quickly to quarantine the systems to prevent further spread of the virus. OIT, FBI and other security agencies are working together to determine a root cause analysis. This ransomware virus was a variant and the state worked with its antivirus software provider to implement a fix today. The state has robust backup and security tools and has no intention of paying ransomware. Teams will continue to monitor the situation closely and will be working into the night.”
The Colorado DOT officials confirmed that the agency will not pay the ransom and it will restore data from backups.
The SamSam ransomware is an old threat, attacks were observed in 2015 and the list of victims is long, many of them belong to the healthcare industry. The attackers spread the malware by gaining access to a company’s internal networks by brute-forcing RDP connections.
Among the victims of the Samsam Ransomware there is the MedStar non-profit group that manages 10 hospitals in the Baltimore and Washington area. Crooks behind the attack on MedStar requested 45 Bitcoins (about US$18,500) for restoring the encrypted files, but the organization refused to pay the Ransom because it had a backup of the encrypted information.
In April 2016, the FBI issued a confidential urgent “Flash” message to the businesses and organizations about the Samsam Ransomware.
Back to the present, the Samsam Ransomware made the headlines in the first days of 2018, the malicious code infected systems of some high-profile targets, including hospitals, an ICS firm, and a city council.

Iran-linked group OilRig used a new Trojan called OopsIE in recent attacks
24.2.2018 securityaffairs BigBrothers APT
According to malware researchers at Palo alto Networks, the Iran-linked OilRig APT group is now using a new Trojan called OopsIE.
The Iran-linked OilRig APT group is now using a new Trojan called OopsIE, experts at Palo Alto Networks observed the new malware being used in recent attacks against an insurance agency and a financial institution in the Middle East.
One of the attacks relied on a variant of the ThreeDollars delivery document, the same malicious document was sent by the threat actor to the UAE government to deliver the ISMInjector Trojan.
In the second attack detected by PaloAlto, the OilRig hackers attempted to deliver the malicious code via a link in a spear phishing message.
“On January 8, 2018, Unit 42 observed the OilRig threat group carry out an attack on an insurance agency based in the Middle East. Just over a week later, on January 16, 2018, we observed an attack on a Middle Eastern financial institution. In both attacks, the OilRig group attempted to deliver a new Trojan that we are tracking as OopsIE.” reads the analysis from Palo Alto Networks.
The first attack occurred on January 8, 2018, the hackers sent two emails to two different email addresses at the target organization within a six minutes time span. Attackers spoofed the email address associated with the Lebanese domain of a major global financial institution.
OilRig launched another attack on January 16, in this case, the attackers downloaded the OopsIE Trojan from the command and control (C&C) server directly. The same organization was hit by OilRig for the second time, the first attacks occurred in 2017.
The researchers explained that the malware is packed with SmartAssembly and obfuscated with ConfuserEx.
The hackers gain persistence by creating a VBScript file and a scheduled task to run itself every three minutes. The OopsIE Trojan communicates with the C&C over HTTP by using the InternetExplorer application object.
“By using the InternetExplorer application object, all C2 related requests will look as if they came from the legitimate browser and therefore will not contain any anomalous fields within the request, such as custom User-Agents. The OopsIE Trojan is configured to use a C2 server hosted at:
www.msoffice365cdn[.]com” states the analysis.
“The Trojan will construct specific URLs to communicate with the C2 server and parses the C2 server’s response looking for content within the tags <pre> and </pre>. The initial HTTP request acts as a beacon”

The Trojan can run a command, upload a file, or download a specified file.
Oilrig will continue to adapt its tactics, the experts believe that it will remain a highly active threat actor in the Middle East region.
“This group has repeatedly shown evidence of a willingness to adapt and evolve their tactics, while also reusing certain aspects as well. We have now observed this adversary deploy a multitude of tools, with each appearing to be some form of iterative variation of something used in the past. However, although the tools themselves have morphed over time, the plays they have executed in their playbook largely remain the same when examined over the attack life cycle,” Palo Alto concludes.
FBI warns of spike in phishing campaigns to gather W-2 information
24.2.2018 securityaffairs BigBrothers
The FBI is warning of a spike in phishing campaigns aimed to steal W-2 information from payroll personnel during the IRS’s tax filing season.
The FBI has observed a significant increase since January of complaints of compromised or spoofed emails involving W-2 information.
“Beginning in January 2017, IRS’s Online Fraud Detection & Prevention (OFDP), which monitors for suspected IRS-related phishing emails, observed an increase in reports of compromised or spoofed emails requesting W-2 information.” states the alert published by the FBI.
W-2 information is a precious commodity for crooks that are showing an increasing interest in tax data.
Law enforcement and security experts observed many variations of IRS and tax-related phishing campaigns, but most effective are mass data thefts, for example, campaigns targeting Human Resource (HR) professionals.
“The most popular method remains impersonating an executive, either through a compromised or spoofed email in order to obtain W-2 information from a Human Resource (HR) professional within the same organization.” continues the alert.
“Individual taxpayers may also be the targeted, but criminals have evolved their tactics to focus on mass data thefts.”
w-2 information
A separate warning od W-2 -related phishing campaigns was issued by the Internal Revenue Service.
“The Form W-2 scam has emerged as one of the most dangerous phishing emails in the tax community. During the last two tax seasons, cybercriminals tricked payroll personnel or people with access to payroll information into disclosing sensitive information for entire workforces.” reads the IRS’s advisory issued in January. “The scam affected all types of employers, from small and large businesses to public schools and universities, hospitals, tribal governments and charities.”
Once cyber criminal obtained the W-2 information, they will request a wire transfer, unfortunately, in the case of businesses and organizations the scam is not discovered for weeks or months.
“The initial email may be a friendly, “hi, are you working today” exchange before the fraudster asks for all Form W-2 information. In several reported cases, after the fraudsters acquired the workforce information, they immediately followed that up with a request for a wire transfer.” continues the advisory.
“In addition to educating payroll or finance personnel, the IRS and Security Summit partners also urge employers to consider creating a policy to limit the number of employees who have authority to handle Form W-2 requests and that they require additional verification procedures to validate the actual request before emailing sensitive data such as employee Form W-2s.”
Phishing scams related W-2 information have been increasing, the number of reports regarding this criminal practice from both victims and non-victims jumped from over 100 in 2016 up to roughly 900 in 2017, The IRS confirmed that more than 200 employers were victimized in 2017.
“Reports to phishing@irs.gov from victims and nonvictims about this scam jumped to approximately 900 in 2017, compared to slightly over 100 in 2016. Last year, more than 200 employers were victimized, which translated into hundreds of thousands of employees who had their identities compromised.” continues the alert.
Let me close with recommendations published by the FBI to avoid being victims of W-2 phishing scams and BEC:
Limit the number of employees within a business who have the authority to approve and/or conduct wire transfers and handle W-2 related requests or tasks
Use out of band authentication to verify requests for W-2 related information or wire transfer requests that are seemingly coming from executives. This may include calling the executive to obtain verbal verification, establishing a phone Personal Identification Number (PIN) to verify the executive’s identity, or sending the executive via text message a one-time code and a phone number to call in order to confirm the wire transfer request
Verify a change in payment instructions to a vendor or supplier by calling to verbally confirm the request. The phone number should not come from the electronic communication, but should instead be taken from a known contact list for that vendor
Maintain a file, preferably in non-electronic form, of vendor contact information for those who are authorized to approve changes in payment instructions
Delay the transaction until additional verifications can be performed such as having staff wait to be contacted by the bank to verify the wire transfer
Require dual-approval for any wire transfer request involving one or more of the following:
A dollar amount over a specific threshold
Trading partners who have not been previously added to a “white list” of approved trading partners to receive wire payments
New trading partners
New bank and/or account numbers for current trading partners
Wire transfers to countries outside of the normal trading pattern
Disappearing bytes: Reverse engineering the MS Office RTF parser
24.2.2018 Kaspersky Exploit
Microsoft Office was a prime target for attacks in 2017. As well as the large number of vulnerabilities discovered and proof-of-concept exploits published, malware authors felt it necessary to prevent detection of ‘one-day’ and ‘old-day’ exploits by antivirus software. It also became clear that using RTF parsing features and peculiarities are no longer enough to effectively evade detection. Along with the rise of MS Office exploitation, when RTF is used as a container for an exploit, we encountered lots of samples that were ‘exploiting’ the implementation of Microsoft Word’s RTF parser to confuse all other third-party RTF parsers, including those used in AV software.
To achieve parsing exactly like that in MS Office, we needed to reverse-engineer it.
I decided to look first at MS Office 2010, because when it comes to parsing it’s better to look at an older implementation. I then compared my findings with those found in newer versions.
An RTF parser comprises a state machine with 37 states, 22 of which are unique:
We’ll look at the most significant states and those that have an influence on the parsing of \objdata, a destination control word that contains the object data. Microsoft OLE links, Microsoft OLE embedded objects, and Macintosh Edition Manager subscriber objects are represented in RTF as objects. These states are:
enum
{
PARSER_BEGIN = 0,
PARSER_CHECK_CONTROL_WORD = 2,
PARSER_PARSE_CONTROL_WORD = 3,
PARSER_PARSE_CONTROL_WORD_NUM_PARAMETER = 4,
PARSER_PARSE_HEX_DATA = 5,
PARSER_PARSE_HEX_NUM_MSB = 7,
PARSER_PARSE_HEX_NUM_LSB = 8,
PARSER_PROCESS_CMD = 0xE,
PARSER_END_GROUP = 0x10,
// …
};
Microsoft Office is shipped without debug symbols, meaning it wasn’t possible to recover the original state names. However, I believe I’ve chosen suitable names according to their underlying functionality.
The first state executed on an opened RTF file is PARSER_BEGIN. In most cases, it’s also executed after processing a control word. The main goal of this state is to determine the next state according to encountered char, destination, and other values stored in the ‘this’ structure and set by control word processors. By default the next state is PARSER_CHECK_CONTROL_WORD.
case PARSER_BEGIN:
// … – checks that we dont need
while (data.pos != data.end)
{
byte = *(uint8_t*)data.pos;
data.pos++;
if (this->bin_size > 0)
{
goto unexpected_char;
}
// …
if (byte == 9)
{
// …
continue;
}
if (byte == 0xA || byte == 0xD)
{
// …
break;
}
if (byte == ‘\\’)
{
uint8_t byte1 = *(uint8_t*)data.pos;
if (byte1 == ‘\”)
{
if (this->destination == listname ||
this->destination == fonttbl ||
this->destination == revtbl ||
this->destination == falt ||
this->destination == leveltext ||
this->destination == levelnumbers ||
this->destination == liststylename ||
this->destination == protusertbl ||
this->destination == lsdlockedexcept)
goto unexpected_char;
state = PARSER_CHECK_CONTROL_WORD;
// …
break;
}
if (byte1 == ‘u’)
{
// …
break;
}
state = PARSER_CHECK_CONTROL_WORD;
// …
break;
}
if (byte == ‘{‘)
{
create_new_group();
// …
break;
}
if (byte == ‘}’)
{
state = PARSER_END_GROUP;
break;
}
unexpected_char:
// it will set next state depending on destination / or go to unexpected_cmd to do more checks and magic
// …
if (this->destination == pict ||
this->destination == objdata ||
this->destination == objalias ||
this->destination == objsect ||
this->destination == datafield ||
this->destination == fontemb ||
this->destination == svb ||
this->destination == macro ||
this->destination == tci ||
this->destination == datastore ||
this->destination == mmconnectstrdata ||
this->destination == mmodsoudldata ||
this->destination == macrosig)
{
state = PARSER_PARSE_HEX_DATA;
data.pos–;
break;
}
// …
break;
}
break;
PARSER_CHECK_CONTROL_WORD will check if the next char is the start of a control word or if it’s a control symbol, and will set the next state accordingly.
case PARSER_CHECK_CONTROL_WORD:
byte = *(uint8_t*)data.pos;
if ((byte >= ‘a’ && byte <= ‘z’) || (byte == ‘ ‘) || (byte >= ‘A’ && byte <= ‘Z’))
{
state = PARSER_PARSE_CONTROL_WORD;
this->cmd_len = 0;
}
else
{
data.pos++;
this->temp[0] = 1;
this->temp[1] = byte;
this->temp[2] = 0;
state = PARSER_PROCESS_CMD;
this->cmd_len = 1;
break;
}
The states PARSER_PARSE_CONTROL_WORD and PARSER_PARSE_CONTROL_WORD_NUM_PARAMETER will store the null-terminated control word that is made up of ASCII alphabetical characters and a null-terminated numeric parameter (if it exists) in a temporary buffer of a fixed size.
case PARSER_PARSE_CONTROL_WORD:
pos = this->temp + 1;
parsed = this->temp + 1;
while (data.pos != data.end)
{
byte = *(uint8_t*)data.pos;
// length of null-terminated strings cmd + num should be <= 0xFF
if ((byte == ‘-‘) || (byte >= ‘0’ && byte <= ‘9’))
{
//if parsed == temp_end
// goto raise_exception
*parsed = 0;
parsed++;
pos = parsed;
if (parsed >= temp_end)
{
parsed = temp_end – 1;
*parsed = 0;
state = PARSER_PROCESS_CMD;
this->cmd_len = pos – (this->temp + 1);
break;
}
data.pos++;
this->cmd_len = pos – (this->temp + 1);
*parsed = byte;
parsed++;
pos = parsed;
state = PARSER_PARSE_CONTROL_WORD_NUM_PARAMETER;
break;
}
if (byte == ‘ ‘)
{
data.pos++;
if (parsed >= temp_end)
{
parsed = temp_end – 1;
}
*parsed = 0;
state = PARSER_PROCESS_CMD;
this->cmd_len = pos – (this->temp + 1);
break;
}
if ((byte >= ‘a’ && byte <= ‘z’) || (byte >= ‘A’ && byte <= ‘Z’))
{
if (parsed – this->temp >= 0xFF)
{
if (parsed >= temp_end)
{
parsed = temp_end – 1;
}
*parsed = 0;
state = PARSER_PROCESS_CMD;
this->cmd_len = pos – (this->temp + 1);
break;
}
//if parsed == temp_end
// goto raise_exception
*parsed = byte;
parsed++;
pos = parsed;
data.pos++;
}
else
{
if (parsed >= temp_end)
{
parsed = temp_end – 1;
}
*parsed = 0;
state = PARSER_PROCESS_CMD;
this->cmd_len = pos – (this->temp + 1);
break;
}
}
break;
case PARSER_PARSE_CONTROL_WORD_NUM_PARAMETER:
while (data.pos != data.end)
{
byte = *(uint8_t*)data.pos;
// length of null-terminated strings cmd + num should be <= 0xFF
if (byte == ‘ ‘)
{
data.pos++;
if (parsed >= temp_end)
{
parsed = temp_end – 1;
}
*parsed = 0;
state = PARSER_PROCESS_CMD;
break;
}
if (byte >= ‘0’ && byte <= ‘9’)
{
if (parsed – this->temp >= 0xFF)
{
if (parsed >= temp_end)
{
parsed = temp_end – 1;
}
*parsed = 0;
state = PARSER_PROCESS_CMD;
break;
}
//if parsed == temp_end
// goto raise_exception
*parsed = byte;
*parsed++;
data.pos++;
}
else
{
if (parsed >= temp_end)
{
parsed = temp_end – 1;
}
*parsed = 0;
state = PARSER_PROCESS_CMD;
break;
}
}
break;
case PARSER_PROCESS_CMD:
case PARSER_SKIP_DATA:
case PARSER_END_GROUP:
case PARSER_SKIP_DATA_CHECK_B:
case PARSER_SKIP_DATA_CHECK_I:
case PARSER_SKIP_DATA_CHECK_N:
case PARSER_SKIP_DATA_GET_BIN_VAL:
case PARSER_SKIP_DATA_INNER_DATA:
this->state = state;
cmd_parser(&data);
state = this->state;
break;
Then it is processed in the state PARSER_PROCESS_CMD that calls another function responsible for processing control words and control symbols. It takes into account the current state and sets the next state.
There are multiple states responsible for parsing hex-data. The most interesting for us is PARSER_PARSE_HEX_DATA – as you can see, it’s set in PARSER_BEGIN if the destination objdata is set.
case PARSER_PARSE_HEX_DATA:
parsed_data = this->temp;
if (this->bin_size <= 0)
{
while (data.pos != data.end)
{
byte = *(uint8_t*)data.pos;
if (byte == ‘{‘ || byte == ‘}’ || byte == ‘\\’)
{
state = PARSER_BEGIN;
if (parsed_data != this->temp)
{
push_data(parsed_data – this->temp);
parsed_data = this->temp;
}
break;
}
if (this->flag & 0x4000)
{
data.pos++;
continue;
}
if (byte >= ‘0’ && byte <= ‘9’)
{
val = byte – 0x30;
}
else if (byte >= ‘a’ && byte <= ‘f’)
{
val = byte – 0x57;
}
else if (byte >= ‘A’ && byte <= ‘F’)
{
val = byte – 0x37;
}
else if (byte == 9 || byte == 0xA || byte == 0xD || byte == 0x20)
{
data.pos++;
continue;
}
else
{
// show message that there are not enough memory
this->flag |= 0x4000;
data.pos++;
continue;
}
if (this->flag & 0x8000)
{
this->hex_data_byte = val << 4;
this->flag &= 0x7FFF;
}
else
{
if (parsed_data == temp_end)
{
push_data(sizeof(this->temp));
parsed_data = this->temp;
}
this->hex_data_byte |= val;
*parsed_data = this->hex_data_byte;
parsed_data++;
this->flag |= 0x8000;
}
data.pos++;
}
}
else
{
if (this->flag & 0x4000)
{
uint32_t size;
if (this->bin_size <= data.end – data.pos)
{
size = this->bin_size;
}
else
{
size = data.end – data.pos;
}
this->bin_size -= size;
data.pos += size;
}
else
{
while (this->bin_size > 0)
{
if (parsed_data == temp_end)
{
push_data(sizeof(this->temp));
parsed_data = this->temp;
}
byte = *(uint8_t*)data.pos;
*parsed_data = byte;
parsed_data++;
data.pos++;
this->bin_size–;
}
}
}
if (parsed_data != this->temp)
{
push_data(parsed_data – this->temp);
parsed_data = this->temp;
}
break;
This state will parse hexadecimal data and binary data if set.
The states PARSER_PARSE_HEX_NUM_MSB and PARSER_PARSE_HEX_NUM_LSB are used together to parse hex values (data of the \panose control word and \’ control symbol).
case PARSER_PARSE_HEX_NUM_MSB:
this->flag |= 0x8000;
this->hex_num_byte = 0;
state = PARSER_PARSE_HEX_NUM_LSB;
case PARSER_PARSE_HEX_NUM_LSB:
// …
byte = *(uint8_t*)data.pos;
data.pos++;
val = 0;
if (byte – ‘0’ <= 9)
{
val = byte – 0x30;
}
else if (byte – ‘a’ <= 5)
{
val = byte – 0x57;
}
else if (byte – ‘A’ <= 5)
{
val = byte – 0x37;
}
this->hex_num_byte |= val << ((this->flag >> 0xF) << 2);
this->flag = ((~this->flag ^ this->flag) & 0x7FFF) ^ ~this->flag;
if (this->flag & 0x8000)
{
// …
state = PARSER_BEGIN;
}
else
{
break;
}
break;
State reset
Looking at PARSER_PARSE_HEX_NUM_MSB, PARSER_PARSE_HEX_NUM_LSB and PARSER_PARSE_HEX_DATA, it is easy to spot a bug. Even if they use a different variable to store the decoded hex value, they use the same bit to determine which nibble is now decoded – high (most significant bits, or MSB) or low (less significant bits, or LSB). And PARSER_PARSE_HEX_NUM_MSB always resets this bit to MSB.
It is therefore possible to make bytes disappear in the PARSER_PARSE_HEX_DATA context by triggering a change of state to PARSER_PARSE_HEX_NUM_MSB.
For this to work it is enough to put \’XX in the data that comes after the \objdata control word. In this case, when the parser encounters \ in state PARSER_PARSE_HEX_DATA it will return to state PARSER_BEGIN and after that will go to state PARSER_PROCESS_CMD. The handler for the \’ control symbol will not change a destination, but will change the next state to PARSER_PARSE_HEX_NUM_MSB. After PARSER_PARSE_HEX_NUM_MSB and PARSER_PARSE_HEX_NUM_LSB control is transferred back to PARSER_BEGIN and eventually to PARSER_PARSE_HEX_DATA because the destination is still equal to objdata. After all that, the next byte will be decoded as a high nibble.
It is also worth noting that PARSER_PARSE_HEX_NUM_LSB does not check if the provided value is a valid hexadecimal; therefore, after \’ there could be absolutely any two bytes.
This behavior can be observed in the following example:
“f\’cc” will be removed from the final result
When control is transferred for the first time to the PARSER_PARSE_HEX_DATA state, after the \objdata control word is processed, the MSB bit is already set. Let’s look at how it happens and how this example will be processed:
After some reverse engineering of the keyword processing function, I found a list of all the control words and their corresponding structures:
With this information we can locate and look at the objdata constructor:
You can see it sets the MSB bit, allocates a new buffer and replaces the old pointer with a new one. Therefore, the data decoded between two \objdata control words is never used.
“d0cf11e0a1b11ae1” will be removed from the final result
Final destination
We know that if \’ or \objdata is put in data, it will change the output. What about other control words and control symbols? There are more than 1500 of them!
Mostly nothing.
As some control words represent a destination, they can’t be used – they change the objdata destination on their own, and to decode an object the objdata destination is needed.
Other control words do not affect objdata destination.
The only one way to change the destination so that it’s possible to return to the objdata destination without losing previously decoded data is to use special symbols – opening brace ({) and closing brace (}). These symbols indicate the start and end of a group.
When the parser encounters the end of a group in state PARSER_BEGIN, the destination that was set before the start of the group will be restored.
Therefore, by putting {\aftncn FF} after \objdata, FF will not get into the decoded data because FF now applies to the destination aftncn and will be handled according to this destination.
However, by using {\aftnnalc FF}, FF will get into the decoded data because the destination is still equal to objdata.
It is also worth noting that {\objdata FF} still can’t be used because the buffer will not be restored.
An accurate list of all destination control words was created with a simple fuzzer.
Fixed-size buffer
Another obfuscation technique that comes to mind while looking at the code of an RTF parser is not related to this ‘MSB’ bug, but can also be used to remove bytes from a hex-stream. The technique’s related to the temporary buffer size and how a control word and numeric parameter are parsed in the states PARSER_PARSE_CONTROL_WORD and PARSER_PARSE_CONTROL_WORD_NUM_PARAMETER. You can see an example of its use in the following screenshot.
In this example the size of the data that will be removed as part of the numeric parameter is calculated using the formula: 0xFF (size of temporary buffer) – 0xB (size of ‘oldlinewrap’) – 2 (null-terminator characters) = 0xF2.
Unnecessary data
While the techniques described above are related to general RTF parsing, the processing of some specific keywords conceals some further confusion.
According to the specification states, if \* was encountered right before a control word or control symbol that was not found in the lookup table, its considered an unknown destination group and all the data up to the closing brace } that closes this group should be discarded. The lookup table in MS Office contains control words that are not present in the specification and it raises concerns that it will be changed in future, affecting parsing of the same document on different versions of MS Office. When the function responsible for processing keywords encounters such cases or one of the specific control words (such as \comment, \generator, \nonshppict and so on), it will set the state PARSER_SKIP_DATA and the number for encountered opening braces { to 1.
enum
{
// …
PARSER_SKIP_DATA = 0xF,
// …
PARSER_SKIP_DATA_CHECK_B = 0x13,
PARSER_SKIP_DATA_CHECK_I = 0x14,
PARSER_SKIP_DATA_CHECK_N = 0x15,
PARSER_SKIP_DATA_GET_BIN_VAL = 0x16,
PARSER_SKIP_DATA_INNER_DATA = 0x17,
// …
};
Kind of magic
During analysis of the PARSER_SKIP_DATA* states I found things that are the opposite not only to the specification but also to the rest of the parser code.
While looking for the \bin control word, this states will skip data, changing the number of encountered opening and closing braces until that number equals zero. The hidden catch lies in the way the numeric parameter is processed.
First of all, the maximum allowed length of the numeric parameter is increased up to 0xFF – it’s calculated without considering the length of the control word.
The second catch is that the numeric parameter is not numeric anymore! The parser allows not only decimal characters but also Latin characters to pass. Then this parameter is passed to custom strtol, making it possible to specify the length of data that should be skipped without considering opening and closing braces as a hexadecimal number.
Obfuscations with the use of these two primitives have not yet been encountered in the wild.
Conclusion
Reverse engineering has proved to be the most effective way to build a parser, and in the case of RTF it would most likely be impossible to achieve the desired behavior otherwise.
Exact parsing depends on small implementation details and algorithmic bugs rather than on a specification that could be confusing or state things that are not true.
Kaspersky Lab products detect all kinds of RTF obfuscation and perform the most correct processing of RTF files, providing the best protection to our end users.
Iranian Hackers Use New Trojan in Recent Attacks
23.2.2018 securityweek CyberSpy
The cyberespionage group known as OilRig and previously linked to Iran has been observed using a new Trojan in recent attacks, Palo Alto Networks reports.
A highly active group mainly targeting organizations in the Middle East, OilRig was attempting to deliver a Trojan called OopsIE in two attacks targeting an insurance agency and a financial institution in the Middle East. While one of the attacks relied on a variant of the ThreeDollars delivery document, the other attempted to deliver the malware to the victim directly, likely via a link in a spear phishing email.
The first attack occurred on January 8, 2018, and started with two emails being sent to two different email addresses at the same organization within a six minutes time span. Both messages originated from an email address associated with the Lebanese domain of a major global financial institution, but researchers from Palo Alto Networks believe the email address was spoofed.
On January 16, OilRig targeted an organization that it had also hit a year ago. The OopsIE Trojan was downloaded from the command and control (C&C) server directly, suggesting that the server was being used for staging as well. It also suggests that group might have changed tactics after the targeted organization took measures to counter known OilRig TTPs following last year’s incident.
The ThreeDollars samples collected in the new attacks were similar to those analyzed in October 2017, using the same lure image (albeit a cropped and edited version) that tricks users into enabling macros. While executing a malicious macro in the background, the malicious document displays a decoy image to lower suspicion, although it is a fake error message.
The macro creates a scheduled task that executes after one minute to decode base64 encoded data using the Certutil application, and another task that executes after two minutes, running a VBScript to execute the OopsIE Trojan and clean up the installation.
Packed with SmartAssembly, the Trojan is obfuscated with ConfuserEx and achieves persistence by creating a VBScript file. It also creates a scheduled task to run itself every three minutes. The malware communicates with the C&C over HTTP, using the InternetExplorer application object.
“The Trojan will construct specific URLs to communicate with the C2 server and parses the C2 server’s response looking for content within the tags <pre> and </pre>. The initial HTTP request acts as a beacon,” the researchers explain.
The Trojan extracts and loads an embedded assembly by concatenating the contents of two resources, a technique the OilRig group was already known to employ.
Based on responses received from the server, the Trojan can run a command, upload a file, or download a specified file.
In addition to the use of the ThreeDollars delivery document, the newly observed attacks overlap with previous incidents involving the OilRig group in that they use the C&C domain msoffice365cdn[.]com. The researchers also linked the domain’s registrant to the office365-management[.]com and office365-technical[.]info domains and believe the OilRig group is behind all of them. The IP msoffice365cdn[.]com resolves to was also associated with the group.
“This group has repeatedly shown evidence of a willingness to adapt and evolve their tactics, while also reusing certain aspects as well. We have now observed this adversary deploy a multitude of tools, with each appearing to be some form of iterative variation of something used in the past. However, although the tools themselves have morphed over time, the plays they have executed in their playbook largely remain the same when examined over the attack life cycle,” Palo Alto concludes.
Report Highlights Challenges of Incident Response
23.2.2018 securityweek Incindent
False Positives Lead to a Surprising Number of Incident Response Investigations
Helsinki, Finland-based security firm F-Secure has analyzed a random sample of incident response investigations conducted by its security consultants. The resulting report (PDF) cannot be considered a scientific analysis of incident response, but nevertheless provides useful observations.
Some of these observations could be expected; others are perhaps surprising. For example, successful attacks are fairly evenly split between opportunistic and targeted, F-Secure found. Since there are far more opportunistic attacks fueled by mass spam and phishing campaigns, the implication is that targeted attacks are, pro rata, very successful.
Within the industry sectors included in the analysis, there are interesting distinctions. For example, successful attacks against the financial and manufacturing sectors are evenly distributed between opportunistic and targeted. Successful attacks against the gaming and public sectors were (within the confines of this report) always targeted; but such attacks against the insurance, media and telecom sectors are always opportunistic.
It would be interesting to conjecture why this might be so. For example, gaming is almost continuously under one form or another of attack, while the public sector is highly regulated. It would be tempting to suggest that a solid security posture can effectively eliminate most opportunistic attacks.
The report notes that targeted attacks use social engineering to a greater extent than opportunistic attacks. This suggests that an important defense against targeted attacks will be user security awareness training.
Opportunistic attacks, however, are more likely to focus on external technology exploits via internet facing services.
"Opportunistic attacks," say the report's authors, "are often initiated with cost-effective target selection techniques, such as mass scanning the internet and attacking a vulnerable service when a new exploit comes out. This can be done in a matter of minutes using tools readily available on the internet." The implication here is that an effective early patching regime will reduce the success of opportunistic attacks.
Another surprise is the high number of insider-instigated successful attacks. While 'internet exploits' tops the list at 21%, this is closely followed by insiders at 20%. Malicious e-mail attachments and phishing attacks (often considered to be the major threats) are at 18% and 16% respectively.
However, one of the biggest surprises in this report is the number of incident response calls that are false positives. False positives are a common problem during network analysis and incident triaging, but it is surprising how many of these false positives result in a call to an incident response specialist firm like F-Secure.
Thirteen percent of F-Secure incident response investigations were false positives; that is, says the report, "were conducted due to IT problems or other issues being misunderstood as security incidents by the reporting organization."
This is nothing like the number of successful attacks that caused actual damage (79%), but more than the meager 8% of investigations into failed attacks.
These figures lead F-Secure to believe that many companies simply do not have adequate internal incident response capabilities, able to detect and stop an incident before it progresses. “Every incident response process begins with the same question: is it an incident? How fast a company can make that determination, how smooth and efficient their processes and procedures are, the quality of their forensics and technology, and how well-trained their staff is, defines the cost of the answer to that question,” says F-Secure principal security consultant Tom Van de Wiele. “Once an organization has the facts based on detection capabilities, and not rumors or assumptions, then the process can continue with the next step which is usually containment and eradication.”
In a related blog post, F-Secure's Adam Pilkey describes three incident response recommendations for companies. The first is that breach evidence can be found in the system logs. "You'll want to collect other evidence too, although exactly what will depend on your organization, infrastructure, threat model, and other factors."
The second is that a method of filtering the collected data will be necessary. Manually will be too time-intensive; and requires expensive expertise. As an example of the volumes to be expected, F-Secure's specialist sensors collected about 2 million events from one customer in one month. Correlation and analytics brought this number down to 25 genuinely suspicious events -- and manual analysis found they contained 15 actual threats.
The third requirement is knowing what to look for. "Anything out of the ordinary should be a potential concern," writes Pilkey. "You should also cross reference your logs against threat intelligence feeds to find any indicators of compromise (such as finding activity from known malicious IPs)."
GitLab Patches Domain Hijacking Vulnerability
23.2.2018 securityweek Vulnerebility
Open source Git repository management system GitLab has addressed a security hole that could have been exploited to hijack users’ custom domains and point them to malicious content.
GitLab Pages is a feature that allows users to create websites for their projects, groups or user accounts, and then connect them to custom domains and TLS certificates.
White hat hackers noticed that no validation was being performed to ensure that the custom domain added to a user’s Pages site was actually theirs.
A custom domain can be added to GitLab Pages by creating a new DNS A record with an IP address for a Pages server. Since no validation was performed when adding custom domains, an attacker could have identified domains with DNS records pointing to the GitLab Pages server and hijack those domains. When users visited the hijacked domains, they would have been served content from the attacker’s repository.
The attack worked against custom domains that were deleted by users but still had the DNS records for the GitLab server active.
Two researchers reported variations of this issue to GitLab via the company’s bug bounty program on HackerOne. GitLab initially decided not to fix anything, but it started taking action after the second report was submitted.
“Attacker can create fake GitLab account(s) using the email(s) from temporary/anonymous email services. Configure fake email addresses with git for further code commits. Create multiple repositories and add domain name from the vulnerable list. The attacker can then: 1) use the static websites as Command and Control centers for their malware / for other malicious intents, 2) phish the customers / visitors of the legitimate domain owners,” one of the researchers explained in the report submitted via HackerOne.
Proof-of-concept (PoC) exploits created by the researchers revealed that there had been hundreds of vulnerable domains.
GitLab initially disabled the functionality for adding custom domains to GitLab Pages, and this week it rolled out a permanent fix by requiring users to verify ownership when adding a custom domain. Verification is done by adding a DNS TXT record containing a token provided by GitLab to the user’s domain.
Some users pointed out on Hacker News that the problem is similar to the issue that caused Let’s Encrypt last month to disable TLS-SNI-01 validation.
GitHub Enforces Stronger Encryption
23.2.2018 securityweek Safety
GitHub this week permanently disabled a series of weak cryptographic standards across its software development platform in an attempt to better protect users.
As of Feb. 22, 2018, the TLSv1/TLSv1.1 standard is no longer used on HTTPS connections to GitHub. The change affects all web, API, and git connections to https://github.com and https://api.github.com, Patrick Toomey, Application Security Engineer, GitHub, says.
The platform also retired the diffie-hellman-group1-sha1 and diffie-hellman-group14-sha1 encryption standards, a move that affects all SSH connections to github.com. This change follows the enabling of the diffie-hellman-group-exchange-sha256 standard on GitHub in September 2017.
The removal of these weak cryptographic standards was initially announced last year, and GitHub has since focused on ensuring that the change won’t have a major impact on its users. At the moment, only a small fraction of traffic uses the deprecated algorithms and clients are expected to automatically transition to the new ones, but some clients are expected to be impacted.
These include older systems that, although no longer maintained, continue to access Git/the GitHub API using the deprecated algorithms. To help mitigate this, the platform disabled support for the old algorithms for one hour on February 8, 2018. This provided a two week grace period for impacted systems to be upgraded.
“As noted above, the vast majority of traffic should be unaffected by this change. However, there are a few remaining clients that we anticipate will be affected. Fortunately, the majority of clients can be updated to work with TLSv1.2,” Toomey notes.
Impacted clients include Git Credential Manager for Windows prior to version 1.14.0, Git clients that shipped with Red Hat 5, 6, and 7 (updating to versions 6.8 and 7.2 or greater should resolve this), JDK releases prior to JDK 8, and Visual Studio (which ships with specific versions of Git for Windows and the Git Credential Manager for Windows).
Newer versions of these programs, however, include support for TLSv1.2 and updating ensures that clients continue to work properly with GitHub even after the deprecation.
Tech Giants Hit by Meltdown, Spectre Respond to Lawmakers
23.2.2018 securityweek Vulnerebility
Intel, AMD, ARM, Apple, Amazon, Google and Microsoft have responded to lawmakers who raised questions last month about the disclosure of the CPU vulnerabilities known as Meltdown and Spectre.
The U.S. House Energy and Commerce Committee announced on January 24 that it had sent letters to the companies hit by the Meltdown/Spectre incident, inquiring about their disclosure process. The tech giants were instructed to respond by February 7 and their responses have now been made public.
The Meltdown and Spectre vulnerabilities, which allow malicious applications to access potentially sensitive data from memory, were discovered independently by researchers at Google and various universities and private companies. Affected vendors were first notified in June 2017 and the disclosure of the flaws was initially planned for January 9, but it was moved to January 3 after some experts figured out that operating system developers had been preparing patches for what appeared to be critical processor flaws.
The U.S. House Energy and Commerce Committee asked impacted vendors about why and who proposed an embargo, when were US-CERT and CERT/CC notified, the impact of the embargo on critical infrastructure and other technology firms, the resources and best practices used in implementing the embargo, and lessons learned regarding multi-party coordinated disclosure.
Overall, the companies said Google Project Zero, whose researchers discovered the vulnerabilities, set the embargo after consultations with affected firms. Project Zero typically gives vendors 90 days to release patches, but the deadline was significantly extended due to the “complex nature of the vulnerability and mitigations.”
None of the companies notified US-CERT and CERT/CC of Meltdown and Spectre prior to their public disclosure. The agencies learned about the flaws through the public disclosure on January 3, and US-CERT was contacted by Intel on that day and again two days later.
The companies told lawmakers that the embargo and the disclosure process were consistent with industry standard practices designed to protect the public against attacks exploiting unpatched vulnerabilities.
In response to questions regarding impact on critical infrastructure, Intel noted that “the generally understood characteristics of most [industrial control systems] suggest that risk to these systems is likely low.” Many of the major ICS vendors have published advisories to warn users of the risks associated with these attack methods.
As for lessons learned, the tech giants claim they are evaluating the situation in an effort to improve their process in the future, and many say they are open to discussions on this topic.
Use of Fake Code Signing Certificates in Malware Surges
23.2.2018 securityweek Virus
There has been surge in the use of counterfeit code signing certificates to evade security detection solutions, despite the high cost such certificates come with, a new Recorded Future report shows.
Fake code signing certificates are used as a layered obfuscation technique in malware distribution campaigns, but these aren’t always stolen from legitimate owners, but rather issued upon request. The certificates are created for the specific buyer and registered using stolen corporate credentials, thus rendering traditional network defenses less effective, Recorded Future says.
Counterfeit certificates have been around for over half a decade, but the first offerings for such certificates were observed on the Dark Web only several years ago.
In March 2015, a user known as C@T offered on a prolific hacking messaging board a Microsoft Authenticode that could sign 32-bit/64-bit executable files, along with Microsoft Office, Microsoft VBA, Netscape Object Signing, and Marimba Channel Signing documents, and Silverlight 4 applications. Furthermore, Apple code signing certificates were also available, Recorded Future's researchers say.
The advertiser claimed the certificates were issued by Comodo, Thawte, and Symantec and registered under legitimate corporations. The seller also said each certificate was unique and would only be assigned to a single buyer. The seller suggested the certificates would increase the success rate of malware installations 30% to 50% and claimed to have sold over 60 certificates in less than six months.
What prevented C@T’s offer to appeal to a large client base was the prohibitive cost of certificates, which can surpass $1,000 per certificate in some instances.
Several years later, three new actors started offering such services, primarily in the Eastern European underground, and two remain active, providing counterfeit certificates to Russian-speaking individuals.
One of the actors specializes in Class 3 certificates (they do not include Extended Validation (EV) assurance) and offers them at $600. The other seller has a broad range of products in the offering, the researchers discovered.
Standard Comodo code signing certificates (without SmartScreen reputation rating) cost $295, while the most trusted EV certificates from Symantec cost $1,599 (a 230% premium over the authentic certificate). Buyers looking to make bulk purchases would pay $1,799 for fully authenticated domains with EV SSL encryption and code signing capabilities.
“According to the information provided by both sellers during a private conversation, to guarantee the issuance and lifespan of the products, all certificates are registered using the information of real corporations. With a high degree of confidence, we believe that the legitimate business owners are unaware that their data was used in the illicit activities,” Recorded Future notes.
All certificates are created per the buyer’s request, individually, and have an average delivery time of two to four days.
A trial one of the vendors conducted revealed that detection rate of the payload executable of a previously unreported Remote Access Trojan (RAT) decreased upon signing with a recently issued Comodo certificate. Testing a non-resident version of the payload revealed that only one security product recognized the file as malicious.
“Network security appliances performing deep packet inspection become less effective when legitimate (legitimate certificate) SSL/TLS traffic is initiated by a malicious implant. Netflow (packet headers) analysis is an important control toward reducing risk, as host-based controls may also be rendered ineffective by legitimate code signing certificates,” the security researchers note.
The counterfeit certificates might have experienced a surge, but they are not expected to become mainstream because of their prohibitive cost when compared to crypting services that are readily available at $10-$30 per each encryption. Nonetheless, more sophisticated attackers and nation-state actors will continue employing code signing and SSL certificates in their operations.
Dozen Flaws Found in Trend Micro Email Encryption Gateway
23.2.2018 securityweek Vulnerebility
Researchers have discovered a dozen vulnerabilities in Trend Micro’s Email Encryption Gateway, including several issues rated critical and high severity. A majority of the flaws have been patched by the vendor.
Core Security revealed this week that its employees found several types of vulnerabilities in the Linux-based email encryption product. The most serious of the security holes can allow a local or remote attacker with access to the targeted system to execute arbitrary commands with root privileges.
Core Security has published an advisory detailing each of the vulnerabilities it has found. The flaws have been assigned the CVE identifiers CVE-2018-6219 through CVE-2018-6230.
The most serious of the flaws, rated critical based on its CVSS score, is CVE-2018-6223, an issue related to missing authentication. System admins can configure the virtual appliance running Email Encryption Gateway during the deployment process through a registration endpoint. The problem is that this endpoint can be accessed without authentication, allowing attackers to set administrator usernames and passwords and make other configuration changes.
Six of the flaws found in Email Encryption Gateway have been rated “high severity,” including an arbitrary file write issue that can lead to command execution, a couple of cross-site scripting (XSS) vulnerabilities, a command execution flaw related to arbitrary log file locations, and the lack of a validation mechanism for software updates.
Other flaws identified by Core Security researchers include SQL and XML external entity (XXE) injections.
Trend Micro informed customers that the vulnerabilities impact Email Encryption Gateway 5.5 build 1111 and earlier running on a virtual appliance. Patches for ten of the flaws are included in version 5.5 build 1129. It’s worth pointing out that it took the vendor more than half a year to release fixes.
A medium severity CSRF issue and a low severity SQL injection vulnerability have not been patched “due to the difficulties of implementing and the negative impact on critical normal product function of the proposed resolutions.” However, Trend Micro did provide some mitigations.
The company also pointed out that the Email Encryption Gateway will reach end of life (EOL) soon and advised customers to migrate to the InterScan Messaging Security product, which provides similar features and functionality.
This was not the first time Core Security researchers discovered vulnerabilities in a Trend Micro product. Back in December, the company disclosed the details of five security holes found in Trend Micro’s Smart Protection Server product.
U.S. Enters Final Stage of Net Neutrality Debate
23.2.2018 securityweek BigBrothers
The Federal Communications Commission (FCC) published its official order (PDF) repealing net neutrality rules in the Federal Register on Thursday. This follows the December vote by the commissioners -- 3-2 in support of Chairman Ajit Pai's campaign to abandon the Open Internet Order that began in 2005 and was finally approved by the FCC in 2010.
The basic tenet of net neutrality is that internet service providers may not favor one customer over another. ISPs contend that basic business principles should allow them to offer discounts to major customers. Neutrality supporters fear that this could only be achieved by charging small customers at a higher rate -- and that this would inevitably affect innovation by favoring the existing large customers. Side effects would include the ISPs effectively having the ability to block websites.
Although the FCC ruling is now official, it won't come into effect until April 23; that is, 60 days after publication in the Federal Register. It still has hurdles. Led by New York State attorney general Eric Shneiderman, 23 states have immediately petitioned (PDF) for a judicial review of the Order. The petition asks the court of appeals for the district of Columbia to determine that the order is "arbitrary, capricious, and abuse of discretion". They claim it violates both the Constitution and the Communications Act of 1934, and they "request that this Court hold unlawful, vacate, enjoin, and set aside the Order."
At the same time, several of the states are planning their own state-level net neutrality laws -- effectively telling the ISPs that if they operate the new FCC rules, they won't be allowed to do business in their states.
In San Francisco, Mayor Mark Farrell, who chairs the city's Blue Ribbon Panel on Municipal Fiber, released recommendations designed to stop ISPs compromising net neutrality principles. The plan is for San Francisco to own its own high-speed fiber network. "On the day the FCC is releasing its plan to repeal net neutrality and vital consumer protections, I am releasing San Francisco's plan to fight back against this misguided move that will dismantle the Internet as we know it," Farrell said in a statement.
Meanwhile, in January, Sen. Ed Markey, D-Mass. gathered the support of all his Democratic colleagues, plus one Republican (Sen. Susan Collins of Maine) seeking to kill the order under the Congressional Review Act. If the Democrats are able to gain one more vote in the Senate to overcome the Republican majority, they will be able to prevent the FCC repealing net neutrality both now and again in the future. In reality, this is unlikely since it will require the Senate Majority Leader and the House Speaker -- both Republicans -- to schedule a vote before April 23.
A Consumer Reports survey of more than 1000 Americans in 2017 showed consumer support for the existing net neutrality rules. "One main finding," says the report, "was that the majority of Americans -- 57 percent -- support the current net neutrality regulations that ban ISPs from blocking or discriminating against lawful content on the internet." Only 16% opposed the existing rules. "An even larger majority -- 67 percent -- said that ISPs shouldn't be allowed to choose which websites, apps, or streaming services their customers can access."
In a statement yesterday, the Consumers Union said, "We urge Senators to listen to the consumers they represent and vote to restore these critical net neutrality rules to ensure that internet service providers aren't the gatekeepers to the internet."
During the public comment period for the repeal of net neutrality, the FCC received millions of comments. The process was not without its critics. At one point, the FCC's website went off-line, supposedly either under the weight of comments being submitted or an unrelated DDoS attack. Neutrality activists, however, claimed that the FCC took the website offline to hinder the receipt of negative public comments.
Since then Schneiderman's office undertook its own investigation into the public comments. Among the millions received by the FCC, it concluded that around 2 million were fraudulent, being submitted by people posing to be others -- both living and dead.
This may be partly the motivation for FCC commissioner Jessica Rosenworcel's comments. Rosenworcel was one of two FCC commissioners to vote against the repeal. "This agency has failed the American public," she said. "It turned a blind eye to all kinds of corruption in our public record, from Russian intervention to fake comments to stolen identities in our files. As a result of the mess the agency created, broadband systems will now have the power to block websites, throttle services and censor online content. This is not right,"
America has entered the final stage of the net neutrality debate. Ajit Pai's new approach is in the driving seat -- but the next 60 days will decide whether he succeeds or not.
Chaos backdoor, a malicious code that returns from the past targets Linux servers
23.2.2018 securityaffairs Virus
Security experts from GoSecure, hackers are launching SSH brute-force attacks on poorly secured Linux servers to deploy a backdoor dubbed Chaos backdoor.
“This post describes a backdoor that spawns a fully encrypted and integrity checked reverse shell that was found in our SSH honeypot,” states the report published by GoSecure.
“We named the backdoor ‘Chaos’, following the name the attacker gave it on the system. After more research, we found out this backdoor was originally part of the ‘sebd’ rootkit that was active around 2013.”
The Chaos backdoor was one of the components of the “sebd” Linux rootkit that appeared in the threat landscape back in 2013, researchers discovered a post on hackforums.net, where a user claims to know how the backdoor was made publicly available.
It seems that the source code of the backdoor was caught by a “researcher” that released it on the forum by changing the name of the backdoor in Chaos to trick members into believing that is was a new threat.
The malicious code is now being used by attackers in the wild to target Linux servers worldwide.
Researchers performed an Internet-wide scan using the handshake extracted from the client in order to determine the number of infected Linux servers and they discovered that this number is quite low, below the 150 marks.

The installation of the Chaos backdoor starts with the attacker downloading a file that pretended to be a jpg from http://xxx.xxx.xxx.29/cs/default2.jpg.
The file was currently a .tar archive containing the Chaos (ELF executable), the client (ELF executable), initrunlevels Shell script, the install Shell script.
“Chaos”, in the tar archive, is the actual backdoor that is installed on the victim’s system and the “Client” file is the client to connect to the installed backdoor.
The backdoor is not sophisticated is doesn’t rely on any exploits, it opens a raw socket on port 8338 on which it listens to commands.
“Any decent firewall would block incoming packets to any ports that have not explicitly been opened for operational purposes,” GoSecure experts say. “However, with Chaos using a raw socket, the backdoor can be triggered on ports running an existing legitimate service.”
To check if your system is infected experts suggest to run the following command as root:
1 netstat –lwp
and analyze the list the processes to determine which are legitimate ones that have listening raw sockets open.
“Because chaos doesn’t come alone but with at least one IRC Bot that has remote code execution capabilities, we advise infected hosts to be fully reinstalled from a trusted backup with a fresh set of credentials.” suggest experts to the owner of infected systems.
Cybersecurity – Tips to Protect Small Business from Cyber Attacks
23.2.2018 securityaffairs Cyber
Small Business is a privileged target of attackers, in fact, there is a high risk of having problems with hackers if you are a large company or even a media player.
Do you have a small company? If the answer is yes, and you think that no cyber attack will ever affect you, think again. Small Business is a privileged target of attackers, in fact, there is a high risk of having problems with hackers, if you are a large company or even a media player.
According to recent reports, more than 40% of cyber attacks are targeting companies with fewer than 500 employees. More disturbing studies show that hackers attack every fifth small company. In most cases, these companies shut down because their security plans do not exist or there is a huge gap in providing total protection.
Cybersecurity is the most important way to ensure that your business does not run the risk of malicious attacks, especially if the people behind them do not show up.
Therefore, it is essential to take strong security measures if you do not want to lose your job for life and trust of your valuable customers. Moreover, prominent organizations expect their confidential information to hide under any circumstances. If you find that this is not the case, your customers will turn to other companies.
To avoid this, we would like to share with you how you can protect your small business from cyber attacks or more simply, tips to protect small business from cyber attacks.
Make as Many Backups as Possible
The reserve is significant if you want to protect all confidential data from cyber attacks and hackers who create malicious software and send it to devices that are explicitly used by small employees are inexorable. If you create multiple backups, you can sleep well at night, knowing that these files, presentations, etc. are present safe and sound. It is important not to get stained forever when it comes to malware.
Application of the Most Powerful Antivirus Program
When using a reliable security solution, it is essential to keep your business altogether.
Do not forget to choose the one antivirus software that protects your computer against all types of malware; antivirus program that eventually needs to detect and eliminate spam, spyware, Trojans, phishing attacks, etc. after selecting the best option for your business, but don’t forget to update it regularly.
Training of Employees
The people who work for you need to know that by clicking on the random links that you received through your professional email can cause significant damages to the company and its secret and confidential information.
The same applies to connections to networks that do not use a secure password. These are just two of the most dangerous practices you should stop right away. How can this be done? For example, you can organize training programs or hold meetings, where safety experts advise, give to employees and safe practices in the workplace against cyber crimes discuss. A better option is to implement security policies and procedures regarding online ethics.
Using Different Terminals Networks Every time for Payments
Using the same network for a payment terminal is a practice that must stop. Never connect it to your business. Keep these two parts separately, because only a few authorized employees can contact them. Therefore, the computers in your network protect the confidential content of cyber attacks.
Using Cybersecurity Insurance Policy
We ensure our cars, our homes, etc. Why do not we do this for our company? Cybersecurity is very useful for cyber threats. How? If a malware attack occurs, your company is responsible.
There is demand, so you must pay a significant amount of money as compensation. With the help of cybersecurity insurance, you can guarantee full coverage of all court fees.
Change Passwords Every in Three Months
Many people use the same password on all our devices, social platforms, etc. More than a year ago, small businesses did the same and increased the risk of cyber attacks. We should Change passwords every three months and do not forget to create strong passwords every time you do so.
The most secure passwords consist of 8-16 characters, which contain special characters, numbers, and letters. If you know you do not have a right memory, the password manager simplifies your work.
OMG botnet, the first Mirai variant that sets up proxy servers on vulnerable devices
23.2.2018 securityaffairs BotNet
Researchers at Fortinet have discovered the OMG botnet, the first Mirai variant that sets up proxy servers on the compromised IoT devices.
A new variant of the infamous Mirai botnet appeared in the threat landscape, it was discovered by researchers at Fortinet that referred it as OMG because of strings containing “OOMGA” in the configuration table.
“For this reason, we decided to name this variant OMG.”“The table, originally encrypted, was decrypted using 0xdeadbeef as the cipher key seed, using the same procedure adopted for the original Mirai. The first thing we noticed are the strings /bin/busybox OOMGA and OOMGA: applet not found.” wrote Fortinet.
The name Mirai was given to the Mirai bot because of the strings /bin/busybox MIRAI and MIRAI: applet not found, which are commands to determine if it has successfully brute-forced its way into the targeted IoT device. These strings are similar with other variations such as Satori/Okiru, Masuta, etc.”
The Mirai botnet was first spotted in August 2016 by the security researcher MalwareMustDie, it was specifically designed to compromise vulnerable or poorly protected IoT. Once Mirai malware compromises an IoT device it recruits it into a botnet primarily used for launching DDoS attacks, such as the one that hit Dyn DNS service.
In October 2016, the Mirai source code was leaked and threat actors in the wild started customizing their Mirai botnet.
The OMG botnet includes most of Mirai’s features and modules, including the attack, killer, and scanner modules, but also adds new ones.
According to Fortinet its configuration includes two strings used to add a firewall rule to ensure traffic on two random ports is allowed.
“This variant also adds and removes some configurations that can be found in the original Mirai code. Two notable additions are the two strings that are used to add a firewall rule to allow traffic on two random ports, which we will discuss in the latter part of the article.” continues the analysis.

After initialization, OMG connects to the command and control (C&C) server, the configuration table analyzed in the post contains the CnC server string, ccnew.mm.my, which resolves to 188.138.125.235.
The malware connects to the C&C port 50023, then it sends a defined data message (0x00000000) to the server to identify itself as a new bot.
In response, the server sends a 5-byte long data string, where the first byte is a command on how the newly recruited device should be used as a proxy server, the two options are:
1 for attack
>1 to terminate the connection.
The OMG botnet leverages the open source software 3proxy as its proxy server and during the set up phase the bot adds firewall rules to allow traffic on the two random ports.
“This variant of Mirai uses 3proxy, an open source software, to serve as its proxy server. The set up begins by generating two random ports that will be used for the http_proxy_portand socks_proxy_port. Once the ports are generated, they are reported to the CnC.” continues the analysis.
“For the proxy to work properly, a firewall rule must be added to allow traffic on the generated ports. As mentioned earlier, two strings containing the command for adding and removing a firewall rule to enable this were added to the configuration table .”
Fortinet experts believe the operators behind the OMG botnet sell access to the IoT proxy server, they highlighted that this is the first Mirai variant that sets up proxy servers on vulnerable IoT devices.
“With this development, we believe that more and more Mirai-based bots are going to emerge with new ways of monetization,” concluded Fortinet.
Further details, including IoCs are reported in the blog post published by Fortinet.
Fraud Campaign Targets Accounts Payable Contacts at Fortune 500 Firms
23.2.2018 securityweek Spam
A new business email compromise (BEC) campaign is targeting accounts payable personnel at Fortune 500 companies in an attempt to trick victims into initiating fraudulent wire transactions to attacker-controlled accounts, IBM warns.
As part of BEC scams, attackers take over or impersonate a trusted user’s email account to target other companies and divert funds to their accounts. Based on phishing and social engineering, such attacks are relatively simple to perform and are attractive to cybercriminals, IBM notes.
As part of the recently observed campaign, attackers used well-crafted social engineering tactics and phishing emails to obtain legitimate credentials from their targets. The emails appeared to come from known contacts and mimicked previous conversations, while in some cases the attackers managed to insert themselves into ongoing conversations between business users.
Posing as the known contact from a vendor or associated company, the attackers then requested that payments be sent to a new bank account number or beneficiary.
By creating mail filters, the attackers ensured they would communicate only with the victim. In some cases, they also found and filled out necessary forms or spoofed supervisor emails to provide victim with additional approval.
The group behind the attacks, IBM says, likely operates out of Nigeria, given the spoofed sender email addresses and IP addresses that were used. However, compromised servers and proxies are often used to hide the attackers’ location.
The actors created spoofed DocuSign login pages on over 100 compromised websites in various geographic locations. Targeted companies were identified in the retail, healthcare, financial and professional services industries, including Fortune 500 companies.
To harvest business user credentials, the attackers sent a mass phishing email to the user’s internal and external contacts, often to several hundreds of them. The message included a link supposedly leading to a business document, but instead redirecting the victim to a fraudulent “DocuSign” portal requesting authentication for download.
Next, the attackers filtered out the stolen credentials and only used those from companies that only require a username and password when employees access their email accounts.
“The attackers specifically targeted personnel involved in the organization’s accounts payable departments to ensure that the victim had access to the company’s bank accounts,” IBM notes.
Following a reconnaissance phase, the attackers engaged with the targeted employee and impersonated vendors or associated companies with established relations to the client. The attackers likely conducted extensive research on the target’s organizational structure and engaged into operations such as impersonating victims, finding and spoofing internal documents, and setting up multiple domains and emails to pose as higher-level authorities.
The attackers set up domains that resembled those of the target company’s vendors, either using a hard-to-identify typo change or registering the vendor’s name with a different top-level domain (TLD). They used these domain names to set up email accounts purporting to belong to known employees and used the accounts to send emails directly to the targets.
“Finally, although the attackers made some grammatical and colloquial mistakes, their English skills were proficient and the few mistakes they made could be easily overlooked by the target. The attackers created a false sense of reality around the target and imparted a sense of urgency to pay, resulting in successful scams involving millions of dollars,” IBM explains.
The attackers either created email rules or auto-deleted all emails delivered from within the user’s company to prevent victims from noticing fraudulent correspondence or unusual messages in their inbox. They also auto-forwarded email responses to different addresses to read them without logging into the compromised accounts.
The security researchers say the attackers had “more financial success using shell corporations and corresponding bank accounts based in Hong Kong or China rather than using consumer bank accounts, in which cases financial institutions were more likely to delay or block large or unusual transactions.”
The shell corporations involved in the BEC scams were registered within the past year, some on the same month payments were requested to the account. Wire transfers associated with BEC scams usually end up in accounts at banks located in China and Hong Kong, IBM notes.
Meltdown patch for OpenBSD is available … let’s wait for feedbacks
23.2.2018 securityaffairs Vulnerebility
OpenBSD releases Version 11 code update that addresses the Meltdown vulnerability by implementing the separation between the kernel and the user memory pages.
OpenBSD addresses the Meltdown vulnerability with the release of a Version 11 code. The update implements the separation between the kernel and the user memory pages.
OpenBSD’s Phillip Guenther provided further details on the implementation.
“When a syscall, trap, or interrupt takes a CPU from userspace to kernel the trampoline code switches page tables, switches stacks to the thread’s real kernel stack, then copies over the necessary bits from the trampoline stack. On return to userspace the opposite occurs: recreate the iretq frame on the trampoline stack, switch stack, switch page tables, and return to userspace.” wrote Guenther.
“Per-CPU page layout mostly inspired by DragonFlyBSD.”
Guenther explained that Per-CPU page layout mostly implemented the approach used in DragonFly BSD.
According to Gunther the impact on performance would be reduced because the approach minimizes the overhead for the management of kernel code and data in the transitions to/from the kernel.
“On Intel CPUs which speculate past user/supervisor page permission checks, use a separate page table for userspace with only the minimum of kernel code and data required for the transitions to/from the kernel.” he added.
“When a syscall, trap, or interrupt takes a CPU from userspace to kernel the trampoline code switches page tables, switches stacks to the thread’s real kernel stack, then copies over the necessary bits from the trampoline stack. On return to userspace the opposite occurs: recreate the iretq frame on the trampoline stack, switch stack, switch page tables, and return to userspace.”Meltdown OpenBSD
A couple of weeks ago, DTrace expert Brendan Gregg developed a “microbenchmark” to measure the performance degradation introduced by the Linux kernel page table isolation (KPTI) patch for the Meltdown CPU vulnerability. The tests demonstrated a degradation between 0.1 per cent and 6 per cent.
Let’s wait for the tests on OpenBSD.
Further technical details on the approach implemented for OpenBSD are available here.
Hackers compromised a Tesla Internal Servers with a Cryptocurrency miner
23.2.2018 securityaffairs Hacking
Cloud security firm RedLock discovered that hackers have compromised the Tesla cloud computing platform to mine cryptocurrency.
Tesla has confirmed that hackers have compromised its cloud computing platform to mine cryptocurrency, after the incident was discovered by cloud security firm RedLock.
The hackers have breached the Tesla cloud servers and have installed a crypto currency miner, the company fixed the issue exploited by the hackers “within hours.”
The attackers gained access to the Tesla’s Amazon Web Services environment on a Kubernetes console that was reportedly not password-protected. The console is used by companies to manage the infrastructure deployed on the cloud hosting providers.
“According to RedLock, the hackers discovered log-in details to Tesla’s Amazon Web Services environment on a Kubernetes console – a system originally designed by Google to manage applications. The console was reportedly not password-protected.” states the BBC.
RedLock experts discovered a “pod” inside the Kubernetes console that stored login credentials for one of Tesla’s AWS cloud infrastructure.
The security breach happened in 2017, according to the company no customer data had been stolen.
“Our initial investigation found no indication that customer privacy or vehicle safety or security was compromised in any way,” said a Tesla spokesman.
According to RedLock, the exposed AWS buckets contained sensitive information, including telemetry data.
“The hackers had infiltrated Tesla’s Kubernetes console which was not password protected. Within one Kubernetes pod, access credentials were exposed to Tesla’s AWS environment which contained an Amazon S3 (Amazon Simple Storage Service) bucket that had sensitive data such as telemetry.” reads a blog post published by RedLock.

Tesla promptly fixed the problem once RedLock notified its discovery.
RedLock added that the security breach was caused by Tesla engineers that forgot to implement an authentication mechanism to the Kubernetes console.
Because they used a custom mining pool, it is unclear how much money this hacker group made.
RedLock confirmed that other companies left their bucket exposed online last year, including Aviva and Gemalto.
Drupal addressed several vulnerabilities in Drupal 8 and 7
23.2.2018 securityaffairs Vulnerebility
The Drupal development team addressed many vulnerabilities in both Drupal 8 and 7, including some flaws rated as “critical”.
Drupal maintainers have fixed many vulnerabilities in Drupal 7 and 8, including some flaws rated as “critical.”
One of the critical security vulnerabilities is related to partial cross-site scripting (XSS) prevention mechanisms that was addressed with Drupal 8.4.5 and 7.57 versions. The popular CMS uses a JavaScript function that doesn’t completely sanitize the input
“Drupal has a Drupal.checkPlain() JavaScript function which is used to escape potentially dangerous text before outputting it to HTML.” reads the advisory. “This function does not correctly handle all methods of injecting malicious HTML, leading to a cross-site scripting vulnerability under certain circumstances.”
The second vulnerability rated as critical affects Drupal 8, it could be exploited by users who have permission to post comments to view content and comments they should not be able to access. The flaw could also allow users to add comments to the content that should not be able to access.
The Drupal team also fixed two moderately critical vulnerabilities in Drupal 7 and other two in Drupal 8. The flaws in Drupal 7:
A Private file access bypass – Drupal fails to check if a user has access to a file before allowing the user to view or download it when the CMS is using a private file system.
A jQuery cross site scripting vulnerability that is present when making Ajax requests to untrusted domains.
while the vulnerabilities in Drupal 8 are:
A Language fallback can be incorrect on multilingual sites with node access controls. Drupal marks the untranslated version of a node as the default fallback for access queries. This fallback is used for languages that do not yet have a translated version of the created node. This can result in an access bypass vulnerability.
A Settings Tray access bypass that could be exploited by users to update certain data that they do not have the permissions for.
Stinná stránka umělé inteligence, inteligentní stroje pomáhají kyberzločincům
22.2.2018 Novinky/Bezpečnost Bezpečnost
Mezinárodní experti bijí na poplach před možností zneužití umělé inteligence ze strany „kriminálníků, teroristů či zločineckých států”. Stostránkovou zprávu napsalo 26 odborníků na umělou inteligenci, kyberzločiny a robotiku včetně expertů z univerzit (Cambridge, Oxford, Yale, Stanford) a z neziskového sektoru (společnosti jako OpenAI, Středisko pro novou americkou bezpečnost či Electronic Frontier Foundation).
Ve zprávě píší, že v příštích deseti letech by mohla zvyšující se efektivnost umělé inteligence posílit počítačovou kriminalitu a teroristé by mohli více využívat drony či roboty. Odborníci také zmiňují možnost snadnější manipulace voleb na sociálních sítích prostřednictvím takzvaných internetových botů, což jsou počítačové programy, které pro svého majitele opakovaně vykonávají nějaké rutinní činnosti.
Tito odborníci vyzývají vlády a další vlivové skupiny k omezení těchto možných hrozeb. "Domníváme se, že útoky, které by snadnější přístup k umělé inteligenci mohl umožnit, budou obzvlášť účinné, přesně cílené a těžko odhalitelné," píše se ve zprávě.
Vyprovokované dopravní nehody
Odborníci zmiňují i některé "hypotetické možnosti" zneužití umělé inteligence. Teroristé by například mohli uzpůsobit systémy umělé inteligence používané třeba v dronech či samořiditelných dopravních prostředcích pro vyprovokování srážek a výbuchů.
Odborníci připomínají i možnost zneužití například úklidového robota v nějakém úřadu, který by se mohl dostal mezi jiné roboty, kteří připravují třeba jídlo. Takovýto robotí vetřelec by pak mohl pomocí výbušniny zaútočit na nějakého úředníka poté, co by jej identifikoval.
Podle jednoho z autorů zprávy a ředitele střediska z Cambridgeské univerzity Seána Ó hÉigeartaigha by se mohla "s větším zneužitím umělé inteligence zvýšit zejména počítačová kriminalita".
Větší záběr by mohly představovat i útoky pomocí tzv. spear phishingu, což je podvodná technika používaná na internetu k získávání citlivých údajů (útočník zasílá e-mail konkrétní osobě; pro tradiční phishing je typické rozeslání obrovského množství mailů).
Velké nebezpečí vidí Seán Ó hÉigeartaigh "v možném zneužití umělé inteligence v politice". "Již jsme zažili, jak se jednotlivci či skupiny snažili zasahovat pomocí internetu do demokratických voleb," připomíná a dodává: "Jestliže umělá inteligence umožní, aby byly tyto útoky silné, jednoduché na zopakování a složité na odhalení, mohlo by to znamenat velký problém pro politickou stabilitu."
Umělá inteligence by mohla sloužit třeba i k výrobě falešných a velmi realistických videí, která by pak mohla být použita k diskreditaci politických činitelů. Do rozvoje umělé inteligence by se mohly zapojit i některé autoritářské státy, které by pak mohly s její pomocí snadněji sledovat své občany.
Před zneužitím varoval i Hawking
Není to poprvé, co se upozorňuje na možné zneužití umělé inteligence. V roce 2014 před tím varoval známý astrofyzik Stephen Hawking, k němuž se v poslední době přidal třeba podnikatel Elon Musk a další. Zveřejněny byly také zprávy například o možném užívání zabijáckých dronů.
Tato nová zpráva přináší "nový pohled na část umělé inteligence, která by mohla přinést nové hrozby nebo změnit existující hrozby v oblastech počítačové, politické i lidské bezpečnosti".
Umělá inteligence, která se objevila v 50. letech 20. století, je obor informatiky zabývající se tvorbou strojů vykazujících známky inteligentního chování. V posledních letech bylo dosaženo pokroku v oblastech kupříkladu vnímání, hlasového rozeznávání či obrazové analýzy.
"V současnosti ještě existuje rozdíl mezi rychlostí výzkumu a možnými aplikacemi novinek. Ještě je čas jednat," říká vědec z Oxfordské univerzity Miles Brundage. Právě na jeho pracovišti začala tato zpráva vznikat.
"Na zmírnění těchto hrozeb by měli spolupracovat vědci na umělou inteligenci, vývojáři robotů a dronů i regulační orgány a politici," říká Seán Ó hÉigeartaigh.
Hackeři se dostali do cloudu Tesly běžícím na Amazonu a těžili kryptoměny
22.2.2018 Novinky/Bezpečnost Hacking
Hackeři se dostali do cloudu Tesly běžícím na Amazonu a těžili kryptoměnyHackeři se dostali do cloudu Tesly běžícím na Amazonu a těžili kryptoměnyHackeři se dostali do cloudu Tesly běžícím na Amazonu a těžili kryptoměnyHackeři se dostali do cloudu Tesly běžícím na Amazonu a těžili kryptoměnyHackeři se dostali do cloudu Tesly běžícím na Amazonu a těžili kryptoměny24 FOTOGRAFIÍ
zobrazit galerii
Bezpečnostní společnost RedLock, která se specializuje na kyberútoky a odhalení děr v systémech, objevila hacknutý účet na AWS (Amazon Wev Services) společnosti Tesla.
Tesla používá cloudovou platformu Amazonu na mnoho věcí, kromě sběru dat z automobilů i analýzu a podobně. RedLock odhalil, že jeden z administračních účtů neměl heslo a hackeři přes něj využívali výkon cloudu k těžení kryptoměn.
V rámci odměn za odhalení chyb Tesla vyplatila RedLocku pouze 3 tisíce dolarů, takže lze předpokládat, že nešlo o nějaký kritický účet, který by měl vliv na celou platformu či zabezpečení uživatelských dat. Ostatně podle vyjádření zástupců šlo pouze o testovací účet pro interní automobily Tesla.
Právě bezpečnost celé platformy je pro automobilový průmysl stále kritičtější. Obzvláště s příchodem autonomních systémů, které budou zpracovávat data z obrovského množství vozů a budou pochopitelně obsahovat i soukromá data o jednotlivých jízdách daných uživatelů. Pro hackery mají taková data jistě vysokou cenu a v nejhorším případě by případné hacknutí mohlo ovlivnit i samotnou funkčnost platformy, která bude v nějaké formě udržovat autonomní vozidla neustále připojená a kontrolovaná.
Rakousko chystá vlastního trojského koně. Bude pomáhat v boji s teroristy na internetu
22.2.2018 Novinky/Bezpečnost BigBrother
Rakouská vláda ve středu schválila balíček opatření umožňujících prostřednictvím sledování komunikace odhalovat závažnou kriminalitu a terorismus. Úřadům tak má být do budoucna umožněno nasazovat do počítačů státní sledovací software, neboli takzvaný „Bundestrojaner” (spolkový trojský kůň), informují rakouská média.
Nasazování špionážních programů do komunikačních aplikací jako jsou Skype nebo WhatsApp jsou jen jedním z opatření, která zahrnuje rozsáhlý balíček přijatý novou pravicovou vládou lidovců (ÖVP) a svobodných (FPÖ).
Zostřena má být celková kontrola veřejného prostoru. Úřady mají získat přístup k obrazovým a zvukovým záznamům z monitorovacích zařízení všech veřejných i soukromých subjektů, jako jsou dopravní podniky, letiště nebo nádraží.
Kromě toho bude systém na rozeznávání státních poznávacích značek evidovat údaje o řidiči, SPZ, značce, typu a barvě každého automobilu.
V případě počátečního podezření na trestný čin mohou úřady telekomunikačním společnostem nařídit uchovávání příslušných dat po dobu až jednoho roku.
Hackeři zneužili cloudový systém Tesly k těžbě kryptoměn
22.2.2018 Novinky/Bezpečnost Hacking
Cloudový systém amerického výrobce elektromobilů Tesla napadli hackeři a využili ho k těžbě kryptoměn. Podle sdělení společnosti RedLock, která se zaměřuje na kybernetickou bezpečnost, pronikli do administrativní konzole Kubernetes, která nebyla chráněna heslem. Dopad útoku na bezpečnost vozidel ani dat zákazníků Tesla zatím nezjistila. Jak uvedl server televize CNBC, ohroženy byly účty na úložišti Amazon Web Services (AWS).
Kubernetes je systém navržený společností Google, zaměřený na optimalizaci cloudových aplikací.
Společnost RedLock nesdělila, jaká kryptoměna byla těžena. Obdobné problémy podle ní měly i další přední firmy včetně britské pojišťovny Aviva a nizozemského výrobce SIM karet Gemalto. Průnik do systémů Tesly však byl sofistikovanější a používal několik různých strategií, aby zabránil odhalení hackerů.
Tesla problém po informaci RedLocku okamžitě vyřešila. Automobilka oznámila, že dopad na ochranu dat klientů ani na bezpečnost vozidel nezjistila. Podle mluvčího se kybernetický útok dotkl jen automobilů používaných zaměstnanci firmy.
Z analýz RedLocku je zřejmé, že poskytovatelé cloudových služeb jako Amazon, Microsoft a Google dělají, co mohou, a žádný z velkých útoků v loňském roce se nestal z důvodu jejich nedbalosti, prohlásil představitel společnosti Gaurav Kumar. "Bezpečnost je však společnou odpovědností. Organizace na všech úrovních jsou povinny sledovat infrastrukturu rizikových konfigurací, neobvyklých aktivit uživatelů a podezřelého síťového provozu," zdůraznil.
Kyberšpionážní skupina z KLDR rozšířila pole působnosti
22.2.2018 Novinky/Bezpečnost BigBrother
Severokorejská kyberšpionážní jednotka, která se v minulosti zaměřovala na jihokorejskou vládu a soukromý sektor, loni výrazně zdokonalila svou činnost a rozšířila pole působnosti do Japonska či na Blízký východ. Podle agentury Reuters to vyplývá ze studie americké společnosti FireEye, která se zabývá bezpečností v kybernetickém prostoru.
Kyberšpionážní jednotka ATP37 (Reaper) podle expertů dříve pracovala pod vedením skupiny Lazarus, která je údajně zodpovědná za kybernetické útoky na společnost Sony Pictures z roku 2014 nebo za šíření vyděračského viru WannaCry. Tím se loni infikovaly statisíce počítačů ve 150 zemích světa. Skupina ATP37 zřejmě funguje už od roku 2012, trvalou hrozbu však začala představovat až v loňském roce.
Jednotka ATP37 se dosud ve své činnosti soustřeďovala pouze na jihokorejskou vládu, armádu, média nebo organizace na ochranu lidských práv a severokorejské přeběhlíky. Podle expertů se však loni nově zaměřila i na japonské organizace spojené s misí OSN pro lidská práva a sankcemi vůči KLDR, vietnamské dopravní a obchodní firmy a finanční společnosti na Blízkém východě.
"Myslíme si, že primárním úkolem ATP37 je shromažďovat informace, které by podpořily strategické, vojenské, politické a ekonomické zájmy Severní Koreje," cituje britský list The Guardian závěry odborníků.
Kybernetické útoky, za nimiž podle expertů stojí severokorejský režim, byly v minulosti zaměřeny na letecké, telekomunikační a finanční podniky. Pchjongjang veškerá obvinění důrazně odmítl.
Google našel další díru ve Windows 10. Starší verze Windows nepostihuje
22.2.2018 Novinky/Bezpečnost Zranitelnosti
Microsoft si myslel, že chybu opravil, ale zřejmě se tak nestalo.
Byl to opět Google, kdo našel díru ve Windows a informace o ní zveřejnil. Shodou okolností je to druhý případ ve velmi krátkém období. Zatímco zmíněná díra v Edgi byla vyhodnocena jako střední hrozba, v tomto případě se budeme bavit o vysoké zneužitelnosti. To je hodnocení od Googlu, Microsoft pak díře přisoudil nálepku důležité, nikoli kritické.
V nově objeveném scénáři útoku dochází ke zneužití funkce SvcMoveFileInheritSecurity tak, že se vydává za uživatele či uživatelku. Pomocí funkce MoveFileEx se útočnice či útočník pokusí přesunout soubor do jiného umístění. Po vyvolání funkce dojde o opuštění modelu vydávání se za uživatele a k pokusu o resetování bezpečnostního popisovače nového souboru tak, aby odpovídal zděditelným oprávněním.
Chyba CVE-2018-0826
K problému dochází pouze při práci se soubory s pevnými odkazy. Pakliže je soubor přesunut do adresáře, jenž disponuje dědičnými položkami pro správu přístupu, je krátce řečeno možné, aby byl soubor díky zděděným oprávněním modifikován tím, kdo útok provádí. Podle Googlu byly dokonce nalezeny dvě velmi podobné chyby.
Jednu interně označil číslem 1427. Jedná se o chybu známou též pod označením CVE-2017-11783 a byla opravena na podzim. Týkala se přitom všech do té doby vydaných verzí Windows 10, ale také Windows 8.1. Druhý problém, na který Google upozornil po vypršení lhůty pro opravu, (Microsoft si vyžádal prodloužení oproti standardním 90 dnům, čemuž bylo vyhověno), viz výše, reklamní gigant interně označuje číslem 1428 a je známa též pod označením CVE-2018-0826.
Podle Microsoftu se tato chyba týká jen Windows 10. Výměna informací mezi Googlem a Microsoftem naznačuje, že si firmy zcela nerozumí. Redmondští tvrdí, že chybu opravili v aktualizacích, jež vydali v rámci únorového záplatovacího úterý. Chybu 1427 považovali za duplikát chyby 1428. Jenže podle Googlu byla ve skutečnosti opravena jen chyba 1427, zatímco chyba 1428 v systému zůstala.
Takže nejde o duplikát, jen o podobnou chybu. Zřejmě nás tedy čeká další oprava. Tato chyba by naštěstí neměla být snadno zneužitelná. Tedy, její zneužití je snadné, ale podmínky pro takový útok jsou jen obtížně splnitelné. Např. útok nelze provést vzdáleně, nelze jej provést ze sandboxu, který nabízí aplikace jako Chrome nebo Edge apod.
Google zveřejnil detaily k díře v prohlížeči Edge. Varoval Microsoft předem, ale ten chybu včas neopravil
22.2.2018 Živě.cz Zranitelnosti
Živě.cz v prohlížeči EdgeTmavé téma prohlížeče EdgePodporuje další technologie HTML5, třeba WebRTC 1.0, a jak vidíte, dokáže i takto zobrazit miniatury otevřených stránekKlepnutím na tlačítko nahoře vlevo můžete uložit otevřené panely na pozdějiEdge docela dobře zobrazuje PDF a nově se naučil i EPUB
Google zveřejnil detaily bezpečnostní chyby v prohlížeči Edge. Microsoft přitom o chybě věděl dopředu, ale ve stanovené lhůtě nedostatky neodstranil, informoval web Neowin.net.
Tým Googlu prostřednictvím Projektu Zero odhalil v listopadu minulého roku zranitelnost prohlížeče Microsoft Edge a poskytl Microsoftu 90 dní na opravu. Pro složitost opravy lhůtu prodloužili o 14 dní, ale ani po tomto termínu chyba nebyla odstraněna.
Zranitelnost dovoluje útočníkovi obejít zabezpečení prohlížeče a vložit škodlivý kód do počítače oběti. Chyba byla označena jako středně závažná. Microsoft je přesvědčen, že tuto záležitost vyřeší do 13. března. Proč se tak nestalo doposud však blíže nevysvětlil.
Mirai Variant Sets Up Proxy Servers on Compromised Devices
22.2.2018 securityweek BotNet IoT
A newly observed variant of the infamous Mirai botnet is capable of setting up proxy servers on the infected Internet of Things (IoT) devices, Fortinet warns.
Mirai is a distributed denial of service (DDoS)-capable malware family that emerged in late 2016. Targeting IoT devices to add them to a botnet and launch powerful attacks, Mirai has been involved on some massive incidents right from the start.
Referred to as OMG because of strings containing "OOMGA" it its configuration table, the malware keeps most of Mirai’s capabilities, but also adds its own features to the mix.
Unlike Mirai, the OMG variant’s configuration includes two strings used to add a firewall rule to ensure traffic on two random ports is allowed, Fortinet discovered.
However, the new malware variation keeps Mirai’s original attack, killer, and scanner modules, which means that it is capable of performing all of the operations that Mirai could, such as killing processes (telnet, ssh, http, and other processes related to other bots), telnet brute-force login, and DDoS attacks.
After initialization, OMG connects to the command and control (C&C) server on port 50023. Once the connection has been established, the malware sends a defined data message to the server to identify itself as a new bot.
The server responds with a 5-byte long data string, where the first byte is a command on how the newly recruited device should be used: 0 if it should be used as a proxy server, 1 for attack, and >1 to terminate the connection.
OMG, the security researchers discovered, uses open source software 3proxy as its proxy server. During setup, it generates two random ports for the http_proxy_port and socks_proxy_port, reports them to the C&C, and adds a firewall rule to allow traffic on these ports.
After enabling the firewall rule, the malware sets up 3proxy with the predefined configuration embedded in its code. The researchers believe the attackers sell access to the IoT proxy server (because the C&C server wasn’t active during investigation, the researchers only performed static analysis).
“This is the first time we have seen a modified Mirai capable of DDOS attacks as well as setting up proxy servers on vulnerable IoT devices. With this development, we believe that more and more Mirai-based bots are going to emerge with new ways of monetization,” Fortinet concludes.
Several Vulnerabilities Patched in Drupal
22.2.2018 securityweek Vulnerebility
Updates released on Wednesday for Drupal 7 and 8 patch several vulnerabilities, including issues rated “critical.” No bug fixes are included in the latest releases.
One of the critical security holes patched by Drupal 8.4.5 and 7.57 is related to incomplete cross-site scripting (XSS) prevention mechanisms.
“Drupal has a Drupal.checkPlain() JavaScript function which is used to escape potentially dangerous text before outputting it to HTML. This function does not correctly handle all methods of injecting malicious HTML, leading to a cross-site scripting vulnerability under certain circumstances,” Drupal said in its advisory.
Another critical flaw, which only affects Drupal 8, allows users who have permission to post comments to view content and comments they should not be able to access. The weakness can also be exploited to add comments to the supposedly restricted content.
While these issues are rated “critical,” it’s worth pointing out that Drupal developers use NIST’s Common Misuse Scoring System to determine the risk level, which means that “critical” is second on the severity scale, after “highly critical.”
The latest Drupal 7 update also patches two moderately critical vulnerabilities. One of them, which developers claim only occurs if a site’s configuration is unusual, is an access bypass issue that can allow users to view or download files on the private file system without Drupal checking if they have access to it.
The second moderately critical flaw in Drupal 7 is a jQuery XSS issue when making Ajax requests to untrusted domains. Drupal 8 is not affected as jQuery was updated to a newer version with the release of Drupal 8.4.0.
Two moderately critical security bugs have also been fixed in Drupal 8, including an access bypass vulnerability related to language fallback on multilingual sites, and an access bypass flaw in the Settings Tray module that could allow users to update certain data without having the necessary permissions.
Finally, Drupal 7 patches a “less critical” external link injection vulnerability that can allow an attacker to trick users into navigating to a malicious site.
Drupal developers informed users that version 8.4.5 is the last release of the 8.4.x series. Users will have to update to Drupal 8.5.0, expected to become available on March 7, to receive bug and security fixes.
Cisco Patches Critical Flaws in UCDM, ESC Products
22.2.2018 securityweek Vulnerebility
Updates released by Cisco for its Unified Communications Domain Manager (UCDM) and Elastic Services Controller (ESC) products patch critical vulnerabilities that can be exploited by remote attackers.
According to Cisco, UCDM releases prior to 11.5(2) are affected by a flaw that allows a remote, unauthenticated attacker to bypass security protections, obtain elevated privileges, and execute arbitrary code.
“The vulnerability is due to insecure key generation during application configuration. An attacker could exploit this vulnerability by using a known insecure key value to bypass security protections by sending arbitrary requests using the insecure key to a targeted application,” Cisco said in its advisory.
The security hole is tracked as CVE-2018-0124 and it was discovered by Cisco itself during internal security testing.
A critical vulnerability was also discovered by Cisco during internal security testing in the company’s ESC product, specifically the authentication functionality of the web-based service portal.
The flaw, tracked as CVE-2018-0121, allows a remote attacker to bypass authentication and gain administrator privileges on the service portal. The authentication mechanism can be bypassed by submitting an empty value when prompted to enter an admin password.
The vulnerability affects ESC 3.0.0 and it has been addressed with the release of version 3.1.0. This version also patches a high severity unauthorized access vulnerability caused by the presence of default credentials for the service portal.
Cisco also informed customers on Wednesday of a high severity denial-of-service (DoS) vulnerability in the Interactive Voice Response (IVR) management connection interface of the company’s Unified Customer Voice Portal (CVP) product. A remote attacker can exploit this flaw to cause a DoS condition by initiating a specially crafted connection to the IP address of the targeted device.
Cisco says there is no evidence that any of these vulnerabilities have been exploited in malicious attacks.
Cisco on Wednesday also released advisories for cross-site scripting (XSS), cross-site request forgery (CSRF) and DoS flaws affecting its UCS Director and Integrated Management Controller Supervisor, Unified Communications Manager, Prime Service, Prime Collaboration, Jabber Client Framework, Data Center Analytics Framework, and Unity Connection products, but they have all been assigned a “medium” severity rating.
Do Business Leaders Listen to Their Own Security Professionals?
22.2.2018 securityweek Cyber
Survey Shows a Disconnect Between Business Leaders and Security Professionals
A new research report published this week claims, "A disconnect about cybersecurity is causing tension among leaders in the C-suite -- and may be leaving companies vulnerable to breaches as a result."
The specific disconnect is over the relative importance between anti-malware and identity control -- but it masks a more persistent issue: do business leaders even listen to their own security professionals?
The basis for this assertion comes from two sources: the Verizon 2017 Data Breach Investigations Report (DBIR), and the report's own research. DBIR states, "81% of hacking-related breaches leveraged either stolen and/or weak passwords." The new research (PDF), conducted by Centrify and Dow Jones Customer Intelligence shows that companies' security officers agree with the view, while their CEOs do not. Centrify surveyed 800 senior executives in November 2017.
According to the new research, 62% of CEOs consider malware to be the primary threat to cybersecurity, while only 35% of their technical officers agree. The technical officers agree with the DBIR that most breaches come through failures in identity and access control. "More than two-thirds (68%) of executives from companies that experienced at least one breach with serious consequences say it would most likely have been prevented by either privileged user identity and access management or user identity assurance. That compares with only 8% who point to anti-malware endpoint controls."
The report, published by Centrify (a firm that delivers Zero Trust Security through what it calls 'Next-Gen Access'), found this to be perhaps the most disturbing of a series of mismatches between the views of technical officers and their CEOs. Another example concerns strategy accountability: 81% of CEOs say they are most accountable for the company's security strategy; while 78% of the technical officers believe it is they who are most accountable.
These figures raise two questions: firstly, are the technical officers correct in their assertion that identity control is more important than anti-malware, or are CEOs correct in their insistence on anti-malware; and secondly, if the technical officers are correct, why do they fail to adequately communicate their views to senior management?
There is no simple answer. Not all practitioners accept the survey results. Steve Lentz, CSO and director of information security at Samsung Research America, doesn't automatically accept that identity is a bigger problem than malware. "I really believe it's the unknown malware that is on many employee PCs that leak info." He quoted an example of two employees visiting from abroad and connecting to his network. "Our network defenses immediately alerted my security team and quarantined the two PCs." One had a keylogger while the other had a password stealer. The implication is that since it is impossible to control all identities all the time it is necessary to have adequate anti-malware.
Martin Zinaich, information security leader at the City of Tampa, FL, believes the problem may stem from different priorities between Business and Security. Business leaders often have "a low user-friction tolerance combined with a high-risk appetite." At the same time, questioning whether malware or identity is the biggest problem is a mistake. "Wasn't last year's big breach at Equifax due to an unpatched Apache Struts vulnerability? Too often for security professionals it is the basics that get missed."
To a degree, the malware/identity issue is a chicken and egg problem. Drew Koenig, security solutions architect at Magenic, takes one view. If "you look at incidents in their entirety, malware is the result of identity security failures." While phishing and poor security behavior is one problem, poor password construction, account sharing, and over-privileged accounts are another. Compromised accounts are the delivery mechanism, he suggests, for the malware that accesses databases and steals sensitive data.
But Joseph Carson, chief security scientist at Thycotic, warns that attackers use social engineering to bypass initial identity controls. "One single click on a malicious link, can download malware onto your computer that can immediately lock up data in a 'ransomware' attack." In this scenario, identity controls won't protect you from the effects of malware.
Boris Vaynberg, co-founder and CEO at Solebit agrees. "Most attacks start with an attacker penetrating into the organization. These attackers use various techniques, most of them including use of malware to secure initial control inside the organization. Once the attacker gets control, the second step is lateral movement. Attackers will then attempt to secure the credentials they are seeking in order to obtain an organization's sensitive data."
Brian Kelly, chief information security leader at Quinnipiac University, accepts that malware may be the vector used to compromise the identity, but adds, "I really keep coming back to the idea that identity is the new perimeter. In a world full of clouds and ubiquitous mobile access, identity is the only thing between you and your data."
The implication is that identity control cannot stop malware. But since we know that anti-malware also cannot guarantee to stop all malware, identity and credential control becomes essential to prevent lateral movement and privilege escalation.
"It's overly simplistic to think that if the organization addresses one specific attack vector, it will prevent all major breaches," warns Lenny Zeltser, VP of products at Minerva Labs. "Attackers can follow different pathways to achieve their objectives. They can steal credentials, elevate access, and cause damage even if the company has strong identity management practices. Identity security is important, so is endpoint defense, so are network safeguards, etc. We cannot focus on a single security layer and neglect the others."
The second implication from the Centrify survey is that either security professionals are failing to deliver their message to business leaders, or business leaders are refusing to listen to their security professionals. Again, there is no simple answer.
Mike Weber, VP at Coalfire Labs, believes there is a business reason for business leaders to be reluctant to listen to their security professionals. "The security landscape changes constantly, and those dynamic changes rarely align with fiscal year planning cycles. To be able to quickly react to the latest threats, a CISO may need to resort to 'overselling' a particular need." The problem here is that business leaders face 'oversells' all the time, and are well-versed in ignoring them.
Brian Kelly suggests the basic problem comes from multiple sources of threat information. "The feeling that malware is the greatest risk may be driven more by media reports than the security team's failure to deliver the correct message. Information Security teams are competing for the CEO's attention, but are also struggling to craft a message that makes sense in context."
Perhaps one of the problems is a basic misunderstanding of the purpose of 'security'. Mike Smart, security strategist at Forcepoint, believes security is like the brake on a car. Business leaders think its purpose is to slow down the car; that is, security slows down business. "Innovators will tell you the opposite," he says. "It's there to give the driver the confidence to go as fast as possible." In this view, security is the enabler of agile business -- but the implication is that security leaders have failed to adequately explain this function to the business leaders.
Dr. Bret Fund, founder and CEO at SecureSet, suggests that most companies have failed to yet establish the partnership between business and security that is necessary for an agile but secure business. "Security managers need to do a better job understanding the business constraints and how, as a security team, they can provide meaningful solutions inside of those realities. Business managers need to do a better job of understanding that security is everyone's responsibility and NOT just the security teams."
There is little disagreement over a disconnect between business leaders and security professionals. Bridging that disconnect is the problem. Koenig believes that the security team needs to own the problem. "In security," he says, "you have to assume everyone outside your team distrusts you. That's an unfortunate reality. So, to improve your delivery, educate instead of present. Put context around what you are reporting. Help them understand that malware is a valid risk, but most breaches are the result of poor identity controls that allows for the delivery of malware. Ultimately for every security report that is delivered you have to answer the hardest question from a business, 'So What?'. Don't tell, explain."
Centrify's survey demonstrates this mismatch in cyber threat understanding between business leaders and security professionals. The report shows that most security professionals believe that 'identity' is the number one control, while business leaders concentrate on malware. It's a nuanced issue. Identity and credential control, such as that provided by Centrify, won't stop all malware -- but it may prevent a malware incident developing into a major breach. How to get business leaders to listen to security professionals remains a continuing problem.
WhatsApp Co-founder Invests $50 Million in Signal
22.2.2018 securityweek Social
Open Whisper Systems, the organization behind the privacy-focused messaging app Signal, announced on Wednesday the launch of the Signal Foundation, with an initial investment of $50 million from WhatsApp co-founder Brian Acton.
The Signal service is used by millions of people and the Signal protocol is used by billions through its integration into popular applications such as WhatsApp, Facebook Messenger and Google Allo.
Despite the success of its product, the Signal team has never had more than seven members and there have only been an average of 2.3 full-time developers.Signal Foundation launches with $50 million investment
With the launch of the Signal Foundation and the $50 million from Acton, Signal will have the resources necessary to expand and accelerate its mission to make private communications accessible to everyone.
“Starting with an initial $50,000,000 in funding, we can now increase the size of our team, our capacity, and our ambitions. This means reduced uncertainty on the path to sustainability, and the strengthening of our long-term goals and values,” said Moxie Marlinspike, founder of Open Whisper Systems and CEO of the Signal Foundation. “Perhaps most significantly, the addition of Brian brings an incredibly talented engineer and visionary with decades of experience building successful products to our team.”
The Signal Foundation is a 501(c)(3) nonprofit organization. Up until now, the Freedom of the Press Foundation acted as a fiscal sponsor for Signal.
Acton, who left WhatsApp and Facebook last year, will serve as executive chairman of the Signal Foundation and will be actively involved in operations and product development.
“After over 20 years of working for some of the largest technology companies in the world, I couldn’t be more excited for this opportunity to build an organization at the intersection of technology and the nonprofit world,” said Acton.
“In the immediate future we are focused on adding to our talented-but-small team and improving Signal Messenger. Our long-term vision is for the Signal Foundation to provide multiple offerings that align with our core mission,” he added.
The Global cost of cybercrime jumped up to $600 Billion
22.2.2018 securityaffairs CyberCrime
The tech giants McAfee and Cisco published to reports that providers further info about the global impact of cybercrime.
Which is the cost of cybercrime? It is hard to provide an effective a good estimation of the overall impact of the numerous phenomena that happen every day, including cyber attacks, data breaches, scams and so on.
The tech giants McAfee and Cisco published to reports that providers further info about the global impact of cybercrime.
According to the report was written by McAfee in collaboration with the Center for Strategic and International Studies (CSIS), the global cost is estimated at $600 billion annually, a disconcerting figure that corresponds to 0.8% of the global GDP. The value is jumped from $500 billion in 2014 to $600 billion (+20%).
“In 2014, taking into account the full range of costs, CSIS estimated that cybercrime cost the world between $345 billion and $445 billion. As a percentage of global GDP, cybercrime cost the global economy 0.62% of GDP in 2014. Using the same methods, CSIS now believe the range is now between $445 billion and $600 billion.” states the report.
The jump is mainly caused by the significant increase of theft of intellectual property and business confidential information, intellectual property theft accounts for at least 25% of overall cybercrime costs.
The cost of cybercrime is distributed among all the countries of the world, no one is immune. The report shows variations by region, that are linked to income levels and level of cybersecurity maturity, the countries with greater losses are the richest ones.

According to the report, Russia leads cybercrime activities worldwide, the reports also highlighted the thin line between crime rings and nation-state actors.
“CSIS believes that Russia leads overall in cybercrime, reflecting the skill of its hacker community and its disdain for western law enforcement. The complex and close relationship between the Russian state and Russian organized crime means that Russia provides a sanctuary for the most advanced cybercriminals, whose attention focuses on the financial sector.” continues the report.
Ransomware are a profitable business for the criminal ecosystem, currently, more than 6,000 black marketplaces offer for sale such kind of malware and related services, an overall offer of more than
45,000 different products.
The second report published by Cisco confirmed the worrisome trends for cybercrime activities, the document is based on interviews with 3,600 CISOs. According to Cisco almost any attack will cost to the victims at least $500,000. The cost dramatically increased for 8% of companies in the Cisco report that admitted that cyber attacks had cost them over $5 million, 11% the companies suffered economic losses between $2.5 million and $4.9 million.
Cisco highlighted the risk of attacks aimed to the supply chain of the companies. these attacks have increased in complexity and frequency.
Let me suggest reading both studies, they offer an interesting analysis of criminal ecosystem and of the overall cost of cybercrime.
Ohrožení podnikových sítí ze strany internetu věcí je realitou
22.2.2018 SecurityWorld IoT
V nedávném seriálu BBC zvaném McMafia převzal hacker vládu nad IT sítí bombajského přístavu pomocí prodejního automatu s jen několika málo bezpečnostními údaji. Ač se takový případ může zdát nepravděpodobný, je hrozba ze strany internetu věcí vůči kriticky důležité infrastruktuře velice reálná. Jak se stále více zařízení připojuje k síti a další a další senzory nachází využít napříč průmyslovými odvětvími, stává se zároveň ohrožení podnikových sítí skrze neaktualizovaná zařízení internetu věcí skutečnou hrozbou. Zprávu přináší server SC Magazine. Jaká jsou tedy fakta za obavami z hacknutí důležitých IT systémů skrze internet věcí?
Hrozba je reálná a nezmizí sama od sebe.
Celosvětově stoupá míra využití zařízení internetu věcí. Majorita sítí je ovšem nepřipravena na takto masivní příliv nových zařízení, a ještě méně jsou připraveny na hackery a další jednotlivce, kteří se pokusí získat přístup k podnikovým sítím a uživatelským datům pro zločinné úmysly.
Gartner předpokládá, že zde do konce roku 2020 bude kolem 20,4 miliard k síti připojených zařízení. Je evidentní, že počet propojených zařízení se bude i nadále zvyšovat. To sice přináší spoustu výhod, ale také vzrůstající bezpečnostní riziko. Jak se sítě stávají dynamičtějšími a neustále rostou, je těžší a těžší identifikovat a spravovat všechna zařízení k nim připojená.
Ta hrozba je tu a je velmi reálná. Rok 2016 přinesl jeden z největších DDoS útoků všech dob – botnet Mirai – který vyřadil z provozu mnoho webových stránek. Útok byl možný díky zařízením internetu věcí, unikátním IP adresám hostujícím malware. Zařízení nejvíce se podílející na útoku? Průmyslové kamery.
Nejnovější potomek botnetu Mirai se nazývá Satori a objevil se v letošním roce, specificky cílí na procesory ARC. Hlavním účelem je krást kryptoměnu Ethereum skrze hackování online těžařských hostů a tajnému nahrazení jejich peněženek.
Mirai a Satori plně odhalují potenciál kybernetických zločinců ozbrojených malwarem a velkým množstvím nezabezpečených zařízení internetu věcí. Jak se stále více zařízení dostává na síť, hrozeb bude přibývat. Více zařízení znamená více bodů, skrze které může útočník zařízení infikovat a následně je využívat při DDoS útocích.
Jak bohužel ukazuje výše zmíněný seriál McMafia, právě klíčová IT infrastruktura je obzvláště ohrožena. Některé příklady podobných útoků na nezbytné systémy ukazuje hned několik hacknutých vodních elektráren mezi roky 2011 a 2016 a také elektrárnu ve Spojených státech, která byla infiltrována hned sedmnáctkrát mezi roky 2013 a 2014. Co je horší: jaderná elektrárna částečně hacknutá v roce 2016.
Množství zařízení připojených k podnikové síti je nejen téměř nemožné spravovat, ale někdy ani nelze jejich počet vůbec zaznamenat. Princip BYOD (buy your own device, kdy zaměstnanec nedostane firemní notebook nebo mobil, ale koupí si vlastní) a zařízení internetu věcí vede k většímu rozšíření zařízení s vlastními IP adresami a výkonem – ale často bez pořádného zabezpečení. Právě tato zařízení se poté pro hackery stávají bodem vniku do podnikových sítí.
Nová chytrá zařízení se nyní zvládají na vaše sítě připojovat samy od sebe. Vše od chytrých telefonů až po bezpečnostní kamery. Tyto zařízení nejsou spravována a mohou se stát nezabezpečenými koncovými body, které výrazně zvýší šanci na hacknutí sítě. A právě tato zařízení se také stávají hlavním cílem hackerů a kybernetických zločinců. Ti díky nim mohou využít LAN přístup na servery nebo, ještě častěji, mohou podobná zařízení sloužit k manipulaci s daty a získání přístupu do sítě.
Většina organizací si nemyslí, že mají do své sítě připojena nějaká zařízení internetu věcí, ale dokud je nehledají, nemohou si být jistí.
Mnoho firem se nyní, oprávněně, obává útoků zvenčí, které by do jejich sítí pronikly. Nejnovější firewally, systémy na prevenci proti vniknutí, pokročilé ochranné systémy a další, to vše hraje roli v obraně. Jak se však k síti připojuje stále více zařízení, je nutné hledět i na hrozby z vnitřku.
Pokud společnosti nemají kvalitní infrastrukturu na podporu zařízení internetu věcí, riskují odhalení svých podnikových sítí zločinným aktivitám. To může vést k devastujícím výsledkům, obzvláště pokud hackeři odhalí zranitelnosti v zařízení internetu věcí s přístupem ke klíčové IT infrastruktuře.
Dobrým začátečním bodem pro firmy, které berou svou bezpečnost vážně v dnešním hyperpropojeném světě, je zvýšit povědomí o všech zařízeních v síti a implementovat centralizovaný systémy správy pro zajištění dodržování všech pravidel.
Najděte je, zhodnoťte je, spravujte je. To musí být nová mantra pro ochranu organizací od všech různých zařízení. Žijeme v časech jako z televize a v kybernetickém světě musíme chránit svá aktiva lépe než ti, kteří byli na televizních obrazovkách hacknuti.
Structure of Cyber Risk Perception Survey Could Distort Findings
22.2.2018 securityweek Cyber
CISOs Barely Mentioned in Report on Global Cyber Risk Perception
The purpose of a new report from cyber insurance firm Marsh, supported by Microsoft's Global Security Strategy and Diplomacy team, is to examine the global state of cyber risk management: "This report provides a lens into the current state of cyber risk management at organizations around the world."
To achieve this, Marsh polled 1,312 senior executives "representing a range of key functions, including information technology, risk management, finance, legal/compliance, senior management, and boards of directors." However, there is no category representing information security, nor any specific indication where a security team fits in the organizational structure.
A reasonable assumption would be cyber security is treated as part of IT, and that if the organization has a CSO or CISO, that position reports directly to the CIO from within the IT structure. That would explain why IT is consistently described as the functional area that is the primary owner and decision-maker for cyber risk management in all companies across all sectors with revenue above $10 million per annum.
But it doesn't reflect reality. While the majority of CISOs might still report to the CIO, this is slowly changing. Some now report directly to the board while others report to the Chief Risk Officer (CRO) or Legal.
Cyber Risk ReportFurthermore, the cyber security function is key to the specification and implementation of any cyber risk mitigation policy (where 'mitigation' equates to risk reduction as opposed to other methods such as risk transfer, which equates to insurance). Human Resources (30 respondents) can help with insider risk definition and response. Procurement can help with security product purchasing (14 respondents). Finance (340 polled) can help with budget planning and financial compliance issues. But none of these will see the full cyber risk threat. While all of these should be involved in cyber risk management, only a dedicated security team is in a position to define and lead it -- and yet there is no cyber security function included in the report.
The decision not to give cyber security its own role, if not the primary role, within the survey has the potential to distort the findings. For example, 41% of the respondents are concerned about financially motivated attacks (which in this survey includes hacktivists), while only 6% are most concerned about politically motivated attacks including state-sponsored attacks.
The question asked was 'With regard to a cyber-attack that delivers destructive malware, which threat actor concerns you the most?" Options on offer included 'Operational error' and 'Human error, such as employee loss of mobile device'; neither of which are commonly associated with the delivery of destructive malware. It is not clear that heads of individual departments would have the nuanced understanding of different cyber threat vectors to provide an accurate view of overall cyber risk.
Another example can be found in the section on reporting. The report states, "53% of chief information security officers, 47% of chief risk officers, and 38% of chief technology/information officers said they provide reports to board members on cyber investment initiatives. Yet only 18% of board members said they receive such information." There is clearly a disconnect between reporting and listening -- and few people in the security industry would question that there is a security information communications problem.
This is the one occurrence of the title 'CISO' in the entire report -- but notice a higher percentage of cyber security officers report on cyber investments than do the IT officers. The implication is that if Security had been separated out from IT, then IT would not so consistently be seen as the primary decision-maker for cyber risk management -- something that most security practitioners might consider worrying given the non-cyber-risk and potentially conflicting business pressures already affecting IT.
This lack of distinction between IT and Security also misses a useful opportunity. The figures show that more reports are delivered by CISOs (percentage-wise) than by CIOs and CTOs. For several years now, CISOs have been on a campaign to improve their own and their security staff's 'soft skills'. Indeed, NIST's National Initiative for Cybersecurity Education (NICE) is this week running a webinar titled, 'Development of Soft Skills That Are in Demand by Cybersecurity Employers'.
NICE states that for cybersecurity employers, "soft skills such as effective communication, problem-solving, creative thinking, resourcefulness, acting as a team player, and flexibility are among the most desirable attributes they are looking for in a new hire." It would be useful if Marsh's figures could show the comparative effectiveness of cyber risk reporting coming from CISOs and CIOs.
Nevertheless, there is useful data and advice within the report. It shows that the majority of companies do not have a method of expressing risk quantitatively (that is, in economic terms). Those that do express their risk tend to do so qualitatively (that is, with capability maturity levels). But understanding the economic effect of different cyber events is essential for both risk mitigation and/or risk transfer. It helps the security team to understand where to concentrate both effort and budget; and it is essential for insurance companies to set realistic insurance premiums.
The figures show that just over half of organizations either have (34%) or plan to buy (22%) cyber insurance. The remainder either have no plans, or specifically plan not to buy insurance -- but a small number (less than 1%) have dropped existing insurance. The primary reason cited for dropping insurance is, "Cyber insurance does not provide adequate coverage for the cost."
The implication is that cyber insurance companies (which include Marsh) have a large potential market Cyber Insurance Market to Top $14 Billion by 2022: Report , but have not yet succeeded in fully making their case. This report does not help by largely ignoring companies' existing cyber risk mitigation specialists.
By not differentiating between the responding company's security function and its IT function, security-specific mitigation is diluted. When SecurityWeek asked Marsh why it hadn't separated the two, Marsh responded, "Don't know exactly what you mean by 'cyber security function' -- a CISO??"
The 'cyber security function' is the work performed by the security team under a variously titled head of cyber security. Although IT and Security must necessarily work together, they have different functions and different priorities, and therefore deserve to be treated separately.
Marsh provided SecurityWeek with a detailed breakdown of the respondents' job functions, answered under the question: "Which functional area most closely describes your position?" The available options were Finance, Risk management, Information technology, Board of directors, Operations, Legal/Compliance/Audit, Human resources, Procurement, and Other. 'Cyber Security' was not an option.
It is the security function that best understands and is most engaged in active risk mitigation. By concentrating the survey on general business leaders with little understanding of, or direct involvement in, cyber risk mitigation, the results inevitably favor the primary alternative; that is 'risk transfer'. Risk transfer is cyber insurance; which is what Marsh provides.
SEC Tells Execs Not to Trade While Investigating Security Incidents
22.2.2018 securityweek BigBrothers
The U.S. Securities and Exchange Commission (SEC) on Wednesday announced updated guidance on how public companies should handle the investigation and disclosure of data breaches and other cybersecurity incidents.
The SEC has advised companies to inform investors in a timely fashion of all cybersecurity incidents and risks – even if the firm has not actually been targeted in a malicious attack. The agency also believes companies should develop controls and procedures for assessing the impact of incidents and risks.
While directors, officers and the people in charge of developing these controls and procedures should be made aware of security risks and incidents, the SEC believes these individuals should refrain from trading securities while in possession of non-public information regarding a significant cybersecurity incident.
SEC Updates Guidance on Data Breach Disclosures
“Public companies should have policies and procedures in place to (1) guard against directors, officers, and other corporate insiders taking advantage of the period between the company’s discovery of a cybersecurity incident and public disclosure of the incident to trade on material nonpublic information about the incident, and (2) help ensure that the company makes timely disclosure of any related material nonpublic information. In addition, we believe that companies are well served by considering the ramifications of directors, officers, and other corporate insiders trading in advance of disclosures regarding cyber incidents that prove to be material,” the SEC said.
These recommendations follow accusations of insider trading against executives at two major companies recently involved in significant cybersecurity incidents. Last year, questions were raised after four Equifax executives sold stock worth $1.8 million just prior to public disclosure of the hack affecting 145 million customers. Equifax claimed that the execs had been unaware of the breach when they sold shares.
Intel’s CEO, Brian Krzanich, faced similar accusations after it was revealed that he had sold all the stock he was legally allowed to, worth roughly $24 million, just before the Meltdown and Spectre vulnerabilities were disclosed. The chipmaker claimed Krzanich’s decision was not related to the disclosure, but some of the lawsuits filed against Intel over the flaws accuse the company of misleading investors.
“We’re all fighting a cyber arms race. However, some organizations have been operating the cyber war while being cloaked. Organizations determine if damage has been done, and how much damage has been done while not being made public. While these undisclosed investigations are being conducted to determine the extent and potential impact of an attack, it’s simply reckless and inappropriate for executives to trade equities, even if they’re on an automated plan,” said Bill Conner, CEO of SonicWall.
“It is good to see the SEC taking action, even if they are reacting on behalf of shareholders to protect them from the massive, headlining breaches that have come so frequent. There’s more to be done by the SEC with respect to cyber guidelines on disclosure and insider trading rules but, this is a solid step in the right direction,” Conner added.
The SEC’s cybersecurity incident disclosure guidance was first released in 2011 and it has now been updated to reinforce and expand previous recommendations. However, some officials, including SEC commissioners Kara Stein and Robert Jackson, believe the agency could have and should have done more.
“I reluctantly support today’s guidance in the hope that it is just the first step toward defeating those who would use technology to threaten our economy. The guidance essentially reiterates years-old staff-level views on this issue. But economists of all stripes agree that much more needs to be done,” Jackson said on Wednesday.
The SEC itself admitted last year that it was the victim of a cyberattack in 2016 that may have allowed hackers to profit through trading on non-public information obtained from its EDGAR filing system.
Singapore Invites Cyberattacks to Strengthen Defenses
22.2.2018 securityweek BigBrothers
Hundreds of hackers have targeted Singapore's defence ministry –- but the attacks were at the government's invitation in an unusual attempt to strengthen cybersecurity.
Authorities said Wednesday they had paid out US$14,750 in prize money to the best of the 264 so-called "white hat" hackers -- specialists who seek to break into networks to check for vulnerabilities -- involved in the project.
The program, which ran from mid-January to early February, was introduced after an embarrassing breach last year which saw hackers steal personal data from about 850 military servicemen and other employees from a defence ministry web portal.
It was run with cybersecurity network HackerOne, which specializes in coordinating "bug bounty programs" in which hackers are rewarded for spotting weaknesses in computer systems.
The top hacker in the contest was a Cyber Security Manager from Ernst and Young Singapore who gave his name only as Darrel and goes by the online moniker "Shivadagger". He was awarded US$5,000.
A total of 97 vulnerability reports were submitted from 34 participants during the program, with 35 reports deemed valid, according to the defence ministry.
David Koh, the defence ministry's cybersecurity chief, hailed the project. "Our systems are now more secure," he said.
While Singapore has some of the most advanced weaponry in the region, Koh said the ministry was at increasing risk of being targeted, and attackers could range from high-school students in their basements to criminals and state-actors.
Zkontrolujte si, jestli je váš firemní počítač chráněn před chybami Meltdown a Spectre
22.2.2018 SecurityWorld Zranitelnosti
Analytická služba Microsoftu Windows Analytics nyní může prozkoumat podnikové počítače s Windows 10, 8.1 a 7 a určit, zda jsou systémy zranitelné vůči vadám Meltdown a Spectre nacházejícím se v procesorech.
Nová schopnost služby Analytics spadající pod sekci „Upgrade Readiness“, tedy připravenost na aktualizaci, představil Terry Myerson, vrcholný představitel firmy zaměřený právě na operační systém Windows. Myerson zranitelnosti nazval „výzvou pro nás všechny,“ neboť vychází z hardwaru jako takového, nikoli ze softwaru.
„K naší službě Windows Analytics jsme přidali možnost nahlásit stav všech zařízení s Windows, které IT odborníci spravují,“ píše Myerson na blogu Microsoftu.
Windows Analytics je shrnující pojem pro tři různé separátní služby: Upgrade Readiness, Update Compliance a Device Health. Zaměřují se na připravenost počítače na aktualizace a také na samotné „zdraví“ stroje. Vychází z telemetrických dat, která Microsoft z osobních počítačů s Windows získává. Windows Analytics jsou dostupné pouze pro zákazníky s licencí Windows Enterprise.
Služba Upgrade Readiness měla původně odhalovat stroje nejvhodnější k aktualizaci z Windows 7 a 8.1 na Windows 10. Doporučuje také ty systémy, které by měli jako první aktualizovat na nejnovější build, tedy verzi systému.
S aktualizací určenou na ověření zabezpečení vůči zranitelnostem Meltdown a Spectre ukáže služba IT administrátorům, zda je antivirový software počítače kompatibilní s aktualizacemi, které Microsoft vydal minulý týden a které mají lépe zabezpečit počítače vůči oběma zranitelnostem.
Upgrade Readiness také určuje, které systémy jsou již proti Meltdownu a Spectru chráněny a ty PC, které mají aktualizace dočasně deaktivovány. Poskytuje rovněž informace o aktualizacích firmwaru, které ve spolupráci s Microsoftem vydává Intel.
Protože Meltdown i Spectre se nachází přímo v procesoru, je nejlepší obranou právě aktualizace firmwaru (tedy kromě celkové fyzické výměny procesoru). Zpočátku se bude Upgrade Readiness zaměřovat jen na Intel, ale podle Myersona „přidáme i CPU partnerů hned jak budou data o nich dostupné Microsoftu“.
Zack Dvorak, programový manažer Microsoftu však varuje, že uživatelé mohou zprvu vidět množství neznámých nebo prázdných polí při využití služby. „Na vylepšení dat poskytovaných službou Upgrade Readiness pracujeme a nové informace vám zobrazíme hned jak to bude možné.“
Google white hackers disclosed critical vulnerabilities in uTorrent clients
22.2.20218 securityaffairs Vulnerebility
White hackers at Google Project Zero have discovered two critical remote code execution vulnerabilities in versions of BitTorrent’s web-based uTorrent Web client and uTorrent Classic desktop client.
With dozens of millions of active users a day, uTorrent is one of the most popular torrent client, the vulnerabilities could be easily exploited by the researchers to deliver a malware on the target computer or view the past downloads.
Project Zero hacker Tavis Ormandy published a detailed analysis of the issues because the vulnerabilities were not fixed in a 90-day period according to the disclosure policy.
utorrent security
The flaws are tied to various JSON-RPC issues, or issues related to the way the web-based apps handle JavaScript Object Notations (JSON) as they relate to the company’s remote procedure call (RPC) servers.
“By default, utorrent create an HTTP RPC server on port 10000 (uTorrent classic) or 19575 (uTorrent web). There are numerous problems with these RPC servers that can be exploited by any website using XMLHTTPRequest(). To be clear, visiting *any* website is enough to compromise these applications.0 reads the technical analysis.”
Both desktop and web-based uTorrent clients use a web interface to display website content, the presence of JSON-RPC issues make possible the attack decribed by Ormandy,
The expert discovered that the issue can allow an attacker to trigger a flaw in the clients by hiding commands inside web pages that interact with uTorrent’s RPC servers.
An attacker can exploit the vulnerability to change the torrent download folder and download a file to any writable location, including the Windows Startup folder and download an executable file, that will be executed on every startup. The attacker could exploit the same flaw to gain access to user’s download activity information.
The researchers explained that a remote exploitation of the flaw requires a DNS rebinding attack that allows a JavaScript code hosted on a website to create a bridge to the local network bypassing the same-origin policy (SOP).
“This requires some simple DNS rebinding to attack remotely, but once you have the (authentication) secret you can just change the directory torrents are saved to, and then download any file anywhere writable,” Ormandy wrote.
“The authentication secret is not the only data accessible within the webroot – settings, crashdumps, logs and other data is also accessible. As this is a complete remote compromise of the default uTorrent web configuration, I didn’t bother looking any further after finding this,” the researcher added.
Tavis Ormandy
✔
@taviso
Hmm, it looks like BitTorrent just added a second token to uTorrent Web. That does not solve the DNS rebinding issue, it just broke my exploit. 😩
10:08 PM - Feb 20, 2018
164
54 people are talking about this
Twitter Ads info and privacy
20 Feb
Tavis Ormandy
✔
@taviso
Hmm, it looks like BitTorrent just added a second token to uTorrent Web. That does not solve the DNS rebinding issue, it just broke my exploit. 😩
Tavis Ormandy
✔
@taviso
I just fixed the exploit and verified it still works. I would recommend asking BitTorrent to resolve this issue if you're affected, and it works in the default configuration so you probably are. Sigh.
10:20 PM - Feb 20, 2018
86
28 people are talking about this
Twitter Ads info and privacy
Ormandy released proof-of-concept (PoC) code for the flaws he discovered.
This week, BitTorrent released an official statement on the matter:
“On December 4, 2017, we were made aware of several vulnerabilities in the uTorrent and BitTorrent Windows desktop clients. We began work immediately to address the issue. Our fix is complete and is available in the most recent beta release (build 3.5.3.44352 released on 16 Feb 2018). This week, we will begin to deliver it to our installed base of users. All users will be updated with the fix automatically over the following days. The nature of the exploit is such that an attacker could craft a URL that would cause actions to trigger in the client without the user’s consent (e.g. adding a torrent).”
Russia-linked Sofacy APT group shift focus from NATO members to towards the Middle East and Central Asia
22.2.20218 securityaffairs APT
Experts from Kaspersky highlighted a shift focus in the Sofacy APT group’s interest, from NATO member countries and Ukraine to towards the Middle East and Central Asia.
The Russia-linked APT28 group (aka Pawn Storm, Fancy Bear, Sofacy, Sednit, Tsar Team and Strontium.) made the headlines again, this time security experts from Kaspersky highlighted a shift focus in their interest, from NATO member countries and Ukraine to towards the Middle East and Central Asia.
“Sofacy, one of the most active APT we monitor, continues to spearphish their way into targets, reportedly widely phishes for credentials, and infrequently participates in server side activity (including host compromise with BeEF deployment, for example). KSN visibility and detections suggests a shift from their early 2017 high volume NATO spearphish targeting towards the middle east and Central Asia, and finally moving their focus further east into late 2017.” states Kaspersky.
The experts analyzed the infections of the Sofacy backdoor tracked as SPLM, CHOPSTICK and X-Agent, the APT group had been increasingly targeting former Soviet countries in Central Asia. The hackers mostly targeted telecoms companies and defense-related organization, primary target were entities in Turkey, Kazakhstan, Armenia, Kyrgyzstan, Jordan and Uzbekistan.
The researchers observed several attacks leveraging the SPLM and the Zebrocy tool between the second and fourth quarters of 2017 against organizations in Asia. The list of targeted countries included China, Mongolia, South Korea and Malaysia.

“This high level of cyber-espionage activity goes back years. In 2011-2012, the group used a relatively tiny implant (known as “Sofacy” or SOURFACE) as their first stage malware, which at the time had similarities with the old Miniduke implants.” states Kaspersky.
“This made us believe the two groups were connected, although it looks they split ways at a certain point, with the original Miniduke group switching to the CosmicDuke implant in 2014. The division in malware was consistent and definitive at that point.”
The Zebrocy tool was used by attackers to collect data from victims, researchers observed its involvement in attacks on accounting firms, science and engineering centers, industrial organizations, ministries, embassies and consulates, national security and intelligence agencies, press and translation services, and NGOs.
The researchers highlighted that the attack infrastructure used in the last attacks pointed to the Sofacy APT, the group has been fairly consistent throughout even if their TTPs were well documented by security firms across the years. Researchers at Kaspersky expect to see some significant changes this year.
“Sofacy set up and maintained multiple servers and c2 for varying durations, registering fairly recognizable domains with privacy services, registrars that accept bitcoin, fake phone numbers, phony individual names, and 1 to 1 email address to domain registration relationships. Some of this activity and patterns were publicly disclosed, so we expect to see more change in their process in 2018. Also, throughout the year and in previous years, researchers began to comment publicly on Sofacy’s fairly consistent infrastructure setup.” continues Kaspersky.
Further details are included in the analysis published by Kaspersky, including Indicators of Compromise (IOCs).
Intel releases Spectre patches for Skylake, Kaby Lake, Coffee Lake
22.2.20218 securityaffairs Vulnerebility
Intel released a stable microcode update to address the Spectre vulnerability for its Skylake, Kaby Lake, and Coffee Lake processors in all their various variants.
Intel has released microcode to address the CVE-2017-5715 Spectre vulnerability for many of its chips, let’s this time the security updates will not cause further problems.
The Spectre attack allows user-mode applications to extract information from other processes running on the same system. It can also be exploited to extract information from its own process via code, for example, a malicious JavaScript can be used to extract login cookies for other sites from the browser’s memory.
The Spectre attack breaks the isolation between different applications, allowing to leak information from the kernel to user programs, as well as from virtualization hypervisors to guest systems.
Problems such as frequent reboots were related to the fix for the CVE-2017-5715 Spectre flaw (Spectre Variant 2) and affected almost any platform, including systems running on Broadwell Haswell CPUs, as well as Ivy Bridge-, Sandy Bridge-, Skylake-, and Kaby Lake-based platforms.

A couple of weeks ago Intel released new microcode for its Skylake processors, now it has announced security updates for Kaby Lake, Coffee Lake and other CPUs.
The microcode is now available for all 6th, 7th, and 8th generation Core processors and also X-series Intel Core products, as well as Xeon Scalable and Xeon D chips.
Intel released the Spectre firmware security updates for the following products:
Anniedale/Moorefield, Apollo Lake, Avoton/Rangeley, Broxton, Cherry View, Coffee Lake, Cougar Mountain, Denverton, Gemini Lake, Kaby Lake, Knights Landing, Knights Mill, Skylake, SoFIA, Tangier, Valleyview/Bay Trail, and XGold.
Intel released beta patches for Broadwell, Gladden, Haswell, some Ivy Bridge, Sandy Bridge, and Skylake Xeon E3 processors. The beta patches have been provided to OEMs for their final validation.
The patches for the remaining chips are either in pre-beta or planning phase.
Both Intel and AMD confirmed are working on processors that will include protections against attacks such as Spectre and Meltdown.
Global Cybercrime Costs $600 Billion Annually: Study
21.2.2018 securityweek CyberCrime
The annual cost of cybercrime has hit $600 billion worldwide, fueled by growing sophistication of hackers and proliferation of criminal marketplaces and cryptocurrencies, researchers said Wednesday.
A report by the security firm McAfee with the Center for Strategic and International Studies found theft of intellectual property represents about one-fourth of the cost of cybercrime in 2017, and that other attacks such as those involving ransomware are growing at a fast pace.
Russia, North Korea and Iran are the main sources of hackers targeting financial institutions, while China is the most active in cyber espionage, the report found.
Criminals are using cutting-edge technologies including artificial intelligence and encryption for attacks in cyberspace, with anonymity preserved by using bitcoin or other cryptocurrency, the researchers said.
"We are seeing the bad actor community taking advantage of the innovation in the technology industry," Steve Grobman, chief technology officer for McAfee, told a news conference in Washington.
Even though these technologies can offer "tremendous value" when used for legitimate purposes, they also can be adopted by criminals to hide their tracks, Grobman said.
The McAfee-CSIS report suggested cybercrime costs were rising from a 2014 estimate of $445 billion.
"We were hoping it would flatten, but we didn't see that," said CSIS vice president James Lewis.
One of the reasons for the increase, according to Lewis, is that "there's a whole 'dark web' phenomenon that creates a safe space for criminals to operate."
These dark web marketplaces, the report noted, allow hackers and other criminals to offer their services or sell tools which can be used for attacks, and to sell stolen credit card numbers or other valuable data.
- 'Russia is the leader' -
Lewis said meanwhile the geopolitical risks of cybercrime are a key element in these attacks.
"Our research bore out the fact that Russia is the leader in cybercrime, reflecting the skill of its hacker community and its disdain for western law enforcement," Lewis said.
"North Korea is second in line, as the nation uses cryptocurrency theft to help fund its regime, and we're now seeing an expanding number of cybercrime centers, including not only North Korea but also Brazil, India and Vietnam."
The report said there is often a connection between governments and the cybercrime community.
It noted that in a massive attack against US-based Yahoo, "one of the cybercriminals who hacked Yahoo at the behest of Russian intelligence services... also used the stolen data for spam and credit card fraud for personal benefit."
The study did not attempt to measure the cost of all malicious activity on the internet, but focused on the loss of proprietary business data, online fraud and financial crimes, manipulation directed toward publicly traded companies, cyber insurance and reputational damage.
The global research report comes days after the White House released a report showing cyberattacks cost the United States between $57 billion and $109 billion in 2016, while warning of a "spillover" effect for the broader economy if certain sectors are hit.
Google Researcher Finds Critical Flaws in uTorrent Apps
21.2.2018 securityweek Vulnerebility
Google researcher Tavis Ormandy discovered several critical vulnerabilities in the classic and web-based versions of BitTorrent’s uTorrent application. Patches have been released, but the expert says not all flaws have been fixed properly.
Ormandy found that the uTorrent Classic and the uTorrent Web apps create an HTTP RPC server on ports 10000 and 19575, respectively. These RPC servers and some vulnerabilities allow remote attackers to take control of the apps with little user interaction.
In the case of uTorrent Web, which is accessed by users via their web browser, the application relies on a random token that is included in every request for authentication. The problem, according to Ormandy, is that the token can be easily obtained by an attacker from the web root folder and abused to take control of the service.
A malicious actor can exploit the flaw to change the torrent download folder and download a file to any writable location. For example, a hacker could change the download directory to the Startup folder in Windows and download an executable file, which would run on every startup.
An exploit can be executed remotely using a DNS rebinding attack, which allows JavaScript code hosted on a website to create a bridge to the local network, effectively bypassing the same-origin policy (SOP).
Ormandy noted that the web root folder also contains other data – not just the authentication token – including settings, logs and crash dump files.
In the case of uTorrent Classic, the Google researcher discovered a vulnerability that allows a malicious website to obtain the targeted user’s download history.
The expert also noticed that the application disables the ASLR and GS exploit mitigations, and that the guest account does not disable some features – the app’s documentation says many features are disabled for security reasons.
Finally, Ormandy found a design flaw related to the use of the Mersenne Twister pseudorandom number generator (PRNG) for creating authentication tokens and cookies, session identifiers, and pairing keys.
The vulnerabilities were reported to BitTorrent on November 27 and they were made public on Tuesday. Ormandy released technical details and proof-of-concept (PoC) code for the more serious of the vulnerabilities he discovered.
The latest beta version of uTorrent Classic (3.5.3 build 44352) patches the flaws, but Ormandy noted that it still disables the ASLR mitigation. BitTorrent says the fixes will be delivered automatically to users over the next days.
As for uTorrent Web, BitTorrent has attempted to implement a patch, but the Google Project Zero researcher says he has managed to bypass it.
BitTorrent VP of Engineering Dave Rees told SecurityWeek that the company only learned of the uTorrent Web vulnerability this week. Nevertheless, the company believes that all vulnerabilities discovered by Ormandy it the two products have been addressed.
uTorrent is not the only torrent application found to be vulnerable to DNS rebinding attacks. In January, Ormandy revealed that he had managed to execute arbitrary code via such an attack against the Transmission client.
Hacker Detection Firm Vectra Networks Raises $36 Million
21.2.2018 securityweek IT
Vectra Networks, a cybersecurity firm that helps customers detect “in-progress” cyberattacks, today announced that it has closed a $36 million Series D funding round, bringing the total amount raised to date by the company to $123 million.
The company said the investment would be used to expand sales and marketing, fuel product development of its Cognito threat hunting platform, and open a new research-and-development (R&D) center in Dublin, Ireland.
Vectra describes its flagship Congito platform as a solution that “performs non-stop, automated threat hunting with always-learning behavioral models to quickly and efficiently find hidden and unknown attackers before they do damage.”
Vectra Networks Logo
The Series D funding round was led by growth equity fund Atlantic Bridge, with the Ireland Strategic Investment Fund (ISIF) and Nissho Electronics Corp. Returning investors Khosla Ventures, Accel Partners, IA Ventures, AME Cloud Ventures, DAG Ventures and Wipro Ventures also participated in the funding.
“This is an exciting investment for ISIF that promises significant economic impact for Ireland,” said Fergal McAleavey, head of private equity at ISIF. “It is encouraging to see Ireland leverage its emerging expertise in artificial intelligence by attracting businesses such as Vectra that are on the leading edge of technology. With cybersecurity becoming critical for all organizations, we are confident Vectra will deliver a strong economic return on our investment while creating high-value R&D employment here in Ireland.”
The new Dublin facility is expected to add up to 100 jobs in Ireland over the next five years, the company said.
Vectra also has R&D facilities in San Jose, Calif., Austin, Texas and Cambridge, Mass.
Malicious RTF Persistently Asks Users to Enable Macros
21.2.2018 securityweek Virus Vulnerebility
A malicious RTF (Rich Text Format) document has been persistently displaying an alert to ask users to enable macros, Zscaler security researchers have discovered.
As part of this unique infection chain, the malicious document forces the victims to execute an embedded VBA macro designed to download the QuasarRAT and NetWiredRC payloads.
While analyzing the attack, the security researchers discovered that the actor included macro-enabled Excel sheets inside the malicious RTF documents, to trick users into allowing the execution of payloads.
The RTF document features the .doc extension and is opened with Microsoft Word. When that happens, a macro warning popup is displayed, prompting the user to either enable or disable the macro.
However, the malicious RTF document repeatedly displays the warning popups even if the targeted user clicks on the “Disable Macros” button. By persistently displaying the alert, the malicious actor increases the chances for the user giving in and allowing the macro to run.
The analyzed malicious RTF contains 10 embedded Excel spreadsheets, meaning that the warning is displayed 10 times. Users can’t stop these popups unless they click through all of them or force-quit Word, Zscaler notes.
The attack relies on the use of “\objupdate” control for the embedded Excel sheet objects (OLE object). This function would trigger the macro code inside the embedded Excel sheet when the RTF document is being loaded in Microsoft Word, thus causing the multiple macro warning popups to appear.
The same “\objupdate” control was observed being abused in attacks leveraging the CVE-2017-0199 vulnerability that Microsoft patched in April last year. The new attack, however, does not exploit this vulnerability or another Office security flaw.
The actor behind this campaign used two variations of the malicious macro. The code executes a PowerShell command to download intermediate payloads using Schtasks and cmd.exe. By performing registry modifications, the malware would also permanently enable macros for Word, PowerPoint, and Excel.
The macro downloads a malicious VBS file which terminates all running Word and Excel instances, downloads a final payload using the HTTPS protocol and executes the payload.
Next, it enables macros for Office and disables protected view settings in the suite, creates a scheduled task to run the downloaded payload after 200 minutes, deletes the scheduled task, and downloads an additional payload to the same location.
Zscaler observed the attack dropping two Remote Access Trojans (RATs), namely NetwiredRC and QuasarRAT. NetwiredRC can find files, launch remote shell, log keystrokes, capture screen, steal passwords, and more. QuasarRAT is free and open source, and is believed to be an evolution of xRAT. It has features such as remote webcam, remote shell, and keylogging.
Intel Releases Spectre Patches for More CPUs
21.2.2018 securityweek Vulnerebility
Intel has released firmware updates that fix the Spectre vulnerability for many of its processors and patches for dozens more are nearly ready for use in production environments.
After the first round of microcode updates released by the company caused problems for many users, including more frequent reboots and unstable systems, Intel started working on a new set of patches that should address these issues.
The company first released new firmware updates for its Skylake processors, but on Tuesday it announced that patches are now also available for Kaby Lake, Coffee Lake and other CPUs. This includes 6th, 7th, and 8th generation, and X-series Intel Core products, as well as Xeon Scalable and Xeon D processors used in data center systems.Intel releases microcode updates to patch Spectre
As of February 21, the following products have Spectre firmware patches ready for use in production environments: Anniedale/Moorefield, Apollo Lake, Avoton/Rangeley, Broxton, Cherry View, Coffee Lake, Cougar Mountain, Denverton, Gemini Lake, Kaby Lake, Knights Landing, Knights Mill, Skylake, SoFIA, Tangier, Valleyview/Bay Trail, and XGold.
Beta patches, which have been provided to OEMs under NDA for validation, are currently available for Broadwell, Gladden, Haswell, some Ivy Bridge, Sandy Bridge, and Skylake Xeon E3 processors.
As for the remaining CPUs, patches are either in pre-beta or planning phase, but pre-mitigation microcode updates, which should be replaced once production fixes are released, are available for many products.
The patches are generally available through OEM firmware updates. Device manufacturers started releasing BIOS updates to patch the Meltdown and Spectre vulnerabilities shortly after their disclosure, but many decided to halt the updates after Intel warned of instability issues. Some vendors have resumed the distribution of firmware updates.
Meltdown attacks are possible due to a vulnerability tracked as CVE-2017-5754, while Spectre attacks are possible due to flaws tracked as CVE-2017-5753 (Variant 1) and CVE-2017-5715 (Variant 2). Meltdown and Spectre Variant 1 can be patched with software updates, but Spectre Variant 2 requires microcode updates for a complete fix.
Both Intel and AMD announced recently that they are working on processors that will have built-in protections against Spectre- and Meltdown-like exploits.
In the meantime, Intel faces more than 30 lawsuits, including ones filed by customers and shareholders, over the Meltdown and Spectre vulnerabilities.
North Korea Cyber Threat 'More Aggressive Than China': US Firm
21.2.2018 securityweek BigBrothers
North Korean hackers are becoming more aggressive than their Chinese counterparts, a leading US cybersecurity firm warned Tuesday, as it identified a Pyongyang-linked group as an "advanced persistent threat".
It was the first time that FireEye had used the designation for a North Korean-based group.
Analysts say the isolated and impoverished but nuclear-armed North has stepped up hacking operations partly to raise money for the cash-strapped regime, which is subject to multiple sanctions over its atomic weapons and ballistic missile programs.
North Korea Cyber ThreatNorth Korea has previously been blamed for the WannaCry ransomware that briefly wreaked havoc around the world last year -- an accusation it angrily denies.
FireEye said North Korean operatives had expanded their targets beyond South Korea and mounted increasingly sophisticated attacks, adding it had identified a suspected North Korean cyberespionage group it dubbed "APT37" -- standing for "advanced persistent threat".
APT37 was "primarily based in North Korea", it said, and its choice of targets "aligns with North Korean state interests".
"We assess with high confidence that this activity is carried out on behalf of the North Korean government," it added.
APT37 has been active at least since 2012, it said, previously focused on "government, military, defence industrial base and media sector" in the rival South before widening its range to include Japan, Vietnam and the Middle East last year, and industries ranging from chemicals to telecommunications.
"This group should be taken seriously," FireEye added.
FireEye's first APT was identified in a 2013 report by company division Mandiant, which said that hackers penetrating US newspapers, government agencies and companies "are based primarily in China and that the Chinese government is aware of them".
One group, it said then, was believed to be a branch of the People's Liberation Army in Shanghai called Unit 61398. Five of its members were later indicted by US federal prosecutors on charges of stealing information from US firms, provoking a diplomatic row between Washington and Beijing.
"We have seen both North Korean and Chinese operations range from simplistic to very technically sophisticated," FireEye's director of intelligence analysis John Hultquist told AFP.
"The sharpest difference between the two really lies in the aggressive nature of North Korean operations," he added.
"Whereas Chinese actors have typically favoured quiet espionage, North Korea has demonstrated a willingness to carry out some very aggressive activity, ranging from attack to outright global crime."
But the WannaCry ransomware, he believes, was the work of a different North Korean group. "Thus far, we have only found APT37 doing the quiet espionage but they are a tool the regime can use aggressively."
The North is known to operate an army of thousands of well-trained hackers that have attacked South Korean firms, institutions and even rights groups helping North Korean refugees.
Its cyberwarfare abilities first came to prominence when it was accused of hacking into Sony Pictures Entertainment to take revenge for "The Interview," a satirical film that mocked its leader Kim Jong Un.
More recently, according to analysts, the North's hackers have stepped up campaigns to raise funds by attacking cryptocurrency exchanges as the value of bitcoin and other cybercurrencies soared.
Top Experts Warn Against 'Malicious Use' of AI
21.2.2018 securityweek Virus
Artificial intelligence could be deployed by dictators, criminals and terrorists to manipulate elections and use drones in terrorist attacks, more than two dozen experts said Wednesday as they sounded the alarm over misuse of the technology.
In a 100-page analysis, they outlined a rapid growth in cybercrime and the use of "bots" to interfere with news gathering and penetrate social media among a host of plausible scenarios in the next five to 10 years.
"Our report focuses on ways in which people could do deliberate harm with AI," said Seán Ó hÉigeartaigh, Executive Director of the Cambridge Centre for the Study of Existential Risk.
"AI may pose new threats, or change the nature of existing threats, across cyber-, physical, and political security," he told AFP.
The common practice, for example, of "phishing" -- sending emails seeded with malware or designed to finagle valuable personal data -- could become far more dangerous, the report detailed.
Currently, attempts at phishing are either generic but transparent -- such as scammers asking for bank details to deposit an unexpected windfall -- or personalised but labour intensive -- gleaning personal data to gain someone's confidence, known as "spear phishing".
"Using AI, it might become possible to do spear phishing at scale by automating a lot of the process" and making it harder to spot, O hEigeartaigh noted.
In the political sphere, unscrupulous or autocratic leaders can already use advanced technology to sift through mountains of data collected from omnipresent surveillance networks to spy on their own people.
"Dictators could more quickly identify people who might be planning to subvert a regime, locate them, and put them in prison before they act," the report said.
Likewise, targeted propaganda along with cheap, highly believable fake videos have become powerful tools for manipulating public opinion "on previously unimaginable scales".
An indictment handed down by US special prosecutor Robert Mueller last week detailed a vast operation to sow social division in the United States and influence the 2016 presidential election in which so-called "troll farms" manipulated thousands of social network bots, especially on Facebook and Twitter.
Another danger zone on the horizon is the proliferation of drones and robots that could be repurposed to crash autonomous vehicles, deliver missiles, or threaten critical infrastructure to gain ransom.
- Autonomous weapons -
"Personally, I am particularly worried about autonomous drones being used for terror and automated cyberattacks by both criminals and state groups," said co-author Miles Brundage, a researcher at Oxford University's Future of Humanity Institute.
The report details a plausible scenario in which an office-cleaning SweepBot fitted with a bomb infiltrates the German finance ministry by blending in with other machines of the same make.
The intruding robot behaves normally -- sweeping, cleaning, clearing litter -- until its hidden facial recognition software spots the minister and closes in.
"A hidden explosive device was triggered by proximity, killing the minister and wounding nearby staff," according to the sci-fi storyline.
"This report has imagined what the world could look like in the next five to 10 years," Ó hÉigeartaigh said.
"We live in a world fraught with day-to-day hazards from the misuse of AI, and we need to take ownership of the problems."
The authors called on policy makers and companies to make robot-operating software unhackable, to impose security restrictions on some research, and to consider expanding laws and regulations governing AI development.
Giant high-tech companies -- leaders in AI -- "have lots of incentives to make sure that AI is safe and beneficial," the report said.
Another area of concern is the expanded use of automated lethal weapons.
Last year, more than 100 robotics and AI entrepreneurs -- including Tesla and SpaceX CEO Elon Musk, and British astrophysicist Stephen Hawking -- petitioned the United Nations to ban autonomous killer robots, warning that the digital-age weapons could be used by terrorists against civilians.
"Lethal autonomous weapons threaten to become the third revolution in warfare," after the invention of machine guns and the atomic bomb, they warned in a joint statement, also signed by Google DeepMind co-founder Mustafa Suleyman.
"We do not have long to act. Once this Pandora's box is opened, it will be hard to close."
Contributors to the new report -- entitled "The Malicious Use of AI: Forecasting, Prevention, and Mitigation" -- also include experts from the Electronic Frontier Foundation, the Center for a New American Security, and OpenAI, a leading non-profit research company.
"Whether AI is, all things considered, helpful or harmful in the long run is largely a product of what humans choose to do, not the technology itself," said Brundage.
Palo Alto Networks Releases New Rugged Firewall
21.2.2018 securityweek Safety
Palo Alto Networks on Tuesday announced that it has updated its PAN-OS operating system and released a new next-generation firewall designed for use in industrial and other harsh environments.
The new PA-220R is a ruggedized NGFW that can be used by various types of organizations, including power plants, utility substations, oil and gas facilities, manufacturing plants, and healthcare organizations. During beta testing, the product was also used for railway systems, defense infrastructure, and even amusement parks.
Palo Alto Networks PA-220R rugged firewall
The PA-220R is designed to withstand extreme temperatures, vibration, humidity, dust, and electromagnetic interference.
Palo Alto Networks said the product works with various industrial applications and protocols, including OSIsoft PI, Siemens S7, Modbus, DNP3, and IEC 60870-5-104.
“For early-engagement customers and many of our expected users of the PA-220R, the situation is that they have industrial assets in harsh environments that have been modernized or are being modernized as part of their OT digital transformation initiatives,” explained Del Rodillas, director of industrial cybersecurity product marketing at Palo Alto Networks. “In many of these initiatives, the automation piece is cutting-edge, but the provisions for cybersecurity are lagging, leaving these organizations exposed.”
“As additional motivation for the security upgrade, some harsh-environment remote sites have grown in complexity and require local segmentation to improve visibility and control over local traffic. There are also use cases which require direct site-to-site connectivity instead of requiring users to go up through SCADA first in order to get to other sites,” Rodillas added.
The PA-220R firewall runs Palo Alto Networks’ PAN-OS operating system, which the company updated to version 8.1 this week.
According to Palo Alto Networks, PAN-OS 8.1 brings many improvements, including simplified implementation of application-based security policies, streamlined decryption of SSL traffic, better performance thanks to new hardware, new management features, and enhanced threat detection and prevention.
Automated Compliance Testing Tool Accelerates DevSecOps
21.2.2018 securityweek Privacy
Chef Software's InSpec 2.0 Compliance Automation Tool Helps Organizations Maintain an Up-to-Date View of Compliance Status
Software developers are urged to include security throughout the development cycle. This requires testing for compliance with both house rules and regulatory requirements before an application is released. Compliance testing is difficult, time-consuming and often subject to human error.
A January survey by Seattle-based software automation firm Chef Software shows that 74% of development teams assess for software compliance issues manually, and half of them remediate manually. Chef further claims that 59% of organizations do not assess for compliance until the code is running in production, and 58% of organizations need days to remediate issues.
Now Chef has released InSpec version 2.0 of its compliance automation technology. InSpec evolved from technology acquired with the purchase of German startup company VulcanoSec in 2015. The latest version improves performance and adds new routines. Chef claims it offers 90% Windows performance gains (30% on Linux/Unix) over InSpec 1.0. New in version 2.0 is the ability to verify AWS and Azure policies (with the potential to eliminate accidental public access to sensitive data in S3 buckets); and more than 30 new built-in resources.
The S3 bucket compliance problem is an example of InSpec's purpose. Earlier this month, two separate exposed databases were discovered in AWS S3 buckets. Last week, FedEx was added to the growing list, with (according to researchers) a database of "more than 119 thousands of scanned documents of US and international citizens, such as passports, driving licenses, security IDs etc."
In each case -- and the many more examples disclosed during 2017 -- the cause was simple: the databases were set for public access. The potential regulatory compliance effects, however, are complex. Just the EU General Data Protection Regulation (GDPR, coming into effect in May 2018) would have left FedEx liable to a fine of up to 4% of its global revenue if any of the 'international citizens' were citizens of the EU. FedEx revenue for 2017 is approximately $60 billion.
In all cases the cause was most likely simple human error. But this discloses a bigger problem within secure and compliant software development: it involves multiple stakeholders with different priorities and, to a degree, different languages of expression. "Compliance requirements are often specified by high level compliance officers in high level ambiguous Word documents," explains Julian Dunn, Chef's director of product marketing.
"But at the implementation level you have the DevOps folks who are in charge of the systems -- but they don't understand ambiguous Word documents. What they understand is code, computer systems and the applications. There's a failure to communicate because everyone uses different tools to do so -- and that just slows down the process."
InSpec 2.0 can verify AWS and Azure policies (with the potential to eliminate public access to sensitive data in S3 buckets); and more than 30 new built-in resources. It provides a simple easy-to-understand code-like method of defining compliance requirements. These requirements are then regularly checked against the company's infrastructure, both cloud and on-prem. A few lines of this code language would solve the S3 bucket exposure problem: "it { should have_mfa_enabled }" and "it { should_not have_access_key }".
Another example could be a database that compliance requires has access controls. For a Red Hat Linux system, the InSpec code would include, "control "ensure_selinux_installed" do", and "it { should be_installed }".
InSpec then regularly checks the infrastructure and detects whether anything is not compliant or has slipped out of compliance with the specified rules. It is part of the InSpec cycle that Chef describes as 'detect, correct, automate'. Detection provides visibility into current compliance status to satisfy audits and drive decision-making; correction is the remediation of issues to improve performance and security; and automation allows for faster application deployment and continuous code risk management.
"We help the customer in the automate phase with pre-defined profiles around the common regulatory requirements," explains Dunn. "But InSpec is fundamentally a generic toolkit for expressing rules and positive and negative outcomes from those rules -- so it deals with everything from soft compliance (rules of the house) all the way through to GDPR, PCI, SOX and so on."
But there is a further benefit. Software development has embraced the concept of DevOps to avoid siloed software development and deployment. Increasing security compliance regulations are now driving the concept of DevSecOps, to bring the security team into the mix. InSpec automatically involves security and compliance with the code development process -- a fully-functioning DevSecOps environment able to improve rather than inhibit the agility of software development is an automatic byproduct of InSpec 2.0.
Control Flow Integrity, a fun and innovative Javascript Evasion Technique
21.2.2018 securityaffairs Hacking
Javascript evasion technique – Security Expert Marco Ramilli detailed a fun and innovative way to evade reverse-engineering techniques based on Javascript technology.
Understanding the real code behind a Malware is a great opportunity for Malware analysts, it would increase the chances to understand what the sample really does. Unfortunately it is not always possible figuring out the “real code”, sometimes the Malware analyst needs to use tools like disassemblers or debuggers in order to guess the real Malware actions. However when the Sample is implemented by “interpreted code” such as (but not limited to): Java, Javascript, VBS and .NET there are several ways to get a closed look to the “code”.
Unfortunately attackers know what the analysis techniques are and often they implement evasive actions in order to reduce the analyst understanding or to make the overall analysis harder and harder. An evasive technique could be implemented to detect if the code runs over a VM or it could be implemented in order to run the code only on given environments or it could be implemented to avoid debugging connectors or again to evade reverse-engineering operations such as de-obfuscations techniques. Today “post” is about that, I’d like to focus my readers attention on a fun and innovative way to evade reverse-engineering techniques based on Javascript technology.
Javascript is getting day-by-day more important in term of attack vector, it is often used as a dropper stage and its implementation is widely influenced by many flavours and coding styles but as a bottom line, almost every Javascript Malware is obfuscated. The following image shows an example of obfuscated javascript payload (taken from one analysis of mine).
Example: Obfuscated Javascript
As a first step the Malware analyst would try to de-obfuscate such a code by getting into it. Starting from simple “cut and paste” to more powerful “substitution scripts” the analyst would try to rename functions and variables in order to split complexity and to make clear what code sections do. But in Javascript there is a nice way to get the callee function name which could be used to understand if a function name changed over the time. That function is the arguments.callee.caller. By using that function the attacker can create a stack trace where it saves the executed function chaining name list. The attacker would grab function names and use them as the key to dynamically decrypt specific and crafted Javascript code. Using this technique the Attacker would have an implicit control flow integrity because if a function is renamed or if the function order is slightly different from the designed one, the resulting “hash” would be different. If the hash is different the generated key would be different as well and it wont be able to decrypt and to launch specific encrypted code.
But lets take a closer look to what I meant. The following snip shows a clear (not obfuscated) example explaining this technique. I decided to show not obfuscated code up here just to make it simple.
var _ = require("underscore");
function keyCharAt(key, i) {
return key.charCodeAt( Math.floor(i % key.length) );
}
function xor_encrypt(key, data) {
return _.map(data, function(c, i) {
return c.charCodeAt(0) ^ keyCharAt(key, i);
});
}
function xor_decrypt(key, data) {
return _.map(data, function(c, i) {
return String.fromCharCode( c ^ keyCharAt(key, i) );
}).join("");
}
function cow001(){
eval(xor_decrypt(arguments.callee.name,[0,0,25,67,95,93,6,65,27,95,87,25,68,34,22,92,89,82,10,0,2,67,16,114,12,1,3,85,94,69,67,59,5,89,87,86,6,29,4,16,120,84,17,10,87,17,23,24]));
}
function pyth001(){
eval(xor_decrypt(arguments.callee.name,[19,22,3,88,0,1,25,89,66]));
}
function pippo(){
pyth001();
}
pippo();
view rawAntiDeobfuscationJavascriptTechnique.js hosted with ❤ by GitHub
Each internal stage evaluates ( eval() ) a content. On row 21 and 25 the function cow001 and pyth001 evaluates xor decrypted contents. The xor_decrypt function takes two arguments: decoding_key and the payload to be decrypted. Each internal stage function uses as decryption key the name of callee by using the arguments.callee.name function. If the function name is the “designed one” (the one that the attacker used to encrypt the payload) the encrypted content would be executed with no exceptions. On the other side if the function name is renamed (by meaning has been changed by the analyst for his convenience) the evaluation function would fail and potentially the attacker could trigger a different code path (by using a simple try and catch statement).
Before launching the Sample in the wild the attacker needs to prepare the “attack path” by developing the malicious Javascript and by obfuscating it. Once the obfuscation took place the attacker needs to use an additional script (such as the following one) to encrypt the payloads according to the obfuscated function names and to replace the newly encrypted payload to the final and encrypted Javascipt file replacing the encrypted payloads with the one encrypted having as a key the encrypted function names.
"use strict"; var _ = require("underscore");
function keyCharAt(key, i) { return key.charCodeAt( Math.floor(i % key.length) ); }
function xor_encrypt(key, data) { return _.map(data, function(c, i) { return c.charCodeAt(0) ^ keyCharAt(key, i); }); }
function xor_decrypt(key, data)
{ return _.map(data, function(c, i)
{ return String.fromCharCode( c ^ keyCharAt(key, i) ); }).join(""); }
var final_payload = "console.log('Malicious Content Triggers Here !')";
var k_final = "cow001";
var encrypted_final = xor_encrypt(k_final,final_payload);
var decrypted_final = xor_decrypt(k_final, encrypted_final); console.log(encrypted_final.toString()); console.log(decrypted_final); var _1_payload = "cow001();";
var k_1 = "pyth001";
var encrypted_1 = xor_encrypt(k_1,_1_payload);
var decrypted_1 = xor_decrypt(k_1, encrypted_1);
console.log(encrypted_1.toString());
console.log(decrypted_1);
view rawAntiDeobfuscationJavascriptPreparationScrypt.js hosted with ❤ by GitHub
The attacker is now able to write a Javascript code owning its own control flow. If the attacker iterates such a concept over and over again, he would block or control the code execution by hitting a complete reverse-engineering evasion technique.
The original post published by Marco Ramilli on his blog at the following URL:
https://marcoramilli.blogspot.it/2018/02/control-flow-integrity-javascript.html
U.S. Justice Department Launches Cybersecurity Task Force
21.2.2018 securityweek BigBrothers
U.S. Attorney General Jeff Sessions announced on Tuesday the launch of a new cybersecurity task force whose role is to help the Department of Justice find ways to combat cyber threats and become more efficient in this area.
The Cyber-Digital Task Force will focus on various types of threats, such as interfering with elections, disrupting critical infrastructure, using the Internet for spreading violent ideologies and recruiting followers, attacks that rely on botnets, the use of technology designed to hide criminal activities and avoid law enforcement, and the theft of personal, corporate and governmental data.
The task force has been instructed to submit a report to the Attorney General on these and other important topics, along with providing initial recommendations, by June 30.
The Cyber-Digital Task Force will be chaired by a senior Justice Department official and will include representatives of the Department’s Criminal Division, the National Security Division, the U.S. Attorney’s Office community, the Office of Legal Policy, the Office of Privacy and Civil Liberties, the Office of the Chief Information Officer, the FBI, ATF, DEA, and the U.S. Marshals Service. Other departments may be invited to participate as well.
“The Internet has given us amazing new tools that help us work, communicate, and participate in our economy, but these tools can also be exploited by criminals, terrorists, and enemy governments,” said Attorney General Sessions. “At the Department of Justice, we take these threats seriously. That is why today I am ordering the creation of a Cyber-Digital Task Force to advise me on the most effective ways that this Department can confront these threats and keep the American people safe.”
The U.S. government has been increasingly concerned about online campaigns whose goal is to interfere with the country’s elections. Russia is widely believed to have meddled in the 2016 presidential election and officials fear it will attempt to do so again in the upcoming midterm elections.
Officials are also concerned about cyberattacks launched by Russia and others against critical infrastructure in the United States.
In response to growing threats, the U.S. government has launched various cybersecurity initiatives. For instance, the Department of Energy is prepared to invest millions in cybersecurity and recently announced the creation of a dedicated office, and the Department of Defense has paid hackers hundreds of thousands of dollars for finding vulnerabilities in its systems.
North Korean APT Group tracked as APT37 broadens its horizons
21.2.2018 securityweek APT
Researchers at FireEye speculate that the APT group tracked as APT37 (aka Reaper, Group123, ScarCruft) operated on behalf of the North Korean government.
Here we are to speak about a nation-state actor dubbed APT37 (aka Reaper, Group123, ScarCruft) that is believed to be operating on behalf of the North Korean government.
APT37 has been active since at least 2012, it made the headlines in early February when researchers revealed that the APT group leveraged a zero-day vulnerability in Adobe Flash Player to deliver malware to South Korean users.
Cyber attacks conducted by the APT37 group mainly targeted government, defense, military, and media organizations in South Korea.
FireEye linked the APT37 group to the North Korean government based on the following clues:
the use of a North Korean IP;
malware compilation timestamps consistent with a developer operating in the North Korea time
zone (UTC +8:30) and follows what is believed to be a typical North Korean workday;
objectives that align with Pyongyang’s interests(i.e. organizations and individuals involved in Korean
Peninsula reunification efforts);
Researchers from FireEye revealed that the nation-state actor also targeted entities in Japan, Vietnam, and even the Middle East in 2017. The hackers targeted organizations in the chemicals, manufacturing, electronics, aerospace, healthcare, and automotive sectors.
“APT37 has likely been active since at least 2012 and focuses on targeting the public and private sectors primarily in South Korea. In 2017, APT37 expanded its targeting beyond the Korean peninsula to include Japan, Vietnam and the Middle East, and to a wider range of industry verticals, including chemicals, electronics, manufacturing, aerospace, automotive and healthcare entities” reads the report published by FireEye.

Experts revealed that in 2017, the APT37 targeted a Middle Eastern company that entered into a joint venture with the North Korean government to provide telecommunications service to the country.
The hackers leveraged several vulnerabilities in Flash Player and in the Hangul Word Processor to deliver several types of malware.
The arsenal of the group includes the RUHAPPY wiper, the CORALDECK exfiltration tool, the GELCAPSULE and HAPPYWORK downloaders, the MILKDROP and SLOWDRIFT launchers, the ZUMKONG infostealer, the audio-capturing tool SOUNDWAVE, and backdoors tracked by FireEye as DOGCALL, KARAE, POORAIM, WINERACK and SHUTTERSPEED.
“North Korea has repeatedly demonstrated a willingness to leverage its cyber capabilities for a variety of purposes, undeterred by notional redlines and international norms. Though they have primarily tapped other tracked suspected North Korean teams to carry out the most aggressive actions, APT37 is an additional tool available to the regime, perhaps even desirable for its relative obscurity.” concludes FireEye.
“We anticipate APT37 will be leveraged more and more in previously unfamiliar roles and regions, especially as pressure mounts on their sponsor.”
Coldroot RAT cross-platform malware targets MacOS without being detected
21.2.2018 securityweek Apple
The former NSA hacker and malware researcher Patrick Wardle is back, this time he spotted a new remote access Trojan dubbed Coldroot RAT.
The Coldroot RAT is a cross-platform that is targeting MacOS systems and the bad news is that AV software is not able to detect it. The malware acts as a keylogger on MacOS systems prior to the OS High Sierra allowing it to capture user passwords and credentials.
Wardle published a detailed analysis of the RAT that is currently available for sale on the underground markets since Jan. 1, 2017, while some versions of the Coldroot RAT code have also been available on GitHub for nearly two years.
The expert explained that the RAT masquerades as an Apple audio driver “com.apple.audio.driver2.app” that when clicked on displays an authentication prompt requesting the victim to provide its MacOS credentials.
“an unflagged file named com.apple.audio.driver2.app caught my eye. It was recently submitted for a scan, in early January. ” wrote Wardle.
“Though currently no AV-engine on VirusTotal flags this application as malicious, the fact it contained a reference to (TCC.db) warranted a closer look.”
Once obtained the credentials the RAT modifies the privacy TCC.db database. The researchers analyzed a sample that once installed attempts to provide the malware with accessibility rights (so that it may perform system-wide keylogging) by creating the
/private/var/db/.AccessibilityAPIEnabled
file and then modifies the privacy database TCC.db that keep track of the applications installed on the machine and the related level of accessibility rights.
“Think, (ab)using AppleScript, sending simulated mouse events via core graphics, or directly interacting with the file system. An example of the latter was DropBox, which directly modified macOS’s ‘privacy database’ (TCC.db) which contains the list of applications that are afforded ‘accessibility’ rights.” Wardle wrote.
“With such rights, applications can then interact with system UIs, other applications, and even intercept key events (i.e. keylogging). By directly modifying the database, one could avoid the obnoxious system alert that is normally presented to the user: ”

Patrick Wardle explained that the RAT gain persistence by installing itself as a launch daemon.
The researcher highlighted that systems running MacOS High Sierra protect TCC.db via System Integrity Protection (SIP).
“Thought this script is executed as root, on newer versions of macOS (Sierra+) it will fail as the privacy database is now protected by SIP,” Wardle added.
The static analysis of the malware revealed the commands it supports that are:
Repeating this process for the other commands reveals the following capabilities:
file/directory list
file/directory rename
file/directory delete
process list
process execute
process kill
download
upload
get active window
remote desktop
shutdown
Patrick Wardle believes that author of the RAT is “Coldzer0” that advertised the malicious code for sale offering the possibility to customize it.
“Besides revealing the likely identify of the malware author, this turns up:
source code for an old (incomplete) version of Coldroot
an informative demo video of the malware
The source code, though (as noted), is both old and incomplete – provides some confirmation of our analysis. For example, the PacketTypes.pas file contains information about the malware’s protocol and tasking commands: “
IPhony už nelze vyřadit z provozu jedinou zprávou. Apple vydal aktualizaci systému
20.2.2018 Novinky/Bezpečnost Apple
Vyřadit prakticky jakýkoliv iPhone z provozu nebyl ještě minulý týden vůbec žádný problém. Operační systém totiž obsahoval chybu, kvůli které bylo jablečné zařízení vyřazeno z provozu poté, co obdrželo zprávu s jedním konkrétním znakem. Společnost Apple však nyní vydala aktualizaci, která tento nepříjemný problém řeší.
Informace o tom, že je možné snadno vyřadit iPhone z provozu, začala internetem kolovat na konci minulého týdne.
Ukázalo se, že iPhony se zhroutí poté, co je na nich zobrazena zpráva obsahující jeden konkrétní znak v telugštině, tedy v třetím nejpoužívanějším indickém jazyce po hindštině a bengálštině. Roli přitom nehrálo, zda se jednalo o SMS zprávu nebo zda byl text zaslán prostřednictvím Twitteru, Skypu či přes e-mail.
Apple’s latest operating system has a bug that could really mess up your phone https://t.co/gqpRzAGKqd
— New York Magazine (@NYMag) February 16, 2018
Takto vypadá znak, který dokázal vyřadit iPhone z provozu.
Ve chvíli, kdy se v jakékoliv aplikaci daný znak zobrazil, aplikace se zasekla a přestala pracovat. V krajním případě – pokud byl znak zobrazen v notifikačním okně – došlo dokonce k pádu celého operačního systému a iPhone se neustále restartoval.
Po pouhých pár dnech přispěchala společnost Apple s opravou, vydána byla v noci na úterý. Uživatelé, kteří si nechtějí nechat od vtipálků a zlomyslných uživatelů výše popsaným způsobem zablokovat své přístroje, by měli tedy co nejdříve provést aktualizaci na iOS 11.2.6.
Dříve trápily uživatele odkazy
Vtipálci – a případně i nefalšovaní záškodníci s nekalými úmysly – tak mají další možnost, jak potrápit uživatele jablečných smartphonů. A historicky to není poprvé.
V roce 2016 se například internetem šířily odkazy na speciální webovou stránku, která dokázala u iPhonů a stolních počítačů od Applu „shodit“ nejen samotný prohlížeč, ale také celý operační systém, jak je vidět i na videu níže.
Stránka obsahuje speciálně upravený kód v JavaScriptu, který zkrátka donutí zařízení provést restart. Jedinou obranou je na podobné odkazy neklikat.
Souborový systém APFS má v High Sierra kritickou chybu. Hrozí při ní ztráta zálohovaných dat
20.2.2018 Živě Apple
Systém High Sierra přinesl na Macy jako jednu v hlavních novinek souborový systém APFS. Ten je optimalizovaný pro SSD a odolnější vůči chybám moderních úložišť. Jak ale nyní zjistil vývojář zálohovací utility Carbon Copy Cloner, obsahuje chybu, při které může dojít ke ztrátě dat.
Týká se primárně dynamických diskových obrazů (sparse), které reprezentují data na externím úložišti, typicky na NASu nebo externím disku. Tam lze vytvořit obraz disku tohoto typu a nasměrovat na něj například zálohovací aplikaci. Obraz disku potom ukazuje právě takovou velikost, jakou zabírají data na fyzickém disku.
Problém ale nastane v případě, že se zaplní cílové fyzické úložiště. Systém ne vždy korektně vrátí hodnotu o zaplněném disku a jeho obraz tak stále ukazuje informaci o volném místu (a předá ji dalším aplikacím). A i přesto, že fyzicky není možné data na externí úložiště zkopírovat, systém přenos dat zobrazí jako úspěšný.
Před odpojením disku dokonce lze takto zkopírovaná data z obrazu otevřít a korektně číst. Po odpojení a znovupřipojení se však samozřejmě stanou nedostupná. To je právě v případě použití se zálohovacími aplikacemi kritickou chybou. Náprava by tak měla ze strany Applu přijít co nejdřív. Více na:
Stovky českých webů těžily virtuální mince
20.2.2018 Novinky/Bezpečnost Bezpečnost
Hned několik stovek českých internetových serverů zatěžovalo nadměrně výkon počítačů a chytrých telefonů svých návštěvníků, ukrývaly se na nich totiž speciální skripty pro těžbu kybernetických mincí, jako jsou například bitcoiny. Upozornil na to serveru Lupa.cz.
Kybernetické měny jsou fenoménem dnešní doby. V loňském roce nalákaly celou řadu uživatelů o stovky procent rostoucí kurzy prakticky všech kybernetických měn. Popularita nicméně rostla také díky tomu, že lidé mohou těžit virtuální mince sami, za jejich pořízení tedy nemusí platit ani korunu.
Pokud mají dostatečně výkonný počítač – případně chytrý telefon –, mohou si nainstalovat speciální software a s jeho pomocí kryptoměny doslova těžit – tento program totiž používá předem nastavené výpočty, jejich výsledkem je zisk virtuálních mincí. Za ty je pak možné nakupovat prakticky cokoliv.
Virus se nestahuje, web stačí jen navštívit
Stejným způsobem mohou těžit také hackeři, kteří internetem masivně šíří nejrůznější těžařské viry. Speciálními skripty, které pracují na stejných principech jako samotné viry, jsou dokonce hojně šířeny také prostřednictvím nejrůznějších webových stránek.
Do počítačů nebo jiných zařízení se tedy žádné škodlivé kódy nestahují. Návštěvníci dotčených webů pomáhají počítačovým pirátům vydělat peníze už jen tím, že web navštíví, neboť výkon jejich počítačů či jiných zařízení byl využíván k těžbě kybernetických mincí.
Objevily se na 950 tuzemských webech, jak vyčíslil bezpečnostní tým CSIRT.CZ.
Kolik lidí infikované stránky navštívilo, zatím není jasné. CSIRT.CZ nicméně kontaktoval provozovatele všech dotčených stránek, aby zjednali nápravu.
Nejrozšířenější těžařské viry
Z prvních třech míst v žebříčku nejrozšířenějších počítačových hrozeb obsadily hned dvě příčky právě těžařské viry. Konkrétně šlo o nezvané návštěvníky CoinHive a Cryptoloot.
CoinHive byl navržen pro těžbu kryptoměny monero bez souhlasu uživatele. Tento škodlivý kód implantuje JavaScript, který využívá procesor koncových uživatelů a negativně ovlivňuje výkon stroje těžbou kryptoměn. Kyberzločinci mohou využít pro těžbu kryptoměn až 65 % celkových zdrojů CPU koncového uživatele, aniž by o tom věděl.
Malware Cryptoloot funguje velmi podobně. Využívá výkon procesoru nebo grafické karty pro těžbu různých virtuálních mincí, které mohou následně počítačoví piráti směnit za skutečné peníze.
„Uživatelé stále častěji nedůvěřují vyskakujícím oknům a bannerové reklamě a využívají software pro blokování reklam, takže webové stránky více a více využívají jako alternativní zdroj příjmů těžbu kryptoměn. Ale často bez svolení a upozornění uživatelů, jejichž stroje jsou pro těžbu využívané,“ prohlásil Peter Kovalčík, SE Manager ve společnosti Check Point.
„Navíc kyberpodvodníci se ve snaze maximalizovat zisk snaží využít nástroje pro těžbu kryptoměn a získat ještě více z výpočetního výkonu uživatelů ve svůj prospěch. Je pravděpodobné, že v příštích měsících bude tento trend ještě výraznější,“ dodal.
Olympijské hry jsou rájem pro hackery. Denně se uskuteční milióny útoků
20.2.2018 Novinky/Bezpečnost Hacking
Zraky snad všech sportovních fanoušků se v posledních týdnech ubírají k Pchjongčchangu, kde se konají 23. zimní olympijské hry. Ty lákají – stejně jako v minulých letech – také počítačové piráty. Bezpečnostní experti varují, že počet útoků v době olympiády vzroste o milióny každý den.
Na útoky počítačových pirátů by měli být připraveni také uživatelé, kteří se do Pchjongčchangu vůbec nevydali a jednotlivá sportovní klání sledují z pohodlí svého obýváku.dynamic-picture-free1__660762
Počítačoví piráti totiž prakticky vždy podobně hojně sledované akce zneužívají k tomu, aby šířili nejrůznější škodlivé kódy. Sázejí především na to, že diváci touží po co nejrychlejších a nejzajímavějších zprávách.
Na sociálních sítích, různých chatovacích skupinách i v nevyžádaných e-mailech je tak možné narazit na odkazy na fotografie i videa o aktuálních výkonech či počtu medailí. Velmi často však takové výzvy směřují na podvodné stránky, kde číhají škodlivé kódy.
Výjimkou nejsou ani odkazy na videa, která však nejdou přehrát. Uživatel údajně pro jejich shlédnutí potřebuje nainstalovat speciální plugin, ve skutečnosti jde však o počítačový virus.
Počty útoků raketově rostou
Útoky nicméně nejsou nijak výjimečné ani v samotném místě konání her. V průběhu pekingských her v roce 2008 bylo podle antivirové společnosti Kaspersky Lab detekováno okolo 190 miliónů kybernetických útoků (12 miliónů denně). V Londýně v roce 2012 jich analytici zaznamenali 200 miliónů a v roce 2014 při hrách v Soči 322 miliónů. Během poslední olympiády v Riu před dvěma lety odborníci odhalili celých 570 milionů útoků.
„Olympijské hry vždy vedle úžasných sportovních výkonů nabízejí i jedinečnou přehlídku nejnovějších technologií, které často předznamenávají další vývoj. Vzhledem k obrovské důležitosti technologií pro bezproblémový chod této události je nezbytné zajistit jejich bezpečnost. Lákají totiž velké množství hackerů, jejichž cílem je narušit hlavní komunikační a informační systémy a způsobit chaos,“ uvedl Mohamad Amin Hasbini, bezpečnostní analytik ve společnosti Kaspersky Lab.
První útok postihl hry v Pchjongčchangu už během předminulého pátku, kdy probíhalo slavnostní zahájení. Tehdy kyberzločinci prováděli nájezdy na webové stránky her a korejské televizní systémy, cílem bylo kompletní vyřazení z provozu.
Šlo o tzv. DDoS útok, při kterém stovky tisíc počítačů začnou přistupovat v jeden okamžik na konkrétní server. Ten zpravidla nezvládne tak vysoké množství požadavků zpracovat a spadne. Pro běžné uživatele se pak takto napadená webová stránka tváří jako nedostupná.
Dva útoky již byly odvráceny
Hackerům však útok nevyšel, neboť na něj byli administrátoři tamních počítačových systémů připraveni. Zástupci Mezinárodního olympijského výboru to bez dalších podrobností potvrdili o několik dní později.
Přestože znají původ útoku, odmítli jej komentovat. Nechtějí prý ohrozit průběh her politickými tahanicemi. „Podobné snahy hackerů nejsou nijak výjimečné. Důležité je, že se nám je podařilo opětovně odrazit a že nijak nebyl ohrožen průběh her,“ zdůraznil pro agenturu Reuters mluvčí Mezinárodního olympijského výboru Mark Adams.
I z dalších zpráv je nicméně zřejmé, že administrátoři mají s počítačovými systémy na olympiádě plné ruce práce. Už od konce loňského roku totiž měl probíhat sofistikovaný hackerský útok na počítače více než tří tisíc klíčových zaměstnanců, kdy by se pomocí škodlivého kódu dostali útočníci k citlivým datům, případně mohli manipulovat na dotčených strojích se zobrazovanými informacemi.
Také tento útok se však podařilo ještě před startem olympiády odvrátit.
Podvod poznají jen pozorní. ČSOB varovala před počítačovými piráty
20.2.2018 Novinky/Bezpečnost Podvod
Počítačoví piráti se v posledních dnech zaměřili na klienty ČSOB, internetem šíří odkaz na podvodné stránky imitující vzhled této banky. Z klientů se snaží vylákat přihlašovací údaje k jejich účtům. Podvodné stránky přitom pozorní uživatelé poznají na první pohled.
Před falešným internetovým bankovnictvím, které imituje vzhled stránek ČSOB, varovali přímo zástupci banky.
„Upozorňujeme na výskyt podvodné stránky v designu ČSOB internetového bankovnictví s cílem získat přihlašovací data do internetového bankovnictví, data o platebních kartách a další důvěrné údaje,“ uvedl mluvčí banky Patrik Madle.

Ukázka podvodné webové stránky
FOTO: ČSOB
Ten zároveň zdůraznil, jak mohou lidé podvodné stránky odhalit. „Pokud se přihlašujete do internetového bankovnictví, zkontrolujte vždy nejdříve řádek s internetovou adresou. V každé chvíli, kdy pracujete s internetovým bankovnictvím nebo se do něj přihlašujete, musí být v adresním řádku vašeho prohlížeče adresa https://ib.csob.cz a vedle ní ikona zámku,“ prohlásil mluvčí.
Zběhlejší uživatelé patrně již vědí, že po kliknutí na zmiňovanou ikonu zámku se zobrazí certifikát potvrzující platnost a ověřující identitu stránky. To se však u těch podvodných nestane.
„V moderních internetových prohlížečích se kontrola provádí automaticky (řádek s adresou stránky zezelená, pozn. red.),“ připomněl Mandle.
Jdou po zůstatku i půjčkách
Pokud důvěřivci své přihlašovací údaje do falešných stránek skutečně zadají, jsou již jen krůček od vybílení bankovního účtu. Se znalostí telefonního čísla je totiž pro podvodníky hračkou vylákat od lidí potvrzovací SMS zprávu, pomocí které mohou například provádět peněžní transakce.
V ohrožení jsou přitom i jedinci, kteří nemají na bankovním účtu příliš mnoho financí. Útočníci mohou touto cestou sjednat bez vědomí majitele klidně i půjčku. A tyto peníze následně vyberou.
Zda kvůli podvodným stránkám přišel nějaký klient skutečně o peníze, však mluvčí banky nekomentoval. „V případě pochybností neváhejte kontaktovat helpdesk elektronického bankovnictví na telefonním čísle 495 800 111,“ dodal mluvčí.
Na pozoru by se měli mít také klienti dalších bank
V současnosti se objevily na síti pouze stránky imitující internetové bankovnictví ČSOB. Není nicméně vyloučeno, že se v dohledné době budou podvodníci vydávat za bankéře také jiného finančního ústavu v Česku.
V minulosti se touto cestou snažili například počítačoví piráti opakovaně napálit klienty České spořitelny. Obezřetnost je tedy na místě.
Agentuře unikla z cloudu osobní data 12 tisíc hvězd sociálních sítí
20.2.2018 Novinky/Bezpečnost Sociální sítě
Únik citlivých osobních dat a kontaktních údajů 12 tisíc známých osobností ze sociálních sítí oznámila marketingová agentura Octoly. Jde o známé tváře, které propagují značky kosmetických a dalších firem, jako jsou Dior, Estée Lauder, Lancôme a Blizzard Entertainment.
Webové stránky agentury Octoly
FOTO: repro octoly.com
Včera 13:27
Firma, která sídlí v Paříži, využívala tyto celebrity k propagování známých značek kosmetiky a dalších produktů. Mezi její klienty patří například společnosti Dior, Estée Lauder, Lancôme nebo Blizzard Entertainment. Společnost však měla špatně nakonfigurováno úložiště dat v cloudu a nešťastnou náhodou se jí podařilo zveřejnit řadu citlivých údajů o těchto vlivných uživatelích sociálních sítí, většinou z Instagramu, Twitteru a YouTubu.
Uniklá data obsahovala skutečná jména propagátorů značek, jejich adresy, telefonní čísla a e-mailové adresy včetně těch, které byly určeny pro používání účtů na PayPalu, a data narození. Nezřídka šlo rovněž o ověřovací tokeny, které mohly být zneužity pro převzetí účtů na sociálních sítích, a tisíce hesel a uživatelských jmen, která patřila různým internetovým účtům tvůrců.
Úložiště obsahovalo rovněž informace o 600 značkách, které využívají služeb marketingové agentury Octoly, a rovněž 12 tisíc zpráv Deep Social, které byly vytvořeny zvlášť pro každého spolupracovníka a představují podrobnou analýzu vlivu těchto osobností sociálních sítí na internetu, různé zájmové a věkové skupiny a informace o značkách, které by mohly nejlépe propagovat.
Interní záznamy o klientech
Součástí balíku informací byly i interní zprávy o klientech, které by mohly poškodit zákazníky agentury, pokud by se dostaly do rukou jejich konkurence. Podle bezpečnostní společnosti UpGuard je únik o to nebezpečnější, že řadu propagátorů značek na sociálních sítích tvoří ženy, jimž nyní hrozí obtěžování, protože byly zveřejněny jejich adresy i telefony. Marketingové agentuře nyní hrozí žaloby ze strany klientů i spolupracovníků.
„Takto citlivá data musí být rozhodně několikanásobně zabezpečena před zneužitím,“ říká bezpečnostní expert společnosti ESET Václav Zubr. „Minimem by měla být dvoufaktorová autentizace, tedy nejen jednoduché uživatelské jméno a heslo, ale také jednorázově generovaný kód zaslaný na mobilní telefon,“ dodává.
Agentura má do jisté míry štěstí, že k úniku osobních dat došlo před letošním květnem, kdy začne platit nová evropská směrnice o ochraně osobních dat (GDPR). Za podobný prohřešek by poté musela zaplatit velmi vysokou pokutu.
CZ.NIC spouští HaaS: honeypot as a service
20.2.2018 Root.cz Zabezpečení
Přesněji, přivítat jste ho mohli v říjnu loňského roku, kdy jsme spustili jeho beta verzi. Z počátku jsme nechávali volnou registraci a ladili první nedostatky, zátěžovou zkouškou pak bylo přesunutí všech uživatelů routerů Turris.
Veškeré problémy a připomínky jsme vyřešili a nic nebránilo tomu spustit ostrý provoz služby HaaS neboli Honeypot as a Service.
Co to vlastně HaaS je a k čemu slouží? Honeypot je speciální aplikace, která simuluje operační systém a dovoluje potenciálnímu útočníkovi se přihlásit přes SSH do koncového zařízení a provést libovolné příkazy nebo třeba stáhnout malware. Nainstalovat si takovou aplikaci není jednoduché a pokud se v ní objeví chyby, může být i nebezpečná. Proto jsme se rozhodli vzít bezpečnostní riziko na sebe a zpřístupnit honeypot jako veřejnou službu, na kterou mohou uživatelé Internetu přesměrovat útoky vedené na jejich routery.
Moc rádi bychom řekli, že stačí na vašem routeru či serveru povolit port 22 a přesměrovat na naše servery, ale není tomu tak. Snažili jsme se však o co nejjednodušší řešení, co se instalace a vývoje týče. Věřte, že jsme minimálně měsíc strávili pouze výběrem proxy, která musí u uživatelů běžet. K čemu proxy je? Pouze k jednomu malému, ale velmi důležitému detailu. Abychom znali IP adresu útočníka, která slouží k následné analýze chování útočníků s cílem odhalení nových, dosud neznámých útoků.
Dobrá zpráva je, že i přes krátkou dobu provozu a porodní bolesti máme hodně dat. S přírůstkem deset tisíc SSH sessions za hodinu, v takto malém počtu uživatelů (aktuálně 1 600 aktivních uživatelů), budeme brzy řešit zajímavé úlohy, jak všechna data stihnout analyzovat. Uděláme pro to maximum, protože botnety volající rm -rf jako první příkaz nás děsí a je třeba s nimi zatočit.
Nasbíraná data využívá Národní bezpečnostní tým CSIRT.CZ pro zkoumání útoků z českých IP adres, o čemž jsou pak majitelé informováni a hlavně vyzváni k nápravě. Největší počet útoků pochází z Číny, proto již spolupracujeme s Taiwanem, aby i u nich mohli zasáhnout. Na spolupráci s dalšími bezpečnostními týmy se pracuje.
NMI18_Materna
Pokud se chcete do projektu zapojit, můžete tak učinit na stránkách haas.nic.cz, kde se zaregistrujete a dle pokynů nainstalujete HaaS proxy (dostupné jako deb a rpm balíček, na PyPI nebo jen tar). V případě zájmu o analýzu dat jsou anonymizovaná data dostupná na stránce s globálními statistiky. Chybí v nich úmyslně použitá hesla, protože jsme zaznamenali nejeden případ, při kterém se uživatel omylem dostal do svého vlastního honeypotu.
Velká část e-mailů putuje internetem nešifrovaně. Kdo to změní?
20.2.2018 Root.cz Zabezpečení
Máme rok 2018 a stále jsme se ještě nevypořádali ani s pořádným šifrováním elektronické pošty. IETF má nyní nová doporučení ohledně šifrování a co možná nejlepší ochrany uživatelů. Jak jsou na tom vaše maily?
Internet Engineering Task Force (IETF) se dlouhodobě snaží o bezpečný a důvěryhodný internet. Nejnovějším příspěvkem na tomto poli je nový standard zavádějící bezpečnější přístup k elektronické poště. Přestože máme rok 2018, stále je v této oblasti co dohánět, protože velká část pošty putuje internetem v otevřené podobě nebo s velmi slabým zabezpečením.
Výsledkem je RFC 8314, ve kterém Chris Newman z Oracle a Keith Moore z Windrock vysvětlují, že v některých případech není komunikace mezi klientem a serverem šifrovaná. Zároveň dokument novelizuje celou řadu předchozích standardů a zavádí přísnější přístup s cílem zajistit uživatelům výrazně vyšší bezpečnost.
Oportunistické šifrování nestačí
Dokument identifikuje hlavní nedostatky v komunikaci mezi e-mailovým klientem (MUA) a servery. Ty mohou být přitom dvojího druhu – pro odesílání pošty (Submission) a příjem pošty (Access). Používají různé protokoly jako Internet Message Access Protocol (IMAP) (RFC3501), Post Office Protocol (POP) (RFC1939) a Simple Mail Transfer Protocol (SMTP) Submission (RFC6409).
Obvykle se při jejich použití používá zabezpečení pomocí Transport Layer Security (TLS) (RFC5246), ale často to není prováděno tím nejlepším způsobem vzhledem k utajení e-mailové komunikaci při přenosu internetem.
Typickým příkladem je takzvané oportunistické (česky příležitostné) šifrování. Předchozí standardy (RFC 2595, 3207 a 3501) totiž doporučovaly používat právě tento způsob. Klient se k serveru připojí běžným otevřeným protokolem bez šifrování a teprve v průběhu komunikace může navrhnout přechod na šifrovanou komunikaci pomocí příkazu STARTTLS.
Konkrétní podoba šifrovaného kanálu pak závisí na dohodnutých schopnostech obou stran. Jinými slovy: pokud o to klient výslovně požádá, může být zahájeno vyjednávání o sestavení nového šifrovaného kanálu pro bezpečnější komunikaci. K němu ovšem vůbec nemusí dojít, pokud se protistrany nedohodnou, přenese se pošta v klidu nešifrovaně. Navíc začátek celé komunikace vždy probíhá v otevřeném prostředí a může tak být odposloucháván nebo manipulován.
Řešení existuje, je jím implicitní šifrování, tedy použití odděleného TCP portu, na kterém se nejprve vždy povinně naváže TLS spojení a teprve v něm probíhá komunikace s poštovním serverem. Čerstvě vydané RFC tedy pro protokoly POP, IMAP, SMTP a další příbuzné doporučuje právě použití této bezpečnější metody.
Klient musí ověřovat certifikáty
Nový dokument zavádí povinnou validaci certifikátů na straně klienta, který se tak musí při navazování spojení řídit RFC 7817. V případě POP3S a IMAPS s tím není problém, protože implicitní TLS je dnes na serverech už velmi rozšířené. Jinak je to ale v případě SMTP, kde je stále ještě častým zvykem používat oportunistické šifrování se STARTTLS. Aby byl přechod pro uživatele pokud možno hladký, měly by servery po přechodné období implementovat jak STARTTLS na portu 587, tak bezpečnější implicitní TLS na portu 465.
TCP port 465 původně vznikl pro TLS variantu SMTP, ale poté se ukázalo, že není možné nijak pomocí MX záznamu signalizovat šifrování (a tedy ani použití jiného portu). Proto se stále pro komunikaci mezi servery používá původní port 25 a vyhrazení nového portu 465 bylo zrušeno. Řada uživatelů ale už mezi tím začala nový port používat pro doručení pošty ze svého klienta s implicitním TLS. Tento postup se nyní formalizuje zavedením nové služby Submissions.
Port 25 není určen pro klienty
Stále rozšířené je použití TCP portu 25 také pro doručení pošty na odesílající server (SMTP Submission), pro které jsou ovšem vyhrazeny už zmíněné porty 587 a 465. Tvůrci nového RFC proto říkají, že by poskytovatelé služeb měli své uživatele co nejdříve přesunout na bezpečnější varianty – ať už oportunistické nebo implicitní. To navíc bez ohledu na to, zda se uživatelé při použití dané služby musejí autentizovat.
Port 25 by tak měl být vyhrazen pro komunikaci mezi servery a klienti by přes něj neměli vůbec poštu na svůj odesílací server předávat. Bohužel je historicky na použití tohoto portu řada uživatelů zvyklá, takže i někteří poskytovatelé poštovních služeb nabízejí přijetí pošty přes tento port. Zároveň ale poskytovatelé připojení často použití portu 25 blokují kvůli boji s odchozím spamem, takže jsou uživatelé chtě něchtě tlačeni do použití správných rozhraní.
Změny na obou stranách
Výše uvedené změny se týkají e-mailových klientů (Thunderbird, Outlook, Apple Mail a dalších), ale také serverů. Ty podle RFC musí implementovat TLS na zmíněných komunikačních protokolech a měly by tak učinit i na jakýchkoliv dalších. Povinně musí TLS umožnit na těch protokolech, kde se uživatel přihlašuje pomocí jména a hesla.
NMI18_Sedivy
Poskytovatelé poštovních služeb by co nejdříve měli ukončit podporu nešifrovaných protokolů, čemuž by měla předcházet postupná migrace uživatelů na šifrované kanály. Za bezpečné se při tom považuje TLS verze 1.1 a vyšší. Server by měl buďto spojení se starší verzí úplně odmítnout nebo přijmout, ale poté zamítnout přihlášení uživatele. Druhá varianta umožňuje navázat komunikaci a poté předat zprávu o důvodu selhání, přináší ale riziko vyzrazení přihlašovacích údajů uživatele. Po nových uživatelích by tak mělo být od začátku požadováno použití TLS alespoň verze 1.1.
RFC 8314 zavádí řadu nových MUST a SHOULD pro obě strany komunikace: klienta i server. Cílem je opustit zastaralé oportunistické šifrování a přinést i do přenosu elektronické pošty podobné standardy, na jaké jsme zvyklí například u HTTPS. Bohužel svět webu a svět elektronické pošty dělí dvě dekády (alespoň po formalizační stránce) a starší protokoly se novým trendům obecně přizpůsobují pomaleji.
Russian Cyberspies Shift Focus From NATO Countries to Asia
20.2.2018 securityweek BigBrothers
The Russia-linked cyber espionage group known as Sofacy, APT28, Fancy Bear, Pawn Storm, Sednit and Strontium has shifted its focus from NATO member countries and Ukraine to Central Asia and even further east, Kaspersky Lab reported on Tuesday.
Sofacy, which is believed to be behind attacks targeting the 2016 presidential election in the United States, has been known to target Ukraine and NATO countries. NATO was heavily targeted in early 2017, including with zero-day exploits, but Kaspersky said the group later started to shift its focus towards the Middle East and Central Asia, which had been less targeted in the first half of the year.
According to the security firm, by mid-2017, detections of a Sofacy backdoor tracked as SPLM, CHOPSTICK and X-Agent showed that the hackers had been increasingly targeting former Soviet countries in Central Asia, including telecoms firms and defense-related organizations. The attacks were aimed at countries such as Turkey, Kazakhstan, Armenia, Kyrgyzstan, Jordan and Uzbekistan.
Attacks involving SPLM and a tool tracked as Zebrocy were increasingly spotted between the second and fourth quarters of 2017 further east. The list of countries where these pieces of malware were detected by Kaspersky includes China, Mongolia, South Korea and Malaysia.
Zebrocy, which allows attackers to collect data from victims, has been used to target various types of organizations, including accounting firms, science and engineering centers, industrial organizations, ministries, embassies and consulates, national security and intelligence agencies, press and translation services, and NGOs.
As for the infrastructure used in these attacks, researchers pointed out that Sofacy has been fairly consistent throughout the years and many of its techniques and patterns have been publicly disclosed. As a result, Kaspersky expects to see some changes this year.
“Sofacy is one of the most active threat actors we monitor, and it continues to spear-phish its way into targets, often on a remarkable global scale,” explained Kurt Baumgartner, principal security researcher at Kaspersky Lab. “Our data and detections show that in 2017, the threat actor further developed its toolset as it moved from high volume NATO spear-phish targeting towards the Middle East and Central Asia, before finally shifting its focus further East. Mass campaigns appear to have given way to subsets of activity and malware involving such tools as Zebrocy and SPLM.”
Apple Fixes Indian Character Crash Bug in iOS, macOS
20.2.2018 securityweek Apple
Updates released by Apple on Monday for iOS, macOS, tvOS and watchOS patch a flaw that causes applications to crash when rendering specific strings of Indian characters.
Someone noticed recently that displaying a string written in India’s Telugu language (జ్ఞా) caused many apps on iOS and macOS to crash. The list of impacted apps includes Twitter, Firefox, Chrome, Safari, WhatsApp, Mail, Thunderbird, Instagram, Slack and others.
Apple became aware of the issue after news of the bug started to spread on social media networks and trolls and pranksters started exploiting it. One individual apparently showed how he could crash the Uber app on drivers’ phones by setting his name to the problematic string and requesting a ride.
SecurityWeek can confirm that conducting a search for the string in any web browser on macOS causes the applications to immediately crash. Attempting to send or receive an email using Mail or Thunderbird has the same effect.
While initially only a certain Telugu string appeared to work, some later noticed that a specific string using characters of India’s Bengali language also caused apps on iOS and macOS to crash. There are several theories on what may be causing the crash, including from Mozilla research engineer Manish Goregaokar and Philippe Verdy of the Unicode Consortium.
Apple tracks the vulnerability as CVE-2018-4124 and describes it as a heap corruption triggered when processing a maliciously crafted string. “A memory corruption issue was addressed through improved input validation,” Apple said.
The company patched the flaw on Monday with the release of macOS High Sierra 10.13.3 Supplemental Update, iOS 11.2.6, watchOS 4.2.3 and tvOS 11.2.6. watchOS and tvOS are affected due to the fact that they are based on iOS. The latest operating system updates don’t fix any other vulnerabilities.
3 Million New Android Malware Samples Discovered in 2017
20.2.2018 securityweek Android
More than 3 million new malware samples targeting the Android operating system were discovered in 2017, marking a slight decrease from the previous year, G Data reports.
The security firm counted 3,002,482 new Android malware samples during 2017, at an average of 8,225 per day, or 343 new malware samples every hour. Although the number is slightly lower when compared to 2016 (when 3,246,284 samples were discovered), the decrease isn’t significant.
In late January, Google revealed that it took down over 700,000 bad apps from Google Play during 2017, a 70% increase compared to the previous year. Many of these programs were copycats – they were either apps packing unacceptable content or malware posing as legitimate apps.
With Android being the most popular mobile operating system out there, it’s no wonder cybercriminals are focused on bypassing Google’s protection mechanisms in their attempt to push malware into the official app store.
This also shows that users should not rely solely on Google’s security features to protect their devices and data. A third-party security program should also be installed and maintained, to detect applications with malicious functions in due time.
Despite the large number of new Android malware samples and that of malicious programs slipping through Google’s protections, the overall security of the operating system appears to be improving, especially with the Internet giant stepping up the platform update process.
Previously, the update process involved multiple steps: the Android team published the open source code, processor providers adapted it to their specific hardware, smartphone providers worked on customizations for the software, network operators also added their own modifications, and only then could an update finally be released.
“Frequently, these concatenated processes take a very long time, so users do not receive the updates until months after they were released by the Android team,” G Data notes.
Lately, Google has been trying to have updates available for all users faster, and initiatives like Project Treble helps in this direction. Through it, a so-called vendor interface is provided, bridging the Android OS framework and the provider’s modifications and making relevant hardware-specific information readily available. Thus, manufacturers can deliver Android updates quickly.
Last year, developers and researchers discovered a total of 841 vulnerabilities among the various versions of Android, making the platform a clear forerunner when it comes to security issues. As a recent Risk Based Security report revealed, the Android-based Pixel/Nexus devices had the most (354) vulnerabilities featuring CSSv2 Scores 9.0 - 10.0 last year.
This leading position could be explained by Android’s open source nature, which provides more people with the opportunity of researching it.
“However, the problem is not only vulnerabilities in the software, but specifically holes in the hardware. Meltdown and Spectre, the serious security holes in processors, which are also present in mobile devices, have again demonstrated how important a speedy security process is so that users receive new updates quickly,” G Data points out.
North Korean Hacking Group APT37 Expands Targets
20.2.2018 securityweek APT
A lesser known hacker group believed to be working on behalf of the North Korean government has been expanding the scope and sophistication of its campaigns, according to a report published on Tuesday by FireEye.
The threat actor is tracked by FireEye as APT37 and Reaper, and by other security firms as Group123 (Cisco) and ScarCruft (Kaspersky). APT37 has been active since at least 2012, but it has not been analyzed as much as the North Korea-linked Lazarus group, which is said to be responsible for high-profile attacks targeting Sony and financial organizations worldwide.
Cisco published a report in January detailing some of the campaigns launched by the threat actor in 2017, but APT37 only started making headlines in early February when researchers revealed that it had been using a zero-day vulnerability in Adobe Flash Player to deliver malware to South Korean users.
APT37, whose goals appear to align with North Korea’s military, political and economic interests, has mainly focused on targeting public and private entities in South Korea, including government, defense, military and media organizations.
However, according to FireEye, the group expanded its attacks to Japan, Vietnam and even the Middle East last year. The list of targets includes organizations in the chemicals, manufacturing, electronics, aerospace, healthcare, and automotive sectors.
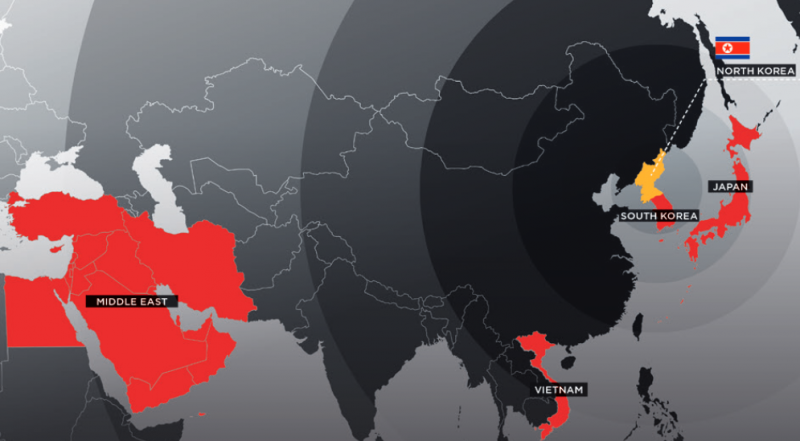
One of the targets in the Middle East was a telecommunications services provider that had entered an agreement with the North Korean government. The deal fell through, which is when APT37 started hacking the Middle Eastern company, likely in an effort to collect information, FireEye said.
APT37 has exploited several Flash Player and Hangul Word Processor vulnerabilities to deliver various types of malware, including the RUHAPPY wiper, the CORALDECK exfiltration tool, the GELCAPSULE and HAPPYWORK downloaders, the MILKDROP and SLOWDRIFT launchers, the ZUMKONG infostealer, the audio-capturing tool SOUNDWAVE, and backdoors tracked by FireEye as DOGCALL, KARAE, POORAIM, WINERACK and SHUTTERSPEED.
This malware has been delivered using social engineering tactics, watering holes, and even torrent sites for wide-scale distribution.
FireEye is highly confident that APT37 is linked to the North Korean government based on several pieces of evidence, including the use of a North Korean IP, malware compilation timestamps consistent with a typical workday in North Korea, and objectives that align with Pyongyang’s interests.
“North Korea has repeatedly demonstrated a willingness to leverage its cyber capabilities for a variety of purposes, undeterred by notional redlines and international norms,” FireEye said in its report. “Though they have primarily tapped other tracked suspected North Korean teams to carry out the most aggressive actions, APT37 is an additional tool available to the regime, perhaps even desirable for its relative obscurity. We anticipate APT37 will be leveraged more and more in previously unfamiliar roles and regions, especially as pressure mounts on their sponsor.”
Neither Kaspersky nor Cisco have explicitly attributed the APT37 attacks to North Korea.
Google to Acquire IoT Management Platform Xively
20.2.2018 securityweek IoT
Google is stepping up its Internet of Things (IoT) game as it has entered into an agreement to acquire Xively, a division of LogMeIn, Inc.
The Xively IoT platform can “help companies in any industry profit from the IoT” and claims to provide “everything needed to build and launch a connected product in months, not years.” It also provides one-click integrations with business tools such as Salesforce.
Formerly known as Cosm and Pachube, LogMeIn acquired Xively in 2011 for approximately $11 million, and will be selling it to Google in a $50 million deal.
Built on LogMeIn’s foundation of security, Xively’s IoT platform is enterprise-ready and is expected to help Google accelerate its customers’ production time when building IoT connected businesses.
“By 2020, it’s estimated that about 20 billion connected things will come online, and analytics and data storage in the cloud are now the cornerstone of any successful IoT solution,” Google says.
The Internet giant is already working on providing a fully managed IoT service via Google Cloud, and the acquisition, which is subject to closing conditions, is expected to complement that.
The resulting product, Google says, would easily and securely connect, manage, and ingest “data from globally dispersed devices.” The platform will pair with the security and scale of Google Cloud, which already provides data analytics and machine learning capabilities to customers.
“Through this acquisition, Cloud IoT Core will gain deep IoT technology and engineering expertise, including Xively’s advanced device management, messaging, and dashboard capabilities. Our customers will benefit from Xively’s extensive feature set and flexible device management platform,” Google says.
While they will continue to invest in their Support-of-Things initiatives, by selling Xively, LogMeIn is exiting the IoT connectivity platform space.
“We believe that Google Cloud, now armed with Xively’s team and great technology – and backed by their platform and developer heritage and reach – are a far better fit for the future of platform leadership,” Bill Wagner, President and CEO, LogMeIn, notes in a blog post.
NIST Proposes Metadata Schema for Evaluating Federated Attributes
20.2.2018 securityweek BigBrothers
NIST's Attribute Metadata Schema Could Help Privacy Compliance in Multi-Domain Transactions
Verifying identities (entities) is one problem. Managing the authorized transactions available to that verified entity is a separate problem. As industry and government increasingly move online, both the complexity and criticality of different possible cross-domain transactions increase. A single verified entity may be authorized for some transactions, but not others.
The decision to authorize or decline access to a protected resource depends upon different attributes (metadata) associated with each entity. In a federated identity and access management (IAM) process, different metadata is obtained from different authoritative providers. The National Institute of Standards and Technology (NIST) recently published 'Attribute Metadata: a Proposed Schema for Evaluating Federated Attributes' (PDF) in order to provide the basis for the evolution of a standardized approach to entity attributes.
This is an internal report (NISTIR 8112) that will not be imposed upon federal agencies, but can be used by both public and private organizations. Its purpose is to allow a system (RP, the relying party) that uses federated IAM to better understand and trust different attributes; to apply more granular and effective access authorizations; and to promote the federation of attributes.
"NIST envisions that the core set of metadata proposed here can serve as a library or menu from which both commercial and federal implementers can draw common semantics, syntaxes, and values to support their specific needs," notes the report. "This will serve as a starting point for the development of a metadata standard that can enable greater federation across markets and sectors."
NIST believes that it could become the foundation for a future attribute confidence scoring structure to help align attribute-based authorizations with an organization's risk environment. Furthermore, it adds, "the ideal metadata schema could be used in both commercial and public-sector implementations, thus serving as a foundation to enable greater federation across markets and sectors."
The NIST proposal comprises two core concepts: Attribute Schema Metadata (ASM, or the attribute's own metadata -- a definition of the attribute); and Attribute Value Metadata (AVM, or the value contained in the metadata). The ASM for an attribute includes its description, allowed values, its format, its verification frequency, and a description of the basis for processing attributes and attribute values.
The AVM defines 15 separate metadata elements around the value contained in an attribute. There are five categories: provenance (3), accuracy (2), currency (3), privacy (5) and classification (2). The provenance category includes three elements: 'origin', which is the name of the entity that issues the attribute; 'provider', which is the name of the entity providing the attribute and might be different to the origin; and 'pedigree', which is the relationship of the attribute value to an authoritative source, such as 'authoritative', 'derived' or 'self-asserted'.
The Classification (security level) metadata comprises two elements: classification and releasability. The classification metadata element could be any one of six values: unclassified, controlled unclassified, confidential, secret, top secret, and company confidential. The releasability element has seven possible values: NATO, NOFORN (no-one foreign), FVEY (only members of the Five Eye allies), public release, for business purposes, do not release, and none.
However, the remaining eight metadata elements have no defined values nor restrictions on what could be included. The five 'privacy' elements are particularly interesting because they can be used both to provide compliance with privacy regulations -- including aspects of the EU's General Data Protection Regulation -- and demonstrate compliance to auditors. The elements are date of consent, type of consent, acceptable uses, cache time limit, and date for data deletion.
Consent is an essential part of user data collection and user data processing. Having the date consent was given, separate data processors have greater legal status in processing user data. The type of consent is equally important. Values could include 'opt-in', 'opt-out' or parental-delegated consent, among others. Since different jurisdictions can demand 'opt-in' consent, or allow 'opt-out' consent, knowing which attribute applies to the data is important for privacy compliance.
The acceptable uses element can be used to specify the use conditions for the entities that receive attributes. Again, since under GDPR and other regulations, user data can only be used for the purposes for which it was collected, it is an aid to ensuring and demonstrating compliance. The NIST document suggests, "organizations or trust frameworks might also maintain their own categories of acceptable uses based on their policies."
The cache time limit reflects the sensitivity of different data, and can be used to specify the maximum time that data may reside in cache memory, perhaps for re-use in other transactions. "In some cases," says NIST, "the time to live may be dictated by regulation or law, and this information needs to be relayed to RP systems so data are handled accordingly. The more sensitive an attribute value, the shorter time it will likely be enabled to live in temporary memory."
The data deletion data attribute simply ensures that a best practice privacy principle can be applied. "Some attribute values may produce little to no privacy risk for individuals," writes NIST. "Other values may add new privacy risks or increase existing privacy risks. A deletion date ensures that sensitive information does not remain in systems indefinitely."
"This NISTIR," says the report, "defines a set of optional elements of an attribute metadata schema to support cross-organization decision making, such as two executive branch agencies, in attribute assertions. It also provides the semantics and syntax required to support interoperability. NIST does not intend to make any of this schema required in federal systems and attribute-based information sharing. Rather, this schema represents a compendium of possible metadata elements to assist in risk-based decision making by an RP. This schema is focused on subjects (individual users); objects and data tagging, while related, are out of scope."
A new multi-stage attack deploys a password stealer without using macros
20.2.2018 securityaffairs Vulnerebility Attack
Security researchers at Trustwave spotted a new malicious campaign that uses a multi-stage attack to deploy a password stealer.
Researchers at Trustwave have spotted a new malware-based campaign that uses a multi-stage infection to deploy a password stealer malware.
Hackers leverage the infamous Necurs botnet to distribute spam emails delivering Microsoft Office documents that embedded malicious macros.
DOCX attachments used by the attackers contain an embedded OLE object that has external references, the external access is provided to remote OLE objects to be referenced in the document.xml.rels.
“Anyone can easily manipulate data in a Word 2007 file programmatically or manually. As shown below, the DOCX attachment contains an embedded OLE object that has external references. This ‘feature’ allows external access to remote OLE objects to be referenced in the document.xml.rels.” states the analysis published by trustwave.
“When user opens the DOCX file, it causes a remote document file to be accessed from the URL: hxxp://gamestoredownload[.]download/WS-word2017pa[.]doc. This is actually a RTF file that is downloaded and executed.”
Once the victim opened the file, it will attempt to trigger the CVE-2017-11882 memory-corruption flaw that was used by many threat actors in the wild, including the Cobalt hacking group. Microsoft fixed the vulnerability in November, the CVE-2017-11882 flaw was discovered by the security researchers at Embedi, it affects the MS Office component EQNEDT32.EXE that is responsible for insertion and editing of equations (OLE objects) in documents.
The component fails to properly handle objects in the memory, a bug that could be exploited by the attacker to execute malicious code in the context of the logged-in user.
Back to the macro-based Multi-Stage attack discovered by Trustwave, the RTF file accessed after the victim opens the DOCX files executes an MSHTA command line to download and execute a remote HTA file.
The HTA file contains VBScript with obfuscated code that decodes to a PowerShell Script designed to eventually downloads and executes a remote binary file that is a Password Stealer Malware.
“The malware steals credentials from email, ftp, and browser programs by concatenating available strings in the memory and usage of the APIs RegOpenKeyExW and PathFileExistsW to check if registry or paths of various programs exist.” continues the analysis.

The password stealer will send data to the command and control server (C&C) via an HTTP POST.
The most interesting aspect of this attack is the use of multiple stages to deliver the final payload, an approach that Trustwave calls unusual.
Malware researchers at Trustwave highlighted that a so long infection chain is more likely to fail compared to other technique implemented in other attacks.
“It’s pretty unusual to find so many stages and vectors being used to download malware. Indeed, this approach can be very risky for the malware author. If any one stage fails, it will have a domino effect on the whole process. Another noticeable point is that the attack uses file types (DOCX, RTF and HTA), that are not often blocked by email or network gateways unlike the more obvious scripting languages like VBS, JScript or WSF.” concludes Trustwave.
The analysis published by Trustwave includes the Indicators of Compromise (IoCs).
Cyberattacks cost the United States between $57 billion and $109 billion in 2016
20.2.2018 securityaffairs BigBrothers
The report published by the White House Council of Economic Advisers examines the cyberattacks cost that malicious cyber activities cause to the U.S. economy.
How much cost cyber attacks to the US? According to a report published by the White House Council of Economic Advisers last week, the cyberattacks cost between $57 billion and $109 billion in 2016, and things can go worse in the future.
“This report examines the substantial economic costs that malicious cyber activity imposes on the U.S. economy. Cyber threats are ever-evolving and may come from sophisticated adversaries. Due to common vulnerabilities, instances of security breaches occur across firms and in patterns that are difficult to anticipate.” states the report.
“Firms in critical infrastructure sectors may generate especially large negative spillover effects into the wider economy.”
The report analyzed the impact of malicious cyber activities on public and private entities, including DoS attacks, sabotage, business disruption, and theft of proprietary data, intellectual property, and sensitive financial and strategic information.
Damages and losses caused by a cyber attack may spill over from the initial target to economically linked organizations. More exposed are critical infrastructure sectors, at attack against companies and organization in this industry could have a severe impact on the US economy.
The document warns of nation-state actors such as Russia, China, Iran, and North Korea, that are well funded and often conduct sophisticated targeted attacks for both sabotage and cyber espionage.
“Finally, and perhaps most important, if a firm owns a critical infrastructure asset, an attack against this firm could cause major disruption throughout the economy.” reads the report.
“Insufficient cybersecurity investment in these sectors exacerbates the risks of cyberattacks and data breaches. The economic implications of attacks against critical infrastructure assets are described in more detail later in the paper. “

The reports also warn of devastating cyberattacks that would target sectors that are internally interconnected and interdependent with other sectors.
The report offered little in the way of new recommendations on improving cybersecurity, but noted that the situation is hurt by “insufficient data” as well as “underinvestment” in defensive systems by the private sector.
“Cyber connectivity is an important driver of productivity, innovation, and growth for the U.S. economy, but it comes at a cost. Companies, individuals, and the government are vulnerable to malicious cyber activity.” concludes the report. “Effective public and private-sector efforts to combat this malicious activity would contribute to domestic GDP growth. However, the ever-evolving nature and scope of cyber threats suggest that additional and continued efforts are critical, and the cooperation between public and private sectors is key.”
RubyGems 2.7.6 addresses several flaws and implements some improvements
20.2.2018 securityaffairs Vulnerebility
The RubyGems 2.7.6 update released last week for RubyGems includes several security improvements and addresses several types of vulnerabilities.
The new RubyGems 2.7.6 release addresses several vulnerabilities in Ruby Gems and implements several security improvements.
The updates prevent path traversal when writing to a symlinked basedir outside of the root and during gem installation.

The updates also address a cross-site scripting (XSS) vulnerability in the homepage attribute when displayed via gem server and an Unsafe Object Deserialization issue in gem owner.
The new RubyGems release raises a security error when there are duplicate files in a package and enforce URL validation on spec homepage attribute.
To update to the latest RubyGems you can run:
gem update --system
Several Vulnerabilities Patched in RubyGems
20.2.2018 securityweek Vulnerebility
An update released last week for RubyGems includes several security improvements and patches for various types of vulnerabilities.
RubyGems 2.7.6 patches path traversal vulnerabilities that exist when writing to a symlinked basedir outside of the root and during gem installation. It also fixes a cross-site scripting (XSS) vulnerability in the homepage attribute when displayed via gem server, and a possible unsafe object deserialization flaw.
This was not the only deserialization issue patched recently in RubyGems. Back in October, developers informed users that an unsafe deserialization vulnerability could have been exploited for remote code execution.
The latest version of RubyGems also includes some security improvements, such as triggering a security error when a package contains duplicate files, enforcing URL validation on the spec homepage attribute, and strictly interpreting octal fields in tar headers.
Yasin Soliman, nmalkin and plover have each been credited for two of the vulnerabilities patched in RubyGems 2.7.6.
A total of five security holes were patched in RubyGems last year. The deserialization issue, tracked as CVE-2017-0903, and an ANSI escape sequence vulnerability identified as CVE-2017-0899 were the only ones rated “high severity” based on their CVSS score.
Other vulnerabilities fixed last year included a DNS request hijacking issue, a denial-of-service (DoS) flaw, and a weakness that could have been exploited by malicious gems to overwrite arbitrary files.
Five vulnerabilities were also patched last year in Ruby itself, including command injection and memory corruption issues.
NIST Working on Global IoT Cybersecurity Standards
20.2.2018 securityweek IoT
NIST is Working Towards International Cybersecurity Standards for the Internet of Things With Draft Interagency Report (NISTIR) 8200
The Internet of Things (IoT) is here and growing. It has the potential to facilitate or obstruct the further evolution of the Fourth Industrial Revolution; largely depending upon whether it is used or abused. Its abusers will be the same criminal and aggressor state actors that currently abuse information systems. But while there are standards and frameworks for defending information networks against aggressors, there are no adequate international standards for securing the internet of things.
In April 2017, the Interagency International Cybersecurity Standardization Working Group (IICS WG) -- established by the National Security Council’s Cyber Interagency Policy Committee (NSC Cyber IPC) -- set up an Internet of Things (IoT) Task Group to determine the current state of international cybersecurity standards development for IoT.
NIST has now published the draft NISTIR document: The Status of International Cybersecurity Standardization for IoT. It is intended to assist the member agencies of the IICS WG Task Group "in their standards planning and to help to coordinate U.S. government participation in international cybersecurity standardization for IoT." NIST is seeking feedback, especially on the information about the state of cybersecurity standardization for IoT, at NISTIR-8200@nist.gov by April 18.
The scope of securing the IoT is a mammoth task. To aid the understanding of this scope, NIST describes the IoT in five separate functional areas: connected vehicles; consumer IoT; health and medical devices; smart buildings, and smart manufacturing (including ICS). There are nuanced differences between securing these functional areas and traditional cyber security. While security has traditionally prioritized confidentiality, integrity and availability (CIA) in that order of priority, for the most part 'availability' is the priority for IoT devices.
Consumer IoT is one area that may be different, with the traditional need for confidentiality (as in privacy) still dominant. Patient privacy is also a consideration for medical devices. But, "In addition to data privacy and patient safety", comments Jun Du, Senior Director and Architect at ZingBox, "we must also put a heavy focus on ensuring uninterrupted service of medical devices. A cyber-attack can bring down the entire hospital by disrupting their service delivery, putting patient lives at risk."
This is the fundamental difference between traditional information security and IoT security -- it is closer to OT than to IT. "The objectives of confidentiality, integrity and availability altogether focus on information security rather than IoT security," adds Du. "When it comes to IoT security, availability of the device is more relevant to business operations than just the security of information. We should focus on availability first, then look at confidentiality and integrity."
Even in consumer IoT, there is an operational element. Many of the threat vectors are similar between IoT and information networks, but the effects of a successful attack could be more dramatic.
The biggest problem for IoT devices, comments Drew Koenig, security solutions architect at Magenic, "are IoT devices that limit or prevent updating and patching. That's the killer; a zero day -- and the only solution is to replace your fridge before someone hacks it and floods your kitchen."
That metaphor traverses NIST's five IoT functional areas: crashed cars, flooded kitchens and locked doors, malfunctioning heart pace makers, stuck elevators and power failures, and failing production lines.
To get the IICS WG Task Group started in its work to discover the current state of international IoT standardization, the NISTIR 8200 compiles a table of potentially relevant existing standards separated into eleven core cybersecurity areas. These areas range from cryptographic techniques and cyber incident management, through IAM and network security, to supply chain risk management to system security engineering.
Each one of these core cybersecurity areas will present its own IoT-specific difficulties. For example, Du comments, "While encryption is a highly recommended security trend, it isn’t without its drawbacks. Encryption can hide valuable details needed by various teams including security researchers, incident response teams, and security vendors in addition to hiding them from hackers. Insider threats may also attempt to leverage end-to-end encryption to evade detection. In order to protect against these risks, IoT vendors should provide limited visibility through exportation of logs, session stats and meta data information."
A wide range of existing and potentially relevant standards are mapped against these core areas, providing links to the standard, the standard developing organization (SDO), and a description of the standard. It becomes the raw material for a gap analysis between existing and necessary standards. Such an analysis is also provided, mapping standards to the core areas across the five functions. Only 'cryptographic techniques' https://www.securityweek.com/review-nist-crypto-standards-and-developmen... and 'IAM' have available standards applicable to four of the five categories; but always with the rider that there is slow uptake of these standards.
The fifth and missing category is medical IoT, which fares worst of all the five categories for existing applicable standards. However, the two core areas of 'IT system security evaluation' and 'network security' have no available standards applicable to any of the five IoT categories. In reality, the entire gap analysis makes depressing viewing: there are no core areas that have standards adequately adopted in any of the five IoT categories. Even where there are standards, uptake is slow.
Missing from this draft document is any standard that requires the ability for firmware updates within the IoT device build. This may be because there is no existing standard that attempts this. Where 'patching' is mentioned in the draft NISTIR document, it is solely for patch management, or remediation where patching is not possible.
"This document is a good start," comments Koenig. The reality, however, is that it will be a long time before any serious benefit comes from the work. He sees two areas of primary concern. The first is a lack of regulation. NIST doesn't regulate the private sector, although its recommendations can be required for the public sector. Even if this work eventually leads to IoT standards recommendations, it will require separate legislation to enforce the recommendations across the private sector. That still won't necessarily address the manufacture of overseas-sourced devices, or the assembly of devices with multiple foreign components.
Without regulation over device manufacture and development, Koenig's second big concern comes into play: "IoT devices that limit or prevent updating and patching. That's the killer," he says.
But even with regulation controlling the manufacture of IoT devices, that still won't necessarily solve the problems. Steve Lentz, CSO and director information security at Samsung Research America has always believed that security teams need to do their own 'due diligence' on products and processes, and not rely on what they are told by vendors. He suspects that standards and regulations "will bring out vendors claiming to provide IoT security. Again, this is where security teams need to do their due diligence and really check/test out these claims," he warns. "IoT is also Wi-Fi which is now everywhere. We need to ensure complete work infrastructure is secure just not the traditional network defenses.
"We need to ensure we thoroughly research solutions that fit our environments," he continued. "The government can give oversight and make recommendations, but we need to find the solution that works best for us."
Macro-Based Multi-Stage Attack Delivers Password Stealer
20.2.2018 securityweek Vulnerebility Attack
A malicious attack uses a multi-stage infection to deploy malware that is capable of stealing passwords from various applications on a victim’s computer, Trustwave reports.
The attack starts with spam emails distributed from the Necurs botnet to deliver macro-enabled documents, such as Word docs, Excel spreadsheets, or PowerPoint presentations, to the targets.
As part of this infection campaign, DOCX attachments containing an embedded OLE object that has external references was used. Thus, external access is provided to remote OLE objects to be referenced in the document.xml.rels, Trustwave explains.
As soon as the user opens the file, a remote document is accessed from the URL hxxp://gamestoredownload[.]download/WS-word2017pa[.]doc. Although it has a .doc extension, the file is actually a RTF document.
Once executed on the victim’s system, the file attempts to exploit the CVE-2017-11882 vulnerability that Microsoft patched last November in the Office’s Equation Editor tool, and which has been already abused in a wide range of attacks.
The RTF file executes an MSHTA command line to download and execute a remote HTA file. In turn, the HTA file contains VBScript with obfuscated code which decodes to a PowerShell Script designed to fetch and run a remote binary file.
This binary is the final payload that turns out to be a password stealer malware family capable of gathering credentials from email, FTP, and browsers installed on the victim’s machine. For that, it concatenates available strings in the memory and uses the RegOpenKeyExW and PathFileExistsW APIs to check if registry or paths of various programs exist.
The malware was observed sending the harvested data to its command and control (C&C) server via a HTTP POST request.
The most interesting aspect of this attack is the use of multiple stages to deliver the final payload, an approach that Trustwave calls unusual. The security researchers also point out that this long infection chain is more likely to fail compared to other, more straightforward attacks.
“Indeed, this approach can be very risky for the malware author. If any one stage fails, it will have a domino effect on the whole process. Another noticeable point is that the attack uses file types (DOCX, RTF and HTA), that are not often blocked by email or network gateways unlike the more obvious scripting languages like VBS, JScript or WSF,” Trustwave concludes.
SIM Hijacking – T-Mobile customers were victims an info disclosure exploit
20.2.2018 securityaffairs Hacking Mobil
Lorenzo Franceschi-Bicchierai published an interesting post on SIM hijacking highlighted the risks for the end users and their exposure to this illegal practice.
In 2017, hackers stole some personal information belonging to T-Mobile customers by exploiting a well-known vulnerability.
A video tutorial titled ‘T-Mobile Info Disclosure exploit’ showing how to use the flaw was also published on the Internet.
Exploiting the vulnerability it is possible to access certain customers’ data, including email addresses, billing account numbers, and the phone’s IMSI numbers.
Such kind of info could be used by hackers in social engineering attack against T-Mobile’s customer support employees with the intent of stealing the victim’s phone number.

The attackers can use them to impersonate the target customer, crooks call the T-Mobile customer care posing as the victim with the intent to trick the operator to issue a new SIM card for the victim’s number.
The crooks activate the new SIM and take control of your phone number, then they can use is to steal the victim’s identity. This is the beginning of the nightmare for the victims that suddenly lose their service.
Many web service leverage on user’s phone number to reset their password, this means that the attackers once activated the new SIM can use it to carry on password reset procedures and take over the victims’ accounts on many web services.
Lorenzo reported many stories of SIM hijacking victims, this is the story of the T-Mobile customer Fanis Poulinakis
“Today I lived a nightmare.
My phone all of the sudden stopped working – I tried to contact T-Mobile through twitter—no phone right?—It took them an hour to let me know that someone must have transferred my number to another carrier and they asked me to call my bank to let them know.
I immediately log in on my bank account and voila! $,2000 were gone.
I’ve spent the whole day between T-Mobile, Chase Bank and trying to understand what happened. What a nightmare.
[…] It is unbelievable—and i think it’s also a negligence from T-Mobile’s side that they don’t make it mandatory to have a password connected to the phone number rather than the social number. […] It’s the first time I’m realizing how vulnerable our information is.”
SIM Hijacking could be a true nightmare for the victims, let me suggest reading the other witnesses reported by Lorenzo in his blog post.
City Union Bank is the last victim of a cyber attack that used SWIFT to transfer funds
20.2.2018 securityaffairs Cyber
The Indian bank Kumbakonam-based City Union Bank announced that cyber criminals compromised its systems and transferred a total of US$1.8 million.
During the weekend, the Russian central bank revealed a new attack against the SWIFT system, unknown hackers have stolen 339.5 million roubles (roughly $6 million) from a Russian bank last year.
Even if the SWIFT international bank transfer system enhanced its security after the string of attacks that targeted it since 2016, the news of a new attack made the headlines.
The victim is the Indian bank Kumbakonam-based City Union Bank that announced that criminals compromised its systems and transferred a total of US$1.8 million.
Taiwan bank hach
On Sunday, February 18, the Kumbakonam-based City Union Bank issued a statement after local media reported that three unauthorized transactions were initiated by staff. The Indian bank confirmed that it has suffered a security breach launched “international cyber-criminals and there is no evidence of internal staff involvement”.
“During our reconciliation process on February 7, it was found out that 3 fraudulent remittances had gone through our SWIFT system to our corespondent banks which were not initiated from our bank’s end. We immediately alerted the correspondent banks to recall the funds,” reads the statement issued by City Union Bank.
The three transactions took place before February 7, when they were discovered during the reconciliation processes.
One transaction of $500,000 that was made through Standard Chartered Bank, New York, to a Dubai based bank was immediately blocked.
A second transaction $372,150 was made through a Standard Chartered Bank account in Frankfurt to a Turkish account, and the third transaction of 1 million dollars was sent through a Bank of America account in New York to a China-based bank.
The City Union Bank confirmed it was working with the Ministry of External Affairs and officials in Turkey and China to recover the funds.
“With the help of Ministry of External Affairs through Consulate General of Shanghai and Istanbul and office of the National Cyber Security Council (PMO) all possible efforts through diplomatic and legal channels are being taken to repatriate the money,” continues the statement.
Summarizing the security features implemented for the SWIFT were able to detect only the transfer to Dubai.
The SWIFT system is now back in operation with “adequate enhanced security”.
At the time of writing the root source of the problem is still unclear
Record-Breaking Number of Vulnerabilities Disclosed in 2017: Report
19.2.2018 securityweek Vulnerebility
Vulnerability QuickView 2017 Vulnerability Trends
A record-breaking number of vulnerabilities were disclosed in 2017, with a total of 20,832 such security flaws, a new report from Risk Based Security shows.
According to the company’s VulnDB QuickView report, last year saw a 31.0% year-on-year increase in the number of vulnerabilities disclosed. The number of flaws recorded by the National Vulnerability Database (NVD) increased as well.
Of all the issues published by Risk Based Security in 2017, 7,900 weren’t documented by MITRE’s Common Vulnerability Enumeration (CVE) and NVD, and 44.5% of these issues had a CVSSv2 score between 7.0 and 10. This, the security firm notes, represents a major risk for organizations worldwide, as they might not even be aware of the fact that those vulnerabilities exist.
In 2017, 39.3% of all published vulnerabilities have CVSSv2 scores above 7.0, 48.5% of them can be exploited remotely, and public exploits exist for 31.5% of the vulnerabilities, the security firm’s report (PDF) reveals. Half (50.6%) of the 2017 vulnerabilities are web-related and 28.9% of these web-related issues are Cross-Site Scripting (XSS) bugs.
The list of top ten vendors with vulnerabilities featuring CVSS scores between 9.0 and 10.0 includes Google (503 flaws), SUSE (301), Canonical (285), Red Hat (274), SGP – a subsidiary of Silent Circle (257), Adobe (256), Mozilla (246), Samsung (228), Oracle (201), and Xerox (198).
The top ten products with vulnerabilities featuring CSSv2 Scores 9.0 - 10.0 include Google Pixel/Nexus devices (354 issues), Ubuntu (285), SilentOS (257), Red Had Enterprise Linux (253), Firefox (246), SUSE Linux Enterprise Desktop (226), Samsung Mobile Devices (226), SUSE Linux Enterprise Server (197), OpenSUSE Leap (196), and FreeFlow Print Server (191).
Last year, at least 44.8% (9,335) of vulnerabilities disclosed were coordinated with the vendor and only 18.6% (3,875) of them were uncoordinated disclosures. Only 5.9% of 2017 vulnerabilities were disclosed as part of vendor or third-party bug bounty programs, the report reveals.
While most of the vulnerabilities disclosed last year (72.8%) have updates or some form of a patch available for them, 23.2% of the issues currently have no known solution. However, 443 of the vulnerabilities reported in 2017 were found to have no risk due to inaccurate disclosures, meaning that no mitigation was necessary for them.
The report also reveals that only 1.7% of all reported vulnerabilities in 2017 were found in SCADA products, down from 2.8% in 2016. 52.2% of the SCADA vulnerabilities were remotely exploitable, 73.5% had an impact on the integrity of the product, and 61.3% were related to improper input validation.
“Organizations that track and triage vulnerability patching saw no relief in 2017, as it was yet another record-breaking year for vulnerability disclosures. The increasingly difficult task of protecting digital assets has never been so critical to businesses as we continue to see a rise in compromised organizations and data breaches. If your vulnerability intelligence solution didn’t offer information on the more than 20,000 vulnerabilities disclosed in 2017, your organization is at an increased risk”, said Brian Martin, VP of Vulnerability Intelligence for Risk Based Security.
Millions Stolen From Russian, Indian Banks in SWIFT Attacks
19.2.2018 securityweek Attack
Malicious hackers attempted to steal millions of dollars from banks in Russia and India by abusing the SWIFT global banking network.
A report published last week by Russia’s central bank on the types of attacks that hit financial institutions in 2017 revealed that an unnamed bank was the victim of a successful SWIFT-based attack.
A copy of the report currently posted on the central bank’s website does not specify how much the hackers stole, but Reuters said they had managed to obtain 339.5 million rubles (roughly $6 million).
According to the organization, the number of targeted attacks aimed at lenders increased in 2017 compared to the previous year. Attackers used widely available tools such as Metasploit, Cobalt Strike, Empire, and Mimikatz to achieve their goals – Cobalt Strike was reportedly used to steal more than 1 billion rubles (roughly $17 million).SWIFT attacks hit Indian, Russian banks
The news comes after Russia’s Globex bank admitted in December that hackers had attempted to steal roughly $940,000 through the SWIFT system. The attackers reportedly only managed to steal a fraction of the amount they targeted.
In India, City Union Bank issued a statement on Sunday saying that it had identified three fraudulent transfers abusing the SWIFT payments messaging system. One transfer of $500,000 through a Standard Chartered Bank account in New York to a bank in Dubai was blocked and the money was recovered.
The second transfer of €300,000 ($372,000) was made to an account at a bank based in Turkey via a Standard Chartered Bank account in Germany. The funds were blocked at the Turkish bank and City Union hopes to recover the money.
The third transfer was for $1 million and it went to a Chinese bank through a Bank of America account. City Union Bank said the funds were claimed by someone using forged documents.
The news comes after reports that India’s Punjab National Bank was the victim of a massive $1.7 billion fraud scheme involving the company’s employees. City Union, however, clarified that this was a “cyber attack initiated by international cyber criminals and there is no evidence of internal staff involvement.”
SWIFT-based attacks made many headlines in the past years ever since hackers successfully stole $81 million from Bangladesh’s central bank in early 2016.
The organization behind the SWIFT system, the Society for Worldwide Interbank Financial Telecommunication, has taken measures to prevent attacks, but malicious actors have continued to target financial institutions in sophisticated campaigns.
Hackers attempted to steal $60 million from a bank in Taiwan, $12 million from a bank in Ecuador, and $1.1 million from a bank in Vietnam.
Over 30 Lawsuits Filed Against Intel for CPU Flaws
19.2.2018 securityweek Vulnerebility
More than 30 lawsuits have been filed by Intel customers and shareholders against the chip giant following the disclosure of the Meltdown and Spectre attack methods.
Three class action lawsuits were filed against Intel within a week of the Meltdown and Spectre flaws being disclosed, but the number had reached 32 by February 15, according to an annual report submitted by Intel to the U.S. Securities and Exchange Commission (SEC).
Lawsuits have been filed in the United States and other countries, and some complaints also target Intel’s directors and executives.
The company faces 30 class action lawsuits filed by customers who claim to have been harmed by Intel’s actions and/or omissions in connection to Meltdown and Spectre. Two securities class action lawsuits claim the company violated securities laws by making false or misleading statements, which had a negative impact on entities that acquired Intel stock between July 27, 2017 and January 4, 2018, when the processor vulnerabilities were disclosed.
“We dispute the claims described above and intend to defend the lawsuits vigorously,” Intel said. “Given the procedural posture and the nature of these cases, including that the proceedings are in the early stages, that alleged damages have not been specified, that uncertainty exists as to the likelihood of a class or classes being certified or the ultimate size of any class or classes if certified, and that there are significant factual and legal issues to be resolved, we are unable to make a reasonable estimate of the potential loss or range of losses, if any, that might arise from these matters.”
Three shareholder derivative lawsuits have also been filed in California against certain Intel officers and members of the company’s board of directors.
“The complaints allege that the defendants breached their duties to Intel in connection with the disclosure of the security vulnerabilities and the failure to take action in relation to alleged insider trading. The complaints seek to recover damages from the defendants on behalf of Intel,” Intel said.
While lawsuits and negative publicity may change the situation in the future, Intel currently does not expect Meltdown and Spectre to have a material financial impact on its business or operations.
AMD, ARM and Apple, whose processors rely on ARM technology, also face lawsuits over the Meltdown and Spectre vulnerabilities.
90 days have passed, Google discloses unpatched flaw in the Microsoft Edge browser
19.2.2018 securityaffairs Vulnerebility
Google Project Zero disclosed details of an unpatched flaw in the Edge browser because Microsoft failed to address it within a 90-day deadline.
White hackers at the Google Project Zero have disclosed details of an unpatched vulnerability in the Edge browser because Microsoft failed to address it within a 90-day deadline according to the Google’s disclosure policy.
The flaw could be exploited by attackers to bypass the Arbitrary Code Guard (ACG) that was implemented in Windows 10 Creators Update alongside Code Integrity Guard (CIG).
The security features allow preventing Edge browser exploits from loading and executing malicious code.
“An application can directly load malicious native code into memory by either 1) loading a malicious DLL/EXE from disk or 2) dynamically generating/modifying code in memory. CIG prevents the first method by enabling DLL code signing requirements for Microsoft Edge. This ensures that only properly signed DLLs are allowed to load by a process. ACG then complements this by ensuring that signed code pages are immutable and that new unsigned code pages cannot be created.” states the description published by Microsoft.

Google Project Zero researcher Ivan Fratric who discovered the vulnerability demonstrated that the ACG feature can be bypassed. The expert reported the issue to Microsoft on November 17, but the tech giant had initially planned to include a fix in the February Patch Tuesday updates, but evidently, something went wrong because “the fix is more complex than initially anticipated.”
The vulnerability was classified as having “medium” severity, Project Zero has published details of the issue in a blog post.
“If a content process is compromised and the content process can predict on which address JIT process is going to call VirtualAllocEx() next (note: it is fairly predictable), content process can: 1. Unmap the shared memory mapped above above using UnmapViewOfFile() 2. Allocate a writable memory region on the same address JIT server is going to write and write an soon-to-be-executable payload there. 3. When JIT process calls VirtualAllocEx(), even though the memory is already allocated, the call is going to succeed and the memory protection is going to be set to PAGE_EXECUTE_READ.” reads the analysis shared by Google.
In February 2017, Fratric published technical details related to a high severity type confusion vulnerability, tracked as CVE-2017-0037, that could have been exploited by attackers to crash Internet Explorer and Edge browser, and under certain circumstance to execute arbitrary code.
Google Discloses Unpatched Edge Vulnerability
19.2.2018 securityweek Vulnerebility
Google Project Zero has made public the details of an unpatched vulnerability affecting the Edge web browser after Microsoft failed to release a patch within a 90-day deadline.
Google Project Zero researcher Ivan Fratric has found a way to bypass Arbitrary Code Guard (ACG), a feature added by Microsoft to Edge in Windows 10 Creators Update alongside Code Integrity Guard (CIG).
The features, introduced in February 2017, are designed to prevent browser exploits from executing malicious code.
“An application can directly load malicious native code into memory by either 1) loading a malicious DLL/EXE from disk or 2) dynamically generating/modifying code in memory,” Microsoft explained. “CIG prevents the first method by enabling DLL code signing requirements for Microsoft Edge. This ensures that only properly signed DLLs are allowed to load by a process. ACG then complements this by ensuring that signed code pages are immutable and that new unsigned code pages cannot be created.”
Fratric showed that the ACG feature can be bypassed and informed Microsoft of his findings on or around November 17. The company had initially planned on patching the vulnerability with its February Patch Tuesday updates, but later determined that “the fix is more complex than initially anticipated.”
Microsoft now expects to release a fix on March 13, but the date exceeds Google Project Zero’s 90-day disclosure deadline so the details of the vulnerability have been made public. Project Zero has classified the flaw as having “medium” severity.
This is not the first time Project Zero has disclosed an unpatched vulnerability found by Fratric in Microsoft’s web browsers. In February 2017, it made public details and proof-of-concept (PoC) code for a high severity type confusion issue that could have been exploited to crash Internet Explorer and Edge, and possibly even execute arbitrary code.
The security hole, tracked as CVE-2017-0037, was fixed by Microsoft in March 2017, roughly two weeks after it was disclosed.
Fratric is the creator of a fuzzer named Domato, which last year helped him uncover tens of vulnerabilities in popular web browser engines.
Cybersecurity Plagued by Insufficient Data: White House
19.2.2018 securityweek BigBrothers
Cyberattacks Are Costly, and Things Could Get Worse: US Report
Cyberattacks cost the United States between $57 billion and $109 billion in 2016, a White House report said Friday, warning of a "spillover" effect for the broader economy if the situation worsens.
A report by the White House Council of Economic Advisers sought to quantify what it called "malicious cyber activity directed at private and public entities" including denial of service attacks, data breaches and theft of intellectual property, and sensitive financial and strategic information.
It warned of malicious activity by "nation-states" and specifically cited Russia, China, Iran, and North Korea.
The report noted particular concern over attacks on so-called critical infrastructure, such as highways, power grids, communications systems, dams, and food production facilities which could lead to important spillover impacts beyond the target victims.
"If a firm owns a critical infrastructure asset, an attack against this firm could cause major disruption throughout the economy," the report said.
It added that concerns were high around cyberattacks against the financial and energy sectors.
"These sectors are internally interconnected and interdependent with other sectors as well as robustly connected to the internet, and are thus at a highest risk for a devastating cyberattack that would ripple through the entire economy," it said.
The report offered little in the way of new recommendations on improving cybersecurity, but noted that the situation is hurt by "insufficient data" as well as "underinvestment" in defensive systems by the private sector.
The document was issued a day after US officials blamed Russia for last year's devastating "NotPetya" ransomware attack, calling it a Kremlin effort to destabilize Ukraine which then spun out of control, hitting companies in the US, Europe and elsewhere.
It said Russia, China, North Korea and other nation-states "often engage in sophisticated, targeted attacks," with a specific emphasis on industrial espionage.
"If they have funding needs, they may conduct ransom attacks and electronic thefts of funds," the report said.
But threats were also seen from "hacktivists," or politically motivated groups, as well as criminal organizations, corporate competitors, company insiders and "opportunists."
In an oft-repeated recommendation, the White House report said more data sharing could help thwart some attacks.
"The field of cybersecurity is plagued by insufficient data, largely because firms face a strong disincentive to report negative news," the report said.
"Cyber protection could be greatly improved if data on past data breaches and cyberattacks were more readily shared across firms."
An APFS Filesystem flaw could lead macOS losing data under certain conditions
19.2.2018 securityaffairs Apple
The Apple expert Mike Bombich discovered an APFS Filesystem vulnerability that could lead macOS losing data under certain conditions.
A few days ago a ‘text bomb‘ bug was reported for Apple iOS and macOS apps, the issue can crash any Apple iPhone, iPad Or Mac.
Now the Apple expert Mike Bombich discovered an APFS Filesystem vulnerability that could lead macOS losing data under certain conditions.
The bug ties the way the operating system handles APFS sparse disk images formatted in Apple filesystem format APFS.
An Apple Disk Image is a disk image commonly used by the macOS operating system is “mounted” as a volume within the Finder. It contains the entire contents and structure of a disk volume, such as USB, CD, DVD, hard disk drive, or network share.
Disk images are commonly used by several Mac apps, for example for backup applications or disk cloning.
The expert discovered that APFS sparse disk images don’t properly manage the volume of the “free disk space” from the sparse disk image, the OS doesn’t correctly report “free disk space” respect the real “free disk space” value.
“Earlier this week I noticed that an APFS-formatted sparsebundle disk image volume showed ample free space, despite that the underlying disk was completely full. Curious, I copied a video file to the disk image volume to see what would happen. The whole file copied without error! I opened the file, verified that the video played back start to finish, checksummed the file – as far as I could tell, the file was intact and whole on the disk image.” wrote Mike Bombich. “When I unmounted and remounted the disk image, however, the video was corrupted. If you’ve ever lost data, you know the kick-in-the-gut feeling that would have ensued. Thankfully, I was just running some tests and the file that disappeared was just test data. Taking a closer look, I discovered two bugs in macOS’s “diskimages-helper” service that lead to this result.”
Bombich explained that data are written into the void because the OS doesn’t warn users that there is no enough space on the underlying hard drive to contain his data.
As described by the expert, the misleading data are still accessible for a short period after the write operation, unfortunately after the next system reboot exceeding files become corrupted and inaccessible.
Bombich is the author of the Mac backup software Carbon Copy Cloner, according to statistics from his software no many users are affected. The expert says that only 7% of all Carbon Copy Cloner users store backups as sparse disk image files and that only 12% of these 7% use APFS-formatted disk images.
The Carbon Copy Cloner software will not support AFPS-formatted sparse disk images until Apple addresses the vulnerability reported by Bombich.
Below a video PoC of the flaw.
“Until Apple resolves this disk images bug, we strongly recommend that people avoid using APFS-formatted sparse disk images for any purpose with any application.” concluded the expert.
Researchers spotted a new malware in the wild, the Saturn Ransomware
19.2.2018 securityaffairs Ransomware
Researchers at the MalwareHunterTeam spotted a new strain of ransomware called Saturn Ransomware, the name derives from the .saturn extension it appends to the name of the encrypted files.
Currently, the malware requests victims of $300 USD payment that doubles after 7 days.
Once infected a system, the Saturn Ransomware checks if it is running in a virtual environment and eventually it halts the execution to avoid being analyzed by researchers.
Then it performs a series of actions to make impossible for the victims restoring the encrypted files, it deletes shadow volume copies, disables Windows startup repair, and to clear the Windows backup catalog.
Below the command executed by the malicious code:
At this point, the Saturn ransomware is ready to encrypt files having certain file types.
The ransomware such as many other threats uses a Tor payment site that is reported in the ransom note dropped on the machine while the Saturn ransomware is encrypting the files.
“While encrypting the computer, Saturn Ransomware will drop ransom notes named #DECRYPT_MY_FILES#.html and #DECRYPT_MY_FILES#.txt and a key file named #KEY-[id].KEY in each folder that it encrypts a file. The key file is used to login to the TOR ransom site, while the ransom note contains brief information on what has happened to the victims files and a link to the TOR payment site at su34pwhpcafeiztt.onion.” wrote Larwrence Abrams from Bleeping Computer.

File encrypted by the Saturn Ransomware (Source Bleeping computer)
The Saturn ransomware also drops a #DECRYPT_MY_FILES#.vbs triggers an audio message to the victims, and it sets your Windows desktop background to #DECRYPT_MY_FILES.BMP.
The authentication to TOR site is made by uploading the key file, then users will display the Saturn Decryptor page for the victim that includes detailed instructions.
Researchers are still analyzing the Saturn ransomware, even if it is being actively distributed, it is still unclear what distribution vector threat actors are using to spread it.
Further information, including the Indicators of compromise (IoCs), are available in the blog post published by Bleeping Computer.
Prosecutor Robert Mueller indicted 13 Russians for a massive operation aimed to influence Presidential election
19.2.2018 securityaffairs BigBrothers
The special prosecutor Robert Mueller has accused thirteen Russian nationals of tampering with the 2016 presidential election and charged them with conspiring against the United States.
Thirteen Russian nationals and three Russian entities have been indicted for a massive operation aimed to influence the 2016 Presidential election.
The special prosecutor Robert Mueller has accused the defendants of tampering with the 2016 US presidential election and charged them with conspiring against the United States.
According to the results of the investigation conducted by the prosecutor, the Internet Research Agency, a Russian organization, and the 13 Russians began targeting the United States back in 2014.
Russian nationals used stolen American identities and local computer infrastructure to influence the 2016 Presidential election, the group deliberately denigrate the candidate Clinton to support Trump.
“Certain Defendants traveled to the United States under false pretenses for the purpose of
collecting intelligence to inform Defendants’ operations. Defendants also procured and used
computer infrastructure, based partly in the United States, to hide the Russian origin of their
activities and to avoid detection by U.S. regulators and law enforcement.” reads the Mueller’s indictment.
“Defendant ORGANIZATION had a strategic goal to sow discord in the U.S. political
system, including the 2016 U.S. presidential election. Defendants posted derogatory information
about a number of candidates, and by early to mid-2016, Defendants’ operations included
supporting the presidential campaign of then-candidate Donald J. Trump (“Trump Campaign”) and
disparaging Hillary Clinton.”
The indictment states the Russian organization since April 2014 created a specific section focused on the US population that acted to influence the sentiment of citizens on the candidates through social media platforms, including Facebook, Instagram, Twitter, and YouTube. By 2014,
The group used VPN services to connect from Russia to the US and manage their network of social media accounts.
The organization would use email addresses such as staceyredneck@gmail.com during its activities.
16 Feb
kadhim (^ー^)ノ
✔
@kadhimshubber
Replying to @kadhimshubber
In September 2017, people apparently continue to write emails in which they say: "the FBI busted our activity (not a joke). So, I got preoccupied with covering tracks together with the colleagues" https://www.justice.gov/file/1035477/download … pic.twitter.com/jZCaq61ork
kadhim (^ー^)ノ
✔
@kadhimshubber
Email addresses the Russians allegedly used with their PayPal accounts include: "staceyredneck@gmail.com" and "wokeaztec@outlook.com" https://www.justice.gov/file/1035477/download … pic.twitter.com/7A6pbdM42I
7:23 PM - Feb 16, 2018
View image on Twitter
2
See kadhim (^ー^)ノ's other Tweets
The Russian propaganda machine created and controlled numerous social media accounts, one of them is the Twitter account “Tennessee GOP,” which used the
handle @TEN_GOP.
“The @TEN_GOP account falsely claimed to be controlled by a U.S. state
political party. Over time, the @TEN_GOP account attracted more than 100,000 online followers.” continues the Indictment.
The group used stolen identities of US citizens to buy political advertisements on social media, they also recruited Americans to spread derogatory information.
We are facing with a powerful and efficient propaganda machine. defendants and their conspirators
constantly monitored their campaign over social media. They measured the
size of the online U.S. audiences reached by their actions and the types of engagement with the
posts.
The activity of the organization was very active in 2016, when defendants posing as American citizens and communicating with Americans began to gather intelligence to better target their campaign.
“In order to carry out their activities to interfere in US political and electoral processes without detection of their Russian affiliation, the Defendants conspired to obstruct the lawful functions of the United States government through fraud and deceit, including by making expenditures in connection with the 2016 US presidential election without proper regulatory disclosure; failing to register as foreign agents carrying out political activities within the United States; and obtaining visas through false and fraudulent statements,” the indictment reads.
Social media giants Facebook and Twitter are both accused of running ads and promoted content for the groups operated by the Organization.
Twitter has admitted the involvement of thousands of bot accounts in Russian propaganda, the company has deleted 200,000 tweets posted by army of trolls used by the Kremlin.
Effective Tips for Internet Safety for Kids You Must Read
19.2.2018 securityaffairs Safety
Online safety for your kids is very important. However, that doesn’t necessarily mean that it needs to be hard work.
The key thing is to learn how to get parental controls set up properly so that you won’t have to worry as much about online safety when your kids start to use the internet for both school projects and entertainment.
There are many ways that the version of the internet that your kids see can be fine-tuned. One option is to use a free content filter that is offered by all of the major providers.
There are also sophisticated software that is available for sale that you can invest in if you feel the need for a more advanced solution.
In order to determine which is best for you, we will be covering some of the major parental control options that are available to you.
In this article, we will be discussing various parent control options that are available to you. However, keep in mind, that although there are some very useful parental control tools that are available – it is still important for you to watch what your children are doing when they are online as much as you can. There is no substitute when it comes to parental supervision of children.
Content filters
All of the major UK broadband providers, including EE, Virgin Media, TalkTalk, Sky, and BT offer content filters as a standard feature.
They block off sites that contain material that is inappropriate for children, like self-harming, pornography, and other nasty material. Access to sites that are known to contain malware and viruses are also restricted. The best internet packages will have this as standard nowadays.
Which broadband providers offer the best security?
You will need to decide whether or not you want to use the filters when you are getting your broadband first set up. The settings can be changed at any time by simply logging into your account. So you can always change your mind on whether you want to use the filters or not.
Software
Some broadband providers offer parental control software as part of their broadband packages. This type of software is widely available. Content filters are network-level filters and are applied to anyone who uses the connection.
By contrast, parental control software affects only the device that it is installed on. So for example, if you install parent control software on your desktop computer, it will not affect what your children are doing when they are using their tablets and phones.
In addition to filtering inappropriate content out, like gambling-related, violent and pornographic sites, some of this software also lets you monitor the online activity of your children and even restrict what times of days certain websites can be used.
This can definitely come in handy. You will finally have a way of keeping them off of sites like Facebook and YouTube when they are supposed to be doing their homework.
In general, any device that is able to access the internet has its own onboard parental control sets that can be tinkered with before allowing your children to use it.
That is particularly helpful if the broadband company provides you with the software that is the kind that applies to just one device at a time.
For example, Apple’s iPad and iPhone, have a broad range of restrictions, and you cause the settings menu to easily access them. You can lock them in place and protect them using a password.
Those devices, in addition to many others, also allow you to disable paid transactions inside of games and apps. That way your kids can run up any bills without you knowing about it!
There is no such thing as a flawless system. That is why it is a very good idea to make use of all of the different tools that are available to you.
When you place restrictions on the way devices can be used and also install software, it makes it double unlikely that your children will be exposed to any unsuitable or harmful material while they are online.
This will help to put your mind at ease, which is so important these days with all of the dangers lurking online.
Web browsers
At times your web browser, which is the program that is used for browsing the internet, allows you to block out certain kinds of websites.
Those settings may be used in conjunction with whatever software you have installed on your computer already which provides you with an added layer of protection.
For example, when the Google Chrome browser is used – which is a free download that is available to use – it includes a feature that allows you to set up different account profiles for managers and supervised users, which gives you full control of how your children can use the internet when they are online.
Once again it is best to use these features of the browser in combination with other parental controls, especially since the settings apply only to the Chrome browser. More tech-savvy, older children can quickly discover a workaround, such as downloading another web browser other than Google Chrome.
Websites
On certain internet platforms and websites, like iTunes, YouTube, and Google, there is a family-friendly filter that can be switched on that should block out any content that isn’t suited for children to see.
Once again, keep in mind that there is no such thing as a flawless system so that is why it makes sense to use these features in combination with other kinds of parental controls.
This is only really effective to use with very young children since older kids can figure out how the filter can be turned off if they get curious enough and want to look at things that they know they aren’t allowed to.
General advice on how to get safe online
Get Safe Online, an internet safety initiative has provided the advice below. We hope you find it helpful to manage your children’s experiences online.
Set some boundaries even before your child gets their first internet connected device – whether it is a console, laptop, tablet, or mobile device. After they have their device, it might be harder to change the settings or how they use it.
Network-level parental controls are offered by all major providers. When you switch to a different broadband package, you will have an option for turning content filtering on, so that adult material is blocked.
Keep in mind that doesn’t mean all bad stuff will be blocked – there is no such thing as a fully effective filter. You will need to stay vigilant and supervise your children.
Have a discussion with your children about what is appropriate and safe to share and post online.
All videos, photos, and comments are part of a person’s ‘digital footprint’ and may be seen by anybody and be available forever on the internet.
Speak with your children about the type of content they view online, along with the precautions they need to take when they are communicating with others online – for example, to never share personal information with strangers.
Keep in mind that services such as YouTube and Facebook have a reason for having minimum age limits of 13 years old. Don’t cave in to pressure – speak with your child’s school and other parents to be sure everyone is on the same page.
Explain to your children that being online doesn’t provide them with protection or anonymity. Make sure that you clearly tell them that they shouldn’t do anything over the internet that they wouldn’t feel completely comfortable doing in real life.
COINHOARDER criminal gang made an estimated $50 million with a Bitcoin phishing campaign
19.2.2018 securityaffairs Phishing
Researchers with Cisco Talos have monitored a bitcoin phishing campaign conducted by a criminal gang tracked as Coinhoarder that made an estimated $50 million by exploiting Google AdWords.
Researchers with Cisco Talos have monitored a bitcoin phishing campaign for several months with the help of the Ukraine Cyberpolice.
The gang, tracked as Coinhoarder, has made an estimated $50 million by exploiting Google AdWords to trick netizens into visiting Bitcoin phishing sites. This is the element that characterized this phishing campaign, Coinhoarder attackers used geo-targeting filters for their ads, the researchers noticed that hackers were targeting mostly Bitcoin owners in Africa.
The Ukrainian authorities located and shut down the servers hosting some of the phishing websites used by crooks. The phishing sites were hosted on the servers of a bulletproof hosting provider located in Ukraine, Highload Systems. The operation was temporarily disrupted but the police haven’t arrested any individual.
“Cisco has been tracking a bitcoin theft campaign for over 6 months. The campaign was discovered internally and researched with the aid of an intelligence sharing partnership with Ukraine Cyberpolice. The campaign was very simple and after initial setup the attackers needed only to continue purchasing Google AdWords to ensure a steady stream of victims.” reads the analysis published by Talos. “This campaign targeted specific geographic regions and allowed the attackers to amass millions in revenue through the theft of cryptocurrency from victims.”
The Coinhoarder group used Google Adwords for black SEO purposes, on February 24, 2017, researchers at Cisco observed a massive phishing campaign hosted in Ukraine targeting the popular Bitcoin wallet site blockchain.info with over 200,000 client queries. Crooks used Google Adwords to poison user search results in order to steal users’ wallets.
Unfortunately, this attack scheme is becoming quite common in the criminal ecosystem, hackers implement it to target many different crypto wallets and exchanges via malicious ads.
The COINHOARDER gang leveraged the typosquatting technique, the hackers used domains imitating the Blockchain.info Bitcoin wallet service in conjunction SSL signed phishing sites in order to appear as legitimate. Based on the number of queries, the researchers confirmed that this is one of the biggest campaigns targeting Blockchain.info to date.
“The COINHOARDER group has made heavy use of typosquatting and brand spoofing in conjunction SSL signed phishing sites in order to appear convincing. We have also observed the threat actors using internationalized domain names.” continues the analysis. “These domains are used in what are called homograph attacks, where an international letter or symbol looks very similar to one in English. Here are some examples from this campaign.
The Punycode (internationalized) version is on the left, the translated (homographic) version on the right:
xn–blockchan-d5a[.]com → blockchaìn[.]com
xn–blokchan-i2a[.]info → blokchaín[.]info”
Talos researchers revealed that one campaign that was conducted between September and December 2017, the group made around $10 million.
“While working with Ukraine law enforcement, we were able to identify the attackers’ Bitcoin wallet addresses and thus, we could track their activity for the period of time between September 2017 to December 2017. In this period alone, we quantified around $10M was stolen.In one specific run, they made $2M within 3.5 week period. ” states Cisco Talos.
Further technical details on the campaign, including Indicators of Compromise are included in the analysis published by Cisco Talos.
Germany’s defense minister: Cyber security is going to be the main focus of this decade.
19.2.2018 securityaffairs BigBrothers
On Saturday, Germany defense minister Ursula von der Leyen told CNBC that cyber attacks are the greatest challenge threatening global stability.
The cybersecurity is a pillar of modern states, the string of recent massive attacks including NotPetya and WannaCry is the demonstration that we are all potential targets.
Cyber attacks could hit governments, private companies and citizens in every time and from every where causing severe problems to the victims and huge financial losses. The cyber risk is directly linked to geopolitical, environmental, technological, and economic risks. A cyber attack could destabilize governments worldwide, it can get a business out of the business.
When journalists asked about the “single greatest threat to global stability,” to the German defense minister, she confirmed the disconcerting scenario.
“I think it’s the cyber threats because whatever adversaries you can think of and even if you talk about Daesh (the terrorist group) they use the cyber domain to fight against us.” Germany’s defense minister Ursula von der Leyen told CNBC.
Germany defense minister urges European states to invest in collective defense
“This decade will be the decade of improvement in cyber security and information ruling,” she added.

Governments and companies are already investing to improve the resilience to cyber attacks of their networks. The Germany defense minister also noticed that Governments are also working to improve their offensive cyber capabilities.
The US and UK are reportedly using cyber soldiers to fight the Islamic State.
The video interview is available at the following link:
https://www.cnbc.com/video/2018/02/17/cyber-threats-biggest-threat-to-stabililty-german-defense-minister-says.html
JenkinsMiner made $3.4 million in a few months by compromising Jenkins servers
19.2.2018 securityaffairs Hacking
Hacker Group Makes $3 Million by Installing Monero Miners on Jenkins Servers
A criminal organization has made $3.4 million by compromising Jenkins servers and installing a Monero cryptocurrency miner dubbed JenkinsMiner.
“The perpetrator, allegedly of Chinese origin, has been running the XMRig miner on many versions of Windows, and has already secured him over $3 million worth of Monero crypto-currency. As if that wasn’t enough though, he has now upped his game by targeting the powerful Jenkins CI server, giving him the capacity to generate even more coins.” states a blog post published by CheckPoint.
Jenkins is the most popular open source automation server, it is maintained by CloudBees and the Jenkins community.
The automation server supports developers build, test and deploy their applications, it has more than 133,000 active installations worldwide with more than 1 million users.

According to the researchers, threat actors behind the massive mining operation were leveraging the CVE-2017-1000353 RCE vulnerability in the Jenkins Java deserialization implementation.
The vulnerability is due to lack of validation of the serialized object, its exploitation allowed the attackers to make Jenkins servers download and install the JenkinsMiner.
“The operation uses a hybridization of a Remote Access Trojan (RAT) and XMRig miner over the past months to target victims around the globe. The miner is capable of running on many platforms and Windows versions, and it seems like most of the victims so far are personal computers. With every campaign, the malware has gone through several updates and the mining pool used to transfer the profits is also changed.” continues the post.
Most of the downloads for the JenkinsMiner are from IP address located in China and assigned to the Huaian government information center, of course, we are not able to determine if the server was compromised or explicitly used by state-sponsored hackers.

Further details and IoCs are included in the analysis published by CheckPoint.
In January, security expert Mikail Tunç analyzed Jenkins servers exposed online discovering that many instances leak sensitive information.
Tunç highlighted that Jenkins typically requires credentials to the code repository and access to an environment in which to deploy the code, usually GitHub, AWS, and Azure. Failure to configure the application correctly can expose data to serious risk.
The researcher discovered that many misconfigured systems provided guest or administrator permissions by default, while others allowed guest or admin access to anyone who registered an account.
Oracle to Acquire Cloud Security Firm Zenedge
17.2.2018 securityweek IT
Oracle said Thursday that it has agreed to acquire cloud security firm Zenedge for an undisclosed sum.
Zenedge offers a suite of services to protect systems deployed in the cloud, on-premise or in hybrid hosting environments, with solutions including a Web Application Firewall (WAF), Distributed Denial of Service (DDoS) protection, and products to secure applications, networks, databases and APIs from attacks. Additionally, the company provides outsourced security monitoring and mitigating attacks
Powered by artificial intelligence (AI), Zenedge's products and 24/7 virtual Security Operations Center (SOC) defend over 800,000 web properties and networks globally.
Oracle says the acquisition of Zenedge expands Oracle Cloud Infrastructure and Oracle's Domain Name System (DNS) capabilities, adding application and network protection that augments existing Oracle security services and partnerships.
“The combination with Zenedge equips Oracle Cloud Infrastructure with integrated, next-generation network and infrastructure security, to address modern security threats,” claims Don Johnson, Senior Vice President of Product Development, Oracle.
According to Crunchbase, Zenedge has raised approximately $13.7 million in funding.
In September 2016, Oracle announced its acquisition of Cloud Access Security Broker (CASB) firm Palerra for an undisclosed sum, followed by an acquisition of Web traffic management firm Dyn in late 2016.
Global Powers Must Address 'Episodes of Cyberwar': UN Chief
17.2.2018 securityweek BigBrothers
World leaders must lay the groundwork on how countries respond to cyberattacks that have proven to be a daunting threat, whether by state actors or criminal enterprises, UN secretary general Antonio Guterres said Friday.
"It is clear we are witnessing in a more or less disguised way cyberwars between states, episodes of cyberwar between states," Guterres said during one of the opening speeches at the Munich Security Conference.
"It's high time to have a serious discussion about the international legal framework in which cyberwars take place," he said.
"The fact is we haven't been able to discuss whether or not the Geneva convention applies to cyberwar and whether international humanitarian law applies to cyberwar."
The United States and Britain on Thursday blamed the Russian military for last year's devastating "NotPetya" ransomware attack, calling it a Kremlin effort to destabilise Ukraine, which spun out of control.
The attacks ended up crippling computer networks in the United States and Europe, including those of some big companies.
Washington has also blamed North Korea for the huge "WannaCry" ransomware attack last May in which more than 300,000 computers were struck in some 150 nations.
"How to respond in cases of permanent violations of cybersecurity? What are the different uses that criminal, terror organisations are making of the web?" Guterres said.
Finding a consensus on how to respond to such attacks is urgent, he said, "especially now that artificial intelligence, that is providing enormous potential for economic development, social development, for the well-being of all, is also in the opinion of many an existential threat for humankind."
"It is necessary to bring together governments, the private sector, those involved in civil society, academics, research centres, in order to be able to establish at least some basic protocols to allow the web to be an effective instrument for the good," he said.
Unknown hackers stole $6 million from a Russian bank via SWIFT system last year
17.2.2018 securityaffairs Hacking
A new attack against the SWIFT system made the headlines again, unknown hackers have stolen 339.5 million roubles (roughly $6 million) from a Russian bank last year.
The news of the attack against the international payments messaging system was reported on Friday by the Russian central bank, this is the last incident of a long string of cyber heists.
“The volume of unsanctioned operations as a result of this attack amounted to 339.5 million roubles,” states the Russian central bank.
“The central bank said it had been sent information about “one successful attack on the work place of a SWIFT system operator.” reported the Reuters agency.
According to a spokesman for the central bank, hackers took control of a computer at a Russian bank and transferred the money to an account they controlled through the payment messaging system.
The spokesman did not provide details about the attack, he quoted Artem Sychev, deputy head of the central bank’s security department, as saying the hackers implemented “a common scheme”.
“When a case of potential fraud is reported to us, we offer our assistance to the affected user to help secure its environment,” said Natasha de Teran, a spokeswoman for SWIFT.
SWIFT highlighted that its “own systems” have never been compromised by attackers in past attacks.
“Brussels-based SWIFT said late last year digital heists were becoming increasingly prominent as hackers use more sophisticated tools and techniques to launch new attacks.” continues the Reuters.
This isn’t the only cyber attacks against a Russian bank that attempted to steal money through the SWIFT system, in December, hackers tried to steal 55 million roubles from Russian state bank Globex.
The string of attacks began with the cyber attack against Bangladesh Bank in February 2016 that resulted in the theft of $81 million.
Even if the SWIFT hasn’t revealed the exact number of victims of the SWIFT hackers, details on some attacks were revealed, such as the attack on Taiwan’s Far Eastern International Bank.
119,000 Scanned IDs of FedEx-owned company Bongo International’s customers exposed online
17.2.2018 securityaffairs Incindent
Researchers discovered an Amazon S3 bucket contains personal information and scans of IDs of some 119,000 US and international citizens.
It has happened again, researchers discovered another unsecured Amazon S3 bucket holding a huge trove of data that was exposed online. The Amazon S3 bucket contains personal information and scans of IDs of some 119,000 US and international citizens, the discovered was made once again by Kromtech security experts earlier this month.
The data belongs to the FedEx-owned company Bongo International that provides support the online sales of North American retailers and brands to consumers in abroad. Bongo was acquired in 2014 by FedEx and was operating with the name FedEx Cross-Border International until it went out of the business in April 2017.
The AWS bucket contained more than 112,000 files, unencrypted information and ID scans of customers from many countries, including the US, Mexico, Canada, various EU countries, Saudi Arabia, Kuwait, Japan, Malaysia, China, Australia.
“Among other stuff, it contained more than 119 thousands of scanned documents of US and international citizens, such as passports, driving licenses, security IDs etc. IDs were accompanied by scanned “Applications for Delivery of Mail Through Agent” forms (PS Form 1583) – which also contained names, home addresses, phone numbers and zip codes.” reads the blog post published by the company.
ZDNet analyzed the documents and found scans of drivers’ licenses, national ID cards, work ID cards, voting cards, utility bills, vehicle registration forms, medical insurance cards, firearms licences, US military identification cards, and credit cards that customers used to verify their identity with the FedEx division.
“Among the exposed files, ZDNet confirmed drivers’ licenses, national ID cards, and work ID cards, voting cards, and utility bills. We also found resumes, vehicle registration forms, medical insurance cards, firearms licences, a few US military identification cards, and even a handful of credit cards that customers used to verify their identity with the FedEx division.” wrote Zack Whittaker on ZDNet.
“One identity card, when we checked, revealed the details of a senior official at the Netherlands’ Ministry of Defense.”
It seems that the Amazon S3 bucket includes data related to anybody who used Bongo International services between 2009 and 2012 and the bad news is that it has been available for public access for many years. As said, FexEx bought the company in 2014, it is likely it was not aware of the data leak at the time of the acquisition.
Amazon S3 bucket
Kromtech tried to contact FedEx without success, the company removed the S3 bucket only after its existence was publicly disclosed.
“After a preliminary investigation, we can confirm that some archived Bongo International account information located on a server hosted by a third-party, public cloud provider is secure,” said FedEx spokesperson Jim McCluskey. “The data was part of a service that was discontinued after our acquisition of Bongo. We have found no indication that any information has been misappropriated and will continue our investigation.”
In October 2017, the Kromtech Security Center released a free scan tool that could allow admins to identify and secure Amazon S3 Buckets belonging to their organizations.
Let me suggest reading the guide published by the company to explain how to secure Amazon S3 buckets.
Oracle WebLogic Server Flaw Exploited to Deliver Crypto-Miners
16.2.2018 securityweek Vulnerebility Exploit CoinMine
Threat actors are exploiting a recently patched vulnerability in Oracle WebLogic Server to infect systems with crypto-currency mining malware, FireEye reports.
Identified as CVE-2017-10271, the vulnerability resides in the WebLogic Server Security Service (WLS Security) in Oracle WebLogic Server versions 12.2.1.2.0 and older, and was addressed by Oracle it its October 2017 Critical Patch Update (CPU).
After proof-of-concept code exploiting the bug was made public in December, activity associated with the exploitation of this vulnerability increased in volume, FireEye's researchers say. Successful exploitation of the flaw on unpatched systems allows attackers to remotely execute arbitrary code.
“We saw evidence of organizations located in various countries – including the United States, Australia, Hong Kong, United Kingdom, India, Malaysia, and Spain, as well as those from nearly every industry vertical – being impacted by this activity,” FireEye reported.
The crypto-currency market boomed recently, and cybercriminals have not been shy in their attempts to take advantage of the market. However, actors involved in crypto-currency mining operations don’t normally target specific organizations, but rather launch attacks that are opportunistic in nature.
Attackers abusing CVE-2017-10271 to infect targeted systems with crypto-miners used various tactics to achieve their purpose, the researchers discovered. Some of the incidents, for example, used PowerShell to drop the miner directly onto the victim’s system and leveraged ShellExecute() for execution.
In other attacks, PowerShell scripts were used to deliver the miner, instead of downloading the executable directly. In addition to downloading the miner, the script would also attempt to achieve persistence through scheduled tasks.
The script would delete the tasks created by other crypto-miners and would kill processes associated with those programs, in addition to being able to connect to mining pools with wallet key. It would also limit CPU usage to avoid suspicion.
Tactics employed in other attacks also involved the use of tools such as Mimikatz and EternalBlue for lateral movement across Windows environments.
The malware would first determine whether the system is 32-bit or 64-bit, to fetch a specific PowerShell script from the command and control (C&C) server. Next, it checks all network adapters and attempts to connect to every system in the network using extracted credentials, to run a PowerShell to drop and run the malware on the targeted system.
The malware uses WMI (Windows Management Instrumentation) for persistence and can perform a Pass-the-Hash attack using NTLM information derived from Mimikatz, to download and execute the malware on remote machines. It sends the stolen credentials to a remote server using an HTTP GET request.
If it fails moving laterally, the malware uses the PingCastle MS17-010 scanner to determine whether the target is vulnerable to EternalBlue.
In scenarios targeting Linux machines, the vulnerability would be exploited to deliver shell scripts that include functionality similar to that of PowerShell scripts. They would attempt to kill already running crypto-miners and then download and execute the malware, in addition to creating a cron job to maintain persistence.
“Use of cryptocurrency mining malware is a popular tactic leveraged by financially-motivated cyber criminals to make money from victims. We’ve observed one threat actor mining around 1 XMR/day, demonstrating the potential profitability and reason behind the recent rise in such attacks,” FireEye says.
Although they might be seen as less risky when compared to ransomware operations, crypto-currency mining malware does pose a variety of risks. Systems infected with crypto-miners might experience slowed performance, but such operations could also be hiding additional malware.
U.S. Energy Department Announces Office for Cyber, Energy Security
16.2.2018 securityweek BigBrothers
The U.S. Department of Energy announced this week that it’s creating a new Office of Cybersecurity, Energy Security, and Emergency Response (CESER).
The new office will be led by an assistant secretary who will report to the undersecretary of energy. The role of the assistant secretary will be to focus on energy infrastructure security and support the DoE’s expanded national security responsibilities.
The CESER office will help the DoE efficiently coordinate preparedness and response to both manmade and natural threats.U.S. Department of Energy launches Office of Cybersecurity, Energy Security, and Emergency Response
“DOE plays a vital role in protecting our nation’s energy infrastructure from cyber threats, physical attack and natural disaster, and as Secretary, I have no higher priority,” said U.S. Secretary of Energy Rick Perry. “This new office best positions the Department to address the emerging threats of tomorrow while protecting the reliable flow of energy to Americans today.”
U.S. President Donald Trump has proposed a budget of $30.6 billion for the DoE, including $96 million allocated for bolstering the department’s cybersecurity and energy security efforts. Overall, the current administration wants to invest $80 billion in IT and cybersecurity, which represents a 5.2 percent increase compared to the previous fiscal year.
Energy facilities in the United States and the Energy Department itself have often been targeted by malicious hackers in the past years.
In response to the increasing threat, the DoE announced a few months ago its intention to invest more than $20 million in cybersecurity, including tools and technologies for enhancing cybersecurity, communication systems for resilient grid architectures, energy delivery systems that can adapt to survive a cyber incident, partnerships for vulnerability mitigation, and identifying energy delivery systems that are inadvertently accessible from the Web.
U.S. Government Contractors Score Poorly on Cyber Risk Tests
16.2.2018 securityweek BigBrothers
Report Analyzes Cyber Risk of Federal Supply Chain
Attacks against the supply chain are not uncommon. It represents the soft underbelly of large organizations that are otherwise well defended. The federal government is not an exception -- in fact, federal agencies are especially reliant on their supply chain; and the security posture of that supply chain is of national importance.
This importance is not unrecognized. The May 2017 presidential Executive Order specified that the supply chain be included in security improvements: it called for a report, "on cybersecurity risks facing the defense industrial base, including its supply chain, and United States military platforms, systems, networks, and capabilities, and recommendations for mitigating these risks."
BitSight this week published an analysis of the security posture of the federal supply chain following the executive order. BitSight is a firm that examines and rates companies' security posture by analyzing visible evidence. It sees indicators of compromise, infected machines, improper configuration, poor security hygiene and potentially harmful user behaviors. From such evidence, it is able to see and compare different organizations. It concludes that the federal supply chain continues to provide a soft underbelly for attacks against federal agencies.
While federal agencies are improving their own security stance, their supply chain is lagging. For its analysis, BitSight researchers took a random sample of over 1,200 U.S. federal government contractors across a range of sectors, and compared the results with the performance of over 120 U.S. federal agencies.
It found a mean performance gap of at least 15 points between the agencies and their contractors. BitSight's ratings are calculated on a scale of 250-900, where a higher score reflects a stronger security posture. "There is a significant gap between the security performance of U.S. federal agencies and their contractors," concludes the analysis. "The mean rating for agencies as of January 2018 was 725. This is markedly higher than any of the other sector of contractors for the U.S. federal government observed in this study."
This mean rating disguises some concerning specifics. For example, nearly one in five users at Technology and Aerospace/Defense contractors have an outdated internet browser, making these employees and their organizations highly susceptible to new variants of malware. "High-profile vulnerabilities like Spectre can exploit outdated browsers as an attack to intercept or compromise data," warns BitSight. "Updating to the latest browser, operating system, or software package is critical to mitigating risks."
Individual risk vectors are graded on a scale from 'A' to 'F'. "Nearly 50% of contractors have a BitSight grade below C for the Protective Technology subcategory of the NIST Cybersecurity Framework," states the report. "This data suggests that many contractors are not implementing best practices for network security, encryption, and email security." Engineering was the worst performing sector in this area, with only 4% achieving an A rate. This compares to 38% of the federal agencies achieving an A grade (which is almost three times the average second-best rate of 13% for Business Services).
Botnet infections are another worrying area. It was highlighted in the Trump executive order, which demanded action "to improve the resilience of the internet and communications ecosystem and to encourage collaboration with the goal of dramatically reducing threats perpetrated by automated and distributed attacks (e.g., botnets)."
Here there is less difference between the agencies and their contractors -- in fact both the Business Services (80%) and Aerospace/Defense (74%) sectors achieved more A grades than the Federal Agencies (73%). However, only Aerospace/Defense equaled the agencies in the low number of F and D grades (both at 4%). In general, however, far more of the subcontractors scored B and below than did the agencies. For reference, BitSight claims, "an organization receiving a B or lower in this category is more than twice as likely to experience a data breach."
It goes on to suggest, "This data suggests that these organizations have ineffective security programs in place and may be experiencing ongoing data breaches."
Security of the supply chain is a problematic issue for all organizations. This BitSight reports suggests that it is a serious problem for federal agencies. “Tens of thousands of government contractors hold sensitive data or perform services on behalf of federal agencies," says Jacob Olcott, VP of Strategic Partnerships at BitSight. "The U.S. government must be focused on evaluating, monitoring and improving the cyber hygiene of these contractors. Recent contractor regulations, like the new DOD requirements, are a start, but are too focused on check-the-box compliance. Cyber is a dynamic risk. By leveraging objective data and continuously monitoring the supply chain, the federal government will better comprehend the danger within its own ecosystem and begin to meaningfully mitigate this risk.”
Cambridge, Mass.-based BitSight Technologies raised $40 million in a Series C funding round in September 2016, bringing the total raised to $95 million.
OpenSSL alpha adds TLS 1.3 support in the alpha version of OpenSSL 1.1.1
16.2.2018 securityaffairs Krypto
OpenSSL adds TLS 1.3 (Transport Layer Security) supports in the alpha version of OpenSSL 1.1.1 that was announced this week.
OpenSSL adds TLS 1.3 supports in the alpha version of OpenSSL 1.1.1 that was announced this week. TLS protocol was designed to allow client/server applications to communicate over the Internet in a secure way preventing message forgery, eavesdropping, and tampering.
“OpenSSL 1.1.1 is currently in alpha. OpenSSL 1.1.1 pre release 1 has now been made available.” states the OpenSSL’s announcement.
“This OpenSSL pre-release has been provided for testing ONLY. It should NOT be used for security critical purposes. The alpha release is available for download via HTTP and FTP from the following master locations (you can find the various FTP mirrors under https://www.openssl.org/source/mirror.html)”
The first Internet-Draft dates back to April 2014, in January it was presented the 23 and will expire on July 9, 2018.
One of the most debated problems when dealing with TLS is the role of so-called middleboxes, many companies need to inspect the traffic for security purposes and TLS 1.3 makes it very hard.
“The reductive answer to why TLS 1.3 hasn’t been deployed yet is middleboxes: network appliances designed to monitor and sometimes intercept HTTPS traffic inside corporate environments and mobile networks. Some of these middleboxes implemented TLS 1.2 incorrectly and now that’s blocking browsers from releasing TLS 1.3. However, simply blaming network appliance vendors would be disingenuous.” reads a blog post published by Cloudflare in December that explained the difficulties of mass deploying for the TLS 1.3.
According to the tests conducted by the IETF working group in December 2017, there was around a 3.25 percent failure rate of TLS 1.3 client connections.
TLS 1.3 will deprecate old cryptographic algorithms entirely, this is the best way to prevent the exploiting of vulnerabilities that affect the protocol and that can be mitigated only when users implement a correct configuration.
In the last few years, researchers discovered several critical issues in the protocol that have been exploited in attacks.
OpenSSL maintainers have completely redesigned the OpenSSL random number generator in the new version.
The new OpenSSL release also includes the implementation for SHA3 and multi-prime RSA, and the support for the SipHash set of pseudorandom functions.
BGP Flaws Patched in Quagga Routing Software
16.2.2018 securityweek Vulnerebility
Several vulnerabilities that could lead to denial-of-service (DoS), information disclosure, and remote code execution have been patched this week in the Quagga routing software suite.
Quagga implements the Open Shortest Path First (OSPF), Routing Information Protocol (RIP), Border Gateway Protocol (BGP) and Intermediate System to Intermediate System (IS-IS) protocols for Unix-like platforms, particularly Linux, Solaris, FreeBSD and NetBSD.
Quagga developers and the CERT Coordination Center (CERT/CC) at Carnegie Mellon University announced this week that Quagga 1.2.3 patches several vulnerabilities affecting the BGP daemon (bpgd).
One of the more serious flaws, rated critical by CERT/CC based on its CVSS score, is CVE-2018-5379, a double-free memory corruption issue related to the processing of certain UPDATE messages containing cluster-list or unknown attributes.
“This issue can be triggered by an optional/transitive UPDATE attribute, that all conforming eBGP speakers should pass along. This means this may triggerable in many affected Quagga bgpd processes across a wide area of a network, because of just one UPDATE message,” Quagga developers explained. “This issue could result in a crash of bgpd, or even allow a remote attacker to gain control of an affected bgpd process.”
Another vulnerability, CVE-2018-5381, can be exploited to cause bgpd to enter an infinite loop and stop responding until it’s restarted. “BGP sessions will drop and not be reestablished,” developers said.
Quagga 1.2.3 also patches CVE-2018-5378, a security hole that can lead to sensitive data from the bgpd process being sent over the network to a configured peer. This can also cause the bgpd process to crash.
The last vulnerability patched by the latest Quagga release is CVE-2018-5378, which developers say has “very low” impact.
Linux distributions, including Ubuntu, Debian and Red Hat, have started publishing advisories describing these vulnerabilities. Regarding CVE-2018-5379, Red Hat said “Glibc's heap protection mitigations render this issue more difficult to exploit, though bypasses may still be possible.”
A Single-Character Message Can Crash Any Apple iPhone, iPad Or Mac
16.2.2018 thehackernews Apple
Only a single character can crash your iPhone and block access to the Messaging app in iOS as well as popular apps like WhatsApp, Facebook Messenger, Outlook for iOS, and Gmail.
First spotted by Italian Blog Mobile World, a potentially new severe bug affects not only iPhones but also a wide range of Apple devices, including iPads, Macs and even Watch OS devices running the latest versions of their operating software.
Like previous 'text bomb' bug, the new flaw can easily be exploited by anyone, requiring users to send only a single character from Telugu—a native Indian language spoken by about 70 million people in the country.
Once the recipient receives a simple message containing the symbol or typed that symbol into the text editor, the character immediately instigates crashes on iPhones, iPads, Macs, Apple Watches and Apple TVs running Apple's iOS Springboard.
Apps that receive the text bomb tries to load the character, but fails and refuses to function properly until the character is removed—which usually can be done by deleting the entire conversation.
iphone-crash-telugu-character
The easiest way to delete the offending message is by asking someone else to send a message to the app that is crashing due to the text bomb. This would allow you to jump directly into the notification and delete the entire thread containing the character.
The character can disable third-party apps like iMessage, Slack, Facebook Messenger, WhatsApp, Gmail, and Outlook for iOS, as well as Safari and Messages for the macOS versions.
Telegram and Skype users appear to be unaffected by the text bomb bug.
Apple was made aware of the text bomb bug at least three days ago, and the company plans to address the issue in an iOS update soon before the release of iOS 11.3 this spring.
The public beta version of iOS 11.3 is unaffected.
Since so many apps are affected by the new text bomb, bad people can use the bug to target Apple users via email or messaging or to create mass chaos by spamming the character across an open social platform.
U.S., Canada, Australia Attribute NotPetya Attack to Russia
16.2.2018 securityweek Ransomware
The United States, Canada, Australia and New Zealand have joined the United Kingdom in officially blaming Russia for the destructive NotPetya attack launched last summer. Moscow has denied the accusations.
In a statement released on Thursday, the White House attributed the June 2017 attack to the Russian military and described it as “the most destructive and costly cyber-attack in history.”
“The attack, dubbed ‘NotPetya,’ quickly spread worldwide, causing billions of dollars in damage across Europe, Asia, and the Americas,” the White House Press Secretary stated. “It was part of the Kremlin’s ongoing effort to destabilize Ukraine and demonstrates ever more clearly Russia’s involvement in the ongoing conflict. This was also a reckless and indiscriminate cyber-attack that will be met with international consequences.”
According to the Australian government, the conclusion that threat actors sponsored by Russia are responsible for the cyberattack was reached based on information from its domestic intelligence agencies and consultation with the U.S. and U.K.
“The Australian Government condemns Russia’s behaviour, which posed grave risks to the global economy, to government operations and services, to business activity and the safety and welfare of individuals,” stated Angus Taylor, Australia’s Minister for Law Enforcement and Cybersecurity. “The Australian Government is further strengthening its international partnerships through an International Cyber Engagement Strategy to deter and respond to the malevolent use of cyberspace.”
Canada’s Communications Security Establishment (CSE) also accused Russia of launching the NotPetya attack based on its own assessment.
“Canada condemns the use of the NotPetya malware to indiscriminately attack critical financial, energy, government, and infrastructure sectors around the world in June 2017,” said CSE Chief Greta Bossenmaier. “As previously stated, the Government of Canada continues to strongly oppose the use of cyberspace for reckless and destructive criminal activities. We remain committed to working with our allies and partners to maintain the open, reliable and secure use of cyber space.”
New Zealand’s Government Communications Security Bureau (GCSB) said that while the country was not directly targeted by NotPetya, the incident did cause disruption to some organizations that had rushed to update their systems after news of the attack broke.
New Zealand has joined the other Five Eyes countries in condemning the attack, but its statement suggests that its attribution of the incident to Russia is based solely on information provided by GCSB’s international partners.
British Foreign Office Minister for Cyber Security Lord Tariq Ahmad said Russia “showed a continued disregard for Ukrainian sovereignty” by launching the NotPetya attack.
Moscow has denied the accusations, describing them as unsubstantiated and groundless. “This is nothing more than the continuation of the Russophobic campaign lacking any evidence,” said Kremlin spokesman Dmitry Peskov.
The NotPetya malware (also known as PetrWrap, exPetr, GoldenEye and Diskcoder.C) affected tens of thousands of systems around the world. Researchers initially believed NotPetya was a piece of ransomware, but a closer analysis revealed that it was actually a destructive wiper.
Rosneft, AP Moller-Maersk, Merck, FedEx, Mondelez International, Nuance Communications, Reckitt Benckiser, and Saint-Gobain reported losing hundreds of millions of dollars due to the attack.
Last year, Five Eyes countries and Japan officially accused North Korea of launching the WannaCry attack.
'DoubleDoor' IoT Botnet Uses Two Backdoor Exploits
16.2.2018 securityweek BotNet
A newly discovered Internet of Things (IoT) botnet is using two exploits to ensure it can not only bypass authentication on targeted devices, but also render additional protections useless, NewSky Security has discovered.
Dubbed DoubleDoor, the botnet allows attackers to takeover devices even if the user has authentication enabled and has added a firewall for additional protection. Specifically, the malware abuses CVE-2015–7755, a Juniper Networks SmartScreen OS exploit, and CVE-2016–10401, a Zyxel modem backdoor exploit (also abused by the Hide ‘N Seek botnet).
What NewSky Security discovered was that the botnet first deploys the infamous Juniper Networks exploit, which essentially allows it to get past firewall authentication. The backdoor was initially discovered in the ScreenOS software running on NetScreen firewalls.
Through this backdoor, the telnet and SSH daemons of Netscreen firewalls become accessible with the hardcoded password <<< %s(un=’%s’) = %u and any username, regardless of whether a valid one or not. In the initial attack cycle of DoubleDoor, the attack was implemented using the username “netscreen,” NewSky's researchers say.
Next, the botnet attempts to deploy the backdoor for ZyXEL PK5001Z devices, which is pretty straight forward as well, using a hardcoded su password as zyad5001. This is a privilege escalation exploit, and the botnet’s operators were also observed performing a “password based attack to get a basic privilege account like admin:CenturyL1nk before going for the superuser,” the researchers say.
The DoubleDoor botnet was also observed performing reconnaissance to ensure the attack was successful and control of the IoT device was achieved.
“DoubleDoor botnet takes care of this, by using a randomized string in every attack. Lack of any standard string will make sure it is not very easy to classify the recon activity as malicious. The strings have one thing in common though, they are always 8 in length,” the security researchers note.
The botnet is currently in a nascent phase, with attacks observed only between Jan. 18 and Jan. 27, 2018. Most of the attacks were observed originating from South Korean IPs. The botnet’s attacks are expected to remain low, mainly because they are only effective if the victim runs a specific unpatched version of Juniper ScreenOS firewall and uses unpatched Zyxel modems.
“Double layer of IoT protection is more common in corporate environments, which don’t rely on built-in IoT authentication and like to protect it with another layer of firewall. Although such corporate devices can be lesser in number, getting control of corporate environment routers can be more valuable for an attacker as it can lead to targeted IoT attacks,” the researchers say.
Financial Regulator's Algorithm Compliance Concerns Are Relevant to All Businesses
16.2.2018 securityweek IT
The UK's financial regulator, the Financial Conduct Authority (FCA), issued a report Monday warning financial companies that it would be looking closely at so-called 'algo trading': "Algorithmic Trading Compliance in Wholesale Markets" (PDF).
Algo (or algorithmic) trading is the use of computer algorithms to buy or sell stock automatically and at speed if certain market conditions are met. The danger is that rapid trading by computers can change the market causing more buying or selling before human traders can intervene and correct the situation. Such algo trading has been blamed as partly responsible for this month's Wall Street sell-off that led to a 4% fall in Standard & Poor's 500-stock index last Monday -- the worst decline since August 2011.
David Murray, Corvil's chief marketing and business development officer, explains the problem. "It takes a person 300-400 milliseconds (thousandths of a second) to blink, and computers can execute a trade in 30-40 microseconds (millionths of a second) -- so it is clear that the new reality of time in an algorithmic world mandates new oversight and controls."
In its new report, compiled in the months preceding last week's Wall Street sell-off, the FCA warns, "In the absence of appropriate systems and controls, the increased speed and complexity of financial markets can turn otherwise manageable errors into extreme events with potentially wide-spread implications." Because of this, it adds, "We will continue to assess whether firms have taken sufficient steps to reduce risks arising from algorithmic trading."
Five key compliance areas are highlighted by the FCA: a full understanding and management of algorithms across the business; robust development and testing processes for algorithms; pre and post trade risk controls; an effective governance and oversight framework; and the ability to monitor for potential conduct issues and thereby reduce market abuse risks.
This isn't just about automated trading with the potential to wobble global financial markets -- it is also about localized and criminal abuse of algorithms. In November 2017, the FCA fined Paul Axel Walter -- subsequently known as 'algo-baiter' -- £60,090 for market abuse via algorithms. Walter was a senior bond trader, working at Bank of America Merrill Lynch (BAML). In 2014, he entered bids into the system that reflected the opposite of his intention. The algorithms reacted to his bids allowing him to subsequently enter his true bids into a market that he had manipulated.
But the issues go beyond just financial trading. "Similar conditions exist not only across global financial markets," explains Murray. "There are similar risks for other algorithmic businesses and use of artificial intelligence."
With the digitization and computer-based automation of all industry, the problems currently highlighted in the financial sector will become an issue for businesses generally. Actions will be triggered by and acted upon by unseen algorithms hidden within the system. It already happens within security products, where decisions can be made without anyone really understanding how or why they were reached. At the same time, outsiders will be able to manipulate the algorithms by feeding them false information, similar to Walter's manipulation of the trading algorithms.
The FCA's five principles for algo compliance are applicable far beyond just financial institutions. Compliance officers and security teams will need to understand their use of algorithms within machine learning and artificial intelligence systems to remain within compliance and defeat both internal and external malicious actors. Key, perhaps, is the second principle: robust development and testing processes. This is particularly relevant where a business develops its own algorithms -- as is common in the financial industry -- rather than relying, blindly, on externally developed algorithms.
Algorithm development is subject to the same pressures as any other software development -- the need to get it complete and operational as quickly as possible. The FCA warns against development procedures that focus on operational effectiveness without considering other issues. An example outside of finance could be automated customer or user profiling without considering the impact of the General Data Protection Regulation (GDPR). Article 22 states, "The data subject shall have the right not to be subject to a decision based solely on automated processing, including profiling, which produces legal effects concerning him or her or similarly significantly affects him or her."
The FCA's advice is good for all software development: "a culture of open communication between different business units, while having a clear separation of roles and independent reviews... by having a separate team that verifies and checks the output and quality of code."
As the algorithms get more complex, they get more difficult to control. "There's often a tradeoff between model or algorithm performance and complexity," explains Endgame's technical director of data science, Hyrum Anderson, "with higher performing models often requiring more model mass. Examples include: more trees in random forest or gradient boosting models, more layers in convolutional neural networks, etc. As a design principal, experienced machine learning researchers try to utilize the principle of Occam's razor -- when many models have similar performance, choose the simpler one."
But he also warns that while simplicity aids in human understanding and verification, and prevents models from making extreme predictions, it also potentially creates the best conditions for adversaries to fool them. While DevOps may be good for software development, DevSecOps would be better for algorithm development to ensure the most secure and reliable outcome.
A second of the FCA's five principles is also relevant to compliance and security teams beyond just the financial industry: the ability to monitor for potential conduct issues. Two aspects of this requirement are particularly relevant: network monitoring for signs of abuse or misuse; and algorithm testing standards and procedures.
The first will become increasingly challenging. Security teams already monitor their networks for anomalous events; but they use algorithms to do so. As algorithmic automation increases throughout industry, security teams will need to find monitoring methods to monitor even the algorithms they use for monitoring other aspects of the business. They will need to be able to detect malicious external actors attempting to subvert the algorithms, and insiders attempting to manipulate the algorithms. This is of course particularly concerning in the financial sector where entire markets, and potentially national economies, could be manipulated for criminal gain -- or individual company share prices manipulated in sophisticated versions of pump and dump schemes.
Corvil's Murray summarizes the problem. "To operate in today’s machine time environments and enable rapid, secure, compliant time to market, businesses require process controls as well as layered technology oversight to assure precision and accuracy of time stamping to establish sequencing, continuous capture and of all electronic business activity, real-time analysis of transactions, and anomaly detection for cyber and abuse surveillance."
Testing the veracity of algorithms will also be a problem. The third-party anti-malware testing industry is struggling to find methods of adequately and objectively testing algo-based endpoint protection systems. As companies begin to develop their own algorithms for their own automation purposes, testing will likely fall on the very people who developed the algorithms. Objectivity may be impossible, and testing may not be effective.
The FCA's algorithmic trading compliance report should be a clarion call for all businesses. The new and emerging world of artificial intelligence -- that is, algorithms -- promises huge benefits for industry in increased speeds and lower costs; just as it does in the financial markets. But whether industry generally has fully examined the security and compliance issues that algorithms bring with them is a separate but urgent question. Algorithmic Trading Compliance in Wholesale Markets is a good starting point.
Dispel Launches Election Security Platform
16.2.2018 securityweek Krypto
Dispel, a U.S.-based company that specializes in secure communication and collaboration systems, on Thursday announced the launch of a new product designed to help protect elections against malicious cyber actors.
According to Dispel, the new solution, which consists of its Election Cyber Defense System (ECDS) and a hardware device named ECDS Wicket, is capable of protecting the integrity of voter, ballot and campaign information. The company says its product can be easily installed even by a novice with only five minutes of training.
The election security platform is designed to automatically tunnel sensitive voting data and ensure that databases and networks cannot be located and attacked by malicious actors. The ECDS Wicket, which needs to be plugged into the reporting center computer, protects communications with two layers of AES-256 encryption with independent 4096-bit RSA keys for the initial exchange.
The device links the reporting center computer to a siloed dataroom where voting data is uploaded. Each dataroom is located in a network protected by Dispel’s Moving Target Defense technology. When the ECDS system is active, the reporting center computer can no longer transmit data to the Internet and can only communicate with election-related sites.
The platform has different systems that can help secure specific voting and campaign-related operations, including voter rolls, vote tabulation, and campaign communications.
For example, when voter rolls are changed, state officials connect with reporting officials through a secure video conferencing page to confirm the identity of the reporting official before granting them access to change the roll. Every change made to the roll is logged and stored in a secure location.
The tabulation system is designed to ensure that voting data is safely transmitted and stored. As for protecting campaign communications, Dispel provides what it calls the Campaign Comms Enclave, which includes secure video conferencing, telephony, messaging, file sharing, VPN, research stations, and logging capabilities for a flat fee of $2,500 per month, $7,500 per quarter, or $25,000 annually.
The voter roll and vote tabulation systems are priced based on the number of Wicket devices, voter rolls, access terminals, and reporting centers needed.
U.S. intelligence officials are convinced that Russia interfered in the 2016 presidential election and they have warned that it will likely attempt to meddle in this year’s midterm elections as well. Threat groups from Russia and other countries could try to interfere and experts warned recently that voting machines and other systems used in the election are vulnerable to hacker attacks.
Dispel told SecurityWeek that it has yet to make any deals with the U.S. government regarding the use of its product at the upcoming elections.
Democrats on Wednesday asked Congress for more than $1 billion in grants for boosting election security, and a product such as the one offered by Dispel could be taken into consideration for protecting votes.
Dispel is also offering its product to governments outside the U.S., but it has yet to actively promote it.
Russian Hackers Sent to U.S. Prison for Stealing 160 Million Bank Card Numbers
16.2.2018 securityweek BigBrothers
A United States Judge this week sent two Russian nationals to prison for their involvement in a hacking scheme that compromised roughly160 million credit card numbers and incurred losses of hundreds of millions.
The two, Vladimir Drinkman, 37, and Dmitriy Smilianets, 34, both of Moscow, were arrested in the Netherlands on June 28, 2012. Smilianets was extradited to the United States on Sept. 7, 2012, while Drinkman was extradited on Feb. 17, 2015.
Drinkman, who previously pleaded guilty before U.S. District Judge Jerome B. Simandle of the District of New Jersey, was sentenced to 144 months in prison. Smilianets, who pleaded guilty in September 2013, was sentenced to 51 months and 21 days in prison.
Drinkman and Smilianets, along with three co-defendants, were charged with hacking into the networks of organizations engaged in financial transactions, retailers operating with financial data, and other institutions with information of interest to the group.
The conspirators hacked the computer networks of NASDAQ, 7-Eleven, Carrefour, JCP, Hannaford, Heartland, Wet Seal, Commidea, Dexia, JetBlue, Dow Jones, Euronet, Visa Jordan, Global Payment, Diners Singapore and Ingenicard, court documents and statements show.
Each of the five defendants played a specific role in the scheme, with Drinkman penetrating network security, gaining access to the corporate victims’ systems, and harvesting valuable data from the compromised networks. Smilianets would sell the stolen data and distribute the proceeds of the scheme to the participants.
The other three co-defendants, namely Alexandr Kalinin, 31, of St. Petersburg, Russia, Roman Kotov, 36, of Moscow, Russia, and Mikhail Rytikov, 30, of Odessa, Ukraine, are fugitives.
The hackers targeted the computer networks of corporate victims to steal information such as user names and passwords, means of identification, credit and debit card numbers, and other personal identification information of cardholders.
The group used SQL injection attacks to penetrate the victims’ networks. The hackers targeted vulnerabilities in SQL (Structured Query Language) databases for initial access, then installed malware on the system to create a backdoor and help them maintain access to the network. They would sometime assault a victim network for months before being able to bypass security.
“The defendants used their access to the networks to install ‘sniffers’, which were programs designed to identify, collect and steal data from the victims’ computer networks. The defendants then used an array of computers located around the world to store the stolen data and ultimately sell it to others,” a Department of Justice announcement reads.
The stolen data was sold through online forums or directly to individuals and organizations for around $10 for a stolen American credit card number and associated data, $50 for a European credit card number and associated data, and $15 for a Canadian credit card number and associated data.
Their customers would encode such data onto the magnetic strip of a blank plastic card and use it to withdraw money from ATMs or make purchases.
To conceal the scheme, the five defendants used various methods, starting with the use of anonymous web-hosting services provided by Rytikov. They also used private and encrypted communication channels and also attempted to evade protections by security software, in addition to modifying settings on victim networks to disable the logging of their actions.
“As a result of the scheme, financial institutions, credit card companies and consumers suffered hundreds of millions in losses – including more than $300 million in losses reported by just three of the corporate victims – and immeasurable losses to the identity theft victims in costs associated with stolen identities and false charges,” DoJ says.
In addition to prison terms, Drinkman and Smilianets were also sentenced to three years of supervised release.
DELL EMC addressed two critical flaws in VMAX enterprise storage systems
16.2.2018 securityaffairs Vulnerebility
Dell EMC addressed two critical vulnerabilities that affect the management interfaces for its VMAX enterprise storage systems.
The Dell EMC’s VMAX Virtual Appliance (vApp) Manager is an essential component of a wide range of the enterprise storage systems.
The first flaw tracked as CVE-2018-1215 is an arbitrary file upload vulnerability that could be exploited by a remote authenticated attacker to potentially upload arbitrary maliciously crafted files in any location on the web server. The flaw received a Common Vulnerability Scoring System (CVSS) base score of 8.8.
“Arbitrary file upload vulnerability A remote authenticated malicious user may potentially upload arbitrary maliciously crafted files in any location on the web server. By chaining this vulnerability with CVE-2018-1216, the attacker may use the default account to exploit this vulnerability.” reads the security advisory.
VMAX enterprise storage systems
The second flaw tracked as CVE-2018-1216 is an undocumented default account in the vApp Manager with a hard-coded password. The flaw received a Common Vulnerability Scoring System (CVSS) base score of 9.8.
“Hard-coded password vulnerability The vApp Manager contains an undocumented default account (ÒsmcÓ) with a hard-coded password that may be used with certain web servlets. A remote attacker with the knowledge of the hard-coded password and the message format may use vulnerable servlets to gain unauthorized access to the system. Note: This account cannot be used to log in via the web user interface.” continues the advisory.
The CVE-2018-1215 could be chained with a second flaw tracked as CVE-2018-1216 to use a hard-coded password to a default account to exploit this vulnerability.
“The vApp Manager which is embedded in Dell EMC Unisphere for VMAX, Dell EMC Solutions Enabler, Dell EMC VASA Virtual Appliances, and Dell EMC VMAX Embedded Management (eManagement) contains multiple security vulnerabilities that may potentially be exploited by malicious users to compromise the affected system.” states the security advisory issued by Dell EMC.
Affected products:
Dell EMC Unisphere for VMAX Virtual Appliance versions prior to 8.4.0.18
Dell EMC Solutions Enabler Virtual Appliance versions prior to 8.4.0.21
Dell EMC VASA Virtual Appliance versions prior to 8.4.0.514
Dell EMC VMAX Embedded Management (eManagement) versions prior to and including 1.4 (Enginuity Release 5977.1125.1125 and earlier)
Dell EMC has removed the default ÒsmcÓ account from new installs, but the company noticed that the account will not be removed after the upgrade of the vApp Manager application.
UK Foreign Office Minister blames Russia for NotPetya massive ransomware attack
16.2.2018 securityaffairs Ransomware
The United Kingdon’s Foreign and Commonwealth Office formally accuses the Russian cyber army of launching the massive NotPetya ransomware attack.
The UK Government formally accuses the Russian cyber army of launching the massive NotPetya ransomware attack.
The United Kingdon’s Foreign and Commonwealth Office “attributed the NotPetya cyber-attack to the Russian Government.”
According to the UK, NotPetya was used to disrupt Ukrainian “financial, energy and government sector” targets, but it went out of control causing severe damages to companies worldwide.

The shipping giant Maersk chair Jim Hagemann Snabe revealed its company reinstalled 45,000 PCs and 4,000 Servers after NotPetya the attack.
In August 2017 the company announced that it would incur hundreds of millions in U.S. dollar losses due to the ransomware massive attack.
The UK considers the attack an intolerable act and will not accept future similar offensives.
“Foreign Office Minister Lord Ahmad has today attributed the NotPetya cyber-attack to the Russian Government. The decision to publicly attribute this incident underlines the fact that the UK and its allies will not tolerate malicious cyber activity.” reads the official statement issued by the UK Government.
“The attack masqueraded as a criminal enterprise but its purpose was principally to disrupt. Primary targets were Ukrainian financial, energy and government sectors. Its indiscriminate design caused it to spread further, affecting other European and Russian business.”
Below the declaration of the Foreign Office Minister for Cyber Security Lord (Tariq) Ahmad of Wimbledon:
“The UK Government judges that the Russian Government, specifically the Russian military, was responsible for the destructive NotPetya cyber-attack of June 2017.
The attack showed a continued disregard for Ukrainian sovereignty. Its reckless release disrupted organisations across Europe costing hundreds of millions of pounds.
The Kremlin has positioned Russia in direct opposition to the West yet it doesn’t have to be that way. We call upon Russia to be the responsible member of the international community it claims to be rather then secretly trying to undermine it.
The United Kingdom is identifying, pursuing and responding to malicious cyber activity regardless of where it originates, imposing costs on those who would seek to do us harm. We are committed to strengthening coordinated international efforts to uphold a free, open, peaceful and secure cyberspace.”
According to Ukraine’s Secret Service (SBY), Russia orchestrated the NotPetya ransomware attack, going public with their accusations just days after the incident.
NotPetya wasn’t the last massive ransomware attack in order of time, in October Bad Rabbit
NotPetya was followed by the Bad Rabbit ransomware that in late October infected systems in many countries wordlwide, most of in East Europe, such as Ukraine and Russia.
Over $100,000 Paid Out in 'Hack the Air Force 2.0'
15.2.2018 securityweek Security
HackerOne on Thursday announced the results of a bug bounty challenge run by the U.S. Air Force on its platform. More than $100,000 were paid out for over 100 vulnerabilities reported during Hack the Air Force 2.0.
The challenge ran between December 9 and January 1. The U.S. Department of Defense paid out a total of $103,883 for 106 valid vulnerability reports submitted by 27 hackers from the U.S., Canada, U.K., Sweden, Netherlands, Belgium and Latvia.
The largest single payout, which is also the highest reward in any federal bug bounty program to date, was $12,500.
Of the 106 flaws, 55 were discovered on the first day of Hack the Air Force 2.0 during a live hacking event at the WeWork Fulton Center inside the Fulton Center subway station in New York City.Hack the Air Force 2.0
Seven U.S. Airmen and 25 civilians earned a total of over $26,000 on the first day, including $10,650 by Mathias Karlsson and Brett Buerhaus, who demonstrated how malicious actors could have breached an unclassified DoD network by exploiting a vulnerability in the Air Force’s website.
“We continue to harden our attack surfaces based on findings of the previous challenge and will add lessons learned from this round,” said Air Force CISO Peter Kim. “This reinforces the work the Air Force is already doing to strengthen cyber defenses and has created meaningful relationships with skilled researchers that will last for years to come.”
The first edition of Hack the Air Force paid out more than $130,000 for 207 valid vulnerability reports. The bug bounty challenges run by the Pentagon on the HackerOne platform since 2016 led to the discovery and patching of more than 3,000 vulnerabilities, with a total of over $400,000 awarded to white hat hackers.
The Pentagon also has a vulnerability disclosure policy that aims to provide guidance to researchers on how to disclose security holes found in the organization’s public-facing websites. While no monetary rewards are being offered, the policy provides a legal avenue for reporting flaws.
U.K. Officially Blames Russia for NotPetya Attack
15.2.2018 securityweek Ransomware
The United Kingdom on Thursday officially accused the Russian government of launching the destructive NotPetya attack, which had a significant financial impact on several major companies.
British Foreign Office Minister for Cyber Security Lord Tariq Ahmad said the June 2017 NotPetya attack was launched by the Russian military and it “showed a continued disregard for Ukrainian sovereignty.”
“The Kremlin has positioned Russia in direct opposition to the West yet it doesn’t have to be that way. We call upon Russia to be the responsible member of the international community it claims to be rather then secretly trying to undermine it,” the official stated.
“The United Kingdom is identifying, pursuing and responding to malicious cyber activity regardless of where it originates, imposing costs on those who would seek to do us harm. We are committed to strengthening coordinated international efforts to uphold a free, open, peaceful and secure cyberspace,” he added.
The U.K. believes that while the NotPetya attack masqueraded as a criminal campaign, its true purpose was to cause disruption. The country’s National Cyber Security Center (NCSC) assessed that the Russian military was “almost certainly” responsible for the attack, which is the highest level of assessment.
The U.K. was also the first to officially accuse North Korea of launching the WannaCry attack. The United States, Canada, Japan, Australia and New Zealand followed suit several weeks later.
Last month, Britain's Defence Secretary Gavin Williamson accused Russia of spying on its critical infrastructure as part of a plan to create “total chaos” in the country.
While the U.S. has not made an official statement on the matter, confidential documents obtained by The Washington Post last month showed that the CIA had also concluded with “high confidence” that the Russian military was behind the NotPetya attack.
Cybersecurity firms and Ukraine, the country hit the hardest by NotPetya, linked the malware to other threats previously attributed to Russia.
The NotPetya malware outbreak affected tens of thousands of systems in more than 65 countries. Researchers initially believed NotPetya (also known as PetrWrap, exPetr, GoldenEye and Diskcoder.C) was a piece of ransomware, but a closer analysis revealed that it was actually a destructive wiper.
Rosneft, AP Moller-Maersk, Merck, FedEx, Mondelez International, Nuance Communications, Reckitt Benckiser, and Saint-Gobain reported losing hundreds of millions of dollars due to the attack.
Intel Offers $250,000 for Side-Channel Exploits
15.2.2018 securityweek Exploit
Intel Opens Bug Bounty Program to All Researchers, Offers up to $250,000 for Flaws Similar to Meltdown and Spectre
Intel on Wednesday announced major changes to its bug bounty program, including that it’s now open to all researchers, and significant rewards for exploits similar to Meltdown and Spectre.
Researchers who find critical hardware vulnerabilities that allow software-based side-channel attacks – just like Meltdown and Spectre – can earn up to $250,000. Flaws classified as high severity are worth up to $100,000, while medium- and low-risk issues are worth up to $20,000 and $5,000, respectively. The severity of a flaw is determined based on its CVSS base score, adjusted depending on the security objectives and threat model of the targeted product.
The part of Intel’s bug bounty program covering side-channel exploits will run until December 31, 2018.
Intel also announced that its bug bounty program is now open to all researchers – it was invitation-only until now. When the company launched this initiative back in March 2017, the maximum reward for hardware vulnerabilities was $30,000, but it has now been increased to $100,000 for critical flaws.
The maximum amount the company is prepared to pay for firmware vulnerabilities has increased from $10,000 to $30,000, and for software flaws from $7,500 to $10,000.
The list of hardware products covered by Intel’s bug bounty program includes processors, chipsets, field-programmable gate array (FPGA) integrated circuits, networking and communications equipment, motherboards, and solid-state drives.
“We believe these changes will enable us to more broadly engage the security research community, and provide better incentives for coordinated response and disclosure that help protect our customers and their data,” said Rick Echevarria, vice president and general manager of Platform Security at Intel.
Intel was made aware of the Spectre and Meltdown attack methods several months before researchers disclosed them, but many are unhappy with the way the company handled the situation.
While Spectre and Meltdown also affect processors from AMD, ARM and IBM, Intel was hit the hardest. The company started releasing microcode updates shortly after the existence of the vulnerabilities was brought to light, but the first round of patches introduced stability problems. Intel started releasing a second round of updates, which should address these issues, only last week.
The company says its future CPUs will include protections against attacks like Meltdown and Spectre.
Researchers Warn Against Knee-Jerk Attribution of 'Olympic Destroyer' Attack
15.2.2018 securityweek Attack
Cyber Attack Attribution
Attribution has become a buzzword in malware analysis. It is very difficult to achieve -- but is necessary in a world that is effectively engaged in the early stages of a geopolitical cyberwar. Malware researchers tend to stop short of saying, 'this country or that actor is behind this attack'. Nevertheless, they are not shy in dropping hints, leaving the reader to make subjective conclusions.
They have done just that with the recent cyber-attacks against the PyeongChang Winter Olympic Games.
The New York Times comments, "Security companies would not say definitively who was behind the attack, but some digital crumbs led to a familiar culprit: Fancy Bear, the Russian hacking group with ties to Russian intelligence services."
Microsoft tweeted, "Fresh analysis of the #cyberattack against systems used in the Pyeongchang #WinterOlympics reveals #EternalRomance SMB exploit."
EternalRomance -- one of the leaked NSA exploits -- along with SMB was employed in the Bad Rabbit ransomware which has been likened to NotPetya which the UK government today ascribed to the Russian intelligence services.
Intezer is a firm that specializes in recognizing code reuse. It has analyzed the Olympic attacks, and comments, "We have found numerous small code fragments scattered throughout different samples of malware in these attacks that are uniquely linked to APT3, APT10, and APT12 which are known to be affiliated with Chinese threat actors."
Recorded Future comments (PDF), "Our own research turned up trivial but consistent code similarities between Olympic Destroyer modules and several malware families used by the Lazarus Group. These include standard but different functions within BlueNoroff Banswift malware, the LimaCharlie family of Lazarus malware from the Novetta Blockbuster report, and a module from the Lazarus SpaSpe malware meant to target domain controllers." Lazarus is, of course, considered to be synonymous with North Korea.
But while saying that there are code similarity hints at connections with North Korea, Recorded Future warns against jumping to any specific conclusion. "The trouble with this technique is that while code similarity can be stated with certainty, down to a percentage of bytes shared, the results are not straightforward and require expert interpretation. The Olympic Destroyer malware is a perfect example of how we can be led astray by this clustering technique when our standard for similarity is too low."
Code analysis suggests that Russia, China or North Korea, or any combination thereof, or all, or none of these state actors were behind the Winter Olympics attack.
Juan Andres Guerrero-Saade, principal security researcher at the Insikt Group at Recorded Future says: “Complex malware operations make us take pause to reevaluate research methods and make sure the research community is not being misled by its own eagerness to attribute attacks."
Priscilla Moriuchi, director of strategic threat development at Recorded Future says: “Attribution continues to be important in cyber-attacks because it shapes the victim, public, and government responses. However, accurate attribution is both more crucial and more difficult to determine than ever because adversaries are constantly evolving new techniques and the expertise required to identify a sophisticated actor keeps increasing.”
This doesn't mean that Recorded Future drops no hints of its own. It notes that this was a sophisticated two-pronged attack probably involving an earlier malware attack designed to steal credentials to be used during the opening ceremony against both the organizers and the infrastructure providers. In other words, it could only be achieved by a highly resourced attacker.
The attack's purpose was disruption rather than absolute destruction. While systems were wiped, they were left able to reboot -- allowing the possibility of eventual data recovery and reinstatement. There is no immediately apparent attempt at extortion -- removing financial motivation and leaving the probability of political motivation.
The 'hints' contained in the code similarity point variously at Russia, China and North Korea. Recorded Future adds another possibility: "The co-occurrence of code overlap in the malware may be indicative of a false flag operation, attempting to dilute evidence and confuse researchers." In other words, without access to 5Eyes-quality wiretaps and intercepted voice conversations (which intelligence agencies would be unwilling to reveal) it is all but impossible to attribute this, or any other cyber-attack, with 100% confidence.
As Recorded Future concludes, "For the time being, attribution remains inconclusive."
SAP Security Notes – February 2018 addresses tens of flaws including High Risk issues
15.2.2018 securityaffairs Vulnerebility
SAP Security Notes – February 2018: SAP Security Notes February 2018 addressed several vulnerabilities including High-Risk flaws.
SAP has released February 2018 Patches that addressed some high-risk vulnerabilities in its software, a total of 26 Security Notes (5 high-, 19 medium- and 2 low-risk). Once again, the missing authorization check is the most common vulnerability type this month.
The Security Notes SAP addresses three cross-site scripting (XSS) vulnerabilities, two directory traversal flaws, two information disclosure bugs, two missing authorization checks, one unrestricted file upload, and other issues.
Affected products are the Internet Graphics Server (IGS), NetWeaver System Landscape Directory, HANA Extended Application Services, ABAP File Interface, SAP CRM, ERP Financials Information System, Netweaver Portal, Netweaver Java Web Application, CRM WebClient UI, BI Launchpad, and SAP HANA.
“On 13th of February 2018, SAP Security Patch Day saw the release of 11 Security Notes. Additionally, there were 3 updates to previously released security notes.” reads the advisory published by SAP.

SAP also addressed previous Security Notes that includes an incorrect authorization check in ERP Logistics, a cross-site request forgery (CSRF) vulnerability in SAP Sybase, and a flaw that ties the way the SAP Note Assistant handles digitally signed notes.
Three critical vulnerabilities were reported by Mathieu Geli, Vahagn Vardanyan, and Vladimir Egorov, researchers at ERPScan security firm.
The details of the issues fixed thanks to the support of the researchers are:
A Missing Authentication check vulnerability in SAP NetWeaver System Landscape Directory (CVSS Base Score: 8.3 CVE-2018-2368). Update is available in SAP Security Note 2565622. An attacker can use Missing authorization check vulnerability for access to a service without any authorization procedures and use service functionality that has restricted access. This can lead to an information disclosure, privilege escalation and other attacks.
A Directory Traversal vulnerability in SAP Internet Sales (CVSS Base Score: 6.6 CVE-2018-2380). Update is available in SAP Security Note 2547431. An attacker can use Directory traversal to access to arbitrary files and directories located in a SAP-server file system including application source code, configuration and system files. It allows to obtain critical technical and business-related information stored in a vulnerable SAP-system.
An Information Disclosure vulnerability in SAP HANA (CVSS Base Score: 5.3 CVE-2018-2369). Update is available in SAP Security Note 2572940. An attacker can use Information disclosure vulnerability for revealing additional information (system data, debugging information, etc) which will help to learn about a system and to plan other attacks.
The most severe vulnerability addressed by the security updates is a missing authentication check in SAP NetWeaver System Landscape Directory tracked as CVE-2018-2368, which received a CVSS base score of 8.3.
The flaw could be exploited by an attacker to access a service without any authorization, a circumstance that could lead to several attacks, including the privilege escalation and information disclosure,
“A Missing Authentication check vulnerability in SAP NetWeaver System Landscape Directory (CVSS Base Score: 8.3 CVE-2018-2368). Update is available in SAP Security Note 2565622. An attacker can use Missing authorization check vulnerability for access to a service without any authorization procedures and use service functionality that has restricted access. This can lead to an information disclosure, privilege escalation and other attacks.” continues ERPScan.
The updates also addressed:
A Directory Traversal vulnerability in SAP Internet Sales (CVSS Base Score: 6.6 CVE-2018-2380) that could be exploited by an attacker to use Directory traversal to access to arbitrary files and directories located in a SAP-server file system including application source code, configuration and system files.
An Information Disclosure vulnerability in SAP HANA (CVSS Base Score: 5.3 CVE-2018-2369). that could be exploited by an attacker for revealing additional information (system data, debugging information, etc).
Other vulnerabilities addressed this month included a directory traversal (CVE-2018-2367) in SAP ABAP File Interface (CVSS base score: 6.6) and a directory traversal (CVE-2018-2380) in SAP Internet Sales (CVSS base score: 6.6).
Further info related to the flaws addressed by SAP are available on the company blog.
Unknown Threat Actor Conducts OPSEC Targeting Middle East
15.2.2018 securityaffairs Hacking
Hackers conduct OPSEC Targeting Middle East – Classified Documents That May Pertain To The Jordanian Research House Dar El-Jaleel Are Being Used As Bait In A Campaign Targeting The Middle East.
The researchers Paul Rascagneres with help of Martin Lee, from CISCO TALOS, described a campaign of targeted attacks against the middle east with key elements present: Geopolitical interest at stake, once documents pertaining Research House Dar EL-Jaleel, that research on Israeli-Palestinian conflict and Sunni-Shia conflict with Iran, are being used.
Second, the extensive use of scripting languages (VBScript, PowerShell, VBA) as part of the attack vector, once they are used to be dynamically loaded and execute VBScript functions stored in a Command & Control server.
Third, the attacker had deployed a series of sophisticated countermeasures to hide his identification using Operation Security (OPSEC), utilization of reconnaissance scripts to validate the victim machine according to his criteria, utilization of CloudFlare system to hide the IP and infrastructure and finally using filters on connections based on User-Agent strings to use the infrastructure for short periods of time before vanishing going offline.
Regarding the analysis in the report, the script campaign is divided into a series of steps to further advance the widespread of the infection. The VBS campaign is composed of 4 steps with additional payloads and 3 distinct functions that are: Reconnaissance, Persistence, and Pivoting.

According to the report the first stage starts with a VBScript named من داخل حرب ايران السرية في سوريا.vbs (“From inside Iran’s secret war in Syria.vbs”) that is aimed to create in the second stage a PowerShell script that will generate a Microsoft Office document named Report.doc and to open it. On the third stage, the opened document contains a macro that creates a WSF (Windows Script File) file to be executed. On the fourth stage the script contains configuration information such as: The hostname of the command and control server, the port used 2095 and the User-Agent.
As the report notice, the User-Agent strings are being used to the identification of targets, while the command and control server filter these strings to only allow connections based in these criteria. The script tries to register the infected system with an HTTP request, which in turn executes an infinite loop to further download and use other payloads. The researchers discovered three types of additional payloads that are the following: s0, s1, and s2. These payloads for WSF scripts are VBScript functions that are loaded and executed in ExecuteGlobal() and GetRef() APIs. The difference between the payloads resides on the number of arguments supplied to execute the function.
The researchers found out a reconnaissance function in the earlier steps of the campaign that was intended to acquire information on the targeted system, verify if it contained significant information or if it was a sandbox machine. The hackers layered out a methodology composed of these steps: first acquiring the serial number of disk volume, and then using a payload to acquire information on any anti-virus software present on the system. Next, by querying ipify.org the hackers tried to obtain the IP address of the infected machines to further obtain the computer name, username, operating system and architecture.
A second function is used to list the drives on the system and its type.
Finally, the researchers cover the remaining two functions: Persistence and Pivoting. Persistence functions were used alongside the reconnaissance functions linked to the WSF script. While the first script was used to persist, the second was used to clean the infected system to cover its tracks. Regarding the Pivoting function, it receives an argument where the PowerShell script executes a second base64 encoded script intended to download shellcode from 176.107.185.246 to be mapped in the memory and then executed.
As the researchers noticed, the hackers behind the campaign had been very careful to protect their infrastructure and their code against the leak. The command and control server was protected by CloudFlare to avoid tracking and difficult the analysis. Furthermore, by using filters on the User-Agents the hackers selected requests that only meet their criteria.
The Threat Actor was only seen active during the morning, on the Central European Time zone, to unleash their attacks and payloads. Once infected the operating system receives the pivot function to disable the firewall and allow the unique IP to receive the shellcode. Next, the server becomes unreachable. The researchers point out: “This high level of OPSEC is exceptional even among presumed state-sponsored threat actors”.
The researchers also noticed some similarities with Jenxcus (Houdini/H-Worn), but it was not clear if it is a new version or an adaption. They for sure agree that it is far more advanced in the resources it presents. The researchers state:
“This document is a weekly report about the major events occurring during the 1st week of November 2017, talking about the most important events happening in Jordan, Iraq, Syria, Lebanon, Palestine, Israel, Russia, ISIS and the ongoing Gulf Countries conflict with Qatar. These campaigns show us that at least one threat actor is interested in and targeting the Middle East. Due to the nature of the decoy documents, we can conclude that the intended targets have an interest in the geopolitical context of the region”.
Sources:
http://www.securityweek.com/actor-targeting-middle-east-shows-excellent-opsec
http://www.securitynewspaper.com/2018/02/10/targeted-attacks-middle-east/
http://blog.talosintelligence.com/2018/02/targeted-attacks-in-middle-east.html
https://blogs.cisco.com/security/talos/targeted-attacks-in-the-middle-east
https://cyware.com/news/targeted-attacks-in-the-middle-east-8e454752
Android Security Bulletin – Google fixed several Critical Code Execution vulnerabilities
15.2.2018 securityaffairs Android
Android Security Bulletin for February 2018 – Google has fixed tens of vulnerabilities for Android OS, including several critical remote code execution (RCE) flaws.
The Android Security Bulletin for February 2018 addresses 26 vulnerabilities in the mobile operating system, most of which are elevation of privilege flaws.
The 2018-02-01 security patch level fixed 7 vulnerabilities, 6 in Media Framework and one issue affecting the System component.
The tech giant has fixed two critical RCE vulnerabilities in Media Framework. The first issue is the CVE-2017-13228 that affects Android 6.0 and newer, the second one, tracked as CVE-2017-13230, impacts Android 5.1.1 and later.

Google also fixed other vulnerabilities in Media Framework, including an information disclosure vulnerability, an elevation of privilege bug, and several denial-of-service flaws.
“The most severe of these issues is a critical security vulnerability in Media framework that could enable a remote attacker using a specially crafted file to execute arbitrary code within the context of a privileged process.” states the advisory.
The most severe of these vulnerabilities is tracked as CVE-2017-13236, it is a System issue that could be exploited by an attacker to achieve remote code execution in the context of a privileged process. The attacker can trigger the flaw via email, web browsing, and MMS when processing media files.
The 2018-02-05 security patch level includes fixes for 19 vulnerabilities in HTC, Kernel, NVIDIA, Qualcomm, and Qualcomm closed-source components.
The most severe flaws included in the 2018-02-05 security patch level are two remote code execution vulnerabilities in Qualcomm components tracked as CVE-2017-15817 and CVE-2017-17760.
Google also released the Pixel / Nexus Security Bulletin that addresses 29 vulnerabilities in Google devices.
“The Pixel / Nexus Security Bulletin contains details of security vulnerabilities and functional improvements affecting supported Google Pixel and Nexus devices (Google devices). For Google devices, security patch levels of 2018-02-05 or later address all issues in this bulletin and all issues in the February 2018 Android Security Bulletin.” states Google.
“All supported Google devices will receive an update to the 2018-02-05 patch level. We encourage all customers to accept these updates to their devices.”
Spam and phishing in 2017
15.2.2018 Kaspersky Analysis Spam
Figures of the year
The share of spam in mail traffic came to 56.63%, down 1.68% against 2016.
The biggest source of spam remains the US (13.21%).
40% of spam emails were less than 2 KB in size.
The most common malware family found in mail traffic was Trojan-Downloader.JS.Sload
The Anti-Phishing system was triggered 246,231,645 times.
9% of unique users encountered phishing
Global events in spam
Spam emails that mention the hottest topics in the world news agenda are a permanent feature of junk traffic. This trend has been observed for several years and is unlikely to change any time soon. Natural disasters in 2017 (hurricanes Irma and Harvey, the earthquake in Mexico) were a gift to fraudsters. “Nigerian” scammers bombarded mailboxes with messages asking for assistance in obtaining the inheritance of deceased relatives and donations for disaster victims, etc. Natural disasters were also a common theme in advertising spam and emails offering jobs and loans.
In 2017 spammers made frequent mention of natural disasters
Sporting events are another favorite topic of spammers. The most popular — and most mentioned in fake giveaway messages — are major soccer competitions and the Olympics. Back in 2016 we picked up emails citing the FIFA 2018 World Cup, and the following year their number increased, with the format and content unchanged. Typically, such emails say that during such-and-such lottery, supposedly held by a well-known organization, the recipient was randomly selected among a million others as the winner of a huge cash prize. Besides money, scammers sometimes promise tickets to competitions. The details are usually outlined in file attachments using official competition and sponsor logos.
“Winning” the lottery can be timed to major sporting events
The “Nigerian” scammers often refer to famous figures. Presidents and other political VIPs are especially in demand. In 2017, one of the most popular figures for fraudsters was US President Donald Trump.
We predict that in 2018 scammers will continue to pay close attention to world events and famous figures so as not to let slip the chance to squeeze ever more money and personal info out of gullible victims.
Cryptocurrencies in spam
Throughout the year we wrote that cryptocurrencies had gained a foothold in advertising spam and fraudulent mailings: all the numerous “Earn from home” schemes, financial pyramids, fake lottery wins, and phishing scams, etc., seem to have been updated and given a cryptocurrency makeover. Let’s try to systematize the various types of cryptocurrency-related spam.
Seminars
As major conferences and seminars are held on blockchain technology, spammers are making increasing use of this topic for their own purposes. The seminars advertised in their mailings don’t overload users with technical details, but promise to teach them how to extract eye-watering profits from cryptocurrencies. Such mailings are relatives of “traditional” spam on the topic “How to make a killing on the stock exchange.”
Example emails advertising “lucrative” seminars
Financial fraud
A specific type of cryptocurrency fraud relates to fake “cloud mining” services. Such services hire out the mining power of their own specialized data centers. Fake sites offer similar services, but on paying up, the user receives neither mining power nor their money back. The crypto version of the classic pyramid scam warrants a special mention: the user “receives” mining income until they enlist other victims (for which there is also a reward). But sooner or later the cash flow stops, and the original investment is not repaid.
Fake “cloud mining” services offer enticing rewards
Sites masquerading as cryptocurrency trading platforms operate in a similar manner. The crucial difference between them and real exchanges is that money can only be invested, not withdrawn. Revenue usually “grows” very quickly, stimulating the user to invest more funds.
On fake cryptocurrency exchanges, experience really isn’t necessary
More subtle are binary options brokers (and their fake counterparts). We covered them in a previous report.
Another type of cryptocurrency fraud is fake services offering to exchange one currency for another, or convert it into “real” money. Scammers lure victims with favorable exchange rates, and then make off with the cash.
The “currency exchange desk” simply pockets the money for itself
Spam is very often used for this kind of fraud because it gives what all scammers crave — anonymity.
Other types of fraud
More traditional types of fraud, such as fake lottery wins, started using bitcoin bait:
Malware
CryptoLocker, whose creators demanded payment in bitcoin, was found in spam far less often than in 2016. That said, we encountered various modifications of Locky, Cerber, Rack, and other ransomware. At the same time, new capabilities such as stealing passwords from cryptocurrency wallets and mining were added to spam-distributed malware.
What’s more, a host of malware was distributed in spam under the guise of bitcoin mining tools or trading instructions.
The attached document was detected as HEUR:Exploit.RTF.Generic
Address databases
Targeted address databases advertised through spam were updated with the email addresses of cryptocurrency users, putting the address owners at risk of a targeted attack (for example, phishing as mentioned above).
Like other hot global issues, cryptocurrency is set be a recurring theme in spam for a very long time to come. And given the juicy rewards on offer, 2018 can expect to see growth in both fraudulent and phishing “cryptocurrency” spam.
Spamming by ethnicity
As we all know, spam peddles everything from potency-enhancing drugs to fake goods by well-known brands — it’s an international phenomenon that knows no geographic boundaries. However, 2017 caught the eye for some more localized spam content.
China and manufacturing
Back in 2016, we wrote about the Chinese habit of using spam to market goods internationally. Nothing changed in 2017: More and more Chinese companies are offering their products in this way.
India and IT
Whereas the Chinese are keen to sell goods on the international market, spam from India is more likely to offer IT services: SEO, web design, mobile apps, and much more:
Russia and seminars
Russian spam is written in, yes, Russian — and is therefore aimed at the domestic market. It too advertises goods and services, but more striking is the range of seminars and training on offer:
America and targeted business spam
In the US, the law governing the distribution of advertising messages operates on the opt-out principle. Accordingly, users can be sent messages until they explicitly unsubscribe from the mailing list in question, for which a link must be provided. The CAN-SPAM Act stipulates many other legal requirements for mailings. The legislation demands that the message body match the subject in terms of topic, there be no automatic collection of addresses, the advertiser’s physical address appear in the text, and much more.
Using the opt-out principle, many small, and sometimes not-so-small, companies send out promotional materials to people who have not subscribed to them. A legal gray area arises from the fact that even if spam-mailing companies are physically located in the US, the emails are distributed worldwide, and most countries operate an opt-in policy, requiring the prior consent of recipients. In other words, some countries at the legislative level consider mailshots to be spam.
A trait of business spam is its very narrow targeting of companies operating in specific areas. Oftentimes, mailings are not directed to the company as a whole, but to people with certain job titles.
Malware and the corporate sector
The number of malicious spam messages in 2017 fell 1.6-fold against 2016. Kaspersky Lab clients registered a total of 145,820,119 triggers of Mail Anti-Virus throughout 2017.
Number of Mail Anti-Virus triggers among Kaspersky Lab clients in 2017
This drop is due to the unstable operation of the Necurs botnet: it mediated the spread of far fewer mailings, and in Q1 2017 was completely idle. Malicious mailshots sent via Necurs were short, not personalized. They were used to try to install cryptolockers from the Locky family on recipients’ computers.
In general, 2017 was marked by a large cluster of malicious, but well-crafted emails, containing fragments of business correspondence matching the company profile, plus the full details of the organizations in whose name they had been sent.
Emails containing malicious objects detected as Backdoor.Java.Adwind.cu
The messages were not mass-distributed, but most likely targeted. Based on the target domain names, it can be assumed that the attackers were primarily interested in the corporate sector, while the tactic of citing previous messages of the addressee suggests in some cases a Business Email Compromise-type attack.
An email containing a malicious object detected as Trojan-PSW.Win32.Fareit.dnak
Malware downloaded onto the victim computer most often had functions for collecting detailed information about the system and its settings (as well as passwords, keystrokes, etc.), and then transferring this data to a remote server. For information about potential targets and perpetrators of such attacks, see our article.
Phishing
Phishing pages migrate to HTTPS
Sites have been moving to HTTPS in increasing numbers, and not just legitimate resources. If a year ago a top tip for users was “check that pages requesting personal data are secure,” today a certificate does not guarantee safety: anyone or anything could be behind it.
Where do scammers get certificates? For domains created specifically for fraudulent purposes, attackers most likely use free 90-day certificates from Let’s Encrypt and Comodo, two certificate authorities. Getting hold of one is simplicity itself.
A phishing site with a free 90-day certificate issued by Let’s Encrypt
What’s more, phishing pages are often located on hacked sites that already have the necessary certificates.
A phishing page located on a hacked site with HTTPS
Scammers also make use of free web hosting with an SSL certificate:
On the topic of free hosting sites, it should be noted that attackers often use services that do not closely monitor user-posted content. It is not uncommon for phishing content to be placed on free hosting sites of well-known companies: this reduces the risk of the page being blacklisted, since it is located on a reputable domain with a high-profile name and a good SSL certificate. And although such services are pro-active in the fight against illegitimate content, phishing pages on their domains are found fairly often.
A phishing page located on the Google Sites service redirecting users to a third-party resource where payment system data is requested
Phishing pages located on the Force.com Sites service
Punycode encoding
Another important rule is to always check the spelling of the domain name, a task made more difficult due to the active use by phishers of Punycode encoding, which helps mask phishing domain names under the domains of well-known brands. Web browsers use Punycode to display Unicode characters in the address bar, but if all the characters in the domain name belong to the character set for one language, the browser displays them not in Punycode format, but in the specified language. Scammers select characters similar or identical to ones in Latin script, and use them to create domain names that resemble those of well-known companies.
The technique is not new, but caused a real stir this year, especially after an article by Chinese researcher Xudong Zheng. As an example, he created a domain with a name that in the address bar was indistinguishable from Apple’s domain. Phishers aren’t always able to find identical symbols, but the results are still look pretty convincing.
Examples of domains displayed in Punycode in browser address bars
Besides the external similarity to the original domain, such domains are more difficult to detect by keywords.
Fake cryptocurrency wallets
Fraudsters are always up to speed on the latest trends, brands, and news hooks. The hype around cryptocurrencies in 2017 reached such a crescendo that even those far removed from the virtual world were snapping up bitcoin, whatever it was.
As a result, cryptocurrency wallets were a very attractive target for phishers. Proof of this is the large number of phishing pages spoofing cryptocurrency wallets. We encountered Coinbase, BitGo, and Xapo, to name just a few. One of the leaders by number of spoofs is blockchain.info.
Examples of phishing pages mimicking user sign-in to popular cryptocurrency wallets
Scammers also spoof popular cryptocurrency services in an attempt to get users to hand over money under the guise of lucrative investments.
A page spoofing the popular Coinbase
Social media fraud
In Q2, social networks were hit by a wave of air ticket giveaways. Scammers set up websites under famous airline brands that were supposedly raffling off tickets. After completing a short survey, the user was redirected to a resource created by the attackers. This could be an infected site, a phishing page prompting to install malware under the guise of a browser update, or a page spreading malicious content, etc.
Examples of Facebook posts with links to various scamming domains
The scheme is not new, but the distribution mechanism in this case is innovative: in winning a “prize,” users themselves shared unsafe content in social media.
For some domains in the scheme, visitor activity statistics were available, according to which just one of the sites was visited by more than 2,500 users worldwide in the space of an hour:
In Q3, scammers shifted their attention to WhatsApp and extended their assortment of fake prizes.
Fake giveaways that began their odyssey in social media migrated to WhatsApp, and the range of prizes expanded
Fake viruses
Cybercriminals often don’t even bother to write malware, using instead fake virus notifications supposedly from common operating systems. Such messages often appear as pop-up ads or as the result of the user being passed through a redirect chain. This might happen after completing a survey, as in the scheme described above.
The scammers’ primary aim is to intimidate and coerce users into calling a “technical support” number where they are offered solutions to disinfect their computer — not free of charge, of course.
Examples of pages showing fake system infection messages
It’s not only Windows users in the firing line. Scammers are targeting Apple products, too.
Example of a page showing a fake system infection message
Under the same guise, cybercrooks also distribute insecure software.
Example of a page showing a fake system infection message and prompting to download a file
Tax refunds
Another eternal topic is tax returns and tax refunds. Public trust in government sites plays an important role in the success of phishing operations in this segment. Exploiting features of the taxation system in different countries, scammers carry out successful attacks in the US, France, Canada, Ireland, and elsewhere.
Examples of phishing pages using the names of tax authorities in different countries
The new iPhone
The release of the new version of the popular smartphone also attracted scammers, with attempts to redirect users to phishing pages mimicking Apple sites growing 1.5-fold in September, when the latest iteration of the flagship series went on sale.
Number of Anti-Phishing triggers on user computers caused by attempts to redirect to phishing sites using the Apple brand, 2017
The launch of Apple’s new smartphone inspired a host of fraudulent schemes, including fake giveaways, sales of counterfeit devices, and classic phishing scams mentioning the brand.
Fake Apple sign-in page
Statistics: spam
Proportion of spam in email traffic
The share of spam in email traffic in 2017 fell by 1.68% to 56.63%.
Proportion of spam in global email traffic, 2017
The lowest share (52.67%) was recorded in December 2017. The highest (59.56%) belonged to September.
Sources of spam by country
In 2017, the US remained the biggest source of spam (13.21%). A 6.59% hike in spam distribution pushed China up to second place (11.25%). Vietnam took bronze (9.85%).
India slipped from third to fourth (7.02%), showing a 3.13% decline in its share of spam. Next came Germany (5.66%, +2.45%) and Russia (5.40%, +1.87%).
In the seventh place was Brazil (3.97%, -0.04%). And in ninth, France (3.71%, -0.32%). Italy rounds off the Top 10 with a score of 1.86%, up 0.62% against 2016.
Source of spam by country, 2017
Spam email size
In 2017, the share of very small emails (up to 2 KB) in spam again dropped sharply, averaging 43.40%, which is 18.76% less than in 2016. The proportion of emails ranging in size from 2 to 5 KB amounted to 5.08%, another significant change.
Spam emails by size, 2017
There was further growth in the share of emails between 5 and 10 KB (9.14%, +2.99%), 10 and 20 KB (16.26%, +1.79%), and 20 and 50 KB (21.23%, +11.15%). Overall, spam in 2017 did not buck the trend of fewer very small emails and rising numbers of average size emails (5-50 KB).
Malicious attachments in email
Malware families
Top 10 malware families in 2017
In 2017, the most common malware family in email traffic was Trojan-Downloader.JS.Sload — a set of JS scripts that download and run other malicious programs on the victim computer, usually encryptors.
Runner-up was last year’s leader Trojan-Downloader.JS.Agent — the typical member of this malware family is an obfuscated JS that uses ADODB.Stream technology to download and run DLL, EXE, and PDF files.
Third place went to the Backdoor.Java.Qrat family — a cross-platform multi-functional backdoor written in Java and sold in the Darknet under the umbrella of Malware-as-a-Service (MaaS). It is generally distributed by email in the form of JAR attachments.
The Worm.Win32.WBVB family took fourth place. It includes executable files written in Visual Basic 6 (both in P-Code mode and Native mode) that are untrusted in KSN.
Trojan-PSW.Win32.Fareit completes the Top 5. This malware family is designed to steal data, such as the credentials of FTP clients installed on infected computers, cloud-storage credentials, browser cookies, and email passwords. Fareit Trojans send the information collected to the attackers’ server. Some members of the family can download and run other malware.
In sixth position was the Trojan-Downloader.MSWord.Agent family. This malware takes the form of a DOC file with an embedded macro written in Visual Basic for Applications (VBA) that runs when the document is opened. The macro downloads another malicious file from the attackers’ site and runs it on the user’s computer.
In seventh is Trojan.PDF.Badur, which poses as a PDF document containing a link to a potentially dangerous site.
Eighth place was occupied by the Trojan-Downloader.VBS.Agent family — a set of VBS scripts that use ADODB.Stream technology to download ZIP archives and run malware extracted from them.
Trojan.WinLNK.Agent found itself in ninth position. Members of this malware family have the extension .lnk and contain links for downloading malicious files or a path for running another malicious executable file.
One more family of Trojan loaders, Trojan.Win32.VBKrypt, props up the Top 10.
Countries targeted by malicious mailshots
In 2017, Germany (16.25%, +2.12%) held on to top spot. China (12.10%) climbed from third to second, adding 4.78% for the year. Russia (6.87%, +1.27%) rounds off the Top 3.
Countries targeted by malicious mailshots, 2017
Further down come Japan (5.32%, -2.27%), Britain (5.04%, -0.13%), Italy (4.89%, -0.55%), and Brazil (4.22%, -0.77%).
Eighth place is taken by Vietnam (2.71%, +0.81%). And ninth by France (2.42%, -1.15%). The Top 10 is rounded off by the UAE (2.34%, +0.82%).
Statistics: phishing
In 2017, the Anti-Phishing system was triggered 246,231,645 times on computers of Kaspersky Lab users as a result of phishing redirection attempts. That is 91,273,748 more than in 2016. In all, 15.9% of our users were targeted by phishers.
Organizations under attack
The rating of organizations targeted by phishing attacks is based on the triggering of the heuristic component in the Anti-Phishing system on user computers. This component detects all instances when the user tries to follow a link in an email or on the Internet to a phishing page in the event that such links have yet to be added to Kaspersky Lab’s databases.
Organizations under attack by category
The lion’s share of heuristic component triggers in 2017 went to pages that mentioned banking organizations (27%, +1.24%). Second place in the rating is the Payment systems category (15.87%, +4.32%), followed by Online stores (10.95%, +0.78%).
Distribution of organizations subject to phishing attacks by category, 2017.
See our financial report (link) for more details about phishing in the financial sector.
Top 3 organizations under attack from phishers
As before, the trend in mass phishing is still to use the most popular brands. By doing so, scammers significantly increase the likelihood of a successful attack. The Top 3 is made of organizations whose names were most often used by phishers (according to the heuristic statistics for triggers on user computers):
Facebook 7.97%
Microsoft Corporation 5.57%
PayPal 4.50%
The geography of attacks
Countries by percentage of attacked users
As in the previous year, Brazil had the highest percentage of attacked unique users out of the total number of users in the country, seeing its score increase by 1.41% to 29.02%.
Percentage of users on whose computers the Anti-Phishing system was triggered out of all Kaspersky Lab users in the country, 2017
Top 10 countries by percentage of attacked users
Brazil 29.02%
Australia 22.51%
China 19.23%
Qatar 18.45%
Bolivia 18.38%
Albania 17.95%
New Zealand 17.85%
Portugal 16.76%
Angola 16.45%
Russia 16.43%
Top 10 countries by percentage of attacked users
The number of attacked users also increased in Australia — by 2.43% to 22.5%. Next come China (19.23%), where the share of attacked users fell by 3.61%, and Qatar (14.45%).
Results
The number of malicious spam messages in 2017 fell 1.6-fold against 2016. This drop is due to the unstable operation of the Necurs botnet, which mediated the spread of far fewer mailings.
In 2018, spammers and phishers will continue to closely monitor world events and famous figures so as not to miss any opportunity to extract money and personal info from their unsuspecting targets. We can expect mailings to refer to the Winter Olympic Games, the FIFA World Cup, the presidential elections in Russia, and other events. What’s more, the first few months of the year are likely to experience a wave of phishing pages and mailshots exploiting the topic of tax refunds, since in many countries April is tax payment month. The theme of cryptocurrency will be popping up in spam for a very long time to come. And given the juicy rewards on offer, 2018 can expect to see growth in both fraudulent and phishing “cryptocurrency” spam.
The number of phishing sites using SSL certificates will surely continue to grow. As will the use of different domain name obfuscation methods.
Kaspersky Files New Lawsuit Over U.S. Government Software Ban
15.2.2018 securityweek
Kaspersky Lab has filed a new lawsuit over the U.S. government’s decision to ban its products in federal agencies, this time challenging the National Defense Authorization Act (NDAA).
The NDAA for Fiscal Year 2018 was signed by President Donald Trump in mid-December and it reinforced the binding operational directive (BOD) issued by the Department of Homeland Security (DHS) in September, which ordered government agencies to stop using products from Kaspersky due to concerns regarding its ties to Russian intelligence.
Kaspersky filed a lawsuit to appeal the BOD on December 18, a few days after President Trump signed the NDAA. Last month, the security firm filed an injunction in an effort to expedite the appeal.
The government filed a response to the injunction earlier this month and Kaspersky responded this week with a new lawsuit that challenges the NDAA as a bill of attainder.
A bill of attainder is a legislative act that singles out an individual or group for punishment without a trial. Legislative bills of attainder are banned by the U.S. constitution.
“Kaspersky Lab has filed an action challenging the constitutionality of Section 1634 (a) and (b) of the National Defense Authorization Act for Fiscal Year 2018, which prohibits any federal entity from using the company’s hardware, software or services. Kaspersky Lab believes that these provisions violate the U.S. Constitution by specifically and unfairly singling out the company for legislative punishment, based on vague and unsubstantiated allegations without any basis in fact,” Kaspersky Lab stated.
“No evidence has been presented of any wrongdoing by the company, or of any misuse of its products. Kaspersky Lab is proven to be one of the world’s leading IT security companies, with a track record of uncovering malicious code and threat actors regardless of their origin or purpose,” the company added.
Kaspersky has attempted to clear its name by launching a new transparency initiative that involves giving partners access to source code and paying significantly larger bug bounties for vulnerabilities found in the firm’s products.
It has also attempted to provide a logical explanation over accusations that its software had been exploited by Russian hackers to steal data belonging to the U.S. National Security Agency (NSA) from a contractor’s device.
Critical Oracle Micros POS Flaw Affects Over 300,000 Payment Systems
1.2.2018 thehackernews Vulnerebility
Oracle has released a security patch update to address a critical remotely exploitable vulnerability that affects its MICROS point-of-sale (POS) business solutions for the hospitality industry.
The fix has been released as part of Oracle's January 2018 update that patches a total of 238 security vulnerabilities in its various products.
According to public disclosure by ERPScan, the security firm which discovered and reported this issue to the company, Oracle's MICROS EGateway Application Service, deployed by over 300,000 small retailers and business worldwide, is vulnerable to directory traversal attack.
If exploited, the vulnerability (CVE-2018-2636) could allow attackers to read sensitive data and receive information about various services from vulnerable MICROS workstations without any authentication.
Using directory traversal flaw, an unauthorized insider with access to the vulnerable application could read sensitive files from the MICROS workstation, including service logs and configuration files.
As explained by the researchers, two such sensitive files stored within the application storage—SimphonyInstall.xml or Dbconfix.xml—contain usernames and encrypted passwords for connecting to the database.
"So, the attacker can snatch DB usernames and password hashes, brute them and gain full access to the DB with all business data. There are several ways of its exploitation, leading to the whole MICROS system compromise," the researchers warned.
"If you believe that gaining access to POS URL is a snap, bear in mind that hackers can find digital scales or other devices that use RJ45, connect it to Raspberry PI, and scan the internal network. That is where they easily discover a POS system. Remember this fact when you pop into a store."
ERPScan has also released a proof-of-concept Python-based exploit, which, if executed on a vulnerable MICROS server, would send a malicious request to get the content of sensitive files in response.
Besides this, Oracle's January 2018 patch update also provides fixes for Spectre and Meltdown Intel processor vulnerabilities affecting certain Oracle products.
Serious Flaws Affect Several ManageEngine Products
1.2.2018 securityweek Vulnerebility
Researchers at Digital Defense have uncovered several potentially serious vulnerabilities in IT management products from ManageEngine, including ones that allow an attacker to take complete control of the affected application. The vendor has released patches to address the flaws.
Zoho-owned ManageEngine provides network, data center, desktop and mobile device, and security solutions to more than 40,000 customers, including three out of every five Fortune 500 company.
One of the flaws found by Digital Defense affects ManageEnegine’s ServiceDesk Plus help desk software. An unauthenticated file upload vulnerability allows an attacker to upload a JavaScript web shell and use it to execute arbitrary commands with SYSTEM privileges.
Experts also discovered several blind SQL injection vulnerabilities that allow an unauthenticated attacker to take complete control of an application and possibly even the underlying host.
These types of flaws have been found in the OpManager network monitoring product, Network Configuration Manager, bandwidth monitoring and traffic analysis product NetFlow Analyzer, firewall configuration and log management product Firewall Analyzer, and IP address management app OpUtils.
These products are also impacted by an enumeration issue that can be exploited to access user information such as usernames, email addresses and phone numbers.
An attacker could gain access to the content of files on the host running ManageEngine applications by leveraging an unauthenticated XML External Entity (XXE) vulnerability.
Digital Defense said ManageEngine promptly responded to its vulnerability reports and released updates for each of the affected applications to address the security holes.
“Application layer vulnerabilities continue to be a key area of focus for software vendors,” said Mike Cotton, vice president of engineering at Digital Defense. “We are pleased to work collaboratively with affected vendors to facilitate prompt resolution, ensuring our clients and enterprises are protected from any potential exploitation of these vulnerabilities.”
Digital Defense recently reported discovering authentication bypass, arbitrary file upload, and path traversal vulnerabilities affecting data protection products from both Dell EMC and VMware.
Malware exploiting Spectre and Meltdown flaws are currently based on available PoC
1.2.2018 securityaffairs Virus
Malware Exploiting Spectre, Meltdown Flaws Emerges
Researchers at the antivirus testing firm AV-TEST have discovered more than 130 samples of malware that were specifically developed to exploit the Spectre and Meltdown CPU vulnerabilities.
The good news is that these samples appear to be the result of testing activities, but experts fear that we could soon start observing attacks in the wild.
Most of the codes obtained by AV-TEST are just recompiled versions of the Proof of Concept code available online. Experts at AV-TEST also found the first JavaScript PoC codes for web browsers like IE, Chrome or Firefox in our database now.
“We also found the first JavaScript PoC codes for web browsers like IE, Chrome or Firefox in our database now.”Andreas Marx, CEO of AV-TEST, told SecurityWeek.
The Meltdown attack could allow attackers to read the entire physical memory of the target machines stealing credentials, personal information, and more.
The Meltdown exploits the speculative execution to breach the isolation between user applications and the operating system, in this way any application can access all system memory.
The Spectre attack allows user-mode applications to extract information from other processes running on the same system. It can also be exploited to extract information from its own process via code, for example, a malicious JavaScript can be used to extract login cookies for other sites from the browser’s memory.
The Spectre attack breaks the isolation between different applications, allowing to leak information from the kernel to user programs, as well as from virtualization hypervisors to guest systems.
On January 17, experts at AV-TEST reported that they had detected 77 malware samples apparently related to the Intel vulnerabilities.
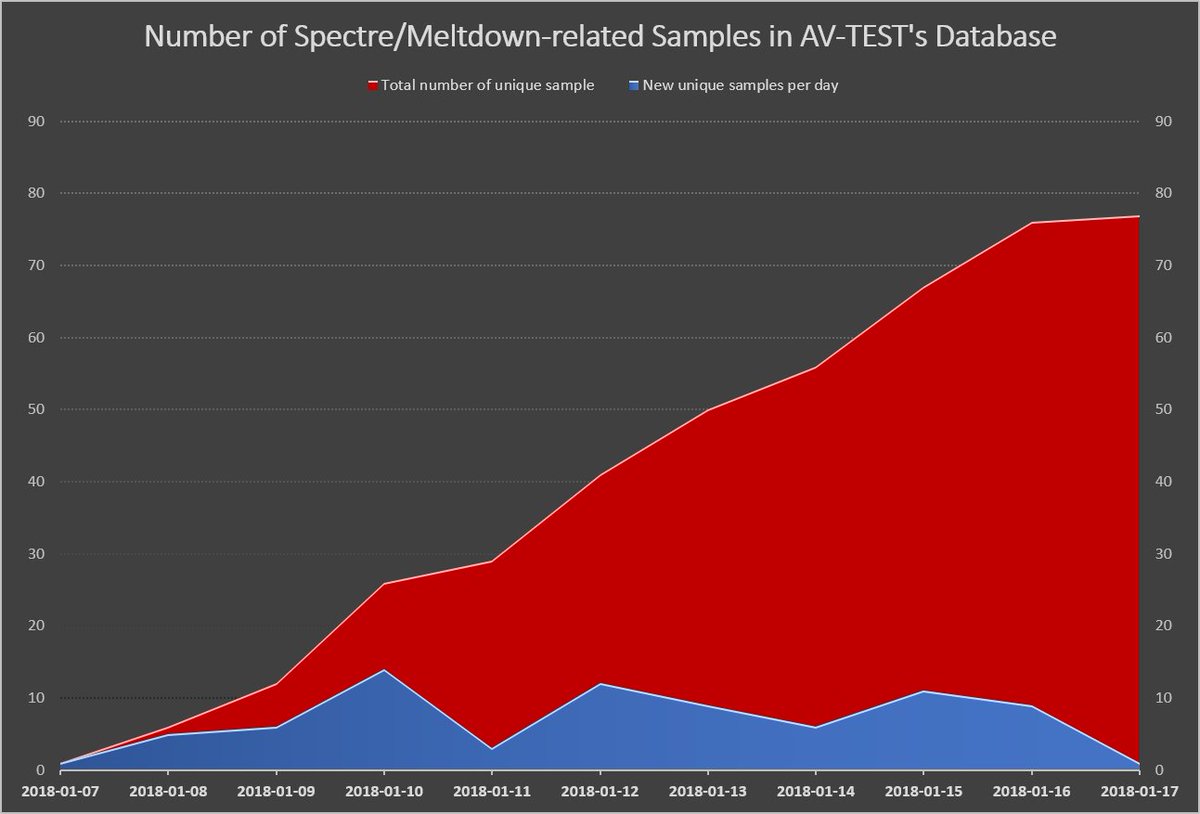
AV-TEST GmbH
✔
@avtestorg
#Spectre & #Meltdown: So far, the AV-TEST Institute discovered 77 samples which appear to be related to recently reported CPU vulnerabilities. #CVE-2017-5715 #CVE-2017-5753 #CVE-2017-5754
2:49 PM - Jan 17, 2018
7 7 Replies 24 24 Retweets 27 27 likes
Twitter Ads info and privacy
The number of malware samples related to Meltdown and Spectre reached pi119 by January 23.
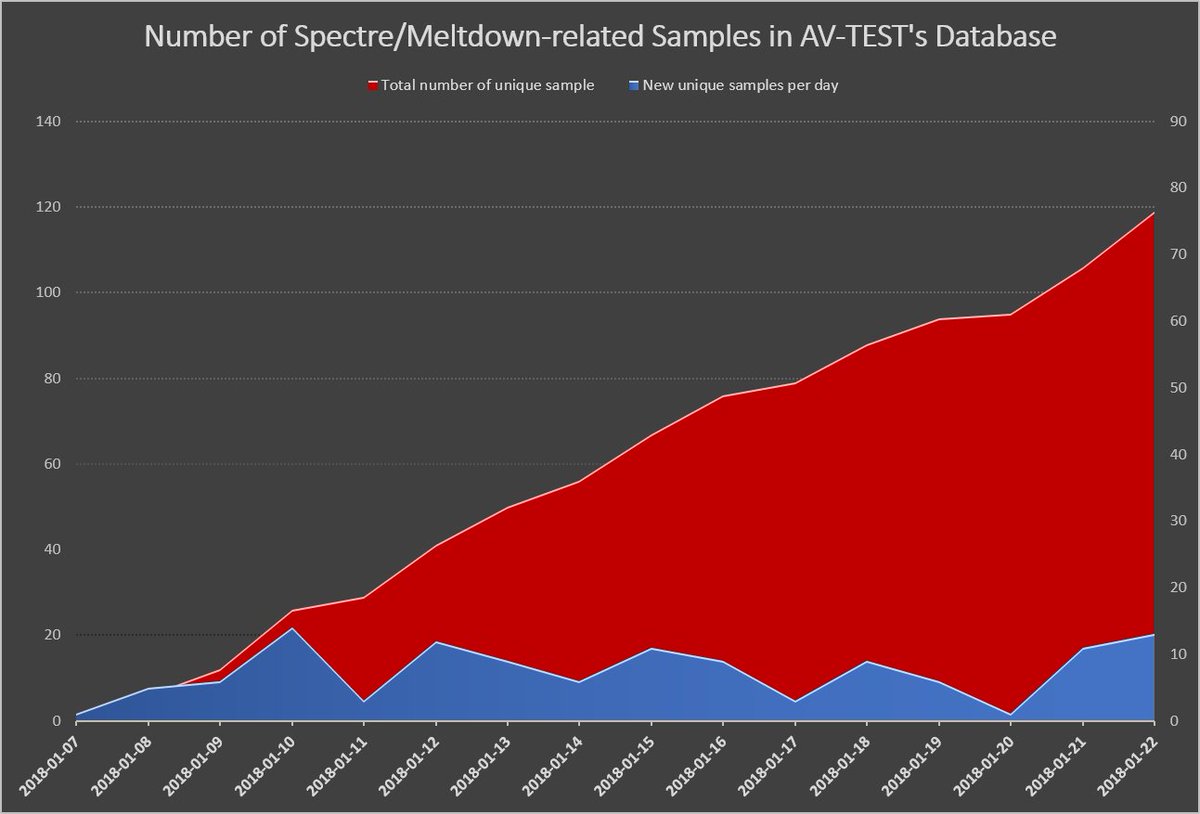
AV-TEST GmbH
✔
@avtestorg
[UPDATE: 2018-01-23] #Spectre & #Meltdown: So far, the AV-TEST Institute discovered 119 samples which appear to be related to recently reported CPU vulnerabilities. #CVE-2017-5715 #CVE-2017-5753 #CVE-2017-5754
SHA256 Hashes: https://plus.google.com/b/100383867141221115206/photos/photo/100383867141221115206/6514266175374877506 …
4:23 PM - Jan 23, 2018
2 2 Replies 14 14 Retweets 24 24 likes
Twitter Ads info and privacy
On January 31, AV-TEST confirmed to be in possession of 139 samples from various sources.

AV-TEST GmbH
✔
@avtestorg
[UPDATE: 2018-01-23] #Spectre & #Meltdown: So far, the AV-TEST Institute discovered 119 samples which appear to be related to recently reported CPU vulnerabilities. #CVE-2017-5715 #CVE-2017-5753 #CVE-2017-5754
SHA256 Hashes: https://plus.google.com/b/100383867141221115206/photos/photo/100383867141221115206/6514266175374877506 …
4:23 PM - Jan 23, 2018
2 2 Replies 14 14 Retweets 24 24 likes
Twitter Ads info and privacy
According to the AV-TEST CEO, several groups of experts are working on a malware that could trigger Intel flaws, most of them are re-engineering the available PoC.
“We aren’t the only ones concerned. Others in the cybersecurity community have clearly taken notice, because between January 7 and January 22 the research team at AV-Test discovered 119 new samples associated with these vulnerabilities,” reads a blog post published by Fortinet. “FortiGuard Labs has analyzed all of the publicly available samples, representing about 83 percent of all the samples that have been collected, and determined that they were all based on proof of concept code. The other 17 percent may have not been shared publicly because they were either under NDA or were unavailable for reasons unknown to us.”
Mozilla fixes a critical remote code execution vulnerability in Firefox
1.2.2018 securityaffairs Vulnerebility
Mozilla has released security updates for Firefox 58 that addresses a critical remote code vulnerability that allows a remote attacker to run arbitrary code on vulnerable systems.
Mozilla has released an update for the Firefox 58 browser (aka Firefox Quantum) that addresses a critical flaw that could be exploited by a remote attacker to execute arbitrary code on computers running the vulnerable version of the browser.
The vulnerability, tracked as CVE-2018-5124, affects Firefox versions 56 through 58, meanwhile, it doesn’t impact Firefox for Android and Firefox 52 ESR.
The development teams behind major Linux distributions have also started rolling out updated packages that fix the flaw.
It was discovered by the Mozilla developer Johann Hofmann.
According to a security advisory published by Cisco, the Firefox 58.0.1 version fixed an ‘arbitrary code execution’ flaw that originates due to ‘insufficient sanitization’ of HTML fragments in chrome-privileged documents (browser UI).
“A vulnerability in Mozilla Firefox could allow an unauthenticated, remote attacker to execute arbitrary code on a targeted system.” states the security advisory.
“The vulnerability is due to insufficient sanitization of HTML fragments in chrome-privileged documents by the affected software. An attacker could exploit the vulnerability by persuading a user to access a link or file that submits malicious input to the affected software. A successful exploit could allow the attacker to execute arbitrary code with the privileges of the user. If the user has elevated privileges, the attacker could compromise the system completely.“
Firefox 58 was released on January 23, it addresses more than 30 vulnerabilities in the popular browser, some of them rated as high severity, including a use-after-free, buffer overflow, and integer overflow flaws.
According to Mozilla, its bug bounty program has already paid out nearly $1 million to white hat hackers who reported vulnerabilities.
Don’t waste time, apply the software updates as soon as possible.